Table of Contents
- Contents
- Setting Up
- Preparations Required Before Use
- Preventing Unauthorized Access
- Setting up Using the Setup Guide
- Logging in as an Administrator
- Setting the Date/Time
- Setting up the Network Environment
- Installing Drivers
- Fax Line Settings
- Setting E-mail/I-Fax Communication
- Connecting to the Other Devices
- Basic Operations
- Parts and Their Functions
- Turning ON the Machine
- Placing Originals
- Loading Paper
- Using the Touch Panel Display
- Logging into the Machine
- Specifying Paper Size and Type
- Specifying Paper Size and Type in the Paper Drawer
- Specifying Paper Size and Type in the Multi-purpose Tray
- Registering Frequently Used Paper Size and Type for the Multi-purpose Tray
- Fixing the Paper Size and Type to Use with the Multi-Purpose Tray
- Registering Free Size Paper (Custom Size Paper)
- Automatically Selecting the Appropriate Paper Source for a Specific Function
- Customizing the Touch Panel Display
- Customizing the <Home> Screen
- Creating a Shortcut for a Frequently Used Function
- Registering a Combination of Frequently Used Functions
- Customizing the Basic Features Screen
- Registering Frequently Used Settings and Destinations as Personal Buttons/Shared Buttons on the <Home> Screen
- Switching the Displayed Language
- Registering Shortcuts for Frequently Used Settings/Registered Items
- Customizing the Screen Display Appearance and the Operational Conditions
- Canceling Send/Print Jobs
- Setting Sounds
- Entering Sleep Mode
- Registering Destinations
- Copying
- Faxing
- Fax Basic Features Screen
- Basic Operations for Sending Faxes
- Receiving Faxes
- Sending Faxes Successfully
- Simplifying Sending Operations
- Useful Functions When Sending
- Various Receiving Methods
- Forwarding Received Documents Automatically
- Checking Status and Log for Sent and Received Documents
- Sending Faxes from Your Computer (PC Fax)
- Using Internet Faxes (I-Fax)
- Sending and Receiving Faxes via the Machine (Remote Fax)
- Printing
- Scanning
- Scan Basic Features Screen
- Basic Operations for Scanning Originals
- Scanning Clearly
- Scanning Efficiently
- Useful Scanning Functions
- Checking Scanned Originals Before Sending/Saving (Preview)
- Sending/Saving at a Specified Time
- Notifying You by E-Mail of the Completion of Sending/Saving
- Scanning with the OCR Function
- Enhancing the Security of Electronic Files
- Recalling Previously Used Settings for Sending/Saving (Previous Settings)
- Setting a File Name
- Specifying E-Mail Settings
- Using Your Computer to Scan (Remote Scan) (Windows)
- Using Other Machines and Memory Media
- Linking with Mobile Devices
- Managing the Machine
- Applying a Security Policy to the Machine
- Managing Users
- Configuring the Network Security Settings
- Restricting the Machine's Functions
- Adding a Digital Signature to Sent Files
- Managing the Machine from a Computer (Remote UI)
- Starting the Remote UI
- Checking the Status and Logs
- Turning OFF/Restarting the Machine
- Registering Destinations via the Remote UI
- Registering User Groups
- Registering a Key and Certificate for Network Communication
- Configuring the Expiration Check Method for Received Certificates
- Generating a Key and Certificate Signing Request (CSR)
- Retrieving/Updating a Certificate from an SCEP Server
- Managing Stored Files
- Managing the Logs
- Importing/Exporting the Setting Data
- Updating the Firmware
- Updating the Firmware (Distribution)
- Setting Scheduled Updates
- Displaying Messages from the Administrator
- Configuring the Visual Message Function
- Sending E-Mail Notification When an Error Occurs
- Installing System Options
- Synchronizing Settings for Multiple Canon Multifunction Printers
- Initializing All Data/Settings
- Functions Linked to Cloud Service
- Settings/Registration
- Maintenance
- Troubleshooting
- Implementing Security Measures
- Appendix
- SIL OPEN FONT LICENSE
Canon C1533iF User Manual
Displayed below is the user manual for C1533iF by Canon which is a product in the Multifunctionals category. This manual has pages.
Related Manuals
imageRUNNER
C1538iF / C1533iF
User's Guide
USRMA-5646-00 2021-02 en Copyright CANON INC. 2021

Contents
Setting Up ............................................................................................................................................................ 2
Preparations Required Before Use ............................................................................................................................. 3
Preventing Unauthorized Access ................................................................................................................................ 4
Setting up Using the Setup Guide ............................................................................................................................... 6
Logging in as an Administrator ................................................................................................................................ 15
Setting the Date/Time ............................................................................................................................................. 17
Setting up the Network Environment ....................................................................................................................... 19
Canceling the Network Setting Lock ...................................................................................................................... 22
Selecting the Network Connection Method ............................................................................................................ 23
Connecting to a Wired LAN .................................................................................................................................. 25
Connecting to a Wireless LAN ............................................................................................................................... 26
Setting Up the Connection Using WPS Push Button Mode .................................................................................. 28
Setting Up the Connection Using WPS PIN Code Mode ...................................................................................... 29
Setting Up Connection by Selecting a Wireless Router ....................................................................................... 30
Setting Up a Connection by Specifying Detailed Settings .................................................................................... 31
Checking the SSID and Network Key ............................................................................................................... 33
Setting an IP Address .......................................................................................................................................... 34
Setting an IPv4 Address ................................................................................................................................. 35
Setting an IPv6 Address ................................................................................................................................. 37
Setting the IPv4 Address of the Sub Line .......................................................................................................... 40
Adapting to the Network Environment .................................................................................................................. 41
Making Ethernet Settings .............................................................................................................................. 42
Setting the Wait Time When Connecting to a Network ....................................................................................... 44
Making DNS Settings ..................................................................................................................................... 45
Making SMB Settings .................................................................................................................................... 50
Making WINS Settings ................................................................................................................................... 52
Registering the LDAP Server .......................................................................................................................... 53
Monitoring and Controlling via SNMP .............................................................................................................. 57
Setting Static Routing .................................................................................................................................... 61
Other Network Settings ................................................................................................................................. 63
Conguring System Data Communication ........................................................................................................ 65
Installing Drivers .................................................................................................................................................... 67
Fax Line Settings ..................................................................................................................................................... 68
Setting E-mail/I-Fax Communication ........................................................................................................................ 70
Connecting to the Other Devices ............................................................................................................................. 75
Basic Operations .......................................................................................................................................... 79
Parts and Their Functions ........................................................................................................................................ 82
Front Side .......................................................................................................................................................... 83
Back Side ........................................................................................................................................................... 86
Interior .............................................................................................................................................................. 88
Feeder ............................................................................................................................................................... 89
Multi-Purpose Tray .............................................................................................................................................. 91
I

Paper Drawer ..................................................................................................................................................... 92
Control Panel ..................................................................................................................................................... 93
Turning ON the Machine ......................................................................................................................................... 95
Turning OFF the Machine ..................................................................................................................................... 96
Placing Originals ..................................................................................................................................................... 97
Loading Paper ....................................................................................................................................................... 102
Basic Paper Loading Method .............................................................................................................................. 103
Loading Envelopes ............................................................................................................................................ 111
Loading Preprinted Paper .................................................................................................................................. 115
Using the Touch Panel Display ............................................................................................................................... 118
Basic Screens on the Touch Panel Display ............................................................................................................ 119
Items Displayed on the <Home> Screen ........................................................................................................ 122
Timeline Display Specications ..................................................................................................................... 125
Items Displayed in the Timeline .................................................................................................................... 127
Basic Operation of the Touch Panel Display ......................................................................................................... 130
Entering Characters .......................................................................................................................................... 135
Logging into the Machine ...................................................................................................................................... 137
List of Items That Can Be Personalized ................................................................................................................ 139
Specifying Paper Size and Type .............................................................................................................................. 141
Specifying Paper Size and Type in the Paper Drawer ............................................................................................. 142
Specifying Paper Size and Type in the Multi-purpose Tray ...................................................................................... 145
Registering Frequently Used Paper Size and Type for the Multi-purpose Tray ........................................................... 148
Fixing the Paper Size and Type to Use with the Multi-Purpose Tray ......................................................................... 151
Registering Free Size Paper (Custom Size Paper) ................................................................................................... 153
Automatically Selecting the Appropriate Paper Source for a Specic Function .......................................................... 154
Customizing the Touch Panel Display ..................................................................................................................... 156
Customizing the <Home> Screen ........................................................................................................................ 159
Creating a Shortcut for a Frequently Used Function .............................................................................................. 162
Registering a Combination of Frequently Used Functions ...................................................................................... 164
Customizing the Basic Features Screen ................................................................................................................ 167
Registering Frequently Used Settings and Destinations as Personal Buttons/Shared Buttons on the <Home> Screen .... 170
Registering Personal Buttons/Shared Buttons ................................................................................................ 171
Switching the Displayed Language ..................................................................................................................... 176
Registering Shortcuts for Frequently Used Settings/Registered Items ..................................................................... 178
Customizing the Screen Display Appearance and the Operational Conditions ........................................................... 180
Canceling Send/Print Jobs ...................................................................................................................................... 183
Setting Sounds ...................................................................................................................................................... 184
Entering Sleep Mode ............................................................................................................................................. 188
Registering Destinations ....................................................................................................................................... 190
About the Address Books of the Machine ............................................................................................................. 192
Registering Destinations in the Address Book ...................................................................................................... 195
Registering Multiple Destinations as a Group ................................................................................................. 205
Editing the Registered Destinations in the Address Book ................................................................................. 208
Registering a Destination in a One-Touch Button .................................................................................................. 210
Registering a Group in a One-Touch Button ................................................................................................... 212
II

Editing the Registered Destinations in One-Touch Buttons ............................................................................... 214
Copying .............................................................................................................................................................. 216
Copy Basic Features Screen ................................................................................................................................... 218
Basic Copy Operations ........................................................................................................................................... 220
Cancelling Copying ........................................................................................................................................... 231
Enhancing and Adjusting Copy Quality ................................................................................................................... 233
Selecting the Type of Original for Copying ........................................................................................................... 234
Adjusting Sharpness for Copying (Sharpness) ...................................................................................................... 235
Erasing Dark Borders When Copying (Erase Frame) ............................................................................................... 236
Adjusting the Color ........................................................................................................................................... 238
One Touch Color Mode ...................................................................................................................................... 240
Copying Eciently ................................................................................................................................................ 242
Copying Multiple Originals onto One Sheet (N on 1) .............................................................................................. 243
Copying Separately Scanned Originals Together (Job Build) ................................................................................... 245
Checking the Copy Results ................................................................................................................................. 247
Copying Immediately by Interrupting Other Jobs .................................................................................................. 249
Functions Useful for Making and Managing Material .............................................................................................. 250
Finishing by Collating/Grouping ......................................................................................................................... 251
Useful Copy Functions ........................................................................................................................................... 253
Shifting the Image ............................................................................................................................................ 254
Notifying You of the Completion of Copying by E-Mail ........................................................................................... 257
Making ID Card Copies ...................................................................................................................................... 259
Skipping Blank Pages When Printing ................................................................................................................... 261
Reducing Copying Operations ................................................................................................................................ 263
Recalling Previously Used Copy Settings (Previous Settings) ................................................................................... 264
Recalling Settings ............................................................................................................................................. 265
Restrictions Regarding the Combination of Functions ............................................................................................. 266
Faxing .................................................................................................................................................................. 271
Fax Basic Features Screen ...................................................................................................................................... 273
Basic Operations for Sending Faxes ....................................................................................................................... 275
Canceling Sending Faxes ................................................................................................................................... 289
Receiving Faxes .................................................................................................................................................... 291
Sending Faxes Successfully .................................................................................................................................... 294
Checking Scanned Images Before Sending (Preview) ............................................................................................. 295
Checking the Connection to the Recipient Before Sending (Direct Send) .................................................................. 297
Sending Faxes Manually (Manual Sending) ........................................................................................................... 298
Notifying You by E-Mail of the Completion of Sending ........................................................................................... 299
Simplifying Sending Operations ............................................................................................................................. 301
Sending Separately Scanned Documents Together (Job Build) ................................................................................ 302
Recalling Previously Used Settings for Sending (Previous Settings) .......................................................................... 304
Useful Functions When Sending ............................................................................................................................. 306
Sending at a Specied Time ............................................................................................................................... 307
III

Saving a Copy of a Sent Document ...................................................................................................................... 309
Various Receiving Methods .................................................................................................................................... 312
Saving Received Documents in the Machine (Memory Reception) ........................................................................... 313
Keeping Received Documents Private ................................................................................................................. 316
Forwarding Received Documents Automatically ..................................................................................................... 318
Checking Status and Log for Sent and Received Documents .................................................................................... 321
Sending Faxes from Your Computer (PC Fax) .......................................................................................................... 324
Sending PC Faxes ............................................................................................................................................. 325
Using Internet Faxes (I-Fax) ................................................................................................................................... 329
Sending I-Faxes ................................................................................................................................................ 330
Receiving I-Faxes .............................................................................................................................................. 338
Sending and Receiving Faxes via the Machine (Remote Fax) .................................................................................... 339
Printing .............................................................................................................................................................. 341
Printing From a Computer ..................................................................................................................................... 343
Canceling Printing ............................................................................................................................................ 346
Checking the Printing Status and History ............................................................................................................. 348
Advanced Functions for Printing ............................................................................................................................ 350
Printing Documents Held in the Machine ............................................................................................................. 351
Printing at a Specied Time (Scheduled Printing) .................................................................................................. 355
Various Printing Methods ...................................................................................................................................... 357
Directly Printing Files without Opening Them ....................................................................................................... 358
Printing Using a Virtual Printer ........................................................................................................................... 360
Printing From Memory Media (Media Print) ......................................................................................................... 363
Printing Using the Microsoft Cloud Service (Universal Print) ................................................................................... 364
Conguring the Universal Print User Settings ................................................................................................. 368
Scanning ........................................................................................................................................................... 372
Scan Basic Features Screen .................................................................................................................................... 374
Basic Operations for Scanning Originals ................................................................................................................ 377
Checking Status and Log for Scanned Documents ................................................................................................ 392
Scanning Clearly ................................................................................................................................................... 394
Adjusting Image Quality .................................................................................................................................... 395
Adjusting Density ............................................................................................................................................. 396
Adjusting Sharpness When Scanning (Sharpness) ................................................................................................. 397
Erasing Dark Borders When Scanning (Erase Frame) ............................................................................................. 398
Scanning Eciently ............................................................................................................................................... 401
Sending/Saving Separately Scanned Documents Together (Job Build) ...................................................................... 402
Useful Scanning Functions .................................................................................................................................... 404
Checking Scanned Originals Before Sending/Saving (Preview) ................................................................................ 405
Sending/Saving at a Specied Time ..................................................................................................................... 407
Notifying You by E-Mail of the Completion of Sending/Saving ................................................................................. 409
Scanning with the OCR Function ......................................................................................................................... 411
Enhancing the Security of Electronic Files ............................................................................................................ 416
IV

Recalling Previously Used Settings for Sending/Saving (Previous Settings) ............................................................... 421
Setting a File Name ........................................................................................................................................... 423
Specifying E-Mail Settings .................................................................................................................................. 425
Using Your Computer to Scan (Remote Scan) (Windows) ......................................................................................... 427
Using Color Network ScanGear 2 ........................................................................................................................ 428
Scanning Originals from an Application ......................................................................................................... 430
Using WSD ....................................................................................................................................................... 432
Scanning Originals Using WSD (WSD Scan) .................................................................................................... 433
Using Other Machines and Memory Media ......................................................................... 437
Using Another Machine or Server - Network .......................................................................................................... 438
Using Memory Media ............................................................................................................................................ 441
Settings Screens for Using Other Machines/Servers/Memory Media ........................................................................ 446
Linking with Mobile Devices ............................................................................................................ 452
Connecting with Mobile Devices ............................................................................................................................ 453
Connecting Directly .......................................................................................................................................... 454
Utilizing the Machine through Applications ........................................................................................................... 458
Using AirPrint ....................................................................................................................................................... 460
Printing with AirPrint ........................................................................................................................................ 465
Scanning with AirPrint ....................................................................................................................................... 468
Faxing with AirPrint .......................................................................................................................................... 470
If AirPrint Cannot Be Used ................................................................................................................................. 472
Printing with Default Print Service (Android) .......................................................................................................... 473
Managing the Machine ........................................................................................................................ 476
Applying a Security Policy to the Machine .............................................................................................................. 478
Using a Password to Protect the Security Policy Settings ........................................................................................ 479
Conguring the Security Policy Settings .............................................................................................................. 481
Security Policy Setting Items .............................................................................................................................. 483
Managing Users .................................................................................................................................................... 489
Conguring the Personal Authentication Management Settings ............................................................................. 492
Registering User Information in the Local Device ............................................................................................ 495
Importing/Exporting User Data .................................................................................................................... 499
Adding and Editing User Information in a CSV File .................................................................................... 503
Registering Server Information .................................................................................................................... 507
Conguring the Authentication Functions ...................................................................................................... 513
Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a Computer .............................. 520
Using Other Convenient Personal Authentication Management Functions ............................................................... 521
Setting the Department ID Management ....................................................................................................... 522
Changing the System Manager ID and PIN .............................................................................................. 523
Conguring the Department ID Management Settings .............................................................................. 525
Using Department IDs to Manage Printing or Remote Scanning via Computer ............................................. 528
Conguring Personal Folders ....................................................................................................................... 529
Using ACCESS MANAGEMENT SYSTEM ........................................................................................................... 533
V

Deleting User Setting Information ...................................................................................................................... 534
Conguring the Network Security Settings ............................................................................................................ 536
Restricting Communication by Using Firewalls ..................................................................................................... 538
Specifying IP Addresses in Firewall Settings ................................................................................................... 539
Specifying MAC Addresses in Firewall Settings ................................................................................................ 542
Conguring the Firewall of the Sub Line ........................................................................................................ 544
Setting a Proxy ................................................................................................................................................. 547
Conguring the Key and Certicate for TLS .......................................................................................................... 549
Generating the Key and Certicate for Network Communication ...................................................................... 552
Conguring the IPSec Settings ........................................................................................................................... 555
Conguring the IEEE 802.1X Authentication Settings ............................................................................................. 561
Restricting the Machine's Functions ...................................................................................................................... 564
Restricting Access to Address Book and Sending Functions .................................................................................... 565
Restricting Use of the Address Book ............................................................................................................. 566
Limiting Available Destinations ..................................................................................................................... 569
Restricting the Fax Sending Functions ........................................................................................................... 571
Restricting Printing from a Computer .................................................................................................................. 573
Restricting the Use of Memory Media .................................................................................................................. 576
Adding a Digital Signature to Sent Files .................................................................................................................. 577
Generating a Device Signature Certicate ............................................................................................................ 578
Registering a User Signature Certicate .............................................................................................................. 579
Managing the Machine from a Computer (Remote UI) ............................................................................................ 581
Starting the Remote UI ...................................................................................................................................... 583
Checking the Status and Logs ............................................................................................................................ 587
Turning OFF/Restarting the Machine ................................................................................................................... 591
Registering Destinations via the Remote UI ......................................................................................................... 592
Sharing an Address List with Specic Users .................................................................................................... 596
Registering User Groups ................................................................................................................................... 598
Registering a Key and Certicate for Network Communication ............................................................................... 600
Conguring the Expiration Check Method for Received Certicates ........................................................................ 605
Generating a Key and Certicate Signing Request (CSR) ......................................................................................... 608
Retrieving/Updating a Certicate from an SCEP Server .......................................................................................... 611
Managing Stored Files ....................................................................................................................................... 617
Managing the Logs ........................................................................................................................................... 620
Importing/Exporting the Setting Data ................................................................................................................. 625
Importing/Exporting All Settings .................................................................................................................. 628
Importing/Exporting the Settings Individually ................................................................................................ 632
Address Book Items .............................................................................................................................. 635
Updating the Firmware ..................................................................................................................................... 640
Updating the Firmware (Distribution) .................................................................................................................. 642
Setting Scheduled Updates ................................................................................................................................ 645
Displaying Messages from the Administrator ....................................................................................................... 647
Conguring the Visual Message Function ............................................................................................................ 649
Sending E-Mail Notication When an Error Occurs ................................................................................................ 652
Installing System Options ..................................................................................................................................... 654
VI

Synchronizing Settings for Multiple Canon Multifunction Printers .......................................................................... 656
Starting Setting Synchronization ......................................................................................................................... 659
Switching the Machines to Synchronize ............................................................................................................... 662
Initializing All Data/Settings .................................................................................................................................. 663
Functions Linked to Cloud Service .......................................................................................................................... 665
Settings/Registration ............................................................................................................................ 670
Settings/Registration Table ................................................................................................................................... 671
Preferences ..................................................................................................................................................... 674
Paper Settings ............................................................................................................................................ 675
Display Settings .......................................................................................................................................... 677
Timer/Energy Settings ................................................................................................................................. 680
Network .................................................................................................................................................... 682
External Interface ....................................................................................................................................... 707
Accessibility ............................................................................................................................................... 708
Volume Settings ......................................................................................................................................... 709
Adjustment/Maintenance .................................................................................................................................. 710
Adjust Image Quality .................................................................................................................................. 711
Adjust Action ............................................................................................................................................. 713
Maintenance .............................................................................................................................................. 714
Function Settings .............................................................................................................................................. 715
Common ................................................................................................................................................... 716
Copy ......................................................................................................................................................... 720
Printer ...................................................................................................................................................... 722
Output Report ...................................................................................................................................... 723
Custom Settings ................................................................................................................................... 724
UFR II .................................................................................................................................................. 727
PCL ..................................................................................................................................................... 728
PS ....................................................................................................................................................... 730
Imaging .............................................................................................................................................. 732
PDF ..................................................................................................................................................... 734
XPS ..................................................................................................................................................... 736
Utility .................................................................................................................................................. 738
Send ......................................................................................................................................................... 739
Receive/Forward ......................................................................................................................................... 748
Store/Access Files ....................................................................................................................................... 751
Print ......................................................................................................................................................... 753
Set Destination ................................................................................................................................................. 755
Management Settings ....................................................................................................................................... 757
User Management ...................................................................................................................................... 758
Device Management ................................................................................................................................... 761
License/Other ............................................................................................................................................ 765
Data Management ...................................................................................................................................... 767
Security Settings ......................................................................................................................................... 768
<Preferences> ....................................................................................................................................................... 770
<Paper Settings> .............................................................................................................................................. 771
<Display Settings> ............................................................................................................................................ 773
VII

<Timer/Energy Settings> ................................................................................................................................... 777
<Network> ....................................................................................................................................................... 782
<External Interface> .......................................................................................................................................... 795
<Accessibility> .................................................................................................................................................. 797
<Adjustment/Maintenance> .................................................................................................................................. 798
<Adjust Image Quality> ..................................................................................................................................... 799
<Adjust Action> ................................................................................................................................................ 804
<Maintenance> ................................................................................................................................................ 805
<Function Settings> .............................................................................................................................................. 807
<Common> ...................................................................................................................................................... 808
<Copy> ............................................................................................................................................................ 817
<Printer> ......................................................................................................................................................... 818
<Send> ............................................................................................................................................................ 820
<Receive/Forward> ........................................................................................................................................... 835
<Store/Access Files> .......................................................................................................................................... 843
<Print> ............................................................................................................................................................ 846
<Set Destination> .................................................................................................................................................. 849
<Management Settings> ....................................................................................................................................... 853
<User Management> ........................................................................................................................................ 854
<Device Management> ...................................................................................................................................... 857
<License/Other> ............................................................................................................................................... 861
<Data Management> ........................................................................................................................................ 864
<Security Settings> ........................................................................................................................................... 866
Maintenance ................................................................................................................................................. 872
Regular Cleaning .................................................................................................................................................. 874
Cleaning the Exterior ........................................................................................................................................ 875
Cleaning the Platen Glass .................................................................................................................................. 876
Cleaning the Feeder .......................................................................................................................................... 878
Replacing the Toner Cartridge ............................................................................................................................... 881
Replacing the Waste Toner Container .................................................................................................................... 885
Replacement Parts ................................................................................................................................................ 888
Checking the Remaining Amount of Consumables .................................................................................................. 891
Adjusting Print Quality .......................................................................................................................................... 893
Adjusting Gradation .......................................................................................................................................... 894
Adjusting Density ............................................................................................................................................. 896
Correcting Color Mismatch ................................................................................................................................ 897
Automatically Adjusting Color Registration and Color Intensity .............................................................................. 898
Making Colors More Vivid .................................................................................................................................. 900
Adjusting Image Size ......................................................................................................................................... 901
Reducing Toner Used When Color Printing .......................................................................................................... 902
Paper Type Management Settings ......................................................................................................................... 903
Checking the Number of Pages for Copy/Print/Fax/Scan ......................................................................................... 908
Printing Reports and Lists ..................................................................................................................................... 909
VIII

Troubleshooting ......................................................................................................................................... 921
If the Machine Does Not Operate ........................................................................................................................... 923
Cannot Print ......................................................................................................................................................... 925
Problems with Printing Results .............................................................................................................................. 926
Problems with Faxes ............................................................................................................................................. 929
Problems with Scanning ........................................................................................................................................ 931
Problems with the Network ................................................................................................................................... 933
Problems with Security ......................................................................................................................................... 937
Other Problems .................................................................................................................................................... 938
A Message or a Number Starting with "#" (an Error Code) Is Displayed .................................................................... 940
A Message Saying to Contact Your Dealer or Service Representative Is Displayed ..................................................... 941
Countermeasures for Each Message ................................................................................................................... 943
Countermeasures for Each Error Code ................................................................................................................ 982
Clearing Paper Jams ............................................................................................................................................ 1008
Paper Jams in the Feeder ................................................................................................................................. 1011
Paper Jams inside the Machine or in the Fixing Unit ............................................................................................ 1013
Paper Jams in a Paper Source ........................................................................................................................... 1017
Implementing Security Measures ............................................................................................. 1023
Various Security Functions .................................................................................................................................. 1024
Appendix ........................................................................................................................................................ 1030
Third Party Software ........................................................................................................................................... 1032
Notice ................................................................................................................................................................ 1033
Feature Highlights .............................................................................................................................................. 1037
Operability .................................................................................................................................................... 1038
Utilizing Personalization ............................................................................................................................ 1039
Productivity ................................................................................................................................................... 1046
Image Quality ................................................................................................................................................ 1047
Manageability ................................................................................................................................................ 1048
Building a Dual Network Environment ......................................................................................................... 1050
Reliability ...................................................................................................................................................... 1053
Oce Compatibility ........................................................................................................................................ 1054
The List of System Functions and Items ............................................................................................................... 1055
Home ............................................................................................................................................................ 1056
Copy ............................................................................................................................................................. 1058
Fax ............................................................................................................................................................... 1060
Scan and Send ............................................................................................................................................... 1062
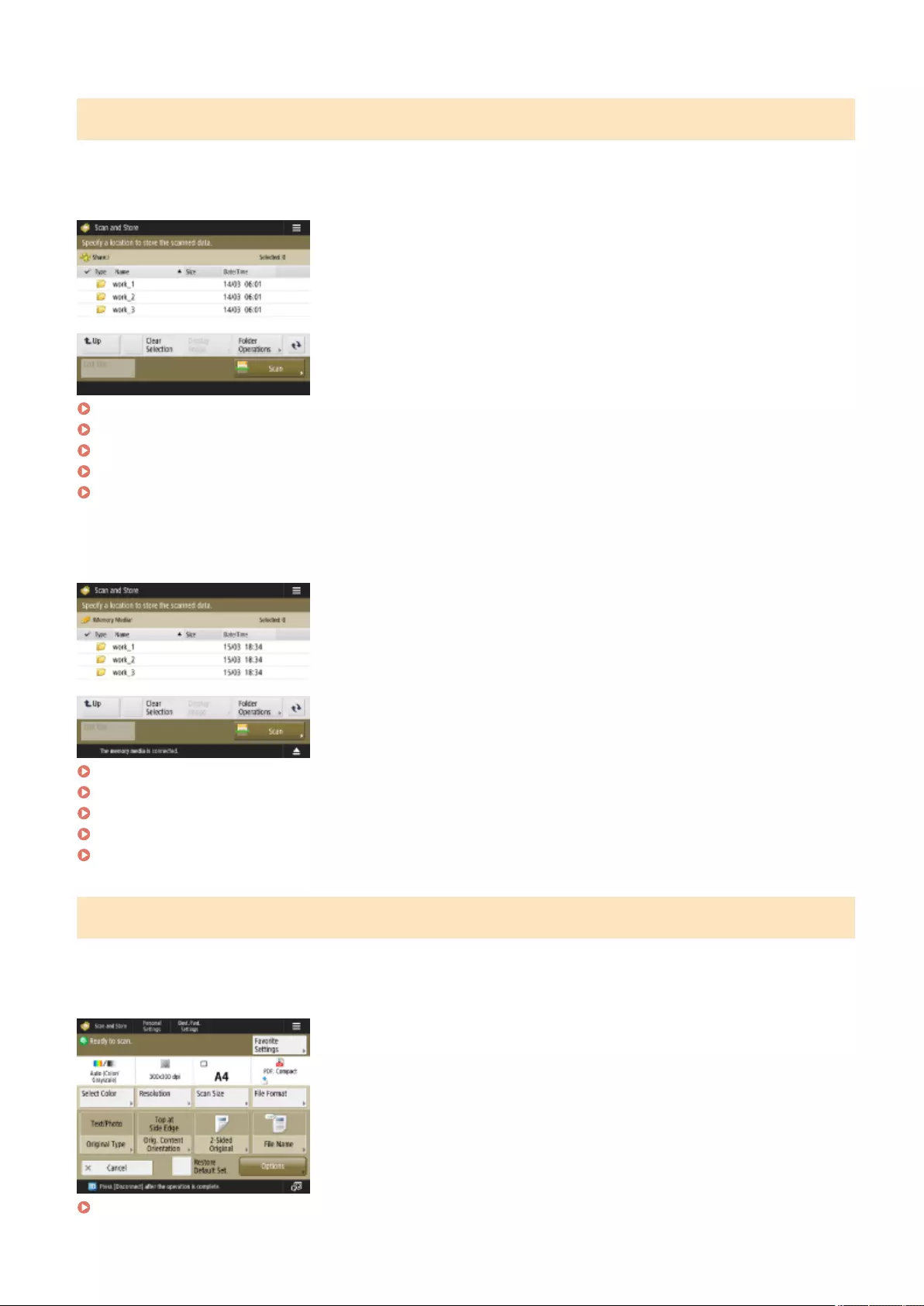
Scan and Store ............................................................................................................................................... 1064
Access Stored Files ......................................................................................................................................... 1068
Fax/I-Fax Inbox .............................................................................................................................................. 1072
Print ............................................................................................................................................................. 1074
Changing Login Services ..................................................................................................................................... 1075
IX

Basic Windows Operations .................................................................................................................................. 1080
System Specications .......................................................................................................................................... 1084
Fax Function .................................................................................................................................................. 1085
Send Functions .............................................................................................................................................. 1086
Printer Functions ............................................................................................................................................ 1088
Management Functions ................................................................................................................................... 1091
System Environment ....................................................................................................................................... 1097
Network Environment ..................................................................................................................................... 1099
System Options .............................................................................................................................................. 1101
Hardware Specications ...................................................................................................................................... 1103
Main Unit ...................................................................................................................................................... 1104
Feeder .......................................................................................................................................................... 1107
Available Paper .............................................................................................................................................. 1109
Paper Feeder PF-D .......................................................................................................................................... 1115
Cassette Feeding Unit-AV ................................................................................................................................. 1116
Copy Card Reader ........................................................................................................................................... 1117
Options .............................................................................................................................................................. 1118
Optional Equipment ........................................................................................................................................ 1119
Paper Feeder PF-D .................................................................................................................................... 1120
Cassette Feeding Unit-AV .......................................................................................................................... 1121
TELEPHONE 6 KIT ..................................................................................................................................... 1122
Copy Card Reader ..................................................................................................................................... 1123
ADF Access Handle-A ................................................................................................................................ 1125
Manuals and Their Contents ................................................................................................................................ 1126
Using User's Guide .............................................................................................................................................. 1127
Screen Layout of User's Guide .......................................................................................................................... 1128
Viewing User's Guide ...................................................................................................................................... 1132
X

Setting Up
Setting Up ............................................................................................................................................................... 2
Preparations Required Before Use ....................................................................................................................... 3
Preventing Unauthorized Access .......................................................................................................................... 4
Setting up Using the Setup Guide ......................................................................................................................... 6
Logging in as an Administrator .......................................................................................................................... 15
Setting the Date/Time ......................................................................................................................................... 17
Setting up the Network Environment ................................................................................................................ 19
Canceling the Network Setting Lock ............................................................................................................... 22
Selecting the Network Connection Method .................................................................................................... 23
Connecting to a Wired LAN ............................................................................................................................. 25
Connecting to a Wireless LAN ......................................................................................................................... 26
Setting Up the Connection Using WPS Push Button Mode ....................................................................... 28
Setting Up the Connection Using WPS PIN Code Mode ............................................................................ 29
Setting Up Connection by Selecting a Wireless Router ............................................................................. 30
Setting Up a Connection by Specifying Detailed Settings ......................................................................... 31
Checking the SSID and Network Key ........................................................................................................ 33
Setting an IP Address ..................................................................................................................................... 34
Setting an IPv4 Address ........................................................................................................................... 35
Setting an IPv6 Address ........................................................................................................................... 37
Setting the IPv4 Address of the Sub Line ................................................................................................. 40
Adapting to the Network Environment ........................................................................................................... 41
Making Ethernet Settings ......................................................................................................................... 42
Setting the Wait Time When Connecting to a Network ............................................................................ 44
Making DNS Settings ............................................................................................................................... 45
Making SMB Settings ............................................................................................................................... 50
Making WINS Settings .............................................................................................................................. 52
Registering the LDAP Server .................................................................................................................... 53
Monitoring and Controlling via SNMP ...................................................................................................... 57
Setting Static Routing .............................................................................................................................. 61
Other Network Settings ........................................................................................................................... 63
Conguring System Data Communication ............................................................................................... 65
Installing Drivers ................................................................................................................................................. 67
Fax Line Settings ................................................................................................................................................. 68
Setting E-mail/I-Fax Communication ................................................................................................................. 70
Connecting to the Other Devices ....................................................................................................................... 75
Setting Up
1
Setting Up
72JY-000
Setting up the usage environment is required before using each function of the machine. First, conrm the processes
to complete "setting up" prior to actual setup. Preparations Required Before Use(P. 3)
◼Administrators and General Users
To manage the machine, it is recommended to construct a system in which someone is appointed as an administrator
and general users operate the machine under the management of an administrator. Administrators decide the rules
for using the machine and operate important setups such as networks and security. Administrators set the access for
each user when necessary.
Carrying out the initial setup of the machine (Setup Guide)
●You can easily set up to start using the machine, such as setting the date and time and networks, by
following the on-screen instructions. Setting up Using the Setup Guide(P. 6)
Setting Up
2
Preparations Required Before Use
72JY-001
Set up the machine in order from steps 1 through 4. For details, click a link to display the corresponding pages. To use
the machine safely, at the same time, conrm Preventing Unauthorized Access(P. 4) .
Step 1 Setting up Using the Setup Guide(P. 6)
Step 2 Setting up the Network Environment(P. 19)
●Set up the network environment not included on the Setup Guide. If you do not start the
Setup Guide, start setting up from this procedure.
Step 3 Installing Drivers(P. 67)
Step 4 Setting E-mail/I-Fax Communication(P. 70)
Setting from the Remote UI
●When you complete setup for the network environment, you can set up the machine from Remote UI
eciently. Starting the Remote UI(P. 583)
Saving setup time by importing data from other machines
●If you have any other Canon multifunction printer and save (export) its registered setup data to a computer
beforehand, setup contents such as address book and paper type setting can be immediately used by
importing them to the machine. Importing/Exporting the Setting Data(P. 625)
Setting Up
3
Preventing Unauthorized Access
72JY-002
This section describes preventive measures against unauthorized access from external networks. For administrators
and users that are using the machine in a network environment, make sure to read this section before use.
Connecting to networks enables you to use various functions such as printing, remote operation from a computer,
sending scanned documents through the Internet, etc. However, for protection against unauthorized access from an
external network, security measures are essential. This section describes some countermeasures against unauthorized
access, which must be implemented before using the machine with a network environment.
Implementing Private IP Addresses(P. 4)
Limiting Communication via a Firewall(P. 5)
Setting up TLS Encryption Communication(P. 5)
Managing the Machine's Information via Passwords(P. 5)
Implementing Private IP Addresses
An IP address is a number that is assigned to a computer on a network. A "global IP address" is used for Internet
connections. A "private IP address" is used for local area networks such as an oce LAN. If your IP address is a global
IP address, unauthorized users on the Internet can attempt to access your local network and risks such as information
leakage become larger. If your address is a private address, only users on a local area network such as the oce LAN
have access.
【Global IP address】
Accessible from outside your network
【Private IP address】
Accessible only from within a local area network
Generally, when setting up an IP address, use a private IP address. For a private IP address, any addresses in the
following ranges can be used. Conrm if the IP address that is currently set is a private IP address.
◼Ranges of Private IP Addresses
●10.0.0.0 to 10.255.255.255
●172.16.0.0 to 172.31.255.255
●192.168.0.0 to 192.168.255.255
For information on how to conrm IP addresses, see Setting an IPv4 Address(P. 35) .
●Even if a global IP address is set for the machine, risk of unauthorized access can be reduced by using a
rewall. Consult your network administrator when you want to operate the machine using a global IP
address.
Setting Up
4
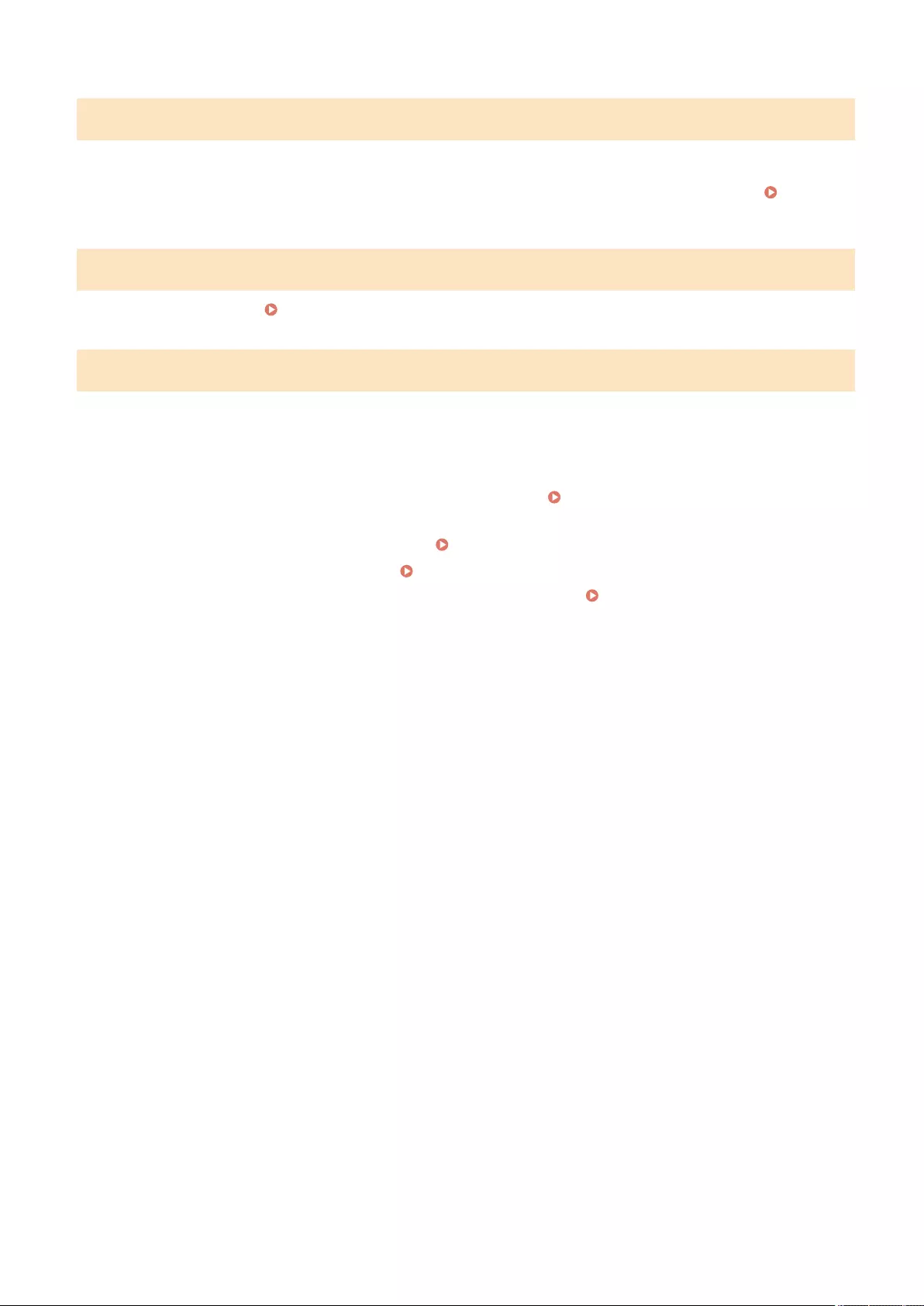
Limiting Communication via a Firewall
A rewall is a system that prevents unauthorized access from external networks in order to prevent attacks or invasion
into the local area network. Access from outside your local network that has potential to be a risk can be shut out
beforehand by limiting communication from a specic external IP address in your network environment. Restricting
Communication by Using Firewalls(P. 538)
Setting up TLS Encryption Communication
For TLS communication, see Starting the Remote UI(P. 583) .
Managing the Machine's Information via Passwords
Even if the machine receives unauthorized access from a malicious third party, risk of information leakage can be
greatly reduced when various information resources in the machine are protected by passwords.
Password for each function / PIN code setting
●Personal authentication management using User Authentication Conguring the Personal Authentication
Management Settings(P. 492)
●PIN code setting for system management contents Changing the System Manager ID and PIN(P. 523)
●PIN code settings for accessing Address Book Restricting Use of the Address Book(P. 566)
These are examples of preventing unauthorized access. For other details, see Managing the Machine(P. 476) and
carry out necessary settings according to your environment.
Setting Up
5

Setting up Using the Setup Guide
72JY-003
PMW-STSG
When the machine is turned ON for the rst time ( Turning ON the Machine(P. 95) ), the initial setup of the
machine begins automatically. You can adjust the basic setup necessary to use the machine. Congure the basic setup
in accordance with each screen, or click a link to display the corresponding page and see details.
Step 1 Specify the language and keyboard layout.
Select the language to be displayed on the screens. Depending on the language, you can
change the layout of the keyboard that is displayed to enter characters.
●Select the language, and press <OK>.
●To change the keyboard layout, press <Set>, select the keyboard layout, and press
<OK>.
●Displaying the button for switching languages will be convenient for frequent
language switching. Switching the Displayed Language(P. 176)
Step 2 Check the paper settings.
Check that the paper loaded in the drawers is correctly specied.
●If the paper sizes are correct, press <OK>.
●For information on the screen and the instructions on how to change the settings,
see Specifying Paper Size and Type in the Paper Drawer(P. 142) .
●If you are not logged in as an administrator, proceed to Step 10.
Step 3 Log in as the Administrator.
Make an authenticated login to congure the settings that require Administrator privileges.
Setting Up
6
●Press <Log In>, and enter the user name and password of a user with administrator
privileges. The default user name for the administrator is "Administrator" and the
default password is "7654321". Press <Log In> again, and press <OK>.
●If you enter the factory default password, the screen prompting you to change the
password is displayed. You can also change the password later. Logging in as an
Administrator(P. 15)
●You can skip the settings that require Administrator privileges and proceed to the next step
by pressing <Skip>. In this case, proceed to Step 10.
Step 4 Specify the user authentication settings.
To enhance the security of the machine, use the machine under a system that uses user
authentication.
●This machine is set to use the user authentication as the login service. For more information,
see Conguring the Personal Authentication Management Settings(P. 492) .
●Press <On> for <Use User Authentication>, press <On> for the login method to use,
and press <Next>.
●If you do not use user authentication, press <Off> for <Use User Authentication>,
press <OK>, and proceed to Step 5.
Specify the following settings if there are no administrators besides the "Administrator"
user registered in the machine.
●To enhance the security of the machine by disabling the "Administrator" user and
registering a new administrator, press <Yes>. In <Register Administrator>, enter
<User Name> and <Password>, and press <OK>. Specify <E-Mail Address>,
Setting Up
7

<Department ID>, and <Display Name> as necessary. For more information, see
Registering User Information in the Local Device(P. 495) . The "Administrator"
user will be disabled the next time you log in.
●To operate as "Administrator," press <No>.
●Select the timing for displaying the login screen. If you select <Display When Func.
Selected>, press <Functions>, select the function to display the login screen for, and
press <OK>. Also, select the setting items on the <Settings/Registration> screen to
display the login screen for.
●If you select <Off> for <Keyboard Authentication>, press <OK>. Proceed to step 5.
●If you select <On> for <Keyboard Authentication>, press <Next>.
●To use authentication via numeric key entry only on the login screen, press <On>,
and press <OK>.
Step 5 Set the date and time.
Specify the date and time of the machine.
●Enter the date and time, and press <OK>.
●Set <Time Zone> and <Daylight Saving Time> as necessary. For more information,
see Setting the Date/Time(P. 17) .
Step 6 Set the IP address.
Specify the settings for network connection.
Setting Up
8
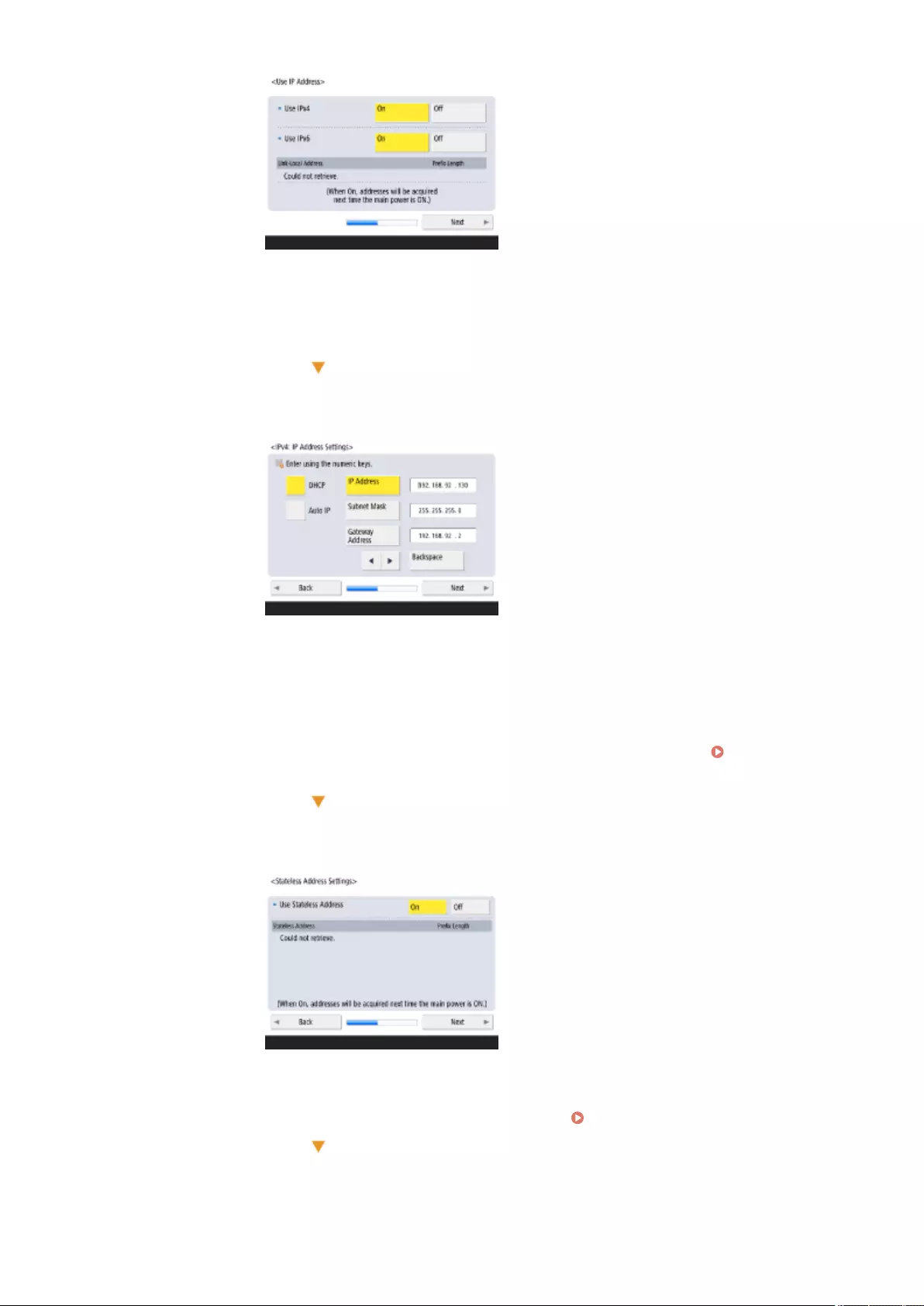
●Press <On> for <Use IPv4> or <Use IPv6>, and press <Next>. You can also use both
IPv4 and IPv6.
●If you press <Off> for <Use IPv4> and <Use IPv6>, and press <OK>, skip the network
settings and proceed to Step 9.
If you press <On> for <Use IPv4>, specify the following settings.
●To obtain the IP address automatically, press <DHCP> or <Auto IP>, and press
<Next> or <OK>.
●To set the IP address manually, clear the selection for <DHCP> or <Auto IP>, press
<IP Address>, <Subnet Mask>, and <Gateway Address> to enter each value, and
press <Next> or <OK>.
●For information on the IPV4 address settings, see Setting an IPv4
Address(P. 35) .
If you press <On> for <Use IPv6>, specify the following settings.
●Press <On> to use the stateless address or <Off> to not use the stateless address,
and press <Next>.
●For information on the IPv6 address, see Setting an IPv6 Address(P. 37) .
After specifying the stateless address, specify the following settings.
Setting Up
9
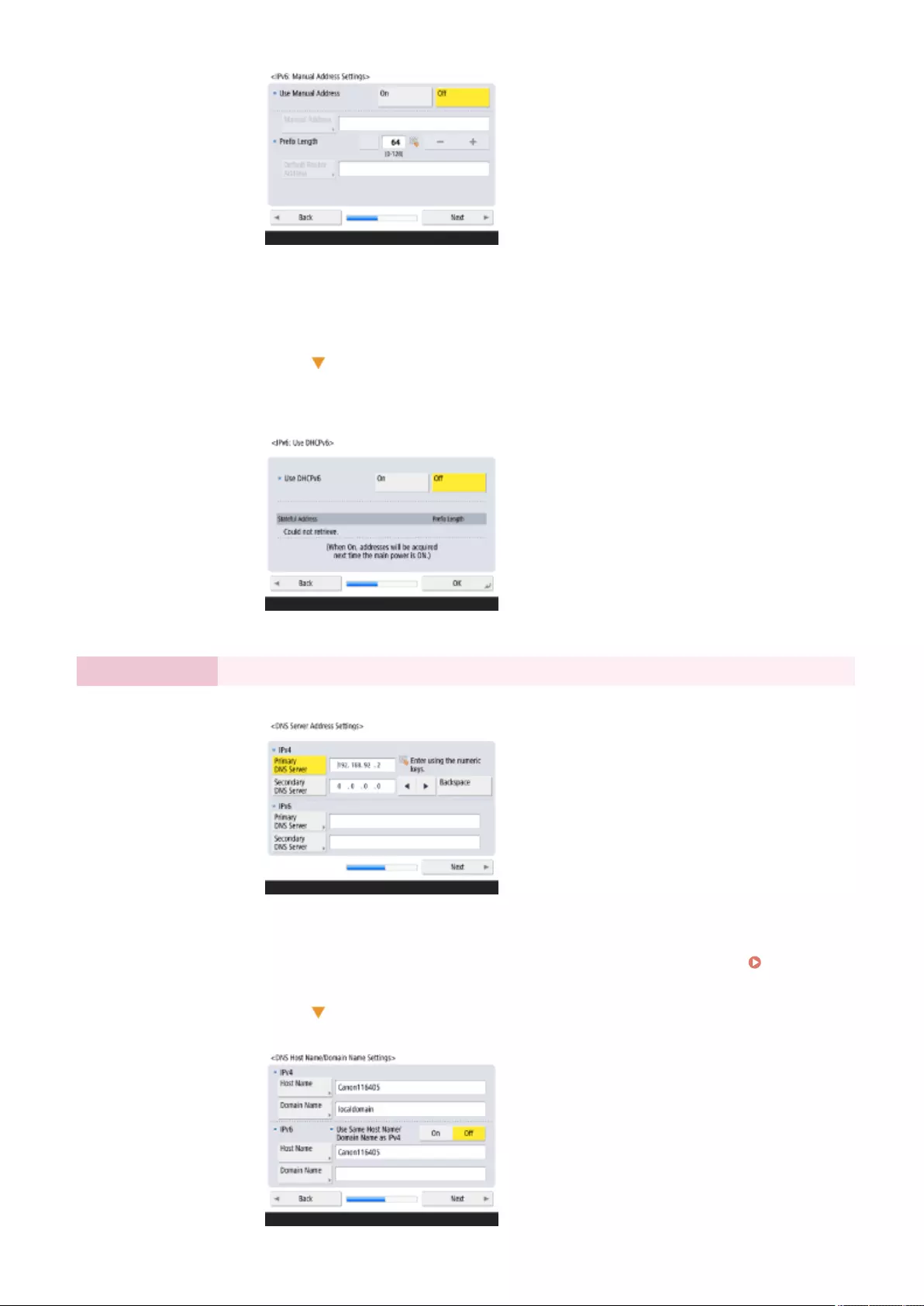
●Press <On> to use the manual address or <Off> no not use the manual address,
and press <Next>.
●To use the manual address, press <Manual Address>, <Prex Length>, and <Default
Router Address> to enter each value.
After specifying the manual address, specify the following settings.
●Press <On> to use DHCPv6 or <Off> to not use DHCPv6, and press <OK>.
Step 7 Specify the DNS settings.
Specify the DNS server address, DNS host name, and DNS domain name.
●Press <Primary DNS Server> and <Secondary DNS Server>, enter IPV4/IPv6 address
for the DNS server, and press <Next>.
●For information on the settings of the DNS server address, see Making DNS
Settings(P. 45) .
Setting Up
10
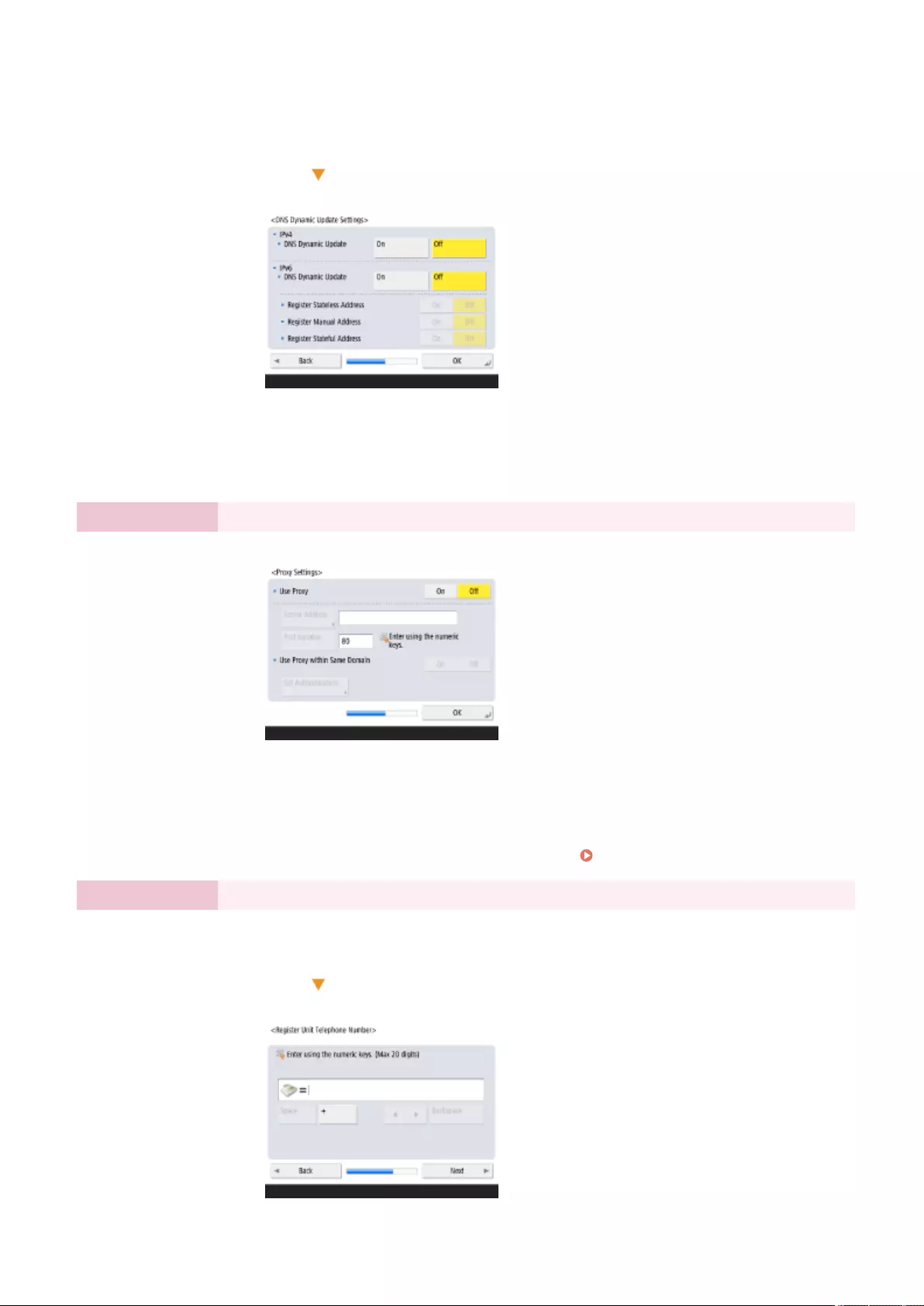
●Press <Host Name> to enter the name of the machine (host name). Press <Domain
Name> to enter the domain name that the machine belongs to, and press <Next>.
●If the settings of IPv4 and IPv6 are the same, press <On> for <Use Same Host
Name/Domain Name as IPv4>.
●To update automatically using the DNS Dynamic Update Settings, press <On> for
<DNS Dynamic Update>, and press <OK>.
●If you set <DNS Dynamic Update> for <IPv6> to <On>, select <On> for the items to
register automatically.
Step 8 Specify the Proxy settings.
Specify the necessary settings to use the Proxy.
●To use the Proxy, press <On>, press <Server Address> and <Port Number> to enter
each value, and press <OK>.
●If you set <Use Proxy within Same Domain> to <On>, press <Set Authentication> to
specify the Proxy authentication settings.
●For information on the Proxy settings, see Setting a Proxy(P. 547) .
Step 9 Specify the fax settings.
Specify the necessary settings to use the fax function.
●Select the country/region, and press <OK>.
●Enter the fax number, and press <Next>.
Setting Up
11

●For information on the fax settings, see Fax Line Settings(P. 68) .
●Press <Set>, enter the user name, and press <Next>.
●Select the line type, and press <Next>.
●Press <Auto RX> when using the fax function only or <Fax/Tel(Auto Switch)> when a
telephone or handset is connected to the machine, and press <OK>.
Step 10 Perform the automatic gradation adjustment.
Adjust the gradation to print clearly.
●Depending on the machine, the procedure differs. For information on the automatic
gradation adjustment, see Adjusting Gradation(P. 894) .
Step 11 Print a report.
You can print the network user list, fax user data list, and adjusted value list.
Setting Up
12
●Press <Start Printing> for the report you want to print.
●When printing is complete, or if you do not print a list, press <OK>.
Step 12 Complete the Setup Guide.
When nishing the Setup Guide, restart the machine to apply the specied settings.
●Press <OK> to restart the machine.
●If you do not use the Setup Guide, press <End Setup Guide> in Step 1.
●You can press (Settings/Register) to individually specify settings congured during the Setup Guide at a
later time.
◼Starting the Setup Guide later
The Setup Guide cannot be started in the following cases.
●If the user authentication or department ID authentication is set.
●If the DepartmentID Authentication is set.
●If the authentication with a card is performed.
(Settings/Register) <Management Settings> <License/Other> <Start Setup Guide>
<Start>
Setting Up
13

●If you start the Setup Guide later and log in as an administrator, Step 3 will not be displayed. Proceed to Step
4.
Setting Up
14
Logging in as an Administrator
72JY-004
Log in as an administrator, otherwise important items regarding the network and security cannot be set. To set up the
user management after the setup is complete, you need to log in as an administrator. The default user name for the
administrator is "Administrator" and the default password is "7654321". When you are going to operate the machine
as "Administrator," change the current password to improve the security. The changed password should be known by
the administrator only.
●You can disable "Administrator" and make a setting to grant administrator privilege to specic users.
Initializing the administrator password
If you have forgotten the password for "Administrator," it can be returned to the default password. Press
(Counter/Device Information) <Device Info./Other> <Initialize Admin. Password> enter the license
key press <Start> <OK>.
●If "Administrator" is disabled, it is enabled when initializing the password. Registering User Information
in the Local Device(P. 495)
●You can prohibit initialization of the administrator password. <Prohibit Initialization of Administrator
Password>(P. 860)
1Press (Settings/Register).
2Press <Log In>.
3Log in with the procedure.
Keyboard authentication
1Set the user name and password.
●Enter the name of a user with administrator privilege, and press <Next>.
●Set the password and press <OK>.
2Press <Log In>.
●If you have not changed the administrator password, the message prompting you to change to a new
password is displayed. Press <Yes> and set a new password. You need to enter the new password
twice to conrm it.
●If you have already changed the administrator password, the functions will be available after you
successfully log in.
Log out after use.
Setting Up
15

◼When logged in as an administrator
After pressing (Settings/Register), the following screen is displayed.
●If you set to <Personal Settings> and change the items that can be personalized, settings are registered as the
personal settings for the users who log into the machine.
●If you set to <Device Settings>, settings are registered as the machine’s settings.
●<Personal Settings> and <Device Settings> are only displayed on the <Settings/Registration> screen if you log in
with administrator privileges.
LINKS
Logging into the Machine(P. 137)
Starting the Remote UI(P. 583)
Setting Up
16

Setting the Date/Time
72JY-005
Adjust the machine's date/time. These settings should be made properly as the date/time is used in cases such as
sending an e-mail automatically at a specied time.
1Press (Settings/Register).
2Press <Preferences> <Timer/Energy Settings> <Date/Time Settings>.
3Enter the date/time.
<Time Zone>
Select the time zone for your area.
To change the time zone, press <Set> and select the time zone.
●UTC is an acronym for Universal Coordinated Time. The standard (time zone) for each country is
determined on the basis of UTC. For communication via the Internet, precise time zone setting is
essential.
<Daylight Saving Time>
To set daylight saving time, press <On> and set the date/time for <Start Date> and <End Date>. To set the
date, specify the day of the week and the week of the month.
●If daylight saving time is set, the time can be put forward an hour compared to the time zone or time
during a specied period in the summer.
Date and time
Enter 4 digits for the year, 4 digits for the month and day, and 4 digits for the time in the same way that
the current time appears on the display.
●The order of the date and time may differ, depending on the country/region.
●Time is entered in 24-hour notation.
●If you make a mistake, press (Clear) and enter again from the year.
Setting Up
17

4Press <OK>.
●If you changed the setting of <Time Zone> or <Daylight Saving Time>, you need to restart the machine by
turning the power OFF. Press the power switch to turn OFF the machine ( Turning OFF the
Machine(P. 96) ). When 10 or more seconds have elapsed after the touch panel display and indicators
turned off, turn ON the machine again ( Turning ON the Machine(P. 95) ).
Setting Up
18
Setting up the Network Environment
72JY-006
0YRY-006 0UUY-006 0UW1-006 1100-006 0X7F-006 0X7H-006 10XJ-006 0X6E-006 0X6W-006 1106-006 0X7C-006 0X7A-006 10YY-006 0WXY-006 0X7E-006 10H3-006 0WR6-006 0WR7-006 108A-006 1116-006 10H4-0JS 0WR5-006 0WR8-006 0YWJ-006 0YWH-006 0YWR-006 0YWK-006 0YWE-006 0YWF-006 0YAS-006 PMW-STNW
To connect the machine to a network, connect the machine to a router using a LAN cable or Wi-Fi and specify a unique
IP address in the network. To specify an IP address, there are two methods: automatic setting and manual setting.
Select one of the methods that is suitable for your communication environment and devices. The machine adopts not
only basic network functions, but also advanced technologies in order to exibly cope with various environments.
Carry out the necessary setup required for your environment.
For safe use
●If you connect the machine to a network without appropriate security measures, there are risks that the
machine might receive unauthorized access from third parties. Set up network security to secure important
data and information. Conguring the Network Security Settings(P. 536)
●You can connect the machine to a computer using a USB cable ( Parts and Their Functions(P. 82) ).
However, if you only connect the machine to a computer using a USB cable without connecting to a network,
operations such using as a scanner or sending/transferring data from the machine to a computer are not
possible.
●You can establish a wireless direct connection between the machine and mobile devices. Connecting
Directly(P. 454)
◼Conrm before handling
Follow the procedure below to make a connection to a network.
Conrm rst.
●Are a computer and a router properly connected using a LAN cable? For details, see
the instruction manual for each device or contact the manufacturers.
●Is setup of the computer network completed? If the setup is not completed, you
cannot use the devices on a network even after completing the following steps.
●Depending on your environment, you may need to change the settings of the
network communication system (half-duplex/full-duplex) and Ethernet type
(1000BASE-T/100BASE-TX/10BASE-T) ( Making Ethernet Settings(P. 42) ). For
details, contact the network administrator.
●To conrm the MAC address, see <Network>(P. 782) .
●To connect to a network employing IEEE802.1X, see Conguring the IEEE 802.1X
Authentication Settings(P. 561) .
Setting Up
19
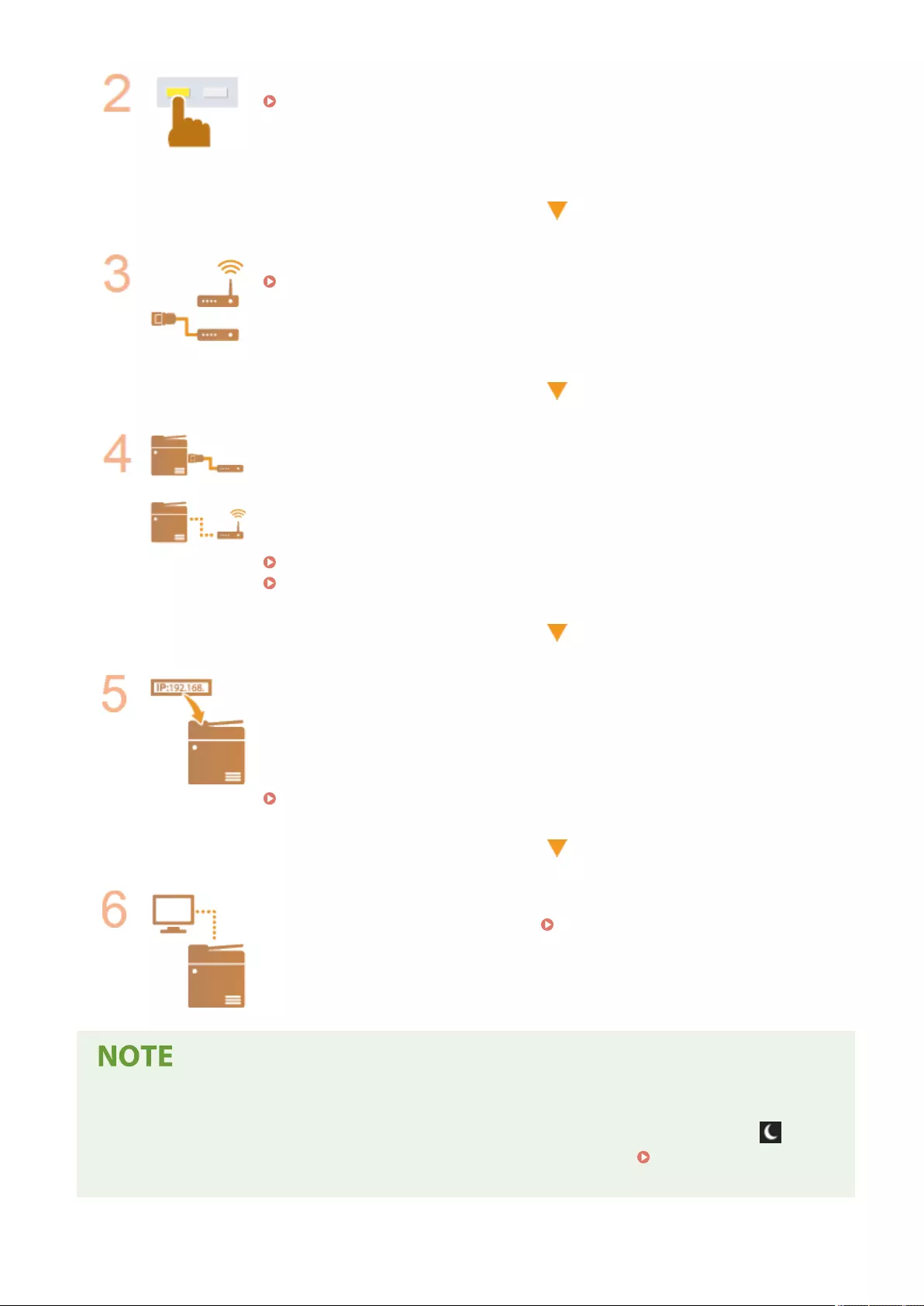
Enable the network settings of the machine.
Canceling the Network Setting Lock(P. 22)
Select a wired LAN or wireless LAN for connection.
Selecting the Network Connection Method(P. 23)
Connect the machine to a router.
●Is the LAN cable connector plugged into the proper place securely? Insert the
connector until it clicks.
●For a wireless LAN connection, check the connection between the machine and the
router.
Connecting to a Wired LAN(P. 25)
Connecting to a Wireless LAN(P. 26)
Set an IP address as necessary.
●Normally, an IP address is automatically allocated by DHCP, so this setting is not
necessary. If you want to use a specic IP address or change the protocol of the
automatic setting of an IP address from DHCP (initial setting) to another, this setting is
necessary.
Setting an IP Address(P. 34)
Conrm that proper connection is completed.
●Start the Remote UI from a computer ( Starting the Remote UI(P. 583) ). If the
Remote UI screen is displayed, the connection is completed.
When <Sleep Mode Energy Use> is set to <Low>
●Depending on the utility software, communication may fail if the machine is in sleep mode. Press
(Energy Saver) to recover from the Sleep mode before conguring this setting. <Sleep Mode Energy
Use>(P. 780)
Setting Up
20

Canceling the Network Setting Lock
72JY-007
By default, a security lock is applied to the network settings in order to prevent unintended changes. Unlock the
security lock to change them.
(Settings/Register) <Preferences> <Network> <Conrm Network Connection Setting
Changes> <On> <OK>
●If <Off> is selected, you cannot view or change the network settings. Also, error messages related to the
network are not displayed.
Setting Up
22
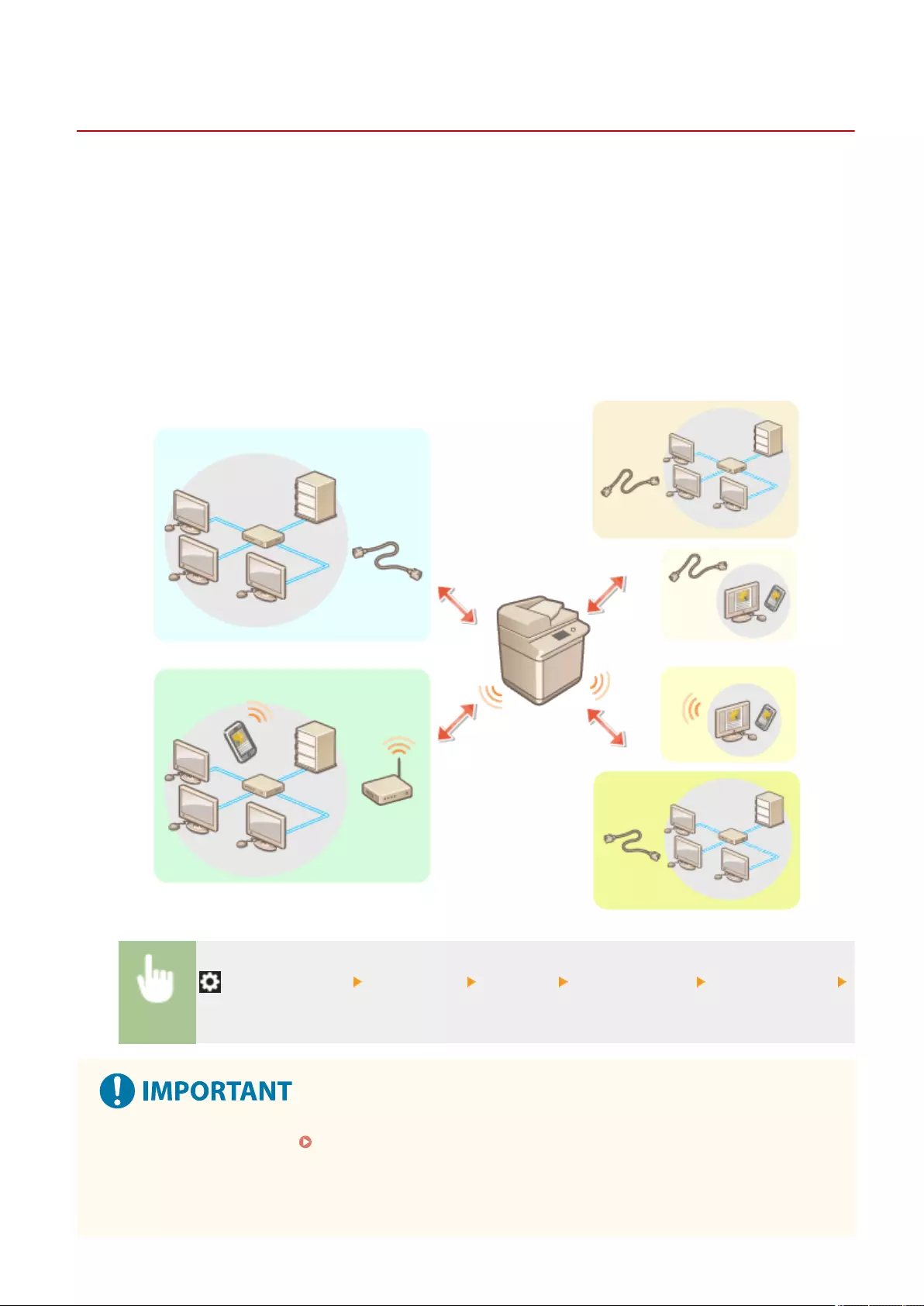
Selecting the Network Connection Method
72JY-008
You can select the method for connecting the machine to computers, etc. The following connection methods are
available.
●Wired LAN only
●Wireless LAN only
●Simultaneous wired LAN and wireless LAN
●Simultaneous wired LAN and another wired LAN
When using simultaneous wired LAN and wireless LAN or simultaneous wired LAN and another wired LAN, the line
connected from the LAN port of the machine is called the "main line" and the line connected from wireless LAN or
another wired LAN is called the "sub line."
(Settings/Register) <Preferences> <Network> <Select Interface> select the interface
<OK>
●When using a sub line, see Feature Highlights(P. 1037) .
If you selected <Wireless LAN> or <Wired LAN + Wireless LAN>
●The settings of <Wireless LAN Settings> are cleared.
●You cannot set wireless LAN as the main line and wired LAN as the sub line.
Setting Up
23
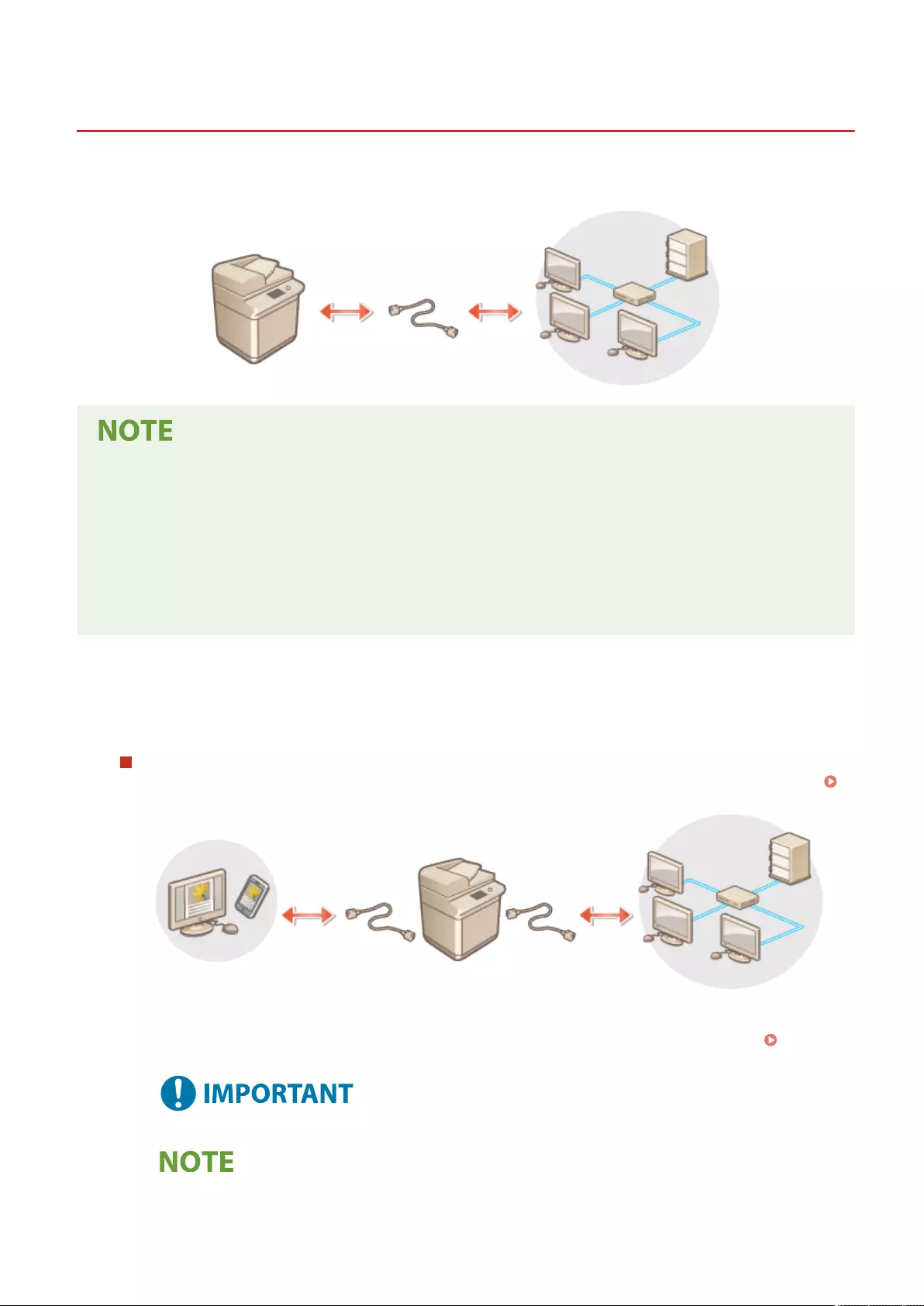
Connecting to a Wired LAN
72JY-009
Connect the machine to a computer via a router using a LAN cable.
●A router and LAN cable are not included with the machine, so please prepare them separately.
●The machine supports 1000BASE-T/100BASE-TX/10BASE-T Ethernet.
●To make a connection using 100BASE-TX/10BASE-T, use a category 5 twisted pair cable. It is recommended to
use an enhanced category 5 twisted pair cable to make a connection using 1000BASE-T.
●If devices supporting 1000BASE-T, 100BASE-TX and 10BASE-T are used together, a device (such as a switching
hub) supporting all of the Ethernet types you use is necessary. For more information, contact your dealer or
service representative.
1Connect the machine to a router using a LAN cable.
●Push the connector in until it clicks into place.
Connecting to a Wired LAN for the Sub Line
When <Wired LAN + Wired LAN> is selected in <Select Interface>, connect the wired LAN for the sub line.
<Select Interface>(P. 790)
1Connect the USB-LAN adapter to the USB port of the machine (far left side of the main unit). Parts and
Their Functions(P. 82)
●Multiple USB-LAN adapters cannot be connected.
●For information on the USB-LAN adapters that can be used, contact your dealer or service
representative.
Setting Up
25
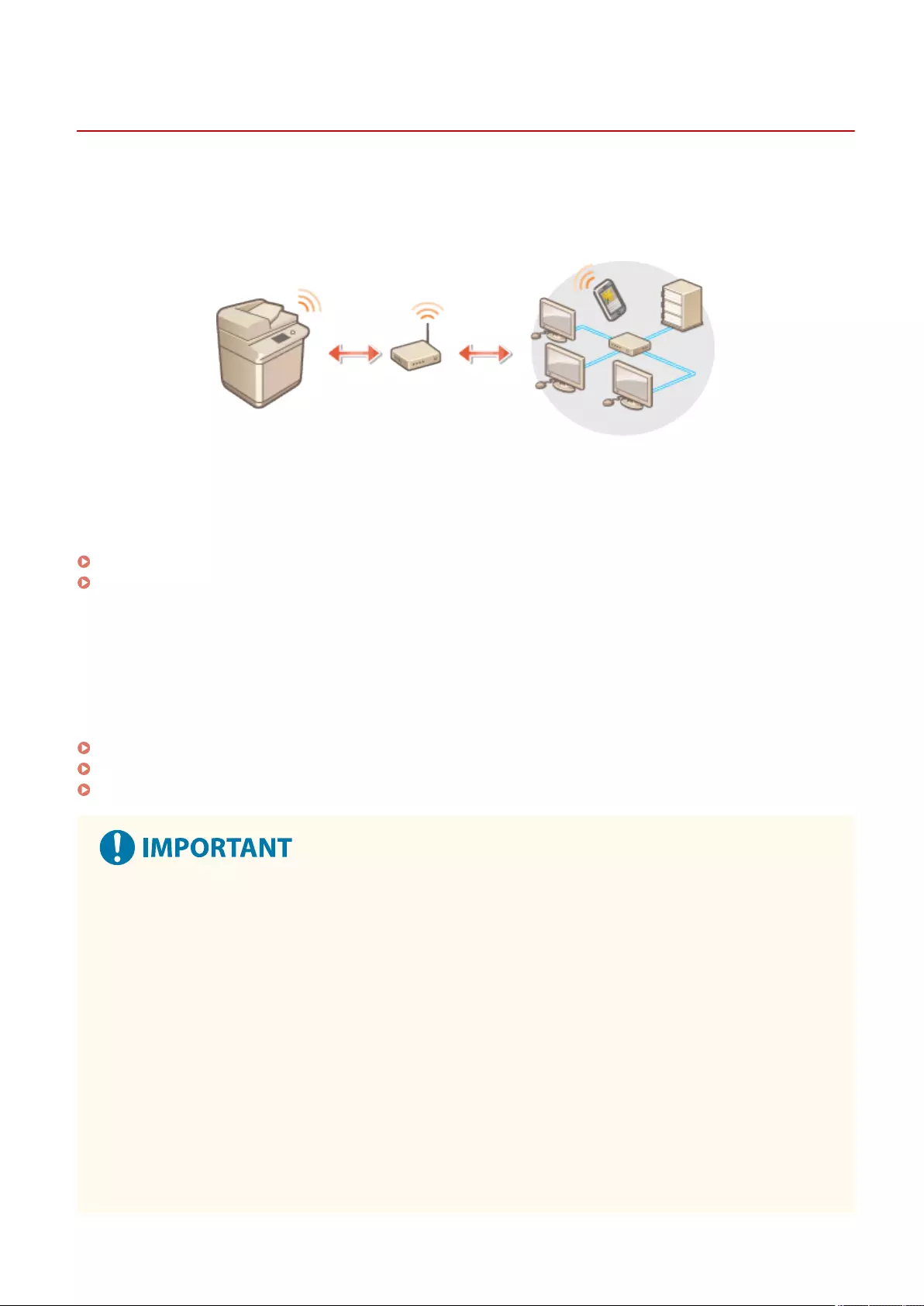
Connecting to a Wireless LAN
72JY-00A
Wirelessly connect the machine to a computer or mobile device via a wireless LAN router (access point). If the wireless
router is equipped with Wi-Fi Protected Setup (WPS), conguring your network is automatic and easy. If the wireless
router does not support with WPS, or if you want to specify authentication and encryption settings in detail, you need
to manually set up the connection. Congure connection on the computer or mobile device side in advance.
◼Setting Up the Connection Using WPS
If your wireless LAN router supports WPS, two setting modes are available: push button mode and PIN code mode.
Setting Up the Connection Using WPS Push Button Mode(P. 28)
Setting Up the Connection Using WPS PIN Code Mode(P. 29)
◼Setting Up the Connection Manually
There are two manual setting methods: manually congure the setting with a wireless LAN router selected, or
manually enter all the required information for wireless LAN connection. Regardless of the method, make sure that
you have the required setup information, including the SSID and network key.
Setting Up Connection by Selecting a Wireless Router(P. 30)
Setting Up a Connection by Specifying Detailed Settings(P. 31)
Checking the SSID and Network Key(P. 33)
●Use wireless LAN connection at your own discretion and at your own risk. If the machine is connected to an
unsecured network, your personal information might be leaked to a third party because radio waves used in
wireless communication can go anywhere nearby, even beyond walls.
●The wireless LAN security that is supported by the machine is listed below. For the wireless security
compatibility of your wireless router, see the instruction manuals for your networking devices or contact
your manufacturer.
128 (104)/64 (40) bit WEP
WPA-PSK (TKIP/AES-CCMP)
WPA2-PSK (TKIP/AES-CCMP)
WPA-EAP (AES-CCMP)
WPA2-EAP (AES-CCMP)
However, WPA-EAP and WPA2-EAP cannot be used if <Wired LAN + Wireless LAN> is selected in <Select
Interface>.
●Depending on the network device, the operation of the wireless LAN router differs. See the instruction
manuals for your networking device for help.
Setting Up
26
●When <Prohibit Use of Weak Encryption> is set to <On> ( <Prohibit Use of Weak Encryption>(P. 869) ),
the machine cannot be connected to the wireless LAN router without the security settings, or either WEP or
TKIP is specied.
●This machine does not come with a wireless router. Have the router ready.
●The wireless router must conform to IEEE 802.11b/g/n and be able to communication in 2.4 GHz bandwidth.
For more information, see the instruction manuals for your networking devices or contact your
manufacturer.
◼Check the settings and information of the wireless LAN
Check the information you set.
(Settings/Register) <Preferences> <Network> <Wireless LAN> <Wireless LAN
Information>
Connecting directly
●You can establish a direct wireless connection between a mobile device and the machine without using a
wireless LAN router. Connecting Directly(P. 454)
Reducing the power consumption
●If you set <Power Save Mode> to <On>, you can regularly set the machine to the power saving mode to
match the signal that the wireless LAN router sends. <Wireless LAN> <Power Save Mode>(P. 790)
Setting Up
27

Setting Up the Connection Using WPS Push Button
Mode
72JY-00C
If your wireless router supports the WPS (Wi-Fi Protected Setup) Push Button mode, you can easily set up a connection
with the WPS button on the router.
(Settings/Register) <Preferences> <Network> <Wireless LAN> <Wireless LAN
Settings> <WPS Push Button Mode> press and hold the WPS button on the wireless router
➠When the wireless LAN router is detected and the conguration is complete, the screen <Connected.> will
be displayed.
●Depending on the networking device, you may need to press and hold the WPS button for 2 seconds or
longer. See the instruction manuals for your networking device for help.
●If the wireless router is set to use WEP authentication, you may not be able to set up connection using WPS.
Setting Up
28
Setting Up the Connection Using WPS PIN Code Mode
72JY-00E
Some WPS (Wi-Fi Protected Setup) routers do not support the Push Button mode. In this case, register the PIN code
generated on the machine to the networking device.
Generating a PIN code on the machine
1Press (Settings/Register).
2Press <Preferences> <Network> <Wireless LAN> <Wireless LAN Settings>
<WPS PIN Code Mode>.
➠A PIN code is generated.
Registering the PIN code to the wireless router
Register the PIN code within two minutes after the PIN code is generated. For details, see the instruction
manual for your networking device.
1Access a wireless router from a computer.
2Display the screen for entering a WPS PIN code.
3Register the generated PIN code to the wireless router.
➠When the wireless LAN router is detected and the conguration is complete, the screen <Connected.> will
be displayed.
●If the wireless router is set to use WEP authentication, you may not be able to set up connection using WPS.
Setting Up
29
Setting Up Connection by Selecting a Wireless Router
72JY-00F
You can search the wireless routers available for connection and select one from the display of the machine. If the
security standard for your wireless LAN router is WEP or WPA/WPA2-PSK, enter a WEP key or PSK for the network key.
Conrm and write down in advance information regarding your SSID, network key, security standard, or
authentication/encryption method, etc. Checking the SSID and Network Key(P. 33)
Security settings
●If the wireless connection is set up by selecting a wireless router, the WEP authentication method is set to
<Open System> or the WPA/WPA2-PSK encryption method is set to <Auto> (AES-CCMP or TKIP). If you want
to select <Shared Key> for WEP authentication or <AES-CCMP> for WPA/WPA2-PSK encryption, set up the
connection in <Enter Manually>. Setting Up a Connection by Specifying Detailed Settings(P. 31)
●If the security standard for your wireless LAN router is WPA/WPA2-EAP, the encryption method is set to AES-
CCMP. Also, specify the IEEE 802.1X authentication settings for the machine before connecting to the
wireless LAN. Conguring the IEEE 802.1X Authentication Settings(P. 561)
1Press (Settings/Register).
2Press <Preferences> <Network> <Wireless LAN> <Wireless LAN Settings>
<Other (Set Manually)>.
3Press <Select Access Point>.
●The machine starts searching for available wireless routers.
4Select a wireless router, and connect to it.
If the security setting of your wireless LAN router is WEP or WPA/WPA2-PSK
1Select the wireless LAN router to use, and press <OK>.
2Press <WEP Key> or <PSK>, and enter the network key.
3Press <OK>.
➠When the conguration is complete, the screen <Connected.> will be displayed.
If the security setting of your wireless LAN router is other than WEP or WPA/WPA2-
PSK
1Select the wireless LAN router to use, and press <OK>.
➠When the conguration is complete, the screen <Connected.> will be displayed.
Setting Up
30

Setting Up a Connection by Specifying Detailed Settings
72JY-00H
If you want to specify the security settings in detail or cannot establish the wireless connection using the other
procedures, manually enter all the required information for the wireless LAN connection. Conrm and write down in
advance information regarding your SSID, network key, security standard, or authentication/encryption method, etc.
Checking the SSID and Network Key(P. 33)
1Press (Settings/Register).
2Press <Preferences> <Network> <Wireless LAN> <Wireless LAN Settings>
<Other (Set Manually)>.
3Press <Enter Manually>.
4Press <SSID>, and enter the SSID that you have checked.
5Specify the security settings in <Security Settings>.
Using WEP
1Press <WEP>.
2Select an authentication method.
●To use the WEP key as a password, press <Shared Key>.
●If you press <Open System>, the machine experiences an authentication is set on the wireless router.
If this happens, the machine automatically changes the setting to <Shared Key> and retries the
connection.
3Select the WEP key that you want to edit.
●Press any of <WEP Key 1> to <WEP Key 4>.
4Enter the network key that you have checked.
5Select the WEP key to use.
6Press <OK>.
Using WPA-PSK or WPA2-PSK
1Press <WPA/WPA2-PSK>.
2Select an encryption method.
●To set the machine to automatically select AES-CCMP or TKIP to match the setting of the wireless
router, press <Auto>.
3Press <PSK>, and enter the network key that you have checked.
4Press <OK>.
Setting Up
31

Using WPA-EAP or WPA2-EAP
1Press <WPA/WPA2-EAP>.
2Press <OK>.
6Press <OK>.
➠ When the wireless LAN router is detected and the conguration is complete, the screen <Connected.> will
be displayed.
Setting Up
32

Checking the SSID and Network Key
72JY-00J
When manually setting up a wireless LAN router connection, it is necessary to specify the SSID, network key, and
security standard, etc., of the wireless LAN router. The SSID and network key may be indicated on these networking
devices. Check your devices before setting up the connection. If the security standard for your wireless LAN router is
WPA/WPA2-EAP, specify the IEEE 802.1X authentication settings for the machine in advance ( Conguring the IEEE
802.1X Authentication Settings(P. 561) ). For more information, see the instruction manuals for your networking
devices or contact your manufacturer.
SSID A name given for identifying a specic wireless LAN. Some other terms used for SSID
include "access point name" and "network name."
Network Key
A keyword or password used for encrypting data or authenticating a network. Some other
terms used for network key include "encryption key," "WEP key," "WPA/WPA2 passphrase,"
"preshared key (PSK)."
Wireless Security
Protocols
(Authentication /
Encryption)
●Security types (WEP/WPA-PSK/WPA2-PSK/WPA-EAP/WPA2-EAP)
●Authentication method (Open System/Shared Key/IEEE 802.1X authentication)
●Encryption method (TKIP/AES-CCMP)
●WPA/WPA2-EAP cannot be used if <Wired LAN + Wireless LAN> is selected in <Select Interface>.
Setting Up
33

Setting an IP Address
72JY-00K
0YRY-00K 1100-00K 10XJ-00K 1106-00K 10YY-00K 10H3-00K 108A-00K 1116-00K 10H4-00K 0YAS-00K
To connect the machine to a network, a unique IP address on the network is required. The machine supports two
versions of IP addresses: "IPv4" and "IPv6." Set and use them according to your environment. You can use either IPv4
or IPv6. You can also use both of them at the same time.
When a connection method with a main line and sub line is selected in <Select Interface>, specify the IP address of the
sub line in <IP Address Settings> in <Sub Line Settings>.
Setting an IPv4 Address(P. 35)
Setting an IPv6 Address(P. 37)
Setting the IPv4 Address of the Sub Line(P. 40)
Setting Up
34

Setting an IPv4 Address
72JY-00L
There are two methods to set an IPv4 address: allocating automatically using DHCP and entering manually. Select
either of the two according to your environment. Conduct a connection test as necessary.
Setting an IPv4 Address(P. 35)
Conducting a Connection Test for an IPv4 Address(P. 36)
Setting an IPv4 Address
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings>.
3Press <Use IPv4> <On> <OK> to enable IPv4 settings.
4Press <IP Address Settings> and set an IP address.
●You can set both automatic allocation and manual allocation. If you set both and set <Release Address Last
Acquired from DHCP Server When Address Cannot Be Acquired> to <Off>, the manually entered IP address is
used when automatic IP address retrieval fails.
Automatic allocation using DHCP
Press <DHCP> or <Auto IP>. Select one of them according to your network environment. If you select both
<DHCP> and <Auto IP>, automatic allocation using DHCP takes priority.
●If you press <Auto IP>, the available IP address is automatically searched in the network (LAN) and the
value for each item is allocated. This function allocates the IP address without using a DHCP server.
However, communication outside of the router range is not available.
●In an environment where both <DHCP> and <Auto IP> cannot be used, if either of the two is selected,
useless communication occurs because the machine tries to check if the service is provided on the
network.
Setting by manual entry
1Conrm that both <DHCP> and <Auto IP> are canceled.
●If either of the two is selected, press the button to cancel.
2Enter the IP address, the subnet mask, and the gateway address.
●Press the button corresponding to each and enter values.
5Press <OK>.
Setting Up
35

6Press (Settings/Register) <Yes>.
Conducting a Connection Test for an IPv4 Address
When the machine is connected properly, the Remote UI login screen can be displayed from the computer ( Starting
the Remote UI(P. 583) ). You can conduct a connection test on the control panel of the machine.
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings>
<PING Command> Enter the address of any other in-use device <Start>
➠When the machine is connected correctly, the <Response from the host.> message is displayed.
●Even though IP addresses are properly set, if the machine is connected to a switching hub, the machine
might not be connected to the network. In this case, delay the timing of the machine's communication start
and try to connect again. Setting the Wait Time When Connecting to a Network(P. 44)
LINKS
Setting an IPv6 Address(P. 37)
Making WINS Settings(P. 52)
Setting Up
36
Setting an IPv6 Address
72JY-00R
The following are the types of IPv6 addresses. Register as necessary. Up to four stateless addresses can be registered.
Conduct a connection test as necessary.
Type Explanation
Link local address Addresses that can be used only in the same link and that are automatically created without setting
anything. Cannot be used out of the router range.
Stateless address Addresses that are created automatically on the basis of the prex notied by a router and the MAC
address of the machine, even in an environment without a DHCP server.
Manual address Addresses that are manually entered. Prex length and a default router address are specied.
Stateful address Addresses that are acquired from the DHCP server.
Setting an IPv6 Address(P. 37)
Conducting a Connection Test for an IPv6 Address(P. 38)
Setting an IPv6 Address
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>.
3Press <Use IPv6> <On> <OK> to enable IPv6 settings.
4Set an IP address.
●Set an IPv6 address according to your environment and purposes.
Setting a stateless address
1Press <Stateless Address Settings>.
2Press <On> <OK>.
Setting a manual address
1Press <Manual Address Settings>.
2Press <On> in <Use Manual Address> and carry out the necessary settings.
Setting Up
37

<Use Manual Address>
Press <On>.
<Manual Address>
Press the <Manual Address> button and enter an address. The following addresses cannot be used.
●Addresses that begin with "ff" (multicast address)
●Addresses that consist only of "0"
●IPv4-compatible addresses (IPv6 addresses in which the upper 96 bits are "0" with an IPv4 address
contained in the lower 32 bits)
●IPv4-mapped addresses (IPv6 addresses in which the upper 96 bits are "0:0:0:0:ffff:" with an IPv4
address contained in the lower 32 bits)
<Prex Length>
The length of the network address section can be changed.
<Default Router Address>
Press <Default Router Address> and enter an address. The following addresses cannot be used.
●Addresses that begin with "ff" (multicast address).
●Addresses that consist only of "0"
If you don't specify an address, leave the column blank.
Setting a stateful address
1Press <Use DHCPv6>.
2Press <On> <OK>.
●Press <On> for <Only Retrieve Stateful Address Prex> to only retrieve the rst half of the stateful
address from the DHCP server using DHCPv6. <Only Retrieve Stateful Address Prex>(P. 783)
5Press (Settings/Register) <Yes>.
Conducting a Connection Test for an IPv6 Address
When the machine is connected properly, the Remote UI login screen can be displayed from a computer ( Starting
the Remote UI(P. 583) ). If you don't have a computer to check it, conrm if a proper connection is completed with
following the steps.
Setting Up
38
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
<PING Command> Enter the address of any other in-use device or the host name <Start>
➠When the machine is connected correctly, the <Response from the host.> message is displayed.
●Even though IP addresses are properly set, if the machine is connected to a switching hub, the machine
might not be connected to the network. In this case, delay the timing of the machine's communication start
and try to make a connection again. Setting the Wait Time When Connecting to a Network(P. 44)
LINKS
Setting an IPv4 Address(P. 35)
Setting Up
39

Setting the IPv4 Address of the Sub Line
72JY-00S
Specify the IPv4 address to use for the sub line.
●Only IPv4 addresses can be used with the sub line.
Only IPv4 addresses can be used with the sub line.
1Press (Settings/Register).
2Press <Preferences> <Network> <Sub Line Settings>.
3Press <IP Address Settings> and set the IP address of the sub line.
●You can also set both automatic assignment and manual entry. If you set both and set <Release Address Last
Acquired from DHCP Server When Address Cannot Be Acquired> to <Off>, the manually entered IP address is
used when automatic IP address retrieval fails.
Automatically Assigning the IP Address with DHCP
Press <DHCP>. Select this item according to the network environment of your wireless LAN.
●If <DHCP> is selected, communication is performed to check whether network services are being provided,
regardless of whether the environment can use DHCP. It is recommended that you deselect this item if
you are not using DHCP.
Manually Entering the IP Address
1Conrm that <DHCP> is deselected.
●If it is selected, press the button to deselect it.
2Enter the IP address and subnet mask.
●Press each button and enter the required setting.
●When connecting to another network via a router, enter the gateway address and also congure
<Static Routing Settings>. Setting Static Routing(P. 61)
4Press <OK>.
5Press (Settings/Register) <Yes>.
Setting Up
40
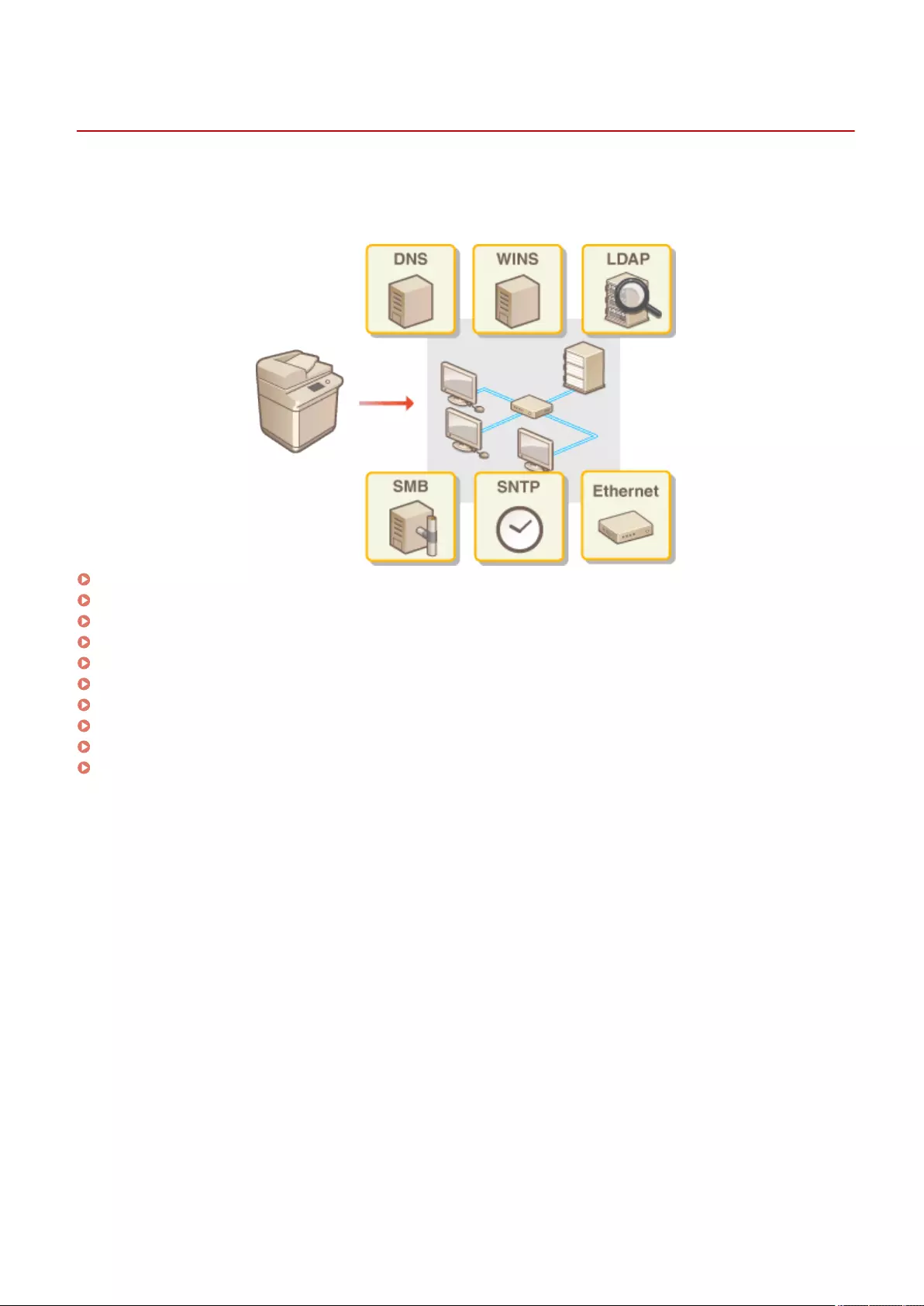
Adapting to the Network Environment
72JY-00U
The scale and form of a network varies depending on the purpose and use. The machine adopts various technologies
for adapting to as many environments as possible. Consult your network administrator and carry out necessary
settings according to your environment.
Making Ethernet Settings(P. 42)
Setting the Wait Time When Connecting to a Network(P. 44)
Making DNS Settings(P. 45)
Making SMB Settings(P. 50)
Making WINS Settings(P. 52)
Registering the LDAP Server(P. 53)
Monitoring and Controlling via SNMP(P. 57)
Setting Static Routing(P. 61)
Other Network Settings(P. 63)
Conguring System Data Communication(P. 65)
Setting Up
41
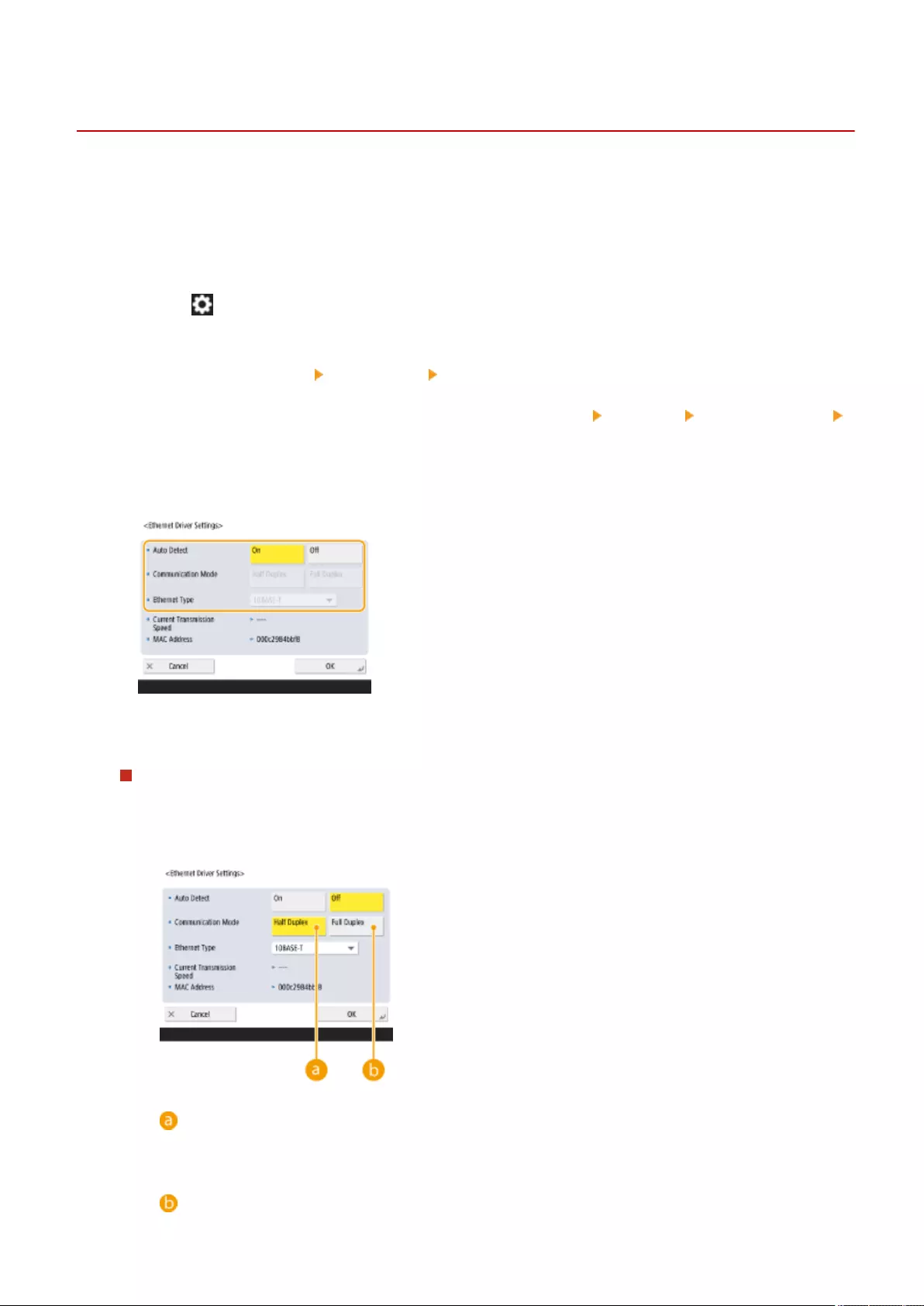
Making Ethernet Settings
72JY-00W
Ethernet is a standard that stipulates communication methods within a LAN. Normally, the communication system
(half-duplex/full-duplex) and Ethernet type (1000BASE-T/100BASE-TX/10BASE-T) can be set automatically. You can set
them separately by switching the setting to manual operation. Register the settings as necessary.
<Ethernet Driver Settings> exists for both the main line and sub line. Congure each as required.
1Press (Settings/Register).
2Press <Preferences> <Network> <Ethernet Driver Settings>.
●To specify the Ethernet settings for the sub line, press <Preferences> <Network> <Sub Line Settings>
<Ethernet Driver Settings>.
3Make Ethernet settings.
●Normally, press <On> in <Auto Detect>. The communication system and Ethernet type are detected and
automatically congured.
Making Ethernet settings manually
1Press <Off> in <Auto Detect>.
2Select the communication system.
<Half Duplex>
Carry out send/receive functions alternately. Select this when the connected router is set for half-
duplex communication.
<Full Duplex>
Setting Up
42

Setting the Wait Time When Connecting to a Network
72JY-00X
If you intend to implement network redundancy by connecting several switching hubs, a mechanism is necessary to
avoid packet looping. In this case, it is effective to determine the roles of the switching ports, but communication may
not be properly transmitted in cases just after changes such as adding a new device to the network. To connect the
machine to such a network, set the waiting time which is the time until the communication starts.
(Settings/Register) <Preferences> <Network> <Waiting Time for Connection at Startup>
Set the waiting time <OK> (Settings/Register) <Yes>
LINKS
Making Ethernet Settings(P. 42)
Setting Up
44

Making DNS Settings
72JY-00Y
0YRY-00X 1100-00X 10XJ-00X 1106-00X 10YY-00X 10H3-00X 108A-00X 1116-00X 10H4-00X 0YAS-00X
The DNS server is a computer which converts the names of devices (domain names) on the Internet into IP addresses.
There are many DNS servers on the Internet worldwide. They cooperate with each other to make correspondence
between domain names and IP addresses. This section describes the steps for setting the machine's DNS server
address, host name, and domain name. You can also set the machine so that an automatic update is carried out if
correspondence between the host name and the IP address is changed. If you set DNS under an IPv6 environment,
conrm if IPv6 addresses can be used ( Setting an IPv6 Address(P. 37) ). In addition, you can make correspondence
with an IP address by acquiring the host name through a DHCP server without manually entering the host name of the
machine.
Making DNS Settings(P. 45)
Using a DHCP Server(P. 48)
Making DNS Settings
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <DNS Settings>.
3Specify a DNS server address.
1Press <DNS Server Address Settings>.
2Carry out the necessary settings.
●According to your environment, enter an IP address of the DNS server.
<IPv4>
●Press <Primary DNS Server>, and enter an IPv4 address of the DNS server.
●If there is a secondary DNS server, enter its IP address. If you don't set a secondary DNS server, enter
"0.0.0.0".
<IPv6>
●Press <Primary DNS Server>, and enter an IPv6 address of the DNS server. You cannot enter
addresses that begin with "ff" (multicast address), addresses that consist of only "0," or local link
addresses.
Setting Up
45
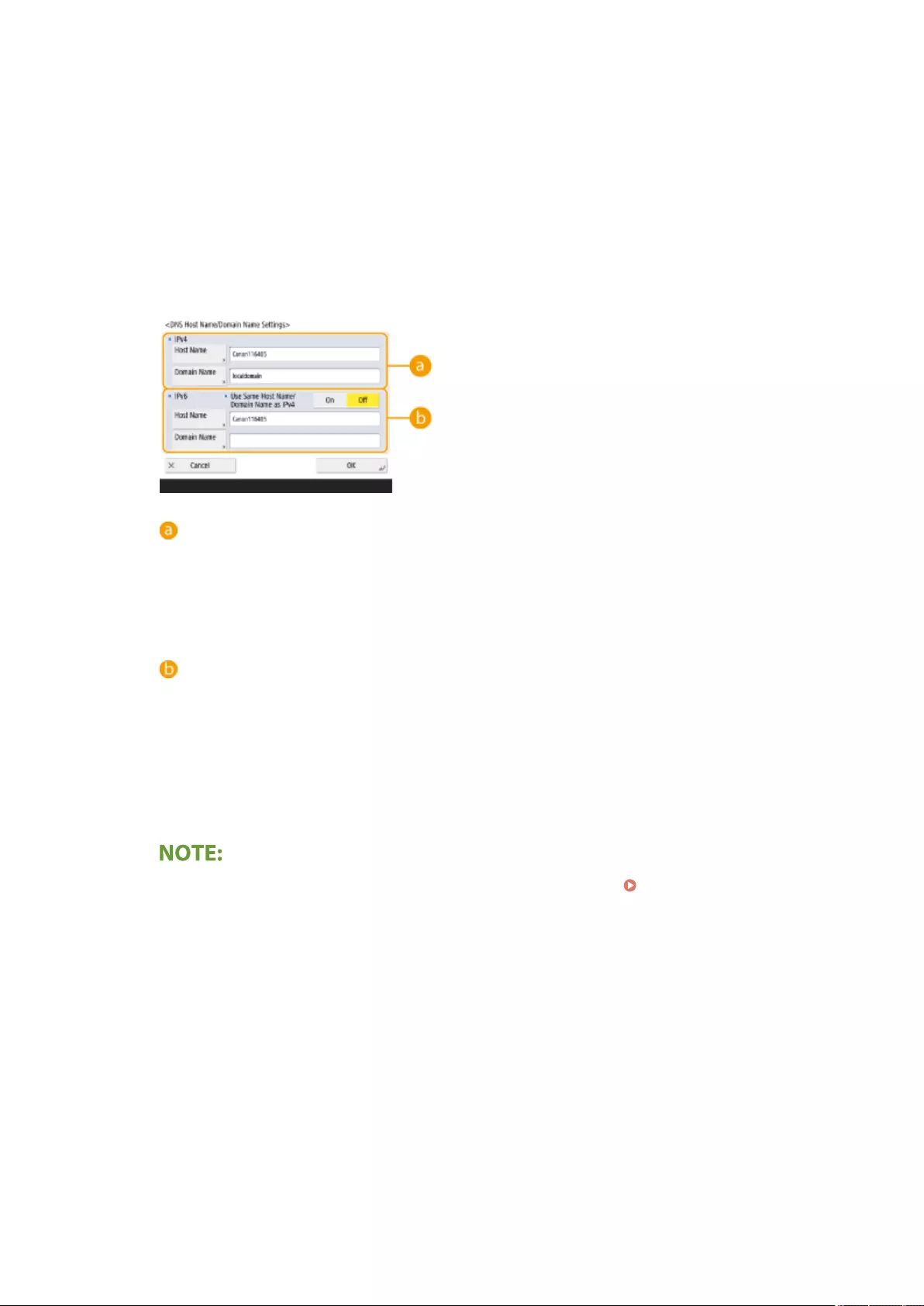
●If there is a secondary DNS server, enter its IP address. You cannot enter addresses that begin with
"ff" (multicast address), addresses that consist of only "0," or local link addresses. This column can be
left blank.
3Press <OK>.
4Specify the machine's host name and domain name.
1Press <DNS Host Name/Domain Name Settings>.
2Carry out the necessary settings.
<IPv4>
●Press <Host Name>, and enter the host name of the machine to register on the DNS server using
alphanumeric characters.
●Press <Domain Name>, and enter the domain name which the machine belongs to using
alphanumeric characters (Example: "example.com").
<IPv6>
●To set the host name and domain name to be the same as IPv4, press <On> in <Use Same Host Name/
Domain Name as IPv4>. To set to be different from those of IPv4, press <Off>.
●To set the host name to be different from IPv4, press <Host Name> and enter the host name of the
machine to register on the DNS server using alphanumeric characters.
●To set the domain name to be different from IPv4, press <Domain Name> and enter the domain name
that the machine belongs to using alphanumeric characters. (Example: "example.com").
●If you set <Use DHCPv6> to <On> for the stateful address settings ( Setting an IPv6
Address(P. 37) ), the manually congured domain name is overwritten. If you set <Use Same Host
Name/Domain Name as IPv4> to <On>, the domain name that is retrieved from DHCPv6 server is
used.
3Press <OK>.
5Set automatic correspondence updates.
1Press <DNS Dynamic Update Settings>.
2Carry out the necessary settings.
Setting Up
46
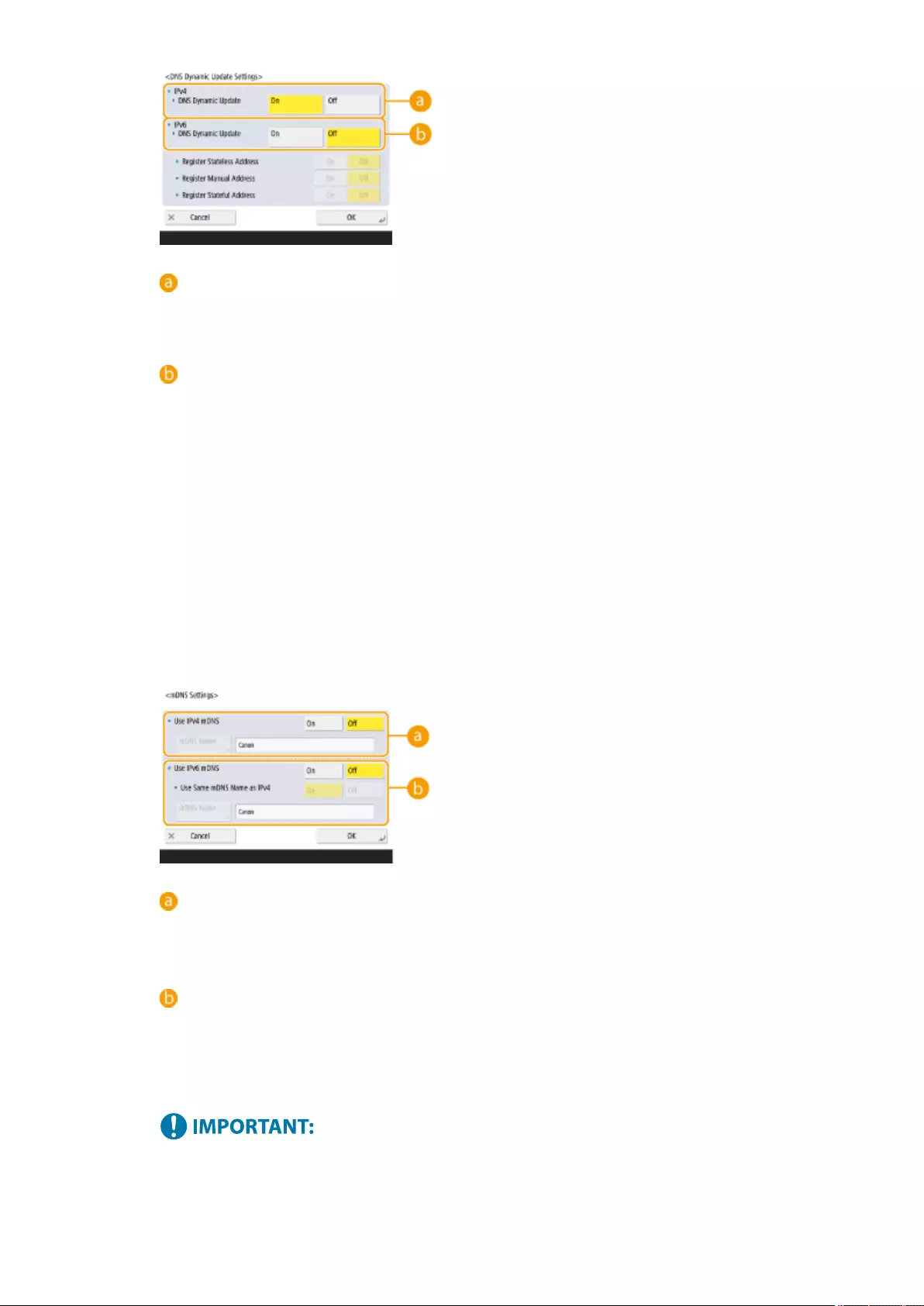
<IPv4>
●To automatically update the information when correspondence between the host name and the IP
address is changed in an environment such as DHCP, press <On> in <DNS Dynamic Update>.
<IPv6>
●To automatically update the information when correspondence between the host name and the IP
address is changed in an environment such as DHCP, press <On> in <DNS Dynamic Update>.
●Turn <On> the address you want to register as a DNS server in <Register Stateless Address>/<Register
Manual Address>/<Register Stateful Address>. Please note that automatic update cannot be carried
out if all are set to <Off>.
3Press <OK>.
6Specify the mDNS settings.
1Press <mDNS Settings>.
2Carry out the necessary settings.
<Use IPv4 mDNS>
●To enable the DNS function in an environment without a DNS server, press <On>.
●Press <mDNS Name>, and enter an mDNS name of your choice using alphanumeric characters.
<Use IPv6 mDNS>
●To enable the DNS function in an environment without a DNS server, press <On>.
●To set the same settings as IPv4 for the mDNS name, press <On> for <Use Same mDNS Name as
IPv4>. To use different settings, press <mDNS Name> and enter an mDNS name of your choice using
alphanumeric characters.
●If you set <Use IPv4 mDNS> to <On>, the machine will not completely enter the Sleep mode.
●If you set <Use IPv6 mDNS> to <On>, the machine will not completely enter the Sleep mode.
3Press <OK>.
Setting Up
47

7Press (Settings/Register) <Yes>.
Using a DHCP Server
You can acquire a host name by using the DHCP server.
●The DHCP optional setting only applies to the main line.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings> or <IPv6
Settings> <DHCP Option Settings>.
3Carry out the necessary setup.
●Some items may not be displayed in <IPv6 Settings>.
<Acquire Host Name>
To acquire a host name through the DHCP server, press <On>.
<DNS Dynamic Update>
To make the DHCP server automatically update information regarding correspondence between the IP
addresses and the host names without using the machine, press <On>.
<Acquire DNS Server Address>
To acquire the DHCP server IP address, press <On>.
<Acquire Domain Name>
To acquire a domain name through the DHCP server, press <On>.
<Acquire WINS Server Address>
To acquire a domain name through the WINS server, press <On>.
<Acquire SMTP Server Address>
To acquire a domain name through the SMTP server, press <On>.
<Acquire POP Server Address>
To acquire a domain name through the POP server, press <On>.
Setting Up
48

4Press <OK>.
5Press (Settings/Register) <Yes>.
Setting Up
49
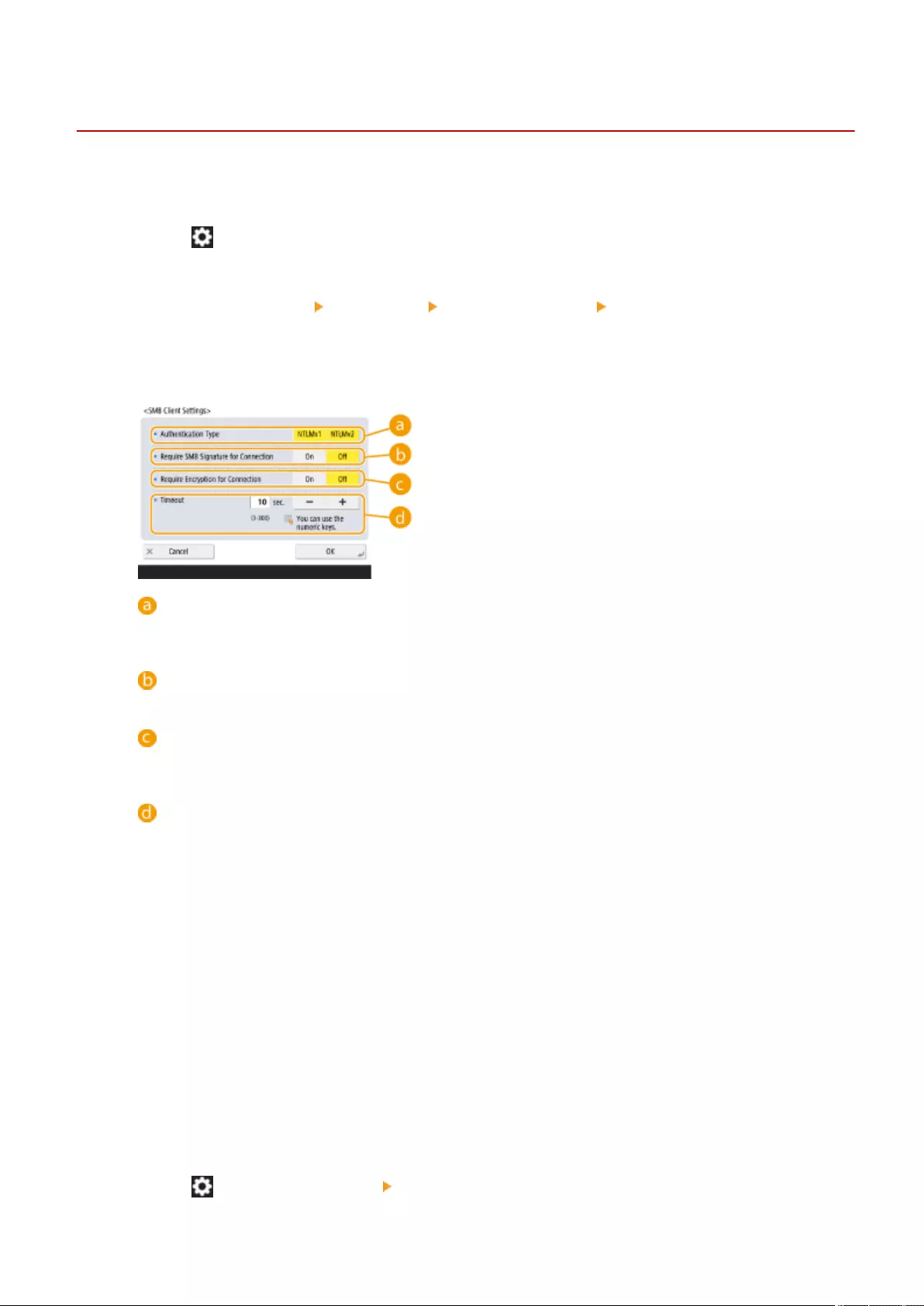
Making SMB Settings
72JY-010
This section describes how to specify the settings to use when the machine connects to a network as an SMB client.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <SMB Client Settings>.
3Specify the required settings.
<Authentication Type>
Select the authentication protocol version. Select either <NTLMv1> or <NTLMv2>, according to the
destination SMB server. You can also select both.
<Require SMB Signature for Connection>
To request an SMB packet signature when connecting to an SMB server, press <On>.
<Require Encryption for Connection>
To request a connection with SMB v3.0 encrypted communication when connecting to an SMB server,
press <On>.
<Timeout>
Set the time until the SMB connection destination responds.
●When sending to an SMB server, the network connection was lost or the response on the server side
was slow, causing a wait time timeout on the machine side before the data could be sent or forwarding
could be completed. If this happens, you may be able to avoid a timeout by increasing the wait time.
4Press <OK>.
5Press <Specify SMB Client Version>, and select the SMB version used by the SMB
client.
6Press <OK>.
7Press (Settings/Register) <Yes>.
Setting Up
50
●When <Require Encryption for Connection> is set to <On>, the machine can only connect to SMB servers that
support SMB v3.0 encrypted communication. When <1.0> and <2.0> are set to <On> for <Specify SMB Client
Version> but <3.0> is not set to <On>, the machine cannot connect to SMB servers that do not support SMB
v3.0 encrypted communication.
●Use the same version of SMB with the SMB server and SMB client. SMB cannot be used if the versions differ.
●Depending on the network settings, an error may be displayed when sending to the SMB server. In this case,
adjust the time in <Timeout>.
LINKS
Making WINS Settings(P. 52)
Setting Up
51
Making WINS Settings
72JY-011
WINS is the name of a solution service that converts a NetBIOS name (a computer name and a printer name on an
SMB network) into an IP address. To use WINS, you need a specied WINS server.
●To register the WINS server on the machine, set <Computer Name/Workgroup Name Settings> for <TCP/IP
Settings>. <Computer Name/Workgroup Name Settings>(P. 783)
●If you set <Use NetBIOS> to <Off> in <Computer Name/Workgroup Name Settings>, the WINS setting is
disabled. Make sure to set <Use NetBIOS> to <On> when using WINS.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <WINS Settings>.
3Press <On> in <WINS Resolution>, and enter the IP address of the WINS server in
<WINS Server Address>.
●If the WINS server IP address is acquired from the DHCP server, the IP address acquired from the DHCP
server has priority.
4Press <OK>.
5Press (Settings/Register) <Yes>.
LINKS
Setting an IPv4 Address(P. 35)
Setting Up
52
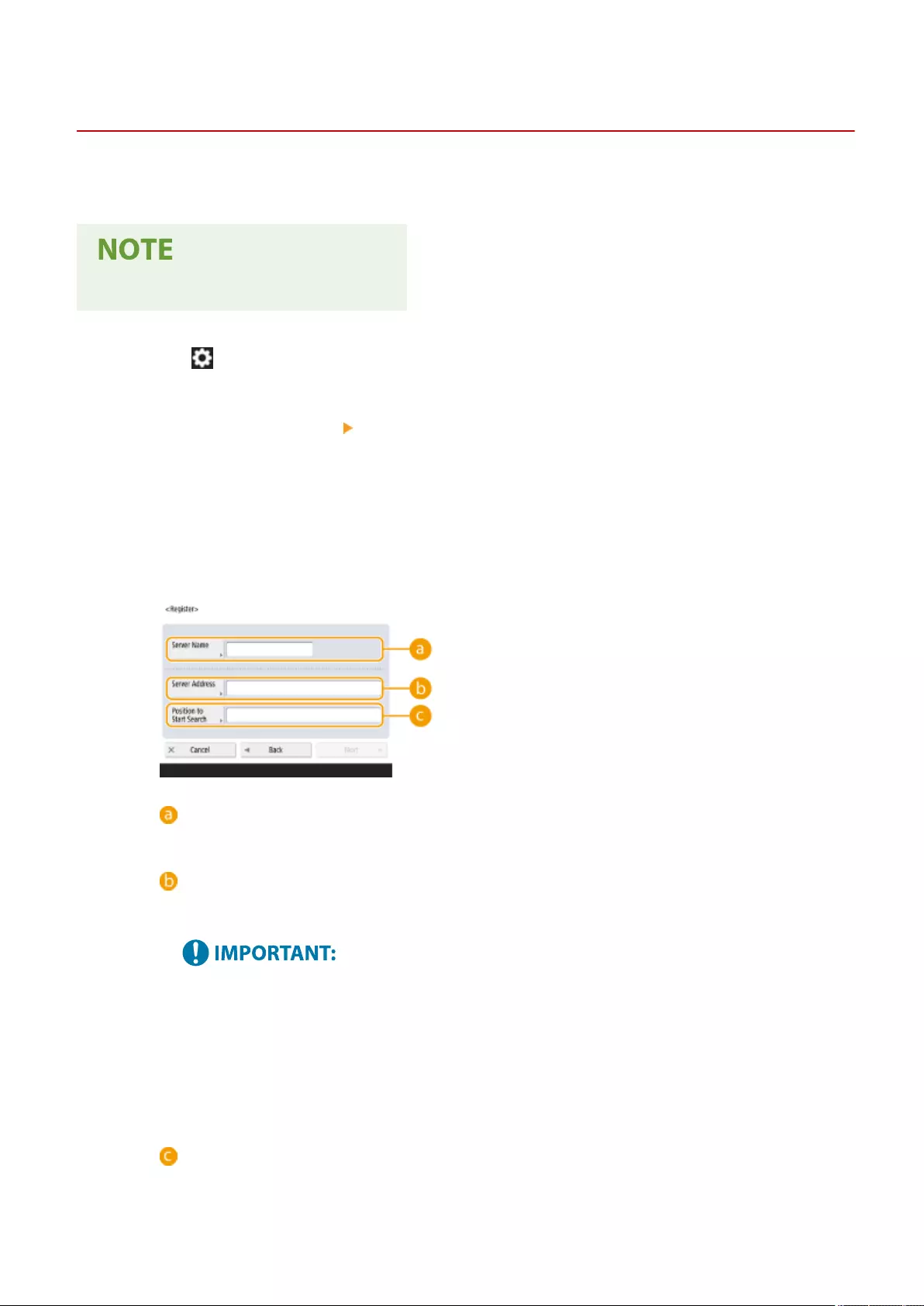
Registering the LDAP Server
72JY-012
In environments where an LDAP sever is employed, fax numbers and e-mail addresses can be searched, specied as
destinations from the machine, and registered in the machine's Address Book.
●You can register up to ve LDAP servers.
1Press (Settings/Register).
2Press <Set Destination> <Register LDAP Server>.
3Register the LDAP server.
1Press <Register>.
2Enter the necessary information.
<Server Name>
Enter a name for the LDAP server.
<Server Address>
Enter the IP address or host name of the LDAP server using alphanumeric characters (Example:
"ldap.example.com").
<Server Address> and DNS
To prevent errors, pay attention to the following when a destination search is carried out from the
machine to the LDAP server.
●When entering the IP address, check if the usable DNS server supports only forward lookup. When
the DNS server supports forward lookup only, press <Do Not Use> or <Use> in <Authentication
Information> in step 4. When selecting <Use (Security Authentication)>, conrm that the DNS server
supports reverse lookup.
<Position to Start Search>
Specify where to start searching in the directory tree of the LDAP server.
●For LDAPv3, you can skip the setting because the machine retrieves automatically the server’s
setting. For LDAPv2, always specify the point.
Setting Up
53
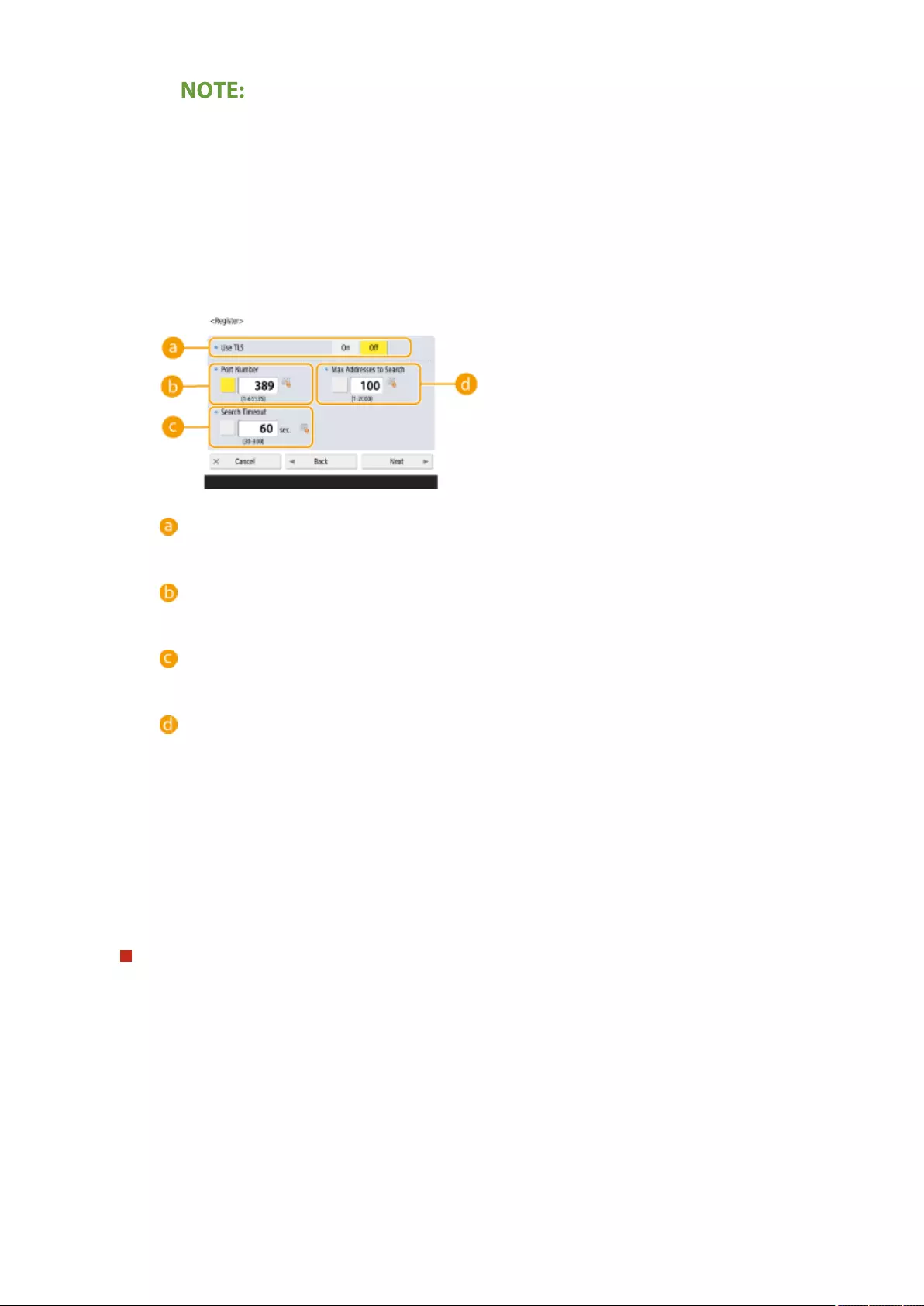
Entering the format of <Position to Start Search>
●When you use Windows Server, enter the domain name of the Active Directory in units of strings
divided by a dot ".". Add "DC=" for each unit and separate them with commas ",".
Example: When the domain name is "john.example.com", enter "DC=john,DC=example,DC=com".
●When you use Lotus Notes Domino, enter the directory tree node identication name (dn) like
"cn=user1,ou=team1,ou=salesdept,o=canon".
3Press <Next>.
4Enter the necessary information.
<Use TLS>
To encode the communication to/from the LDAP server using TLS, press <On>.
<Port Number>
Enter the port number used when communicating to/from the LDAP server.
<Search Timeout>
Specify in seconds how long the search can continue.
<Max Addresses to Search>
Specify how many destinations can be searched.
5Press <Next>.
4Set authentication information.
●Specify authentication methods according to the settings of the LDAP server.
●You can check the connection by pressing <Check Connection> after specifying the settings.
When authenticating using login information
Enter the user name and the password used as authentication information.
1Press <Use> in <Authentication Information>.
2Select the combination of the server LDAP version and character encoding, and press <Next>.
Setting Up
54

3Enter the user name and the password and carry out the necessary settings.
<User Name>
Enter the user name of the machine registered on the LDAP server.
Entering the format of the user name
●When you use Windows Server, enter in the format of "(Windows domain name)\(Windows user
name)".
Example: When the Windows domain name is "example" and Windows user name is "user1", enter
"example\user1".
●When you use Lotus Notes Domino, enter the authenticated user identication name (dn) like
"cn=user1,ou=team1,ou=salesdept,o=canon".
<Password>
Enter the password registered on the LDAP server. When the password is entered, <Conrm> is
displayed for conrmation. Enter the password again.
<Display Authentication Screen When Searching>
When searching destinations, to display the user name and password entry screen, press <On>.
4Press <OK>.
When authenticating using encoded data
Authentication can be done more safely by encoding the data exchange. When this measure is employed, the
LDAP version and character code information are set to <ver.3(UTF-8)>. The time of the machine and LDAP
server need to be synchronized.
1Press <Use (Security Authentication)> in <Authentication Information>.
2Press <Next>.
3Enter the user name and the password and carry out the necessary settings.
Setting Up
55

<User Name>
Enter the username of the machine registered in the LDAP server (Example:"user1").
<Password>
Enter the password registered on the LDAP server. When the password is entered, <Conrm> is
displayed for conrmation. Enter the password again.
<Domain Name>
Enter the domain name of the machine.
<Display Authentication Screen When Searching>
When searching destinations, to display the user name and password entry screen, press <On>.
4Press <OK>.
When authenticating anonymously without using login information
1Press <Do Not Use> in <Authentication Information>.
2Select the combination of the LDAP version and the character code of the server.
3Press <Next>.
4Press <OK>.
LINKS
Registering Server Information(P. 507)
<Set Destination>(P. 849)
Making SNTP Settings(P. 63)
Setting Up
56
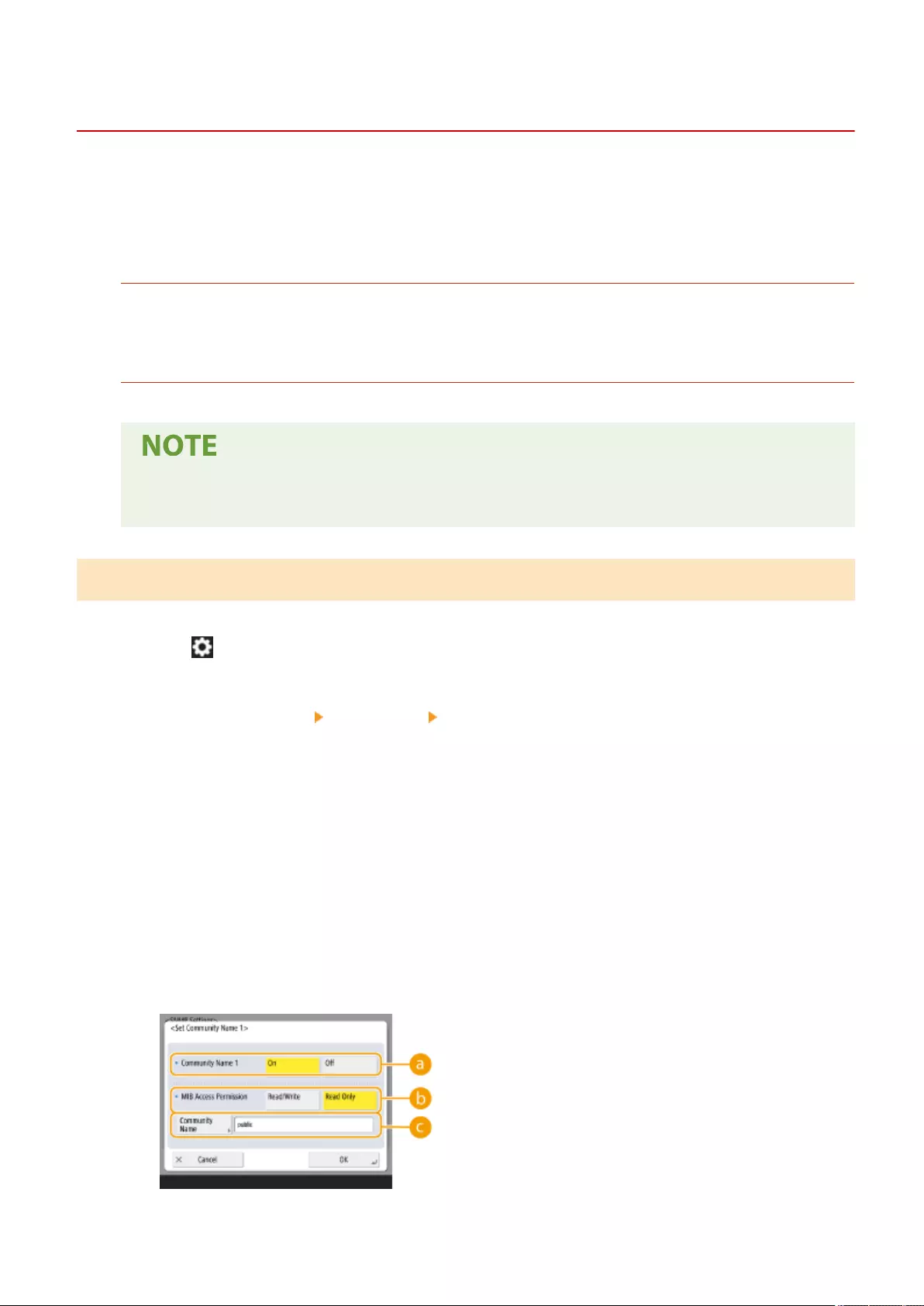
Monitoring and Controlling via SNMP
72JY-013
SNMP is a protocol for monitoring and controlling communication devices on a network on the basis of a management
information database called MIB. You can check the machine's error information and the number of prints through a
computer. The machine supports SNMPv1 and SNMPv3 in which security functions are enhanced. You can use either
of the two or both. Set each function according to your environment and purposes.
SNMPv1
SNMPv1 determines the communication range on the basis of information called community name. However,
as community names are sent to networks as plain text, they may be vulnerable to security issues. To ensure
safety, invalidate SNMPv1 and use SNMPv3.
SNMPv3
SNMPv3 enables you to implement network device management with strong security functions.
●When SNMP management software is usable, you can set, monitor, and control the machine through
a computer. For details, see your software's instruction manuals.
Setting SNMPv1/SNMPv3
1Press (Settings/Register).
2Press <Preferences> <Network> <SNMP Settings>.
3Set SNMPv1.
1Press <On> in <Use SNMPv1>.
●If you don't use SNMPv1, press <Off>.
2Press <Set Dedicated Community>, <Set Community Name 1> or <Set Community Name 2>.
●The exclusive community is a community (group) prepared for managers using device management
software. To use the exclusive community, press <Set Dedicated Community>. To specify a general
community, press <Set Community Name 1> or <Set Community Name 2>.
3Set the community.
Setting Up
57

<Dedicated Community>/<Community Name 1>/<Community Name 2>
To use the selected community, press <On>. When you don't want to use the community, press <Off>.
<MIB Access Permission>
For each community, select MIB access privileges from <Read/Write> or <Read Only>.
<Community Name>
Enter a community name that you belong to using alphanumeric characters. If you select <Set
Dedicated Community>, you cannot set an exclusive community name.
4Press <OK>.
4Set SNMPv3.
1Press <On> in <Use SNMPv3>.
●If you don't use SNMPv3, press <Off>.
2Press <Administrator Settings>.
3Specify the necessary settings, and press <OK>.
<Use Administrator>
If you use Administrator, set to <On>.
<Encryption Password>
If you use a password which is different from the authentication, deselect <Use Same Password as for
Authentication>, press <Encryption Password>, and enter the password.
●If "Administrator" is disabled, you cannot set <Administrator Settings> (the setting of <Use
Administrator> is xed to <Off>).
4Press <User Settings> <Register>.
5Enter the necessary information.
Setting Up
58

<User Name>
Enter a user name using alphanumeric characters.
●You cannot use the characters "Administrator" for a user name to register. If you want to use the
characters "Administrator," you need to set <Use Administrator> to <Off> under <Administrator
Settings>.
<MIB Access Permission>
Select MIB access privileges from <Read/Write> or <Read Only>.
<Security Settings>
Set a combination of authentication and encoding. Select <Auth. Yes/Encrypt. Yes>, <Auth. Yes/
Encrypt. No>, or <Auth. No/Encrypt. No>.
6Press <Next>.
7Enter the necessary information.
<Authentication Algorithm>
Select <MD5>, <SHA1>, or <SHA2> according to your environment. For <SHA2>, select from four hash
lengths (224 bit, 256 bit, 384 bit, or 512 bit).
<Authentication Password>
Enter a password to use for authentication. When the password is entered, <Conrm> is displayed for
conrmation. Enter the password again.
<Encryption Algorithm>
Select <DES> or <AES> according to your environment.
<Encryption Password>
Enter a password to use for encoding. When the password is entered, <Conrm> is displayed for
conrmation. Enter the password again.
8Press <OK> <OK>.
9Press <OK>.
Setting Up
59
5Congure settings in <Retrieve Printer Mngt. Information from Host>.
●If you set to <On>, you can periodically acquire printer management information such as printing protocol
from a computer on the network by using SNMP.
6Press <OK>.
7Press (Settings/Register) <Yes>.
●When using SNMPv1 and SNMPv3 in combination, it is recommended to set MIB access privileges for
SNMPv1 to <Read Only>. If you set <Read/Write>, almost all of the machine's operations become practicable
and the strong security functions of SNMPv3 will not be effective. Access privileges to MIB can be set in
either SNMPv1 or SNMPv3. In SNMPv3, you can set them for each user.
Setting Up
60
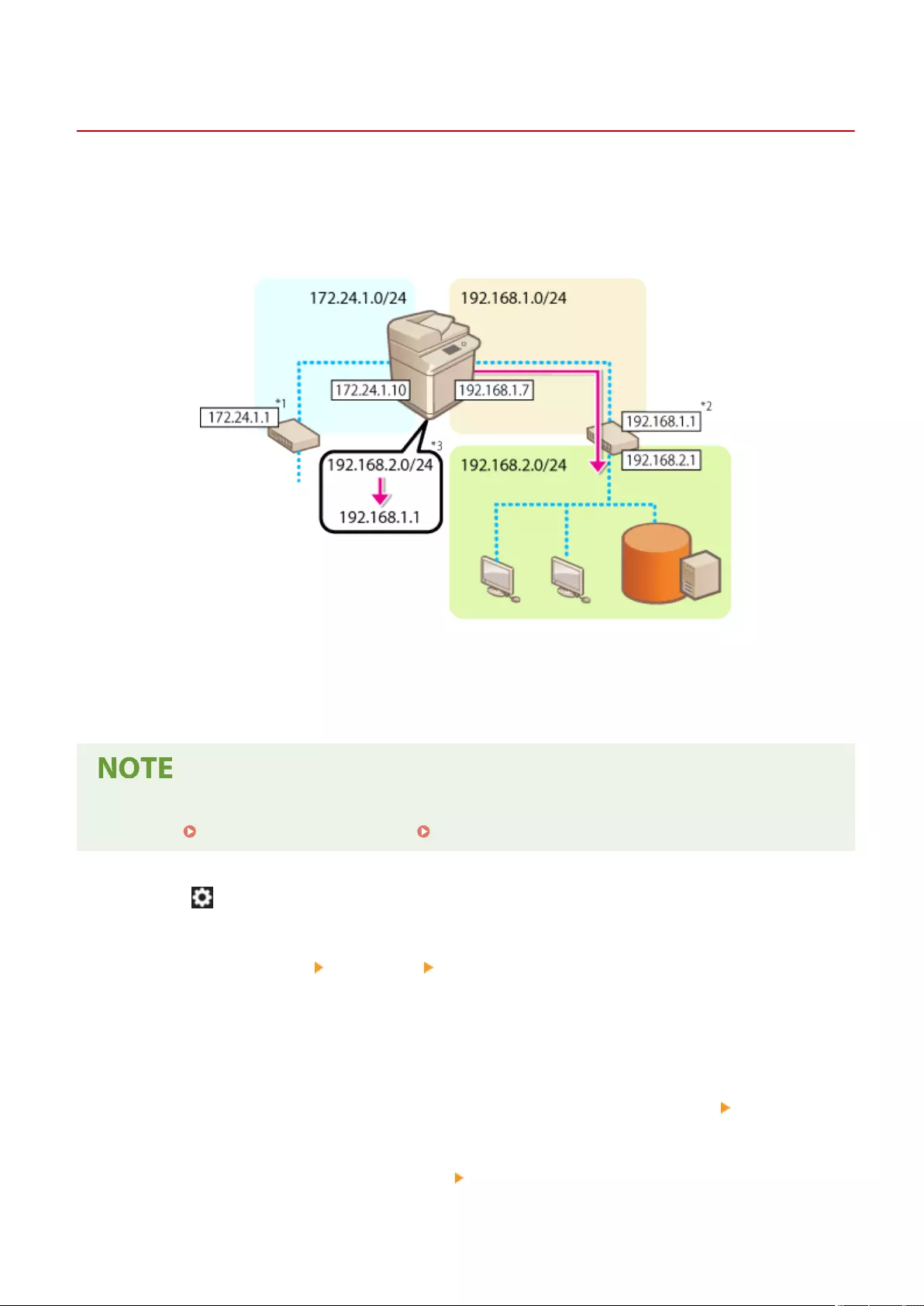
Setting Static Routing
72JY-014
You can set static routing to manually specify the network route.
For example, when sending data from a machine connected to other networks via a router with both the main line and
sub line, the data can be sent via the gateway of the sub line instead of the gateway of the main line that is normally
used.
*1 Main line gateway
*2 Sub line gateway
*3 Static routing settings
●When connecting to another network via a router, enter the gateway address in <IP Address Settings> in
advance. Setting an IPv4 Address(P. 35) Setting the IPv4 Address of the Sub Line(P. 40)
1Press (Settings/Register).
2Press <Preferences> <Network> <Static Routing Settings>.
3Press <On> for <Static Routing Settings>.
4Select the line to register the static routing information from the list press <Edit>.
5Enter <Address> and <Prex Length> press <Next>.
●Press each button and enter the required setting.
Setting Up
61

6Enter the gateway address press <OK> <OK>.
7Press (Settings/Register) <Yes>.
●The route order is displayed in <Order> on the static routing settings screen.
●You can register up to 16 devices that can be connected.
●The success/failure of the static routing settings is displayed in <Routing Regist.>. An error message is also
displayed on the bottom of the screen.
●When failure is indicated in <Routing Regist.>, select the static routing settings that failed and set the
address and gateway address again.
Setting Up
62
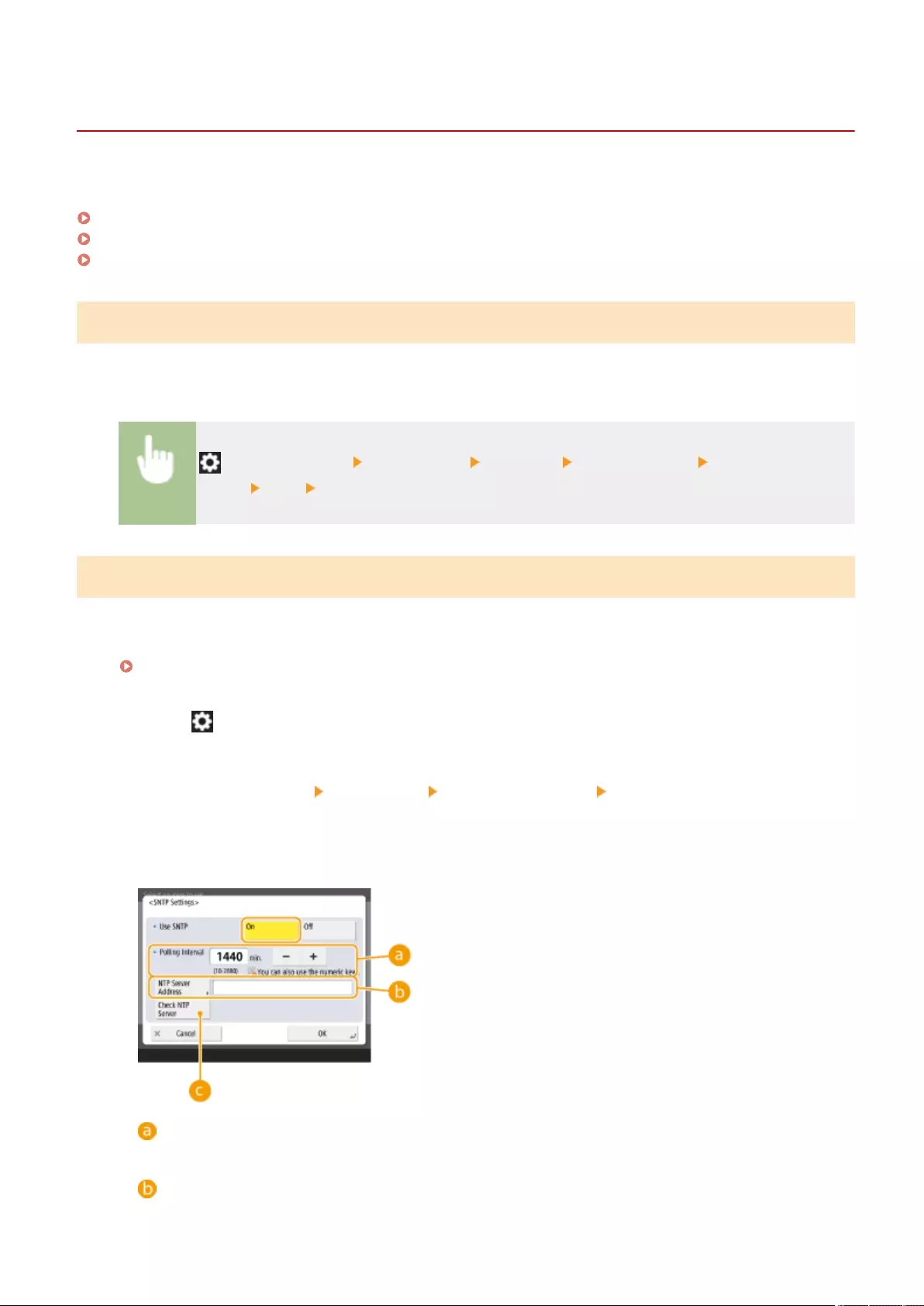
Other Network Settings
72JY-015
Set the following according to your network environment.
Setting the PASV Mode of FTP(P. 63)
Making SNTP Settings(P. 63)
Monitoring the Machine From Device Management Systems(P. 64)
Setting the PASV Mode of FTP
PASV is an FTP communication mode that is used during le transfer. Press <On> for this setting to enable the
machine to connect to an FTP server even if the machine is within a rewall. Conrm beforehand that the PASV mode
is set on the FTP server side.
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <Use FTP PASV
Mode> <On> <OK>
Making SNTP Settings
SNTP is a protocol to adjust time using a time server on the network. SNTP is used when time needs to be adjusted
between the machine and the server in cases when security authentication is done at the time of accessing an LDAP
server. Set the time difference (time zone) beforehand because actions are based on Coordinated Universal Time
(UTC). Setting the Date/Time(P. 17)
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <SNTP Settings>.
3Press <On> in <Use SNTP> and carry out the necessary settings.
<Polling Interval>
Specify the prescribed interval in minutes to adjust the time.
<NTP Server Address>
Setting Up
63

Enter the IP address of the NTP server. When the DNS server is used, instead of an IP address, you can
enter "host name.domain name" (FQDN) using alphanumeric characters. (Example: "ntp.example.com").
<Check NTP Server>
You can check the communication status between a registered server and the SNTP. When a connection is
made properly, "OK" is displayed. However, only the communication status is conrmed and time
adjustment is not carried out.
●To perform time synchronization via SNTP with the NTP server, setting the time zone where the
machine is used is required in advance. Setting the Date/Time(P. 17)
4Press <OK>.
5Press (Settings/Register) <Yes>.
Monitoring the Machine From Device Management Systems
When device management software is employed, you can collect/manage various information such as setting
information, address information, and device failure information on the network through the server.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <Multicast Discovery
Settings>.
3Set <Response> to <On>, press <Scope Name> and enter a scope name.
●Enter a scope name specied using Multicast Discovery Settings in <Scope Name>.
4Press <OK>.
5Press (Settings/Register) <Yes>.
LINKS
<Network>(P. 782)
Setting Up
64
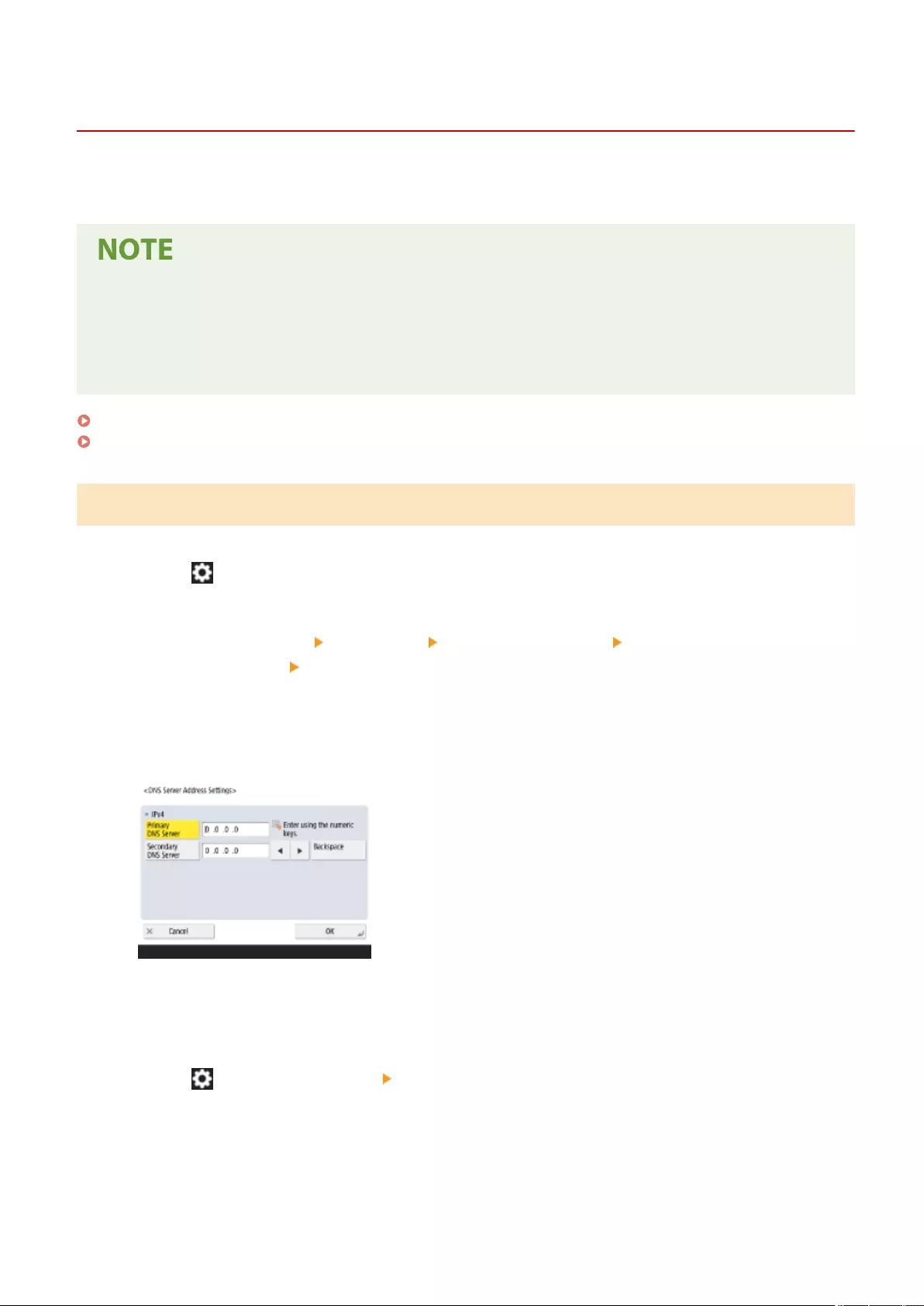
Conguring System Data Communication
72JY-016
The settings described in this section are required to use the sub line for performing DNS name resolution and data
communication via a proxy. Administrator or NetworkAdmin privileges are required to specify these settings.
●The DNS server address setting and proxy settings for the sub line can only be used for specic system data
communication, such as using the sub line to access a rmware distribution server. They cannot be used for
a regular internet connection. When using a DNS server or proxy server for the sub line for applications
other than system data communication, register the addresses and port numbers to use with the sub line in
the settings of the main line.
Setting the DNS of the Sub Line(P. 65)
Proxy Settings of the Sub Line(P. 66)
Setting the DNS of the Sub Line
1Press (Settings/Register).
2Press <Preferences> <Network> <Sub Line Settings> <Settings for System Data
Communication> <DNS Server Address Settings>.
3Specify the required settings.
●Enter the IP address of the DNS server, according to your environment.
4Press <OK>.
5Press (Settings/Register) <Yes>.
Setting Up
65
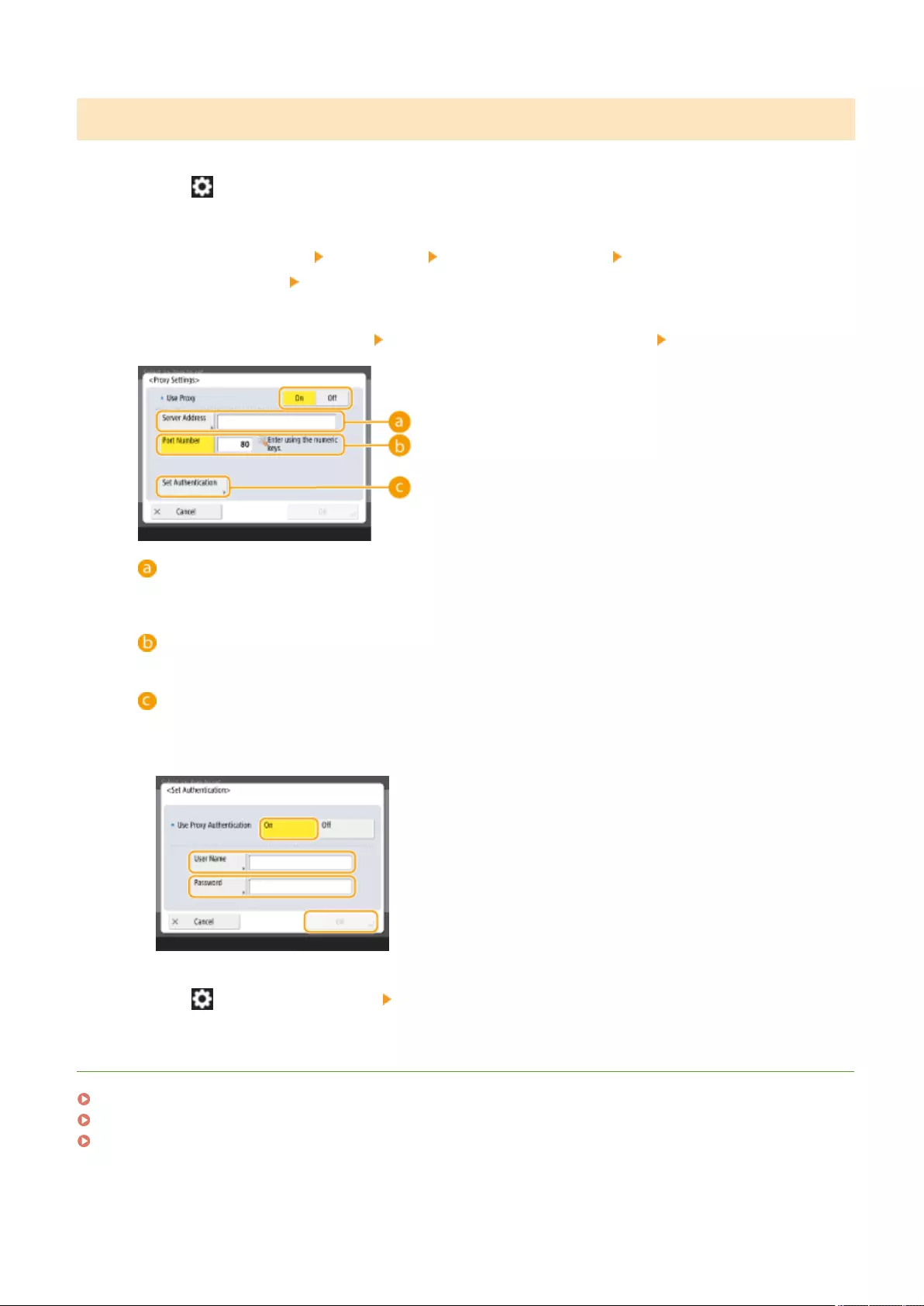
Proxy Settings of the Sub Line
1Press (Settings/Register).
2Press <Preferences> <Network> <Sub Line Settings> <Settings for System Data
Communication> <Proxy Settings>.
3Press <On> for <Use Proxy> congure the required settings press <OK>.
<Server Address>
Enter the address of the proxy server to use. Specify the settings, such as the IP address and host name,
according to your environment.
<Port Number>
Enter the port number of the proxy server.
<Set Authentication>
Press this to set the authentication information when using the authentication function of a proxy server.
Press <On> on the displayed screen, enter the user name and password for proxy authentication, and
press <OK>.
4Press (Settings/Register) <Yes>.
LINKS
Selecting the Network Connection Method(P. 23)
Making DNS Settings(P. 45)
Setting a Proxy(P. 547)
Setting Up
66
Installing Drivers
72JY-017
140K-015 PMW-INDR
Install the printer driver, fax driver, and drivers for other system options as well as related software on your computer.
1Make preparations before installation.
●Equip the main unit with optional equipment ( Optional Equipment(P. 1119) ).
●Install the drivers and software to use from the included CD/DVD-ROM or by downloading them from the
Canon website for your country/region accessed via the URL indicated below.
(https://global.canon/en/support/)
●The latest versions of drivers and software are uploaded to the Canon website when they become
available. Download them as needed after checking the operating environment for your machine.
●Some functions of drivers and software may not be available depending on the model of the machine or
operating environment.
●Some drivers may not be fully compatible with the operating system you are using. Check the driver
compatibility with latest versions of operating systems on the Canon website.
2Carry out installation of the drivers.
●For details on the installation, see the manuals for the drivers and software you want to use.
●If communication via the relevant IP address is not permitted in <Firewall Settings>, you cannot install the
driver. For more information, see Specifying IP Addresses in Firewall Settings.
●After you have installed the driver, if communication via the IP address of the computer you have installed it
on is not permitted in <Firewall Settings>, you cannot print or send a fax from that computer.
Setting Up
67
Fax Line Settings
72JY-018
To use the fax on the machine, register the fax number and company or department name to be displayed/printed at
the receiving party's fax machine when sending a fax. Also, set the communication channel type.
To use the fax function
●The optional product is required for faxing. System Options(P. 1101)
1Press (Settings/Register).
2Press <Function Settings> <Send> <Fax Settings> <Set Line>.
3Press <Line 1> <Register Unit Telephone Number>.
4Enter a fax number and press <OK>.
●The fax number you registered will be notied to the recipient.
5Enter a name in <Register Unit Name> and press <OK>.
●The name you registered will be notied to the recipient.
●Instead of the unit name you specied, you can show or print the sender's name. Basic Operations for
Sending Faxes(P. 275)
6Select a line type in <Select Line Type>, press <OK>.
●If you are not sure what kind of line type you are using, please contact your dealer or service representative,
or the sales oce of your telephone company.
Congure the setting according to the fax option.
●You can set to display a destination's phone number on the screen or report in <Set Number Display>.
<Receive/Forward>(P. 835) <Fax Settings>
●You can set to automatically switch of the incoming fax and incoming call in <RX Mode>. <Receive/
Forward>(P. 835) <Fax Settings>
LINKS
Setting Up
68

Setting E-mail/I-Fax Communication
72JY-019
0YRY-017 0UUY-00Y 0UW1-00Y 1100-017 0X7F-017 0X7H-017 10XJ-017 0X6E-017 0X6W-017 1106-017 0X7C-017 0X7A-017 10YY-017 0WXY-017 0X7E-017 10H3-017 0WR6-017 0WR7-017 108A-017 1116-017 10H4-017 0WR5-017 0WR8-017 0YWJ-016 0YWH-017 0YWR-016 0YWK-017 0YWE-017 0YWF-017 0YAS-017 PMW-STCM
To directly send scanned documents via e-mail/I-fax without going through a computer, you need to congure
communication settings such as a mail server, authentication methods, etc. Generally, an SMTP server is used for
sending, and an SMTP server or a POP3 sever is used for receiving. You can set encoding and other parameters. For
details about necessary settings, contact the Internet service provider or network administrators.
1Press (Settings/Register).
2Press <Function Settings> <Send> <E-Mail/I-Fax Settings> <Communication
Settings>.
3Set communication.
1Specify the basic settings.
<E-Mail Address>
Enter the machine's e-mail address.
●You can specify any name as the user name (part at the left of @ mark). Enter the registered host
name at the right of the @ mark.
<SMTP Server>
Enter an SMTP server name (or an IP address).
●After specifying the settings, check the connection for <SMTP Server>.
<Use POP RX>
Press <On> when you want to receive e-mails and I-faxes using a POP3 server.
<Use SMTP RX>
Press <On> when you want to make the machine an SMTP server to receive e-mails and I-faxes. Be
aware that you cannot receive via SMTP if you don't register the host name of the machine on the DNS
server.
2Press <Next>.
3Specify the POP server settings.
Setting Up
70
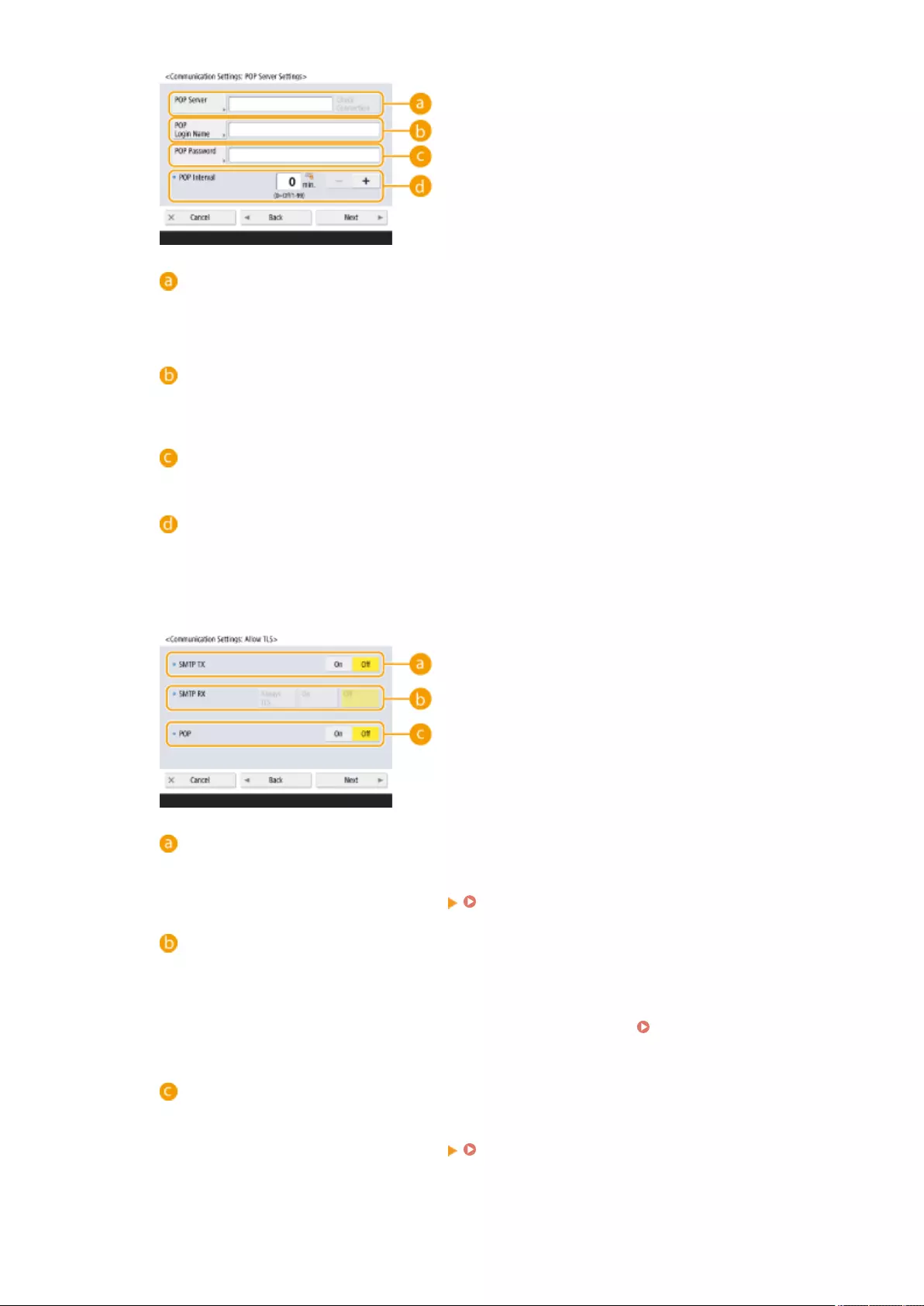
<POP Server>
Enter a POP3 server name (or an IP address).
●After specifying the settings, check the connection for <POP Server>.
<POP Login Name>
To use a POP3 server, enter the user name of the specied mail account using alphanumeric
characters.
<POP Password>
To use a POP3 server, enter the password of the specied mail account.
<POP Interval>
You can set the interval to automatically issue POP in minutes.
4Press <Next>.
5Specify the settings for encrypted communication.
<SMTP TX>
To encode the communication to/from the SMTP server using TLS, press <On>. When <On> is set, you
can conrm the TLS server certicate during communication with the server and add CN to the
verication items. <E-Mail/I-Fax Settings> <Conrm TLS Certicate for SMTP TX>(P. 827)
<SMTP RX>
To encode communication using TLS when receiving e-mails and I-faxes using the SMTP server, press
<Always TLS> or <On>. When you don't want to receive data other than encoded data, select <Always
TLS>.
●To encrypt SMTP reception with TLS, prepare the key pair in advance. Conguring the Key and
Certicate for TLS(P. 549)
<POP>
To encode the communication to/from the POP3 server using TLS, press <On>. When <On> is set, you
can conrm the TLS server certicate during communication with the server and add CN to the
verication items. <E-Mail/I-Fax Settings> <Conrm TLS Certicate for POP RX>(P. 827)
6Press <Next>.
Setting Up
71

Setting POP authentication before sending
POP authentication before sending (POP before SMTP) is a conrmation of users by the POP server
(reception mail server) before sending, which is a function to block unauthorized e-mails sent by third parties.
1Specify each item.
<POP Authentication Method>
Set the authentication methods of the POP3 server. To encode the password during authentication,
select <APOP>. To authenticate users when receiving mail (POP), select <POP AUTH>.
<POP Authentication Before Sending>
To perform authentication using the POP3 server, press <On>.
Setting SMTP authentication
SMTP authentication (SMTP AUTH) veries users by checking user names and passwords when e-mails are
sent. It can also encode SMTP communication (sent and received).
1Specify each item.
<SMTP Authentication (SMTP AUTH)>
To use SMTP authentication, press <On>, enter the user name and password of the specied mail
accounts in <User Name> and <Password>.
User name and password
●<User Name> and <Password> for <SMTP Authentication (SMTP AUTH)> are also used when
forwarding received documents.
●Forwarding is performed as "Fixed Device Authentication" regardless of the <Information Used for
SMTP Server Authentication> settings. ( <Information Used for SMTP Server
Authentication>(P. 816) )
<Display Authent. Screen When Sending>
When sending e-mails and I-faxes, to display the user name and password entry screen, press <On>.
Setting Up
72

When setting SMTP authentication
●Specify the authentication method using one of the following three methods.
●Fixed Device Authentication
●Entering the authentication information when sending
●Registering information for each user
Fixed Device Authentication: When <User Name> and <Password> entered into <SMTP
Authentication (SMTP AUTH)> are used and the authentication screen (<Log in to SMTP Server>)
is not displayed when sending
●Specify the settings as follows.
●<SMTP Authentication (SMTP AUTH)>: <On>
●<User Name>: Enter the user name.
●<Password>: Enter the password.
●<Display Authent. Screen When Sending>: <Off>
●<Information Used for SMTP Server Authentication>(P. 816) : <Device Settings>
Entering the authentication information when sending: When <User Name> and <Password>
entered into <SMTP Authentication (SMTP AUTH)> are used and the authentication screen (<Log
in to SMTP Server>) is displayed when sending
●<User Name> and <Password> entered into <SMTP Authentication (SMTP AUTH)> are entered as the
authentication information when sending.
●When <User Name> and <Password> for <SMTP Authentication (SMTP AUTH)> are not entered
(blank), the authentication information when sending is also blank.
●Specify the settings as follows.
●<SMTP Authentication (SMTP AUTH)>: <On>
●<User Name>: Enter the user name.
●<Password>: Enter the password.
●<Display Authent. Screen When Sending>: <On>
●<Information Used for SMTP Server Authentication>(P. 816) : <Device Settings>
Registering information for each user: When <Registered Info. for Each User> is used and the
authentication screen (<Log in to SMTP Server>) is not displayed when sending
●SMTP authentication is performed using the user name and password registered in the local device.
●Specify the settings as follows.
●<SMTP Authentication (SMTP AUTH)>: <On>
●<Display Authent. Screen When Sending>: <Off>
●<Information Used for SMTP Server Authentication>(P. 816) : <Registered Info. for
Each User>
4Press <OK>.
●Depending on your environment, you might need to specify the SMTP/POP3 port number. For details,
contact the Internet service provider or the network administrators. <Specify Port Number for SMTP
TX/POP RX>(P. 826)
Setting Up
73
Connecting to the Other Devices
72JY-01A
The machine can be connected to a computer (Windows server) or Advanced Space of other Canon multifunction
printers on a network. The machine can print/send data saved in the connected Windows server or Advanced Space.
●To connect the machine to the storage spaces on other multifunction printers, settings of the other printers
are also necessary.
1Press (Settings/Register).
2Press <Function Settings> <Store/Access Files> <Network Settings>.
3Specify each item.
Registering multifunction printers to connect to
Register the Windows server or Advanced Space of other multifunction printers to connect to.
1Press <Network Place Settings> <Register>.
2Enter the necessary information and press <OK>.
<Name>
Enter the name of the Advanced Space to connect to. As a name entered here is displayed on the list
at the time of access, enter a name that is easy to read.
<Protocol>
Select <SMB> or <WebDAV>, depending on whether the Windows server or Advanced Space of
destination is made available as an SMB server or WebDAV.
<Location>/<Host Name>
<Location> is displayed when you select <SMB>, and <Host Name>is displayed when you select
<WebDAV> in the protocol setting.
●Enter the address in <Location> as "\\ (host name or IP address) \share" to connect to a shared
space, or "\\ (host name or IP address) \users" to connect to personal space.
●Enter the address in <Host Name> as "https:// (host name or IP address)", and press <Next>. Then,
enter "/share" for the shared space or "/users" for the personal space in <Folder Path>.
Setting Up
75
●Do not register something other than the Advanced Space of another imageRUNNER ADVANCE series
machine or a Windows server which is opened externally, as this may cause the machine to
malfunction.
Controlling communication protocols
Select the communication protocol to use when making an external reference to a Windows server or Advanced
Space of other Canon multifunction printers on a network. However, if only one of them is used, you can
increase the security by disabling unnecessary settings.
1Press <Protocol for External Reference>.
2Press <On> of the protocol you use, then press <OK>.
●When connection via SMB is not used, set the <SMB> setting to <Off>. When connection via WebDAV is
not used, set the <WebDAV> setting to <Off>.
Verifying the certicate when connecting
When the Windows server or Advanced Space to connect to is set to use TLS, you can verify the TLS server
certicate sent from the connected device when connecting. Because a connection will be canceled if an error
occurs, attacks such as identity theft by third parties can be prevented.
1Press <Conrm TLS Certicate for Network Access>.
2Press <On> <OK>.
●When you press <On>, the screen for adding the verication items is displayed. If you need to verify
the CN (Common Name), add a check mark.
●If you do not verify the certicate, TLS communication is performed, even with an invalid certicate.
LINKS
Using Other Machines and Memory Media(P. 437)
<Store/Access Files>(P. 843)
Conguring the Key and Certicate for TLS(P. 549)
Setting Up
76

Basic Operations
Basic Operations ............................................................................................................................................... 79
Parts and Their Functions ................................................................................................................................... 82
Front Side ....................................................................................................................................................... 83
Back Side ........................................................................................................................................................ 86
Interior ........................................................................................................................................................... 88
Feeder ............................................................................................................................................................ 89
Multi-Purpose Tray ......................................................................................................................................... 91
Paper Drawer ................................................................................................................................................. 92
Control Panel .................................................................................................................................................. 93
Turning ON the Machine ..................................................................................................................................... 95
Turning OFF the Machine ............................................................................................................................... 96
Placing Originals ................................................................................................................................................. 97
Loading Paper .................................................................................................................................................... 102
Basic Paper Loading Method ........................................................................................................................ 103
Loading Envelopes ....................................................................................................................................... 111
Loading Preprinted Paper ............................................................................................................................ 115
Using the Touch Panel Display ......................................................................................................................... 118
Basic Screens on the Touch Panel Display .................................................................................................... 119
Items Displayed on the <Home> Screen ................................................................................................ 122
Timeline Display Specications .............................................................................................................. 125
Items Displayed in the Timeline ............................................................................................................. 127
Basic Operation of the Touch Panel Display ................................................................................................. 130
Entering Characters ...................................................................................................................................... 135
Logging into the Machine ................................................................................................................................. 137
List of Items That Can Be Personalized ......................................................................................................... 139
Specifying Paper Size and Type ........................................................................................................................ 141
Specifying Paper Size and Type in the Paper Drawer .................................................................................... 142
Specifying Paper Size and Type in the Multi-purpose Tray ............................................................................ 145
Registering Frequently Used Paper Size and Type for the Multi-purpose Tray .............................................. 148
Fixing the Paper Size and Type to Use with the Multi-Purpose Tray .............................................................. 151
Registering Free Size Paper (Custom Size Paper) .......................................................................................... 153
Automatically Selecting the Appropriate Paper Source for a Specic Function ............................................. 154
Customizing the Touch Panel Display .............................................................................................................. 156
Customizing the <Home> Screen .................................................................................................................. 159
Basic Operations
77

Creating a Shortcut for a Frequently Used Function ..................................................................................... 162
Registering a Combination of Frequently Used Functions ............................................................................ 164
Customizing the Basic Features Screen ........................................................................................................ 167
Registering Frequently Used Settings and Destinations as Personal Buttons/Shared Buttons on the <Home>
Screen .......................................................................................................................................................... 170
Registering Personal Buttons/Shared Buttons ....................................................................................... 171
Switching the Displayed Language ............................................................................................................... 176
Registering Shortcuts for Frequently Used Settings/Registered Items ......................................................... 178
Customizing the Screen Display Appearance and the Operational Conditions ............................................. 180
Canceling Send/Print Jobs ................................................................................................................................. 183
Setting Sounds ................................................................................................................................................... 184
Entering Sleep Mode ......................................................................................................................................... 188
Registering Destinations .................................................................................................................................. 190
About the Address Books of the Machine ..................................................................................................... 192
Registering Destinations in the Address Book .............................................................................................. 195
Registering Multiple Destinations as a Group ........................................................................................ 205
Editing the Registered Destinations in the Address Book ...................................................................... 208
Registering a Destination in a One-Touch Button ......................................................................................... 210
Registering a Group in a One-Touch Button .......................................................................................... 212
Editing the Registered Destinations in One-Touch Buttons .................................................................... 214
Basic Operations
78
Basic Operations
72JY-01C
This chapter describes basic operations, such as how to use the control panel and touch panel display, as well as how
to load paper and originals.
◼Parts and Their Functions
This section describes the exterior and interior parts of the machine and their functions, as well as how to use the keys
on the control panel. Parts and Their Functions(P. 82)
◼Turning ON the Machine
This section describes how to turn the machine ON or OFF. Turning ON the Machine(P. 95)
◼Using the Touch Panel Display
This section describes how to use the buttons on the touch panel display to perform various operations, such as
adjusting and checking the settings. This section also describes how to enter text and numbers, which are necessary
for operations such as registering information in the Address Book and sending faxes. Using the Touch Panel
Display(P. 118)
Basic Operations
79

◼Logging into the Machine
This section describes how to log in when a login screen is displayed. Logging into the Machine(P. 137)
◼Placing Originals
This section describes how to place originals on the platen glass and in the feeder. Placing Originals(P. 97)
◼Loading Paper
This section describes how to load the paper into the paper drawer and multi-purpose tray. Loading Paper(P. 102)
◼Customizing the Touch Panel Display
This section describes how to arrange buttons and customize menus, making it easier to use the screens displayed on
the touch panel. Customizing the Touch Panel Display(P. 156)
Basic Operations
80
◼Specifying the Sound Settings
This section describes how to specify the settings for sounds, such as those produced when fax sending is complete or
when an error occurs. Setting Sounds(P. 184)
◼Entering Sleep Mode
This section describes how to set sleep mode. Entering Sleep Mode(P. 188)
◼Registering Destinations
This section describes how to register destinations in the Address Book or one-touch buttons for sending faxes or
scanned documents. Registering Destinations(P. 190)
Basic Operations
81

Parts and Their Functions
72JY-01E
This section describes the parts of the machine (front side and interior) and how they function. This section also
describes how to place originals and how to load paper, as well as the names and usage of the keys on the control
panel. Read this section for tips on how to use the machine properly.
Front Side(P. 83)
Back Side(P. 86)
Interior(P. 88)
Feeder(P. 89)
Multi-Purpose Tray(P. 91)
Paper Drawer(P. 92)
Control Panel(P. 93)
Basic Operations
82
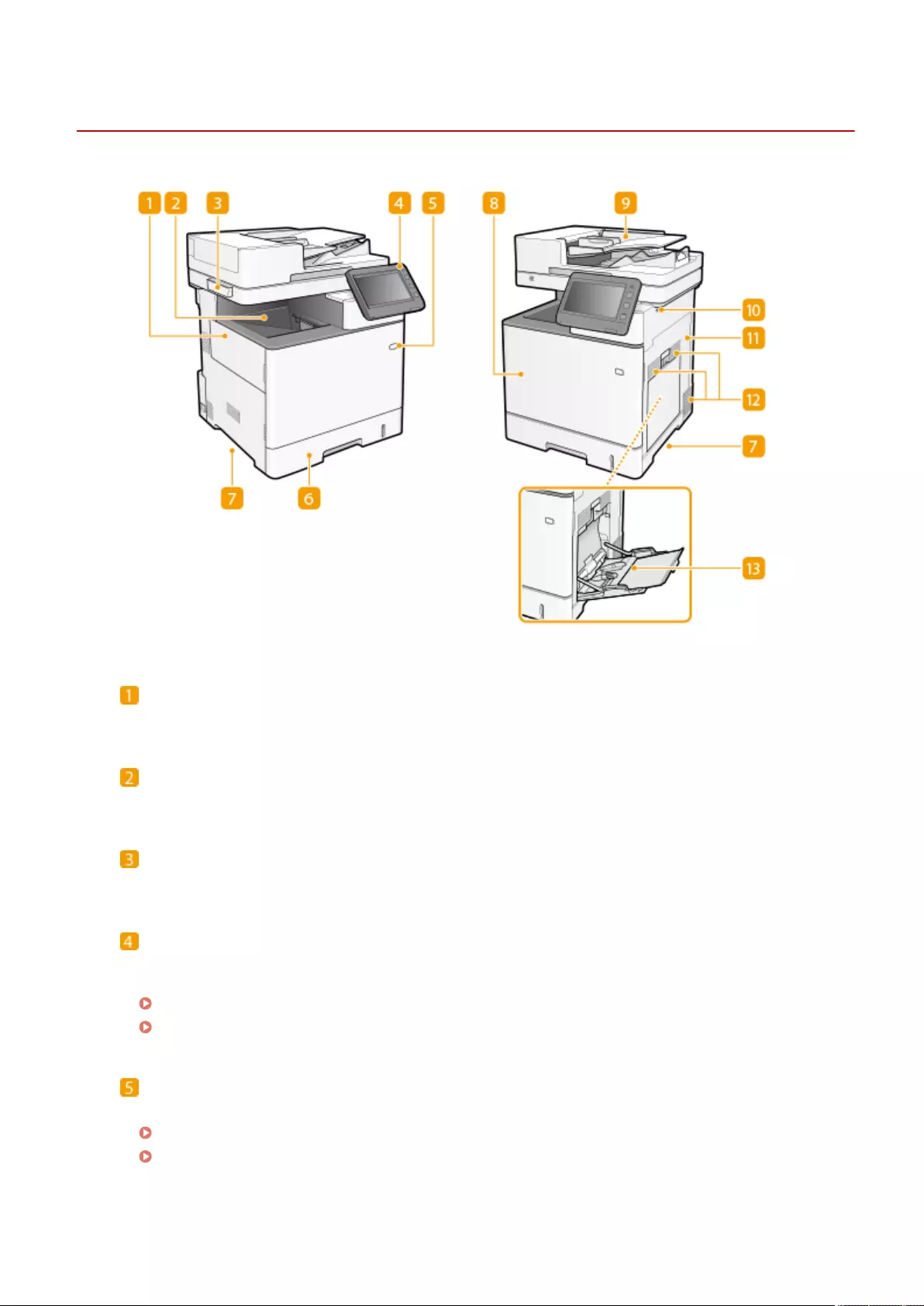
Front Side
72JY-01F
Left cover
Open the left cover when replacing the waste toner container.
Output tray
Printed paper is output to the output tray.
Glass cleaning sheet storage box
Use this box to store the cloth for cleaning the platen glass.
Control Panel
The control panel consists of Home key, a display, status indicators, etc. You can perform all the operations
and specify settings from the control panel.
Control Panel(P. 93)
Basic Screens on the Touch Panel Display(P. 119)
Power switch
Press the power switch when turning ON or OFF the machine.
Turning ON the Machine(P. 95)
Turning OFF the Machine(P. 96)
Basic Operations
83
Paper drawer
Load the type of paper you frequently use into the paper drawer.
Paper Drawer(P. 92)
Basic Paper Loading Method(P. 103)
Lift handles
Hold the lift handles when carrying the machine.
Front cover
Open the front cover when replacing toner cartridges. Replacing the Toner Cartridge(P. 881)
Feeder
Automatically feeds originals into the machine for scanning. When two or more sheets are loaded in the
feeder, originals can be scanned continuously. Feeder(P. 89)
USB memory port (Front-right side of the machine)
You can connect devices such as a USB memory device to the machine. Connecting a USB Memory
Device(P. 84)
●Some types of memory media may not be able to save data correctly.
●The USB port (front-right side of the machine) supports USB 2.0.
Right cover
Open the right cover when clearing paper jams. Clearing Paper Jams(P. 1008)
Ventilation slot
Air from inside the machine is vented out to cool down the inside of the machine. Note that placing objects in
front of the ventilation slots prevents ventilation.
Multi-purpose tray
Load the paper into the multi-purpose tray when you want to temporarily use a type of paper different from
that which is loaded in the paper drawer.
Multi-Purpose Tray(P. 91)
Basic Paper Loading Method(P. 103)
Connecting a USB Memory Device
You can connect a USB memory device to the USB ports located on the right side of the machine, and directly
print data from the USB memory device. Originals scanned using the machine can also be saved directly to the
USB memory device.
Using Memory Media(P. 441)
Basic Operations
84

●Make sure that the USB memory device is oriented properly when connecting it to the machine. If it is not
connected properly, it may cause the USB memory device or machine to malfunction.
●Make sure to follow the proper procedure when removing the USB memory device. Inserting/Removing
Memory Media(P. 442) Failure to do so may cause the USB memory device or machine to malfunction.
●The machine only supports FAT32/exFAT format USB memory device.
Unsupported devices and usages
●Memory media with security functions
●Memory media that does not meet the USB specication
●Memory card readers connected via USB
●Connecting memory media via an extension cable
●Connecting memory media via a USB hub
Basic Operations
85
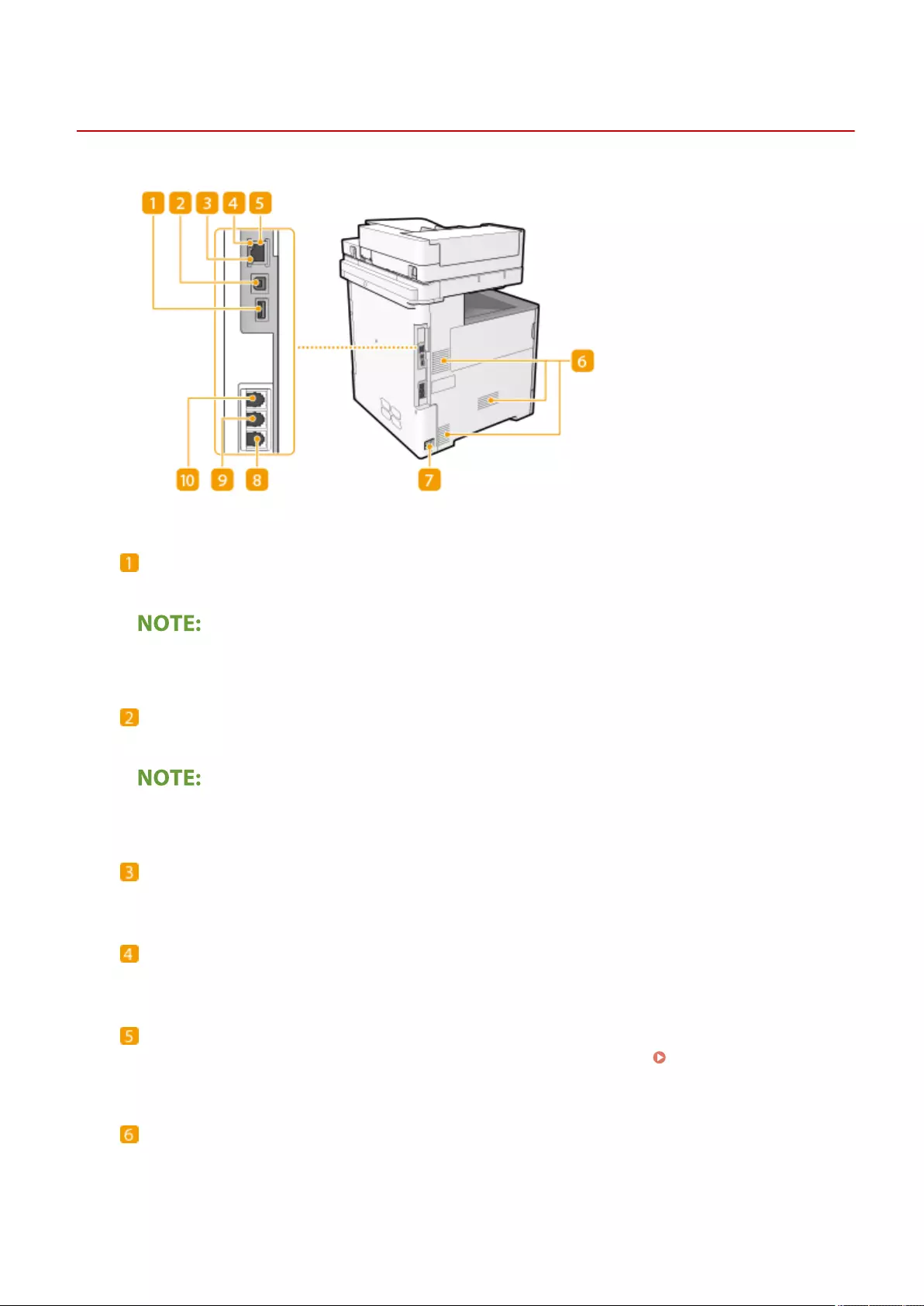
Back Side
72JY-01H
USB port (for USB device connection)
You can connect devices such as an external hard disk to the machine.
●The USB port (for USB device connection) supports USB 2.0.
USB port (for computer connection)
Connect a USB cable when connecting the machine and a computer.
●The USB port (for computer connection) supports USB 2.0.
LNK indicator
The LNK indicator blinks green when the machine is properly connected to a network.
ACT indicator
The ACT indicator blinks while data is being sent or received.
LAN port
Connect a LAN cable when connecting the machine to a wired LAN router, etc. Setting up the Network
Environment(P. 19)
Ventilation slot
Air from inside the machine is vented out to cool down the inside of the machine. Note that placing objects in
front of the ventilation slots prevents ventilation.
Basic Operations
86
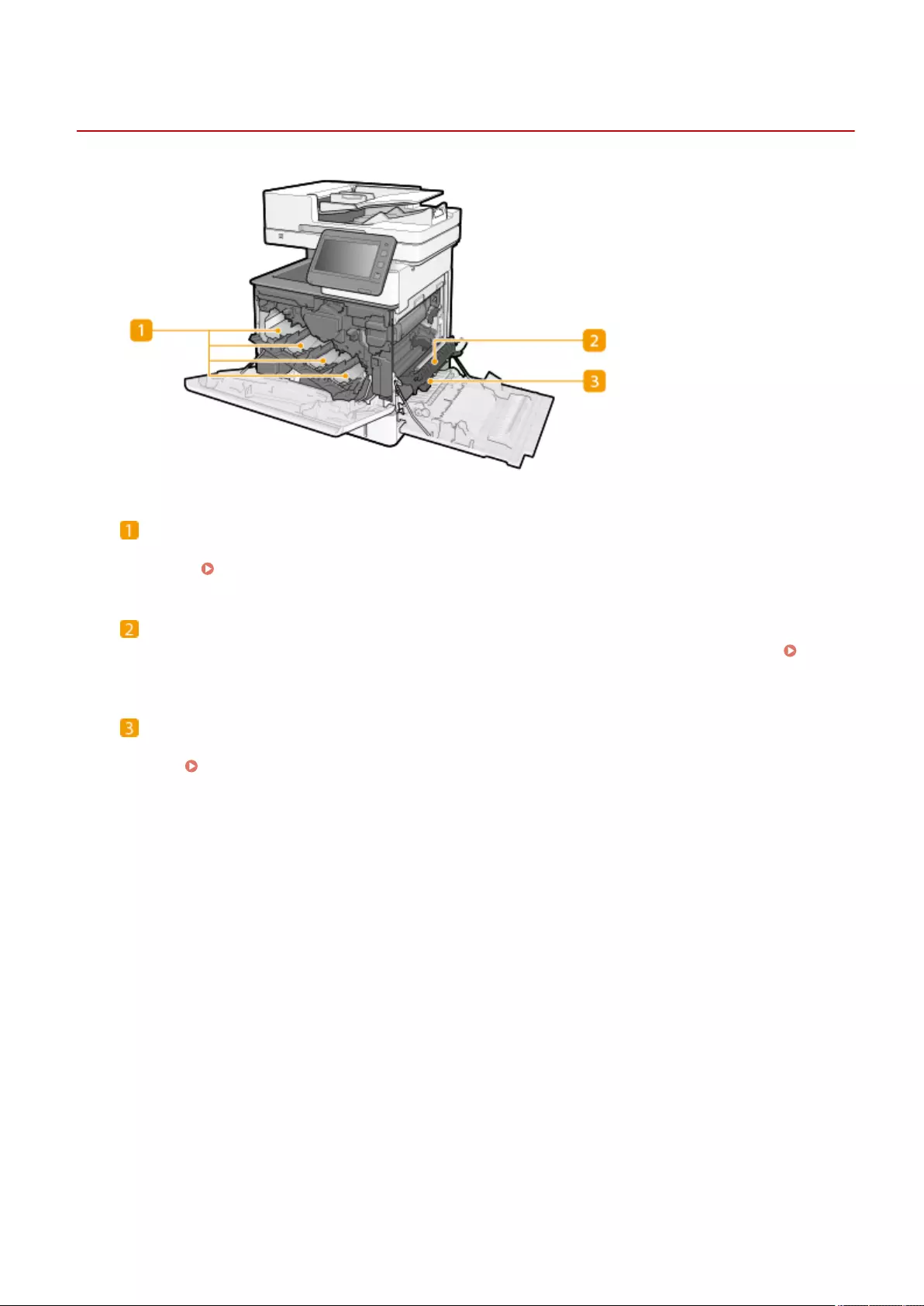
Interior
72JY-01J
Toner slots
Load the toner cartridges in these slots: Y (yellow) in the leftmost slot, followed by M (magenta), C (cyan), and
K (black). Replacing the Toner Cartridge(P. 881)
Transfer unit
If there is a paper jam inside the machine, raise the transport guide to remove the jammed paper.
Clearing Paper Jams(P. 1008)
Transport guide
If paper has jammed inside the machine, lift up the transfer unit and open this guide to remove the jammed
paper. Clearing Paper Jams(P. 1008)
Basic Operations
88
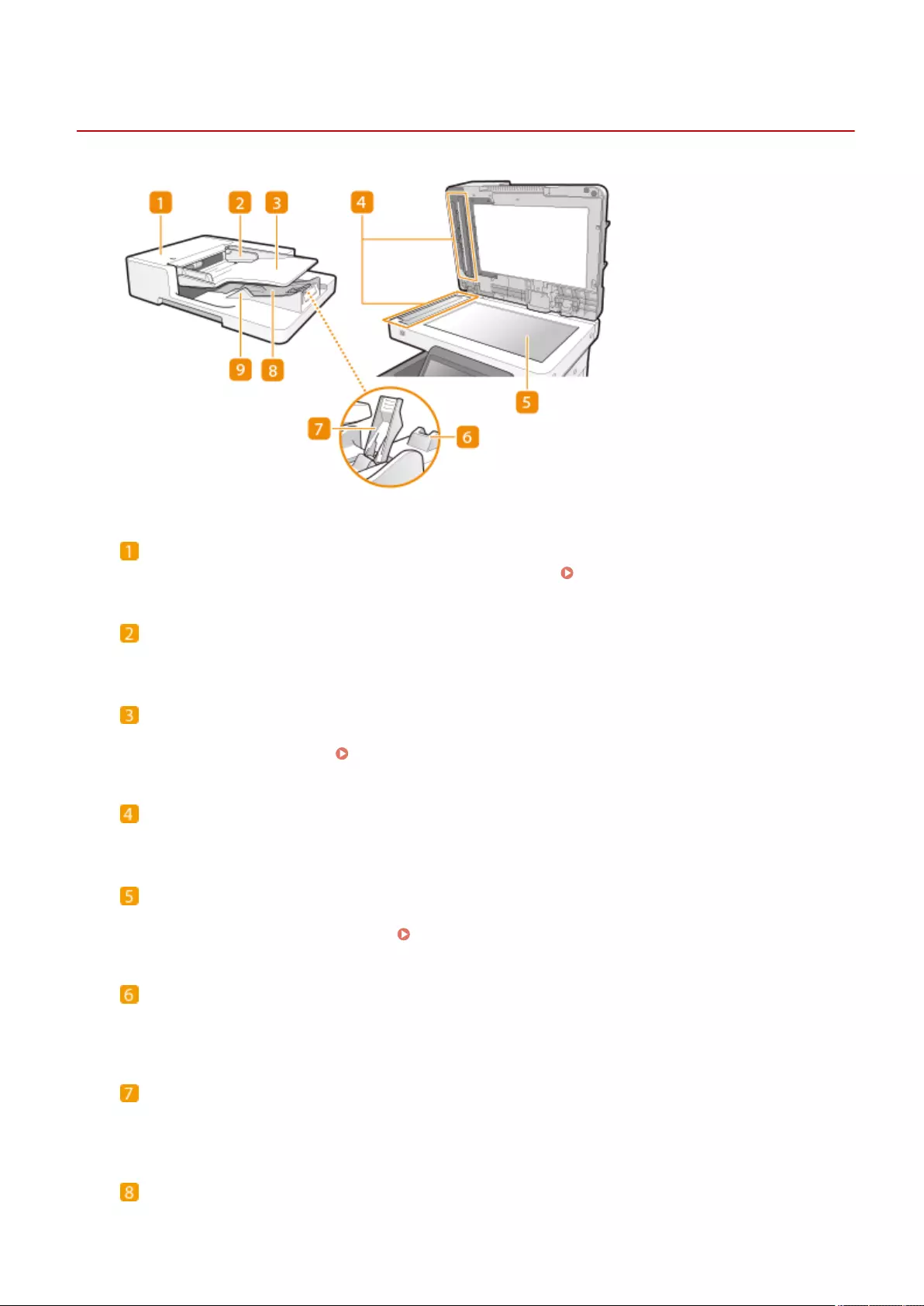
Feeder
72JY-01K
Feeder cover
Open this cover when removing originals jammed in the feeder. Paper Jams in the Feeder(P. 1011)
Slide guides
Adjust these guides according to the width of an original.
Original supply tray
Originals placed here are automatically fed into the feeder. When two or more sheets are loaded, originals
can be scanned continuously. Placing Originals(P. 97)
Document feed scanning area
Originals placed in the feeder are scanned in this area.
Platen glass
When scanning books, thick originals, thin originals, and other originals that cannot be scanned using the
feeder, place them on the platen glass. Placing Originals(P. 97)
Original output tray extension
Pull out this tray when scanning large-sized originals to prevent them from dropping over the edge of the
feeder.
Original stopper
When outputting large originals, raising the original stopper prevents the originals from slipping off the tray
or drooping over the end.
Original output tray
Scanned originals are output here.
Basic Operations
89

Original retainer
Holds down originals to support outputting originals neatly.
●If a thick original such as a book or magazine is placed on the platen glass, do not press down hard on the
feeder.
●Do not place any objects in the original output area. Doing so may cause damage to the originals.
●Regularly clean the feeder and platen glass in order to obtain proper print results. Regular
Cleaning(P. 874)
Basic Operations
90
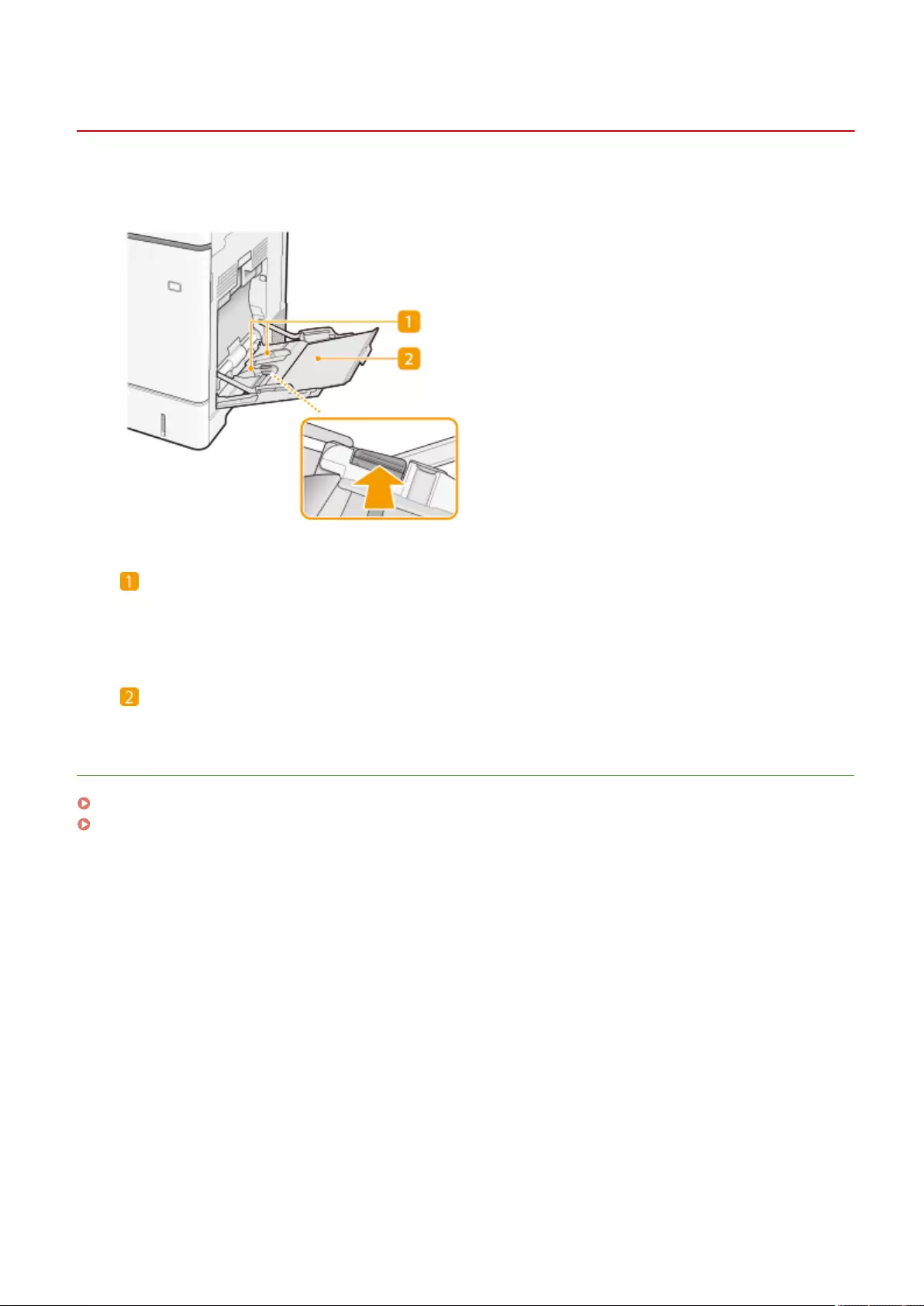
Multi-Purpose Tray
72JY-01L
Use the multi-purpose tray when you want to print on a type of paper that is not loaded in the paper drawer, such as
labels or envelopes.
Paper guides
Adjust the paper guides to exactly the width of the loaded paper to ensure that paper is fed straight into the
machine. Press the lock release lever that is marked with arrow in the illustration to release the lock and slide
the paper guides.
Paper tray
Pull out the paper tray when loading paper.
LINKS
Loading Paper in the Multi-Purpose Tray(P. 107)
Loading Envelopes in the Multi-Purpose Tray(P. 113)
Basic Operations
91
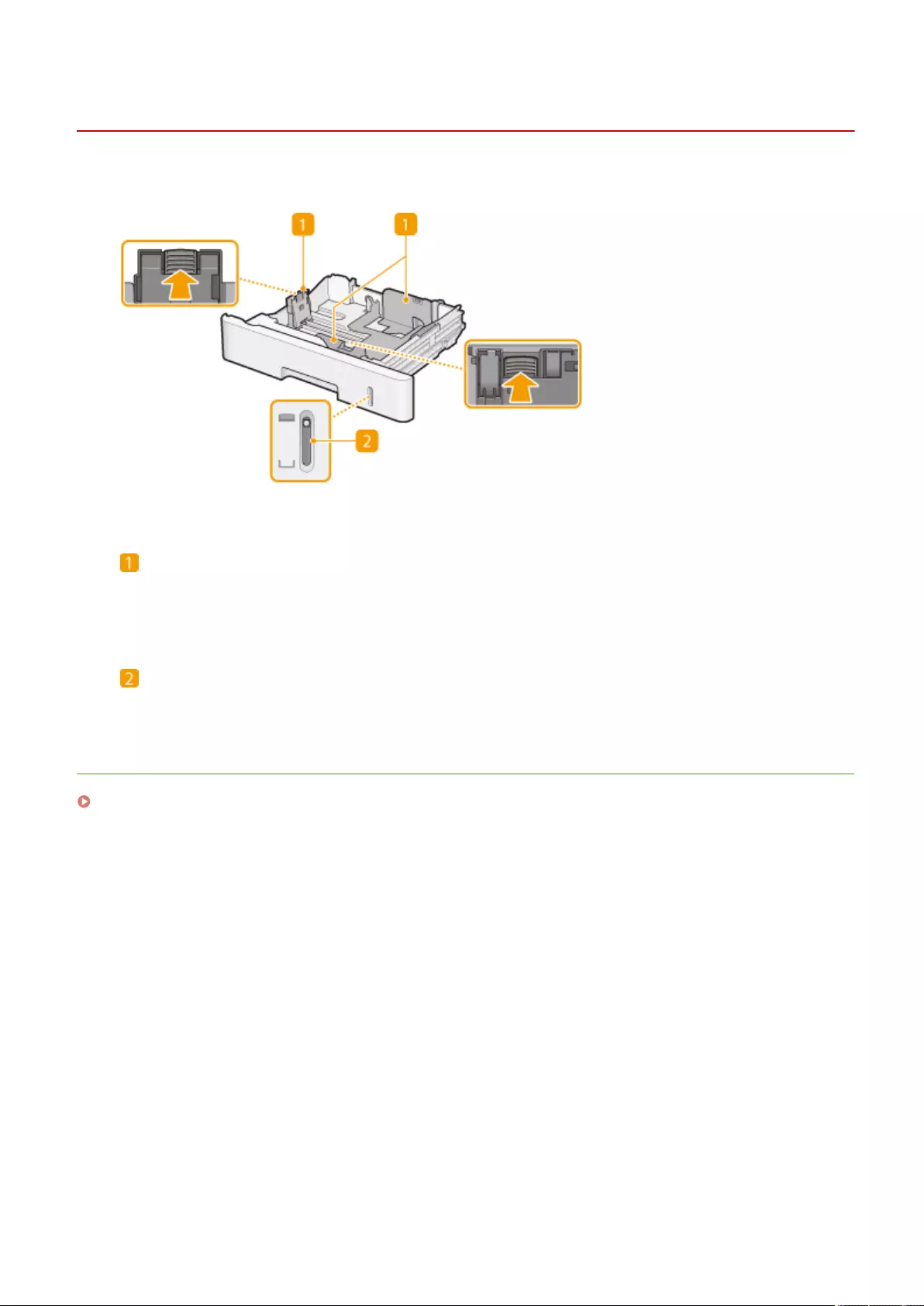
Paper Drawer
72JY-01R
Paper guides
Adjust the paper guides to exactly the size of the loaded paper to ensure that paper is fed straight into the
machine. Press the lock release levers that are marked with arrows in the illustrations to release the locks
and slide the paper guides.
Paper level indicator
Indicates the remaining amount of paper. The mark moves downward as the remaining amount of paper
decreases.
LINKS
Loading Paper in the Paper Drawer(P. 103)
Basic Operations
92
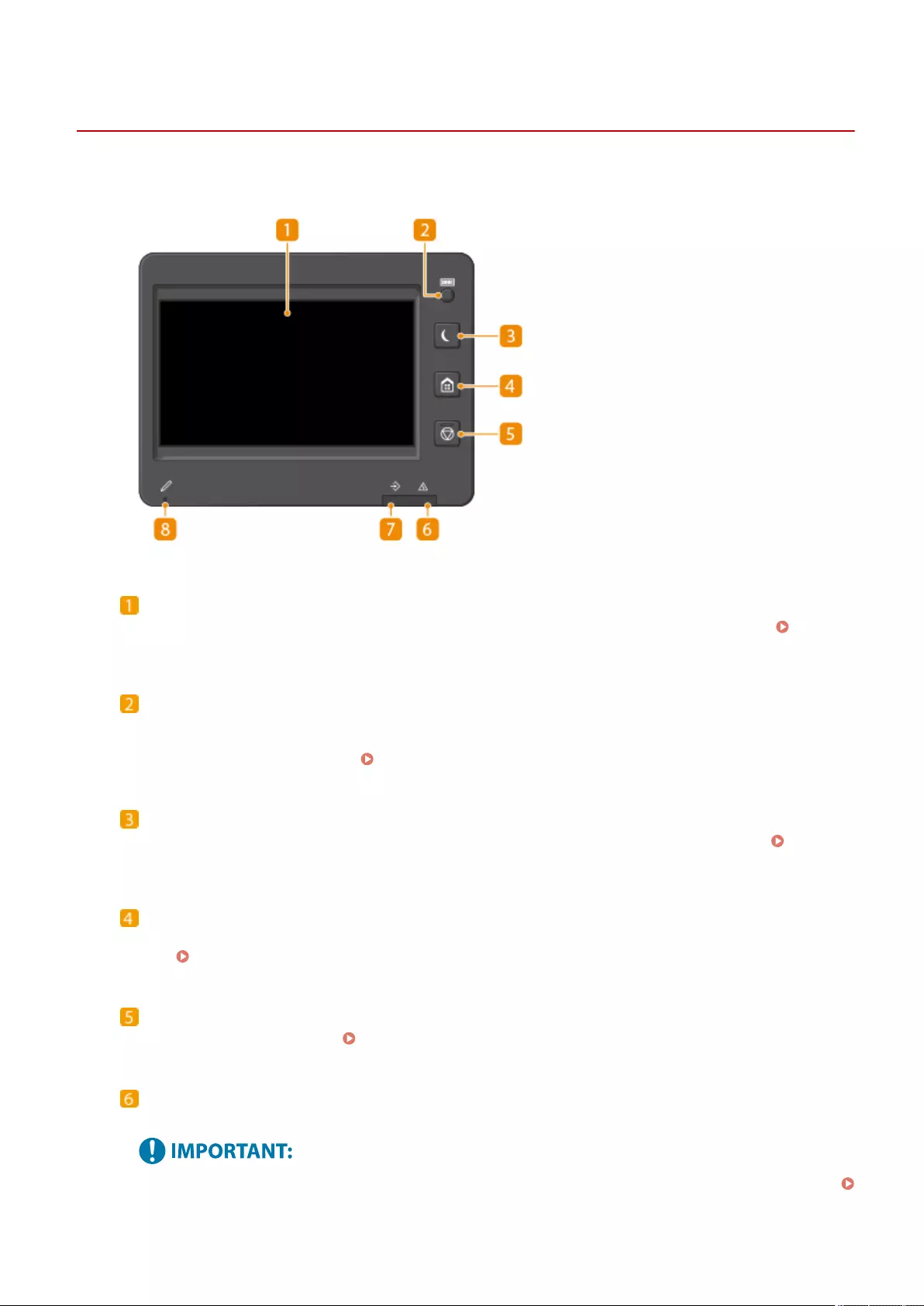
Control Panel
72JY-01S
This section describes the names and usage of the keys on the control panel.
Touch panel display
In addition to the settings screen for each function, the error status is also shown on this display. Using
the Touch Panel Display(P. 118)
[Counter/Device Information] key
Press to display the total number of pages used for operations such as copying or printing on the touch
panel display. You can also check the serial number and IP address of the machine, and the device
information of optional products. Checking the Number of Pages for Copy/Print/Fax/Scan(P. 908)
[Energy Saver] key
Press to put the machine into sleep mode. The key lights up when the machine is in sleep mode. Entering
Sleep Mode(P. 188)
[Home] key
Press to display the Home screen, which provides access to the setting menu and functions such as copy and
scan. Customizing the <Home> Screen(P. 159)
[Stop] key
Stops a send job or a print job. Canceling Send/Print Jobs(P. 183)
Error indicator
Blinks or lights up when an error such as a paper jam occurs.
●If the Error indicator blinks, follow the instructions that appear on the touch panel display.
Troubleshooting(P. 921)
Basic Operations
93

●If the Error indicator maintains a steady red light, contact your dealer or service representative.
Processing/Data indicator
Blinks while operations such as sending or printing are being performed. Lights up green when there are
originals waiting to be processed.
Panel Touch Pen
Use when operating the touch panel display, such as to enter characters.
Basic Operations
94
Turning ON the Machine
72JY-01U
This section describes how to turn ON the machine.
1Make sure that the power plug is rmly inserted into the power outlet.
2Press the power switch.
➠The startup screen appears on the touch panel display.
●You can select the screen displayed immediately after the machine is turned ON. <Use Default Screen
After Startup/Restoration>(P. 859)
●The response of the touch panel display and keys on the control panel may not be optimal immediately after
the machine is turned ON.
●If the machine is connected to a powered off Mac computer by USB cable, the computer may turn on
automatically when this machine does. In this case, disconnect the USB cable from the machine. You may
also be able to solve this problem by using a USB hub between the machine and the computer.
LINKS
Turning OFF the Machine(P. 96)
Basic Operations
95
Turning OFF the Machine
72JY-01W
This section describes how to turn OFF the machine.
Check the machine's operation status before turning it OFF
●Do not turn OFF the machine while using the Fax/I-fax function. I-fax or fax documents cannot be sent or
received when the machine is turned OFF.
●Do not turn OFF the machine if the <Backing up stored data from Remote UI...> message is displayed on the
touch panel display. Doing so may cause the machine to fail to back up the stored data.
●If the machine is turned OFF during scanning or printing, a paper jam may occur.
●You can shut down the machine from the Remote UI. Turning OFF/Restarting the Machine(P. 591)
1Press the power switch.
●The machine may take some time to completely shut down. Do not remove the power plug until the display
and lamps turn OFF.
●To restart the machine, wait for at least 10 seconds after the system is turned off, and then turn the machine
back ON. When <Quick Startup Settings for Main Power> is enabled, wait for at least 20 seconds to restart
the machine. <Quick Startup Settings for Main Power>(P. 777)
LINKS
Turning ON the Machine(P. 95)
Basic Operations
96
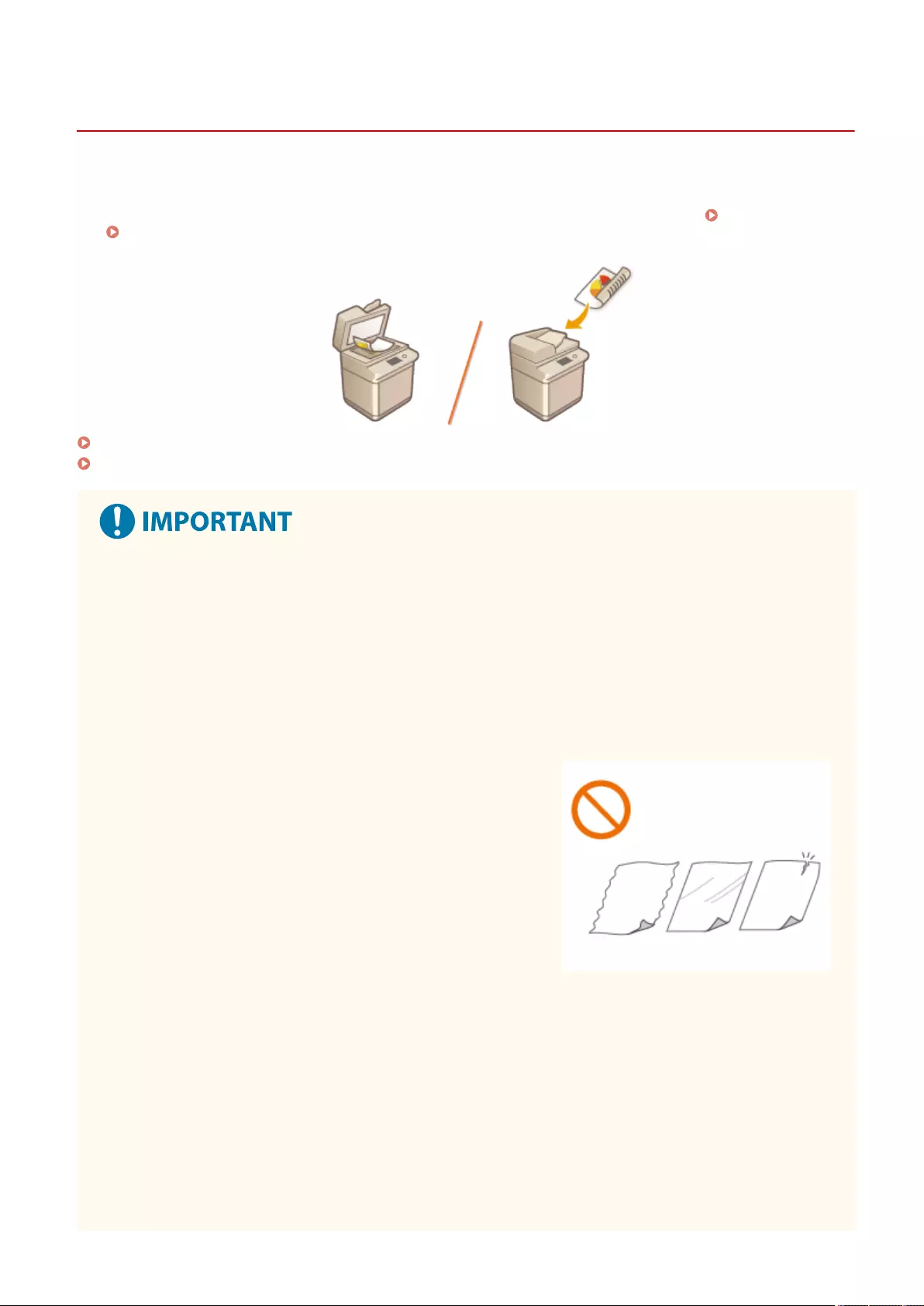
Placing Originals
72JY-01X
Place your originals on the platen glass or in the feeder. For originals such as books and thick/thin paper which cannot
be loaded in the feeder, place the original on the platen glass. If you want to scan 2-sided originals or continue to scan
several sheets of originals, place them in the feeder. For information on loadable sizes, etc., see Main Unit(P. 1104)
and Feeder(P. 1107) .
Placing Originals on the Platen Glass(P. 98)
Placing Originals in the Feeder(P. 99)
Use originals that are completely dry
●When placing originals, make sure that any glue, ink, or correction uid on the originals has completely
dried.
To avoid paper jams
●The use of stiff or elastic paper may result in paper jams in some operating environments. Such paper
should be loosened up slightly before being loaded.
●Do not place the following types of originals in the feeder as this may cause paper jams:
- Wrinkled or creased paper
- Carbon paper or carbon-backed paper
- Curled or rolled paper
- Coated paper
- Torn originals
- Originals with large holes
- Onion skin or thin paper
- Stapled or clipped originals
- Paper printed by a thermal transfer printer
- Transparencies
- Originals with notes attached
- Originals pasted together
- Originals placed in a clear le
- Business cards made of materials other than paper (fabric,
leather, plastic, etc.)
- Business cards made of rough or uneven paper, such as
washi (traditional Japanese paper)
- Business cards with special nishes, such as embossing or foil
Basic Operations
97
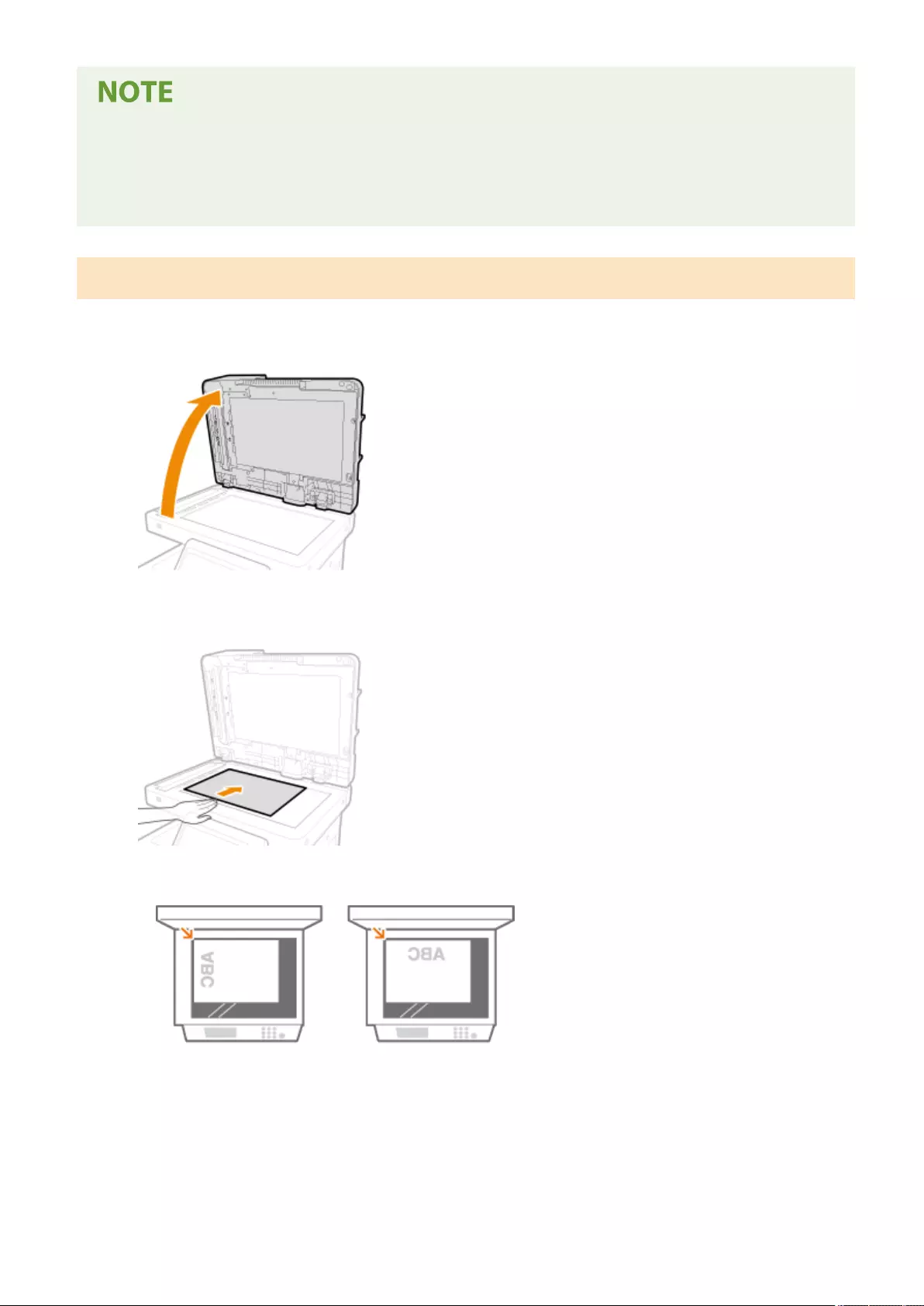
To scan originals more accurately
●Originals placed in the feeder are scanned while being fed into the machine. On the other hand, originals
placed on the platen glass remain in a xed position while they are scanned. To ensure more accurate
scanning results, placing originals on the platen glass is recommended.
Placing Originals on the Platen Glass
1Open the feeder.
2Place the original face down on the platen glass.
●Align the corner of the original with the top-left corner of the platen glass, and place the original so that the
top and the bottom are properly positioned, as shown in the following illustrations.
3Gently close the feeder.
➠The original is ready for scanning.
●Before starting the scanning, specify the paper size and scanning size to match the size of the original.
●When scanning is complete, remove the original from the platen glass.
Basic Operations
98
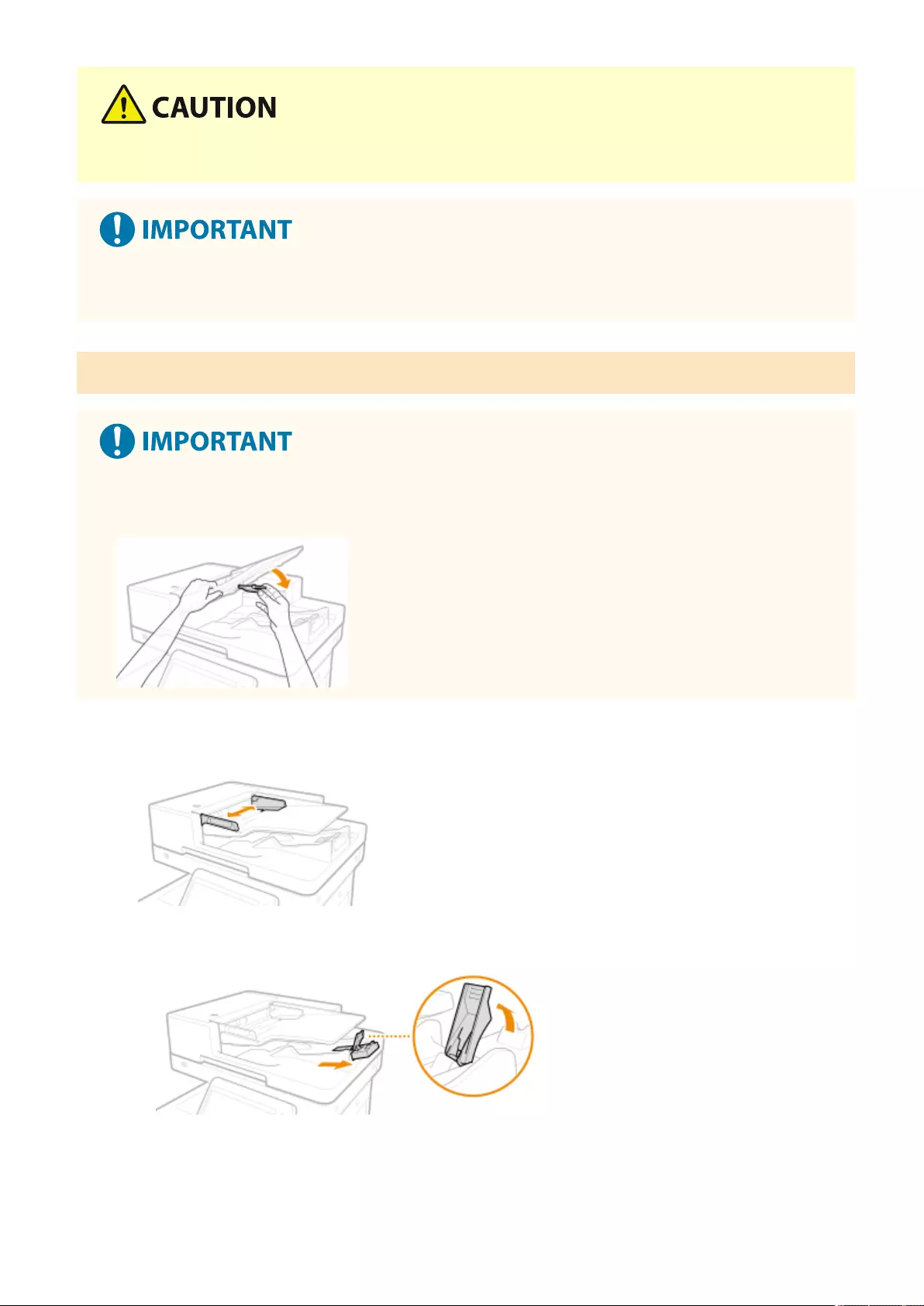
●When closing the feeder, take care that your eyes are not exposed to light emitted through the platen glass.
●If a thick original such as a book or magazine is placed on the platen glass, do not press down hard on the
feeder.
Placing Originals in the Feeder
●Do not place items in the original output tray, as doing so may cause damage to your originals.
●Check that the original retainer is lowered.
1Align the slide guides to t the size of your originals.
●When loading originals that are LGL size, pull out the original output tray extension and raise the original
stopper to prevent the ends of the originals from drooping over the end of the tray.
●If the output originals are not stacked evenly, just raise the original stopper.
2Fan the original stack and align the edges.
Basic Operations
99
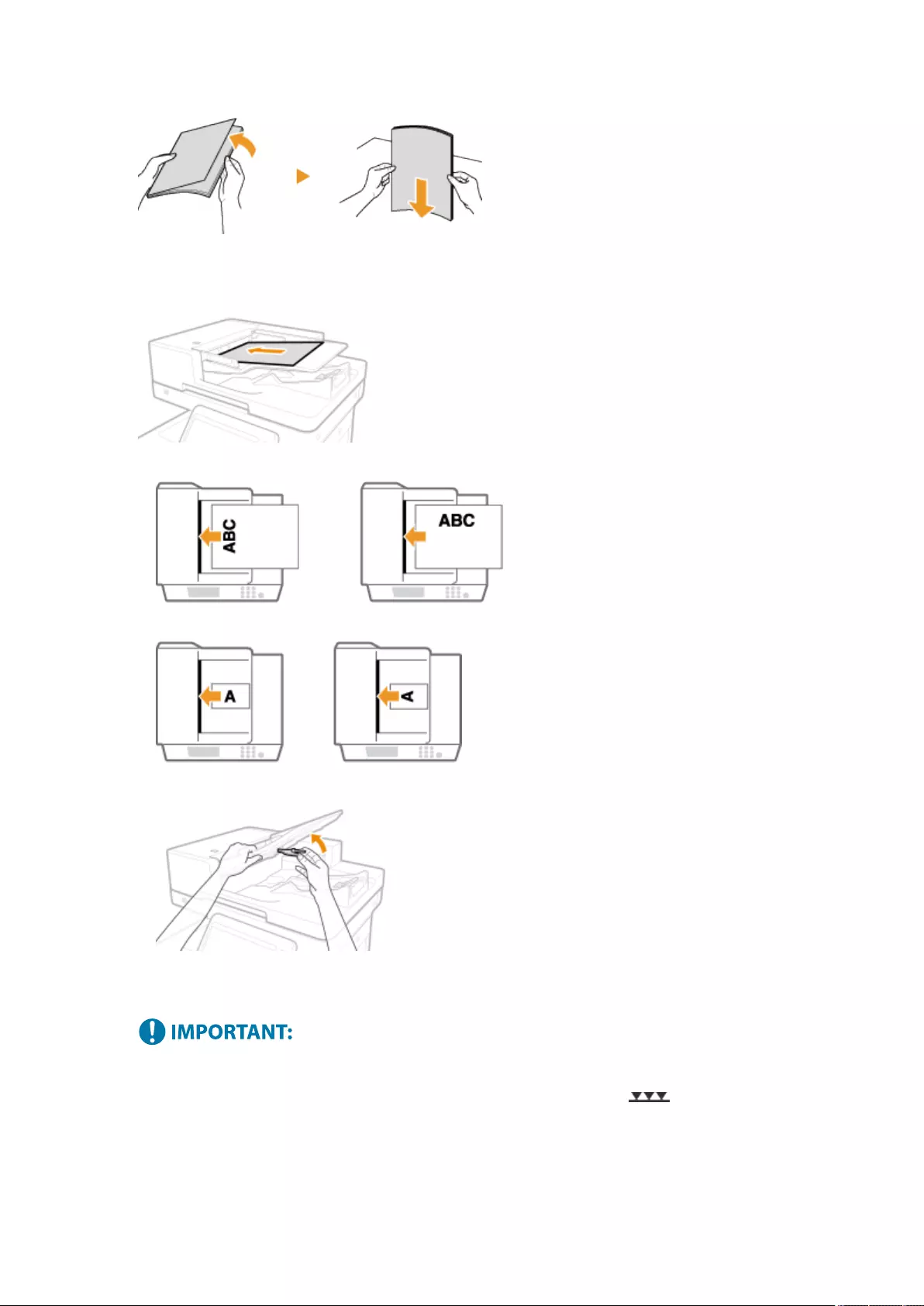
●Fan the original stack in small batches, and align the edges by lightly tapping the stack on a at surface a few
times.
3Place the originals face up and as far into the feeder as they will go.
●Place the original so that its top and bottom are properly positioned, as shown in the following illustrations.
●Load originals with short edges of 87 mm or less oriented as shown in the following illustrations.
●When scanning thin originals (52 g/m² or less) or A6R size or smaller originals, raise the original retainer.
➠Originals are ready for scanning.
●Before starting the scanning, specify the paper size and scanning size to match the size of the original.
Load limit lines
●Make sure that the original stack does not exceed the load limit lines ( ). If you place originals that
exceed the limit, they may not be scanned or may cause a paper jam.
When placing an original that is folded
●Always smooth out any folds in your originals before placing them into the feeder.
Align the slide guides securely against the edges of the original
Basic Operations
100
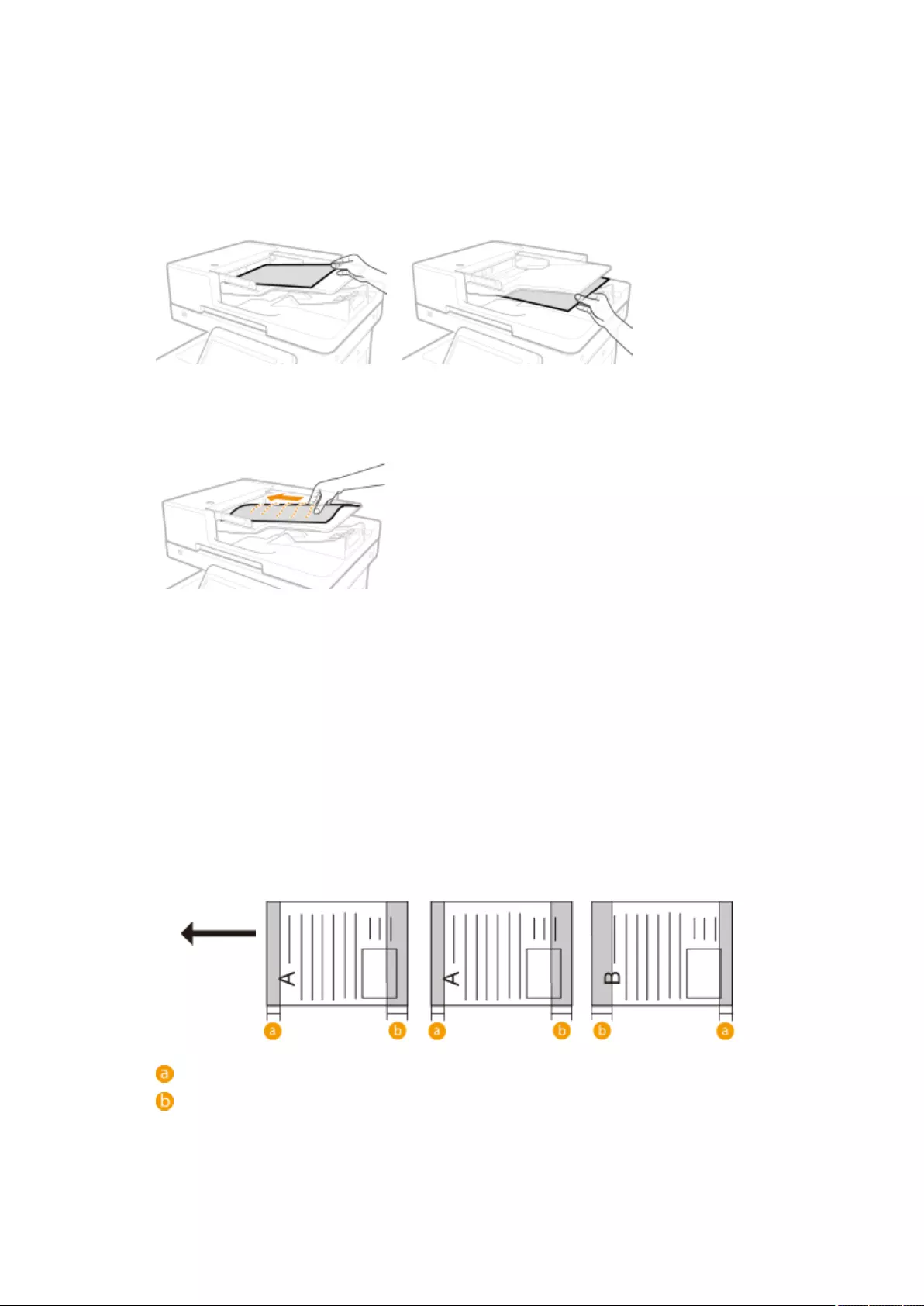
●Slide guides that are too loose or too tight can cause misfeeds or paper jam.
While originals are being scanned
●Do not add or remove originals.
When scanning long strip originals
●If you scan long originals (which have a length of up to 630 mm), support the originals by hand when
scanning and outputting paper.
When placing thin paper originals
●Thin originals may become creased, if used in a high temperature or high humidity environment.
●It may be dicult to place thin paper originals. In this case, lightly bend the paper while placing it.
●Make sure that you do not push too hard when placing the original. The original may not be fed correctly,
or may cause a paper jam.
When repeatedly scanning the same original
●It is recommended that you do not repeatedly scan the same original more than ve times (this varies
depending on paper quality). The original may fold or become wrinkled, or become dicult to send.
Color original scan range
●When a color original is scanned with a setting made for automatic color discrimination, it may be
identied as a black-and-white document if it contains color portions only in the gray areas as shown in
the following gure.
1-sided originals 2-sided originals
Front side Back side
Paper feed
direction
: 10 mm
: 17 mm
●To scan originals as color document, set the machine to Full Color mode.
Basic Operations
101

Loading Paper
72JY-01Y
You can load the paper into the paper drawer or multi-purpose tray. For more information about available paper types
and sizes, see Available Paper(P. 1109) . To obtain the optimum printing results, make sure to correctly specify the
size and type of paper that is loaded. Specifying Paper Size and Type(P. 141)
Basic Paper Loading Method(P. 103)
Loading Envelopes(P. 111)
Loading Preprinted Paper(P. 115)
●Before using any paper, conrm the precautions regarding paper and the correct way to store it.
Available Paper(P. 1109)
●Loading paper while stock remains may cause a multiple sheet feed or a paper jam. If there is paper
remaining, it is recommended that you wait until all of it has been used before loading more paper.
●Do not load different sizes or types of paper together.
LINKS
Registering Free Size Paper (Custom Size Paper)(P. 153)
Paper Feeder PF-D(P. 1120)
Cassette Feeding Unit-AV(P. 1121)
Basic Operations
102
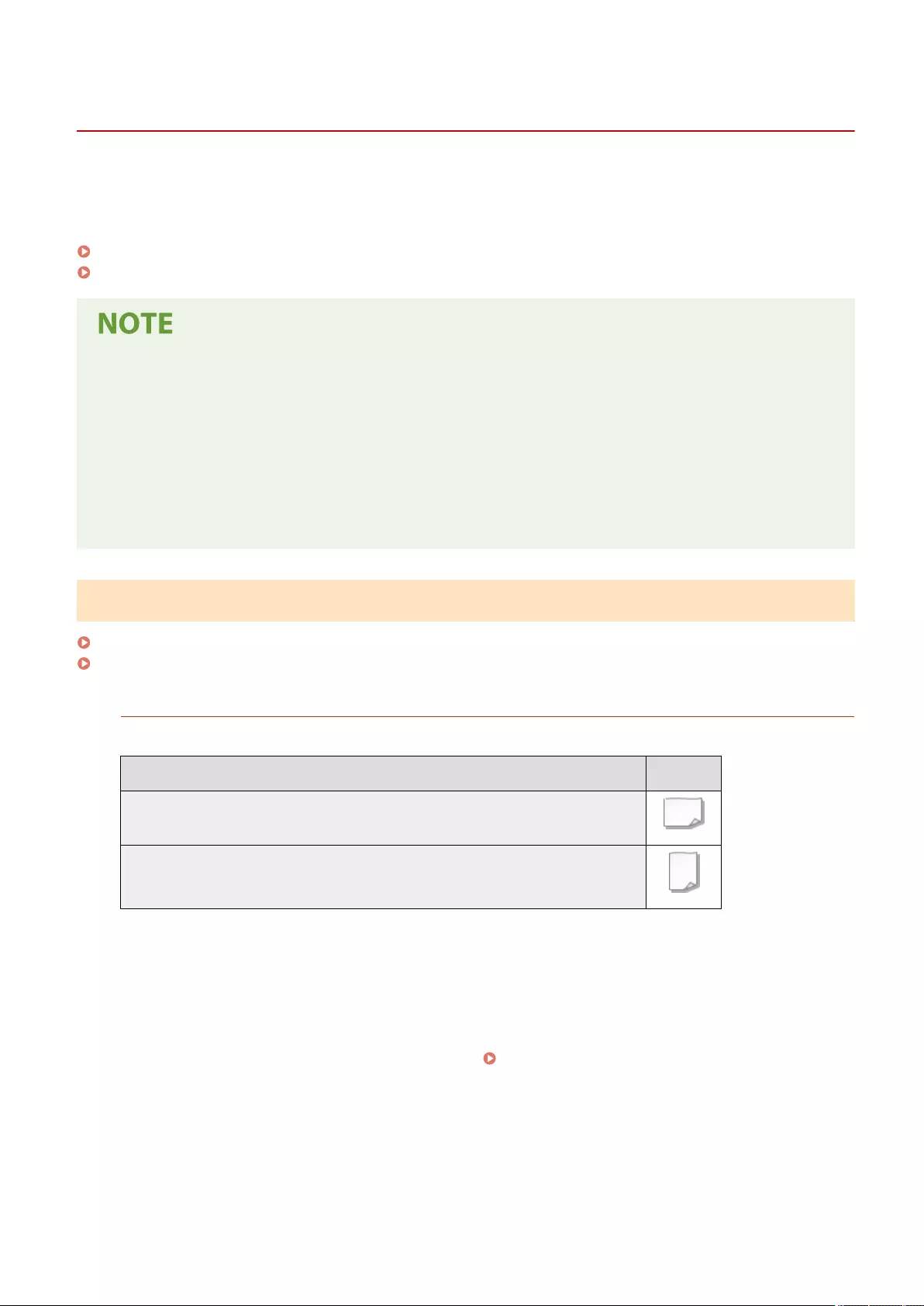
Basic Paper Loading Method
72JY-020
This section describes the general method for loading paper such as plain or recycled paper. Load frequently used
paper types or sizes in the paper drawer. When temporarily using paper that is not loaded in the paper drawer, load it
in the multi-purpose tray.
Loading Paper in the Paper Drawer(P. 103)
Loading Paper in the Multi-Purpose Tray(P. 107)
● For the optional Paper Feeder PF-D or Cassette Feeding Unit-AV, follow the procedure of paper drawer to
load paper.
●If there are instructions on the paper package about which side of the paper to load, follow those
instructions.
●Paper may overlap when it is fed or a paper jam may occur, depending on the cut surface of the paper.
Changing the paper orientation and loading it again may reduce the effect of the cut surface.
●If paper runs out and printing is stopped, load a new paper stack. Printing restarts after the new paper stack
is loaded.
Loading Paper in the Paper Drawer
Loading Standard Size Paper(P. 103)
Loading a Custom Size Paper(P. 105)
Paper Orientation
See the table below to load available paper in correct orientation.
Paper Orientation
A4, B5, A5 (landscape), A6, Legal*, Letter, Statement, Executive, 16K, Custom (landscape)
A5 (portrait), Custom (portrait)
* Can be loaded only in the optional Paper Feeder PF-D or Cassette Feeding Unit-AV.
◼Loading Standard Size Paper
To load paper whose size is found in the paper size markings on the paper drawer, use the following procedure. For
paper whose size is not found in the paper size markings, see Loading a Custom Size Paper(P. 105) .
1Pull out the paper drawer until it stops.
Basic Operations
103
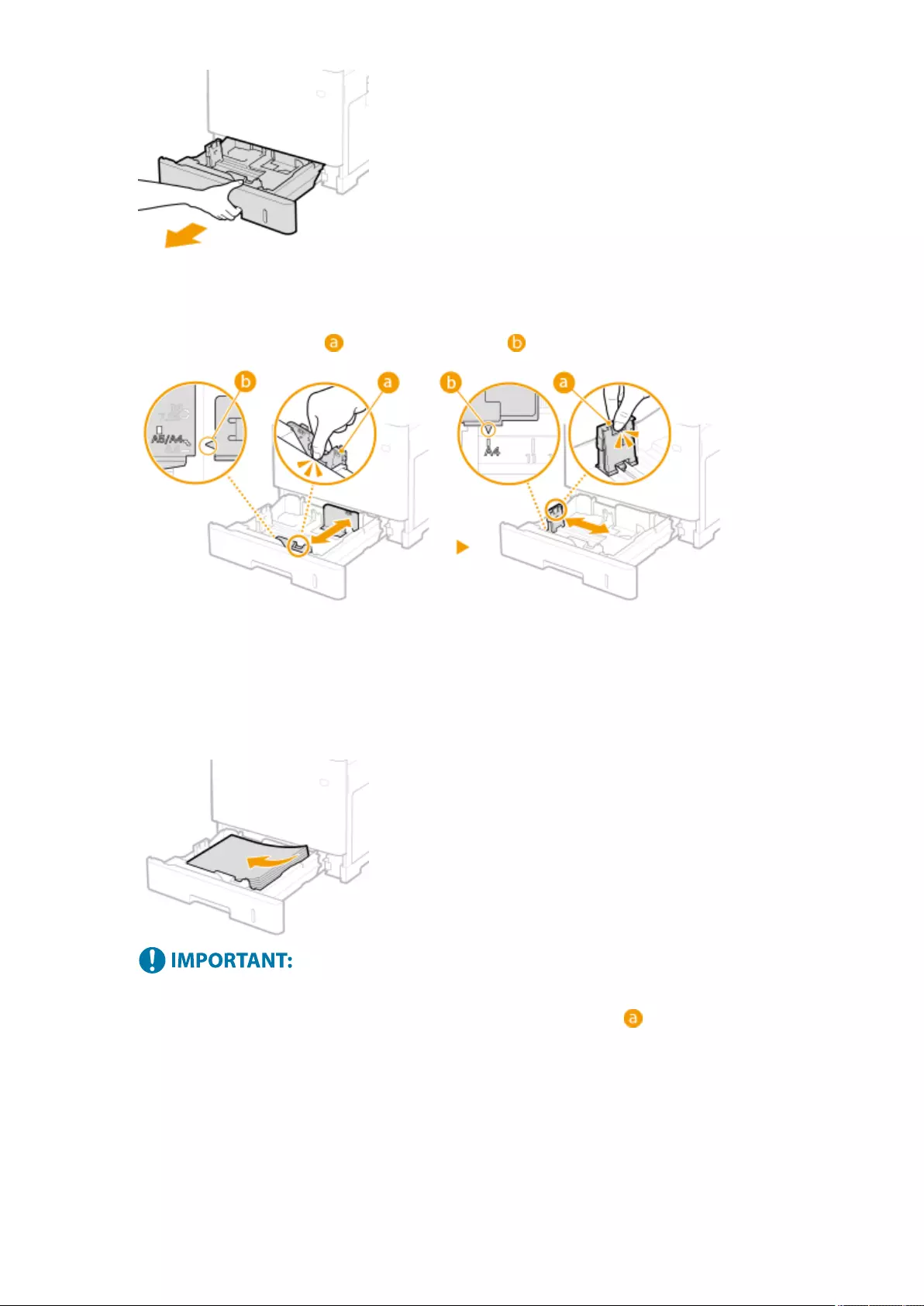
2Adjust the positions of the paper guides to the paper size you want to use.
●Press the lock release lever ( ) to align the projection ( ) to the appropriate paper size marking.
3Load the paper so that the edge of the paper stack is aligned against the paper guide
on the left side of the paper drawer.
●Insert the paper with the print side face up.
●Fan the paper stack well, and tap it on a at surface to align the edges.
Do not exceed the load limit line when loading paper
●Make sure that the paper stack does not exceed the load limit line ( ). Loading too much paper can
cause paper jams.
Basic Operations
104
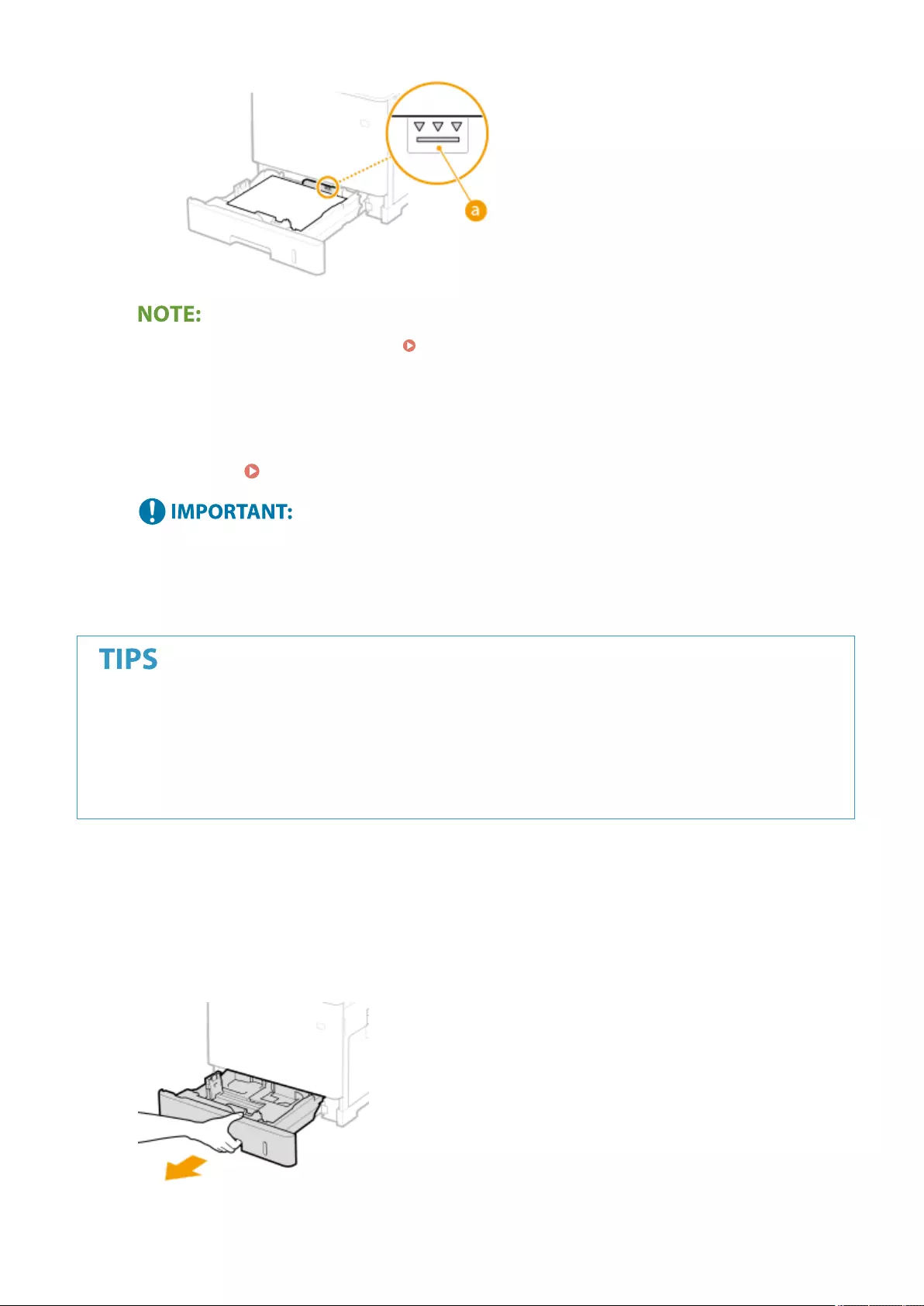
●When loading paper with a logo, see Loading Preprinted Paper(P. 115) .
4Set the paper drawer.
»Continue to Specifying Paper Size and Type in the Paper Drawer(P. 142)
When changing the paper size or type
●The factory default settings for paper size and type are <A4> and <Plain 2>, respectively. If you load a
different size or type of paper into the machine, make sure to change the setting. If you do not change the
paper size or type setting, the machine cannot print properly.
Printing on the back side of printed paper (2nd Side of 2-Sided Page)
●You can print on the back side of printed paper. Flatten any curls on the printed paper and insert it into the
multi-purpose tray, with the side to print face down (previously printed side face up). Then press <2nd Side
of 2-Sided Page> on the screen for selecting the paper type.
●Use only the paper printed with this machine.
◼Loading a Custom Size Paper
To load custom size paper or other paper whose size is not found in the paper size markings on the paper drawer, use
the following procedure.
1Pull out the paper drawer until it stops.
Basic Operations
105
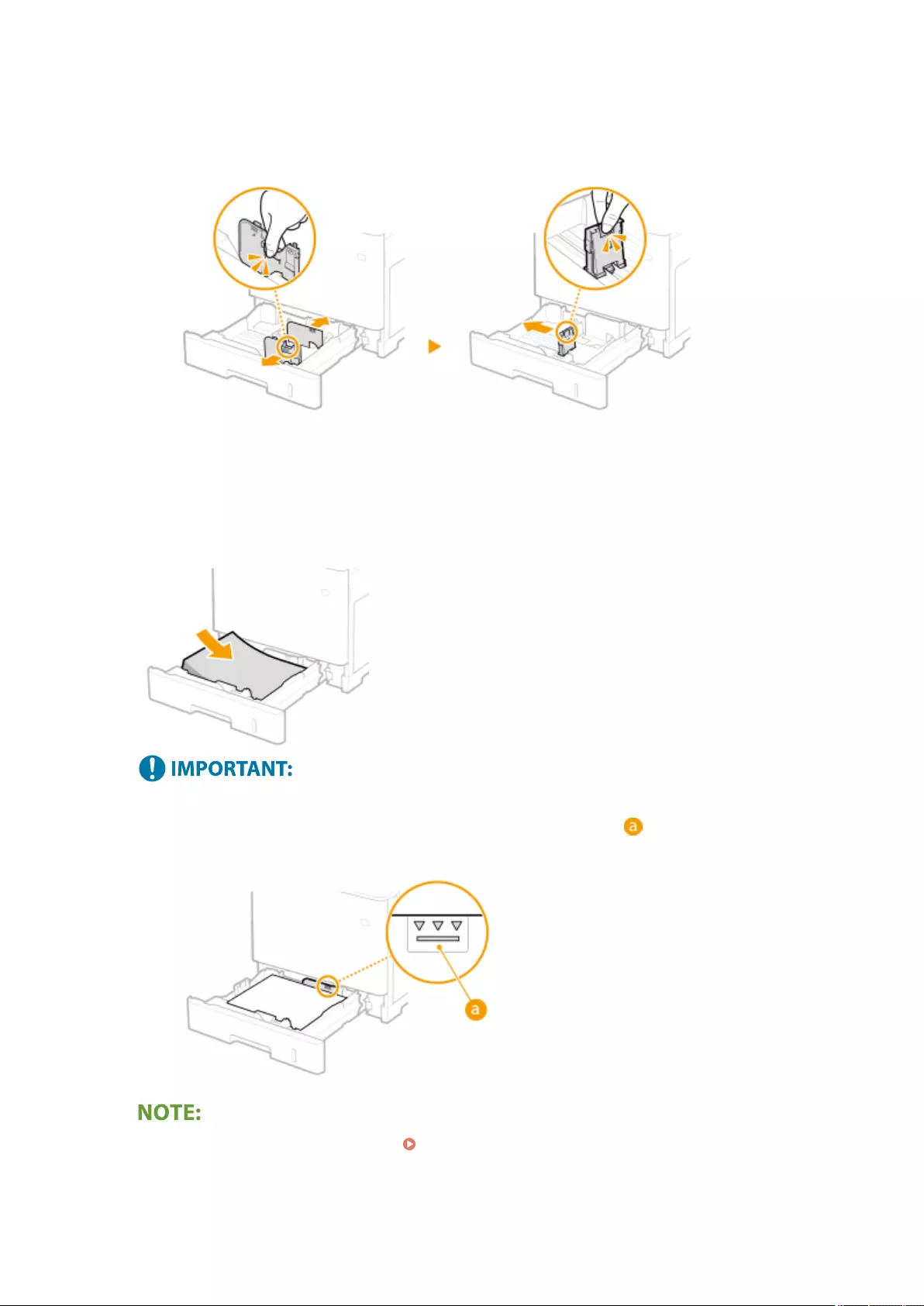
2Slide the paper guides apart.
●Press the lock release lever to slide the paper guides outward.
3Load the paper so that the edge of the paper stack is aligned against the right side of
the paper drawer.
●Place the paper stack with the print side face up.
●Fan the paper stack well, and tap it on a at surface to align the edges.
Do not exceed the load limit line when loading paper
●Make sure that the paper stack does not exceed the load limit line ( ). Loading too much paper can
cause paper jams.
●When loading paper with a logo, see Loading Preprinted Paper(P. 115) .
4Align the paper guides against the edges of the paper.
Basic Operations
106
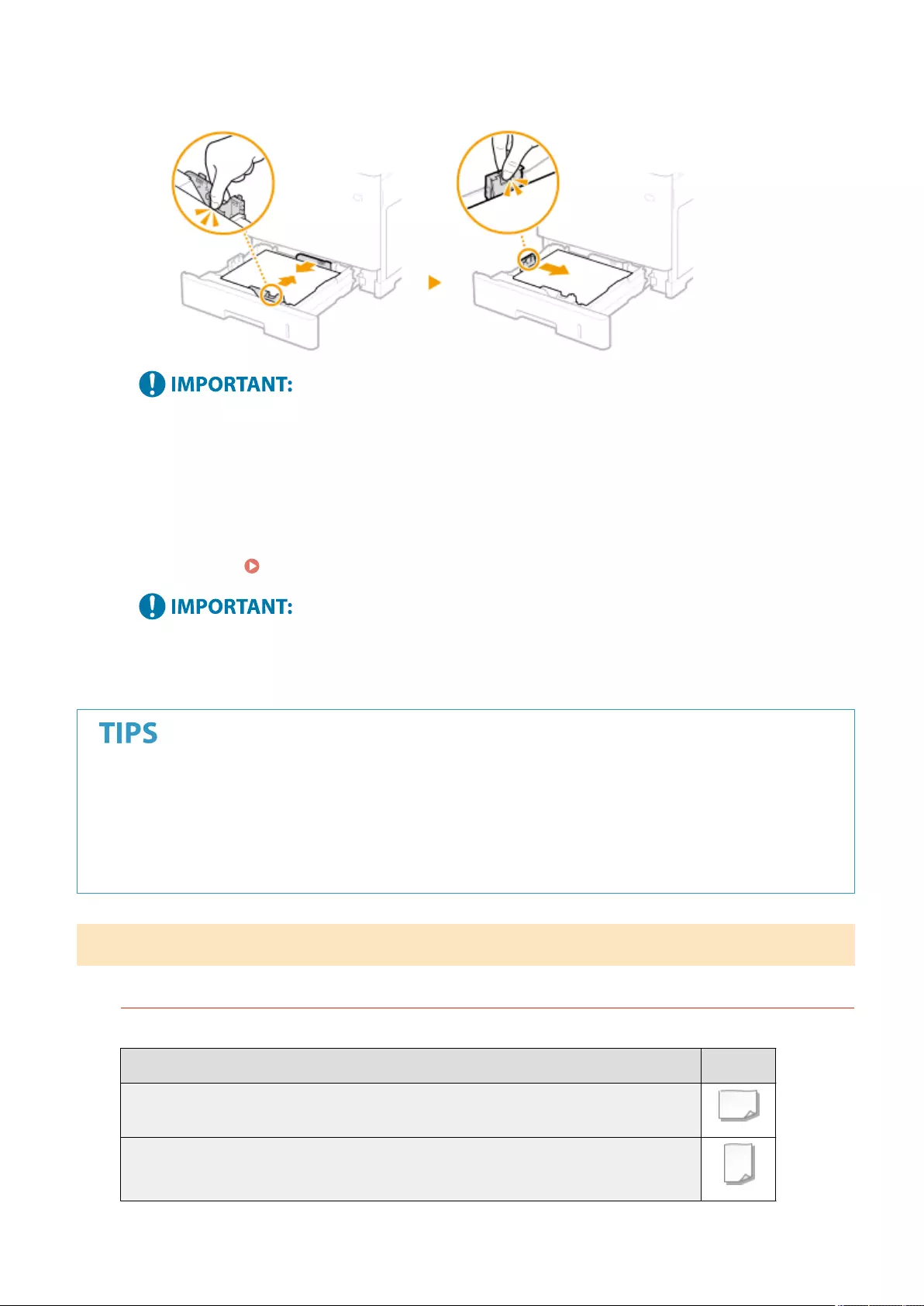
●Press the lock release lever and slide the paper guides inward until they are aligned securely against the
edges of the paper.
Align the paper guides securely against the edges of the paper
●Paper guides that are too loose or too tight can cause misfeeds or paper jams.
5Set the paper drawer.
»Continue to Specifying Paper Size and Type in the Paper Drawer(P. 142)
When changing the paper size or type
●If you load a different size or type of paper into the machine, make sure to change the settings. If you do
not change the paper size or type setting, the machine cannot print properly.
Printing on the back side of printed paper (2nd Side of 2-Sided Page)
●You can print on the back side of printed paper. Flatten any curls on the printed paper and insert it into the
multi-purpose tray, with the side to print face down (previously printed side face up). Then press <2nd Side
of 2-Sided Page> on the screen for selecting the paper type.
●Use only the paper printed with this machine.
Loading Paper in the Multi-Purpose Tray
Paper Orientation
See the table below to load available paper in correct orientation.
Paper Orientation
A4, B5, A5 (landscape), A6, Legal, Letter, Statement, Executive, 16K, Custom (landscape), Envelope
A5 (portrait), Custom (portrait)
Basic Operations
107
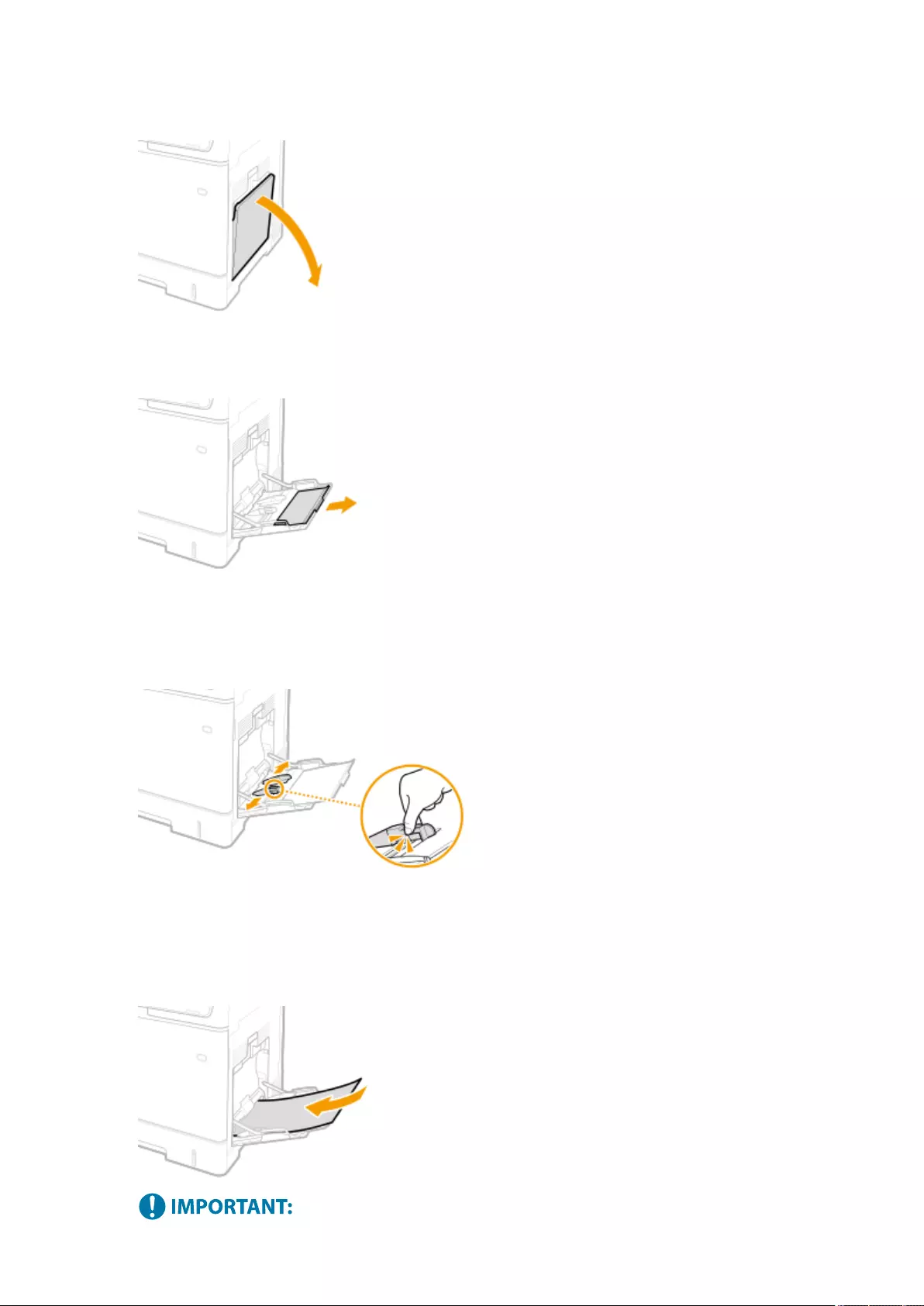
1Open the cover.
2Pull out the paper tray.
3Spread the paper guides apart.
●Press the lock release lever to slide the paper guides outward.
4Insert the paper into the multi-purpose tray until the paper stops.
●Insert the paper with the print side face down.
●Fan the paper stack well, and tap it on a at surface to align the edges.
Basic Operations
108
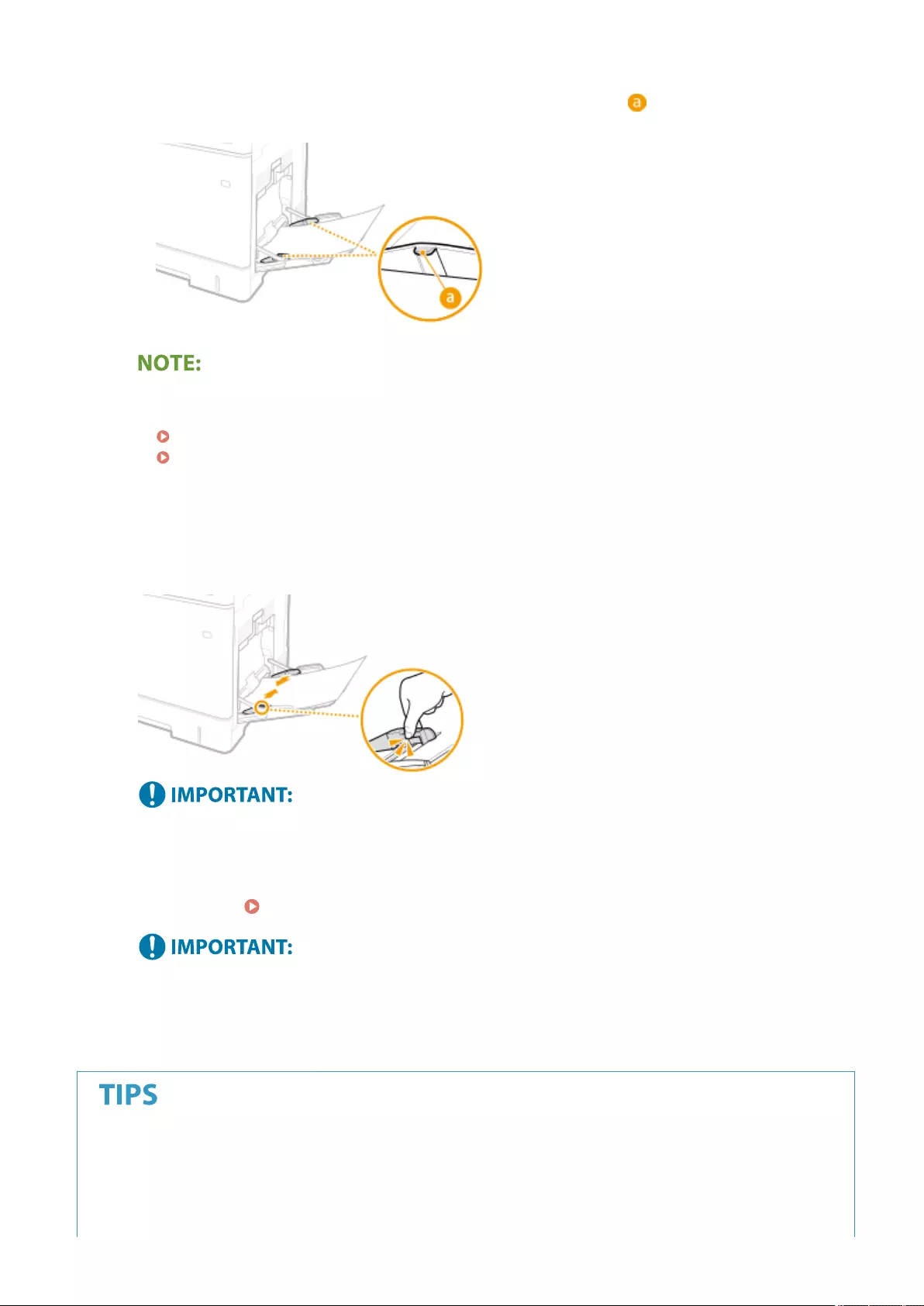
Do not exceed the load limit guide when loading paper
●Make sure that the paper stack does not exceed the load limit guide ( ). Loading too much paper can
cause paper jams.
●If you use envelopes or paper with a logo mark, pay attention to the orientation when loading them in the
paper source.
Loading Envelopes(P. 111)
Loading Preprinted Paper(P. 115) .
5Align the paper guides against the edges of the paper.
●Press the lock release lever and slide the paper guides inward until they are aligned securely against the
edges of the paper.
Align the paper guides securely against the edges of the paper
●Paper guides that are too loose or too tight can cause misfeeds or paper jams.
»Continue to Specifying Paper Size and Type in the Multi-purpose Tray(P. 145)
When changing the paper size or type
●The factory default settings for paper size and type are <A4> and <Plain 2>, respectively. If you load a
different size or type of paper into the machine, make sure to change the setting. If you do not change the
paper size or type setting, the machine cannot print properly.
Printing on the back side of printed paper (2nd Side of 2-Sided Page)
●You can print on the back side of printed paper. Flatten any curls on the printed paper and insert it into the
multi-purpose tray, with the side to print face down (previously printed side face up). Then press <2nd Side
of 2-Sided Page> on the screen for selecting the paper type.
Basic Operations
109
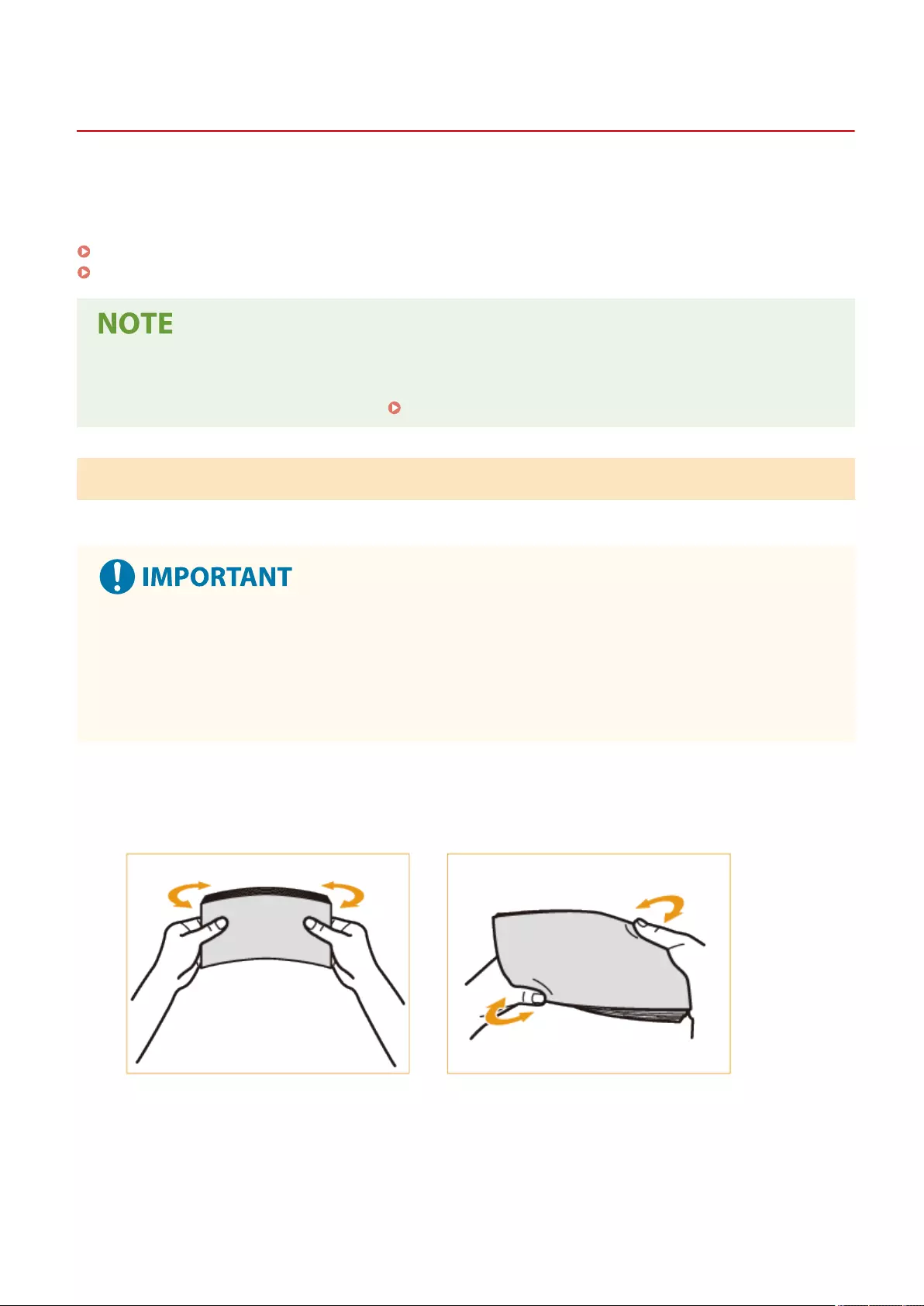
Loading Envelopes
72JY-021
Load envelopes in the paper drawer or multi-purpose tray. When printing on envelopes, to prevent paper jams and
wrinkles, make sure to atten any curls on envelopes before loading them. Also pay attention to the orientation of
envelopes and which side is face up.
Before Loading Envelopes(P. 111)
Loading Envelopes in the Multi-Purpose Tray(P. 113)
●This section describes how to load envelopes with the proper orientation, as well as procedures that you
need to complete before loading envelopes. For a description of the general procedure for loading
envelopes in the multi-purpose tray, see Basic Paper Loading Method(P. 103) .
Before Loading Envelopes
Follow the procedure below to prepare the envelopes before loading.
●Do not use envelopes that have glue attached to their aps, as the glue may melt due to the heat and
pressure of the xing unit.
●Envelopes may become creased, depending on the type of envelopes or the conditions in which they are
stored.
●Streaks may appear where envelopes overlap.
1Flatten any curls.
●Pick up about ve envelopes. Flatten any curls, and loosen the stiff areas in the four corners.
Basic Operations
111
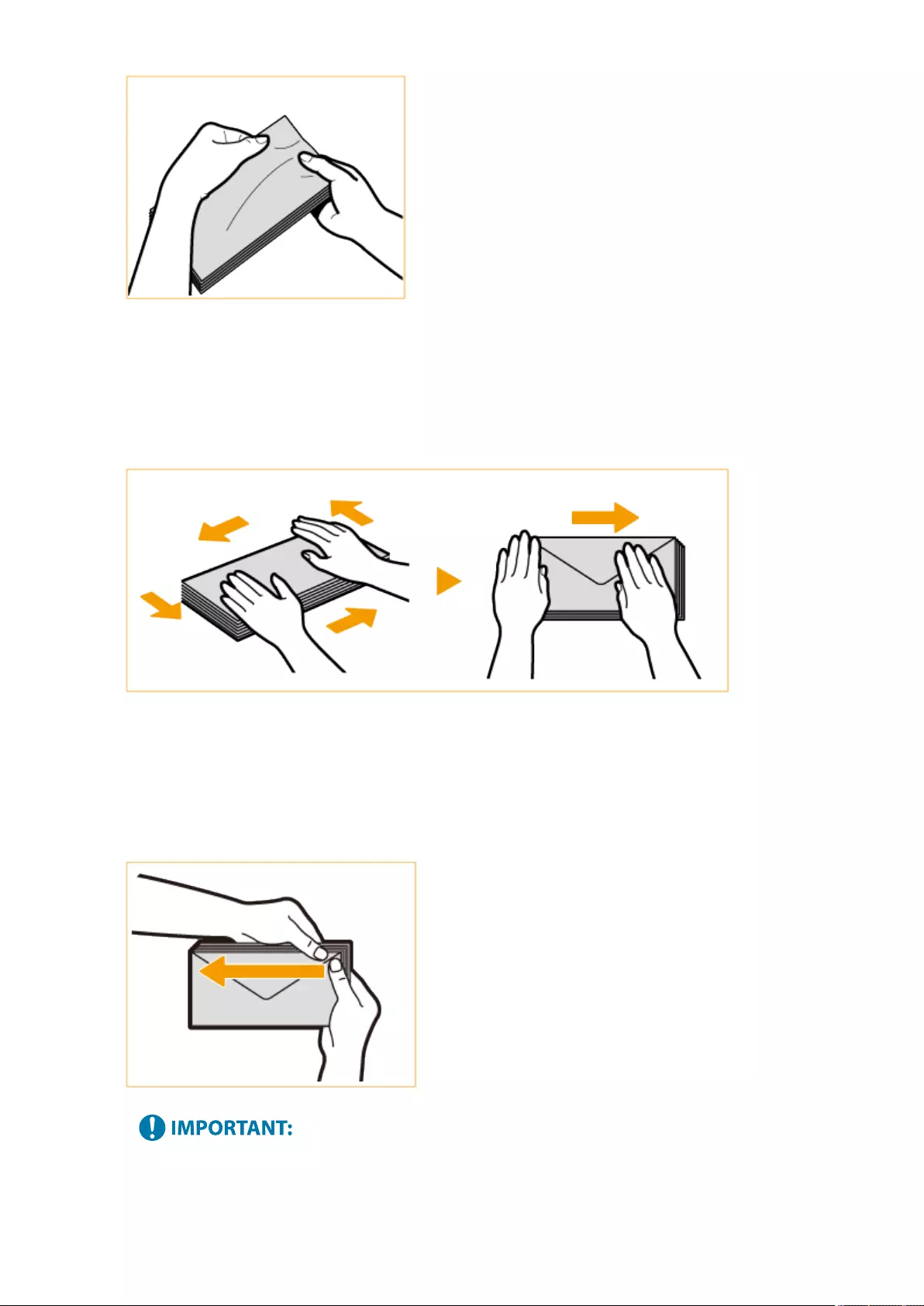
●Repeat this step ve times for each set of ve envelopes.
2Smooth the envelopes out, and remove any air inside them.
●Place the envelopes on a at surface, and move your hands in the direction of the arrows to remove the air
inside the envelopes.
●Repeat this step ve times for each set of ve envelopes.
3Press down on the four sides.
●Press down rmly on all four sides. In particular, carefully press down on the side facing the direction in
which the envelopes will be fed. Press down rmly so that the ap stays at.
●Failure to rmly press down on the ap may result in a paper jam. If this happens, press down rmly on all
four sides of each individual envelope.
Basic Operations
112
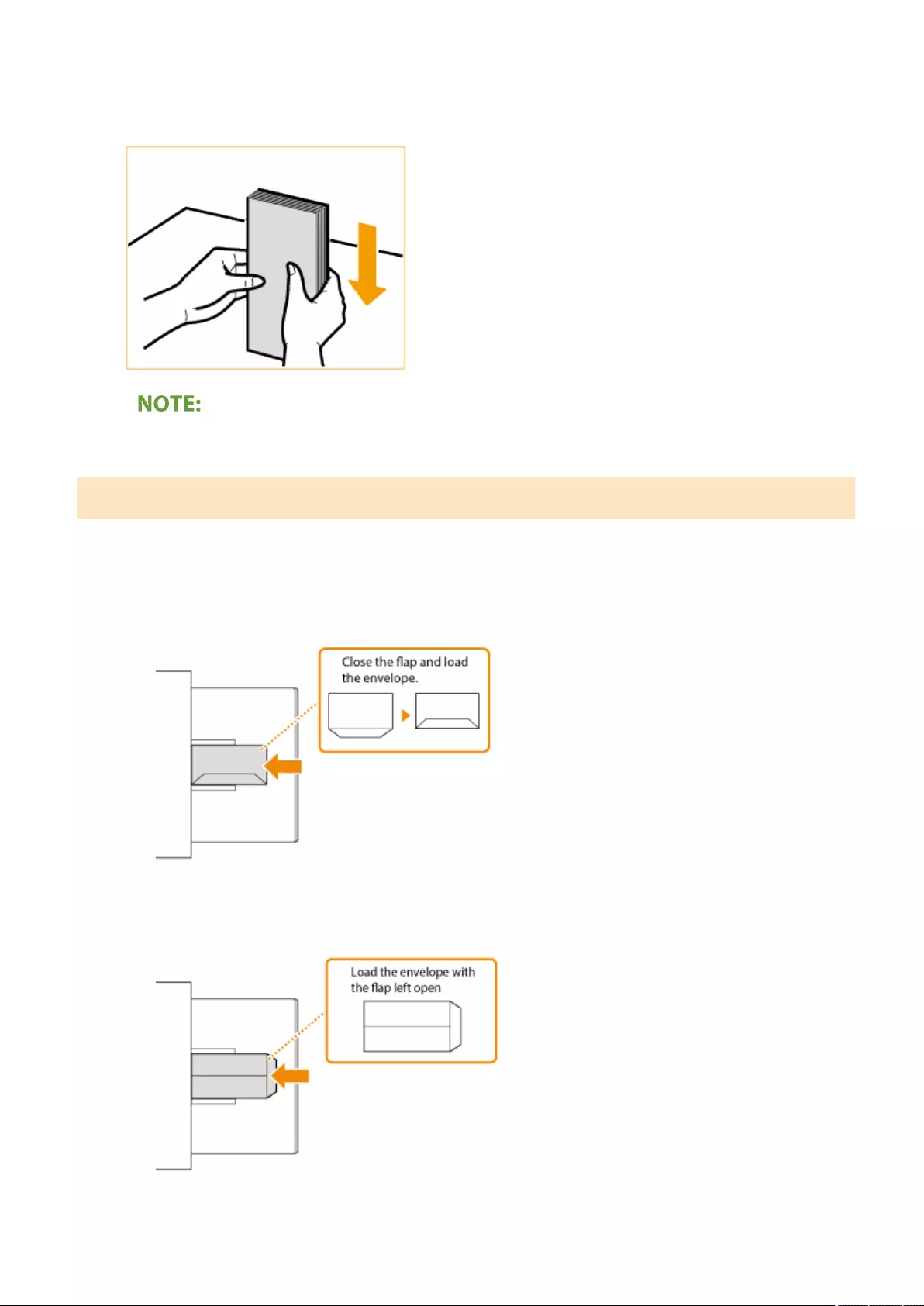
4Align the envelopes on a at surface.
●Check that no envelopes are tucked underneath the ap of the envelope above or below them.
Loading Envelopes in the Multi-Purpose Tray
Load the envelopes as indicated below, with the front side of the envelopes (the side without the glued areas)
face down (recommended).
Yougatanaga 3, ISO-5, Monarch, No.10, DL
Close the aps, and load the envelopes so that their aps are on the near side.
Nagagata 3
Load the envelopes so that their aps are on the right side.
Basic Operations
113

●Make sure that the paper stack does not exceed the load limit guide. If the envelopes are not fed properly
even if they have been prepared according to the procedures, load the envelopes individually in the multi-
purpose tray instead of loading several envelopes together.
●Do not print on the reverse side of the envelopes (the side with the glued areas).
●When you print on envelopes, remove them from the output tray 10 at a time.
Basic Operations
114
Loading Preprinted Paper
72JY-022
When you load paper that has been preprinted with a logo, pay attention to the orientation of the paper regardless of
whether you use the paper drawer or the multi-purpose tray. Load the paper properly so that printing is performed on
the same side as the logo.
Loading Paper with Logos in the Paper Drawer(P. 116)
Loading Paper with Logos in the Multi-Purpose Tray(P. 116)
When performing a copy operation, also pay attention to the orientation of the original
document
●Place the original in the feeder with the side to copy face up, or place the original on the platen glass with
the side to copy face down, as shown in the following illustrations.
Feeder (A portrait layout document) Platen glass (A portrait layout document)
Feeder (A landscape layout document) Platen glass (A landscape layout document)
●Also, of the copy settings, make sure that <Original Content Orientation> is set correctly. Basic Copy
Operations(P. 220)
●This section describes how to load preprinted paper with the proper orientation. For a description of the
general procedure for loading paper in the paper drawer or multi-purpose tray, see Basic Paper Loading
Method(P. 103) .
Basic Operations
115
●This section describes how to load preprinted paper when performing one-sided copying/printing. When
performing two-sided copying/printing using preprinted paper, load paper by interpreting that the
indications in this section referring to the facing of the paper mean the opposite.
●To ensure that pages are printed on the proper side of preprinted paper irrespective of one-sided or two-
sided printing, you can use the following setting methods.
- By specifying the paper type each time to print: load the paper type registered with "Preprinted Paper" set
to <On> in <Paper Type Management Settings>, specify that paper type and then perform the printing.
- By specifying the paper source each time to print: load paper in the paper source for which <Switch Paper
Feed Method> is set to <Print Side Priority>, specify that paper source and then perform the printing.
●Proper manner of loading preprinted paper when "Preprinted Paper" is set to <On> in <Paper Type
Management Settings> or when <Switch Paper Feed Method> is set to <Print Side Priority>
- Paper drawer: the logo side face down
- Paper source other than the paper drawer: the logo side face up
Loading Paper with Logos in the Paper Drawer
The loading method varies depending on whether the orientation of the logo printed paper is portrait or landscape.
Load the paper with the logo printed side (the side to print) face up, as shown in the following illustrations.
Portrait orientation paper The printing results
Landscape orientation paper (printing) The printing results
Landscape orientation paper (copying) The printing results
Loading Paper with Logos in the Multi-Purpose Tray
The loading method varies depending on whether the orientation of the logo printed paper is portrait or landscape.
Load the paper with the logo printed side (the side to print) face down, as shown in the following illustrations.
Basic Operations
116
Portrait orientation paper The printing results
Landscape orientation paper (printing) The printing results
Landscape orientation paper (copying) The printing results
Basic Operations
117
Using the Touch Panel Display
72JY-023
The display of the machine is a touch panel that can be operated by touching directly with your ngers. The screen is
used not only for basic functions such as copying and scanning, but also to display various settings, text input,
communication status and error messages. In this manual, however, "touch" is indicated as "press."
Basic Screens on the Touch Panel Display(P. 119)
Basic Operation of the Touch Panel Display(P. 130)
Entering Characters(P. 135)
Regarding the handling of the touch panel display
●Do not press the touch panel display too hard. Doing so may break the touch panel display.
●Do not use an object with a sharp end, such as a mechanical pencil or ballpoint pen. Doing so may scratch
the surface of the touch panel display or break it.
●Placing objects on the display or wiping the display may cause the touch panel to react and lead to a
malfunction.
●Peel off the protective lm from the touch panel display before use.
●You can customize menus and rearrange frequently used buttons for easier access. You can also combine
multiple settings into one button to simplify operations. Customizing the Touch Panel Display(P. 156)
Adjust the brightness of the touch panel display
Adjust Brightness
If it is hard to see the content of the touch panel display, adjust the brightness by operating the control panel.
<Adjust Brightness> adjust the brightness with <+> or <-> <Close>
LINKS
Control Panel(P. 93)
Basic Operations
118
Basic Screens on the Touch Panel Display
72JY-024
This section describes the various screens displayed on the touch panel display.
Home
<Home> Screen
The <Home> screen is displayed when you press (Home). The <Home> screen displays a list of function
buttons and acts as the entrance to various functions. Items Displayed on the <Home> Screen(P. 122)
Basic Features Screen of Each Function
On the <Home> screen, press the function buttons to display the Basic Features screen where you can access
basic functions such as copying, faxing and scanning. Though the display and setting items on the Basic
Features screen differ depending on functions, you can change the settings to suit your needs. Customizing
the Basic Features Screen(P. 167)
Example: Copy Basic Features screen
Items displayed differ depending on functions.
Copy Basic Features Screen(P. 218)
Fax Basic Features Screen(P. 273)
Scan Basic Features Screen(P. 374)
<Settings/Registration> Screen
Press (Settings/Register) to display the <Settings/Registration> screen. Press this key rst to make changes
for each setting, such as paper settings, display settings, and network settings. On this screen, you can also
register destinations, such as e-mail addresses and fax numbers.
Settings/Registration(P. 670)
Registering Destinations(P. 190)
Basic Operations
119

Current menu level
The screen names of the current level and one level above are displayed.
Setting item list
Setting items that belong to the current menu level are displayed in a list.
●When there is no menu under the lower level, the setting screen is displayed.
Status Monitor
<Status Monitor> Screen
When you press (Status Monitor), the <Status Monitor> screen is displayed. On this screen, you can check
the printing status and transmission status, as well as the remaining amount of toner and memory level.
Status and logs of copy/print/transmission/saved documents
The current status or log of the selected item is displayed. You can cancel copying, printing, and fax
transmission on this screen.
Cancelling Copying(P. 231)
Canceling Sending Faxes(P. 289)
Scan Basic Features Screen(P. 374)
Canceling Printing(P. 346)
Checking the Printing Status and History(P. 348)
Consumables
You can check the status of the machine, such as the amount of toner or paper remaining and memory
levels.
Hardware Specications(P. 1103)
Checking the Remaining Amount of Consumables(P. 891)
Basic Operations
120
Error Screen
In some cases when an error occurs, instructions on how to respond to the error are displayed. Follow the on-
screen instructions to solve the problem. Countermeasures for Each Message(P. 943)
Example: When a paper jam occurs
●Press displayed on the <Home> screen and the Basic Features screen to customize the screen such as
rearranging buttons or creating a shortcut key. Customizing the Touch Panel Display(P. 156)
●You can change settings regarding the screen display, such as which screen appears immediately after
turning ON the machine, and whether the message appears for remaining paper and toner. <Display
Settings>(P. 773)
●You can set the screen to be displayed when a certain amount of time has passed without operation.
<Function After Auto Reset>(P. 779)
LINKS
Control Panel(P. 93)
Basic Operations
121
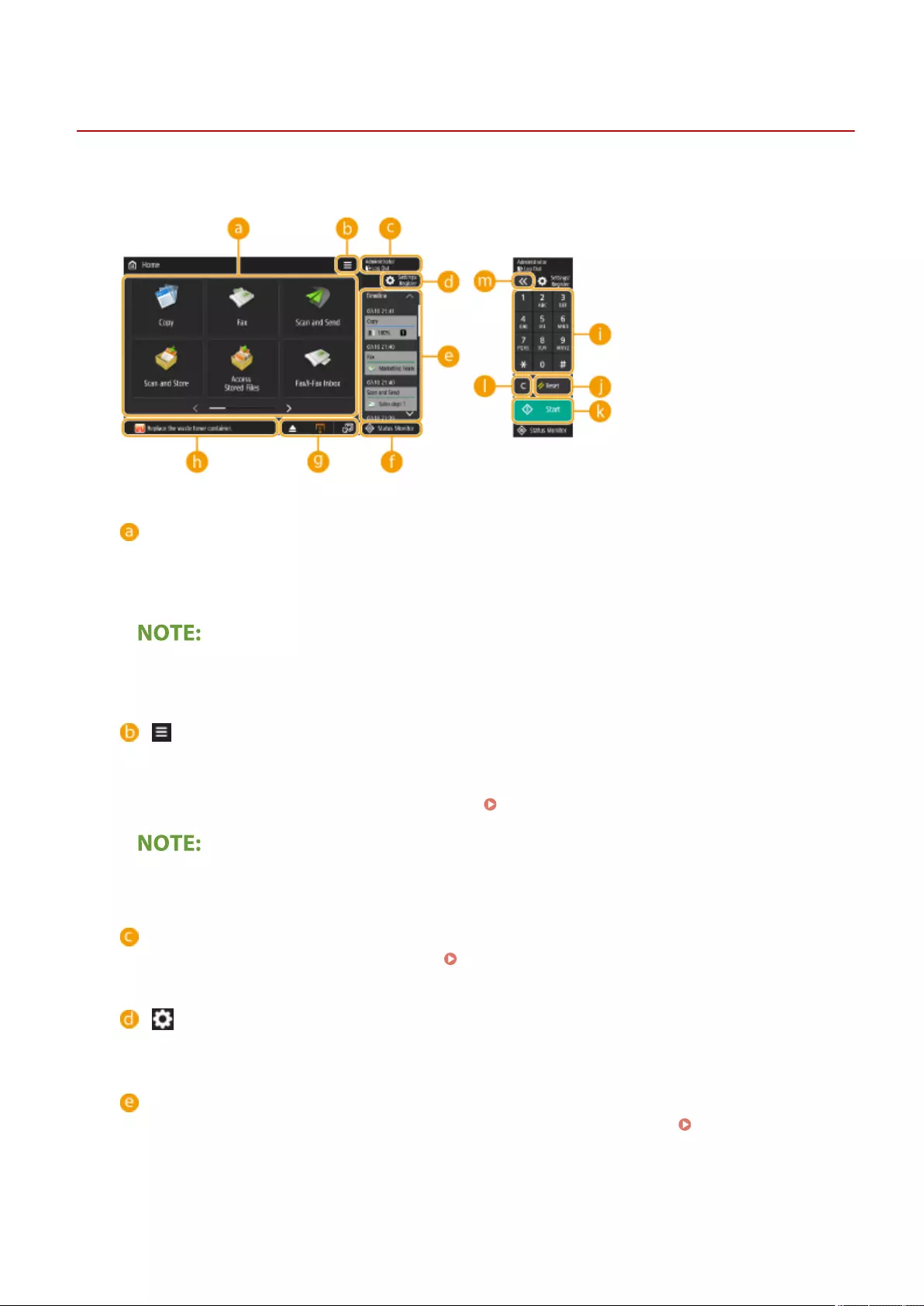
Home
Items Displayed on the <Home> Screen
72JY-025
This section describes the items displayed on the <Home> screen.
Function buttons
These buttons enable you to open the basic function screens, such as "Copy" and "Scan and Send".
When frequently used settings and destinations are registered as <Personal>/<Shared>, they are added as
buttons.
●When you press and hold a button, the settings related to the button appear.
This button enables you to customize and manage the <Home> screen. You can also display the menu by
pressing and holding the background.
Customizing the <Home> screen enables you to change the background and button size. Management
settings enable you to display/hide the timeline, etc. Customizing the <Home> Screen(P. 159)
●You can also display <Menu> by pressing and holding the background of the <Home> screen.
<Log In>/<Log Out>
You can log in/log out by pressing this button. Logging into the Machine(P. 137)
(Settings/Register)
You can display the <Settings/Register> screen by pressing this button.
<Timeline>
You can display the setting history and notices for some functions. For details, see Timeline Display
Specications(P. 125) .
Basic Operations
122

(Status Monitor)
You can check the print status, fax sending/receiving status, usage history, etc. It also enables you to check
the amount of remaining paper and toner, the error status, etc. Using the Touch Panel Display(P. 118)
Button display area
The following three types of buttons are displayed from left to right, according to the usage status and state
of the machine. The displayed buttons differ according to the model of your machine and its optional
equipment.
●Button for removing USB memory
: Memory media removal conrmation screen
●Button to the procedure for recovery/replacement/supply
: Paper jam recovery procedure screen
: Staple jam recovery procedure screen or staple cartridge replacement procedure screen
: Toner cartridge replacement procedure screen
: Waste toner container replacement procedure screen
: Staple waste/punch waste/trim waste removal procedure screen
: Replacement part replacement procedure screen
●<Switch Language/Keyboard> button
: Display language/keyboard switching screen
Status display area
The status of the machine, processes that are executing, errors, etc. are displayed via messages and icons.
Countermeasures for Each Message(P. 943)
Numeric keys
Numeric keys ([0] to [9], [*], [#])
Press to enter numerical values, *, and #. Entering Characters(P. 135)
Reset
(Reset)
Press to cancel the settings and restore the previously specied settings.
Start
(Start)
Press to start copying or scanning documents. You can adjust the touch time required to begin the start
process. <Start Key Touch Recognition Delay>(P. 804)
Clear
(Clear)
Press to clear entered values or characters.
Numeric key enlargement/reduction
/
Press to widen or narrow the range of the numeric keys displayed on the screen.
Basic Operations
123

● to are displayed on screens other than the <Home> screen.
Basic Operations
124
Timeline Display Specications
72JY-026
The following two types of information are displayed in the timeline.
Setting History(P. 125)
Notices(P. 126)
●For information on the icons and items displayed in the timeline, see Items Displayed in the
Timeline(P. 127) .
●A timeline can be displayed for each login user. If not logged in, a shared timeline can be displayed for users
who do not use authentication, such as unauthenticated users and guest users. Change the settings for
<Allow Non-Authentication Users to Use Timeline> and <Allow Each Login User to Use Timeline> according
to your needs. Customizing the <Home> Screen(P. 159)
●The timeline for users that do not use authentication, such as unauthenticated users and guest users, is
retained when <Quick Startup Settings for Main Power>(P. 777) is set to <On> and quick startup is
performed. When the power is turned OFF with <Quick Startup Settings for Main Power>(P. 777) set to
<Off> or quick startup could not be performed, the timeline for users that do not use authentication, such as
unauthenticated users and guest users, is deleted.
●The timeline cannot be imported/exported. Importing/Exporting the Setting Data(P. 625)
Setting History
The timeline is convenient for users who repeatedly use the same settings and destinations for a function such
as "Copy" and "Scan and Send". The history of settings used are automatically added to the timeline and can be
pressed to recall the same settings.
The timeline displays the settings of the following functions.
●Copy
●Fax
●Scan and Send
●Scan and Store (Network)
●Access Stored Files (Printing Network les)
●The latest 10 items of history are retained as the timeline in chronological order. The history of earlier jobs is
deleted from the timeline. When the job before last is used again, the order of the top two jobs is switched
but the number of jobs in the timeline does not change. However, if the settings are changed after being
recalled, they are deemed to be new settings.
Basic Operations
125

●To delete history that has been automatically added or store the settings of that history to the <Home>
screen as a Personal button/Shared button, press and hold the history. However, <Display Conrmation
Screen When Recalling> and <Start Operation for Recall (Operation starts when button is pressed.)> cannot
be set when registering a Personal button/Shared button from the timeline. Registering Personal
Buttons/Shared Buttons(P. 171)
●When <Restrict Resending from Log> is set to <On>, the history of "Fax" and "Scan and Send" is not retained
in the timeline.
●The following passwords can be included in the timeline for each login user.
- Login passwords to destination le servers for Scan and Send
- Encryption passwords for Scan and Store (<Password Required to Open Document> and <Password
Required to Change Permission>)
●Whether to include the password in the timeline of the logged in user can be changed in <Prohibit
Caching of Authentication Password>(P. 866) . However, the password in <Password> for the fax function
is retained in the timeline, regardless of the <Prohibit Caching of Authentication Password>(P. 866)
setting.
●The password is not retained in the timeline for unauthenticated users or guest users regardless of the
<Prohibit Caching of Authentication Password>(P. 866) setting. However, if the password in <Password>
for the fax function is set, it is not displayed in the timeline.
●If <Manage Address Book Access Numbers>(P. 849) is set to <On>, the send job log ("Fax" and "Scan
and Send") for unauthenticated users and guest users is not displayed in the timeline.
●The setting history of the user that is logged in can be shared with multiple machines as personalization
data using setting synchronization. List of Items That Can Be Personalized(P. 139)
●With Access Stored Files, les are saved to the timeline together with the settings they are printed with. You
cannot select another le and reuse the settings only. The corresponding timeline settings also cannot be
used if a le has been deleted or moved.
Notices
Notices are displayed when the user that is logged in has unprinted jobs. Printing can be executed by displaying
the print screen from the displayed timeline.
●Notices are not displayed in the timeline if <Personal> is set to <Off> in <Job List Display
Settings>(P. 847) .
●If <Display Other User Jobs>(P. 846) is set to <On>, the total number of unprinted jobs for the user that
is logged in and unprinted jobs for other users is displayed in the notices.
Basic Operations
126
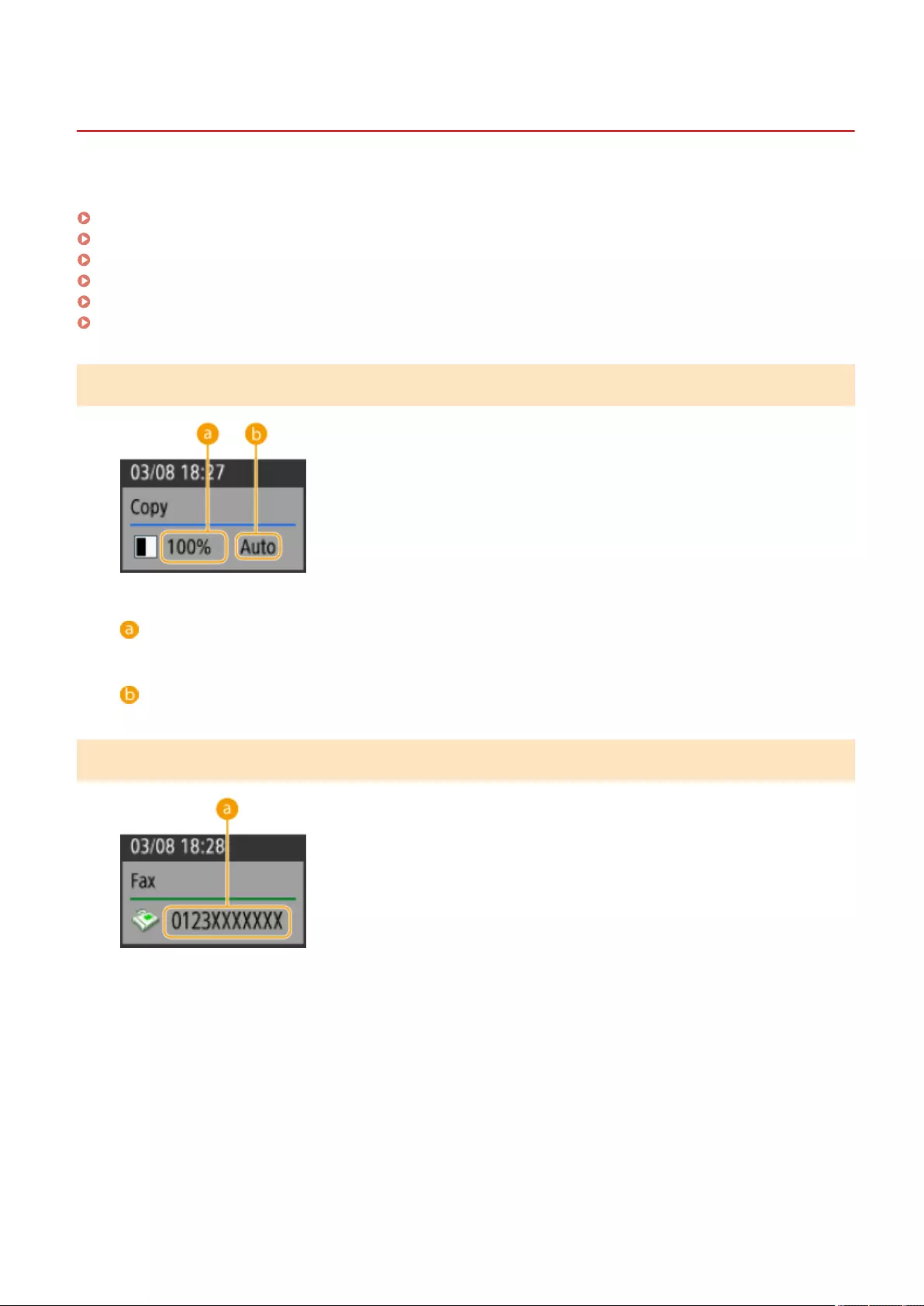
Timeline
Items Displayed in the Timeline
72JY-027
The items displayed in the timeline differ according to the function. The items for each function are described here.
Copy(P. 127)
Fax(P. 127)
Scan and Send(P. 128)
Scan and Store (Network)(P. 128)
Access Stored Files (Network)(P. 128)
Print(P. 129)
Copy
Zoom ratio
Paper source
Fax
Basic Operations
127
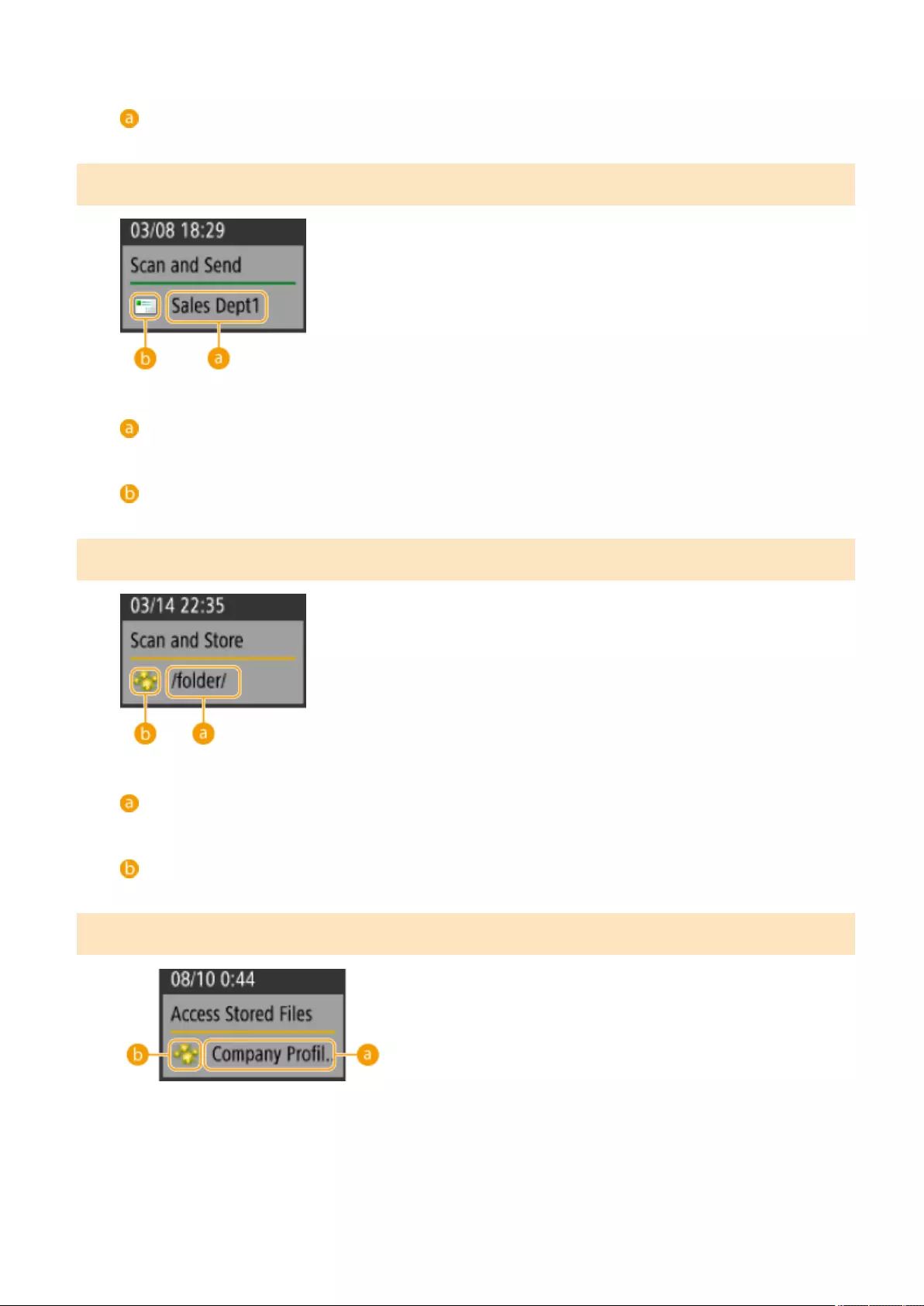
Destination
Scan and Send
First destination
Destination type of the rst destination
Scan and Store (Network)
Folder name
Mail Box icon
Access Stored Files (Network)
Basic Operations
128
File name
Mail Box type
●When multiple les are selected, the name of the le selected rst is displayed.
Print
Number of jobs waiting to be printed
Basic Operations
129
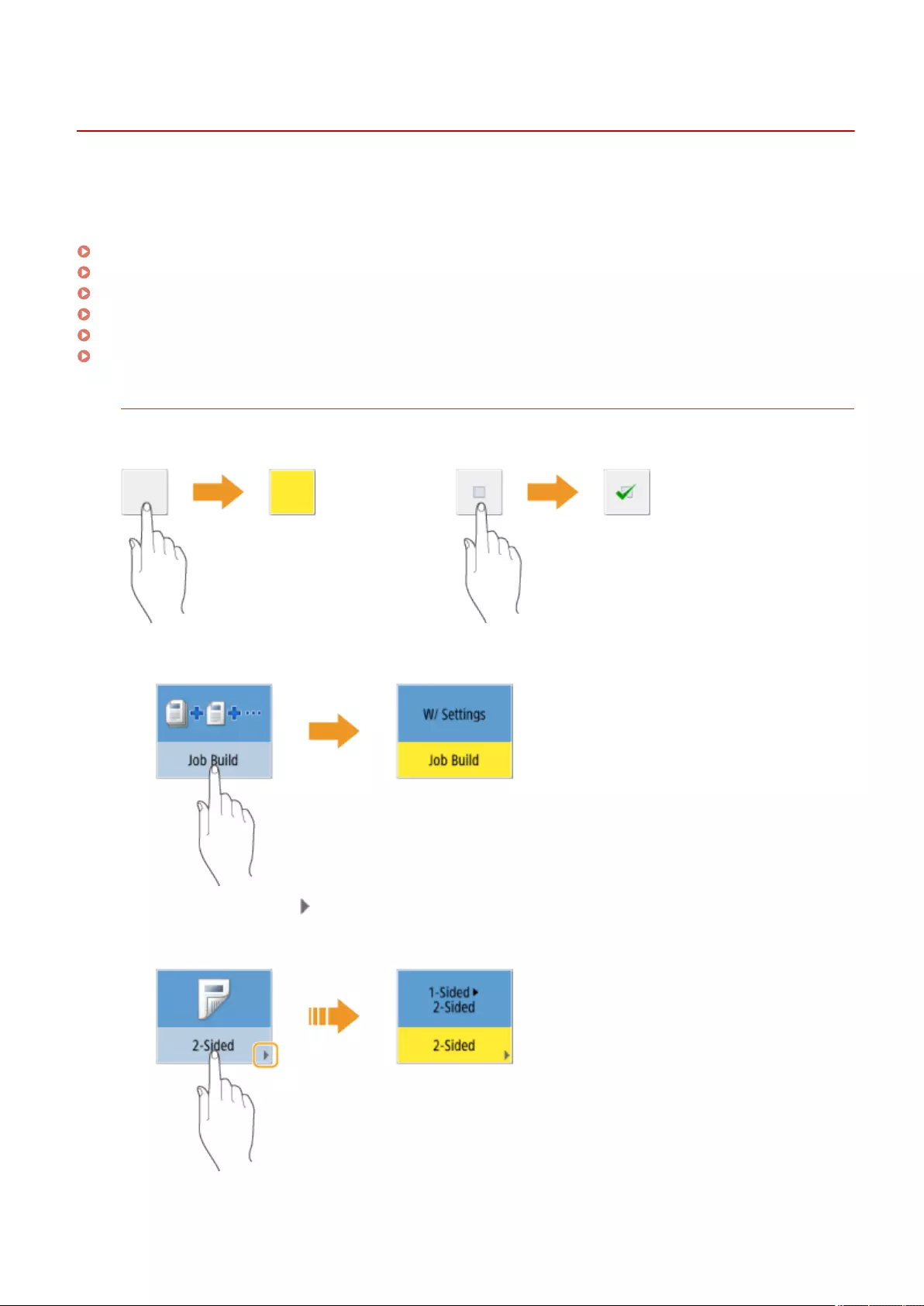
Basic Operation of the Touch Panel Display
72JY-028
Even though functions and settings are different, the operation methods for buttons displayed on the screen and the
procedure to select items are the same. This section describes the operation methods for buttons frequently displayed
on the screen as well as how to select items.
Selecting a Button(P. 130)
Selecting an Item from Drop-down List(P. 131)
Adjusting a Value to Increase or Decrease(P. 131)
Applying/Canceling Settings(P. 131)
Switching Pages(P. 132)
Changing the Display Order in the List(P. 132)
Selecting a Button
When you press a button, the button color may change or a check mark may be added to indicate that it has
been selected.
●Press the function setting button to display the setting status in the upper section of a button and the color
of the lower section is changed.
●Press a button in which is located in the lower-right to display the setting screen. When the setting is
made, the setting status is displayed in the upper section of the button and the color of lower section is
changed.
●When a button is displayed in a lighter color, you cannot select that button. Such displays appear depending
on login status or because its related function cannot be used as another function has been set.
Basic Operations
130
Selecting an Item from Drop-down List
Press a button in which is located in the right to display the drop-down list. Press the item on a list to select
an item.
Adjusting a Value to Increase or Decrease
Press the <-> or <+> buttons to decrease or increase values, such as when adjusting the density. Each time you
press the button, the slider ( ) moves to increase or decrease the numerical value. By holding down the
button, you can change the value quickly.
Applying/Canceling Settings
Press <OK> to apply settings and press <Cancel Settings> to discard the changes and restore the previous
settings.
●In addition, buttons such as <Cancel> which cancels the setting and returns to the previous screen, <Next>
which applies the setting to proceed to the next screen, <Back> which returns to the previous setting screen
and <Close> which closes the screen currently open are displayed.
Basic Operations
131
Switching Pages
When a list display is two pages or more, press / or / to switch the page. Press to jump to the
rst page, press to jump to the last page.
Changing the Display Order in the List
When there are multiple jobs/les in a list, you can press <Name> or <Date/Time> to sort the list of items. When
is displayed, items are displayed in ascending order, or when is displayed, items are displayed in
descending order.
●Sorting conditions differ depending on the function you are using.
●If you log in with personal authentication management, the sorting condition that was last used is
retained. List of Items That Can Be Personalized(P. 139)
Tutorial
View the function guide
Press <Tutorial> to display a screen that introduces what you can do with the functions of the machine as well
as tips for using copy, scan, etc. View this screen when you want to learn more about what functions are
available and how to use them.
Basic Operations
132
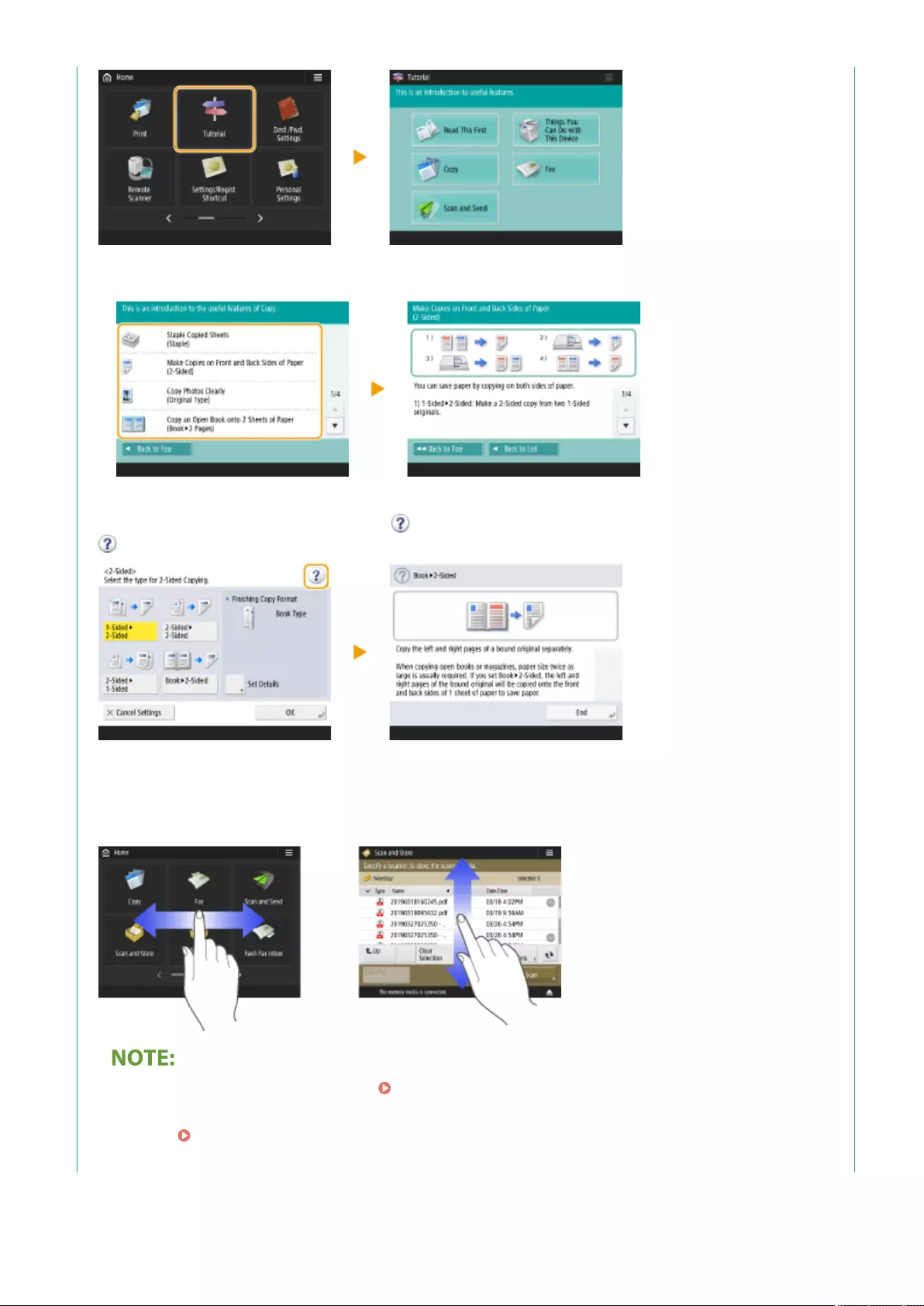
Example: Tutorial for Copy functions
●When you select an item from the list, the tutorial screen is displayed.
Use the Help function
Depending on the function being displayed, is sometimes displayed on the upper-right of the screen. Press
to check the description and operation method of the function.
●Press <End> to return to the previous screen.
Operate in the same manner as with a smartphone (ick/drag-and-drop)
On some screens, you can switch the page or scroll by icking your nger up/down or left/right on the screen as
you would with a smartphone.
●You can also disable ick operations. <Use Flick Function>(P. 797)
●Flick operations and drag-and-drop operations cannot be used when <Invert Screen Colors> is set to
<On>. <Invert Screen Colors>(P. 797)
On screens with movable buttons, the buttons can be dragged and dropped to move them.
Basic Operations
133
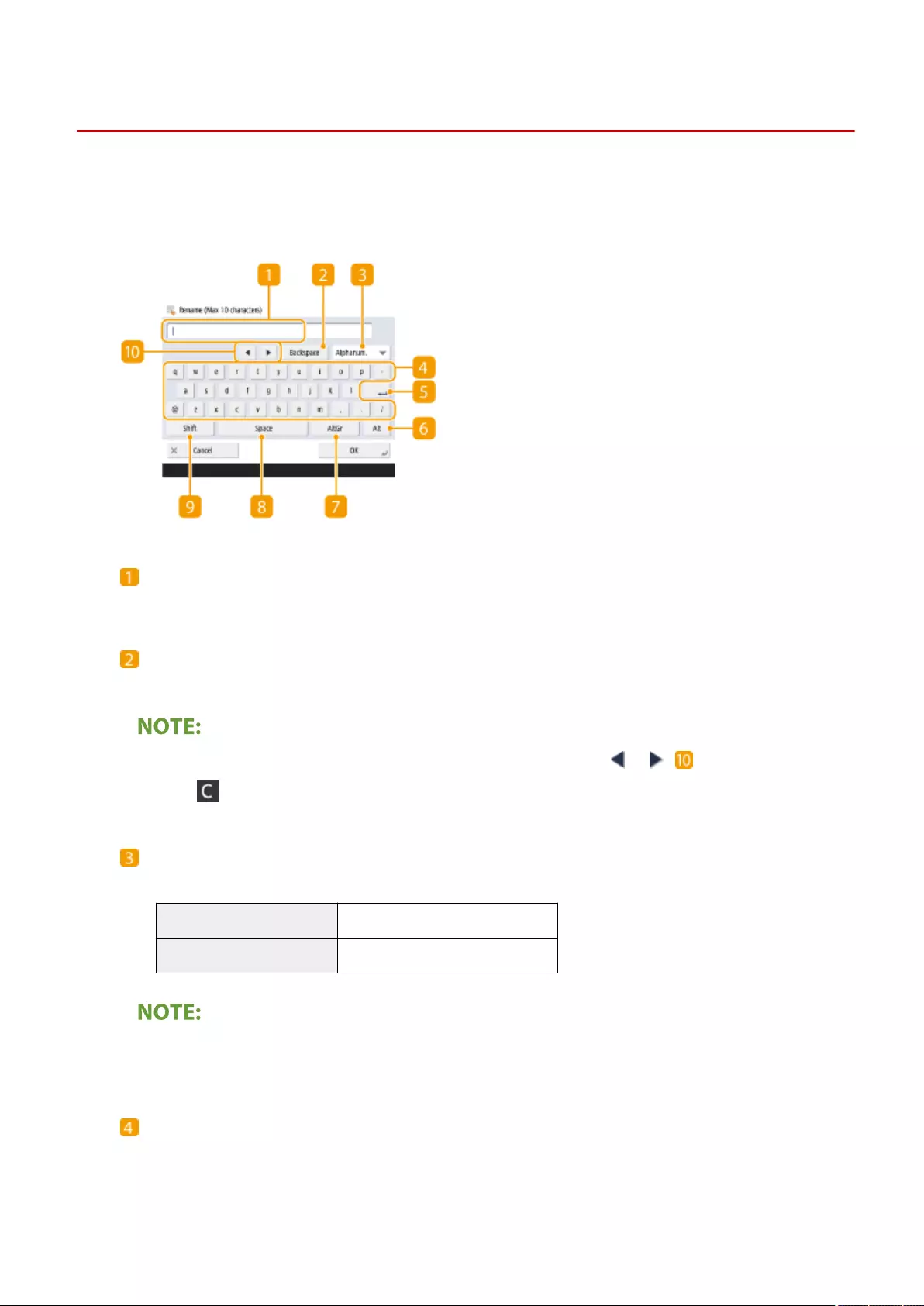
Entering Characters
72JY-029
For screens that require alphanumeric entries, enter characters using the keys on the touch panel display. To enter
numbers, you can also use the numeric keys on the right of the touch panel display.
Example: <Alphanum.> mode
Character input eld
Characters entered are displayed.
<Backspace> button
Each time you press the button, you can delete a character to the left of the cursor one by one.
●If a character you want to delete is not to the left of the cursor, press or ( ) to move the cursor.
●Press (Clear) if you want to delete all the characters you entered.
Entry mode button
Select the entry mode from the drop-down list.
<Alphanum.> Alphanumeric character entry mode
<Symbol> Symbol entry mode
●You may not be able to select the entry mode because the type of characters that you can enter is
predetermined for some screens.
Character input button
The same keyboard layout as that of a computer.
Basic Operations
135

Enter button
Press to start a new line.
<Alt> button
Press to display only the numeric keys.
<AltGr> button
Press to display characters with accent marks.
<Space> button
Press to enter a space.
<Shift> button
Press to enter uppercase characters or symbols.
Cursor button
Move the cursor in the input eld.
When displaying the numeric keys icon
●When < You can use numeric keys.> is displayed, you can enter numerical values using the
numeric keys on the right of the touch panel display.
Example: <XY Ratio> setting screen
●When < Enter using the numeric keys.> is displayed, only the numeric keys on the right of the
touch panel display can be used for entering numbers.
Enter characters from the USB keyboard
To enter characters, you can also use a USB keyboard by connecting it to the USB port ( Front
Side(P. 83) ). Note the following points when entering from a USB keyboard.
●Set <Use AddOn Driver for USB Input Device> in <USB Settings> to <Off>. <Use AddOn Driver for
USB Input Device>(P. 795)
●You can only enter ASCII characters from a USB keyboard.
●Keys that are not displayed on the keyboard screen of the touch panel display, such as Delete, End,
Tab, Esc, and function keys, cannot be used on a USB keyboard.
●The entering sound of a USB keyboard is produced based on the <Entry Tone> and <Invalid Entry
Tone> settings on the sound setting screen. Setting Sounds(P. 184)
Basic Operations
136
Log In
Logging into the Machine
72JY-02A
0YRY-022 1100-022 10XJ-022 1106-022 10YY-022 10H3-022 108A-022 1116-022 10H4-022 0YAS-022
When the login screen is displayed, registered authorized users are required to log in to continue operating the
machine. To log in, each user must enter his or her own user name and password. This ensures the security of the
machine. Also, the users can use the machine as conveniently as possible by customizing (personalizing) the display
and the settings according to their preferences. The items displayed on the login screen vary depending on the user
management settings. Perform the login operation based on the items that are displayed.
When the User Name and Password Input Screen Is Displayed(P. 137)
●For the functions and settings that can be personalized, see List of Items That Can Be
Personalized(P. 139) .
●If you are not using the Personalization function, set <Enable Use of Personal Settings> ( <Enable Use of
Personal Settings>(P. 859) ) to <Off>.
●If <Auto Reset Time> is set, the user is automatically logged out when no operations are performed for a
specied period. <Auto Reset Time>(P. 778)
When the User Name and Password Input Screen Is Displayed
Use the on-screen keyboard to enter the user name and password.
1Press <User Name>.
●If the login user's cache is remaining, you can also select the user name from the login history drop-down
list. When a user name is selected, press <Password> and proceed to step 3.
2Enter the user name and press <Next>.
3Enter the password and press <OK>.
4Select the login destination from the <Login Destination> drop-down list, and press
<Log In>.
➠When login is successful, the machine functions become available.
●Log out after use.
Basic Operations
137
●You can log into the machine using the copy card. For details about the copy card, see Copy Card
Reader(P. 1123) .
●You can specify whether to save passwords entered during login in the cache. <Prohibit Caching of
Authentication Password>(P. 866)
●If you set <Display Button to Change Password on Settings Menu> to <On>, the password can be changed
from on the top right of the login screen. <Display Button to Change Password on Settings
Menu>(P. 854)
●You can specify whether to save or delete the login user's cache. <Number of Caches for Login
Users>(P. 854)
LINKS
Using the Touch Panel Display(P. 118)
Customizing the Touch Panel Display(P. 156)
Managing Users(P. 489)
Starting the Remote UI(P. 583)
Basic Operations
138
List of Items That Can Be Personalized
72JY-02C
The following items can be personalized for each login user.
Category Setting Value Corresponding Settings
Display language *1*2 Display language and
keyboard layout
<Switch Language/Keyboard>(P. 773)
Accessibility *1*2 Key Repetition Settings <Key Repetition Settings>(P. 797)
Invert Screen Colors <Invert Screen Colors>(P. 797)
Initial screen *1*2 Screen displayed after
logging in
<Default Screen After Startup/Restoration>(P. 773)
Home *1*2 Personal buttons Personal buttons ( Registering Personal Buttons/
Shared Buttons(P. 171) )
Timeline*3*5 Timeline ( Items Displayed on the <Home>
Screen(P. 122) )
Home settings Customizing the <Home> Screen(P. 159)
Network SSID, Network key,
Automatically Enable/
Disable Direct Connection
at Login/Logout
<Personal SSID and Network Key Settings>(P. 792) ,
<Access Point Mode Settings>(P. 791)
Default job settings *1*2*3 Copy <Change Default Settings>(P. 817)
Fax <Change Default Settings>(P. 830)
Scan and Send*4 <Change Default Settings>(P. 820)
Scan and Store*4 <Change Default Settings>(P. 843)
Access Stored Files <Change Default Settings>(P. 844)
Shortcuts *1*2 Copy <Register Options Shortcuts>(P. 817)
Fax <Register Options Shortcuts>(P. 830)
Scan and Send <Register Options Shortcuts>(P. 820)
Previous Settings *1*3*5 Copy Recalling Previously Used Copy Settings (Previous
Settings)(P. 264)
Fax Recalling Previously Used Settings for Sending
(Previous Settings)(P. 304)
Scan and Send*4 Recalling Previously Used Settings for Sending/
Saving (Previous Settings)(P. 421)
Address Book Personal address lists*1 Registering Destinations via the Remote UI(P. 592) ,
Registering Destinations in the Address Book(P. 195)
Group address books*1*6
(user group address list 01
to user group address list
50)
Basic Operations
139
Category Setting Value Corresponding Settings
Conditions for changing the list order *5 Scan and Store Saving Scanned Documents to Another Machine or
Server(P. 438) , Scanning Documents and Saving to
Memory Media(P. 443)
Access Stored Files Printing a File on Another Machine or Server(P. 439) ,
Printing Files on Memory Media(P. 444)
Print Printing Documents Held in the Machine(P. 351)
Automatic print after login settings Auto Print User Jobs When
Logging In
<Auto Print User Jobs When Logging In>(P. 848)
Other Keychain*1 -
*1 Deleted when <Delete Oldest User Settings> is specied. <Action When Maximum Number of Users
Exceeded>(P. 859)
*2 When a client machine synchronizes custom settings for the rst time, the synchronization of this item may not nish
before the machine starts up.
*3 When synchronizing custom settings, this item can be specied for individual machines within the scope of data
sharing. (Other settings for the server machine are required on the machine with server function.)
*4 Even if this item is set to be shared, destinations are left blank and not synchronized.
*5 This item cannot be imported from another machine or exported to another machine. Importing/Exporting the
Setting Data(P. 625)
*6 It is necessary to use the login service that supports the group function (User Authentication supports the group
function).
◼Items That Cannot Be Personalized but Can Be Synchronized by Synchronizing Custom
Settings
The following items cannot be personalized but can be shared between multiple Canon multifunction printers
by synchronizing custom settings.
●Destination for sharing user group address lists Registering Destinations via the Remote UI(P. 592)
●Home settings (when not logged in) Customizing the <Home> Screen(P. 159)
●Set <Shared across All Devices> to share the <Shared> and <Wallpaper Settings> (when not logged in)
settings of the <Home> screen with all client machines using synchronization of custom settings. If
you want to manage these settings for each client machine separately, select <Device-Specic (Not
Shared)> when starting the service for the rst time (when no client machines are connected to the
server machine). The data may be initialized if the scope of data sharing is changed after the service is
started. (Other settings for the server machine are required on the machine with server function.)
●For information on the keychain, see Managing Users(P. 489) .
●When the <Switch Language/Keyboard>, <Accessibility>, and <Personal SSID and Network Key
Settings> settings could not be reected immediately after logging in, they can be reected when it
becomes possible. For more information, see Starting Setting Synchronization(P. 659) .
Basic Operations
140

Specifying Paper Size and Type
72JY-02E
You must specify the paper size and type settings to match the paper that is loaded. Make sure to change the paper
settings when you load paper that is different from the previously loaded paper.
Specifying Paper Size and Type in the Paper Drawer(P. 142)
Specifying Paper Size and Type in the Multi-purpose Tray(P. 145)
Registering Frequently Used Paper Size and Type for the Multi-purpose Tray(P. 148)
Fixing the Paper Size and Type to Use with the Multi-Purpose Tray(P. 151)
Registering Free Size Paper (Custom Size Paper)(P. 153)
Automatically Selecting the Appropriate Paper Source for a Specic Function (P. 154)
●If the setting does not match the size and type of loaded paper, a paper jam or printing error may occur.
Basic Operations
141
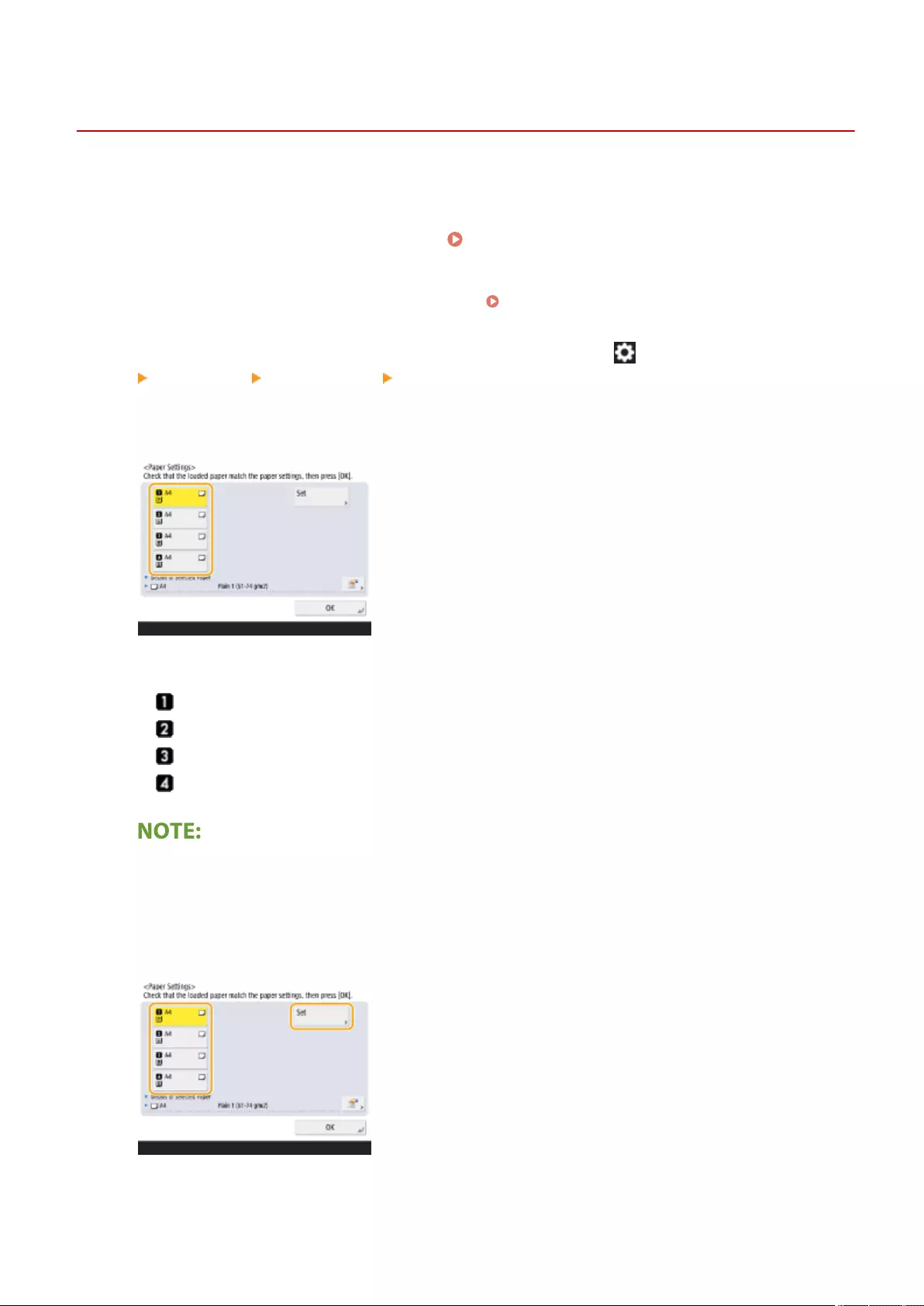
Specifying Paper Size and Type in the Paper Drawer
72JY-02F
PMW-SPDR
1Load the paper in the paper drawer. Basic Paper Loading Method(P. 103)
●If <Conrm When Loading Paper in Paper Drawer> is set to <On> , the <Paper Settings> screen is displayed
when the paper drawer is inserted into the machine. <Conrm When Loading Paper in Paper
Drawer>(P. 775)
●If <Conrm When Loading Paper in Paper Drawer> is set to <Off>, press (Settings/Register)
<Preferences> <Paper Settings> <Paper Settings> to display the <Paper Settings> screen.
2Check the paper size that is displayed.
●The paper sources are represented by the following icons, respectively. Note that the paper source
indications differ depending on the options installed.
: The paper drawer 1
: The paper drawer 2
: The paper drawer 3
: The paper drawer 4
●If the displayed paper size is different from the loaded paper size, the paper may not be loaded properly.
Load the paper again.
3If the displayed paper size/type is different from the loaded paper size/type, select
the paper source in which paper is loaded and press <Set> .
4Select the paper size and press <Next> .
Basic Operations
142
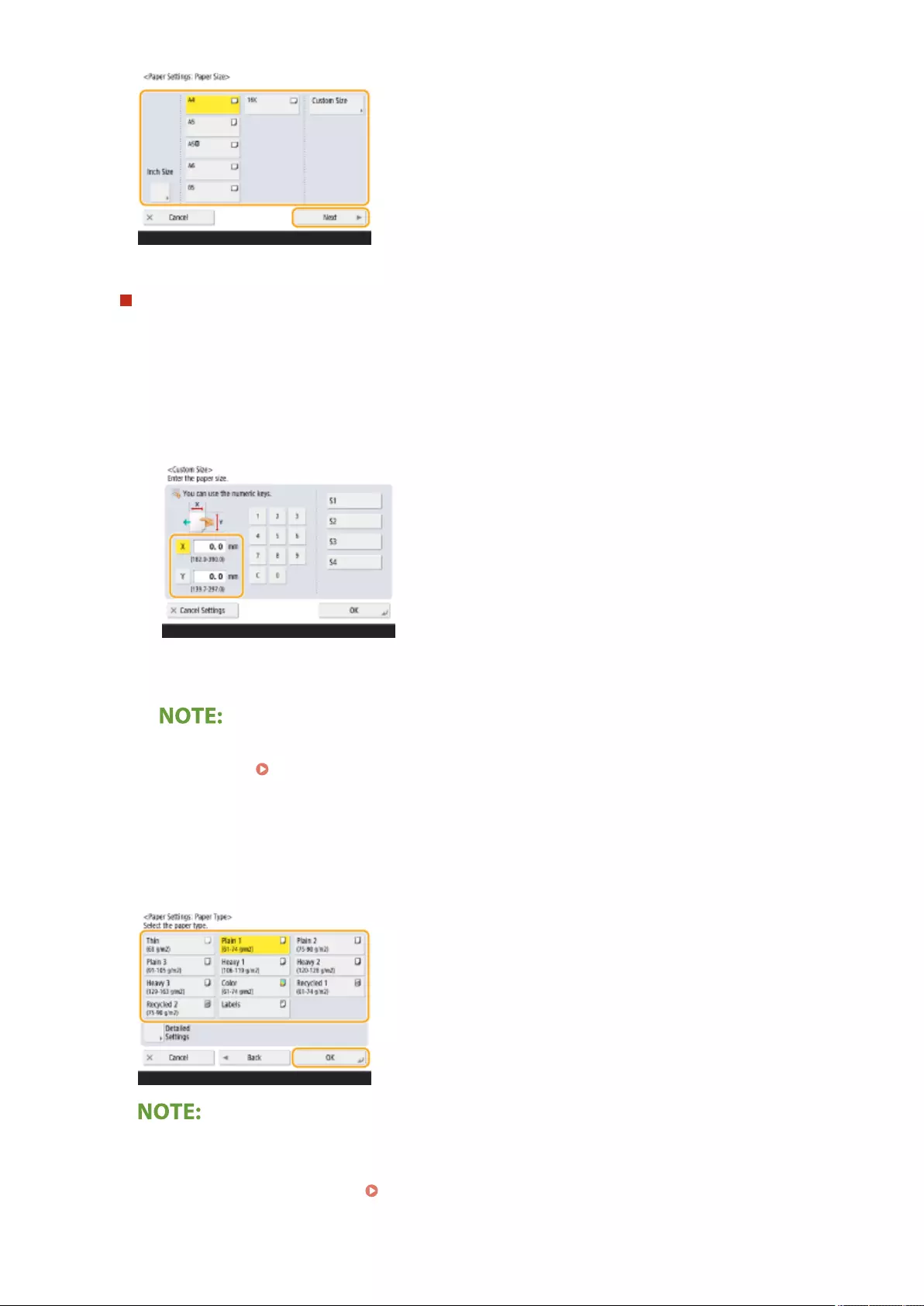
When loading custom size paper
0UUY-023 0UW1-023 0YRY-02C 0X7F-02A 0X7H-02A 1100-02C 0X6E-02A 0X6W-02A 10XJ-02C 0X7C-02A 0X7A-02A 1106-02C 0WXY-02A 0X7E-02A 10YY-02C 10H3-02C 0WR6-02A 0WR7-02A 108A-02C 1116-02C 10H4-02C 0WR5-02A 0WR8-02A 0YWJ-029 0YWH-02A 0YWR-029 0YWK-02A 0YWE-02A 0YWF-02A 0YAS-02E
Specify the size of paper loaded in the paper drawer.
1Select the paper drawer in which paper is loaded and press <Custom Size>.
2Specify the length of the <X> side and <Y> side.
●Press <X> or <Y> to enter the length of each side using the numeric keys.
●If you register the paper size you use frequently on buttons <S1> to <S4>, you can call them up with
one touch. Registering Free Size Paper (Custom Size Paper)(P. 153)
3Press <OK>.
5Select the paper type and press <OK>.
●If the paper type loaded is not displayed, press <Detailed Settings> to select from a list.
●If the paper type of the paper that you have loaded is not listed on the detailed setting screen, you can
register it in the paper type list. Paper Type Management Settings(P. 903)
Basic Operations
143
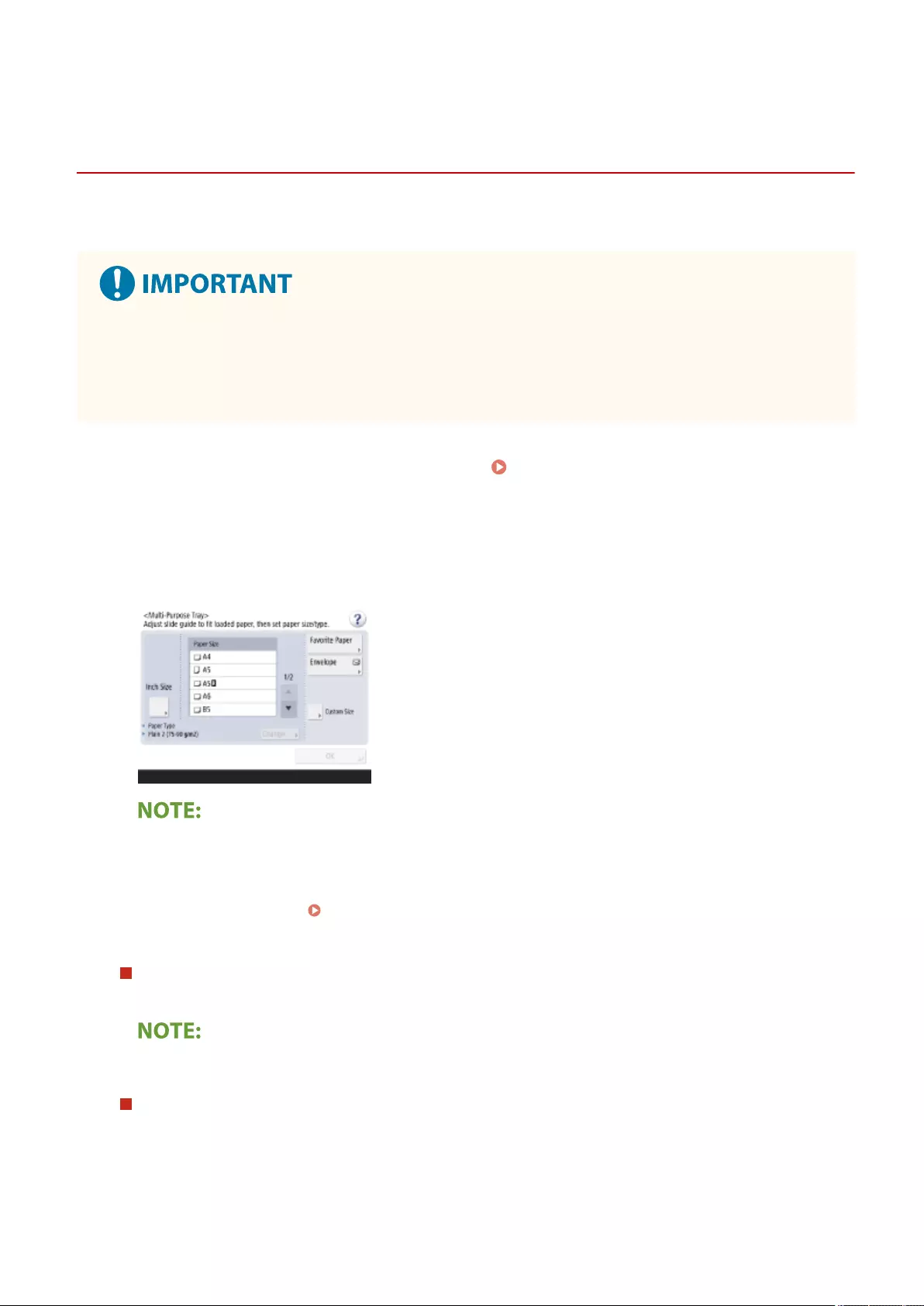
Specifying Paper Size and Type in the Multi-purpose
Tray
72JY-02H
PMW-SPMT
●If <Paper Feed Mode for Printer Driver Jobs with MP Tray> is set to <On>, printer driver settings are
prioritized when the multi-purpose tray is specied as the paper source for jobs from the printer driver.
●A paper jam or other printing problems may occur if the size and type of paper specied in the printer driver
do not match those of the actual paper loaded in the multi-purpose tray.
1Load the paper in the multi-purpose tray. Loading Paper in the Multi-Purpose
Tray(P. 107)
➠The screen for specifying the paper size and type is displayed.
2Specify the paper size.
●If the displayed paper size is different from the loaded paper size, the paper may not be loaded properly.
Load the paper again.
●If you press <Favorite Paper> and register the frequently used paper size on buttons, you can call them up
with a simple press. Registering Frequently Used Paper Size and Type for the Multi-purpose
Tray(P. 148)
When loading standard size paper
Select the paper size from <Paper Size>.
●Press <Inch Size> to select an inch paper size.
When loading custom size paper
0UUY-024 0UW1-024 0YRY-02E 0X7F-02C 0X7H-02C 1100-02E 0X6E-02C 0X6W-02C 10XJ-02E 0X7C-02C 0X7A-02C 1106-02E 0WXY-02C 0X7E-02C 10YY-02E 10H3-02E 0WR6-02C 0WR7-02C 108A-02E 1116-02E 10H4-02E 0WR5-02C 0WR8-02C 0YWJ-02A 0YWH-02C 0YWR-02A 0YWK-02C 0YWE-02C 0YWF-02C 0YAS-02F
1Press <Custom Size>.
2Specify the length of the <X> side and <Y> side.
Basic Operations
145
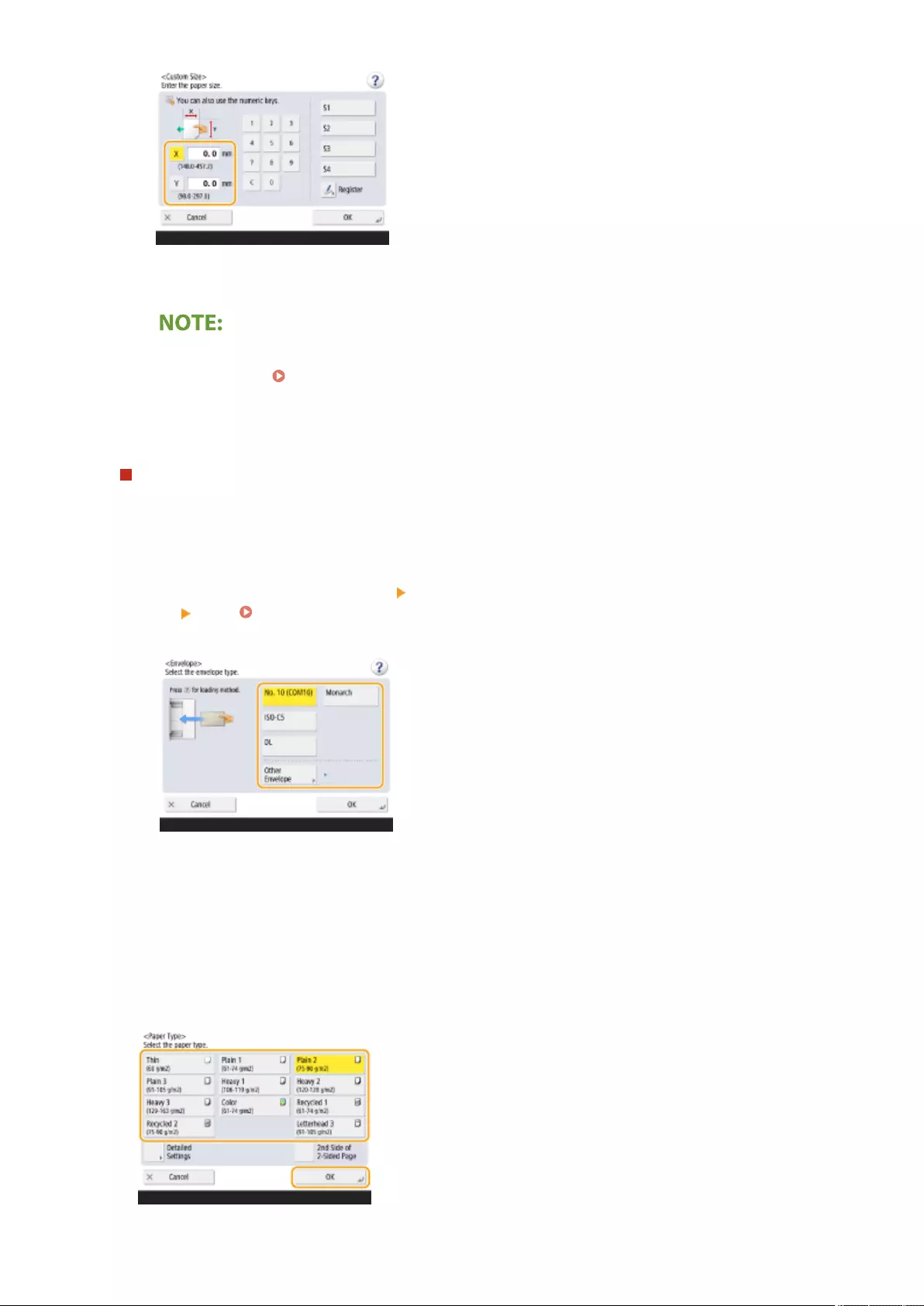
●Press <X> or <Y> to enter the length of each side using the numeric keys.
●If you register the paper size you use frequently on buttons <S1> to <S4>, you can call them up with a
simple press. Registering Free Size Paper (Custom Size Paper)(P. 153)
3Press <OK>.
When loading envelopes
1Press <Envelope>.
●The envelope paper type cannot be selected from the details screen of <Paper Type>. To select the
envelope paper type, register the paper type in <Register Favorite Paper (Multi-Purpose Tray)>, then
press <Favorite Paper> in step 2 the button to which the envelope paper type has been registered
<OK>. Registering Frequently Used Paper Size and Type for the Multi-purpose Tray(P. 148)
2Select the type of envelopes.
●Press <OK> and proceed to step 5.
3Press <Change> in <Paper Type>.
4Select the paper type and press <OK>.
Basic Operations
146
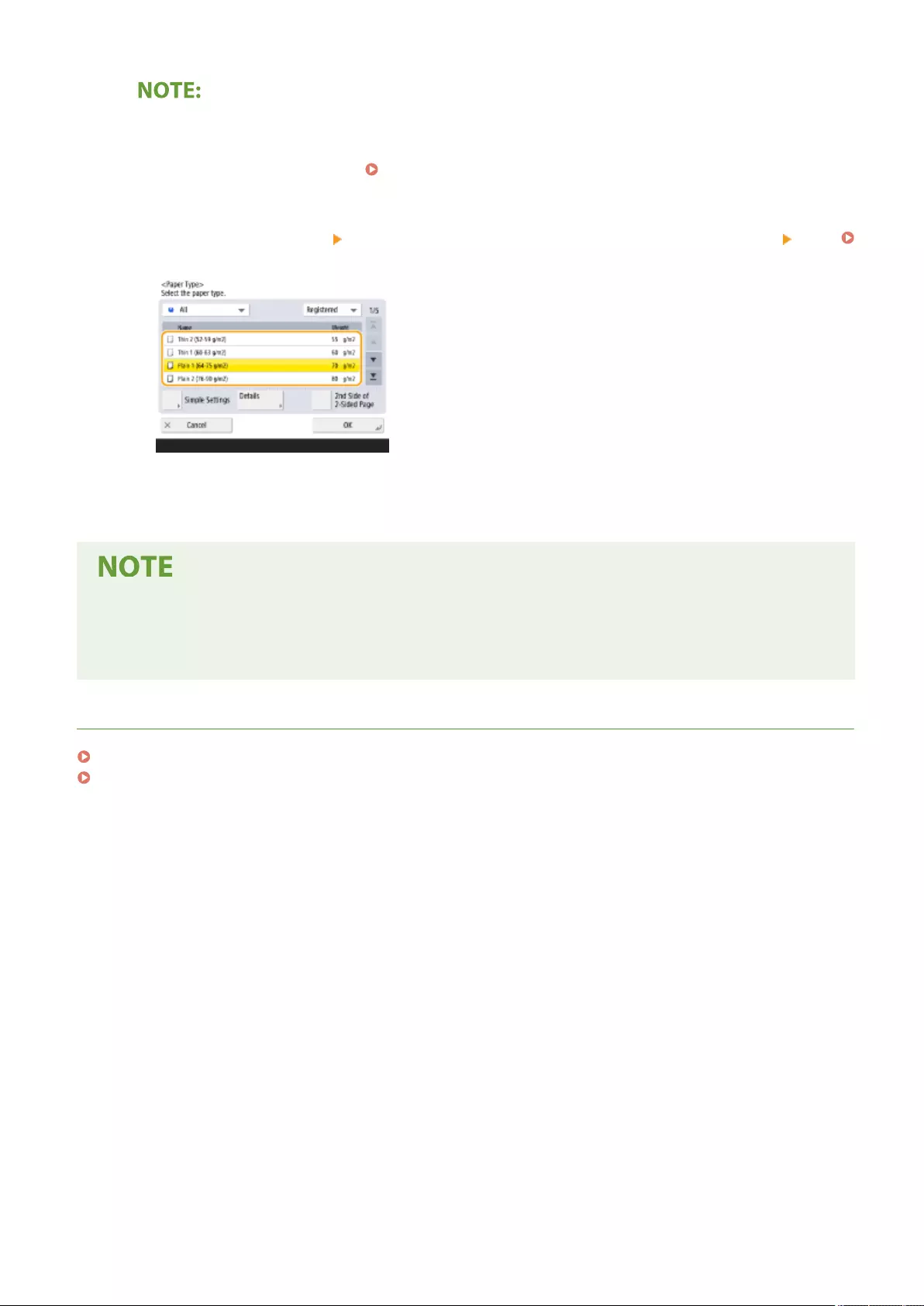
●If the paper type loaded is not displayed, press <Detailed Settings> to select from a list.
●If the paper type of the paper that you have loaded is not listed on the detailed setting screen, you can
register it in the paper type list. Paper Type Management Settings(P. 903)
●The envelope paper type cannot be selected from the details screen of <Paper Type>. To select the
envelope paper type, register the paper type in <Register Favorite Paper (Multi-Purpose Tray)>, then press
<Favorite Paper> in step 2 the button to which the envelope paper type has been registered <OK>.
Registering Frequently Used Paper Size and Type for the Multi-purpose Tray(P. 148)
5Press <OK>.
If a screen other than that for specifying the paper size and type is displayed
●If a message prompting you to adjust the paper guide is displayed, adjust the width of the paper guide
again and press <OK>.
LINKS
Hardware Specications(P. 1103)
<Prioritize Printer Driver Settings for Jobs with MP Tray>(P. 818)
Basic Operations
147
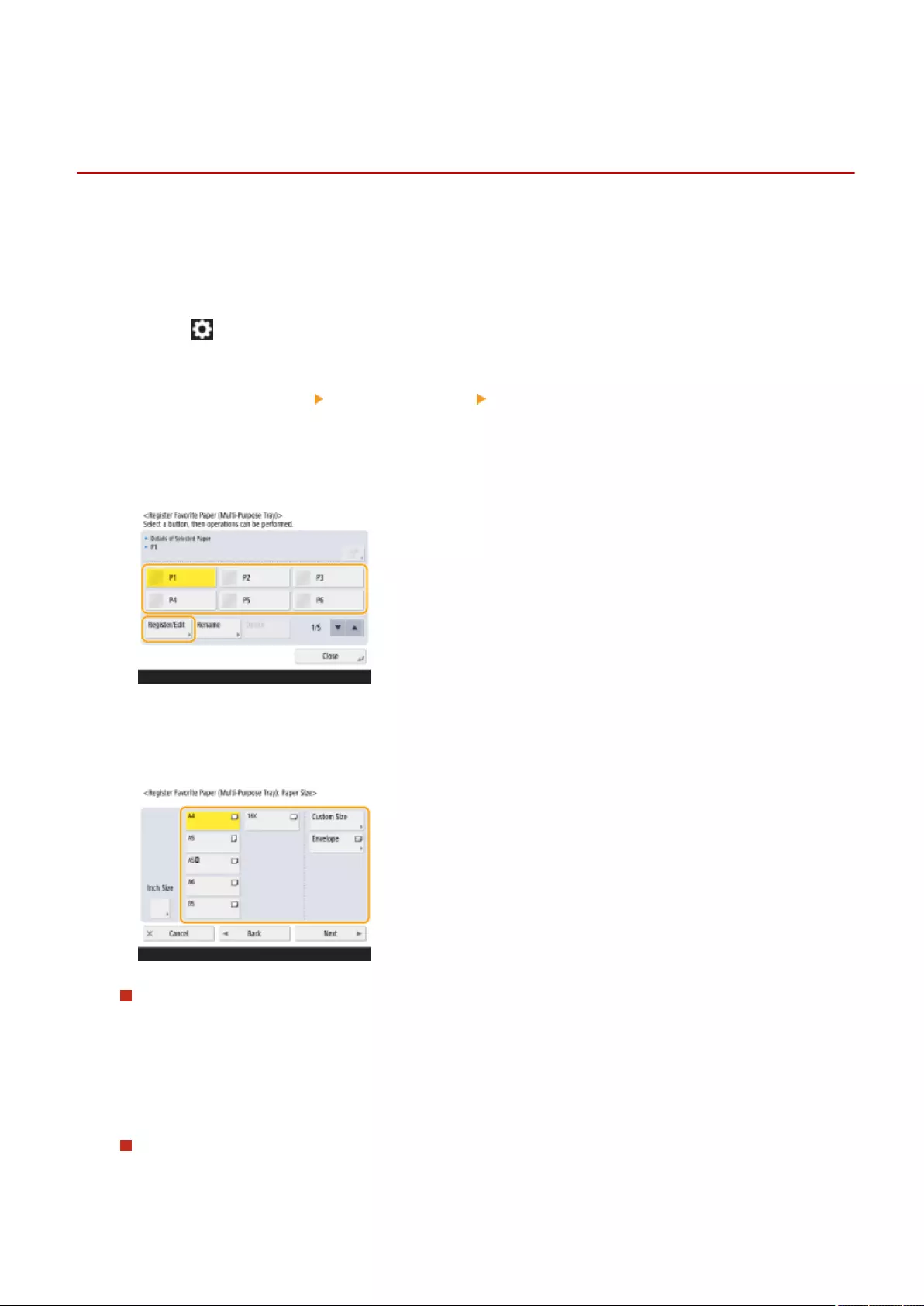
Registering Frequently Used Paper Size and Type for
the Multi-purpose Tray
72JY-02J
If you use a specic size and type of paper by loading in the multi-purpose tray, you can register that paper in advance
as "Favorite Paper" for the multi-purpose tray. "Favorite Paper" can easily be called up from the screen which is
displayed when you load the paper in the multi-purpose tray, so that you can save the time and labor to make size and
type settings each time you use the specic paper.
1Press (Settings/Register).
2Press <Preferences> <Paper Settings> <Register Favorite Paper (Multi-Purpose
Tray)>.
3Select a button to register and press <Register/Edit>.
●You can change the registered name by pressing <Rename>.
4Select the paper size.
When registering standard size paper
1Select the standard size paper.
2Press <Next>.
When registering custom size paper
1Press <Custom Size>.
Basic Operations
148
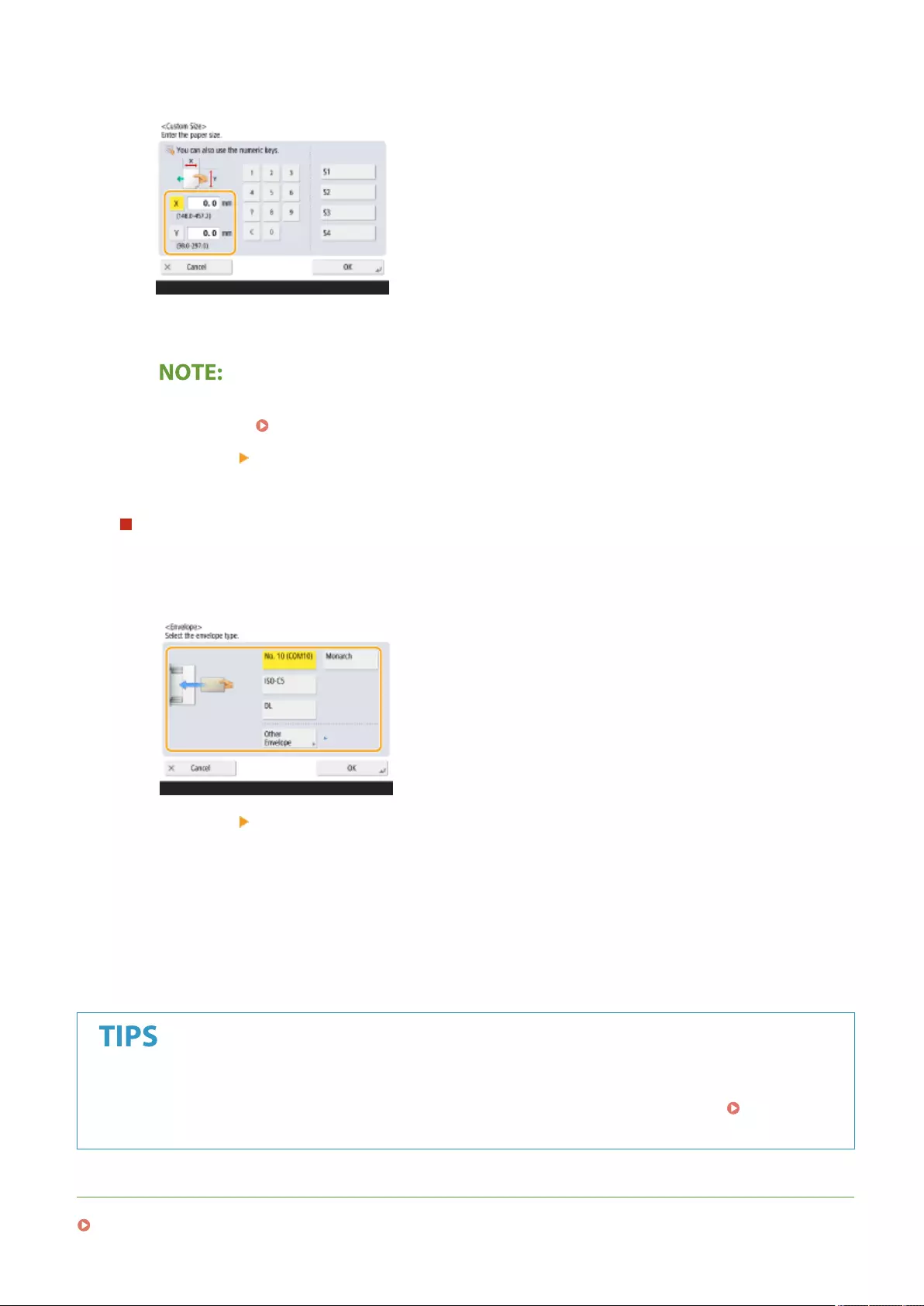
2Specify the length of the <X> side and <Y> side.
●Press <X> or <Y> to enter the length of each side using the numeric keys.
●If you register the paper size you use frequently on buttons <S1> to <S4>, you can call them up with
one touch. Registering Free Size Paper (Custom Size Paper)(P. 153)
3Press <OK> <Next>.
When registering envelopes
1Press <Envelope>.
2Select the type of envelopes.
3Press <OK> <Next>.
5Select the paper type and press <OK>.
6Press <Close>.
●If <Always Specify> under <Multi-Purpose Tray Defaults> is set to <Favorite Paper>, a screen is displayed to
allow you to select your "Favorite Paper" when you load the paper in the multi-purpose tray. <Multi-
Purpose Tray Defaults>(P. 771)
LINKS
Loading Paper in the Multi-Purpose Tray(P. 107)
Basic Operations
149
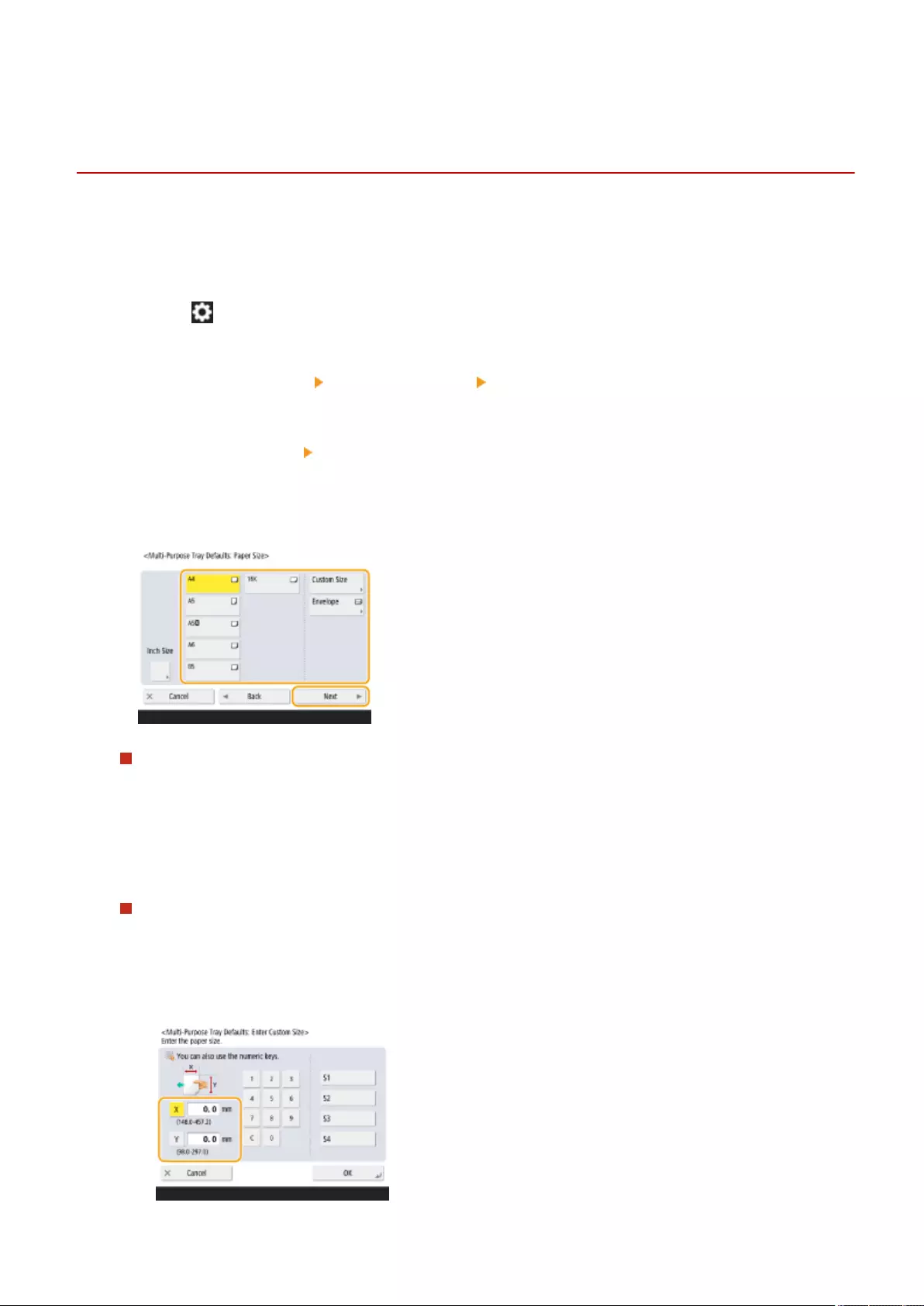
Fixing the Paper Size and Type to Use with the Multi-
Purpose Tray
72JY-02K
If you always use the same paper size and type with the multi-purpose tray, it is recommended that you x the paper
size and type settings for the multi-purpose tray. This is convenient because you can save the time and labor to make
settings each time you load paper in the multi-purpose tray.
1Press (Settings/Register).
2Press <Preferences> <Paper Settings> <Multi-Purpose Tray Defaults>.
3Press <Use Preset> <Register>.
4Select the paper size.
When registering standard size paper
1Select the standard size paper.
2Press <Next>.
When registering custom size paper
1Press <Custom Size>.
2Specify the length of the <X> side and <Y> side.
Basic Operations
151
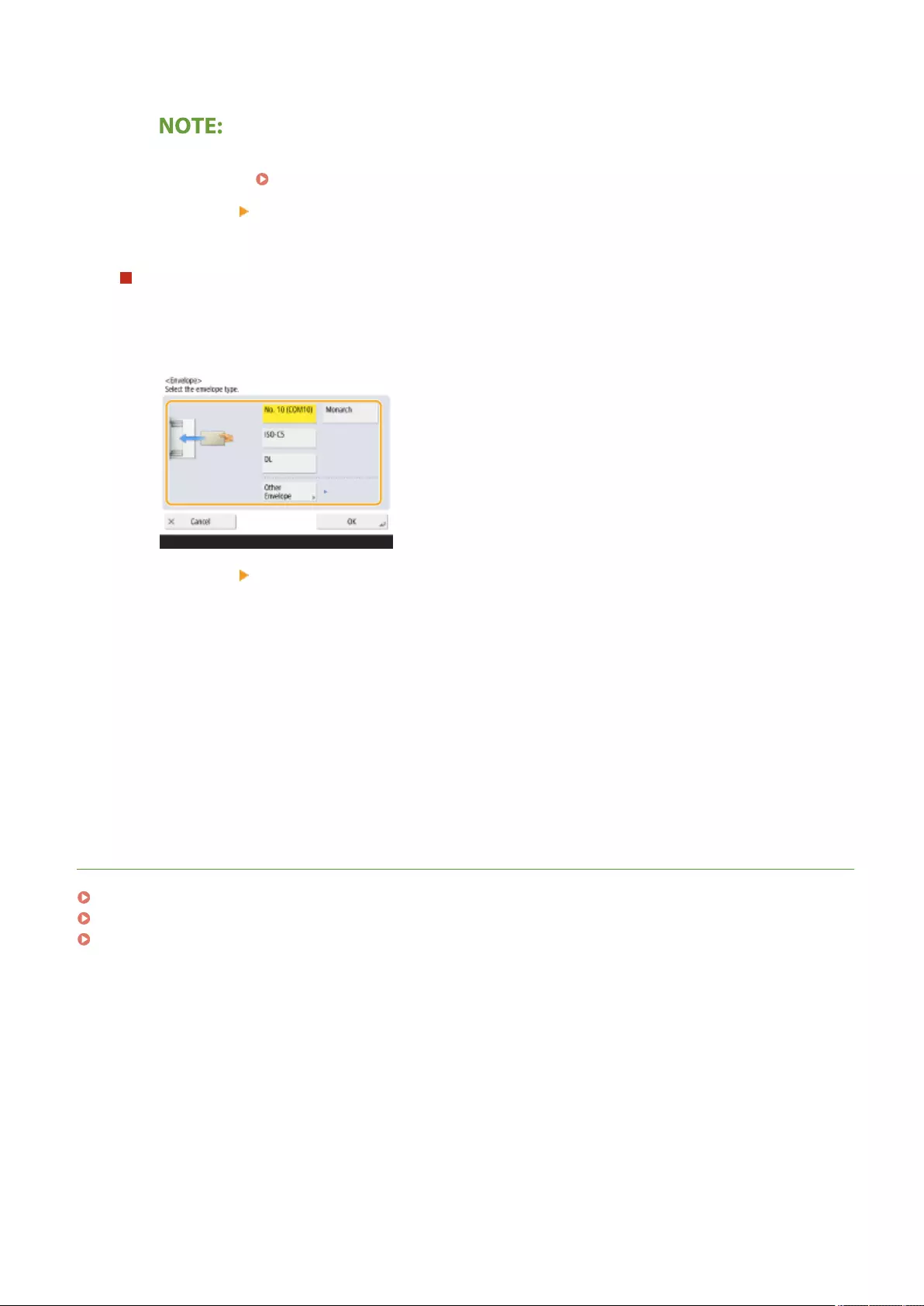
●Press <X> or <Y> to enter the length of each side using the numeric keys.
●If you register the paper size you use frequently on buttons <S1> to <S4>, you can call them up with
one touch. Registering Free Size Paper (Custom Size Paper)(P. 153)
3Press <OK> <Next>.
When registering envelopes
1Press <Envelope>.
2Select the type of envelopes.
3Press <OK> <Next>.
5Select the paper type and press <OK>.
6Press <OK>.
7Press <Close>.
LINKS
Loading Paper in the Multi-Purpose Tray(P. 107)
Hardware Specications(P. 1103)
Registering Frequently Used Paper Size and Type for the Multi-purpose Tray(P. 148)
Basic Operations
152

Registering Free Size Paper (Custom Size Paper)
72JY-02L
You can register up to four frequently used free sizes of paper. The paper sizes registered here are displayed on the
paper size selection screen for the paper drawer and multi-purpose tray ( Specifying Paper Size and Type in the
Paper Drawer(P. 142) or Specifying Paper Size and Type in the Multi-purpose Tray(P. 145) ).
1Press (Settings/Register).
2Press <Preferences> <Paper Settings> <Register Custom Size>.
3Select a button from <S1> to <S4> and press <Register/Edit>.
●You can assign an easy to remember name to the button by pressing <Rename>.
4Set the paper size and press <OK>.
●Specify the length of the <X> side and <Y> side. Press <X> or <Y> to enter the length of each side using the
numeric keys.
5Press <Close>.
LINKS
Basic Paper Loading Method(P. 103)
Basic Operations
153
Automatically Selecting the Appropriate Paper Source
for a Specic Function
72JY-02R
Paper sources in which <Paper Source Auto Selection> are set to <On> will be automatically selected when <Select
Paper> is set to <Auto>.
Paper sources in which <Paper Source Auto Selection> are set to <Off> will not be selected unless they are selected
manually.
●To the paper source to be selected automatically, one of the following paper types must be selected for each
paper source.
- If <Consider Paper Type> is set to <On>
●1-Sided Printing: Thin, Plain, Recycled
●2-Sided Printing: Thin*1, Plain, Recycled
- If <Consider Paper Type> is set to <Off>
●1-Sided Printing: Thin*1, Plain, Recycled, Heavy*1, Color*1 (in white)
●2-Sided Printing: Thin*1, Plain, Recycled, Heavy*1, Color*1 (in white)
*1 Only paper that can be printed on both sides are available. For more information, see Paper Available for Two-Sided
Copying/Two-Sided Printing(P. 1113) .
●When the copy ratio is set to <Auto>, a paper source will not be selected automatically.
●When one of the following modes is set, a paper source will not be selected automatically.
- N on 1, Copy ID Card
●It is necessary to select at least one paper source. However, you cannot set only the multi-purpose tray to
<On>.
1Press (Settings/Register).
2Press <Function Settings> <Common> <Paper Feed Settings> <Paper Source
Auto Selection>.
3Select the function.
●<Other> enables you to make settings for a paper source that is used for outputting reports.
4Select <On> for each paper source that you want to be selected automatically.
If you selected <Copy> in step 3
Set whether to consider the paper type.
●If you select the <Consider Paper Type> check box: when the current paper source runs out of paper, copying
is halted even if another paper source is loaded with paper of the same size, unless the type of that paper is
the same as with the paper in question. Pressing (Start) again displays the paper selection screen.
Basic Operations
154

●If you deselect the <Consider Paper Type> check box: when the current paper source runs out of paper,
automatic paper source switching is performed and copying is continued if another paper source is loaded
with paper of the same size, regardless of the paper type.
If you selected <Printer> in step 3
Set whether to put multiple paper sources in a group. If paper source grouping is specied, paper source
selection is automatically performed within a group when you print by specifying any paper source
belonging to that group. To specify paper source grouping, select the <Use Group> check box, press
<Change> to select a group which you want to put each paper source in, and press <OK>.
5Press <OK> <OK>.
Basic Operations
155
Customizing the Touch Panel Display
72JY-02S
In order to more easily use the <Home> screen and the Basic Features screen of each function, you can customize the
screen by rearranging buttons or creating shortcut buttons. In addition, you can work more eciently by registering
the settings already specied for frequently used functions to <Personal>/<Shared>, or the Personal Settings to
customize the operation environment to your preferences.
Customizing the <Home> Screen
The order, size, and number of buttons displayed on the <Home> screen can be changed, and the background
image can be changed. <Home Management Settings> enables you to congure the timeline display settings
and display/hide the function buttons.
Customizing the <Home> Screen(P. 159)
Creating a Shortcut
Function shortcut buttons can be displayed on each function screen. Registering frequently used functions is
convenient because it enables functions to be continuously used without returning to the <Home> screen.
Creating a Shortcut for a Frequently Used Function(P. 162)
Registering Favorite Settings
If you frequently use the same combination of settings for copy, fax, and scan, it is convenient that you have
those settings registered as <Favorite Settings>.
Basic Operations
156
Registering a Combination of Frequently Used Functions(P. 164)
Customizing the Basic Features Screen
You can change the setting buttons that are displayed on the Basic Features screens (for copy, fax, and scan).
You can also display a different Basic Features screen customized for each logged-in user.
Customizing the Basic Features Screen(P. 167)
Creating the <Personal>/<Shared> Button
It is possible to freely register frequently used functions and setting procedures on the <Home> screen.
Registering Frequently Used Settings and Destinations as Personal Buttons/Shared Buttons on the
<Home> Screen(P. 170)
Changing the Language Displayed
You can change the language displayed on the touch panel display and keyboard.
Switching the Displayed Language(P. 176)
Basic Operations
157
Creating the Settings/Registration Shortcut
You can create a shortcut for any setting item that is displayed with a press of (Settings/Register). If you
frequently use a setting item provided at a very deep level, you can conveniently use the shortcut for that item
to quickly switch the display.
Registering Shortcuts for Frequently Used Settings/Registered Items(P. 178)
Settings for Each User (Personal Settings)
The displays and operation environment can be changed for each user.
Customizing the Screen Display Appearance and the Operational Conditions(P. 180)
LINKS
Using the Touch Panel Display(P. 118)
Basic Operations
158

Customizing the <Home> Screen
72JY-02U
This section describes what can be customized and managed from the items displayed when is pressed on the
<Home> screen.
●Depending on the setting for <Allow Home Screen Customization for Common Use> and the privileges of the
login user, a screen for selecting either <Customize for Personal Use> or <Customize for Common Use> may
be displayed when <Move Buttons>, <Edit Buttons>, <Home Screen Layout Settings>, or <Wallpaper
Settings> is selected.
- <Customize for Personal Use>: Select this to customize the Home screen for the current login user. The
default settings for <Customize for Personal Use> follow the settings for <Customize for Common Use>.
- <Customize for Common Use>: Select this to customize the Home screen for the users who have no
personalized screen, such as non-login users, Guest users, etc. The settings in <Customize for Common
Use> are applied until the authenticated user congures <Customize for Personal Use>.
●If the settings in <Customize for Common Use> are changed, the changes are also reected to <Customize
for Personal Use> until the authenticated user congures <Customize for Personal Use>.
●<Home> screen settings can be imported/exported between machines that support the <Home> screen.
Importing/Exporting the Setting Data(P. 625)
●<Home> screen settings are not imported to machines that support the <Quick Menu> screen but do not
support the <Home> screen.
●Even if any of the settings in <Home Management Settings for Personal Use> is disabled when exporting,
personal settings are exported if they are already congured.
<Move Buttons>
You can move function buttons and Personal buttons/Shared buttons.
<Edit Buttons>
Only <Move:> can be used for function buttons.
<Rename>, <Delete>, and <Move> can be used for Personal buttons/Shared buttons.
<Home Screen Layout Settings>
You can select one of the following items for the size and number of buttons displayed on a single screen.
●<3 large buttons per page>
●<6 large buttons per page>
●<9 medium buttons per page>
●<12 medium-small buttons per page>
Basic Operations
159

●<15 small buttons per page>
<Wallpaper Settings>
You can change the background image.
<Home Management Settings>
The following settings are available. (Red and bold text indicates the default setting.)
●<Allow Home Screen Customization for Common Use>: <On>/<Off>
●<Allow Non-Authentication Users to Use Timeline>: <On>/<Off>
●<Allow Each Login User to Use Timeline>: <On>/<Off>
●<Return to Home After Job is Performed>: <On>/<Off>
●<Restrict Function Display>: Select the functions or AddOn applications to hide on the <Home> screen.
●<Home Management Settings for Personal Use>: The following settings can be congured.
- <Allow Registration/Editing of Personal Buttons>: <On>/<Off>
- <Allow Use of Move Buttons When Customizing for Personal Use>: <On>/<Off>
- <Allow Use of Home Screen Layout Set. When Customizing for Personal Use>: <On>/<Off>
- <Allow Use of Wallpaper Settings When Customizing for Personal Use>: <On>/<Off>
●Operating this setting requires administrator privileges.
●<Allow Home Screen Customization for Common Use>
When set to On, General users and users that are not logged in can register shared buttons and customize
the Home screen for common use.
●<Return to Home After Job is Performed>
When set to On, the Home screen will be displayed after performing jobs using Shared buttons, Personal
buttons or Timeline.
●History is not retained in the timeline when a user is not logged in and <Allow Non-Authentication Users to
Use Timeline> is set to <Off>, or when a user is logged in and <Allow Each Login User to Use Timeline> is
set to <Off>.
●When <Enable Use of Personal Settings> is disabled, <Home Management Settings for Personal Use> is
grayed out and personal settings cannot be used. <Enable Use of Personal Settings>(P. 859)
●<Allow Registration/Editing of Personal Buttons>
Disable this to hide personal buttons.
●If <Allow Use of Move Buttons When Customizing for Personal Use> is disabled after moving buttons on
the personalized screen with <Allow Use of Move Buttons When Customizing for Personal Use> enabled,
buttons become unable to be moved on the personalized screen but their position is retained.
●<Allow Use of Home Screen Layout Set. When Customizing for Personal Use>
Disable this to apply the settings in <Device Settings>.
●<Allow Use of Wallpaper Settings When Customizing for Personal Use>
Disable this to apply the settings in <Device Settings>.
<Function Shortcut Button Settings>
You can register function buttons as shortcuts. Select the registration destination, and then the function to
register.
●Operating this setting requires administrator privileges.
Basic Operations
160

●If you do not use shortcuts, select <Unassigned> from the list.
Basic Operations
161
Creating a Shortcut for a Frequently Used Function
72JY-02W
You can create a shortcut button for the functions on the <Home> screen. Use this button to access a different
function without returning to the <Home> screen. To create a shortcut, log in with administrator privileges. Logging
into the Machine(P. 137)
●Shortcuts that can be registered: 4
1Press . <Home> Screen(P. 119)
2Press <Function Shortcut Button Settings>.
3Select a number for the shortcut to be created.
4Select the function you want to create a shortcut for.
Basic Operations
162

●Select the function from the list. You can check the position of the shortcut selected and the function
assigned to it in the preview screen on the left of the list.
●If you do not use shortcuts, select <Unassigned> from the list.
5Press <OK>.
Basic Operations
163
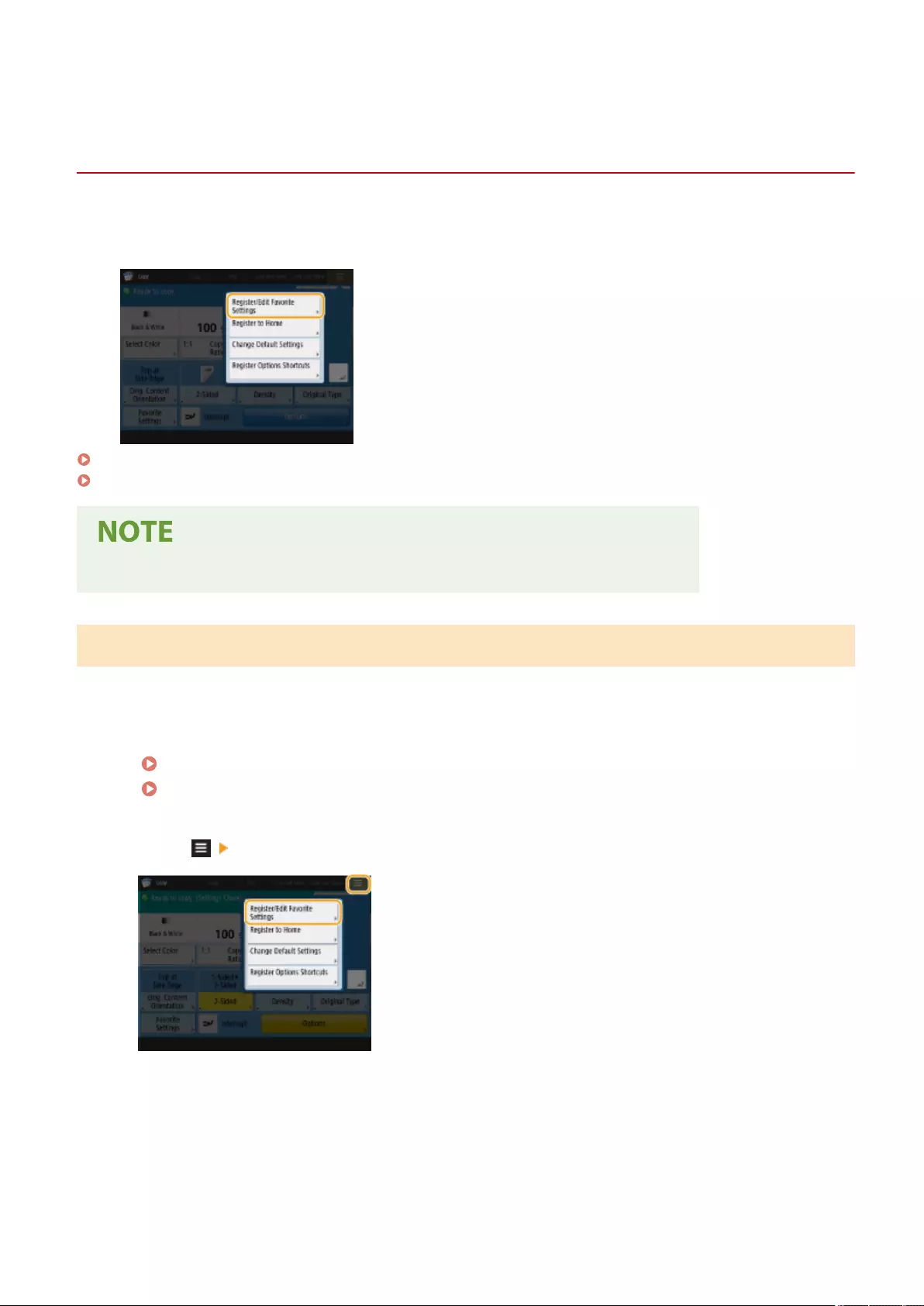
Favorite SettingsFavorite SettingsFavorite Settings
Registering a Combination of Frequently Used
Functions
72JY-02X
If you use the same settings every time for the Copy, Fax, or Scan function or want to save complicated settings, you
can register settings as favorite settings, which can then be conveniently recalled.
Registering Settings(P. 164)
Recalling Registered Settings(P. 165)
●The settings stored in memory are not deleted, even if the main power is turned OFF.
Registering Settings
Example: Copy Function
1Press <Copy>, and specify the settings you want to register.
<Home> Screen(P. 119)
Basic Copy Operations(P. 220)
2Press <Register/Edit Favorite Settings>.
3Select a button, and press <Register>.
Basic Operations
164

●To change a button name, select the button, press <Rename>, and enter the new name.
●To delete registered settings, select the button and press <Delete>.
●The name for the button is not deleted. To change a key name, press <Rename>.
●If an address included in a favorite settings button is deleted from the address book, it is also deleted from
the settings registered in the favorite settings button.
●If you select <Device Login Auth. Info.> for <Information Used for File TX/Browsing Authentication>, a
password for a le destination cannot be stored in <Favorite Settings>.
4Press <Yes> <Close>.
●For certain functions, press <Next>, enter a comment as necessary, and press <OK>. You can set <Show
Comments> to <On> to display comments.
●<The information for the new le destination specied may include a password. Do you want to
include the password when registering? (Press [No] to register the destination without the
password.)>
If the above messages is displayed when registering <Favorite Settings> for <Scan and Send>,
perform the following operations.
- If you want to recall favorite settings without entering a password, press <Yes> to retain the
password information.
- If you want to recall favorite settings by entering a password, press <No> to delete the password
information. (If you often import favorite settings to other devices, you can require a password to
be entered each time to prevent users from impersonating other users.)
Recalling Registered Settings
Example: Copy Function
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
●With <Fax> and <Scan and Send>, you can change the default screen to the <Favorite Settings> screen.
- Scan and Send: <Default Screen>(P. 820)
- Fax: <Default Screen>(P. 830)
Basic Operations
165
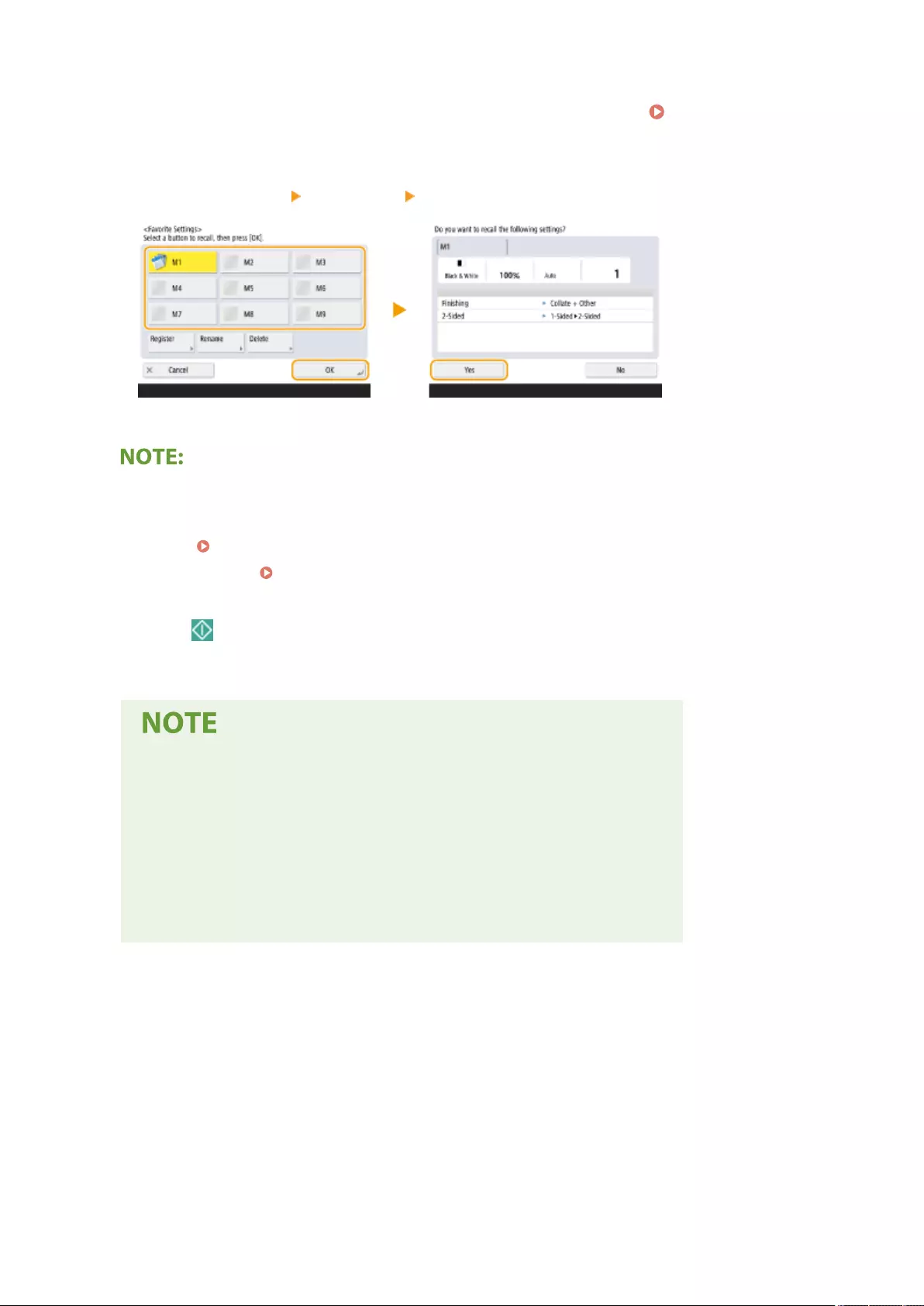
3Press <Favorite Settings> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Select the button press <OK> <Yes>.
●You can also change the settings you recall after pressing <Yes>.
●For the Copy/Scan and Send function, you can also set the machine not to display the conrmation screen
when the registered settings are recalled.
- Copy: <Display Conrmation for Favorite Settings>(P. 817)
- Scan and Send: <Display Conrmation for Favorite Settings>(P. 820)
5Press (Start).
➠Copying starts.
●The limit to the number of <Favorite Settings> you can register is as follows.
- Copy: 9
- Fax: 18
- Scan and Send: 18
- Scan and Store (Network/Memory Media): 9
- JPEG/TIFF les in Access Stored Files (Network/Memory Media): 9
- PDF/XPS les in Access Stored Files (Network/Memory Media): 9
Basic Operations
166
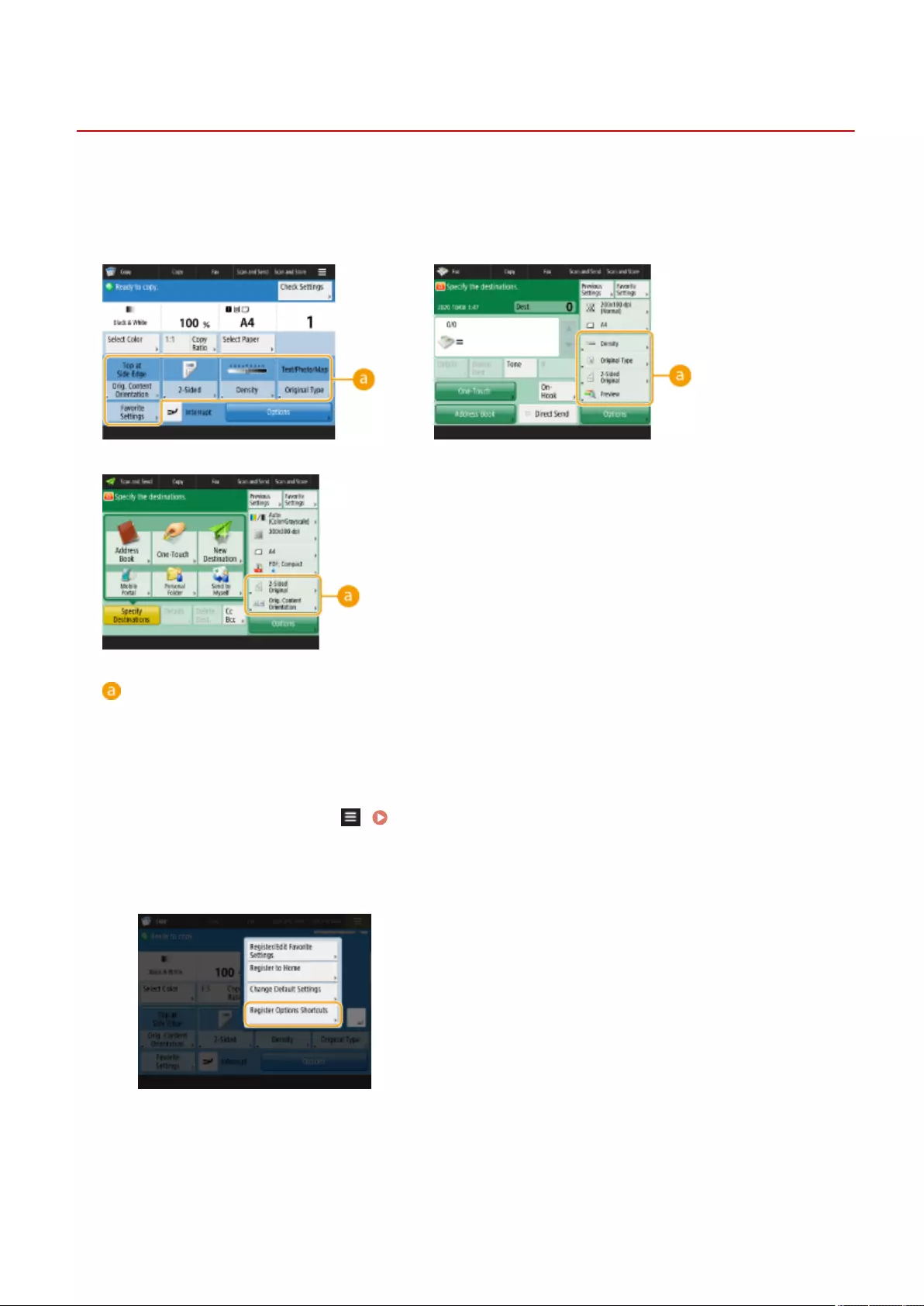
Options ShortcutsOptions ShortcutsOptions Shortcuts
Customizing the Basic Features Screen
72JY-02Y
The setting buttons that are displayed on the Basic Features screens (for copy, fax, and scan) can be changed with
other setting buttons in <Options>. By locating frequently used setting buttons on the Basic Features screen, you can
use functions more eciently. In addition, by logging in with personal authentication management, you can display a
different Basic Features screen customized for each user.
Copy Basic Features screen
Fax Basic Features screen
Scan Basic Features screen
Buttons that can be replaced
Example: Copy Basic Features screen
1Press <Copy> and press . <Home> Screen(P. 119)
2Press <Register Options Shortcuts>.
3Select a button to be replaced.
Basic Operations
167
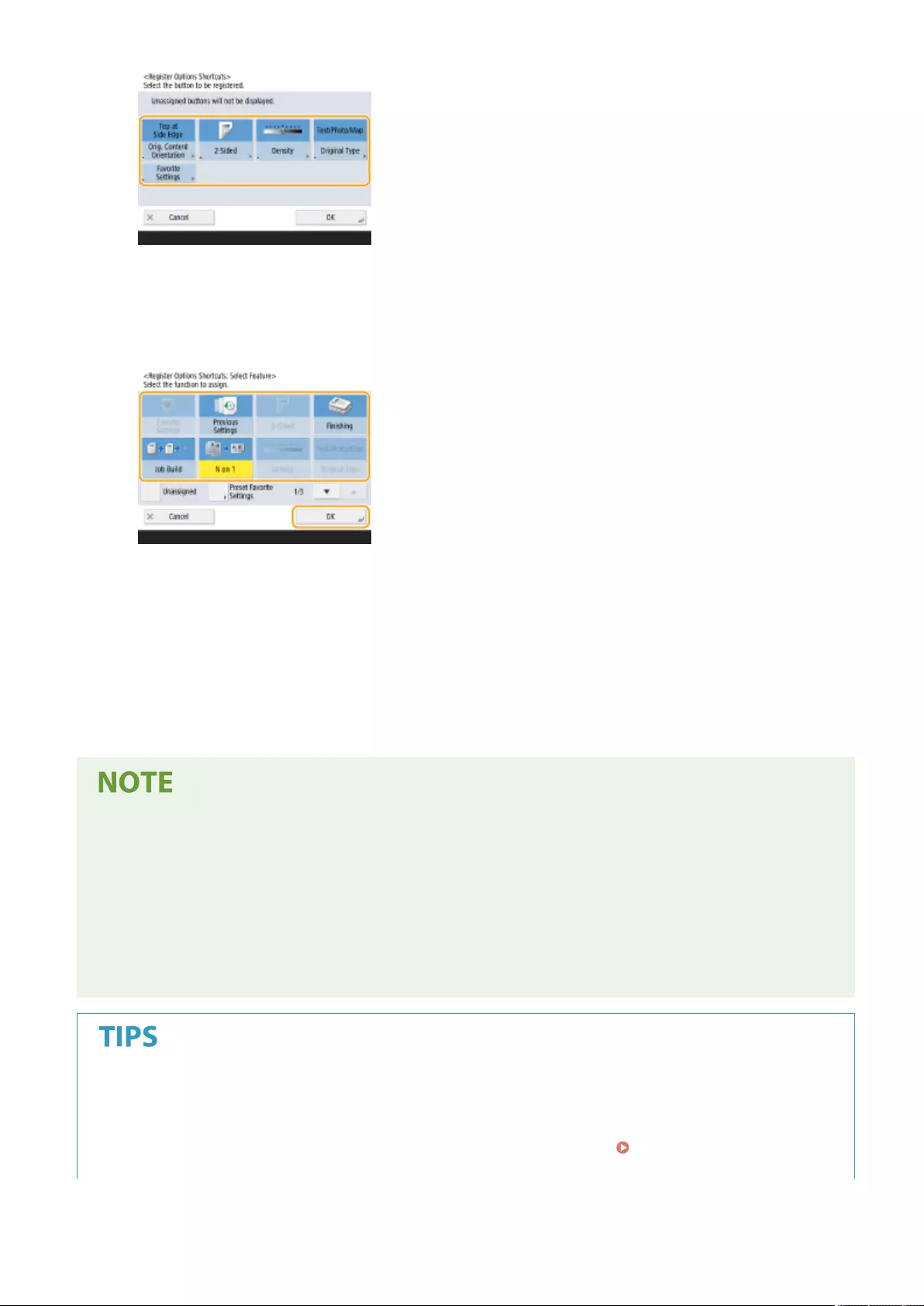
●Buttons displayed here are currently being displayed on the Basic Features screen. Buttons selected in this
step will not be displayed on the Basic Features screen.
4Select a button you want to display on the Basic Features screen and press <OK>.
●If you do not want to display the button, press <Unassigned>.
●For the Copy function, you can register the congured favorite settings as a shortcut from <Preset Favorite
Settings>.
5Press <OK>.
➠By replacing with the button selected in step 3, the new button selected in step 4 is displayed on the Basic
Features screen.
●The number of setting items located on the Basic Features screen and the location to be displayed differ
depending on functions.
●A shortcut button is not displayed if <Unassigned> is set as a shortcut.
●The limit to the number of shortcuts for <Options> you can register is as follows.
- Copy: 5
- Fax: 4
- Scan and Send: 2
Registering in <Favorite Settings>
●In <Favorite Settings>, you can register frequently used procedures for copying, as well as frequently
specied destinations and settings for scanning. For more information, see Registering a Combination
of Frequently Used Functions(P. 164) .
Basic Operations
168
Changing the default setting on the Basic Features screen
●After changing the settings for each function, you can register the current settings as a default on the Basic
Features screen by pressing followed by <Change Default Settings>. If you log into the machine with
personal authentication management ( Logging into the Machine(P. 137) ) before performing this
setting, it is registered as your own personal default setting ( List of Items That Can Be
Personalized(P. 139) ).
Basic Operations
169
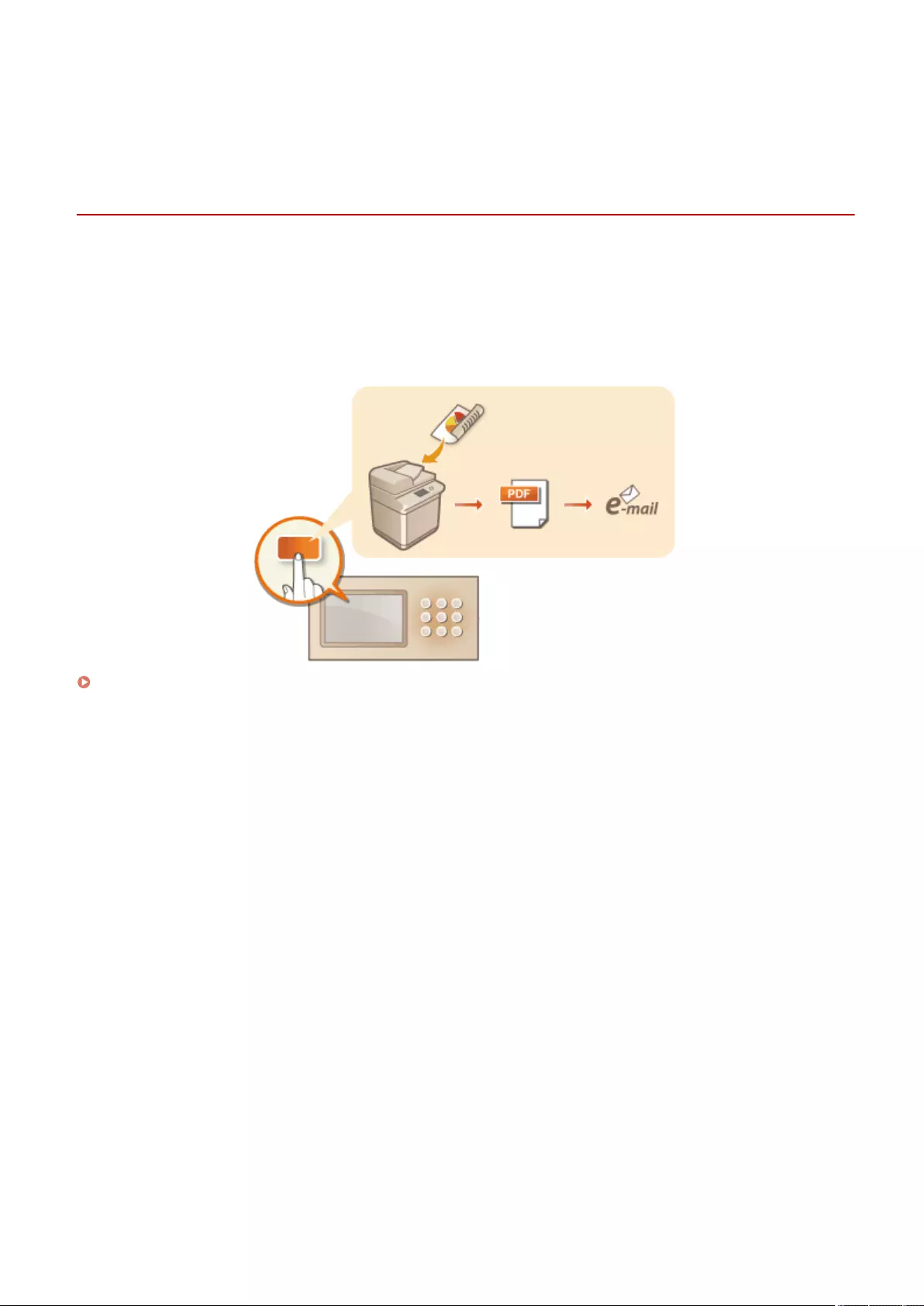
Personal/Shared
Registering Frequently Used Settings and Destinations
as Personal Buttons/Shared Buttons on the <Home>
Screen
72JY-030
Frequently used settings and destinations can be registered to the <Home> screen as Personal buttons/Shared
buttons to recall those settings with a single button.
Shared buttons can be used by all users.
Personal buttons can only be used by login users.
Registering Personal Buttons/Shared Buttons(P. 171)
Basic Operations
170
Registering Personal Buttons/Shared Buttons
72JY-031
You can register Personal buttons for your own use, or Shared buttons that can be shared with all users.
●To register a Personal button, you need to log in with personal authentication management. Conguring
the Personal Authentication Management Settings(P. 492)
●If you select <Device Login Auth. Info.> for <Information Used for File TX/Browsing Authentication>, a
password for a le destination is not stored in a Personal button. <Information Used for File TX/
Browsing Authentication>(P. 816)
●For information on the maximum number of Personal buttons and Shared buttons that can be registered,
see Management Functions(P. 1091) .
●Personal buttons cannot be changed to Shared buttons, and vice-versa. To do so, recall the settings and
register another button from .
●Press and hold a button to change its name/comment or move/delete it. The same operations (changing the
name/comment of a button or moving/deleting a button) can be performed from on the <Home>
screen. Customizing the <Home> Screen(P. 159)
●Personal buttons can be shared between multiple devices by synchronizing personalized data. List of
Items That Can Be Personalized(P. 139)
Settings that can be registered in Personal buttons/Shared buttons
Functions and settings that can be registered in Personal buttons/Shared buttons are indicated below.
●Settings that can be registered in <Favorite Settings> for the <Copy> function Reducing Copying
Operations(P. 263)
●<Fax> function settings of the machine Basic Operations for Sending Faxes(P. 275)
●Settings that can be registered in <Favorite Settings> for the <Scan and Send> function Useful Scanning
Functions(P. 404)
●Settings that can be registered in <Favorite Settings> for the <Scan and Store> function Scan Settings
Screen in <Scan and Store>(P. 446)
●Save locations for the <Scan and Store> and <Access Stored Files> functions Using Other Machines and
Memory Media(P. 437)
●Shortcuts to the Basic Features screen for the <Fax/I-Fax Inbox> function
●Access to a server and the login password can be registered to Personal buttons/Shared buttons. This is
convenient for skipping password entry when recalling the registered button. If you want to set password in
the settings stored in the registered button, as you often import settings in a Personal button or Shared
button to another machine and you want to prevent users from pretending to be other users, exclude a
password when registering.
Importing/exporting the registered buttons
●You can import and export the registered Personal/Shared buttons from the Remote UI. Importing/
Exporting All Settings(P. 628)
●Batch import of Personal buttons/Shared buttons may not be available, depending on the model of the
machine to import from. For more information, contact your dealer or service representative.
Example: Registering copy function
1Press <Copy> specify the copy settings. <Home> Screen(P. 119)
Basic Operations
171
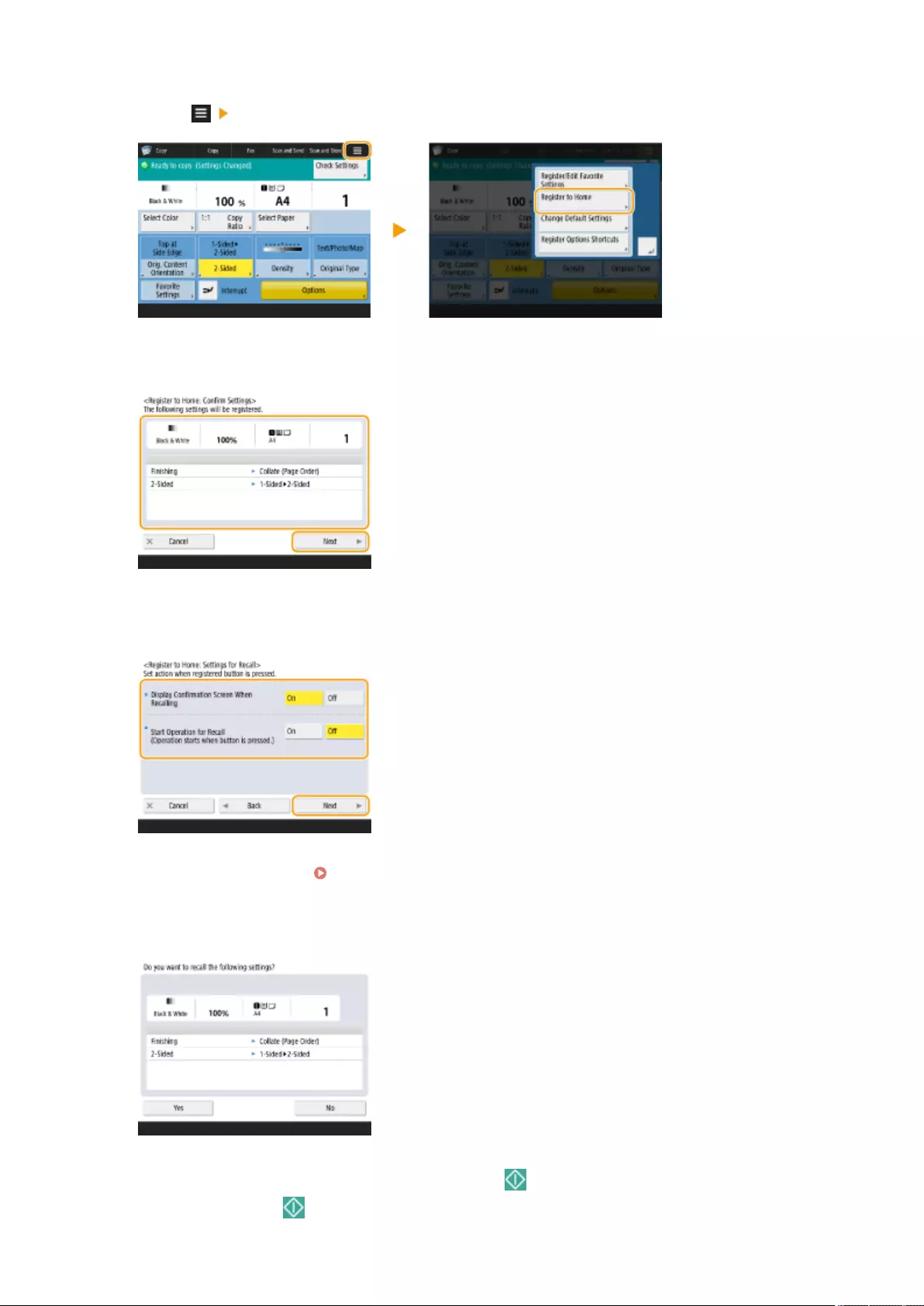
2Press <Register to Home> when the setting is complete.
3Conrm the settings and press <Next>.
4Specify the action that is performed when the registered button is pressed, and press
<Next>.
●The setting described below results in a different operation immediately after pressing the registered button.
For more information, see Executing Personal Buttons/Shared Buttons(P. 173) .
●If you select <On> for <Display Conrmation Screen When Recalling>, the conrmation screen below is
displayed when you press the registered button. Select <Off> if you do not want to display the conrmation
screen.
●If you select <On> for <Start Operation for Recall (Operation starts when button is pressed.)>, copying starts
when you press the registered button without pressing (Start). Select <Off> if you want to start copying
manually by pressing (Start).
Basic Operations
172
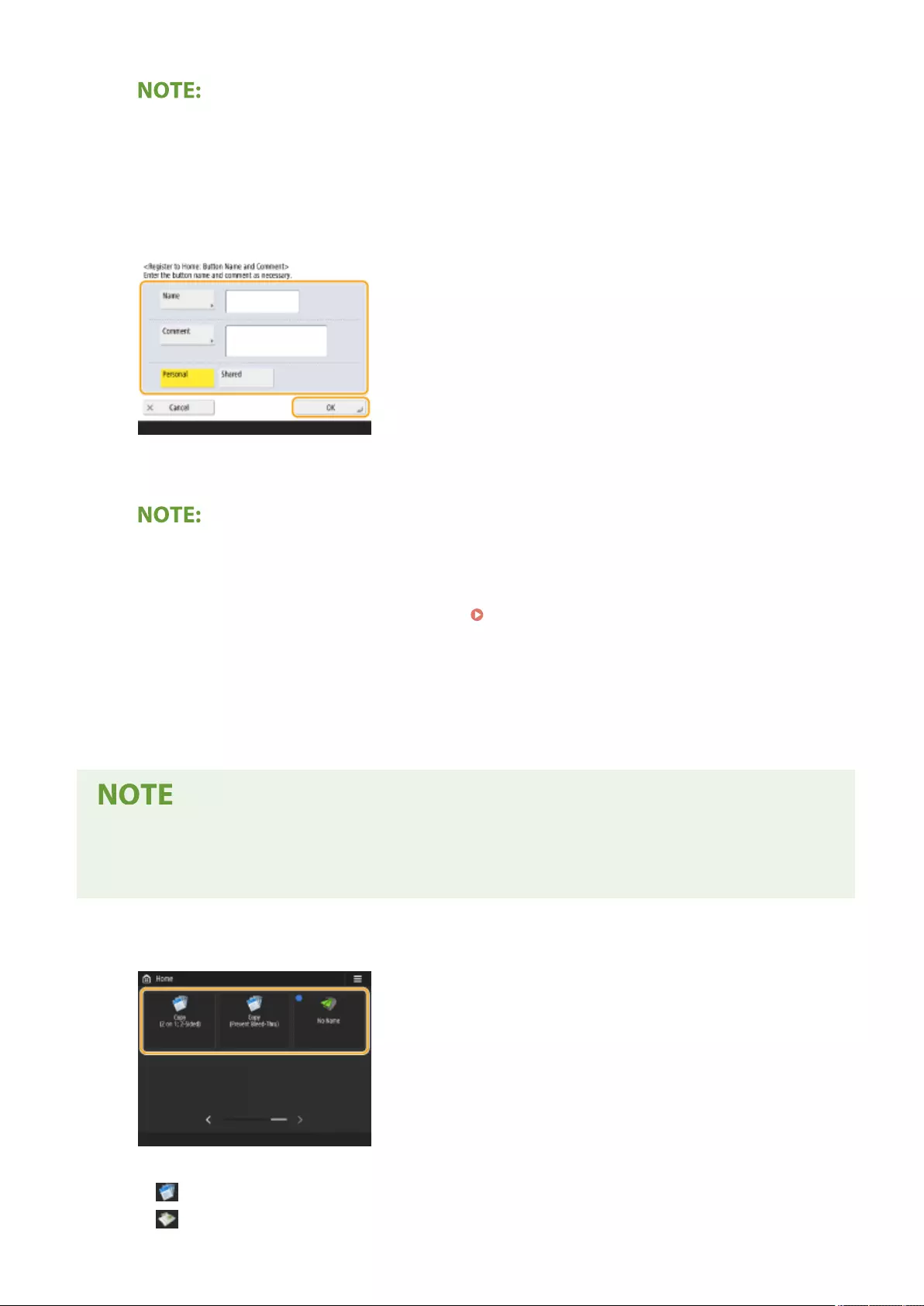
●If you select <On> for both <Display Conrmation Screen When Recalling> and <Start Operation for Recall
(Operation starts when button is pressed.)>, copying starts after you select <Yes> on the conrmation
screen.
5Enter the button name and a comment, select <Personal> or <Shared>, and press
<OK>.
●Press <Name> or <Comment> to enter. It is convenient if you enter a setting name in <Name> and a memo
in <Comment>.
●To register a button for yourself only, press <Personal>. To register a button to share with other users,
press <Shared>.
●When <12 medium-small buttons per page> is set for <Home Screen Layout Settings>, <Comment> is not
displayed for Personal buttons/Shared buttons. Customizing the <Home> Screen(P. 159)
◼Executing Personal Buttons/Shared Buttons
This section describes how to execute Personal buttons/Shared buttons. The procedure for executing the function
differs according to the settings specied when registering the Personal button/Shared button and the registered
function.
●The destinations registered in the one-touch buttons on the Quick Menu of the client machine are not
updated even if those registered in the one-touch buttons of a server machine are updated. Conrm if the
destination is updated when you cannot send to the registered destinations.
1Press the button you want to use.
●Each icon indicates the function type as shown below.
<Copy>
<Fax>
Basic Operations
173

<Scan and Send>
<Scan and Store>
<Access Stored Files>
<Fax/I-Fax Inbox>
●You can also execute the content of the button with the following procedure: press and hold the Personal
button/Shared button press <Recall>.
2Perform the following operation according to the content registered in the button.
When <Display Conrmation Screen When Recalling> is set to <On>
A conrmation screen asking whether to recall the settings is displayed.
●If <Start Operation for Recall (Operation starts when button is pressed.)> is set to <On>, operations
registered in the button start when you press <Yes>.
●If <Start Operation for Recall (Operation starts when button is pressed.)> is set to <Off>, the setting screen
is displayed when you press <Yes>. This enables you to change the settings before pressing (Start) to
start.
When <Display Conrmation Screen When Recalling> is set to <Off>
●If <Start Operation for Recall (Operation starts when button is pressed.)> is set to <On>, operations
registered in the button start immediately.
●If <Start Operation for Recall (Operation starts when button is pressed.)> is set to <Off>, the setting screen
is displayed. This enables you to change the settings before pressing (Start) to start.
When you select <Scan and Store> function button
The folder specied as the save location for the scanned documents is displayed. Scan the documents you want
to save.
Using Other Machines and Memory Media(P. 437)
When you select <Access Stored Files> function button
The specied save folder is displayed. Select a le in the folder for sending or printing.
Using Other Machines and Memory Media(P. 437)
When you select the <Fax/I-Fax Inbox> function button
The registered settings screen is displayed. Proceed with the operation that you want to perform.
Printing Documents in the Memory RX Inbox(P. 313)
Basic Operations
174

Switching the Displayed Language
72JY-032
You can change the language and keyboard layout displayed on the touch panel display. If you switch languages
frequently, it is convenient to use the <Switch Language/Keyboard> button. Follow the procedure below to show this
button on the touch panel display.
Switching the Displayed Language and Keyboard Layout(P. 176)
Showing the <Switch Language/Keyboard> Button on the Touch Panel Display(P. 176)
Switching the Displayed Language and Keyboard Layout
1Press (Settings/Register).
2Press <Preferences> <Display Settings> <Switch Language/Keyboard>.
3Select a language from the list and press <OK>.
●For some languages, the keyboard layout can be changed. After selecting the language, press <Set>, select
the layout type, and press <OK>.
Showing the <Switch Language/Keyboard> Button on the Touch Panel
Display
1Press (Settings/Register).
2Press <Preferences> <Display Settings> <Display Switch Language/Keyboard
Button>.
3Press <On> <OK>.
Basic Operations
176
●If you set it to <On>, appears at the bottom of the touch panel display. You can switch the currently
displayed language to another by pressing the <Switch Language/Keyboard> button, selecting the desired
language from the list, and then press <OK>.
●You can change the displayed language for each login user. Customizing the Screen Display
Appearance and the Operational Conditions(P. 180)
Basic Operations
177

Settings/Regist. Shortcut
Registering Shortcuts for Frequently Used Settings/
Registered Items
72JY-033
You can register shortcuts for the settings that are displayed when you press (Settings/Register), in <Settings/
Regist. Shortcut>. This allows you to quickly display even those settings that are congured deep in the menu
hierarchy.
●If <Settings/Regist. Shortcut> is not displayed on the <Home> screen, press <Home Management
Settings> <Restrict Function Display> <Set> set <Settings/Regist. Shortcut> to be displayed.
●Shortcuts that can be registered: 10
1Press <Settings/Regist. Shortcut>. <Home> Screen(P. 119)
2Press <Register>.
3Select the button in which you want to register settings.
●You can select the assigned button to change the registered settings.
4Select the settings to register as shortcuts and press <OK>.
Basic Operations
178

●If you do not want to register settings, select <Unassigned>.
Basic Operations
179

Personal Settings
Customizing the Screen Display Appearance and the
Operational Conditions
72JY-034
Individual users can customize the operational conditions to meet their preferences. For example, users who are
English speakers can make a setting so that the English version of touch panel display appears when logging in, and
other users can register their own SSID and network key to enable the machine to be easily connected to their mobile
device. Because these settings are only enabled when the user who congured the settings logs in, they do not affect
the settings of other users.
●To use personal settings, you need to log in with personal authentication management. Managing
Users(P. 489)
Available settings
The settings listed below can be congured.
●The language used on the touch panel display
●Accessibility functions for users who have diculty seeing or performing input operations on the touch
panel display
●Personal access point (personal SSID/network key)
●Automatically printing jobs after logging in
1Press <Personal Settings>. <Home> Screen(P. 119)
●When the login screen is displayed, log in. Logging into the Machine(P. 137)
2Press the setting button that you want to congure.
To set the displayed language
Press <Switch Language/Keyboard>, select a language from the list, and press <OK>.
Basic Operations
180
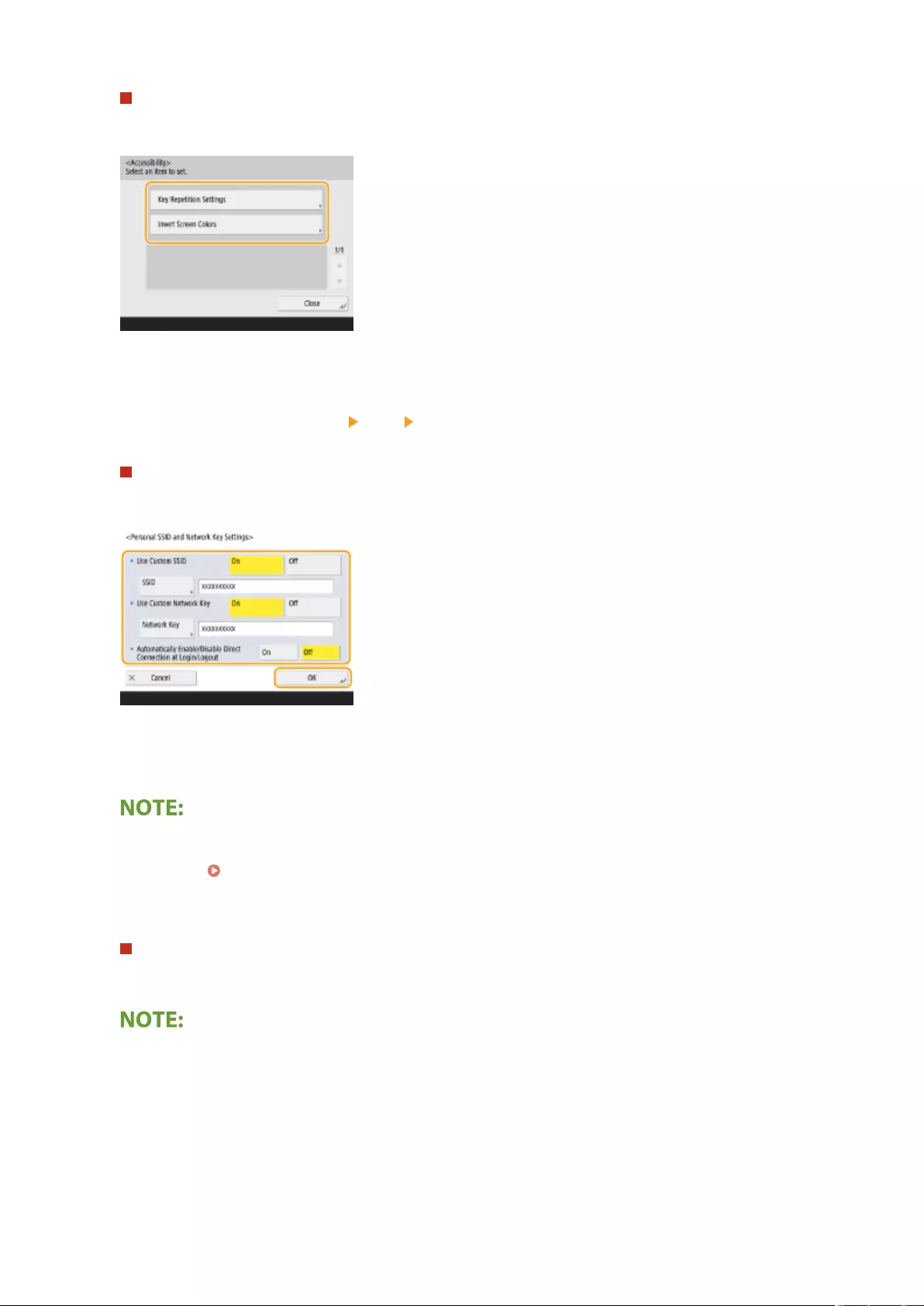
To set accessibility
Press <Accessibility>, and select the setting you want to congure.
●Press <Key Repetition Settings> to change the speed at which the same character is entered repeatedly
when a button is held down. This setting may prevent users from inadvertently entering the same
character more than once when performing input operations slowly.
●Press <Invert Screen Colors> <On> <OK> to invert the screen colors and make text easier to read.
To specify a personal SSID and network key
Press <Personal SSID and Network Key Settings>, specify a personal SSID and network key, and press <OK>.
●When <Automatically Enable/Disable Direct Connection at Login/Logout> is set to <On>, direction
connections are possible when logging in without the need to press <Enable> for <Direct Connection> in
<Mobile Portal>.
●This setting can be used when <Use Personal SSID and Network Key> is set to <On> in <Access Point Mode
Settings>. <Access Point Mode Settings>(P. 791)
●Only one mobile device may connect at a time when a personal SSID and network key are set.
Auto Print User Jobs When Logging In
●Press <On> to enable the <Auto Print User Jobs When Logging In> setting.
●This setting is disabled if any of the following settings is specied.
-If <Use User Authentication> is set to <Off>
- If <Enable Auto Print Function When Logging In> is set to <Off>
- If <Enable Use of Personal Settings> is set to <Off>
- If <Use ACCESS MANAGEMENT SYSTEM> is set to <On>
- If <Only Allow Encrypted Print Jobs> is set to <On>
- If <Personal> of <Job List Display Settings> is set to <Off>
Basic Operations
181

- If <Display Warning When Starting to Print> of <Held Jobs Warning Settings> is set to <On>
●For details on this function, see Printing Documents Held in the Machine(P. 351) .
Set the screen that is displayed when the machine starts
●If the machine is congured so that users are required to log in when it starts up ( Specifying When to
Display the Login Screen(P. 517) ), <Default Screen After Startup/Restoration> is displayed as an item in
<Personal Settings>. The screen that is displayed after the machine starts up can be set for each user.
LINKS
List of Items That Can Be Personalized(P. 139)
Switching the Displayed Language(P. 176)
<Accessibility>(P. 797)
<Access Point Mode Settings>(P. 791)
Basic Operations
182

Canceling Send/Print Jobs
72JY-035
If you press (Stop) on the control panel while a send/print job is being processed and a screen that leads to <Send
Jobs>/<Print Jobs> is being displayed, the ongoing send/print job is paused, and <Send Jobs>/<Print Jobs> appears.
Select the job that you want to cancel, and press <Cancel>.
●Screens that lead to <Send Jobs>/<Print Jobs>
-<Home> screen
- <Print> screen
- Top screens of (Status Monitor) (<Copy/Print>, <Send>, <Receive>, <Store>, <Consumables/Others>)
- <Visual Message Settings> screen
●If you press (Stop) on the control panel while a send/fax job is being processed and the <Fax>/<Scan and
Send> screen is being displayed, a pop-up screen that directly cancels the ongoing job appears. When
multiple jobs are in process, you can set which job to cancel: the job that was last made, or the job that is in
the process of sending. ( <Job to Cancel When Stop Is Pressed>(P. 825) )
●If there is a job that was started after pressing (Stop) on the control panel, the job is performed.
●For instructions on canceling jobs from the <Copy> screen or <Fax> screen, see Cancelling
Copying(P. 231) or Canceling Sending Faxes(P. 289) .
Basic Operations
183
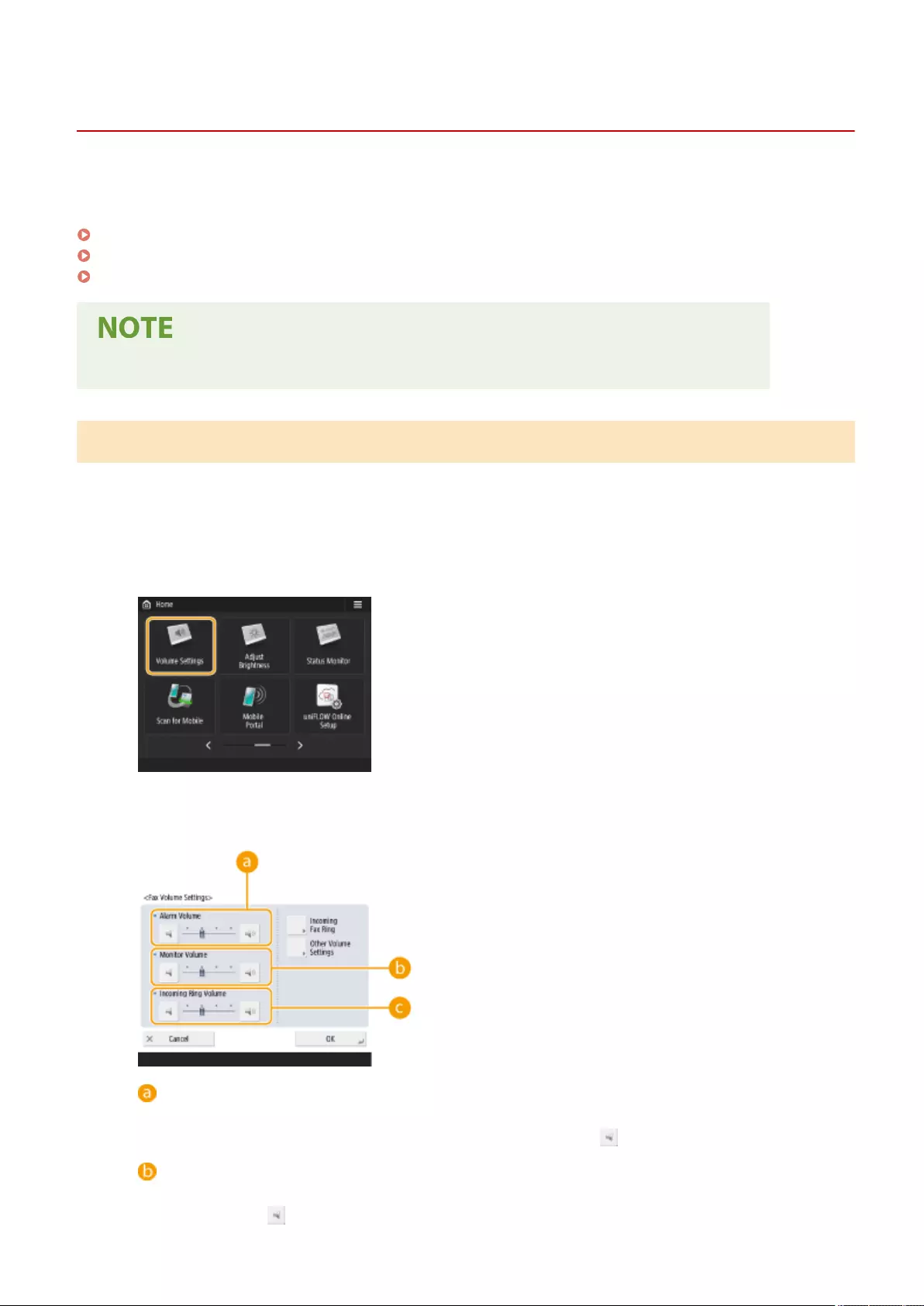
Volume Settings
Setting Sounds
72JY-036
You can adjust the volume of sounds produced by the machine when sending/receiving a fax. In addition to setting
sounds for faxes, you can specify whether or not conrmation and warning sounds are produced.
Adjusting the Volume for Sending/Receiving Faxes(P. 184)
Setting the Incoming Fax Tone(P. 185)
Setting the Conrmation Sound and Warning Sound(P. 186)
This setting works only for Line 1 (the standard line). Use this setting with Line 1 (the standard line).
Adjusting the Volume for Sending/Receiving Faxes
You can adjust the volume of sounds produced for fax functions, such as the communication and cancellation sounds
during fax transmission, or the sound to indicate that a received fax is nished printing. You can also set whether or
not a sound is produced for the Fax Memory Lock sending/receiving result.
1Press <Volume Settings>.
2Adjust the volume or specify the setting, and press <OK>.
<Alarm Volume>
Adjust the volume of sound that is produced when fax transmission is canceled, or when a received fax is
nished printing. If you do not want a sound to be produced, press all the way to the left.
<Monitor Volume>
Adjust the volume of sound that is produced when sending a fax. If you do not want a sound to be
produced, press all the way to the left.
Basic Operations
184
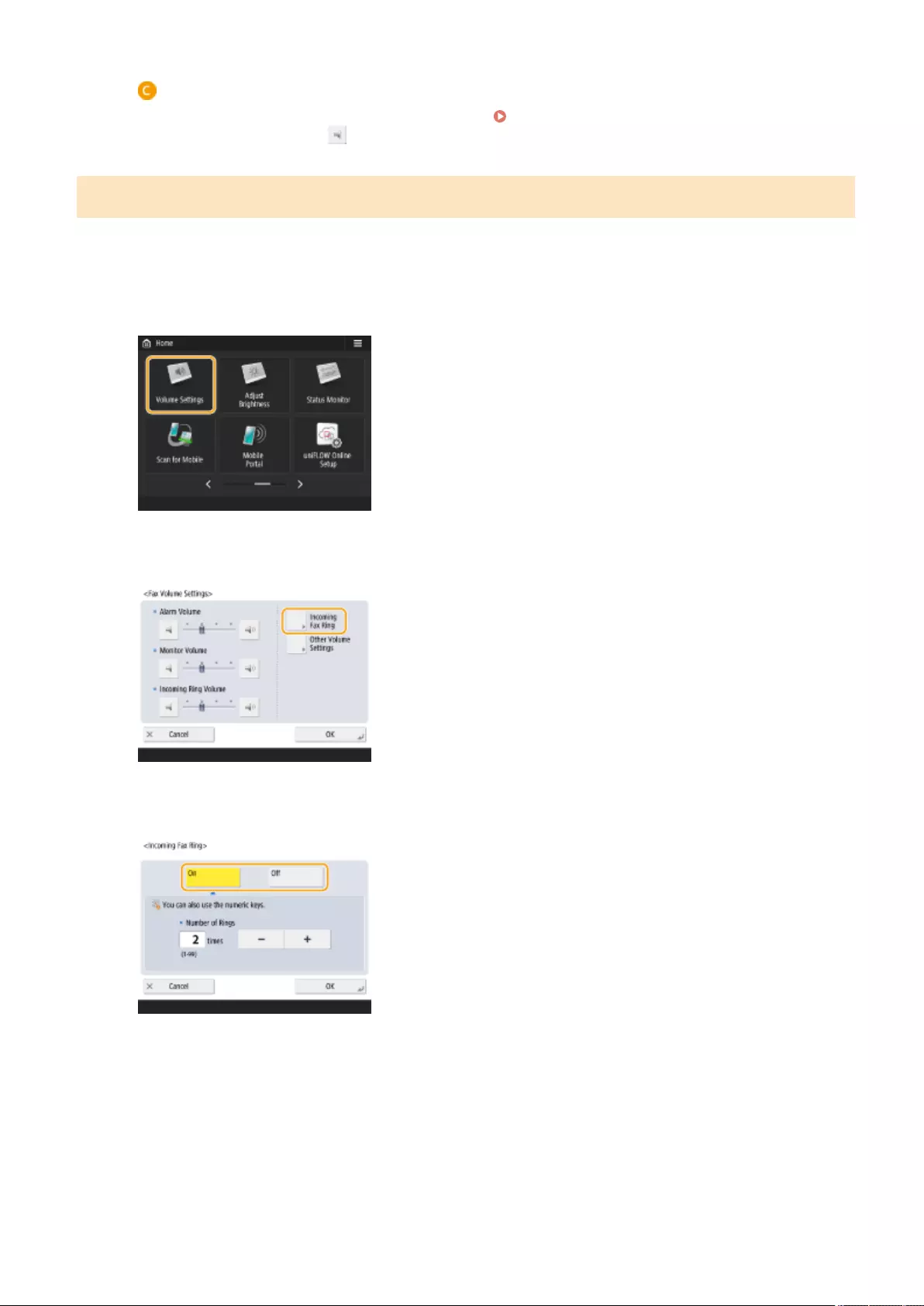
<Incoming Ring Volume>
Press to adjust the volume of incoming faxes when <RX Mode>(P. 840) is set to <Fax/Tel(Auto Switch)>.
To mute the sound, press several times to set the volume to the far left.
Setting the Incoming Fax Tone
You can set the incoming fax tone not only when the TELEPHONE 6 KIT is installed but also when a commercial
telephone is connected.
1Press <Volume Settings>.
2Press <Incoming Fax Ring>.
3Set the incoming tone.
●Select <On> to emit the incoming tone or <Off> to not. If you selected <Off>, proceed to step 5.
4Select the incoming tone count.
Basic Operations
185
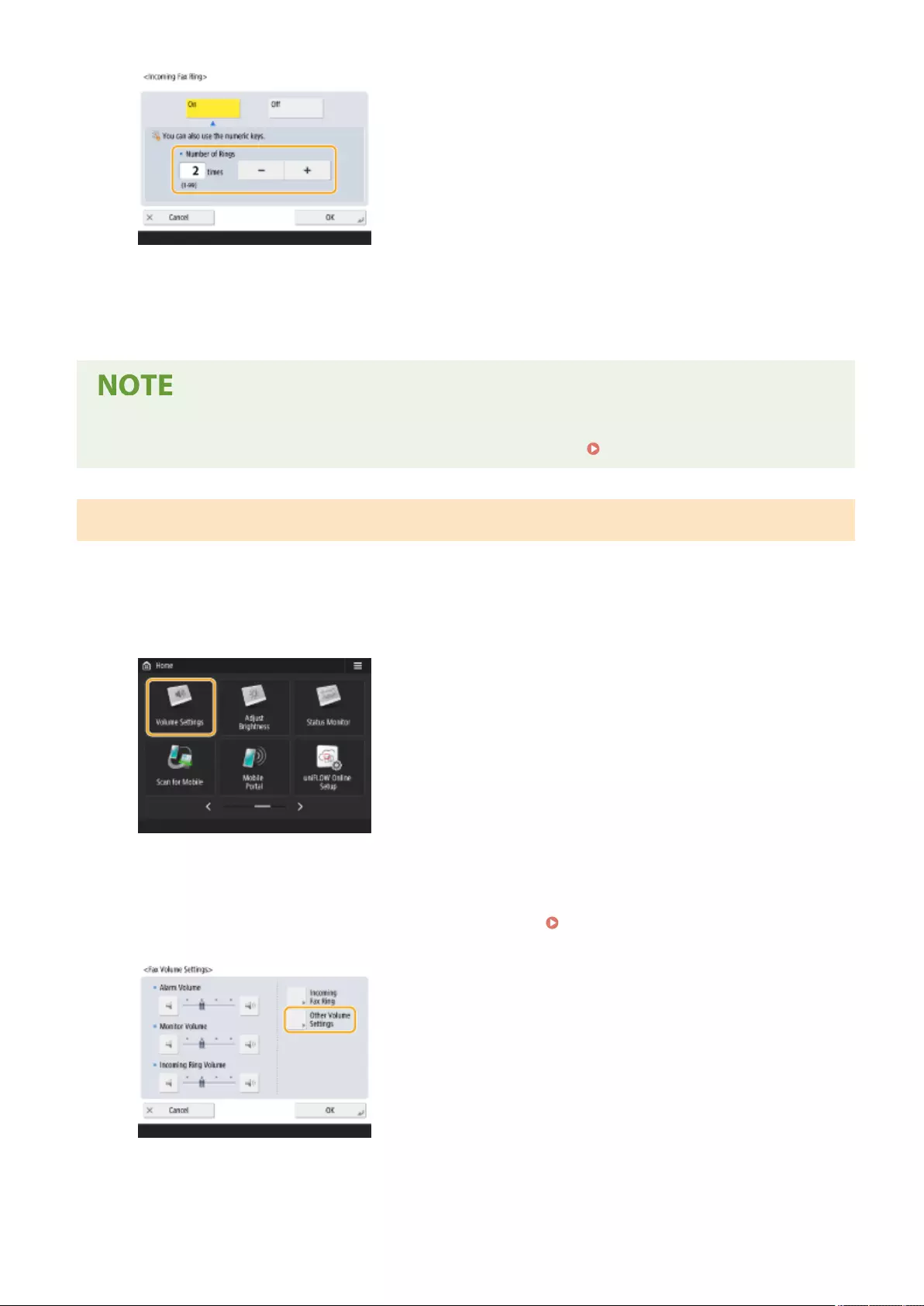
●Set the count using <->/<+> or the numeric keys.
5Press <OK>.
●Even if the incoming tone is set to <Off>, the incoming tone will be emitted when a fax arrives during the
Sleep mode if the power consumption during Sleep mode is set to low. <Sleep Mode Energy Use>(P. 780)
Setting the Conrmation Sound and Warning Sound
The machine produces sounds in a variety of situations, such as when control panel keys or touch panel buttons are
pressed, or when a malfunction occurs. You can specify whether or not set each sound individually.
1Press <Volume Settings>.
2Press <Other Volume Settings>.
●If the option to enable use of the fax function is not installed ( System Options(P. 1101) ), <Volume
Settings> is displayed.
3Set each conrmation sound/warning sound and press <Close>.
Basic Operations
186

Setting Items Description
<Entry Tone> Sound produced each time a key on the control panel or a button on the touch panel
display is pressed
<Invalid Entry Tone> Sound produced when an invalid key/button operation is performed, or when you
enter a number outside the valid setting range
<Restock Supplies Tone> Sound produced when the amount of toner is low
<Forgot Original Tone> Sound produced if original is remained on the platen glass after operation is nished
<Error Tone> Sound produced when a malfunction such as paper jam or operational error occurs
<Job Done Tone> Sound produced when an operation such as copying or scanning is complete
<Sleep Mode Tone> Sound produced when the machine enters sleep mode, or when the machine is
turned OFF if you set <Quick Startup Settings for Main Power> to <On>. (Depending
on the situations, the machine does not startup quickly and the tone does not sound.)
<Login Tone> Sound produced when login is successful
<Memory RX/TX End Tone> Sound produced when Fax Memory Lock sending/receiving completes without an
error Saving Received Documents in the Machine (Memory Reception)(P. 313)
<Memory RX/TX Error Tone> Sound produced when Fax Memory Lock sending/receiving completes with an error
Saving Received Documents in the Machine (Memory Reception)(P. 313)
4Press <OK>.
LINKS
TELEPHONE 6 KIT(P. 1122)
Basic Operations
187

Entering Sleep Mode
72JY-037
The sleep mode function reduces power consumption by temporarily disabling some internal operations of the
machine. You can put the machine into sleep mode simply by pressing (Energy Saver) on the control panel. When
the machine is in sleep mode, the touch panel display turns off and (Energy Saver) lights up. Control
Panel(P. 93)
●The machine may not enter sleep mode depending on the machine's operation status and conditions.
●If the machine does not enter the Sleep mode for an extended period of time, automatic calibration is
performed to maintain image quality. Calibration may affect the life of the toner cartridge.
●The Processing/Data indicator ashes or maintains a steady green light even when the machine enters the
Sleep mode.
Exiting Sleep Mode
The machine exits the sleep mode when one of the following operations is performed:
●When (Energy Saver) is pressed on the control panel*1
●When originals are placed in the feeder
●When the feeder is opened
●When paper is loaded in/removed from the multi-purpose tray*1
●When a cover on the machine is opened/closed*1
*1 Some models of the machine do not support this function.
When You Want to Set the Auto Sleep Timer
You can use the <Auto Sleep Time> setting to automatically put the machine into sleep mode. If you want to
change the amount of time that elapses before the machine enters auto sleep mode, follow the procedure
below.
(Settings/Register) <Preferences> <Timer/Energy Settings> <Auto Sleep Time> or
to set the amount of time that elapses before the machine automatically enters sleep mode
<OK>.
●You can set the time range to automatically enter sleep mode by the day of the week. <Auto Sleep
Weekly Timer>(P. 780)
Energy Consumption in Sleep Mode
You can set the amount of energy that the machine consumes when it is in sleep mode. Follow the procedure
below to set the amount of energy consumed in sleep mode.
Basic Operations
188

(Settings/Register) <Preferences> <Timer/Energy Settings> set <Sleep Mode Energy
Use> to <Low> or <High>.
Basic Operations
189
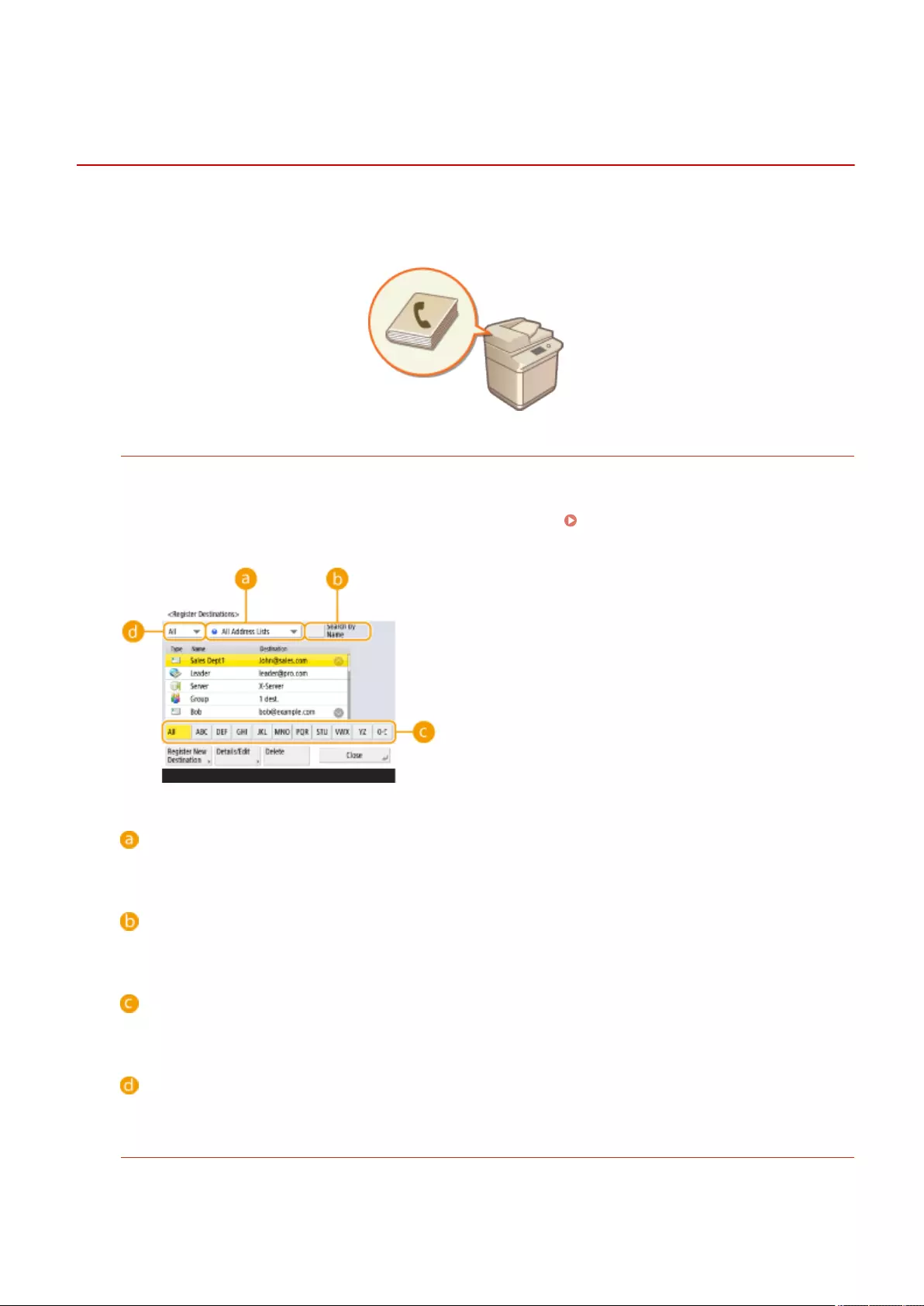
Dest./Fwd. Settings
Registering Destinations
72JY-038
PMW-RGDS
Destinations for sending faxes and scanned data can be registered in the Address Book or one-touch buttons.
Address Book
If you want to register many destinations or classify them by department or business partner, register them in
the Address Book. The Address Book allows you to search destinations by the rst character of the name or by
selecting a destination type such as fax or e-mail. You can register destinations for all users, destinations for
your own use, and destinations that only an administrator can edit. Registering Destinations in the Address
Book(P. 195)
Address list drop-down list
Select an address list for a department or business partner.
<Search by Name>
Enter the destination name.
First letter button
Select the alphanumeric button for the rst character of the destination name.
Destination type drop-down list
Select the button to lter destinations by destination type such as fax or e-mail.
One-Touch Button
You can register frequently used destinations in one-touch buttons to simplify operations. The one-touch
buttons with registered destinations are displayed on the touch panel display, enabling you to quickly search
Basic Operations
190
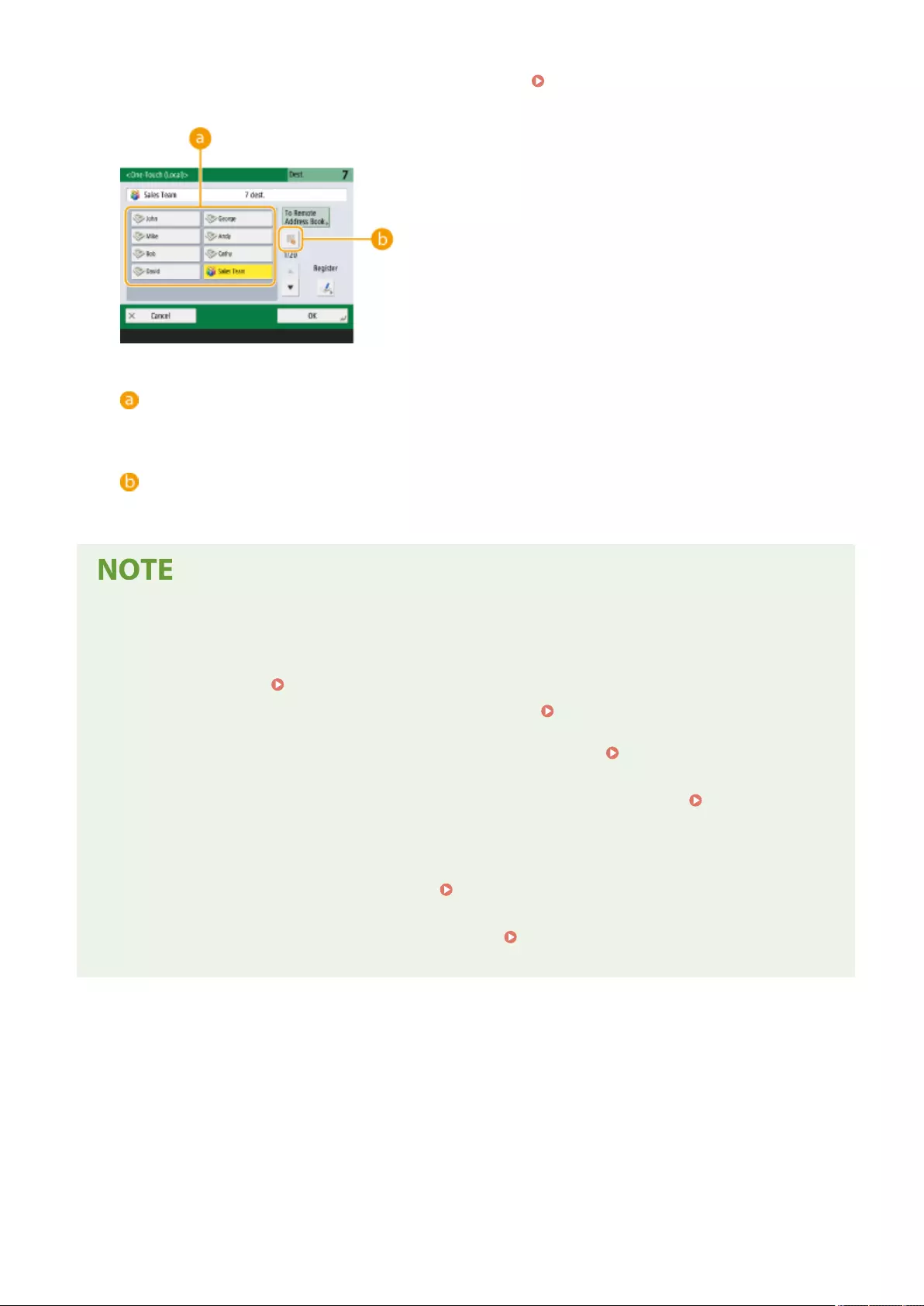
and specify the destinations with the simple press of a button. Registering a Destination in a One-Touch
Button(P. 210)
One-touch button
You can easily specify the desired destination with the simple press of a button.
One-touch number button
You can enter the three-digit number of a registered one-touch button if it is not shown on the touch panel
display.
For the administrator
●The Address Book and one-touch buttons can be exported/imported. This can be used for backup data if a
failure occurs or to simplify the procedure for registering destinations between supported machines. For
more information, see Importing/Exporting the Settings Individually(P. 632) .
●The Address Book can be personalized for each logged-in user ( List of Items That Can Be
Personalized(P. 139) ). Furthermore, the Synchronize Custom Settings facility can be used to enable the
Address Book to be shared by a number of Canon multifunction printers ( Synchronizing Settings for
Multiple Canon Multifunction Printers(P. 656) ).
●You can set a password to avoid unauthorized editing or deletion in the Address Book. Setting a PIN for
Address Book(P. 566)
●If there are destinations that you do not want to display in the Address Book or if you want to limit user
access to destinations, enter an access number when registering a destination. To use the access number, it
is necessary to activate the setting in advance in Restricting Access to Destinations Registered in the
Address Book(P. 567) .
●Congure User Group Address Lists from the Remote UI. ( Registering Destinations via the Remote
UI(P. 592) )
Basic Operations
191

About the Address Books of the Machine
72JY-039
Local Address Book and Remote Address Book
Local Address Book: The address book stored on the storage device of the machine. This address book is
comprised of the following address lists.
●Address List 01 to 10
●Address List, One-Touch
●Address List for Administrator
●Personal Address List
●User Group Address List 01 to 50
Remote Address Book: The address book of another Canon machine connected to the machine via a network. It
can be accessed in the same way as the Local Address Book to specify destinations.
●To use a Remote Address Book, it is necessary to register the Remote Address Book to access on the
client machine ( <Set Destination>(P. 849) <Acquire Remote Address Book>) and make the
Remote Address Book open on the server machine ( <Set Destination>(P. 849) <Make Remote
Address Book Open>).
●Up to eight machines including this machine can be connected as client machines at the same time to
the server machine with the Remote Address Book that is opened externally. However, if the server
machine is performing other network communication during this time, the number of machines that
can connect may be reduced. If the machine cannot connect, a network error notice is sent.
●The server machine destinations registered in Favorite Settings and the <Personal>/<Shared> button
of the client machine are not updated when the destinations are updated on the server machine.
Conrm if the destination is updated when you cannot send to the registered destinations.
●Destinations registered in the Remote Address Book cannot be edited/deleted from a client machine.
To edit/delete destinations in the Remote Address Book, edit/delete the Local Address Book on the
server that discloses the Remote Address Book.
Overview of Address Lists
◼Address List 01 to 10
Address lists that are open to all users.
◼Address List, One-Touch
The one-touch button destinations displayed on the <Fax> screen and <Scan and Send> screen. Only the one-
touch buttons for fax destinations are displayed on the <Fax> screen. Fax destinations are also displayed on the
<Scan and Send> screen if <Enable Fax in Scan and Send Function> is set to <On>.
Basic Operations
192
◼Address List for Administrator
Used to register destinations used in <Forwarding Settings> and <Archive TX Document>.
◼Personal Address List
The personal address list displayed when user authentication is used.
◼User Group Address List 01 to 50
The group address list available to a group of users when user authentication is used. A User Group Address
List corresponds to a single user group.
●<Use Personal Address List> and <Use User Group Address List> must be enabled to use <Use
Personal Address List>(P. 852) and <Use User Group Address List>(P. 852) .
●To use a User Group Address List, it is necessary to create a user group in advance ( Registering
User Information in the Local Device(P. 495) ) and associate the created user group with the User
Group Address List ( Registering Destinations via the Remote UI(P. 592) ).
Moving/Copying Destination Addresses
The table below indicates whether destination addresses can be moved or copied between the various address
books.
Move/Copy to:
Address List 01 to 10,
Address List for
Administrator
Personal
Address List
User Group
Address List 01 to
50
Move/
Copy from:
Address List 01 to 10,
Address List for
Administrator
Move Copy Copy
Personal Address List Copy -- Move
User Group Address List 01
to 50 Copy Move Move
Destination addresses cannot be moved/copied in the following situations.
●Situations when destination addresses cannot be copied to <Address List 1> to <Address List 10>
- When a general user is performing the operation and <Address Book PIN> has been set but the
user has not entered the PIN
- When the user is performing the operation from the control panel and <Use User Group Address
List> is set to <On (Browse Only)> (Copying can be performed from the Remote UI)
●Situations when destination addresses cannot be copied to the <Personal Addr. List>
- When <Use Personal Address List> is set to <Off>
- When <Use User Group Address List> is set to <On (Browse Only)>
●Situations when destination addresses cannot be moved/copied to "User Group Address List 01 to 50"
Basic Operations
193
- When <Use User Group Address List> is set to <On (Browse Only)> or <Off>
Differences in Address List Types
Address List
01 to 10
Address
List, One-
Touch
Address List for
Administrator
Personal
Address List
User Group
Address List
01 to 50
People who can use the address book All users All users Administrator
DeviceAdmin
Each logged-
in user
Each user
group*1
Address Book PIN (registration restriction) Yes Yes No No No
Manage Address Book Access Numbers function Yes No No No No
Printing the address list Yes Yes Yes No No
Can be set as a <Forwarding Destination> in
<Forwarding Settings> Yes Yes Yes No No
Can be set with <URL Send Settings> in <Set
Fax/I-Fax Inbox> Yes Yes Yes No No
Can be set as a notication destination of <Job
Done Notice> Yes Yes Yes No No
Can be set as <Reply-to> Yes Yes Yes No No
Creating <Group> in an address list Yes Yes Yes Yes Yes
*1 Only the user groups that the user logged in on the control panel belongs to can be accessed. All User Group Address Lists can
be accessed when a user with Administrator privileges logs in from the Remote UI.
●For information on the maximum number of destinations that can be registered to each address list,
see Management Functions(P. 1091) "Max. Destinations Registered to Address Book."
●The maximum number of Personal Address Lists and User Group Address Lists that can be stored in
the machine depends on the limit in the user settings information. See Management
Functions(P. 1091) "Maximum number of users whose setting information can be saved in the
machine."
Basic Operations
194
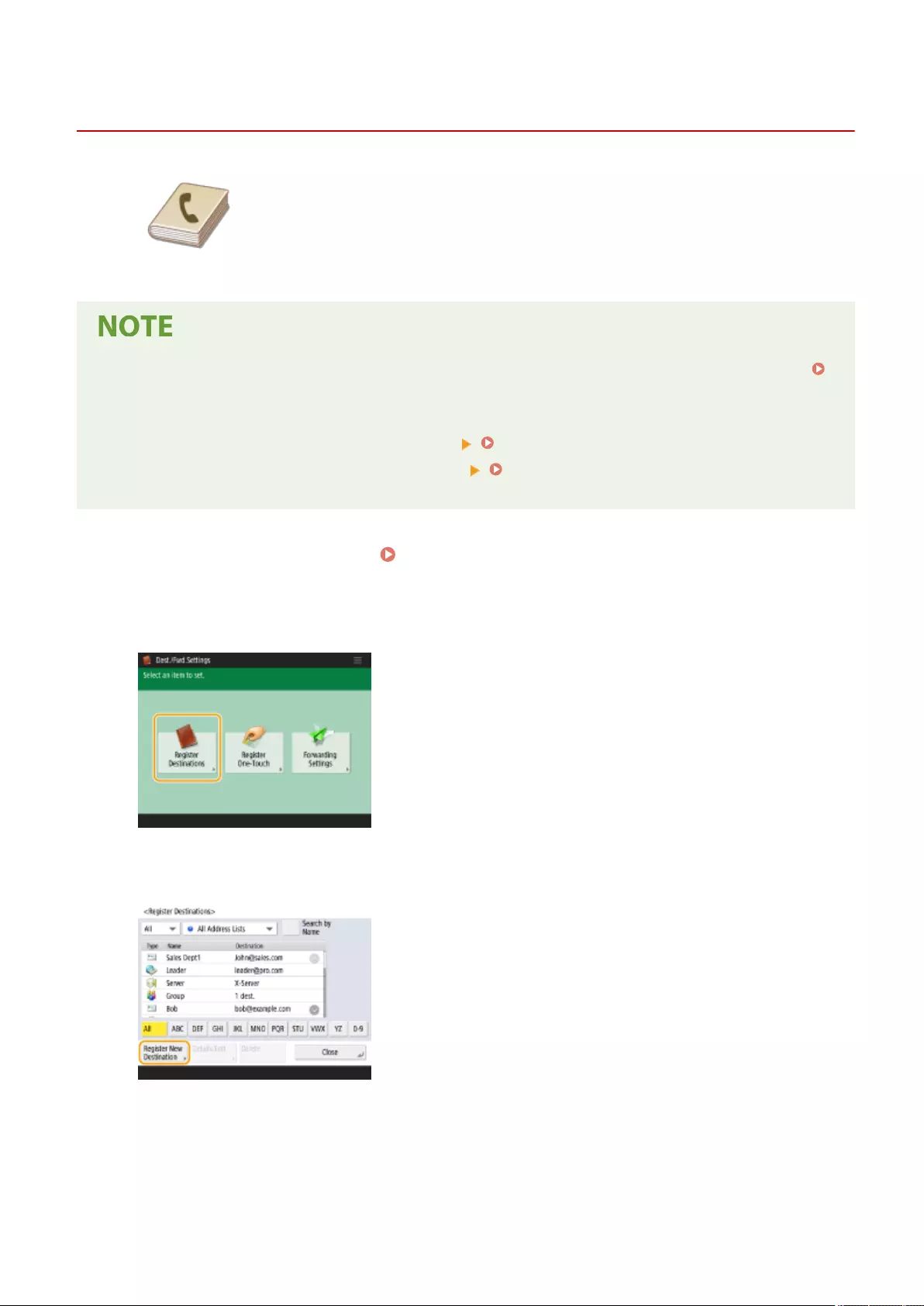
Registering Destinations in the Address Book
72JY-03A
You can register a recipient's fax number or an e-mail address that can be used
when sending scanned documents in the Address Book. You can also register an I-
fax destination, a le server folder location (IP address and path), and the storage
(Advanced Space) of a Canon multifunction printer in the Address Book as a
destination.
●To register a destination for your own use, you need to log in with personal authentication management.
Managing Users(P. 489)
●Registering/editing/deleting of destinations can also be performed from the following screens:
- <Address Book> on the Fax Basic Features screen Basic Operations for Sending Faxes(P. 275)
- <Address Book> on the Scan Basic Features screen Basic Operations for Scanning Originals(P. 377)
1Press <Dest./Fwd. Settings>. <Home> Screen(P. 119)
2Press <Register Destinations>.
3Press <Register New Destination>.
4Select the type of destination to register.
Basic Operations
195

●Select <Fax>, <E-Mail>, <I-Fax>, or <File> as the type of destination to register.
5Select where to register the destination from the address list drop-down list.
●If you want to register the destination for your own use, select <Personal Addr. List>.
●If you want to register the destination which only an administrator can edit, select <Address List for Admin.>.
●If you want to share the destination with a registered user group, select a registered User Group Address
List.
●<Address List 1> to <Address List 10> can be regarded as 10 separate address books. Classifying an
address list by departments or by business partners makes them easier to nd when specifying a
destination. It is also easier to manage an address list if you change their names to department name or
business partner name ( <Rename Address List>(P. 849) ).
●You can also manage User Group Address Lists by enabling only the administrator to register/edit
destinations from the Remote UI. (<Set Destination> <Use User Group Address List>(P. 852) )
6Press <Name> enter the destination name, and press <Next>.
7Congure the settings according to the type of destination selected in step 4.
Fax
1Enter the fax number.
Basic Operations
196
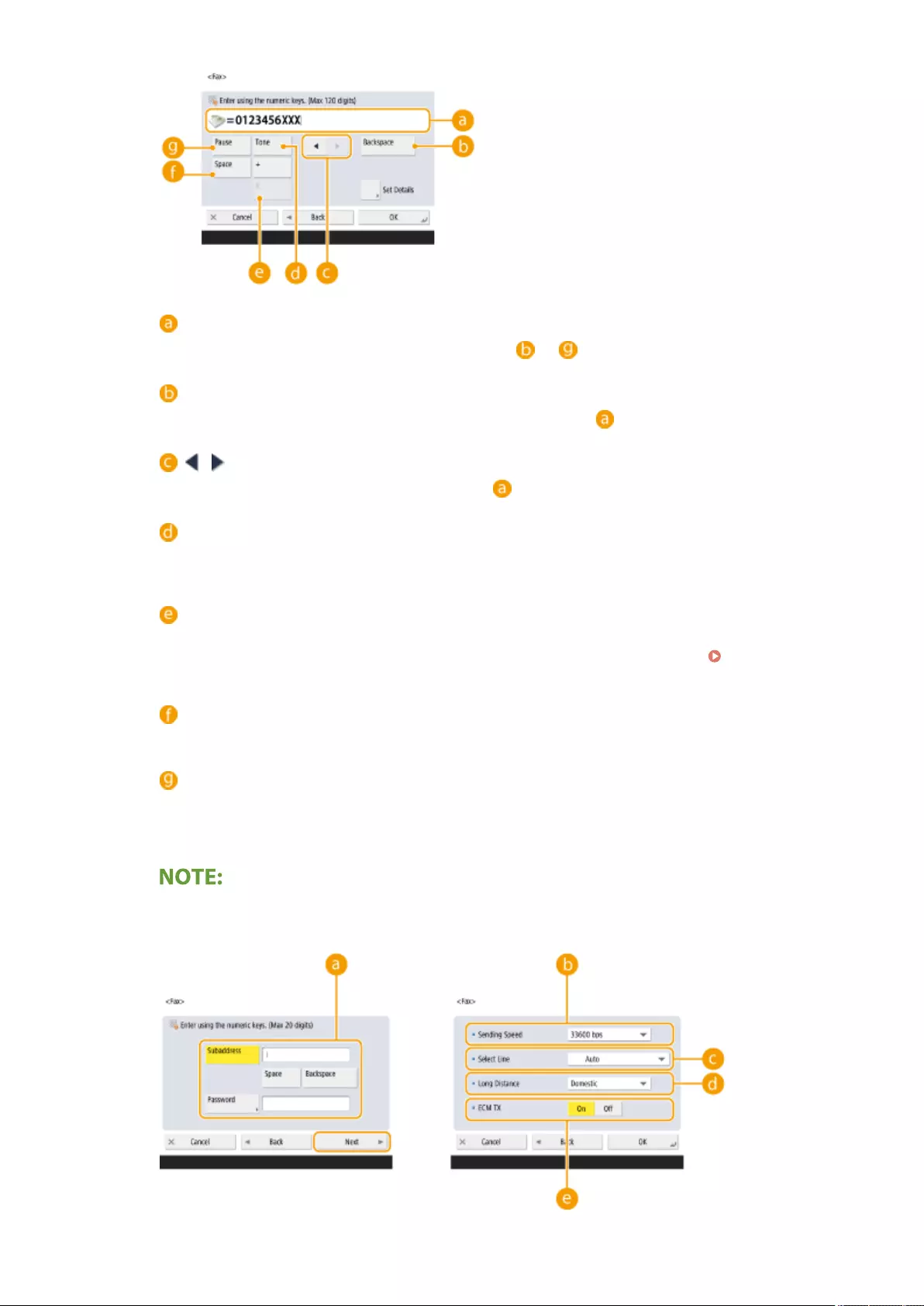
Fax number eld
Enter the fax number using the numeric keys. Enter to as necessary.
<Backspace>
Delete numbers to the left of the cursor in the fax number eld ( ) one by one.
/
Press when moving the fax number eld cursor ( ) to the left or right.
<Tone>
If you press this button, the character "T" (tone) is inserted. Even if you are using pulse dial, numbers
following "T" will be sent using tone dial.
<R> key
If the machine is connected to a PBX (Private Branch Exchange), press this button before entering the
destination. If this button is not available, you need to register the R-key settings. <R-Key
Setting>(P. 833)
<Space>
Enter a blank space between numbers to make them easier to read.
<Pause>
If you press this button, the character "P" (pause) is inserted. When sending a fax overseas, insert
pauses after the international access code or fax number. This helps to improve the connection.
●You cannot insert a pause at the beginning of a number.
2Press <Set Details> and specify settings as necessary.
Basic Operations
197

<Subaddress>/<Password>
Specify when sending or receiving documents to increase security by attaching a subaddress and
password to all of your fax transactions. Basic Operations for Sending Faxes(P. 275)
<Sending Speed>
Depending on the recipient's fax machine or the status of the line, a transmission error may occur due
to the transmission speed. If errors occur frequently, lower this setting value.
<Select Line>
If you have additional telephone lines, you can select the line to use for sending a fax.
<Long Distance>
If transmission errors occur frequently when you make overseas calls, select <International (1)>. If
errors persist, change the setting to <International (2)> or <International (3)>.
<ECM TX>
Select <On> to correct image errors. Select <Off> if the recipient's fax machine does not support the
Error Correction Mode (ECM).
●To send faxes using ECM, it is also necessary to set <Fax Settings> <ECM TX>(P. 831) to <On>.
●Although there are items you can set in the fax setting ( Fax Basic Features Screen(P. 273) ), it is
convenient to set them here if you want to change the sending conditions for each destination.
●Set <Auto Adjust Communication Speed When Using VoIP>(P. 834) to <On> to send and receive
faxes more accurately when the line or other party is prone to errors. If you set this to <On>, the
communication speed is limited to 14,400 bps or slower, which reduces errors.
E-mail
1Press <E-Mail Address> enter the e-mail address.
2Select <On> or <Off> in <Divide Data>.
If the size of the data being sent exceeds the maximum limit ( <Maximum Data Size for
Sending>(P. 827) ), select whether you want to divide the data by size or by page.
●If you select <On>, the data is divided into smaller sizes that do not exceed the limit and is sent in
several sections. The recipient's e-mail software must be able to combine the data received.
●If you select <Off>, the number of pages to be sent at one time decreases and the total transmission is
divided into several sections. For example, 10 pages of data are transmitted twice, 5 pages each time.
Therefore, your counterpart receives two e-mails. However, if you send data that cannot be separated
into pages, such as JPEG, a transmission error occurs.
Basic Operations
198
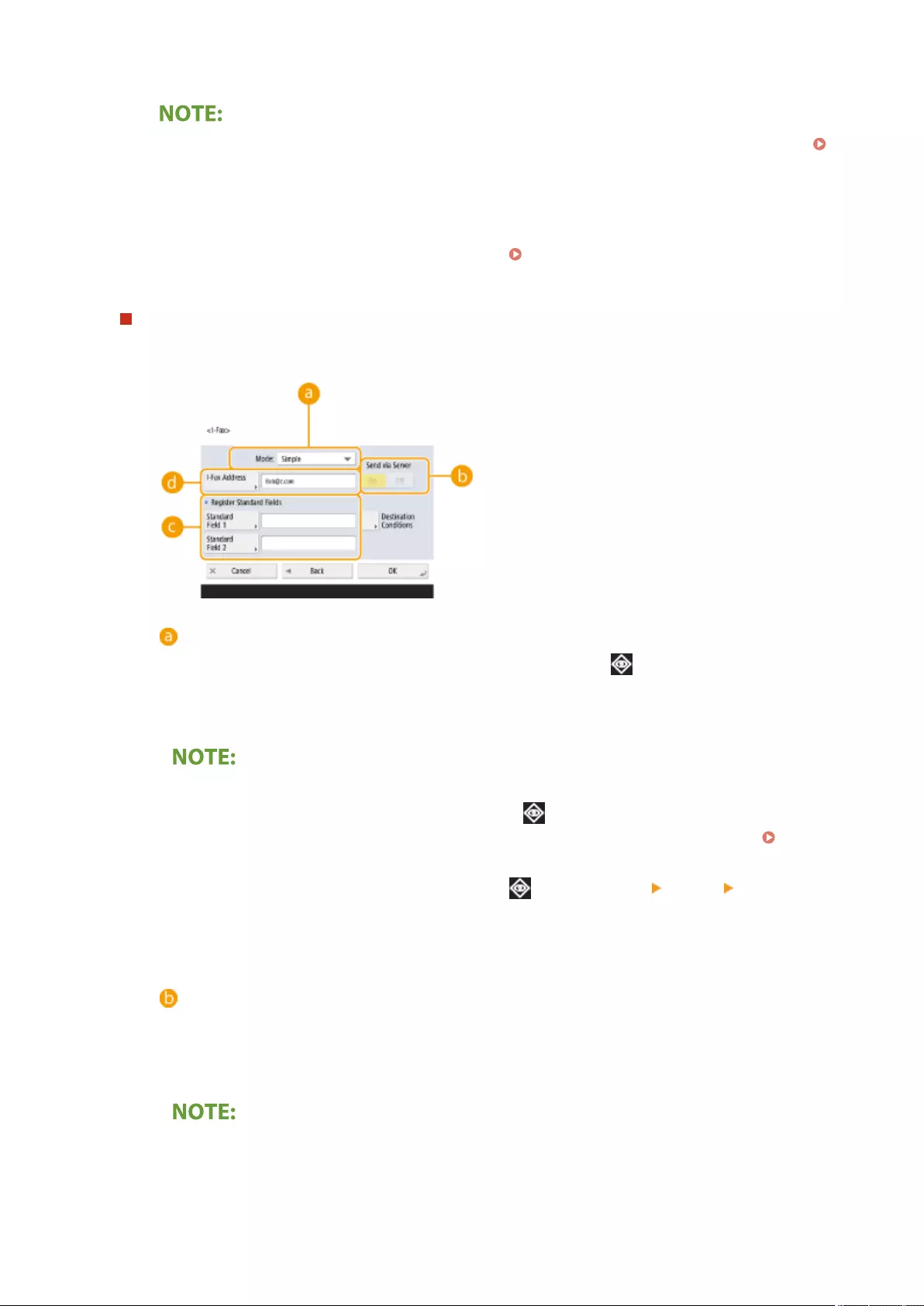
●When the domain to use is xed, you can skip domain entry. You can register a domain name to
<Auto Add Specied Domain to Dest. Without Domain>(P. 830) and enable <When Sending E-Mail>
in advance to automatically add a domain when sending, without the need to enter "@" and the
domain name.
●You can register frequently used domain names in <Register'd Characters> on the keyboard, and you
can recall them when entering an e-mail address. <Registered Characters for Keyboard>(P. 774)
I-fax
1Specify settings as necessary.
<Mode:>
You can select the type of sending results that are displayed when (Status Monitor) is pressed.
Select <Full> if you want to check whether an I-fax is delivered to the recipient's machine, or select
<Simple> if you want to check whether an I-fax is delivered to a mail server. Note that you cannot
conrm the delivery status if the recipient's machine does not support the <Mode:> function.
●If you send an I-fax using the <Full> mode to a machine that does not support the <Full> mode,
<Awaiting result...> is displayed when you press (Status Monitor) to check the delivery status,
even if the transmission is complete. It continues to be displayed until the time set in <Full Mode
TX Timeout>(P. 829) passes.
●You can check the delivery status by pressing (Status Monitor) <Send> <Job Log>. If the
document was sent successfully, <OK> will be displayed, if it failed to send, <NG> will be displayed,
and if the results cannot be conrmed, <--> will be displayed. In the Simple mode, even if the
delivery was successful, <--> will be displayed because delivery conrmation cannot be carried out.
<Send via Server>
Specify whether or not to send I-faxes to destinations via the mail server. Select <On> if you want to
send I-faxes via the mail server. Select <Off> if you want to send data directly to a recipient on the same
local area network (LAN). By sending directly to a recipient, you can send large amounts of data without
placing a burden on the mail server.
●To send an I-fax that is not in an IP address format such as "user name@[the recipient's IP address]"
without using a mail server, settings such as an MX (Mail eXchange) record need to be congured
on the DNS server. Ask your Network administrator whether or not this type of setting is available.
Basic Operations
199

●When you set <Off> in <Send via Server>, you are required to set <On> in <Use Send via
Server>(P. 829) in advance. If this setting is <Off>, the setting in <Send via Server> cannot be
changed. It is recommended to set <Allow MDN Not via Server>(P. 829) to <On>.
●Even if you set <Send via Server> to <Off>, delivery conrmation of documents sent using the Full
mode is carried out via the server.
<Register Standard Fields>
This setting is required for using an Internet fax service. If you do not use an Internet fax service, this
setting is not necessary. For more information, contact your Internet service provider.
<I-Fax Address>
●Enter the I-fax address using the following format: adv01@example.com.
●When sending to a recipient on the same network, use the following format: adv01@[192.168.11.100]
(the recipient device name@[IP address]).
●When the domain to use is xed, you can skip domain entry. You can register a domain name to
<Auto Add Specied Domain to Dest. Without Domain>(P. 830) and enable <When Sending I-Fax>
in advance to automatically add a domain when sending, without the need to enter "@" and the
domain name.
●You can register frequently used domain names in <Register'd Characters> on the keyboard, and you
can recall them when entering an I-fax address. <Registered Characters for Keyboard>(P. 774)
2Press <Destination Conditions> specify each setting and press <OK>.
<Paper Size>
Set the paper size that the recipient can receive. Specify this setting after checking whether the paper
size of the data to send matches the specications of the recipient's device.
- <A4/LTR>: Sends with the A4/LTR size.
- <A4/LTR> + <B4>: Sends with the A4/LTR size or B4 size.
- <A4/LTR> + <A3/11x17>: Sends with the A4/LTR size or A3/11" x 17" size.
- <A4/LTR> + <B4> + <A3/11x17>: Sends with the A4/LTR size, B4 size, or A3/11" x 17" size.
●If the paper size of the scanned data is smaller than the sizes set in <Paper Size>, the data is sent
with the smallest paper size set in <Paper Size> with blank margins.
●If the paper size of the scanned data is larger than the sizes set in <Paper Size>, the data is reduced
and sent with the largest paper size set in <Paper Size>.
●Set the destination conditions according to the specications of the recipient's machine. If the paper
size of the data to send is larger than the paper sizes that can be used with the recipient's device,
the image may be clipped or cut off.
<Compression Method>
Select compression method. The compression rate is highest for MMR, followed by MR, and then MH.
The higher the compression rate, the shorter the required transmission time.
Basic Operations
200

<Resolution>
Select a higher value to increase the resolution and image quality. However, the higher the resolution,
the longer the required transmission time.
<Divide Data>
If the size of the data being sent exceeds the maximum limit ( <Maximum Data Size for
Sending>(P. 827) ), select whether you want to divide the data by size or by page.
●If you select <On>, the data is divided into smaller sizes that do not exceed the limit and is sent in
several sections. The recipient's device must be able to combine the data received.
●If you select <Off> in <Send via Server> ( ) in step 1 for conguring the I-fax setting, the data is
sent without being divided, even if it exceeds the maximum limit.
●Set the destination conditions according to the specications of the recipient's machine. If you set
conditions that the recipient's machine does not support, a transmission error may occur.
File server/Advanced Space
1Enter the host name of the le server/Advanced Space which transmits data.
●Ask your Network administrator about the information on the le server/Advanced Space.
<Protocol>
Select a protocol for the le server from <Windows (SMB)>, <FTP> and <WebDAV>.
When sending a document to the Advanced Space, select <Windows (SMB)> or <WebDAV>.
●If you select <Windows (SMB)>, the <Search Host> and <Browse> buttons are displayed. You can
easily specify a le server/Advanced Space by searching or viewing the network.
●You can register up to ve Directory servers used in <Browse>.
<Host Name>
Enter the host name of the le server/Advanced Space.
●If you select <FTP> for protocol, enter <Host Name> as follows.
When TLS is disabled
Example:
To save to the Shared Space: ftp://<host name>/share
To save to the Personal Space: ftp://<host name>/users
When TLS is enabled
Basic Operations
201

Example:
To save to the Shared Space: ftps://<host name>/share
To save to the Personal Space: ftps://<host name>/users
When sending a document to the Advanced Space, enter <Host Name> as follows.
●If you select <Windows (SMB)> for the protocol
Example:
To save to the Shared Space: \\192.168.100.50\share
To save to the Personal Space: \\192.168.100.50\users
●If you select <WebDAV> for protocol, enter <Host Name> as follows and press <Next>.
When TLS is disabled
Example:
To save to the Shared Space: http://<IP address or host name>/
To save to the Personal Space: http://<IP address or host name>/
When TLS is enabled
Example:
To save to the Shared Space: https://<IP address or host name>/
To save to the Personal Space: https://<IP address or host name>/
<Check Connection>
Press this button after entering the host name to conrm the connection with the le server/Advanced
Space.
●If you are using a login service such as personal authentication management, it is necessary to
enter <User Name> and <Password>.
2Congure the le server/Advanced Space information.
●Ask your Network administrator about the le server/Advanced Space information and the folder.
<Folder Path>
Specify the folder's directory to which data is sent.
When sending a document to the Advanced Space with <WebDAV> selected for the protocol, enter
<Folder Path> as follows.
Example:
To save to the Shared Space: /share
To save to the Personal Space: /users
<Password>
Enter the login password of the le server/Advanced Space.
<Conrm Before Sending>
By enabling <Conrm Before Sending>, a screen requiring password entry is displayed before sending,
even if a password is entered in ( ).
Basic Operations
202
<User Name>
Enter the login user name of the le server/Advanced Space.
●When the le server/Advanced Space destination is included in the group ( Registering Multiple
Destinations as a Group(P. 205) ), set <Conrm Before Sending> to <Off>. If it is set to <On>, you
cannot send data.
●If you specify the destination for which you activate <Conrm Before Sending> as the forwarding
destination, the screen to enter the password does not appear. The registered password is used and
forwarding is performed.
●You can use different authentication information from the user name in ( ) and password in ( )
to register to the address book. For more information, see <Information Used for File TX/
Browsing Authentication>(P. 816) .
●If you set <Protocol> to <Windows (SMB)> or <FTP>, specifying a folder that does not exist in <Folder
Path> will result in the folder being automatically created and les being stored within. However, a
sending error will occur if you specify a folder with multiple levels.
●When checking a WebDAV connection, the HEAD method of HTTP is used to check the connection.
The folder specied in <Folder Path> is accessed using the HEAD method. If access via the HEAD
method is prohibited for the corresponding folder, an error occurs for the connection check.
Examples of settings that prohibit access via the HEAD method are indicated below.
●IIS7: Access cannot be performed via the HEAD method unless [Source] is selected in the
access permissions for the WebDAV authoring rules of the target folder.
●Apache: Access cannot be performed via the HEAD method unless HEAD is described using
the [Limit] directive in httpd.conf.
8Press <OK> <Close>.
●When destinations are managed by access numbers, enter the access number ( Restricting Access to
Destinations Registered in the Address Book(P. 567) ) after pressing <Next> in step 8.
●If you try to send to a le server/Advanced Space in which <Conrm Before Sending> is set to <On>, a
screen appears prompting you to enter a user name and password. In this case, enter the previously set
password. If you want to register a le server/Advanced Space in a group address, set <Conrm Before
Sending> to <Off>. You cannot send to a group address including a le server/Advanced Space in which
<Conrm Before Sending> is set to <On>.
●Multiple destinations registered in the Address Book can be combined into a group. For details, see
Registering Multiple Destinations as a Group(P. 205) .
●To change or delete the information of destinations registered in the Address Book, see Editing the
Registered Destinations in the Address Book(P. 208) .
●UPN can be used only if you are sending to a computer belonging to a domain operated with Active
Directory.
Basic Operations
203
If the LDAP server has already been registered in the machine ( Registering the LDAP Server(P. 53) ), you
can search for destinations and register them in the Address Book. Press <Dest./Fwd. Settings> <Register
Destinations> <Register New Destination> <Register from LDAP Server> and search for destinations using
<Search by Conditions>.
●When the user name and password are correct but the search result is empty, check the time setting both
on the LDAP server and the machine. If the time setting between the LDAP server and the machine differs by
ve minutes or more, a search cannot be performed.
●If multiple destinations are displayed as search results, you can register up to 256 of them at one time.
●The information that can be obtained via the LDAP server consists of only names and fax numbers/
addresses. Register other information from <Details/Edit> as necessary.
●You cannot search for destinations on an LDAP server from both the control panel and the Remote UI at the
same time.
●When searching for destinations on an LDAP server from the control panel of the machine, you can specify
four search conditions. On the other hand, when searching for destinations on an LDAP server from the
Remote UI, you can only specify one search condition.
●You may need to enter the user name and password. Enter the user name and password of the machine
registered in the LDAP server. If authentication information is not used, search with the user name and
password elds in the Remote UI left blank.
Specifying/registering destinations from the send history
●You can specify destinations and register destinations to the address book from the send history on the
<Status Monitor> screen. This saves you the effort of directly entering the address, and also helps avoid
sending to an incorrect destination due to entering the wrong address.
- When specifying a destination: (Status Monitor) <Send> <Job Log> select the destination to
send to <Specify as Send Destination> <OK>
- When registering a destination: (Status Monitor) <Send> <Job Log> select the destination to
register <Register Destination> register the destination from the registration screen for each
destination type
Checking Status and Log for Sent and Received Documents(P. 321)
Checking Status and Log for Scanned Documents(P. 392)
LINKS
Basic Operations for Sending Faxes(P. 275)
Basic Operations for Scanning Originals(P. 377)
Using Other Machines and Memory Media(P. 437)
<Change Default Display of Address Book>(P. 849)
<Set Destination>(P. 849)
Basic Operations
204
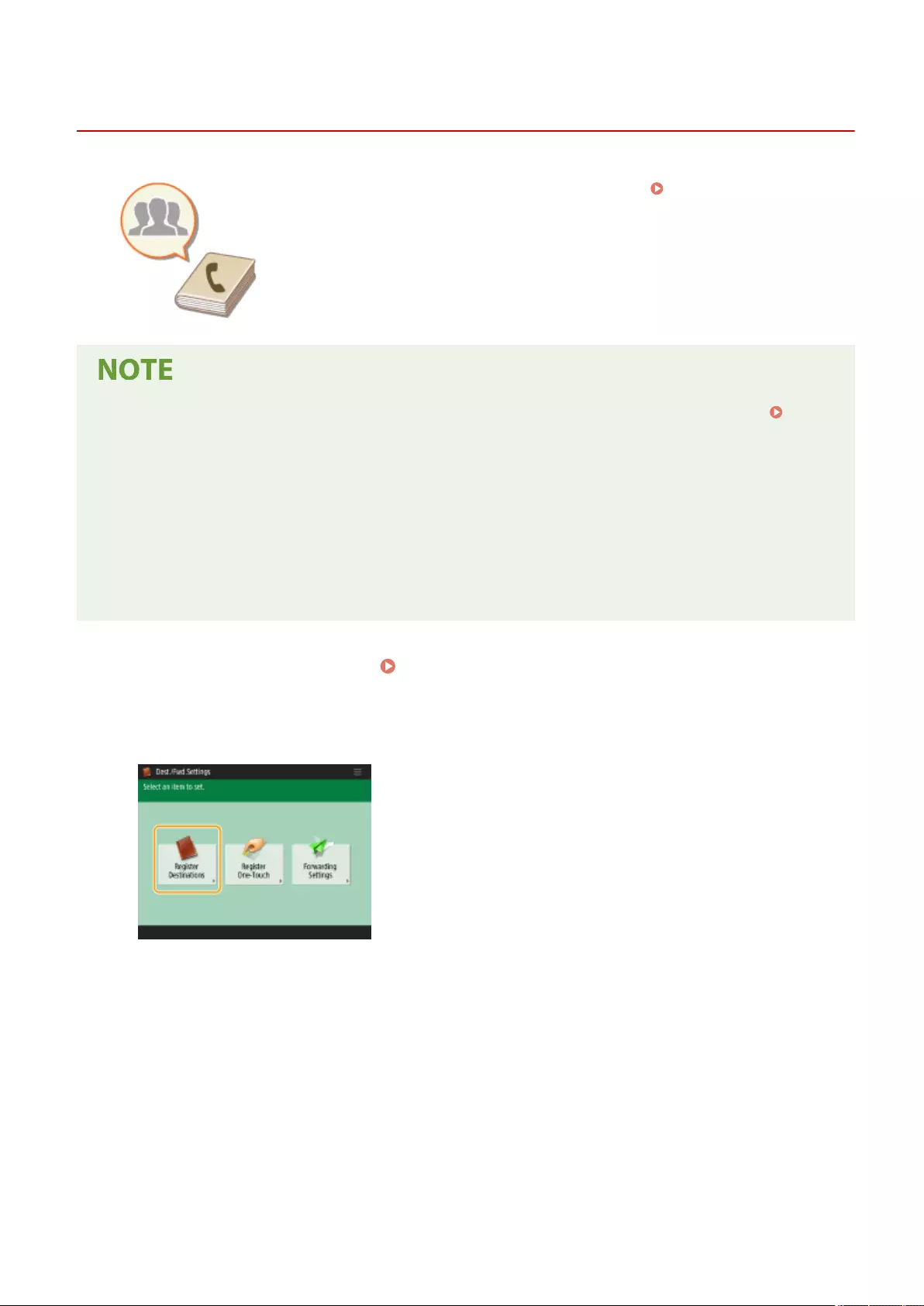
Registering Multiple Destinations as a Group
72JY-03C
Multiple destinations registered in the Address Book( Registering Destinations
in the Address Book(P. 195) ) can be combined into a group. You can use this
feature to send documents and back up data at the same time because different
types of destinations can be registered in the same group. For example, you can
register e-mail addresses and le server IP addresses together in one group.
●To register a group that contains destinations for your own use, you need to log into the machine.
Logging into the Machine(P. 137)
●You cannot register new destinations in a group address. Register destinations in the Address Book in
advance.
●Only destinations in the same address list can be grouped. Destinations registered in a different address list
cannot be grouped.
●You can register up to 256 destinations in a group address.
●Since each address entry is treated as a single entry, if you register a fax number in a group address, the fax
number and group address entry are counted as two separate entries.
1Press <Dest./Fwd. Settings>. <Home> Screen(P. 119)
2 Press <Register Destinations>.
3Press <Register New Destination>.
4Press <Group>.
Basic Operations
205
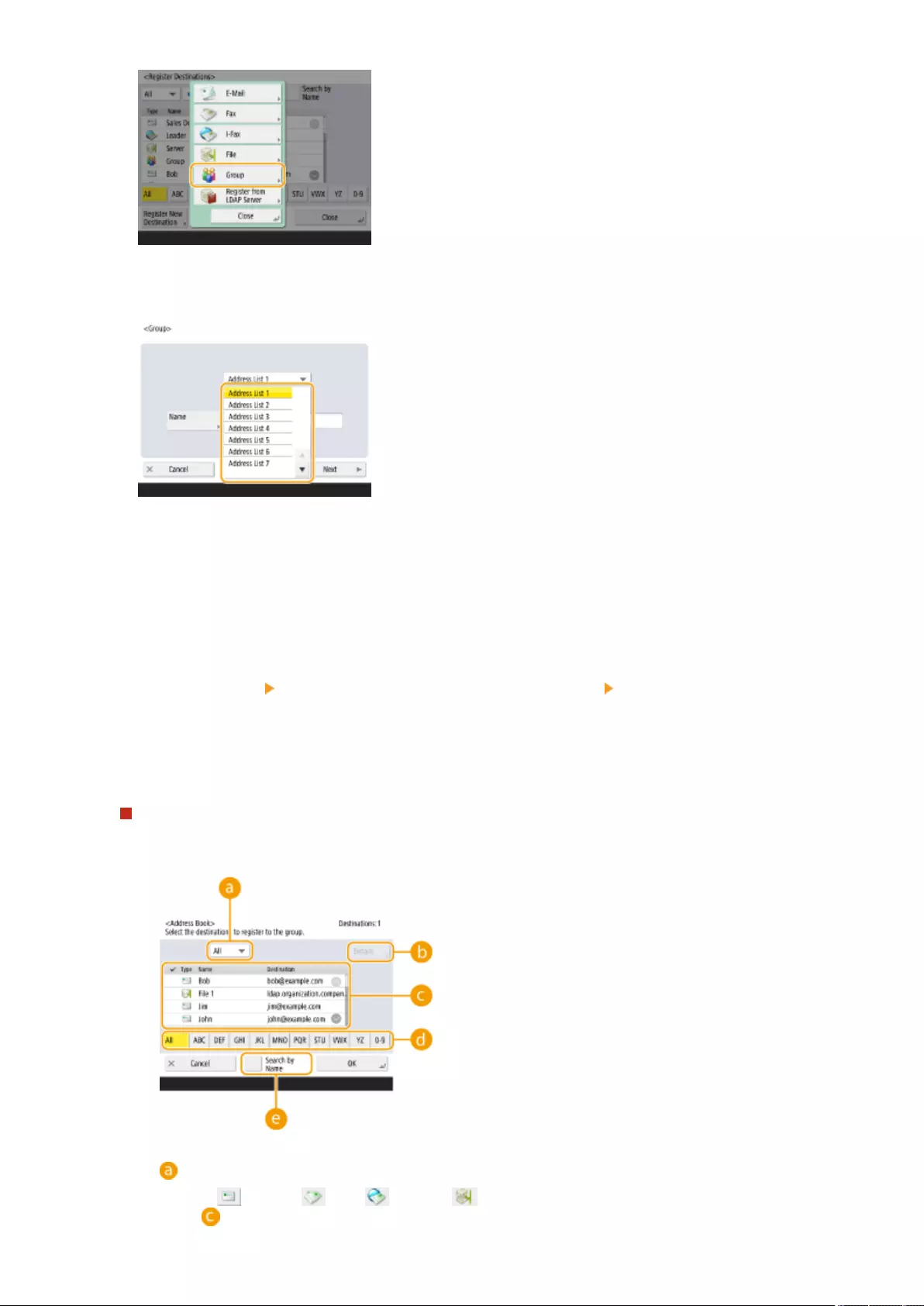
5Select where to register the group from the address list drop-down list.
●You can create a group from the destinations registered in the selected address list. For example, if you
select <Address List 2>, you cannot add a destination registered in <Address List 1> to the group. The created
group is registered in the address list you select in this step.
●If you want to register a group that contains destinations for your own use, select <Personal Addr. List>.
●If you want to register destinations in a group which only an administrator can edit, select <Address List for
Admin.>.
6Press <Name> enter the group name, and press <OK> <Next>.
7Select the destinations you want to include in the group.
When you select <Add from Address Book>
1Select the destinations you want to register in a group, and press <OK>.
Destination type drop-down list
Select (e-mail), (fax), (I-fax) or (le) to lter the destinations displayed in the address
list ( ). Press <All> to display all registered destinations.
Basic Operations
206

<Details>
Select a destination and press <Details> if you want to check the settings of the destination. Press <OK>
to return to the previous screen.
Destination list
Destinations registered in the address list that you selected in step 6 are displayed. From this list, select
the destinations you want to register in a group.
●When destinations are managed by access numbers, they are not displayed in the list unless you
enter the access number ( Restricting Access to Destinations Registered in the Address
Book(P. 567) ) after pressing <Access No.>.
First letter button
Select the alphanumeric button for the rst character of the destination name. Press <All> to display all
registered destinations.
<Search by Name>
Enter the destination name. Press <Search by Name> again to return to the previous screen.
8Press <OK> <Close>.
●When destinations are managed by access numbers, enter the access number ( Restricting Access to
Destinations Registered in the Address Book(P. 567) ) after pressing <Next> in step 8.
●If you try to send to a le server in which <Conrm Before Sending> is set to <On>, a screen appears
prompting you to enter a user name and password. In this case, enter the previously set password. If you
want to register a le server in a group address, set <Conrm Before Sending> to <Off>. You cannot send
to a group address including a le server in which <Conrm Before Sending> is set to <On>.
Basic Operations
207
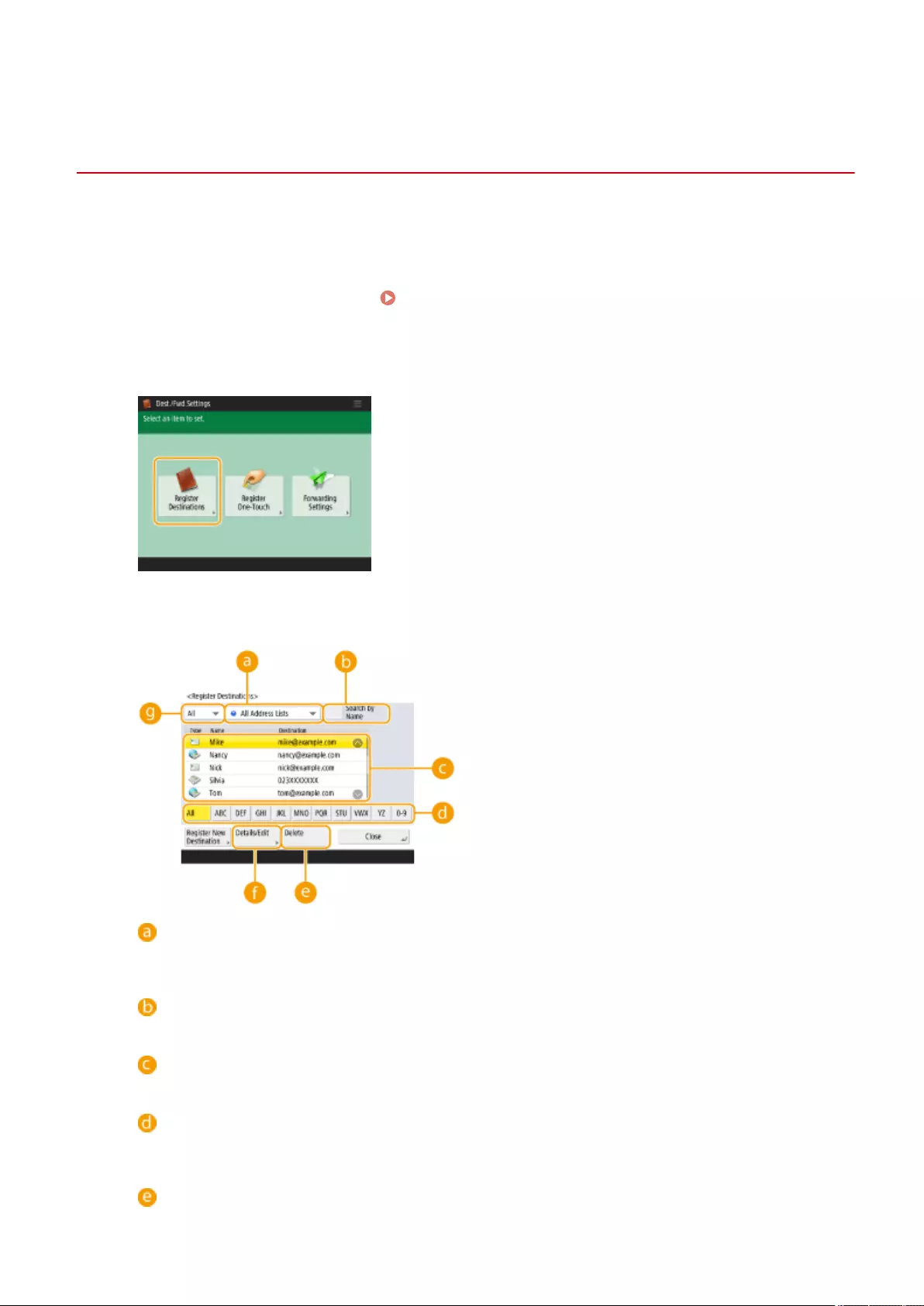
Editing the Registered Destinations in the Address
Book
72JY-03E
0YRY-039 0UUY-02X 0UW1-02X 1100-039 0X7F-035 0X7H-035 10XJ-039 0X6E-035 0X6W-035 1106-039 0X7C-035 0X7A-035 10YY-039 0WXY-035 0X7E-035 10H3-039 0WR6-035 0WR7-035 108A-039 1116-039 10H4-039 0WR5-035 0WR8-035 0YWJ-034 0YWH-035 0YWR-034 0YWK-035 0YWE-035 0YWF-035 0YAS-038
After registering destinations, you can change or delete their settings.
1Press <Dest./Fwd. Settings>. <Home> Screen(P. 119)
2Press <Register Destinations>.
3Select the destination you want to edit.
Address list drop-down list
Select <Personal Addr. List>, <Address List 1> to <Address List 10> or <Address List for Admin.> to lter the
destinations to be displayed in the address list.
<Search by Name>
Enter the destination name. Press <Search by Name> again to return to the previous screen.
Destination list
Select the destination you want to edit or delete.
First letter button
Select the alphanumeric button for the rst character of the destination name. Press <All> to display all
registered destinations.
<Delete>
Basic Operations
208

Press to delete the destination.
<Details/Edit>
Press to check or edit the settings of destinations.
Destination type drop-down list
Select (e-mail), (fax), (I-fax), (le), or (group) to lter the destinations displayed in the
address list ( ). Press <All> to display all registered destinations.
●When destinations are managed by access numbers, enter the access number ( Restricting Access
to Destinations Registered in the Address Book(P. 567) ) after pressing <Access No.>.
●Destinations in <Personal Address List> are only displayed for the login user that registered them. Even
if you have administrator privileges, you cannot view or edit the destinations in <Personal Address List>
for other users.
4Press <Details/Edit>.
●If you want to delete a destination, select the destination and press <Delete> <Yes>.
5Edit the settings of the destination.
●For details about how to edit the settings, see Registering Destinations in the Address Book(P. 195) .
6Press <OK> <Close>.
Basic Operations
209
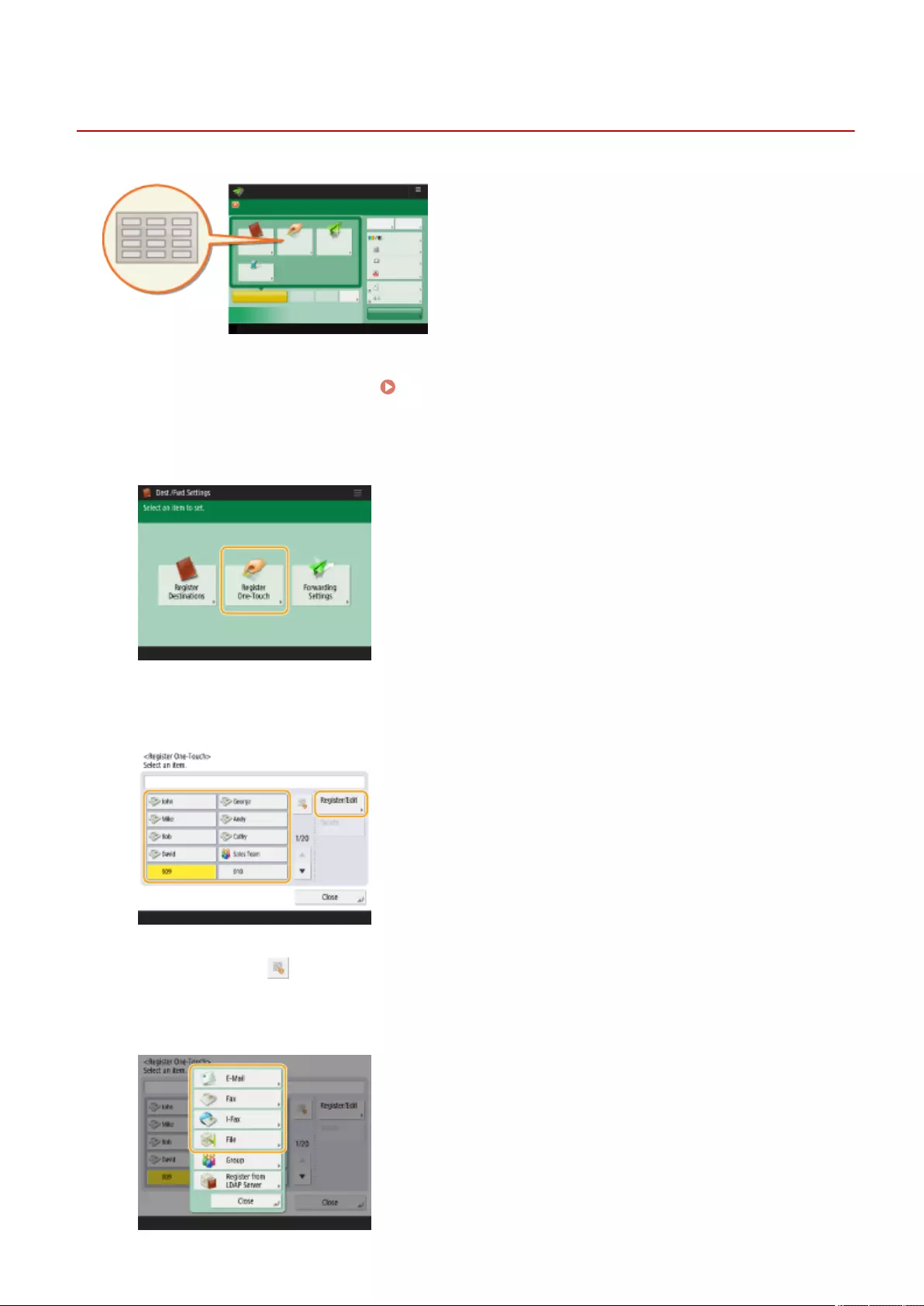
Registering a Destination in a One-Touch Button
72JY-03F
It is convenient to register a frequently used destination in a
one-touch button. This enables you to quickly specify a
destination with the simple press of a button. In addition to
registering a fax number or e-mail address in a one-touch
button, you can also register a le server folder location (IP
address and path) to use when storing scanned data.
1Press <Dest./Fwd. Settings>. <Home> Screen(P. 119)
2Press <Register One-Touch>.
3Select the one-touch number to register the destination in, and press <Register/
Edit>.
●A three-digit number (001 to 200) is assigned to each one-touch button. You can also specify a one-touch
button by pressing and entering the three-digit number using the numeric keys.
4Select the type of destination to register.
Basic Operations
210
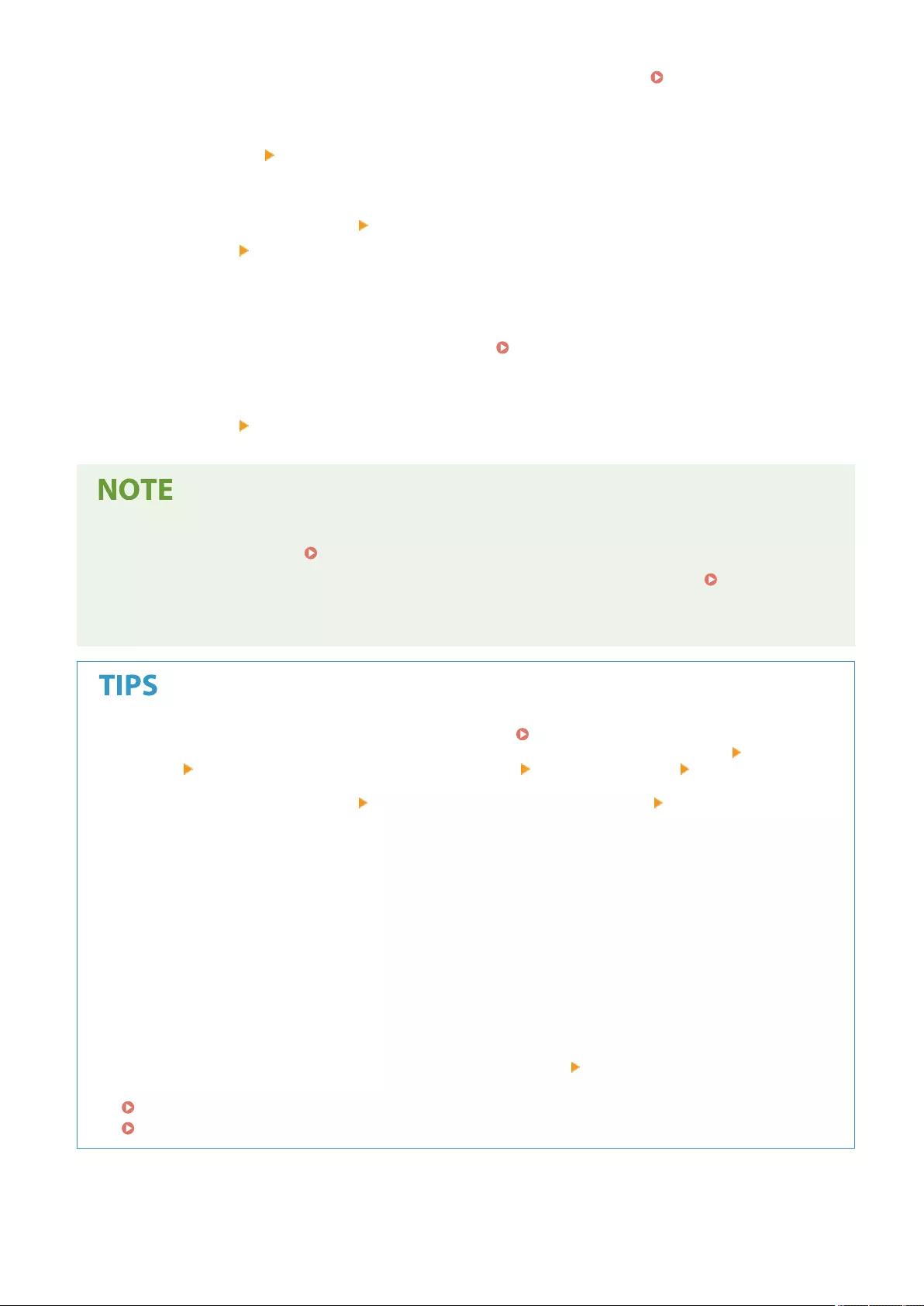
●Select <Fax>, <E-Mail>, <I-Fax>, or <File> as the type of destination to register. Registering Destinations in
the Address Book(P. 195)
5Press <Name> enter the destination name, and press <OK>.
6Press <One-Touch Name> enter the one-touch button name to be displayed, and
press <OK> <Next>.
7Congure the settings according to the type of destination selected in step 4.
●For more information about the settings, see step 7 in Registering Destinations in the Address
Book(P. 195) .
8Press <OK> <Close>.
●Destinations registered in one-touch buttons can be combined into a group and registered as a single
destination. For details, see Registering a Group in a One-Touch Button(P. 212) .
●To change or delete the information of destinations registered in one-touch buttons, see Editing the
Registered Destinations in One-Touch Buttons(P. 214) .
●Destinations stored in one-touch buttons also appear in the Local Address Book.
If the LDAP server has already been registered in the machine ( Registering the LDAP Server(P. 53) ), you
can search for destinations and register them in one-touch buttons. Press <Dest./Fwd. Settings> <Register
One-Touch> select the one-touch button you want to register press <Register/Edit> <Register from LDAP
Server> and search for destinations using <Search by Conditions>. After conrming the settings of the
destination, press <One-Touch Name> enter the one-touch name to be displayed press <OK>.
●When the user name and password are correct but the search result is empty, check the time setting both
on the LDAP server and the machine. If the time setting between the LDAP server and the machine differs by
ve minutes or more, a search cannot be performed.
●Unlike the Address Book, you cannot select more than one destination at a time to register.
●The information that can be obtained via the LDAP server consists of only names and fax numbers/
addresses. Register other information from <Details/Edit> as necessary.
Registering an address from the send history
●You can register a destination in a one-touch button from sent job logs in the <Status Monitor> screen. This
saves the labor of manually entering a fax number and other destination information, and contributes to
prevention of wrong transmission due to use of destination information registered incorrectly. When you
specify an address in sent job logs and press <Register Destination> <One-Touch>, a screen for
registering various items of destination information in a one-touch button.
Checking Status and Log for Sent and Received Documents(P. 321)
Checking Status and Log for Scanned Documents(P. 392)
Basic Operations
211
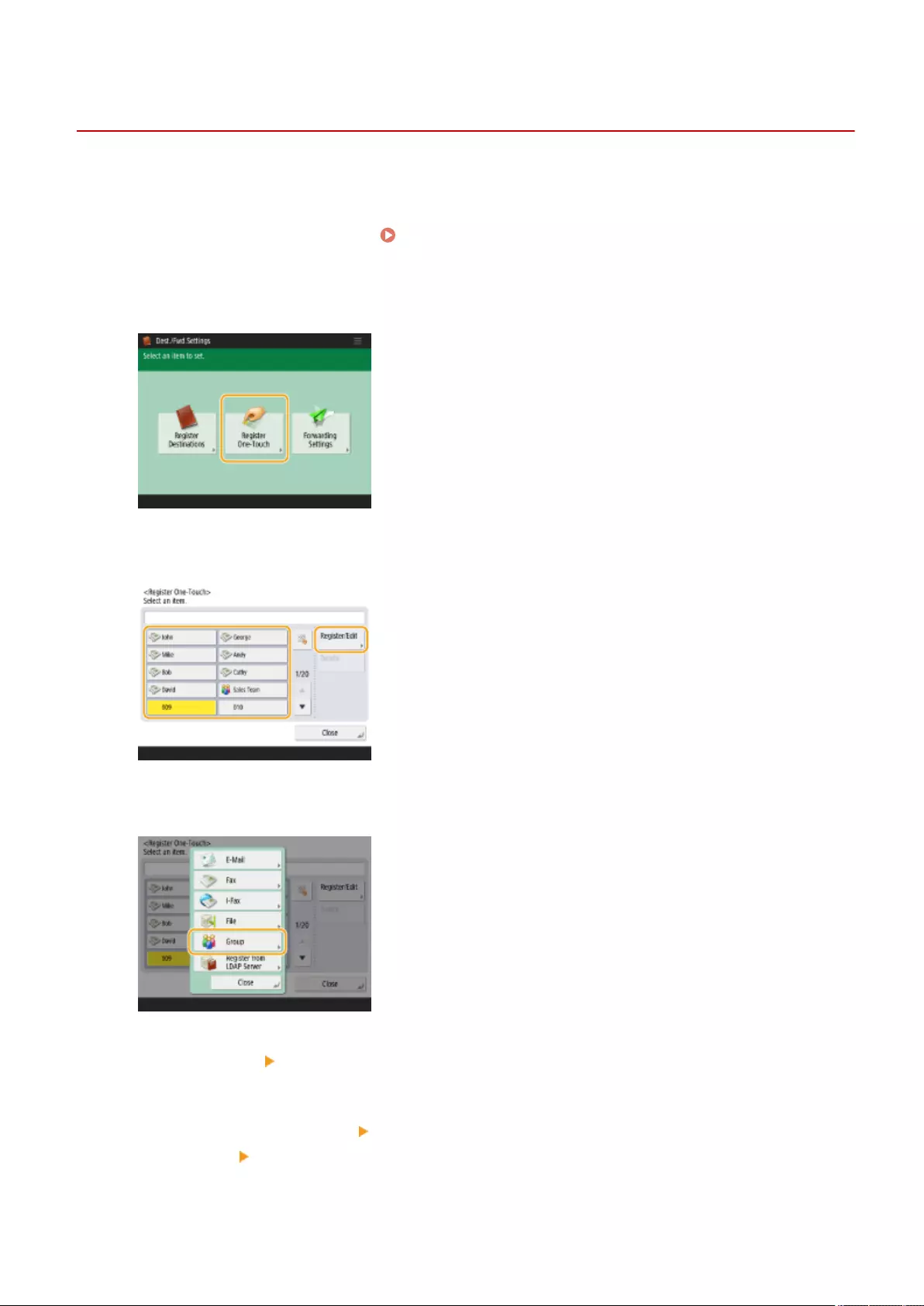
Registering a Group in a One-Touch Button
72JY-03H
Destinations registered in one-touch buttons can be combined into a group and registered as a single destination.
1Press <Dest./Fwd. Settings>. <Home> Screen(P. 119)
2Press <Register One-Touch>.
3Select the one-touch button you want to register and press <Register/Edit>.
4Press <Group>.
5Press <Name> enter the group name, and press <OK>.
6Press <One-Touch Name> enter the one-touch button name to be displayed, and
press <OK> <Next> .
7Select the destinations you want to register in a group.
Basic Operations
212

●If you want to select a destination from a one-touch button, press <Add from One-Touch> select the
destination press <OK>.
8Press <OK> <Close>.
Basic Operations
213
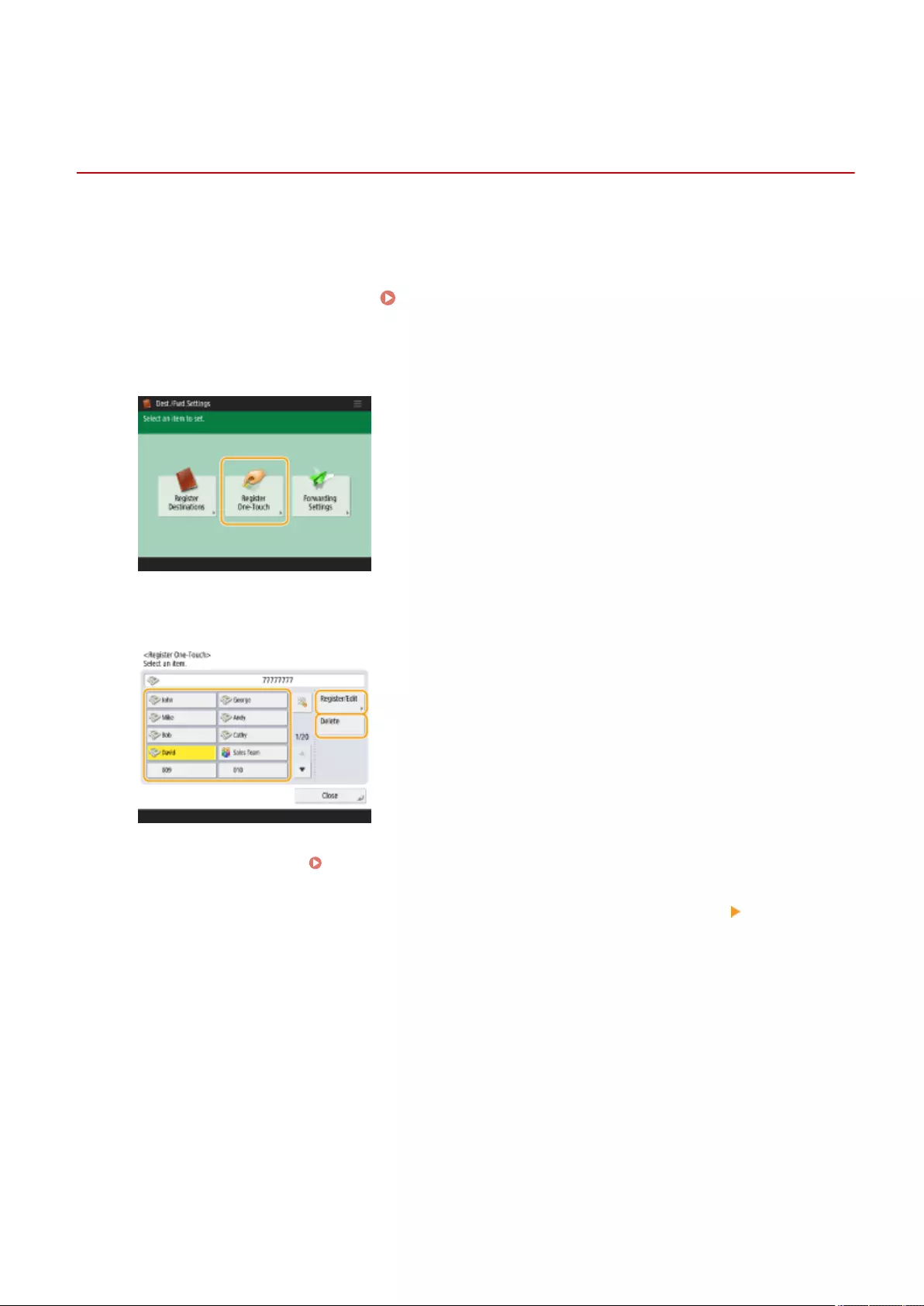
Editing the Registered Destinations in One-Touch
Buttons
72JY-03J
0YRY-03C 0UUY-030 0UW1-030 1100-03C 0X7F-037 0X7H-037 10XJ-03C 0X6E-037 0X6W-037 1106-03C 0X7C-037 0X7A-037 10YY-03C 0WXY-037 0X7E-037 10H3-03C 0WR6-037 0WR7-037 108A-03C 1116-03C 10H4-03C 0WR5-037 0WR8-037 0YWJ-036 0YWH-037 0YWR-036 0YWK-037 0YWE-037 0YWF-037 0YAS-03A
After registering destinations, you can change or delete their settings.
1Press <Dest./Fwd. Settings>. <Home> Screen(P. 119)
2Press <Register One-Touch>.
3Select the one-touch button you want to edit or delete.
●If you want to edit the settings of the one-touch button, press <Register/Edit>. For details about how to edit
the settings, see step 7 in Registering Destinations in the Address Book(P. 195) . Press <OK> after you
nish editing.
●If you want to delete a one-touch button, select the one-touch button and, press <Delete> <Yes>.
4Press <Close>.
Basic Operations
214

Copying
Copying ................................................................................................................................................................ 216
Copy Basic Features Screen .............................................................................................................................. 218
Basic Copy Operations ...................................................................................................................................... 220
Cancelling Copying ....................................................................................................................................... 231
Enhancing and Adjusting Copy Quality ............................................................................................................ 233
Selecting the Type of Original for Copying ................................................................................................... 234
Adjusting Sharpness for Copying (Sharpness) .............................................................................................. 235
Erasing Dark Borders When Copying (Erase Frame) ..................................................................................... 236
Adjusting the Color ....................................................................................................................................... 238
One Touch Color Mode ................................................................................................................................. 240
Copying Eciently ............................................................................................................................................ 242
Copying Multiple Originals onto One Sheet (N on 1) ..................................................................................... 243
Copying Separately Scanned Originals Together (Job Build) ......................................................................... 245
Checking the Copy Results ........................................................................................................................... 247
Copying Immediately by Interrupting Other Jobs ......................................................................................... 249
Functions Useful for Making and Managing Material .................................................................................... 250
Finishing by Collating/Grouping ................................................................................................................... 251
Useful Copy Functions ....................................................................................................................................... 253
Shifting the Image ........................................................................................................................................ 254
Notifying You of the Completion of Copying by E-Mail ................................................................................. 257
Making ID Card Copies ................................................................................................................................. 259
Skipping Blank Pages When Printing ............................................................................................................ 261
Reducing Copying Operations .......................................................................................................................... 263
Recalling Previously Used Copy Settings (Previous Settings) ........................................................................ 264
Recalling Settings ......................................................................................................................................... 265
Restrictions Regarding the Combination of Functions ................................................................................... 266
Copying
215
Copy
Copying
72JY-03K
PMW-CPIG
This chapter describes basic copy operations and various other useful functions.
◼Introduction to Basic Copy Operations
This section describes the Copy Basic Features screen and basic copy operations.
Copy Basic Features Screen(P. 218)
Basic Copy Operations(P. 220)
Cancelling Copying(P. 231)
◼Enhancing Quality and Eciency
This section describes functions useful for enhancing copy quality and operational eciency such as adjusting
sharpness to obtain clearer print results and combining multiple originals to eciently copy them at once.
Enhancing and Adjusting Copy Quality(P. 233)
Copying Eciently(P. 242)
◼Making Handouts
This section describes copy functions that enable you to create documents suitable for distribution and management
with page numbers, reference numbers, etc.
Functions Useful for Making and Managing Material(P. 250)
Copying
216
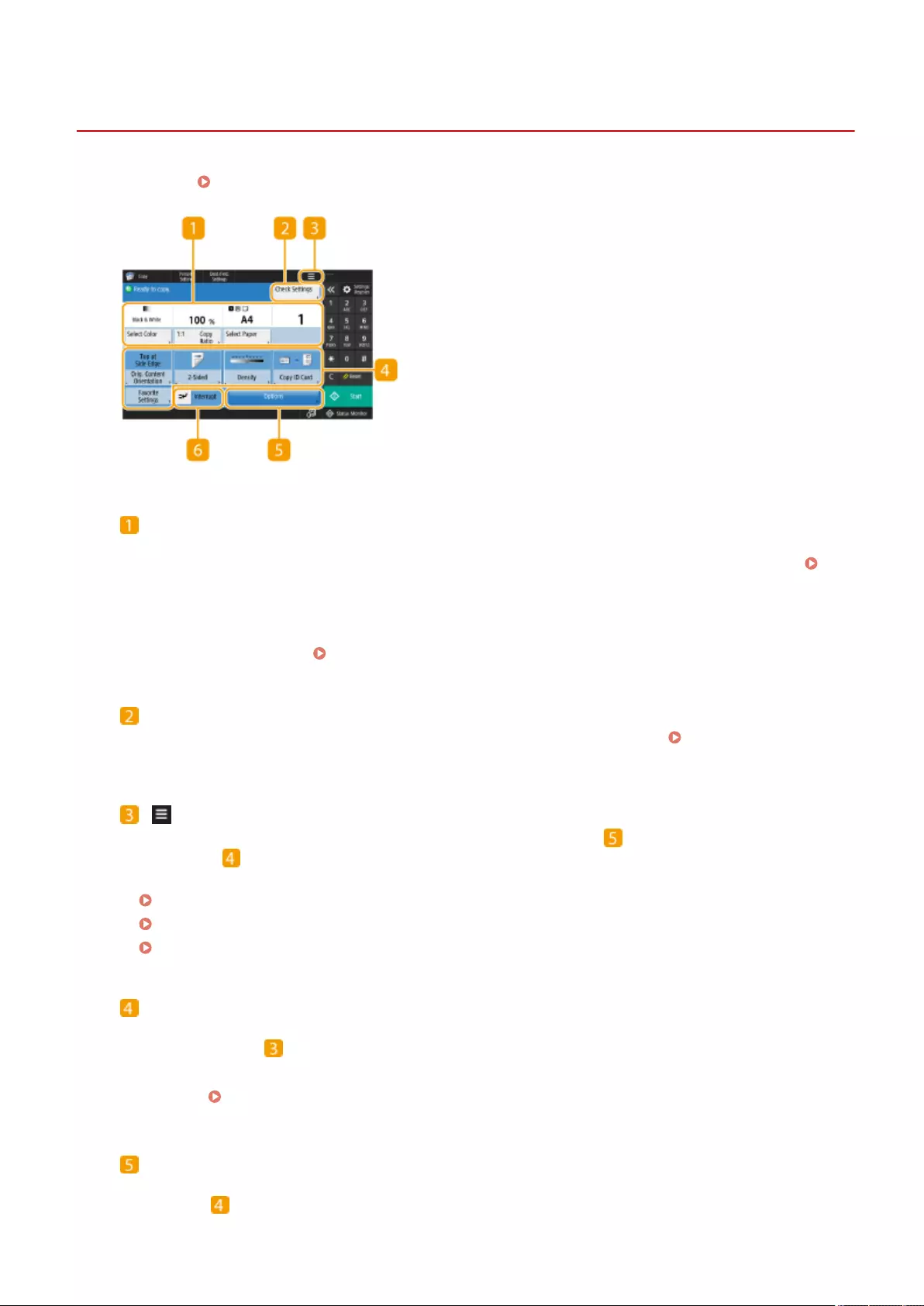
Copy Basic Features Screen
72JY-03L
Pressing <Copy> ( <Home> Screen(P. 119) ) displays the Copy Basic Features screen.
1:1
Current setting status and setting buttons
Displays setting status such as the copy ratio, paper size, and number of copies. Make sure to conrm the
settings in order to copy properly. To change the settings, press the button under the display section. Basic
Copy Operations(P. 220)
●If you press <1:1>, you can make copies the same size as your original.
●Depending on the number of copies and settings, <Copy Sample> is displayed to check the copy result by
printing a sample copy. Checking the Copy Results(P. 247)
<Check Settings>
You can check the settings in the list. You can also make changes to the settings. Basic Copy
Operations(P. 220)
Press this icon to register the current settings in <Favorite Settings> of or to change the buttons
displayed in . You can also register the current settings in Personal buttons or Shared buttons on the
Home screen.
Registering a Combination of Frequently Used Functions(P. 164)
Customizing the Basic Features Screen(P. 167)
Registering Personal Buttons/Shared Buttons(P. 171)
Function setting buttons
Displays the most frequently used buttons from <Options>. The setting status is displayed on the buttons.
You can also press to change which buttons are displayed.
●If the button for the function that you want to use is not displayed, press <Options> and select the desired
button. Basic Copy Operations(P. 220)
Options
<Options>
Displays all of the function setting buttons. For convenience, you can display frequently used function setting
buttons in .
Copying
218
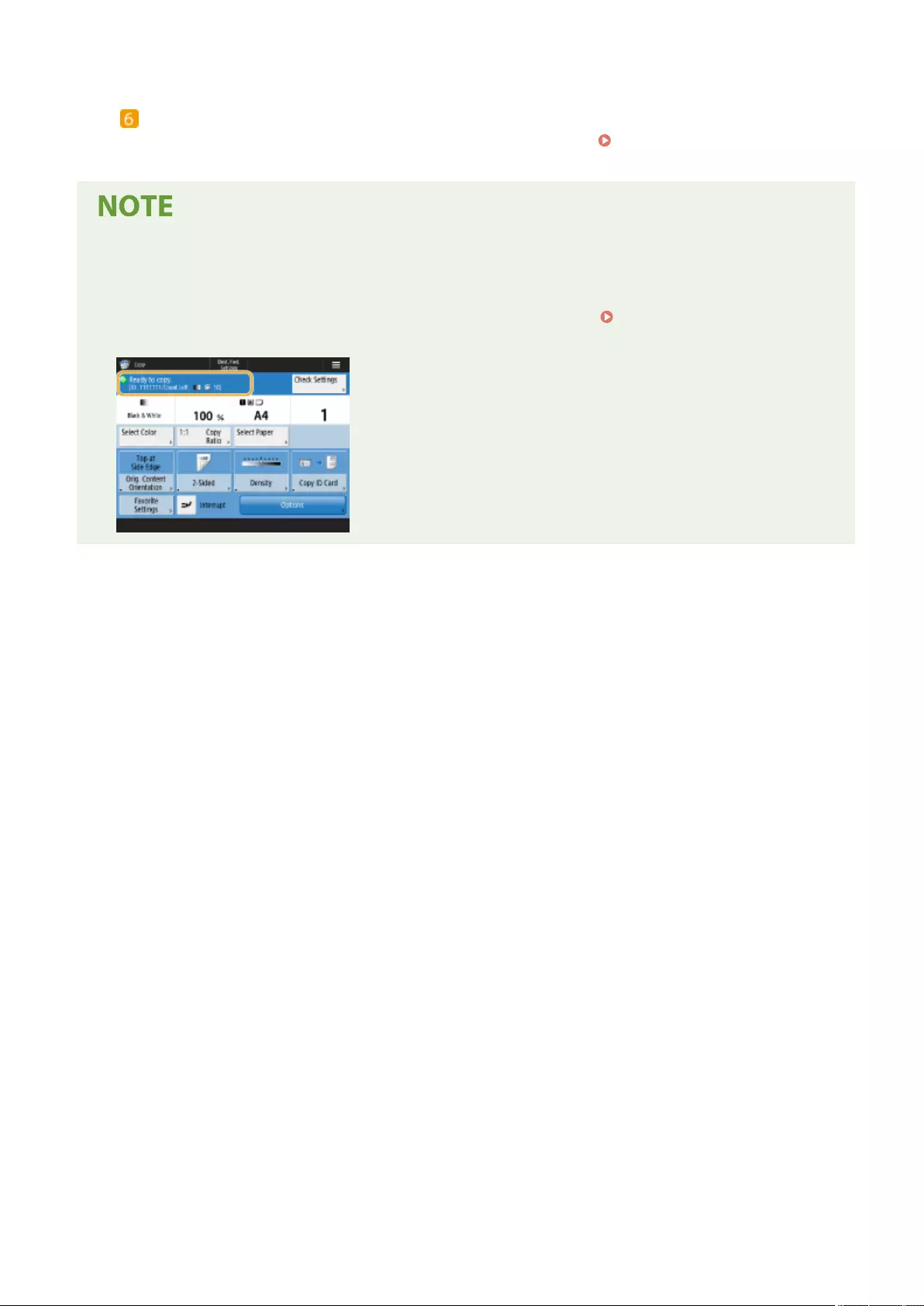
<Interrupt>
You can interrupt waiting copy jobs and make your copy immediately. Copying Immediately by
Interrupting Other Jobs(P. 249)
●Some functions cannot be used in combination with each other. Buttons that cannot be selected are
displayed in light gray.
●The number of pages remaining is displayed if a page limit is set with Department ID Management. For
information on setting Department ID Management and page limits, see Conguring the Department ID
Management Settings(P. 525) .
Copying
219
Basic Copy Operations
72JY-03R
This section describes the basic operations for copying.
1Place the document. Placing Originals(P. 97)
●If <Auto Collate> is set to <On>, the Collate mode is automatically set when you place your originals in the
feeder. <Auto Collate>(P. 817)
2Press <Copy>. <Home> Screen(P. 119)
3Enter the number of copies using the numeric keys on the Copy Basic Features
screen. Copy Basic Features Screen(P. 218)
4Specify the copy settings as necessary.
Select Color
Selecting Color Copying or Black and White Copying
Copy RatioCopy Ratio
Enlarging or Reducing Copies
Select Paper
Selecting Copy Paper
2-Sided
2-Sided Copying
DensityDensity
Adjusting Image Quality of Copies
Original Content Orientation
Specifying the Orientation of the Original
Selecting Color Copying or Black and White Copying
You can select the color mode for copying. For example, this enables you to save toner
by copying color originals in black and white, or copying tickets with a single color
such as red or blue to indicate the date they are distributed.
1Press <Select Color>.
2Select the color to copy with.
Copying
220
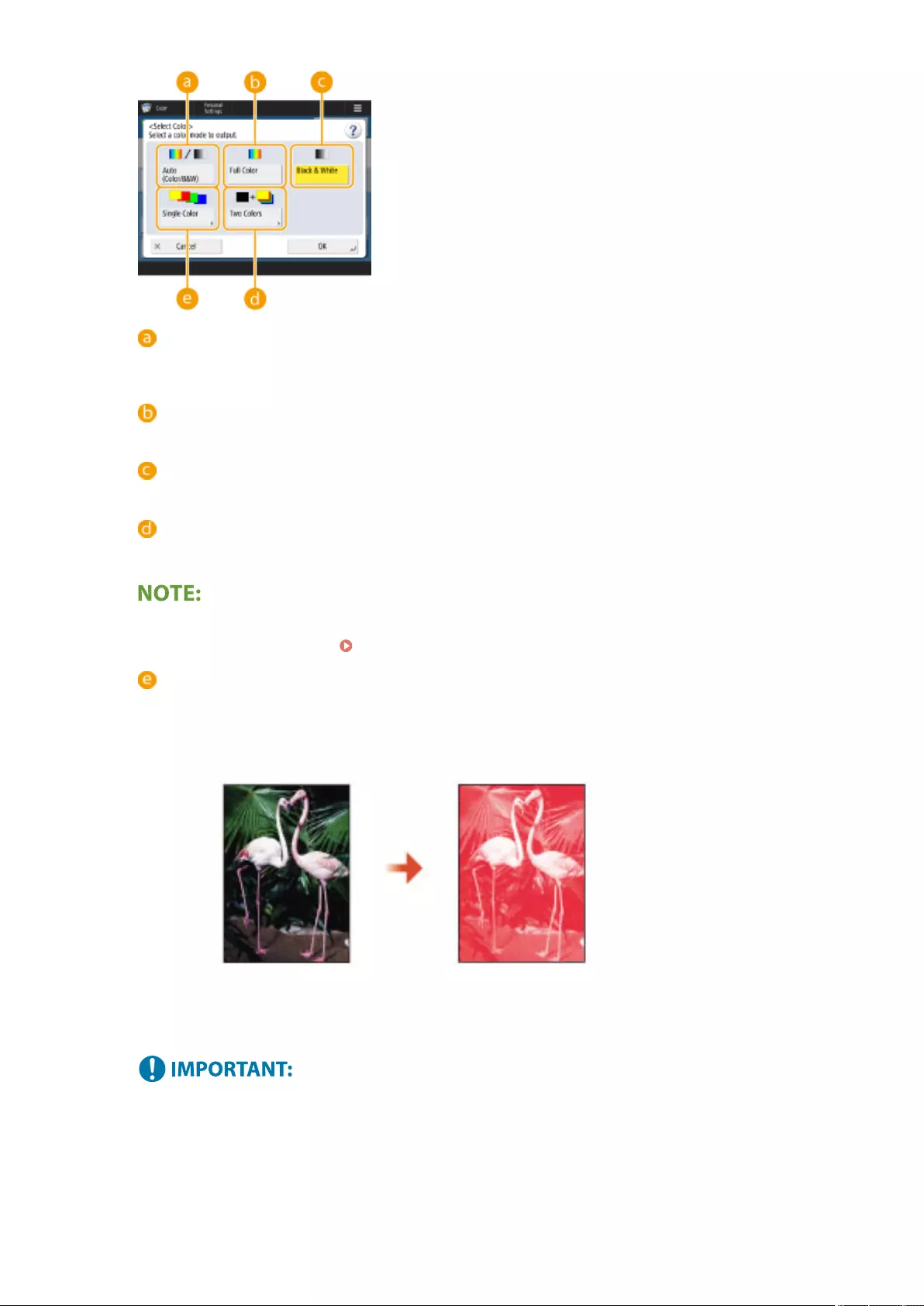
<Auto (Color/B&W)>
Automatically detects the color of the original. Color pages are copied in four colors (CMYK), and black and
white pages are copied in black (K) only.
<Full Color>
Copies in four colors (CMYK), regardless of the color of the original.
<Black & White>
Copies in black (K) only, regardless of the color of the original.
<Two Colors>
Copies in black and the color you specify. Select <Red>, <Green>, <Blue>, <Yellow>, <Magenta>, or <Cyan>.
●You can set whether to replace a chromatic color other than the specied color (or approximate color) with
black or the specied color. <Chromatic Color Conversion for Two Colors Printing>(P. 809)
<Single Color>
Copies with the color you specify only. Select <Red>, <Green>, <Blue>, <Yellow>, <Magenta>, or <Cyan>.
Example: If you copy with red
3Press <OK>.
●Depending on the state of the color original, it may be detected as black and white when scanned, even if
you set <Auto (Color/B&W)>. To avoid this, set the color mode to <Full Color>.
●When the Auto (Color/B&W) mode is set, black-and-white copies are output at the same speed as colour
copies.
●If a black-and-white document is copied in the <Full Color>, <Single Color>, or <Two Colors> mode, it is
counted as a color copy.
Copying
221

Enlarging or Reducing Copies
You can enlarge or reduce copies from standard document sizes to other standard
paper sizes.
Enlarging or Reducing Copies with Standard Paper Sizes
You can enlarge or reduce by specifying the copy ratio (%). You can specify the
vertical and horizontal ratios individually.
Enlarging or Reducing Copies by Specifying the Copy Ratio
You can enlarge or reduce to automatically t the paper size selected.
Enlarging and Reducing Copies to Fit Paper Size
◼Enlarging or Reducing Copies with Standard Paper Sizes
1Press <Copy Ratio>.
2To reduce, select the copy ratio from , to enlarge, select the copy ratio from ,
and press <OK>.
Copying
222

◼Enlarging or Reducing Copies by Specifying the Copy Ratio
1Press <Copy Ratio>.
2Specify the copy ratio and press <OK>.
●To specify vertical and horizontal ratios individually, press <XY Ratio> and then specify the ratios for each.
Depending on the ratio, the image on the printout may be rotated by 90 degrees.
◼Enlarging and Reducing Copies to Fit Paper Size
1Press <Select Paper>.
2Select paper and press <OK>.
3Press <Copy Ratio>.
4Press <Auto>.
4Select the size of the original, and press <OK>.
Copying
223
●When copying in equal copy ratio to paper that has the same size as the original document, the edges
of the copied document may be slightly missing. To avoid this, reduce the document by pressing
<Copy Ratio> <Fit to Page> to obtain the missing edges of the document.
●If you select <Fit to Page>, <Shift> is automatically set to <Center>.
●You cannot scan highly transparent originals, such as transparencies, using the Auto setting for Copy
Ratio. Use the Preset Zoom or Zoom by Percentage mode instead.
Selecting Copy Paper
If you want to copy free size documents or documents of high transparency, or if you
want to copy with paper set in the multi-purpose tray, you need to select paper
manually.
1Press <Select Paper>.
2Select paper and press <OK>.
●Pressing enables you to conrm detailed information of the paper selected.
●Be sure to correctly set the paper type. If the type of paper is not set correctly, it may adversely affect image
quality. If a service repair is needed, contact your dealer or service representative.
●Take care when copying an original with an image that extends all the way to the edges. If you copy on the
same size paper, the periphery of the original image may be cut off slightly on the copy. For more
information on how much may be cut off, see Hardware Specications(P. 1103) .
Copying
224
2-Sided Copying
You can copy 1-sided documents on both sides of the paper. You can also copy a 2-
sided document on both sides of the paper, or on two separate sheets.
Copying 1-Sided to 2-Sided
Copying 2-Sided to 2-Sided
Copying 2-Sided to 1-Sided
●Place the document in a proper orientation as shown in the illustrations below.
●Documents of heavy or thin paper cannot be placed in the feeder. Place the document on the platen
glass. In this case, place the document in a proper orientation as shown in the illustrations below.
●When making 2-sided copies, functions of some settings such as the paper size and type are limited.
For more information, see Hardware Specications(P. 1103) .
◼Copying 1-Sided to 2-Sided
When copying a horizontally long document, place the document in landscape orientation.
1Press <Options> <2-Sided>.
2Press <1-Sided 2-Sided>.
Copying
225
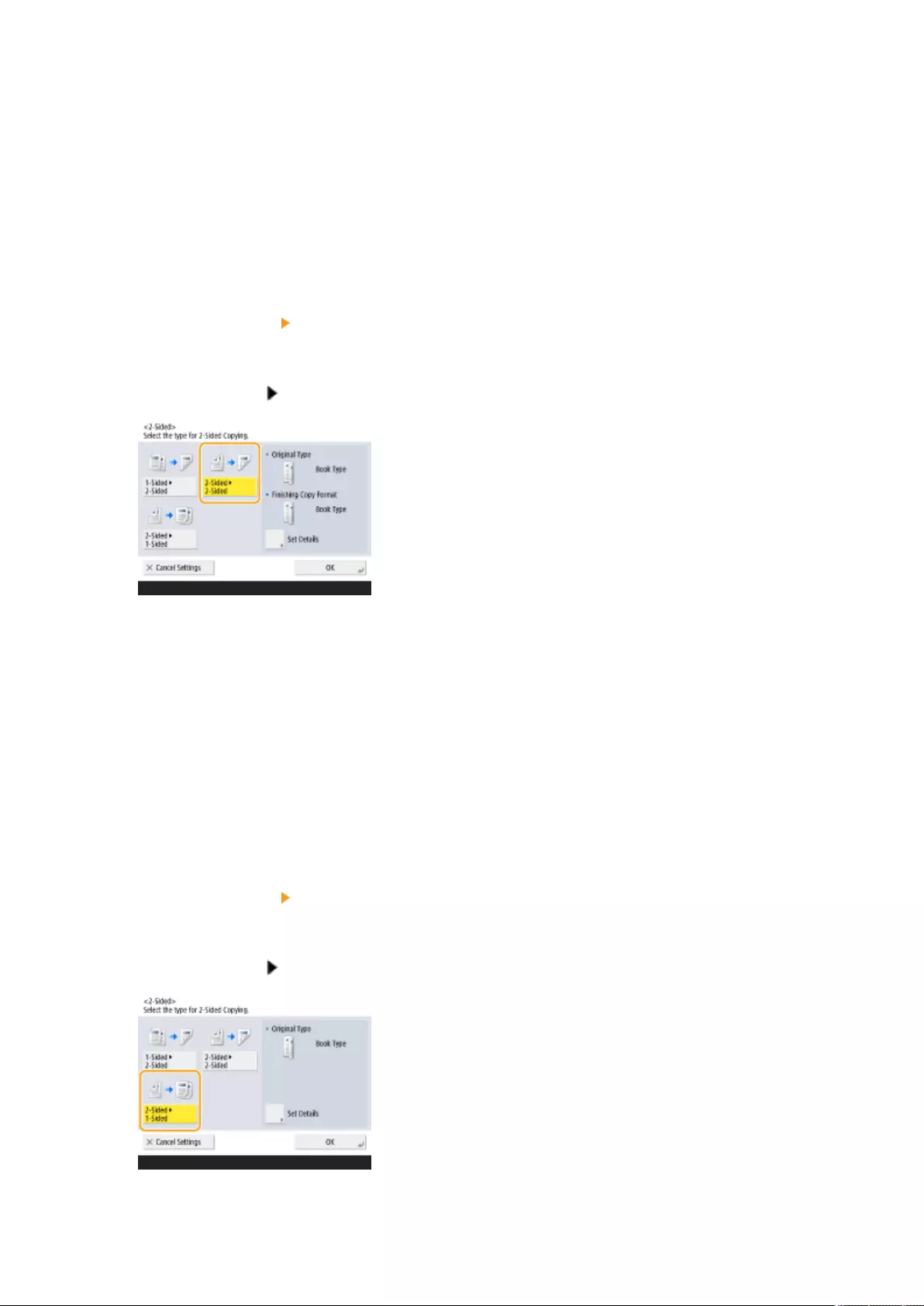
3Set <Finishing Copy Format> and press <OK>.
●To change the print orientation, press <Set Details>. Select <Book Type> to make the front and back sides of
the printout have the same top-bottom orientation. Select <Calendar Type> to make the front and back sides
of the printout have opposite top-bottom orientations.
◼Copying 2-Sided to 2-Sided
1Press <Options> <2-Sided>.
2Press <2-Sided 2-Sided>.
3Set <Original Type> and <Finishing Copy Format>, and press <OK>.
●To specify the document orientation and change the print orientation, press <Set Details>. Select <Book
Type> when the front and back sides of the document have the same top-bottom orientation. Select
<Calendar Type> when the front and back sides of the document have opposite top-bottom orientations. You
can also set the page orientation of the printout with <Book Type> or <Calendar Type>.
◼Copying 2-Sided to 1-Sided
Place the document in the feeder.
1Press <Options> <2-Sided>.
2Press <2-Sided 1-Sided>.
Copying
226

3Set <Original Type> and press <OK>.
●To specify the document orientation, press <Set Details>. Select <Book Type> when the front and back sides
of the document have the same top-bottom orientation. Select <Calendar Type> when the front and back
sides of the document have opposite top-bottom orientations.
Adjusting Image Quality of Copies
You can adjust density of the entire document. For example, increasing copy density
enables you to easily read faint characters written in pencil.
Adjusting the Density of Copies
You can adjust density of the background. This enables you to make clear copies of
originals such as newspapers or originals with colored backgrounds.
Adjusting the Density of the Background of Copies
◼Adjusting the Density of Copies
1Press <Options> <Density>.
2Adjust density and press <OK>.
●Press to decrease density. Press to increase density.
◼Adjusting the Density of the Background of Copies
1Press <Options> <Density>.
2Press <Adjust> in <Background Density>.
Copying
227

●To adjust the background automatically, press <Auto> and proceed to step 4.
3Adjust density and press <OK>.
●Press <-> to decrease the density of the entire background. Press <+> to increase the density of the entire
background.
●Depending on the colors of documents, sections other than the background may be affected.
●Press <+> to scan the blue text of documents such as receipts or invoices clearly.
●Press <-> to remove the background when scanning originals like newspapers or originals with a colored
background.
●If you press <Adjust> <Adjust Each Color>, you can adjust the background density by color.
4Press <OK>.
Specifying the Orientation of the Original
You can specify the orientation of an original placed on the platen glass or into the
feeder as horizontal or vertical.
1Press <Options> <Original Content Orientation>.
2Select the orientation of the original.
Copying
228
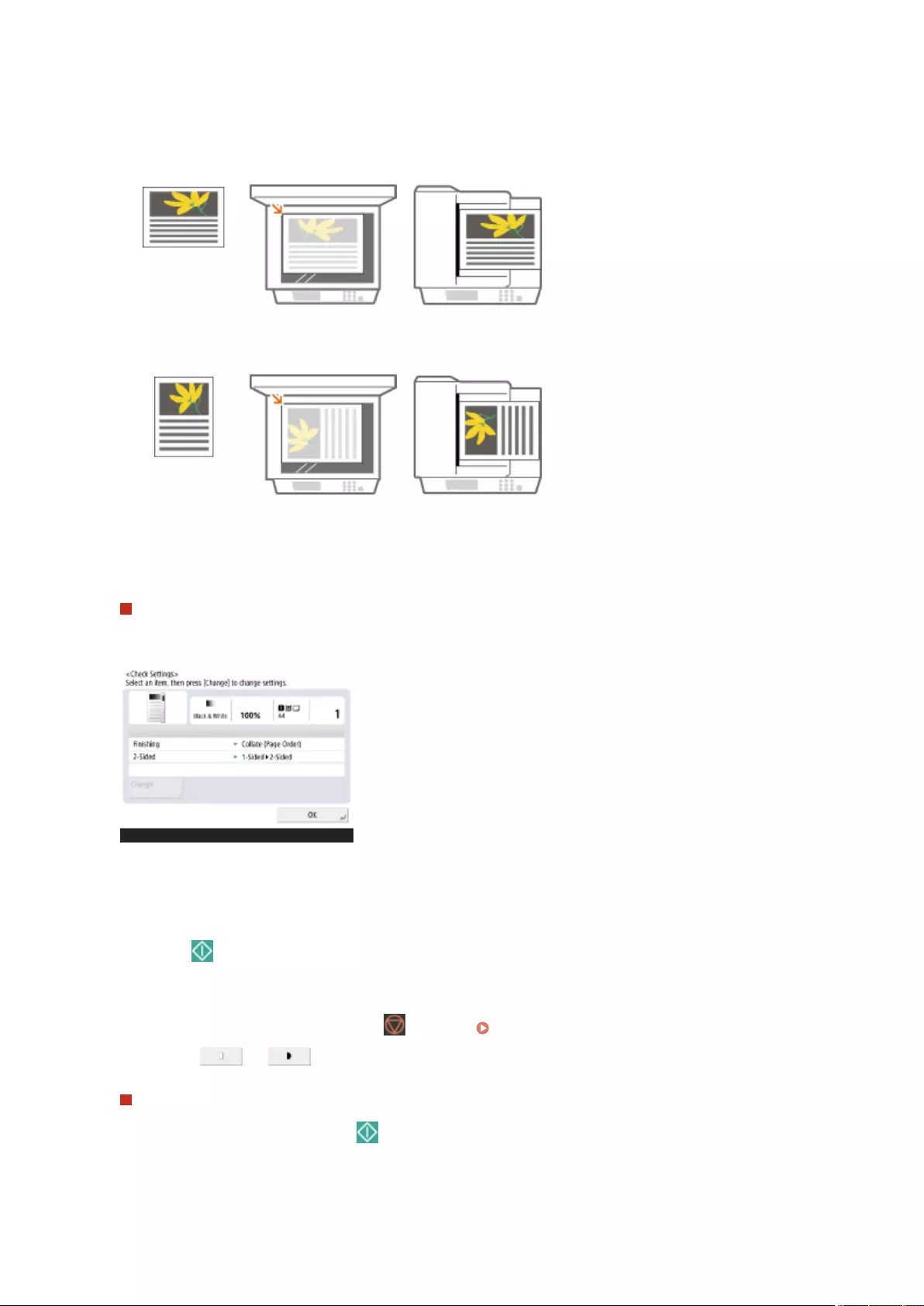
●Select <Top at Far Edge> for horizontally-oriented originals, or <Top at Side Edge> for vertically-oriented
originals.
For Originals in Portrait Orientation
Type of Original Platen Glass Feeder
For Originals in Landscape Orientation
Type of Original Platen Glass Feeder
3Press <OK>.
Check Settings
Conrm settings before copying
If you press <Check Settings>, the list of the specied settings is displayed.
●If you select a setting on the list and press <Change>, you can change the setting. After changing the
setting, press <OK>.
1Press (Start).
➠Copying starts.
●To cancel copying, press <Cancel> or (Stop). Cancelling Copying(P. 231)
●Pressing or during copying enables you to adjust density.
When <Press the [Start] key to scan the next original.> is displayed
Place the next document and press (Start). After scanning all of the documents, press <Start Copying> to
start copying.
Copying
229
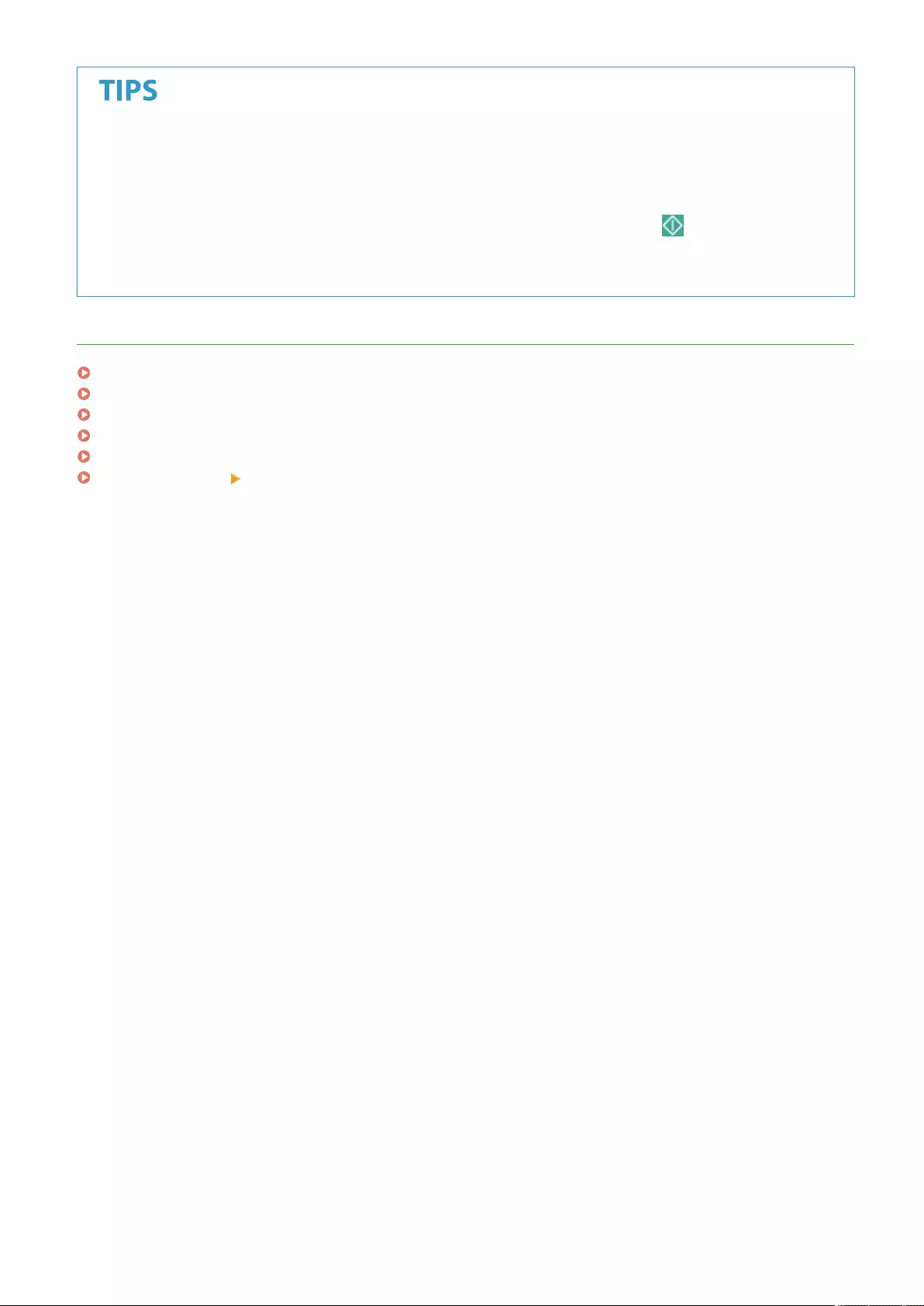
Reserving a copy
●Scanning can be performed in advance, even if the machine is preparing to print or printing. This function is
called "Reserved copy." For example, to perform reserved copy while the printing or waiting screen is
displayed, press <Close>, specify the copy settings in the usual manner, and press (Start).
●You can specify up to 50 jobs to be reserved, including the current job. Interrupt copy jobs are not included
in this count.
LINKS
Copy Basic Features Screen(P. 218)
Specifying Paper Size and Type(P. 141)
Hardware Specications(P. 1103)
Loading Paper in the Multi-Purpose Tray(P. 107)
Optional Equipment(P. 1119)
<Common>(P. 808) <Paper Output Settings>
Copying
230

Cancelling Copying
72JY-03S
You can cancel copying while scanning originals or cancel waiting copy jobs.
◼Canceling Copying While Scanning
The following screen is displayed while scanning originals. Press <Cancel> to cancel copying.
●If you press (Stop) on the control panel while the Copy Basic Features screen is being displayed, the
copy job is paused and, the message <<Stop>Select the Copy job you want to cancel.> and the list of copy
jobs are displayed. You can select the copy job from the list and cancel the job by pressing <Cancel>.
●If you log in with personal authentication management and log out after pressing (Stop) on the
control panel to display the message <<Stop>Select the Copy job you want to cancel.> and the list of copy
jobs, the last job that the logged out user executed is canceled and other jobs are resumed.
◼Canceling Waiting Copy Jobs
1Press <Status Monitor>.
2Press <Copy/Print> <Job Status>.
3Select <Copy> from the drop-down list and display waiting copy jobs.
Copying
231
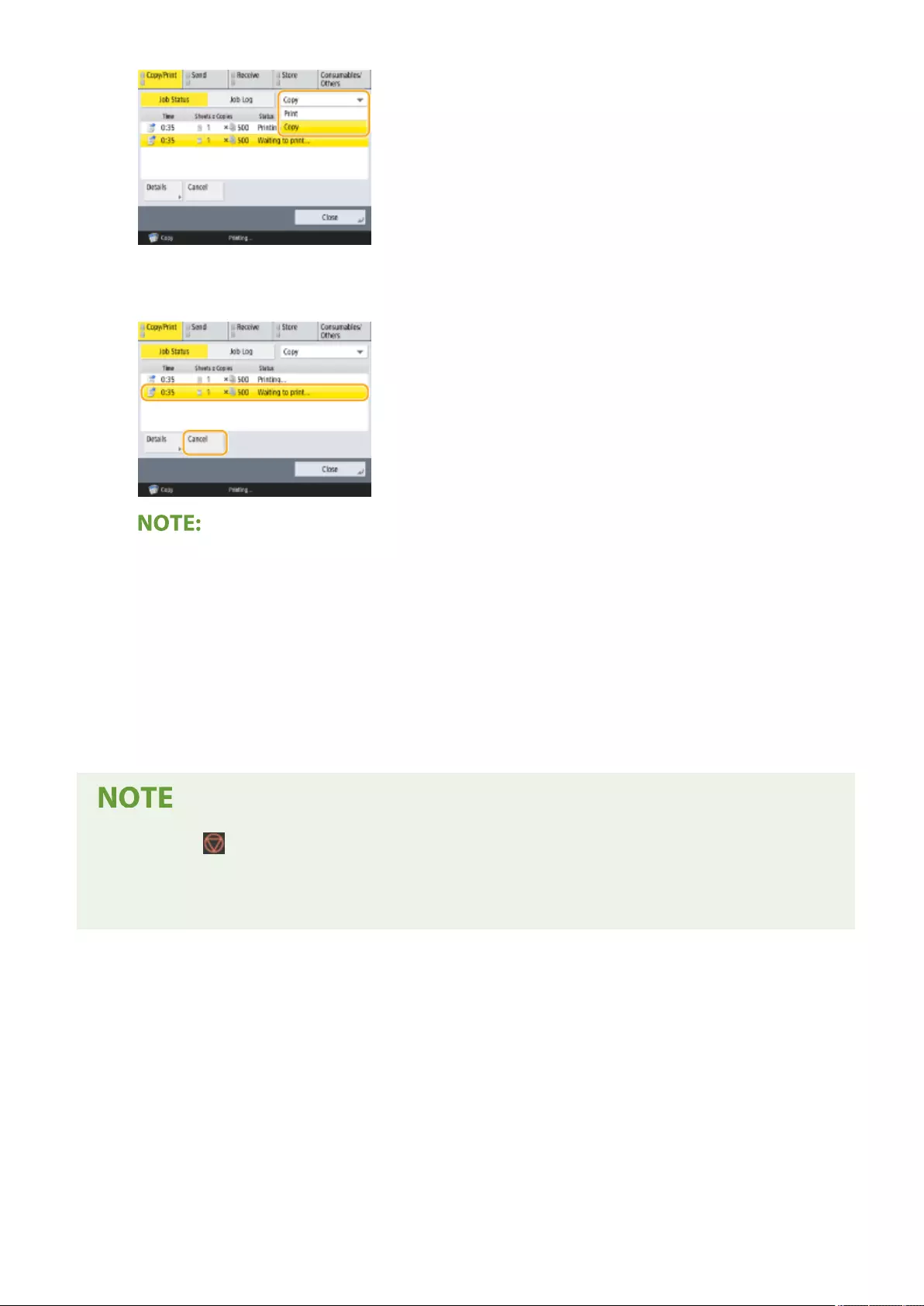
4Select the copy job to cancel and press <Cancel>.
●If you press <Details>, detailed information such as the number of copies and the Department ID is
displayed.
5Press <Yes>.
➠Copying stops.
6Press <Close>.
●If you press (Stop) on the control panel when copy jobs are waiting, all the copy jobs are paused and
then the message <<Stop>Select the Copy job you want to cancel.> and the list of the copy jobs are
displayed. You can select a copy job from the list and cancel the copy job by pressing <Cancel>. If you want
to resume copying, press <Resume Copying>.
Copying
232
Enhancing and Adjusting Copy Quality
72JY-03U
You can enhance the copy quality by making ne adjustments such as adjusting sharpness and erasing unnecessary
dark borders.
Selecting the Type of Original
for Copying(P. 234)
Adjusting Sharpness for Copying
(Sharpness)(P. 235)
Erasing Dark Borders When
Copying (Erase Frame)(P. 236)
Adjusting the Color(P. 238) One Touch Color Mode(P. 240)
Copying
233

Original TypeOriginal Type
Selecting the Type of Original for Copying
72JY-03W
You can select the optimal image quality for the copy depending on the type of
original such as originals with only characters or magazines with photographs.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Original Type>.
5Select the type of original.
●To adjust the text/photo processing priority level, press <Adjust Level> select <Text Priority> or <Photo
Priority>.
6Press <OK> <Close>.
7Press (Start).
➠Copying starts.
Copying
234

SharpnessSharpness
Adjusting Sharpness for Copying (Sharpness)
72JY-03X
You can copy the image with clear contours and lines by increasing the sharpness, or
soften the copied image by decreasing the sharpness. Use this function when you
want to sharpen blurred text and diagrams, or to reduce moire (a striped, wavy
pattern) to smooth the nished image.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Sharpness>.
5Adjust sharpness and press <OK>.
●Set the sharpness to <High> when you want to copy originals containing text or ne lines. Set the sharpness
to <Low> when you want to copy originals containing printed photographs or other halftones.
6Press <Close>.
7Press (Start).
➠Copying starts.
Copying
235
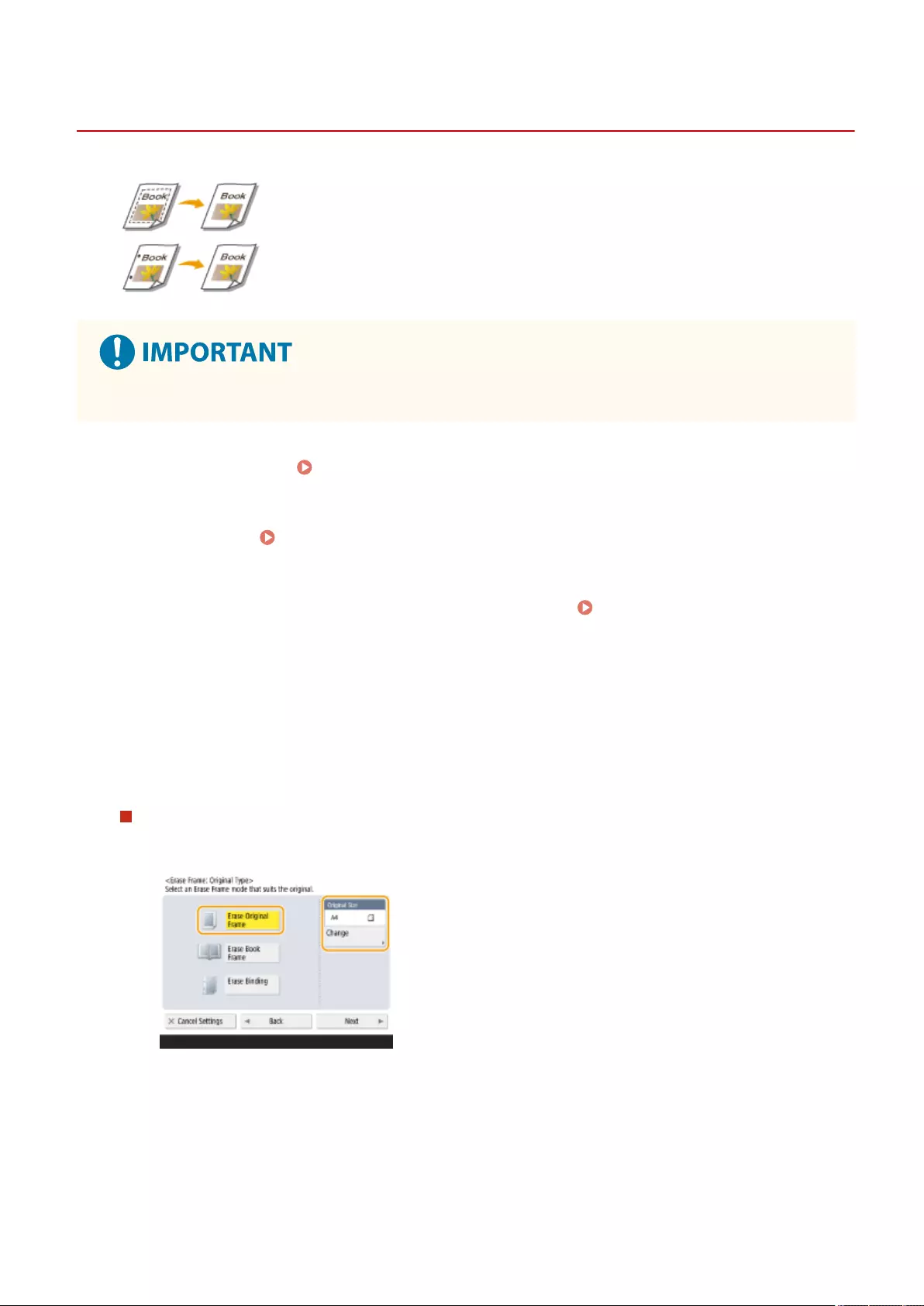
Erase FrameErase Frame
Erasing Dark Borders When Copying (Erase Frame)
72JY-03Y
When copying originals that are smaller than the output paper size, frame lines of
the originals may appear in the copied image. When copying thick books, dark
borders may appear. <Erase Frame> enables you to erase these frame lines and dark
borders. You can also set the machine to not copy punch holes in the originals.
●Place originals with punch holes on the platen glass. Placing them in the feeder may result in damage.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Erase Frame>.
5Specify erasing type and width.
Erasing the frames in copies of documents
1Press <Erase Original Frame> and set <Original Size>.
●If the size displayed in <Original Size> is different from the size of the original you set, press <Change>
to select the size.
2Press <Next>.
3Enter the width of the frame to erase.
Copying
236

Erasing the dark borders in copies of books
You can erase the dark borders both in the center and contour lines that appear when you copy facing pages
in a book.
1Press <Erase Book Frame> and conrm <Original Size>.
●If the size displayed in <Original Size> is different from the size of the book you set, press <Change> to
select the size.
2Press <Next>.
3Press <Center> or <Sides>, and enter each erasing width.
Erasing punch holes in copies of documents
1Press <Erase Binding>.
2Press <Next>.
3Specify the position of the punch holes, and enter the erasing width.
●If you want to adjust the width for each border independently, press <Erase Original Frame> or <Erase
Book Frame>, and then press <Adjust Independently> to enter the erasing widths.
6Press <OK> <Close>.
7Press (Start).
➠Copying starts.
Copying
237
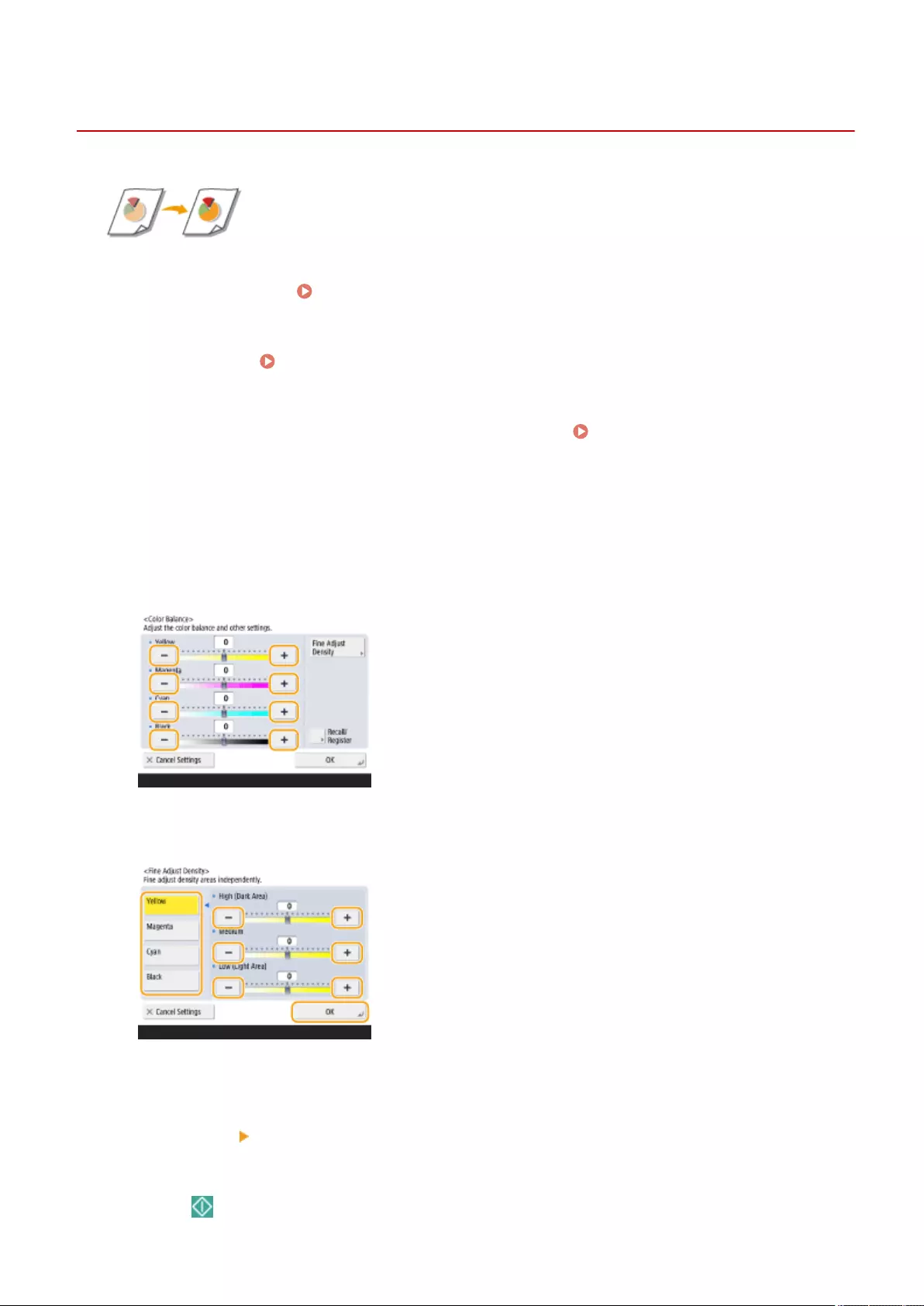
Color BalanceColor Balance
Adjusting the Color
72JY-040
Adjust the density of yellow, magenta, cyan, and black separately.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Color Balance>.
5Press <-> or <+> for each color to adjust the color balance.
6Press <Fine Adjust Density>, and perform other adjustments as necessary.
●Select a color and adjust its density level by its density area using the <-> or <+> button. When adjustment is
complete, press <OK>.
7Press <OK> <Close>.
8Press (Start).
Copying
238
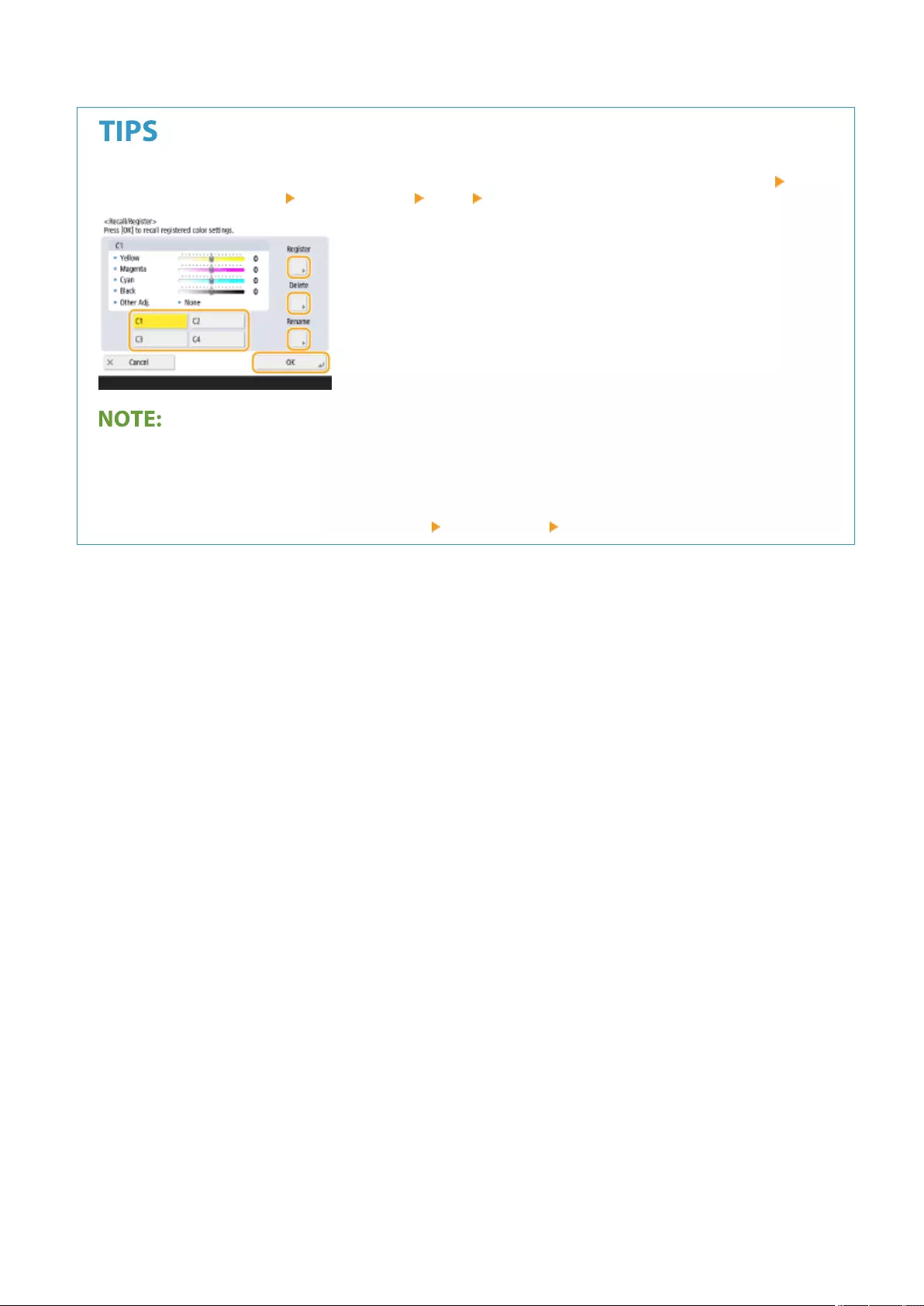
➠Copying starts.
You can register up to four settings after adjustment. After adjusting the color, press <Recall/Register> select
a button from <C1> to <C4> press <Register> <Yes> <OK>.
●To recall registered settings, press <Recall/Register>, select a button, and press <OK>.
●You can change the button names of <C1> to <C4>. Select the button to change, press <Rename>, and enter
a new name.
●To delete registered settings, select the button press <Delete> <Yes>.
Copying
239

Adjust One-Touch ColorAdjust One-Touch Color
One Touch Color Mode
72JY-041
You can intuitively select the image quality with a single button, such as having subtle
colors or having a retro nish like an old photograph.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Adjust One-Touch Color>.
5Select the desired image quality.
Example adjustment:
Original
Vivid Colors
Copying
240

Tranquil Colors
Lighten Image
Darken Image
Highlight Reproduction
Sepia Tone
●If you select <Highlight Reproduction>, the image quality is adjusted so that highlights are not blown out.
●You can select multiple types of image quality at the same time. However, <Vivid Colors> and <Tranquil
Colors> cannot be selected at the same time, and <Lighten Image>, <Darken Image>, and <Highlight
Reproduction> cannot be selected at the same time.
6Press <OK> <Close>.
7Press (Start).
➠Copying starts.
●The settings in <Options> <Color Balance> automatically change according to the image quality
you select.
●If you select <Sepia Tone>, <Single Color (Sepia Tone) > is displayed in <Select Color> on the Basic
Features screen.
Copying
241
Copying Eciently
72JY-042
You can save paper by copying several originals onto one sheet or checking the copy result before making copies.
Copying Multiple Originals onto
One Sheet (N on 1)(P. 243)
Copying Separately Scanned
Originals Together (Job Build)
(P. 245)
Checking the Copy
Results(P. 247)
Copying Immediately by Interrupting Other Jobs(P. 249)
Copying
242

N on 1N on 1
Copying Multiple Originals onto One Sheet (N on 1)
72JY-043
You can copy several pages of originals onto a single sheet. This function enables
you to copy with a smaller amount of paper than the original number of pages.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <N on 1>.
5Select the way to arrange pages and select the original size and paper size for
copying.
●Select how many pages to be arranged onto a single sheet of paper. You can change the arrangement order
as well.
●To make 2-sided copies, or to scan 2-sided originals to make 1-sided copies, press <2-Sided Settings>. For
more information on the setting, see "2-Sided Copying" in step 4 of Basic Copy Operations(P. 220) .
●Pressing <Change> in <Original Size> enables you to select the size of original and pressing <Change> in
<Paper Size> enables you to select the paper size.
6Press <OK> <Close>.
7Press (Start).
➠Copying starts.
Copying
243

Originals must all be the same size.
●If you set <N on 1>, <Shift> is automatically set to <Center>.
Copying
244

Job BuildJob Build
Copying Separately Scanned Originals Together (Job
Build)
72JY-044
Even if you have too many originals to be placed in the feeder at once, you can scan
the originals separately and copy them as a batch of documents. Originals scanned
with both the feeder and the platen glass also can be copied at one time.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Job Build> <Close>.
5Press (Start) to scan the originals.
➠When scanning is complete, the screen appears prompting you to scan the next original.
6Place the next original and press (Start) to scan the original.
●Repeat this step until you nish scanning all of the originals.
●To change the scan settings, press <Change Settings>.
●The following functions can be used in <Change Settings>: You need to set the necessary scan settings in
advance, since you cannot change the other functions during the Job Build mode.
-<Select Color>
- <Copy Ratio>
- <2-Sided Original>
- <Density>
- <Original Type>
●If you specify the <N on 1 > mode together with the Job Build mode, you cannot change <Select Color>,
<Copy Ratio>, and <Density> in <Change Settings>.
7Press <Start Copying>.
Copying
245

➠Copying starts.
Copying
246

Checking the Copy Results
72JY-045
Prior to a large amount of copying, you can check the copy result by printing a copy
sample. Conrming the copy results enables you to eliminate output mistakes.
●<Copy Sample> appears only if you set to make multiple copies and one of the following settings at the same
time.
-Collate (Page Order)
Copy Sample
Checking the Copy Result by Making a Copy (Copy Sample)
When you specied multiple numbers of copies, you can rst make a copy of your whole original to check the result
and then start making the rest of the copies. You can also copy only specic pages of your original.
1Place the originals in the feeder. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Enter the number of copies, and specify the copy settings according to your purpose
and objective. Basic Copy Operations(P. 220)
4Press <Copy Sample> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
5Select pages for the copy sample and press <OK>.
●If you want to copy all of the pages, select <All Pages>.
●To copy specic pages, select <Specied Pages>. Enter the pages by pressing <First Page> or <Last Page>.
Copying
247
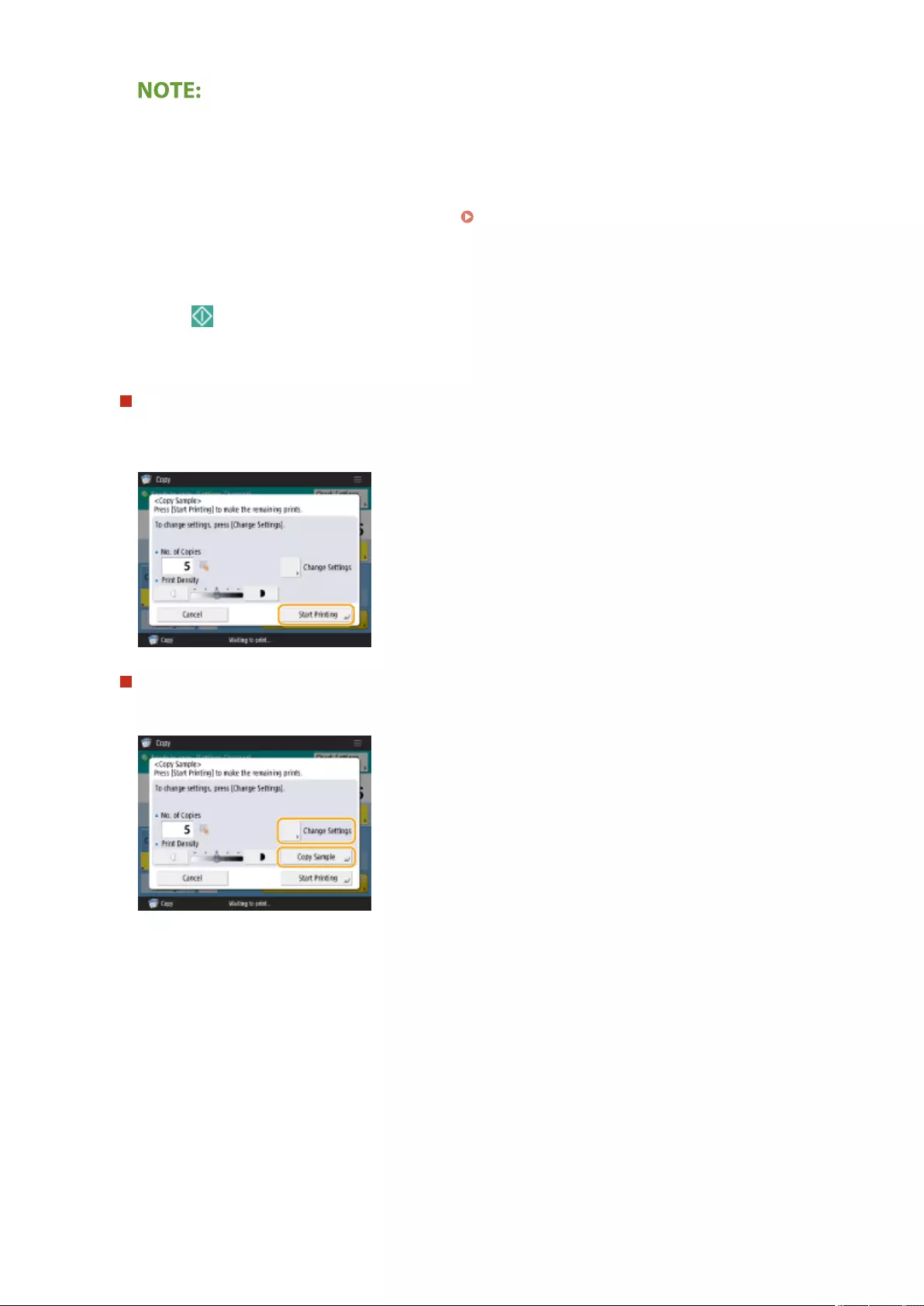
If you select <All Pages>
●If you select <All Pages>, the machine's counter counts the sample set as a copy.
If you select <Specied Pages>
●Specify the pages based on the output page numbers. For example, if the number of pages of document is
10 and you copy with the 2 on 1 setting ( Copying Multiple Originals onto One Sheet (N on 1)
(P. 243) ), the number of nished pages becomes 5. If you want to copy the seventh to tenth pages of the
original, specify the fourth page for <First Page> and the fth page for <Last Page>.
6Press (Start) to scan the originals, and press <Start Copying>.
➠The copy sample is printed. Check the result.
If there is no problem with the copy result
Press <Start Printing> to print the number of copies you specied. If you selected <All Pages> in step 5, the
number of copies minus one is printed. If you select <Specied Pages> in step 5, the total number of copies is
printed.
If you want to change settings
Press <Change Settings> to change the settings. <Copy Sample> is displayed after the settings are changed.
Copy a sample again.
Copying
248
Interrupt
Copying Immediately by Interrupting Other Jobs
72JY-046
You can copy immediately even while another operation is being performed. This is
convenient for cases in which you only want to copy several pages urgently, but
another person's output will not nish soon.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Interrupt> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Specify the copy settings as necessary. Basic Copy Operations(P. 220)
5Press (Start).
➠The previous job is paused and interrupt copying starts.
●To cancel interrupt copying, press <Interrupt> again before pressing (Start).
●When interrupt copying nishes, the previous job restarts automatically.
●During interrupt copying, you cannot perform another interrupt copying. After the current interrupt copying
nishes, perform the next interrupt copying.
●Even when the number of reserved copy jobs has reached its limit, interrupt copying can still be performed.
You can interrupt jobs with a reserved copy job ( Basic Copy Operations(P. 220) ).
●To interrupt the current job and perform a reserved copy job, press <Status Monitor> <Copy/Print> <Job
Status> Select the document to copy <Interrupt/Priority Print> <Interrupt and Print>.
●To perform a reserved copy job right after the current job nishes, press <Status Monitor> <Copy/Print>
<Job Status> Select the document to copy with the rst priority <Interrupt/Priority Print> <Priority
Print>.
Copying
249

Finishing (Collate/Group)
Finishing by Collating/Grouping
72JY-048
When copying two copies or more from the feeder, you can select collating or
grouping for the order of printouts. Select "Collate" to print in sequential page order.
Select "Group" to print bundles of each page, as in 10 sheets for the rst page, 10
sheets for the second page, and so forth.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Finishing>.
5Press <Collate (Page Order)> or <Group (Same Pages)>.
6Press <OK> <Close>.
7Press (Start).
➠Copying starts.
●Depending on the paper type, you cannot use nishing functions. Hardware Specications(P. 1103)
When placing an original on the platen glass
●Pressing <Options> <Job Build> on the Copy Basic Features screen enables you to use the Collate/Group
function even if the original is placed on the platen glass.
Copying
251

Insert a job separator between each page during a group output
●If you select <Group (Same Pages)>, you can insert a job separator between each group. For more
information, see <Job Separator Between Groups>. <Copy>(P. 817) <Job Separator Between Groups>
When conguring settings in <Access Stored Files>
●You can use nishing functions only when printing PDF/XPS les.
Copying
252

Shift
Shifting the Image
72JY-04A
This function enables you to make copies with the entire image shifted towards an
edge or the center of the page. Shift the image when you want to make blank space
on the page to input or arrange text and images on material.
Shifting the Image to an Edge or the Center(P. 255)
Specifying Moving Distance(P. 255)
Shift Direction Settings
●Depending on the orientation of the original and the location where it is placed, the direction to which the
image will be shifted will differ.
- When the original is placed on the platen glass
Top at Side Edge: Image will shift to the right and/or bottom.
Top at Far Edge: Image will shift to the left and/or bottom.
- When the original is placed in the feeder
Top at Side Edge: Image will shift to the left or right, and/or bottom.
Top at Far Edge: Image will shift to the top or bottom, and/or right.
●If using the By Position function: The image will shift but its position will be adjusted so that the entire
image is copied without being cut off.
●If using the By Numeric Keys function: The copied image may be cut off.
Copying
254

Shifting the Image to an Edge or the Center
You can make margins around the image by copying to paper larger than the original or by reducing the copied image
to a size smaller than the paper size. When these margins are available, the image can be shifted to an edge or the
center of the paper.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Shift>.
5Press <By Position> <Next>.
6Select the direction to move the image.
●Press an arrow button or <Center> to select the direction of movement.
7Press <OK> <Close>.
8Press (Start).
➠Copying starts.
Shift
Specifying Moving Distance
If no blank space exists because the original image and the output paper are the same size, or if you want to shift
images by a few millimeters, specify the moving distance.
1Place the original. Placing Originals(P. 97)
Copying
255

2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Shift>.
5Press <By Numeric Keys> <Next>.
6Specify the position to move to.
●Press <Set> in <Front Side> and specify the moving distance. Press the up/down/left/right buttons indicating
directions and enter the moving distance using the numeric keys.
●If you want to move the image on the back side when copying both sides, the <Back Side> setting is needed.
To move to the same position as the front side, press <Same as Front Side>. To move symmetrically, press
<Opposite to Front Side>. To move to a position different from the front side, press <Set> and enter the
moving distance.
7Press <OK> <Close>.
8Press (Start).
➠Copying starts.
Copying
256
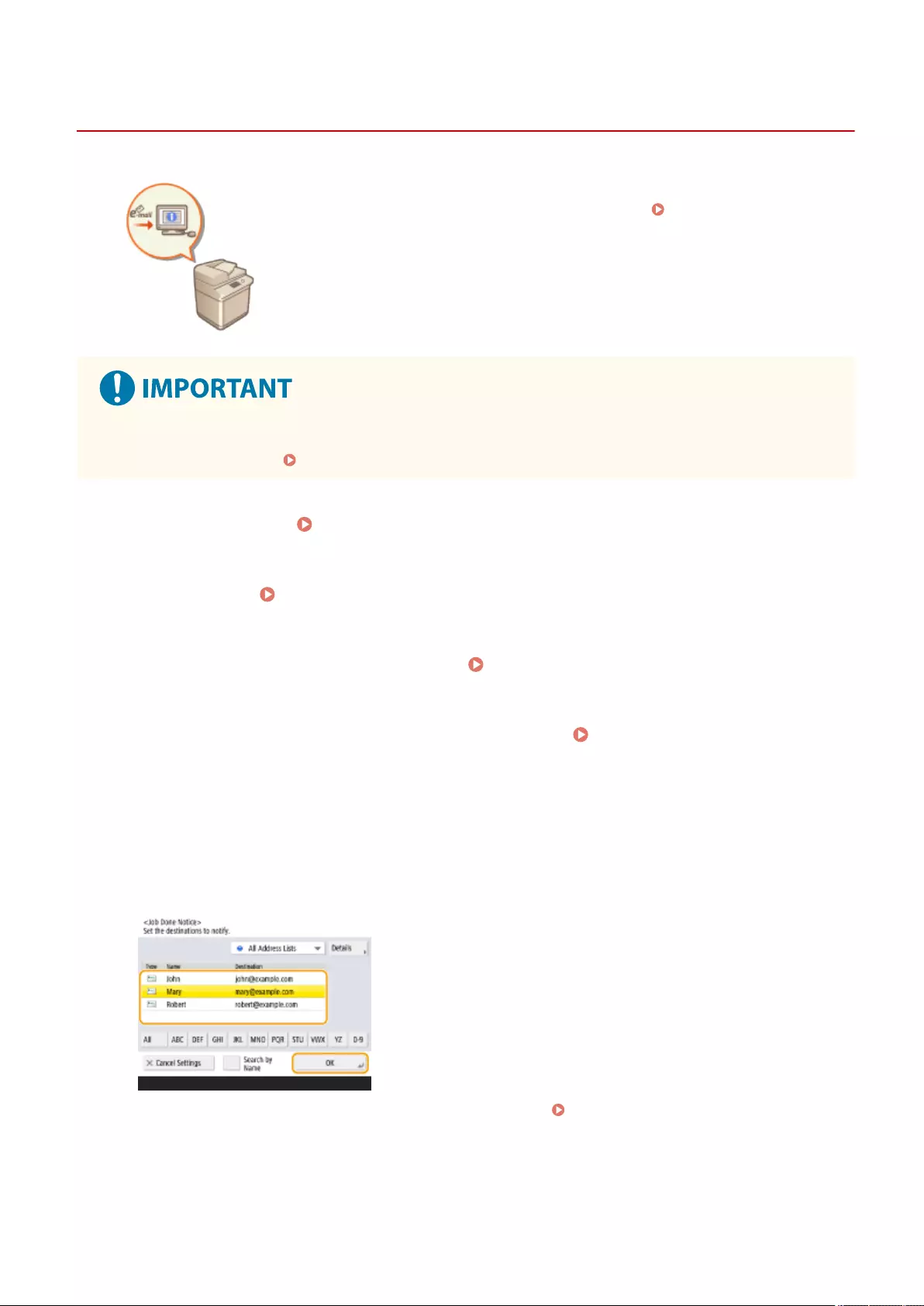
Job Done Notice
Notifying You of the Completion of Copying by E-Mail
72JY-04C
You can receive an e-mail notifying you that originals are nished copying. When
performing a large copying job or reservation copies ( Basic Copy
Operations(P. 220) ), you do not need to wait beside the machine for the print
completion.
●The destination for the notication e-mail needs to be specied from the Address Book. Register the desired
destination beforehand. Registering Destinations in the Address Book(P. 195)
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Specify the copy settings as necessary. Basic Copy Operations(P. 220)
4Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
5Press <Job Done Notice>.
6Select an e-mail address from the Address Book and press <OK>.
●For information on how to view and use the Address Book, see Address Book(P. 190) .
7Press <Close>.
Copying
257

8Press (Start).
➠Documents are scanned and copying starts. When copying is complete, the notication e-mail is sent to
the specied address.
Copying
258
Copy ID Card
Making ID Card Copies
72JY-04E
This function enables you to copy both the front and back of an ID card onto a single
sheet of paper. This function is useful when copying ID cards (identication cards)
such as driver's licenses, because the orientation and print position of the images of
both sides of the ID card are aligned automatically according to the paper size.
●Place the ID card on the platen glass. Place the ID card face down with its corner aligned with the top-left
corner of the platen glass, as shown below. The Copy ID Card mode cannot be used when the ID card is
placed in the feeder.
●If another original is set in the feeder, you cannot start copying. Remove the original from the feeder.
●Only A4 paper can be used for <Copy ID Card>.
1Place the ID card on the platen glass face down. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Copy ID Card>.
5Press <Change>, select the paper to use, and press <OK>.
Copying
259

6Press <OK> <Close>.
7Press (Start) to scan the front side.
➠Once scanning is completed, a screen will appear notifying you that preparations to scan the back side are
complete.
8Turn the ID card over so that its back side is facing down and press (Start) to scan
the back side.
➠After the back side is scanned, printing starts automatically.
Copying
260
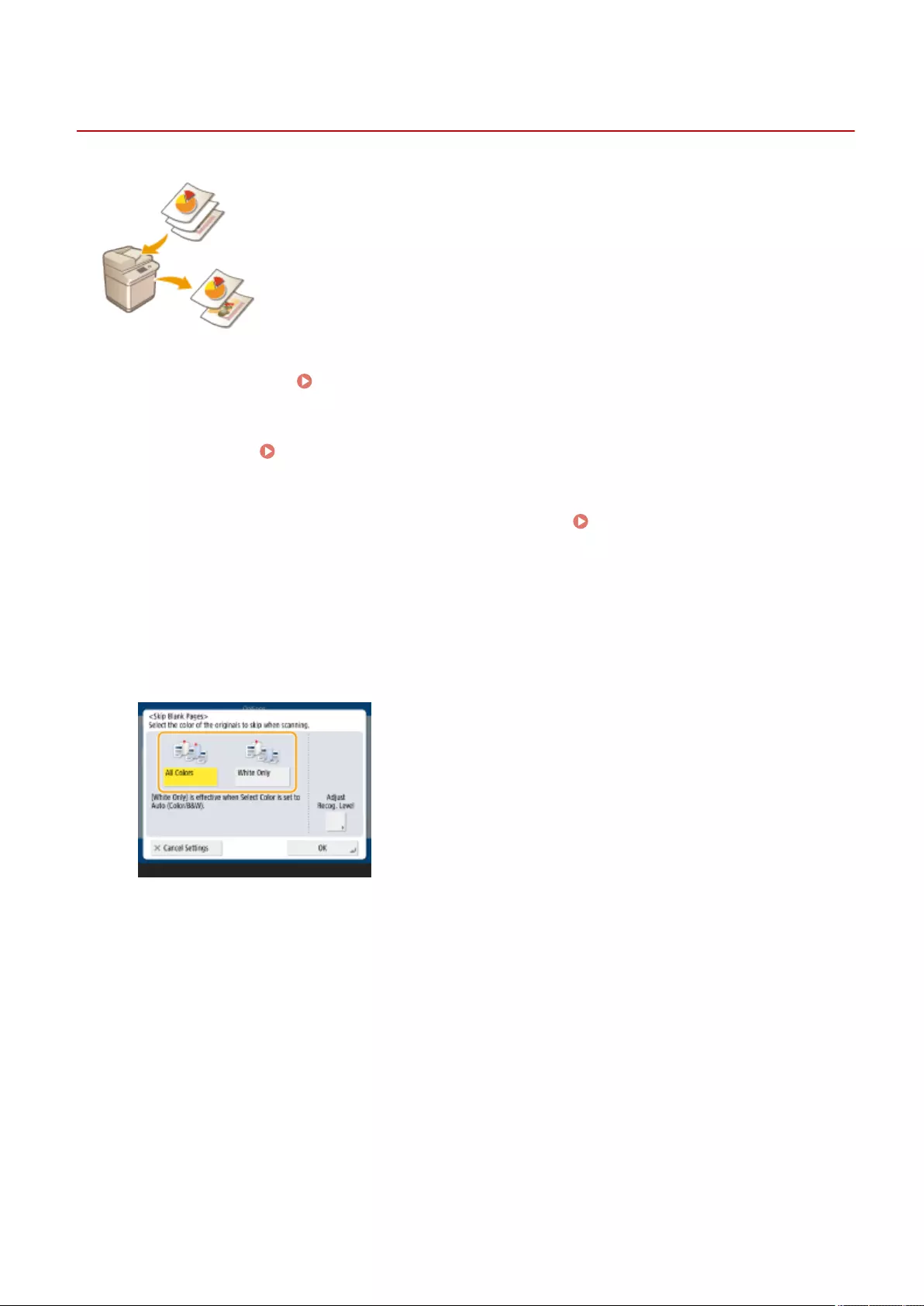
Skip Blank PagesSkip Blank Originals
Skipping Blank Pages When Printing
72JY-04F
The machine can detect blank pages when scanning, and print all the pages except
blank pages.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Skip Blank Pages>.
5Select the color of the originals to skip.
●To skip blank originals regardless of their color, select <All Colors>. To skip blank originals only in white,
select <White Only>.
●If a setting other than <Auto (Color/B&W)> is set in <Select Color>, the same operations as <All Colors> is
performed even if you select <White Only>.
6Press <Adjust Recog. Level>, set the accuracy to detect blank paper, and then press
<OK>.
Copying
261

➠Pressing <+> makes the detection accuracy higher.
7Press <OK> <Close>.
8Press (Start).
➠Copying starts.
●If the size of the original is smaller than the scan size setting, it may not be skipped correctly.
●To check the number of pages that have been printed, follow the procedures below:
- (Status Monitor) <Copy/Print> <Job Log> select a document <Details> check the number
displayed for <No. of Orig. Pages>.
- The status screen and report display the number including blank paper. Checking the Status of
Copies/Prints(P. 587)
- The copy counter is not incremented for blank paper that is saved. However, the scan counter is
incremented for those pages.
Copying
262

Previous Settings
Recalling Previously Used Copy Settings (Previous
Settings)
72JY-04J
You can recall the previously used copy settings. The details of the recalled setting
can be changed before copying.
●The three most recent settings that were stored in memory are not deleted even when the main power is
turned Off.
1Place the original. Placing Originals(P. 97)
2Press <Copy>. <Home> Screen(P. 119)
3Press <Options> on the Copy Basic Features screen. Copy Basic Features
Screen(P. 218)
4Press <Previous Settings>.
5Select the setting to recall and press <OK>.
●When personal authentication management is in use, the machine recalls the settings specied in the past by
the user who is logging in to the machine.
6Press (Start).
➠Copying starts.
Copying
264
Restrictions Regarding the Combination of Functions
72JY-04L
The following tables show the unavailable combinations of settings when you want to set more than one function at a
time.
◼Functions that Cannot Be Used in Combination
"Functions that Cannot Be Used in Combination" indicate the following:
●Functions that cannot be set because the buttons for them are greyed out when the function on the left column is
set.
●Functions that cannot be set because the buttons for them are not displayed (depending on the optional products
available for use) when the function on the left column is set.
●Functions that cannot be set in combination with the function on the left column because a message appears when
(Start) is pressed and copying does not start.
●Functions that cannot be set in combination with the function on the left column because a message appears on
the operation guide of the touch panel display and copying starts without the supposedly set functions being
activated. (Example: If you selected and tried to copy on paper to which the Finish mode cannot be applied.)
●Functions that cannot be set in combination with the function on the left column because the paper source that
contains the paper to be used for copying cannot be selected.
◼Functions that Have Priority when Set Last
"Functions that Have Priority when Set Last" indicate the following:
●The function that you set last is enabled, and the function that you set rst is canceled or the buttons for them are
greyed out, when the function on the left column is set in combination with these functions.
●For information on the paper sizes and types that can be used with the <2-Sided> and <Finishing>
modes, see Available Paper(P. 1109) .
●For information on the optional product required to use each function, see Optional
Equipment(P. 1119) and System Options(P. 1101) .
Copy Basic Features Screen(P. 266)
Options Screen (1/3)(P. 267)
Options Screen (2/3)(P. 268)
Options Screen (3/3)(P. 269)
Copy Basic Features Screen
Function Functions that Cannot
Be Used in Combination Functions that Have Priority when Set Last
Select Color
Auto (Color/
B&W)
Full Color, Black & White, Single Color, Two Colors,
Adjust One-Touch Color (Sepia Tone)
Full Color Auto (Color/B&W), Black & White, Single Color,
Two Colors, Adjust One-Touch Color (Sepia Tone)
Copying
266
Black & White Auto (Color/B&W), Full Color, Single Color, Two
Colors, Adjust One-Touch Color (Sepia Tone)
Single Color Adjust One-Touch Color
(Sepia Tone)
Auto (Color/B&W), Full Color, Black & White, Two
Colors
Two Colors Adjust One-Touch Color
(Sepia Tone)
Auto (Color/B&W), Full Color, Black & White,
Single Color
Copy Ratio
1:1 (100%) Copy Ratio (Manual), Copy Ratio (Preset Zoom),
Copy Ratio (Auto), XY Ratio
Manual Copy ID Card Direct (100%), Copy Ratio (Preset Zoom), Copy
Ratio (Auto), XY Ratio
Preset Zoom Copy ID Card Direct (100%), Copy Ratio (Manual), Copy
Ratio (Auto), XY Ratio
Auto Copy ID Card Direct (100%), Copy Ratio (Manual), Copy Ratio
(Preset Zoom), XY Ratio
XY Ratio Copy ID Card Direct (100%), Copy Ratio (Manual), Copy Ratio
(Preset Zoom), Copy Ratio (Auto)
Fit to Page
N on 1, Copy ID Card,
Erase Original Frame,
Erase Book Frame, Erase
Binding
Select Paper
Paper source Select Paper (Custom Size)
Custom Size N on 1 Select Paper (Paper source), Copy ID Card
Copy Sample Copy ID Card Group (Same Pages)
Interrupt Copy ID Card
Options Screen (1/3)
Function Functions that Cannot Be Used in
Combination
Functions that Have Priority
when Set Last
2-Sided
1-Sided>2-Sided Copy ID Card 2-Sided>2-Sided, 2-Sided>1-
Sided
2-Sided>2-Sided Copy ID Card 1-Sided>2-Sided, 2-Sided>1-
Sided
2-Sided>1-Sided Copy ID Card 1-Sided>2-Sided, 2-Sided>2-
Sided
Finishing
Collate (Page Order) Copy ID Card, Group (Same
Pages)
Group (Same Pages) Copy ID Card, Copy Sample Collate (Page Order)
Job Build Copy ID Card
Copying
267
N on 1
Fit to Page, Select Paper (Custom
Size), Copy ID Card, Erase Original
Frame, Erase Book Frame, Shift (By
Numeric Keys), Skip Blank Pages
Density
Auto Photo, Text/Photo Density (Adjust)
Adjust Density (Auto)
Original Type
Text/Photo/Map Photo, Text
Photo Text/Photo/Map, Text
Text Text/Photo/Map, Photo
Options Screen (2/3)
Function Functions that Cannot Be Used in
Combination
Functions that Have Priority
when Set Last
Color Balance Yellow, Magenta,
Cyan, Black
Adjust One-Touch Color
(Lighten Image, Darken
Image, Highlight
Reproduction)
Adjust One-Touch Color
Lighten Image,
Darken Image,
Highlight
Reproduction
Color Balance (Yellow,
Magenta, Cyan, Black)
Sepia Tone Select Color (Single Color, Two Colors)
Select Color (Auto (Color/
B&W), Full Color, Black &
White)
Erase Frame
Erase Original
Frame Fit to Page, N on 1, Copy ID Card Erase Book Frame, Erase
Binding
Erase Book Frame Fit to Page, N on 1, Copy ID Card Erase Original Frame, Erase
Binding
Erase Binding Fit to Page, Copy ID Card Erase Original Frame, Erase
Book Frame
Shift
By Position Copy ID Card Shift (By Numeric Keys)
By Numeric Keys N on 1, Copy ID Card Shift (By Position)
Copy ID Card
Copy Ratio (Manual), Copy Ratio (Preset
Zoom), Copy Ratio (Auto), XY Ratio, Fit to
Page, Select Paper (Custom Size), 1-
Sided>2-Sided, 2-Sided>2-Sided, 2-
Sided>1-Sided, N on 1, Erase Original
Frame, Erase Book Frame, Erase
Binding, Shift (By Position), Shift (By
Numeric Keys), Job Build, Collate (Page
Order), Group (Same Pages), Copy
Sample, Interrupt, Skip Blank Pages
Copying
268
Options Screen (3/3)
Function Functions that Cannot Be Used in Combination Functions that Have Priority when Set Last
Skip Blank Pages N on 1, Copy ID Card
Copying
269

Faxing
Faxing ................................................................................................................................................................... 271
Fax Basic Features Screen ................................................................................................................................. 273
Basic Operations for Sending Faxes ................................................................................................................. 275
Canceling Sending Faxes .............................................................................................................................. 289
Receiving Faxes ................................................................................................................................................. 291
Sending Faxes Successfully ............................................................................................................................... 294
Checking Scanned Images Before Sending (Preview) ................................................................................... 295
Checking the Connection to the Recipient Before Sending (Direct Send) ...................................................... 297
Sending Faxes Manually (Manual Sending) ................................................................................................... 298
Notifying You by E-Mail of the Completion of Sending ................................................................................. 299
Simplifying Sending Operations ....................................................................................................................... 301
Sending Separately Scanned Documents Together (Job Build) ..................................................................... 302
Recalling Previously Used Settings for Sending (Previous Settings) .............................................................. 304
Useful Functions When Sending ....................................................................................................................... 306
Sending at a Specied Time .......................................................................................................................... 307
Saving a Copy of a Sent Document ............................................................................................................... 309
Various Receiving Methods .............................................................................................................................. 312
Saving Received Documents in the Machine (Memory Reception) ................................................................ 313
Keeping Received Documents Private .......................................................................................................... 316
Forwarding Received Documents Automatically ............................................................................................ 318
Checking Status and Log for Sent and Received Documents ......................................................................... 321
Sending Faxes from Your Computer (PC Fax) .................................................................................................. 324
Sending PC Faxes ......................................................................................................................................... 325
Using Internet Faxes (I-Fax) .............................................................................................................................. 329
Sending I-Faxes ............................................................................................................................................ 330
Receiving I-Faxes .......................................................................................................................................... 338
Sending and Receiving Faxes via the Machine (Remote Fax) ......................................................................... 339
Faxing
270
Fax
Faxing
72JY-04R
PMW-FXIG
This chapter introduces the basic methods for sending and receiving faxes as well as convenient fax functions you can
use according to your needs.
◼Introduction to Basic Operations
This section describes the Fax Basic Features screen and the basic sending and receiving methods.
Fax Basic Features Screen(P. 273)
Basic Operations for Sending Faxes(P. 275)
Receiving Faxes(P. 291)
Checking Status and Log for Sent and Received
Documents(P. 321)
◼Successfully, Easily, Conveniently
You can nd and choose among various sending and receiving methods right for you. Fully using functions can
provide you with an ecient way to send and receive faxes.
Sending Faxes Successfully(P. 294)
Simplifying Sending Operations(P. 301)
Useful Functions When Sending(P. 306)
Various Receiving Methods(P. 312)
Forwarding Received Documents Automatically(P. 318)
◼Sending Faxes from Your Computer
You can directly fax a document saved on a computer. This method can eliminate the need to print, saving paper and
toner, as well as make the images and ne print on documents more clear.
Sending Faxes from Your Computer (PC Fax)(P. 324)
Faxing
271

◼Using Fax Functions More Fully
This section describes how to send and receive faxes via the Internet. You can also learn how to use a multifunction
printer without the ability to fax for sending and receiving faxes via other multifunction printers on the network.
Using Internet Faxes (I-Fax)(P. 329)
Sending and Receiving Faxes via the Machine (Remote Fax)
(P. 339)
Faxing
272

Fax Basic Features Screen
72JY-04S
Pressing <Fax> ( <Home> Screen(P. 119) ) displays the Fax Basic Features screen.
Destination
Displays the destination's name, the fax number, and the number of destinations you specied.
<Details>
Enables you to check the detailed information of the destination displayed in .
<Delete Dest.>
Enables you to delete the destination displayed in .
Tone
<Tone>
If you press this button when specifying the destination, the character "T" (tone) is inserted. Even if you are
using pulse dial, numbers following "T" will be sent using tone dial. Press this button when using fax
information services.
<One-Touch>
Enables you to specify a fax destination registered in one-touch buttons.
<Address Book>
Enables you to specify a fax destination registered in the Address Book.
<On-Hook>
Press to send a fax document manually. Sending Faxes Manually (Manual Sending)(P. 298)
<Direct Send>
Press to check the connection to the recipient's fax machine before scanning originals. Checking the
Connection to the Recipient Before Sending (Direct Send)(P. 297)
Options
Faxing
273

<Options>
Displays all of the function setting buttons. For convenience, you can display frequently used function setting
buttons in .
Function setting buttons
Displays the most frequently used buttons from <Options>. The setting status is displayed on the buttons.
You can also press to change which buttons are displayed.
●If the button for the function that you want to use is not displayed, press <Options> and select the
desired button. Basic Operations for Sending Faxes(P. 275)
Current setting status and setting buttons
Displays setting status such as the resolution. Make sure to conrm the settings in order to scan properly. To
change the settings, press the desired button. Basic Operations for Sending Faxes(P. 275)
<Favorite Settings>
Register frequently used scan settings here in advance to easily recall them when necessary. Registering a
Combination of Frequently Used Functions(P. 164)
Press this icon to register the current settings in <Favorite Settings> of and change the button displayed
in .
Registering a Combination of Frequently Used Functions(P. 164)
Customizing the Basic Features Screen(P. 167)
<Previous Settings>
Press to recall the previously specied settings. Recalling Previously Used Settings for Sending
(Previous Settings)(P. 304)
R
<R>
Press to use the R key. Basic Operations for Sending Faxes(P. 275)
●You can select whether to hide the Address Book and one-touch buttons to restrict use of the Address Book.
<Restrict Address Book Use>(P. 820)
●Some functions cannot be used in combination with each other. Buttons that cannot be selected are
displayed in light gray.
●The total number of specied destinations is displayed on the top of the screen.
LINKS
Registering Destinations(P. 190)
Faxing
274
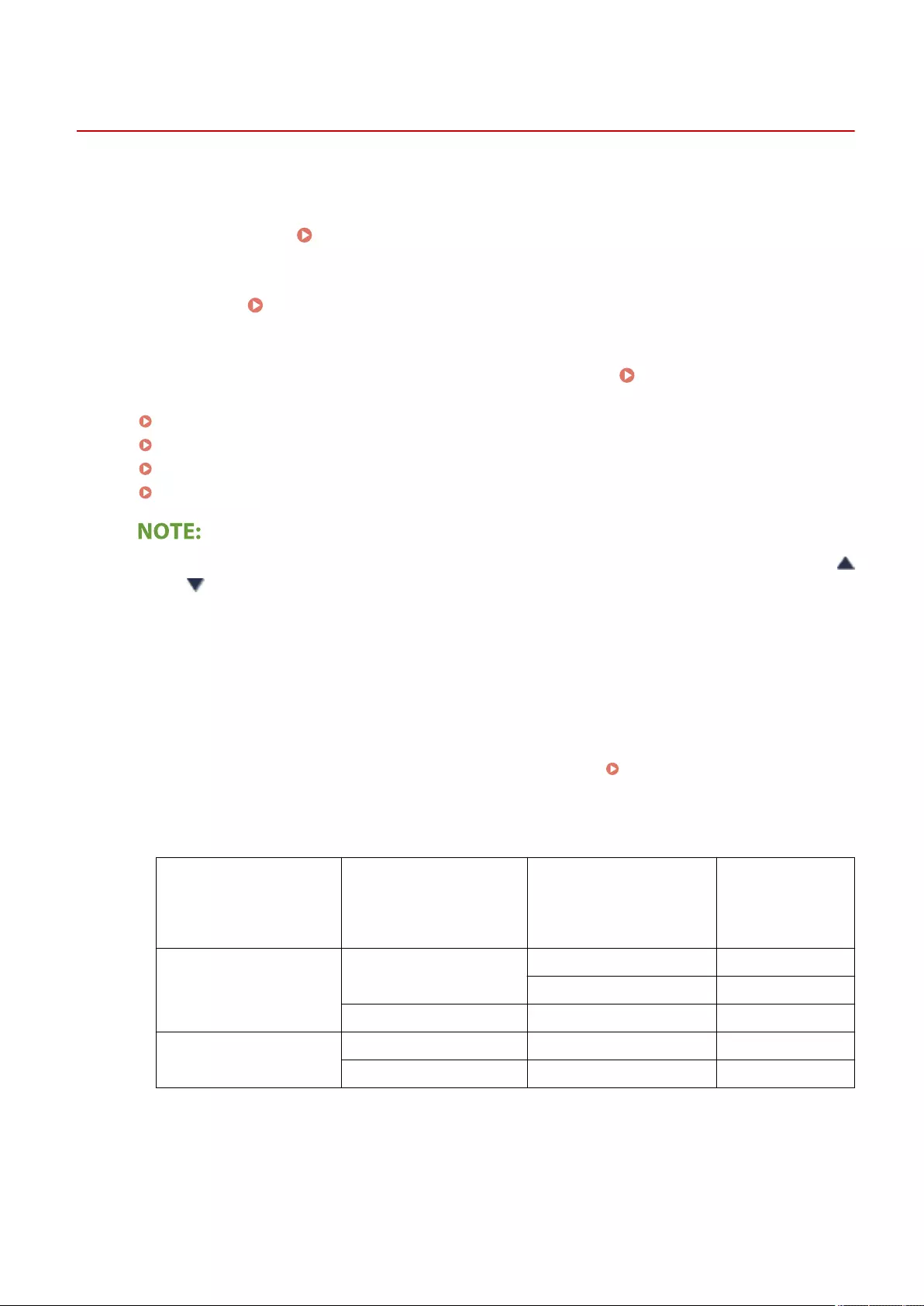
Basic Operations for Sending Faxes
72JY-04U
This section describes the basic operations for sending fax documents.
1Place the original. Placing Originals(P. 97)
2Press <Fax>. <Home> Screen(P. 119)
3Specify the destination on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
Address Book
Specifying Destinations from the Address Book
One-Touch
Specifying Destinations from One-Touch Buttons
Entering Destinations Manually
Specifying Destinations in the LDAP Server
DetailsDelete Dest.
●To check the detailed information about the specied destination, select the desired destination using
and and press <Details>. To delete a destination from the specied destinations, press <Delete Dest.>.
●You can only change destinations from <Details> specied using the New Destination and destinations
obtained via an LDAP server.
●<ECM TX>, <Sending Speed>, and <Long Distance> do not appear when you specify a destination from the
Remote Address Book.
●If the server machine is performing the System Manager information settings, authentication between the
server machine and the client machine is performed while the client machine is obtaining the Remote
Address Book/one-touch buttons. Authentication is performed by matching the System Manager ID and
System Manager PIN set by the server machine and client machine. Changing the System Manager ID
and PIN(P. 523)
The availability of the Remote Address Book/one-touch buttons depends on the status of the System
Manager information settings for the server machine and client machine, as shown below.
When the server machine
is performing the System
Manager information
settings
When the client machine is
performing the System
Manager information
settings
The System Manager ID
and System PIN for the
server machine and client
machine match
Can use the
Remote Address
Book/One-Touch
Button
Performing Performing Matches Yes
Does Not Match No
Not Performing - No
Not Performing Performing - Yes
Not Performing - Yes
Faxing
275
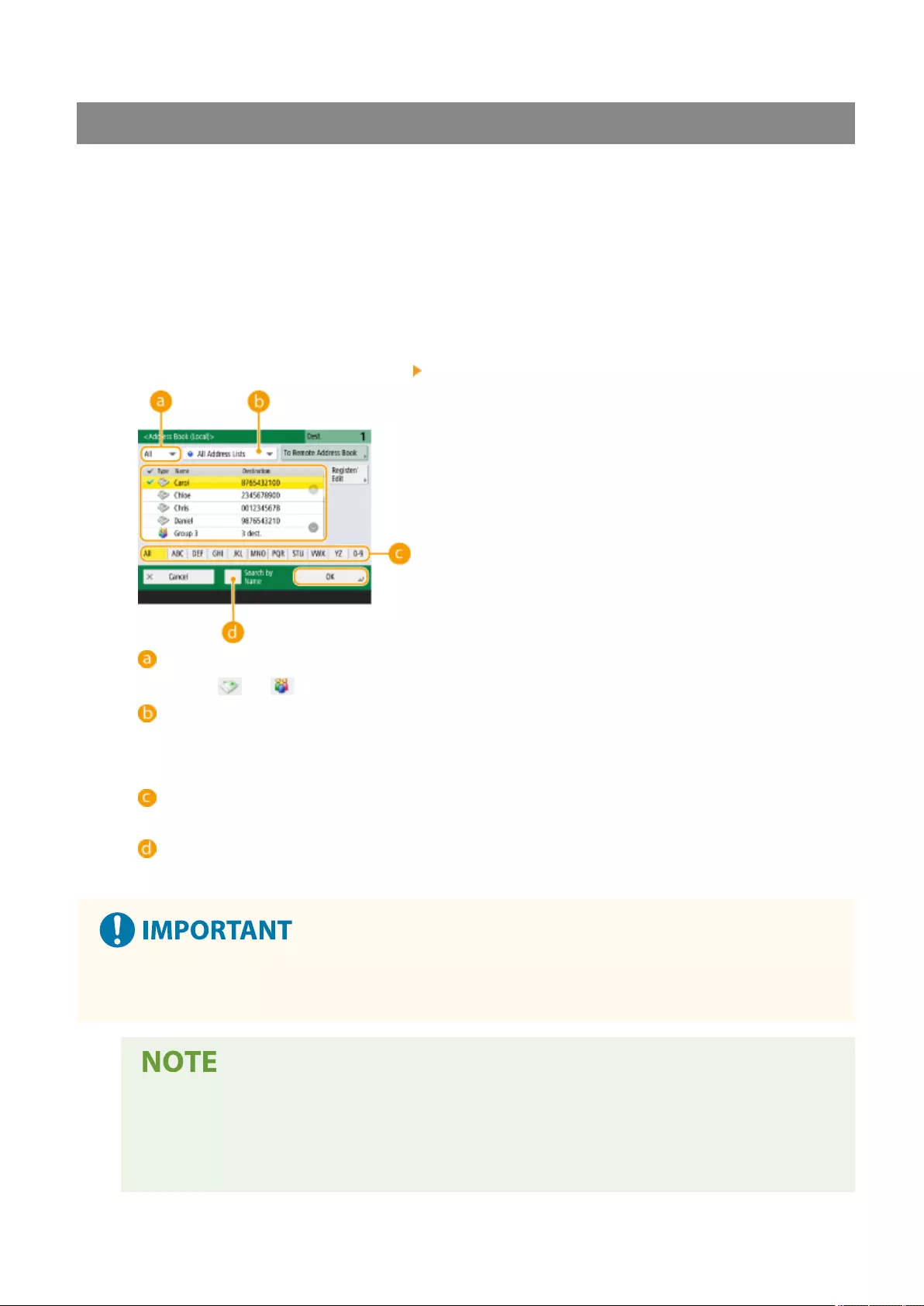
Specifying Destinations from the Address Book
1Press <Address Book>.
2Select the destination and press <OK>.
●If an access number is set when the destination is registered, press <Access No.> and enter the access
number using the numeric keys. The corresponding destination is displayed in the Address Book.
●To use the Remote Address Book, press <To Remote Address Book>. When <Change Address Book> is
displayed, press <Change Address Book> <Remote>.
Destination type drop-down list
Pressing and displays fax and group destinations, respectively.
Address list drop-down list
Enables you to display a specic group of destinations. When you are logged in to the machine with
personal authentication management, selecting <Personal Addr. List> displays your personal Address
Book.
Search buttons by rst letter
Enables you to narrow down a search by the rst letter of the destination name.
<Search by Name>
Enables you to search the destination by the name you are entering.
●If you select the group destination containing destinations other than fax destinations, sending a fax is not
allowed.
●<Register New Destination>, <Details/Edit>, and <Delete> in <Register/Edit> on the <Address Book
(Local)> screen can be used to register new destinations, check details, and edit/delete destinations.
●To use the Remote Address Book, it is necessary to congure the server machine settings. Set to open
the Remote Address Book externally on the server machine.
Faxing
276
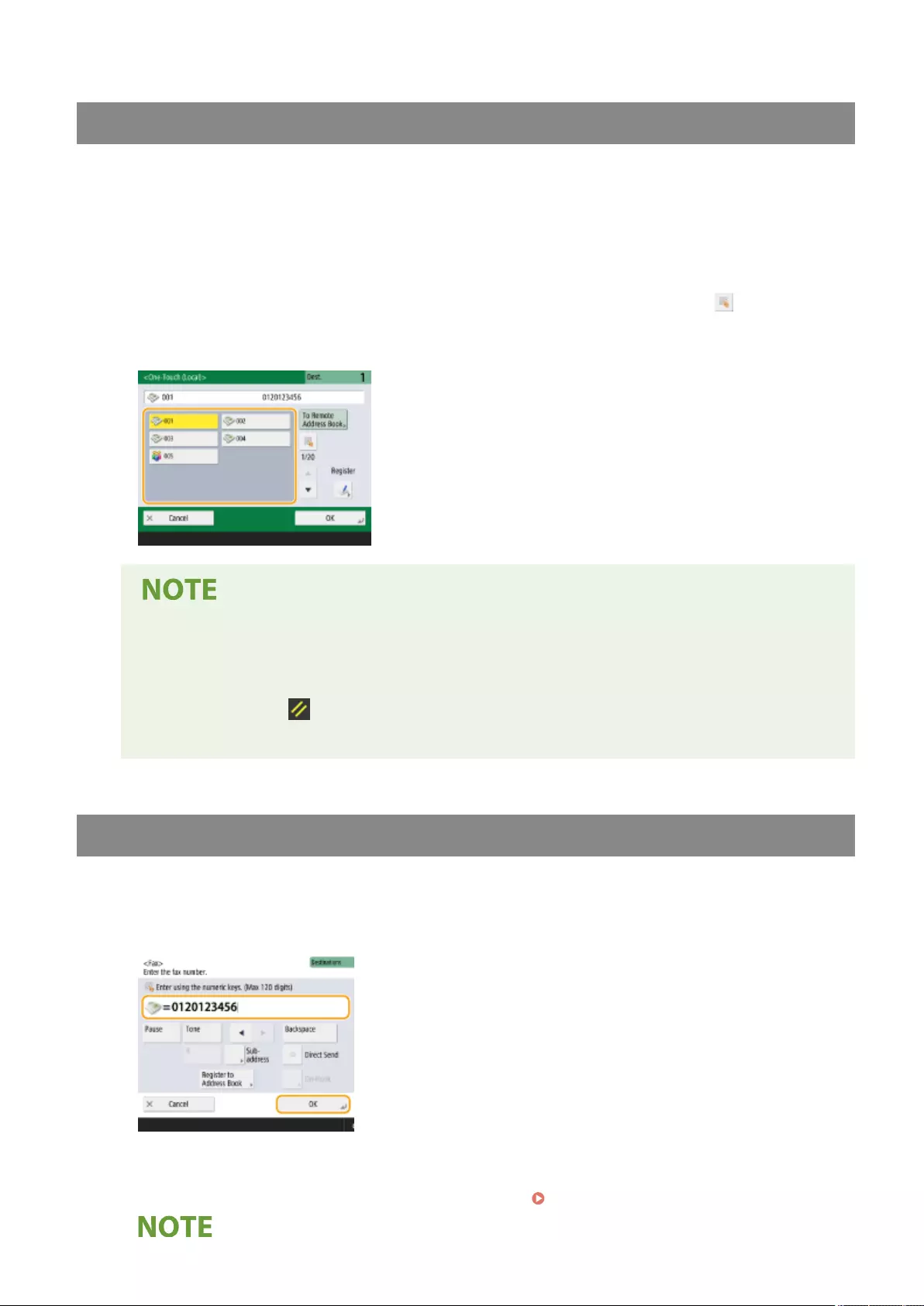
Specifying Destinations from One-Touch Buttons
1Press <One-Touch>.
2Select the desired one-touch button and press <OK>.
●To specify the destination using a one-touch button number (one-touch number), press and enter the
number for the desired one-touch button.
●To use the Remote Address Book, press <To Remote Address Book>.
●The destinations registered in the one-touch buttons of the server machine are updated in the
following times:
- When a fax job has been sent on the client machine
- When you press (Reset) on the client machine
- When Auto Reset is activated on the client machine
Entering Destinations Manually
You can specify destinations manually that are not registered in the Address Book or one-touch buttons.
1Enter a fax number using the numeric keys and press <OK>.
●To add another fax number, repeat this step.
●If the machine is connected to a PBX (Private Branch Exchange), press <R> before entering the destination. If
<R> is not available, you need to register the R-key settings. <R-Key Setting>(P. 833)
Faxing
277

●You can press <Register to Address Book> to register the entered destination. Set the required conditions,
and specify <Name> and <Address Book>. For information on the settings, see Registering
Destinations in the Address Book(P. 195) .
To send faxes overseas
●Enter the international access number, the country code, and the fax number, in that order. If you
cannot successfully connect to the destination overseas, press <Pause> to insert a pause between a
number and the next number.
To send faxes with a subaddress
●The machine supports the use of ITU-T* standard subaddresses. If the recipient's fax machine is
compatible with the use of ITU-T subaddresses, you can enhance the condentiality of sent
documents using a subaddress and password. To send a document with a subaddress, enter a fax
number, press <Subaddress> or <Set Details>, and then enter the subaddress and password.
* Stands for International Telecommunication Union-Telecommunication Standardization Sector, which is the group
that makes recommendations towards the standardization of worldwide telecommunications.
Specifying Destinations in the LDAP Server
You can search and specify destinations registered in the LDAP server.
1Press <Address Book>.
2Press <To LDAP Server>.
●When <Change Address Book> is displayed, press <Change Address Book> <LDAP Server>.
●If the network password input screen is displayed, enter the user name and password and press <OK>.
3When searching destinations in the LDAP server, press either <Search by Name> or
<Search by Conditions>.
Faxing
278
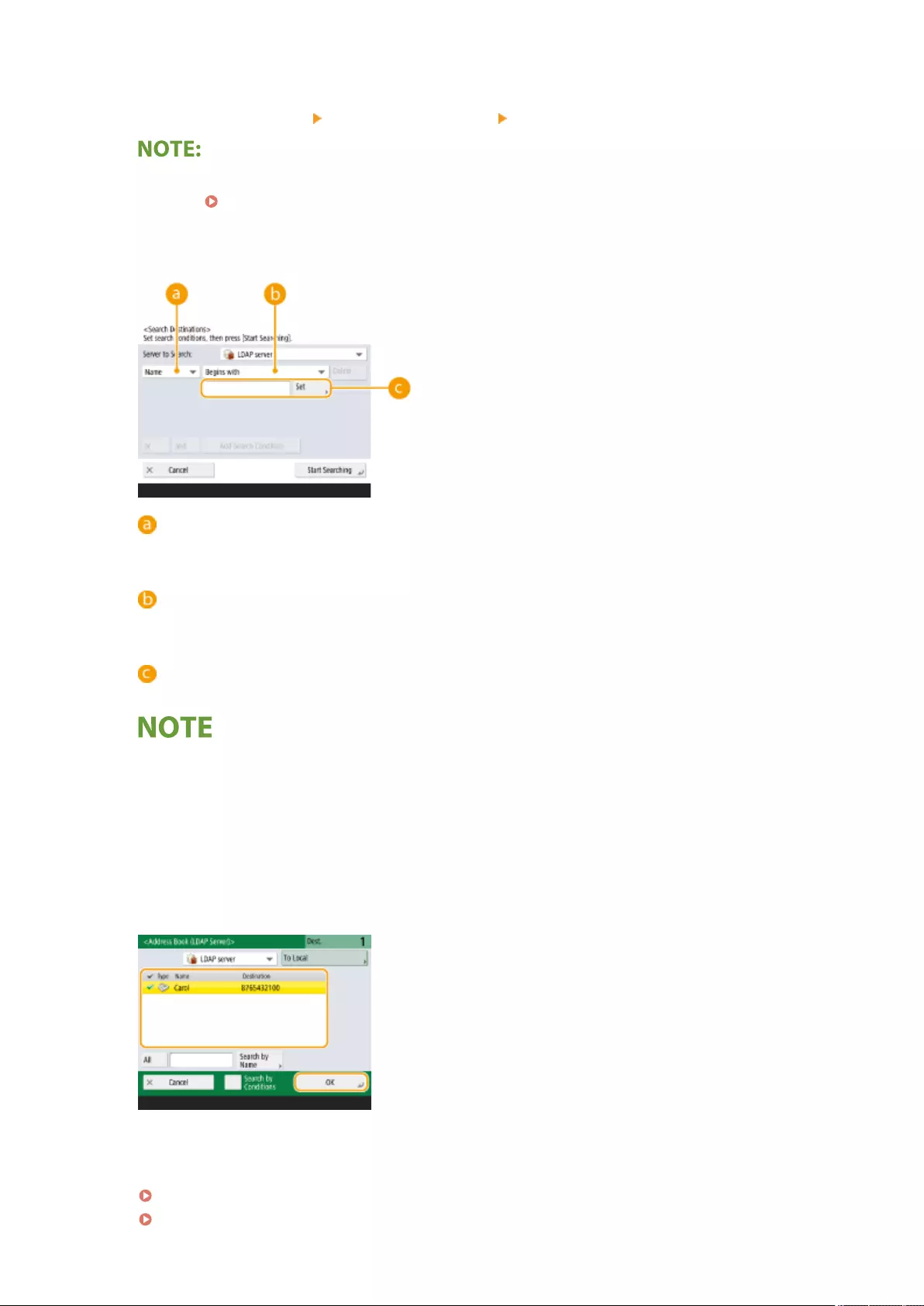
■When searching by name
Press <Search by Name> enter the text to search press <OK>.
●You can specify attributes used when performing "Search by Name" for a destination from the LDAP
server. <Settings for Search by Name When Using LDAP Server>(P. 851)
■When searching by conditions
Press <Search by Conditions>, specify the search conditions on the screen, and press <Start Searching>.
Search categories
Select a criterion to search for destinations from name, fax number, organization name, and organization
unit (department name, etc.)
Search conditions
Select a search condition such as a destination name that contains "John" and a department name that
begins with "Development."
Search characters
Press <Set> and enter search characters for the search condition.
To search with multiple conditions
●You can search destinations with multiple conditions. Specify the rst search condition, press <Add Search
Condition>, and then select <or> or <and> for the next condition.
To change conditions and search again
●Press <Delete> to delete the specied contents, and specify the conditions again.
4Select the destination and press <OK>.
4Specify the scan settings as necessary.
Scan Size2-Sided Original
Specifying How to Scan Originals
ResolutionDensityOriginal TypeSharpness
Adjusting Image Quality
Erase Frame
Faxing
279

Erasing Dark Borders (Erase Frame)
Specifying How to Scan Originals
If you are scanning free size/highly transparent originals, or the edge of image is
missing when scanning, you need to manually specify the scanning size.
Specifying the Scanning Size of Originals
The machine can automatically scan both the front and back sides of an original.
Scanning Both Sides of Originals
◼Specifying the Scanning Size of Originals
1Press the setting button for scanning size.
2Select the scanning size and press <OK>.
●To scan the original in A4, select <A4>.
When scanning a free size original
Place the original in the feeder and select <Free Size>.
When specifying the values of scanning size
Place the original on the platen glass/in the feeder, select <Custom>, and enter the length and width of the
original.
●When a scanning size smaller than the minimum size that can be scanned with the feeder is set, scanning
cannot be performed with the feeder. For information on the document sizes that can be scanned with the
feeder, see Feeder(P. 1107) .
Faxing
280

When scanning a long original
Place the original in the feeder and select <Long Original>.
To register the scanning size
●If you frequently specify the scanning size with the same values, press <Custom> <Register Size>
and register the size to quickly recall the setting for convenience.
◼Scanning Both Sides of Originals
Place the original in the feeder. For landscape-oriented originals, place them horizontally.
1Press <Options> <2-Sided Original>.
2Select <Book Type> or <Calendar Type> and press <OK>.
●Select <Book Type> for originals whose images on the front and back sides face the same direction, or
<Calendar Type> for originals whose images on the front and back sides face in opposite directions.
3Press <Close>.
Adjusting Image Quality
You can select the resolution suitable for your type of original. The higher the
resolution is, the clearer the image becomes, but the longer it takes to send.
Selecting Resolution
Faxing
281
Specifying the type of original such as documents with characters only or magazines
with photographs enables you to send with optimal image quality.
Selecting the Type of Original
You can adjust the density of the entire original. For example, increasing the density
enables you to easily read faint characters written in pencil.
Adjusting the Density of the Entire Original
You can adjust the density of the background. You can clearly send originals with a
colored background or thin originals such as newspapers whose characters and
images on the back side are transparently visible.
Adjusting the Density of the Background
You can scan the image with clear contours and lines by increasing the sharpness, or
soften the image by decreasing the sharpness. Use this function when you want to
sharpen blurred text and diagrams, or to reduce moire (a shimmering, wavy pattern)
to smoothen the nished image.
Adjusting Sharpness (Sharpness)
◼Selecting Resolution
1Press the setting button for resolution.
2Select the resolution and press <OK>.
Faxing
282
●A lower resolution is suitable for originals containing text only, while a higher resolution is suitable for
originals containing photographs. The higher the resolution is, the more nely originals can be scanned.
●When a resolution higher than 200 dpi x 400 dpi is set, even if <Speed/Image Quality Priority for Black &
White Scan> is set to <Quality Priority>, the setting is not enabled.
◼Selecting the Type of Original
1Press <Options> <Original Type>.
2Select the type of original and press <OK>.
●To adjust the text/photo processing priority level, press <Adjust Level> select <Text Priority> or <Photo
Priority>.
3Press <Close>.
◼Adjusting the Density of the Entire Original
1Press <Options> <Density>.
2Adjust the density and press <OK>.
●Press to decrease the density. Press to increase the density.
3Press <Close>.
◼Adjusting the Density of the Background
1Press <Options> <Density>.
2Press <Adjust> in <Background Density>.
Faxing
283
●To adjust the background automatically, press <Auto> and proceed to step 4.
3Adjust the density and press <OK>.
●If <-> is pressed, the density of the entire background decreases. If <+> is pressed, the density of the entire
background increases.
●Depending on the colors of originals, sections other than the background may be affected.
4Press <OK> <Close>.
◼Adjusting Sharpness (Sharpness)
●The setting for <Sharpness> is invalid when all of the conditions below are met. The setting is reected in
the image displayed for <Preview>, but not for the actual scanned image.
- <Original Type>: <Text>
- <Resolution>: <200x100 dpi (Normal)>
1Press <Options> <Sharpness>.
2Adjust the sharpness and press <OK>.
●To sharpen blurred text, adjust the control to <High>.
●To reduce moire when scanning originals that contain printed photos, such as magazines or pamphlets,
adjust the control to <Low>.
3Press <Close>.
Erasing Dark Borders (Erase Frame)
When scanning originals that are smaller than the scanning size, frame lines of the originals may appear in the
scanned image. When scanning a thick book, dark borders may appear. This function enables you to erase
these frame lines and dark borders. You can also set the machine to not copy punch holes in the originals.
●Place the original with punch holes on the platen glass. Placing in the feeder may result in damage.
1Press <Options> <Erase Frame>.
2Specify the erasing type and width.
Faxing
284
Erasing the frames in copies of documents
1Press <Erase Original Frame> and check <Original Size>.
●If the size displayed in <Original Size> is different from the size of the original, press <Change> to
select the size. You can only set the Erase Original Frame mode for the original sizes shown on the
touch panel display.
2Press <Next>.
3Enter the width of the frame to erase.
Erasing dark borders in copies of books
You can erase the dark borders both in the center and contour lines that appear when you scan facing pages
in a book.
1Press <Erase Book Frame> and check <Original Size>.
●If the size displayed in <Original Size> is different from the size of the book, press <Change> to select
the size. You can only set the Erase Book Frame mode for the original sizes shown on the touch panel
display.
2Press <Next>.
3Press <Center> or <Sides> and enter each erasing width.
Erasing punch holes in copies of documents
1Press <Erase Binding>.
2Press <Next>.
Faxing
285

3Enter the erasing width.
●If you want to adjust the width for each border independently, press <Erase Original Frame> or
<Erase Book Frame> <Next> < Adjust Independently> enter the erasing widths.
●If you are using <Erase Binding>, the borders you do not select are also erased by 4 mm.
3Press <OK> <Close>.
5Press (Start).
➠Originals are scanned and sending starts.
●To cancel scanning, press <Cancel> or (Stop) <Yes>.
When <Press the [Start] key to scan the next original.> is displayed
Place the next original to scan and press (Start). When scanning all of the originals is complete, press <Start
Sending> to send the fax.
●To cancel sending, see Canceling Sending Faxes(P. 289) .
To check the total number of specied destinations
●The total number of specied destinations is displayed on the top of the screen. This enables you to conrm
that the number of destinations is correct before sending.
To send with the sender information
●You can send with the sender's name and fax number. <TX Terminal ID>(P. 821)
To check the statuses for sent documents
●On the <Status Monitor> screen, you can check the statuses for sent documents. This screen enables you to
send faxes again or cancel sending after checking the statuses. Checking Status and Log for Sent and
Received Documents(P. 321)
●When <Display Notication When Job Is Accepted> is set to <On>, the <Status Monitor> screen can be
displayed from the following screen that is shown after a send job is received. <Display Notication
When Job Is Accepted>(P. 825)
Faxing
286

When a transmission error occurs because the recipient's line is busy
●The machine automatically redials after a certain period of time. You can change the settings such as how
many times the machine redials and the interval between redials. <Auto Redial>(P. 832)
TX Result Report
To print the report for the results of sending
●On the Fax Basic Features screen, pressing <Options> <TX Result Report> enables you to set to
automatically print the report listing the results of sending.
●To set this for each job from <Options>, it is necessary to select <For Error Only> or <Off> in <TX Result
Report>(P. 820) , and then set <Allow Printing from Options> to <On>.
When photos in the sent image are too dark or light colors in the background of color
originals cannot be removed
●The quality of the sent image may be able to be improved if the following conditions/settings are met.
- Job type: Fax (Memory Sending) or Scan and Send (Fax/I-fax)
- <Select Color>: <Black & White> (Scan and Send)
- <Original Type>: <Text>
- <Density> <Background Density>: <Auto>
- <Resolution>: 200 dpi x 400 dpi, 300 dpi x 300 dpi*, 400 dpi x 400 dpi, or 600 dpi x 600 dpi*
*Can be set for Scan and Send
-<Speed/Image Quality Priority for Black & White Scan> Fax/I-Fax Send Jobs: <Quality Priority> (
<Speed/Image Quality Priority for Black & White Scan>(P. 811) )
Saving a copy of a sent document
●You can set the machine so that a copy of a sent document is automatically saved in a le server. The copy is
converted into an electric le such as PDF and saved, allowing you to easily check the contents from your
computer. Saving a Copy of a Sent Document(P. 309)
Sender Name (TTI)Sender Name (TTI)
Selecting a sender's name
●On the Basic Fax Features screen, pressing <Options> <Sender Name (TTI)> enables you to select a name
from a list of registered sender's names to include in the sender information. <Register Sender Name
(TTI)>(P. 831)
●If logging in using User Authentication, the login name appears in <100> of Sender Name (TTI).
Checking scanned images before sending
●You can check scanned images on the preview screen before sending. Checking Scanned Images Before
Sending (Preview)(P. 295)
Faxing
287

Registering frequently used settings
●You can combine frequently used destinations and scan settings into a button of the machine for later use.
By pressing the registered button when scanning originals, you can quickly complete your settings.
Registering a Combination of Frequently Used Functions(P. 164)
LINKS
Canceling Sending Faxes(P. 289)
Sending Faxes Successfully(P. 294)
Simplifying Sending Operations(P. 301)
Useful Functions When Sending(P. 306)
Registering Destinations(P. 190)
Registering the LDAP Server(P. 53)
Managing Users(P. 489)
<Set Destination>(P. 849)
Faxing
288

Canceling Sending Faxes
72JY-04W
You can cancel scanning originals or sending faxes that are being sent or waiting to be sent.
◼Canceling Scanning Originals
1Press <Cancel> on the displayed screen or (Stop).
2Press <Yes>.
➠Scanning originals is canceled.
◼Canceling Sending Faxes Being Sent or Waiting to Be Sent
1Press <To Status Mntr.> on the displayed screen.
2Press <Send> <Job Status>.
3Select <Fax>.
➠A list of jobs being sent or waiting to be sent is displayed.
4Select the job to cancel and press <Cancel>.
5Press <Yes>.
➠Sending the fax is canceled.
Faxing
289
To immediately cancel a job that is being sent
If you press (Stop) on the control panel to cancel a fax job while it is being sent, the message <Is it OK to
cancel the following Send job?> appears. Press <Yes> to cancel sending the fax.
●You can select <Latest Received Job> or <Job Being Sent> to choose the job to cancel. <Job to
Cancel When Stop Is Pressed>(P. 825)
●Press (Stop) when there are multiple send jobs to display the screen for selecting the send job
to cancel. If the send job you want to cancel is not displayed, press <Check Other Jobs> to display
<Send Jobs>. Select the job that you want to cancel, and press <Cancel>.
LINKS
Basic Operations for Sending Faxes(P. 275)
Checking Status and Log for Sent and Received Documents(P. 321)
Faxing
290
Receiving Faxes
72JY-04X
This section describes the methods for receiving faxes and how to set up the machine to receive faxes. You need to
complete some procedures for using fax functions before specifying the receiving settings. Setting the Fax
Reception Method(P. 840)
●The machine can print received fax documents on A4 or Letter size paper. If received fax documents are
printed on other paper sizes, a portion of the page may not be printed or a page may be printed on two
separate sheets of paper.
◼Methods for Receiving Faxes
The machine provides the following receiving methods. Select the method that best suits your needs and then set it up
by following the procedure in <RX Mode>(P. 840) .
<Auto RX>
Dedicated to receiving faxes
The machine receives faxes automatically. Even if someone makes a call to you, you cannot
talk to the caller.
<Fax/Tel (Auto
Switch)>
When the call is a fax
The machine receives the fax automatically.
When the call is a telephone call
An incoming call rings. Pick up the handset to answer the call.
●You need to connect your telephone or the optional handset to the machine beforehand.
<Answering
Machine>
When the call is a fax
After an incoming call rings, the machine receives the fax automatically.
When the call is a telephone call
The answering machine activates, enabling the caller to leave a message. If you pick up the
handset before the answering machine starts recording a message, you can talk with the
caller.
●You need to connect your answering machine to the machine beforehand.
●Set the answering machine to answer after a few rings.
●We recommend that you add approximately 4 seconds of silence at the beginning of the
message or set the maximum recording time to 20 seconds.
<Manual RX>
When the call is a fax
An incoming call rings. Pick up the handset. If you hear a beep, select (Home)
<Fax> <On-Hook> <Start RX> to receive faxes.
Faxing
291

When the call is a telephone call
An incoming call rings. Pick up the handset. If you do not hear a beep, start your
conversation.
●You need to connect your telephone or the optional handset to the machine beforehand.
●You can set the machine to automatically receive faxes when an incoming call rings within
a specied timeframe. <Switch to Auto RX>(P. 841)
<Net Switch>*1 The machine distinguishes between fax and telephone calls. This mode is only available for
certain countries and requires a subscription to a network switch service.
●You need to connect your telephone or the optional handset to the machine beforehand.
*1 Indicates items that may not be displayed on the Settings/Registration screen, depending on the region.
●Depending on the type of telephone connected to it, the machine may not be able to send or receive faxes
properly.
●If you are connecting an external telephone with fax functions, set the telephone to not receive faxes
automatically.
●If you pick up the telephone handset and hear a beep, the call is a fax. You can receive the fax just by using
the telephone to enter a specic ID number. <Remote RX>(P. 840)
●You can save paper when printing.
<Print on Both Sides>(P. 835)
<Reduce Fax RX Size>(P. 835)
●You can include information, such as reception time, in received documents when printing. <Print RX
Page Footer>(P. 835)
●If you set the machine to check a reception password for subaddress communication, you can prevent the
machine from receiving spam faxes. <RX Password>(P. 842)
●Setting <Forward Temporarily Stored File to Memory RX Inbox> to <Yes> enables you to forward received
documents to the storage location of the machine (Memory RX Inbox) if they cannot be printed due to paper
jams or lack of paper. In this case, <Fax Memory Lock>/<Use I-Fax Memory Lock> is automatically set to
<On>, and forwarded documents can be checked from the screen. Also, forwarded documents can be
Faxing
292

printed later. ( Saving Received Documents in the Machine (Memory Reception)(P. 313) ) To return to
normal printing, set <Fax Memory Lock>/<Use I-Fax Memory Lock> to <Off>.
LINKS
Various Receiving Methods(P. 312)
Forwarding Received Documents Automatically(P. 318)
Checking Status and Log for Sent and Received Documents(P. 321)
Faxing
293
Sending Faxes Successfully
72JY-04Y
This section describes how to avoid potential sending errors caused by incorrectly scanning documents or a busy line,
etc.
Checking Scanned Images Before Sending
(Preview)(P. 295)
Checking the Connection to the Recipient Before
Sending (Direct Send)(P. 297)
Sending Faxes Manually (Manual Sending)
(P. 298)
Notifying You by E-Mail of the Completion of
Sending(P. 299)
Faxing
294

Preview
Checking Scanned Images Before Sending (Preview)
72JY-050
You can check scanned images on the preview screen before sending. You can also
delete, move, or switch pages on the preview screen.
●The original cannot be checked before sending with the Direct Sending or Manual Sending mode, even if
<Preview> is set.
1Place the original. Placing Originals(P. 97)
2Press <Fax>. <Home> Screen(P. 119)
3Specify the destination on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Specify the scan settings as necessary. Basic Operations for Sending Faxes(P. 275)
5Press <Options> <Preview> <Close>.
6Press (Start).
➠Originals are scanned and the preview screen appears.
●To cancel scanning, press <Cancel> or (Stop) <Yes>.
When <Press the [Start] key to scan the next original.> is displayed
Place the next original to scan and press (Start). When scanning all of the originals is complete, press
<Preview and Send> to display the preview screen.
7Check the scanned images on the preview screen.
●Edit the scanned image on the preview screen as necessary.
Faxing
295

To delete a page
You can delete the page currently displayed on the preview screen.
1Press <Delete Page>.
To move a page
You can move a page to the specied destination.
1Press <Edit Scanned Data>.
2Press <Move Pg. Position>.
3Enter the page numbers corresponding to <Move Page> and <Behind Page>.
4Press <OK>.
To switch the locations of pages
You can switch the locations of specied pages.
1Press <Edit Scanned Data>.
2Press <Switch Pg Position>.
3Enter the page numbers corresponding to <Target Page A> and <Target Page B>.
4Press <OK>.
8Press <Start Sending>.
➠Sending starts.
Faxing
296

Direct Send
Checking the Connection to the Recipient Before
Sending (Direct Send)
72JY-051
To successfully send faxes to the destination you intend, you can check beforehand
that the recipient is connected and ready to start communication. As the machine
bypasses memory when scanning originals, you can send faxes even if there is no
memory available.
1Place the original. Placing Originals(P. 97)
●To send multiple pages, place the originals in the feeder. When the original is placed on the platen glass, only
one page can be sent.
2Press <Fax>. <Home> Screen(P. 119)
3Specify the destination on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Specify the scan settings as necessary. Basic Operations for Sending Faxes(P. 275)
5Press <Options> <Direct Send> <Close>.
6Press (Start).
➠The machine dials the recipient's number. When the machine connects the call, originals are scanned and
sending starts.
●The machine does not start sending when the recipient's line is busy.
Direct Send is not available in the following cases
●Any of the following scan settings are specied: <2-Sided Original>/<Erase Frame>/<Job Build>/<Delayed
Send>
●Multiple destinations are specied.
●<Limit Functions> is set to <Off> for any function when the machine is in Department ID Management.
Conguring the Department ID Management Settings(P. 525)
Faxing
297
On-Hook
Sending Faxes Manually (Manual Sending)
72JY-052
You can manually send fax documents after checking that the destination is ready to
receive fax transmissions.
●If you have added additional lines, you can only use Line 1 (the standard line) for manual sending.
●If the control card is removed while a call is being made by pressing <On-Hook> with the Copy Card Reader
attached, the line is disconnected.
1Place the original. Placing Originals(P. 97)
●When you want to send multiple pages, place originals in the feeder. When the original is placed on the
platen glass, you can only send one page.
2Press <Fax>. <Home> Screen(P. 119)
3Press <On-Hook> on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Enter the recipient's phone number.
5Make sure that you hear the recipient or a high-pitched tone.
6Press (Start).
➠Originals are scanned and sending starts.
Manual Sending is not available in the following cases
●Any of the following scan settings are specied: <2-Sided Original>/<Erase Frame>/<Job Build>/<Delayed
Send>
●<Limit Functions> is set to <Off> for any function when the machine is in Department ID Management.
Conguring the Department ID Management Settings(P. 525)
Faxing
298
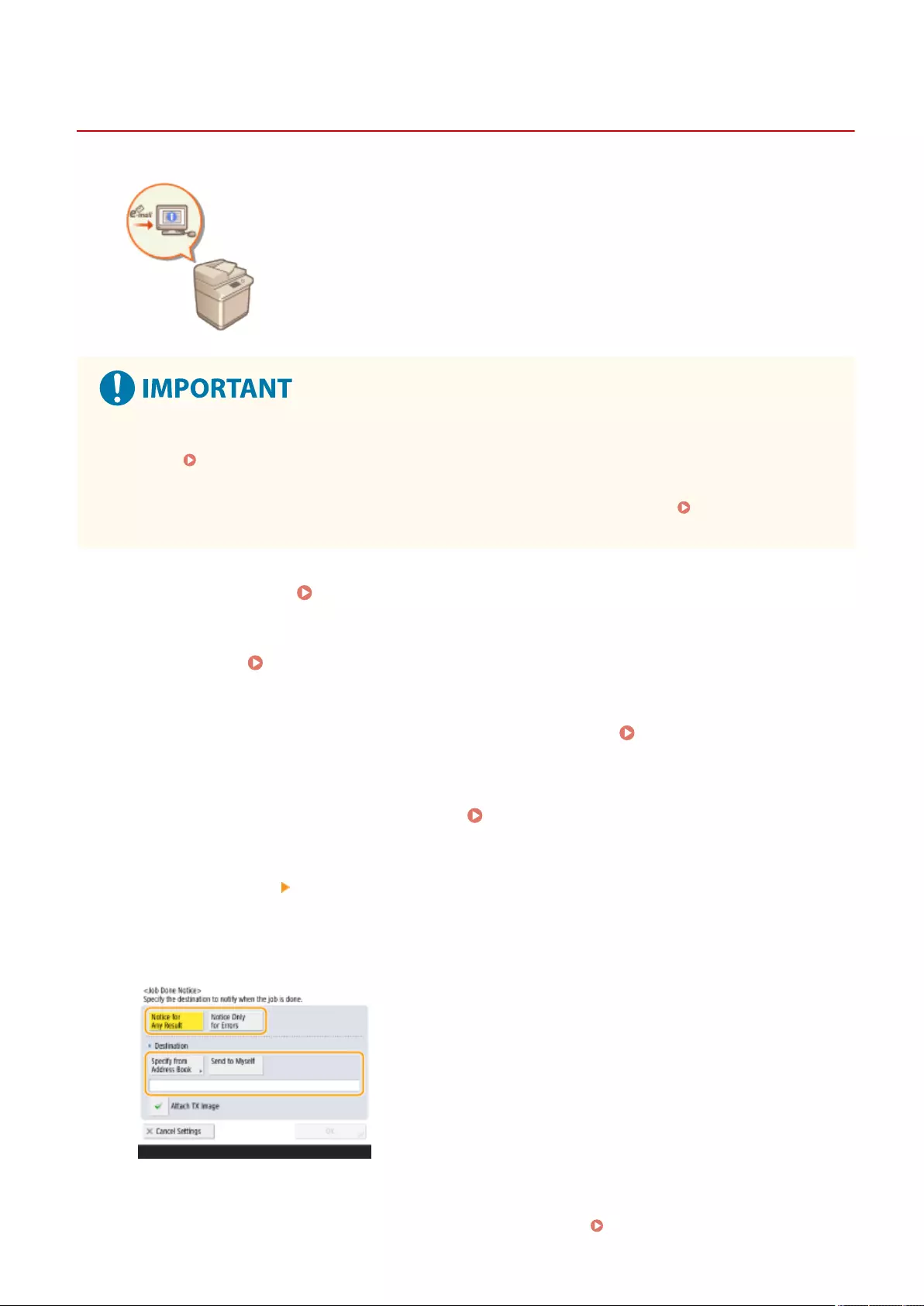
Job Done Notice
Notifying You by E-Mail of the Completion of Sending
72JY-053
You can receive an e-mail notifying you that sending documents is complete. Even if
documents are waiting to be sent, you can use your computer or portable device to
check whether sending documents is complete, giving you reassurance. When an
error occurs, you are notied of destinations whose documents failed to be sent.
●To select the destination to notify from <Address Book>, it is necessary to register the destination in
advance. Registering Destinations in the Address Book(P. 195)
●To select <Send to Myself> as the destination to notify, it is necessary to register your e-mail address in the
user information in advance, and log in using personal authentication management. Registering User
Information in the Local Device(P. 495)
1Place the original. Placing Originals(P. 97)
2Press <Fax>. <Home> Screen(P. 119)
3Specify the destination on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Specify the scan settings as necessary. Basic Operations for Sending Faxes(P. 275)
5Press <Options> <Job Done Notice>.
6Select the notication timing, and set the destination to notify.
●If you select <Notice for Any Result>, a notication e-mail is sent for each send job. If you select <Notice Only
for Errors>, a notication e-mail is sent only when an error occurs.
●For more information on how to view and use the Address Book, see Address Book(P. 190) .
Faxing
299

●If you want to check the content of the sent document, select <Attach TX Image> to attach the rst page of
the document as a PDF le to a notication e-mail.
7Press <OK> <Close>.
8Press (Start).
➠Originals are scanned and sending starts. When sending is complete, the notication e-mail is sent to the
specied address.
Faxing
300
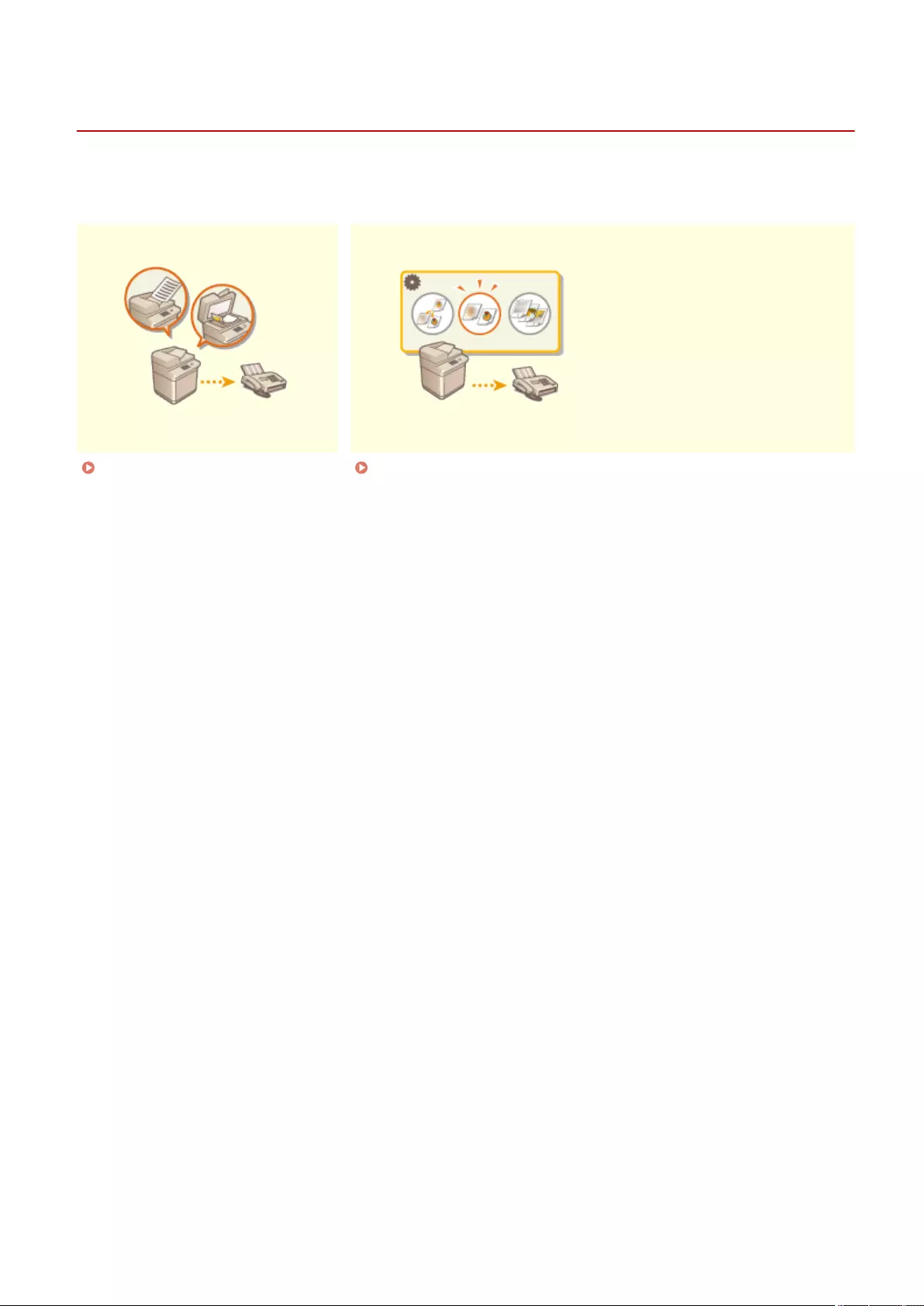
Simplifying Sending Operations
72JY-054
You can send separately scanned documents together. By recalling previously used settings, you can simplify sending
operations.
Sending Separately Scanned
Documents Together (Job Build)
(P. 302)
Recalling Previously Used Settings
for Sending (Previous Settings)
(P. 304)
Faxing
301
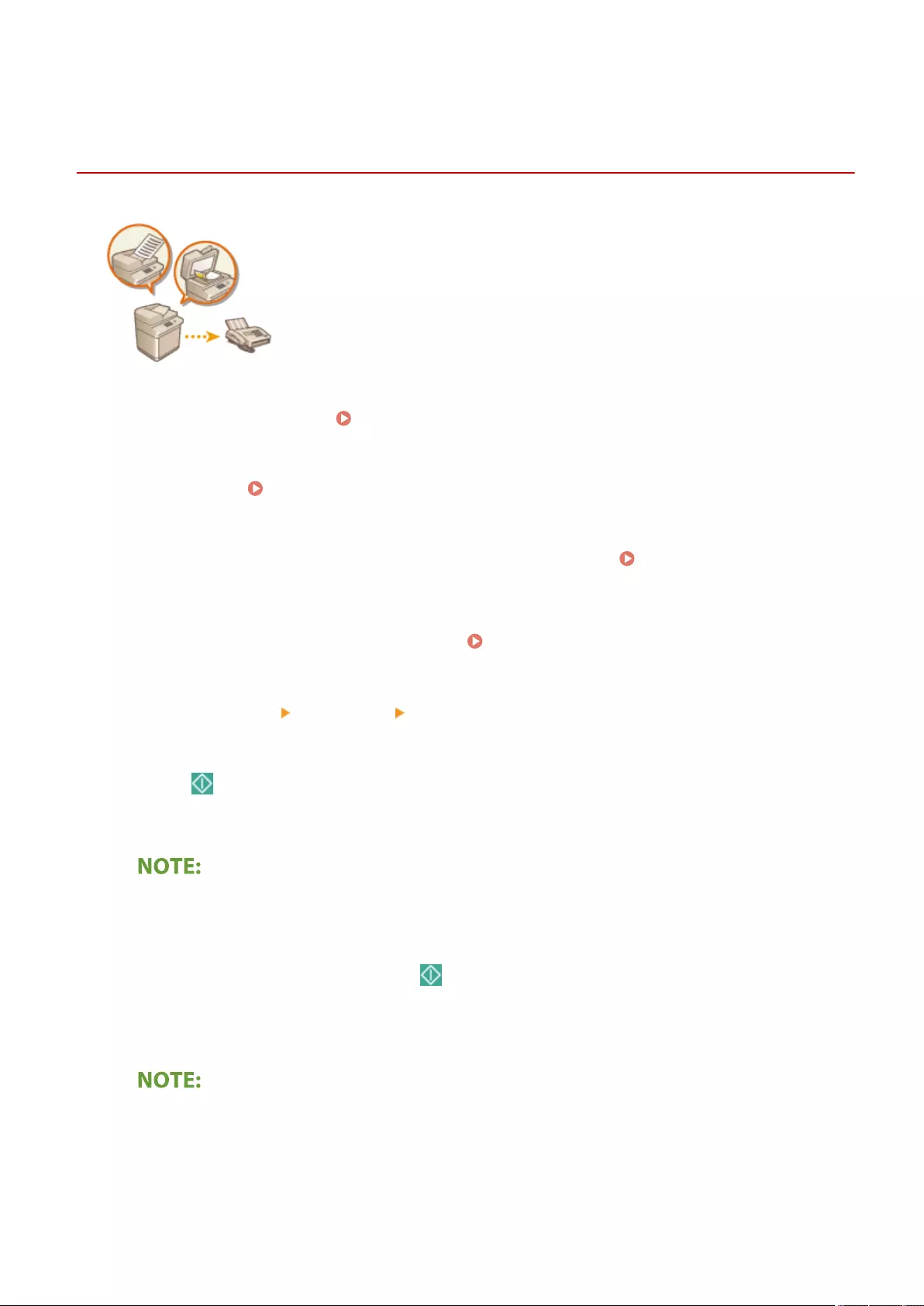
Job Build
Sending Separately Scanned Documents Together (Job
Build)
72JY-055
Even if you have too many originals to be placed in the feeder at the same time, you
can scan the originals separately and send them as a batch of documents.
Documents scanned with both the feeder and the platen glass can also be sent at
the same time.
1Place the rst original. Placing Originals(P. 97)
2Press <Fax>. <Home> Screen(P. 119)
3Specify the destination on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Specify the scan settings as necessary. Basic Operations for Sending Faxes(P. 275)
5Press <Options> <Job Build> <Close>.
6Press (Start) to scan the original.
➠When scanning is complete, the screen appears prompting you to scan the next original.
●If you place your originals in the feeder, remove the originals from the original output area when the
scanning of each batch is complete.
7Place the next original and press (Start).
●Repeat this step until you nish scanning all of the originals.
●To change the scan settings, press <Change Settings>.
●The following functions can be used in <Change Settings>. You cannot change the setting for the other
functions while in the Job Build mode. You need to specify the necessary scan settings in advance.
- <Scan Size>
- <2-Sided Original>
- <Density>
Faxing
302

- <Original Type>
●When scanning and sending 1-sided originals and 2-sided originals together, if the rst document you
scan is a 2-sided original, set <2-Sided Original>. When scanning a 1-sided original, disable the <2-Sided
Original> setting in <Change Settings>.
8Press <Start Sending>.
➠All scanned documents are combined into one and sent to the specied destination.
Faxing
303

Previous Settings
Recalling Previously Used Settings for Sending
(Previous Settings)
72JY-056
You can recall the destinations specied in the past. Their scan settings such as
density are also recalled at the same time.
●You can store a series of destination, scan, or send settings specied before pressing (Start) as a single
group of Previous Settings.
●The three most recent settings that were stored in memory are not deleted even when the main power is
turned OFF.
●When you use fax information services, you cannot specify a destination that is stored in the Address List or
use the Previous Settings mode.
1Place the original. Placing Originals(P. 97)
2Press <Fax>. <Home> Screen(P. 119)
3Press <Previous Settings> on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Select the log to recall and press <OK>.
➠The destination and its scan settings are specied according to the selected log.
●When personal authentication management is in use, the machine recalls the settings specied in the past by
the user who are logging in to the machine.
●You can change the recalled settings before sending.
Faxing
304

5Press (Start).
➠Originals are scanned and sending starts.
●If you set <Manage Address Book Access Numbers> to <On>, you cannot recall settings from memory.
●If you set any address type to <On> in <Restrict New Destinations>, the currently stored Previous Settings are
deleted.
LINKS
Managing Users(P. 489)
Faxing
305
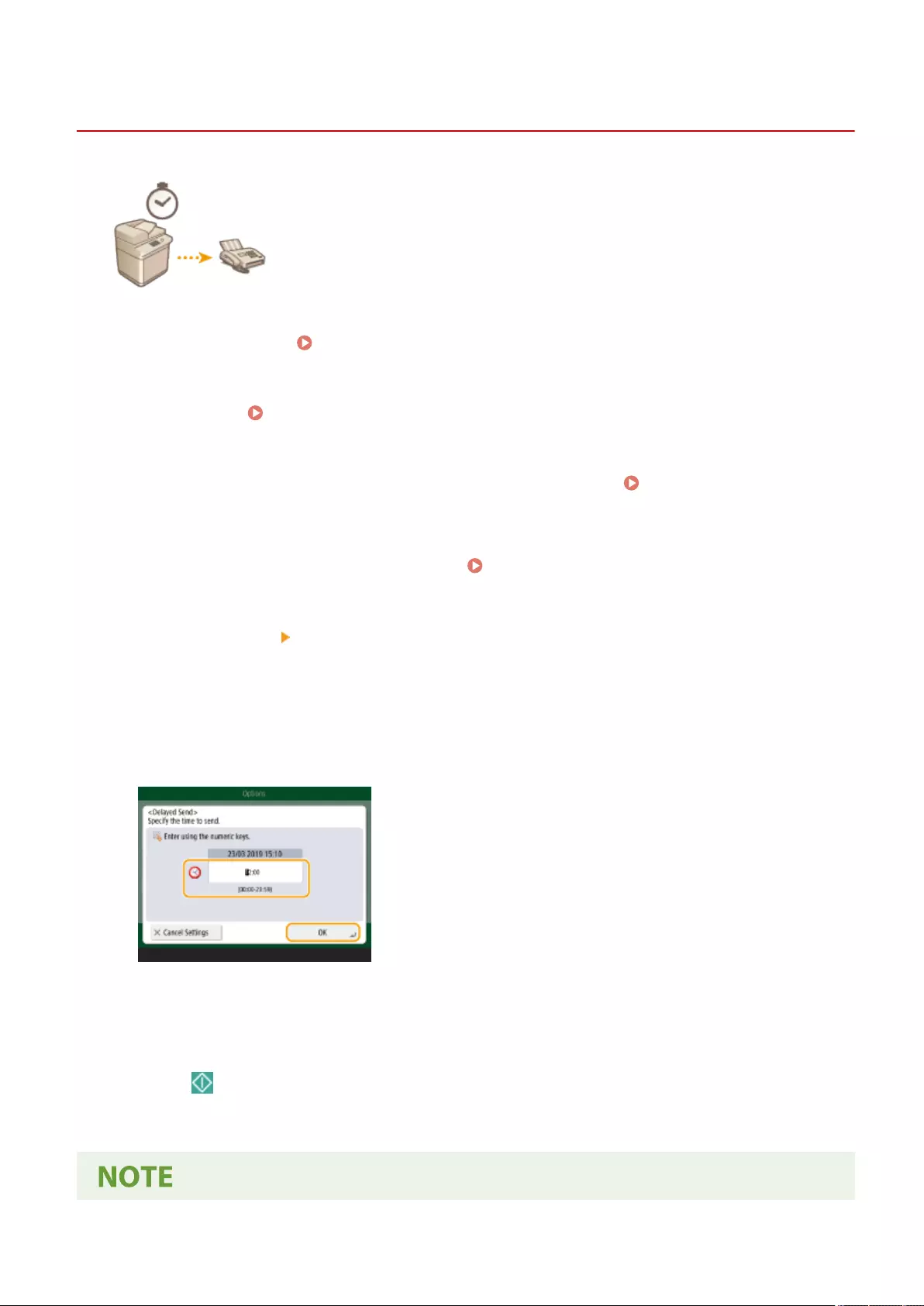
Delayed Send
Sending at a Specied Time
72JY-058
You can scan originals in advance and send the scanned documents at a specied
time.
1Place the original. Placing Originals(P. 97)
2Press <Fax>. <Home> Screen(P. 119)
3Specify the destination on the Fax Basic Features screen. Fax Basic Features
Screen(P. 273)
4Specify the scan settings as necessary. Basic Operations for Sending Faxes(P. 275)
5Press <Options> <Delayed Send>.
6Enter the time to send and press <OK>.
●Enter all four digits of the time. For example, for 5 minutes past 7, enter "0705" and for 18 minutes past 23,
enter "2318."
7Press <Close>.
8Press (Start).
➠Originals are scanned and sent at the specied time.
Faxing
307

Saving a Copy of a Sent Document
72JY-059
You can save a copy of a sent fax in a pre-specied destination (e-mail or le server,
etc.) Depending on the destination, the saved fax copy is converted into another
digital le format such as PDF, thus keeping documents organized and manageable.
This method also helps you easily manage logs because a folder categorized by
sender name or date is automatically created in the specied destination on the
server.
●A copy of a document is saved even if a sending error occurs.
●Depending on the type of destination, the following restrictions may apply.
- E-Mail: An e-mail without a message is sent.
- Fax/I-Fax: The sent fax cannot be saved as an electronic le.
Registering the Storage Location and File Format
In order to back up fax documents, it is necessary to register settings such as the storage location and le format in
advance.
●You cannot perform Direct Sending if you set <Archive TX Document> to <On>.
●This setting automatically switches to <Off> in the following cases. Specify the destination again or return
the setting to <On> as required.
- When the backup destination has been deleted from the address book
- When an address book has been imported from the Remote UI Importing/Exporting the Setting
Data(P. 625)
- When an address book has been received from Address Book Management Software. <Import/Export
from Addr. Book Management Software>(P. 857)
1Press (Settings/Register) <Function Settings> <Send> <Common Settings>
<Archive TX Document>.
2Press <On> for <Use Archive TX Document>.
Faxing
309
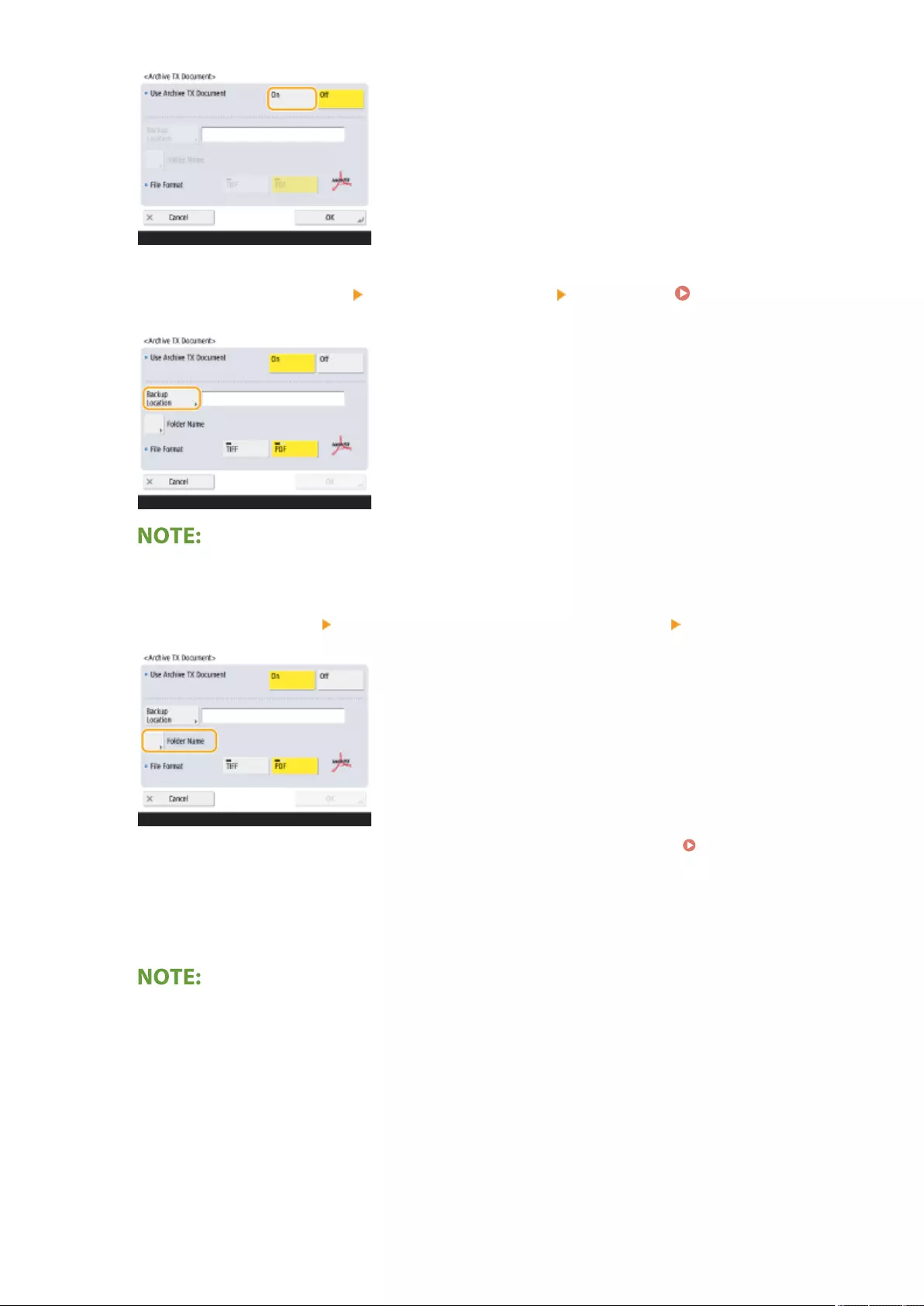
3Press <Backup Location> select the destination press <OK>. Registering
Destinations in the Address Book(P. 195)
●A destination in <Personal Addr. List> cannot be specied as the destination.
4Press <Folder Name> set how to organize the created folders press <OK>.
●You can select <Sender Information>, <Date>, or <Off> to categorize folder names. <Archive TX
Document>(P. 825)
●File names are specied by send date and time, job number, sender information, destination information,
and result information.
Example: 201603151005_0050_John_1112223333_OK.pdf
Sender information
●Information regarding the sender is displayed in the following situations.
- Sender Name: When <Sender Name (TTI)> is set to <W/Settings>
- User Name: When <Sender Name (TTI)> is set to <No Settings>, and the user is authenticated
- Line Name: When <Sender Name (TTI)> is set to <No Settings>, the user is not authenticated, and the user
name is registered for the line used to send the fax
- Telephone Number: When <Sender Name (TTI)> is set to <No Settings>, the user is not authenticated, and
the user telephone number is registered, but the user name is not registered, for the line used to send the
fax
- ----: When none of the above information is available
Faxing
310
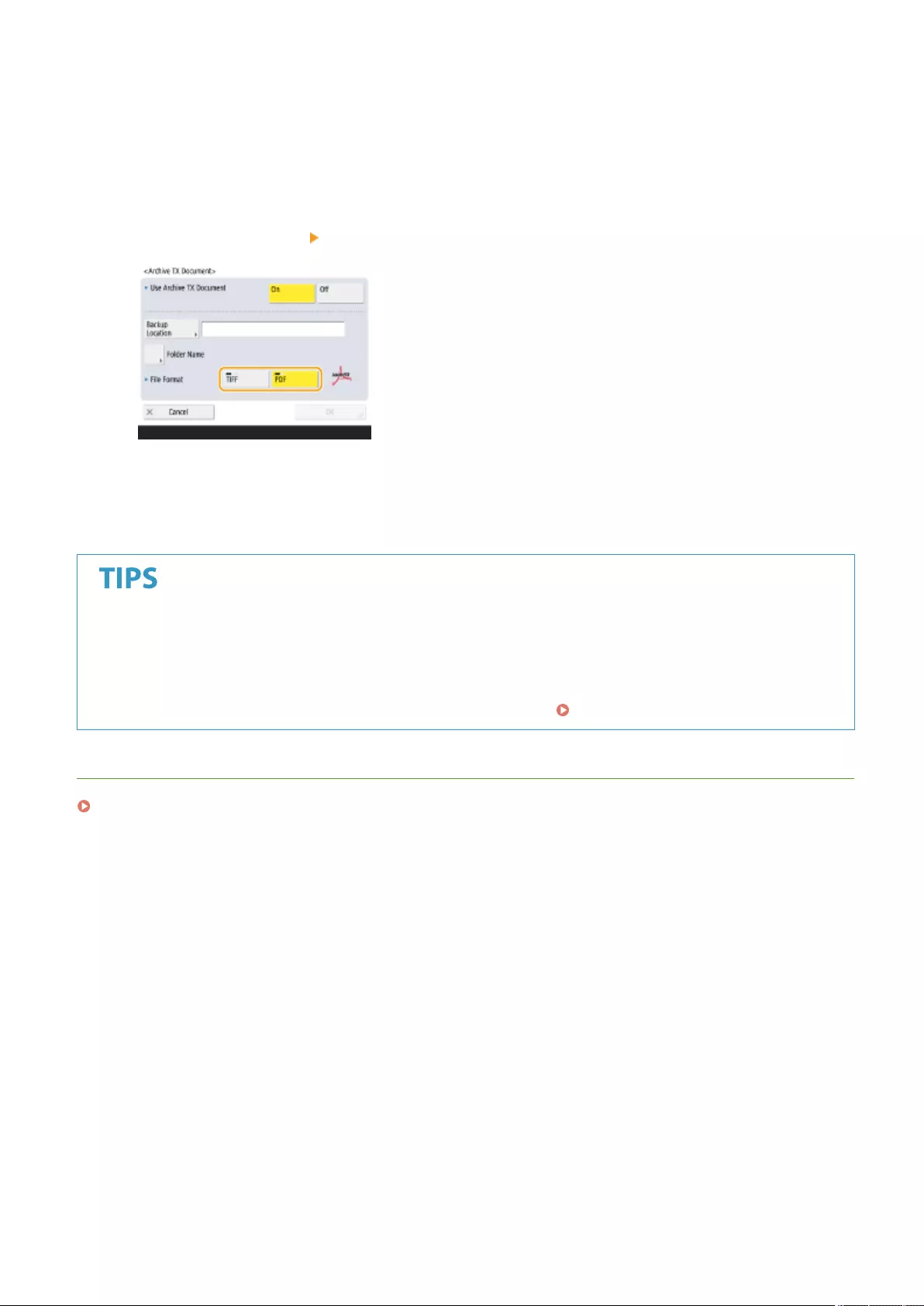
Destination information
●Information regarding the destination is displayed in the following situations.
- Destination Unit Name: When the destination unit name is available
- Telephone Number: When the destination unit name is not available
- Destination name of rst successful sending: When performing a sequential broadcast transmission
5Press <File Format> select the le format for saving the sent data.
6Press <OK>.
●Registration is complete.
Specifying multiple destinations including a fax destination
●You can save a copy of a sent document by sending to multiple destinations which include a fax destination
from the Scan Basic Features screen. To display fax destinations on the Scan Basic Features screen, it is
necessary to set <Enable Fax in Scan and Send Function> to <On>. <Display Fax Function>(P. 773)
LINKS
Basic Operations for Sending Faxes(P. 275)
Faxing
311

Various Receiving Methods
72JY-05A
The machine can be set to temporarily save received documents in it without printing. By checking and selecting
documents you want to print, you can save paper. There is also a function to receive and keep condential documents
private.
●If image les attached to received I-fax documents are not compatible with this machine, the machine does
not process (print, forward, or store) these les. The les are deleted instead. In this case, the names of the
deleted les and the message "No programs can process the le attachment." are printed with the text of
the received I-fax.
Saving Received Documents in the Machine (Memory
Reception)(P. 313)
Keeping Received Documents
Private(P. 316)
Faxing
312

Fax/I-Fax Inbox
Saving Received Documents in the Machine (Memory
Reception)
72JY-05C
You can have incoming documents saved in the storage location (Memory RX Inbox)
of the machine without printing. By printing just what you need and deleting
unnecessary documents such as direct mails from the Memory RX Inbox, you can
save paper.
Saving in the Memory RX Inbox(P. 313)
Printing Documents in the Memory RX Inbox(P. 313)
Fax Memory LockI-Fax Memory Lock
Saving in the Memory RX Inbox
To use this function, you need to activate the memory reception function rst ( <Use Fax Memory Lock>(P. 837)
and <Use I-Fax Memory Lock>(P. 837) ), and then follow the procedure below to specify the settings so that
incoming documents can be received in memory.
1Press <Fax/I-Fax Inbox>. <Home> Screen(P. 119)
2Press <Memory RX Inbox>.
●If the password is set for the Memory RX Inbox, the screen appears prompting you to enter the password (
<Memory RX Inbox PIN>(P. 837) ). Enter the password and press <OK>.
Memory RX Inbox
3Select <Memory RX Inbox> and set <Fax Memory Lock> to <On>.
●To receive I-faxes in memory, set <I-Fax Memory Lock> to <On>.
Print
Printing Documents in the Memory RX Inbox
When the Processing/Data indicator on the control panel maintains a steady green, follow the following procedures to
check/print saved documents.
1Press <Fax/I-Fax Inbox>. <Home> Screen(P. 119)
Faxing
313

2Press <Memory RX Inbox>.
Divided Data RX Inbox
Divided Data RX Inbox
Pressing <Divided Data RX Inbox> enables you to check the receive status of an I-fax that has been divided into
several parts before being sent, and the remaining capacity of the Divide Data RX Inbox.
The following can be performed using <Divided Data RX Inbox>.
Divided Data List
●Pressing <Divided Data List> enables you to check the document list.
DeletePrint When Deleted
●Pressing <Delete> enables you to delete a document that was divided and sent. Selecting <Print When
Deleted> enables you to set the machine to print the divided received data document when it is deleted.
3Select <Memory RX Inbox>.
➠A list of saved documents is displayed.
4Select a document to print and press <Print>.
DetailsDisplay Image
●Pressing <Details> enables you to check information about the document, including senders' names and the
number of pages received. Pressing <Display Image> enables you to check the contents of the document as
well as select and delete pages.
Delete
●Pressing <Delete> <Yes> deletes the document. You cannot delete multiple documents simultaneously. To
delete multiple documents, select and delete one document at a time.
Send
●Pressing <Send> enables you to specify destinations to send the document. To delete the document from the
Fax/I-Fax Inbox after sending, press <Delete File After Sending> before sending.
Select All (Max 32 les)Clear Selection
●Pressing <Select All (Max 32 les)> enables you to select the documents at once. When a document is
selected, <Clear Selection> is displayed enabling you to clear all selections.
●To print all the documents in memory, press <Off> for <Fax Memory Lock> or <I-Fax Memory Lock>. You
can skip step 5.
●You cannot print multiple documents simultaneously. To print multiple documents, select and print one
document at a time.
5Press <Start Printing>.
➠Once a document is printed, it is automatically deleted from memory.
Faxing
314
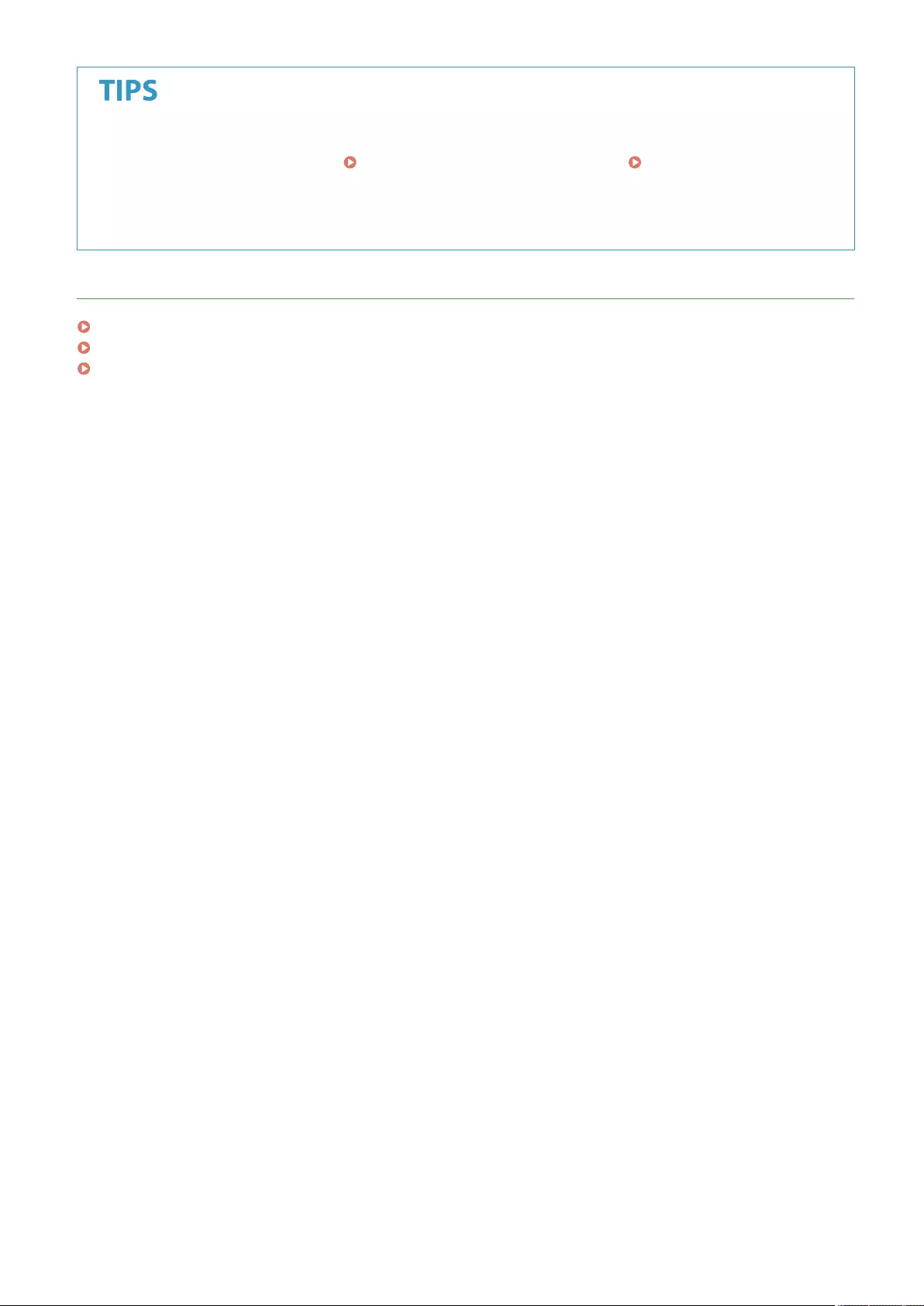
●You can specify a day of the week or the time such as on weekends or night time during which received
documents are saved in memory. <Memory Lock Start Time>(P. 838) and <Memory Lock End
Time>(P. 838)
●Registering an arbitrary level of the Memory RX Inbox to the <Personal>/<Shared> button enables
operations to be executed quickly and eciently.
LINKS
Basic Operations for Sending Faxes(P. 275)
Sending I-Faxes(P. 330)
Basic Operations for Scanning Originals(P. 377)
Faxing
315
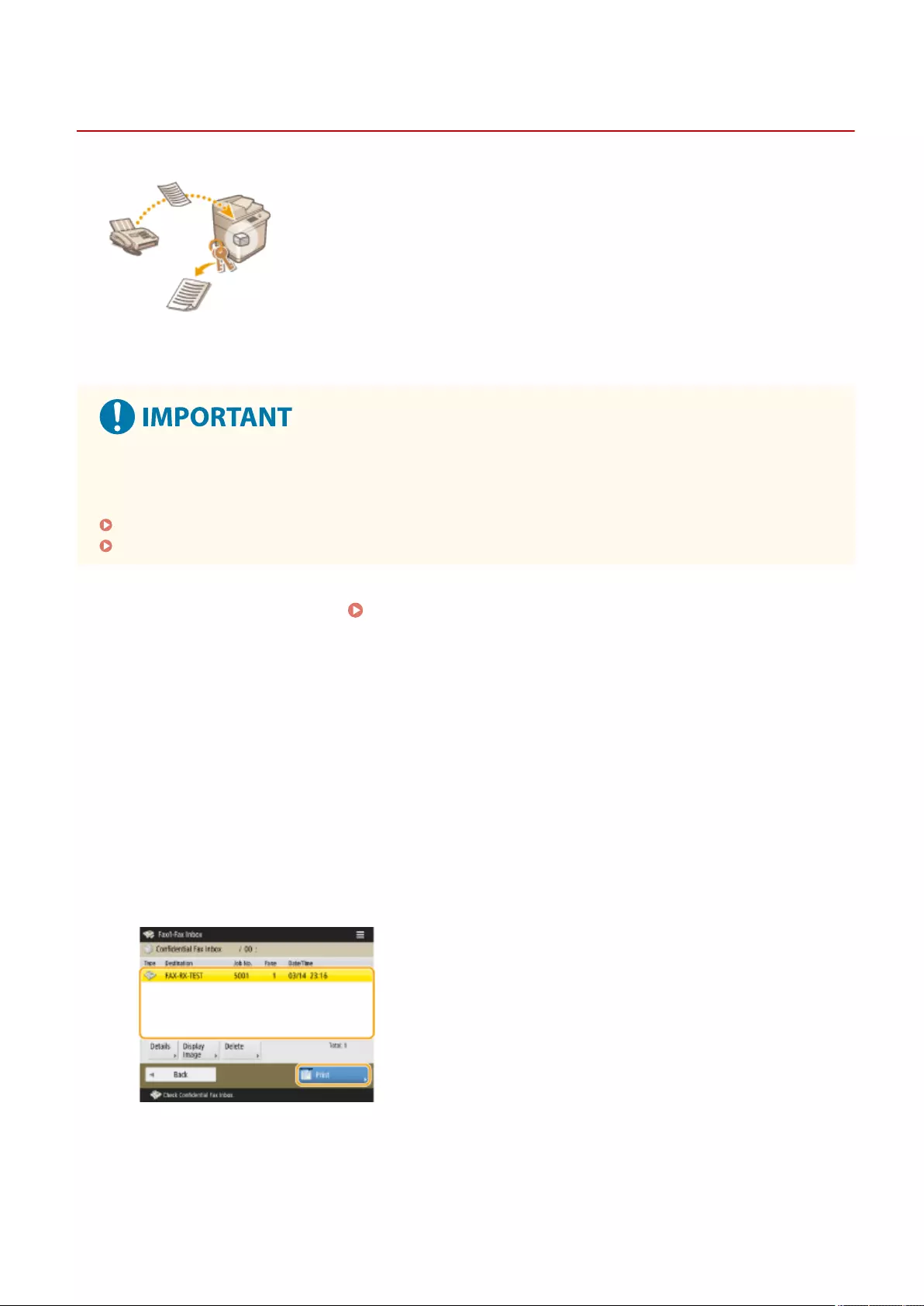
Print
Keeping Received Documents Private
72JY-05E
This function is to save in the specied storage location (Condential Fax Inbox) the
received documents that match specic conditions. The Condential Fax Inbox
contains multiple boxes, and each box can be protected by password. By specifying a
condition such as saving all documents from Company A in Box No. 10, you are
allowed to only check the documents you need. This function also enables you to
prevent unauthorized persons from seeing condential documents unintentionally
by setting a password. When the Processing/Data indicator on the control panel
maintains a steady green, follow the following procedures to check/print saved
documents.
To use this function
●Some settings such as the save location and password for documents need to be registered beforehand.
Forwarding Received Documents Automatically(P. 318)
<Set/Register Condential Fax Inboxes>(P. 836)
1Press <Fax/I-Fax Inbox>. <Home> Screen(P. 119)
2Press <Condential Fax Inbox>.
3Select the box where documents are saved.
●If the password is set for the box, the screen appears prompting you to enter the password. Enter the
password and press <OK>.
➠A list of saved documents is displayed.
4Select the document to print and press <Print>.
DetailsDisplay Image
●Pressing <Details> enables you to check information about the document, including senders' names and the
number of pages received.
●Pressing <Display Image> enables you to check the contents of the document as well as select and delete
pages.
Delete
Faxing
316

●Pressing <Delete> <Yes> deletes the document. You cannot delete multiple documents simultaneously. To
delete multiple documents, select and delete one document at a time.
●You cannot print multiple documents simultaneously. To print multiple documents, select and print one
document at a time.
5Press <Start Printing>.
●To delete the document to print, press <Delete File After Printing> before printing.
➠Printing starts.
●You can set to receive the URL of the save location by e-mail when receiving documents. Just entering the
URL in the address bar of a Web browser enables you to check the contents of documents from your
computer through the Remote UI. <Set/Register Condential Fax Inboxes>(P. 836)
●Registering an arbitrary level of Condential Fax Inbox to the <Personal>/<Shared> button enables
operations to be executed quickly and eciently.
LINKS
Managing the Machine from a Computer (Remote UI)(P. 581)
Faxing
317
Forwarding Received Documents Automatically
72JY-05F
You can set to forward received documents to specied destinations. Fax numbers
as well as e-mail addresses and shared folders in computers can be specied as
forwarding destinations.
Forwarding All Documents Automatically (Forwarding All)
The machine forwards all received documents to specied destinations. This method is useful when you want to
get faxes even if you are out of the oce. You can also set to print forwarded documents or receive an e-mail
notifying you that forwarding documents is complete.
Forwarding Automatically by Specied Conditions (Conditional Forwarding)
The machine forwards received documents that only match the specic conditions, such as sender's fax number
and received dates/times. For example, you can set conditions such as forwarding documents from Company A
to all branch oces and forwarding documents received on holidays to e-mail addresses. Just like with the
Forwarding All method above, you can also set to print forwarded documents or receive an e-mail notifying you
that forwarding documents is complete.
Conguring Forwarding Settings
To use automatic forwarding, it is necessary to specify the forwarding destination and le format, etc., in advance.
1Press (Settings/Register) <Function Settings> <Receive/Forward> <Common
Settings> <Forwarding Settings>.
●You can also display the <Forwarding Settings> screen by pressing <Dest./Fwd. Settings>( <Home>
Screen(P. 119) ) <Forwarding Settings>.
2Press <Register>.
3Press <Condition Name> and enter the name.
Faxing
318
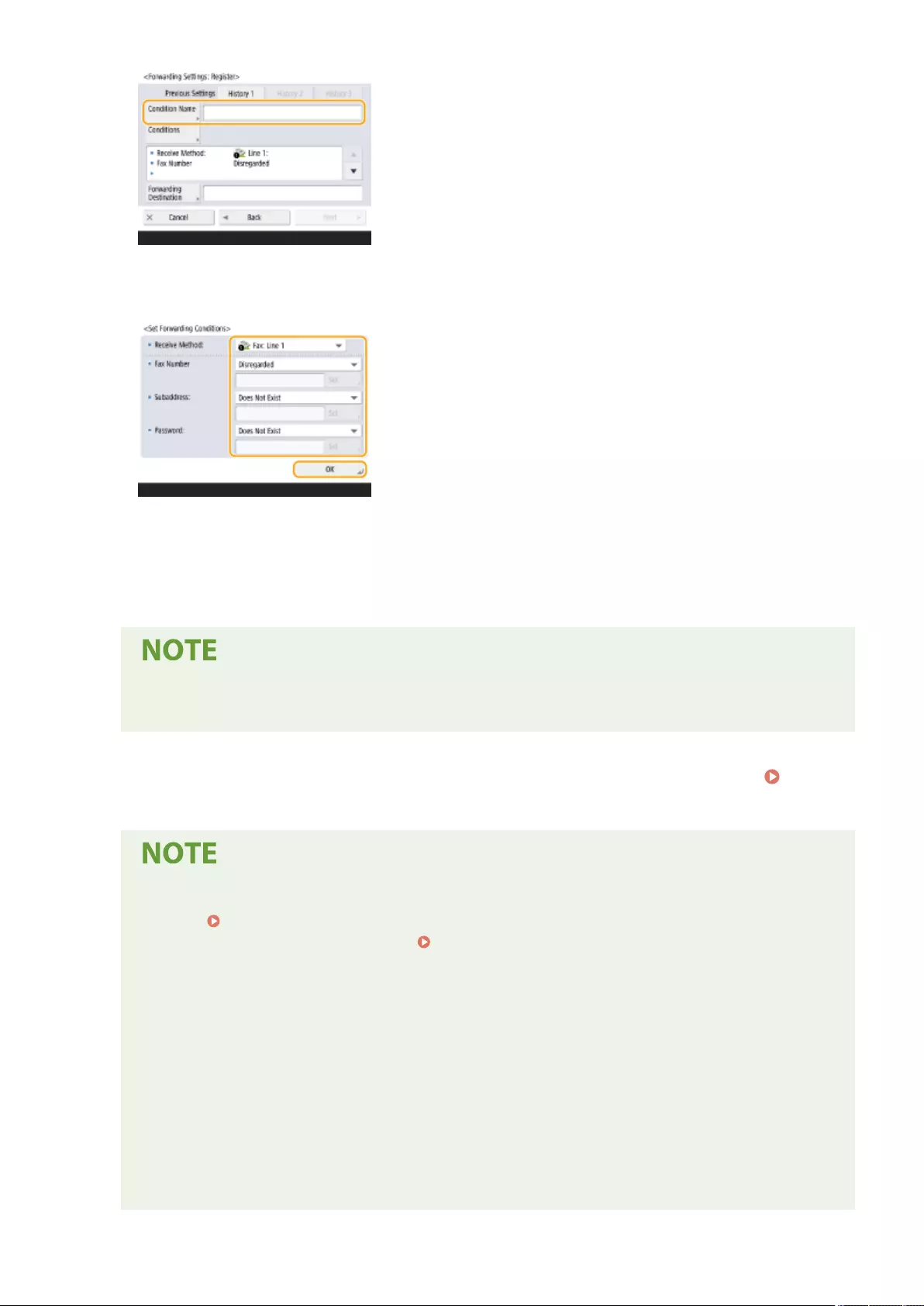
4Press <Conditions> and specify the conditions for the destinations to forward.
●A document will be forwarded if it is received from a destination that meets the conditions specied here.
Example: Forwarding a fax from 1111111111
●Receive Method: <Fax>
●Fax Number: Select <Equals> from the drop-down list and enter "1111111111."
●You cannot change <Receive Method> after registering <Forwarding Settings>. To use forwarding
settings with <Receive Method> changed, you have to register the forwarding settings again.
5Press <Forwarding Destination> and specify the destination to forward to.
Registering Destinations in the Address Book(P. 195)
●A destination in <Personal Address List> cannot be specied as the forwarding destination.
●When <Acquire Address Book>(P. 851) is set to <On>, forwarding destinations can also be
selected from a remote address book. About the Address Books of the Machine(P. 192)
●You can store received fax/I-fax les in the Condential Fax Inbox by specifying it as a forwarding
destination.
●If a Condential Fax Inbox is selected as the forwarding destination, the following settings cannot be
used.
- File Name
- Store/Print Received File
- Forwarding Done Notice
- File Format
●If you select a fax number as the forwarding destination, the subaddress and password registered in
the Address Book are ignored.
Faxing
319
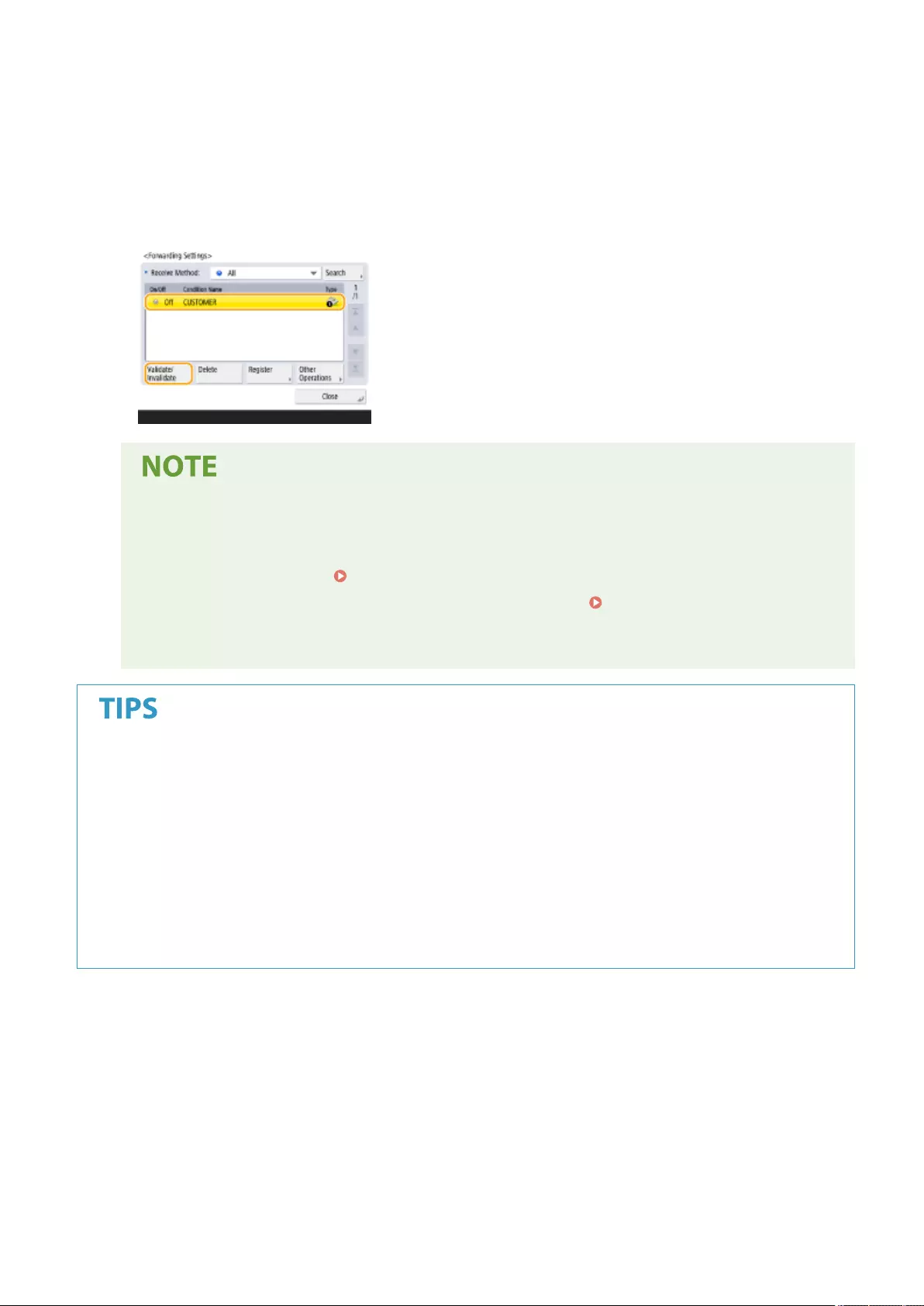
6Press <OK>.
●This completes the registration.
7Select the registered forwarding settings and press <Validate/Invalidate> to switch
the forwarding conditions to <On>.
●You cannot specify a WebDAV server as an I-fax forwarding destination.
●If you specify a destination for which <Conrm Before Sending> is enabled as a forwarding
destination, the screen to enter the password does not appear. The registered password is used and
forwarding is performed. Registering Destinations(P. 190)
●Documents with forwarding errors are handled according to the <Handle Files with Forwarding
Errors>(P. 836) settings.
●You can store up to 1,000 forwarding settings.
●Selecting <Forward without Conditions> enables you to forward all received documents that do not meet the
specied conditions to the desired destination.
●You can forward to multiple destinations by specifying a group destination in <Forwarding Destination>.
●<Specify Fwd. Time> enables you to specify the time and day to perform forwarding.
●If you set <Forwarding Done Notice>, you can send an e-mail notifying that forwarding documents is
complete. You can select <Notice Only for Errors>, so that you are not notied of a successful forwarding.
●If you set <Store/Print Received File> to <On>, you can store or print the received le by following the
Memory Lock settings. The received le is stored if Memory Lock is <On> and it is printed if Memory Lock is
<Off>.
Faxing
320
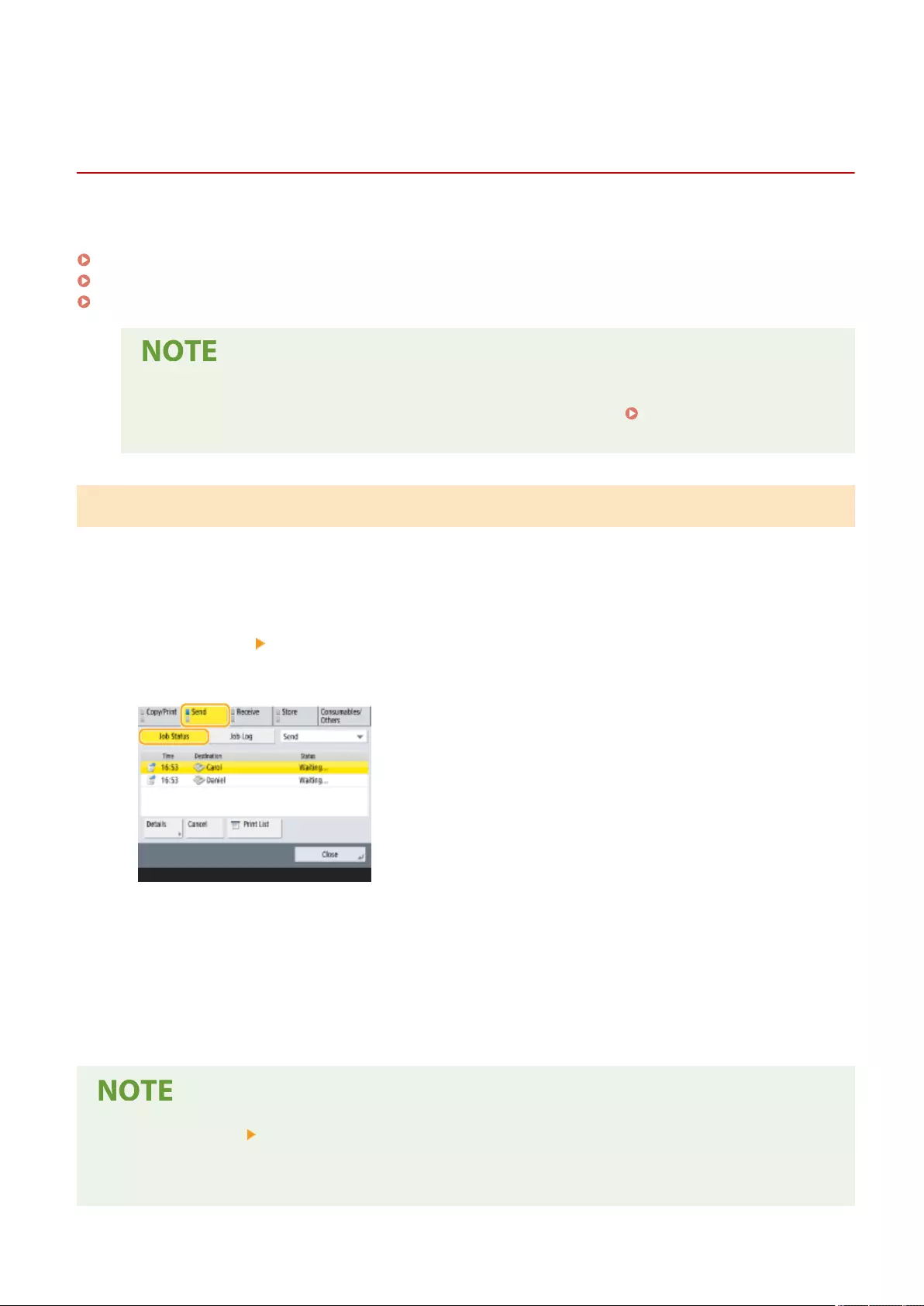
Checking Status and Log for Sent and Received
Documents
72JY-05H
You can check the statuses and communication logs for sent and received documents.
Checking the Statuses for Sent Documents(P. 321)
Checking the Statuses for Received Documents(P. 322)
Checking If Documents Are Sent or Received Successfully(P. 323)
●When personal authentication management is used, you can restrict users from performing
operations on the jobs of other users on the <Status Monitor> screen. <Restrict Access to Other
User Jobs>(P. 857)
Checking the Statuses for Sent Documents
1Press <Status Monitor>.
2Press <Send> <Job Status>.
●To display only fax documents, select <Fax> from the drop-down list in the upper-right of the screen.
3Check the statuses.
●Selecting a document and pressing <Details> enables you to check detailed information such as the
destinations and the number of pages.
●Selecting a document and pressing <Cancel> enables you to cancel sending. You cannot select multiple jobs
and cancel them all at once. Select and cancel one job at a time.
●Pressing <Details> <Resend> enables you to resend the documents that failed to send. To specify another
destination, press <Change Destination>. For documents with multiple destinations specied using the same
sending method, press <Broadcast List>, select a destination, and then press <Resend> or <Change
Destination>.
Faxing
321

●You can resend documents when <Delete Failed TX Jobs> is set to <Off> ( <Delete Failed TX
Jobs>(P. 821) ). Note that you cannot resend the documents sent with Direct Send/Manual Sending/PC fax.
●You can change the destinations of documents that are set to be sent at a specied time as well as
documents that failed to send. Note that you cannot change the destinations for documents with multiple
destinations specied that are being sent, or when entering a new destination is restricted ( Limiting
Available Destinations(P. 569) ).
●The destination can be changed for a job that is canceled because of transmission errors, or a job that is
waiting to be sent in the Delayed Send mode.
●You cannot change multiple destinations at one time. Also, you cannot change the destinations in a group at
one time.
Checking the Statuses for Received Documents
1Press <Status Monitor>.
2Press <Receive> <Job Status>.
●To display only fax documents, select <Fax> from the drop-down list in the upper-right of the screen.
3Check the statuses.
●Selecting a document and pressing <Details> enables you to check detailed information such as the sender's
names and the number of pages.
●Selecting a document and pressing <Cancel> enables you to cancel receiving. You cannot select multiple jobs
and cancel them all at once. Select and cancel one job at a time.
●If you press <Check I-Fax RX>, reception starts if an I-fax has been received by the POP server. You can
display <Check I-Fax RX> by selecting <Forward> from the drop-down list on the top right of the screen.
●To use <Check I-Fax RX>, set <POP> to <On> in <Communication Settings> to enable the machine to receive
via POP. Setting E-mail/I-Fax Communication(P. 70)
●You can automatically receive I-faxes in the following cases: Setting E-mail/I-Fax Communication(P. 70)
-<POP Interval> in <Communication Settings> is set to a value other than '0'.
-I-faxes are received with SMTP without going via a server.
Faxing
322

Checking If Documents Are Sent or Received Successfully
1Press <Status Monitor>.
2Press <Send> or <Receive> <Job Log>.
●To display only fax documents, select <Fax> from the drop-down list in the upper-right of the screen.
3Check if documents are sent or received successfully.
●<OK> is displayed in the <Result> column when a document was sent or received successfully. If <NG> is
displayed, this shows that a document failed to be sent or received because it was canceled or there was
some error.
●You can check the error code by selecting a document and pressing <Details>. You can check the causes and
solutions for errors based on error codes. Countermeasures for Each Error Code(P. 982)
●Pressing <Communic Mngt Rprt.> or <Fax Activity Report> prints a log list of sent and received documents
displayed on the screen.
Registering an address from the send history
●You can register an address to the Address Book or a one-touch button via the send history on the <Status
Monitor> screen. This saves you the effort of directly entering the fax number, and also helps avoid sending
a fax to an incorrect number due to entering the wrong fax number.
Registering Destinations in the Address Book(P. 195)
Registering a Destination in a One-Touch Button(P. 210)
LINKS
Sending at a Specied Time(P. 307)
Checking the Connection to the Recipient Before Sending (Direct Send)(P. 297)
Sending Faxes Manually (Manual Sending)(P. 298)
Sending Faxes from Your Computer (PC Fax)(P. 324)
Printing a List of Usage History(P. 910)
Outputting a Communication Result Report(P. 912)
Faxing
323

Sending Faxes from Your Computer (PC Fax)
72JY-05J
You can send fax documents created on your computer directly from your computer, just like printing operations. This
method eliminates the need to print documents for faxing, allowing you to save paper. To use this function, you need
to install a fax driver in your computer ( Installing Drivers(P. 67) ).
Sending PC Faxes(P. 325)
◼Help for fax driver
Clicking [Help] (Windows) or (Mac OS) on the fax driver setting screen displays the Help screen. For information
that is not in the User's Guide, including driver features and how to set up those features, see Help.
Faxing
324
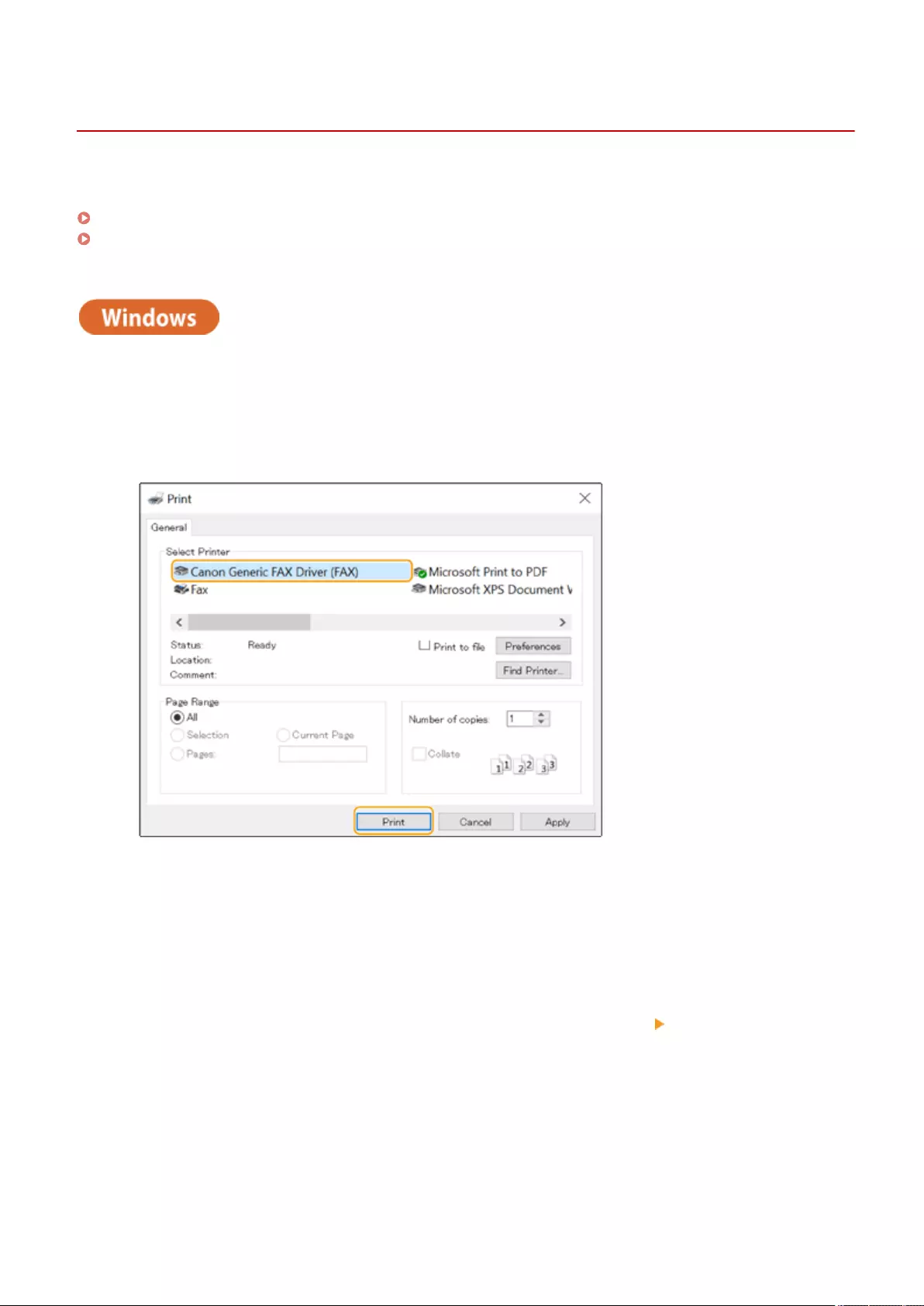
Sending PC Faxes
72JY-05K
This section describes the basic ow of sending PC faxes from a computer.
For Windows(P. 325)
For Mac OS(P. 326)
For Windows
1Open a document and display the print screen.
2Select the machine and click [Print] or [OK].
3Click the [Enter Destination] tab, and specify the communication mode and fax
number you are using.
●[* Communication Mode]: Make sure that [G3] is selected.
●[* Fax Number/URI]: Make sure that [Fax Number] is selected.
●[* Fax Number]: Enter a fax number.
●If you need to specify a number to dial an outside line, click [Detailed Settings] [Add Outside Dialing Prex
to G3/IP Fax Number], and enter a fax number in the [G3] text box.
Faxing
325
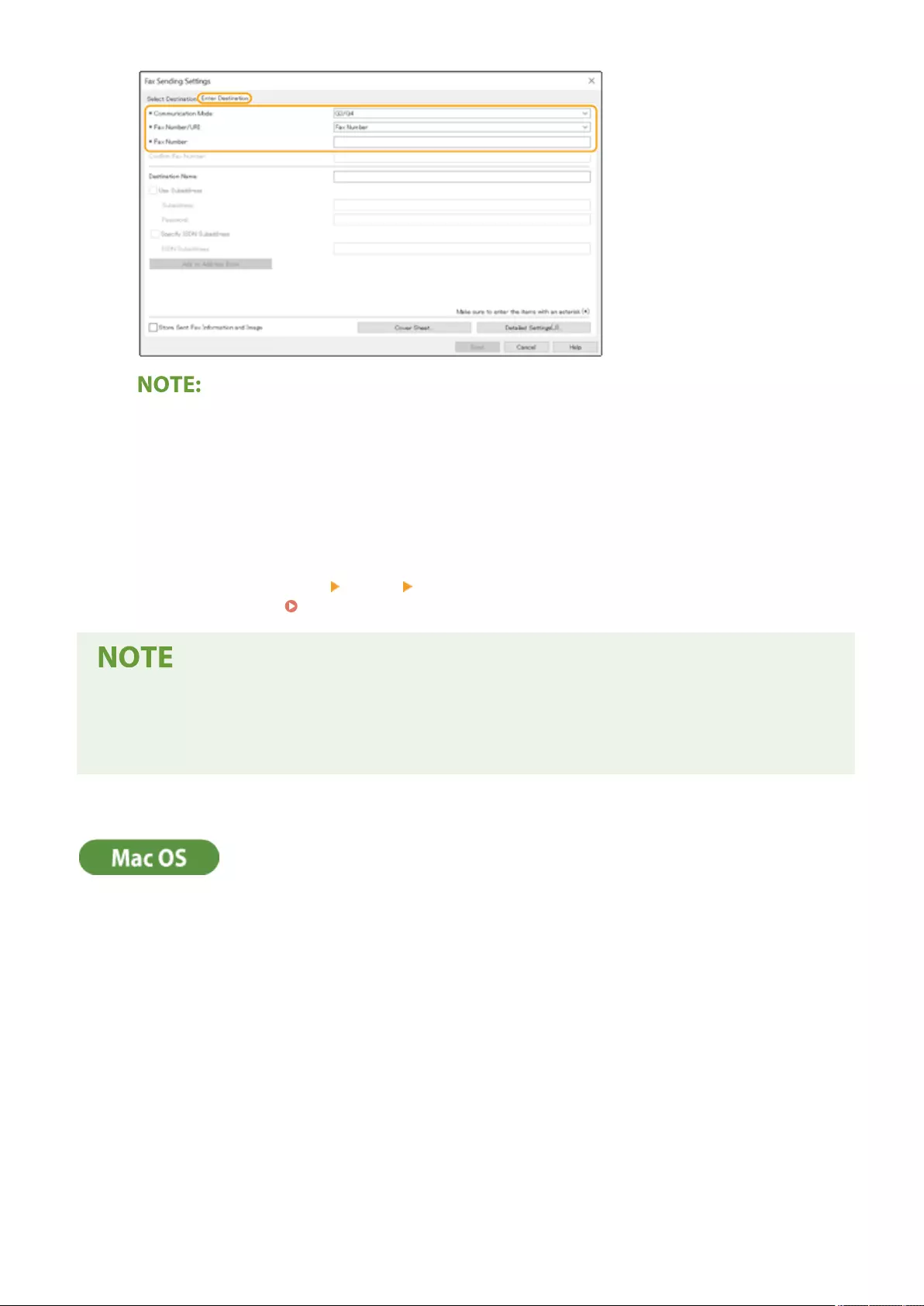
●If [Conrm Fax Number/URI when Setting Destination] is set in the [Security Settings] dialog box, enter the
specied fax number in [Conrm Fax Number]. For details, see Help for fax driver.
4Click [Send].
➠Sending starts.
●To cancel sending, double-click the printer icon displayed in the task tray of the desktop, select the le to
cancel, and click [Document] [Cancel] [Yes]. If the icon is not displayed, you can cancel from the control
panel of the machine. Checking Status and Log for Sent and Received Documents(P. 321)
When the department ID and password or the user name and password input screen is
displayed
●Enter the department ID and password or the user name and password.
For Mac OS
1Open a document and display the print screen.
2Select the machine and click [Show Details].
Faxing
326
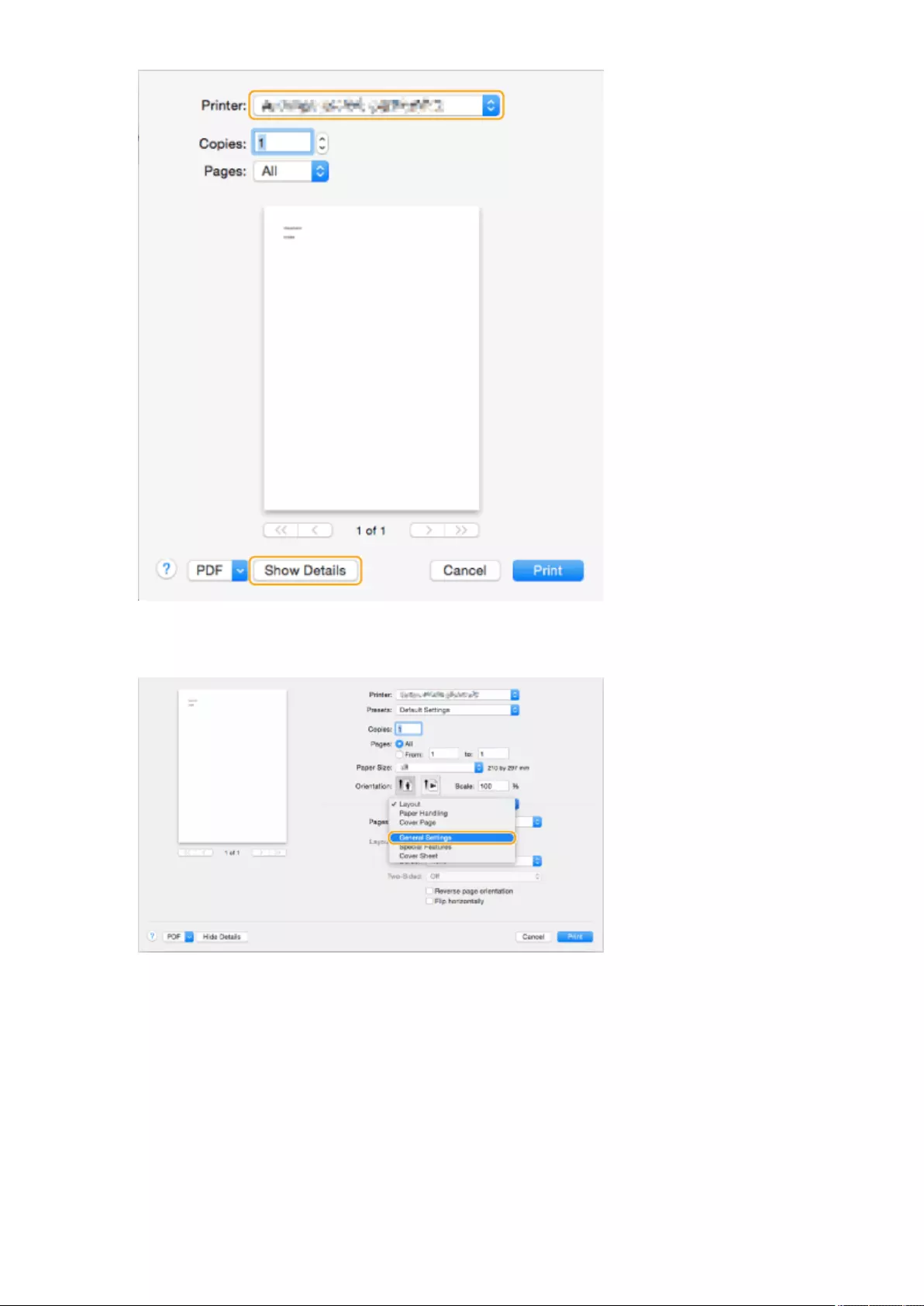
3Click [General Settings].
4Click [Add Destination].
Faxing
327
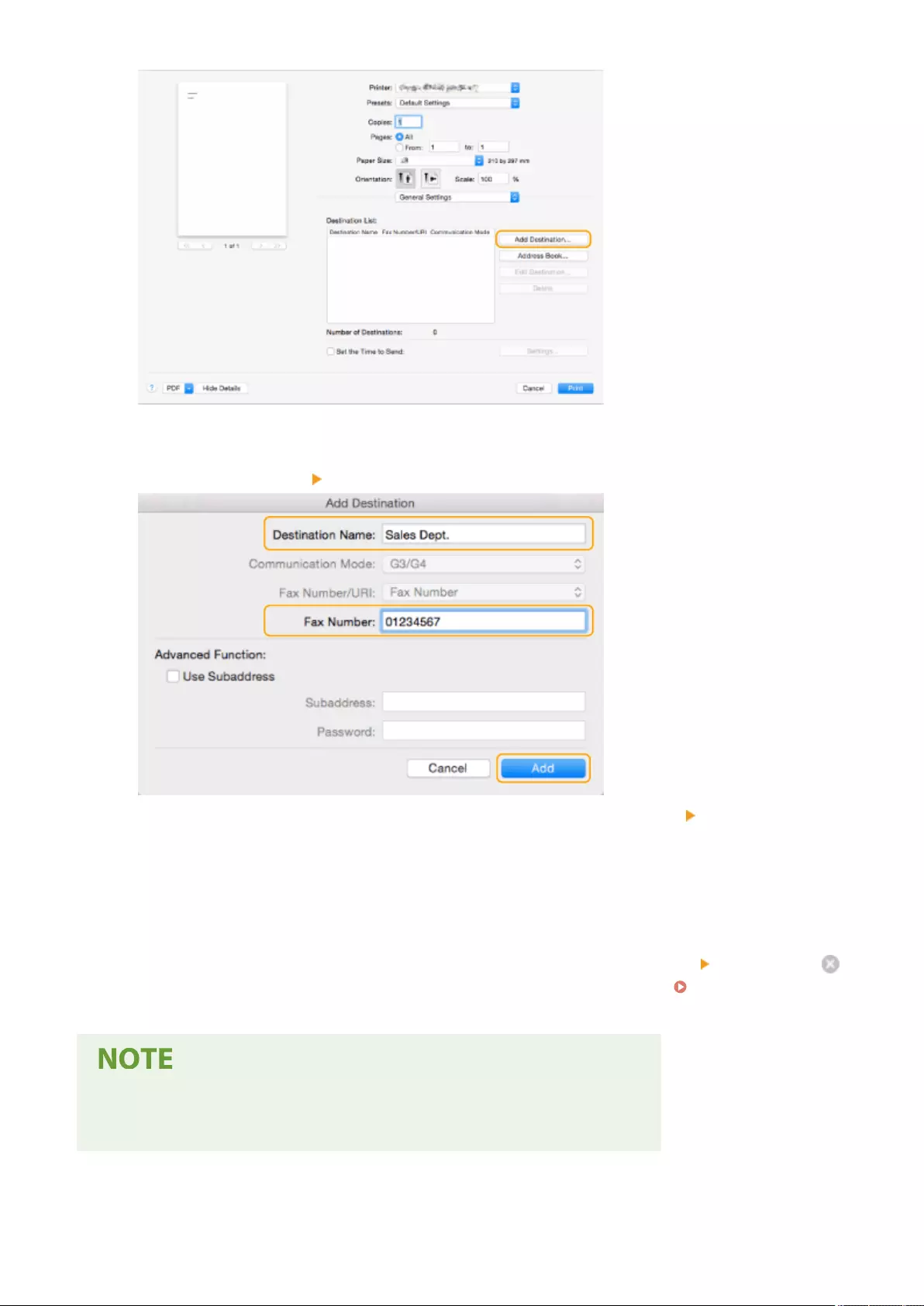
5Enter the destination name in [Destination Name] and fax number in [Fax Number],
and then click [Add] [Cancel].
●If you need to specify a number to dial an outside line, click [Outside Dialing Prex] [Settings] on the
[Special Features] panel, and then enter the number.
6Click [Print].
➠Sending starts.
●To cancel sending, click the printer icon displayed in the Dock, select the le to cancel click [Delete] or .
If the icon is not displayed, you can cancel from the control panel of the machine. Checking Status and
Log for Sent and Received Documents(P. 321)
When the department ID and password input screen is displayed
●Enter the department ID and password.
Faxing
328
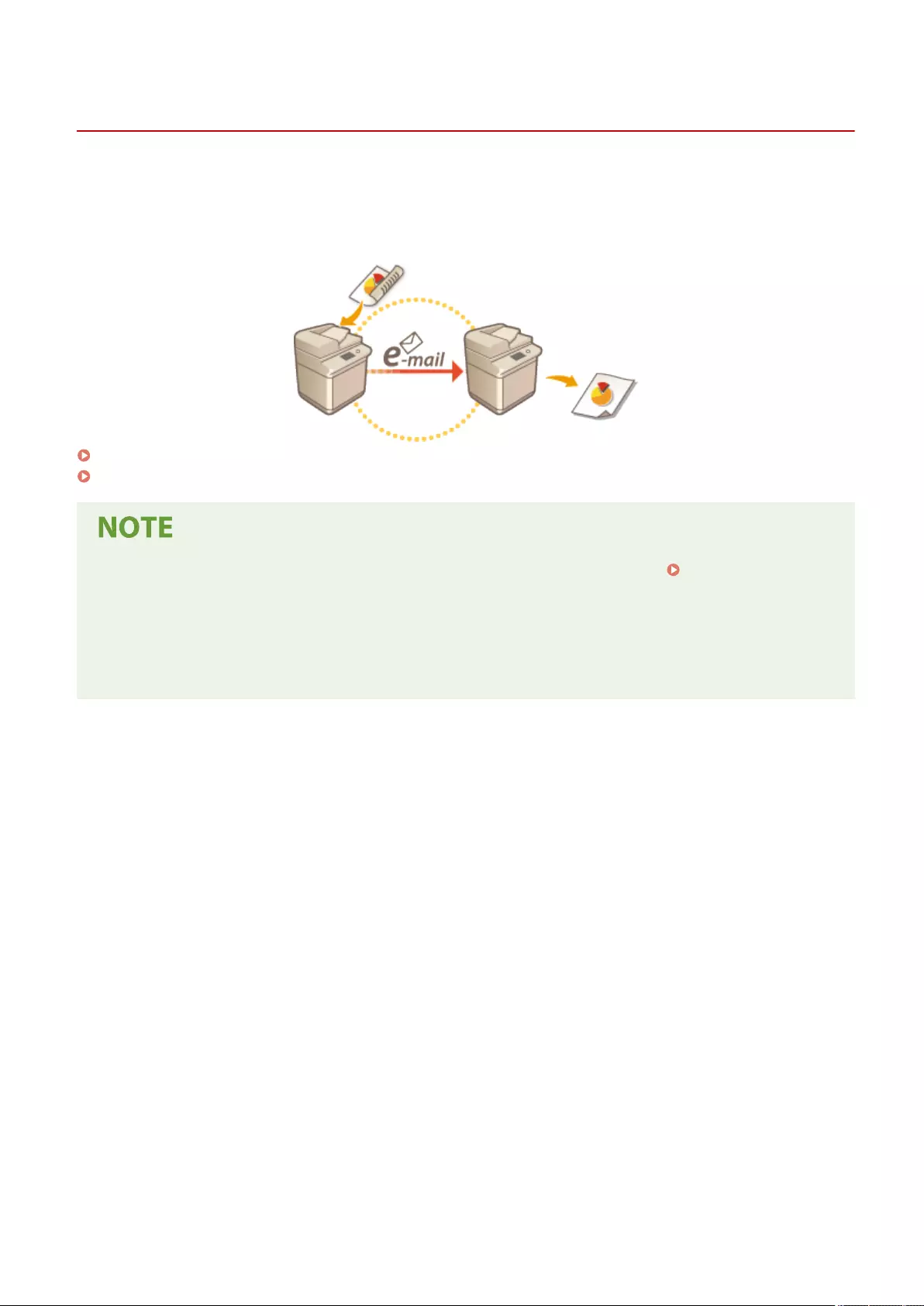
Using Internet Faxes (I-Fax)
72JY-05L
Internet fax (I-fax) is a function to send and receive faxes via the Internet. Scanned documents are converted into TIFF
format image and are sent as e-mail attachments. Even if you are sending to a distant place or you have lots of
documents to send, you do not have to worry about transmission costs because telephone lines are not used. With
this function, you can also send and receive I-faxes between devices in the same network using an oce LAN.
Sending I-Faxes(P. 330)
Receiving I-Faxes(P. 338)
●To send documents to an e-mail address used on a computer or mobile device, see Basic Operations for
Scanning Originals(P. 377) .
●Standards for I-fax are dened by ITU-T (International Telecommunication Union - Telecommunication
Standardization Sector). You can send and receive with other manufacturer's machines as long as that
machine is ITU-T compliant. The machine is compliant with Recommendation T.37 (Procedures for the
transfer of facsimile data via store-and-forward on the Internet).
Faxing
329
Sending I-Faxes
72JY-05R
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
Specifying Destinations from the Address Book
Specifying Destinations from One-Touch Buttons
Entering Destinations Manually
Specifying Destinations in the LDAP Server
●You can only change destinations from <Details> specied using the New Destination and destinations
obtained via an LDAP server.
●If the server machine is performing the System Manager information settings, authentication between the
server machine and the client machine is performed while the client machine is obtaining the Remote
Address Book/one-touch buttons. Authentication is performed by matching the System Manager ID and
System Manager PIN set by the server machine and client machine. Changing the System Manager ID
and PIN(P. 523)
The availability of the Remote Address Book/one-touch buttons depends on the status of the System
Manager information settings for the server machine and client machine, as shown below.
When the server machine
is performing the System
Manager information
settings
When the client machine is
performing the System
Manager information
settings
The System Manager ID
and System PIN for the
server machine and client
machine match
Can use the
Remote Address
Book/One-Touch
Button
Performing Performing Matches Yes
Does Not Match No
Not Performing - No
Not Performing Performing - Yes
Not Performing - Yes
Specifying Destinations from the Address Book
1Press <Address Book>.
2Select the destination and press <OK>.
Faxing
330
●If an access number is set when the destination is registered, press <Access No.> and enter the access
number using the numeric keys. The corresponding destination is displayed in the Address Book.
●To use the Remote Address Book, press <To Remote Address Book>. When <Change Address Book> is
displayed, press <Change Address Book> <Remote>.
Destination type drop-down list
Pressing and displays I-fax and group destinations, respectively.
Address list drop-down list
Enables you to display a specic group of destinations. When you are logged in to the machine with
personal authentication management, selecting <Personal Addr. List> displays your personal Address
Book.
Search buttons by rst letter
Enables you to narrow down a search by the rst letter of the destination name.
<Search by Name>
Enables you to search the destination by the name you are entering.
●To use the Remote Address Book, it is necessary to congure the server machine settings. Set to open
the Remote Address Book externally on the server machine.
Specifying Destinations from One-Touch Buttons
1Press <One-Touch>.
2Select the desired one-touch button and press <OK>.
●To specify the destination using a one-touch button number (one-touch number), press and enter the
number for the desired one-touch button.
●To use the Remote Address Book, press <To Remote Address Book>.
Faxing
331
●The destinations registered in the one-touch buttons of the server machine are updated in the
following times:
- When a fax job has been sent on the client machine
- When you press (Reset) on the client machine
- When Auto Reset is activated on the client machine
Entering Destinations Manually
You can specify destinations manually that are not registered in the Address Book or one-touch buttons.
1Press <New Destination> <I-Fax>.
2Select the transmission mode.
●If you want to set the machine so that you can check the sending result of a document on the <Status
Monitor> screen, select <Full>. If not, select <Simple>. Note that the recipient also needs to support the
transmission mode in order to check the sending result. Depending on the recipient's machine, sending an I-
fax is not allowed unless you select <Simple>.
●If you send an I-fax to a destination that does not support the transmission mode, the <Status Monitor>
screen displays <Awaiting result...> even if sending is complete. This message is displayed until the time
set for <Full Mode TX Timeout> passes. <Full Mode TX Timeout>(P. 829)
3Enter the I-fax destination.
Faxing
332
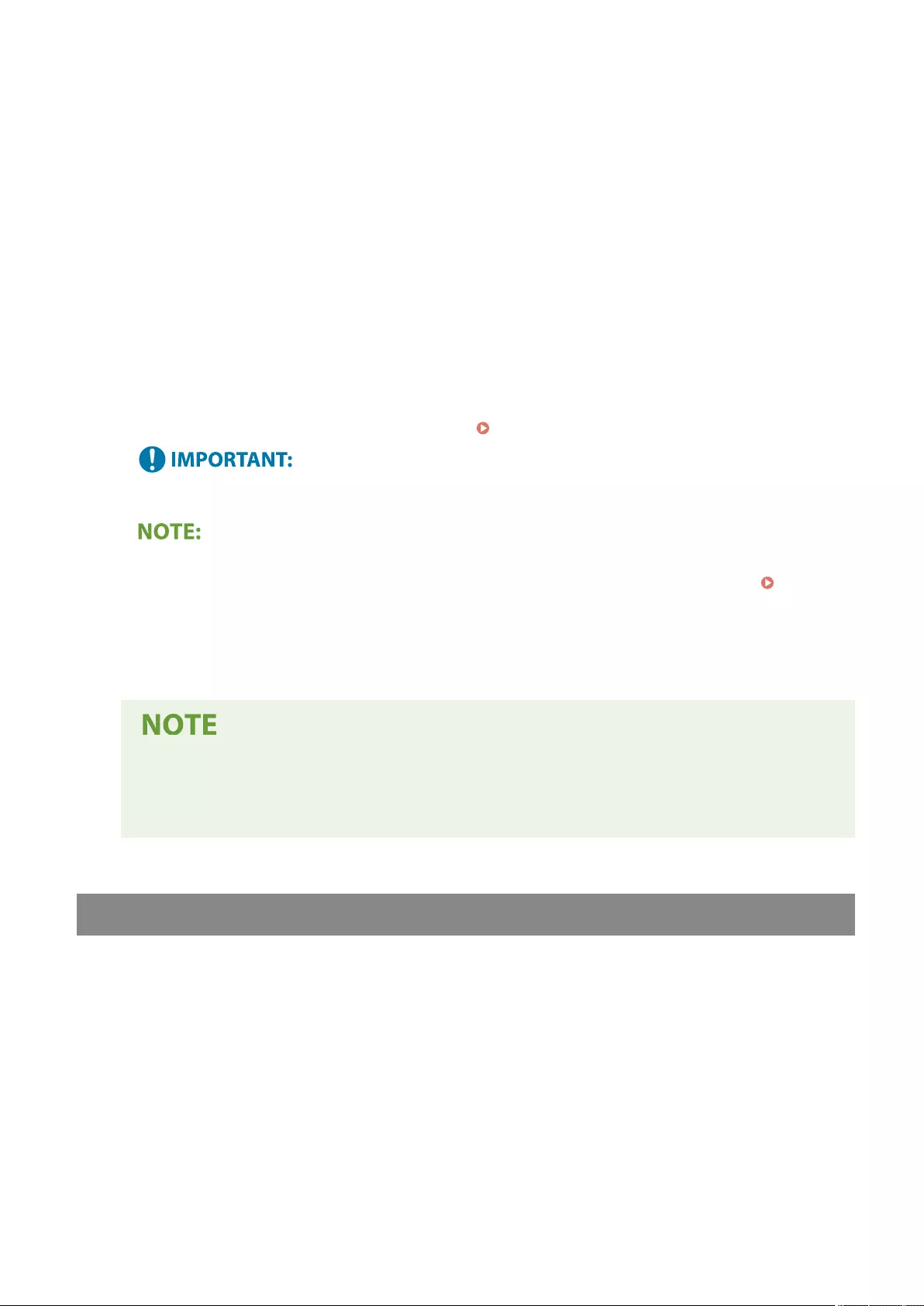
●Press <I-Fax Address>, enter the destination, and then press <OK>. The destination needs to be specied in a
format such as "adv01@example.com." To send to a device within the same network, enter the destination in
a format such as "adv01@192.168.11.100 (recipient's name@IP address)."
4Press <Destination Conditions>.
5Specify the receiving conditions the recipient supports and press <OK>.
●Be sure to check the receiving functions the recipient supports before specifying the conditions.
●To add another I-fax address, press <Next Destination> and repeat steps 2 through 5.
●In <Compression Method>, the compression ratio of les increases in the order of MH→MR→MMR, and
shortens transmission time.
●In <Divide Data>, select <On> to divide large amounts of document data for sending. If the recipient does not
have the function to combine divided data, select <Off>. For the <Off> setting, a transmission error occurs
when the size of send data exceeds a certain value. <Maximum Data Size for Sending>(P. 827)
●Specifying the conditions the recipient does not support may cause a transmission error.
●You can press <Register to Address Book> to register the entered destination. Set the required conditions,
and specify <Name> and <Address Book>. For information on the settings, see Registering
Destinations in the Address Book(P. 195) .
6Press <OK>.
To send to a device within the same network
●When sending an I-fax to a device within the same network, you can send directly to the device
without going through the mail server. Set <Send via Server> to <Off> before sending an I-fax.
Specifying Destinations in the LDAP Server
You can search and specify destinations registered in the LDAP server.
1Press <Address Book>.
2Press <To LDAP Server>.
Faxing
333
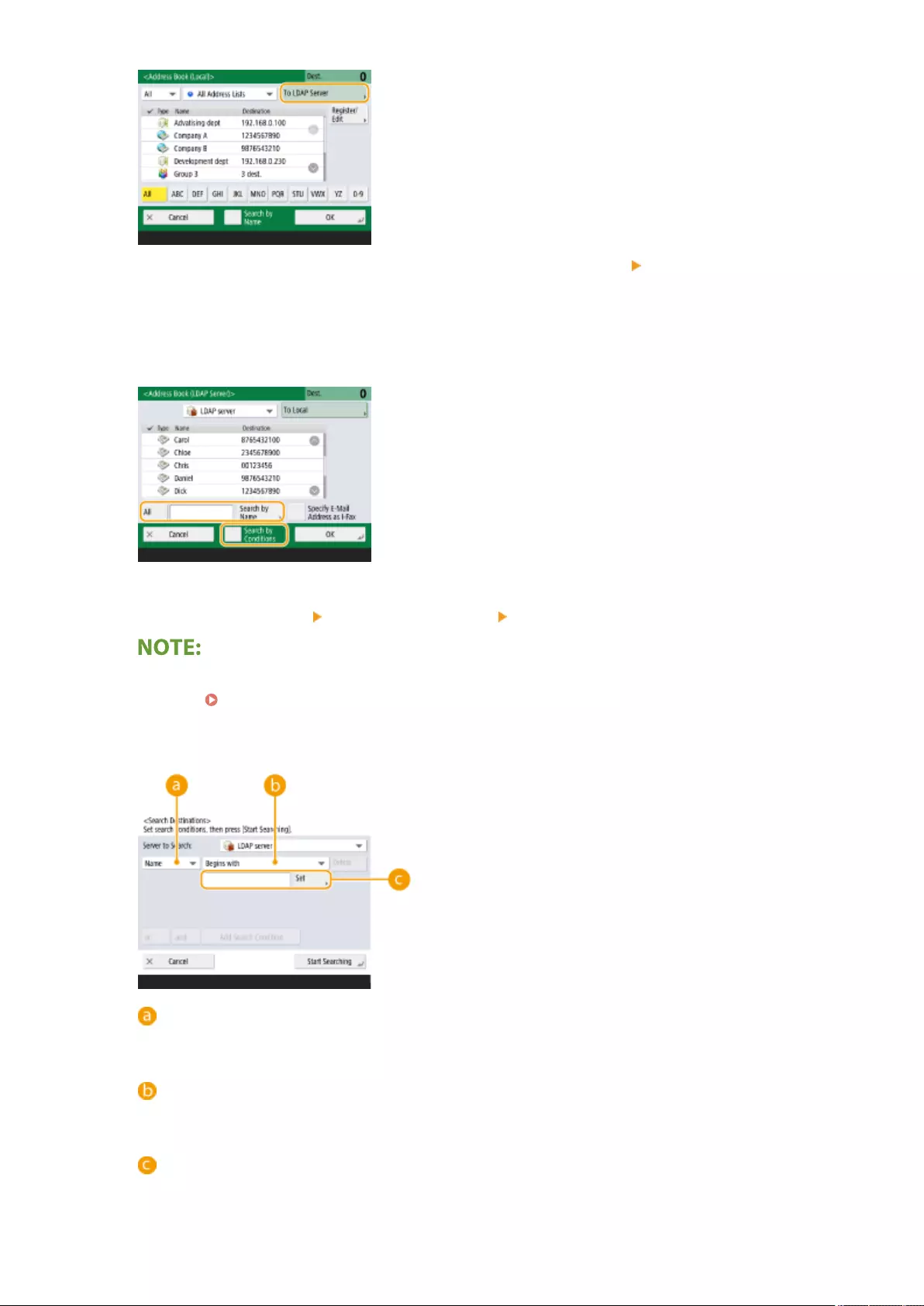
●When <Change Address Book> is displayed, press <Change Address Book> <LDAP Server>.
●If the network password input screen is displayed, enter the user name and password and press <OK>.
3When searching destinations in the LDAP server, press either <Search by Name> or
<Search by Conditions>.
■When searching by name
Press <Search by Name> enter the text to search press <OK>.
●You can specify attributes used when performing "Search by Name" for a destination from the LDAP
server. <Settings for Search by Name When Using LDAP Server>(P. 851)
■When searching by conditions
Press <Search by Conditions>, specify the search conditions on the screen, and press <Start Searching>.
Search categories
Select a criterion to search for destinations from name, fax number, organization name, and organization
unit (department name, etc).
Search conditions
Select a search condition such as a destination name that contains "John" and a department name that
begins with "Development."
Search characters
Press <Set> and enter search characters for the search condition.
Faxing
334
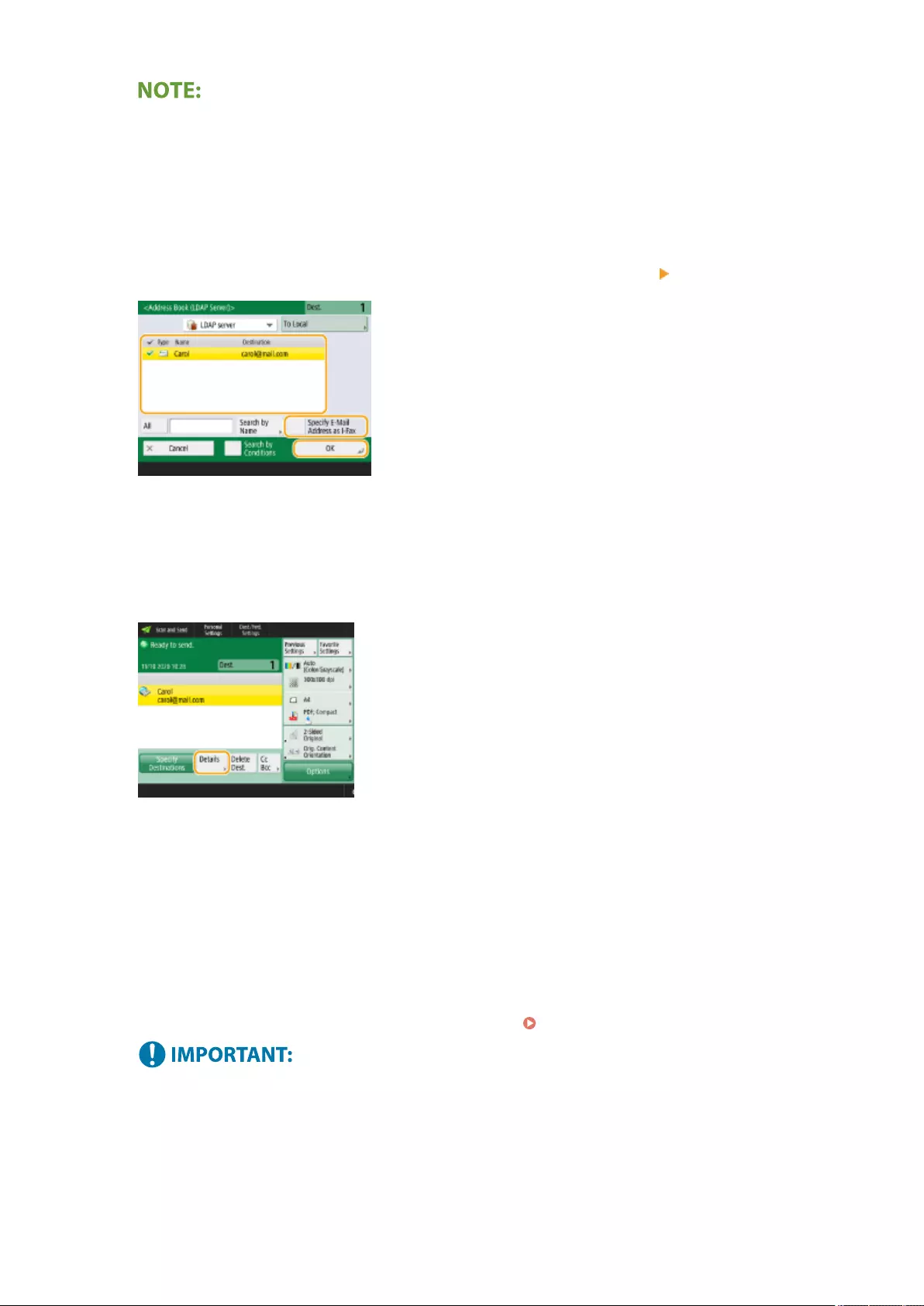
To search with multiple conditions
●You can search destinations with multiple conditions. Specify the rst search condition, press <Add Search
Condition>, and then select <or> or <and> for the next condition.
To change conditions and search again
●Press <Delete> to delete the specied contents, and specify the conditions again.
4Select destination and press <Specify E-Mail Address as I-Fax> <OK>.
5Check the displayed message and press <OK>.
6Press <Details>.
7Specify the receiving conditions the recipient supports and press <OK>.
●Press <Destination Conditions> and select the functions the recipient supports. Be sure to check the receiving
functions the destination before specifying the conditions.
●In <Compression Method>, the compression ratio of les increases in the order of MH→MR→MMR, so
shortens transmission time.
●In <Divide Data>, select <On> to divide send large amounts of document data for sending. If the recipient
does not have the function to combine divided data, select <Off>. For the <Off> setting, a transmission error
occurs when the size of send data exceeds a certain value. <Maximum Data Size for Sending>(P. 827)
●Specifying the conditions the recipient does not support may cause a transmission error.
8Press <OK>.
Faxing
335
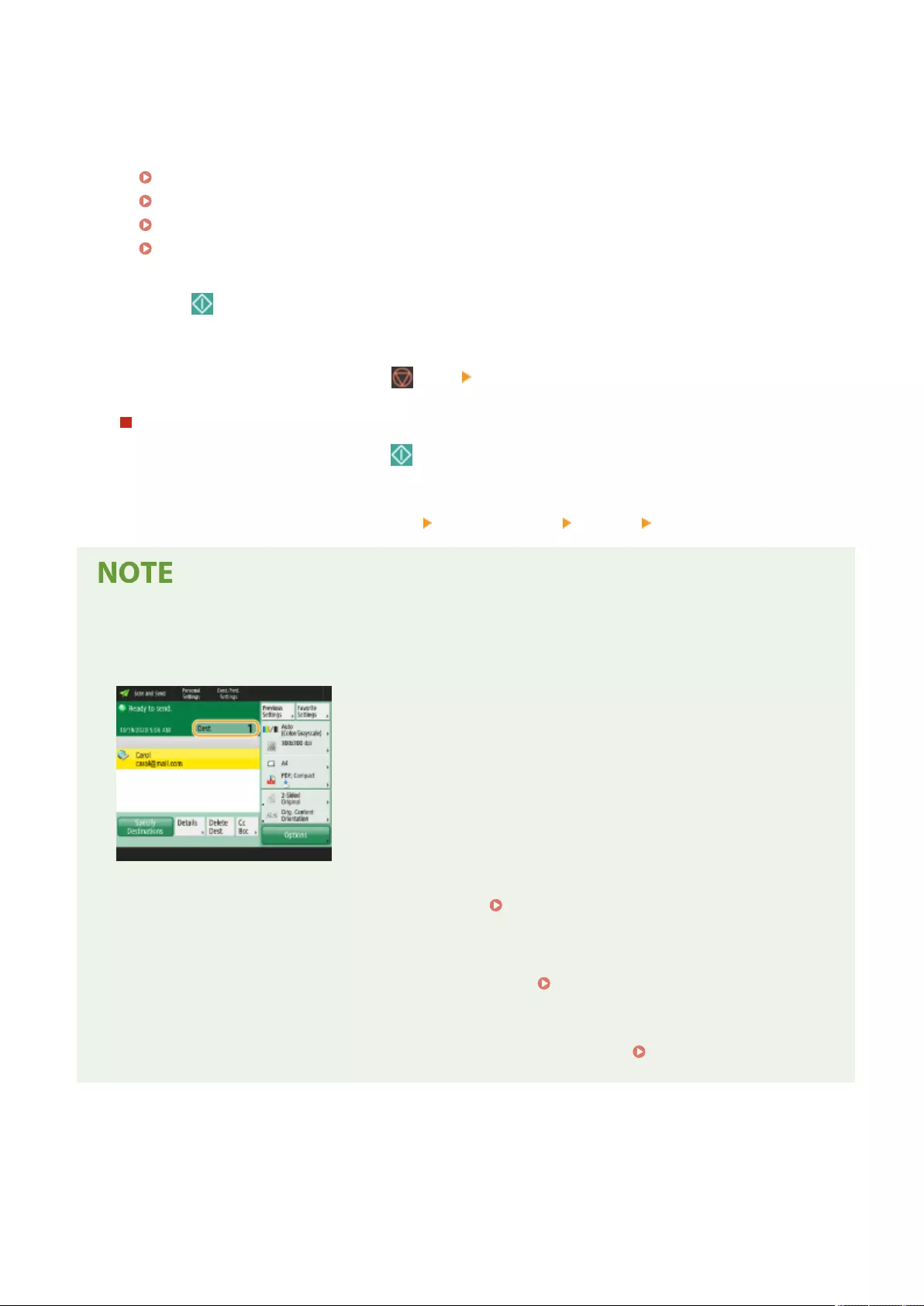
4Press <Options> and specify the scan settings as necessary.
●See the following for details.
Basic Operations for Scanning Originals(P. 377)
Scanning Clearly(P. 394)
Scanning Eciently(P. 401)
Useful Scanning Functions(P. 404)
5Press (Start).
➠Originals are scanned and sending starts.
●To cancel scanning, press <Cancel> or (Stop) <Yes>.
When <Press the [Start] key to scan the next original.> is displayed
Place the next original to scan and press (Start). When scanning all of the originals is complete, press <Start
Sending> to send the I-fax.
●To cancel sending, press <To Status Mntr.> select a document <Cancel> <Yes>.
To check the total number of specied destinations
●The total number of specied destinations is displayed on the top of the screen. This enables you to conrm
that the number of destinations is correct before sending.
To send with the sender information
●You can send with the sender's name and I-fax address. <TX Terminal ID>(P. 821)
To check the statuses for sent documents
●On the <Status Monitor> screen, you can check the statuses for sent documents. This screen enables you to
send faxes again or cancel sending after checking the statuses. Checking Status and Log for Sent and
Received Documents(P. 321)
●When <Display Notication When Job Is Accepted> is set to <On>, the <Status Monitor> screen can be
displayed from the following screen that is shown after a send job is received. <Display Notication
When Job Is Accepted>(P. 825)
Faxing
336
To print the report for the results of sending
●On the Scan Basic Features screen, pressing <Options> <TX Result Report> enables you to set to
automatically print the report listing the results of sending. Checking Status and Log for Sent and
Received Documents(P. 321)
●To set this for each job from <Options>, it is necessary to select <For Error Only> or <Off> in <TX Result
Report>(P. 820) , and then set <Allow Printing from Options> to <On>.
To send les securely
●Using TLS communication enables you to send an encrypted le. Conguring the Key and Certicate for
TLS(P. 549)
When photos in the sent image are too dark or light colors in the background of color
originals cannot be removed
●The quality of the sent image may be able to be improved if the following conditions/settings are met.
- Job type: Fax (Memory Sending) or Scan and Send (Fax/I-fax)
- <Select Color>: <Black & White> (Scan and Send)
- <Original Type>: <Text>
- <Density> <Background Density>: <Auto>
- <Resolution>: 200 dpi x 400 dpi, 300 dpi x 300 dpi*, 400 dpi x 400 dpi, or 600 dpi x 600 dpi*
*Can be set for Scan and Send
- <Speed/Image Quality Priority for Black & White Scan> Fax/I-Fax Send Jobs: <Quality Priority> <Speed/
Image Quality Priority for Black & White Scan>(P. 811)
Checking scanned images before sending
●You can check scanned images on the preview screen before sending. Checking Scanned Originals
Before Sending/Saving (Preview)(P. 405)
Registering frequently used settings
●You can combine frequently used destinations and scan settings into a button of the machine for later use.
By pressing the registered button when scanning originals, you can quickly complete your settings.
Registering a Combination of Frequently Used Functions(P. 164)
LINKS
Registering Destinations(P. 190)
Registering the LDAP Server(P. 53)
<Set Destination>(P. 849)
Faxing
337
Receiving I-Faxes
72JY-05S
◼When an I-fax is received
The Processing/Data indicator on the control panel blinks green. When receiving is complete, the document is
automatically printed and the indicator turns off.
●To cancel receiving, press <Status Monitor> <Receive> <Job Status> select a document <Cancel>.
●You can specify the time before reception is canceled when receiving a divided I-fax and the subsequent
data cannot be received. Data received by the specied time is printed. <Divided Data RX
Timeout>(P. 839)
◼To receive I-faxes manually
Press <Status Monitor> <Receive> <Job Log> <Check I-Fax RX>. Pressing <Fax/I-Fax Inbox>( <Home>
Screen(P. 119) ) <Memory RX Inbox> <Divided Data RX Inbox> enables you to check the receiving statuses of I-
faxes divided and their data size.
●You can save paper when printing.
<Print on Both Sides>(P. 835)
<Reduce Fax RX Size>(P. 835)
●You can include information, such as reception time, in received documents when printing. <Print RX
Page Footer>(P. 835)
LINKS
Various Receiving Methods(P. 312)
Forwarding Received Documents Automatically(P. 318)
Checking Status and Log for Sent and Received Documents(P. 321)
Faxing
338
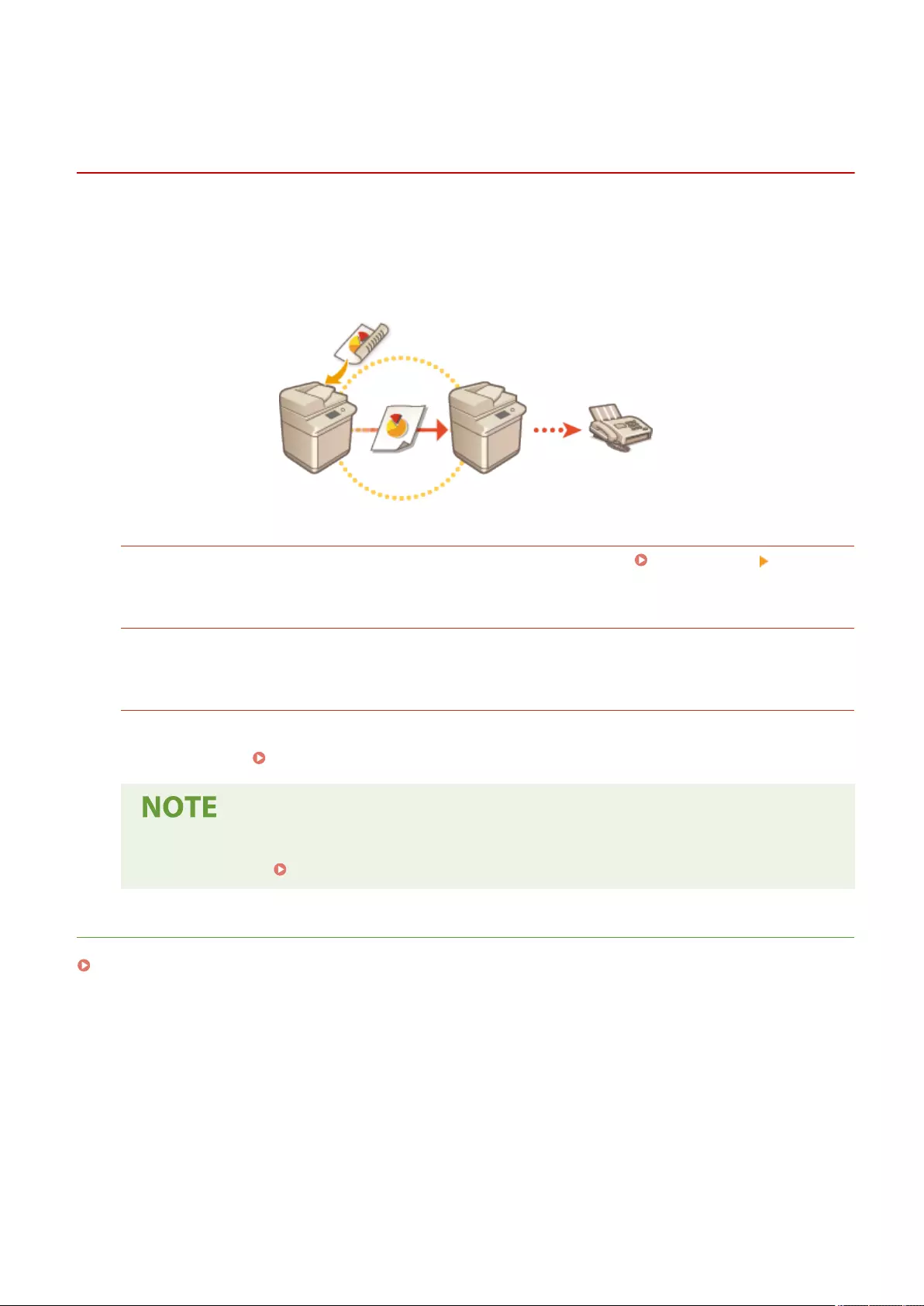
Sending and Receiving Faxes via the Machine (Remote
Fax)
72JY-05U
By specifying this machine as a relay, you can send and receive faxes from another multifunction printer on the same
network, even if it does not have fax functionality. This is called the Remote Fax function. When using this function, the
machine with fax functionality (this machine) and the machine without fax functionality can be likened to a server
machine and client machine, respectively. Sharing fax functionality and communication lines reduces introduction
costs and offers an ecient use of fax functions.
Before Using a Remote Fax
You must specify settings in advance to use this machine as a server machine. <Send>(P. 820) <Remote
Fax Settings>
Sending a Fax
When sending a fax, you only need to operate the client machine. There is no need to operate the server
machine (this machine).
Receiving a Fax
Faxes received by a server machine (this machine) are converted to I-faxes and forwarded to a client machine
via the network. You must specify settings for the server machine (this machine) in advance in order to forward
to a client machine. <Forwarding Settings>(P. 836)
●The sender information of a fax sent from the client machine is printed according to the setting in the
server machine. <TX Terminal ID>(P. 821)
LINKS
Receiving I-Faxes(P. 338)
Faxing
339

Printing
Printing ................................................................................................................................................................ 341
Printing From a Computer ................................................................................................................................ 343
Canceling Printing ........................................................................................................................................ 346
Checking the Printing Status and History ..................................................................................................... 348
Advanced Functions for Printing ...................................................................................................................... 350
Printing Documents Held in the Machine ..................................................................................................... 351
Printing at a Specied Time (Scheduled Printing) ......................................................................................... 355
Various Printing Methods ................................................................................................................................. 357
Directly Printing Files without Opening Them .............................................................................................. 358
Printing Using a Virtual Printer ..................................................................................................................... 360
Printing From Memory Media (Media Print) ................................................................................................. 363
Printing Using the Microsoft Cloud Service (Universal Print) ........................................................................ 364
Conguring the Universal Print User Settings ........................................................................................ 368
Printing
340
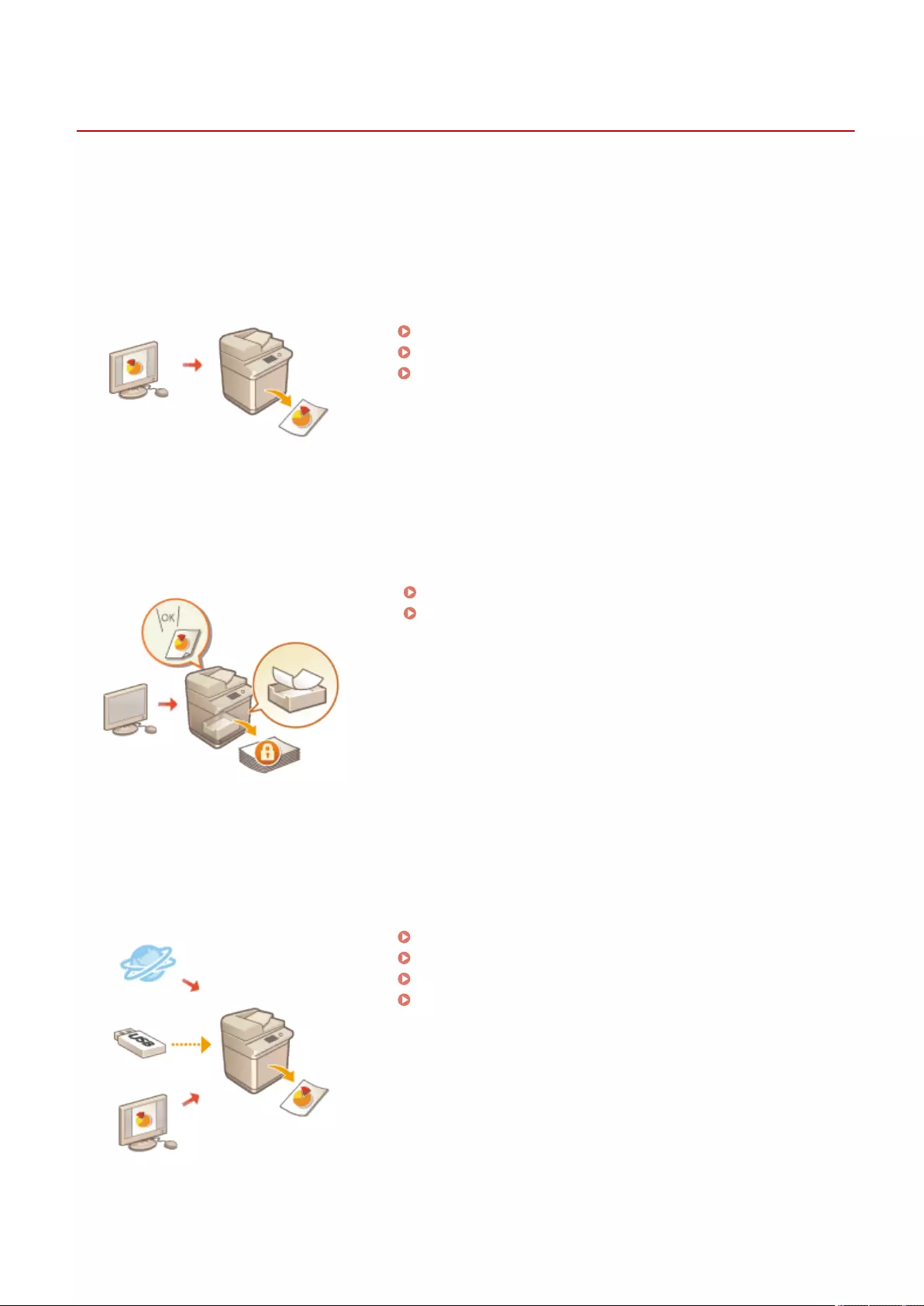
Printing
72JY-05W
PMW-PTIG
You can print documents and images prepared on a computer. This section introduces basic procedures and
convenient printing functions.
◼Introduction of basic operations
This section describes the basic operation methods when printing from a computer.
Printing From a Computer(P. 343)
Canceling Printing(P. 346)
Checking the Printing Status and History(P. 348)
◼Advanced functions for printing
This section introduces functions used when you want to print a sample set or edit the document before printing large
quantities, avoid to leave or to be copied printed paper, etc.
Printing Documents Held in the Machine(P. 351)
Printing at a Specied Time (Scheduled Printing)(P. 355)
◼Printing in various environments
This section introduces printing methods for printing without the printer driver of the machine such as printing
without your computer during a business trip, etc.
Directly Printing Files without Opening Them(P. 358)
Printing Using a Virtual Printer(P. 360)
Printing From Memory Media (Media Print)(P. 363)
Printing Using the Microsoft Cloud Service (Universal Print)
(P. 364)
Printing
341
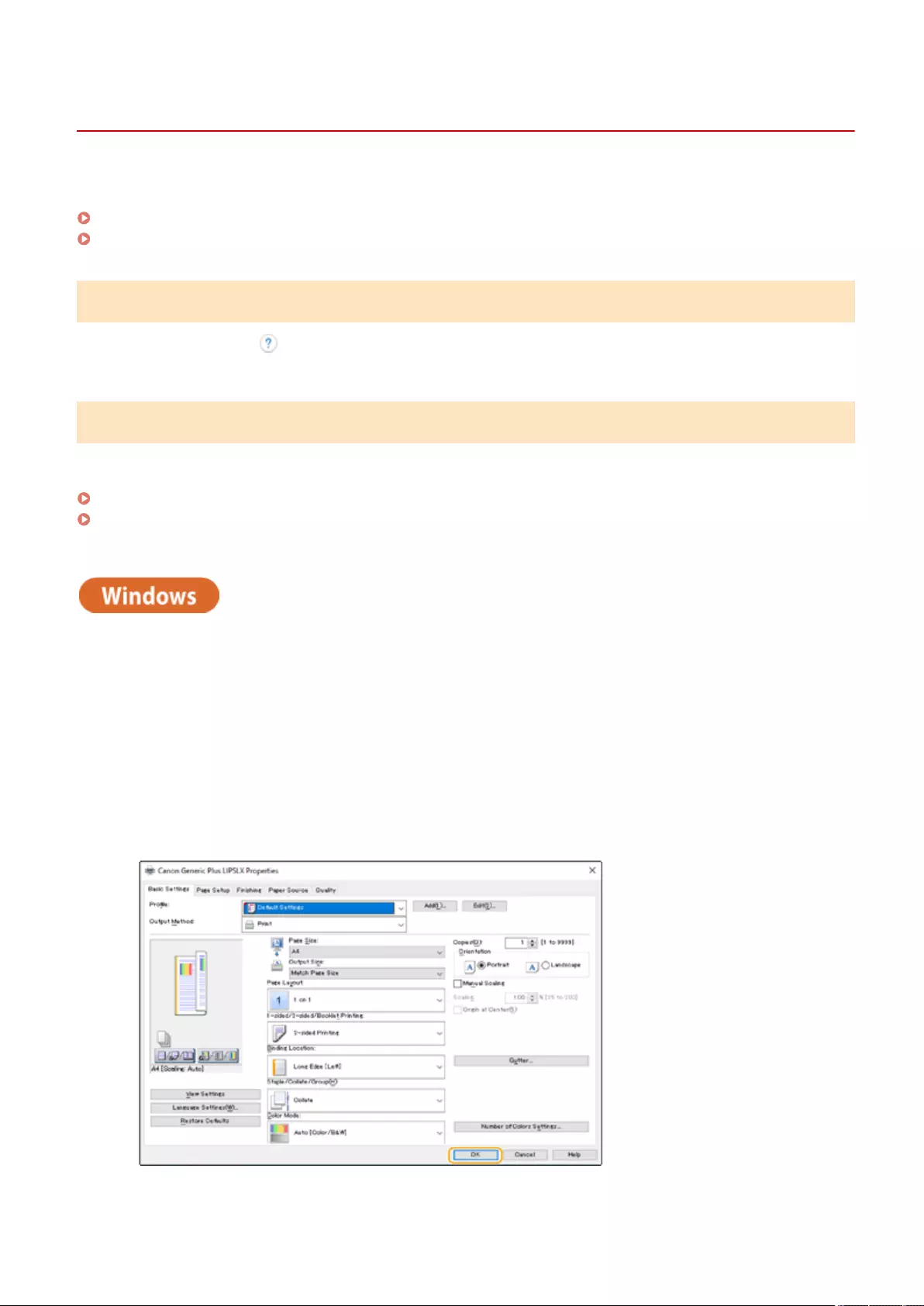
Printing From a Computer
72JY-05X
This section describes basic printing from a computer with the printer driver installed.
Help for Printer Drivers(P. 343)
Basic Printing Operations(P. 343)
Help for Printer Drivers
Clicking [Help] (Window) or (Mac OS) on the printer driver setting screen displays the Help screen. For information
that is not in the User's Guide, including about driver features and how to set up those features, see Help.
Basic Printing Operations
This section describes the basic ow when printing from a computer.
In case of Windows(P. 343)
In case of Mac OS(P. 344)
In case of Windows
1Open a document and display the print screen.
2Select the machine and click [Preferences] or [Properties].
3Specify the print settings as necessary and click [OK].
●Switch tabs as necessary to specify the desired print settings.
Printing
343
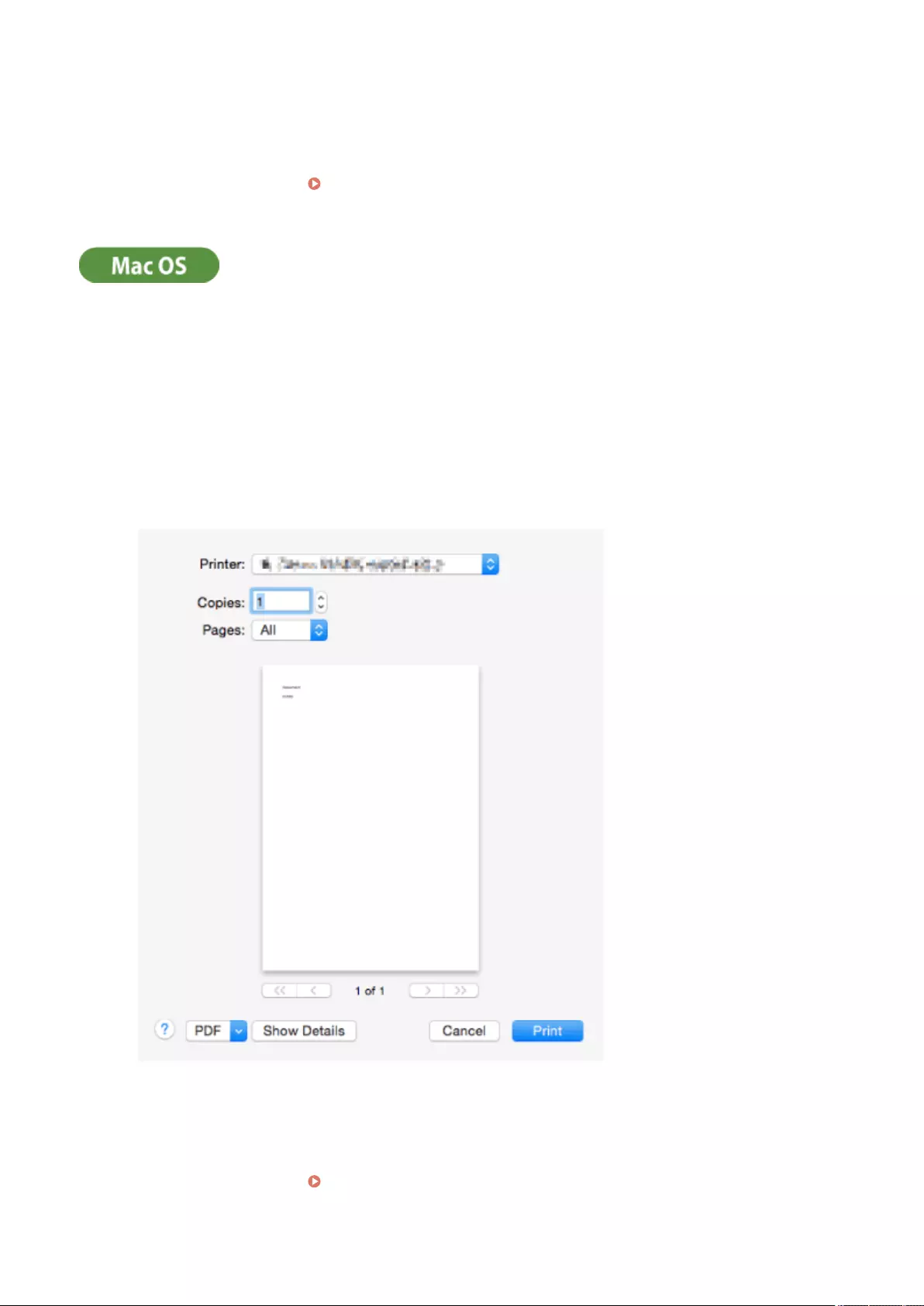
4Click [Print] or [OK].
➠Printing starts.
●If you want to cancel, see Canceling Printing(P. 346) .
In case of Mac OS
1Open a document and display the print screen.
2Select the machine.
3Specify the print settings as necessary.
●After selecting the setting panel from the drop-down list, set for printing on each panel.
4Click [Print].
➠Printing starts.
●If you want to cancel, see Canceling Printing(P. 346) .
Printing
344
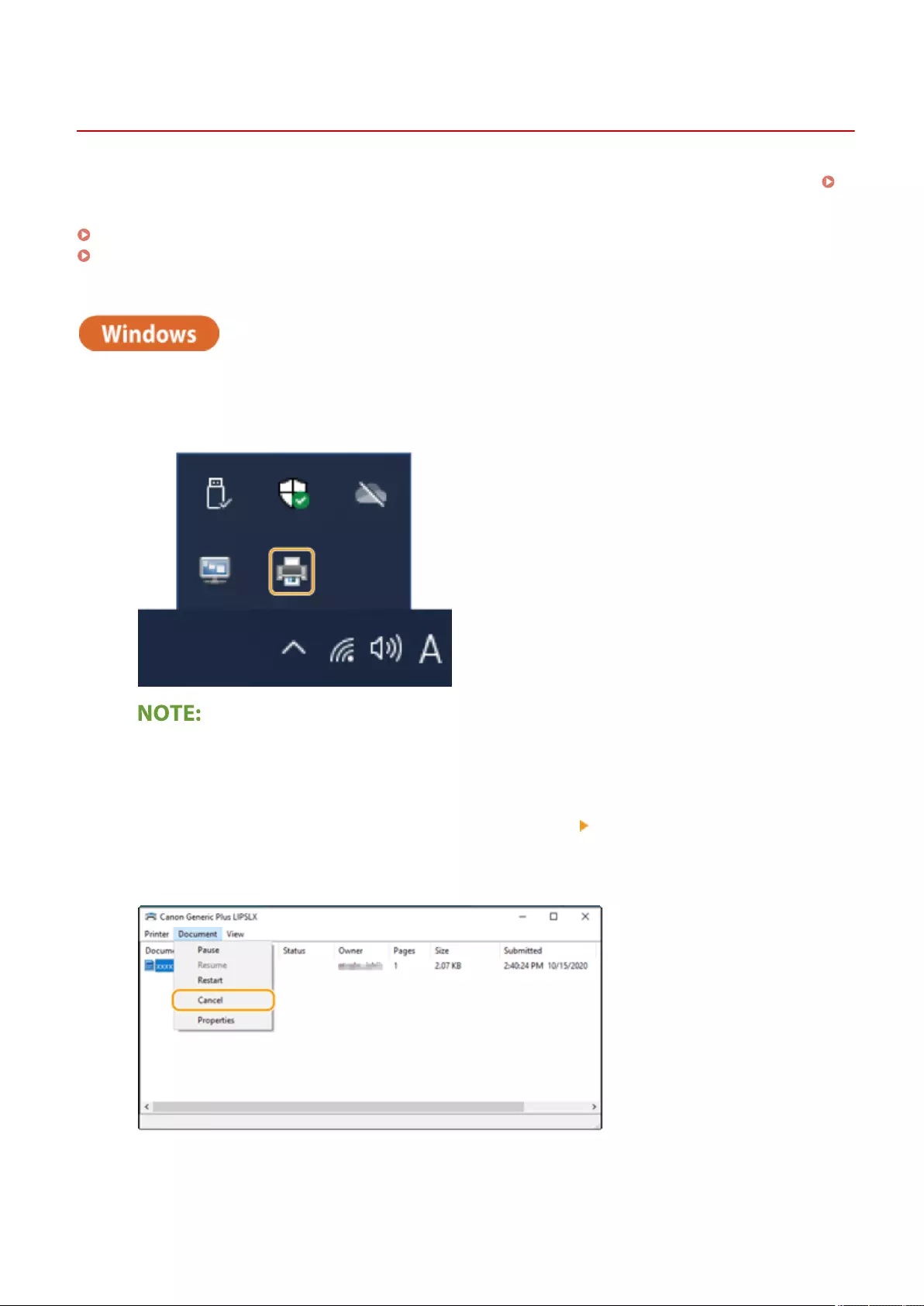
Canceling Printing
72JY-05Y
You can cancel printing before it has nished. You can also cancel a print job on the control panel of the machine.
Checking the Printing Status and History(P. 348)
In case of Windows(P. 346)
In case of Mac OS(P. 347)
In case of Windows
1Double-click the printer icon on the system tray in the lower-right of the screen.
When the printer icon is not displayed
●Open the printer folder, and click or double-click the icon for the machine.
2Select the document to cancel and click [Document] [Cancel].
●If you cannot nd the document to cancel, the document is already sent to the machine. In that case, you
cannot cancel the printing on the computer.
3Click [Yes].
➠Printing is canceled.
Printing
346
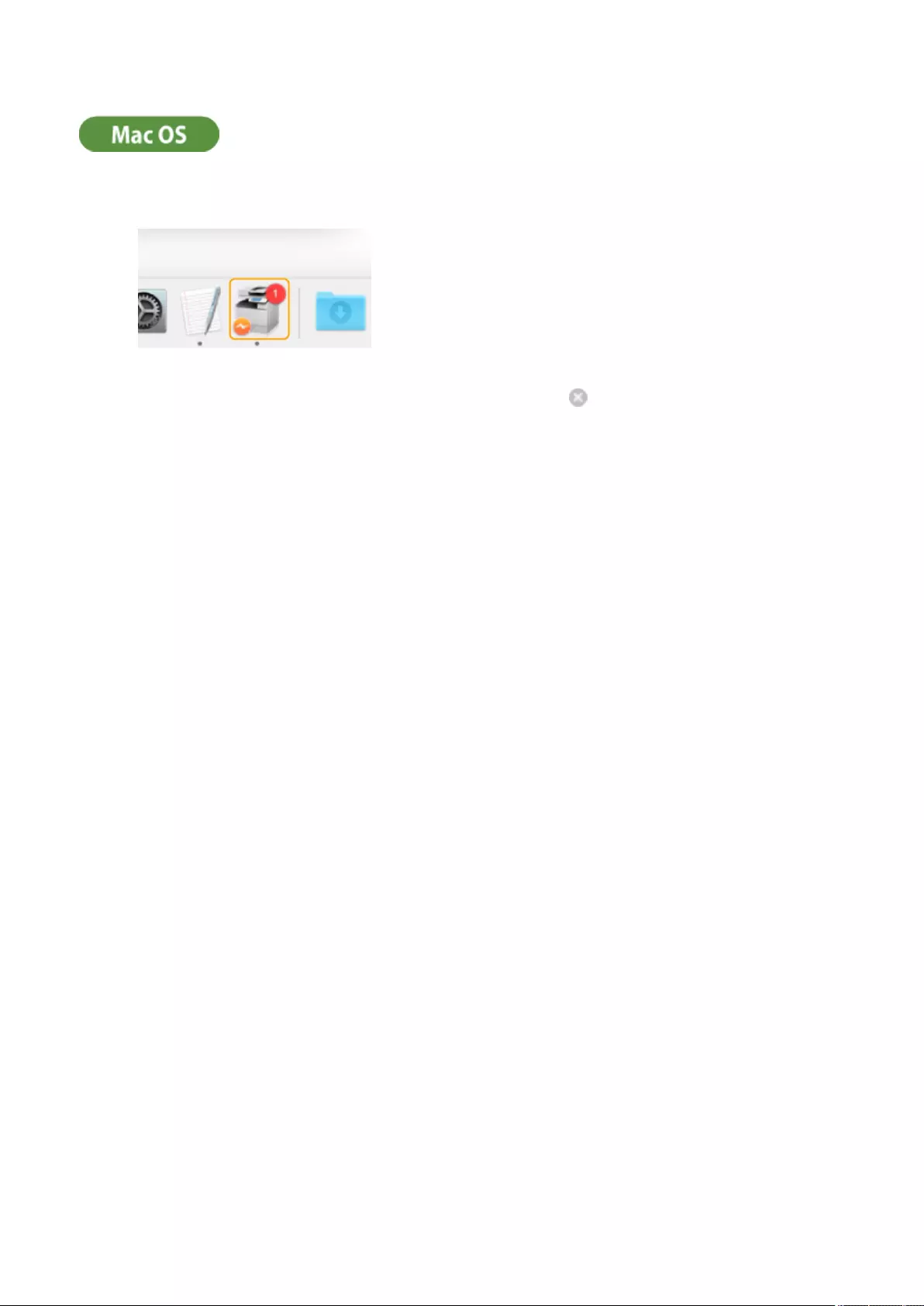
In case of Mac OS
1Click the printer icon displayed on the Dock.
2Select the document to cancel and click [Delete] or .
➠Printing is canceled.
Printing
347

Checking the Printing Status and History
72JY-060
You can check the wait status for print jobs and whether or not an error has occurred during printing. Operations such
as printing the document ahead of other documents and temporarily suspending or canceling printing are possible as
well.
●When personal authentication management is used, you can restrict users from performing operations on
the jobs of other users on the <Status Monitor> screen. <Restrict Access to Other User Jobs>(P. 857)
1Press (Status Monitor).
2Press <Copy/Print> <Job Status>.
●To display only the documents to be printed, select <Print> from the drop-down list in the upper-right of the
screen.
3Check the status.
●Pressing <Details> after selecting a document, enables you to cancel printing, to check the status of the job,
etc.
●Pressing <Cancel> after selecting a document, enables you to cancel printing.
●When pressing <Interrupt/Priority Print> after selecting a document, <Interrupt and Print> and <Priority
Print> appear. Press <Interrupt and Print> to suspend a print job in process and immediately start printing
the document selected. Press <Priority Print> to jump the selected document to the top of the waiting list,
and print it after printing the print job in progress.
●To ignore an error and continue printing, press <Details> select a document <Skip Error>.
●To forcibly print any unprinted job in the machine, press <Details> select a document <Paper Feed>.
●You cannot interrupt an interrupt print job with another job. If you try to interrupt an interrupt print job, the
job is started after the current interrupt job is complete.
Printing
348

◼Checking the printing history
Press <Job Log> to display a list of printed documents. If a document is printed without problems, the <Result> column
displays <OK>. If <NG> is displayed, it shows that printing was canceled or an error occurred.
●To see the detailed information, press <Details> after selecting a document.
●To print a history list, press <Print List>.
LINKS
Canceling Printing(P. 346)
Printing
349

Print
Printing Documents Held in the Machine
72JY-062
You can temporarily hold print data in the machine and print it from the control
panel when required.
You can also set the machine to always hold print data. The Secure Print function can
be used even when the Forced Hold setting is disabled.
<Forced Hold>(P. 846)
Restricting Printing from a Computer(P. 573)
●The Forced Hold mode needs to be set in advance. <Print> <Forced Hold>(P. 846)
●Up to 200 users can use this mode. If a document which is shared with several people is retained in the
machine, only the user who sends the job is counted.
●You can store up to 2,000 jobs.
●At least 4 GB is guaranteed for storing retained documents.
●The maximum size of a retained document that can be stored is 2 GB.
●The documents retained in the machine are saved even if the machine is turned OFF.
●Note that documents are automatically deleted after a specied period of time passes. Please consult your
administrator regarding the length of this time period.
1Press <Print>. <Home> Screen(P. 119)
2Select a document.
Personal/Shared/Group
<Personal>/<Shared>/<Group>
●<Personal>: Displays the documents sent by the user who is logged in.
●<Shared>: Documents held based on specic conditions according to forced hold settings are displayed.
All users can display/print these documents.
●<Group>: Displays documents that have the same group information as the user who is logged in. Uses
Department IDs to identify groups.
Printing
351
Document list
●Documents which match the document type selected in the drop-down list and their related
information are displayed in a list format.
●When a document is selected, which indicates "selected" is displayed. When multiple documents
are selected, the numbers in the center of are displayed as 1, 2, 3 ... in the order selected. When
you press a selected document, the selection is canceled.
●Press <Date/Time> to sort the documents by date/time, in ascending ( ) or descending ( ) order.
●If you log in with personal authentication management, the last sorting condition is retained. List of
Items That Can Be Personalized(P. 139)
●Secured print or encrypted secured print documents display next to the number of sheets x number
of copies on the job list.
●If <Display Warning on Job List Screen> is set to <On> in <Held Jobs Warning Settings>, is displayed
on the job list for documents that match the specied conditions. If <Display Warning on Job List
Screen> is set to <On> in <Held Jobs Warning Settings>, a warning pop-up is displayed when printing,
for documents that match the specied conditions. <Held Jobs Warning Settings>(P. 847)
●You can print from here if the printer driver output method is set to [Secured Print].
Jobs to Be PrintedJobs PrintedScheduled Print
<Jobs to Be Printed>/<Jobs Printed>/<Scheduled Print>
When selecting an unprinted document, conrm that <Jobs to Be Printed> is selected.
Update button
Updates the document list.
Start Printing
<Start Printing>
Executes printing.
Other Operations
<Other Operations>
●<Cancel Printing>:Cancels printing.
●<Delete Job>:Deletes documents.
●<Display Image>:Enables you to check the contents of the document as well as select and delete
pages.
●You cannot restore a page that has been deleted.
●You cannot delete a page from <Display Image> if it is the only page there.
●Previews may not be available with <Display Image>, depending on the settings of the printer driver.
●For information on the page description languages that enable previewing and the le formats for
direct printing, see Printer Functions.
●<Delete Page> from <Display Image> of the PrintRelease function of Canon PRINT Business is not
supported.
●If the message < Failed to delete the page. > is displayed when deleting a page, press <Delete Page> in
< Preview > again.
Print Settings
<Print Settings>/<Print Set. for Selected Jobs>
You can edit the printing settings such as number of copy. You can also change the print settings when
multiple documents are selected.
●You can print a sample set with the settings specied in Print Settings by pressing <Print Sample>.
●Depending on changed settings, the document may not be printed correctly.
Printing
352
●If you change the settings on <Print Settings>/<Print Set. for Selected Jobs>, the document in which the
new settings are applied is displayed in <Printed>.
●If you select general print jobs, secured print jobs, and encrypted secured print jobs at the same time,
you cannot change the print settings of them at once.
●The settings may not be able to be changed in <Print Settings>, depending on the settings of the printer
driver.
●For information on the page description languages that enable the conguration of print settings and
the le formats for direct printing, see Printer Functions(P. 1088) .
●You cannot change the print settings of multiple jobs at once when using the PrintRelease function of
Canon PRINT Business.
Select All (Max 100 jobs)Clear Selection
<Select All (Max 100 jobs)>/<Clear Selection>
If a document is not selected in , <Select All (Max 100)> is displayed, which enables you to select all the
documents in the document list. When documents are selected, <Clear Selection> is displayed enabling
you to cancel the entire selection.
●The messages <Some jobs could not be stored after being received.> and <Some jobs have been deleted.>
may be displayed if an error occurs when receiving a document or a document is automatically deleted
because its retention period has elapsed, etc. In this case, press to cancel the message.
3Press <Start Printing>.
➠Printing starts.
●To cancel printing, select the job to cancel in <Jobs Printed>, and select <Cancel Printing>. You can also
press (Stop) on the control panel and select the job to cancel from <Print Jobs>. For information on
canceling jobs with the Stop key, see Canceling Send/Print Jobs(P. 183) .
Automatically Printing Forced Hold Print Jobs after Logging In
You can set to automatically print jobs when a user logs in. When the administrator has set <Enable Auto
Print Function When Logging In>(P. 847) to <On>, users that are logged in with personal authentication
management can set whether automatic printing is performed or not. Set <Auto Print User Jobs When
Logging In>(P. 848) to <On> to perform automatic printing. The setting is retained for each user. List of
Items That Can Be Personalized(P. 139)
●The following jobs are not automatically printed even if this setting is enabled.
- <Personal> jobs of other users, <Shared> jobs, and <Group> jobs
- Printed jobs
- Encrypted secure printing jobs
- Secure printing jobs (when <Require PIN for Printing/Displaying User Jobs> is set to <On> in <PIN
Settings for Secure Print Jobs>(P. 847) )
●When multiple jobs are held, they are printed in the display order of <Date>.
Printing
353

●A maximum of 100 jobs can be printed with a single login operation.
●If jobs are already held, this setting is enabled by logging in again after setting <Auto Print User Jobs
When Logging In> to <On>.
Printing More Safely with Encrypted Secure Print
By using Encrypted Secure Printing, you can send encrypted printing data to a machine from your computer. This
enables you to reduce the risk of information leaks when sending printed data, and to print more safely. Use this
especially when printing highly condential documents.
●The document with Encrypted Secure Printing is displayed along with on the setting change screen.
●To print the encrypted document, you must enter the password. The password must be the same as the
password you set on the printer driver.
●For information on setting items, see "Help" by clicking [Help] on the printer driver setting screen (Windows
only).
●Encrypted Secure Print cannot be used with Mac OS.
●To use encrypted secure printing, display the printer folder right-click the icon for the machine select
[Printer properties] see the [Help] on the [Encrypted-P]tab. For information on displaying the printer
folder, see Displaying the Printer Folder(P. 1080) .
Printing
354
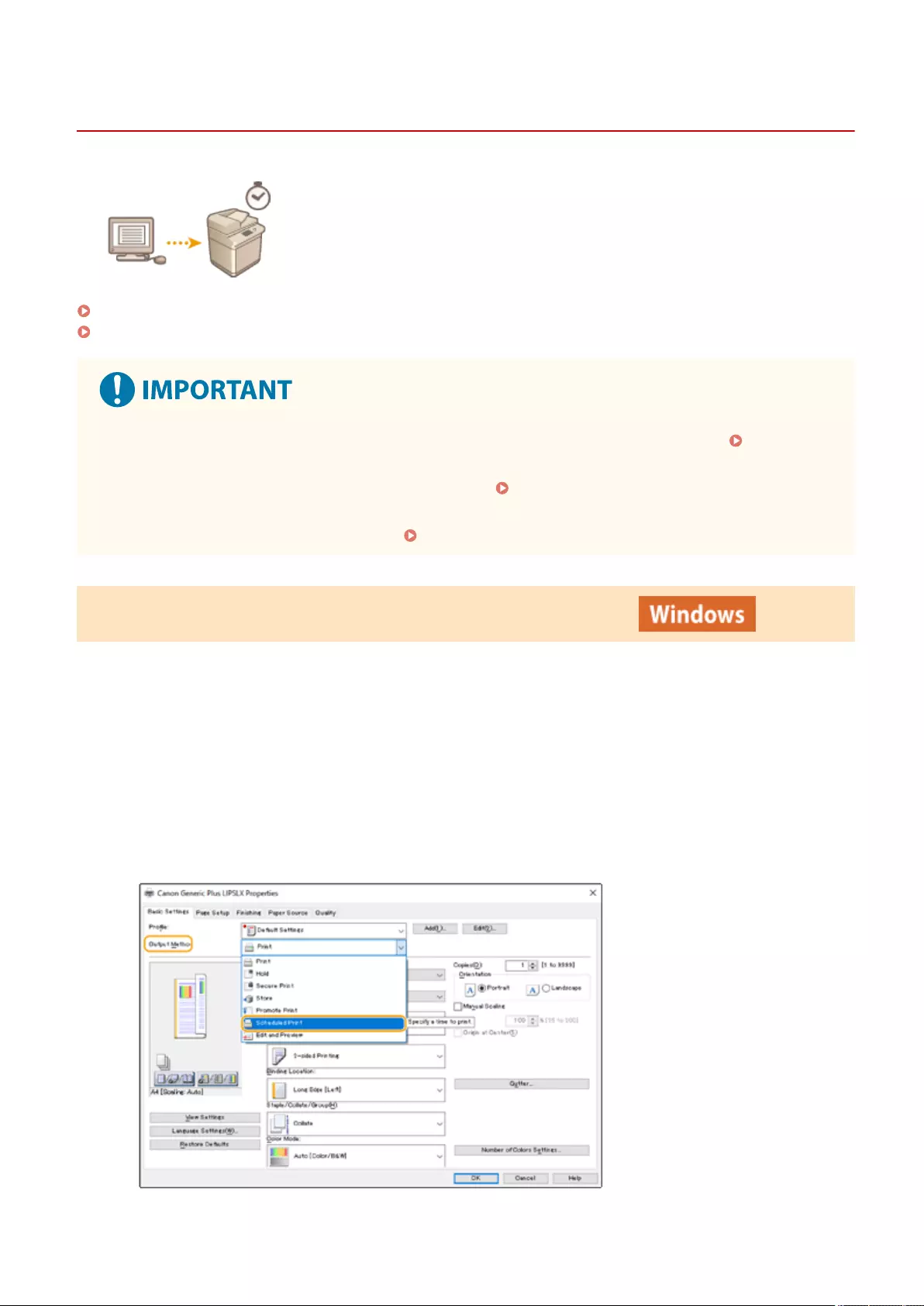
Printing at a Specied Time (Scheduled Printing)
72JY-063
You can set a time to start printing, which is useful when printing large amounts of
documents at night, etc.
Sending Scheduled Print Documents from a Computer (Windows)(P. 355)
Checking the Scheduled Print Jobs(P. 356)
●To use the scheduled print function, it is necessary to set <Forced Hold> to <Off> in advance. <Forced
Hold>(P. 846)
●To use the scheduled print function, it is necessary to set <Use ACCESS MANAGEMENT SYSTEM>(P. 862)
to <Off> in advance.
●The scheduled print jobs are deleted when <Use ACCESS MANAGEMENT SYSTEM>(P. 862) is set to <On>.
Sending Scheduled Print Documents from a Computer (Windows)
1Open the document and display the print screen.
●For information on displaying the print screen, see the help for the application.
2Select the machine, and click [Details] or [Properties].
3Select [Scheduled Print] for [Output Method].
Printing
355

4Specify [Print Start Time] in [Scheduled Print Details], and click [OK].
5Congure the print settings as necessary, and click [OK].
6Click [Print] or [OK].
➠The document is sent to the machine.
●The scheduled print jobs are executed according to the time set in the machine. Conrm that the time set in
the machine matches that of your computer in advance.
●If a print job is scheduled at a time longer than 24 hours in advance, the job is canceled.
●A print start time between 0:00 and 23:59 is specied on the printer driver screen, but the time is processed
in the format year, month, day, hour, minute, and second (with the second xed to 0).
Checking the Scheduled Print Jobs
1Press <Print>. <Home> Screen(P. 119)
2Press <Scheduled Print>, and check the print jobs waiting to be output.
●The scheduled print date and time can be checked in <Scheduled>.
●To delete a print job, select the document, and press <Delete Job>.
●Scheduled print jobs are deleted after they are executed. They are also not displayed in <Jobs Printed>.
Printing
356
Various Printing Methods
72JY-064
This section introduces printing method using the Remote UI, or how to print a le stored in memory media.
Directly Printing Files without
Opening Them(P. 358)
Printing Using a Virtual
Printer(P. 360)
Printing From Memory Media
(Media Print)(P. 363)
Printing Using the Microsoft
Cloud Service (Universal Print)
(P. 364)
Printing
357
Directly Printing Files without Opening Them
72JY-065
By using remote UI, it is possible to print les saved on a computer or network
directly from the machine without using the printer driver. You do not need to open
les on the computer for printing.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Direct Print] on the portal page. Remote UI Screen(P. 585)
3Select a le format and then a le.
4Specify the print settings as necessary.
●If a password is set for the PDF le, press [Specify PDF File] enter the password in [Document Password].
When printing PDF les linked to the policy server, select [Specify PDF File] enter the policy server user
name in [Policy Server User Name] and the policy server password in [Policy Server Password].
●To print the PDF le which is prohibited for printing, or to print PDF les that only allow low-resolution
printing in high resolution, enter the master password.
●Depending on the selected paper size, PDF/XPS les may be canceled on printing.
5Click [Start Printing].
➠Printing starts.
Printing
358

●Do not click [Start Printing] repeatedly during le transfer. Otherwise, le malfunction may occur and the le
may not be transferred.
●Printing may not be performed properly depending on the data.
●If printing with Direct Print is not possible or the printing position deviates, opening les from the
application and using the printer driver may enable proper printing.
Printing
359
Printing Using a Virtual Printer
72JY-066
A virtual printer enables you to use LPD printing or FTP printing with the print
settings registered as a virtual printer in advance. For example, registering
settings such as the paper type, number of copies, and two-sided printing in
advance eliminates the need to specify these settings for each job.
Adding a Virtual Printer(P. 360)
Printing with a Virtual Printer(P. 361)
●Set <Forced Hold>(P. 846) to <Off>. If <Forced Hold> is set when a job is executed, the results may
differ depending on the settings. Conguring the Forced Hold Printing Settings(P. 573)
- If the job matches the set conditions for <Job Action> and <Cancel>: The job is canceled.
- If the job matches the set conditions for <Job Action> and <Print>: The job is printed according to
the virtual printer.
- If the job matches the set conditions for <Job Action> and <Hold as Shared Job>: The virtual printer
is disabled and the job is held in the machine.
●For Secure Print and Encrypted Secure Print, the virtual printer is disabled and the job is held in the
machine.
●Set <LPD Print Settings>(P. 784) to <On> to perform LPD printing.
●Set <FTP Print Settings>(P. 785) to <On> to perform FTP printing.
●The page description language and le format that can be used with a virtual printer is PS and PDF.
Adding a Virtual Printer
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Printer] [Virtual Printer Management].
4Click [Add Virtual Printer].
Printing
360
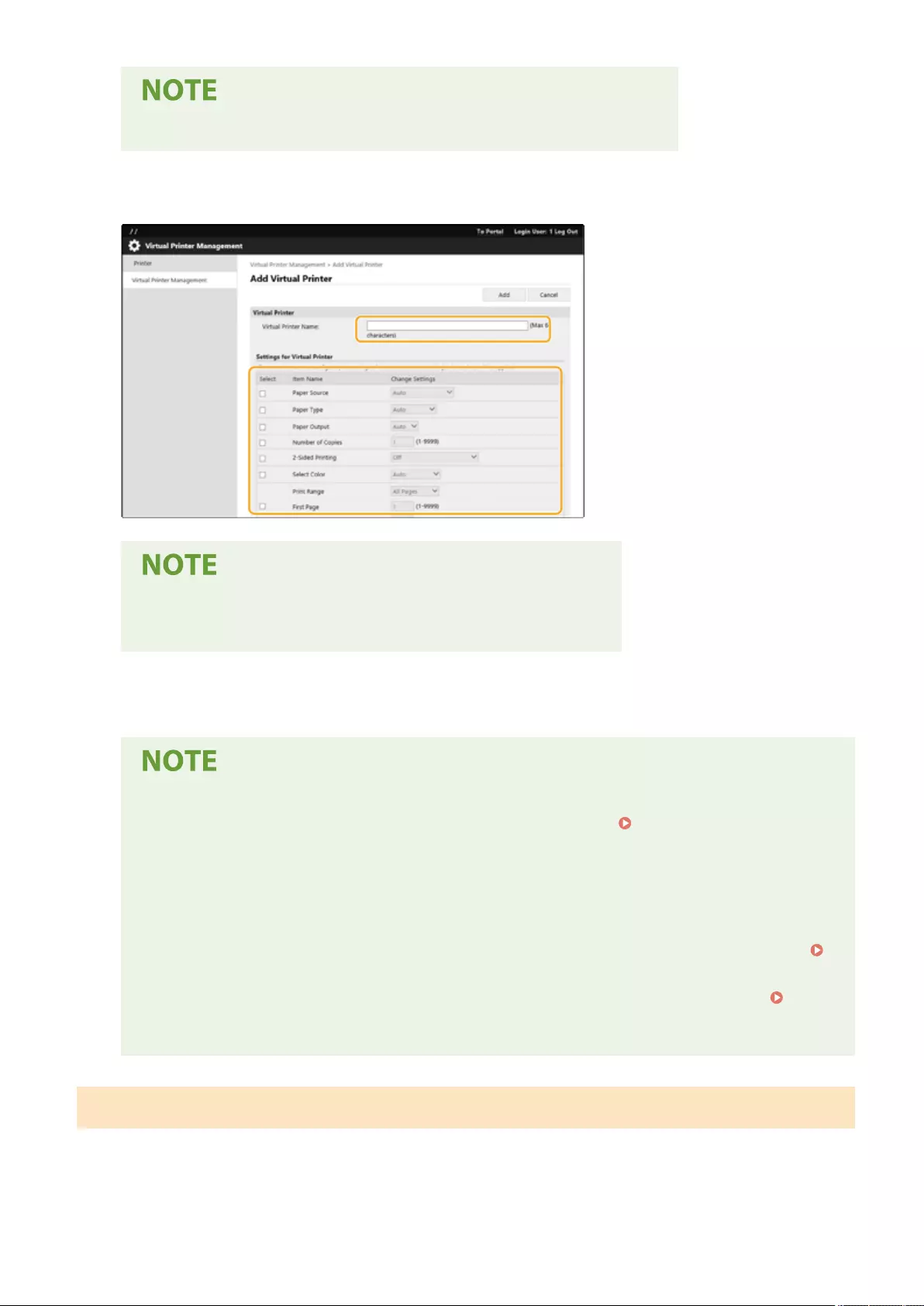
●Operations cannot be performed from multiple browsers at the same time.
5Enter the virtual printer name and specify the required settings.
●Multiple virtual printers with the same name cannot be registered.
●A maximum of 20 virtual printers can be registered.
6Click [Add].
●You are required to log in to the Remote UI with any of the following privileges to perform this
setting. For more information, see the items in [Select Role to Set:] in Registering User
Information in the Local Device(P. 495) .
- Administrator
- DeviceAdmin
- NetworkAdmin
●This setting can be imported/exported with models that support batch importing of this setting.
Importing/Exporting the Setting Data(P. 625)
●This setting is included in [Settings/Registration Basic Information] when batch exporting.
Importing/Exporting All Settings(P. 628)
Printing with a Virtual Printer
For LPD printing
●LPR -S [IP address of the machine] -P [virtual printer name] [le name]
Example: Printing "sample.pdf" with a virtual printer named "001"
lpr -S IP address of the machine -P 001 sample.pdf
Printing
361

For FTP printing
●put [le name] [virtual printer name]
Example: Printing "sample.pdf" with a virtual printer named "001"
> put sample.pdf 001
Printing
362

Printing From Memory Media (Media Print)
72JY-067
It is possible to print les saved on memory media directly from the machine without
using a computer. This is convenient when printing after bringing data back from an
outside location or when printing data you have brought with you to a business
destination.
Using memory media
●For available memory media and information on inserting/removing memory media, see Connecting a
USB Memory Device(P. 84) .
●For instructions on using memory media, see Using Memory Media(P. 441) .
●Depending on the le format, an optional product may be required. System Options(P. 1101)
Printing
363
Printing Using the Microsoft Cloud Service (Universal
Print)
72JY-0LF
Universal Print is a service that enables you to print documents via the Microsoft
cloud. Universal Print drivers are included as a standard feature in Windows 10, so
there is no need to install printer drivers for each computer. This also eliminates the
need for printer servers, thereby enabling cost reductions and reducing the
workload on network administrators.
Conditions of Use
To use Universal Print, you must rst register as a Microsoft 365 service user and use the Azure Active Directory
Service.
●Printing Using the Microsoft Cloud Service (Universal Print)
-For communication using a sub-line
Required Settings
Administrator settings
Use the Remote UI to register this machine in Azure Active Directory. Registering This Machine in Azure
Active Directory(P. 365)
User settings
Congure your computer so that Universal Print can be used. Conguring a Printer Registered in Azure
Active Directory on the Computer(P. 367)
When a proxy server is used
●To use Universal Print via a proxy server, you must also congure the proxy settings on your
computer.
Associating Users and Universal Print Jobs
You can associate Universal Print jobs with users authenticated through User Authentication. You can still use
Universal Print without conguring these settings. Conguring the Universal Print User Settings(P. 368)
Printing with Universal Print
See the Microsoft website for information on printing with Universal Print.
Printing
364
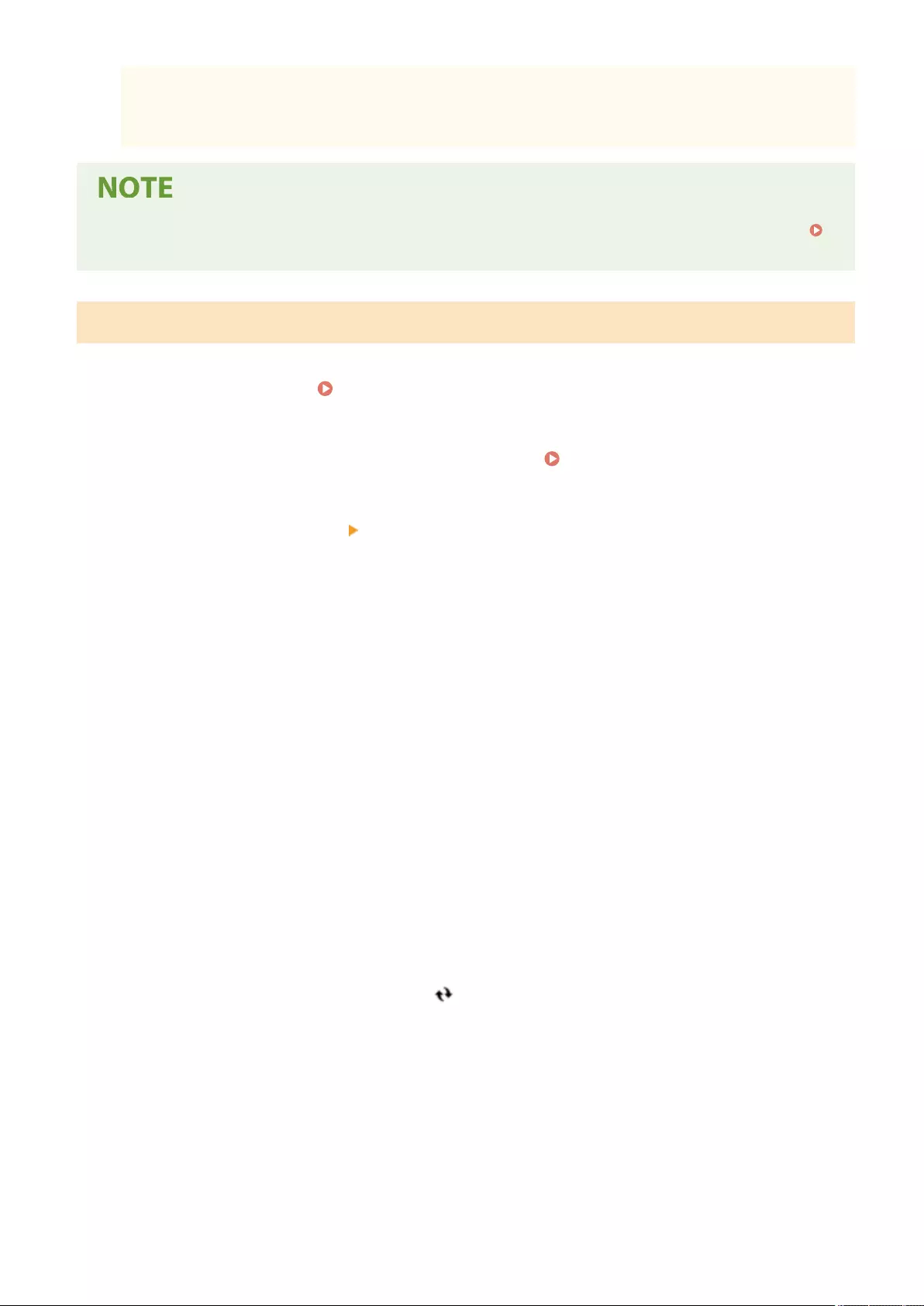
●In some operating systems, print errors or problems with the print results may occur. See Universal
Print Troubleshooting on the Microsoft website for information on the compatibility of your operating
system.
●If Forced Hold printing is enabled, Universal Print jobs will run as specied in the <Forced Hold> settings.
<Forced Hold>(P. 846)
Registering This Machine in Azure Active Directory
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Network Settings] [Settings for Universal Print].
4Click [Edit...] for [Basic Settings].
5Select the [Use Universal Print] checkbox and enter the printer name in the [Printer
Name] eld.
●To verify the server certicate sent from the server, select the [Verify Server Certicate] checkbox.
●To add CN (Common Name) to the items to be veried, select the [Add CN to Verication Items] checkbox.
●Change the [Application ID], [Azure Active Directory Authentication URL] or [Azure Active Directory
Registration URL] settings according to your cloud environment.
6Click [OK].
7Click [Register...] in [Registration Status].
8Wait a few seconds, and then click .
Printing
365
9Click the URL link displayed for [URL for Registration].
10 Follow the instructions on the screen to register the machine.
11 Wait a few minutes, and then click in the Remote UI screen.
➠Once registration is completed, [Registered] appears in [Registration Status].
12 View the Universal Print management screen of Azure Active Directory in your web
browser.
13 Select the registered machine and click [Share Printer].
●To change the name displayed on the computer, enter the new name in [Printer Share Name], and then click
[Share Printer].
➠[Printer shared.] appears at the top right of the screen.
14 Click [Members], and then click [Add].
15 Select the members and groups who will use the registered printer from the list.
●The selected members and groups will be able to use the printer.
◼To Delete a Registered Printer
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Network Settings] [Settings for Universal Print].
Printing
366

4Click [Registration Status] for [Unregister].
5Click [OK].
6View the Azure Active Directory device management screen in your web browser.
7Select the model to be deleted and click [Delete].
Conguring a Printer Registered in Azure Active Directory on the Computer
1Click [Settings] [Accounts].
2Click [Access work or school] [Connect].
3Follow the on-screen instructions to sign in to your Microsoft 365 account.
4Click [Home] [Devices].
5Click [Printers & scanners] [Add a printer or scanner].
6Select a registered printer from the list.
Printing
367
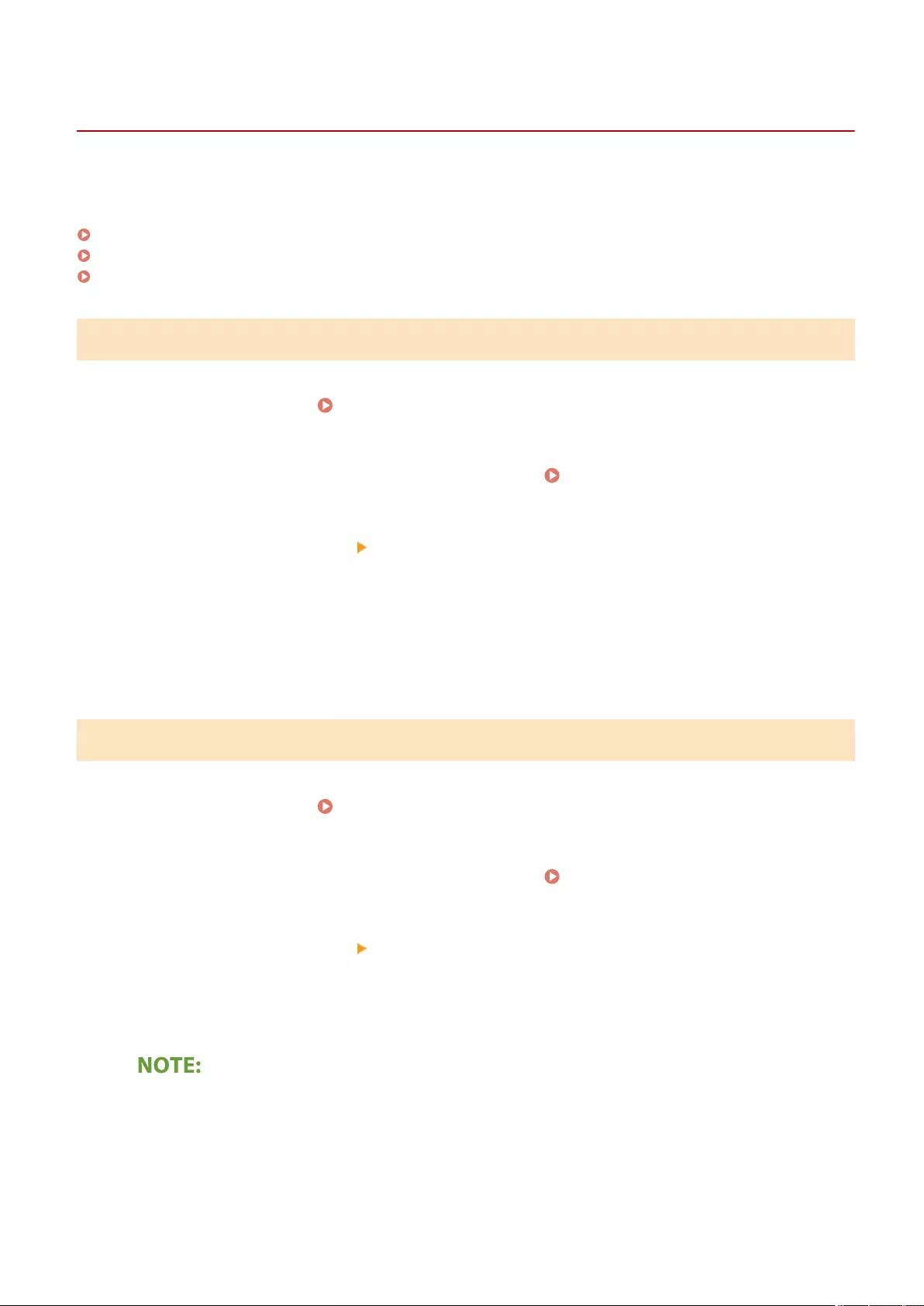
Conguring the Universal Print User Settings
72JY-0LH
Congure these settings if you want to manage users authenticated through User Authentication and their associated
Universal Print jobs. Universal Print can still be run without conguring these settings.
Set by the User(P. 368)
Set by the Administrator(P. 368)
Set by the Administrator Using a CSV File(P. 369)
Set by the User
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Enter [User Name for Universal Print:] in [Information for Universal Print].
●In [User Name for Universal Print:], enter the email address or phone number used in the Microsoft 365
account.
Set by the Administrator
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Click [Edit...] for the user to be set.
If the Universal Print user is not registered
●Click [Add User] and register the user information. When registering the user information, enter the [User
Name for Universal Print:] in [Information for Universal Print].
5Enter [User Name for Universal Print:] in [Information for Universal Print].
Printing
368

●In [User Name for Universal Print:], enter the email address or phone number used in the Microsoft 365
account.
6Click [Update].
Set by the Administrator Using a CSV File
You can associate User Authentication users with a Microsoft 365 account by editing a CSV le.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management] [Settings for Universal
Print].
4Click [Start Exporting].
●If there is no user information that is associated with a Microsoft 365 account, you cannot congure the
settings using a CSV le. Click [Add Association...], add the associated user and then click [Start Exporting].
5Editing the exported CSV le
●Enter a registered user name in "mcp_uid".
●In "azureaccount_name", enter the email address or phone number used in the Microsoft 365 account.
6Click [Import...] and specify the le edited in step 5.
7Click [Start Importing].
●If the authentication method is set to [Picture Login] and [User Registration Method:] is set to [Register
Automatically When Job Is Received], the following information is registered as the user information for a
job executed by the Microsoft 365 account called "user1@example.com".
- Settings registered in the user database
User name: user1@example.com
- Universal Print settings
User name: user1
Microsoft 365 account: example.com
- Information displayed on the login screen for Picture Login
user1
example.com
Printing
369

Scanning
Scanning .............................................................................................................................................................. 372
Scan Basic Features Screen ............................................................................................................................... 374
Basic Operations for Scanning Originals ......................................................................................................... 377
Checking Status and Log for Scanned Documents ....................................................................................... 392
Scanning Clearly ................................................................................................................................................ 394
Adjusting Image Quality ............................................................................................................................... 395
Adjusting Density ......................................................................................................................................... 396
Adjusting Sharpness When Scanning (Sharpness) ........................................................................................ 397
Erasing Dark Borders When Scanning (Erase Frame) .................................................................................... 398
Scanning Eciently ........................................................................................................................................... 401
Sending/Saving Separately Scanned Documents Together (Job Build) .......................................................... 402
Useful Scanning Functions ............................................................................................................................... 404
Checking Scanned Originals Before Sending/Saving (Preview) ..................................................................... 405
Sending/Saving at a Specied Time .............................................................................................................. 407
Notifying You by E-Mail of the Completion of Sending/Saving ...................................................................... 409
Scanning with the OCR Function ................................................................................................................... 411
Enhancing the Security of Electronic Files ..................................................................................................... 416
Recalling Previously Used Settings for Sending/Saving (Previous Settings) .................................................. 421
Setting a File Name ...................................................................................................................................... 423
Specifying E-Mail Settings ............................................................................................................................. 425
Using Your Computer to Scan (Remote Scan) (Windows) ............................................................................... 427
Using Color Network ScanGear 2 .................................................................................................................. 428
Scanning Originals from an Application ................................................................................................. 430
Using WSD .................................................................................................................................................... 432
Scanning Originals Using WSD (WSD Scan) ............................................................................................ 433
Scanning
371
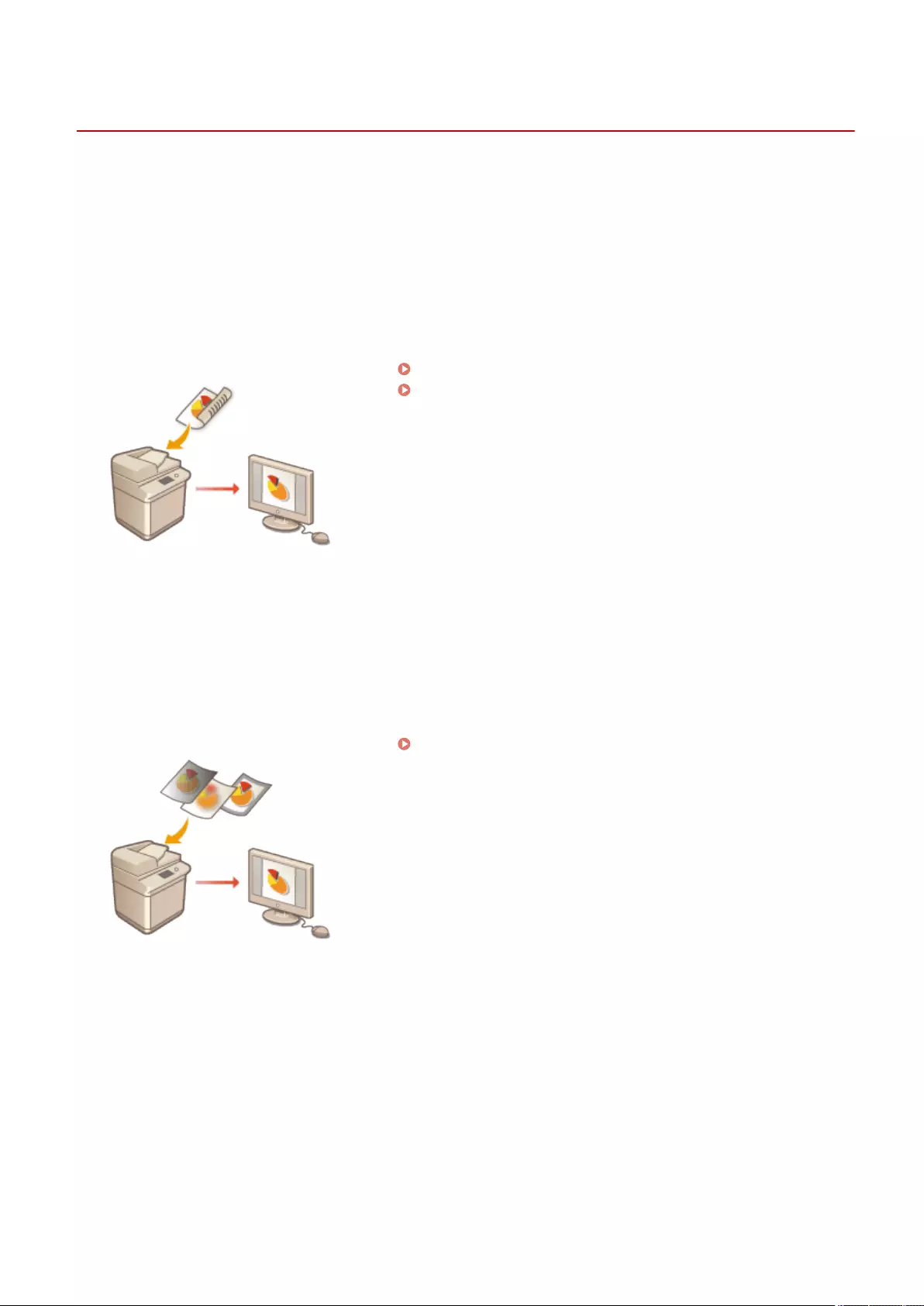
Scan and Send
Scanning
72JY-068
PMW-SCIG
Scanning paper originals enables you to convert them into electronic les, such as PDF, commonly supported by a
computer. Converted les can be sent as e-mail attachments from the machine, or saved in a le server. This chapter
describes a variety of useful functions for easy scanning as well as basic operations.
◼Introduction to Basic Operations
This section describes the Scan Basic Features screen and the basic sending/saving methods.
Scan Basic Features Screen(P. 374)
Basic Operations for Scanning Originals(P. 377)
◼Scanning Clearly
This section describes the methods to solve problems such as blurry photographs, illegible text due to dark paper, and
the appearance of dark borders.
Scanning Clearly(P. 394)
◼Scanning Various Types of Originals
Even if your original contains a large number of pages, you can easily scan it.
Scanning
372

Scanning Eciently(P. 401)
◼Eciently, Reliably, Safely
This section describes a variety of functions useful for increasing working eciency, avoiding operation errors, and
enhancing security.
Useful Scanning Functions(P. 404)
◼Scanning Using a Computer
If you are editing a scanned document in a computer, save directly into the computer for convenience.
Using Your Computer to Scan (Remote Scan) (Windows)(P. 427)
Scanning
373
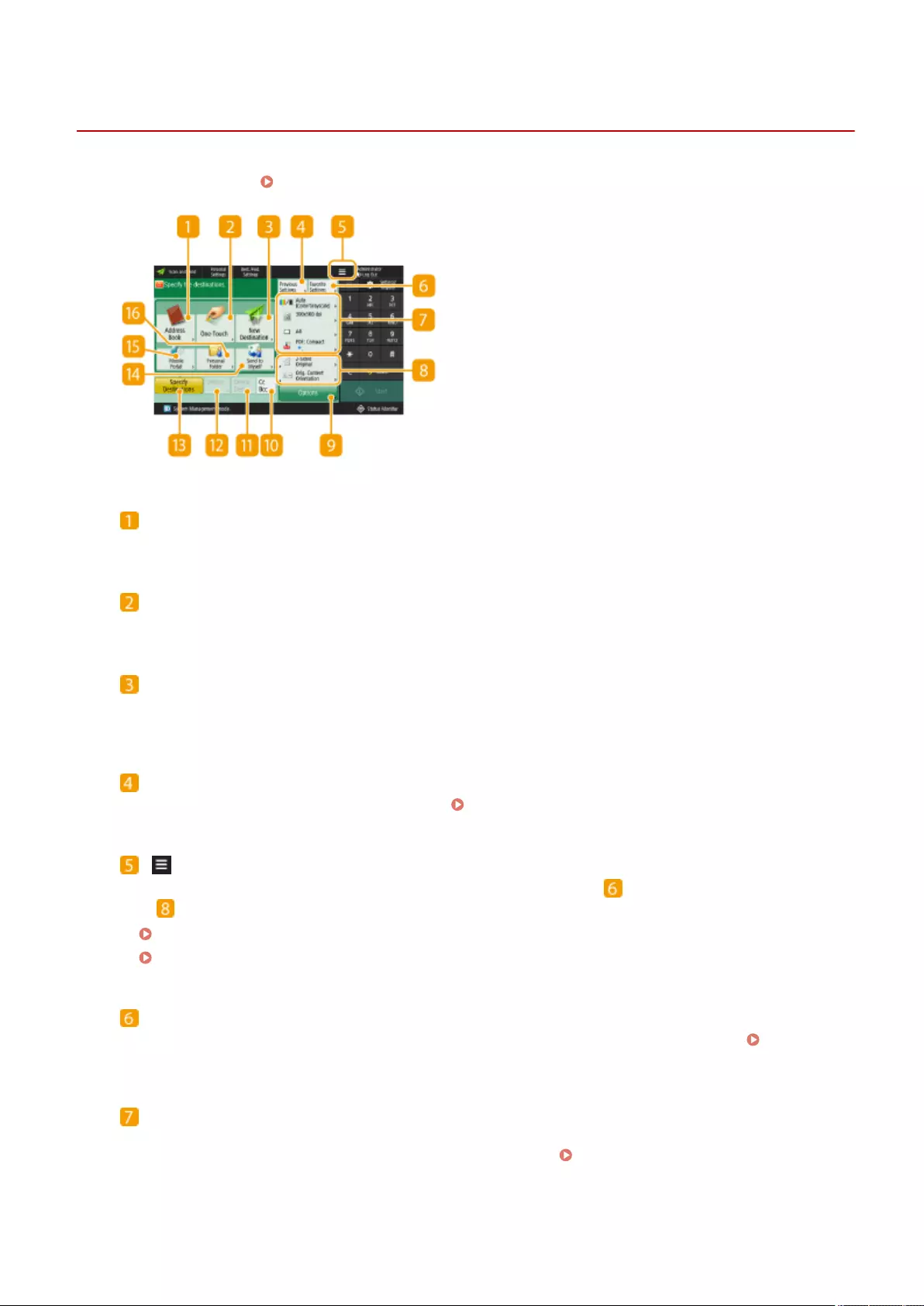
Scan Basic Features Screen
72JY-069
Pressing <Scan and Send> ( <Home> Screen(P. 119) ) displays the Scan Basic Features screen.
<Address Book>
Enables you to specify a sending destination and a save location registered in the Address Book.
<One-Touch>
Enables you to specify a sending destination and a save location registered in one-touch buttons.
<New Destination>
Enables you to specify destinations manually that are not registered in the Address Book or one-touch
buttons.
<Previous Settings>
Press to recall the previously specied settings. Basic Operations for Scanning Originals(P. 377)
Press this icon to register the current settings in <Favorite Settings> of and change the button displayed
in .
Managing the Machine(P. 476)
Customizing the Basic Features Screen(P. 167)
<Favorite Settings>
Register frequently used scan settings here in advance to easily recall them when necessary. Managing
the Machine(P. 476)
Current setting status and setting buttons
Displays setting status such as the resolution and le formats. Make sure to conrm the settings in order to
scan properly. To change the settings, press the desired button. Basic Operations for Scanning
Originals(P. 377)
Scanning
374
Function setting buttons
Displays the most frequently used buttons from <Options>. You can also press to change which buttons
are displayed.
●If the button for the function that you want to use is not displayed, press <Options> and select the desired
button. Basic Operations for Scanning Originals(P. 377)
OptionsOptions
<Options>
Displays all of the function setting buttons. For convenience, you can display frequently used function setting
buttons in .
<Cc Bcc>
Enables you to specify e-mail destinations as Cc or Bcc. Basic Operations for Scanning Originals(P. 377)
<Delete Dest.>
Enables you to delete the specied destination.
<Details>
Enables you to check the detailed information about the specied destination.
<Specify Destinations>
Displays the methods for specifying destinations or a list of specied destinations.
<Send to Myself>
Enables you to directly specify your own e-mail address. This button is available only when you are logged in
to the machine with personal authentication management. Managing Users(P. 489)
<Mobile Portal>
Enables you to specify a destination from the address book of a mobile device.
Basic Operations for Scanning Originals(P. 377)
<Personal Folder>
Enables you to specify your personal folder registered as a save location. This button is available only when
you are logged in to the machine with personal authentication management.
Conguring Personal Folders(P. 529)
Managing Users(P. 489)
●You can select whether to hide the Address Book and one-touch buttons to restrict use of the Address Book.
<Restrict Address Book Use>(P. 820)
●Some functions cannot be used in combination with each other. Buttons that cannot be selected are
displayed in light gray.
●The total number of specied destinations is displayed on the top right of the screen.
Scanning
375
Basic Operations for Scanning Originals
72JY-06A
PMW-BASC
This section describes the basic operations for scanning originals.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
Address BookAddress Book
Specifying Destinations from the Address Book
One-TouchOne-Touch
Specifying Destinations from One-Touch Buttons
New DestinationNew Destination
Entering Destinations Manually
Specifying Destinations in the LDAP Server
Send to MyselfSend to Myself
Specifying Your Own E-Mail Address
Personal FolderPersonal Folder
Specifying Personal Folder
Mobile Portal
Specifying Destinations from the Address Book of a Mobile Device
Cc BccCc Bcc
Specifying Addresses in Cc/Bcc
Specify DestinationsSpecify Destinations
●To specify multiple destinations, press <Specify Destinations> and specify an additional destination.
Delete Dest.Delete Dest.
●To delete a destination, select the destination you want to delete, and press <Delete Dest.>.
DetailsDetails
●You can select a destination and press <Details> to conrm the detailed information for the destination.
●You can only change destinations from <Details> specied using the New Destination and destinations
obtained via an LDAP server.
●If the server machine is performing the System Manager information settings, authentication between the
server machine and the client machine is performed while the client machine is obtaining the Remote
Address Book/one-touch buttons. Authentication is performed by matching the System Manager ID and
System Manager PIN set by the server machine and client machine. Changing the System Manager ID
and PIN(P. 523)
The availability of the Remote Address Book/one-touch buttons depends on the status of the System
Manager information settings for the server machine and client machine, as shown below.
When the server machine
is performing the System
Manager information
settings
When the client machine is
performing the System
Manager information
settings
The System Manager ID
and System PIN for the
server machine and client
machine match
Can use the
Remote Address
Book/One-Touch
Button
Performing Performing Matches Yes
Does Not Match No
Not Performing - No
Not Performing Performing - Yes
Not Performing - Yes
Scanning
377

Specifying Destinations from the Address Book
1Press <Address Book>.
2Select the destination and press <OK>.
●If an access number is set when the destination is registered, press <Access No.> and enter the access
number using the numeric keys. The corresponding destination is displayed in the Address Book.
●To use the Remote Address Book, press <To Remote Address Book>. When <Change Address Book> is
displayed, press <Change Address Book> <Remote>.
Destination type drop-down list
Pressing , , and displays e-mail, le server, and group destinations, respectively.
Address list drop-down list
When you are logged in to the machine with personal authentication management, selecting <Personal
Addr. List> displays your personal Address Book. You can also display dedicated user group address lists
(User Group Address Lists) in which you are included.
Search buttons by rst letter
Enables you to narrow down a search by the rst letter of the destination name.
<Search by Name>
Enables you to search the destination by the name you are entering.
●<Register New Destination>, <Details/Edit>, and <Delete> in <Register/Edit> on the <Address Book
(Local)> screen can be used to register new destinations, check details, and edit/delete destinations.
Registering Destinations(P. 190)
●To use the Remote Address Book, it is necessary to congure the server machine settings. Set to open
the Remote Address Book externally on the server machine.
Scanning
378
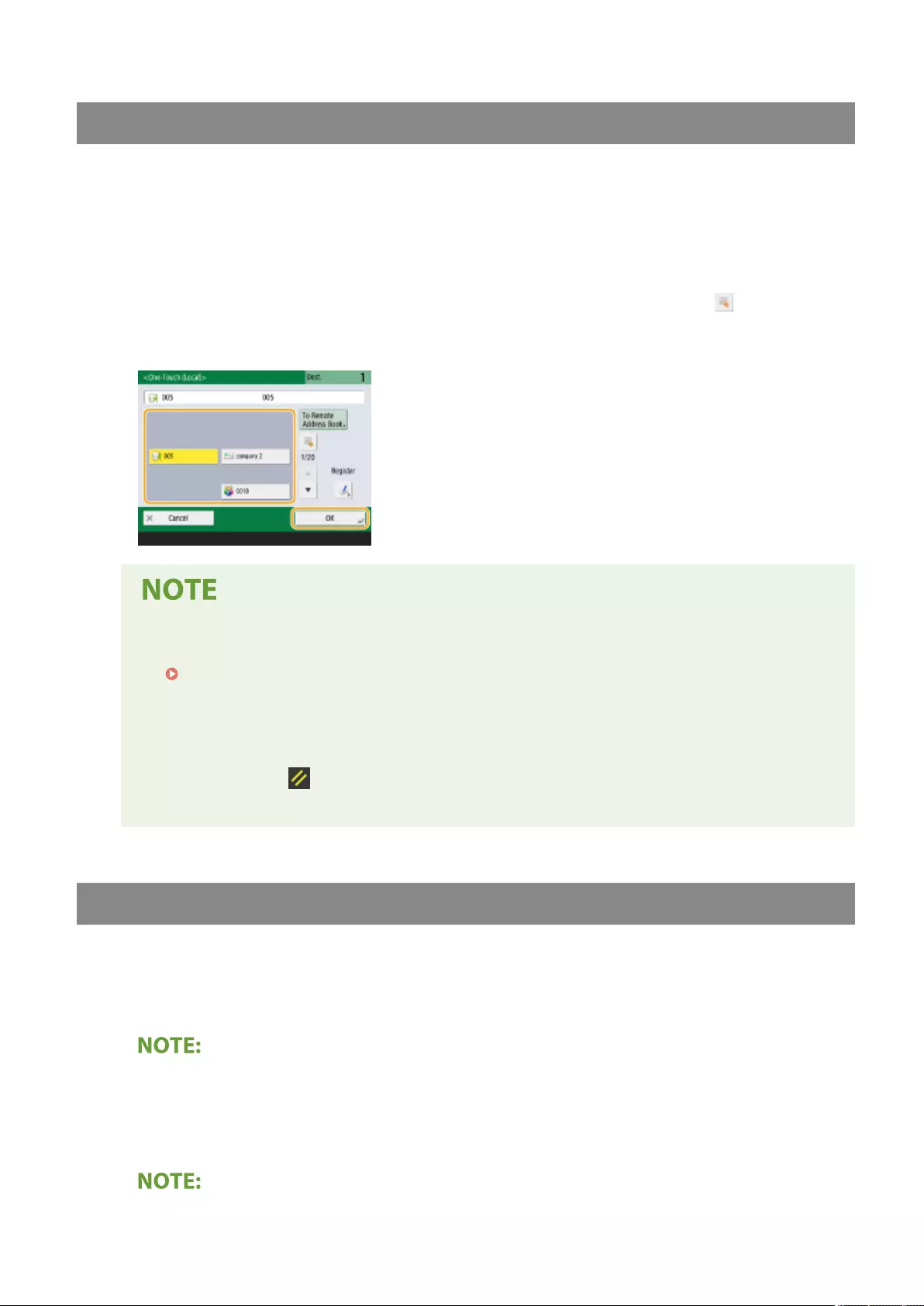
Specifying Destinations from One-Touch Buttons
1Press <One-Touch>.
2Select the desired one-touch button and press <OK>.
●To specify the destination using a one-touch button number (one-touch number), press and enter the
number for the desired one-touch button.
●To use the Remote Address Book, press <To Remote Address Book>.
●To select a destination from the <One-Touch> screen after scanning, set <One-Touch> for <Default
Screen>. The work required for sending scanned documents to the same destination can be reduced.
<Send>(P. 820)
●The destinations registered in the one-touch buttons of the server machine are updated in the
following times:
- When a fax job has been sent on the client machine
- When you press (Reset) on the client machine
- When Auto Reset is activated on the client machine
Entering Destinations Manually
You can specify destinations manually that are not registered in the Address Book or one-touch buttons.
1Press <New Destination> and select <E-Mail> or <File>.
●Selecting <I-Fax> enables you to send scanned documents as a fax via the Internet.
2Specify the destination and press <OK>.
Scanning
379

●You can press <Register to Address Book> to register the entered destination. Set the required conditions,
specify <Name>, and specify the address list from the address list drop-down list. For information on the
settings, see Registering Destinations in the Address Book(P. 195) .
●If you select <File> in step 1, specify the settings such as the IP address of a le server and the path of the
save location folder. For details about the setting items, consult your network administrator.
Specifying Destinations in the LDAP Server
You can search and specify destinations registered in the LDAP server.
1Press <Address Book>.
2Press <To LDAP Server>.
●When <Change Address Book> is displayed, press <Change Address Book> <LDAP Server>.
●If the network password input screen is displayed, enter the user name and password and press <OK>.
3When searching destinations in the LDAP server, press either <Search by Name> or
<Search by Conditions>.
When searching by name
Press <Search by Name> enter the text to search press <OK>.
You can specify attributes used when performing "Search by Name" for a destination from the LDAP server.
<Settings for Search by Name When Using LDAP Server>(P. 851)
When searching by conditions
Press <Search by Conditions>, specify the search conditions on the screen, and press <Start Searching>.
Scanning
380

Search categories
Select a criterion to search for destinations from name, e-mail address, organization name, and
organization unit (department name, etc).
Search conditions
Select a search condition such as a destination name that contains "John" and a department name that
begins with "Development."
Search characters
Press <Set> and enter search characters for the search condition.
●A maximum of 2,000 destinations can be displayed in the search results.
To search with multiple conditions
●You can search destinations with multiple conditions. Specify the rst search condition, press <Add Search
Condition>, and then select <or> or <and> for the next condition.
To change conditions and search again
●Press <Delete> to delete the specied contents, and specify the conditions again.
4Select the destination and press <OK>.
Specifying Your Own E-Mail Address
You can specify the e-mail address of the user who is logged in to the machine with personal authentication
management.
1Press <Send to Myself>.
➠The e-mail address of the user who is logged in to the machine is specied as the destination.
Scanning
381

Specifying Personal Folder
You can specify the personal folder of the user who is logged in to the machine with personal authentication
management.
1Specify <Personal Folder>.
➠The personal folder of the user who is logged in to the machine is specied as destination.
Specifying Destinations from the Address Book of a Mobile Device
You can specify a destination from the address book of a mobile device.
●Only e-mail destinations can be specied from the address book of a mobile device.
●To use this function, you must install the "Canon PRINT Business" application to your mobile device.
Utilizing the Machine through Applications(P. 458)
1Connect to the mobile device. Connecting with Mobile Devices(P. 453)
2Send the address from the mobile device to the machine.
●For detailed information on operations using the mobile device, see the Help of the application.
●You can send information including the subject, message body, and le name from the mobile device to
the machine. Specifying E-Mail Settings(P. 425)
Specifying Addresses in Cc/Bcc
E-mail addresses can be specied in Cc (Carbon copy) and Bcc (Blind carbon copy).
1Press <Cc Bcc>.
2Press <Cc> or <Bcc> <Specify Destinations>.
Scanning
382

●To move a destination from Cc or Bcc, press <To/Bcc|Cc> or <To/Cc|Bcc> and specify the destination to
move to To, Cc, or Bcc.
3Specify the destination press <OK>.
●For information on specifying the destination, see the method for specifying each type of destination.
●A destination other than an e-mail destination can be specied with <Specify Destinations>, but cannot be
specied in Cc or Bcc or moved to Cc or Bcc.
4Specify the scan settings as necessary.
File FormatFile Format
Selecting a File Format
Resolution
Selecting Resolution
Scan Size
Specifying the Scanning Size of Originals
Select Color
Selecting Color Scan/Black & White Scan
2-Sided Original
Scanning Both Sides of Originals
Selecting a File Format
Scanned originals are converted into electronic les such as PDF. Select the le
format according to your purposes and environment of use.
1Press the setting button for le format.
Scanning
383
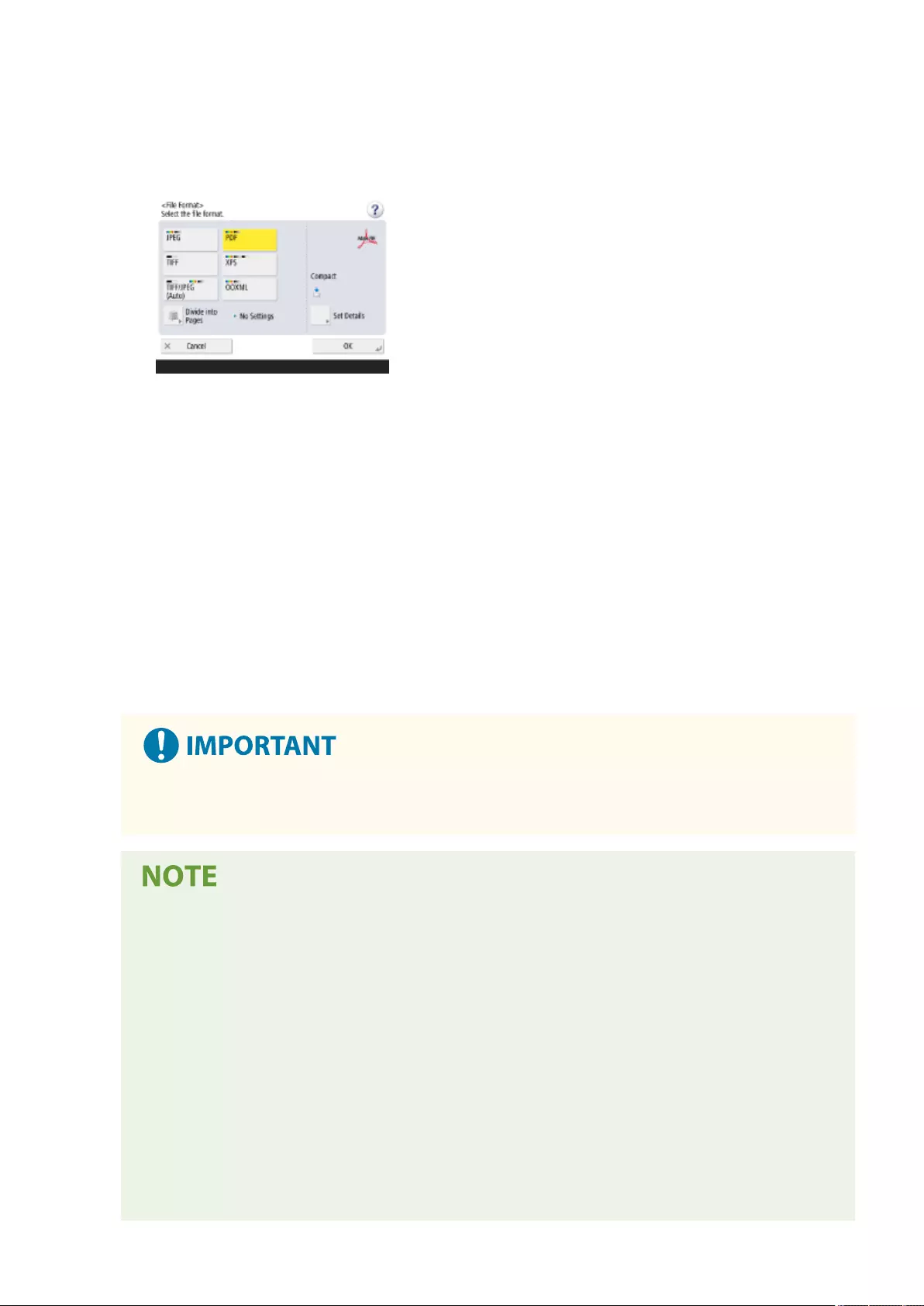
2Select the le format.
●If you select <PDF>, <XPS>, or <OOXML>, you can specify various additional settings.
●If you selected <JPEG> or <TIFF>, there are no further operations. Press <OK>.
<JPEG>
This le format is suitable for photographic originals. Multiple-page originals will be divided into one le
per page.
<TIFF>
This le format is suitable for graphical originals. Originals are scanned in black and white.
<PDF>
This le format is suitable for text documents. Documents can be displayed in the same way on any
computer, regardless of the operating system used.
<XPS>
This is a le format taken from Windows Vista. Documents can be displayed in the same way on any
Windows computer, regardless of the operating system used.
<OOXML>
This le format can be edited in Microsoft Oce Word or PowerPoint.
●You cannot select <OOXML> if you are sending a le stored in <Memory RX Inbox> of <Fax/I-Fax
Inbox>.
●<PDF; Trace&Smooth> is only valid with the following settings:
-Select Color: Color mode other than the Black-and-White mode
- Resolution: 300 dpi x 300 dpi
●<PDF; Compact> or <XPS; Compact> is only valid with the following settings:
- Select Color: Color mode other than the Black-and-White mode
- Resolution: 300 dpi x 300 dpi
●<Word> documents to which <OOXML> is set can only be sent with the following settings.
- Select Color: Color mode other than the Black & White mode
- Resolution: 300 dpi x 300 dpi
●<PowerPoint> documents to which <OOXML> is set can only be sent with the following settings.
- Select Color: Color mode other than the Black & White mode
- Resolution: 300 dpi x 300 dpi or 600 dpi x 600 dpi
Scanning
384
●If you select <PDF; Trace&Smooth>, the machine may be unable to recognize which parts of the
scanned document are text and line drawings, depending on the scanned document.
●The text and background of PDF les containing outline data may become misaligned, and text and
line drawings may not be displayed, depending on the version of Adobe Illustrator used to open the
PDF.
When creating les by pages
●To scan a multiple-page original and save each page as a separate le instead of saving all pages as a
single le, press <Divide into Pages>.
●To specify the number of pages to include in each le, after pressing <Divide into Pages>, specify the
desired number of pages. To save each page as a separate le, specify <1> for the number of pages.
●If you select <TIFF/JPEG>, each page will automatically be created as a separate le according to the
Select Color mode.
- When Black & White is set for the Select Color mode: TIFF
- When a setting other than Black & White is set for the Select Color mode: JPEG
●You cannot specify the number of pages to include in one le if you are currently using the <Scan and
Store> function.
Installing an option can expand functions for scanning to create les. For information on the required optional
products and on the le formats, see System Options(P. 1101) .
Selecting Resolution
To scan an original clearly, increase the resolution. To reduce the le size, decrease
the resolution.
1Press the setting button for resolution.
2Select the resolution and press <OK>.
●Depending on the le format you are selecting, the resolution that you can select is limited.
Scanning
385
●When <Fax> or <I-Fax> is specied for the destination and a resolution higher than 300 dpi is set,
even if <Speed/Image Quality Priority for Black & White Scan> is set to <Quality Priority>, the setting is
not enabled.
Specifying the Scanning Size of Originals
If you are scanning free size/highly transparent originals, or the edge of image is
missing when scanning, you need to manually specify the scanning size.
1Press the setting button for scanning size.
2Select the scanning size and press <OK>.
●To scan the original in A4, select <A4>.
When scanning a free size original
Place the original in the feeder and select <Free Size>.
When specifying the values of scanning size
Place the original on the platen glass/in the feeder, select <Custom>, and enter the height and width of the
original.
●When a scanning size smaller than the minimum size that can be scanned with the feeder is set, scanning
cannot be performed with the feeder. For information on the document sizes that can be scanned with the
feeder, see Feeder(P. 1107) .
Scanning
386
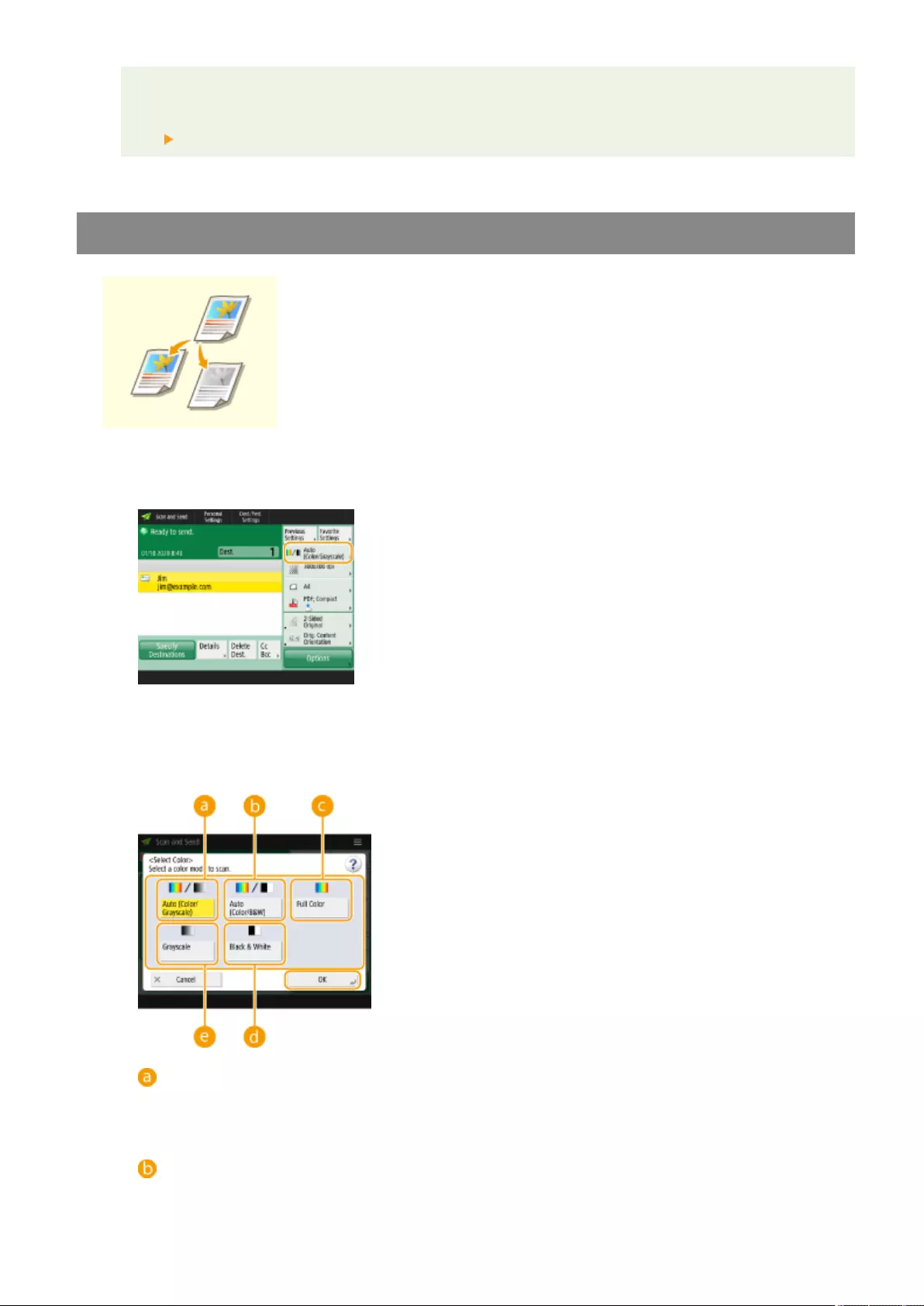
To register the scanning size
●If you frequently specify the scanning size with the same values, register the size in <Custom>
<Register Size> to quickly recall the setting for convenience.
Selecting Color Scan/Black & White Scan
You can specify color when scanning original.
1Press the setting button for color.
2Select the color and press <OK>.
●Depending on the le format you are selecting, the setting item that you can select is limited.
<Auto (Color/Grayscale)>
Determines automatically what color is used for scanning according to the color of an original. For
example, color pages are scanned in color, and monochrome pages are scanned in grayscale
(monochrome gradation).
<Auto (Color/B&W)>
Determines automatically what color is used for scanning according to the color of an original. For
example, colored pages are scanned in color, and monochrome pages are scanned in black and white.
Scanning
387

Select this mode when text is faint with <Auto (Color/Grayscale)>, or when the original mainly consists of
text.
<Full Color>
Scans in color regardless of a document's color. Depending on the state of the color original, it may be
detected as black and white when scanned, even if you set <Auto (Color/B&W)>. To avoid this, set the color
mode to <Full Color>.
<Black & White>
Scans in black and white regardless of an original's color. This mode is automatically set for the TIFF le
format.
<Grayscale>
Scans in grayscale regardless of an original's color. This mode uses different shades of color, such as black,
dark gray, gray, light gray, and white, making color look more natural and beautiful compared with <Black
& White>.
●If a black-and-white original is scanned in the Full Color mode, it is counted as a color scan.
●If you select <JPEG> as the le format, <Black & White> is changed to <Grayscale>.
●If you select <TIFF> as the le format, <Black & White> is set.
●If <OOXML> is selected as the le format, you can only send in <Auto (Color/Grayscale)>, <Full Color>, or
<Grayscale>.
Scanning Both Sides of Originals
The machine can automatically scan both the front and back sides of an original.
●Place the original in the feeder.
●If you want to scan each side of the 2-sided originals placed on the platen glass, specify the <Job
Build> settings. Sending/Saving Separately Scanned Documents Together (Job Build)(P. 402)
1Press <2-Sided Original>.
2Select <Book Type> or <Calendar Type> and press <OK>.
Scanning
388

●Select <Book Type> for originals whose images on the front and back sides face the same direction, or
<Calendar Type> for originals whose images on the front and back sides face in opposite directions.
5Press (Start).
➠Originals are scanned and sending/saving starts.
●To cancel scanning, press <Cancel> or (Stop) <Yes>.
When <Press the [Start] key to scan the next original.> is displayed
Place the next original to scan and press (Start). When scanning all of the originals is complete, press <Start
Sending> to send/save the le.
●Depending on the communication settings, you may be prompted to enter the user name and password.
Setting E-mail/I-Fax Communication(P. 70)
To check the total number of specied destinations
●The total number of specied destinations is displayed on the top right of the screen. This enables you to
conrm that the number of destinations is correct before sending.
To immediately cancel a job that is being sent
If you press (Stop) on the control panel while a job is being sent, the message <Is it OK to cancel the
following Send job?> appears. Press <Yes> to cancel sending.
●You can select <Latest Received Job> or <Job Being Sent> to choose the job to cancel. <Job to Cancel
When Stop Is Pressed>(P. 825)
●Press (Stop) when there are multiple send jobs to display the screen for selecting the send job to cancel.
If the send job you want to cancel is not displayed, press <Check Other Jobs> to display <Send Jobs>. Select
the job that you want to cancel, and press <Cancel>.
To check the statuses for sent/saved documents
●On the <Status Monitor> screen, you can check the statuses for sent/saved documents. This screen enables
you to send/save documents again or cancel sending/saving after checking the statuses. Checking Status
and Log for Scanned Documents(P. 392)
Scanning
389

●When <Display Notication When Job Is Accepted> is set to <On>, the <Status Monitor> screen can be
displayed from the following screen that is shown after a send job is received. <Display Notication
When Job Is Accepted>(P. 825)
TX Result ReportTX Result Report
To print the report for the results of sending/saving
●On the Scan Basic Features screen, pressing <Options> <TX Result Report> enables you to set to
automatically print the report listing the results of sending/saving.
●To set this for each job from <Options>, it is necessary to select <For Error Only> or <Off> in <TX Result
Report>(P. 820) , and then set <Allow Printing from Options> to <On>.
File name
When a le is sent/saved, its le name is automatically set based on the following format. You can change the
setting so that a different name can be assigned. Setting a File Name(P. 423)
●When sending by e-mail
"Job numbers (four digits)_page numbers (three digits).le extension name" format, such as "1042_001.jpg"
●When saving in a le server
"The year, month, day, hour, minute, and second the le is saved (14 digits).le extension name" format,
such as "20151030133541.jpg"
E-mail subject
●The subject entered in <Default Subject> is automatically set ( <Default Subject>(P. 828) ). If you specify a
different subject, change the setting, or specify each time you send an e-mail ( Specifying E-Mail
Settings(P. 425) ).
Orig. Content Orientation
Determining the top and bottom of the original
●You can set the orientation of the document before scanning so that its top and bottom are positioned
correctly when the sent/saved le is displayed on a computer.
●Press <Options> on the Scan Basic Features screen <Orig. Content Orientation> <Top at Far Edge>
<OK>.
Specifying multiple destinations including faxes
●Setting <Enable Fax in Scan and Send Function> to <On> enables you to specify fax destinations from the
Scan Basic Features screen ( <Display Fax Function>(P. 773) ). This setting is useful for specifying
multiple destinations including faxes, such as when saving a copy of a sent fax in a le server.
Checking scanned images before sending/saving
●You can check scanned images on the preview screen before sending/saving. Checking Scanned
Originals Before Sending/Saving (Preview)(P. 405)
Registering frequently used settings
●You can combine frequently used destinations and scan settings into a button of the machine for later use.
By pressing the registered button when scanning originals, you can quickly complete your settings.
Registering a Combination of Frequently Used Functions(P. 164)
Scanning
390
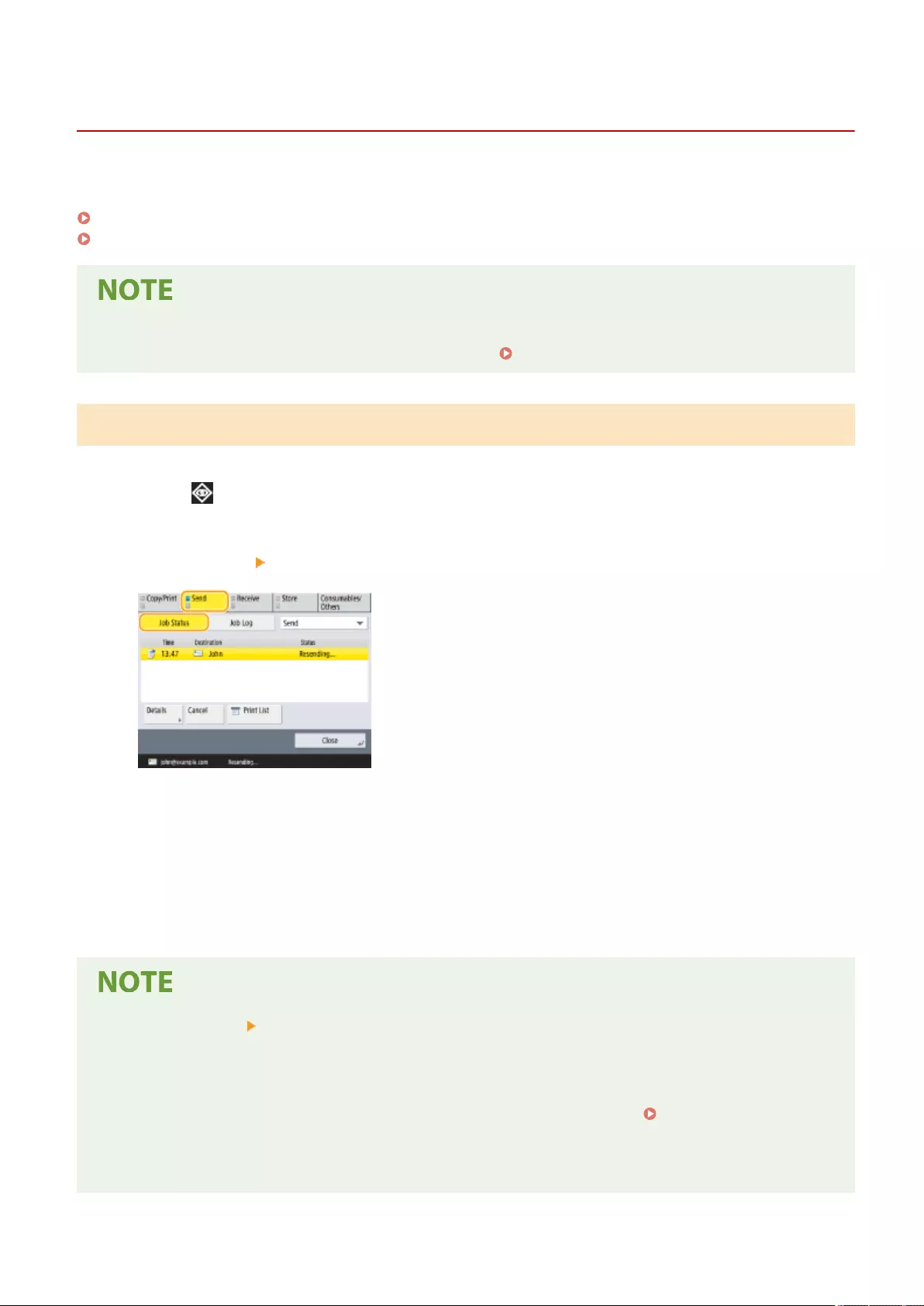
Checking Status and Log for Scanned Documents
72JY-06C
You can check the statuses and communication logs for sent and saved documents.
Checking the Statuses for Sent/Saved Documents(P. 392)
Checking If Documents Are Sent or Saved Successfully(P. 393)
●When personal authentication management is used, you can restrict users from performing operations on
the jobs of other users on the <Status Monitor> screen. <Restrict Access to Other User Jobs>(P. 857)
Checking the Statuses for Sent/Saved Documents
1Press <Status Monitor>.
2Press <Send> <Job Status>.
3Check the statuses.
●Selecting a document and pressing <Details> enables you to check detailed information such as destinations
and the number of pages.
●Selecting a document and pressing <Cancel> enables you to cancel sending/saving.
●Pressing <Print List> prints a status list of sent/saved documents displayed on the screen.
●Pressing <Details> <Resend> enables you to resend/resave the documents that failed to send/save. To
specify another destination, press <Change Destination>. For documents with multiple destinations
specied using the same sending/saving method, press <Broadcast List>, select a destination, and then
press <Resend> or <Change Destination>.
●You can resend/resave documents when <Delete Failed TX Jobs> is set to <Off>. <Delete Failed TX
Jobs>(P. 821)
●You can change the destinations of documents that are set to be sent/saved at a specied time as well as
documents that failed to send/save. Note that you cannot change the destinations for documents with
Scanning
392
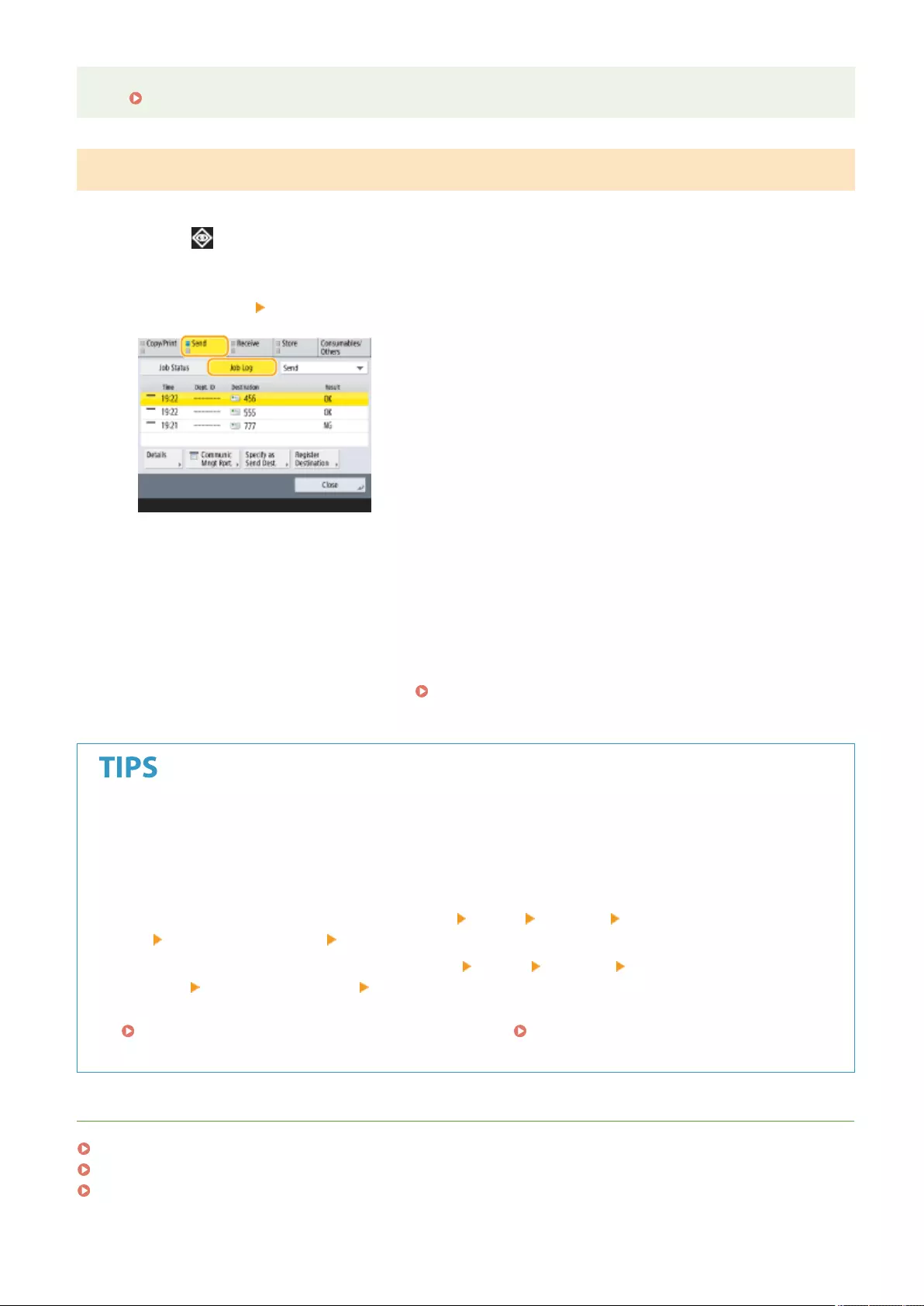
multiple destinations specied that are being sent/saved, or when entering a new destination is restricted
( Restricting New Destinations(P. 569) ).
Checking If Documents Are Sent or Saved Successfully
1Press <Status Monitor>.
2Press <Send> <Job Log>.
3Check if documents are sent or saved successfully.
●<OK> is displayed in the <Result> column when a document was sent or saved successfully. If <NG> is
displayed, this shows that a document failed to be sent or saved because it was canceled or there was some
error.
●You can check the error code by selecting a job and pressing <Details>. You can check the causes and
solutions for errors based on error codes. Countermeasures for Each Error Code(P. 982)
●By pressing <Communic Mngt Rprt.>, the displayed send/save log can be printed as a list.
Specifying/registering destinations from the send history
●You can specify destinations and register destinations to the address book from the send history on the
<Status Monitor> screen. This saves you the effort of directly entering the address, and also helps avoid
sending to an incorrect destination due to entering the wrong address.
- When specifying a destination: <Status Monitor> <Send> <Job Log> select the destination to send
to <Specify as Send Dest.> <OK>
- When registering a destination: <Status Monitor> <Send> <Job Log> select the destination to
register <Register Destination> register the destination from the registration screen for each
destination type
Registering Destinations in the Address Book(P. 195) Registering a Destination in a One-Touch
Button(P. 210)
LINKS
Sending/Saving at a Specied Time(P. 407)
Printing a List of Usage History(P. 910)
Outputting a Communication Result Report(P. 912)
Scanning
393
Scanning Clearly
72JY-06E
For catalogs with many photographs included, reports written in pencil, and thick magazines, adjusting the density
and sharpness and erasing unnecessary shadows can scan originals clearly.
Adjusting Image Quality(P. 395) Adjusting Density(P. 396) Adjusting Sharpness When
Scanning (Sharpness)(P. 397)
Erasing Dark Borders When
Scanning (Erase Frame)(P. 398)
Scanning
394

Original Type
Adjusting Image Quality
72JY-06F
You can scan with optimal image quality suitable for your type of original. For
example, making the color tone beautiful for originals with photos, while making the
contrast sharp for text-only originals, which makes it easy to read.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Press <Options> <Original Type>.
5Select the type of original and press <OK>.
●To adjust the text/photo processing priority level, press <Adjust Level> select <Text Priority> or <Photo
Priority>.
6Press <Close>.
7Press (Start).
➠Originals are scanned and sending/saving starts.
●If the phenomenon called moire (striped pattern noise) occurs when scanning an original, adjust the
sharpness. Adjusting Sharpness When Scanning (Sharpness)(P. 397)
Scanning
395

Density
Adjusting Density
72JY-06H
You can scan originals more clearly by manually adjusting the density according to
the contents of the original. For example, increasing the density enables you to
easily read faint characters written in pencil.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Press <Options> <Density>.
5Adjust the density and press <OK>.
●Press to decrease the density. Press to increase the density.
To adjust the density of the background
●You can send/store documents such as newspapers, or documents with colored backgrounds clearly.
Press <Auto> to automatically adjust the background density.
●Press <Adjust> to manually adjust the background density, and adjust the background density of each
color in <Adjust Each Color>.
6Press <Close>.
7Press (Start).
➠Originals are scanned and sending/saving starts.
Scanning
396

Sharpness
Adjusting Sharpness When Scanning (Sharpness)
72JY-06J
You can scan the image with clear contours and lines by increasing the sharpness, or
soften the image by decreasing the sharpness. Use this function when you want to
sharpen blurred text and diagrams, or to reduce moire (a shimmering, wavy pattern)
to smoothen the nished image.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Press <Options> <Sharpness>.
5Adjust the sharpness and press <OK>.
●To sharpen blurred text, adjust the control to <High>.
●To reduce moire when scanning originals that contain printed photos, such as magazines or pamphlets,
adjust the control to <Low>.
6Press <Close>.
7Press (Start).
➠Originals are scanned and sending/saving starts.
Scanning
397
Erase Frame
Erasing Dark Borders When Scanning (Erase Frame)
72JY-06K
When scanning originals that are smaller than the scanning size, frame lines of the
originals may appear in the scanned image. When scanning a thick book, dark
borders may appear. This function enables you to erase these frame lines and dark
borders. You can also set the machine to not copy punch holes in the originals.
●Place the original with punch holes on the platen glass. Placing in the feeder may result in damage.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Press <Options> <Erase Frame>.
5Specify the erasing type and width.
Erasing the frames in copies of documents
1Press <Erase Original Frame> and check <Original Size>.
●If the size displayed in <Original Size> is different from the size of the original, press <Change> to
select the size. Only the original sizes shown on the touch panel display can be scanned.
2Press <Next>.
3Enter the width of the frame to erase.
Scanning
398
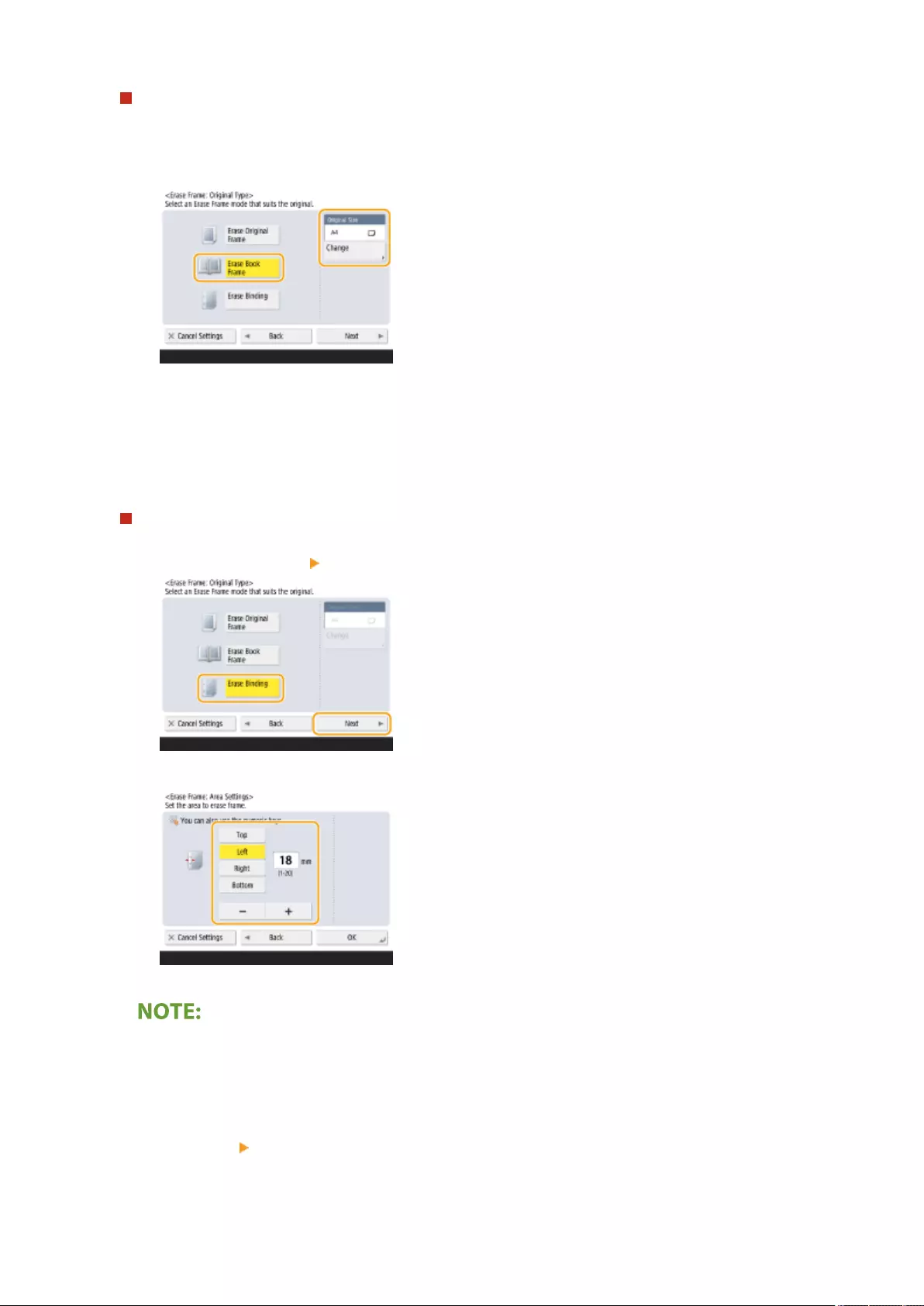
Erasing dark borders in copies of books
You can erase the dark borders both in the center and contour lines that appear when you scan facing pages
in a book.
1Press <Erase Book Frame> and check <Original Size>.
●If the size displayed in <Original Size> is different from the size of the book, press <Change> to select
the size. Only the original sizes shown on the touch panel display can be scanned.
2Press <Next>.
3Press <Center> or <Sides> and enter each erasing width.
Erasing punch holes in copies of documents
1Press <Erase Binding> <Next>.
2Select the punch hole location and enter the erasing width.
●If you want to adjust the width for each border independently, press <Erase Original Frame> or <Erase
Book Frame>, and then press <Adjust Independently> to enter the erasing widths.
●If you are using <Erase Binding>, the borders you do not select are also erased by 4 mm.
6Press <OK> <Close>.
Scanning
399

7Press (Start).
➠Originals are scanned and sending/saving starts.
Scanning
400

Job Build
Sending/Saving Separately Scanned Documents
Together (Job Build)
72JY-06R
Even if you have too many originals to be placed in the feeder at the same time, you
can scan the originals separately and send/save them as a batch of documents.
Originals scanned with both the feeder and the platen glass can also be sent/saved
at the same time.
1Place the rst original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Press <Options> <Job Build> <Close>.
6Press (Start) to scan the original.
➠When scanning is complete, the screen appears prompting you to scan the next original.
●If you place your originals in the feeder, remove the originals from the original output area when the
scanning of each batch is complete.
7Place the next original and press (Start).
●Repeat this step until you nish scanning all of the originals.
●To change the scan settings, press <Change Settings>.
●If you want to scan one-sided and two-sided originals and store them as two-sided documents, divide the
originals into one-sided and two-sided batches. For example, if the rst batch consists of two-sided
originals, set the <2-Sided Original> mode. Thereafter, you have to manually set or cancel the <2-Sided
Original> mode for each batch of originals that you scan.
Scanning
402

●The following functions can be used in <Change Settings>. Other functions must be congured in advance,
as they cannot be changed during the Job Build mode.
- <Select Color>
- <Scan Size>
- <2-Sided Original>
- <Density>
- <Original Type>
8Press <Start Sending>.
➠All scanned documents are combined into one and sent/saved to the specied destination.
Scanning
403
Useful Scanning Functions
72JY-06S
The machine has various useful functions, including notifying you of the completion of sending/saving scanned
originals.
Checking Scanned Originals
Before Sending/Saving (Preview)
(P. 405)
Sending/Saving at a Specied
Time(P. 407)
Notifying You by E-Mail of the
Completion of Sending/Saving(P. 409)
Scanning with the OCR
Function(P. 411)
Enhancing the Security of
Electronic Files(P. 416)
Recalling Previously Used Settings
for Sending/Saving (Previous
Settings)(P. 421)
Setting a File Name(P. 423) Specifying E-Mail
Settings(P. 425)
Scanning
404
Preview
Checking Scanned Originals Before Sending/Saving
(Preview)
72JY-06U
You can check scanned originals on the preview screen before sending/saving. You
can also delete, move, or switch pages on the preview screen.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Press <Options> <Preview> <Close>.
6Press (Start).
➠Originals are scanned and the preview screen appears.
●To cancel scanning, press <Cancel> or (Stop) <Yes>.
When <Press the [Start] key to scan the next original.> is displayed
Place the next original to scan and press (Start). When scanning all of the originals is complete, press
<Preview and Send> to display the preview screen.
7Check the scanned originals on the preview screen.
●Edit the scanned original on the preview screen as necessary.
To delete a page
You can delete the page currently displayed on the preview screen.
1Press <Delete Page>.
Scanning
405

To move a page
You can move a page to the specied destination.
1Press <Edit Scanned Data>.
2Press <Move Pg. Position>.
3Enter the page numbers corresponding to <Move Page> and <Behind Page>.
4Press <OK>.
To switch the locations of pages
You can switch the locations of specied pages.
1Press <Edit Scanned Data>.
2Press <Switch Pg Position>.
3Enter the page numbers corresponding to <Target Page A> and <Target Page B>.
4Press <OK>.
8Press <Start Sending>.
➠Sending/saving starts.
Scanning
406
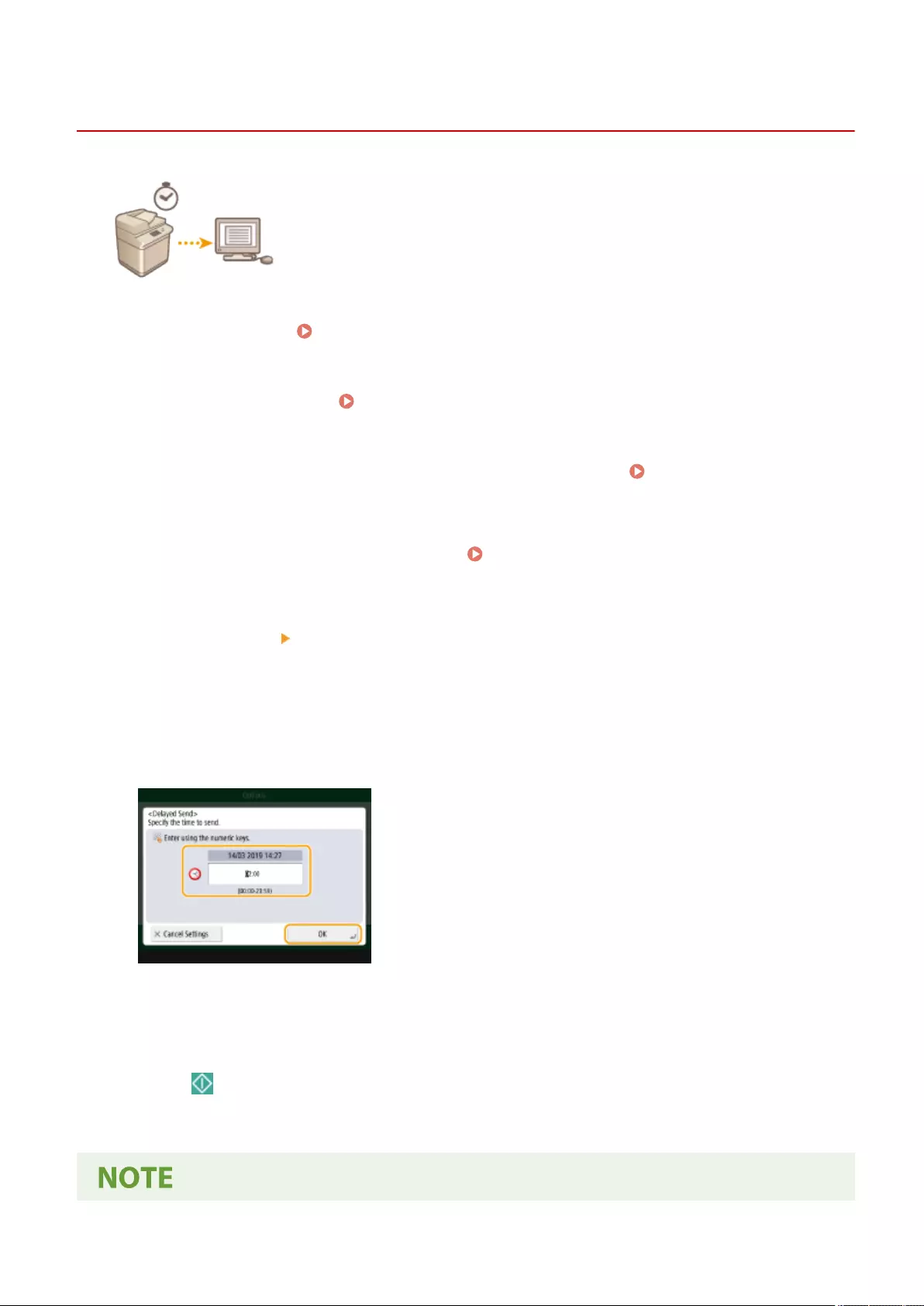
Delayed SendDelayed Send
Sending/Saving at a Specied Time
72JY-06W
You can scan originals in advance and send/save the scanned documents at a
specied time.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Press <Options> <Delayed Send>.
6Enter the time to send/save and press <OK>.
●Enter all four digits of the time. For example, for 5 minutes past 7, enter "0705" and for 18 minutes past 23,
enter "2318."
7Press <Close>.
8Press (Start).
➠Originals are scanned and sent/saved at the specied time.
Scanning
407
●You can check on the <Status Monitor> screen whether sending/saving is complete or not. Checking
Status and Log for Scanned Documents(P. 392)
●You can reserve up to 64 jobs for delayed sending. However, the actual number of send jobs that the
machine can handle may be fewer than 64, depending on the following conditions:
- When multiple documents are being sent at the same time
- When large documents are being sent
- When a large amount of memory is being used for the Fax/I-Fax Inbox
LINKS
Notifying You by E-Mail of the Completion of Sending/Saving(P. 409)
Scanning
408
Job Done NoticeJob Done Notice
Notifying You by E-Mail of the Completion of Sending/
Saving
72JY-06X
You can receive an e-mail notifying that sending/saving documents is complete. Even
if documents are waiting to be sent/saved, you can use your computer or portable
device to check whether sending documents is complete, giving you reassurance.
When an error occurs, you are notied of destinations whose documents failed to be
sent/saved.
●To select the destination to notify from <Address Book>, it is necessary to register the destination in
advance. Registering Destinations in the Address Book(P. 195)
●To select <Send to Myself> as the destination to notify, it is necessary to register your e-mail address in the
user information in advance, and log in using personal authentication management. Registering User
Information in the Local Device(P. 495)
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Press <Options> <Job Done Notice>.
6Specify the notication condition and the destination to notify.
Scanning
409
●If you select <Notice for Any Result>, a notication e-mail is sent for each send job. If you select <Notice Only
for Errors>, a notication e-mail is sent only when an error occurs.
●For more information on how to view and use the Address Book, see Address Book(P. 190) .
●If you want to check the content of the sent document, select <Attach TX Image> to attach the rst page of
the document as a PDF le to a notication e-mail.
7Press <OK> <Close>.
8Press (Start).
➠Originals are scanned and sending/saving starts. When sending/saving is complete, the notication e-mail
is sent to the specied address.
Scanning
410
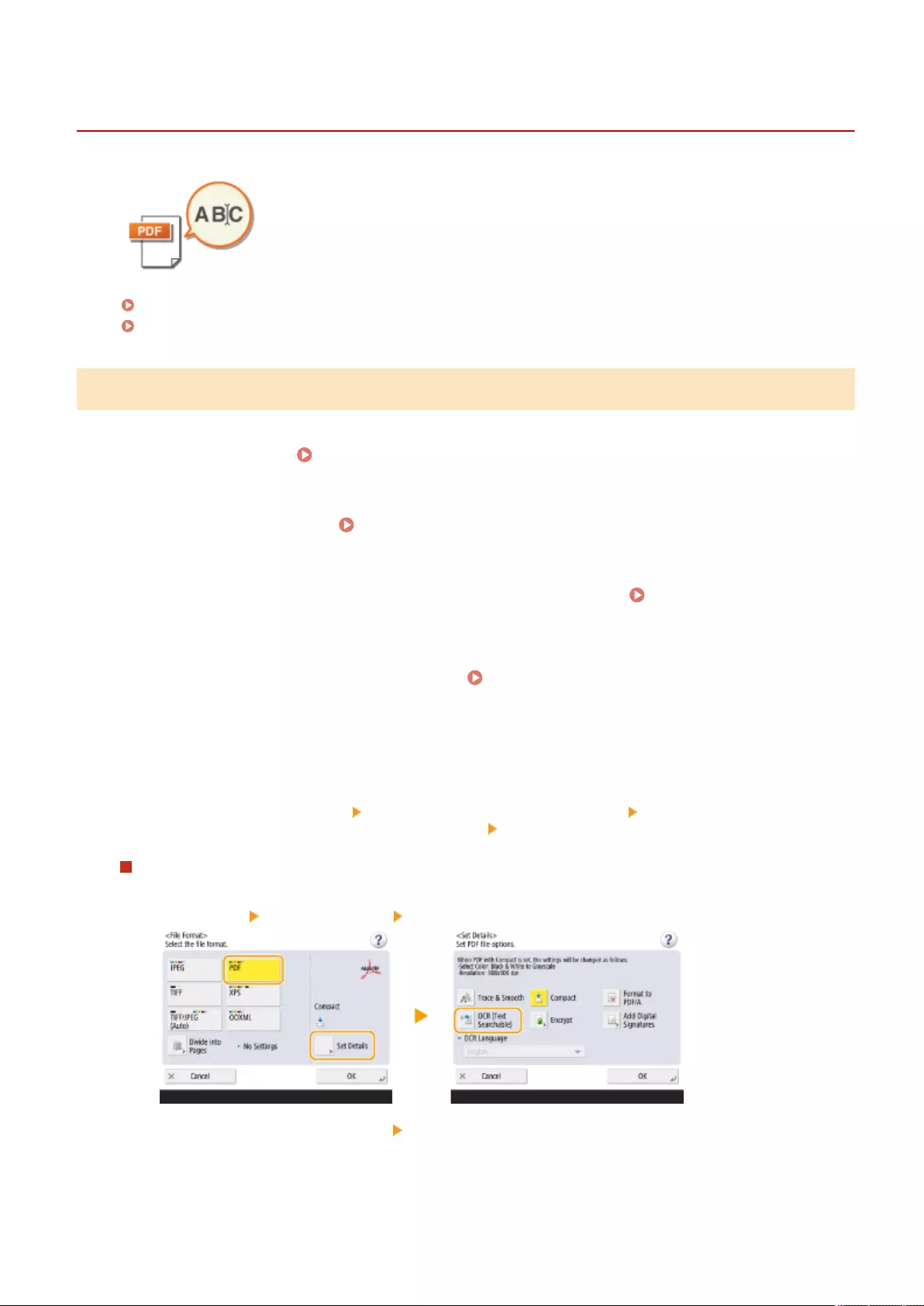
Scanning with the OCR Function
72JY-06Y
This mode enables you to perform OCR (optical character recognition) to extract data
that can be recognized as text from the scanned image and create a PDF/XPS/OOXML
(pptx/docx) le that is searchable. You can also set <Compact> if you select PDF or
XPS as the le format.
Scanning with OCR(P. 411)
OCR Results Are Not Satisfactory(P. 413)
Scanning with OCR
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Select a le format.
If you want to separate multiple images and send them as separate les, each of which consists of only one
page, press <Divide into Pages> enter the number of pages to divide by press <OK>. If you want to scan
the images as a single le, press <Divide into Pages> <Cancel Settings>.
To select PDF
1Select <PDF> press <Set Details> <OCR (Text Searchable)>.
2Select the language to use for OCR press <OK>.
Scanning
411

To select XPS
1Select <XPS> press <Set Details> <OCR (Text Searchable)>.
2Select a language to use for OCR press <OK>.
To select the Word format for OOXML
1Select <OOXML> select <Word> from the drop-down list.
●To change a language to use for OCR, press <Set Details> <Change> select a language or
language group press <OK>.
To select the PowerPoint format for OOXML
1Select <OOXML> select <PowerPoint> from the drop-down list.
●To change the language used for OCR, press <Set Details> <Change> select the language press
<OK>.
6Press <OK>.
Scanning
412
●If you select <PDF; OCR>, <XPS; OCR>, or <OOXML; OCR> as the le format, and <Smart Scan> is set to
<On> in <OCR (Text Searchable) Settings>, the orientation of the original is detected, and the
document is automatically rotated if necessary before it is sent. <OCR (Text Searchable)
Settings>(P. 813)
●If you select <PDF> or <XPS> as the le format, you can set <Compact> and <OCR (Text Searchable)>
at the same time. In that case, <PDF; Compact> or <XPS; Compact> is displayed as the le format on
the Scan and Send Basic Features screen.
●If you select <Word> for <OOXML>, you can set to delete the scanned background images. You can
generate Word les which are easy to edit without unwanted images. <Include Background
Images in Word File>(P. 814)
●Select one language or one group according to the language used in the originals to scan. Settings
and Languages for OCR Processing(P. 413)
OCR Results Are Not Satisfactory
When you create text-searchable PDF/XPS/OOXML les, OCR (Optical Character Recognition) may not be properly
processed. This may be because the settings on the machine, or the language, character type or format of the original
document are not appropriate for OCR processing.
◼Checking the Machine Settings and Supported Languages
You can improve OCR processing by customizing the machine settings regarding character recognition according to
the originals, or by using suitable character types or fonts in the originals so that the machine can recognize the
characters.
◼Settings and Languages for OCR Processing
Item Details
Language Settings for Character
Recognition
When a language is specied with OCR selected in <File Format>:
Characters are recognized based on the language you select for each le format.
When a language is not specied with OCR selected in <File Format>:
Characters are recognized based on the language you select in <Switch Language/
Keyboard> ( <Switch Language/Keyboard>(P. 773) ).*1
Recognizable Asian Languages Japanese, Chinese (Simplied), Chinese (Traditional), Korean
Recognizable Character Types and Fonts (Asian Languages)(P. 414)
Recognizable European Languages
and Language Groups
Languages:
English, French, Italian, German, Spanish, Dutch, Portuguese, Albanian, Catalan, Danish,
Finnish, Icelandic, Norwegian, Swedish, Croatian, Czech, Hungarian, Polish, Slovak,
Estonian, Latvian, Lithuanian, Russian, Greek, Turkish
Language Groups:
Western European (ISO)*2, Central European (ISO)*3, Baltic (ISO)*4
Recognizable Character Types and Fonts (European Languages)(P. 414)
*1 Displayed languages in the list may vary. If you select English, French, Italian, German, Spanish, Thai, or Vietnamese,
the selected language is recognized as Western European (ISO).
*2 Including English, French, Italian, German, Spanish, Dutch, Portuguese, Albanian, Catalan, Danish, Finnish, Icelandic,
Norwegian, and Swedish.
*3 Including Croatian, Czech, Hungarian, Polish, and Slovak.
Scanning
413
*4 Including Estonian, Latvian, and Lithuanian.
◼Recognizable Character Types and Fonts (Asian Languages)
Item Details
Recognizable Character Types Japanese:
Alphanumeric characters, Kana characters, Kanji characters (JIS rst level, and some
of the JIS second level), Symbols
Chinese (Simplied):
Alphanumeric characters, Chinese characters, Symbols (GB2312-80)
Chinese (Traditional):
Alphanumeric characters, Chinese characters, Symbols (Big5)
Korean:
Alphanumeric characters, Chinese characters, Hangul characters, Symbols
(KSC5601)
Recognizable Fonts ●Multiple fonts are supported. (Ming-cho type is recommended.)
●Italicized characters cannot be recognized.
Fonts Used for Converted Characters (Only
when Word is selected as the le format)
Japanese:
Asian characters: MS Mincho
European characters: Century
Chinese (Simplied):
Asian characters: SimSun
European characters: Calibri
Chinese (Traditional):
Asian characters: PMingLiU
European characters: Calibri
◼Recognizable Character Types and Fonts (European Languages)
Item Details
Recognizable Character Types Alphanumeric characters, Special characters of the recognized
language*, Symbols
Recognizable Fonts ●Multiple fonts are supported. (Times, Century, and Arial are
recommended.)
●Italicized characters can be recognized.
Fonts Used for Converted Characters (Only when Word is
selected as the le format)
●Calibri
●Italic style is not reproduced.
* The following special Greek characters can be recognized. Special characters for each language can also be recognized.
Some special characters cannot be recognized depending on the languages.
Α, Β, Γ, Δ, Ε, Ζ, Η, Θ, Ι, Κ, Λ, Μ, Ν, Ξ, Ο, Π, Ρ, Σ, Τ, Υ, Φ, Χ, Ψ, Ω, α, β, γ, δ, ε, ζ, η, θ, ι, κ, λ, μ, ν, ξ, ο, π, ρ, σ, τ,υ, φ, χ, ψ, ω
◼Checking the Format of the Original Documents
Use originals suitable for OCR processing to improve the processing accuracy when creating searchable PDF/XPS/
OOXML les.
Scanning
414
Item Details
Original Format Printed documents, Word processor documents (documents consisting of text, graphics,
photographs, or tables, and with no character slant)
Text Format ●Horizontal and vertical writing (documents containing both horizontal and vertical
writing can also be recognized)
●Only horizontal writing can be recognized for European languages and Korean text.
●One to three column documents with no complex column settings
Character Size 8 to 40 point
Table Format (For Word Format Only) Tables that meet the following conditions:
●Tables consist of squares divided with solid lines
●Tables with up to 32 columns
●Tables with up to 32 rows
Some originals suitable for OCR processing may not be processed properly.
●High accuracy may not be achieved with originals including a large amount of text on each page.
●Characters may be replaced with unintended characters or be missing due to the background color of the
original, form and size of characters, or slanted characters.*
●Paragraphs, line breaks, or tables may not be reproduced.*
●Some parts of illustrations, photographs, or seal impressions may be recognized as characters and be
replaced with characters.*
* When Word is selected as the le format.
Scanning
415
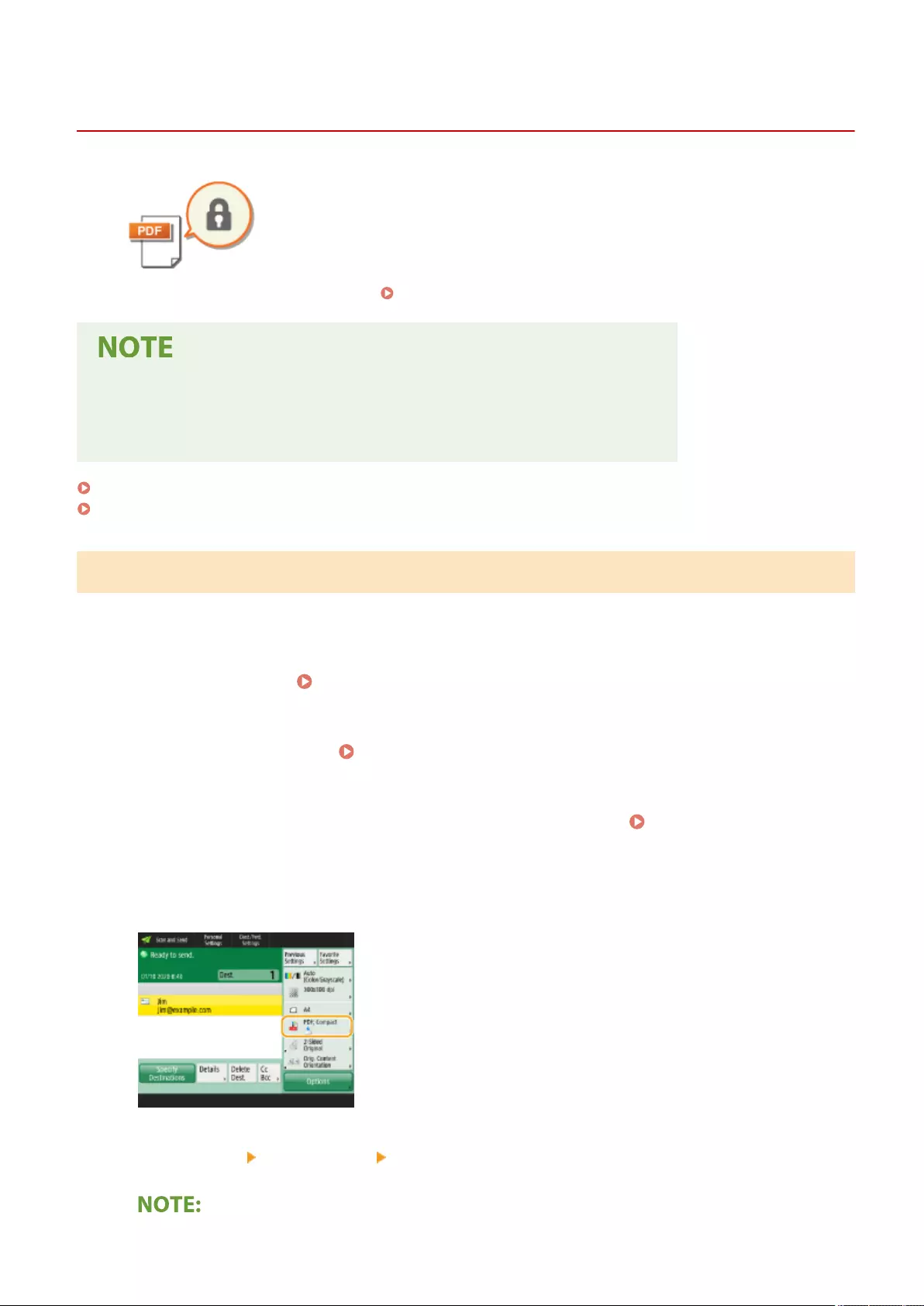
Enhancing the Security of Electronic Files
72JY-070
Electronic les are vulnerable to security threats, such as those of les being viewed
easily and tampered without leaving any traces. When scanning important papers,
you can enhance the security of the les by encrypting or adding a digital signature
to them.
For information on the optional products required to use this function and the le
formats, see System Options(P. 1101) .
●Only PDF les can be encrypted.
●PDF and XPS les can have digital signatures.
●For PDF les, the encryption and digital signature functions can be used together.
Performing Encryption(P. 416)
Adding a Digital Signature(P. 418)
Performing Encryption
Setting a password when scanning an original enables PDF les to be encrypted for sending/saving. This helps reduce
the risk of the les being viewed or edited by others.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Press the setting button for le format.
5Press <PDF> <Set Details> <Encrypt>.
Scanning
416

●To perform encryption, it is necessary to disable <Format to PDF/A>.
●You cannot set the Encrypted PDF mode when <Auto (OCR)> is set for <File Name>.
●This mode can be used only if an e-mail address or le server is specied as the destination.
6Set the password and press <OK>.
<Encryption Level>
Select the encryption level. If you want to use <Acrobat 9.0 or Equivalent/256-bit AES> rather than
<Acrobat 10.0 or Equivalent/256-bit AES> as the encryption level, use this setting to change the selections
you can make. <256-bit AES Settings for Encrypted PDF>(P. 814)
<Password Required to Open Document>
Enables you to set the password that is required when opening the le. Press <Password Required to
Open Document> <Password to Open Doc.> to enter the password.
<Password Required to Change Permission>
Enables you to set the password that is required when printing the le or editing the le, such as deleting
pages, as well as to specify the operations that are allowed. Press <Password Required to Change
Permission> <Permission Password> to enter the password, and then press <Set Details> and specify
the operations to be permitted.
●<Allow Printing>
-<Do Not Allow>: Printing is not allowed.
(Even if you select <Do Not Allow>, the document can be printed if it is opened with the permission
password in Adobe Acrobat 5 or earlier.)
- <Allow (Low Resolution Only)>: Only low-resolution printing is allowed.
(Appears only if you select <Acrobat 6.0 or Later/128-bit RC4>, <Acrobat 7.0 or Later/128-bit AES>, <Acrobat
9.0 or Equivalent/256-bit AES>, or <Acrobat 10.0 or Equivalent/256-bit AES>.)
- <Allow>: Printing is allowed.
●<Allow Changes>
- <Do Not Allow>: Changing of les is not allowed.
- <Insert, Delete, or Rotate Pages>: Inserting, deleting, and rotating pages are allowed. (Appears only if you
select <Acrobat 6.0 or Later/128-bit RC4>, <Acrobat 7.0 or Later/128-bit AES>, <Acrobat 9.0 or Equivalent/
256-bit AES>, or <Acrobat 10.0 or Equivalent/256-bit AES>.)
- <Signature Field Signing>: If there is already a signature eld in the PDF, adding a digital signature to that
signature eld is allowed. (Appears only if you select <Acrobat 6.0 or Later/128-bit RC4>, <Acrobat 7.0 or
Later/128-bit AES>, <Acrobat 9.0 or Equivalent/256-bit AES>, or <Acrobat 10.0 or Equivalent/256-bit AES>.)
- <Commenting and Signature Field Signing>: Adding comments, and adding a digital signature to a
signature eld (if there is already a signature eld in the PDF) are allowed.
- <Changes but Add Comments/Extract Pages>: Changes to the document are allowed, except for adding
comments and extracting pages. (Appears only if you select <Acrobat 3.0 or Later/40-bit RC4>.)
- <Changes but Extract Pages>: Changing of les except for extracting pages is allowed.
Scanning
417

●<Enable Copying and Extraction of Images/Text>
- Appears only if you select an item other than <Acrobat 3.0 or Later/40-bit RC4> for <Encryption Level>. If
you select this item, you can copy or extract image/text from the scanned le.
●<Enable Access for Visually Impaired>
- Appears only if you select an item other than <Acrobat 3.0 or Later/40-bit RC4> for <Encryption Level>.
Selecting this item enables functions for reading aloud the text inside a le for the visually impaired.
●<Enable Accessibility, Copy, Extraction of Image/Text>
- Appears only if you select <Acrobat 3.0 or Later/40-bit RC4> for <Encryption Level>. Selecting this key sets
both <Enable Copying and Extraction of Images/Text> and <Enable Access for Visually Impaired> at the
same time.
●If you are logging in to the machine with personal authentication management ( Managing
Users(P. 489) ), the <Store Password> button is displayed. Pressing this button saves the passwords
you entered so that you can eliminate the need to enter passwords for the next setting.
●One password can be stored for each user. If you enter a new password when a password is already
stored, the existing password is overwritten (the password is deleted if it is left blank).
●You cannot set the same password for both <Password to Open Doc.> and <Permission Password>.
●If you leave <Password to Open Doc.> or <Permission Password> empty, the stored password is
erased.
●If you log in using User Authentication when all of the following conditions are true, multiple
passwords may exist. In this case, a message conrming whether or not to use the password stored
in <Store Password> may appear. Press <Yes> to use the password stored in <Store Password>. Press
<No> to use the password registered in Favorite Settings.
- A password is stored in <Store Password>
- An encrypted PDF le is stored in Favorite Settings
- The encrypted PDF le is recalled and sent from Favorite Settings
●To set digital signatures when <Password Required to Change Permission> is set, set <Allow
Changes> to <Changes but Extract Pages>.
●Even if you set restrictions for a PDF le with <Permission Password>, some of the restrictions may be
ignored if the reader opens the PDF with certain software.
7Press (Start).
➠Originals are scanned and sending/saving starts.
Adding a Digital Signature
You can convert scanned originals into PDF/XPS les with a digital signature. A digital signature is similar to the act of
signing and sealing papers, which enables you to check who created the le and if the le was tampered or forged
after it was signed. For detailed information about a digital signature and its settings, see Adding a Digital
Signature to Sent Files(P. 577) .
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
Scanning
418
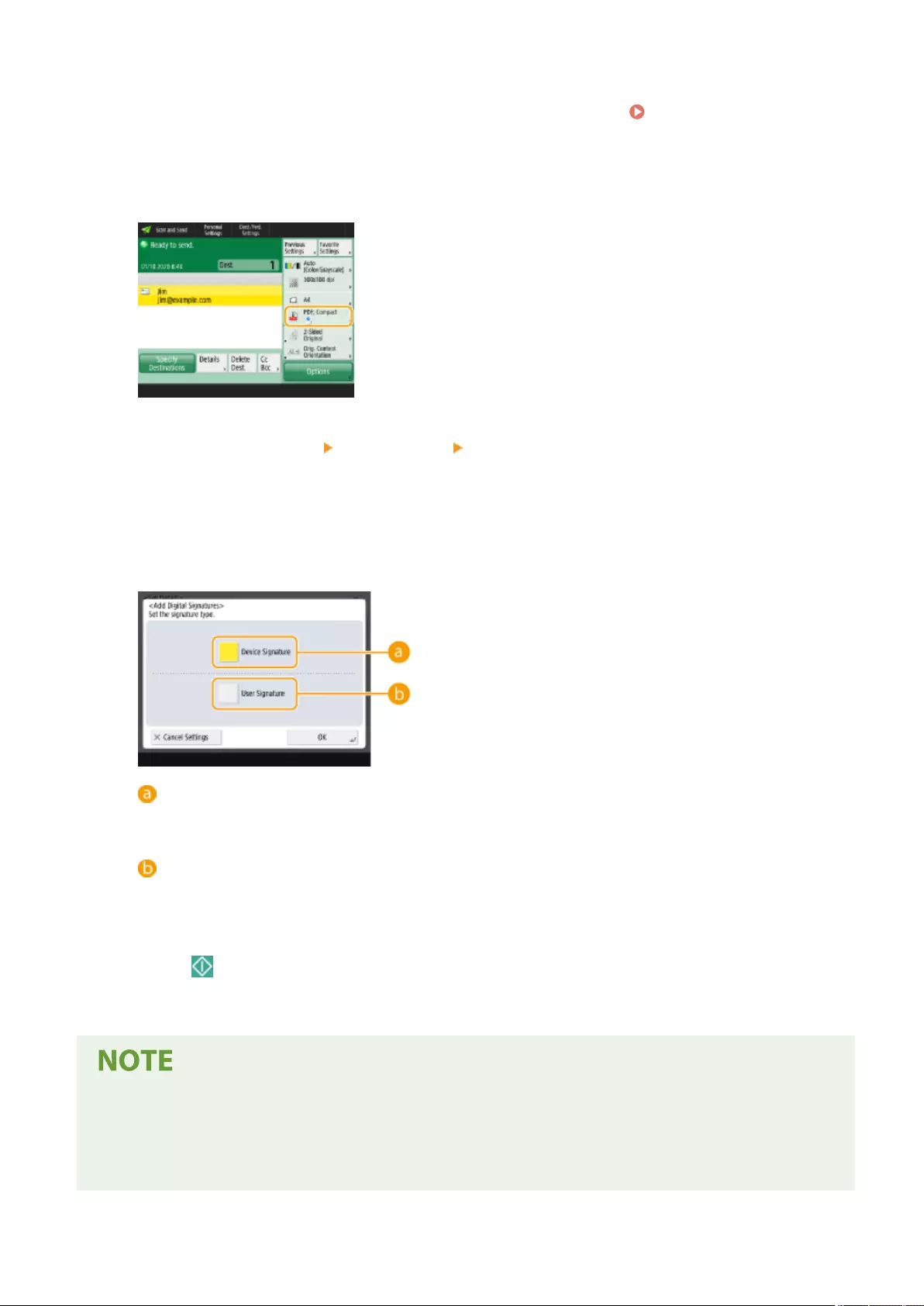
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Press the setting button for le format.
5Press <PDF> or <XPS> <Set Details> <Add Digital Signatures>.
●If you do not log in to the machine with personal authentication management and select <XPS>, press <Add
Device Signature>.
6Select the digital signature and press <OK>.
<Device Signature>
The name of the machine is added to the le as a signature. The reader can verify that the le is scanned
from the machine.
<User Signature>
The name of the user who logs in to the machine with personal authentication management is added to
the le as a signature. The reader can verify that the le is scanned by the user.
7Press (Start).
➠Originals are scanned and sending/saving starts.
Making a digital signature recognized at a glance by the reader (visible signature) (only
for a PDF le)
●Pressing <Visible Signatures> makes the signature appear on the rst page of the le, enabling the reader to
check at a glance who created the le.
Scanning
419
When using together with PDF le encryption
●If you want to set a password for <Password Required to Change Permission> when encrypting a PDF le,
select <Changes but Extract Pages> for <Allow Changes>. Performing Encryption(P. 416)
●Setting S/MIME enables you to send an e-mail with a digital signature as well as encryption. <S/MIME
Settings>(P. 826)
LINKS
Managing Users(P. 489)
Scanning
420
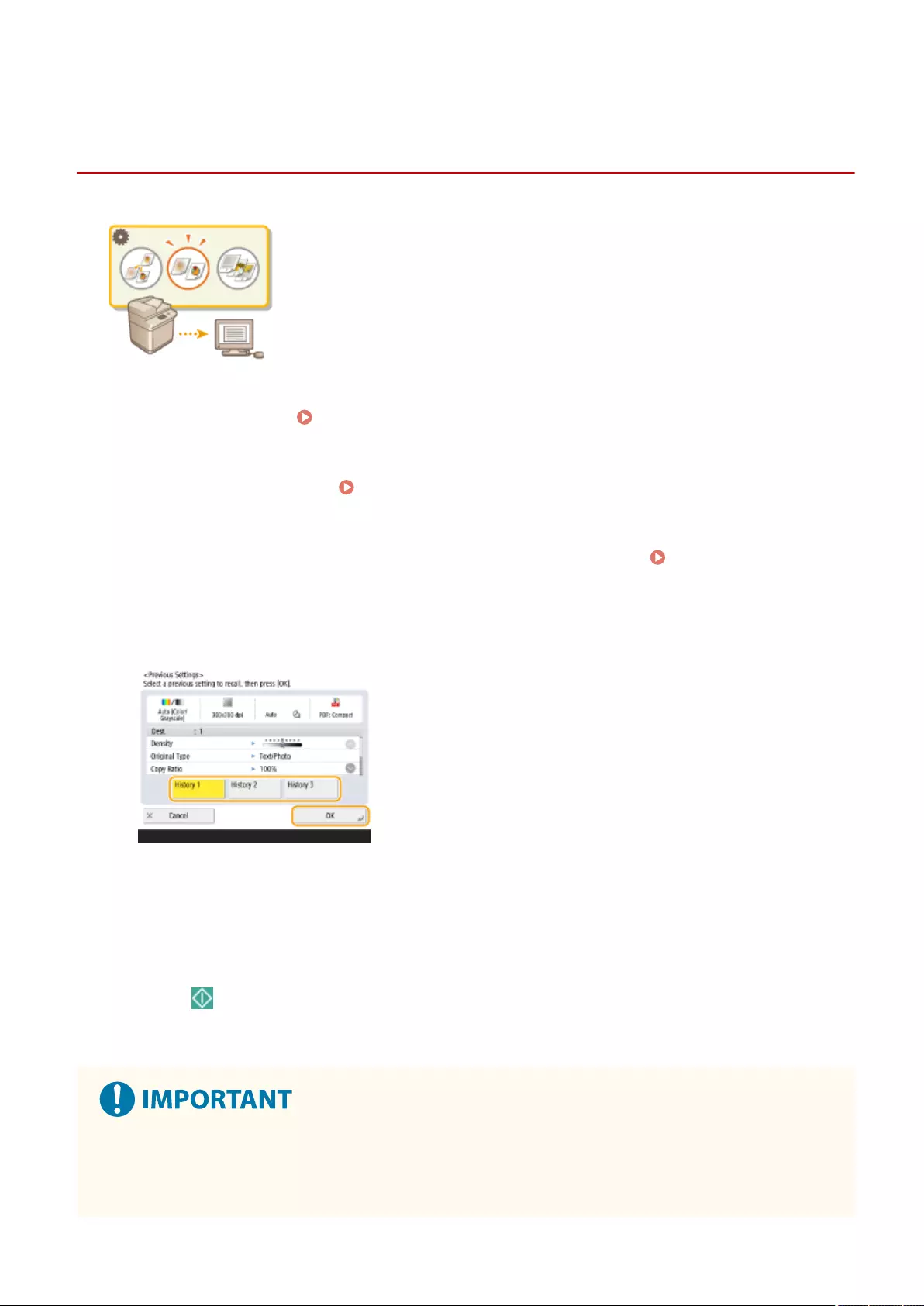
Previous Settings
Recalling Previously Used Settings for Sending/Saving
(Previous Settings)
72JY-071
You can recall destinations specied in the past. Their scan settings such as density
are also recalled at the same time.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Press <Previous Settings> on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Select the log to recall and press <OK>.
➠The destination and its scan settings are specied according to the selected log.
●When personal authentication management is in use, the machine recalls the settings specied in the past by
the user who are logging in to the machine.
●You can change the recalled settings before sending/saving.
5Press (Start).
➠Originals are scanned and sending/saving starts.
●If you set <Manage Address Book Access Numbers> to <On>, you cannot recall recently used settings.
●If you set any address type to <On> in <Restrict New Destinations>, the currently stored Previous Settings
are deleted.
Scanning
421
File NameFile Name
Setting a File Name
72JY-072
A scanned document is sent/saved with its le name automatically assigned. If you
want to change the le name of documents so that the contents can be guessed
from the name, specify the following settings before scanning.
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Press <Options> <File Name>.
6Press <File Name>, enter the le name, and then press <OK>.
●If you use characters such as "\", "/", ":", "*", "?", "<", ">", or "|" in the document name, you are unable to send
the le to le servers that run on operating systems that do not recognize such characters.
7Press <OK> <Close>.
8Press (Start).
➠Originals are scanned and sending/saving starts.
●When sending a document by e-mail, it is sent with its le name assigned in the format of "entered le
name_page numbers (three digits).le extension," such as "business log_001.jpg." If you do not enter a le
name, the format will be "Job numbers (four digits)_page numbers (three digits).le extension."
●When saving a document in a le server, it is saved with its le name assigned in the format of "entered le
name_the year, month, day, hour, minute, and second the le is saved (14 digits).le extension," such as
"business log_20151030133541.jpg." If you do not enter a le name, the format will be "the year, month, day,
hour, minute, and second the le is saved (14 digits). le extension."
●Pressing to add a check mark to <Rmv Date/Job No. from File Name> excludes the data/time and the job
number from the le name.
Scanning
423
●If you are saving a document in a le server, selecting <Divide into Pages> when specifying a le format
adds a page number (ve digits) at the end of a le name.
Extracting a text block in the document for use as its le name
●If you set <OCR (Text Searchable)> for <PDF>, <XPS>, or <OOXML> in <File Format>, and then press <Auto
(OCR)> for <File Name>, the text in the original is extracted and automatically entered into <File Name>. The
maximum number of characters to be extracted can be set in <Max Number of Char. for File Name> for
<OCR (Text Searchable) Settings>(P. 813) .
●You cannot set <Encrypt> and <Auto (OCR)> at the same time.
●If you manually enter the le name and set <Auto (OCR)>, the extracted text is appended to the end of the
lename. Characters over the character limit will be cut off.
Editing a le name from the Remote UI
●If you register a le name in a state where <File Name> is set in <Favorite Settings>, you can edit the le
name from the Remote UI.
Start the Remote UI click [Settings/Registration] [Function Settings] [Send]
[Favorite Settings]
●The le name generated with <Auto (OCR)> is not reected to the following items:
- The send job status (status display (on the bottom of the touch panel display))
- TX Report
- <File Name> in the job log
LINKS
System Options(P. 1101)
Performing Encryption(P. 416)
Scanning
424
Specifying E-Mail Settings
72JY-073
You can specify the subject, body, reply-to address, and priority used when sending
your documents as e-mail attachments.
●The reply-to address needs to be specied from among those registered in the Address Book. Register the
desired address in the Address Book beforehand. Registering Destinations in the Address Book(P. 195)
●You can specify a destination from the address book of a mobile device. You can also send information
including the subject, body, and le name from the mobile device to the machine. Scan Basic Features
Screen(P. 374)
1Place the original. Placing Originals(P. 97)
2Press <Scan and Send>. <Home> Screen(P. 119)
3Specify the destination on the Scan Basic Features screen. Scan Basic Features
Screen(P. 374)
4Specify the scan settings as necessary. Basic Operations for Scanning
Originals(P. 377)
5Press <Options> and specify e-mail settings.
Subject/MessageSubject/Message
To specify subject/body
1Press <Subject/Message>.
2Press <Subject>, enter the subject, and then press <OK>.
●If nothing is entered, the subject entered in <Default Subject> is automatically set. <Default
Subject>(P. 828)
3Press <Message>, enter the body, and then press <OK>.
4Press <OK>.
Scanning
425

●If you send the subject/body from a mobile device to the machine, the complete sent text may not appear
in the entry eld. If this happens, press <Cancel Settings> on the subject/body entry screen.
Reply-toReply-to
To specify reply-to address
1Press <Reply-to>.
2Select a reply-to address and press <OK>.
●For instructions on how to specify destinations, see Basic Operations for Scanning
Originals(P. 377) .
●When you send an e-mail, the selected destination is set as the reply-to e-mail address when the recipient
replies.
●When you send an I-fax, a Full mode delivery conrmation message is sent to the selected reply-to
address.
●If you set a login service for the machine and set <Specify Authentication User for Reply-To> to <On>, the
e-mail address of the login user appears as the reply-to address.
E-Mail PriorityE-Mail Priority
To specify priority
1Press <E-Mail Priority>.
2Select a priority level and press <OK>.
6Press <Close>.
7Press (Start).
➠Originals are scanned and sending starts.
Scanning
426
Scanner
Using Your Computer to Scan (Remote Scan) (Windows)
72JY-074
You can scan originals placed on the machine by operating your computer. There are two methods for scanning, using
the "Color Network ScanGear 2" scanner driver supplied with the machine and the WSD function available for
Windows.
Using Color Network ScanGear 2 to Scan
You can scan originals directly into your favorite application for editing. This method is useful when you want to
edit scanned photos in Photoshop or want to paste scanned picture into a Word document. Using Color
Network ScanGear 2(P. 428)
Using WSD to Scan
Even if you do not have a dedicated scanner driver, you can scan an original easily from a computer using the
WSD function available for Windows. Using WSD(P. 432)
Scanning
427

Using Color Network ScanGear 2
72JY-075
You can scan an original by starting Color Network ScanGear 2 from an application such as Adobe Photoshop and
Microsoft Oce Word. Scanned documents can be edited or saved using the application's functions. You need to
complete some procedures before using Color Network ScanGear 2. Preparing to Use Color Network ScanGear
2(P. 428)
Scanning Originals from an Application(P. 430)
●For information about system environments in which Color Network ScanGear 2 can be used, see Help for
Color Network ScanGear 2.
●Depending on the version of the Windows operating system you are using, the Color Network ScanGear 2
screens in this section may differ from your screens.
●Starting Color Network ScanGear 2 requires TWAIN-compliant applications. Check Help for each application
to determine whether it supports TWAIN or not.
◼Help for Color Network ScanGear 2
Clicking [Help] [Color Network ScanGear 2 Help] on the Color Network ScanGear 2 screen displays the Help screen.
For information that is not in the User's Guide, including driver features and how to set up those features, see Help.
◼Preparing to Use Color Network ScanGear 2
After installing Color Network ScanGear 2 on a computer ( Installing Drivers(P. 67) ), follow the following
procedures to connect Color Network ScanGear 2 to the machine.
1Click [Start] the list of applications [Color Network ScanGear 2] [Color Network
ScanGear 2 Tool].
2Search the machine.
Specifying the IP address or host name of the machine
1Click [Specify Address] and enter the IP address or host name of the machine in the [IP Address or Host
Name] text box.
Searching for the machine automatically
1Click [Search for Scanners on the Network].
2Select [IP Address] or [IP Address or Host Name] from the [Address Displayed in Search Result] drop-
down list and click [Search].
3Click to select the machine from the [Search Results] list box.
Scanning
428
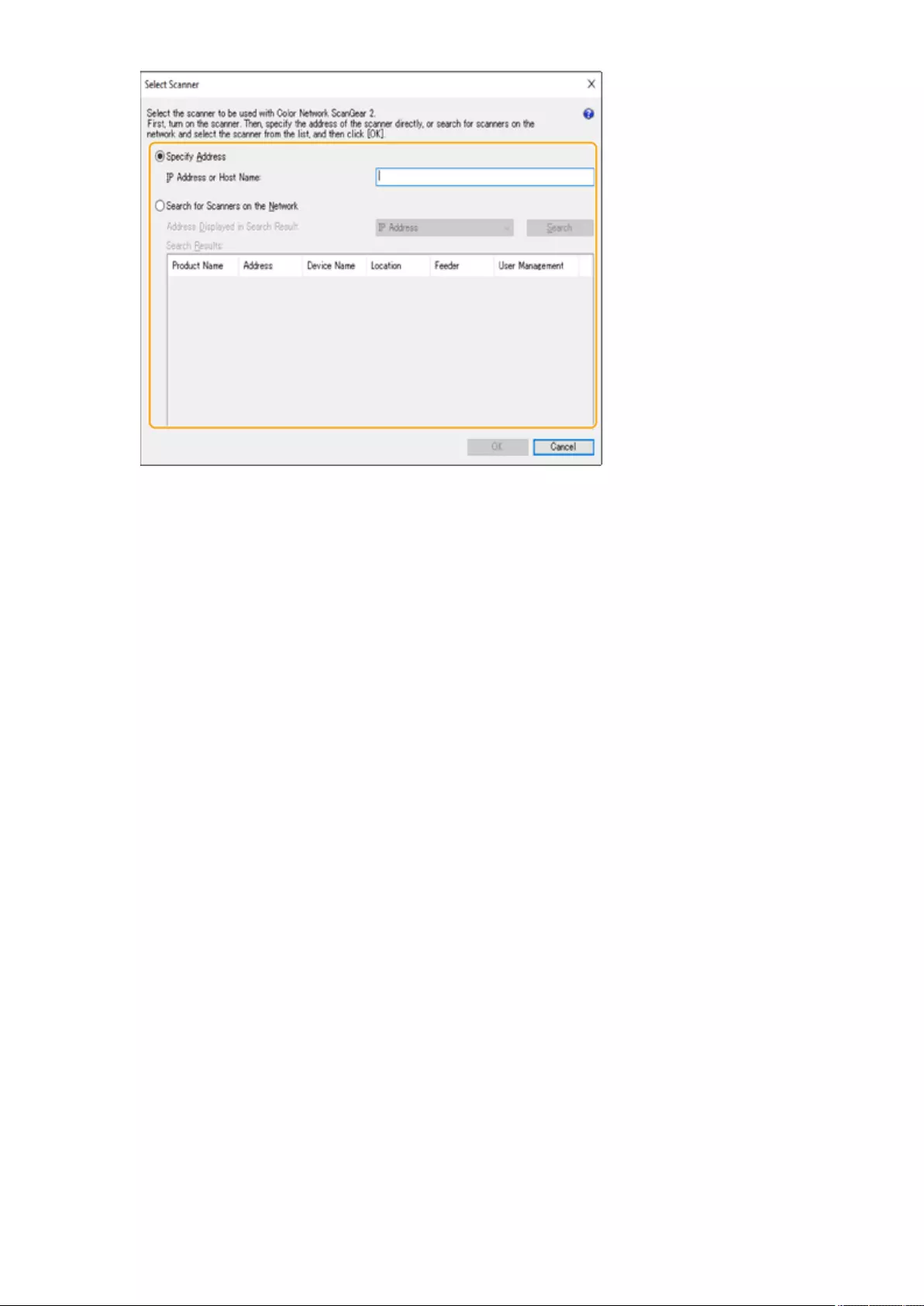
3Click [OK].
●The [Select Scanner] dialog box closes.
4Check that this machine is selected and click [Exit].
●To check if it can be connected properly, click [Test Connection].
Scanning
429

Scanning Originals from an Application
72JY-076
This section describes the method for scanning an original by starting Color Network ScanGear 2 from an application.
You can also scan a part of the original by specifying the scanning area.
From the control panel
1Place the original. Placing Originals(P. 97)
●To specify the scanning area, place the original on the platen glass.
●To scan multiple pages successively, place the originals in the feeder.
2Press <Scanner>. <Home> Screen(P. 119)
3Press <Online>.
➠Now you are ready for scanning from your computer.
●During the online state, other functions such as copying are not available.
●You can also set the machine to automatically go online. <Auto Online>(P. 812)
From a computer
4From the application menu, select the command that starts the scanning.
●Color Network ScanGear 2 starts. For more information, see the instruction manual for each application.
5At [Scanning Method] of the [Basic Settings] tab, select the location where the
original is placed.
●When placing the original on the platen glass, select [Platen Glass].
●When placing a 1-sided original in the feeder, select [Feeder (1-sided)]. For 2-sided originals, select [Feeder (2-
sided)].
Scanning
430
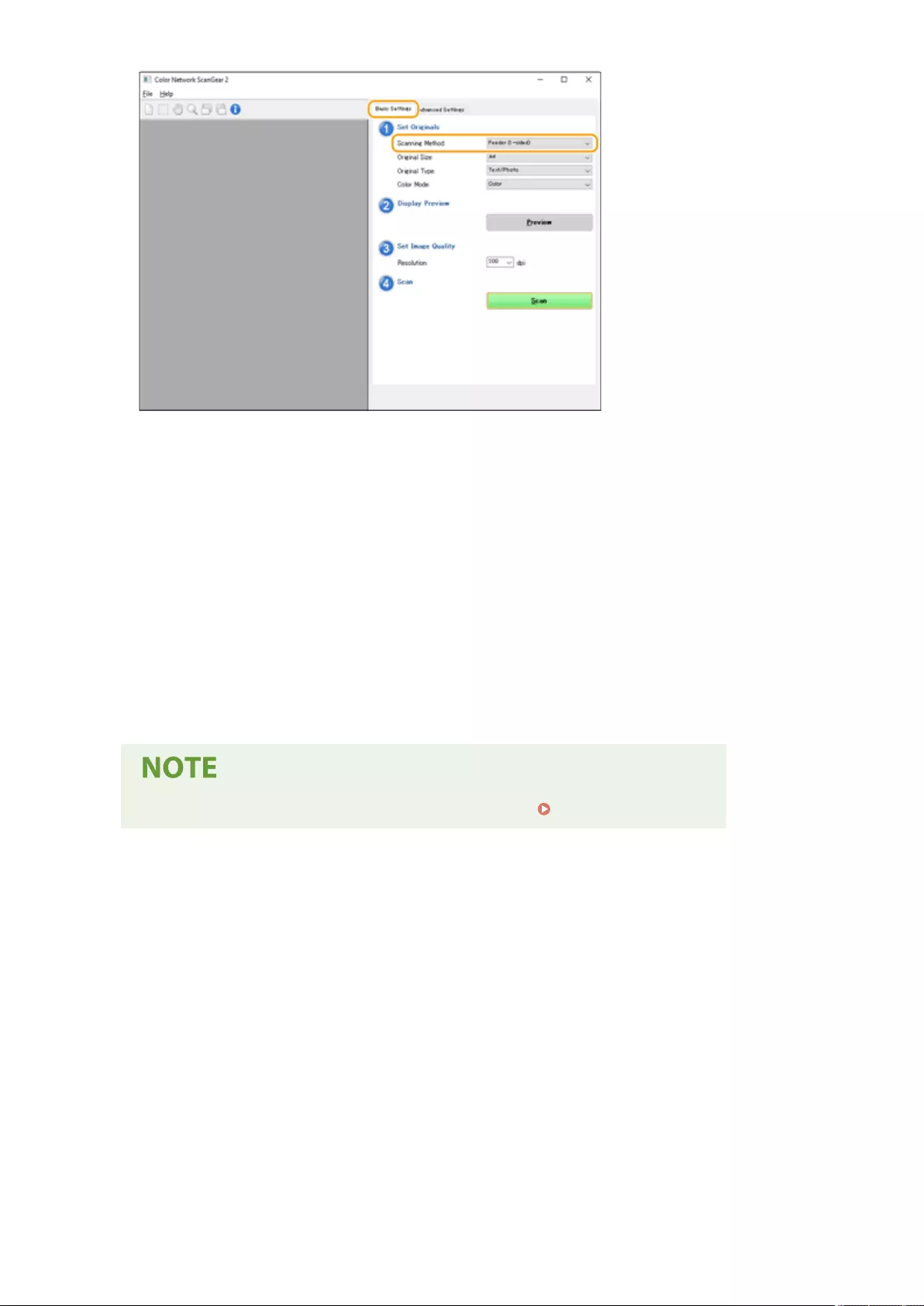
6Specify the scan settings as necessary.
●You can specify the color, resolution, and original size for scanning. Clicking the [Advanced Settings] tab
enables you to perform detailed settings such as original orientation. For more information, see Help for
Color Network ScanGear 2.
7Click [Scan].
➠Scanning an original starts.
●When scanning is complete, the Color Network ScanGear 2 screen closes and the scanned original is
displayed on the application screen.
●When the scanning operations are complete, press <Oine> on the <Scanner> screen.
●You can also set the machine to automatically go oine. <Auto Oine>(P. 812)
Scanning
431
Using WSD
72JY-077
"WSD (Web Services on Devices)" is a function to search devices located on the network. Using WSD enables you to
automatically nd the machine on the network from a computer, and start scanning the original on the machine. This
function is called "WSD Scan." You need to complete some procedures before using WSD Scan. Preparing for WSD
Scan(P. 432)
Scanning Originals Using WSD (WSD Scan)(P. 433)
In the following cases, WSD Scan is not available.
●ACCESS MANAGEMENT SYSTEM is activated Using ACCESS MANAGEMENT SYSTEM(P. 533)
●DepartmentID Authentication is in use as a login service Changing Login Services(P. 1075)
◼Preparing for WSD Scan
From the control panel
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <WSD Settings>.
3Press <On> for <Use WSD Scan>.
4Press <OK>.
From a computer
5Click [Start] [Settings] [Devices] [Printers & scanners].
6Click [Add a printer or scanner].
7Select the device to use click [Add a device].
●If this machine is not displayed, a Firewall setting problem may exist. For more information, see the
instruction manual of the computer.
Scanning
432
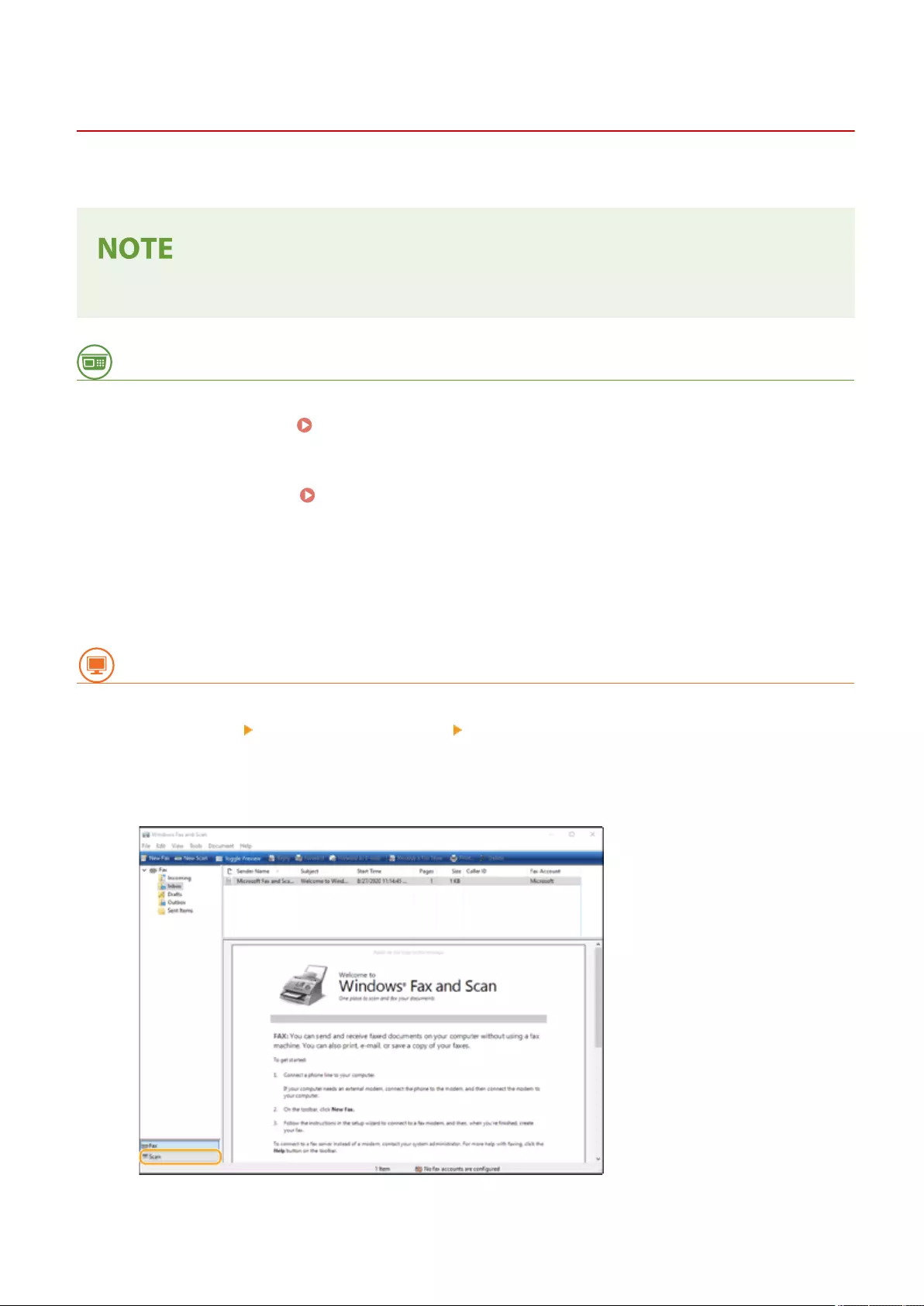
Scanning Originals Using WSD (WSD Scan)
72JY-078
This section describes how to scan originals from a computer using WSD.
●The available scanning size is A4(LTR). Note that even if you place an original larger than A4(LTR), only
A4(LTR) size is scanned.
From the control panel
1Place the original. Placing Originals(P. 97)
2Press <WSD Scan>. <Home> Screen(P. 119)
3Press <Allow Remote Scanner>.
➠Now you are ready for scanning from your computer.
From a computer
4Click [Start] [Windows Accessories] [Windows Fax and Scan].
5Click [Scan].
Scanning
433
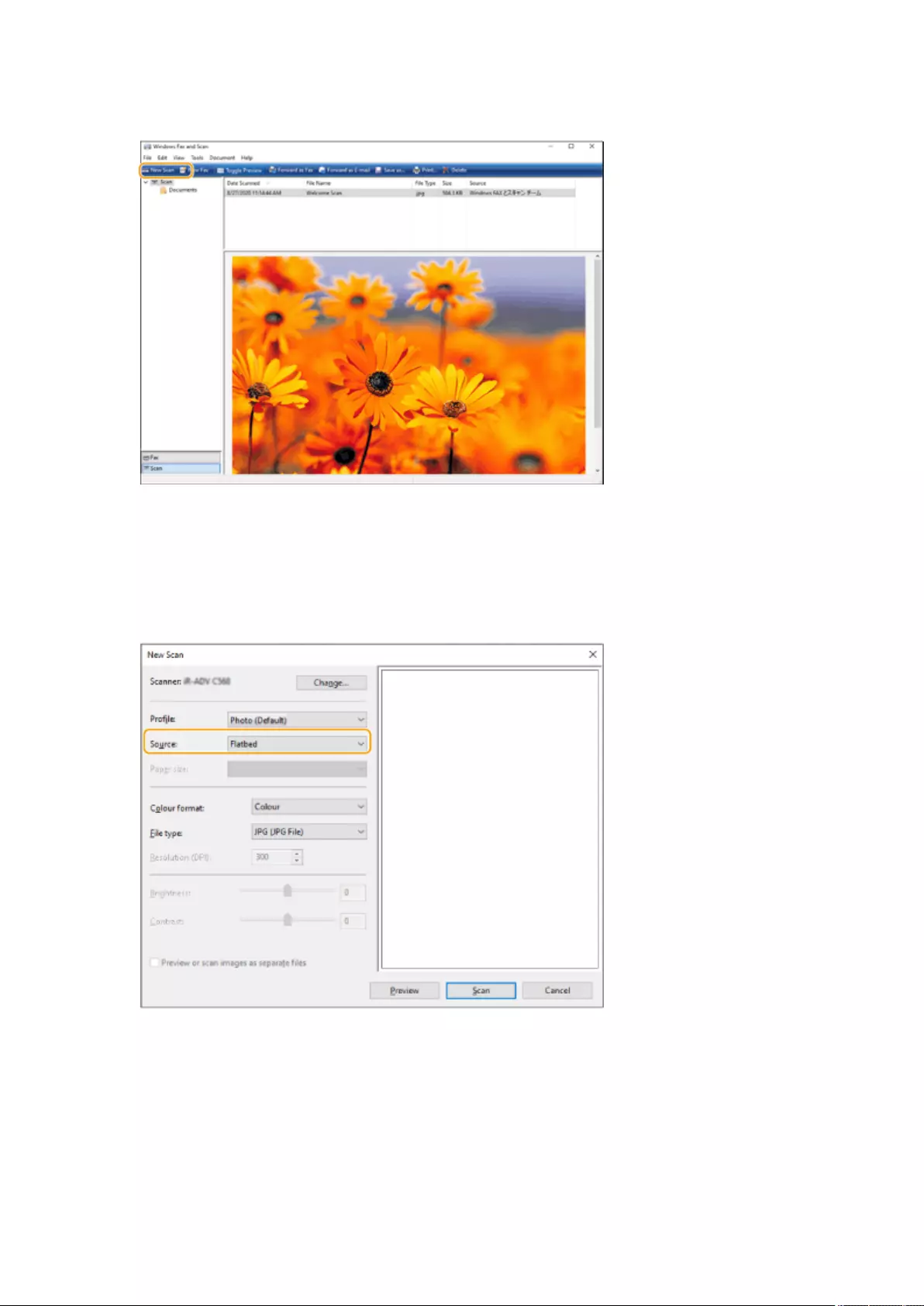
6Click [New Scan].
●When the [Select Device] dialog box is displayed, select the machine and click [OK].
7From the [Source] drop-down list, select the location where the original is placed.
●When placing the original on the platen glass, select [Flatbed]. When placing in the feeder, select [Feeder
(Scan one side)].
8Specify the scan settings as necessary.
●Selecting the type of original from the [Prole] drop-down list enables you to make adjustments for the
optimal image quality. For originals mainly consisting of text, select [Document]. For originals consisting of
photographs only, select [Photo (Default)].
●From the [File type] drop-down list, select the le format for the saved image of the scanned original.
●To check the scanned image with the specied settings reected, click [Preview].
Scanning
434
9Click [Scan].
➠Scanning an original starts.
●When scanning is complete, the scanned document is displayed in the list of les on the [Windows Fax and
Scan] screen and saved in the [Scanned Documents] folder of [Documents].
Registering frequently used scan settings
●If you always scan with the same settings, follow the procedures below to register the settings. You can
easily and conveniently recall them when scanning.
Select [Add prole] from the [Prole] drop-down list Specify the scan settings you want to register Enter
a name in the [Prole name] text box Click [Save Prole]
Sending the document to a computer using WSD
●You can also send the scanned document to computers on the network that support WSD. In this case, press
<WSD Scan> select the computer you want to send to <Enable>. The [Windows Fax and Scan] screen
and the folder open in the computer, and the scanned document is displayed.
●Up to 40 destination computers are displayed.
Scanning
435

Using Other Machines and Memory
Media
Using Other Machines and Memory Media .................................................................................... 437
Using Another Machine or Server - Network ................................................................................................... 438
Using Memory Media ........................................................................................................................................ 441
Settings Screens for Using Other Machines/Servers/Memory Media ............................................................ 446
Using Other Machines and Memory Media
436
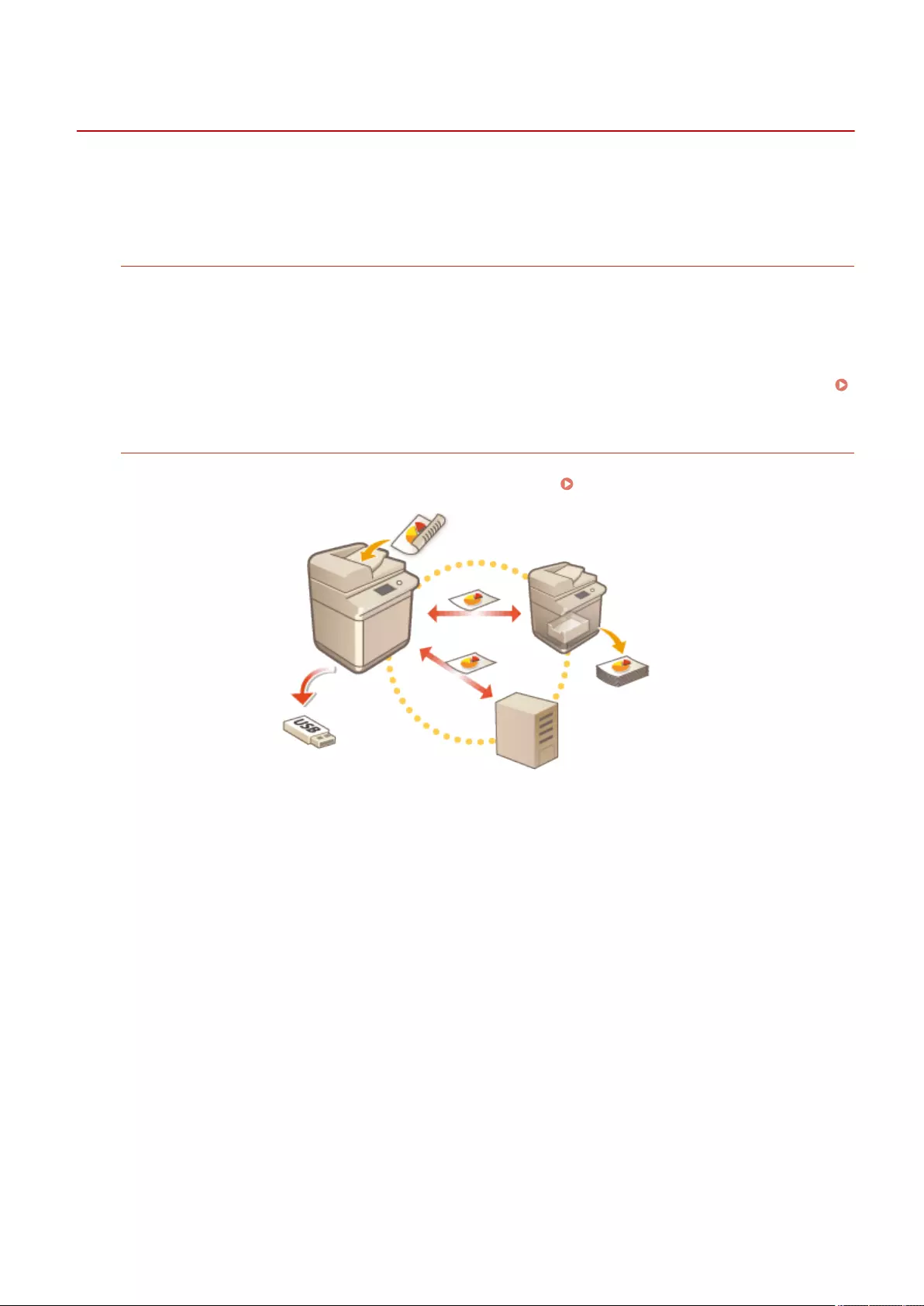
Scan and StoreAccess Stored Files
Using Other Machines and Memory Media
72JY-0LK
The machine can directly use data saved on other Canon machines connected to the network and data saved on
memory media. This enables data to be printed, and folder and le operations to be performed. Documents can also
be scanned with this machine and directly saved to another machine or memory media.
Using Machines Connected to the Network
By registering the following locations as connection destinations for the machine, they can be directly accessed
and used from the machine.
●Shared space (Advanced Space) of another Canon machine
●Windows server
You can directly use the le management of the Windows server or the Advanced Space of another machine.
Using Another Machine or Server - Network(P. 438)
Using Memory Media Such as USB Memory
You can also use the data on a computer not connected to the network via memory media compliant with the
USB standard. Preparations are required for using memory media. Using Memory Media(P. 441)
Using Other Machines and Memory Media
437
NetworkNetwork
Using Another Machine or Server - Network
72JY-0LL
This section describes the procedure for using a Windows server or the Advanced Space of another machine
connected to the network. This enables you to print saved les and directly save scanned documents.
Saving Scanned Documents to Another Machine or Server(P. 438)
Printing a File on Another Machine or Server(P. 439)
Using Personal Folders
●If you are logged in with personal authentication management, you can use the dedicated folders provided
for each user (Personal folders). By specifying a folder on a server connected to the network as a personal
folder, it can be directly accessed from the machine. Conguring Personal Folders(P. 529)
Saving Scanned Documents to Another Machine or Server
Required Preparations
Register the Advanced Space of another machine or Windows server as a connection destination. Connecting
to the Other Devices(P. 75)
1Place the original. Placing Originals(P. 97)
2Press <Scan and Store> <Network>.
➠The connection destinations registered in the machine are displayed.
3Select the connection destination, and log in.
When the login screen is displayed, enter the user name and password to log in. If the login screen is not
displayed, proceed to the next step.
Up
●To go back up one folder level, press <Up>.
Check Storage Information
●You can press <Check Storage Information> <Details> to check the information for the connection
destination.
Scan
4Display the folder to save to, and press <Scan>.
➠The settings screen for scanning is displayed.
●You can press <Name> or <Date/Time> to sort the display.
Folder OperationsFolder Operations
●In <Folder Operations>, you can check the information of a folder, rename a folder, create a new folder, or
delete a folder.
Update
●Press to refresh the display.
Using Other Machines and Memory Media
438

5Congure the scan settings.
Specify the le name and le format, and congure the scan settings as required. Scan Settings Screen in
<Scan and Store>(P. 446)
6Press (Start) to start scanning and save the le.
➠The scanning screen is displayed. When saving is complete, the connection destination selected in step 4
is displayed.
●To cancel scanning, press <Cancel> or (Stop).
●If you have another original to scan, place the original and repeat the procedure in step 6.
If <Start Storing> is displayed
When all of the originals have been scanned, press <Start Storing> to save the le.
➠The store location selected in step 4 is displayed.
7Conrm that the le has been saved.
●If you did not specify a le name in step 5, the date and time that the le was saved is used as the le name.
Display Image
●You can press <Display Image> to check the content of the le.
●You can press <Status Monitor> <Store> <Job Log> to check whether the le has been saved correctly. If
<NG> is displayed, the le has not been saved correctly. Repeat step 6.
If <Disconnect> is displayed
When your operations are complete, press <Disconnect> to log out from the connection destination.
Printing a File on Another Machine or Server
Required Preparations
Register the Advanced Space of another machine or Windows server as a connection destination. Connecting
to the Other Devices(P. 75)
1Press <Access Stored Files> <Network>.
➠The connection destinations registered in the machine are displayed.
2Select the connection destination, and log in.
When the login screen is displayed, enter the user name and password to log in. If the login screen is not
displayed, proceed to the next step.
Up
●To go back up one folder level, press <Up>.
Check Storage Information
●You can press <Check Storage Information> <Details> to check the information for the connection
destination.
Print
3Select the le to print, and press <Print>.
Using Other Machines and Memory Media
439
You can select up to six les in the same folder to print together. The les are printed in the selected order.
Clear SelectionSearch
You can deselect a le by selecting the le again. To deselect all les, press <Clear Selection>.
●Press <Search> to search for les and folders in the folder that is currently displayed. To not include
subfolders when searching, select <Do Not Include Subfolders>.
Display Image
●You can press <Display Image> to check the content of the le.
Edit File
●In <Edit File>, you can check the information of a le, rename a le, or delete a le.
Update
●Press to refresh the display.
4If the <Select Paper> screen is displayed, select the paper to use.
If not, proceed to the next step.
5Enter the number of copies to make using the numeric keys.
If multiple les are selected, press <Change No. of Copies> and enter the number of copies.
6Congure the print settings.
Congure the two-sided printing, nishing settings, and other print settings as required.
If a password is required for printing a PDF le, press <Options> <Password to Open Doc.> <Encryption
Password> or <Policy Password>, and enter the password.
*You cannot print multiple PDF les with different passwords simultaneously. Print Settings Screen in
<Access Stored Files>(P. 448)
7Press <Start Printing>.
➠The printing screen is displayed. When printing is complete, the le selection screen in step 3 is displayed.
●If the password entry screen is displayed, enter the password set in the PDF le.
●To cancel printing, press <Cancel>.
Using Other Machines and Memory Media
440
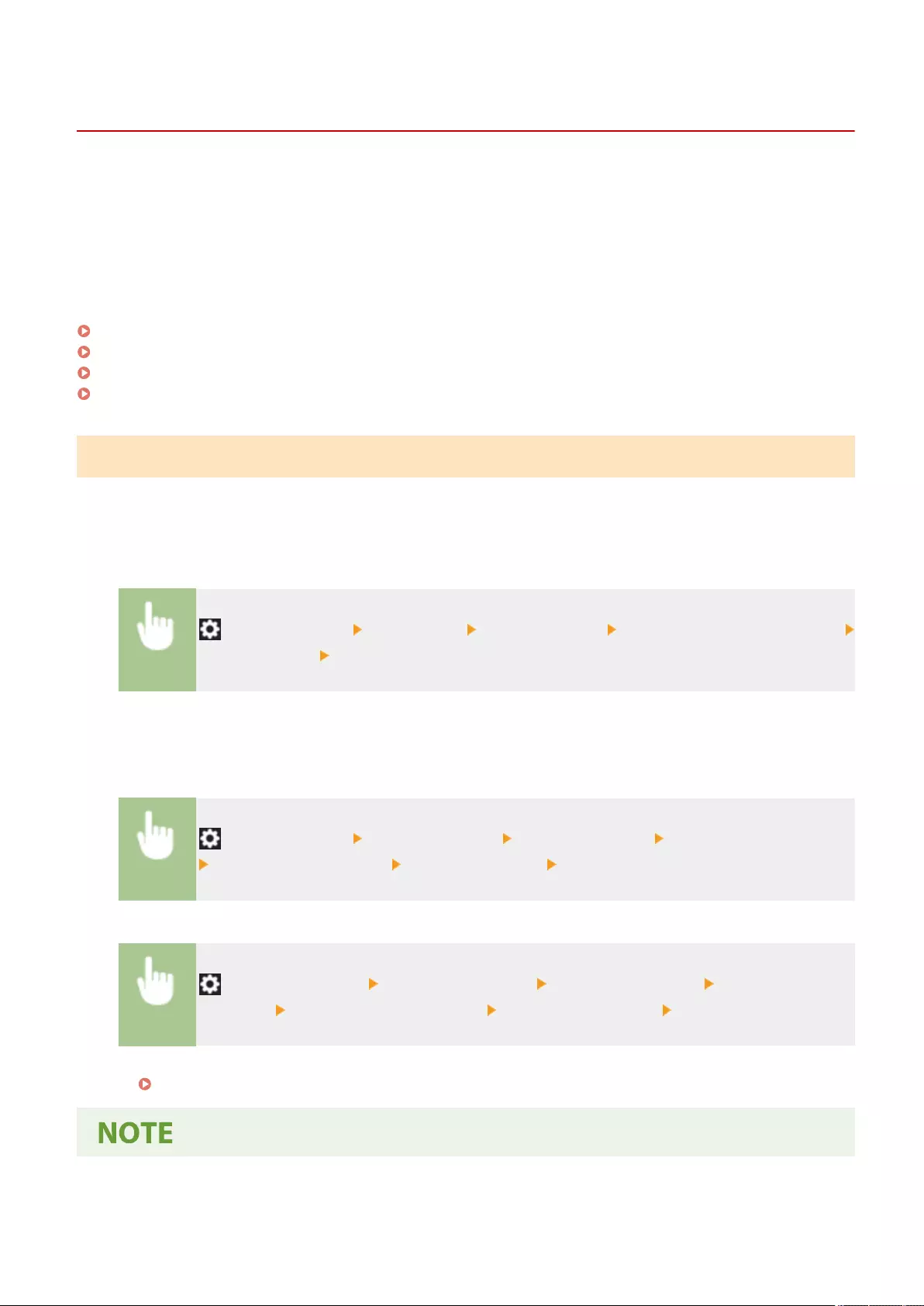
Memory MediaMemory Media
Using Memory Media
72JY-0LR
You can directly insert memory media to the machine and use it.
Memory media compliant with the USB 2.0 standard is supported. FAT32/exFAT format memory media is supported.
The following devices and usage methods are not supported.
●Memory media with security functions
●Memory card readers connected via USB
●USB extension cables or USB hubs
Preparing to Use Memory Media(P. 441)
Inserting/Removing Memory Media(P. 442)
Scanning Documents and Saving to Memory Media(P. 443)
Printing Files on Memory Media(P. 444)
Preparing to Use Memory Media
When using memory media, perform the following preparations in advance.
◼Displaying the Memory Media as a Store Location
(Settings/Register) <Preferences> <Display Settings> <Store Location Display Settings>
<Memory Media> <On>
◼Enabling Memory Media for Scanning/Printing
When Using the Scan Function
(Settings/Register) <Function Settings> <Store/Access Files> <Memory Media Settings>
<Use Scan/Print Function> <Use Scan Function> <On>
When Using the Print Function
(Settings/Register) <Function Settings > <Store/Access Files > <Memory Media
Settings > <Use Scan/Print Function > <Use Print Function > <On >
If memory media is not recognized although it is connected correctly, set <Use AddOn Driver for USB Storage Device>
to <Off>. <Use AddOn Driver for USB Storage Device>(P. 795)
Using Other Machines and Memory Media
441
Displaying a shortcut to available functions when memory media Is Inserted
●Set <Select Option When Connecting Memory Media> to <On>. When memory media is inserted, a screen
such as the following is displayed and the corresponding functions can be immediately executed. <Select
Option When Connecting Memory Media>(P. 845)
*To display the shortcuts, insert the memory media after canceling the sleep mode. Exiting Sleep
Mode(P. 188)
Inserting/Removing Memory Media
Inserting memory media incorrectly or in the wrong direction may cause problems with the machine or the memory
media.
◼Inserting Memory Media
Insert the USB memory into the USB port on the right side of the machine with the correct orientation.
◼Removing Memory Media
1Press , select the memory media to remove, and press <Remove>.
2When the message <Ready to safely remove the memory media.> is displayed, remove the memory
media.
Using Other Machines and Memory Media
442
Scanning Documents and Saving to Memory Media
1Insert the memory media into the USB port of the machine. Inserting/Removing
Memory Media(P. 442)
2Place the original. Placing Originals(P. 97)
3Press <Scan and Store> <Memory Media>.
➠The connected memory media is displayed.
4Select the memory media.
Up
●To go back up one folder level, press <Up>.
Check Media Information
●You can press <Check Media Information> <Details> to check the information for the memory media.
Scan
5Display the folder to save to, and press <Scan>.
➠The settings screen for scanning is displayed.
●You can press <Name> or <Date/Time> to sort the display.
Folder OperationsFolder Operations
●In <Folder Operations>, you can check the information of a folder, rename a folder, create a new folder, or
delete a folder.
Update
●Press to refresh the display.
6Congure the scan settings.
Specify the le name and le format, and congure the scan settings as required. Scan Settings Screen in
<Scan and Store>(P. 446)
7Press (Start) to start scanning and save the le.
➠The scanning screen is displayed. When saving is complete, the connection destination selected in step 5
is displayed.
●To cancel scanning, press <Cancel> or (Stop).
●If you have another original to scan, place the original and repeat the procedure in step 7.
If <Start Storing> is displayed
When all of the originals have been scanned, press <Start Storing> to save the le.
➠The store location selected in step 5 is displayed.
8Conrm that the le has been saved.
●If you did not specify a le name in step 6, the date and time that the le was saved is used as the le name.
Display Image
Using Other Machines and Memory Media
443
●You can press <Display Image> to check the content of the le.
●You can press <Status Monitor> <Store> <Job Log> to check whether the le has been saved correctly. If
<NG> is displayed, the le has not been saved correctly. Repeat step 7.
9Correctly remove the memory media. Inserting/Removing Memory Media(P. 442)
Incorrectly removing the memory media may cause problems with the machine or the memory media.
Printing Files on Memory Media
1Insert the memory media into the USB port of the machine. Inserting/Removing
Memory Media(P. 442)
2Press <Access Stored Files> <Memory Media>.
➠ The connected memory media is displayed.
3Select the memory media.
Up
●To go back up one folder level, press <Up>.
Check Media Information
●You can press <Check Media Information> <Details> to check the information for the memory media.
Print
4Select the le to print, and press <Print>.
You can select up to six les in the same folder to print together. The les are printed in the selected order.
Clear SelectionSearch
You can deselect a le by selecting the le again. To deselect all les, press <Clear Selection>.
●Press <Search> to search for les and folders in the folder that is currently displayed. To not include
subfolders when searching, select <Do Not Include Subfolders>.
Display Image
●You can press <Display Image> to check the content of the le.
Update
●Press to refresh the display.
Edit File
●In <Edit File>, you can check the information of a le, rename a le, or delete a le.
5If the <Select Paper> screen is displayed, select the paper to use.
If not, proceed to the next step.
6Enter the number of copies to make using the numeric keys.
If multiple les are selected, <Change No. of Copies> is displayed. Press this button when changing the
number of copies.
7Congure the print settings.
Congure the two-sided printing, nishing settings, and other print settings as required.
●You cannot print multiple PDF les with different passwords simultaneously.
●To print a PDF le with a password, press <Options> <Password to Open Doc.> <Encryption Password>,
and enter the password.
Using Other Machines and Memory Media
444

●To print a PDF le linked with a policy server, press <Options> <Password to Open Doc.> <Policy
Password>, and enter the user name and password. Print Settings Screen in <Access Stored
Files>(P. 448)
8Press <Start Printing>.
➠The printing screen is displayed. When printing is complete, the le selection screen in step 4 is displayed.
●If the password entry screen is displayed, enter the password set in the PDF le.
●To cancel printing, press <Cancel>.
9Correctly remove the memory media. Inserting/Removing Memory Media(P. 442)
Incorrectly removing the memory media may cause problems with the machine or the memory media.
Using Other Machines and Memory Media
445

Settings Screens for Using Other Machines/Servers/
Memory Media
72JY-0LS
The following screens are displayed when scanning originals from <Scan and Store> and printing les from <Access
Stored Files>.
Scan Settings Screen in <Scan and Store>(P. 446)
Options Screen in <Scan and Store>(P. 447)
Print Settings Screen in <Access Stored Files>(P. 448)
Options Screen in <Access Stored Files>(P. 449)
Scan Settings Screen in <Scan and Store>
This screen is for conguring the scan settings when scanning from <Scan and Store>.
You can register the current settings as favorite settings or default settings, or register them to the <Home>
screen as Shared buttons or Personal buttons. Registering Personal Buttons/Shared Buttons(P. 171)
Message Display Area (Top)
A message indicating the current state is displayed.
The remaining number of pages that can be scanned is also displayed if a page limit is set with Department ID
Management.
Favorite Settings
<Favorite Settings>
Change the scan settings to the registered settings.
Scan Settings
The buttons for changing the scan settings and the current settings are displayed.
Select Color
<Select Color>
Specify the color.
Resolution
<Resolution>
Increase the resolution to scan the originals more clearly.
Decrease the resolution to reduce the le size.
Scan Size
<Scan Size>
Specify the size of the originals to save.
File Format
<File Format>
Select the format of the les to save.
If <Divide into Pages> is specied, a three digit page number is appended to the end of the le name.
*Optional products may be required, depending on the le format. File Formats and the Need for
Optional Products(P. 1101)
Original Type
<Original Type>
Using Other Machines and Memory Media
446

Select the scanning mode and scanning priority for text/photos according to the type of originals, such as
originals containing only text or originals including photos.
Original Content Orientation
<Original Content Orientation>
Set this mode to x the orientation for scanning to horizontal or vertical.
2-Sided Original
<2-Sided Original>
Set this mode to scan both the front and back sides of the original.
●Select <Book Type> if the front and back sides of the original have the same top-bottom orientation.
●Select <Calendar Type> if the front and back sides of the original have the opposite top-bottom orientation.
File Name
<File Name>
Specify the le name of the les to save.
●\ / : , * ? " < > | cannot be used.
●You cannot use a period (.) or space for the rst or last character of the le name.
Options
<Options>
Congure the settings for scanning the originals more clearly. Options Screen in <Scan and
Store>(P. 447)
Restore Default Set.
<Restore Default Set.>
Change the scan settings to the registered settings.
Options Screen in <Scan and Store>
This screen is displayed by pressing <Options> on the scan settings screen in <Scan and Store>. It enables you to
congure the settings for scanning the originals more clearly.
Erase Frame
<Erase Frame>
Set this mode to eliminate border lines, shadows, or binding holes, etc.
Job Build
<Job Build>
Set this mode to scan originals in sequence and store the result as one le, when it is impossible to scan them
all at once.
Sharpness
<Sharpness>
Set this mode to scan blurry text and diagrams clearly or reduce the moiré effect and smoothen photos.
Density
<Density>
Adjust the density according to the original.
Faint text written in pencil can be made easier to read by increasing the density.
Preview
<Preview>
Set this mode to display a preview screen to check the le content after scanning originals.
*You can delete, move, or switch pages on the preview screen.
Using Other Machines and Memory Media
447
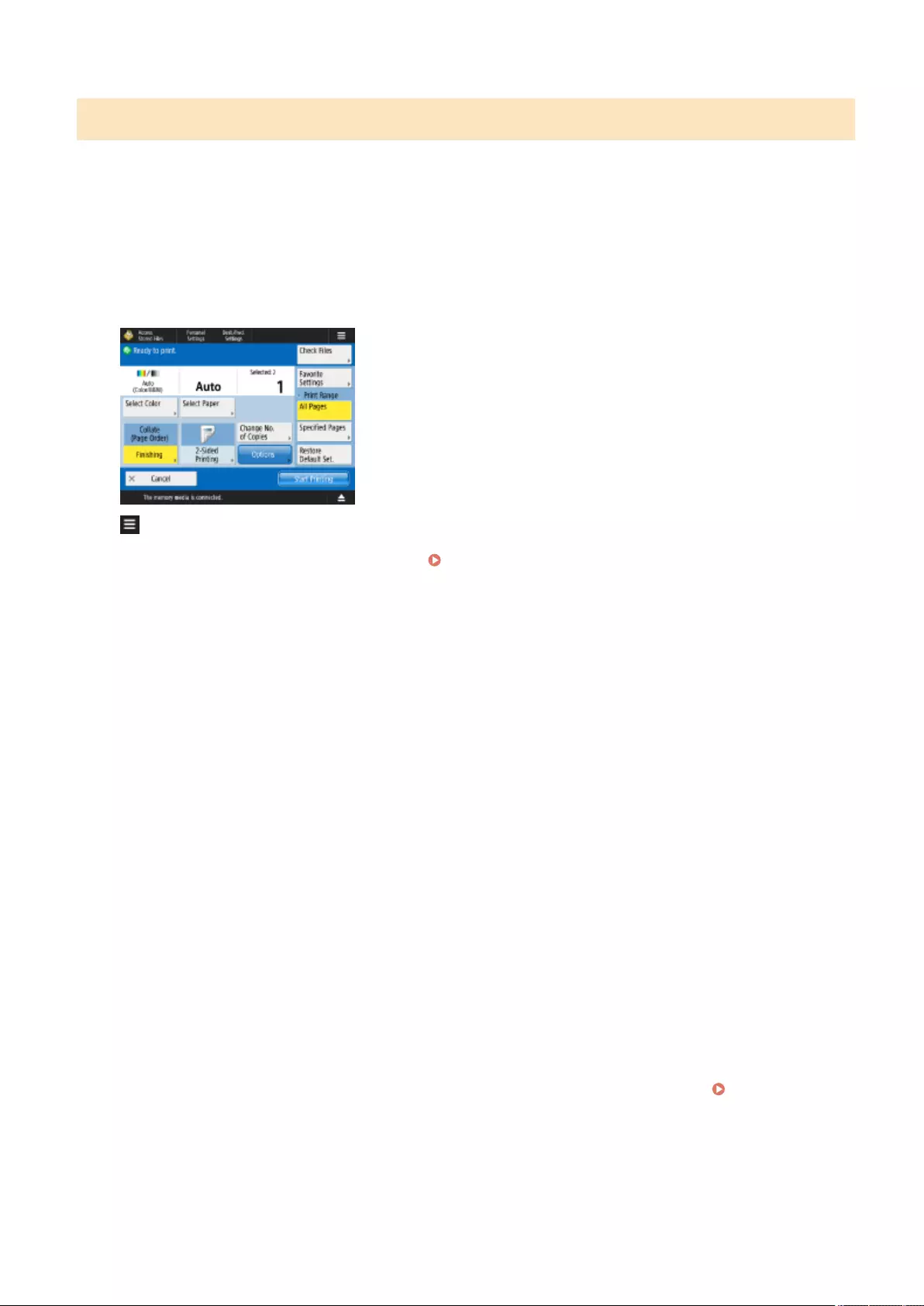
Print Settings Screen in <Access Stored Files>
This screen is for conguring print settings when printing from <Access Stored Files>.
When printing multiple les in a different format together, you can set the following print settings.
●<Select Color>
●<Select Paper>
●<Change No. of Copies>
●<2-Sided Printing>
You can register the current settings as favorite settings or default settings, or register them to the <Home>
screen as Shared buttons or Personal buttons. Registering Personal Buttons/Shared Buttons(P. 171)
Message Display Area (Top)
A message indicating the current state is displayed.
The remaining number of pages that can be printed is also displayed if a page limit is set with Department ID
Management.
Check Files
<Check Files>
You can check the information and content of the selected le.
Print Settings
The buttons for changing the print settings and the current settings are displayed.
Select Color
<Select Color>
Specify the color.
Select Paper
<Select Paper>
Select the paper to print on.
When printing a PDF le to both sides of the paper, it is necessary to select the paper size to print on in
<Select Paper> if the front and back pages are of a different size.
Change No. of CopiesChange No. of Copies
<Change No. of Copies>
This mode is available only when multiple les are selected. Press this button when changing the number of
copies.
Finishing (Collate/Group)
<Finishing>
Set this mode to congure the nishing settings when printing PDF/XPS les.
2-Sided Printing
<2-Sided Printing>
Specify the opening type when printing on both sides of the paper.
When printing a PDF le to both sides of the paper, it is necessary to select the paper size to print on in
<Select Paper> if the front and back pages are of a different size.
Options
<Options>
Congure the settings for printing the scanned documents more clearly and eciently. Options Screen in
<Access Stored Files>(P. 449)
Favorite Settings
<Favorite Settings>
Change the print settings to the registered settings.
Print Range
Print Range
When printing a le with two pages or more, specify the pages to print.
Restore Default Set.
Using Other Machines and Memory Media
448

<Restore Default Set.>
Change the print settings to the registered settings.
Options Screen in <Access Stored Files>
This screen is displayed by pressing <Options> on the print settings screen in <Access Stored Files>. It enables you to
congure the settings for printing the documents more clearly. The available settings may differ, depending on the
format of the le to print.
Printing PDF les
Printing image les
Resolution
<Resolution>
Set <Superne (1200 dpi)> to print more clearly.
Halftones
<Halftones>
Select the halftone printing mode to match the le you want to print.
●<Resolution>: Set this mode to enable ne printing so that the outlines of text data, etc. are clearer. This
mode is optimal for printing data containing a lot of text or ne lines.
●<Gradation>: Set this mode to enable printing with both smooth gradations and suitable outlines. You can
adjust this setting to smoothly print shapes and graphs using gradation.
●<Error Diffusion>: Suitable for sharply printing the contours of CAD data, and data that includes text and ne
lines, etc.
Match Paper Size
<Match Paper Size>
Set this mode to automatically enlarge/reduce when printing PDF/XPS les.
Enlarge Print Area
<Enlarge Print Area>
Set this mode to narrow the blank borders at each side of the page and enlarge the print area.
Print Comments
<Print Comments>
Set this mode to add comments when printing PDF les.
Password to Open Doc.
<Password to Open Doc.>
Enter the password required for printing the PDF le.
*You cannot print multiple PDF les with different passwords simultaneously.
●<Encryption Password>: When printing a PDF le with a password set, enter that password.
●<Policy Password>: When printing a PDF le with a server security policy applied, enter the password set in
the policy.
Skip Blank Pages
<Skip Blank Pages>
Set this mode to automatically detect blank pages included in les and not print them.
Enlarge/Reduce
<Enlarge/Reduce>
Set this mode to automatically enlarge/reduce the image size according to the paper size when printing image
les.
Image Orientation
Using Other Machines and Memory Media
449

<Image Orientation>
Set this mode to automatically detect the aspect ratio of the image le and print it vertically or horizontally as
required. You can also manually specify to print vertically or horizontally.
Print Position
<Print Position>
You can set the print area to the center or the top left when printing an image le.
Using Other Machines and Memory Media
450

Linking with Mobile Devices
Linking with Mobile Devices .................................................................................................................... 452
Connecting with Mobile Devices ...................................................................................................................... 453
Connecting Directly ...................................................................................................................................... 454
Utilizing the Machine through Applications .................................................................................................... 458
Using AirPrint .................................................................................................................................................... 460
Printing with AirPrint .................................................................................................................................... 465
Scanning with AirPrint .................................................................................................................................. 468
Faxing with AirPrint ...................................................................................................................................... 470
If AirPrint Cannot Be Used ............................................................................................................................ 472
Printing with Default Print Service (Android) .................................................................................................. 473
Linking with Mobile Devices
451
Linking with Mobile Devices
72JY-07W
Linking the machine with mobile devices such as smart phones and tablets enables you to easily print and scan using
applications. In addition, you can operate the machine from mobile devices via remote control to conrm printing
status and change the settings of the machine.
Connecting with Mobile Devices(P. 453)
Utilizing the Machine through Applications(P. 458)
Using AirPrint(P. 460)
Printing with Default Print Service (Android)(P. 473)
●Depending on your mobile device, the machine may not operate correctly.
Linking with Mobile Devices
452
Mobile Portal
Connecting with Mobile Devices
72JY-07X
There are two methods to connect the mobile devices with the machine, "Connecting via a Wireless LAN Router" and
"Direct connection." Select a connection method in accordance with the communication environment and the device
you are using.
Perform communication with mobile devices from <Mobile Portal> ( <Home> Screen(P. 119) ). You can conrm the
information of connected mobile devices, etc., from here.
◼Connecting via a Wireless LAN Router
For information on how to connect a mobile device to your wireless LAN router, see the manuals provided with the
devices, or contact the manufacturer.
Connect with the machine using either a wired LAN or wireless LAN router. Setting up the Network
Environment(P. 19)
●If you connect to the machine via a wireless LAN router, you can conrm details of the machine on the <LAN
Connection> screen by pressing <Mobile Portal> ( <Home> Screen(P. 119) ) <LAN Connection>.
◼Connecting Directly
Directly connect a mobile device to the machine wirelessly without using wireless LAN. It is possible to immediately
connect to the machine wirelessly even outside of a wireless LAN environment. Connecting Directly(P. 454)
Linking with Mobile Devices
453
Connecting Directly
72JY-07Y
Even in an environment without a wireless LAN router, you can still directly connect your mobile device to the machine
via "Access Point Mode" or "Wi-Fi Direct," which enable connections between the device and the machine without the
need to congure complicated settings.
Preparing to Connect Directly(P. 454)
Connecting Directly (Access Point Mode)(P. 455)
Connecting Directly (Wi-Fi Direct)(P. 456)
Preparing to Connect Directly
Establish a connection by using Access Point Mode in the following order.
Check the network settings of the machine.
●Press (Settings/Register) <Preferences> <Network> <TCP/IP Settings>
<IPv4 Settings> set <Use IPv4> to <On>.
Prepare the mobile device.
●Congure the mobile device to enable Wi-Fi connection.
Prepare the machine for connection.
●Press (Settings/Register) <Preferences> <Network> <Direct Connection
Settings> set <Use Direct Connection> to <On>.
●Press (Settings/Register) <Preferences> <Network> <Direct Connection
Settings> select the type of direct connection to use in <Direct Connection Type>.
●Press <Mobile Portal> ( <Home> Screen(P. 119) ) <Direct Connection>
<Enable>.
●If <Wireless LAN> or <Wired LAN + Wireless LAN> is selected in <Select Interface>,
<Wi-Fi Direct> cannot be used in <Direct Connection Type>. <Select
Interface>(P. 790)
●If <Automatically Enable/Disable Direct Connection at Login/Logout> is set to <On>
in <Personal SSID and Network Key Settings>, direct connections are possible when
Linking with Mobile Devices
454

logging in without pressing <Mobile Portal> <Direct Connection> <Enable>.
<Personal SSID and Network Key Settings>(P. 792)
●For details on using Canon PRINT Business, see the related manuals. (https://global.canon/gomp/)
●If the message <Cannot be used with the current settings. Contact the system manager.> is displayed
on the top of the touch panel display and <Enable> cannot be pressed, conrm that <Use Direct
Connection> is set to <On>. If <Use Direct Connection> is set to <On> but <Enable> cannot be
pressed, change the IP address in <IP Address Settings for Direct Connection>. <Use Direct
Connection>(P. 791) <IP Address Settings for Direct Connection>(P. 792)
●When using the Access Point Mode, if the machine is started with <Always Keep Enabled If SSID/
Network Key Specied> set to <On>, direct connections are possible without pressing <Mobile Portal>
<Enable>. <Always Keep Enabled If SSID/Network Key Specied>(P. 792)
Connecting Directly (Access Point Mode)
●It may take some time for connection between the machine and the mobile device to be established.
◼Connecting Manually
1With the machine as the connection destination, congure the wireless LAN settings
on your mobile device, using the SSID and network key information shown on the
touch panel display of the machine.
2After completing the desired operations, press <Disconnect>.
◼Connecting with a QR Code
For Canon PRINT Business
1Start Canon PRINT Business on the mobile device.
2Read the QR code shown on the touch panel display of the machine.
3After completing the desired operations, press <Disconnect>.
Linking with Mobile Devices
455
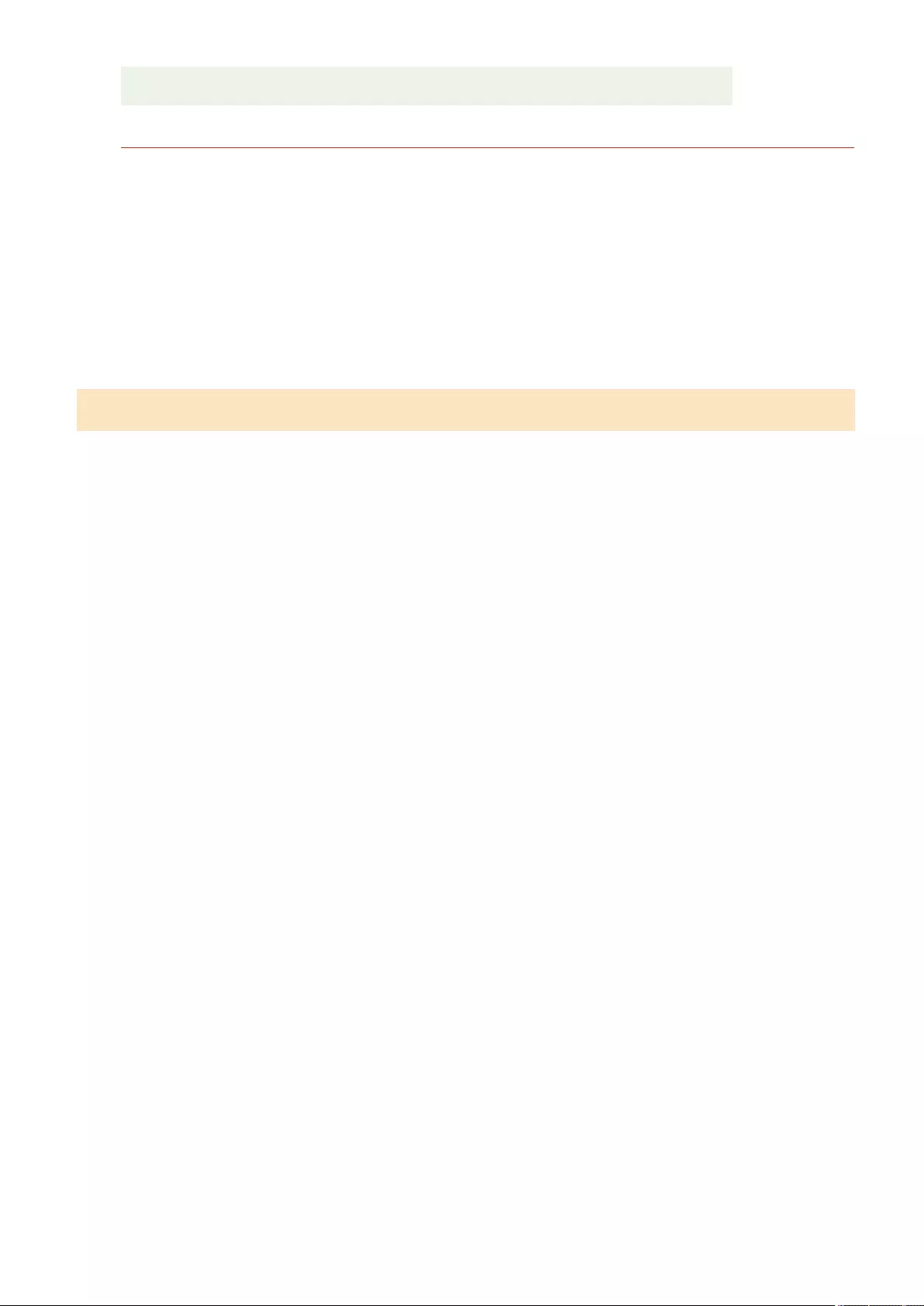
●If you cannot read the QR code, update Canon PRINT Business to the latest version.
For devices using iOS (iOS11 or later)
1Start the standard camera app on the iOS device.
2Read the QR code shown on the touch panel display of the machine.
3After completing the desired operations, press <Disconnect>.
Connecting Directly (Wi-Fi Direct)
◼Connecting to the Machine from a Mobile Device
1Start a direct connection on the mobile device.
●Open the Wi-Fi Direct screen from the Wi-Fi settings screen of the mobile device, and tap the machine from
the list of Wi-Fi Direct devices that have been detected.
➠A message indicating that a connection request has been received from the mobile device is displayed on
the touch panel display of the machine.
2Press <Yes> on the touch panel display of the machine.
➠A connection between the machine and the mobile device is started.
3After completing the desired operations, press <Disconnect>.
◼Connecting to a Mobile Device from the Machine
1Press the name of the device to directly connect to from the list displayed on the
touch panel display, and press <Connect>.
➠A screen for selecting whether to allow a connection to the mobile device is displayed.
2Tap [Yes] on the screen of the mobile device.
➠A connection between the machine and the mobile device is started.
3After completing the desired operations, press <Disconnect>.
Linking with Mobile Devices
456

●To check the connected mobile devices, press <Mobile Dev. Info> on the <Direct Connection> screen.
●While connecting via direct connection, you may not be able to connect to the Internet depending on the
mobile device you are using.
●The connection standby status ends if a wireless connection is not performed from the mobile device within
ve minutes of the device name being displayed.
●If the status without data transmission between a mobile device and the machine continues during
communication by direct connection, the communication may end.
●Power saving performance of sleep mode degrades while connecting via direct connection.
●When you nish the desired operation, be sure to terminate the connection between the machine and the
mobile device. If they remain connected, power saving performance of sleep mode degrades.
●If you use the direct connection, do not set the IP address manually on the mobile device. Doing so may
prevent proper communication after using the direct connection.
Linking with Mobile Devices
457

Utilizing the Machine through Applications
72JY-080
Print by using applications from a mobile device connected to the machine. Various applications including those
exclusive to Canon are supported. Use properly in accordance with your device, the application, and the situation.
◼Canon PRINT Business
An application for printing, etc. from mobile devices that support iOS/Android. No operations on the machine are
necessary to perform printing. For information on supported operating systems, detailed setting methods, and
operational procedures, see the Help of the application or the Canon website (https://global.canon/gomp/).
●Canon PRINT Business can be downloaded free of charge, but the customer is responsible for any fees
regarding internet connection.
◼Printing with Canon Print Service
You can easily print from the menu of applications that support the Android print subsystem. For more information on
supported operating systems and detailed settings and procedures, see the Canon website (https://global.canon/
gomp/).
◼Printing and Scanning with Mopria®
The machine also supports Mopria®. Using Mopria® enables you to print from mobile devices that support Android
using common operations and settings, even if manufacturers and models differ. For example, if you are using
printers supporting Mopria® made by multiple manufacturers or a printer supporting Mopria® that is located in a
place you are visiting, you can print without installing an application exclusive for each manufacturer or model.
Mopria® can also be used to directly import the data scanned with the machine to mobile devices that support
Android. For more information on supporting models or operation environments, see http://www.mopria.org.
Conrming Mopria®settings
Log in to the Remote UI with Administrator privileges ( Starting the Remote UI(P. 583) )
[Settings/Registration] [Network Settings] [Mopria Settings] select the [Use Mopria] check
box [OK]
●If you enable the Mopria® setting, <Use Network Link Scan> also changes to <On>.
●To use the Mopria® scan service, <Use Network Link Scan> must be set to <On>.
Linking with Mobile Devices
458

<TCP/IP Settings> <Use Network Link Scan>(P. 787)
◼Printing from Windows Phone (Windows 10 Mobile and Later)
You can perform printing from a Windows Phone without downloading a dedicated application or installing a driver.
Make sure that the <Use WSD Printing>, <Use WSD Browsing>, and <Multicast Discovery Settings> are enabled.
<WSD Settings>(P. 785)
<Multicast Discovery Settings>(P. 786)
Scan for Mobile
Scan for Mobile
●The application, "Scan for Mobile" enables you to use the Scan function of the machine from the mobile
device. You can operate the machine from your mobile device to scan originals, and then send the image
that you scanned on the machine to your mobile device using WebDAV communication.
Linking with Mobile Devices
459

Using AirPrint
72JY-081
This section describes the settings required to use AirPrint and the procedure for printing, scanning, and sending
faxes from Apple devices.
AirPrint Settings
Conguring AirPrint Settings(P. 460)
Displaying the Screen for AirPrint(P. 462)
Functions of the AirPrint
Printing with AirPrint(P. 465)
Scanning with AirPrint(P. 468)
Faxing with AirPrint(P. 470)
Troubleshooting
If AirPrint Cannot Be Used(P. 472)
Conguring AirPrint Settings
You can register information, including the name of the machine and installation location, that is used for identifying
the machine. The settings required for using AirPrint can be congured remotely using the Remote UI.
◼Conguring Settings Using the Remote UI
1Start the Remote UI and log on in System Manager Mode. Starting the Remote
UI(P. 583)
2Click [Settings/Registration].
●If you are using a mobile device, such as an iPad, iPhone, or iPod touch, read "click" as "tap" in this section.
3Click [Network Settings] [AirPrint Settings].
4Specify the required settings, and click [OK].
Linking with Mobile Devices
460
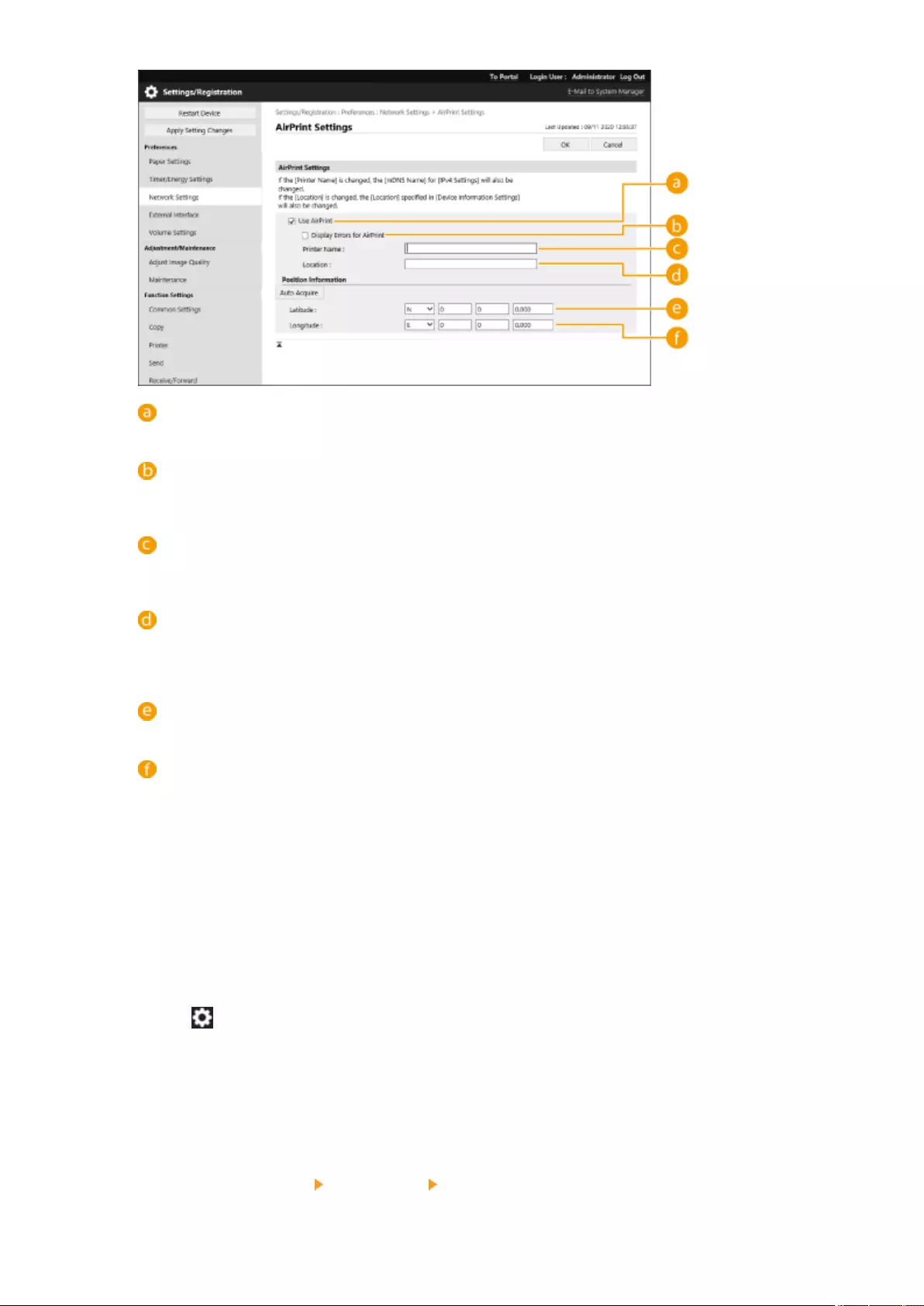
[Use AirPrint]
Select the check box to enable AirPrint. To disable AirPrint, clear the check box.
[Display Errors for AirPrint]
Specify whether to display an error screen on the control panel if printing cannot be performed as
expected due to a problem with the print data when printing with AirPrint.
[Printer Name]
Enter the name of the machine. If an mDNS name has already been registered in [mDNS Settings]
([Network Settings] in [Preferences] (Settings/Registration)), the registered name is displayed.
[Location]
Enter the location of the machine. If a location has already been registered in [Device Information
Settings] ([Device Management] in [Management Settings] (Settings/Registration)), the registered name is
displayed.
[Latitude]
Enter the latitude of the location where the machine is installed.
[Longitude]
Enter the longitude of the location where the machine is installed.
5Restart the machine.
●Turn OFF the machine, wait at least 10 seconds, and then turn it ON.
◼Conguring Settings from the Touch Panel Display
1Press (Settings/Register) .
2Press <Log In>.
●Enter the System Manager ID and System PIN.
3Press <Preferences> <Network> <Use AirPrint>.
Linking with Mobile Devices
461

4Press <On> <OK>.
If you select [Use AirPrint], the following settings in <TCP/IP Settings> are set to <On>.
●Use HTTP
●IPP Print Settings
●Use IPv4 mDNS
●Use IPv6 mDNS
●Use Network Link Scan
●If you change [Printer Name] that you have once specied, you may be unable to print any more from the
Mac that has been able to be used for printing so far. This phenomenon occurs because <mDNS Name> (
Making DNS Settings(P. 45) ) of IPv4 is also changed automatically. In this case, add the machine to the
Mac again.
●When AirPrint is in-use, <Use Same mDNS Name as IPv4> is xed to <On> for the mDNS name of IPv6.
●Entering the printer name makes it easier to identify multiple printers that support AirPrint.
Displaying the Screen for AirPrint
You can display the screen for AirPrint, on which you can not only access the AirPrint Settings but also view
information about consumables, such as paper and toner cartridge. Further, you can congure security function
settings.
◼Displaying from a Mac
1Click [System Preferences] in the Dock on the desktop [Printers & Scanners].
2Select the machine, and click [Options & Supplies].
3Click [Show Printer Webpage].
4Logging in to the Remote UI
●To change the AirPrint settings, it is necessary to log in as an administrator.
◼Conguring the Screen for AirPrint
If you log in with administrator privileges, you can also change the AirPrint settings from the page for AirPrint.
Linking with Mobile Devices
462
[AirPrint]
Enables you to check the values entered in the AirPrint settings, such as the name and location of the
machine. You can click [Edit...] to change the settings.
[Print Security Settings]
Specify the settings required to print using TLS and authentication.
If <IPP Print Settings> is already set, the existing settings are displayed. The values registered in [Print
Security Settings] change according to the values in <IPP Print Settings>.
[Scan Security Settings]
Specify the settings required to scan using TLS.
If <Use TLS> in <Use Network Link Scan> is already set, the existing settings are displayed. The values
registered in [Scan Security Settings] change according to the value in <Use TLS> in <Use Network Link Scan>.
[User Management]
You can add/edit users to authenticate. Managing Users(P. 489)
[TLS Settings]
Enables you to change the key and certicate used for TLS. Conguring the Key and Certicate for
TLS(P. 549)
[Key and Certicate Settings]
Enables you to generate and install a key and certicate, or request a certicate to be issued. Conguring
the Key and Certicate for TLS(P. 549)
◼Checking Consumables and the Device Version
You can check information regarding the paper sources of the machine, the remaining amount of toner, and the
device version.
Linking with Mobile Devices
463

Trademarks
Apple, Bonjour, iPad, iPhone, iPod touch, Mac, macOS, OS X and Safari are trademarks of Apple Inc., registered in the
U.S. and other countries. AirPrint and the AirPrint logo are trademarks of Apple Inc.
iOS is a trademark or registered trademark of Cisco in the U.S. and other countries and is used under license.
Linking with Mobile Devices
464

Printing with AirPrint
72JY-082
You can print from an iPad, iPhone, iPod touch, or Mac without using a printer driver.
Printing from an iPad, iPhone, or iPod touch(P. 465)
Printing from a Mac(P. 466)
System Requirements
One of the following Apple devices is required to print with AirPrint.
●iPad (all models)
●iPhone (3GS or later)
●iPod touch (3rd generation or later)
●Mac (Mac OS X 10.7 or later)*
* OS X 10.9 or later when using a USB connection
Network Environment
One of the following environments is required.
●An environment where an Apple device and the machine are connected to the same LAN
●An environment where an Apple device and the machine are connected directly
●An environment where a Mac is connected to the machine via USB
Printing from an iPad, iPhone, or iPod touch
1Make sure that the machine is turned ON and connected to the Apple device.
●For how to make sure of this, see Setting up the Network Environment(P. 19) .
●For information on the Direct Connection, see Connecting Directly(P. 454) .
2From the application on your Apple device, tap to display the menu options.
3Tap [Print].
Linking with Mobile Devices
465
4Select this machine from [Printer].
➠The printers connected to the network are displayed here. Select this machine in this step.
●The screen for selecting the machine in [Printer] is not displayed for applications that do not support
AirPrint. In this case, printing cannot be performed.
5Specify the print settings as necessary.
●The available settings and paper sizes differ depending on the application you are using.
6Tap [Print].
➠Printing starts.
Checking the print status
●During printing, press the Home button of the Apple device twice tap [Print].
Printing from a Mac
1Make sure that the machine is turned ON and connected to the Mac.
●For how to make sure of this, see Setting up the Network Environment(P. 19) .
2From your Mac, add the machine in [System Preferences] [Printers & Scanners].
●If the machine has already been added for scanning or sending faxes, this operation is not required.
3Open a document in an application and display the print dialog box.
●How to display the print dialog box differs for each application. For more information, see the instruction
manual for the application you are using.
4Select the machine in the print dialog box.
➠The printers added to the Mac are displayed. Select the machine in this step.
5Specify the print settings as necessary.
●The available settings and paper sizes differ depending on the application you are using.
Linking with Mobile Devices
466

Scanning with AirPrint
72JY-083
You can use AirPrint to transfer the data scanned by the machine directly to a Mac.
System Requirements
To scan with AirPrint, you need a Mac with OS X 10.9 or later installed. To scan using TLS, you need a Mac with
OS X 10.11 or later installed.
Network Environment
One of the following environments is required.
●An environment where an Apple device and the machine are connected to the same LAN
●An environment where a Mac is connected to the machine via USB
●For scanning, it is required to set <Use Network Link Scan> to <On>. <TCP/IP Settings> <Use Network
Link Scan>(P. 787)
●A rmware update may also be required. Updating the Firmware(P. 640)
●You cannot scan while settings for operations are being made, or while the machine is performing any
operation whatsoever.
Scanning from a Mac
1Make sure that the machine is turned ON and connected to the Mac.
●For how to make sure of this, see Setting up the Network Environment(P. 19) .
2From your Mac, add the machine in [System Preferences] [Printers & Scanners].
●If the machine has already been added for printing or sending faxes, this operation is not required.
3Select this machine from the list of printers in [Printers & Scanners].
4Click [Scan].
Linking with Mobile Devices
468

5Click [Open Scanner].
➠The [Scanner] screen is displayed.
6Congure the scan settings as necessary.
7Click [Scan].
➠The document is scanned, and the image is displayed.
Linking with Mobile Devices
469

Faxing with AirPrint
72JY-084
You can send faxes from a Mac in almost the same way as when you print from a Mac.
System Requirements
To send faxes with AirPrint, you need a Mac with OS X 10.9 or later installed.
Network Environment
One of the following environments is required.
●An environment where an Apple device and the machine are connected to the same LAN
●An environment where a Mac is connected to the machine via USB
●A rmware update may be required to send faxes. Updating the Firmware(P. 640)
Faxing from a Mac
1Make sure that the machine is turned ON and connected to the Mac.
●For how to make sure of this, see Setting up the Network Environment(P. 19) .
2From your Mac, add the machine in [System Preferences] [Printers & Scanners].
●If the machine has already been added for printing or sending faxes, this operation is not required.
3Open a document in an application and display the print dialog box.
●How to display the print dialog box differs for each application. For more information, see the instruction
manual for the application you are using.
4Select this machine in the print dialog box.
Linking with Mobile Devices
470

➠The printers added to the Mac are displayed. Select the fax driver of the machine in this step.
5Specify the destination.
6Click [Fax].
➠Fax sending starts.
Linking with Mobile Devices
471

If AirPrint Cannot Be Used
72JY-085
If AirPrint cannot be used, try taking the following solutions.
●Make sure that the machine is turned ON. If the machine is turned ON, rst turn it OFF, then wait for at least 10
seconds and then turn it back ON to check if the problem is solved.
●Make sure that no error messages are displayed on the machine.
●Make sure that Apple devices and the machine are connected to the same LAN. If the machine is turned ON, it may
take several minutes before the machine is ready for communication.
●Make sure that Bonjour on your Apple device is enabled.
●Make sure that the machine is congured to enable operations from a computer even when no department ID and
password are entered.
●For printing, make sure that the paper is loaded in the machine and the machine has sucient toner levels
remaining. Displaying the Screen for AirPrint(P. 462)
●For scanning, make sure that the machine's setting for Network Link Scan is <On>. <TCP/IP Settings> <Use
Network Link Scan>(P. 787)
Linking with Mobile Devices
472
Printing with Default Print Service (Android)
72JY-086
If your Android terminal supports Default Print Service, you can print from the Default Print Service of your Android
terminal.
To print with the machine using Default Print Service, it is necessary to enable Mopria®.
Conrming Mopria®settings
Log in to the Remote UI with Administrator privileges ( Starting the Remote UI(P. 583) )
[Settings/Registration] [Network Settings] [Mopria Settings] select the [Use Mopria] check
box [OK]
●If you enable the Mopria® setting, <Use Network Link Scan> also changes to <On>.
●To use the Mopria® scan service, <Use Network Link Scan> must be set to <On>.
<TCP/IP Settings> <Use Network Link Scan>(P. 787)
●In order to use the Canon machine/printer from the Default Print Service of your Android terminal, you must
rst congure the following settings on your Android terminal.
●Enable Default Print Service.
●Disable or uninstall Mopria®.
●Disable or uninstall Canon Print Service.
Linking with Mobile Devices
473

Managing the Machine
Managing the Machine ............................................................................................................................... 476
Applying a Security Policy to the Machine ....................................................................................................... 478
Using a Password to Protect the Security Policy Settings .............................................................................. 479
Conguring the Security Policy Settings ....................................................................................................... 481
Security Policy Setting Items ......................................................................................................................... 483
Managing Users ................................................................................................................................................. 489
Conguring the Personal Authentication Management Settings .................................................................. 492
Registering User Information in the Local Device .................................................................................. 495
Importing/Exporting User Data ............................................................................................................. 499
Adding and Editing User Information in a CSV File .......................................................................... 503
Registering Server Information ............................................................................................................. 507
Conguring the Authentication Functions ............................................................................................. 513
Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a Computer .............. 520
Using Other Convenient Personal Authentication Management Functions .................................................. 521
Setting the Department ID Management .............................................................................................. 522
Changing the System Manager ID and PIN ..................................................................................... 523
Conguring the Department ID Management Settings ................................................................... 525
Using Department IDs to Manage Printing or Remote Scanning via Computer .............................. 528
Conguring Personal Folders ................................................................................................................ 529
Using ACCESS MANAGEMENT SYSTEM ................................................................................................... 533
Deleting User Setting Information ................................................................................................................ 534
Conguring the Network Security Settings .................................................................................................... 536
Restricting Communication by Using Firewalls ............................................................................................. 538
Specifying IP Addresses in Firewall Settings ........................................................................................... 539
Specifying MAC Addresses in Firewall Settings ...................................................................................... 542
Conguring the Firewall of the Sub Line ................................................................................................ 544
Setting a Proxy ............................................................................................................................................. 547
Conguring the Key and Certicate for TLS .................................................................................................. 549
Generating the Key and Certicate for Network Communication .......................................................... 552
Conguring the IPSec Settings ..................................................................................................................... 555
Conguring the IEEE 802.1X Authentication Settings ................................................................................... 561
Restricting the Machine's Functions ................................................................................................................ 564
Restricting Access to Address Book and Sending Functions ......................................................................... 565
Restricting Use of the Address Book ...................................................................................................... 566
Limiting Available Destinations .............................................................................................................. 569
Restricting the Fax Sending Functions ................................................................................................... 571
Managing the Machine
474

Restricting Printing from a Computer ........................................................................................................... 573
Restricting the Use of Memory Media .......................................................................................................... 576
Adding a Digital Signature to Sent Files .......................................................................................................... 577
Generating a Device Signature Certicate .................................................................................................... 578
Registering a User Signature Certicate ....................................................................................................... 579
Managing the Machine from a Computer (Remote UI) ................................................................................... 581
Starting the Remote UI ................................................................................................................................. 583
Checking the Status and Logs ....................................................................................................................... 587
Turning OFF/Restarting the Machine ............................................................................................................ 591
Registering Destinations via the Remote UI ................................................................................................. 592
Sharing an Address List with Specic Users ........................................................................................... 596
Registering User Groups .............................................................................................................................. 598
Registering a Key and Certicate for Network Communication .................................................................... 600
Conguring the Expiration Check Method for Received Certicates ............................................................. 605
Generating a Key and Certicate Signing Request (CSR) ............................................................................... 608
Retrieving/Updating a Certicate from an SCEP Server ................................................................................ 611
Managing Stored Files .................................................................................................................................. 617
Managing the Logs ....................................................................................................................................... 620
Importing/Exporting the Setting Data .......................................................................................................... 625
Importing/Exporting All Settings ........................................................................................................... 628
Importing/Exporting the Settings Individually ....................................................................................... 632
Address Book Items ........................................................................................................................ 635
Updating the Firmware ................................................................................................................................ 640
Updating the Firmware (Distribution) ........................................................................................................... 642
Setting Scheduled Updates ........................................................................................................................... 645
Displaying Messages from the Administrator ............................................................................................... 647
Conguring the Visual Message Function ..................................................................................................... 649
Sending E-Mail Notication When an Error Occurs ....................................................................................... 652
Installing System Options ................................................................................................................................ 654
Synchronizing Settings for Multiple Canon Multifunction Printers ............................................................... 656
Starting Setting Synchronization .................................................................................................................. 659
Switching the Machines to Synchronize ........................................................................................................ 662
Initializing All Data/Settings ............................................................................................................................ 663
Functions Linked to Cloud Service ................................................................................................................... 665
Managing the Machine
475
Managing the Machine
72JY-087
To reduce the various risks associated with using this machine, such as the leakage of personal information or
unauthorized use by third parties, constant and effective security measures are required. Designate an administrator
to handle important machine settings, such as the user management and security settings, to ensure that the machine
is used safely.
◼Conguring the Basic Management System
Applying a Security Policy to the Machine(P. 478)
Managing Users(P. 489)
Conguring the Network Security Settings(P. 536)
◼Limiting Risks from Negligence, Operation Errors, and Misuse
Restricting the Machine's Functions(P. 564)
Adding a Digital Signature to Sent Files(P. 577)
◼Ensuring Effective Management
Managing the Machine from a Computer (Remote UI)
(P. 581)
Synchronizing Settings for Multiple Canon
Multifunction Printers(P. 656)
Managing the Machine
476

Applying a Security Policy to the Machine
72JY-088
It is a common practice for organizations to adopt a security policy that denes basic information security objectives
and standards, which requires information devices such as computers and multifunctional printers to be operated
accordingly. On this machine, multiple settings related to security policy can be managed in batch via the Remote UI,
and a dedicated password can be set up so that only the information security administrator is able to modify the
settings. Before conguring these settings, make sure that the Remote UI is set up to use TLS. Starting the Remote
UI(P. 583)
Using a Password to Protect the Security Policy Settings(P. 479)
Conguring the Security Policy Settings(P. 481)
Security Policy Setting Items(P. 483)
●The purpose of the security policy settings is to manage all functions and settings related to information
security, and not to actually prevent information leakage itself.
Managing the Machine
478
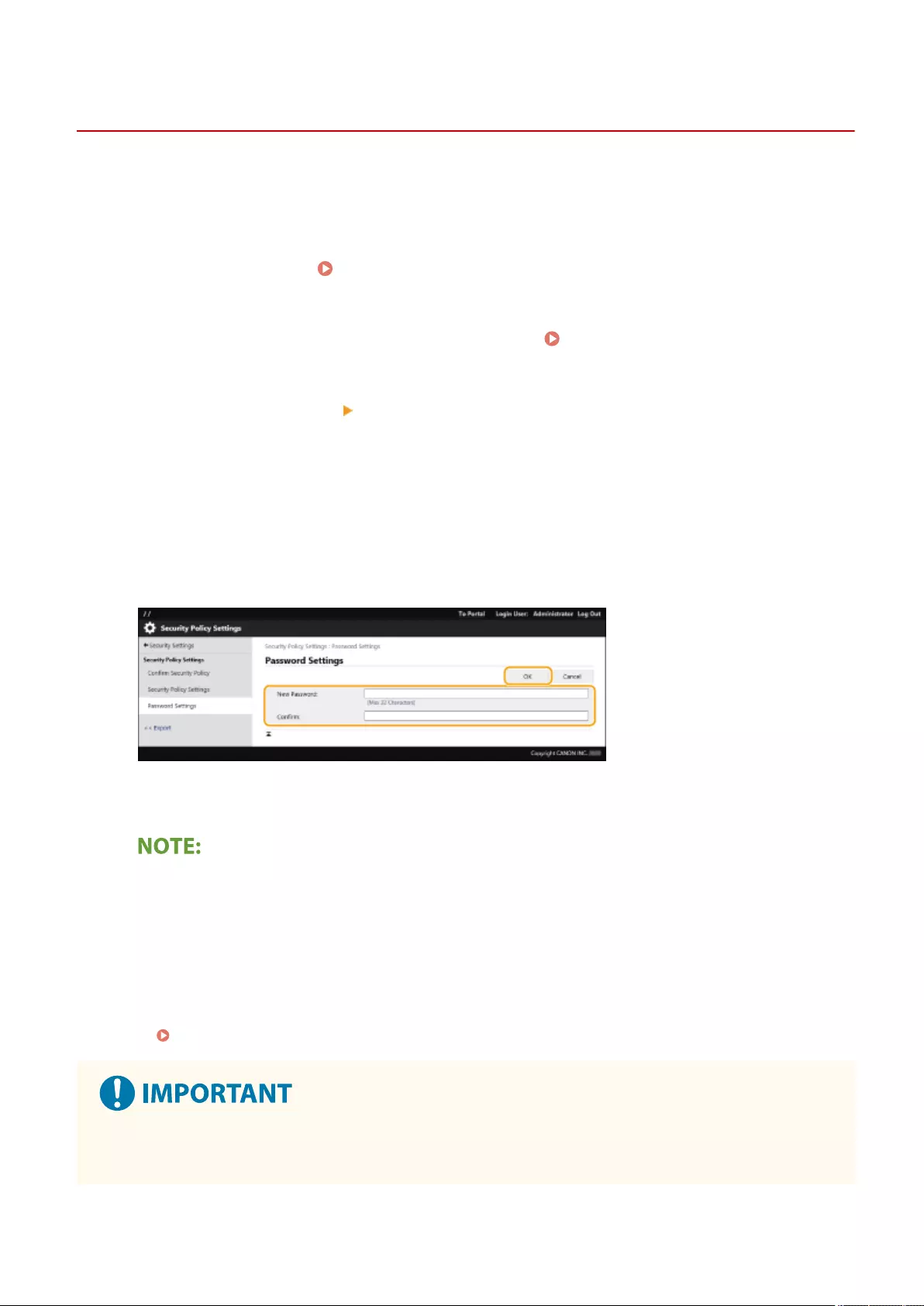
Using a Password to Protect the Security Policy Settings
72JY-089
It is recommended that you use a password to protect the machine settings related to security policy. By setting a
password, the privilege for modifying the security policy settings can be restricted only to the information security
administrators who know the password.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Security Settings] [Security Policy Settings].
➠The [Conrm Security Policy] page is displayed.
4Click [Password Settings].
5Enter a password and click [OK].
●Use alphanumeric characters or symbols for the password.
●Make sure that the password is entered correctly, and enter the new password again in [Conrm:].
To change the password
●Enter the current password in [Current Password:] and the new password in [New Password:], then enter
the new password again in [Conrm:] and click [OK].
To remove the password
●Enter the current password in [Current Password:], and click [OK] without entering any value for [New
Password:] or [Conrm:] (leave them blank). If an input character limit has been congured in [Password
Settings Policy], a value must be entered for this setting. Cancel the limit before removing the password.
Security Policy Setting Items(P. 483)
●Make sure that you do not forget your password. If you forget your password, contact your dealer or service
representative.
Managing the Machine
479

●To set/change the password, it is necessary to log in to the Remote UI with one of the following privileges.
-Administrator
- DeviceAdmin
- NetworkAdmin
●If a password is set, it will be required for authentication in order to initialize the machine. After
authentication is performed and the machine is initialized, the password will be deleted. Initializing All
Data/Settings(P. 663)
Managing the Machine
480
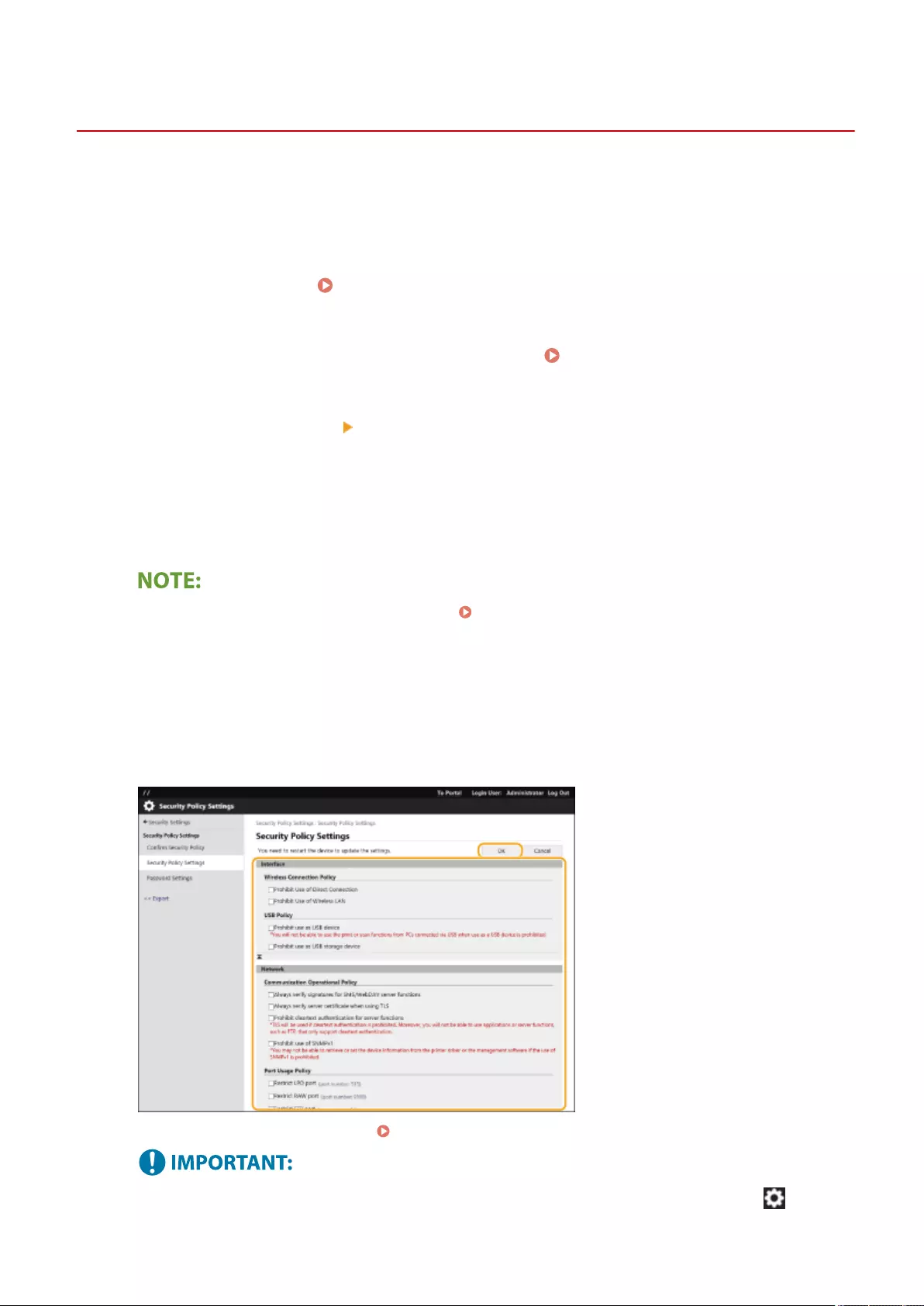
Conguring the Security Policy Settings
72JY-08A
Machine settings related to information security can be applied and managed in batch. It is recommended that the
information security administrator in charge of managing your security policy apply the security policy to the machine
in accordance with the policy of your organization. To congure the security policy, log in to the Remote UI with
Administrator privileges.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Security Settings] [Security Policy Settings].
4Click [Security Policy Settings].
➠The setting precautions are displayed. Make sure to read and understand the contents.
●If no password has been congured ( Using a Password to Protect the Security Policy
Settings(P. 479) ), read the contents and click [OK] to proceed to step 6.
5Enter the password and click [Log In].
6Congure the necessary items and click [OK].
●For information on the settings, see Security Policy Setting Items(P. 483) .
●The settings related to items indicated with a check mark here cannot be changed using (Settings/
Register) or the Remote UI.
Managing the Machine
481

●For any machine settings that were changed when the security policy settings were applied, you cannot
simply clear the check box to restore the previously set value. To change the settings, use (Settings/
Register) or the Remote UI.
7Click [OK].
●If a security policy has been congured, a message indicating that functions and operations are restricted
is displayed when the <Settings/Registration> screen is displayed on the control panel or the Remote UI.
◼Applying the Security Policy Settings to Another Device
You can import and export the machine's security policy settings. By applying the same policy to multiple devices*, you
can manage all of the devices in your organization using identical settings. Importing/Exporting the Setting
Data(P. 625)
* Only Canon devices that are compatible with security policy settings
●The security policy settings can only be imported if the security policy setting password on the exporting
machine matches that of the importing machine, or if no password has been set for the importing machine.
If no password has been set for the importing machine, the password congured for the exporting machine
is set to the importing machine.
Managing the Machine
482
Security Policy Setting Items
72JY-08C
The setting items related to the security policy of the machine are described below. Select the check boxes for the
items that you want to apply on the setting screen.
◼[Interface]
[Wireless Connection Policy]
Prevent unauthorized access by prohibiting wireless connections.
[Prohibit Use of Direct Connection] <Use Direct Connection> and <Always Keep Enabled If SSID/
Network Key Specied> are set to <Off>. It is not possible to
access the machine from mobile devices.
Connecting
Directly(P. 454)
<Network>(P. 782)
[Prohibit Use of Wireless LAN] If <Select Interface> is set to <Wireless LAN> or <Wired LAN +
Wireless LAN>, it changes to <Wired LAN>. Wireless connections
can no longer be made via a wireless LAN router or access
point.
<Select
Interface>(P. 790)
[USB Policy]
Prevent unauthorized access and data breaches by prohibiting USB connection.
[Prohibit use as USB device] <Use as USB Device> is set to <Off>. It is not possible to
connect to a computer via USB.
<Use as USB Device>(P. 795)
[Prohibit use as USB storage device] <Use USB Storage Device> is set to <Off>. It is not possible
to use USB storage devices.
<Use USB Storage
Device>(P. 796)
◼[Network]
[Communication Operational Policy]
Increase the security of communications by requiring the verication of signatures and certicates.
[Always verify signatures for SMS/
WebDAV server functions]
There are no setting items that the security policy is
applied to for the machine.
-
[Always verify server certicate
when using TLS]
The following settings are set to <On>, and a check mark
is added to <CN>.
●<Conrm TLS Certicate for WebDAV TX>
●<Conrm TLS Certicate for FTPS TX >
●<Conrm TLS Certicate for SMTP TX>
●<Conrm TLS Certicate for POP RX>
●<Conrm TLS Certicate for Network Access>
●<Conrm TLS Certicate Using AddOn Application>
●<Conrm TLS Certicate for LDAP Server Access>
The following settings are set to <On>.
●[License/Other] [Visual Message Settings]
[Conrm Certicate for TLS Communication]
●[License/Other] [Visual Message Settings] [Add
CN to Verication Items]
<Conrm TLS Certicate for
WebDAV TX>(P. 823)
<Conrm TLS Certicate for
FTPS TX>(P. 823)
<Conrm TLS Certicate for
SMTP TX>(P. 827)
<Conrm TLS Certicate for POP
RX>(P. 827)
<Conrm TLS Certicate for
Network Access>(P. 845)
<Conrm TLS Certicate Using
AddOn Application>(P. 861)
<Conrm TLS Certicate for
LDAP Server Access>(P. 850)
Conguring the Visual Message
Function(P. 649)
Managing the Machine
483
During TLS communication, verication will be
performed for digital certicates with common names.
[Prohibit cleartext authentication
for server functions]
<Use FTP Printing> in <FTP Print Settings> is set to <Off>,
<SMTP RX> in <E-Mail/I-Fax Settings>
<Communication Settings> is set to <Always TLS>,
<Dedicated Port Authentication Method> in <Network> is
set to <Mode 2>. When using the machine as a server,
plain text authentication and functions that use plain
text authentication are not available.
<FTP Print Settings>(P. 785)
<Communication
Settings>(P. 826)
<Dedicated Port Authentication
Method>(P. 788)
[Prohibit use of SNMPv1] In <SNMP Settings>, <Use SNMPv1> is set to <Off>. It is
not possible to use SNMPv1 when obtaining device
information from the computer.
<SNMP Settings>(P. 787)
●This setting does not apply to communication with IEEE 802.1X networks, even if the check box is selected
for [Always verify server certicate when using TLS].
●If [Prohibit cleartext authentication for server functions] is selected and your device management software
or driver version is old, it may not be possible to connect to the machine. Ensure that you are using the
latest versions.
[Port Usage Policy]
Prevent external breaches by closing unused ports.
[Restrict LPD port (port number: 515)] <LPD Print Settings> is set to <Off>. It is not possible to
perform LPD printing.
<LPD Print
Settings>(P. 784)
[Restrict RAW port (port number: 9100)] <RAW Print Settings> is set to <Off>. It is not possible to
perform RAW printing.
<RAW Print
Settings>(P. 784)
[Restrict FTP port (port number: 21)] In <FTP Print Settings>, <Use FTP Printing> is set to <Off>.
It is not possible to perform FTP printing.
<FTP Print
Settings>(P. 785)
[Restrict WSD port (port number: 3702,
60000)]
In <WSD Settings>, <Use WSD Printing>, <Use WSD
Browsing>, and <Use WSD Scan> are all set to <Off>. It is
not possible to use WSD functions.
<WSD Settings>(P. 785)
[Restrict BMLinkS port (port number:
1900)]
There are no setting items that the security policy is
applied to for the machine.
-
[Restrict IPP port (port number: 631)] The <IPP Print Settings> and <Use Mopria> options are all
set to <Off>. It is not possible to print using IPP or
Mopria™.
<IPP Print
Settings>(P. 785)
<Use Mopria>(P. 789)
[Restrict SMB port (port number: 139, 445)] There are no setting items that the security policy is
applied to for the machine.
-
[Restrict SMTP port (port number: 25)] In <E-Mail/I-Fax Settings> <Communication Settings>,
<SMTP RX> is set to <Off>. SMTP reception is not
possible.
<Communication
Settings>(P. 826)
[Restrict dedicated port (port number:
9002, 9006, 9007, 9011-9015, 9017-9019,
9022, 9023, 9025, 20317, 47545-47547)]
<Dedicated Port Settings> is set to <Off>. It is not
possible to use dedicated ports.
<Dedicated Port
Settings>(P. 788)
[Restrict Remote Operator's Software port
(port number: 5900)]
<Remote Operation Settings> is set to <Off>. It is not
possible to use remote operation functions.
<Remote Operation
Settings>(P. 862)
Managing the Machine
484
[Restrict SIP (IP Fax) port (port number:
5004, 5005, 5060, 5061, 49152)]
There are no setting items that the security policy is
applied to for the machine.
-
[Restrict mDNS port (port number: 5353)] In <mDNS Settings>, the <Use IPv4 mDNS> and <Use
IPv6 mDNS> options are set to <Off> and <Use Mopria> is
set to <Off>. It is not possible to search the network or
perform automatic settings using mDNS. It is also not
possible to print using Mopria™.
<mDNS
Settings>(P. 783)
<Use Mopria>(P. 789)
[Restrict SLP port (port number: 427)] In <Multicast Discovery Settings>, <Response> is set to
<Off>. It is not possible to search the network or perform
automatic settings using SLP.
<Multicast Discovery
Settings>(P. 786)
[Restrict SNMP port (port number: 161)] In <SNMP Settings>, the <Use SNMPv1> and <Use
SNMPv3> options are set to <Off>, and <Display Scan for
Mobile> is set to <Off>. It is not possible to obtain device
information from the computer or congure settings
using SNMP.
<SNMP
Settings>(P. 787)
<Display Scan for
Mobile>(P. 776)
◼[Authentication]
[Authentication Operational Policy]
Prevent unregistered users from performing unauthorized operations by implementing secure user authentication.
[Prohibit guest users to use
device]
The following settings are set to <On>.
●<User Management> <Authentication Management>
<Use User Authentication>
●<Restrict Job from Remote Device w/out User Authent.>
●[Login for Unregistered Users:] [Allow unregistered
users to log in as Guest User]
<Login Screen Display Settings> is set to <Displ When Dev
Operation Start>.
It becomes [Standard Authentication Mode] if [Guest
Authentication Mode] is set for [Authentication Mode:] in
[Remote UI Authentication].
In addition, [Guest Authentication Mode] can no longer be
selected for [Authentication Mode:] in [Remote UI
Authentication].
Unregistered users cannot log in to the machine, and print
jobs from computers are canceled.
<Use User
Authentication>(P. 854)
<Login Screen Display
Settings>(P. 854)
<Restrict Job from Remote
Device w/out User
Authent.>(P. 855)
ACCESS MANAGEMENT SYSTEM
Administrator Guide
[Force setting of auto logout] <Auto Reset Time> is enabled. The user is automatically
logged out if no operations are performed for a specied
period of time. Select [Time Until Logout:] on the Remote UI
setting screen.
<Auto Reset Time>(P. 778)
[Password Operational Policy]
Impose strict limits for password operations.
[Prohibit caching of password for
external servers]
<Prohibit Caching of Authentication Password> is set
to <On>, and [Save authentication information for
login users] is set to [Off]. Users will always be
required to enter a password when accessing an
external server.
<Prohibit Caching of
Authentication
Password>(P. 866)
Registering Server
Information(P. 507)
Managing the Machine
485
[Display warning when default
password is in use]
<Display Warning When Default Password Is in Use>
is set to <On>. A warning message will be displayed
whenever the machine's factory default password is
used.
<Display Warning When
Default Password Is in
Use>(P. 866)
[Prohibit use of default password for
remote access]
<Allow Use of Default Password for Remote Access>
is set to <Off>. It is not possible to use the factory
default password when accessing the machine from
a computer.
<Allow Use of Default
Password for Remote
Access>(P. 867)
[Password Settings Policy]
Prevent third parties from easily guessing passwords by setting a minimum level of complexity and a period of validity
for user authentication passwords.
[Set minimum number of characters for
password]
<Minimum Length Settings> is set to <On>. It is not
possible to set a password with fewer characters than
the number specied for [Minimum Number of
Characters] on the Remote UI setting screen.
<Minimum Length
Settings>(P. 867)
[Set password validity period] <Validity Period Settings> is set to <On>. A period of
validity is set for the password. Specify the period in
[Validity Period:] on the Remote UI setting screen.
<Validity Period
Settings>(P. 867)
[Prohibit use of 3 or more identical
consecutive characters]
<Prohibit Use of 3 or More Identical Consec.
Characters> is set to <On>. It is not possible to set a
password that includes the same character repeated
three or more times consecutively.
<Prohibit Use of 3 or More
Identical Consec.
Characters>(P. 867)
[Force use of at least 1 uppercase
character]
<Use at Least 1 Uppercase Character> is set to <On>.
Passwords are required to include at least one
uppercase alphabetic character.
<Use at Least 1 Uppercase
Character>(P. 868)
[Force use of at least 1 lowercase
character]
<Use at Least 1 Lowercase Character> is set to <On>.
Passwords are required to include at least one
lowercase alphabetic character.
<Use at Least 1 Lowercase
Character>(P. 868)
[Force use of at least 1 digit] <Use at Least 1 Digit> is set to <On>. Passwords are
required to include at least one numeric character.
<Use at Least 1
Digit>(P. 868)
[Force use of at least 1 symbol] <Use at Least 1 Symbol> is set to <On>. Passwords are
required to include at least one symbol.
<Use at Least 1
Symbol>(P. 869)
[Lockout Policy]
Block users from logging in for a specied period of time after a certain number of consecutive invalid login attempts.
[Enable lockout] In <Lockout Settings>, <Enable Lockout> is set to <On>. Specify the
values for [Lockout Threshold] and [Lockout Period] on the Remote UI
setting screen.
<Lockout
Settings>(P. 866)
◼[Key/Certicate]
Protect important data by preventing the use of weak encryption, or by saving encrypted user passwords and keys in a
designated hardware component.
[Prohibit use of weak encryption] <Prohibit Use of Weak Encryption> is set to <On>. It is not
possible to use weak encryption. When the check box is
selected, [Prohibit use of key/certicate with weak
encryption] can be selected.
<Prohibit Use of Weak
Encryption>(P. 869)
Managing the Machine
486
[Prohibit use of key/certicate with weak
encryption]
In <Prohibit Use of Weak Encryption>, <Prohibit Use of
Key/Certicate with Weak Encryption> is set to <On>. It is
not possible to use a key or certicate with weak
encryption.
<Prohibit Use of Weak
Encryption>(P. 869)
[Use TPM to store password and key] There are no setting items that the security policy is
applied to for the machine.
-
◼[Log]
You can periodically survey how the machine is used, by requiring logs to be recorded.
[Force recording of audit log] <Display Job Log> is set to <On>, <Retrieve Job Log with
Management Software> in <Display Job Log> is set to <Allow>,
<Save Audit Log> is set to <On>, <Retrieve Network
Authentication Log> is set to <On>, and <Use Login Name as
User Name for Print Jobs> is set to <On>. Audit logs are always
recorded.
<Display Job Log>(P. 858)
<Save Audit Log>(P. 858)
<Retrieve Network
Authentication Log>(P. 858)
<Use Login Name as User
Name for Print Jobs>(P. 793)
[Force SNTP settings] In <SNTP Settings>, <Use SNTP> is set to <On>. Time
synchronization via SNTP is required. Enter a value for [NTP
Server Address] on the Remote UI setting screen.
<SNTP Settings>(P. 785)
◼[Job]
[Printing Policy]
Prevent information leakage from occurring when printing.
[Prohibit immediate printing of
received jobs]
The following settings are set to <On>.
●<Fax Memory Lock> in the Fax/I-Fax Inbox
●<I-Fax Memory Lock> in the Fax/I-Fax Inbox
●<Set Fax/I-Fax Inbox> <Use Fax Memory Lock>
●<Set Fax/I-Fax Inbox> <Use I-Fax Memory Lock>
●<Forced Hold>
<Handle Files with Forwarding Errors> is set to <Store/
Print>.
<Memory Lock End Time> is set to <Off>.
Only <Hold as Shared Job> can be set for the operation
conditions of <Forced Hold>.
Printing does not occur immediately, even when printing
operations are performed.
<Handle Files with Forwarding
Errors>(P. 836)
<Use Fax Memory Lock>(P. 837)
<Use I-Fax Memory
Lock>(P. 837)
<Memory Lock End
Time>(P. 838)
<Forced Hold>(P. 846)
Saving Received Documents in
the Machine (Memory Reception)
(P. 313)
[Sending/Receiving Policy]
Limit the sending operations for destinations, and limit how received data is processed.
[Allow sending only to registered
addresses]
In <Restrict New Destinations>, the <Fax>, <E-Mail>, <I-
Fax>, and <File> options are set to <On>. It is only
possible to send to destinations that are registered in the
Address Book.
<Restrict New
Destinations>(P. 823)
[Force conrmation of fax number] <Conrm Entered Fax Number> is set to <On>. Users are
required to enter a fax number again for conrmation
when sending a fax.
<Conrm Entered Fax
Number>(P. 833)
Managing the Machine
487

[Prohibit auto forwarding] <Use Forwarding Settings> is set to <Off>. It is not
possible to automatically forward faxes.
<Use Forwarding
Settings>(P. 836)
◼[Storage]
Delete unnecessary data in the memory of the machine to prevent information leaks.
[Force complete deletion of data] There are no setting items that the security policy is applied to for the machine. -
Managing the Machine
488
Managing Users
72JY-08E
You can ensure a higher level of security and eciency by utilizing a user authentication application (login service) to
manage the users of the machine ( Login Service(P. 489) ). It is recommended that the administrator manage all
users in accordance with your operating environment and required security measures. User Management
Functions(P. 489)
Conguring the Personal Authentication Management Settings(P. 492)
Using Other Convenient Personal Authentication Management Functions(P. 521)
Deleting User Setting Information(P. 534)
Login Service
A user authentication application (login service) called "User Authentication" is used as the primary method of
managing the users of the machine. With the User Authentication login service, personal authentication can be
performed for users based on the user name and password registered for each user. The user information is checked
either on the database inside the machine or on an external authentication server. With the ability to precisely dene
which functions are available to each user, you can personalize machine operations and improve security by limiting
access to certain functions. It may also be possible to use Department ID Management to manage groups, depending
on the device used for authentication.
●If you are not using the Personalization function, set <Enable Use of Personal Settings> ( <Enable Use of
Personal Settings>(P. 859) ) to <Off>.
User Management Functions
User management can provide the advantages described below. To protect important data and reduce costs, you can
limit access to the machine and dene the range of operations that are available to users.
Preventing Unauthorized Use by Third Parties
Because machine usage is limited to approved users, information leakage due to unauthorized use by third
parties is prevented, even if the machine is located in a busy area that is open to outside parties.
Managing the Machine
489
Setting the Privilege Levels
With personal authentication management, you can dene the range of available operations by specifying the
role (privilege level) for each user. For example, you can select the Administrator role to allow full access
privileges, the NetworkAdmin role to allow conguration of network-related settings, or the DeviceAdmin role
to allow the conguration of device information settings and the settings for keys and certicates that are
required when using particular functions. By selecting and assigning various privilege levels to administrators,
you can operate more effectively as a team in handling a wide range of machine management tasks.
Setting Usage Restrictions
Personal authentication management enables a user with Administrator privileges to manage the range of
operations that are available to users. The ability to set function restrictions for each user provides you with
more precise control in user management.
Managing Groups of Users
Users can be assigned to groups based on Department ID (Department ID Management), enabling you to check
the total number of printed or scanned pages for each Department ID. You can also set specic limits for each
Department ID, such as a maximum of 500 printed pages or a maximum of 200 copied pages. This function can
help boost cost awareness and provide hints on how to improve your operations.
Optimizing the Settings for Each User
Various settings can be saved for each user and applied at login. Users can create Personal buttons, and they
can specify a Personal folder on the network. It is also possible for the machine to remember passwords once
they have been entered, enabling users to log in again without entering the password.
Associating User Accounts with Keychains for Smooth Operations
●When authentication information different from the authentication information used when logging in is
required, the authentication information has to be entered once, but does not need to be entered again
once authentication is successful. This authentication information is called a keychain. Since keychains are
Managing the Machine
490

associated with user accounts, authentication information does not need to be entered again, even if the
power of the machine is turned OFF.
Associating User Accounts with Department IDs to Restrict the Number of Copies and
Prints
●User Authentication user accounts can be associated with Department IDs. By specifying copy and print
restrictions for Department IDs in advance, you can apply restrictions on the number of copies or prints for
each department that a user belongs to. For information on associating user accounts with Department IDs,
see Registering User Information in the Local Device(P. 495) . For information on specifying
restrictions according to department, see Conguring the Department ID Management
Settings(P. 525) .
Managing the Machine
491

Conguring the Personal Authentication Management
Settings
72JY-08F
The User Authentication login service performs personal authentication based on the information registered for each
user, enabling you to limit the users who can access the machine. User information registration (authentication) can
be performed on this machine and on an external server. You can congure the authentication system to use only this
machine as the authentication device, or you can additionally specify an Active Directory or LDAP authentication server
on the network as an authentication device to utilize the existing user information registered on the server (
Authentication Device(P. 492) ). Administrators can also specify which functions are available to each individual user,
such as "user A is prohibited from making copies" or "user B is allowed to use all machine functions." For the user login
method, you can enter authentication information or select a user ( Login Method(P. 492) ). Before conguring the
user authentication settings, decide the authentication device and login method. Conguring Personal
Authentication Management with User Authentication(P. 493)
Registering User Information in the Local Device(P. 495)
Importing/Exporting User Data(P. 499)
Registering Server Information(P. 507)
Conguring the Authentication Functions(P. 513)
Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a Computer(P. 520)
Authentication Device
The authentication devices described below can be used for personal authentication management. Each type of
authentication device requires a different environment and settings. Conrm your system environment before
conguring. System Specications(P. 1084)
Local Device (This Machine)
User information is managed on the database inside the machine. User information is registered and edited via
the control panel or the Remote UI. When the local device is congured as a standalone authentication device,
Department ID Management can also be performed at the same time. Registering User Information in the
Local Device(P. 495)
Active Directory/LDAP Server
In addition to the local device, you can specify an LDAP server or Windows Server with Active Directory installed
as the authentication device. One advantage of using this type of device is that the users registered on the
server can be added as general users without any changes. To provide administrator privileges to a user, the
user must be assigned to a specic administrator group on the Active Directory or LDAP server. To specify the
additional authentication device, you must register the information of the server used for authentication.
Registering Server Information(P. 507)
Login Method
The user login methods described below are available for personal authentication management. It is also possible to
use these methods in combination with each other. For more information on login operations, see Logging into the
Machine(P. 137) .
Managing the Machine
492
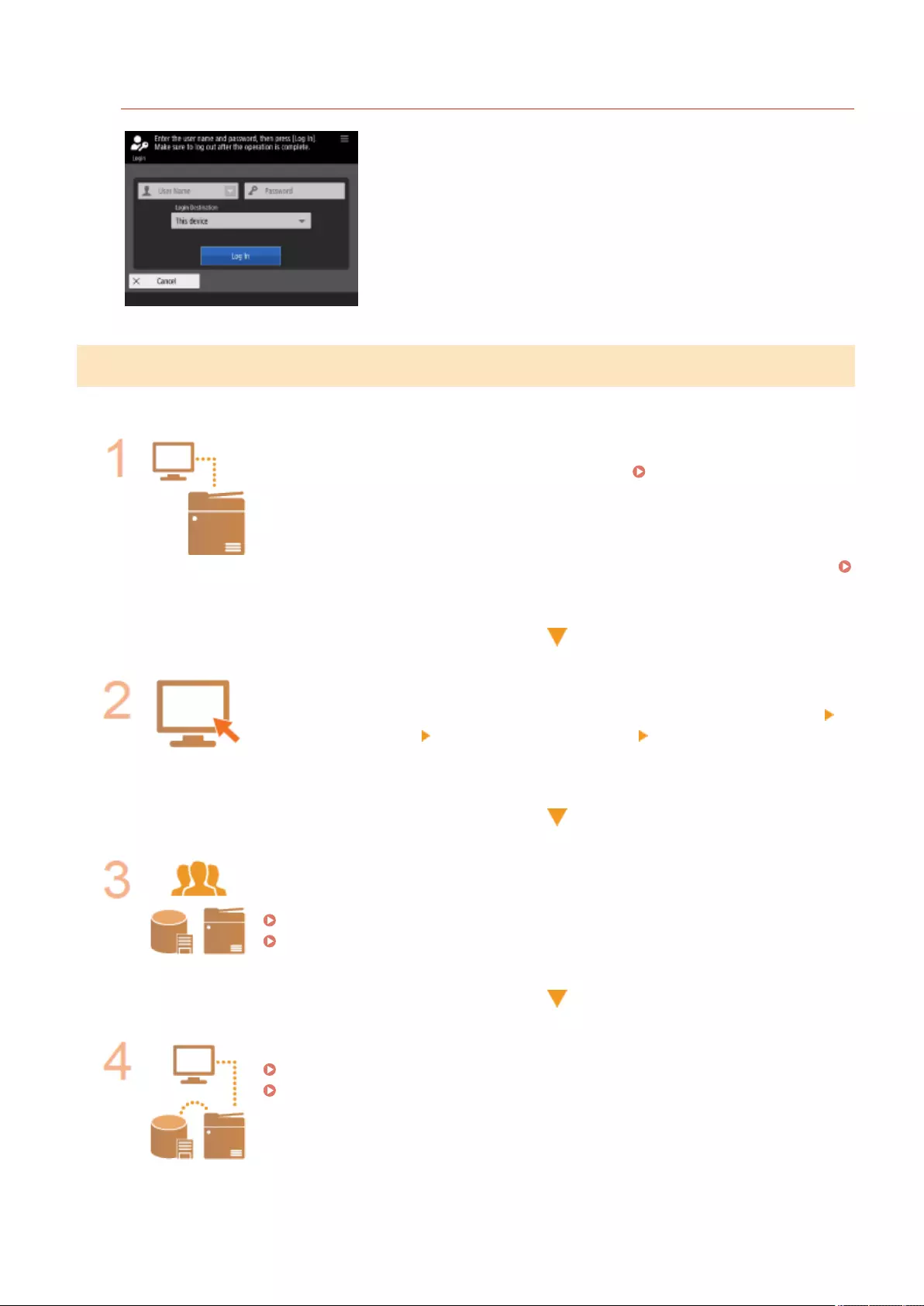
Keyboard Authentication
With this method, users log in by entering their user name and
password using the keyboard displayed on the control panel. This
method is available regardless of the authentication device that is used.
Conguring Personal Authentication Management with User Authentication
Congure the personal authentication management settings in the order described below.
Check the basic conguration.
●Is the machine properly connected to the computer? Setting up the Network
Environment(P. 19)
●If you are using an authentication server, have the DNS settings been congured for
the machine?
●If you are using an authentication server, have the date and time been properly set?
Setting the Date/Time(P. 17)
Check the login service.
●Log in to the Remote UI with Administrator privileges, click [Settings/Registration]
[User Management] [Authentication Management] [Authentication Service
Information], and check that the login service is indicated as User Authentication.
Congure the authentication server settings.
●Register user information on the local device and specify the authentication server.
Registering User Information in the Local Device(P. 495)
Registering Server Information(P. 507)
Select the user authentication system.
Conguring the Authentication Functions(P. 513)
Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a
Computer(P. 520)
Managing the Machine
493

●Make sure to log out after you nish using the Remote UI. If you close the Remote UI without logging out, it
may take a long time to log in next time.
●If you want to limit authentication method to User Authentication (restrict use of System Manager ID for
authentication) when the machine is accessed from a device management software or driver, make sure to
set <Prohibit Authentication Using Department ID and PIN> to <On>. <Prohibit Authentication Using
Department ID and PIN>(P. 866)
Managing the Machine
494

Registering User Information in the Local Device
72JY-08H
To perform personal authentication management, you must rst register user
information in the database of the machine.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
Disabling "Administrator"
●"Administrator" is registered as the default administrator name (user name). This user cannot be deleted
but it can be disabled after adding a user with "Administrator" privileges. Logging in as an
Administrator(P. 15)
4Click [Add User].
To edit user information
●Click [Edit] for the user information that you want to edit, make the necessary changes, and click [Update].
To delete user information
●Select the check box for the user information that you want to delete, and click [Delete] [OK].
5Enter the necessary information.
Managing the Machine
495
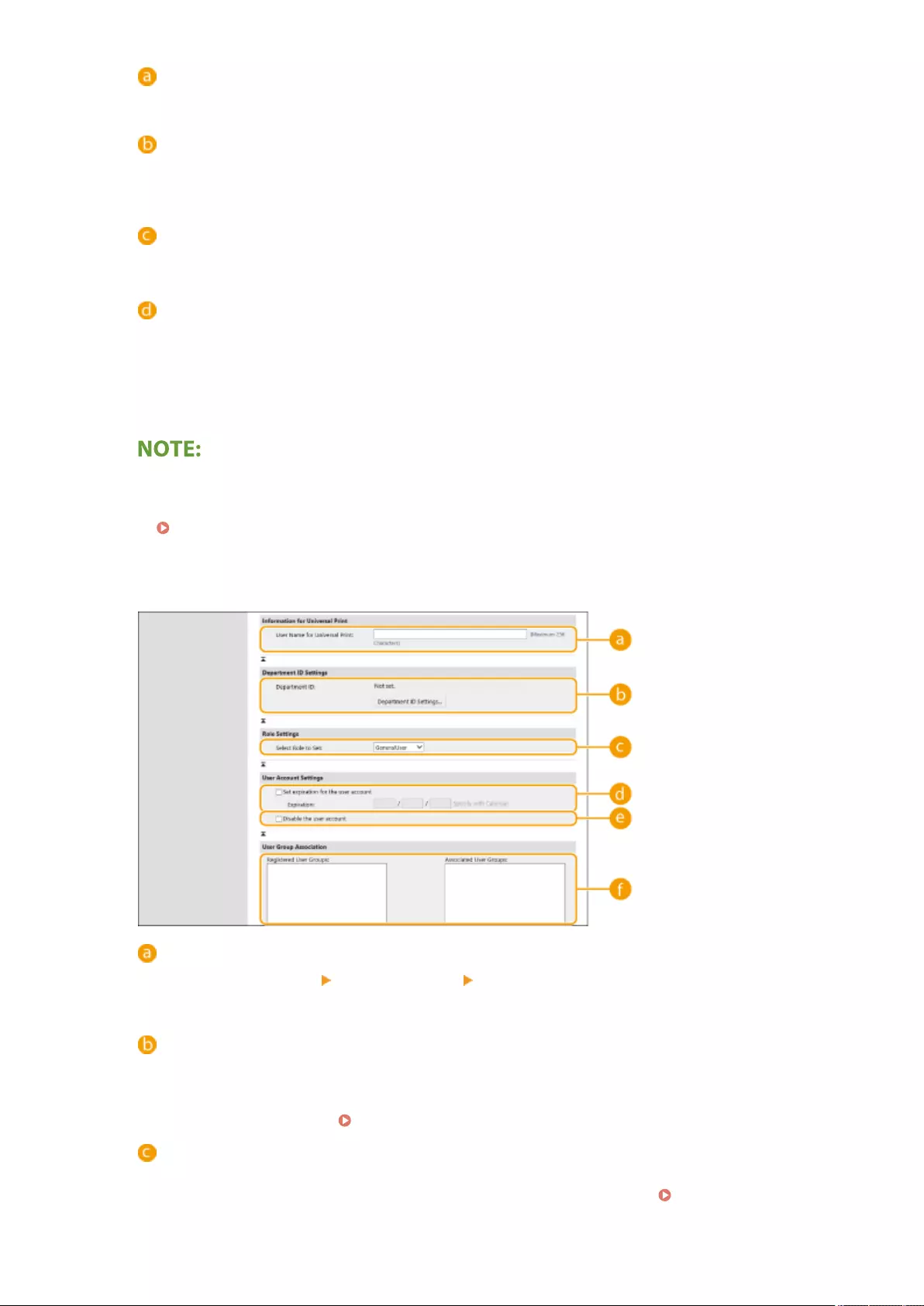
[User Name:] / [Password:] / [Conrm:]
Enter the user name and password. For conrmation, enter the password again in [Conrm:]. Single-byte
or double-byte characters can be used for the user name.
[No Expiry for Password]
Select the check box to set the password of the user to register to have no expiration date. This setting can
be specied when [Set password validity period] is set to [Off] in [Password Settings Policy] in
[Authentication] in [Security Policy Settings].
[Displayed As:]
Enter the name of the user. The display name is displayed as the user name for forced hold printing and
used as the sender name when sending e-mail.
[E-Mail Address:]
Enter the e-mail address that the user is using on devices such as computers. When sending scanned
documents, this address will be displayed along with the sender's name. This address is also used when
sending documents by using <Send to Myself>.
When an I-fax is sent, the e-mail address registered here is displayed in the Sender line on the recipient
device.
●It is also possible for general users to change their own password and PIN.
●Selecting the [Allow e-mail address settings] check box enables general users to specify e-mail addresses.
Conguring the User Login Methods and Authentication Devices(P. 513)
6Specify other required settings.
[User Name for Universal Print:]
If [Settings/Registration] [Network Settings] [Settings for Universal Print] is enabled, you can enter
the email address or phone number used in the Microsoft 365 account of the user with which Universal
Print jobs are associated.
[Department ID:]
When using Department ID Management, you must click [Department ID Settings...] and select the
Department ID from the list to assign to the user. First, register the necessary Department IDs in [Register
New Department...] on the list screen. If the Department ID that you specify here is later deleted, make
sure to change this setting. Conguring the Department ID Management Settings(P. 525)
[Select Role to Set:]
The user privileges (roles) listed below can be selected. Also specify the settings here when adding an
administrator. The available setting items vary depending on the privileges ( Settings/
Managing the Machine
496
Registration(P. 670) ). In addition, you can create your own roles. Using ACCESS MANAGEMENT
SYSTEM(P. 533)
[Administrator] Allows all operations as an administrator of the machine.
[GeneralUser] Allows general user privileges.
[DeviceAdmin] Allows operations that are available to general users, along with the ability to change
settings related to basic functions such as copying, printing, sending, and receiving.
[NetworkAdmin] Allows operations that are available to general users, along with the ability to change
network-related settings.
[Set expiration for the user account]
When setting a period of validity for the account, select the check box and enter a value for [Expiration].
[Disable the user account]
Select the check box to temporarily disable the account.
[User Group Association]
When you want to assign the user to a group, select a registered user group from the list and click [Add].
This setting is not displayed when using Department IDs as user groups. Conguring the User Login
Methods and Authentication Devices(P. 513)
7Click [Add].
Conguring settings via the control panel
●You can also register user information by pressing (Settings/Register) <Management Settings>
<User Management> <Authentication Management> <Register/Edit Authentication User>. <Register/
Edit Authentication User>(P. 854)
Creating user groups
●Address Lists in the Address Book can be shared between users who are registered in a user group.
Registering User Groups(P. 598)
Check for unregistered Department IDs
●If you click [Check Unregistered Department ID...] on the screen displayed in step 4, you can nd out
Department IDs that are not registered in the machine by checking Department IDs assigned to the users
against Department IDs registered in the machine.
Batch settings for Department IDs
●If you click [Batch Settings for Department ID...] on the screen displayed in step 4, you can create new
Department IDs and apply settings for all users.
●If the user name is comprised of numbers and is seven digits or fewer, the same number is assigned to the
same user as the Department ID. If the password of the same user is registered as a number that is seven
digits or fewer, it is also set as the PIN for that Department ID.
●If the user name and password do not meet the above conditions, a Department ID is automatically
assigned starting from 0000001, and 0 (none) is set for the PIN.
Managing the Machine
497

Registering the Department ID as the User Name
●If you click [Add User Using Department ID...] on the screen in step 4, a new user with the same name as the
Department ID is registered. When keyboard authentication is used, authentication can be performed using
numeric key entry only.
LINKS
Registering Server Information(P. 507)
Conguring the Authentication Functions(P. 513)
Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a Computer(P. 520)
Managing the Machine
498
Importing/Exporting User Data
72JY-08J
You can save user information stored in the machine to a computer (export), as well as load user information from
other machines into the machine you are using (import). This is useful when you want to register multiple users at
once.
Exporting User Data(P. 499)
Automatically Importing User Data(P. 499)
Manually Importing User Data(P. 501)
●For information on editing a CSV le for importing, see Adding and Editing User Information in a CSV
File(P. 503) .
●If duplicates of data exist in a CSV le for importing, the version of the data that was read rst will be
prioritized and registered.
●It is recommended that you export the registered/edited user data to make a backup copy.
Exporting User Data
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Click [Export].
5Select the le format, and click [Start Export].
●User information created in the le format that can be used with User Authentication is exported. The le
extension is "csv."
6Follow the instructions on the screen to specify the location to store the le.
➠The csv le is stored.
Automatically Importing User Data
You can automatically update user data by periodically importing import les stored in a specied location.
Managing the Machine
499
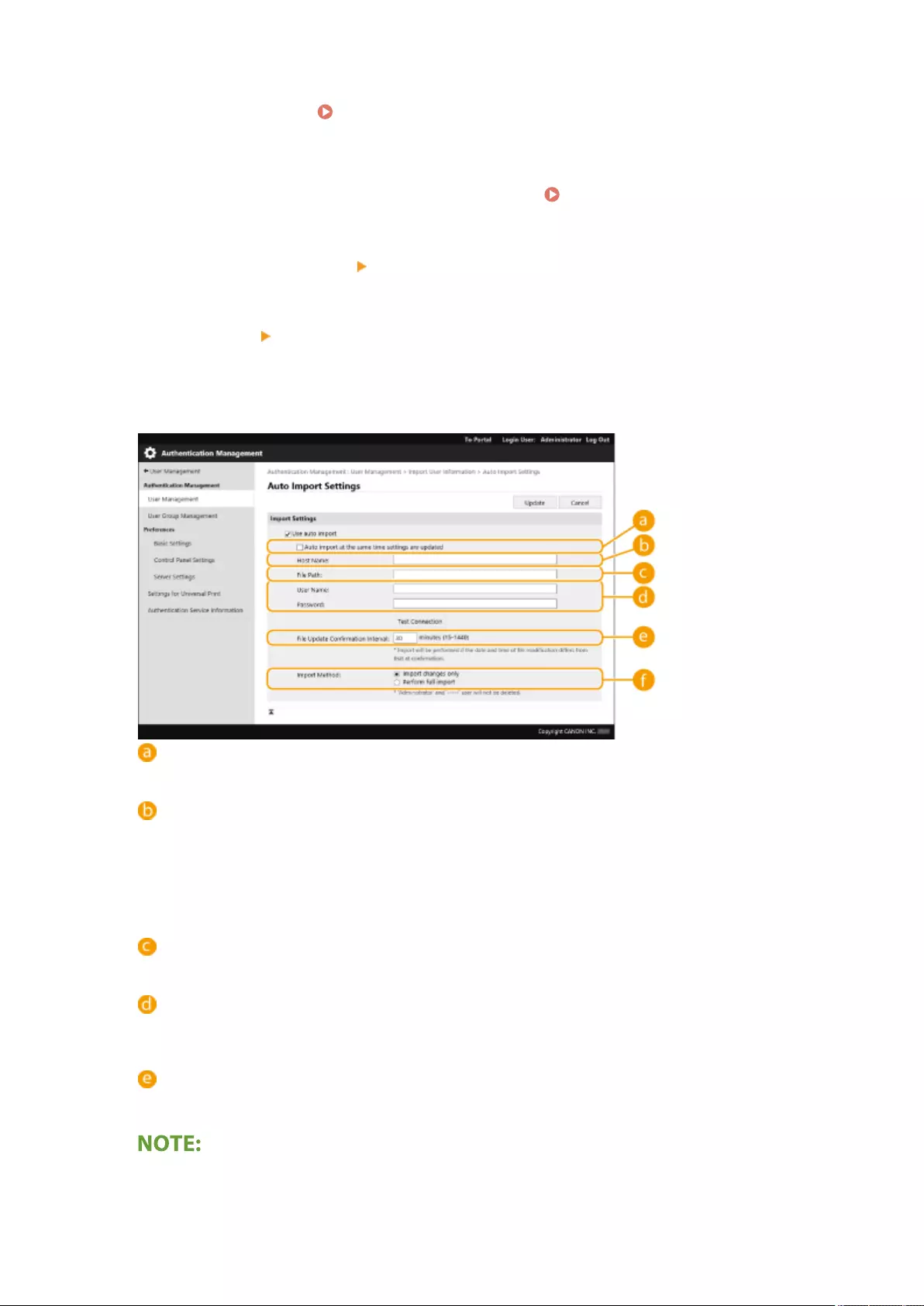
1Start the Remote UI. Starting the Remote
UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Click [Import] [Auto Import Settings...].
5Select the check box for [Use auto import] and specify the required settings.
[Auto import at the same time settings are updated]
Click the [Update] button to start importing.
[Host Name:]
Enter the host name of the server to access, along with the path that require authentication.
Example:
●\\Host Name
●\\IP Address\Shared Folder Name
[File Path:]
Enter the path of the le for importing.
[User Name:]/[Password:]
Enter the user name and password required to log in to the computer in which the le for importing is
stored.
[File Update Conrmation Interval:]
You can specify the interval in minutes for checking for les to import.
●If the operation cannot be performed at the specied time because the machine is turned OFF or is
completely in the Sleep mode, the operation is performed and information is reected when the machine
recovers.
Managing the Machine
500

[Import Method:]
Select whether to import only updated or added user data, or all user data.
●If you select [Perform full import] and a user with the same user name is already registered, the user
information is overwritten.
●When importing information of a user who accesses the Advanced Space with SMB, specify the
appropriate value in the "password" column. If you export the data from the machine and import it to the
other machine without performing the above operation, authentication may fail. (The value is "********"
when exported.)
●When performing a complete import, any users not listed in the imported les are deleted from the
machine. However, "-----" and "Administrator", which are registered by default, will remain even if they are
not listed in the imported les.
●"User Authentication Format" is the only le format that is supported. Also, the "uid" column is required.
●Note that if you are using a server that does not support SMBv3.0 encrypted communication, user data
travels unencrypted across communication paths while it is being obtained.
6Click [Test Connection], conrm that you can connect, and then click [Update].
Manually Importing User Data
You can manually specify data for importing and update user information.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Click [Import] [Manual Import Settings...]
5Specify the required settings.
Managing the Machine
501

[File Path:]
Specify the path of the le for importing.
[File Format:]
Select the le format for importing.
●<Simple Device Login Format>:
Imports user information exported from a Canon machine using the Local Device Authentication of
SSO-H. The le extension is "ldif."
●<User Access Control for Advanced Space Format>:
Imports user information exported from a Canon machine with Advanced Space user access control.
The le extension is "csv."
●<User Authentication Format>:
Imports user information created in the le format that can be used with User Authentication. The le
extension is "csv."
[Import Method:]
Select whether to import only updated or added user data, or all user data.
●If you select [Perform full import] and a user with the same user name is already registered, the user
information is overwritten.
●When importing information of a user who accesses the Advanced Space with SMB, specify the
appropriate value in the "password" column. If you export the data from the machine and import it to the
other machine without performing the above operation, authentication may fail. (The value is "********"
when exported.)
●When performing a complete import, any users not listed in the imported les are deleted from the
machine. However, "-----" and "Administrator", which are registered by default, will remain even if they are
not listed in the imported les.
[Application Timing:]
Select [Apply immediately] or [Specify the date and time]. If you select [Specify the date and time], enter
the desired date and time or the time only.
●If the user information cannot be reected at the specied time because the machine is turned OFF or is
completely in the Sleep mode, the information is reected when the machine recovers.
6Click [Start Import]
●If the Department ID (dept_id) and PIN (dept_pin) are written in the imported CSV le, [Check Unregistered
Department ID] will be displayed after importing is complete. Perform Department ID registration.
Managing the Machine
502
Adding and Editing User Information in a CSV File
72JY-08K
This section describes the content of each column in a CSV le used for importing or exporting. Refer to this section
when editing CSV les.
However, if "No" is written in the "Change Required" section for a particular column, do not change the content of that
column.
Column Name Change
Required
Valid
Characters
Invalid
Characters
Compatibility
With Remote
UI Screen
Notes
uid Yes 1 to 32
characters
Control
characters,
single-byte
spaces, and
the following
characters:
\ / : * ? | < >
[ ] ; , = + @ "
●Must be input when importing.
●"@" may be available depending on
a setting. <Allow Use of @ in
User Name>(P. 855)
password Yes 0 to 32
characters
within the
ISO885915
character set
Control
characters
●Output as "********" (* x 8) when
exporting.
●When updating the password,
"********" will be deleted and
overwritten by the new password.
However, when importing changes,
even if you leave the eld
unspecied (blank), it will not be
overwritten as empty (blank), but
will instead retain the existing value.
●If this item is omitted when
importing changes, the existing
user will carry over the original
password.
cn Yes 0 to 32
characters
Control
characters
N/A
cn;lang-ja;phonetic Yes 0 to 32
characters
Control
characters
See "Notes." Displayed as "phonetic" if the display
language is set to "Japanese."
cardIdList Yes Card ID: a
number up to
eight
alphanumeric
characters
You can
specify up to
1,000 items.
Non-single-
byte
alphanumeric
characters
See "Notes." ●Exported only if the optional Copy
Card Reader is attached.
●Multiple items of card information
are connected with a semi-colon (;).
●This item appears between "e-mail
address" and "icon image" when the
optional Copy Card Reader is
attached.
mail Yes Combination
of 0 to 256
alphanumeric
characters and
symbols
Control
characters
N/A
avatorImgPath No - - Cannot be changed. Automatically
assigned when specifying icon images.
Managing the Machine
503
Column Name Change
Required
Valid
Characters
Invalid
Characters
Compatibility
With Remote
UI Screen
Notes
dept_id Yes A number up
to seven digits
Non-single-
byte numeric
characters
N/A
dept_pin Yes A number up
to seven digits
Non-single-
byte numeric
characters
N/A
roleName Yes 0 to 32
characters
Control
characters,
single-byte
spaces, and
the following
characters:
\ / : * ? | < >
[ ] ; , = + @ " &
If this item is omitted, or if a name is
specied that is not registered in role
management, it will be changed to the
initial role setting.
accountExpires Yes See "Notes." See "Notes." YYYYMMDD format. "235959" is
automatically added as the time after
importing.
accountDisabled Yes 1 or 0 Any character
besides "1"
(disable) or "0"
(enable)
N/A
group Yes 0 to 64
characters.
You can
specify up to
10 items.
Control
characters,
single-byte
spaces, and
special
symbols.
The "Group name" registered in the
user group management is written
here. If the user belongs to multiple
groups, group names are connected
with a "|".
createDate Yes See "Notes." See "Notes." -
(N/A)
●Output in the
"TYYYYMMDDhhmmssmmm"
format when exporting. (The "T" is
added in order to prevent
corruption of the text.)
●When importing, input the
information in one of the following
formats.
●YYYYMMDDhhmmssmmm
●TYYYYMMDDhhmmssmmm
●YYYYMMDD
●TYYYYMMDD
●If you omit this item, the date and
time of importing is used for the
date and time of registration for
new users. For existing users, the
original registration date and time
are carried over.
lastLoginDate Yes See "Notes." See "Notes." -
(N/A)
●The date and time that the user last
logged in are stored.
●Output in the
"TYYYYMMDDhhmmssmmm"
format when exporting. (The "T" is
Managing the Machine
504
Column Name Change
Required
Valid
Characters
Invalid
Characters
Compatibility
With Remote
UI Screen
Notes
added in order to prevent
corruption of the text.)
●When importing, input the
information in one of the following
formats.
●YYYYMMDDhhmmssmmm
●TYYYYMMDDhhmmssmmm
●YYYYMMDD
●TYYYYMMDD
●Used for determining whether a
user has logged in and whether to
perform automatic user deletion.
●If you omit this item, the date and
time that the user last logged in are
blank for new users. For existing
users, date and time that the user
last logged in are carried over.
dc No 0 to 32
characters
Control
characters
-
(N/A)
Cannot be changed. It will be
automatically assigned for the following
users.
●Users registered following server
authentication
uuid No - - - Cannot be changed. Automatically
assigned during user registration.
sdl_digest No - - - Cannot be changed. Automatically
generated when registering/changing
password.
uac_advbox_digest1 No - - - Cannot be changed. Automatically
generated when registering/changing
password.
uac_advbox_digest2 No - - - Cannot be changed. Automatically
generated when registering/changing
password.
pin_digest No - - - Cannot be changed. Automatically
generated when registering/changing
PIN.
server_user_g No - - - Cannot be changed. This is an
identication ag for the user
registered after completing server
authentication.
server_user_gp_key No - - - Cannot be changed. This is the group to
which the user who is registered after
completing server authentication
belongs.
Managing the Machine
505
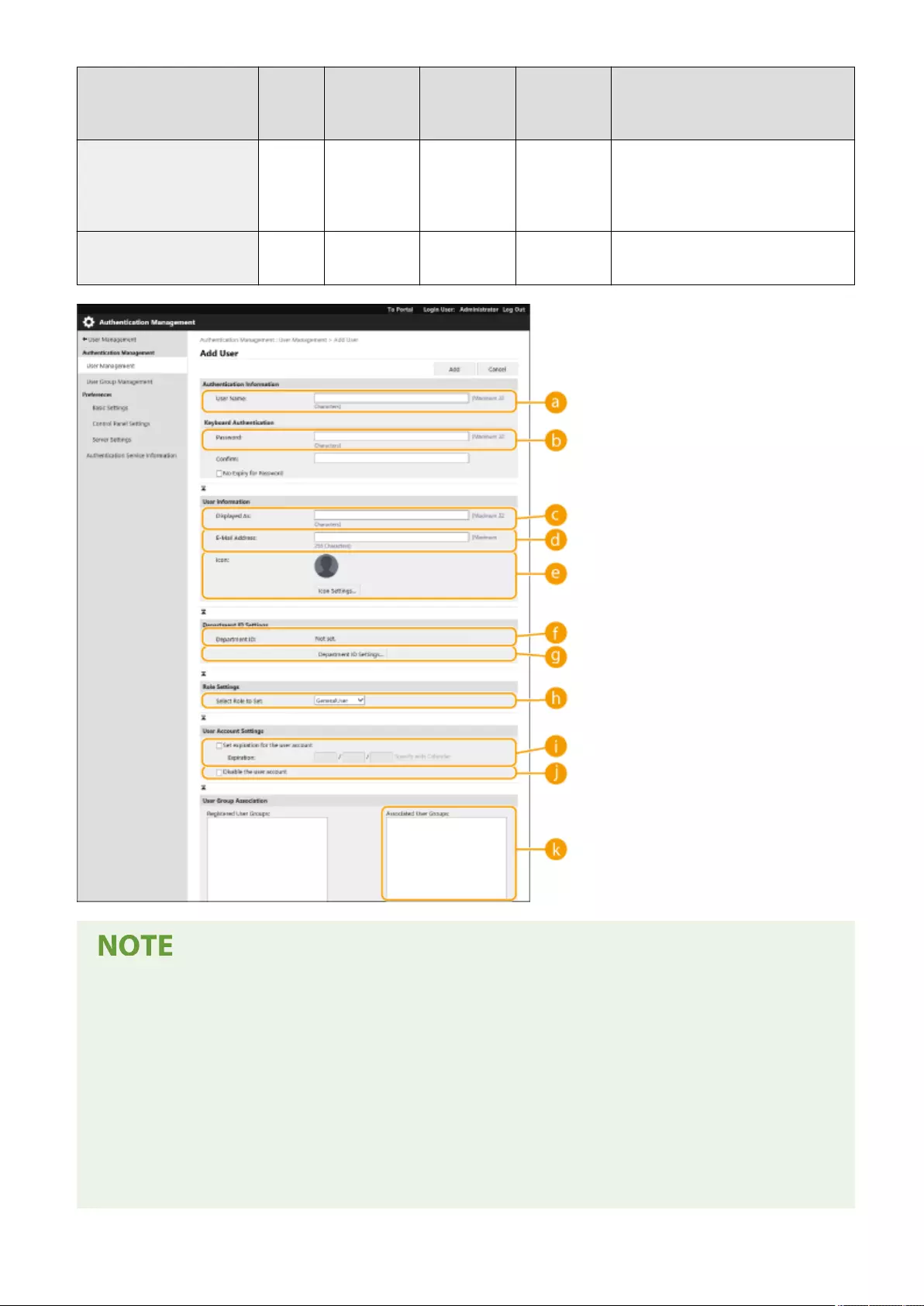
Column Name Change
Required
Valid
Characters
Invalid
Characters
Compatibility
With Remote
UI Screen
Notes
server_user_gp_value No - - - Cannot be changed. This is the group to
which the user who is registered after
completing server authentication
belongs.
CharSet - - - - For UTF8, "CharSet:UTF8" will be written
in the column line.
●The line at the beginning of the le is the column line.
●Items names may not appear in sequence.
●The encodings supported by CSV les are UTF-8, SJIS, BIG5, GB2312, and Korean.
●Text strings in exported CSV les are surrounded by ″[″ and ″]″ if any of the following conditions apply. When
editing a CSV le and adding new text strings that meet the following conditions, surround any such text
strings with "[" and "]".
- Numbers starting with "0"
- Numbers greater than 12 digits
- Text strings surrounded by "[" and "]"
Managing the Machine
506
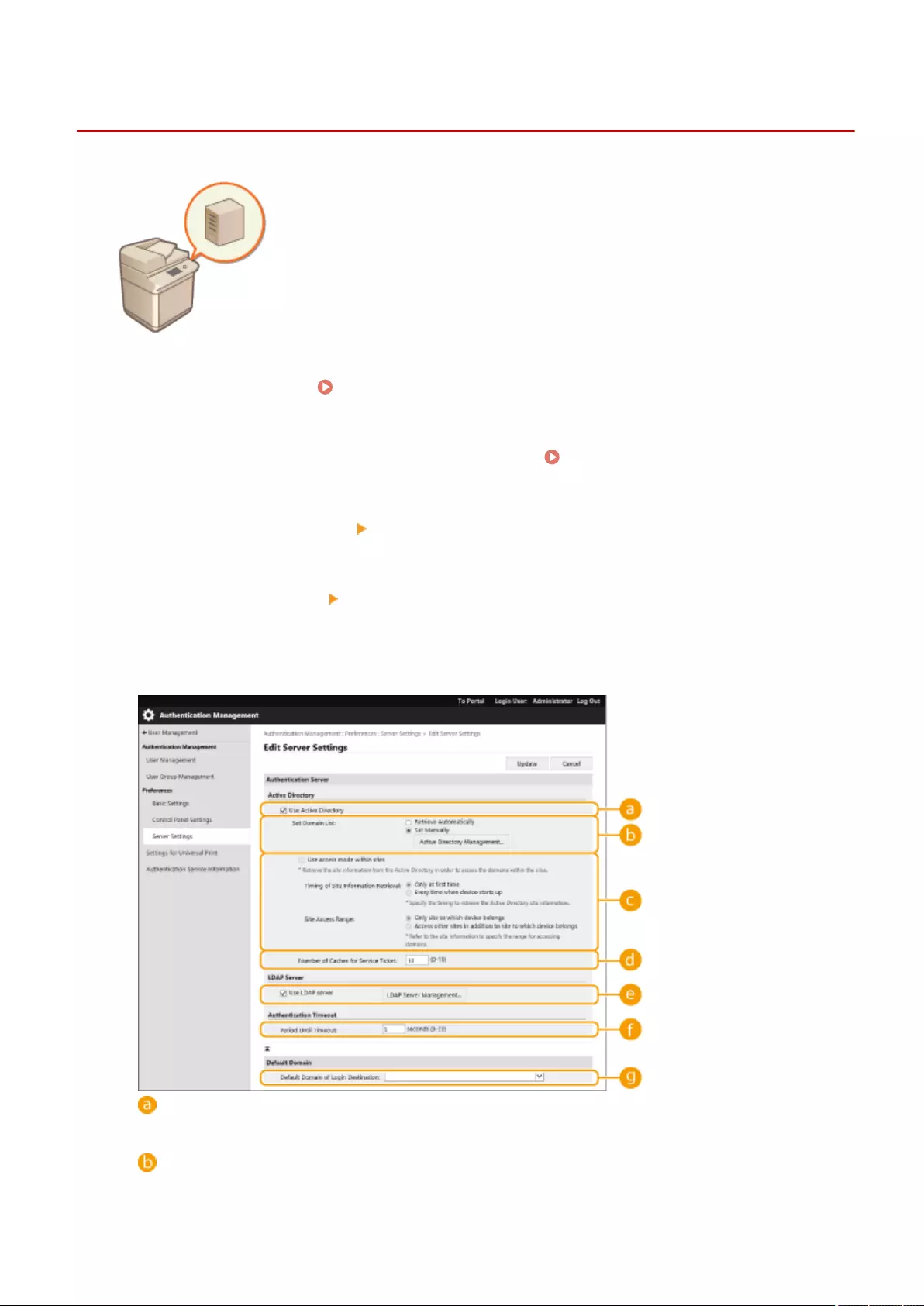
Registering Server Information
72JY-08L
To specify an Active Directory or LDAP server as an additional authentication device,
you must register the information of the server used for authentication. Conduct a
connection test as necessary.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Click [Server Settings] [Edit...].
5Set the authentication server and domain information.
[Use Active Directory]
Select the check box when using Active Directory.
[Set Domain List:]
Select whether the Active Directory information of the login destination is retrieved automatically or
entered manually. To enter it manually, select [Set Manually] and add the domain of the login destination
in [Active Directory Management...].
Managing the Machine
507
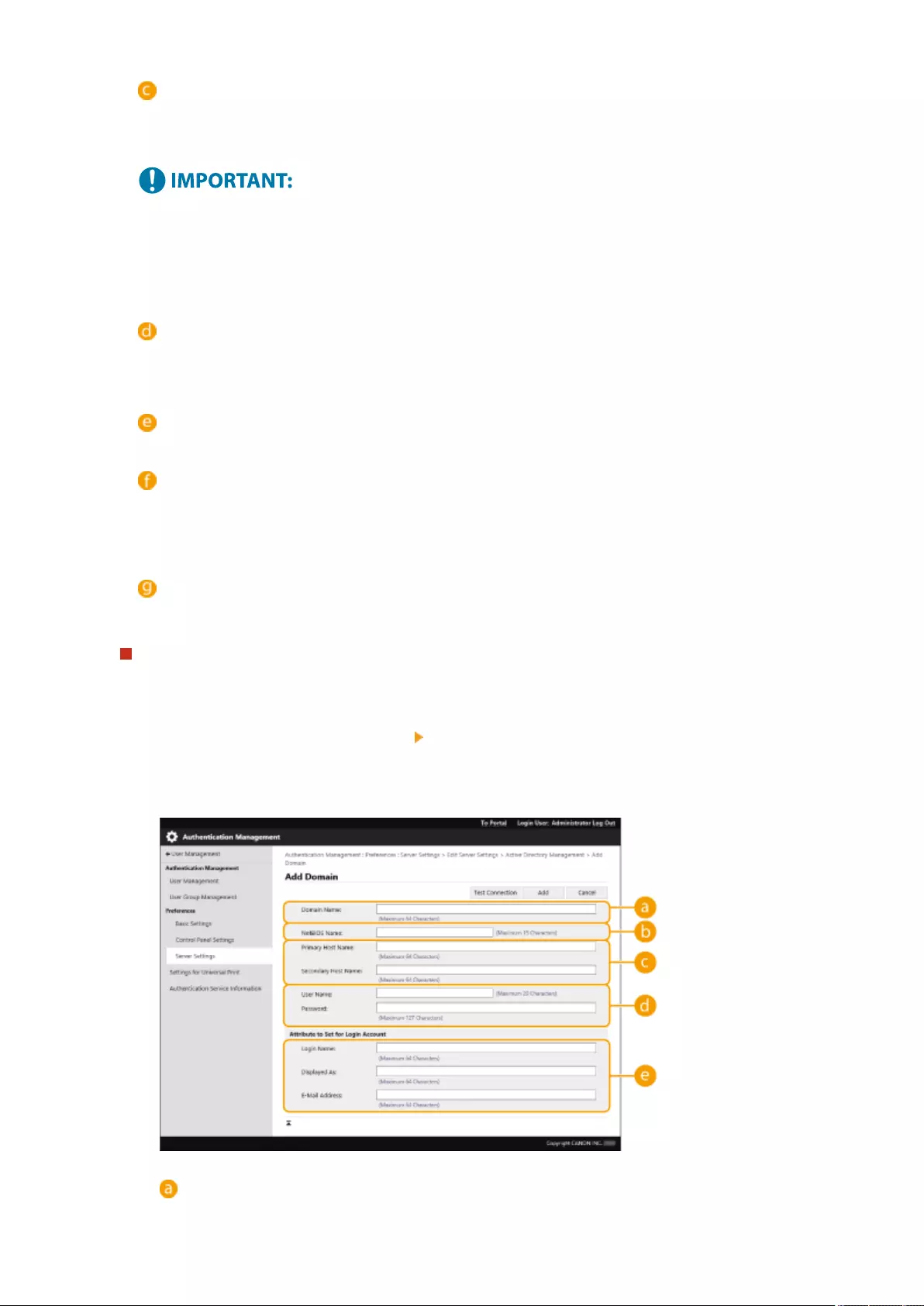
[Use access mode within sites]
Select the check box if there are multiple Active Directory servers and you want to assign access priority to
the Active Directory located in the same site as the machine. Change the settings for [Timing of Site
Information Retrieval:] and [Site Access Range:] as necessary.
●Even when [Only site to which device belongs] in [Site Access Range:] is set, the machine may access sites
outside the site it belongs to when performing domain controller access during the startup process.
However, access to domain controllers in the same site as the machine is prioritized. As an exception, if
domain controllers in the same site cannot be accessed but domain controllers outside the site can be
accessed, priority is given to accessing domain controllers outside the site.
[Number of Caches for Service Ticket:]
Specify the number of service tickets that the machine can hold. A service ticket is an Active Directory
function that acts as a record of a previous login, which reduces the amount of time it takes for the same
user to log in next time.
[Use LDAP server]
Select the check box when using an LDAP server.
[Period Until Timeout:]
Specify the time limit for attempting to connect to the authentication server and the time limit for waiting
for a response. When [Save authentication information for login users] is enabled, if you cannot log in
within the time limit specied here, login is attempted using the authentication information saved in the
cache.
[Default Domain of Login Destination:]
Specify the domain that has connection priority.
Manually specifying the Active Directory domain
1Select the check box for [Use Active Directory] and select [Set Manually] for [Set Domain List:].
2Click [Active Directory Management...] [OK].
3Click [Add Domain...].
4Enter the necessary information.
[Domain Name:]
Managing the Machine
508
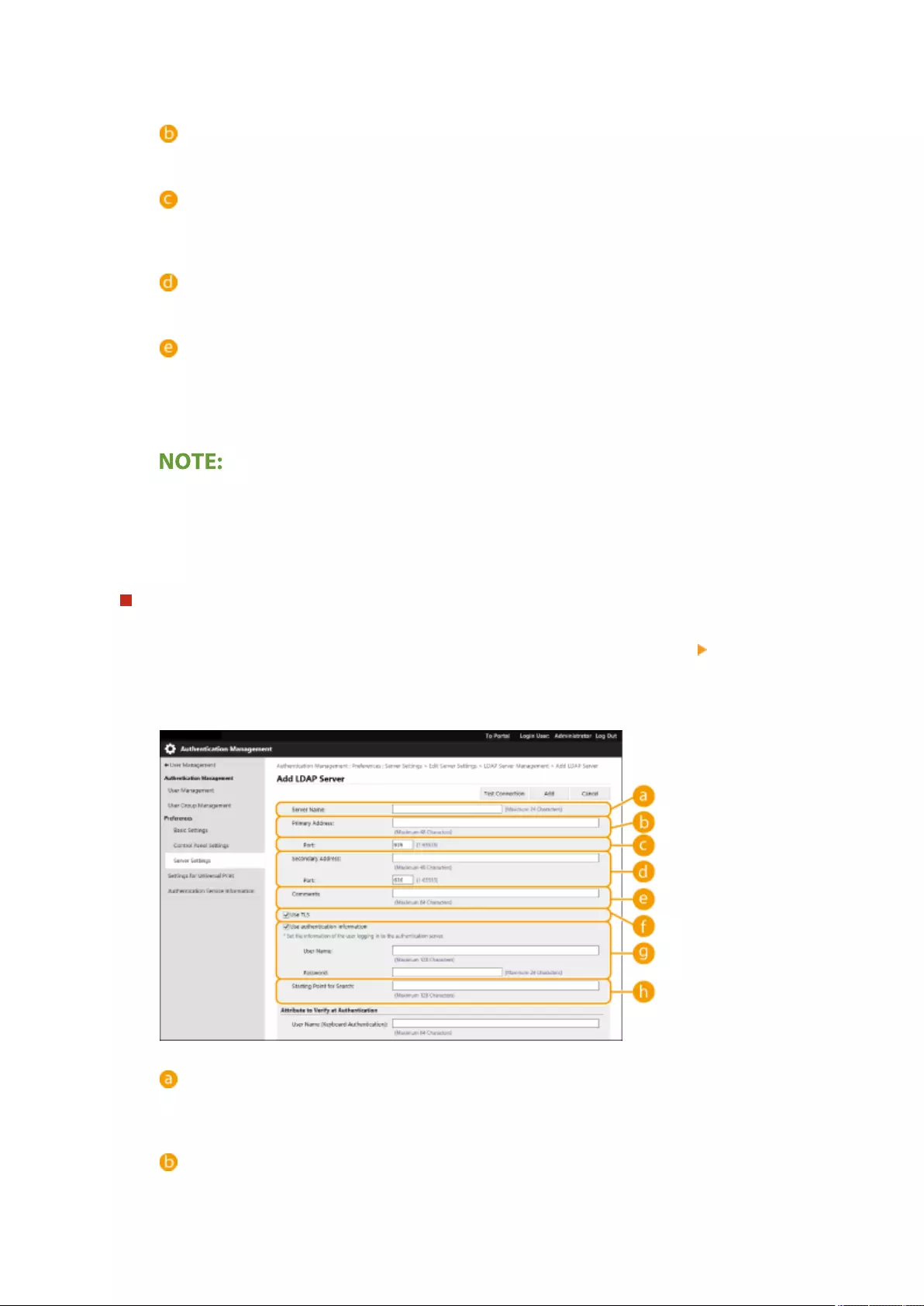
Enter the domain name of the Active Directory that is the login destination (Example:
company.domain.com).
[NetBIOS Name]
Enter the NetBIOS domain name (Example: company).
[Primary Host Name:] / [Secondary Host Name:]
Enter the host name of the Active Directory server (Example: ad-server1). When using a secondary
server, specify the name in [Secondary Host Name:].
[User Name:] / [Password:]
Enter the user name and password to use for accessing and searching the Active Directory server.
[Login Name:] / [Displayed As] / [E-Mail Address]
Specify the data elds (attribute names) for the login name, display name, and e-mail address of each
user account on the Active Directory server (Example: sAMAccountName, cn, mail).
5Click [Test Connection] to conrm that connection is possible, and then click [Add].
To edit server information
●Click [Edit] for the server information that you want to edit, make the necessary changes, and click
[Update].
Registering LDAP server information
1Select the check box for [Use LDAP server] and click [LDAP Server Management...] [OK].
2Click [Add Server...].
3Enter the LDAP server information.
[Server Name]
Enter the name for the LDAP server. The name "localhost" cannot be used. The server name may not
include spaces.
[Primary Address]
Enter the IP address or host name of the LDAP server (Example: ldap.example.com). The loopback
address (127.0.0.1) cannot be used.
Managing the Machine
509

[Port:]
Enter the port number used for communicating with the LDAP server. Use the same setting that is
congured on the server. If you do not enter a number, it is automatically set to "636" when the check
box is selected for [Use TLS], or it is set to "389" when the check box is cleared.
[Secondary Address:] / [Port:]
When using a secondary server in your environment, enter the IP address and the port number.
[Comments]
Enter a description or note as necessary.
[Use TLS]
Select the check box when using TLS encryption for communications with the LDAP server.
[Use authentication information]
Clear the check box to allow anonymous access to the LDAP server, only if the LDAP server is set to
allow anonymous access. When using the user name and password for authentication, select the check
box and enter values for [User Name:] and [Password:].
[Starting Point for Search:]
Specify the location (level) to search for user information when LDAP server authentication is
performed.
4Specify how to set the attribute names and domain name.
[User Name (Keyboard Authentication):]
Specify the LDAP data eld (attribute name) for the user name on the LDAP server (Example: uid).
[Login Name:] / [Display Name] / [E-Mail Address]
Specify the LDAP data elds (attribute names) for the login name, display name, and e-mail address of
each user account on the LDAP server (Example: uid, cn, mail).
[Specify the domain name] / [Specify the attribute name for domain name acquisition]
Select how to set the domain name of the login destination. To specify the domain name directly, select
[Specify the domain name] and enter the domain name. To specify an LDAP data eld (attribute name)
from which to acquire the domain name on the LDAP server, select [Specify the attribute name for
domain name acquisition] and enter the attribute name (Example: dc).
5Click [Test Connection] to conrm that connection is possible, and then click [Add].
To edit server information
Managing the Machine
510
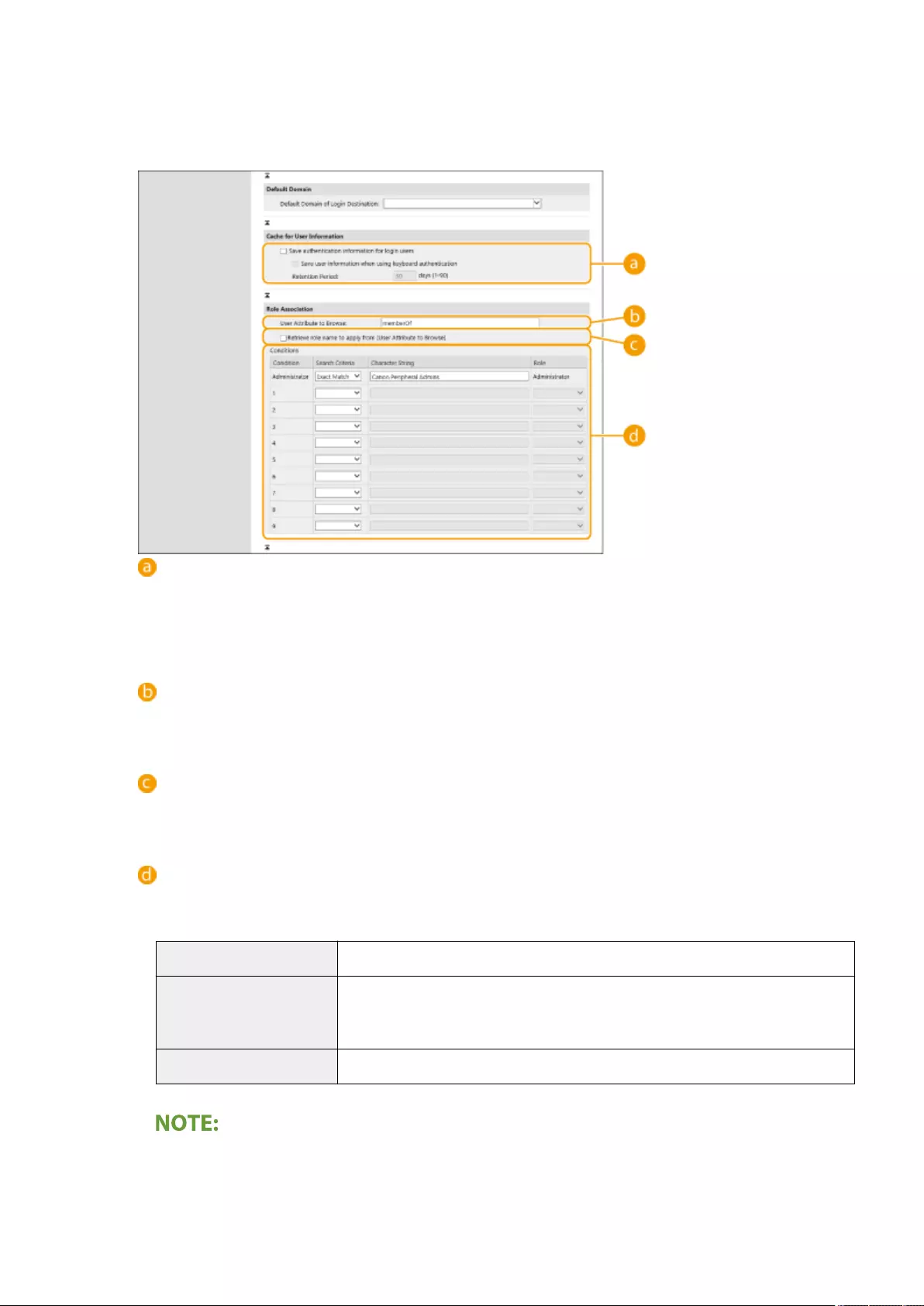
●Click [Edit] for the server information that you want to edit, make the necessary changes, and click [Update].
6Enter the user information and set the privileges.
[Save authentication information for login users]
Select the check box to save the authentication information of users who log in via the control panel.
Select the [Save user information when using keyboard authentication] check box to save the information
of users who log in using keyboard authentication to the cache. After the settings are congured, the
saved authentication information can be used for login, even if the machine is unable to connect to the
server. Change the [Retention Period:] setting as necessary.
[User Attribute to Browse:]
Enter the data eld (attribute name) on the referenced server that is used to determine user privileges
(roles). Normally, you can use the preset value of "memberOf", which indicates the group that the user
belongs to.
[Retrieve role name to apply from [User Attribute to Browse]]
Select the check box to use the character string registered in the data eld on the server specied in [User
Attribute to Browse:] for the role name. Before conguring, check the role names that can be selected on
the machine, and register them on the server.
[Conditions]
You can set the conditions that determine user privileges. The conditions below are applied in the order
that they are listed.
[Search Criteria] Select the search criteria for [Character String].
[Character String]
Enter the character string that is registered to the attribute specied in [User Attribute
to Browse:]. To set the privileges based on the group that user belongs to, enter the
group name.
[Role] Select the privileges that apply to users who match the criteria.
The [Conditions] settings when using Active Directory servers
●"Canon Peripheral Admins" is set in advance as the Administrator user group. Assign different privileges
to the other groups created on the server.
Managing the Machine
511

7Click [Update].
8Restart the machine. Restarting the Machine(P. 591)
DNS Settings
The following settings are required if the port number used for Kerberos on the Active Directory side is
changed.
●Information for the Kerberos service of Active Directory must be registered as an SRV record as follows:
●Service: "_kerberos"
●Protocol: "_udp"
●Port number: The port number used by the Kerberos service of the Active Directory domain (zone)
●Host offering this service: Host name of the domain controller that is actually providing the Kerberos
service of the Active Directory domain (zone)
LINKS
Registering User Information in the Local Device(P. 495)
Conguring the Authentication Functions(P. 513)
Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a Computer(P. 520)
Managing the Machine
512
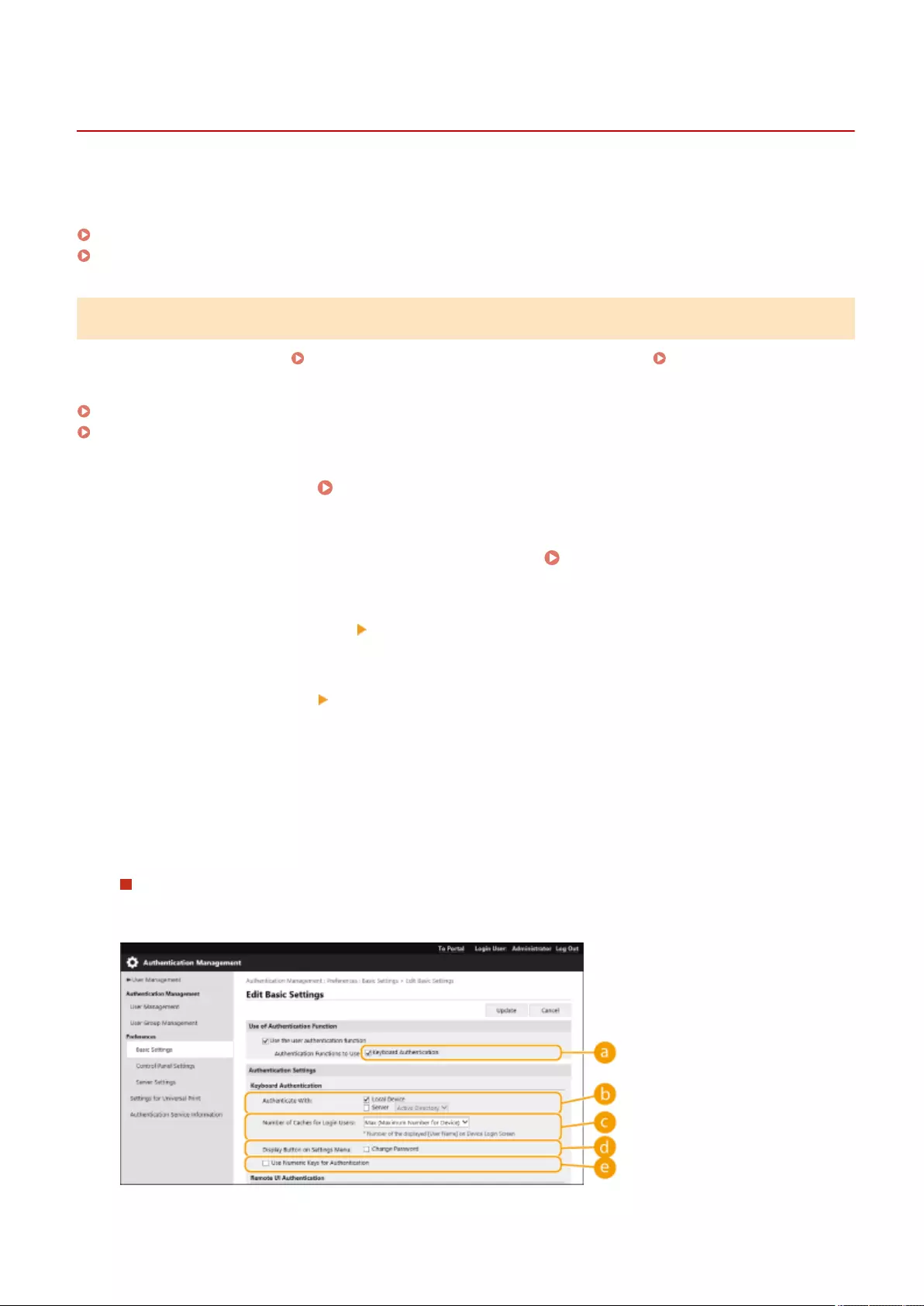
Conguring the Authentication Functions
72JY-08R
You can congure the user login methods, authentication devices, and other authentication functions based on your
system environment and needs. You can also specify how the login screen is displayed.
Conguring the User Login Methods and Authentication Devices(P. 513)
Specifying When to Display the Login Screen(P. 517)
Conguring the User Login Methods and Authentication Devices
Specify the user login methods ( Login Method(P. 492) ) and authentication devices ( Authentication
Device(P. 492) ). Note that the authentication devices need to be set up before conguring the settings below.
Registering User Information in the Local Device(P. 495)
Registering Server Information(P. 507)
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management].
4Click [Basic Settings] [Edit...].
5Select the check box for [Use the user authentication function] and specify the
required settings.
●Select the login methods that you want to use, and specify detailed settings such as authentication device
settings.
Using keyboard authentication
Congure the settings below when using keyboard authentication.
Managing the Machine
513
[Authentication Functions to Use:]
Select the check box for [Keyboard Authentication].
[Authenticate With:]
Select the user authentication device.
●Select the check box for [Local Device] if you are using the database inside this machine to manage user
information.
●When using an external authentication server, select [Server] and specify the type of server.
[Number of Caches for Login Users:]
The names of users who previously logged in can be displayed in a drop-down list on the login screen on the
machine. Select [0] to hide the login history, and select [1] to display only the name of the user who logged in
most recently.
[Display Button on Settings Menu:]
Select the check box to add the <Change Password> button to the menu that is displayed when pressing
on the top right corner of the login screen.
[Use Numeric Keys for Authentication]
If this function is enabled and the user name and password are comprised of numbers only, authentication
can be performed with numeric key entry only.
Conguring detailed settings for authentication functions
You can congure detailed settings for the personal authentication functions.
Managing the Machine
514
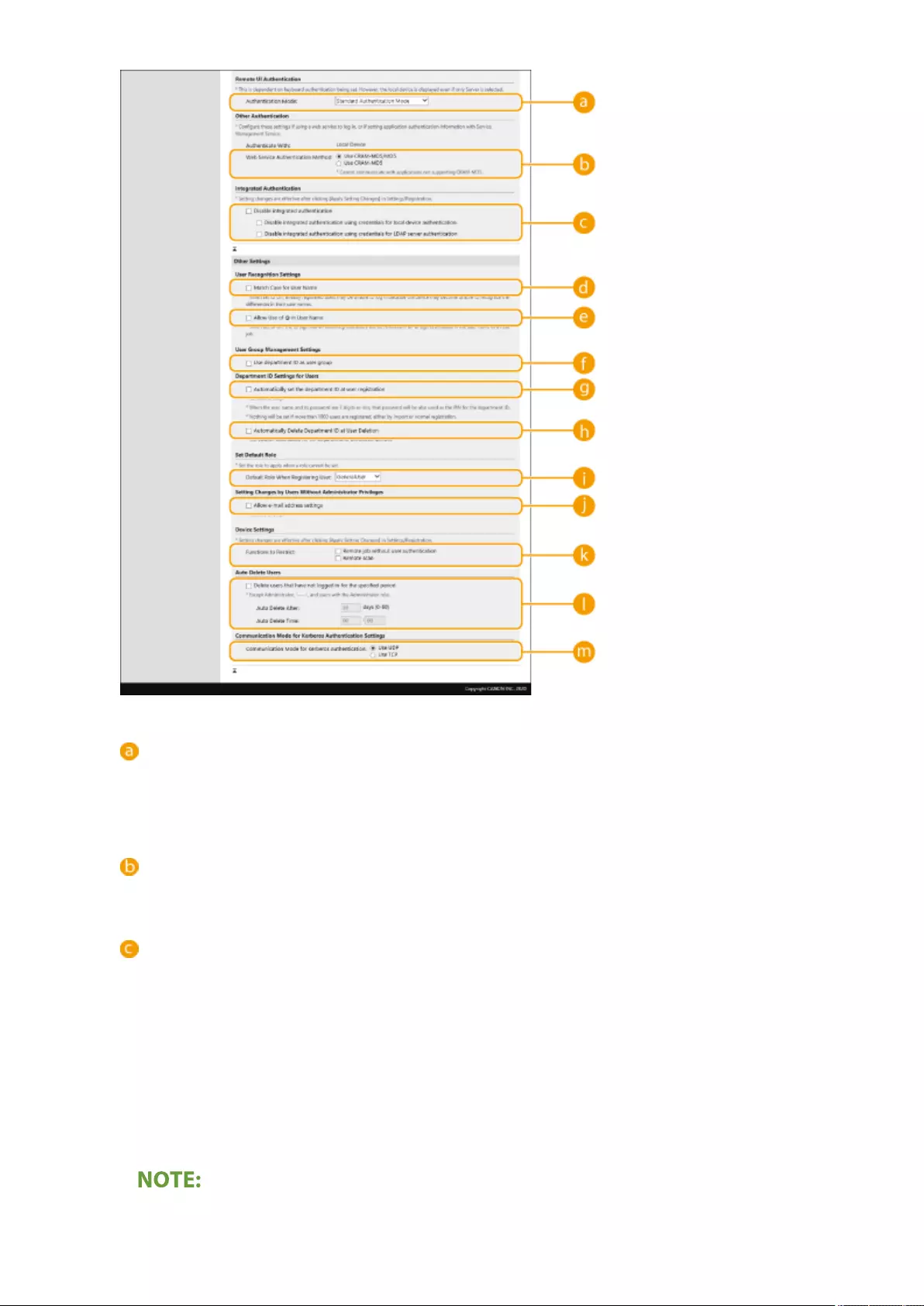
[Authentication Mode:]
Select the authentication mode to use for Remote UI login. When [Guest Authentication Mode] is selected,
unregistered users can also log in by clicking [Log In (Guest)]. Select [Administrator Authentication Mode] to
only allow users with Administrator privileges to log in.
[Web Service Authentication Method:]
Select the local device authentication method to use for communications with Web service applications.
[Disable integrated authentication]
Integrated authentication is a function that enables the authentication information used when logging in to
be used when logging in at other times. Select the check box to disable the integrated authentication
function.
●To disable the integrated authentication function only for logged-in users who are registered in the local
device, select the check box for [Disable integrated authentication using credentials for local device
authentication].
●To disable the integrated authentication function only for logged-in users who are registered in the LDAP
server, select the check box for [Disable integrated authentication using credentials for LDAP server
authentication].
Managing the Machine
515

●When integrated authentication is disabled, a separate user name and password must be registered in
order to access the folders and boxes listed below.
●Personal folder
●LDAP server
●Shared folder/FTP server/WebDAV server
●Advanced Space
●Integrated authentication is valid while the session is valid.
[Match Case for User Name]
If this function is set, you can set whether user names are case-sensitive.
●It is recommended that this is set together with <Function Settings> <Print> <Match Case for User
Name>.
[Allow Use of @ in User Name]
Select whether to allow "@" to be used in user names.
[Use department ID as user group]
Select the check box to use Department IDs as the user groups ( Registering User Information in the
Local Device(P. 495) ) to which users are registered.
[Automatically set the department ID at user registration]
Select the check box to automatically allocate a Department ID when you register/edit a user via the Remote
UI. A new Department ID will not be allocated if one has already been allocated. This setting can only be
specied from the Remote UI.
●If the user name is comprised of numbers and is seven digits or fewer, the same number is assigned to
the same user as the Department ID. If the password of the same user is registered as a number that is
seven digits or fewer, it is also set as the PIN for that Department ID.
●If the user name and password do not meet the above conditions, a Department ID is automatically
assigned starting from 0000001, and 0 (none) is set for the PIN.
●In the following cases, the Department ID is not registered automatically.
●If a user is registered from the control panel of the machine
●If 1,000 Department IDs are already registered
●If 1,001 or more users are already registered
[Automatically Delete Department ID at User Deletion]
If this check box is selected, when a user is deleted, the department ID assigned to the user is automatically
deleted. Counter information assigned to the corresponding department ID is also deleted. If multiple users
are registered to the department ID, it is not automatically deleted.
[Default Role When Registering User:]
Select the role to apply to users in situations such as when no privileges are set.
Managing the Machine
516

[Allow e-mail address settings]
Select the check box to enable users without Administrator privileges to specify their own e-mail addresses in
their user accounts.
[Functions to Restrict:]
Select the check boxes for functions that cannot be used when personal authentication management is
enabled.
[Delete users that have not logged in for the specied period]
Select the check box to delete users registered in the local device who have not logged in to the machine for
a specied period of time. Make sure to also specify the number of days before automatic deletion and the
time it is executed.
●If you set [Auto Delete After:] to [0], all accounts other than the administrator are deleted at the time set in
[Auto Delete Time:].
●If the accounts cannot be deleted at the specied time because the machine is turned OFF or is completely
in sleep mode, the accounts are deleted the next time that the machine starts.
●If a user has never logged in before, the date and time that the user was registered is displayed as the
time that the user last logged in.
[Communication Mode for Kerberos Authentication]
Select the communication method used for Kerberos authentication.
6Click [Update].
7Restart the machine. Restarting the Machine(P. 591)
●The authentication method selected for [Web Service Authentication Method:] is also used when performing
personal authentication with address book management software. <Import/Export from Addr. Book
Management Software>(P. 857)
Specifying When to Display the Login Screen
You can specify when to display the login screen by selecting either "when you start using the machine" or "after a
function button is pressed." If "after a function button is pressed" is selected, you can specify the functions that
require user login. Functions that are not specied are available to unregistered users.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
Managing the Machine
517
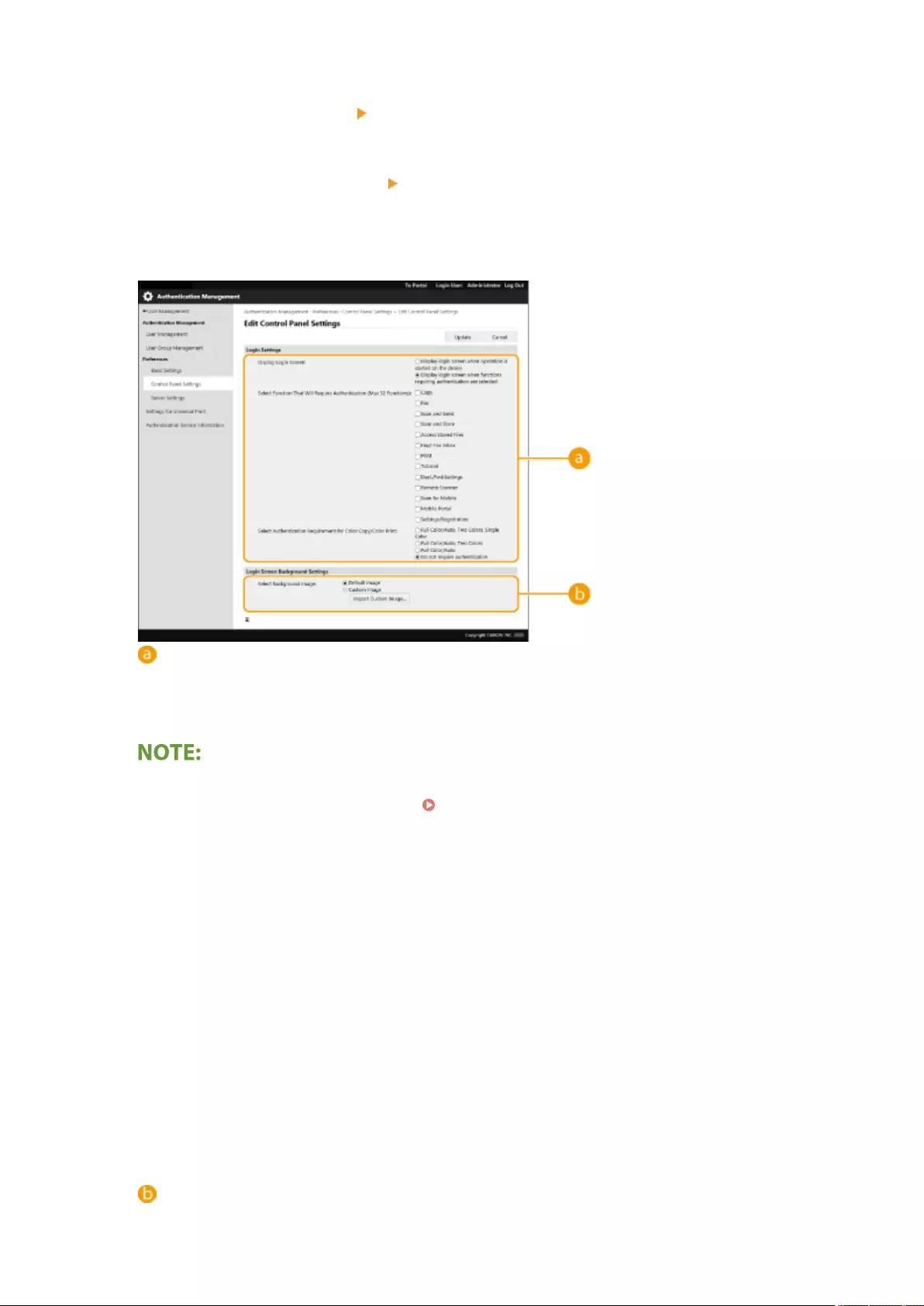
3Click [User Management] [Authentication Management].
4Click [Control Panel Settings] [Edit...].
5Congure the settings as necessary.
[Login Settings]
In [Display Login Screen:], select when the login screen is displayed.
If you selected [Display login screen when functions requiring authentication are selected], also select the
functions to display the login screen for.
●If you change this setting, <Restrict Access to Other User Jobs> may be set to <On>. The relationship
between the settings is indicated below. <Restrict Access to Other User Jobs>(P. 857)
●When the [Display login screen when operation is started on the device] check box is selected:
<Copy/Print>, <Send>, and <Store> in <Restrict Access to Other User Jobs> are set to <On>
●When the [Display login screen when functions requiring authentication are selected] check box is
selected and the [Copy], [Access Stored Files], or [Print] check box is selected in [Select Function That
Will Require Authentication]:
<Copy/Print> in <Restrict Access to Other User Jobs> is set to <On>
●When the [Display login screen when functions requiring authentication are selected] check box is
selected and the [Fax] or [Scan and Send] check box is selected in [Select Function That Will Require
Authentication]:
<Send> in <Restrict Access to Other User Jobs> is set to <On>
●When the [Display login screen when functions requiring authentication are selected] check box is
selected and the [Scan and Store] check box is selected in [Select Function That Will Require
Authentication]:
<Store> in <Restrict Access to Other User Jobs> is set to <On>
●If you want to set <Restrict Access to Other User Jobs> to <Off>, set it to <Off> after this setting is
complete.
[Login Screen Background Settings]
You can specify a background image for the login screen.
Managing the Machine
518

Using Personal Authentication to Manage Printing/
Faxing/Remote Scanning via a Computer
72JY-08S
You can apply personal authentication management to printing, faxing, and remote scanning ( Using Your
Computer to Scan (Remote Scan) (Windows)(P. 427) ) via a computer. This can provide greater security, as the
machine does not accept these operations unless the user is identied.
(Settings/Register) <Management Settings> <User Management> <Authentication
Management> <Restrict Job from Remote Device w/out User Authent.> <On>
<OK> (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>
LINKS
Registering User Information in the Local Device(P. 495)
Registering Server Information(P. 507)
Conguring the Authentication Functions(P. 513)
Managing the Machine
520
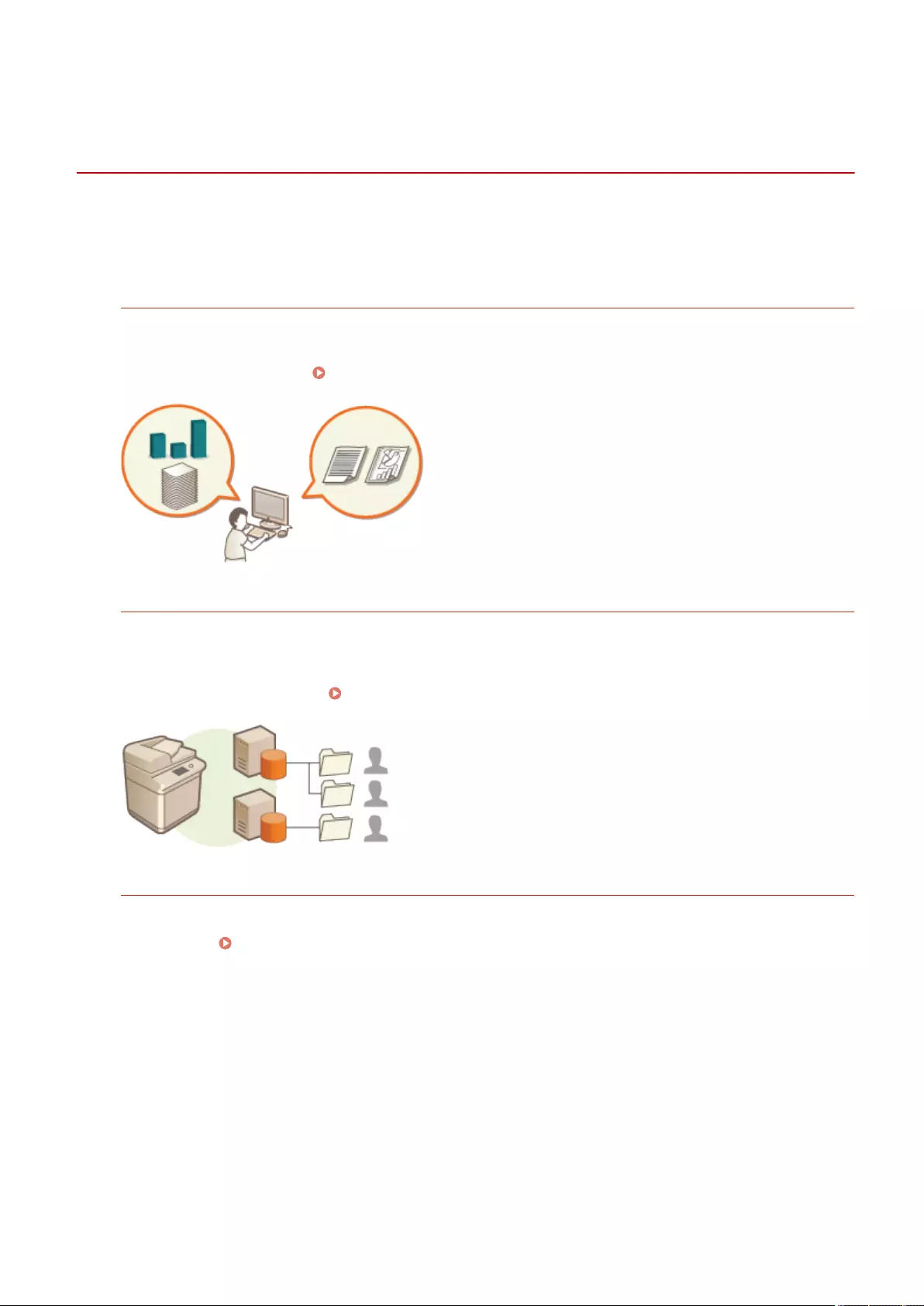
Using Other Convenient Personal Authentication
Management Functions
72JY-08U
Personal authentication management provides a variety of advantages in addition to user authentication. This section
describes some of the other convenient functions that use personal authentication to expand the capabilities of
multifunctional printers, such as managing user groups or creating Personal folders for individual users.
Department ID Management
Users registered in the machine can be organized into groups such as the departments that they belong to, and
managed based on their Department ID. This function lets you check the total number of pages used for each
Department ID, or set maximum limits on the number of pages that each group can use for copying or printing,
which can help reduce costs. Setting the Department ID Management(P. 522)
Personal Folder
Personal folders are dedicated folders for individuals that can be specied as the destination for scanned
documents from <Network> in <Scan and Send> and <Scan and Store> and accessing les from <Network> in
<Access Stored Files>, and can be created in shared folders or le servers. Registering a Personal folder makes
it easy for users to send documents to themselves, which can effectively prevent information leakage due to
sending to wrong destinations. Conguring Personal Folders(P. 529)
ACCESS MANAGEMENT SYSTEM
An environment that uses ACCESS MANAGEMENT SYSTEM can provide more precise control in user
management, by allowing you to create new privilege levels and dene which functions are available to each
privilege level. Using ACCESS MANAGEMENT SYSTEM(P. 533)
Managing the Machine
521

Setting the Department ID Management
72JY-08W
Users can be organized into groups such as the departments that they belong to, and managed based on their
Department ID. First, create all of the Department IDs that are to be managed, and assign users to each one (
Registering User Information in the Local Device(P. 495) ). After assigning users to Department IDs, enable
Department ID Management. To perform the same type of management for printing/scanning from a computer,
congure the additional required settings. Administrator privileges are required in order to congure these settings.
Changing the System Manager ID and PIN(P. 523)
Conguring the Department ID Management Settings(P. 525)
Using Department IDs to Manage Printing or Remote Scanning via Computer(P. 528)
Managing the Machine
522
Changing the System Manager ID and PIN
72JY-08X
When Department ID Management is enabled, Department IDs must be set for users before they can log in. The
System Manager ID and System Manager PIN are both set to "7654321" by default, but it is recommended to change
them for security reasons. Follow the procedure below to change them.
●Make sure that you do not forget the System Manager PIN. If you forget the System Manager PIN, contact
your dealer or service representative.
●This setting is not a default User Authentication administrator setting. To specify this setting for a user with
administrator privileges in User Authentication, set [Select Role to Set:] to "Administrator". Registering
User Information in the Local Device(P. 495)
1Press (Settings/Register).
2Press <Management Settings> <User Management> <System Manager
Information Settings>.
3Make the necessary changes to the System Manager settings, and press <OK>.
<System Manager ID>
Enter a number of 7 digits or less for the new System Manager ID.
<System Manager PIN>
Enter a number of 7 digits or less for the new System Manager PIN, and press <Conrm>. For
conrmation, enter the PIN again and press <OK>.
<System Manager Name> / <E-Mail Address> / <Contact Information> / <Comment>
Enter information about the administrator as necessary.
●You cannot register a System Manager ID or PIN consisting only of 0s, such as "00" or "0000000".
Managing the Machine
523

●Even if you enter fewer than seven digits, zeros are added to the start of the number, and a seven digit
number is set.
●When the optional Copy Card Reader is attached, the System Manager ID and System Manager PIN are
reset to "7654321". Optional Equipment(P. 1119)
●You can also make entering seven digits a requirement for the System Manager ID and System Manager
PIN. For more information, contact your dealer or service representative.
LINKS
Conguring the Department ID Management Settings(P. 525)
Registering User Information in the Local Device(P. 495)
Managing the Machine
524
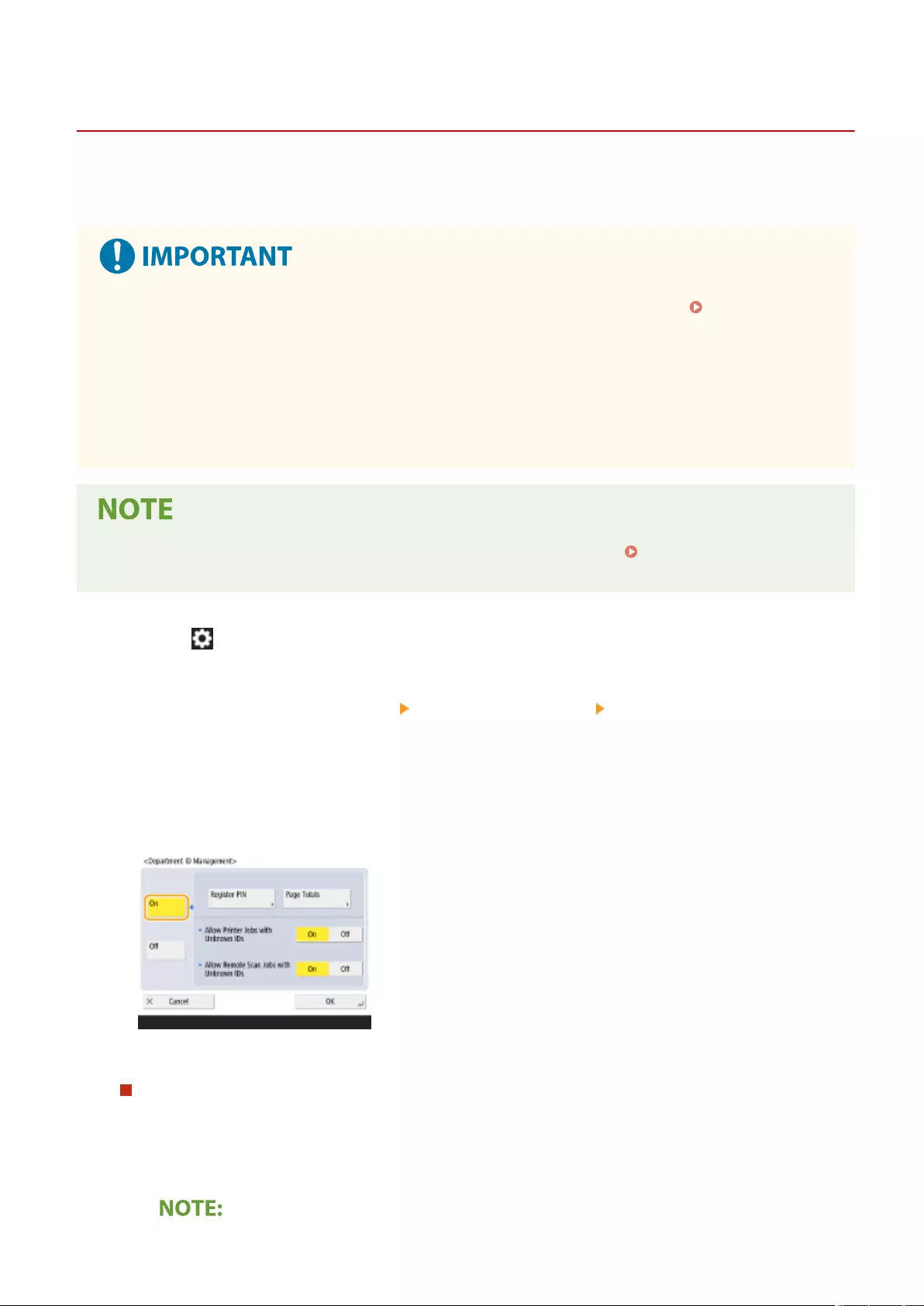
Conguring the Department ID Management Settings
72JY-08Y
You can organize and manage users in groups based on Department ID. Follow the procedure below to congure
Department ID Management and enable the machine to count the number of pages used for printing and scanning.
●Make sure that Department IDs have been set for the users registered in the machine. Registering User
Information in the Local Device(P. 495)
●Department ID Management is only valid for users who are registered to the local device.
●If you login as a user with Administrator privileges, a System Manager ID and PIN are automatically
assigned, and managed as Department ID.
●If Department ID Management is activated through the Copy Card Reader, the Department IDs assigned to
the cards are used. Therefore, you cannot register Department IDs.
●For information on the number of Department IDs that you can register, see Management
Functions(P. 1091) .
1Press (Settings/Register).
2Press <Management Settings> <User Management> <Department ID
Management>.
3Press <On>.
➠Department ID Management is enabled.
●To disable Department ID Management, press <Off>.
Registering Department IDs and PINs
1Press <Register PIN>.
2Press <Register>.
Managing the Machine
525
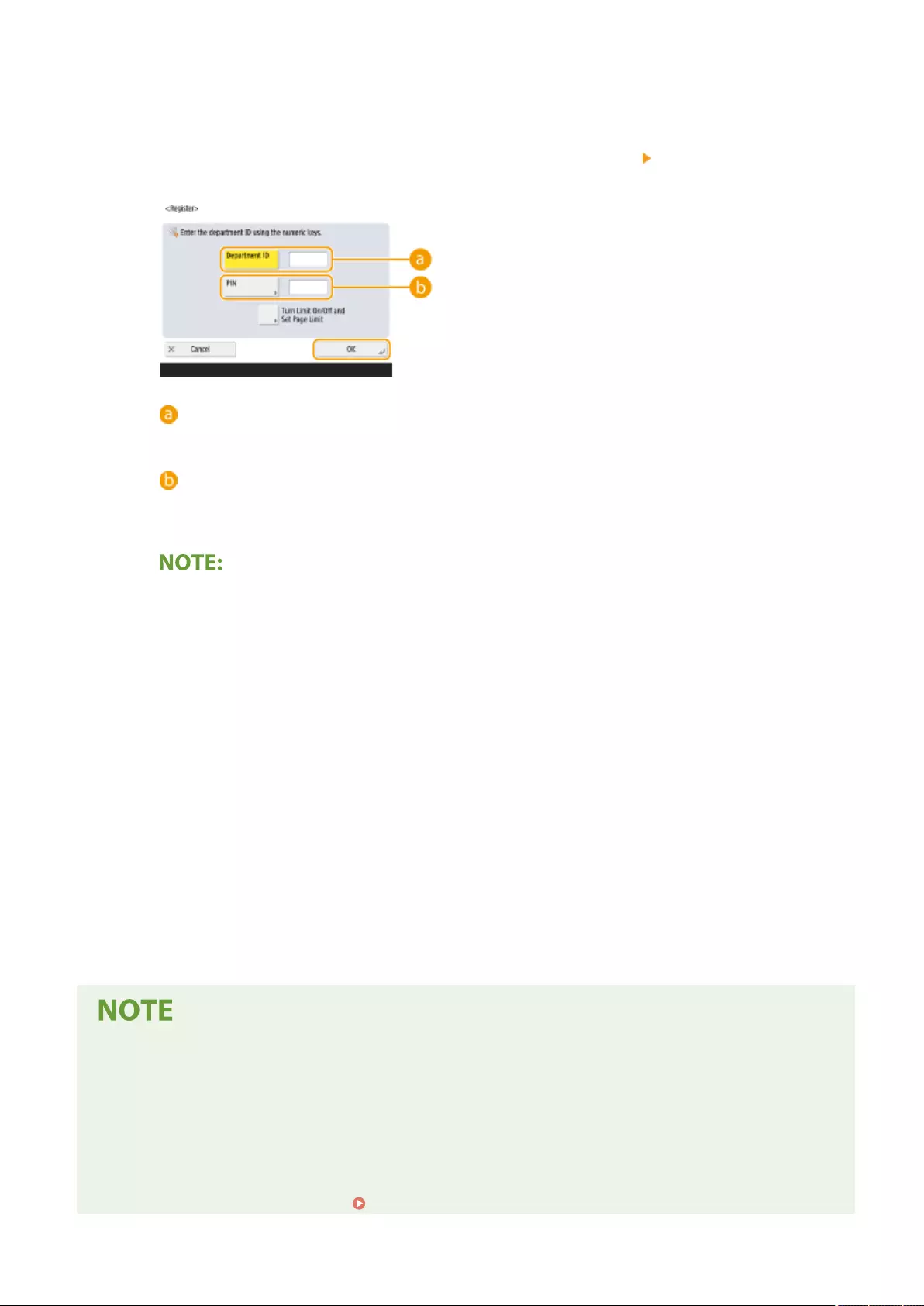
To edit Department ID settings
●Select the Department ID that you want to edit, and press <Edit> to display the Edit screen.
To delete Department ID settings
●Select the Department ID that you want to delete, and press <Delete> <Yes>.
3Enter the Department ID and PIN, and press <OK>.
<Department ID>
Enter a number of 7 digits or less for the Department ID.
<PIN>
Enter a number of 7 digits or less for the PIN, and press <Conrm>. For conrmation, enter the PIN
again and press <OK>. If you do not want to set a PIN, leave this item blank.
●You cannot register a Department ID or PIN consisting only of 0s, such as "00" or "0000000".
●Even if you enter fewer than seven digits, zeros are added to the start of the number, and a seven
digit number is set.
●You can press <Turn Limit On/Off and Set Page Limit> to set the total number of pages that the
department is allowed to use for copying, scanning, and printing.
●You can also make entering seven digits a requirement for Department IDs and PINs. For more
information, contact your dealer or service representative.
●The machine stops printing if any one of the color or black-and-white page limits is reached while
printing a document that contains both color and black-and-white areas.
●The machine stops copying if any one of the total color or black-and-white print or copy limits is
reached while copying a document that contains both color and black-and-white areas.
4Press <OK>.
4Press <OK>.
To check the page counts
●If you want to check the total number of pages used by each Department ID for copies, prints, and scans
(including faxes), press <Page Totals> on the screen displayed in step 3. The page counts do not include
blank pages or sample prints used for checking items such as gradation adjustment.
Logging In Using a Department ID and PIN
●By registering a user with the same name as a department ID, login operations can be performed using a
registered department ID and PIN. Registering User Information in the Local Device(P. 495)
Managing the Machine
526
The login screen can either be displayed when starting an operation or after a function is selected.
Specifying When to Display the Login Screen(P. 517)
Changing the Login Service
●The machine uses "User Authentication" (personal authentication management) as the login service.
However, you can change the login service to "DepartmentID Authentication" using SMS. Changing Login
Services(P. 1075)
LINKS
Using Department IDs to Manage Printing or Remote Scanning via Computer(P. 528)
Managing the Machine
527
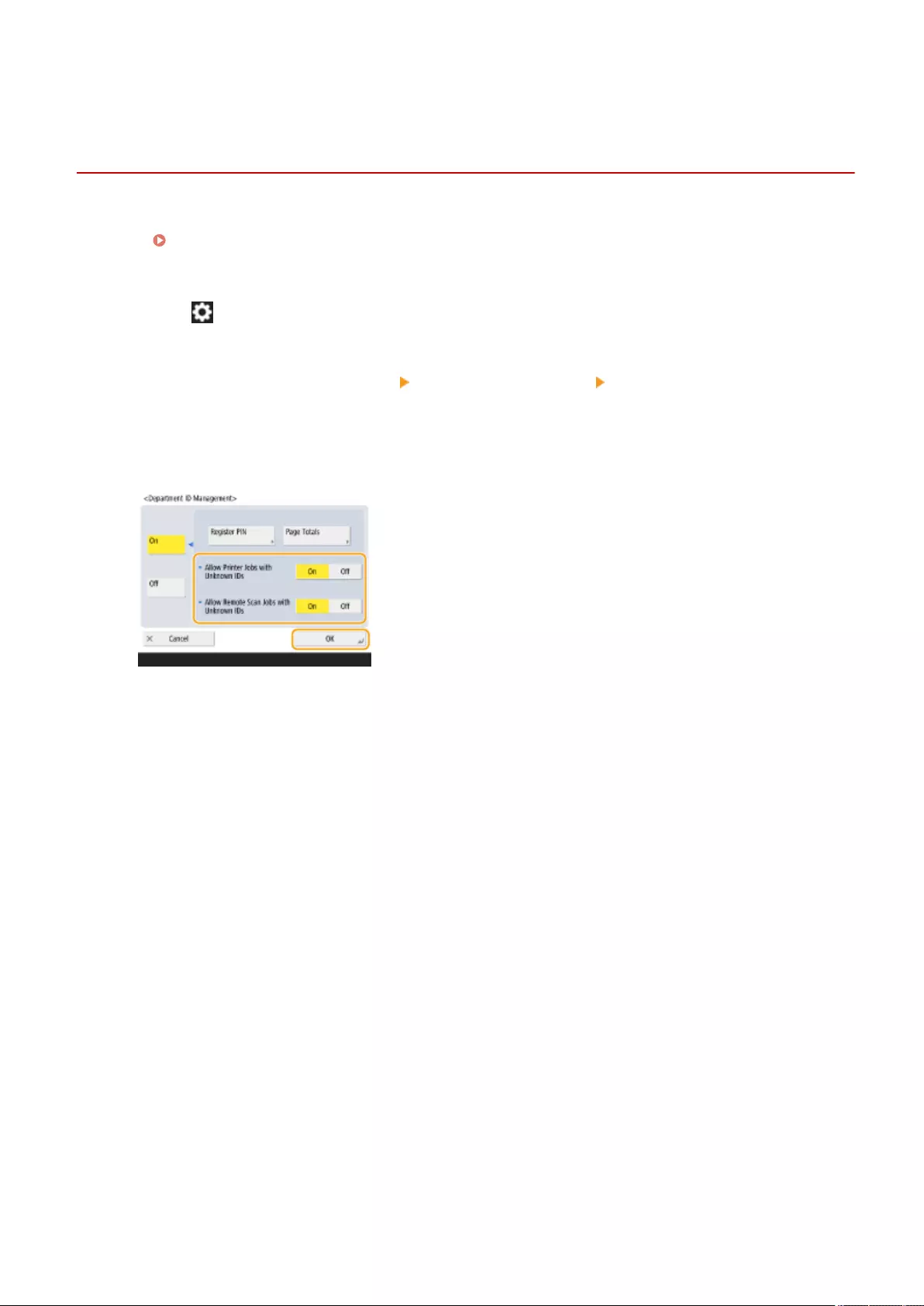
Using Department IDs to Manage Printing or Remote
Scanning via Computer
72JY-090
You can use Department ID Management to manage printing and remote scanning operations performed via a
computer ( Using Your Computer to Scan (Remote Scan) (Windows)(P. 427) ). Use this function when you would
like to improve security or monitor the number of pages that are printed.
1Press (Settings/Register).
2Press <Management Settings> <User Management> <Department ID
Management>.
3Select <Off> for the functions that you want to manage, then press <OK>.
If <Off> is selected, a Department ID must be entered when executing a corresponding job.
Managing the Machine
528
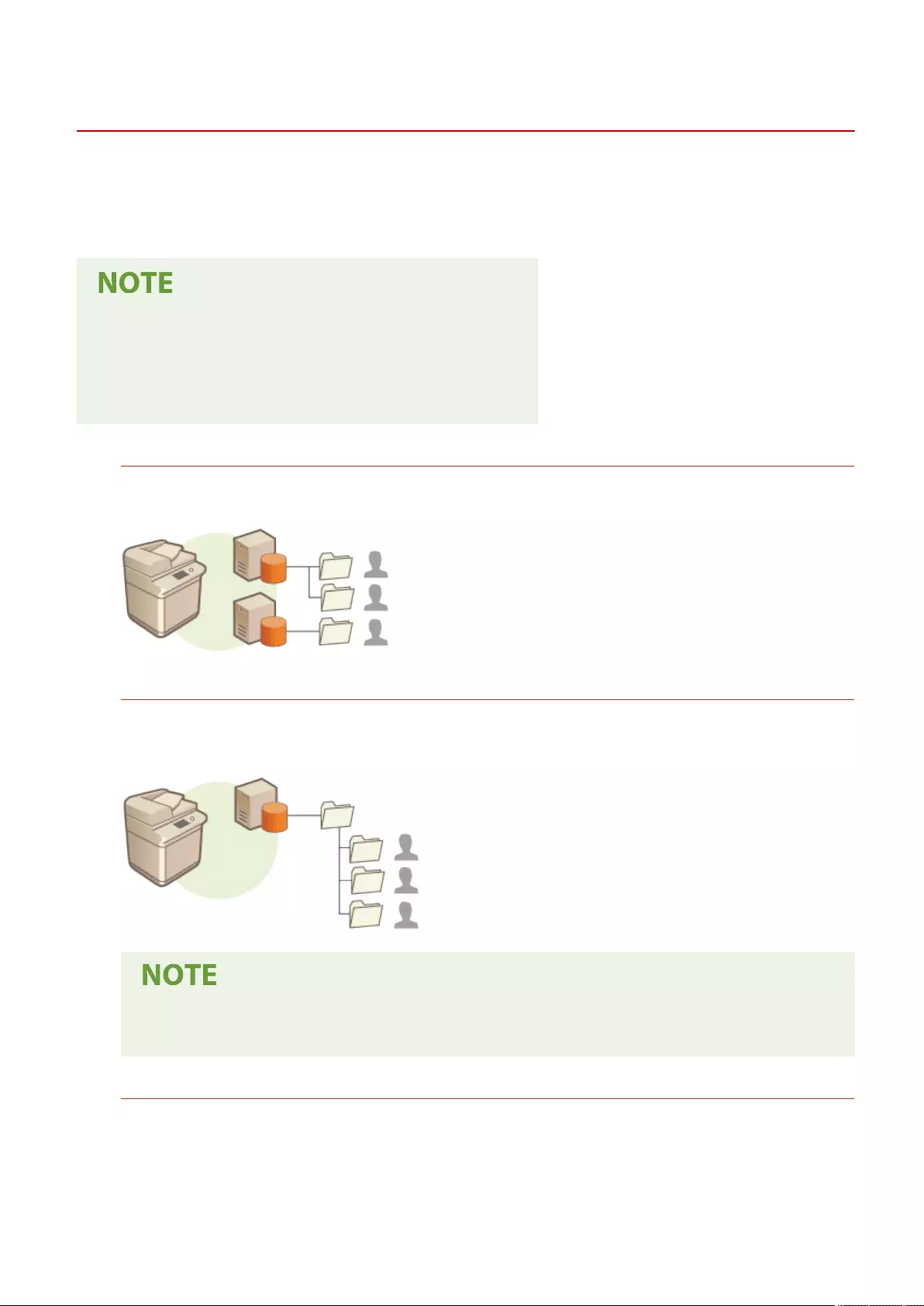
Conguring Personal Folders
72JY-091
A Personal folder is an individual folder that can be used by the user logged in with personal authentication
management. Shared folders and le servers can be specied and used as a Personal folder.
An administrator with Administrator privileges selects the method for specifying Personal folders. The login users
specify Personal folders based on the setting specied by the administrator.
●A Personal folder is a folder shared by the following screens.
- <Scan and Send>
- <Network> in <Scan and Store>
- <Network> in <Access Stored Files>
Creating Folders in Any Location Specied by Users
Users create a Personal folder in any location they desire. This enables each user to send documents to a folder
in a familiar location.
Creating Folders in a Home Folder Specied by the Administrator
A folder for each user name is created inside a parent folder (home folder) specied by the administrator.
Personal folders are easier to manage because they are all kept together in one location. A Windows (SMB)
shared folder or WebDAV server can be specied.
●If you set up the home folder on the WebDAV server, folders for all users must be prepared
beforehand.
Creating Folders in a Location Specied by the Server
Personal folders are specied based on the folder information registered in an authentication server, such as
the homeDirectory attribute of Active Directory in Windows. Only a Windows (SMB) shared folder can be
specied.
Managing the Machine
529

Setting How to Specify the Location of Personal Folders
1Press (Settings/Register).
2Press <Function Settings> <Send> <Common Settings> <Personal Folder
Specication Method>.
●This setting is the same as the following setting. The settings are in different locations, but they perform the
same function.
(Settings/Register) <Function Settings> <Store/Access Files> <Network Settings> <Personal
Folder Specication Method>
3Select how to specify the location of Personal folders.
Creating folders in any location specied by users
Press <Register for Each User> <OK>. Each user can specify the location of the Personal folder.
Creating folders in a home folder specied by the administrator
1Press <Home Folder> <Set>.
2Specify the home folder and press <OK>.
Managing the Machine
530
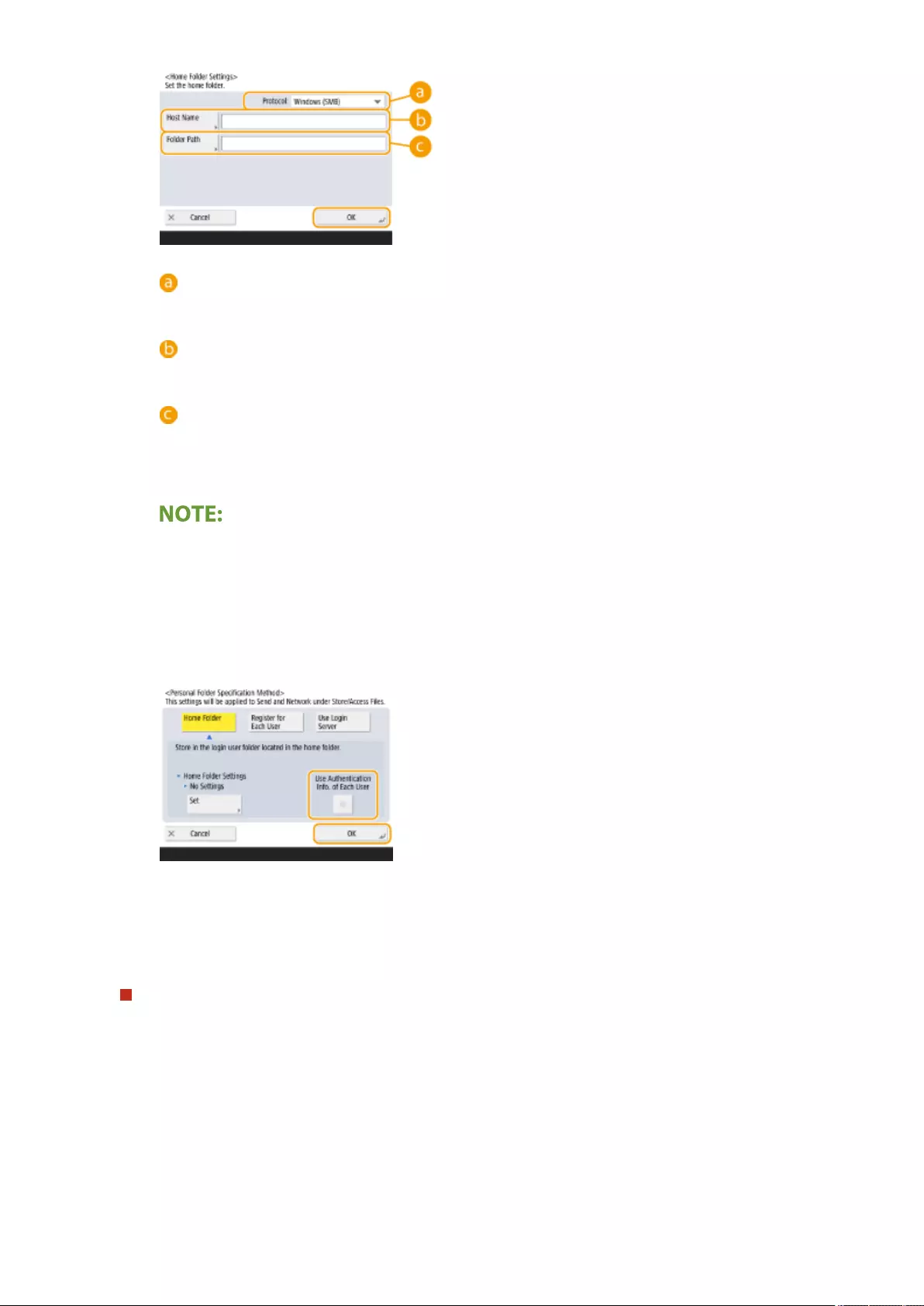
<Protocol>
Select the protocol to use when accessing Personal folders.
<Host Name>
Enter the host name or IP address of the computer where you want to create the home folder.
<Folder Path>
Enter the folder path for the home folder. For example, enter "users\public\share" for a home folder
created inside a subfolder named "share" in the "Public" folder on the C: drive (path:
"C:\users\public\share").
●You may not be able to specify the path if there are too many folder levels.
3Select the authentication information to use, and press <OK>.
●To use a separate user name and password for the Personal folder, press <Use Authentication Info. of
Each User> to add a check mark. Remove the check mark to use the same user name and password
entered at login. If a check mark is added to this item, a user name and password must be registered
for each user.
A folder is created inside a home folder, with the following names.
●If a check mark is added to <Use Authentication Info. of Each User>: the user name specied by a user
●If no check mark is added to <Use Authentication Info. of Each User>: the user name used for logging
in
Creating folders in a location specied by the server
1Press <Use Login Server>.
2Select the authentication information to use, and press <OK>.
●To use a separate user name and password for the Personal folder, press <Use Authentication Info. of
Each User> to add a check mark. Remove the check mark to use the same user name and password
entered at login. If a check mark is added to this item, a user name and password must be registered
for each user.
Managing the Machine
531

●The authentication information required for accessing a personal folder (user name and password)
cannot be retrieved from Active Directory. If <Use Authentication Info. of Each User> is selected, the
user name and password for logging in to the machine with keyboard authentication are registered as
authentication information for accessing a personal folder.
●It is necessary to use the login service that supports this function. For more information, consult your
dealer or service representative.
●If you are using User Authentication, congure a folder in "homeDir" which is a user attribute in the
Active Directory, using the "\\host name\folder path" format.
Registering a Personal folder and authentication information for each user
●If <Personal Folder Specication Method> is set to <Register for Each User>, register one of the following as
the Personal folder for each user. The registered settings are the same and the same Personal folder is
registered, no matter where the setting is congured.
- <Scan and Send> <Register/Edit Information for Each User> <Personal Folder>
- <Scan and Store> <Network> <Register/Edit Information for Each User> <Personal Folder>
- <Access Stored Files> <Network> <Register/Edit Information for Each User> <Personal
Folder>
Managing the Machine
532
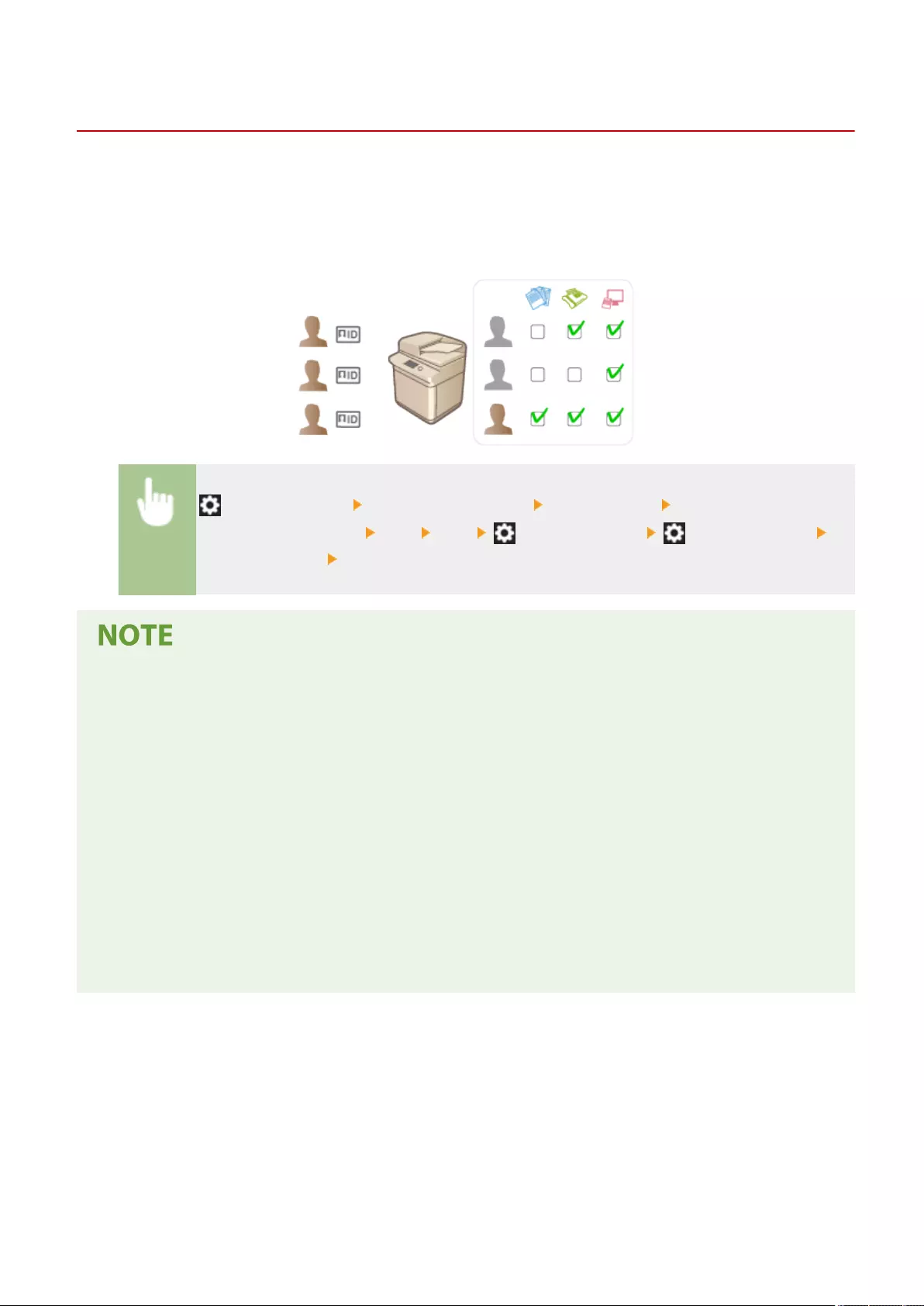
Using ACCESS MANAGEMENT SYSTEM
72JY-092
In an environment that uses ACCESS MANAGEMENT SYSTEM, it is possible to dene which functions are available to
each privilege level (role), as well as create new roles. This provides more precise control in user management by
enabling you to specify which functions are available to each individual user. For example, you can prohibit user A
from copying, while allowing user B to use all functions. Follow the procedure below to enable ACCESS MANAGEMENT
SYSTEM functions.
(Settings/Register) <Management Settings> <License/Other> <Use ACCESS
MANAGEMENT SYSTEM> <On> <OK> (Settings/Register) (Settings/Register)
<Apply Set. Chng.> <Yes>
●If this setting is set to <On>, <Use User Authentication> in Settings/Registration is also set to <On>. To set
<Use User Authentication> to <Off>, rst set this setting to <Off>.
●If you set this function to <On>, the following settings in Settings/Registration are disabled.
- Setting a PIN for Address Book
- Restricting New Destinations
●Similar restrictions can be set for roles using the ACCESS MANAGEMENT SYSTEM. For details, see ACCESS
MANAGEMENT SYSTEM Administrator Guide.
●Even if you change this setting from <On> to <Off>, the following settings in Settings/Registration do not
automatically return to their previous values. Change the settings manually.
- Setting a PIN for Address Book
- Restricting New Destinations
●For more information on system requirements and how to create and edit roles, see ACCESS MANAGEMENT
SYSTEM Administrator Guide.
Managing the Machine
533

Deleting User Setting Information
72JY-093
You can delete unnecessary user setting information. User setting information is a type of table that includes data
about where and what settings have been congured for users. Setting information is registered automatically, and
some setting information must be manually deleted because it remains even after a user has been deleted. To delete
user setting information, log in to the Remote UI with Administrator privileges.
●You can also set to automatically delete user setting information when the maximum amount of information
that can be registered has been reached. <Action When Maximum Number of Users
Exceeded>(P. 859)
●For information on the maximum amount of user setting information that can be registered, see System
Specications(P. 1084) .
●The User Setting Information that the User Setting Information Management can link with User
Authentication is as follows:
●Information of Personal buttons/Shared buttons ( Registering Frequently Used Settings and
Destinations as Personal Buttons/Shared Buttons on the <Home> Screen(P. 170) )
●Keychain information ( Managing Users(P. 489) )
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [User Setting Information Management Service] on the portal page. Remote
UI Screen(P. 585)
3Delete the user setting information.
Deleting the setting information for all users
Click [Delete All User Setting Information] [Yes].
Deleting the setting information for individual users
1Click [Select User and Delete Setting Information].
2Select the check box for the user with the setting information that you want to delete, and click [Delete]
[Yes].
Deleting the shared setting information of all users
Click [Delete Shared Setting Information of All Users] [Yes].
Managing the Machine
534
Deleting the setting information for all user groups
Click [Delete All User Group Setting Information] [Yes].
Deleting the setting information for individual user groups
1Click [Select User Group and Delete Setting Information].
2Select the check box for the user group with the setting information that you want to delete, and click
[Delete] [Yes].
●The changed user setting information is enabled when the machine is restarted. It may take some
time until the old user setting information is deleted. Wait for a while and restart the machine.
LINKS
Conguring the Personal Authentication Management Settings(P. 492)
Managing the Machine
535
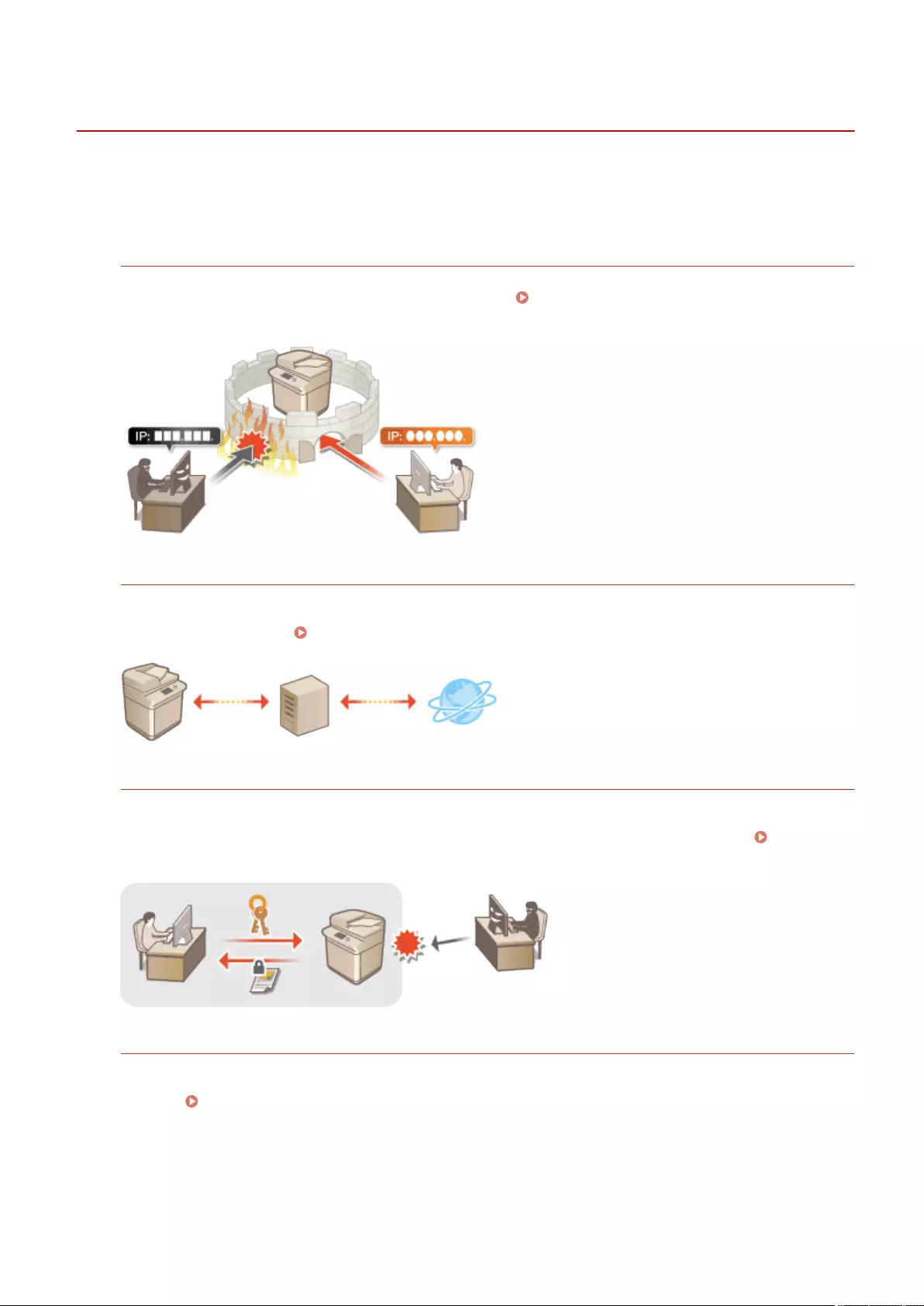
Conguring the Network Security Settings
72JY-094
Authorized users may incur unanticipated losses from attacks by malicious third parties, such as sning, spoong,
and tampering of data as it ows over a network. To protect your important and valuable information from these
attacks, the machine supports the following features to enhance security and secrecy.
Firewall Settings
Unauthorized access by third parties, as well as network attacks and breaches, can be blocked by only allowing
communication with devices that have a specic IP address. Restricting Communication by Using
Firewalls(P. 538)
Proxy Settings
When the client devices are connected to an external network, communication is established through the proxy
server. When the proxy server is used, websites can be browsed more safely, therefore, security can be
expected to be enhanced. Setting a Proxy(P. 547)
TLS Encrypted Communication
TLS is a protocol for encryption for data sent over a network and is often used for communication via a Web
browser or an e-mail application. TLS enables secure network communication when accessing the machine in a
variety of situations, such as when using the Remote UI or address book management software. Conguring
the Key and Certicate for TLS(P. 549)
IPSec Communication
While TLS only encrypts data used on a specic application, such as a Web browser or an e-mail application,
IPSec encrypts the whole (or payloads of) IP packets. This enables IPSec to offer a more versatile security system
than TLS. Conguring the IPSec Settings(P. 555)
Managing the Machine
536

IEEE 802.1X Authentication
If a device tries to connect and start communicating on an 802.1X network, the device must go through user
authentication in order to prove that the connection is made by an authorized user. Authentication information
is sent to and checked by a RADIUS server, which permits or rejects communication to the network depending
on the authentication result. If authentication fails, a LAN switch (or an access point) blocks access from the
outside of the network. The machine can connect to an 802.1X network as a client device. Conguring the
IEEE 802.1X Authentication Settings(P. 561)
Managing the Machine
537

Restricting Communication by Using Firewalls
72JY-095
By conguring packet ltering to only allow communication with devices that have a specic IP address or MAC
address, you can reduce the risk of unauthorized access by outside third parties. Administrator or NetworkAdmin
privileges are required in order to congure these settings.
Specifying IP Addresses in Firewall Settings(P. 539)
Specifying MAC Addresses in Firewall Settings(P. 542)
Conguring the Firewall of the Sub Line(P. 544)
Managing the Machine
538
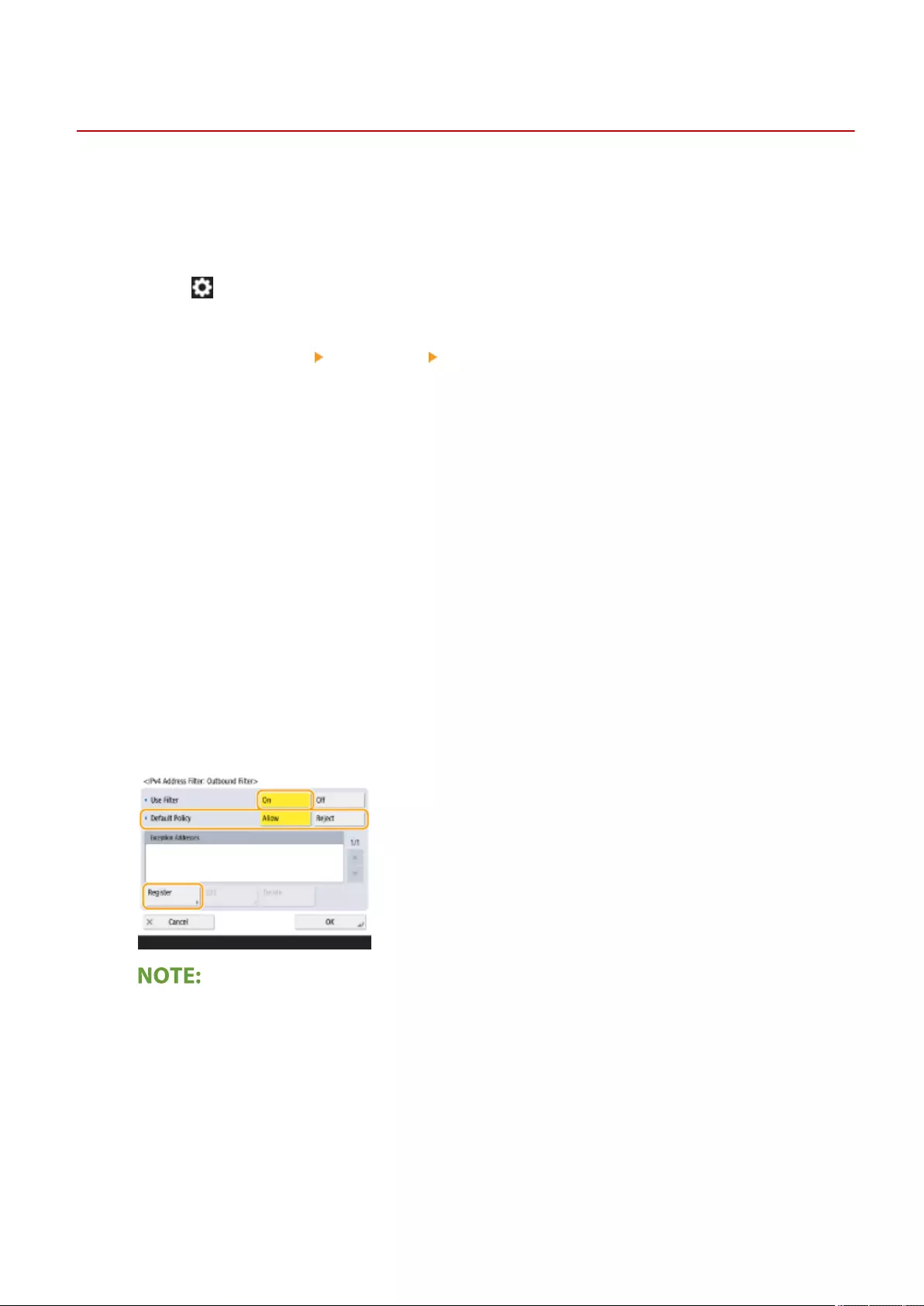
Specifying IP Addresses in Firewall Settings
72JY-096
You can set whether to allow or reject communication with a device that has a specic IP address. After conguring the
IP addresses in the rewall settings, you can check the results in the log of blocked communication requests. You can
also set whether to allow or reject ICMP communications such as PING commands, etc., after specifying rewall
settings.
1Press (Settings/Register).
2Press <Preferences> <Network> <Firewall Settings>.
3Press <IPv4 Address Filter> or <IPv6 Address Filter>.
●Select the lter setting that corresponds to the IP address set on the machine.
4Select <Outbound Filter> or <Inbound Filter>.
●To restrict data sent from the machine to a computer, select <Outbound Filter>.
●To restrict data received from a computer, select <Inbound Filter>.
●To restrict data communication but allow only ICMP communications such as PING commands, etc., set
<Always Allow Sending/Receiving Using ICMP> to <On>.
5Set <Use Filter> to <On>, select <Default Policy>, then press <Register>.
●For <Default Policy>, select <Reject> to only allow communication with devices that have an IP address
specied in <Exception Addresses> in the next step, or select <Allow> to reject communication with them.
●If <Reject> is selected for <Default Policy>, the restrictions do not apply to sending to multicast or
broadcast addresses.
6Set the exception addresses.
When using IPv4 When using IPv6
Managing the Machine
539
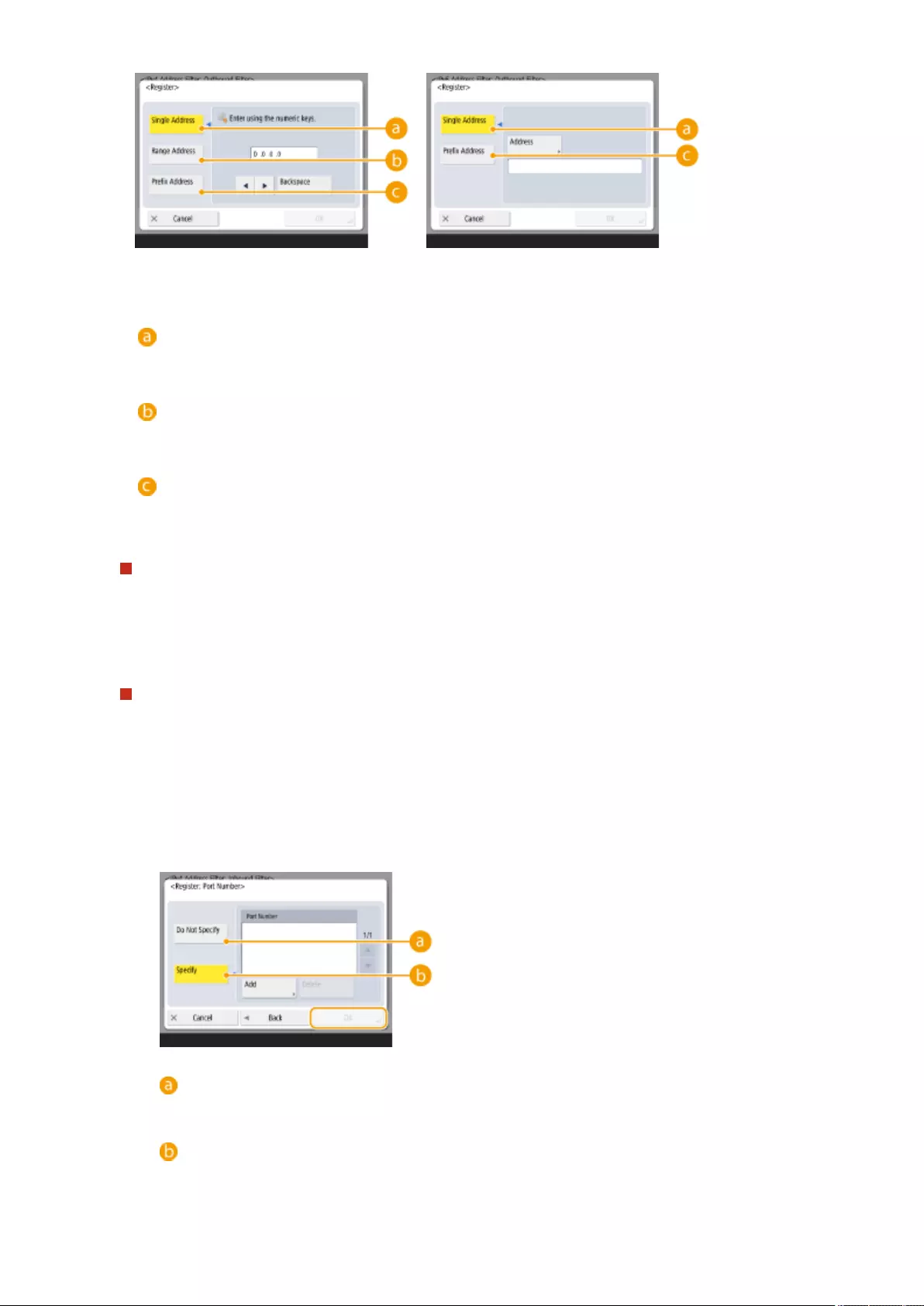
●Specify the IP addresses to designate as exceptions of the <Default Policy> option selected in the previous
step. Select one of the input methods described below.
<Single Address>
Enter an individual IP address to designate as an exception. In the case of IPv6, press <Address> to display
the input screen.
<Range Address>
Specify a range of IP addresses. Enter a separate address for <First Address> and <Last Address>. It is not
possible to enter IPv6 addresses.
<Prex Address>
Specify a range of IP addresses using a prex (network address). Enter a network address for <Address>,
and specify the network address length in <Prex Length>.
Setting exception addresses for the outbound lter
1Select the IP address input method, and enter the exception addresses.
2Press <OK>.
Setting exception addresses for the inbound lter
1Select the IP address input method, and enter the exception addresses.
2Press <Next>.
3Set the port number if necessary, and press <OK>.
●Select whether to specify a port number. You can congure detailed communication restrictions by
specifying a port number for the exception address.
<Do Not Specify>
The exception address setting applies to all communication received from the specied IP address.
<Specify>
The exception address setting only applies to communication received from the specied IP address
using the designated port number. Press <Add>, enter the port number, and press <OK>. You can
register up to 50 ports per one exception address for both IPv4/IPv6.
Managing the Machine
540
To edit an exception address
●On the screen displayed in step 5, select the exception address that you want to edit, and press <Edit> to
display the edit screen.
7Press <OK>.
8Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
Checking the blocked communication requests in the log
●The latest 100 communications blocked by the rewall can be displayed from (Settings/Register)
<Preferences> <Network> <Firewall Settings> <IP Address Block Log>. The history of blocked
communications can be exported from the Remote UI in the CSV format. Exporting a Log as a
File(P. 622)
●If <Default Policy> is set to <Reject>, the history of communication blocked by the rewall is not displayed in
<IP Address Block Log>.
LINKS
Specifying MAC Addresses in Firewall Settings(P. 542)
Managing the Machine
541
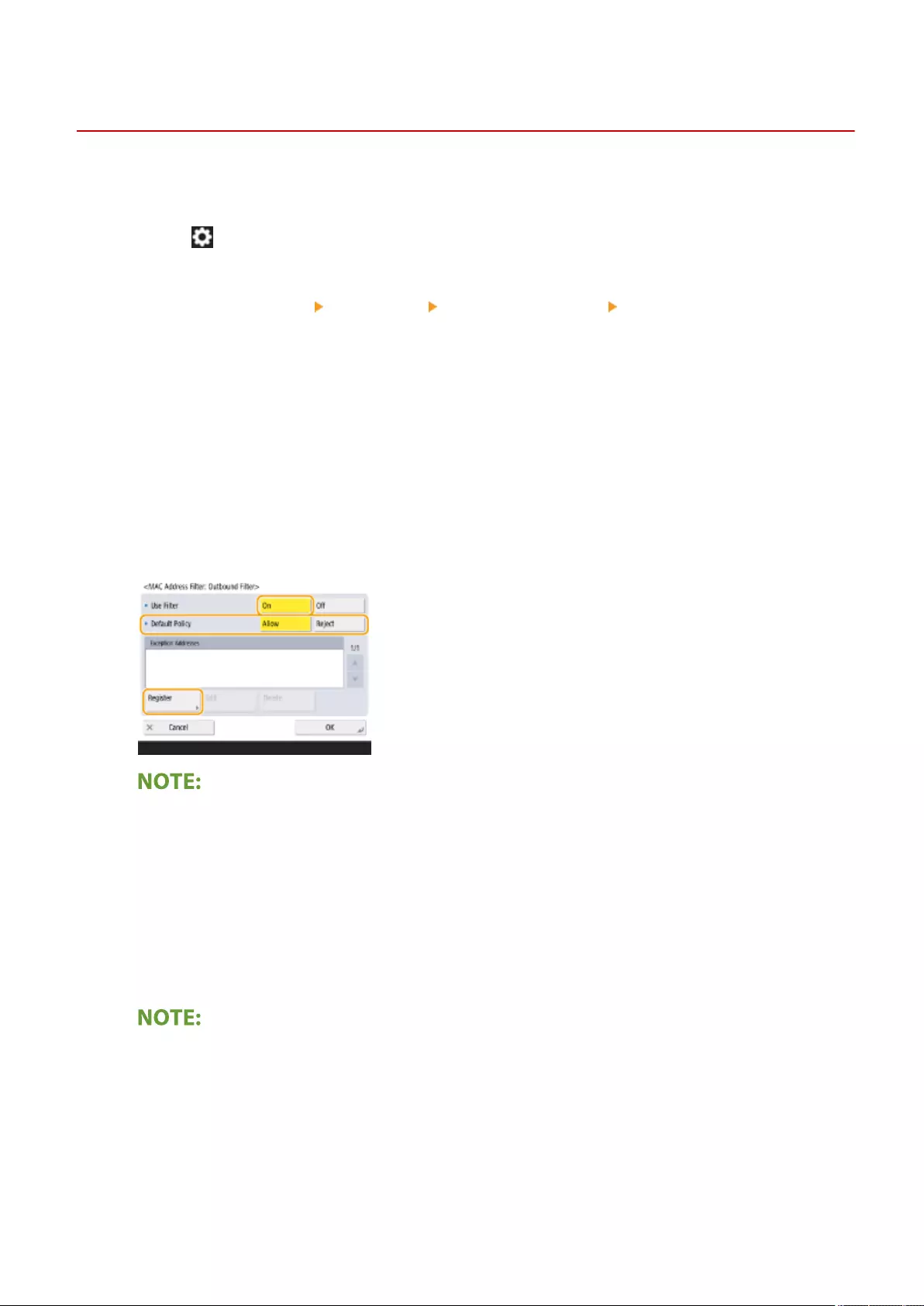
Specifying MAC Addresses in Firewall Settings
72JY-097
You can set whether to allow or reject communication with a device that has a specic MAC address.
1Press (Settings/Register).
2Press <Preferences> <Network> <Firewall Settings> <MAC Address Filter>.
3Select <Outbound Filter> or <Inbound Filter>.
●To restrict data sent from the machine to a computer, select <Outbound Filter>.
●To restrict data received from a computer, select <Inbound Filter>.
4Set <Use Filter> to <On>, select <Default Policy>, then press <Register>.
●For <Default Policy>, select <Reject> to only allow communication with devices that have a MAC address
specied in <Exception Addresses> in the next step, or select <Allow> to reject communication with them.
●If <Reject> is selected for <Default Policy>, the restrictions do not apply to sending to multicast or broadcast
addresses.
5Enter the exception addresses, and press <OK>.
●Specify the MAC addresses to designate as exceptions of the <Default Policy> option selected in the previous
step.
●You can register 100 exception addresses for <Outbound Filter> and <Inbound Filter>.
To edit an exception address
●On the screen displayed in step 4, select the exception address that you want to edit, and press <Edit> to
display the edit screen.
6Press <OK>.
Managing the Machine
542
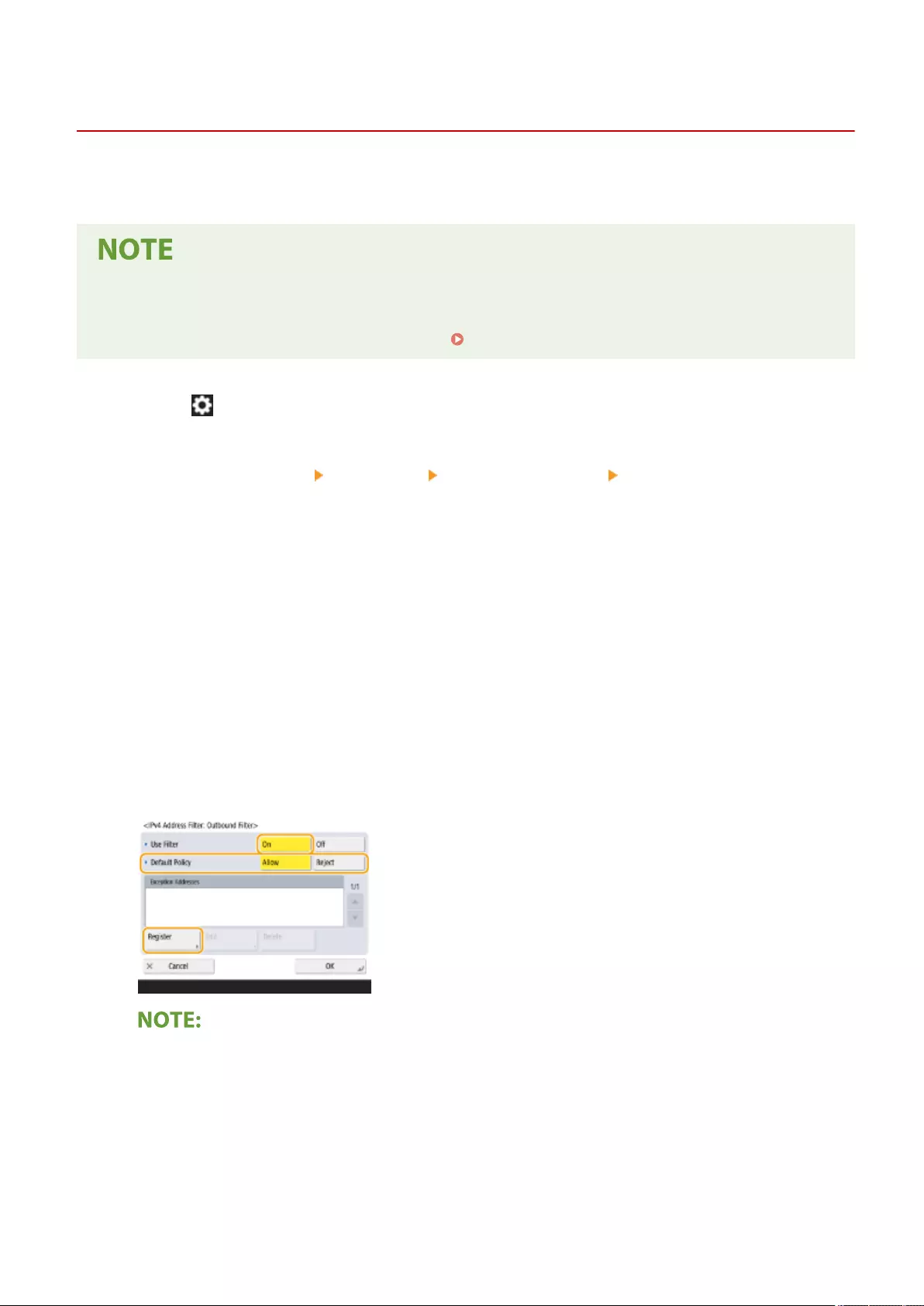
Conguring the Firewall of the Sub Line
72JY-098
You can set whether to allow communication only with devices that have the specied IP address for communication
with the sub line.
●Only IPv4 addresses can be registered for the sub line.
●For information on the exception addresses and exception port numbers that can be used for
communication and are registered by default, see Management Functions(P. 1091) .
1Press (Settings/Register).
2Press <Preferences> <Network> <Sub Line Settings> <Firewall Settings>.
3Press <IPv4 Address Filter>.
4Select <Outbound Filter> or <Inbound Filter>.
●To restrict data sent from the machine to a computer, select <Outbound Filter>.
●To restrict data received from a computer, select <Inbound Filter>.
5Set <Use Filter> to <On>, select <Default Policy>, then press <Register>.
●For <Default Policy>, select <Reject> to only allow communication with devices that have an IP address
specied in <Exception Addresses> in the next step, or select <Allow> to reject communication with them.
●If <Reject> is selected for <Default Policy>, the restrictions do not apply to sending to multicast or
broadcast addresses.
6Set the exception addresses.
Managing the Machine
544
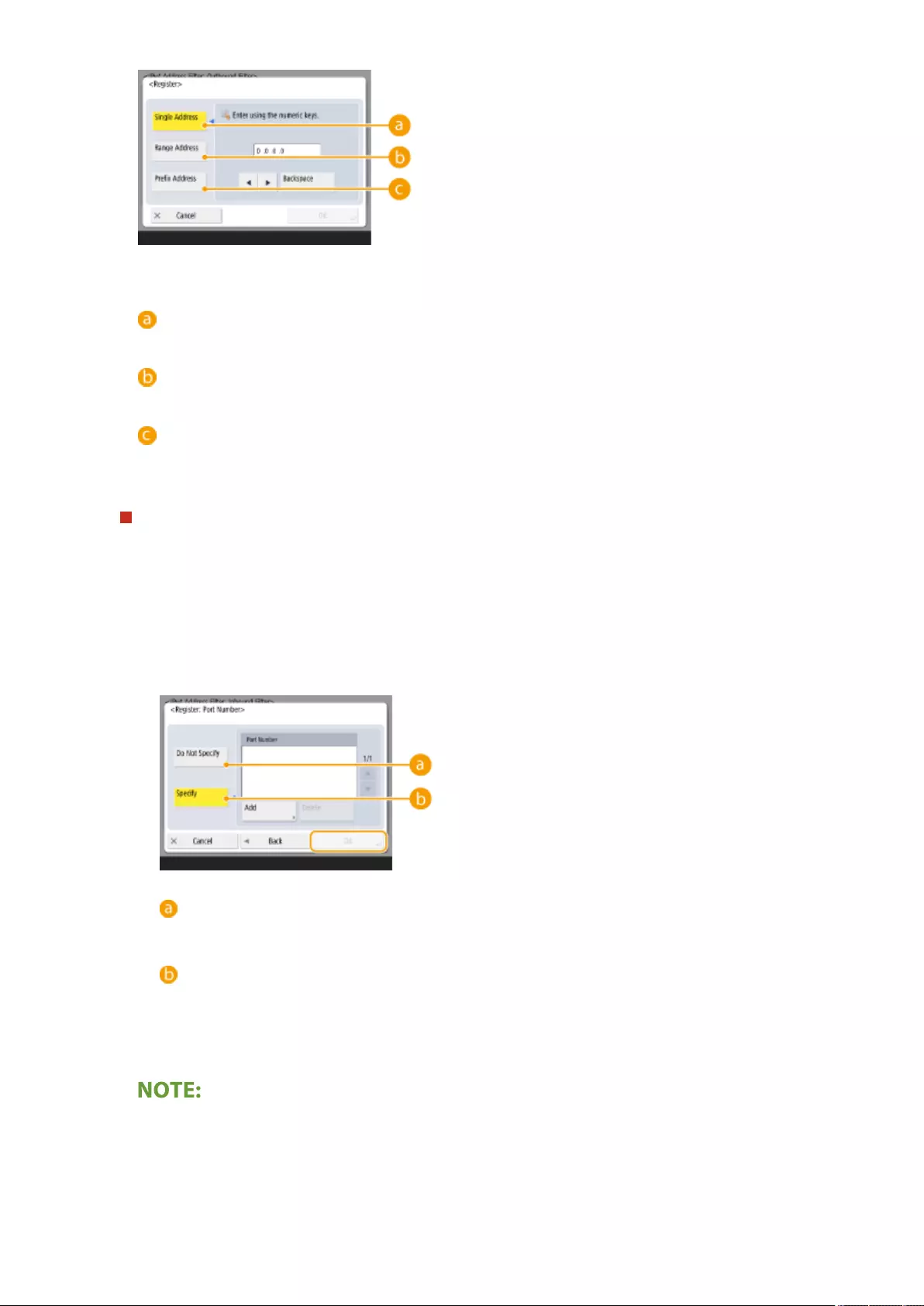
●Specify the IP addresses to designate as exceptions of the <Default Policy> option selected in the previous
step. Select one of the input methods described below.
<Single Address>
Enter an individual IP address to designate as an exception.
<Range Address>
Specify a range of IP addresses. Enter a separate address for <First Address> and <Last Address>.
<Prex Address>
Specify a range of IP addresses using a prex (network address). Enter a network address for <Address>,
and specify the network address length in <Prex Length>.
Setting exception addresses for the transmission lter/reception lter
1Select the IP address input method, and enter the exception addresses.
2Press <Next>.
3Set the port number if necessary, and press <OK>.
●Select whether to specify a port number. You can congure detailed communication restrictions by
specifying a port number for the exception address.
<Do Not Specify>
The exception address setting applies to all communication received from the specied IP address.
<Specify>
The exception address setting only applies to communication received from the specied IP address
using the designated port number. Press <Add>, enter the port number, and press <OK>. You can
register up to 50 ports per one exception address.
To edit an exception address
●On the screen displayed in step 5, select the exception address that you want to edit, and press <Edit> to
display the edit screen.
Managing the Machine
545

7Press <OK>.
8Press <Close> <Yes>.
Checking the blocked communication requests in the log
●The latest 100 communications blocked by the rewall can be displayed from (Settings/Register)
<Preferences> <Network> <Firewall Settings> <IP Address Block Log>. The history of blocked
communications can be exported from the Remote UI in the CSV format. Exporting a Log as a
File(P. 622)
●If <Default Policy> is set to <Reject>, the history of communication blocked by the rewall is not displayed in
<IP Address Block Log>.
Managing the Machine
546

Setting a Proxy
72JY-099
A proxy (or HTTP proxy server) refers to a computer or software that carries out HTTP communication for other
devices, especially when communicating with resources outside the network, such as when browsing Web sites. The
client devices connect to the outside network through the proxy server, and do not communicate directly to the
resources outside. Setting a proxy not only facilitates management of trac between in-house and outside networks
but also blocks unauthorized access and consolidates anti-virus protection for enhanced security. Administrator or
NetworkAdmin privileges are required in order to congure these settings.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <Proxy Settings>.
3Set <Use Proxy> to <On>, congure the necessary settings, and press <OK>.
<Server Address>
Enter the address of the proxy server to use. Specify the IP address or host name depending on your
environment.
<Port Number>
Enter the port number of the proxy server to use.
<Use Proxy within Same Domain>
Select <On> if you want to use the proxy server even when communicating with devices in the same
domain.
●This setting is only displayed for the proxy settings screen of the main line.
<Set Authentication>
To use the proxy server authentication function, press this and congure the authentication information.
On the screen that is displayed, press <On>, enter the user name and password to use for proxy
authentication, and press <OK>.
Managing the Machine
547
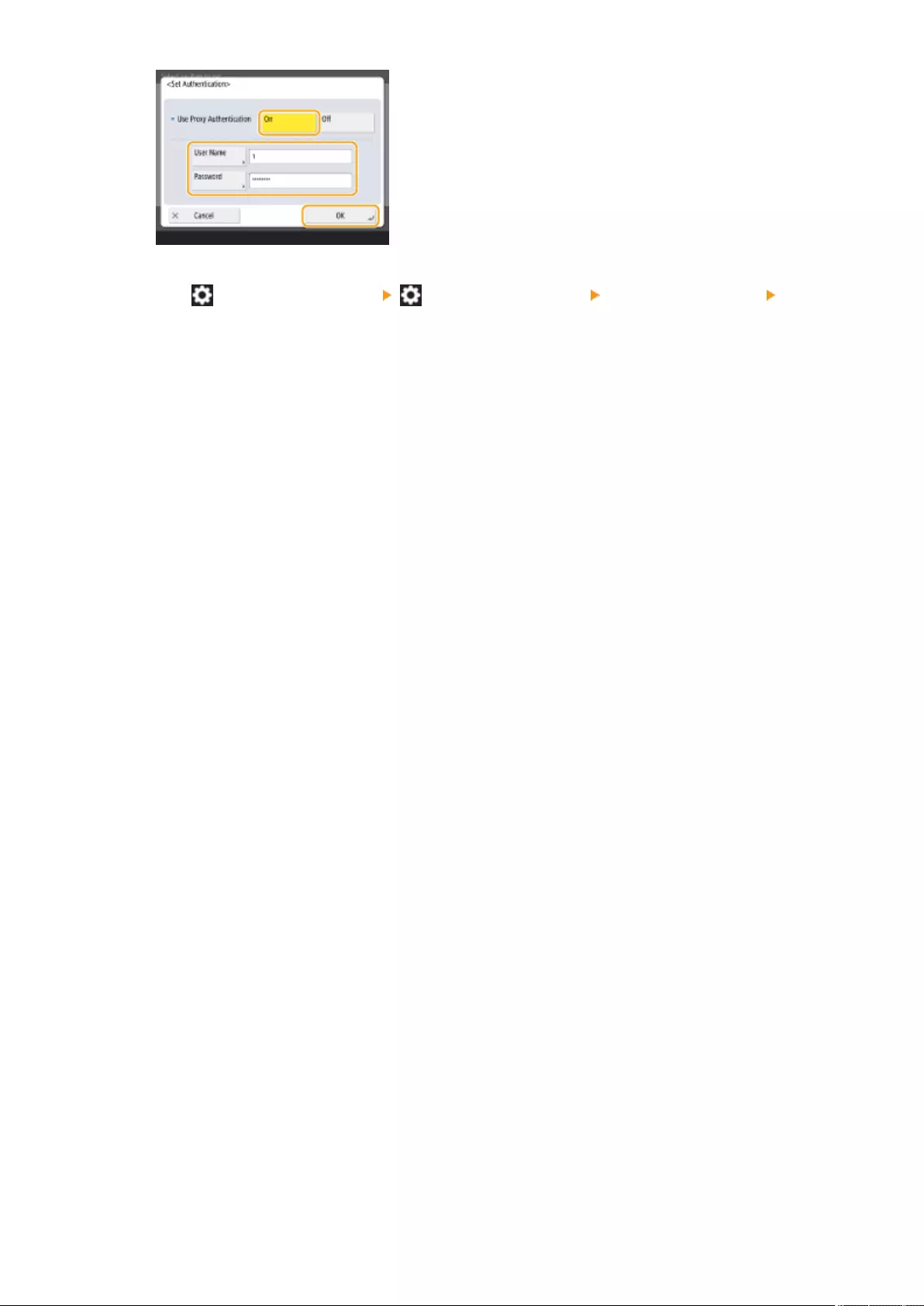
4Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
Managing the Machine
548
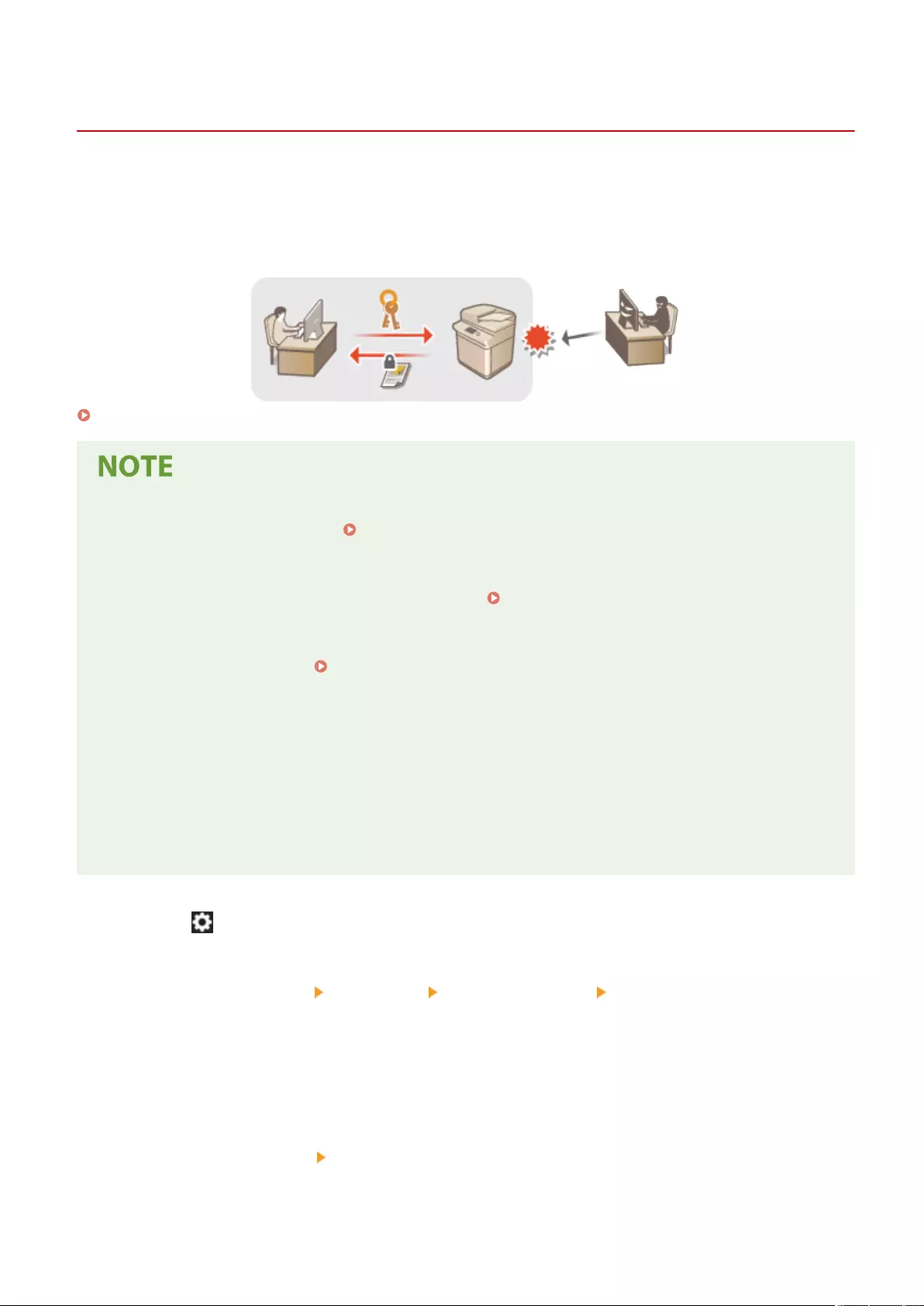
Conguring the Key and Certicate for TLS
72JY-09A
You can use TLS encrypted communication to prevent sning, spoong, and tampering of data that is exchanged
between the machine and other devices such as computers. When conguring the settings for TLS encrypted
communication, you must specify a key and certicate (server certicate) to use for encryption. You can use the key
and certicate that are preinstalled in the machine, or you can generate your own or acquire them from a certication
authority. Administrator or NetworkAdmin privileges are required in order to congure these settings.
Generating the Key and Certicate for Network Communication(P. 552)
●If you want to use a key and certicate that you generate yourself, generate the key and certicate before
performing the procedure below. Generating the Key and Certicate for Network
Communication(P. 552)
●If you want to use a key and certicate that you acquire from a certication authority (CA), register the key
and certicate before performing the procedure below. Registering a Key and Certicate(P. 600)
●If you set <Format Encryption Method to FIPS 140-2> to <On>,you can make the TLS communication
encryption method comply with the United States government-approved FIPS (Federal Information
Processing Standards) 140-2. <Format Encryption Method to FIPS 140-2>(P. 869)
●If <Format Encryption Method to FIPS 140-2> is set to <On>, an error will occur when you try to specify a
certicate for TLS that uses an algorithm not recognized by FIPS (lower than RSA2048bit).
●A communication error will occur if you set <Format Encryption Method to FIPS 140-2> to <On>, and send to
a remote party that does not support FIPS-recognized encryption algorithms.
●If <Format Encryption Method to FIPS 140-2> is set to <On>, <CHACHA20-POLY1305> and <X25519> switch
to <Off>.
●If <CHACHA20-POLY1305> or <X25519> is set to <On>, <Format Encryption Method to FIPS 140-2> switches
to <Off>.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <TLS Settings>.
3Press <Key and Certicate>.
4Select the key and certicate to use for TLS encrypted communication, and press
<Set as Default Key> <Yes>.
Managing the Machine
549

●If you want to use the preinstalled key and certicate, select <Default Key>.
●TLS encrypted communication cannot use <Device Signature Key>, which is used for the device signature,
or <AMS>, which is used for access restrictions.
5Press <OK>.
6Press <Specify Allowed Versions>.
7Specify <Specify Allowed Versions> and <Minimum Version> press <OK>.
8Set each algorithm press <OK>.
The following combinations of TLS version and algorithm are available.
: Available
-: Unavailable
Algorithm
TLS Version
<TLS 1.3> <TLS 1.2> <TLS 1.1> <TLS 1.0>
<Encryption Algo Settings>
<AES-CBC (256-bit)> -
<AES-GCM (256-bit)> - -
<3DES-CBC> -
<AES-CBC (128-bit)> -
<AES-GCM (128-bit)> - -
Managing the Machine
550
<CHACHA20-POLY1305> - - -
<Key Exchange Algo Settings>
<RSA> -
<ECDHE>
<X25519> - - -
<Signature Algo Settings>
<RSA>
<ECDSA>
<HMAC Algo Settings>
<SHA1> -
<SHA256> - -
<SHA384> - -
9Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
➠The machine restarts, and the settings are applied.
LINKS
Starting the Remote UI(P. 583)
Setting E-mail/I-Fax Communication(P. 70)
Managing the Machine
551

Generating the Key and Certicate for Network
Communication
72JY-09C
The machine can generate the key and certicate (server certicate) used for TLS
encrypted communication. If you want to start using TLS encrypted communication
immediately, it is convenient to use the key and certicate that are preinstalled in the
machine. If necessary, have an administrator generate a key and certicate. Note,
however, that TLS encrypted communication is not enabled simply by generating a
key and certicate. Conguring the Key and Certicate for TLS(P. 549)
●If you want to use a server certicate with a CA signature, you can generate the key along with a CSR,
instead of the certicate. Generating a Key and CSR(P. 608)
1Press (Settings/Register).
2Press <Management Settings> <Device Management> <Certicate Settings>
<Generate Key> <Generate Network Communication Key>.
3Congure the necessary items for the key, and press <Next>.
<Key Name>
Enter a name for the key. Use a name that will be easy to nd when displayed in a list.
<Signature Algorithm>
Select the hash algorithm to use for the signature. The available hash algorithms vary depending on the
key length ( System Specications(P. 1084) ). A key length of 1024 bits or more can support SHA384
and SHA512 hash algorithms. If <RSA> is selected for , and <Generate Key: Key Length (bit) Settings> is
set to <1024> or more for , the SHA384 and SHA512 hash algorithms can be selected.
<Key Algorithm>
Select the key algorithm. If <RSA> is selected, <Generate Key: Key Length (bit) Settings> is displayed as a
setting item for . If <ECDSA> is selected, <Generate Key: Key Type Settings> is displayed instead.
Managing the Machine
552

<Generate Key: Key Length (bit) Settings> / <Generate Key: Key Type Settings>
Specify the key length if <RSA> is selected for , or specify the key type if <ECDSA> is selected. In both
cases, a higher value provides greater security but reduces the communication processing speed.
4Congure the necessary items for the certicate, and press <Generate Key>.
<Validity Start Date> / <Validity End Date>
Enter the validity start and end date.
<Country/Region>/ <State> / <City> / <Organization> / <Organization Unit>
Select the country code from the list, and enter the location and the organization name.
<Common Name>
Enter the IP address or FQDN.
●When performing IPPS printing in a Windows environment, make sure to enter the machine's IP
address.
●A DNS server is required in order to enter the FQDN of the machine. Enter the IP address if a DNS server
is not used.
Managing keys and certicates
You can check the detailed settings or delete keys and certicates on the screen that is displayed when
you press (Settings/Register) <Management Settings> <Device Management> <Certicate
Settings> <Key and Certicate List>. If the list of keys and certicates is not displayed, press <Key and
Certicate List for This Device> to display it.
●If is displayed, the key is corrupted or invalid.
●If is not displayed, the certicate for the key does not exist.
●If you select a key and certicate and press <Certicate Details>, detailed information about the
certicate is displayed. You can also press <Verify Certicate> on this screen to check whether the
certicate is valid.
●To delete keys and certicates, select the ones that you want to delete, and press <Delete> <Yes>.
Managing the Machine
553
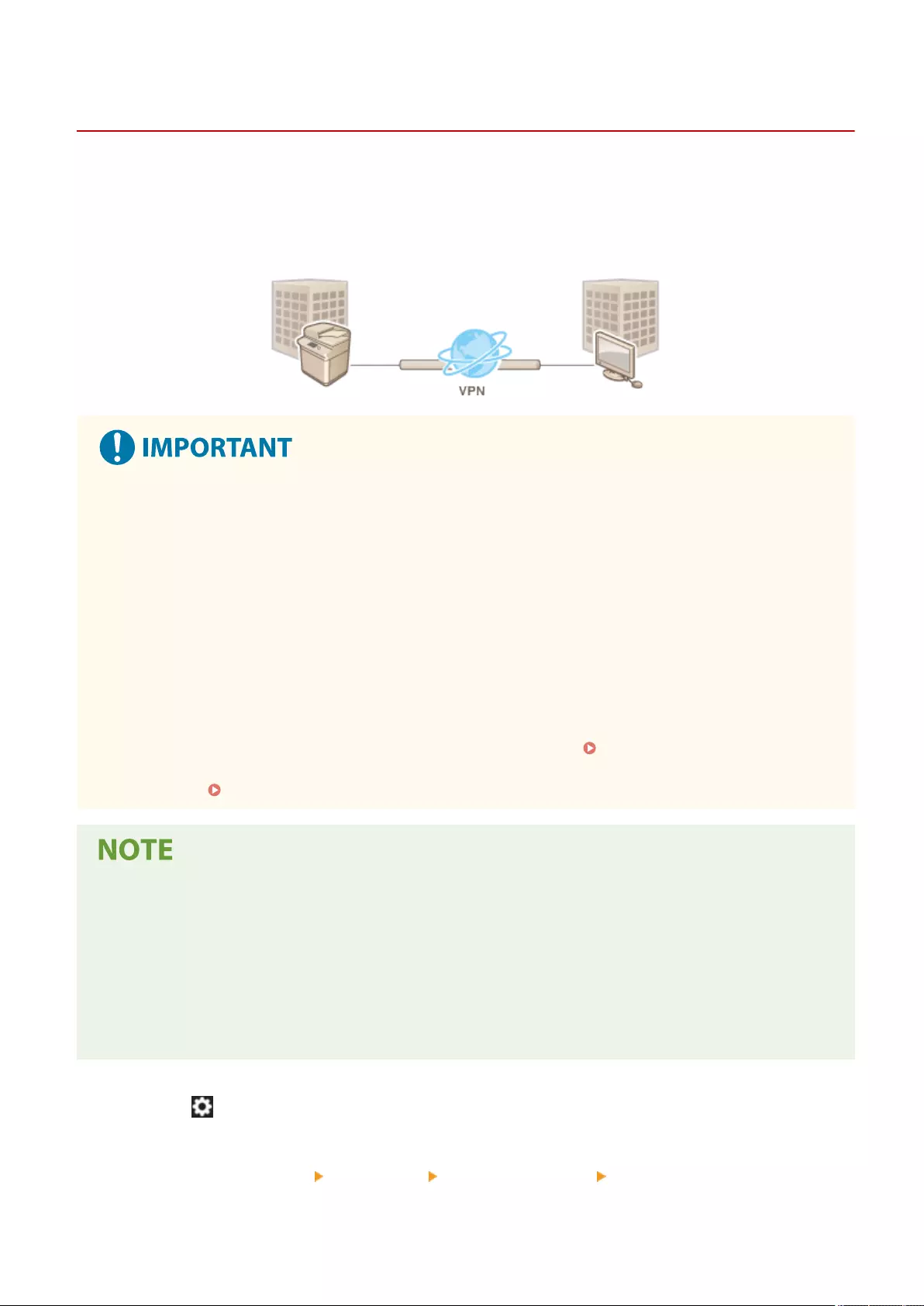
Conguring the IPSec Settings
72JY-09E
By using IPSec, you can prevent third parties from intercepting or tampering with IP packets transported over the IP
network. Because IPSec adds security functions to IP, a basic protocol suite used for the Internet, it can provide
security that is independent of applications or network conguration. To perform IPSec communication with this
machine, you must congure settings such as the application parameters and the algorithm for authentication and
encryption. Administrator or NetworkAdmin privileges are required in order to congure these settings.
Communication mode
●This machine only supports transport mode for IPSec communication. As a result, authentication and
encryption is only applied to the data portions of IP packets.
Key exchange protocol
This machine supports Internet Key Exchange version 1 (IKEv1) for exchanging keys based on the Internet
Security Association and Key Management Protocol (ISAKMP). For the authentication method, set either the pre-
shared key method or the digital signature method.
●When setting the pre-shared key method, you need to decide on a passphrase (pre-shared key) in advance,
which is used between the machine and the IPSec communication peer.
●When setting the digital signature method, use a CA certicate and a PKCS#12 format key and certicate to
perform mutual authentication between the machine and the IPSec communication peer. For more
information on registering new CA certicates or keys/certicates, see Registering a Key and Certicate
for Network Communication(P. 600) . Note that SNTP must be congured for the machine before it uses
this method. Making SNTP Settings(P. 63)
●Regardless of the setting of <Format Encryption Method to FIPS 140-2> for IPSec communication, an
encryption module which has already obtained FIPS140-2 certication will be used.
●In order to make IPSec communication comply with FIPS 140-2, you must set the key length of both DH and
RSA for IPSec communication to 2048-bit or longer in the network environment that the machine belongs to.
●Only the key length for DH can be specied from the machine.
●Take note when conguring your environment, as there are no settings for RSA in the machine.
●You can register up to 10 security policies.
1Press (Settings/Register).
2Press <Preferences> <Network> <TCP/IP Settings> <IPSec Settings>.
Managing the Machine
555
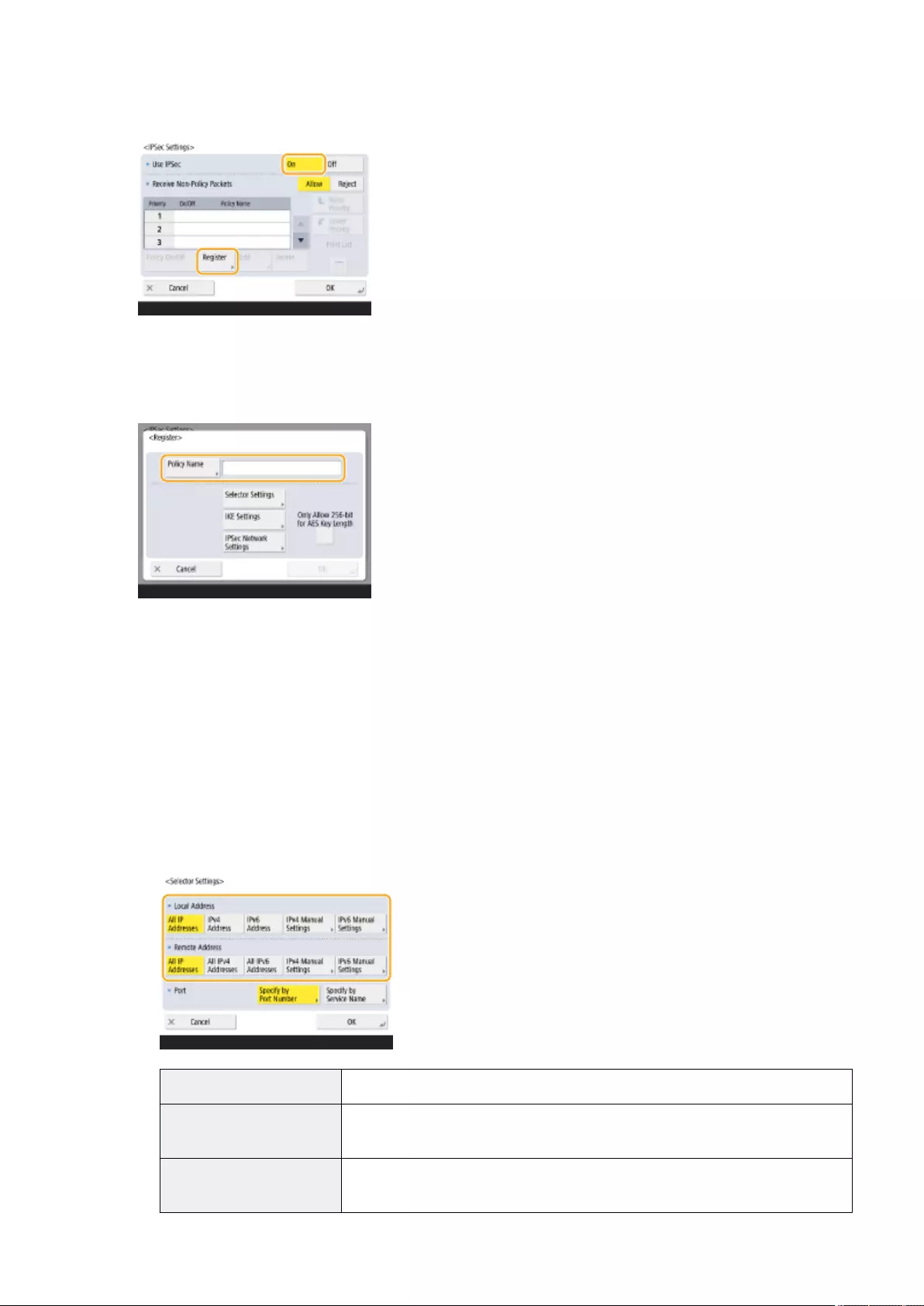
3Set <Use IPSec> to <On>, and press <Register>.
4Specify a name for the policy.
●Press <Policy Name>, enter the name, and press <OK>.
●Canon multifunction printers support two key lengths for the AES encryption method: 128 bit and 256 bit. To
restrict the key length to 256 bit and meet CC authentication standards, set <Only Allow 256-bit for AES Key
Length> to <On>.
5Congure the IPSec application parameters.
1Press <Selector Settings>.
2Specify the IP address to apply the IPSec policy to.
●Specify the IP address of this machine in <Local Address>, and specify the IP address of the
communication peer in <Remote Address>.
<All IP Addresses> IPSec is applied to all sent and received IP packets.
<IPv4 Address> IPSec is applied to IP packets sent to and received from the IPv4 address of this
machine.
<IPv6 Address> IPSec is applied to IP packets sent to and received from the IPv6 address of this
machine.
Managing the Machine
556

<All IPv4 Addresses> IPSec is applied to IP packets sent to and received from the IPv4 address of the
communication peer.
<All IPv6 Addresses> IPSec is applied to IP packets sent to and received from the IPv6 address of the
communication peer.
<IPv4 Manual Settings>
Specify the IPv4 address to apply IPSec to.
●Select <Single Address> to enter an individual IPv4 address.
●Select <Address Range> to specify a range of IPv4 addresses. Enter a separate
address for <First Address> and <Last Address>.
●Select <Subnet Settings> to specify a range of IPv4 addresses using a subnet
mask. Enter separate values for <Address> and <Subnet Mask>.
<IPv6 Manual Settings>
Specify the IPv6 address to apply IPSec to.
●Select <Single Address> to enter an individual IPv6 address.
●Select <Address Range> to specify a range of IPv6 addresses. Enter a separate
address for <First Address> and <Last Address>.
●Select <Specify Prex> to specify a range of IPv6 addresses using a prex. Enter
separate values for <Address> and <Prex Length>.
3Specify the port to apply IPSec to.
●Press <Specify by Port Number> to use port numbers when specifying the ports that IPSec applies to.
Select <All Ports> to apply IPSec to all port numbers. To apply IPSec to a specic port number, press
<Single Port> and enter the port number. After specifying the ports, press <OK>. Specify the port of
this machine in <Local Port>, and specify the port of the communication peer in <Remote Port>.
●Press <Specify by Service Name> to use service names when specifying the ports that IPSec applies to.
Select the service in the list, press <Service On/Off> to set it to <On>, and press <OK>.
4Press <OK>.
6Congure the authentication and encryption settings.
1Press <IKE Settings>.
2Congure the necessary settings.
Managing the Machine
557

<IKE Mode>
Select the operation mode for the key exchange protocol. Security is enhanced if you select <Main>
because the IKE session itself is encrypted, but the speed of the session is slower than with
<Aggressive>, which does not encrypt the entire session.
<Validity>
Set the expiration period of the generated IKE SA.
<Authentication Method>
Select one of the authentication methods described below.
<Pre-Shared Key Method>
Set the same passphrase (pre-shared key) that is set for the communication peer.
Press <Shared Key>, enter the character string to use as the shared key, and
press <OK>.
<Digital Sig. Method>
Set the key and certicate to use for mutual authentication with the
communication peer. Press <Key and Certicate>, select the key and certicate to
use, and press <Set as Default Key> <Yes> <OK>.
<Authentication/Encryption Algorithm>
Select either <Auto> or <Manual Settings> to set how to specify the authentication and encryption
algorithm for IKE phase 1. If you select <Auto>, an algorithm that can be used by both this machine
and the communication peer is set automatically. If you want to specify a particular algorithm, select
<Manual Settings> and congure the settings below.
<Authentication> Select the hash algorithm.
<Encryption> Select the encryption algorithm.
<DH Group> Select the group for the Die-Hellman key exchange method to set the key
strength.
3Press <OK>.
●When <IKE Mode> is set to <Main> on the <IKE Settings> screen and <Authentication Method> is set
to <Pre-Shared Key Method>, the following restrictions apply when registering multiple security
policies.
●Pre-shared key method key: when specifying multiple remote IP addresses to which a security
policy is to be applied, all shared keys for that security policy are identical (this does not apply when
a single address is specied).
●Priority: when specifying multiple remote IP addresses to which a security policy is to be applied,
the priority of that security policy is below security policies for which a single address is specied.
Managing the Machine
558
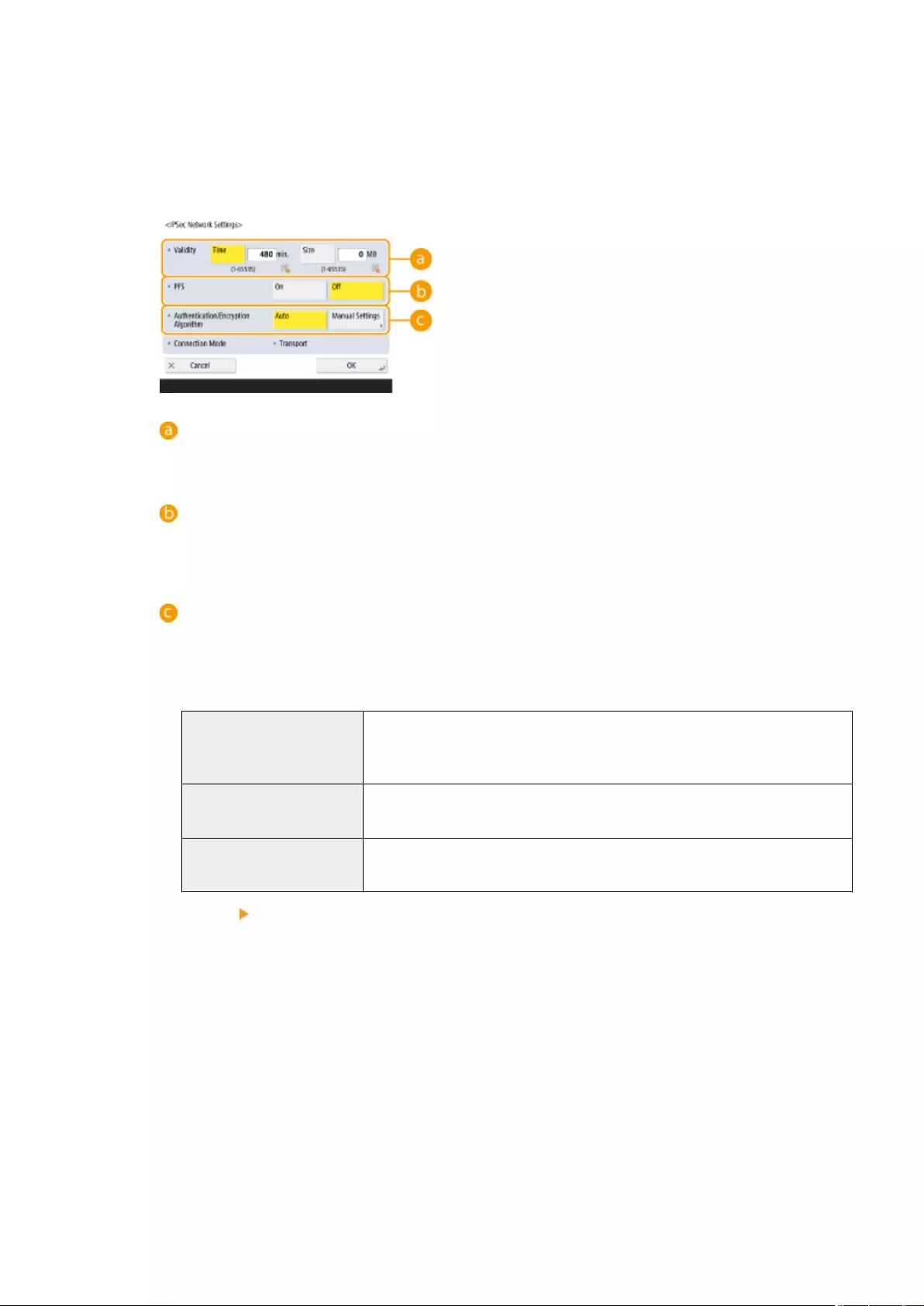
7Congure the IPSec communication settings.
1Press <IPSec Network Settings>.
2Congure the necessary settings.
<Validity>
Set the expiration period of the generated IPSec SA. Make sure to set either <Time> or <Size>. If you
set both, the setting with the value that is reached rst is applied.
<PFS>
If you set the Perfect Forward Secrecy (PFS) function to <On>, the secrecy of the encryption key is
increased, but the communication speed is slower. In addition, the PFS function must be enabled on
the communication peer device.
<Authentication/Encryption Algorithm>
Select either <Auto> or <Manual Settings> to set how to specify the authentication and encryption
algorithm for IKE phase 2. If you select <Auto>, the ESP authentication and encryption algorithm is set
automatically. If you want to specify a particular authentication method, press <Manual Settings> and
select one of the authentication methods below.
<ESP>
Authentication and encryption are both performed. Select the algorithm for <ESP
Authentication> and <ESP Encryption>. Select <NULL> if you do not want to set
the authentication or encryption algorithm.
<ESP (AES-GCM)> AES-GCM is used as the ESP algorithm, and authentication and encryption are
both performed.
<AH (SHA1)> Authentication is performed, but data is not encrypted. SHA1 is used as the
algorithm.
3Press <OK> <OK>.
8Enable the registered policies and check the order of priority.
●Select the registered policies from the list, and press <Policy On/Off> to turn them <On>.
●Policies are applied in the order that they are listed, starting at the top. If you want to change the order of
priority, select a policy in the list and press <Raise Priority> or <Lower Priority>.
●If you do not want to send or receive packets that do not correspond to the policies, select <Reject> for
<Receive Non-Policy Packets>.
9Press <OK>.
Managing the Machine
559

10 Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
Managing IPSec policies
You can edit policies on the screen displayed in step 3.
●To edit the details of a policy, select the policy in the list and press <Edit>.
●To disable a policy, select the policy in the list and press <Policy On/Off>.
●To delete a policy, select the policy in the list and press <Delete> <Yes>.
Managing the Machine
560

Conguring the IEEE 802.1X Authentication Settings
72JY-09F
In a network environment that uses IEEE 802.1X authentication, unauthorized network access is blocked by a LAN
switch (authenticator) that only grants access privileges to client devices (supplicants) that are authorized by the
authentication server (RADIUS server). To connect this machine to an IEEE 802.1X network, settings such as the
authentication method used by the authentication server must be congured on the machine. Administrator or
NetworkAdmin privileges are required in order to congure these settings.
IEEE 802.1X Authentication Method
The machine supports the authentication methods described below. You must register a CA certicate before
using any of these authentication methods. Registering a CA Certicate(P. 601)
EAP-TLS (Extensible Authentication Protocol-Transport Level Security)
The machine and the authentication server authenticate each other by mutually sending certicates. A CA
certicate must be registered on the machine to verify the certicate (server certicate) sent from the
authentication server. In addition, a PKCS#12 format key and certicate (client certicate) must be specied
in this setting, so that the authentication server can authenticate the machine. Register these items before
conguring the settings ( Registering a Key and Certicate(P. 600) ). This authentication method cannot
be used in combination with the other methods.
EAP-TTLS (EAP-Tunneled TLS)
Only the authentication server sends a certicate. A CA certicate must be registered on the machine to
verify the certicate (server certicate) sent from the authentication server. In addition, a user name and
password need to be specied in these settings, so that the authentication server can authenticate the
machine. Microsoft Challenge Handshake Authentication Protocol Version 2 (MS-CHAPv2) or Password
Authentication Protocol (PAP) can be selected as the internal authentication protocol to support EAP-TTLS.
PEAP (Protected EAP)
Only the authentication server sends a certicate. A CA certicate must be registered on the machine to
verify the certicate (server certicate) sent from the authentication server. In addition, a user name and
password need to be specied in these settings, so that the authentication server can authenticate the
machine. Only MS-CHAPv2 can be selected as the internal authentication protocol to support PEAP.
Setting the IEEE 802.1X Authentication Method
1Press (Settings/Register).
2Press <Preferences> <Network> <IEEE 802.1X Settings>.
Managing the Machine
561

3Press <On> for <Use IEEE 802.1X> <Next>, and congure the necessary settings.
<Login Name>
Enter the name (EAP Identity) of the login user to receive IEEE 802.1X authentication.
<Verify Authent. Server Certicate>
Set this setting to <On> when verifying server certicates sent from an authentication server.
<Verify Authentication Server Name>
To verify a common name in the server certicate, select <On> in <Verify Authentication Server Name>,
and enter the name of the authentication server registered by the login user in <Authentication Server
Name>.
4Select the authentication method and congure the necessary settings.
Selecting EAP-TLS
1Press <On> for <Use TLS>, and press <Key and Certicate>.
2In the list, select the key and certicate to use, and press <Set as Default Key>.
3Press <OK>.
Selecting EAP-TTLS
1Press <Off> for <Use TLS>, and press <Next>.
2Press <On> for <Use TTLS>.
3Select <MSCHAPv2> or <PAP>, and press <OK>.
4Enter the user name and password.
●Press <User Name> or <Password>, and enter the information. If you enter a name for <User Name>,
disable <Use Login Name as User Name>.
●If you want to set <User Name> to the same login name that was entered in step 3, press <Use Login
Name as User Name>.
Managing the Machine
562

●<Conrm> is displayed when you enter a password and press <OK>. For conrmation, enter the
password again and press <OK>.
Selecting PEAP
1Press <Off> for <Use TLS>, and press <Next>.
2Press <On> for <Use PEAP>.
3Enter the user name and password.
●Press <User Name> or <Password>, and enter the information. If you enter a name for <User Name>,
disable <Use Login Name as User Name>.
●If you want to set <User Name> to the same login name that was entered in step 3, press <Use Login
Name as User Name>.
●<Conrm> is displayed when you enter a password and press <OK>. For conrmation, enter the
password again and press <OK>.
5Press <OK>.
6Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
Managing the Machine
563
Restricting the Machine's Functions
72JY-09H
You can restrict the use of certain functions that may lead to information leaks or that are subject to misuse. It is also
possible to completely disable the use of individual functions.
Restricting Access to Address Book and Sending Functions
You can set a PIN for the Address Book so that general users cannot make any changes, and you can limit the
destinations that can be specied when sending faxes and scans. You can also set individual access numbers for
specic contacts whose information you do not want to make available to everyone, so that only the users who
know the number can access the destination. Restricting Access to Address Book and Sending
Functions(P. 565)
Restricting Printing from a Computer
You can prohibit all users from printing documents from a computer, or only allow printing if the user is
authorized on the machine. You can also congure the machine so that only Encrypted Secure Print documents
can be printed. Restricting Printing from a Computer(P. 573)
Restricting the Use of Memory Media
Although memory media such as USB memory devices provide convenience, they also increase the potential for
security risks such as information leakage. You can set access restrictions for memory media based on your
security policy. Restricting the Use of Memory Media(P. 576)
Managing the Machine
564
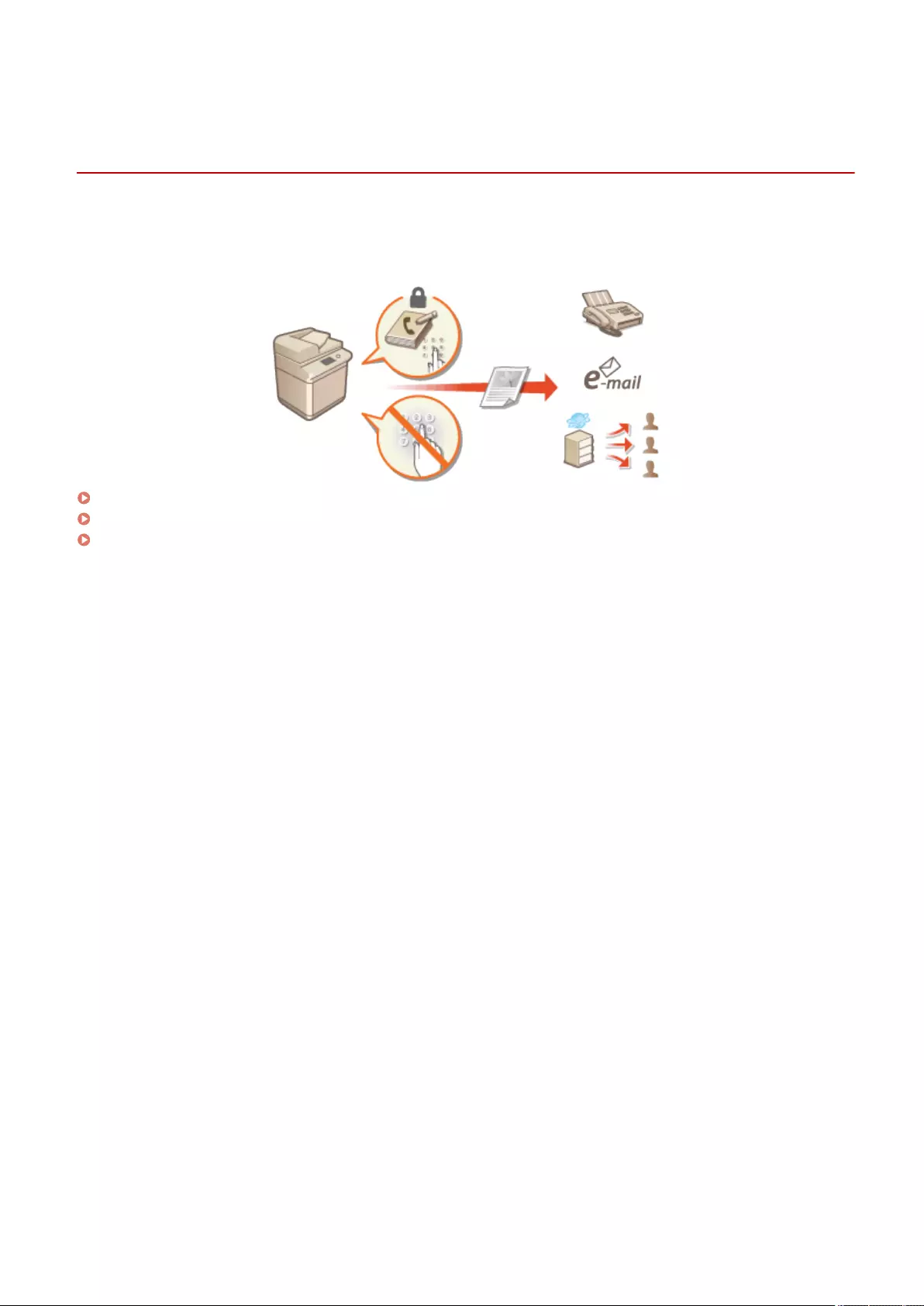
Restricting Access to Address Book and Sending
Functions
72JY-09J
You can set a PIN for the Address Book to prevent users from editing destination information, or you can restrict the
available sending destinations to reduce the risk of information leakage. You can also prevent documents from being
sent to unintended recipients by requiring users to enter the fax number twice for conrmation before sending.
Restricting Use of the Address Book(P. 566)
Limiting Available Destinations(P. 569)
Restricting the Fax Sending Functions(P. 571)
Managing the Machine
565
Restricting Use of the Address Book
72JY-09K
You can prevent the leakage of sensitive or personal information from the Address
Book by setting a PIN or preventing certain destinations from being displayed in the
Address Book. You can also hide the Address Book itself. Administrator privileges are
required in order to congure these settings.
Setting a PIN for Address Book(P. 566)
Restricting Access to Destinations Registered in the Address Book(P. 567)
Hiding the Address Book(P. 567)
Setting a PIN for Address Book
The Address Book can be set to require users to enter a PIN in order to add new entries to the Address Book or edit
existing entries. This can reduce the risk of unauthorized editing of the Address Book. Note, however, that even if a
PIN is set for the Address Book, a user who logs in with Administrator privileges can add and edit entries without
entering the required PIN.
1Press (Settings/Register).
2Press <Set Destination> <Address Book PIN> <Set>.
3Set the PIN for editing the Address Book.
●Enter the PIN and press <Conrm>. For conrmation, enter the PIN again and press <OK>.
●You cannot set a PIN that consists only of zeros, such as "00" or "0000000".
●To disable the PIN, press (Clear) to erase the PIN (leave the text box blank), and press <OK>.
4Press <OK>.
Managing the Machine
566

In addition to setting the Address Book PIN, you can further enhance security by performing the following
operations:
●Restricting the addition of new destinations Limiting Available Destinations(P. 569)
●Disabling the PC fax function Restricting Fax Sending from a Computer(P. 571)
Restricting Access to Destinations Registered in the Address Book
You can set an access number for important business contacts and other destinations in the Address Book that you do
not want to display to all users. Destinations with a registered access number are only displayed to users who enter
the correct access number. Follow the procedure below to enable the access number registration function.
●If the access number registration function is enabled, users cannot specify a destination using <Previous
Settings>.
(Settings/Register) <Set Destination> <Manage Address Book Access Numbers> <On>
<OK>
●After conguring this setting, register the access numbers in the Address Book.
●You can enter up to seven digits for the access number. If you enter fewer than seven digits, the machine
stores the access number with leading zeros.
Example: If <321> is entered, <0000321> is stored.
●You cannot store an access number with only zeros as the number, such as <0000000>.
●If you enter a number that begins in zeros, such as <02> or <002>, the zeros are ignored and the number is
registered as <0000002>, the same as if you had simply entered <2>.
Hiding the Address Book
Set whether to hide the Address Book and one-touch buttons. You can specify separate settings for Fax as well as Scan
and Send.
Managing the Machine
567

Hiding the Fax Address Book and One-Touch Buttons
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Restrict Address Book
Use> <On> <OK>
Hiding the Scan and Send Address Book and One-Touch Buttons
(Settings/Register) <Function Settings> <Send> <Common Settings> <Restrict Address
Book Use> <On> <OK>
LINKS
Registering Destinations in the Address Book(P. 195)
Registering Destinations via the Remote UI(P. 592)
Managing the Machine
568
Limiting Available Destinations
72JY-09L
You can set restrictions on the destinations that can be
specied. For example, you can limit the destinations to those
that are registered in the Address book or LDAP server. With
personal authentication management, you can restrict the
send destination to the user's own e-mail address or to a folder
that is specied in advance. You can also restrict the domains
that can be specied as destinations. By restricting the send
destinations, you can prevent information leakage that may
occur due to operation errors or misuse. Administrator or
DeviceAdmin privileges are required in order to congure
these settings.
●Some of the restrictions on the destinations that are described below may not be available when ACCESS
MANAGEMENT SYSTEM is enabled. Using ACCESS MANAGEMENT SYSTEM(P. 533)
Restricting New Destinations(P. 569)
Restricting E-Mail Destination to <Send to Myself>(P. 570)
Restricting File Send Destination to Personal Folder(P. 570)
Restricting the Domain of Send Destination(P. 570)
Restricting New Destinations
The destinations that can be specied when sending faxes or scanned documents can be restricted to those registered
in the Address Book or one-touch buttons, those registered in <Favorite Settings> or <Send to Myself>, or those that
can be searched on the LDAP server. When this function is enabled, users cannot specify destinations using
alphanumeric character input.
1Press (Settings/Register).
2Press <Function Settings> <Send> <Common Settings> <Restrict New
Destinations>.
3Select the functions that you want to restrict new destinations for.
Managing the Machine
569
4Press <On> <OK>.
Restricting E-Mail Destination to <Send to Myself>
You can set restrictions so that users who log in with personal authentication can only send scanned documents to
their own e-mail address. To use this function, an e-mail address must be registered in the user information. Congure
the user information before performing the procedure below.
(Settings/Register) <Function Settings> <Send> <Common Settings> <Limit E-Mail to
Send to Myself> <On> <OK>
Restricting File Send Destination to Personal Folder
You can set restrictions so that users who log in with personal authentication can only send scanned documents to
their Personal folder ( Conguring Personal Folders(P. 529) .)
(Settings/Register) <Function Settings> <Send> <Common Settings> <Restrict File TX
to Personal Folder> <On> <OK>
Restricting the Domain of Send Destination
You can restrict e-mail and I-fax destinations so that only addresses in a specic domain are available. When a domain
is specied, you can also set whether to allow sending to subdomains.
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings> <Restrict
Destination Domain> Select <On> for <Restrict Sending to Domains> <Register> Specify the
destination domain <OK> Select <Allow> or <Reject> for <Send to Subdomain> <OK>
<OK>
●You can register up to three domains.
LINKS
Basic Operations for Sending Faxes(P. 275)
Basic Operations for Scanning Originals(P. 377)
Managing the Machine
570
Restricting the Fax Sending Functions
72JY-09R
You can set various restrictions for sending faxes, which can prevent sending errors and information leakage to third
parties. Administrator privileges are required in order to congure these settings.
Conrming Fax Numbers before Sending(P. 571)
Restricting Fax Sending from a Computer(P. 571)
Displaying a Conrmation Screen for Fax Destinations(P. 571)
Restricting Sequential Broadcasting(P. 572)
Restricting Sending from Log(P. 572)
Conrming Fax Numbers before Sending
You can require users to enter a fax number twice for conrmation before sending faxes, to prevent misdialing. This
setting can also be congured with DeviceAdmin privileges.
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Conrm Entered Fax
Number> <On> <OK>
Restricting Fax Sending from a Computer
You can prohibit users from sending faxes from a computer ( Sending Faxes from Your Computer (PC Fax)
(P. 324) ). This setting can also be congured with DeviceAdmin privileges.
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Allow Fax Driver
TX> <Off> <OK>
Displaying a Conrmation Screen for Fax Destinations
You can set the machine to display a conrmation screen when sending to a fax destination. This can help prevent fax
sending errors.
Managing the Machine
571
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Conrm Before
Sending When Fax Dest. Included> <On> Select <Only for Seq. Broadcast> or <All> <OK>
(Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>
●<Only for Seq. Broadcast> and <All> cannot be selected if sequential broadcasting is restricted (
Restricting Sequential Broadcasting(P. 572) ).
●When the function for conrming the fax number before sending ( Conrming Fax Numbers before
Sending(P. 571) ) is enabled, the conrmation screen is not displayed if there is only one destination.
Restricting Sequential Broadcasting
You can restrict the sequential broadcasting function, which enables users to send a fax to multiple recipients in
succession.
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Restrict Sequential
Broadcast When Fax Dest. Included> <On> <OK> (Settings/Register) (Settings/
Register) <Apply Set. Chng.> <Yes>
Restricting Sending from Log
You can prohibit users from being able to specify a previously used destination from the log. After conguring this
setting, previously used destinations cannot be selected from the log when sending faxes.
(Settings/Register) <Function Settings> <Send> <Common Settings> <Restrict
Resending from Log> <On> <OK>
LINKS
Basic Operations for Sending Faxes(P. 275)
Managing the Machine
572
Restricting Printing from a Computer
72JY-09S
You can restrict printing from a computer ( Printing From a Computer(P. 343) ) so that only specic types of
documents can be printed. You can also congure the machine so that documents are not printed until the user is
authorized on the machine ( Printing Documents Held in the Machine(P. 351) ). You can also restrict the machine
to only print Encrypted Secure Print ( Printing More Safely with Encrypted Secure Print(P. 354) ) documents,
which can prevent information leakage due to unattended printouts or unprotected print data. Administrator or
DeviceAdmin privileges are required in order to congure these settings.
Prohibiting Printing from a Computer(P. 573)
Conguring the Forced Hold Printing Settings(P. 573)
Allowing Only Encrypted Secure Print(P. 575)
Prohibiting Printing from a Computer
You can prohibit users from printing documents from a computer.
(Settings/Register) <Function Settings> <Printer> <Restrict Printer Jobs> <On>
Select the restriction exceptions <OK>
Conguring the Forced Hold Printing Settings
When printing documents from a computer, you can hold print data in the machine
and prevent documents from being printed immediately ( Printing Documents
Held in the Machine(P. 351) ). You can congure settings so that printing cannot be
performed until the user is authorized on the machine, which ensures greater
security and reduces the risk of other people viewing or inadvertently picking up
sensitive documents. Administrator privileges are required in order to congure
these settings.
1Press (Settings/Register).
2Press <Function Settings> <Print> <Forced Hold>.
3Press <On>, set the necessary conditions, and then press <OK>.
●You can set detailed conditions for holding printer jobs, such as the user or IP address. If no conditions are
set, all print jobs are held except for jobs from unidentied users. If no conditions are set and a print job
from an unidentied user is received, it is canceled without being held.
Managing the Machine
573

Setting the conditions for holding documents
1Press <Register>.
2Set the conditions for holding documents, and press <OK>.
<Condition Name>
Enter a name for the condition. Use a name that will be easy to identify when displayed in a list.
<Job Condition>
The types of conditions listed below can be selected.
<User Name> Specify a particular user name as the condition. If this is left blank, print
documents for which the user cannot be identied will be targeted.
<IP Address> Specify a particular IP address as the condition. You can also specify a
range of IP addresses.
<Input Method> Specify a particular printing protocol as the condition.
<Job Action>
Select how to handle documents that match the conditions. When <Hold as Shared Job> is selected, you
can set <ID for Substitution> to specify the user name output to the log when printing. Select <Cancel>
to discard the document.
<Target>
You can set either a value specied by the operation target, or one not specied.
3Set the order in which to apply the conditions, and press <OK>.
●The conditions are applied in the order that they are listed, starting at the top. If you want to change
the order, select a condition in the list and press <Raise Priority> or <Lower Priority>.
●To edit the details of a condition, select it in the list and press <Details/Edit>.
●To disable a condition, select it in the list and press <Validate/Invalidate>.
●To delete a condition, select it in the list and press <Delete> <Yes>.
Conguring the detailed settings for forced hold printing
●You can congure detailed settings for documents that are held for printing, such as how long to save them
and how to display them. <Print>(P. 846)
Managing the Machine
574

Allowing Only Encrypted Secure Print
You can congure the machine to only allow printing of Encrypted Secure Print documents from a computer, which
can prevent information leakage due to unprotected print data. With this setting, documents cannot be printed using
normal printing operations. Users are required to enter a password on the machine when printing Encrypted Secure
Print documents. Printing More Safely with Encrypted Secure Print(P. 354)
(Settings/Register) <Function Settings> <Print> <Only Allow Encrypted Print Jobs>
<On> <OK> (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>
Managing the Machine
575
Restricting the Use of Memory Media
72JY-09U
Although memory media such as USB memory devices provide convenience, they can also be a source of information
leakage if they are not properly managed. This section describes the procedures for prohibiting the use of memory
media, as well as for restricting the ability to save scanned documents on memory media, or print data saved on
memory media. Administrator or DeviceAdmin privileges are required in order to congure these settings.
(Settings/Register) <Function Settings> <Store/Access Files> <Memory Media Settings>
<Use Scan/Print Function> Select <Off> for <Use Scan Function> or <Use Print Function>
<OK> (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>
LINKS
Using Memory Media(P. 441)
Printing From Memory Media (Media Print)(P. 363)
Managing the Machine
576
Adding a Digital Signature to Sent Files
72JY-09W
By adding a digital signature to a scanned document that is sent in a particular le format, you can certify that the
document has not been altered and is guaranteed by the creator. The machine can add a device signature or user
signature to documents.
Device Signature
The device signature uses a key and certicate mechanism, enabling the recipient
of a scanned document to verify that it was created on this machine. The
recipient can check what machine was used to create the document, as well as
whether the document has been altered. Before you can add a device signature,
the key and certicate (device certicate) used for the device signature needs to
be created on the machine. Generating a Device Signature
Certicate(P. 578)
User Signature
The user signature is linked with personal authentication management functions,
enabling the recipient of a scanned document to verify who created it. As with
the device signature, the user signature enables the recipient to check whether
the document was altered after the signature was added. A system option is
required in order to use this function ( System Options(P. 1101) ). Before you
can add a user signature, a key and certicate (user certicate) needs to be
registered for each user via the Remote UI. Registering a User Signature
Certicate(P. 579)
●For information on validating certicates, registering certicates in the trusted certicates list, and verifying
signatures on the reader side, see the documentation for the software that supports the PDF format (such
as Adobe Reader/Adobe Acrobat).
●You can set multiple digital signatures for a le. In this case, device signatures are applied before user
signatures.
●If a recipient veries a PDF or XPS that has had multiple signatures added to it using software that supports
the PDF format (such as Adobe Reader/Adobe Acrobat) or the XPS format (such as XPS Viewer), only the last
signature added to the le remains valid. The device signature causes the document to be handled as if it
has been altered.
●You cannot forward a received I-fax document with a user signature from the machine.
Displaying a digital signature (visible signature)
Digital signature information can be displayed on the rst page of the document, making it easy for the reader
to see that a digital signature has been added. Only PDF documents support visible signatures. Adding a
Digital Signature(P. 418)
Managing the Machine
577
Generating a Device Signature Certicate
72JY-09X
The key and certicate (device certicate) required when adding a device signature
can be generated on the machine. Designate an administrator to generate these
items. Once they are generated, you can add a digital signature to scanned
documents that are sent in a particular le format. Adding a Digital
Signature(P. 418)
(Settings/Register) <Management Settings> <Device Management> <Certicate
Settings> <Generate Key> <Generate/Update Device Signature Key> <Yes> <OK>
Key and certicate for device signature
●The generated key and certicate are registered with the name "Device Signature Key". You can register only
one key and certicate for the device signature.
Managing the key and certicate for device signature
You can check the detailed settings of the key and certicate on the screen that is displayed when you press
(Settings/Register) <Management Settings> <Device Management> <Certicate Settings> <Key
and Certicate List> <Key and Certicate List for This Device>.
●If is displayed, the key is corrupted or invalid. You can update the key and certicate by conguring the
settings again.
●If you select <Device Signature Key> and press <Certicate Details>, detailed information about the device
signature certicate is displayed. You can also press <Verify Certicate> on this screen to check whether the
certicate is valid.
●The PDF/XPS le contains sender information that the reader of the le can use to validate the reliability of
the device signature by matching it with the SHA-1 message digest number. You can verify this information
in <Certicate Thumbprint> on this machine.
Ensuring that a device signature is always added when sending
●You can congure the machine so that a device signature is always added to scanned documents that are
sent in a particular le format, regardless of the user settings. You can also restrict the le formats used
when sending documents, which ensures that no documents can be sent without a device signature.
Administrator or DeviceAdmin privileges are required in order to congure these settings. <Common
Settings> <Always Add Device Signature to Send>(P. 824)
LINKS
Generating the Key and Certicate for Network Communication(P. 552)
Registering a Key and Certicate for Network Communication(P. 600)
Registering a User Signature Certicate(P. 579)
Managing the Machine
578
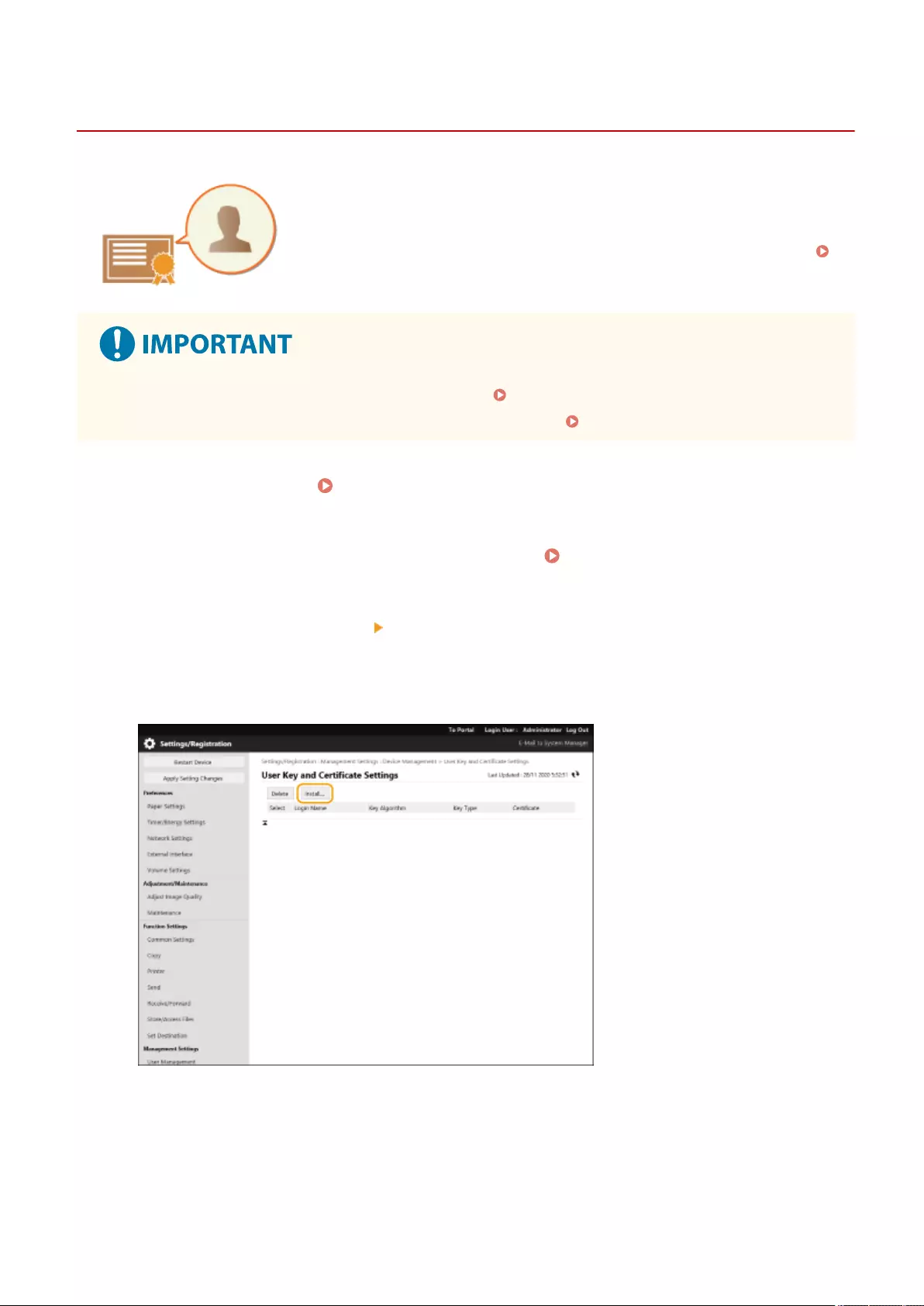
Registering a User Signature Certicate
72JY-09Y
The key and certicate (user certicate) required when adding a user signature can
be registered via the Remote UI. Designate an administrator to register these items.
Once they are registered, users who log in with personal authentication can add a
digital signature to scanned documents that are sent in a particular le format.
Adding a Digital Signature(P. 418)
●A system option is required in order to use this function. System Options(P. 1101)
●You may not be able to register some types of keys and certicates. System Specications(P. 1084)
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [User Key and Certicate Settings].
4Click [Install...].
5Register the certicate.
Managing the Machine
579
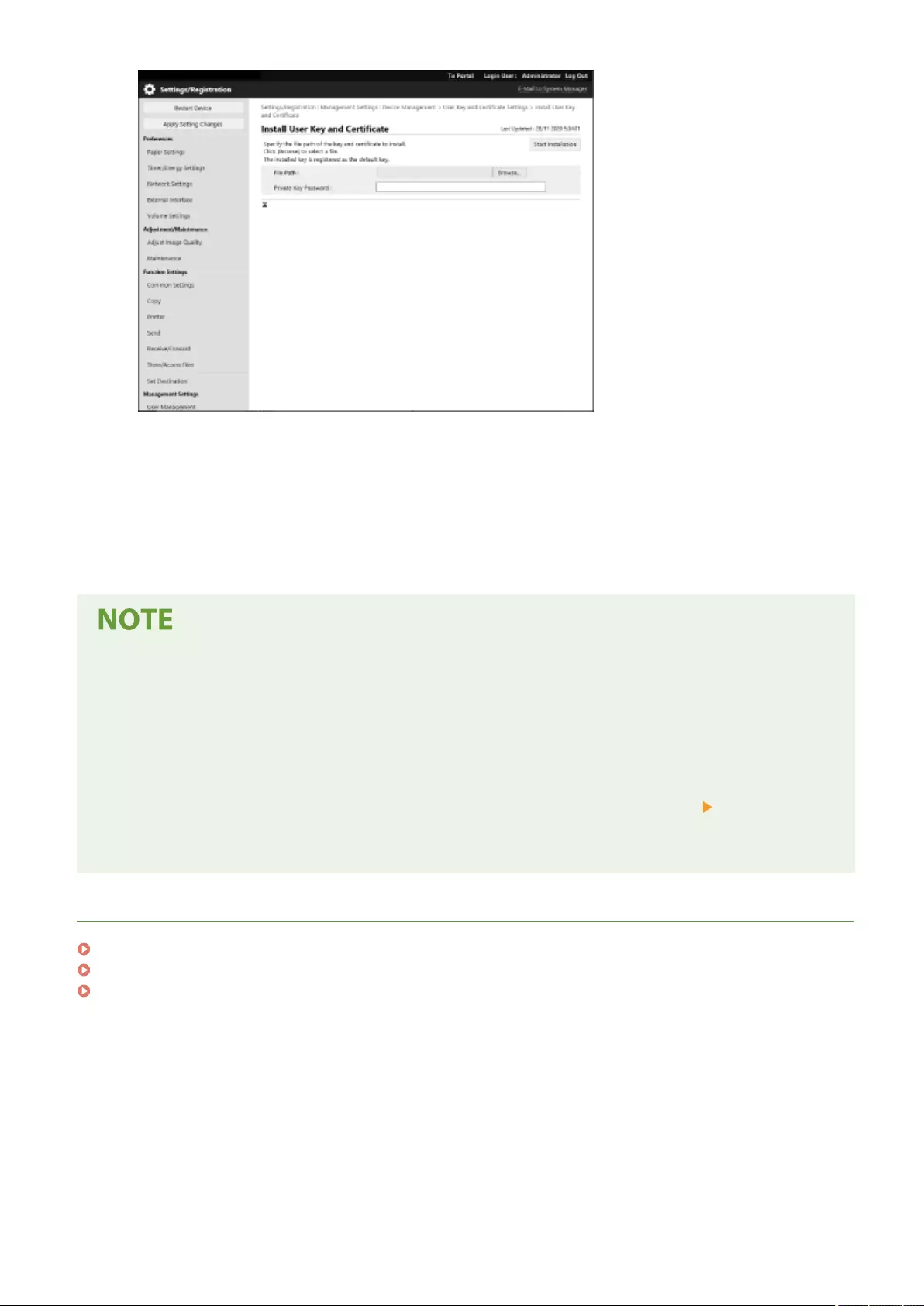
1Click [Browse...], and specify the le (user certicate) to install.
●You may not be able to specify the le name if it is too long.
2Enter the password of the private key.
●In [Private Key Password], enter the password registered to the key.
3Click [Start Installation].
Managing the keys and certicates for user signature
You can check the detailed settings or delete keys and certicates on the screen displayed in step 4.
●If you log in with Administrator privileges, the keys and certicates for all user signatures are displayed. For
users who do not log in with Administrator privileges, only the key and certicate of the logged in user are
displayed.
●Click a login name to display detailed information about the certicate.
●To delete keys and certicates, select the ones that you want to delete, and click [Delete] [OK].
●For information on the certicate authority that issues the User Certicate for each user compatible with the
machine for adding a user certicate, see the notice included with the optional product.
LINKS
Generating the Key and Certicate for Network Communication(P. 552)
Registering a Key and Certicate for Network Communication(P. 600)
Generating a Device Signature Certicate(P. 578)
Managing the Machine
580
Managing the Machine from a Computer (Remote UI)
72JY-0A0
You can remotely operate the machine from your computer's Web browser to perform operations such as checking
the printing status, changing the machine settings, or editing the Address Book. This convenient feature enables you
to remain at your desk while operating the machine. To perform remote operation, enter the IP address of the
machine in your Web browser and open the Remote UI portal page. For more information on the system requirements
for the Remote UI, see System Specications(P. 1084) .
How to Use the Remote UI
This section describes the Remote UI login procedure and the features of the Remote UI main screen.
Starting the Remote UI(P. 583)
Checking the Status of Waiting Documents and the Machine
This section describes how to check the status of copied, printed, sent, and received documents, as well as error
information and the remaining amount of paper.
Checking the Status and Logs(P. 587)
Other Functions Available Using the Remote UI
This section describes various other convenient functions that can be performed via computer using the
Remote UI, such as editing the Address Book, checking les in the Fax/I-Fax Inbox from a computer, and
backing up the machine settings in case they are needed.
Turning OFF/Restarting the Machine(P. 591)
Registering Destinations via the Remote
UI(P. 592)
Sharing an Address List with Specic
Users(P. 596)
Registering User Groups(P. 598)
Registering a Key and Certicate for Network
Communication(P. 600)
Conguring the Expiration Check Method for
Received Certicates(P. 605)
Generating a Key and Certicate Signing
Request (CSR)(P. 608)
Retrieving/Updating a Certicate from an
SCEP Server(P. 611)
Managing Stored Files(P. 617)
Managing the Logs(P. 620)
Managing the Machine
581

Importing/Exporting the Setting
Data(P. 625)
Updating the Firmware(P. 640)
Updating the Firmware (Distribution)(P. 642)
Setting Scheduled Updates(P. 645)
Displaying Messages from the
Administrator(P. 647)
Conguring the Visual Message
Function(P. 649)
Sending E-Mail Notication When an Error
Occurs(P. 652)
When using a proxy server
●You cannot access the machine via a proxy server. If a proxy server is used in your environment, congure
your Web browser to bypass the proxy server and access the machine directly.
Managing the Machine
582
Starting the Remote UI
72JY-0A1
To start the Remote UI, enter the IP address of the machine in your Web browser. Check the IP address congured for
the machine before performing this operation. Setting an IP Address(P. 34)
For security reasons, you cannot log in to the Remote UI using the default password (7654321) for the Administrator
user. Log in to the Remote UI after changing the password of the Administrator user from the control panel.
(Settings/Register) <Management Settings> <User Management> <Authentication
Management> <Register/Edit Authentication User> change the password for "Administrator"
●When both the machine and the Active Directory server are set as user authentication devices (
Conguring the User Login Methods and Authentication Devices(P. 513) ), the time setting of the Active
Directory server needs to match that of the machine.
Using TLS encryption for communication
●When you want to encrypt the Remote UI communication, congure the TLS key and certicate (
Conguring the Key and Certicate for TLS(P. 549) ), go to the <Remote UI Settings> setting ( <Remote
UI Settings>(P. 862) ) and set <Use TLS> to <On>, then turn the machine OFF and back ON.
Logging in to the Remote UI using the default password of the Administrator user
●You can also set to allow logging in to the Remote UI using the default password of the Administrator user.
( (Settings/Register) <Management Settings> <Security Settings> <Authentication/Password
Settings> <Password Settings> <Allow Use of Default Password for Remote Access> <On>)
Starting the Remote UI(P. 583)
Setting the Timeout Time after Logging In to the Remote UI(P. 584)
Remote UI Screen(P. 585)
Starting the Remote UI
1Start the Web browser.
2Enter the IP address of the machine, and press the [ENTER] key on the computer
keyboard.
Managing the Machine
583
●Enter "http://<IP address of the machine>/" in the address input eld.
●When using an IPv6 address, enclose the IP address portion in brackets ([ ]) (Example: http://
[fe80:2e9e:fcff:fe4e:dbce]/).
If the Remote UI does not start
●If the login screen is not displayed in step 3 of this procedure, clear the Web browser's cache and enter the
IP address again.
If a message related to security is displayed
●A warning message may be displayed if the Remote UI communication is encrypted. If there are no
problems with the certicate or TLS settings, you can continue using the Web browser.
3Log in to the Remote UI.
●Enter a registered user name and password in [User Name] and [Password], select the login destination in
[Login Destination], and click [Log In].
●If [Log In (Guest)] is displayed, unregistered users can click this button and log in as general users.
●With some user authentication settings, the Remote UI may skip the login screen and display the main
screen (portal page) directly. Remote UI Screen(P. 585)
4Check that the Remote UI portal page is displayed. Remote UI Screen(P. 585)
●When using the Remote UI to operate the machine, do not use the Web browser's [Back] button. The page
may not change properly if you use the [Back] button.
Setting the Timeout Time after Logging In to the Remote UI
The user is automatically logged out if no operations are performed for a certain period of time after logging in to the
Remote UI. You can set the time until the user is logged out.
Start the Remote UI [Settings/Registration] [Network Settings] [Session Settings] [Timeout
After Logging in to Remote UI] set the timeout time after login [OK]
Managing the Machine
584
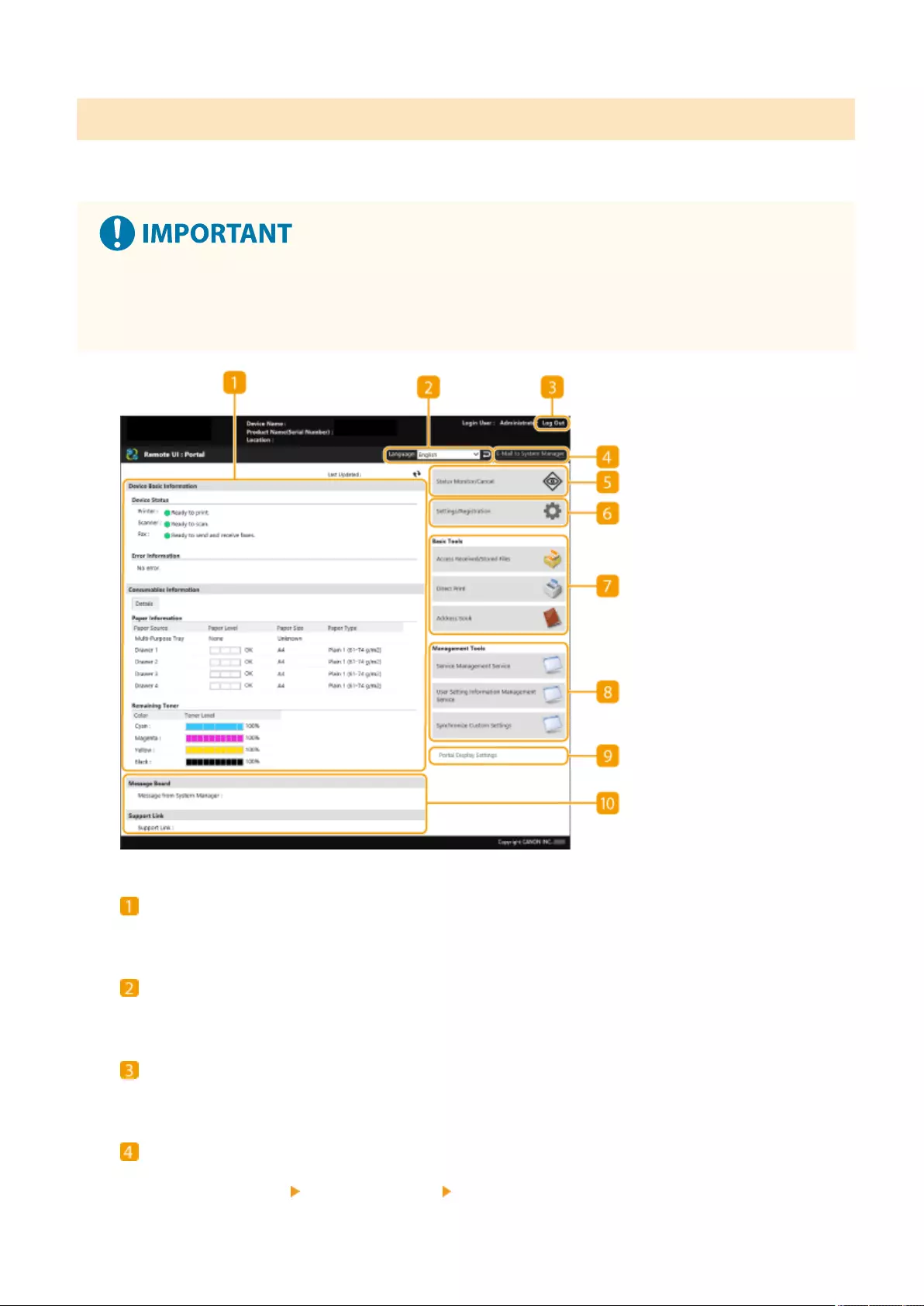
Remote UI Screen
The portal page shown below is displayed when you log in to the Remote UI. This section describes the items
displayed on the portal page and the basic operations.
●Some display items and functions are only available if you log in with Administrator privileges.
●If multiple users are operating the Remote UI at the same time or the control panel of the machine is being
operated at the same time as the Remote UI, the last operation that is performed is effective.
Device information
The current machine status is displayed, along with information about errors, consumables, etc.
Display language
You can switch the language that is displayed on the Remote UI screen.
[Log Out]
Log out from the Remote UI and return to the login page.
[E-Mail to System Manager]
Create an e-mail message to send to the administrator. The administrator's e-mail address can be set in
[Settings/Registration] [User Management] [System Manager/Contact Person Information Settings].
Managing the Machine
585
[Status Monitor/Cancel]
You can check the status of jobs or cancel processing. You can also check detailed information about the
amount of remaining toner and paper, etc. Checking the Status and Logs(P. 587)
[Settings/Registration]
You can change the machine settings. You can save the setting details to a computer, or import them from a
computer to the machine. Importing/Exporting the Setting Data(P. 625)
●You can use either the control panel or the Remote UI to change most machine settings, but some settings
can only be changed using one or the other.
[Basic Tools]
You can perform operations such as printing documents or registering/editing destinations.
Managing Stored Files(P. 617)
Directly Printing Files without Opening Them(P. 358)
Registering Destinations via the Remote UI(P. 592)
[Management Tools]
You can manage applications and user setting information ( Deleting User Setting Information(P. 534) ).
[Portal Display Settings]
You can change the order in which the [Basic Tools] and [Management Tools] buttons are displayed on the
portal page.
Messages/support
Messages from the administrator are displayed, along with links to machine support information.
Displaying Messages from the Administrator(P. 647)
●To update the current page with the latest information, click .
LINKS
Settings/Registration(P. 670)
Managing the Machine
586
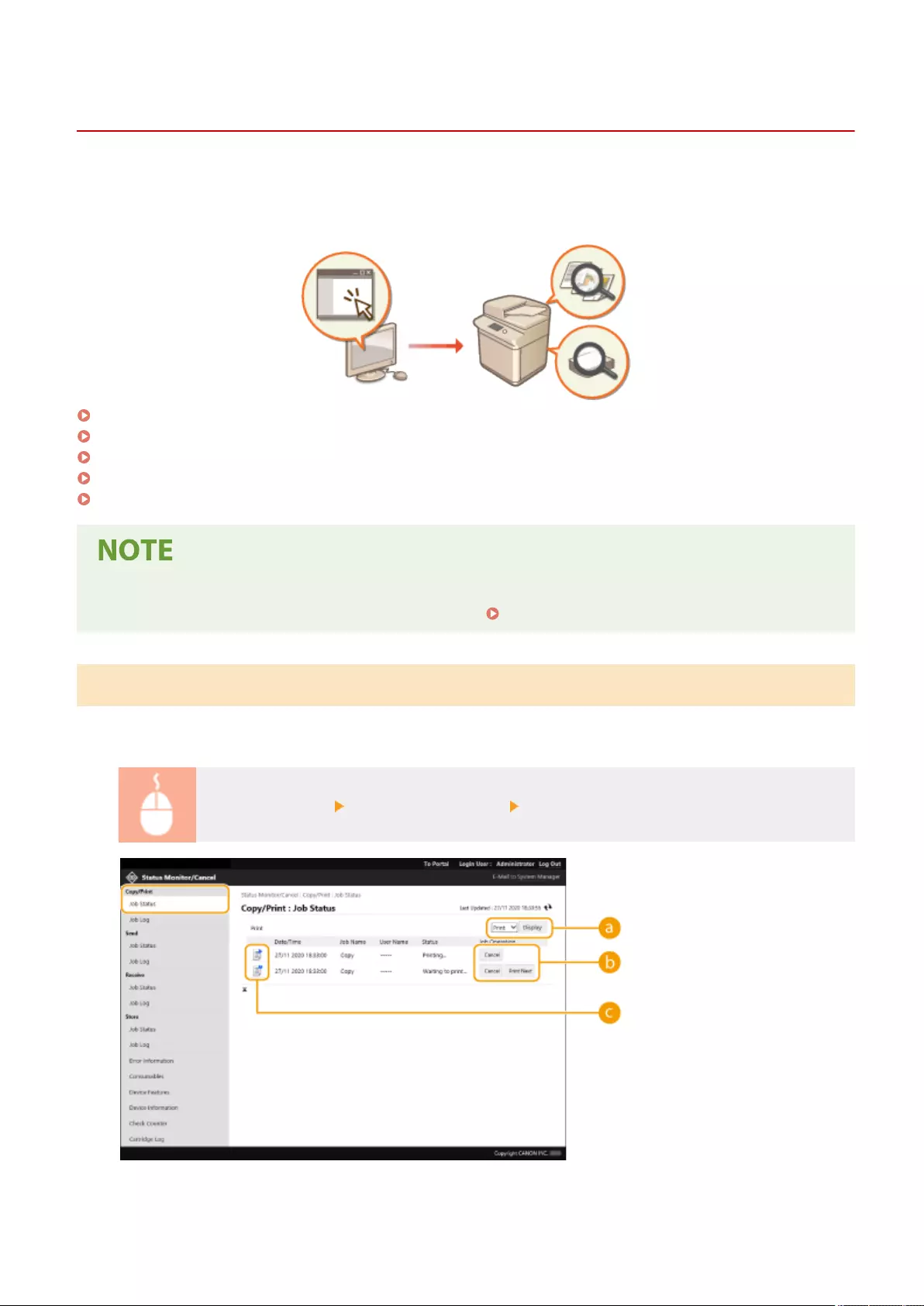
Checking the Status and Logs
72JY-0A2
You can use the Remote UI to check the status of documents that are waiting to be processed, as well as the logs for
documents that have been processed. You can also check the status of the machine, such as error information and the
remaining amount of consumables.
Checking the Status of Copies/Prints(P. 587)
Checking the Status of Sent/Received Documents(P. 588)
Checking the Status of Stored Documents(P. 589)
Checking the Job Log(P. 589)
Checking the Machine Status(P. 590)
●When personal authentication management is used, you can restrict users from performing operations on
the jobs of other users on the <Status Monitor> screen. <Restrict Access to Other User Jobs>(P. 857)
Checking the Status of Copies/Prints
You can check the status of documents that are waiting to be copied or printed. You can also output a document
before the others, or cancel a document.
Start the Remote UI [Status Monitor/Cancel] [Job Status] under [Copy/Print]
Managing the Machine
587
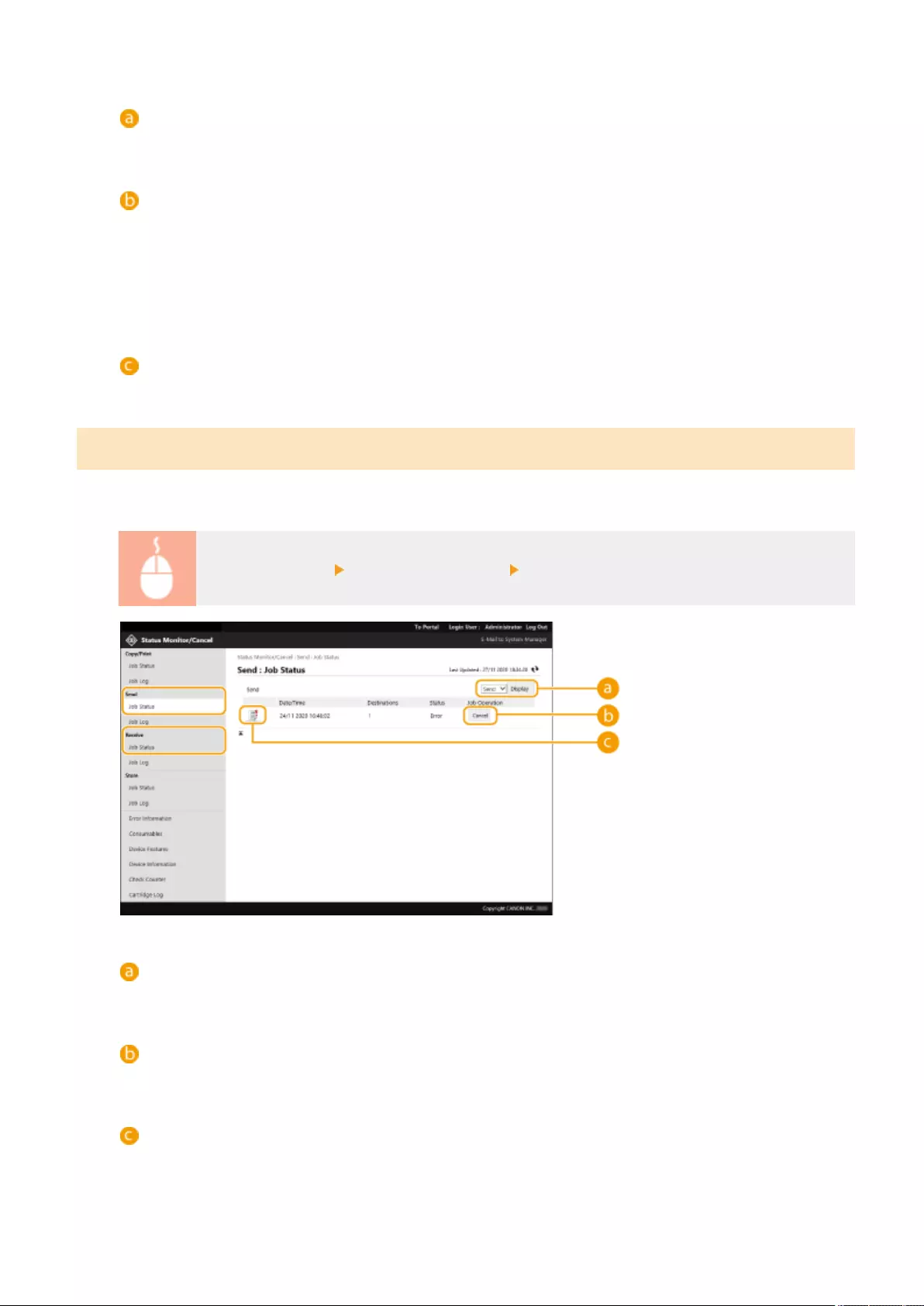
Function selection
Select the function that you want to check, and click [Display].
Operation buttons
●[Cancel]: Copying or printing is canceled. The canceled document is deleted and cannot be recovered.
●[Print Next]: The document is output immediately after the current document is complete.
●[Pause]: Documents that are being printed from a computer are paused. You cannot pause documents
that are being copied. Press [Resume] to resume printing a document that was paused.
Document icon
Click the icon to display detailed information about the document.
Checking the Status of Sent/Received Documents
You can check the status of faxes and e-mails that are waiting to be sent, faxes that have been received, and faxes that
are waiting to be forwarded. You can also cancel the process for sending and receiving documents.
Start the Remote UI [Status Monitor/Cancel] [Job Status] under [Send] or [Receive]
Function selection
Select the function that you want to check, and click [Display].
[Cancel]
Document sending or receiving is canceled. The canceled document is deleted and cannot be recovered.
Document icon
Click the icon to display detailed information about the document.
Managing the Machine
588
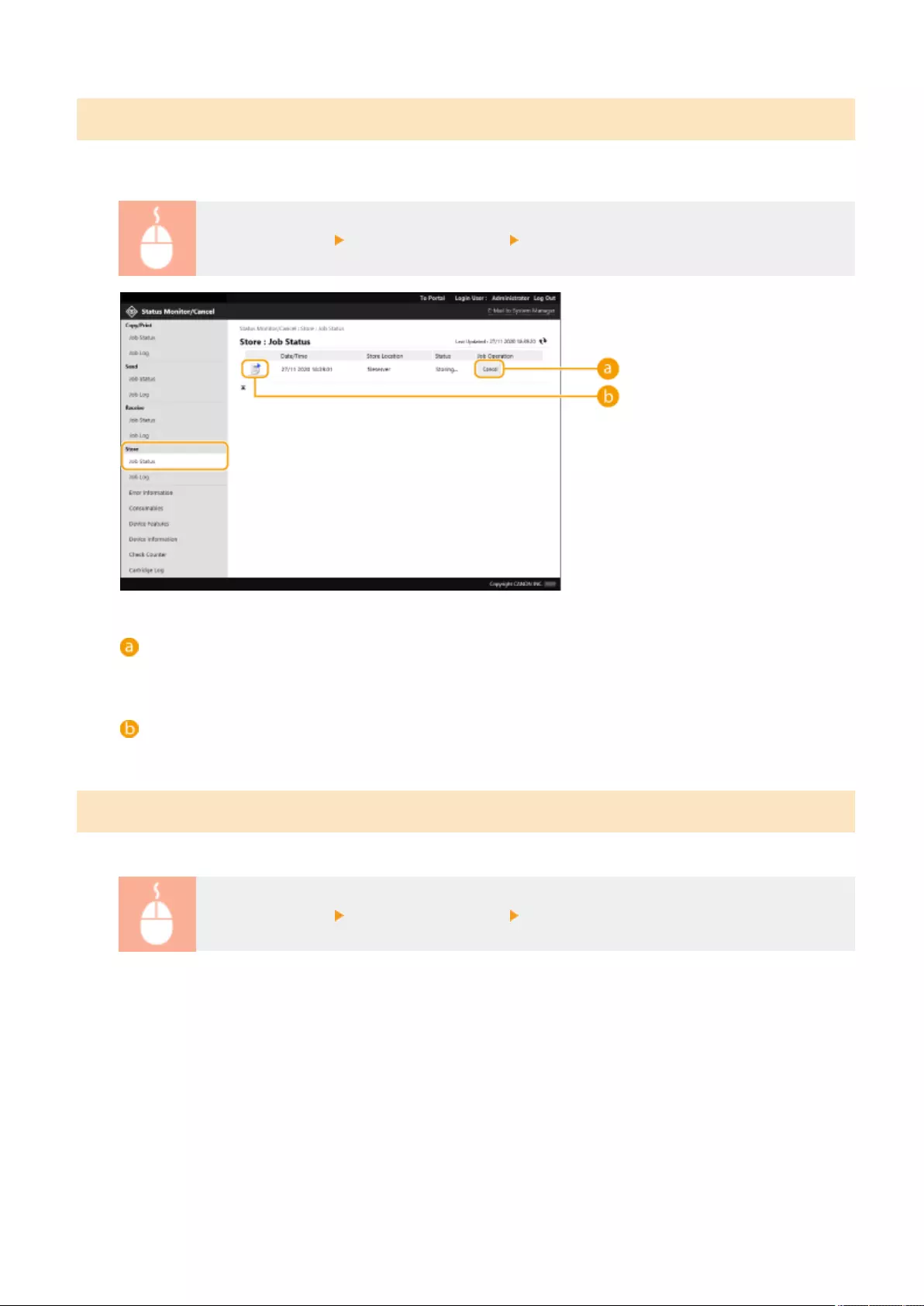
Checking the Status of Stored Documents
You can check the status of documents that are waiting to be stored. You can also cancel the process for storing
documents.
Start the Remote UI [Status Monitor/Cancel] [Job Status] under [Store]
[Cancel]
Document storing is canceled. The canceled document is deleted and cannot be recovered.
Document icon
Click the icon to display detailed information about the document.
Checking the Job Log
You can display a log for documents that were copied, printed, sent, received, or stored.
Start the Remote UI [Status Monitor/Cancel] [Job Log]
Managing the Machine
589
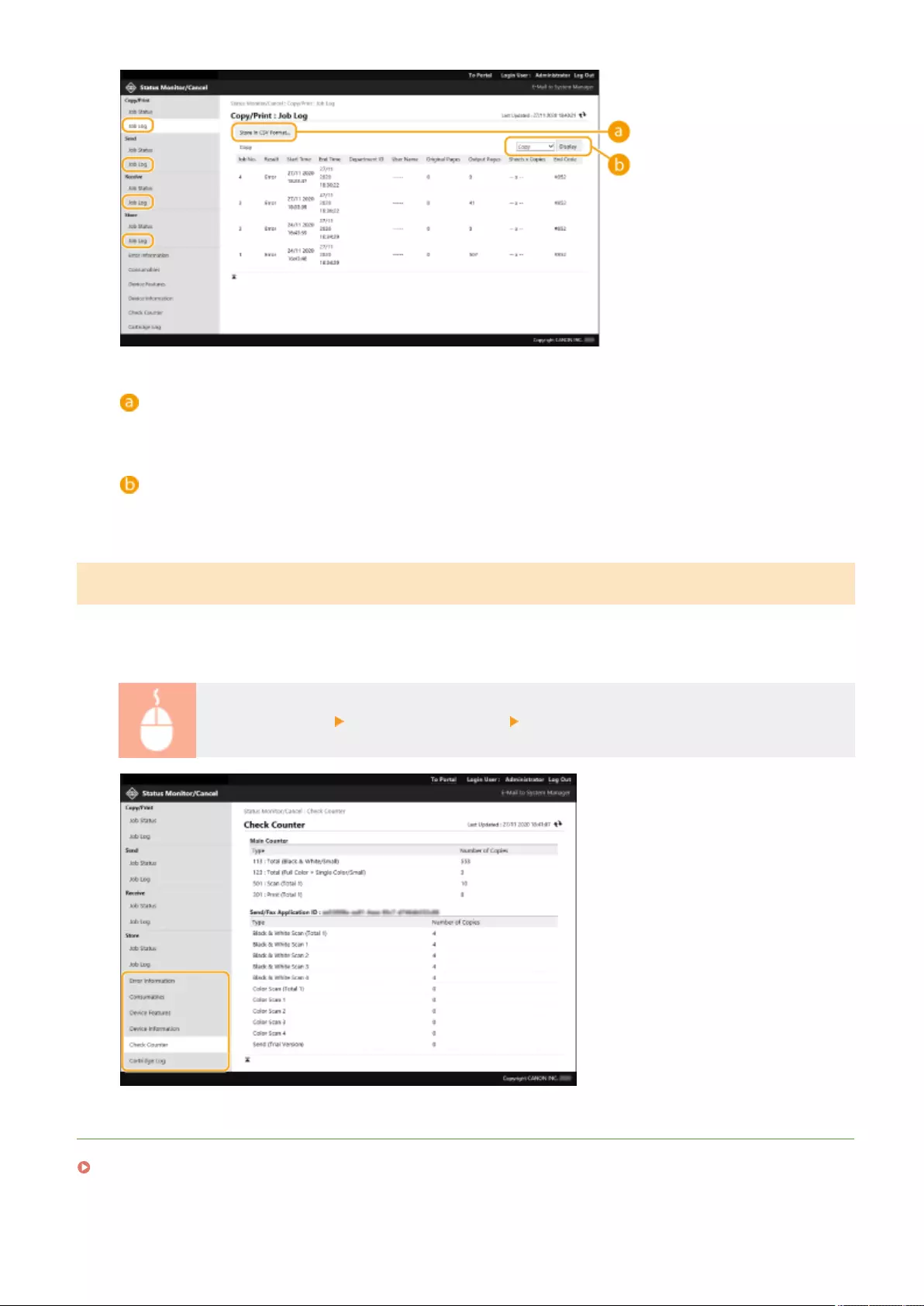
[Store in CSV Format...]
The log data can be exported and saved as a CSV le (*.csv) on the computer.
Function selection
Select the function that you want to check, and click [Display]. The displayed functions may vary depending
on your machine model and optional equipment.
Checking the Machine Status
You can check a variety of information about the machine, such as error information, the amount of remaining paper
and toner, information about attached optional equipment, and the total number of pages that have been printed up
to now.
Start the Remote UI [Status Monitor/Cancel] Select the item that you want to check
LINKS
Starting the Remote UI(P. 583)
Managing the Machine
590
Turning OFF/Restarting the Machine
72JY-0A3
You can use the Remote UI to shut down or restart the machine.
●When the machine is turned OFF or restarted, any documents that are being printed or sent are canceled.
Turning OFF the Machine(P. 591)
Restarting the Machine(P. 591)
Turning OFF the Machine
Start the Remote UI [Settings/Registration] [Device Management] [Remote Shutdown]
[Start]
Restarting the Machine
Start the Remote UI [Settings/Registration] [Restart Device] [Perform Restart] [OK]
If optional equipment is not recognized after restart
●The machine may not recognize optional equipment after it is restarted. If this happens, turn OFF the power
of the optional equipment, and then turn it back ON.
LINKS
Starting the Remote UI(P. 583)
Turning ON the Machine(P. 95)
Turning OFF the Machine(P. 96)
Managing the Machine
591
Registering Destinations via the Remote UI
72JY-0A4
PMW-RGUI
You can use the Remote UI to register destinations in the Address Book. You can also check the registered details and
edit the Address Book.
●For instructions on sharing an address list, see Sharing an Address List with Specic Users(P. 596) .
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Address Book] on the portal page. Remote UI Screen(P. 585)
3Register the destination.
●For more information on address lists, see Registering Destinations in the Address Book(P. 195) .
1Click the address list in which to register the destination ([Personal Address List], User Group Address
Lists, [Address List 01] to [Address List 10], or [Address List for Administrators]).
●[Personal Address List] is for the exclusive use of the logged-in user, and is only available when
personal authentication management is enabled.
●[Address List for Administrators] is only available to administrators who log in with Administrator or
DeviceAdmin privileges.
●If the page for entering a PIN is displayed, enter the PIN and click [OK].
●If you want to share the destination with a registered user group, select a registered User Group
Address List.
●You can also manage User Group Address Lists by enabling only users with Administrator privileges to
register/edit destinations from the Remote UI. (<Set Destination> <Use User Group Address
List>(P. 852) )
2Click [Register New Destination...].
3Select the destination type and click [Set].
Managing the Machine
592
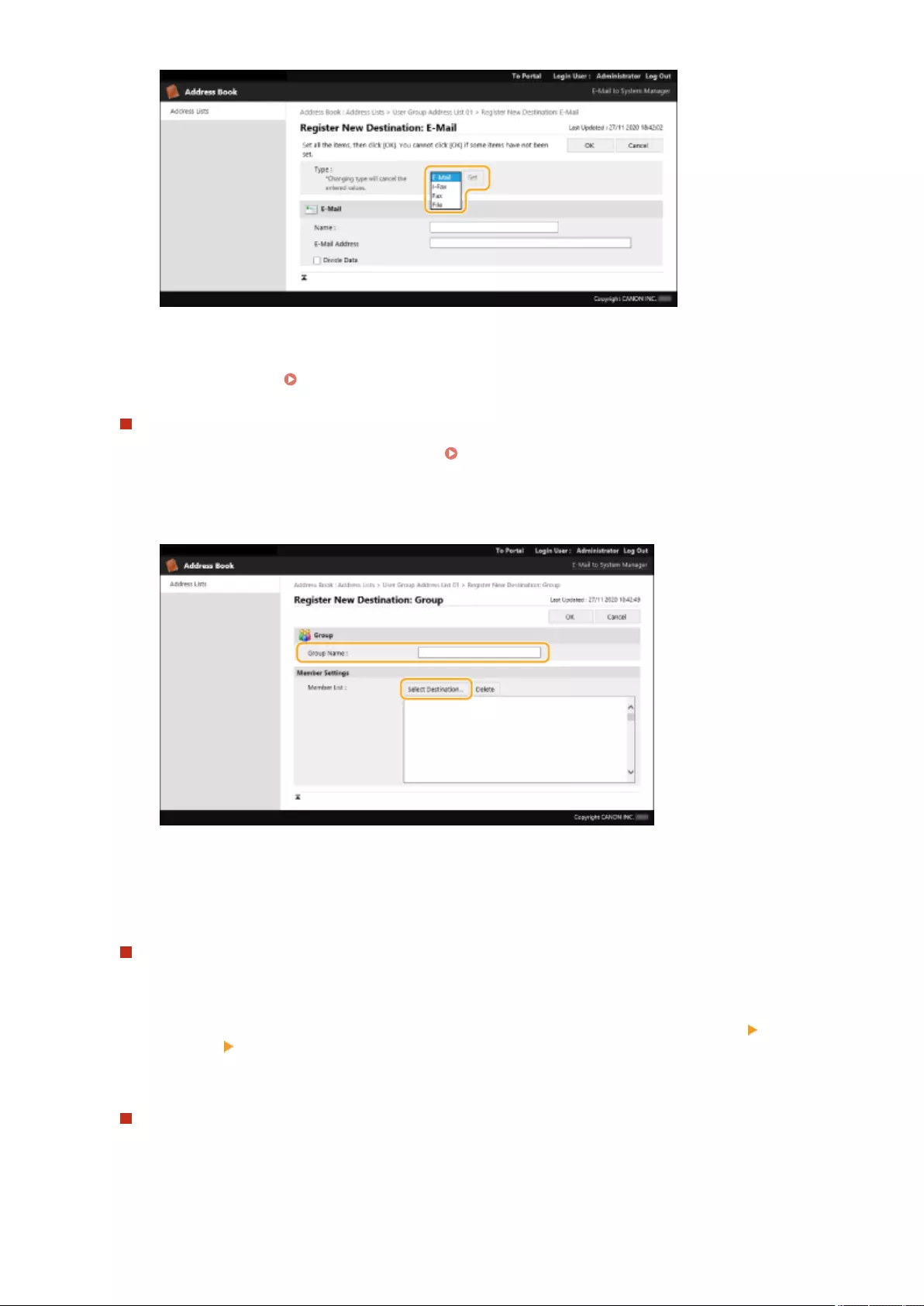
4Register the necessary information and click [OK].
●The displayed items vary depending on the destination type. For more information on the information
to register, see Registering Destinations in the Address Book(P. 195) .
Registering a group destination
For more information on group destinations, see Registering Multiple Destinations as a Group(P. 205) .
1Click [Register New Group...].
2Enter a name for the group in [Group Name], and click [Select Destination...] for [Member List].
3Select the check box for the destinations that you want to register to the group, and click [OK].
4Click [OK].
Registering a name for the address list
Click [Register Address List Name...] or [Register/Change Address List Name...], enter the name, and click
[OK].
You can set to also change the name of the user group address book when a user group name is changed.
Log in to the Remote UI as a user with Administrator privileges, press [Settings/Registration] [Set
Destination] [Personal Address List/User Group Address List Settings], and select the [Apply User Group
Name Change to User Group Address List Name] check box. [Apply User Group Name Change to User Group
Address List Name] is only available when personal authentication management is enabled.
Checking/editing destination details
You can click the [Type] icon or name of a destination to check the details of the destination. To edit the
destination, click [Edit], change the registered details, and click [OK].
Managing the Machine
593
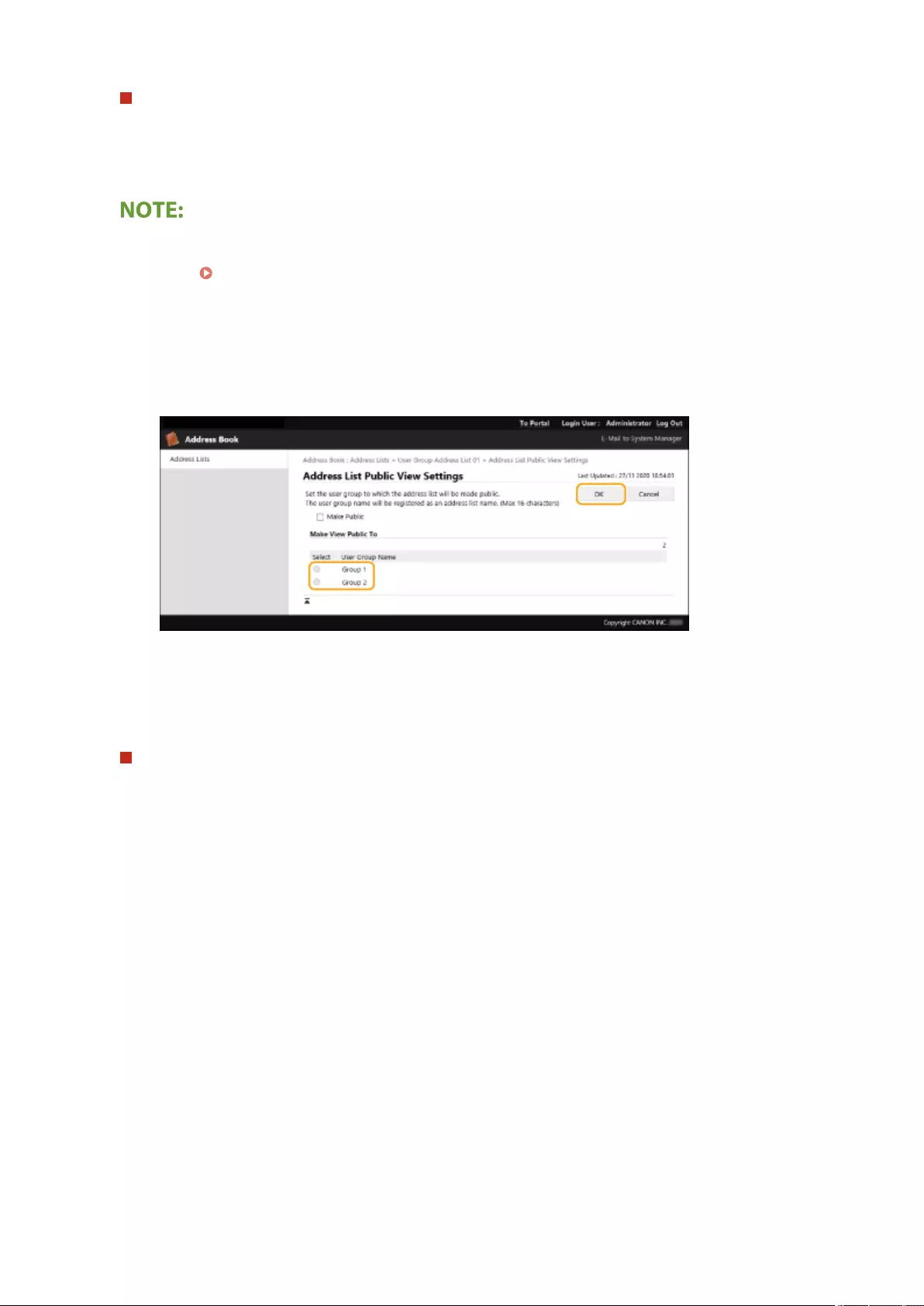
Registering to a user group address list
When using personal authentication management, an address list can be shared between users in the same
user group. First, set up the user group that will share the address list, then register the destinations that you
want to share.
●Users can be registered to a user group to share the address lists in an address book between registered
users. Registering User Groups(P. 598)
1Click the address list in which to register the destination ([User Group Address List 01] to [User Group
Address List 50]).
2Click [Public View Settings...].
3Select the group in which to share the address list, and click [OK].
4Click [Register New Destination...] or [Register New Group...].
5Register the necessary information and click [OK].
Registering to a one-touch button
1Click [Address List One-Touch].
2Click [Not Registered] or an unregistered one-touch number.
●[Not Registered] is displayed in [Name] for unregistered one-touch buttons.
●To display one-touch buttons that are not shown in the list, select the range of numbers in [List
Number], then click [Display].
Managing the Machine
594
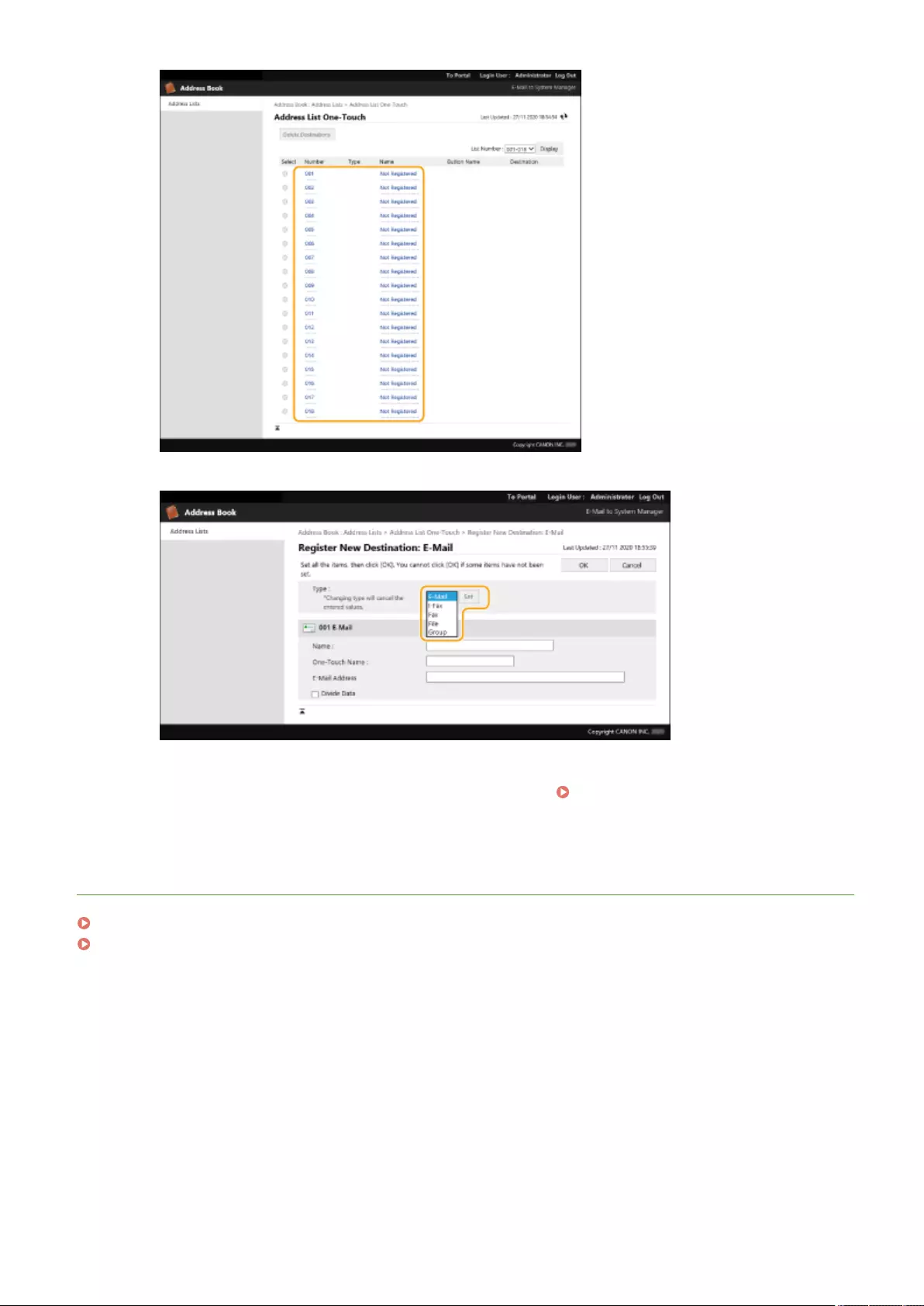
3Select the destination type and click [Set].
4Register the necessary information and click [OK].
●For more information on the information to register, see Registering a Destination in a One-
Touch Button(P. 210) .
LINKS
Registering Destinations(P. 190)
Restricting Use of the Address Book(P. 566)
Managing the Machine
595
Sharing an Address List with Specic Users
72JY-0A5
You can use a user group address list to share an address list between specic users. This is useful when using a
shared address list within the same department.
Procedure for Sharing Addresses
Follow the procedure below.
Registering Users.
●Register the users to share with. Registering User Information in the Local
Device(P. 495)
If you are using Server Authentication, proceed to step 2.
Registering a Group to Share
●Register a user group. Registering User Groups(P. 598)
Setting the Group Share Destination
●Specify the group created in step 2 in [Public View Settings...] from the address list in
which to register the destination. Registering Destinations via the Remote
UI(P. 592)
Managing the Machine
596

●To add new users to an existing group, set the destination group when registering the users in step 1.
Managing the Machine
597
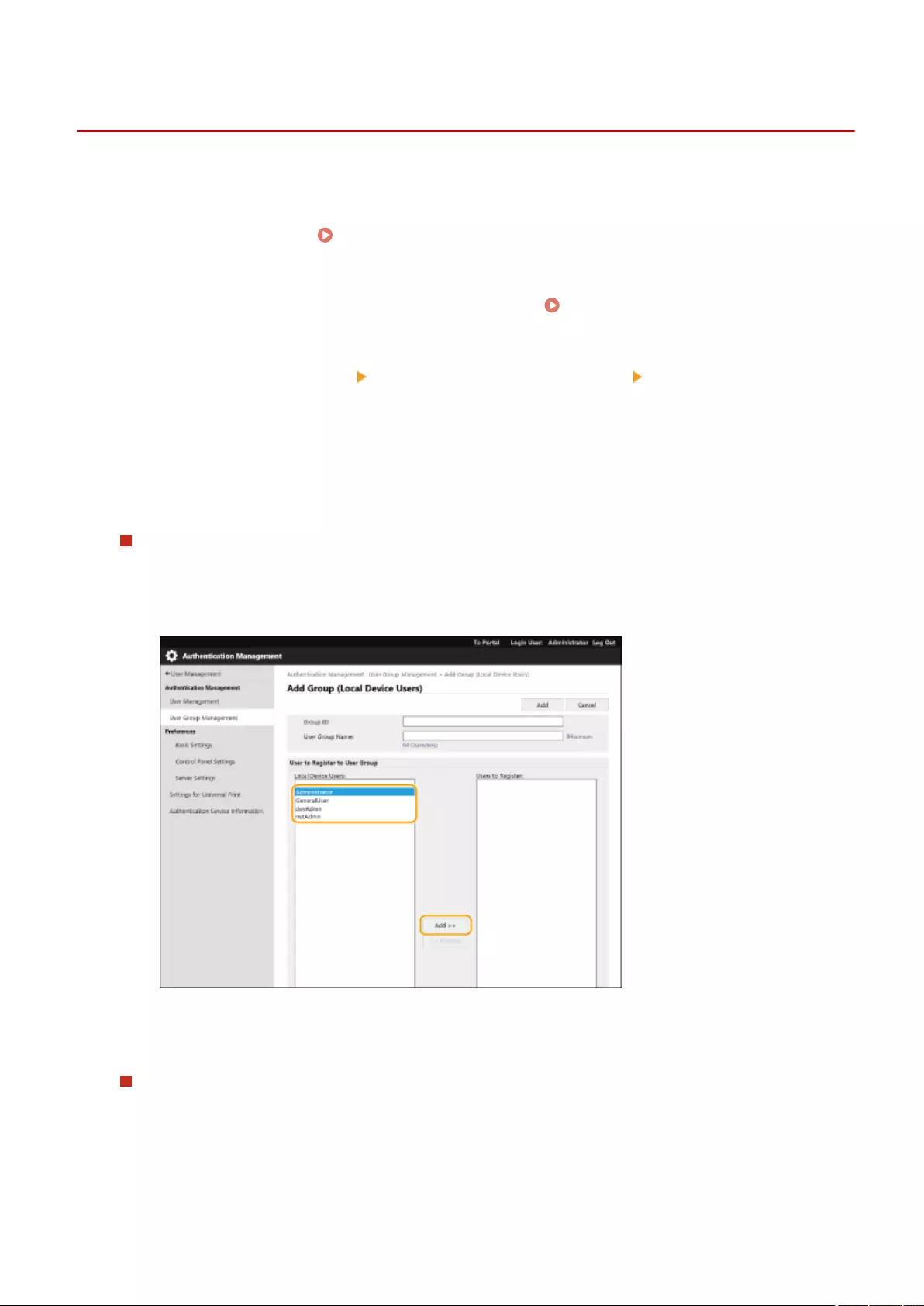
Registering User Groups
72JY-0A6
Register user groups. User group address lists can be shared between registered user groups.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [User Management] [Authentication Management] [User Group
Management].
4Click [Add Group (Local Device Users)...] or [Add Group (Other Users)...].
●Select [Add Group (Other Users)...] if Server Authentication is set.
Adding Groups to a Local Device
1Enter the group ID and user group name.
2Select the users to include in the user group, and click [Add >>].
3Click [Add].
Adding Groups to an Authentication Server
1Enter the group ID, user group name, attribute name, and attribute value.
2Click [Add].
Managing the Machine
598

●For [Attribute Name:], enter the "Attribute Name" (such as company name, department or position) managed
by the server authentication destination (ActiveDirectory, LDAP server, etc.). For example, enter "company" or
"department".
●For [Attributes:], input the values you wish to extract as a group from the values listed for "Attribute Name" in
the server. For example, you may enter "Company A" for the company name, and "Sales 1" for the
department name.
Managing the Machine
599
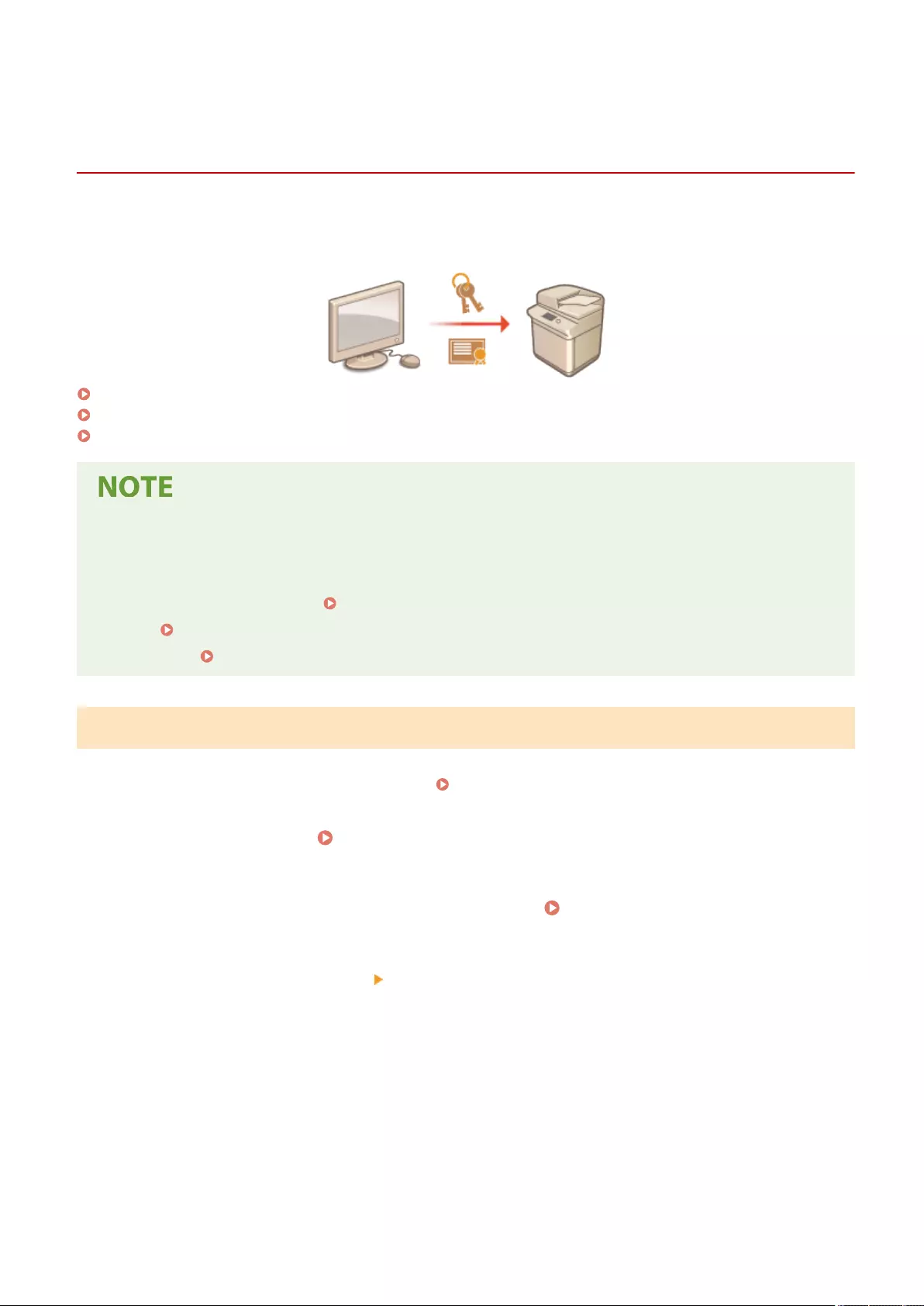
Registering a Key and Certicate for Network
Communication
72JY-0A7
You can use the Remote UI to register keys/certicates, CA certicates, and S/MIME certicates to the machine from
your computer. Designate an administrator to register these items.
Registering a Key and Certicate(P. 600)
Registering a CA Certicate(P. 601)
Registering an S/MIME Certicate(P. 602)
The communication methods listed below use a key/certicate or CA certicate. If you want to use a registered
key and certicate in actual communication, you need to specify the key and certicate in the settings for each
communication method. However, an X.509 DER format CA certicate does not need to be specied in the
settings for each communication method. You can use it simply by registering it to the machine.
●TLS encrypted communication Conguring the Key and Certicate for TLS(P. 549)
●IPSec Conguring the IPSec Settings(P. 555)
●IEEE 802.1X Conguring the IEEE 802.1X Authentication Settings(P. 561)
Registering a Key and Certicate
Keys and certicates (server certicates) can be registered via the Remote UI. For information on the keys and
certicates that can be registered on the machine, see System Specications(P. 1084) .
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Key and Certicate Settings].
4Click [Register Key and Certicate...].
5Click [Install...].
6Install the key and certicate.
Managing the Machine
600
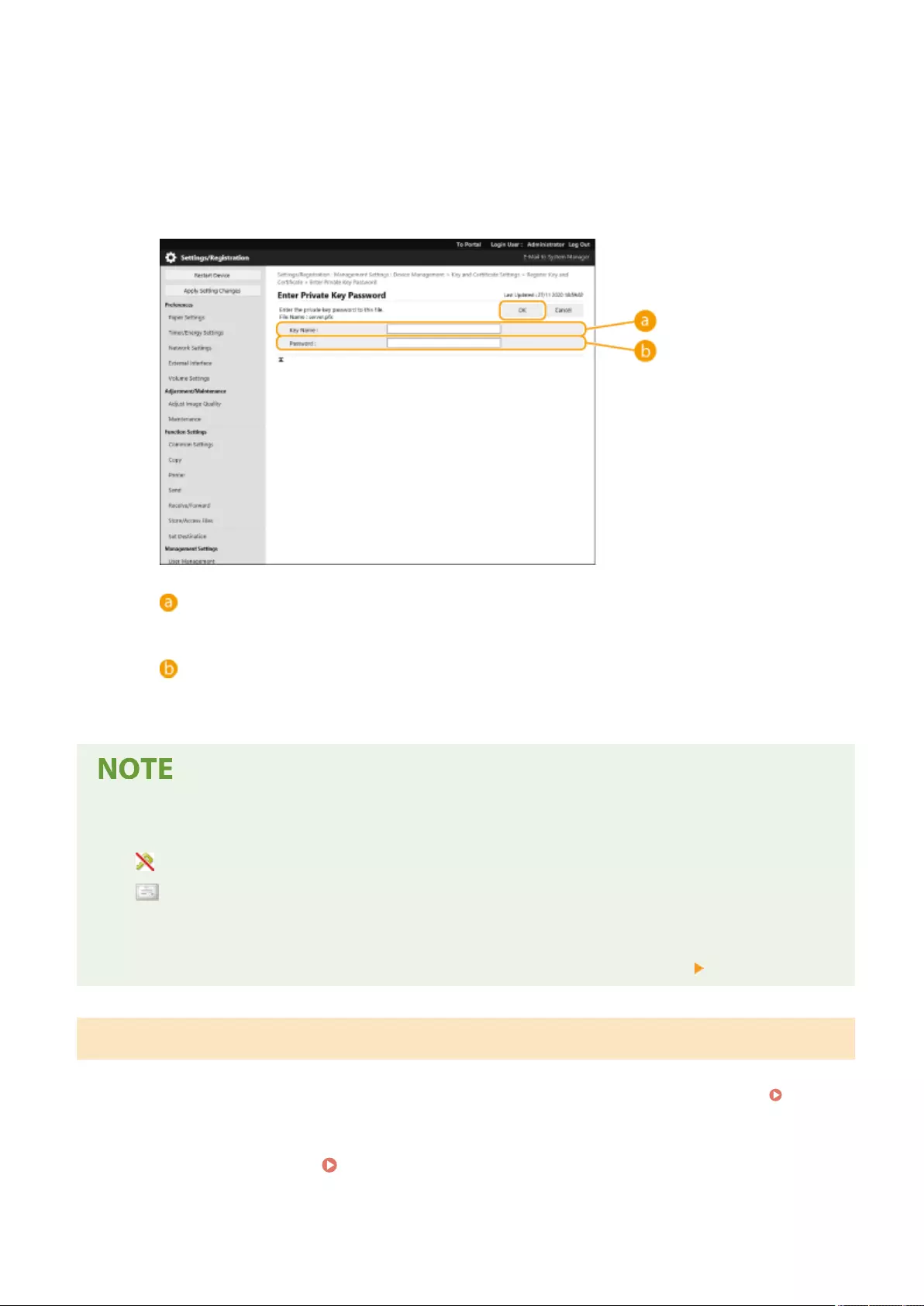
●Click [Browse...], specify the les (key and certicate) to install, and click [Start Installation].
7Register the key and certicate.
1Select the key and certicate that you want to register, and click [Register].
2Enter the key name and password, and click [OK].
[Key Name]
Use alphanumeric characters to enter the name of the key that was registered to the machine.
[Password]
Use alphanumeric characters to enter the password of the private key that is set for the le to
register.
Managing keys and certicates
You can check the detailed settings or delete keys and certicates on the screen displayed in step 4.
●If is displayed, the key is corrupted or invalid.
●If is displayed, the certicate for the key does not exist.
●Click a key name to display detailed information about the certicate. You can also click [Verify Certicate] on
this screen to check whether the certicate is valid.
●To delete a key and certicate, select the one that you want to delete, and click [Delete] [OK].
Registering a CA Certicate
X.509 DER format CA certicates are preinstalled in the machine. You can register a new CA certicate if it is required
by a particular function. For information on the CA certicates that can be registered on the machine, see System
Specications(P. 1084) .
1Start the Remote UI. Starting the Remote UI(P. 583)
Managing the Machine
601
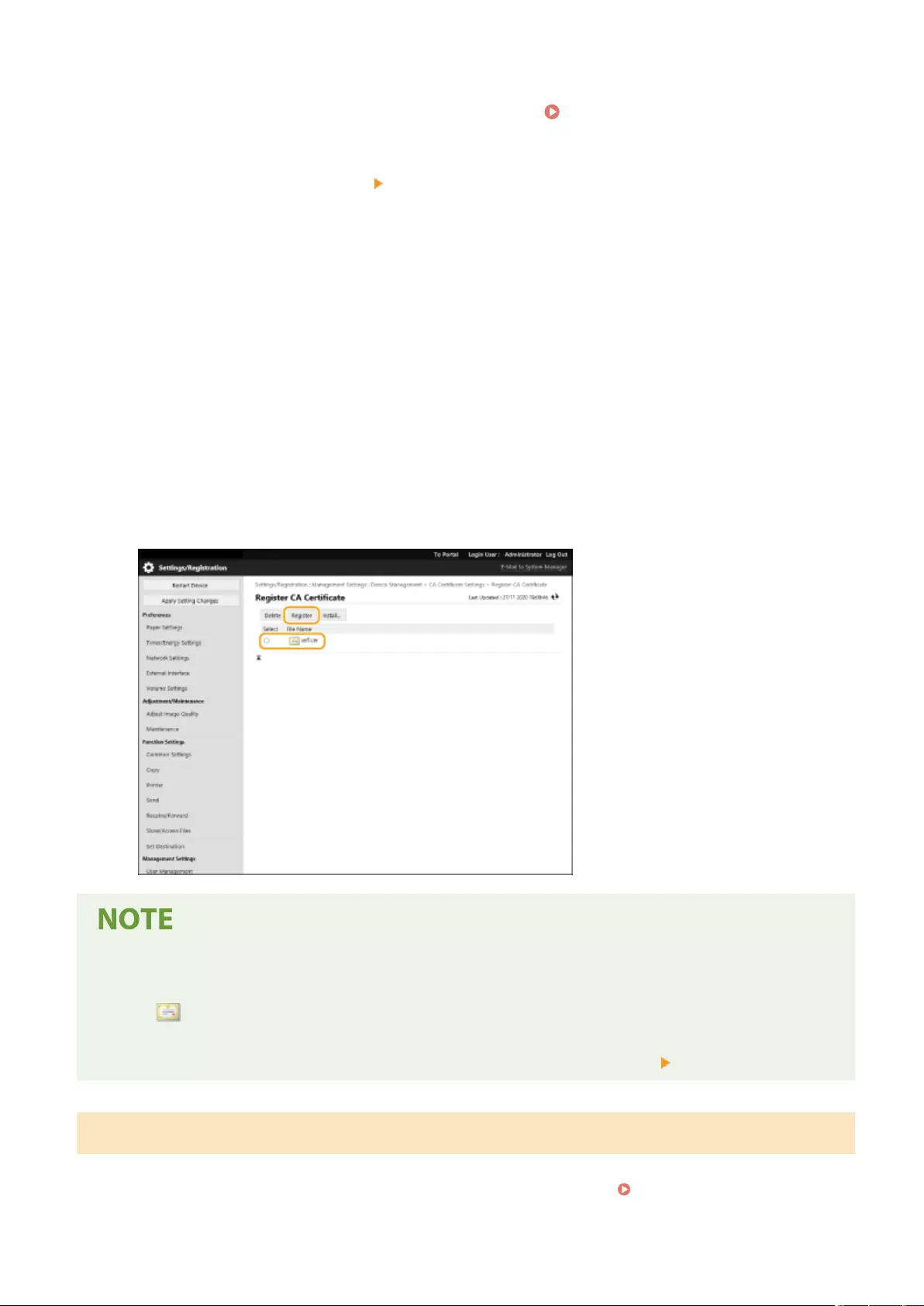
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [CA Certicate Settings].
4Click [Register CA Certicate...].
5Click [Install...].
6Install the CA certicate.
●Click [Browse...], specify the le (CA certicate) to install, and click [Start Installation].
7Register the CA certicate.
●Select the CA certicate that you want to register, and click [Register...].
Managing CA certicates
You can check the detailed settings or delete CA certicates on the screen displayed in step 4.
●Click to display detailed information about the CA certicate. You can also click [Verify Certicate] on
this screen to check whether the CA certicate is valid.
●To delete a CA certicate, select the one that you want to delete, and click [Delete] [OK].
Registering an S/MIME Certicate
You can register a public key certicate (S/MIME certicate) to use for encrypting e-mail/I-fax with S/MIME. For
information on the S/MIME certicates that can be registered on the machine, see System Specications(P. 1084) .
Managing the Machine
602
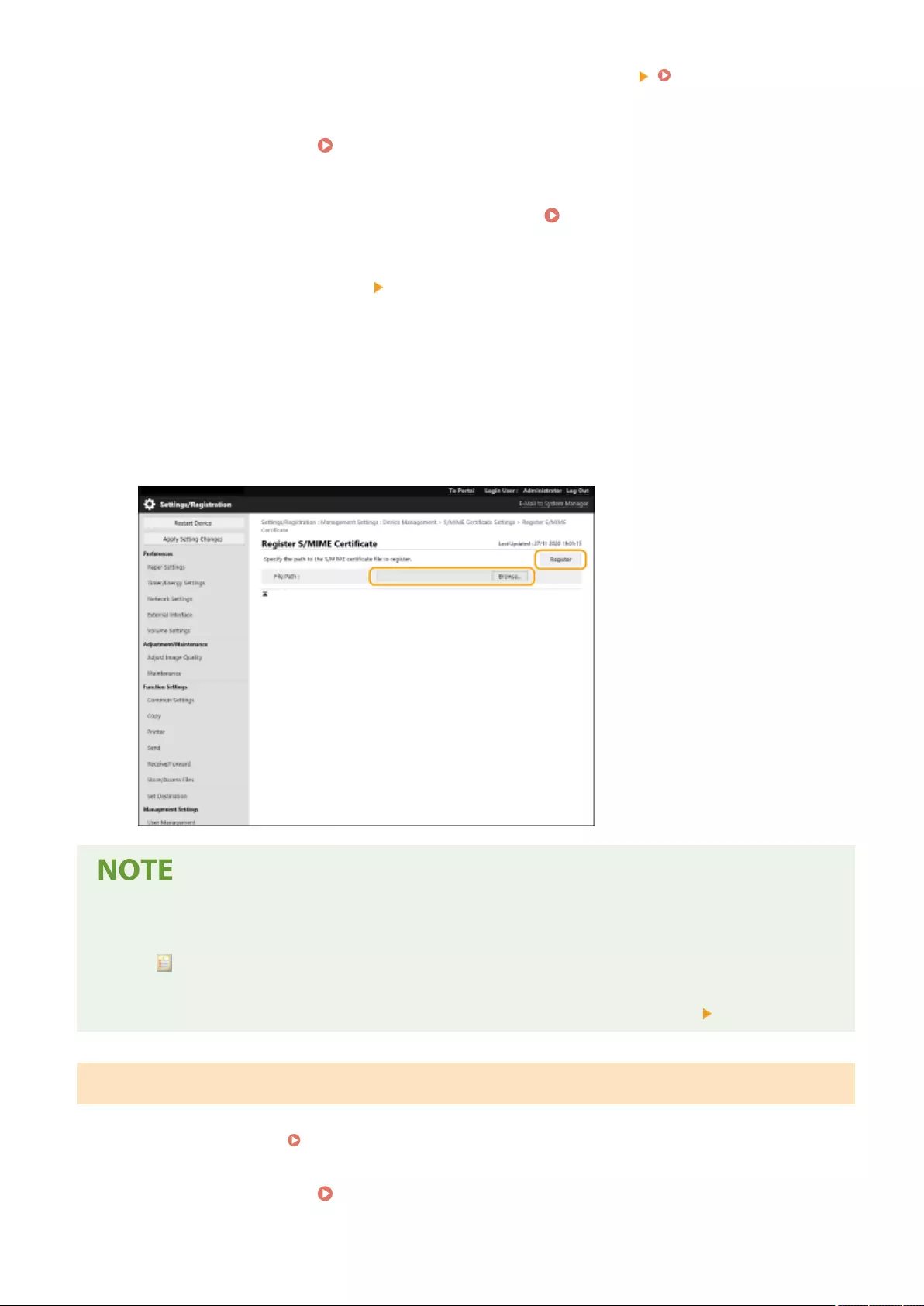
For information on how to congure the S/MIME settings, see <E-Mail/I-Fax Settings> <S/MIME
Settings>(P. 826) .
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [S/MIME Certicate Settings].
4Click [Register S/MIME Certicate...].
5Register the S/MIME certicate.
●Click [Browse...], specify the le (S/MIME certicate) to register, and click [Register].
Managing S/MIME certicates
You can check the detailed settings or delete S/MIME certicates on the screen displayed in step 4.
●Click to display detailed information about the S/MIME certicate. You can also click [Verify Certicate] on
this screen to check whether the S/MIME certicate is valid.
●To delete an S/MIME certicate, select the one that you want to delete, and click [Delete] [OK].
Registering a Certicate Revocation List (CRL)
You can use the Remote UI to register a certicate revocation list (CRL). For information on the CRLs that can be
registered on the machine, see System Specications(P. 1084) .
1Start the Remote UI. Starting the Remote UI(P. 583)
Managing the Machine
603
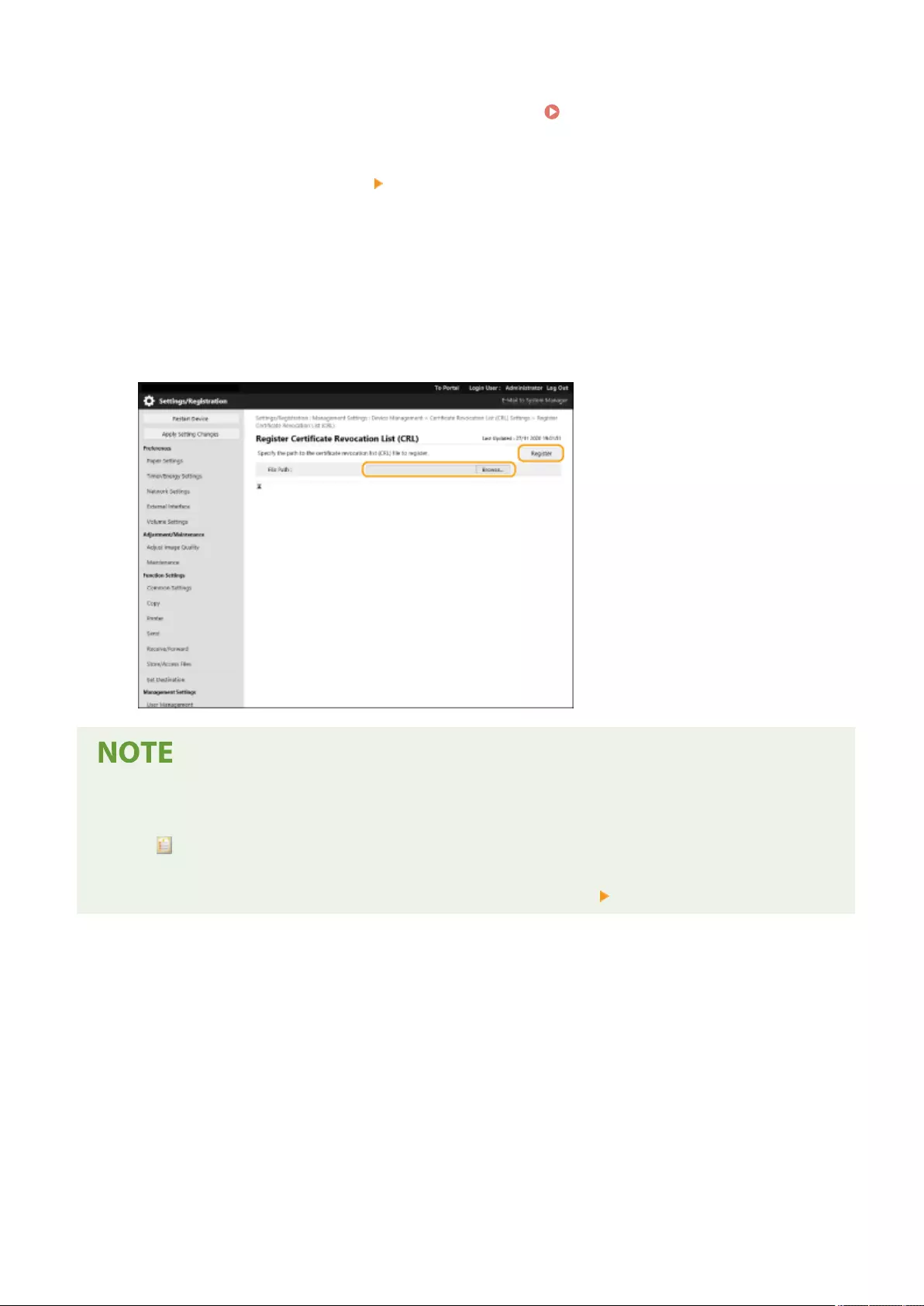
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Certicate Revocation List (CRL) Settings].
4Click [Register CRL...].
5Register the CRL.
●Click [Browse...], specify the le (CRL) to register, and click [Register].
Managing CRLs
You can check the detailed settings or delete CRLs on the screen displayed in step 4.
●Click to display detailed information about it. You can also click [Verify CRL] on this screen to check
whether the CRL is valid.
●To delete a CRL, select the one that you want to delete, and click [Delete] [OK].
Managing the Machine
604
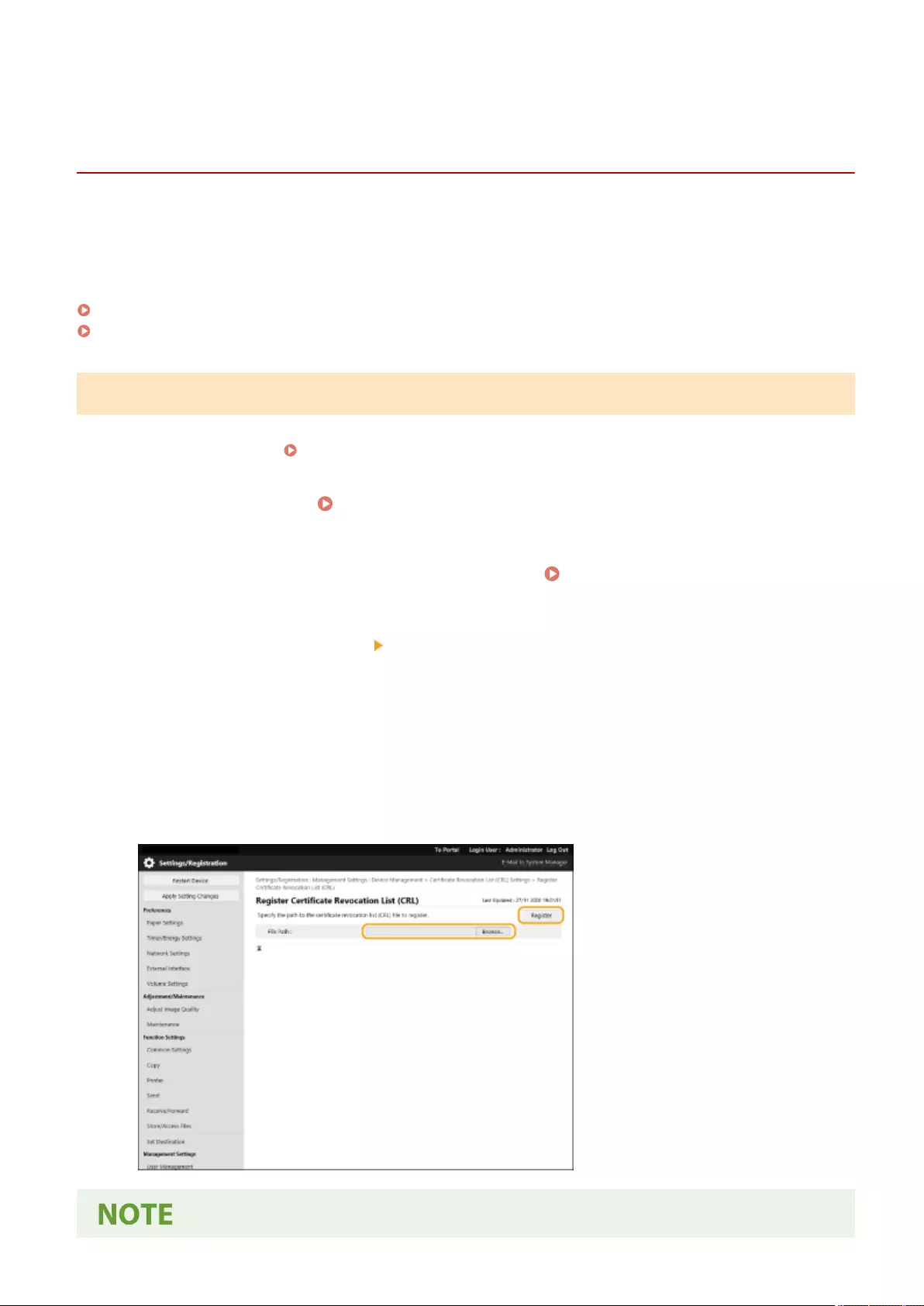
Conguring the Expiration Check Method for Received
Certicates
72JY-0A8
There are two methods for verifying whether certicates received from the other party in communication are valid:
Comparing with the certicate revocation list (CRL) registered in the machine and querying an OCSP (online certicate
status protocol) responder (a server that supports OCSP). Set the method for checking the expiration of certicates
according to your environment. This registration can only be performed by the administrator.
Registering a Certicate Revocation List (CRL)(P. 605)
Conguring the Online Certicate Status Protocol (OCSP)(P. 606)
Registering a Certicate Revocation List (CRL)
You can use the Remote UI to register a certicate revocation list (CRL). For information on the CRLs that can be
registered on the machine, see System Specications(P. 1084) .
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Certicate Revocation List (CRL) Settings].
4Click [Register CRL...].
5Register the CRL.
●Click [Browse...], specify the le (CRL) to register, and click [Register].
Managing the Machine
605
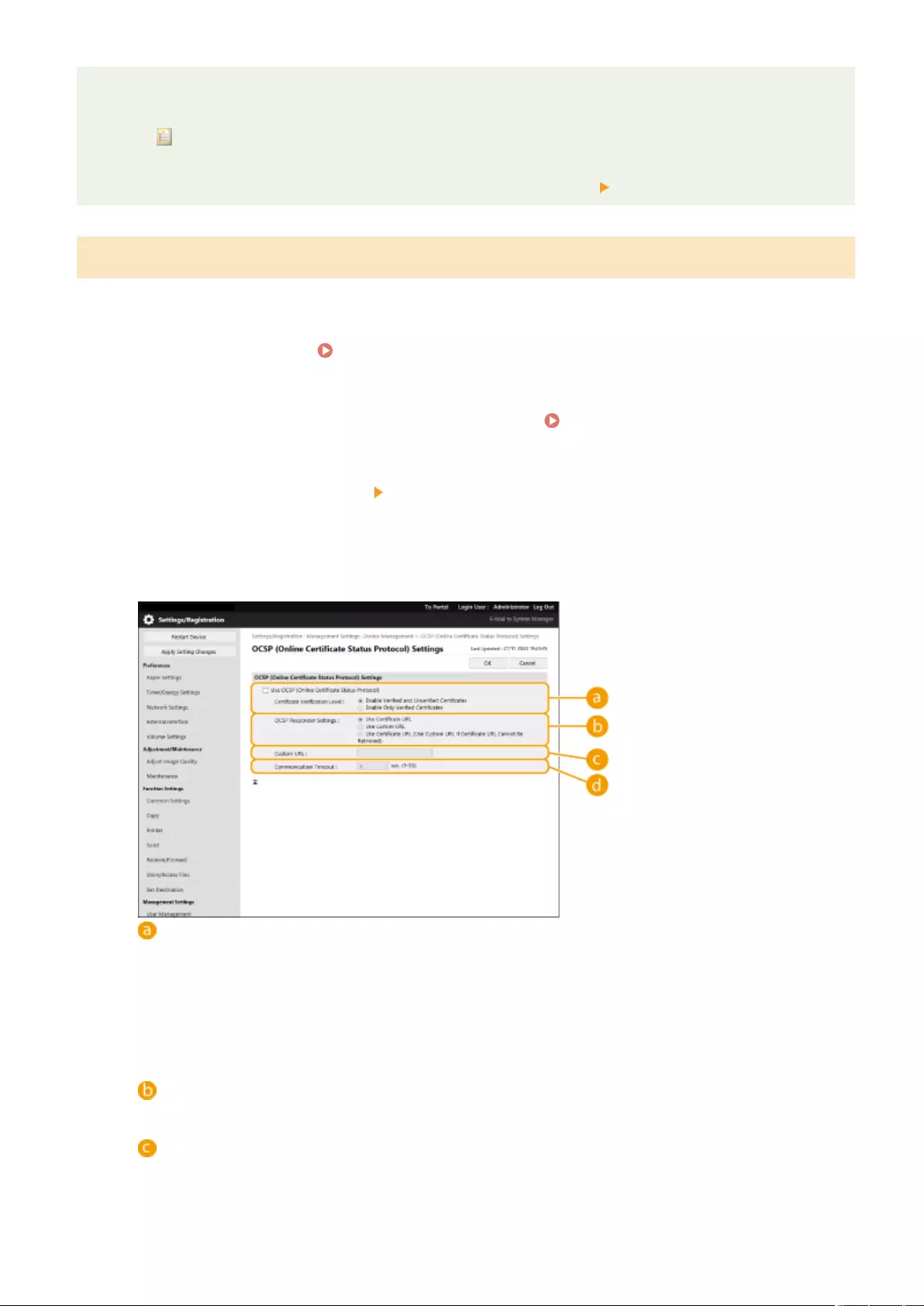
Managing CRLs
You can check the detailed settings or delete CRLs on the screen displayed in step 4.
●Click to display detailed information about it. You can also click [Verify CRL] on this screen to check
whether the CRL is valid.
●To delete a CRL, select the one that you want to delete, and click [Delete] [OK].
Conguring the Online Certicate Status Protocol (OCSP)
You can congure the certicate verication level and the OCSP responder to connect to.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [OCSP (Online Certicate Status Protocol) Settings].
4Select the check box for [Use OCSP (Online Certicate Status Protocol)], and
congure the online certicate status protocol (OCSP).
[Certicate Verication Level]
Set whether to disable certicates in situations such as the following:
●When the machine cannot connect to the OCSP responder
●When a timeout occurs
●When expiration cannot be checked, such as when the result of checking the expiration of a certicate
via the OCSP responder is unknown
[OCSP Responder Settings]
Specify the URL for connecting to the OCSP responder.
[Custom URL]
When [Use custom URL] or [Use Certicate URL (Use Custom URL If Certicate URL Cannot Be Retrieved)]
is selected, enter the URL of the OCSP responder (ASCII code only, maximum 255 characters).
Managing the Machine
606

[Communication Timeout]
Set the time until communication with the OCSP responder times out. The connection is canceled if there
is no response from the OCSP responder within the set time.
5Click [OK].
Managing the Machine
607
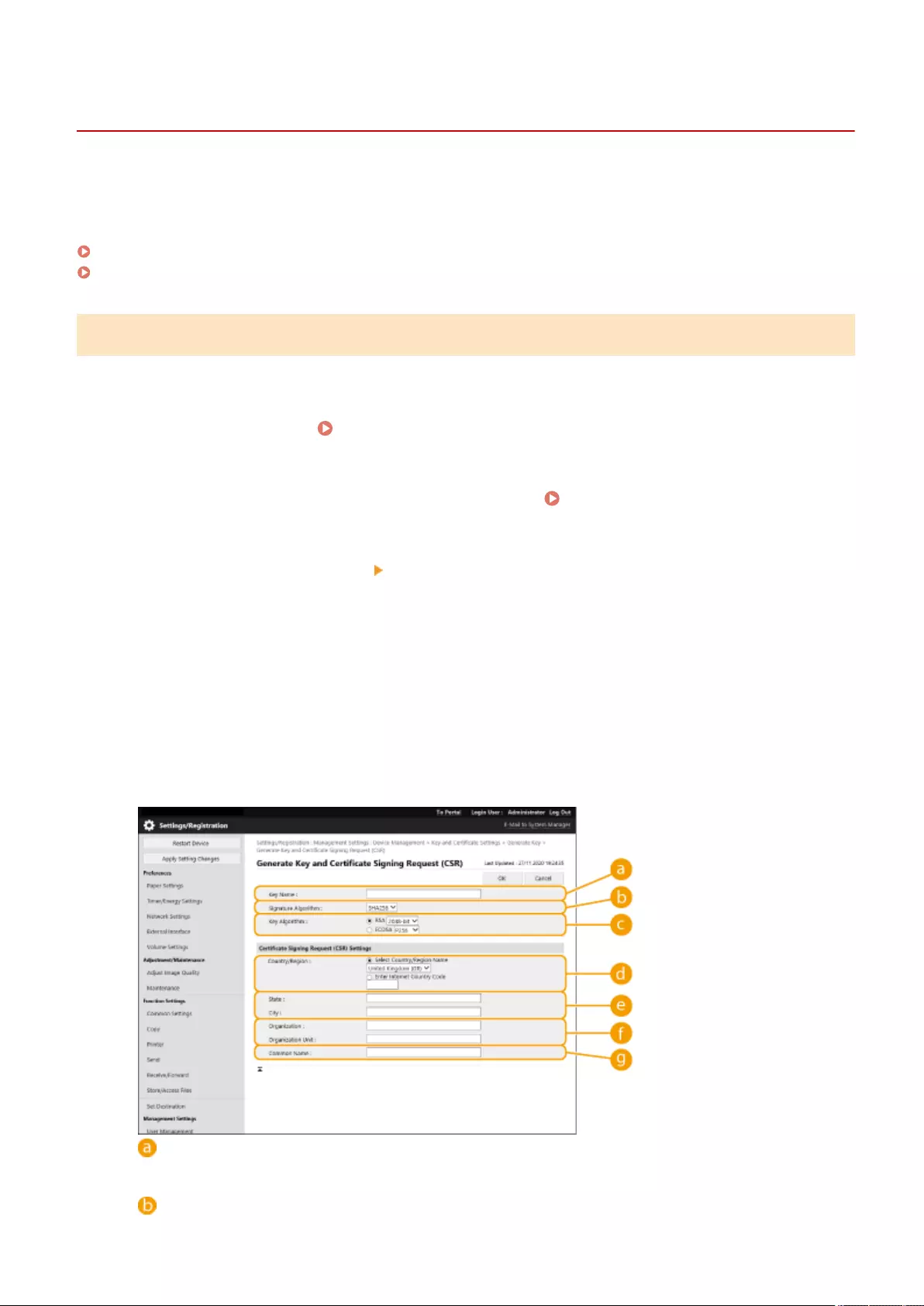
Generating a Key and Certicate Signing Request (CSR)
72JY-0A9
Certicates generated on this machine do not have a CA signature, which may cause communication errors with some
communication peers. To request a certicate with a CA signature, certicate signing request (CSR) data is required. A
user who logs in with administrator privileges can generate a CSR.
Generating a Key and CSR(P. 608)
Registering a Certicate to a Key(P. 609)
Generating a Key and CSR
You can generate a key and CSR on the machine. You can also display the CSR data on the screen and export it as a le.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Key and Certicate Settings].
4Click [Generate Key...].
5Click [Key and Certicate Signing Request (CSR)].
6Congure the necessary items for the key and certicate.
[Key Name]
Enter a name for the key. Use a name that will be easy to nd when displayed in a list.
[Signature Algorithm]
Managing the Machine
608
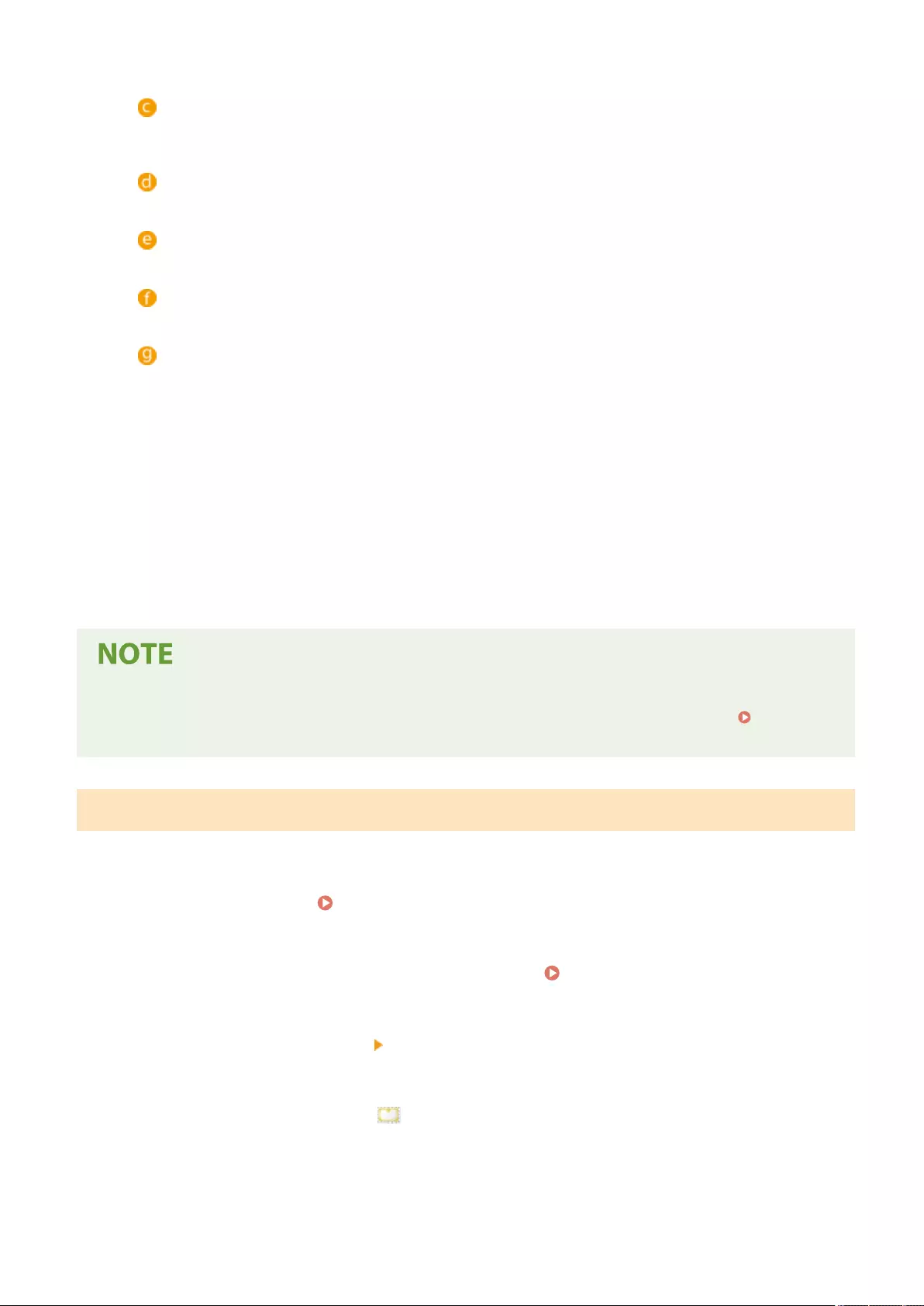
Select the hash algorithm to use for the signature.
[Key Algorithm]
Select the key algorithm, and specify the key length if [RSA] is selected, or specify the key type if [ECDSA] is
selected.
[Country/Region]
Select the country code from the list, or enter it directly.
[State]/[City]
Enter the location.
[Organization]/[Organization Unit]
Enter the organization name.
[Common Name]
Enter the IP address or FQDN.
●When performing IPPS printing in a Windows environment, make sure to enter the machine's IP
address.
●A DNS server is required in order to enter the FQDN of the machine. Enter the IP address if a DNS server
is not used.
7Click [OK].
➠The CSR data is displayed.
●If you want to save the CSR data to a le, click [Store in File] and specify the save location.
●The key that generated the CSR is displayed on the key and certicate list screen, but you cannot use it by
itself. To use this key, you need to register the certicate that is later issued based on the CSR. Registering
a Certicate to a Key(P. 609)
Registering a Certicate to a Key
You can register the certicate that was applied for and issued based on the CSR.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Key and Certicate Settings].
4In the [Certicate] list, click for the certicate that you want to register.
Managing the Machine
609
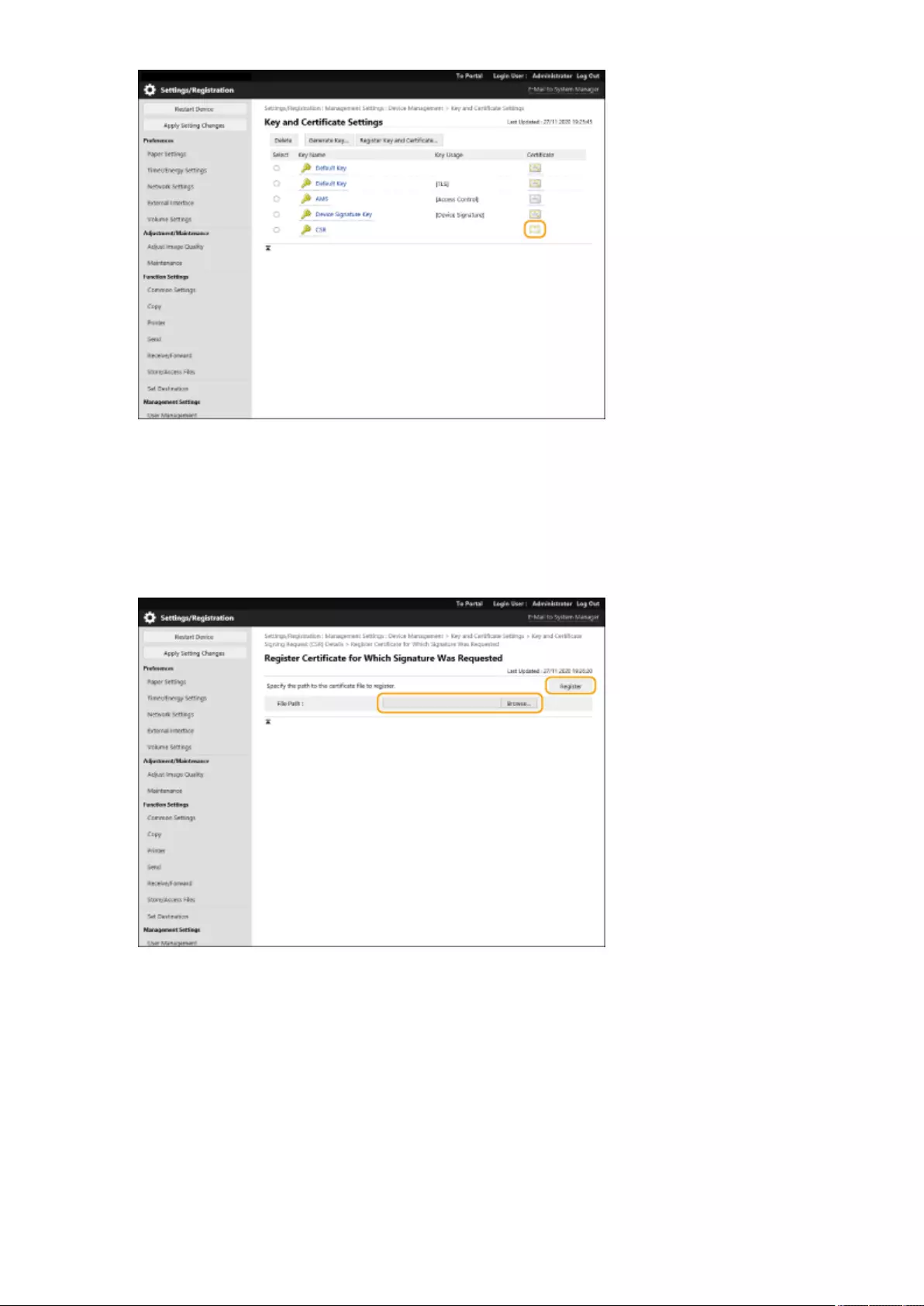
5Click [Register Certicate...].
6Register the certicate.
●Click [Browse...], specify the le (certicate) to register, and click [Register].
Managing the Machine
610
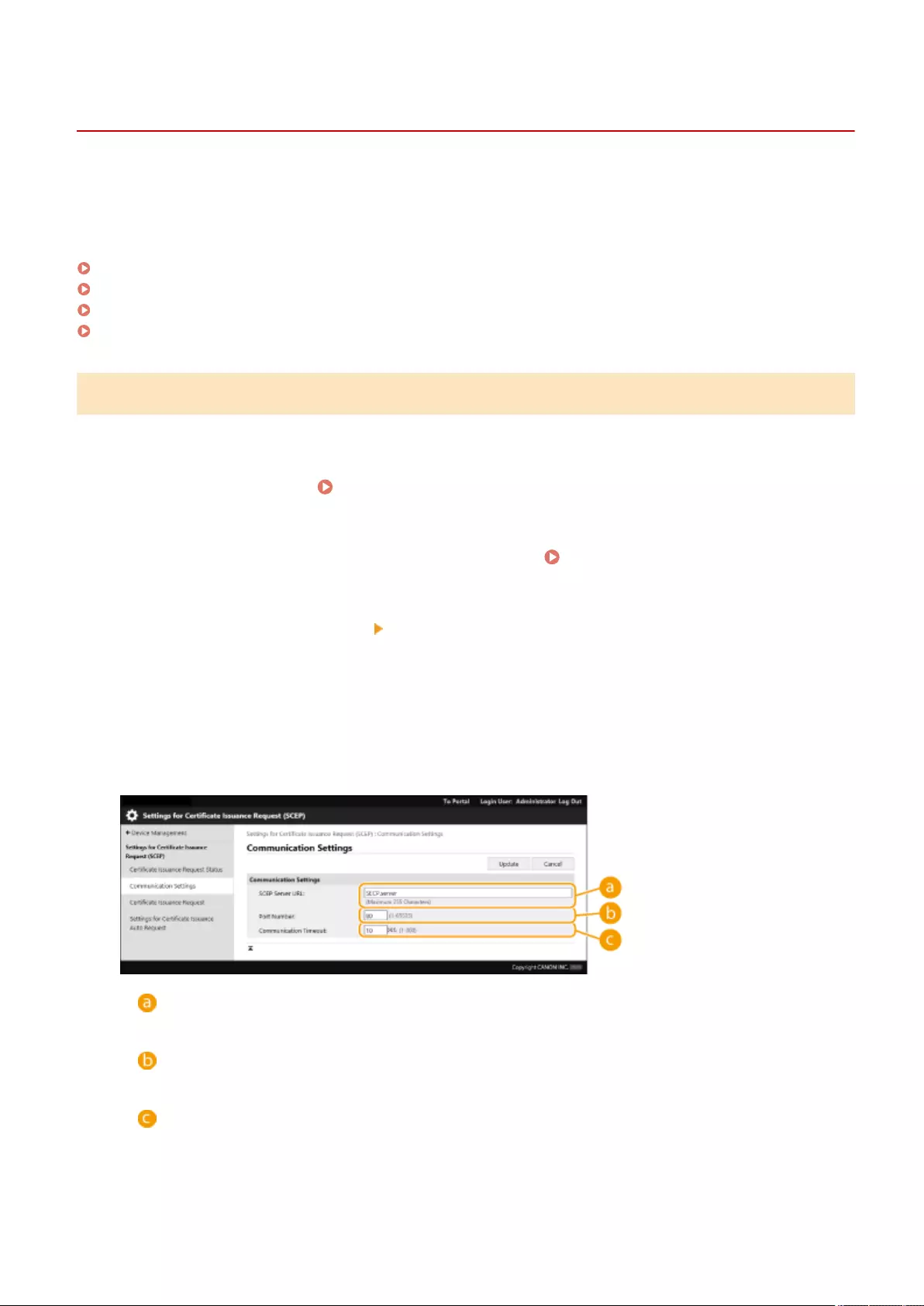
Retrieving/Updating a Certicate from an SCEP Server
72JY-0AA
A request for issuing the certicate required for keys generated with the machine can be sent to an SCEP (Simple
Certicate Enrollment Protocol) server that manages certicates. Certicates issued from the SCEP server are
automatically registered to the machine. Administrator privileges are required to send a request for issuing a
certicate.
Specifying the Communication Settings of the SCEP Server(P. 611)
Requesting a Certicate to Be Issued(P. 612)
Requesting a Certicate to Be Issued at the Specied Time(P. 613)
Checking the Status of Requesting a Certicate to Be Issued(P. 615)
Specifying the Communication Settings of the SCEP Server
You can specify the settings for communicating with the SCEP server.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Settings for Certicate Issuance Request (SCEP)].
4Click [Communication Settings].
5Set the required communication settings.
[SCEP Server URL:]
Specify the URL of the SCEP server to connect to.
[Port Number:]
Enter the port number to use for communicating with the SCEP server.
[Communication Timeout:]
Enter the timeout time for communication with the SCEP server. The connection is canceled if there is no
response from the SCEP server within the set time.
Managing the Machine
611
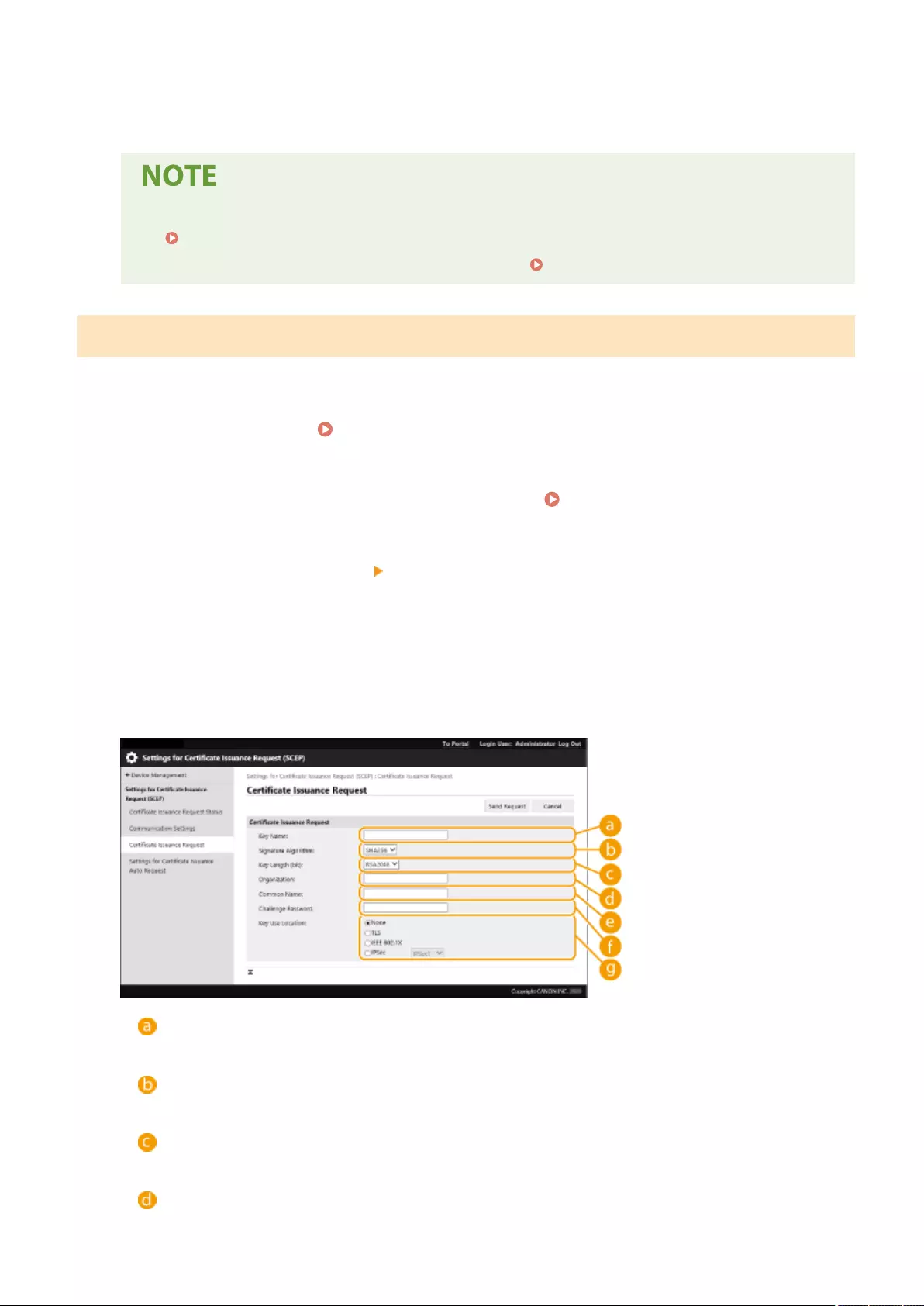
6Click [Update].
●The settings cannot be updated when [Enable Timer for Certicate Issuance Auto Request] is selected.
Requesting a Certicate to Be Issued at the Specied Time(P. 613)
●For information on the supported versions of SCEP, see Management Functions(P. 1091) .
Requesting a Certicate to Be Issued
You can manually request a certicate to be issued.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Settings for Certicate Issuance Request (SCEP)].
4Click [Certicate Issuance Request].
5Set the items required for requesting a certicate to be issued.
[Key Name:]
Enter the name for the key. Enter a name that will be easy to nd when displayed in a list.
[Signature Algorithm:]
Select the hash function to use for the signature.
[Key Length (bit):]
Select the key length.
[Organization:]
Managing the Machine
612

Enter the organization name.
[Common Name:]
Enter the IP address or FQDN.
●When performing IPPS printing in a Windows environment, make sure to enter the IP address of the
machine.
●A DNS server is required to enter the FQDN of the machine. Enter the IP address of the machine if a
DNS server is not used.
[Challenge Password:]
When a password is set on the SCEP server side, enter the challenge password included in the request
data (PKCS#9) for requesting a certicate to be issued.
[Key Use Location:]
Select the destination where the key will be used. When [IPSec] is selected, select the IPSec of the
destination from the drop-down list.
●When selecting something other than [None], enable the various functions in advance. If a certicate is
successfully obtained with the various functions disabled, the certicate is assigned as the destination,
but the various functions are not automatically enabled.
6Click [Send Request].
7Click [Restart].
●A manual request for issuing a certicate cannot be sent when [Enable Timer for Certicate Issuance
Auto Request] is selected. Requesting a Certicate to Be Issued at the Specied Time(P. 613)
●The information set here is not saved to the storage of the machine.
Requesting a Certicate to Be Issued at the Specied Time
You can set to automatically request a certicate to be issued at a specied time.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Settings for Certicate Issuance Request (SCEP)].
4Click [Settings for Certicate Issuance Auto Request].
Managing the Machine
613
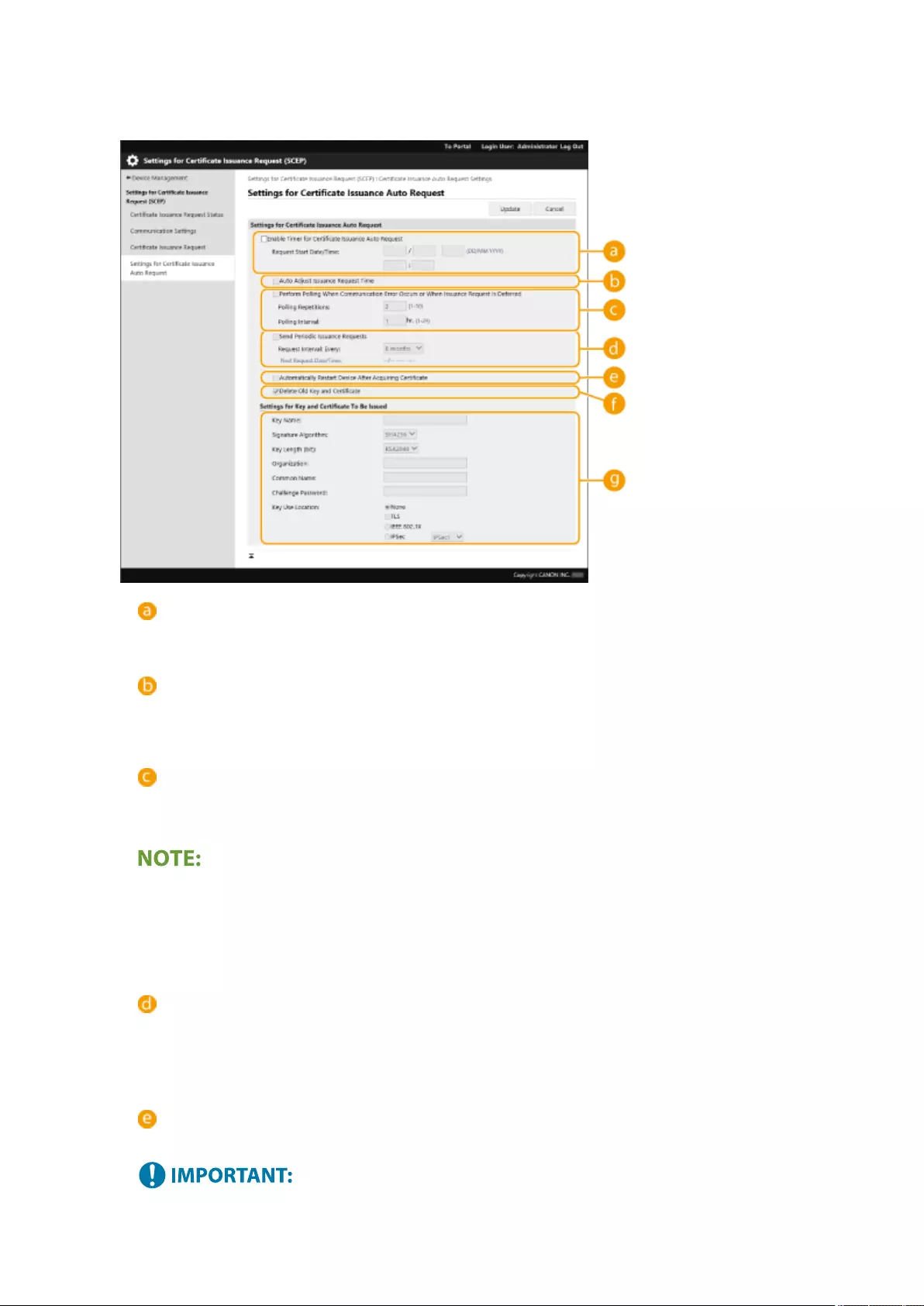
5Set the items required for requesting a certicate to be issued.
[Enable Timer for Certicate Issuance Auto Request]
Select this to automatically request a certicate to be issued at a specied time, and specify the start date/
time in [Request Start Date/Time:].
[Auto Adjust Issuance Request Time]
Select this to adjust the time to send the request. This reduces load on the SCEP server when multiple
multifunction printers send a request at the same time. The time is randomly adjusted 1 to 600 seconds
from the time specied in [Request Start Date/Time:].
[Perform Polling When Communication Error Occurs or When Issuance Request Is Deferred]
Select this to check the status of the SCEP server when a communication error has occurred or when a
certicate issue request is pending. Specify the number of polling times and polling interval.
●In the following cases, polling is not performed and an error occurs.
- When the machine has exceeded the limit of keys and certicates it can hold
- When an error is included in the retrieved response data
- When an error occurs on the SCEP server side
[Send Periodic Issuance Requests]
Select this to periodically send an automatic request for a certicate to be issued, and specify the interval
in [Request Interval: Every:].
When an automatic request for a certicate to be issued is performed successfully, the next date/time to
issue a request is displayed in [Next Request Date/Time:].
[Automatically Restart Device After Acquiring Certicate]
Select this to restart the machine after the certicate is retrieved.
●The machine is restarted even during batch importing/exporting.
Managing the Machine
614
[Delete Old Key and Certicate]
Select this to overwrite the old key and certicate.
●The key and certicate with the same destination for use are overwritten.
●The default key is not overwritten.
[Settings for Key and Certicate To Be Issued]
Enter the information for the key to generate. For information on the settings, see step 5 of Requesting
a Certicate to Be Issued(P. 612) .
6Click [Update].
Checking the Status of Requesting a Certicate to Be Issued
The certicate requested and issued based on the CSR is registered in the key.
Start the Remote UI click [Settings/Registration] [Device Management] [Certicate Issuance
Request Status].
●The following statuses are displayed in [Status].
- [To Be Processed]: The next date/time to issue a request is displayed in [Request Date/Time].
- [Processing...]: Polling is being performed.
- [Error]: An error such as a communication error or key upper limit exceeded error has occurred.
- [Successful]: The date/time that the certicate was successfully issued is displayed in [Request Date/Time].
●The information displayed in [Details] in [Error] is indicated below.
[Details] Cause
Deferred The pending status was returned from the SCEP server.
Key and Certicate Registration Limit Error The limit to the number of keys and certicates that can be
registered in the machine was reached.
Communication Error (TOP ERROR) Connection to the SCEP server failed/a communication
timeout occurred.
Communication Error (TOP ERROR <HTTP status
code>)
An HTTP error occurred.
Communication Error (SCEP ERROR Fail Info 0) Unrecognized or unsupported algorithm.
Communication Error (SCEP ERROR Fail Info 1) Integrity check (meaning signature verication of the CMS
message) failed.
Communication Error (SCEP ERROR Fail Info 2) Transaction not permitted or supported.
Communication Error (SCEP ERROR Fail Info 3) The signingTime attribute from the CMS
authenticatedAttributes was not suciently close to the
system time.
Managing the Machine
615

[Details] Cause
Communication Error (SCEP ERROR Fail Info 4) No certicate could be identied matching the provided
criteria.
●History for the last 20 certicates is displayed. When the number of certicates exceeds 20, the oldest
information is overwritten.
●This setting can be imported/exported with models that support batch importing of this setting.
Importing/Exporting the Setting Data(P. 625)
●When performing batch exporting, this setting is included in [Settings/Registration Basic
Information]. Importing/Exporting All Settings(P. 628)
LINKS
Conguring the Key and Certicate for TLS(P. 549)
Conguring the IEEE 802.1X Authentication Settings(P. 561)
Conguring the IPSec Settings(P. 555)
Managing the Machine
616
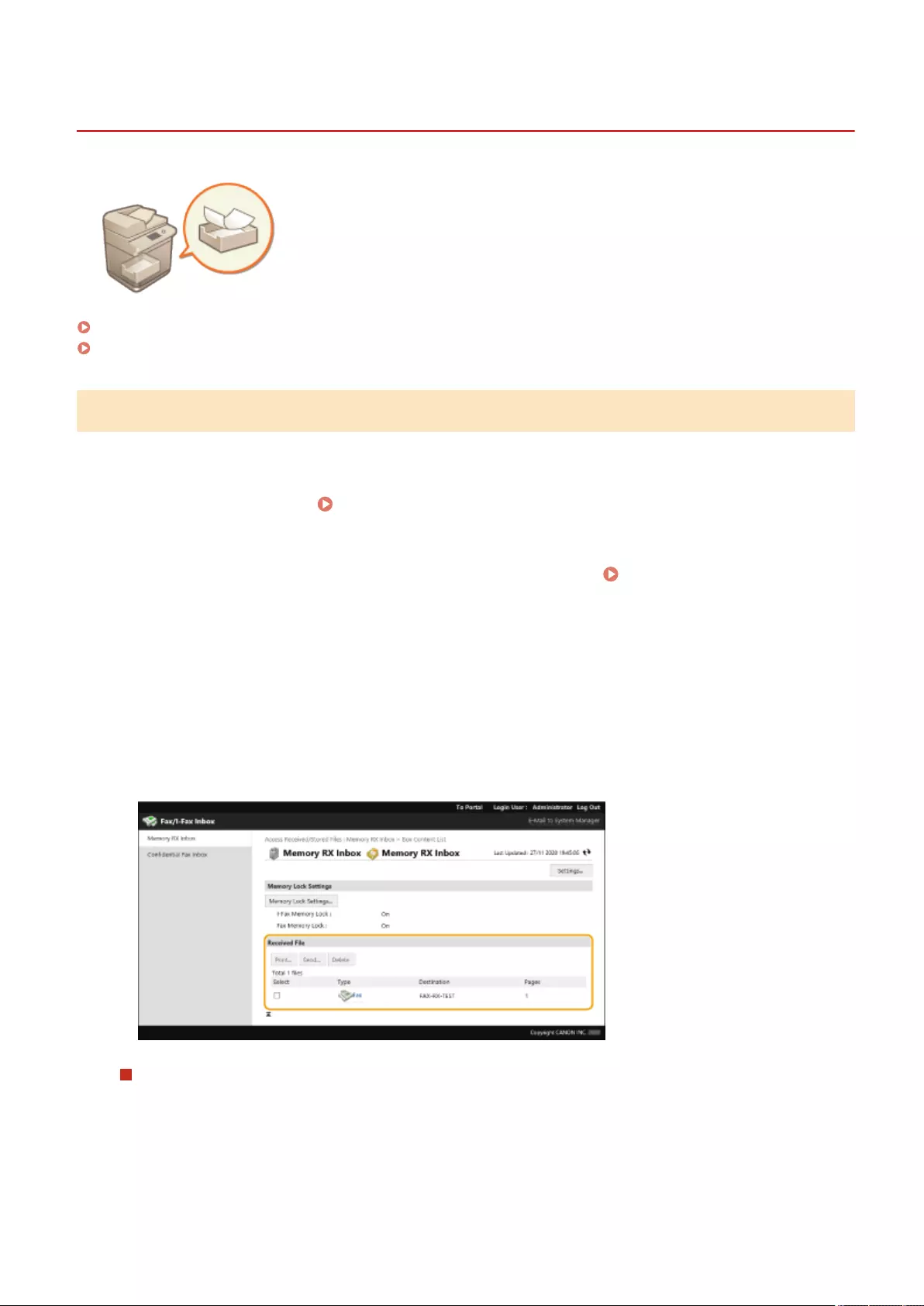
Managing Stored Files
72JY-0AC
You can use the Remote UI to print, send, or delete faxes and I-faxes that are
temporarily stored in the Fax/I-Fax Inbox.
Managing Documents Temporarily Stored in Memory RX Inbox(P. 617)
Managing Documents Temporarily Stored in Condential Fax Inbox(P. 618)
Managing Documents Temporarily Stored in Memory RX Inbox
You can print or forward faxes and I-faxes that are temporarily stored in the Memory RX Inbox using Memory Lock.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Access Received/Stored Files] on the portal page. Remote UI Screen(P. 585)
3Select [Memory RX Inbox] and click [Memory RX Inbox].
●If the page for entering a PIN is displayed, enter the PIN and click [OK].
4Select the document and perform the desired operation.
●Click the [Type] icon to display detailed information about the document.
Printing a document
1Select the check box for a document that you want to print, and click [Print...].
●You can select multiple documents.
2Click [Start Printing].
Managing the Machine
617
●Documents are automatically deleted after they are printed.
Forwarding a document
1Select the check box for a document that you want to forward, and click [Send...].
●You can select multiple documents.
2Click [Select Destination], select the destination, and click [OK].
●You can click [Move to Top], [Move Up], [Move Down], or [Move to Bottom] to change the order in
which the les are forwarded.
●You can click [Settings...] in [Set Details] to change the send settings. You can also change detailed
settings of the le in [File Settings]. Scanning(P. 372)
●If you select the check box for [Delete File After Sending], documents are automatically deleted after
they are forwarded.
3Click [OK].
Deleting a le
1Select the check box for the le that you want to delete.
2Click [Delete] [OK].
To check I-faxes that were divided when received
●Click [Divided Data RX Inbox] on the screen displayed in step 3 to display a list of I-faxes that were divided
when received. Receiving I-Faxes(P. 338)
To set a PIN for Memory RX Inbox
●You can change the PIN for the Memory RX Inbox by clicking [Settings...] on the screen displayed in step 4
and adding a check mark to [Set PIN].
To congure Memory Lock settings
●You can set whether to receive faxes and I-faxes in the Memory RX Inbox by clicking [Memory Lock
Settings...] on the screen displayed in step 4.
Managing Documents Temporarily Stored in Condential Fax Inbox
You can print or delete faxes and I-faxes that are temporarily stored in the Condential Fax Inbox.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Access Received/Stored Files] on the portal page. Remote UI Screen(P. 585)
Managing the Machine
618
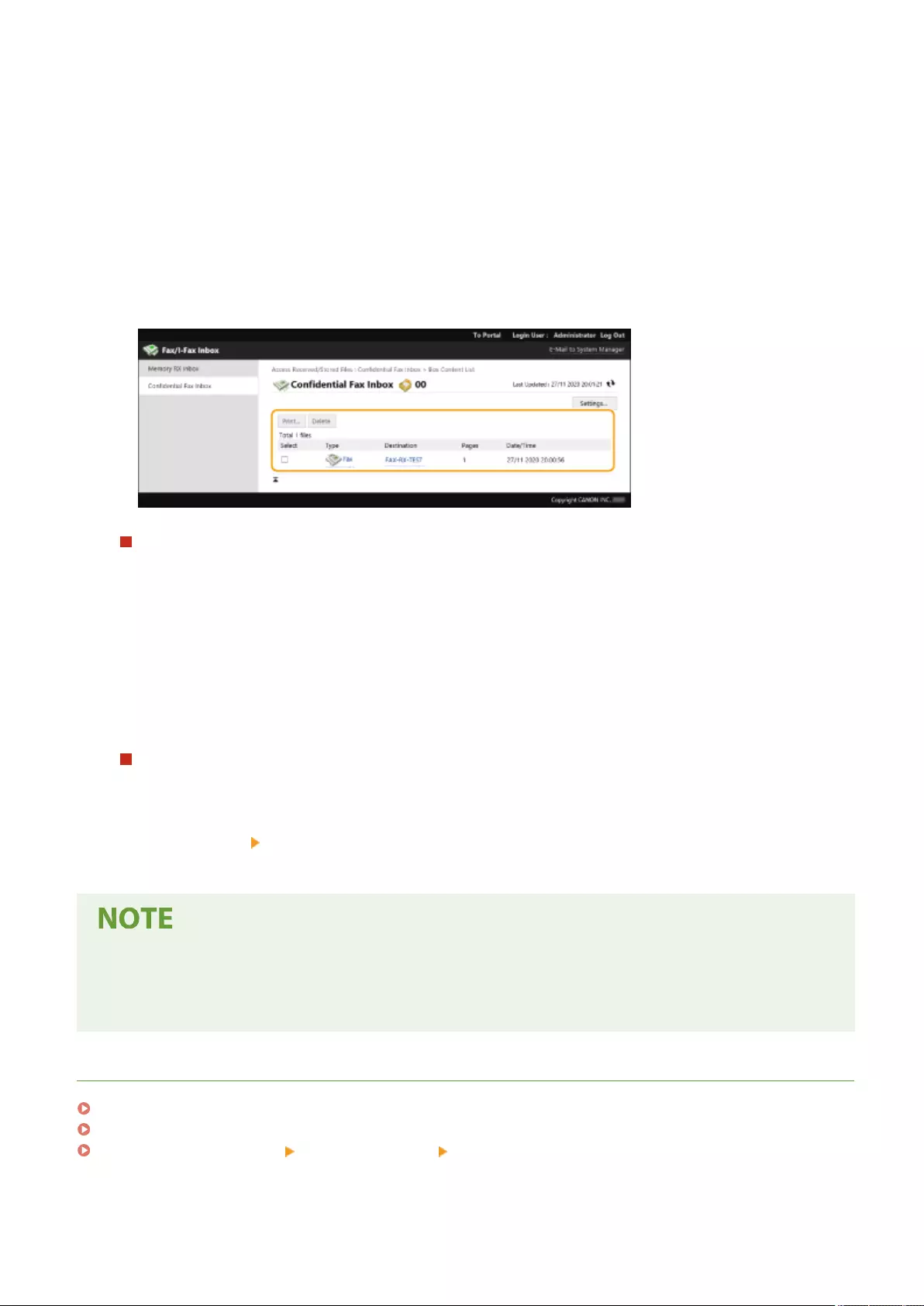
3Select [Condential Fax Inbox] and click the number of the desired Condential Fax
Inbox.
●If the page for entering a PIN is displayed, enter the PIN and click [OK].
●You can also specify a Condential Fax Inbox by entering its number in [Box Number (00-49)] and clicking
[Open...].
4Select the document and perform the desired operation.
●Click the [Type] icon to display detailed information about the document.
Printing a document
1Select the check box for a document that you want to print, and click [Print...].
●You can select multiple documents.
2Click [Start Printing].
●If you select the check box for [Delete File After Printing], documents are automatically deleted after
they are printed.
Deleting a le
1Select the check box for the le that you want to delete.
2Click [Delete] [OK].
To change the settings of a Condential Fax Inbox
●You can change the name and PIN for the selected Condential Fax Inbox by clicking [Settings...] on the
screen displayed in step 4.
LINKS
Saving Received Documents in the Machine (Memory Reception)(P. 313)
Keeping Received Documents Private(P. 316)
<Receive/Forward>(P. 835) <Common Settings> <Set Fax/I-Fax Inbox>
Managing the Machine
619
Managing the Logs
72JY-0AE
You can use the logs to check or analyze how the machine is being used. A variety of information about each operation
is recorded in the logs, such as the operation date/time, user name, operation type, function type, and operation
result. For more information on the types of logs, see System Specications(P. 1084) . Administrator privileges are
required in order to manage the logs.
Starting Log Recording(P. 620)
Exporting Logs Automatically(P. 621)
Exporting a Log as a File(P. 622)
Deleting the Logs(P. 622)
Sending Logs via the Syslog Protocol(P. 623)
●If Audit Log Collection is enabled and an error occurs in the memory area managed by this function,
initialization is automatically performed and then an error screen appears.
●If you can obtain the audit log from before the error occurred, click [Download Audit Log] to obtain the
log, and then click [OK].
●If you cannot obtain the audit log from before the error occurred, click [OK].
●When initialization is completed, Audit Log Collection is resumed, and the automatic initialization process is
recorded in the log.
Starting Log Recording
Follow the procedure below to start recording logs.
Start the Remote UI [Settings/Registration] [Device Management] [Export/Clear Audit Log]
[Audit Log Information] Click [Start] for [Audit Log Collection]
●If Sleep Mode Energy Use is set to [High], logs are not collected when the machine enters the Sleep mode.
●When generating a network connection log, mail box authentication log, mail box document operation log,
or machine management log, click [Device Management] [Save Audit Log] select the check box for
[Save Audit Log] click [OK] [Apply Setting Changes].
Managing the Machine
620
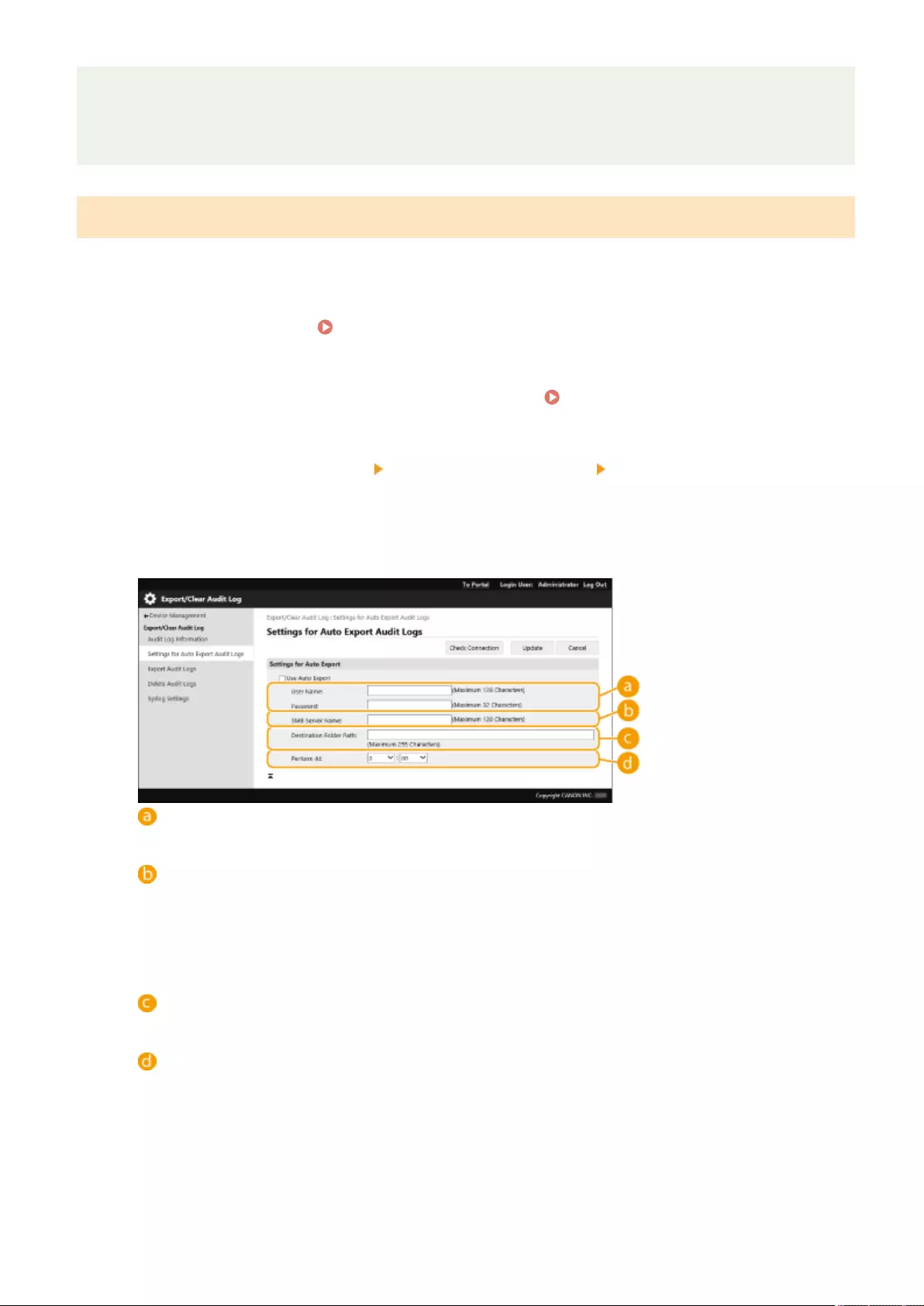
●If the power of the machine is turned OFF while collecting logs due to a power outage, etc., collection starts
again when the machine restarts, from the log that was being collected before the power turned OFF.
●If you stop log collection while logs are being collected, the logs for the period that log collection was
stopped are not collected when log collection is next started.
Exporting Logs Automatically
You can set the machine to automatically export audit logs to a specied folder at a predetermined time each day, or
when the number of audit logs reaches 95% of the maximum number (approximately 38,000).
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Export/Clear Audit Log] [Settings for Auto Export
Audit Logs].
4Select the check box for [Use Auto Export] and specify the required settings.
[User Name:] / [Password:]
Enter the user name and password necessary for logging into a server to which logs are exported.
[SMB Server Name:]
Enter the host name of the SMB server to export log les to, along with the path that requires
authentication.
●\\Host Name
●\\IP Address\Shared Folder Name
[Destination Folder Path:]
Enter the path for the folder in which to store the log les.
[Perform At:]
You can specify the time at which to perform exporting.
5Click [Check Connection], conrm that you can connect, and then click [Update].
●Audit logs will now be automatically exported. The le extension is "csv."
Managing the Machine
621
●After automatic exporting of the audit logs has succeeded, the collected audit logs are automatically
deleted. Audit logs cannot be deleted manually.
●After automatic exporting and deleting of the audit logs have succeeded, each log is generated. If other log
collections do not occur by the next automatic export time, the audit log will not be automatically exported.
●You can also manually export audit logs from the Remote UI. Exporting a Log as a File(P. 622)
●If automatic exporting fails, the machine will retry multiple times. An error message is displayed on the
control panel of the machine if automatic exporting fails even once.
●Specify an SMB server for Windows Server 2012 or later, or Windows 8 or later.
●If the machine is turned OFF, exporting will not be performed, even at the specied time. Also, it will not be
performed when the machine recovers.
●If the machine is in the Sleep mode, it will automatically recover and perform exporting at the specied time.
●Note that if you are using a server that does not support SMB v3.0 encrypted communication, audit log data
travels unencrypted across communication paths while it is being automatically exported.
●Depending on your environment, automatic exporting of logs may be performed later than the specied
time.
6Follow the instructions on the screen to specify the location to store the les.
➠The csv les are stored.
Exporting a Log as a File
The various logs can be exported and saved to a computer as CSV les, which can be opened using a CSV le editor or
a text editor.
●When exporting logs as les, use TLS or IPSec. Conguring the IPSec Settings(P. 555)
Start the Remote UI [Settings/Registration] [Device Management] [Export/Clear Audit Log]
[Export Audit Logs] [Export] Follow the on-screen instructions to save the le
●If you want to automatically delete all logs after they are exported, select the check box for [Delete logs from
device after export] before clicking [Export]. If you then click [Cancel], exporting is canceled and the logs are
deleted, even if they were not nished being exported as les.
●Log collection is stopped while the export process is being performed.
Deleting the Logs
You can delete all of the collected logs.
Managing the Machine
622
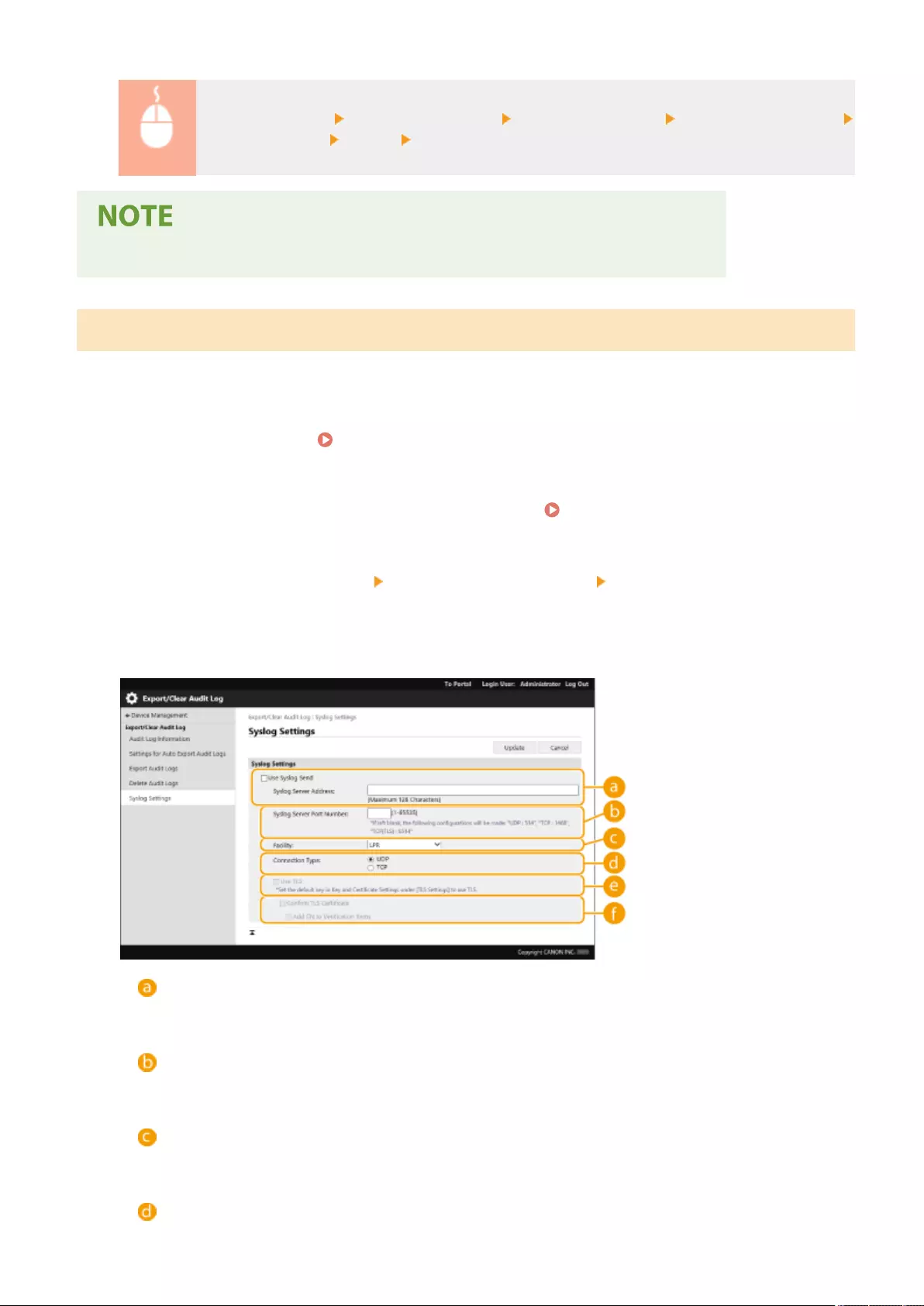
Start the Remote UI [Settings/Registration] [Device Management] [Export/Clear Audit Log]
[Delete Audit Logs] [Delete] [Yes]
●If [Settings for Auto Export Audit Logs] is enabled, you cannot manually delete audit logs.
Sending Logs via the Syslog Protocol
Syslog Information can be sent to an SIEM (security information/event management) system. Linking with an SIEM
system enables various information analyzed from realtime alert information to be centrally managed.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [Export/Clear Audit Log] [Syslog Settings].
4Select [Use Syslog Send], and specify the required settings.
[Syslog Server Address:]
Specify the address of the Syslog server to connect to. Enter the necessary information, such as IP address
and host name, according to your environment.
[Syslog Server Port Number:]
Enter the port number used by the Syslog server for Syslog communication. If left blank, the port number
dened in RFC (UDP: 514, TCP: 1468, TCP (TLS): 6514) is used.
[Facility:]
Specify the type of log messages to send. Select one of the following: [Local0] to [Local7], [Log Alert], [Log
Audit], [Security Messages], or [LPR] dened in RFC.
[Connection Type:]
Managing the Machine
623
Specify the communication type ([UDP]/[TCP]).
[Use TLS]
Select this to use TLS to encrypt information communicated with the Syslog server.
●When [TCP] is selected in [Connection Type:], you can set to use TLS.
[Conrm TLS Certicate]/[Add CN to Verication Items]
Set whether to verify the TLS server certicate sent when connecting and its CN (Common Name).
5Click [Update].
●A slight time lag occurs after the error for some audit logs, because Syslog transmission is performed after
polling every 30 seconds.
●The supported RFCs are 5424 (Syslog format), 5425 (TLS), and 5426 (UDP).
LINKS
Starting the Remote UI(P. 583)
Conguring the Key and Certicate for TLS(P. 549)
Managing the Machine
624
Importing/Exporting the Setting Data
72JY-0AF
Machine data such as Address Book destinations, user setting information, and various setting values can be exported
and saved to a computer. Exported data can also be imported into the machine from a computer. Data exported from
the machine can be imported into other Canon multifunction printers, making it easier to congure the settings on a
new machine, such as when you purchase a replacement. For more information on the setting items that can be
imported, see Settings/Registration Table(P. 671) . When importing or exporting, you can specify whether to
import or export all of the machine data, or only particular data.
Importing/Exporting All Settings(P. 628)
Importing/Exporting the Settings Individually(P. 632)
Designate an administrator to manage operations
●Designate an administrator with Administrator privileges to perform data import/export operations. When
data is imported, Address Book information, user settings, network settings, and other data are overwritten,
which may prevent some functions from working properly or cause problems with machine operation.
Exercise caution when importing data.
Do not turn OFF the machine until importing or exporting is complete
●It may take several minutes for the process to complete. Do not turn OFF the machine before the process is
complete. Doing so may result in data loss or cause the machine to malfunction.
●The following functions/processes cannot be carried out while importing/exporting data:
- Send jobs
- Forwarding jobs
- Fax/I-fax jobs
- Report print jobs
- Scan and Store in Network/Memory Media (during scanning or storing)
- Individual Importing/Individual Exporting
- Importing/Exporting from Address Book Management Software
- Batch Importing/Batch Exporting
- Importing/Exporting Personal button/Shared button
- Update process for the Register/Update Software function
- Synchronizing Custom Settings*
- Operating from the touch panel display of the machine
- Operating from the Remote UI
- Using the Remote Address Book
- Putting the machine to the sleep mode
* If the settings are being synchronized (including when currently being paused/entering a paused state),
the synchronization process of data related to personalized setting values, and group management data
is paused.
Managing the Machine
625
●Importing/exporting data cannot be performed while the following functions/processes are being carried
out:
- Send jobs
- Forwarding jobs
- Fax/I-fax jobs
- Report print jobs
- Scan and Store in Network/Memory Media (during scanning or storing)
- Individual Importing/Individual Exporting
- Importing/Exporting from Address Book Management Software
- Batch Importing/Batch Exporting
- Importing/Exporting Personal button/Shared button
- Update process for the Register/Update Software function
- Synchronizing Custom Settings*
- Using the Remote Address Book
- Processing the shutdown of the machine
- Displaying error code
* If the settings are being synchronized (including when currently being paused/entering a paused state),
you cannot import/export data related to personalized setting values, and group management data.
Do not import or export in different display languages
●If the display language differs between the exporting machine and the importing machine, the setting
values may corrupt, causing malfunction of the machine.
Do not edit exported les.
●Do not open and edit exported XML les, as this may cause the machine to malfunction.
When importing to a Canon multifunction printer other than this machine
●Some settings may not be imported. Settings/Registration Table(P. 671)
When using a password to protect the security policy settings
●The security policy settings can only be imported if the security policy setting password on the exporting
machine matches that of the importing machine, or if no password has been set for the importing machine.
If no password has been set for the importing machine, the password congured for the exporting machine
is set to the importing machine.
When synchronizing custom settings
●If synchronization of custom settings (client) is started, the importing and exporting of data subject to
synchronization (including the Address Book) become restricted. For information on synchronization of
custom settings, see Synchronizing Settings for Multiple Canon Multifunction Printers(P. 656) . For
information on the data subject to synchronization of custom settings, see List of Items That Can Be
Personalized(P. 139) . For information on conditions and restrictions when importing and exporting during
synchronization of custom settings, see Conditions for Removing Restrictions on the Importing/
Exporting of Settings and Other Items(P. 627) .
Importing Data after Starting Synchronization of Custom Settings (Client)
Follow the procedure below to import the data, and then synchronize the data.
Managing the Machine
626
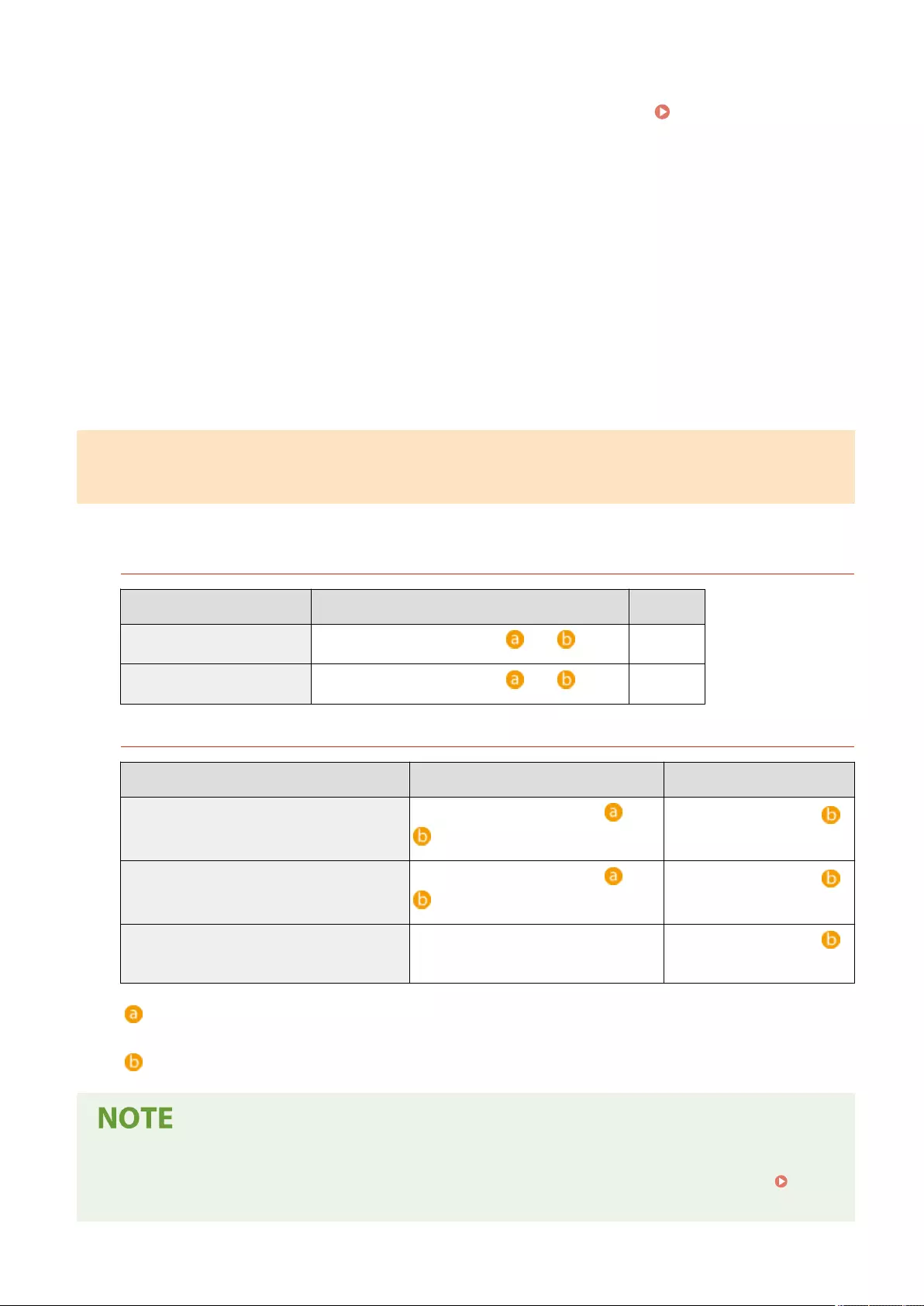
1Stop synchronization of custom settings on a client machine. Starting Setting
Synchronization(P. 659)
2To import data for existing users/groups, back up the data, and delete the data for
the users/groups that will be imported from the server machine.
●For information on the procedure, see the instruction manuals of the machine with the server function.
3Import the data to add to the client machine that has synchronization stopped.
4Synchronize the client machine with the server machine.
Conditions for Removing Restrictions on the Importing/Exporting of Settings
and Other Items
Importing/exporting becomes possible if the corresponding conditions are met for the items described below.
Batch Importing/Batch Exporting
Export Import
Personal Setting Information Only possible if both conditions and are met Unavailable
User Group Address List Only possible if both conditions and are met Unavailable
Individual Importing/Individual Exporting
Export Import
Personal Setting Information (all)
Only possible if both conditions and
are met
Only possible if condition
is met
User Group Address List (all)
Only possible if both conditions and
are met
Only possible if condition
is met
User Group Address List 01 to User Group
Address List 20
Not possible (there is no function for
exporting individual Address Books)
Only possible if condition
is met
:Execution is only possible for 15 minutes following successful preparation for exporting user data during
synchronization of custom settings (server).
:Execution is only possible if the connection destination of the server/client machine is "localhost:8443".
●For information on the procedure for preparing to export user data, see the instruction manuals of the
machine with the server function. For information on the procedure for importing address lists, see
Importing Settings Individually(P. 633) .
Managing the Machine
627

Importing/Exporting All Settings
72JY-0AH
You can export all of the setting data from the machine and save it to a computer, and then import it when conguring
the settings on a new machine, such as when you purchase a replacement. If you want to congure the same settings
on two or more Canon multifunction printers*, you can simply export all settings from one machine and import them
all to the others, eliminating the need to congure each machine separately. To perform these operations, log in to the
Remote UI with Administrator privileges.
* Only models that support the import/export of all settings
Exporting All Settings(P. 628)
Importing All Settings(P. 629)
Exporting All Settings
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Data Management] [Export].
4Select the check box for [Select All].
●Specic items can also be exported. For information on which Settings/Registration items correspond with
which items of the batch export function of the Remote UI, see Settings/Registration Table(P. 671) .
5Enter the password in [Encryption Password] select the security level from
[Security Level] click [Start Exporting] [OK].
●The password in [Encryption Password] will be required when importing the exported setting data. Use
alphanumeric characters.
●For conrmation, enter the password again in [Conrm].
●To encrypt all the settings data, select [Level 2] in [Security Level].
Managing the Machine
628
●It may take some time for the screen to change. Do not click [Start Exporting] more than once.
●When importing settings data to another model that does not support the setting in [Security Level], select
[Level 1].
6Click [Check Status].
●If the [Cannot be used when exporting.] message is displayed, do not use the Remote UI to perform the
operations.
7Click [Start Downloading].
8Follow the on-screen instructions to specify where to save the data.
To export all setting data without using a computer
●You can export all setting data to memory media such as a USB memory device. <Import/Export>
<Export to USB Memory>(P. 864)
Importing All Settings
You can import all setting data that was exported to a computer. When importing, the previously congured setting
values are overwritten. Note, however, that some machine models may not be able to import all setting items.
Settings/Registration Table(P. 671)
Managing the Machine
629

Check the System Manager information
●When importing the Department ID Management settings to a different multifunctional printer with
Department ID Management enabled, the System Manager information is overwritten, which may prevent
you from logging in with the previous System Manager ID and PIN. Before performing this operation, make
sure to check the System Manager information that is saved on the exporting machine.
When applying security policy settings
●The security policy settings can only be imported if the security policy setting password of the exporting
machine matches that of the importing machine, or if no password has been set for the importing machine.
If no password has been set for the importing machine, the password congured for the exporting machine
is automatically set to the importing machine.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Data Management] [Import].
4Click [Browse...], and specify the le to import.
5Enter the password in [Decryption Password], and click [Start Importing] [OK].
●In [Decryption Password], enter the same password that was entered when the setting data was exported.
●Select the check box for [Create Import/Export Result Report] if you want to output the import results as a
CSV le.
➠The data of the selected le is imported into the machine.
Managing the Machine
630

6Click [OK] [Check Status].
●The machine may need to be restarted, depending on the imported data. Click [Perform Restart].
●If you select the check box for [Create Import/Export Result Report] in the previous step, click [Settings/
Registration] [Data Management] [Import/Export Results] [Create Report] to export the import
results.
To import all setting data without using a computer
●You can import all setting data from memory media such as a USB memory device. <Import/Export>
<Import from USB Memory>(P. 864)
●Only one report le is saved. The next time a batch import is executed, the existing report le is deleted.
●Reports are created in the following language.
- If the display language of the machine is set to Japanese immediately after the import process: Japanese
- If the display language of the machine is set to something other than Japanese immediately after the
import process: English
Managing the Machine
631

Importing/Exporting the Settings Individually
72JY-0AJ
You can import/export only the address lists in the Address Book. Administrator privileges are required in order to
perform these operations.
Exporting Settings Individually(P. 632)
Importing Settings Individually(P. 633)
●For information on editing an Address Book CSV le for importing, see Address Book Items(P. 635) .
Exporting Settings Individually
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Data Management], and select the settings to export.
When exporting address lists
1Click [Address Lists] in [Import/Export Individually].
2Click [Export...].
●If the page for entering a PIN is displayed, enter the PIN and click [OK].
3Congure the necessary settings.
Managing the Machine
632

[Address Lists]
Select the address lists to export. Note that after the address lists are saved, the names of the address
lists revert back to the factory defaults.
[Security Level]
You can set the security level if [Custom Format] is selected in [File Format]. When [Level 1] is selected,
you can import to all Canon multifunction printers. When [Level 2] is selected, the password for the
address list data is encrypted using a more secure method than [Level 1]. However, the data can only
be imported to the machine models that support the [Level 2] setting (models on which the [Security
Level] setting is displayed).
[File Format]
Select the le format of the data to be exported. Select [Custom Format] when you intend to import all
information registered in address lists to another Canon multifunction printer, or select [LDAP Format]
or [CSV Format] if the le is to be used by a computer application. Note, however, that if [LDAP Format]
is selected, only the e-mail addresses and fax numbers are saved.
To set a password for exported data
●Set <Include Password When Exporting Address Book> to <On> ( <Include Password When
Exporting Address Book>(P. 850) ). When this setting is congured, the items for entering the
password are displayed on the [Export Address Lists] screen. If a password has been set, the data can
only be imported if the correct password is entered.
To edit data exported in the CSV format
●For information on each column in the Address Book, see Address Book Items(P. 635) .
●Data may not be able to be imported correctly when importing to an old version of the machine.
4Click [Start Exporting].
5Follow the on-screen instructions to specify where to save the data.
Importing Settings Individually
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Data Management], and select the settings to import.
When importing address lists
1Click [Address Lists] in [Import/Export Individually].
2Click [Import...].
●If the page for entering a PIN is displayed, enter the PIN and click [OK].
Managing the Machine
633

3Congure the necessary settings.
[Address Lists]
Select the address list that is the import destination.
[Import Method]
Select [Add] if you want to add the imported destinations without deleting the current address list, or
select [Delete and Overwrite] if you want to delete the current address list and overwrite the data with
the imported destinations.
[File Path]
Click [Browse...], and specify the le to import.
[File Format]
Select the le format of the data to be imported. Select [Custom Format] for les in the dedicated
format for Canon multifunction printers (*.abk), select [LDAP Format] for LDAP format les (*.ldif), or
select [CSV Format] for CSV format les (*.csv).
[Decrypt Address List Authentication Information]
When importing encrypted les, select the check box and enter the same password that was entered
when the setting data was exported.
4Click [Start Importing] [OK].
●The machine may need to be restarted depending on the settings to import. Restarting the
Machine(P. 591)
LINKS
Importing/Exporting All Settings(P. 628)
Restricting Use of the Address Book(P. 566)
Managing the Machine
634

Address Book Items
72JY-0AK
This section describes each column of the Address Book. Refer to this section when editing CSV les.
Header
Header Name Required Notes
# Canon AddressBook CSV version:
0x0002 Yes Fixed value
# CharSet: UTF-8 Yes Fixed value
# dn: xed
Yes
(Required for
One-touch
button Address
Book)
Indicates that the destination name is handled as a one-
touch button. Entry is only required when the import
destination is a one-touch button Address Book.
Added when exporting from a one-touch button Address
Book, so there is no need to add this item again when
importing.
# SubAddressBookName: Address Book
name Yes
Enter the Address Book name after the colon (:), with a space
in between. If the Address Book is unnamed, leave the space
after the colon (:) blank.
# DB Version: 0x010a Yes Fixed value
# Crypto Version: 2 No Leave this section blank if you are creating a new Address
Book CSV le.
# Crypto Attribute: pwd No Leave this section blank if you are creating a new Address
Book CSV le.
●The presence a header relating to "Crypt" in a header indicates that the password attribute is
encrypted. However, when entering this information into a newly-created CSV le, or when editing the
pwd attribute of an exported CSV le, encryption cannot be performed in a manner that allows the
machine to correctly decode. In such cases, delete the corresponding portion from the header.
Body
Attribute Name Description Required Notes
objectclass Object class (destination
type) Yes
Indicates the type of destination. The required
attribute varies according to this value. Enter
one of the following.
●For e-mail: email
●For G3 fax: g3fax
●For IP fax: ipfax
●For fax: ifax
●For le server (SMB, FTP, WebDAV):
remotelesystem
●For group: groupds
Managing the Machine
635
cn Destination name No Enter in UTF-8 character code. Otherwise, the
destination name will be left blank.
cnread Phonetic alphabet No Displayed as "phonetic" if the display language
is set to "Japanese".
cnshort One-touch button name No Enter in UTF-8 character code. Otherwise, the
one-touch button name will be left blank.
subdbid Address Book number No
Specify which Address Book to import to in the
Remote UI. Not required when writing to a CSV
le.
mailaddress E-mail address
Yes
(Required for
certain
destination
types)
This attribute is required for e-mail and I-fax
destinations.
dialdata Fax number
Yes
(Required for
certain
destination
types)
This attribute is required for fax destinations.
However, it is not required if the destination is
an IP fax using a URI.
uri The URI used with an IP fax
Yes
(Required for
certain
destination
types)
Only usable for IP fax destinations. This
attribute is required if you do not specify a fax
number for an IP fax.
For an IP fax destination using a URI, you must
also specify the "URI ag" (see below).
url File server destination host
name
Yes
(Required for
certain
destination
types)
This attribute is required for le server
destinations. You can only use letters and
symbols.
path File path for le server
destination No You can only use letters and symbols.
protocol Protocol
Yes
(Required for
certain
destination
types)
This attribute is required for le server
destinations. Enter one of the following.
●For SMB: smb
●For FTP: ftp
●For WebDAV: addonprotocol0225
username
User name used when
logging in to a le server
destination
Yes
(Required for
certain
destination
types)
This attribute is required for FTP le server
destinations. The user ID is required to log in
to a le sending destination, and therefore is
also required for le sending destinations
using authentication, such as SMB and
WebDAV.
pwd
Password used when
logging in to a le server
destination
No This attribute is required for le sending
destinations using authentication.
member A member of a group
destination
Yes
(Required for
certain
destination
types)
This attribute is required for group
destinations.
Managing the Machine
636
indxid A serial number allocated
to a destination Yes
This attribute is required if the import
destination is a one-touch button Address
Book. This number becomes the one-touch
button number. In other cases, enter a
number from 201 to 1,800.
enablepartial Setting for dividing data
when sending an e-mail No Enter either "on" or "off".
sub Subaddress of a le server
destination No
faxprotocol Fax protocol No
Enter one of the following.
●g3
●ecm
ecm Indicates the use of ECM. No Enter either "on" or "off".
txstartspeed Starting transmission
speed for faxing No
Enter one of the following.
●2400
●4800
●7200
●9600
●14400
●33600
commode
Fax communication mode
Setting regarding
international sending
No
Enter one of the following.
●For PSTN domestic line: domestic
●For PSTN international line 1:
international1
●For PSTN international line 2:
international2
●For PSTN international line 3:
international3
lineselect Selected fax line No
Enter one of the following. Otherwise, "auto" is
used.
●For lines 1 to 4: line1, line2, line3, or line4
●For automatic line specication: auto
uricommode IP fax communication
mode
Yes
(Required for
certain
destination
types)
This is the chosen communication mode for IP
faxes. This attribute is required if you use IP
faxing, and are sending to a fax destination.
Enter one of the following.
●For G3: ip_g3
●For intranet: ip_lsv
●For a VoIP gateway: ip_gw
uriag The ag for a URI used with
an IP fax
Yes
(Required for
certain
destination
types)
This attribute is required if the destination is
an IP fax, and you use a URI instead of a fax
number. Enter either "TRUE" or "FALSE". If you
use a URI, enter "TRUE".
pwdinputag
Setting for requesting
password input per
transmission
No Enter either "on" or "off".
Managing the Machine
637
ifaxmode I-Fax mode (simple/full) No Enter either "simple" or "full".
transsvcstr1 I-fax relay service text
string 1 No Enter total of up to 40 alphanumeric
characters and symbols.
transsvcstr2 I-fax relay service text
string 2 No Enter total of up to 16 alphanumeric
characters and symbols.
ifaxdirectmode I-fax direct sending No Enter either "on" or "off".
documenttype I-fax document type No
Enter one of the following.
●To send in color: cl
●To send in black and white: bw
bwpapersize Paper size allowable when
sending an I-fax No
bwcompressiontype Compression format used
when sending an I-fax No
bwpixeltype Color space allowable when
sending an I-fax No
bwbitsperpixel Bit count allowable when
sending an I-fax No
bwresolution Resolution allowable when
sending an I-fax No
clpapersize Paper size allowable when
sending a color I-fax No
clcompressiontype Compression format used
when sending a color I-fax No Fixed as "jpeg".
clpixeltype Color space allowable when
sending a color I-fax No Fixed as "rgb".
clbitsperpixel Bit count allowable when
sending a color I-fax No Fixed as "8".
clresolution Resolution allowable when
sending a color I-fax No
accesscode Access code No Enter up to seven numbers.
uuid A UUID for identifying a
destination No This item is not necessary when creating a new
CSV le.
cnreadlang Phonetic alphabet
character code No
Displayed as "phonetic" if the display language
is set to "Japanese". Enter the language code
to use. For Japanese (SJIS), enter "ja".
enablesfp Unused No This item is unused, and therefore does not
need to be entered.
memberobjectuuid
Used for Personal Address
List/User Group Address
List
No
loginusername
Used for Personal Address
List/User Group Address
List
No
Managing the Machine
638
logindomainname
Used for Personal Address
List/User Group Address
List
No
usergroupname
Used for Personal Address
List/User Group Address
List
No
personalid
Used for Personal Address
List/User Group Address
List
No
Managing the Machine
639

Update Firmware
Updating the Firmware
72JY-0AL
New rmware is periodically released to add new functions or resolve issues with
existing functions. If new rmware is available, follow the procedure below to update
it on the machine. Administrator privileges are required in order to update the
rmware.
Checking the Firmware Version(P. 640)
Updating the Firmware(P. 641)
●Do not perform the following operations while updating the rmware. Doing so may cause a critical error.
- Turn OFF the main power
- Remove the LAN cable
- Perform communication (such as printing) with the machine from another computer or application*1
-Congure the sleep settings of your computer*2
*1 When updating the rmware in a network environment, ensure that other users do not perform operations such as
printing.
*2 The rmware may not be updated correctly if the computer enters the sleep mode.
Preparing to update the rmware
●Download the latest rmware from the Canon website (https://global.canon/).
●Back up the machine data and settings in case the rmware update is not performed properly.
Importing/Exporting the Setting Data(P. 625)
Note regarding the update process
●The machine restarts several times.
●The update process is interrupted if jobs remain.
●The screen switches several times during the update process. It may take some time for the screen to
switch, but do not close the browser until the update process is complete.
Checking the Firmware Version
Check the rmware version of the machine before updating the rmware and after updating the rmware.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Status Monitor/Cancel] on the portal page. Remote UI Screen(P. 585)
Managing the Machine
640
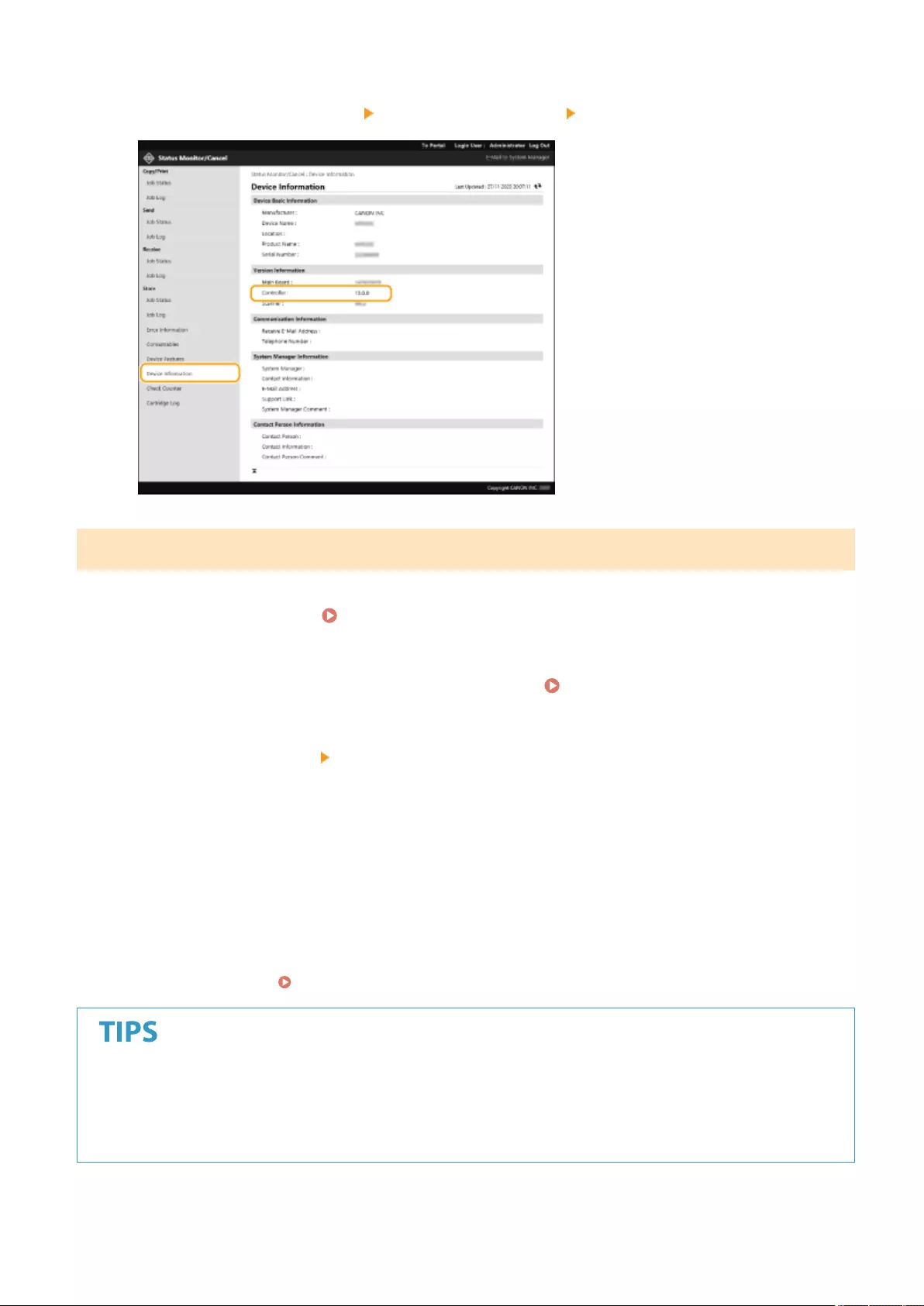
3Click [Device Information] [Version Information] check [Controller].
Updating the Firmware
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [License/Other] [Register/Update Software].
4Click [Manual Update].
5Click [Browse...], select the rmware update to use, and click [Update].
➠When the <The process has stopped because there are one or more unnished jobs. Restart the device
manually in order to start the process. The browser may be closed.> message appears, turn the machine
OFF and back ON. Turning OFF/Restarting the Machine(P. 591)
Updating the Firmware from the Home Screen
●Firmware updates can also be performed from <Update Firmware> on the Home screen.
Administrator privileges are required for this operation.
Managing the Machine
641
Updating the Firmware (Distribution)
72JY-0AR
If the machine has access to the Internet, you can download the latest rmware for
the machine from Canon's distribution server. This might be more exible and
convenient than the other update method ( Updating the Firmware(P. 640) )
because both manual and automatic update options are available, enabling you to
download the rmware at a specied time or as soon as the latest version is
available. Administrator privileges are required in order to perform these
operations.
Preparing to update the rmware
●Back up the machine data and settings in case the rmware update is not performed properly.
Importing/Exporting the Setting Data(P. 625)
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [License/Other] [Register/Update Software].
4Perform a communication test.
●Test whether you can access the distribution server over the network.
1Click [Display Logs/Communication Test].
2Click [Communication Test] [Yes].
➠The results of the communication test are displayed.
●If [Could not connect to distribution server. Check the distribution server and network.] is displayed,
check that the LAN cable is connected and the network settings are congured properly. Setting up
Using the Setup Guide(P. 6)
5Click [Distributed Update] [Conrm New Firmware].
6Congure the necessary settings.
Managing the Machine
642

[Current Version]/[Applicable Firmware]
You can check the current rmware version and new one respectively.
[Release Note]
Important information is displayed. Make sure to read and understand the contents.
[Distribution Schedule]
To download the rmware immediately, select [Distribute now]. To automatically download the rmware
at a specied date and time, select [Distribute at specied date and time] and specify the date and time in
[Year]/[Month]/[Date]/[Time]. You can schedule a time within a week in advance.
[Timing to Apply]
To automatically apply the rmware immediately after downloading is complete, select [Apply immediately
after distribution]. To automatically apply the rmware at a specied date and time, select [Apply at
specied date and time] and specify the date and time in [Year]/[Month]/[Date]/[Time]. You can also select
[Apply manually] to manually apply the rmware.
[Updated Module Only]
Select [On] to perform an incremental update (download only the difference between the current and new
rmware versions). If you want to download the entire rmware, select [Off]. Note that some rmware
versions do not support incremental update.
[E-Mail Address]
Enter your e-mail address. The distribution server sends the update status to the e-mail address entered
here.
[Comments]
Enter a description or note to add to the e-mail. If you manage multiple machines, enter the device name
so that you can easily identify the received update status.
7Click [Execute] [OK].
●If the license agreement screen is displayed, check the information and click [I Agree].
●If [Apply immediately after distribution] or [Apply at specied date and time] is selected in the previous
step, the machine automatically restarts immediately after the rmware is applied. If [Apply manually] is
selected, you need to apply the downloaded rmware manually. Applying the Downloaded
Firmware(P. 644)
Managing the Machine
643
●Changing the distributed update settings again may delete the downloaded rmware or cancel the
scheduled settings.
Canceling the distribution schedule
●On the screen displayed in step 5, click [Delete Scheduled Distribution] [Yes].
Automatically check for new rmware (scheduled update)
●If you click [Scheduled Update Settings] [Edit] in step 5, you can set the machine to periodically access the
distribution server for new rmware. If new rmware is available, it is downloaded to update the rmware
on the machine. Setting Scheduled Updates(P. 645)
◼Applying the Downloaded Firmware
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [License/Other] [Register/Update Software].
4Click [Distributed Update] [Apply Firmware] [OK].
●The machine automatically restarts immediately after the rmware is applied.
To delete the rmware
●Click [Delete Firmware] [OK].
Conguring settings via the control panel
●You can also access and congure the distributed update settings by pressing (Settings/Register)
<Management Settings> <License/Other> <Register/Update Software> <Update Firmware>.
<License/Other>(P. 861)
Managing the Machine
644
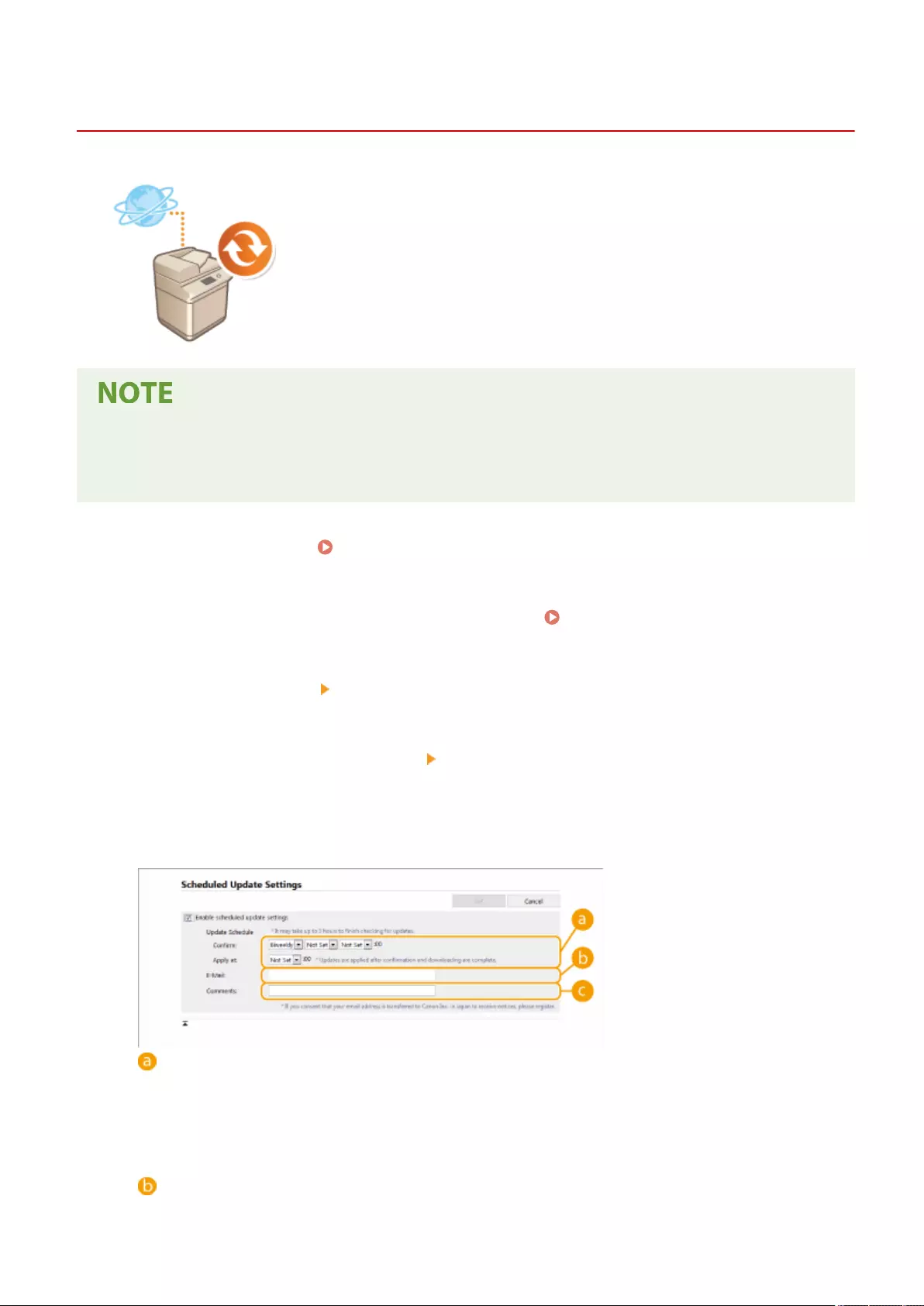
Setting Scheduled Updates
72JY-0AS
You can set the machine to regularly check for new applicable rmware and
automatically update the rmware of the machine.
●This operation can only be performed by a user with the required privileges.
●If the downloading of the rmware is not complete, or the downloaded rmware has not been applied, you
cannot perform a scheduled update.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [License/Other] [Register/Update Software].
4Click [Scheduled Update Settings] [Edit...].
5Select the check box for [Enable scheduled update settings], and congure the
necessary settings.
[Update Schedule]
[Conrm]
Select the cycle ([Biweekly] or [Weekly], a day ([Sun] to [Sat]), and the time). The time is displayed in 24-
hour notation. The rmware check may take up to 3 hours to complete from the specied time.
[Apply at]
Select the time to apply downloaded rmware.
[E-Mail]
Managing the Machine
645
Enter the e-mail address of the administrator. You can receive e-mails regarding the update status that is
sent from the distribution server.
[Comments]
Enter the comment that will automatically be added to the e-mail. If the model name is entered, you can
identify which device status the e-mail is about.
●If previously downloaded rmware has not been applied by scheduled update, the next scheduled
update is not performed.
●If Scheduled Update is set, a rmware update is applied at the specied time after the new rmware
is downloaded from the distribution server. After application is complete, the machine automatically
restarts.
6Click [Set].
Managing the Machine
646
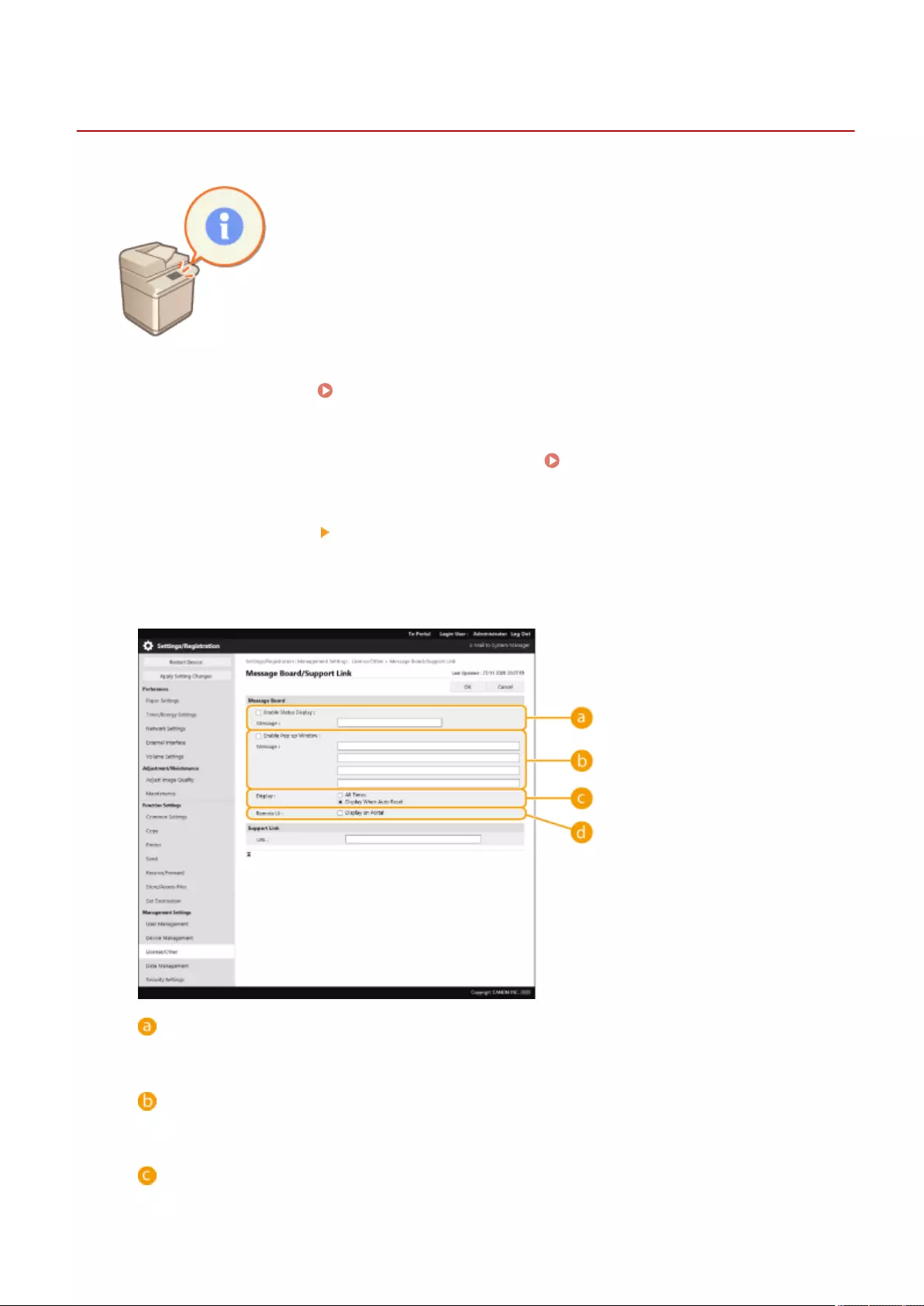
Displaying Messages from the Administrator
72JY-0AU
You can display messages to users on the touch panel display. Messages can be
displayed at the bottom of the touch panel display or in a separate pop-up window,
and you can select which display method to use based on the type of message or
user. When a message is displayed in a pop-up window, you can also display the
same message on the Remote UI portal page. Administrator privileges are required
in order to congure these settings.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [License/Other] [Message Board/Support Link].
4Enter the message, and click [OK].
[Enable Status Display]
To display the message at the bottom of the touch panel display, select the check box and enter the
message in [Message]. Use this setting for displaying operational tips and other low-priority messages.
[Enable Pop-up Window]
To display the message in a pop-up window on the touch panel display, select the check box and enter the
message in [Message]. Use this setting for displaying high-priority messages.
[Display]
Select the display method for the pop-up window.
Managing the Machine
647
[All Times] The pop-up window is displayed continuously, and the machine cannot be operated.
Use this setting for messages such as an out-of-service notice.
[Display When Auto Reset]
The pop-up window is displayed when no operations are performed for a specied
period of time, or when the machine is restarted. Use this setting for messages such
as a maintenance schedule notice.
[Remote UI]
If you select the check box, the message shown in the pop-up window is also displayed on the Remote UI
portal page.
Canceling the message display
●Clear the check boxes for [Enable Status Display], [Enable Pop-up Window], and [Remote UI]. If you also want
to delete the message contents, remove the text that was entered in the [Message] text boxes.
LINKS
<Timer/Energy Settings>(P. 777)
Managing the Machine
648

Visual Message
Conguring the Visual Message Function
72JY-0AW
The Visual Message function enables you to display simple content and messages on the touch panel display.
Displaying messages from the administrator or event notications, etc. on the touch panel display enables the
machine to be used as an information sharing tool in the oce.
●When the Visual Message function is set, content can be checked from <Visual Message> on the (Home),
regardless of the above timing.
●Set a le saved on a le server or in the Advanced Box of another Canon multifunctional printer on the same
network as the content to display. Using Other Machines and Memory Media(P. 437)
●You can also set a website on the internet as the content via a proxy server. The proxy settings used for this
function are the same as the settings in <Proxy Settings>(P. 787) .
●The content is displayed when printing starts if the forced hold print function is enabled and the [Display
When Print Job Starts] check box is selected.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [License/Other] [Visual Message Settings] [Display Settings].
4Set the display timing and content.
Managing the Machine
649

Setting the Display Timing
[Display After Logout/Auto Reset]
Select this check box to display the content after logging out or after the auto reset mode activates.
The setting to display the content after logging out is enabled when <Login Screen Display Settings> is set
to <Display When Device Operation Starts>. To display the content after the auto reset mode activates, set
<Auto Reset Time> to 1 minute or longer.
[Display After Login]
Select this check box.to display the content after logging in. This is enabled when <Login Screen Display
Settings> is set to <Display When Device Operation Starts>.
[Display When Print Job Starts]
Select this check box to display the content when printing starts. This is enabled when forced hold printing
is set.
Setting the Content for Each Display Timing
[SMB]
Select the check box to access the content to display via [SMB].
[HTTP/WebDAV]
Select the check box to access the content to display via [HTTP/WebDAV].
Managing the Machine
650
[File Path:]
Enter the path to the content to display.
Example:
●[SMB] : \\server01\share\signage.jpg
●[HTTP/WebDAV] : https://webdav-server1/signage.html
[User Name:]/[Password:]
Enter the user name and password necessary for logging into the Advanced Space or le server.
[Conrm Certicate for TLS Communication]/[Add CN to Verication Items]
Set whether to verify the TLS server certicate sent when connecting and its CN (Common Name).
5Click [OK].
●To display the content after the Auto Reset mode initiates, set <Auto Reset Time> to one minute or longer.
●For information on the le formats and data sizes that can be displayed, see Management
Functions(P. 1091) .
●This setting can only be specied by a user with Administrator privileges.
●This setting can be imported/exported. The same setting can be imported to multiple devices (only Canon
devices that support the Visual Message function) to display the same notice or information on multiple
devices. Importing/Exporting the Setting Data(P. 625)
●[File Path:] is imported/exported with this setting. If a le in the Advanced Space is specied and displayed
on the exporting machine, perform one of the following operations:
- Manually copy the le in the Advanced Space of the exporting machine to the Advanced Space of the
importing machine.
- Change [File Path:] to the path where the le exists.
●If you are going to perform login operations, perform them after closing the Visual Message screen.
Logging into the Machine(P. 137)
●If the Copy Card Reader is attached, the content is not displayed.
LINKS
<Login Screen Display Settings>(P. 854)
<Use User Authentication>(P. 854)
<Auto Reset Time>(P. 778)
Managing the Machine
651
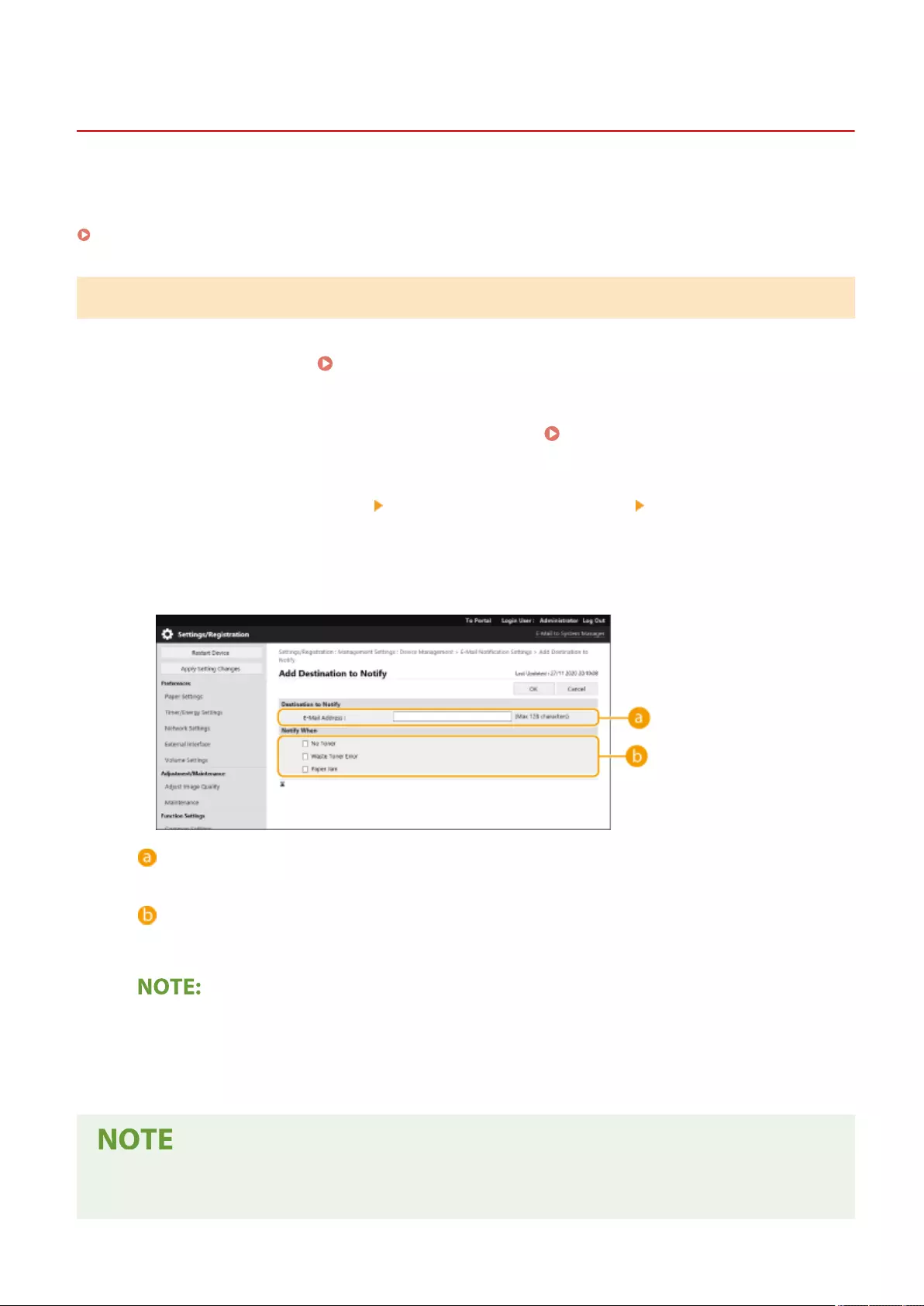
Sending E-Mail Notication When an Error Occurs
72JY-0AX
You can notify an e-mail address specied in advance when toner needs replacing or a paper jam needs to be cleared,
etc.
Specifying the Destination and the Information to Send(P. 652)
Specifying the Destination and the Information to Send
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Settings/Registration] on the portal page. Remote UI Screen(P. 585)
3Click [Device Management] [E-Mail Notication Settings] [Add Destination to
Notify...].
4Specify settings as necessary.
[Destination to Notify]
Enter the e-mail address.
[Notify When]
Select the information to send.
●You can register up to ve destinations.
5Click [OK].
●The result of sending the e-mail can be checked in [Status Monitor/Cancel] in [Job Log].
●This setting can only be specied by a user with Administrator privileges.
Managing the Machine
652
Installing System Options
72JY-0AY
When using system options, you may need to log in with Administrator privileges to
register licenses. To register a license, you will need the number that is printed on
the license access number certicate. Make sure you have it with you before you
start. You can perform license registration even if the machine is not connected to
the network.
1Perform a communication test.
●Test whether you can register the license over the network.
1Press (Settings/Register).
2Press <Management Settings> <License/Other> <Register/Update Software> <Software
Management Settings>.
3Press <Test Communication>.
➠The <Do you want to test communication?> message is displayed.
4Press <Yes>.
➠The results of the communication test are displayed.
●If <NG> is displayed, check that the LAN cable is connected and the network settings are congured
properly. Setting up Using the Setup Guide(P. 6)
●If you cannot connect to the network, register the license oine. When Registration Cannot Be
Performed over the Network(P. 655)
2Press (Settings/Register).
3Press <Management Settings> <License/Other> <Register/Update Software>
<Install Applications/Options>.
4Press <License Access Number>, and enter the license access number.
5Conrm the number, and press <Start>.
6Select the function to install, and press <Install>.
●If the license agreement screen is displayed, check the information and press <I Agree>.
7Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
Managing the Machine
654
◼When Registration Cannot Be Performed over the Network
If for some reason the machine is unable to connect to the network, register the license oine. First obtain a license
key using a computer connected to the network, then register it by entering it into the machine. To obtain a license
key, you will need the number that is printed on the license access number certicate, along with the serial number of
the machine.
1Access the license issuing website (http://www.canon.com/lms/license/) and obtain
the license key.
●Follow the on-screen instructions and enter the license access number and serial number to obtain the
license key.
2Press (Settings/Register).
3Press <Management Settings> <License/Other> <Register License>.
4Enter the license key.
5Press <Start> <OK>.
6Press (Settings/Register) (Settings/Register) <Apply Set. Chng.> <Yes>.
Conrming the serial number
●The serial number is displayed in the bottom left of the screen when you press the [Counter/Device
Information] key. It can also be conrmed from the Remote UI portal page.
Managing the Machine
655
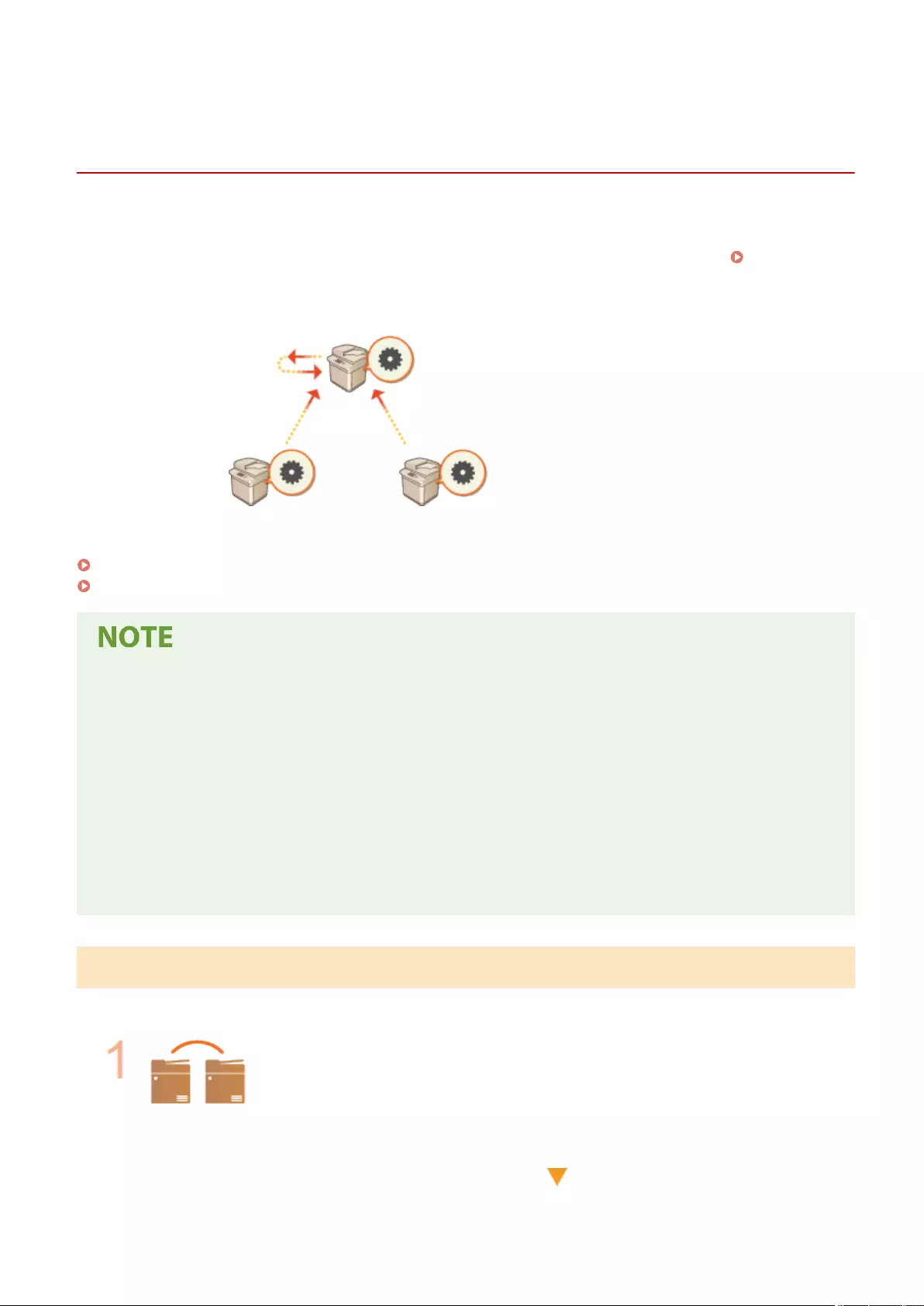
Synchronizing Settings for Multiple Canon
Multifunction Printers
72JY-0C0
You can synchronize the personalized data of multiple Canon multifunction printers on a network. This enables the
address book and Personal button/Shared button, etc. specied and registered on a single machine to be used on
other machines that are synchronized. For information on the items subject to synchronization, see List of Items
That Can Be Personalized(P. 139)
Server/Client Machine
Client Machine Client Machine
Starting Setting Synchronization(P. 659)
Switching the Machines to Synchronize(P. 662)
●This machine does not have a server function. It operates as a client machine.
●Enable the server function on the machine with the server function, and connect this machine as a client
machine.
●Up to 10 machines including the server machine can be synchronized.
●Synchronized values may not be reected, depending on the optional products and the machine
conguration.
●A server machine can either be used as a server machine that does not synchronize its own data, or as both
a server and client machine (server/client machine).
●If you do not start client functions on the server machine, data specied on the server machine will not be
reected in client machines.
Procedure for Synchronizing
Specify synchronization as indicated below.
Initial Check
●Are the machines to synchronize correctly connected to the network?
Managing the Machine
656
Exporting the User Data
●It is recommended that you export the user data for backup purposes. Importing/
Exporting the Setting Data(P. 625)
Specifying the Server Machine Settings
●Start synchronization on the server machine. For information on the procedure, see
the instruction manuals of the machine with the server function.
Specifying the Detailed Synchronization Settings
●Specify the detailed synchronization settings on the server machine. For information
on the procedure, see the instruction manuals of the machine with the server
function.
Starting Synchronization
●Specify the connection destination on the client machines and start synchronization.
Starting Setting Synchronization(P. 659)
Checking Synchronization
●Check the detailed synchronization settings, registered users, and connected
machines on the server machine. For information on the procedure, see the
instruction manuals of the machine with the server function.
●To change the scope of sharing, etc. after starting synchronization, shut down all the client machines,
change the settings on the server machine, and start all the client machines again.
●Synchronization starts after the client machines are restarted.
●When a client machine starts and connects to the server machine, the user data registered in both the
server machine and client machine is overwritten with the user data in the server machine, and the user
data set in the client machine is deleted. To use the user data in a client machine to be connected to, delete
the corresponding data from the server machine via [Delete User Data] in [Synchronize Custom Settings
(Server)] before starting the client machine.
●If different data exists for the same user in multiple client machines that are started in succession, the user
data in the client machine that rst connected to the server is used for synchronization.
Managing the Machine
657
: Data of user 1
: Other data of user 1
: Data of user 2
: Data of user 3
User data of client machine A
●The rst client machine that
connected to the server.
●Has the data of user 1 and
user 2 registered.
User data of client machine
B
●Has the other data of user
1 and the data of user 3
registered.
User data registered in the server
machine
●The data of user 1 registered in
the server machine is
synchronized using the data of
client machine A.
●If a problem occurs in the server machine or a client machine after starting synchronization, the data with
[Device-Specic (Not Shared)] set for its scope of sharing in the machine with the problem returns to its
default settings and is not restored.
●To synchronize custom settings between machines, the machine authentication settings and group
management settings must be the same. For information on specifying the same authentication settings,
see the instructions for the login application. For group management settings, it is recommended that the
settings in one machine are exported and imported into the other machines. When Department IDs are
used for group management, set the same Department IDs for each machine.
●To synchronize the information regarding the network places for keychains, the order that the network
places are registered must be the same in all machines.
●If a machine you are using is an older version, registered shortcuts and keychains may not be synchronized.
●When synchronization of custom settings is performed, <Delete Oldest User Settings> is set to <Action
When Maximum Number of Users Exceeded>(P. 859) for server/client machines and client machines and
cannot be changed.
●If synchronization of custom settings (client) is started, the data subject to synchronization (including the
Address Book) becomes unable to be imported or exported. For information on importing/exporting
settings data, see Importing/Exporting the Setting Data(P. 625) . For information on the data subject to
synchronization of custom settings, see List of Items That Can Be Personalized(P. 139) .
Managing the Machine
658
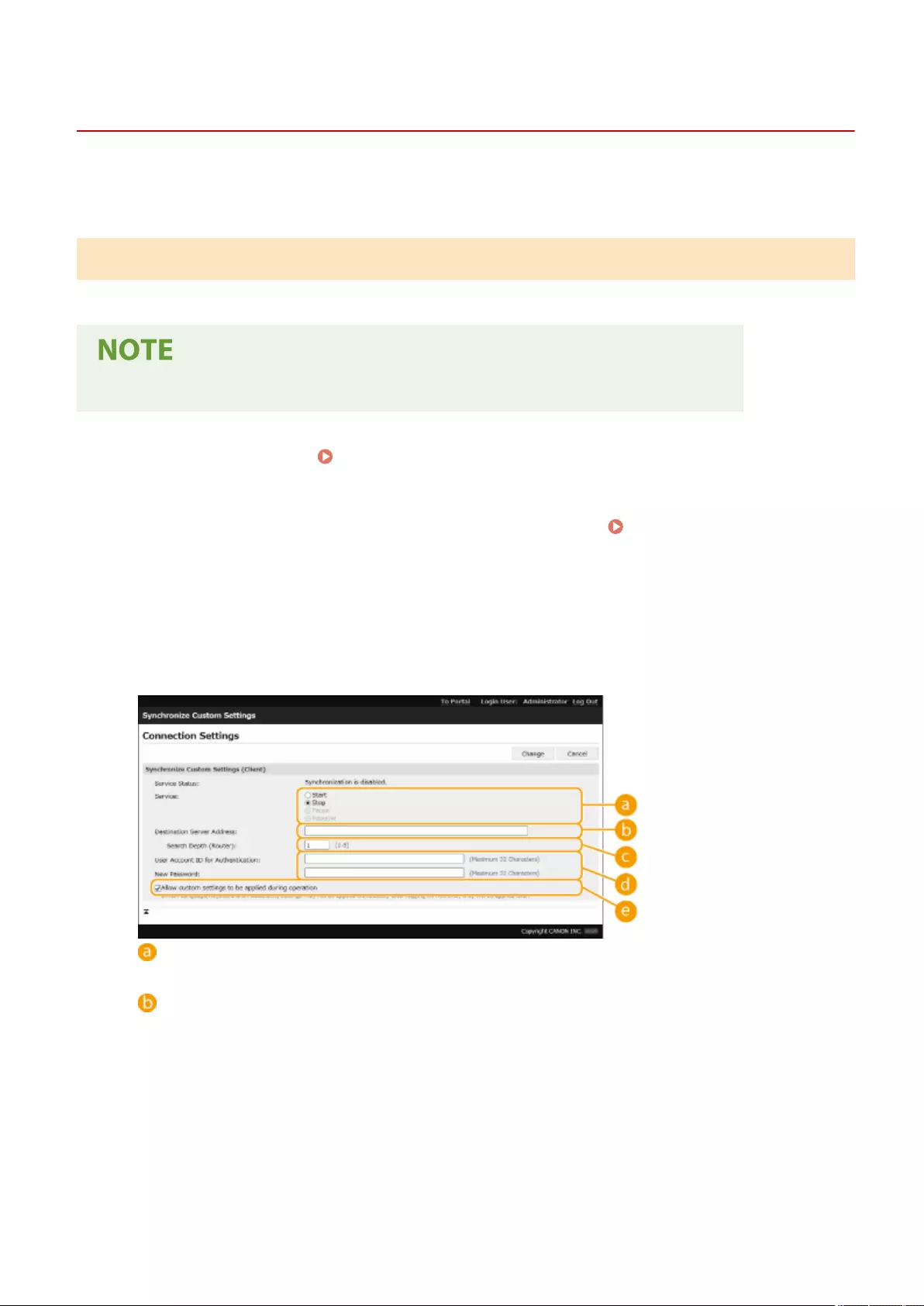
Starting Setting Synchronization
72JY-0C1
Use the Remote UI to specify the settings for starting synchronization and start synchronization. Administrator
privileges are required for registration.
Synchronizing Custom Settings
Specify the settings for the client machine.
●Other settings for the server machine are required on the machine with the server function.
1Start the Remote UI. Starting the Remote UI(P. 583)
2Click [Synchronize Custom Settings] on the portal page. Remote UI Screen(P. 585)
3Click [Change Connection Destination...].
4Specify the required settings.
[Service]
Select [Start].
[Destination Server Address:]
Enter the IP address or host name of the server machine. When specifying the port number, "8443" must
be specied. The port number can be omitted. If this is left blank, the server machine is automatically
discovered.
●Example settings (IPv4):
Using an IP address: 192.168.18.138
Using a host name: v4.server.canon.com
●Example settings (IPv6):
Using an IP address: fe80::65f0:82cb:b3d6:e6bc
Using a host name: v6.server.canon.com
When specifying the port number: [fe80::65f0:82cb:b3d6:e6bc]:8443
Managing the Machine
659

[Search Depth (Router):]
Enter the number of routers to hop (the number of routers to communicate through). If this value is too
small, the server machine may not be discovered with network discovery. If you do not want to
communicate through routers, specify "1".
[User Account ID for Authentication:]/[New Password:]
Enter the ID and password of a user account with Administrator privileges for the machine to use as the
server machine.
[Allow custom settings to be applied during operation]
Select the check box to reect the <Switch Language/Keyboard>, <Accessibility>, and <Personal SSID and
Network Key Settings> settings when it becomes possible if they could not be reected immediately after
logging in.
●In the following cases, synchronization can be set without performing step 4.
- When the machines to synchronize are within the same router.
- When <Use User Authentication> is set to <On> on the server machine (see <Use User
Authentication>(P. 854) ) and User Authentication is set as the login service (see Changing
Login Services(P. 1075) )
- When nothing is entered in [User Account ID for Authentication:] on the client machines (the item is
null)
- When the service for synchronizing custom settings is started on the server machine (if the machine
is a server/client machine, the setting can be changed by starting the server service and the client
service at the same time)
- When there is only one server machine for synchronizing custom settings on the same network
●If the network settings of the server machine include both IPv4 and IPv6, and if IPv6 is prioritized and
the client machine disables IPv6, the client machine cannot connect via search. Enter the IPv4 address
for the destination server address.
5Click [Change].
6Restart the machine. Turning OFF/Restarting the Machine(P. 591)
●Continue to congure the synchronization settings on the machine with the server function.
Checking the Communication Log for Synchronization
●You can check the communication log from the screen for synchronizing custom settings. The log can
also be downloaded as a le.
●"Warning" is recorded as the level when the server machine cannot communicate temporarily.
●"Error" is recorded as the level when the maximum amount of data that can be registered has been
exceeded or authentication with the server machine fails.
Simple Synchronization Settings
●Synchronization of custom settings can be started from the control panel for Canon multifunction
printers within the same router.
- For a client machine:
Managing the Machine
660

Press (Settings/Register) <Management Settings> <Device Management> set
<Synchronize Custom Settings (Client)> to <Enable>.
●User Authentication must be enabled as the authentication method.
Note When Canceling Synchronization
●When a client machine cancels synchronization of custom settings, the client machine will become
unable to retrieve the settings for each user registered in the server machine. Therefore note that the
personalized data of a machine that was a client machine may not have the latest data after
synchronization of custom settings has been canceled.
Managing the Machine
661
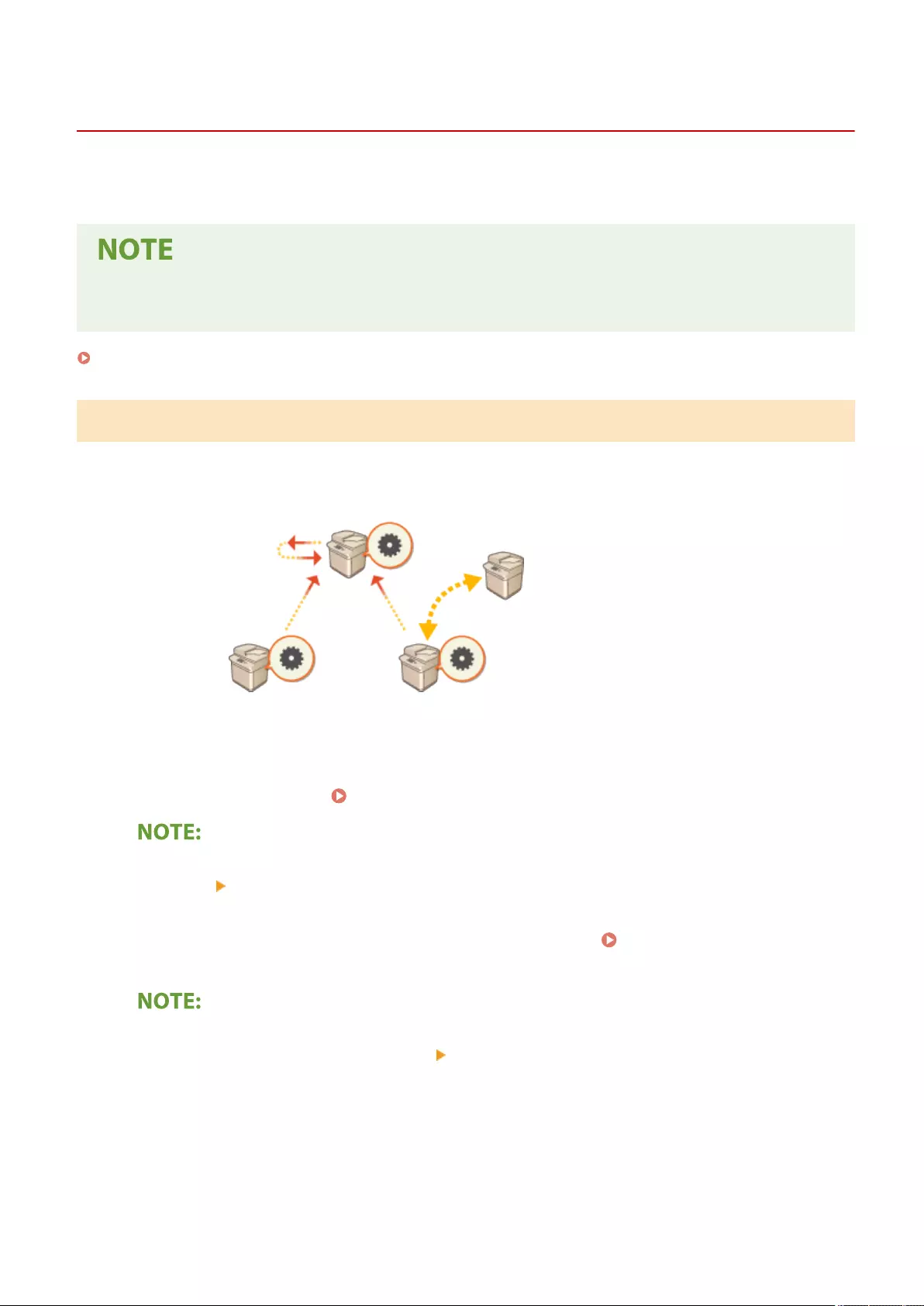
Switching the Machines to Synchronize
72JY-0C2
This section describes the procedure for switching the machines to synchronize after starting synchronization of
custom settings.
●For information on changing the server machine, see the instruction manuals of the machine with the server
function.
Changing a Client Machine(P. 662)
Changing a Client Machine
Follow this procedure to change a client machine to a new machine.
Server Machine (Server/Client Machine)
Client Machine Client Machine
1Stop synchronization from [Synchronize Custom Settings] in the Remote UI of the
target client machine. Starting Setting Synchronization(P. 659)
●If the client machine cannot be operated, delete the target client machine in [Synchronize Custom Settings
(Server)] [Conrm Device Information] in the Remote UI of the server machine (server/client machine).
2Conguring Synchronization on a New Client Machine. Starting Setting
Synchronization(P. 659)
●If synchronization was not correctly stopped on a client machine or if the client machine was not deleted
in [Synchronize Custom Settings (Server)] [Conrm Device Information] in the Remote UI of the server
machine (server/client machine), that client machine will be counted as still in use.
Managing the Machine
662
Initializing All Data/Settings
72JY-0C3
You can restore all of the machine settings to the factory default values. Since data
remaining in the memory is overwritten with meaningless values, this prevents
external leaks of condential data when disposing of the machine. Administrator
privileges are required in order to perform initialization.
●Before initializing, make sure that there are no documents being processed or waiting to be processed.
These documents will be deleted when initialization is performed.
●Do not turn OFF the machine during initialization. Doing so may lead to defects in the memory of the
machine.
●Initialization may take 30 minutes or more to complete. The machine cannot be used during the initialization
process.
●If you perform <Initialize All Data/Settings>(P. 865) when the Copy Card Reader is attached, it is
necessary to reinstall the Copy Card Reader. For more information, contact your dealer or service
representative.
Before performing initialization
Back up your important data or export it as a le.
●Machine setting information Importing/Exporting the Setting Data(P. 625)
●User authentication information registered in the local device for personal authentication management
Registering User Information in the Local Device(P. 495)
When using a password to protect the security policy settings
●You need to enter the password to initialize the machine settings. Using a Password to Protect the
Security Policy Settings(P. 479)
1Press (Settings/Register).
2Press <Management Settings> <Data Management> <Initialize All Data/
Settings>.
3Press <Yes>.
➠Initialization is performed. After the process is complete, the machine restarts and the Initialize All Data/
Settings Report is printed.
●When the <A security policy is applied to this device.> message is displayed, a password must be entered by
the security administrator. For more information, contact your security administrator. Applying a Security
Policy to the Machine(P. 478)
Managing the Machine
663
●Although the job log information can be deleted by initializing all data/settings, the result of printing the
Initialize All Data/Settings Report is recorded in the print log. Checking the Printing Status and
History(P. 348)
●It is also possible to individually select some machine settings and restore their factory default values.
Settings/Registration(P. 670)
Managing the Machine
664
uniFLOW Online Setup
Functions Linked to Cloud Service
72JY-0C4
You can check the usage status of the device and the user by linking to cloud service, depending on the model of the
machine you are using.
uniFLOW Online Express(P. 665)
uniFLOW Online Express
By creating "tenants" in the cloud, and registering the user information and devices, you can use the following
functions without building a server.
●For instructions on creating and accessing a tenant, contact your dealer or service representative.
●For details on uniFLOW Online Express, see " First Steps Guide ".
◼"Authentication Function" That Creates a Secure Device Usage Environment
By registering users and devices to uniFLOW Online Express, you can create a secure and personalized print
environment without the need for a local server. In this environment, for example, you can help prevent troubles
where a user takes away prints left by someone else, or you can customize the device screen only for yourself.
The following can be performed using the authentication function of uniFLOW Online Express:
●Managing the user information for the authentication function
●Managing the authentication information such as ID cards and PIN codes
●Switching the authentication method and authentication system*
*For administrators only
Managing the Machine
665

◼"Accounting and Reporting Function" That Enables Checking Logs and Costs
This function calculates the usage of devices registered/connected to the same tenant on uniFLOW Online Express,
and then creates a report. By linking with the authentication function of uniFLOW Online Express, this function enables
you to check the usage log of each user, and create cost tables for each copied/scanned page so that you can
calculate/check the cost for each device.
◼"Simple Scan Function" That Sends Scanned Data to an E-Mail Address or in the Cloud
This function enables you to send scanned documents to your e-mail address (Scan to Myself), or directly store them in
the external cloud service.
Main Specications
Authentication Function
User registration method ●Linking the Oce 365TM account
●Uploading in CSV format
●Registering users via e-mail
●Manual entry
User authentication system ●Microsoft Azure Active Directory
●Oce 365TM integrated with Active Directory Federation Services
●Active Directory in your company
●Linking with external SNS services (Single Sign-On)
Authentication method ●PIN code
●ID card
Managing the Machine
666

●ID card + PIN code
Accounting and Reporting Function
Report type ●Usage log of each user
●Usage log of each device
●Copy/print/scan/fax logs of all users
●Copy/print/scan/fax logs of all devices (all periods)
●Copy/print/scan/fax logs of all devices (specied period)
Simple Scan Function
Send/store function Scan to Myself (Sending an e-mail), Scan to Google Drive
File format TIFF, PDF
Managing the Machine
667

Settings/Registration
Settings/Registration .................................................................................................................................. 670
Settings/Registration Table .............................................................................................................................. 671
Preferences .................................................................................................................................................. 674
Paper Settings ....................................................................................................................................... 675
Display Settings ..................................................................................................................................... 677
Timer/Energy Settings ........................................................................................................................... 680
Network ................................................................................................................................................. 682
External Interface .................................................................................................................................. 707
Accessibility ........................................................................................................................................... 708
Volume Settings ..................................................................................................................................... 709
Adjustment/Maintenance ............................................................................................................................. 710
Adjust Image Quality ............................................................................................................................. 711
Adjust Action ......................................................................................................................................... 713
Maintenance .......................................................................................................................................... 714
Function Settings .......................................................................................................................................... 715
Common ................................................................................................................................................ 716
Copy ...................................................................................................................................................... 720
Printer ................................................................................................................................................... 722
Output Report ................................................................................................................................. 723
Custom Settings .............................................................................................................................. 724
UFR II .............................................................................................................................................. 727
PCL .................................................................................................................................................. 728
PS .................................................................................................................................................... 730
Imaging .......................................................................................................................................... 732
PDF ................................................................................................................................................. 734
XPS .................................................................................................................................................. 736
Utility .............................................................................................................................................. 738
Send ...................................................................................................................................................... 739
Receive/Forward .................................................................................................................................... 748
Store/Access Files .................................................................................................................................. 751
Print ....................................................................................................................................................... 753
Set Destination ............................................................................................................................................. 755
Management Settings .................................................................................................................................. 757
User Management ................................................................................................................................. 758
Device Management .............................................................................................................................. 761
License/Other ........................................................................................................................................ 765
Data Management ................................................................................................................................. 767
Settings/Registration
668

Security Settings .................................................................................................................................... 768
<Preferences> .................................................................................................................................................... 770
<Paper Settings> .......................................................................................................................................... 771
<Display Settings> ........................................................................................................................................ 773
<Timer/Energy Settings> .............................................................................................................................. 777
<Network> .................................................................................................................................................... 782
<External Interface> ..................................................................................................................................... 795
<Accessibility> .............................................................................................................................................. 797
<Adjustment/Maintenance> ............................................................................................................................. 798
<Adjust Image Quality> ................................................................................................................................ 799
<Adjust Action> ............................................................................................................................................ 804
<Maintenance> ............................................................................................................................................. 805
<Function Settings> .......................................................................................................................................... 807
<Common> ................................................................................................................................................... 808
<Copy> ......................................................................................................................................................... 817
<Printer> ...................................................................................................................................................... 818
<Send> ......................................................................................................................................................... 820
<Receive/Forward> ....................................................................................................................................... 835
<Store/Access Files> ..................................................................................................................................... 843
<Print> .......................................................................................................................................................... 846
<Set Destination> .............................................................................................................................................. 849
<Management Settings> ................................................................................................................................... 853
<User Management> .................................................................................................................................... 854
<Device Management> ................................................................................................................................. 857
<License/Other> ........................................................................................................................................... 861
<Data Management> .................................................................................................................................... 864
<Security Settings> ....................................................................................................................................... 866
Settings/Registration
669

Settings/Register
Settings/Registration
72JY-0C5
You can customize the machine based on your environment and needs by conguring settings described in this
chapter. To start conguration, press (Settings/Register).
This section describes what each item in the setting menu can congure.
●Some of the settings may not be displayed depending on the conguration of optional equipment installed
on the machine.
●Some changes may not be reected immediately, depending on the settings. In this case, it is necessary to
perform one of the following.
●Press <Yes> on the screen conrming whether you want to make changes.
●Press (Settings/Register) <Apply Set. Chng.>.
●Restart the machine.
◼<Personal Settings> and <Device Settings>
When User Authentication ( Managing Users(P. 489) ) is enabled, <Personal Settings> and <Device Settings> are
displayed on the screen after you log in with Administrator privileges by pressing (Settings/Register). If you select
<Personal Settings> and change the items that can be personalized, settings are registered as the personal settings
for the user who is logged into the machine ( List of Items That Can Be Personalized(P. 139) ). If you select
<Device Settings>, settings are registered as the settings of the machine. If you log in as a user without Administrator
privileges, just like when selecting <Personal Settings>, if you change settings that can be personalized, settings are
registered as personal settings without being registered as device settings.
Settings/Registration
670

Settings/Registration Table
72JY-0C6
The following settings can be selected or stored on the Settings/Registration screen:
Preferences(P. 674)
Adjustment/Maintenance(P. 710)
Function Settings(P. 715)
Set Destination(P. 755)
Management Settings(P. 757)
●Some of the settings may not be displayed depending on the conguration of optional equipment installed on the machine.
●Some changes may not be reected immediately, depending on the settings. In this case, it is necessary to perform one of the
following.
●Press <Yes> on the screen conrming whether you want to make changes.
●Press (Settings/Register) <Apply Set. Chng.>.
●Restart the machine.
●The settings that can be specied differ between administrators and general users, and vary depending on restrictions
imposed by the administrator.
◼Description of the Settings
Describes the functions of each setting item on Settings/Registration. The settings that can be operated vary depending on the user
authority and the machine you use. Setting items and values are written under Setting Description. The factory defaults are written in bold
red characters.
◼"DeviceAdmin" and "NetworkAdmin"
The "DeviceAdmin" and "NetworkAdmin" items are written for each item in the Settings/Registration table. If the administrator role is
specied for the machine, users with Administrator privileges can change all of the settings, while general users are restricted and can
change only some of the settings. Meanwhile, users with DeviceAdmin or NetworkAdmin privileges can change certain settings even while
those settings are restricted. For those settings, "Yes" or "No" indicates whether the settings can be changed with DeviceAdmin and
NetworkAdmin privileges.
◼"Can be set in Remote UI"
The "Can be set in Remote UI" item is written for each item in the Settings/Registration table. "Yes" or "No" indicates if the settings can/
cannot be set in the Remote UI.
◼Import All Function
The "Import All Function" item is written in the Settings/Registration table. Depending on whether a setting item can be batch imported, "A",
"B", "C", or "No" is written. "A", "B", and "C" refer to the following cases.
Settings/Registration
671
Case A
Importing all to your machine
Restoring the settings information to your machine for backups.
Export
Import
Settings Information
Case B
Importing all to the same model machine
Applies to machines of the same series as this machine.
Export
Settings Information
Import
Case C
Importing all to the different model machine
Applies to models that support batch importing.
Export
Settings Information
Import
◼Name of Item When Exporting with the Remote UI
This section indicates which Settings/Registration items correspond with which items of the batch export function of the Remote UI. "-" is
indicated for items that are not imported/exported. Importing/Exporting All Settings(P. 628)
The items that can be selected for the batch export function of the Remote UI are indicated below.
Items That Can Be Selected with the Batch Export Function
Settings/Registration Basic Information
Paper Type Management Settings
Settings for Printer Settings
Download Prole for Printer Settings
Settings/Registration
672

Forwarding Settings
Box Settings
Department ID Management Settings
Key Settings
Certicate/Certicate Revocation List (CRL) Settings
Visual Message Settings
Home Settings
Favorite Settings
Address Book
User Group Address List
Authentication User Management
Security Policy Settings
Personal Setting Information*
AddOn Application Setting Information
* For information on the settings that are included in [Personal Setting Information], see List of Items That Can Be
Personalized(P. 139) . Select an item in "Name of Item When Exporting with the Remote UI" listed on the Settings/Registration table when
exporting the value (which you set from <Device Settings>) from the Remote UI. <Personal Settings> and <Device Settings>(P. 670)
Settings/Registration
673

Preferences
72JY-0C7
Paper Settings(P. 675)
Display Settings(P. 677)
Timer/Energy Settings(P. 680)
Network(P. 682)
External Interface(P. 707)
Accessibility(P. 708)
Volume Settings(P. 709)
●Some items can be set using the Remote UI. Use the control panel of the device to set items which cannot be set using the
Remote UI.
●The names may be different on the Remote UI.
Settings/Registration
674
Paper Settings
72JY-0C8
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import
All
Function
Name of Item
When Exporting
with the
Remote UI
<Paper Settings>
Paper Source
<Set>:
●<Paper Settings: Paper Size>
<A4>, <A5>, <A5R>, <A6>, <B5>,
<16K>
<Custom Size>, <Inch Size>
●<Paper Settings: Paper Type>
<Thin (60 g/m2)>, <Plain 1 (61-74
g/m2)>, <Plain 2 (75-90 g/m2)>,
<Plain 3 (91-105 g/m2)>, <Heavy
1 (106-119 g/m2)>, <Heavy 2
(120-128 g/m2))>, <Heavy 3
(129-163 g/m2))>, <Color (61-74
g/m2)>, <Recycled 1 (61-74 g/
m2)>, <Recycled 2 (75-90 g/
m2)>, <Labels>
<Detailed Settings>
Yes Yes Yes*1 B*2
Settings/
Registration
Basic
Information
<Paper Type Management Settings>
<Details/Edit>
●<Name>, <Category>, <Basis
Weight>, <Finish>, <Type>,
<Color>, <Use as Template
Paper>, <Humid Environment
Mode>, <Output Ppr. Stick
Prevnt. Mode>, <Reduce Img
Defect by Ppr Dust>, <Adj. Paper
Convey. in MP Tray>, <Reduce
Thin Paper Waviness>, <Reduce
Thin/Plain Ppr Wrinkles>,
<Reduce Envelope Wrinkles>
<Duplicate>, <Delete>
Yes No Yes C*3
Paper Type
Management
Settings
<Register Favorite Paper (Multi-
Purpose Tray)>
<P1> to <P30>:
<Register/Edit>, <Rename>, <Delete> Yes Yes No B
Settings/
Registration
Basic
Information
<Multi-Purpose Tray Defaults>
●<Use Preset> (<Register>)
●<Always Specify> (<Standard>,
<Favorite Paper>)
Yes Yes No B
Settings/
Registration
Basic
Information
<Register Custom Size> <S1> to <S4>:
<Register/Edit>, <Rename>, <Delete> Yes Yes No B Settings/
Registration
Settings/Registration
675

Basic
Information
*1: <Custom Size> cannot be set from the Remote UI.
*2: <Custom Size> cannot be imported with the Import All function.
*3: <Use as Template Paper> is categorized as "A".
Settings/Registration
676
Display Settings
72JY-0C9
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Default Screen After Startup/Restoration>
<Home>, <Copy>,
<Fax>*1, <Scan and
Send>, <Scan and Store>,
<Access Stored Files>,
<Fax/I-Fax Inbox>,
<Remote Scanner>,
<Tutorial>, <Dest./Fwd.
Settings>, <Print>,
<Update Firmware>,
<WSD Scan>, <Scan for
Mobile>, <Mobile Portal>,
<uniFLOW Online Setup>
No No No C
Settings/
Registration Basic
Information
<Open Status Monitor
Screen>: <On>, <Off>
<Default Screen (Status Monitor)>
<Default Status Type>:
<Copy/Print>, <Send>,
<Receive>, <Store>,
<Consumables/Others>
Yes Yes No C
Settings/
Registration Basic
Information
<Status/Log>: <Job
Status>, <Job Log>
<Details> (<Copy/Print>,
<Job Status>): <Print>,
<Copy>
<Details> (<Send>, <Job
Status>): <Send>, <Fax>
<Details> (<Receive>, <Job
Status>): <Fax>,
<Forward>
<Details> (<Copy/Print>,
<Job Log>): <Copy>,
<Printer>, <Local Print>,
<Received Job Print>,
<Print Report>
<Details> (<Send>, <Job
Log>): <Send>, <Fax>
<Details> (<Receive>, <Job
Log>): <Receive>, <Fax>
Settings/Registration
677
<Display Fax Function>*1
<On>, <Off>
No No No C
Settings/
Registration Basic
Information
<Enable Fax in Scan and
Send Function>: <On>,
<Off>
<Store Location Display Settings>
<Network>: <On>, <Off>
No No No C
Settings/
Registration Basic
Information
<Memory Media>: <On>,
<Off>
<Switch Language/Keyboard> <Language>, <Keyboard
Layout> Yes Yes No C
Settings/
Registration Basic
Information
<Display Switch Language/Keyboard Button> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Use Keyboard Shift Lock Feature> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Registered Characters for Keyboard> <Register/Edit>, <Delete> Yes Yes No C
Settings/
Registration Basic
Information
<Display Remaining Paper Message> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<No. of Copies/Job Duration Status> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Notify to Clean Original Scanning Area> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Paper Type Selection Screen Priority> <Simple>, <Detailed> Yes Yes No C
Settings/
Registration Basic
Information
<Switch Millimeter/Inch Entry> <Millimeter>, <Inch> Yes Yes No C
Settings/
Registration Basic
Information
<Conrm When Loading Paper in Paper
Drawer> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Display Logged-in User Name>
<At Screen Top> (<User
Name>, <Display Name>),
<At Screen Bottom>,
<Off>
No No No C
Settings/
Registration Basic
Information
<Display Remaining Toner Error Message> <On>, <Off> Yes No No C
Settings/
Registration Basic
Information
<Delete Remaining Toner Error> <On>, <Off> Yes Yes No C -
Settings/Registration
678
<IP Address Display Settings> <On>, <Off> No Yes No C
Settings/
Registration Basic
Information
<Display Scan for Mobile> <On>, <Off> No Yes No C
Settings/
Registration Basic
Information
<Display Mobile Portal> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Display QR Code on Mobile Portal> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
*1: Indicates items that appear only when the appropriate optional products are available for use.
Settings/Registration
679
Timer/Energy Settings
72JY-0CA
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Adjust Time> 00:00 to 23:59, in one minute
increments Yes Yes No No -
<Date/Time Settings>
Date and Time Setting (12
digit number) No No Yes No
Settings/
Registration Basic
Information
<Time Zone>: UTC-12:00 to
UTC+00:00 to UTC+14:00 No No Yes C
Settings/
Registration Basic
Information
<Daylight Saving Time>:
<On>, <Off>No No Yes C
Settings/
Registration Basic
Information
<Start Date> (<Month>/
<Day>/<Time> (0 to 23)),
<End Date> (<Month>/<Day>/
<Time> (0 to 23))
No No Yes C
Settings/
Registration Basic
Information
<Time Format> <24 Hour>, <12 Hour> No No Yes C
Settings/
Registration Basic
Information
<Quick Startup Settings for Main Power> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Auto Reset Time>
0 min=Off, 10 to 50 seconds
in 10 second increments, 1 to
2 to 9 minutes in one minute
increments
Yes Yes Yes C
Settings/
Registration Basic
Information
<Restrict Auto Reset Time> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Function After Auto Reset> <Default Function>,
<Selected Function> Yes Yes Yes C
Settings/
Registration Basic
Information
<Auto Shutdown Time> 0 hr=Off, 1 to 4 to 8 hours in
one hour increments No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
680
<Auto Shutdown Weekly Timer>
<Sunday> to <Saturday>,
00:00 to 23:59, in one minute
increments
No No Yes C
Settings/
Registration Basic
Information
<Auto Sleep Time>
10 secs, 1 min, 2 mins, 10
mins, 15 mins, 20 mins, 30
mins, 40 mins, 50 mins, 1 hr,
90 mins, 2 hrs
Yes Yes Yes C
Settings/
Registration Basic
Information
<Sleep Mode Energy Use> <Low>, <High> Yes Yes Yes C
Settings/
Registration Basic
Information
<Auto Sleep Weekly Timer>
<Sunday> to <Saturday>,
00:00 to 23:59, in one minute
increments
Yes Yes Yes C
Settings/
Registration Basic
Information
<Time Settings for Auto Adjust Gradation>
<Sunday> to <Saturday>,
00:00 to 23:59, in one minute
increments
Yes Yes Yes C
Settings/
Registration Basic
Information
<Sleep Mode Exit Time Settings> 00:00 to 23:59, in one minute
increments Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
681
Network
72JY-0CC
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
●<Output Report>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Output Report> <Yes>, <No> Yes Yes Yes No -
●<Conrm Network Connection Setting Changes>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Conrm Network Connection Setting
Changes> <On>, <Off> No Yes No C Settings/Registration
Basic Information
●<TCP/IP Settings>: <IPv4 Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Use IPv4> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<IP Address Settings>
<IP Address>: <0.0.0.0> No Yes Yes A Settings/Registration
Basic Information
<Subnet Mask>: <0.0.0.0> No Yes Yes C Settings/Registration
Basic Information
<Gateway Address>:
<0.0.0.0>No Yes Yes C Settings/Registration
Basic Information
<DHCP>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Auto IP>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<DHCP Option Settings>
<Acquire Host Name>:
<On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<DNS Dynamic Update>:
<On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<Acquire DNS Server
Address>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
Settings/Registration
682
<Acquire Domain Name>:
<On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Acquire WINS Server
Address>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Acquire SMTP Server
Address>: <On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<Acquire POP Server
Address>: <On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<Release Address Last
Acquired from DHCP
Server When Address
Cannot Be Acquired>*1:
<On>, <Off>
No Yes Yes C Settings/Registration
Basic Information
<PING Command> <IPv4 Address>: <0.0.0.0> No Yes No No -
*1 This setting can only be specied from the Remote UI.
●<TCP/IP Settings>: <IPv6 Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Use IPv6> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Stateless Address Settings> <Use Stateless Address>:
<On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Manual Address Settings>
<Use Manual Address>:
<On>, <Off>No Yes Yes A Settings/Registration
Basic Information
<Manual Address> (IPv6
Address (39 characters
maximum))
No Yes Yes A Settings/Registration
Basic Information
<Prex Length>: 1 to 64 to
128 No Yes Yes A Settings/Registration
Basic Information
<Default Router Address>
(39 characters maximum) No Yes Yes A Settings/Registration
Basic Information
<Use DHCPv6> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<PING Command>
<IPv6 Address> (39
characters maximum) No Yes No No -
<Host Name> No Yes No No -
<Only Retrieve Stateful Address Prex> <On>, <Off> Yes No Yes C Settings/Registration
Basic Information
<DHCP Option Settings>
<Acquire DNS Server
Address>: <On>, <Off> Yes No Yes C Settings/Registration
Basic Information
Settings/Registration
683
<Acquire Domain Name>:
<On>, <Off> Yes No Yes C Settings/Registration
Basic Information
●<TCP/IP Settings>: <DNS Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<DNS Server Address Settings>
<IPv4>
<Primary DNS Server> No Yes Yes C Settings/Registration
Basic Information
<Secondary DNS Server> No Yes Yes C Settings/Registration
Basic Information
<IPv6>
<Primary DNS Server> No Yes Yes C Settings/Registration
Basic Information
<Secondary DNS Server> No Yes Yes C Settings/Registration
Basic Information
<DNS Host Name/Domain Name Settings>
<IPv4>
<Host Name>:
Canon****** ("******"
represents the last six
digits of a MAC address.)
No Yes Yes A Settings/Registration
Basic Information
<Domain Name> No Yes Yes A Settings/Registration
Basic Information
<IPv6>
<Use Same Host Name/
Domain Name as IPv4>:
<On>, <Off>
No Yes Yes A Settings/Registration
Basic Information
<Host Name>:
Canon****** ("******"
represents the last six
digits of a MAC address.)
No Yes Yes A Settings/Registration
Basic Information
<Domain Name> No Yes Yes A Settings/Registration
Basic Information
<DNS Dynamic Update Settings>
<IPv4> <DNS Dynamic Update>:
<On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<IPv6>
<DNS Dynamic Update>:
<On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<Register Stateless
Address>: <On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<Register Manual Address>:
<On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<Register Stateful
Address>: <On>, <Off>No Yes Yes C Settings/Registration
Basic Information
Settings/Registration
684
<mDNS Settings>
<Use IPv4 mDNS>: <On>,
<Off> No Yes Yes C Settings/Registration
Basic Information
<mDNS Name> (63
characters maximum) No Yes Yes C Settings/Registration
Basic Information
<Use IPv6 mDNS>: <On>,
<Off> No Yes Yes C Settings/Registration
Basic Information
<Use Same mDNS Name as
IPv4>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<mDNS Name> (63
characters maximum) No Yes Yes C Settings/Registration
Basic Information
●<TCP/IP Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Computer Name/Workgroup Name
Settings>
<Computer Name> (15
characters maximum):
Canon****** ("******"
represents the last six digits
of a MAC address.)
No Yes Yes A
Settings/
Registration Basic
Information
<Workgroup Name> (15
characters maximum):
WORKGROUP
No Yes Yes A
Settings/
Registration Basic
Information
<Comment> (48 characters
maximum) No Yes Yes A
Settings/
Registration Basic
Information
<Use NetBIOS>: <On>, <Off> No Yes Yes A
Settings/
Registration Basic
Information
<SMB Client Settings>
<Authentication Type>:
<NTLMv1>, <NTLMv2>No Yes Yes C
Settings/
Registration Basic
Information
<Require SMB Signature for
Connection>: <On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<Require Encryption for
Connection>: <On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<Timeout>: 3 to 3 0 to 300
sec. No Yes Yes C
Settings/
Registration Basic
Information
<Specify SMB Client Version> <1.0>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
685
<2.0>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<3.0>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<WINS Settings>
<WINS Resolution>: <On>,
<Off>No Yes Yes C
Settings/
Registration Basic
Information
<WINS Server Address> (IP
Address) No Yes Yes C
Settings/
Registration Basic
Information
<LPD Print Settings>
<On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<LPD Banner Page>: <On>,
<Off>No Yes Yes C
Settings/
Registration Basic
Information
<RX Timeout>: 1 to 5 to 60
(min.) No Yes Yes C
Settings/
Registration Basic
Information
<RAW Print Settings>
<On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Bidirectional
Communication>: <On>,
<Off>
No Yes Yes C
Settings/
Registration Basic
Information
<RX Timeout>: 1 to 5 to 60
(min.) No Yes Yes C
Settings/
Registration Basic
Information
<SNTP Settings>
<Use SNTP>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Polling Interval>: 10 to
1440 to 2880 min. No Yes Yes C
Settings/
Registration Basic
Information
<NTP Server Address> (IP
Address or Host Name) No Yes Yes C
Settings/
Registration Basic
Information
<Check NTP Server> No Yes Yes No -
<FTP Print Settings>
<Use FTP Printing>: <On>,
<Off>No Yes Yes C
Settings/
Registration Basic
Information
<User Name>: guest No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
686
<Password>: 7654321 No Yes Yes C
Settings/
Registration Basic
Information
<Use UTF-8 to Display Name of FTP Print
Job> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<WSD Settings>
<Use WSD Printing>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<Use WSD Browsing>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<Use WSD Scan>: <On>,
<Off>No Yes Yes C
Settings/
Registration Basic
Information
<Use FTP PASV Mode> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<IPP Print Settings>
<On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Allow When Using TLS>:
<On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<Use Authentication>: <On>,
<Off>No Yes Yes C
Settings/
Registration Basic
Information
<Multicast Discovery Settings>
<Response>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Scope Name> No Yes Yes C
Settings/
Registration Basic
Information
<Sleep Mode Notication Settings>*1
<Notify>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Port Number>: 1 to 11427
to 65535 No Yes Yes C
Settings/
Registration Basic
Information
<Number of Routers to
Traverse>: 0 to 3 to 254 No Yes Yes C
Settings/
Registration Basic
Information
<Notication Interval>: 60 to
600 to 65535 sec. No Yes Yes C
Settings/
Registration Basic
Information
<Use HTTP> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
687
<TLS Settings>
<Key and Certicate>
<Set as Default Key>: <Yes>,
<No> No Yes Yes No -
<Certicate Details>
(<Version>, <Serial
Number>, <Signature
Algorithm>, <Issued To>,
<Validity Start Date>,
<Validity End Date>,
<Issuer>, <Public Key>,
<Certicate Thumbprint>,
<Issued To (Altn. Name)>,
<Verify Certicate>)
No Yes Yes No -
<Display Use Location>
(Displays what the key pair is
being used for)
No Yes Yes No -
<Specify Allowed Versions>
<Maximum Version>: <TLS
1.0>, <TLS 1.1>, <TLS 1.2>,
<TLS 1.3>
No Yes Yes C
Settings/
Registration Basic
Information
<Minimum Version>: <TLS
1.0>, <TLS 1.1>, <TLS 1.2>,
<TLS 1.3>
No Yes Yes C
Settings/
Registration Basic
Information
<Encryption Algo Settings>
<AES-CBC (256-bit)>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<AES-GCM (256-bit)>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<3DES-CBC>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<AES-CBC (128-bit)>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<AES-GCM (128-bit)>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<CHACHA20-POLY1305>:
<On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Key Exchange Algo Settings>
<RSA>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<ECDHE>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<X25519>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
688
<Signature Algo Settings>
<RSA>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<ECDSA>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<HMAC Algo Settings>
<SHA1>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<SHA256>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<SHA384>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Proxy Settings>
<Use Proxy>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Server Address> (IP
Address or FQDN) No Yes Yes C
Settings/
Registration Basic
Information
<Port Number>: 1 to 80 to
65535 No Yes Yes C
Settings/
Registration Basic
Information
<Use Proxy within Same
Domain>: <On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<Set Authentication>
<Use Proxy Authentication>:
<On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<User Name> (24 characters
maximum) No Yes Yes C
Settings/
Registration Basic
Information
<Password> (24 characters
maximum) No Yes Yes C
Settings/
Registration Basic
Information
<Conrm Auth. Info. When in Auth.
Management Mode> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
*1 This setting can only be specied from the Remote UI.
●<TCP/IP Settings>: <IPSec Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import
All
Function
Name of Item
When Exporting
with the
Remote UI
Settings/Registration
689
<Use IPSec> <On>, <Off> No Yes Yes C
Settings/
Registration
Basic
Information
<Receive Non-Policy Packets> <Allow>, <Reject> No Yes Yes C
Settings/
Registration
Basic
Information
<Policy On/Off> <On>, <Off> No Yes Yes C
Settings/
Registration
Basic
Information
<Register> <Policy Name> (24 characters
maximum) No Yes Yes C
Settings/
Registration
Basic
Information
<Selector Settings>
<Local Address> (<All IP Addresses>,
<IPv4 Address>, <IPv6 Address>,
<IPv4 Manual Settings>, <IPv6
Manual Settings>)
No Yes Yes C
Settings/
Registration
Basic
Information
●<IPv4 Manual Settings> (<Single
Address>, <Address
Range>(<First Address>, <Last
Address>), <Subnet
Settings>(<Address>, <Subnet
Mask>))
No Yes Yes C
Settings/
Registration
Basic
Information
●<IPv6 Manual Settings> (<Single
Address>(<Address>), <Address
Range> (<First Address>, <Last
Address>), <Specify Prex>
(<Address>, <Prex Length>))
No Yes Yes C
Settings/
Registration
Basic
Information
●<Prex Length> (1 to 64 to 128) No Yes Yes C
Settings/
Registration
Basic
Information
<Remote Address>(<All IP
Addresses>, <All IPv4 Addresses>,
<All IPv6 Addresses>, <IPv4 Manual
Settings>, <IPv6 Manual Settings>)
No Yes Yes C
Settings/
Registration
Basic
Information
●<IPv4 Manual Settings>(<Single
Address>, <Address
Range>(<First Address>, <Last
Address>), <Subnet
Settings>(<Address>, <Subnet
Mask>))
No Yes Yes C
Settings/
Registration
Basic
Information
●<IPv6 Manual Settings> (<Single
Address>(<Address>), <Address
Range> (<First Address>, <Last
Address>), <Specify Prex>
(<Address>, <Prex Length>))
No Yes Yes C
Settings/
Registration
Basic
Information
●<Prex Length> (1 to 64 to 128) No Yes Yes C Settings/
Registration
Settings/Registration
690
Basic
Information
<Port> (<Specify by Port Number>,
<Specify by Service Name>) No Yes Yes C
Settings/
Registration
Basic
Information
●<Specify by Port
Number>(<Local Port>(<All
Ports>, <Single Port>), <Remote
Port>(<All Ports>, <Single
Port>))
No Yes Yes C
Settings/
Registration
Basic
Information
●<Single Port> (1 to 65535) No Yes Yes C
Settings/
Registration
Basic
Information
●<Specify by Service Name>
<Service On/Off>: <On>, <Off> No Yes Yes C
Settings/
Registration
Basic
Information
<IKE Settings>
<IKE Mode>: <Main>, <Aggressive> No Yes Yes C
Settings/
Registration
Basic
Information
<Validity>: 1 to 480 to 65535 min. No Yes Yes C
Settings/
Registration
Basic
Information
<Authentication Method>: <Pre-
Shared Key Method> (<Shared
Key>), <Digital Sig. Method> (<Key
and Certicate>)
No Yes Yes C
Settings/
Registration
Basic
Information
●<Key and Certicate>:
<Set as Default Key> No Yes Yes C
Settings/
Registration
Basic
Information
●<Key and Certicate>:
<Certicate Details>(<Version>,
<Serial Number>, <Signature
Algorithm>, <Issued To>,
<Validity Start Date>, <Validity
End Date>, <Issuer>, <Public
Key>, <Certicate Thumbprint>,
<Issued To (Altn. Name)>,
<Verify Certicate>)
No Yes Yes C
Settings/
Registration
Basic
Information
●<Key and Certicate>: <Display
Use Location>(Displays what the
key pair is being used for)
No Yes Yes C
Settings/
Registration
Basic
Information
<Authentication/Encryption
Algorithm> (<Auto>, <Manual
Settings>)
No Yes Yes C
Settings/
Registration
Basic
Information
Settings/Registration
691
<Authentication/Encryption
Algorithm>: <Manual Settings>
●<Authentication>
<SHA1>: <On>, <Off>
<SHA2>: <On>, <Off>
No Yes Yes C
Settings/
Registration
Basic
Information
●<Encryption>
<3DES-CBC>: <On>, <Off>
<AES-CBC>: <On>, <Off>
No Yes Yes C
Settings/
Registration
Basic
Information
●<DH Group>
<Group 14 (2048)>: <On>, <Off>
<ECDH-P256>: <On>, <Off>
<ECDH-P384>: <On>, <Off>
No Yes Yes C
Settings/
Registration
Basic
Information
<IPSec Network Settings>
<Validity>
<Time>: <On>, <Off> No Yes Yes C
Settings/
Registration
Basic
Information
●<On>: (1 to 480 to 65535min.) No Yes Yes C
Settings/
Registration
Basic
Information
<Validity>
<Size>: <On>, <Off>No Yes Yes C
Settings/
Registration
Basic
Information
●<On>: (0 to 1 to 65535 MB) No Yes Yes C
Settings/
Registration
Basic
Information
<PFS>: <On>, <Off> No Yes Yes C
Settings/
Registration
Basic
Information
<Authentication/Encryption
Algorithm>: <Auto>, <Manual
Settings>
No Yes Yes C
Settings/
Registration
Basic
Information
<Authentication/Encryption
Algorithm>: <Manual Settings>
(<ESP>, <ESP (AES-GCM)>, <AH
(SHA1)>)
No Yes Yes C
Settings/
Registration
Basic
Information
<ESP> Settings:
●<ESP Authentication>
<SHA1>: <On>, <Off>
<NULL>: <On>, <Off>
No Yes Yes C
Settings/
Registration
Basic
Information
●<ESP Encryption>
<3DES-CBC>: <On>, <Off>
<AES-CBC>: <On>, <Off>
<NULL>: <On>, <Off>
No Yes Yes C
Settings/
Registration
Basic
Information
Settings/Registration
692
<ESP (AES-GCM)> Settings: None No Yes Yes C
Settings/
Registration
Basic
Information
<AH (SHA1)> Settings: None No Yes Yes C
Settings/
Registration
Basic
Information
<Connection Mode>:
Transport (display only) No Yes Yes C
Settings/
Registration
Basic
Information
<Only Allow 256-bit for AES Key
Length> <On>, <Off> No Yes Yes No -
<Edit> - No Yes Yes No -
<Delete> - No Yes Yes No -
<Print List> <Yes>, <No> No Yes Yes No -
●<TCP/IP Settings>
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<TCP/IP Option Settings>*1
<Use Window Scale
Option>: <On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<MTU Size>: 600 to
1500 bytes (600-1500) No Yes Yes C Settings/Registration
Basic Information
<Use Network Link Scan>
<On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Use TLS>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
*1 This setting can only be specied from the Remote UI.
●<SNMP Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Use SNMPv1> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Set Dedicated Community>
<Dedicated Community>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
693
<MIB Access Permission>:
<Read/Write>, <Read Only>No Yes Yes C
Settings/
Registration Basic
Information
<Set Community Name 1>
<Community Name 1>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<MIB Access Permission>:
<Read/Write>, <Read Only>No Yes Yes C
Settings/
Registration Basic
Information
<Community Name>: public No Yes Yes C
Settings/
Registration Basic
Information
<Set Community Name 2>
<Community Name 2>: <On>,
<Off>No Yes Yes C
Settings/
Registration Basic
Information
<MIB Access Permission>:
<Read/Write>, <Read Only>No Yes Yes C
Settings/
Registration Basic
Information
<Community Name>: public2 No Yes Yes C
Settings/
Registration Basic
Information
<Use SNMPv3> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Administrator Settings>
<Use Administrator>: <On>,
<Off> No Yes Yes C
Settings/
Registration Basic
Information
<Encryption Password> No Yes Yes C
Settings/
Registration Basic
Information
<Use Same Password as for
Authentication>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<User Settings>
<User On/Off>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Register> (<User Name>, <MIB
Access Permission> (<Read/
Write>, <Read Only>), <Security
Settings> (<Auth. Yes/Encrypt.
Yes>, <Auth. Yes/Encrypt. No>,
<Auth. No/Encrypt. No>),
<Authentication
Algorithm> (<MD5>, <SHA1>,
<SHA2-224>, <SHA2-256>,
<SHA2-384>, <SHA2-512>),
<Authentication Password>,
<Encryption Algorithm> (<DES>,
<AES>), <Encryption Password>)
No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
694
<Details/Edit> (<User Name>,
<MIB Access
Permission> (<Read/Write>,
<Read Only>), <Security
Settings> (<Auth. Yes/Encrypt.
Yes>, <Auth. Yes/Encrypt. No>,
<Auth. No/Encrypt. No>),
<Authentication
Algorithm> (<MD5>, <SHA1>,
<SHA2-224>, <SHA2-256>,
<SHA2-384>, <SHA2-512>),
<Authentication Password>,
<Encryption Algorithm> (<DES>,
<AES>), <Encryption Password>)
No Yes Yes C
Settings/
Registration Basic
Information
<Delete> No Yes Yes No -
<Retrieve Printer Mngt. Information from
Host> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
●<Format Host Resources MIB to RFC2790>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Format Host Resources MIB to RFC2790> <On>, <Off> No Yes No C Settings/Registration
Basic Information
●<Dedicated Port Settings>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the Remote
UI
<Dedicated Port Settings> <On>, <Off> No Yes Yes C Settings/Registration Basic
Information
●<Dedicated Port Authentication Method>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Dedicated Port Authentication Method> <Mode 1>, <Mode
2> No Yes Yes C Settings/Registration
Basic Information
●<Use Spool Function>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the Remote
UI
<Use Spool Function> <On>, <Off> No Yes Yes C Settings/Registration Basic
Information
●<Waiting Time for Connection at Startup>
Settings/Registration
695
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Waiting Time for Connection at Startup> 0 to 300 sec. No Yes Yes C Settings/Registration
Basic Information
●<Ethernet Driver Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Ethernet Driver Settings>
<Auto Detect>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
●<Communication Mode>
(Off): <Half Duplex>, <Full
Duplex>
No Yes Yes C
Settings/
Registration Basic
Information
●<Ethernet Type> (Off):
<10BASE-T>, <100BASE-TX>,
<1000BASE-T>
No Yes Yes C
Settings/
Registration Basic
Information
<Current Transmission Speed>:
Display Only No Yes Yes No -
<MAC Address>: Display only No Yes Yes No -
●<IEEE 802.1X Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Use IEEE 802.1X> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Login Name> Login Name No Yes Yes C Settings/Registration
Basic Information
<Verify Authent. Server Certicate> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Verify Authentication Server Name> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Authentication Server Name> Authentication Server Name No Yes Yes C Settings/Registration
Basic Information
<Use TLS> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Key and Certicate> <Set as Default Key> No Yes Yes No -
Settings/Registration
696
<Certicate Details> (<Version>,
<Serial Number>, <Signature
Algorithm>, <Issued To>,
<Validity Start Date>, <Validity
End Date>, <Issuer>, <Public
Key>, <Certicate Thumbprint>,
<Issued To (Altn. Name)>,
<Verify Certicate>)
No Yes Yes No -
<Display Use Location> (Key and
Certicate) No Yes Yes No -
<Use TTLS>
<On>, <Off> No Yes Yes C Settings/Registration
Basic Information
●<<TTLS Settings (TTLS
Protocol)>>: <MSCHAPv2>,
<PAP>
No Yes Yes C Settings/Registration
Basic Information
<Use PEAP> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<User Name>
Name of the user to be
authenticated with IEEE802.1X
authentication
No Yes Yes C Settings/Registration
Basic Information
<Password>
Password of the user to be
authenticated with IEEE802.1X
authentication
No Yes Yes C Settings/Registration
Basic Information
<Use Login Name as User Name> <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
●<Firewall Settings>: <IPv4 Address Filter>
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Outbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Default Policy>: <Allow>, <Reject> No Yes Yes C
Settings/
Registration Basic
Information
<Register> (Up to 16 IPv4
addresses), <Details/Edit>, <Delete> No Yes Yes C
Settings/
Registration Basic
Information
●<Register>
<Single Address>, <Range
Address> (<First Address>,
<Last Address>), <Prex
Address> (<Address>, <Prex
Length>)
No Yes Yes C
Settings/
Registration Basic
Information
●<Details/Edit>
<Single Address>, <Range
Address> (<First Address>,
<Last Address>), <Prex
No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
697
Address> (<Address>, <Prex
Length>)
●<Prex Length> (1 to 32) No Yes Yes C
Settings/
Registration Basic
Information
<Inbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Default Policy>: <Allow>, <Reject> No Yes Yes C
Settings/
Registration Basic
Information
<Register> (Up to 16 IPv4
addresses), <Details/Edit>, <Delete> No Yes Yes C
Settings/
Registration Basic
Information
●<Register>
<Single Address>, <Range
Address> (<First Address>,
<Last Address>), <Prex
Address> (<Address>, <Prex
Length>), <Port Number> (<Do
Not Specify>, <Specify>)
●<Specify> (<Port Number>):
<Add>, <Delete>
No Yes Yes C
Settings/
Registration Basic
Information
●<Details/Edit>
<Single Address>, <Range
Address> (<First Address>,
<Last Address>), <Prex
Address> (<Address>, <Prex
Length>), <Port Number> (<Do
Not Specify>, <Specify>)
No Yes Yes C
Settings/
Registration Basic
Information
●<Prex Length> (1 to 32) No Yes Yes C
Settings/
Registration Basic
Information
<Always Allow Sending/Receiving Using
ICMP> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
●<Firewall Settings>: <IPv6 Address Filter>
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Outbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C
Settings/
Registration
Basic Information
<Default Policy>: <Allow>, <Reject> No Yes Yes C
Settings/
Registration
Basic Information
<Register> (Up to 16 IPv6
addresses), <Details/Edit>, <Delete> No Yes Yes C
Settings/
Registration
Basic Information
Settings/Registration
698
●<Register>
<Single Address> (<Address>),
<Prex Address> (<IPv6
Prex>, <Prex Length>)
No Yes Yes C
Settings/
Registration
Basic Information
●<Details/Edit>
<Single Address> (<Address>),
<Prex Address> (<IPv6
Prex>, <Prex Length>)
No Yes Yes C
Settings/
Registration
Basic Information
●<Prex Length> (0 to 128) No Yes Yes C
Settings/
Registration
Basic Information
<Inbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C
Settings/
Registration
Basic Information
<Default Policy>: <Allow>, <Reject> No Yes Yes C
Settings/
Registration
Basic Information
<Register> (Up to 16 IPv6
addresses), <Details/Edit>, <Delete> No Yes Yes C
Settings/
Registration
Basic Information
●<Register>
<Single Address> (<Address>),
<Prex Address> (<IPv6
Prex>, <Prex Length>), <Port
Number> (<Do Not Specify>,
<Specify>)
●<Specify> (<Port Number>):
<Add>, <Delete>
No Yes Yes C
Settings/
Registration
Basic Information
●<Details/Edit>
<Single Address> (<Address>),
<Prex Address> (<IPv6
Prex>, <Prex Length>), <Port
Number> (<Do Not Specify>,
<Specify>)
No Yes Yes C
Settings/
Registration
Basic Information
●<Prex Length> (0 to 128) No Yes Yes C
Settings/
Registration
Basic Information
<Always Allow Sending/Receiving Using
ICMPv6> <On>, <Off> No Yes Yes C
Settings/
Registration
Basic Information
●<Firewall Settings>: <MAC Address Filter>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Outbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Default Policy>:
<Allow>, <Reject> No Yes Yes C Settings/Registration
Basic Information
Settings/Registration
699
<Register> (Up to 100
Mac addresses), <Edit>,
<Delete>
No Yes Yes C Settings/Registration
Basic Information
<Inbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Default Policy>:
<Allow>, <Reject> No Yes Yes C Settings/Registration
Basic Information
<Register> (Up to 100
Mac addresses), <Edit>,
<Delete>
No Yes Yes C Settings/Registration
Basic Information
●<Firewall Settings>: <IP Address Block Log>
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<IP Address Block Log>
<Date>, <Type>, <IP
Address>, <Port
Number>, <Result>,
<Details>
No Yes Yes No -
●<Use Mopria>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the Remote
UI
<Use Mopria> <On>, <Off> No Yes Yes C Settings/Registration Basic
Information
●<Use AirPrint>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the Remote
UI
<Use AirPrint> <On>, <Off> No Yes Yes C Settings/Registration Basic
Information
●<Display Errors for AirPrint>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the Remote
UI
<Display Errors for AirPrint> <On>, <Off> No Yes Yes C Settings/Registration Basic
Information
●<Settings for Universal Print>*1
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
Settings/Registration
700
<Basic Settings>
<Use Universal Print> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Verify Server Certicate> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Add CN to Verication Items> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Printer Name> OIP_PRINTER No Yes Yes A
Settings/
Registration Basic
Information
<Application ID> f9fc375cc7ba-4e5c-
b213-23affd792cc1 No Yes Yes C
Settings/
Registration Basic
Information
<Azure Active Directory Authentication
URL>
https://
login.microsoftonline.com/
organizations/oauth2/v2.0
No Yes Yes C
Settings/
Registration Basic
Information
<Azure Active Directory Registration
URL>
https://
register.print.microsoft.com/api/
v1.0/register
No Yes Yes C
Settings/
Registration Basic
Information
<Registration Status> <URL for Registration>
<Code for Registration> No Yes Yes -
Settings/
Registration Basic
Information
*1 This setting can only be specied from the Remote UI.
●<Device Position Information Settings>
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Device Position Information Settings>
<Latitude>: Specify the
latitude. No Yes Yes No -
<Longitude>: Specify
the longitude. No Yes Yes No -
●<Select Interface>
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Select Interface>
<Wired LAN>, <Wireless
LAN>, <Wired LAN + Wired
LAN>, <Wired LAN +
Wireless LAN>
No Yes No C Settings/Registration
Basic Information
●<Wireless LAN>: <Wireless LAN Settings>
Settings/Registration
701
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When
Exporting with
the Remote UI
<WPS Push Button Mode>
<WPS PIN Code Mode>
<Other (Set Manually)>
<Select Access Point>
Select the access point and security
type from the list No Yes No No -
WEP authentication: <Enter
Network Key (WEP)> (<WEP Key>:
Enter the WEP key)
No Yes No No -
WPA/WPA2-PSK encryption: <Enter
Network Key (PSK)> (<PSK>: Enter
the WPA/WPA2-PSK Passphrase)
No Yes No No -
<Enter Manually>
<SSID>: Enter SSID No Yes No No -
<Security Settings>: <None>,
<WEP>, <WPA/WPA2-PSK>, <WPA/
WPA2-EAP>
No Yes No No -
●<Security Settings> (<WEP>)
<IEEE 802.11 Authent.>
(<Open System>, <Shared
Key>), <WEP Key 1>, <WEP Key
2>, <WEP Key 3>, <WEP Key 4>
●<Security Settings> (<WPA/
WPA2-PSK>)
<Encryption Method> (<Auto>,
<AES-CCMP>), <PSK>
No Yes No No -
●<Wireless LAN>: <Wireless LAN Information>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Wireless LAN Information>
<All> No Yes Yes No -
<Details> No Yes Yes No -
●<Wireless LAN>: <Power Save Mode>
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the Remote
UI
<Power Save Mode> <On>, <Off> No Yes Yes C Settings/Registration Basic
Information
●<Direct Connection Settings>
Settings/Registration
702
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Use Direct Connection> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Direct Connection Type> <Access Point Mode>,
<Wi-Fi Direct> No Yes Yes C
Settings/
Registration Basic
Information
<Device Name for Wi-Fi Direct>
Device Name for Wi-Fi
Direct (Max 32
characters): Device
Name
No Yes Yes No
Settings/
Registration Basic
Information
<Time Until Direct Connection Session Is
Terminated>
0 = None, 1 to 30 to 60
min. No Yes Yes C
Settings/
Registration Basic
Information
<Access Point Mode Settings>
<Use Personal SSID and
Network Key>: <On>,
<Off>
No Yes Yes C
Settings/
Registration Basic
Information
<Use Custom SSID>:
<On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<SSID>: Enter SSID No Yes Yes C
Settings/
Registration Basic
Information
<Use Custom Network
Key>: <On>, <Off>No Yes Yes C
Settings/
Registration Basic
Information
<Network Key>: Enter
the network key No Yes Yes C
Settings/
Registration Basic
Information
<Always Keep Enabled If SSID/Network Key
Specied> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<IP Address Settings for Direct Connection> 192.168.22.1 No Yes Yes C
Settings/
Registration Basic
Information
<Personal SSID and Network Key Settings>
<Use Custom SSID>:
<On>, <Off>Yes Yes No C Personal Setting
Information
<SSID>: Enter personal
SSID. Yes Yes No C Personal Setting
Information
<Use Custom Network
Key>: <On>, <Off>Yes Yes No C Personal Setting
Information
<Network Key>: Enter
personal network key. Yes Yes No C Personal Setting
Information
Settings/Registration
703
<Automatically Enable/
Disable Direct
Connection at Login/
Logout>: <On>, <Off>
Yes Yes No C Personal Setting
Information
<Use Login Name as User Name for Print Jobs> <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
●<Sub Line Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<IP Address Settings>
<DHCP>: <On>, <Off> No Yes No C
Settings/
Registration Basic
Information
<IP Address>: <0.0.0.0> No Yes No A
Settings/
Registration Basic
Information
<Subnet Mask>: <0.0.0.0> No Yes No C
Settings/
Registration Basic
Information
<Gateway Address>:
<0.0.0.0>No Yes No C
Settings/
Registration Basic
Information
<Priority Line for Communication with
Mobile Devices> <Main Line>, <Sub Line> No Yes No C
Settings/
Registration Basic
Information
<Ethernet Driver Settings>
<Auto Detect>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
●<Communication Mode>
(Off): <Half Duplex>,
<Full Duplex>
No Yes Yes C
Settings/
Registration Basic
Information
●<Ethernet Type> (Off):
<10BASE-T>, <100BASE-
TX>, <1000BASE-T>
No Yes Yes C
Settings/
Registration Basic
Information
<Current Transmission
Speed>: Display Only No Yes Yes C
Settings/
Registration Basic
Information
<MAC Address>: Display only No Yes Yes C
Settings/
Registration Basic
Information
●<Sub Line Settings>: <Firewall Settings>: <IPv4 Address Filter>
Item Setting Description DeviceAdmin NetworkAdmin Can be
set in
Import All
Function
Name of Item
When Exporting
Settings/Registration
704
Remote
UI
with the Remote
UI
<Outbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Default Policy>: <Allow>, <Reject> No Yes Yes C
Settings/
Registration Basic
Information
<Register> (Up to 16 IPv4
addresses), <Details/Edit>, <Delete> No Yes Yes C
Settings/
Registration Basic
Information
●<Register>
<Single Address>, <Range
Address> (<First Address>, <Last
Address>), <Prex Address>
(<Address>, <Prex Length>),
<Port Number>(<Do Not
Specify>, <Specify>)
●<Specify>(<Port Number>):
<Add>, <Delete>
No Yes Yes C
Settings/
Registration Basic
Information
●<Details/Edit>
<Single Address>, <Range
Address> (<First Address>, <Last
Address>), <Prex Address>
(<Address>, <Prex Length>),
<Port Number>(<Do Not
Specify>, <Specify>)
No Yes Yes C
Settings/
Registration Basic
Information
<Prex Length> (1 to 32) No Yes Yes C
Settings/
Registration Basic
Information
<Inbound Filter>
<Use Filter>: <On>, <Off> No Yes Yes C
Settings/
Registration Basic
Information
<Default Policy>: <Allow>, <Reject> No Yes Yes C
Settings/
Registration Basic
Information
<Register> (Up to 16 IPv4
addresses), <Details/Edit>, <Delete> No Yes Yes C
Settings/
Registration Basic
Information
●<Register>
<Single Address>, <Range
Address> (<First Address>, <Last
Address>), <Prex Address>
(<Address>, <Prex Length>),
<Port Number>(<Do Not
Specify>, <Specify>)
●<Specify>(<Port Number>):
<Add>, <Delete>
No Yes Yes C
Settings/
Registration Basic
Information
●<Details/Edit>
<Single Address>, <Range
Address> (<First Address>, <Last
Address>), <Prex Address>
(<Address>, <Prex Length>),
No Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
705
<Port Number>(<Do Not
Specify>, <Specify>)
<Prex Length> (1 to 32) No Yes Yes C
Settings/
Registration Basic
Information
●<Sub Line Settings>: <Settings for System Data Communication>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<DNS Server Address Settings>
<Primary DNS Server> No Yes Yes C Settings/Registration
Basic Information
<Secondary DNS Server> No Yes Yes C Settings/Registration
Basic Information
<Proxy Settings>
<Use Proxy>: <On>, <Off> No Yes Yes C Settings/Registration
Basic Information
<Server Address> (IP
Address or FQDN) No Yes Yes C Settings/Registration
Basic Information
<Port Number>: 1 to 80 to
65535 No Yes Yes C Settings/Registration
Basic Information
<Set Authentication>
<Use Proxy Authentication>:
<On>, <Off>No Yes Yes C Settings/Registration
Basic Information
<User Name> (24 characters
maximum) No Yes Yes C Settings/Registration
Basic Information
<Password> (24 characters
maximum) No Yes Yes C Settings/Registration
Basic Information
●<Static Routing Settings>
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Static Routing Settings>
<Use Static Routing>: <On>,
<Off>No Yes No C Settings/Registration
Basic Information
<Edit>, <Delete> No Yes No No -
●<Edit>
<Address>(<0.0.0.0>), <Prex
Length>(1 to 32), <Gateway
Address>(<0.0.0.0>)
No Yes No C Settings/Registration
Basic Information
Settings/Registration
706
External Interface
72JY-0CE
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting
Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<USB Settings>
<Use as USB Device> <On>, <Off> No No Yes C Settings/Registration
Basic Information
<Use AddOn Driver for USB Input Device> <On>, <Off> No No Yes C Settings/Registration
Basic Information
<Use AddOn Driver for USB Storage Device> <On>, <Off> No No Yes C Settings/Registration
Basic Information
<Use USB Storage Device> <On>, <Off> Yes No Yes C Settings/Registration
Basic Information
<Restrict Auto Installation of Printer Driver> <On>, <Off> No No Yes C Settings/Registration
Basic Information
Settings/Registration
707
Accessibility
72JY-0CF
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting
Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Key Repetition Settings>
<Standard>,
<Slightly Slow>,
<Slow>
Yes Yes No C Settings/Registration Basic
Information
<Invert Screen Colors> <On>, <Off> Yes Yes No C Settings/Registration Basic
Information
<Use Flick Function> <On>, <Off> Yes Yes No C Settings/Registration Basic
Information
Settings/Registration
708
Volume Settings
72JY-0CH
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Fax Volume Settings>
<Alarm Volume> 0 to 1 to 3 Yes Yes Yes C
Settings/
Registration Basic
Information
<Monitor Volume> 0 to 1 to 3 Yes Yes Yes C
Settings/
Registration Basic
Information
<Incoming Ring Volume> 0 to 1 to 3 Yes Yes Yes C
Settings/
Registration Basic
Information
<Incoming Fax Ring>
<On>, <Off>
When <On> is selected: Ring
Count: 1 to 2 to 99
Yes Yes Yes C
Settings/
Registration Basic
Information
<Other Volume Settings>
<Entry Tone>: <On>, <Off>
<Invalid Entry Tone>: <On>,
<Off>
<Restock Supplies Tone>: <On>,
<Off>
<Forgot Original Tone>: <On>,
<Off>
<Error Tone>: <On>, <Off>
<Job Done Tone>: <On>, <Off>
<Sleep Mode Tone>: <On>, <Off>
<Login Tone>: <On>, <Off>
<Memory RX/TX End Tone>:
<On>, <Off>
<Memory RX/TX Error Tone>:
<On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
709
Adjust Image Quality
72JY-0CK
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Auto Adjust Gradation>
When <Full Adjust> is set:
Paper Select, <Start
Printing>, <Start Scanning>
Yes Yes No No -
When <Quick Adjust> is
set:
<Start>
<Correct Density>
<Copy>: <Light>, <Dark> (9
levels)
<B&W Send/Scan and
Store (Other Than Mail
Box)>: <Light>, <Dark> (9
levels)
<Color Scan for Send/Scan
and Store>: <Light>,
<Dark> (9 levels)
Yes Yes No C
Settings/
Registration Basic
Information
<Auto Correct Color Shift> <Start> Yes Yes No No -
<Settings for Auto Full Calibration>
<Timing for Auto Full
Calibration at Startup> :
<After Printing First Job>,
<After Main Power ON>
Yes Yes Yes A
Settings/
Registration Basic
Information
<Frequency for Auto Full
Calibration> : <Normal>,
<High>
Yes Yes Yes B
Settings/
Registration Basic
Information
<Full Color Printing Vividness Settings> <Standard>, <Level 1>,
<Level 2> Yes Yes No A
Settings/
Registration Basic
Information
<Fine Adjust Zoom>
<X>:
-1.0 % to 0 % to +1.0 % (in
0.1 % increments)
<Y>:
-1.0 % to 0 % to +1.0 % (in
0.1 % increments)
Yes Yes No A
Settings/
Registration Basic
Information
<Adjust Toner Volume Used for Color
Printing> <Off>, <Level 1>, <Level 2> Yes No No A
Settings/
Registration Basic
Information
<Special Processing>
Settings/Registration
711
<Waterdrop Pattern Prevention Mode> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<Adjust Fixing Temperature> <Low>, <Standard>, <High
1>, <High 2> Yes No Yes B
Settings/
Registration Basic
Information
<Curl Prevention Mode>
<Mode 1>: <On >, <Off
>
<Mode 2>: <On>, <Off>
Yes No Yes B
Settings/
Registration Basic
Information
<Paper Slipping Prevention Mode> <Off>, <Mode 1>, <Mode
2> Yes No Yes B
Settings/
Registration Basic
Information
<Auto Clean Secondary Transfer Roller> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<White Streak Prevention Mode> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<Correct Fixing When Using Plain Paper> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<Correct Tail End Fixing When Using Plain
Paper> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<Plain Paper Fill Area Image Adjustment
Mode> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<Heavy Paper Fill Area Image Adjustment
Mode> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
<Envelope Sealing Prevention Mode> <On>, <Off> Yes No Yes B
Settings/
Registration Basic
Information
Settings/Registration
712

Adjust Action
72JY-0CL
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Start Key Touch Recognition Delay> -1 to 0 to +7 No No No C Settings/Registration Basic
Information
Settings/Registration
713
Maintenance
72JY-0CR
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Clean Feeder> <Start> Yes Yes No No -
<Clean Pressure Roller for Fixing> Paper Select, <Start> Yes Yes No No -
<Original Scanning Area Cleaning Method> Displays the Cleaning
Method Yes Yes No No -
<Check Maintenance Method>
<Replace Toner Cartridge>
Displays the toner
cartridge replacement
method
Yes Yes No No -
<Replace Waste Toner Container>
Displays the waste toner
container replacement
method
Yes Yes No No -
<Remove Jammed Paper (Example)> Displays the jammed
paper removal method Yes Yes No No -
<Control Detected Condensation>
<On> (<Jobs to Restrict
When Condensation is
Detected>: <Only
Received Jobs>, <All
Jobs>), <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
714
Common
72JY-0CU
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote UI
<Paper Feed Settings>
<Paper Source Auto Selection>
<Copy>, <Printer>,
<Access Stored Files>,
<Receive/Fax>, <Other>
Yes Yes Yes B
Settings/
Registration Basic
Information
●<MP Tray>: <On>,
<Off>Yes Yes Yes B
Settings/
Registration Basic
Information
●Other: <On>, <Off> Yes Yes Yes B
Settings/
Registration Basic
Information
<Copy>: <Consider Paper
Type>: <On>, <Off> Yes Yes Yes B
Settings/
Registration Basic
Information
<Printer>: <Use Group>:
<On>, <Off>Yes Yes Yes B
Settings/
Registration Basic
Information
<Switch Paper Feed Method>
<MP Tray> and Other:
<Speed Priority>, <Print
Side Priority>
Yes Yes Yes B
Settings/
Registration Basic
Information
<Suspended Job Timeout>
<On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
0 to 5 to 999min. Yes Yes Yes C
Settings/
Registration Basic
Information
<Paper Output Settings>
<Job Separator Between Jobs>
<On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Change> (Select Paper
Source) Yes Yes Yes C
Settings/
Registration Basic
Information
<Job Separator Between Copies> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
716
<copies> (1 to 10 to 9999) Yes Yes Yes C
Settings/
Registration Basic
Information
<Change> (Select Paper
Source) Yes Yes Yes C
Settings/
Registration Basic
Information
<Print Settings>
<Print Priority>
<Copy>: 1, 2, 3 Yes Yes Yes C
Settings/
Registration Basic
Information
<Printer>: 1, 2, 3 Yes Yes Yes C
Settings/
Registration Basic
Information
<Access Strd. Files>,
<Receive/Fax>, <Other>:
1, 2, 3
Yes Yes Yes C
Settings/
Registration Basic
Information
<Text/Photo Priority When Recognized as
B&W by ACS>
<Text Priority>, <Photo
Priority>Yes Yes Yes B
Settings/
Registration Basic
Information
<Chromatic Color Conversion for Two
Colors Printing>
<All Chromatic Colors>,
<Similar Chromatic Clr.> Yes Yes Yes C
Settings/
Registration Basic
Information
<Default Settings for Output Report>
<2-Sided Printing> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Auto Delete Suspended Jobs>
<On>, <Off> No No Yes C
Settings/
Registration Basic
Information
0 to 5 to 999 min. No No Yes C
Settings/
Registration Basic
Information
<Scan Settings>
<Feeder Jam Recovery Method> <From 1st Page>, <From
Suspnd. Original> Yes Yes Yes B
Settings/
Registration Basic
Information
<Streak Prevention> <On>, <Off> Yes Yes Yes B
Settings/
Registration Basic
Information
<Speed/Image Quality Priority for Black &
White Scan>
<Fax/I-Fax Send Jobs>:
<Speed Priority>,
<Quality Priority>
<All Send Jobs Except
Fax/I-Fax Jobs>: <Speed
Priority>, <Quality
Priority>
Yes Yes Yes B
Settings/
Registration Basic
Information
Settings/Registration
717
<Speed/Image Quality Priority for Scan
from Feeder>
<Speed Priority>,
<Quality Priority> Yes Yes Yes B
Settings/
Registration Basic
Information
<Remote Scan Gamma Value>
<Gamma 1.0>, <Gamma
1.4>, <Gamma 1.8>,
<Gamma 2.2>
Yes Yes Yes B
Settings/
Registration Basic
Information
<Auto Online> <On>, <Off> Yes No No C
Settings/
Registration Basic
Information
<Auto Oine> <On>, <Off> Yes No No C
Settings/
Registration Basic
Information
<Generate File>
<Image Quality Level for Compact>
<Image Level in Text/
Photo Mode or Photo
Mode>: <Data Size
Priority>, <Normal>,
<Quality Priority>
<Image Level in Text
Mode>: <Data Size
Priority>, <Normal>,
<Quality Priority>
Yes Yes Yes C
Settings/
Registration Basic
Information
<OCR (Text Searchable) Settings>
<Smart Scan>: <On>,
<Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Max Number of Char.
for File Name>: 1 to 24 Yes Yes Yes C
Settings/
Registration Basic
Information
<Trace & Smooth Settings>
<Outline Graphics>:
<On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Graphics Recognition
Level>: <Normal>,
<Moderate>, <High>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Background Image
Level>: <Data Size
Priority>, <Normal>,
<Quality Priority>
Yes Yes Yes C
Settings/
Registration Basic
Information
<OOXML Settings>
<Background Image
Level>: <Quality Priority>,
<Standard>, <Data Size
Priority>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Color Image
Recognition Level>:
<High>, <Standard>, <Do
Not Recognize>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Color Image Line Width
Recognition>: <On>,
<Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
718
<Include Background Images in Word
File> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Specify Minimum PDF Version> <Do Not Specify>, <1.5>,
<1.6>, <1.7> Yes Yes Yes C
Settings/
Registration Basic
Information
<Format PDF to PDF/A> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<256-bit AES Settings for Encrypted PDF>
<Acrobat 9.0 or
Equivalent>, <Acrobat
10.0 or Equivalent>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Rotate Scanned Image When
Generating PDF> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Set Authentication Method>
<Information Used for LDAP Server
Authentication>
<Device Settings>,
<Device Login Auth.
Info.>, <Registered Info.
for Each User>
Yes No Yes C
Settings/
Registration Basic
Information
<Information Used for SMTP Server
Authentication>
<Device Settings>,
<Registered Info. for
Each User>
Yes No Yes C
Settings/
Registration Basic
Information
<Information Used for File TX/Browsing
Authentication>
<Standard>, <Device
Login Auth. Info.>,
<Registered Info. for Each
User>
Yes No Yes C
Settings/
Registration Basic
Information
Settings/Registration
719
Copy
72JY-0CW
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Register/Edit Favorite Settings>
<M1> to <M9>:<Register>,
<Rename>, <Delete>,
<Check Content>
Yes Yes No C Favorite Settings
<Display Conrmation for Favorite Settings> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Change Default Settings> <Register>, <Initialize> Yes Yes No C Favorite Settings
<Register Options Shortcuts>
Shortcut 1: Each mode,
<Orig. Content
Orientation>
Yes Yes No C Favorite Settings
Shortcut 2: Each mode, <2-
Sided>Yes Yes No C Favorite Settings
Shortcut 3: Each mode,
<Density>Yes Yes No C Favorite Settings
Shortcut 4: Each mode,
<Copy ID Card>Yes Yes No C Favorite Settings
Shortcut 5: Each mode,
<Favorite Settings>Yes Yes No C Favorite Settings
<Auto Collate> <On>, <Off> Yes Yes No B
Settings/
Registration Basic
Information
<Select Color Settings for Copy>
<Use Auto (Color/B&W)>:
<On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Use Full Color>:<On>,
<Off> Yes No Yes C
Settings/
Registration Basic
Information
<Use Single Color>:<On>,
<Off> Yes No Yes C
Settings/
Registration Basic
Information
<Use Two Colors>:<On>,
<Off> Yes No Yes C
Settings/
Registration Basic
Information
Settings/Registration
720

<Job Separator Between Groups>
<On>, <Off>
<Change> (Select Paper
Source)
Yes Yes No B
Settings/
Registration Basic
Information
Settings/Registration
721
Printer
72JY-0CX
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Output Report> Output Report(P. 723) - - - - -
<Printer Settings>
<Custom Settings> Custom
Settings(P. 724) - - - - -
<UFR II> UFR II(P. 727) - - - - -
<PCL> PCL(P. 728) - - - - -
<PS> PS(P. 730) - - - - -
<Imaging> Imaging(P. 732) - - - - -
<PDF> PDF(P. 734) - - - - -
<XPS> XPS(P. 736) - - - - -
<Utility> Utility(P. 738) - - - - -
<Restrict Printer Jobs>
<On>, <Off> Yes No Yes C Settings for
Printer Settings
When <On> is selected:
●<Select Jobs to Allow>:
<Reserved Jobs>
Yes No Yes C Settings for
Printer Settings
<PDL Selection (Plug and Play)>
<UFR II>, <PCL6>, <PS3>,
<UFR II (V4)>, <Fax>, <PCL6
(V4)>
Yes No Yes C Settings for
Printer Settings
<Prioritize Printer Driver Settings for Jobs
with MP Tray> <On>, <Off> Yes Yes Yes C Settings for
Printer Settings
<PS Password Settings> <SystemParams Password>,
<StartJob Password> No No Yes C Settings for
Printer Settings
<Paper Feed Mode When Using PCL
Emulation>
<Mode 0>, <Mode 1>,
<Mode 2> No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
722
Output Report
72JY-0CY
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<PCL>
<Conguration Page> <Yes>, <No> Yes Yes Yes No -
<Font List> <Yes>, <No> Yes Yes Yes No -
<PS>
<Conguration Page> <Yes>, <No> Yes Yes Yes No -
<Font List> <Yes>, <No> Yes Yes Yes No -
Settings/Registration
723
Custom Settings
72JY-0E0
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Copies> 1 to 9999 Yes Yes Yes C Settings for
Printer Settings
<2-Sided Printing> <On>, <Off> Yes Yes Yes C Settings for
Printer Settings
<Paper Feed>
<Default Paper Feed Source> <Auto>, <MP Tray>, <Drawer 1>,
<Drawer 2>, <Drawer 3> Yes Yes Yes B Settings for
Printer Settings
<Default Paper Size>
<Letter>, <Legal>, <A4>, <A5>, <A6>,
<B5>, <16K>, <Executive>,
<Statement>, <Env. NAGAGATA 3>,
<Env. YOGATANAGA3>, <Env. No.
10>, <Envelope ISO-C5>, <Envelope
DL>, <Envelope Monarch>
Yes Yes Yes B Settings for
Printer Settings
<Default Paper Type>
<Thin>, <Plain 1>, <Plain 2>, <Plain
3>, <Heavy 1>, <Heavy 2>, <Heavy
3>, <Heavy 4>, <Heavy 5>, <Color>,
<Recycled 1>, <Recycled 2>,
<Labels>, <Letterhead 1>,
<Letterhead 2>, <Letterhead 3>,
<Letterhead 4>, <Letterhead 5>,
<Letterhead 6>, <Letterhead 7>,
<Bond>, <Envelope>
Yes Yes Yes B Settings for
Printer Settings
<Paper Size Override> <On>, <Off> Yes Yes Yes C Settings for
Printer Settings
<Paper Output>
<Finishing> <Finishing>:<Off>, <Collate>,
<Group> Yes Yes Yes C Settings for
Printer Settings
<Print Quality>
<Density>*1
<Cyan>: -8 to +8; 0
<Magenta>: -8 to +8; 0
<Yellow>: -8 to +8; 0
<Black>: -8 to +8; 0
Yes Yes Yes C Settings for
Printer Settings
<Density (Fine Adjust)>*1
<Cyan>:
<High>: -8 to +8; 0
<Medium>: -8 to +8; 0
<Low>: -8 to +8; 0
Yes Yes Yes C Settings for
Printer Settings
Settings/Registration
724
<Magenta>:
<High>: -8 to +8; 0
<Medium>: -8 to +8; 0
<Low>: -8 to +8; 0
<Yellow>:
<High>: -8 to +8; 0
<Medium>: -8 to +8; 0
<Low>: -8 to +8; 0
<Black>:
<High>: -8 to +8; 0
<Medium>: -8 to +8; 0
<Low>: -8 to +8; 0
<Toner Save> <On>, <Off> Yes Yes Yes C Settings for
Printer Settings
<Gradation> <Standard>, <High 1>, <High 2> Yes Yes Yes B Settings for
Printer Settings
<Resolution> <1200 dpi>, <600 dpi> Yes Yes Yes B Settings for
Printer Settings
<Sharpness (Photo)> -1 to +3; 0Yes Yes Yes C Settings for
Printer Settings
<Special Smoothing Mode> <Mode 1>, <Mode 2>, <Mode 3>,
<Mode 4>, <Mode 5>, <Mode 6> Yes Yes Yes B Settings for
Printer Settings
<Toner Volume Correction> <Normal>, <Grad. Priority>, <Text
Priority> Yes Yes Yes C Settings for
Printer Settings
<Line Control> <Res. Priority>, <Grad. Priority> Yes Yes Yes C Settings for
Printer Settings
<Width Adjustment>
<Width Adjustment>: <On>, <Off>
<Target for Width Adjust.>*1: <Text>,
<Line>, <Text and Line>, <All>
Yes Yes Yes B Settings for
Printer Settings
<Advanced Smoothing>
<Advanced Smoothing>: <Off>,
<Level 1>, <Level 2>
<Apply to Graphics>: <On>, <Off>
<Apply to Text>: <On>, <Off>
Yes Yes Yes C Settings for
Printer Settings
<Gradation Smoothing>
<Gradation Smoothing>: <Off>,
<Level 1>, <Level 2>
<Apply to Graphics>: <On>, <Off>
<Apply to Images>: <On>, <Off>
Yes Yes Yes C Settings for
Printer Settings
<Enhance Text for B&W Print> <On>, <Off> Yes Yes Yes C Settings for
Printer Settings
<Layout>
<Binding Location> <Long Edge>, <Short Edge> Yes Yes Yes C Settings for
Printer Settings
<Gutter> -50.0 mm to +50.0 mm; 0.0 mm Yes Yes Yes C Settings for
Printer Settings
<Offset Short Edge (Front)> -50.0 mm to +50.0 mm; 0.0 mm Yes Yes Yes C Settings for
Printer Settings
Settings/Registration
725
<Offset Long Edge (Front)> -50.0 mm to +50.0 mm; 0.0 mm Yes Yes Yes C Settings for
Printer Settings
<Offset Short Edge (Back)> -50.0 mm to +50.0 mm; 0.0 mm Yes Yes Yes C Settings for
Printer Settings
<Offset Long Edge (Back)> -50.0 mm to +50.0 mm; 0.0 mm Yes Yes Yes C Settings for
Printer Settings
<Auto Error Skip> <On>, <Off> Yes Yes Yes C Settings for
Printer Settings
<Timeout>
<Timeout>: <On>, <Off>
<Timeout>: 5 seconds to 300
seconds; 15 seconds
Yes Yes Yes C Settings for
Printer Settings
<Personality>*1 <Auto>, <PS>, <PCL>, <Imaging>,
<PDF>, <XPS> Yes Yes Yes C Settings for
Printer Settings
<Mode Priority>*1 <None>, <PS>, <PCL>, <PDF>, <XPS> Yes Yes Yes C Settings for
Printer Settings
<Auto Select>*1
<PS>: <On>, <Off>
<PCL>: <On>, <Off>
<XPS>: <On>, <Off>
<Imaging>: <On>, <Off>
<PDF>: <On>, <Off>
Yes Yes Yes C Settings for
Printer Settings
<Color Mode> <Auto (Color/B&W)>, <Black &
White> Yes Yes Yes C Settings for
Printer Settings
<Compressed Image Output> <Output>, <Display Error> Yes Yes Yes C Settings for
Printer Settings
<Initialize> <Yes>, <No> Yes Yes No No -
*1 Indicates items that appear only when the appropriate optional product is available for use or the appropriate setting is specied.
Settings/Registration
726
UFR II
72JY-0E1
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Halftones>
<Err Diffusion(600dpi
Only)>:<On>, <Off>Yes Yes
Yes B Settings for Printer
Settings
<Text>: <Resolution>,
<Gradation> Yes Yes
<Graphics>: <Resolution>,
<Gradation>Yes Yes
<Image>: <Resolution>,
<Gradation>Yes Yes
<Matching Method>
<General>, <Perceptual>,
<Colorimetric>, <Vivid
Photo>, <Download
Prole>
Yes Yes Yes C Settings for Printer
Settings
<Gray Compensation>
<Text>: <On>, <Off> Yes Yes
Yes B Settings for Printer
Settings
<Graphics>: <On>, <Off> Yes Yes
<Image>: <On>, <Off> Yes Yes
<Paper Save> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
Settings/Registration
727
PCL
72JY-0E2
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Paper Save> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Orientation> <Portrait>, <Landscape> Yes Yes Yes C Settings for Printer
Settings
<Font Source> <Internal>, <Soft/External> Yes Yes No C Settings for Printer
Settings
<Font Number>
0 to 104; 0 (If the Font Source
setting is Internal.)
1 to 999; 1 (If the Font Source
setting is Soft/External.)
Yes Yes Yes C Settings for Printer
Settings
<Point Size>*1 4.00 to 999.75 <point>; 12.00
<point> Yes Yes Yes C Settings for Printer
Settings
<Pitch>*1 0.44 to 99.99 <cpi>; 10.00 <cpi> Yes Yes Yes C Settings for Printer
Settings
<Form Lines> 5 to 128 <lines>; 64 <lines> Yes Yes Yes C Settings for Printer
Settings
<Character Code>
<ARABIC8>, <DESKTOP>,
<GREEK8>, <HEBREW7>,
<HEBREW8>, <ISO4>, <ISO6>,
<ISO11>, <ISO15>, <ISO17>,
<ISO21>, <ISO60>, <ISO69>,
<ISOCYR>, <ISOGRK>, <ISOHEB>,
<ISOL1>, <ISOL2>, <ISOL5>,
<ISOL6>, <ISOL9>, <LEGAL>,
<MATH8>, <MCTEXT>, <MSPUBL>,
<PC8>, <PC8DN>,
<PC8GRK>,<PC8TK>, <PC775>,
<PC850>, <PC851>, <PC852>,
<PC858>, <PC862>, <PC864>,
<PC866>, <PC1004>, <PIFONT>,
<PSMATH>, <PSTEXT>, <ROMAN8>,
<ROMAN9>, <VNINTL>, <VNMATH>,
<VNUS>, <WIN30>, <WINARB>,
<WINBALT>, <WINCYR>,
<WINGRK>, <WINL1>, <WINL2>,
<WINL5>
Yes Yes Yes C Settings for Printer
Settings
<Custom Paper> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
Settings/Registration
728
<Unit of Measure>*1 <Millimeters>, <inches> Yes Yes Yes C Settings for Printer
Settings
<X dimension>*1 127.0 mm to 355.6 mm; 355.6 mm Yes Yes Yes B Settings for Printer
Settings
<Y dimension>*1 76.2 mm to 216.0 mm; 216.0 mm Yes Yes Yes B Settings for Printer
Settings
<Append CR to LF> <Yes>, <No> Yes Yes Yes C Settings for Printer
Settings
<Enlarge A4 Print Width> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Halftones>
<Err Diffusion(600dpi Only) >:
<On>, <Off>
Yes Yes Yes B Settings for Printer
Settings
<Text>: <Resolution>, <Gradation>
<Graphics>: <Resolution>,
<Gradation>
<Image>: <Resolution>,
<Gradation>
<Matching Method>
<General>, <Perceptual>,
<Colorimetric>, <Vivid Photo>,
<Download Prole>
Yes Yes Yes C Settings for Printer
Settings
<Gray Compensation>
<Text>: <On>, <Off>
Yes Yes Yes B Settings for Printer
Settings
<Graphics>: <On>, <Off>
<Image>: <On>, <Off>
<BarDIMM> <Enable>, <Disable> Yes Yes Yes C Settings for Printer
Settings
<FreeScape>*1 <Off>, <~>, <">, <#>, <$>, </>, <\>,
<?>, <{>, <}>, <|> Yes Yes Yes C Settings for Printer
Settings
*1 Indicates items that appear only when the appropriate optional product is available for use or the appropriate setting is specied.
Settings/Registration
729
PS
72JY-0E3
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Paper Save> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Job Timeout> 0 to 3600 seconds; 0 second Yes Yes Yes C Settings for Printer
Settings
<Print PS Errors> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Line Renement> <On>, <On (Slim)>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Pure Black Text> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Black Overprint>*1 <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<RGB Source Prole>
<sRGB>, <Gamma 1.5>, <Gamma
1.8>, <Gamma 2.4>, <None>,
<Download Prole>
Yes Yes Yes No -
<CMYK Simulation Prole>
<JapanColor(Canon>, <US Web
Ctd(Canon>, <Euro Standard>,
<None>, <Download Prole>
Yes Yes Yes No -
<Use Grayscale Prole> <On>, <Off> Yes Yes Yes No -
<Output Prole>
<Text>: <Normal>, <Photo>, <TR
Normal>, <TR Photo>,
<Download Prole>
<Graphics>: <Normal>, <Photo>,
<TR Normal>, <TR Photo>,
<Download Prole>
<Image>: <Normal>, <Photo>,
<TR Normal>, <TR Photo>,
<Download Prole>
Yes Yes Yes No -
<Matching Method> <Perceptual>, <Saturation>,
<Colorimetric> Yes Yes Yes C Settings for Printer
Settings
<Halftones>
<Err Diffusion(600dpi Only)>:
<On>, <Off>
Yes Yes Yes B Settings for Printer
Settings
<Text>: <Resolution>,
<Gradation>
Settings/Registration
730
<Graphics>: <Resolution>,
<Gradation>
<Image>: <Resolution>,
<Gradation>
<Brightness>*1 85% to 115%; 100% Yes Yes Yes C Settings for Printer
Settings
<Composite Overprint> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Grayscale Conversion>*1 <sRGB>, <NTSC>, <Uniform RGB> Yes Yes Yes C Settings for Printer
Settings
*1 Indicates items that appear only when the appropriate optional product is available for use or the appropriate setting is specied.
Settings/Registration
731
Imaging
72JY-0E4
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Image Orientation> <Auto>, <Vertical>,
<Horizontal> Yes Yes Yes C Settings for Printer
Settings
<Zoom> <Off>, <Auto> Yes Yes Yes C Settings for Printer
Settings
<Print Position> <Auto>, <Center>, <Top
Left> Yes Yes Yes C Settings for Printer
Settings
<Show Warnings> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Enlarge Print Area> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Matching Method>
<General>, <Perceptual>,
<Colorimetric>, <Vivid
Photo>, <Download
Prole>
Yes Yes Yes C Settings for Printer
Settings
<Photo Correct. (Color Only)>
<Photo Optimizer PRO> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Red-Eye Correction>
<Red-Eye Correction>:
<On>, <Off>
Yes Yes Yes C Settings for Printer
Settings
<Red-Eye Correction
Level>: <Weak>,
<Standard>, <Strong>
<Face Brightener>
<Face Brightener>: <On>,
<Off>
Yes Yes Yes C Settings for Printer
Settings
<Face Brightener Level>:
<Weak>, <Standard>,
<Strong>
<Halftones>
<Resolution>,
<Gradation>, <Error
Diffusion>
Yes Yes Yes B Settings for Printer
Settings
<Gray Compensation> <On>, <Off> Yes Yes Yes B Settings for Printer
Settings
<Grayscale Conversion>*1 <sRGB>, <NTSC>,
<Uniform RGB> Yes Yes Yes C Settings for Printer
Settings
Settings/Registration
732

*1 Indicates items that appear only when the appropriate optional product is available for use or the appropriate setting is specied.
Settings/Registration
733
PDF
72JY-0E5
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Paper Save> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Enlarge/Reduce to Fit Size> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Enlarge Print Area> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<N on 1> <Off>, <2 on 1>, <4 on 1>, <6 on
1>, <8 on 1>, <9 on 1>, <16 on 1> Yes Yes Yes C Settings for Printer
Settings
<Comment Print> <Off>, <Auto> Yes Yes Yes C Settings for Printer
Settings
<Line Renement> <On>, <On (Slim)>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Pure Black Text> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Black Overprint>*1 <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<RGB Source Prole>
<sRGB>, <Gamma 1.5>,<Gamma
1.8>, <Gamma 2.4>,<None>,
<Download Prole>
Yes Yes Yes No -
<CMYK Simulation Prole>
<JapanColor(Canon>, <US Web
Ctd(Canon>, <Euro Standard>,
<None>, <Download Prole>
Yes Yes Yes No -
<Use Grayscale Prole> <On>, <Off> Yes Yes Yes No -
<Output Prole>
<Text>: <Normal>, <Photo>, <TR
Normal>, <TR Photo>, <Download
Prole>
<Graphics>: <Normal>, <Photo>,
<TR Normal>, <TR Photo>,
<Download Prole>
<Image>: <Normal>, <Photo>, <TR
Normal>, <TR Photo>, <Download
Prole>
Yes Yes Yes No -
<Matching Method> <Perceptual>, <Saturation>,
<Colorimetric> Yes Yes Yes C Settings for Printer
Settings
Settings/Registration
734
<Halftones>
<Err Diffusion(600dpi Only)>:
<On>, <Off>
Yes Yes Yes B Settings for Printer
Settings
<Text>: <Resolution>,
<Gradation>
<Graphics>: <Resolution>,
<Gradation>
<Image>: <Resolution>,
<Gradation>
<Brightness>*1 85% to 115%; 100% Yes Yes Yes C Settings for Printer
Settings
<Composite Overprint> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Grayscale Conversion>*1 <sRGB>, <NTSC>, <Uniform RGB> Yes Yes Yes C Settings for Printer
Settings
*1 Indicates items that appear only when the appropriate optional product is available for use or the appropriate setting is specied.
Settings/Registration
735
XPS
72JY-0E6
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Paper Save> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Matching Method>
<General>, < Perceptual>,
<Colorimetric>, <Vivid
Photo>, <Download Prole>
Yes Yes Yes C Settings for Printer
Settings
<Photo Correct. (Color Only))>
<Photo Optimizer PRO> <On>, <Off> Yes Yes Yes C Settings for Printer
Settings
<Red-Eye Correction>
<Red-Eye Correction>: <On>,
<Off>
Yes Yes Yes C Settings for Printer
Settings
<Red-Eye Correction
Level>*1: <Weak>,
<Standard>, <Strong>
<Face Brightener>
<Face Brightener>: <On>,
<Off>
Yes Yes Yes C Settings for Printer
Settings
<Face Brightener Level>*1 :
<Weak>, <Standard>,
<Strong>
<Halftones>
<Err Diffusion(600dpi Only)>:
<On>, <Off>
Yes Yes Yes B Settings for Printer
Settings
<Text>: <Gradation>,
<Resolution>
<Graphics>: <Gradation>,
<Resolution>
<Image>: <Gradation>,
<Resolution>
<Gray Compensation>
<Text>: <On>, <Off>
Yes Yes Yes B Settings for Printer
Settings
<Graphics>: <On>, <Off>
<Image>: <On>, <Off>
<Grayscale Conversion>*1 <Text>: <sRGB>, <NTSC>,
<Uniform RGB> Yes Yes Yes C Settings for Printer
Settings
Settings/Registration
736

<Graphics>: <sRGB>,
<NTSC>, <Uniform RGB>
<Image>: <sRGB>, <NTSC>,
<Uniform RGB>
*1 Indicates items that appear only when the appropriate optional product is available for use or the appropriate setting is specied.
Settings/Registration
737
Utility
72JY-0E7
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin Can be set in
Remote UI
Import All
Function
Name of Item When
Exporting with the
Remote UI
<Initialize PCL Storage> <Yes>, < No> Yes Yes No No -
<Initialize PS Storage> <Yes>, <No> Yes Yes No No -
<Reset Printer> <Yes>, <No> Yes Yes No No -
Settings/Registration
738
Send
72JY-0E8
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Output Report>
<TX/RX User Data List> <Yes>, <No> Yes Yes Yes No -
<Fax User Data List> <Yes>, <No> Yes Yes Yes No -
<Common Settings>
<Register Favorite Settings>
Conrm Settings Yes Yes No C Favorite Settings
Select Location: <M1> to <M18> Yes Yes No C Favorite Settings
<Show Comments>:
<On>, <Off>Yes Yes No C
Settings/
Registration Basic
Information
<Name>, <Comment> Yes Yes No C Favorite Settings
<Edit Favorite Settings>
Select the Button: <M1> to
<M18>
Yes Yes No C
Favorite Settings
Settings/
Registration Basic
Information
<Show Comments>:
<On>, <Off>
<Delete>, <Check Content>,
<Rename>
<Display Conrmation for Favorite
Settings> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Default Screen>
<Standard>, <One-Touch>,
<Favorite Settings>, <Address
Book>
Yes Yes No C
Settings/
Registration Basic
Information
<Restrict Address Book Use> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Change Default Settings> <Register>, <Initialize> Yes Yes No C Favorite Settings
<Register Options Shortcuts>
<Shortcut 1>:
<2-Sided Original>, Each mode,
<Unassigned> Yes Yes No C Favorite Settings
<Shortcut 2>:
Settings/Registration
739
<Orig. Content Orientation>,
Each mode, <Unassigned>
<TX Result Report>
<For Error Only>, <On>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
When <For Error Only> is
selected:
<Allow Printing from Options>:
<On>, <Off>
<Report with TX Image>: <On>,
<Off>
When <On> is selected:
<Report with TX Image>: <On>,
<Off>
When <Off> is selected:
<Allow Printing from Options>:
<On>, <Off>
<Report with TX Image>: <On>,
<Off>
<Communication Management Report>
<Print/Send for Each Specied
No. of Transm.>: <Print>,
<Send>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
Number of transmissions: 100
to 1000
<Print/Send at Specied Time>:
<Print>, <Send>, <Off>
Specify Print Time: 00:00 to
23:59
<Print Send/Receive Jobs
Separately>: On, Off
<Destination>
<TX Terminal ID>
<Print>, <Do Not Print>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Print Position>: <Inside Image
Area>, <Outside Image Area>
<Display Destination Unit
Name>: <On>, <Off>
<Mark Number As>: <Fax>,
<TEL>
<Delete Failed TX Jobs> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Retry Times> 0 to 3 to 5 times Yes Yes Yes C
Settings/
Registration Basic
Information
<Data Compression Ratio> <High Ratio>, <Normal>, <Low
Ratio> Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
740
<YCbCr TX Gamma Value> <Gamma 1.0>, <Gamma 1.4>,
<Gamma 1.8>, <Gamma 2.2> Yes Yes Yes C
Settings/
Registration Basic
Information
<Use Divided Chunk Send for WebDAV
TX> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Conrm TLS Certicate for WebDAV
TX>
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<CN>: On, Off
<Conrm TLS Certicate for FTPS TX>
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<CN>:On, Off
<Restrict New Destinations>
<Fax>: <On>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
<E-Mail>: <On>, <Off>
<I-Fax>: <On>, <Off>
<File>: <On>, <Off>
<Always Add Device Signature to Send>
<On>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<Restrict File Formats>: <On>,
<Off>
<Limit E-Mail to Send to Myself> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Restrict File TX to Personal Folder> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Personal Folder Specication Method>
<Home Folder>, <Register for
Each User>, <Use Login Server>
Yes No Yes C
Settings/
Registration Basic
Information
When <Home Folder> is
selected:
<Set>, <Use Authentication Info.
of Each User>
<Set>: <Protocol>(<Windows
(SMB)>, <WebDAV>), <Host
Name>, <Folder Path>
When <Use Login Server> is
selected:
<Use Authentication Info. of
Each User>
<Restrict Resending from Log> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Archive TX Document>
<Use Archive TX
Document>:<On>, <Off>Yes No Yes C
Settings/
Registration Basic
Information
Settings/Registration
741
When <On> is selected:
<Backup Location>: Select
Addresses, Address Details,
Register Addresses
<Folder Name>: <Sender
Information>, <Date>, <Off (Do
Not Create)>
<File Format>: <TIFF>, <PDF>
<Display Notication When Job Is
Accepted> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Job to Cancel When Stop Is Pressed> <Latest Received Job>, <Job
Being Sent> Yes No Yes C
Settings/
Registration Basic
Information
<E-Mail/I-Fax Settings>
<Register Unit Name> Register Unit Name Yes Yes Yes C
Settings/
Registration Basic
Information
<Communication Settings>
<E-Mail Address>: Enter the E-
Mail Address Yes Yes Yes A
Settings/
Registration Basic
Information
<SMTP Server>: Enter the SMTP
Server Yes Yes Yes C
Settings/
Registration Basic
Information
<Use POP RX>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Use SMTP RX>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<POP Server>: Enter the POP
Server Yes Yes Yes C
Settings/
Registration Basic
Information
<POP Login Name>: Enter the
POP Login Name Yes Yes Yes A
Settings/
Registration Basic
Information
<POP Password>: Enter the POP
Password Yes Yes Yes A
Settings/
Registration Basic
Information
<POP Interval>: 0 to 99 minutes Yes Yes Yes C
Settings/
Registration Basic
Information
<SMTP TX>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<SMTP RX>: <Always TLS>,
<On>, <Off>Yes Yes Yes C
Settings/
Registration Basic
Information
Settings/Registration
742
<POP>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<POP Authentication Method>:
<Standard>, <APOP>, <POP
AUTH>
Yes Yes Yes C
Settings/
Registration Basic
Information
<SMTP Authentication (SMTP
AUTH)>: <On>, <Off>Yes Yes Yes C
Settings/
Registration Basic
Information
<POP Authentication Before
Sending>: <On>, <Off>Yes Yes Yes C
Settings/
Registration Basic
Information
<Display Authent. Screen When
Sending>: <On>, <Off>Yes Yes Yes C
Settings/
Registration Basic
Information
<Specify Port Number for SMTP TX/POP
RX>
<SMTP TX>: 1 to 25 to 65535
<POP RX>: 1 to 110 to 65535 Yes Yes Yes C
Settings/
Registration Basic
Information
<S/MIME Settings>
<Encryption Settings>: <Always
Encrypt>, <Only Encrypt If
Certicate>, <Do Not Encrypt>
<Add Digital Signatures>: <On>,
<Off>
Yes No Yes C
Settings/
Registration Basic
Information
<Set Details>:
<Encryption Algorithm>:
<3DES>, <AES128>, <AES256>
<Signature Algorithm>:
<SHA1>, <SHA256>, <SHA384>,
<SHA512>
<Verify Sig. upon Receipt>:
<On>, <Off>
<Print Sig. upon Receipt>:
<On>, <Off>
<Conrm TLS Certicate for SMTP TX>
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<CN>: On, Off
<Conrm TLS Certicate for POP RX>
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<CN>: On, Off
<Maximum Data Size for Sending> 0 to 3 to 99 MB Yes No Yes C
Settings/
Registration Basic
Information
<Default Subject> Enter the Subject, Attached
Image Yes No Yes C
Settings/
Registration Basic
Information
<Specify Authentication User for Reply-
To> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
Settings/Registration
743
<Specify Authentication User as
Sender> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Allow Unregistered Users to Send E-
Mail> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Full Mode TX Timeout> 1 to 24 to 99 hr. Yes No Yes C
Settings/
Registration Basic
Information
<Print MDN/DSN upon Receipt> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Use Send via Server> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Allow MDN Not via Server> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Restrict Destination Domain>
<Restrict Sending to Domains>:
<On>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<Register>, <Details/Edit>,
<Delete>
<Auto Complete for Entering E-Mail
Addresses>
<Off>, <Address Book (Local)>,
<LDAP Server> Yes No No C
Settings/
Registration Basic
Information
<Auto Add Specied Domain to Dest.
Without Domain>
<Domain Name>
<When Sending E-Mail>: <On>,
<Off>
<When Sending I-Fax>: <On>,
<Off>
Yes No No C
Settings/
Registration Basic
Information
<Fax Settings>
<Register Favorite Settings>
Conrm Settings Yes Yes No C Favorite Settings
Select Location: <M1> to <M18> Yes Yes No C Favorite Settings
<Show Comments>: <On>,
<Off>Yes Yes No C
Settings/
Registration Basic
Information
<Name>, <Comment> Yes Yes No C Favorite Settings
<Edit Favorite Settings>
Select the Button: <M1> to
<M18>
Yes Yes No C
Favorite Settings
Settings/
Registration Basic
Information
<Show Comments>: <On>,
<Off>
<Delete>, <Check Content>,
<Rename>
Settings/Registration
744
<Display Conrmation for Favorite
Settings> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Default Screen>
<Standard>, <One-Touch>,
<Favorite Settings>, <Address
Book>
Yes Yes No C
Settings/
Registration Basic
Information
<Restrict Address Book Use> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Change Default Settings> <Register>, <Initialize> Yes Yes No C Favorite Settings
<Register Options Shortcuts>
<Shortcut 1>:
<Density>, Each mode,
<Unassigned>
Yes Yes No C Favorite Settings
<Shortcut 2>:
<Original Type>, Each mode,
<Unassigned>
<Shortcut 3>:
<2-Sided Original>, Each mode,
<Unassigned>
<Shortcut 4>:
<Preview>, Each mode,
<Unassigned>
<Register Sender Name (TTI)> <Register/Edit>, <Delete> Yes Yes Yes C
Settings/
Registration Basic
Information
<Use Authentication User Name as
Sender Name> <On>, <Off> Yes No No C
Settings/
Registration Basic
Information
<Off-Hook Alarm>*1 <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<ECM TX> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Set Pause Time> 1 to 4 to 15 sec. Yes Yes Yes C
Settings/
Registration Basic
Information
<Auto Redial>*2
<On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Set Details>:
<Number of Redials>: 1 to 2 to
10 times
<Redial Interval>: 2 to 99
minutes
<Redial When TX Error>: <Error
and 1st Page>, <All Pages>,
<Off>
Settings/Registration
745
<Check Dial Tone Before Sending>*2 <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Fax TX Result Report>
<For Error Only>, <On>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
When <For Error Only> is
selected:
<Report with TX Image>: <On>,
<Off>
When <On> is selected:
<Report with TX Image>: <On>,
<Off>
<Fax Activity Report>
<Print/Send for Each Specied
No. of Transm.>: <Print>,
<Send>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
Number of transmissions: 40 to
1000
<Print/Send at Specied Time>:
<Print>, <Send>, <Off>
Specify Print Time: 00:00 to
23:59
<Print Send/Receive Jobs
Separately>: On, Off
<Destination>
<Set Line>
<Line 1> - Yes No No No -
<Register Unit Telephone
Number> Enter the User Telephone No. Yes No Yes A
Settings/
Registration Basic
Information
<Register Unit Name> Enter the Unit Name Yes No Yes A
Settings/
Registration Basic
Information
<TX Start Speed>
<33600 bps>, <14400 bps>,
<9600 bps>, <7200 bps>, <4800
bps>, <2400 bps>
Yes No Yes C
Settings/
Registration Basic
Information
<R-Key Setting>
<PSTN>, <PBX>
When <PBX> is selected:
<Prex> (20 digits maximum),
<Hooking>
Yes No Yes C
Settings/
Registration Basic
Information
<Conrm Entered Fax Number> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Allow Fax Driver TX> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Conrm Before Sending When Fax
Dest. Included>
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
Settings/Registration
746
<Only for Seq. Broadcast>,
<All>
<Restrict Sequential Broadcast When
Fax Dest. Included> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Remote Fax Settings>
<Use Remote Fax> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Auto Adjust Communication Speed
When Using VoIP> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
*1 Indicates items that can be selected only when the optional handset is connected to the machine.
*2 Indicates items that may not be displayed on the Settings/Registration screen or that may have different default setting, depending on
the region.
Settings/Registration
747
Receive/Forward
72JY-0E9
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Output Report>
<TX/RX User Data List> <Yes>, <No> Yes Yes Yes No -
<Fax User Data List> <Yes>, <No> Yes Yes Yes No -
<Common Settings>
<Print on Both Sides> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Reduce Fax RX Size>
<On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
●<Reduction Mode>:
<Auto>, <Fixed>
●<Reduction Ratio>: 75 to
90% to 97%
●<Reduction Direction>:
<Vertical & Horizontal>,
<Vertical Only>
<Print RX Page Footer> <Print>, <Do Not Print> Yes Yes Yes C
Settings/
Registration Basic
Information
<Interrupt and Print RX Jobs> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Use Forwarding Settings> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Handle Files with Forwarding Errors> <Always Print>, <Store/Print>,
<Off> Yes No Yes C
Settings/
Registration Basic
Information
Settings/Registration
748
<Forwarding Settings>
<Receive Method:>, <Validate/
Invalidate>, <Delete>,
<Register>, <Other
Operations>(<Forward without
Conditions>, <Details/Edit>,
<Print List>, <E-Mail Priority>),
<Search>
Yes No Yes No*1 Forwarding
Settings *2
<Set Fax/I-Fax Inbox>
<Set/Register Condential Fax
Inboxes>
<Box No.>: 00 to 49 Yes Yes No C Box Settings
<Register Box Name> Yes Yes No C Box Settings
<PIN> Yes Yes No C Box Settings
<URL Send Settings> Yes Yes No C Box Settings
<Initialize> Yes Yes No No -
<Memory RX Inbox PIN> <Set>: <PIN>, <Conrm> Yes No No C Box Settings
<Use Fax Memory Lock> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Use I-Fax Memory Lock> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Memory Lock Start Time>
<Everyday> (1 to 5), <Specify
Days> (<Sun> to <Sat>, 1 to 5),
<Off>
Yes No Yes C
Settings/
Registration Basic
Information
<Memory Lock End Time>
<Everyday> (1 to 5), <Specify
Days> (<Sun> to <Sat>, 1 to 5),
<Off>
Yes No Yes C
Settings/
Registration Basic
Information
<Divided Data RX Timeout> 0 to 24 to 99 hr. Yes No Yes C
Settings/
Registration Basic
Information
<Forward Temporarily Stored File to
Memory RX Inbox> <Yes>, <No> Yes Yes No No -
<Always Send Notice for RX Errors> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Fax Settings>
<ECM RX> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<RX Mode>
<Auto RX>, <Fax/Tel(Auto
Switch)>, <Answering
Machine>, <Manual RX>, <Net
Switch>*3 Yes Yes Yes C
Settings/
Registration Basic
Information
When <Fax/Tel(Auto Switch)> is
selected:
<RX Mode: Set Details>
Settings/Registration
749
●<Time Until Ringing
Starts>: 0 to 8 *4 to 30 sec.
●<Ringing Period>: 15 to 22
*4 to 300 sec.
●<Action After Ringing
Period Is Over>: <End
Communication>,
<Receive Fax>
<Remote RX>
<On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
Remote RX ID: 00 to 25 to 99
<Switch to Auto RX>
<On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Ring Time Until Auto RX>: 1 to
15 to 99 sec.
<Fax RX Result Report> <For Error Only>, <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Condential Fax Inbox RX Report> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<RX Start Speed>
<33600 bps>, <14400 bps>,
<9600 bps>, <7200 bps>, <4800
bps>, <2400 bps>
Yes No Yes C
Settings/
Registration Basic
Information
<RX Password> <Set>: <Password>, <Conrm> Yes No Yes C
Settings/
Registration Basic
Information
*1 <Register>, <Forward without Conditions>, <Details/Edit>, <E-Mail Priority> : C
*2 <E-Mail Priority> :Settings/Registration Basic Information
*3 Indicates items that may not be displayed on the Settings/Registration screen, depending on the region.
*4 Indicates items with default setting that may differ, depending on the region.
Settings/Registration
750
Store/Access Files
72JY-0EA
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Common Settings>
<Scan and Store Settings>
<Register/Edit Favorite Settings>
<Register>, <Rename>,
<Delete>, <Check Content>
(<M1> to <M9>)
Yes Yes No C Favorite Settings
<Change Default Settings> <Register>, <Initialize> Yes Yes No C Favorite Settings
<Access Stored Files Settings>
<Register/Edit Favorite Settings>
<Register>, <Rename>,
<Delete>, <Check Content>
(<M1> to <M9>)
Yes Yes No C Favorite Settings
<Change Default Settings> <Register>, <Initialize> Yes Yes No C Favorite Settings
<Limit Box PIN to 7 Digits/Restrict
Access> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Network Settings>
<Network Place Settings>
<Register> (<Name>,
<Protocol>, <Location>), <Edit>
(<Name>, <Protocol>,
<Location>), <Details>,
<Delete>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Protocol for External Reference> <SMB>: <On>, <Off>
<WebDAV>: <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Conrm TLS Certicate for Network
Access>
<On>, <Off> No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
●<Add Items to Verify>:
<CN>: <On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
<Personal Folder Specication Method>
<Home Folder>, <Register for
Each User>, <Use Login
Server> No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
751
When <Home Folder> is
selected:
●<Set>, <Use
Authentication Info. of
Each User>
<Set>: <Protocol>(<Windows
(SMB)>, <WebDAV>),<Host
Name>, <Folder Path>
When <Use Login Server> is
selected:
●<Use Authentication Info.
of Each User>
<Memory Media Settings>
<Use Scan/Print Function>
<Use Scan Function>: <On>,
<Off>Yes No Yes C
Settings/
Registration Basic
Information
<Use Print Function>: <On>,
<Off>Yes No Yes C
Settings/
Registration Basic
Information
<Select Option When Connecting
Memory Media> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
Settings/Registration
752
Print
72JY-0EC
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Forced Hold>
<On>, <Off>
When <On> is selected:
●<Validate/Invalidate>,
<Register>, <Details/Edit>,
<Delete>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Job Storage Period> 10, 20, 30 min., 1, 2, 3, 6, 12
hr., 1, 2, 3 days Yes Yes No C
Settings/
Registration Basic
Information
<Delete Job After Printing> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Only Allow Encrypted Print Jobs> <On>, <Off> Yes Yes Yes C*1
Settings/
Registration Basic
Information
<Include Domain as User Recognition
Condition> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Display Other User Jobs> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Restrict Deletion of Other User Jobs> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Match Case for User Name> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Job List Display Settings>
<Personal>: <On>, <Off>
<Shared>: <On>, <Off>
<Group>: <On>, <Off>
When two or more of
personal/shared/group are set
to <On>:
<Personal>, <Shared>,
<Group>
Yes Yes No C
Settings/
Registration Basic
Information
Settings/Registration
753
<Held Jobs Warning Settings>
<Display Warning on Job List
Screen>: <On>, <Off>
<Display Warning When
Starting to Print>: <On>, <Off>
When <On> is selected:
<If Print Jobs with Specied
Number of Pages or More Are
Included>: <On>, <Off> (1 to
100 to 9999)
<If 1-Sided Print Jobs Are
Included>: <On>, <Off>
<If Color Print Jobs Are
Included>: <On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
<PIN Settings for Secure Print Jobs>
<Require PIN for Printing/
Displaying User Jobs>: <On>,
<Off>
<Require PIN for Job Deletion>:
<On>, <Off>
Yes Yes Yes C
Settings/
Registration Basic
Information
<Enable Auto Print Function When Logging
In> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Auto Print User Jobs When Logging In> <On>, <Off> Yes Yes No No
Settings/
Registration Basic
Information
*1 If the license for encrypted secure printing is validated.
Settings/Registration
754
Set Destination
72JY-0EE
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Address Lists>
<Address List 1> to
<Address List 10>, <One-
Touch>, <Address List for
Admin.>, <Print List>
Yes Yes Yes No -
<Register Destinations>
<Register New
Destination>, <Details/
Edit>, <Delete>, <Search
by Name>
Yes Yes Yes*1 C Address Book
<Rename Address List>
<Address List 1> to
<Address List 10>,
<Rename>
Yes Yes Yes C Address Book
<Register One-Touch> <001> to <200>,
<Register/Edit>, <Delete> Yes Yes Yes C Address Book
<Change Default Display of Address Book> <Local>, <LDAP Server>,
<Remote> Yes Yes No C
Settings/
Registration Basic
Information
<Address Book PIN>
<Set>:
<PIN>: Enter the PIN (7
digits maximum)
<Conrm>
No No Yes C
Settings/
Registration Basic
Information
<Manage Address Book Access Numbers> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Include Password When Exporting Address
Book> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Register LDAP Server>
<Register>, <Details/
Edit>, <Delete>, <Print
List>
Yes Yes Yes B
Settings/
Registration Basic
Information
<Auto Search When Using LDAP Server> <On>, <Off> Yes Yes No C
Settings/
Registration Basic
Information
<Conrm TLS Certicate for LDAP Server
Access>
<On>, <Off>
Yes No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
<CN>: On, Off
Settings/Registration
755
<Change Default LDAP Search Conditions> <Register>, <Initialize> Yes Yes No No -
<Register/Edit LDAP Search Attribute>
<Not Registered 1>, <Not
Registered 2>:
<Register/Edit>, <Delete>
Yes Yes Yes B
Settings/
Registration Basic
Information
<Settings for Search by Name When Using
LDAP Server>
<Name Type for Search
Attribute>:
cn, commonname,
fullName, displayName,
sn, givenName, Custom
Yes No No C
Settings/
Registration Basic
Information
<Filter>:
Contains, Does Not
Contain, Equals, Differs
from, Begins with, Ends
with
<Acquire Remote Address Book>
<Acquire Address Book> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Remote Address Book Server Address> Enter the IP Address or
Host Name Yes Yes Yes C
Settings/
Registration Basic
Information
<Communication Timeout> 15 to 30 to 120 sec. Yes Yes Yes C
Settings/
Registration Basic
Information
<Fax TX Line Auto Select Adjustment> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Make Remote Address Book Open>
<Make Address Book Open> <On>, <Off> Yes Yes Yes C
Settings/
Registration Basic
Information
<Use Personal Address List> <On>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
<Use User Group Address List> <On>, <On (Browse
Only)>, <Off> Yes No Yes C
Settings/
Registration Basic
Information
*1 <Server to Search:>: No
Settings/Registration
756
User Management
72JY-0EH
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import
All
Function
Name of Item
When Exporting
with the Remote
UI
<Authentication Management>
<Change Password>*1 (32 characters maximum) Yes Yes Yes C Authentication
User Management
<Register/Edit Authentication User> <Register>, <Details/Edit>,
<Delete> No No Yes C Authentication
User Management
<Use User Authentication>
<On>, <Off>
When <On> is selected:
●<Keyboard Authentication>:
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
<Keyboard Authentication>
<Number of Caches for Login
Users>
<0>, <1>, <Max (Maximum No.
for Device)>No No Yes C
Settings/
Registration Basic
Information
<Display Button to Change
Password on Settings Menu> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Use Numeric Keys for
Authentication> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Login Screen Display Settings>
<Displ When Dev Operation
Start>, <Display When Func.
Selected>
No No Yes C
Settings/
Registration Basic
Information
When <Display When Func.
Selected> is selected:
●<Require Authentication
For>: <Functions>, <Color
Copy/Print> (<None (No
Authentication Required)>,
<Full Color>, <Full Color/Two
Colors>, <Full Color/Two
Colors/Single Color>)
No No Yes C
Settings/
Registration Basic
Information
●<Require Authentication in
Settings/Registration For>*2:
<All Items>, <Administrator
Items Only>
No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
758
<Functions to Restrict>
<Print from Drivers without AMS
Printer Driver Add-in>: <Restrict>,
<Do Not Restrict>
No No Yes C
Settings/
Registration Basic
Information
<Remote Scan>: <Restrict>, <Do
Not Restrict>No No Yes C
Settings/
Registration Basic
Information
<Restrict Job from Remote Device
w/out User Authent.> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Default Role When Registering User>
<Administrator>,
<GeneralUser>, <DeviceAdmin>,
<NetworkAdmin>,
<PowerUser>*2, <LimitedUser>*2
No No Yes C
Settings/
Registration Basic
Information
<Match Case for User Name> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Allow Use of @ in User Name> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<System Manager Information Settings>
<System Manager ID>: 7654321
(Seven digits maximum)
<System Manager PIN>: 7654321
(Seven digits maximum)
<System Manager Name>
<E-Mail Address>
<Contact Information>
<Comment>
No No Yes C
Department ID
Management
Settings
<Department ID Management> <On>, <Off> No No Yes C
Department ID
Management
Settings
<Register PIN>
<Register>, <Edit>, <Delete>,
<Limit Functions>*3 No No Yes C
Department ID
Management
Settings
When <Register>/<Edit> is
selected:
<Department ID>, <PIN>, <Turn
Limit On/Off and Set Page Limit>
No No Yes C
Department ID
Management
Settings
When <Turn Limit On/Off and Set
Page Limit> is selected:
●<Total Print Limit>:
<On>, <Off>
Page Limit (0 to 999999)
●<Total Color Print Limit>:
<On>, <Off>
Page Limit (0 to 999999)
●<Total Black & White Print
Limit>: <On>, <Off>
Page Limit (0 to 999999)
No No Yes C
Department ID
Management
Settings
When <Set Copy Limit> is
selected:
●<Color Copy Limit>:
Settings/Registration
759
<On>, <Off>
Page Limit (0 to 999999)
●<Black & White Copy Limit>:
<On>, <Off>
Page Limit (0 to 999999)
When <Set Scan Limit> is
selected:
●<Color Scan Limit>: <On>,
<Off>
Page Limit (0 to 999999)
●<Black & White Scan Limit>:
<On>, <Off>
Page Limit (0 to 999999)
When <Set Print Limit Details> is
selected:
●<Color Print Limit>: <On>,
<Off>
Page Limit (0 to 999999)
●<Black & White Print Limit>:
<On>, <Off>
Page Limit (0 to 999999)
<Page Totals> <Clear>, <Print List>, <Clear All
Totals> No No Yes No -
<Allow Printer Jobs with Unknown
IDs> <On>, <Off> No No Yes C
Department ID
Management
Settings
<Allow Remote Scan Jobs with
Unknown IDs> <On>, <Off> No No Yes C
Department ID
Management
Settings
<Allow Black & White Copy/Print
Jobs>*3 <On>, <Off> No No Yes C
Department ID
Management
Settings
<Allow Black & White Printer Jobs> <On>, <Off> No No Yes C
Department ID
Management
Settings
*1 Indicates items that appear only if you are logged in as a user with privileges other than Administrator privileges when User
Authentication is being used.
*2 Indicates items that appear only if ACCESS MANAGEMENT SYSTEM is enabled.
*3 Indicates items that appear only if DepartmentID Authentication is set as the login service.
Settings/Registration
760
Device Management
72JY-0EJ
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be
set in
Remote
UI
Import All
Function
Name of Item
When
Exporting with
the Remote UI
<Device Information Settings>
<Device Name> No No Yes A
Settings/
Registration
Basic
Information
<Location> No No Yes A
Settings/
Registration
Basic
Information
<Import/Export from Addr. Book
Management Software>
<On>, <Off>
●When <On> is selected:
<Use User Authentication
When Importing>: <On>,
<Off>
No No No C
Settings/
Registration
Basic
Information
<Conrm Device Signature Certicate>
<Version>, <Serial Number>,
<Signature Algorithm>, <Issued
To>, <Validity Start Date>,
<Validity End Date>, <Issuer>,
<Public Key>, <Certicate
Thumbprint>, <Issued To (Altn.
Name)>, <Verify Certicate>
Yes Yes Yes No -
<Conrm User Signature Certicate>*2
<Version>, <Serial Number>,
<Signature Algorithm>, <Issued
To>, <Validity Start Date>,
<Validity End Date>, <Issuer>,
<Public Key>, <Certicate
Thumbprint>, <Issued To (Altn.
Name)>, <Verify Certicate>
Yes Yes Yes No -
<Certicate Settings>
<Generate Key>
<Generate Network Communication
Key>
<Key Name> Yes Yes Yes No -
<Signature Algorithm>:
<SHA256>, <SHA384>, <SHA512> Yes Yes Yes No -
<Key Algorithm>: <RSA>,
<ECDSA> Yes Yes Yes No -
●When <RSA> is selected: Yes Yes Yes No -
Settings/Registration
761
<Generate Key: Key Length
(bit) Settings>: <512>, <1024>,
<2048>, <4096>
●When <ECDSA> is selected:
<Generate Key: Key Type
Settings>: <P256>, <P384>,
<P521>
Yes Yes Yes No -
<Validity Start Date>: Date,
Month, Year (01/01/2000 -
31/12/2037)
Yes Yes Yes No -
<Validity End Date>: Date,
Month, Year (01/01/2000 -
31/12/2037)
Yes Yes Yes No -
<Country/Region>: Country/
Region name and code Yes Yes Yes No -
<State> Yes Yes Yes No -
<City> Yes Yes Yes No -
<Organization> Yes Yes Yes No -
<Organization Unit> Yes Yes Yes No -
<Common Name> (IP address of
the machine or FQDN (41
characters maximum))
Yes Yes Yes No -
<Generate/Update Device Signature
Key> <Yes>, <No> Yes Yes Yes C Key Settings
<Generate/Update Key for Access
Control> <Yes>, <No> Yes Yes Yes No -
<Key and Certicate List>
<Key and Certicate List for Users>*2
<Certicate Details>: (<Version>,
<Serial Number>, <Signature
Algorithm>, <Issued To>,
<Validity Start Date>, <Validity
End Date>, <Issuer>, <Public
Key>, <Certicate Thumbprint>,
<Issued To (Altn. Name)>, <Verify
Certicate>)
Yes Yes Yes C*3*4
Certicate/
Certicate
Revocation List
(CRL) Settings
<Delete> Yes Yes Yes No -
<Key and Certicate List for This
Device>*2
<Certicate Details>: (<Version>,
<Serial Number>, <Signature
Algorithm>, <Issued To>,
<Validity Start Date>, <Validity
End Date>, <Issuer>, <Public
Key>, <Certicate Thumbprint>,
<Issued To (Altn. Name)>, <Verify
Certicate>)
Yes Yes Yes C*3*4
Certicate/
Certicate
Revocation List
(CRL) Settings
<Delete> Yes Yes Yes No -
<Display Use Location> (Key and
Certicate) Yes Yes Yes C Certicate/
Certicate
Settings/Registration
762
Revocation List
(CRL) Settings
<CA Certicate List>
<Certicate Details>: (<Version>,
<Serial Number>, <Signature
Algorithm>, <Issued To>,
<Validity Start Date>, <Validity
End Date>, <Issuer>, <Public
Key>, <Certicate Thumbprint>,
<Issued To (Altn. Name)>, <Verify
Certicate>)
Yes Yes Yes C*3
Certicate/
Certicate
Revocation List
(CRL) Settings
<Delete> Yes Yes Yes No -
<Certicate Revocation List (CRL)>
<CRL Details>: <Version>,
<Signature Algorithm>, <Valid
From>, <Next Update>, <Issuer>,
<Serial No. List>
Yes Yes Yes C*3
Certicate/
Certicate
Revocation List
(CRL) Settings
<Delete> Yes Yes Yes No -
<Register Key and Certicate>
<Register> Yes Yes Yes No -
<Delete> Yes Yes Yes No -
<Register CA Certicate>
<Register> Yes Yes Yes No -
<Delete> Yes Yes Yes No -
<OCSP (Online Certicate Status
Protocol) Settings>
<Use OCSP (Online Certicate
Status Protocol)>: <On>, <Off>
When <On> is selected:
●<Certicate Verication
Level>:
<Enable Unveried
Certicates>: <On>, <Off>
●<OCSP Responder Settings>:
●<URL>: <Retrieve from
Certicate>, <Custom>,
<Retrieve from Cert./
Custom>
●<Custom URL>
●<Communication Timeout>:
1 to 3 to 30 sec.
Yes Yes Yes C
Settings/
Registration
Basic
Information
<Display Job Status Before Authentication> <On>, <Off> No No Yes C
Settings/
Registration
Basic
Information
<Restrict Access to Other User Jobs>
<Copy/Print>: <On>, <Off>
<Send>: <On>, <Off>
<Receive>: <On>, <Off>
<Store>: <On>, <Off>
No No Yes C
Settings/
Registration
Basic
Information
<Display Job Log>
<On>, <Off> No No Yes C
Settings/
Registration
Basic
Information
When <Off> is selected: No No Yes C Settings/
Registration
Settings/Registration
763
●<Retrieve Job Log with
Management Software>:
<Allow>, <Do Not Allow>
Basic
Information
<Save Audit Log> <On>, <Off> No No Yes C
Settings/
Registration
Basic
Information
<Retrieve Network Authentication Log> <On>, <Off> No No Yes C
Settings/
Registration
Basic
Information
<Store Key Operation Log> <On>, <Off> No No Yes C
Settings/
Registration
Basic
Information
<Restrict Service Representative Access> <On>, <Off (Auth. Needed)>,
<Off>No No Yes C
Settings/
Registration
Basic
Information
<Synchronize Custom Settings (Client)>
Before synchronizing: <Enable>,
<Pause>
After synchronizing: <Disable>,
<Resume>
No No Yes No -
<Manage Personal Settings>
<Enable Use of Personal Settings> <On>, <Off> No No No C
Settings/
Registration
Basic
Information
<Action When Maximum Number of
Users Exceeded>
<Delete Oldest User Settings>,
<Discard New User Settings>No No No C
Settings/
Registration
Basic
Information
<Use Default Screen After Startup/
Restoration> <On>, <Off> No No No C
Settings/
Registration
Basic
Information
<Prohibit Initialization of Administrator
Password> <On>, <Off> No No No No -
<Restrict Special Mode Operations> <On>, <Off> No No No C
Settings/
Registration
Basic
Information
*1 Imports the registered distribution destination.
*2 Indicates items that appear only when the appropriate optional equipment is available for use.
*3 Supports only algorithms that can be imported from the Remote UI.
*4 Keys and certicates are exported in the PKCS#12 format.
Settings/Registration
764
License/Other
72JY-0EK
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Register License> 24 characters maximum No No No No -
<AddOn Settings>
<Print System Information> <Yes>, <No> No No No No -
<Use TLS> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Conrm TLS Certicate Using AddOn
Application>
<On>, <Off>
When <On> is selected:
●<Add Items to Verify>:
<CN>: On, Off
No No Yes C
Settings/
Registration Basic
Information
<Use DNS Caching>
<On (Unltd. Use)>, <On
(Specify Period)>, <Off>
When <On (Specify Period)>
is selected:
●<Period of Validity>: 1 to
60 to 120 sec.
No No Yes C
Settings/
Registration Basic
Information
<Use Proxy Settings of This Device> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Add X-FRAME-OPTIONS to HTTP
Header> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Remote UI Settings>
<On>, <Off> No No No C
Settings/
Registration Basic
Information
When <On> is selected:
●<Use TLS>: <On>, <Off>No No Yes C
Settings/
Registration Basic
Information
<Delete Message Board Contents> <Yes>, <No> No No No No -
<Remote Operation Settings>
<On>, <Off> No No Yes C
Settings/
Registration Basic
Information
When <On> is selected: No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
765
●<Password>: 8
characters maximum
(Only alphanumeric
characters)
<Use ACCESS MANAGEMENT SYSTEM> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Register/Update Software>
<Install Applications/
Options>, <Update
Firmware>, <Software
Management Settings>,
<Scheduled Update>
No No Yes No -
<Start Setup Guide> <Start> No No No No -
<Allow Use of Print Function from Mobile> <On>, <Off> No No No C*1
Settings/
Registration Basic
Information
*1 Only for machines that support the Forced Hold function.
Settings/Registration
766
Data Management
72JY-0EL
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Import/Export>
<Import from USB Memory>
<Store Import Result
in Device>: <On>,
<Off>
<Store Import Result
in USB>: <On>, <Off>
<Decryption
Password>
No No No No -
<Export to USB Memory> <Encryption
Password> No No No No -
<Import Result Report> <Yes>, <No> No No No No -
<Restrict Import/Export from Web
Service> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Initialize All Data/Settings> <Yes>, <No> No No No No -
Settings/Registration
767
Security Settings
72JY-0ER
●For information on the items ("A", "B", "C", and "No") in the "Import All Function" column, see Import All Function(P. 671) .
Item Setting Description DeviceAdmin NetworkAdmin
Can be set
in Remote
UI
Import All
Function
Name of Item
When Exporting
with the Remote
UI
<Authentication/Password Settings>
<Authentication Function Settings>
<Prohibit Authentication Using
Department ID and PIN> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Lockout Settings>
<Enable Lockout>: <On>,
<Off>No No Yes C
Settings/
Registration Basic
Information
When <On> is selected:
●<Lockout
Threshold>: 1 to10
times
●<Lockout Period>: 1
to 60 min.
No No Yes C
Settings/
Registration Basic
Information
<Password Settings>
<Prohibit Caching of Authentication
Password> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Display Warning When Default
Password Is in Use> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Allow Use of Default Password for
Remote Access> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Minimum Length Settings> <On> (1 to 32
Characters), <Off>No No Yes C
Settings/
Registration Basic
Information
<Validity Period Settings> <On> (1 to 180 days),
<Off>No No Yes C
Settings/
Registration Basic
Information
<Prohibit Use of 3 or More Identical
Consec. Characters> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
768
<Use at Least 1 Uppercase Character> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Use at Least 1 Lowercase Character> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Use at Least 1 Digit> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Use at Least 1 Symbol> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<Encryption Settings>
<Prohibit Use of Weak Encryption>
<On>, <Off>
<On> is selected:
●<Prohibit Use of
Key/Certicate with
Weak Encryption>:
<On>, <Off>
No No Yes C
Settings/
Registration Basic
Information
<Format Encryption Method to FIPS
140-2> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<System Verication Settings>
<Verify System at Startup> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
<McAfee Embedded Control> <On>, <Off> No No Yes C
Settings/
Registration Basic
Information
Settings/Registration
769
<Preferences>
72JY-0ES
Item Description
<Paper Settings>(P. 771) This section describes how to register paper settings.
<Display Settings>(P. 773) This section describes the display settings for the touch panel display.
<Timer/Energy Settings>(P. 777) This section describes the timer settings and energy settings.
<Network>(P. 782) This section describes the network settings.
<External Interface>(P. 795) This section describes the USB settings.
<Accessibility>(P. 797) This section describes settings for improving accessibility, such as the speed of repetition
when keys are held down, and whether to use ick operations.
Settings/Registration
770
<Paper Settings>
72JY-0EU
This section describes how to register paper to use.
<Paper Settings>
(Settings/Register) <Preferences> <Paper Settings>
You can register the paper size and type for each paper source. This setting enables you to achieve the
appropriate print results. Specifying Paper Size and Type in the Paper Drawer(P. 142)
●If you have changed the size or type of paper loaded in the paper source when <Conrm When
Loading Paper in Paper Drawer> is set to <Off>, make sure to change this setting as well.
<Paper Type Management Settings>
(Settings/Register) <Preferences> <Paper Settings>
You can register/edit various customer paper types (user dened paper types), besides the default paper types
registered in the machine. Paper Type Management Settings(P. 903)
<Register Favorite Paper (Multi-Purpose Tray)>
(Settings/Register) <Preferences> <Paper Settings>
You can easily specify paper settings by registering paper frequently used in the multi-purpose tray in a button.
"Favorite Paper" can be easily recalled from the screen displayed when paper is loaded. Registering
Frequently Used Paper Size and Type for the Multi-purpose Tray(P. 148)
<Multi-Purpose Tray Defaults>
(Settings/Register) <Preferences> <Paper Settings>
You can set the method for selecting the paper to use in the multi-purpose tray. If you always use the same
paper size/type in the multi-purpose tray, it is convenient to register the paper in <Use Preset>. Fixing the
Paper Size and Type to Use with the Multi-Purpose Tray(P. 151)
●If you use various types of paper in the multi-purpose tray, select <Always Specify>. If you frequently use
multiple types of paper, you can eliminate the procedure for selecting the paper type by registering the
paper types in advance. Registering Frequently Used Paper Size and Type for the Multi-purpose
Tray(P. 148)
●When the following conditions are met, you can press <Temp. Change Ppr. in MP Tray> on the paper
selection screen of <Copy> and <Access Stored Files> to change the paper size/type to load from the
multi-purpose tray:
- If paper is loaded in the multi-purpose tray
- If this setting is set to <Use Preset>
- If <Prioritize Printer Driver Settings for Jobs with MP Tray>(P. 818) is set to <On>
Settings/Registration
771

<Register Custom Size>
(Settings/Register) <Preferences> <Paper Settings>
You can register frequently used free sizes of paper. The paper sizes registered here are displayed on the paper
size selection screen for the paper drawer and multi-purpose tray. Registering Free Size Paper (Custom Size
Paper)(P. 153)
Settings/Registration
772

<Display Settings>
72JY-0EW
This section describes the display settings for the touch panel display.
<Default Screen After Startup/Restoration>
(Settings/Register) <Preferences> <Display Settings>
You can set the default screen displayed at startup/restoration.
●Depending on the authentication method specied in personal authentication management, the Log
In screen may be displayed before the screen set in <Default Screen After Startup/Restoration> is
displayed.
●When the login service is changed to Department ID Authentication and <Limit Functions> for
<Department ID Management> is used, the <Home> screen or the login screen for entering the
Department ID/PIN may be displayed before the screen set in <Default Screen After Startup/
Restoration>, depending on the settings.
<Default Screen (Status Monitor)>
(Settings/Register) <Preferences> <Display Settings>
You can change the screen that is displayed when you press (Status Monitor).
<Display Fax Function>
(Settings/Register) <Preferences> <Display Settings>
You can set the machine to display the Fax function on the <Home> screen. If you choose to display the Fax
function, you can also select whether to display <Fax> in <Scan and Send>. Doing so enables you to send to fax,
e-mail, and I-fax destinations at the same time.
<Store Location Display Settings>
(Settings/Register) <Preferences> <Display Settings>
You can change the destinations that are displayed when you press <Scan and Store> or <Access Stored Files>.
<Switch Language/Keyboard>
(Settings/Register) <Preferences> <Display Settings>
You can select the language/keyboard displayed on the touch panel display.
Settings/Registration
773

●Some messages may not be displayed properly in the selected language. In this case, restart the
machine. Some messages may not change even after the machine is restarted.
●If Server Authentication + Local Device Authentication are set using personal authentication
management, and there is a difference between the language set on the machine and the one set in
Active Directory, the sender's full name will not appear in e-mail messages sent to the recipient.
<Display Switch Language/Keyboard Button>
(Settings/Register) <Preferences> <Display Settings>
You can display the button that enables you to switch the language and keyboard layout. The button is
displayed on the bottom line of the touch panel display.
<Use Keyboard Shift Lock Feature>
(Settings/Register) <Preferences> <Display Settings>
If you press <Shift> on the keyboard screen, you can enter an uppercase letter. You can specify the shift lock
settings for entering uppercase letters continuously or for entering text which begins with an uppercase letter.
<Registered Characters for Keyboard>
(Settings/Register) <Preferences> <Display Settings>
You can register strings often used when entering E-Mail/I-Fax destinations using the keyboard.
<Display Remaining Paper Message>
(Settings/Register) <Preferences> <Display Settings>
You can set to display a message indicating that the remaining paper loaded in a paper source is low.
<No. of Copies/Job Duration Status>
(Settings/Register) <Preferences> <Display Settings>
The number of copies specied and the approximate time before the current job completes are displayed on
the bottom line of the touch panel display.
●The accuracy of the approximate times that appear on the bottom line of the touch panel display may
vary, depending on the status of the machine.
●The approximate time does not appear when the wait time is less than one minute.
<Notify to Clean Original Scanning Area>
(Settings/Register) <Preferences> <Display Settings>
You can set the machine to display the message that prompts you to clean the scanning area when the machine
detects stains in the document feed scanning area.
<Paper Type Selection Screen Priority>
(Settings/Register) <Preferences> <Display Settings>
Settings/Registration
774
You can set whether to prioritize the simple (<Simple>) or detailed (<Detailed>) setting screen when you display
the screen to select the paper type.
<Switch Millimeter/Inch Entry>
(Settings/Register) <Preferences> <Display Settings>
You can set whether to enter numeric values in millimeters or inches on the various numeric entry screens.
<Conrm When Loading Paper in Paper Drawer>
(Settings/Register) <Preferences> <Display Settings>
You can set whether to display the <Paper Settings> screen when the paper drawer is inserted into the machine.
●The <Paper Settings> screen is not displayed in the following cases.
- When paper is loaded because it has run out during a job
- When a paper jam is removed
- When a screen for executing, canceling, or conrming jobs is displayed
- When the paper is set in (Settings/Register) <Preferences> <Paper Settings> <Paper
Settings>
<Display Logged-in User Name>
(Settings/Register) <Preferences> <Display Settings>
You can select whether to display the user name/display name on the touch panel display.
●If DepartmentID Authentication is set as the login service and <Department ID Management> is set to
<On>, the Department ID is displayed when <At Screen Bottom> is selected. It is not displayed on the
top of the screen.
●If User Authentication is set as the login service, <User Name> is displayed when <At Screen Bottom>
is selected.
<Display Remaining Toner Error Message>
(Settings/Register) <Preferences> <Display Settings>
Displays a warning screen that enables you to identify which color is running low when remaining toner is low.
This message is useful, as it enables you to prepare a new toner cartridge in advance, etc.
●The warning screen prompting you to prepare a new toner cartridge is displayed.
●If you press <Close> on the warning screen to close the screen, you can perform normal operations.
However, the warning screen will appear every time the machine returns from sleep mode or when
the main power is turned ON.
Settings/Registration
775

●If you have already prepared a new toner cartridge, etc., and the notication becomes unnecessary,
perform the <Delete Remaining Toner Error> operation.
●The message indicating the status remains on the bottom of the screen, regardless of this setting.
<Delete Remaining Toner Error>
(Settings/Register) <Preferences> <Display Settings>
You can delete the warning screen which appears when the remaining toner is low if <Display Remaining Toner
Error Message> is set to <On>.
●The warning screen will appear again when a different color toner becomes low, if <Display
Remaining Toner Error Message> is set to <On>.
<IP Address Display Settings>
(Settings/Register) <Preferences> <Display Settings>
You can set whether to display the IP address on the counter information screen.
●This setting is only valid when <Use IPv4> is set to <On>.
<Display Scan for Mobile>
(Settings/Register) <Preferences> <Display Settings>
You can set whether to enable the <Scan for Mobile> setting, which sends scanned data to mobile devices such
as smartphones and tablets.
<Display Mobile Portal>
(Settings/Register) <Preferences> <Display Settings>
You can set whether to display <Mobile Portal> on the <Home> screen.
<Display QR Code on Mobile Portal>
(Settings/Register) <Preferences> <Display Settings>
You can set whether to display a QR code on the <Mobile Portal> screen. Using a QR code saves you the effort
of entering the IPv4 address of the machine.
Settings/Registration
776

<Timer/Energy Settings>
72JY-0EX
This section describes the timer settings and energy settings.
<Adjust Time>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can adjust the time in minutes.
●Even if you change the time from 23:59 to 00:00, the date will not be changed.
<Date/Time Settings>
(Settings/Register) <Preferences> <Timer/Energy Settings>
Setting the current date and time is very important. For instructions on how to congure the setting, see
Setting the Date/Time(P. 17) .
<Time Format>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set whether to display the time in 24-hour notation or 12-hour notation.
●You can also specify to automatically synchronize the date and time with a server on the network
using SNTP. Making SNTP Settings(P. 63)
<Quick Startup Settings for Main Power>
(Settings/Register) <Preferences> <Timer/Energy Settings>
If you set this function to <On>, you can reduce the time it takes until you can perform operations on the screen
and scan originals after the power is turned ON.
●When this function is enabled
- Standby power is consumed even when the power is turned OFF.
- A tone sounds when the machine is turned ON, or when the machine is turned OFF if you set <Sleep
Mode Tone> in <Other Volume Settings> to <On>. (However, the machine may not be able to start
up quickly and the tone may not sound, depending on the status of the machine.)
●Even if this function is set to 'On', the machine does not startup quickly in the following situations:
- When any of the network settings below are set to 'On'
Settings/Registration
777

●Wi-Fi
- When turning ON the main power of the machine after turning OFF the main power in any of the
conditions below
●More than 110 hours have elapsed after quick startup
●Operating jobs
●Jobs are reserved
●Just after using telephone lines
●Backing up data
●Accessing to the machine via network
●After specifying settings which require restarting the machine
●Error is occurred
●Using the Limited Functions mode
●The power cord is disconnected after turning OFF the main power
●AddOn applications which do not support quick startup are installed on the machine
- When turning ON the main power of the machine in 20 seconds after turning OFF the main power
- When turning ON the main power of the machine after eight hours have passed since the machine
was turned OFF
- When turning ON the main power of the machine after turning OFF the main power from the
Remote UI
<Auto Reset Time>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can specify the time period in which you are logged out and the touch panel display returns to the default
setting automatically.
●If the login service is being used, the machine automatically logs out the user when the Auto Reset
Time elapses.
●The screen displayed after the Auto Reset initiates differs depending on the following settings.
-Setting 1: The settings in [Visual Message Settings] (when [When to Display] is set to [After Logout/
Auto Reset])
●When Visual Message is not set or after the displayed Visual Message screen is closed, the screen
that is specied in Setting 2 is displayed.
- Setting 2: The settings in <Function After Auto Reset>
●When <Default Function> is set, the screen specied in <Default Screen After Startup/Restoration>
(Setting 3) is displayed.
●When <Selected Function> is set, the function before the Auto Reset initiates is displayed. (The
specied settings and entered values for each function will be cleared.) However, the <Selected
Function> settings may not be correctly reected, and the screen specied in <Default Screen After
Startup/Restoration> may be displayed.
- Setting 3: The settings in <Default Screen After Startup/Restoration>
Settings/Registration
778

<Restrict Auto Reset Time>
(Settings/Register) <Preferences> <Timer/Energy Settings>
If you set this function to <On>, general users become unable to set <Auto Reset Time> and <Function After
Auto Reset>.
<Function After Auto Reset>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set whether the default screen set for <Default Screen After Startup/Restoration> in <Preferences> or
the immediately previous screen is displayed at startup after the Auto Reset initiates.
●If Visual Message is set to be displayed after the Auto Reset mode initiates, the Visual Message screen
is displayed rst, regardless of this setting. Conguring the Visual Message Function(P. 649)
<Auto Shutdown Time>
(Settings/Register) <Preferences> <Timer/Energy Settings>
With the Auto Shutdown, if the touch panel display of the machine is idle for a certain period of time after it has
entered the Sleep mode, the machine automatically shuts down.
●This function is not displayed if the fax board is installed. If it is displayed, set <Auto Shutdown Time>
to <0>, and contact your dealer or service representative.
●Even when operating the machine from the Remote UI, the machine automatically shuts down if the
touch panel display of the machine is idle for a certain period of time. A malfunction may occur
particularly if the machine automatically shuts down while importing. Set <Auto Shutdown Time> to
<0> when importing data.
●The Auto Shutdown may not be performed, depending on the usage conditions of the machine.
<Auto Shutdown Weekly Timer>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set the time that the machine automatically shuts down each day of the week. If you use this function,
you do not have to shut down the machine manually every day.
Settings/Registration
779
●If both <Auto Shutdown Time> and <Auto Shutdown Weekly Timer> are set, priority is given to <Auto
Shutdown Time>.
<Auto Sleep Time>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set the time until the machine automatically enters the Sleep mode if no operations are performed.
●It is recommended that the default value is used for this setting.
<Sleep Mode Energy Use>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set the amount of energy that the machine consumes when it is in the Sleep mode.
●If the machine is connected to a computer using a USB cable, depending on the timing for entering
the sleep mode, the machine may be unable to receive data correctly. Reactivate the machine from
the sleep mode, then execute the job again.
●The energy consumption level may be the same as when <High> is set even when <Low> is set,
depending on the status of the machine.
●If the energy consumption level is set to <Low>, communication failure may occur, depending on the
network utility software you are using. To avoid this, press the Energy Saver key to cancel the Sleep
mode before using the machine.
<Auto Sleep Weekly Timer>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set the time that the machine automatically enters the Sleep mode each day of the week.
●If you set both the <Auto Sleep Time> and <Auto Sleep Weekly Timer>, the <Auto Sleep Time> setting
is given priority.
Settings/Registration
780
<Time Settings for Auto Adjust Gradation>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can automatically perform the automatic gradation adjustment at a set time every day.
<Sleep Mode Exit Time Settings>
(Settings/Register) <Preferences> <Timer/Energy Settings>
You can set the time for recovering from the Sleep mode.
Settings/Registration
781
<Network>
72JY-0EY
This section describes the network settings.
<Output Report>
(Settings/Register) <Preferences> <Network>
You can print the settings in <Network>. Printing a List of Settings(P. 917)
<Conrm Network Connection Setting Changes>
(Settings/Register) <Preferences> <Network>
If this setting is set to <On>, you can change network settings. If errors related to network connections occur,
an error message appears on the touch panel display of the machine. Canceling the Network Setting
Lock(P. 22)
<Use IPv4>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings>
Set whether to use IPv4. Setting an IPv4 Address(P. 35)
<IP Address Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings>
Specify the IPv4 address. Setting an IPv4 Address(P. 35)
<DHCP Option Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings>
Specify the optional settings for DHCP. Using a DHCP Server(P. 48)
<PING Command>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv4 Settings>
Tests whether the IPv4 address is set correctly. Conducting a Connection Test for an IPv4 Address(P. 36)
<Use IPv6>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Specify whether to use IPv6. Setting an IPv6 Address(P. 37)
<Stateless Address Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Specify the IPv6 stateless address. Setting an IPv6 Address(P. 37)
<Manual Address Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Specify the IPv6 address manually. Setting an IPv6 Address(P. 37)
Settings/Registration
782
<Use DHCPv6>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Specify whether to obtain the IPv6 address from the DHCP server. Setting an IPv6 Address(P. 37)
<PING Command>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Check whether the IPv6 address is correctly specied. Conducting a Connection Test for an IPv6
Address(P. 38)
<Only Retrieve Stateful Address Prex>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Specify whether to obtain only the former half of the stateful address from the DHCP server by using DHCPv6.
<DHCP Option Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPv6 Settings>
Specify the optional settings for DHCP. Using a DHCP Server(P. 48)
<DNS Server Address Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <DNS Settings>
Specify the DNS server address settings. Making DNS Settings(P. 45)
<DNS Host Name/Domain Name Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <DNS Settings>
Specify the host name and domain name of the machine. Making DNS Settings(P. 45)
<DNS Dynamic Update Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <DNS Settings>
Specify whether to perform the automatic update when the mapping between the host name and IP address is
changed on an environment such as DHCP. Making DNS Settings(P. 45)
<mDNS Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <DNS Settings>
Specify settings for using the DNS function on a system that does not have a DNS server. Making DNS
Settings(P. 45)
<Computer Name/Workgroup Name Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the name of the machine on the network and the name of the workgroup it belongs to. If your
environment does not have workgroups, create a workgroup in Windows and enter the name of that
workgroup.
Settings/Registration
783
●If you set <Use NetBIOS> to <Off>, <WINS Settings> is disabled. Make sure to set <Use NetBIOS> to
<On> when using WINS.
<SMB Client Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the settings to use when the machine connects to a network as an SMB client. Making SMB
Settings(P. 50)
<Specify SMB Client Version>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the version of SMB to use with the SMB client. Making SMB Settings(P. 50)
●Use the same version of SMB with the SMB server and SMB client. SMB cannot be used if the versions
differ.
<WINS Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for Windows Internet Name Service (WINS). Making WINS Settings(P. 52)
●If you set <Use NetBIOS> to <Off> in <Computer Name/Workgroup Name Settings>, this setting is
disabled.
<LPD Print Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for LPD printing. To use LPD printing, press <On> and set the time until the job is automatically
canceled when the print data cannot be received due to a communication error, etc.
●Banner pages are set to be output by print job. Even if <LPD Banner Page> is set to <On>, banner
pages are not output for print jobs that are set to not output a banner page.
<RAW Print Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Settings/Registration
784
Specify settings for RAW printing. To use RAW printing, press <On> and set whether to use bidirectional
communication and the time until the job is automatically canceled when the print data cannot be received due
to a communication error, etc.
<SNTP Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for Simple Network Time Protocol (SNTP). Making SNTP Settings(P. 63)
<FTP Print Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for FTP printing. To use FTP printing, press <On>, and set <User Name> and <Password> as
necessary.
<Use UTF-8 to Display Name of FTP Print Job>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify whether to use UTF-8 for displaying le names when you perform FTP print.
<WSD Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the WSD settings. To use WSD (Web Service on Devices) for the print application, set <Use WSD Printing>
to <On>. To use WSD to retrieve the information for the machine, set <Use WSD Browsing> to <On>.
To use the WSD Scan function, set <Use WSD Scan> to <On>. Using WSD(P. 432)
●If you set <Use WSD Printing> to <On>, <Use WSD Browsing> and <Use HTTP> are also set to <On>.
●If you set <Use WSD Scan> to <On>, <Use HTTP> is also set to <On>.
<Use FTP PASV Mode>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify whether to use the FTP PASV mode. Setting the PASV Mode of FTP(P. 63)
<IPP Print Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for IPP printing. To use IPP printing, press <On> and set whether to only allow communication
data encrypted with TLS (IPP printing) and whether to use IPP authentication.
●If you set this to <On>, <Use HTTP> is also set to <On>.
●To perform IPPS printing, a key pair to use is required. You can use a preinstalled key pair or an
original key pair generated by the machine as the key to use. For information on the key to use and
the method for generating an original key pair, see Generating the Key and Certicate for
Network Communication(P. 552) or Registering a Key and Certicate for Network
Communication(P. 600) . If you select <RSA> for <Key Algorithm> when generating the key to use for
Settings/Registration
785

network communication, set a key length of <1024> or longer. IPPS printing may not be able to be
performed correctly if a key length of <512> is set, depending on the operating system you are using.
●To use the IPP authentication function by setting <Use Authentication> to <On>, the user information
of the machine is used as the user and password for IPP authentication. Make sure to register the
user information in advance when using the IPP authentication function. Registering User
Information in the Local Device(P. 495)
<Multicast Discovery Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the multicast discovery settings. Monitoring the Machine From Device Management
Systems(P. 64)
<Sleep Mode Notication Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for multicast sending of the Sleep mode notications on the network.
●This setting can only be specied from the Remote UI.
<Use HTTP>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Enable or disable HTTP setting.
●By specifying this setting as <On>, you can open a necessary port. However, it is recommended that
you specify it as <Off>, if a port is not used. If you leave the port open, an unauthorized user may
access the machine.
If you set this to <Off>, the following settings are also set to <Off>.
●<Remote UI Settings>
●<IPP Print Settings>
●<Use WSD Scan> and <Use WSD Printing> in <WSD Settings>
●<Use WebDAV Server>
<TLS Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Settings/Registration
786
You can set a key pair, TLS version, and encryption algorithm to use after conrming that a machine uses TLS
encrypted communication. Conguring the Key and Certicate for TLS(P. 549)
<Proxy Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify settings for the proxy. Setting a Proxy(P. 547)
<Conrm Auth. Info. When in Auth. Management Mode>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify whether the machine checks authentication information when you print using the V4 printer driver.
●If there is no key to use for TLS communication or it is corrupted, this setting is disabled.
Conguring the Key and Certicate for TLS(P. 549)
<IPSec Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the IPSec settings. Conguring the IPSec Settings(P. 555)
<TCP/IP Option Settings>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify the TCP option window scale and MTU size.
●This setting can only be specied from the Remote UI.
<Use Network Link Scan>
(Settings/Register) <Preferences> <Network> <TCP/IP Settings>
Specify whether to use Network Link Scan.
<SNMP Settings>
(Settings/Register) <Preferences> <Network>
Specify the SNMP settings. Monitoring and Controlling via SNMP(P. 57)
<Format Host Resources MIB to RFC2790>
(Settings/Register) <Preferences> <Network>
Specify whether the host resources MIB is compliant with the specications of RFC2790.
Settings/Registration
787
<Dedicated Port Settings>
(Settings/Register) <Preferences> <Network>
Specify whether to congure/refer to detailed information of the machine from the Canon drivers or utility
software.
●If the setting is set to <Off>, some application that uses dedicated port may not be used.
<Dedicated Port Authentication Method>
(Settings/Register) <Preferences> <Network>
Specify the authentication method for the dedicated port.
●If the setting is set to <Mode 2>, communication using a dedicated port uses a secure mode.
Accordingly, you may not be able to connect from device management software or drivers, etc.
<Use Spool Function>
(Settings/Register) <Preferences> <Network>
Specify whether to spool print jobs that are sent to the machine in the storage device of the machine.
<Waiting Time for Connection at Startup>
(Settings/Register) <Preferences> <Network>
Specify the waiting time for connecting to a network from when the machine starts. Setting the Wait Time
When Connecting to a Network(P. 44)
<Ethernet Driver Settings>
(Settings/Register) <Preferences> <Network>
Specify the Ethernet driver settings. Making Ethernet Settings(P. 42)
<IEEE 802.1X Settings>
(Settings/Register) <Preferences> <Network>
Specify the settings for IEEE 802.1X. Conguring the IEEE 802.1X Authentication Settings(P. 561)
●If you set <IEEE 802.1X Settings> to <On>, the machine will not completely enter the Sleep mode.
Settings/Registration
788
<Outbound Filter>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <IPv4 Address Filter>
Specify the outbound lter. Specifying IP Addresses in Firewall Settings(P. 539)
<Inbound Filter>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <IPv4 Address Filter>
Specify the inbound lter. Specifying IP Addresses in Firewall Settings(P. 539)
<Always Allow Sending/Receiving Using ICMP>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <IPv4 Address Filter>
Specify whether to always allow ICMP communication.
<Outbound Filter>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <IPv6 Address Filter>
Specify the outbound lter. Specifying IP Addresses in Firewall Settings(P. 539)
<Inbound Filter>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <IPv6 Address Filter>
Specify the inbound lter. Specifying IP Addresses in Firewall Settings(P. 539)
<Always Allow Sending/Receiving Using ICMPv6>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <IPv6 Address Filter>
Specify whether to always allow ICMPv6 communication.
<Outbound Filter>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <MAC Address Filter>
Specify the outbound lter. Specifying MAC Addresses in Firewall Settings(P. 542)
<Inbound Filter>
(Settings/Register) <Preferences> <Network> <Firewall Settings> <MAC Address Filter>
Specify the inbound lter. Specifying MAC Addresses in Firewall Settings(P. 542)
<IP Address Block Log>
(Settings/Register) <Preferences> <Network> <Firewall Settings>
Displays the log for blocking with an IP address lter. Specifying IP Addresses in Firewall Settings(P. 539)
<Use Mopria>
(Settings/Register) <Preferences> <Network>
Specify whether to print data directly from mobile devices that support Mopria®, such as smartphones and
tablets. Utilizing the Machine through Applications(P. 458)
Settings/Registration
789
<Use AirPrint>
(Settings/Register) <Preferences> <Network>
Specify whether to print directly from an iPhone, iPad, iPod Touch, or Mac that supports AirPrint. Using
AirPrint(P. 460)
<Display Errors for AirPrint>
(Settings/Register) <Preferences> <Network>
Specify whether to display an error screen on the control panel if printing cannot be performed as expected due
to a problem with the print data when printing with AirPrint.
If this is set to <On>, an error screen is displayed on the control panel. Cancel the job after checking the error
screen. If this is set to <Off>, an error screen is not displayed on the control panel but the job remains in the job
history with <NG> indicated.
<Settings for Universal Print>
(Settings/Register) <Preferences> <Network>
Specify the Universal Print settings. Printing Using the Microsoft Cloud Service (Universal Print)(P. 364)
●This setting can only be specied from the Remote UI.
<Device Position Information Settings>
(Settings/Register) <Preferences> <Network>
Specify the device position information settings. Using AirPrint(P. 460)
<Select Interface>
(Settings/Register) <Preferences> <Network>
Select whether to use a wired LAN or wireless LAN by itself, a wired LAN and wireless LAN simultaneously, or a
wired LAN and another wired LAN simultaneously. Selecting the Network Connection Method(P. 23)
<Wireless LAN Settings>
(Settings/Register) <Preferences> <Network> <Wireless LAN>
Specify the wireless LAN settings. Connecting to a Wireless LAN(P. 26)
<Wireless LAN Information>
(Settings/Register) <Preferences> <Network> <Wireless LAN>
Displays the setting information of wireless LAN. Check the settings and information of the wireless
LAN(P. 27)
<Power Save Mode>
(Settings/Register) <Preferences> <Network> <Wireless LAN>
Specify whether to set the machine to the power save mode periodically, according to the signals sent by a
wireless LAN router. Connecting to a Wireless LAN(P. 26)
Settings/Registration
790
<Use Direct Connection>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify whether to use direct connection. Connecting Directly(P. 454)
<Direct Connection Type>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Select the type of direct connection. Connecting Directly(P. 454)
●If Wi-Fi Direct is selected, only one mobile device can connect.
<Device Name for Wi-Fi Direct>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify the device name to use for direct connections (Wi-Fi Direct).
●"-XY_Canon10" (where XY are random letters) is automatically appended to the device name for Wi-Fi
Direct, unless the device name is 22 characters or more, in which case "-XY_Canon10" is not
appended.
<Time Until Direct Connection Session Is Terminated>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify the time before communication is automatically terminated when there is a prolonged period of no data
transmission/reception while communicating using direct connection.
●This setting is disabled if <Always Keep Enabled If SSID/Network Key Specied> is set to <On>.
<Access Point Mode Settings>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify the settings for access point mode.
Settings/Registration
791
When <Use Personal SSID and Network Key> is set to <On>
●Information on the user and SSID/network key when logging in is associated and stored in the
machine. Only one mobile device can be connected.
When <Use Personal SSID and Network Key> is set to <Off>
●If both <Use Custom SSID> and <Use Custom Network Key> are set to <On>, multiple mobile devices
can be connected at the same time. A maximum of ve devices can be connected at the same time.
●If either or both <Use Custom SSID> and <Use Custom Network Key> are set to <Off>, a random SSID
or network key is used to connect each time. Only one mobile device can be connected.
<Always Keep Enabled If SSID/Network Key Specied>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
If <Specify SSID to Use> and <Specify Network Key to Use> are enabled in <Access Point Mode Settings>, direct
connections can be made without pressing <Enable> in <Direct Connection> in <Mobile Portal>.
●The machine can connect with multiple mobile devices at the same time. A maximum of ve devices
can be connected at the same time.
●If this is set to <On>, the <Time Until Direct Connection Session Is Terminated> setting is disabled.
●If this is set to <On>, the machine will not enter the Sleep mode completely.
<IP Address Settings for Direct Connection>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify the IP address to distribute to mobile devices connecting using direct connection.
●The IP address distributed to mobile devices may be up to nine numbers greater than the value of the
specied IP address.
<Personal SSID and Network Key Settings>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify an SSID and network key for each user when logging in and connecting using a direct connection. To set
an SSID, set <Use Custom SSID> to <On>, and enter the SSID. To set a network key, set <Use Custom Network
Key> to <On>, and enter the network key.
If <Automatically Enable/Disable Direct Connection at Login/Logout> is set to <On>, direct connections are
possible when logging in without pressing <Mobile Portal> <Direct Connection> <Enable>.
Settings/Registration
792
●When specifying this setting as an administrator, select <Personal Settings> on the Settings/
Registration screen.
<Use Login Name as User Name for Print Jobs>
(Settings/Register) <Preferences> <Network> <Direct Connection Settings>
Specify whether to display the login name as the user name of print jobs that are printed using direct
connection.
<IP Address Settings>
(Settings/Register) <Preferences> <Network> <Sub Line Settings>
Specify the IPv4 address to use with a wireless LAN (sub line) when using both a wired LAN and wireless LAN at
the same time.
<Priority Line for Communication with Mobile Devices>
(Settings/Register) <Preferences> <Network> <Sub Line Settings>
Select the line to connect mobile devices to when using both a wired LAN (main line) and wireless LAN (sub line)
at the same time.
<Ethernet Driver Settings>
(Settings/Register) <Preferences> <Network> <Sub Line Settings>
Specify the Ethernet driver settings for the sub line. Making Ethernet Settings(P. 42)
<Outbound Filter>
(Settings/Register) <Preferences> <Network> <Sub Line Settings> <Firewall Settings> <IPv4
Address Filter>
Specify the transmission lter in the sub line settings. Conguring the Firewall of the Sub Line(P. 544)
<Inbound Filter>
(Settings/Register) <Preferences> <Network> <Sub Line Settings> <Firewall Settings> <IPv4
Address Filter>
Specify the reception lter in the sub line settings. Conguring the Firewall of the Sub Line(P. 544)
<DNS Server Address Settings>
(Settings/Register) <Preferences> <Network> <Sub Line Settings> <Settings for System Data
Communication>
Specify the DNS server address settings for the sub line. Setting the DNS of the Sub Line(P. 65)
<Proxy Settings>
(Settings/Register) <Preferences> <Network> <Sub Line Settings> <Settings for System Data
Communication>
Specify the proxy settings for the sub line. Setting a Proxy(P. 547)
<Static Routing Settings>
(Settings/Register) <Preferences> <Network>
Settings/Registration
793

<External Interface>
72JY-0F0
This section describes the USB settings.
<Use as USB Device>
(Settings/Register) <Preferences> <External Interface> <USB Settings>
You can set whether to use the machine as a USB device.
●If this is set to <Off>, print and scan jobs from a computer connected via USB cable cannot be
performed.
●Changes in settings are effective after performing <Apply Setting Changes> on the Top screen of the
Settings/Registration.
<Use AddOn Driver for USB Input Device>
(Settings/Register) <Preferences> <External Interface> <USB Settings>
You can set whether to use the AddOn driver for USB input device connections.
●Depending on the type of AddOn application that uses device such as a keyboard or card reader, you
may need to set this to <On>. To check whether you need to set this to <On>, see the manual for the
AddOn application you are using, or contact your dealer or service representative.
●Changes in settings are effective after performing <Apply Setting Changes> on the Top screen of the
Settings/Registration.
<Use AddOn Driver for USB Storage Device>
(Settings/Register) <Preferences> <External Interface> <USB Settings>
You can set whether to use the AddOn driver for USB external storage.
●Depending on the type of AddOn application that uses USB external memory device, you may need to
set this to <On>. To check whether you need to set this to <On>, see the manual for the AddOn
application you are using, or contact your dealer or service representative.
Settings/Registration
795
●Changes in settings are effective after performing <Apply Setting Changes> on the Top screen of the
Settings/Registration.
<Use USB Storage Device>
(Settings/Register) <Preferences> <External Interface> <USB Settings>
You can set whether to allow the use of USB external storage devices.
●Changes in settings are effective after performing <Apply Setting Changes> on the Top screen of the
Settings/Registration.
<Restrict Auto Installation of Printer Driver>
(Settings/Register) <Preferences> <External Interface> <USB Settings>
This enables you to prevent a new printer driver from being installed when switching machines with multiple
machines connected via USB.
●Set this to <Off> when using a USB hub to connect multiple machines.
●Changes in settings are effective after performing <Apply Setting Changes> on the Top screen of the
Settings/Registration.
Settings/Registration
796

<Accessibility>
72JY-0F1
This section describes settings for improving accessibility, such as the speed at which the same character is entered
repeatedly when a key is held down, and reversing the contrast of the touch panel display.
<Key Repetition Settings>
(Settings/Register) <Preferences> <Accessibility>
You can set the amount of time before characters start repeating when you hold down a key on the touch panel
display, as well as the interval between repetitions.
<Invert Screen Colors>
(Settings/Register) <Preferences> <Accessibility>
You can invert the screen colors of the touch panel display. If you nd it hard to view the display even after
adjusting the brightness, try specifying this setting.
●Flick operations and drag-and-drop operations cannot be used when <Invert Screen Colors> is set to
<On>. Operate in the same manner as with a smartphone (ick/drag-and-drop)(P. 133)
●<Invert Screen Colors> is enabled for the following screens.
- Copy
- Scan and Send
- Fax
- Print
- Scan and Store
- Access Stored Files
- Fax/I-Fax Inbox
- Dest./Fwd. Settings
- Status Monitor
- Error screen (no paper)
<Use Flick Function>
(Settings/Register) <Preferences> <Accessibility>
You can set whether to use ick operations.
●The following functions are not affected by this setting.
- Flick operations on the <Display Image> screen
- AddOn applications
Settings/Registration
797
<Adjustment/Maintenance>
72JY-0F2
Item Description
<Adjust Image Quality>(P. 799) This section describes how to adjust image quality for copying and printing.
<Adjust Action>(P. 804) This section describes settings regarding device operation.
<Maintenance>(P. 805) This section describes how to use the auto cleaning function for the main unit and feeder.
Settings/Registration
798
<Adjust Image Quality>
72JY-0F3
This section describes how to adjust image quality for copying and printing.
<Auto Adjust Gradation>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
If the gradation of the printing is signicantly different from the original document, this correction adjusts the
printing so that it more closely matches the original document. Adjusting Gradation(P. 894)
●It is recommended that you select <Full Adjust> when performing an automatic gradation
adjustment. Select <Quick Adjust> for a quick, but less complete adjustment between regular full
adjustment recalibrations.
●Test pages are not counted as part of the copy or print total page counts.
<Correct Density>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
If the density of the printing is signicantly different from the original document, this adjusts the scan density
to be closer to the original. Adjusting Density(P. 896)
<Auto Correct Color Shift>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
If the colors of printing run or blur, color mismatch (color misregistration) may have occurred. This correction
adjusts the printing so that color mismatch does not occur. Correcting Color Mismatch(P. 897)
<Settings for Auto Full Calibration>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
The machine performs automatic adjustment (calibration) in order to prevent color misregistration and ensure
that the original color intensity is correctly reproduced. You can set the timing and frequency for performing
calibration. Automatically Adjusting Color Registration and Color Intensity(P. 898)
<Full Color Printing Vividness Settings>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
This setting enables you to make colors more saturated when performing color printing. Making Colors
More Vivid(P. 900)
Settings/Registration
799
●This setting is only effective for copying. Changes in settings are effective after performing <Apply
Setting Changes>.
<Fine Adjust Zoom>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
If the size of the image copied is signicantly different from the original document, ne adjustment is
performed so that the printing more closely matches the size of the original document. Adjusting Image
Size(P. 901)
<Adjust Toner Volume Used for Color Printing>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
By adjusting the amount of toner used when color printing, you may be able to reduce problems such as
streaks and irregularities. Reducing Toner Used When Color Printing(P. 902)
<Waterdrop Pattern Prevention Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
You can set <Waterdrop Pattern Prevention Mode> for when a splattered image, white patches, streaks, etc.
appear on the halftone images of twosided print jobs. Immediately after you turn ON the machine in a low
temperature environment, if the halftone reproduction of the printout becomes signicantly different from the
original document, set this mode to <On>.
●If you set <Waterdrop Pattern Prevention Mode>, the printing speed for the rst sheet becomes
slower.
<Adjust Fixing Temperature>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
You can reduce image quality problems that occur due to an inappropriate xing unit temperature by adjusting
the xing temperature.
●Set this in the following cases. The print results may be improved.
- <Low>: Set this when the same unintended image is repeated, as indicated below.
- <High 1>: Set this when the toner of the printed images peels off.
- <High 2>: Set this when the improvements of <High 1> are insucient.
●Set <Standard> to not use either setting.
Settings/Registration
800

●The printing speed is slower when <High 2> is set.
●Toner peeling may be able to be improved without changing this setting, by changing the paper type
and usage environment.
<Curl Prevention Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
You can set <Curl Prevention Mode> to reduce curling on the end of paper due to the heat and pressure of the
xing unit during printing.
●If this setting is set to <On>, it may affect the printing quality.
●If setting <Mode 1> to <On> does not reduce curling, set <Mode 2> to <On>. If setting both <Mode 1>
and <Mode 2> does not reduce curling, set <Mode 1> and <Mode 2> to <Off> and set <Switch Paper
Feed Method> to <Print Side Priority>.
<Paper Slipping Prevention Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
Paper may not be fed correctly when printing or print quality may be reduced, depending on the usage
environment.
●<Mode 1> : Set this when printing documents with large amounts of images or text on each page.
However, the print speed will be slower.
●<Mode 2> : Set this when printing documents with small amounts of images or text on each page. The
print speed will not be reduced as much as <Mode 1>.
●<Off>: Set this when you do not want the print speed to be reduced. However, the print quality will
not be improved.
<Auto Clean Secondary Transfer Roller>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
The secondary transfer roller is cleaned after executing a print job with free size specied. Set this when the
back side of the paper is dirty.
<White Streak Prevention Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
White streaks may appear in the printed image. This setting may improve this problem.
●When set to <On>, the print density will be lighter.
Settings/Registration
801

<Correct Fixing When Using Plain Paper>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
Smudges may appear in the printed image, depending on the paper type and usage environment. This setting
may improve this problem.
●When set to <On>, the print speed will be slower.
<Correct Tail End Fixing When Using Plain Paper>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
Colors may become darker at the tail end of printed images because toner is insuciently xed. This setting
may improve this problem.
●When set to <On>, the print speed will be slower.
<Plain Paper Fill Area Image Adjustment Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
The nish quality may be able to be improved by enabling this setting when using plain paper with a smooth
surface.
●If you set this setting to <On> when using plain paper without a smooth surface, xing problems may
occur.
<Heavy Paper Fill Area Image Adjustment Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
The nish quality may be able to be improved by enabling this setting when using heavy paper without a
smooth surface.
●If you set this setting to <On> when using paper with a smooth surface, xing problems may occur.
Settings/Registration
802
<Envelope Sealing Prevention Mode>
(Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality> <Special Processing>
You can set <Envelope Sealing Prevention Mode> to prevent the glue on envelope aps from melting and
sealing due to the heat and pressure of the xing unit during envelope printing.
●This setting is only enabled during envelope printing.
●If this setting is set to <On>, the quality of the image may be adversely affected.
Settings/Registration
803
<Adjust Action>
72JY-0F4
This section describes settings regarding device operation.
<Start Key Touch Recognition Delay>
(Settings/Register) <Adjustment/Maintenance> <Adjust Action>
You can set the time until the machine recognizes that (Start) has been pressed. Setting a longer time
prevents unintentional jobs due to (Start) being accidentally pressed.
Settings/Registration
804
<Maintenance>
72JY-0F5
This section describes how to use the auto cleaning function for the main unit and feeder.
<Clean Feeder>
(Settings/Register) <Adjustment/Maintenance> <Maintenance>
If streaks appear on originals scanned with the feeder or paper that is printed, execute <Clean Feeder>.
Cleaning the Feeder(P. 878)
<Clean Pressure Roller for Fixing>
(Settings/Register) <Adjustment/Maintenance> <Maintenance>
If printed paper is dirty, execute <Clean Pressure Roller for Fixing>.
<Original Scanning Area Cleaning Method >
(Settings/Register) <Adjustment/Maintenance> <Maintenance>
Start the video that shows how to clean the platen glass.
<Replace Toner Cartridge>
(Settings/Register) <Adjustment/Maintenance> <Maintenance> <Check Maintenance Method>
Plays the sample video explaining the method for replacing toner cartridges. You can play this sample video
even when replacement is not necessary, so that you may understand the process in advance.
<Replace Waste Toner Container>
(Settings/Register) <Adjustment/Maintenance> <Maintenance> <Check Maintenance Method>
Plays the sample video explaining the method for replacing the waste toner container. You can play this sample
video even when replacement is not necessary, so that you may understand the process in advance.
<Remove Jammed Paper (Example)>
(Settings/Register) <Adjustment/Maintenance> <Maintenance> <Check Maintenance Method>
Plays the sample video explaining the method for removing jammed paper. You can play this sample video even
when paper is not jammed, so that you may understand the process in advance.
<Control Detected Condensation>
(Settings/Register) <Adjustment/Maintenance> <Maintenance>
Set whether to start the process to remove condensation when condensation is detected inside the machine. If
you set this mode to <On>, the process to remove condensation is automatically performed.
●During the process to remove condensation, printing may not be performed correctly resulting in the paper
being blank.
●To maintain the effect of the process to remove condensation going when this mode is set to <On>, it is
necessary to keep the machine's power ON.
Settings/Registration
805

●Print jobs that are carried out during the process to remove condensation are restricted by the <Jobs
to Restrict When Condensation is Detected> settings.
- <Only Received Jobs>: Regardless of the <Use Fax Memory Lock>/<Use I-Fax Memory Lock>
settings, the received fax/I-fax data is stored in Memory RX Inbox and cannot be printed during the
process to remove condensation. Reports that are automatically output at the specied time cannot
be printed.
- <All Jobs>: All print data cannot be printed during the process to remove condensation.
● If you select <On> and press <OK>, a screen asking whether to immediately perform the process to
remove condensation is displayed. If you want to immediately start the process to remove
condensation, press <Yes>.
Settings/Registration
806

<Function Settings>
72JY-0F6
This section describes the settings for functions such as Copy, Printer, and Fax.
●Some settings can only be set by the Administrator.
●Some of the settings may not be displayed depending on the conguration of optional equipment installed
on the machine.
Item Description
<Common>(P. 808) This section describes settings for functions such as Paper Feed Settings, Paper Output Settings,
Print Settings, Scan Settings, and Generate File.
<Copy>(P. 817) This section describes how to specify the copy settings.
<Printer>(P. 818) This section describes how to specify printer settings.
<Send>(P. 820) This section describes how to specify scan and send settings.
<Receive/Forward>(P. 835) This section describes how to receive E-mail and fax settings.
<Store/Access Files>(P. 843) This section describes the settings for scanning originals and printing stored les.
<Print>(P. 846) This section describes the print settings.
Settings/Registration
807
<Common>
72JY-0F7
This section describes settings for functions such as Paper Feed Settings, Paper Output Settings, Print Settings, Scan
Settings, and Generate File.
●Some of the settings may not be displayed depending on the conguration of optional equipment installed
on the machine.
<Paper Source Auto Selection>
(Settings/Register) <Function Settings> <Common> <Paper Feed Settings>
You can congure the paper source that will be used when copying/printing with <Select Paper> set to <Auto>.
This setting also functions when the paper in the current paper source runs out during copying/printing.
Automatically Selecting the Appropriate Paper Source for a Specic Function (P. 154)
<Switch Paper Feed Method>
(Settings/Register) <Function Settings> <Common> <Paper Feed Settings>
When regularly using paper with logos such as letterheads, while printing in both one-sided and two-sided, you
can set this setting to <Print Side Priority> to print the rst page on the front side for both one-sided and two-
sided, without having to change the paper orientation. Loading Preprinted Paper(P. 115)
●The settings for Automatic Paper Selection and Auto Drawer Switching are disabled for paper sources
with <Print Side Priority> set. The print speed is also slower when performing one-sided printing.
●<Print Side Priority> is only enabled when paper that can be printed on both sides is set ( Paper
Available for Two-Sided Copying/Two-Sided Printing(P. 1113) ). For other paper, the message
<Load paper.> appears and the paper is not fed, or the <Print Side Priority> setting is disabled.
●For instructions on loading paper, see Loading Preprinted Paper(P. 115) .
<Suspended Job Timeout>
(Settings/Register) <Function Settings> <Common> <Paper Feed Settings>
If this setting is set to <On> and a job is suspended due to a lack of paper, etc., the machine automatically prints
the next job after the specied time period.
●If a job is suspended because paper has run out during the job, the next job is not processed even
after the designated suspension time elapses.
Settings/Registration
808

●To automatically delete suspended jobs, see <Auto Delete Suspended Jobs>(P. 810) .
<Job Separator Between Jobs>
(Settings/Register) <Function Settings> <Common> <Paper Output Settings>
This enables you to insert the specied paper at the start of each job when multiple jobs are printed
consecutively.
<Job Separator Between Copies>
(Settings/Register) <Function Settings> <Common> <Paper Output Settings>
This enables you to insert the specied paper each number of copy sets to divide the sets. If you set this, paper
is inserted when printing with Collate (Page Order).
●If you are using the Group (Same Pages) mode, you cannot insert job separation sheets between copy
sets.
<Print Priority>
(Settings/Register) <Function Settings> <Common> <Print Settings>
A job that has a higher set priority can be set to print after the job currently being processed is complete.
●If the same printing priority has been specied for multiple functions, printing starts with the rst
processed print job.
●Priority printing does not take place until the current job is complete. However, if the current job is
paused, the printing of another job may start, depending on its settings.
<Text/Photo Priority When Recognized as B&W by ACS>
(Settings/Register) <Function Settings> <Common> <Print Settings>
You can set the quality to use when an original is detected to be black-and-white with auto color selection.
●If you set <Text Priority> in this setting and your original is determined as black-and-white by the
<Auto (Color/B&W)> mode in <Select Color>, the original is processed as if you selected <Text> as the
original type setting, even if you select a mode other than <Text> for <Original Type> in <Copy>.
<Chromatic Color Conversion for Two Colors Printing>
(Settings/Register) <Function Settings> <Common> <Print Settings>
Settings/Registration
809

You can select the specied color to use when printing using the two-color mode, which prints in black and a
specied color. The two-color mode can be set for copying or printing. This setting is reected in both the two-
color mode for printing and the two-color mode for copying.
●All Chromatic Colors: When specifying the color to use for all chromatic colors other than black in the original
(or image data).
●Approximate Colors Only: When using the color for only the specied color (or approximate color) and using
black for all other chromatic colors in the original (or image data).
Example Replaced Colors and Settings
When the two-color mode is specied for an original (or image data) including the following colors, the colors
are replaced as indicated below.
●Colors included in the original (or image data): Red, orange, blue, black
●Red specied for the two-color mode
Original (or image data) "All Chromatic Colors" "Approximate Colors Only"
Red Red Red
Orange Red Red
Blue Red Black
Black Black Black
<2-Sided Printing>
(Settings/Register) <Function Settings> <Common> <Print Settings> <Default Settings for Output
Report>
You can specify the 2-Sided Printing for printing reports such as Send TX Report and Communication
Management Report.
<Auto Delete Suspended Jobs>
(Settings/Register) <Function Settings> <Common> <Print Settings>
If this setting is set to <On> and a job is suspended due to a paper jam, etc., the machine automatically deletes
the job after the specied time period.
●To retain a suspended job without automatically deleting it, see <Suspended Job
Timeout>(P. 808) .
<Feeder Jam Recovery Method>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
Settings/Registration
810
You can select whether scanning will start again from the rst page of the original or the page of the original in
which scanning was interrupted if a paper jam occurs in the feeder.
●Direct sending of faxes does not support this setting. If a paper jam occurs while performing direct
sending, the job will be canceled. In this case, set the job again.
●Depending on the location of a paper jam, it can be dicult to determine whether document
scanning has been completed. If you have set <From Suspnd. Original> for <Feeder Jam Recovery
Method> and you do not nd until which page the document has been scanned, it is recommended
that you cancel the job, and then execute it again.
●Select one of the following.
- <From 1st Page>: Place the originals in the feeder again, and then restart scanning from the rst
page of the document. The originals will be fed automatically until the page of the document in
which scanning is interrupted.
- <From Suspnd. Original>: Place the originals that were not scanned because of a paper jam in the
feeder, and then start scanning all the remaining originals again.
<Streak Prevention>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
You can set whether to detect and prevent streaks when scanning originals.
●When <On> is selected, extremely thin lines may be detected as streaks.
<Speed/Image Quality Priority for Black & White Scan>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
You can set whether priority is given to scanning speed or to image quality when performing black and white
scanning.
●Set <Quality Priority> to ensure the reproduction of yellow colors in originals.
<Speed/Image Quality Priority for Scan from Feeder>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
Settings/Registration
811
You can set whether priority is given to scanning speed or to image quality when scanning originals from the
feeder.
●This setting applies to the Copy function and AddOn applications using the Copy function.
<Remote Scan Gamma Value>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
You can set the gamma value to use when scanning color documents into your computer through the Network
Scan function. Select the gamma value most suited to your computer settings so that you can print the
document with the optimal density.
<Auto Online>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
Set this to <On> to automatically enable the remote scanner function when you press <Scanner> ( <Home>
Screen(P. 119) ).
●When the remote scanner function is enabled, you cannot use <Copy> and <Scan and Store>.
●You can specify the time period in which you are logged out and the touch panel display returns to
the default setting automatically.
<Auto Oine>
(Settings/Register) <Function Settings> <Common> <Scan Settings>
If the machine is connected to a network that is online, scanning is not possible with <Copy> or <Scan and
Store>. If you set <Auto Oine> to <On>, the machine automatically goes oine when the time set in <Auto
Reset Time> in <Preferences> (Settings/Registration) has elapsed.
●If <Auto Reset Time> is set to <0>, the machine automatically goes oine after approximately two
minutes.
●You can specify the time period in which you are logged out and the touch panel display returns to
the default setting automatically.
<Image Quality Level for Compact>
(Settings/Register) <Function Settings> <Common> <Generate File>
Settings/Registration
812

If you select PDF/XPS (Compact) as the le format when using <Scan and Send> or <Scan and Store>, you can
set the image quality level of the document.
●This setting is disabled when sending a fax or I-fax.
●If you scan an original with many colors when <Text> is selected for the original type, the data size
and image quality will vary following compression, according to the selected image level. However, if
the original is in monochrome or has few colors, it does not matter which image level you select.
<OCR (Text Searchable) Settings>
(Settings/Register) <Function Settings> <Common> <Generate File>
If you select <OCR (Text Searchable)> for <PDF>, <XPS>, or <OOXML> as the le format, you can set the Smart
Scan setting, and set the number of characters used for the Auto (OCR) in File Name. Smart Scan is a mode that
determines the text direction and rotates the data, so that the document will be in the correct orientation when
viewing the document on a computer. Auto (OCR) in File Name is a mode that automatically uses the rst text
scanned by OCR in the document as its le name. Auto (OCR) in File Name is specied in <File Name> in
<Options> on the Scan and Send screen. Setting a File Name(P. 423)
●You cannot use the Auto (OCR) in File Name mode and the Encrypted PDF mode at the same time
when sending a le.
<Trace & Smooth Settings>
(Settings/Register) <Function Settings> <Common> <Generate File>
You can change the recognition rate of line drawings of the original when creating a le with outline graphics.
●If you increase the value in <Graphics Recognition Level>, the data size also increases. It is
recommended that you rst use <Normal>, and if desirable results are not obtained, try increasing
the recognition level to <Moderate> or <High>.
●This setting is disabled when sending a fax or I-fax.
<OOXML Settings>
(Settings/Register) <Function Settings> <Common> <Generate File>
You can specify the background image level, color image recognition level, and color image line width
recognition when creating les with Oce Open XML le format.
Settings/Registration
813

●This setting is disabled when sending a fax or I-fax.
●Color image settings are only valid with PowerPoint.
<Include Background Images in Word File>
(Settings/Register) <Function Settings> <Common> <Generate File>
When generating Word les from scanned originals, you can delete the image detected as the background in
the Word les. It becomes easier to edit Word les because unnecessary images are deleted.
<Specify Minimum PDF Version>
(Settings/Register) <Function Settings> <Common> <Generate File>
You can specify the minimum version to assign when generating PDF les.
●Depending on the functions set for the PDF les, the version assigned may be higher than that
specied with this setting.
<Format PDF to PDF/A>
(Settings/Register) <Function Settings> <Common> <Generate File>
You can create PDF les compliant with PDF/A-1b. This is suited for long-term storage because it guarantees
that the visual quality of the PDF does not change with the machine or viewing software.
This setting is linked with the following default settings:
●<File Format> in <Scan and Send>
●<File Format> in <Scan and Store>
●<File Format> in <Forwarding Settings>
●This setting is disabled when sending a fax or I-fax.
●The following PDF functions cannot be set if <Format PDF to PDF/A> is set to <On>.
-Encryption
- Visible Signature
<256-bit AES Settings for Encrypted PDF>
(Settings/Register) <Function Settings> <Common> <Generate File>
When generating an encrypted PDF le, you can select <Acrobat 3.0 or Later/40-bit RC4>, <Acrobat 6.0 or Later/
128-bit RC4>, <Acrobat 7.0 or Later/128-bit AES>, or <Acrobat 10.0 or Equivalent/256-bit AES> as the PDF
Settings/Registration
814
encryption level. If you want to use <Acrobat 9.0 or Equivalent/256-bit AES> rather than <Acrobat 10.0 or
Equivalent/256-bit AES> as the encryption level, use this setting to change the selections you can make.
●This setting is disabled when sending a fax or I-fax.
<Rotate Scanned Image When Generating PDF>
(Settings/Register) <Function Settings> <Common> <Generate File>
The following operations are performed when scanning and generating a PDF le.
●<On>: The data to generate is rotated.
●<Off>: The data to generate is not rotated, but information for rotating the image is added to the PDF header
to enable it to be rotated in a viewer.
●Set the vertical orientation of the original in <Orig. Content Orientation>.
●If <On> is set, le generation takes slightly longer compared to <Off>.
●PDF les generated with <Off> set may be displayed without the correct rotation, depending on the
viewer.
●Even if <On> is set, the generated PDF les may be the same as when <Off> is set, depending on the
type of PDF le and the conditions when scanning.
<Information Used for LDAP Server Authentication>
(Settings/Register) <Function Settings> <Common> <Set Authentication Method>
You can specify the authentication method for accessing an LDAP server.
●When <Device Settings> is set
-The information set in Registering the LDAP Server(P. 53) is used.
●When <Device Login Auth. Info.> is set
-The authentication information used when logging into the machine is used.
●When <Registered Info. for Each User> is set
- The authentication information of the LDAP server is registered for each user.
●<Device Login Auth. Info.> is available only when using the same authentication information for
logging in to the machine and accessing the LDAP server, and when using a login service which
supports Integrated Authentication. For information whether the login service you are using supports
Integrated Authentication, contact your dealer or service representative.
●When <Registered Info. for Each User> is selected, each user sets the user name and password used
for LDAP authentication on the Send Basic Features screen <Register/Edit Information for
Each User> <LDAP Server Authentication Information>.
Settings/Registration
815
<Information Used for SMTP Server Authentication>
(Settings/Register) <Function Settings> <Common> <Set Authentication Method>
You can specify the authentication method for accessing an SMTP server.
●If you select <Device Settings>
-Uses the information that was set in <Communication Settings: Authentication Settings> ( Setting
E-mail/I-Fax Communication(P. 70) ).
●If you select <Registered Info. for Each User>
- Registers and uses SMTP server authentication information for each user.
●If <Registered Info. for Each User> is selected, each user has to press <Scan and Send>
<Register/Edit Information for Each User> set the user name and password used for SMTP
authentication in <SMTP Server Authentication Information>.
<Information Used for File TX/Browsing Authentication>
(Settings/Register) <Function Settings> <Common> <Set Authentication Method>
You can specify the authentication method for accessing a le server.
●<Device Login Auth. Info.> is only valid for SMB and WebDAV.
●When <Standard> is set
- The information set in Registering Destinations in the Address Book(P. 195) is used.
●When <Device Login Auth. Info.> is set
-The authentication information used when logging into the machine is used.
●Even if this is set to <Device Login Authentication Information>, a user name and password need to
be entered when accessing a le server to send/access les if the user is logged in to the machine
using Picture Login.
●When <Registered Info. for Each User> is set
- The authentication information of the le server is registered for each user.
●When <Registered Info. for Each User> is selected, each user sets the user name and password used
for le server authentication on the Send Basic Features screen <Register/Edit Information
for Each User> <Authentication Information for File TX/Browsing>.
Settings/Registration
816
<Copy>
72JY-0F8
This section describes how to specify the copy settings.
<Register/Edit Favorite Settings>
(Settings/Register) <Function Settings> <Copy>
You can register a combination of settings frequently used when copying to a single button. You can also assign
a name to the button. Registering a Combination of Frequently Used Functions(P. 164)
<Display Conrmation for Favorite Settings>
(Settings/Register) <Function Settings> <Copy>
You can select whether to display a conrmation screen when recalling "Favorite Settings."
<Change Default Settings>
(Settings/Register) <Function Settings> <Copy>
You can change the settings registered as default for the <Copy> function. Customizing the Basic Features
Screen(P. 167)
<Register Options Shortcuts>
(Settings/Register) <Function Settings> <Copy>
You can register/change modes in the shortcut keys displayed on the Copy Basic Features screen. This feature is
useful when you want to register functions frequently used from <Options> and <Favorite Settings>.
<Auto Collate>
(Settings/Register) <Function Settings> <Copy>
If this setting is set to <On>, the machine can automatically switch to <Collate (Page Order)> for the nishing
mode when originals are placed in the feeder. This is useful when making multiple sets of copies, because you
do not need to remember to select the Finishing mode.
<Select Color Settings for Copy>
(Settings/Register) <Function Settings> <Copy>
You can restrict the use of the color mode in <Select Color> when copying.
<Job Separator Between Groups>
(Settings/Register) <Function Settings> <Copy>
When copying two copies or more with <Group (Same Pages)> in <Finishing>, you can insert sheets between
each page group. If you select <On>, select a paper source.
Settings/Registration
817
<Printer>
72JY-0F9
This section describes the printer settings.
<Output Report>
(Settings/Register) <Function Settings> <Printer>
You can print reports for the machine settings.
<Printer Settings>
(Settings/Register) <Function Settings> <Printer>
Specify the printer settings.
For more information, see Setting the Machine (PS/PCL/UFR II Printer).
<Restrict Printer Jobs>
(Settings/Register) <Function Settings> <Printer>
If this setting is set to <On>, you can restrict jobs from the printer driver.
<PDL Selection (Plug and Play)>
(Settings/Register) <Function Settings> <Printer>
Select default Page Description Language (PDL).
<Prioritize Printer Driver Settings for Jobs with MP Tray>
(Settings/Register) <Function Settings> <Printer>
You can prioritize printer driver settings over the paper settings in the machine when printing a job with the
multi-purpose tray specied as the paper source.
●When the following conditions are met, you can press <Temp. Change Ppr. in MP Tray> on the paper
selection screen of <Copy> and <Access Stored Files> to change the paper size/type to load from the
multi-purpose tray:
- If paper is loaded in the multi-purpose tray
- If this setting is set to <On>
- If <Multi-Purpose Tray Defaults>(P. 771) is set to <Use Preset>
●If the paper size specied in the printer driver greatly differs from the paper size set in the multi-
purpose tray, an error message is displayed.
<PS Password Settings>
(Settings/Register) <Function Settings> <Printer>
You can specify the password that restricts the use of the control command prepared by the PS printer.
Settings/Registration
818
●<SystemParams Password> is a password that allows changes to the system parameter, and <StartJob
Password> is a password that allows startjob, exitserver operator to perform. For more information,
check PostScript language specications.
<Paper Feed Mode When Using PCL Emulation>
(Settings/Register) <Function Settings> <Printer>
You can set the paper source used for the PCL5 PaperSource command.
●For details on each setting, see Setting the Machine (PS/PCL/UFR II Printer).
Settings/Registration
819
<Send>
72JY-0FA
This section describes how to specify the Scan and Send settings.
<TX/RX User Data List>
(Settings/Register) <Function Settings> <Send> <Output Report>
You can print a list of the send/receive settings registered in the machine. Printing Reports and
Lists(P. 909)
<Fax User Data List>
(Settings/Register) <Function Settings> <Send> <Output Report>
You can print a list of the fax settings registered in the machine. Printing Reports and Lists(P. 909)
<Register Favorite Settings>/<Edit Favorite Settings>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can register frequently used settings in a button of the machine for later use when scanning. You can also
assign a name to a button and enter a comment. You can also delete or rename registered settings.
Registering a Combination of Frequently Used Functions(P. 164)
<Display Conrmation for Favorite Settings>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to display a conrmation screen when recalling "Favorite Settings."
<Default Screen>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can specify the screen to display when <Scan and Send> or the Reset key is pressed.
<Restrict Address Book Use>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to hide the Address Book and one-touch buttons on the Scan Basic Features screen, etc.,
as well as whether to restrict use of the Address Book.
<Change Default Settings>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can change the settings registered as default for the <Scan and Send> function.
<Register Options Shortcuts>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can register modes in the shortcut keys displayed on the <Scan and Send> screen. This feature is useful
when you want to register frequently used functions. Customizing the Basic Features Screen(P. 167)
<TX Result Report>
(Settings/Register) <Function Settings> <Send> <Common Settings>
Settings/Registration
820
A TX Result Report is a report that enables you to check whether documents were sent correctly to their
intended destinations. The machine can be set to print this report automatically after documents are sent or
only when a transmission error occurs. You can also specify the setting to print the rst part of the document as
part of the report to remind you of the document's contents. TX Result Report(P. 914)
<Allow Printing from Options> can be set if <For Error Only> or <Off> is selected. If you set <Allow Printing from
Options> to <On>, you can set whether to print a TX report from <Options> for each job.
●When sending a color document, <Report with TX Image> cannot be used to attach an image
converted to black-and-white.
●This setting links with the <TX Result Report> setting in <Options> for each function.
<Communication Management Report>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can print or send document sending/receiving logs as a report. The machine can be set to print or send this
report when a specied number of communications (100 to 1,000) is reached or at a specied time. The send/
receive reports can also be printed or sent separately.
When the report is sent as data, it is sent in the CSV le format. Communication Management
Report(P. 912)
<TX Terminal ID>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to add the sender information to the top of a sent document when sending a fax/I-fax.
Information such as the fax number, name, and I-fax address of the machine is printed, enabling the recipient
to check who sent the document.
●The settings of the server machine are used when sending remote faxes.
●The information registered in <Register Unit Telephone Number> and <Register Unit Name> is
printed as the sender information. Fax Line Settings(P. 68)
●When printing the sender's name instead of the unit name, register the name in <Register Sender
Name (TTI)>(P. 831) and specify it from <Sender Name (TTI)>. Faxing(P. 271)
<Delete Failed TX Jobs>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to automatically delete a document from memory when the sending/saving error
occurs. Selecting <Off> enables you to resend/resave the documents that failed to send/save.
●If this mode is set to <Off>, the status of any job with a forwarding error will be saved in <Job Status>
on the <Status Monitor> screen.
Settings/Registration
821
<Retry Times>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can set the number of times that the machine tries to automatically resend data when the data cannot be
sent because the recipient is busy sending or receiving, or when an error occurs.
●This setting is disabled when sending faxes.
<Data Compression Ratio>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can set the compression ratio for color/grayscale scanned data.
●If you want to select compact or trace & smooth for the PDF le format or select compact for the XPS
le format, it is recommended that you set <Data Compression Ratio> to <Normal> or <Low Ratio>. If
you set it to <High Ratio>, images may be output in low quality even if you select <Quality Priority> in
<Generate File> <Image Quality Level for Compact>.
●This setting is disabled when sending faxes.
<YCbCr TX Gamma Value>
(Settings/Register) <Function Settings> <Send> <Common Settings>
If you are sending a document in color or grayscale, you can specify the gamma value to use when converting
scanned RGB image data to YCbCr. You can reproduce the image with the optimal image quality at the recipient
by setting an appropriate gamma value.
●This setting is disabled for the following le formats:
-PDF; Compact
- XPS; Compact
- PDF; Trace&Smooth
●This setting is disabled when sending faxes.
<Use Divided Chunk Send for WebDAV TX>
(Settings/Register) <Function Settings> <Send> <Common Settings>
Settings/Registration
822
You can divide data into chunks when sending with WebDAV. Chunked encoding is a function for sending a le
with an unknown size by dividing it into chunks of a known length. It enables the sending time to be reduced
because it is not necessary to calculate the size of the le before sending it.
●You may not be able to send les with chunked encoding, depending on certain conditions for the
WebDAV server and proxy server.
<Conrm TLS Certicate for WebDAV TX>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can check whether the TLS server certicate is valid when sending with WebDAV. You can verify the validity
of the certicate and reliability of the certicate chain, as well as conrm the CN (Common Name).
●If you do not verify the certicate, TLS communication is performed, even with an invalid certicate.
●If there is a problem with the certicate, WebDAV sending will fail.
<Conrm TLS Certicate for FTPS TX>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can check whether the TLS server certicate is valid when sending with FTPS. You can verify the validity of
the certicate and reliability of the certicate chain, as well as conrm the CN (Common Name).
<Restrict New Destinations>
(Settings/Register) <Function Settings> <Send> <Common Settings>
When sending faxes and scanned data, the available destinations can be limited to the following three ways, to
ensure that users cannot specify the destination by entering text.
- Destinations registered in the address book and one-touch buttons
- Destinations set in <Favorite Settings> and <Send to Myself>
- Destinations that can be searched for with an LDAP server
Restricting the Entry of New Destinations
1Press (Settings/Register).
2Press <Function Settings> <Send> <Common Settings> <Restrict New Destinations>.
3Select the functions you want to restrict destination entry for.
Settings/Registration
823
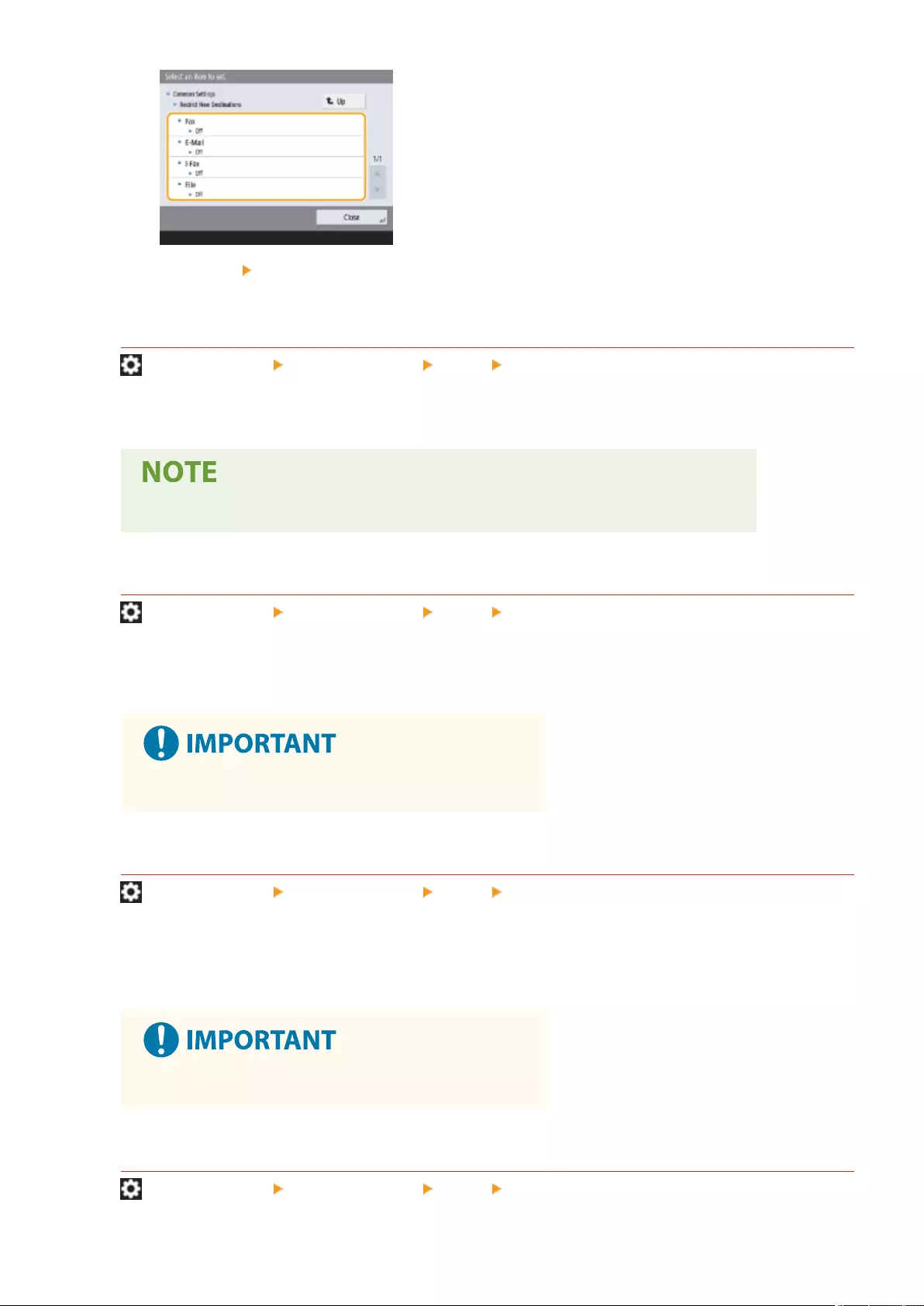
4Press <On> <OK>.
<Always Add Device Signature to Send>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to always add a device signature to sent PDF/XPS les.
●If you set <Restrict File Formats> to <On>, les other than PDF/XPS les cannot be sent.
<Limit E-Mail to Send to Myself>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can limit the destination that can be specied when sending e-mail to the e-mail address of the user that is
logged in. This setting enables you to prevent information leaks due to transmission to a wrong destination.
●This setting applies to users with the GeneralUser role.
<Restrict File TX to Personal Folder>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can limit the destination that can be specied when saving to a le server to the dedicated folder of the
user that is logged in. This setting enables you to prevent information leaks due to transmission to a wrong
destination.
●This setting applies to users with the GeneralUser role.
<Personal Folder Specication Method>
(Settings/Register) <Function Settings> <Send> <Common Settings>
Settings/Registration
824

A Personal folder is an individual folder that can be used by the user logged in with personal authentication
management. Shared folders and le servers can be specied and used as a Personal folder. Conguring
Personal Folders(P. 529)
●A Personal folder is a folder shared by the following screens.
- <Scan and Send>
- <Network> in <Scan and Store>
- <Network> in <Access Stored Files>
<Restrict Resending from Log>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to prevent users from recalling the logs for the destinations and scan settings specied
in the past. Selecting <On> hides the <Previous Settings> buttons from both the Fax Basic Features screen and
the Scan Basic Features screen.
<Archive TX Document>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can save a copy of a sent fax in a pre-specied destination (e-mail or le server, etc.). Saving a Copy of a
Sent Document(P. 309)
<Display Notication When Job Is Accepted>
(Settings/Register) <Function Settings> <Send> <Common Settings>
You can select whether to display a screen prompting you to check the communication status after sending/
saving documents using <Fax> or <Scan and Send> ( <Home> Screen(P. 119) ).
<Job to Cancel When Stop Is Pressed>
(Settings/Register) <Function Settings> <Send> <Common Settings>
Select the send job to cancel when the Stop key is pressed while a send job of the Fax function or the Scan and
Send function is being processed. You can select either <Latest Received Job> or <Job Being Sent>.
●If you selected <Job Being Sent> and the machine has multiple fax lines that are currently being used
for sending, the last of those jobs is canceled.
<Register Unit Name>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can register the name of your company or department as the unit name. The registered name is displayed/
printed at the recipient as the sender information when you send an e-mail/I-fax.
Settings/Registration
825
●The registered unit name is used as the e-mail address display name, in the format "unit name <e-
mail address>".
●You can enter up to 24 characters for the unit name.
●The e-mail address used in the login service appears in the From eld on the recipient's machine for
e-mail messages and I-fax documents. Registering User Information in the Local Device(P. 495)
●If you press <E-Mail/I-Fax Settings> set <Specify Authentication User as Sender> to <On>, the e-mail
address registered for the login user is displayed as the sender's name in the From eld for the
recipient, regardless of the login service being used.
<Communication Settings>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can specify the settings for a mail server and an authentication method that you are using for e-mails/I-
faxes. Setting E-mail/I-Fax Communication(P. 70)
●If you set shorter than 10 minutes (excluding '0 min') for <POP Interval>, the machine will not
completely enter the Sleep mode.
●The machine can only receive I-faxes and communication error notices.
<Specify Port Number for SMTP TX/POP RX>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can change the port number of the SMTP and POP.
<S/MIME Settings>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can set S/MIME. If you set S/MIME, you can add a digital signature or encrypt the e-mail when using the e-
mail/I-fax function.
Setting E-Mail Encryption
1Press (Settings/Register).
2Press <Function Settings> <Send> <E-Mail/I-Fax Settings> <S/MIME Settings>.
3Set encryption and the digital signature.
4Press <OK>.
Settings/Registration
826
●It is necessary to register the public key certicate of the recipient in advance. Generating the Key
and Certicate for Network Communication(P. 552)
<Conrm TLS Certicate for SMTP TX>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can check whether the TLS server certicate is valid when sending with SMTP. You can verify the validity of
the certicate and reliability of the certicate chain, as well as conrm the CN (Common Name).
●If you do not verify the certicate, TLS communication is performed, even with an invalid certicate.
●If there is a problem with the certicate, SMTP sending will fail.
<Conrm TLS Certicate for POP RX>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can check whether the TLS server certicate is valid when receiving with POP. You can verify the validity of
the certicate and reliability of the certicate chain, as well as conrm the CN (Common Name).
●If you do not verify the certicate, TLS communication is performed, even with an invalid certicate.
●If there is a problem with the certicate, POP receiving will fail.
<Maximum Data Size for Sending>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can set the maximum data size for outgoing e-mail messages and I-fax documents. If an e-mail message
exceeds this data size limit, it is split up into several e-mail messages before being sent. However, if an I-fax
transmission exceeds the data size limit, it is handled as an error, and not sent.
●If you enter '0' MB as the data size, there is no size limit on the data that is sent.
●Set the maximum data size for sending lower than the data limit for the mail server.
Settings/Registration
827

<Default Subject>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can set the subject to specify automatically if you do not enter a subject when sending an e-mail/I-fax.
<Specify Authentication User for Reply-To>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can select whether to set the e-mail address of a user who logs in to the machine with personal
authentication management as the reply-to address when sending an e-mail/I-fax.
●If logging in using User Authentication, the login name appears in <100> of the Sender Name (TTI)
list. If <On> is selected, the login name in <100> is automatically set as the <Sender Name (TTI)> in
<Options>.
●If you enter an e-mail address as the reply-to destination in <Options> when sending an e-mail
message or I-fax document, that e-mail address is given priority, even if <Specify Authentication User
for Reply-To> is set to <On>.
<Specify Authentication User as Sender>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can select whether to display the e-mail address of a user who logs in to the machine with personal
authentication management in the From eld as the sender of received e-mail.
●If this mode is set to <Off>, users that are logged in as guests using a login service such as User
Authentication can still perform sending, even if <Allow Unregistered Users to Send E-Mail> is set to
<Off>.
<Allow Unregistered Users to Send E-Mail>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
When the machine is in use with personal authentication management, you can select whether to allow the
sending of an e-mail from a user whose e-mail address is not registered in the machine. If <Off> is selected,
users with their e-mail addresses registered can only send e-mails.
●If you set <Specify Authentication User as Sender> to <Off>, the address registered in the Device
Information settings is displayed at the receiving end.
Settings/Registration
828

<Full Mode TX Timeout>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can set the time before sending operations automatically terminate if an MDN (notication e-mail
conrming the transmission result) is not received from the recipient when sending an I-fax in the <Full> mode.
<Print MDN/DSN upon Receipt>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
In I-fax Full Mode, e-mail messages are sent to the machine from the recipient and the mail server, notifying
you whether I-faxes are sent to destinations successfully or not. You can select whether to print these
notication e-mails when the machine receives them.
●I-fax delivery can also be conrmed in the TX Result Report. TX Result Report(P. 914)
<Use Send via Server>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can select whether to allow users to change the setting of <Send via Server> when sending I-faxes.
●For I-fax, if <Send via Server> is set to <Off>, there is no size limit on the data that is sent, even if you
enter the maximum data size for sending.
<Allow MDN Not via Server>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
The machine receiving the I-fax can send an MDN (a notication e-mail for checking the sending result) to the IP
address of the sending machine without going through a mail server.
<Restrict Destination Domain>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can set to only allow sending to addresses in a specied domain when sending an e-mail or I-fax.
<Auto Complete for Entering E-Mail Addresses>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can set to automatically display e-mail addresses registered in the Address Book or an LDAP server based
on the initial characters of an e-mail address entry.
●E-mail addresses that are stored with an access number do not appear.
Settings/Registration
829

<Auto Add Specied Domain to Dest. Without Domain>
(Settings/Register) <Function Settings> <Send> <E-Mail/I-Fax Settings>
You can register frequently used domain names in advance to eliminate the need to enter a domain when
specifying an address because a domain name with @ is automatically appended. If you want to send to
"123@example.com", register the domain name "example.com". If you specify an address that already includes
a domain with this setting on, the domains in this setting are invalid.
●Note the following when importing the Address Book to another device.
- Since this setting follows the settings of the device you are using, the domain may differ from that
assigned by the device. Check this setting before using it with another device.
- If you import addresses without domain information to a device that does not have this setting, you
may not be able to send because the addresses are invalid.
<Register Favorite Settings>/<Edit Favorite Settings>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can register frequently used settings in a button of the machine for later use when sending a fax. You can
also assign a name to a button and enter a comment. You can also delete or rename registered settings.
Registering a Combination of Frequently Used Functions(P. 164)
<Display Conrmation for Favorite Settings>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can select whether to display a conrmation screen when recalling "Favorite Settings."
<Default Screen>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can specify the screen to display when <Fax> or the Reset key is pressed.
<Restrict Address Book Use>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can select whether to hide the Address Book and one-touch buttons on the Fax Basic Features screen, etc.
as well as whether to restrict use of the Address Book.
<Change Default Settings>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can change the settings registered as default for the <Fax> function.
<Register Options Shortcuts>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can register modes in the shortcut keys displayed on the <Fax> screen. Customizing the Basic Features
Screen(P. 167)
Settings/Registration
830

<Register Sender Name (TTI)>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can register any name as the sender name, such as the section or department's name, or an individual's
name, and edit/delete registered names. The registered name is printed on paper at the recipient as the sender
information when you send a fax.
●You can store up to 99 sender names (01 to 99).
<Use Authentication User Name as Sender Name>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
If logging in with personal authentication management, the login name appears in <100> on the <Sender Name
(TTI)> screen. If <On> is selected, the login name in <100> is used as the default setting for the sender name.
●If this setting is set to <Off>, the user name in <00> is used as the default setting for the sender name.
For instructions on registering a user name, see Fax Line Settings(P. 68) .
<Off-Hook Alarm>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
If the optional handset is not returned to the machine correctly after sending or receiving a fax, the user is
notied with an alarm.
●This setting works only for Line 1 (the standard line).
<ECM TX>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can set whether to use ECM in the fax transmission protocol. ECM checks for fax data errors and corrects
them.
●If the communication speed appears to be extremely slow, you may be able to improve the speed by
setting to <Off>.
●Even when you set ECM, errors can sometimes occur due to a poor telephone line connection.
Settings/Registration
831

●The conditions for successful ECM transmission are indicated below.
- ECM transmission is enabled with this setting
- The destination supports ECM
- <ECM TX> was set to <On> when registering the destination address to the Address Book
Registering Destinations in the Address Book(P. 195)
<Set Pause Time>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can set the number of seconds to pause when sending faxes. Some overseas dialing may not be successful
when dialing the international access code, country code, and the destination's telephone number all at once. In
such cases, inserting a pause after the international access code can make it easier to connect.
●Pauses entered at the end of dialed fax numbers are always 10 seconds long.
<Auto Redial>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
Auto Redial enables the machine to automatically redial the recipient's fax number if the recipient cannot be
reached due to a busy line, or if a sending error occurs. If you activate this setting, you can set how many times
the machine redials, the redial interval, and whether the document should be resent when there is an error.
<Check Dial Tone Before Sending>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
If you are sending a fax from your machine at the same time another fax machine (made by a company other
than Canon) is trying to send you a fax, your fax may end up being redirected to that fax machine, instead of
the original destination you had intended. Activating this setting enables you to avoid such sending problems.
<Fax TX Result Report>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
A Fax TX Result Report is a report that enables you to check whether faxes were sent correctly to their intended
destinations. The machine can be set to print this report automatically after documents are sent or only when a
transmission error occurs. You can also specify the setting to print the rst part of the document as part of the
report to remind you of the document's content. Fax TX Result Report(P. 915)
<Fax Activity Report>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can print or send fax document sending/receiving logs as a report. The machine can be set to print or send
this report when a specied number of communications (40 to 1,000) is reached or at a specied time. The
send/receive reports can also be printed or sent separately.
When the report is sent as data, it is sent in the CSV le format. Fax Activity Report(P. 914)
Settings/Registration
832
<Register Unit Telephone Number>
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Set Line> <Line X>
You can register the fax number to use when the fax is used on the machine. The registered fax number is
printed on paper at the recipient as the sender information when you send a fax. Fax Line Settings(P. 68)
<Register Unit Name>
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Set Line> <Line X>
You can register the name of your company or department as the unit name. The registered name is printed on
paper at the recipient as the sender information when you send a fax. Fax Line Settings(P. 68)
<TX Start Speed>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can change the send start speed. This setting is useful when there is diculty initiating the sending of a
document due to a poor line condition.
●If your document transmission is slow in starting, this may mean that the telephone lines in your area
are in poor condition. Select a slower speed. You can select <33600 bps>, <14400 bps>, <9600 bps>,
<7200 bps>, <4800 bps>, or <2400 bps>.
●Set <Auto Adjust Communication Speed When Using VoIP>(P. 834) to <On> to send and receive
faxes more accurately when the line or other party is prone to errors. The communication speed is
limited to <14400 bps> or slower, which reduces errors. If <Auto Adjust Communication Speed When
Using VoIP> is set to <Off>, the speed returns to the value displayed in <TX Start Speed>.
<R-Key Setting>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
If your machine is connected through a PBX (Private Branch Exchange), it is necessary to set the access method.
You can set the PBX type to <Prex> or <Hooking>. If you register the outside line access number in the R-key,
you can easily access the outside line.
<Conrm Entered Fax Number>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
To prevent sending a fax to an incorrect destination, you can select whether to display an entry conrmation
screen when entering a fax number.
<Allow Fax Driver TX>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can select whether to allow sending a fax from a computer.
<Conrm Before Sending When Fax Dest. Included>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can select whether to display a destination conrmation screen when sending to destinations containing
faxes. This helps prevent you from sending a fax to an incorrect destination.
Settings/Registration
833
<Restrict Sequential Broadcast When Fax Dest. Included>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can select whether to restrict sending to multiple destinations containing faxes at the same time.
<Use Remote Fax>
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Remote Fax Settings>
You can specify whether to use the machine as a server machine for the Remote Fax function.
●If you want to use the machine as a Remote Fax server machine, press <Network> set <Dedicated
Port Settings> to <On>.
<Auto Adjust Communication Speed When Using VoIP>
(Settings/Register) <Function Settings> <Send> <Fax Settings>
You can send and receive faxes more accurately when the line or other party is prone to errors.
●If you set this to <On>, the communication speed is limited to <14400 bps> or slower in the following
settings, which reduces errors. If you set this to <Off>, the speeds return to their original values.
- <Sending Speed> for destinations registered in the Address Book or one-touch buttons
Registering Destinations in the Address Book(P. 195)
- The transmission speed set in <TX Start Speed> <TX Start Speed>(P. 833)
- The reception speed set in <RX Start Speed> <RX Start Speed>(P. 841)
Settings/Registration
834
<Receive/Forward>
72JY-0FC
This section describes how to specify receive settings.
<TX/RX User Data List>
(Settings/Register) <Function Settings> <Receive/Forward> <Output Report>
You can print a list of the send/receive settings registered in the machine. TX/RX User Data List(P. 917)
<Fax User Data List>
(Settings/Register) <Function Settings> <Receive/Forward> <Output Report>
You can print a list of the fax settings registered in the machine. Fax User Data List(P. 917)
<Print on Both Sides>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can select whether to print received documents on both sides of paper.
<Reduce Fax RX Size>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can select whether to reduce received documents so that the whole document is printed within the
printable area of the paper.
●If this setting is set to <Off>, the image size of the received le is not reduced to t the size of the
paper. If the size of the image exceeds the printable area, the image is divided into equal sections and
printed onto separate sheets of paper.
●If you select <Auto> in <Reduction Mode>, the image size is automatically reduced by a suitable
reduction ratio. This ratio can range from the value set for <Reduction Ratio>, up to 100% of the
received document size.
<Print RX Page Footer>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can select whether to print information, such as reception time and page number, at the bottom of
received documents.
●When an e-mail without a body is received, the From information and Subject information (up to 24
characters for each) is printed at the top of the rst page of the attachment le.
Settings/Registration
835
<Interrupt and Print RX Jobs>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can set to suspend other jobs to print faxes/I-faxes when the machine receives them.
<Use Forwarding Settings>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can select whether to forward received documents to other destinations such as the Condential Fax Inbox
of the machine and an external le server. If you select <On>, specify the forwarding conditions in <Forwarding
Settings>.
<Handle Files with Forwarding Errors>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can set how the machine handles documents that fail to be forwarded.
●If you press <Common Settings> set <Delete Failed TX Jobs> to <Off>, the documents with
forwarding errors will be saved on the <Status Monitor> screen, and the documents will not be
processed according to the settings you specied here.
●If you select <Store/Print> when Memory Lock is set, the documents with forwarding errors will be
saved.
●If you select <Store/Print> when Memory Lock is not set, the documents with forwarding errors will be
printed.
<Forwarding Settings>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can specify the conditions for forwarding received documents. You can also set to forward all incoming
documents to a specied destination without specifying any conditions. Forwarding Received Documents
Automatically(P. 318)
<Set/Register Condential Fax Inboxes>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can assign a name for each Condential Fax Inbox as well as set a PIN.
Setting/Registering Condential Fax Inboxes
1Press (Settings/Register).
2Press <Function Settings> <Receive/Forward> <Common Settings>.
3Press <Set Fax/I-Fax Inbox>.
4Press <Set/Register Condential Fax Inboxes>.
5Select the box number specify each setting, and press <OK>.
Settings/Registration
836
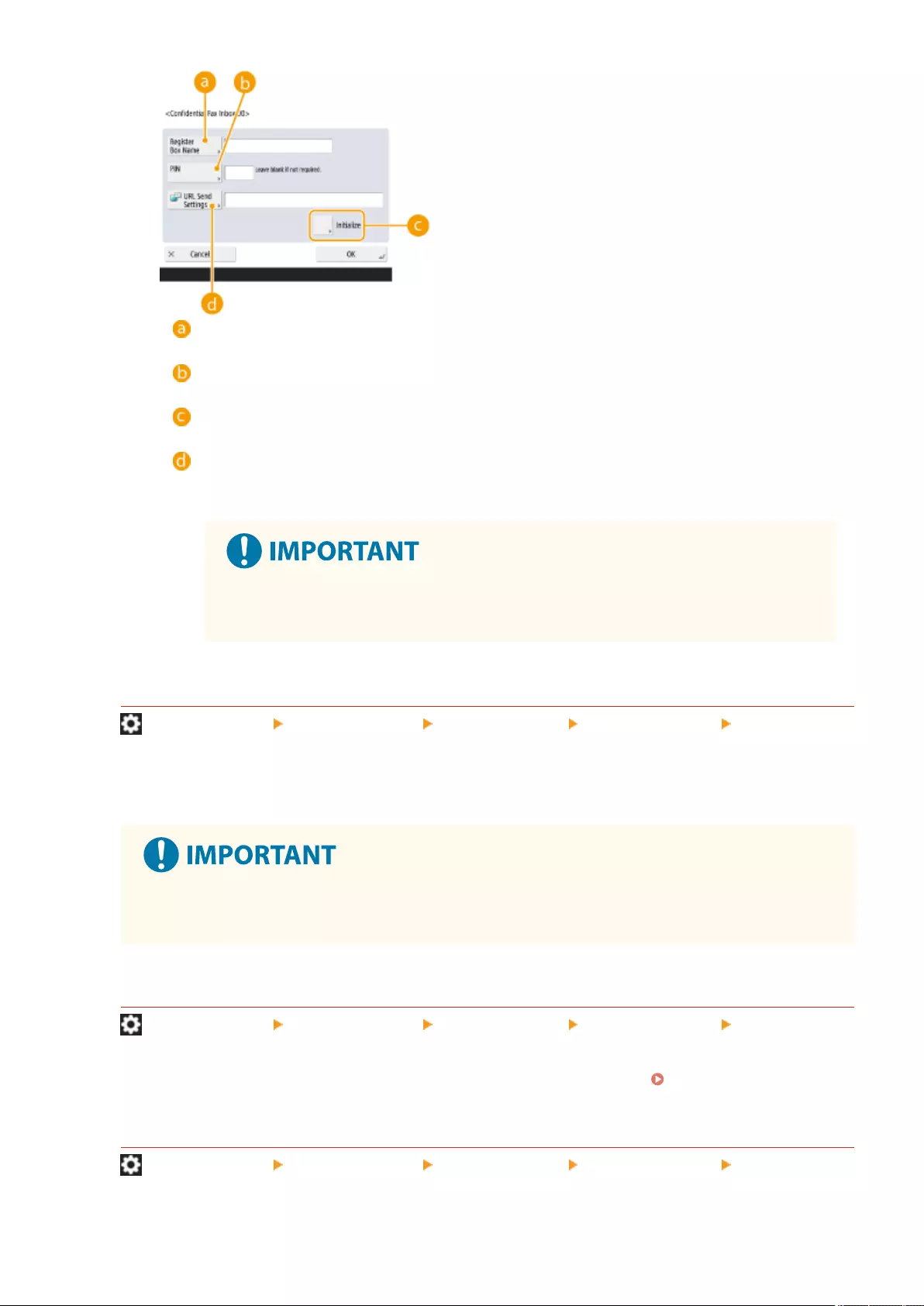
<Register Box Name>
Register a name for the box.
<PIN>
Enter the PIN for the box.
<Initialize>
Initializes the box.
<URL Send Settings>
Enables the URL for a box with documents saved can be sent via e-mail or checked on the Remote UI
screen.
●Since there is no way to check a registered PIN, make sure that you write down the
PIN that you enter, and keep it in a safe place.
<Memory RX Inbox PIN>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can set a PIN for the Memory RX Inbox.
●Since there is no way to check a registered PIN, make sure that you write down the PIN that you
enter, and keep it in a safe place.
<Use Fax Memory Lock>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can select whether to save received fax documents in the Memory RX Inbox. Saving Received
Documents in the Machine (Memory Reception)(P. 313)
<Use I-Fax Memory Lock>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
Settings/Registration
837

You can select whether to save received I-fax documents in the Memory RX Inbox. Saving Received
Documents in the Machine (Memory Reception)(P. 313)
<Memory Lock Start Time>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can specify the time to activate the Memory Reception function. The machine will automatically switch to
the Memory Reception mode at the specied time.
Setting the Start Time for Memory Reception
1Press (Settings/Register).
2Press <Function Settings> <Receive/Forward> <Common Settings>.
3Press <Set Fax/I-Fax Inbox>.
4Press <Memory Lock Start Time>, and specify the required settings.
<Everyday>
Set the time that memory reception starts.
<Specify Days>
Set the day of the week and time that memory reception starts.
<Off>
Select this when you do not want to set a memory reception start time.
●You can set <Everyday> for the memory reception start time and <Specify Days> for
the memory reception end time (or vice-versa).
<Memory Lock End Time>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can specify the time to deactivate the Memory Reception function. The machine will automatically cancel
the Memory Reception mode at the specied time.
Setting the End Time for Memory Reception
1Press (Settings/Register).
2Press <Function Settings> <Receive/Forward> <Common Settings>.
3Press <Set Fax/I-Fax Inbox>.
Settings/Registration
838
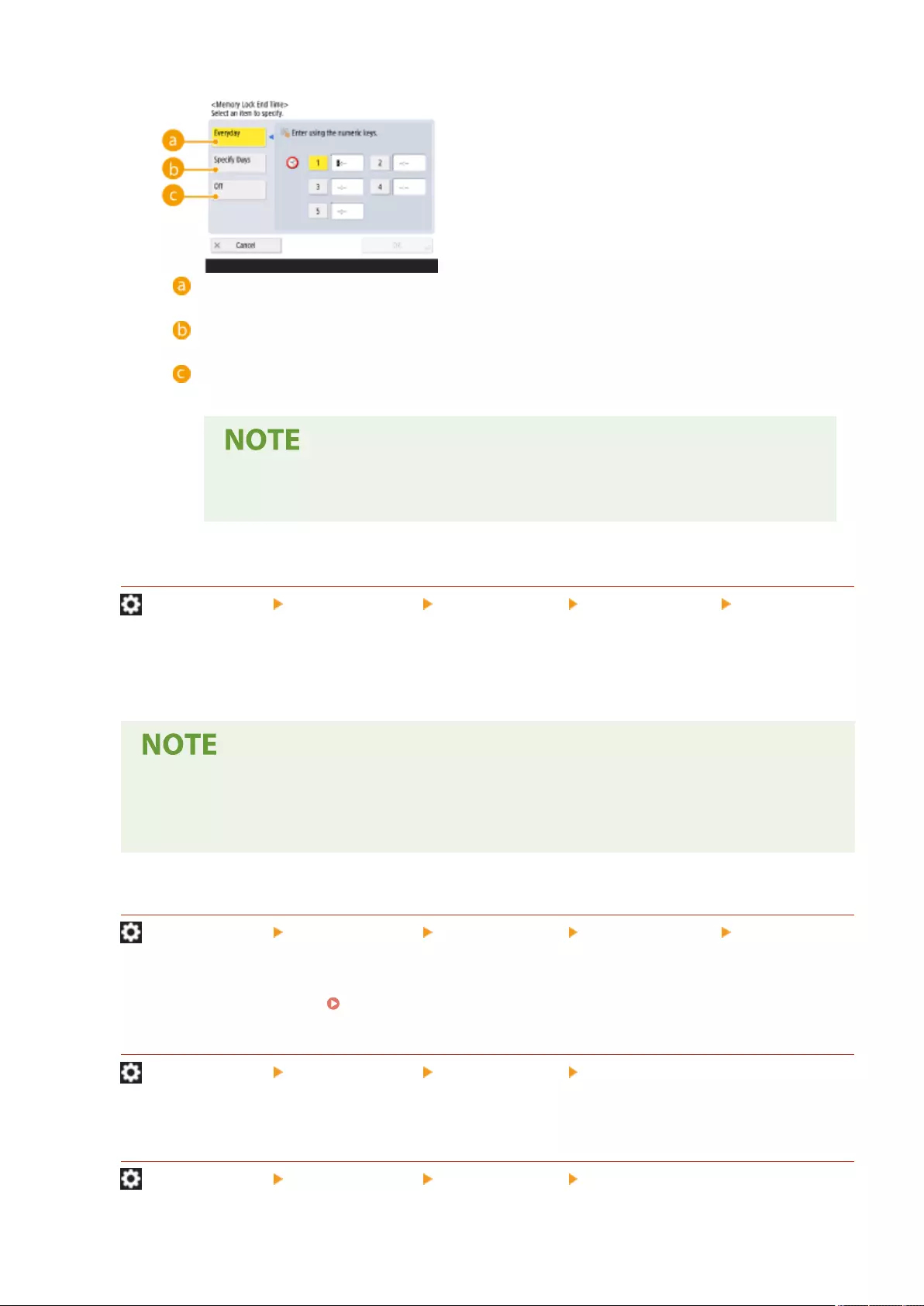
4Press <Memory Lock End Time>, and specify the required settings.
<Everyday>
Set the time that memory reception ends.
<Specify Days>
Set the day of the week and time that memory reception ends.
<Off>
Select this when you do not want to set a memory reception end time.
●You can set <Everyday> for the memory reception start time and <Specify Days> for
the memory reception end time (or vice-versa).
<Divided Data RX Timeout>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can specify the time before reception is canceled when receiving a divided I-fax and the subsequent data
cannot be received. Data received by the specied time is printed.
●If you delete divided data, it cannot be combined to form a complete document, even if the remaining
divided data is received later.
●Divided data cannot be printed as a regular image unless it has been combined.
<Forward Temporarily Stored File to Memory RX Inbox>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings> <Set Fax/I-Fax
Inbox>
You can specify whether to automatically forward received documents to the Memory RX Inbox if they cannot
be printed due to an error, etc. Saving Received Documents in the Machine (Memory Reception)(P. 313)
<Always Send Notice for RX Errors>
(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
You can select whether to notify the sender that an I-fax was not received successfully.
<ECM RX>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
Settings/Registration
839

You can receive faxes using the Error Correction Mode (ECM).
●To perform a communication using ECM, ECM needs to be set in both the sending machine and this
machine.
●Even when you set ECM, errors can sometimes occur due to a poor telephone line connection.
<RX Mode>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
You can set the fax reception method.
Setting the Fax Reception Method
1Press (Settings/Register).
2Press <Function Settings> <Receive/Forward> <Fax Settings>.
3Press <RX Mode>.
4Select the reception method.
●If you selected something other than <Fax/Tel(Auto Switch)>, press <OK>.
●If you selected <Fax/Tel(Auto Switch)>, specify the required settings.
<Time Until Ringing Starts>
Set the time until the incoming fax tone is emitted after receiving a call.
<Ringing Period>
Set the time to continue emitting the incoming fax tone.
<Action After Ringing Period Is Over>
Set the operation for the machine when the phone is not answered with the incoming fax tone emitted.
●The machine may not emit a tone even when a call is received, depending on the
settings.
<Remote RX>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
Settings/Registration
840
You can receive faxes using the dial operation of a telephone connected to the machine. If you pick up the
handset and the other party is a fax machine, you can enter the ID number specied here from the telephone to
receive the fax.
●If a one digit number is set, make sure to enter a zero before the number when entering the ID
number from the telephone. For example, if "09" is set, enter "0" then "9" as the ID number from the
telephone.
●Since the ID number is sent with a push tone, an ID number cannot be entered from a telephone
incompatible with push tones (such as a rotary dial telephone).
<Switch to Auto RX>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
You can set the machine to automatically switch to automatic reception after the specied time elapses when
manual reception is set.
<Fax RX Result Report>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
A Fax RX Result Report is a report that enables you to check whether faxes were received correctly. The machine
can be set to print this report automatically after documents are received or only when a reception error occurs.
Fax RX Result Report(P. 916)
<Condential Fax Inbox RX Report>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
A Condential Fax Inbox RX Report is a report that enables you to check whether documents were received in
the Condential Fax Inbox correctly. The machine can be set to print this report automatically after documents
are received. Condential Fax Inbox RX Report(P. 916)
<RX Start Speed>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
You can change the receive start speed. This setting is useful when there is diculty initiating the receiving of a
document due to a poor line condition.
●Set <Auto Adjust Communication Speed When Using VoIP>(P. 834) to <On> to send and receive
faxes more accurately when the line or other party is prone to errors. The communication speed is
limited to <14400 bps> or slower, which reduces errors. If <Auto Adjust Communication Speed When
Using VoIP> is set to <Off>, the speed returns to the value displayed in <RX Start Speed>.
Settings/Registration
841
<RX Password>
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
You can set an ITU-T standard password. If a subaddress is not set in a document that was received from
another party using the ITU-T standard, a reception password check takes place. If the password found does
not match the password set with this setting, or if a password is not attached to the document, the document is
not received.
●Priority is given to the subaddress password if the received document is set with a subaddress, even if
an RX password is set.
●ITU-T stands for International Telecommunication Union-Telecommunication Standardization Sector,
which is the group that makes recommendations toward the standardization of worldwide
telecommunications.
Settings/Registration
842
<Store/Access Files>
72JY-0FE
This section describes the settings for storing scanned documents and printing stored les.
<Register/Edit Favorite Settings>
(Settings/Register) <Function Settings> <Store/Access Files> <Common Settings> <Scan and Store
Settings>
You can register frequently used settings in a button of the machine for later use when saving. You can also
assign your favorite name to a button and check registered settings. Registering a Combination of
Frequently Used Functions(P. 164)
Specifying Settings in Advance
To register/edit these settings, specify the settings from (Settings/Register) after performing the
following procedure in advance.
1Press <Scan and Store>. <Home> Screen(P. 119)
2Select the location to save the le.
3Press <Scan>.
4Specify the scan settings to register.
<Change Default Settings>
(Settings/Register) <Function Settings> <Store/Access Files> <Common Settings> <Scan and Store
Settings>
You can change the settings registered as default for the <Scan and Store> function.
Specifying Settings in Advance
To register/edit these settings, specify the settings from (Settings/Register) after performing the
following procedure in advance.
1Press <Scan and Store>. <Home> Screen(P. 119)
2Select the location to save the le.
3Press <Scan>.
4Specify the scan settings to register.
<Register/Edit Favorite Settings>
(Settings/Register) <Function Settings> <Store/Access Files> <Common Settings> <Access Stored
Files Settings>
You can register frequently used settings in a button of the machine for later use when printing. You can also
assign your favorite name to a button and check registered settings. Registering a Combination of
Frequently Used Functions(P. 164)
Settings/Registration
843
Specifying Settings in Advance
To register/edit these settings, specify the settings from (Settings/Register) after performing the
following procedure in advance.
1Press <Access Stored Files>. <Home> Screen(P. 119)
2Select the location where the le to use is saved.
3Select a le and press <Print>.
4Specify the print settings to register.
<Change Default Settings>
(Settings/Register) <Function Settings> <Store/Access Files> <Common Settings> <Access Stored
Files Settings>
You can change the settings registered as default for the <Access Stored Files> function.
Specifying Settings in Advance
To register/edit these settings, specify the settings from (Settings/Register) after performing the
following procedure in advance.
1Press <Access Stored Files>. <Home> Screen(P. 119)
2Select the location where the le to use is saved.
3Select a le and press <Print>.
4Specify the print settings to register.
<Limit Box PIN to 7 Digits/Restrict Access>
(Settings/Register) <Function Settings> <Store/Access Files> <Common Settings>
If you set this setting to <On>, users are forced to set a seven-digit PIN, thus enhancing security.
●This setting is also applied to the Memory RX Inbox and Condential Fax Inbox.
<Network Place Settings>
(Settings/Register) <Function Settings> <Store/Access Files> <Network Settings>
You can register the Advanced Space of another imageRUNNER ADVANCE series machine or a Windows server
as an external reference. Connecting to the Other Devices(P. 75)
<Protocol for External Reference>
(Settings/Register) <Function Settings> <Store/Access Files> <Network Settings>
You can select the protocol to use when accessing the Advanced Space of another imageRUNNER ADVANCE
series machine or a Windows server which is opened externally. Connecting to the Other Devices(P. 75)
Settings/Registration
844
<Conrm TLS Certicate for Network Access>
(Settings/Register) <Function Settings> <Store/Access Files> <Network Settings>
You can conrm whether the TLS server certicate is valid when accessing the Advanced Space of another
imageRUNNER ADVANCE series machine or a Windows server. You can verify the validity of the certicate and
reliability of the certicate chain, as well as conrm the CN (Common Name). Connecting to the Other
Devices(P. 75)
<Personal Folder Specication Method>
(Settings/Register) <Function Settings> <Store/Access Files> <Network Settings>
A Personal folder is an individual folder that can be used by the user logged in with personal authentication
management. Shared folders and le servers can be specied and used as a Personal folder. Conguring
Personal Folders(P. 529)
●A Personal folder is a folder shared by the following screens.
- <Scan and Send>
- <Network> in <Scan and Store>
- <Network> in <Access Stored Files>
<Use Scan/Print Function>
(Settings/Register) <Function Settings> <Store/Access Files> <Memory Media Settings>
Specifying this setting enables you to save documents stored in memory media, as well as print les in memory
media. Restricting the Use of Memory Media(P. 576)
<Select Option When Connecting Memory Media>
(Settings/Register) <Function Settings> <Store/Access Files> <Memory Media Settings>
You can set whether to display shortcuts to available functions when memory media is connected.
Connecting a USB Memory Device(P. 84)
Settings/Registration
845
<Print>
72JY-0FF
This section describes the print settings.
<Forced Hold>
(Settings/Register) <Function Settings> <Print>
Specify the settings for the forced hold printing. Conguring the Forced Hold Printing Settings(P. 573)
<Job Storage Period>
(Settings/Register) <Function Settings> <Print>
Specify the time period for storing jobs.
<Delete Job After Printing>
(Settings/Register) <Function Settings> <Print>
Specify whether to delete jobs after they are printed.
<Only Allow Encrypted Print Jobs>
(Settings/Register) <Function Settings> <Print>
You can set the machine to only receive encrypted secure print jobs from computers.
<Include Domain as User Recognition Condition>
(Settings/Register) <Function Settings> <Print>
Specify whether to determine print jobs of a login user by "user name + domain name" or only "user name".
Depending on your environment, if print jobs are not correctly determined as My Jobs, they can be correctly
determined as jobs of the login user by selecting <Off> and excluding "domain name".
<Display Other User Jobs>
(Settings/Register) <Function Settings> <Print>
Specify whether to display the jobs from users other than the authorized user.
<Restrict Deletion of Other User Jobs>
(Settings/Register) <Function Settings> <Print>
Specify whether to allow jobs of users other than the authorized user to be deleted when the jobs of users other
than the authorized user are displayed.
<Match Case for User Name>
(Settings/Register) <Function Settings> <Print>
Specify whether to set the machine to distinguish uppercase and lowercase characters for user names.
●This setting is applied to the whole user names including domain names.
Settings/Registration
846
●It is recommended that this is set together with <User Management> in <Authentication
Management> <Match Case for User Name> <Management Settings>.
<Job List Display Settings>
(Settings/Register) <Function Settings> <Print>
Specify the job types to be included in the job list, and the job type to be selected by default.
●You cannot specify <On> for <Group> only in <Job List Display Settings>. Either <Personal> or
<Shared> must also be set to <On>.
<Held Jobs Warning Settings>
(Settings/Register) <Function Settings> <Print>
Specify the method for sending Job Hold alerts.
<PIN Settings for Secure Print Jobs>
(Settings/Register) <Function Settings> <Print>
You can set whether to require a PIN to be entered when printing, displaying images, or deleting with the
Secured Print function.
●For the Encrypted Secure Print function, you can only set whether to require a PIN to be entered
when deleting. In addition, it is necessary to enter a PIN to print a document/display the preview
regardless of the values specied in <Require PIN for Printing/Displaying User Jobs>.
<Enable Auto Print Function When Logging In>
(Settings/Register) <Function Settings> <Print>
You can set whether to allow forced hold print jobs to be automatically printed when each user logs in.
●This setting is disabled if any of the following settings is specied.
-<Use User Authentication> is <Off>
- <Enable Use of Personal Settings> is <Off>
- <Use ACCESS MANAGEMENT SYSTEM> is <On>
- <Only Allow Encrypted Print Jobs> is <On>
- <Personal> for <Job List Display Settings> is <Off>
Settings/Registration
847
- <Display Warning When Starting to Print> for <Held Jobs Warning Settings> is <On>
<Auto Print User Jobs When Logging In>
(Settings/Register) <Function Settings> <Print>
You can set whether to automatically print forced hold print jobs after logging in. Automatically Printing
Forced Hold Print Jobs after Logging In(P. 353)
●This setting is disabled if any of the following settings is specied.
-<Use User Authentication> is <Off>
- <Enable Auto Print Function When Logging In> is <Off>
- <Enable Use of Personal Settings> is <Off>
- <Use ACCESS MANAGEMENT SYSTEM> is <On>
- <Only Allow Encrypted Print Jobs> is <On>
- <Personal> for <Job List Display Settings> is <Off>
- <Display Warning When Starting to Print> for <Held Jobs Warning Settings> is <On>
Settings/Registration
848

<Set Destination>
72JY-0FH
You can specify the settings for registering and changing destinations.
<Address Lists>
(Settings/Register) <Set Destination>
You can print a list of destinations registered in the Address Book or one-touch buttons. Printing a List of
Settings(P. 917)
●Even if you set <Manage Address Book Access Numbers>(P. 849) to <On>, all destinations
including those stored with access numbers are printed.
<Register Destinations>
(Settings/Register) <Set Destination>
You can register destinations to the address book of the machine. Registering Destinations in the Address
Book(P. 195)
<Rename Address List>
(Settings/Register) <Set Destination>
You can rename each address list.
<Register One-Touch>
(Settings/Register) <Set Destination>
You can register destinations to the one-touch buttons of the machine. Registering a Destination in a One-
Touch Button(P. 210)
<Change Default Display of Address Book>
(Settings/Register) <Set Destination>
You can specify the type of the Address Book to display when you press <Address Book> on the Fax Basic
Features screen or the Scan and Send Basic Features screen.
<Address Book PIN>
(Settings/Register) <Set Destination>
You can set a PIN for the Address Book. Restricting Use of the Address Book(P. 566)
<Manage Address Book Access Numbers>
(Settings/Register) <Set Destination>
You can select whether to allow users to set an access number for a destination when registering in the Address
Book. Restricting Use of the Address Book(P. 566)
Settings/Registration
849
<Include Password When Exporting Address Book>
(Settings/Register) <Set Destination>
If you set this setting to <On>, you can select whether to include the passwords registered for destinations
when exporting the Address Book using the Remote UI.
●You can set whether to export the following passwords:
-The password for subaddress transmission set in fax destinations
- The authentication password set for le server destinations
<Register LDAP Server>
(Settings/Register) <Set Destination>
You can specify the settings of an LDAP server, such as a server name and server address, you are using when
searching for or registering destinations. Registering the LDAP Server(P. 53)
<Auto Search When Using LDAP Server>
(Settings/Register) <Set Destination>
If you set this setting to <On>, you can immediately start searches when accessing an LDAP server from the
control panel of the machine.
●Automatic searches are only performed for the rst LDAP server registered, which is displayed on the
top of the LDAP server drop-down list.
<Conrm TLS Certicate for LDAP Server Access>
(Settings/Register) <Set Destination>
You can select whether to verify TLS certicates when connected to an LDAP server.
<Change Default LDAP Search Conditions>
(Settings/Register) <Set Destination>
You can register frequently used search conditions as the default settings for searching an LDAP server.
Registering the Default Search Conditions for Each LDAP Server
1Press (Settings/Register).
2Press <Set Destination> <Change Default LDAP Search Conditions> <Register>.
●To restore the default search conditions, press <Initialize>.
3Congure the search conditions.
Settings/Registration
850
4Press <OK>.
●You may have to set up the LDAP servers beforehand, depending on the network environment.
●Searching by organization/organizational unit may not be possible, depending on the information
registered in an LDAP server.
●You can add other search attributes. <Register/Edit LDAP Search Attribute>(P. 851)
<Register/Edit LDAP Search Attribute>
(Settings/Register) <Set Destination>
You can add search items to use when searching an LDAP server.
LDAP Search Attributes
1Press (Settings/Register).
2Press <Set Destination> <Register/Edit LDAP Search Attribute>.
3Select <Not Registered 1> or <Not Registered 2>, and press <Register/Edit>.
●To edit a search attribute, select a registered attribute, and press <Register/Edit>.
●To delete a search attribute, press <Delete>.
4Specify <Display Name> and <Attribute Name>, and press <OK> <Close>.
●You cannot edit or delete names, <E-Mail>, <Fax>, <Organization> or <Organization Unit>.
<Settings for Search by Name When Using LDAP Server>
(Settings/Register) <Set Destination>
You can specify the attribute used when searching an LDAP server for destinations by name using "Search by
Name."
Conguring to "Search by Name" for LDAP Searches
1Press (Settings/Register).
2Press <Set Destination> <Settings for Search by Name When Using LDAP Server>.
3Set <Name Type for Search Attribute> and <Filter>, and press <OK>.
<Acquire Address Book>
(Settings/Register) <Set Destination> <Acquire Remote Address Book>
Settings/Registration
851

You can specify whether to use the Address book of another machine on the network as the Remote Address
Book.
<Remote Address Book Server Address>
(Settings/Register) <Set Destination> <Acquire Remote Address Book>
You can specify the IP address or the host name of a device that opens the Remote Address Book externally.
The IP address can be specied using IPv4 or IPv6.
<Communication Timeout>
(Settings/Register) <Set Destination> <Acquire Remote Address Book>
You can set the communication timeout. When a device opening a Remote Address Book does not respond
within the specied time, the machine stops trying to obtain destinations from the device.
<Fax TX Line Auto Select Adjustment>
(Settings/Register) <Set Destination> <Acquire Remote Address Book>
You can set whether to automatically select the fax line instead of using the line registered to the destination,
when sending a fax to a destination obtained from a Remote Address Book.
<Make Address Book Open>
(Settings/Register) <Set Destination> <Make Remote Address Book Open>
You can select whether to open the Address Book of this machine to another machine on a network.
<Use Personal Address List>
(Settings/Register) <Set Destination>
You can select whether to use a personal Address Book of a user who logs in to the machine with personal
authentication management.
<Use User Group Address List>
(Settings/Register) <Set Destination>
You can restrict the use of <User Group Address List>. However, when an administrator accesses the machine
from the Remote UI, they can register/edit <User Group Address List> regardless of this setting.
●You can set to also change the name of the user group address book when a user group name is
changed. Log in to the Remote UI as a user with Administrator privileges, press [Settings/
Registration] [Set Destination] [Personal Address List/User Group Address List Settings] select
the [Apply User Group Name Change to User Group Address List Name] check box.
Settings/Registration
852
<Management Settings>
72JY-0FJ
You can congure the settings related to management of users, devices, and data, etc., for secure and ecient use of
the machine.
Item Description
<User Management>(P. 854) You can congure the settings for managing users of the machine with a user authentication
application.
<Device Management>(P. 857) You can manage information about the hardware and operations, as well as various data
required when using the machine functions.
<License/Other>(P. 861) You can register licenses and congure the settings related to the software and system
options available for the machine.
<Data Management>(P. 864) You can congure settings to utilize the machine settings or data such as address lists.
<Security Settings>(P. 866) You can specify the settings related to the user authentication function, password, and
encryption.
Settings/Registration
853

<User Management>
72JY-0FK
You can congure the settings for managing users of the machine with a user authentication application.
<Change Password>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
The users registered in the machine can change their own login password. This setting is not displayed for
users that have logged in with Administrator privileges.
<Register/Edit Authentication User>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select to register users in the machine and specify the user information, such as the password and privilege
level. Registering User Information in the Local Device(P. 495)
<Use User Authentication>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select whether to enable the personal authentication management function. You can also select which login
methods to use for user authentication. Conguring the User Login Methods and Authentication
Devices(P. 513)
<Number of Caches for Login Users>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
<Keyboard Authentication>
Select whether to display the names of users who previously logged in in a drop-down list on the login screen.
Select <0> to hide the login history, and select <1> to display only the name of the user who logged in most
recently. Conguring the User Login Methods and Authentication Devices(P. 513)
<Display Button to Change Password on Settings Menu>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
<Keyboard Authentication>
Select whether to allow users to change passwords by using on the top right corner of the login screen.
Conguring the User Login Methods and Authentication Devices(P. 513)
<Use Numeric Keys for Authentication>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
<Keyboard Authentication>
If the user name and password are comprised of numbers only, authentication can be performed with numeric
key entry only.
<Login Screen Display Settings>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Specify when to display the login screen by selecting either "when you start using the machine" or "after a
function button is pressed." If "after a function button is pressed" is selected, you can specify the functions that
require user login. Specifying When to Display the Login Screen(P. 517)
Settings/Registration
854
●If you change this setting, <Restrict Access to Other User Jobs>(P. 857) may be set to <On>. For
more information, see Specifying When to Display the Login Screen(P. 517) .
<Functions to Restrict>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select whether to restrict use of particular functions when personal authentication management is enabled.
Conguring the User Login Methods and Authentication Devices(P. 513)
●Changes in settings are effective after performing <Apply Set. Chng.>.
<Restrict Job from Remote Device w/out User Authent.>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select whether to apply personal authentication management to printing, faxing, and remote scanning via a
computer. Using Personal Authentication to Manage Printing/Faxing/Remote Scanning via a
Computer(P. 520)
<Default Role When Registering User>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select the role to apply to users in situations such as when no privileges are set. Conguring the User Login
Methods and Authentication Devices(P. 513)
<Match Case for User Name>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select whether user names are case-sensitive.
●It is recommended that this is set together with <Function Settings> <Print> <Match Case for
User Name>.
<Allow Use of @ in User Name>
(Settings/Register) <Management Settings> <User Management> <Authentication Management>
Select whether to allow "@" to be used in user names.
<System Manager Information Settings>
(Settings/Register) <Management Settings> <User Management>
Set the System Manager information for the machine. Changing the System Manager ID and PIN(P. 523)
Settings/Registration
855
<Device Management>
72JY-0FL
You can specify settings related to the management of the device and optional products.
<Device Information Settings>
(Settings/Register) <Management Settings> <Device Management>
Enter the name and the installation location to identify the machine.
<Import/Export from Addr. Book Management Software>
(Settings/Register) <Management Settings> <Device Management>
Set whether to import or access the address books of address book management software.
●When user authentication is performed, setting <Use User Authentication When Importing> to <On>
enables only address books for which user authentication has been performed to be imported.
<Conrm Device Signature Certicate>
(Settings/Register) <Management Settings> <Device Management>
Check the detailed settings of a device signature certicate. You can also check whether the certicate is valid.
<Conrm User Signature Certicate>
(Settings/Register) <Management Settings> <Device Management>
Check the detailed settings of a user signature certicate available for the logged-in user. You can also check
whether the certicate is valid.
<Certicate Settings>
(Settings/Register) <Management Settings> <Device Management>
You can manage the keys/certicates, CA certicates, or certication revocation list (CRL) used in the machine.
You can also set the Online Certicate Status Protocol (OCSP).
Generating the Key and Certicate for Network Communication(P. 552)
Generating a Device Signature Certicate(P. 578)
Registering a User Signature Certicate(P. 579)
Generating a Key and Certicate Signing Request (CSR)(P. 608)
Conguring the Expiration Check Method for Received Certicates(P. 605)
<Display Job Status Before Authentication>
(Settings/Register) <Management Settings> <Device Management>
Select whether to restrict access to the <Status Monitor> screen when using a login service.
<Restrict Access to Other User Jobs>
(Settings/Register) <Management Settings> <Device Management>
Settings/Registration
857
Select whether to restrict users from performing operations on the jobs of other users on the <Status Monitor>
screen when User Authentication is used.
●If you change <Login Screen Display Settings>(P. 854) , this setting may be set to <On>. For more
information, see Specifying When to Display the Login Screen(P. 517) .
<Display Job Log>
(Settings/Register) <Management Settings> <Device Management>
Select whether to display job logs on the <Status Monitor> screen. You can also select whether to allow device
management software to retrieve job logs from the machine. Basic Screens on the Touch Panel
Display(P. 119)
<Save Audit Log>
(Settings/Register) <Management Settings> <Device Management>
Select whether to start log recording. For information on the types of logs, see System
Specications(P. 1084) .
Starting Log Recording(P. 620)
System Specications(P. 1084)
●If this is set to <On>, the <Adjust Time>(P. 777) setting cannot be used.
●Changes in settings are effective after performing <Apply Set. Chng.>.
<Retrieve Network Authentication Log>
(Settings/Register) <Management Settings> <Device Management>
Select whether to start log recording for authentication performed when the machine is accessed via the
network, such as when printing from a computer or accessing the Advanced Space.
<Store Key Operation Log>
(Settings/Register) <Management Settings> <Device Management>
Select whether to save a log of the key operations performed by users. By analyzing the stored logs, you can
survey how the machine is being used.
●When the log is output, PINs, passwords, and information obfuscated by the settings for <Restrict
Access to Other User Jobs>, etc., are output as masked characters. Therefore, condential information
cannot be leaked externally.
Settings/Registration
858
●For information on interpreting and outputting saved logs, contact your dealer or service
representative.
<Restrict Service Representative Access>
(Settings/Register) <Management Settings> <Device Management>
You can set the machine to restrict changes in user information or security-related settings when the machine is
inspected or repaired by your dealer or service representative.
●Even when this is not set to <On>, you can check the audit log for past operations if the service
representative has changed user information or security-related settings.
<Synchronize Custom Settings (Client)>
(Settings/Register) <Management Settings> <Device Management>
You can synchronize the personalized data of multiple Canon multifunction printers on a network. Even for the
server machine, it is necessary to enable this setting if you wish to operate the machine as the client machine.
Starting Setting Synchronization(P. 659)
<Enable Use of Personal Settings>
(Settings/Register) <Management Settings> <Device Management> <Manage Personal Settings>
Select whether to enable users that are logged into the machine to use the Personalization function, such as the
display language, accessibility settings, and the screen to display after startup/restoration.
<Action When Maximum Number of Users Exceeded>
(Settings/Register) <Management Settings> <Device Management> <Manage Personal Settings>
Select how the machine processes personal settings for users or groups (user setting information) when the
number for which the machine can save various settings exceeds the limit.
●For information on the data deleted when <Delete Oldest User Settings> is specied, see List of
Items That Can Be Personalized(P. 139) .
●To completely erase data manually instead of deleting it automatically, follow the procedure
described in Deleting User Setting Information(P. 534) .
●For information on the limit of user or group personal settings (user setting information) that the
machine can save, see System Specications(P. 1084) .
<Use Default Screen After Startup/Restoration>
(Settings/Register) <Management Settings> <Device Management> <Manage Personal Settings>
Select whether to enable each user to set the screen displayed on startup/restoration.
Settings/Registration
859
<Prohibit Initialization of Administrator Password>
(Settings/Register) <Management Settings> <Device Management>
Specify whether to restrict operations of <Initialize Admin. Password> ([Counter/Device Information] key
<Device Info./Other>).
<Restrict Special Mode Operations>
(Settings/Register) <Management Settings> <Device Management>
Select whether to restrict use of Special Mode, which is provided for the purpose of maintenance by service
representatives.
Settings/Registration
860
<License/Other>
72JY-0FR
You can register licenses and congure the settings related to the software and system options available for the
machine.
<Register License>
(Settings/Register) <Management Settings> <License/Other>
Enter the license key for a system option that can be used on the machine. Installing System
Options(P. 654)
<Print System Information>
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings>
You can print a report containing information on the applications and some of the system applications installed
in the machine. Printing a List of Settings(P. 917)
<Use TLS>
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings>
Select whether to use TLS communication when an AddOn application is used by accessing the machine via a
Web browser.
●You need to congure the key and certicate before setting this setting to <On>. Conguring the
Key and Certicate for TLS(P. 549)
●Changes made for this setting are also applied to <Use TLS> in <Remote UI Settings>(P. 862) .
●Changes in settings are effective after performing <Apply Set. Chng.>.
<Conrm TLS Certicate Using AddOn Application>
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings>
Select whether to verify TLS server certicates and their common names (CN) when TLS communication is used
for an AddOn application.
<Use DNS Caching>
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings>
Select whether to save DNS information from successful searches via an AddOn application to memory. You can
also set an expiration date if you choose to save information temporarily.
<Use Proxy Settings of This Device>
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings>
Select whether to use the proxy settings of the machine with AddOn applications. Setting a Proxy(P. 547)
<Add X-FRAME-OPTIONS to HTTP Header>
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings>
Settings/Registration
861
When the HTTP server returns a response, it appends X-FRAME-OPTIONS to the header to prevent contents
created by other servers from overlapping.
<Remote UI Settings>
(Settings/Register) <Management Settings> <License/Other>
Select whether to use the Remote UI to operate the machine and change settings.
●Changes in settings are effective after performing <Apply Set. Chng.>.
<Delete Message Board Contents>
(Settings/Register) <Management Settings> <License/Other>
Select to delete messages from the administrator that are displayed on the control panel.
●When <OK> is displayed on a message board, press <OK> to operate the machine. To clear a message
board without <OK> displayed, you need to use the Remote UI.
<Remote Operation Settings>
(Settings/Register) <Management Settings> <License/Other>
Select whether to enable the Remote Operation function. This function enables you to specify settings and
process jobs from a computer by displaying the screen of the touch panel display on the computer screen.
●When remote operation is performed, the following settings cannot be changed or executed.
-<Job Storage Period>(P. 846)
<Use ACCESS MANAGEMENT SYSTEM>
(Settings/Register) <Management Settings> <License/Other>
Select whether to use ACCESS MANAGEMENT SYSTEM. Using ACCESS MANAGEMENT SYSTEM(P. 533)
●Changes in settings are effective after performing <Apply Set. Chng.>.
Settings/Registration
862
<Register/Update Software>
(Settings/Register) <Management Settings> <License/Other>
You can install system options/AddOn applications in the machine. Installing System Options(P. 654)
<Start Setup Guide>
(Settings/Register) <Management Settings> <License/Other>
You can follow the wizard instructions to congure the machine's initial settings. Setting up Using the Setup
Guide(P. 6)
<Allow Use of Print Function from Mobile>
(Settings/Register) <Management Settings> <License/Other>
If this setting is set to <On>, you can perform operations from a mobile device for documents stored in <Print>.
Settings/Registration
863

<Data Management>
72JY-0FS
You can congure settings to utilize the machine settings or data such as address lists.
<Import from USB Memory>
(Settings/Register) <Management Settings> <Data Management> <Import/Export>
You can import all the settings information from a USB memory device.
●If USB memory is already connected to the machine, that USB memory will be recognized as the
media to use for importing, even if you connect new USB memory. Press remove the
connected USB memory insert the desired USB memory.
<Export to USB Memory>
(Settings/Register) <Management Settings> <Data Management> <Import/Export>
You can export all the settings information into a USB memory device.
●You cannot select which settings to export when exporting to USB memory. All settings are batch
exported.
●If USB memory is already connected to the machine, that USB memory will be recognized as the
media to use for exporting, even if you connect new USB memory. Press remove the
connected USB memory insert the desired USB memory.
<Import Result Report>
(Settings/Register) <Management Settings> <Data Management> <Import/Export>
Select to print a report of import results.
●Reports are printed in the following language.
- If the display language of the machine is set to Japanese immediately after the import process:
Japanese
- If the display language of the machine is set to something other than Japanese immediately after
the import process: English
Settings/Registration
864

<Restrict Import/Export from Web Service>
(Settings/Register) <Management Settings> <Data Management> <Import/Export>
Select whether to restrict import and export operations with Web applications other than the Remote UI.
●Changes in settings are effective after performing <Apply Set. Chng.>.
<Initialize All Data/Settings>
(Settings/Register) <Management Settings> <Data Management>
Select to restore all of the machine settings to the factory default values and completely erase the data stored in
the machine. It is not normally necessary to use this setting, but it is useful to erase personal or condential
information when disposing of the machine. Initializing All Data/Settings(P. 663)
Settings/Registration
865

<Security Settings>
72JY-0FU
You can specify the settings related to the user authentication function, password, and encryption.
<Prohibit Authentication Using Department ID and PIN>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Authentication Function Settings>
Select whether to prohibit authentication with a Department ID and PIN when operating from the printer/
scanner. If <On> is selected, authentication with System Manager ID and PIN is also prohibited when operating
from a device management software.
●Jobs that are restricted by this setting are forcibly canceled on the machine.
<Lockout Settings>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Authentication Function Settings>
Select whether to block users from logging in for a specied period of time after a certain number of
consecutive invalid login attempts. This setting does not apply to authentication with a Department ID or PIN,
or authentication for the Mail Box.
●Users may be blocked from logging in before a specied number of consecutive invalid login
attempts if login operations are performed on Windows or other operating systems, or from
applications that use FTP, IPP, SNMPv3, SMB, or WebDAV.
<Prohibit Caching of Authentication Password>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
Select whether to prohibit caching of a password that is entered at login.
●Passwords are not saved to the timeline of unauthenticated users or guest users, regardless of this
setting.
<Display Warning When Default Password Is in Use>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
Settings/Registration
866

Select whether to display the screen for changing the password when the Administrator logs in to the machine
using the default user name and password.
●If the password has expired, the screen for changing the password appears, regardless of this setting.
<Allow Use of Default Password for Remote Access>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
Select whether to allow the default password to be used when logging in from the Remote UI.
<Minimum Length Settings>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can set the minimum number of characters required when registering a password to prevent the
simplication of passwords. When a password length is set, a user cannot be registered with a blank password.
●This setting applies to personal authentication management, not to Department ID and PIN.
●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Validity Period Settings>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can set a password expiration period to force users to periodically change their password, in order to
prevent the simplication of passwords.
●This setting applies to personal authentication management, not to Department ID and PIN.
●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Prohibit Use of 3 or More Identical Consec. Characters>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can restrict passwords so that the same character cannot be used consecutively three or more times.
Settings/Registration
867

●This setting applies to personal authentication management, not to Department ID and PIN.
●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Use at Least 1 Uppercase Character>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can restrict passwords so that only passwords which include at least one uppercase character can be
registered.
●This setting applies to personal authentication management, not to Department ID and PIN.
●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Use at Least 1 Lowercase Character>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can restrict passwords so that only passwords which include at least one lowercase character can be
registered.
●This setting applies to personal authentication management, not to Department ID and PIN.
●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Use at Least 1 Digit>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can restrict passwords so that only passwords which include at least one number can be registered.
●This setting applies to personal authentication management, not to Department ID and PIN.
Settings/Registration
868

●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Use at Least 1 Symbol>
(Settings/Register) <Management Settings> <Security Settings> <Authentication/Password Settings>
<Password Settings>
You can restrict passwords so that only passwords which include at least one symbol can be registered.
●This setting applies to personal authentication management, not to Department ID and PIN.
●Password restriction settings are valid for passwords that are registered/edited after the restrictions
are set. When a password that is already registered exceeds the restrictions for these settings, a
screen prompting to change the password is displayed when user authentication is performed.
<Prohibit Use of Weak Encryption>
(Settings/Register) <Management Settings> <Security Settings> <Encryption Settings>
Select whether to restrict the use of weak encryption, or a key and certicate with weak encryption.
Management Functions(P. 1091)
●This setting applies to functions such as IPSec, TLS, Kerberos, S/MIME, wireless LAN, and SNMPv3.
●The machine may not be able to communicate with devices that only support weak encryption.
●Even if the use of weak encryption is restricted, it may be allowed depending on the certicate (root
certicate).
●For information on the algorithms prohibited when this setting is set to <On>, see System
Specications(P. 1084) .
<Format Encryption Method to FIPS 140-2>
(Settings/Register) <Management Settings> <Security Settings> <Encryption Settings>
Specify whether to make the function using encryption comply with FIPS 140-2.
●This setting is available for TLS and AddOn applications.
●This setting is only available for AddOn applications that use a FIPS provider.
●For information on the algorithms prohibited when this setting is set to <On>, see System
Specications(P. 1084) .
Settings/Registration
869
<Verify System at Startup>
(Settings/Register) <Management Settings> <Security Settings> <System Verication Settings>
You can set the machine to verify the integrity of the rmware and applications installed in the machine during
startup.
●This function restarts the machine not only when the setting is changed from <Off> to <On> but also
when <OK> is pressed without changing the setting from <On>. To avoid restarting the machine
without changing the setting from <On>, press <No> on the conrmation screen and then press
<Cancel> on the screen for this function.
●When this function is set to <On>, startup takes longer than when it is set to <Off> because system
verication is performed.
●The following events and results are recorded to the device management log. Managing the
Logs(P. 620)
Event Result
Firmware verication Success
Verication of the applications installed in the machine Failure
●If an error code is displayed on the screen when the machine is started with this setting set to <On>,
contact your dealer or service representative.
<McAfee Embedded Control>
(Settings/Register) <Management Settings> <Security Settings> <System Verication Settings>
When the machine is operating, the McAfee Embedded Control function is used to prevent unauthorized
program modication and the execution of unauthorized programs, for improved system reliability.
●To set this function to <On>, it is necessary to set <Verify System at Startup> to <On> in advance.
●When this function is set to <On>, startup takes longer than when it is set to <Off>.
Settings/Registration
870

Maintenance
Maintenance ..................................................................................................................................................... 872
Regular Cleaning ............................................................................................................................................... 874
Cleaning the Exterior .................................................................................................................................... 875
Cleaning the Platen Glass ............................................................................................................................. 876
Cleaning the Feeder ..................................................................................................................................... 878
Replacing the Toner Cartridge ......................................................................................................................... 881
Replacing the Waste Toner Container ............................................................................................................. 885
Replacement Parts ............................................................................................................................................ 888
Checking the Remaining Amount of Consumables ......................................................................................... 891
Adjusting Print Quality ..................................................................................................................................... 893
Adjusting Gradation ..................................................................................................................................... 894
Adjusting Density ......................................................................................................................................... 896
Correcting Color Mismatch ........................................................................................................................... 897
Automatically Adjusting Color Registration and Color Intensity ................................................................... 898
Making Colors More Vivid ............................................................................................................................. 900
Adjusting Image Size .................................................................................................................................... 901
Reducing Toner Used When Color Printing ................................................................................................... 902
Paper Type Management Settings ................................................................................................................... 903
Checking the Number of Pages for Copy/Print/Fax/Scan ............................................................................... 908
Printing Reports and Lists ................................................................................................................................ 909
Maintenance
871
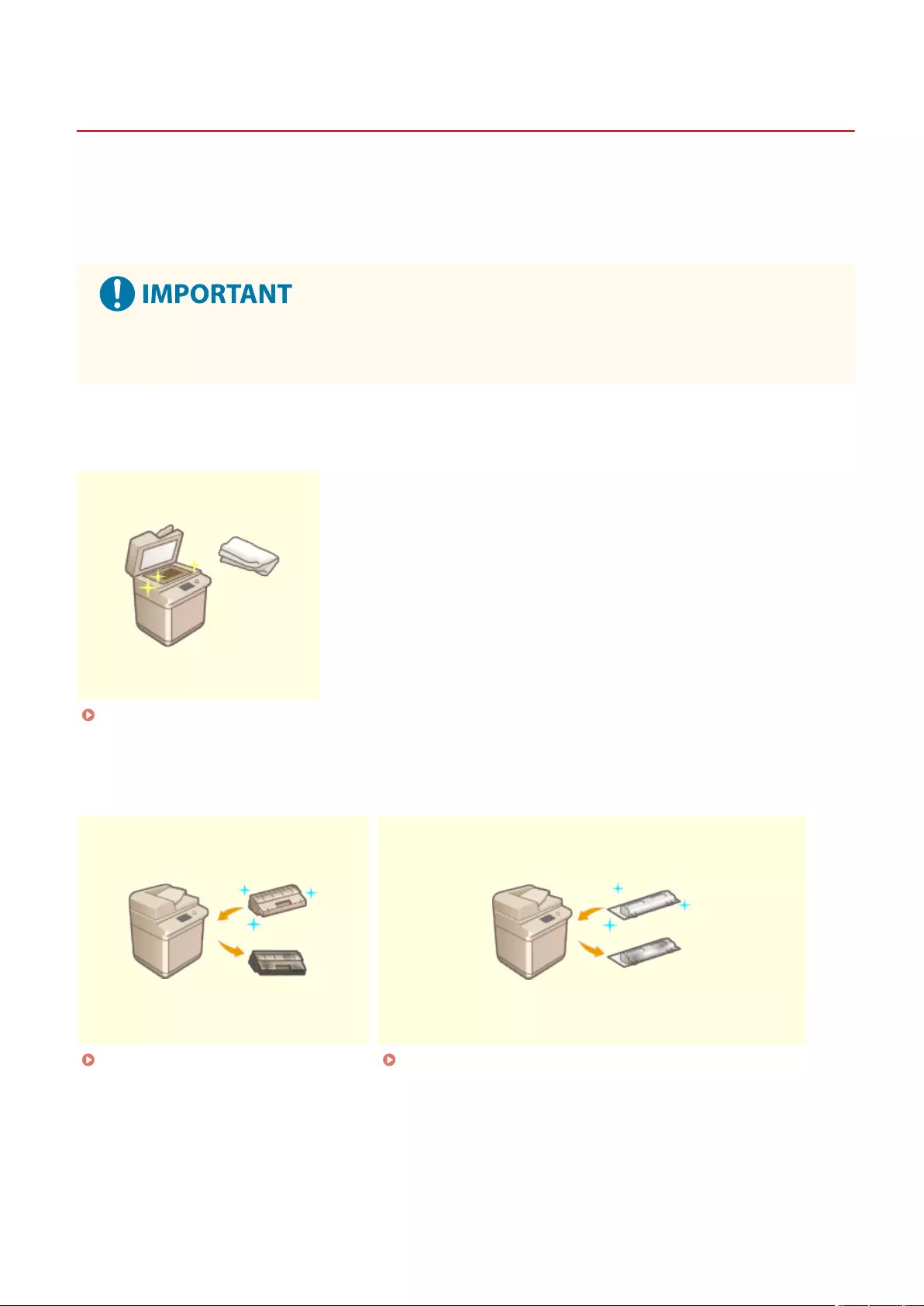
Maintenance
72JY-0FW
PMW-MNTC
This section describes the maintenance and management of the machine, such as regular cleaning and the
replacement of consumables. It also describes the maintenance service provided by Canon. For information on
precautions to take during maintenance, see the Important Safety Instructions.
●The minimum holding period for performance parts for repairs and toner cartridges is seven (7) years after
production of the machine model is discontinued.
◼Basic Cleaning
Regular Cleaning(P. 874)
◼Replacing Consumables
Replacing the Toner Cartridge(P. 881) Replacing the Waste Toner Container(P. 885)
Maintenance
872
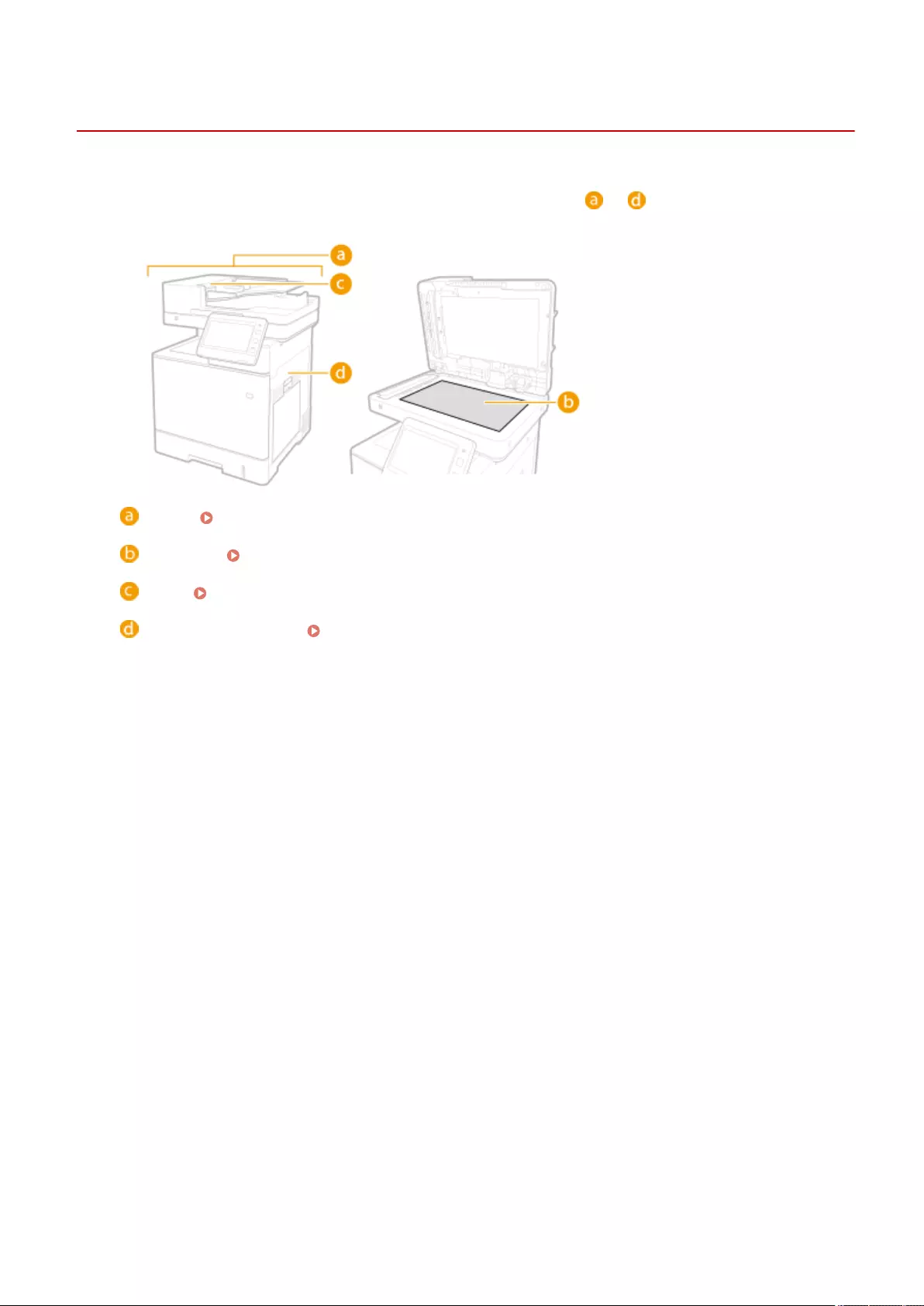
Regular Cleaning
72JY-0FX
It is recommended that you periodically clean the machine to prevent loss of print quality and enable you to use the
machine comfortably and safely. Clean the machine in the order indicated by to below.
Exterior Cleaning the Exterior(P. 875)
Platen glass Cleaning the Platen Glass(P. 876)
Feeder Cleaning the Feeder(P. 878)
Pressure roller for xing <Clean Pressure Roller for Fixing>(P. 805)
Maintenance
874

Cleaning the Exterior
72JY-0FY
Periodically wipe the surface of the machine to keep it clean.
1Turn the power OFF, and remove the power plug from the power outlet.
Turning OFF the Machine(P. 96)
●Check the operation status of the machine before turning the power OFF. You can turn the power OFF
even if the machine is executing an operation, but this may cause the operation to be interrupted or data
to become damaged.
2Wipe the surface of the machine.
●Wet a soft cloth with water or diluted mild detergent, wring the cloth out well, and wipe the machine.
●Wait until the moisture has completely dried before proceeding to the next step.
3Insert the power plug into the power outlet, and turn the power ON.
Turning ON the Machine(P. 95)
Maintenance
875

Cleaning the Platen Glass
72JY-0H0
If the platen glass is dirty, originals may not be scanned clearly, or the size of the original may not be detected clearly.
1Turn the power OFF, and remove the power plug from the power outlet.
Turning OFF the Machine(P. 96)
●Check the operation status of the machine before turning the power OFF. You can turn the power OFF
even if the machine is executing an operation, but this may cause the operation to be interrupted or data
to become damaged.
2Open the feeder.
3Wipe the reverse side of the feeder and the platen glass.
Wipe the platen glass.
●Wipe the platen glass with the included cleaning cloth.
●If the cleaning sheet is dirty, rinse it in water and dry it before using it.
Wipe the reverse side of the feeder.
●If you cannot remove the dirt, wet a soft cloth with water and wring it out well, then wipe the
reverse side of the feeder with it. Afterwards, wipe the reverse side of the feeder with a soft
and dry cloth. Wait until the moisture has completely dried before proceeding to the next
step.
Maintenance
876

If you cannot remove the dirt
●Wet a soft cloth with mild detergent and wring it out well, then wipe the machine with it. Afterwards, wipe
the machine with a soft and dry cloth.
4Gently close the feeder.
5Insert the power plug into the power outlet, and turn the power ON.
Turning ON the Machine(P. 95)
Maintenance
877
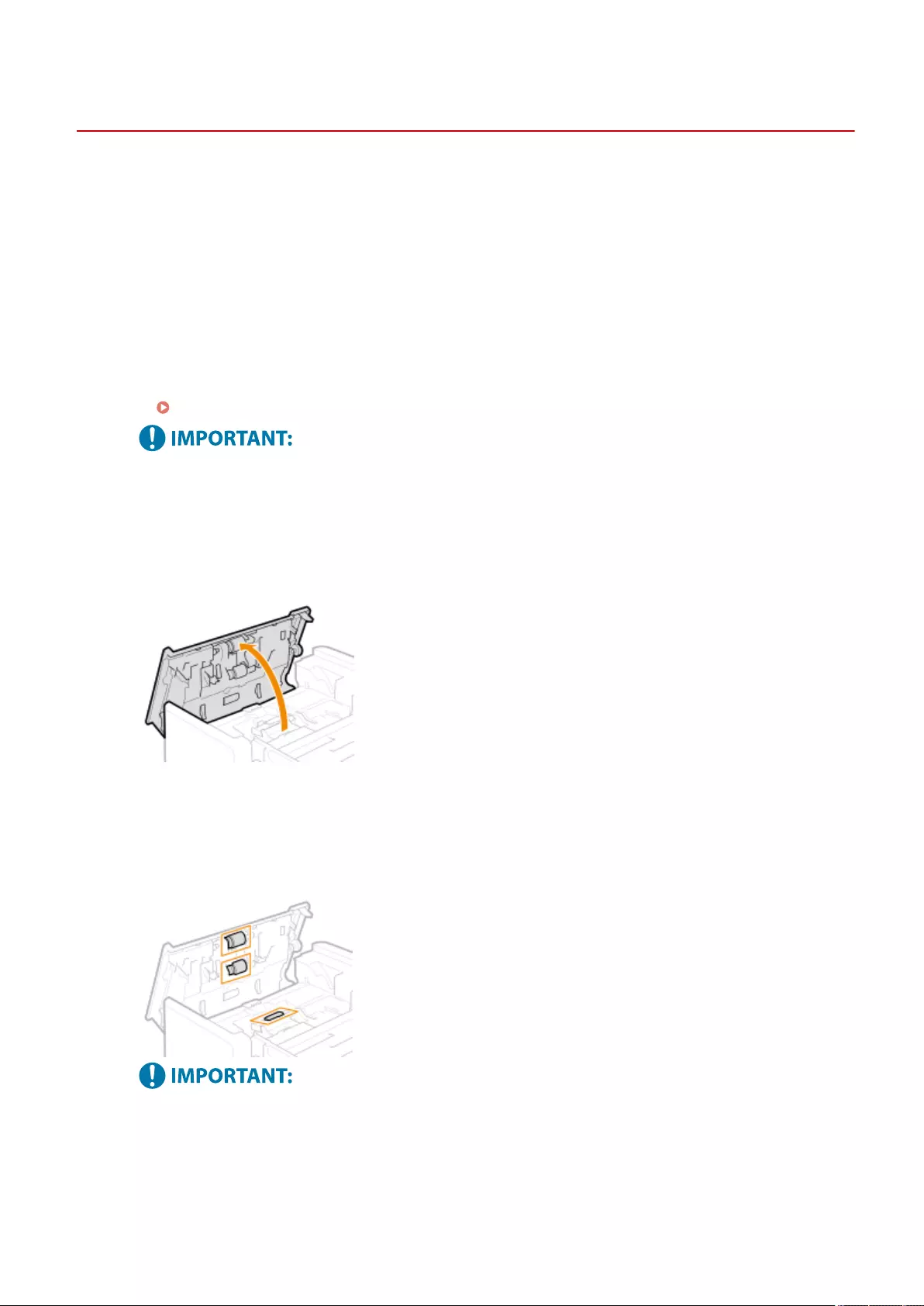
Cleaning the Feeder
72JY-0H1
If any of the following problems occurs when the document is scanned from the feeder, then perform feeder
cleaning.
●The document cannot be scanned clearly
●The size of the document cannot be detected correctly
●The document gets dirty during scanning
●Paper jam occurs frequently
1Turn the power OFF, and remove the power plug from the power outlet.
Turning OFF the Machine(P. 96)
●Check the operation status of the machine before turning the power OFF. You can turn the power OFF
even if the machine is executing an operation, but this may cause the operation to be interrupted or data
to become damaged.
2Open the feeder cover.
3Clean the rollers inside the feeder cover.
●Wet a soft cloth with water and wring it out well, then wipe the rollers. Afterwards, wipe the rollers with a soft
and dry cloth.
●If the rollers and surrounding areas are very dirty, clean them out. To do this, wet a cloth with water and
wring it out well, then wipe the dirty areas. Afterwards, wipe the areas with a soft and dry cloth.
Maintenance
878
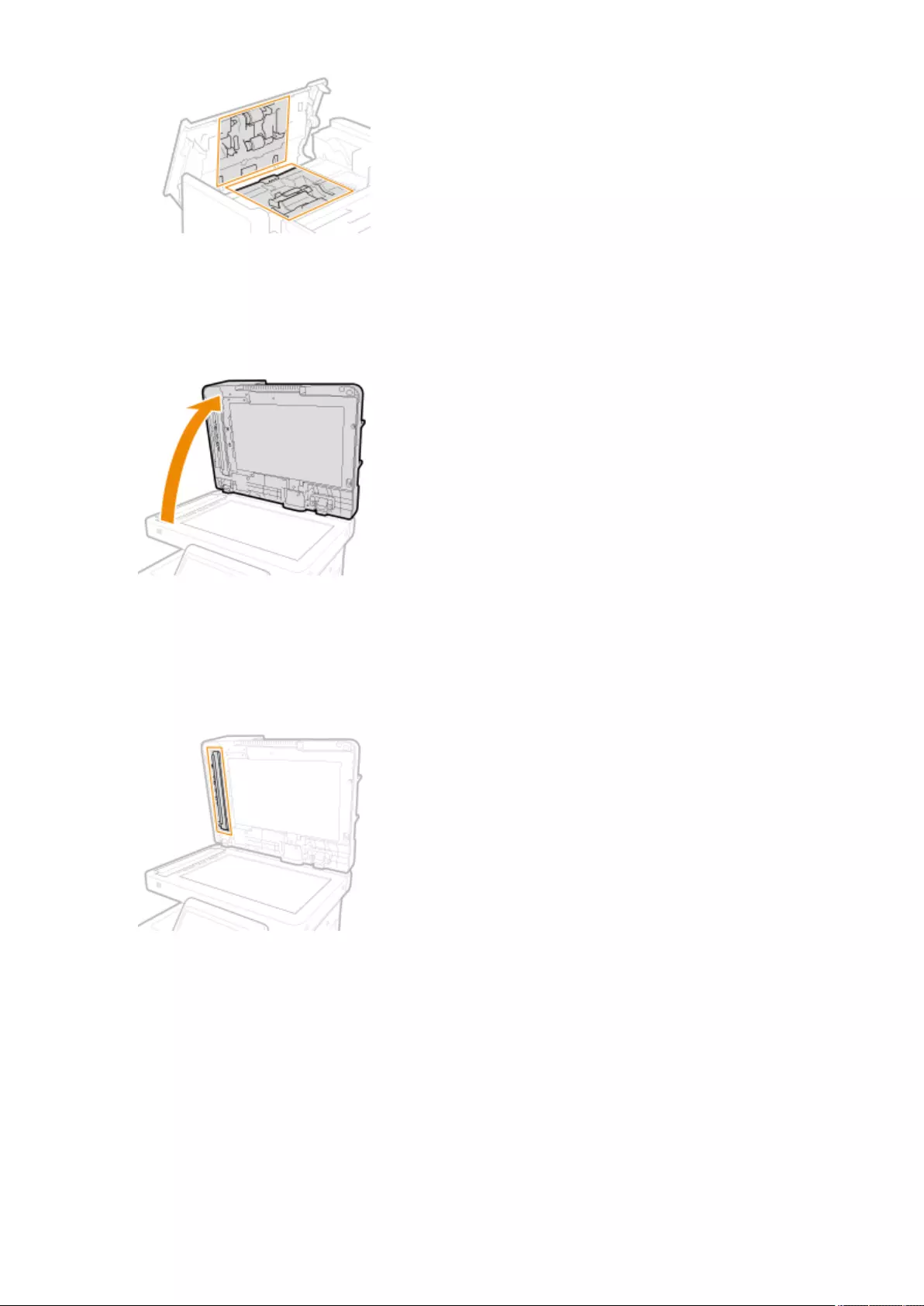
4Gently close the feeder cover.
5Open the feeder.
6Wipe the document feed scanning area on the feeder side.
●Wipe the thin glass strip.
●Wipe the area with the included cleaning cloth. If you cannot remove the dirt, wet a soft cloth with water and
wring it out well, then wipe the machine with it. Afterwards, wipe the machine with a soft and dry cloth.
●Wait until the moisture has completely dried before proceeding to the next step.
7Wipe the document feed scanning area on the platen glass side.
●Wipe the thin glass strip.
●Wipe the area with the included cleaning cloth. If you cannot remove the dirt, wet a soft cloth with water and
wring it out well, then wipe the machine with it. Afterwards, wipe the machine with a soft and dry cloth.
Maintenance
879
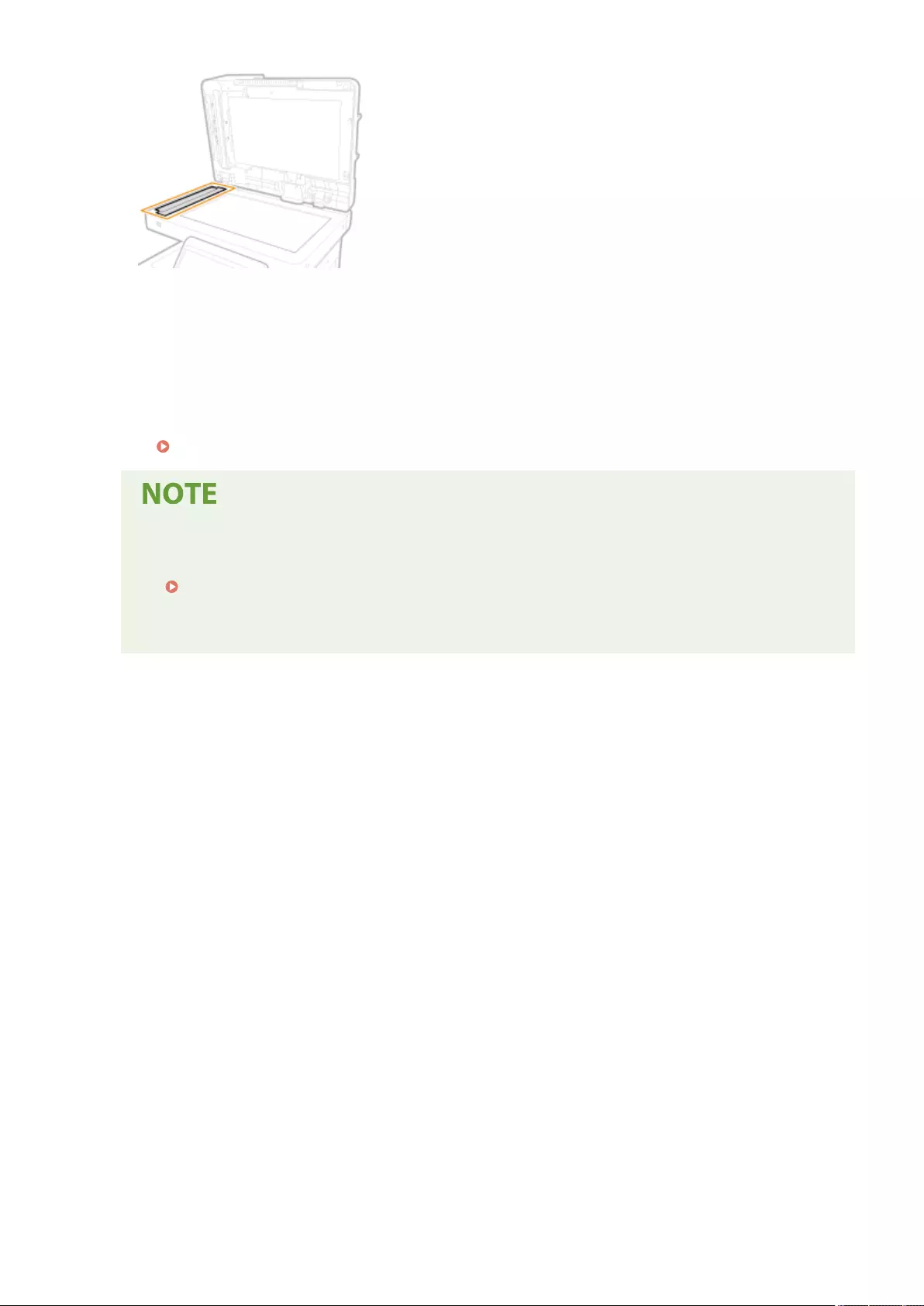
●Wait until the moisture has completely dried before proceeding to the next step.
8Gently close the feeder.
9Insert the power plug into the power outlet, and turn the power ON.
Turning ON the Machine(P. 95)
If streaks still appear on the originals or paper after the feeder cleaning operation
●Load about 10 sheets of A4 size paper in the feeder and perform the following procedure to execute
<Clean Feeder>(P. 805) . When a message indicating that cleaning is complete is displayed, try
using the feeder to copy an original to check if the problem has been resolved.
●It takes approximately 10 seconds to clean the feeder.
Maintenance
880
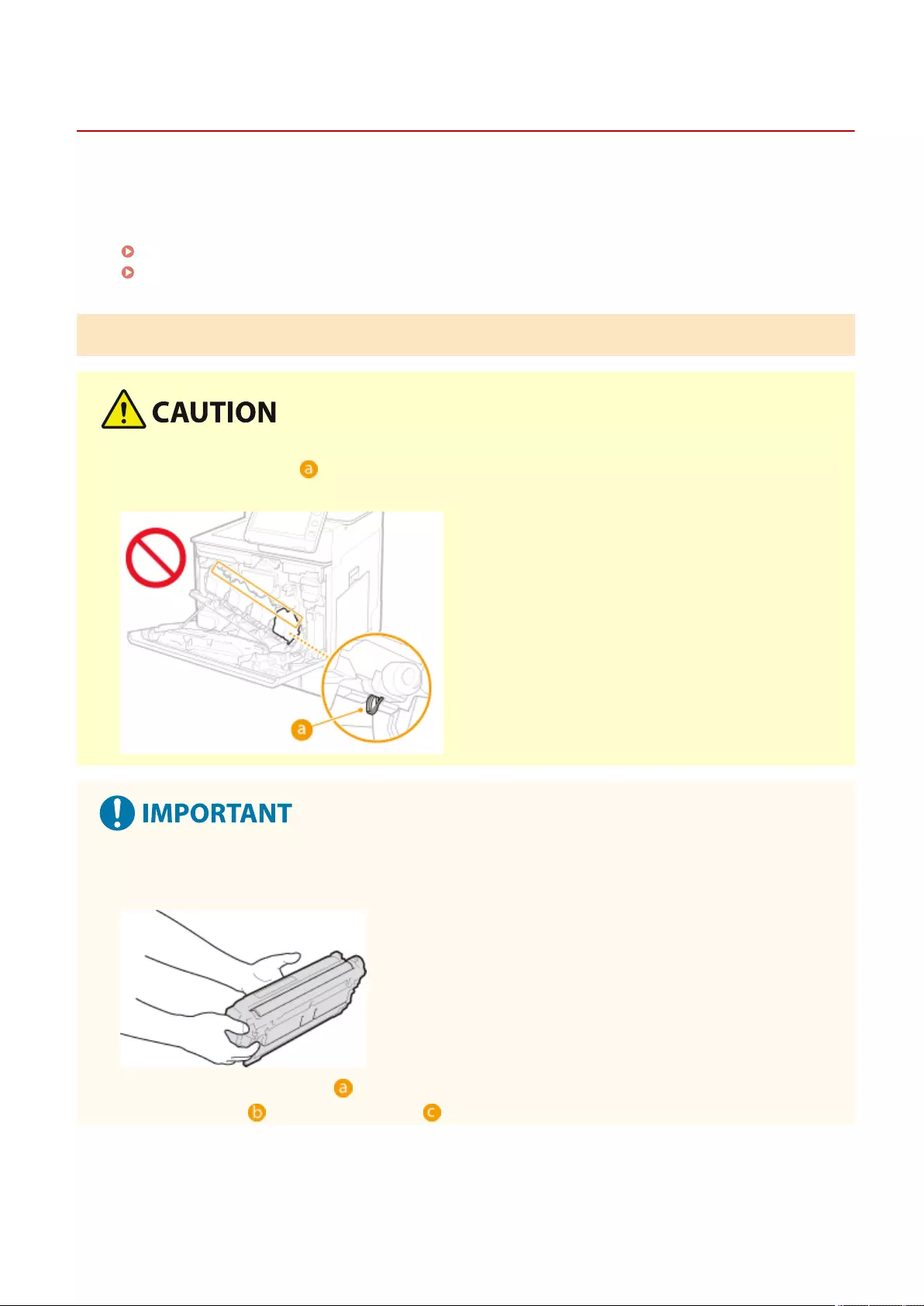
Replacing the Toner Cartridge
72JY-0H2
When toner starts running low or has run out, a message is displayed prompting you to prepare a new toner cartridge
or perform toner cartridge replacement. Prepare a new toner cartridge or perform toner cartridge replacement
according to the displayed message.
Cautions When Replacing the Toner Cartridge(P. 881)
Procedure for Replacing the Toner Cartridge(P. 882)
Cautions When Replacing the Toner Cartridge
●Do not touch the contacts ( ) inside the machine. Doing so may result in damage to the machine.If you
cannot remove the paper, contact your dealer or service representative.
●Do not replace toner cartridges until the message prompting you to do so appears.
●Be sure to hold the toner cartridge using the handle.
●To avoid scratching the surface ( ) of the drum inside the machine or exposing it to light. Do not touch the
electrical contacts ( ) or the toner memory ( ).
Maintenance
881
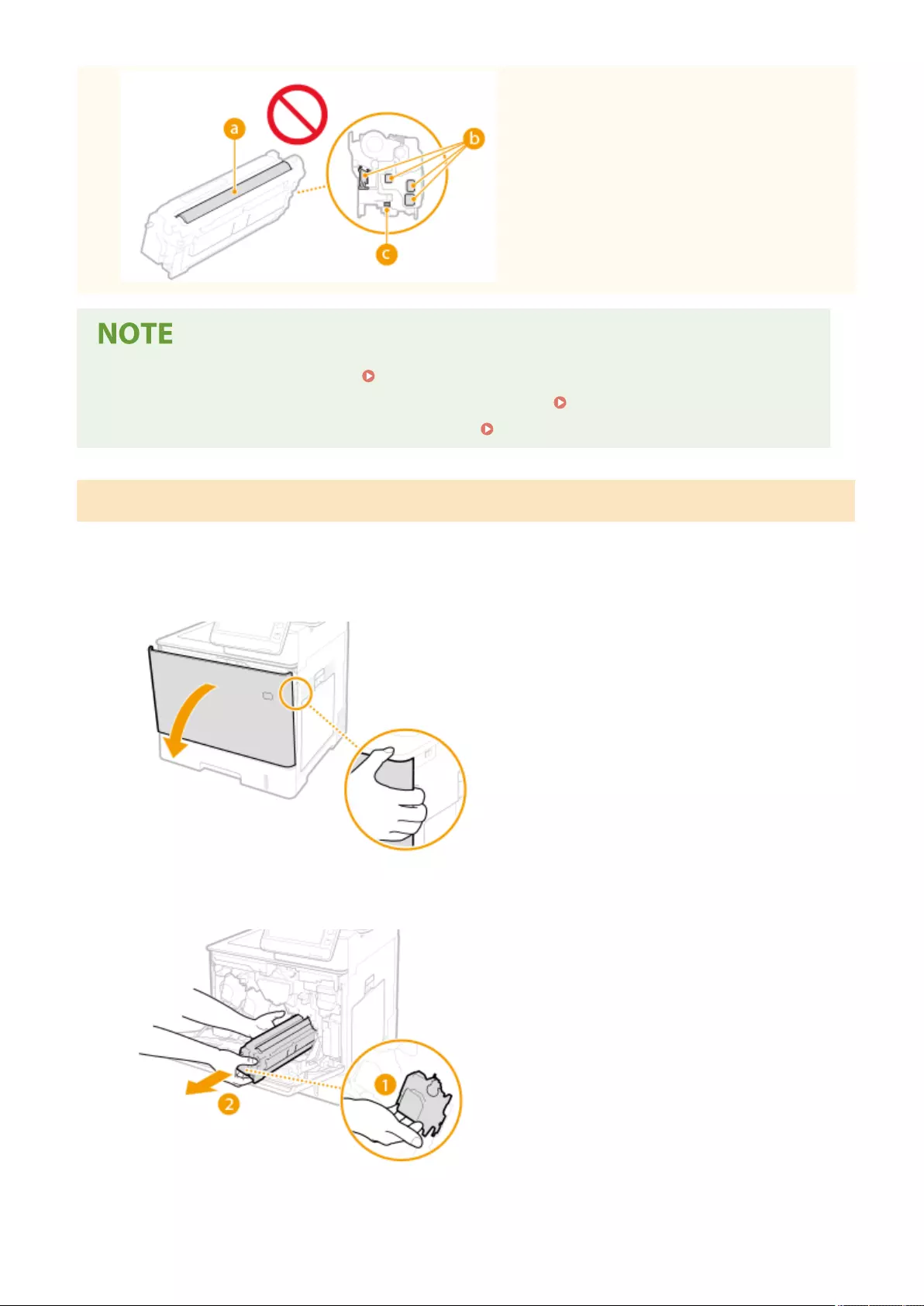
●For details about each message, see Countermeasures for Each Message(P. 943) .
●For information on the product numbers for toner cartridges, see Consumables(P. 888) .
●You can check the current amount of toner remaining. Checking the Remaining Toner Level(P. 891)
Procedure for Replacing the Toner Cartridge
When replacing toner cartridges, follow the instructions shown in the video along with those written below.
1Open the front cover.
2Pull out the toner cartridge.
3Remove the replacement toner cartridge from the protective case.
Maintenance
882
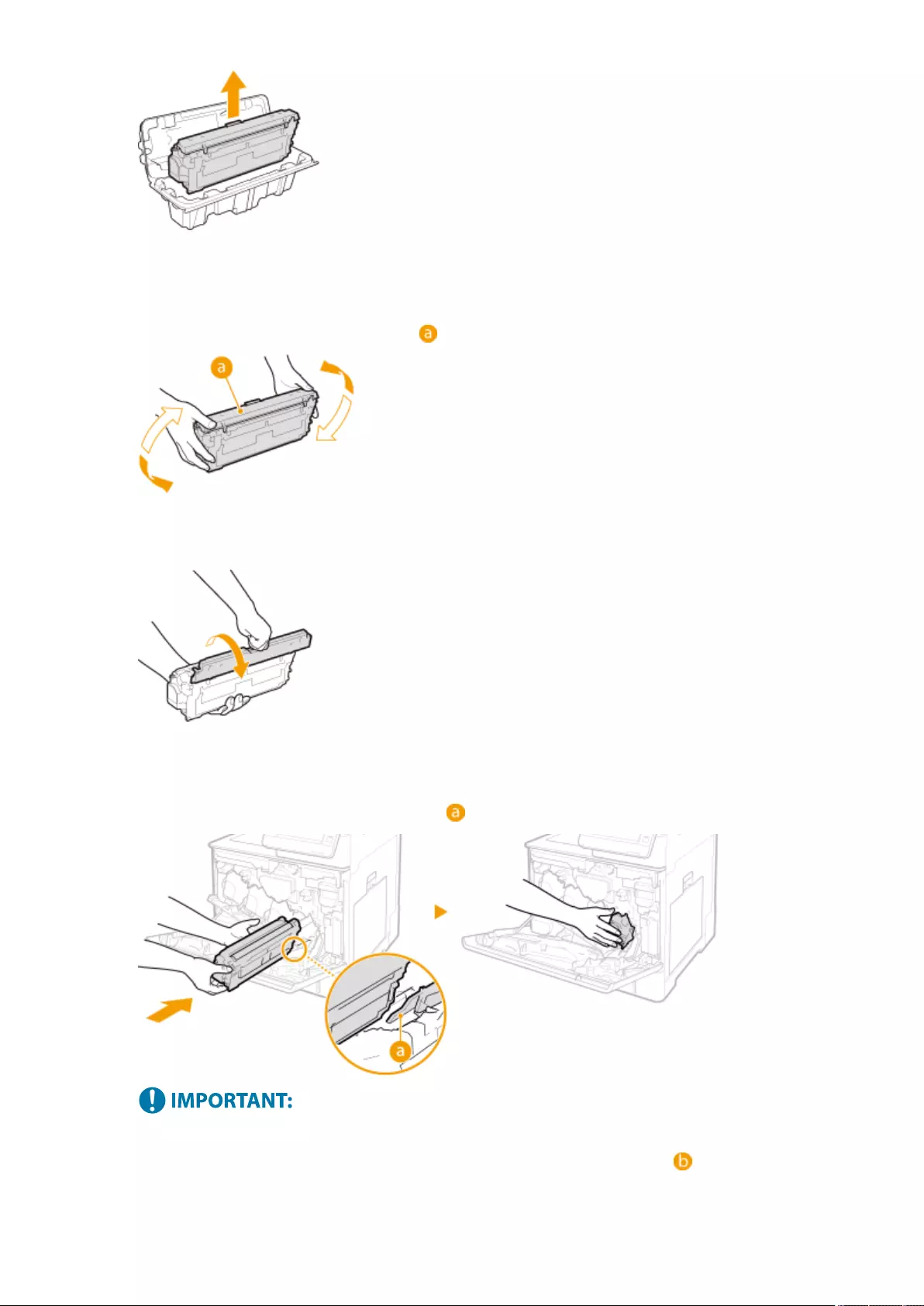
4Shake the toner cartridge ve or six times as shown below to evenly distribute the
toner inside the cartridge, and then place it on a at surface.
●De not remove the drum protective cover ( ) in this step.
5Remove the drum protective cover.
6Install the toner cartridge.
●Align the toner cartridge with the toner guide ( ) and push it into the slot until it stops.
●Be careful that the drum portion does not get hit against the mouth of the slot.
●Place the toner cartridge into the slot marked with the appropriate color label ( ).
Maintenance
883

7Close the front cover.
Maintenance
884
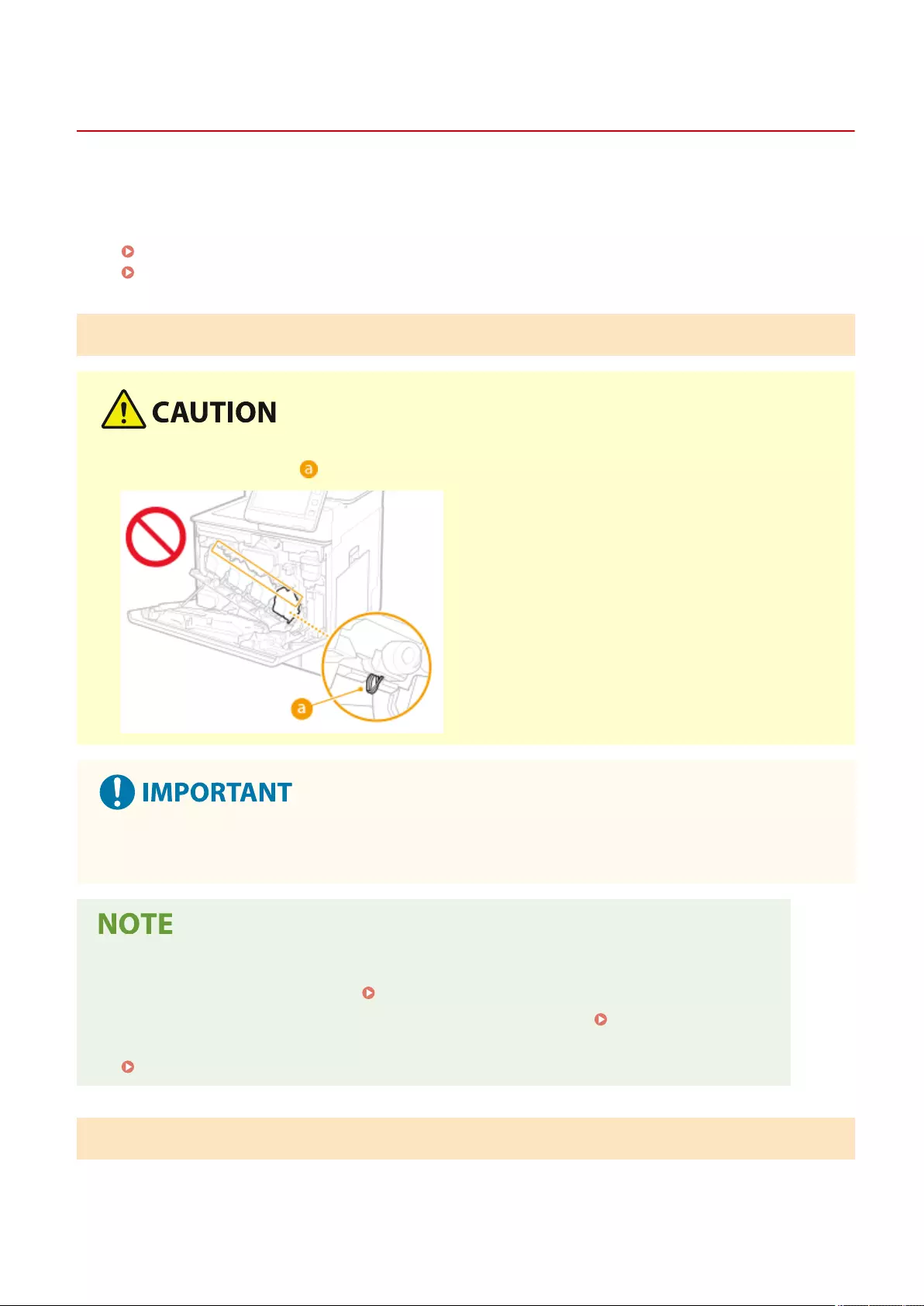
Replacing the Waste Toner Container
72JY-0H3
When the waste toner container is almost full or completely full, a message is displayed prompting you to prepare a
new waste toner container or perform waste toner container replacement. Prepare a new waste toner container or
perform waste toner container replacement according to the displayed message.
Cautions When Replacing the Waste Toner Container(P. 885)
Procedure for Replacing the Waste Toner Container(P. 885)
Cautions When Replacing the Waste Toner Container
●Do not touch the contacts ( ) inside the machine. Doing so may result in damage to the machine.
●Do not replace the waste toner container before the message prompting you to replace it appears on the
touch panel display.
●The waste toner container is a container for collecting unused toner that remains when printing.
●For details about each message, see Countermeasures for Each Message(P. 943) .
●For information on the model number of the waste toner container, see Consumables(P. 888) .
●You can check the current amount of space remaining in the waste toner container.
Checking the Space Remaining in the Waste Toner Container(P. 891)
Procedure for Replacing the Waste Toner Container
When replacing the waste toner container, the procedure is also displayed on the screen. Check the information
displayed on the screen in addition to the following procedure.
Maintenance
885
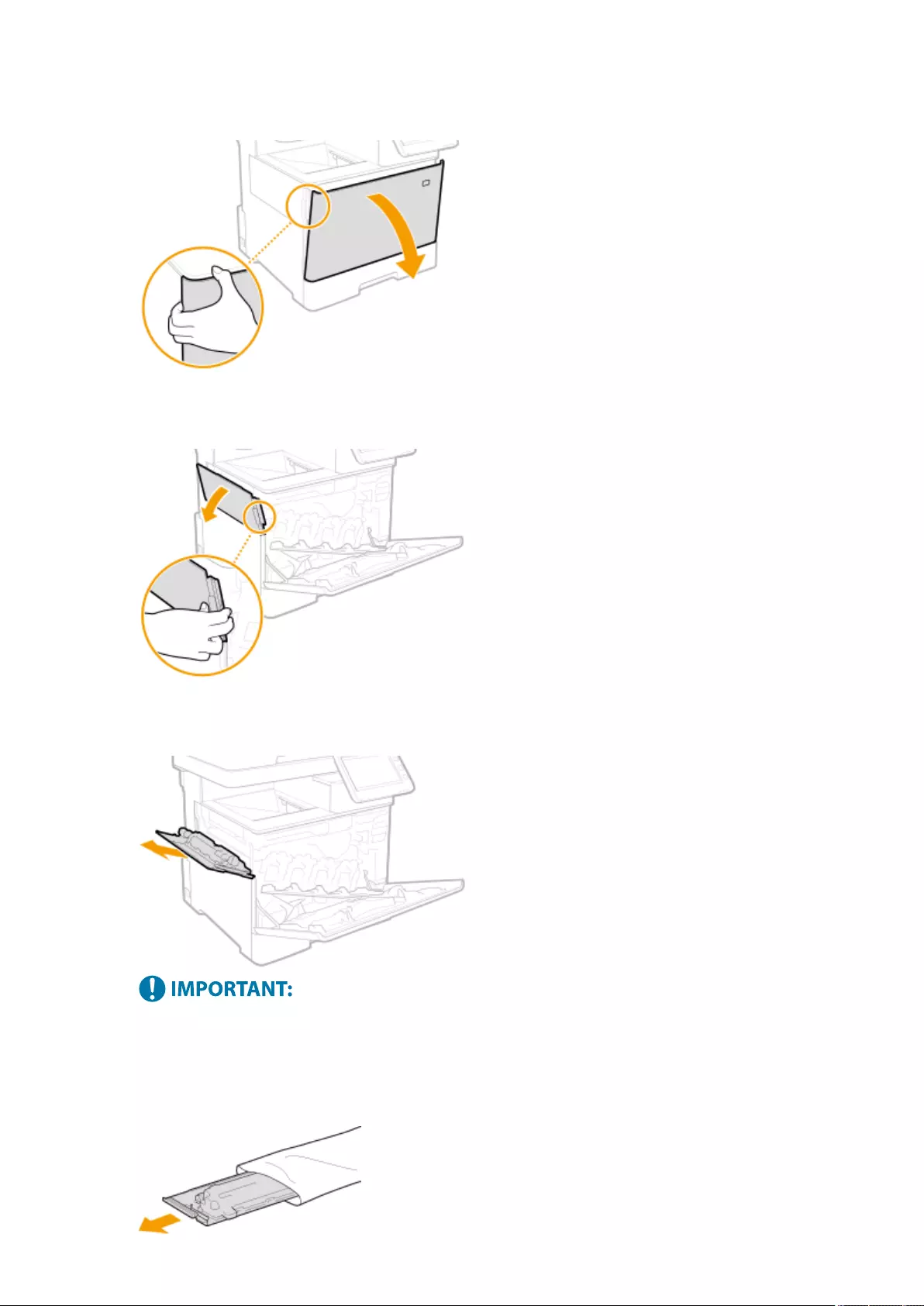
1Open the front cover.
2Open the left cover.
3Remove the waster toner container together with the left cover.
●Be careful not to tilt the container. Tilting the waster toner container will result in spilling of collected
toner.
4Remove the waste toner container from the protective case.
Maintenance
886
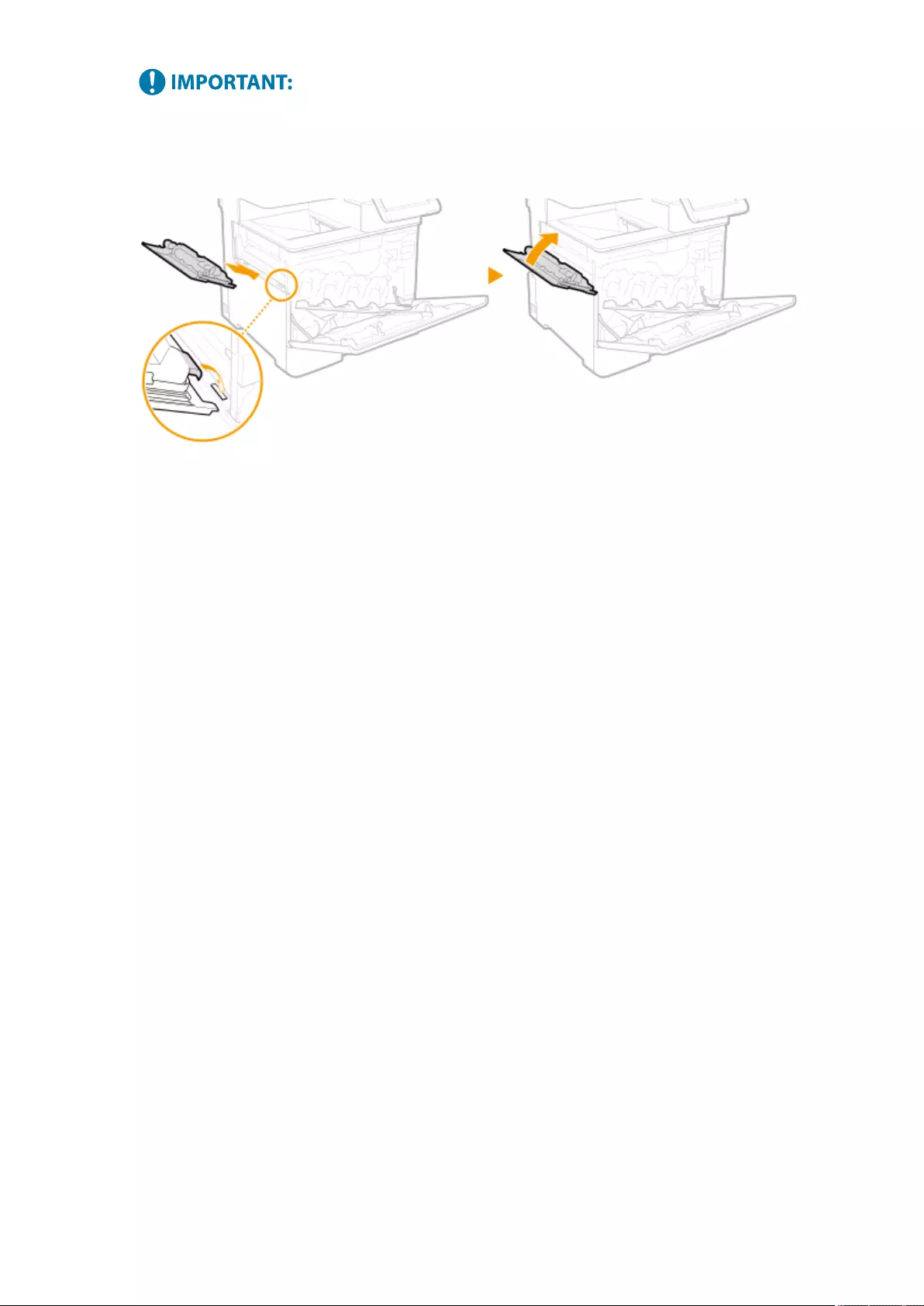
●Do not disassemble or modify the waste toner container.
5Install the new waste toner container and close the left cover.
6Close the front cover.
Maintenance
887
Replacement Parts
72JY-0H4
This section describes the replacement parts (consumables/consumable parts) used by the machine. Follow the
precautions when handling and storing the replacement parts.
Genuine Consumables
Canon continuously develops technology innovations in Canon manufactured Toner,
Cartridge, and Parts, specically designed for use in Canon Multi-Functional machines.
Experience the benets of optimal print performance, print volume and high quality
outputs, achieved through Canon's new advanced technologies. Therefore, the use of
Canon genuine consumables is recommended for your Canon Multi-Functional machines.
Consumables(P. 888)
Consumable Parts(P. 889)
●Depending on the installation environment, printing paper size, or document type, you may need to replace
consumables before the end of the estimated lifetime.
●To maintain print quality, the machine performs automatic calibration in accordance with changes in the
environmental conditions. The machine may also perform automatic calibration when it is turned ON or
recovers from sleep mode. Calibration uses the toner, and accordingly it may result in a decrease of lifetime
of the toner cartridges.
●The color toner cartridges are used even in black and white printing. Therefore, much use of black and white
printing may also result in decrease in the remaining number of printable pages for each color.
●You can check the current amount of replacement parts remaining.
Checking the Remaining Amount of Consumables(P. 891)
Consumables
◼Toner Cartridge for Replacement
Model name Genuine Canon toner Weight
imageRUNNER C1538iF
imageRUNNER C1533iF
●Canon Toner T10 Black
●Canon Toner T10 Cyan
●Canon Toner T10 Magenta
●Canon Toner T10 Yellow
●Black: Approx. 1.0 kg
●Cyan, Magenta, Yellow: Approx. 0.9 kg
●Canon Toner T10L Black
●Canon Toner T10L Cyan
●Canon Toner T10L Magenta
●Canon Toner T10L Yellow
●Approx. 0.9 kg
Maintenance
888
Storing toner cartridges in an improper location or environment may cause problems such as data loss.
●Store toner cartridges in the following conditions:
- Storage temperature range: 0-35ºC
- Storage humidity range: 35% to 85% RH (relative humidity, condensation-free)*
*Even within the approved storage humidity range, water droplets (condensation) may develop inside the toner cartridge if
the temperatures inside and outside the toner cartridge differ. Condensation will adversely affect the print quality.
●Store unopened until immediately prior to use.
●Do not store toner cartridges upright or upside down.
●Do not store toner cartridges in the following locations:
- Locations exposed to open ames
- Locations exposed to direct sunlight or bright light for ve minutes or more
- Locations exposed to excessively salty air
- Locations heavily exposed to corrosive gases (e.g. aerosol sprays or ammonia)
- Very hot and/or humid locations
- Locations subject to dramatic changes in temperature and humidity likely to cause condensation
- Very dusty locations
- Locations within the reach of children
●Store the packaging material safely for future use. It will be needed for situations such as storing the
machine with the toner cartridges removed.
●Canon reserves the right to reposition, reshape, add or remove packaging material without notice.
Be careful of counterfeit toners
●Please be aware that there are counterfeit Canon toners in the marketplace. Use of counterfeit toner may
result in poor print quality or machine performance. Canon is not responsible for any malfunction, accident
or damage caused by the use of counterfeit toner.
For more information, see global.canon/ctc.
●For information on the collection of used toner cartridges, see the Notice(P. 1033) .
Consumable Parts
◼Waste Toner Container
Make sure to use the dedicated waste toner container for this machine.
Maintenance
889

●Waste Toner Box WT-B1
The average number of pages that can be printed per waste toner container is 54,000 sheets
(paper size assumed to be A4 or Letter).
●When replacing the waste toner container Replacing the Waste Toner Container(P. 885)
◼ADF Maintenance Kit
Follow the instructions provided to your dealer or service representative.
●DR-208
Maintenance
890
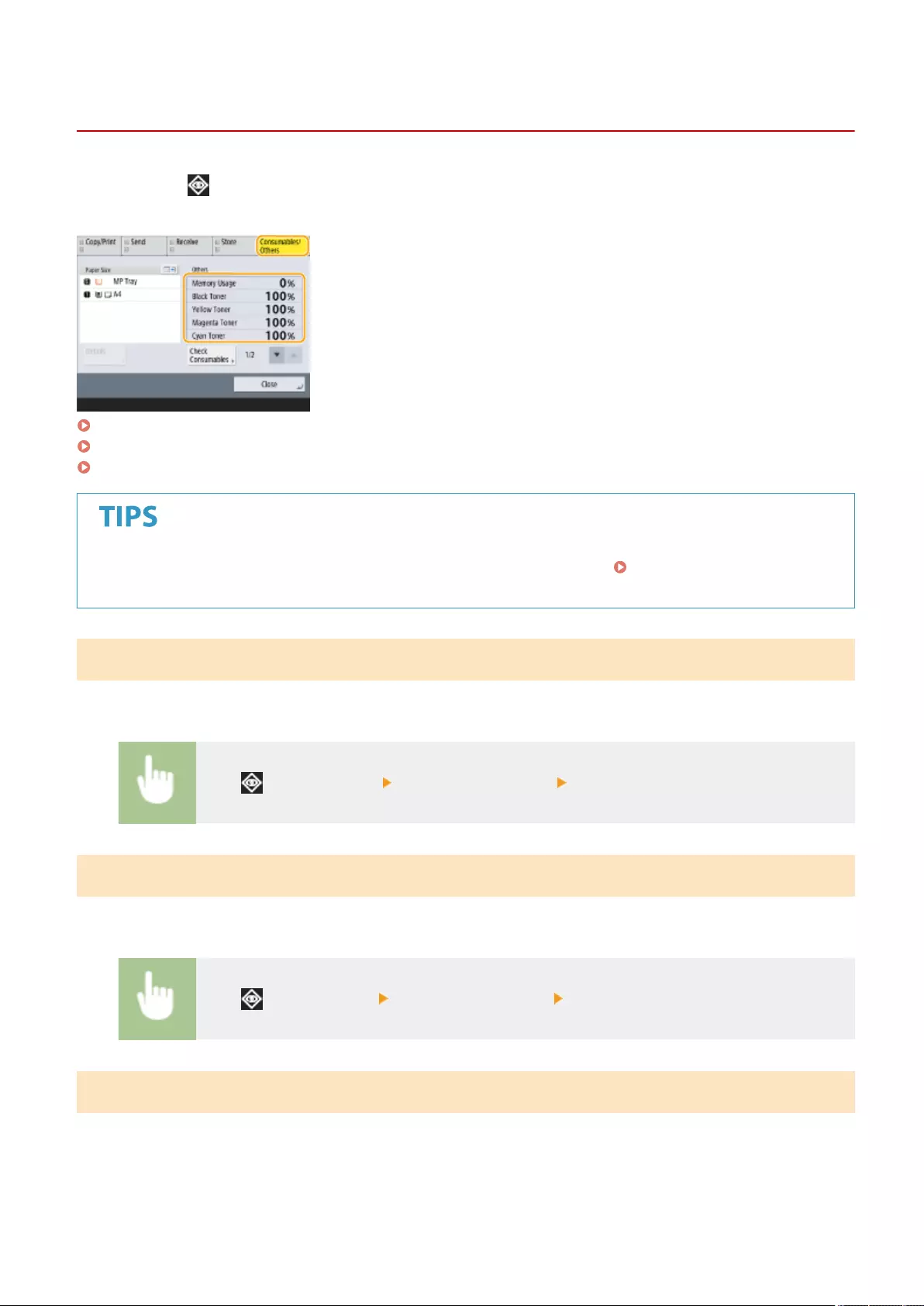
Checking the Remaining Amount of Consumables
72JY-0H5
When you press (Status Monitor), the Status Monitor screen is displayed, allowing you to check the toner level or
other status indications.
Checking the Remaining Toner Level(P. 891)
Checking the Space Remaining in the Waste Toner Container(P. 891)
Checking the Detailed Status of Consumables(P. 891)
●You can check the remaining amount of consumables from the Remote UI. Checking the Machine
Status(P. 590)
Checking the Remaining Toner Level
It is recommended that you check the remaining toner level before printing a large job to determine whether or not to
prepare a new toner cartridge.
Press (Status Monitor) <Consumables/Others> check the remaining toner level.
Checking the Space Remaining in the Waste Toner Container
It is recommended that you check the space remaining in the waste toner container before performing a large job to
determine whether or not to prepare a new waste toner container.
Press (Status Monitor) <Consumables/Others> check <Waste Toner>.
Checking the Detailed Status of Consumables
Check the detailed status of consumables.
Maintenance
891
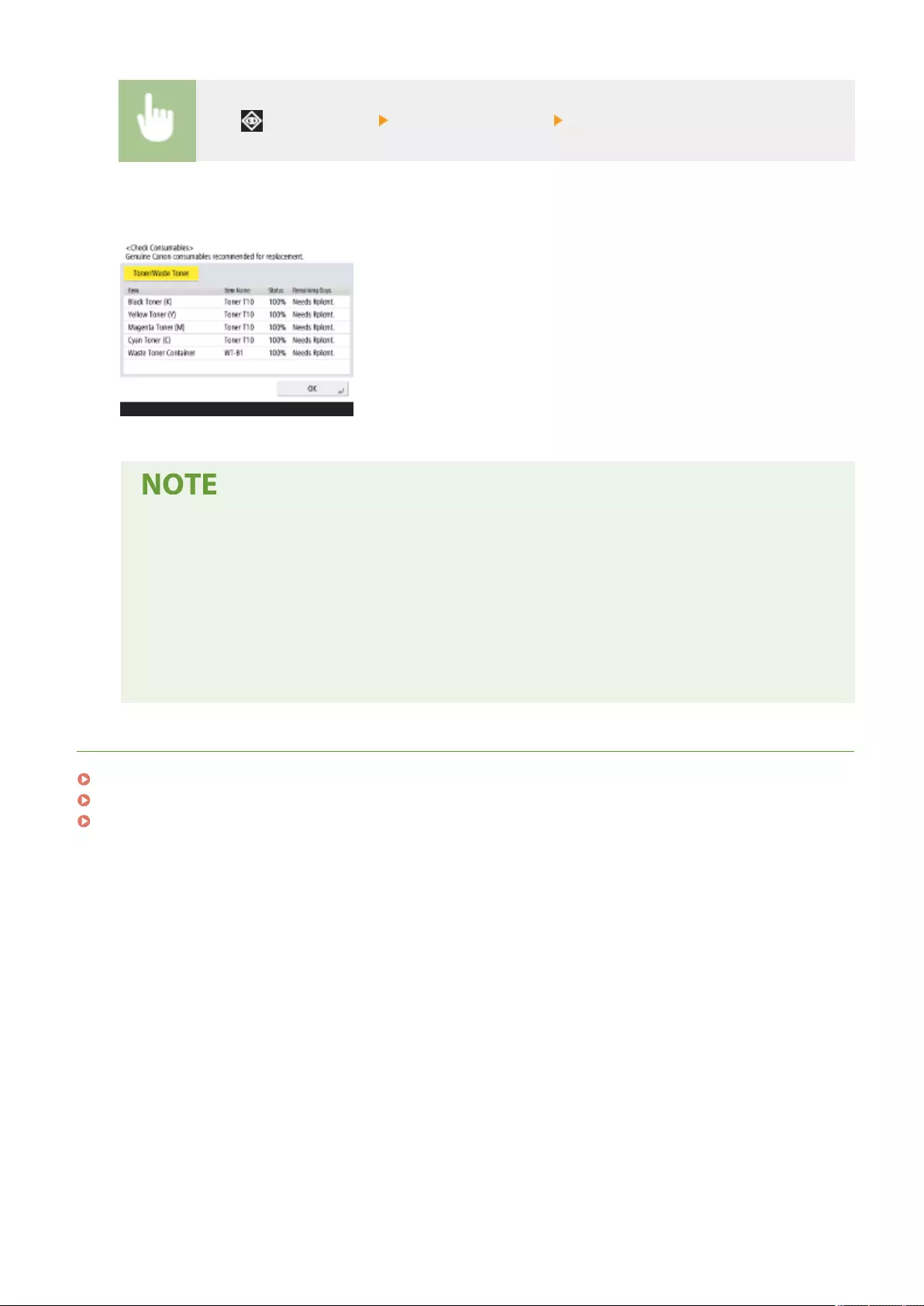
Press (Status Monitor) <Consumables/Others> <Check Consumables>.
◼<Toner/Waste Toner> Screen
<Item>, <Item Name>, <Status>, and <Remaining Days> are displayed.
●<Remaining Days> displays the expected number of days remaining until replacement is required,
based on past usage.
●Even if <Needs Rplcmt.> is displayed in <Remaining Days>, do not perform replacement until a
message prompting you to replace consumables is displayed in the status display area (at the bottom
of the touch panel display).
●The measurement for <Remaining Days> does not complete for a while after the machine starts
operation, and <1 year or more> is displayed during this time. The remaining days displayed after this
time may be extremely small temporarily.
LINKS
Replacing the Toner Cartridge(P. 881)
Replacing the Waste Toner Container(P. 885)
Countermeasures for Each Message(P. 943)
Maintenance
892

Adjusting Print Quality
72JY-0H6
Adjust the settings below if printing results are not satisfactory.
◼Gradation Adjustment
If color gradation reproducibility has become so poor that the printed gradation differs markedly from the print
data, make adjustments to improve color gradation reproducibility.
Adjusting Gradation(P. 894)
◼Density Correction
If the density of the printing is signicantly different from the original document, this adjusts the scan density
to be closer to the original.
Adjusting Density(P. 896)
◼Color Mismatch Correction
If the colors of printing run or blur, color mismatch (color misregistration) may have occurred. The problem may
be improved by performing color mismatch correction.
Correcting Color Mismatch(P. 897)
◼Automatically Adjusting Color Registration and Color Intensity
Automatic adjustment (calibration) is performed in order to prevent color misregistration and ensure that the
original color intensity is correctly reproduced.
Automatically Adjusting Color Registration and Color Intensity(P. 898)
◼Vividness Setting
You can increase the saturation of colors for color printing.
Making Colors More Vivid(P. 900)
◼Image Size Adjustment
If the size of the image copied is slightly different from the original, ne adjustment is performed so that the
printed size more closely matches the size of the original.
Adjusting Image Size(P. 901)
◼Toner Amount Reduction
You can prevent excessive toner from being xed onto paper to reduce print failure such as poor toner xing or
bleed-through.
Reducing Toner Used When Color Printing(P. 902)
Maintenance
893

Adjusting Gradation
72JY-0H7
0UUY-0J6 0UW1-0HR 0YRY-0HL 0X7F-0L6 0X7H-0KR 1100-0HU 0X6E-0L6 0X6W-0KR 10XJ-0HU 0X7C-0L6 0X7A-0KR 1106-0HU 0WXY-0L7 0X7E-0KR 10YY-0HU 10H3-0HR 0WR6-0LC 0WR7-0KY 108A-0HS 1116-0HS 10H4-0HR 0WR5-0LC 0WR8-0KY 0YWJ-0JK 0YWH-0KR 0YWR-0JC 0YWK-0KR 0YWE-0L6 0YWF-0KR 0YAS-0HU
If the gradation of the printing result is signicantly different from the original document when you copy or print an
image, you can perform adjustment (calibration) to correct the gradation.
●Frequently performing calibration may affect the life of the toner cartridge.
●Performing calibration when the toner level is low may adversely affect the color balance. If this symptom
occurs, it is recommended that you replace the toner cartridge that is low. Checking the Remaining
Toner Level(P. 891)
●Automatic calibration is performed according to changes in the status and environment of the machine.
Full Adjustment
Correct the gradation of an image accurately and optimize reproducibility during printing. Optimized information will
be retained until the next accurate correction.
●You can use the following paper sizes/types.
-Size: A4, LTR
- Type: Thin, Plain 1 to 3, Recycled 1 to 2
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Auto Adjust Gradation> <Full Adjust>.
2Select the paper and press <OK>.
3Press <Start Printing>.
➠A test page is printed.
Maintenance
894

4Place the test page on the platen glass.
●Place the test page sheet in the machine in a manner that its side on which the four color stripes are printed
faces down and the black stripe faces toward the back side of the machine.
5Close the feeder and press <Start Scanning>.
➠The machine starts scanning the test page.
6Open the feeder, and remove the test page.
7Repeat steps 3 to 6.
●To complete the adjustment, print the test page two times, and scan it each time it is printed.
Quick Adjustment
This adjustment maintains the optimized status that was acquired by <Full Adjust>. If the result of this adjustment is
not satisfactory, perform <Full Adjust>.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Auto Adjust Gradation> <Quick Adjust>.
2Press <Start>.
Maintenance
895
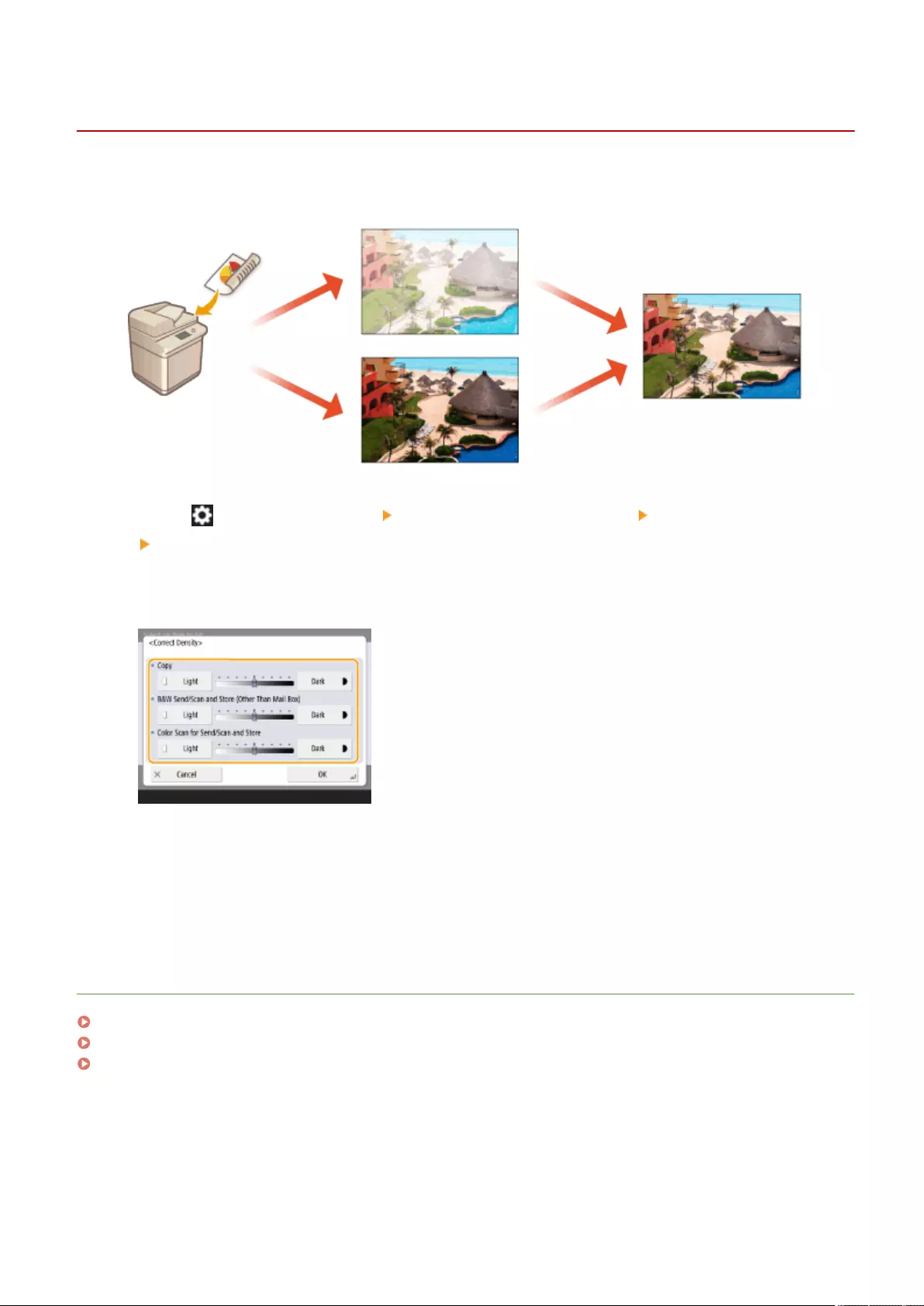
Adjusting Density
72JY-0H8
If the density of the printing is signicantly different from the original document, follow the procedure below to adjust
the scan density to be closer to the original.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Correct Density>.
2Adjust the density.
●When set to the <Dark> side, areas printed with the maximum density are increased. When set to the <Light>
side, lled areas, text, and lines may be printed like halftones with dots missing. This setting should mainly
be used to adjust the intermediate densities.
3Press <OK>.
LINKS
Basic Copy Operations(P. 220)
Basic Operations for Sending Faxes(P. 275)
Basic Operations for Scanning Originals(P. 377)
Maintenance
896
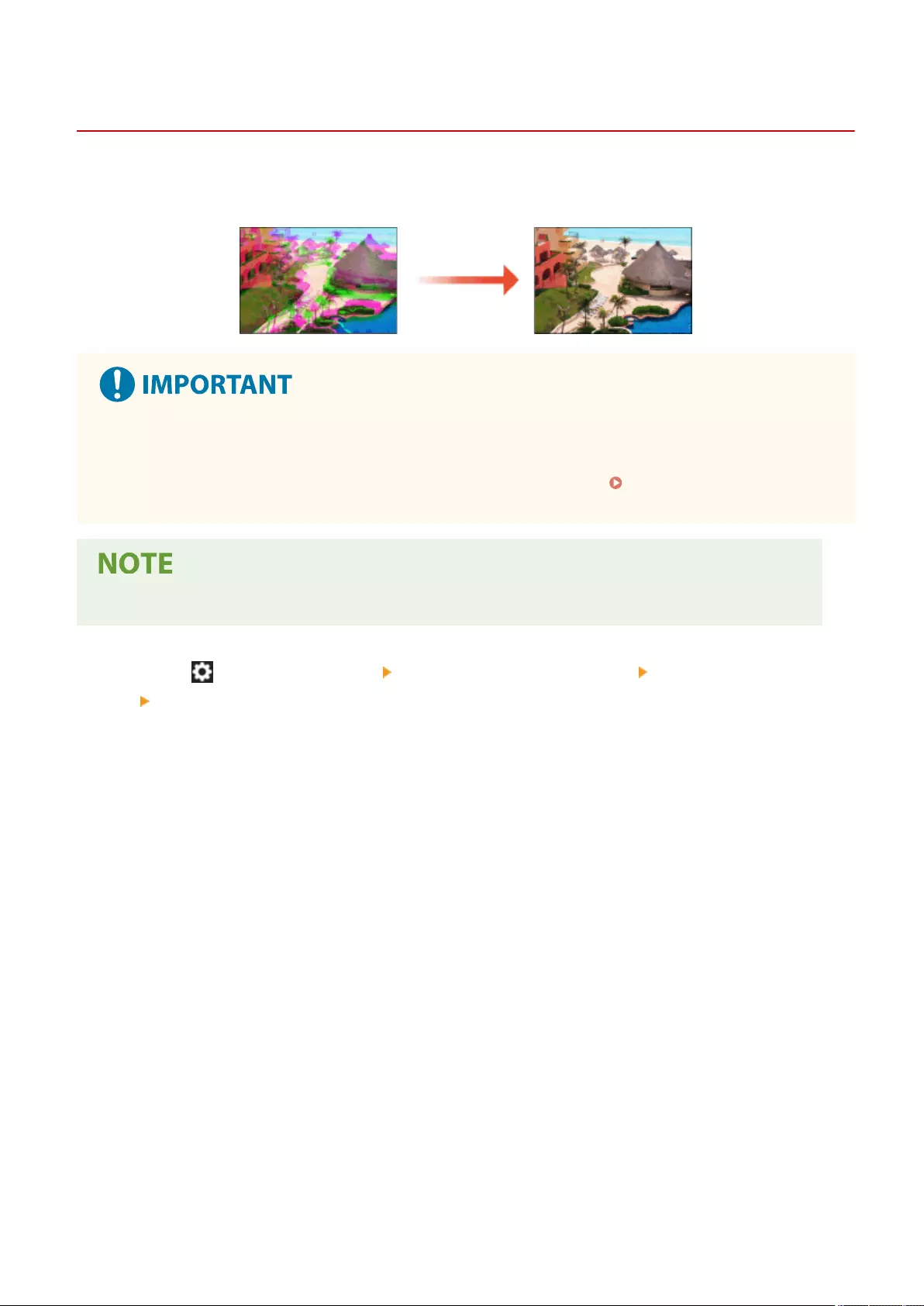
Correcting Color Mismatch
72JY-0H9
If the print positions slightly shift for the respective colors, use the following procedure to perform color print
mismatch correction (calibration).
●Frequently performing calibration may affect the life of the toner cartridge.
●Performing calibration when the toner level is low may adversely affect the color balance. If this symptom
occurs, it is recommended that you replace the toner cartridge that is low. Checking the Remaining
Toner Level(P. 891)
●Automatic calibration is performed according to changes in the status and environment of the machine.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Auto Correct Color Shift>.
2Press <Start>.
Maintenance
897

Automatically Adjusting Color Registration and Color
Intensity
72JY-0LJ
The machine performs automatic adjustment (calibration) in order to prevent color misregistration and ensure that
the original color intensity is correctly reproduced. You can set the timing and frequency for performing calibration.
Color misregistration is the phenomenon that occurs when the print position shifts slightly for each color and
results in a blurry print result that is out of focus.
Image with color misregistration Image without color misregistration
Color intensity refers to the intensity of colors such as red, yellow, green, blue, and purple.
Color intensity not reproduced Original Color intensity reproduced
●Frequently performing calibration may affect the life of the toner cartridge.
●Performing calibration when the toner level is low may adversely affect the color balance. If this symptom
occurs, it is recommended that you replace the toner cartridge that is low. Checking the Remaining
Toner Level(P. 891)
●Automatic calibration is performed according to changes in the status and environment of the machine.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Settings for Auto Full Calibration>.
2Set <Timing for Auto Full Calibration at Startup> and <Frequency for Auto Full
Calibration>.
Timing for Auto Full Calibration at Startup
Select the timing for automatically performing calibration after the power is turned ON.
Maintenance
898

Frequency for Auto Full Calibration
Set the frequency for automatically performing calibration. Set this item to <High> if color misregistration
often occurs.
Maintenance
899

Making Colors More Vivid
72JY-0HA
If you want to obtain color printouts with increased saturation of colors as compared to the print data, use the
following procedure to congure the necessary settings.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Full Color Printing Vividness Settings>.
2Select the level.
●<Standard> prints with the same color as the original.
●<Level 1> prints with more saturated colors than the original. <Level 2> prints with even more saturated
colors.
3Press <OK>.
Maintenance
900

Adjusting Image Size
72JY-0HC
If the size of the copied image slightly differs from the original, use the following procedure to make ne adjustment
of the image size. You can adjust the magnication of the horizontal width and vertical width, respectively.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Fine Adjust Zoom>.
2Adjust the image size.
●Set the magnication of <X> for horizontal width adjustment, and the magnication of <Y> for vertical width
adjustment.
3Press <OK>.
LINKS
Basic Copy Operations(P. 220)
Maintenance
901
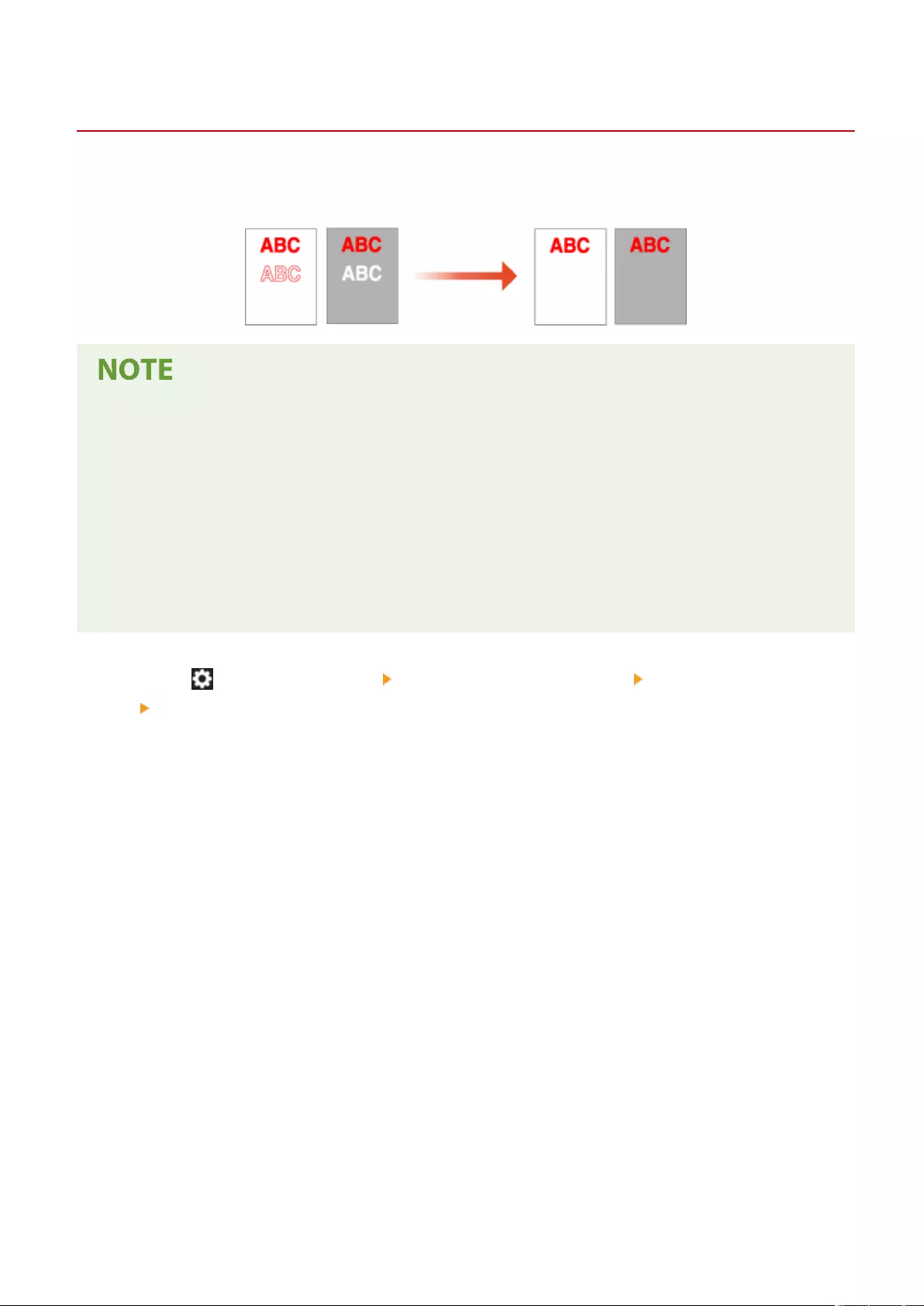
Reducing Toner Used When Color Printing
72JY-0HE
Fixing of excessive toner onto paper may cause color print failures such as generation of afterimages of highly dense
characters or lines. Reducing the amount of toner to be xed may improve this failure.
●This function may improve the following failures.
- Toner scattering around deep color areas of printed images
- Poor toner xing in a low-temperature environment
- Darkening of images printed on transparencies at the time of projection
- Bleed-through appearing when copying originals from 2-sided printing
●This function is enabled when in the <Copy>, <Print>, or <Access Stored Files> menu, <Use Full Color> is
selected under <Select Color> or <Use Auto (Color/Black & White)> is selected, that is, when the current print
mode is recognized as full color.
●Use of this function may give an adverse effect on color printing quality.
1Press (Settings/Register) <Adjustment/Maintenance> <Adjust Image Quality>
<Adjust Toner Volume Used for Color Printing>.
2Select the toner volume setting and press <OK>.
●<Off> prints with the standard toner volume.
●<Level 1> prints deep color areas with a bit smaller toner volume than the standard volume.
●<Level 2> generally prints with a reduced toner volume.
Maintenance
902

Paper Type Management Settings
72JY-0HF
You can register and edit detailed information of frequently used paper types as the <Custom Type>.
To register a new paper type, rst duplicate the paper type that resembles the new type in order to copy all of the
internal operational parameters. This procedure copies the suitable settings to the new paper type from the registered
custom paper easily.
You can also improve printing quality and paper feeding trouble by editing the custom paper, depending on the
characteristics.
●It is necessary to log in as an administrator to register custom paper types or change the settings of
registered custom paper types. Logging into the Machine(P. 137)
●When you register the custom paper type, you cannot specify the paper source. For more information on
registering the paper source, see Specifying Paper Size and Type in the Paper Drawer(P. 142) .
●You can import/export the registered custom paper type information, and share it with another Canon
machine. Importing/Exporting the Settings Individually(P. 632)
Registering frequently used paper types(P. 903)
Items that can be specied(P. 904)
Registering frequently used paper types
1Press (Settings/Register).
2Press <Preferences> <Paper Settings> <Paper Type Management Settings>.
3Specify the settings.
Paper type drop-down list
Enables you to select the paper type to display.
Sort List By
Maintenance
903
Enables you to change the display order of the list.
<Details/Edit>
Displays details for the selected paper type on the <Details/Edit> screen. If you select a custom paper type,
you can edit it.
<Duplicate>
Duplicates the selected paper type as a custom paper type.
<Delete>
Deletes the selected custom paper type.
<Change>
Appears on the <Details/Edit> screen for the custom paper type and enables you to change the settings
for the selected item.
●You can only edit/delete custom paper types.
4Press <OK> .
Items that can be specied
The following items can be specied.
◼Name
You can change the name of the custom paper type.
●When you register the settings for the custom paper type, make sure to change its name. You cannot
change the settings of the default paper types registered in the machine.
◼Basis Weight
You can change the basis weight of the custom paper type.
●If you enter a value that is different from the actual weight of the set paper, paper jams may occur, and the
quality of the image may be adversely affected.
◼Finish
You can change the Finish setting of Custom Type you have registered.
Maintenance
904

●If you select a nishing type which is different from that of the loaded paper, paper jams may occur, and the
quality of the image may be adversely affected.
◼Type
You can change the Type setting of Custom Type you have registered.
●If you select a paper type which is different from that of the loaded paper, paper jams may occur, and the
quality of the image may be adversely affected.
◼Color
You can change the color of the custom paper type.
●If you select a color which is different from that of the loaded paper, paper jams may occur, and the quality
of the image may be adversely affected.
◼Use as Template Paper
You can set this mode to <On> to use preprinted paper (paper which has logos already printed on it), such as a
letterhead.
●The custom paper type with <On> set for <Use as Template Paper> is not automatically selected in the
following cases.
- When the paper type for printing is set to <Auto>
- If <Paper Source Auto Selection> is set to <On> and <Consider Paper Type> is set to <Off> when copying
●Methods for loading paper if <Use as Template Paper> is set to <On>:
-Paper drawer of the main unit: the side with a logo facing down
- Paper source other than a paper drawer of the main unit: the side with a logo facing up
◼<Humid Environment Mode>
Print problems may occur due to humidity in the environment of the machine. This setting may improve this problem.
Maintenance
905

●Set this in the following cases. The print results may be improved.
- <High Humidity>: Set this if the print density is light or irregular when using the machine in a high
humidity environment.
- <Low Humidity 1>: Set this if images and text are blurred when using the machine in a low humidity
environment.
- <Low Humidity 2>: Set this if images show toner scattering or shaded parts of the image have white
patches (areas left white) when using the machine in a low humidity environment.
●Set <Standard> to not use either setting.
◼<Output Ppr. Stick Prevnt. Mode>
Paper may get stuck together when performing two-sided printing, depending on the image density of the print data.
This setting may improve this problem.
●<Mode 2> is better at preventing pages from being stuck together than <Mode 1>, but the print speed
becomes slower when performing two-sided printing.
◼<Reduce Img Defect by Ppr Dust>
Using paper with a large amount of paper dust may cause images to be printed faintly or with streaks. This setting
may improve this problem.
●When set to <On>, the print speed may be slower.
◼<Adj. Paper Convey. in MP Tray>
Corrects paper feeding problems that occur due to a low paper feeding speed when feeding from the multi-purpose
tray.
●When set to <On>, the print speed may be slower.
◼<Reduce Thin Paper Waviness>
This setting may improve wrinkling or curling when printing on thin paper.
●When set to <On>, printing may be faint.
Maintenance
906
◼<Reduce Thin/Plain Ppr Wrinkles>
Wrinkling may occur when printing on Thin, Plain 1, Plain 2, or Plain 3. This setting may improve this problem.
●When set to <On>, the print speed may be slower.
◼<Reduce Envelope Wrinkles>
Wrinkling may occur when printing on envelopes. This setting may improve this problem.
●When set to <On>, printing may be faint.
Maintenance
907

Checking the Number of Pages for Copy/Print/Fax/Scan
72JY-0HH
On the touch panel display, you can check the total number of pages for copying, faxing, scanning, and printing.
1Press (Counter/Device Information).
Control Panel(P. 93)
2Check the total number of copied, scanned, and printed pages.
●If you want to check the total number of pages that were scanned and sent, press <Check Send/Fax
Counter>.
●Press <Monitoring Service> <Communication Test> to check communication with the remote monitoring
server. When this function is executed, information on the machine is periodically sent to the remote
monitoring server. It is necessary to enable communication between the machine and the server providing
the service in order to use this function.
●You can print a list that shows the number of pages used for copying, printing, scanning, and faxing.
Printing a Report on the Number of Copied and Printed Pages(P. 909)
●You can also check the counter information for each AddOn. Press <Check AddOn Counter> on the screen in
step 2. If you press <Device Info./Other> <Check Device Conguration> on the same screen, you can check
the options installed in the machine.
●For information on the count conditions, contact your dealer or service representative.
Maintenance
908
Printing Reports and Lists
72JY-0HJ
You can print reports and lists to check information such as the total number of copied pages, communication results,
and machine settings.
Printing a Report on the Number of Copied and Printed Pages(P. 909)
Printing a List of Usage History(P. 910)
Outputting a Communication Result Report(P. 912)
Printing a List of Settings(P. 917)
Printing a Report on the Number of Copied and Printed Pages
Counter Report
You can print a report to check the total number of all copied and printed pages, as well as the total number of
scanned pages and faxed pages.
(Counter/Device Information) <Print List> <Yes>
Page Count List
You can print a list to check the total number of pages* that were copied, printed, and scanned for each
Department ID. To print this list, you need to log in with administrator privileges. Logging into the
Machine(P. 137)
(Settings/Register) <Management Settings> <User Management> <Department ID
Management> <On> <Page Totals> <Print List> Select the items to print <Start
Printing>
●Department ID Management must be set in order to calculate the Page Count List for each
Department ID. Setting the Department ID Management(P. 522)
●With the Remote UI Page Count List, you can check how many pages have been printed or scanned by
individual user names linked to a Department ID. To display the list, Starting the Remote
UI(P. 583) click [Settings/Registration] [User Management] [Department ID Management].
However, note that user names will not be displayed if multiple users are allocated to the same
Department ID, or if you are using DepartmentID Authentication as the login service.
●The Page Count List can also be saved as a CSV le using the Remote UI. Starting the Remote
UI(P. 583) click [Settings/Registration] [User Management] [Department ID
Management] [Store in CSV Format...].
* In this report, the numbers are based on copied or printed sides of the page. For example, the count is 1 if you print on one side
of a page, and the count is 2 if you print on both sides of the page.
Maintenance
909
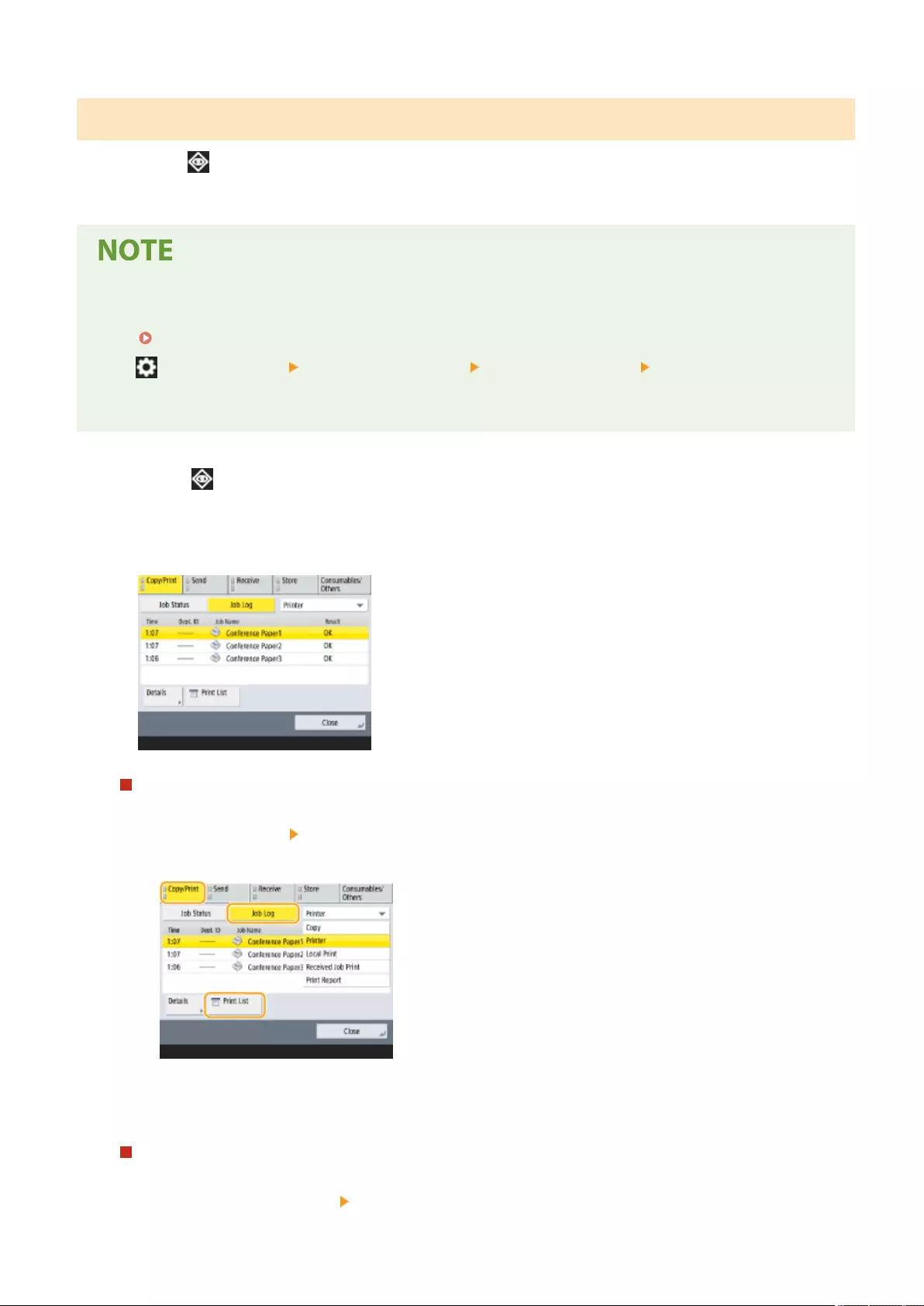
Printing a List of Usage History
When you press (Status Monitor), the Status Monitor screen is displayed, allowing you to check the usage history
for each function, such as copying, printing, sending e-mail, sending/receiving faxes/I-faxes, etc. From this screen, you
can also print the usage history for each function.
●If "NG" appears in the "RESULT" column in the printed list, check the three-digit number preceded by "#" to
nd the reason and solutions.
Countermeasures for Each Error Code(P. 982)
●If (Settings/Register) <Management Settings> <Device Management> <Restrict Access to Other
User Jobs> is set to <On>, jobs other than those of the logged-in user are displayed as "***" and cannot be
operated. If you log in with administrator privileges, the jobs of all users are displayed.
1Press (Status Monitor).
2Display the usage history of each function and print a list.
Copy/print log
1Press <Copy/Print> <Job Log>.
2Select the items you want to print, and press <Print List>.
3Press <Yes>.
Sending/receiving log
1Press <Send> or <Receive> <Job Log>.
Maintenance
910
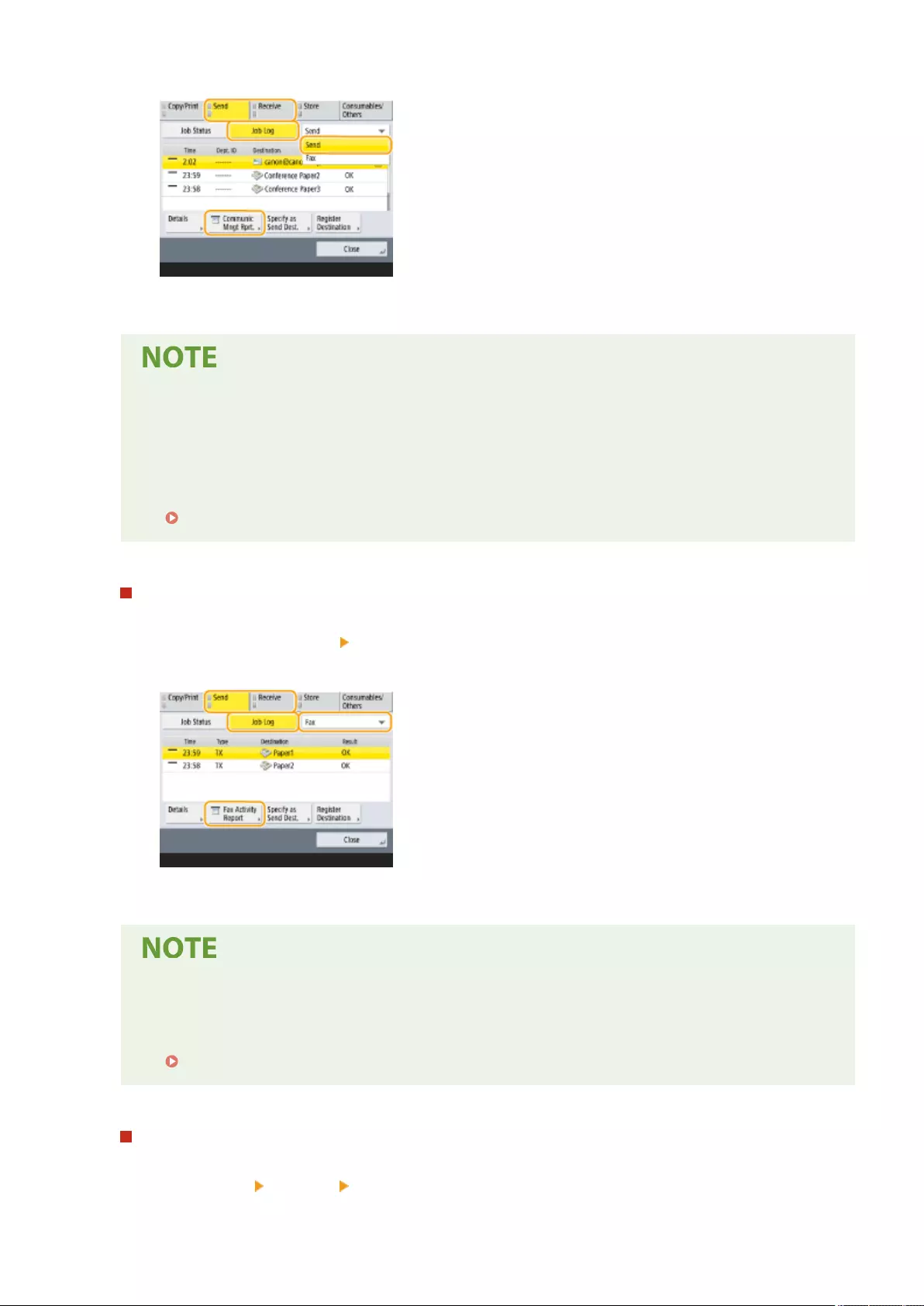
2Select <Send> or <Receive> from the list, and press <Communic Mngt Rprt.>.
3Press <Start Printing>.
●For documents sent by e-mail, the list indicates the sending results between the machine and the mail
server, not between the machine and the destination.
●If you select <Output Specif'd No. of Transm.> in step 3, you can specify the number of log results that
appear in the list.
●You can specify whether or not to print the list automatically.
Communication Management Report(P. 912)
Fax sending/receiving log
1Press <Send> or <Receive> <Job Log>.
2Select <Fax> from the list, and press <Fax Activity Report>.
3Press <Start Printing>.
●If you select <Output Specif'd No. of Transm.> in step 3, you can specify the number of log results that
appear in the list.
●You can specify whether or not to print the list automatically.
Fax Activity Report(P. 914)
Storage log
1Press <Store> <Job Log> <Print List>.
Maintenance
911

2Press <Yes>.
●There are two types of store locations printed as the protocol. If one of the following conditions is
met, the corresponding store location is printed.
- Memory Media: If the data is stored in a removable media such as USB memory from <Scan and
Store>
- Network: If the data is stored in the Windows server from <Scan and Store>
Outputting a Communication Result Report
You can print a list of results for sending/receiving fax, e-mail, or I-fax, and results for storing items in the le server. A
report is set to be printed automatically or printed only when an error occurs. However, you can change the setting to
print only at a specied time or not to print at all. In addition, you can send the report to a specied destination as a
CSV le.
●If "NG" appears in the "RESULT" column in the printed list, check the three-digit number preceded by "#"to
nd the reason and solutions.
Countermeasures for Each Error Code(P. 982)
●If (Settings/Register) <Management Settings> <Device Management> <Restrict Access to Other
User Jobs> is set to <On>, jobs other than those of the logged-in user are displayed as "***" and cannot be
operated. If you log in with administrator privileges, the jobs of all users are displayed.
Communication Management Report
You can congure the machine to automatically print the report or send it as a CSV le to destinations
registered in the Address Book when the specied number of communication results, including sent or received
faxes, e-mails, and I-faxes, as well as items saved in the le server, is reached. You can also congure the
machine to print the report or send it as a CSV le at a specied time.
1Press (Settings/Register).
2Press <Function Settings> <Send> <Common Settings> <Communication
Management Report>.
3Congure the necessary settings, and press <OK>.
Maintenance
912

<Print/Send for Each Specied No. of Transm.>
Select this to print/send a report when the specied number of communication results is reached. Set the
number of communication results using the numeric keys.
<Print/Send at Specied Time>
Select this to print/send a report at the specied time. Set the time using the numeric keys.
<Print Send/Receive Jobs Separately>
Select this to output separate reports for send jobs and receive jobs.
<Destination>
Specify the destination.
●Press <Destination> <To Remote Address Book> to specify the destination to the destinations registered
in a remote address book.
Local Address Book and Remote Address Book(P. 192)
●You cannot congure the settings for the Communication Management Report while <Display Job Log> in
<Management Settings> is set to <Off>. In addition, if you change <Display Job Log> in <Management
Settings> from <Off> to <On>, <Print/Send for Each Specied No. of Transm.> and <Print/Send at Specied
Time> in the Communication Management Report automatically changes to <Off>.
<Display Job Log>(P. 858)
●For documents sent by e-mail, the report indicates the sending results between the machine and the
mail server, not between the machine and the destination.
●You can manually print a Communication Management Report from a list in the usage history.
Sending/receiving log(P. 910)
When setting to print a report at a specied time
●If a report is set to print at a specied time, the 100 most recent results are printed, with the most
recent results rst. If the number of results exceeds 100, the older results are not printed.
When setting the machine to send the report as a CSV le at a specied time
●The 2,000 most recent results are exported to a CSV le, which is sent at the specied time. If the
number of results exceeds 2,000 by the specied time for le sending, the older results are not
exported.
Maintenance
913
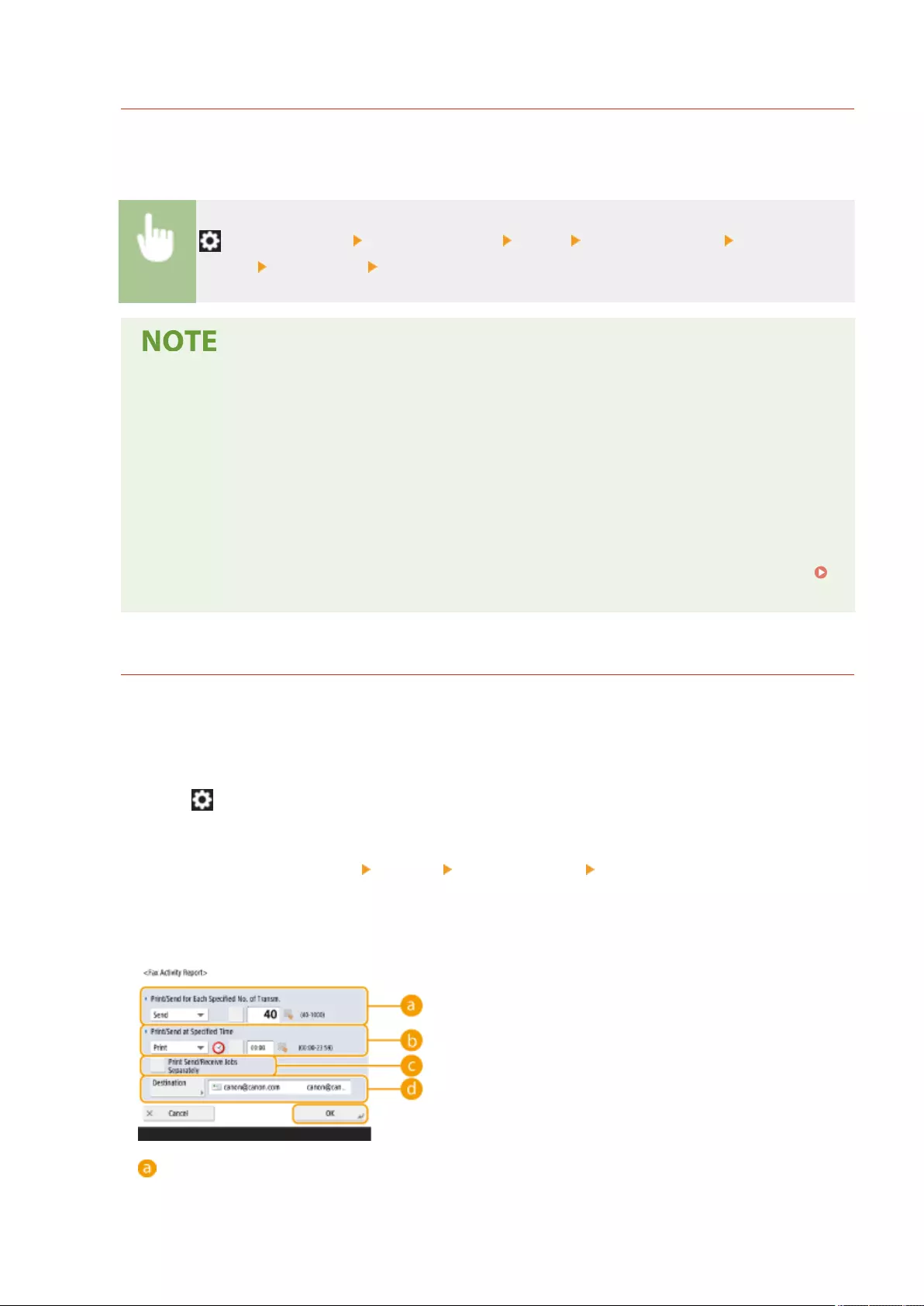
TX Result Report
You can congure the machine to automatically print the report for sending results, including sent faxes, e-
mails, and I-faxes, as well as items saved in the le server. You can also congure the setting to print the report
only when an error occurs. You are required to log in with administrator privileges to print this report.
(Settings/Register) <Function Settings> <Send> <Common Settings> <TX Result
Report> Set the report <OK>
●Even if you set <Report with TX Image> to <On> in the report settings, the image of the sent original
does not appear in a report when an encrypted PDF is sent.
●If the fax board is installed, the results of fax transmissions are printed. In addition, a Fax TX Result
Report is printed with the TX Result Report, if <Fax TX Result Report> is set to <For Error Only> or
<On>.
●For documents sent by e-mail, the report indicates the sending results between the machine and the
mail server, not between the machine and the destination.
●Send jobs originating from the fax driver are omitted from this report.
●If unnecessary streaks or shadows appear around the sent document, use <Erase Original Frame>.
Erasing Dark Borders When Scanning (Erase Frame)(P. 398)
Fax Activity Report
You can congure the machine to automatically print a report on fax sending and receiving or send it as a CSV
le to destinations registered in the Address Book when the specied number of sent or received faxes is
reached. You can also congure the machine to print the report or send it as a CSV le at a specied time.
1Press (Settings/Register).
2Press <Function Settings> <Send> <Fax Settings> <Fax Activity Report>.
3Congure the necessary settings, and press <OK>.
<Print/Send for Each Specied No. of Transm.>
Select this to print/send a report when the specied number of communication results is reached. Set the
number of communication results using the numeric keys.
Maintenance
914
<Print/Send at Specied Time>
Select this to print/send a report at the specied time. Set the time using the numeric keys.
<Print Send/Receive Jobs Separately>
Select this to output separate reports for send jobs and receive jobs.
<Destination>
Specify the destination.
●Press <Destination> <To Remote Address Book> to specify the destination to the destinations registered
in a remote address book.
Local Address Book and Remote Address Book(P. 192)
●You cannot congure the settings for the Fax Activity Report while <Display Job Log> in <Management
Settings> is set to <Off>. In addition, if you change <Display Job Log> in <Management Settings> from <Off>
to <On>, <Print/Send for Each Specied No. of Transm.> and <Print/Send at Specied Time> in the Fax
Activity Report automatically changes to <Off>.
<Display Job Log>(P. 858)
●You can manually print a Fax Activity Report from a list in the usage history.
Fax sending/receiving log(P. 911)
●The name of the remote party registered in the Address Book is printed when sending to a
destination selected from the Address Book. If sending by entering a number with the numeric keys,
the Transmitting Subscriber Identication (TSI) is printed if it could be acquired from the recipient.
When setting to print a report at a specied time
●If a report is set to print at a specied time, the 40 most recent results are printed, with the most
recent results rst. If the number of results exceeds 40, the older results are not printed.
When setting the machine to send the report as a CSV le at a specied time
●The 2,000 most recent results are exported to a CSV le, which is sent at the specied time. If the
number of results exceeds 2,000 by the specied time for le sending, the older results are not
exported.
Fax TX Result Report
You can congure the machine to automatically print the report each time a fax is sent. You can also congure
the setting to print the report only when an error occurs.
(Settings/Register) <Function Settings> <Send> <Fax Settings> <Fax TX Result Report>
Set the report <OK>
Maintenance
915

●A Fax Multi TX Report is printed when <Fax TX Result Report> is set to <On> and broadcast
transmission is performed.
●Even if you set <Report with TX Image> to <On> in the report settings, the image of the sent original
does not appear in a report when a fax is directly sent to the destination using direct sending (
Checking the Connection to the Recipient Before Sending (Direct Send)(P. 297) ) or manual
sending ( Sending Faxes Manually (Manual Sending)(P. 298) ).
●If unnecessary streaks or shadows appear around the sent document, use <Erase Original Frame>.
Erasing Dark Borders When Scanning (Erase Frame)(P. 398)
●If <TX Result Report> is set to <For Error Only> or <On>, a TX Result Report is printed with the Fax TX
Result Report.
Fax RX Result Report
You can set a Fax RX Result Report to print automatically every time a fax is received. It is also possible to set the
report to print only when an error occurs.
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings> <Fax RX
Result Report> Set the report <OK>
Condential Fax Inbox RX Report
You can congure the machine to automatically print the report when a received fax is saved in the Condential
Fax Inbox. You can also congure the setting so that the report is not printed.
(Settings/Register) <Function Settings> <Receive/Forward> <Fax Settings>
<Condential Fax Inbox RX Report> Set the report <OK>
●Even though <Off> is set in this setting, if Fax RX Result Report(P. 916) is enabled, a report is
printed when a fax is saved in the Condential Fax Inbox.
Printer Report
You can print a report of printer functions, such as the font list and status.
(Settings/Register) <Function Settings> <Printer> <Output Report> Select the printer
function Follow the on-screen instructions to select the item to be printed
Maintenance
916
Printing a List of Settings
Information and settings registered in the machine such as registered destinations, send/receive settings, fax settings,
forwarding conditions, etc. can be printed as a list.
Address Lists
You can print a list of destinations registered in the Address Book or in one-touch buttons.
(Settings/Register) <Set Destination> <Address Lists> Select the address book or one-
touch buttons to print <Print List> <Yes>
TX/RX User Data List
You can print a list of the settings congured for <Send> and <Receive/Forward> under (Settings/Register).
(Settings/Register) <Function Settings> <Send> or <Receive/Forward> <Output Report>
<TX/RX User Data List> <Yes>
●Items that have been changed from their default settings are printed with an asterisk (*) next to
them.
Fax User Data List
You can print a list of the settings congured for fax function by using <Send> and <Receive/Forward> under
(Settings/Register).
(Settings/Register) <Function Settings> <Send> or <Receive/Forward> <Output Report>
<Fax User Data List> <Yes>
●Items that have been changed from their default settings are printed with an asterisk (*) next to
them.
Forwarding Settings
You can print a list of the settings congured for fax and I-fax forwarding by using <Receive/Forward> under
(Settings/Register). You are required to log in with administrator privileges to print this list.
Maintenance
917

(Settings/Register) <Function Settings> <Receive/Forward> <Common Settings>
<Forwarding Settings> <Other Operations> <Print List> <Yes>
Network Setting List
You can print a list of the settings congured for <Network> in <Preferences> under (Settings/Register).
(Settings/Register) <Preferences> <Network> <Output Report> <Yes>
●Items that have been changed from their default settings are printed with an asterisk (*) next to
them.
●The following items are automatically generated from unique information of the machine by default
and when the settings are initialized, and have an asterisk (*) next to them.
- IPv4 Host Name
- IPv6 Host Name
- mDNS Name (mDNS Settings)
- Current Transmission Speed (Ethernet Driver Settings)
System Information list
You can print a report containing information on the applications and some of the system applications installed
in the machine. You are required to log in with administrator privileges to print this list.
(Settings/Register) <Management Settings> <License/Other> <AddOn Settings> <Print
System Information> <Yes>
LDAP Server Registration List
You can print a list of LDAP server settings registered in the machine. You are required to log in with
administrator privileges to print this list.
(Settings/Register) <Set Destination> <Register LDAP Server> <Print List> <Yes>
IPSec Policy List
You can print a list of IPSec policy settings registered in the machine. You are required to log in with
administrator privileges to print this list.
Maintenance
918
(Settings/Register) <Preferences> <Network> <TCP/IP Settings> <IPSec Settings>
<Print List> <Yes>
●Lists can be printed only if A4 or LTR (plain, recycled, thin, or color) is loaded in a paper source whose
settings in <Other> in <Paper Source Auto Selection> in <Function Settings> (Settings/Register) are set
to <On>. However, if <Consider Paper Type> for <Copy> is set to <On> in <Paper Source Auto
Selection>, you cannot print from a paper source with color paper specied.
Automatically Selecting the Appropriate Paper Source for a Specic Function (P. 154)
Maintenance
919

Troubleshooting
Troubleshooting ............................................................................................................................................. 921
If the Machine Does Not Operate ..................................................................................................................... 923
Cannot Print ...................................................................................................................................................... 925
Problems with Printing Results ........................................................................................................................ 926
Problems with Faxes ......................................................................................................................................... 929
Problems with Scanning ................................................................................................................................... 931
Problems with the Network ............................................................................................................................. 933
Problems with Security ..................................................................................................................................... 937
Other Problems ................................................................................................................................................. 938
A Message or a Number Starting with "#" (an Error Code) Is Displayed ........................................................ 940
A Message Saying to Contact Your Dealer or Service Representative Is Displayed ....................................... 941
Countermeasures for Each Message ............................................................................................................ 943
Countermeasures for Each Error Code ......................................................................................................... 982
Clearing Paper Jams ........................................................................................................................................ 1008
Paper Jams in the Feeder ............................................................................................................................ 1011
Paper Jams inside the Machine or in the Fixing Unit ................................................................................... 1013
Paper Jams in a Paper Source ..................................................................................................................... 1017
Troubleshooting
920
Troubleshooting
72JY-0HK
PMW-TROB
If a problem occurs while you are using the machine, check the following items rst. If the problem cannot be solved
or an inspection is required, contact your dealer or service representative.
◼What kind of problem do you have?
If the Machine Does Not Operate(P. 923) Cannot Print(P. 925)
Problems with Printing Results(P. 926) Problems with Faxes(P. 929)
Problems with Scanning(P. 931) Problems with the Network(P. 933)
A Message or a Number Starting with "#" (an Error Code) Is
Displayed(P. 940)
Problems with Security(P. 937)
Other Problems(P. 938) Clearing Paper Jams(P. 1008)
Troubleshooting
921

Troubleshooting
922
If the Machine Does Not Operate
72JY-0HL
If a problem occurs while you are using the machine, check the following before contacting your dealer or service
representative.
Check This First(P. 923)
If the machine does not respond to computer operations(P. 923)
When the authentication screen (login screen) is displayed(P. 924)
Check This First
Is a message displayed on the touch panel display?
●A message is displayed on the touch panel display when an error or a problem occurs while operating the
machine.
A Message or a Number Starting with "#" (an Error Code) Is Displayed(P. 940)
Is (Energy Saver) lit?
●If it is lit, press (Energy Saver) to cancel the Sleep mode.
Is the machine connected to a computer correctly?
●Check the network connection of the machine and the computer.
Setting up the Network Environment(P. 19)
If the machine does not respond to computer operations
Restart the machine.
●If the machine does not respond even though its power is turned ON, turn the power OFF ( Turning OFF
the Machine(P. 96) ). Conrm that the power cord is connected correctly, wait 10 or more seconds after
the main power is turned OFF, and then turn the power back ON ( Turning ON the Machine(P. 95) ).
Check whether the driver is installed correctly.
●For information on installing the driver, see Installing Drivers(P. 67) .
Check whether the IP address of the machine is correct.
●Check the IP address settings, and change them if they are incorrect. For information on the settings, see
Setting up Using the Setup Guide(P. 6) .
Troubleshooting
923

Cannot Print
72JY-0HR
Check This First
Is the Processing/Data indicator (on the control panel) ashing or lit?
●If it is ashing or lit, there is a document that is being processed or waiting to be processed. Wait for the
processing to nish or select the document that you want to prioritize from the screen for checking the
printing status.
Checking the Printing Status and History(P. 348)
Printing Documents Held in the Machine(P. 351)
Is a message displayed on the touch panel display?
●A message is displayed on the touch panel display when an error or a problem occurs while operating the
machine.
A Message or a Number Starting with "#" (an Error Code) Is Displayed(P. 940)
Is <Auto Select> set to <No>?
●To switch to the appropriate operation mode, change all items or the items you are using to <Yes>. For
more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
Is forced hold printing enabled?
●If it is enabled, documents may not be printed, depending on their settings.
Conguring the Forced Hold Printing Settings(P. 573)
Are you printing via a print server using the LPR command?
●When continuously printing PDF data using the LPR command, execute one job at a time at the interval set
in <Timeout>. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
Troubleshooting
925
Problems with Printing Results
72JY-0HS
The printed image is displaced or skewed.(P. 926)
Images are uneven or faint.(P. 926)
Black streaks appear.(P. 926)
Bleedthrough occurs.(P. 926)
Images are not printed on the intended side of the paper.(P. 927)
Images are not printed in the intended size.(P. 927)
The orientation does not match on both sides of the paper when using two-sided printing.(P. 927)
The printed image is displaced or skewed.
Are the paper guides misaligned?
●Match the paper guides with the paper loaded in the paper source.
Images are uneven or faint.
Is the paper damp?
●Replace the paper with paper that is not damp.
Are the gradation and density set appropriately?
●Perform gradation adjustment.
Adjusting Gradation(P. 894)
Black streaks appear.
Is the document feed scanning area dirty?
●Clean the document feed scanning area.
Cleaning the Feeder(P. 878)
Bleedthrough occurs.
Is the density of backgrounds set appropriately?
●If bleed-through is observed with the print result, adjusting the density of background can improve the
problem, giving a ne print.
Basic Copy Operations(P. 220)
Basic Operations for Sending Faxes(P. 275)
Adjusting Density(P. 396)
Troubleshooting
926
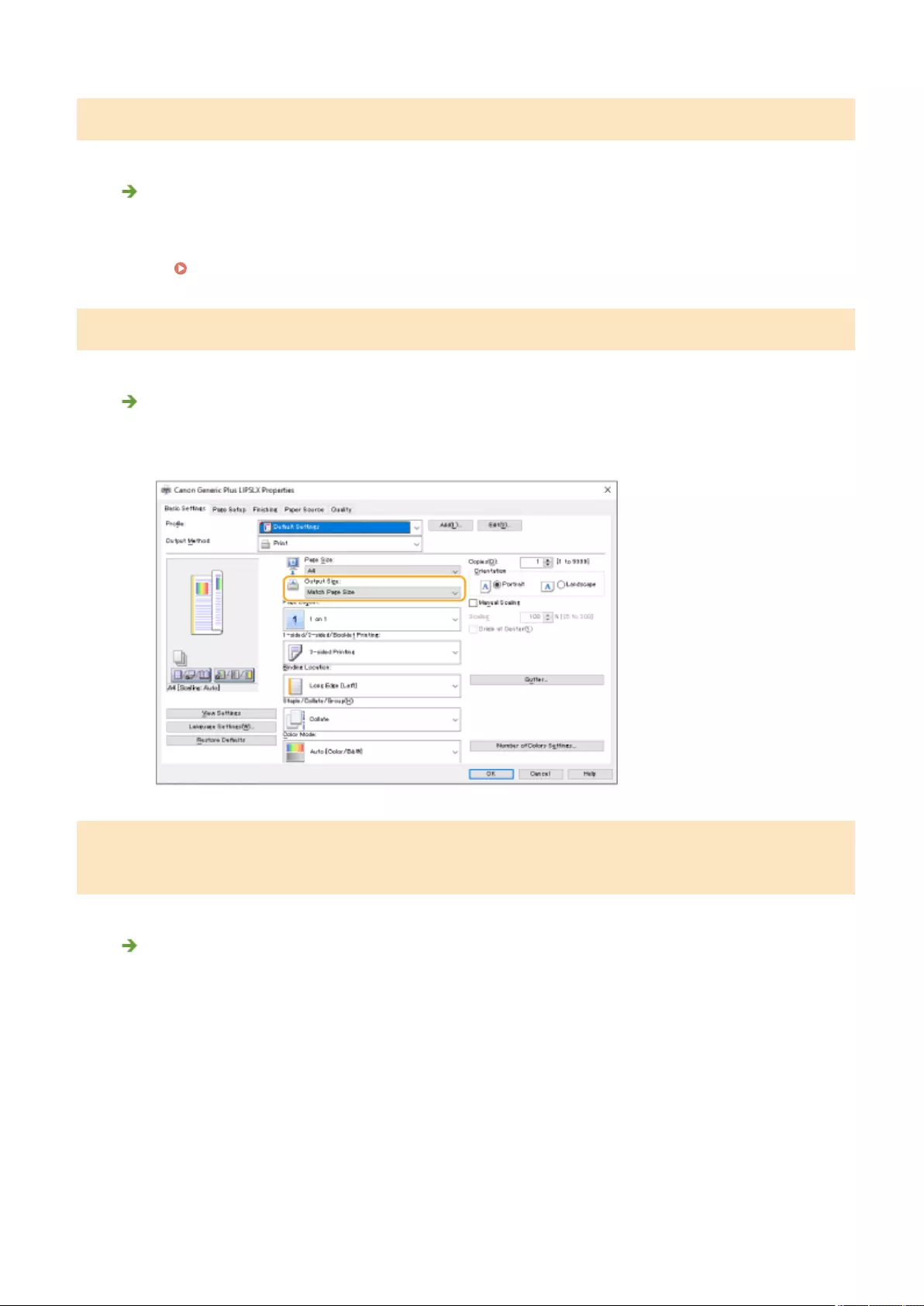
Images are not printed on the intended side of the paper.
Is the orientation of the loaded paper correct?
●Check the orientation and side of the paper that is facing up. Load the paper again if it is incorrectly
orientated.
Loading Paper(P. 102)
Images are not printed in the intended size.
Do the original size and size of the paper that is loaded match?
●Replace the paper that is loaded with paper of the size you want to print on.
●Match [Output Size] in the printer driver with the size of paper to print on.
The orientation does not match on both sides of the paper when using two-
sided printing.
Are the settings for two-sided printing correct?
●Follow the procedure below to check the print settings.
1Select the orientation of the original on the print settings screen of the application.
2On the [Basic Settings] screen of the driver, set [Orientation] to the same orientation you set in
step 1.
Troubleshooting
927
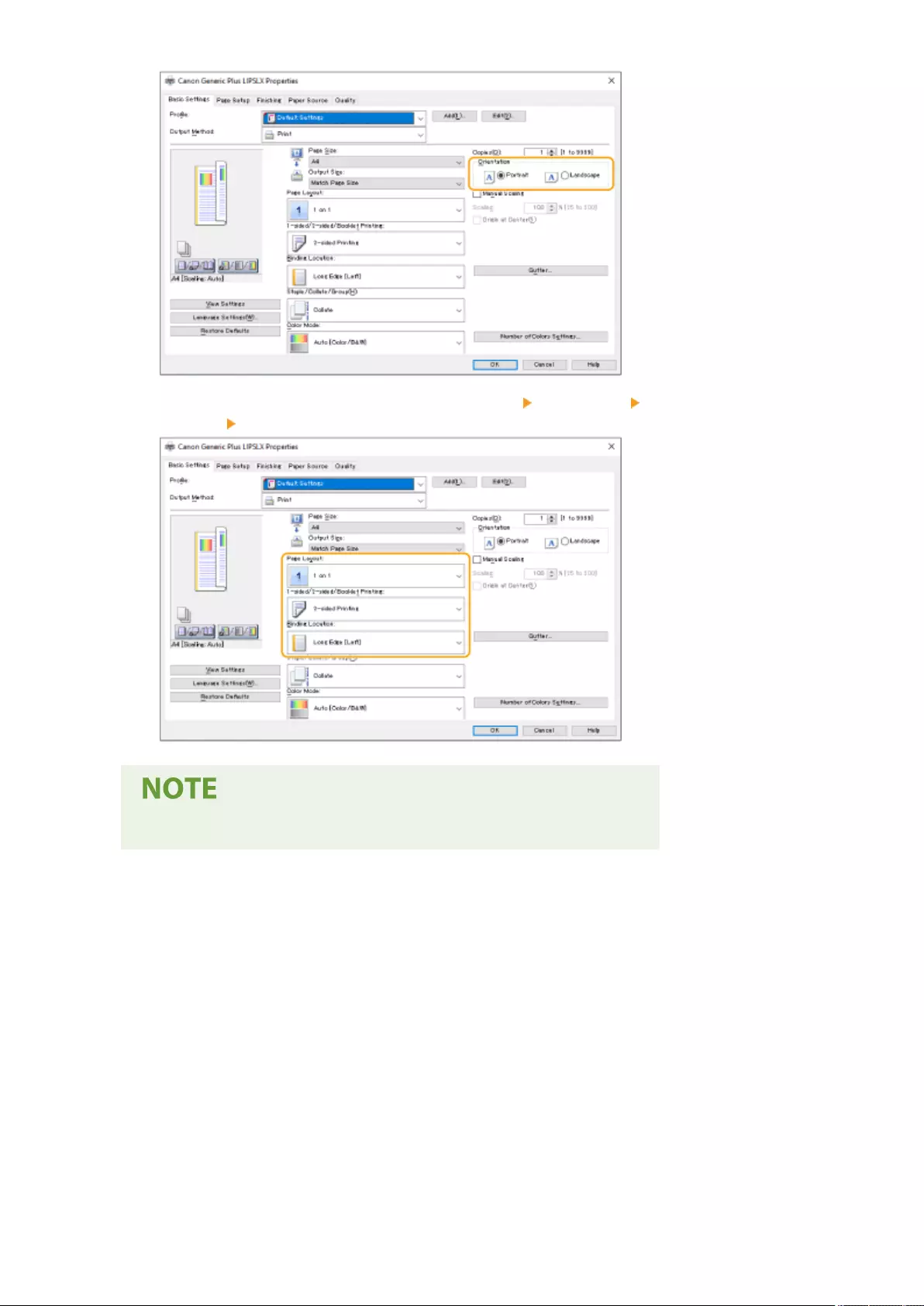
3While checking the print preview, set [Page Layout] [Page Order] [1-sided/2-sided/Booklet
Printing] [Binding Location].
●[Page Order] is displayed when [Page Layout] is set to [2 on 1] or higher.
Troubleshooting
928
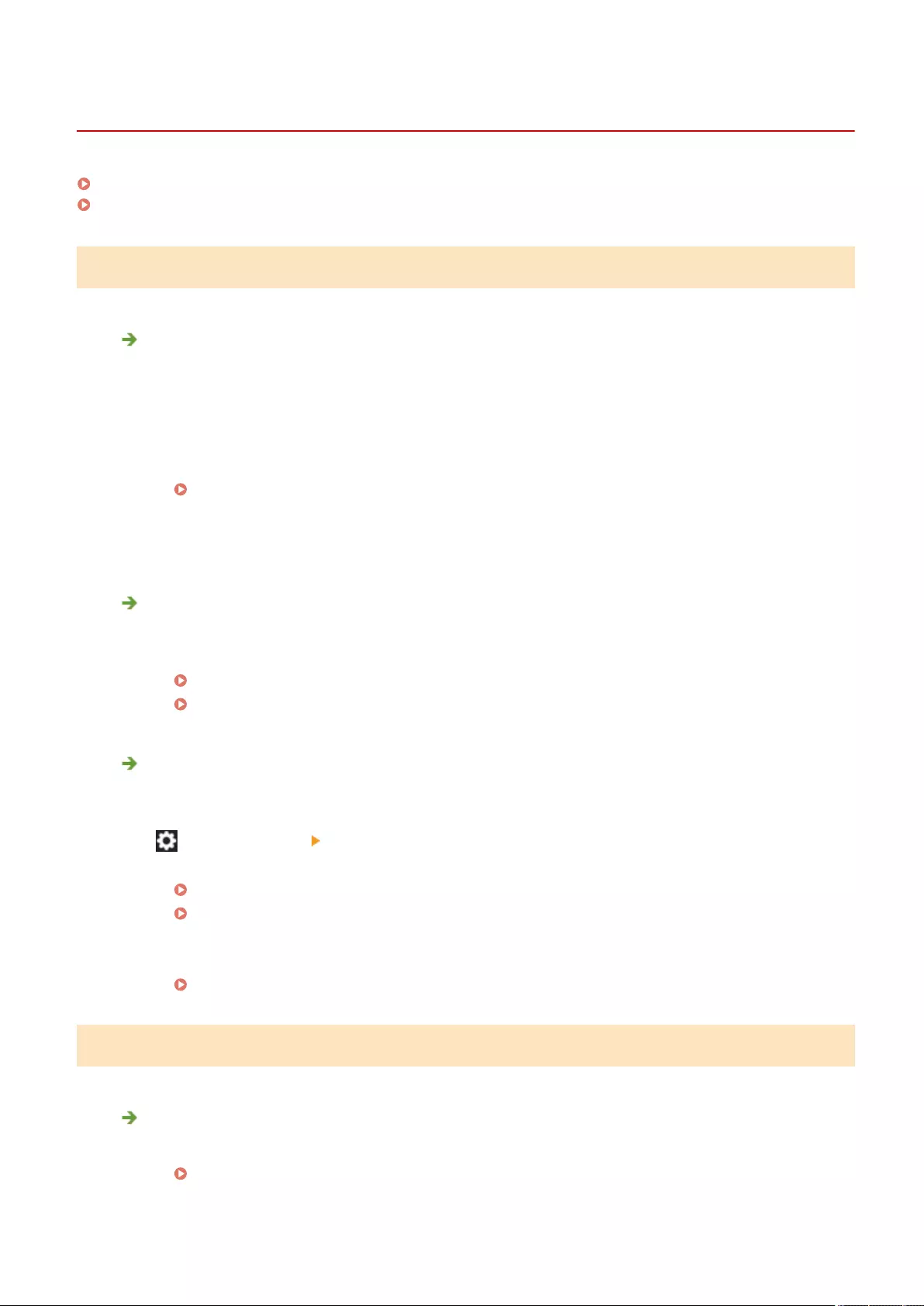
Problems with Faxes
72JY-0HU
Faxes cannot be sent or forwarded.(P. 929)
Cannot receive faxes.(P. 929)
Faxes cannot be sent or forwarded.
If no faxes can be sent
●Call the destination fax from the machine to check whether the phone line is connected in the wrong
location.
If the dial tone of the phone line cannot be heard
The modular cable (phone line for faxing) is disconnected or inserted in the wrong location. Check the
modular cable and insert it in the correct location.
Parts and Their Functions(P. 82)
If the machine cannot connect to the destination fax machine (you cannot hear the fax tone)
There may be a problem with the other party or the service provider. Contact the other party.
If faxes cannot be forwarded
●Check the forwarding destination registered in the address book or one-touch button, and change it if it is
incorrect.
Editing the Registered Destinations in the Address Book(P. 208)
Editing the Registered Destinations in One-Touch Buttons(P. 214)
If you are using an optical line or an IP phone line
●Communication errors may occur, depending on the line quality. For more information, contact your
service provider. You may be able to reduce communication errors by lowering the transmission speed in
(Settings/Register) <TX Start Speed>. You can also set the transmission speed for each destination
from the preferences for the address book or one-touch buttons.
<TX Start Speed>(P. 833)
Registering Destinations in the Address Book(P. 195)
●You can also use <Auto Adjust Communication Speed When Using VoIP> to limit the communication speed
to reduce errors.
<Auto Adjust Communication Speed When Using VoIP>(P. 834)
Cannot receive faxes.
Does the machine have sucient free memory?
●Delete unnecessary documents in the memory of the machine.
Saving Received Documents in the Machine (Memory Reception)(P. 313)
Troubleshooting
929

Check the number preceded by "#", and refer to the appropriate
countermeasure.
●If fax reception or transmission fails, a number (error code) preceded by "#" is displayed on the touch
panel display or in a communication management report. You can refer to the necessary countermeasures
according to the error code.
Countermeasures for Each Error Code(P. 982)
Troubleshooting
930
Problems with Scanning
72JY-0HW
Cannot send documents to a server using the scan and send function.(P. 931)
Cannot send scanned documents via e-mail.(P. 931)
Black streaks appear in scanned documents.(P. 931)
Bleedthrough occurs in scanned documents.(P. 932)
Cannot send documents to a server using the scan and send function.
Are the server settings such as the password correct?
●If the login password, etc. of the server (computer) has been changed, make sure to also change the
settings registered in the address book or one-touch buttons.
Editing the Registered Destinations in the Address Book(P. 208)
Editing the Registered Destinations in One-Touch Buttons(P. 214)
Cannot send scanned documents via e-mail.
Is the information for the destination correct?
●Change the settings registered in the address book or one-touch buttons.
Editing the Registered Destinations in the Address Book(P. 208)
Editing the Registered Destinations in One-Touch Buttons(P. 214)
Are the settings for the SMTP server or DNS server correct?
●If no e-mail can be sent, set the SMTP server and DNS server correctly. Also, if the port number for SMTP
Send or receiving with POP are different from the default, specify the correct port numbers in <Specify
Port Number for SMTP TX/POP RX>(P. 826) .
Setting E-mail/I-Fax Communication(P. 70)
Making DNS Settings(P. 45)
Black streaks appear in scanned documents.
Is the document feed scanning area dirty?
●Clean the document feed scanning area.
Cleaning the Feeder(P. 878)
Troubleshooting
931
Problems with the Network
72JY-0HX
Problems with Connections(P. 933)
Problems with Wireless Connections(P. 934)
Problems with Connections
Cannot set up the network.
●Check whether <Conrm Network Connection Setting Changes> is set to <On>.
<Conrm Network Connection Setting Changes>(P. 782)
An unintended destination is dialed up.
●If a dial-up router is on the network to which the machine is connected, the machine connects to a
destination other than the intended destination, depending on the settings of the machine or dial-up
router. This may result in subscriber line charges and call charges. Check the following.
●If the dial-up router does not have to send packets via broadcast, change the router settings to ensure
that it sends packets via a method other than broadcast. If it is necessary to allow broadcasting with the
dial-up router, check whether an unnecessary destination is set.
●Check whether the host name and IP address of the le server and mail server, etc. set in the machine are
correct.
●If the DNS server is on an external server, use the IP address instead of the host name for the destination,
even when connecting to devices on the same network as the machine.
●If the DNS server is on the network that the machine is connected to, check whether the information for
devices connected to an external network is registered on the DNS server, and whether it is correct.
Cannot recognize the machine from a computer.
●If the IP address of the computer where the Remote UI and utility software are executed is not allowed for
sending and receiving in <Firewall Settings>, the information for the machine cannot be displayed on the
computer. Check whether the settings are correct.
Specifying IP Addresses in Firewall Settings(P. 539)
●When using device management software, set <Set Dedicated Community> to <On>, and select <Read/
Write> for <MIB Access Permission>. Also set <Dedicated Port Settings> to <On>.
Monitoring and Controlling via SNMP(P. 57)
●The machine cannot be recognized when utility software is used to access the machine with a community
name other than the SNMP community name set in the machine. Check the SNMP community name.
Monitoring and Controlling via SNMP(P. 57)
●If the message "An error has occurred." is displayed in the Web browser and the Remote UI cannot be
started, invalid cache data may remain. Clear the cache of the Web browser.
●If the machine enters the Sleep mode, it may not be able to be recognized from a computer. Cancel the
Sleep mode or change <Sleep Mode Energy Use> to <High>.
<Sleep Mode Energy Use>(P. 780)
Troubleshooting
933
Problems with Wireless Connections
Cannot connect wireless LAN and wired LAN at the same time.
●You cannot connect wireless LAN and wired LAN at the same time. USB and wireless LAN or USB and wired
LAN can be used at the same time.
The Remote UI is not displayed.
●Are <Use HTTP> and <Remote UI Settings> set to <On>?
<Use HTTP>(P. 786)
Starting the Remote UI(P. 583)
●If you are connected with wireless LAN, restart the Remote UI after checking whether the IP address is set
correctly.
Conducting a Connection Test for an IPv4 Address(P. 36)
Conducting a Connection Test for an IPv6 Address(P. 38)
●If you are connected with wired LAN, restart the Remote UI after checking whether the IP address is set
correctly and the cable is connected correctly.
Connecting to a Wired LAN(P. 25)
Starting the Remote UI(P. 583)
●Are you using a proxy server? If so, add the IP address of the machine in "Exceptions" (addresses to not
use a proxy for) in the proxy server settings of the Web browser.
●Is communication with computers restricted in the rewall? If the Remote UI cannot be displayed because
the settings are incorrect, set <IPv4 Address Filter>, <IPv6 Address Filter>, or <MAC Address Filter> to
<Off> from the control panel of the machine.
Restricting Communication by Using Firewalls(P. 538)
<Network>(P. 782) <IPv4 Address Filter>
<Network>(P. 782) <IPv6 Address Filter>
<Network>(P. 782) <MAC Address Filter>
Cannot connect to the network.
●The IP address may have failed to be set. Set the IP address again.
Setting an IP Address(P. 34)
●If you are connected with wireless LAN, check whether the machine can connect to the network.
If you cannot connect to a wireless LAN(P. 935)
If you do not know the IP address that was set.
●Press the (Counter/Device Information) key and check the IP address.
Control Panel(P. 93)
●If you want to know the details of the settings or change the settings, press (Settings/Register) and
check the IP address.
Setting an IP Address(P. 34)
Troubleshooting
934
Cannot change from wired LAN to wireless LAN or wireless LAN to wired LAN.
●Did you also switch the LAN setting from the control panel of the machine? You cannot change the
connection method of the machine unless you do so.
Selecting the Network Connection Method(P. 23)
If you do not know the SSID and network key of the wireless LAN router to
connect to or the SSID is not displayed on the screen.
●Check whether the SSID is displayed on the wireless LAN router or its box.
Checking the SSID and Network Key(P. 33)
The SSID of the wireless LAN router to connect to is not displayed in the list of
access points.
●Check whether the SSID of the wireless LAN router that you made a note of is correct.
Checking the SSID and Network Key(P. 33)
●If the SSID of the wireless LAN router is not disclosed (if it is using the stealth function*), set the wireless
LAN router to disclose the SSID.
* This function prevents the SSID of a wireless LAN router from being automatically detected.
●Check whether the machine is connected to the network.
If you cannot connect to a wireless LAN(P. 935)
If you cannot connect to a wireless LAN
Check the status of the computer.
●Is setup of the computer and wireless LAN router complete?
●Are any of cables of the wireless LAN router (power cable, LAN cable, etc.)
disconnected?
●Is the wireless LAN router turned ON?
If the problem is still not resolved:
●Turn all the devices off, and then on again.
●After waiting a while, check whether you can connect to the network.
Check whether the machine is turned ON.
If the machine is turned ON, turn it OFF, and then ON again.
Check the installation location of the machine and wireless LAN router.
●Are the machine and wireless LAN router too far away from each other?
●Is there an obstacle such as a wall between the machine and wireless LAN
router?
●Are there any devices that emit electromagnetic waves nearby, such as a
microwave or digital cordless telephone?
Troubleshooting
935
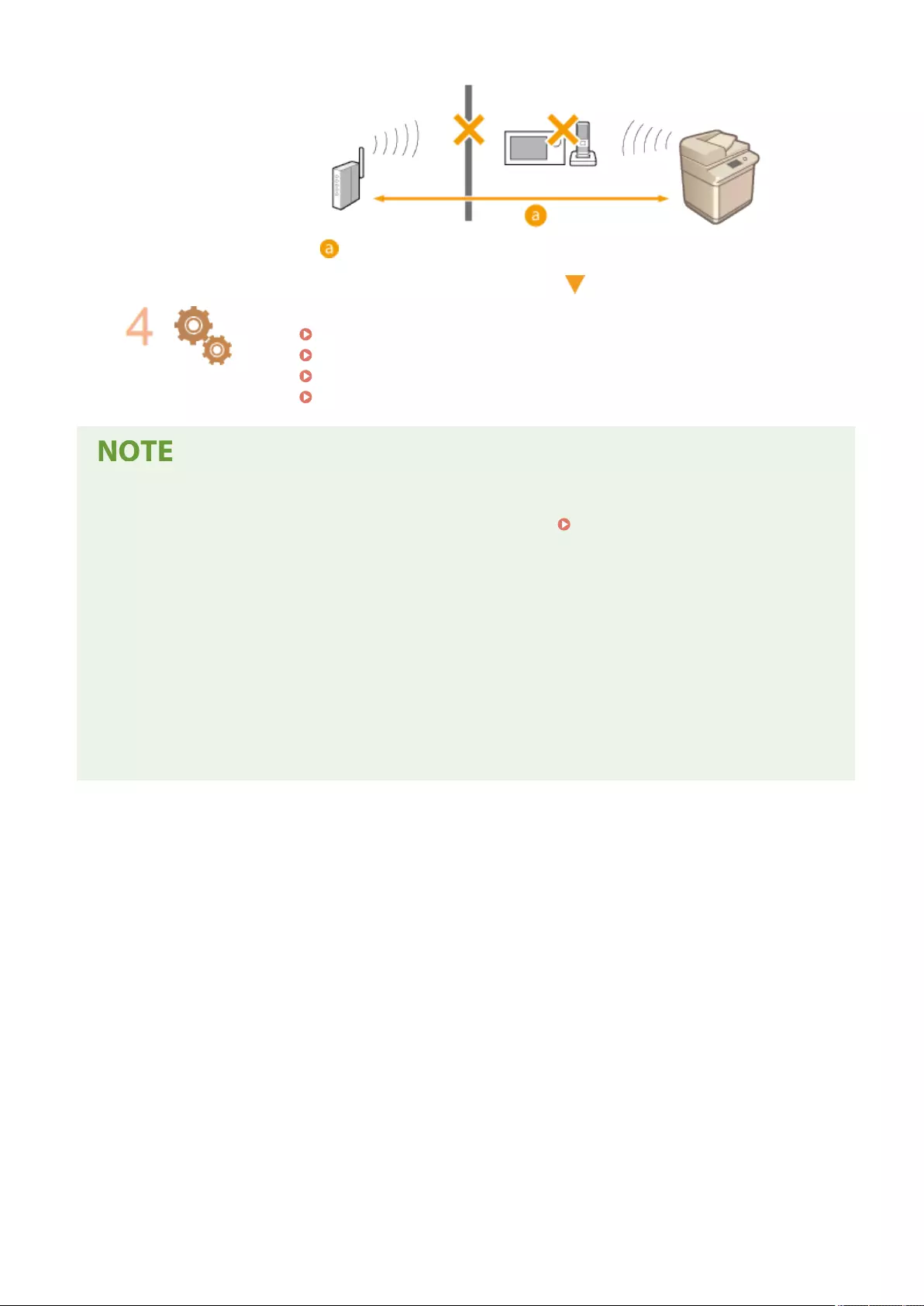
: Within 50 m
Specify the following settings again.
Setting Up the Connection Using WPS Push Button Mode(P. 28)
Setting Up the Connection Using WPS PIN Code Mode(P. 29)
Setting Up Connection by Selecting a Wireless Router(P. 30)
Setting Up a Connection by Specifying Detailed Settings(P. 31)
If settings require manual entry
●If the wireless LAN router is set as follows, perform manual entry ( Setting Up a Connection by
Specifying Detailed Settings(P. 31) ):
- ANY rejection* is enabled.
- An automatically generated WEP key (hexadecimal) is set.
- The stealth function is enabled.
* A wireless LAN router function for refusing connections if the device trying to connect has "ANY" or "blank" set for the SSID.
If it is necessary to change the settings on the wireless LAN router side
●If the wireless LAN router is set as follows, change the settings on the router side:
- MAC address ltering is set.
- WEP is selected or WPA/WPA2 encryption is set for the TKIP when communicating only with IEEE 802.11n.
Troubleshooting
936
Problems with Security
72JY-0HY
The settings in <Settings/Register> are not restored even though the check box is deselected in the security
policy settings.(P. 937)
Cannot import security policy settings.(P. 937)
A security administrator password entry screen is displayed even though no password is set.(P. 937)
The settings in <Settings/Register> are not restored even though the check
box is deselected in the security policy settings.
●Items changed with security policy settings applied are not restored simply by deselecting the check box.
Deselect the check box, and change the corresponding settings from the (Settings/Register) button, or
from [Settings/Registration] in the Remote UI.
Cannot import security policy settings.
●Have you set a different security policy password from the source device? Remove the password in the
destination device or set the same password as the source device.
Using a Password to Protect the Security Policy Settings(P. 479)
A security administrator password entry screen is displayed even though no
password is set.
●If you import security policy settings, the same password is set for the destination device if a security
policy password is set in the source device. Check the password of the source device.
Troubleshooting
937
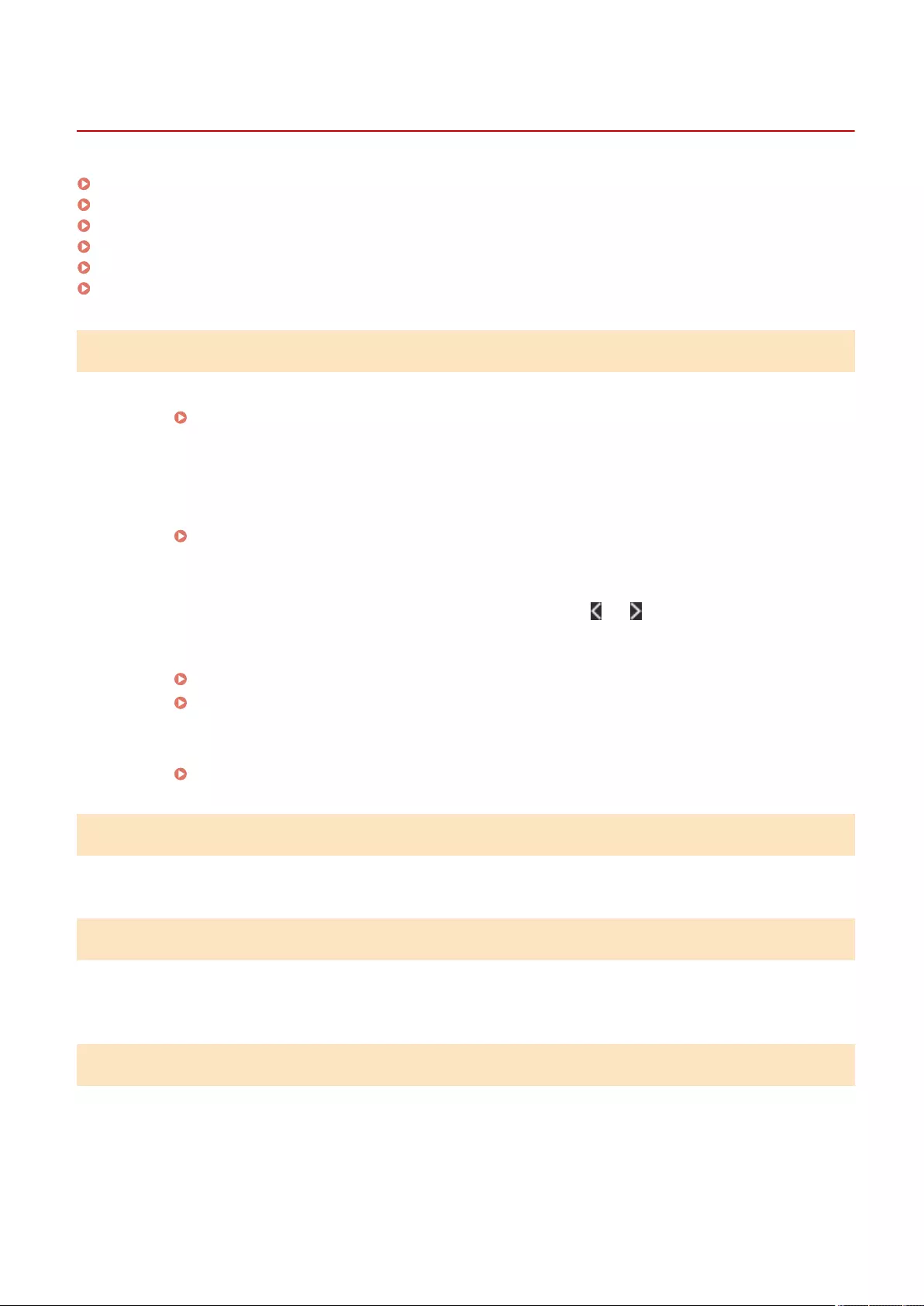
Other Problems
72JY-0J0
Cannot press a button, select an item, or an item is not displayed.(P. 938)
Some settings imported from another device are not reected.(P. 938)
Log les are garbled.(P. 938)
Log events are not recorded even though log collection was started.(P. 938)
The setting for long-strip originals is not displayed.(P. 939)
The setting for K-size paper is not displayed.(P. 939)
Cannot press a button, select an item, or an item is not displayed.
●Some settings can only be used by the administrator. They cannot be used by general users.
Settings/Registration(P. 670)
●The system administrator limits the functions that general users can use to prevent unauthorized use, and
restricts the use of functions.
●The functions that can be used with User Authentication are managed by the administrator. These
functions can be used by logging in using an ID with access privileges.
Logging into the Machine(P. 137)
●Functions cannot be used because the optional equipment or system options that they require are not
installed.
●The buttons displayed on the screen have been changed. Press or at the bottom of the screen to
switch the display, or press <Options> and search for the desired button. For a Basic Features screen,
press <Options> and search for the desired button.
Customizing the <Home> Screen(P. 159)
Customizing the Basic Features Screen(P. 167)
●The settings are managed with security policy settings. To change the settings, it is necessary to log in to
the Remote UI with administrator privileges.
Conguring the Security Policy Settings(P. 481)
Some settings imported from another device are not reected.
●If a security policy is set, settings that violate the security policy cannot be imported.
Log les are garbled.
●When opening CSV les with Microsoft Excel, the content may not be recognized as text strings and may
become garbled as a result. If this happens, open the les with a CSV le editor or text editor.
Log events are not recorded even though log collection was started.
●Results may not be reected in a log le if it is retrieved immediately after log collection is started. Since it
takes some time to collect logs, retrieve the log le again after waiting a while.
Troubleshooting
938

The setting for long-strip originals is not displayed.
●You can use long-strip originals by changing the machine settings. For more information, contact your
dealer or service representative.
The setting for K-size paper is not displayed.
●You can use K-size paper by changing the machine settings. For more information, contact your dealer or
service representative.
Troubleshooting
939

A Message or a Number Starting with "#" (an Error
Code) Is Displayed
72JY-0J1
0UUY-0KJ 0UW1-0JS 0YRY-0JR 0X7F-0RH 0X7H-0LR 1100-0JW 0X6E-0RH 0X6W-0LR 10XJ-0JW 0X7C-0RH 0X7A-0LR 1106-0JW 0WXY-0RJ 0X7E-0LR 10YY-0JW 10H3-0JS 0WR6-0RS 0WR7-0LY 108A-0JU 1116-0JU 10H4-0JS 0WR5-0RS 0WR8-0LY 0YWJ-0KK 0YWH-0LL 0YWR-0KC 0YWK-0LL 0YWE-0RH 0YWF-0LL 0YAS-0S4
If a message is displayed on the screen of the machine or the Remote UI, or a number starting with "#" (an error code)
is displayed on the details screen for job log or a communication management report, refer to the following to check
the remedy.
A Message Saying to Contact Your Dealer or Service Representative Is Displayed(P. 941)
Countermeasures for Each Message(P. 943)
Countermeasures for Each Error Code(P. 982)
Troubleshooting
940
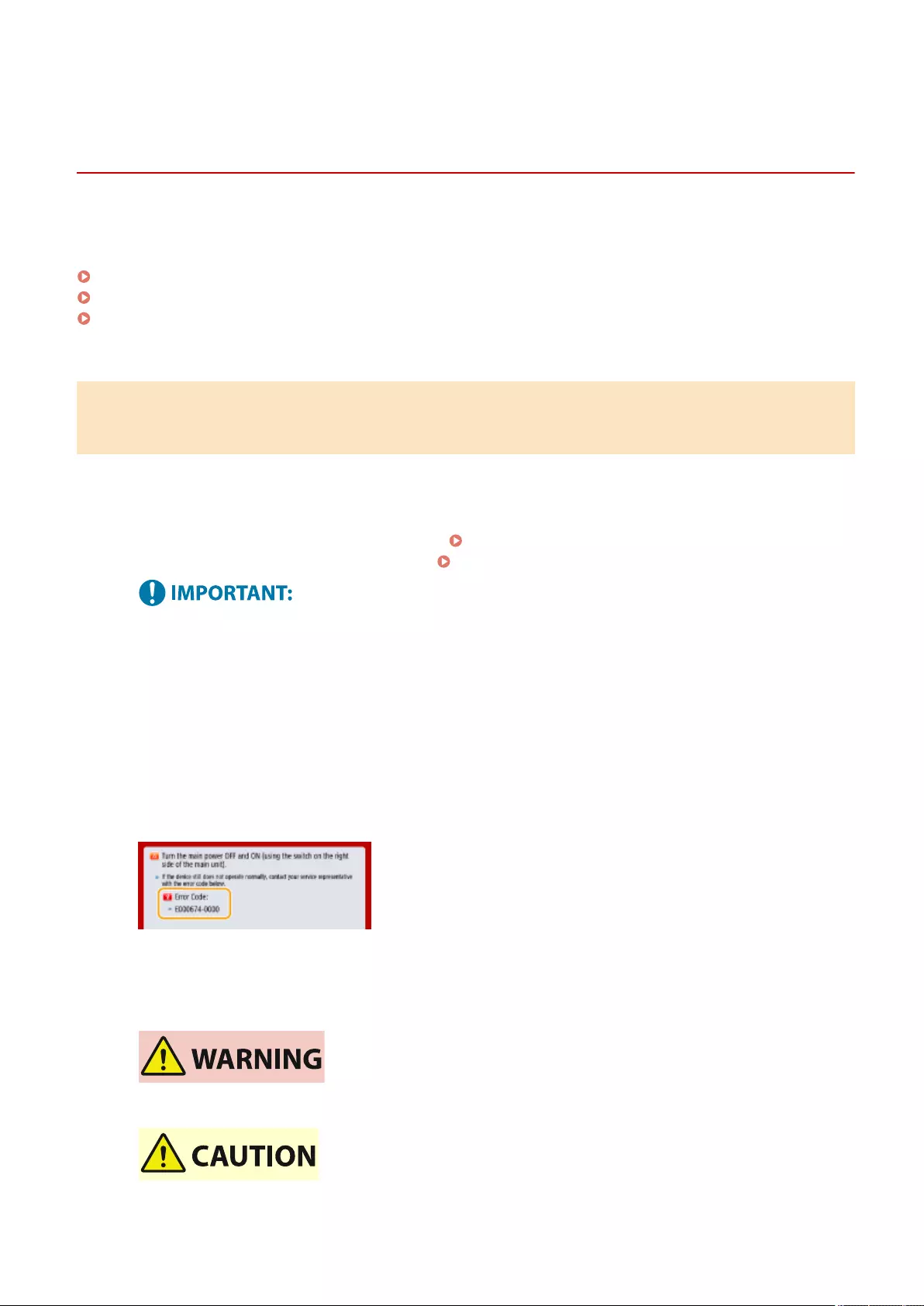
A Message Saying to Contact Your Dealer or Service
Representative Is Displayed
72JY-0J2
If the machine cannot operate normally due to a problem, a message is displayed on the touch panel display. Check
the reference according to the displayed message.
When a message saying to contact your dealer or service representative is displayed(P. 941)
When the <Limited Functions Mode> button is displayed(P. 942)
When the <This function is currently unavailable. You can use other functions from [Home].> message is
displayed(P. 942)
When a message saying to contact your dealer or service representative is
displayed
1Restart the machine.
●Press the power switch to turn the power OFF ( Turning OFF the Machine(P. 96) ), wait for longer than 10
seconds, and then turn the power ON again ( Turning ON the Machine(P. 95) ).
●Note that data waiting to be processed is erased when you turn the power OFF.
2If the message is still displayed, prepare the following information.
●Product name
●Your dealer or service representative where you purchased the machine
●The problem (the specic operation you performed and the result and symptom, etc.)
●Code displayed on the touch panel display
Multiple codes may be displayed.
3Turn the power of the machine OFF, pull out the power plug, and contact your dealer
or service representative.
●Do not connect or disconnect the power cord with wet hands, as this may result in electrical shock.
Troubleshooting
941
●Always grasp the power plug when disconnecting the power cord. Pulling on the power cord may expose
or snap the core wire, or otherwise damage the power cord. If the power cord is damaged, this could
cause current to leak, resulting in a re or electrical shock.
When the <Limited Functions Mode> button is displayed
You can continue to use the machine before resolving the problem by limiting functions.
1Press <Limited Functions Mode>.
2Press <Yes> to restart the machine.
●The machine is restarted with the Limited Functions mode.
●When the problem is resolved, the message prompting you to contact your dealer or service representative
disappears from the bottom left of the screen.
Functions available when the Print function is limited:
0UUY-0XS 0UW1-0Y4 0YRY-0JS 0X7F-0JK 0X7H-0JK 1100-0JX 0X6E-0JK 0X6W-0JK 10XJ-0JX 0X7C-0JK 0X7A-0JK 1106-0JX 0WXY-0JL 0X7E-0JK 10YY-0JX 10H3-0JU 0WR6-0JU 0WR7-0JU 108A-0JW 1116-0JW 10H4-0JU 0WR5-0JU 0YWJ-0HA 0YWH-0JK 0YWR-0H5 0YWK-0JK 0YWE-0JK 0YWF-0JK 140K-04Y
Fax, Scan, Remote Scanner, Tutorial, Quick Menu, Status Monitor, Remote UI
Functions available when the Scan function is limited:
Access Stored Files, Fax/I-Fax Inbox, Print, Tutorial, Quick Menu, Status Monitor, Remote UI
●Depending on the error, the process for storing system information is performed after the error
occurs. Do not turn OFF the machine until the process is complete.
When the <This function is currently unavailable. You can use other functions
from [Home].> message is displayed
140K-04Y 0YRY-0JS 1100-0JX 10XJ-0JX 1106-0JX 10YY-0JX
This message is displayed when you select a restricted function while in limited function mode or if the Print or Scan
function is restricted. Select a different function from the <Home> screen. For the available functions, see ( When
the <Limited Functions Mode> button is displayed(P. 942) ).
Troubleshooting
942
Countermeasures for Each Message
72JY-0J3
If an error occurs during scanning or printing, or if a problem occurs with the network connection or settings, a
message appears on the machine display or the Remote UI screen. For details about each message and solutions to
the problems, refer to the messages below. Also, if a six-digit number is displayed when you are logging in, see If a
six-digit number is displayed when you are logging in(P. 975) .
23 MEMORY FULL
There is insucient memory to register overlay forms and external characters, etc.
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer to increase the free memory, and
then try printing again. However, note that initializing the printer will erase all the print data in the
memory of the machine. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online
manual site.
●Press <Skip Error>, and continue printing. However, the data that could not be registered due to a lack of
memory will not be printed.
27 JOB REJECT
The specied emulation does not exist.
●Specify emulation that the machine supports. For more details, see Setting the Machine (PS/PCL/UFR II
Printer) via the online manual site.
●Press <Skip Error> to skip the printing that an error occurred for. You can perform the following printing.
33 WORK FULL
Could not print because the dedicated work memory was insucient.
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer to increase the free memory, and
then try printing again. However, note that initializing the printer will erase all the data in the memory of
the machine. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
●Press <Skip Error>, and continue printing. However, the data for which an error was displayed will not be
printed correctly. Also note that registered data such as overlay forms and macros may be deleted.
52 IMAGEMODE REJECT
Data that cannot be processed was sent while printing an image.
●Press <Skip Error> to skip the printing that an error occurred for. However, the data for which an error was
displayed will not be printed.
●Perform printing again using a printer driver that supports the data format of the image.
The Active Directory site information is invalid. Contact the system manager.
The site information of Active Directory is not set correctly.
●Check whether <Timing of Site Information Retrieval:> and <Site Access Range:> are set correctly in <Use
of Access Mode within Sites:>.
Troubleshooting
943
Could not verify CRL.
Could not conrm the CA certicate of the certicate authority that issued the certicate revocation list
(CRL).
●Register the CA certicate of the certicate authority that issued the certicate revocation list (CRL).
Registering a CA Certicate(P. 601)
D1 Replot Buffer Full
Could not redraw because data could not be registered to the replot buffer.
●Press <Skip Error>, and continue printing. However, the data that caused the error will not be printed
correctly. For information on the replot buffer, see Print.
D1 Div. Print. Bffr Full
Could not perform divided printing because data could not be registered to the buffer for divided
printing.
●Cancel printing ( Canceling Printing(P. 346) ), set <Divide Mode> to <No> and <Enlarge/Reduce> to
<Auto> in the HP-GL setup menu, specify the output paper size, and perform printing again. However, the
data will be enlarged/reduced when printed. For more details, see Print.
●Press <Skip Error>, and continue printing. However, the data that could not be registered will not be
printed correctly. For information on divided printing, see Print.
D1 Polygon Buffer Full
Could not draw because data could not be registered to the polygon buffer.
●Press <Skip Error>, and continue printing. However, the data that could not be registered will not be
printed correctly. For information on the polygon buffer, see Print.
D0-nn error (nn is two alphanumeric characters)
The printer stopped operating normally due to an unknown problem.
●Restart the machine. Press the power switch to turn the power OFF ( Turning OFF the Machine(P. 96) ),
wait for longer than 10 seconds, and then turn the power ON again ( Turning ON the Machine(P. 95) ).
If the message is still displayed after restarting the machine, make a note of the message and contact your
dealer or service representative.
Could not send the new PIN via e-mail. Check the settings.
Could not send an e-mail for resetting the PIN.
●Check whether an e-mail address is set.
●Check the e-mail settings and network settings.
FF FONT FULL
Could not register font information in the font table because there were too many fonts to register.
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer to increase the free memory, and
then try printing again. However, note that initializing the printer will erase all the data in the memory of
the machine. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
Troubleshooting
944

●Press <Skip Error>, and continue printing. However, the data that could not be registered will not be
printed correctly.
FM DL SIZE ERROR n (n is a single alphanumeric character)
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM DL SCALE ERROR n (n is a single alphanumeric character)
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM DL FONT MEMORY FULL
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM FILE ACCESS ERROR
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM SC WORK MEM. ERROR n (n is a single alphanumeric character)
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM ALIGNMENT ERROR
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM FONT PARSE ERROR
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM FONT MEMORY FULL
The printer stopped operating normally due to an unknown problem.
Troubleshooting
945
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
FM WORK MEMORY ERROR
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
IEEE 802.1X error. Set the correct authentication information.
The client authentication information is not set correctly.
●Check whether the authentication method and authentication information (key and certicate, user name
and password, and CA certicate) are set correctly.
IEEE 802.1X error. No reply from the destination.
An error occurred while communicating with the authenticator.
●Check whether the authenticator (LAN switch) and RADIUS server are set correctly.
IEEE 802.1X error. Cannot analyze the certicate.
Failed to analyze the server certicate sent from the RADIUS server.
●Check the content of the server certicate of the RADIUS server.
IEEE 802.1X error. The certicate is incorrect.
An error occurred when using the server certicate sent from the RADIUS server as a CA certicate for
validation.
●Check the content of the server certicate of the RADIUS server and the CA certicate registered in the
machine.
Registering a CA Certicate(P. 601)
IEEE 802.1X error. The certicate has expired.
The server certicate sent from the RADIUS server has expired.
●Check the expiration date of the server certicate of the RADIUS server.
IEEE 802.1X error. Change the authentication password.
The password has expired.
●Set a new password.
IEEE 802.1X error. Check the authentication settings.
The authentication method set in the machine and the authentication method set in the RADIUS server
do not match.
●Check the authentication method set in the machine and the RADIUS server, and set the correct
authentication method.
Troubleshooting
946
Set the IP address.
The IP address of the machine is not set.
●Set the IP address in <TCP/IP Settings>, and restart the machine.
Setting an IP Address(P. 34)
Cannot register PDF with Format to PDF/A as default. All other settings have been
registered.
You tried to register a default value for <Scan and Send>, <Scan and Store>, or <Access Strd. Files>, while
the <Format PDF to PDF/A> settings for the <PDF> le format was changed.
●You cannot register default settings if you change the <Format PDF to PDF/A> setting for the <PDF> le
format. Register default settings after changing settings other than the <Format PDF to PDF/A> setting.
Check the server name in the SMB server settings.
A computer or printer with the same name as the SMB server is registered in the WINS database.
●If <WINS Resolution> is set to <On> in <WINS Settings>, do not register a computer or printer with the
same name as the SMB server in <Computer Name/Workgroup Name Settings> in <TCP/IP Settings>.
Making WINS Settings(P. 52)
<Computer Name/Workgroup Name Settings>(P. 783)
A computer or printer with the same name as the SMB server exists in the workgroup that the machine
belongs to.
●Do not register a computer or printer with the same name as the SMB server in <Computer Name/
Workgroup Name Settings> in <TCP/IP Settings>.
<Computer Name/Workgroup Name Settings>(P. 783)
TLS Error
The WebDAV server does not support TLS encrypted communication.
●Set TLS on the WebDAV server side, according to your environment.
The proxy server does not support TLS encrypted communication.
●If the WebDAV client connects to the internet via a proxy, set TLS on the proxy server side.
Cannot delete the default key because it is in use by TLS or other settings. Check the
settings.
The key and certicate you are trying to delete is being used in TLS encrypted communications.
●Set all TLS settings to <Off> to stop TLS encrypted communication.
TCP/IP Error
Could not automatically retrieve the address with DHCP and Auto IP.
●If the address cannot be automatically retrieved with DHCP and Auto IP, <IP Address> in <IPv4 Settings> is
set to 0.0.0.0. Set the correct IPv4 address. In addition, if you selected <Wired LAN + Wireless LAN> in
<Select Interface>, correctly congure the IPv4 address of the wireless LAN (sub line).
Setting an IPv4 Address(P. 35)
<IP Address Settings>(P. 782) (<Sub Line Settings>)
Troubleshooting
947
0.0.0.0 is set as a xed IPv4 address in <IP Address> in <IPv4 Settings>.
●Set the correct IPv4 address.
Setting an IPv4 Address(P. 35)
<IP Address Settings>(P. 782) (<Sub Line Settings>)
The IPv6 address is not set correctly.
Check the following. It may take several minutes until the stateless address is decided.
●Check whether <Use IPv6> is set to <On> in <IPv6 Settings>.
●When using a stateless address or DHCPv6, check whether each address has been retrieved.
●If the address has not been retrieved, check the settings of the router and the DHCPv6 server.
Setting an IPv6 Address(P. 37)
The address of the DNS server is not set correctly.
●Check whether the address of the DNS server is set correctly in <IPv4> or <IPv6>.
Making DNS Settings(P. 45)
Could not send to the TCP/IP protocol stack.
●Check whether the IPv4 address or IPv6 address is set correctly in <IPv4 Settings> or <IPv6 Settings>.
Setting an IPv4 Address(P. 35)
Setting an IPv6 Address(P. 37)
Out of resources. Wait a moment, then try again.
TCP/IP resources were insucient while continuously sending or after continuously sending with FTP or
Windows (SMB).
●Try again after waiting a while.
Check the TCP/IP.
The TCP/IP of the machine is not operating.
●Check the IP address, DHCP, and Auto IP settings in <TCP/IP Settings>.
Setting an IPv4 Address(P. 35)
●If you selected <Wired LAN + Wireless LAN> in <Select Interface>, check the settings for the IP address and
DHCP in <Sub Line Settings>.
<IP Address Settings>(P. 782) (<Sub Line Settings>)
Check the TCP/IP. (Main Line)
The IP address of the main line is set to "0.0.0.0".
●Set a different IP address.
Setting an IPv4 Address(P. 35)
Check the TCP/IP. (Sub Line)
The IP address of the sub line is set to "0.0.0.0".
●Set a different IP address.
Setting the IPv4 Address of the Sub Line(P. 40)
Troubleshooting
948
Universal Print: A server communication error occurred.
The machine is not connected to the network correctly.
●Check the machine and network settings, and try connecting again. Could not communicate because a
server error occurred.
●Check whether the server is operating normally. Communication with the server is blocked due to rewall
settings.
●Congure the rewall settings to allow communication.
Universal Print: Could not authenticate with server.
An error has occurred during server authentication.
●Restart the machine. If the message still appears after restarting the machine, make a note of the
message and contact your dealer or service representative.
Universal Print: The certicate has expired.
The expiration date of the certicate has expired.
●Delete this machine from Azure Active Directory and the computer, re-register the machine, and then
update the certicate.
Universal Print: An internal error occurred.
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message still appears after restarting the machine, make a note of the
message and contact your dealer or service representative.
Universal Print: The printer is not registered.
This machine was deleted from Azure Active Directory and could not be communicated with.
●Re-register this machine in Azure Active Directory.
Check the wired LAN adapter connected to the USB port.
Multiple USB-LAN adapters are connected, or the USB-LAN adapter is not connected/recognized.
●Check the connection of the USB-LAN adapter.
Connecting to a Wired LAN for the Sub Line(P. 25)
●If you reconnected the USB-LAN adapter, restart the machine.
Front Side(P. 83)
XPS Print Range Error
There are no pages that can be processed in the specied range for printing.
●Specify a correct page range.
XPS Image Data Error
Failed to extend the image data.
Troubleshooting
949

●Replace the image data in the XPS le and try printing again.
XPS Spool Memory Full
There is insucient memory to process the XPS data.
●Restart the machine and try printing again. If you still cannot print, divide the pages into multiple les and
print them separately.
XPS Data Error
An invalid command is specied due to corrupt data, etc. and processing cannot continue.
●Perform printing again using XPS data in a format supported by the machine.
XPS Unsupport Image Err
An unsupported data format is included.
●Convert the data to the TIFF or JPEG format and try printing again.
XPS Font Error
Failed to analyze the font data.
●Replace the font data in the XPS le and try printing again.
XPS Page Data Error
Cannot generate pages because the descriptions are incorrect.
●Perform printing again using XPS data in a format supported by the machine.
XPS Memory Full
There is insucient memory to process the XPS data.
●Press <Skip Error>, and continue printing. However, pages that include the data that caused the error may
not be printed correctly.
You do not have privileges to access the XXX page.
You tried to log in as a user without the required privileges.
●Log in as a user with the required privileges.
The account has expired. Contact the system manager.
The certicate may have expired.
●Conrm the expiration date of for the certicate registered in the machine. If the certicate has expired,
register a certicate within the validity period.
Registering a Key and Certicate for Network Communication(P. 600)
The expiration date of the account has expired.
●Conrm the expiration date of the corresponding account.
Troubleshooting
950

Access point connection error. Check Wireless LAN Information.
The access point could not be found.
●Check the wireless LAN settings.
Check the settings and information of the wireless LAN(P. 27)
AP Mode: Ended due to an error.
No data was sent or received between the machine and the connected mobile device for over three
minutes.
●Check the connection between the machine and the mobile device.
AP Mode: Ended because no other device could be found.
Cannot nd a mobile device capable of connection.
●Check the network settings of the mobile device, and then connect by holding it near the machine.
Depending on your mobile device, the machine may not operate correctly. If you cannot successfully
connect, contact your dealer or service representative.
AP Mode: Max no. of devices that can connect has been reached.
Cannot connect because the number of mobile devices which can connect simultaneously has reached
the upper limit.
●Disconnect any unnecessary mobile devices, or wait until other mobile devices have disconnected.
AP Mode: Connected to other devices.
Cannot connect because the machine is already connected to another device.
●Wait until the connection to the other device has terminated.
Following toner cartridges have reached end of their lifetimes. Replacing the toner
cartridges is recommended. Printing can be continued by pressing [Resume Printing],
but problems due to using those cartridges are not covered by warranty.
The toner cartridge has expired.
●It is generally recommended that you replace the toner cartridge, but it is also possible to continue
printing. However, in that case, the quality of printing cannot be guaranteed.
Procedure for Replacing the Toner Cartridge(P. 882)
Could not delete authentication information because an error occurred.
The authentication information could not be deleted because an unknown error occurred.
●Contact your dealer or service representative.
Could not set authentication information because an error occurred.
The authentication information could not be set because an unspecied error occurred.
●Contact your dealer or service representative.
Troubleshooting
951
An error occurred. Contact the system manager.
The selected user has already been deleted.
●Log in as the Administrator and register the button again.
An unexpected system error occurred.
●Check the operations and log in again. If you still cannot log in, consult your system administrator.
No response.
Could not send because an error occurred in the server.
●Check whether the server is operating normally.
The machine is not connected to the network correctly.
●Check the machine and network settings, and try connecting again.
Setting up the Network Environment(P. 19)
Could not send e-mail or an I-fax because an error occurred in TCP/IP.
●Check the machine and network settings, and try connecting again.
Setting up the Network Environment(P. 19)
Replace the waste toner container.
The waste toner container is full, so printing is not possible any longer.
●Follow the instructions on the screen to replace the waste toner container.
Procedure for Replacing the Waste Toner Container(P. 885)
Cannot recall the settings because the function for the button does not exist.
A personal button or shared button that includes a function not supported by the machine was used.
●If you have imported personal buttons/shared buttons registered in another imageRUNNER ADVANCE
series device, buttons not supported by the machine may be included. Register the personal buttons/
shared buttons again in the machine.
Cannot recall the settings because the function for the button is disabled. Enable the
function, then try again.
The operation could not be executed by pressing the button because the function to use has been
stopped.
●Press the button after enabling the function that was stopped to be used.
Synchronize Custom Settings: Log in again for synchronization.
There is an inconsistency between the synchronization data of the server machine and that of the client
machine synchronizing custom settings.
●Log out, and then log in again.
Troubleshooting
952
Synchronize Custom Settings: Some settings are restricted.
The client machine was synchronizing custom settings, but the server machine is turned OFF or is not
operating normally.
●Turn the server machine ON.
●If the server machine is operating normally, check that its network cable is connected before checking the
network settings.
Synchronize Custom Settings: An error occurred.
An error occurred during synchronization startup.
●Conrm that the address of the destination server is correct for the synchronization of custom settings
(client).
●If the synchronization of custom settings (client) is complete, restart synchronization.
●Restart the machine.
●If the problem is not resolved even after restarting the machine, check the followings.
1. You can ping the IP address set for the destination
2. The address of the destination server is correctly displayed
Synchronize Custom Settings: Enabling synchronization...
Processing to begin synchronization of custom settings is being performed.
●Wait until processing is complete.
Synchronize Custom Settings: Server authentication error.
Authentication with the server machine could not be achieved.
●Check that the authentication user ID and new password for the synchronization of custom settings
(client) are the same as the authentication user ID and password with administrator privileges in the
server machine.
●If the synchronization of custom settings (client) is complete, restart synchronization.
●Restart the machine.
Synchronize Custom Settings: Cannot nd the server.
The server machine for synchronization of custom settings could not be found using Auto Search.
●Conrm that the server machine is turned ON.
●If the server machine is operating normally, check that its network cable is connected before checking the
network settings.
●Conrm the usable conditions for Auto Search. Starting Setting Synchronization(P. 659)
●Without using Auto Search, manually specify the server address of the destination for the synchronization
of custom settings (client), and the search depth (router).
●If the synchronization of custom settings (client) is complete, restart synchronization.
●Restart the machine.
Synchronize Custom Settings: Cannot identify the server.
Multiple server machines for the synchronization of custom settings were found using Auto Search.
Troubleshooting
953
●Manually specify the server machine or shut down all unnecessary server machines that are currently
running so that only one remains.
When specifying the server machine manually
●Without using Auto Search, manually specify the server address of the destination for the synchronization
of custom settings (client), and the search depth (router). Starting Setting Synchronization(P. 659)
When shutting down unnecessary servers that are currently running
●Even if the network settings of the server machine include both IPv4 and IPv6, if IPv6 is prioritized and the
client machine disables IPv6, the client machine cannot connect via search. Enter the IPv4 address for the
destination server address.
●If the synchronization of custom settings (client) is complete, restart synchronization and then restart the
machine.
Check the covers.
The cover of optional equipment is open.
●Check whether the covers of optional equipment are closed.
An error occurred when auto exporting the audit log.
The data could not be exported because a server error occurred.
●Check that the server is functioning normally.
The machine is not connected to the network correctly.
●Check the settings of the machine and the network, and try connecting again.
The automatic export settings are incorrect.
●Check that the automatic export settings are correct ( Exporting Logs Automatically(P. 621) ).
Failed to generate Device Signature Key. Set the e-mail address in Communication
Settings.
To use device signatures, you must rst congure the e-mail address of the machine.
●Congure the e-mail address of the machine ( Setting E-mail/I-Fax Communication(P. 70) ), and then
generate a key for device signatures ( Generating a Device Signature Certicate(P. 578) ).
The function may be stopped. Buttons could not be imported.
When importing data, buttons with functions not supported by the machine were included.
●Check whether all the buttons have been imported to the machine.
Routing registration failed. Check Static Routing Settings.
There is an entry that routing table registration failed for in the static routing settings.
●Check the registered destination address and gateway address, and specify the correct settings.
Setting Static Routing(P. 61)
Remove the original from the platen glass.
An original remains on the platen glass.
●Remove the original from the platen glass, and place another original.
Troubleshooting
954
The original scanning area (feeder) is dirty.
The document feed scanning area (on the feeder side) is dirty.
●Clean the document feed scanning area.
Cleaning the Feeder(P. 878)
Original scanning area (thin glass strip) is dirty.
The document feed scanning area (the long and thin glass strip) is dirty.
●Clean the document feed scanning area.
Cleaning the Feeder(P. 878)
Return the originals to their correct order, then press the [Start] key.
Scanning stopped because an unknown problem occurred in the feeder.
●Scan the original again from the rst page.
Return the originals to their correct order, then press the [Start] key. (The data size of
the scanned original exceeds the limit. Settings will be automatically corrected and the
originals will be scanned again.)
Scanning was canceled because the data of the scanned document exceeded the maximum size that can
be handled by the machine.
●Scan the original again from the rst page. If you still cannot scan the original, you may be able to scan by
lowering the setting in <Sharpness>, and setting <Original Type> to <Text>.
The device is currently being used by another user. Wait a while, and then try to
perform the operation again.
You cannot use the machine when it is being used by another user.
●Try again after waiting a while.
The number of search results exceeds the limit. Change search conditions, then try
again.
Destinations exceeding the maximum number of search results were found.
●Narrow the search conditions and try searching again.
●Increase the maximum number of search results in <Max Addresses to Search> in <Register LDAP Server>.
Registering the LDAP Server(P. 53)
The search condition includes characters that cannot be used with the selected server.
"\" is used in the search conditions.
●Remove the "\" from the search conditions and try searching again.
If an uneven number of "(" or ")" are included or an "*" is included inside parentheses, search conditions
are not established.
●Set a correct combination of characters, and try searching again.
Troubleshooting
955
If <LDAP Server Version and Character Code> is set to <ver.2 (JIS)>, only ASCII code (0x20 to 0x7E)
characters can be used.
●Remove the invalid characters and try searching again.
An error occurred when verifying.
The certicate is invalid.
●Register the correct certicate and specify the settings again.
Conguring the Key and Certicate for TLS(P. 549)
Registering a Key and Certicate for Network Communication(P. 600)
This CRL is invalid.
The certicate revocation list (CRL) may be corrupt, or a signing algorithm not supported by the machine
may be used.
●Register the correct certicate revocation list (CRL).
Registering a Certicate Revocation List (CRL)(P. 603)
This CRL has expired.
The start date for the certicate revocation list (CRL) may be set to a date in the future.
●Check the start date of the certicate registered in the machine. If the start date is set to a date in the
future, use the certicate on a day after that date.
Registering a Certicate Revocation List (CRL)(P. 603)
The date and time set on the machine may be incorrect.
●Check the date and time setting of the machine.
Setting the Date/Time(P. 17)
Cannot register because the algorithm of this key is not supported.
You tried to register the key and certicate le of an unsupported encryption algorithm.
●Register the key and certicate le of a supported encryption algorithm.
Registering a Key and Certicate(P. 600)
System Specications(P. 1084)
Cannot set as the default key because this key is corrupted or invalid.
The key specied for the machine cannot be set because it is corrupted.
●Register the key again.
Generating the Key and Certicate for Network Communication(P. 552)
Registering a Key and Certicate(P. 600)
This certicate has been revoked.
The certicate is included in the certicate revocation list (CRL).
●Register a new certicate.
Registering a Key and Certicate for Network Communication(P. 600)
Troubleshooting
956
This certicate is invalid.
The certicate is invalid.
●Register the correct certicate and specify the settings again.
Conguring the Key and Certicate for TLS(P. 549)
Registering a Key and Certicate for Network Communication(P. 600)
This certicate has expired.
The certicate may have expired.
●Check the expiration date of the certicate registered in the machine. If the certicate has expired, register
a valid certicate.
Registering a Key and Certicate for Network Communication(P. 600)
The date and time set on the machine may be incorrect.
●Check the date and time setting of the machine.
Setting the Date/Time(P. 17)
No response from the server. Check the settings.
The specied server may have a problem such as not being specied correctly, not being turned on, or
having insucient resources.
●Try specifying the server again after waiting a while. If there is still no response from the server, select
another server.
Cannot start searching because the server version settings are incorrect. Check the
settings.
A different server LDAP version is set in the LDAP server and the machine.
●Change the setting in <LDAP Server Version and Character Code> in <Register LDAP Server> to "ver.2" to
match the LDAP server.
Registering the LDAP Server(P. 53)
Check the server.
You tried to access the server without using a proxy.
●Check whether the WebDAV server settings are correct.
●Check whether the proxy settings are correct.
Setting a Proxy(P. 547)
Access to the destination is not allowed.
●Check whether the WebDAV server settings are correct.
You tried to access the server via a proxy without using TLS encrypted communication.
●Set <Use Divided Chunk Send for WebDAV TX> to <Off>.
<Use Divided Chunk Send for WebDAV TX>(P. 822)
The proxy server failed to communicate with an upstream server.
●Check whether the WebDAV server and proxy server settings are correct.
Troubleshooting
957
An HTTP protocol version not supported by the WebDAV server was used in a request from the WebDAV
client.
●Check whether the WebDAV server settings are correct.
The disk space of the WebDAV server is insucient for the request from the WebDAV client.
●Make sucient disk space for the request available on the WebDAV server.
The appropriate paper size, A4, is not available.
Paper of the optimal size selected with Automatic Paper Selection has not been loaded.
●Load paper of the displayed size.
<Paper Source Auto Selection> is set to <Off>.
●Specify the paper drawer manually.
●Set a paper source loaded with the optimal paper size to <On> in <Paper Source Auto Selection>.
<Paper Source Auto Selection>(P. 808)
Paper of a type that cannot be selected with Automatic Paper Selection is loaded.
●Specify the paper drawer manually.
●If you are copying, select the <Consider Paper Type> check box in <Paper Source Auto Selection>.
<Paper Source Auto Selection>(P. 808)
Sub line was disconnected due to a subnet mask conict.
The network addresses of the main line and sub line conict.
●Check the IP address and subnet mask settings of the main line and sub line.
Setting an IP Address(P. 34)
There are too many subdirectories.
The maximum number of characters was exceeded because the number of levels was too deep.
●The destination cannot be specied. Specify another destination.
Remove all the output paper.
Paper has accumulated in the output tray.
●Remove all paper from the output tray.
The contents of the specied le may be incorrect.
You tried to register a button by specifying a different le when importing.
●Register the correct le and try importing again.
The default key is not set. Check TLS Settings.
The key and certicate (TLS server certicate) are not registered.
●To use TLS encrypted communication, rst register the key to be used.
Conguring the Key and Certicate for TLS(P. 549)
Troubleshooting
958
The default key is not set. Check the Key and Certicate List settings in Certicate
Settings.
The key and certicate (TLS server certicate) are not registered.
●Register a key and certicate for performing TLS encrypted communication.
Generating the Key and Certicate for Network Communication(P. 552)
Registering a Key and Certicate(P. 600)
A wired LAN adapter that cannot be used has been connected.
A USB-LAN adapter that cannot be used with the machine is connected.
●For information on the USB-LAN adapters that can be used, contact your dealer or service representative.
Connecting to a Wired LAN for the Sub Line(P. 25)
Could not verify the certicate.
The CA certicate of a certicate authority could not be conrmed.
●Register a CA certicate issued by a certicate authority.
Cannot connect.
Failed to perform proxy authentication.
●Check whether the proxy settings are correct.
Setting a Proxy(P. 547)
Cannot edit/delete the paper because it is being used for other settings in Settings/
Registration.
You tried to edit or delete paper that was registered in another setting via <Paper Type Management
Settings>.
●The paper is registered as "Favorite Paper" in <Register Favorite Paper (Multi-Purpose Tray)> and <Multi-
Purpose Tray Defaults>. Cancel the registration.
Registering Frequently Used Paper Size and Type for the Multi-purpose Tray(P. 148)
Check Computer Name in Settings/Registration.
A computer or printer with the same name is registered in the WINS database.
●When <WINS Resolution> in <WINS Settings> is set to <On>, do not register a computer or printer with a
name already listed in <Computer Name/Workgroup Name Settings> in <TCP/IP Settings>.
Making WINS Settings(P. 52)
<Computer Name/Workgroup Name Settings>(P. 783)
A printer or computer with the same name already exists in the same workgroup as this machine.
●Do not register a computer or printer with a name already listed in <Computer Name/Workgroup Name
Settings> in <TCP/IP Settings>.
<Computer Name/Workgroup Name Settings>(P. 783)
Troubleshooting
959
A toner cartridge of the wrong color may have been inserted. If this toner cartridge is
used, a malfunction may occur. Check the inserted toner cartridge.
The color of the inserted toner cartridge may be incorrect.
●Make sure to check the status of the inserted toner cartridge.
To continue using the toner cartridge, press <I Agree>. If you select this option, the operation of the
machine is not guaranteed.
To replace the toner cartridge, press <Cancel>.
If you are not sure about the remedies, contact your dealer or service representative from which you
purchased the toner cartridge.
Cannot change the settings because the selected key is being used.
The key and certicate you are trying to delete is being used in TLS encrypted communications.
●Set all TLS settings to <Off> to stop TLS encrypted communication.
Cannot nd the selected server. Check the settings.
The host name cannot be identied when the authentication information of the LDAP server is set to
<Use (Security Authentication)>.
●Check whether the settings in <DNS Settings> are correct.
<Network>(P. 782) <TCP/IP Settings>
●Check whether the settings on the DNS server side are correct.
The IP address could not be identied.
●Check whether the settings in <DNS Settings> are correct.
<Network>(P. 782) <TCP/IP Settings>
●Check whether the settings on the DNS server side are correct.
Cannot connect to the selected server. Check the settings.
Could not connect to the IP address/port.
●Check whether the server address and port number in <Register LDAP Server> are correct.
Registering the LDAP Server(P. 53)
●Check whether the LDAP server is operating normally.
●If <Authentication Information> is set to <Use (Security Authentication)> for the LDAP server, check
whether UDP packets are blocked by the lter.
●Check whether the gateway address set in <TCP/IP Settings> is correct.
Setting an IPv4 Address(P. 35)
The setting item specied from Settings Menu cannot currently be used. Contact the
system manager.
The selected settings menu cannot be changed or is not available.
●Contact your system administrator.
The selected button may be unavailable. Contact the system manager.
The selected user does not exist.
Troubleshooting
960

●Log in as the Administrator and register the button again.
"Administrator" has been disabled.
●Select a user with administrator privileges.
Could not send.
The data to send is too large.
●Reduce the size of the data and try sending again.
Session timed out. Wait a moment, then try to access the database again.
The session timed out because the specied length of time elapsed.
●Try accessing again after waiting a while. If the session continues to time out, restart the machine.
Cannot complete searching due to timeout. Check the settings.
The search could not be completed within the specied time.
●Increase the length of the timeout time in <Search Timeout> in <Register LDAP Server>.
Registering the LDAP Server(P. 53)
Could not execute because the le contains unsupported data.
The page cannot be generated due to incorrect content.
●Try printing again using data in a format compatible with the machine.
Direct Connection: Ended due to an error.
Failed to connect to the mobile device, or no data was sent or received between the machine and the
connected mobile device for a certain period of time.
●Check the connection between the machine and the mobile device.
Direct Connection: Ended because no other dev. could be found.
Cannot nd a mobile device capable of connection.
●Check the network settings of the mobile device, and then connect by holding it near the machine.
Depending on your mobile device, the machine may not operate correctly. If you cannot successfully
connect, contact your dealer or service representative.
A non-Canon toner cartridge may be inserted, so information about remaining toner
cannot be detected properly.
A toner cartridge for which the print quality cannot be guaranteed may be installed.
●To continue using the toner cartridge, press <I Agree>. If you select this option, the operation of the
machine is not guaranteed.
Adjusting gradation... Wait a moment.
The machine is performing auto adjustment.
Troubleshooting
961
●Printing will automatically resume when the adjustment is complete. Wait a while.
Could not access the database. Restart the device.
Failed to access the user database because it is corrupt, etc.
●Restart the machine.
Digital Sig. Cert. Access Error
Could not access the device certicate when sending the device signature.
●Check the content of the device certicate registered in the machine.
Generating a Device Signature Certicate(P. 578)
Certicate Expiration Date Error
The certicate has expired.
●Check the expiration date of the certicate.
Time Stamp Digital Sig. Error
The time stamp license le is corrupt.
●Check the status of the time stamp license le.
The password of the time stamp license le is incorrect.
●Check the password of the time stamp license le, and set the correct password.
The time stamp module of the machine is not functioning correctly.
●Restart the machine.
●If it still does not function correctly, contact your dealer or service representative.
Cannot log in because multiple users are registered under the same user name.
Contact the system manager.
The user name could not be distinguished because user names are set to be not case-sensitive.
●Change the settings to make user names case-sensitive, or register another user name.
Cannot register any new buttons because the number of registered buttons has
reached the limit. Buttons already registered can be overwritten.
The button cannot be registered because the maximum number of buttons has been exceeded.
●Overwrite an existing button or delete unnecessary buttons.
Customizing the <Home> Screen(P. 159)
Troubleshooting
962

Cannot import because the number of buttons for registration has exceeded the upper
limit.
Buttons cannot be registered while importing because the maximum number of personal buttons/
shared buttons has been exceeded.
●Delete unnecessary personal buttons/shared buttons, and import the data again.
Could not register because the number of registered users has reached the limit.
Cannot register the user because the number of users has exceeded the upper limit.
●Delete any unnecessary users.
Replace the toner cartridge. (XXXX)
The toner in the toner cartridge has run out, and printing cannot be performed.
●Pressing the icon displayed at the bottom right of the screen displays a motion video to give the
instructions for toner cartridge replacement. Follow these instructions to replace the toner cartridge.
Replacing the Toner Cartridge(P. 881)
●The "XXXX" in the message indicates the toner color.
●When black toner or all the toners have run out, you need not perform the operation of pressing the
icon at the bottom right of the screen. The toner cartridge replacement screen is automatically
displayed, which allows you to perform the replacement procedure in accordance with the instructions
given by motion video.
Cannot recognize the inserted toner cartridge. A non-Canon toner cartridge may be
inserted, so information about remaining toner cannot be detected properly.
A toner cartridge for which the print quality cannot be guaranteed may be installed.
●To continue using the toner cartridge, press <I Agree>. If you select this option, the operation of the
machine is not guaranteed.
Cannot recognize the toner cartridge. Pull out the toner cartridge, then insert it again
or information about remaining toner won't be detected properly.
The toner cartridge may not be correctly inserted, the toner cartridge may have been damaged, or a
toner cartridge with the wrong model number may be inserted.
●Reinsert the toner cartridge. Make sure to check the status of the inserted container. For instructions on
checking the model number of the toner cartridge, see Consumables(P. 888) .
To continue using the toner cartridge, press <Close> or <I Agree>. If you select this option, the operation
of the machine is not guaranteed.
To replace the toner cartridge, press <Cancel>.
If you are not sure about the remedies, contact your dealer or service representative from which you
purchased the toner cartridge.
XXXX toner is low. Replacement is not yet needed.
Toner in the toner cartridge is running out.
Troubleshooting
963

●You can continue printing, but at this time you should prepare a new toner cartridge to have it available
when needed.
●This message may not be displayed depending on your contract.
●The "XXXX" in the message indicates the toner color.
The entered PIN is incorrect.
An incorrect PIN was entered.
●Enter the PIN again.
●If you do not know the correct PIN, contact the administrator.
The authentication server is not running. Contact the system manager.
The LAN cable is disconnected.
●Connect the LAN cable.
The Active Directory server is not running.
●Start the Active Directory server.
The KDC service of Active Directory is stopped.
●Follow the procedure below to check the status of the service.
1 Start the "Service" management tool of Active Directory.
2 Check whether the Active Directory server is operating normally.
Communication with the Active Directory * server is blocked by the rewall.
●Stop blocking the default port 88.
* If Active Directory is set as the login destination, communication is normally performed with the UDP protocol using port 88, but
the data may be processed with the TCP protocol if it exceeds a certain size.
Cannot nd the authentication server. Contact the system manager.
The LAN cable is disconnected.
●Connect the LAN cable.
The primary/secondary DNS server settings of the machine are incorrect or not set.
●Check and adjust the DNS server settings of the machine.
The DNS server specied in the machine is not running or its service is stopped.
●Follow the procedure below to check the status and settings of the DNS server.
1 Check whether the DNS server specied in the machine is running.
2 Start the "Service" management tool of the DNS server.
3 Check the status in <DNS Server>, and if <Enable> is not displayed, right-click and select <Enable>.
Check whether the host record exists in the DNS server.
●Check whether a host record exists in the DNS server, and whether the forwarder settings are correct.
No password is set on the authentication server side. Contact the system manager.
An appropriate password was not set on the server side when conguring or upgrading Active Directory.
Troubleshooting
964
●Reset the password of the corresponding account, and specify the settings again.
Cannot log in because anonymous access to the authentication server is not allowed.
Contact the system manager.
Anonymous access is not allowed on the LDAP server.
●On the information input screen of the LDAP server, select <Use authentication information>, and then
specify the user name and password according to what is registered in the LDAP server.
Registering Server Information(P. 507)
The account information necessary to log in to the authentication server is invalid.
Contact the system manager.
The user name or password is not set correctly.
●Conrm the authentication user ID and password, and whether the user has administrator privileges.
The attributes specied in the server settings are not set correctly.
●Conrm that the attributes are correct. Also, make sure that the elds (attribute names) do not contain
invalid values.
Registering Server Information(P. 507)
The administrator account information specied in the server settings is not set correctly. Alternatively,
the user could not log in as an administrator.
●Specify the correct administrator account information.
The information for the server settings is insucient.
●Conrm that the attributes necessary for logging in are set correctly.
Registering Server Information(P. 507)
A competing IP address was found on the network.
The IPv4 address set for the machine already exists in the same network as the machine.
●Change the IP address of the machine in <IP Address> in <IPv4 Settings> so that it does not conict with
the IP address of another device.
Setting an IPv4 Address(P. 35)
An IP address conict was detected on the network (Main Line).
The IPv4 address set for the main line of the machine already exists on the same network as the
machine.
●Change the IP address of the main line of the machine so that it does not conict with the IP address of
another device.
Setting an IPv4 Address(P. 35)
An IP address conict was detected on the network (Sub Line).
The IPv4 address set for the sub line of the machine already exists on the same network as the machine.
●Change the IP address of the sub line of the machine so that it does not conict with the IP address of
another device.
Setting the IPv4 Address of the Sub Line(P. 40)
Troubleshooting
965
Could not perform the operation because a network error occurred.
Writing from an external source is not allowed.
●Set <Prohibit Writing from External> for the destination to <Off>.
The full path (the folder name indicating the lename and destination to save) is too long.
●Shorten the folder name or le name or change the destination to save so that the number of characters
for the path is 256 characters or fewer, including "/share" or "users".
Check the network connection.
The cable is not connected to the machine correctly.
●Check whether the LAN cable is connected correctly. If you had to connect it again, restart the machine.
Connecting to a Wired LAN(P. 25)
The machine is not connected to the network.
●If you want to use the machine without connecting to a network, set <Conrm Network Connection
Setting Changes> to <Off>.
<Conrm Network Connection Setting Changes>(P. 782)
Check the network connection. (Main Line)
The machine and the LAN cable of the main line are not connected correctly.
●Check whether the LAN cable is connected correctly. If you had to connect it again, restart the machine.
Connecting to a Wired LAN(P. 25)
The machine is not connected to the network.
●If you want to use the machine without connecting to a network, set <Conrm Network Connection
Setting Changes> to <Off>.
<Conrm Network Connection Setting Changes>(P. 782)
Check the network connection. (Sub Line)
The machine and the LAN cable of the sub line are not connected correctly.
●Check whether the LAN cable is connected correctly. If you had to connect it again, restart the machine.
Front Side(P. 83)
The machine is not connected to the network.
●If you want to use the machine without connecting to a network, set <Conrm Network Connection
Setting Changes> to <Off>.
<Conrm Network Connection Setting Changes>(P. 782)
Scanning was canceled because the originals were not correctly fed.
A paper jam occurred in the feeder because multiple originals were fed together.
●Remove the originals from the feeder, and place them again.
A paper jam occurred in the feeder because an invalid type of original was fed.
●Remove the invalid original ( Placing Originals(P. 97) ), and place an appropriate type of original.
Troubleshooting
966
Remove the jammed originals from the feeder and any originals left in the feeder tray,
then place them back in the feeder tray and press the [Start] key.
Scanning was canceled because the original is jammed in the feeder.
●You need to restart the scanning with the sheet jammed in the feeder. Put together the unscanned sheets
of original neatly, reload them in the feeder, and then press (Start).
Remove the original from the feeder.
You are using a function that cannot be used when an original is placed in the feeder.
●Place the original on the platen glass.
Performing multiple jobs...
Multiple jobs such as print and send jobs are executing at the same time as the scan operation.
●Wait a while until the scan operation resumes.
Cannot log in because an authentication error occurred in Department ID
Management. Contact the system manager.
When using User Authentication, Department ID Management is enabled but Department IDs have not
been assigned to users.
●If you are a general user, ask your administrator to assign you a Department ID.
●If you are an administrator user, ask the Department ID Management administrator to assign you a
Department ID. If no administrator users can log in, contact your dealer or service representative.
PDL Invalid DLG Input
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL DLG Rendering Error
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL DLG Unknown Error
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL DLG Memory Full
The work memory was insucient when the system was processing data (in particular, graphic
processing and text processing).
Troubleshooting
967

●Press <Skip Error>, and continue printing. However, pages that include the data that caused the error may
not be printed correctly.
PDL DLG Mem. Alloc. Err
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL GL Orig. Pt Unknown
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL GL Coord.Result
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL Invalid GL Input
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL GL Range Check
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL GL Memory Full
The work memory was insucient when the system was processing data (in particular, graphic
processing and text processing).
●Press <Skip Error>, and continue printing. However, pages that include the data that caused the error may
not be printed correctly.
PDL GL Mem. Alloc. Err
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL IMG Refer. Data Err
The TIFF or JPEG data includes data that cannot be processed with the machine.
Troubleshooting
968
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer to increase the free memory, and
then try printing again. However, note that initializing the printer will erase all the data in the memory of
the machine. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
PDL IMG Initial. Err
The memory for printing the TIFF or JPEG data was insucient.
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer to increase the free memory, and
then try printing again. However, note that initializing the printer will erase all the data in the memory of
the machine. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
PDL IMG Process. Error
An unknown problem occurred while processing the TIFF or JPEG data.
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer, and try printing again. However,
note that initializing the printer will erase all the data in the memory of the machine. For more details, see
Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
PDL IMG Invalid Data
The TIFF or JPEG data includes data that cannot be processed with the machine.
●Cancel printing ( Canceling Printing(P. 346) ), and check the TIFF or JPEG data.
●Press <Skip Error>, and continue printing. However, the data that caused the error will not be printed.
Data that cannot be processed by the machine because the machine has the same IP address as another
device, etc. was sent.
●Cancel printing ( Canceling Printing(P. 346) ), check the IP address in <TCP/IP Settings>, and change
the IP address if necessary.
Setting an IP Address(P. 34)
PDL IMG Work Memory Full
The memory for processing the TIFF or JPEG data was insucient.
●Cancel printing ( Canceling Printing(P. 346) ), initialize the printer to increase the free memory, and
then try printing again. However, note that initializing the printer will erase all the data in the memory of
the machine. For more details, see Setting the Machine (PS/PCL/UFR II Printer) via the online manual site.
●Press <Skip Error>, and continue printing. However, the data that caused the error will not be printed.
PDL nn Rendering Error (nn is the module name)
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL PDF Error
PDF data that cannot be processed with the machine was sent.
●Cancel printing ( Canceling Printing(P. 346) ), optimize the PDF using Adobe Acrobat, and try printing
again.
●Cancel printing ( Canceling Printing(P. 346) ), open the PDF le in an application, and try printing again
using the printer driver.
Troubleshooting
969
●If the above-mentioned remedies do not solve the problem, make a note of the message and contact your
dealer or service representative.
PDL PDF Data Decode Err
The password for printing the PDF le is incorrect.
●Enter the correct password, and try printing again.
Printing is not allowed in the security settings of the PDF le.
●Change the PDF le to allow printing in an application for editing PDF les.
If the PDF le is linked with a policy server, the policy server cannot be accessed.
●Check whether the policy server is turned on.
●Check whether the machine, policy server, and network are operating normally.
PDL PDF Memory Full
There is insucient memory to process the PDF data.
●Cancel printing ( Canceling Printing(P. 346) ), optimize the PDF by adjusting settings such as the image
resolution using Adobe Acrobat (to reduce the size of the data to print at one time), and perform printing
again.
●Cancel printing ( Canceling Printing(P. 346) ), divide the pages of the PDF data in Adobe Acrobat into
multiple les, and try printing again.
●Cancel printing ( Canceling Printing(P. 346) ), open the PDF le in an application, and try printing again
using the printer driver.
PDL RIP Process. Error
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL XPS Error
An undened error occurred.
●Restart the machine and try again. If the message is still displayed, make a note of the message and
contact your dealer or service representative.
PDL XPS Initialize Error
An unknown error such as not being able to retrieve memory during initialization occurred.
●Restart the machine and try again. If the message is still displayed, make a note of the message and
contact your dealer or service representative.
PDL XPS Rendering Error
An error occurred in the rendering system.
●Restart the machine and try again. If the message is still displayed, make a note of the message and
contact your dealer or service representative.
Troubleshooting
970

PDL Image Comp. Error
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL Rendering Timeout
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL Data Transfer Error
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
PDL Reg. Access Error
The printer stopped operating normally due to an unknown problem.
●Restart the machine. If the message is still displayed after restarting the machine, make a note of the
message and contact your dealer or service representative.
Cannot recall the button settings because other operations are being performed.
The
<Personal>/<Shared> cannot be called when another function is being executed.
●Call the <Personal>/<Shared> after the operations for the other function are complete.
Register to Home will be canceled and you will be returned to the function screen
because you do not have permission to register buttons. Log in as an administrator,
then try again.
Registering personal buttons/shared buttons is restricted in user authentication.
●Register the button after logging in as an administrator.
The password does not meet the policy requirements. Change the password.
The entered password violates the password policy.
●Enter a password that complies with the password policy. If you do not know the password policy, consult
your system administrator.
A toner cartridge that cannot be used with this device has been inserted, so printing is
currently unavailable. Make sure the specied toner cartridge for this device is
inserted.
A toner cartridge that can be used with the machine has not been loaded.
Troubleshooting
971
●Load the toner cartridge that can be used with the machine. For instructions on checking the model
number of the toner cartridge, see Replacement Parts(P. 888) .
To continue using the toner cartridge, press <Close>. If you select this option, the operation of the machine is
not guaranteed.
If you are not sure about the remedies, contact your dealer or service representative from which you
purchased the toner cartridge.
Timer settings for this device and the authentication server may not be synchronized.
Contact the system manager.
The date and time settings of the machine and the authentication server are different.
●Synchronize the date and time settings of the machine and the authentication server.
Wireless LAN communication error. Turn main power OFF & ON.
An unknown error occurred when conguring the wireless LAN connection.
●Restart the machine. Press the power switch to turn the power OFF ( Turning OFF the Machine(P. 96) ),
wait for longer than 10 seconds, and then turn the power ON again ( Turning ON the Machine(P. 95) ).
Wireless LAN communic. error. Check Wireless LAN Information.
An unknown error occurred when conguring the wireless LAN connection.
●Check the wireless LAN settings.
Check the settings and information of the wireless LAN(P. 27)
Cannot send because the memory is full. Wait a moment, then try again.
The fax could not be sent because there was insucient memory.
●Lower the resolution and try sending again.
●Delete unnecessary documents in the memory of the machine to free up space.
Printing Documents in the Memory RX Inbox(P. 313)
Using Another Machine or Server - Network(P. 438)
●If this message is displayed frequently, contact your dealer or service representative.
Could not perform the operation because the memory is full.
When using the Scan and Store function, scanning was canceled because the memory became full while
scanning the original.
●Press <OK> to return to the Basic Features screen. Delete unnecessary data to increase the free space, and
try scanning the original again.
Scanning will be canceled because the memory is full. Do you want to print the scanned
pages?
When using the Copy function, scanning was canceled because the memory became full while scanning
the original.
●Press <Yes> to copy the scanned pages. Scan the remaining originals after copying is complete.
Troubleshooting
972
Scanning will be canceled because the memory is full. Wait a moment, then try again.
When using the Copy function, scanning was canceled because the memory became full while scanning
the original.
●Press <OK> to return to the Basic Features screen. Scan the remaining originals after the current copy
operation is complete.
Scanning will be canceled because the memory is full. Do you want to send the scanned
pages?
When using the Fax or Scan and Send function, scanning was canceled because the memory became full
while scanning the original.
●Press <Yes> to send the scanned pages. Scan the remaining originals after sending is complete.
Scanning will be canceled because the memory is full. Do you want to store the scanned
pages?
When using the Scan and Store function, scanning was canceled because the memory became full while
scanning the original.
●Press <Yes> to save the scanned pages. Scan the remaining originals after saving is complete.
The amount of data stored for registered users has reached the limit. You can perform
operations, but no data (job setting logs, personal settings content, etc.) can be stored
this time. To be able to store data from the next time you log in, unnecessary data must
be deleted from other users. Contact the system manager or refer to the manual for
details.
The user setting information could not be saved because the maximum number of users who can be
registered was exceeded.
●To save new user setting information, delete any unnecessary user setting information.
Deleting User Setting Information(P. 534)
If you are not using the Personalization function, delete user setting information, and then set <Enable
Use of Personal Settings> ( <Enable Use of Personal Settings>(P. 859) ) to <Off>.
●You can specify settings to automatically delete old user setting information if the number of users who
can be registered is exceeded.
<Action When Maximum Number of Users Exceeded>(P. 859)
Register to Home will be canceled because you are not logged in. Return to the
function screen, log in, then try again.
Registering shared buttons is restricted in user authentication.
●Register the button after logging in as an administrator.
Check the user name, password, or settings.
An incorrect user name or password was set for the LDAP server authentication information.
●Check whether the user name and password in <Register LDAP Server> are correct.
Registering the LDAP Server(P. 53)
An incorrect domain name was set for the LDAP server authentication information.
Troubleshooting
973
●Check whether the domain name in <Register LDAP Server> is correct.
Registering the LDAP Server(P. 53)
Load paper.
The paper in the paper source has run out.
●Load paper in the paper source displayed on the touch panel display.
Loading Paper(P. 102)
The paper guides in the paper source are in the wrong position.
●Adjust the paper guides according to the edges of the paper. Depending on the cut edge of the paper,
multiple sheets of paper may be fed together when printing, which can cause paper jams. This can be
reduced by changing the orientation of the loaded paper.
The paper settings differ from the paper that is loaded.
●Check the paper settings in <Consumables/Others> in (Status Monitor). If the paper settings are
incorrect, match them with the paper that is loaded. Paper settings can be specied for all the paper sizes
and types set in the paper drawers and multi-purpose tray in (Settings/Register) <Preferences>
<Paper Settings>.
Specifying Paper Size and Type(P. 141)
The paper settings of the driver or application differ from the paper that is loaded.
●Check the paper settings on the [Printing Preferences] screen of the printer driver, and if the paper
settings are incorrect, match them with the paper that is loaded.
Scanning was canceled because the data size of the scanned original exceeds the limit.
Scanning may be possible if sharpness is reduced, or Original Type is set to Text.
Scanning was canceled because the data of the scanned document exceeded the maximum size that can
be handled by the machine.
●You may be able to scan by lowering the setting in <Sharpness>, and setting <Original Type> to <Text>.
Information set by the currently logged-in user will not be stored.
The user setting information cannot be saved because the maximum number of users who can be
registered was exceeded.
●To save new user setting information, delete any unnecessary user setting information.
Deleting User Setting Information(P. 534)
●You can specify settings to automatically delete old user setting information if the number of users who
can be registered is exceeded.
<Action When Maximum Number of Users Exceeded>(P. 859)
Login failed. Anonymous access to the authentication server is not allowed. Contact the
system manager.
Anonymous access is not allowed in the LDAP server.
●Select the check box in <Use authentication information> on the screen for entering information on the
LDAP server, and set the user name and password according to the information registered in the LDAP
server.
Registering Server Information(P. 507)
Troubleshooting
974

Login failed. The account information necessary to log in to the authentication server is
invalid. Contact the system manager.
The user name or password is not set correctly.
●On the screen for entering the information for the LDAP server, set the correct settings according to the
settings registered in the LDAP server.
Registering Server Information(P. 507)
Cannot log in. Check the login destination.
The login destination information entered on the mobile device side is incorrect.
●Conrm that you have specied the correct login destination, and then log in again.
Cannot store the password because the number of passwords stored for each user has
reached the limit.
The login user password cannot be registered because the maximum number of passwords has been
exceeded.
●Delete unnecessary password information.
If a six-digit number is displayed when you are logging in
If an error occurs when you are logging in, a six-digit number may be displayed below the message. Take the
necessary measure depending on the six-digit number displayed.
310001
Communication with the authentication server failed.
●Check the network cables from the machine and the domain controller (Active Directory).
●Check whether the domain controller is down.
●Check whether name resolution is working correctly with the DNS server set for the machine on the
domain controller.
●Try again after augmenting the current value of [Period Until Timeout:] in the Active Directory settings.
310002
When [Use access mode within sites] is enabled on the machine, the site information of Active Directory
is not set correctly.
●Check whether the site setting on Active Directory is valid.
310003
The network environment is not yet ready.
●Check again after a while.
●Check whether name resolution to the specied domain name is working correctly (the address can be
identied) with the DNS server set for the machine, and then make adjustments as necessary.
●The DNS server set for the machine cannot be found, or it is currently unable to communicate. Check the
conguration and the communication environment.
Troubleshooting
975

322000
A server error has occurred during Kerberos authentication.
●In Active Directory, clear the check box for [Do not require Kerberos preauthentication], which is an
account option for the logged-in user account. Alternatively, check whether Active Directory is used
properly.
322006
The objective user does not exist on the authentication server.
●Check whether the authentication user or search user exists on the domain controller to authenticate.
322012
In Active Directory, the check box for [Smart card is required for interactive logon], which is an account
option for the logged-in user account, is selected.
●In Active Directory, clear the check box for [Smart card is required for interactive logon], which is an
account option for the logged-in user account. After clearing the check box, be sure to reset the password.
When resetting the password, you can use the same password instead of a new one.
322018
The validity period of the account has expired.
●Check the validity period of the account in question.
322023
The validity period of the password has expired.
●Change the password.
●In Active Directory, check the setting of the account options for the logged-in user account.
322024
The user name or password is wrong when keyboard authentication is performed.
●Check the password of the authentication user or search user.
322029
The attempt to communicate with the writable domain controller failed.
●Check the network cable from the writable domain controller.
●Check whether the writable domain controller is down.
●Check whether name resolution is working correctly with the DNS server on the writable domain
controller.
●Try again after augmenting the current value of [Period Until Timeout:] in the Active Directory settings.
322037
The date and time settings are not identical between the machine and the authentication server.
Troubleshooting
976

●Ensure that the date and time settings are identical between the machine and the authentication server.
322xxx
A Kerberos authentication error.
●A Kerberos error code is displayed in place of xxx.
323000
An error has occurred during LDAP server authentication.
●Check whether Active Directory or LDAP service is used properly.
323008
An LDAP server authentication error has occurred in relation to TLS/non-TLS communication.
●Check the communication settings (TLS/non-TLS) of the server.
●Check whether the communication settings on the device side are identical to those on the server side.
323048
You are attempting to log in as an anonymous user for LDAP server authentication.
●Check whether the LDAP service setting permits anonymous user authentication.
323049/323053
The user information for LDAP server authentication is not set correctly.
●Check the user name and password of the authentication user or search user.
●Check whether the authentication user or search user is invalid, whether their validity period has expired,
and whether they are account-locked.
323xxx
An LDAP server authentication (LDAPBind) error.
●An LDAPBind error code is displayed in place of xxx.
324000
An error has occurred during LDAP server search.
●Check whether Active Directory or LDAP service is used properly.
324xxx
LDAP server search (LDAPSearch) error.
●An LDAPSearch error code is displayed in place of xxx.
325000
An error has occurred during LDAP server authentication.
Troubleshooting
977

●Check whether Active Directory or LDAP service is used properly.
325010
You have attempted to perform registration to a read-only domain controller.
●If the domain controller congured in Active Directory is of the read-only type, no user information editing
functions (registering/deleting cards, changing PIN) are available. To use the user information registration
function, congure a writable domain controller.
325050
The search user set in the Administrator settings page does not have update authority (write access).
●Check whether the search user is granted write access to the user attribute that you are going to modify.
325067
You are attempting to modify an attribute of a Relative Distinguished Name (RDN) such as cn attribute.
●You are attempting to modify an attribute of a Relative Distinguished Name (RDN) such as cn attribute.
The information of such attribute cannot be modied, so specify another attribute.
325xxx
An LDAP server update error.
●An LDAPModify error code is displayed in place of xxx.
331000
User authentication failed.
●Check the user name and password. If the user name and password are correct, contact your system
manager.
331001
The user name has not been entered.
●Enter the user name.
331002
Cannot nd the user.
●Check the user name and password. If the user name and password are correct, contact your system
manager. The user may not exist on the LDAP server, or the search user may not have read access to
attribute information of the relevant account.
331003
You are using a card that is not registered on the authentication server.
●Check whether you are using a valid card.
Troubleshooting
978

331004
Card information is double registered on the authentication server.
●Contact your system manager.
331005
The validity period of the logged-in user has expired.
●Contact your system manager.
331006
The validity value of the card and that on the authentication server are different from each other.
●Check whether you are using a valid card. If you are using a valid card, contact your system manager.
331007
A validity value outside the range is set on the authentication server.
●Check whether the server is operated with the correct attribute of validity value.
331008
The account of the logged-in user is locked out.
●Contact your system manager.
331009
The user ID of the account you are using to log in to the machine is invalid. Or the Active Directory
settings may not be correct.
●Check whether all of the required attributes are set correctly.
●In Active Directory, clear the check box for [Do not require Kerberos preauthentication], which is an
account option for the logged-in user account.
331010
To perform authentication for a specic function, you have attempted to log in as a user who is not
permitted to use that function.
●Contact your system manager.
331011
Login to perform authentication for a specic function failed.
●Check which functions the logged-in user is able to use.
331012
The PIN of the logged-in user is invalid.
●Enter the PIN again.
Troubleshooting
979

331013
The account of the logged-in user is invalid.
●Contact your system manager.
332000
User information updating failed.
●Updating the user information failed. Check whether the user information you used for updating is valid
and whether invalid information is not specied for updating.
332001
Already registered card information.
●The card of the logged-in user is already registered. Check whether you are using a valid card. Or contact
your system manager.
332002
An invalid attribute was specied for user information updating.
●When card information editing functions are used, it is not permitted to make registration with
sAMAccountName or userPrincipalName attribute in the Active Directory settings. One solution is to use
other attribute.
332003
An invalid login name was specied for user information updating.
●It is not permitted to register the name of the logged-in user (login name). Check the user name and
contact your system manager.
332004
An invalid display name was specied for user information updating.
●It is not permitted to register the display name of the logged-in user. Check the display name attribute
value on the server being referred to, and contact your system manager.
332005
An invalid domain name was specied for user information updating.
●It is not permitted to register the domain name for the logged-in user. Check the domain name you have
selected and contact your system manager.
332006
An invalid email address was specied for user information updating.
●It is not permitted to register the email address of the logged-in user. Check the email address attribute
value on the server being referred to, and contact your system manager.
Troubleshooting
980

332007
An invalid role was specied for user information updating.
●Check the attribute value for determining the privileges on the side of the server being referred to, and
contact your system manager.
332008
The maximum registerable number of users was exceeded during user information updating.
●Contact your system manager.
Troubleshooting
981

Countermeasures for Each Error Code
72JY-0J4
0YRY-0JW 1100-0K0 10XJ-0K0 1106-0K0 10YY-0K0 10H3-0JX 108A-0JY 1116-0JY 10H4-0JX 0YAS-0K2
When printing or scanning is not completed normally or fax transmission or reception fails, a number starting with "#"
(an error code) is displayed on the details screen for job log or a communication management report ( Printing
Reports and Lists(P. 909) ). Perform the countermeasure required for the error code.
●Some error codes may not be displayed, depending on your machine.
#001 to #800
#001(P. 983) #003(P. 983) #005(P. 983) #009(P. 983) #010(P. 983)
#011(P. 984) #012(P. 984) #018(P. 984) #019(P. 984) #022(P. 984)
#025(P. 985) #033(P. 985) #034(P. 985) #035(P. 985) #037(P. 985)
#040(P. 986) #054(P. 986) #080(P. 986) #081(P. 986) #082(P. 986)
#083(P. 986) #084(P. 987) #099(P. 987) #102(P. 987) #107(P. 987)
#401(P. 987) #402(P. 987) #403(P. 987) #404(P. 988) #406(P. 988)
#407(P. 988) #409(P. 988) #410(P. 988) #411(P. 988) #701(P. 988)
#702(P. 989) #703(P. 989) #704(P. 989) #705(P. 989) #706(P. 989)
#711(P. 990) #712(P. 990) #713(P. 990) #715(P. 990) #716(P. 990)
#749(P. 990) #751(P. 990) #752(P. 991) #753(P. 991) #755(P. 991)
#759(P. 992) #761(P. 992) #762(P. 992) #766(P. 992) #769(P. 992)
#770(P. 993) #771(P. 993) #772(P. 993) #773(P. 993)
#801 to #999
#801(P. 994) #802(P. 994) #803(P. 994) #804(P. 995) #805(P. 995)
#806(P. 995) #807(P. 995) #809(P. 995) #810(P. 995) #813(P. 996)
#815(P. 996) #816(P. 996) #818(P. 996) #819(P. 996) #820(P. 996)
#821(P. 996) #822(P. 997) #825(P. 997) #827(P. 997) #828(P. 997)
#829(P. 997) #830(P. 997) #831(P. 997) #832(P. 998) #833(P. 998)
#834(P. 998) #835(P. 998) #837(P. 998) #838(P. 999) #839(P. 999)
#841(P. 999) #842(P. 999) #843(P. 999) #844(P. 999) #845(P. 1000)
#846(P. 1000) #847(P. 1000) #848(P. 1000) #851(P. 1001) #852(P. 1001)
#853(P. 1001) #856(P. 1001) #857(P. 1001) #858(P. 1001) #859(P. 1001)
#860(P. 1001) #861(P. 1002) #862(P. 1002) #863(P. 1002) #864(P. 1002)
#865(P. 1002) #866(P. 1002) #868(P. 1003) #869(P. 1003) #870(P. 1003)
#871(P. 1003) #872(P. 1003) #873(P. 1003) #874(P. 1003) #875(P. 1004)
Troubleshooting
982

#876(P. 1004) #877(P. 1004) #878(P. 1004) #879(P. 1004) #880(P. 1004)
#881(P. 1005) #882(P. 1005) #883(P. 1005) #884(P. 1005) #885(P. 1005)
#886(P. 1005) #889(P. 1005) #899(P. 1006) #904(P. 1006) #905(P. 1006)
#919(P. 1006) #923(P. 1006) #925(P. 1006) #927(P. 1006) #928(P. 1007)
#929(P. 1007) #934(P. 1007) #939(P. 1007) #995(P. 1007)
◼#001
A paper jam occurred.
●After removing the paper jam, check the documents and the settings, and then scan again.
◼#003
Communication that exceeds the specied time (64 minutes) causes an error.
●Lower the resolution and try sending again.
Basic Operations for Sending Faxes(P. 275)
●When receiving a document, ask the other party to lower the resolution when scanning or divide the
document into multiple parts.
◼#005
There was no response from the other party for 35 seconds.
●Check that the other party can communicate, and try sending again.
The device of the other party is not a model that supports G3.
●Check the device of the other party.
◼#009
Paper has run out.
●Load paper.
Loading Paper(P. 102)
The paper deck/paper drawer is not inserted correctly.
●Insert the paper deck/paper drawer in all the way.
Basic Paper Loading Method(P. 103)
◼#010
Paper has run out.
●Load paper.
Loading Paper(P. 102)
Troubleshooting
983

◼#011
The document to send was not placed correctly.
●Place the original correctly and try sending again from the start of the procedure.
◼#012
Could not send because the device of the other party does not have any paper.
●Tell the other party to load paper.
◼#018
There was no response when redialing.
●Check that the other party can communicate, and redial again.
Could not send because the other party was making a call, etc.
●Check that the other party can communicate, and try sending again.
Could not send because the settings of the device of the other party do not match.
●Check the settings of the other party, and try sending again.
◼#019
When sending a fax from a remote fax client machine, sending could not be performed because the
memory of the remote fax server machine became full.
●Try sending again after the other sending to the remote fax server machine is complete.
●Delete unnecessary documents and error documents from the remote fax server machine to free up
space.
The document could not be sent because the memory of the machine is full.
●Delete unnecessary documents and documents with errors to make more memory available.
When performing memory sending, the image could not be stored in the memory.
●Perform memory sending again.
●Send the document with direct sending.
There was a problem with the scanned image when performing direct sending.
●Perform direct sending again.
◼#022
Forwarding could not be performed because the content of the group destination specied as the
forwarding destination was deleted or only included a Mail Box.
●Specify another destination, and try sending again.
When sending to a destination registered in the address book, sending could not be performed because
the destination was deleted from the address book while the machine was waiting to send.
●Specify another destination, and try sending again.
Sending from the fax driver is not allowed.
Troubleshooting
984

●Set <Allow Fax Driver TX> to <On>, and try sending again. Restricting the Fax Sending
Functions(P. 571)
◼#025
When sending a fax from a remote fax client machine, a line that does not exist in the remote fax server
machine was specied.
●Check the number of lines in the server machine, and try sending again after matching the remote fax
transmission settings of the client machine with the number of lines on the server machine.
◼#033
The device of the other party does not support condential communication or subaddresses.
●Send without using condential communication or subaddresses.
◼#034
The condential storage location in the device of the other party specied for condential
communication was not found.
●Check the condential storage location in the device of the other party, and try sending again.
The memory was insucient in the device of the other party.
●Ask the other party to free up some space.
◼#035
The device of the other party does not support the forwarding function or subaddresses.
●Directly send to the other party.
◼#037
The document could not be copied or received because there was insucient memory available.
●Organize documents in the Memory RX Inbox to make more memory available.
Printing Documents in the Memory RX Inbox(P. 313)
●If you are copying a document with more than 100 pages in one operation, divide the document into two
or more parts and then copy.
Data containing more than 1,000 pages was received.
●The machine deletes any pages after the 999th page, and prints or stores the remaining 999 pages. Tell
the other party to send the 1,000th and subsequent pages again.
When performing delayed sending or redial sending, the image data of the document to send was not
found in memory.
●Scan the original again, and try sending again.
●Select direct sending when sending again.
Could not send to multiple destinations because the machine had insucient free memory.
●Delete unnecessary documents and error documents to free up space.
●Divide the document into two or more parts, and then try sending the document again.
Troubleshooting
985

●Lower the resolution and try sending again.
◼#040
When sending a fax from a remote fax client machine, sending could not be performed because the
memory of the remote fax server machine was insucient.
●Delete unnecessary documents and error documents from the remote fax server machine to free up
space.
●Divide the document into two or more parts, and then try sending the document again.
●Lower the resolution and try sending again.
The document could not be sent because the memory of the machine is full.
●Delete unnecessary documents and documents with errors to make more memory available.
●Divide the sending operation into multiple batches instead of sending the document to all destinations at
once.
●Lower the resolution, and then send the document again.
◼#054
The sending process was canceled because the unit telephone number and unit name were not
registered.
●Try sending again after registering the unit telephone number and unit name.
<Send>(P. 820) <Fax Settings> <Set Line>
<Register Unit Telephone Number>(P. 833)
<Register Unit Name>(P. 825)
◼#080
A subaddress is not set in the device of the other party.
●Check the subaddress of the other party, and try sending again.
◼#081
A password is not set in the device of the other party.
●Check the password of the other party, and try sending again.
◼#082
Polling transmission is not congured in the device of the other party.
●Tell the other party to congure polling transmission, and perform polling reception again.
◼#083
The subaddress and password of the machine and the device of the other party did not match when
performing polling reception.
●Check that the subaddress and password of the machine and the device of the other party match, and try
sending again.
Troubleshooting
986

◼#084
Cannot perform polling reception because the password is not supported by the device of the other
party.
●Perform polling reception without using a password.
◼#099
The operation was canceled before it was complete.
●Perform the operation again.
◼#102
The subaddress and password do not match.
●Check the subaddress and password of the other party, and try sending again.
There was insucient memory in the recipient's machine.
●Ask the recipient to make more memory available.
◼#107
The document could not be sent because there was insucient memory available.
●Lower the resolution or divide the document into two or more parts, and then try sending the document
again.
●Delete unnecessary les to make more memory available.
Saving Received Documents in the Machine (Memory Reception)(P. 313)
●If this problem occurs frequently, contact your dealer or service representative.
◼#401
The memory media or le server is full, or the number of les that can be saved in the root directory (the
top level folder inside the memory media) has been exceeded.
●Delete unnecessary les from the memory media or le server, or create a new folder and move existing
les to that folder to create room in the root directory.
◼#402
The image transfer failed when transferring to the memory media because an invalid character (such
as \) was included in the specied lename.
●Change the lename to the correct lename.
◼#403
The le could not be saved because a le with the same name already exists. Normally, automatic
renaming is performed to append a number between 1 and 999 to the lename when a le with the same
name exists, but the le could not be saved because les with the numbers 1 to 999 appended to them
already exist.
●Change the lename and save the le again.
Troubleshooting
987

◼#404
Writing failed because the write protect switch of the memory media was enabled.
●Disable the write protect switch of the memory media.
◼#406
Writing failed due to one of the following possible causes:
Memory media was removed while the le was being written to it.
The Advanced Space of another machine on the network was deleted while the le was being written
to it.
●Check that the memory media is inserted or that the Advanced Space of another machine on the network
is available, and read the le again.
The image transfer failed when transferring to the memory media because an unspecied error
occurred. (The connected memory media may be formatted with an unsupported le system.)
●Check the status of the memory media and conrm that it is formatted with a le system supported by the
machine (FAT32/exFAT). Then, try performing the procedure again.
The size of the le exceeded the upper limit.
●Lower the resolution or reduce the number of pages, and perform the operation again.
◼#407
The length of the full path to the specied le (or folder) exceeds the maximum supported length.
●Change the lename so that the length of the full path is within 256 characters, or change the destination
folder.
◼#409
The le could not be saved because the maximum number of les that can be saved in the destination
has been reached.
●Change the destination to save the le.
◼#410
Storing cannot be performed because there are too many jobs waiting to be stored.
●Perform the operation again when the other jobs are complete.
◼#411
The le are already locked by the other operations.
●Wait a while, and perform the operation again.
◼#701
The Department ID does not exist, or the PIN was changed.
Troubleshooting
988

●If you are using User Authentication, assign Department IDs to users. If you are using DepartmentID
Authentication, enter the new Department ID and PIN to log in again.
The reception setting in <Allow Printer Jobs with Unknown IDs> or <Allow Remote Scan Jobs with
Unknown IDs> is set to <Off>.
●Set <Allow Printer Jobs with Unknown IDs> and <Allow Remote Scan Jobs with Unknown IDs> in
<Department ID Management> to <On>.
Setting the Department ID Management(P. 522)
Sending could not be performed because the remote fax client machine failed authentication to the
remote fax server machine.
●If Department ID Management is set in the remote fax server machine, log in to the remote fax client
machine using the Department ID and PIN set in the remote fax server machine.
◼#702
Sending could not be performed because the memory was full.
●Wait a while. Try sending again after the other sending is complete.
◼#703
An error occurred while converting the image.
●Lower the resolution, and then send the document again.
Could not write because the image area of the memory is full.
●Try sending again after the other sending is complete.
●Delete unnecessary les in the Fax/I-Fax Inbox. If there is still a problem, restart the machine.
Turning ON the Machine(P. 95)
◼#704
An unknown error occurred when retrieving destination information from the address book.
●Check the destination settings. If there is still a problem, restart the machine.
Turning ON the Machine(P. 95)
◼#705
Sending was canceled because the image data size exceeded the maximum value set in Settings/
Register.
●Adjust the maximum data size for sending. Select a lower resolution or reduce the number of images sent
at once when using the I-fax function to ensure that the maximum data size for sending is not exceeded.
Divide the data, depending on the conditions of the other party.
<Maximum Data Size for Sending>(P. 827)
◼#706
An address book was being imported/exported from the Remote UI or another sending component was
in use.
●Try sending again after the other operation is complete.
Troubleshooting
989

◼#711
The memory is full. You may be able to send if you delete unnecessary les in memory.
●Try sending again after deleting unnecessary les in memory.
◼#712
The memory is full. Try executing again after deleting unnecessary les in memory.
●Try sending again after deleting unnecessary les in memory.
◼#713
The document in Fax/I-Fax Inbox was deleted before sending the URL.
●Try sending again after saving the required document in the Fax/I-Fax Inbox.
◼#715
The certicate to use was not found when sending an e-mail with a digital signature attached.
●When using a device signature, set the e-mail address of the machine ( Setting E-mail/I-Fax
Communication(P. 70) ), and then generate a certicate for device signatures ( Generating a Device
Signature Certicate(P. 578) ). If a certicate for device signatures has already been generated, generate
it again.
●Check whether an expired certicate or revoked certicate is being used. In addition, check whether the
certicate chain is invalid.
◼#716
The destination public key certicate could not be found.
●Register the destination public key certicate in the machine.
Registering an S/MIME Certicate(P. 602)
●Check whether an expired certicate or revoked certicate is being used. In addition, check whether the
certicate chain is invalid.
◼#749
The operation could not be performed because a service call message is displayed.
●Turn the main power OFF, and turn the main power ON again. If the operation still cannot be performed
correctly, turn the main power switch OFF, remove the power plug from the outlet, and contact your
dealer or service representative.
Turning OFF the Machine(P. 96)
Turning ON the Machine(P. 95)
◼#751
The server is not running or the network is disconnected (either you could not connect to the
destination, or the connection was lost before the job could be completed).
●Check whether the server is operating normally.
Troubleshooting
990

●Check the status of the network.
●If the destination is using IIS 6.0 with Windows Server 2003 and digest authentication is used as the
authentication method of the WebDAV server, set <Use Divided Chunk Send for WebDAV TX> to <On> to
send with WebDAV via a proxy using TLS communication.
<Use Divided Chunk Send for WebDAV TX>(P. 822)
The IP address is not set.
●Check <TCP/IP Settings> in <Preferences>.
<Network>(P. 782) <TCP/IP Settings>
Could not send to an SMB server (including the Advanced Space of another imageRUNNER ADVANCE
series machine disclosed with SMB) because a le server is being browsed using Windows (SMB).
●If an error occurs with delayed sending, close the <Browse> screen, and scan and send the document
again.
●If an error occurs when forwarding a received fax/I-fax le to an SMB server, scan a printed copy of the
received le, and send it to the forwarding destination.
Basic Operations for Scanning Originals(P. 377)
●You can avoid errors by using FTP as the protocol for sending to servers.
◼#752
The server is not running or the network is disconnected.
●Check whether the SMTP server is operating normally.
●Check the status of the network.
The SMTP server name setting for e-mail/I-fax is incorrect or the e-mail address or domain name is not
set.
●Check the SMTP server name, e-mail address, and domain name settings in <Communication Settings>.
Setting E-mail/I-Fax Communication(P. 70)
◼#753
A TCP/IP error (Socket or Select error, etc.) occurred when sending e-mail or when sending a fax from a
remote fax client machine.
●Check the status of the network cable and connector. If there is still a problem, restart the machine.
Turning ON the Machine(P. 95)
◼#755
Could not send a fax from a remote fax client machine because TCP/IP is not operating correctly.
●Check <TCP/IP Settings> in <Preferences>.
<Network>(P. 782) <TCP/IP Settings>
The IP address is not set.
●Check <TCP/IP Settings> in <Preferences>.
<Network>(P. 782) <TCP/IP Settings>
●If you selected <Wired LAN + Wireless LAN> or <Wired LAN + Wired LAN> in <Select Interface>, also check
<Sub Line Settings> in <Preferences>.
When the machine was turned ON, an IP address was not assigned to the machine by DHCP or Auto IP.
<Network>(P. 782) <Sub Line Settings>
Troubleshooting
991

When the machine was turned ON, an IP address was not assigned to the machine by DHCP or Auto IP.
●Check <TCP/IP Settings> in <Preferences>.
<Network>(P. 782) <TCP/IP Settings>
●If you selected <Wired LAN + Wireless LAN> or <Wired LAN + Wired LAN> in <Select Interface>, also check
<Sub Line Settings> in <Preferences>.
When the machine was turned ON, an IP address was not assigned to the machine by DHCP or Auto IP.
<Network>(P. 782) <Sub Line Settings>
◼#759
An error occurred when sending the URL of the Mail Box in which a le was saved.
●Contact your administrator.
◼#761
When sending a PDF/XPS le with a digital signature, the le could not be sent because the certicate or
key pair set in the machine was corrupt or could not be accessed.
●When sending a PDF/XPS le with a user signature, check whether the user certicate is corrupt. If the
user certicate is corrupt, install it again.
Adding a Digital Signature to Sent Files(P. 577)
Registering a User Signature Certicate(P. 579)
●When sending a PDF/XPS le with a device signature, check whether the device certicate is corrupt. If the
device certicate is corrupt, generate it again.
Generating a Device Signature Certicate(P. 578)
◼#762
Could not send to a domain not registered as an allowed domain because <Restrict Destination Domain>
is set to <On>.
●Set <Restrict Destination Domain> to <Off> or register the domain as an allowed domain, and try sending
again.
Restricting the Domain of Send Destination(P. 570)
◼#766
The certicate to use when sending a PDF/XPS le with a digital signature has expired.
●Update the certicate or use a certicate that has not expired.
●If the certicate has not expired, set the time of the machine correctly.
Setting the Date/Time(P. 17)
◼#769
The number of trials allowed for the send function reached the upper limit.
●If you want to continue using this function, purchase the ocial optional product.
Troubleshooting
992

◼#770
When sending with WebDAV, sending could not be performed because TLS communication was not
supported on the WebDAV server side or proxy server side.
●Check the WebDAV server settings.
●Check the proxy server if you are sending via a proxy.
Sending could not be performed because a validation error occurred when validating the TLS server
certicate when sending with WebDAV because <Conrm TLS Certicate for WebDAV TX> is set to <On>.
●Check whether the CA certicate used to sign the TLS server certicate on the WebDAV server side is
registered in the machine.
●Check whether the TLS server certicate on the WebDAV server side is correct.
●Check whether the TLS server certicate is a self-signed certicate.
The operation could not be completed because a validation error occurred when validating the TLS
server certicate when accessing another server because <Conrm TLS Certicate for Network Access> is
set to <On>.
●Check whether the CA certicate used to sign the TLS server certicate of the Advanced Space of the other
imageRUNNER ADVANCE series machine disclosed as a WebDAV server is registered in the machine.
●Check whether the TLS server certicate of the Advanced Space of the other imageRUNNER ADVANCE
series machine disclosed as a WebDAV server is correct.
●Check whether the TLS server certicate is a self-signed certicate.
◼#771
The remote fax server address setting is incorrect.
●Check <Remote Fax TX Settings>.
The remote fax server is not running.
●Check whether the remote fax server is operating normally.
The network is disconnected.
●Check the status of the network.
Could not connect to the remote fax server because the DNS server could not be connected to.
●Check the DNS server name setting.
Making DNS Settings(P. 45)
●Check whether the DNS server is operating normally.
◼#772
The network is disconnected.
●Check the status of the network.
◼#773
PDF functions that are not available when <Format PDF to PDF/A> is set to <On > are selected.
●Cancel the Encrypt, and Visible Signatures settings. Alternatively, set <Format PDF to PDF/A> to <Off>.
<Format PDF to PDF/A>(P. 814)
Troubleshooting
993

◼#801
A timeout error occurred due to a problem on the mail server side when communicating with the SMTP
server to send an e-mail or send or receive an I-fax.
●Check whether the SMTP server is operating normally.
●Check the status of the network.
An error was returned from the SMTP server when connecting with SMTP. The address setting is
incorrect. An error occurred due to a problem on the server side when sending to a le server.
●Check whether SMTP is operating normally, the status of the network, the destination settings, and the
status and settings of the le server.
The user name and password required when sending e-mail have not been set.
●Check <SMTP Authentication (SMTP AUTH)> in <Authent./Encryption>.
Setting SMTP authentication(P. 72)
You sent to a destination that does not have write privileges.
●Check the destination settings.
A le with the same name existed when sending to a le server that does not allow les to be
overwritten.
●Change the settings of the le server to enable les to be overwritten. Alternatively, contact the server
administrator.
●Change the lename.
The folder name or password specied when sending to a le server was incorrect.
●Check the folder name or password.
◼#802
The SMTP server name specied in <Communication Settings> is incorrect.
●Check the SMTP server name set in <Communication Settings>.
Setting E-mail/I-Fax Communication(P. 70)
The DNS server address specied in <DNS Settings> is incorrect.
●Check the DNS server address specied in the DNS settings.
Making DNS Settings(P. 45)
Connection to the DNS server failed.
●Check that the DNS server is functioning normally.
The settings for the FTP server specied as the destination are incorrect.
●Check the FTP server specied as the destination.
Connection to the FTP server failed.
●Check that the FTP server is functioning normally.
◼#803
The connection was interrupted due to reasons on the recipient's side before all of the pages could be
sent.
●Re-enter the group destination, and try sending again.
Troubleshooting
994

◼#804
When sending to a le server, no folders matched the specied path.
●Check the destination.
You do not have access privileges for the folder or le. Alternatively, the folder or le may have been
deleted by another operation.
●Allow access to the folder on the server side. Alternatively, contact the server administrator.
◼#805
Could not send to the SMB server because there was insucient free space on the server side.
●Delete unnecessary documents and error documents from the server to free up space. Alternatively,
contact the server administrator.
◼#806
The user name or password specied when sending to a le server was incorrect.
●Check the user name or password.
The destination specied when sending an e-mail/I-fax was incorrect.
●Check the e-mail/I-fax destination.
◼#807
You do not have access privileges for the specied directory.
●Set access privileges for the server directory or send to a directory that you have access privileges for.
Alternatively, contact your administrator.
◼#809
When sending to an SMB server, a le with the same name already exists and overwriting of les is not
allowed.
●Change the lename and try sending again.
●Change the settings of the SMB server to enable les to be overwritten. Alternatively, contact the server
administrator.
When sending to an SMB server, the response on the server side was slow, causing a wait time timeout
on the machine side before the data could be sent or forwarding could be completed.
●Set a longer timeout time in <Timeout> on the SMB client.
Making SMB Settings(P. 50)
◼#810
A POP server connection error occurred when an I-fax was received.
●Check the POP server settings in <Communication Settings>.
Setting E-mail/I-Fax Communication(P. 70)
●Check whether the POP server is operating correctly. Check the status of the network.
Troubleshooting
995

An error was returned from the POP server when connecting to the POP server. Alternatively, a timeout
error occurred on the server side.
●Check the POP server settings in <Communication Settings>.
Setting E-mail/I-Fax Communication(P. 70)
●Check whether the POP server is operating correctly. Check the status of the network.
◼#813
A POP server authentication error (user account error or password error) occurred when an I-fax was
received.
●Check the POP server settings in <Communication Settings>.
Setting E-mail/I-Fax Communication(P. 70)
◼#815
You cannot log on to the le server because the machine is printing a document sent to that server.
Simultaneous connections are not possible.
●Wait for a few moments before trying to send the data again. Alternatively, stop the PServer.
◼#816
Printing could not be performed because the maximum number of prints set in Department ID
Management was exceeded.
●Contact your System Manager.
◼#818
The received data was in a le format that cannot be printed.
●Tell the other party to change the le format and send again.
◼#819
Data that cannot be handled was received. The MIME information is invalid.
●Tell the other party to check the settings and send again.
◼#820
Data that cannot be handled was received. The BASE64 or uuencode is invalid.
●Tell the other party to check the settings and send again.
◼#821
Data that cannot be handled was received. A TIFF analysis error occurred.
●Tell the other party to check the settings and send again.
Troubleshooting
996

◼#822
Data that cannot be handled was received. The image cannot be decoded.
●Tell the other party to check the settings and send again.
◼#825
The Department ID and PIN of a job being executed or a reserved job were deleted, or the PIN was
changed.
●Execute the job again using the changed Department ID and PIN.
◼#827
Data that cannot be handled was received. Unsupported MIME information was included.
●Tell the other party to check the settings and send again.
◼#828
HTML data was received.
●Tell the other party to change to a format other than HTML and send again.
◼#829
Data containing more than 1,000 pages was received.
●The machine deletes any pages after the 999th page, and prints or stores the remaining 999 pages. Tell
the other party to send the 1,000th and subsequent pages again.
◼#830
A DSN error notication was received because the I-fax address or destination conditions were incorrect.
●Check the specied I-fax address and the destination conditions.
A DSN error notication was received because the size of the le that was sent exceeded the size allowed
by the mail server.
●Change the setting in <Maximum Data Size for Sending> so that the size of the le to send does not
exceed the size allowed by the mail server.
<Maximum Data Size for Sending>(P. 827)
●Check the status of the mail server, DNS server, and network.
◼#831
An I-fax document could not be received using SMTP because of the Receive Filter setting in Firewall
Settings.
●Reset the Receive Filter setting in Firewall Settings.
Specifying IP Addresses in Firewall Settings(P. 539)
Troubleshooting
997

◼#832
Could not send DSN mail because e-mail settings and network settings were not specied in
<Communication Settings>.
●Check <Communication Settings>, <DNS Settings>, and <IP Address Settings>.
Setting E-mail/I-Fax Communication(P. 70)
Making DNS Settings(P. 45)
Setting an IP Address(P. 34)
DSN mail could not be sent due to a problem with the mail server or DNS server.
●Check the status of the mail server and DNS server.
◼#833
MDN (Message Disposition Notication) mail could not be sent because the TCP/IP settings were not
specied.
●Check <Communication Settings>, <DNS Settings>, and <IP Address Settings>.
Setting E-mail/I-Fax Communication(P. 70)
Making DNS Settings(P. 45)
Setting an IP Address(P. 34)
MDN (Message Disposition Notication) mail could not be sent due to a problem with the mail server or
DNS server.
●Check the status of the mail server and DNS server.
◼#834
An MDN error notication was received because the I-fax address or destination conditions were
incorrect.
●Check the specied I-fax address and the destination conditions.
An MDN error notication was received because a problem occurred in the mail server or network.
●Check the status of the mail server and network.
An MDN error notication was received because a problem such as a full memory occurred at the other
party.
●Check the conditions and status of the other party.
◼#835
The maximum number of text lines that can be received with I-fax was exceeded.
●Tell the other party to reduce the number of text lines in the message body and send again.
◼#837
A connection request was received from a host whose connection is restricted by the Receive Filter
settings in Firewall Settings.
●Check the Receive Filter settings in Firewall Settings. This may also represent a hacking attempt via
unauthorized access.
Specifying IP Addresses in Firewall Settings(P. 539)
Troubleshooting
998

◼#838
The license required to use the send function has expired.
●Purchase a license for the send function.
◼#839
The user name or password set in <Communication Settings> is incorrect.
●Check the user name and password settings for SMTP authentication (SMTP AUTH) in <Communication
Settings>.
Setting E-mail/I-Fax Communication(P. 70)
◼#841
An encryption algorithm shared with the mail server does not exist for e-mail and I-fax transmission.
●Set <Allow TLS (POP)> or <Allow TLS (SMTP TX)> in <Communication Settings> to <Off>.
Setting E-mail/I-Fax Communication(P. 70)
●Add a common encryption algorithm to the mail server settings.
◼#842
The mail server requested authentication using a client certicate for e-mail and I-fax transmission.
●Set <Allow TLS (POP)> or <Allow TLS (SMTP TX)> in <Communication Settings> to <Off>.
Setting E-mail/I-Fax Communication(P. 70)
●Change mail server settings so that a client certicate is not requested.
Sending could not be performed because a validation error occurred when validating the TLS server
certicate when sending with SMTP because <Conrm TLS Certicate for SMTP TX> is set to <On>.
●Use the Remote UI to check whether the CA certicate used to sign the TLS server certicate on the SMTP
server side is registered in the machine.
●Check whether the TLS server certicate on the SMTP server side is correct.
●Check whether the TLS server certicate is a self-signed certicate.
◼#843
There is a great difference between the time of the KDC (Key Distribution Center) server and the time set
in the machine.
●Adjust the current date and time in <Date/Time Settings>.
Setting the Date/Time(P. 17)
●Adjust the current time set in the KDC (Key Distribution Center) server.
◼#844
Failed to perform TLS encrypted communication with the POP server when sending with POP before
SMTP.
●Check the TLS encrypted communication settings of the POP server.
Troubleshooting
999

●Set <Allow TLS (POP)> to <Off> in <Communication Settings>. If the problem is not resolved, set <POP
Authentication Before Sending> to <Off> in <Communication Settings>, and switch to a setting other than
POP before SMTP.
Setting E-mail/I-Fax Communication(P. 70)
Sending could not be performed because a validation error occurred when validating the TLS server
certicate when communicating with the POP server because <Conrm TLS Certicate for POP RX> is set
to <On>.
●Use the Remote UI to check whether the CA certicate used to sign the TLS server certicate on the POP
server side is registered in the machine.
●Check whether the TLS server certicate on the POP server side is correct.
●Check whether the TLS server certicate is a self-signed certicate.
◼#845
Failed to perform POP authentication (POP AUTH) when sending with POP before SMTP.
●Check the settings in <POP Server>, <POP Login Name>, and <POP Password> in <Communication
Settings>.
Setting E-mail/I-Fax Communication(P. 70)
●Check the POP authentication settings of the POP server.
●Select <Standard> or <APOP> in <POP Authentication Method> in <Communication Settings>. If the
problem is not resolved, set <POP Authentication Before Sending> to <Off> in <Communication Settings>,
and switch the communication settings to something other than POP before SMTP.
Setting E-mail/I-Fax Communication(P. 70)
◼#846
Failed to perform POP authentication (APOP) when sending with POP before SMTP.
●Check the settings in <POP Server>, <POP Login Name>, and <POP Password> in <Communication
Settings>.
Setting E-mail/I-Fax Communication(P. 70)
●Check the APOP settings of the POP server.
●Select <Standard> or <POP AUTH> in <POP Authentication Method> in <Communication Settings>. If the
problem is not resolved, set <POP Authentication Before Sending> to <Off> in <Communication Settings>,
and switch the communication settings to something other than POP before SMTP.
Setting E-mail/I-Fax Communication(P. 70)
◼#847
Could not save the received le in a Condential Fax Inbox because the memory of the Mail Box or Fax/I-
Fax Inbox was full.
●Delete unnecessary les in the Condential Fax Inbox or Memory RX Inbox.
Printing Documents in the Memory RX Inbox(P. 313)
Keeping Received Documents Private(P. 316)
◼#848
An error occurred when combining an e-mail that was divided and sent.
Troubleshooting
1000

●The divided data may have been deleted. If you delete divided data, it cannot be combined to form a
completed document, even if the remaining data is received later. Ask the sender to send the data again.
◼#851
The printer job could not be stored because the memory is full.
●Check the amount of available memory, and execute the job again.
◼#852
The power was turned OFF while the job was being executed.
●Check that the power cable and plug are securely connected, and execute the job again.
◼#853
The memory is full.
●Reduce the number of pages or check that the number of jobs waiting to be processed has decreased, and
execute the job again.
◼#856
The executed operation was canceled because the memory area for temporarily saving data became full.
●Contact your administrator.
◼#857
Printing was canceled due to the job being canceled while being received, or due to timeout.
●If timeout has occurred, check the status of the network.
◼#858
The data is invalid.
●Check that the print protocol is supported by the machine, as well as the print settings.
◼#859
A compression error occurred with the image data.
●Check the original and the settings, and then try scanning again.
◼#860
Recovery failed after a paper jam, or an incompatible page description language or settings which
cannot be combined were included.
●Check the paper or job settings.
Troubleshooting
1001

◼#861
An error occurred while processing the print data or image data.
●Check the image size and paper size, as well as the color specication settings.
◼#862
Settings are included which are not supported, cannot be combined, or otherwise exceed the limits of
the machine.
●Check the job settings.
◼#863
The job was canceled because initialization operations were performed while the print data was being
processed.
●Execute the job again.
◼#864
Could not correctly recognize the external controller, or an error occurred while forwarding print data.
●Check the controller and the print data.
◼#865
The required functions for printing are currently restricted.
●Check the machine and the job settings.
◼#866
The job was canceled by the security related settings.
●If you are executing a job from the printer driver, use the user information of the appropriate privileges.
●If you are executing a job from the control panel, login as a user with the appropriate privileges.
The security related settings are as follows.
●<Restrict Job from Remote Device w/out User Authent.> is <On>
●<Prohibit Authentication Using Department ID and PIN> is <On>
●<Use ACCESS MANAGEMENT SYSTEM> is <On>
- <Print from Drivers without AMS Printer Driver Add-in> is <Restrict>
- The print function is restricted by the user role settings*
*For information on the user roll settings, see the ACCESS MANAGEMENT SYSTEM Administrator Guide.
Troubleshooting
1002

◼#868
When sending with WebDAV, communication with the destination failed, and access via a proxy was
requested (received HTTP Error 305: Use Proxy).
●Check the WebDAV server settings.
●Check the proxy settings.
Setting a Proxy(P. 547)
◼#869
When sending with WebDAV, a response indicating that authentication failed was received from the
destination (received HTTP Error 401: Unauthorized).
●Check the user name or password.
●Check the WebDAV server security settings.
◼#870
When sending with WebDAV, a response indicating that the request was rejected was received from the
destination (received HTTP Error 403: Forbidden).
●Try sending again after waiting a while.
●Check the destination settings.
●Check the WebDAV server settings.
◼#871
When sending with WebDAV, a response indicating that the specied folder was not found was received
from the destination (HTTP Error 404: Not Found/409: Conict/410: Gone).
●Check the destination settings.
◼#872
When sending with WebDAV, a response indicating that access is not allowed was received from the
destination (received HTTP Error 405: Method Not Allowed).
●Check the WebDAV server settings.
◼#873
When sending with WebDAV, a response indicating that proxy authentication failed was received from
the destination (received HTTP Error 407: Proxy Authentication Required).
●Check the proxy settings.
Setting a Proxy(P. 547)
◼#874
When sending with WebDAV, a response indicating that a timeout occurred was received from the
destination (received HTTP Error 408: Request Timeout).
●Try sending again after waiting a while.
Troubleshooting
1003

●Check the WebDAV server settings.
◼#875
When sending with WebDAV, a response indicating that chunk transmission was refused was received
from the destination (received HTTP Error 411: Length Required).
●Set <Use Divided Chunk Send for WebDAV TX> to <Off>.
<Use Divided Chunk Send for WebDAV TX>(P. 822)
●Check the WebDAV server settings.
◼#876
When sending with WebDAV, a response indicating that the size of the data was too large was received
from the destination (received HTTP Error 413: Request Entity Too Large).
●Check the WebDAV server settings.
◼#877
When sending with WebDAV, a response indicating that the URI (host name and path to folder) was too
long was received from the destination (received HTTP Error 414: Request-URI Too Long).
●Check the WebDAV server settings.
◼#878
When sending with WebDAV, a response indicating that an unexpected situation preventing the request
from being executed occurred on the server side was received from the destination (received HTTP Error
500: Internal Server Error).
●Check the WebDAV server settings.
◼#879
When sending with WebDAV, a response indicating that the server does not support the necessary
functions to execute the request was received from the destination (received HTTP Error 501: Not
Implemented).
●Check the WebDAV server settings.
●When sending via a proxy with non-TLS communication, set <Use Divided Chunk Send for WebDAV TX> to
<Off>.
<Use Divided Chunk Send for WebDAV TX>(P. 822)
◼#880
When sending with WebDAV, a response indicating that communication with an upstream server failed
was received from the proxy server (received HTTP Error 502: Bad Gateway).
●Check the WebDAV server settings.
●Check the proxy server settings.
Troubleshooting
1004

◼#881
When sending with WebDAV, a response indicating that requests currently cannot be handled was
received from the destination (received HTTP Error 503: Service Unavailable).
●Check the WebDAV server settings.
◼#882
When sending with WebDAV, a response indicating that communication with an upstream server failed
was received from the proxy server (received HTTP Error 504: Gateway Timeout).
●Check the WebDAV server settings.
●Check the proxy server settings.
◼#883
When sending with WebDAV, a response indicating that the server does not support the necessary
functions to execute the request was received from the destination (received HTTP Error 505: HTTP
Version Not Supported).
●Check the WebDAV server settings.
◼#884
When sending with WebDAV, a response indicating that disk space required for the request could not be
secured on the server side was received from the destination (received HTTP Error 507: Insucient
Storage).
●Check the WebDAV server settings.
◼#885
When sending with WebDAV, an unexpected error response was received from the server.
●Check the WebDAV server settings.
●Check the proxy server settings.
◼#886
When sending with WebDAV, a response indicating that the request was invalid was received from the
destination (received HTTP Error 400: Bad Request).
●When sending via a proxy with non-TLS communication, set <Use Divided Chunk Send for WebDAV TX> to
<Off>.
<Use Divided Chunk Send for WebDAV TX>(P. 822)
◼#889
The original could not be scanned or printed because it was embedded with job restriction information.
●Check the job restriction information or contact your administrator.
Troubleshooting
1005

◼#899
E-mail or I-fax transmission completed normally. However, the transmission may not have been received
by the other party because it is relayed by multiple servers.
●Ask whether the other party received the transmission, as necessary.
The fax was sent normally from the remote fax client. However, reception may be incomplete because
the transmission was relayed via a remote fax server.
●Check whether the fax was sent in the transmission results of the remote fax server.
●Check the status of the server and network.
●Ask the recipient to check that the document was received properly.
◼#904
Destinations registered in <Favorite Settings> are not updated when the Address Book is retrieved using
device information delivery from an iR/imagePRESS series machine connected to the network.
●Register <Favorite Settings> again from the touch panel display of the machine.
◼#905
The job could not be executed because a network error occurred.
●Check the path length and access privileges of the server, and whether the le or folder is in use.
◼#919
A syntax error or a PostScript error that exceeds device restrictions, etc. was detected.
●Set <Print PS Errors> (Settings/Register) to <On>, submit the job again, conrm the contents of the PostScript
error, then execute the job after resolving the error. For more details, see "Setting the Machine (PS/PCL/UFR
II Printer)" via the online manual site.
◼#923
Could not print on the specied side of the cover, or body.
●Change to a paper type that is compatible with two-sided printing, and execute the job again.
◼#925
A transmission error occurred from the fax driver.
●An image size that cannot be sent was specied. Check the size of the image.
◼#927
A transmission error occurred from the fax driver.
●Font that cannot be processed is included in the data received by the machine from a computer. Check the
received data.
Troubleshooting
1006

◼#928
A transmission error occurred from the fax driver.
●The memory is full, or the data size has exceeded the size that can be processed at one time. Delete
unnecessary data or check the data size.
◼#929
A transmission error occurred from the fax driver.
●A network error occurred when the machine was receiving data from a computer. Check the network
connections and settings.
◼#934
An error occurred for a print job, and the job was deleted because the specied time period elapsed.
●Resolve the error and execute the job again.
●You can also change the time period before deletion or disable automatic deletion from <Auto Delete
Suspended Jobs> (Settings/Register).
<Auto Delete Suspended Jobs>(P. 810)
◼#939
Printing was canceled due to an error that occurred while processing the image data.
●Execute the job again.
◼#995
Reserved communication jobs were cleared.
●Perform the operation again, as necessary.
Troubleshooting
1007
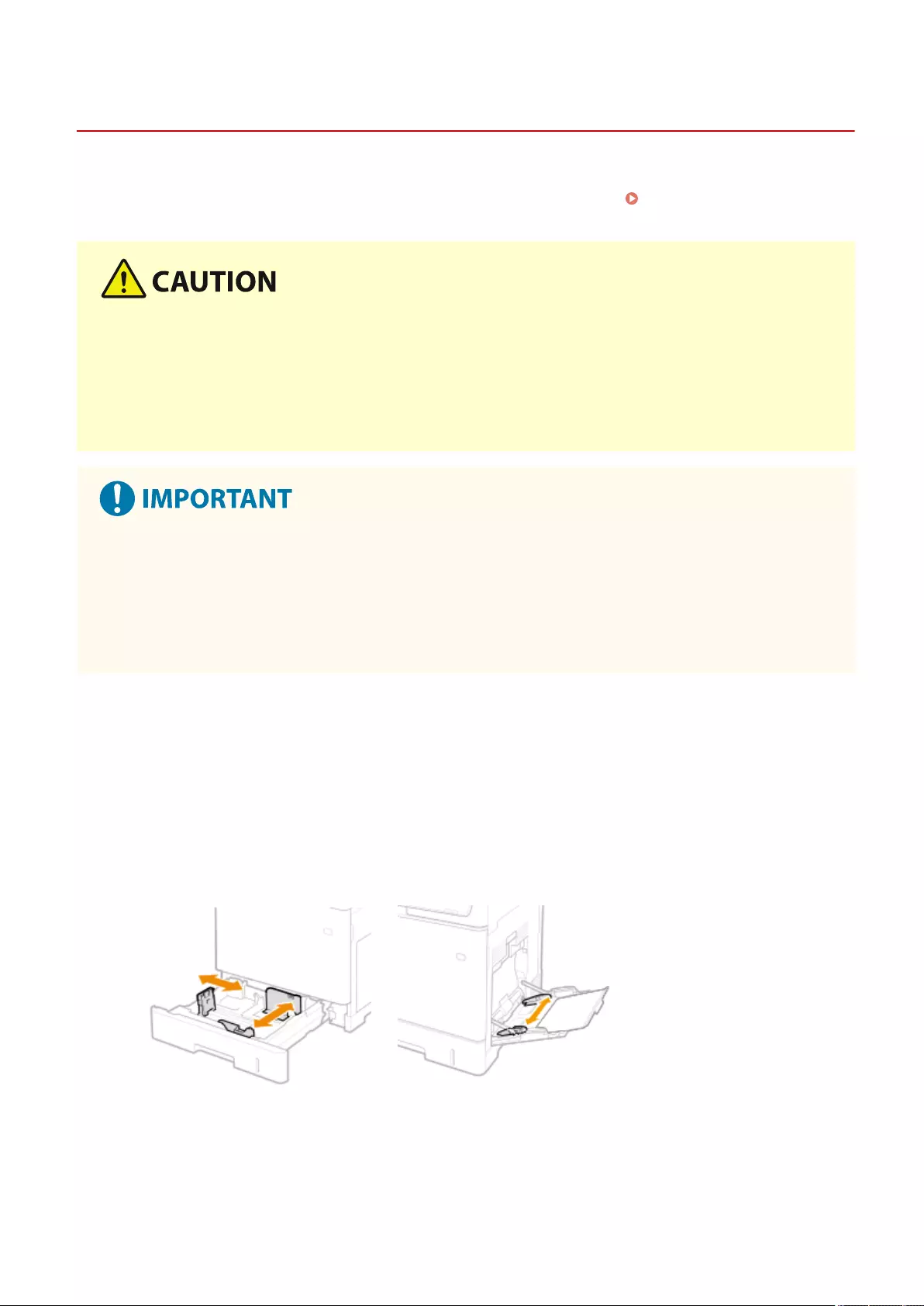
Clearing Paper Jams
72JY-0J5
If a paper jam occurs, a message, the location of the paper jam, and the procedure for clearing it are displayed on the
screen. If you do not know how to clear the paper jam from viewing the screen, see Paper Jam Locations(P. 1009)
to clear the paper jam. For information on cautions when clearing paper jams, see the Important Safety Instructions.
●Do not forcibly remove the jammed paper from the machine. Forcibly removing the paper may result in
injury or damage parts of the machine.
- If you cannot remove the paper, contact your dealer or service representative.
●When all paper jams have been cleared, immediately remove your hands from the machine and optional
equipment so that your clothing and hands do not get caught in the rollers.
Cautions when clearing paper jams
●When clearing paper jams, do not turn the power OFF. Data being printed is erased when you turn the
power OFF.
- Take particular care when a fax is being received.
●When the paper gets torn, be sure to remove the torn pieces so that they do not remain.
◼If Paper Jams Frequently Occur
If paper jams frequently occur even though there are no problems with the machine and its optional
equipment, check the following.
Are the paper guides misaligned?
●Match the paper guides with the paper loaded in the paper source.
Do sheets of paper overlap when being fed?
●If paper jams occur due to overlapping of sheets of paper when being fed, reload the paper by changing the
orientation.
Troubleshooting
1008

Is the paper type correct?
●On the <Status Monitor> screen, check the paper type. <Status Monitor> Screen(P. 120)
●If the paper loaded in a paper source differs from the paper type setting, see Loading Paper(P. 102) to set
the paper type again.
Do pieces of paper remain in the machine?
●Pieces of paper may remain in the machine after removing a paper jam. Open the location where the paper
was jammed, and remove any pieces of paper (Do not forcibly remove the jammed paper from the machine.
Forcibly removing the paper may result in injury or damage parts of the machine. If you cannot remove the
paper, contact your dealer or service representative.).
Paper Jam Locations
For information on the paper jam locations and the method for clearing paper jams, see the following diagram and
references.
Feeder Paper Jams in the Feeder(P. 1011)
Inside the main unit Paper Jams inside the Machine or in the Fixing Unit(P. 1013)
Paper drawer Paper Jams in a Paper Source(P. 1017)
●Paper may not actually be jammed in the location you check. Even in this case, follow the instructions
on the screen to check all the locations.
Troubleshooting
1009

●The screen indicating that there is a paper jam is repeatedly displayed until you clear the paper jam.
●If you press <Close> on the screen indicating that there is a paper jam, you may be able to continue to
perform operations and specify settings without immediately removing the paper jam.
●Do not remove paper from a location other than that displayed as a paper jam location on the screen.
This may cause paper jams in other locations or missing pages in output documents.
Troubleshooting
1010
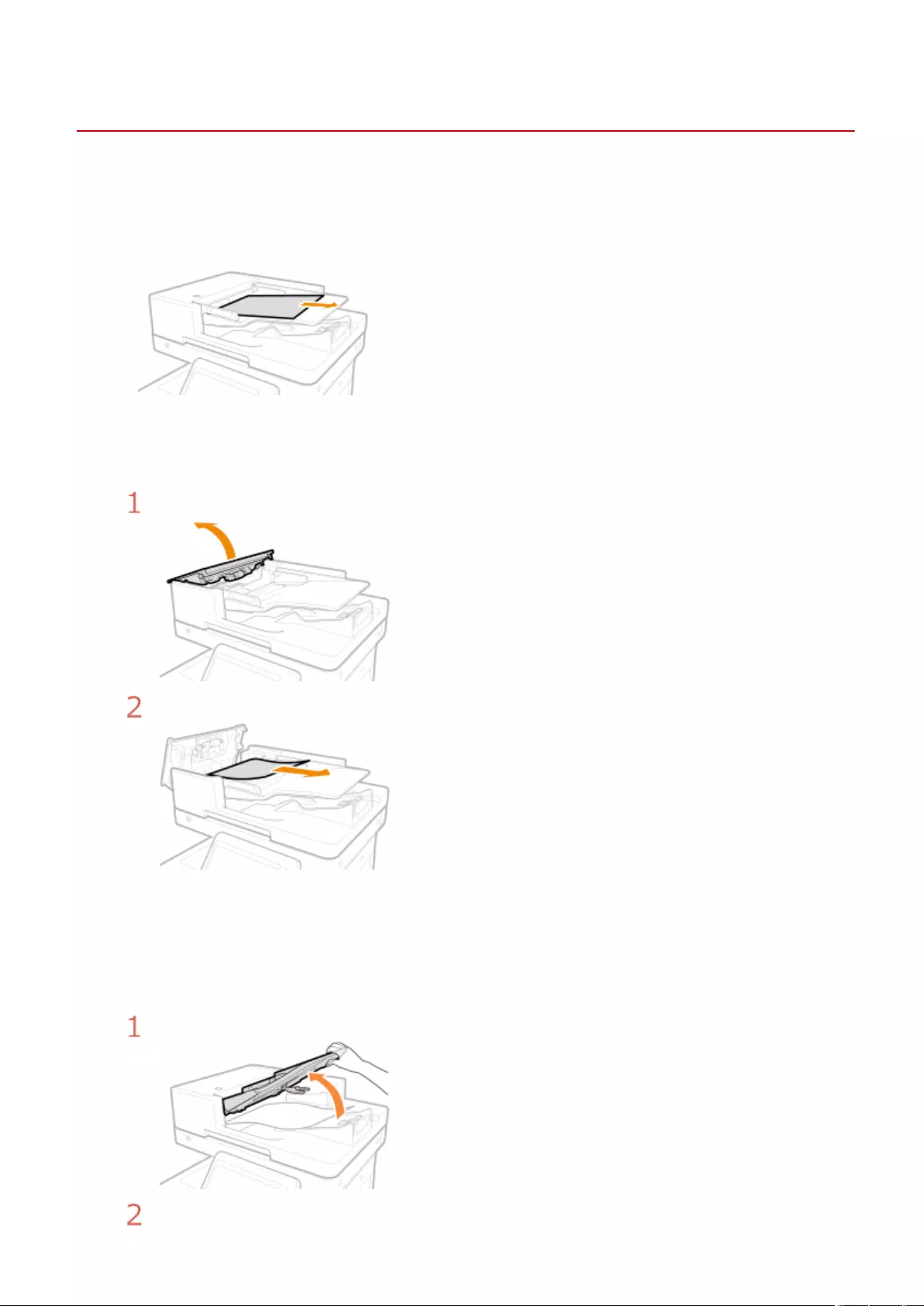
Paper Jams in the Feeder
72JY-0J6
Check the paper jam location on the screen, and follow the procedure below to remove the original.
1Remove the originals in the original supply tray.
2Check whether an original is jammed in the feeder cover.
Open the feeder cover.
If an original is jammed, gently pull it out in the direction of the arrow.
●If you cannot remove the jammed original, proceed to the next step without forcibly
removing it.
3Check whether an original is jammed in the original output tray.
Lift the original supply tray.
If an original is jammed, gently pull it out in the direction of the arrow.
Troubleshooting
1011
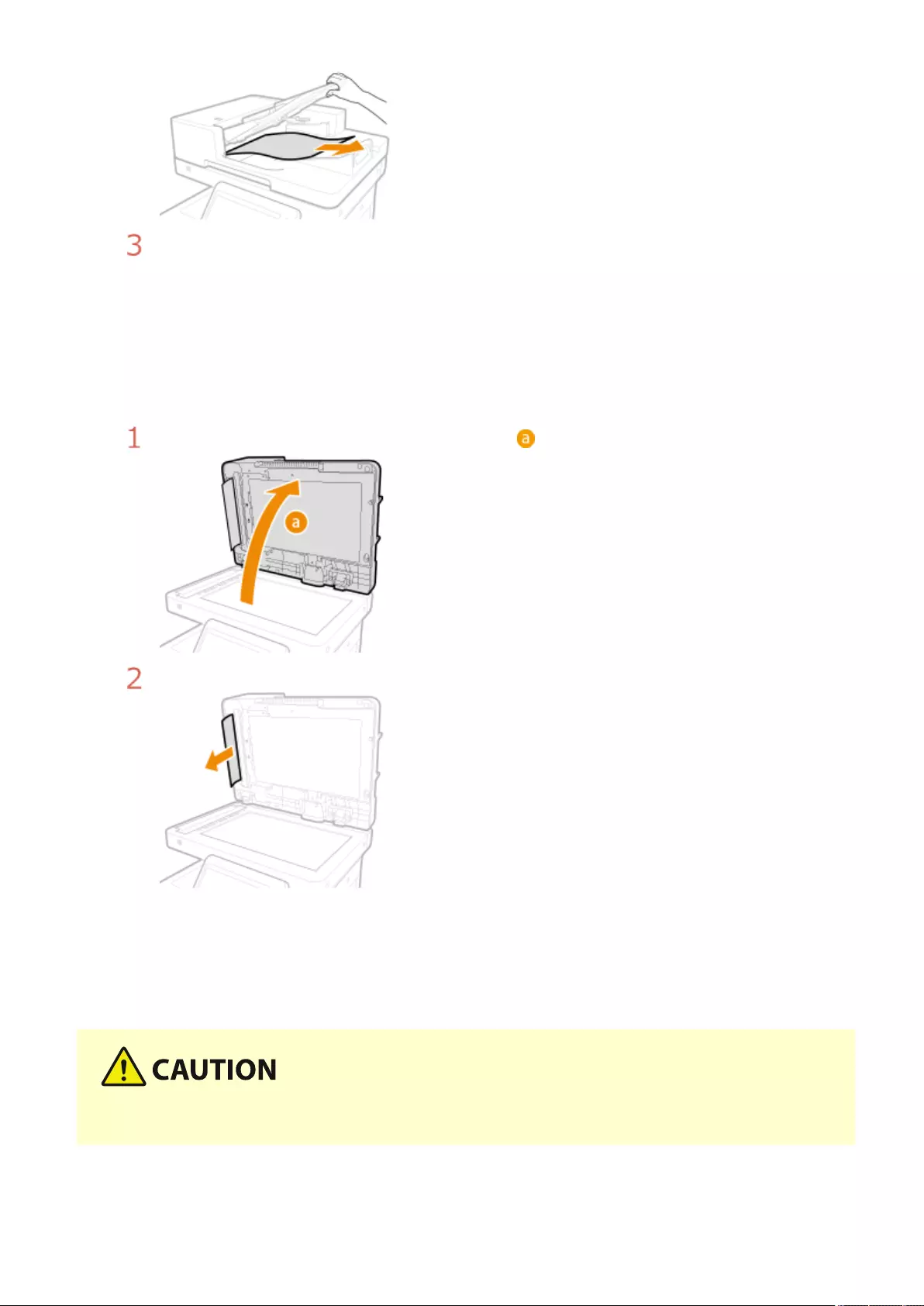
Return the original supply tray back into position.
4After removing all jammed originals, close the feeder cover.
5Lift up the feeder, and check if there is a jammed original.
Lift up the feeder, and check the position indicated by .
If an original is jammed, gently pull it out in the direction of the arrow.
6Return the feeder to its original position.
●Continue following the instructions on the screen to proceed with the interrupted operation or continue
clearing paper jams.
●When closing the feeder, take care that your eyes are not exposed to light emitted through the platen glass.
Troubleshooting
1012
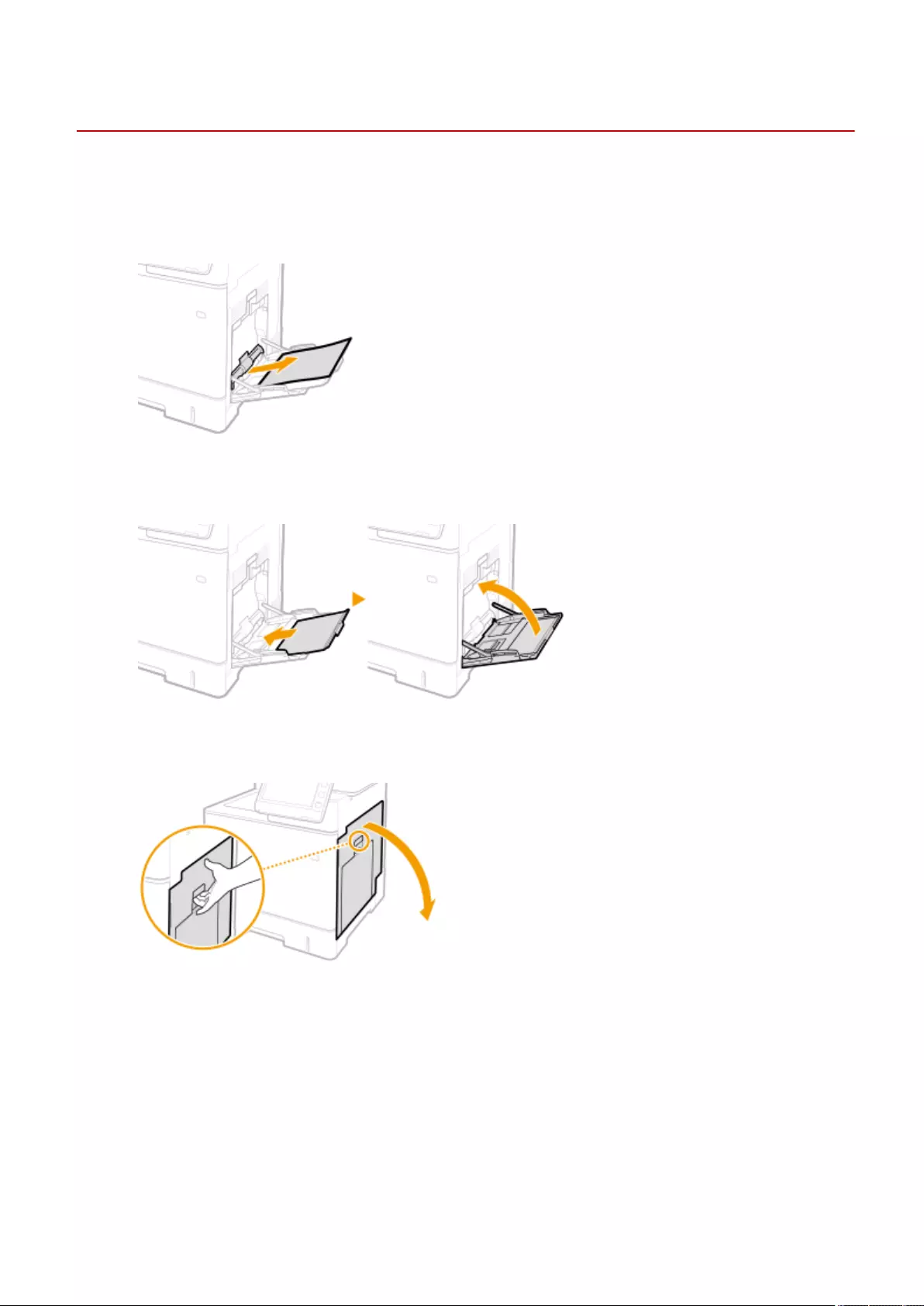
Paper Jams inside the Machine or in the Fixing Unit
72JY-0J7
Check the paper jam location on the screen, and follow the procedure below to remove the paper.
1Gently pull out the paper.
2Close the tray.
3Open the right cover.
4Gently pull out the paper.
Troubleshooting
1013
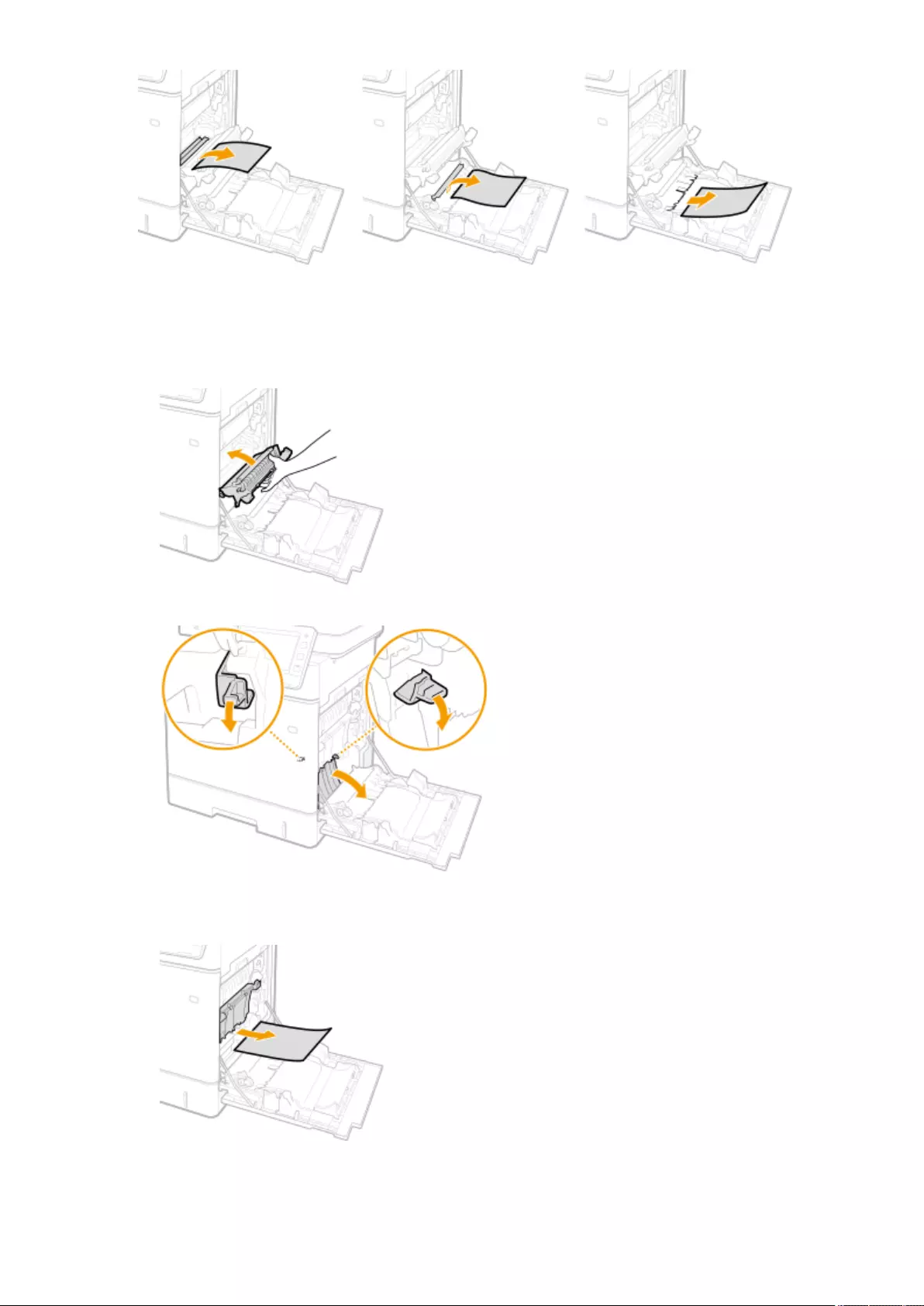
5Remove the jammed paper in the delivery unit.
1Lift up the delivery unit.
2Lower the green levers on both sides of the transport guide.
3Gently pull out the paper.
●Pull out the paper while holding it as horizontally as possible to prevent unxed toner from falling.
6Check whether there is a paper jam in the xing unit.
Troubleshooting
1014
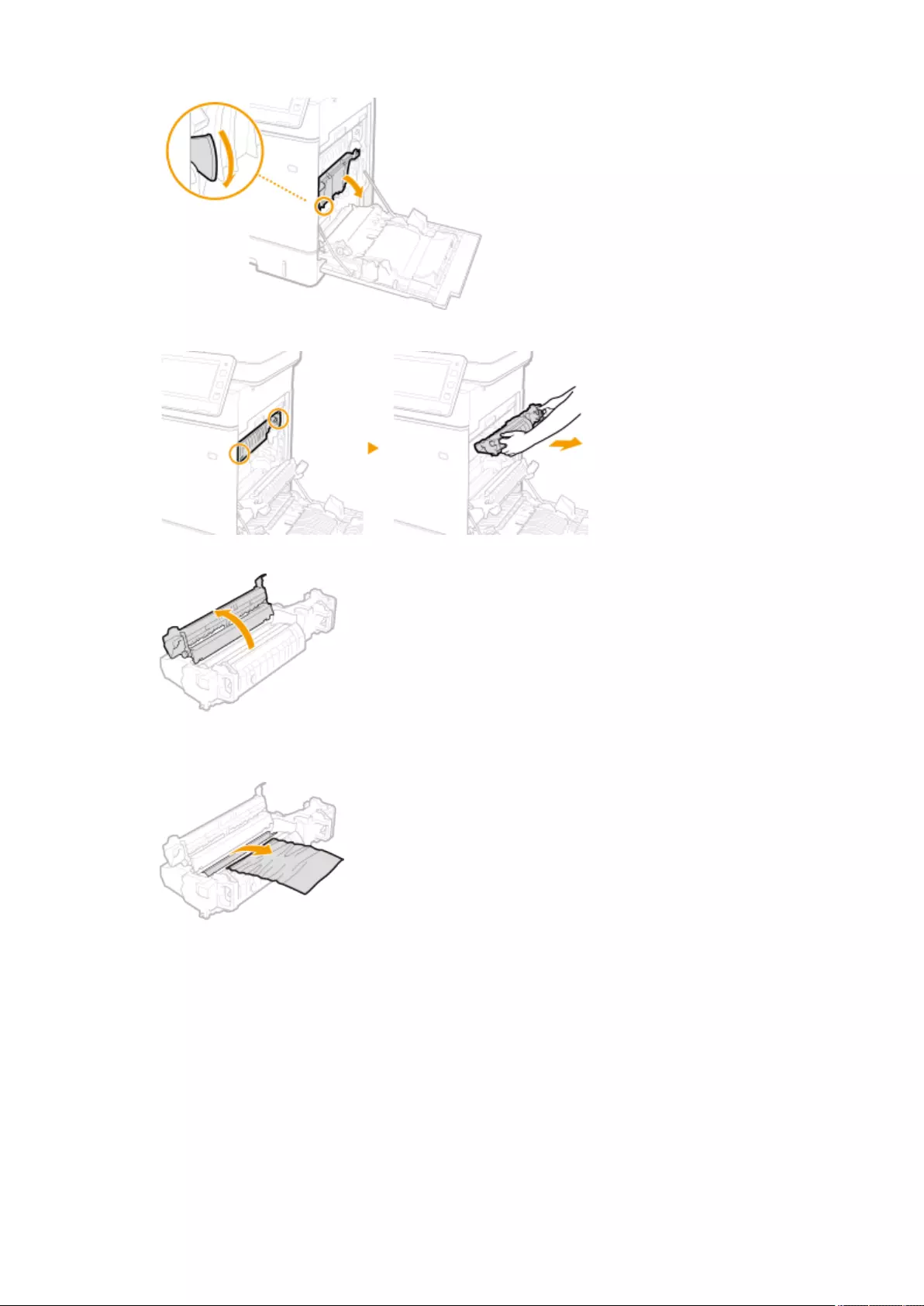
1Turn the delivery unit downward.
2Hold the handles on both sides of the xing unit, and pull out the xing unit straight toward you.
3Open the cover.
4Gently pull out the paper.
●Pull out the paper while holding it as horizontally as possible to prevent unxed toner from falling.
5Close the cover.
6Gently pull out the paper.
●Determine in which way you can pull out the jammed paper more easily, and try that way rst.
●Pull out the paper while holding it as horizontally as possible to prevent unxed toner from falling.
Troubleshooting
1015
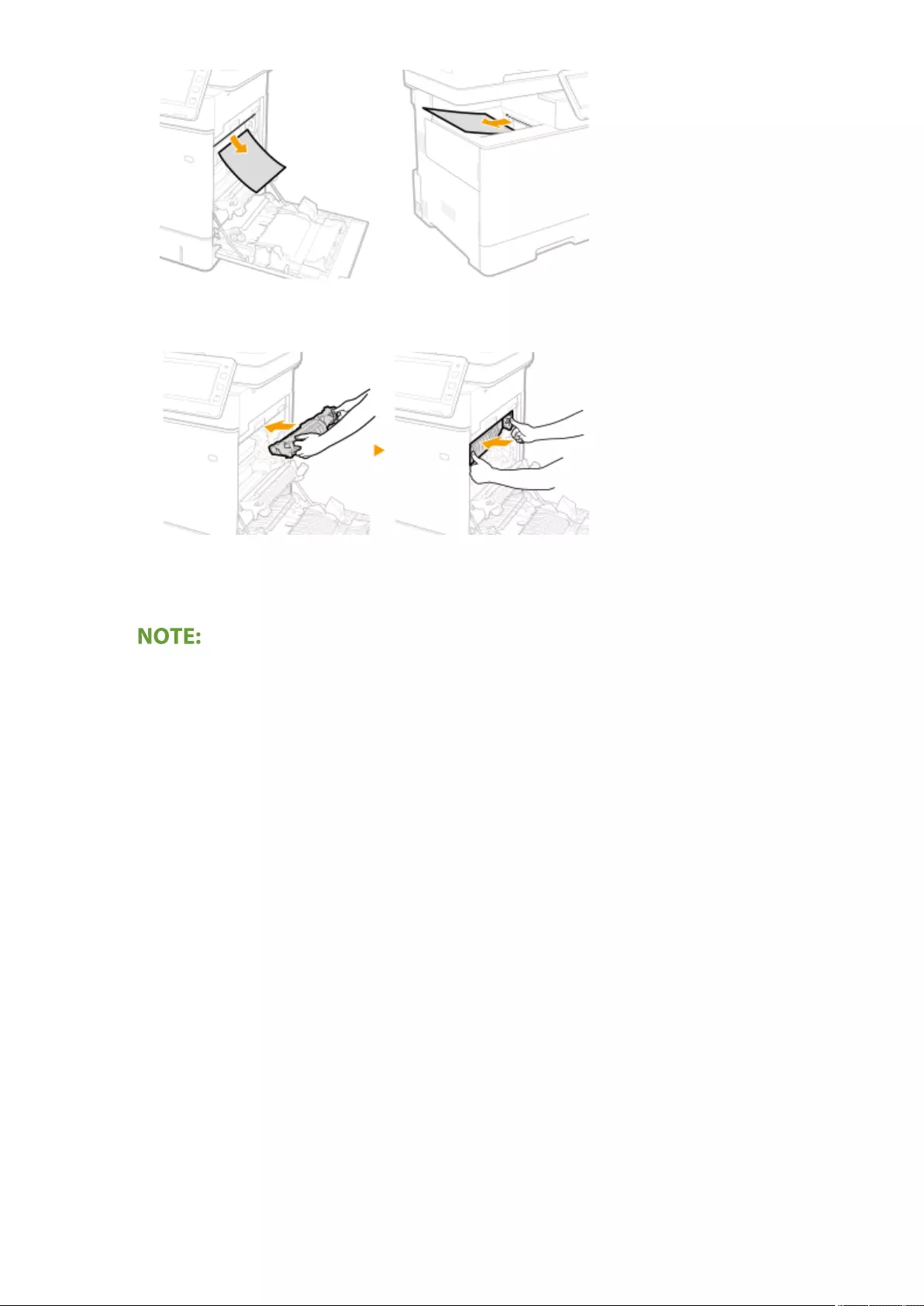
7Place the xing unit back into position.
●Fully push it in until it cannot go any further.
7Close the right cover.
When the message is still displayed
●Paper may be jammed in other locations. Check other locations, and remove jammed paper if any. If the
message is still displayed, check whether the right cover is securely closed.
Troubleshooting
1016
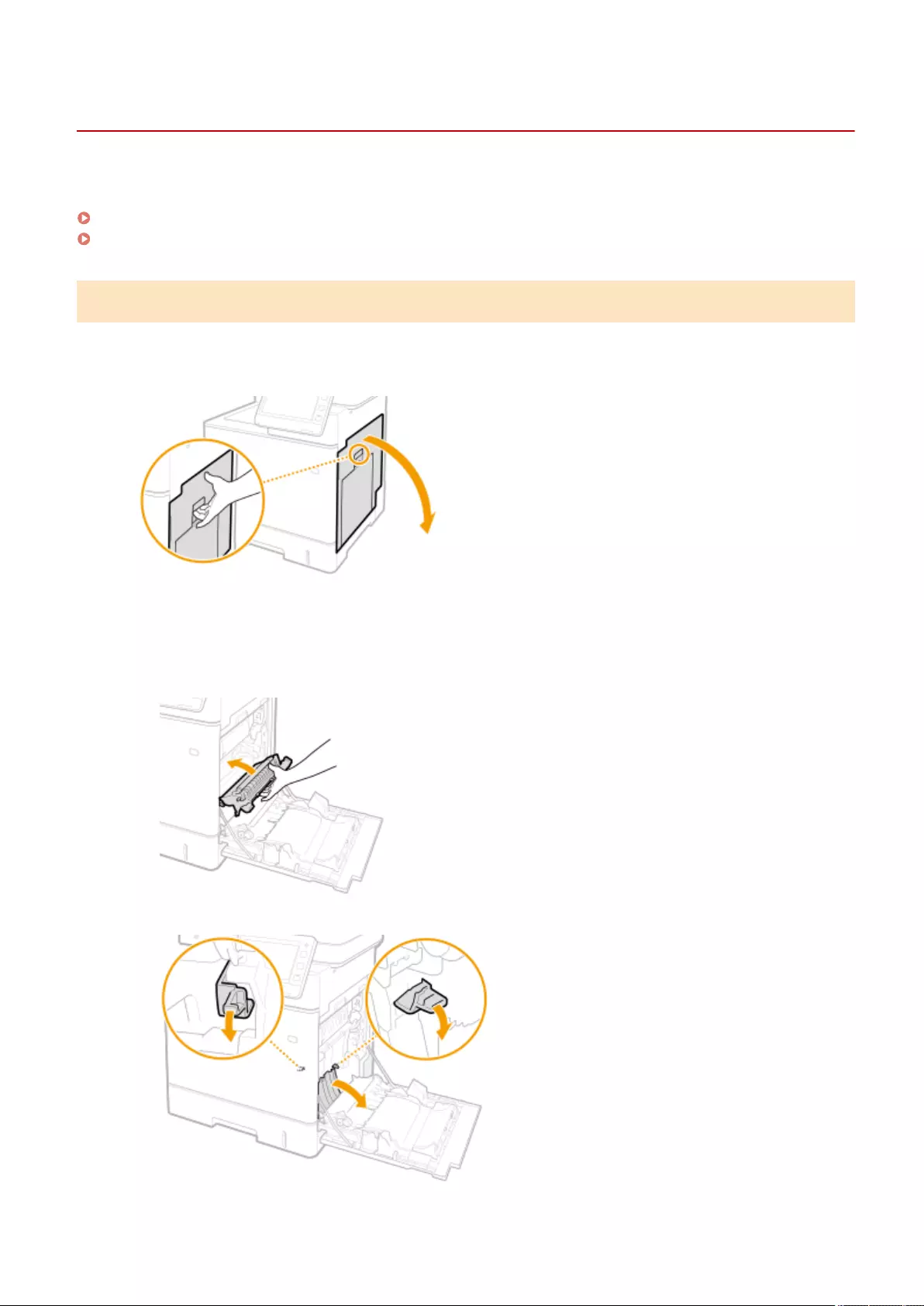
Paper Jams in a Paper Source
72JY-0J8
Check the paper jam location on the screen, and follow the procedure below to remove the paper.
Clearing Paper Jams in Paper Drawers 1(P. 1017)
Clearing Paper Jams in Paper Drawers 2, 3 and 4 (Optional)(P. 1018)
Clearing Paper Jams in Paper Drawers 1
1Open the right cover.
2Remove the jammed paper in the delivery unit.
1Lift up the delivery unit.
2Lower the green levers on both sides of the transport guide.
3Gently pull out the paper.
Troubleshooting
1017
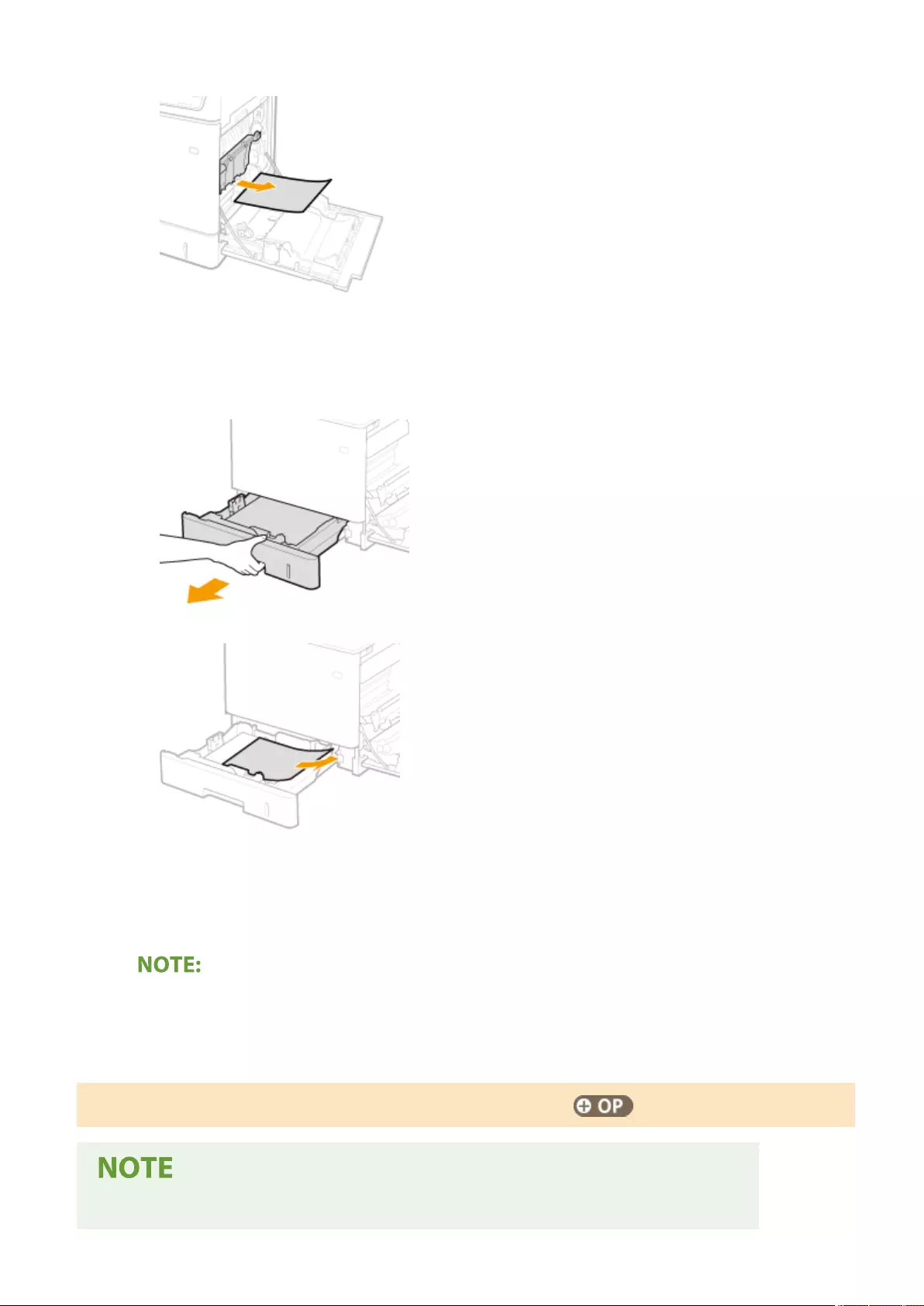
●Pull out the paper while holding it as horizontally as possible to prevent unxed toner from falling.
3Remove the jammed paper in the paper drawer.
1Pull out the paper drawer until it stops.
2Gently pull out the paper.
3Set the paper drawer.
4Close the right cover.
When the message is still displayed
●Paper may be jammed in other locations. Check other locations, and remove jammed paper if any. If the
message is still displayed, check whether the right cover is securely closed.
Clearing Paper Jams in Paper Drawers 2, 3 and 4 (Optional)
●Remove jammed paper in Paper Drawers 3 and 4 with the same procedure as Paper Drawer 2.
Troubleshooting
1018
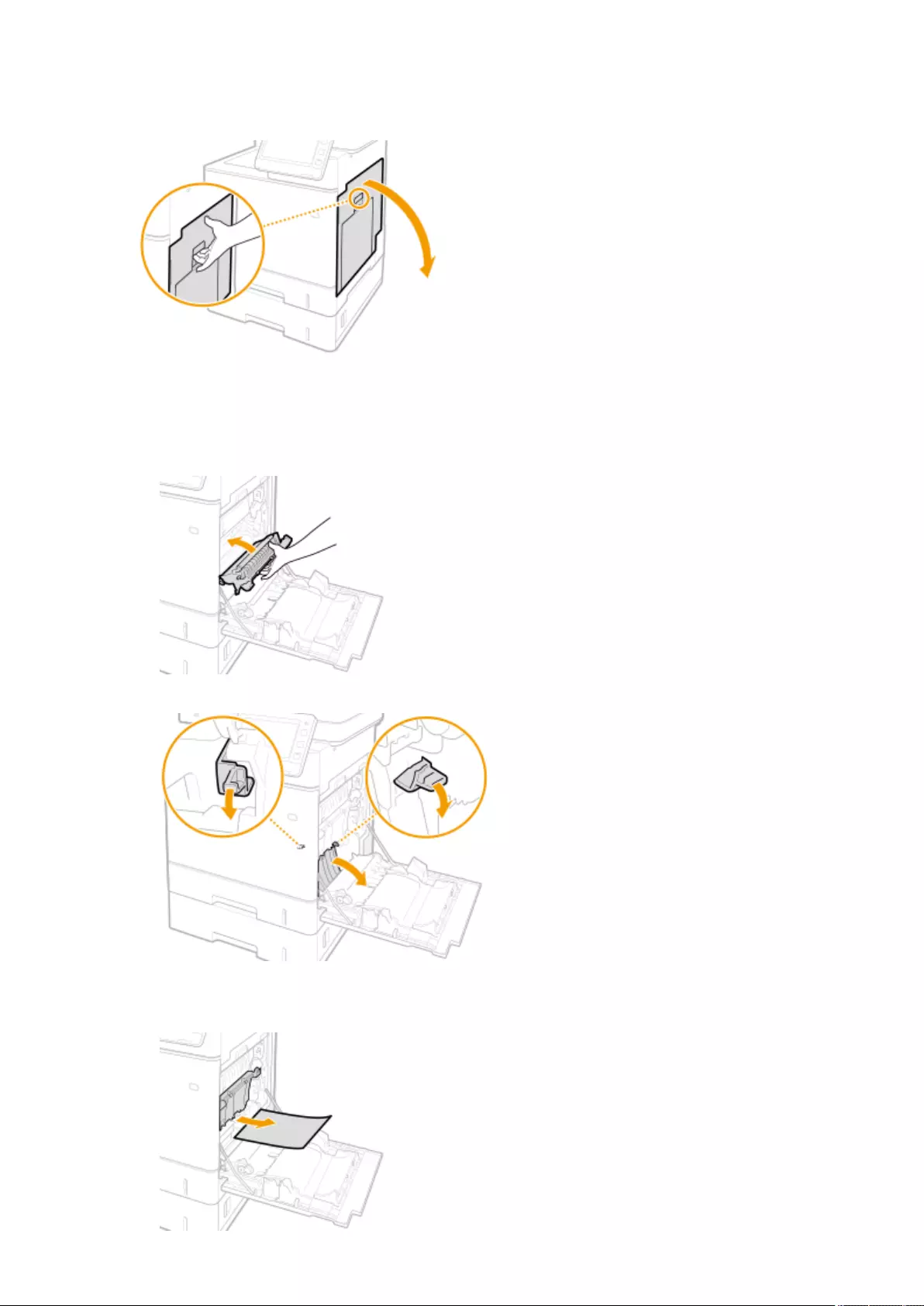
1Open the right cover.
2Remove the jammed paper in the delivery unit.
1Lift up the delivery unit.
2Lower the green levers on both sides of the transport guide.
3Gently pull out the paper.
●Pull out the paper while holding it as horizontally as possible to prevent unxed toner from falling.
Troubleshooting
1019
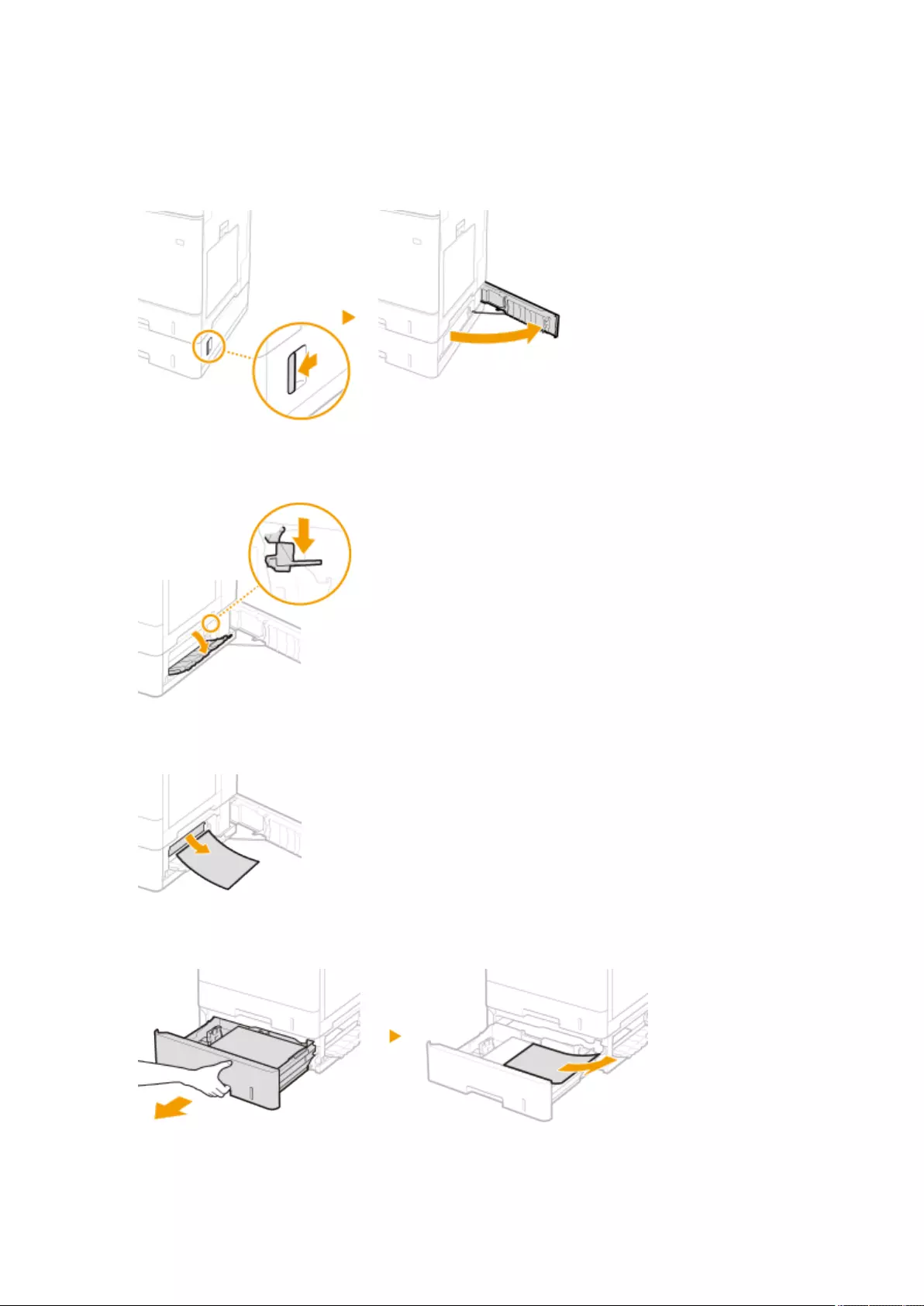
3Close the right cover.
4Open the right cover of the paper feeder.
5Lower the green lever to open the transport guide.
6Gently pull out the paper.
7Pull out the paper drawer until it stops, and gently pull out the paper.
8Set the paper drawer.
Troubleshooting
1020

9Close the right cover of the paper feeder.
When the message is still displayed
●Paper may be jammed in other locations. Check other locations, and remove jammed paper if any. If the
message is still displayed, check whether the right cover is securely closed.
Troubleshooting
1021

Implementing Security Measures
Implementing Security Measures ...................................................................................................... 1023
Various Security Functions ............................................................................................................................. 1024
Implementing Security Measures
1022

Implementing Security Measures
72JY-0J9
Saving important data to the machine and sharing information via the machine enable the machine to be used more
effectively. It also raises the value the machine provides as an information asset.
The machine provides various functions for enhancing security, such as preventing information leaks, preventing
unauthorized access, and protecting condential information.
Using these security functions together enables you to use the machine securely.
Various Security Functions(P. 1024)
Implementing Security Measures
1023

Various Security Functions
72JY-0JA
Do you feel uneasy about the following problems?
●Unattended output
●Unauthorized access
●Faxes sent to the wrong destination
●Forgetting to erase condential data on the machine
The machine provides various security functions for minimize the risk of information leakage and unauthorized access.
This section describes functions that are effective in certain situations.
Preventing Documents Leaks and Modication(P. 1024)
Preventing Unauthorized Access to the Network(P. 1025)
Preventing Trouble Caused by Erroneous Sending(P. 1025)
Preventing Leaks of Condential Information during Operation of the Machine(P. 1027)
●Implementing security measures does not guarantee that all information will be protected.
●Using the Import All function enables multiple devices to be managed with the same settings. Importing/
Exporting the Setting Data(P. 625)
Preventing Documents Leaks and Modication
When managing condential documents, it is necessary to handle problems
such as leaks, loss, and modication. The machine is equipped with security
functions designed to prevent paper and electronic documents from leakage
and tampering, such as not starting printing until the user logs in at the
device, and attaching a signature to PDF documents.
Use the following functions as security measures for preventing document
leaks and modication, etc.
Forced Hold
To avoid leaving printed material, accidental information leakage, misprinting, etc., the administrator can set to
store the document before printing. Printing Documents Held in the Machine(P. 351)
Encrypted Secure Print
By using Encrypted Secure Printing, you can send encrypted printing data to a machine from your computer.
This enables you to reduce the risk of information leaks when sending printed data, and to print more safely.
Printing More Safely with Encrypted Secure Print(P. 354)
Implementing Security Measures
1024

Add Digital Signatures
You can increase the reliability of documents created on the machine by adding digital signatures to scanned
documents. The digital signature is added using a key and certicate mechanism, which enables you to identify
the device and/or user that created the document, while ensuring that the data has not been altered. Adding
a Digital Signature to Sent Files(P. 577)
Encrypted PDF
Setting a password when scanning an original enables PDF les to be encrypted for sending/saving. This helps
reduce the risk of the les being viewed or edited by others. Performing Encryption(P. 416)
Preventing Unauthorized Access to the Network
Although Cloud services have made it easier to exchange data via the
Internet, communication can still be intercepted or modied by malicious
third parties due to network vulnerabilities. The machine provides various
measures for increasing network security, such as only allowing
communication with specic IP addresses and encrypting data for
communication.
Use the following functions as security measures for preventing unauthorized
network access, etc.
Firewall Settings
Unauthorized access by third parties, as well as network attacks and breaches, can be blocked by only allowing
communication with devices that have a specic IP address. Restricting Communication by Using
Firewalls(P. 538)
Proxy Settings
You can provide greater security by using a proxy server for connections outside the network, such as when
browsing websites. Setting a Proxy(P. 547)
TLS Settings
TLS is a protocol for encryption for data sent over a network and is often used for communication via a Web
browser or an e-mail application. TLS enables secure network communication when accessing the machine in a
variety of situations, such as when using the Remote UI or distributing device information. Conguring the
Key and Certicate for TLS(P. 549)
IPSec Settings
While TLS only encrypts data used on a specic application, such as a Web browser or an e-mail application,
IPSec encrypts the whole (or payloads of) IP packets. This enables IPSec to offer a more versatile security system
than TLS. Conguring the IPSec Settings(P. 555)
IEEE 802.1X Settings
If a device tries to connect and start communicating on an 802.1X network, the device must go through user
authentication in order to prove that the connection is made by an authorized user. Authentication information
is sent to and checked by a RADIUS server, which permits or rejects communication to the network depending
on the authentication result. If authentication fails, a LAN switch (or an access point) blocks access from the
outside of the network. The machine can connect to an 802.1X network as a client device. Conguring the
IEEE 802.1X Authentication Settings(P. 561)
Preventing Trouble Caused by Erroneous Sending
Implementing Security Measures
1025

Erroneous sending to the wrong destination or careless mistakes such as
entering the wrong fax number can lead to leaks of condential information.
The machine provides various measures for increasing security when
sending, such as limiting the destinations that can be sent to and forcing the
fax number to be entered twice before sending.
Use the following functions as security measures for preventing trouble
caused by erroneous sending.
Address Book PIN
You can set an access number for important business contacts and other destinations in the Address Book that
you do not want to display to all users. Restricting Access to Destinations Registered in the Address
Book(P. 567)
Manage Address Book Access Numbers
You can prevent the leakage of sensitive or personal information from the Address Book by setting a PIN or
preventing certain destinations from being displayed in the Address Book. You can also hide the Address Book
itself. Hiding the Address Book(P. 567)
Restrict Address Book Use
Set whether to hide the Address Book and one-touch buttons. You can specify separate settings for Fax as well
as Scan and Send. Restricting Use of the Address Book(P. 566)
Restrict New Destinations
The destinations that can be specied when sending faxes or scanned documents can be restricted to those
registered in the Address Book or one-touch buttons, those registered in <Favorite Settings> or <Send to
Myself>, or those that can be searched on the LDAP server. Restricting New Destinations(P. 569)
Limit E-Mail to Send to Myself
You can set restrictions so that users who log in with personal authentication can only send scanned documents
to their own e-mail address. Restricting E-Mail Destination to <Send to Myself>(P. 570)
Restrict File TX to Personal Folder
You can set restrictions so that users who log in with personal authentication can only send scanned documents
to their Personal folder. Restricting File Send Destination to Personal Folder(P. 570)
Restrict Sending to Domains
You can restrict e-mail and I-fax destinations so that only addresses in a specic domain are available. When a
domain is specied, you can also set whether to allow sending to subdomains. Restricting the Domain of
Send Destination(P. 570)
Conrm Entered Fax Number
You can require users to enter a fax number twice for conrmation before sending faxes, to prevent misdialing.
Conrming Fax Numbers before Sending(P. 571)
Allow Fax Driver TX
You can prohibit users from sending faxes from a computer. Restricting Fax Sending from a
Computer(P. 571)
Implementing Security Measures
1026

Conrm Before Sending When Fax Dest. Included
You can set the machine to display a conrmation screen when sending to a fax destination. Displaying a
Conrmation Screen for Fax Destinations(P. 571)
Previewing Documents before Sending
You can check scanned images on the preview screen before sending. Checking Scanned Images Before
Sending (Preview)(P. 295)
Preventing Leaks of Condential Information during Operation of the
Machine
The machine generates value as an information asset by storing important
data. Preventing condential information from remaining on the machine
after disposal is another important security measure. The machine provides
various measures for increasing security of operation, such as preventing
unregistered users from operating the machine, and completely erasing
temporary job data when the machine is started.
Use the following functions as security measures for preventing leaks of
condential information during operation of the machine.
Verify System at Startup
The integrity of the rmware, system, and AddOn applications in the machine is veried during startup.
<Verify System at Startup>(P. 870)
McAfee Embedded Control
When the machine is operating, the McAfee Embedded Control function is used to prevent unauthorized
program modication and the execution of unauthorized programs, for improved system reliability. <McAfee
Embedded Control>(P. 870)
Personal Authentication Management
A user name and password can be used to perform personal authentication of users. Preventing unauthorized
access by third parties and setting usage restrictions can maintain a higher level of security and enable more
ecient operation of the machine. Managing Users(P. 489)
Initialize All Data/Settings
You can restore all of the machine settings to the factory default values. Since data remaining in the memory is
overwritten with meaningless values, this prevents external leaks of condential data when disposing of the
machine. Initializing All Data/Settings(P. 663)
Security Policy Settings
A security policy describes company-wide rules regarding information security. With this machine, multiple
settings related to a security policy can be set together. Applying a Security Policy to the Machine(P. 478)
Allow Use of Default Password for Remote Access
You can set the machine to not allow users to log in to the Remote UI using the default password (7654321) of
the "Administrator" user for security reasons. <Allow Use of Default Password for Remote Access>(P. 867)
Implementing Security Measures
1027

Appendix
Appendix ........................................................................................................................................................... 1030
Third Party Software ....................................................................................................................................... 1032
Notice ............................................................................................................................................................... 1033
Feature Highlights .......................................................................................................................................... 1037
Operability ................................................................................................................................................. 1038
Utilizing Personalization ...................................................................................................................... 1039
Productivity ................................................................................................................................................ 1046
Image Quality ............................................................................................................................................. 1047
Manageability ............................................................................................................................................. 1048
Building a Dual Network Environment ................................................................................................. 1050
Reliability .................................................................................................................................................... 1053
Oce Compatibility .................................................................................................................................... 1054
The List of System Functions and Items ........................................................................................................ 1055
Home ......................................................................................................................................................... 1056
Copy ........................................................................................................................................................... 1058
Fax ............................................................................................................................................................. 1060
Scan and Send ............................................................................................................................................ 1062
Scan and Store ........................................................................................................................................... 1064
Access Stored Files ..................................................................................................................................... 1068
Fax/I-Fax Inbox ........................................................................................................................................... 1072
Print ........................................................................................................................................................... 1074
Changing Login Services ................................................................................................................................. 1075
Basic Windows Operations ............................................................................................................................. 1080
System Specications ..................................................................................................................................... 1084
Fax Function ............................................................................................................................................... 1085
Send Functions ........................................................................................................................................... 1086
Printer Functions ........................................................................................................................................ 1088
Management Functions .............................................................................................................................. 1091
System Environment .................................................................................................................................. 1097
Network Environment ................................................................................................................................ 1099
System Options .......................................................................................................................................... 1101
Hardware Specications ................................................................................................................................. 1103
Main Unit .................................................................................................................................................... 1104
Feeder ........................................................................................................................................................ 1107
Appendix
1028

Available Paper ........................................................................................................................................... 1109
Paper Feeder PF-D ...................................................................................................................................... 1115
Cassette Feeding Unit-AV ........................................................................................................................... 1116
Copy Card Reader ....................................................................................................................................... 1117
Options ............................................................................................................................................................ 1118
Optional Equipment ................................................................................................................................... 1119
Paper Feeder PF-D ............................................................................................................................... 1120
Cassette Feeding Unit-AV ..................................................................................................................... 1121
TELEPHONE 6 KIT ................................................................................................................................ 1122
Copy Card Reader ................................................................................................................................ 1123
ADF Access Handle-A ........................................................................................................................... 1125
Manuals and Their Contents .......................................................................................................................... 1126
Using User's Guide .......................................................................................................................................... 1127
Screen Layout of User's Guide .................................................................................................................... 1128
Viewing User's Guide .................................................................................................................................. 1132
Appendix
1029
Appendix
72JY-0JC
This chapter contains the technical specications of this machine, descriptions of options, instructions on how to use
the User's Guide, disclaimers, copyright information, and other important information for customers. Read this
chapter as necessary.
◼Machine Specications
You can check the specications of the machine, feeder, network environment, copy, scan, etc.
Hardware Specications(P. 1103)
System Specications(P. 1084)
◼Changing the Login Service
See this section to change the login service for user authentication.
Changing Login Services(P. 1075)
◼Using Optional Equipment
See this section to check the optional equipment and the system options to use the machine more eciently.
Options(P. 1118)
Optional Equipment(P. 1119)
System Options(P. 1101)
◼Referencing the Manual of This Machine
See the following section(s) to read instructions on how to use the various manuals and the User's Guide (this manual)
that help you understand machine's functions and operating procedures.
Appendix
1030
Manuals and Their Contents(P. 1126)
Using User's Guide(P. 1127)
◼Others
This section describes basic OS operations and includes disclaimers, copyright information, and other information.
Third Party Software(P. 1032)
Feature Highlights(P. 1037)
Basic Windows Operations(P. 1080)
Notice(P. 1033)
Appendix
1031

Third Party Software
72JY-0JE
For information related to third-party software, click the following icon(s).
Third-Party Services
THIRD PARTY LICENSE README
Third-Party Software Included in This Manual
Appendix
1032

Notice
72JY-0JF
◼IPv6Ready Logo
The protocol stack included in this machine has obtained the IPv6 Ready Logo Phase-2
established by the IPv6 Forum.
◼Product Information required by COMMISSION REGULATION (EU) No 801/2013 amending
Regulation (EC) No 1275/2008
Power consumption of the product in networked standby if wired network ports are connected and all wireless
network ports are activated (if they are available at the same time).
Model Name Power consumption of the product in networked standby
imageRUNNER C1538iF / C1533iF 3.0 W or less
●The above value(s) are the actual values for single machine, chosen arbitrarily, and may therefore vary from
the value of the machine in use. Optional network ports are not connected and/or activated in the
measurement.
◼WEEE and Battery Directives
Only for European Union and EEA (Norway, Iceland and Liechtenstein)
These symbols indicate that this product is not to be disposed of with your household waste, according to the WEEE
Directive (2012/19/EU), the Battery Directive (2006/66/EC) and/or national legislation implementing those Directives.
If a chemical symbol is printed beneath the symbol shown above, in accordance with the Battery Directive, this
indicates that a heavy metal (Hg = Mercury, Cd = Cadmium, Pb = Lead) is present in this battery or accumulator at a
concentration above an applicable threshold specied in the Battery Directive.
This product should be handed over to a designated collection point, e.g., on an authorized one-for-one basis when
you buy a new similar product or to an authorized collection site for recycling waste electrical and electronic
equipment (EEE) and batteries and accumulators. Improper handling of this type of waste could have a possible
impact on the environment and human health due to potentially hazardous substances that are generally associated
with EEE.
Your cooperation in the correct disposal of this product will contribute to the effective usage of natural resources.
Appendix
1033

For more information about the recycling of this product, please contact your local city oce, waste authority,
approved scheme or your household waste disposal service or visit www.canon-europe.com/sustainability/approach/.
◼Environmental Information
Reducing your environmental impact while saving money
Power Consumption and Activation Time
The amount of electricity a device consumes depends on the way the device is used. This product is designed and set
in a way to allow you to reduce your electricity costs. After the last print it switches to Ready Mode. In this mode it can
print again immediately if required. If the product is not used for a time, the device switches to its Power Save Mode.
The devices consume less power (Watt) in these modes.
If you wish to set a longer Activation Time or would like to completely deactivate the Power Save Mode, please
consider that this device may then only switch to a lower energy level after a longer period of time or not at all.
Canon does not recommend extending the Activation Times from the optimum ones set as default.
Energy Star ®
The Energy Star® programme is a voluntary scheme to promote the development and purchase of energy ecient
models, which help to minimise environmental impact.
Products which meet the stringent requirements of the Energy Star® programme for both environmental benets and
the amount of energy consumption will carry the Energy Star® logo accordingly.
Paper types
This product can be used to print on both recycled and virgin paper (certied to an environmental stewardship
scheme), which complies with EN12281 or a similar quality standard. In addition it can support printing on media
down to a weight of 64g/m2.
Lighter paper means less resources used and a lower environmental footprint for your printing needs.
Duplex printing (Standard duplex printing products only)
Duplex printing capability enables you to print on both sides automatically, and therefore helps to reduce the use of
valuable resources by reducing your paper consumption.
The duplex function has been auto enabled during the set up and driver installation and Canon strongly recommends
that you do not disable this function. You should continue to use the duplex function to reduce the environmental
impact of your work with this product at all times.
◼When disposing of used toner cartridges
●To protect the environment and make more effective use of resources, Canon promotes the recovery and recycling
of used toner cartridges. Please cooperate in the recovery of toner cartridges (resource reuse). For details on
resource reuse, see the Canon website:
global.canon/ctc
When disposing of toner cartridges, pack them in their original packaging to prevent toner dispersal and dispose of
the cartridges in accordance with your local government instructions.
◼Installation
●If you nd the machine's operation to be noisy in some operating modes or due to your surroundings, we
recommend setting up the machine in a separate location from your oce.
●If you nd the machine's operation to be noisy in some operating modes or due to your surroundings, we
recommend setting up the machine in a separate location from your oce.
●Machines with storage devices such as hard disks may not operate properly when used at high altitudes (3,000
meters above sea level or higher).
Appendix
1034

◼Trademarks
Mopria®, the Mopria® Logo and the Mopria® Alliance logo are registered trademarks and service marks of Mopria
Alliance, Inc. in the United States and other countries. Unauthorized use is strictly prohibited.
This product contains the Universal Font Scaling Technology or UFST® under license from Monotype Imaging, Inc.
UFST® is a trademark of Monotype Imaging, Inc. registered in the United States Patent and Trademark Oce and may
be registered in certain jurisdictions.
UFST: Copyright © 1989 - 1996, 1997, 2003, 2004, 2008, 2014, all rights reserved, by Monotype Imaging Inc.
Adobe, Acrobat and Reader are registered trademarks of Adobe Systems Incorporated in the United States and/or
other countries.
Apple, Bonjour, iPad, iPhone, iPod touch, Safari, Mac, macOS and OS X are trademarks of Apple Inc.
Google Chrome and Android are trademarks of Google LCC.
Portions of this software are copyright © 2007 The FreeType Project(www.freetype.org).
All rights reserved.
Java is a registered trademark of Oracle and /or its aliates.
Adobe, PostScript, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems
Incorporated in the United States and/or other countries.
Copyright © 2007 -08 Adobe Systems Incorporated. All rights reserved.
Protected by U.S. Patents 5,737,599; 5,781,785; 5,819,301; 5,929,866; 5,943,063; 6,073,148; 6,515,763; 6,639,593;
6,754,382; 7,046,403; 7,213,269; 7,242,415; Patents pending in the U.S. and other countries.
All instances of the name PostScript in the text are references to the PostScript language as dened by Adobe Systems
Incorporated unless otherwise stated. The name PostScript also is used as a product trademark for Adobe Systems'
implementation of the PostScript language interpreter.
Except as otherwise stated, any reference to a "PostScript printing device," "PostScript display device," or similar item
refers to a printing device, display device or item (respectively) that contains PostScript technology created or licensed
by Adobe Systems Incorporated and not to devices or items that purport to be merely compatible with the PostScript
language.
Adobe, the Adobe logo, PostScript, the PostScript logo, and PostScript 3 are either registered trademarks or
trademarks of Adobe Systems Incorporated in the United States and/or other countries.
Linux is a registered trademark of Linus Torvalds. Microsoft and Windows are either registered trademarks or
trademarks of Microsoft Corporation in the United States and/or other countries.
All other trademarks are the property of their respective owners.
Appendix
1035

The PDF logo is a trademark or registered trademark of Adobe Systems Incorporated in the United States and other
countries.
Copyright © 2008 Adobe Systems Incorporated. All rights reserved.
Protected by U.S. Patents 6,185,684; 6,205,549; 7,213,269; 7,272,628; 7,278,168; Patents pending in the U.S. and other
countries.
All instances of the name PostScript in the text are references to the PostScript language as dened by Adobe Systems
Incorporated unless otherwise stated. The name PostScript also is used as a product trademark for Adobe Systems'
implementation of the PostScript language interpreter.
Except as otherwise stated, any reference to a "PostScript printing device," "PostScript display device," or similar item
refers to a printing device, display device or item (respectively) that contains PostScript technology created or licensed
by Adobe Systems Incorporated and not to devices or items that purport to be merely compatible with the PostScript
language.
Adobe, the Adobe logo, Adobe LiveCycle® Policy Server, PostScript, the PostScript Logo, and PostScript 3 are either
registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries.
All other trademarks are the property of their respective owners.
All brand names and product names appearing on this manual are registered trademarks or trademarks of their
respective owners.
All other trademarks are the property of their respective owners.
◼Disclaimers
●The information in this document is subject to change without notice.
●CANON INC. MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS MATERIAL, EITHER EXPRESS OR IMPLIED,
EXCEPT AS PROVIDED HEREIN, INCLUDING WITHOUT LIMITATION, THEREOF, WARRANTIES AS TO MARKETABILITY,
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OF USE, OR NON-INFRINGEMENT. CANON INC. SHALL
NOT BE LIABLE FOR ANY DIRECT, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY NATURE, OR LOSSES OR
EXPENSES RESULTING FROM THE USE OF THIS MATERIAL.
●If you are unable to view the manual in PDF format, download Adobe Acrobat Reader from the Adobe Systems
website (https://get.adobe.com/reader/).
◼Copyright
Reproduction of the contents of this document in whole or in part without prior permission is prohibited.
Appendix
1036

Feature Highlights
72JY-0JH
This section highlights six ways in which you can use the machine to its fullest potential.
Customizable functions for greater ease-of-use
Operability(P. 1038)
Superior productivity to help your business' daily operations run more smoothly
Productivity(P. 1046)
Clearer images thanks to high-quality image printing and corrective functions
Image Quality(P. 1047)
Expanded capabilities and easier management
Manageability(P. 1048)
Convenience and peace of mind
Reliability(P. 1053)
An energy-saving design that's environmentally friendly
Oce Compatibility(P. 1054)
Appendix
1037
Operability
72JY-0JJ
This section describes how to use simple operations and customizable functions to operate the machine more easily.
User-Friendly Operation Screens User Friendly Customization (Personalization)
The touch panel display can be operated with
smartphone-like operations such as ick
operations.
Basic Operation of the Touch Panel
Display(P. 130)
The operation screens, settings, and functions of the machine
can be customized according to user preferences. This is called
"personalization."
The user must be logged in to personal authentication in order
to use personalization.
Utilizing Personalization(P. 1039)
List of Items That Can Be Personalized(P. 139)
Appendix
1038
Utilizing Personalization
72JY-0JK
Have you ever experienced the following?
●Accidentally copying with the settings of the previous user
●Frequently conguring the same combination of settings
The machine has a personalization function that enables settings to be registered for each login user by using
personal authentication management. For example, two-sided copying can be set as the default copy mode and the
initial screen after logging in can be set to the Scan and Store Basic Features screen.
The customized settings can also be synchronized with other Canon machines on the same network and used on any
machine.
The personalization function helps to improve operability and security, and reduce costs.
●The user must be in a position to use the personal authentication function in order to use personalization.
For information on personal authentication, contact your device administrator. Managing Users(P. 489)
●The settings that were personalized for each user can be synchronized with other Canon machines on the
same network and used on all synchronized machines. Synchronizing Settings for Multiple Canon
Multifunction Printers(P. 656)
●For details on the settings that can be personalized, see List of Items That Can Be Personalized(P. 139) .
◼Screen Personalization
Changing the Display Language
for Each User (Switch Language/
Keyboard)(P. 1041)
Displaying a Frequently Used
Screen as the Initial Screen
(Default Screen After Startup/
Restoration / Default Screen
(Status Monitor))(P. 1041)
Preventing Repeated Entry of
the Same Character (Key
Repetition Settings)(P. 1042)
Appendix
1039
Improving the Screen Visibility
(Invert Screen Colors)(P. 1042)
◼Setting Personalization
Specifying Frequently Used
Settings as the Default Settings
(Change Default Settings)(P. 1042)
Creating Shortcuts to Setting
Items at a Deep Level (Register
Options Shortcuts)(P. 1043)
Recalling Past Settings for
Copying (Previous Settings)
(P. 1043)
Making the Job List Easy to See
(Sorting the Job List)(P. 1043)
Managing Destinations in
Personal Address Lists/User Group
Address Lists (Personal Addr. List /
User Group Address List)(P. 1044)
Enabling Multiple Settings to Be
Set with a Single Button
(<Personal>/<Shared>)(P. 1044)
Appendix
1040
◼Function Personalization
Printing Important Documents
at the Machine (Forced Hold)
(P. 1044)
Directly Storing Scanned Data on
a Server (Personal Folder)(P. 1045)
Sending the Scanned Document
to Your Own E-Mail Address (Send
to Myself)(P. 1045)
Screen Personalization
Changing the Display Language for Each User (Switch Language/Keyboard)
The language of the screen can be changed to the liking of each login
user.
For example, the machine can display the screen in English for a certain
user, and then switch the display language to French when another user
logs in.
The keyboard layout of the touch panel display can also be changed.
Customizing the Screen Display Appearance and the Operational
Conditions(P. 180)
Displaying a Frequently Used Screen as the Initial Screen (Default Screen After Startup/
Restoration / Default Screen (Status Monitor))
The screen displayed after logging in and after the machine returns from
sleep mode can be set.
For example, the operation screen (Basic Features screen) for <Copy> and
<Fax>, the destination selection screen for <Scan and Store>, and the
<Status Monitor> screen for checking the job status can be set as the
initial screen.
<Default Screen After Startup/Restoration>(P. 773)
A frequently used job status/log screen can be registered as the default
screen displayed when <Status Monitor> is pressed.
<Default Screen (Status Monitor)>(P. 773)
Appendix
1041
Preventing Repeated Entry of the Same Character (Key Repetition Settings)
This setting enables you to adjust the time until entry of the same
character is repeated.
For example, if you press and hold the <a> key for a certain period of time,
the letter "a" begins to be entered repeatedly. This can be prevented for
people who want to work slowly, by adjusting the response speed of the
touch panel display.
Customizing the Screen Display Appearance and the Operational
Conditions(P. 180)
Improving the Screen Visibility (Invert Screen Colors)
The screen can be displayed with reversed colors.
For example, the screen colors can be reversed to make it easier to read
for users that have trouble with the default colors.
Customizing the Screen Display Appearance and the Operational
Conditions(P. 180)
Setting Personalization
Specifying Frequently Used Settings as the Default Settings (Change Default Settings)
Frequently used settings can be registered as the default settings.
For example, if a user frequently uses the two-sided mode, it can be set by
default to eliminate the need to specify it every time the user operates the
machine.
<Change Default Settings>(P. 817) (Copy)
<Change Default Settings>(P. 830) (Fax)
<Change Default Settings>(P. 820) (Scan and Send)
<Change Default Settings>(P. 843) (Scan and Store)
<Change Default Settings>(P. 844) (Access Stored Files)
Appendix
1042

Creating Shortcuts to Setting Items at a Deep Level (Register Options Shortcuts)
Shortcuts for frequently used settings can be registered to the Copy Basic
Features screen, the Fax Basic Features screen, and the Scan and Send
Basic Features screen.
For example, if a user frequently uses the <N on 1> mode in <Options> of
the Copy function, a shortcut to the <N on 1> mode can be displayed on
the Copy Basic Features screen, so that you can recall the <N on 1> mode
with one press of a button instead of going all the way down to the
<Options> screen.
Customizing the Basic Features Screen(P. 167)
Recalling Past Settings for Copying (Previous Settings)
The previously used <Copy> settings, and the previously used <Fax> and
<Scan and Send> settings and destinations are retained in the machine.
When copying with the same settings used in the past, the user can recall
the previously used settings to eliminate the need to specify the same
settings.
Recalling Previously Used Copy Settings (Previous Settings)(P. 264)
Recalling Previously Used Settings for Sending (Previous Settings)
(P. 304)
Recalling Previously Used Settings for Sending/Saving (Previous
Settings)(P. 421)
Making the Job List Easy to See (Sorting the Job List)
The job list can be sorted using the order of names, dates, etc., to make it
easier to nd the desired job or document.
The sorting order is retained for the next time the user logs in.
Changing the Display Order in the List(P. 132)
Appendix
1043
Managing Destinations in Personal Address Lists/User Group Address Lists (Personal
Addr. List / User Group Address List)
Destinations can be separated and managed using personal address lists
and user group address lists.
For example, you can manage destinations used for your own personal
customers in your personal address list and destinations shared within a
group in a user group address list.
Registering Destinations in the Address Book(P. 195)
Enabling Multiple Settings to Be Set with a Single Button (<Personal>/<Shared>)
<Personal> buttons and <Shared> buttons can be used to eliminate the
need to set the same combination of settings separately.
For example, a user can set the <2-Sided> and <N on 1> modes together.
By registering these settings in a <Personal> button, this combination of
settings can be recalled with a single button press.
By registering the settings in a <Shared> button, they can be conveniently
used by other users.
Registering Frequently Used Settings and Destinations as Personal
Buttons/Shared Buttons on the <Home> Screen(P. 170)
Function Personalization
Printing Important Documents at the Machine (Forced Hold)
Important documents can be prevented from being printed out until the
user is present at the machine.
Forced hold printing enables you to check your print job at the machine
before printing, so that you can cancel unnecessary jobs, or prevent other
users from taking your documents away.
Printing Documents Held in the Machine(P. 351)
Appendix
1044
Directly Storing Scanned Data on a Server (Personal Folder)
The data scanned with the machine can be stored on a server on the same
network.
For example, a user can create a personal folder on an SMB server in the
oce and directly save data scanned with the machine. This prevents data
from becoming mixed up with the data of other users.
Conguring Personal Folders(P. 529)
Sending the Scanned Document to Your Own E-Mail Address (Send to Myself)
Users can easily send scanned documents to their own e-mail address.
For example, when sending a document to the e-mail address of a
customer as a PDF le, a user can press <Send to Myself> displayed on the
Scan and Send Basic Features screen, etc. to also send the PDF le to their
own e-mail address.
Scan Basic Features Screen(P. 374)
Appendix
1045
Productivity
72JY-0JL
This section describes how to use the machine's superior productivity to help your daily business operations run more
smoothly.
Using the Machine Immediately after Turning it ON
(Quick Startup)
Specifying <Quick Startup Settings for Main Power> reduces the time required
for the machine to start up after turning the main power ON, enabling
smoother operations.
<Quick Startup Settings for Main Power>(P. 777)
Appendix
1046
Image Quality
72JY-0JR
This section describes functions that help to produce crisp and clear images, such as high-quality image printing and
corrective functions.
Adjusting Print Quality Sending Clearer Faxes
You can achieve more satisfying print results by using
corrective functions such as gradation adjustment and
density correction.
Adjusting Print Quality(P. 893)
Reproduction can be enhanced on the receiving end by
setting a corresponding gamma value when sending
faxes.
<YCbCr TX Gamma Value>(P. 822)
Appendix
1047
Manageability
72JY-0JS
This section describes how to expand the capabilities of the machine and make management easier.
Dual Network Environment Using the Control Panel as a Tool for Sharing Information
(Visual Message Function)
A dual network environment using wired LAN and
wireless LAN or wired LAN and another wired LAN
can be used.
Building a Dual Network Environment(P. 1050)
Content and messages set by the administrator can be
displayed on the touch panel display to inform users. This
function is useful for sharing information in the oce.
Conguring the Visual Message Function(P. 649)
Connecting to the Wireless LAN Linking with Mobile Devices
A wireless LAN is built into the machine, enabling you
to connect a computer or mobile device to the
machine, as well as install it in a separate location.
Connecting to a Wireless LAN(P. 26)
You can directly print data saved in a mobile device from
the machine, or use the machine to scan data to a mobile
device. You can also use your mobile device to specify
settings for forced hold printing in the machine.
Linking with Mobile Devices(P. 452)
Appendix
1048
Easily Moving the Address Book Operating an Oce Security Policy
You can export the Address Book registered in the
machine, and import it to another machine. You can also
export the Address Book in the CSV le format and edit it
on a computer.
Importing/Exporting the Settings Individually(P. 632)
A security policy describes company-wide rules
regarding information security. With this machine,
multiple settings related to a security policy can be set
together.
Applying a Security Policy to the Machine(P. 478)
Sharing Settings between Multiple Machines
Personalized settings and Address Books can be synchronized and shared
between multiple machines. Settings specied on a single machine are reected
in all synchronized machines.
Synchronizing Settings for Multiple Canon Multifunction Printers(P. 656)
Appendix
1049
Building a Dual Network Environment
72JY-0JU
Do you have separate machines in each department or oor of the same oce for security purposes?
In addition to single connections with a wired LAN or wireless LAN, this machine enables dual network environments
with both a wired LAN and wireless LAN or a wired LAN and another wired LAN via a USB-LAN adapter*. This makes it
easy to build network environments where employees use the main line and customers use a sub line with restricted
functionality. It also contributes to reduced costs as it is not necessary to install a machine for each network
environment.
* For information on the supported USB-LAN adapters, contact your dealer or service representative.
This machine and the User's Guide refer to the main wired LAN in a dual network as the "main line". The sub wireless
LAN or another wired LAN in a dual network is referred to as the "sub line."
Flow of Settings Required for a Dual Network(P. 1050)
Cautions When Using the Sub Line(P. 1051)
Flow of Settings Required for a Dual Network
In a dual network, the main line and sub line have separate settings. This section describes the settings required for
the sub line network.
●Specify the wired LAN/wireless LAN settings common to the main and sub lines, as required.
Connecting to a Wired LAN(P. 25)
Connecting to a Wireless LAN(P. 26)
Connecting to a Wired LAN(P. 25)
Connecting to a Wireless LAN(P. 26)
Step 1 Selecting the Network Connection Method(P. 23)
●Select <Wired LAN + Wireless LAN> or <Wired LAN + Wired LAN>.
Step 2 Setting the IPv4 Address of the Sub Line(P. 40)
Appendix
1050
●Specify the IPv4 address settings from <IP Address Settings> in <Sub Line Settings>. When
using static routing, also set a gateway address.
Step 3 Making Ethernet Settings(P. 42) *
●Set this when using a wired LAN via a USB-LAN adapter for the sub line.
* Specify the required settings according to your environment.
Step 4 Conguring the Firewall of the Sub Line(P. 544) *
●Register the port numbers of the functions to use/restrict in the rewall settings of the sub
line.
* Specify the required settings according to your environment.
Step 5 Setting Static Routing(P. 61) *
●Set static routing when connecting to another network via a router.
* Specify the required settings according to your environment.
Step 6 Conguring System Data Communication(P. 65) *
●Set this when performing specic system data communication, such as accessing a rmware
distribution server in environments where DNS name resolution or network connections via
a proxy cannot be used.
* Specify the required settings according to your environment.
Cautions When Using the Sub Line
The network functions set in the machine can all be used for the main line. However, the functions that can be used
with the sub line are limited.
Appendix
1051

●The DNS server and WINS server settings cannot be used at the same time as the main line.
●<DNS Server Address Settings> and <Proxy Settings> in <Settings for System Data Communication> can only
be used for specic system data communication, such as using the sub line to access a rmware distribution
server. When using a DNS server or proxy server for the sub line for applications other than system data
communication, register the addresses and port numbers to use with the sub line in the settings of the main
line.
Making DNS Settings(P. 45)
Setting a Proxy(P. 547)
◼Functions Restricted for the Sub Line
The following network functions cannot be used with the sub line.
●IPv6 address settings
●IEEE802.1X authentication
●IPsec
●NetBIOS
●FTP (ACTIVE mode)
●DHCP Option Settings
●DNS Dynamic Update Settings
●Multicast Discovery Settings
●Setting the IP address via AutoIP
●Firewall settings via MAC address lter
●Browsing using the SMB protocol
The following functions and services cannot be used, due to the above limitations.
●Building a printing/accounting system that performs server connections via an AddOn application
●Building an authentication system for an Active Directory server
●File sending using DNS name resolution or NetBIOS name resolution from the SMB or WebDAV protocol*1
●Automatic discovery of other multifunction printers on the sub line side using multicast discovery*1
●Functions such as the following that use the IP address of the main line
- [Security Policy Settings]
- <Make Remote Address Book Open>
- Batch importing/batch exporting
- Visual Message
●Color Network ScanGear 2
●Universal Print
*1 Specify the IP address directly.
Appendix
1052
Reliability
72JY-0JW
This section describes how to use the machine with greater convenience and peace of mind.
Managing Saved Copies of Faxes
(Automatically Saving Images of Sent Faxes)
Digitizing and Managing Communication
Management Reports
You can digitize and save sent faxes and automatically save
them in a specied folder. Information related to sending is
automatically added to the le name, enabling you to
effectively manage faxes.
Saving a Copy of a Sent Document(P. 309)
In addition to printing logs for sending and receiving
(communication management reports), you can also
save them as CSV les and manage them on a
computer.
Outputting a Communication Result
Report(P. 912)
Preventing Forgotten Originals after Scanning Conrming Maintenance Procedures on the Touch
Panel Display
(Videos)
When scanning originals is complete, the user is notied
of forgotten originals via a message on the touch panel
display or warning sound, etc.
Setting Sounds(P. 184)
You can conrm procedures for replenishing
consumables and cleaning by viewing videos on the
touch panel display.
<Maintenance>(P. 805)
Appendix
1053
Oce Compatibility
72JY-0JX
This section describes how to use the machine in an environmentally-friendly manner.
Using the Sleep Mode to Save Power During Standby
The machine saves power by switching to the Sleep mode or Energy Saver mode when not in use. Users can also
save power by only starting up the functions they require when the machine recovers from the Sleep mode.
Entering Sleep Mode(P. 188)
<Timer/Energy Settings>(P. 777)
Appendix
1054
Home
72JY-0K0
◼Shortcut
Log In(P. 137)
Timeline(P. 127)
Status Monitor(P. 120)
◼Operation button list
Numeric key enlargement/reduction(P. 123)
Settings/Register(P. 670)
Numeric keys(P. 123)
Clear(P. 123)
Reset(P. 123)
Start(P. 123)
◼Function button list
Copy(P. 216)
Fax(P. 271)
Scan and Send(P. 372)
Scan and Store(P. 437)
Access Stored Files(P. 437)
Fax/I-Fax Inbox(P. 313)
Print(P. 351)
Tutorial(P. 132)
Dest./Fwd. Settings(P. 190)
Scanner(P. 427)
Settings/Regist. Shortcut(P. 178)
Personal Settings(P. 180)
Status Monitor(P. 120)
Appendix
1056
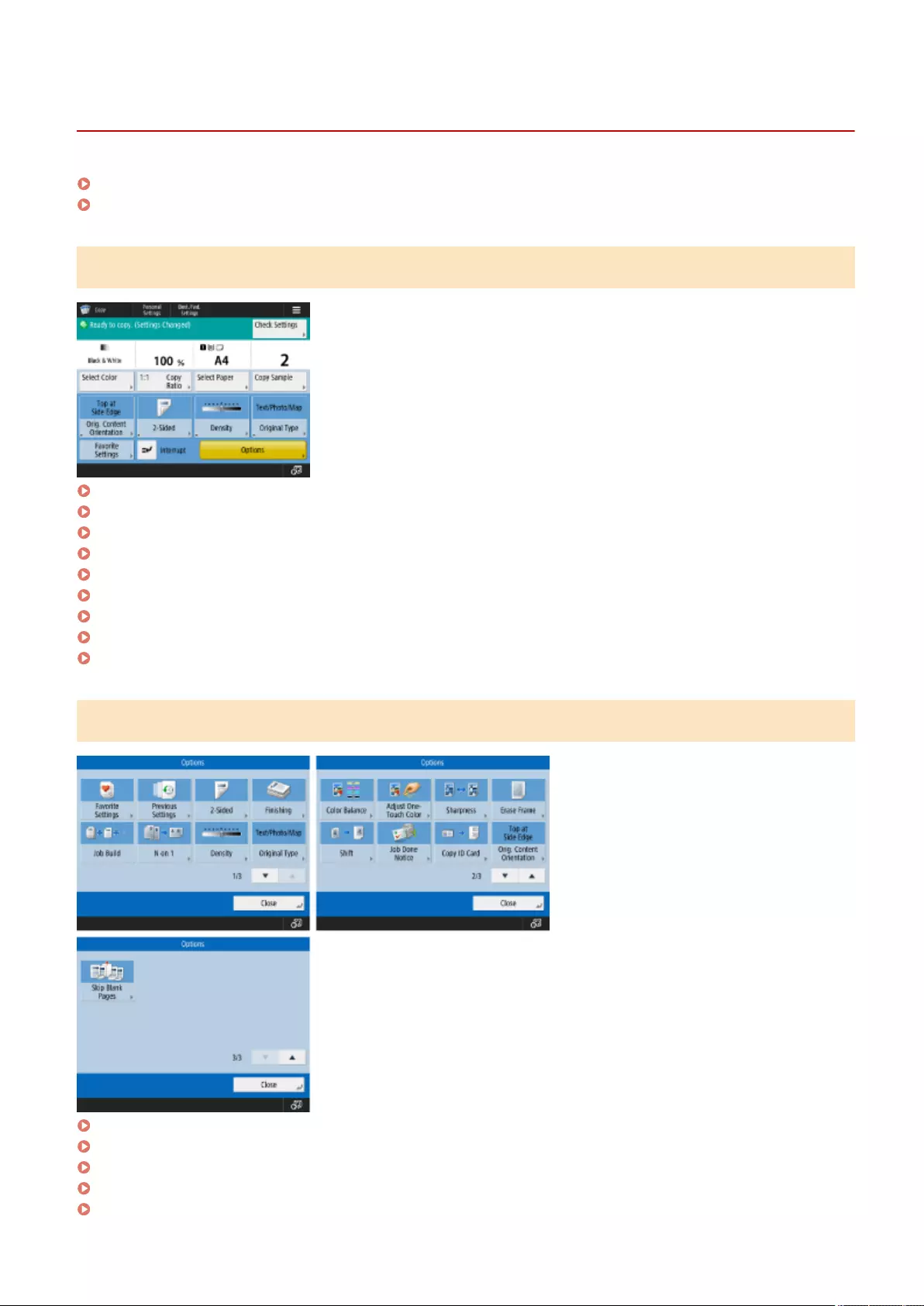
Copy
72JY-0K1
Copy Basic Features Screen(P. 1058)
Options(P. 1058)
Copy Basic Features Screen
Select Color(P. 220)
1:1(P. 218)
Copy Ratio(P. 220)
Select Paper(P. 220)
Copy Sample(P. 247)
Check Settings(P. 229)
Options Shortcuts(P. 167) 1 to 5
Interrupt(P. 249)
Options(P. 218)
Options
Favorite Settings(P. 164)
Previous Settings(P. 264)
2-Sided(P. 220)
Finishing (Collate/Group)(P. 251)
Job Build(P. 245)
Appendix
1058

Fax
72JY-0K2
Fax Basic Features Screen(P. 1060)
Options(P. 1060)
Fax Basic Features Screen
Details(P. 275)
Delete Dest.(P. 275)
Tone(P. 273)
R(P. 274)
Previous Settings(P. 304)
Favorite Settings(P. 164)
Resolution(P. 279)
Scan Size(P. 279)
Options Shortcuts(P. 167) 1 to 4
One-Touch(P. 275)
Address Book(P. 275)
On-Hook(P. 298)
Direct Send(P. 297)
Options(P. 273)
Options
Original Type(P. 279)
2-Sided Original(P. 279)
Density(P. 279)
Sharpness(P. 279)
Erase Frame(P. 279)
Job Build(P. 302)
Sender Name (TTI)(P. 287)
Direct Send(P. 297)
Delayed Send(P. 307)
Appendix
1060

Scan and Send
72JY-0K3
Scan and Send Basic Features Screen(P. 1062)
Options(P. 1063)
Scan and Send Basic Features Screen
Address Book(P. 377)
One-Touch(P. 377)
New Destination(P. 377)
Mobile Portal(P. 377)
Personal Folder(P. 377)
Send to Myself(P. 377)
Specify Destinations(P. 377)
Details(P. 377)
Delete Dest.(P. 377)
Cc Bcc(P. 377)
Previous Settings(P. 421)
Favorite Settings(P. 164)
Select Color(P. 383)
Resolution(P. 383)
Scan Size(P. 383)
File Format(P. 383)
Options Shortcuts(P. 167) 1 to 2
Options(P. 375)
Appendix
1062
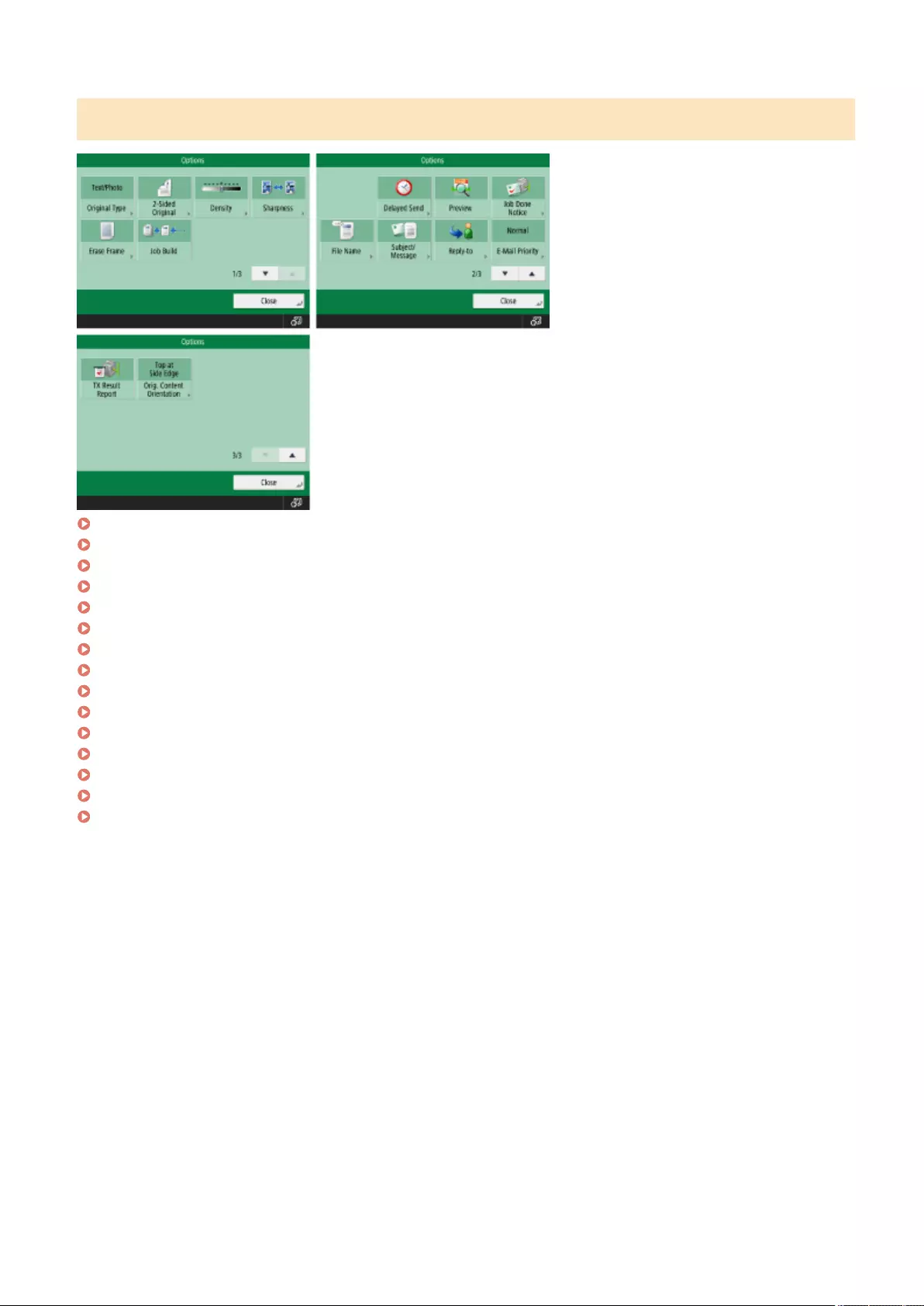
Options
Original Type(P. 395)
2-Sided Original(P. 383)
Density(P. 396)
Sharpness(P. 397)
Erase Frame(P. 398)
Job Build(P. 402)
Delayed Send(P. 407)
Preview(P. 405)
Job Done Notice(P. 409)
File Name(P. 423)
Subject/Message(P. 425)
Reply-to(P. 426)
E-Mail Priority(P. 426)
TX Result Report(P. 390)
Orig. Content Orientation(P. 390)
Appendix
1063

Scan and Store
72JY-0K4
Storage Selection Screen(P. 1064)
File Selection Screen(P. 1065)
Scan Screen(P. 1065)
Options(P. 1066)
●Some of the modes described here are referring to the modes of the <Copy> or <Scan and Send> function.
Storage Selection Screen
Network(P. 438)
Memory Media(P. 441)
◼Network
Check Storage Information(P. 438)
◼Memory Media
Check Media Information(P. 443)
Appendix
1064
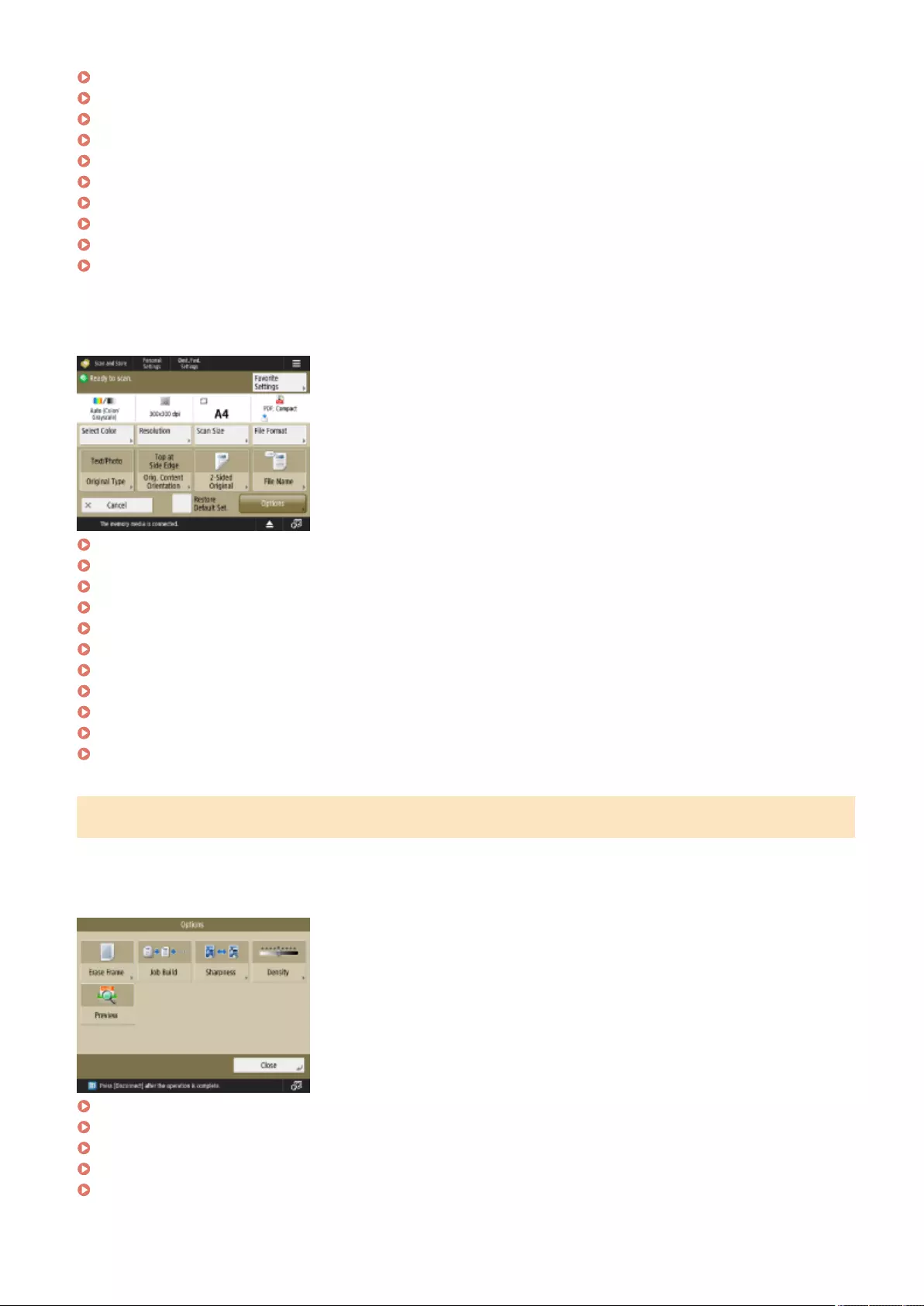
Resolution(P. 446)
Scan Size(P. 446)
File Format(P. 446)
Original Type(P. 446)
Original Content Orientation(P. 447)
2-Sided Original(P. 447)
File Name(P. 447)
Favorite Settings(P. 446)
Restore Default Set.(P. 447)
Options(P. 447)
◼Memory Media
Select Color(P. 446)
Resolution(P. 446)
Scan Size(P. 446)
File Format(P. 446)
Original Type(P. 446)
Original Content Orientation(P. 447)
2-Sided Original(P. 447)
File Name(P. 447)
Favorite Settings(P. 446)
Restore Default Set.(P. 447)
Options(P. 447)
Options
◼Network
Erase Frame(P. 447)
Job Build(P. 447)
Sharpness(P. 447)
Density(P. 447)
Preview(P. 447)
Appendix
1066

Access Stored Files
72JY-0K5
Storage Selection Screen(P. 1068)
File Selection Screen(P. 1069)
Print Settings Screen(P. 1070)
Options(P. 1071)
●Some of the modes described here are referring to the mode of the <Copy> function.
Storage Selection Screen
Network(P. 438)
Memory Media(P. 441)
◼Network
Check Storage Information(P. 439)
◼Memory Media
Check Media Information(P. 444)
Appendix
1068
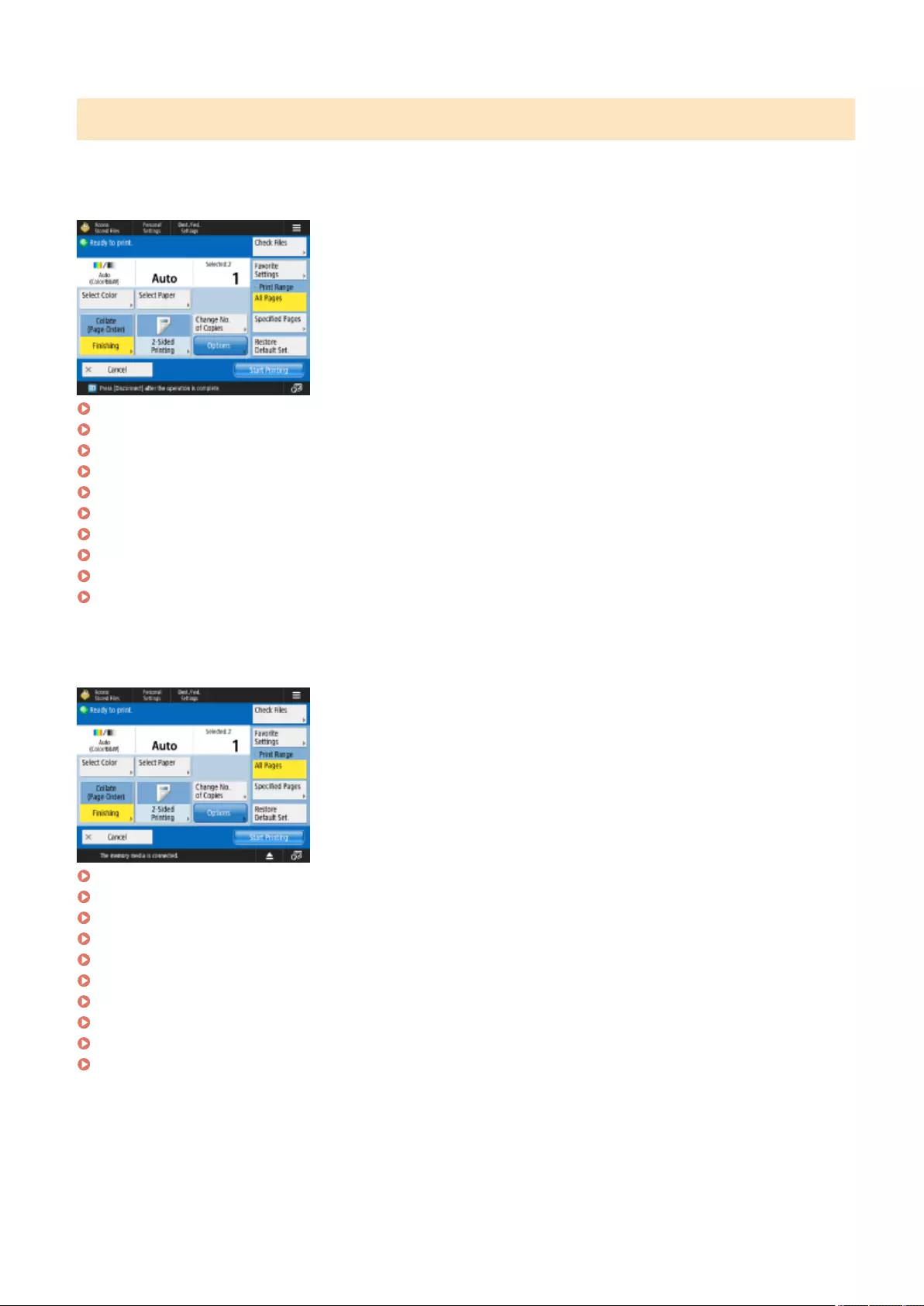
Print Settings Screen
◼Network
Select Color(P. 448)
Select Paper(P. 448)
Finishing (Collate/Group)(P. 448)
2-Sided Printing(P. 448)
Change No. of Copies(P. 448)
Options(P. 448)
Check Files(P. 448)
Favorite Settings(P. 448)
Print Range(P. 448)
Restore Default Set.(P. 448)
◼Memory Media
Select Color(P. 448)
Select Paper(P. 448)
Finishing (Collate/Group)(P. 448)
2-Sided Printing(P. 448)
Change No. of Copies(P. 448)
Options(P. 448)
Check Files(P. 448)
Favorite Settings(P. 448)
Print Range(P. 448)
Restore Default Set.(P. 448)
Appendix
1070

Options
◼Network
Resolution(P. 449)
Halftones(P. 449)
Match Paper Size(P. 449)
Enlarge Print Area(P. 449)
Print Comments(P. 449)
Password to Open Doc.(P. 449)
Skip Blank Pages(P. 449)
Enlarge/Reduce(P. 449)
Image Orientation(P. 449)
Print Position(P. 450)
◼Memory Media
Resolution(P. 449)
Halftones(P. 449)
Match Paper Size(P. 449)
Enlarge Print Area(P. 449)
Print Comments(P. 449)
Password to Open Doc.(P. 449)
Skip Blank Pages(P. 449)
Enlarge/Reduce(P. 449)
Image Orientation(P. 449)
Print Position(P. 450)
Appendix
1071
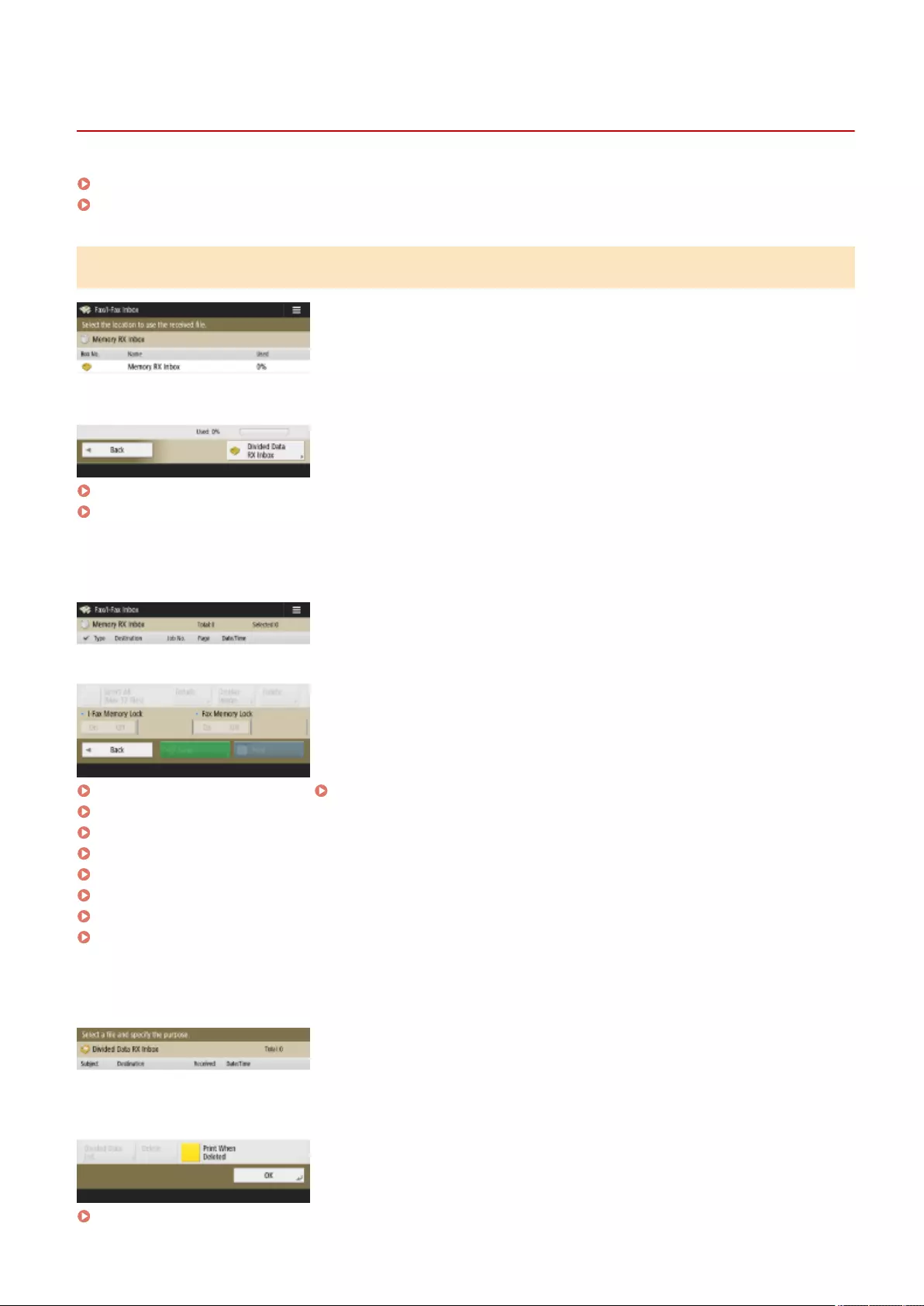
Fax/I-Fax Inbox
72JY-0K6
Memory RX Inbox(P. 1072)
Condential Fax Inbox(P. 1073)
Memory RX Inbox
Memory RX Inbox(P. 313)
Divided Data RX Inbox(P. 314)
◼Memory RX Inbox
Select All (Max 32 les)(P. 314) / Clear Selection(P. 314)
Details(P. 314)
Display Image(P. 314)
Delete(P. 314)
I-Fax Memory Lock(P. 313)
Fax Memory Lock(P. 313)
Send(P. 314)
Print(P. 313)
◼Divided Data RX Inbox
Divided Data List(P. 314)
Appendix
1072
Changing Login Services
72JY-0K8
The application to implement user authentication is called the "Login Service." The machine is set to use "User
Authentication (personal authentication management)" for the login service by default. If you want to use
"DepartmentID Authentication," change the login service in the SMS.
Changing the Login Service(P. 1075)
Setting When Using DepartmentID Authentication(P. 1076)
Changing the Login Service
1Log in to the Remote UI. Starting the Remote UI(P. 583)
2Click [Service Management Service] on the portal page.
3Click [System Application Management] [Start] in [SMS Installer Service (Password
Authentication)].
➠The status becomes [Started].
4Click [Enhanced System Application Management] [Switch] in [DepartmentID
Authentication].
➠The status becomes [Start after Restart].
5Restart the machine. Restarting the Machine(P. 591)
➠The machine restarts and the changed settings are reected.
When DepartmentID Authentication is started
●If you click [Service Management Service] on the portal page of the Remote UI, the login screen to the
SMS is displayed. For security purposes, the machine is congured not to permit login with the
default password dedicated for the SMS. Press (Settings/Register) Management Settings>
<Security Settings> <Authentication/Password Settings> <Password Settings> temporally set
<Allow Use of Default Password for Remote Access> to <On>.
●After logging in to the SMS with the default password, restore the original security level by changing
the default password and then resetting <Allow Use of Default Password for Remote Access> to <Off>.
●"meapSmsLogin" is set as the login password dedicated for the SMS. If you log in with
"meapSmsLogin," the screen for changing the password is displayed. For security purposes, follow
the on-screen instructions to change the password.
●The password for the SMS can be changed with [Change Password] in [System Management].
Appendix
1075

●Make sure that you do not forget your password. Otherwise, you will not be able to access SMS. In
this case, contact your dealer or service representative.
Return to User Authentication
●Select [Enhanced System Application Management] [User Authentication], click [Switch], and restart
the machine. If you will not use SMS Installer Service (Password Authentication), after restart of the
machine select [System Application Management] [SMS Installer Service (Password
Authentication)], and click [Stop].
Setting When Using DepartmentID Authentication
When implementing Department ID Management with the DepartmentID Authentication, make sure that the
administrator (system administrator) manages the Department IDs and PINs. To enhance security, log in with the
system administrator's ID (System Manager ID) and make sure to change the system administrator's ID and PIN.
Which users become administrator or general users depends on whether Department ID Management and System
Manager Settings are set, as indicated in the table below.
Department ID Management System Manager
Settings Administrator General Users
On
Set System Manager Users authenticated with a Department
ID and PIN not for the System Manager
Not Set Users authenticated with a
Department ID and PIN None
Off
Set System Manager Users other than the System Manager
Not Set All users None
◼Changing the System Manager ID and PIN
1Press (Settings/Register) <Log In>.
2Enter <System Manager ID> and <System Manager PIN> and press <Log In>.
●Immediately after the DepartmentID Authentication has started, both the System Manager ID and PIN
are set as "7654321."
●You cannot register a Department ID or PIN consisting only of 0s, such as "00" or "0000000".
●Even if you enter fewer than seven digits, zeros are added to the start of the number, and a seven
digit number is set. However, the zeros at the start of the number can be omitted when logging in. For
example, even if you enter <2>, <02>, or <002>, the PIN is set as <0000002>. However, you can log in
by entering <2>, <02>, or <002>.
3Press <Management Settings> <User Management> <System Manager Information Settings>.
4Enter the necessary information and press<OK>.
●Enter the same PIN again for conrmation, and press <OK>.
●If you install the Copy Card Reader after changing the System Manager ID and PIN, the ID and PIN
return to "7654321."
Appendix
1076

●When the machine is equipped with the Copy Card Reader, the numbers assigned to each card (1 to
1000 by the factory default) cannot be registered as the System Manager ID and PIN.
◼Enabling Department ID Management
To enable Department ID Management with the DepartmentID Authentication, you need to register the
Department ID and PIN.
1Press (Settings/Register) Management Settings> <User Management> <Department ID
Management>.
2Press <On>.
●If you want to manage only with the System Manager ID and PIN without implementing Department
ID Management, press <Off>.
●If you want to return the login service to the User Authentication and use the Department IDs, set
Department ID Management of the DepartmentID Authentication to <Off> and start the User
Authentication. Then assign Department IDs to users and set Department ID Management of the User
Authentication to <On>.
3Press <Register PIN> <Register>.
4Enter <Department ID> and <PIN> press <OK>.
●Enter the same PIN again for conrmation, and press <OK>.
●You cannot register a Department ID or PIN consisting only of 0s, such as "00" or "0000000".
●Even if you enter fewer than seven digits, zeros are added to the start of the number, and a seven
digit number is set. However, the zeros at the start of the number can be omitted when logging in. For
example, even if you enter <2>, <02>, or <002>, the PIN is set as <0000002>. However, you can log in
by entering <2>, <02>, or <002>.
●If you do not set a PIN, you can use the machine by entering only the Department ID.
5Press <OK> <OK>.
◼Login Operation When Department ID Management Using the DepartmentID
Authentication is Enabled
When Department ID Management is enabled, you need to log in to use the machine.
Logging in from the control panel
Enter <Department ID> and <PIN> press <Log In>.
Appendix
1077
When Department ID Management is not implemented
●When only the System Manager ID and PIN are set without Department ID Management, you need to
log in to the machine only when you want to congure the settings that require the administrator's
authority. Press (Settings/Register) Log In>, enter <System Manager ID> and <System Manager
PIN>, and press <Log In>.
Logging in from the Remote UI
Enter the Department ID in [Department ID] and PIN in [PIN], and click [Log In].
When Department ID Management is not implemented
●When only the System Manager ID and PIN are set without Department ID Management, the login
methods differ between the system administrator and general users. For the system administrator,
enter [System Manager ID]/[System Manager PIN], and then click [Log In (Administrator)]. General
users do not need to enter the Department ID and PIN. Click [Log In (General User)].
◼Implementing Function Restrictions and User Management
Congure the settings as necessary.
Checking page totals
(Settings/Register) Management Settings> <User Management> <Department ID
Management> <Page Totals> Check the page total
Appendix
1078
Setting the maximum number of pages for copy/print/scan
(Settings/Register) Management Settings> <User Management> <Department ID
Management> <Register PIN> Select Department ID <Edit> <Turn Limit On/Off and Set
Page Limit> Press <On> for functions to restrict Enter the number of pages <OK> <OK>
<OK> <OK>
Setting Department ID Management on functions other than copy/print
(Settings/Register) Management Settings> <User Management> <Department ID
Management> <Register PIN> <Limit Functions> Press <On> for functions to set
Department ID Management on <OK> <OK> <OK>
Deleting Department IDs
(Settings/Register) Management Settings> <User Management> <Department ID
Management> <Register PIN> Select the Department ID <Delete> <Yes> <OK> <OK>
Blocking Printer Jobs and Remote Scan Jobs When Department ID is Unknown
(Settings/Register) Management Settings> <User Management> <Department ID
Management> Set <Allow Printer Jobs with Unknown IDs> or <Allow Remote Scan Jobs with
Unknown IDs> to <Off> <OK>
Not authenticate black and white copy/print jobs when using Department ID
Management
(Settings/Register) <Management Settings> <User Management> <Department ID
Management> Set <Allow Black & White Copy/Print Jobs> or <Allow Black & White Printer Jobs> to
<Off> <OK>
LINKS
Conguring the Personal Authentication Management Settings(P. 492)
Appendix
1079

Basic Windows Operations
72JY-0K9
Displaying the Printer Folder(P. 1080)
Displaying Shared Printers in the Print Server(P. 1080)
Checking the LPR/RAW Printer Port(P. 1082)
When Printing from the Windows Store App(P. 1083)
●Depending on the computer that you use, the operation may differ.
◼Displaying the Printer Folder
Windows Server 2012
Right-click the lower-left corner of the screen select [Control Panel] [View devices and printers].
Windows 8.1/Server 2012 R2
Right-click [Start] select [Control Panel] [View devices and printers].
Windows 10
[ ] select [Windows System] [Control Panel] [Hardware and Sound] [Devices and Printers].
Windows Server 2016
Right-click [ ] select [Control Panel] [Hardware] [Devices and Printers].
◼Displaying Shared Printers in the Print Server
1Open Windows Explorer.
Windows Server 2012
Right-click the lower-left corner of the screen select [File Explorer].
Windows 8.1/Server 2012 R2
Right-click [Start] select [File Explorer].
Windows 10/Server 2016
Right-click [ ] select [File Explorer]
2Select [Network] or [My Network Places] and double-click the computer set up as a
print server.
●To view computers on the network, you may need to turn on network discovery or search the network for
computers.
Appendix
1080
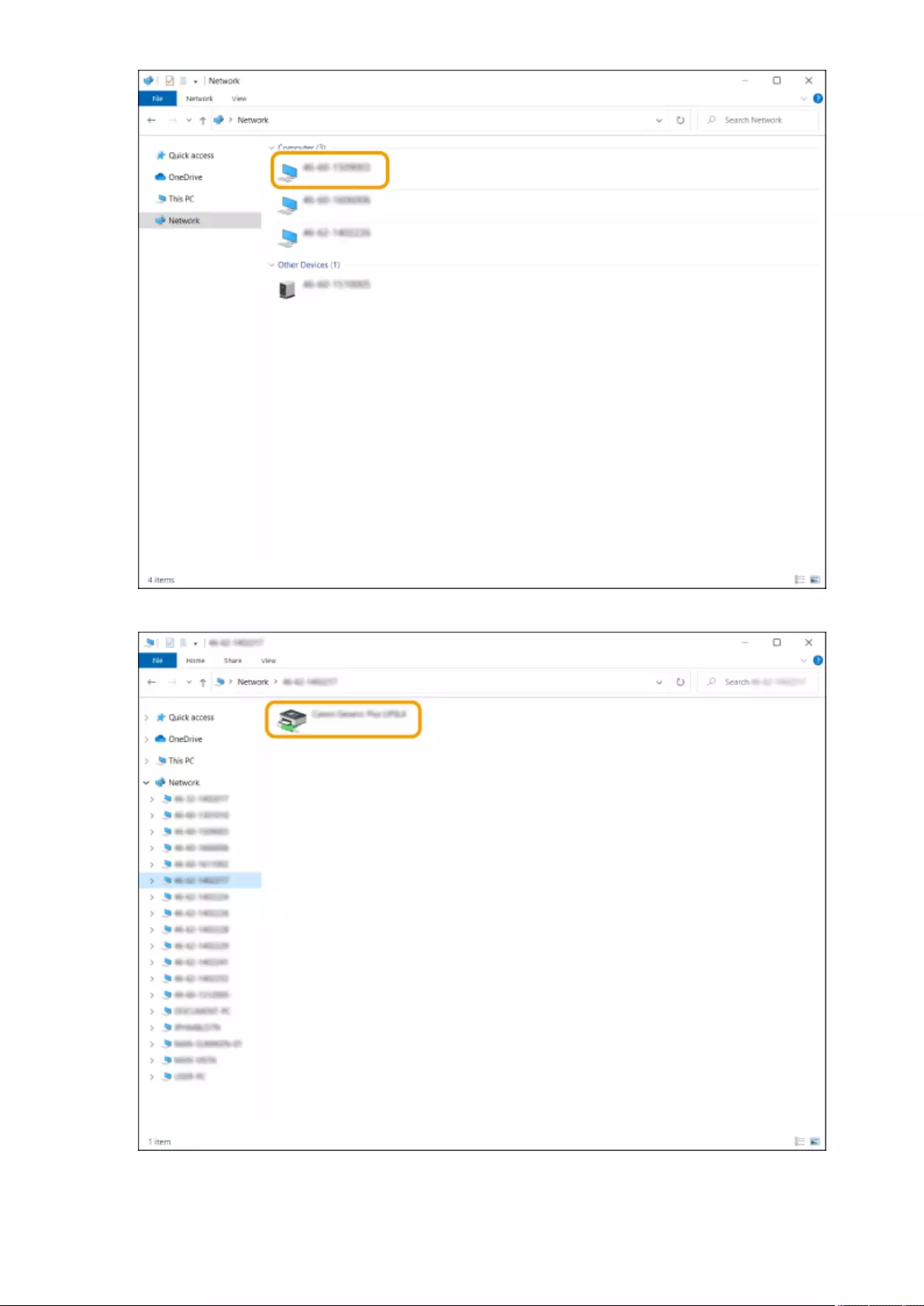
➠The shared printer is displayed.
Appendix
1081
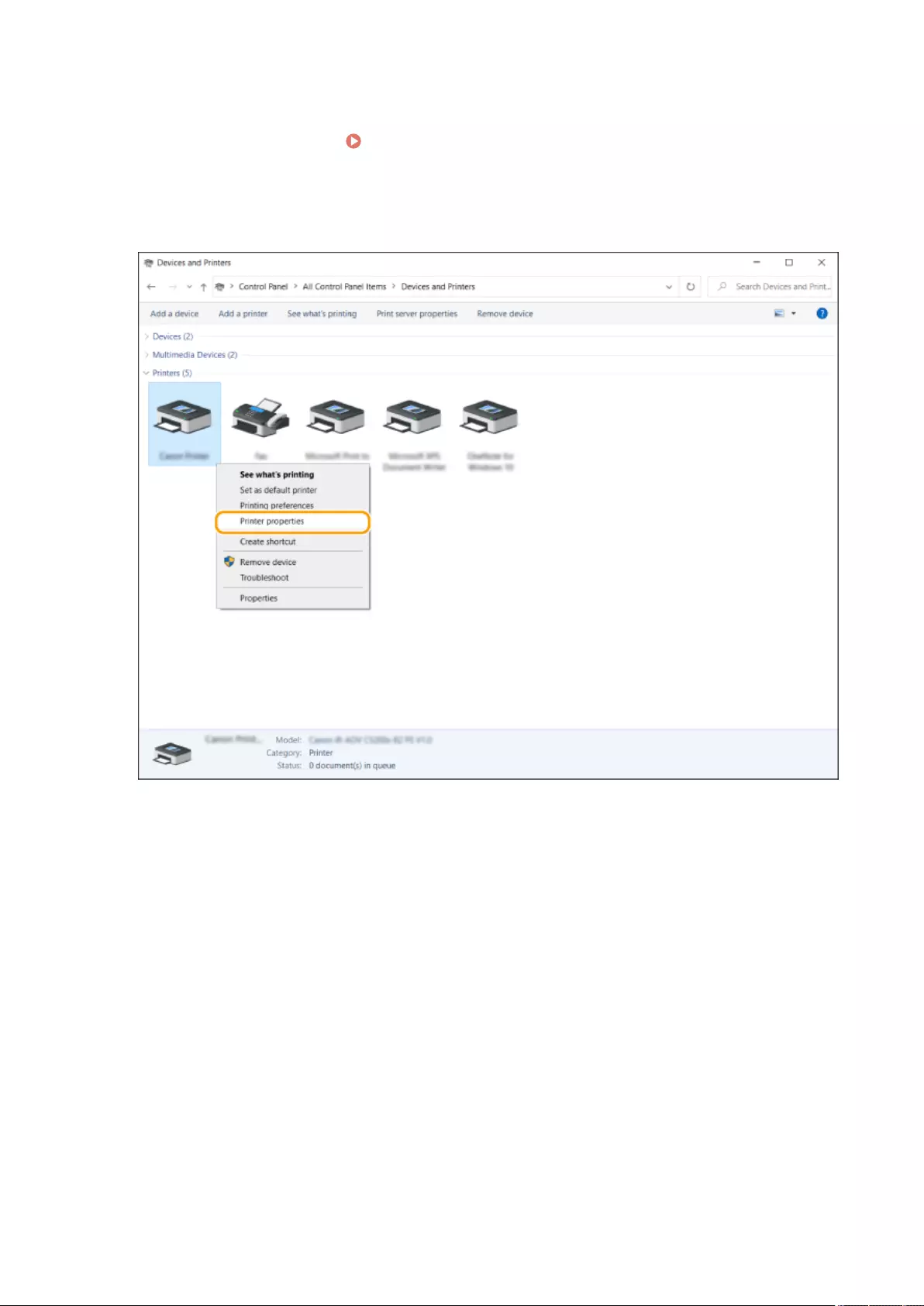
◼Checking the LPR/RAW Printer Port
1Open the printer folder. Displaying the Printer Folder(P. 1080)
2Right-click your printer icon of the machine and click [Printer properties] (or
[Properties]).
3Check the port settings.
●Click the [Ports] tab.
●Make sure that the correct port is selected for the printer.
Appendix
1082
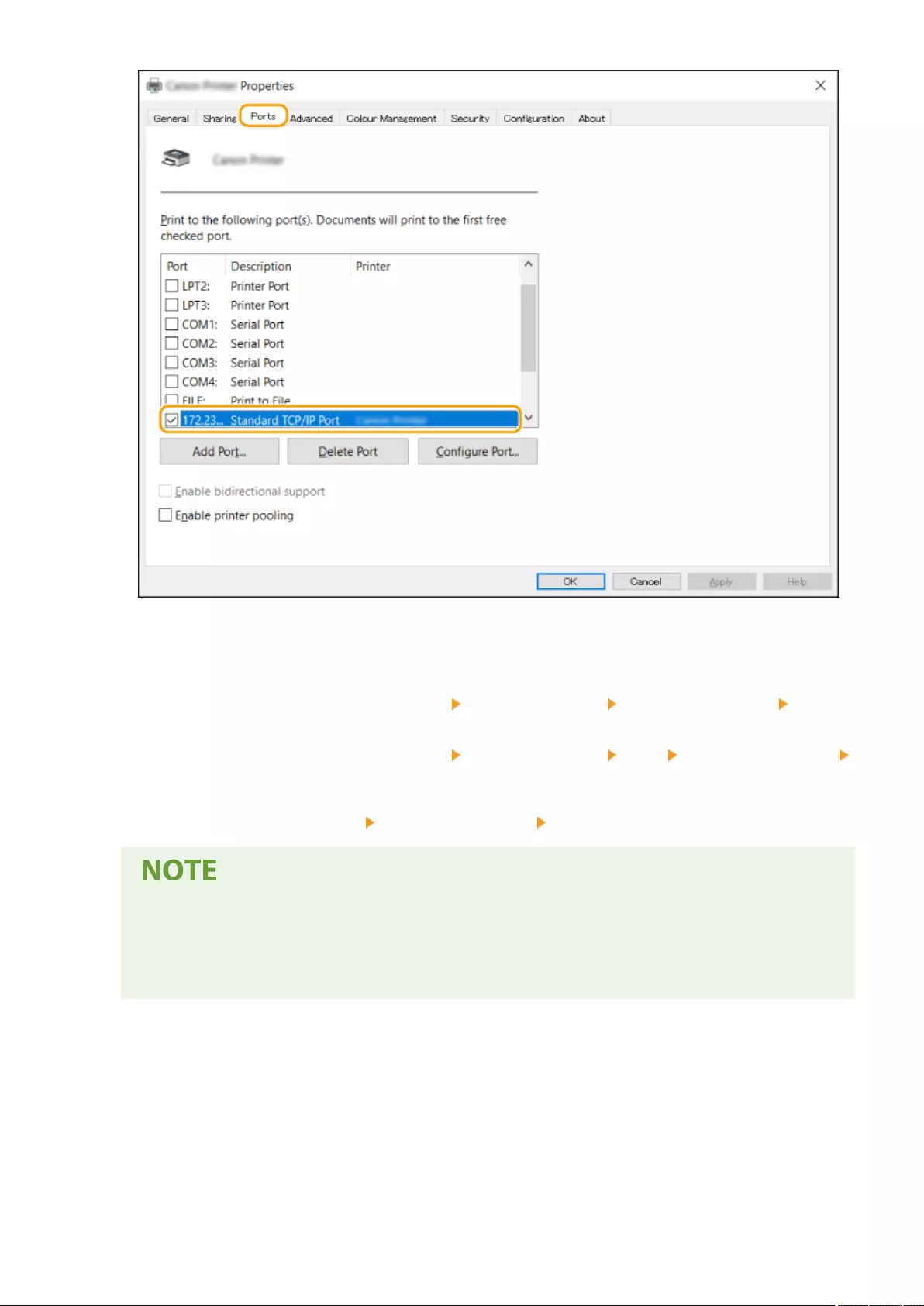
◼When Printing from the Windows Store App
Windows Server 2012
Display the charms on the right side of the screen Tap or click [Devices] The driver that you use [Print].
Windows 8.1/Server 2012 R2
Display the charms on the right side of the screen Tap or click [Devices] [Print] The driver that you use
[Print].
Windows 10
Tap or click [Print] on the application The driver that you use [Print].
●If you print using this method, only a limited number of print settings are available.
●If the message [The printer requires your attention. Go to the desktop to take care of it.] is displayed,
go to the desktop and follow the instructions in the displayed dialog box. This message appears when
the machine is set to display the user name during printing and similar instances.
Appendix
1083

System Specications
72JY-0KA
This section presents the system specications for this product. Specications are subject to change without notice for
product improvement or future release.
◼Functional Specications
Fax Function(P. 1085)
Send Functions(P. 1086)
Printer Functions(P. 1088)
Management Functions(P. 1091)
◼Environment To Use the Machine
System Environment(P. 1097)
Network Environment(P. 1099)
System Options(P. 1101)
Appendix
1084
Fax Function
72JY-0KC
Telephone Line Used *1 Public Switched Telephone Network (PSTN)
Scan Line Density Normal
G3: 8 dot/mm x 3.85 line/mm
Fine
G3: 8 dot/mm x 7.7 line/mm
Super-Fine
G3: 8 dot/mm x 15.4 line/mm
Ultra-Fine
G3: 16 dot/mm x 15.4 line/mm
Transmission Speed Super G3: 33.6 kbps
G3: 14.4 kbps
Compression Method MH, MR, MMR, JBIG
Transmission Type Super G3, G3
Sending Original Sizes A4, B5*2, A5*2, A6*2, LGL, LTR, and STMT
Receiving Paper Sizes A4, B5, A5, LGL, LTR, STMT, and 16K
No. of Memory RX Jobs Up to 320 jobs
Transmission Times JBIG: Approximately 2.6 seconds (When sending A4 Canon original paper, Normal 8 dot/mm x 3.85
line/mm ECM (JBIG))
*1 When using an IP telephone service, facsimile communication may not be performed normally via an IP telephone
line. It is recommended to use facsimile communication via a general telephone (Public Switched Telephone Network)
line.
*2 Sent as A4.
◼Max. Destinations for Sequential Broadcast Transmission
●You can specify and send to up to 256 destinations at the one time. (If you specify a group, which is made up of
several destinations, each destination is counted as a separate destination.)
Appendix
1085
Send Functions
72JY-0KE
◼Push Scan
Type Color Scanner
Max. Original Scanning Size Depends on copy specications
Resolution for Scan 100x100 dpi, 150x150 dpi, 200x100 dpi (Normal), 200x200 dpi (Fine), 200x400 dpi (Superne),
300x300 dpi, 400x400 dpi (Ultrane)*1, 600x600 dpi*1
Scanning Speed See the feeder specications
Interface 1000 Base-T/100 Base-TX/10 Base-T (IEEE 802.3 compliant)
Protocol Supported File: FTP (TCP/IP), SMB (TCP/IP), WebDAV
E-mail/I-Fax: SMTP (send), POP3 (receive)
Output Format TIFF (MMR), JPEG*2, PDF (Compact, OCR (Text Searchable), Format to PDF/A, Trace & Smooth,
Encrypt), XPS (Compact, OCR (Text Searchable)), PDF/XPS (Device Signature, User Signature), Oce
Open XML (PowerPoint, Word)
*1 Available only when <Black & White> is selected.
*2 Single-Page only.
◼Pull Scan
Max. Original Scanning Size Depends on copy specications
Color mode Color/Black-and-White Auto Switch, Color, Black-and-White, Grayscale
Resolution for Scan 75 dpi x 75 dpi, 100 dpi x 100 dpi, 150 dpi x 150 dpi, 200 dpi x 200 dpi, 300 dpi x 300 dpi, 400 dpi x
400 dpi*1, 600 dpi x 600 dpi*1
Compatible OS Windows 7/Windows 8.1/Windows 10/Windows Server 2008 /Windows Server 2008 R2/Windows
Server 2012/Windows Server 2012 R2/Windows Server 2016/Windows Server 2019
Interface USB2.0High・Speed, 1000Base-T/100Base-TX/10Base-T (IEEE 802.3 compliant)
Protocol Supported TCP/IP
Driver TWAIN compliant, WIA Compliant
*1 Available only when <Black & White> is selected.
Appendix
1086

◼Internet/Intranet FAX
Communication Protocol Internet FAX
SMTP (send*1)/POP3 (receive*2)
Intranet FAX
SMTP (send/receive*1)
I-Fax Communication Mode Simple mode, Full mode (ITU-T T.37 and W-NET FAX compliant)
Max. Original Size A4
Resolution 200 dpi x 100 dpi, 200 dpi x 200 dpi, 200 dpi x 400 dpi*3, 300 dpi x 300 dpi*3, 400 dpi x 400 dpi*3,
600 dpi x 600 dpi*3
*1 Supports SMTP authentication and encrypted communication (TLS) during SMTP send/receive.
*2 Supports APOP/POP before SMTP and encrypted communication (TLS) during POP RX.
*3 Available depending on settings of the other party (capability setting of the receiving machine).
◼Max. Destinations for Sequential Broadcast Transmission
●You can specify and send to up to 256 destinations at the one time. (If you specify a group, which is made up of
several destinations, each destination is counted as a separate destination.)
◼Max. Number of Pages That Can Be Sent with One Job
●The maximum number of pages that can be sent with one job is 999 for a one-sided original or 1,000 for a two-
sided original.
●The maximum number of send jobs that the machine can handle is 64. However, the actual number
of send jobs that the machine can handle may be less than 64, depending on the following conditions:
- When multiple documents are being sent at the same time
- When large documents are being sent
- When a large amount of memory is being used for the Fax/I-Fax Inbox
Appendix
1087
Printer Functions
72JY-0KF
◼UFR II Printer Function
Type Internal
Print Size Depends on copy specications
Print Speed Depends on copy specications
Data Processing Resolution 600 dpi x 600 dpi, 1200 dpi x 1200 dpi
Page Description Language (PDL) UFR II
Protocol Supported TCP/IP (LPD/Port9100/IPP/IPPS/FTP/WSD)
Compatible OS ●Windows 8.1/Windows 10/Windows Server 2012/Windows Server 2012 R2/Windows Server
2016/Windows Server 2019
●Mac OS X (10.11 and later)
Resident Fonts None
Interface USB2.0High・Speed, 1000Base-T/100Base-TX/10Base-T (IEEE 802.3 compliant)
◼PCL Printer Function
Type Internal
Print Size Depends on copy specications
Print Speed Depends on copy specications
Data Processing Resolution 600 dpi x 600 dpi, 1200 dpi x 1200 dpi
Page Description Language (PDL) PCL5, PCL6
Protocol Supported TCP/IP (LPD/Port9100/IPP/IPPS/FTP/WSD)
Compatible OS Windows 8.1/Windows 10/Windows Server 2012/Windows Server 2012 R2/Windows Server
2016/Windows Server 2019
Resident Fonts 93 Roman, 10 Bitmap fonts, 2 OCR fonts, Andalé Mono WT J/K/S/T*1 (Japanese, Korean,
Simplied Chinese, and Traditional Chinese) , Barcode fonts*2
Appendix
1088
Interface USB2.0High・Speed, 1000Base-T/100Base-TX/10Base-T (IEEE 802.3 compliant)
*1 Requires optional PCL International Font Set
*2 Require optional Barcode Printing Kit
◼PS Printer Function
Type Internal
Print Size Depends on copy specications
Print Speed Depends on copy specications
Data Processing Resolution 600 dpi x 600 dpi, 1200 dpi x 1200 dpi
Page Description Language (PDL) Adobe PostScript 3
Protocol Supported TCP/IP (LPD/Port9100/IPP/IPPS/FTP/WSD)
Compatible OS Driver
●Windows 8.1/Windows Server 2012/Windows Server 2012 R2/Windows Server 2016/
Windows Server 2019
●Mac OS X (10.11 and later)
PPD
●Windows 8.1/Windows 10
●Mac OS X (10.10 and later)
Resident Fonts 136 Styles
Interface USB2.0High・Speed, 1000Base-T/100Base-TX/10Base-T (IEEE 802.3 compliant)
◼Functions That Can Be Used with Each Page Description Language and File Format
Functions that can be used with each page description language and le format when using the forced hold print
function are indicated below.
Available Functions Page Description Language File Format
(When Printing with the Direct Print function)
UFR II PS*4XPS PCL*5PDF JPEG TIFF
Print
Change Settings - -
No. of Copies - -
Print Range*1 - - -
Appendix
1089
Available Functions Page Description Language File Format
(When Printing with the Direct Print function)
UFR II PS*4XPS PCL*5PDF JPEG TIFF
Select Color*2 - -
2-Sided Printing - -
Select Paper*1*3 - - -
N on 1 - - - -
Toner Save*1 - -
Display Image - - -
Delete Page - - - - -
*1 You cannot change the print settings when multiple documents are selected.
*2 If a print job that has been made with [Color Mode] set to [Black & White], you cannot change it to <Auto (Color/Black
& White)> or <Two Colors> in the print settings when the job is forcibly retained in the machine.
*3 You cannot change the paper source if different sizes of paper are specied in the print job.
*4 Settings can only be changed for jobs from the Canon PS3 printer driver, excluding PPD.
*5 Settings can be changed, or the preview can be displayed only for PCL XL.
●Depending on changed settings, the document may not be printed correctly.
Appendix
1090

Management Functions
72JY-0KH
◼Information Registered in User Authentication
Up to 5,001 users can be registered.
◼Registering Department IDs
Up to 1,000 Department IDs can be registered.
◼Authentication Functions
●When an Active Directory server is specied as an authentication server, the following system environment is
required.
Software (operating system): Windows Server 2008 SP2*1/Windows Server 2008 R2 SP1/Windows Server 2012*2/
Windows Server 2012 R2*2/Windows Server 2016*2/Windows Server 2019*2
*1 64-bit operating systems are not supported.
*2 Users cannot log in with Active Directory authentication if Kerberos Armoring is enabled for KDCrelated policies (group policies). Make
sure to disable Kerberos Armoring.
●Kerberos encryption methods for the Active Directory authentication supported by the current version of User
Authentication are as follows.
Encryption method
●128-bit AES (Advanced Encryption Standard)
●256-bit AES (Advanced Encryption Standard)
●DES (Data Encryption Standard)
●RC4
●The available encryption methods may vary, depending on the Active Directory settings.
●Of the available encryption methods, the one with the highest cipher strength is automatically selected.
●When specifying an Active Directory server as an authentication server, use the following ports*1 on the server.
To communicate with a DNS server: port number 53
To communicate with a KDC (Key Distribution Center): port number 88
To communicate with a server for LDAP directory service (can be changed to an arbitrary port
number for the LDAP service): port number 389
*1 The above port numbers are default values. These numbers may vary depending on the selected settings.
●When specifying an LDAP server as an authentication server, the following system environment is required.
Appendix
1091
Software: OpenLDAP
Operating system: Requirements are pursuant to the product specications of the LDAP server.
●When specifying an LDAP server as an authentication server, use the following ports*1 on the server.
To communicate with the LDAP server using LDAP (when TLS is enabled): port number 636
To communicate with the LDAP server using LDAP (when TLS is disabled): port number 389
*1 The port numbers can be changed according to the LDAP server settings.
◼Firewall Settings
●When specifying IP addresses in rewall settings, up to 16 IP addresses (or ranges of IP addresses) can be specied
for both IPv4 and IPv6.
●When specifying MAC addresses in rewall settings, up to 100 MAC addresses can be specied.
●The exception addresses and exception port numbers that can be used for communication using the sub line and
are registered by default are indicated below.
Exception addresses: 0.0.0.1 to 255.255.255.255
Exception port numbers: 53, 67, 68, 80, 161, 443, 515*, 631*, 3702, 5353, 5357, 5358, 8000*, 8080, 8443*, 9013,
9100*, 10443*, 20010*, 47545
* Inbound lter only
◼Registration of Certicates (User Signature Keys/Certicates, CA Certicates, S/MIME
Certicates)
●The algorithms and formats of keys and certicates that can be registered are as follows.
RSA signature algorithm: SHA-1/SHA-256/SHA-384*1/SHA-512*1/MD2*2/MD5*2
RSA public-key algorithm (key length): RSA (512 bits*2/1024 bits/2048 bits/4096 bits*2)
DSA signature algorithm: SHA-1
DSA public-key algorithm (key length): DSA (1024 bits/2048 bits/3072 bits)
ECDSA signature algorithm: SHA-1/SHA-256/SHA-384/SHA-512
ECDSA public-key algorithm (key length): ECDSA (P256/P384/P521)
Certicate format:
User Signature Keys/Certicates: PKCS#12*3
Keys, Certicates: PKCS#12*4
Appendix
1092

CA Certicates, S/MIME Certicates: X.509 DER/PEM
File extension:
User Signature Keys/Certicates: pfx/p12
Keys, Certicates: pfx/p12*4
CA Certicates, S/MIME Certicates: cer/pem
Maximum number of registerable certicates:
User Signature Keys/Certicates: 100 (one user certicate per user)
Keys, Certicates: 6*4
CA Certicates: 150
S/MIME Certicates: 2,000
*1 Available only when the key algorithm is 1024 bits or more.
*2 Cannot be used for user signatures
*3 Available only when installed by using the Remote UI.
*4 Used for TLS, IEEE802.1x, IPSec, and device signatures.
◼Registration of Certicate Revocation Lists (CRL)
Up to 50 certicate revocation lists (CRL) can be registered. Note, however, that CRL cannot be registered in the
following cases.
●The data size of the CRL exceeds 1 MB.
●An unsupported signature algorithm is being used.
●The number of revoked certicates registered in one CRL le exceeds 1,000.
◼Denition of "Weak Encryption"
When <Prohibit Use of Weak Encryption> is set to <On>, the use of the following algorithms are prohibited.
Hash: MD4, MD5, SHA-1
HMAC: HMAC-MD5
Common key cryptosystem: RC2, RC4, DES
Public key cryptosystem: RSA encryption (512 bits/1024 bits), RSA signature (512 bits/1024 bits), DSA (512 bits/1024
bits), DH (512 bits/1024 bits)
●Even when <Prohibit Use of Key/Certicate with Weak Encryption> is set to <On>, the hash algorithm SHA-1,
which is used for signing a root certicate, can be used.
Appendix
1093
◼FIPS 140-2 Standard Algorithm
When <Format Encryption Method to FIPS 140-2> is set to <On>, the following algorithms are prohibited from use.
Hash: MD4, MD5, SHA-1 (for a purpose other than TLS)
Common key cryptosystem: RC2, RC4, DES, PBE
Public key cryptosystem: RSA encryption (512 bits/1024 bits), RSA signature (512 bits/1024 bits), DSA signature (512
bits/1024 bits), DH (512 bits/1024 bits)
◼Log Management
●The following types of logs can be managed on the machine. Collected logs can be exported in the CSV le format.
Log Type
Number
Indicated as
"Log Type" in
the CSV File
Description
User Authentication
Log 4098
This log contains information related to the authentication status
of user authentication (login/logout and user authentication
success/failure), the
registering/changing/deleting of user information managed with
User Authentication, and the management (adding/editing/
deleting) of roles with the ACCESS MANAGEMENT SYSTEM.
Job Log 1001 This log contains information related to the completion of
copy/fax/scan/send/print jobs.
Transmission Log 8193 The log contains information related to transmissions.
File Save Log 8196
This log contains information related to the saving of les to the
Network (Advanced Space of other machines) and Memory
Media.
Mail Box Operation Log 8197
This log contains information related to the operations
performed on data in the Memory RX Inbox and the Condential
Fax Inbox.
Mail Box Authentication Log 8199 This log contains information related to the authentication status
of the Memory RX Inbox and the Condential Fax Inbox.
Machine Management Log 8198
This log contains information related to the starting/shutting
down of the machine and changes made to the settings
using (Settings/Register). The Machine Management Log
also records changes in user information or security-related
settings when the machine is inspected or repaired by your
dealer or service representative.
Network Authentication Log 8200 This log is recorded when IPSec communication fails.
Export/Import All Log 8202 This log contains information related to the importing/exporting
of the settings by using the Export All/Import All function.
Appendix
1094
Mail Box Backup Log 8203 This log contains information related to the Memory RX Inbox
and the Condential Fax Inbox.
Application/Software Management
Screen Operation Log 3101
This is an operation log for SMS (Service Management Service),
software registration/updates, and AddOn application installers,
etc.
Security Policy Log 8204 This log contains information related to the setting status of the
security policy settings.
Group Management Log 8205 This log contains information related to the setting status
(registering/editing/deleting) of the user groups.
System Maintenance Log 8206 This log contains information related to rmware updates and
backup/restoration of the AddOn application, etc.
Authentication Print Log 8207 This log contains information and the operation history related
to the forced hold print jobs.
Setting Synchronization Log 8208
This log contains information related to the synchronization of
machine settings. Synchronizing Settings for Multiple Canon
Multifunction Printers(P. 656)
Log for Audit Log Management 3001
This log contains information related to the starting and ending
of this function (the Audit Log Management function), as well as
the exporting of logs, etc.
●Logs can contain up to 40,000 records. When the number of records exceeds 40,000, they are deleted, with
the oldest records rst.
◼Import/Export of the Setting Data
See Settings/Registration Table(P. 671) .
◼Max. Buttons Registered on the <Home> Screen
●Max. number of Personal buttons: 60 per user (total of 12,000 for all users)
●Max. number of Shared buttons: 60
◼Max. Destinations Registered to Address Book
●Address Lists 1 to 10/ Address List for Administrator: 1,600
●One-Touch Address List: 200
●Personal Address List: 25
●Group Address List: 4,000*1 (10 groups*2 x 400 destinations*3)
*1 Total 20,000 for all groups
*2 Max. number of groups per user (a total of 50 groups can be registered in a device)
*3 Max. number of destinations per group
Appendix
1095
◼Images That Can Be Imported for Login Screen Background
●File Size: 1,024 KB
●File Extension: jpg, jpeg, or png
●Image Size: 640 pixels x 442 pixels or smaller
◼Visual Message Specications
File Format JPEG, PNG, BMP, GIF, Animated GIF, and HTML (on the intranet/internet)
Communication Protocol SMB, WebDAV, HTTP
Maximum size of the contents Max. 10 MB
Image Size
Other than HTML: 639 pixels x 400 pixels*
* If the image is larger than the above size, it is displayed in a reduced size without
changing its aspect ratio. If the image is smaller than the above size, it is displayed
without changing the size.
HTML: over 639 pixels x 400 pixels can be used (by scrolling through them)
◼SCEP Server Support
Only the Network Device Enrollment Service (NDES) of Windows Server 2008 R2/Windows Server 2012 R2/Windows
Server 2016 is supported.
Appendix
1096

System Environment
72JY-0KJ
WSD Scan ●Windows 8.1
●Windows 10
System requirements for the Remote
UI *1
Windows
●Internet Explorer 11
●Microsoft Edge
●Google Chrome
Mac OS
●Safari 11 or later
●Google Chrome
Compatible mail forwarding server
software
●Microsoft Exchange Server 2013
●Microsoft Exchange Server 2016
●Microsoft Exchange Server 2019
●Sendmail 8.14.7
Compatible mail receiving server
software
●Microsoft Exchange Server 2013
●Microsoft Exchange Server 2016
●Microsoft Exchange Server 2019
●Qpopper 4.1.0
File servers available as destinations
for le transmission
FTP
●Windows Server 2012: Internet Information Services 8.0
●Windows 8.1/Windows Server 2012 R2: Internet Information Services 8.5
●Windows 10/Windows Server 2016/Windows Server 2019: Internet Information
Services 10
●CentOS 7
Windows (SMB)
●Windows 8.1
●Windows 10
●Windows Server 2012 R2
●Windows Server 2016
●Windows Server 2019
●Mac OS X 10.13
●Mac OS X 10.14
●Mac OS X 10.15
●CentOS 7
WebDAV
●Windows Server 2012: Internet Information Services 8.0
●Windows 8.1/Windows Server 2012 R2: Internet Information Services 8.5
●Windows 10/Windows Server 2016/Windows Server 2019: Internet Information
Services 10
●Mac OS X 10.13
●Mac OS X 10.14
●Mac OS X 10.15
Appendix
1097
●CentOS 7
Types of LDAP servers ●Windows Server 2012 with Active Directory
●Windows Server 2012 R2 with Active Directory
●Windows Server 2016 with Active Directory
●Windows Server 2019 with Active Directory
System requirements for the User's
Guide
Windows
●Internet Explorer 9 and later
●Microsoft Edge
●Firefox
●Firefox ESR
●Chrome (Online browsing only)
Linux
●Firefox
Mac OS
●Safari
●Firefox
●Chrome (Online browsing only)
iOS
●Safari (Online browsing only)
Android
●Chrome (Online browsing only)
*1 Before changing the settings of the machine, set your Web browser to enable all cookies and use JavaScript.
Appendix
1098
Network Environment
72JY-0KK
◼Wired LAN Specications
Interface (Primary line/Secondary line) 10Base-T/100Base-TX/1000Base-T (RJ-45)
Protocol Supported TCP/IP
●Frame type: Ethernet II
●Print applications: LPD/Raw/IPP/IPPS/FTP/WSD/Mopria/AirPrint/Windows 10
Mobile Print
●For precautions related to the sub line, see Cautions When Using the Sub Line(P. 1051) .
◼Wireless LAN Specications
Standard IEEE 802.11b, IEEE 802.11g, IEEE 802.11n
Transmission Scheme ●IEEE 802.11b (Modulation system: DS-SS)
●IEEE 802.11g (Modulation system: OFDM method)
●IEEE 802.11n (Modulation system: OFDM method)
Frequency Range 2.412 to 2.472 GHz
Maximum Radio-Frequency Power Transmitted +14.08 dBm
Security (encryption method) Infrastructure Mode
●128 (104)/64 (40) bit WEP
●WPA-PSK (TKIP/AES-CCMP)
●WPA2-PSK (TKIP/AES-CCMP)
●WPA-EAP (AES-CCMP)
●WPA2-EAP (AES-CCMP)
Access Point Mode
WPA2-PSK (AES-CCMP)
Wi-Fi Direct Mode
WPA2-PSK (AES-CCMP)
Connection Method WPS (Wi-Fi Protected Setup), Manual setup
Appendix
1099
Port Numbers Available for Direct Connection
Type Port Number Protocol
TCP
515 LPD
9100 RAW
80, 8000, 8080 HTTP
631 IPP
443, 10443 IPPS
443, 8443 HTTPS
9013 CPCA (unique Canon protocol)
5357, 5358 WSD
UDP
161 SNMP
5353 mDNS
67, 68 DHCPv4
3702 WSD
47545 CPCA (unique Canon protocol)
Appendix
1100

System Options
72JY-0KL
By installing system-related options, you can further enhance the performance of the machine.
File Formats and the Need for Optional Products(P. 1101)
◼Barcode Printing Kit
This option enables you to print barcodes. For more details, see Bar Code Printing via the online manual site.
◼PCL International Font Set
This option enables you to add the following fonts for a PCL printer. As a result, you can output using multiple
languages in a SAP Unicode environment.
●Andale® and WorldType® Collection J (Japanese Version)
●Andale® and WorldType® Collection K (Korean Version)
●Andale® and WorldType® Collection S (Simplied Chinese Version)
●Andale® and WorldType® Collection T (Traditional Chinese Version)
In order to support differences in character design depending on the region, four font versions are enabled.
◼Universal Send Trace & Smooth PDF Kit
This option is useful when using the Send function on the machine. It enables you to convert the text and line
drawings of a scanned image to scalable outline data. The outline data (Trace) can be extracted and used in Adobe
Illustrator. The smoothing process can also be applied to the text of the outline data to make it appear less jagged
when viewed on a computer monitor or in print.
◼Universal Send Digital User Signature Kit
This option enables you to use the Send function on the machine with security. It enables you to send a PDF or XPS le
with a unique digital user signature obtained from a certicate authority. This enables the recipient of a PDF or XPS le
to verify which user signed it. Adding a Digital Signature to Sent Files(P. 577)
◼Copy Card Reader
This option enables you to perform Department ID Management through authentication with control card. For details,
see Copy Card Reader(P. 1123) .
File Formats and the Need for Optional Products
products may be required, depending on the le format and function you want to use. See the following table.
-: Standard function
: Optional products required
File Format (Detailed Setting) Scan and Send / Scan and Store
JPEG -
Appendix
1101

File Format (Detailed Setting) Scan and Send / Scan and Store
TIFF -
PDF; Trace & Smooth
PDF; Compact -
PDF (OCR (Text Searchable)) -
PDF (Encrypt) -
PDF (Device Signature) -
PDF (User Signature)
PDF (Format to PDF/A) -
XPS (Compact) -
XPS (OCR (Text Searchable)) -
XPS (Device Signature) -
XPS (User Signature)
OOXML (Word) -
OOXML (PowerPoint) -
●The following le formats can be used with the Access Stored Files function: JPEG, TIFF, PDF, XPS. To print
les in other formats, move the les to your computer and print via the printer driver, etc.
Appendix
1102

Hardware Specications
72JY-0KR
This section presents the specications of the main unit and optional equipment of this product. Note that the
specications are subject to change without notice for product improvement or future release.
◼Machine Specications
Main Unit(P. 1104)
Feeder(P. 1107)
Available Paper(P. 1109)
◼Specications of Optional Equipment
Paper Feeder PF-D(P. 1115)
Cassette Feeding Unit-AV(P. 1116)
Copy Card Reader(P. 1117)
Appendix
1103

Main Unit
72JY-0KS
Name Canon imageRUNNER C1538iF / C1533iF
Type Desktop
Resolution for Reading ●600 dpi x 600 dpi
●300 dpi x 600 dpi
●300 dpi x 300 dpi
Resolution for Writing 600 dpi x 600 dpi
Number of Tones 256
Acceptable Originals Sizes of Original
Up to 216.0 mm x 355.6 mm
Types of Original
●Sheet and book
Copy Size/Copy Paper Paper Sizes
Paper Drawer
●Max: 216.0 mm x 297.0 mm
●Min: 101.6 mm x 148.0 mm
Multi-Purpose Tray
●Max: 216.0 mm x 355.6 mm
●Min: 76.2 mm x 127.0 mm
Margin
●Top: 4.0 mm ± 2.0 mm
●Left: 4.0 mm ± 2.0 mm
Paper Weight
●Paper Drawer: 60 g/m² to 163 g/m²
●Multi-Purpose Tray: 60 g/m² to 216 g/m²
Paper Type Available Paper(P. 1109)
Warm-Up Time *1 After Powering ON
60 seconds or less*2
Returning from the Sleep mode
10 seconds or less
First Copy Time ●Color: 6.9 seconds or less
●Black and White: 5.9 seconds or less
Copy Speed *3(Plain A4/LTR, 100%) imageRUNNER C1538iF
●38 sheets/minute (A4)
Appendix
1104

●40 sheets/minute (LTR)
imageRUNNER C1533iF
●33 sheets/minute (A4)
●35 sheets/minute (LTR)
Scanning Speed
(A4/LTR)
Full Color
●1.42 seconds/sheet (A4)
●1.33 seconds/sheet (LTR)
Black-and-White
●1.42 seconds/sheet (A4)
●1.33 seconds/sheet (LTR)
Magnication Regular Paper Size
400%, 200%, 141.4%, 100%, 70.7%, 50%, 25%
Magnication error of Direct (100%)
●Vertical: ±1.30%
●Horizontal: ±1.30%
Zoom
25% to 400% (in 1% increments)
Paper Feeding System/Capacity
*4
Paper Drawer
●550 sheets (80 g/m² / 75 g/m²)
●640 sheets (64 g/m²)
●Paper other than above: height 60 mm or less
Multi-Purpose Tray
●100 sheets (80 g/m² / 75 g/m² / 64 g/m²)
●Paper other than above: height 11 mm or less
Inner Tray Capacity 200 sheets (80 g/m² / 75 g/m² / 64 g/m²)*4
Multiple Copies 999 sheets
Power Source imageRUNNER C1538iF
●220 V - 240 V a.c., 50/60 Hz, 4.0 A
imageRUNNER C1533iF
●220 V - 240 V a.c., 50/60 Hz, 3.9 A
Power Consumption *1 Maximum Power Consumption
1,500 W or less
When the machine is in the Sleep mode
Approximately 1.1 W
When the main power switch is turned OFF
●When <Quick Startup Settings for Main Power> is set to <On>: Approximately 1.1 W
●When <Quick Startup Settings for Main Power> is set to <Off>: 0.4 W or less
Dimensions
(W x D x H)
500 mm x 556 mm x 640 mm
Appendix
1105

Weight
(Toner cartridges excluded)
Main Unit
Approximately 37 kg
Consumables
Consumables(P. 888)
Installation Space
(W x D)
717 mm x 785 mm (When the paper drawer is pulled out and the multi-purpose tray is
opened.)
*Provide a space of 100 mm or more around the machine.
Memory Capacity RAM: 2 GB
eMMC: 30 GB
Environmental Conditions Temperature: 10 °C to 30 °C
Humidity: 20 % to 80 % RH (no condensation)
*1 May vary depending on the environment and conditions under which the machine is being used.
*2 If <Quick Startup Settings for Main Power> is set to "On", it takes 4 seconds until the key operation on the touch panel
display is available after turning on the main power of the machine. Depending on the situations, the machine does not
startup quickly.
*3 The copy speed on A4/LTR size plain paper on one-side printing is measured during continuous copying. Copy speeds
vary depending on the output resolution, the paper type and size, and the paper feeding direction. Copy speeds on
smaller paper sizes may be slower. Plus, the machine may experience downtime or decrease the copy speed in the
middle of a continuous copy run to adjust the temperature inside the machine or maintain the optimal print quality.
*4 May vary depending on the installation environment and paper to use.
Appendix
1106

Feeder
72JY-0KU
Original Feeding Mechanism Automatic Document Feeder
Original Size/Type Size of Originals
Max: 216.0 mm x 355.6 mm*1*2
Min: 48.0 mm x 128.0 mm*3
Weight of Originals
Full Color:
●1-sided/2-sided Scanning: 64 g/m² to 128 g/m²
Black-and-White:
●1-sided Scanning (A/B Series): 42 g/m² to 128 g/m²
●1-sided Scanning (Inch Series): 50 g/m² to 128 g/m²
●2-sided Scanning: 50 g/m² to 128 g/m²
Business card originals: 80 g/m² to 220 g/m² (0.1 mm to 0.23 mm thick)
Narrow width originals smaller than A6R except for business card: 50 g/m² to 128 g/m²
Long originals: 60 g/m² to 90 g/m²
Original Tray Capacity ●100 sheets (80 g/m² / 75 g/m² / 64 g/m²)
●10 sheets (50 g/m² or less)
●10 mm in height or less (more than 80 g/m²)
●Business card originals: 25 sheets
●Long originals: 1 sheets
Original Scanning Speed
(A4/LTR)
1-sided Scanning
Scanning (300 dpi x 300 dpi)
●Full Color:
95 pages/minute (A4)
100 pages/minute (LTR)
●Black-and-White:
95 pages/minute (A4)
100 pages/minute (LTR)
Copying (600 dpi x 600 dpi)
●Full Color: 50 pages/minute
●Black-and-White: 50 pages/minute
2-sided Scanning
Scanning (300 dpi x 300 dpi)
●Full Color:
145 pages/minute (A4)
150 pages/minute (LTR)
●Black-and-White:
150 pages/minute (A4)
155 pages/minute (LTR)
Copying (600 dpi x 600 dpi)
●Full Color: 50 pages/minute
●Black-and-White: 50 pages/minute
*1 Long Original: 355.6 mm to 630.0 mm (only one original for one-sided scanning)
*2 Business card originals: 55.0 mm x 91.0 mm
Appendix
1107

*3 Business card originals: 48.0 mm x 85.0 mm
Appendix
1108
Available Paper
72JY-0KW
The paper types that can be used with this machine are shown in the following table.
For available paper with options attached, see the specications of respective options.
Also, conrm the precautions regarding paper use.
Supported Paper Sizes(P. 1109)
Supported Paper Types(P. 1111)
Precautions Regarding Paper(P. 1113)
Storing Paper Printed With the Machine(P. 1114)
Supported Paper Sizes
Paper Sizes Paper Source (Standard) Paper Source (Optional)
Paper Drawer 1 Multi-Purpose Tray Paper Feeder PF-D Cassette Feeding Unit-AV
A4
A5
A5R
A6
B5
16K
LTR
LGL -
STMT
EXEC
Custom Size
(76.2 mm x 127.0 mm to 216.0 mm x 355.6 mm)
*1 *2 *2
No.10 (COM10) -- -
ISO-C5 - - -
DL - - -
Monarch - - -
Appendix
1109
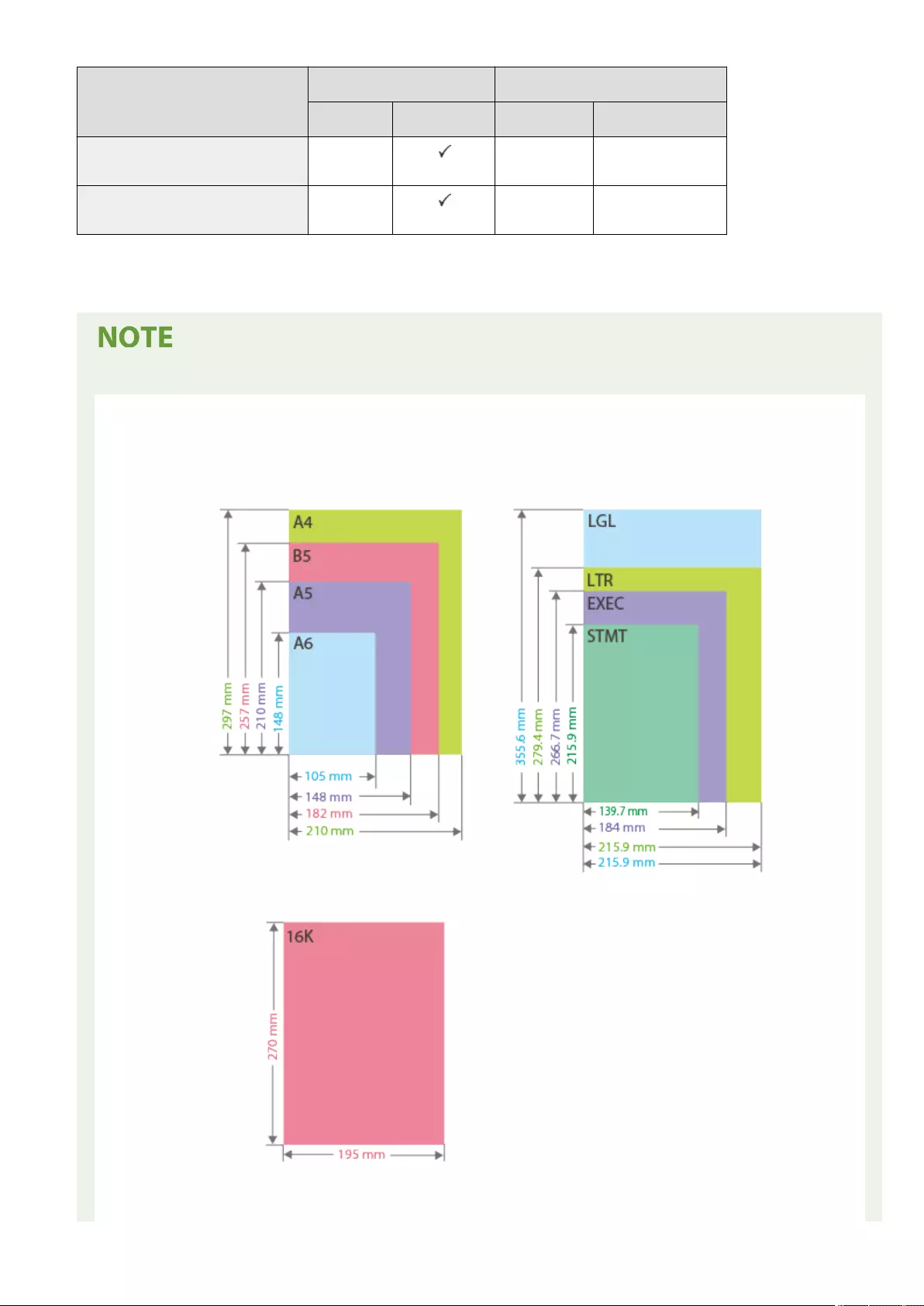
Paper Sizes Paper Source (Standard) Paper Source (Optional)
Paper Drawer 1 Multi-Purpose Tray Paper Feeder PF-D Cassette Feeding Unit-AV
Nagagata 3 - - -
Yougatanaga 3 - - -
*1 You can use custom size settings ranging from 101.6 mm x 148.0 mm to 216.0 mm x 297.0 mm.
*2 You can use custom size settings ranging from 101.6 mm x 148.0 mm to 216.0 mm x 355.6 mm.
Paper sizes supported by this machine
●The following table shows most of the sizes of paper and envelope that can be used with the machine.
Appendix
1110
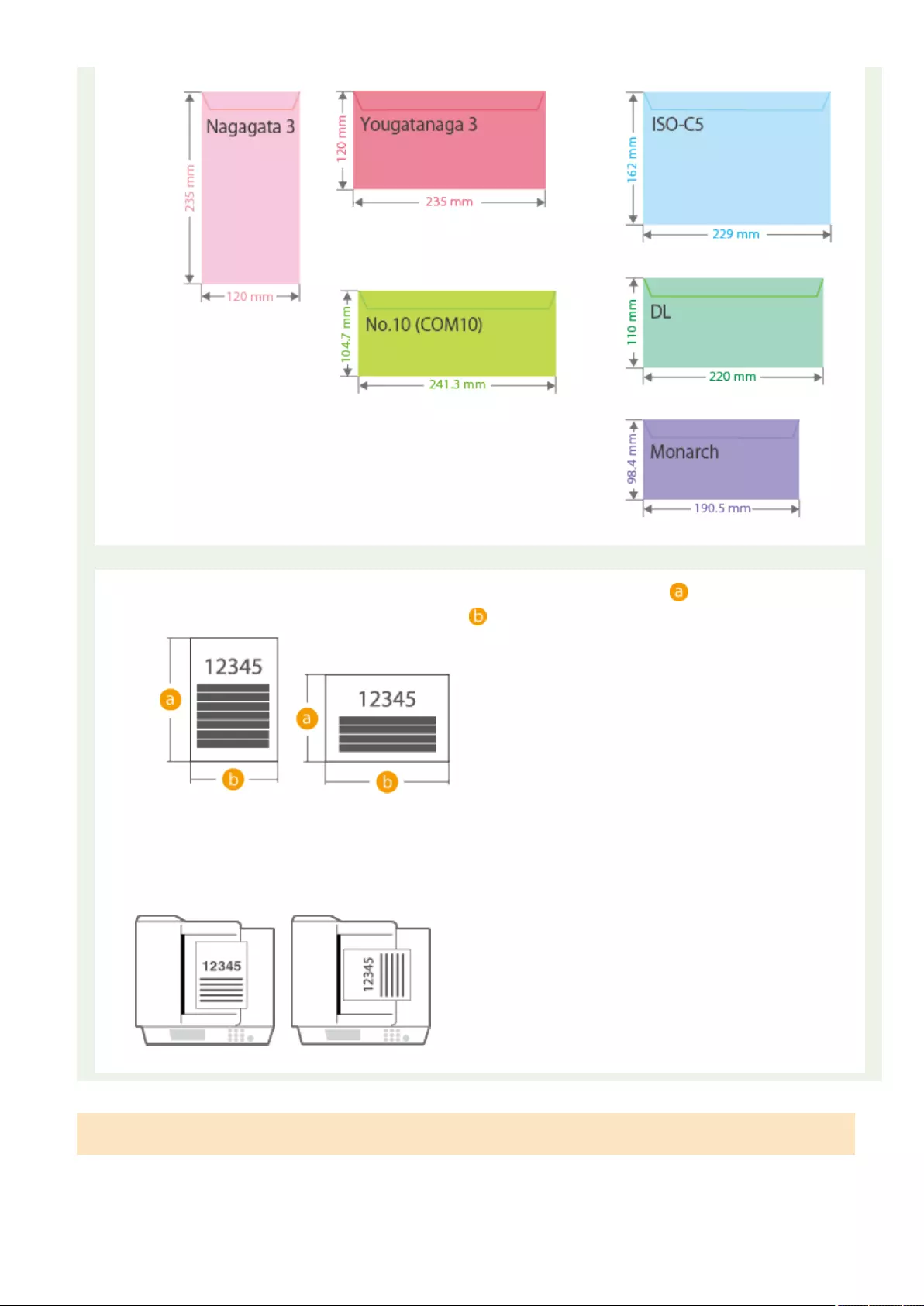
"Vertical" side and "Horizontal" side of paper
●In the User's Guide, regardless of the paper orientation, the side of paper perpendicular ( ) to the front of the machine is
referred to as the "vertical" side while the side parallel ( ) to the front of the machine is referred to as the "horizontal" side.
●In the User's Guide, loading paper with the longer side perpendicular to the front of the machine is referred to as placing in
"portrait orientation" while loading paper with the longer side horizontal to the front of the machine is referred to as placing in
"landscape orientation."
Portrait orientation Landscape orientation
Supported Paper Types
Chlorine-free paper can be used with this machine.
Appendix
1111
Paper Type Paper Weight Paper Source (Standard) Paper Source (Optional)
Paper Drawer 1 Multi-Purpose Tray Paper Feeder PF-D Cassette Feeding Unit-AV
Thin 60 g/m²
Plain 1 61 to 74 g/m²
Plain 2 75 to 90 g/m²
Plain 3 91 to 105 g/m²
Heavy 1 106 to 119 g/m²
Heavy 2 120 to 128 g/m²
Heavy 3 129 to 163 g/m²
Heavy 4 164 to 200 g/m² - - -
Heavy 5 201 to 216 g/m² - - -
Color 61 to 74 g/m²
Recycled 1 *1 61 to 74 g/m²
Recycled 2 *1 75 to 90 g/m²
Letterhead 1 61 to 74 g/m²
Letterhead 2 75 to 90 g/m²
Letterhead 3 91 to 105 g/m²
Letterhead 4 106 to 119 g/m²
Letterhead 5 120 to 128 g/m²
Letterhead 6 129 to 163 g/m²
Letterhead 7 164 to 200 g/m² - - -
Labels 118 to 130 g/m² -
Bond 1 60 to 74 g/m²
Bond 2 75 to 105 g/m²
Appendix
1112

Paper Type Paper Weight Paper Source (Standard) Paper Source (Optional)
Paper Drawer 1 Multi-Purpose Tray Paper Feeder PF-D Cassette Feeding Unit-AV
Envelope 80 to 100 g/m² - - -
*1 You can use 100% recycled paper.
◼Paper Available for Two-Sided Copying/Two-Sided Printing
●When performing 2-sided copying or 2-sided printing, use paper that meets the following requirements.
Paper size: A4, B5, A5R, LGL, LTR, EXEC, 16K, Custom Size (148.0 mm x 210.0 mm to 216.0 mm x 355.6 mm)
Paper type: Thin, Plain 1, Plain 2, Plain 3, Heavy 1, Heavy 2, Heavy 3, Recycled 1, Recycled 2, Letterhead 1, Letterhead 2, Letterhead 3,
Letterhead 4, Letterhead 5, Letterhead 6, Bond 1, and Bond 2
Paper weight: 60 g/m² to 163 g/m²
If using other paper, use <2nd Side of 2-Sided Page> to copy/print on the back side of printed paper.
Precautions Regarding Paper
Do not use the following types of paper
Doing so may cause a paper jam or other printing problems.
●Wrinkled or creased paper
●Curled or rolled paper
●Torn paper
●Damp paper
●Very thin paper
●Thin straw paper
●Paper printed by a thermal transfer printer
●The reverse side of paper which has been printed by a thermal transfer printer
●Highly textured paper
●Glossy paper
When using paper
●Only use paper that has fully acclimatized to the environment in which this machine is installed. Using paper that has been stored
under different temperature or humidity may cause paper jams or result in poor print quality.
Paper handling and storage
●We recommend using the paper immediately after opening the package. Rewrap any remaining paper in its original package, and store
it on a at surface.
●Keep the paper wrapped in its original package to protect the paper from moisture or dryness.
●Do not store the paper in such a way that may cause it to curl or fold.
●Do not store the paper vertically or stack too much paper.
Appendix
1113

●Do not store the paper in direct sunlight, or in a place subject to high humidity, dryness, or drastic changes in temperature or humidity.
When printing on paper that has absorbed moisture
●Steam may emit from the paper output area, or water droplets may form around the paper output area. There is nothing unusual
about any of these occurrences, which occur when the heat generated from xing toner on the paper causes moisture in the paper to
evaporate (most likely to occur at low room temperatures).
Storing Paper Printed With the Machine
Be aware of the following precautions when handling and storing paper printed using the machine.
◼Storing Printed Paper
●Store the paper on a at surface.
●Do not store paper together with items made from PVC (polyvinyl chloride), such as clear folders. The toner may melt, causing paper to
become stuck to PVC-based material.
●Store paper so that it does not become folded or wrinkled. Doing so may cause the toner to come off.
●If you intend to store paper for long periods (two or more years), preserve them in a binder, etc.
●Long-term storage may cause paper to discolor, which in turn may cause print to appear discolored.
●Do not store paper in places with high temperatures.
◼Precautions when sticking printouts with adhesive
●Be sure to use insoluble adhesive.
●Test the adhesive on an unneeded printout before using.
●Before stacking printouts that stuck with adhesive, check that the adhesive completely dried.
Appendix
1114

Copy Card Reader
72JY-0L0
Available Cards Magnetic
Card Readout Method Magnetic readout
Magnetic Card Reading Direction Face up
Store/Replay Replay
Dimensions
(W x D x H)
88 mm x 96 mm x 40 mm (excluding the attachment kit and cable)
Weight Approximately 200 g (including the attachment kit and cable)
Appendix
1117

Options
72JY-0L1
The functionality of the machine can be expanded by installing options to the machine.
◼Available Options
Optional Equipment(P. 1119)
System Options(P. 1101)
◼Finding Options According to Your Purposes
To add paper drawers
Paper Feeder PF-D(P. 1120)
Cassette Feeding Unit-AV(P. 1121)
Making and receiving calls
TELEPHONE 6 KIT(P. 1122)
To use the authentication function to manage users by department
Copy Card Reader(P. 1123)
To use a support tool when closing the feeder
ADF Access Handle-A(P. 1125)
●Some of the settings may not be displayed depending on the conguration of optional equipment installed
on the machine.
Appendix
1118
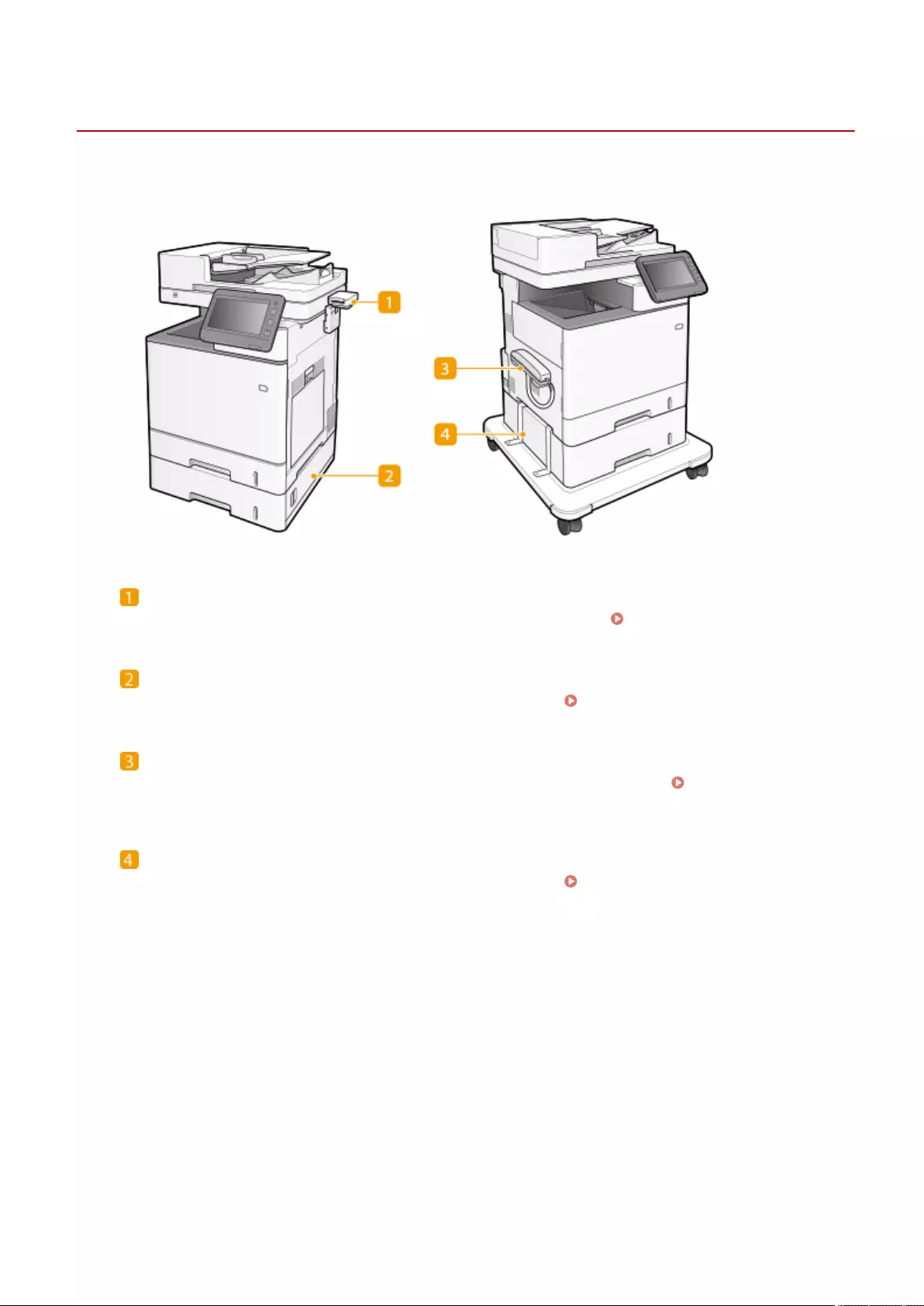
Optional Equipment
72JY-0L2
By combining options, you can use functions more eciently.
Copy Card Reader
You can implement Department ID Management using the card reader. Copy Card Reader(P. 1123)
Paper Feeder PF-D
Load frequently used paper in the paper drawer of this product. Paper Feeder PF-D(P. 1120)
TELEPHONE 6 KIT
You can send a fax manually. You can also use this handset to make a phone call. TELEPHONE 6
KIT(P. 1122)
Cassette Feeding Unit-AV
Load frequently used paper in the paper drawer of this product. Cassette Feeding Unit-AV(P. 1121)
Appendix
1119
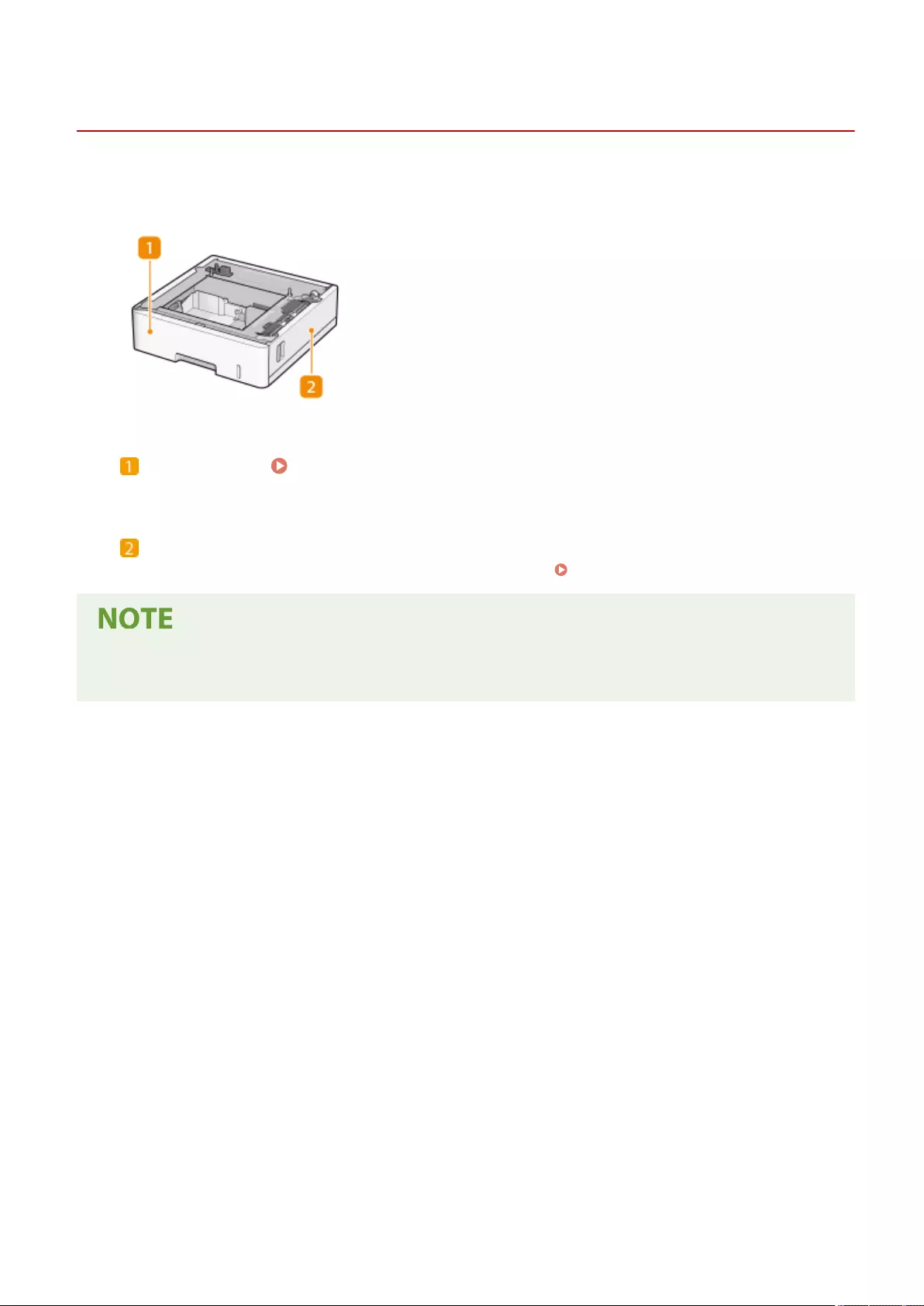
Paper Feeder PF-D
72JY-0L3
Enables you to add a paper drawer. Loading different sized paper in the optional paper drawer enables reduced work
for switching paper.
Paper drawer Basic Paper Loading Method(P. 103)
Load Paper.
Right cover
Open this cover when clearing a paper jam inside the machine. Paper Jams in a Paper Source(P. 1017)
●Up to two units of the Paper Feeder PF-D can be attached. The Cassette Feeding Unit-AV can be attached
further so that up to three paper sources can be added.
Appendix
1120
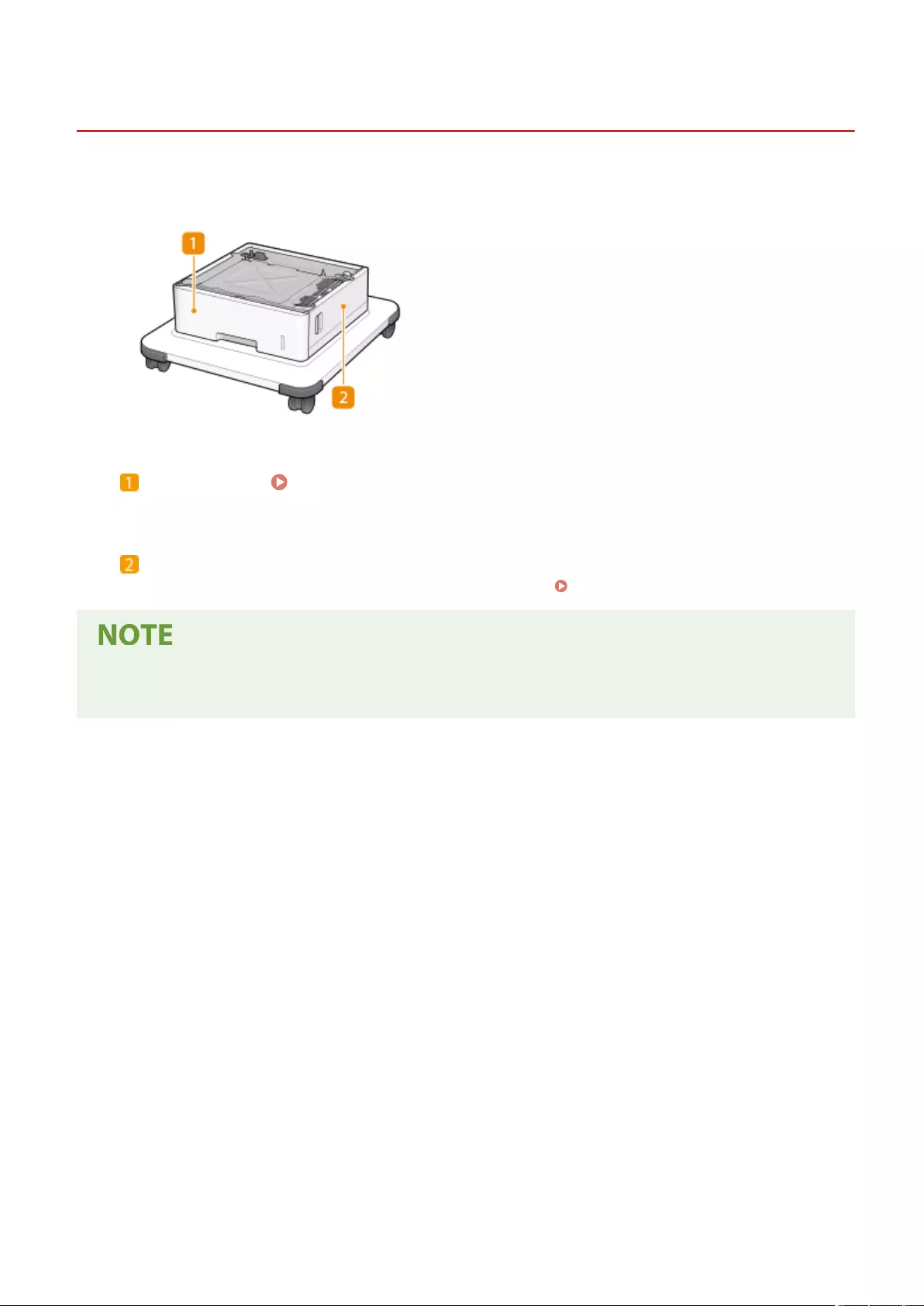
Cassette Feeding Unit-AV
72JY-0L4
Enables you to add a paper drawer. Loading different sized paper in the optional paper drawer enables reduced work
for switching paper.
Paper drawer Basic Paper Loading Method(P. 103)
Load Paper.
Right cover
Open this cover when clearing a paper jam inside the machine. Paper Jams in a Paper Source(P. 1017)
●Up to two units of the Paper Feeder PF-D can be attached on top of the Cassette Feeding Unit-AV. Up to
three paper sources can be added.
Appendix
1121
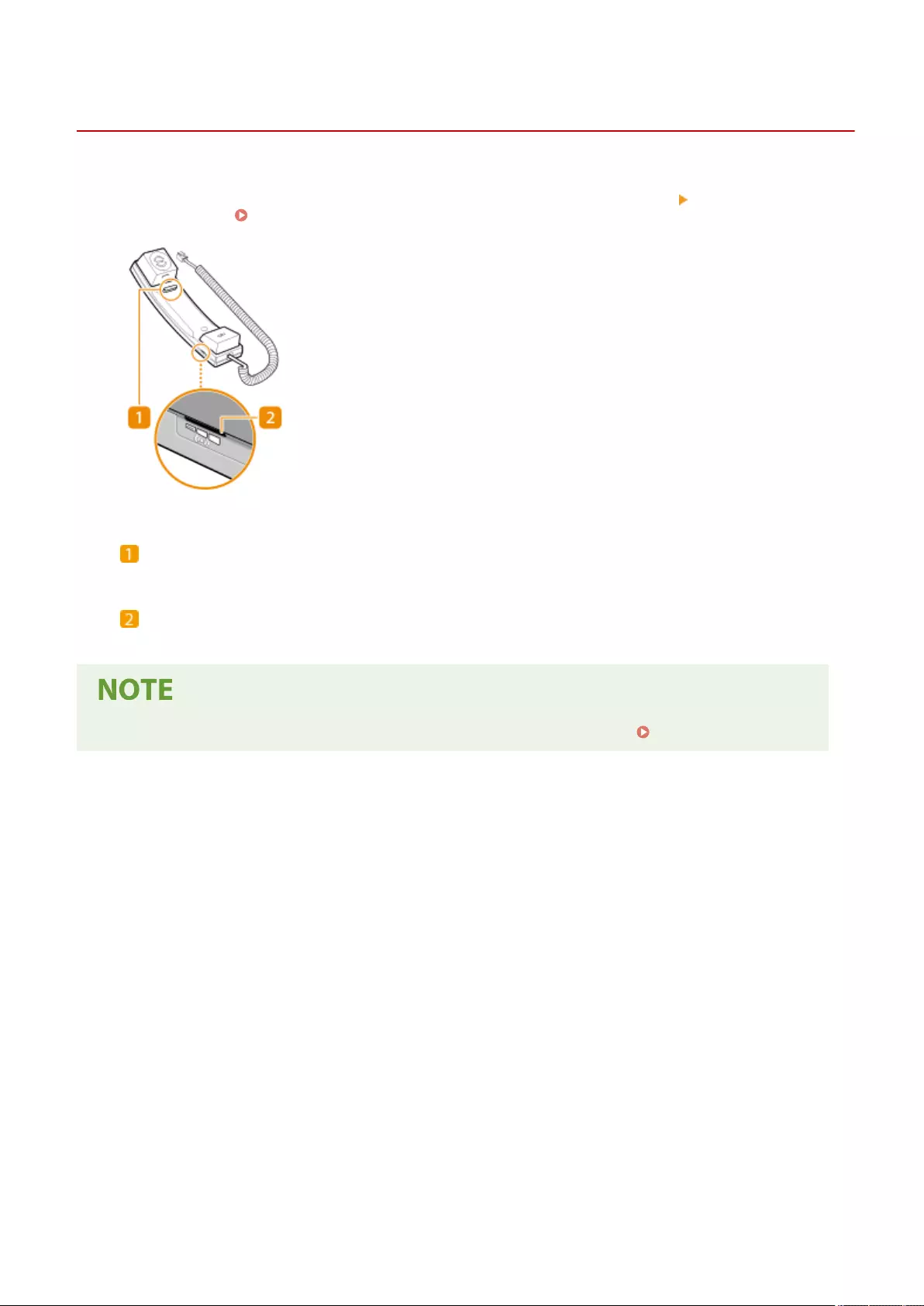
TELEPHONE 6 KIT
72JY-0L5
By connecting the TELEPHONE 6 KIT to the machine, you can make and receive calls the same way as an ordinary
telephone. For switching the receive modes between fax and telephone, see <Fax Settings> <RX Mode>. For making
and receiving calls, see Sending Faxes Manually (Manual Sending)(P. 298) .
Hook button
Ring volume switch
You can set the volume of the telephone ring to high, low, or off.
●If the handset experiences howling, reduce the alarm volume and call volume. Setting Sounds(P. 184)
Appendix
1122
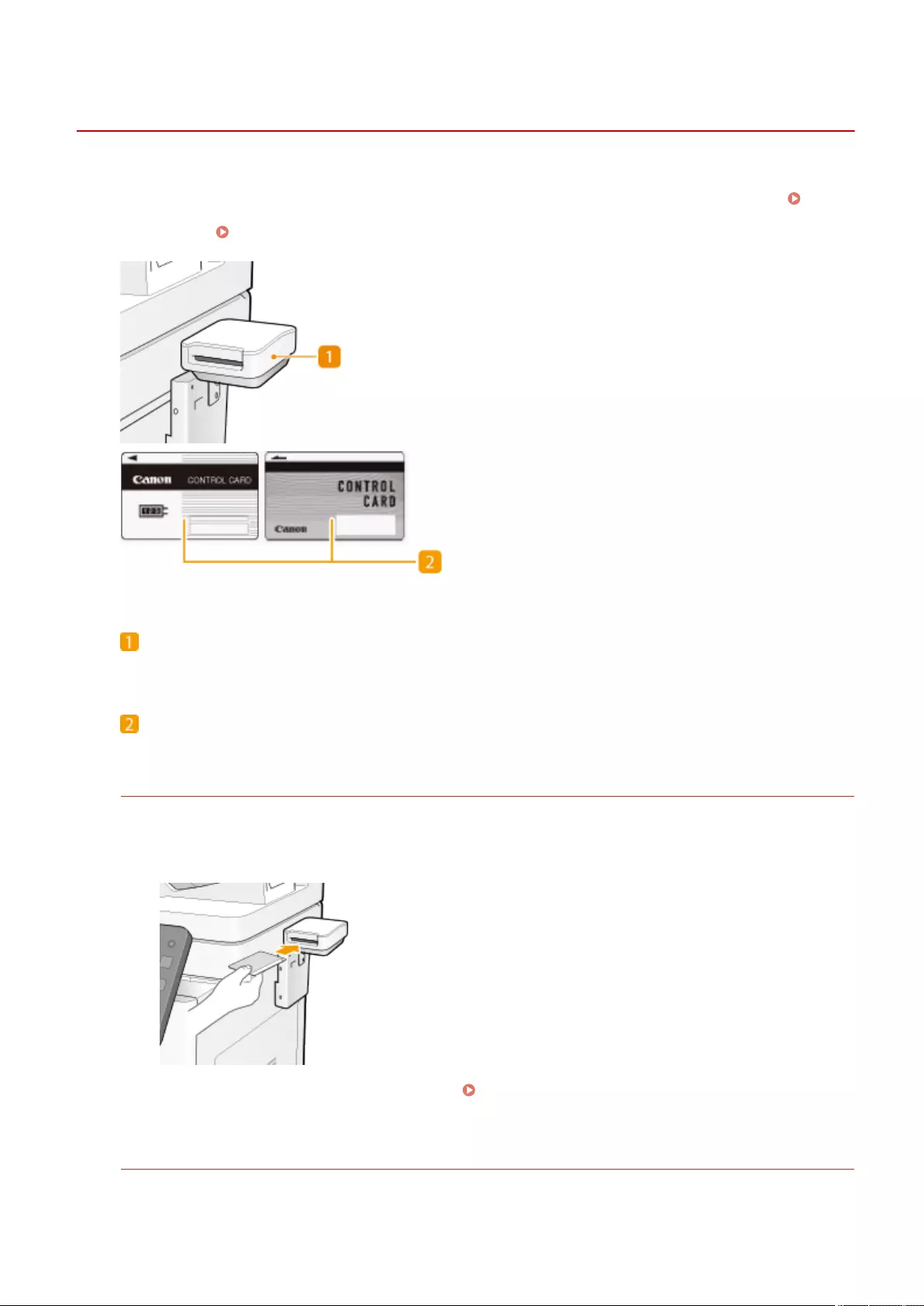
Copy Card Reader
72JY-0L6
If you install the "Copy Card Reader" to the machine, you can perform Department ID Management using the control
card. Users are required to authenticate themselves before starting an operation such as copying or faxing (
Conguring the Department ID Management Settings(P. 525) ). For the maximum registerable number of
Department IDs, see Management Functions(P. 1091) .
Card slot
Insert a control card.
Control card
Control cards used with the "Copy Card Reader."
Inserting a card
1Conrm that the screen to insert a control card is displayed.
2Conrm the direction of the control card and insert it into the card slot.
3Conrm that the <Home> screen is displayed. <Home> Screen(P. 119)
Removing the card
1Remove the control card from the card slot.
Appendix
1123
2Conrm that the screen to set a control card is displayed.
●If you set the Server Authentication user authentication system of User Authentication as the login service
(including when performing Server Authentication with the 'Server Authentication + Local Device
Authentication' user authentication system), you cannot use the Copy Card Reader. Managing
Users(P. 489)
●If the <Home> screen does not appear when the control card is inserted, check if the control card is inserted
in the correct direction and that the control card is not damaged or prohibited from use.
Appendix
1124

ADF Access Handle-A
72JY-0L7
This option helps you to close the feeder.
ADF access handle
Hook the edge of the handle to the tip of the feeder to gently close it.
Appendix
1125
Manuals and Their Contents
72JY-0L8
The manuals listed below are included with the machine. Refer to them as necessary.
Important Safety Instructions The content described in this manual is for the prevention of damage to
property and injury to users of the machine and others.
Setup Guide This manual outlines the initial settings on the machine required when
the machine is turned on for the rst time; and describes how to install
the software and driver.
Using the Setup Guide This manual describes the initial setup procedures required when the
machine is turned on for the rst time. If you view this manual with a
mobile device like a smartphone, you can perform the initial setup by
comparing the display on the machine and the screenshots on this
manual.
User's Guide (This Manual) This manual describes all the functions of the machine. You can browse
information by category or enter a keyword to search for pages on a
specic topic. Using User's Guide(P. 1127)
Setting the Machine (PS/PCL/UFR II
Printer)
This manual describes how to use the PS/PCL/UFR II printer.
ACCESS MANAGEMENT SYSTEM This manual describes how to use ACCESS MANAGEMENT SYSTEM.
V_201012
For the manuals with , access here .
Appendix
1126

Using User's Guide
72JY-0L9
The User's Guide is a manual that can be viewed on your computer or smartphone, etc. This section describes the
screen layout of the User's Guide and how to view the User's Guide. It also describes how to make settings for the
display of the User's Guide.
◼Screen Layout of User's Guide
This section explains the User's Guide screen layout and how to use the buttons on the screen. Screen Layout of
User's Guide(P. 1128)
◼Viewing User's Guide
This section describes what you should be familiar to when viewing the User's Guide, including the meanings of the
marks used in the User's Guide and how the keys on the control panel and the buttons on the computer screen are
represented in the User's Guide. Viewing User's Guide(P. 1132)
◼Setting the Display of the User's Guide
You can change the character size used in the User's Guide, and switch the screen layout to one that is appropriate to
the device on which the User's Guide is displayed.
●If you are unable to view the manual in PDF format, download Adobe Acrobat Reader from the Adobe
Systems website (https://get.adobe.com/reader/).
How to nd the topic you are looking for
Search the contents
●You can nd the page you are looking for by selecting the topic from the Contents on the left side of the
screen.
Search by keyword
●Perform a search by entering a keyword, such as "fax" or "wireless LAN," and the pages containing the
keyword are displayed. You can nd the page you are looking for from those results. You can also enter
phrases such as "connecting to a network." The keyword search also supports the AND Boolean to search for
multiple keywords. For the details of the search screen and how to operate the screen, see
Search(P. 1130) .
Appendix
1127
Screen Layout of User's Guide
72JY-0LA
The User's Guide is divided into different screens, and the content of each screen varies.
Top Page
Appears when the User's Guide starts.
/
Click to display all items underneath chapters. Click to return to the original list.
/
Click to switch between the table of contents and the search display. When the table of contents is displayed,
each click on switches between hiding and showing the display. When the search display is shown, each
click on switches between hiding and showing the display.
Appendix
1128
Click to specify settings such as text size, layout, and display method for the User's Guide.
Click to display information on how to view the User's Guide, how to perform a search, and other
information.
/
Click to display the previous or following topic.
[Notice]
Click to view important information you should know when using the machine.
Topic Page
Contains information about how to congure and use the machine.
Navigation
See what chapter topic you are currently viewing.
Click to go to the corresponding page. To return to the previous page, click "Back" on your Web browser.
●When you click the icon, the current page may go dark and a pop-up window may appear. To return to the
page, click [Close] in the pop-up window.
Appendix
1129
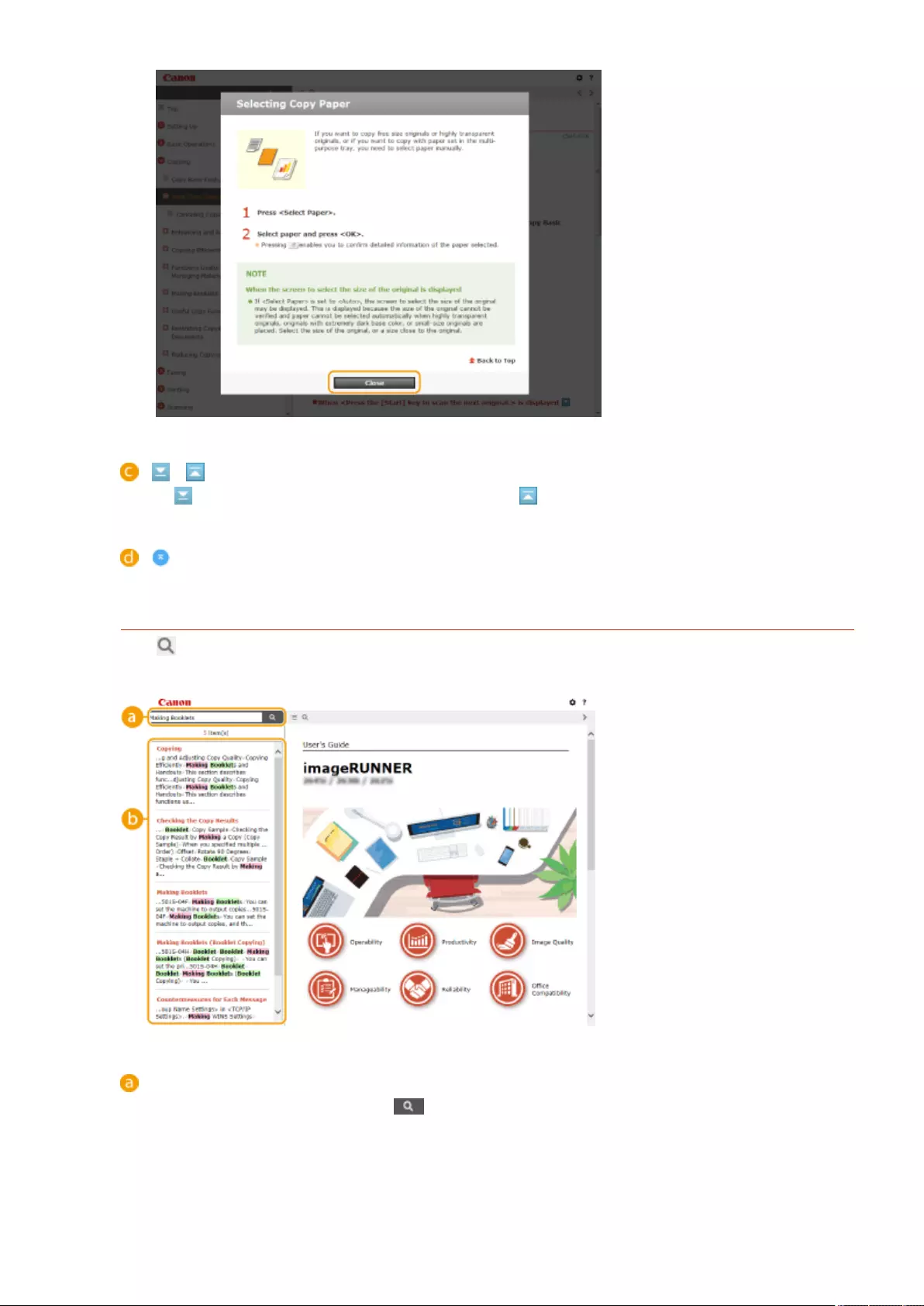
/
Click to display the hidden detailed descriptions. Click to close the detailed descriptions.
Click to return to the page top.
Search
Click to display the search screen. Contains a text box to perform a search by keyword and nd the page
you are looking for.
[Enter keyword(s) here]
Enter a keyword or keywords and click to display the search results. You can search for pages
containing all the keywords by separating the keywords by a space (blank). Also you can only search for
pages containing an exact phrase by enclosing the keywords in double quotation marks.
Appendix
1130

Search result
Displays the search results of the pages that contain the specied keywords. From the results, locate the
page you are looking for and click the topic title of the page.
●The keywords appear in bold in the pages displayed as search results.
Appendix
1131
Viewing User's Guide
72JY-0LC
This section describes the marks, buttons, screens, and other items used in the User's Guide. The warnings and
cautions are also given in the "Important Safety Instructions" included with the machine. See also these instructions.
Marks
Cautions regarding safety, restrictions and cautions regarding the handling of the machine, useful tips, and
other information are indicated using the marks below.
Indicates a warning concerning operations that may lead to death or serious
personal injury if not performed correctly. To ensure that you use the machine
safely, always observe these warnings.
Indicates a precaution for preventing the risk of personal injury or property
damage other than a product fault due to improper use of the machine. To
ensure that you use the machine safely, always observe these cautions.
Indicates an operation that must not be performed. Read these items
carefully, and make sure not to perform the described operations.
Indicates important operational requirements and restrictions that should
always be observed when using this machine. Always observe these
important items to avoid malfunctions, faults or property damage due to
improper machine operation.
Indicates a clarication of an operation, or contains additional explanations
for a procedure.
Indicates useful functions or tips for using the machine.
Keys and buttons
Keys on the control panel, buttons displayed on the touch panel display and buttons on the computer screen
are indicated as follows.
Type Example
Keys on the control panel
Buttons on the touch panel display*
<Function Settings>
<Cancel>
Buttons and other text interfaces displayed on the computer display [Preferences]
[OK]
* Operation to touch a button on the touch panel display is indicated as "Press" in the User's Guide.
Screen
Screens used in the User's Guide may differ from the screen display of your machine depending on the model,
optional equipment, and version.
Appendix
1132

●Depending on the OS you are using, a portion of the indicated screen content may differ from your
computer.
●The screen content for drivers and software may differ due to version upgrades.
Illustrations
Illustrations used in the User's Guide are from "imageRUNNER C1538iF" unless otherwise specically noted.
Appendix
1133

1
Third-Party Services
If you use third-party services through the PRODUCT, use of the services are subjected the conditions
below.
When you access and/or obtain some third party content (such as text, images, videos, audios, or
software) through the SOFTWARE, except as expressly permitted by the content owner or by
applicable law, you may not (a) scrape, build databases or otherwise create permanent copies of such
content, or keep cached copies longer than permitted by the cache header; (b) copy, translate, modify,
create a derivative work of, sell, lease, lend, convey, distribute, publicly display or sublicense to any
third party; (c) misrepresent the source or ownership; and (d) remove, obscure, or alter any copyright,
trademark or other proprietary rights notices, falsify or delete any author attributions, legal notices
or other labels of the origin or source of material.

2
The Software Subjected to Other License Conditions
Please refer to Contents of Software and respective License terms below, for more detail and
corresponding license conditions.
Contents of Software
Names of Software page
Adobe PostScript 3 .......................................................................................................................... 6
Adobe PDF Scan Library ................................................................................................................ 13
Bootstrap ...................................................................................................................................... 16
Crypto API ..................................................................................................................................... 17
expat ............................................................................................................................................ 18
flipsnap ........................................................................................................................................ 20
fontconfig ..................................................................................................................................... 21
freetype2 ...................................................................................................................................... 22
HarfBuzz ....................................................................................................................................... 27
HttpClient2.0 Alpha1 Release ........................................................................................................ 28
iw ................................................................................................................................................. 30
JAVA SE ......................................................................................................................................... 31
jQuery .......................................................................................................................................... 32
jQueryUI ....................................................................................................................................... 33
JSEncrypt....................................................................................................................................... 34
libcurl ........................................................................................................................................... 37
libjingle ........................................................................................................................................ 50
libjpeg .......................................................................................................................................... 51
libpcap ......................................................................................................................................... 52
libpng ........................................................................................................................................... 53
memcached .................................................................................................................................. 56
Net-SNMP ..................................................................................................................................... 57
OpenSSL ....................................................................................................................................... 65
OSGi Release 5 .............................................................................................................................. 77
pango (part of OpenTypeCode) ..................................................................................................... 83
pixman ......................................................................................................................................... 84
Protocol Buffers ............................................................................................................................ 86
servlet.jar ..................................................................................................................................... 87
SQLite ........................................................................................................................................... 91
Wi-Fi Test Suite ............................................................................................................................. 92
X Window System .......................................................................................................................... 93

3
XKCP ........................................................................................................................................... 184
xkeyboard-config ....................................................................................................................... 185
wpa_supplicant-2.6 .................................................................................................................... 191
4
This product partly contains the following Software.
(1) Please access <https://global.canon/en/oss/scd/index.html> to fill the request form so that you
receive an e-mail with the URL to download the source code; or
(2) Please send us a letter in writing with the following information, so that you receive the source
code via postal mail.
In case you have chosen this (2), WE MAY CHARGE YOU no more than the cost of performing this
distribution.
(i) Your Address (Country/Region, ZIP code, Address, Your name) [mandatory]
(ii) Your e-mail address (for the purpose of possible communication with us) [optional]
(iii) Name of the model that you purchased [mandatory].
(iv) Platform Version. Please see the <Check Device Configuration> display on the control panel.
[mandatory]
(v) Product ID number labeled on the back of the main unit. [mandatory]
- Addressee:
Open Source Promotion Division, Canon Inc.
30-2, Shimomaruko 3-chome, Ohta-ku,
Tokyo 146-8501, Japan
- Please see Privacy Notice at Canon Global <https://global.canon/>.
Please refer to Contents of Software and respective License terms below, for more detail and
corresponding license conditions
Contents of Software
Names of Software page
compat-wireless ......................................................................................................................... 193
fusermount ................................................................................................................................. 193
Linux .......................................................................................................................................... 193
WLAN USB Driver ......................................................................................................................... 193
atk .............................................................................................................................................. 201
cairo ........................................................................................................................................... 201
glib ............................................................................................................................................. 201
glibc ........................................................................................................................................... 201
GTK+ .......................................................................................................................................... 201
json-glib..................................................................................................................................... 201
libfuse ........................................................................................................................................ 201

5
Libnl ........................................................................................................................................... 201
libusb ......................................................................................................................................... 201
pango (except OpenTypeCode) ................................................................................................... 201
iproute ........................................................................................................................................ 210
Squid .......................................................................................................................................... 220
webkit ........................................................................................................................................ 266

6
Adobe PostScript 3
Copyright 2007-2008 Adobe Systems Incorporated and its licensors. All rights reserved.
Portions include software under the following terms:
______________________________________________________________________________________
This product contains either BSAFE and/or TIPEM software by RSA Security Inc.
______________________________________________________________________________________
Portions of Pool.c_Copyright 1987 - NeXT, Inc., and portions of Graphics.c_Copyright 1988 NeXT,
Inc. as an unpublished work. All Rights Reserved.
______________________________________________________________________________________
The Apache Software License, Version 1.1
This product includes software developed by the Apache Software Foundation
(http://www.apache.org/).
Portions Copyright (c) 1998-2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. The end-user documentation included with the redistribution, if any, must include the following
acknowledgment:
"This product includes software developed by the Apache Software Foundation
(http://www.apache.org/)."
Alternately, this acknowledgment may appear in the software itself, if and wherever such third-party
acknowledgments normally appear.
4. The names "Xerces" and "Apache Software Foundation" must not be used to endorse or promote
products derived from this software without prior written permission. For written permission, please
contact apache@apache.org.
5. Products derived from this software may not be called "Apache", nor may "Apache" appear in their
name, without prior written permission of the Apache Software Foundation.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING,

7
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION
OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the Apache
Software Foundation and was originally based on software copyright (c) 1999, International Business
Machines, Inc., http://www.ibm.com. For more information on the Apache Software Foundation,
please see <http://www.apache.org/>.
______________________________________________________________________________________
This product includes software developed by the University of California, Berkeley and its contributors.
Portions Copyright (c) 1990 The Regents of the University of California. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. All advertising materials mentioning features or use of this software must display the following
acknowledgement:
This product includes software developed by the University of California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may be used to endorse or
promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS

8
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
______________________________________________________________________________________
Portions Copyright (c) 1985, 1986 The Regents of the University of California. All rights reserved.
This code is derived from software contributed to Berkeley by James A. Woods, derived from original
work by Spencer Thomas and Joseph Orost.
Redistribution and use in source and binary forms are permitted provided that the above copyright
notice and this paragraph are duplicated in all such forms and that any documentation, advertising
materials, and other materials related to such distribution and use acknowledge that the software
was developed by the University of California, Berkeley. The name of the University may not be used
to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTIBILITY AND FITNESS
FOR A PARTICULAR PURPOSE.
Portions Copyright (c) 1993 X Consortium
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the "Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS ORIMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THEX CONSORTIUM BE LIABLE
FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER INAN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR INCONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall not be used in advertising or
otherwise to promote the sale, use or other dealings in this Software without prior written
authorization from the X Consortium.

9
______________________________________________________________________________________
NOTICE REGARDING SABLOTRON
March 27, 2003
Portions of this product are based on Modifications created from the Original Code known as the
"Sablotron XSLT Processor". The Sablotron XSLT Processor is subject to the Mozilla Public License
Version 1.1 (the "License"). You may obtain a copy of
the License at http://www.mozilla.org/MPL/
Software distributed under the License is distributed on an "AS IS" basis, WITHOUT WARRANTY OF
ANY KIND, either express or implied. See the License for the specific language governing rights and
limitations under the License.
The Original Code is the Sablotron XSLT Processor.
The Initial Developer of the Original Code is Ginger Alliance Ltd. Portions created by Ginger Alliance
are Copyright (C) 2000 Ginger Alliance Ltd. All Rights Reserved.
Pursuant to sections 3.2 and 3.6 of the License, the Modifications created by Adobe Systems
Incorporated are available as Source Code. The Modifications may be downloaded via the Internet
from:
http://partners.adobe.com/asn/tech/xml/sablotron/index.jsp
The Original Code may be downloaded via the Internet from:
https://sourceforge.net/projects/sablotron/
______________________________________________________________________________________
This product includes software developed by the University of California, Berkeley and its contributors.
Portions Copyright (c) 1982, 1986, 1987, 1988, 1989, 1990, 1991, 1992, 1993, 1994 The Regents
of the University of California. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions

10
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. All advertising materials mentioning features or use of this software must display the following
acknowledgement: This product includes software developed by the University of California,
Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may be used to endorse or
promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
______________________________________________________________________________________
Portions Copyright (c) 2001 by Andrei Alexandrescu. This code accompanies the book:
Alexandrescu, Andrei. "Modern C++ Design: Generic Programming and Design Patterns Applied".
Copyright (c) 2001. Addison-Wesley.
Permission to use, copy, modify, distribute and sell this software for any purpose is hereby granted
without fee, provided that the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation. The author or Addison-
Welsey Longman make no representations about the suitability of this software for any purpose. It is
provided "as is" without express or implied warranty.
______________________________________________________________________________________
Portions developed by the University of California, Berkeley.
______________________________________________________________________________________
Portions Copyright © 1991-2005 Unicode, Inc. All rights reserved. Distributed under the Terms of
Use in http://www.unicode.org/copyright.html.
Permission is hereby granted, free of charge, to any person obtaining a copy of the Unicode data files
and associated documentation (the "Data Files") or Unicode software and associated documentation
(the "Software") to deal in the Data Files or Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, and/or sell copies of the Data Files or
Software, and to permit persons to whom the Data Files or Software are furnished to do so, provided
that (a) the above copyright notice(s) and this permission notice appear in all copies of the Data Files

11
or Software, (b) both the above copyright notice(s) and this permission notice appear in associated
documentation, and (c) there is clear notice in each modified Data File or in the Software as well as
in the documentation associated with the Data File(s) or Software that the data or software has been
modified.
THE DATA FILES AND SOFTWARE ARE PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR
A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
COPYRIGHT HOLDER OR HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY
SPECIAL INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM
LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THE
DATA FILES OR SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising or
otherwise to promote the sale, use or other dealings in these Data Files or Software without prior
written authorization of the copyright holder.
Unicode and the Unicode logo are trademarks of Unicode, Inc., and may be registered in some
jurisdictions. All other trademarks and registered trademarks mentioned herein are the property of
their respective owners.
______________________________________________________________________________________
Adobe shall retain and reproduce, and require its Sublicensees to retain and reproduce JIM's following
copyright notice within each copy of the licensed programs in any form, in whole or in part: "© 1981,
1990 JMI Consultants, Inc. All rights reserved."
______________________________________________________________________________________
This product includes software developed by the University of California, Berkeley and its contributors.
Portions Copyright (c) 1990, 1993 The Regents of the University of California. All rights reserved.
This code is derived from software contributed to Berkeley by Chris Torek.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.

12
3. All advertising materials mentioning features or use of this software must display the following
acknowledgement:
This product includes software developed by the University of California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may be used to endorse or
promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
______________________________________________________________________________________
The Loki Library
Portions Copyright (c) 2001 by Andrei Alexandrescu // This code accompanies the book:
Alexandrescu, Andrei. "Modern C++ Design: Generic Programming and Design Patterns Applied".
Copyright (c) 2001. Addison-Wesley.
Permission to use, copy, modify, distribute and sell this software for any purpose is hereby granted
without fee, provided that the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation. The author or Addison-
Wesley Longman make no representations about the suitability of this software for any purpose. It is
provided "as is" without express or implied warranty.
______________________________________________________________________________________
Updated Information/Additional Third Party Code Information available at
http://www.adobe.com/go/thirdparty .
______________________________________________________________________________________

13
Adobe PDF Scan Library
Portions use software under the following terms:
______________________________________________________________________________________
This product contains either BSAFE and/or TIPEM software by RSA Security Inc.
______________________________________________________________________________________
This product includes software developed by the Apache Software Foundation
(http://www.apache.org/).
Copyright (c) 1998-2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. The end-user documentation included with the redistribution, if any, must include the following
acknowledgment:
"This product includes software developed by the Apache Software Foundation
(http://www.apache.org/)."
Alternately, this acknowledgment may appear in the software itself, if and wherever such third-party
acknowledgments normally appear.
4. The names "Xerces" and "Apache Software Foundation" must not be used to endorse or promote
products derived from this software without prior written permission. For written permission, please
contact apache@apache.org.
5. Products derived from this software may not be called "Apache", nor may "Apache" appear in their
name, without prior written permission of the Apache Software Foundation.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION
OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT

14
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the Apache
Software Foundation and was originally based on software copyright (c) 1999, International Business
Machines, Inc., http://www.ibm.com. For more information on the Apache Software Foundation,
please see <http://www.apache.org/>.
______________________________________________________________________________________
March 27, 2003
Portions of this product are based on Modifications created from the Original Code known as the
"Sablotron XSLT Processor". The Sablotron XSLT Processor is subject to the Mozilla Public License
Version 1.1 (the "License"). You may obtain a copy of
the License at http://www.mozilla.org/MPL/
Software distributed under the License is distributed on an "AS IS" basis, WITHOUT WARRANTY OF
ANY KIND, either express or implied. See the License for the specific language governing rights and
limitations under the License.
The Original Code is the Sablotron XSLT Processor.
The Initial Developer of the Original Code is Ginger Alliance Ltd. Portions created by Ginger Alliance
are Copyright (C) 2000 Ginger Alliance Ltd. All Rights Reserved.
Pursuant to sections 3.2 and 3.6 of the License, the Modifications created by Adobe Systems
Incorporated are available as Source Code. The Modifications may be downloaded via the Internet
from:
http://partners.adobe.com/asn/tech/xml/sablotron/index.jsp
The Original Code may be downloaded via the Internet from:
https://sourceforge.net/projects/sablotron/
______________________________________________________________________________________
Portions Copyright (c) 1997-1999 Silicon Graphics Computer Systems, Inc.
Permission to use, copy, modify, distribute and sell this software and its documentation for any
purpose is hereby granted without fee, provided that the above copyright notice appear in all copies

15
and that both that copyright notice and this permission notice appear in supporting documentation.
Silicon Graphics makes no representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
______________________________________________________________________________________
The Loki Library
Portions Copyright (c) 2001 by Andrei Alexandrescu . This code accompanies the book:
Alexandrescu, Andrei. "Modern C++ Design: Generic Programming and Design Patterns Applied".
Portions Copyright (c) 2001. Addison-Wesley. Permission to use, copy, modify, distribute and sell
this software for any purpose is hereby granted without fee, provided that the above copyright notice
appear in all copies and that both that copyright notice and this permission notice appear in
supporting documentation. The author or Addison-Wesley Longman make no representations about
the suitability of this software for any purpose. It is provided "as is" without express or implied
warranty.
______________________________________________________________________________________
Updated Information/Additional Third Party Code Information available at
http://www.adobe.com/go/thirdparty .
______________________________________________________________________________________

16
Bootstrap
The MIT License (MIT)
Copyright (c) 2011-2014 Twitter, Inc
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.

17
Crypto API
COPYRIGHT INFORMATION
Copyright (c) 2000 The Legion Of The Bouncy Castle (http://www.bouncycastle.org)
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the "Software"), to deal in the Software without restriction,
including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

18
expat
Copyright (c) 1998, 1999, 2000 Thai Open Source Software Center Ltd
and Clark Cooper
Copyright (c) 2001, 2002, 2003, 2004, 2005, 2006 Expat maintainers.
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the "Software"), to deal in the Software without restriction,
including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright (c) 1998, 1999, 2000 Thai Open Source Software Center Ltd
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the "Software"), to deal in the Software without restriction,
including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF

19
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

20
flipsnap
The MIT License (MIT)
Copyright(c) 2011 PixelGrid, Inc.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

21
fontconfig
Copyright © 2001,2003 Keith Packard
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Keith Packard not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Keith Packard makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
KEITH PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KEITH PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.

22
freetype2
The FreeType Project LICENSE
----------------------------
2006-Jan-27
Copyright 1996-2002, 2006 by
David Turner, Robert Wilhelm, and Werner Lemberg
Introduction
============
The FreeType Project is distributed in several archive packages;
some of them may contain, in addition to the FreeType font engine,
various tools and contributions which rely on, or relate to, the
FreeType Project.
This license applies to all files found in such packages, and
which do not fall under their own explicit license. The license
affects thus the FreeType font engine, the test programs,
documentation and makefiles, at the very least.
This license was inspired by the BSD, Artistic, and IJG
(Independent JPEG Group) licenses, which all encourage inclusion
and use of free software in commercial and freeware products
alike. As a consequence, its main points are that:
o We don't promise that this software works. However, we will be
interested in any kind of bug reports. (`as is' distribution)
o You can use this software for whatever you want, in parts or
full form, without having to pay us. (`royalty-free' usage)
o You may not pretend that you wrote this software. If you use

23
it, or only parts of it, in a program, you must acknowledge
somewhere in your documentation that you have used the
FreeType code. (`credits')
We specifically permit and encourage the inclusion of this
software, with or without modifications, in commercial products.
We disclaim all warranties covering The FreeType Project and
assume no liability related to The FreeType Project.
Finally, many people asked us for a preferred form for a
credit/disclaimer to use in compliance with this license. We thus
encourage you to use the following text:
"""
Portions of this software are copyright © <year> The FreeType
Project (www.freetype.org). All rights reserved.
"""
Please replace <year> with the value from the FreeType version you
actually use.
Legal Terms
===========
0. Definitions
--------------
Throughout this license, the terms `package', `FreeType Project',
and `FreeType archive' refer to the set of files originally
distributed by the authors (David Turner, Robert Wilhelm, and
Werner Lemberg) as the `FreeType Project', be they named as alpha,
beta or final release.
`You' refers to the licensee, or person using the project, where
`using' is a generic term including compiling the project's source
code as well as linking it to form a `program' or `executable'.

24
This program is referred to as `a program using the FreeType
engine'.
This license applies to all files distributed in the original
FreeType Project, including all source code, binaries and
documentation, unless otherwise stated in the file in its
original, unmodified form as distributed in the original archive.
If you are unsure whether or not a particular file is covered by
this license, you must contact us to verify this.
The FreeType Project is copyright (C) 1996-2000 by David Turner,
Robert Wilhelm, and Werner Lemberg. All rights reserved except as
specified below.
1. No Warranty
--------------
THE FREETYPE PROJECT IS PROVIDED `AS IS' WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO,
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. IN NO EVENT WILL ANY OF THE AUTHORS OR COPYRIGHT HOLDERS
BE LIABLE FOR ANY DAMAGES CAUSED BY THE USE OR THE INABILITY TO
USE, OF THE FREETYPE PROJECT.
2. Redistribution
-----------------
This license grants a worldwide, royalty-free, perpetual and
irrevocable right and license to use, execute, perform, compile,
display, copy, create derivative works of, distribute and
sublicense the FreeType Project (in both source and object code
forms) and derivative works thereof for any purpose; and to
authorize others to exercise some or all of the rights granted
herein, subject to the following conditions:
o Redistribution of source code must retain this license file
(`FTL.TXT') unaltered; any additions, deletions or changes to
the original files must be clearly indicated in accompanying

25
documentation. The copyright notices of the unaltered,
original files must be preserved in all copies of source
files.
o Redistribution in binary form must provide a disclaimer that
states that the software is based in part of the work of the
FreeType Team, in the distribution documentation. We also
encourage you to put an URL to the FreeType web page in your
documentation, though this isn't mandatory.
These conditions apply to any software derived from or based on
the FreeType Project, not just the unmodified files. If you use
our work, you must acknowledge us. However, no fee need be paid
to us.
3. Advertising
--------------
Neither the FreeType authors and contributors nor you shall use
the name of the other for commercial, advertising, or promotional
purposes without specific prior written permission.
We suggest, but do not require, that you use one or more of the
following phrases to refer to this software in your documentation
or advertising materials: `FreeType Project', `FreeType Engine',
`FreeType library', or `FreeType Distribution'.
As you have not signed this license, you are not required to
accept it. However, as the FreeType Project is copyrighted
material, only this license, or another one contracted with the
authors, grants you the right to use, distribute, and modify it.
Therefore, by using, distributing, or modifying the FreeType
Project, you indicate that you understand and accept all the terms
of this license.
4. Contacts
-----------

26
There are two mailing lists related to FreeType:
o freetype@nongnu.org
Discusses general use and applications of FreeType, as well as
future and wanted additions to the library and distribution.
If you are looking for support, start in this list if you
haven't found anything to help you in the documentation.
o freetype-devel@nongnu.org
Discusses bugs, as well as engine internals, design issues,
specific licenses, porting, etc.
Our home page can be found at
http://www.freetype.org
--- end of FTL.TXT ---

27
HarfBuzz
Copyright (C) 2006 Behdad Esfahbod
Copyright (C) 1998-2004 David Turner and Werner Lemberg
Copyright (C) 2008 Nokia Corporation and/or its subsidiary(-ies)
Copyright (C) 2004,2007 Red Hat, Inc.
Permission is hereby granted, without written agreement and without license or royalty fees, to use,
copy, modify, and distribute this software and its documentation for any purpose, provided that the
above copyright notice and the following two paragraphs appear in all copies of this software.
IN NO EVENT SHALL THE COPYRIGHT HOLDER BE LIABLE TO ANY PARTY FOR DIRECT, INDIRECT,
SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OF THIS SOFTWARE
AND ITS DOCUMENTATION, EVEN IF THE COPYRIGHT HOLDER HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
THE COPYRIGHT HOLDER SPECIFICALLY DISCLAIMS ANY WARRANTIES, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE SOFTWARE PROVIDED HEREUNDER IS ON AN "AS IS" BASIS, AND THE COPYRIGHT HOLDER HAS
NO OBLIGATION TO PROVIDE MAINTENANCE, SUPPORT, UPDATES, ENHANCEMENTS, OR
MODIFICATIONS.

28
HttpClient2.0 Alpha1 Release
This product includes software developed by the Apache Software Foundation
(http://www.apache.org/) and is subject to the following terms and conditions.
Copyright (c) 2001 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification,
are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this
list of conditions and the following disclaimer in the documentation and/or other
materials provided with the distribution.
3. The end-user documentation included with the redistribution, if any, must
include the following acknowledgement:
"This product includes software developed by the Apache Software Foundation
(http://www.apache.org/)."
Alternately, this acknowledgement may appear in the software itself, if and
wherever such third-party acknowledgements normally appear.
4. The names "The Jakarta Project", "Commons", "Xerces", "Crimson", "Velocity",
and "Apache Software Foundation" must not be used to endorse or promote
products derived from this software without prior written permission. For written
permission, please contact apache@apache.org.
5. Products derived from this software may not be called "Jakarta", "Commons",
"Xerces" "Crimson", "Velocity", or "Apache", nor may "Jakarta", "Commons",
"Xerces" "Crimson", "Velocity", or "Apache" appear in their names without prior
written permission of the Apache Group.

29
NO WARRANTY
THIS SOFTWARE IS PROVIDED "AS IS" AND ANY EXPRESSED OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE APACHE SOFTWARE FOUNDATION OR ITS CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on
behalf of the Apache Software Foundation. For more information on the Apache
Software Foundation, please see <http://www.apache.org/>.

30
iw
Copyright (c) 2007, 2008 Johannes Berg
Copyright (c) 2007 Andy Lutomirski
Copyright (c) 2007 Mike Kershaw
Copyright (c) 2008-2009 Luis R. Rodriguez
Permission to use, copy, modify, and/or distribute this software for any
purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR
ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.

31
JAVA SE
a. Java Technology Restrictions. You may not create, modify, or change the behavior of classes,
interfaces, of subpackages that are in any way identified as “Java”, “Javax”, “Sun” or similar
convention as specified by Oracle in any naming convention designation.
b. Trademarks and Logos. You shall acknowledge that Oracle owns the Java trademark and all
Java-related trademarks, logos and icons including the Coffee Cup and Duke (“Java Marks”) and
agree to: (a) comply with the Java Trademark Guidelines at
http://www.oracle.com/us/legal/trademarks/index.html; (b) not do anything harmful to or
inconsistent with Oracle’s rights in the Java Marks; and (c) assist Oracle in protecting those rights,
including assigning to Oracle any right acquired by You in any Java Mark.
c. Source Code. JAVA SE may contain source code that, unless expressly licensed for other
purposes, is provided solely for reference purpose pursuant to the terms applicable to JAVA SE.
d. Third Party Code. The additional copyright notices and license terms applicable to portions of
the JAVA SE are forth in the THIRDPARTYLICENSEREADME.txt file.
e. Commercial Features. Your use of the Commercial Features for any commercial or production
purpose requires a separate license from Oracle. “Commercial Features” means those features
identified in Table 1-1 (Commercial Features In Java SE Product Editions) of the Program
Documentation accessible at
http://www.oracle.com/technetwork/java/javase/documentation/index.html.

32
jQuery
Copyright (C) 2005, 2014 jQuery Foundation, Inc.
https://jquery.org/license/
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the "Software"), to deal in the Software without restriction,
including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

33
jQueryUI
Copyright (c) 2014 jQuery Foundation and other contributors
http://jqueryui.com/
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the "Software"), to deal in the Software without restriction,
including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

34
JSEncrypt
Copyright (c) 2008-2013 Lapo Luchini <lapo@lapo.it>
Permission to use, copy, modify, and/or distribute this software for any
purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR
ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
---------
* Copyright (c) 2003-2005 Tom Wu
* All Rights Reserved.
*
* Permission is hereby granted, free of charge, to any person obtaining
* a copy of this software and associated documentation files (the
* "Software"), to deal in the Software without restriction, including
* without limitation the rights to use, copy, modify, merge, publish,
* distribute, sublicense, and/or sell copies of the Software, and to
* permit persons to whom the Software is furnished to do so, subject to
* the following conditions:
*
* The above copyright notice and this permission notice shall be
* included in all copies or substantial portions of the Software.
*
* THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
* EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
* WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
*
* IN NO EVENT SHALL TOM WU BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
* INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES WHATSOEVER

35
* RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT ADVISED OF
* THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY, ARISING OUT
* OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
*
* In addition, the following condition applies:
*
* All redistributions must retain an intact copy of this copyright notice
* and disclaimer.
---------
CONTAINS CODE FROM YUI LIBRARY SEE LICENSE @ http://yuilibrary.com/license/
The 'jsrsasign'(RSA-Sign JavaScript Library) License
Copyright (c) 2010-2013 Kenji Urushima
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
---------
The MIT License (MIT)
Copyright (c) 2013 AllPlayers.com

36
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal in the
Software without restriction, including without limitation the rights to use,
copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the
Software, and to permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION
OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
---------
The MIT License (MIT)
Copyright(c) 2011 TJ Holowaychuk <tj@vision-media.ca>
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.

37
libcurl
COPYRIGHT AND PERMISSION NOTICE
Copyright (c) 1996 - 2019, Daniel Stenberg, daniel@haxx.se, and many contributors, see the
THANKS file.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2010, DirecTV, Contact: Eric Hu, <ehu@directv.com>.
Copyright (C) 2010 - 2018, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A

38
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2012 - 2016, Linus Nielsen Feltzing, <linus@haxx.se>
Copyright (C) 2012 - 2017, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2015 - 2017, Daniel Stenberg, <daniel@haxx.se>, et al.
Copyright (C) 2012 - 2014, Linus Nielsen Feltzing, <linus@haxx.se>
All rights reserved.

39
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2014 - 2017, Steve Holme, <steve_holme@hotmail.com>.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE

40
Copyright (C) 2012 - 2015, Daniel Stenberg, <daniel@haxx.se>, et al.
Copyright (C) 2010, Howard Chu, <hyc@highlandsun.com>
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2010, Howard Chu, <hyc@highlandsun.com>
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

41
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 1998 - 2016, Florin Petriuc, <petriuc.florin@gmail.com>
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2012 - 2017, Nick Zitzmann, <nickzman@gmail.com>.
Copyright (C) 2012 - 2018, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A

42
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2014 - 2016, Steve Holme, <steve_holme@hotmail.com>.
Copyright (C) 2015 - 2017, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2010 - 2011, Hoi-Ho Chan, <hoiho.chan@gmail.com>
Copyright (C) 2012 - 2018, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.

43
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2012 - 2018, Daniel Stenberg, <daniel@haxx.se>, et al.
Copyright (C) 2010 , 2011, Hoi-Ho Chan, <hoiho.chan@gmail.com>
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE

44
Copyright (C) 2010, Howard Chu, <hyc@openldap.org>
Copyright (C) 2011 - 2018, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2012 - 2016, Marc Hoersken, <info@marc-hoersken.de>
Copyright (C) 2012, Mark Salisbury, <mark.salisbury@hp.com>
Copyright (C) 2012 - 2018, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,

45
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2012, Marc Hoersken, <info@marc-hoersken.de>, et al.
Copyright (C) 2012 - 2017, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2014, Bill Nagel <wnagel@tycoint.com>, Exacq Technologies
Copyright (C) 2016-2018, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.

46
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE
Copyright (C) 2009, Markus Moeller, <markus_moeller@compuserve.com>
Copyright (C) 2012 - 2017, Daniel Stenberg, <daniel@haxx.se>, et al.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
COPYRIGHT AND PERMISSION NOTICE

47
Copyright (C) 2012 - 2017, Daniel Stenberg, <daniel@haxx.se>, et al.
Copyright (C) 2009, 2011, Markus Moeller, <markus_moeller@compuserve.com>
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not be used in advertising
or otherwise to promote the sale, use or other dealings in this Software without prior written
authorization of the copyright holder.
* Copyright (C) 2017 - 2018 Red Hat, Inc.
*
* Authors: Nikos Mavrogiannopoulos, Tomas Mraz, Stanislav Zidek,
* Robert Kolcun, Andreas Schneider
*
* This software is licensed as described in the file COPYING, which
* you should have received as part of this distribution. The terms
* are also available at https://curl.haxx.se/docs/copyright.html.
*
* You may opt to use, copy, modify, merge, publish, distribute and/or sell
* copies of the Software, and permit persons to whom the Software is
* furnished to do so, under the terms of the COPYING file.
*
* This software is distributed on an "AS IS" basis, WITHOUT WARRANTY OF ANY
* KIND, either express or implied.
# Copyright (C) 1994 X Consortium

48
#
# Permission is hereby granted, free of charge, to any person obtaining a copy
# of this software and associated documentation files (the "Software"), to
# deal in the Software without restriction, including without limitation the
# rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
# sell copies of the Software, and to permit persons to whom the Software is
# furnished to do so, subject to the following conditions:
#
# The above copyright notice and this permission notice shall be included in
# all copies or substantial portions of the Software.
#
# THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
# IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
# FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
# X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
# AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNEC-
# TION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. +
#
# Except as contained in this notice, the name of the X Consortium shall not
# be used in advertising or otherwise to promote the sale, use or other deal-
# ings in this Software without prior written authorization from the X Consor-
# tium.
* Copyright (C) 1996-2001 Internet Software Consortium.
*
* Permission to use, copy, modify, and distribute this software for any
* purpose with or without fee is hereby granted, provided that the above
* copyright notice and this permission notice appear in all copies.
*
* THE SOFTWARE IS PROVIDED "AS IS" AND INTERNET SOFTWARE CONSORTIUM
* DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE INCLUDING ALL
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL
* INTERNET SOFTWARE CONSORTIUM BE LIABLE FOR ANY SPECIAL, DIRECT,
* INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING
* FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
* NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION
* WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.

49
* Copyright (c) 1995, 1996, 1997, 1998, 1999, 2017 Kungliga Tekniska Högskolan
* (Royal Institute of Technology, Stockholm, Sweden).
* Copyright (c) 2001 - 2017 Daniel Stenberg
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* 3. Neither the name of the Institute nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE INSTITUTE AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE INSTITUTE OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE. */

50
libjingle
Copyright 2004--2007, Google Inc.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. The name of the author may not be used to endorse or promote products derived from this
software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF
USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.

51
libjpeg
"this software is based in part on the work of the Independent JPEG Group.".

52
libpcap
License: BSD
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. The names of the authors may not be used to endorse or promote products derived from this
software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

53
libpng
* If you modify libpng you may insert additional notices immediately following
* this sentence.
*
* libpng version 1.2.6, August 15, 2004, is
* Copyright (c) 2004 Glenn Randers-Pehrson, and is
* distributed according to the same disclaimer and license as libpng-1.2.5
* with the following individual added to the list of Contributing Authors
* Cosmin Truta
*
* libpng versions 1.0.7, July 1, 2000, through 1.2.5, October 3, 2002, are
* Copyright (c) 2000-2002 Glenn Randers-Pehrson, and are
* distributed according to the same disclaimer and license as libpng-1.0.6
* with the following individuals added to the list of Contributing Authors
*
* Simon-Pierre Cadieux
* Eric S. Raymond
* Gilles Vollant
*
* and with the following additions to the disclaimer:
*
* There is no warranty against interference with your enjoyment of the
* library or against infringement. There is no warranty that our
* efforts or the library will fulfill any of your particular purposes
* or needs. This library is provided with all faults, and the entire
* risk of satisfactory quality, performance, accuracy, and effort is with
* the user.
*
* libpng versions 0.97, January 1998, through 1.0.6, March 20, 2000, are
* Copyright (c) 1998, 1999, 2000 Glenn Randers-Pehrson
* Distributed according to the same disclaimer and license as libpng-0.96,
* with the following individuals added to the list of Contributing Authors:
*
* Tom Lane
* Glenn Randers-Pehrson

54
* Willem van Schaik
*
* libpng versions 0.89, June 1996, through 0.96, May 1997, are
* Copyright (c) 1996, 1997 Andreas Dilger
* Distributed according to the same disclaimer and license as libpng-0.88,
* with the following individuals added to the list of Contributing Authors:
*
* John Bowler
* Kevin Bracey
* Sam Bushell
* Magnus Holmgren
* Greg Roelofs
* Tom Tanner
*
* libpng versions 0.5, May 1995, through 0.88, January 1996, are
* Copyright (c) 1995, 1996 Guy Eric Schalnat, Group 42, Inc.
*
* For the purposes of this copyright and license, "Contributing Authors"
* is defined as the following set of individuals:
*
* Andreas Dilger
* Dave Martindale
* Guy Eric Schalnat
* Paul Schmidt
* Tim Wegner
*
* The PNG Reference Library is supplied "AS IS". The Contributing Authors
* and Group 42, Inc. disclaim all warranties, expressed or implied,
* including, without limitation, the warranties of merchantability and of
* fitness for any purpose. The Contributing Authors and Group 42, Inc.
* assume no liability for direct, indirect, incidental, special, exemplary,
* or consequential damages, which may result from the use of the PNG
* Reference Library, even if advised of the possibility of such damage.
*
* Permission is hereby granted to use, copy, modify, and distribute this
* source code, or portions hereof, for any purpose, without fee, subject
* to the following restrictions:
*

55
* 1. The origin of this source code must not be misrepresented.
*
* 2. Altered versions must be plainly marked as such and
* must not be misrepresented as being the original source.
*
* 3. This Copyright notice may not be removed or altered from
* any source or altered source distribution.
*
* The Contributing Authors and Group 42, Inc. specifically permit, without
* fee, and encourage the use of this source code as a component to
* supporting the PNG file format in commercial products. If you use this
* source code in a product, acknowledgment is not required but would be
* appreciated.

56
memcached
Copyright (c) 2003, Danga Interactive, Inc.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above
copyright notice, this list of conditions and the following disclaimer
in the documentation and/or other materials provided with the
distribution.
* Neither the name of the Danga Interactive nor the names of its
contributors may be used to endorse or promote products derived from
this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
"AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

57
Net-SNMP
Various copyrights apply to this package, listed in various separate
parts below. Please make sure that you read all the parts.
---- Part 1: CMU/UCD copyright notice: (BSD like) -----
Copyright 1989, 1991, 1992 by Carnegie Mellon University
Derivative Work - 1996, 1998-2000
Copyright 1996, 1998-2000 The Regents of the University of California
All Rights Reserved
Permission to use, copy, modify and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appears in all copies and
that both that copyright notice and this permission notice appear in
supporting documentation, and that the name of CMU and The Regents of
the University of California not be used in advertising or publicity
pertaining to distribution of the software without specific written
permission.
CMU AND THE REGENTS OF THE UNIVERSITY OF CALIFORNIA DISCLAIM ALL
WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL CMU OR
THE REGENTS OF THE UNIVERSITY OF CALIFORNIA BE LIABLE FOR ANY SPECIAL,
INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING
FROM THE LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
---- Part 2: Networks Associates Technology, Inc copyright notice (BSD) -----
Copyright (c) 2001-2003, Networks Associates Technology, Inc

58
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of the Networks Associates Technology, Inc nor the
names of its contributors may be used to endorse or promote
products derived from this software without specific prior written
permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS
IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 3: Cambridge Broadband Ltd. copyright notice (BSD) -----
Portions of this code are copyright (c) 2001-2003, Cambridge Broadband Ltd.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,

59
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* The name of Cambridge Broadband Ltd. may not be used to endorse or
promote products derived from this software without specific prior
written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS'' AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN
IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 4: Sun Microsystems, Inc. copyright notice (BSD) -----
Copyright © 2003 Sun Microsystems, Inc., 4150 Network Circle, Santa Clara,
California 95054, U.S.A. All rights reserved.
Use is subject to license terms below.
This distribution may include materials developed by third parties.
Sun, Sun Microsystems, the Sun logo and Solaris are trademarks or registered
trademarks of Sun Microsystems, Inc. in the U.S. and other countries.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:

60
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of the Sun Microsystems, Inc. nor the
names of its contributors may be used to endorse or promote
products derived from this software without specific prior written
permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS
IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 5: Sparta, Inc copyright notice (BSD) -----
Copyright (c) 2003-2012, Sparta, Inc
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.

61
* Neither the name of Sparta, Inc nor the names of its contributors may
be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS
IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 6: Cisco/BUPTNIC copyright notice (BSD) -----
Copyright (c) 2004, Cisco, Inc and Information Network
Center of Beijing University of Posts and Telecommunications.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of Cisco, Inc, Beijing University of Posts and
Telecommunications, nor the names of their contributors may
be used to endorse or promote products derived from this software
without specific prior written permission.

62
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS
IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 7: Fabasoft R&D Software GmbH & Co KG copyright notice (BSD) -----
Copyright (c) Fabasoft R&D Software GmbH & Co KG, 2003
oss@fabasoft.com
Author: Bernhard Penz <bernhard.penz@fabasoft.com>
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* The name of Fabasoft R&D Software GmbH & Co KG or any of its subsidiaries,
brand or product names may not be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS'' AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF

63
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN
IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 8: Apple Inc. copyright notice (BSD) -----
Copyright (c) 2007 Apple Inc. All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above
copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided
with the distribution.
3. Neither the name of Apple Inc. ("Apple") nor the names of its
contributors may be used to endorse or promote products derived
from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF
USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT
OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
SUCH DAMAGE.
---- Part 9: ScienceLogic, LLC copyright notice (BSD) -----

64
Copyright (c) 2009, ScienceLogic, LLC
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of ScienceLogic, LLC nor the names of its
contributors may be used to endorse or promote products derived
from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
HOLDERS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING,
BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS
OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.

65
OpenSSL
OpenSSL License
---------------
/*
=============================================================
=======
* Copyright (c) 1998-2011 The OpenSSL Project. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
*
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
*
* 4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
*
* 5. Products derived from this software may not be called "OpenSSL"
* nor may "OpenSSL" appear in their names without prior written
* permission of the OpenSSL Project.
*
* 6. Redistributions of any form whatsoever must retain the following

66
* acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)"
*
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
*
=============================================================
=======
*
* This product includes cryptographic software written by Eric Young
* (eay@cryptsoft.com). This product includes software written by Tim
* Hudson (tjh@cryptsoft.com).
*
*/
Original SSLeay License
-----------------------
/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
*
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions

67
* apply to all code found in this distribution, be it the RC4, RSA,
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
*
* Copyright remains Eric Young's, and as such any Copyright notices in
* the code are not to be removed.
* If this package is used in a product, Eric Young should be given attribution
* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* "This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)"
* The word 'cryptographic' can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specific code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT

68
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence
* [including the GNU Public Licence.]
*/
/*
* Copyright (c) 2002 Bob Beck <beck@openbsd.org>
* Copyright (c) 2002 Theo de Raadt
* Copyright (c) 2002 Markus Friedl
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*
*/
/*

69
* Copyright (c) 2004, Richard Levitte <richard@levitte.org>
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*/
/* Copyright (c) 2014, Google Inc.
*
* Permission to use, copy, modify, and/or distribute this software for any
* purpose with or without fee is hereby granted, provided that the above
* copyright notice and this permission notice appear in all copies.
*
* THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
* WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
* MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY
* SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
* WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION
* OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
* CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.

70
*/
OpenSSL License
---------------
/*
=============================================================
=======
* Copyright (c) 1998-2018 The OpenSSL Project. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
*
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
*
* 4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
*
* 5. Products derived from this software may not be called "OpenSSL"
* nor may "OpenSSL" appear in their names without prior written
* permission of the OpenSSL Project.
*
* 6. Redistributions of any form whatsoever must retain the following
* acknowledgment:

71
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)"
*
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
*
=============================================================
=======
*
* This product includes cryptographic software written by Eric Young
* (eay@cryptsoft.com). This product includes software written by Tim
* Hudson (tjh@cryptsoft.com).
*
*/
Original SSLeay License
-----------------------
/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
*
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions
* apply to all code found in this distribution, be it the RC4, RSA,

72
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
*
* Copyright remains Eric Young's, and as such any Copyright notices in
* the code are not to be removed.
* If this package is used in a product, Eric Young should be given attribution
* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* "This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)"
* The word 'cryptographic' can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specific code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY

73
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence
* [including the GNU Public Licence.]
*/
=============================================================
=======
* Copyright (c) 1998-2008 The OpenSSL Project. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
*
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
*
* 4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
*
* 5. Products derived from this software may not be called "OpenSSL"
* nor may "OpenSSL" appear in their names without prior written
* permission of the OpenSSL Project.

74
*
* 6. Redistributions of any form whatsoever must retain the following
* acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)"
*
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
*
=============================================================
=======
/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
*
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions
* apply to all code found in this distribution, be it the RC4, RSA,
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
*
* Copyright remains Eric Young's, and as such any Copyright notices in
* the code are not to be removed.

75
* If this package is used in a product, Eric Young should be given attribution
* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* "This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)"
* The word 'cryptographic' can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specific code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence

76
* [including the GNU Public Licence.]
*/

77
OSGi Release 5
Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1. Definitions.
"License" shall mean the terms and conditions for use, reproduction,
and distribution as defined by Sections 1 through 9 of this document.
"Licensor" shall mean the copyright owner or entity authorized by
the copyright owner that is granting the License.
"Legal Entity" shall mean the union of the acting entity and all
other entities that control, are controlled by, or are under common
control with that entity. For the purposes of this definition,
"control" means (i) the power, direct or indirect, to cause the
direction or management of such entity, whether by contract or
otherwise, or (ii) ownership of fifty percent (50%) or more of the
outstanding shares, or (iii) beneficial ownership of such entity.
"You" (or "Your") shall mean an individual or Legal Entity
exercising permissions granted by this License.
"Source" form shall mean the preferred form for making modifications,
including but not limited to software source code, documentation
source, and configuration files.
"Object" form shall mean any form resulting from mechanical
transformation or translation of a Source form, including but
not limited to compiled object code, generated documentation,
and conversions to other media types.
"Work" shall mean the work of authorship, whether in Source or

78
Object form, made available under the License, as indicated by a
copyright notice that is included in or attached to the work
(an example is provided in the Appendix below).
"Derivative Works" shall mean any work, whether in Source or Object
form, that is based on (or derived from) the Work and for which the
editorial revisions, annotations, elaborations, or other modifications
represent, as a whole, an original work of authorship. For the purposes
of this License, Derivative Works shall not include works that remain
separable from, or merely link (or bind by name) to the interfaces of,
the Work and Derivative Works thereof.
"Contribution" shall mean any work of authorship, including
the original version of the Work and any modifications or additions
to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner
or by an individual or Legal Entity authorized to submit on behalf of
the copyright owner. For the purposes of this definition, "submitted"
means any form of electronic, verbal, or written communication sent
to the Licensor or its representatives, including but not limited to
communication on electronic mailing lists, source code control systems,
and issue tracking systems that are managed by, or on behalf of, the
Licensor for the purpose of discussing and improving the Work, but
excluding communication that is conspicuously marked or otherwise
designated in writing by the copyright owner as "Not a Contribution."
"Contributor" shall mean Licensor and any individual or Legal Entity
on behalf of whom a Contribution has been received by Licensor and
subsequently incorporated within the Work.
2. Grant of Copyright License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
copyright license to reproduce, prepare Derivative Works of,
publicly display, publicly perform, sublicense, and distribute the
Work and such Derivative Works in Source or Object form.
3. Grant of Patent License. Subject to the terms and conditions of

79
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
(except as stated in this section) patent license to make, have made,
use, offer to sell, sell, import, and otherwise transfer the Work,
where such license applies only to those patent claims licensable
by such Contributor that are necessarily infringed by their
Contribution(s) alone or by combination of their Contribution(s)
with the Work to which such Contribution(s) was submitted. If You
institute patent litigation against any entity (including a
cross-claim or counterclaim in a lawsuit) alleging that the Work
or a Contribution incorporated within the Work constitutes direct
or contributory patent infringement, then any patent licenses
granted to You under this License for that Work shall terminate
as of the date such litigation is filed.
4. Redistribution. You may reproduce and distribute copies of the
Work or Derivative Works thereof in any medium, with or without
modifications, and in Source or Object form, provided that You
meet the following conditions:
(a) You must give any other recipients of the Work or
Derivative Works a copy of this License; and
(b) You must cause any modified files to carry prominent notices
stating that You changed the files; and
(c) You must retain, in the Source form of any Derivative Works
that You distribute, all copyright, patent, trademark, and
attribution notices from the Source form of the Work,
excluding those notices that do not pertain to any part of
the Derivative Works; and
(d) If the Work includes a "NOTICE" text file as part of its
distribution, then any Derivative Works that You distribute must
include a readable copy of the attribution notices contained
within such NOTICE file, excluding those notices that do not
pertain to any part of the Derivative Works, in at least one
of the following places: within a NOTICE text file distributed

80
as part of the Derivative Works; within the Source form or
documentation, if provided along with the Derivative Works; or,
within a display generated by the Derivative Works, if and
wherever such third-party notices normally appear. The contents
of the NOTICE file are for informational purposes only and
do not modify the License. You may add Your own attribution
notices within Derivative Works that You distribute, alongside
or as an addendum to the NOTICE text from the Work, provided
that such additional attribution notices cannot be construed
as modifying the License.
You may add Your own copyright statement to Your modifications and
may provide additional or different license terms and conditions
for use, reproduction, or distribution of Your modifications, or
for any such Derivative Works as a whole, provided Your use,
reproduction, and distribution of the Work otherwise complies with
the conditions stated in this License.
5. Submission of Contributions. Unless You explicitly state otherwise,
any Contribution intentionally submitted for inclusion in the Work
by You to the Licensor shall be under the terms and conditions of
this License, without any additional terms or conditions.
Notwithstanding the above, nothing herein shall supersede or modify
the terms of any separate license agreement you may have executed
with Licensor regarding such Contributions.
6. Trademarks. This License does not grant permission to use the trade
names, trademarks, service marks, or product names of the Licensor,
except as required for reasonable and customary use in describing the
origin of the Work and reproducing the content of the NOTICE file.
7. Disclaimer of Warranty. Unless required by applicable law or
agreed to in writing, Licensor provides the Work (and each
Contributor provides its Contributions) on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
implied, including, without limitation, any warranties or conditions
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
PARTICULAR PURPOSE. You are solely responsible for determining the

81
appropriateness of using or redistributing the Work and assume any
risks associated with Your exercise of permissions under this License.
8. Limitation of Liability. In no event and under no legal theory,
whether in tort (including negligence), contract, or otherwise,
unless required by applicable law (such as deliberate and grossly
negligent acts) or agreed to in writing, shall any Contributor be
liable to You for damages, including any direct, indirect, special,
incidental, or consequential damages of any character arising as a
result of this License or out of the use or inability to use the
Work (including but not limited to damages for loss of goodwill,
work stoppage, computer failure or malfunction, or any and all
other commercial damages or losses), even if such Contributor
has been advised of the possibility of such damages.
9. Accepting Warranty or Additional Liability. While redistributing
the Work or Derivative Works thereof, You may choose to offer,
and charge a fee for, acceptance of support, warranty, indemnity,
or other liability obligations and/or rights consistent with this
License. However, in accepting such obligations, You may act only
on Your own behalf and on Your sole responsibility, not on behalf
of any other Contributor, and only if You agree to indemnify,
defend, and hold each Contributor harmless for any liability
incurred by, or claims asserted against, such Contributor by reason
of your accepting any such warranty or additional liability.
END OF TERMS AND CONDITIONS
APPENDIX: How to apply the Apache License to your work.
To apply the Apache License to your work, attach the following
boilerplate notice, with the fields enclosed by brackets "[]"
replaced with your own identifying information. (Don't include
the brackets!) The text should be enclosed in the appropriate
comment syntax for the file format. We also recommend that a
file or class name and description of purpose be included on the
same "printed page" as the copyright notice for easier
identification within third-party archives.

82
Copyright [yyyy] [name of copyright owner]
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.

83
pango (part of OpenTypeCode)
Copyright (C) 2009 Red Hat, Inc.
Copyright (C) 1998-2004 David Turner and Werner Lemberg
Copyright (C) 2004,2007 Red Hat, Inc.
Copyright (C) 2004,2007,2009 Red Hat, Inc.
Copyright (C) 2007,2008,2009 Red Hat, Inc.
Copyright (C) 2007 Chris Wilson
Permission is hereby granted, without written agreement and without
license or royalty fees, to use, copy, modify, and distribute this
software and its documentation for any purpose, provided that the
above copyright notice and the following two paragraphs appear in
all copies of this software.
IN NO EVENT SHALL THE COPYRIGHT HOLDER BE LIABLE TO ANY PARTY FOR
DIRECT, INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES
ARISING OUT OF THE USE OF THIS SOFTWARE AND ITS DOCUMENTATION, EVEN
IF THE COPYRIGHT HOLDER HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
THE COPYRIGHT HOLDER SPECIFICALLY DISCLAIMS ANY WARRANTIES, INCLUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE. THE SOFTWARE PROVIDED HEREUNDER IS
ON AN "AS IS" BASIS, AND THE COPYRIGHT HOLDER HAS NO OBLIGATION TO
PROVIDE MAINTENANCE, SUPPORT, UPDATES, ENHANCEMENTS, OR MODIFICATIONS.

84
pixman
The following is the 'standard copyright' agreed upon by most contributors,
and is currently the canonical license, though a modification is currently
under discussion. Copyright holders of new code should use this license
statement where possible, and append their name to this list.
Copyright 1987, 1988, 1989, 1998 The Open Group
Copyright 1987, 1988, 1989 Digital Equipment Corporation
Copyright 1999, 2004, 2008 Keith Packard
Copyright 2000 SuSE, Inc.
Copyright 2000 Keith Packard, member of The XFree86 Project, Inc.
Copyright 2004, 2005, 2007, 2008 Red Hat, Inc.
Copyright 2004 Nicholas Miell
Copyright 2005 Lars Knoll & Zack Rusin, Trolltech
Copyright 2005 Trolltech AS
Copyright 2007 Luca Barbato
Copyright 2008 Aaron Plattner, NVIDIA Corporation
Copyright 2008 Rodrigo Kumpera
Copyright 2008 André Tupinambá
Copyright 2008 Mozilla Corporation
Copyright 2008 Frederic Plourde
Copyright 2009 Sun Microsystems, Inc.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,

85
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.

86
Protocol Buffers
Copyright 2008, Google Inc.
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions
and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of
conditions and the following disclaimer in the documentation and/or other materials provided with
the distribution.
* Neither the name of Google Inc. nor the names of its contributors may be used to endorse or
promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
Code generated by the Protocol Buffer compiler is owned by the owner of the input file used when
generating it. This code is not standalone and requires a support library to be linked with it. This
support library is itself covered by the above license.

87
servlet.jar
Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1. Definitions.
"License" shall mean the terms and conditions for use, reproduction, and distribution as defined by
Sections 1 through 9 of this document.
"Licensor" shall mean the copyright owner or entity authorized by the copyright owner that is
granting the License.
"Legal Entity" shall mean the union of the acting entity and all other entities that control, are
controlled by, or are under common control with that entity. For the purposes of this definition,
"control" means (i) the power, direct or indirect, to cause the direction or management of such
entity, whether by contract or otherwise, or (ii) ownership of fifty percent (50%) or more of the
outstanding shares, or (iii) beneficial ownership of such entity.
"You" (or "Your") shall mean an individual or Legal Entity exercising permissions granted by this
License.
"Source" form shall mean the preferred form for making modifications, including but not limited to
software source code, documentation source, and configuration files.
"Object" form shall mean any form resulting from mechanical transformation or translation of a
Source form, including but not limited to compiled object code, generated documentation, and
conversions to other media types.
"Work" shall mean the work of authorship, whether in Source or Object form, made available under
the License, as indicated by a copyright notice that is included in or attached to the work (an
example is provided in the Appendix below).
"Derivative Works" shall mean any work, whether in Source or Object form, that is based on (or
derived from) the Work and for which the editorial revisions, annotations, elaborations, or other
modifications represent, as a whole, an original work of authorship. For the purposes of this
License, Derivative Works shall not include works that remain separable from, or merely link (or
bind by name) to the interfaces of, the Work and Derivative Works thereof.
"Contribution" shall mean any work of authorship, including the original version of the Work and
any modifications or additions to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner or by an individual or Legal
Entity authorized to submit on behalf of the copyright owner. For the purposes of this definition,
"submitted" means any form of electronic, verbal, or written communication sent to the Licensor or
its representatives, including but not limited to communication on electronic mailing lists, source

88
code control systems, and issue tracking systems that are managed by, or on behalf of, the
Licensor for the purpose of discussing and improving the Work, but excluding communication that
is conspicuously marked or otherwise designated in writing by the copyright owner as "Not a
Contribution."
"Contributor" shall mean Licensor and any individual or Legal Entity on behalf of whom a
Contribution has been received by Licensor and subsequently incorporated within the Work.
2. Grant of Copyright License.
Subject to the terms and conditions of this License, each Contributor hereby grants to You a
perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable copyright license to
reproduce, prepare Derivative Works of, publicly display, publicly perform, sublicense, and
distribute the Work and such Derivative Works in Source or Object form.
3. Grant of Patent License.
Subject to the terms and conditions of this License, each Contributor hereby grants to You a
perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable (except as stated in this
section) patent license to make, have made, use, offer to sell, sell, import, and otherwise transfer
the Work, where such license applies only to those patent claims licensable by such Contributor
that are necessarily infringed by their Contribution(s) alone or by combination of their
Contribution(s) with the Work to which such Contribution(s) was submitted. If You institute patent
litigation against any entity (including a cross-claim or counterclaim in a lawsuit) alleging that the
Work or a Contribution incorporated within the Work constitutes direct or contributory patent
infringement, then any patent licenses granted to You under this License for that Work shall
terminate as of the date such litigation is filed.
4. Redistribution.
You may reproduce and distribute copies of the Work or Derivative Works thereof in any medium,
with or without modifications, and in Source or Object form, provided that You meet the following
conditions:
You must give any other recipients of the Work or Derivative Works a copy of this License; and
You must cause any modified files to carry prominent notices stating that You changed the files;
and
You must retain, in the Source form of any Derivative Works that You distribute, all copyright,
patent, trademark, and attribution notices from the Source form of the Work, excluding those
notices that do not pertain to any part of the Derivative Works; and
If the Work includes a "NOTICE" text file as part of its distribution, then any Derivative Works that
You distribute must include a readable copy of the attribution notices contained within such
NOTICE file, excluding those notices that do not pertain to any part of the Derivative Works, in at
least one of the following places: within a NOTICE text file distributed as part of the Derivative
Works; within the Source form or documentation, if provided along with the Derivative Works; or,
within a display generated by the Derivative Works, if and wherever such third-party notices

89
normally appear. The contents of the NOTICE file are for informational purposes only and do not
modify the License. You may add Your own attribution notices within Derivative Works that You
distribute, alongside or as an addendum to the NOTICE text from the Work, provided that such
additional attribution notices cannot be construed as modifying the License.
You may add Your own copyright statement to Your modifications and may provide additional or
different license terms and conditions for use, reproduction, or distribution of Your modifications,
or for any such Derivative Works as a whole, provided Your use, reproduction, and distribution of
the Work otherwise complies with the conditions stated in this License.
5. Submission of Contributions.
Unless You explicitly state otherwise, any Contribution intentionally submitted for inclusion in the
Work by You to the Licensor shall be under the terms and conditions of this License, without any
additional terms or conditions. Notwithstanding the above, nothing herein shall supersede or
modify the terms of any separate license agreement you may have executed with Licensor regarding
such Contributions.
6. Trademarks.
This License does not grant permission to use the trade names, trademarks, service marks, or
product names of the Licensor, except as required for reasonable and customary use in describing
the origin of the Work and reproducing the content of the NOTICE file.
7. Disclaimer of Warranty.
Unless required by applicable law or agreed to in writing, Licensor provides the Work (and each
Contributor provides its Contributions) on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS
OF ANY KIND, either express or implied, including, without limitation, any warranties or conditions
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. You
are solely responsible for determining the appropriateness of using or redistributing the Work and
assume any risks associated with Your exercise of permissions under this License.
8. Limitation of Liability.
In no event and under no legal theory, whether in tort (including negligence), contract, or
otherwise, unless required by applicable law (such as deliberate and grossly negligent acts) or
agreed to in writing, shall any Contributor be liable to You for damages, including any direct,
indirect, special, incidental, or consequential damages of any character arising as a result of this
License or out of the use or inability to use the Work (including but not limited to damages for loss
of goodwill, work stoppage, computer failure or malfunction, or any and all other commercial
damages or losses), even if such Contributor has been advised of the possibility of such damages.
9. Accepting Warranty or Additional Liability.
While redistributing the Work or Derivative Works thereof, You may choose to offer, and charge a
fee for, acceptance of support, warranty, indemnity, or other liability obligations and/or rights
consistent with this License. However, in accepting such obligations, You may act only on Your own
behalf and on Your sole responsibility, not on behalf of any other Contributor, and only if You agree

90
to indemnify, defend, and hold each Contributor harmless for any liability incurred by, or claims
asserted against, such Contributor by reason of your accepting any such warranty or additional
liability.
END OF TERMS AND CONDITIONS
APPENDIX: How to apply the Apache License to your work
To apply the Apache License to your work, attach the following boilerplate notice, with the fields
enclosed by brackets "[]" replaced with your own identifying information. (Don't include the
brackets!) The text should be enclosed in the appropriate comment syntax for the file format. We
also recommend that a file or class name and description of purpose be included on the same
"printed page" as the copyright notice for easier identification within third-party archives.
Copyright [yyyy] [name of copyright owner]
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.

91
SQLite
SQLite Copyright
All of the code and documentation in SQLite has been dedicated to the public domain by the
authors. All code authors, and representatives of the companies they work for, have signed
affidavits dedicating their contributions to the public domain and originals of those signed
affidavits are stored in a firesafe at the main offices of Hwaci. Anyone is free to copy, modify,
publish, use, compile, sell, or distribute the original SQLite code, either in source code form or as a
compiled binary, for any purpose, commercial or non-commercial, and by any means.
The previous paragraph applies to the deliverable code and documentation in SQLite - those parts
of the SQLite library that you actually bundle and ship with a larger application. Some scripts used
as part of the build process (for example the "configure" scripts generated by autoconf) might fall
under other open-source licenses. Nothing from these build scripts ever reaches the final
deliverable SQLite library, however, and so the licenses associated with those scripts should not be
a factor in assessing your rights to copy and use the SQLite library.
All of the deliverable code in SQLite has been written from scratch. No code has been taken from
other projects or from the open internet. Every line of code can be traced back to its original
author, and all of those authors have public domain dedications on file. So the SQLite code base is
clean and is uncontaminated with licensed code from other projects.

92
Wi-Fi Test Suite
The ISC License
Copyright (c) 2015 Wi-Fi Alliance
Permission to use, copy, modify, and/or distribute this software for any purpose with or without fee
is hereby granted, provided that the above copyright notice and this permission notice appear in all
copies.
THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY
SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.

93
X Window System
Copyright 1984 - 1996, 1998, 2002 The Open Group
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of The Open Group shall not be
used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from The Open Group.
Copyright (c) 1991, 2002, 2004 - 2009 Oracle and/or its affiliates. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.

94
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright © 1999 - 2001, 2003, 2004, 2008 Keith Packard
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Keith Packard not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Keith Packard makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
KEITH PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KEITH PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright © 2001,2003 Keith Packard
Copyright © 2007 Eric Anholt
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Keith Packard not be used in

95
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Keith Packard makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
KEITH PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KEITH PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright © 2007, 2009 Red Hat, Inc.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Soft-
ware"), to deal in the Software without restriction, including without
limitation the rights to use, copy, modify, merge, publish, distribute,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, provided that the above copyright
notice(s) and this permission notice appear in all copies of the Soft-
ware and that both the above copyright notice(s) and this permission
notice appear in supporting documentation.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABIL-
ITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY
RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS INCLUDED IN
THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL INDIRECT OR CONSE-
QUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFOR-
MANCE OF THIS SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall
not be used in advertising or otherwise to promote the sale, use or

96
other dealings in this Software without prior written authorization of
the copyright holder.
Copyright 1990, 1991 Network Computing Devices;
Portions Copyright 1987 by Digital Equipment Corporation
Permission to use, copy, modify, distribute, and sell this software and
its documentation for any purpose is hereby granted without fee, provided
that the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Network Computing Devices or Digital
not be used in advertising or publicity pertaining to distribution
of the software without specific, written prior permission.
Network Computing Devices and Digital make no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
NETWORK COMPUTING DEVICES AND DIGITAL DISCLAIM ALL WARRANTIES WITH
REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL NETWORK COMPUTING DEVICES
OR DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR
PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS
ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF
THIS SOFTWARE.
Copyright 1987 – 1991, 1993, 1996,1997 by Digital Equipment Corporation, Maynard,
Massachusetts.
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of Digital not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.

97
DIGITAL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright (c) 1997, 1999 - 2003 The XFree86 Project Inc.
All Rights Reserved.
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of The XFree86 Project
Inc. shall not be used in advertising or otherwise to promote the
sale, use or other dealings in this Software without prior written
authorization from The XFree86 Project Inc..
Copyright (C) 1991-2000 Silicon Graphics, Inc. All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:

98
The above copyright notice including the dates of first publication and
either this permission notice or a reference to
http://oss.sgi.com/projects/FreeB/
shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
SILICON GRAPHICS, INC. BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of Silicon Graphics, Inc.
shall not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization from
Silicon Graphics, Inc.
Copyright 1984 – 1989, 1994, 1995 by Hewlett-Packard Company
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of Hewlett-Packard not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
HEWLETT-PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
HEWLETT-PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.

99
Except as contained in this notice, the name of the Hewlett-Packard
Company shall not be used in advertising or otherwise to promote the
sale, use or other dealings in this Software without prior written
authorization from the Hewlett-Packard Company.
Copyright (c) 1993 - 1997 by Silicon Graphics Computer Systems, Inc.
Permission to use, copy, modify, and distribute this
software and its documentation for any purpose and without
fee is hereby granted, provided that the above copyright
notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting
documentation, and that the name of Silicon Graphics not be
used in advertising or publicity pertaining to distribution
of the software without specific prior written permission.
Silicon Graphics makes no representation about the suitability
of this software for any purpose. It is provided "as is"
without any express or implied warranty.
SILICON GRAPHICS DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. IN NO EVENT SHALL SILICON
GRAPHICS BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH
THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1998-2001 by Juliusz Chroboczek
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:

100
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
(C) Copyright IBM Corporation 2006, 2007
(C) Copyright Eric Anholt 2006
Copyright 2007, 2008, 2009 Sun Microsystems, Inc.
Copyright 2009 Red Hat, Inc.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to
deal in the Software without restriction, including without limitation on
the rights to use, copy, modify, merge, publish, distribute, sub license,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT. IN NO EVENT SHALL
IBM AND/OR THEIR SUPPLIERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS
IN THE SOFTWARE.

101
Copyright (c) 2008 Juan Romero Pardines
Copyright (c) 2008 Mark Kettenis
Permission to use, copy, modify, and distribute this software for any
purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR
ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (C) 2003-2006,2008 Jamey Sharp, Josh Triplett
Copyright © 2009 Red Hat, Inc.
Copyright 1990-1992,1999,2000,2004,2009,2010 Oracle and/or its affiliates.
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING

102
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright 1985, 1986, 1987, 1988, 1989, 1990, 1991, 1994, 1996 X Consortium
Copyright 2000 The XFree86 Project, Inc.
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization
from the X Consortium.
Copyright 1985 - 1991 by Digital Equipment Corporation
Portions Copyright 1990, 1991 by Tektronix, Inc.
Permission to use, copy, modify and distribute this documentation for
any purpose and without fee is hereby granted, provided that the above
copyright notice appears in all copies and that both that copyright notice

103
and this permission notice appear in all copies, and that the names of
Digital and Tektronix not be used in in advertising or publicity pertaining
to this documentation without specific, written prior permission.
Digital and Tektronix makes no representations about the suitability
of this documentation for any purpose.
It is provided ``as is'' without express or implied warranty.
Copyright (c) 1999 - 2000 Free Software Foundation, Inc.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
FREE SOFTWARE FOUNDATION BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR
IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the Free Software Foundation
shall not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization from the
Free Software Foundation.
(c) Copyright 1990 1991 Tektronix, Inc.
All Rights Reserved
This file is a component of an X Window System-specific implementation
of Xcms based on the TekColor Color Management System. TekColor is a

104
trademark of Tektronix, Inc. The term "TekHVC" designates a particular
color space that is the subject of U.S. Patent No. 4,985,853 (equivalent
foreign patents pending). Permission is hereby granted to use, copy,
modify, sell, and otherwise distribute this software and its
documentation for any purpose and without fee, provided that:
1. This copyright, permission, and disclaimer notice is reproduced in
all copies of this software and any modification thereof and in
supporting documentation;
2. Any color-handling application which displays TekHVC color
cooordinates identifies these as TekHVC color coordinates in any
interface that displays these coordinates and in any associated
documentation;
3. The term "TekHVC" is always used, and is only used, in association
with the mathematical derivations of the TekHVC Color Space,
including those provided in this file and any equivalent pathways and
mathematical derivations, regardless of digital (e.g., floating point
or integer) representation.
Tektronix makes no representation about the suitability of this software
for any purpose. It is provided "as is" and with all faults.
TEKTRONIX DISCLAIMS ALL WARRANTIES APPLICABLE TO THIS SOFTWARE,
INCLUDING THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE. IN NO EVENT SHALL TEKTRONIX BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA, OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE, OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR THE PERFORMANCE OF THIS SOFTWARE.
Copyright 1992 by Oki Technosystems Laboratory, Inc.
Copyright 1992 by Fuji Xerox Co., Ltd.
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear

105
in supporting documentation, and that the name of Oki Technosystems
Laboratory and Fuji Xerox not be used in advertising or publicity
pertaining to distribution of the software without specific, written
prior permission.
Oki Technosystems Laboratory and Fuji Xerox make no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
OKI TECHNOSYSTEMS LABORATORY AND FUJI XEROX DISCLAIM ALL WARRANTIES
WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL OKI TECHNOSYSTEMS
LABORATORY AND FUJI XEROX BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE
OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1990 - 1994 by FUJITSU LIMITED
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of FUJITSU LIMITED
not be used in advertising or publicity pertaining to distribution
of the software without specific, written prior permission.
FUJITSU LIMITED makes no representations about the suitability of
this software for any purpose.
It is provided "as is" without express or implied warranty.
FUJITSU LIMITED DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL FUJITSU LIMITED BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.

106
Copyright (c) 1995 David E. Wexelblat. All rights reserved
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL DAVID E. WEXELBLAT BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of David E. Wexelblat shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization
from David E. Wexelblat.
Copyright 1990, 1991 by OMRON Corporation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name OMRON not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. OMRON makes no representations

107
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
OMRON DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL OMRON BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTUOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1985, 1986, 1987, 1988, 1989, 1990, 1991 by
Digital Equipment Corporation
Portions Copyright 1990, 1991 by Tektronix, Inc
Rewritten for X.org by Chris Lee <clee@freedesktop.org>
Permission to use, copy, modify, distribute, and sell this documentation
for any purpose and without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
Chris Lee makes no representations about the suitability for any purpose
of the information in this document. It is provided ¥`¥`as-is'' without
express or implied warranty.
Copyright 1993 by Digital Equipment Corporation, Maynard, Massachusetts,
Copyright 1994 by FUJITSU LIMITED
Copyright 1994 by Sony Corporation
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the names of Digital, FUJITSU
LIMITED and Sony Corporation not be used in advertising or publicity

108
pertaining to distribution of the software without specific, written
prior permission.
DIGITAL, FUJITSU LIMITED AND SONY CORPORATION DISCLAIMS ALL WARRANTIES
WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL DIGITAL, FUJITSU LIMITED
AND SONY CORPORATION BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1991 by the Open Software Foundation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Open Software Foundation
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. Open Software
Foundation makes no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
OPEN SOFTWARE FOUNDATION DISCLAIMS ALL WARRANTIES WITH REGARD TO
THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL OPEN SOFTWARE FOUNDATIONN BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1990, 1991, 1992, 1993, 1994 by FUJITSU LIMITED
Copyright 1993, 1994 by Sony Corporation

109
Permission to use, copy, modify, distribute, and sell this software and
its documentation for any purpose is hereby granted without fee, provided
that the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of FUJITSU LIMITED and Sony Corporation
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. FUJITSU LIMITED and
Sony Corporation makes no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
FUJITSU LIMITED AND SONY CORPORATION DISCLAIMS ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL FUJITSU LIMITED OR SONY CORPORATION BE LIABLE
FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE
USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1991, 1992, 1993, 1994 by FUJITSU LIMITED
Copyright 1993 by Digital Equipment Corporation
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of FUJITSU LIMITED and
Digital Equipment Corporation not be used in advertising or publicity
pertaining to distribution of the software without specific, written
prior permission. FUJITSU LIMITED and Digital Equipment Corporation
makes no representations about the suitability of this software for
any purpose. It is provided "as is" without express or implied
warranty.
FUJITSU LIMITED AND DIGITAL EQUIPMENT CORPORATION DISCLAIM ALL
WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL

110
FUJITSU LIMITED AND DIGITAL EQUIPMENT CORPORATION BE LIABLE FOR
ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER
IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF
THIS SOFTWARE.
Copyright 1992, 1993 by FUJITSU LIMITED
Copyright 1993 by Fujitsu Open Systems Solutions, Inc.
Copyright 1994 by Sony Corporation
Permission to use, copy, modify, distribute and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of FUJITSU LIMITED,
Fujitsu Open Systems Solutions, Inc. and Sony Corporation not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
FUJITSU LIMITED, Fujitsu Open Systems Solutions, Inc. and
Sony Corporation make no representations about the suitability of
this software for any purpose. It is provided "as is" without
express or implied warranty.
FUJITSU LIMITED, FUJITSU OPEN SYSTEMS SOLUTIONS, INC. AND SONY
CORPORATION DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS,
IN NO EVENT SHALL FUJITSU OPEN SYSTEMS SOLUTIONS, INC., FUJITSU LIMITED
AND SONY CORPORATION BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE
OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1993 by SunSoft, Inc.
Copyright 1999-2000 by Bruno Haible

111
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the names of SunSoft, Inc. and
Bruno Haible not be used in advertising or publicity pertaining to
distribution of the software without specific, written prior
permission. SunSoft, Inc. and Bruno Haible make no representations
about the suitability of this software for any purpose. It is
provided "as is" without express or implied warranty.
SunSoft Inc. AND Bruno Haible DISCLAIM ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL SunSoft, Inc. OR Bruno Haible BE LIABLE
FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT
OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1991 by the Open Software Foundation
Copyright 1993 by the TOSHIBA Corp.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Open Software Foundation and TOSHIBA
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. Open Software
Foundation and TOSHIBA make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
OPEN SOFTWARE FOUNDATION AND TOSHIBA DISCLAIM ALL WARRANTIES WITH REGARD TO
THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL OPEN SOFTWARE FOUNDATIONN OR TOSHIBA BE

112
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1988 by Wyse Technology, Inc., San Jose, Ca.,
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name Wyse not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
WYSE DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright 1991 by the Open Software Foundation
Copyright 1993, 1994 by the Sony Corporation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Open Software Foundation and
Sony Corporation not be used in advertising or publicity pertaining to
distribution of the software without specific, written prior permission.
Open Software Foundation and Sony Corporation make no
representations about the suitability of this software for any purpose.

113
It is provided "as is" without express or implied warranty.
OPEN SOFTWARE FOUNDATION AND SONY CORPORATION DISCLAIM ALL
WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL OPEN
SOFTWARE FOUNDATIONN OR SONY CORPORATION BE LIABLE FOR ANY SPECIAL,
INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM
LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1992, 1993 by FUJITSU LIMITED
Copyright 1993 by Fujitsu Open Systems Solutions, Inc.
Permission to use, copy, modify, distribute and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of FUJITSU LIMITED and
Fujitsu Open Systems Solutions, Inc. not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission.
FUJITSU LIMITED and Fujitsu Open Systems Solutions, Inc. makes no
representations about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
FUJITSU LIMITED AND FUJITSU OPEN SYSTEMS SOLUTIONS, INC. DISCLAIMS ALL
WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL FUJITSU OPEN SYSTEMS
SOLUTIONS, INC. AND FUJITSU LIMITED BE LIABLE FOR ANY SPECIAL, INDIRECT
OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE
OF THIS SOFTWARE.
Copyright 1993, 1994 by Sony Corporation

114
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of Sony Corporation
not be used in advertising or publicity pertaining to distribution
of the software without specific, written prior permission.
Sony Corporation makes no representations about the suitability of
this software for any purpose. It is provided "as is" without
express or implied warranty.
SONY CORPORATION DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL SONY CORPORATION BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1986, 1998 The Open Group
Copyright (c) 2000 The XFree86 Project, Inc.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
X CONSORTIUM OR THE XFREE86 PROJECT BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,

115
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of the X Consortium or of the
XFree86 Project shall not be used in advertising or otherwise to promote the
sale, use or other dealings in this Software without prior written
authorization from the X Consortium and the XFree86 Project.
Copyright 1990, 1991 by OMRON Corporation, NTT Software Corporation,
and Nippon Telegraph and Telephone Corporation
Copyright 1991 by the Open Software Foundation
Copyright 1993 by the FUJITSU LIMITED
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of OMRON, NTT Software, NTT, and
Open Software Foundation not be used in advertising or publicity
pertaining to distribution of the software without specific,
written prior permission. OMRON, NTT Software, NTT, and Open Software
Foundation make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
OMRON, NTT SOFTWARE, NTT, AND OPEN SOFTWARE FOUNDATION
DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT
SHALL OMRON, NTT SOFTWARE, NTT, OR OPEN SOFTWARE FOUNDATION BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1988 by Wyse Technology, Inc., San Jose, Ca,
Copyright 1987 by Digital Equipment Corporation, Maynard, Massachusetts,

116
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name Digital not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
DIGITAL AND WYSE DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL DIGITAL OR WYSE BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1991, 1992 by Fuji Xerox Co., Ltd.
Copyright 1992, 1993, 1994 by FUJITSU LIMITED
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of Fuji Xerox,
FUJITSU LIMITED not be used in advertising or publicity pertaining
to distribution of the software without specific, written prior
permission. Fuji Xerox, FUJITSU LIMITED make no representations
about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
FUJI XEROX, FUJITSU LIMITED DISCLAIM ALL WARRANTIES WITH
REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL FUJI XEROX,
FUJITSU LIMITED BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL

117
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 2006 Josh Triplett
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
(c) Copyright 1996 by Sebastien Marineau and Holger Veit
<marineau@genie.uottawa.ca>
<Holger.Veit@gmd.de>
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:

118
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
HOLGER VEIT BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of Sebastien Marineau or Holger Veit
shall not be used in advertising or otherwise to promote the sale, use or other
dealings in this Software without prior written authorization from Holger Veit or
Sebastien Marineau.
Copyright 1990, 1991 by OMRON Corporation, NTT Software Corporation,
and Nippon Telegraph and Telephone Corporation
Copyright 1991 by the Open Software Foundation
Copyright 1993 by the TOSHIBA Corp.
Copyright 1993, 1994 by Sony Corporation
Copyright 1993, 1994 by the FUJITSU LIMITED
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of OMRON, NTT Software, NTT, Open
Software Foundation, and Sony Corporation not be used in advertising
or publicity pertaining to distribution of the software without specific,
written prior permission. OMRON, NTT Software, NTT, Open Software
Foundation, and Sony Corporation make no representations about the
suitability of this software for any purpose. It is provided "as is"
without express or implied warranty.
OMRON, NTT SOFTWARE, NTT, OPEN SOFTWARE FOUNDATION, AND SONY

119
CORPORATION DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT
SHALL OMRON, NTT SOFTWARE, NTT, OPEN SOFTWARE FOUNDATION, OR SONY
CORPORATION BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER
IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT
OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 2000 by Bruno Haible
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of Bruno Haible not
be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. Bruno Haible
makes no representations about the suitability of this software for
any purpose. It is provided "as is" without express or implied
warranty.
Bruno Haible DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN
NO EVENT SHALL Bruno Haible BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE
OR PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 2007-2009, Troy D. Hanson
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright

120
notice, this list of conditions and the following disclaimer.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS
IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER
OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
Copyright 1992, 1993 by TOSHIBA Corp.
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted, provided
that the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of TOSHIBA not be used in advertising
or publicity pertaining to distribution of the software without specific,
written prior permission. TOSHIBA make no representations about the
suitability of this software for any purpose. It is provided "as is"
without express or implied warranty.
TOSHIBA DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
TOSHIBA BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright IBM Corporation 1993

121
All Rights Reserved
License to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of IBM not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
IBM DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS, AND
NONINFRINGEMENT OF THIRD PARTY RIGHTS, IN NO EVENT SHALL
IBM BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright 1990, 1991 by OMRON Corporation, NTT Software Corporation,
and Nippon Telegraph and Telephone Corporation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of OMRON, NTT Software, and NTT
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. OMRON, NTT Software,
and NTT make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
OMRON, NTT SOFTWARE, AND NTT, DISCLAIM ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL OMRON, NTT SOFTWARE, OR NTT, BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES

122
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (C) 2001-2006 Bart Massey, Jamey Sharp, and Josh Triplett.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person
obtaining a copy of this software and associated
documentation files (the "Software"), to deal in the
Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute,
sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice shall
be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY
KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE
WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR
PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS
BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the names of the authors
or their institutions shall not be used in advertising or
otherwise to promote the sale, use or other dealings in this
Software without prior written authorization from the
authors.
Copyright 1988 – 1990, 1992, 1994, 1995 Network Computing Devices

123
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of NCD. not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. NCD. makes no representations about the
suitability of this software for any purpose. It is provided "as is"
without express or implied warranty.
NCD. DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL NCD.
BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION
OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1991,1993 by Digital Equipment Corporation, Maynard, Massachusetts,
and Olivetti Research Limited, Cambridge, England.
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the names of Digital or Olivetti
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
DIGITAL AND OLIVETTI DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THEY BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.

124
Copyright 1999, 2005, 2006 Sun Microsystems, Inc. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright (c) 1989 X Consortium, Inc. and Digital Equipment Corporation.
Copyright (c) 1992 X Consortium, Inc. and Intergraph Corporation.
Copyright (c) 1993 X Consortium, Inc. and Silicon Graphics, Inc.
Copyright (c) 1994, 1995 X Consortium, Inc. and Hewlett-Packard Company.
Permission to use, copy, modify, and distribute this documentation for
any purpose and without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
Digital Equipment Corporation, Intergraph Corporation, Silicon
Graphics, Hewlett-Packard, and the X Consortium make no
representations about the suitability for any purpose of the
information in this document. This documentation is provided ``as is''
without express or implied warranty.
Copyright © 2007 Red Hat, Inc

125
Copyright © 2008,2009 Sun Microsystems, Inc. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright (c) 1997 by Mark Leisher
Copyright (c) 1998-2003 by Juliusz Chroboczek
Copyright (c) 1998 Go Watanabe, All rights reserved.
Copyright (c) 1998 Kazushi (Jam) Marukawa, All rights reserved.
Copyright (c) 1998 Takuya SHIOZAKI, All rights reserved.
Copyright (c) 1998 X-TrueType Server Project, All rights reserved.
Copyright (c) 2003-2004 After X-TT Project, All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.

126
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
Copyright 1999, 2000 SuSE, Inc.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of SuSE not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. SuSE makes no representations about the
suitability of this software for any purpose. It is provided "as is"
without express or implied warranty.
SuSE DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL SuSE
BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION
OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1991, 1993
The Regents of the University of California. All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.

127
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement:
This product includes software developed by the University of
California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors
may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
SUCH DAMAGE.
Copyright (c) 1998-1999 Shunsuke Akiyama <akiyama@jp.FreeBSD.org>.
All rights reserved.
Copyright (c) 1998-1999 X-TrueType Server Project, All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS ``AS IS'' AND

128
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
SUCH DAMAGE.
Copyright © 2000 Compaq Computer Corporation
Copyright © 2002 Hewlett-Packard Company
Copyright © 2006 Intel Corporation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and
that the name of the copyright holders not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. The copyright holders make no representations
about the suitability of this software for any purpose. It is provided "as
is" without express or implied warranty.
THE COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE
OF THIS SOFTWARE.
Copyright 1991 by Digital Equipment Corporation, Maynard, Massachusetts,
and the Massachusetts Institute of Technology, Cambridge, Massachusetts.

129
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the names of Digital or MIT not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
DIGITAL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
XFREE86 PROJECT BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the XFree86 Project shall not
be used in advertising or otherwise to promote the sale, use or other dealings

130
in this Software without prior written authorization from the XFree86 Project.
Copyright (c) 2004 The Unichrome Project. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHOR(S) OR COPYRIGHT HOLDER(S) BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright (C) 2001-2006 Bart Massey, Jamey Sharp, and Josh Triplett.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person
obtaining a copy of this software and associated
documentation files (the "Software"), to deal in the
Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute,
sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice shall
be included in all copies or substantial portions of the

131
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY
KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE
WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR
PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS
BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the names of the authors
or their institutions shall not be used in advertising or
otherwise to promote the sale, use or other dealings in this
Software without prior written authorization from the
authors.
Copyright © 2006-2008 Peter Hutterer
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.

132
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany.
Copyright 1993 by David Dawes <dawes@xfree86.org>
Copyright 2002 by SuSE Linux AG, Author: Egbert Eich
Copyright 1994-2002 by The XFree86 Project, Inc.
Copyright 2002 by Paul Elliott
Copyright © 2008 University of South Australia
Copyright 2008 by Chris Salch
Copyright © 2008, 2009 Red Hat, Inc.
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without
fee, provided that the above copyright notice appear in all copies
and that both that copyright notice and this permission notice
appear in supporting documentation, and that the name of the authors
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. The authors make no
representations about the suitability of this software for any
purpose. It is provided "as is" without express or implied
warranty.
THE AUTHORS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN
NO EVENT SHALL THE AUTHORS BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 2005 Adam Jackson.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
on the rights to use, copy, modify, merge, publish, distribute, sub
license, and/or sell copies of the Software, and to permit persons to whom

133
the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT. IN NO EVENT SHALL
ADAM JACKSON BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright (c) 1992-2003 by The XFree86 Project, Inc.
Copyright 1997 by Metro Link, Inc.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE COPYRIGHT HOLDER(S) OR AUTHOR(S) BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the copyright holder(s)
and author(s) shall not be used in advertising or otherwise to promote
the sale, use or other dealings in this Software without prior written

134
authorization from the copyright holder(s) and author(s).
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany.
Copyright 1993 by David Dawes <dawes@xfree86.org>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and
that the names of Thomas Roell and David Dawes not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. Thomas Roell and David Dawes make no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
THOMAS ROELL AND DAVID DAWES DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS.
IN NO EVENT SHALL THOMAS ROELL OR DAVID DAWES BE LIABLE FOR ANY SPECIAL,
INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM
LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1992 by Rich Murphey <Rich@Rice.edu>
Copyright 1993 by David Dawes <dawes@xfree86.org>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Rich Murphey and David Dawes
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. Rich Murphey and
David Dawes make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.

135
RICH MURPHEY AND DAVID DAWES DISCLAIM ALL WARRANTIES WITH REGARD TO
THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL RICH MURPHEY OR DAVID DAWES BE LIABLE FOR
ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1992 by Orest Zborowski <obz@Kodak.com>
Copyright 1993 by David Dawes <dawes@xfree86.org>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Orest Zborowski and David Dawes
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. Orest Zborowski
and David Dawes make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
OREST ZBOROWSKI AND DAVID DAWES DISCLAIMS ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL OREST ZBOROWSKI OR DAVID DAWES BE LIABLE
FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Portions based on kbdrate.c from util-linux 2.9t, which is
Copyright 1992 Rickard E. Faith. Distributed under the GPL.
This program comes with ABSOLUTELY NO WARRANTY.
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany

136
Copyright 1993 by David Dawes <dawes@XFree86.org>
Copyright 1999 by David Holland <davidh@iquest.net)
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and
that the names of Thomas Roell, David Dawes, and David Holland not be used
in advertising or publicity pertaining to distribution of the software
without specific, written prior permission. Thomas Roell, David Dawes, and
David Holland make no representations about the suitability of this software
for any purpose. It is provided "as is" without express or implied
warranty.
THOMAS ROELL, DAVID DAWES, AND DAVID HOLLAND DISCLAIM ALL WARRANTIES WITH
REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS. IN NO EVENT SHALL THOMAS ROELL, DAVID DAWES, OR DAVID HOLLAND
BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION
OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany.
Copyright 1993 by David Dawes <dawes@xfree86.org>
Copyright 2002 by SuSE Linux AG, Author: Egbert Eich
Copyright 1994-2002 by The XFree86 Project, Inc.
Copyright 2002 by Paul Elliott
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of copyright holders not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. The copyright holders
make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or

137
implied warranty.
THE COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1998 by Kazutaka YOKOTA <yokota@zodiac.mech.utsunomiya-u.ac.jp>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Kazutaka YOKOTA not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Kazutaka YOKOTA makes no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
KAZUTAKA YOKOTA DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KAZUTAKA YOKOTA BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1997,1998 by UCHIYAMA Yasushi
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting

138
documentation, and that the name of UCHIYAMA Yasushi not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. UCHIYAMA Yasushi makes no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
UCHIYAMA YASUSHI DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL UCHIYAMA YASUSHI BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 2001 - 2005 by J. Kean Johnston <jkj@sco.com>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name J. Kean Johnston not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. J. Kean Johnston makes no
representations about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
J. KEAN JOHNSTON DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL J. KEAN JOHNSTON BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 2002, 2003, 2005 Tungsten Graphics, Inc., Cedar Park, Texas.
All Rights Reserved.

139
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sub license, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice (including the
next paragraph) shall be included in all copies or substantial portions
of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.
IN NO EVENT SHALL TUNGSTEN GRAPHICS AND/OR ITS SUPPLIERS BE LIABLE FOR
ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT,
TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright (c) 2005 Jesse Barnes <jbarnes@virtuousgeek.org>
Copyright © 2002 David Dawes
Copyright 1998-1999 Precision Insight, Inc., Cedar Park, Texas.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sub license, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice (including the
next paragraph) shall be included in all copies or substantial portions
of the Software.

140
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.
IN NO EVENT SHALL PRECISION INSIGHT AND/OR ITS SUPPLIERS BE LIABLE FOR
ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT,
TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright © 2006 - 2010 Intel Corporation
Copyright © 2007 Red Hat, Inc.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Copyright 2000 by Alan Hourihane, Sychdyn, North Wales, UK.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Alan Hourihane not be used in
advertising or publicity pertaining to distribution of the software without

141
specific, written prior permission. Alan Hourihane makes no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
ALAN HOURIHANE DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL ALAN HOURIHANE BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 2000 Intel Corporation. All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sub license, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice (including the
next paragraph) shall be included in all copies or substantial portions
of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.
IN NO EVENT SHALL INTEL, AND/OR ITS SUPPLIERS BE LIABLE FOR ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR
THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright 2001 VA Linux Systems Inc., Fremont, California.
Copyright © 2002 by David Dawes
All Rights Reserved.

142
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
on the rights to use, copy, modify, merge, publish, distribute, sub
license, and/or sell copies of the Software, and to permit persons to whom
the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT. IN NO EVENT SHALL
ATI, VA LINUX SYSTEMS AND/OR THEIR SUPPLIERS BE LIABLE FOR ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE
USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright © 2000-2001 Juliusz Chroboczek
Copyright © 1998 Egbert Eich
Copyright © 2006-2007 Intel Corporation
Copyright © 2006 Nokia Corporation
Copyright © 2006-2008 Peter Hutterer
Copyright © 2006 Adam Jackson
Copyright © 2009 NVIDIA Corporation
Copyright © 1999 Keith Packard
Copyright © 2007-2009 Red Hat, Inc.
Copyright © 2005-2008 Daniel Stone
Copyright © 2006-2009 Simon Thum
Copyright © 1987, 2003-2006, 2008-2009 Sun Microsystems, Inc.
Copyright © 2006 Luc Verhaegen
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation

143
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright (C) 1994-2003 The XFree86 Project, Inc. All Rights Reserved.
Copyright (C) Colin Harrison 2005-2008
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal in
the Software without restriction, including without limitation the rights to
use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies
of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FIT-
NESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
XFREE86 PROJECT BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the XFree86 Project shall not

144
be used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from the XFree86 Project.
Copyright 1985-1998, 2001 The Open Group
Copyright 2002 Red Hat Inc., Durham, North Carolina.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of The Open Group shall not be
used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from The Open Group.
Copyright (c) 1987, 1989-1990, 1992-1995 X Consortium
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in

145
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall not be
used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from the X Consortium.
Copyright © 1999-2000 SuSE, Inc.
Copyright © 2007, 2008 Red Hat, Inc.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of SuSE not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. SuSE makes no representations about the
suitability of this software for any purpose. It is provided "as is"
without express or implied warranty.
SuSE DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL SuSE
BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION
OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1987-1991, 1993 by Digital Equipment Corporation, Maynard, Massachusetts.
Copyright 1991 Massachusetts Institute of Technology, Cambridge, Massachusetts.
Copyright 1991, 1993 Olivetti Research Limited, Cambridge, England.

146
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of Digital not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
DIGITAL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright 1987 by Digital Equipment Corporation, Maynard, Massachusetts,
Copyright 1994 Quarterdeck Office Systems.
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the names of Digital and
Quarterdeck not be used in advertising or publicity pertaining to
distribution of the software without specific, written prior
permission.
DIGITAL AND QUARTERDECK DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT
OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS

147
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE
OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1997 Digital Equipment Corporation.
All rights reserved.
This software is furnished under license and may be used and copied only in
accordance with the following terms and conditions. Subject to these
conditions, you may download, copy, install, use, modify and distribute
this software in source and/or binary form. No title or ownership is
transferred hereby.
1) Any source code used, modified or distributed must reproduce and retain
this copyright notice and list of conditions as they appear in the
source file.
2) No right is granted to use any trade name, trademark, or logo of Digital
Equipment Corporation. Neither the "Digital Equipment Corporation"
name nor any trademark or logo of Digital Equipment Corporation may be
used to endorse or promote products derived from this software without
the prior written permission of Digital Equipment Corporation.
3) This software is provided "AS-IS" and any express or implied warranties,
including but not limited to, any implied warranties of merchantability,
fitness for a particular purpose, or non-infringement are disclaimed.
In no event shall DIGITAL be liable for any damages whatsoever, and in
particular, DIGITAL shall not be liable for special, indirect,
consequential, or incidental damages or damages for lost profits, loss
of revenue or loss of use, whether such damages arise in contract,
negligence, tort, under statute, in equity, at law or otherwise, even
if advised of the possibility of such damage.
Copyright 2001-2005 Red Hat Inc., Durham, North Carolina.
Copyright (c) 2003 by the XFree86 Project, Inc.
All Rights Reserved.

148
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation on the rights to use, copy, modify, merge,
publish, distribute, sublicense, and/or sell copies of the Software,
and to permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice (including the
next paragraph) shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NON-INFRINGEMENT. IN NO EVENT SHALL RED HAT AND/OR THEIR SUPPLIERS
BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Copyright © 2006 Red Hat, Inc.
(C) Copyright 1998-1999 Precision Insight, Inc., Cedar Park, Texas.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sub license,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.

149
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT. IN NO EVENT SHALL
RED HAT, INC, OR PRECISION INSIGHT AND/OR THEIR SUPPLIERS BE LIABLE FOR ANY
CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT
OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR
THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Copyright (c) 1995 X Consortium
Copyright 2004 Red Hat Inc., Durham, North Carolina.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation on the rights to use, copy, modify, merge,
publish, distribute, sublicense, and/or sell copies of the Software,
and to permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NON-INFRINGEMENT. IN NO EVENT SHALL RED HAT, THE X CONSORTIUM,
AND/OR THEIR SUPPLIERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium
shall not be used in advertising or otherwise to promote the sale,
use or other dealings in this Software without prior written
authorization from the X Consortium.

150
Copyright 1998-2000 Precision Insight, Inc., Cedar Park, Texas.
Copyright 2000 VA Linux Systems, Inc.
Copyright (c) 2002, 2008, 2009 Apple Computer, Inc.
Copyright (c) 2003-2004 Torrey T. Lyons.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sub license, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice (including the
next paragraph) shall be included in all copies or substantial portions
of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.
IN NO EVENT SHALL PRECISION INSIGHT AND/OR ITS SUPPLIERS BE LIABLE FOR
ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT,
TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
(C) Copyright IBM Corporation 2002 - 2007
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sub license,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:

151
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT. IN NO EVENT SHALL
IBM,
AND/OR THEIR SUPPLIERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Copyright (c) 1997, 1998 Metro Link Incorporated
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of the Metro Link shall not be
used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from Metro Link.

152
Copyright 1995-1998 by Metro Link, Inc.
Copyright (c) 1997 Matthieu Herrb
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Metro Link, Inc. not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Metro Link, Inc. makes no
representations about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
METRO LINK, INC. DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL METRO LINK, INC. BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 2000 by Conectiva S.A. (http://www.conectiva.com)
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL

153
CONECTIVA LINUX BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of Conectiva Linux shall
not be used in advertising or otherwise to promote the sale, use or other
dealings in this Software without prior written authorization from
Conectiva Linux.
Copyright (c) 2001, Andy Ritger aritger@nvidia.com
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
o Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
o Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer
in the documentation and/or other materials provided with the
distribution.
o Neither the name of NVIDIA nor the names of its contributors
may be used to endorse or promote products derived from this
software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
"AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT
NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING,
BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN

154
ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
Copyright 1992 Vrije Universiteit, The Netherlands
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted, provided
that the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of the Vrije Universiteit not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. The Vrije Universiteit makes no
representations about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
The Vrije Universiteit DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL The Vrije Universiteit BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1998 by Concurrent Computer Corporation
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of Concurrent Computer
Corporation not be used in advertising or publicity pertaining to
distribution of the software without specific, written prior
permission. Concurrent Computer Corporation makes no representations
about the suitability of this software for any purpose. It is
provided "as is" without express or implied warranty.

155
CONCURRENT COMPUTER CORPORATION DISCLAIMS ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL CONCURRENT COMPUTER CORPORATION BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY
DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright © 2004 Nokia
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Nokia not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Nokia makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
NOKIA DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL NOKIA BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
(c)Copyright 1988,1991 Adobe Systems Incorporated.
All rights reserved.
Permission to use, copy, modify, distribute, and sublicense this software and its
documentation for any purpose and without fee is hereby granted, provided that
the above copyright notices appear in all copies and that both those copyright
notices and this permission notice appear in supporting documentation and that

156
the name of Adobe Systems Incorporated not be used in advertising or publicity
pertaining to distribution of the software without specific, written prior
permission. No trademark license to use the Adobe trademarks is hereby
granted. If the Adobe trademark "Display PostScript"(tm) is used to describe
this software, its functionality or for any other purpose, such use shall be
limited to a statement that this software works in conjunction with the Display
PostScript system. Proper trademark attribution to reflect Adobe's ownership
of the trademark shall be given whenever any such reference to the Display
PostScript system is made.
ADOBE MAKES NO REPRESENTATIONS ABOUT THE SUITABILITY OF THE SOFTWARE FOR ANY
PURPOSE. IT IS PROVIDED "AS IS" WITHOUT EXPRESS OR IMPLIED WARRANTY. ADOBE
DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED
WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-
INFRINGEMENT OF THIRD PARTY RIGHTS. IN NO EVENT SHALL ADOBE BE LIABLE TO YOU
OR ANY OTHER PARTY FOR ANY SPECIAL, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY
DAMAGES WHATSOEVER WHETHER IN AN ACTION OF CONTRACT,NEGLIGENCE, STRICT
LIABILITY OR ANY OTHER ACTION ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE. ADOBE WILL NOT PROVIDE ANY TRAINING OR OTHER
SUPPORT FOR THE SOFTWARE.
Adobe, PostScript, and Display PostScript are trademarks of Adobe Systems
Incorporated which may be registered in certain jurisdictions.
Copyright 1989 Network Computing Devices, Inc., Mountain View, California.
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted, provided
that the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of N.C.D. not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. N.C.D. makes no representations about the
suitability of this software for any purpose. It is provided "as is"
without express or implied warranty.

157
Copyright 1992, 1993 Data General Corporation;
Copyright 1992, 1993 OMRON Corporation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that the
above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and that
neither the name OMRON or DATA GENERAL be used in advertising or publicity
pertaining to distribution of the software without specific, written prior
permission of the party whose name is to be used. Neither OMRON or
DATA GENERAL make any representation about the suitability of this software
for any purpose. It is provided "as is" without express or implied warranty.
OMRON AND DATA GENERAL EACH DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS,
IN NO EVENT SHALL OMRON OR DATA GENERAL BE LIABLE FOR ANY SPECIAL, INDIRECT
OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE
OF THIS SOFTWARE.
Copyright © 1998-2004, 2006 Keith Packard
Copyright © 2000-2002 Keith Packard, member of The XFree86 Project, Inc.
Copyright (c) 2002 Apple Computer, Inc.
Copyright (c) 2003 Torrey T. Lyons.
All Rights Reserved.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Keith Packard not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Keith Packard makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.

158
KEITH PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KEITH PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright © 1999 Keith Packard
Copyright © 2000 Compaq Computer Corporation
Copyright © 2002 MontaVista Software Inc.
Copyright © 2005 OpenedHand Ltd.
Copyright © 2006 Nokia Corporation
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of the authors and/or copyright holders
not be used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission. The authors and/or
copyright holders make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
THE AUTHORS AND/OR COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL THE AUTHORS AND/OR COPYRIGHT HOLDERS BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1993 by Davor Matic
Permission to use, copy, modify, distribute, and sell this software

159
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation. Davor Matic makes no representations about
the suitability of this software for any purpose. It is provided "as
is" without express or implied warranty.
Copyright (C) 2001-2004 Harold L Hunt II All Rights Reserved.
Copyright (C) Colin Harrison 2005-2008
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NONINFRINGEMENT. IN NO EVENT SHALL HAROLD L HUNT II BE LIABLE FOR
ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of Harold L Hunt II
shall not be used in advertising or otherwise to promote the sale, use
or other dealings in this Software without prior written authorization
from Harold L Hunt II.
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany.

160
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Thomas Roell not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Thomas Roell makes no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
THOMAS ROELL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THOMAS ROELL BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany
Copyright 1993 by David Wexelblat <dwex@goblin.org>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Thomas Roell and David Wexelblat
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. Thomas Roell and
David Wexelblat makes no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
THOMAS ROELL AND DAVID WEXELBLAT DISCLAIMS ALL WARRANTIES WITH REGARD TO
THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THOMAS ROELL OR DAVID WEXELBLAT BE LIABLE FOR
ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF

161
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1990,91,92,93 by Thomas Roell, Germany.
Copyright 1991,92,93 by SGCS (Snitily Graphics Consulting Services), USA.
Permission to use, copy, modify, distribute, and sell this software
and its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and
that both that copyright notice and this permission notice appear
in supporting documentation, and that the name of Thomas Roell nor
SGCS be used in advertising or publicity pertaining to distribution
of the software without specific, written prior permission.
Thomas Roell nor SGCS makes no representations about the suitability
of this software for any purpose. It is provided "as is" without
express or implied warranty.
THOMAS ROELL AND SGCS DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THOMAS ROELL OR SGCS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1998 by Alan Hourihane, Wigan, England.
Copyright 2000-2002 by Alan Hourihane, Flint Mountain, North Wales.
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Alan Hourihane not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Alan Hourihane makes no representations
about the suitability of this software for any purpose. It is provided

162
"as is" without express or implied warranty.
ALAN HOURIHANE DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL ALAN HOURIHANE BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1995 Kaleb S. KEITHLEY
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL Kaleb S. KEITHLEY BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of Kaleb S. KEITHLEY
shall not be used in advertising or otherwise to promote the sale, use
or other dealings in this Software without prior written authorization
from Kaleb S. KEITHLEY

163
Copyright (c) 1997 Matthieu Herrb
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Matthieu Herrb not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Matthieu Herrb makes no
representations about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
MATTHIEU HERRB DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL MATTHIEU HERRB BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 2004, Egbert Eich
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to
deal in the Software without restriction, including without limitation the
rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
sell copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
EGBERT EICH BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CON-

164
NECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of Egbert Eich shall not
be used in advertising or otherwise to promote the sale, use or other deal-
ings in this Software without prior written authorization from Egbert Eich.
Copyright 1993 by David Wexelblat <dwex@goblin.org>
Copyright 2005 by Kean Johnston <jkj@sco.com>
Copyright 1993 by David McCullough <davidm@stallion.oz.au>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of David Wexelblat not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. David Wexelblat makes no representations
about the suitability of this software for any purpose. It is provided
"as is" without express or implied warranty.
DAVID WEXELBLAT DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL DAVID WEXELBLAT BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1992 by Orest Zborowski <obz@Kodak.com>
Copyright 1993 by David Wexelblat <dwex@goblin.org>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Orest Zborowski and David Wexelblat

165
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. Orest Zborowski
and David Wexelblat make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
OREST ZBOROWSKI AND DAVID WEXELBLAT DISCLAIMS ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL OREST ZBOROWSKI OR DAVID WEXELBLAT BE LIABLE
FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1995-1999 by Frederic Lepied, France. <fred@sugix.frmug.fr.net>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Frederic Lepied not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Frederic Lepied makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
FREDERIC LEPIED DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL FREDERIC LEPIED BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 1992 by Rich Murphey <Rich@Rice.edu>
Copyright 1993 by David Wexelblat <dwex@goblin.org>

166
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of Rich Murphey and David Wexelblat
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. Rich Murphey and
David Wexelblat make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
RICH MURPHEY AND DAVID WEXELBLAT DISCLAIM ALL WARRANTIES WITH REGARD TO
THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL RICH MURPHEY OR DAVID WEXELBLAT BE LIABLE FOR
ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright © 2003-2004 Anders Carlsson
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Anders Carlsson not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Anders Carlsson makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
ANDERS CARLSSON DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL ANDERS CARLSSON BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER

167
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (C) 2003 Anders Carlsson
Copyright © 2003-2004 Eric Anholt
Copyright © 2004 Keith Packard
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Eric Anholt not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Eric Anholt makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
ERIC ANHOLT DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL ERIC ANHOLT BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1998 Todd C. Miller <Todd.Miller@courtesan.com>
Permission to use, copy, modify, and distribute this software for any
purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND TODD C. MILLER DISCLAIMS ALL
WARRANTIES WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL TODD C. MILLER BE LIABLE
FOR ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION

168
OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright © 2003-2004 Philip Blundell
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Philip Blundell not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Philip Blundell makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
PHILIP BLUNDELL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL PHILIP BLUNDELL BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1994-2003 by The XFree86 Project, Inc.
Copyright 1997 by Metro Link, Inc.
Copyright 2003 by David H. Dawes.
Copyright 2003 by X-Oz Technologies.
Copyright (c) 2004, X.Org Foundation
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:

169
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE COPYRIGHT HOLDER(S) OR AUTHOR(S) BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the copyright holder(s)
and author(s) shall not be used in advertising or otherwise to promote
the sale, use or other dealings in this Software without prior written
authorization from the copyright holder(s) and author(s).
Copyright 1990,91 by Thomas Roell, Dinkelscherben, Germany
Copyright 1993 by David Wexelblat <dwex@goblin.org>
Copyright 1999 by David Holland <davidh@iquest.net>
Copyright © 2000 Compaq Computer Corporation
Copyright © 2002 Hewlett-Packard Company
Copyright © 2004, 2005, 2008 Red Hat, Inc.
Copyright © 2004 Nicholas Miell
Copyright © 2005 Trolltech AS
Copyright © 2006 Intel Corporation
Copyright © 2004 - 2007 Keith Packard
Copyright © 2008 George Sapountzis <gsap7@yahoo.gr>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and
that the name of the copyright holders not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. The copyright holders make no representations
about the suitability of this software for any purpose. It is provided "as

170
is" without express or implied warranty.
THE COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN
AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright © 2000 Keith Packard, member of The XFree86 Project, Inc.
2005 Lars Knoll & Zack Rusin, Trolltech
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Keith Packard not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Keith Packard makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
THE COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN
AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright 1987, 1998 The Open Group
Copyright © 1998-1999, 2001 The XFree86 Project, Inc.
Copyright © 2000 VA Linux Systems, Inc.

171
Copyright (c) 2000, 2001 Nokia Home Communications
Copyright © 2007, 2008 Red Hat, Inc.
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, and/or sell copies of the Software, and to permit persons
to whom the Software is furnished to do so, provided that the above
copyright notice(s) and this permission notice appear in all copies of
the Software and that both the above copyright notice(s) and this
permission notice appear in supporting documentation.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT
OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR
HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL
INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING
FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION
WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Except as contained in this notice, the name of a copyright holder
shall not be used in advertising or otherwise to promote the sale, use
or other dealings in this Software without prior written authorization
of the copyright holder.
Copyright 1996 by Thomas E. Dickey <dickey@clark.net>
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in

172
supporting documentation, and that the name of the above listed
copyright holder(s) not be used in advertising or publicity pertaining
to distribution of the software without specific, written prior
permission.
THE ABOVE LISTED COPYRIGHT HOLDER(S) DISCLAIM ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL THE ABOVE LISTED COPYRIGHT HOLDER(S) BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1998-1999 Precision Insight, Inc., Cedar Park, Texas.
Copyright (c) 2001 Andreas Monitzer.
Copyright (c) 2001-2004 Greg Parker.
Copyright (c) 2001-2004 Torrey T. Lyons
Copyright (c) 2002-2003 Apple Computer, Inc.
Copyright (c) 2004-2005 Alexander Gottwald
Copyright (c) 2002-2009 Apple Inc.
Copyright (c) 2007 Jeremy Huddleston
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE ABOVE LISTED COPYRIGHT HOLDER(S) BE LIABLE FOR ANY CLAIM, DAMAGES OR

173
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name(s) of the above copyright
holders shall not be used in advertising or otherwise to promote the sale,
use or other dealings in this Software without prior written authorization.
Copyright (C) 1999,2000 by Eric Sunshine <sunshine@sunshineco.com>
Copyright (C) 2001-2005 by Thomas Winischhofer, Vienna, Austria.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. The name of the author may not be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN
NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED
TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
Copyright (C) 2005 Bogdan D. bogdand@users.sourceforge.net

174
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal in
the Software without restriction, including without limitation the rights to
use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies
of the Software, and to permit persons to whom the Software is furnished to do
so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHOR BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the author shall not be used in
advertising or otherwise to promote the sale, use or other dealings in this
Software without prior written authorization from the author.
Copyright © 2002 David Dawes
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL

175
THE AUTHOR(S) BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of the author(s) shall
not be used in advertising or otherwise to promote the sale, use or other
dealings in this Software without prior written authorization from
the author(s).
Copyright (C) 1996-1999 SciTech Software, Inc.
Copyright (C) David Mosberger-Tang
Copyright (C) 1999 Egbert Eich
Copyright (C) 2008 Bart Trojanowski, Symbio Technologies, LLC
Permission to use, copy, modify, distribute, and sell this software and
its documentation for any purpose is hereby granted without fee,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of the authors not be used
in advertising or publicity pertaining to distribution of the software
without specific, written prior permission. The authors makes no
representations about the suitability of this software for any purpose.
It is provided "as is" without express or implied warranty.
THE AUTHORS DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE AUTHORS BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF
USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR
OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright 2005-2006 Luc Verhaegen.
Permission is hereby granted, free of charge, to any person obtaining a

176
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE COPYRIGHT HOLDER(S) OR AUTHOR(S) BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Copyright 1995 by Robin Cutshaw <robin@XFree86.Org>
Copyright 2000 by Egbert Eich
Copyright 2002 by David Dawes
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of the above listed copyright holder(s)
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. The above listed
copyright holder(s) make(s) no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
THE ABOVE LISTED COPYRIGHT HOLDER(S) DISCLAIM(S) ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL THE ABOVE LISTED COPYRIGHT HOLDER(S) BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY
DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER

177
IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1997-2004 by Marc Aurele La France (TSI @ UQV), tsi@xfree86.org
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and
that the name of Marc Aurele La France not be used in advertising or
publicity pertaining to distribution of the software without specific,
written prior permission. Marc Aurele La France makes no representations
about the suitability of this software for any purpose. It is provided
"as-is" without express or implied warranty.
MARC AURELE LA FRANCE DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO
EVENT SHALL MARC AURELE LA FRANCE BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE
OF THIS SOFTWARE.
Copyright 1990, 1991 by Thomas Roell, Dinkelscherben, Germany
Copyright 1992 by David Dawes <dawes@XFree86.org>
Copyright 1992 by Jim Tsillas <jtsilla@damon.ccs.northeastern.edu>
Copyright 1992 by Rich Murphey <Rich@Rice.edu>
Copyright 1992 by Robert Baron <Robert.Baron@ernst.mach.cs.cmu.edu>
Copyright 1992 by Orest Zborowski <obz@eskimo.com>
Copyright 1993 by Vrije Universiteit, The Netherlands
Copyright 1993 by David Wexelblat <dwex@XFree86.org>
Copyright 1994, 1996 by Holger Veit <Holger.Veit@gmd.de>
Copyright 1997 by Takis Psarogiannakopoulos <takis@dpmms.cam.ac.uk>
Copyright 1994-2003 by The XFree86 Project, Inc
Permission to use, copy, modify, distribute, and sell this software and its

178
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the names of the above listed copyright holders
not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission. The above listed
copyright holders make no representations about the suitability of this
software for any purpose. It is provided "as is" without express or
implied warranty.
THE ABOVE LISTED COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS, IN NO EVENT SHALL THE ABOVE LISTED COPYRIGHT HOLDERS BE
LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY
DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER
IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (C) 2000 Jakub Jelinek (jakub@redhat.com)
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
JAKUB JELINEK BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

179
Copyright (C) 2000 Keith Packard
2004 Eric Anholt
2005 Zack Rusin
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of copyright holders not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Copyright holders make no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
THE COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS, IN NO EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN
AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
Copyright © 2007 OpenedHand Ltd
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of OpenedHand Ltd not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. OpenedHand Ltd makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
OpenedHand Ltd DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,

180
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL OpenedHand Ltd BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1989, 1990, 1993, 1994
The Regents of the University of California. All rights reserved.
This code is derived from software contributed to Berkeley by
Chris Torek.
This code is derived from software contributed to Berkeley by
Michael Rendell of Memorial University of Newfoundland.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
4. Neither the name of the University nor the names of its contributors
may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY

181
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
SUCH DAMAGE.
Copyright 1987 by Apollo Computer Inc., Chelmsford, Massachusetts.
Copyright 1989 by Hewlett-Packard Company.
All Rights Reserved
Permission to use, duplicate, change, and distribute this software and
its documentation for any purpose and without fee is granted, provided
that the above copyright notice appear in such copy and that this
copyright notice appear in all supporting documentation, and that the
names of Apollo Computer Inc., the Hewlett-Packard Company, or the X
Consortium not be used in advertising or publicity pertaining to
distribution of the software without written prior permission.
HEWLETT-PACKARD MAKES NO WARRANTY OF ANY KIND WITH REGARD
TO THIS SOFWARE, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. Hewlett-Packard shall not be liable for errors
contained herein or direct, indirect, special, incidental or
consequential damages in connection with the furnishing,
performance, or use of this material.
Copyright 1993, 1994 NCR Corporation - Dayton, Ohio, USA
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted, provided
that the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name NCR not be used in advertising
or publicity pertaining to distribution of the software without specific,
written prior permission. NCR makes no representations about the
suitability of this software for any purpose. It is provided "as is"

182
without express or implied warranty.
NCR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN
NO EVENT SHALL NCR BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
(c) Copyright 1996 by Sebastien Marineau and Holger Veit
<marineau@genie.uottawa.ca>
<Holger.Veit@gmd.de>
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
HOLGER VEIT BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the name of Sebastien Marineau or
Holger Veit shall not be used in advertising or otherwise to promote
the sale, use or other dealings in this Software without prior written
authorization from Holger Veit or Sebastien Marineau.

183
Copyright © 2003 Keith Packard, Noah Levitt
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of Keith Packard not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. Keith Packard makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
KEITH PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KEITH PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.

184
XKCP
# Implementation by the Keccak Team, namely, Guido Bertoni, Joan Daemen,
#Michael Peeters, Gilles Van Assche and Ronny Van Keer,
#hereby denoted as "the implementer".
# To the extent possible under law, the implementer has waived all copyright
# and related or neighboring rights to the source code in this file.
# http://creativecommons.org/publicdomain/zero/1.0/

185
xkeyboard-config
Copyright 1996 by Joseph Moss
Copyright (C) 2002-2007 Free Software Foundation, Inc.
Copyright (C) Dmitry Golubev <lastguru@mail.ru>, 2003-2004
Copyright (C) 2004, Gregory Mokhin <mokhin@bog.msu.ru>
Copyright (C) 2006 Erdal Ronahî
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of the copyright holder(s) not be used in
advertising or publicity pertaining to distribution of the software without
specific, written prior permission. The copyright holder(s) makes no
representations about the suitability of this software for any purpose. It
is provided "as is" without express or implied warranty.
THE COPYRIGHT HOLDER(S) DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE COPYRIGHT HOLDER(S) BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1996 Digital Equipment Corporation
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:

186
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL DIGITAL EQUIPMENT CORPORATION BE LIABLE FOR ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR
THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the Digital Equipment
Corporation shall not be used in advertising or otherwise to promote
the sale, use or other dealings in this Software without prior written
authorization from Digital Equipment Corporation.
Copyright 1996, 1998 The Open Group
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of The Open Group shall
not be used in advertising or otherwise to promote the sale, use or

187
other dealings in this Software without prior written authorization
from The Open Group.
Copyright 2004-2005 Sun Microsystems, Inc. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright (c) 1996 by Silicon Graphics Computer Systems, Inc.
Permission to use, copy, modify, and distribute this
software and its documentation for any purpose and without
fee is hereby granted, provided that the above copyright
notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting
documentation, and that the name of Silicon Graphics not be
used in advertising or publicity pertaining to distribution
of the software without specific prior written permission.
Silicon Graphics makes no representation about the suitability
of this software for any purpose. It is provided "as is"

188
without any express or implied warranty.
SILICON GRAPHICS DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. IN NO EVENT SHALL SILICON
GRAPHICS BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH
THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1996 X Consortium
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization
from the X Consortium.

189
Copyright (C) 2004, 2006 Ævar Arnfjörð Bjarmason <avarab@gmail.com>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization of
the copyright holder.
Copyright (C) 1999, 2000 by Anton Zinoviev <anton@lml.bas.bg>
This software may be used, modified, copied, distributed, and sold,
in both source and binary form provided that the above copyright
and these terms are retained. Under no circumstances is the author
responsible for the proper functioning of this software, nor does
the author assume any responsibility for damages incurred with its
use.
Permission is granted to anyone to use, distribute and modify
this file in any way, provided that the above copyright notice
is left intact and the author of the modification summarizes

190
the changes in this header.
This file is distributed without any expressed or implied warranty.

191
wpa_supplicant-2.6
wpa_supplicant and hostapd
--------------------------
Copyright (c) 2002-2016, Jouni Malinen <j@w1.fi> and contributors
All Rights Reserved.
These programs are licensed under the BSD license (the one with
advertisement clause removed).
If you are submitting changes to the project, please see CONTRIBUTIONS
file for more instructions.
This package may include either wpa_supplicant, hostapd, or both. See
README file respective subdirectories (wpa_supplicant/README or
hostapd/README) for more details.
Source code files were moved around in v0.6.x releases and compared to
earlier releases, the programs are now built by first going to a
subdirectory (wpa_supplicant or hostapd) and creating build
configuration (.config) and running 'make' there (for Linux/BSD/cygwin
builds).
License
-------
This software may be distributed, used, and modified under the terms of
BSD license:
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are
met:
1. Redistributions of source code must retain the above copyright

192
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. Neither the name(s) of the above-listed copyright holder(s) nor the
names of its contributors may be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
"AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

193
compat-wireless
fusermount
Linux
WLAN USB Driver
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public License is intended to guarantee your freedom to share and
change free software--to make sure the software is free for all its users. This General Public License
applies to most of the Free Software Foundation's software and to any other program whose
authors commit to using it. (Some other Free Software Foundation software is covered by the GNU
Lesser General Public License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses
are designed to make sure that you have the freedom to distribute copies of free software (and
charge for this service if you wish), that you receive source code or can get it if you want it, that you
can change the software or use pieces of it in new free programs; and that you know you can do
these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or
to ask you to surrender the rights. These restrictions translate to certain responsibilities for you if
you distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give
the recipients all the rights that you have. You must make sure that they, too, receive or can get the
source code. And you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license
which gives you legal permission to copy, distribute and/or modify the software.

194
Also, for each author's protection and ours, we want to make certain that everyone understands
that there is no warranty for this free software. If the software is modified by someone else and
passed on, we want its recipients to know that what they have is not the original, so that any
problems introduced by others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger
that redistributors of a free program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any patent must be licensed for
everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the
copyright holder saying it may be distributed under the terms of this General Public License. The
"Program", below, refers to any such program or work, and a "work based on the Program" means
either the Program or any derivative work under copyright law: that is to say, a work containing the
Program or a portion of it, either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in the term "modification".) Each
licensee is addressed as "you".
Activities other than copying, distribution and modification are not covered by this License; they are
outside its scope. The act of running the Program is not restricted, and the output from the
Program is covered only if its contents constitute a work based on the Program (independent of
having been made by running the Program). Whether that is true depends on what the Program
does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in
any medium, provided that you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to this
License and to the absence of any warranty; and give any other recipients of the Program a copy of
this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work
based on the Program, and copy and distribute such modifications or work under the terms of
Section 1 above, provided that you also meet all of these conditions:

195
a) You must cause the modified files to carry prominent notices stating that you changed the files
and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is
derived from the Program or any part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License.
c) If the modified program normally reads commands interactively when run, you must cause it,
when started running for such interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a notice that there is no warranty (or
else, saying that you provide a warranty) and that users may redistribute the program under these
conditions, and telling the user how to view a copy of this License. (Exception: if the Program itself
is interactive but does not normally print such an announcement, your work based on the Program
is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are
not derived from the Program, and can be reasonably considered independent and separate works
in themselves, then this License, and its terms, do not apply to those sections when you distribute
them as separate works. But when you distribute the same sections as part of a whole which is a
work based on the Program, the distribution of the whole must be on the terms of this License,
whose permissions for other licensees extend to the entire whole, and thus to each and every part
regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written
entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with
a work based on the Program) on a volume of a storage or distribution medium does not bring the
other work under the scope of this License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code
or executable form under the terms of Sections 1 and 2 above provided that you also do one of the
following:

196
a) Accompany it with the complete corresponding machine-readable source code, which must be
distributed under the terms of Sections 1 and 2 above on a medium customarily used for software
interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a
charge no more than your cost of physically performing source distribution, a complete machine-
readable copy of the corresponding source code, to be distributed under the terms of Sections 1
and 2 above on a medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding
source code. (This alternative is allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such an offer, in accord with
Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to it.
For an executable work, complete source code means all the source code for all modules it
contains, plus any associated interface definition files, plus the scripts used to control compilation
and installation of the executable. However, as a special exception, the source code distributed
need not include anything that is normally distributed (in either source or binary form) with the
major components (compiler, kernel, and so on) of the operating system on which the executable
runs, unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated
place, then offering equivalent access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not compelled to copy the source
along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided
under this License. Any attempt otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License. However, parties who have
received copies, or rights, from you under this License will not have their licenses terminated so
long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by modifying or distributing the
Program (or any work based on the Program), you indicate your acceptance of this License to do so,

197
and all its terms and conditions for copying, distributing or modifying the Program or works based
on it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient
automatically receives a license from the original licensor to copy, distribute or modify the Program
subject to these terms and conditions. You may not impose any further restrictions on the
recipients' exercise of the rights granted herein. You are not responsible for enforcing compliance
by third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other
reason (not limited to patent issues), conditions are imposed on you (whether by court order,
agreement or otherwise) that contradict the conditions of this License, they do not excuse you from
the conditions of this License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a consequence you may
not distribute the Program at all. For example, if a patent license would not permit royalty-free
redistribution of the Program by all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to refrain entirely from distribution
of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the
balance of the section is intended to apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right
claims or to contest validity of any such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is implemented by public license practices.
Many people have made generous contributions to the wide range of software distributed through
that system in reliance on consistent application of that system; it is up to the author/donor to
decide if he or she is willing to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest
of this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by patents or
by copyrighted interfaces, the original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding those countries, so that

198
distribution is permitted only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the General Public
License from time to time. Such new versions will be similar in spirit to the present version, but may
differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version number of
this License which applies to it and "any later version", you have the option of following the terms
and conditions either of that version or of any later version published by the Free Software
Foundation. If the Program does not specify a version number of this License, you may choose any
version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution
conditions are different, write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free Software Foundation; we sometimes
make exceptions for this. Our decision will be guided by the two goals of preserving the free status
of all derivatives of our free software and of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE
PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN
WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS"
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD
THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR
OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE
PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL,
SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO
USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO
OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.

199
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the public, the
best way to achieve this is to make it free software which everyone can redistribute and change
under these terms.
To do so, attach the following notices to the program. It is safest to attach them to the start of each
source file to most effectively convey the exclusion of warranty; and each file should have at least
the "copyright" line and a pointer to where the full notice is found.
one line to give the program's name and an idea of what it does.
Copyright (C) yyyy name of author
This program is free software; you can redistribute it and/or
modify it under the terms of the GNU General Public License
as published by the Free Software Foundation; either version 2
of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program; if not, write to the Free Software
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this when it starts in an interactive
mode:
Gnomovision version 69, Copyright (C) year name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details
type `show w'. This is free software, and you are welcome
to redistribute it under certain conditions; type `show c'
for details.

200
The hypothetical commands `show w' and `show c' should show the appropriate parts of the
General Public License. Of course, the commands you use may be called something other than
`show w' and `show c'; they could even be mouse-clicks or menu items--whatever suits your
program.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a
"copyright disclaimer" for the program, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright
interest in the program `Gnomovision'
(which makes passes at compilers) written
by James Hacker.
signature of Ty Coon, 1 April 1989
Ty Coon, President of Vice
This General Public License does not permit incorporating your program into proprietary programs.
If your program is a subroutine library, you may consider it more useful to permit linking
proprietary applications with the library. If this is what you want to do, use the GNU Lesser General
Public License instead of this License.

201
atk
cairo
glib
glibc
GTK+
json-glib
libfuse
Libnl
libusb
pango (except OpenTypeCode)
GNU LESSER GENERAL PUBLIC LICENSE
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
[This is the first released version of the Lesser GPL. It also counts
as the successor of the GNU Library Public License, version 2, hence
the version number 2.1.]
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public Licenses are intended to guarantee your freedom to share and
change free software--to make sure the software is free for all its users.
This license, the Lesser General Public License, applies to some specially designated software
packages--typically libraries--of the Free Software Foundation and other authors who decide to use
it. You can use it too, but we suggest you first think carefully about whether this license or the
ordinary General Public License is the better strategy to use in any particular case, based on the
explanations below.
When we speak of free software, we are referring to freedom of use, not price. Our General Public
Licenses are designed to make sure that you have the freedom to distribute copies of free software
(and charge for this service if you wish); that you receive source code or can get it if you want it;
that you can change the software and use pieces of it in new free programs; and that you are
informed that you can do these things.

202
To protect your rights, we need to make restrictions that forbid distributors to deny you these
rights or to ask you to surrender these rights. These restrictions translate to certain responsibilities
for you if you distribute copies of the library or if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you must give the
recipients all the rights that we gave you. You must make sure that they, too, receive or can get the
source code. If you link other code with the library, you must provide complete object files to the
recipients, so that they can relink them with the library after making changes to the library and
recompiling it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the library, and (2) we offer you
this license, which gives you legal permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that there is no warranty for the free
library. Also, if the library is modified by someone else and passed on, the recipients should know
that what they have is not the original version, so that the original author's reputation will not be
affected by problems that might be introduced by others.
Finally, software patents pose a constant threat to the existence of any free program. We wish to
make sure that a company cannot effectively restrict the users of a free program by obtaining a
restrictive license from a patent holder. Therefore, we insist that any patent license obtained for a
version of the library must be consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the ordinary GNU General Public
License. This license, the GNU Lesser General Public License, applies to certain designated libraries,
and is quite different from the ordinary General Public License. We use this license for certain
libraries in order to permit linking those libraries into non-free programs.
When a program is linked with a library, whether statically or using a shared library, the
combination of the two is legally speaking a combined work, a derivative of the original library. The
ordinary General Public License therefore permits such linking only if the entire combination fits its
criteria of freedom. The Lesser General Public License permits more lax criteria for linking other
code with the library.
We call this license the "Lesser" General Public License because it does Less to protect the user's
freedom than the ordinary General Public License. It also provides other free software developers
Less of an advantage over competing non-free programs. These disadvantages are the reason we
use the ordinary General Public License for many libraries. However, the Lesser license provides
advantages in certain special circumstances.
For example, on rare occasions, there may be a special need to encourage the widest possible use
of a certain library, so that it becomes a de-facto standard. To achieve this, non-free programs
must be allowed to use the library. A more frequent case is that a free library does the same job as
widely used non-free libraries. In this case, there is little to gain by limiting the free library to free
software only, so we use the Lesser General Public License.

203
In other cases, permission to use a particular library in non-free programs enables a greater
number of people to use a large body of free software. For example, permission to use the GNU C
Library in non-free programs enables many more people to use the whole GNU operating system,
as well as its variant, the GNU/Linux operating system.
Although the Lesser General Public License is Less protective of the users' freedom, it does ensure
that the user of a program that is linked with the Library has the freedom and the wherewithal to
run that program using a modified version of the Library.
The precise terms and conditions for copying, distribution and modification follow. Pay close
attention to the difference between a "work based on the library" and a "work that uses the library".
The former contains code derived from the library, whereas the latter must be combined with the
library in order to run.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License Agreement applies to any software library or other program which contains a notice
placed by the copyright holder or other authorized party saying it may be distributed under the
terms of this Lesser General Public License (also called "this License"). Each licensee is addressed as
"you".
A "library" means a collection of software functions and/or data prepared so as to be conveniently
linked with application programs (which use some of those functions and data) to form
executables.
The "Library", below, refers to any such software library or work which has been distributed under
these terms. A "work based on the Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a portion of it, either verbatim or with
modifications and/or translated straightforwardly into another language. (Hereinafter, translation is
included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for making modifications to it. For a
library, complete source code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to control compilation and installation of
the library.
Activities other than copying, distribution and modification are not covered by this License; they are
outside its scope. The act of running a program using the Library is not restricted, and output from
such a program is covered only if its contents constitute a work based on the Library (independent
of the use of the Library in a tool for writing it). Whether that is true depends on what the Library
does and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library's complete source code as you
receive it, in any medium, provided that you conspicuously and appropriately publish on each copy
an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to
this License and to the absence of any warranty; and distribute a copy of this License along with the
Library.

204
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Library or any portion of it, thus forming a work
based on the Library, and copy and distribute such modifications or work under the terms of
Section 1 above, provided that you also meet all of these conditions:
• a) The modified work must itself be a software library.
• b) You must cause the files modified to carry prominent notices stating that you changed
the files and the date of any change.
• c) You must cause the whole of the work to be licensed at no charge to all third parties
under the terms of this License.
• d) If a facility in the modified Library refers to a function or a table of data to be supplied
by an application program that uses the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that, in the event an application does
not supply such function or table, the facility still operates, and performs whatever part of its
purpose remains meaningful.
(For example, a function in a library to compute square roots has a purpose that is entirely well-
defined independent of the application. Therefore, Subsection 2d requires that any application-
supplied function or table used by this function must be optional: if the application does not supply
it, the square root function must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are
not derived from the Library, and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those sections when you distribute
them as separate works. But when you distribute the same sections as part of a whole which is a
work based on the Library, the distribution of the whole must be on the terms of this License,
whose permissions for other licensees extend to the entire whole, and thus to each and every part
regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written
entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library with the Library (or with a
work based on the Library) on a volume of a storage or distribution medium does not bring the
other work under the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public License instead of this
License to a given copy of the Library. To do this, you must alter all the notices that refer to this
License, so that they refer to the ordinary GNU General Public License, version 2, instead of to this
License. (If a newer version than version 2 of the ordinary GNU General Public License has appeared,
then you can specify that version instead if you wish.) Do not make any other change in these
notices.

205
Once this change is made in a given copy, it is irreversible for that copy, so the ordinary GNU
General Public License applies to all subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of the Library into a program that is
not a library.
4. You may copy and distribute the Library (or a portion or derivative of it, under Section 2) in
object code or executable form under the terms of Sections 1 and 2 above provided that you
accompany it with the complete corresponding machine-readable source code, which must be
distributed under the terms of Sections 1 and 2 above on a medium customarily used for software
interchange.
If distribution of object code is made by offering access to copy from a designated place, then
offering equivalent access to copy the source code from the same place satisfies the requirement to
distribute the source code, even though third parties are not compelled to copy the source along
with the object code.
5. A program that contains no derivative of any portion of the Library, but is designed to work with
the Library by being compiled or linked with it, is called a "work that uses the Library". Such a work,
in isolation, is not a derivative work of the Library, and therefore falls outside the scope of this
License.
However, linking a "work that uses the Library" with the Library creates an executable that is a
derivative of the Library (because it contains portions of the Library), rather than a "work that uses
the library". The executable is therefore covered by this License. Section 6 states terms for
distribution of such executables.
When a "work that uses the Library" uses material from a header file that is part of the Library, the
object code for the work may be a derivative work of the Library even though the source code is
not. Whether this is true is especially significant if the work can be linked without the Library, or if
the work is itself a library. The threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data structure layouts and accessors, and
small macros and small inline functions (ten lines or less in length), then the use of the object file is
unrestricted, regardless of whether it is legally a derivative work. (Executables containing this
object code plus portions of the Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may distribute the object code for the work
under the terms of Section 6. Any executables containing that work also fall under Section 6,
whether or not they are linked directly with the Library itself.
6. As an exception to the Sections above, you may also combine or link a "work that uses the
Library" with the Library to produce a work containing portions of the Library, and distribute that
work under terms of your choice, provided that the terms permit modification of the work for the
customer's own use and reverse engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the Library is used in it and that
the Library and its use are covered by this License. You must supply a copy of this License. If the

206
work during execution displays copyright notices, you must include the copyright notice for the
Library among them, as well as a reference directing the user to the copy of this License. Also, you
must do one of these things:
• a) Accompany the work with the complete corresponding machine-readable source code
for the Library including whatever changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked with the Library, with the complete
machine-readable "work that uses the Library", as object code and/or source code, so that the user
can modify the Library and then relink to produce a modified executable containing the modified
Library. (It is understood that the user who changes the contents of definitions files in the Library
will not necessarily be able to recompile the application to use the modified definitions.)
• b) Use a suitable shared library mechanism for linking with the Library. A suitable
mechanism is one that (1) uses at run time a copy of the library already present on the user's
computer system, rather than copying library functions into the executable, and (2) will operate
properly with a modified version of the library, if the user installs one, as long as the modified
version is interface-compatible with the version that the work was made with.
• c) Accompany the work with a written offer, valid for at least three years, to give the same
user the materials specified in Subsection 6a, above, for a charge no more than the cost of
performing this distribution.
• d) If distribution of the work is made by offering access to copy from a designated place,
offer equivalent access to copy the above specified materials from the same place.
• e) Verify that the user has already received a copy of these materials or that you have
already sent this user a copy.
For an executable, the required form of the "work that uses the Library" must include any data and
utility programs needed for reproducing the executable from it. However, as a special exception,
the materials to be distributed need not include anything that is normally distributed (in either
source or binary form) with the major components (compiler, kernel, and so on) of the operating
system on which the executable runs, unless that component itself accompanies the executable.
It may happen that this requirement contradicts the license restrictions of other proprietary libraries
that do not normally accompany the operating system. Such a contradiction means you cannot use
both them and the Library together in an executable that you distribute.
7. You may place library facilities that are a work based on the Library side-by-side in a single
library together with other library facilities not covered by this License, and distribute such a
combined library, provided that the separate distribution of the work based on the Library and of
the other library facilities is otherwise permitted, and provided that you do these two things:
• a) Accompany the combined library with a copy of the same work based on the Library,
uncombined with any other library facilities. This must be distributed under the terms of the
Sections above.

207
• b) Give prominent notice with the combined library of the fact that part of it is a work
based on the Library, and explaining where to find the accompanying uncombined form of the
same work.
8. You may not copy, modify, sublicense, link with, or distribute the Library except as expressly
provided under this License. Any attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under this License will not have
their licenses terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Library or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by modifying or distributing the
Library (or any work based on the Library), you indicate your acceptance of this License to do so,
and all its terms and conditions for copying, distributing or modifying the Library or works based
on it.
10. Each time you redistribute the Library (or any work based on the Library), the recipient
automatically receives a license from the original licensor to copy, distribute, link with or modify
the Library subject to these terms and conditions. You may not impose any further restrictions on
the recipients' exercise of the rights granted herein. You are not responsible for enforcing
compliance by third parties with this License.
11. If, as a consequence of a court judgment or allegation of patent infringement or for any other
reason (not limited to patent issues), conditions are imposed on you (whether by court order,
agreement or otherwise) that contradict the conditions of this License, they do not excuse you from
the conditions of this License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a consequence you may
not distribute the Library at all. For example, if a patent license would not permit royalty-free
redistribution of the Library by all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to refrain entirely from distribution
of the Library.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the
balance of the section is intended to apply, and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right
claims or to contest validity of any such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system which is implemented by public license practices.
Many people have made generous contributions to the wide range of software distributed through
that system in reliance on consistent application of that system; it is up to the author/donor to
decide if he or she is willing to distribute software through any other system and a licensee cannot
impose that choice.

208
This section is intended to make thoroughly clear what is believed to be a consequence of the rest
of this License.
12. If the distribution and/or use of the Library is restricted in certain countries either by patents or
by copyrighted interfaces, the original copyright holder who places the Library under this License
may add an explicit geographical distribution limitation excluding those countries, so that
distribution is permitted only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
13. The Free Software Foundation may publish revised and/or new versions of the Lesser General
Public License from time to time. Such new versions will be similar in spirit to the present version,
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library specifies a version number of
this License which applies to it and "any later version", you have the option of following the terms
and conditions either of that version or of any later version published by the Free Software
Foundation. If the Library does not specify a license version number, you may choose any version
ever published by the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free programs whose distribution
conditions are incompatible with these, write to the author to ask for permission. For software
which is copyrighted by the Free Software Foundation, write to the Free Software Foundation; we
sometimes make exceptions for this. Our decision will be guided by the two goals of preserving the
free status of all derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE
LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN
WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE LIBRARY "AS IS"
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE LIBRARY IS WITH YOU. SHOULD
THE LIBRARY PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR
CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE
LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL,
SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO
USE THE LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE LIBRARY TO
OPERATE WITH ANY OTHER SOFTWARE), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.

209
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Libraries
If you develop a new library, and you want it to be of the greatest possible use to the public, we
recommend making it free software that everyone can redistribute and change. You can do so by
permitting redistribution under these terms (or, alternatively, under the terms of the ordinary
General Public License).
To apply these terms, attach the following notices to the library. It is safest to attach them to the
start of each source file to most effectively convey the exclusion of warranty; and each file should
have at least the "copyright" line and a pointer to where the full notice is found.
one line to give the library's name and an idea of what it does.
Copyright (C) year name of author
This library is free software; you can redistribute it and/or
modify it under the terms of the GNU Lesser General Public
License as published by the Free Software Foundation; either
version 2.1 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
Lesser General Public License for more details.
You should have received a copy of the GNU Lesser General Public
License along with this library; if not, write to the Free Software
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Also add information on how to contact you by electronic and paper mail.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a
"copyright disclaimer" for the library, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in
the library `Frob' (a library for tweaking knobs) written
by James Random Hacker.
signature of Ty Coon, 1 April 1990
Ty Coon, President of Vice
That's all there is to it!

210
iproute
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
License is intended to guarantee your freedom to share and change free
software--to make sure the software is free for all its users. This
General Public License applies to most of the Free Software
Foundation's software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by
the GNU Library General Public License instead.) You can apply it to
your programs, too.
When we speak of free software, we are referring to freedom, not
price. Our General Public Licenses are designed to make sure that you
have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it
if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid
anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether
gratis or for a fee, you must give the recipients all the rights that
you have. You must make sure that they, too, receive or can get the

211
source code. And you must show them these terms so they know their
rights.
We protect your rights with two steps: (1) copyright the software, and
(2) offer you this license which gives you legal permission to copy,
distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain
that everyone understands that there is no warranty for this free
software. If the software is modified by someone else and passed on, we
want its recipients to know that what they have is not the original, so
that any problems introduced by others will not reflect on the original
authors' reputations.
Finally, any free program is threatened constantly by software
patents. We wish to avoid the danger that redistributors of a free
program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any
patent must be licensed for everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and
modification follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains
a notice placed by the copyright holder saying it may be distributed
under the terms of this General Public License. The "Program", below,
refers to any such program or work, and a "work based on the Program"
means either the Program or any derivative work under copyright law:
that is to say, a work containing the Program or a portion of it,
either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in
the term "modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of

212
running the Program is not restricted, and the output from the Program
is covered only if its contents constitute a work based on the
Program (independent of having been made by running the Program).
Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's
source code as you receive it, in any medium, provided that you
conspicuously and appropriately publish on each copy an appropriate
copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty;
and give any other recipients of the Program a copy of this License
along with the Program.
You may charge a fee for the physical act of transferring a copy, and
you may at your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion
of it, thus forming a work based on the Program, and copy and
distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices
stating that you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in
whole or in part contains or is derived from the Program or any
part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License.
c) If the modified program normally reads commands interactively
when run, you must cause it, when started running for such
interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a
notice that there is no warranty (or else, saying that you provide
a warranty) and that users may redistribute the program under
these conditions, and telling the user how to view a copy of this
License. (Exception: if the Program itself is interactive but
does not normally print such an announcement, your work based on

213
the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Program,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Program, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program
with the Program (or with a work based on the Program) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may copy and distribute the Program (or a work based on it,
under Section 2) in object code or executable form under the terms of
Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable
source code, which must be distributed under the terms of Sections
1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three
years, to give any third party, for a charge no more than your
cost of physically performing source distribution, a complete
machine-readable copy of the corresponding source code, to be
distributed under the terms of Sections 1 and 2 above on a medium
customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer

214
to distribute corresponding source code. (This alternative is
allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such
an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for
making modifications to it. For an executable work, complete source
code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to
control compilation and installation of the executable. However, as a
special exception, the source code distributed need not include
anything that is normally distributed (in either source or binary
form) with the major components (compiler, kernel, and so on) of the
operating system on which the executable runs, unless that component
itself accompanies the executable.
If distribution of executable or object code is made by offering
access to copy from a designated place, then offering equivalent
access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not
compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program
except as expressly provided under this License. Any attempt
otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under
this License will not have their licenses terminated so long as such
parties remain in full compliance.
5. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the
Program), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Program or works based on it.

215
6. Each time you redistribute the Program (or any work based on the
Program), the recipient automatically receives a license from the
original licensor to copy, distribute or modify the Program subject to
these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties to
this License.
7. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent
license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under
any particular circumstance, the balance of the section is intended to
apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.

216
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding
those countries, so that distribution is permitted only in or among
countries not thus excluded. In such case, this License incorporates
the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions
of the General Public License from time to time. Such new versions will
be similar in spirit to the present version, but may differ in detail to
address new problems or concerns.
Each version is given a distinguishing version number. If the Program
specifies a version number of this License which applies to it and "any
later version", you have the option of following the terms and conditions
either of that version or of any later version published by the Free
Software Foundation. If the Program does not specify a version number of
this License, you may choose any version ever published by the Free Software
Foundation.
10. If you wish to incorporate parts of the Program into other free
programs whose distribution conditions are different, write to the author
to ask for permission. For software which is copyrighted by the Free
Software Foundation, write to the Free Software Foundation; we sometimes
make exceptions for this. Our decision will be guided by the two goals
of preserving the free status of all derivatives of our free software and
of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED

217
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest
possible use to the public, the best way to achieve this is to make it
free software which everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest
to attach them to the start of each source file to most effectively
convey the exclusion of warranty; and each file should have at least
the "copyright" line and a pointer to where the full notice is found.
<one line to give the program's name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This program is free software; you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation; either version 2 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,

218
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program; if not, write to the Free Software
Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this
when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) year name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
This is free software, and you are welcome to redistribute it
under certain conditions; type `show c' for details.
The hypothetical commands `show w' and `show c' should show the appropriate
parts of the General Public License. Of course, the commands you use may
be called something other than `show w' and `show c'; they could even be
mouse-clicks or menu items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a "copyright disclaimer" for the program, if
necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision' (which makes passes at compilers) written by James Hacker.
<signature of Ty Coon>, 1 April 1989
Ty Coon, President of Vice
This General Public License does not permit incorporating your program into
proprietary programs. If your program is a subroutine library, you may
consider it more useful to permit linking proprietary applications with the
library. If this is what you want to do, use the GNU Library General

219
Public License instead of this License.
* Copyright (c) 1982, 1986, 1993
* The Regents of the University of California. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 4. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.

220
Squid
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
59 Temple Place, Suite 330, Boston, MA 02111, USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
License is intended to guarantee your freedom to share and change free
software--to make sure the software is free for all its users. This
General Public License applies to most of the Free Software
Foundation's software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by
the GNU Library General Public License instead.) You can apply it to
your programs, too.
When we speak of free software, we are referring to freedom, not
price. Our General Public Licenses are designed to make sure that you
have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it
if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid
anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether
gratis or for a fee, you must give the recipients all the rights that
you have. You must make sure that they, too, receive or can get the

221
source code. And you must show them these terms so they know their
rights.
We protect your rights with two steps: (1) copyright the software, and
(2) offer you this license which gives you legal permission to copy,
distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain
that everyone understands that there is no warranty for this free
software. If the software is modified by someone else and passed on, we
want its recipients to know that what they have is not the original, so
that any problems introduced by others will not reflect on the original
authors' reputations.
Finally, any free program is threatened constantly by software
patents. We wish to avoid the danger that redistributors of a free
program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any
patent must be licensed for everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and
modification follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains
a notice placed by the copyright holder saying it may be distributed
under the terms of this General Public License. The "Program", below,
refers to any such program or work, and a "work based on the Program"
means either the Program or any derivative work under copyright law:
that is to say, a work containing the Program or a portion of it,
either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in
the term "modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of

222
running the Program is not restricted, and the output from the Program
is covered only if its contents constitute a work based on the
Program (independent of having been made by running the Program).
Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's
source code as you receive it, in any medium, provided that you
conspicuously and appropriately publish on each copy an appropriate
copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty;
and give any other recipients of the Program a copy of this License
along with the Program.
You may charge a fee for the physical act of transferring a copy, and
you may at your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion
of it, thus forming a work based on the Program, and copy and
distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices
stating that you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in
whole or in part contains or is derived from the Program or any
part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License.
c) If the modified program normally reads commands interactively
when run, you must cause it, when started running for such
interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a
notice that there is no warranty (or else, saying that you provide
a warranty) and that users may redistribute the program under
these conditions, and telling the user how to view a copy of this
License. (Exception: if the Program itself is interactive but
does not normally print such an announcement, your work based on

223
the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Program,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Program, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program
with the Program (or with a work based on the Program) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may copy and distribute the Program (or a work based on it,
under Section 2) in object code or executable form under the terms of
Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable
source code, which must be distributed under the terms of Sections
1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three
years, to give any third party, for a charge no more than your
cost of physically performing source distribution, a complete
machine-readable copy of the corresponding source code, to be
distributed under the terms of Sections 1 and 2 above on a medium
customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer

224
to distribute corresponding source code. (This alternative is
allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such
an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for
making modifications to it. For an executable work, complete source
code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to
control compilation and installation of the executable. However, as a
special exception, the source code distributed need not include
anything that is normally distributed (in either source or binary
form) with the major components (compiler, kernel, and so on) of the
operating system on which the executable runs, unless that component
itself accompanies the executable.
If distribution of executable or object code is made by offering
access to copy from a designated place, then offering equivalent
access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not
compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program
except as expressly provided under this License. Any attempt
otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under
this License will not have their licenses terminated so long as such
parties remain in full compliance.
5. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the
Program), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Program or works based on it.

225
6. Each time you redistribute the Program (or any work based on the
Program), the recipient automatically receives a license from the
original licensor to copy, distribute or modify the Program subject to
these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties to
this License.
7. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent
license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under
any particular circumstance, the balance of the section is intended to
apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.

226
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding
those countries, so that distribution is permitted only in or among
countries not thus excluded. In such case, this License incorporates
the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions
of the General Public License from time to time. Such new versions will
be similar in spirit to the present version, but may differ in detail to
address new problems or concerns.
Each version is given a distinguishing version number. If the Program
specifies a version number of this License which applies to it and "any
later version", you have the option of following the terms and conditions
either of that version or of any later version published by the Free
Software Foundation. If the Program does not specify a version number of
this License, you may choose any version ever published by the Free Software
Foundation.
10. If you wish to incorporate parts of the Program into other free
programs whose distribution conditions are different, write to the author
to ask for permission. For software which is copyrighted by the Free
Software Foundation, write to the Free Software Foundation; we sometimes
make exceptions for this. Our decision will be guided by the two goals
of preserving the free status of all derivatives of our free software and
of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED

227
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
Appendix: How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest
possible use to the public, the best way to achieve this is to make it
free software which everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest
to attach them to the start of each source file to most effectively
convey the exclusion of warranty; and each file should have at least
the "copyright" line and a pointer to where the full notice is found.
<one line to give the program's name and a brief idea of what it does.>
Copyright (C) 19yy <name of author>
This program is free software; you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation; either version 2 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,

228
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public Licensealong with this program; if not,
write to the Free Software
Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111, USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this
when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) 19yy name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
This is free software, and you are welcome to redistribute it
under certain conditions; type `show c' for details.
The hypothetical commands `show w' and `show c' should show the appropriate
parts of the General Public License. Of course, the commands you use may
be called something other than `show w' and `show c'; they could even be
mouse-clicks or menu items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a "copyright disclaimer" for the program, if
necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision' (which makes passes at compilers) written by James Hacker.
<signature of Ty Coon>, 1 April 1989
Ty Coon, President of Vice
This General Public License does not permit incorporating your program into
proprietary programs. If your program is a subroutine library, you may
consider it more useful to permit linking proprietary applications with the
library. If this is what you want to do, use the GNU Library General
Public License instead of this License.

229
///////////////////////////
GNU LESSER GENERAL PUBLIC LICENSE
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
[This is the first released version of the Lesser GPL. It also counts
as the successor of the GNU Library Public License, version 2, hence
the version number 2.1.]
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
Licenses are intended to guarantee your freedom to share and change
free software--to make sure the software is free for all its users.
This license, the Lesser General Public License, applies to some
specially designated software packages--typically libraries--of the
Free Software Foundation and other authors who decide to use it. You
can use it too, but we suggest you first think carefully about whether
this license or the ordinary General Public License is the better
strategy to use in any particular case, based on the explanations below.
When we speak of free software, we are referring to freedom of use,
not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge
for this service if you wish); that you receive source code or can get
it if you want it; that you can change the software and use pieces of
it in new free programs; and that you are informed that you can do
these things.
To protect your rights, we need to make restrictions that forbid

230
distributors to deny you these rights or to ask you to surrender these
rights. These restrictions translate to certain responsibilities for
you if you distribute copies of the library or if you modify it.
For example, if you distribute copies of the library, whether gratis
or for a fee, you must give the recipients all the rights that we gave
you. You must make sure that they, too, receive or can get the source
code. If you link other code with the library, you must provide
complete object files to the recipients, so that they can relink them
with the library after making changes to the library and recompiling
it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the
library, and (2) we offer you this license, which gives you legal
permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that
there is no warranty for the free library. Also, if the library is
modified by someone else and passed on, the recipients should know
that what they have is not the original version, so that the original
author's reputation will not be affected by problems that might be
introduced by others.
Finally, software patents pose a constant threat to the existence of
any free program. We wish to make sure that a company cannot
effectively restrict the users of a free program by obtaining a
restrictive license from a patent holder. Therefore, we insist that
any patent license obtained for a version of the library must be
consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the
ordinary GNU General Public License. This license, the GNU Lesser
General Public License, applies to certain designated libraries, and
is quite different from the ordinary General Public License. We use
this license for certain libraries in order to permit linking those
libraries into non-free programs.
When a program is linked with a library, whether statically or using

231
a shared library, the combination of the two is legally speaking a
combined work, a derivative of the original library. The ordinary
General Public License therefore permits such linking only if the
entire combination fits its criteria of freedom. The Lesser General
Public License permits more lax criteria for linking other code with
the library.
We call this license the "Lesser" General Public License because it
does Less to protect the user's freedom than the ordinary General
Public License. It also provides other free software developers Less
of an advantage over competing non-free programs. These disadvantages
are the reason we use the ordinary General Public License for many
libraries. However, the Lesser license provides advantages in certain
special circumstances.
For example, on rare occasions, there may be a special need to
encourage the widest possible use of a certain library, so that it becomes
a de-facto standard. To achieve this, non-free programs must be
allowed to use the library. A more frequent case is that a free
library does the same job as widely used non-free libraries. In this
case, there is little to gain by limiting the free library to free
software only, so we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free
programs enables a greater number of people to use a large body of
free software. For example, permission to use the GNU C Library in
non-free programs enables many more people to use the whole GNU
operating system, as well as its variant, the GNU/Linux operating
system.
Although the Lesser General Public License is Less protective of the
users' freedom, it does ensure that the user of a program that is
linked with the Library has the freedom and the wherewithal to run
that program using a modified version of the Library.
The precise terms and conditions for copying, distribution and
modification follow. Pay close attention to the difference between a
"work based on the library" and a "work that uses the library". The

232
former contains code derived from the library, whereas the latter must
be combined with the library in order to run.
GNU LESSER GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License Agreement applies to any software library or other
program which contains a notice placed by the copyright holder or
other authorized party saying it may be distributed under the terms of
this Lesser General Public License (also called "this License").
Each licensee is addressed as "you".
A "library" means a collection of software functions and/or data
prepared so as to be conveniently linked with application programs
(which use some of those functions and data) to form executables.
The "Library", below, refers to any such software library or work
which has been distributed under these terms. A "work based on the
Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a
portion of it, either verbatim or with modifications and/or translated
straightforwardly into another language. (Hereinafter, translation is
included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for
making modifications to it. For a library, complete source code means
all the source code for all modules it contains, plus any associated
interface definition files, plus the scripts used to control compilation
and installation of the library.
Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of
running a program using the Library is not restricted, and output from
such a program is covered only if its contents constitute a work based
on the Library (independent of the use of the Library in a tool for
writing it). Whether that is true depends on what the Library does
and what the program that uses the Library does.

233
1. You may copy and distribute verbatim copies of the Library's
complete source code as you receive it, in any medium, provided that
you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact
all the notices that refer to this Licen se and to the absence of any
warranty; and distribute a copy of this License along with the
Library.
You may charge a fee for the physical act of transferring a copy,
and you may at your option offer warranty protection in exchange for a
fee.
2. You may modify your copy or copies of the Library or any portion
of it, thus forming a work based on the Library, and copy and
distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) The modified work must itself be a software library.
b) You must cause the files modified to carry prominent notices
stating that you changed the files and the date of any change.
c) You must cause the whole of the work to be licensed at no
charge to all third parties under the terms of this License.
d) If a facility in the modified Library refers to a function or a
table of data to be supplied by an application program that uses
the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that,
in the event an application does not supply such function or
table, the facility still operates, and performs whatever part of
its purpose remains meaningful.
(For example, a function in a library to compute square roots has
a purpose that is entirely well-defined independent of the
application. Therefore, Subsection 2d requires that any
application-supplied function or table used by this function must
be optional: if the application does not supply it, the square

234
root function must still compute square roots.)
These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Library,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Library, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote
it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library
with the Library (or with a work based on the Library) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public
License instead of this License to a given copy of the Library. To do
this, you must alter all the notices that refer to this License, so
that they refer to the ordinary GNU General Public License, version 2,
instead of to this License. (If a newer version than version 2 of the
ordinary GNU General Public License has appeared, then you can specify
that version instead if you wish.) Do not make any other change in
these notices.
Once this change is made in a given copy, it is irreversible for
that copy, so the ordinary GNU General Public License applies to all
subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of
the Library into a program that is not a library.

235
4. You may copy and distribute the Library (or a portion or
derivative of it, under Section 2) in object code or executable form
under the terms of Sections 1 and 2 above provided that you accompany
it with the complete corresponding machine-readable source code, which
must be distributed under the terms of Sections 1 and 2 above on a
medium customarily used for software interchange.
If distribution of object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the
source code from the same place satisfies the requirement to
distribute the source code, even though third parties are not
compelled to copy the source along with the object code.
5. A program that contains no derivative of any portion of the
Library, but is designed to work with the Library by being compiled or
linked with it, is called a "work that uses the Library". Such a
work, in isolation, is not a derivative work of the Library, and
therefore falls outside the scope of this License.
However, linking a "work that uses the Library" with the Library
creates an executable that is a derivative of the Library (because it
contains portions of the Library), rather than a "work that uses the
library". The executable is therefore covered by this License.
Section 6 states terms for distribution of such executables.
When a "work that uses the Library" uses material from a header file
that is part of the Library, the object code for the work may be a
derivative work of the Library even though the source code is not.
Whether this is true is especially significant if the work can be
linked without the Library, or if the work is itself a library. The
threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data
structure layouts and accessors, and small macros and small inline
functions (ten lines or less in length), then the use of the object
file is unrestricted, regardless of whether it is legally a derivative
work. (Executables containing this object code plus portions of the

236
Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may
distribute the object code for the work under the terms of Section 6.
Any executables containing that work also fall under Section 6,
whether or not they are linked directly with the Library itself.
6. As an exception to the Sections above, you may also combine or
link a "work that uses the Library" with the Library to produce a
work containing portions of the Library, and distribute that work
under terms of your choice, provided that the terms permit
modification of the work for the customer's own use and reverse
engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the
Library is used in it and that the Library and its use are covered by
this License. You must supply a copy of this License. If the work
during execution displays copyright notices, you must include the
copyright notice for the Library among them, as well as a reference
directing the user to the copy of this License. Also, you must do one
of these things:
a) Accompany the work with the complete corresponding
machine-readable source code for the Library including whatever
changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked
with the Library, with the complete machine-readable "work that
uses the Library", as object code and/or source code, so that the
user can modify the Library and then relink to produce a modified
executable containing the modified Library. (It is understood
that the user who changes the contents of definitions files in the
Library will not necessarily be able to recompile the application
to use the modified definitions.)
b) Use a suitable shared library mechanism for linking with the
Library. A suitable mechanism is one that (1) uses at run time a
copy of the library already present on the user's computer system,
rather than copying library functions into the executable, and (2)

237
will operate properly with a modified version of the library, if
the user installs one, as long as the modified version is
interface-compatible with the version that the work was made with.
c) Accompany the work with a written offer, valid for at
least three years, to give the same user the materials
specified in Subsection 6a, above, for a charge no more
than the cost of performing this distribution.
d) If distribution of the work is made by offering access to copy
from a designated place, offer equivalent access to copy the above
specified materials from the same place.
e) Verify that the user has already received a copy of these
materials or that you have already sent this user a copy.
For an executable, the required form of the "work that uses the
Library" must include any data and utility programs needed for
reproducing the executable from it. However, as a special exception,
the materials to be distributed need not include anything that is
normally distributed (in either source or binary form) with the major
components (compiler, kernel, and so on) of the operating system on
which the executable runs, unless that component itself accompanies
the executable.
It may happen that this requirement contradicts the license
restrictions of other proprietary libraries that do not normally
accompany the operating system. Such a contradiction means you cannot
use both them and the Library together in an executable that you
distribute.
7. You may place library facilities that are a work based on the
Library side-by-side in a single library together with other library
facilities not covered by this License, and distribute such a combined
library, provided that the separate distribution of the work based on
the Library and of the other library facilities is otherwise
permitted, and provided that you do these two things:

238
a) Accompany the combined library with a copy of the same work
based on the Library, uncombined with any other library
facilities. This must be distributed under the terms of the
Sections above.
b) Give prominent notice with the combined library of the fact
that part of it is a work based on the Library, and explaining
where to find the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute
the Library except as expressly provided under this License. Any
attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your
rights under this License. However, parties who have received copies,
or rights, from you under this License will not have their licenses
terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Library or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Library (or any work based on the
Library), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Library or works based on it.
10. Each time you redistribute the Library (or any work based on the
Library), the recipient automatically receives a license from the
original licensor to copy, distribute, link with or modify the Library
subject to these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties with
this License.
11. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not

239
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Library at all. For example, if a patent
license would not permit royalty-free redistribution of the Library by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Library.
If any portion of this section is held invalid or unenforceable under any
particular circumstance, the balance of the section is intended to apply,
and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Library under this License may add
an explicit geographical distribution limitation excluding those countries,
so that distribution is permitted only in or among countries not thus
excluded. In such case, this License incorporates the limitation as if
written in the body of this License.
13. The Free Software Foundation may publish revised and/or new
versions of the Lesser General Public License from time to time.
Such new versions will be similar in spirit to the present version,

240
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library
specifies a version number of this License which applies to it and
"any later version", you have the option of following the terms and
conditions either of that version or of any later version published by
the Free Software Foundation. If the Library does not specify a
license version number, you may choose any version ever published by
the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free
programs whose distribution conditions are incompatible with these,
write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free
Software Foundation; we sometimes make exceptions for this. Our
decision will be guided by the two goals of preserving the free status
of all derivatives of our free software and of promoting the sharing
and reuse of software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO
WARRANTY FOR THE LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE LAW.
EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR
OTHER PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE
LIBRARY IS WITH YOU. SHOULD THE LIBRARY PROVE DEFECTIVE, YOU ASSUME
THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY
AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU
FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE
LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A

241
FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER SOFTWARE), EVEN IF
SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Libraries
If you develop a new librar y, and you want it to be of the greatest
possible use to the public, we recommend making it free software that
everyone can redistribute and change. You can do so by permitting
redistribution under these terms (or, alternatively, under the terms of the
ordinary General Public License).
To apply these terms, attach the following notices to the library. It is
safest to attach them to the start of each source file to most effectively
convey the exclusion of warranty; and each file should have at least the
"copyright" line and a pointer to where the full notice is found.
<one line to give the library's name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This library is free software; you can redistribute it and/or
modify it under the terms of the GNU Lesser General Public
License as published by the Free Software Foundation; either
version 2.1 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
Lesser General Public License for more details.
You should have received a copy of the GNU Lesser General Public
License along with this library; if not, write to the Free Software
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Also add information on how to contact you by electronic and paper mail.

242
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a "copyright disclaimer" for the library, if
necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the
library `Frob' (a library for tweaking knobs) written by James Random Hacker.
<signature of Ty Coon>, 1 April 1990
Ty Coon, President of Vice
That's all there is to it!
=============================================================
==========
* Translation Snippets provided by Squid Project Translators held in
* copyright for open distribution.
*
* Translation Snippets provided by Rosetta Project Translators held in
* copyright for open distribution.
*
* Copyright 2009
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE

243
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
see TRANSLATORS file for current contributing translators holding copyrights.
* Livingston Enterprises, Inc.
* 6920 Koll Center Parkway
* Pleasanton, CA 94566
*
* Copyright 1992 Livingston Enterprises, Inc.
*
* Permission to use, copy, modify, and distribute this software for any
* purpose and without fee is hereby granted, provided that this
* copyright and permission notice appear on all copies and supporting
* documentation, the name of Livingston Enterprises, Inc. not be used
* in advertising or publicity pertaining to distribution of the
* program without specific prior permission, and notice be given
* in supporting documentation that copying and distribution is by
* permission of Livingston Enterprises, Inc.
*
* Livingston Enterprises, Inc. makes no representations about
* the suitability of this software for any purpose. It is
* provided "as is" without express or implied warranty.
*
* The new parts of the code is Copyright (C) 1998 R.M. van Selm <selm@cistron.nl>
* with modifications
* Copyright (C) 2004 Henrik Nordstrom <hno@squid-cache.org>
* Copyright (C) 2006 Henrik Nordstrom hno@squid-cache.org
=============================================================
=================

244
Copyright (C) 2004 Henrik Nordstrom
Permission to use, copy, modify, and distribute this software for any purpose
and without fee is hereby granted, provided that this copyright and permission
notice appear on all copies and supporting documentation, the name of Henrik
Nordstrom. not be used in advertising or publicity pertaining to distribution
of the program without specific prior permission.
The author makes no representations about the suitability of this documentation
for any purpose. It isprovided "as is" without express or implied warranty.
Henrik Nordstrom <hno@squid-cache.org>
=============================================================
=================
Copyright 1988, 1989 by Carnegie Mellon University
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of CMU not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
CMU DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
CMU BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
* Copyright 1997 by Carnegie Mellon University

245
*
* All Rights Reserved
*
* Permission to use, copy, modify, and distribute this software and its
* documentation for any purpose and without fee is hereby granted,
* provided that the above copyright notice appear in all copies and that
* both that copyright notice and this permission notice appear in
* supporting documentation, and that the name of CMU not be
* used in advertising or publicity pertaining to distribution of the
* software without specific, written prior permission.
*
* CMU DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
* ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
* CMU BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
* ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
* WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
* ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
* SOFTWARE.
*
* Author: Ryan Troll ryan+@andrew.cmu.edu
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
// (c) 1997 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY

246
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
===========================================
// (c) 1997 - 2000 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.

247
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
//
// File: socket.hh
// Sun May 3 1998
//
// (c) 1998 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Books: W. Richard Steven, "Advanced Programming in the UNIX Environment",
// Addison-Wesley, 1992.
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
//
// Revision 1.3 1999/01/19 11:00:50 voeckler
// Linux glibc2 fixes for socket size parameters.
//

248
// Revision 1.2 1998/08/27 15:23:39 voeckler
// added TCP_NODELAY options at several places.
//
// Revision 1.1 1998/08/13 21:52:55 voeckler
// Initial revision
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
//
// File: squid-tlv.cc
// Tue Jun 15 1999
//
// (c) 1999 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
//
// Revision 1.1 1999/06/15 21:10:16 voeckler
// Initial revision

249
//
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
//
// File: conffile.cc
// Fri Sep 15 2000
//
// (c) 2000 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
//
// Revision 1.1 2000/09/21 09:44:53 voeckler
// Initial revision
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
//
// File: convert.hh

250
// Thu Oct 30 1997
//
// (c) 1997 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
//
// Revision 1.2 1999/01/19 11:00:50 voeckler
// added bool type workaround.
//
// Revision 1.1 1998/08/13 21:38:04 voeckler
// Initial revision
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
//
// File: copyout.cc
// Tue Jun 15 1999
//

251
// (c) 1999 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
//
// Revision 1.2 1999/06/16 13:05:26 voeckler
// mmap file copying on Solaris.
//
// Revision 1.1 1999/06/15 21:10:47 voeckler
// Initial revision
* Copyright (c) 2009-2014, Treehouse Networks Ltd. New Zealand
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*

252
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
* FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE
* COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
* INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING,
* BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
* CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN
* ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
* POSSIBILITY OF SUCH DAMAGE.
* Copyright 2004 The Aerospace Corporation. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions, and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions, and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. The name of The Aerospace Corporation may not be used to endorse or
* promote products derived from this software.
*
* THIS SOFTWARE IS PROVIDED BY THE AEROSPACE CORPORATION "AS IS" AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AEROSPACE CORPORATION BE LIABLE

253
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* Copyright (c) 1995
* Bill Paul <wpaul@ctr.columbia.edu>. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* This product includes software developed by Bill Paul.
* 4. Neither the name of the author nor the names of any co-contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY Bill Paul AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*

254
* EUI-64 conversion and lookup routines
* Copyright (C) 1995, 1996, 1997, and 1998 WIDE Project.
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the project nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE PROJECT AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE PROJECT OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* Copyright (c) 1980, 1983, 1988, 1993
* The Regents of the University of California. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.

255
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* This product includes software developed by the University of
* California, Berkeley and its contributors.
* 4. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
* Copyright (c) 1987, 1993, 1994
* The Regents of the University of California. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*

256
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
* Copyright (c) 1988, 1989, 1993
* The Regents of the University of California. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.

257
* Copyright (c) 1990, 1993
* The Regents of the University of California. All rights reserved.
*
* This code is derived from software contributed to Berkeley by
* Chris Torek.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
* Copyright (c) 2004 by Internet Systems Consortium, Inc. ("ISC")
* Copyright (c) 1996,1999 by Internet Software Consortium.
*
* Permission to use, copy, modify, and distribute this software for any
* purpose with or without fee is hereby granted, provided that the above
* copyright notice and this permission notice appear in all copies.
*

258
* THE SOFTWARE IS PROVIDED "AS IS" AND ISC DISCLAIMS ALL WARRANTIES
* WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
* MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL ISC BE LIABLE FOR
* ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
* WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
* ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT
* OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
* Copyright (c) 2007 Todd C. Miller <Todd.Miller@courtesan.com>
*
* Permission to use, copy, modify, and distribute this software for any
* purpose with or without fee is hereby granted, provided that the above
* copyright notice and this permission notice appear in all copies.
*
* THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
* WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
* MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR
* ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
* WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
* ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
* OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright 1988, 1989 by Carnegie Mellon University
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of CMU not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
CMU DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
CMU BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,

259
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
* -
* Portions Copyright (c) 1993 by Digital Equipment Corporation.
*
* Permission to use, copy, modify, and distribute this software for any
* purpose with or without fee is hereby granted, provided that the above
* copyright notice and this permission notice appear in all copies, and that
* the name of Digital Equipment Corporation not be used in advertising or
* publicity pertaining to distribution of the document or software without
* specific, written prior permission.
*
* THE SOFTWARE IS PROVIDED "AS IS" AND DIGITAL EQUIPMENT CORP. DISCLAIMS ALL
* WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES
* OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL DIGITAL EQUIPMENT
* CORPORATION BE LIABLE FOR ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL
* DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR
* PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS
* ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
* SOFTWARE.
Copyright 1989 by Carnegie Mellon University
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of CMU not be
used in advertising or publicity pertaining to distribution of the
software without specific, written prior permission.
CMU DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
CMU BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR

260
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
// (c) 1999 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
* Livingston Enterprises, Inc.
* 6920 Koll Center Parkway
* Pleasanton, CA 94566
*
* Copyright 1992 Livingston Enterprises, Inc.
* Copyright 1997 Cistron Internet Services B.V.
*
* Permission to use, copy, modify, and distribute this software for any

261
* purpose and without fee is hereby granted, provided that this
* copyright and permission notice appear on all copies and supporting
* documentation, the name of Livingston Enterprises, Inc. not be used
* in advertising or publicity pertaining to distribution of the
* program without specific prior permission, and notice be given
* in supporting documentation that copying and distribution is by
* permission of Livingston Enterprises, Inc.
*
* Livingston Enterprises, Inc. makes no representations about
* the suitability of this software for any purpose. It is
* provided "as is" without express or implied warranty.
This program is based on code from Livingston Enterprises, Inc. and parts are
COPYRIGHT NOTICE SQUID_RAD_AUTH
Copyright (C) 1992-1995 Livingston Enterprises, Inc and Cistron Internet Services
B.V. who both have given permission to modify and distribute those parts. The new
parts of the code is Copyright (C) 1998 R.M. van Selm <selm@cistron.nl> with
modifications Copyright (C) 2004 Henrik Nordstrom <hno@squid-cache.org>
Permission to use, copy, modify, and distribute this software for any purpose
and without fee is hereby granted, provided that this copyright and permission
notice appear on all copies and supporting documentation, the name of
Livingston Enterprises, Inc. not be used in advertising or publicity pertaining
to distribution of the program without specific prior permission, and notice be
given in supporting documentation that copying and distribution is by
permission of Livingston Enterprises, Inc. and Cistron Internet Services B.V.
Neither Livingston Enterprises, Inc. nor Cistron Internet Services B.V. nor I
(R.M. van Selm) make representations about the suitability of this software for
any purpose. It isprovided "as is" without express or implied warranty.
// Author: Jens-S. V?ckler <voeckler@rvs.uni-hannover.de>
// File: signal.cc
// Date: Sat Feb 28 1998
// Compiler: gcc 2.7.2.x series
//

262
// Books: W. Richard Steven, "Advanced Programming in the UNIX Environment",
// Addison-Wesley, 1992.
//
// (c) 1998 Lehrgebiet Rechnernetze und Verteilte Systeme
// Universit?t Hannover, Germany
//
// Permission to use, copy, modify, distribute, and sell this software
// and its documentation for any purpose is hereby granted without fee,
// provided that (i) the above copyright notices and this permission
// notice appear in all copies of the software and related documentation,
// and (ii) the names of the Lehrgebiet Rechnernetze und Verteilte
// Systeme and the University of Hannover may not be used in any
// advertising or publicity relating to the software without the
// specific, prior written permission of Lehrgebiet Rechnernetze und
// Verteilte Systeme and the University of Hannover.
//
// THE SOFTWARE IS PROVIDED "AS-IS" AND WITHOUT WARRANTY OF ANY KIND,
// EXPRESS, IMPLIED OR OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY
// WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
//
// IN NO EVENT SHALL THE LEHRGEBIET RECHNERNETZE UND VERTEILTE SYSTEME OR
// THE UNIVERSITY OF HANNOVER BE LIABLE FOR ANY SPECIAL, INCIDENTAL,
// INDIRECT OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES
// WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER OR NOT
// ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF LIABILITY,
// ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
// SOFTWARE.
=============================================================
=================
compat/os/opensolaris_10_netdb.h:
* Copyright (c) 2001 Mike Barcroft <mike@FreeBSD.org>
* Copyright (c) 1990, 1993
* The Regents of the University of California. All rights reserved.
*
* This code is derived from software contributed to Berkeley by

263
* Chris Torek.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the University nor the names of its contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
=============================================================
=================
(C) Copyright Ion Gaztanaga 2005-2009.
Distributed under the Boost Software License, Version 1.0
Boost Software License - Version 1.0 - August 17th, 2003
Permission is hereby granted, free of charge, to any person or organization
obtaining a copy of the software and accompanying documentation covered by
this license (the "Software") to use, reproduce, display, distribute,
execute, and transmit the Software, and to prepare derivative works of the
Software, and to permit third-parties to whom the Software is furnished to

264
do so, all subject to the following:
The copyright notices in the Software and this entire statement, including
the above license grant, this restriction and the following disclaimer,
must be included in all copies of the Software, in whole or in part, and
all derivative works of the Software, unless such copies or derivative
works are solely in the form of machine-executable object code generated by
a source language processor.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NON-INFRINGEMENT. IN NO EVENT
SHALL THE COPYRIGHT HOLDERS OR ANYONE DISTRIBUTING THE SOFTWARE BE LIABLE
FOR ANY DAMAGES OR OTHER LIABILITY, WHETHER IN CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
=============================================================
=================
# This originates from X11R5 (mit/util/scripts/install.sh), which was
# later released in X11R6 (xc/config/util/install.sh) with the
# following copyright and license.
#
# Copyright (C) 1994 X Consortium
#
# Permission is hereby granted, free of charge, to any person obtaining a copy
# of this software and associated documentation files (the "Software"), to
# deal in the Software without restriction, including without limitation the
# rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
# sell copies of the Software, and to permit persons to whom the Software is
# furnished to do so, subject to the following conditions:
#
# The above copyright notice and this permission notice shall be included in
# all copies or substantial portions of the Software.
#
# THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
# IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
# FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE

265
# X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN
# AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNEC-
# TION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. +
#
# Except as contained in this notice, the name of the X Consortium shall not
# be used in advertising or otherwise to promote the sale, use or other deal-
# ings in this Software without prior written authorization from the X Consor-
# tium.
#
#
# FSF changes to this file are in the public domain.
#
# Calling this script install-sh is preferred over install.sh, to prevent
# 'make' implicit rules from creating a file called install from it
# when there is no Makefile.
#
# This script is compatible with the BSD install script, but was written
# from scratch.

266
webkit
/*
* Copyright (C) 2008 – 2010, 2012 Google Inc. All rights reserved.
* Copyright (C) 2005, 2006, 2008 – 2011, 2013 Apple Inc. All Rights Reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions are
* met:
*
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following disclaimer
* in the documentation and/or other materials provided with the
* distribution.
* * Neither the name of Google Inc. nor the names of its
* contributors may be used to endorse or promote products derived from
* this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2007, 2008, 2010 Apple Inc. All rights reserved.
* Copyright (C) 2007 Justin Haygood (jhaygood@reaktix.com)
*

267
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*
*
* Note: The implementations of InterlockedIncrement and InterlockedDecrement are based
* on atomic_increment and atomic_exchange_and_add from the Boost C++ Library. The license
* is virtually identical to the Apple license above but is included here for completeness.
*
* Boost Software License - Version 1.0 - August 17th, 2003
*
* Permission is hereby granted, free of charge, to any person or organization
* obtaining a copy of the software and accompanying documentation covered by
* this license (the "Software") to use, reproduce, display, distribute,
* execute, and transmit the Software, and to prepare derivative works of the
* Software, and to permit third-parties to whom the Software is furnished to
* do so, all subject to the following:
*

268
* The copyright notices in the Software and this entire statement, including
* the above license grant, this restriction and the following disclaimer,
* must be included in all copies of the Software, in whole or in part, and
* all derivative works of the Software, unless such copies or derivative
* works are solely in the form of machine-executable object code generated by
* a source language processor.
*
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
* FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NON-INFRINGEMENT. IN NO EVENT
* SHALL THE COPYRIGHT HOLDERS OR ANYONE DISTRIBUTING THE SOFTWARE BE LIABLE
* FOR ANY DAMAGES OR OTHER LIABILITY, WHETHER IN CONTRACT, TORT OR OTHERWISE,
* ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
* DEALINGS IN THE SOFTWARE.
*/
/*
* Copyright (C) 2008 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE

269
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006 - 2010, 2013 Apple Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2003 - 2013 Apple Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright

270
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 1999-2000 Harri Porten (porten@kde.org)
* Copyright (C) 2003, 2007, 2008, 2012 Apple Inc. All Rights Reserved.
*
* This library is free software; you can redistribute it and/or
* modify it under the terms of the GNU Lesser General Public
* License as published by the Free Software Foundation; either
* version 2 of the License, or (at your option) any later version.
*
* This library is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* Lesser General Public License for more details.
*
* You should have received a copy of the GNU Lesser General Public
* License along with this library; if not, write to the Free Software
* Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
*
*/

271
/*
* Copyright (C) 2011 University of Szeged
* Copyright (C) 2011 Zoltan Herczeg
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY UNIVERSITY OF SZEGED ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL UNIVERSITY OF SZEGED OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
The GNU General Public License (GPL-2.0)
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
Preamble

272
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public License is intended to guarantee your freedom to share and
change free software--to make sure the software is free for all its users. This General Public License
applies to most of the Free Software Foundation's software and to any other program whose
authors commit to using it. (Some other Free Software Foundation software is covered by the GNU
Library General Public License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses
are designed to make sure that you have the freedom to distribute copies of free software (and
charge for this service if you wish), that you receive source code or can get it if you want it, that you
can change the software or use pieces of it in new free programs; and that you know you can do
these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or
to ask you to surrender the rights. These restrictions translate to certain responsibilities for you if
you distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give
the recipients all the rights that you have. You must make sure that they, too, receive or can get the
source code. And you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license
which gives you legal permission to copy, distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain that everyone understands
that there is no warranty for this free software. If the software is modified by someone else and
passed on, we want its recipients to know that what they have is not the original, so that any
problems introduced by others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger
that redistributors of a free program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any patent must be licensed for
everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION

273
0. This License applies to any program or other work which contains a notice placed by the
copyright holder saying it may be distributed under the terms of this General Public License. The
"Program", below, refers to any such program or work, and a "work based on the Program" means
either the Program or any derivative work under copyright law: that is to say, a work containing the
Program or a portion of it, either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in the term "modification".) Each
licensee is addressed as "you".
Activities other than copying, distribution and modification are not covered by this License; they are
outside its scope. The act of running the Program is not restricted, and the output from the
Program is covered only if its contents constitute a work based on the Program (independent of
having been made by running the Program). Whether that is true depends on what the Program
does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in
any medium, provided that you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to this
License and to the absence of any warranty; and give any other recipients of the Program a copy of
this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work
based on the Program, and copy and distribute such modifications or work under the terms of
Section 1 above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the files
and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is
derived from the Program or any part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License.
c) If the modified program normally reads commands interactively when run, you must cause it,
when started running for such interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a notice that there is no warranty (or
else, saying that you provide a warranty) and that users may redistribute the program under these

274
conditions, and telling the user how to view a copy of this License. (Exception: if the Program itself
is interactive but does not normally print such an announcement, your work based on the Program
is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are
not derived from the Program, and can be reasonably considered independent and separate works
in themselves, then this License, and its terms, do not apply to those sections when you distribute
them as separate works. But when you distribute the same sections as part of a whole which is a
work based on the Program, the distribution of the whole must be on the terms of this License,
whose permissions for other licensees extend to the entire whole, and thus to each and every part
regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written
entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with
a work based on the Program) on a volume of a storage or distribution medium does not bring the
other work under the scope of this License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code
or executable form under the terms of Sections 1 and 2 above provided that you also do one of the
following:
a) Accompany it with the complete corresponding machine-readable source code, which must be
distributed under the terms of Sections 1 and 2 above on a medium customarily used for software
interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a
charge no more than your cost of physically performing source distribution, a complete machine-
readable copy of the corresponding source code, to be distributed under the terms of Sections 1
and 2 above on a medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding
source code. (This alternative is allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such an offer, in accord with
Subsection b above.)

275
The source code for a work means the preferred form of the work for making modifications to it.
For an executable work, complete source code means all the source code for all modules it
contains, plus any associated interface definition files, plus the scripts used to control compilation
and installation of the executable. However, as a special exception, the source code distributed
need not include anything that is normally distributed (in either source or binary form) with the
major components (compiler, kernel, and so on) of the operating system on which the executable
runs, unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated
place, then offering equivalent access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not compelled to copy the source
along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided
under this License. Any attempt otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License. However, parties who have
received copies, or rights, from you under this License will not have their licenses terminated so
long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by modifying or distributing the
Program (or any work based on the Program), you indicate your acceptance of this License to do so,
and all its terms and conditions for copying, distributing or modifying the Program or works based
on it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient
automatically receives a license from the original licensor to copy, distribute or modify the Program
subject to these terms and conditions. You may not impose any further restrictions on the
recipients' exercise of the rights granted herein. You are not responsible for enforcing compliance
by third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other
reason (not limited to patent issues), conditions are imposed on you (whether by court order,
agreement or otherwise) that contradict the conditions of this License, they do not excuse you from
the conditions of this License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a consequence you may
not distribute the Program at all. For example, if a patent license would not permit royalty-free

276
redistribution of the Program by all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to refrain entirely from distribution
of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the
balance of the section is intended to apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right
claims or to contest validity of any such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is implemented by public license practices.
Many people have made generous contributions to the wide range of software distributed through
that system in reliance on consistent application of that system; it is up to the author/donor to
decide if he or she is willing to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest
of this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by patents or
by copyrighted interfaces, the original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding those countries, so that
distribution is permitted only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the General Public
License from time to time. Such new versions will be similar in spirit to the present version, but may
differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version number of
this License which applies to it and "any later version", you have the option of following the terms
and conditions either of that version or of any later version published by the Free Software
Foundation. If the Program does not specify a version number of this License, you may choose any
version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution
conditions are different, write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free Software Foundation; we sometimes

277
make exceptions for this. Our decision will be guided by the two goals of preserving the free status
of all derivatives of our free software and of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE
PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN
WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS"
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD
THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR
OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE
PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL,
SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO
USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO
OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the public, the
best way to achieve this is to make it free software which everyone can redistribute and change
under these terms.
To do so, attach the following notices to the program. It is safest to attach them to the start of each
source file to most effectively convey the exclusion of warranty; and each file should have at least
the "copyright" line and a pointer to where the full notice is found.
One line to give the program's name and a brief idea of what it does.
Copyright (C) <year> <name of author>

278
This program is free software; you can redistribute it and/or modify it under the terms of the GNU
General Public License as published by the Free Software Foundation; either version 2 of the
License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without
even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if not,
write to the Free Software Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-1307
USA
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this when it starts in an interactive
mode:
Gnomovision version 69, Copyright (C) year name of author Gnomovision comes with ABSOLUTELY
NO WARRANTY; for details type `show w'. This is free software, and you are welcome to redistribute
it under certain conditions; type `show c' for details.
The hypothetical commands `show w' and `show c' should show the appropriate parts of the
General Public License. Of course, the commands you use may be called something other than
`show w' and `show c'; they could even be mouse-clicks or menu items--whatever suits your
program.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a
"copyright disclaimer" for the program, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program `Gnomovision' (which makes
passes at compilers) written by James Hacker.
signature of Ty Coon, 1 April 1989
Ty Coon, President of Vice
This General Public License does not permit incorporating your program into proprietary programs.
If your program is a subroutine library, you may consider it more useful to permit linking

279
proprietary applications with the library. If this is what you want to do, use the GNU Library General
Public License instead of this License.
GNU Lesser General Public License
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc. 59 Temple Place, Suite 330, Boston, MA
02111-1307 USA Everyone is permitted to copy and distribute verbatim copies of this license
document, but changing it is not allowed.
[This is the first released version of the Lesser GPL. It also counts as the successor of the GNU
Library Public License, version 2, hence the version number 2.1.]
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public Licenses are intended to guarantee your freedom to share and
change free software--to make sure the software is free for all its users.
This license, the Lesser General Public License, applies to some specially designated software
packages--typically libraries--of the Free Software Foundation and other authors who decide to use
it. You can use it too, but we suggest you first think carefully about whether this license or the
ordinary General Public License is the better strategy to use in any particular case, based on the
explanations below.
When we speak of free software, we are referring to freedom of use, not price. Our General Public
Licenses are designed to make sure that you have the freedom to distribute copies of free software
(and charge for this service if you wish); that you receive source code or can get it if you want it;
that you can change the software and use pieces of it in new free programs; and that you are
informed that you can do these things.
To protect your rights, we need to make restrictions that forbid distributors to deny you these
rights or to ask you to surrender these rights. These restrictions translate to certain responsibilities
for you if you distribute copies of the library or if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you must give the
recipients all the rights that we gave you. You must make sure that they, too, receive or can get the
source code. If you link other code with the library, you must provide complete object files to the
recipients, so that they can relink them with the library after making changes to the library and
recompiling it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the library, and (2) we offer you
this license, which gives you legal permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that there is no warranty for the free
library. Also, if the library is modified by someone else and passed on, the recipients should know

280
that what they have is not the original version, so that the original author's reputation will not be
affected by problems that might be introduced by others.
Finally, software patents pose a constant threat to the existence of any free program. We wish to
make sure that a company cannot effectively restrict the users of a free program by obtaining a
restrictive license from a patent holder. Therefore, we insist that any patent license obtained for a
version of the library must be consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the ordinary GNU General Public
License. This license, the GNU Lesser General Public License, applies to certain designated libraries,
and is quite different from the ordinary General Public License. We use this license for certain
libraries in order to permit linking those libraries into non-free programs.
When a program is linked with a library, whether statically or using a shared library, the
combination of the two is legally speaking a combined work, a derivative of the original library. The
ordinary General Public License therefore permits such linking only if the entire combination fits its
criteria of freedom. The Lesser General Public License permits more lax criteria for linking other
code with the library.
We call this license the "Lesser" General Public License because it does Less to protect the user's
freedom than the ordinary General Public License. It also provides other free software developers
Less of an advantage over competing non-free programs. These disadvantages are the reason we
use the ordinary General Public License for many libraries. However, the Lesser license provides
advantages in certain special circumstances.
For example, on rare occasions, there may be a special need to encourage the widest possible use
of a certain library, so that it becomes a de-facto standard. To achieve this, non-free programs
must be allowed to use the library. A more frequent case is that a free library does the same job as
widely used non-free libraries. In this case, there is little to gain by limiting the free library to free
software only, so we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free programs enables a greater
number of people to use a large body of free software. For example, permission to use the GNU C
Library in non-free programs enables many more people to use the whole GNU operating system,
as well as its variant, the GNU/Linux operating system.
Although the Lesser General Public License is Less protective of the users' freedom, it does ensure
that the user of a program that is linked with the Library has the freedom and the wherewithal to
run that program using a modified version of the Library.
The precise terms and conditions for copying, distribution and modification follow. Pay close
attention to the difference between a "work based on the library" and a "work that uses the library".
The former contains code derived from the library, whereas the latter must be combined with the
library in order to run.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION

281
0. This License Agreement applies to any software library or other program which contains a notice
placed by the copyright holder or other authorized party saying it may be distributed under the
terms of this Lesser General Public License (also called "this License"). Each licensee is addressed as
"you".
A "library" means a collection of software functions and/or data prepared so as to be conveniently
linked with application programs (which use some of those functions and data) to form
executables.
The "Library", below, refers to any such software library or work which has been distributed under
these terms. A "work based on the Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a portion of it, either verbatim or with
modifications and/or translated straightforwardly into another language. (Hereinafter, translation is
included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for making modifications to it. For a
library, complete source code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to control compilation and installation of
the library.
Activities other than copying, distribution and modification are not covered by this License; they are
outside its scope. The act of running a program using the Library is not restricted, and output from
such a program is covered only if its contents constitute a work based on the Library (independent
of the use of the Library in a tool for writing it). Whether that is true depends on what the Library
does and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library's complete source code as you
receive it, in any medium, provided that you conspicuously and appropriately publish on each copy
an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to
this License and to the absence of any warranty; and distribute a copy of this License along with the
Library.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Library or any portion of it, thus forming a work
based on the Library, and copy and distribute such modifications or work under the terms of
Section 1 above, provided that you also meet all of these conditions:
a) The modified work must itself be a software library.
b) You must cause the files modified to carry prominent notices stating that you changed the files
and the date of any change.
c) You must cause the whole of the work to be licensed at no charge to all third parties under the
terms of this License.
d) If a facility in the modified Library refers to a function or a table of data to be supplied by an
application program that uses the facility, other than as an argument passed when the facility is

282
invoked, then you must make a good faith effort to ensure that, in the event an application does
not supply such function or table, the facility still operates, and performs whatever part of its
purpose remains meaningful.
(For example, a function in a library to compute square roots has a purpose that is entirely well-
defined independent of the application. Therefore, Subsection 2d requires that any application-
supplied function or table used by this function must be optional: if the application does not supply
it, the square root function must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are
not derived from the Library, and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those sections when you distribute
them as separate works. But when you distribute the same sections as part of a whole which is a
work based on the Library, the distribution of the whole must be on the terms of this License,
whose permissions for other licensees extend to the entire whole, and thus to each and every part
regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written
entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library with the Library (or with a
work based on the Library) on a volume of a storage or distribution medium does not bring the
other work under the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public License instead of this
License to a given copy of the Library. To do this, you must alter all the notices that refer to this
License, so that they refer to the ordinary GNU General Public License, version 2, instead of to this
License. (If a newer version than version 2 of the ordinary GNU General Public License has appeared,
then you can specify that version instead if you wish.) Do not make any other change in these
notices.
Once this change is made in a given copy, it is irreversible for that copy, so the ordinary GNU
General Public License applies to all subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of the Library into a program that is
not a library.
4. You may copy and distribute the Library (or a portion or derivative of it, under Section 2) in
object code or executable form under the terms of Sections 1 and 2 above provided that you
accompany it with the complete corresponding machine-readable source code, which must be
distributed under the terms of Sections 1 and 2 above on a medium customarily used for software
interchange.
If distribution of object code is made by offering access to copy from a designated place, then
offering equivalent access to copy the source code from the same place satisfies the requirement to

283
distribute the source code, even though third parties are not compelled to copy the source along
with the object code.
5. A program that contains no derivative of any portion of the Library, but is designed to work with
the Library by being compiled or linked with it, is called a "work that uses the Library". Such a work,
in isolation, is not a derivative work of the Library, and therefore falls outside the scope of this
License.
However, linking a "work that uses the Library" with the Library creates an executable that is a
derivative of the Library (because it contains portions of the Library), rather than a "work that uses
the library". The executable is therefore covered by this License. Section 6 states terms for
distribution of such executables.
When a "work that uses the Library" uses material from a header file that is part of the Library, the
object code for the work may be a derivative work of the Library even though the source code is
not. Whether this is true is especially significant if the work can be linked without the Library, or if
the work is itself a library. The threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data structure layouts and accessors, and
small macros and small inline functions (ten lines or less in length), then the use of the object file is
unrestricted, regardless of whether it is legally a derivative work. (Executables containing this
object code plus portions of the Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may distribute the object code for the work
under the terms of Section 6. Any executables containing that work also fall under Section 6,
whether or not they are linked directly with the Library itself.
6. As an exception to the Sections above, you may also combine or link a "work that uses the
Library" with the Library to produce a work containing portions of the Library, and distribute that
work under terms of your choice, provided that the terms permit modification of the work for the
customer's own use and reverse engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the Library is used in it and that
the Library and its use are covered by this License. You must supply a copy of this License. If the
work during execution displays copyright notices, you must include the copyright notice for the
Library among them, as well as a reference directing the user to the copy of this License. Also, you
must do one of these things:
a) Accompany the work with the complete corresponding machine-readable source code for the
Library including whatever changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked with the Library, with the complete
machine-readable "work that uses the Library", as object code and/or source code, so that the user
can modify the Library and then relink to produce a modified executable containing the modified
Library. (It is understood that the user who changes the contents of definitions files in the Library
will not necessarily be able to recompile the application to use the modified definitions.)

284
b) Use a suitable shared library mechanism for linking with the Library. A suitable mechanism is one
that (1) uses at run time a copy of the library already present on the user's computer system, rather
than copying library functions into the executable, and (2) will operate properly with a modified
version of the library, if the user installs one, as long as the modified version is interface-
compatible with the version that the work was made with.
c) Accompany the work with a written offer, valid for at least three years, to give the same user the
materials specified in Subsection 6a, above, for a charge no more than the cost of performing this
distribution.
d) If distribution of the work is made by offering access to copy from a designated place, offer
equivalent access to copy the above specified materials from the same place.
e) Verify that the user has already received a copy of these materials or that you have already sent
this user a copy.
For an executable, the required form of the "work that uses the Library" must include any data and
utility programs needed for reproducing the executable from it. However, as a special exception,
the materials to be distributed need not include anything that is normally distributed (in either
source or binary form) with the major components (compiler, kernel, and so on) of the operating
system on which the executable runs, unless that component itself accompanies the executable.
It may happen that this requirement contradicts the license restrictions of other proprietary libraries
that do not normally accompany the operating system. Such a contradiction means you cannot use
both them and the Library together in an executable that you distribute.
7. You may place library facilities that are a work based on the Library side-by-side in a single
library together with other library facilities not covered by this License, and distribute such a
combined library, provided that the separate distribution of the work based on the Library and of
the other library facilities is otherwise permitted, and provided that you do these two things:
a) Accompany the combined library with a copy of the same work based on the Library, uncombined
with any other library facilities. This must be distributed under the terms of the Sections above.
b) Give prominent notice with the combined library of the fact that part of it is a work based on the
Library, and explaining where to find the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute the Library except as expressly
provided under this License. Any attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under this License will not have
their licenses terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Library or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by modifying or distributing the
Library (or any work based on the Library), you indicate your acceptance of this License to do so,

285
and all its terms and conditions for copying, distributing or modifying the Library or works based
on it.
10. Each time you redistribute the Library (or any work based on the Library), the recipient
automatically receives a license from the original licensor to copy, distribute, link with or modify
the Library subject to these terms and conditions. You may not impose any further restrictions on
the recipients' exercise of the rights granted herein. You are not responsible for enforcing
compliance by third parties with this License.
11. If, as a consequence of a court judgment or allegation of patent infringement or for any other
reason (not limited to patent issues), conditions are imposed on you (whether by court order,
agreement or otherwise) that contradict the conditions of this License, they do not excuse you from
the conditions of this License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a consequence you may
not distribute the Library at all. For example, if a patent license would not permit royalty-free
redistribution of the Library by all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to refrain entirely from distribution
of the Library.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the
balance of the section is intended to apply, and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right
claims or to contest validity of any such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system which is implemented by public license practices.
Many people have made generous contributions to the wide range of software distributed through
that system in reliance on consistent application of that system; it is up to the author/donor to
decide if he or she is willing to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest
of this License.
12. If the distribution and/or use of the Library is restricted in certain countries either by patents or
by copyrighted interfaces, the original copyright holder who places the Library under this License
may add an explicit geographical distribution limitation excluding those countries, so that
distribution is permitted only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
13. The Free Software Foundation may publish revised and/or new versions of the Lesser General
Public License from time to time. Such new versions will be similar in spirit to the present version,
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library specifies a version number of
this License which applies to it and "any later version", you have the option of following the terms

286
and conditions either of that version or of any later version published by the Free Software
Foundation. If the Library does not specify a license version number, you may choose any version
ever published by the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free programs whose distribution
conditions are incompatible with these, write to the author to ask for permission. For software
which is copyrighted by the Free Software Foundation, write to the Free Software Foundation; we
sometimes make exceptions for this. Our decision will be guided by the two goals of preserving the
free status of all derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE
LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN
WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE LIBRARY "AS IS"
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE LIBRARY IS WITH YOU. SHOULD
THE LIBRARY PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR
CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE
LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL,
SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO
USE THE LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE LIBRARY TO
OPERATE WITH ANY OTHER SOFTWARE), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Libraries
If you develop a new library, and you want it to be of the greatest possible use to the public, we
recommend making it free software that everyone can redistribute and change. You can do so by
permitting redistribution under these terms (or, alternatively, under the terms of the ordinary
General Public License).
To apply these terms, attach the following notices to the library. It is safest to attach them to the
start of each source file to most effectively convey the exclusion of warranty; and each file should
have at least the "copyright" line and a pointer to where the full notice is found.
<one line to give the library's name and an idea of what it does.> Copyright (C) <year> <name of
author>

287
This library is free software; you can redistribute it and/or modify it under the terms of the GNU
Lesser General Public License as published by the Free Software Foundation; either version 2.1 of
the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without
even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU Lesser General Public License for more details.
You should have received a copy of the GNU Lesser General Public License along with this library; if
not, write to the Free Software Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-
1307 USA
Also add information on how to contact you by electronic and paper mail.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a
"copyright disclaimer" for the library, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the library `Frob' (a library for tweaking
knobs) written by James Random Hacker.
signature of Ty Coon, 1 April 1990
Ty Coon, President of Vice
That's all there is to it!
Mozilla Public License, version 2.0
1. Definitions
1.1. “Contributor”
means each individual or legal entity that creates, contributes to the creation of, or owns Covered
Software.
1.2. “Contributor Version”
means the combination of the Contributions of others (if any) used by a Contributor and that
particular Contributor’s Contribution.
1.3. “Contribution”
means Covered Software of a particular Contributor.
1.4. “Covered Software”
means Source Code Form to which the initial Contributor has attached the notice in Exhibit A, the
Executable Form of such Source Code Form, and Modifications of such Source Code Form, in each
case including portions thereof.
1.5. “Incompatible With Secondary Licenses”
means
a. that the initial Contributor has attached the notice described in Exhibit B to the Covered
Software; or
b. that the Covered Software was made available under the terms of version 1.1 or earlier of
the License, but not also under the terms of a Secondary License.

288
1.6. “Executable Form”
means any form of the work other than Source Code Form.
1.7. “Larger Work”
means a work that combines Covered Software with other material, in a separate file or files, that is
not Covered Software.
1.8. “License”
means this document.
1.9. “Licensable”
means having the right to grant, to the maximum extent possible, whether at the time of the initial
grant or subsequently, any and all of the rights conveyed by this License.
1.10. “Modifications”
means any of the following:
a. any file in Source Code Form that results from an addition to, deletion from, or
modification of the contents of Covered Software; or
b. any new file in Source Code Form that contains any Covered Software.
1.11. “Patent Claims” of a Contributor
means any patent claim(s), including without limitation, method, process, and apparatus claims, in
any patent Licensable by such Contributor that would be infringed, but for the grant of the License,
by the making, using, selling, offering for sale, having made, import, or transfer of either its
Contributions or its Contributor Version.
1.12. “Secondary License”
means either the GNU General Public License, Version 2.0, the GNU Lesser General Public License,
Version 2.1, the GNU Affero General Public License, Version 3.0, or any later versions of those
licenses.
1.13. “Source Code Form”
means the form of the work preferred for making modifications.
1.14. “You” (or “Your”)
means an individual or a legal entity exercising rights under this License. For legal entities, “You”
includes any entity that controls, is controlled by, or is under common control with You. For
purposes of this definition, “control” means (a) the power, direct or indirect, to cause the direction
or management of such entity, whether by contract or otherwise, or (b) ownership of more than fifty
percent (50%) of the outstanding shares or beneficial ownership of such entity.
2. License Grants and Conditions
2.1. Grants
Each Contributor hereby grants You a world-wide, royalty-free, non-exclusive license:
a. under intellectual property rights (other than patent or trademark) Licensable by such
Contributor to use, reproduce, make available, modify, display, perform, distribute, and otherwise

289
exploit its Contributions, either on an unmodified basis, with Modifications, or as part of a Larger
Work; and
b. under Patent Claims of such Contributor to make, use, sell, offer for sale, have made,
import, and otherwise transfer either its Contributions or its Contributor Version.
2.2. Effective Date
The licenses granted in Section 2.1 with respect to any Contribution become effective for each
Contribution on the date the Contributor first distributes such Contribution.
2.3. Limitations on Grant Scope
The licenses granted in this Section 2 are the only rights granted under this License. No additional
rights or licenses will be implied from the distribution or licensing of Covered Software under this
License. Notwithstanding Section 2.1(b) above, no patent license is granted by a Contributor:
a. for any code that a Contributor has removed from Covered Software; or
b. for infringements caused by: (i) Your and any other third party’s modifications of Covered
Software, or (ii) the combination of its Contributions with other software (except as part of its
Contributor Version); or
c. under Patent Claims infringed by Covered Software in the absence of its Contributions.
This License does not grant any rights in the trademarks, service marks, or logos of any Contributor
(except as may be necessary to comply with the notice requirements in Section 3.4).
2.4. Subsequent Licenses
No Contributor makes additional grants as a result of Your choice to distribute the Covered
Software under a subsequent version of this License (see Section 10.2) or under the terms of a
Secondary License (if permitted under the terms of Section 3.3).
2.5. Representation
Each Contributor represents that the Contributor believes its Contributions are its original
creation(s) or it has sufficient rights to grant the rights to its Contributions conveyed by this
License.
2.6. Fair Use
This License is not intended to limit any rights You have under applicable copyright doctrines of fair
use, fair dealing, or other equivalents.
2.7. Conditions
Sections 3.1, 3.2, 3.3, and 3.4 are conditions of the licenses granted in Section 2.1.
3. Responsibilities
3.1. Distribution of Source Form
All distribution of Covered Software in Source Code Form, including any Modifications that You
create or to which You contribute, must be under the terms of this License. You must inform
recipients that the Source Code Form of the Covered Software is governed by the terms of this
License, and how they can obtain a copy of this License. You may not attempt to alter or restrict the
recipients’ rights in the Source Code Form.

290
3.2. Distribution of Executable Form
If You distribute Covered Software in Executable Form then:
a. such Covered Software must also be made available in Source Code Form, as described in
Section 3.1, and You must inform recipients of the Executable Form how they can obtain a copy of
such Source Code Form by reasonable means in a timely manner, at a charge no more than the cost
of distribution to the recipient; and
b. You may distribute such Executable Form under the terms of this License, or sublicense it
under different terms, provided that the license for the Executable Form does not attempt to limit
or alter the recipients’ rights in the Source Code Form under this License.
3.3. Distribution of a Larger Work
You may create and distribute a Larger Work under terms of Your choice, provided that You also
comply with the requirements of this License for the Covered Software. If the Larger Work is a
combination of Covered Software with a work governed by one or more Secondary Licenses, and the
Covered Software is not Incompatible With Secondary Licenses, this License permits You to
additionally distribute such Covered Software under the terms of such Secondary License(s), so that
the recipient of the Larger Work may, at their option, further distribute the Covered Software under
the terms of either this License or such Secondary License(s).
3.4. Notices
You may not remove or alter the substance of any license notices (including copyright notices,
patent notices, disclaimers of warranty, or limitations of liability) contained within the Source Code
Form of the Covered Software, except that You may alter any license notices to the extent required
to remedy known factual inaccuracies.
3.5. Application of Additional Terms
You may choose to offer, and to charge a fee for, warranty, support, indemnity or liability
obligations to one or more recipients of Covered Software. However, You may do so only on Your
own behalf, and not on behalf of any Contributor. You must make it absolutely clear that any such
warranty, support, indemnity, or liability obligation is offered by You alone, and You hereby agree
to indemnify every Contributor for any liability incurred by such Contributor as a result of warranty,
support, indemnity or liability terms You offer. You may include additional disclaimers of warranty
and limitations of liability specific to any jurisdiction.
4. Inability to Comply Due to Statute or Regulation
If it is impossible for You to comply with any of the terms of this License with respect to some or all
of the Covered Software due to statute, judicial order, or regulation then You must: (a) comply with
the terms of this License to the maximum extent possible; and (b) describe the limitations and the
code they affect. Such description must be placed in a text file included with all distributions of the
Covered Software under this License. Except to the extent prohibited by statute or regulation, such
description must be sufficiently detailed for a recipient of ordinary skill to be able to understand it.
5. Termination

291
5.1. The rights granted under this License will terminate automatically if You fail to comply with any
of its terms. However, if You become compliant, then the rights granted under this License from a
particular Contributor are reinstated (a) provisionally, unless and until such Contributor explicitly
and finally terminates Your grants, and (b) on an ongoing basis, if such Contributor fails to notify
You of the non-compliance by some reasonable means prior to 60 days after You have come back
into compliance. Moreover, Your grants from a particular Contributor are reinstated on an ongoing
basis if such Contributor notifies You of the non-compliance by some reasonable means, this is the
first time You have received notice of non-compliance with this License from such Contributor, and
You become compliant prior to 30 days after Your receipt of the notice.
5.2. If You initiate litigation against any entity by asserting a patent infringement claim (excluding
declaratory judgment actions, counter-claims, and cross-claims) alleging that a Contributor Version
directly or indirectly infringes any patent, then the rights granted to You by any and all Contributors
for the Covered Software under Section 2.1 of this License shall terminate.
5.3. In the event of termination under Sections 5.1 or 5.2 above, all end user license agreements
(excluding distributors and resellers) which have been validly granted by You or Your distributors
under this License prior to termination shall survive termination.
6. Disclaimer of Warranty
Covered Software is provided under this License on an “as is” basis, without warranty of any kind,
either expressed, implied, or statutory, including, without limitation, warranties that the Covered
Software is free of defects, merchantable, fit for a particular purpose or non-infringing. The entire
risk as to the quality and performance of the Covered Software is with You. Should any Covered
Software prove defective in any respect, You (not any Contributor) assume the cost of any necessary
servicing, repair, or correction. This disclaimer of warranty constitutes an essential part of this
License. No use of any Covered Software is authorized under this License except under this
disclaimer.
7. Limitation of Liability
Under no circumstances and under no legal theory, whether tort (including negligence), contract, or
otherwise, shall any Contributor, or anyone who distributes Covered Software as permitted above,
be liable to You for any direct, indirect, special, incidental, or consequential damages of any
character including, without limitation, damages for lost profits, loss of goodwill, work stoppage,
computer failure or malfunction, or any and all other commercial damages or losses, even if such
party shall have been informed of the possibility of such damages. This limitation of liability shall
not apply to liability for death or personal injury resulting from such party’s negligence to the
extent applicable law prohibits such limitation. Some jurisdictions do not allow the exclusion or
limitation of incidental or consequential damages, so this exclusion and limitation may not apply to
You.
8. Litigation

292
Any litigation relating to this License may be brought only in the courts of a jurisdiction where the
defendant maintains its principal place of business and such litigation shall be governed by laws of
that jurisdiction, without reference to its conflict-of-law provisions. Nothing in this Section shall
prevent a party’s ability to bring cross-claims or counter-claims.
9. Miscellaneous
This License represents the complete agreement concerning the subject matter hereof. If any
provision of this License is held to be unenforceable, such provision shall be reformed only to the
extent necessary to make it enforceable. Any law or regulation which provides that the language of
a contract shall be construed against the drafter shall not be used to construe this License against a
Contributor.
10. Versions of the License
10.1. New Versions
Mozilla Foundation is the license steward. Except as provided in Section 10.3, no one other than the
license steward has the right to modify or publish new versions of this License. Each version will be
given a distinguishing version number.
10.2. Effect of New Versions
You may distribute the Covered Software under the terms of the version of the License under which
You originally received the Covered Software, or under the terms of any subsequent version
published by the license steward.
10.3. Modified Versions
If you create software not governed by this License, and you want to create a new license for such
software, you may create and use a modified version of this License if you rename the license and
remove any references to the name of the license steward (except to note that such modified
license differs from this License).
10.4. Distributing Source Code Form that is Incompatible With Secondary Licenses
If You choose to distribute Source Code Form that is Incompatible With Secondary Licenses under
the terms of this version of the License, the notice described in Exhibit B of this License must be
attached.
Exhibit A - Source Code Form License Notice
This Source Code Form is subject to the terms of the Mozilla Public License, v. 2.0. If a copy of the
MPL was not distributed with this file, You can obtain one at http://mozilla.org/MPL/2.0/.
If it is not possible or desirable to put the notice in a particular file, then You may include the notice
in a location (such as a LICENSE file in a relevant directory) where a recipient would be likely to look
for such a notice.
You may add additional accurate notices of copyright ownership.
Exhibit B - “Incompatible With Secondary Licenses” Notice
This Source Code Form is “Incompatible With Secondary Licenses”, as defined by the Mozilla Public
License, v. 2.0.

293
/*
* Copyright (C) 2010 - 2013 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2004, 2006 Apple Computer, Inc. All rights reserved.
* Copyright (C) 2006 Alexey Proskuryakov <ap@nypop.com>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.

294
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2003, 2006, 2007, 2008, 2010 Apple Inc. All rights reserved.
* Copyright (C) 2005, 2008, 2010 Nokia Corporation and/or its subsidiary(-ies)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

295
*/
/*
* Copyright (C) 2010, The Android Open Source Project
* Copyright (C) 2012 Samsung Electronics. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE INC. AND ITS CONTRIBUTORS ``AS IS''
* AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
* THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE INC. OR ITS CONTRIBUTORS
* BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
* CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
* SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
* INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
* CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF
* THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2008, 2010 Apple Computer, Inc. All rights reserved.
* Copyright (C) 2009, 2010, 2012, 2013 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright

296
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2003, 2008, 2009 Apple Inc. All rights reserved.
* Copyright 2010, The Android Open Source Project
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT

297
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2008 - 2012 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions are
* met:
*
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following disclaimer
* in the documentation and/or other materials provided with the
* distribution.
* * Neither the name of Google Inc. nor the names of its
* contributors may be used to endorse or promote products derived from
* this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2008, 2009, 2012, 2013 Apple Inc. All rights reserved.
* Copyright (C) 2008 Cameron Zwarich <cwzwarich@uwaterloo.ca>
* Copyright (C) 2012 Igalia, S.L.

298
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright 2008, 2010 The Android Open Source Project
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*

299
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (c) 2012 Motorola Mobility, Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY MOTOROLA MOBILITY, INC. AND ITS CONTRIBUTORS
* ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
* THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL MOTOROLA MOBILITY, INC. OR ITS
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
* OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
* WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF
* THE POSSIBILITY OF SUCH DAMAGE.
*/

300
/*
* Copyright (C) 1999 Lars Knoll (knoll@kde.org)
* Copyright (C) 2003 - 2011 Apple Inc. All rights reserved.
* Copyright (C) 2009 - 2012 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE INC. AND ITS CONTRIBUTORS ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE INC. OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
* ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
* SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2012 Google Inc. All rights reserved.
* Copyright (C) 2013 Apple Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions are
* met:
*
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Neither the name of Google Inc. nor the names of its
* contributors may be used to endorse or promote products derived from

301
* this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2010 Alex Milowski (alex@milowski.com). All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

302
*/
/*
* Copyright (C) 2006, 2007, 2008, 2009 Apple Inc. All rights reserved.
* Copyright (C) 2008 Nokia Corporation and/or its subsidiary(-ies)
* Copyright (C) 2008, 2009 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2007, 2008, 2009 Apple Inc. All rights reserved.
* Copyright (C) 2008, 2009 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions

303
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2007 Apple Inc. All rights reserved.
* Copyright (C) 2008 Collabora, Ltd. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE

304
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* CSS Media Query
*
* Copyright (C) 2006 Kimmo Kinnunen <kimmo.t.kinnunen@nokia.com>.
* Copyright (C) 2010 Nokia Corporation and/or its subsidiary(-ies).
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/

305
/*
* Copyright (C) 2011, 2012, 2013 Adobe Systems Incorporated. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above
* copyright notice, this list of conditions and the following
* disclaimer.
* 2. Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following
* disclaimer in the documentation and/or other materials
* provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE
* LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
* OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
* TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
* THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*/
/*
* Copyright (C) 2012 Intel Corporation. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above

306
* copyright notice, this list of conditions and the following
* disclaimer.
* 2. Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following
* disclaimer in the documentation and/or other materials
* provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE
* LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
* OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
* TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
* THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*/
/*
* Copyright (C) 2005 Frerich Raabe <raabe@kde.org>
* Copyright (C) 2006, 2009 Apple Inc.
* Copyright (C) 2007 Alexey Proskuryakov <ap@webkit.org>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR
* IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES

307
* OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.
* IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
* INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2008, 2010 Apple Inc. All rights reserved.
* Copyright (C) 2008, 2009 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
* Copyright (C) 2009, 2010 Google, Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*

308
* Copyright (C) 2011 - 2013 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions are
* met:
*
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Neither the name of Google Inc. nor the names of its
* contributors may be used to endorse or promote products derived from
* this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2011 University of Szeged
* Copyright (C) 2011 Gabor Loki <loki@webkit.org>
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.

309
*
* THIS SOFTWARE IS PROVIDED BY UNIVERSITY OF SZEGED ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL UNIVERSITY OF SZEGED OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2011 Google Inc. All rights reserved.
* Copyright (C) 2012 Intel Corporation. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions are
* met:
*
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following disclaimer
* in the documentation and/or other materials provided with the
* distribution.
* * Neither the name of Google Inc. nor the names of its
* contributors may be used to endorse or promote products derived from
* this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT

310
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2007, 2008 Apple Inc. All rights reserved.
* Copyright (C) 2007 Justin Haygood (jhaygood@reaktix.com)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2009 Alex Milowski (alex@milowski.com). All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions

311
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2010 Adam Barth. All Rights Reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,

312
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2009 Apple Inc. All Rights Reserved.
* Copyright (C) 2012 Igalia S.L.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2011 Google Inc. All rights reserved.
* Copyright (C) 2012 Motorola Mobility Inc.
*
* Redistribution and use in source and binary forms, with or without

313
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2003, 2004, 2006, 2007, 2009, 2010 Apple Inc. All rights reserved.
* Copyright (C) 2005, 2010 Nokia Corporation and/or its subsidiary(-ies)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR

314
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006 Samuel Weinig (sam.weinig@gmail.com)
* Copyright (C) 2004, 2005, 2006 Apple Computer, Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2010 University of Szeged
* Copyright (C) 2010 Zoltan Herczeg

315
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY UNIVERSITY OF SZEGED ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL UNIVERSITY OF SZEGED OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2005 Frerich Raabe <raabe@kde.org>
* Copyright (C) 2006, 2009 Apple Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR

316
* IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
* OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.
* IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
* INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2012 Patrick Gansterer <paroga@paroga.com>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2009 Alex Milowski (alex@milowski.com). All rights reserved.
* Copyright (C) 2010 Apple Inc. All rights reserved.

317
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2008, 2009, 2010, 2012, 2013 Apple Inc. All rights reserved.
* Copyright (C) 2008 Cameron Zwarich <cwzwarich@uwaterloo.ca>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived

318
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2011 Adobe Systems Incorporated. All rights reserved.
* Copyright (C) 2012 Apple Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above
* copyright notice, this list of conditions and the following
* disclaimer.
* 2. Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following
* disclaimer in the documentation and/or other materials
* provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE
* LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
* OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY

319
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
* TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
* THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*/
/*
* Copyright (C) 2004, 2005, 2006, 2007 Nikolas Zimmermann <zimmermann@kde.org>
* Copyright (C) 2004, 2005 Rob Buis <buis@kde.org>
* Copyright (C) 2005 Eric Seidel <eric@webkit.org>
* Copyright (C) 2010 Zoltan Herczeg <zherczeg@webkit.org>
* Copyright (C) 2011 University of Szeged
* Copyright (C) 2011 Renata Hodovan <reni@webkit.org>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY UNIVERSITY OF SZEGED ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL UNIVERSITY OF SZEGED OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2003, 2006, 2009 Apple Inc. All rights reserved.

320
* Copyright (C) 2006 Rob Buis <buis@kde.org>
* Copyright (C) 2007-2008 Torch Mobile, Inc.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2011 Ericsson AB. All rights reserved.
* Copyright (C) 2012 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer
* in the documentation and/or other materials provided with the

321
* distribution.
* 3. Neither the name of Ericsson nor the names of its contributors
* may be used to endorse or promote products derived from this
* software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright 2010 Apple Inc. All rights reserved.
* Copyright (C) 2012 Samsung Electronics. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR

322
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2012, 2013 Intel Corporation. All rights reserved.
* Copyright (C) 2007, 2008, 2012 Apple Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above
* copyright notice, this list of conditions and the following
* disclaimer.
* 2. Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following
* disclaimer in the documentation and/or other materials
* provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE
* LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
* OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
* TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
* THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*/
/*
* Copyright (C) 2009 Alex Milowski (alex@milowski.com). All rights reserved.

323
* Copyright (C) 2010 François Sausset (sausset@gmail.com). All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2010 Nokia Corporation and/or its subsidiary(-ies)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE

324
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright 2008, The Android Open Source Project
* Copyright (C) 2012 Research In Motion Limited. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*

325
* Copyright (C) 2009, 2012 Apple Inc. All rights reserved.
* Copyright (C) 2010 Patrick Gansterer <paroga@paroga.com>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2003, 2006 Apple Computer, Inc. All rights reserved.
* Copyright (C) 2006 Samuel Weinig <sam.weinig@gmail.com>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*

326
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2010 University of Szeged
* Copyright (C) 2010 Renata Hodovan (hodovan@inf.u-szeged.hu)
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY UNIVERSITY OF SZEGED ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL UNIVERSITY OF SZEGED OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

327
*/
// Copyright 2010 the V8 project authors. All rights reserved.
// Redistribution and use in source and binary forms, with or without
// modification, are permitted provided that the following conditions are
// met:
//
// * Redistributions of source code must retain the above copyright
// notice, this list of conditions and the following disclaimer.
// * Redistributions in binary form must reproduce the above
// copyright notice, this list of conditions and the following
// disclaimer in the documentation and/or other materials provided
// with the distribution.
// * Neither the name of Google Inc. nor the names of its
// contributors may be used to endorse or promote products derived
// from this software without specific prior written permission.
//
// THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
// "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
// LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
// A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
// OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
// SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
// LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
// DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
// THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
// (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
// OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
/*
* Copyright (C) 2007 Alexey Proskuryakov (ap@nypop.com)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright

328
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE COMPUTER, INC. ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL APPLE COMPUTER, INC. OR
* CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
* EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
* PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
* PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
* OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2007, 2008, 2010 Apple Inc. All rights reserved.
* Copyright (C) 2007 Justin Haygood (jhaygood@reaktix.com)
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES

329
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2008 Apple Inc. All rights reserved.
* Copyright (C) 2008 Cameron Zwarich <cwzwarich@uwaterloo.ca>
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2007, 2008, 2009, 2011 Apple Inc. All rights reserved.

330
* Copyright (C) 2008, 2009 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
* Copyright (C) Research In Motion Limited 2009. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2006, 2007, 2008, 2009, 2010, 2011 Apple Inc. All rights reserved.
* Copyright (C) 2008 Nokia Corporation and/or its subsidiary(-ies)
* Copyright (C) 2008, 2009 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
* Copyright (C) 2008 Alp Toker <alp@atoker.com>
* Copyright (C) Research In Motion Limited 2009. All rights reserved.
* Copyright (C) 2011 Kris Jordan <krisjordan@gmail.com>
* Copyright (C) 2011 Google Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without

331
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of Apple Computer, Inc. ("Apple") nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY APPLE AND ITS CONTRIBUTORS "AS IS" AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
* ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
* THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 1999 Lars Knoll (knoll@kde.org)
* Copyright (C) 2004-2005 Allan Sandfeld Jensen (kde@carewolf.com)
* Copyright (C) 2006, 2007 Nicholas Shanks (webkit@nickshanks.com)
* Copyright (C) 2005, 2006, 2007, 2008, 2009, 2010, 2011, 2012 Apple Inc. All rights reserved.
* Copyright (C) 2007 Alexey Proskuryakov <ap@webkit.org>
* Copyright (C) 2007, 2008 Eric Seidel <eric@webkit.org>
* Copyright (C) 2008, 2009 Torch Mobile Inc. All rights reserved. (http://www.torchmobile.com/)
* Copyright (c) 2011, Code Aurora Forum. All rights reserved.
* Copyright (C) Research In Motion Limited 2011. All rights reserved.
* Copyright (C) 2012 Google Inc. All rights reserved.
*
* This library is free software; you can redistribute it and/or
* modify it under the terms of the GNU Library General Public

332
* License as published by the Free Software Foundation; either
* version 2 of the License, or (at your option) any later version.
*
* This library is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* Library General Public License for more details.
*
* You should have received a copy of the GNU Library General Public License
* along with this library; see the file COPYING.LIB. If not, write to
* the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor,
* Boston, MA 02110-1301, USA.
*/
/* Copyright (C) 2012 Motorola Mobility Inc. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions are
* met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the distribution.
* 3. Neither the name of Motorola Mobility Inc. nor the names of its
* contributors may be used to endorse or promote products derived from this
* software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT

333
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
/*
* Copyright (C) 2011 Google Inc. All rights reserved.
* Copyright (C) 2011 Ericsson AB. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
*
* THIS SOFTWARE IS PROVIDED BY APPLE INC. AND ITS CONTRIBUTORS ``AS IS'' AND ANY
* EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
* DISCLAIMED. IN NO EVENT SHALL APPLE INC. OR ITS CONTRIBUTORS BE LIABLE FOR ANY
* DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
* (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
* ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
* SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/

DO NOT TRANSLATE OR LOCALIZE.
-----------------------------
%% This notice is provided with respect to ASM Bytecode Manipulation
Framework v5.0, which may be included with JRE 8, and JDK 8, and
OpenJDK 8.
--- begin of LICENSE ---
Copyright (c) 2000-2011 France Telecom
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. Neither the name of the copyright holders nor the names of its
contributors may be used to endorse or promote products derived from
this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
CONTRIBUTORS "AS IS"
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED
TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR
CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR

CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF
THE POSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
--------------------------------------------------------------------------------
%% This notice is provided with respect to BSDiff v4.3, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright 2003-2005 Colin Percival
All rights reserved
Redistribution and use in source and binary forms, with or without
modification, are permitted providing that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR

PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING
IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to CodeViewer 1.0, which may be
included with JDK 8.
--- begin of LICENSE ---
Copyright 1999 by CoolServlets.com.
Any errors or suggested improvements to this class can be reported as
instructed on CoolServlets.com. We hope you enjoy this program... your
comments will encourage further development! This software is distributed
under the terms of the BSD License. Redistribution and use in source and
binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation

and/or other materials provided with the distribution.
Neither name of CoolServlets.com nor the names of its contributors may be
used to endorse or promote products derived from this software without
specific prior written permission.
THIS SOFTWARE IS PROVIDED BY COOLSERVLETS.COM AND CONTRIBUTORS
``AS IS'' AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE
LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE."
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Cryptix AES 3.2.0, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---

Cryptix General License
Copyright (c) 1995-2005 The Cryptix Foundation Limited.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are
met:
1. Redistributions of source code must retain the copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in
the documentation and/or other materials provided with the
distribution.
THIS SOFTWARE IS PROVIDED BY THE CRYPTIX FOUNDATION LIMITED AND
CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED.
IN NO EVENT SHALL THE CRYPTIX FOUNDATION LIMITED OR CONTRIBUTORS
BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN
IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.

--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to CUP Parser Generator for
Java 0.10k, which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright 1996-1999 by Scott Hudson, Frank Flannery, C. Scott Ananian
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted, provided
that the above copyright notice appear in all copies and that both the
copyright notice and this permission notice and warranty disclaimer appear in
supporting documentation, and that the names of the authors or their
employers not be used in advertising or publicity pertaining to distribution of
the software without specific, written prior permission.
The authors and their employers disclaim all warranties with regard to
this software, including all implied warranties of merchantability and fitness.
In no event shall the authors or their employers be liable for any special,
indirect or consequential damages or any damages whatsoever resulting from
loss of use, data or profits, whether in an action of contract, negligence or
other tortious action, arising out of or in connection with the use or
performance of this software.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Document Object Model (DOM) Level 2
& 3, which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---

W3C SOFTWARE NOTICE AND LICENSE
http://www.w3.org/Consortium/Legal/2002/copyright-software-20021231
This work (and included software, documentation such as READMEs, or other
related items) is being provided by the copyright holders under the following
license. By obtaining, using and/or copying this work, you (the licensee)
agree that you have read, understood, and will comply with the following terms
and conditions.
Permission to copy, modify, and distribute this software and its
documentation, with or without modification, for any purpose and without fee
or royalty is hereby granted, provided that you include the following on ALL
copies of the software and documentation or portions thereof, including
modifications:
1.The full text of this NOTICE in a location viewable to users of the
redistributed or derivative work.
2.Any pre-existing intellectual property disclaimers, notices, or terms and
conditions. If none exist, the W3C Software Short Notice should be included
(hypertext is preferred, text is permitted) within the body of any
redistributed or derivative code.
3.Notice of any changes or modifications to the files, including the date
changes were made. (We recommend you provide URIs to the location from
which the code is derived.)
THIS SOFTWARE AND DOCUMENTATION IS PROVIDED "AS IS," AND
COPYRIGHT HOLDERS
MAKE NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED,
INCLUDING BUT NOT
LIMITED TO, WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY
PARTICULAR
PURPOSE OR THAT THE USE OF THE SOFTWARE OR DOCUMENTATION WILL
NOT INFRINGE ANY

THIRD PARTY PATENTS,COPYRIGHTS, TRADEMARKS OR OTHER RIGHTS.
COPYRIGHT HOLDERS WILL NOT BE LIABLE FOR ANY DIRECT, INDIRECT,
SPECIAL
OR CONSEQUENTIAL DAMAGES ARISING OUT OF ANY USE OF THE SOFTWARE
OR
DOCUMENTATION. The name and trademarks of copyright holders may NOT be used
in advertising or publicity pertaining to the software without specific,
written prior permission. Title to copyright in this software and any
associated documentation will at all times remain with copyright holders.
____________________________________
This formulation of W3C's notice and license became active on December 31
2002. This version removes the copyright ownership notice such that this
license can be used with materials other than those owned by the W3C, reflects
that ERCIM is now a host of the W3C, includes references to this specific
dated version of the license, and removes the ambiguous grant of "use".
Otherwise, this version is the same as the previous version and is written so
as to preserve the Free Software Foundation's assessment of GPL compatibility
and OSI's certification under the Open Source Definition. Please see our
Copyright FAQ for common questions about using materials from our site,
including specific terms and conditions for packages like libwww, Amaya, and
Jigsaw. Other questions about this notice can be directed to
site-policy@w3.org.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Dynalink v0.5, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (c) 2009-2013, Attila Szegedi

All rights reserved.Redistribution and use in source and binary forms, with or
without modification, are permitted provided that the following conditions are
met:* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer. * Redistributions in
binary form must reproduce the above copyright notice, this list of
conditions and the following disclaimer in the documentation and/or other
materials provided with the distribution. * Neither the name of Attila
Szegedi nor the names of its contributors may be used to endorse or promote
products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
CONTRIBUTORS "AS IS"AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR
CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THEPOSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Elliptic Curve Cryptography, which

may be included with JRE 8, JDK 8, and OpenJDK 8.
You are receiving a copy of the Elliptic Curve Cryptography library in source
form with the JDK 8 and OpenJDK 8 source distributions, and as object code in
the JRE 8 & JDK 8 runtimes.
In the case of the JRE 8 & JDK 8 runtimes, the terms of the Oracle license do
NOT apply to the Elliptic Curve Cryptography library; it is licensed under the
following license, separately from Oracle's JDK & JRE. If you do not wish to
install the Elliptic Curve Cryptography library, you may delete the library
named libsunec.so (on Solaris and Linux systems) or sunec.dll (on Windows
systems) from the JRE bin directory reserved for native libraries.
--- begin of LICENSE ---
GNU LESSER GENERAL PUBLIC LICENSE
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
[This is the first released version of the Lesser GPL. It also counts
as the successor of the GNU Library Public License, version 2, hence
the version number 2.1.]
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
Licenses are intended to guarantee your freedom to share and change
free software--to make sure the software is free for all its users.
This license, the Lesser General Public License, applies to some

specially designated software packages--typically libraries--of the
Free Software Foundation and other authors who decide to use it. You
can use it too, but we suggest you first think carefully about whether
this license or the ordinary General Public License is the better
strategy to use in any particular case, based on the explanations below.
When we speak of free software, we are referring to freedom of use,
not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge
for this service if you wish); that you receive source code or can get
it if you want it; that you can change the software and use pieces of
it in new free programs; and that you are informed that you can do
these things.
To protect your rights, we need to make restrictions that forbid
distributors to deny you these rights or to ask you to surrender these
rights. These restrictions translate to certain responsibilities for
you if you distribute copies of the library or if you modify it.
For example, if you distribute copies of the library, whether gratis
or for a fee, you must give the recipients all the rights that we gave
you. You must make sure that they, too, receive or can get the source
code. If you link other code with the library, you must provide
complete object files to the recipients, so that they can relink them
with the library after making changes to the library and recompiling
it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the
library, and (2) we offer you this license, which gives you legal
permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that
there is no warranty for the free library. Also, if the library is
modified by someone else and passed on, the recipients should know
that what they have is not the original version, so that the original
author's reputation will not be affected by problems that might be

introduced by others.

Finally, software patents pose a constant threat to the existence of
any free program. We wish to make sure that a company cannot
effectively restrict the users of a free program by obtaining a
restrictive license from a patent holder. Therefore, we insist that
any patent license obtained for a version of the library must be
consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the
ordinary GNU General Public License. This license, the GNU Lesser
General Public License, applies to certain designated libraries, and
is quite different from the ordinary General Public License. We use
this license for certain libraries in order to permit linking those
libraries into non-free programs.
When a program is linked with a library, whether statically or using
a shared library, the combination of the two is legally speaking a
combined work, a derivative of the original library. The ordinary
General Public License therefore permits such linking only if the
entire combination fits its criteria of freedom. The Lesser General
Public License permits more lax criteria for linking other code with
the library.
We call this license the "Lesser" General Public License because it
does Less to protect the user's freedom than the ordinary General
Public License. It also provides other free software developers Less
of an advantage over competing non-free programs. These disadvantages
are the reason we use the ordinary General Public License for many
libraries. However, the Lesser license provides advantages in certain
special circumstances.
For example, on rare occasions, there may be a special need to
encourage the widest possible use of a certain library, so that it becomes
a de-facto standard. To achieve this, non-free programs must be
allowed to use the library. A more frequent case is that a free
library does the same job as widely used non-free libraries. In this
case, there is little to gain by limiting the free library to free

software only, so we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free
programs enables a greater number of people to use a large body of
free software. For example, permission to use the GNU C Library in
non-free programs enables many more people to use the whole GNU
operating system, as well as its variant, the GNU/Linux operating
system.
Although the Lesser General Public License is Less protective of the
users' freedom, it does ensure that the user of a program that is
linked with the Library has the freedom and the wherewithal to run
that program using a modified version of the Library.
The precise terms and conditions for copying, distribution and
modification follow. Pay close attention to the difference between a
"work based on the library" and a "work that uses the library". The
former contains code derived from the library, whereas the latter must
be combined with the library in order to run.

GNU LESSER GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND
MODIFICATION
0. This License Agreement applies to any software library or other
program which contains a notice placed by the copyright holder or
other authorized party saying it may be distributed under the terms of
this Lesser General Public License (also called "this License").
Each licensee is addressed as "you".
A "library" means a collection of software functions and/or data
prepared so as to be conveniently linked with application programs
(which use some of those functions and data) to form executables.
The "Library", below, refers to any such software library or work
which has been distributed under these terms. A "work based on the
Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a
portion of it, either verbatim or with modifications and/or translated
straightforwardly into another language. (Hereinafter, translation is
included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for
making modifications to it. For a library, complete source code means
all the source code for all modules it contains, plus any associated
interface definition files, plus the scripts used to control compilation
and installation of the library.
Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of
running a program using the Library is not restricted, and output from
such a program is covered only if its contents constitute a work based
on the Library (independent of the use of the Library in a tool for
writing it). Whether that is true depends on what the Library does
and what the program that uses the Library does.

1. You may copy and distribute verbatim copies of the Library's
complete source code as you receive it, in any medium, provided that
you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact
all the notices that refer to this License and to the absence of any
warranty; and distribute a copy of this License along with the
Library.
You may charge a fee for the physical act of transferring a copy,
and you may at your option offer warranty protection in exchange for a
fee.

2. You may modify your copy or copies of the Library or any portion
of it, thus forming a work based on the Library, and copy and
distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) The modified work must itself be a software library.
b) You must cause the files modified to carry prominent notices
stating that you changed the files and the date of any change.
c) You must cause the whole of the work to be licensed at no
charge to all third parties under the terms of this License.
d) If a facility in the modified Library refers to a function or a
table of data to be supplied by an application program that uses
the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that,
in the event an application does not supply such function or
table, the facility still operates, and performs whatever part of
its purpose remains meaningful.
(For example, a function in a library to compute square roots has
a purpose that is entirely well-defined independent of the
application. Therefore, Subsection 2d requires that any
application-supplied function or table used by this function must
be optional: if the application does not supply it, the square
root function must still compute square roots.)
These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Library,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Library, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the

entire whole, and thus to each and every part regardless of who wrote
it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library
with the Library (or with a work based on the Library) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public
License instead of this License to a given copy of the Library. To do
this, you must alter all the notices that refer to this License, so
that they refer to the ordinary GNU General Public License, version 2,
instead of to this License. (If a newer version than version 2 of the
ordinary GNU General Public License has appeared, then you can specify
that version instead if you wish.) Do not make any other change in
these notices.

Once this change is made in a given copy, it is irreversible for
that copy, so the ordinary GNU General Public License applies to all
subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of
the Library into a program that is not a library.
4. You may copy and distribute the Library (or a portion or
derivative of it, under Section 2) in object code or executable form
under the terms of Sections 1 and 2 above provided that you accompany
it with the complete corresponding machine-readable source code, which
must be distributed under the terms of Sections 1 and 2 above on a
medium customarily used for software interchange.
If distribution of object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the
source code from the same place satisfies the requirement to
distribute the source code, even though third parties are not
compelled to copy the source along with the object code.
5. A program that contains no derivative of any portion of the
Library, but is designed to work with the Library by being compiled or
linked with it, is called a "work that uses the Library". Such a
work, in isolation, is not a derivative work of the Library, and
therefore falls outside the scope of this License.
However, linking a "work that uses the Library" with the Library
creates an executable that is a derivative of the Library (because it
contains portions of the Library), rather than a "work that uses the
library". The executable is therefore covered by this License.
Section 6 states terms for distribution of such executables.
When a "work that uses the Library" uses material from a header file
that is part of the Library, the object code for the work may be a
derivative work of the Library even though the source code is not.
Whether this is true is especially significant if the work can be

linked without the Library, or if the work is itself a library. The
threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data
structure layouts and accessors, and small macros and small inline
functions (ten lines or less in length), then the use of the object
file is unrestricted, regardless of whether it is legally a derivative
work. (Executables containing this object code plus portions of the
Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may
distribute the object code for the work under the terms of Section 6.
Any executables containing that work also fall under Section 6,
whether or not they are linked directly with the Library itself.

6. As an exception to the Sections above, you may also combine or
link a "work that uses the Library" with the Library to produce a
work containing portions of the Library, and distribute that work
under terms of your choice, provided that the terms permit
modification of the work for the customer's own use and reverse
engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the
Library is used in it and that the Library and its use are covered by
this License. You must supply a copy of this License. If the work
during execution displays copyright notices, you must include the
copyright notice for the Library among them, as well as a reference
directing the user to the copy of this License. Also, you must do one
of these things:
a) Accompany the work with the complete corresponding
machine-readable source code for the Library including whatever
changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked
with the Library, with the complete machine-readable "work that
uses the Library", as object code and/or source code, so that the
user can modify the Library and then relink to produce a modified
executable containing the modified Library. (It is understood
that the user who changes the contents of definitions files in the
Library will not necessarily be able to recompile the application
to use the modified definitions.)
b) Use a suitable shared library mechanism for linking with the
Library. A suitable mechanism is one that (1) uses at run time a
copy of the library already present on the user's computer system,
rather than copying library functions into the executable, and (2)
will operate properly with a modified version of the library, if
the user installs one, as long as the modified version is
interface-compatible with the version that the work was made with.
c) Accompany the work with a written offer, valid for at

least three years, to give the same user the materials
specified in Subsection 6a, above, for a charge no more
than the cost of performing this distribution.
d) If distribution of the work is made by offering access to copy
from a designated place, offer equivalent access to copy the above
specified materials from the same place.
e) Verify that the user has already received a copy of these
materials or that you have already sent this user a copy.
For an executable, the required form of the "work that uses the
Library" must include any data and utility programs needed for
reproducing the executable from it. However, as a special exception,
the materials to be distributed need not include anything that is
normally distributed (in either source or binary form) with the major
components (compiler, kernel, and so on) of the operating system on
which the executable runs, unless that component itself accompanies
the executable.
It may happen that this requirement contradicts the license
restrictions of other proprietary libraries that do not normally
accompany the operating system. Such a contradiction means you cannot
use both them and the Library together in an executable that you
distribute.

7. You may place library facilities that are a work based on the
Library side-by-side in a single library together with other library
facilities not covered by this License, and distribute such a combined
library, provided that the separate distribution of the work based on
the Library and of the other library facilities is otherwise
permitted, and provided that you do these two things:
a) Accompany the combined library with a copy of the same work
based on the Library, uncombined with any other library
facilities. This must be distributed under the terms of the
Sections above.
b) Give prominent notice with the combined library of the fact
that part of it is a work based on the Library, and explaining
where to find the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute
the Library except as expressly provided under this License. Any
attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your
rights under this License. However, parties who have received copies,
or rights, from you under this License will not have their licenses
terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Library or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Library (or any work based on the
Library), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Library or works based on it.
10. Each time you redistribute the Library (or any work based on the
Library), the recipient automatically receives a license from the
original licensor to copy, distribute, link with or modify the Library

subject to these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties with
this License.

11. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Library at all. For example, if a patent
license would not permit royalty-free redistribution of the Library by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Library.
If any portion of this section is held invalid or unenforceable under any
particular circumstance, the balance of the section is intended to apply,
and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Library under this License may add
an explicit geographical distribution limitation excluding those countries,
so that distribution is permitted only in or among countries not thus

excluded. In such case, this License incorporates the limitation as if
written in the body of this License.
13. The Free Software Foundation may publish revised and/or new
versions of the Lesser General Public License from time to time.
Such new versions will be similar in spirit to the present version,
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library
specifies a version number of this License which applies to it and
"any later version", you have the option of following the terms and
conditions either of that version or of any later version published by
the Free Software Foundation. If the Library does not specify a
license version number, you may choose any version ever published by
the Free Software Foundation.

14. If you wish to incorporate parts of the Library into other free
programs whose distribution conditions are incompatible with these,
write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free
Software Foundation; we sometimes make exceptions for this. Our
decision will be guided by the two goals of preserving the free status
of all derivatives of our free software and of promoting the sharing
and reuse of software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO
WARRANTY FOR THE LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE
LAW.
EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS
AND/OR
OTHER PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO,
THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF
THE
LIBRARY IS WITH YOU. SHOULD THE LIBRARY PROVE DEFECTIVE, YOU
ASSUME
THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO
IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY
MODIFY
AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED ABOVE, BE LIABLE TO
YOU
FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE
THE

LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES
OR A
FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER SOFTWARE), EVEN
IF
SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF
SUCH
DAMAGES.
END OF TERMS AND CONDITIONS

How to Apply These Terms to Your New Libraries
If you develop a new library, and you want it to be of the greatest
possible use to the public, we recommend making it free software that
everyone can redistribute and change. You can do so by permitting
redistribution under these terms (or, alternatively, under the terms of the
ordinary General Public License).
To apply these terms, attach the following notices to the library. It is
safest to attach them to the start of each source file to most effectively
convey the exclusion of warranty; and each file should have at least the
"copyright" line and a pointer to where the full notice is found.
<one line to give the library's name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This library is free software; you can redistribute it and/or
modify it under the terms of the GNU Lesser General Public
License as published by the Free Software Foundation; either
version 2.1 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU
Lesser General Public License for more details.
You should have received a copy of the GNU Lesser General Public
License along with this library; if not, write to the Free Software
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Also add information on how to contact you by electronic and paper mail.
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a "copyright disclaimer" for the library, if
necessary. Here is a sample; alter the names:

Yoyodyne, Inc., hereby disclaims all copyright interest in the
library `Frob' (a library for tweaking knobs) written by James Random Hacker.
<signature of Ty Coon>, 1 April 1990
Ty Coon, President of Vice
That's all there is to it!
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to ECMAScript Language
Specification ECMA-262 Edition 5.1 which may be included with
JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright notice
Copyright c 2011 Ecma International
Ecma International
Rue du Rhone 114
CH-1204 Geneva
Tel: +41 22 849 6000
Fax: +41 22 849 6001
Web: http://www.ecma-international.org
This document and possible translations of it may be copied and furnished to
others, and derivative works that comment on or otherwise explain it or assist
in its implementation may be prepared, copied, published, and distributed, in
whole or in part, without restriction of any kind, provided that the above
copyright notice and this section are included on all such copies and derivative
works. However, this document itself may not be modified in any way, including
by removing the copyright notice or references to Ecma International, except as
needed for the purpose of developing any document or deliverable produced by

Ecma International (in which case the rules applied to copyrights must be
followed) or as required to translate it into languages other than English. The
limited permissions granted above are perpetual and will not be revoked by Ecma
International or its successors or assigns. This document and the information
contained herein is provided on an "AS IS" basis and ECMA INTERNATIONAL
DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT
LIMITED TO ANY
WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT
INFRINGE ANY OWNERSHIP
RIGHTS OR ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS
FOR A PARTICULAR
PURPOSE." Software License
All Software contained in this document ("Software)" is protected by copyright
and is being made available under the "BSD License", included below. This
Software may be subject to third party rights (rights from parties other than
Ecma International), including patent rights, and no licenses under such third
party rights are granted under this license even if the third party concerned is
a member of Ecma International. SEE THE ECMA CODE OF CONDUCT IN PATENT
MATTERS
AVAILABLE AT http://www.ecma-international.org/memento/codeofconduct.htm FOR
INFORMATION REGARDING THE LICENSING OF PATENT CLAIMS THAT ARE
REQUIRED TO
IMPLEMENT ECMA INTERNATIONAL STANDARDS*. Redistribution and use in
source and
binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation and/or
other materials provided with the distribution.
3. Neither the name of the authors nor Ecma International may be used to endorse

or promote products derived from this software without specific prior written
permission.
THIS SOFTWARE IS PROVIDED BY THE ECMA INTERNATIONAL "AS IS" AND
ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT
SHALL ECMA INTERNATIONAL BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING
IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY
OF SUCH DAMAGE.
--- end of LICENSE ---
%% This notice is provided with respect to Dynalink library which is included
with the Nashorn technology.
--- begin of LICENSE ---
Copyright (c) 2009-2013, Attila Szegedi
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright

notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of the copyright holder nor the names of
contributors may be used to endorse or promote products derived from
this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
CONTRIBUTORS "AS
IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL COPYRIGHT
HOLDER
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
%% This notice is provided with respect to Joni library which is included
with the Nashorn technology.
--- begin of LICENSE ---
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal in
the Software without restriction, including without limitation the rights to
use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies
of the Software, and to permit persons to whom the Software is furnished to do

so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE
SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to FontConfig 2.5, which may be
included with JRE 8, JDK 8, and OpenJDK 8 source distributions on
Linux and Solaris.
--- begin of LICENSE ---
Copyright c 2001,2003 Keith Packard
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that the
above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and that
the name of Keith Packard not be used in advertising or publicity pertaining

to distribution of the software without specific, written prior permission.
Keith Packard makes no representations about the suitability of this software
for any purpose. It is provided "as is" without express or implied warranty.
KEITH PACKARD DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL KEITH
PACKARD BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL
DAMAGES OR ANY
DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to IAIK PKCS#11 Wrapper,
which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
IAIK PKCS#11 Wrapper License
Copyright (c) 2002 Graz University of Technology. All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.

2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. The end-user documentation included with the redistribution, if any, must
include the following acknowledgment:
"This product includes software developed by IAIK of Graz University of
Technology."
Alternately, this acknowledgment may appear in the software itself, if and
wherever such third-party acknowledgments normally appear.
4. The names "Graz University of Technology" and "IAIK of Graz University of
Technology" must not be used to endorse or promote products derived from this
software without prior written permission.
5. Products derived from this software may not be called "IAIK PKCS Wrapper",
nor may "IAIK" appear in their name, without prior written permission of
Graz University of Technology.
THIS SOFTWARE IS PROVIDED "AS IS" AND ANY EXPRESSED OR IMPLIED
WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE
LICENSOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY,
OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR

OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE
POSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to ICU4C 4.0.1 and ICU4J 4.4, which
may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (c) 1995-2010 International Business Machines Corporation and others
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, and/or sell copies of the
Software, and to permit persons to whom the Software is furnished to do so,
provided that the above copyright notice(s) and this permission notice appear
in all copies of the Software and that both the above copyright notice(s) and
this permission notice appear in supporting documentation.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD
PARTY RIGHTS. IN
NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS INCLUDED IN THIS
NOTICE BE
LIABLE FOR ANY CLAIM, OR ANY SPECIAL INDIRECT OR CONSEQUENTIAL

DAMAGES, OR ANY
DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not
be used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization of the copyright holder.
All trademarks and registered trademarks mentioned herein are the property of
their respective owners.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to IJG JPEG 6b, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
This software is copyright (C) 1991-1998, Thomas G. Lane.
All Rights Reserved except as specified below.
Permission is hereby granted to use, copy, modify, and distribute this
software (or portions thereof) for any purpose, without fee, subject to these
conditions:
(1) If any part of the source code for this software is distributed, then this
README file must be included, with this copyright and no-warranty notice
unaltered; and any additions, deletions, or changes to the original files
must be clearly indicated in accompanying documentation.
(2) If only executable code is distributed, then the accompanying
documentation must state that "this software is based in part on the work of
the Independent JPEG Group".
(3) Permission for use of this software is granted only if the user accepts

full responsibility for any undesirable consequences; the authors accept
NO LIABILITY for damages of any kind.
These conditions apply to any software derived from or based on the IJG code,
not just to the unmodified library. If you use our work, you ought to
acknowledge us.
Permission is NOT granted for the use of any IJG author's name or company name
in advertising or publicity relating to this software or products derived from
it. This software may be referred to only as "the Independent JPEG Group's
software".
We specifically permit and encourage the use of this software as the basis of
commercial products, provided that all warranty or liability claims are
assumed by the product vendor.
--- end of LICENSE ---
--------------------------------------------------------------------------------
%% This notice is provided with respect to Joni v1.1.9, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,

EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE
SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to JOpt-Simple v3.0, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (c) 2004-2009 Paul R. Holser, Jr.
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,

EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES
OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT
HOLDERS BE
LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN
ACTION
OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
--- end of LICENSE ---
--------------------------------------------------------------------------------
%% This notice is provided with respect to JSON, which may be included
with JRE 8 & JDK 8.
--- begin of LICENSE ---
Copyright (c) 2002 JSON.org
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
The Software shall be used for Good, not Evil.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR

IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE
SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Kerberos functionality, which
which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
(C) Copyright IBM Corp. 1999 All Rights Reserved.
Copyright 1997 The Open Group Research Institute. All rights reserved.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Kerberos functionality from
FundsXpress, INC., which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (C) 1998 by the FundsXpress, INC.
All rights reserved.

Export of this software from the United States of America may require
a specific license from the United States Government. It is the
responsibility of any person or organization contemplating export to
obtain such a license before exporting.
WITHIN THAT CONSTRAINT, permission to use, copy, modify, and
distribute this software and its documentation for any purpose and
without fee is hereby granted, provided that the above copyright
notice appear in all copies and that both that copyright notice and
this permission notice appear in supporting documentation, and that
the name of FundsXpress. not be used in advertising or publicity pertaining
to distribution of the software without specific, written prior
permission. FundsXpress makes no representations about the suitability of
this software for any purpose. It is provided "as is" without express
or implied warranty.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED
WARRANTIES OF MERCHANTIBILITY AND FITNESS FOR A PARTICULAR
PURPOSE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Kronos OpenGL headers, which may be
included with JDK 8 and OpenJDK 8 source distributions.
--- begin of LICENSE ---
Copyright (c) 2007 The Khronos Group Inc.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and/or associated documentation files (the "Materials"), to

deal in the Materials without restriction, including without limitation the
rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
sell copies of the Materials, and to permit persons to whom the Materials are
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Materials.
THE MATERIALS ARE PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE MATERIALS OR THE USE OR OTHER
DEALINGS IN THE
MATERIALS.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% Portions Copyright Eastman Kodak Company 1992
-------------------------------------------------------------------------------
%% This notice is provided with respect to libpng 1.5.4, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
This copy of the libpng notices is provided for your convenience. In case of

any discrepancy between this copy and the notices in the file png.h that is
included in the libpng distribution, the latter shall prevail.
COPYRIGHT NOTICE, DISCLAIMER, and LICENSE:
If you modify libpng you may insert additional notices immediately following
this sentence.
This code is released under the libpng license.
libpng versions 1.2.6, August 15, 2004, through 1.5.4, July 7, 2011, are
Copyright (c) 2004, 2006-2011 Glenn Randers-Pehrson, and are
distributed according to the same disclaimer and license as libpng-1.2.5
with the following individual added to the list of Contributing Authors
Cosmin Truta
libpng versions 1.0.7, July 1, 2000, through 1.2.5 - October 3, 2002, are
Copyright (c) 2000-2002 Glenn Randers-Pehrson, and are
distributed according to the same disclaimer and license as libpng-1.0.6
with the following individuals added to the list of Contributing Authors
Simon-Pierre Cadieux
Eric S. Raymond
Gilles Vollant
and with the following additions to the disclaimer:
There is no warranty against interference with your enjoyment of the
library or against infringement. There is no warranty that our
efforts or the library will fulfill any of your particular purposes
or needs. This library is provided with all faults, and the entire
risk of satisfactory quality, performance, accuracy, and effort is with
the user.
libpng versions 0.97, January 1998, through 1.0.6, March 20, 2000, are

Copyright (c) 1998, 1999 Glenn Randers-Pehrson, and are
distributed according to the same disclaimer and license as libpng-0.96,
with the following individuals added to the list of Contributing Authors:
Tom Lane
Glenn Randers-Pehrson
Willem van Schaik
libpng versions 0.89, June 1996, through 0.96, May 1997, are
Copyright (c) 1996, 1997 Andreas Dilger
Distributed according to the same disclaimer and license as libpng-0.88,
with the following individuals added to the list of Contributing Authors:
John Bowler
Kevin Bracey
Sam Bushell
Magnus Holmgren
Greg Roelofs
Tom Tanner
libpng versions 0.5, May 1995, through 0.88, January 1996, are
Copyright (c) 1995, 1996 Guy Eric Schalnat, Group 42, Inc.
For the purposes of this copyright and license, "Contributing Authors"
is defined as the following set of individuals:
Andreas Dilger
Dave Martindale
Guy Eric Schalnat
Paul Schmidt
Tim Wegner
The PNG Reference Library is supplied "AS IS". The Contributing Authors
and Group 42, Inc. disclaim all warranties, expressed or implied,
including, without limitation, the warranties of merchantability and of
fitness for any purpose. The Contributing Authors and Group 42, Inc.

assume no liability for direct, indirect, incidental, special, exemplary,
or consequential damages, which may result from the use of the PNG
Reference Library, even if advised of the possibility of such damage.
Permission is hereby granted to use, copy, modify, and distribute this
source code, or portions hereof, for any purpose, without fee, subject
to the following restrictions:
1. The origin of this source code must not be misrepresented.
2. Altered versions must be plainly marked as such and must not
be misrepresented as being the original source.
3. This Copyright notice may not be removed or altered from any
source or altered source distribution.
The Contributing Authors and Group 42, Inc. specifically permit, without
fee, and encourage the use of this source code as a component to
supporting the PNG file format in commercial products. If you use this
source code in a product, acknowledgment is not required but would be
appreciated.
A "png_get_copyright" function is available, for convenient use in "about"
boxes and the like:
printf("%s",png_get_copyright(NULL));
Also, the PNG logo (in PNG format, of course) is supplied in the
files "pngbar.webp" and "pngbar.jpg (88x31) and "pngnow.webp" (98x31).
Libpng is OSI Certified Open Source Software. OSI Certified Open Source is a
certification mark of the Open Source Initiative.
Glenn Randers-Pehrson
glennrp at users.sourceforge.net

July 7, 2011
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to libungif 4.1.3, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
The GIFLIB distribution is Copyright (c) 1997 Eric S. Raymond
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN
THE SOFTWARE.

--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Little CMS 2.5, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Little CMS
Copyright (c) 1998-2011 Marti Maria Saguer
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE
SOFTWARE.

--- end of LICENSE ---
-------------------------------------------------------------------------------
%% Lucida is a registered trademark or trademark of Bigelow & Holmes in the
U.S. and other countries.
-------------------------------------------------------------------------------
%% This notice is provided with respect to Mesa 3D Graphics Library v4.1,
which may be included with JRE 8, JDK 8, and OpenJDK 8 source distributions.
--- begin of LICENSE ---
Mesa 3-D graphics library
Version: 4.1
Copyright (C) 1999-2002 Brian Paul All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the "Software"),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL

BRIAN PAUL BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR
IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Mozilla Network Security
Services (NSS), which is supplied with the JDK test suite in the OpenJDK
source code repository. It is licensed under Mozilla Public License (MPL),
version 2.0.
The NSS libraries are supplied in executable form, built from unmodified
NSS source code labeled with the "NSS_3.13.1_RTM" release tag.
The NSS source code is available in the OpenJDK source code repository at:
jdk/test/sun/security/pkcs11/nss/src
The NSS libraries are available in the OpenJDK source code repository at:
jdk/test/sun/security/pkcs11/nss/lib
--- begin of LICENSE ---
Mozilla Public License Version 2.0
==================================
1. Definitions
--------------
1.1. "Contributor"
means each individual or legal entity that creates, contributes to
the creation of, or owns Covered Software.

1.2. "Contributor Version"
means the combination of the Contributions of others (if any) used
by a Contributor and that particular Contributor's Contribution.
1.3. "Contribution"
means Covered Software of a particular Contributor.
1.4. "Covered Software"
means Source Code Form to which the initial Contributor has attached
the notice in Exhibit A, the Executable Form of such Source Code
Form, and Modifications of such Source Code Form, in each case
including portions thereof.
1.5. "Incompatible With Secondary Licenses"
means
(a) that the initial Contributor has attached the notice described
in Exhibit B to the Covered Software; or
(b) that the Covered Software was made available under the terms of
version 1.1 or earlier of the License, but not also under the
terms of a Secondary License.
1.6. "Executable Form"
means any form of the work other than Source Code Form.
1.7. "Larger Work"
means a work that combines Covered Software with other material, in
a separate file or files, that is not Covered Software.
1.8. "License"
means this document.
1.9. "Licensable"
means having the right to grant, to the maximum extent possible,

whether at the time of the initial grant or subsequently, any and
all of the rights conveyed by this License.
1.10. "Modifications"
means any of the following:
(a) any file in Source Code Form that results from an addition to,
deletion from, or modification of the contents of Covered
Software; or
(b) any new file in Source Code Form that contains any Covered
Software.
1.11. "Patent Claims" of a Contributor
means any patent claim(s), including without limitation, method,
process, and apparatus claims, in any patent Licensable by such
Contributor that would be infringed, but for the grant of the
License, by the making, using, selling, offering for sale, having
made, import, or transfer of either its Contributions or its
Contributor Version.
1.12. "Secondary License"
means either the GNU General Public License, Version 2.0, the GNU
Lesser General Public License, Version 2.1, the GNU Affero General
Public License, Version 3.0, or any later versions of those
licenses.
1.13. "Source Code Form"
means the form of the work preferred for making modifications.
1.14. "You" (or "Your")
means an individual or a legal entity exercising rights under this
License. For legal entities, "You" includes any entity that
controls, is controlled by, or is under common control with You. For
purposes of this definition, "control" means (a) the power, direct
or indirect, to cause the direction or management of such entity,

whether by contract or otherwise, or (b) ownership of more than
fifty percent (50%) of the outstanding shares or beneficial
ownership of such entity.
2. License Grants and Conditions
--------------------------------
2.1. Grants
Each Contributor hereby grants You a world-wide, royalty-free,
non-exclusive license:
(a) under intellectual property rights (other than patent or trademark)
Licensable by such Contributor to use, reproduce, make available,
modify, display, perform, distribute, and otherwise exploit its
Contributions, either on an unmodified basis, with Modifications, or
as part of a Larger Work; and
(b) under Patent Claims of such Contributor to make, use, sell, offer
for sale, have made, import, and otherwise transfer either its
Contributions or its Contributor Version.
2.2. Effective Date
The licenses granted in Section 2.1 with respect to any Contribution
become effective for each Contribution on the date the Contributor first
distributes such Contribution.
2.3. Limitations on Grant Scope
The licenses granted in this Section 2 are the only rights granted under
this License. No additional rights or licenses will be implied from the
distribution or licensing of Covered Software under this License.
Notwithstanding Section 2.1(b) above, no patent license is granted by a
Contributor:

(a) for any code that a Contributor has removed from Covered Software;
or
(b) for infringements caused by: (i) Your and any other third party's
modifications of Covered Software, or (ii) the combination of its
Contributions with other software (except as part of its Contributor
Version); or
(c) under Patent Claims infringed by Covered Software in the absence of
its Contributions.
This License does not grant any rights in the trademarks, service marks,
or logos of any Contributor (except as may be necessary to comply with
the notice requirements in Section 3.4).
2.4. Subsequent Licenses
No Contributor makes additional grants as a result of Your choice to
distribute the Covered Software under a subsequent version of this
License (see Section 10.2) or under the terms of a Secondary License (if
permitted under the terms of Section 3.3).
2.5. Representation
Each Contributor represents that the Contributor believes its
Contributions are its original creation(s) or it has sufficient rights
to grant the rights to its Contributions conveyed by this License.
2.6. Fair Use
This License is not intended to limit any rights You have under
applicable copyright doctrines of fair use, fair dealing, or other
equivalents.
2.7. Conditions

Sections 3.1, 3.2, 3.3, and 3.4 are conditions of the licenses granted
in Section 2.1.
3. Responsibilities
-------------------
3.1. Distribution of Source Form
All distribution of Covered Software in Source Code Form, including any
Modifications that You create or to which You contribute, must be under
the terms of this License. You must inform recipients that the Source
Code Form of the Covered Software is governed by the terms of this
License, and how they can obtain a copy of this License. You may not
attempt to alter or restrict the recipients' rights in the Source Code
Form.
3.2. Distribution of Executable Form
If You distribute Covered Software in Executable Form then:
(a) such Covered Software must also be made available in Source Code
Form, as described in Section 3.1, and You must inform recipients of
the Executable Form how they can obtain a copy of such Source Code
Form by reasonable means in a timely manner, at a charge no more
than the cost of distribution to the recipient; and
(b) You may distribute such Executable Form under the terms of this
License, or sublicense it under different terms, provided that the
license for the Executable Form does not attempt to limit or alter
the recipients' rights in the Source Code Form under this License.
3.3. Distribution of a Larger Work
You may create and distribute a Larger Work under terms of Your choice,
provided that You also comply with the requirements of this License for
the Covered Software. If the Larger Work is a combination of Covered

Software with a work governed by one or more Secondary Licenses, and the
Covered Software is not Incompatible With Secondary Licenses, this
License permits You to additionally distribute such Covered Software
under the terms of such Secondary License(s), so that the recipient of
the Larger Work may, at their option, further distribute the Covered
Software under the terms of either this License or such Secondary
License(s).
3.4. Notices
You may not remove or alter the substance of any license notices
(including copyright notices, patent notices, disclaimers of warranty,
or limitations of liability) contained within the Source Code Form of
the Covered Software, except that You may alter any license notices to
the extent required to remedy known factual inaccuracies.
3.5. Application of Additional Terms
You may choose to offer, and to charge a fee for, warranty, support,
indemnity or liability obligations to one or more recipients of Covered
Software. However, You may do so only on Your own behalf, and not on
behalf of any Contributor. You must make it absolutely clear that any
such warranty, support, indemnity, or liability obligation is offered by
You alone, and You hereby agree to indemnify every Contributor for any
liability incurred by such Contributor as a result of warranty, support,
indemnity or liability terms You offer. You may include additional
disclaimers of warranty and limitations of liability specific to any
jurisdiction.
4. Inability to Comply Due to Statute or Regulation
---------------------------------------------------
If it is impossible for You to comply with any of the terms of this
License with respect to some or all of the Covered Software due to
statute, judicial order, or regulation then You must: (a) comply with
the terms of this License to the maximum extent possible; and (b)

describe the limitations and the code they affect. Such description must
be placed in a text file included with all distributions of the Covered
Software under this License. Except to the extent prohibited by statute
or regulation, such description must be sufficiently detailed for a
recipient of ordinary skill to be able to understand it.
5. Termination
--------------
5.1. The rights granted under this License will terminate automatically
if You fail to comply with any of its terms. However, if You become
compliant, then the rights granted under this License from a particular
Contributor are reinstated (a) provisionally, unless and until such
Contributor explicitly and finally terminates Your grants, and (b) on an
ongoing basis, if such Contributor fails to notify You of the
non-compliance by some reasonable means prior to 60 days after You have
come back into compliance. Moreover, Your grants from a particular
Contributor are reinstated on an ongoing basis if such Contributor
notifies You of the non-compliance by some reasonable means, this is the
first time You have received notice of non-compliance with this License
from such Contributor, and You become compliant prior to 30 days after
Your receipt of the notice.
5.2. If You initiate litigation against any entity by asserting a patent
infringement claim (excluding declaratory judgment actions,
counter-claims, and cross-claims) alleging that a Contributor Version
directly or indirectly infringes any patent, then the rights granted to
You by any and all Contributors for the Covered Software under Section
2.1 of this License shall terminate.
5.3. In the event of termination under Sections 5.1 or 5.2 above, all
end user license agreements (excluding distributors and resellers) which
have been validly granted by You or Your distributors under this License
prior to termination shall survive termination.
************************************************************************

* *
* 6. Disclaimer of Warranty *
* ------------------------- *
* *
* Covered Software is provided under this License on an "as is" *
* basis, without warranty of any kind, either expressed, implied, or *
* statutory, including, without limitation, warranties that the *
* Covered Software is free of defects, merchantable, fit for a *
* particular purpose or non-infringing. The entire risk as to the *
* quality and performance of the Covered Software is with You. *
* Should any Covered Software prove defective in any respect, You *
* (not any Contributor) assume the cost of any necessary servicing, *
* repair, or correction. This disclaimer of warranty constitutes an *
* essential part of this License. No use of any Covered Software is *
* authorized under this License except under this disclaimer. *
* *
************************************************************************
************************************************************************
* *
* 7. Limitation of Liability *
* -------------------------- *
* *
* Under no circumstances and under no legal theory, whether tort *
* (including negligence), contract, or otherwise, shall any *
* Contributor, or anyone who distributes Covered Software as *
* permitted above, be liable to You for any direct, indirect, *
* special, incidental, or consequential damages of any character *
* including, without limitation, damages for lost profits, loss of *
* goodwill, work stoppage, computer failure or malfunction, or any *
* and all other commercial damages or losses, even if such party *
* shall have been informed of the possibility of such damages. This *
* limitation of liability shall not apply to liability for death or *
* personal injury resulting from such party's negligence to the *
* extent applicable law prohibits such limitation. Some *
* jurisdictions do not allow the exclusion or limitation of *

* incidental or consequential damages, so this exclusion and *
* limitation may not apply to You. *
* *
************************************************************************
8. Litigation
-------------
Any litigation relating to this License may be brought only in the
courts of a jurisdiction where the defendant maintains its principal
place of business and such litigation shall be governed by laws of that
jurisdiction, without reference to its conflict-of-law provisions.
Nothing in this Section shall prevent a party's ability to bring
cross-claims or counter-claims.
9. Miscellaneous
----------------
This License represents the complete agreement concerning the subject
matter hereof. If any provision of this License is held to be
unenforceable, such provision shall be reformed only to the extent
necessary to make it enforceable. Any law or regulation which provides
that the language of a contract shall be construed against the drafter
shall not be used to construe this License against a Contributor.
10. Versions of the License
---------------------------
10.1. New Versions
Mozilla Foundation is the license steward. Except as provided in Section
10.3, no one other than the license steward has the right to modify or
publish new versions of this License. Each version will be given a
distinguishing version number.
10.2. Effect of New Versions

You may distribute the Covered Software under the terms of the version
of the License under which You originally received the Covered Software,
or under the terms of any subsequent version published by the license
steward.
10.3. Modified Versions
If you create software not governed by this License, and you want to
create a new license for such software, you may create and use a
modified version of this License if you rename the license and remove
any references to the name of the license steward (except to note that
such modified license differs from this License).
10.4. Distributing Source Code Form that is Incompatible With Secondary
Licenses
If You choose to distribute Source Code Form that is Incompatible With
Secondary Licenses under the terms of this version of the License, the
notice described in Exhibit B of this License must be attached.
Exhibit A - Source Code Form License Notice
-------------------------------------------
This Source Code Form is subject to the terms of the Mozilla Public
License, v. 2.0. If a copy of the MPL was not distributed with this
file, You can obtain one at http://mozilla.org/MPL/2.0/.
If it is not possible or desirable to put the notice in a particular
file, then You may include the notice in a location (such as a LICENSE
file in a relevant directory) where a recipient would be likely to look
for such a notice.
You may add additional accurate notices of copyright ownership.
Exhibit B - "Incompatible With Secondary Licenses" Notice

---------------------------------------------------------
This Source Code Form is "Incompatible With Secondary Licenses", as
defined by the Mozilla Public License, v. 2.0.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to PC/SC Lite for Suse Linux v.1.1.1,
which may be included with JRE 8, JDK 8, and OpenJDK 8 on Linux and Solaris.
--- begin of LICENSE ---
Copyright (c) 1999-2004 David Corcoran <corcoran@linuxnet.com>
Copyright (c) 1999-2004 Ludovic Rousseau <ludovic.rousseau (at) free.fr>
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement:
This product includes software developed by:
David Corcoran <corcoran@linuxnet.com>
http://www.linuxnet.com (MUSCLE)
4. The name of the author may not be used to endorse or promote products
derived from this software without specific prior written permission.
Changes to this license can be made only by the copyright author with

explicit written consent.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED.
IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT
NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS
OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
USE OF
THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to PorterStemmer v4, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
See: http://tartarus.org/~martin/PorterStemmer
The software is completely free for any purpose, unless notes at the head of
the program text indicates otherwise (which is rare). In any case, the notes
about licensing are never more restrictive than the BSD License.
In every case where the software is not written by me (Martin Porter), this
licensing arrangement has been endorsed by the contributor, and it is

therefore unnecessary to ask the contributor again to confirm it.
I have not asked any contributors (or their employers, if they have them) for
proofs that they have the right to distribute their software in this way.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Relax NG Object/Parser v.20050510,
which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (c) Kohsuke Kawaguchi
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions: The above copyright
notice and this permission notice shall be included in all copies or
substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER

DEALINGS IN THE
SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to RelaxNGCC v1.12, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (c) 2000-2003 Daisuke Okajima and Kohsuke Kawaguchi.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. The end-user documentation included with the redistribution, if any, must
include the following acknowledgment:
"This product includes software developed by Daisuke Okajima
and Kohsuke Kawaguchi (http://relaxngcc.sf.net/)."
Alternately, this acknowledgment may appear in the software itself, if and
wherever such third-party acknowledgments normally appear.
4. The names of the copyright holders must not be used to endorse or promote
products derived from this software without prior written permission. For

written permission, please contact the copyright holders.
5. Products derived from this software may not be called "RELAXNGCC", nor may
"RELAXNGCC" appear in their name, without prior written permission of the
copyright holders.
THIS SOFTWARE IS PROVIDED "AS IS" AND ANY EXPRESSED OR IMPLIED
WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.IN NO EVENT SHALL
THE APACHE
SOFTWARE FOUNDATION OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF
USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE,
EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to SAX 2.0.1, which may be included
with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
SAX is free!

In fact, it's not possible to own a license to SAX, since it's been placed in
the public domain.
No Warranty
Because SAX is released to the public domain, there is no warranty for the
design or for the software implementation, to the extent permitted by
applicable law. Except when otherwise stated in writing the copyright holders
and/or other parties provide SAX "as is" without warranty of any kind, either
expressed or implied, including, but not limited to, the implied warranties
of merchantability and fitness for a particular purpose. The entire risk as
to the quality and performance of SAX is with you. Should SAX prove
defective, you assume the cost of all necessary servicing, repair or
correction.
In no event unless required by applicable law or agreed to in writing will
any copyright holder, or any other party who may modify and/or redistribute
SAX, be liable to you for damages, including any general, special, incidental
or consequential damages arising out of the use or inability to use SAX
(including but not limited to loss of data or data being rendered inaccurate
or losses sustained by you or third parties or a failure of the SAX to
operate with any other programs), even if such holder or other party has been
advised of the possibility of such damages.
Copyright Disclaimers
This page includes statements to that effect by David Megginson, who would
have been able to claim copyright for the original work. SAX 1.0
Version 1.0 of the Simple API for XML (SAX), created collectively by the
membership of the XML-DEV mailing list, is hereby released into the public
domain.
No one owns SAX: you may use it freely in both commercial and non-commercial
applications, bundle it with your software distribution, include it on a
CD-ROM, list the source code in a book, mirror the documentation at your own

web site, or use it in any other way you see fit.
David Megginson, sax@megginson.com
1998-05-11
SAX 2.0
I hereby abandon any property rights to SAX 2.0 (the Simple API for XML), and
release all of the SAX 2.0 source code, compiled code, and documentation
contained in this distribution into the Public Domain. SAX comes with NO
WARRANTY or guarantee of fitness for any purpose.
David Megginson, david@megginson.com
2000-05-05
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to SoftFloat version 2b, which may be
included with JRE 8, JDK 8, and OpenJDK 8 on Linux/ARM.
--- begin of LICENSE ---
Use of any of this software is governed by the terms of the license below:
SoftFloat was written by me, John R. Hauser. This work was made possible in
part by the International Computer Science Institute, located at Suite 600,
1947 Center Street, Berkeley, California 94704. Funding was partially
provided by the National Science Foundation under grant MIP-9311980. The
original version of this code was written as part of a project to build
a fixed-point vector processor in collaboration with the University of
California at Berkeley, overseen by Profs. Nelson Morgan and John Wawrzynek.
THIS SOFTWARE IS DISTRIBUTED AS IS, FOR FREE. Although reasonable effort
has been made to avoid it, THIS SOFTWARE MAY CONTAIN FAULTS THAT WILL AT

TIMES RESULT IN INCORRECT BEHAVIOR. USE OF THIS SOFTWARE IS
RESTRICTED TO
PERSONS AND ORGANIZATIONS WHO CAN AND WILL TAKE FULL
RESPONSIBILITY FOR ALL
LOSSES, COSTS, OR OTHER PROBLEMS THEY INCUR DUE TO THE SOFTWARE,
AND WHO
FURTHERMORE EFFECTIVELY INDEMNIFY JOHN HAUSER AND THE
INTERNATIONAL COMPUTER
SCIENCE INSTITUTE (possibly via similar legal warning) AGAINST ALL LOSSES,
COSTS, OR OTHER PROBLEMS INCURRED BY THEIR CUSTOMERS AND
CLIENTS DUE TO THE
SOFTWARE.
Derivative works are acceptable, even for commercial purposes, provided
that the minimal documentation requirements stated in the source code are
satisfied.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Sparkle 1.5,
which may be included with JRE 8 on Mac OS X.
--- begin of LICENSE ---
Copyright (c) 2012 Sparkle.org and Andy Matuschak
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all

copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE
SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% Portions licensed from Taligent, Inc.
-------------------------------------------------------------------------------
%% This notice is provided with respect to Thai Dictionary, which may be
included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Copyright (C) 1982 The Royal Institute, Thai Royal Government.
Copyright (C) 1998 National Electronics and Computer Technology Center,
National Science and Technology Development Agency,
Ministry of Science Technology and Environment,
Thai Royal Government.

Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE
SOFTWARE.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Unicode 6.2.0 & CLDR 21.0.1
which may be included with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
Unicode Terms of Use
For the general privacy policy governing access to this site, see the Unicode

Privacy Policy. For trademark usage, see the UnicodeR Consortium Name and
Trademark Usage Policy.
A. Unicode Copyright.
1. Copyright c 1991-2013 Unicode, Inc. All rights reserved.
2. Certain documents and files on this website contain a legend indicating
that "Modification is permitted." Any person is hereby authorized,
without fee, to modify such documents and files to create derivative
works conforming to the UnicodeR Standard, subject to Terms and
Conditions herein.
3. Any person is hereby authorized, without fee, to view, use, reproduce,
and distribute all documents and files solely for informational
purposes in the creation of products supporting the Unicode Standard,
subject to the Terms and Conditions herein.
4. Further specifications of rights and restrictions pertaining to the use
of the particular set of data files known as the "Unicode Character
Database" can be found in Exhibit 1.
5. Each version of the Unicode Standard has further specifications of
rights and restrictions of use. For the book editions (Unicode 5.0 and
earlier), these are found on the back of the title page. The online
code charts carry specific restrictions. All other files, including
online documentation of the core specification for Unicode 6.0 and
later, are covered under these general Terms of Use.
6. No license is granted to "mirror" the Unicode website where a fee is
charged for access to the "mirror" site.
7. Modification is not permitted with respect to this document. All copies
of this document must be verbatim.
B. Restricted Rights Legend. Any technical data or software which is licensed
to the United States of America, its agencies and/or instrumentalities

under this Agreement is commercial technical data or commercial computer
software developed exclusively at private expense as defined in FAR 2.101,
or DFARS 252.227-7014 (June 1995), as applicable. For technical data, use,
duplication, or disclosure by the Government is subject to restrictions as
set forth in DFARS 202.227-7015 Technical Data, Commercial and Items (Nov
1995) and this Agreement. For Software, in accordance with FAR 12-212 or
DFARS 227-7202, as applicable, use, duplication or disclosure by the
Government is subject to the restrictions set forth in this Agreement.
C. Warranties and Disclaimers.
1. This publication and/or website may include technical or typographical
errors or other inaccuracies . Changes are periodically added to the
information herein; these changes will be incorporated in new editions
of the publication and/or website. Unicode may make improvements and/or
changes in the product(s) and/or program(s) described in this
publication and/or website at any time.
2. If this file has been purchased on magnetic or optical media from
Unicode, Inc. the sole and exclusive remedy for any claim will be
exchange of the defective media within ninety (90) days of original
purchase.
3. EXCEPT AS PROVIDED IN SECTION C.2, THIS PUBLICATION AND/OR
SOFTWARE IS
PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND EITHER
EXPRESS, IMPLIED,
OR STATUTORY, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTIES
OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON-
INFRINGEMENT.
UNICODE AND ITS LICENSORS ASSUME NO RESPONSIBILITY FOR
ERRORS OR
OMISSIONS IN THIS PUBLICATION AND/OR SOFTWARE OR OTHER
DOCUMENTS WHICH
ARE REFERENCED BY OR LINKED TO THIS PUBLICATION OR THE
UNICODE WEBSITE.

D. Waiver of Damages. In no event shall Unicode or its licensors be liable for
any special, incidental, indirect or consequential damages of any kind, or
any damages whatsoever, whether or not Unicode was advised of the
possibility of the damage, including, without limitation, those resulting
from the following: loss of use, data or profits, in connection with the
use, modification or distribution of this information or its derivatives.
E.Trademarks & Logos.
1. The Unicode Word Mark and the Unicode Logo are trademarks of Unicode,
Inc. “The Unicode Consortium” and “Unicode, Inc.” are trade names of
Unicode, Inc. Use of the information and materials found on this
website indicates your acknowledgement of Unicode, Inc.’s exclusive
worldwide rights in the Unicode Word Mark, the Unicode Logo, and the
Unicode trade names.
2. The Unicode Consortium Name and Trademark Usage Policy (“Trademark
Policy”) are incorporated herein by reference and you agree to abide by
the provisions of the Trademark Policy, which may be changed from time
to time in the sole discretion of Unicode, Inc.
3. All third party trademarks referenced herein are the property of their
respective owners.
Miscellaneous.
1. Jurisdiction and Venue. This server is operated from a location in the
State of California, United States of America. Unicode makes no
representation that the materials are appropriate for use in other
locations. If you access this server from other locations, you are
responsible for compliance with local laws. This Agreement, all use of
this site and any claims and damages resulting from use of this site are
governed solely by the laws of the State of California without regard to
any principles which would apply the laws of a different jurisdiction.
The user agrees that any disputes regarding this site shall be resolved
solely in the courts located in Santa Clara County, California. The user
agrees said courts have personal jurisdiction and agree to waive any

right to transfer the dispute to any other forum.
2. Modification by Unicode. Unicode shall have the right to modify this
Agreement at any time by posting it to this site. The user may not
assign any part of this Agreement without Unicode’s prior written
consent.
3. Taxes. The user agrees to pay any taxes arising from access to this
website or use of the information herein, except for those based on
Unicode’s net income.
4. Severability. If any provision of this Agreement is declared invalid or
unenforceable, the remaining provisions of this Agreement shall remain
in effect.
5. Entire Agreement. This Agreement constitutes the entire agreement
between the parties.
EXHIBIT 1
UNICODE, INC. LICENSE AGREEMENT - DATA FILES AND SOFTWARE
Unicode Data Files include all data files under the directories
http://www.unicode.org/Public/, http://www.unicode.org/reports/, and
http://www.unicode.org/cldr/data/. Unicode Data Files do not include PDF
online code charts under the directory http://www.unicode.org/Public/.
Software includes any source code published in the Unicode Standard or under
the directories http://www.unicode.org/Public/,
http://www.unicode.org/reports/, and http://www.unicode.org/cldr/data/.
NOTICE TO USER: Carefully read the following legal agreement. BY DOWNLOADING,
INSTALLING, COPYING OR OTHERWISE USING UNICODE INC.'S DATA FILES
("DATA
FILES"), AND/OR SOFTWARE ("SOFTWARE"), YOU UNEQUIVOCALLY ACCEPT,
AND AGREE TO
BE BOUND BY, ALL OF THE TERMS AND CONDITIONS OF THIS AGREEMENT. IF
YOU DO NOT

AGREE, DO NOT DOWNLOAD, INSTALL, COPY, DISTRIBUTE OR USE THE DATA
FILES OR
SOFTWARE.
COPYRIGHT AND PERMISSION NOTICE
Copyright c 1991-2012 Unicode, Inc. All rights reserved. Distributed under the
Terms of Use in http://www.unicode.org/copyright.html.
Permission is hereby granted, free of charge, to any person obtaining a copy
of the Unicode data files and any associated documentation (the "Data Files")
or Unicode software and any associated documentation (the "Software") to deal
in the Data Files or Software without restriction, including without
limitation the rights to use, copy, modify, merge, publish, distribute, and/or
sell copies of the Data Files or Software, and to permit persons to whom the
Data Files or Software are furnished to do so, provided that (a) the above
copyright notice(s) and this permission notice appear with all copies of the
Data Files or Software, (b) both the above copyright notice(s) and this
permission notice appear in associated documentation, and (c) there is clear
notice in each modified Data File or in the Software as well as in the
documentation associated with the Data File(s) or Software that the data or
software has been modified.
THE DATA FILES AND SOFTWARE ARE PROVIDED "AS IS", WITHOUT
WARRANTY OF ANY
KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE
WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NONINFRINGEMENT OF THIRD
PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS
INCLUDED IN
THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL INDIRECT OR
CONSEQUENTIAL
DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR
PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER

TORTIOUS
ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THE
DATA FILES OR SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not
be used in advertising or otherwise to promote the sale, use or other dealings
in these Data Files or Software without prior written authorization of the
copyright holder.
Unicode and the Unicode logo are trademarks of Unicode, Inc. in the United
States and other countries. All third party trademarks referenced herein are
the property of their respective owners.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to UPX v3.01, which may be included
with JRE 8 on Windows.
--- begin of LICENSE ---
Use of any of this software is governed by the terms of the license below:
ooooo ooo ooooooooo. ooooooo ooooo
`888' `8' `888 `Y88. `8888 d8'
888 8 888 .d88' Y888..8P
888 8 888ooo88P' `8888'
888 8 888 .8PY888.
`88. .8' 888 d8' `888b
`YbodP' o888o o888o o88888o
The Ultimate Packer for eXecutables

Copyright (c) 1996-2000 Markus Oberhumer & Laszlo Molnar
http://wildsau.idv.uni-linz.ac.at/mfx/upx.html
http://www.nexus.hu/upx
http://upx.tsx.org
PLEASE CAREFULLY READ THIS LICENSE AGREEMENT, ESPECIALLY IF YOU
PLAN
TO MODIFY THE UPX SOURCE CODE OR USE A MODIFIED UPX VERSION.
ABSTRACT
========
UPX and UCL are copyrighted software distributed under the terms
of the GNU General Public License (hereinafter the "GPL").
The stub which is imbedded in each UPX compressed program is part
of UPX and UCL, and contains code that is under our copyright. The
terms of the GNU General Public License still apply as compressing
a program is a special form of linking with our stub.
As a special exception we grant the free usage of UPX for all
executables, including commercial programs.
See below for details and restrictions.
COPYRIGHT
=========
UPX and UCL are copyrighted software. All rights remain with the authors.
UPX is Copyright (C) 1996-2000 Markus Franz Xaver Johannes Oberhumer
UPX is Copyright (C) 1996-2000 Laszlo Molnar
UCL is Copyright (C) 1996-2000 Markus Franz Xaver Johannes Oberhumer

GNU GENERAL PUBLIC LICENSE
==========================
UPX and the UCL library are free software; you can redistribute them
and/or modify them under the terms of the GNU General Public License as
published by the Free Software Foundation; either version 2 of
the License, or (at your option) any later version.
UPX and UCL are distributed in the hope that they will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program; see the file COPYING.
SPECIAL EXCEPTION FOR COMPRESSED EXECUTABLES
============================================
The stub which is imbedded in each UPX compressed program is part
of UPX and UCL, and contains code that is under our copyright. The
terms of the GNU General Public License still apply as compressing
a program is a special form of linking with our stub.
Hereby Markus F.X.J. Oberhumer and Laszlo Molnar grant you special
permission to freely use and distribute all UPX compressed programs
(including commercial ones), subject to the following restrictions:
1. You must compress your program with a completely unmodified UPX
version; either with our precompiled version, or (at your option)
with a self compiled version of the unmodified UPX sources as
distributed by us.
2. This also implies that the UPX stub must be completely unmodfied, i.e.

the stub imbedded in your compressed program must be byte-identical
to the stub that is produced by the official unmodified UPX version.
3. The decompressor and any other code from the stub must exclusively get
used by the unmodified UPX stub for decompressing your program at
program startup. No portion of the stub may get read, copied,
called or otherwise get used or accessed by your program.
ANNOTATIONS
===========
- You can use a modified UPX version or modified UPX stub only for
programs that are compatible with the GNU General Public License.
- We grant you special permission to freely use and distribute all UPX
compressed programs. But any modification of the UPX stub (such as,
but not limited to, removing our copyright string or making your
program non-decompressible) will immediately revoke your right to
use and distribute a UPX compressed program.
- UPX is not a software protection tool; by requiring that you use
the unmodified UPX version for your proprietary programs we
make sure that any user can decompress your program. This protects
both you and your users as nobody can hide malicious code -
any program that cannot be decompressed is highly suspicious
by definition.
- You can integrate all or part of UPX and UCL into projects that
are compatible with the GNU GPL, but obviously you cannot grant
any special exceptions beyond the GPL for our code in your project.
- We want to actively support manufacturers of virus scanners and
similar security software. Please contact us if you would like to
incorporate parts of UPX or UCL into such a product.

Markus F.X.J. Oberhumer Laszlo Molnar
markus.oberhumer@jk.uni-linz.ac.at ml1050@cdata.tvnet.hu
Linz, Austria, 25 Feb 2000
Additional License(s)
The UPX license file is at http://upx.sourceforge.net/upx-license.html.
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to Xfree86-VidMode Extension 1.0,
which may be included with JRE 8, JDK 8, and OpenJDK 8 on Linux and Solaris.
--- begin of LICENSE ---
Version 1.1 of XFree86 ProjectLicence.
Copyright (C) 1994-2004 The XFree86 Project, Inc. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicence, and/or sell
copies of the Software, and to permit persons to whom the Software is furnished
to do so,subject to the following conditions:
1. Redistributions of source code must retain the above copyright
notice,this list of conditions, and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution, and in the same place

and form as other copyright, license and disclaimer information.
3. The end-user documentation included with the redistribution, if any,must
include the following acknowledgment: "This product includes
software developed by The XFree86 Project, Inc (http://www.xfree86.org/) and
its contributors", in the same place and form as other third-party
acknowledgments. Alternately, this acknowledgment may appear in the software
itself, in the same form and location as other such third-party
acknowledgments.
4. Except as contained in this notice, the name of The XFree86 Project,Inc
shall not be used in advertising or otherwise to promote the sale, use
or other dealings in this Software without prior written authorization from
The XFree86 Project, Inc.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED
WARRANTIES,INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO
EVENT SHALL THE XFREE86 PROJECT, INC OR ITS CONTRIBUTORS BE
LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL,SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO,PROCUREMENT OF SUBSTITUTE
GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING
IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH
DAMAGE.

--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to X Window System 6.8.2, which may be
included with JRE 8, JDK 8, and OpenJDK 8 on Linux and Solaris.
--- begin of LICENSE ---
Licenses
The X.Org Foundation March 2004
1. Introduction
The X.org Foundation X Window System distribution is a compilation of code and
documentation from many sources. This document is intended primarily as a
guide to the licenses used in the distribution: you must check each file
and/or package for precise redistribution terms. None-the-less, this summary
may be useful to many users. No software incorporating the XFree86 1.1 license
has been incorporated.
This document is based on the compilation from XFree86.
2. XFree86 License
XFree86 code without an explicit copyright is covered by the following
copyright/license:
Copyright (C) 1994-2003 The XFree86 Project, Inc. All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:

The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
XFREE86 PROJECT BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF
OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
Except as contained in this notice, the name of the XFree86 Project shall not
be used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization from the XFree86 Project.
3. Other Licenses
Portions of code are covered by the following licenses/copyrights. See
individual files for the copyright dates.
3.1. X/MIT Copyrights
3.1.1. X Consortium
Copyright (C) <date> X Consortium
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell

copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE X
CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall not be
used in advertising or otherwise to promote the sale, use or other dealings in
this Software without prior written authorization from the X Consortium.
X Window System is a trademark of X Consortium, Inc.
3.1.2. The Open Group
Copyright <date> The Open Group
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that the
above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation.
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.

THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO
EVENT SHALL THE
OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of The Open Group shall not be
used in advertising or otherwise to promote the sale, use or other dealings in
this Software without prior written authorization from The Open Group. 3.2.
Berkeley-based copyrights:
o
3.2.1. General
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. The name of the author may not be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR
IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES

OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO
EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER
IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE
POSSIBILITY OF SUCH DAMAGE. 3.2.2. UCB/LBL
Copyright (c) 1993 The Regents of the University of California. All rights
reserved.
This software was developed by the Computer Systems Engineering group at
Lawrence Berkeley Laboratory under DARPA contract BG 91-66 and contributed to
Berkeley.
All advertising materials mentioning features or use of this software must
display the following acknowledgement: This product includes software
developed by the University of California, Lawrence Berkeley Laboratory.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the

documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement: This product includes software
developed by the University of California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may
be used to endorse or promote products derived from this software without
specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS''
AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE
LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. 3.2.3.
The
NetBSD Foundation, Inc.
Copyright (c) 2003 The NetBSD Foundation, Inc. All rights reserved.
This code is derived from software contributed to The NetBSD Foundation by Ben
Collver <collver1@attbi.com>

Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement: This product includes software
developed by the NetBSD Foundation, Inc. and its contributors.
4. Neither the name of The NetBSD Foundation nor the names of its
contributors may be used to endorse or promote products derived from this
software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE NETBSD FOUNDATION, INC. AND
CONTRIBUTORS ``AS
IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE FOUNDATION OR CONTRIBUTORS BE
LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE

USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. 3.2.4.
Theodore
Ts'o.
Copyright Theodore Ts'o, 1994, 1995, 1996, 1997, 1998, 1999. All rights
reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
and the entire permission notice in its entirety, including the disclaimer
of warranties.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. he name of the author may not be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESS OR IMPLIED
WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE, ALL OF WHICH ARE HEREBY
DISCLAIMED. IN NO
EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER

IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF NOT
ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE. 3.2.5. Theo de Raadt and Damien Miller
Copyright (c) 1995,1999 Theo de Raadt. All rights reserved. Copyright (c)
2001-2002 Damien Miller. All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESS OR
IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO
EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER
IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED

OF THE
POSSIBILITY OF SUCH DAMAGE. 3.2.6. Todd C. Miller
Copyright (c) 1998 Todd C. Miller <Todd.Miller@courtesan.com>
Permission to use, copy, modify, and distribute this software for any purpose
with or without fee is hereby granted, provided that the above copyright
notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND TODD C. MILLER DISCLAIMS ALL
WARRANTIES
WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL TODD C. MILLER BE
LIABLE FOR
ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY
DAMAGES
WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER
IN AN ACTION
OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE. 3.2.7.
Thomas
Winischhofer
Copyright (C) 2001-2004 Thomas Winischhofer
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.

3. The name of the author may not be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS'' AND ANY EXPRESSED
OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO
EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER
IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE
POSSIBILITY OF SUCH DAMAGE. 3.3. NVIDIA Corp
Copyright (c) 1996 NVIDIA, Corp. All rights reserved.
NOTICE TO USER: The source code is copyrighted under U.S. and international
laws. NVIDIA, Corp. of Sunnyvale, California owns the copyright and as design
patents pending on the design and interface of the NV chips. Users and
possessors of this source code are hereby granted a nonexclusive, royalty-free
copyright and design patent license to use this code in individual and
commercial software.
Any use of this source code must include, in the user documentation and
internal comments to the code, notices to the end user as follows:
Copyright (c) 1996 NVIDIA, Corp. NVIDIA design patents pending in the U.S. and

foreign countries.
NVIDIA, CORP. MAKES NO REPRESENTATION ABOUT THE SUITABILITY OF
THIS SOURCE
CODE FOR ANY PURPOSE. IT IS PROVIDED "AS IS" WITHOUT EXPRESS OR
IMPLIED
WARRANTY OF ANY KIND. NVIDIA, CORP. DISCLAIMS ALL WARRANTIES WITH
REGARD TO
THIS SOURCE CODE, INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE. IN NO EVENT SHALL NVIDIA, CORP. BE
LIABLE
FOR ANY SPECIAL, INDIRECT, INCIDENTAL, OR CONSEQUENTIAL DAMAGES,
OR ANY
DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN
ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOURCE CODE. 3.4.
GLX Public
License
GLX PUBLIC LICENSE (Version 1.0 (2/11/99)) ("License")
Subject to any third party claims, Silicon Graphics, Inc. ("SGI") hereby
grants permission to Recipient (defined below), under Recipient's copyrights
in the Original Software (defined below), to use, copy, modify, merge,
publish, distribute, sublicense and/or sell copies of Subject Software
(defined below), and to permit persons to whom the Subject Software is
furnished in accordance with this License to do the same, subject to all of
the following terms and conditions, which Recipient accepts by engaging in any
such use, copying, modifying, merging, publishing, distributing, sublicensing
or selling:
1. Definitions.

(a) "Original Software" means source code of computer software code which
is described in Exhibit A as Original Software.
(b) "Modifications" means any addition to or deletion from the substance
or structure of either the Original Software or any previous
Modifications. When Subject Software is released as a series of files, a
Modification means (i) any addition to or deletion from the contents of a
file containing Original Software or previous Modifications and (ii) any
new file that contains any part of the Original Code or previous
Modifications.
(c) "Subject Software" means the Original Software or Modifications or the
combination of the Original Software and Modifications, or portions of any
of the foregoing.
(d) "Recipient" means an individual or a legal entity exercising rights
under, and complying with all of the terms of, this License. For legal
entities, "Recipient" includes any entity which controls, is controlled
by, or is under common control with Recipient. For purposes of this
definition, "control" of an entity means (a) the power, direct or
indirect, to direct or manage such entity, or (b) ownership of fifty
percent (50%) or more of the outstanding shares or beneficial ownership of
such entity.
2. Redistribution of Source Code Subject to These Terms. Redistributions of
Subject Software in source code form must retain the notice set forth in
Exhibit A, below, in every file. A copy of this License must be included in
any documentation for such Subject Software where the recipients' rights
relating to Subject Software are described. Recipient may distribute the
source code version of Subject Software under a license of Recipient's choice,
which may contain terms different from this License, provided that (i)
Recipient is in compliance with the terms of this License, and (ii) the
license terms include this Section 2 and Sections 3, 4, 7, 8, 10, 12 and 13 of
this License, which terms may not be modified or superseded by any other terms
of such license. If Recipient distributes the source code version under a
different license Recipient must make it absolutely clear that any terms which

differ from this License are offered by Recipient alone, not by SGI. Recipient
hereby agrees to indemnify SGI for any liability incurred by SGI as a result
of any such terms Recipient offers.
3. Redistribution in Executable Form. The notice set forth in Exhibit A must
be conspicuously included in any notice in an executable version of Subject
Software, related documentation or collateral in which Recipient describes the
user's rights relating to the Subject Software. Recipient may distribute the
executable version of Subject Software under a license of Recipient's choice,
which may contain terms different from this License, provided that (i)
Recipient is in compliance with the terms of this License, and (ii) the
license terms include this Section 3 and Sections 4, 7, 8, 10, 12 and 13 of
this License, which terms may not be modified or superseded by any other terms
of such license. If Recipient distributes the executable version under a
different license Recipient must make it absolutely clear that any terms which
differ from this License are offered by Recipient alone, not by SGI. Recipient
hereby agrees to indemnify SGI for any liability incurred by SGI as a result
of any such terms Recipient offers.
4. Termination. This License and the rights granted hereunder will terminate
automatically if Recipient fails to comply with terms herein and fails to cure
such breach within 30 days of the breach. Any sublicense to the Subject
Software which is properly granted shall survive any termination of this
License absent termination by the terms of such sublicense. Provisions which,
by their nature, must remain in effect beyond the termination of this License
shall survive.
5. No Trademark Rights. This License does not grant any rights to use any
trade name, trademark or service mark whatsoever. No trade name, trademark or
service mark of SGI may be used to endorse or promote products derived from
the Subject Software without prior written permission of SGI.
6. No Other Rights. This License does not grant any rights with respect to the
OpenGL API or to any software or hardware implementation thereof or to any
other software whatsoever, nor shall any other rights or licenses not
expressly granted hereunder arise by implication, estoppel or otherwise with

respect to the Subject Software. Title to and ownership of the Original
Software at all times remains with SGI. All rights in the Original Software
not expressly granted under this License are reserved.
7. Compliance with Laws; Non-Infringement. Recipient shall comply with all
applicable laws and regulations in connection with use and distribution of the
Subject Software, including but not limited to, all export and import control
laws and regulations of the U.S. government and other countries. Recipient may
not distribute Subject Software that (i) in any way infringes (directly or
contributorily) the rights (including patent, copyright, trade secret,
trademark or other intellectual property rights of any kind) of any other
person or entity or (ii) breaches any representation or warranty, express,
implied or statutory, which under any applicable law it might be deemed to
have been distributed.
8. Claims of Infringement. If Recipient at any time has knowledge of any one
or more third party claims that reproduction, modification, use, distribution,
import or sale of Subject Software (including particular functionality or code
incorporated in Subject Software) infringes the third party's intellectual
property rights, Recipient must place in a well-identified web page bearing
the title "LEGAL" a description of each such claim and a description of the
party making each such claim in sufficient detail that a user of the Subject
Software will know whom to contact regarding the claim. Also, upon gaining
such knowledge of any such claim, Recipient must conspicuously include the URL
for such web page in the Exhibit A notice required under Sections 2 and 3,
above, and in the text of any related documentation, license agreement or
collateral in which Recipient describes end user's rights relating to the
Subject Software. If Recipient obtains such knowledge after it makes Subject
Software available to any other person or entity, Recipient shall take other
steps (such as notifying appropriate mailing lists or newsgroups) reasonably
calculated to inform those who received the Subject Software that new
knowledge has been obtained.
9. DISCLAIMER OF WARRANTY. SUBJECT SOFTWARE IS PROVIDED ON AN "AS
IS" BASIS,
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED,

INCLUDING, WITHOUT
LIMITATION, WARRANTIES THAT THE SUBJECT SOFTWARE IS FREE OF
DEFECTS,
MERCHANTABLE, FIT FOR A PARTICULAR PURPOSE OR NON- INFRINGING. SGI
ASSUMES NO
RISK AS TO THE QUALITY AND PERFORMANCE OF THE SOFTWARE. SHOULD
ANY SOFTWARE
PROVE DEFECTIVE IN ANY RESPECT, SGI ASSUMES NO COST OR LIABILITY
FOR ANY
SERVICING, REPAIR OR CORRECTION. THIS DISCLAIMER OF WARRANTY
CONSTITUTES AN
ESSENTIAL PART OF THIS LICENSE. NO USE OF ANY SUBJECT SOFTWARE IS
AUTHORIZED
HEREUNDER EXCEPT UNDER THIS DISCLAIMER.
10. LIMITATION OF LIABILITY. UNDER NO CIRCUMSTANCES AND UNDER NO
LEGAL THEORY,
WHETHER TORT (INCLUDING, WITHOUT LIMITATION, NEGLIGENCE OR
STRICT LIABILITY),
CONTRACT, OR OTHERWISE, SHALL SGI OR ANY SGI LICENSOR BE LIABLE FOR
ANY
DIRECT, INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF
ANY
CHARACTER INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF
GOODWILL, WORK
STOPPAGE, LOSS OF DATA, COMPUTER FAILURE OR MALFUNCTION, OR ANY
AND ALL OTHER
COMMERCIAL DAMAGES OR LOSSES, EVEN IF SUCH PARTY SHALL HAVE BEEN
INFORMED OF
THE POSSIBILITY OF SUCH DAMAGES. THIS LIMITATION OF LIABILITY SHALL
NOT APPLY
TO LIABILITY FOR DEATH OR PERSONAL INJURY RESULTING FROM SGI's
NEGLIGENCE TO
THE EXTENT APPLICABLE LAW PROHIBITS SUCH LIMITATION. SOME
JURISDICTIONS DO NOT
ALLOW THE EXCLUSION OR LIMITATION OF INCIDENTAL OR

CONSEQUENTIAL DAMAGES, SO
THAT EXCLUSION AND LIMITATION MAY NOT APPLY TO RECIPIENT.
11. Indemnity. Recipient shall be solely responsible for damages arising,
directly or indirectly, out of its utilization of rights under this License.
Recipient will defend, indemnify and hold harmless Silicon Graphics, Inc. from
and against any loss, liability, damages, costs or expenses (including the
payment of reasonable attorneys fees) arising out of Recipient's use,
modification, reproduction and distribution of the Subject Software or out of
any representation or warranty made by Recipient.
12. U.S. Government End Users. The Subject Software is a "commercial item"
consisting of "commercial computer software" as such terms are defined in
title 48 of the Code of Federal Regulations and all U.S. Government End Users
acquire only the rights set forth in this License and are subject to the terms
of this License.
13. Miscellaneous. This License represents the complete agreement concerning
subject matter hereof. If any provision of this License is held to be
unenforceable, such provision shall be reformed so as to achieve as nearly as
possible the same economic effect as the original provision and the remainder
of this License will remain in effect. This License shall be governed by and
construed in accordance with the laws of the United States and the State of
California as applied to agreements entered into and to be performed entirely
within California between California residents. Any litigation relating to
this License shall be subject to the exclusive jurisdiction of the Federal
Courts of the Northern District of California (or, absent subject matter
jurisdiction in such courts, the courts of the State of California), with
venue lying exclusively in Santa Clara County, California, with the losing
party responsible for costs, including without limitation, court costs and
reasonable attorneys fees and expenses. The application of the United Nations
Convention on Contracts for the International Sale of Goods is expressly
excluded. Any law or regulation which provides that the language of a contract
shall be construed against the drafter shall not apply to this License.
Exhibit A

The contents of this file are subject to Sections 2, 3, 4, 7, 8, 10, 12 and 13
of the GLX Public License Version 1.0 (the "License"). You may not use this
file except in compliance with those sections of the License. You may obtain a
copy of the License at Silicon Graphics, Inc., attn: Legal Services, 2011 N.
Shoreline Blvd., Mountain View, CA 94043 or at
http://www.sgi.com/software/opensource/glx/license.html.
Software distributed under the License is distributed on an "AS IS" basis. ALL
WARRANTIES ARE DISCLAIMED, INCLUDING, WITHOUT LIMITATION, ANY
IMPLIED
WARRANTIES OF MERCHANTABILITY, OF FITNESS FOR A PARTICULAR
PURPOSE OR OF NON-
INFRINGEMENT. See the License for the specific language governing rights and
limitations under the License.
The Original Software is GLX version 1.2 source code, released February, 1999.
The developer of the Original Software is Silicon Graphics, Inc. Those
portions of the Subject Software created by Silicon Graphics, Inc. are
Copyright (c) 1991-9 Silicon Graphics, Inc. All Rights Reserved. 3.5. CID
Font Code Public License
CID FONT CODE PUBLIC LICENSE (Version 1.0 (3/31/99))("License")
Subject to any applicable third party claims, Silicon Graphics, Inc. ("SGI")
hereby grants permission to Recipient (defined below), under SGI's copyrights
in the Original Software (defined below), to use, copy, modify, merge,
publish, distribute, sublicense and/or sell copies of Subject Software
(defined below) in both source code and executable form, and to permit persons
to whom the Subject Software is furnished in accordance with this License to
do the same, subject to all of the following terms and conditions, which
Recipient accepts by engaging in any such use, copying, modifying, merging,
publication, distributing, sublicensing or selling:
1. Definitions.

a. "Original Software" means source code of computer software code that is
described in Exhibit A as Original Software.
b. "Modifications" means any addition to or deletion from the substance or
structure of either the Original Software or any previous Modifications.
When Subject Software is released as a series of files, a Modification
means (i) any addition to or deletion from the contents of a file
containing Original Software or previous Modifications and (ii) any new
file that contains any part of the Original Code or previous
Modifications.
c. "Subject Software" means the Original Software or Modifications or the
combination of the Original Software and Modifications, or portions of any
of the foregoing.
d. "Recipient" means an individual or a legal entity exercising rights
under the terms of this License. For legal entities, "Recipient" includes
any entity that controls, is controlled by, or is under common control
with Recipient. For purposes of this definition, "control" of an entity
means (i) the power, direct or indirect, to direct or manage such entity,
or (ii) ownership of fifty percent (50%) or more of the outstanding shares
or beneficial ownership of such entity.
e. "Required Notice" means the notice set forth in Exhibit A to this
License.
f. "Accompanying Technology" means any software or other technology that
is not a Modification and that is distributed or made publicly available
by Recipient with the Subject Software. Separate software files that do
not contain any Original Software or any previous Modification shall not
be deemed a Modification, even if such software files are aggregated as
part of a product, or in any medium of storage, with any file that does
contain Original Software or any previous Modification.
2. License Terms. All distribution of the Subject Software must be made
subject to the terms of this License. A copy of this License and the Required

Notice must be included in any documentation for Subject Software where
Recipient's rights relating to Subject Software and/or any Accompanying
Technology are described. Distributions of Subject Software in source code
form must also include the Required Notice in every file distributed. In
addition, a ReadMe file entitled "Important Legal Notice" must be distributed
with each distribution of one or more files that incorporate Subject Software.
That file must be included with distributions made in both source code and
executable form. A copy of the License and the Required Notice must be
included in that file. Recipient may distribute Accompanying Technology under
a license of Recipient's choice, which may contain terms different from this
License, provided that (i) Recipient is in compliance with the terms of this
License, (ii) such other license terms do not modify or supersede the terms of
this License as applicable to the Subject Software, (iii) Recipient hereby
indemnifies SGI for any liability incurred by SGI as a result of the
distribution of Accompanying Technology or the use of other license terms.
3. Termination. This License and the rights granted hereunder will terminate
automatically if Recipient fails to comply with terms herein and fails to cure
such breach within 30 days of the breach. Any sublicense to the Subject
Software that is properly granted shall survive any termination of this
License absent termination by the terms of such sublicense. Provisions which,
by their nature, must remain in effect beyond the termination of this License
shall survive.
4. Trademark Rights. This License does not grant any rights to use any trade
name, trademark or service mark whatsoever. No trade name, trademark or
service mark of SGI may be used to endorse or promote products derived from or
incorporating any Subject Software without prior written permission of SGI.
5. No Other Rights. No rights or licenses not expressly granted hereunder
shall arise by implication, estoppel or otherwise. Title to and ownership of
the Original Software at all times remains with SGI. All rights in the
Original Software not expressly granted under this License are reserved.
6. Compliance with Laws; Non-Infringement. Recipient shall comply with all
applicable laws and regulations in connection with use and distribution of the

Subject Software, including but not limited to, all export and import control
laws and regulations of the U.S. government and other countries. Recipient may
not distribute Subject Software that (i) in any way infringes (directly or
contributorily) the rights (including patent, copyright, trade secret,
trademark or other intellectual property rights of any kind) of any other
person or entity, or (ii) breaches any representation or warranty, express,
implied or statutory, which under any applicable law it might be deemed to
have been distributed.
7. Claims of Infringement. If Recipient at any time has knowledge of any one
or more third party claims that reproduction, modification, use, distribution,
import or sale of Subject Software (including particular functionality or code
incorporated in Subject Software) infringes the third party's intellectual
property rights, Recipient must place in a well-identified web page bearing
the title "LEGAL" a description of each such claim and a description of the
party making each such claim in sufficient detail that a user of the Subject
Software will know whom to contact regarding the claim. Also, upon gaining
such knowledge of any such claim, Recipient must conspicuously include the URL
for such web page in the Required Notice, and in the text of any related
documentation, license agreement or collateral in which Recipient describes
end user's rights relating to the Subject Software. If Recipient obtains such
knowledge after it makes Subject Software available to any other person or
entity, Recipient shall take other steps (such as notifying appropriate
mailing lists or newsgroups) reasonably calculated to provide such knowledge
to those who received the Subject Software.
8. DISCLAIMER OF WARRANTY. SUBJECT SOFTWARE IS PROVIDED ON AN "AS
IS" BASIS,
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED,
INCLUDING, WITHOUT
LIMITATION, WARRANTIES THAT THE SUBJECT SOFTWARE IS FREE OF
DEFECTS,
MERCHANTABLE, FIT FOR A PARTICULAR PURPOSE OR NON-INFRINGING. SGI
ASSUMES NO
RISK AS TO THE QUALITY AND PERFORMANCE OF THE SOFTWARE. SHOULD
ANY SOFTWARE

PROVE DEFECTIVE IN ANY RESPECT, SGI ASSUMES NO COST OR LIABILITY
FOR ANY
SERVICING, REPAIR OR CORRECTION. THIS DISCLAIMER OF WARRANTY
CONSTITUTES AN
ESSENTIAL PART OF THIS LICENSE. NO USE OF ANY SUBJECT SOFTWARE IS
AUTHORIZED
HEREUNDER EXCEPT UNDER THIS DISCLAIMER.
9. LIMITATION OF LIABILITY. UNDER NO CIRCUMSTANCES AND UNDER NO
LEGAL THEORY,
WHETHER TORT (INCLUDING, WITHOUT LIMITATION, NEGLIGENCE OR
STRICT LIABILITY),
CONTRACT, OR OTHERWISE, SHALL SGI OR ANY SGI LICENSOR BE LIABLE FOR
ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT,
TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SUBJECT
SOFTWARE OR
THE USE OR OTHER DEALINGS IN THE SUBJECT SOFTWARE. SOME
JURISDICTIONS DO NOT
ALLOW THE EXCLUSION OR LIMITATION OF CERTAIN DAMAGES, SO THIS
EXCLUSION AND
LIMITATION MAY NOT APPLY TO RECIPIENT TO THE EXTENT SO DISALLOWED.
10. Indemnity. Recipient shall be solely responsible for damages arising,
directly or indirectly, out of its utilization of rights under this License.
Recipient will defend, indemnify and hold SGI and its successors and assigns
harmless from and against any loss, liability, damages, costs or expenses
(including the payment of reasonable attorneys fees) arising out of
(Recipient's use, modification, reproduction and distribution of the Subject
Software or out of any representation or warranty made by Recipient.
11. U.S. Government End Users. The Subject Software is a "commercial item"
consisting of "commercial computer software" as such terms are defined in
title 48 of the Code of Federal Regulations and all U.S. Government End Users
acquire only the rights set forth in this License and are subject to the terms

of this License.
12. Miscellaneous. This License represents the complete agreement concerning
subject matter hereof. If any provision of this License is held to be
unenforceable by any judicial or administrative authority having proper
jurisdiction with respect thereto, such provision shall be reformed so as to
achieve as nearly as possible the same economic effect as the original
provision and the remainder of this License will remain in effect. This
License shall be governed by and construed in accordance with the laws of the
United States and the State of California as applied to agreements entered
into and to be performed entirely within California between California
residents. Any litigation relating to this License shall be subject to the
exclusive jurisdiction of the Federal Courts of the Northern District of
California (or, absent subject matter jurisdiction in such courts, the courts
of the State of California), with venue lying exclusively in Santa Clara
County, California, with the losing party responsible for costs, including
without limitation, court costs and reasonable attorneys fees and expenses.
The application of the United Nations Convention on Contracts for the
International Sale of Goods is expressly excluded. Any law or regulation that
provides that the language of a contract shall be construed against the
drafter shall not apply to this License.
Exhibit A
Copyright (c) 1994-1999 Silicon Graphics, Inc.
The contents of this file are subject to the CID Font Code Public License
Version 1.0 (the "License"). You may not use this file except in compliance
with the License. You may obtain a copy of the License at Silicon Graphics,
Inc., attn: Legal Services, 2011 N. Shoreline Blvd., Mountain View, CA 94043
or at http://www.sgi.com/software/opensource/cid/license.html
Software distributed under the License is distributed on an "AS IS" basis. ALL
WARRANTIES ARE DISCLAIMED, INCLUDING, WITHOUT LIMITATION, ANY
IMPLIED
WARRANTIES OF MERCHANTABILITY, OF FITNESS FOR A PARTICULAR

PURPOSE OR OF
NON-INFRINGEMENT. See the License for the specific language governing rights
and limitations under the License.
The Original Software (as defined in the License) is CID font code that was
developed by Silicon Graphics, Inc. Those portions of the Subject Software (as
defined in the License) that were created by Silicon Graphics, Inc. are
Copyright (c) 1994-1999 Silicon Graphics, Inc. All Rights Reserved.
[NOTE: When using this text in connection with Subject Software delivered
solely in object code form, Recipient may replace the words "this file" with
"this software" in both the first and second sentences.] 3.6. Bitstream Vera
Fonts Copyright
The fonts have a generous copyright, allowing derivative works (as long as
"Bitstream" or "Vera" are not in the names), and full redistribution (so long
as they are not *sold* by themselves). They can be be bundled, redistributed
and sold with any software.
The fonts are distributed under the following copyright:
Copyright (c) 2003 by Bitstream, Inc. All Rights Reserved. Bitstream Vera is a
trademark of Bitstream, Inc.
Permission is hereby granted, free of charge, to any person obtaining a copy
of the fonts accompanying this license ("Fonts") and associated documentation
files (the "Font Software"), to reproduce and distribute the Font Software,
including without limitation the rights to use, copy, merge, publish,
distribute, and/or sell copies of the Font Software, and to permit persons to
whom the Font Software is furnished to do so, subject to the following
conditions:
The above copyright and trademark notices and this permission notice shall be
included in all copies of one or more of the Font Software typefaces.
The Font Software may be modified, altered, or added to, and in particular the

designs of glyphs or characters in the Fonts may be modified and additional
glyphs or characters may be added to the Fonts, only if the fonts are renamed
to names not containing either the words "Bitstream" or the word "Vera".
This License becomes null and void to the extent applicable to Fonts or Font
Software that has been modified and is distributed under the "Bitstream Vera"
names.
The Font Software may be sold as part of a larger software package but no copy
of one or more of the Font Software typefaces may be sold by itself.
THE FONT SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY
KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF
COPYRIGHT, PATENT,
TRADEMARK, OR OTHER RIGHT. IN NO EVENT SHALL BITSTREAM OR THE
GNOME FOUNDATION
BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, INCLUDING ANY
GENERAL,
SPECIAL, INDIRECT, INCIDENTAL, OR CONSEQUENTIAL DAMAGES, WHETHER
IN AN ACTION
OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF THE USE OR
INABILITY TO
USE THE FONT SOFTWARE OR FROM OTHER DEALINGS IN THE FONT
SOFTWARE.
Except as contained in this notice, the names of Gnome, the Gnome Foundation,
and Bitstream Inc., shall not be used in advertising or otherwise to promote
the sale, use or other dealings in this Font Software without prior written
authorization from the Gnome Foundation or Bitstream Inc., respectively. For
further information, contact: fonts at gnome dot org. 3.7. Bigelow & Holmes
Inc and URW++ GmbH Luxi font license
Luxi fonts copyright (c) 2001 by Bigelow & Holmes Inc. Luxi font instruction

code copyright (c) 2001 by URW++ GmbH. All Rights Reserved. Luxi is a
registered trademark of Bigelow & Holmes Inc.
Permission is hereby granted, free of charge, to any person obtaining a copy
of these Fonts and associated documentation files (the "Font Software"), to
deal in the Font Software, including without limitation the rights to use,
copy, merge, publish, distribute, sublicense, and/or sell copies of the Font
Software, and to permit persons to whom the Font Software is furnished to do
so, subject to the following conditions:
The above copyright and trademark notices and this permission notice shall be
included in all copies of one or more of the Font Software.
The Font Software may not be modified, altered, or added to, and in particular
the designs of glyphs or characters in the Fonts may not be modified nor may
additional glyphs or characters be added to the Fonts. This License becomes
null and void when the Fonts or Font Software have been modified.
THE FONT SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY
KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTIES OF
MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF
COPYRIGHT, PATENT,
TRADEMARK, OR OTHER RIGHT. IN NO EVENT SHALL BIGELOW & HOLMES
INC. OR URW++
GMBH. BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
INCLUDING ANY
GENERAL, SPECIAL, INDIRECT, INCIDENTAL, OR CONSEQUENTIAL DAMAGES,
WHETHER IN
AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF THE
USE OR
INABILITY TO USE THE FONT SOFTWARE OR FROM OTHER DEALINGS IN THE
FONT
SOFTWARE.

Except as contained in this notice, the names of Bigelow & Holmes Inc. and
URW++ GmbH. shall not be used in advertising or otherwise to promote the sale,
use or other dealings in this Font Software without prior written
authorization from Bigelow & Holmes Inc. and URW++ GmbH.
For further information, contact:
info@urwpp.de or design@bigelowandholmes.com
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to zlib v1.2.5, which may be included
with JRE 8, JDK 8, and OpenJDK 8.
--- begin of LICENSE ---
version 1.2.5, July 18th, 2005
Copyright (C) 1995-2005 Jean-loup Gailly and Mark Adler
This software is provided 'as-is', without any express or implied
warranty. In no event will the authors be held liable for any damages
arising from the use of this software.
Permission is granted to anyone to use this software for any purpose,
including commercial applications, and to alter it and redistribute it
freely, subject to the following restrictions:
1. The origin of this software must not be misrepresented; you must not
claim that you wrote the original software. If you use this software
in a product, an acknowledgment in the product documentation would be
appreciated but is not required.
2. Altered source versions must be plainly marked as such, and must not be

misrepresented as being the original software.
3. This notice may not be removed or altered from any source distribution.
Jean-loup Gailly Mark Adler
jloup@gzip.org madler@alumni.caltech.edu
--- end of LICENSE ---
-------------------------------------------------------------------------------
%% This notice is provided with respect to the following which may be
included with JRE 8, JDK 8, and OpenJDK 8, except where noted:
Apache Commons Math 2.2
Apache Derby 10.10.1.2 [included with JDK 8]
Apache Jakarta BCEL 5.2
Apache Jakarta Regexp 1.4
Apache Santuario XML Security for Java 1.5.4
Apache Xalan-Java 2.7.1
Apache Xerces Java 2.10.0
Apache XML Resolver 1.1
Dynalink 0.5
--- begin of LICENSE ---
Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1. Definitions.
"License" shall mean the terms and conditions for use, reproduction,
and distribution as defined by Sections 1 through 9 of this document.

"Licensor" shall mean the copyright owner or entity authorized by
the copyright owner that is granting the License.
"Legal Entity" shall mean the union of the acting entity and all
other entities that control, are controlled by, or are under common
control with that entity. For the purposes of this definition,
"control" means (i) the power, direct or indirect, to cause the
direction or management of such entity, whether by contract or
otherwise, or (ii) ownership of fifty percent (50%) or more of the
outstanding shares, or (iii) beneficial ownership of such entity.
"You" (or "Your") shall mean an individual or Legal Entity
exercising permissions granted by this License.
"Source" form shall mean the preferred form for making modifications,
including but not limited to software source code, documentation
source, and configuration files.
"Object" form shall mean any form resulting from mechanical
transformation or translation of a Source form, including but
not limited to compiled object code, generated documentation,
and conversions to other media types.
"Work" shall mean the work of authorship, whether in Source or
Object form, made available under the License, as indicated by a
copyright notice that is included in or attached to the work
(an example is provided in the Appendix below).
"Derivative Works" shall mean any work, whether in Source or Object
form, that is based on (or derived from) the Work and for which the
editorial revisions, annotations, elaborations, or other modifications
represent, as a whole, an original work of authorship. For the purposes
of this License, Derivative Works shall not include works that remain
separable from, or merely link (or bind by name) to the interfaces of,
the Work and Derivative Works thereof.

"Contribution" shall mean any work of authorship, including
the original version of the Work and any modifications or additions
to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner
or by an individual or Legal Entity authorized to submit on behalf of
the copyright owner. For the purposes of this definition, "submitted"
means any form of electronic, verbal, or written communication sent
to the Licensor or its representatives, including but not limited to
communication on electronic mailing lists, source code control systems,
and issue tracking systems that are managed by, or on behalf of, the
Licensor for the purpose of discussing and improving the Work, but
excluding communication that is conspicuously marked or otherwise
designated in writing by the copyright owner as "Not a Contribution."
"Contributor" shall mean Licensor and any individual or Legal Entity
on behalf of whom a Contribution has been received by Licensor and
subsequently incorporated within the Work.
2. Grant of Copyright License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
copyright license to reproduce, prepare Derivative Works of,
publicly display, publicly perform, sublicense, and distribute the
Work and such Derivative Works in Source or Object form.
3. Grant of Patent License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
(except as stated in this section) patent license to make, have made,
use, offer to sell, sell, import, and otherwise transfer the Work,
where such license applies only to those patent claims licensable
by such Contributor that are necessarily infringed by their
Contribution(s) alone or by combination of their Contribution(s)
with the Work to which such Contribution(s) was submitted. If You
institute patent litigation against any entity (including a

cross-claim or counterclaim in a lawsuit) alleging that the Work
or a Contribution incorporated within the Work constitutes direct
or contributory patent infringement, then any patent licenses
granted to You under this License for that Work shall terminate
as of the date such litigation is filed.
4. Redistribution. You may reproduce and distribute copies of the
Work or Derivative Works thereof in any medium, with or without
modifications, and in Source or Object form, provided that You
meet the following conditions:
(a) You must give any other recipients of the Work or
Derivative Works a copy of this License; and
(b) You must cause any modified files to carry prominent notices
stating that You changed the files; and
(c) You must retain, in the Source form of any Derivative Works
that You distribute, all copyright, patent, trademark, and
attribution notices from the Source form of the Work,
excluding those notices that do not pertain to any part of
the Derivative Works; and
(d) If the Work includes a "NOTICE" text file as part of its
distribution, then any Derivative Works that You distribute must
include a readable copy of the attribution notices contained
within such NOTICE file, excluding those notices that do not
pertain to any part of the Derivative Works, in at least one
of the following places: within a NOTICE text file distributed
as part of the Derivative Works; within the Source form or
documentation, if provided along with the Derivative Works; or,
within a display generated by the Derivative Works, if and
wherever such third-party notices normally appear. The contents
of the NOTICE file are for informational purposes only and
do not modify the License. You may add Your own attribution
notices within Derivative Works that You distribute, alongside

or as an addendum to the NOTICE text from the Work, provided
that such additional attribution notices cannot be construed
as modifying the License.
You may add Your own copyright statement to Your modifications and
may provide additional or different license terms and conditions
for use, reproduction, or distribution of Your modifications, or
for any such Derivative Works as a whole, provided Your use,
reproduction, and distribution of the Work otherwise complies with
the conditions stated in this License.
5. Submission of Contributions. Unless You explicitly state otherwise,
any Contribution intentionally submitted for inclusion in the Work
by You to the Licensor shall be under the terms and conditions of
this License, without any additional terms or conditions.
Notwithstanding the above, nothing herein shall supersede or modify
the terms of any separate license agreement you may have executed
with Licensor regarding such Contributions.
6. Trademarks. This License does not grant permission to use the trade
names, trademarks, service marks, or product names of the Licensor,
except as required for reasonable and customary use in describing the
origin of the Work and reproducing the content of the NOTICE file.
7. Disclaimer of Warranty. Unless required by applicable law or
agreed to in writing, Licensor provides the Work (and each
Contributor provides its Contributions) on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
implied, including, without limitation, any warranties or conditions
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
PARTICULAR PURPOSE. You are solely responsible for determining the
appropriateness of using or redistributing the Work and assume any
risks associated with Your exercise of permissions under this License.
8. Limitation of Liability. In no event and under no legal theory,
whether in tort (including negligence), contract, or otherwise,

unless required by applicable law (such as deliberate and grossly
negligent acts) or agreed to in writing, shall any Contributor be
liable to You for damages, including any direct, indirect, special,
incidental, or consequential damages of any character arising as a
result of this License or out of the use or inability to use the
Work (including but not limited to damages for loss of goodwill,
work stoppage, computer failure or malfunction, or any and all
other commercial damages or losses), even if such Contributor
has been advised of the possibility of such damages.
9. Accepting Warranty or Additional Liability. While redistributing
the Work or Derivative Works thereof, You may choose to offer,
and charge a fee for, acceptance of support, warranty, indemnity,
or other liability obligations and/or rights consistent with this
License. However, in accepting such obligations, You may act only
on Your own behalf and on Your sole responsibility, not on behalf
of any other Contributor, and only if You agree to indemnify,
defend, and hold each Contributor harmless for any liability
incurred by, or claims asserted against, such Contributor by reason
of your accepting any such warranty or additional liability.
END OF TERMS AND CONDITIONS
APPENDIX: How to apply the Apache License to your work.
To apply the Apache License to your work, attach the following
boilerplate notice, with the fields enclosed by brackets "[]"
replaced with your own identifying information. (Don't include
the brackets!) The text should be enclosed in the appropriate
comment syntax for the file format. We also recommend that a
file or class name and description of purpose be included on the
same "printed page" as the copyright notice for easier
identification within third-party archives.
Copyright [yyyy] [name of copyright owner]

Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
implied.
See the License for the specific language governing permissions and
limitations under the License.
--- end of LICENSE ---
-------------------------------------------------------------------------------

This Font Software is licensed under the SIL Open Font License,
Version 1.1.
This license is copied below, and is also available with a FAQ at:
http://scripts.sil.org/OFL
-----------------------------------------------------------
SIL OPEN FONT LICENSE Version 1.1 - 26 February 2007
-----------------------------------------------------------
PREAMBLE
The goals of the Open Font License (OFL) are to stimulate worldwide
development of collaborative font projects, to support the font
creation efforts of academic and linguistic communities, and to
provide a free and open framework in which fonts may be shared and
improved in partnership with others.
The OFL allows the licensed fonts to be used, studied, modied and
redistributed freely as long as they are not sold by themselves. The
fonts, including any derivative works, can be bundled, embedded,
redistributed and/or sold with any software provided that any reserved
names are not used by derivative works. The fonts and derivatives,
however, cannot be released under any other type of license. The
requirement for fonts to remain under this license does not apply to
any document created using the fonts or their derivatives.
DEFINITIONS
"Font Software" refers to the set of les released by the Copyright
Holder(s) under this license and clearly marked as such. This may
include source les, build scripts and documentation.
"Reserved Font Name" refers to any names specied as such after the
copyright statement(s).
"Original Version" refers to the collection of Font Software
components as distributed by the Copyright Holder(s).
"Modied Version" refers to any derivative made by adding to,
deleting, or substituting -- in part or in whole -- any of the
components of the Original Version, by changing formats or by porting
the Font Software to a new environment.
"Author" refers to any designer, engineer, programmer, technical
writer or other person who contributed to the Font Software.
PERMISSION & CONDITIONS
Permission is hereby granted, free of charge, to any person obtaining
a copy of the Font Software, to use, study, copy, merge, embed,
modify, redistribute, and sell modied and unmodied copies of the
Font Software, subject to the following conditions:
SIL OPEN FONT LICENSE
1134

1) Neither the Font Software nor any of its individual components, in
Original or Modied Versions, may be sold by itself.
2) Original or Modied Versions of the Font Software may be bundled,
redistributed and/or sold with any software, provided that each copy
contains the above copyright notice and this license. These can be
included either as stand-alone text les, human-readable headers or
in the appropriate machine-readable metadata elds within text or
binary les as long as those elds can be easily viewed by the user.
3) No Modied Version of the Font Software may use the Reserved Font
Name(s) unless explicit written permission is granted by the
corresponding Copyright Holder. This restriction only applies to the
primary font name as presented to the users.
4) The name(s) of the Copyright Holder(s) or the Author(s) of the Font
Software shall not be used to promote, endorse or advertise any
Modied Version, except to acknowledge the contribution(s) of the
Copyright Holder(s) and the Author(s) or with their explicit written
permission.
5) The Font Software, modied or unmodied, in part or in whole,
must be distributed entirely under this license, and must not be
distributed under any other license. The requirement for fonts to
remain under this license does not apply to any document created using
the Font Software.
TERMINATION
This license becomes null and void if any of the above conditions are
not met.
DISCLAIMER
THE FONT SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT
OF COPYRIGHT, PATENT, TRADEMARK, OR OTHER RIGHT. IN NO EVENT SHALL THE
COPYRIGHT HOLDER BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
INCLUDING ANY GENERAL, SPECIAL, INDIRECT, INCIDENTAL, OR CONSEQUENTIAL
DAMAGES, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF THE USE OR INABILITY TO USE THE FONT SOFTWARE OR FROM
OTHER DEALINGS IN THE FONT SOFTWARE.
SIL OPEN FONT LICENSE
1135