Zyxel USG2200 User Manual
Displayed below is the user manual for USG2200 by Zyxel which is a product in the Hardware Firewalls category. This manual has pages.
Related Manuals

1/782
www.zyxel.com
ZyWALL/USG/ATP /VPN Series
ATP100/ ATP100W/ ATP200/ ATP500/ ATP700 / ATP800
USG20-VPN / USG20W-VPN / USG40 / USG40W /
USG60 / USG60W / USG110 / UGS210 / USG310/
USG1100 /USG1900 / USG2200-VPN
USG FLEX 100/ USG FLEX 200/ USG FLEX 500
VPN50 / VPN100 /VPN300 /VPN1000
Security Firewalls
Edition 5, June/2020
Handbook
Default Login Details
LAN Port IP Address
https://192.168.1.1
User Name
admin
Password
1234

2/782
www.zyxel.com
copyright © 2020 ZyXEL Communications Corporation
Table of Content
How to Configure Site-to-site IPSec VPN with Amazon VPC .................. 20
Set Up the IPSec VPN Tunnel on the Amazon VPC ............................ 21
Set Up the IPSec VPN Tunnel on the ZyWALL/USG ............................. 25
Test the IPSec VPN Tunnel ..................................................................... 31
What Could Go Wrong? ....................................................................... 32
How to Configure Site-to-site IPSec VPN with Microsoft (MS) Azure ..... 33
Set Up the IPSec VPN Tunnel on the ZyWALL/USG ............................. 34
Set Up the IPSec VPN Tunnel on the MS Azure ................................... 39
Test the IPSec VPN Tunnel ..................................................................... 46
What Could Go Wrong? ...................................................................... 49
How to Configure GRE over IPSec VPN Tunnel ........................................ 50
Set Up the ZyWALL/USG GRE over IPSec VPN Tunnel of Corporate
Network (HQ) ......................................................................................... 51
Set Up the ZyWALL/USG GRE over IPSec VPN Tunnel of Corporate
Network (Branch) .................................................................................. 56
Test the GRE over IPSec VPN Tunnel .................................................... 60
What Could Go Wrong? ....................................................................... 61
How to Configure Site-to-site IPSec VPN Where the Peer has a Static IP
Address ....................................................................................................... 63
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(Branch) .................................................................................................. 68
Test the IPSec VPN Tunnel ..................................................................... 72
What Could Go Wrong? ...................................................................... 73
How to Configure Site-to-site IPSec VPN Where the Peer has a Dynamic
IP Address ................................................................................................... 75
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(HQ) ........................................................................................................ 75
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(Branch has a Dynamic IP Address) ................................................... 79
Test the IPSec VPN Tunnel ..................................................................... 83

3/782
www.zyxel.com
What Could Go Wrong? ...................................................................... 85
How to Configure IPSec Site to Site VPN while one Site is behind a NAT
router ........................................................................................................... 87
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(HQ) ........................................................................................................ 87
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(Branch) .................................................................................................. 91
Set Up the NAT Router (Using ZyWALL USG device in this example) 95
Test the IPSec VPN Tunnel ..................................................................... 97
What Could Go Wrong? ....................................................................... 98
How to Configure Hub-and-Spoke IPSec VPN ........................................ 99
Set Up the IPSec VPN Tunnel on the ZyWALL/USG by Using VPN
Concentrator Hub_HQ-to-Branch_A ................................................ 100
Hub_HQ-to-Branch_B .......................................................................... 104
Hub_HQ Concentrator ....................................................................... 108
Spoke_Branch_A ................................................................................. 109
Spoke_Branch_B .................................................................................. 114
Test the IPSec VPN Tunnel ................................................................... 119
What Could Go Wrong? .................................................................... 123
Set Up the IPSec VPN Tunnel of ZyWALL/USG without Using VPN
Concentrator Hub_HQ-to-Branch_A ................................................ 125
Hub_HQ-to-Branch_B .......................................................................... 128
Spoke_Branch_A ................................................................................. 131
Spoke_Branch_B .................................................................................. 134
Test the IPSec VPN Tunnel ................................................................... 137
What Could Go Wrong? .................................................................... 140
How to Use Dual-WAN to Perform Fail-Over on VPN Using the VPN
Concentrator ............................................................................................ 142
Set Up the IPSec VPN Tunnel on the ZyWALL/USG Hub_HQ-to-
Branch_A .............................................................................................. 143
Hub_HQ-to-Branch_B .......................................................................... 146
Hub_HQ Concentrator ....................................................................... 149
Spoke_Branch_A ................................................................................. 150
Spoke_Branch_B .................................................................................. 153

4/782
www.zyxel.com
Test the IPSec VPN Tunnel ................................................................... 157
What Could Go Wrong? .................................................................... 160
How to Configure IPSec VPN with ZyWALL IPSec VPN Client ............... 161
Set Up the ZyWALL/USG IPSec VPN Tunnel ....................................... 162
Set Up the ZyWALL IPSec VPN Client ................................................. 166
Test the IPSec VPN Tunnel ................................................................... 169
What Can Go Wrong? ........................................................................ 171
How to Configure Site-to-site IPSec VPN with FortiGate ....................... 173
Set Up the IPSec VPN Tunnel on the ZyWALL/USG ........................... 174
Set Up the IPSec VPN Tunnel on the FortiGate ................................. 177
Test the IPSec VPN Tunnel ................................................................... 182
What Could Go Wrong? .................................................................... 183
How to Configure Site-to-site IPSec VPN with WatchGuard ................ 185
Set Up the IPSec VPN Tunnel on the ZyWALL/USG ........................... 186
Set Up the IPSec VPN Tunnel on the WatchGuard .......................... 189
Test the IPSec VPN Tunnel ................................................................... 195
What Could Go Wrong? .................................................................... 196
How to Configure Site-to-site IPSec VPN with Cisco ............................. 198
Set Up the IPSec VPN Tunnel on the ZyWALL/USG ........................... 199
Set Up the IPSec VPN Tunnel on the Cisco ....................................... 204
Test the IPSec VPN Tunnel ................................................................... 209
What Could Go Wrong? .................................................................... 211
How to Configure Site-to-site IPSec VPN with a SonicWALL router ..... 212
Set Up the IPSec VPN Tunnel on the ZyWALL/USG ........................... 213
Set Up the IPSec VPN Tunnel on the SonicWALL .............................. 220
Test the IPSec VPN Tunnel ................................................................... 224
What Could Go Wrong? .................................................................... 226
How to Configure IPSec VPN Failover .................................................... 229
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(HQ) ...................................................................................................... 230
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(Branch) ................................................................................................ 233
Set up the WAN Trunk (ZyWALL/USG_HQ) ........................................ 238

5/782
www.zyxel.com
Set up the Failover Command Line (ZyWALL/USG HQ) .................. 239
Test the IPSec VPN Tunnel ................................................................... 240
What Could Go Wrong? .................................................................... 242
How to Configure L2TP over IPSec VPN while the ZyWALL/USG is behind
a NAT router .............................................................................................. 244
Set Up the L2TP VPN Tunnel on the ZyWALL/USG_HQ ...................... 245
Set Up the NAT Router (Using ZyWALL USG device in this example)
............................................................................................................... 249
Test the L2TP over IPSec VPN Tunnel .................................................. 252
What Could Go Wrong? ..................................................................... 255
How to Configure L2TP VPN with Android 5.0 Mobile Devices ............ 257
Set Up the L2TP VPN Tunnel on the ZyWALL/USG ............................. 258
Set Up the L2TP VPN Tunnel on the Android Device ........................ 262
Test the L2TP over IPSec VPN Tunnel ................................................. 265
What Could Go Wrong? .................................................................... 267
How to Configure L2TP VPN with iOS 8.4 Mobile Devices ..................... 269
Set Up the L2TP VPN Tunnel on the ZyWALL/USG ............................. 269
Set Up the L2TP VPN Tunnel on the iOS Device ................................ 275
Test the L2TP over IPSec VPN Tunnel ................................................. 276
What Could Go Wrong? .................................................................... 279
How to Import ZyWALL/USG Certificate for L2TP over IPsec in Windows 10
................................................................................................................... 281
Set Up the L2TP VPN Tunnel on the ZyWALL/USG ............................. 281
Export a Certificate from ZyWALL/USG and Import it to Windows 10
Operating System ............................................................................... 286
Set Up the L2TP VPN Tunnel on the Windows 10 ............................... 291
Test the L2TP over IPSec VPN Tunnel ................................................. 296
What Could Go Wrong? .................................................................... 298
How to Import ZyWALL/USG Certificate for L2TP over IPsec in IOS mobile
phone ........................................................................................................ 300
Set Up the L2TP VPN Tunnel on the ZyWALL/USG ............................. 300
Export a Certificate from ZyWALL/USG and Import it to iOS Mobile
Phone ................................................................................................... 305

6/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the iOS Mobile Device ................... 305
Test the L2TP over IPSec VPN Tunnel ................................................. 308
What Could Go Wrong? .................................................................... 310
How to Import ZyWALL/USG Certificate for L2TP over IPsec in Android
mobile phone ........................................................................................... 311
Set Up the L2TP VPN Tunnel on the ZyWALL/USG ............................. 312
Export a Certificate from ZyWALL/USG and Import it to Android
Mobile Phone ...................................................................................... 316
Set Up the L2TP VPN Tunnel on the Android Mobile Device ........... 317
Test the L2TP over IPSec VPN Tunnel ................................................. 320
What Could Go Wrong? .................................................................... 322
How to Configure the L2TP VPN with Apple MAC OS X 10.11 Operating
System ....................................................................................................... 324
Set Up the L2TP VPN Tunnel on the ZyWALL/USG ............................. 324
Set Up the L2TP VPN Tunnel on the Apple MAC OS X 10.11 El
Capitan Operating System ................................................................ 329
Test the L2TP over IPSec VPN Tunnel ................................................. 332
What Could Go Wrong? .................................................................... 334
How to configure if I want user can only see SSL VPN Login button in
web portal login page ............................................................................. 336
Set Up the DNS Service ........................................................................ 337
Set Up the ZyWALL/USG SSL VPN Setting ............................................ 337
Set Up the ZyWALL/USG System Setting ............................................. 338
Test the SSL VPN ................................................................................... 339
How to Deploy SSL VPN with Apple Mac OS X 10.10 Operating System
................................................................................................................... 343
Set Up the SSL VPN Tunnel on the ZyWALL/USG ............................... 344
Set Up the SSL VPN Tunnel on the Apple MAC OS X 10.10 Operating
System ................................................................................................... 347
Test the SSL VPN Tunnel ....................................................................... 351
What Could Go Wrong? .................................................................... 354
How To Configure SSL VPN for Remote Access Mobile Devices ......... 356
Set Up the SSL VPN Tunnel on the ZyWALL/USG ............................... 357

7/782
www.zyxel.com
Test the SSL VPN Tunnel ....................................................................... 360
What Could Go Wrong? .................................................................... 362
How to Configure an SSL VPN Tunnel (with SecuExtender version 4.0.0.1)
on the Windows 10 Operating System ................................................... 363
Set up the SSL VPN Tunnel with Windows 10 .................................... 363
What Can Go Wrong? ....................................................................... 367
How to redirect multiple LAN interface traffic to the VPN tunnel ........ 369
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(HQ) ...................................................................................................... 370
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(Branch) ................................................................................................ 373
Set up the Policy Route (ZyWALL/USG_HQ) ..................................... 377
Set up the Policy Route (ZyWALL/USG_Branch) .............................. 378
Test the IPSec VPN Tunnel ................................................................... 380
What Could Go Wrong? .................................................................... 381
How to Create VTI and Configure VPN Failover with VTI ...................... 383
VTI Deployment Flow .......................................................................... 383
Set Up the ZyWALL/USG VTI of Corporate Network (HQ) ............... 384
Set Up the ZyWALL/USG VTI of Corporate Network (Branch) ........ 389
Test the IPSec VPN Tunnel .................................................................. 395
What Can Go Wrong? ....................................................................... 397
How to configure the USG when using a Cloud Based SIP system ..... 399
Set Up the SIP ALG ............................................................................... 400
Test result .............................................................................................. 400
What could go wrong? ...................................................................... 401
How to block HTTPS websites by Domain Filter without applying SSL
Inspection ................................................................................................. 401
Set Up the Content Filter on the ZyWALL/USG ................................. 402
Set Up the Security Policy on the ZyWALL/USG ............................... 405
Set Up the System Policy on the ZyWALL/USG ................................. 405
Test the Result ...................................................................................... 405
How to Configure Content Filter 2.0 with Geo IP Blocking ................... 408
Set Up the Address Objet with Geo IP on the ZyWALL/USG ........... 409

8/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG ............................... 409
Test the Result ...................................................................................... 410
What Could Go Wrong? .................................................................... 411
How to Configure Content Filter 2.0 with HTTPs Domain Filter .............. 412
Application Scenario .......................................................................... 412
Set Up the Content Filter on the ZyWALL/USG .................................. 413
Set Up the Security Policy on the ZyWALL/USG ............................... 415
Set Up the System Policy on the ZyWALL/USG ................................. 416
Test the Result ...................................................................................... 417
What Could Wrong? ........................................................................... 417
How to block the client accessing to certain country using Geo IP and
Content Filter ............................................................................................ 418
Check Geo IP License Status on the ZyWALL/USG ........................... 419
Set Up the Address Objet with Geo IP on the ZyWALL/USG ........... 420
Set Up the Security Policy on the ZyWALL/USG ............................... 421
Test the Result ...................................................................................... 422
How to Restrict Web Portal access from the Internet ........................... 425
Set Up the ZyWALL/USG System Setting ............................................. 425
Test the Web Access ........................................................................... 426
How to Setup and Configure Daily Report ............................................. 429
Set Up the ZyWALL/USG Email Daily Report Setting ........................... 430
Test the Daily Log Report .................................................................... 431
What Could Go Wrong? .................................................................... 433
How to Setup and Configure Email Logs ............................................... 434
Set Up the ZyWALL/USG Email Logs Setting ........................................ 435
Test the Email Log ................................................................................ 436
What Could Go Wrong? .................................................................... 437
How to Setup and send logs to a Syslog Server .................................... 438
Set Up the Syslog Server (Use Papertrail syslog in this example) ....... 438
Set Up the ZyWALL/USG Remote Server Setting ................................ 441
Test the Remote Server ....................................................................... 442
What Could Go Wrong? .................................................................... 443
How to Setup and send logs to a Vantage Reports Server .................. 444

9/782
www.zyxel.com
Set Up the VRPT Server ........................................................................ 445
Set Up the ZyWALL/USG Remote Server Setting ................................ 448
Test the Remote Server ....................................................................... 449
What Could Go Wrong? .................................................................... 449
How to Setup and send logs to the USB storage ................................... 450
Set Up the USB System Settings ........................................................... 451
Set Up the USB Log Storage ................................................................ 452
Check the USG Log Files .................................................................... 453
How to Setup IPv6 Interfaces for Pure IPv6 Routing .............................. 454
Setting Up the IPv6 Interface ............................................................. 455
Set up the Prefix Delegation and Router Advertisement ............... 457
Test ........................................................................................................ 461
What Can Go Wrong? ....................................................................... 462
Test ........................................................................................................ 464
How to Perform and Use the Packet Capture Feature on the
ZyWALL/USG ............................................................................................. 464
Set Up the Packet Capture Feature ................................................... 465
Check the Capture Files ..................................................................... 468
How to Automatically Reboot the ZyWALL/USG by Schedule ............. 469
Set Up the Shell Script .......................................................................... 470
Set Up the Schedule Run ..................................................................... 471
Check the Reboot Status ................................................................... 473
How To Schedule YouTube Access ........................................................ 475
Set Up the Schedule on the ZyWALL/USG ......................................... 475
Create the Application Objects on the ZyWALL/USG ..................... 476
Set Up SSL Inspection on the ZyWALL/USG ........................................ 476
Set Up the Security Policy on the ZyWALL/USG ................................. 477
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System ............................................................................... 478
Test the Result ...................................................................................... 484
What Could Go Wrong? .................................................................... 484
How to continuously run a ZySH script ................................................... 486
Set Up the Shell Script .......................................................................... 486

10/782
www.zyxel.com
Set Up the Schedule Run ..................................................................... 488
Check the Result ................................................................................. 488
How To Register Your Device and Services at myZyXEL.com ............. 489
Account Creation ............................................................................... 490
Device Registration ............................................................................. 492
Service Registration (In the Case of Standard License) ................. 493
Device Management (In the Case of Registering Bundled Licenses)
............................................................................................................... 494
Refresh Service .................................................................................... 495
What Could Go Wrong? .................................................................... 495
How To Exempt Specific Users From Security Control .......................... 497
Set Up the Security Policy on the ZyWALL/USG for Employees ....... 498
Set Up the Security Policy on the ZyWALL/USG for Executives ........ 500
Test the Result ...................................................................................... 502
What Could Go Wrong? .................................................................... 503
How To Detect and Prevent TCP Port Scanning with ADP .................... 504
Set Up the ADP Profile on the ZyWALL/USG ...................................... 505
Test the Result ...................................................................................... 508
What Could Go Wrong? .................................................................... 509
How To Block Facebook ......................................................................... 510
Set Up the Content Filter on the ZyWALL/USG .................................. 511
Set Up the SSL Inspection on the ZyWALL/USG ................................. 511
Set Up the Security Policy on the ZyWALL/USG ................................. 513
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System ............................................................................... 514
Test the Result ...................................................................................... 519
What Could Go Wrong? .................................................................... 520
How To Exempt Specific Users From a Blocked Website ..................... 521
Set Up the Security Policy on the ZyWALL/USG for Employees ....... 522
Set Up the Security Policy on the ZyWALL/USG for Executives ........ 524
Test the Result ...................................................................................... 527
What Could Go Wrong? .................................................................... 528
How To Control Access To Google Drive ............................................... 529

11/782
www.zyxel.com
Set Up the SSL Inspection on the ZyWALL/USG ................................. 530
Set Up the Security Policy on the ZyWALL/USG ................................. 531
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System ............................................................................... 531
Test the Result ...................................................................................... 537
What Could Go Wrong? .................................................................... 538
How To Block HTTPS Websites Using Content Filtering and SSL Inspection
................................................................................................................... 539
Set Up the Content Filter on the ZyWALL/USG .................................. 540
Set Up SSL Inspection on the ZyWALL/USG ........................................ 541
Set Up the Security Policy on the ZyWALL/USG ................................. 543
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System ............................................................................... 544
Test the Result ...................................................................................... 549
What Could Go Wrong? .................................................................... 550
How To Block the Spotify Music Streaming Service .............................. 551
Set Up IDP Profile on the ZyWALL/USG ............................................... 552
Test the Result ...................................................................................... 553
What Could Go Wrong? .................................................................... 554
How does Anti-Malware work ................................................................ 555
Enable Anti-Malware function to protecting your traffic ............... 556
Test the result ....................................................................................... 557
Additional configuration ........................................................................... 557
What can go wrong ........................................................................... 558
How to Configure an Email Security Policy with Mail Scan and DNSBL559
Set Up the Email Security on ATP Series .............................................. 559
Test the result ....................................................................................... 562
What can go wrong ........................................................................... 563
How to Configure Botnet Filter on ATP series? ....................................... 564
Prerequisites before setting up Botnet Filter function ..................... 565
License activation ............................................................................... 565
Update Botnet Filter Signatures ......................................................... 565
Set Up the IP Blocking on the ATP series ........................................... 567

12/782
www.zyxel.com
Test the Result ...................................................................................... 567
Set up the URL Blocking on the ATP series ........................................ 568
Test the Result ...................................................................................... 568
How to Use Sandboxing to Detect Unknown Malware ........................ 570
Set Up Sandboxing on ATP ................................................................. 571
Test the Result ....................................................................................... 573
What Can Go Wrong? ........................................................................ 576
How to Configure Bandwidth Management for FTP and HTTP Traffic .. 577
Set Up the Bandwidth Management for FTP on the ZyWALL/USG 578
Set Up the Bandwidth Management for HTTP on the ZyWALL/USG
............................................................................................................... 579
Set Up the Bandwidth Management Global Setting on the
ZyWALL/USG ......................................................................................... 581
Test the Result ...................................................................................... 582
What Could Go Wrong? .................................................................... 583
How to Limit BitTorrent or Other Peer-to-Peer Traffic ............................. 584
Set Up the Application Patrol Profile on the ZyWALL/USG ............... 585
Set Up the Bandwidth Management for BitTorrent on the
ZyWALL/USG ......................................................................................... 586
Set Up the Bandwidth Management Global Setting on the
ZyWALL/USG ......................................................................................... 588
Test the Result ...................................................................................... 588
What Could Go Wrong? .................................................................... 589
How to Configure a Trunk for WAN Load Balancing with a Static or
Dynamic IP Address ................................................................................. 590
Set Up the Available Bandwidth on WAN1 Interfaces on the
ZyWALL/USG ......................................................................................... 591
Set Up the Available Bandwidth on WAN2 Interfaces on the
ZyWALL/USG ......................................................................................... 592
Set Up the WAN Trunk on the ZyWALL/USG ...................................... 592
Test the Result ...................................................................................... 593
What Could Go Wrong? .................................................................... 594

13/782
www.zyxel.com
How to Configure DNS Inbound Load Balancing to balance DNS Queries
Among Interfaces .................................................................................... 595
Set Up the DNS Inbound Load Balancing on the ZyWALL/USG ..... 596
Set Up the NAT Rule on the ZyWALL/USG ......................................... 597
Test the Result ...................................................................................... 598
What Could Go Wrong? .................................................................... 599
How to Manage Voice Traffic ................................................................. 600
Set Up the SIP ALG on the ZyWALL/USG ........................................... 601
Set Up the Bandwidth Management for SIP on the ZyWALL/USG . 601
Set Up the Bandwidth Management for P2P on the ZyWALL/USG 602
Set Up the Bandwidth Management for FTP on the ZyWALL/USG 603
Test the Result ...................................................................................... 605
What Could Go Wrong? .................................................................... 606
How to Manage ZyWALL/USG Configuration Files ................................ 607
Rename the Configuration Files from the ZyWALL/USG ................. 608
Download the Configuration Files on the ZyWALL/USG ................. 608
Copy the Configuration Files on the ZyWALL/USG .......................... 609
Apply the Configuration Files on the ZyWALL/USG ......................... 610
Upload the Configuration Files from the ZyWALL/USG ................... 611
What Could Go Wrong? .................................................................... 611
How to Manage ZyWALL/USG Firmware ................................................ 612
Download the Current Firmware Version from ZyXEL.com ............ 613
Upload the Firmware on the ZyWALL/USG ....................................... 614
What Could Go Wrong? .................................................................... 617
How to Get Started Using the Wizards .................................................... 618
Set Up the Internet Access (Ethernet) Wizard on the ZyWALL/USG
............................................................................................................... 618
Set Up the Internet Access (PPPoE) Wizard on the ZyWALL/USG .. 622
Set Up the Internet Access (PPTP) Wizard on the ZyWALL/USG ..... 625
Set Up the Wireless Settings Wizard on the ZyWALL/USG ................ 629
Set Up the Device Registration on the ZyWALL/USG ...................... 631
How to Configure the 3G/LTE Interface on the ZyWALL/USG as a WAN
Backup ...................................................................................................... 633

14/782
www.zyxel.com
Set Up the 3G/LTE Interface on the ZyWALL/USG ........................... 634
Set Up the Trunk on the ZyWALL/USG ............................................... 635
Test the Result ...................................................................................... 636
What Could Go Wrong? .................................................................... 637
How to Configure Two Different WAN Interfaces with Different IP
Addresses in the Same VLAN .................................................................. 638
Set Up the Port Grouping on the ZyWALL/USG ................................ 639
Set Up the VLAN on the ZyWALL/USG ............................................... 639
Set Up the Routing on the ZyWALL/USG ........................................... 641
Test the Result ...................................................................................... 641
What Could Go Wrong? .................................................................... 642
How to Let a Server Use the Same Public IP Address as the WAN
Interface Using the Bridge Interface ...................................................... 642
Set Up the Bridge Interface on the ZyWALL/USG ............................ 643
Test the Result ...................................................................................... 645
What Could Go Wrong? .................................................................... 646
How to Allow Public Access to a Server Behind ZyWALL/USG ............ 646
Set Up the NAT on the ZyWALL/USG ................................................. 647
Set Up the Security Policy on the ZyWALL/USG ............................... 648
Test the Result ...................................................................................... 649
What Could Go Wrong? .................................................................... 649
How to Set Up a WiFi Network with ZyXEL APs ....................................... 651
Set Up the AP Management on the ZyWALL/USG .......................... 652
Test the Result ...................................................................................... 654
What Could Go Wrong? .................................................................... 655
How to Set Up Guest WiFi Network Accounts ........................................ 656
Set Up the WiFi Guest Account, Address Range and Service Rule on
the ZyWALL/USG .................................................................................. 657
Set Up the Web Authentication on the ZyWALL/USG ..................... 659
Set Up the Security Policy on the ZyWALL/USG ............................... 660
Test the Result ...................................................................................... 661
What Could Go Wrong? .................................................................... 664

15/782
www.zyxel.com
How to create a Wi-Fi VLAN interfaces to separate staff network and
Guest network .......................................................................................... 666
Set up Wi-Fi VLAN interfaces .............................................................. 667
Test result .............................................................................................. 677
What could go wrong ........................................................................ 679
How to Set Up WiFi Networks with Microsoft Active Directory
Authentication .......................................................................................... 681
Set Up the Wi-Fi Guest Account and Authentication Method on the
ZyWALL/USG ......................................................................................... 682
Set Up the Active Directory Server Account on the ZyWALL/USG 683
Set Up the Security Policy on the ZyWALL/USG ............................... 684
Test the Result ...................................................................................... 685
What Could Go Wrong? .................................................................... 687
How to Set Up IPv6 Interfaces for Pure IPv6 Routing ............................. 688
Enable the IPv6 on the ZyWALL/USG ................................................ 689
Set Up the WAN IPv6 Interface on the ZyWALL/USG ....................... 690
Set Up the LAN IPv6 Interface on the ZyWALL/USG ........................ 690
Test the Result ...................................................................................... 691
What Could Go Wrong? .................................................................... 693
How to Set Up an IPv6 6to4 Tunnel ......................................................... 693
Set Up the LAN IPv6 Interface on the ZyWALL/USG ........................ 694
Set Up the 6to4 Tunnel on the ZyWALL/USG .................................... 696
Test the Result ...................................................................................... 697
What Could Go Wrong? .................................................................... 698
How to Set Up an IPv6-in-IPv4 Tunnel ..................................................... 698
Set Up the LAN IPv6 Interface on the ZyWALL/USG ........................ 699
Set Up the 6to4 Tunnel on the ZyWALL/USG .................................... 700
Set Up the Policy Route on the ZyWALL/USG ................................... 701
Test the Result ...................................................................................... 702
What Could Go Wrong? .................................................................... 703
How to Update Firmware Automatically from a USB Storage .............. 704
Automatic USB Firmware Upgrade Flow ............................................... 704
Enable the USB Firmware Upgrade Function by CLI Command ... 705

16/782
www.zyxel.com
Save the Firmware on the USB ........................................................... 705
Plug the USB into the Device ............................................................. 706
The Device Checks Running Partition for the Model ID and the
Firmware Version ................................................................................. 706
Check Firmware Status ....................................................................... 707
What Can Go Wrong? ........................................................................ 708
How to Configure DHCP Option 60 – Vendor Class Identifier .............. 710
DHCP Option 60 Deployment Flow ....................................................... 711
Setting Up DHCP Option 60 on the Web GUI ................................... 711
Setting Up DHCP Option 60 on the CLI ............................................. 712
Test DHCP Option 60 ........................................................................... 713
What Can Go Wrong? ....................................................................... 713
How to Configure Device HA Pro ........................................................... 714
Device HA Pro License ....................................................................... 715
Behavior of the Device HA Pro .......................................................... 715
Device-HA Pro Setting Screen ........................................................... 715
Suggestions .......................................................................................... 717
How do I Configure Device HA Pro in My Current Environment? . 718
What can go wrong? ......................................................................... 722
How to Upgrade Firmware on HA Pro Synchronized Devices? ........... 723
Firmware Upgrade Flow ..................................................................... 724
Running Firmware Version .................................................................. 724
Running Firmware Partition ................................................................ 724
Synchronization Status ........................................................................ 725
Upload the Firmware to the Active Device ..................................... 726
Test the Result ....................................................................................... 727
How to Downgrade Firmware on HA Pro Synchronized Devices? ...... 728
Firmware Downgrade Flow ................................................................ 729
Configuration File Backup .................................................................. 729
Switch Passive Device to Active Mode ............................................ 729
Ethernet Cable and Heartbeat Port Disconnection ....................... 730
Firmware Downgrade on Device 1 ................................................... 730
Backup Configuration Apply ............................................................. 731

17/782
www.zyxel.com
Connect All Ethernet Cables Back on Device 1 ............................. 732
Firmware Downgrade on Device 2 ................................................... 732
Enable Device HA Pro on Device 2 .................................................. 733
Test the Result ....................................................................................... 733
Appendix. Edit the Configuration File ......................................................... 734
How to replace one defect device of HA Pro ....................................... 736
Scenario and Topology ...................................................................... 736
Before redeploy the HA-Pro environment ........................................ 737
After received the New device (Device 3) ..................................... 738
Configuration on Device 1 ................................................................. 739
Configuration on Device 3 ................................................................. 739
Verification ........................................................................................... 741
How to reboot the Active device to the standby partition when two
partitions has different firmware version ................................................ 743
Change Partition Flow ........................................................................ 744
Check Firmware Version on Active and Passive devices .............. 744
Reboot passive device(Device 1) by standby partition ................ 745
Reboot active device(Device 1) by standby partition .................. 745
Make sure passive device(Device 1) sync process successfully ... 746
Configuration changed scenario ..................................................... 746
How to restore configuration file in Device HA mode? ........................ 748
Configuration file restore flow ............................................................ 749
Unplug all active device network link (Device 1), let network service
runs on passive device. ...................................................................... 749
Upload configuration file to active device (Device 1). ................. 749
Apply configuration file on active device (Device 1) .................... 750
Connect all network cables on Device 1. ....................................... 751
Reset passive device to system default. .......................................... 751
Deploy Device HA .............................................................................. 751
Make sure that passive device (Device 2) sync process successfully
............................................................................................................... 752
How to Check HA Pro Synchronization Status ......................................... 753
Check the sync status on web GUI ................................................... 753
Check the sync status on console .................................................... 754

18/782
www.zyxel.com
A. Check the synchronization status on Active device ............. 754
B. Check the synchronization status on Passive device ............ 755
C. Fail cases ..................................................................................... 757
D. Exception case .......................................................................... 758
What Can Go Wrong? ........................................................................ 759
How to setup Two-Factor Authentication for admin login ................... 760
Setup SMTP function on your device ................................................ 760
Create admin type user on device .................................................. 761
Setup Two-Factor Authentication for admin on your device ........ 762
Test the Result ....................................................................................... 763
What Can Go Wrong? ........................................................................ 765
How to configure Email Security for Phishing mail? .............................. 767
How it works ......................................................................................... 767
Set up Phishing on ATP ........................................................................ 768
Test the Result ....................................................................................... 769
What Can Go Wrong? ........................................................................ 769
How to setup Email to SMS ...................................................................... 771
Setup SMTP function on your device ................................................ 771
Setup Email to SMS Provider configuration ...................................... 772
Create admin type user on device .................................................. 773
Setup Two-Factor Authentication for admin on your device ........ 773
Test the Result ....................................................................................... 774
What Can Go Wrong? ........................................................................ 776
How to Use IP Reputation to Detect Threats .......................................... 777
Activating Reputation Filter Service .................................................. 778
Enabling IP Blocking on ATP ............................................................... 778
Selecting specific type of IP addresses to block ............................. 779
Adding IP addresses to white list and black list ............................... 779
Monitoring statistics for IP detection ................................................. 780
Test the Result ....................................................................................... 780
What Can Go Wrong? ........................................................................ 782

19/782
www.zyxel.com
20/782
www.zyxel.com
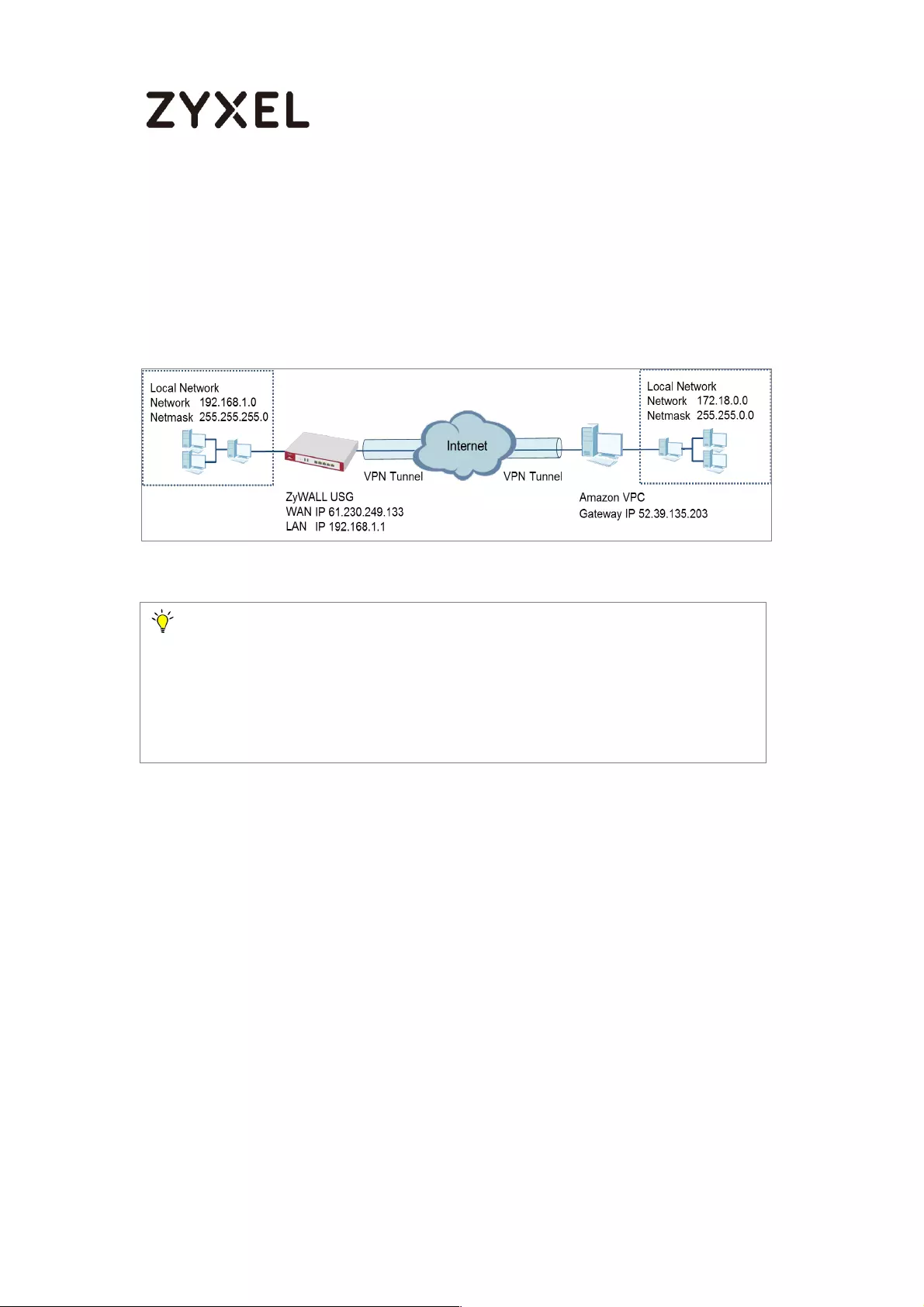
How to Configure Site-to-site IPSec VPN with Amazon VPC
This example shows how to use the VPN Setup Wizard to create a site-to-site
VPN between a ZyWALL/USG and an Amazon VPC platform. The example
instructs how to configure the VPN tunnel between each site. When the VPN
tunnel is configured, each site can be accessed securely.
ZyWALL/USG Site-to-site IPSec VPN with Amazon VPC
Note:
All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks.
This example was tested using USG110 (Firmware Version: ZLD 4.25) and Amazon
VPC (June, 2016).
21/782
www.zyxel.com
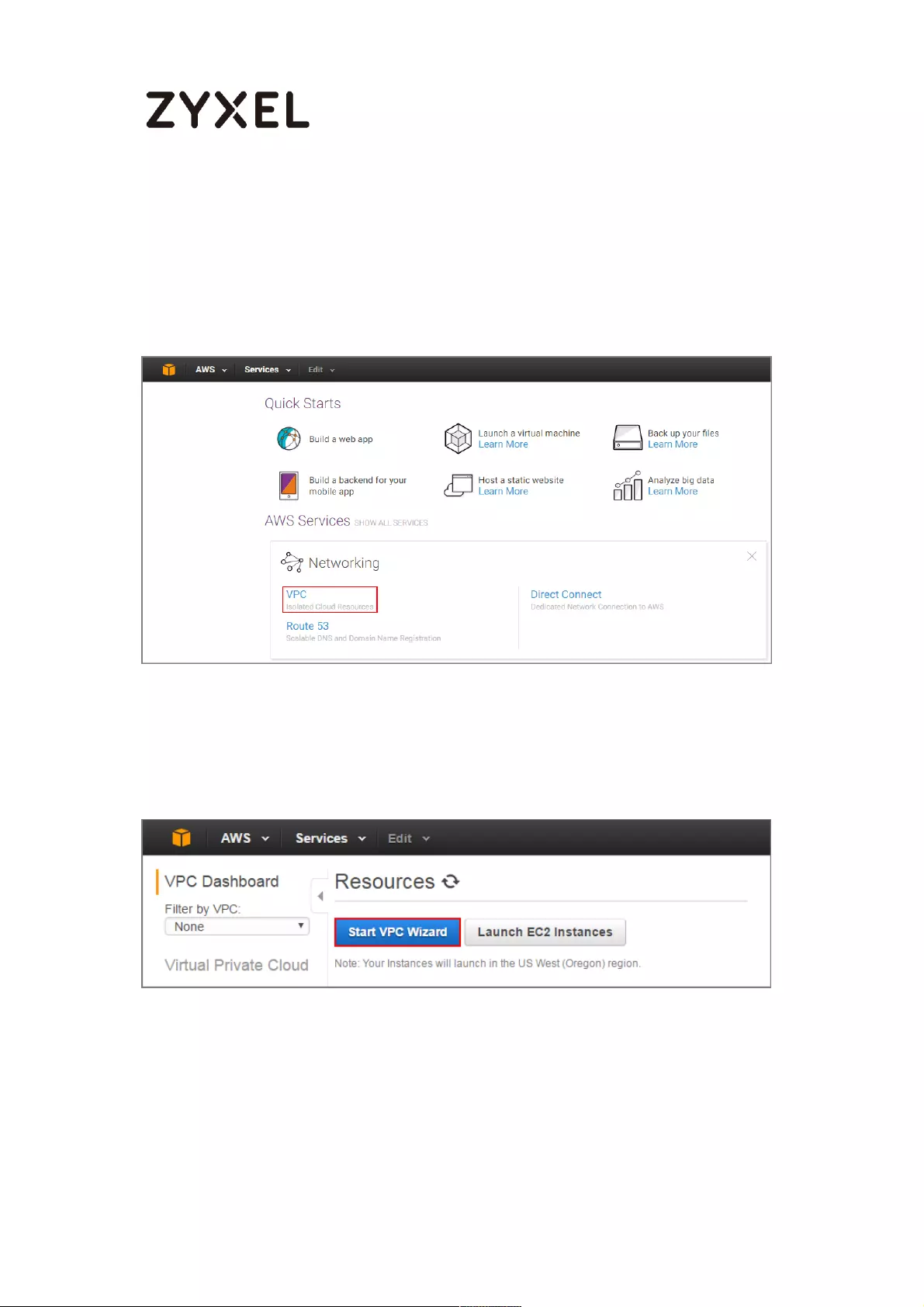
Set Up the IPSec VPN Tunnel on the Amazon VPC
1 Sign into the Amazon AWS Management Console. Go to Networking > VPC.
Amazon AWS Management Console > Networking > VPC
2 In the upper left-hand of the screen, click Start VPC Wizard.
Amazon VPC Management Console > Networking > VPC > Start VPC Wizard
3 Select a VPC Configuration, select VPC with a Private Subnet Only and Hardware
VPN Access, and then click Select.
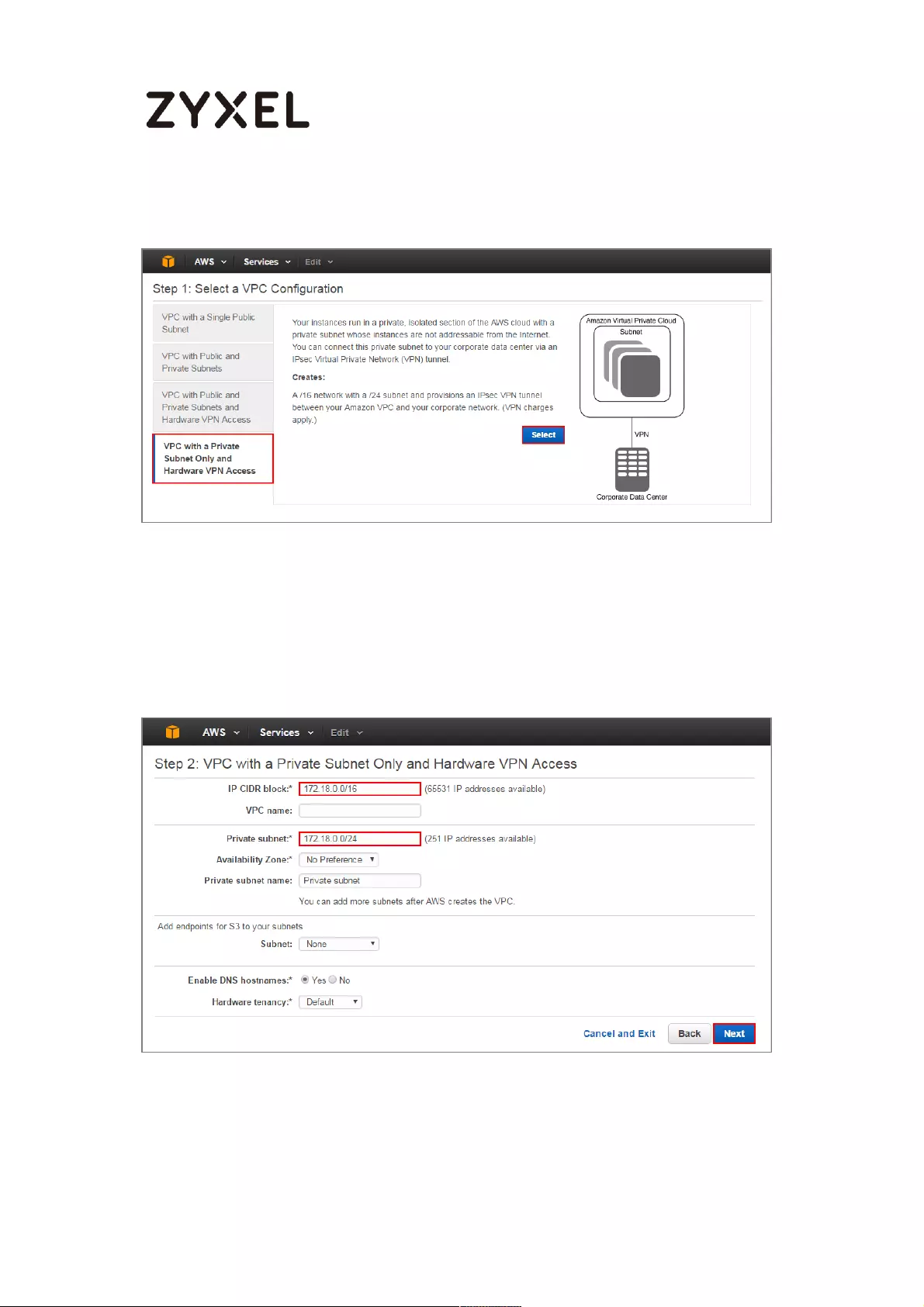
22/782
www.zyxel.com
Select a VPC Configuration > VPC with a Private Subnet Only and Hardware VPN
Access
4 VPC with a Private Subnet Only and Hardware VPN, add your IP CIDR block and
Private subnet. Click Next.
VPC with a Private Subnet Only and Hardware VPN
23/782
www.zyxel.com
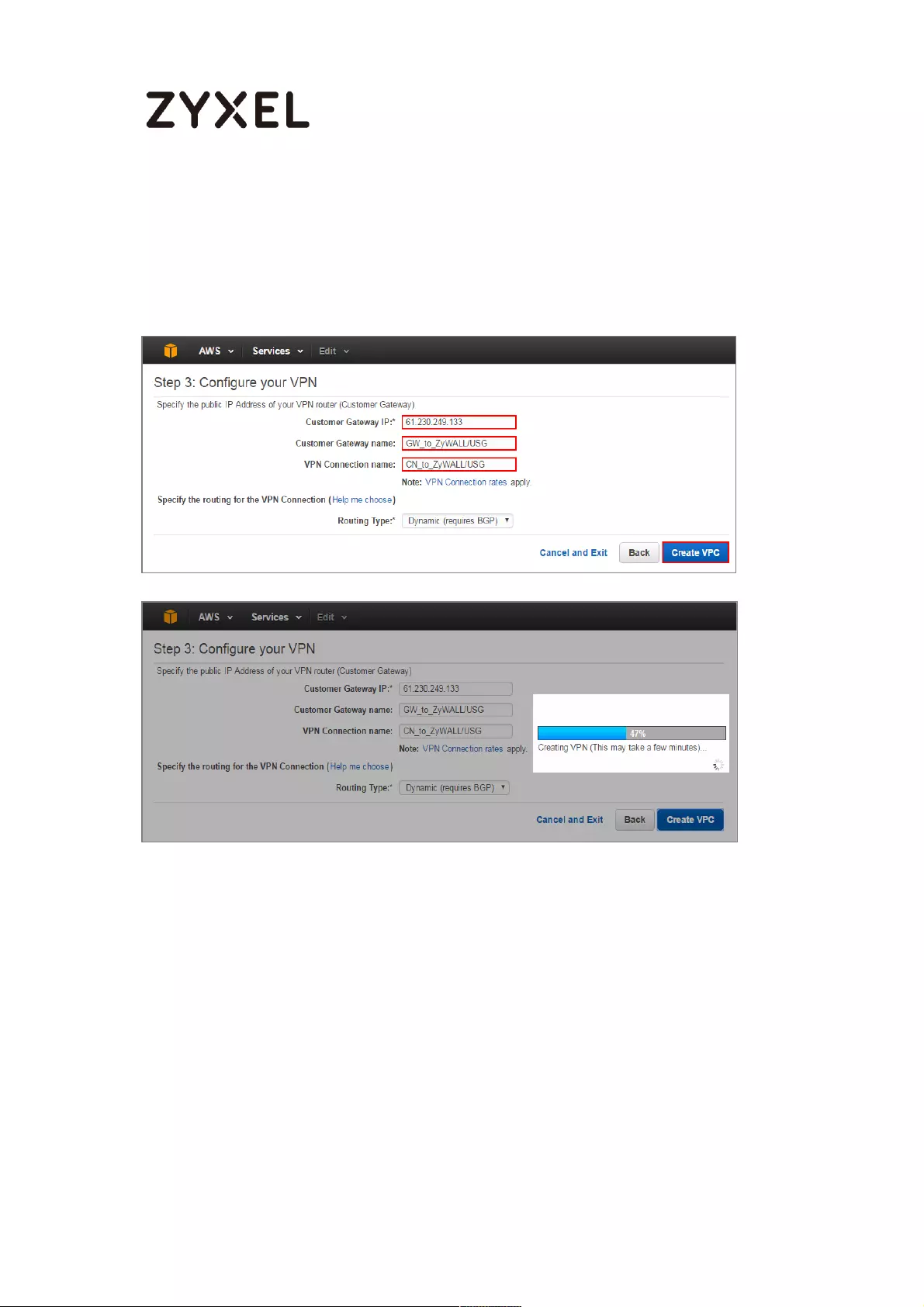
5 Configure your VPN, add your ZyWALL/USG public IP address into Customer
Gateway IP. Name your Customer Gateway name and VPN Connection name.
Click Create VPC at the bottom of the blade.
Configure your VPN
6 In the VPC Dashboard, go to VPN Connections. Select Download Configuration
from the upper bar. Select Vendor and Platform to be Generic. Click Yes,
Download.
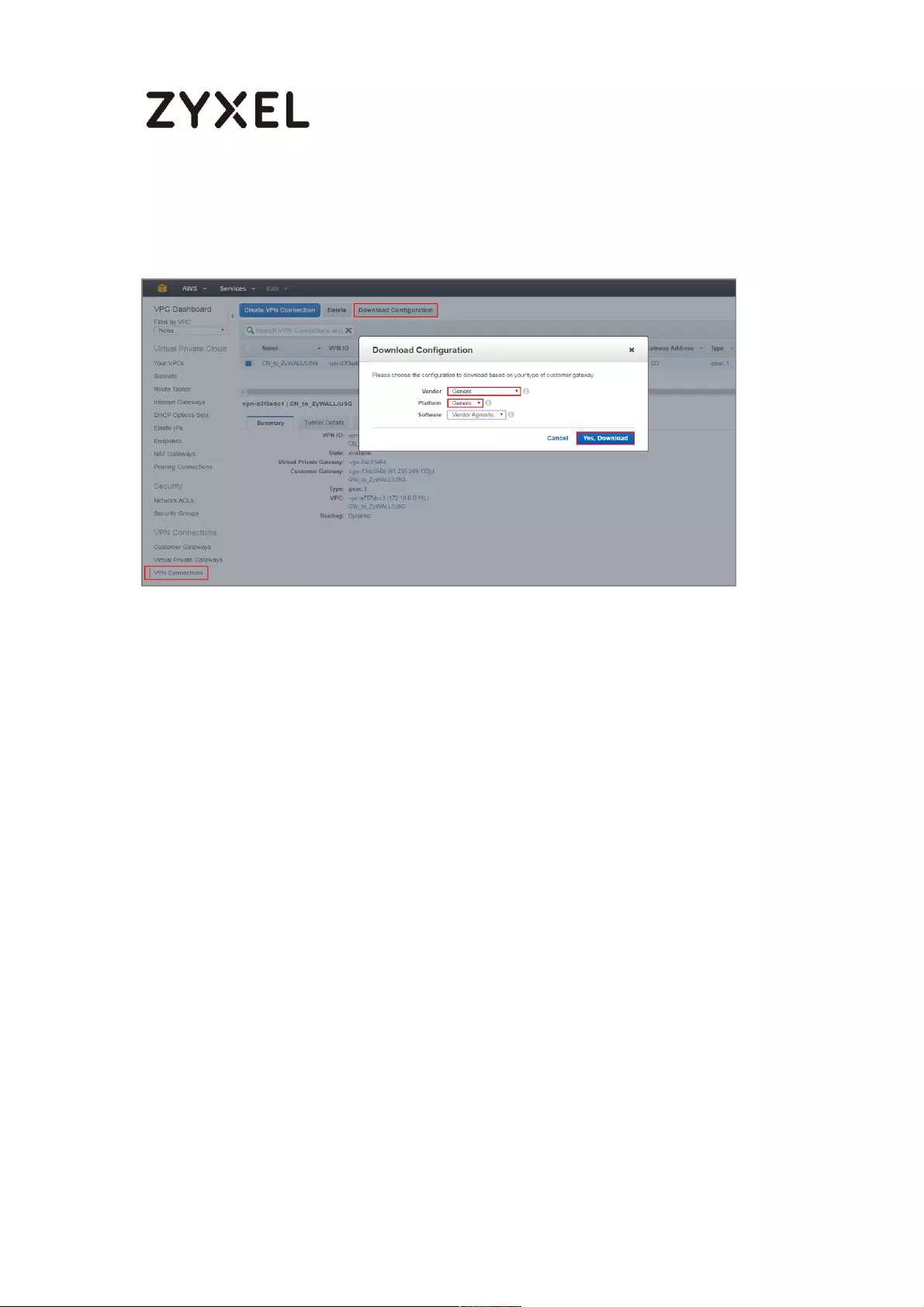
24/782
www.zyxel.com
VPC Dashboard > VPN Connections
7 Open the downloaded configuration txt. file, it displays IKE SA, IPSec SA and
Gateway IP address. Please make sure all the settings match your ZyWALL/USG’s
setting.
Configuration txt. File

25/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG
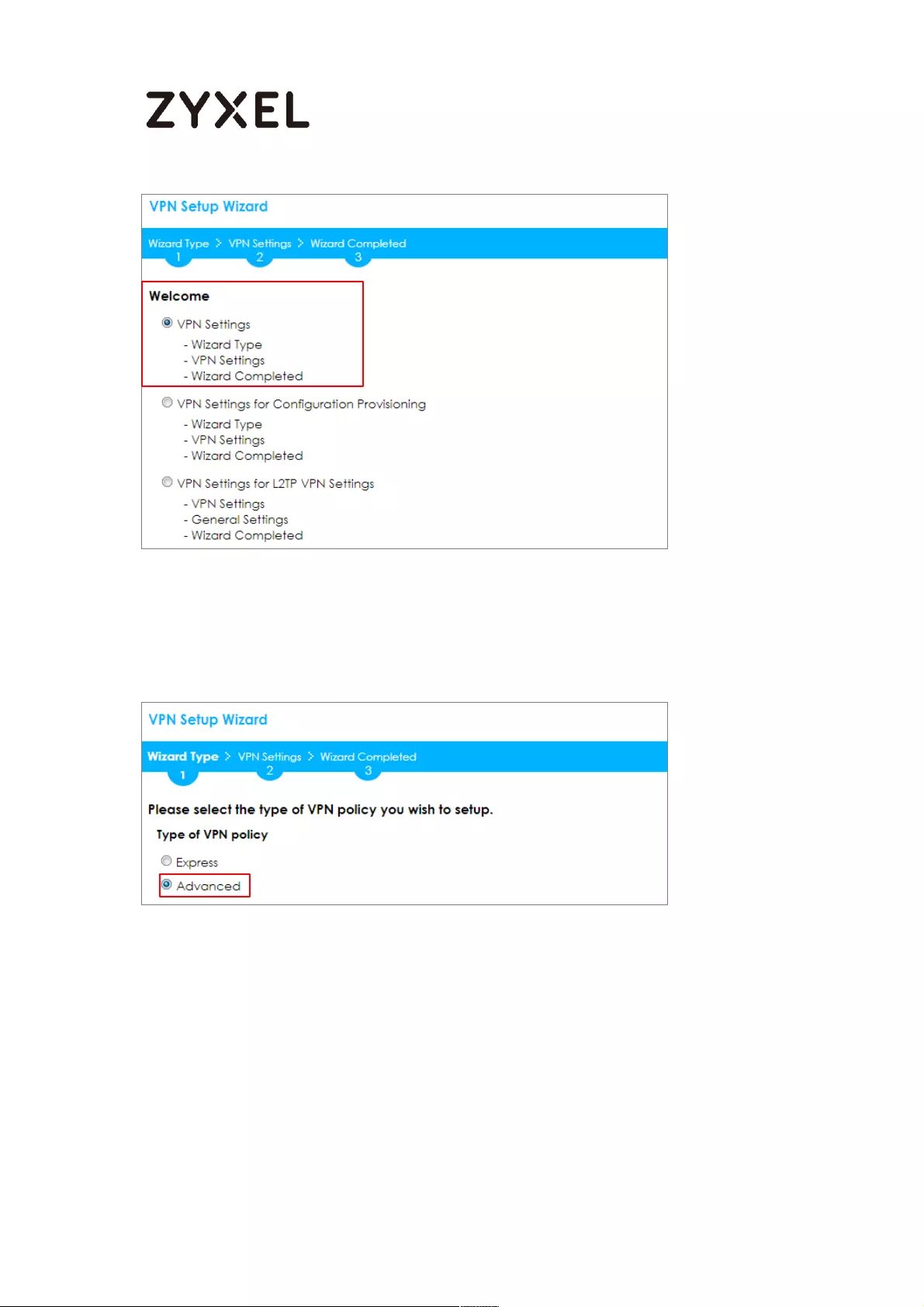
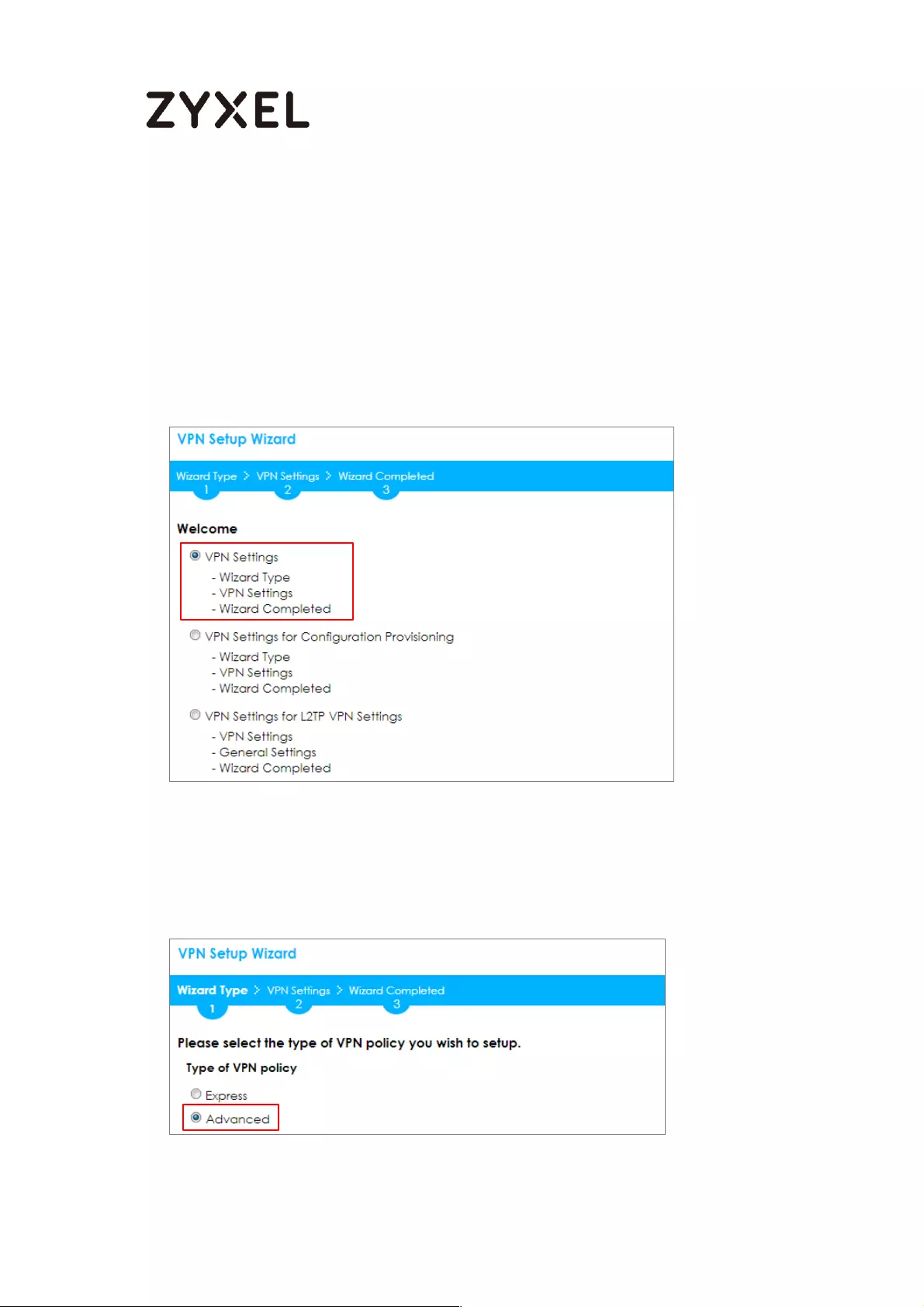
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the Amazon VPC. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
26/782
www.zyxel.com
Choose Advanced to create a VPN rule with the customize phase 1, phase 2
settings and authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type
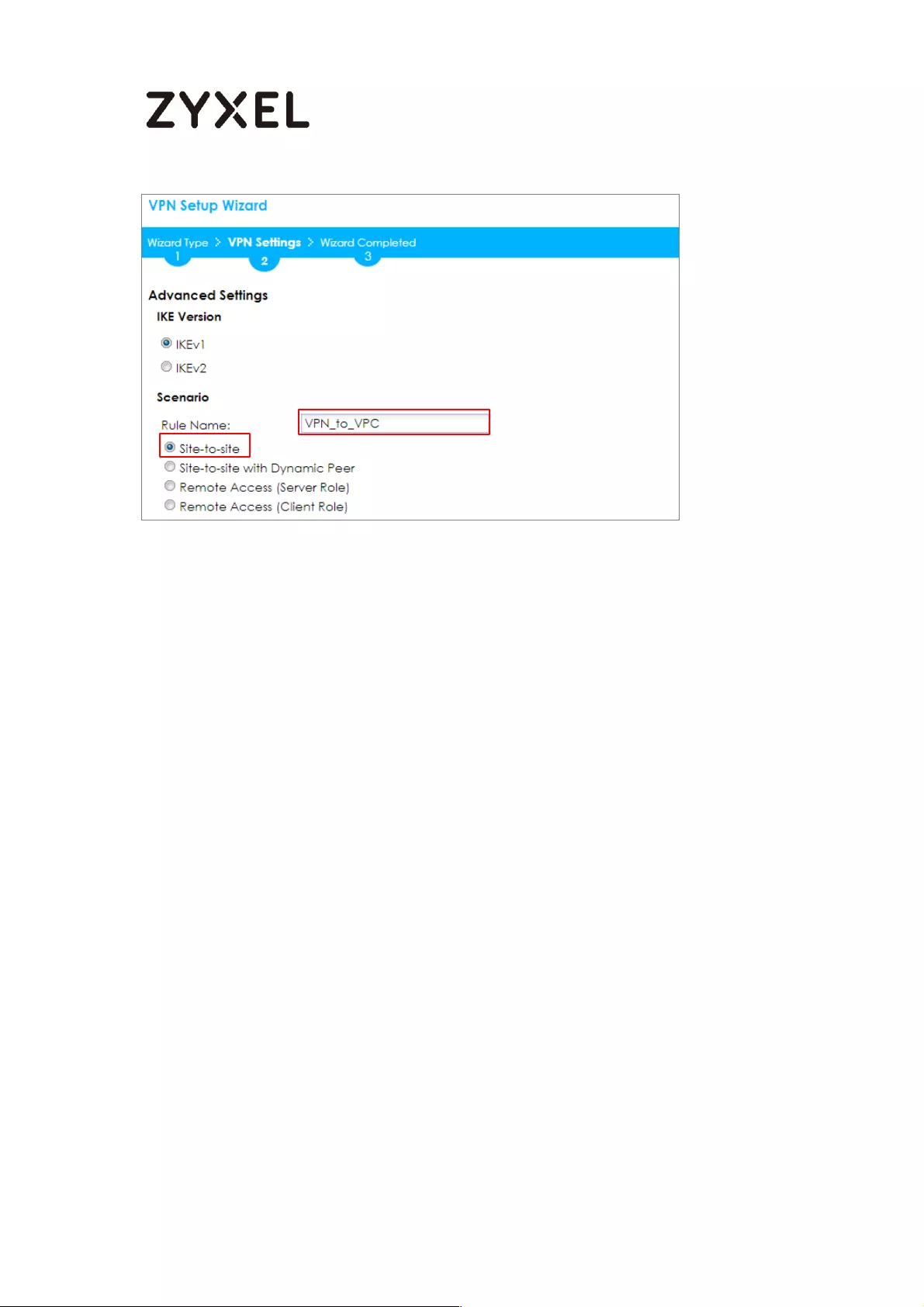
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select
the rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
27/782
www.zyxel.com
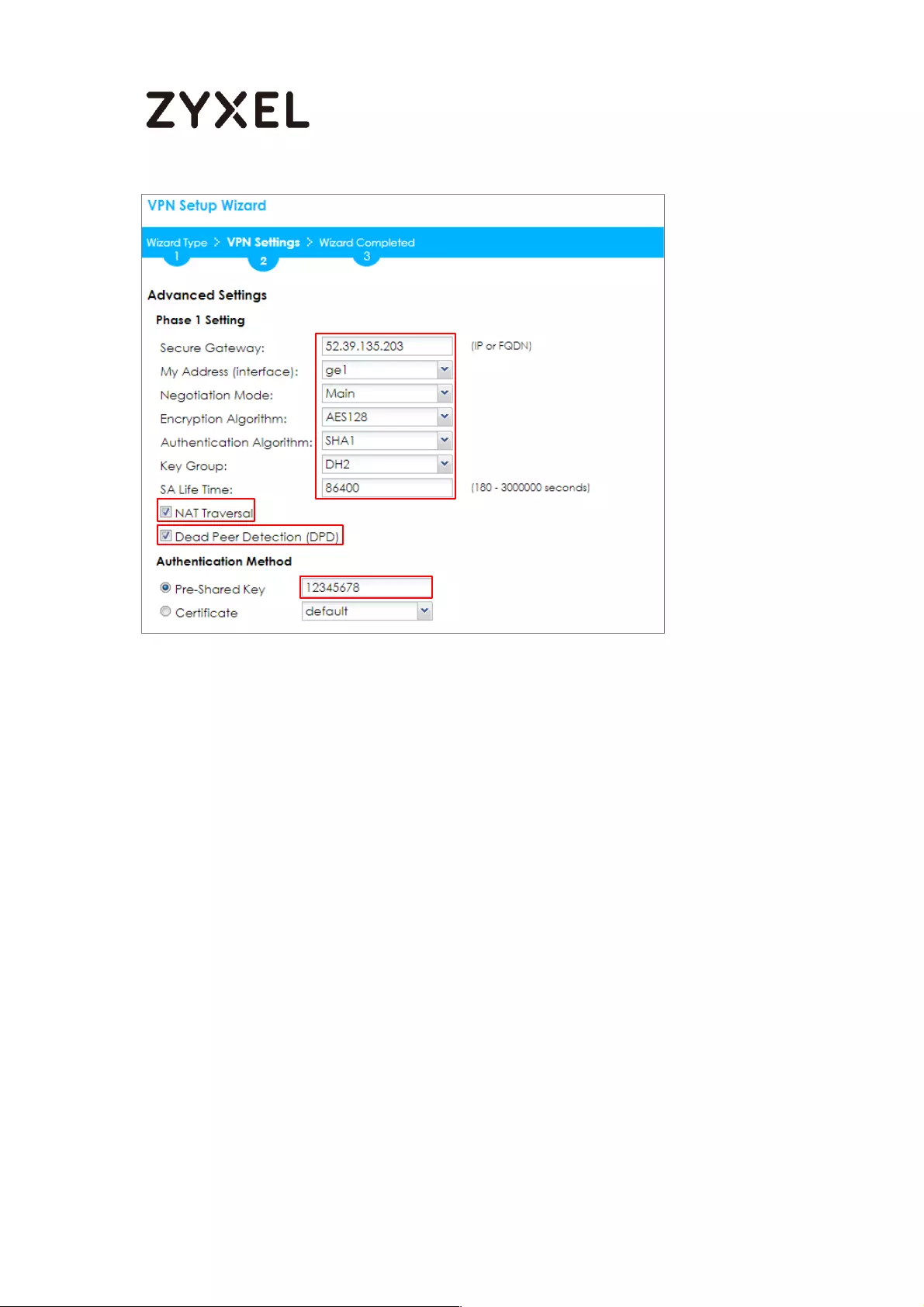
Then, configure the Secure Gateway IP as the peer Amazon VPC’s Gateway IP
address (in the example, 52.39.135.203); select My Address to be the interface
connected to the Internet.
Set the Negotiation, Encryption, Authentication, Key Group and SA Life Time
which Amazon VPC supports. Type a secure Pre-Shared Key.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Phase 1
Setting)
28/782
www.zyxel.com
Continue to Phase 2 Settings to select the Encapsulation, Encryption,
Authentication, and SA Life Time settings which Amazon VPC supports.
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the Amazon VPC. Click OK.

29/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Phase 2 Setting)
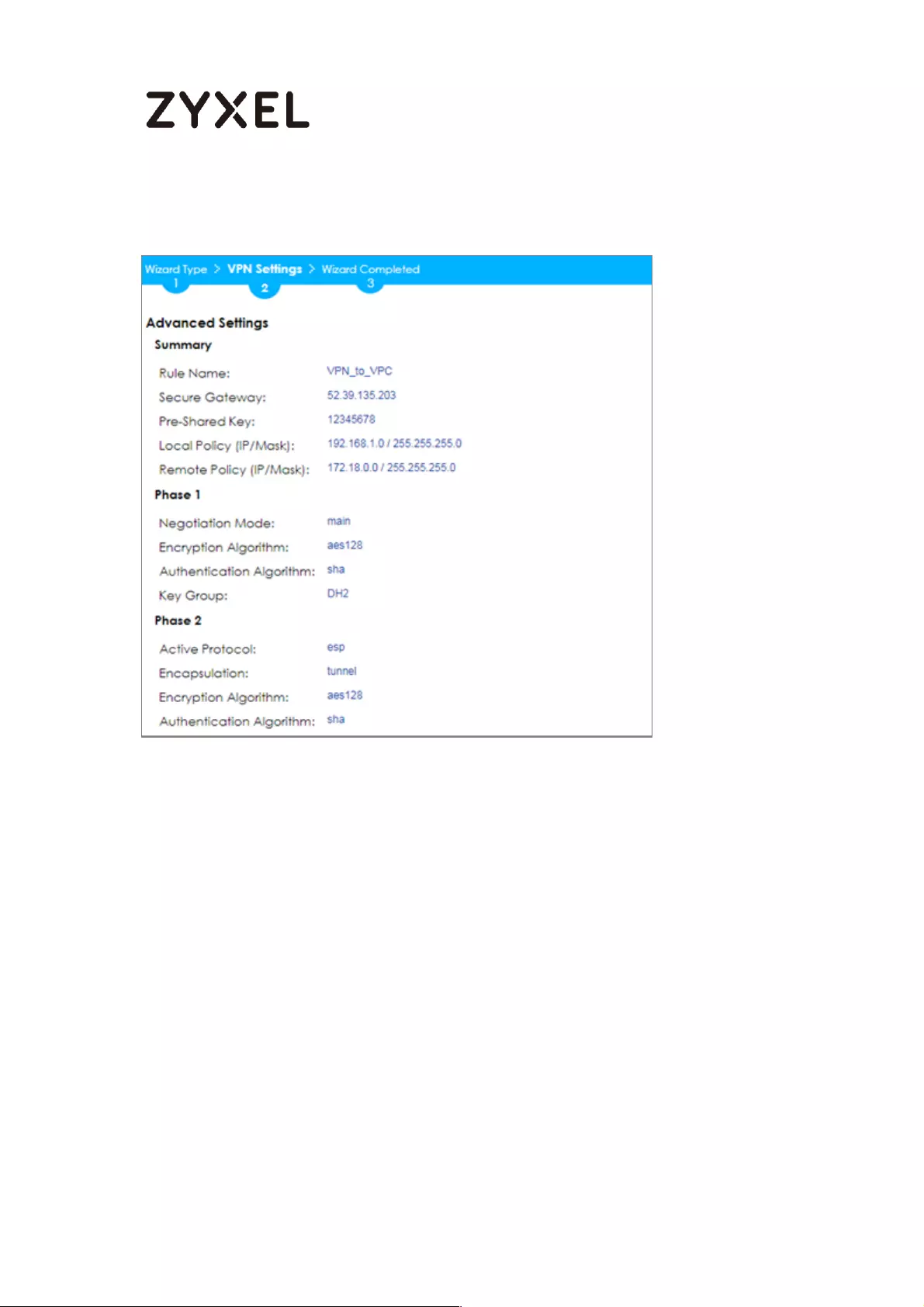
30/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
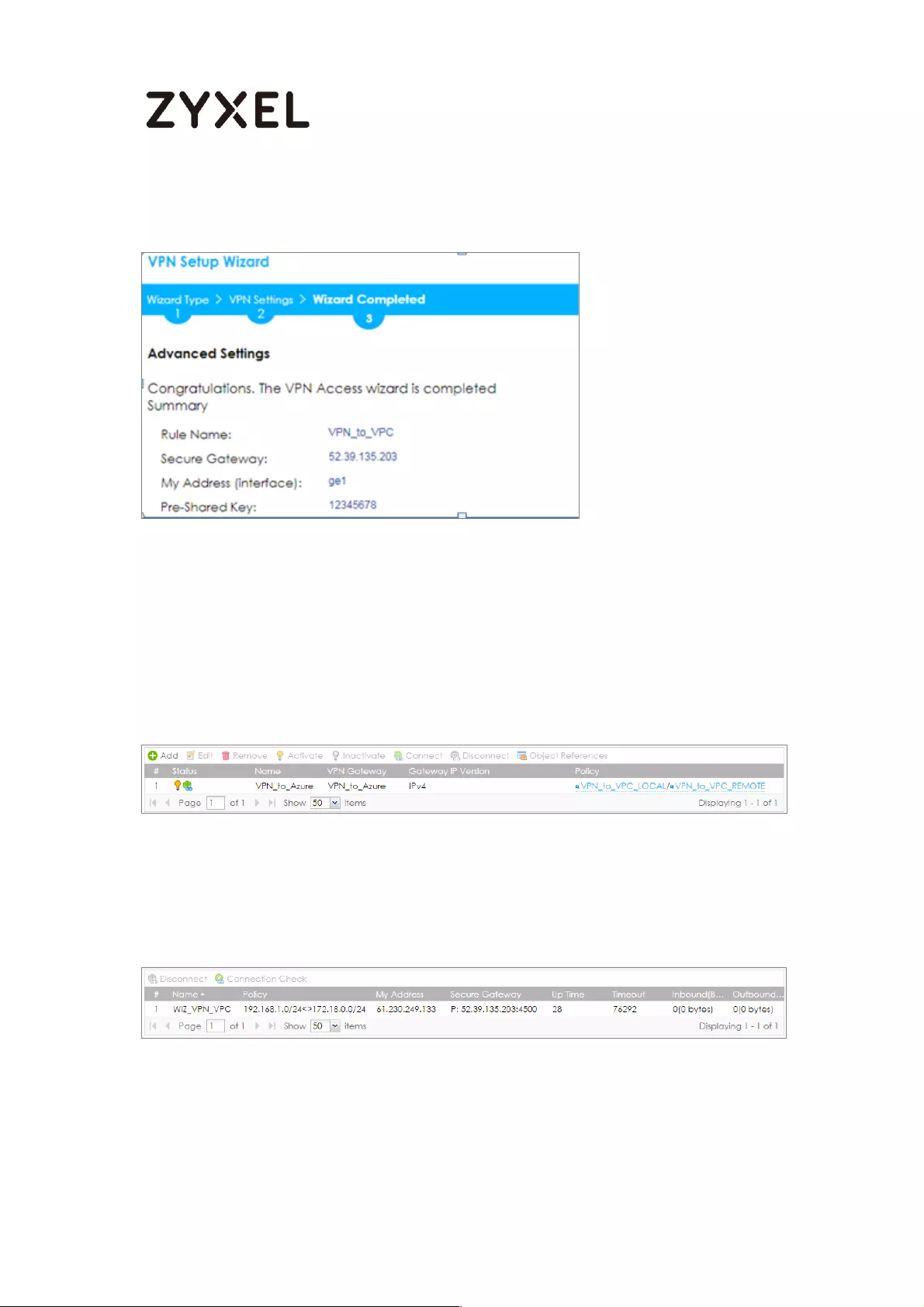
31/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up
Time and the Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > IPSec
To test whether or not a tunnel is working, ping from a Local LAN to AWS VPC private
Subnet for verification. Ensure that both computers have Internet access.
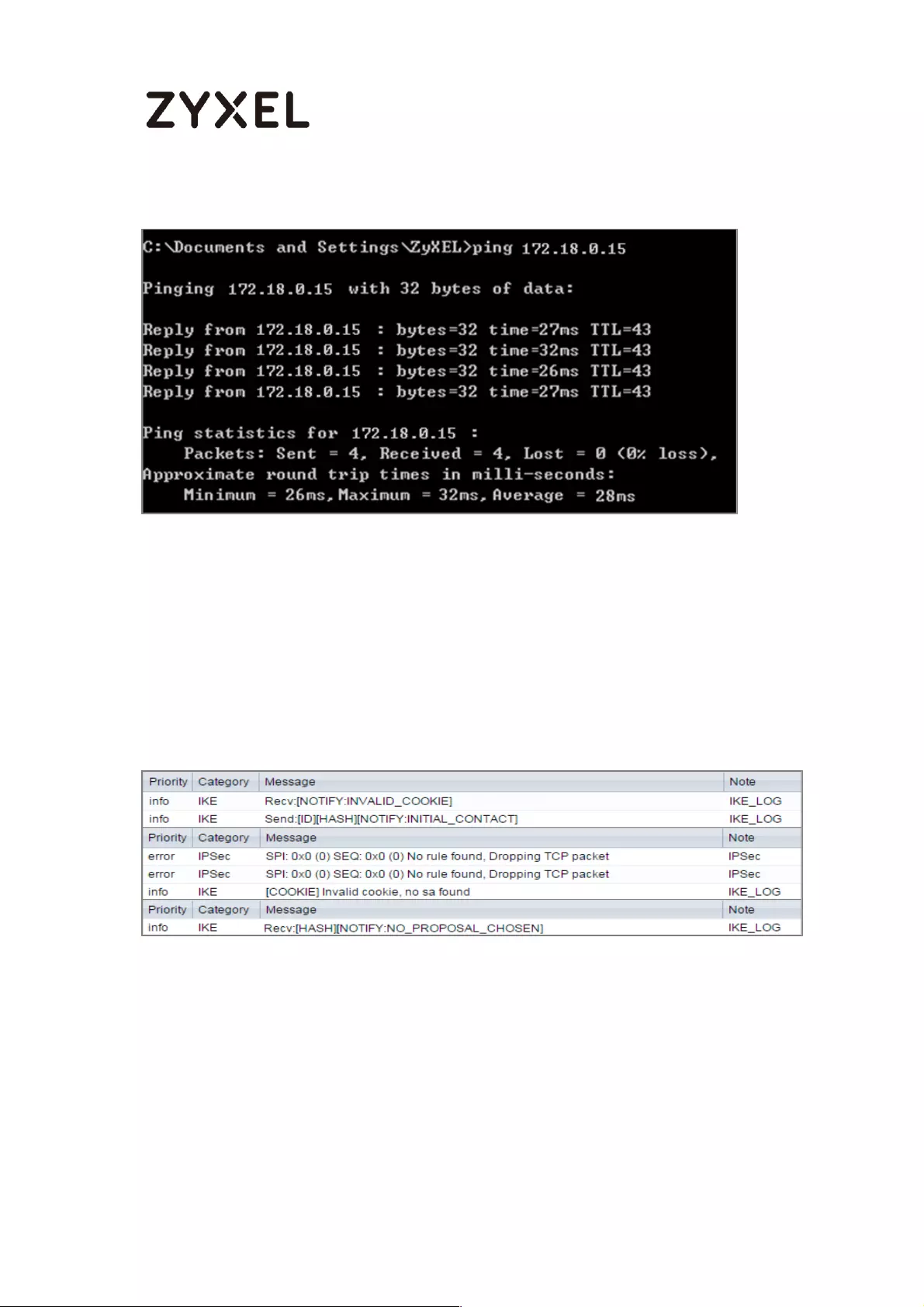
32/782
www.zyxel.com
Ping from Local LAN to AWS VPC private Subnet for verification:
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase
1 Settings. Make sure your ZyWALL/USG Phase 1 Settings are supported in the
Amazon VPC IKE Phase 1 setup list.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log
message, please check ZyWALL/USG Phase 2 Settings. Make sure your
ZyWALL/USG Phase 2 Settings are supported in the Amazon VPC IKE Phase 2
setup list.
MONITOR > Log

33/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN with Microsoft (MS)
Azure
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
between a ZyWALL/USG and a Microsoft (MS) Azure platform. The example
instructs how to configure the VPN tunnel between each site. When the VPN
tunnel is configured, each site can be accessed securely.
ZyWALL Site-to-site IPSec VPN with Microsoft (MS) Azure
Note:
1. All network IP addresses and subnet masks are used as examples in this article. Please
replace them with your actual network IP addresses and subnet masks. This example was
tested using USG40 (Firmware Version: ZLD 4.25) and MS Azure (April, 2016).
34/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the MS Azure. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Advanced to create a VPN rule with the customize phase 1, phase 2
settings and authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type

35/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Then, configure the Secure Gateway IP as the peer MS Azure’s Gateway IP
address (in the example, 13.75.42.148); select My Address to be the interface
connected to the Internet.
Set the Negotiation, Encryption, Authentication, Key Group and SA Life Time which
MS Azure supports. Please make sure you disable Dead Peer Detection (DPD)
which is not supported in the MS Azure IKEv1 Policy-based. Type a secure Pre-
Shared Key.
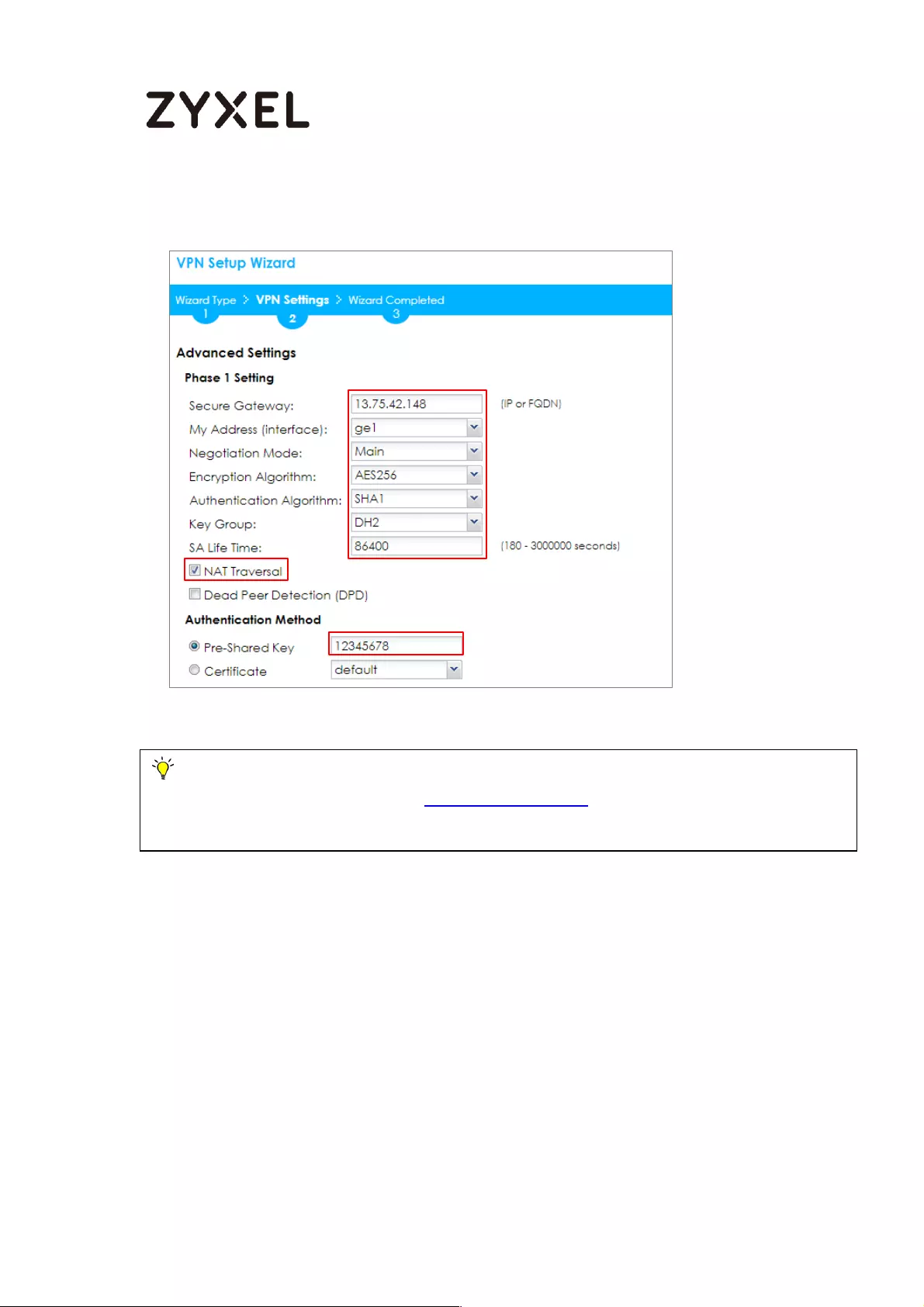
36/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Phase
1 Setting)
Note: For more information about the IPsec Parameters supported in MS Azure, see the
Microsoft Azure Documentation About VPN devices for Site-to-Site VPN Gateway
connections.
37/782
www.zyxel.com
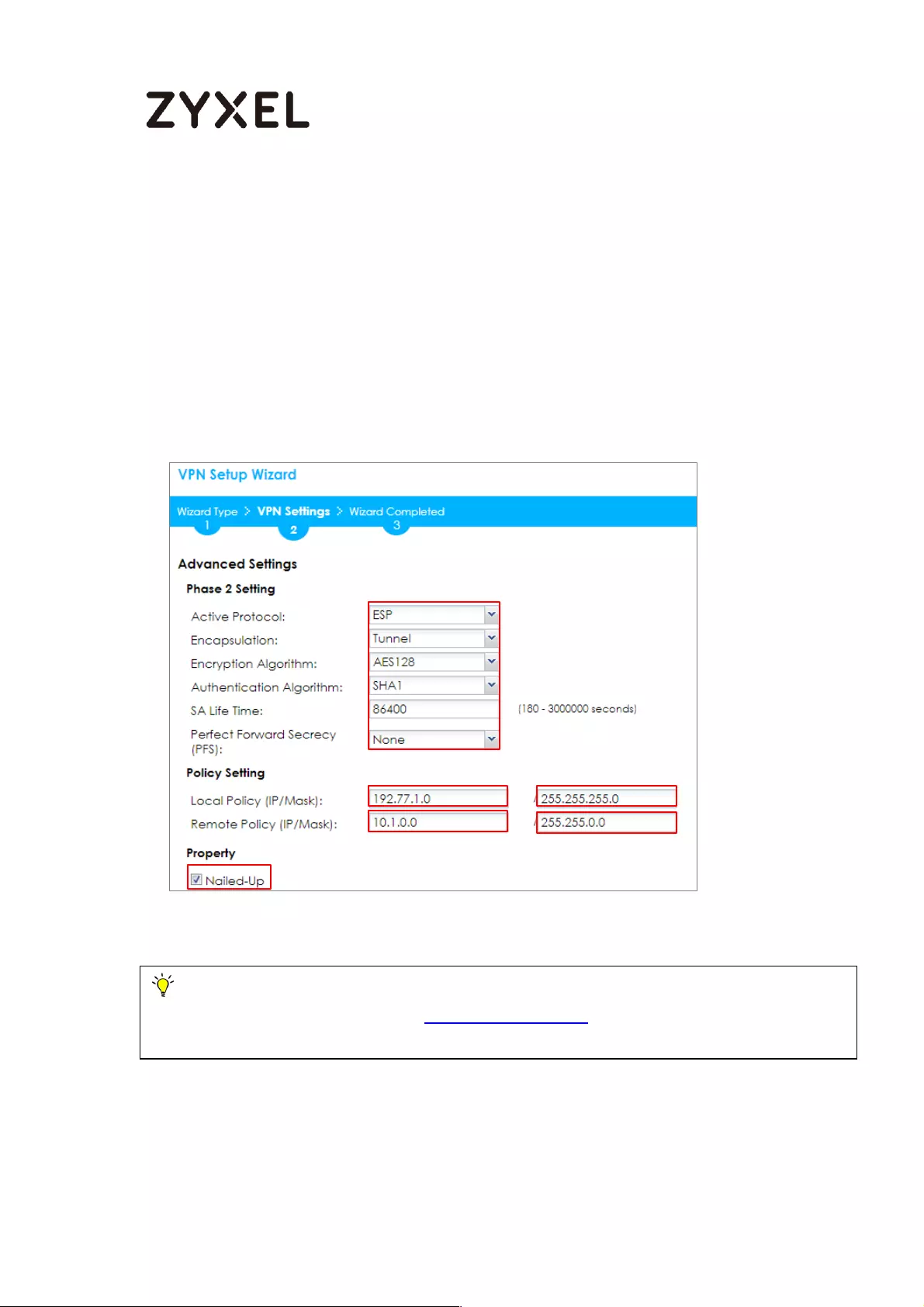
Continue to Phase 2 Settings to select the Encapsulation, Encryption,
Authentication, and SA Life Time settings which MS Azure supports.
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the MS Azure. Click OK.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Phase
2 Setting)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Note: For more information about the IPsec Parameters supported in MS Azure, see the
Microsoft Azure Documentation About VPN devices for Site-to-Site VPN Gateway
connections.
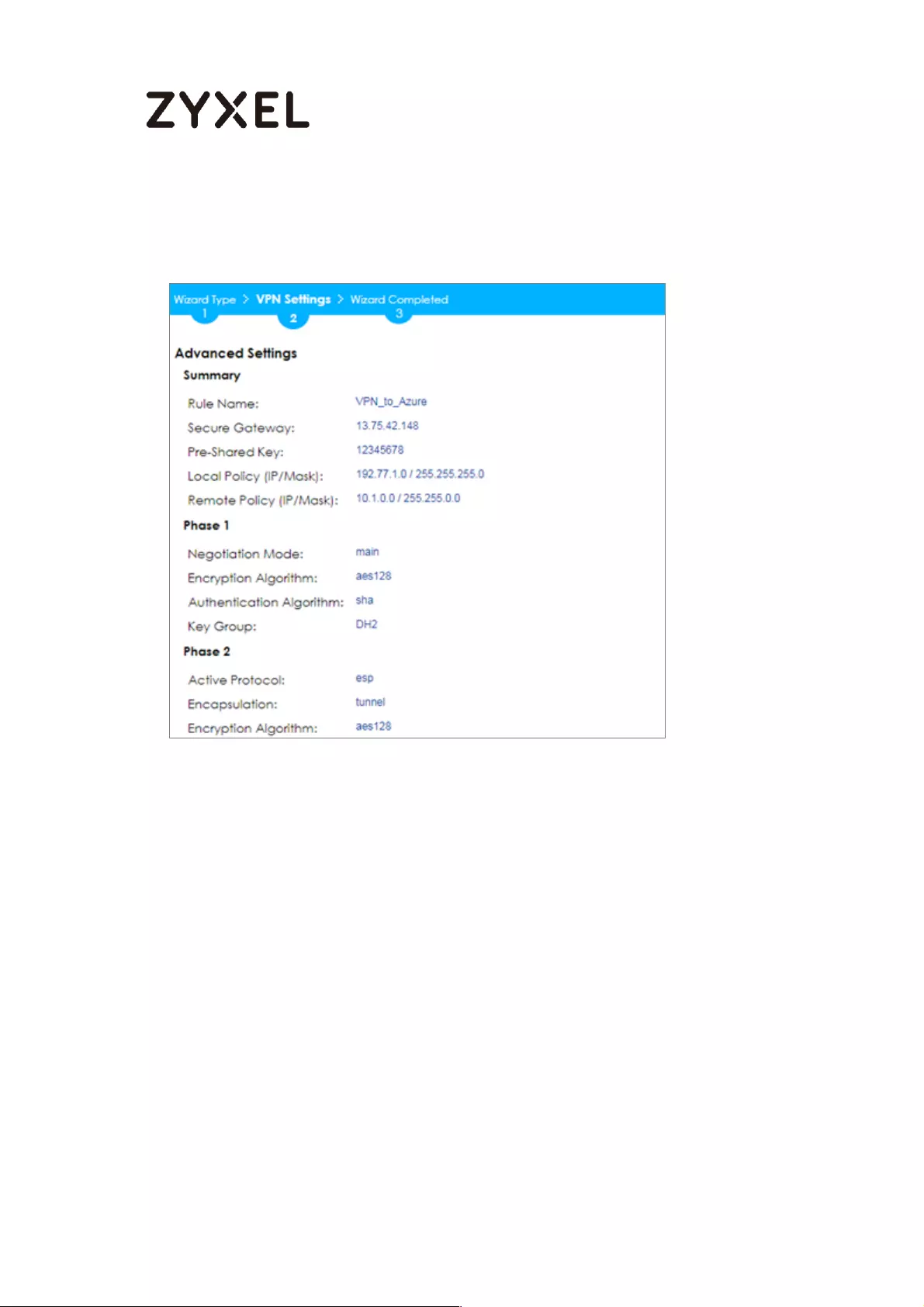
38/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.

39/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Set Up the IPSec VPN Tunnel on the MS Azure
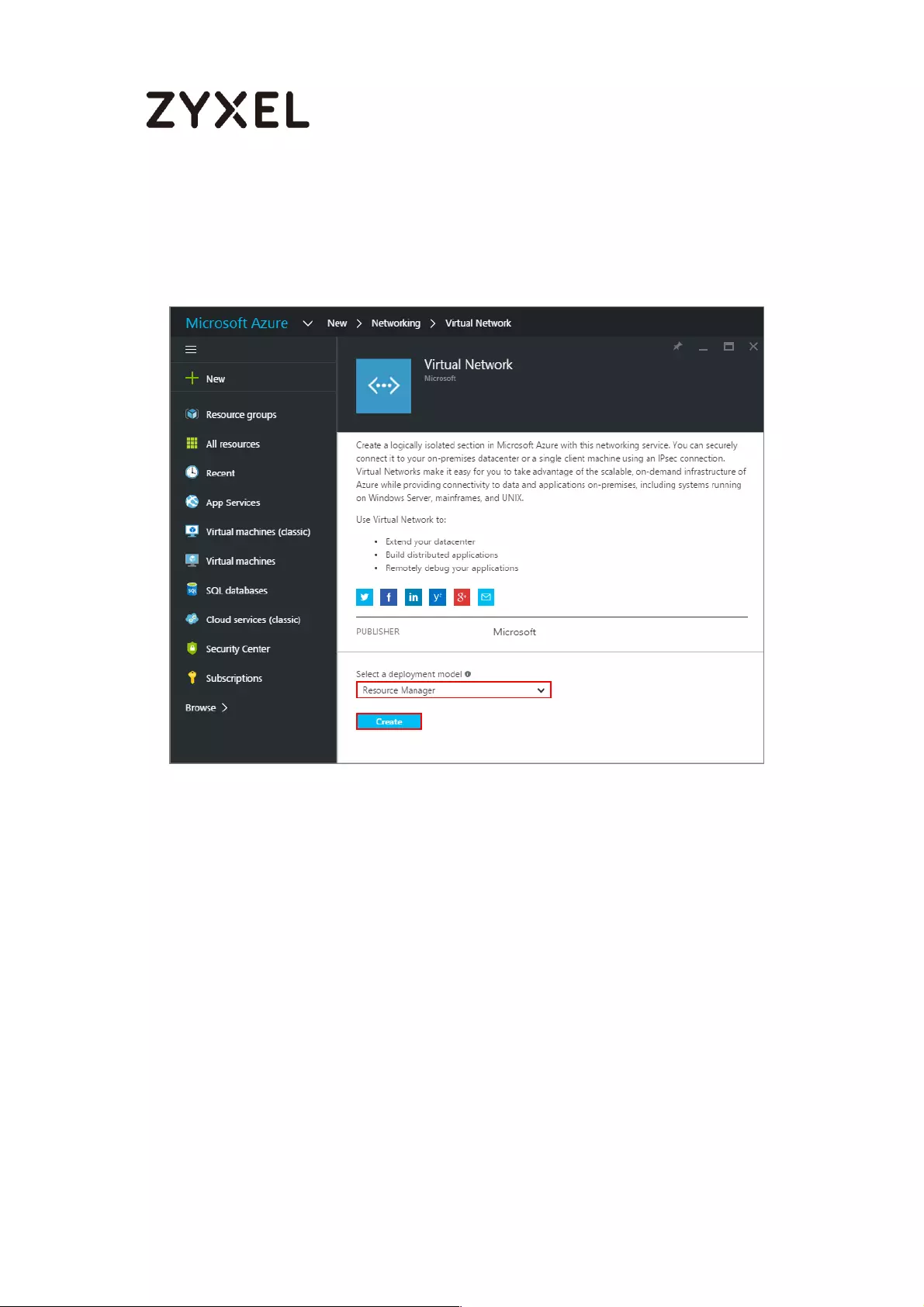
Sign into the Windows Azure Management Portal. In the upper left-hand corner of
the screen, click +New > Networking > Virtual Network.
Azure portal > New > Networking > Virtual Network
40/782
www.zyxel.com
Near the bottom of the Virtual Network blade, from the Select a deployment
model list, select Resource Manager, and then click Create.
New > Networking > Virtual Network > Select a deployment model
On the Create virtual network page, enter the NAME for the VPN network. For
example, VPN_Vnet_to_USG. Add your Address Space, Subnet name and a single
Subnet address range.
Click Resource group and either select an existing resource group, or create a
new one by typing a name for your new resource group. For example, RG_USG.
LOCATION is directly related to the physical location (region) where the virtual
machines (VMs) reside. The region associated with the virtual network cannot be
changed after it has been created.
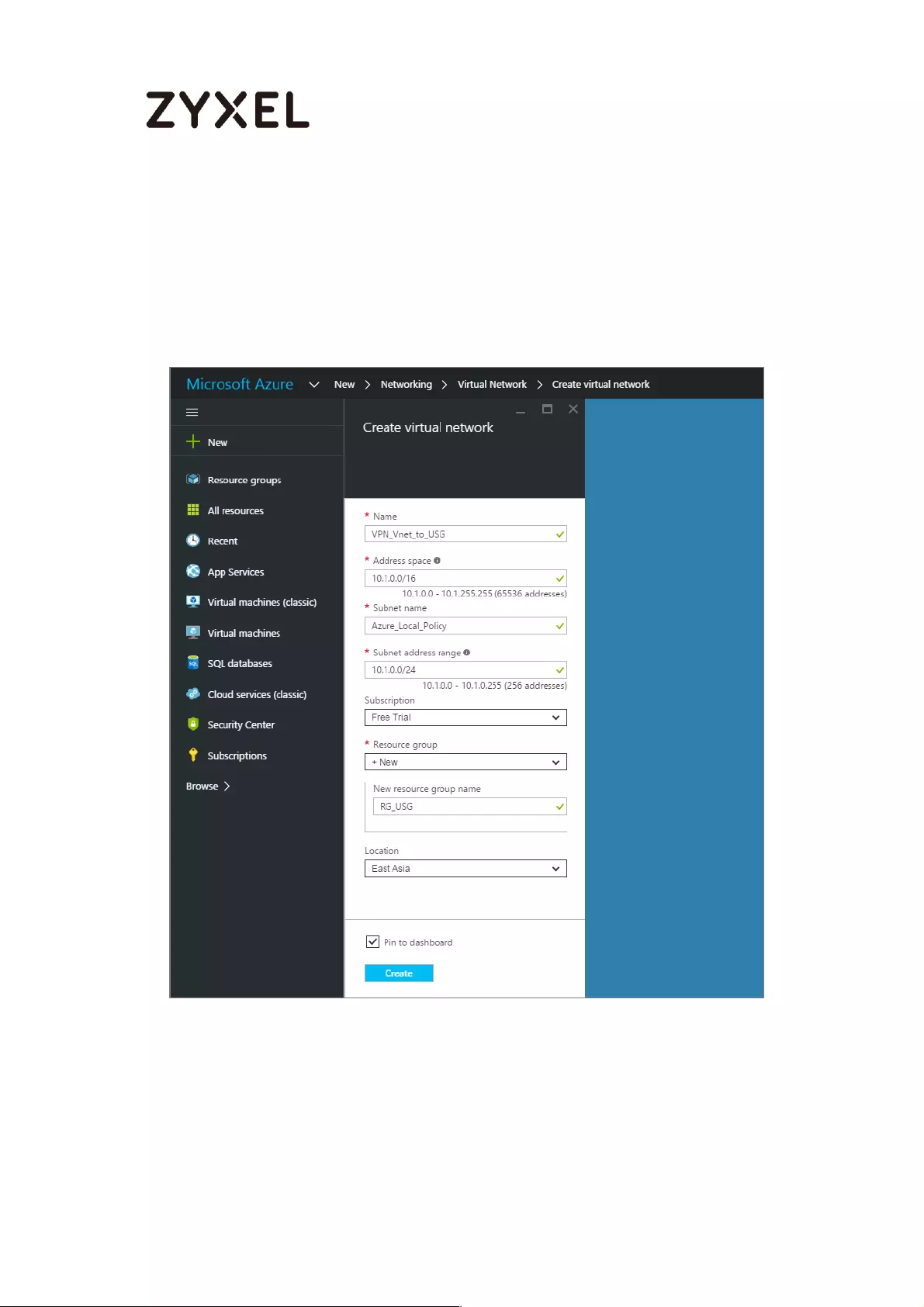
41/782
www.zyxel.com
Then, click the Create button. After clicking Create, you will see a tile on your
dashboard that will reflect the progress of your VNet. The tile will change as the
VNet is being created.
New > Networking > Virtual Network > Create virtual network
In the portal, navigate to the virtual network to which you just created. On the
blade for your virtual network, click the Settings icon at the top of the blade to
expand the Setting blade to Subnets > Add > Add Subnet. Name your subnet
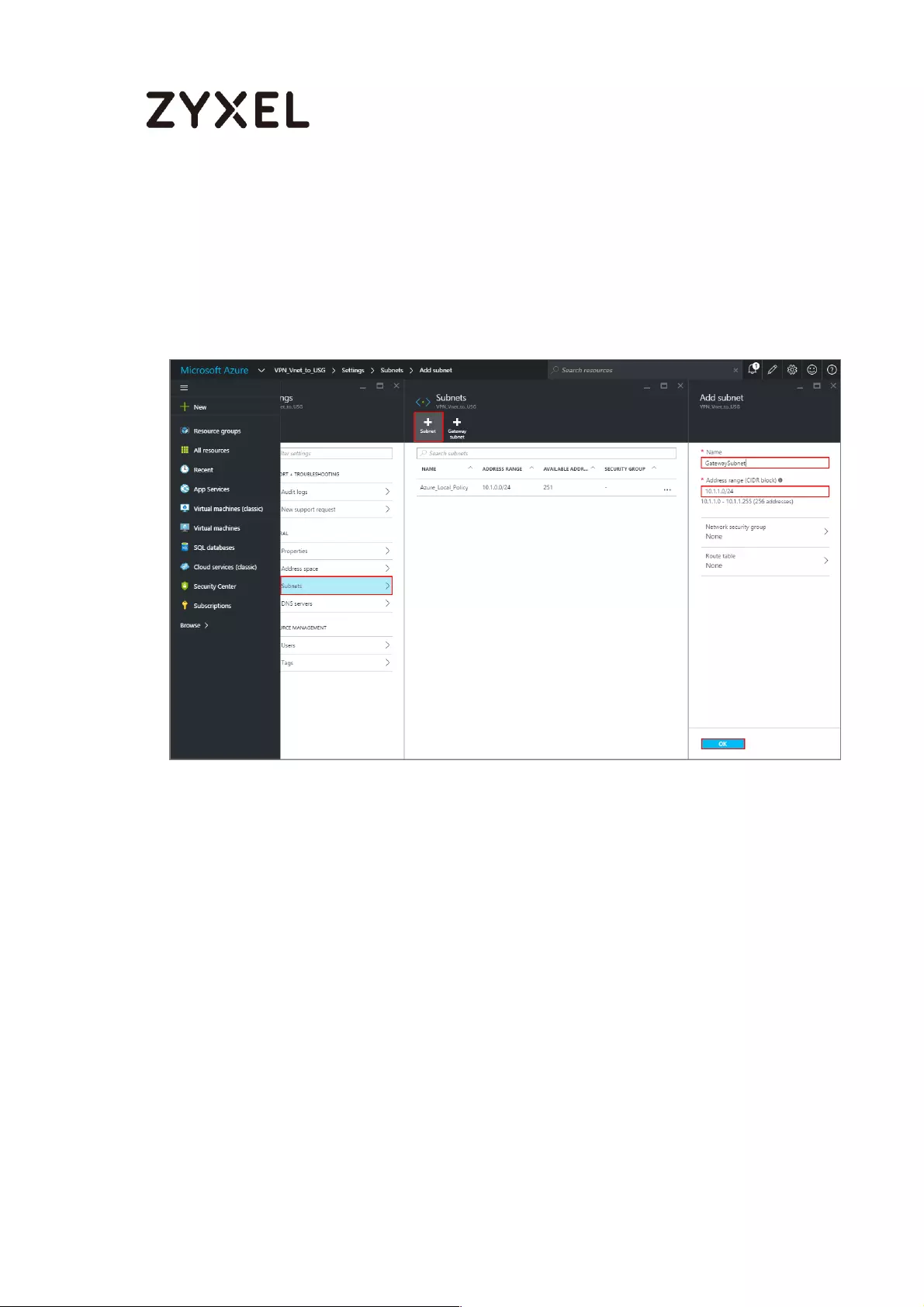
42/782
www.zyxel.com
GatewaySubnet. You should not name it anything else, or the gateway will not
work. Add the IP Address range for your gateway. Click OK at the bottom of the
blade to create the subnet.
VPN Vnet_to_USG > Settings > Subnet > Add subnet
In the portal, go to New, then Networking. Select Virtual network gateway from
the list. On the Create virtual network gateway blade Name field, name your
gateway. Next, choose the Virtual network that you want to deploy this gateway
to.
Click the arrow (>) to open the Choose public IP address blade. Then click Create
New to open the Create public IP address blade. Input a Name for your public IP
address. Note that this is not asking for an IP address. The IP address will be
assigned dynamically. Rather, this is the name of the IP address object that the
address will be assigned to. Click OK to save your changes.

43/782
www.zyxel.com
For Gateway type, select VPN. For VPN type, select Policy-based. For Resource
Group, the resource group is determined by the Virtual Network that you select.
For Location, make sure it's showing the location that both your Resource Group
and VNet exist in.
New > Networking > Create virtual network gateway > Choose public IP address >
Create public IP address
In the Azure Portal, navigate to New > Networking > Local network gateway. The
local network gateway refers to your ZyWALL/USG public IP and local subnet
settings.
On the Create local network gateway blade, specify a Name for your
ZyWALL/USG gateway object.
Specify public IP address of your ZyWALL/USG. It cannot be behind NAT and has
to be reachable by Azure. Address space refers to the address ranges on your
ZyWALL/USG local network. For Resource Group, select the resource group that
you created before. For Location, if you are creating a new local network
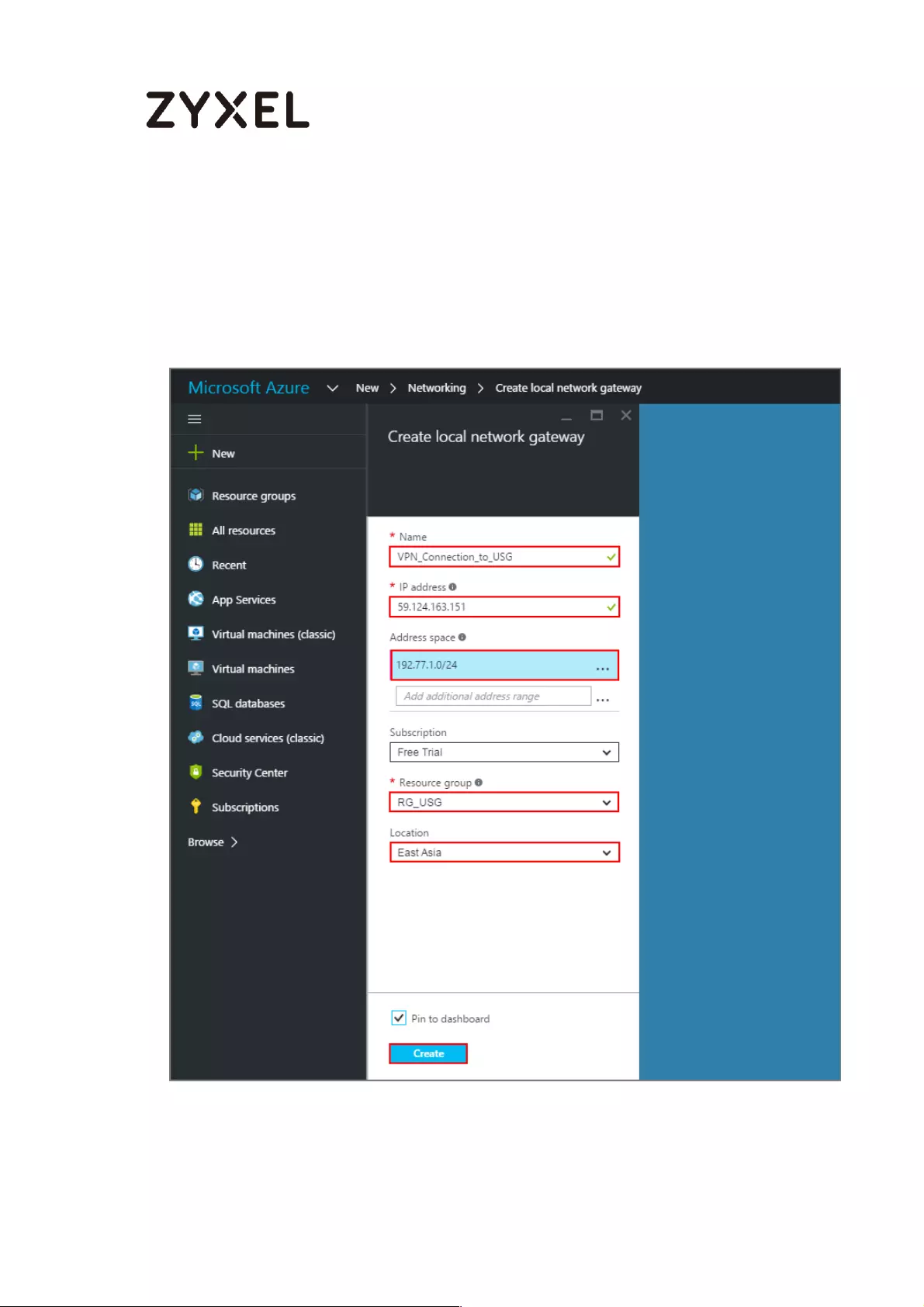
44/782
www.zyxel.com
gateway, you can use the same location as the virtual network gateway. But, this
is not required. The local network gateway can be in a different location.
Click Create to create the local network gateway.
New > Networking > Local network gateway
45/782
www.zyxel.com
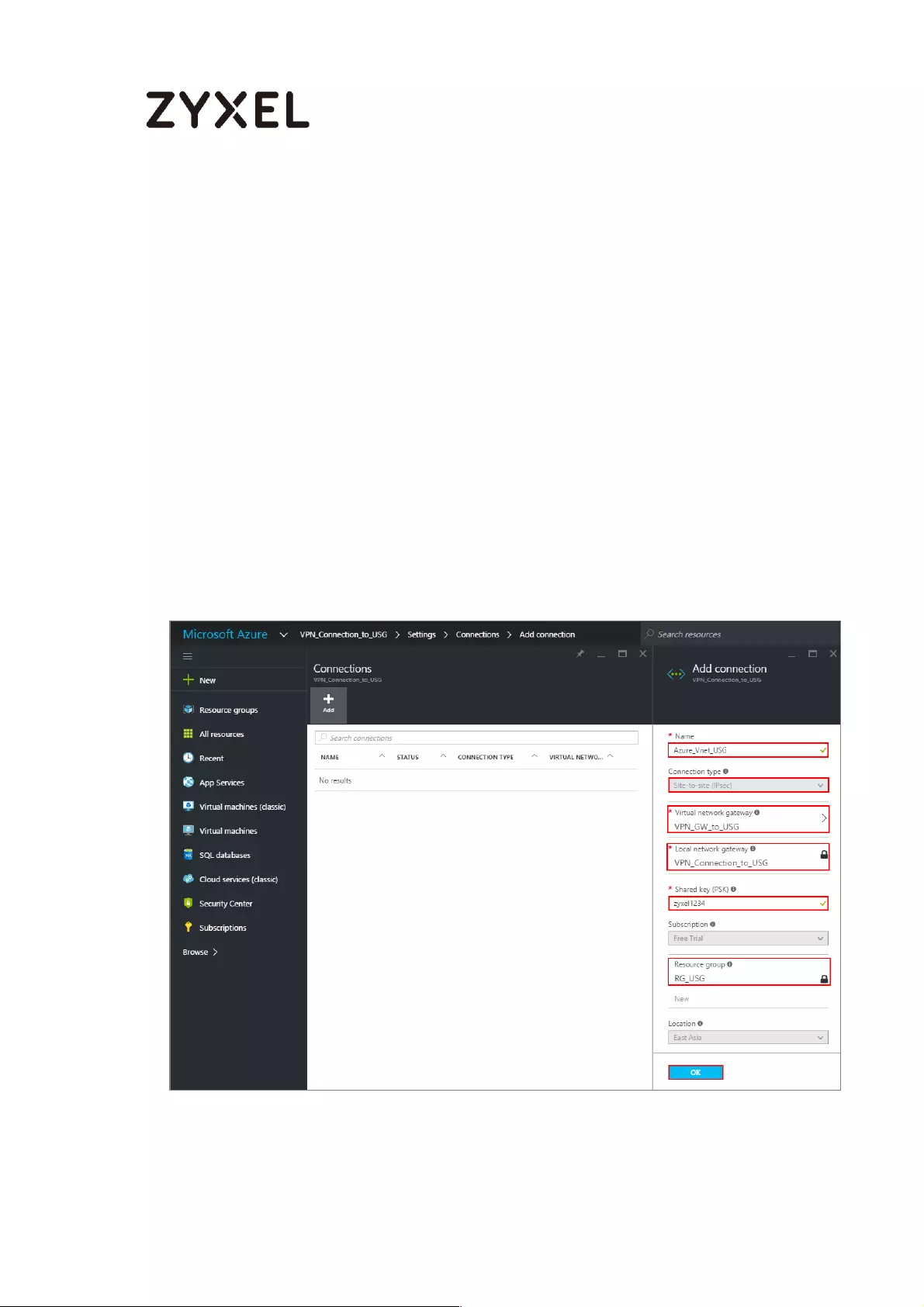
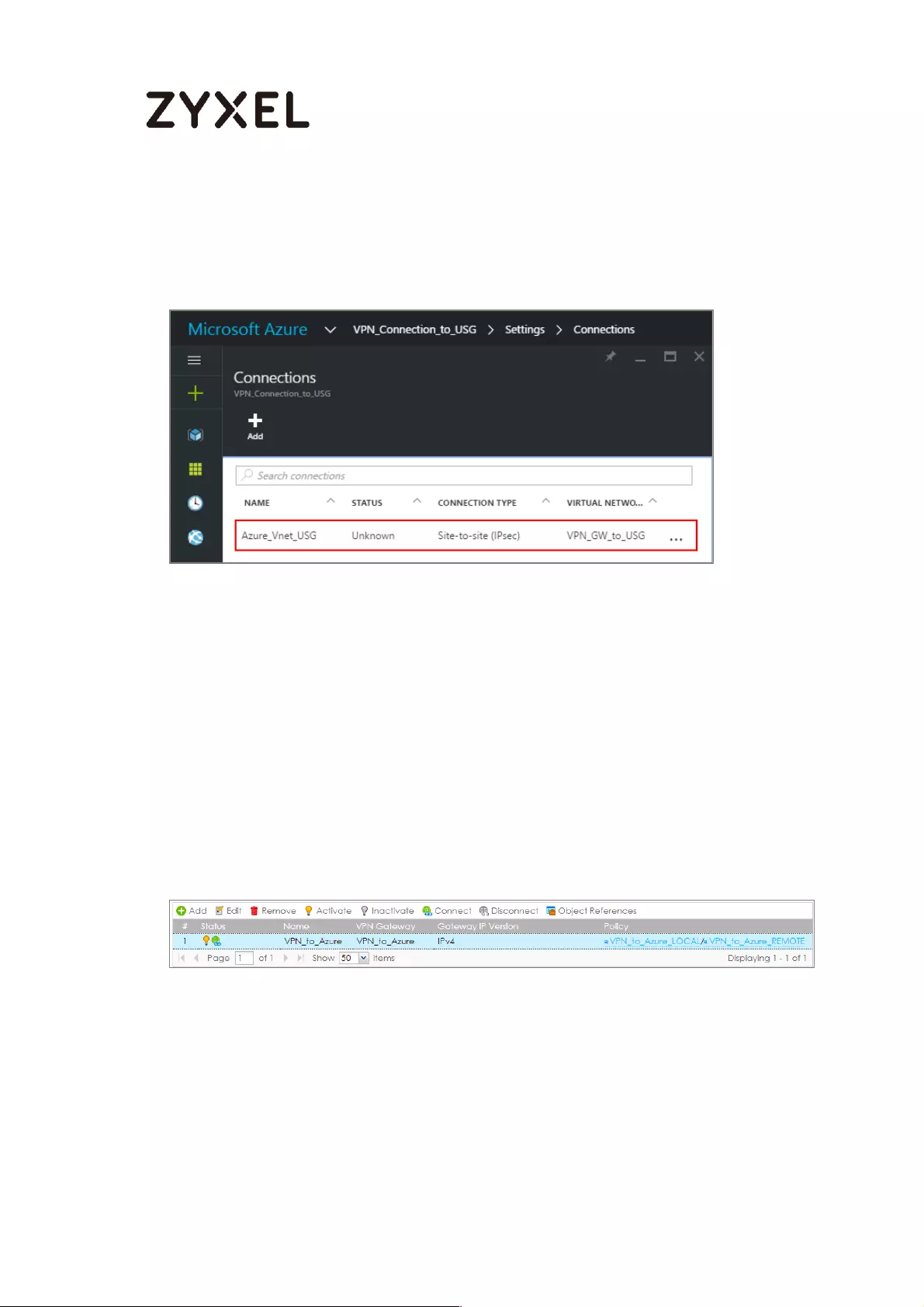
Locate your virtual network gateway (VPN_Connection_to_USG in this example)
and click Settings > Connection > Add connection, Name your connection. For
Connection type, select Site-to-site (IPSec). For Virtual network gateway, the
value is fixed because you are connecting from this gateway (VPN_GW_to_USG in
this example).
For Local network gateway, select the local network gateway that you want to
use (VPN_Connection_to_USG in this example).
For Shared Key (PSK), the value here must match the value that you are using for
your ZyWALL/USG device. For Resource Group, select the resource group that you
created before. Click OK to create your connection.
VPN_Connection_to_USG > Settings > Connections > Add connection
46/782
www.zyxel.com
When the connection is complete, you'll see it appear in the Connections blade
for your Gateway.
VPN_Connection_to_USG > Settings > Connections
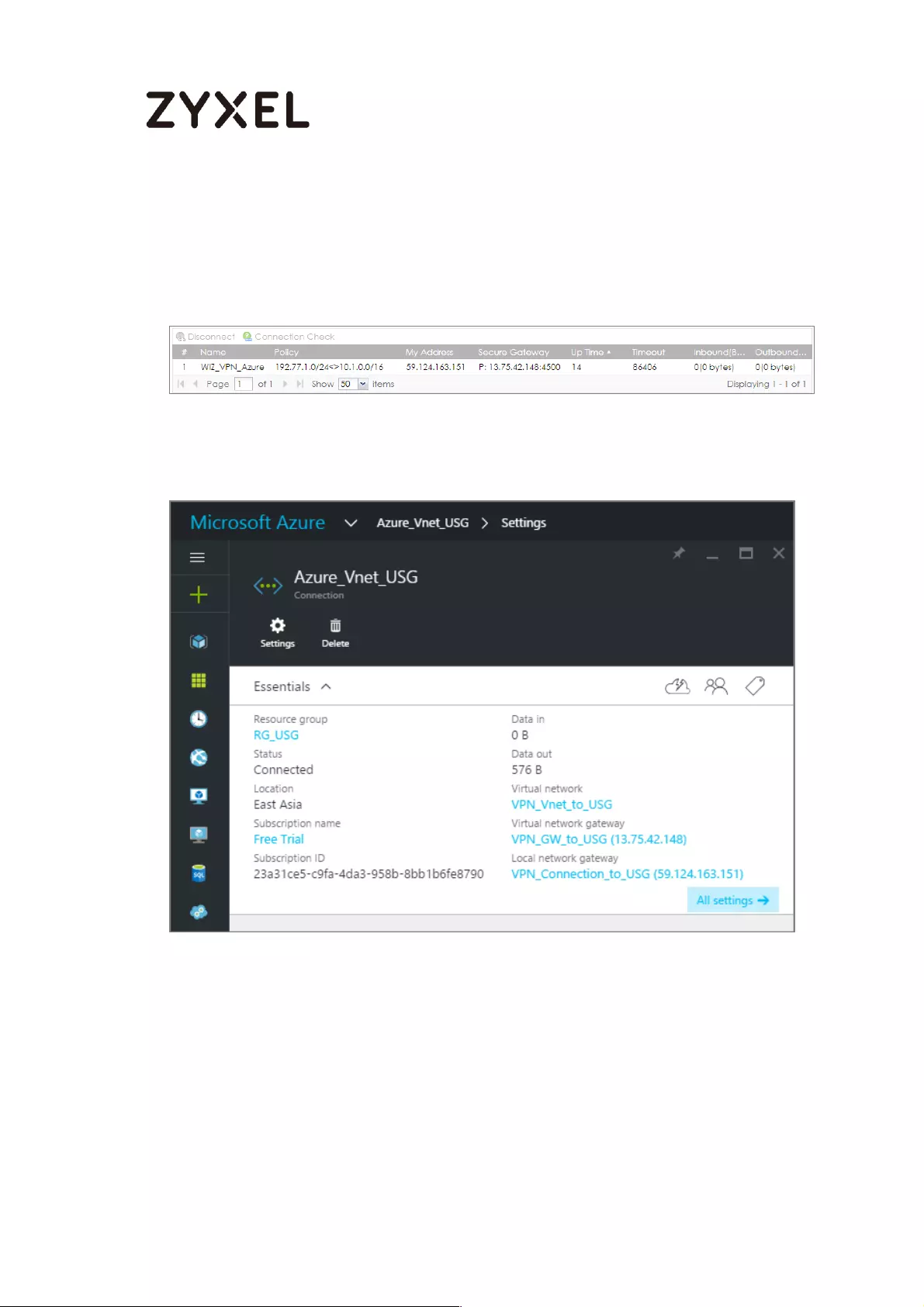
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
47/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > IPSec
Go to Azure_Vnet_USG > Settings to check the tunnel DATA IN and DATA OUT.
VPN > VPN Settings > Currently Active VPN Tunnels
48/782
www.zyxel.com
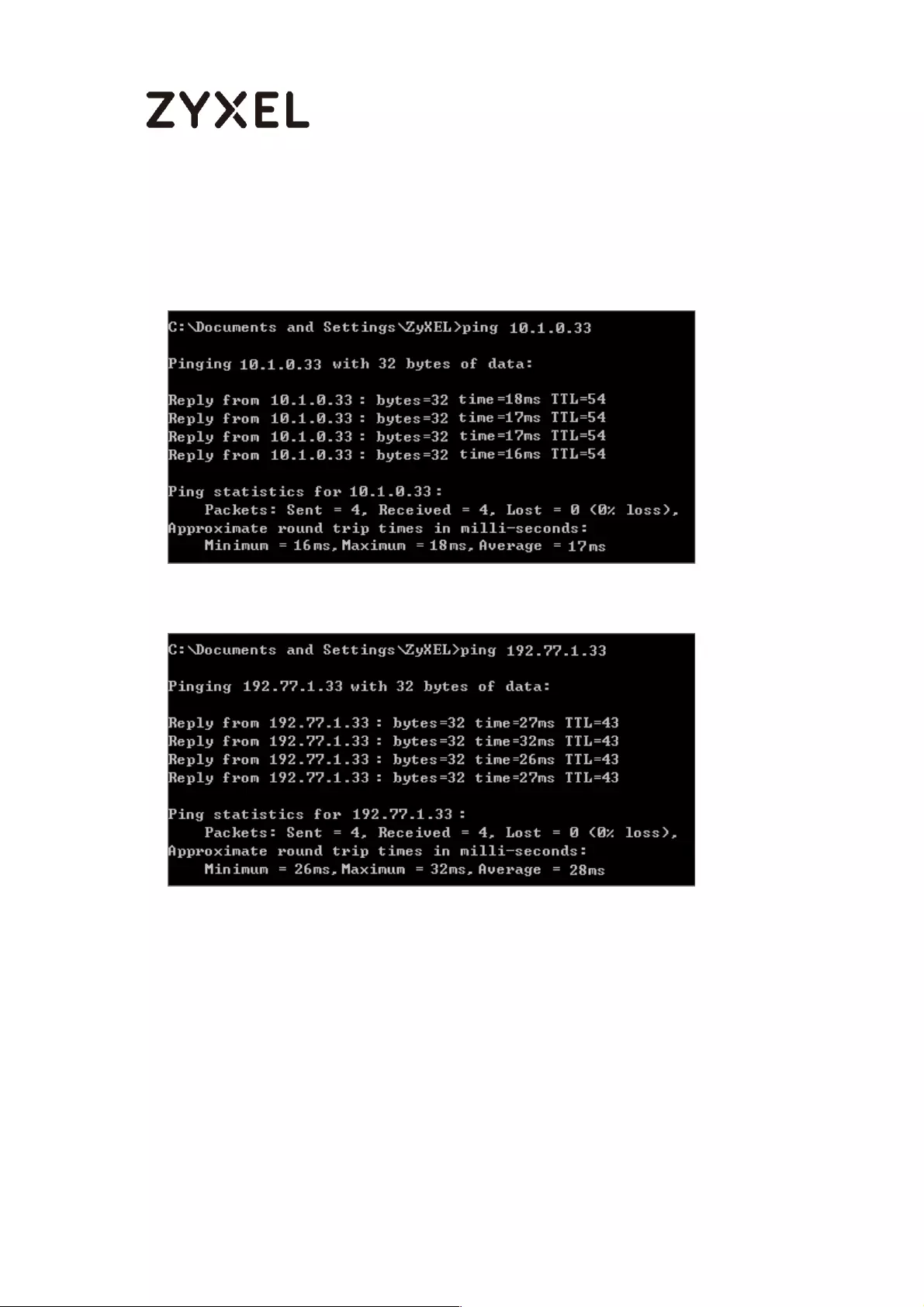
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access.
PC behind ZyWALL/USG > Window 7 > cmd > ping 10.1.0.33
PC behind MS Azure> Window 7 > cmd > ping 192.77.1.33
49/782
www.zyxel.com
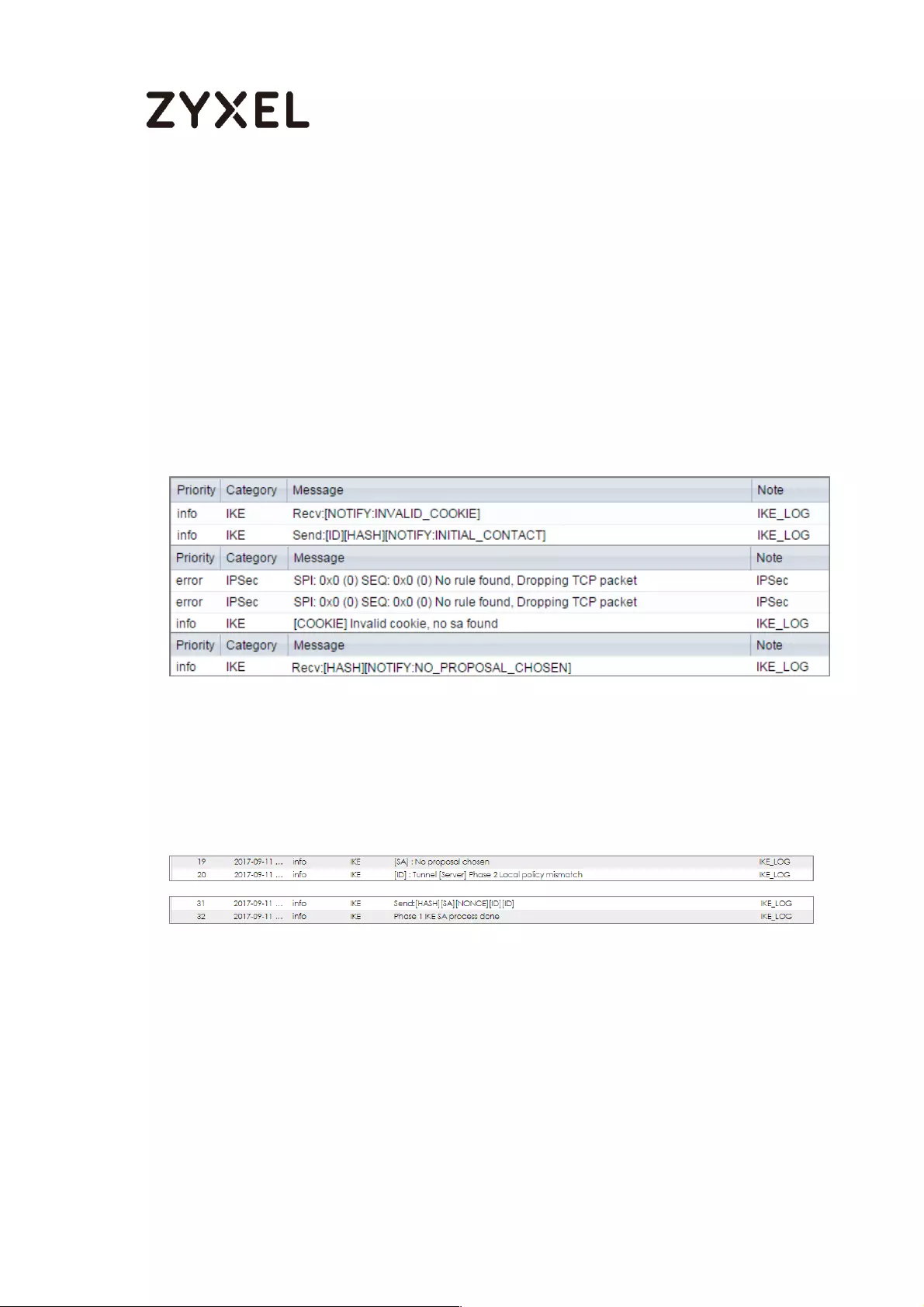
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Make sure your ZyWALL/USG Phase 1 Settings are supported in the MS
Azure IKE Phase 1 setup list.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG Phase 2 Settings. Make sure your ZyWALL/USG Phase 2
Settings are supported in the MS Azure IKE Phase 2 setup list.
MONITOR > Log
50/782
www.zyxel.com
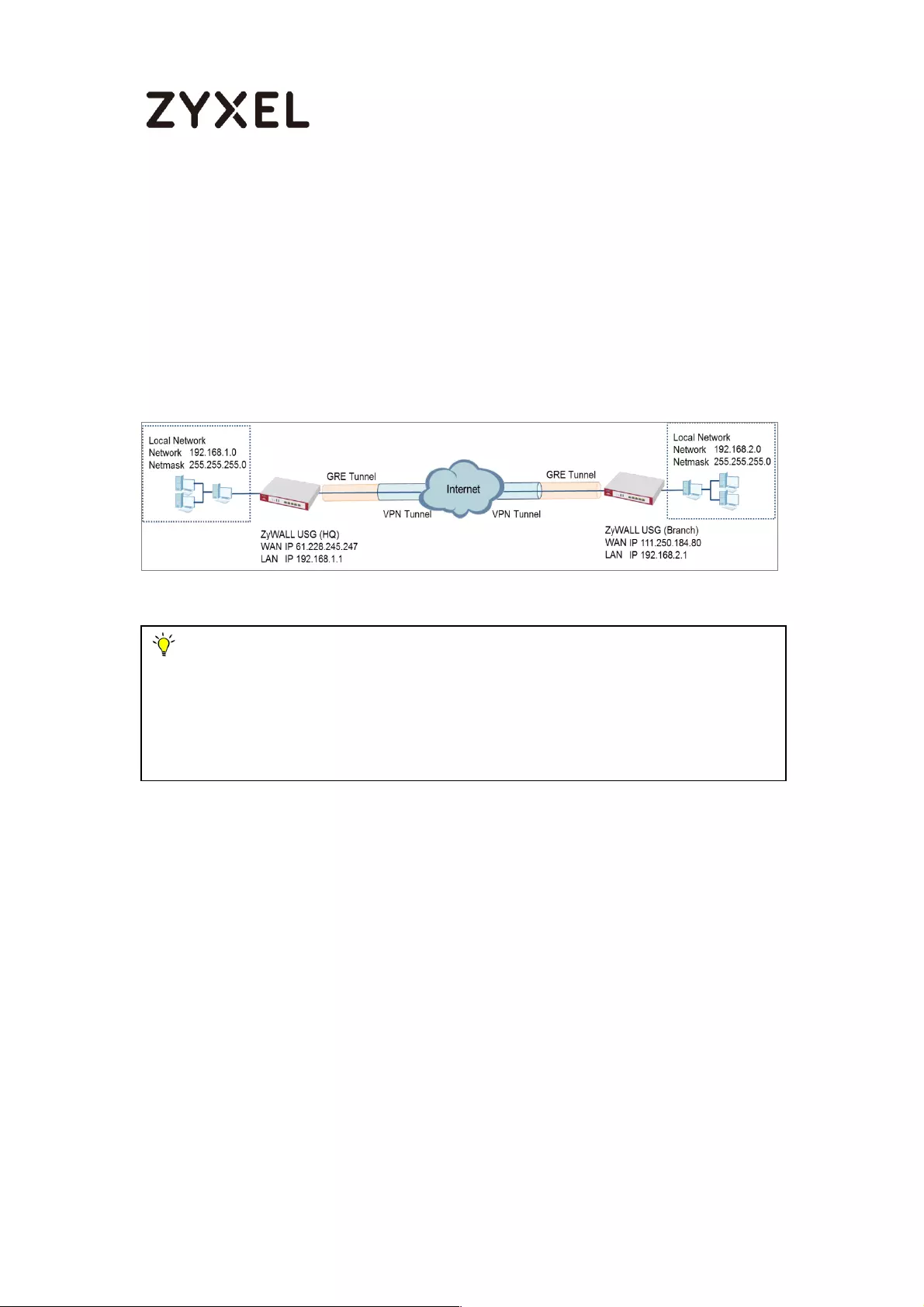
How to Configure GRE over IPSec VPN Tunnel
This example shows how to use the VPN Setup Wizard to create a GRE over
IPSec VPN tunnel between ZyWALL/USG devices. The example instructs how to
configure the VPN tunnel between each site. When the GRE over IPSec VPN
tunnel is configured, each site can be accessed securely.
ZyWALL/USG GRE over IPSec VPN
Note:
All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This
example was tested using USG110 (Firmware Version: ZLD 4.25) and ZyWALL 310
(Firmware Version: ZLD 4.25).

51/782
www.zyxel.com
Set Up the ZyWALL/USG GRE over IPSec VPN Tunnel of
Corporate Network (HQ)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the FortiGate. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
52/782
www.zyxel.com
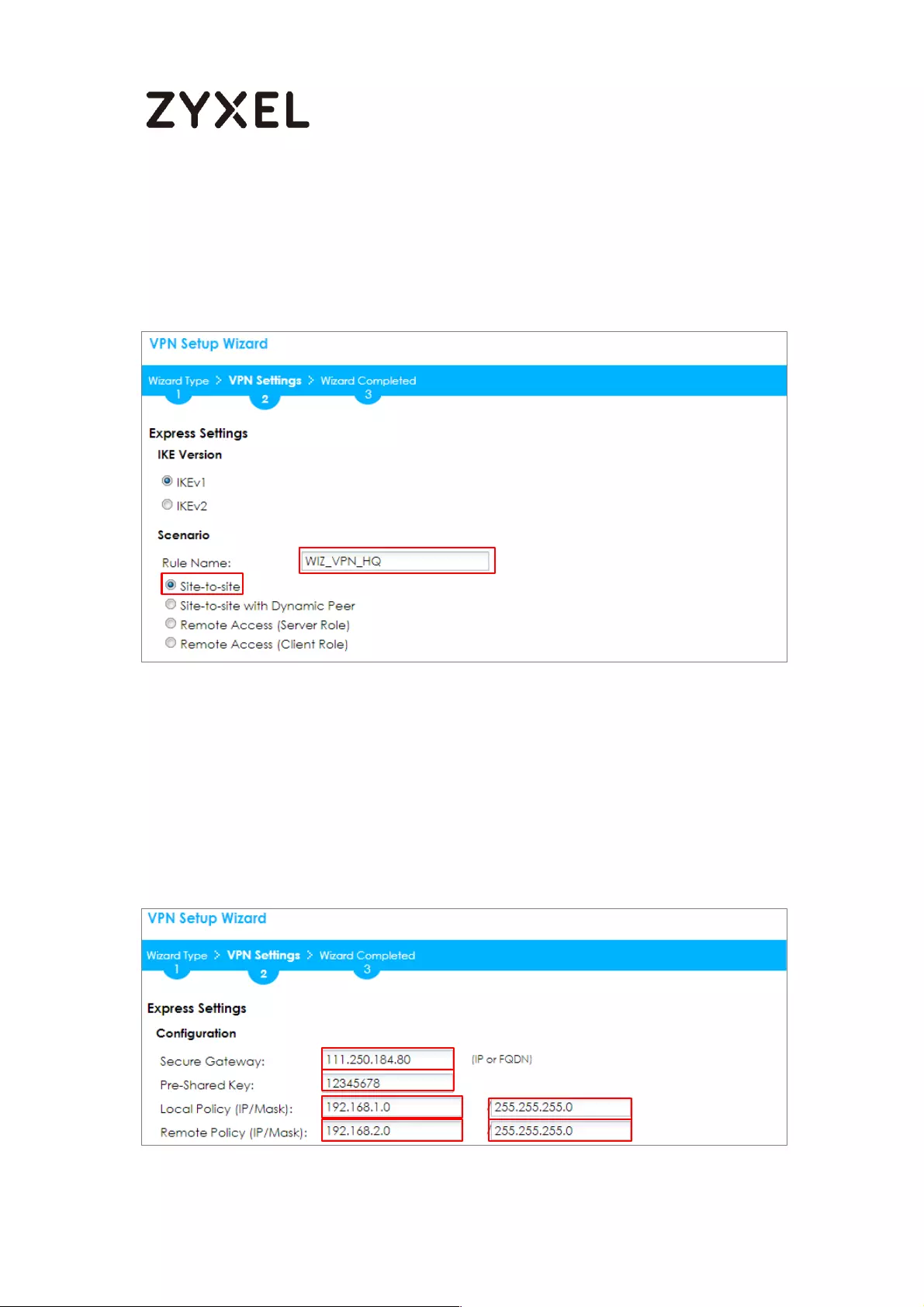
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Select the rule to
be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the Branch’s WAN IP address (in the example,
111.250.184.80). Then, type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG (HQ) and Remote Policy to be the IP address range of the network
connected to the ZyWALL/USG (Branch).
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
53/782
www.zyxel.com
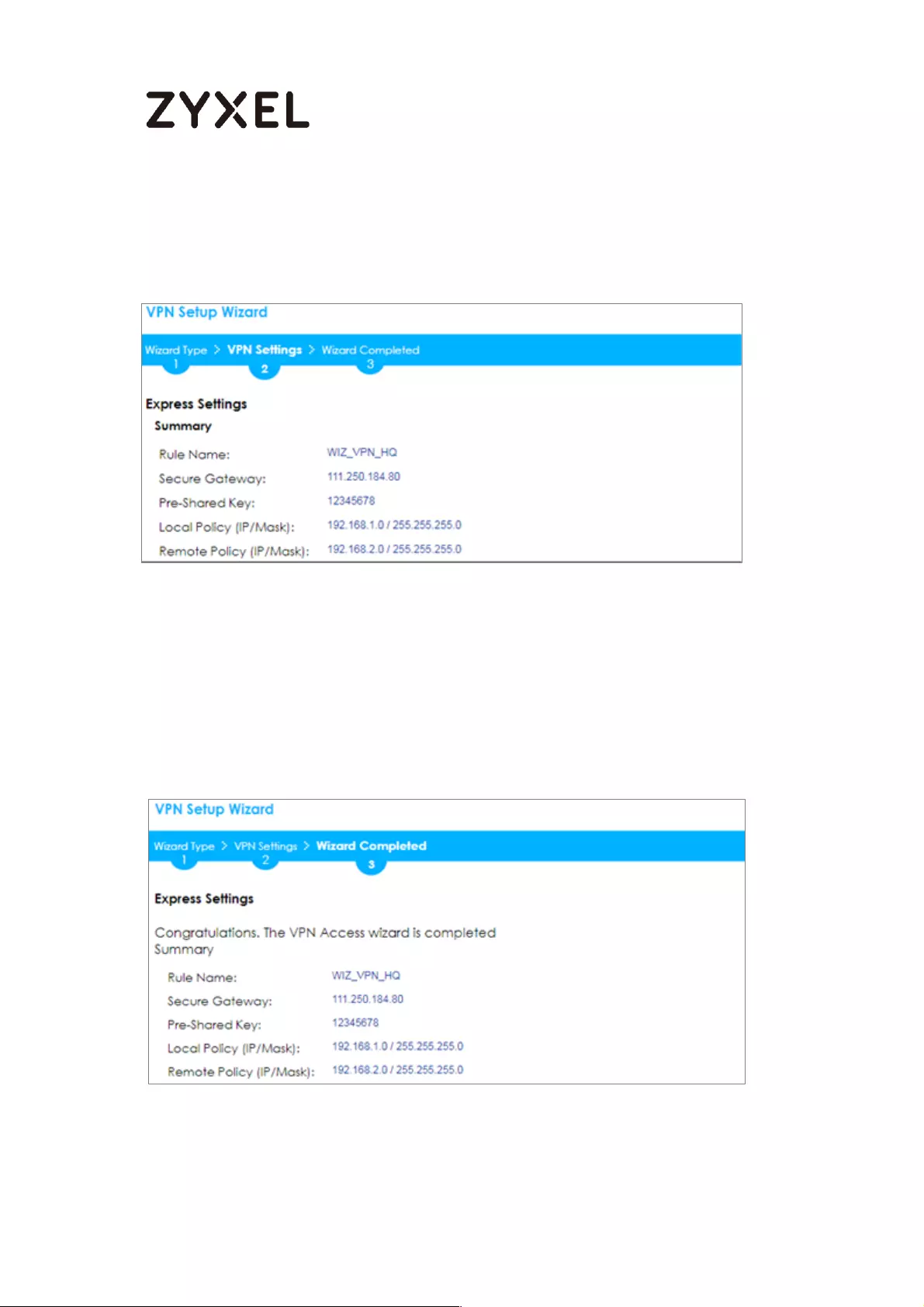
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
54/782
www.zyxel.com
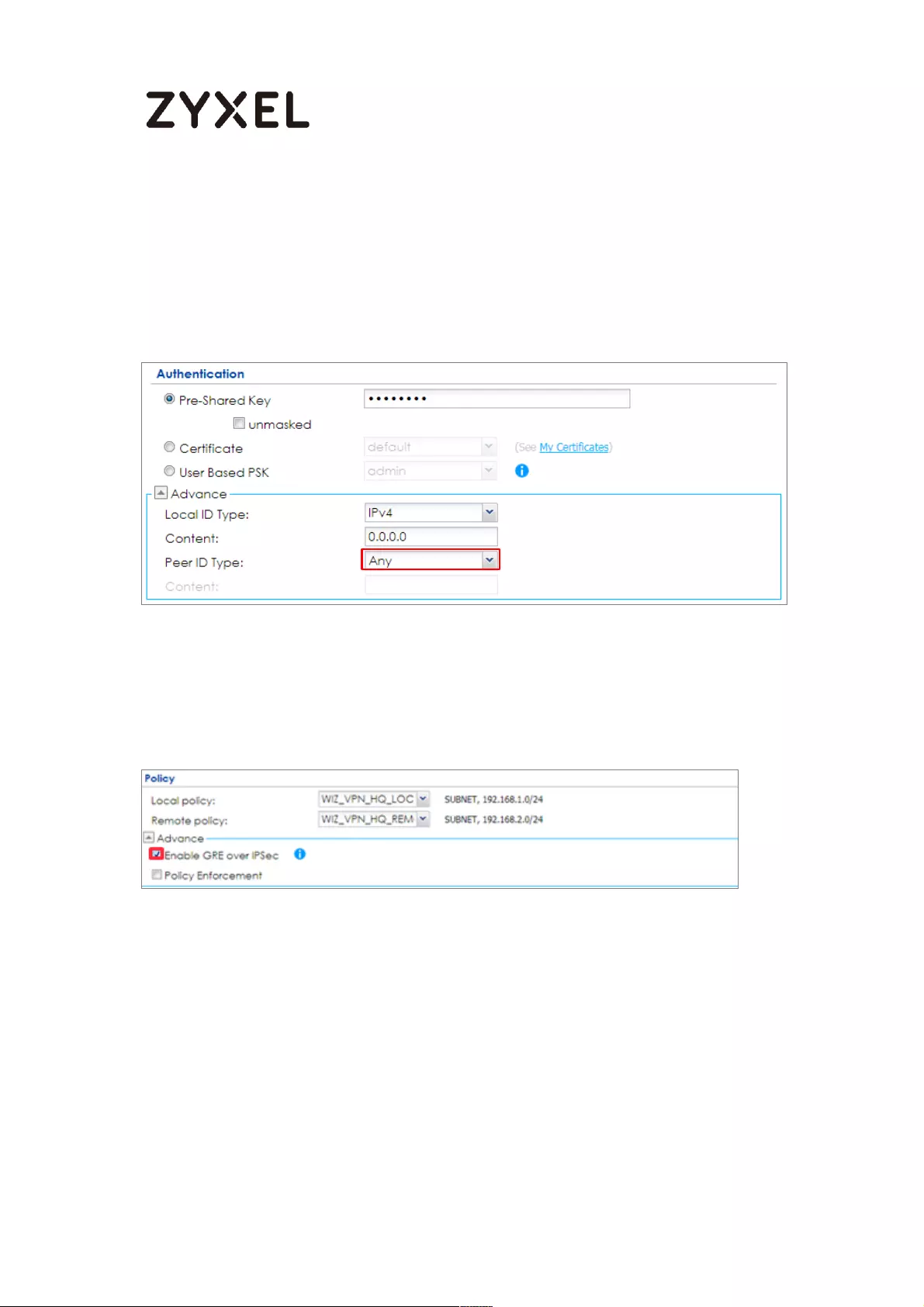
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings. Configure Authentication > Peer ID Type as Any to let the ZyWALL/USG
does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection > Show Advanced
Settings > Policy. Select Enable GRE over IPSec.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Show Advanced
Settings > Policy
The GRE tunnel runs between the IPsec public interface on the HQ unit and the
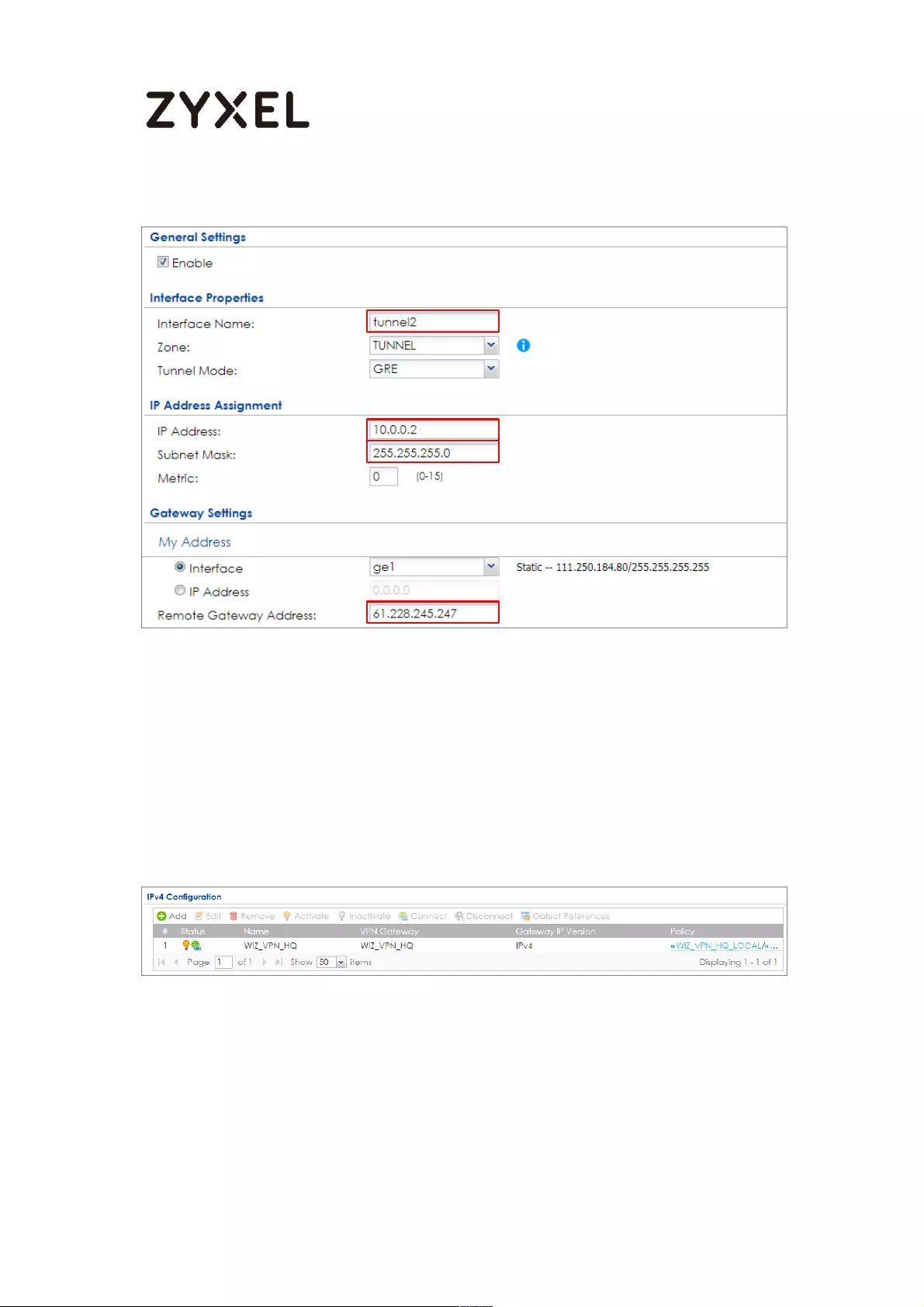
Branch unit. Go to CONFIGURATION > Network > Interface > Tunnel > Add. Enter
the Interface Name (The format is tunnelx, where x is 0 - 3.). Enter the IP Address
and Subnet Mask for this interface. Specify My Address to be the interface or IP
address to use as the source address for the packets this interface tunnels to the
remote gateway. Enter Remote Gateway Address to be the IP address or
domain name of the remote gateway to this tunnel traffic.
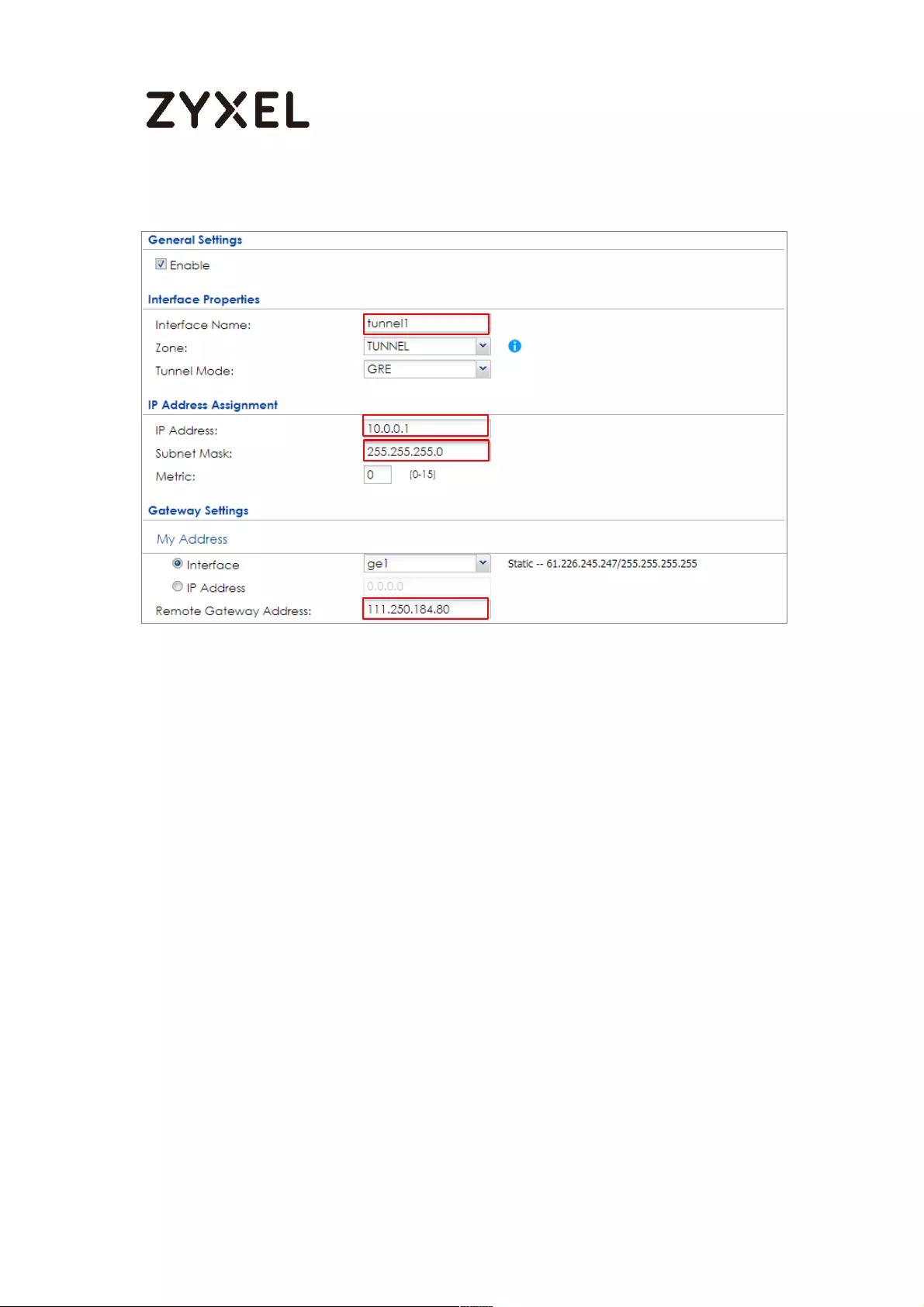
55/782
www.zyxel.com
CONFIGURATION > Network > Interface > Tunnel > Add
56/782
www.zyxel.com
Set Up the ZyWALL/USG GRE over IPSec VPN Tunnel of
Corporate Network (Branch)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the FortiGate. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
57/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Select the rule to
be Site-to-site. Click Next.
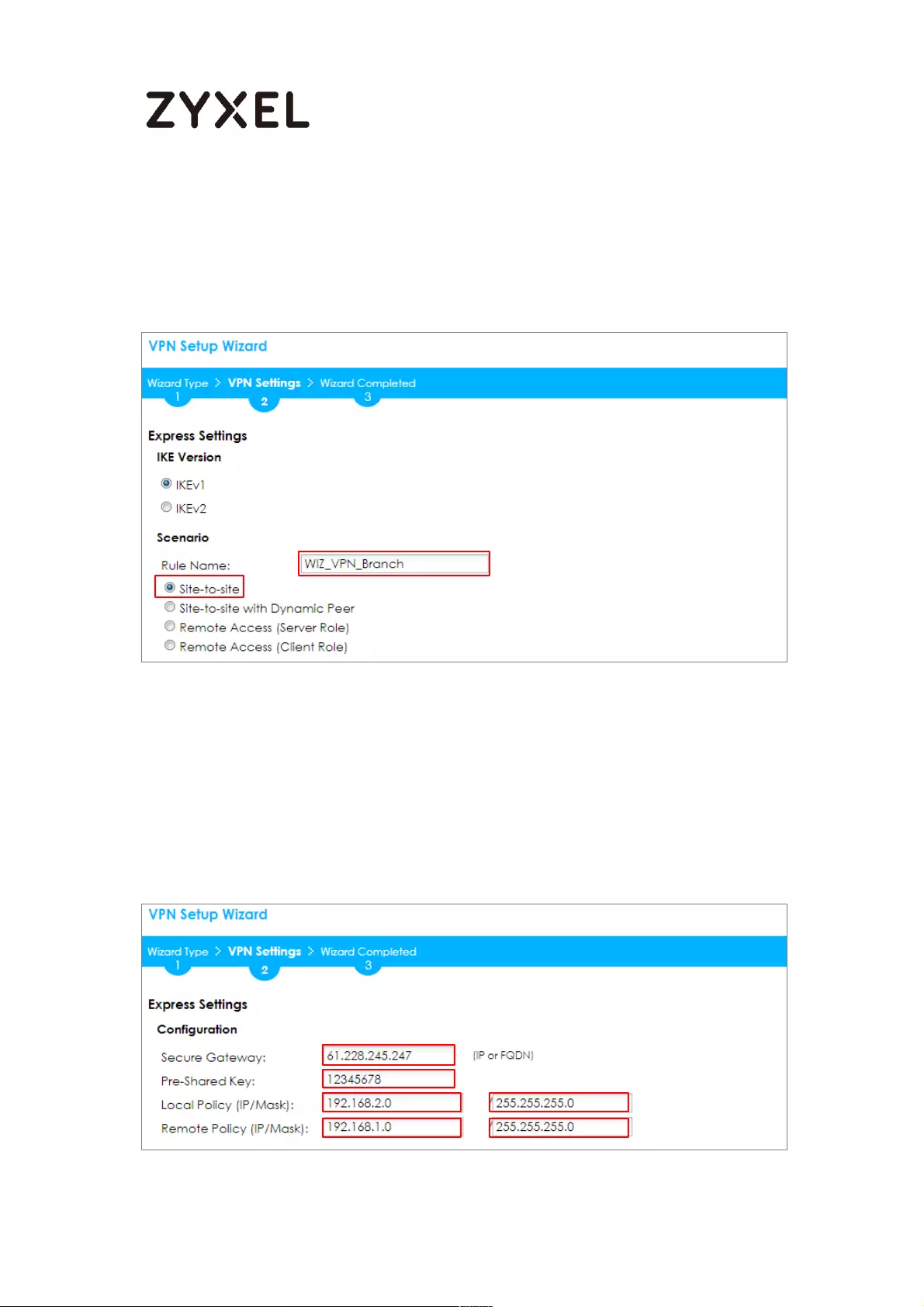
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the HQ’s WAN IP address (in the example,
61.228.245.247). Then, type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG (Branch) and Remote Policy to be the IP address range of the
network connected to the ZyWALL/USG (HQ).
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
58/782
www.zyxel.com
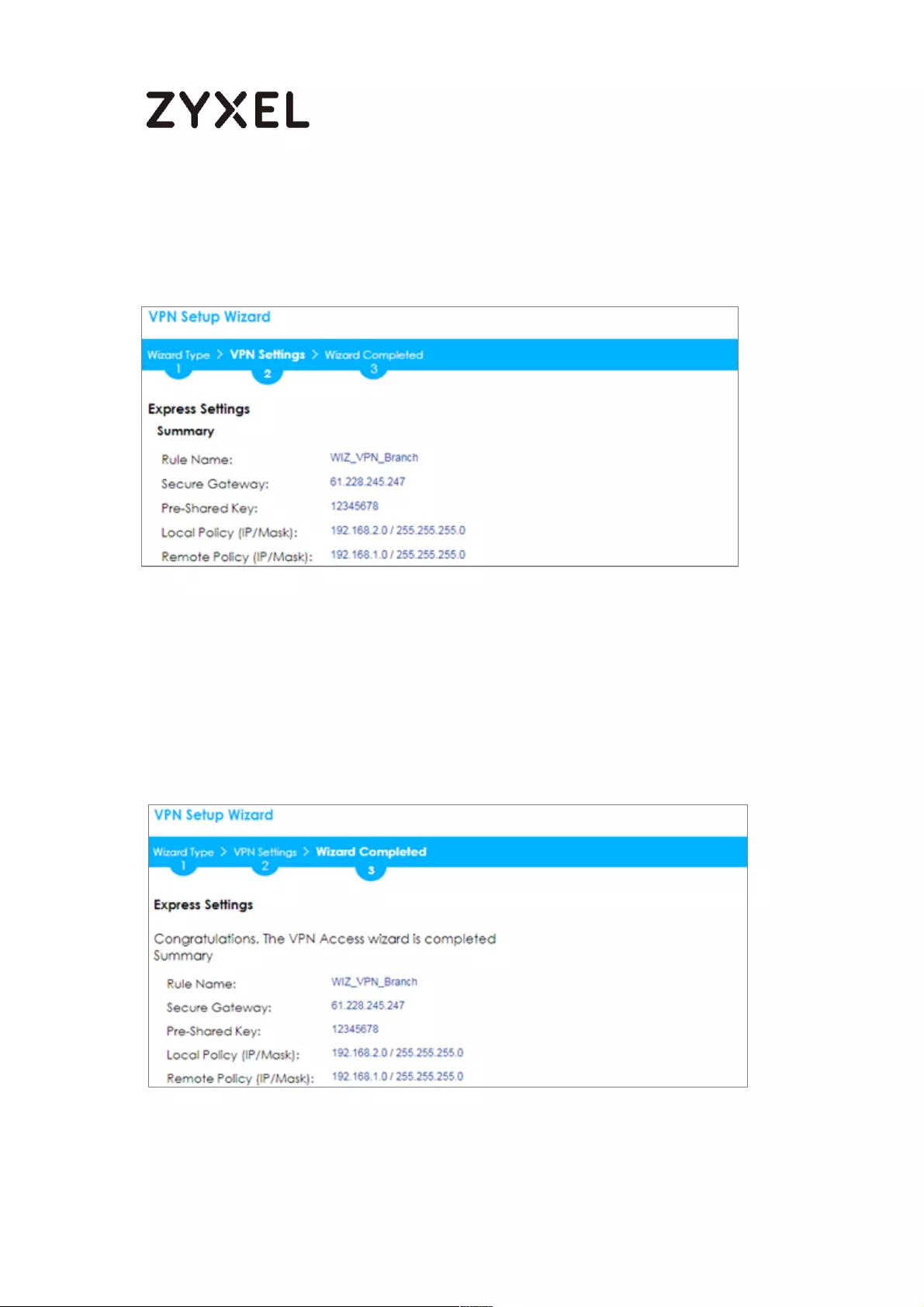
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed

59/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings. Configure Authentication > Peer ID Type as Any to let the ZyWALL/USG
does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection > Show Advanced
Settings > Policy. Select Enable GRE over IPSec.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Show Advanced
Settings > Policy
The GRE tunnel runs between the IPsec public interface on the Branch unit and
the HQ unit. Go to CONFIGURATION > Network > Interface > Tunnel > Add. Enter
the Interface Name (The format is tunnelx, where x is 0 - 3.). Enter the IP Address
and Subnet Mask for this interface. Specify My Address to be the interface or IP
address to use as the source address for the packets this interface tunnels to the
remote gateway. Enter Remote Gateway Address to be the IP address or
domain name of the remote gateway to this tunnel traffic.
60/782
www.zyxel.com
CONFIGURATION > Network > Interface > Tunnel > Add
Test the GRE over IPSec VPN Tunnel
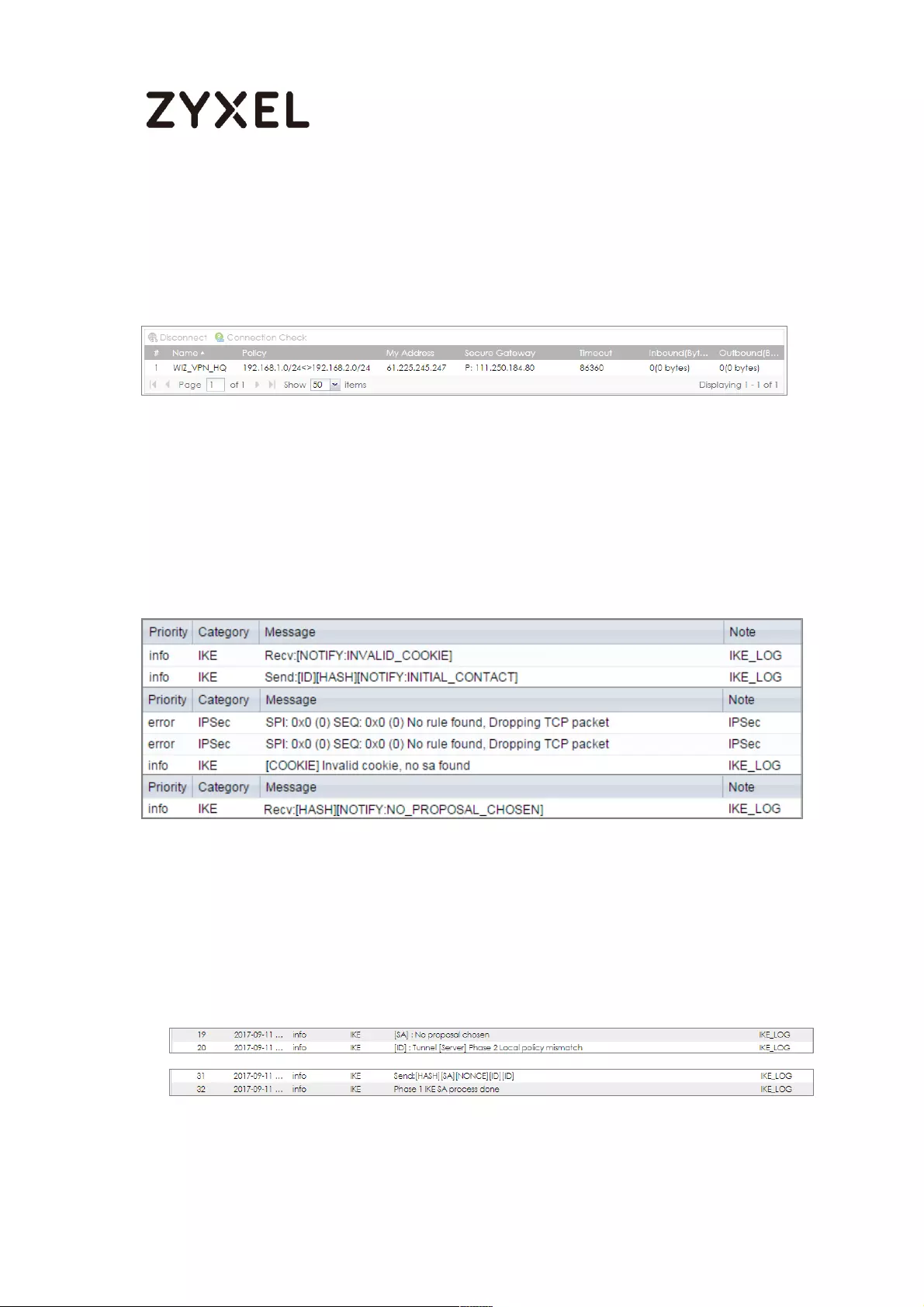
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
61/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up
Time and Inbound (Bytes)/Outbound (Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
What Could Go Wrong?
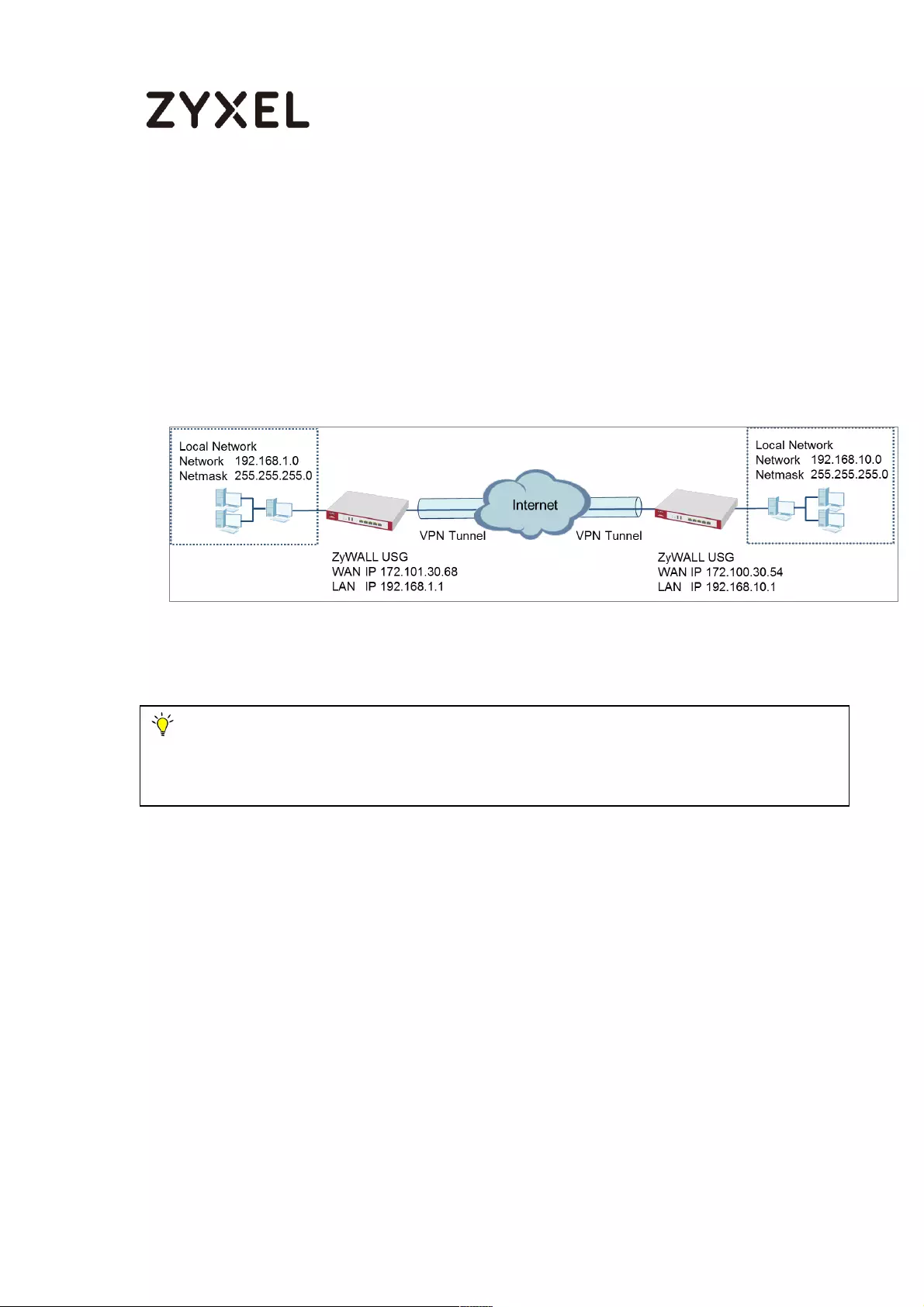
If you see below [info] or [error] log message, please check ZyWALL/USG Phase
1 Settings. Make sure your ZyWALL/USG Phase 1 Settings are supported in the
Amazon VPC IKE Phase 1 setup list.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log
message, please check ZyWALL/USG Phase 2 Settings. Make sure your
ZyWALL/USG Phase 2 Settings are supported in the Amazon VPC IKE Phase 2
setup list.
MONITOR > Log

62/782
www.zyxel.com
63/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN Where the Peer has
a Static IP Address
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
with the Peer has a Static IP Address. The example instructs how to configure the
VPN tunnel between each site. When the VPN tunnel is configured, each site can
be accessed securely.
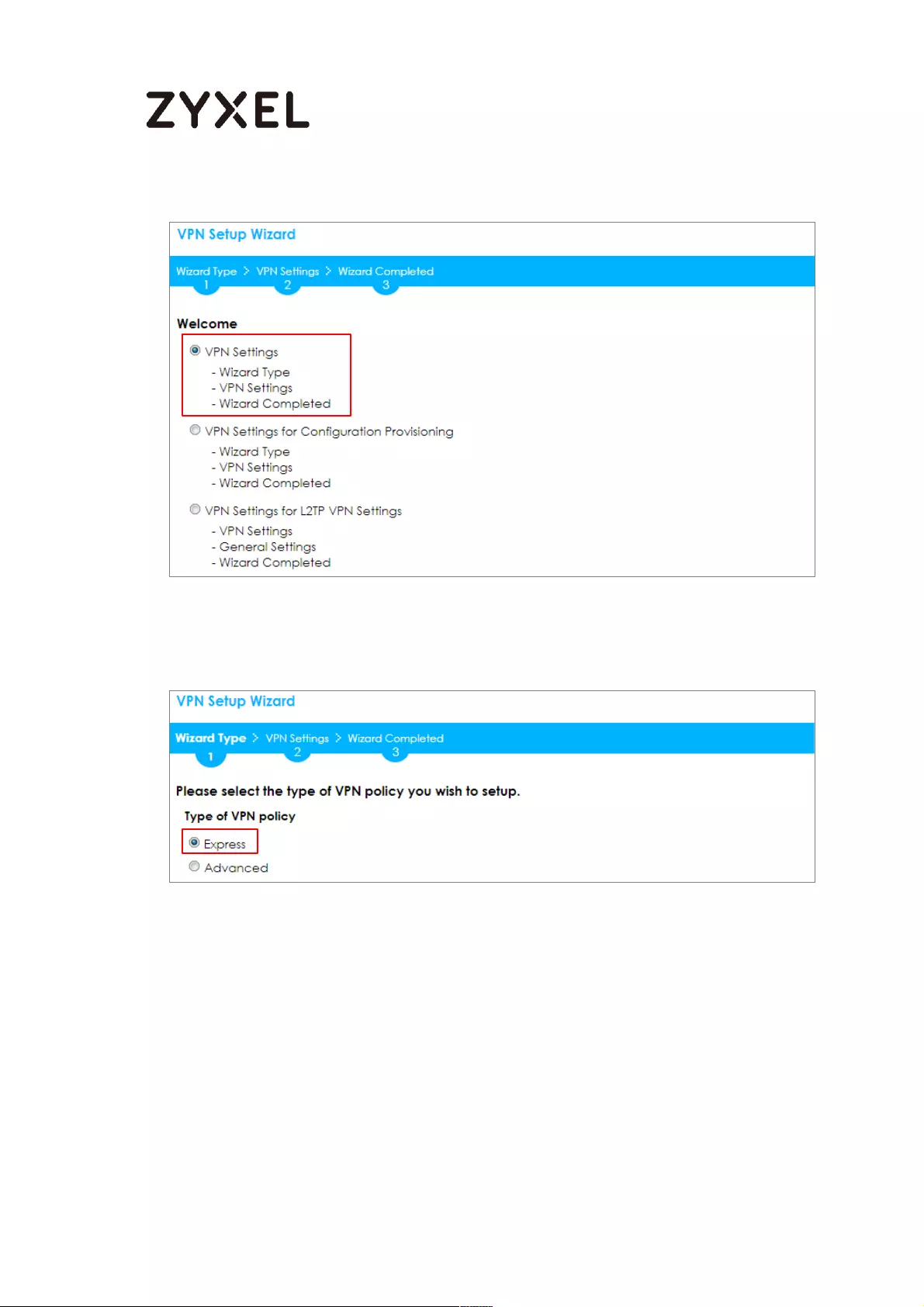
ZyWALL Site-to-site IPSec VPN with a Static IP Address Peer
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network (HQ)In the
ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings wizard
to create a VPN rule that can be used with the remote ZyWALL/USG. Click Next.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
64/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type

65/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
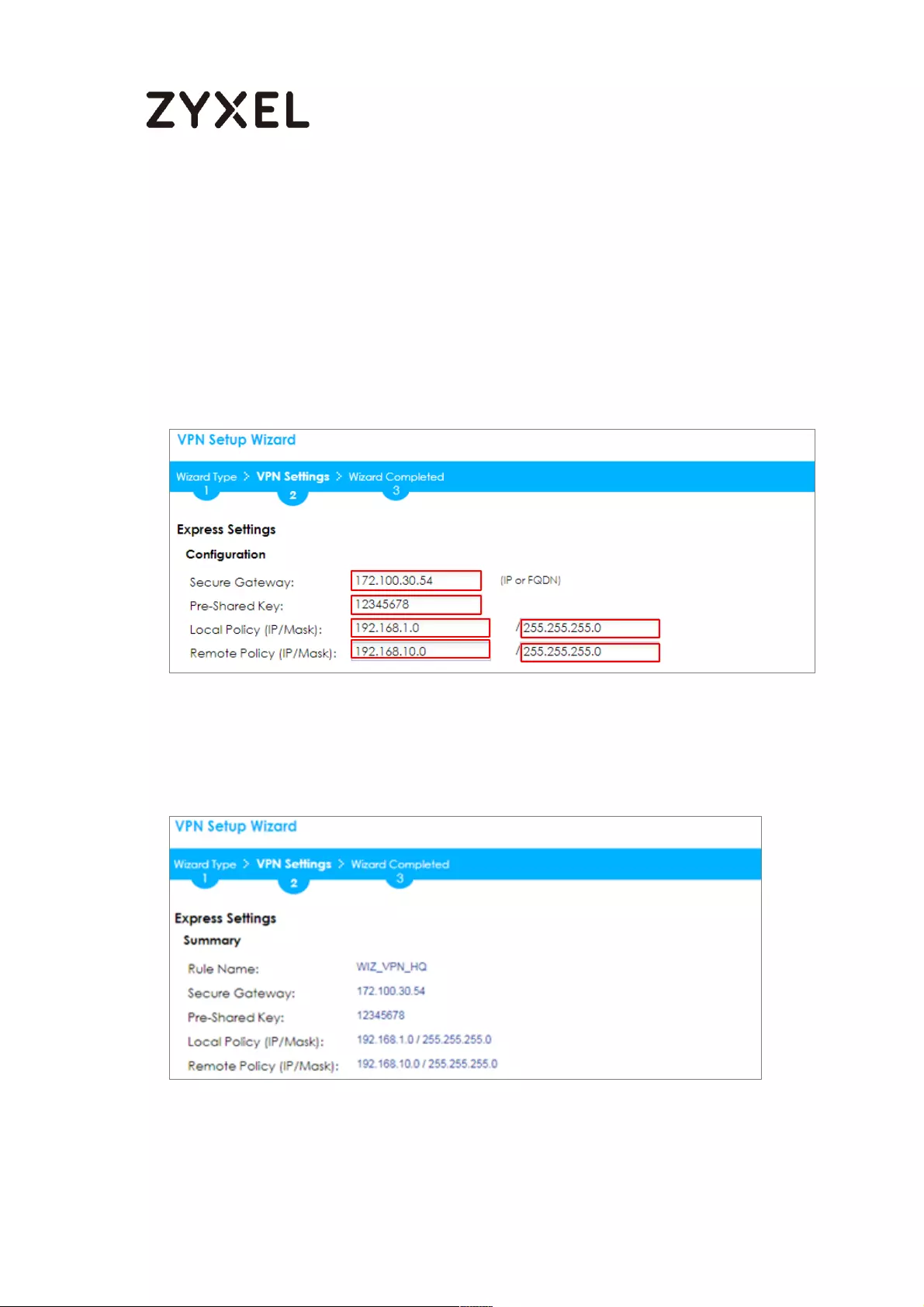
66/782
www.zyxel.com
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.100.30.54). Type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the peer ZyWALL/USG.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
67/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
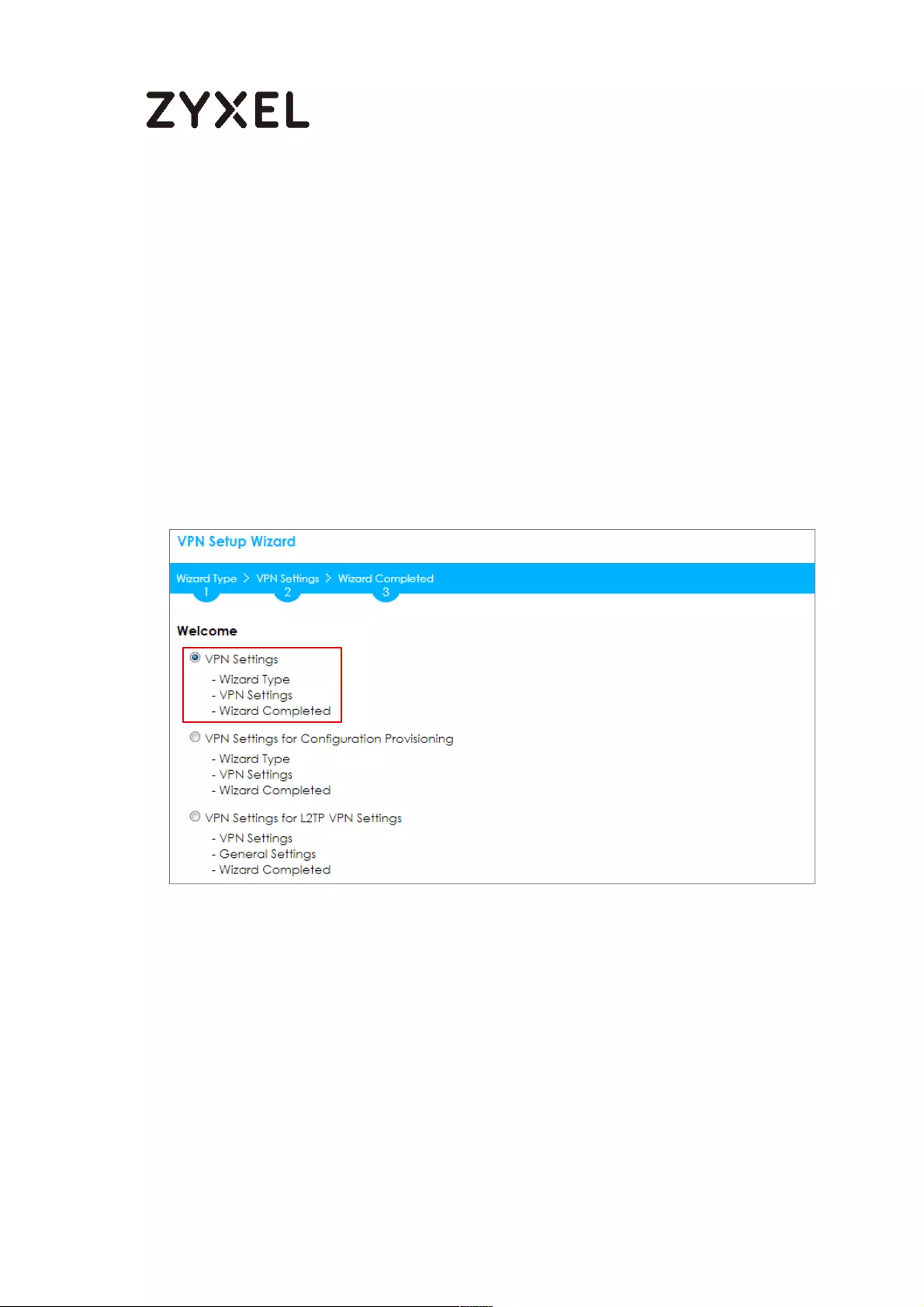
68/782
www.zyxel.com
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(Branch)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
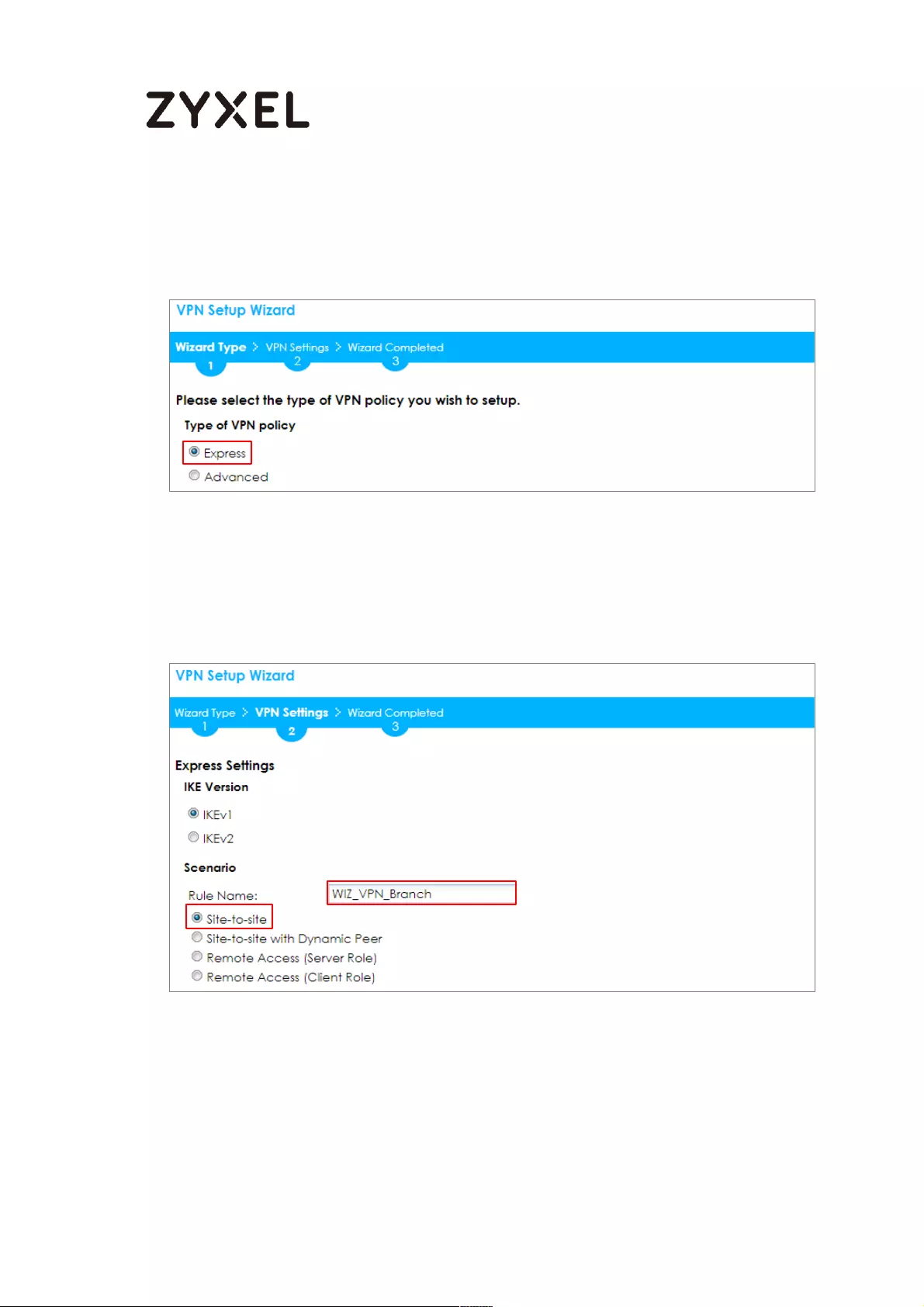
69/782
www.zyxel.com
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and to use a pre-shared key. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Click
Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
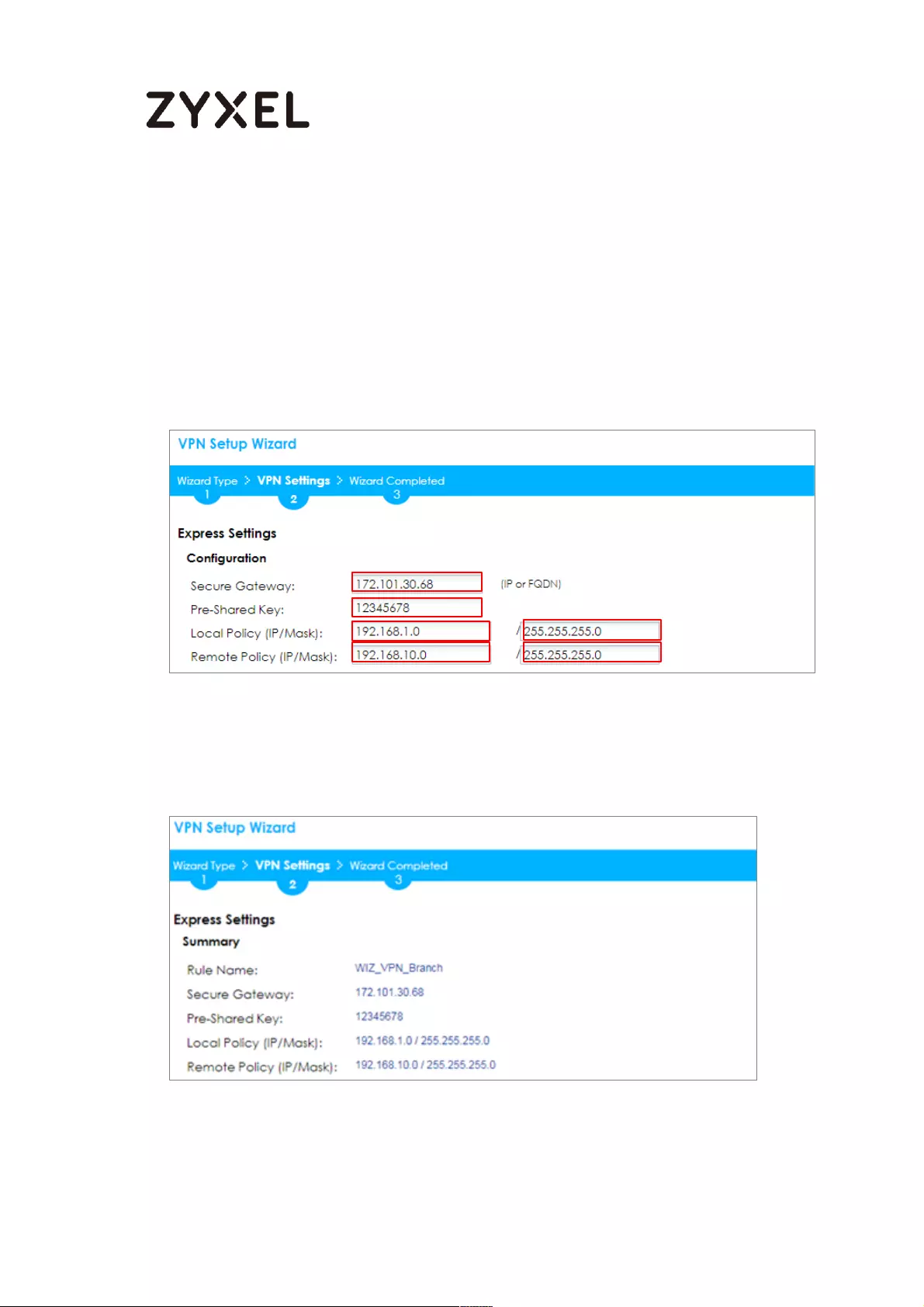
70/782
www.zyxel.com
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.101.30.68). Type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the peer ZYWALL/USG.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
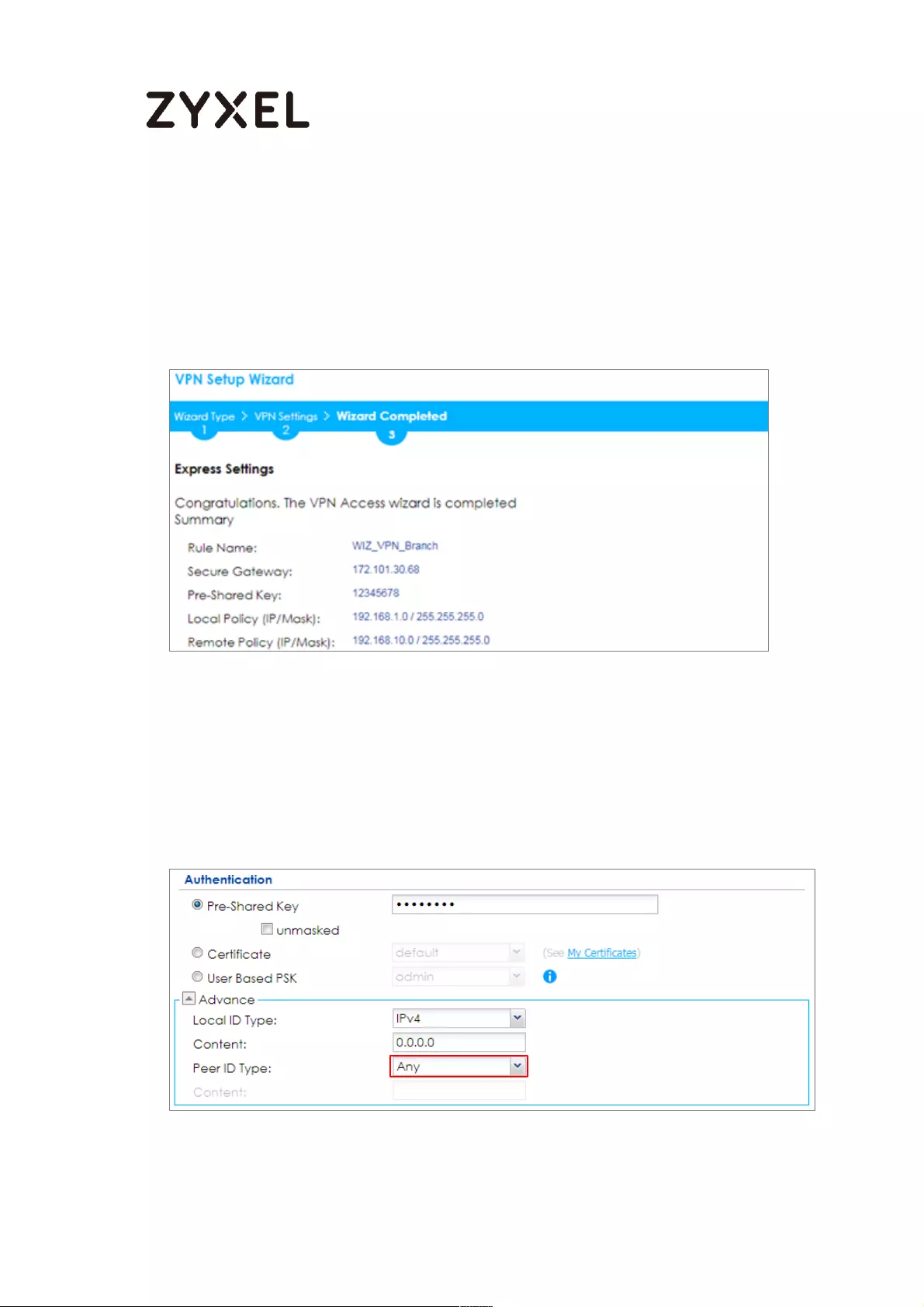
71/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
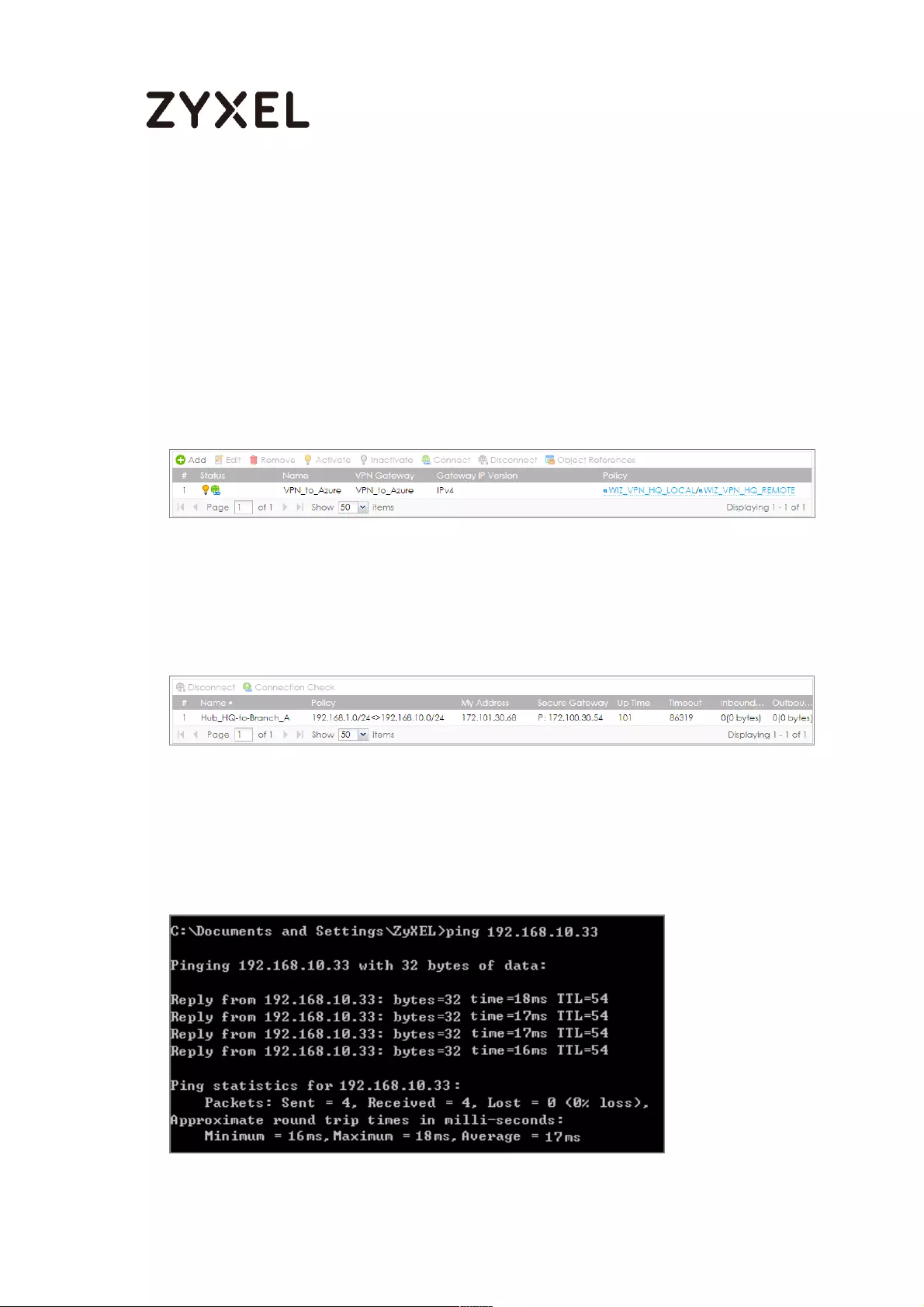
72/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZYWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC at HQ Office > Window 7 > cmd > ping 192.168.10.33
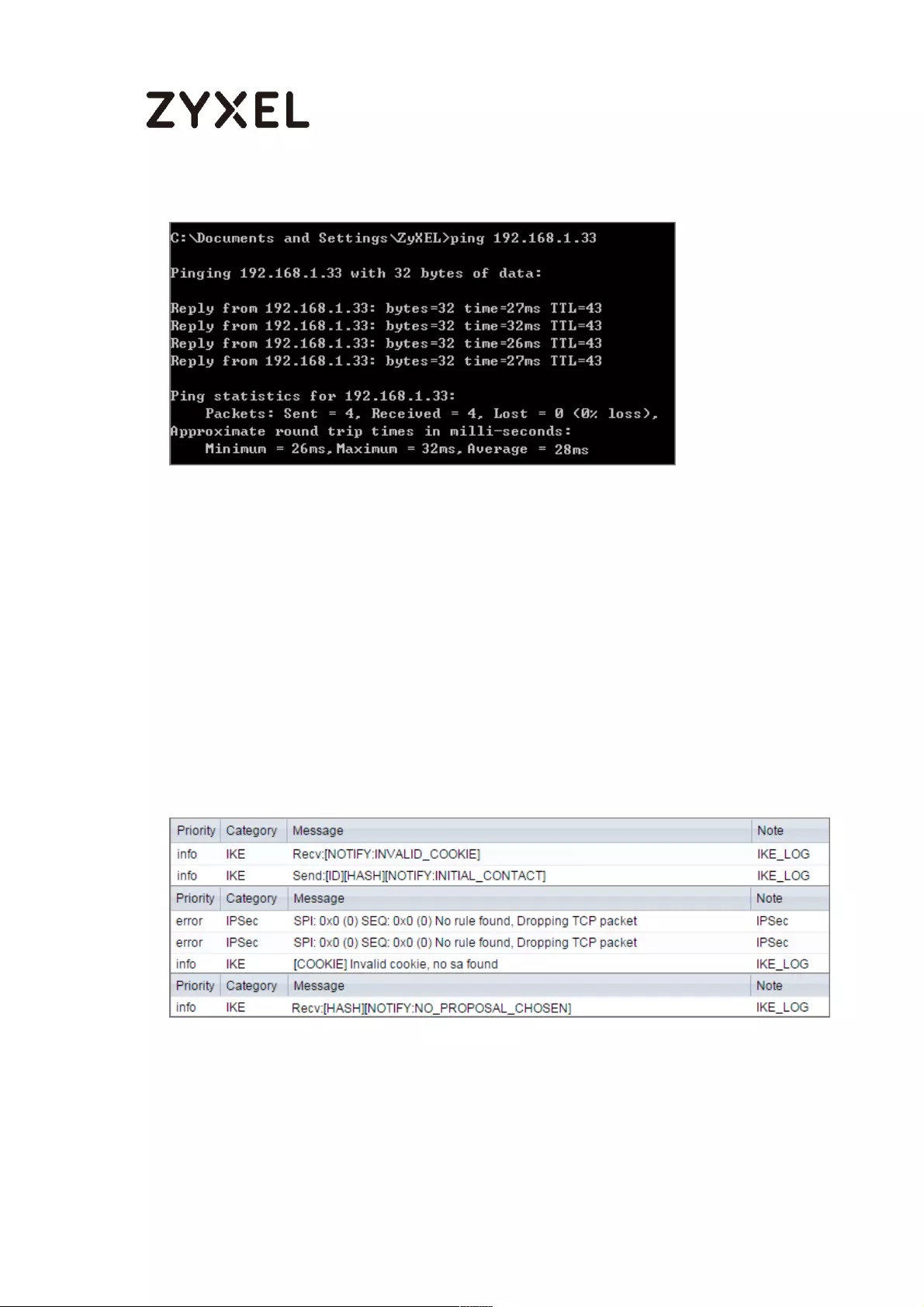
73/782
www.zyxel.com
PC at Branch Office > Window 7 > cmd > ping 192.168.1.33
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG at the HQ and Branch sites must use the same Pre-
Shared Key, Encryption, Authentication method, DH key group and ID Type to
establish the IKE SA.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG Phase 2 Settings. Both ZyWALL/USG at the HQ and
Branch sites must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
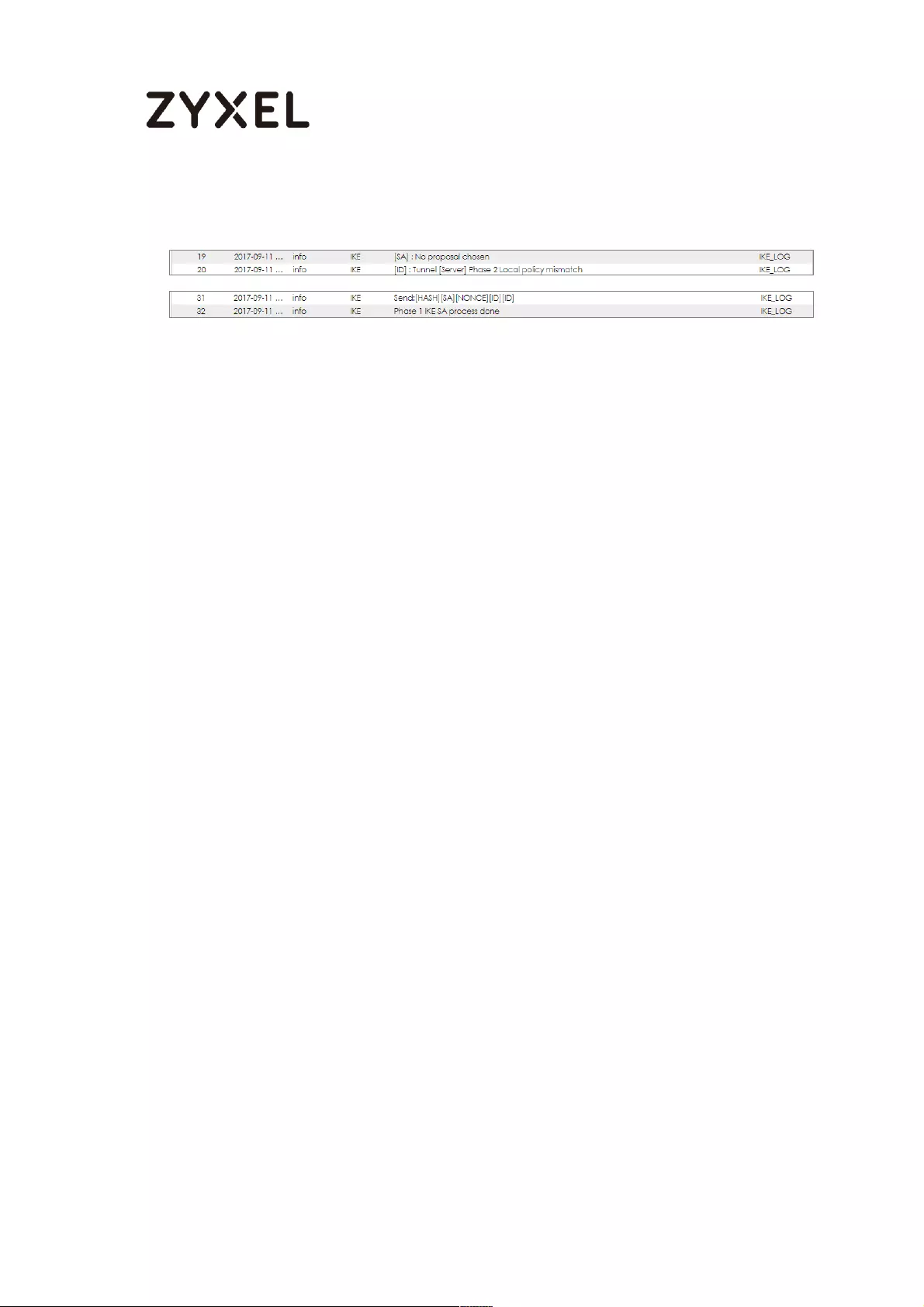
74/782
www.zyxel.com
MONITOR > Log
Make sure the both ZyWALL/USG at the HQ and Branch sites security policies
allow IPSec VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP
uses IP protocol 50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.
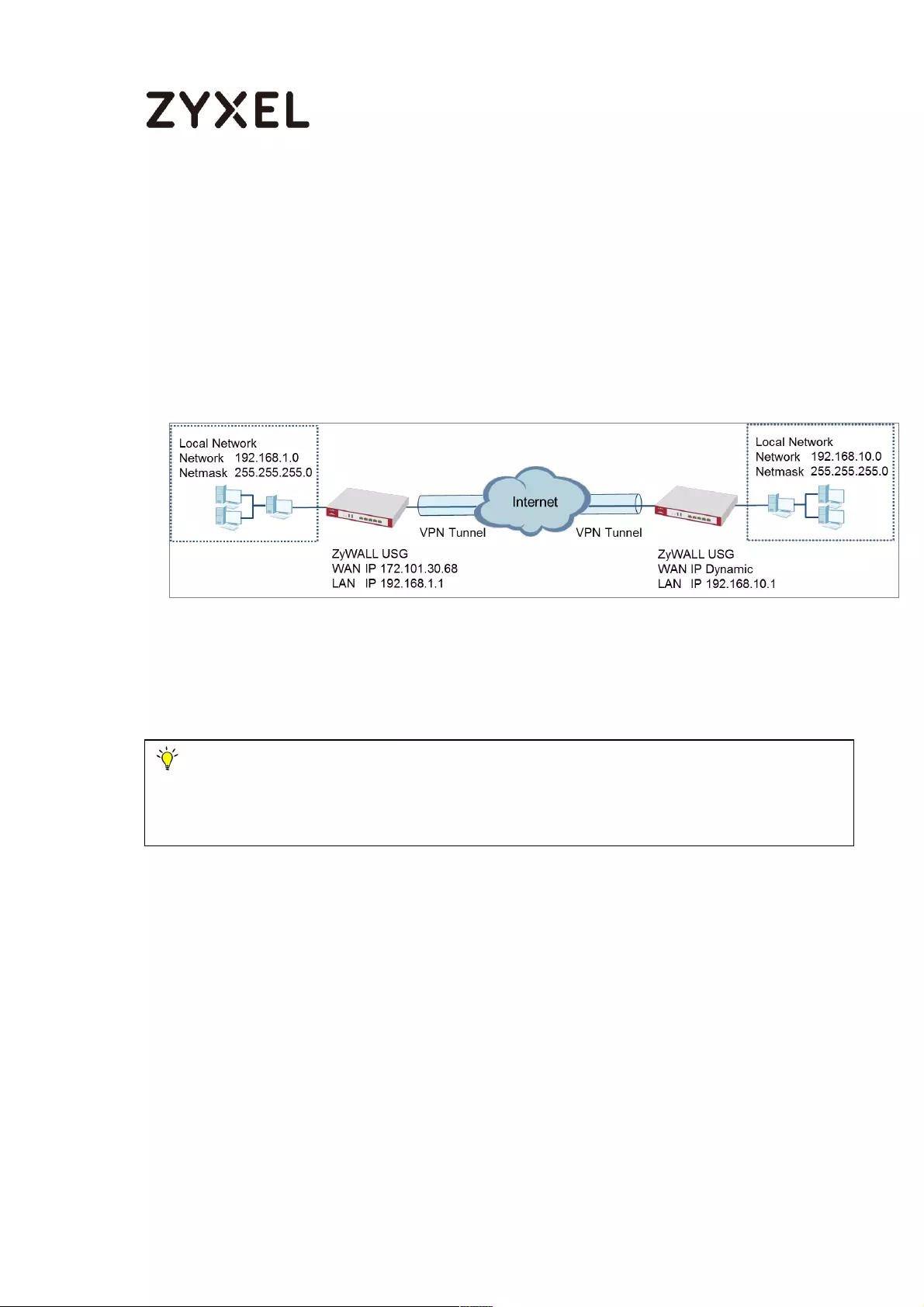
75/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN Where the Peer has a
Dynamic IP Address
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
with the Peer has a Dynamic IP Address. The example instructs how to configure
the VPN tunnel between each site. When the VPN tunnel is configured, each site
can be accessed securely.
ZyWALL Site-to-site IPSec VPN with a Dynamic IP Address Peer
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
76/782
www.zyxel.com
(HQ)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
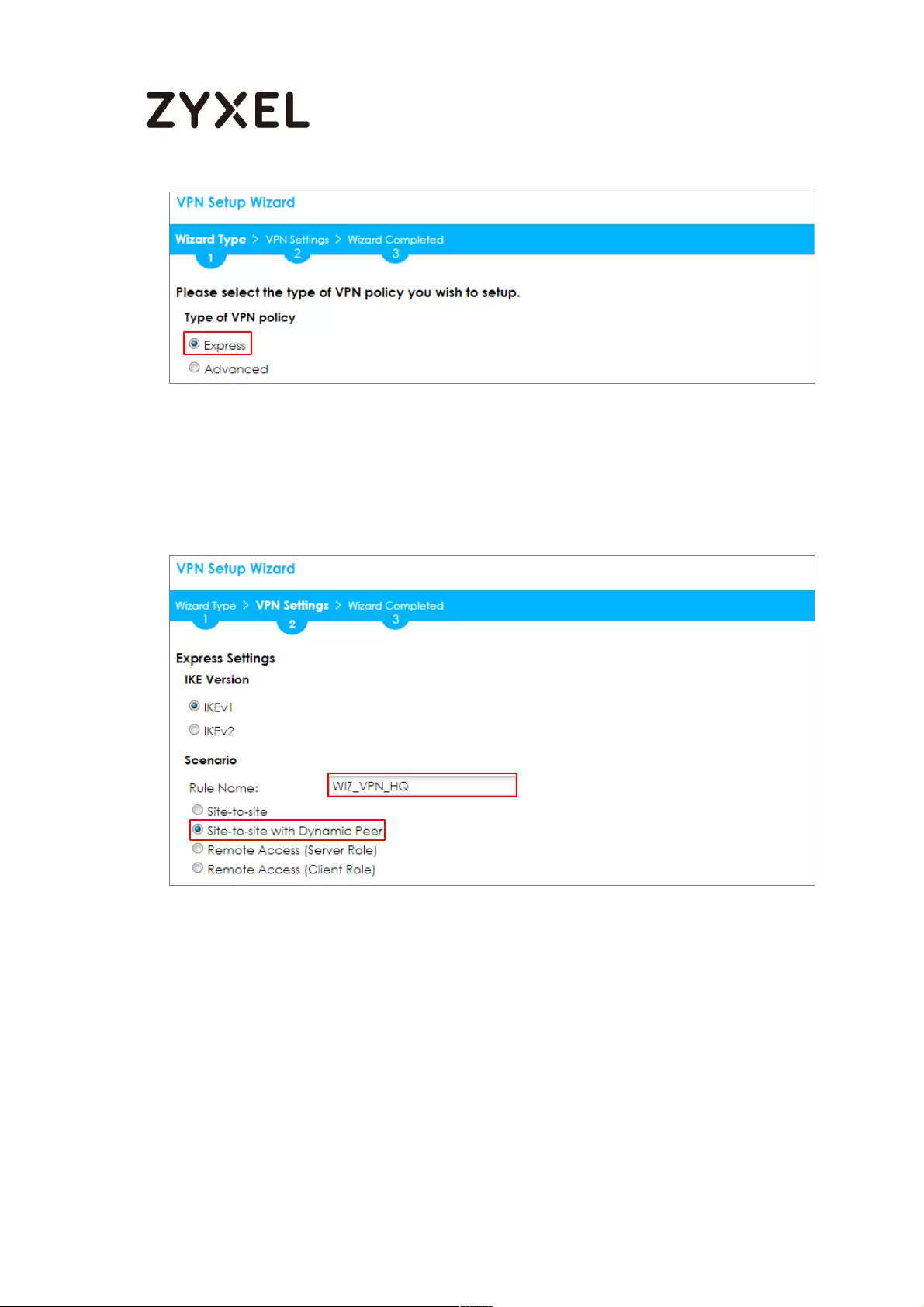
77/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site with Dynamic Peer. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Type a secure Pre-Shared Key (8-32 characters). Then, set Local Policy to be the
IP address range of the network connected to the ZyWALL/USG and Remote
Policy to be the IP address range of the network connected to the peer
ZYWALL/USG.
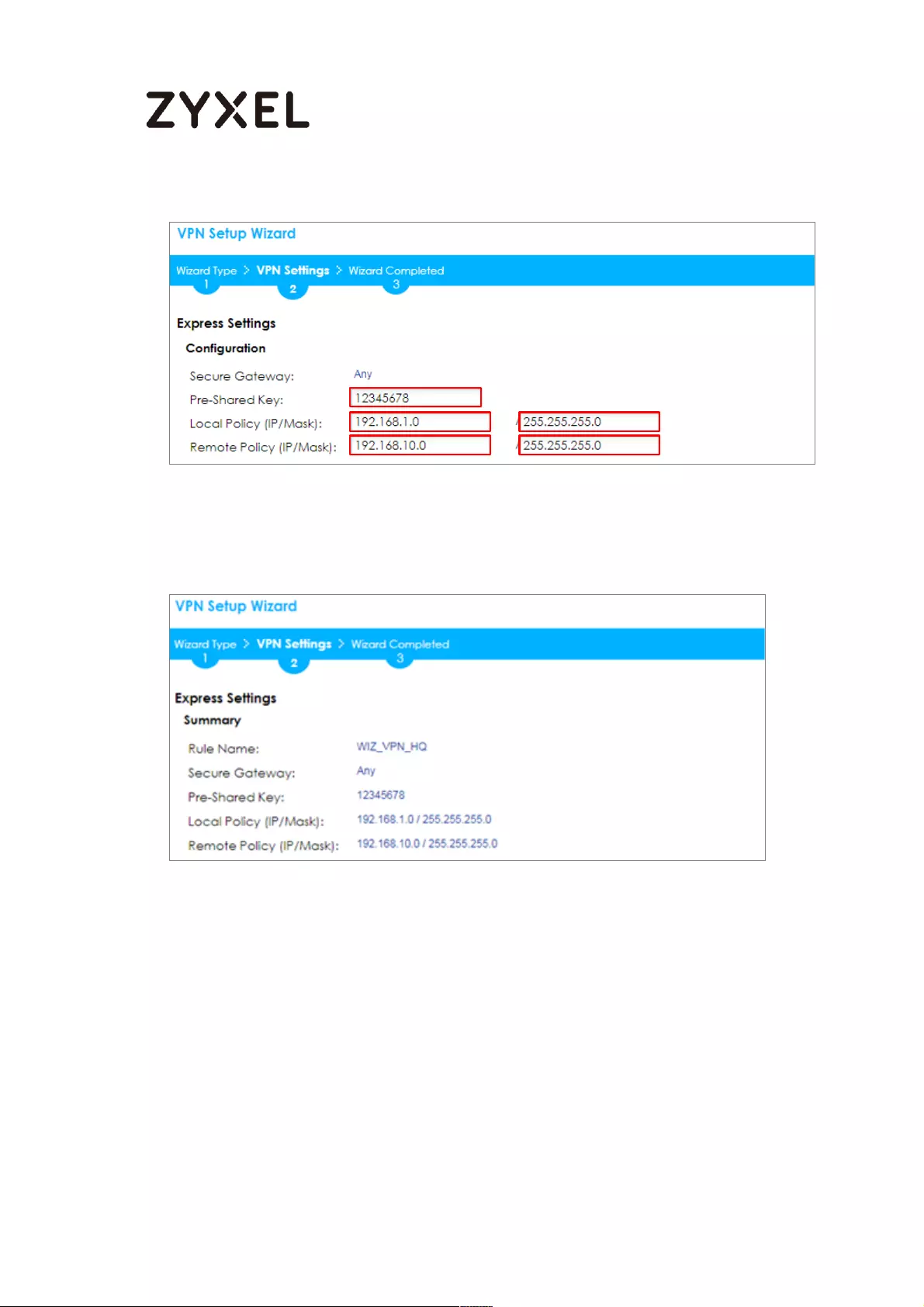
78/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings > Wizard completed
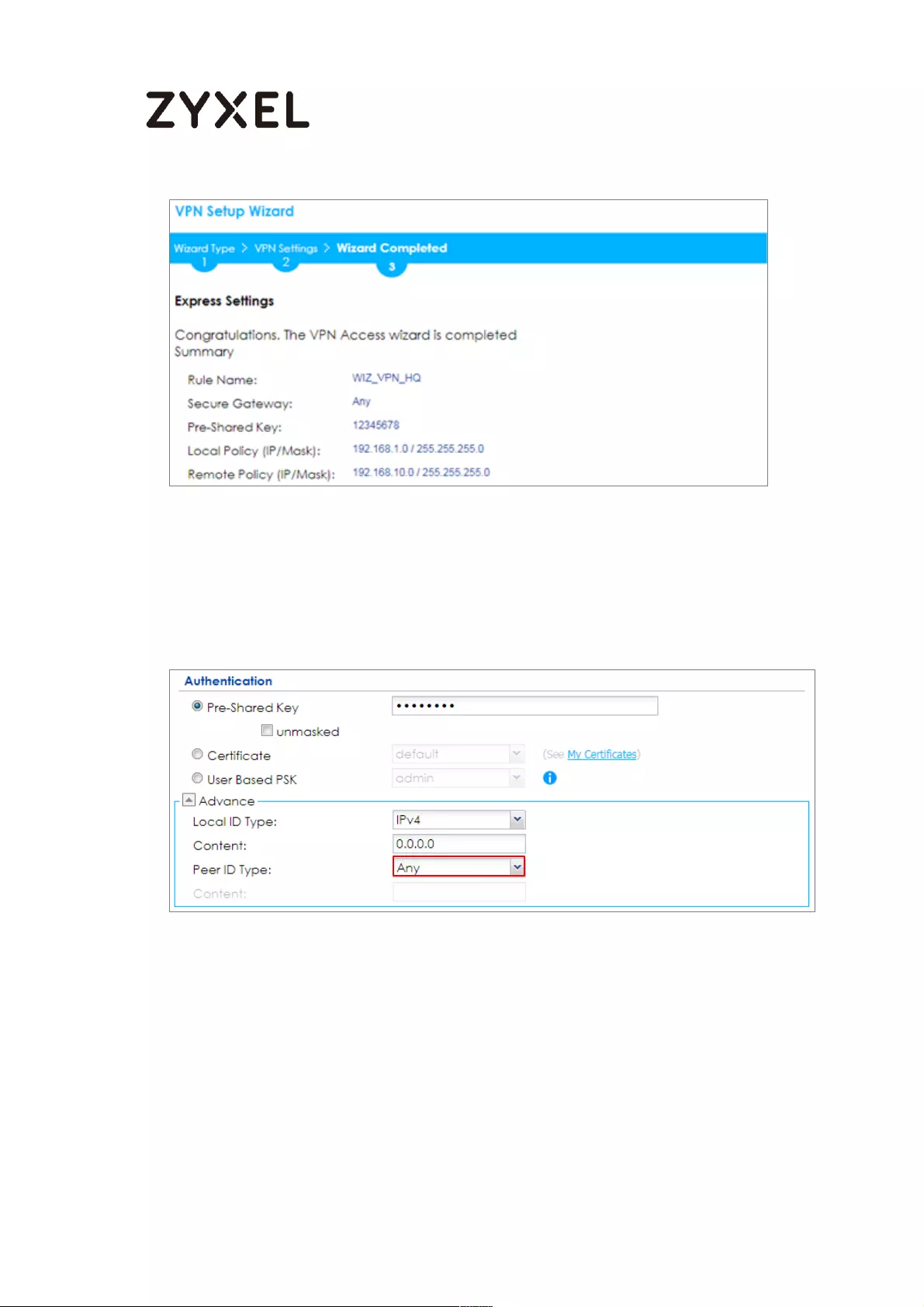
79/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
80/782
www.zyxel.com
(Branch has a Dynamic IP Address)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings to
create a Site-to-site VPN Rule Name.
Quick Setup > VPN Setup Wizard > WelcomeQuick Setup > VPN Setup Wizard >
Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and to use a pre-shared key. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
81/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Click
Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.101.30.68). Type a secure Pre-Shared Key (8-32 characters).
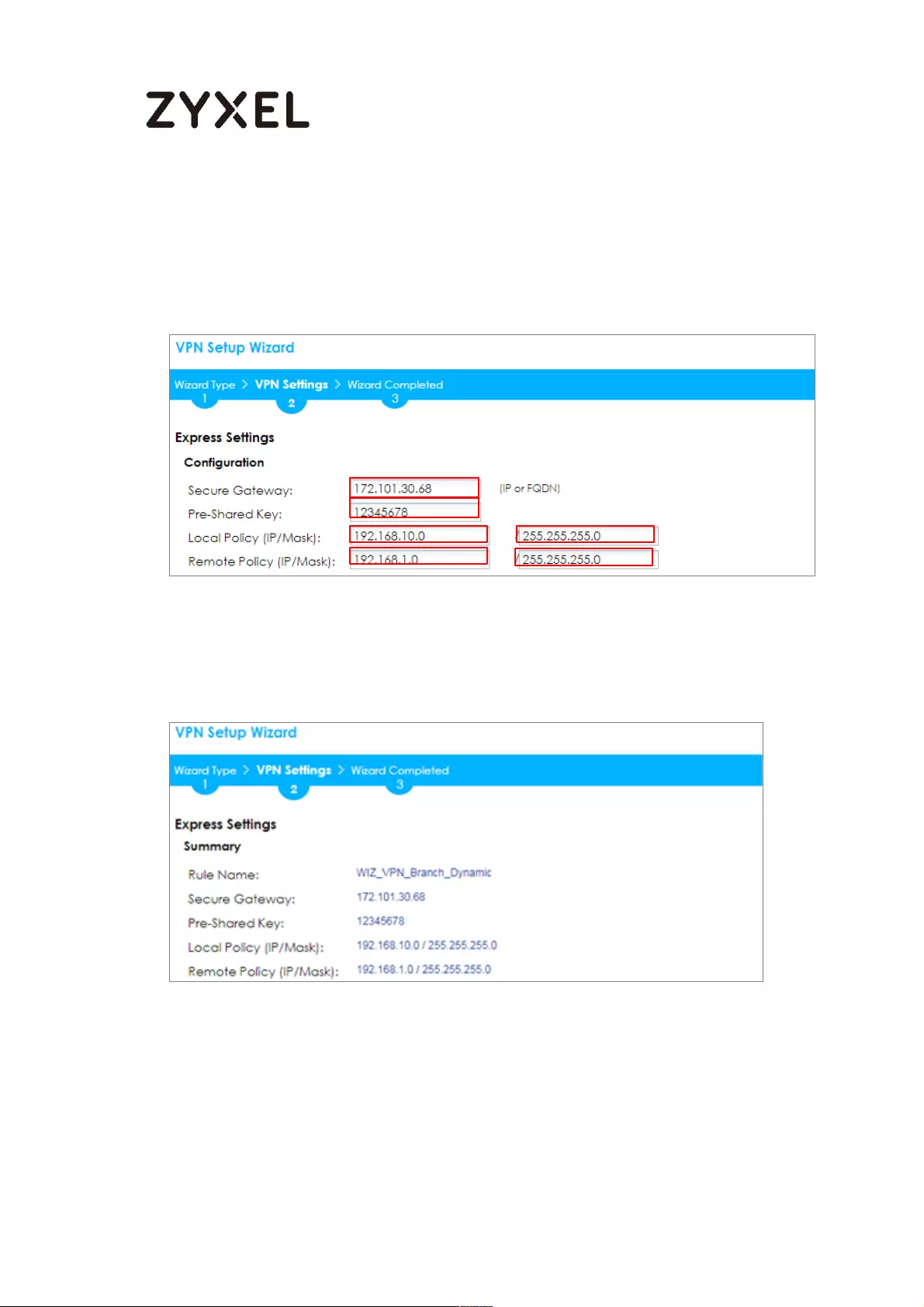
82/782
www.zyxel.com
Set Local Policy to be the ZyWALL/USG local IP address that can use the VPN
tunnel and set Remote Policy to the peer ZyWALL/USG local IP address that can
use the VPN tunnel. Click OK.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
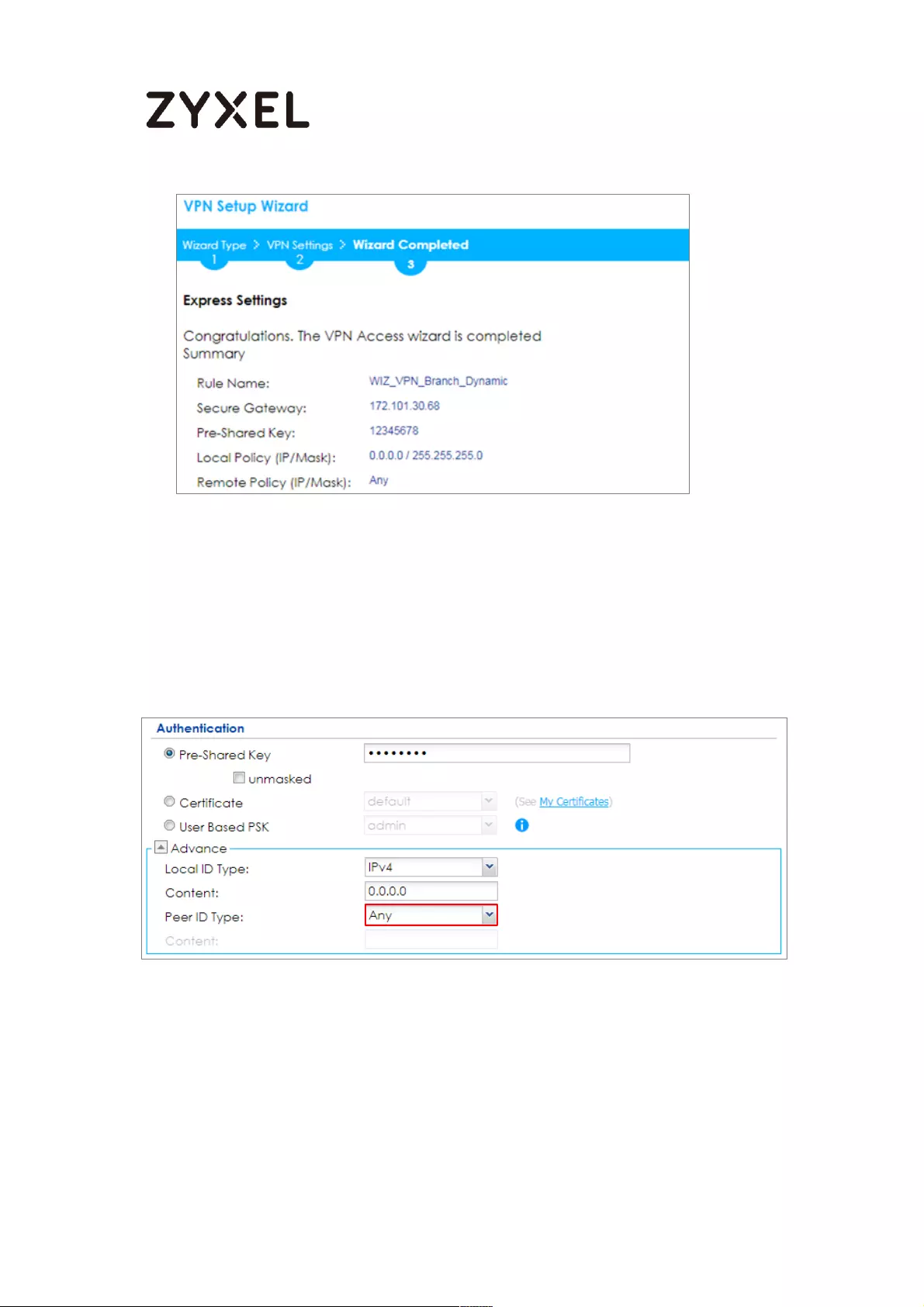
83/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
Test the IPSec VPN Tunnel
The Site-to-site VPN with Dynamic Peer can only initiate the VPN tunnel from the
peer has a dynamic IP Address. Go to CONFIGURATION > VPN > IPSec VPN > VPN
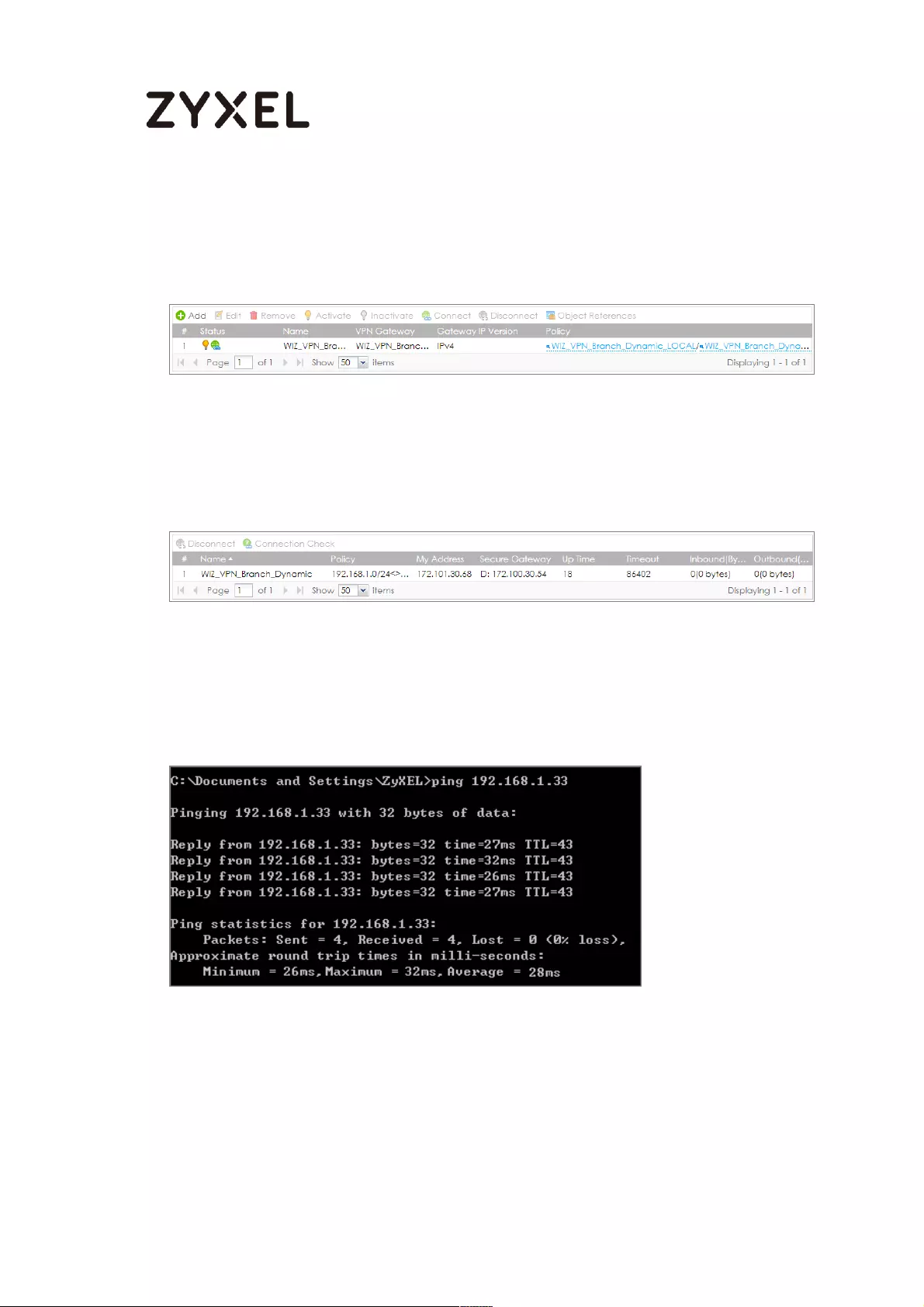
84/782
www.zyxel.com
Connection, click Connect on the upper bar. The Status connect icon is lit when
the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time and
Inbound(Bytes)/Outbound(Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC at HQ Office > Window 7 > cmd > ping 192.168.10.33
PC at Branch Office > Window 7 > cmd > ping 192.168.1.33
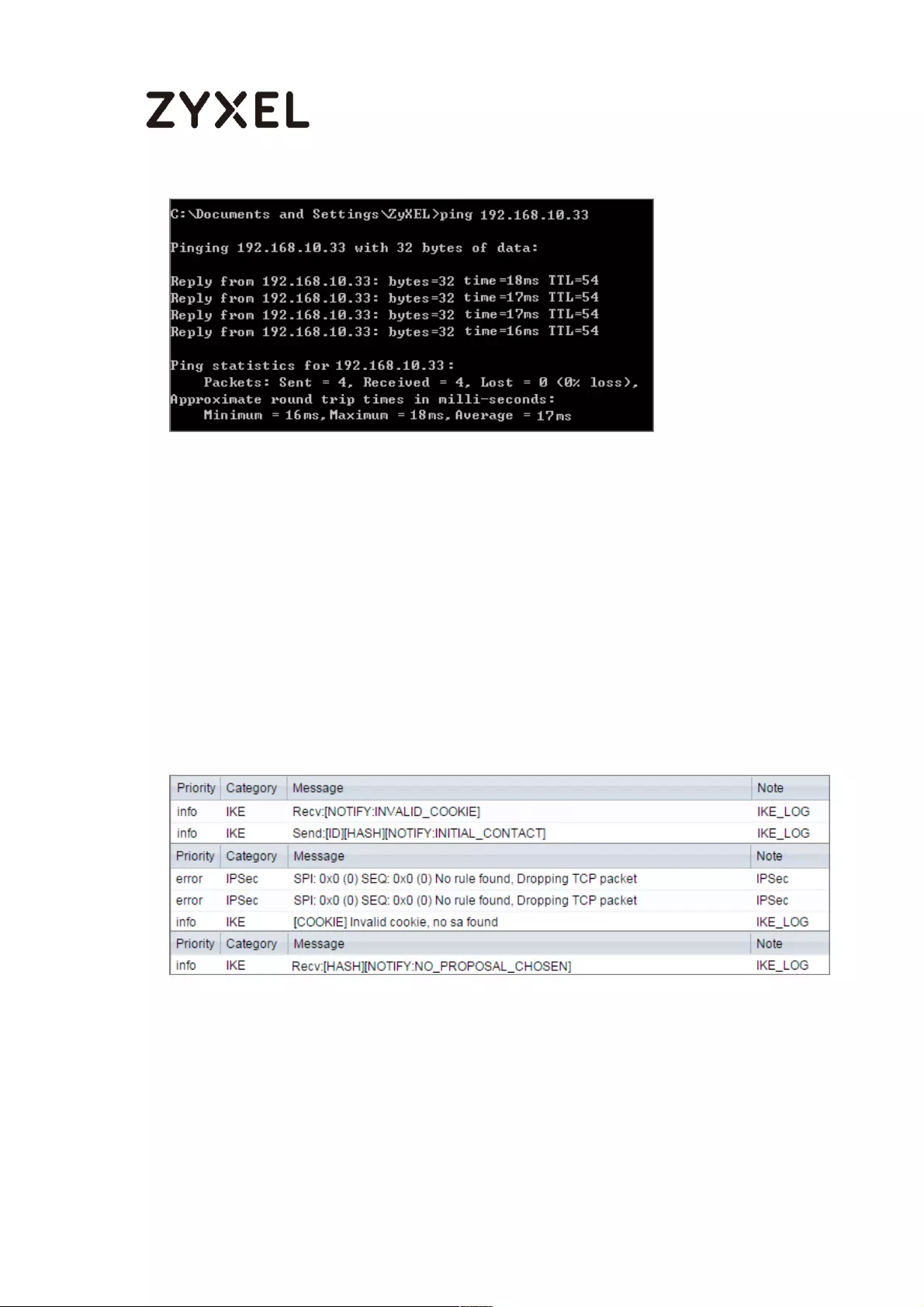
85/782
www.zyxel.com
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG at the HQ and Branch sites must use the same Pre-
Shared Key, Encryption, Authentication method, DH key group and ID Type to
establish the IKE SA.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG Phase 2 Settings. Both ZyWALL/USG at the HQ and
Branch sites must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.

86/782
www.zyxel.com
MONITOR > Log
Make sure the both ZyWALL/USG at the HQ and Branch sites security policies
allow IPSec VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP
uses IP protocol 50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.
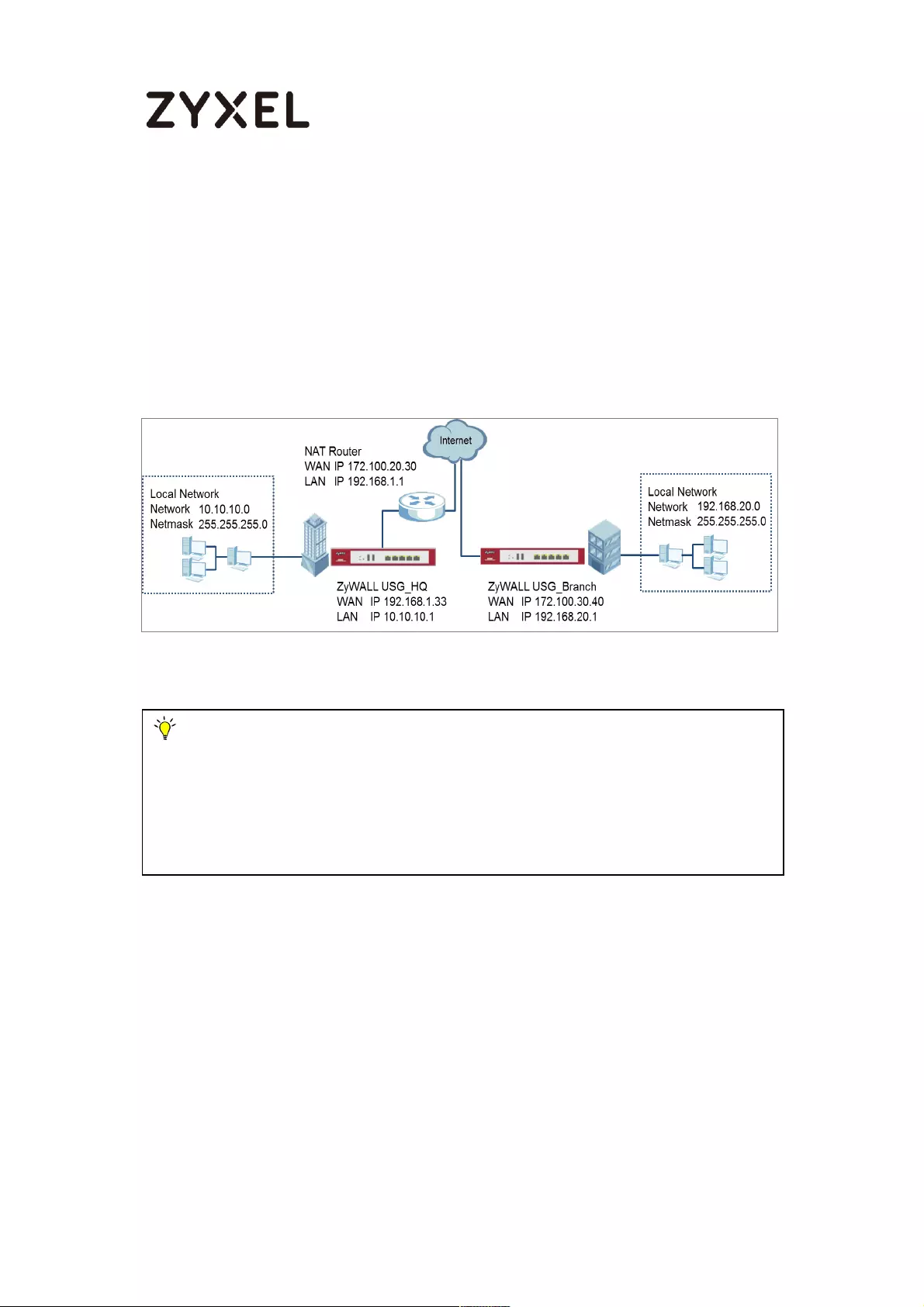
87/782
www.zyxel.com
How to Configure IPSec Site to Site VPN while one Site is
behind a NAT router
This example shows how to use the VPN Setup Wizard to create a IPSec Site to
Site VPN tunnel between ZyWALL/USG devices. The example instructs how to
configure the VPN tunnel between each site while one Site is behind a NAT
router. When the IPSec Site to Site VPN tunnel is configured, each site can be
accessed securely.
ZyWALL/USG Site to Site VPN while one Site is behind a NAT router
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate
Note:
All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks.
This example was tested using USG110 (Firmware Version: ZLD 4.25) and
ZyWALL 310 (Firmware Version: ZLD 4.25).
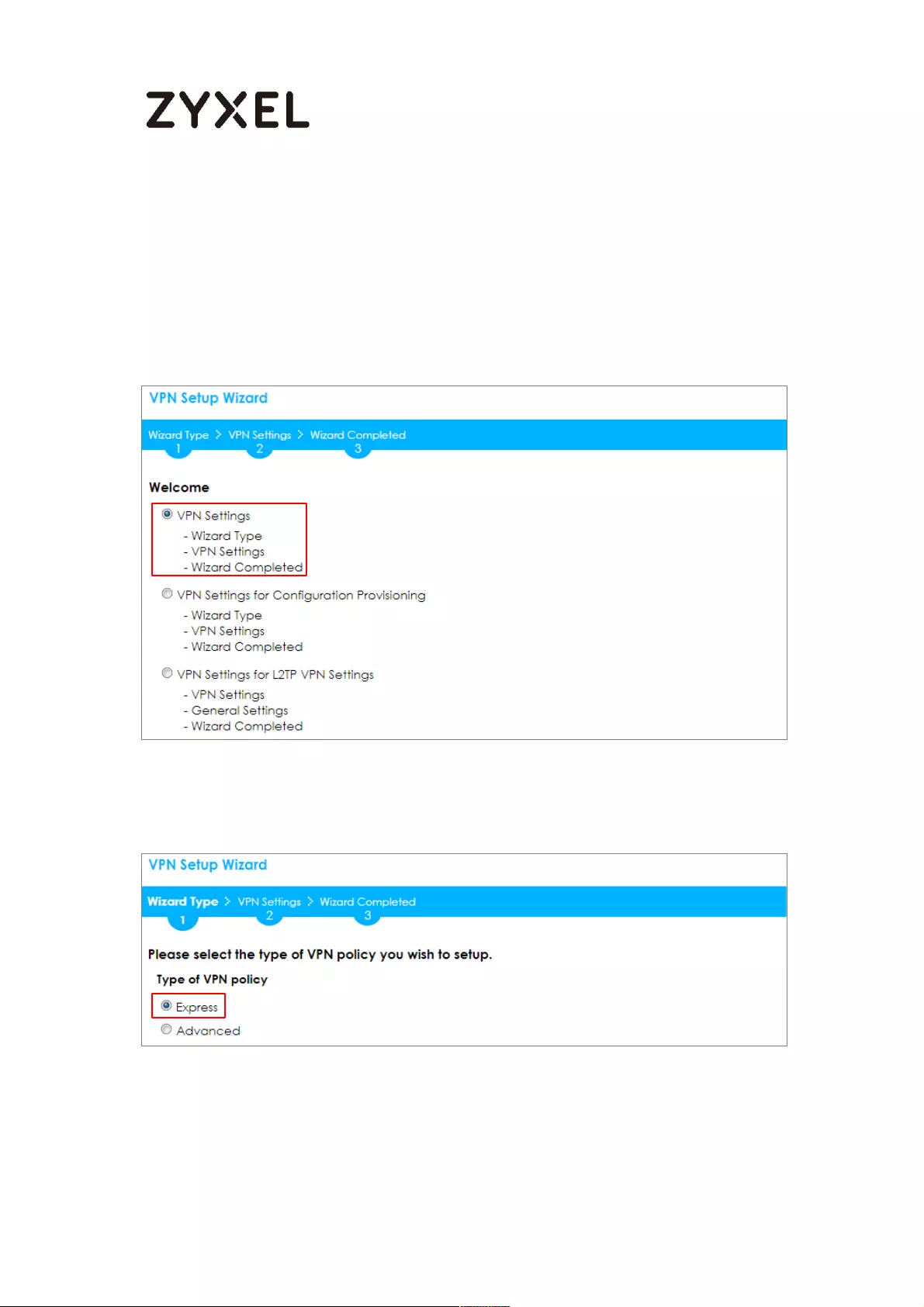
88/782
www.zyxel.com
Network (HQ)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the FortiGate. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Select the rule to
be Site-to-site. Click Next.

89/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the Branch’s WAN IP address (in the example,
172.100.30.40). Then, type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG (HQ) and Remote Policy to be the IP address range of the network
connected to the ZyWALL/USG (Branch).
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
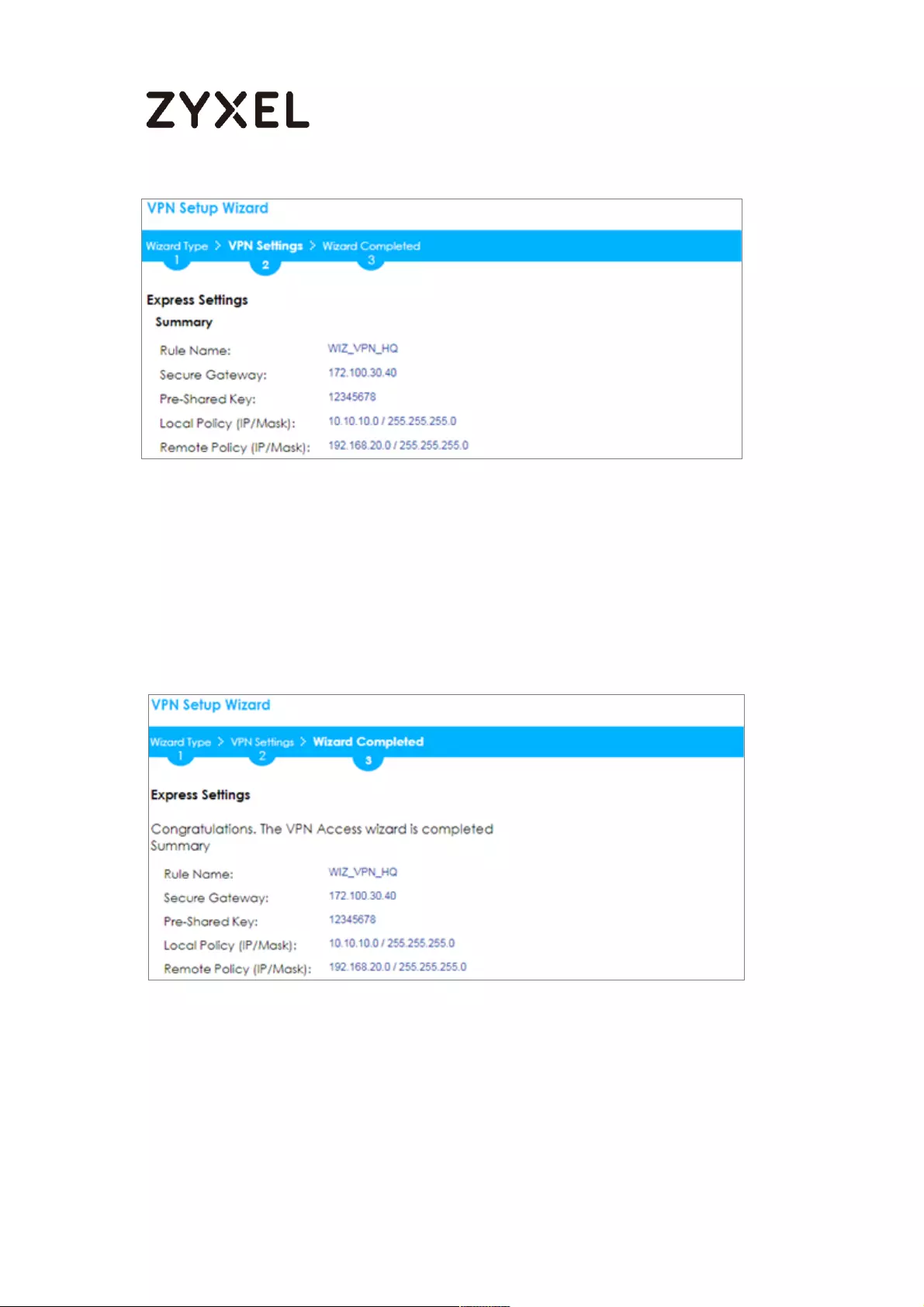
90/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings. Configure Authentication > Peer ID Type as Any to let the ZyWALL/USG
does not require to check the identity content of the remote IPSec router.

91/782
www.zyxel.com
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate
Network (Branch)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the FortiGate. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
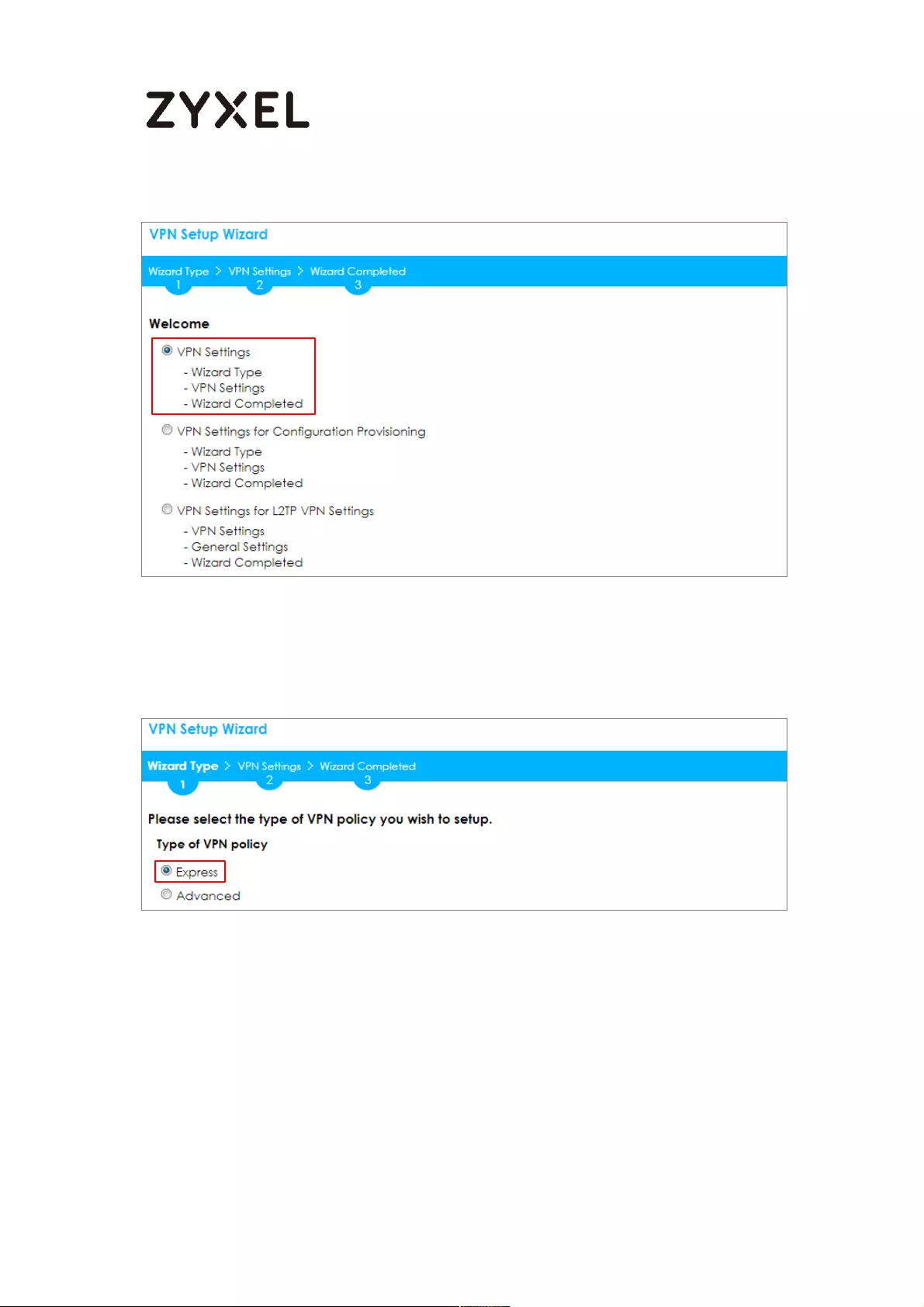
92/782
www.zyxel.com
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Select the rule to
be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
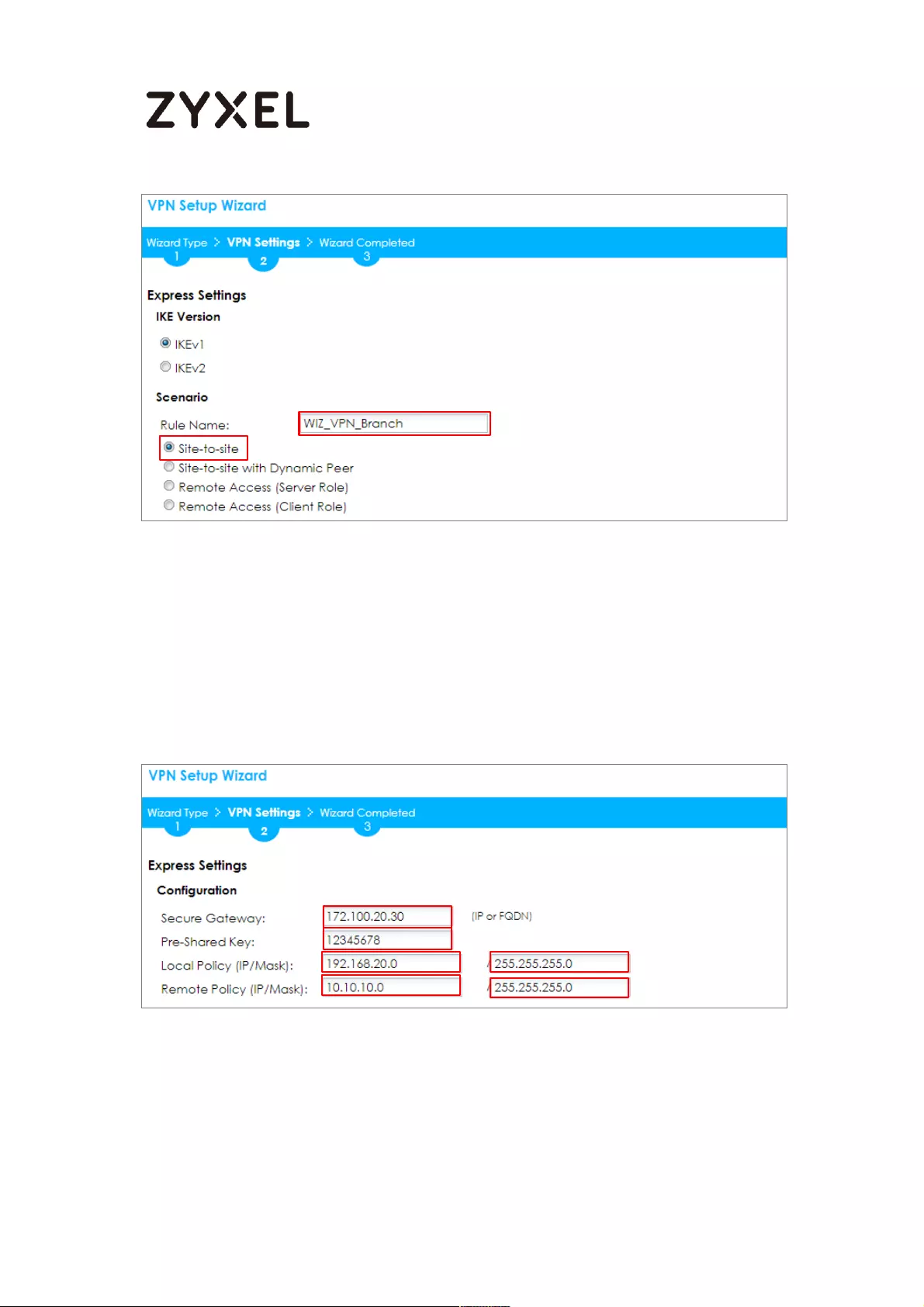
93/782
www.zyxel.com
Configure Secure Gateway IP as the Branch’s WAN IP address (in the example,
172.100.20.30). Then, type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG (HQ) and Remote Policy to be the IP address range of the network
connected to the ZyWALL/USG (Branch).
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
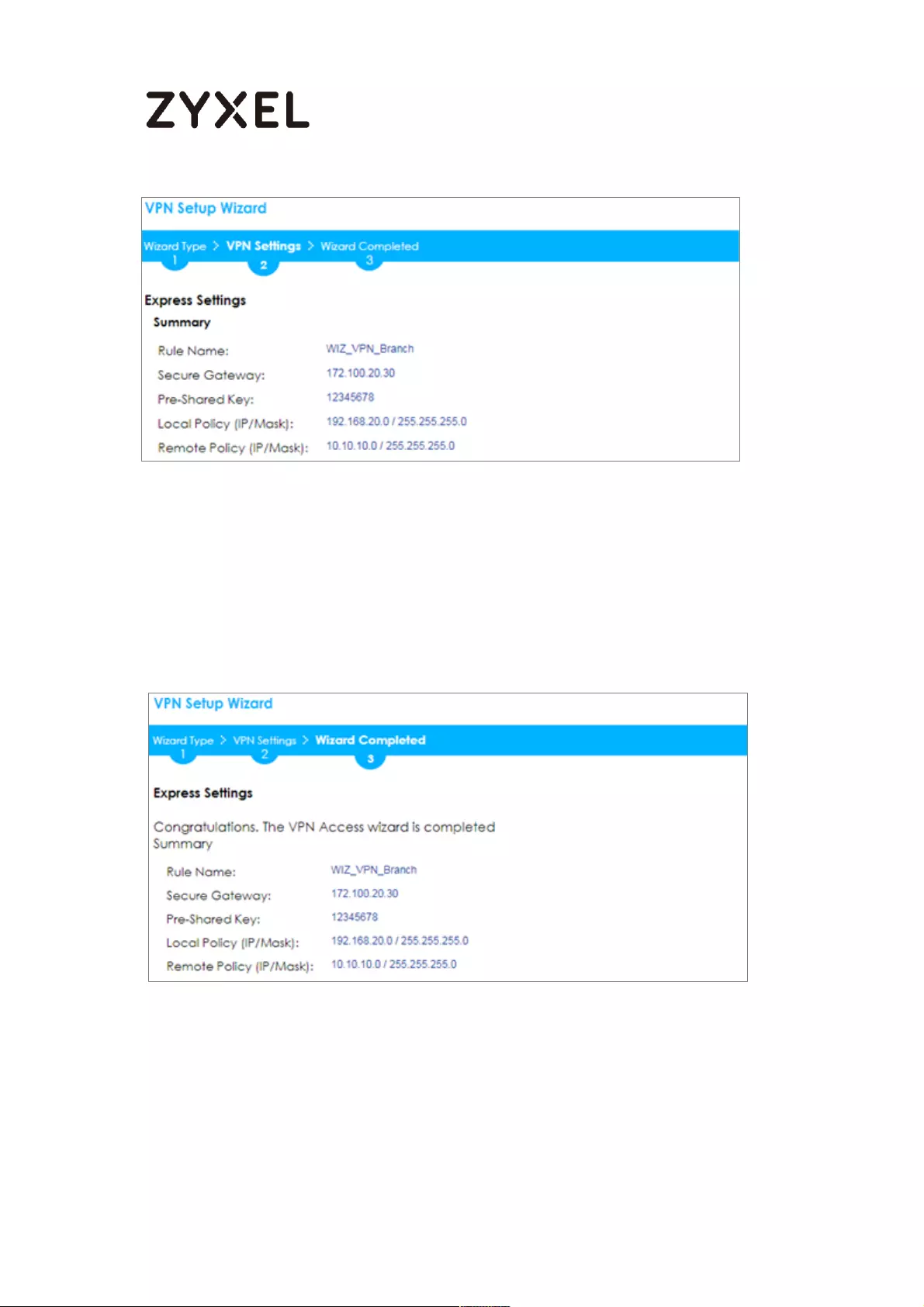
94/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings. Configure Authentication > Peer ID Type as Any to let the ZyWALL/USG
does not require to check the identity content of the remote IPSec router.
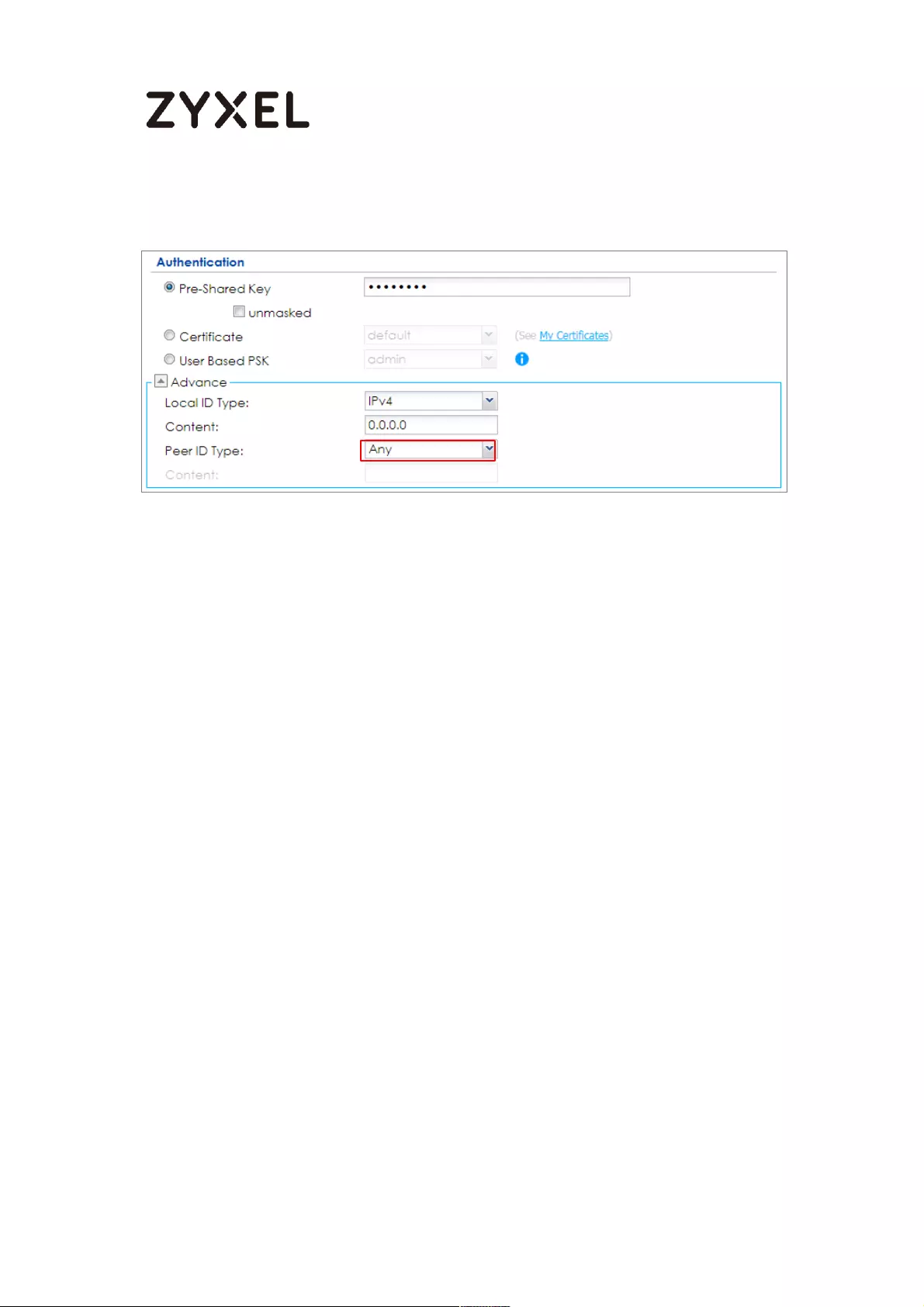
95/782
www.zyxel.com
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Set Up the NAT Router (Using ZyWALL USG device in this
example)
Go to CONFIGURATION > Network > NAT > Add. Select the Incoming Interface
on which packets for the NAT rule must be received. Specified the User-
96/782
www.zyxel.com
Defined Original IP field and Type the translated destination IP address that this
NAT rule supports.
CONFIGURATION > Network > NAT > Add
Go to CONFIGURATION > Security Policy > Policy Control. IP forwarding must be
enabled at the firewall for the following IP protocols and UDP ports:
IP protocol = 50 → Used by data path (ESP)
IP protocol = 51 → Used by data path (AH)
UDP Port Number = 500 → Used by IKE (IPSec control path)
UDP Port Number = 4500 → Used by NAT-T (IPsec NAT traversal)
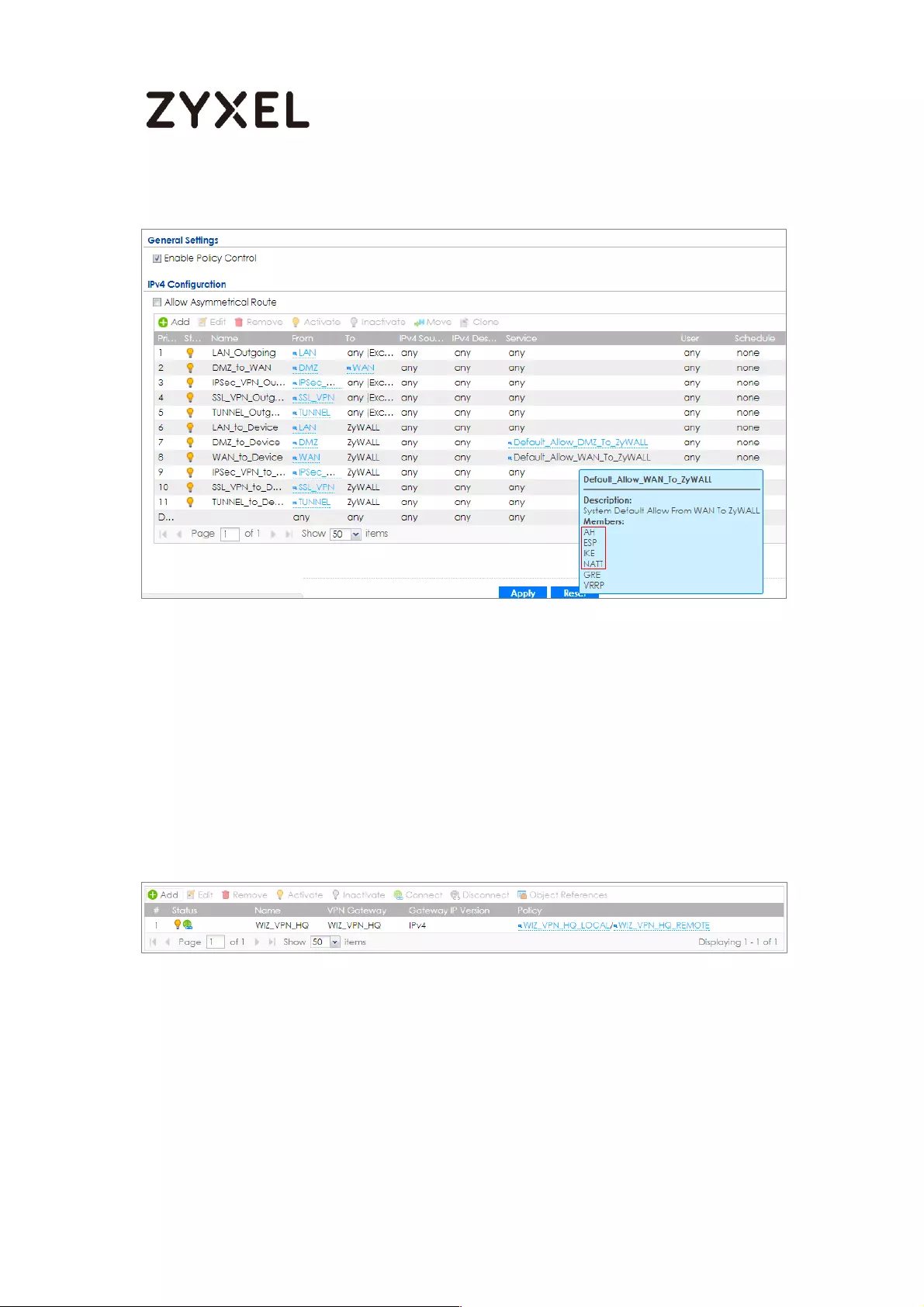
97/782
www.zyxel.com
CONFIGURATION > Security Policy > Policy Control
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up
Time and Inbound (Bytes)/Outbound (Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
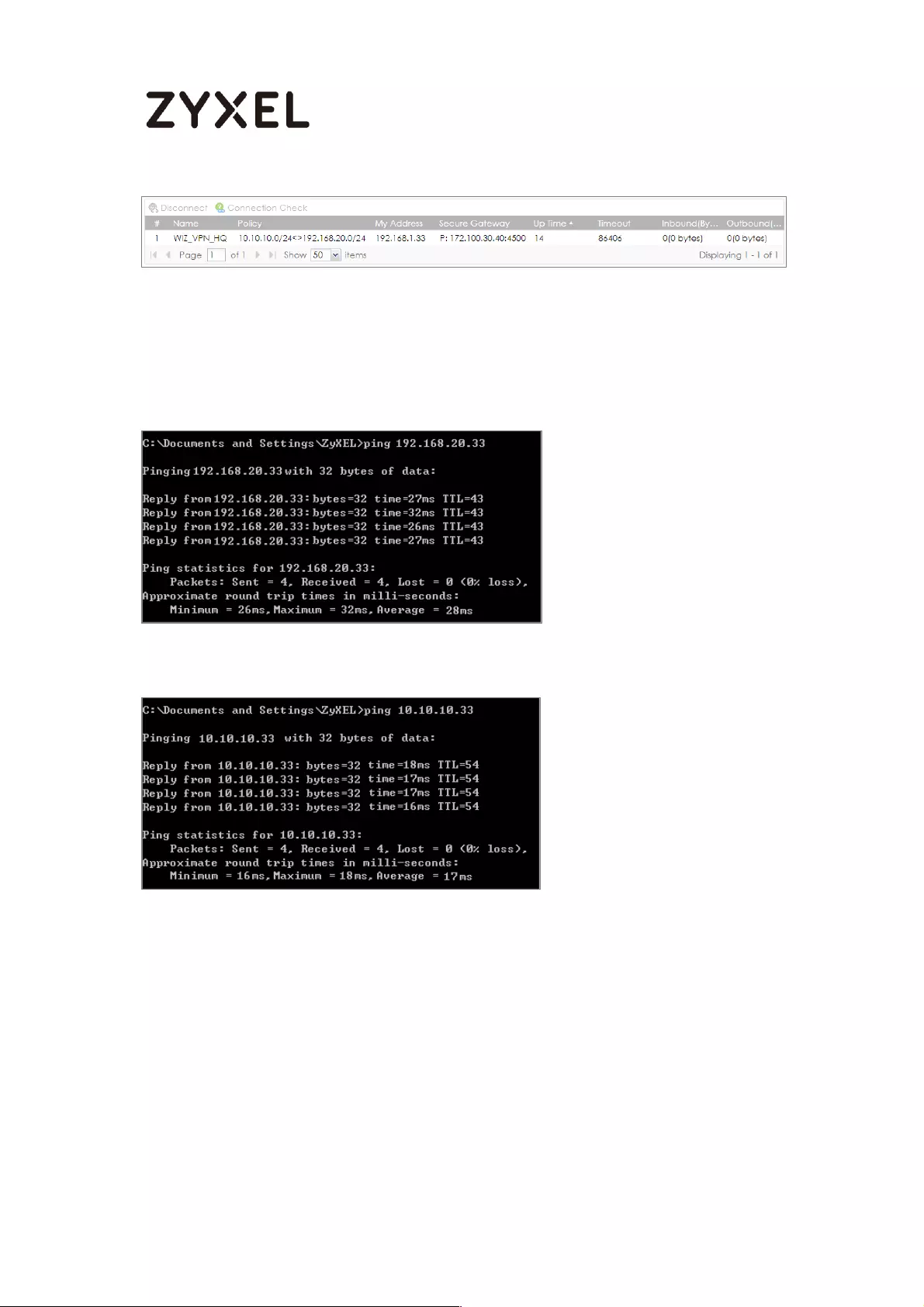
98/782
www.zyxel.com
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC behind ZyWALL/USG (HQ) > Window 7 > cmd > ping 192.168.20.33
PC behind ZyWALL/USG (Branch) > Window 7 > cmd > ping 10.10.10.33
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase
1 Settings. Both ZyWALL/USG at the HQ and Branch sites must use the same Pre-
Shared Key, Encryption, Authentication method, DH key group and ID Type to
establish the IKE SA.
MONITOR > Log
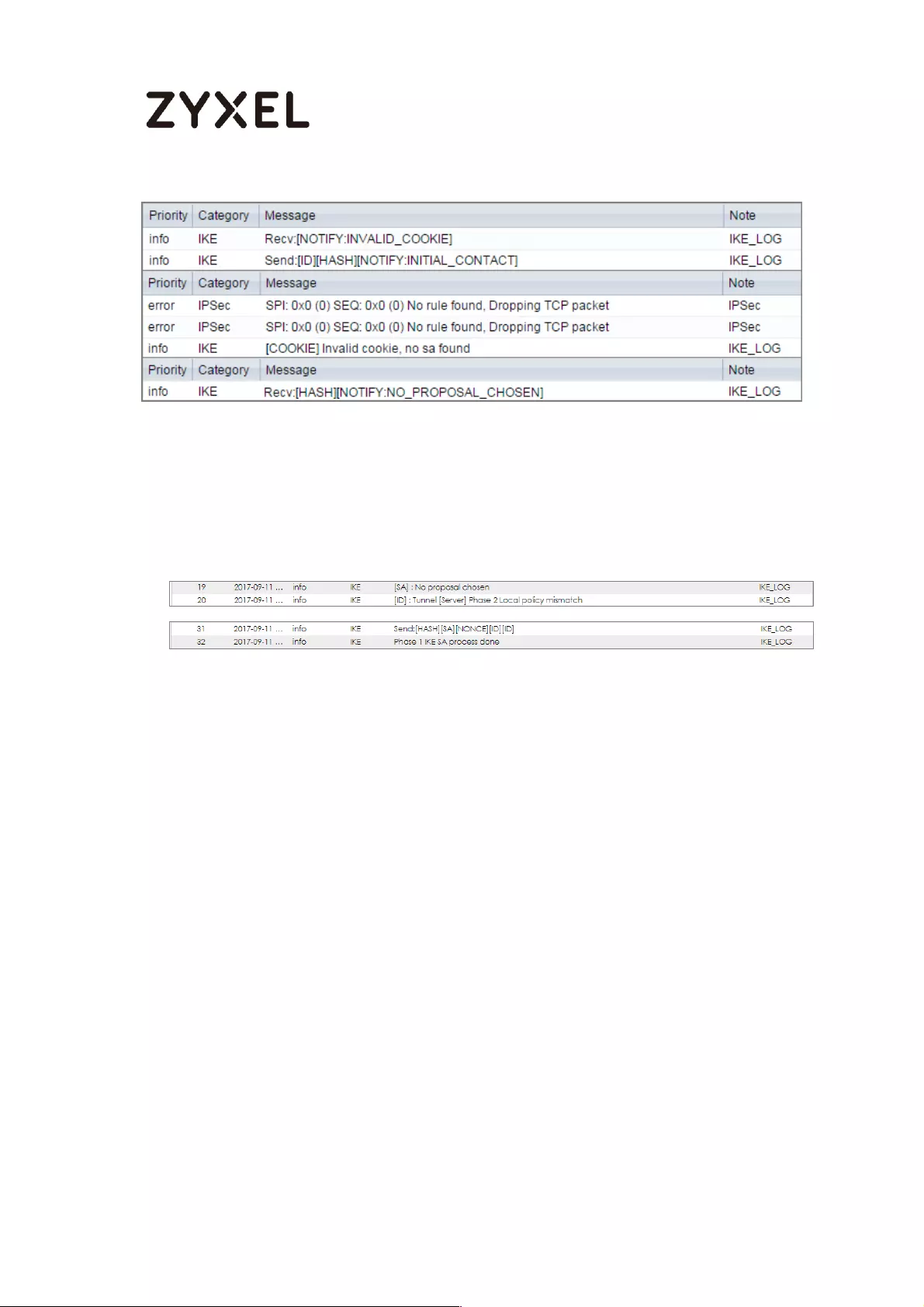
99/782
www.zyxel.com
If you see that Phase 1 IKE SA process done but still get below [info] log
message, please check ZyWALL/USG Phase 2 Settings. Both ZyWALL/USG at the
HQ and Branch sites must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
MONITOR > Log
Make sure the both ZyWALL/USG at the HQ and Branch sites security policies
allow IPSec VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP
uses IP protocol 50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.
How to Configure Hub-and-Spoke IPSec VPN
This is an example of a hub-and-spoke VPN with the HQ ZyWALL/USG as the hub
and spoke VPNs to Branches A and B. When the VPN tunnel is configured, traffic
passes between branches via the hub (HQ). Traffic can also pass between
spoke-and-spoke through the hub. Here are two methods to set up hub-and-
spoke VPN connections: 1. With VPN Concentrator 2. Without VPN Concentrator.
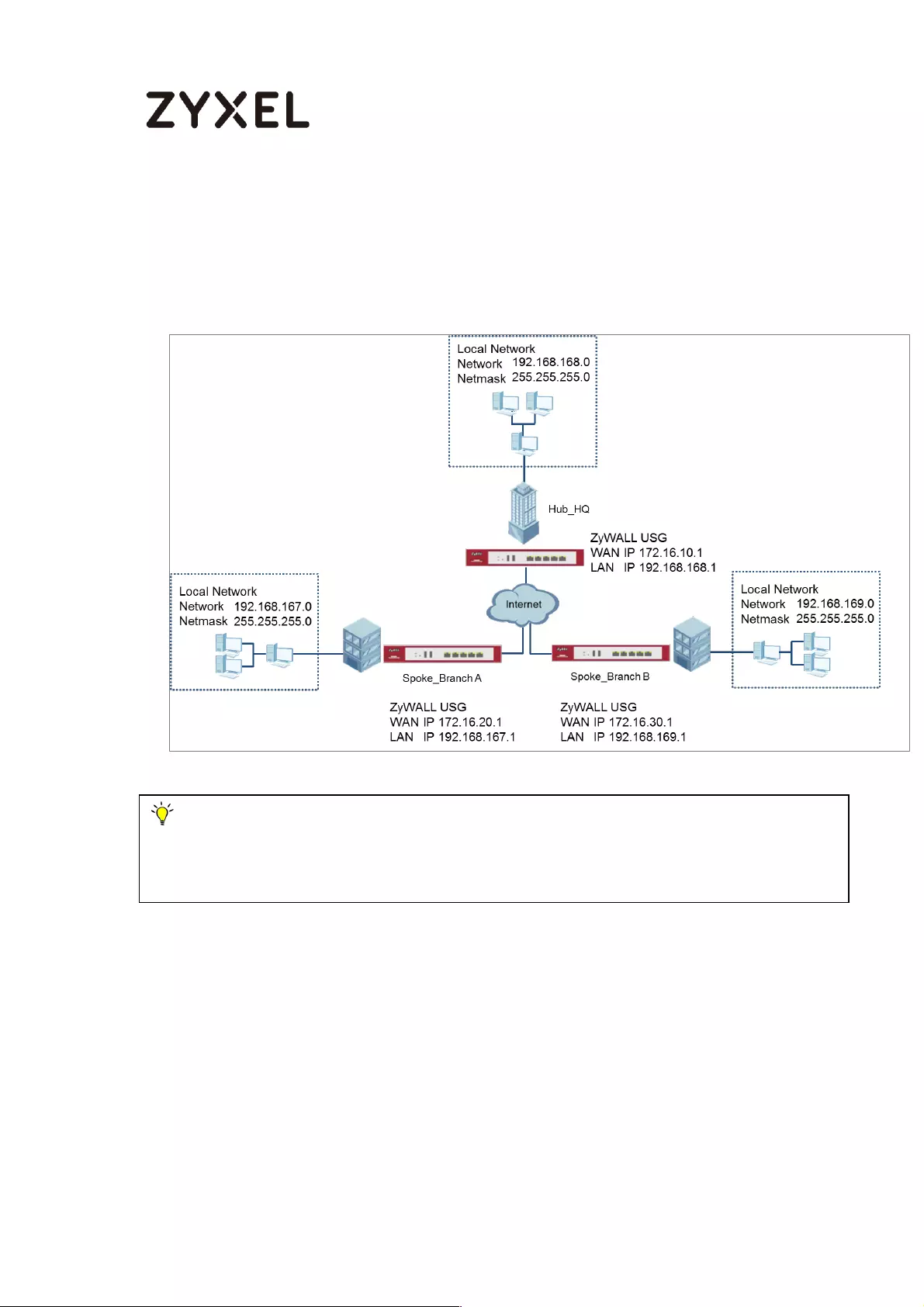
100/782
www.zyxel.com
With just two branch offices, you could just manually set up VPN tunnels between
HQ and the branches. With many branches it's best to use the VPN Concentrator
to set up branch-HQ tunnels automatically.
ZyWALL/USG Hub-and-Spoke VPN Example
Set Up the IPSec VPN Tunnel on the ZyWALL/USG by Using VPN
Concentrator Hub_HQ-to-Branch_A
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
101/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)

102/782
www.zyxel.com
Then, configure the Secure Gateway IP as the Branch A’s Gateway IP address (in
the example, 172.16.20.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Branch A’s Pre-Shared Key.
Set Local Policy to be the IP address range of the network connected to the
Hub_HQ and Remote Policy to be the IP address range of the network connected
to the Branch A. Click OK.
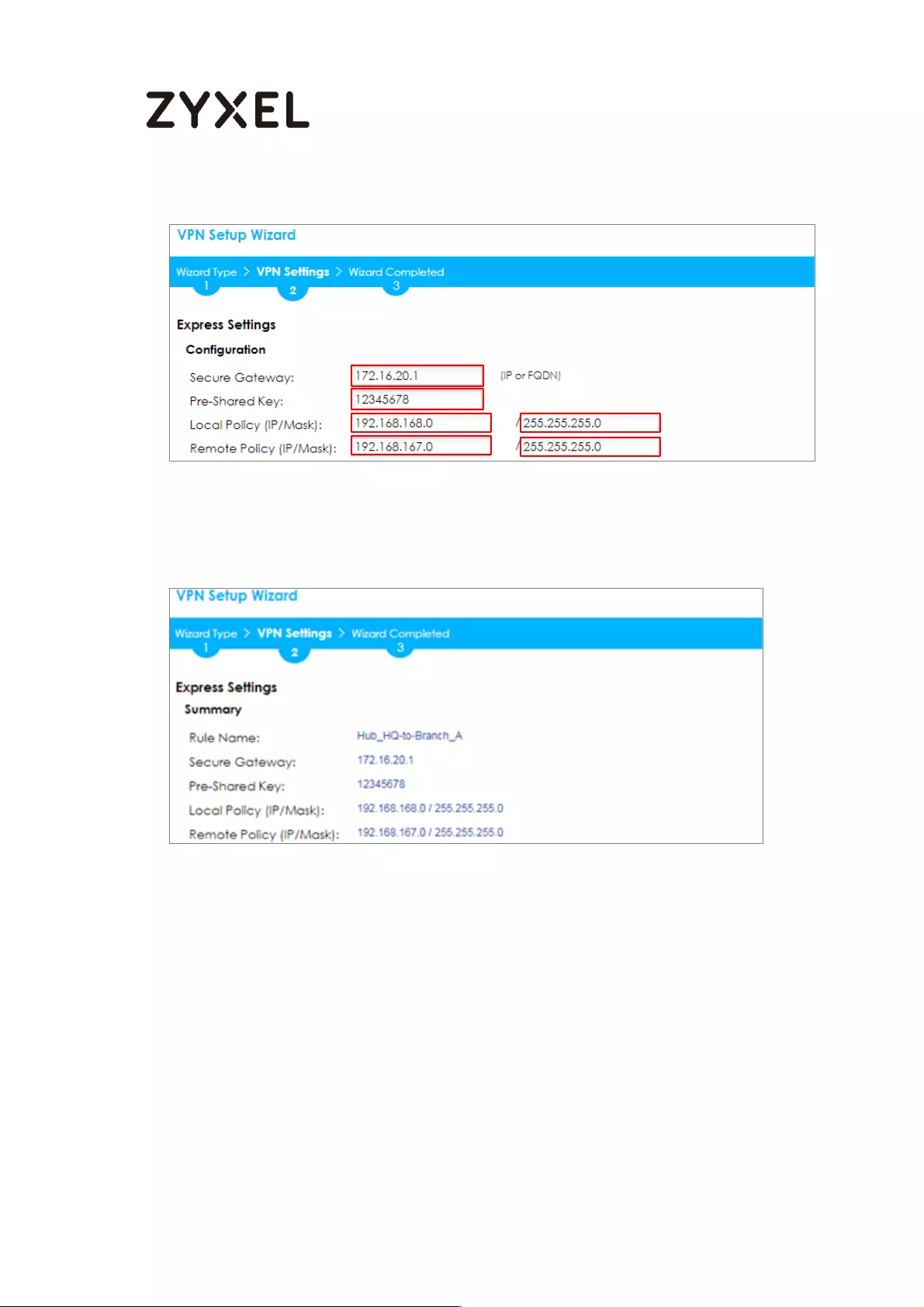
103/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings > Wizard
Completed
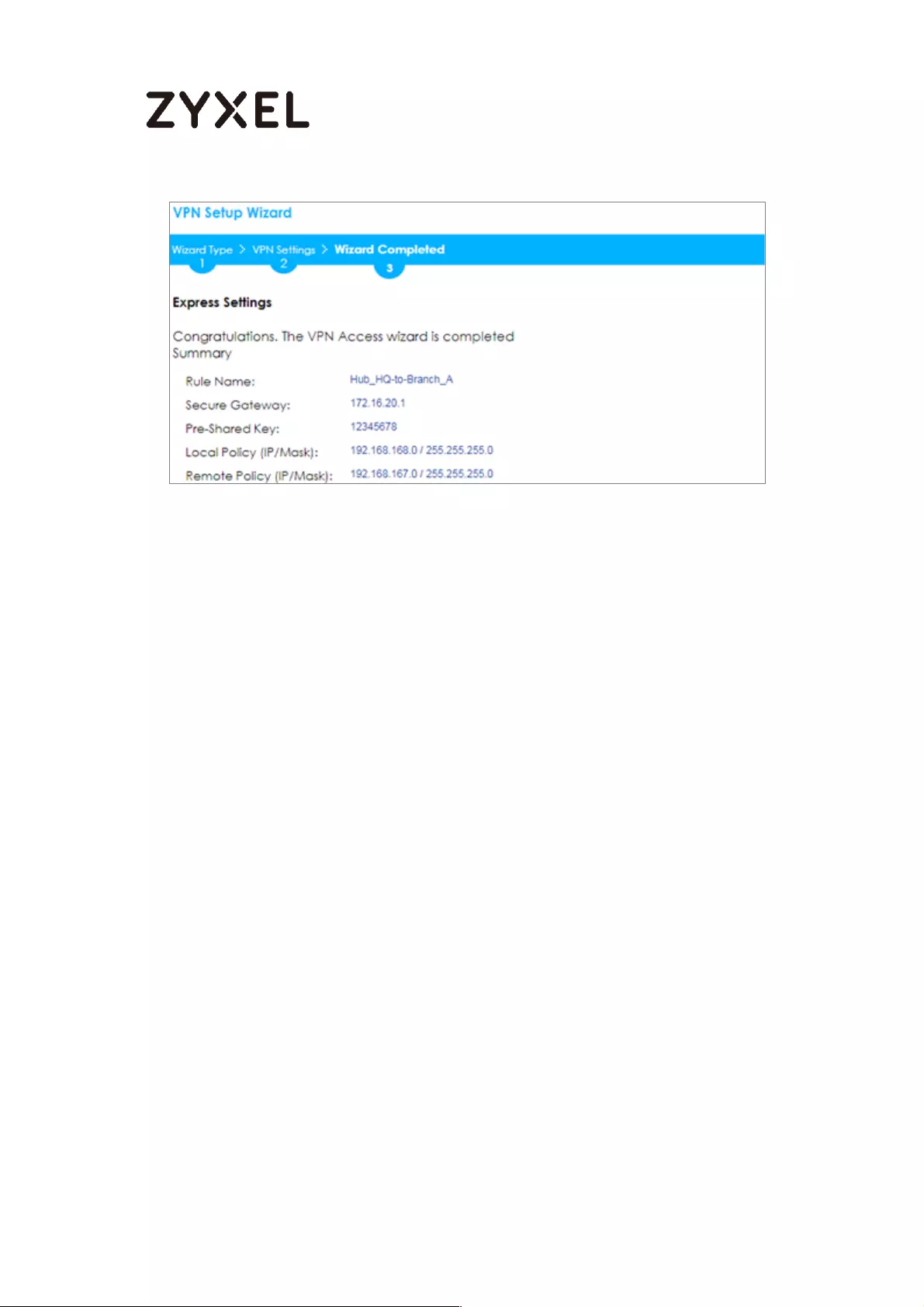
104/782
www.zyxel.com
Hub_HQ-to-Branch_B
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
105/782
www.zyxel.com
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)

106/782
www.zyxel.com
Then, configure the Secure Gateway IP as the Branch B’s Gateway IP address (in
the example, 172.16.30.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Branch B’s Pre-Shared Key.
Set Local Policy to be the IP address range of the network connected to the
Hub_HQ and Remote Policy to be the IP address range of the network connected
to the Branch B. Click OK.
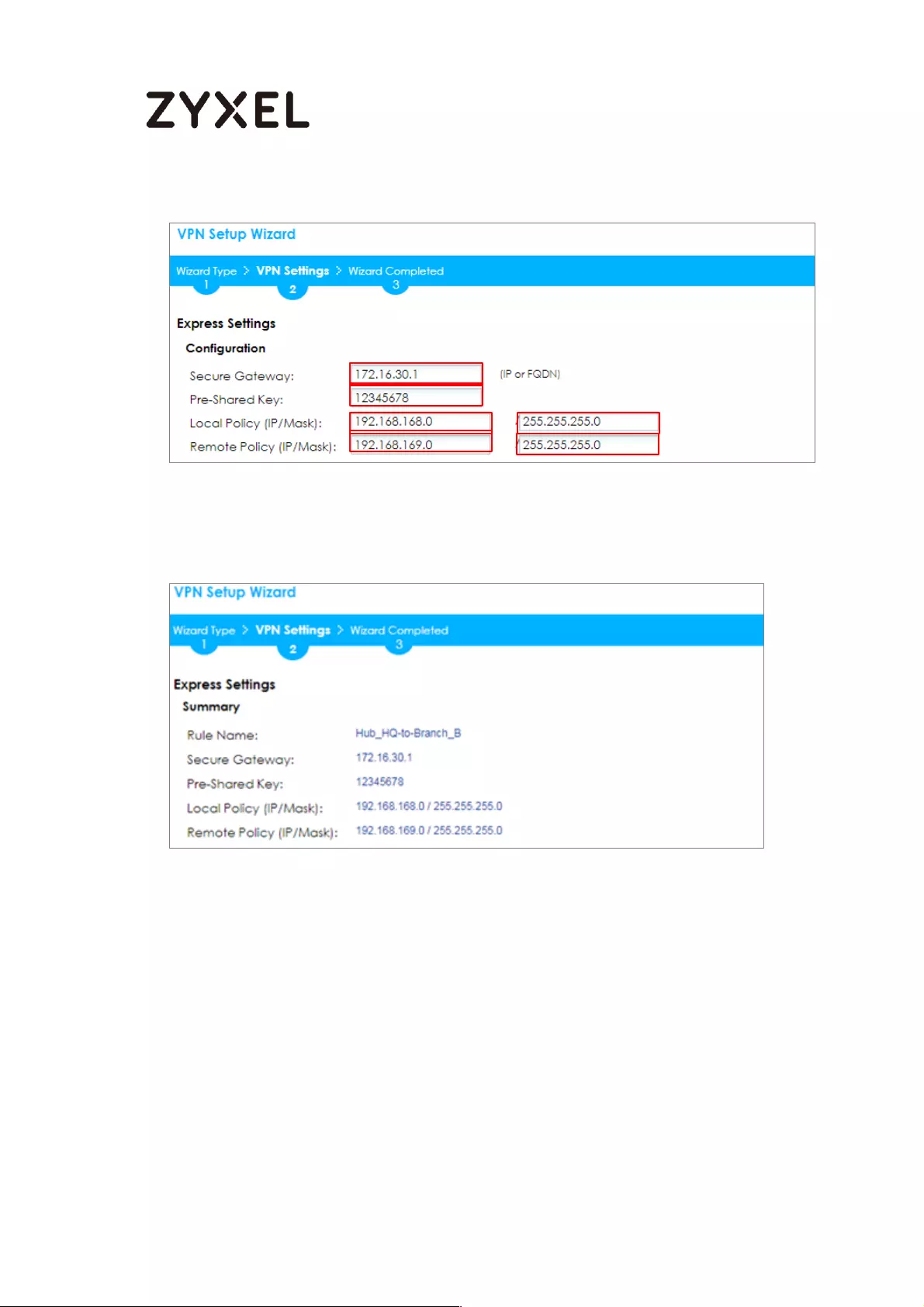
107/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings > Wizard
Completed
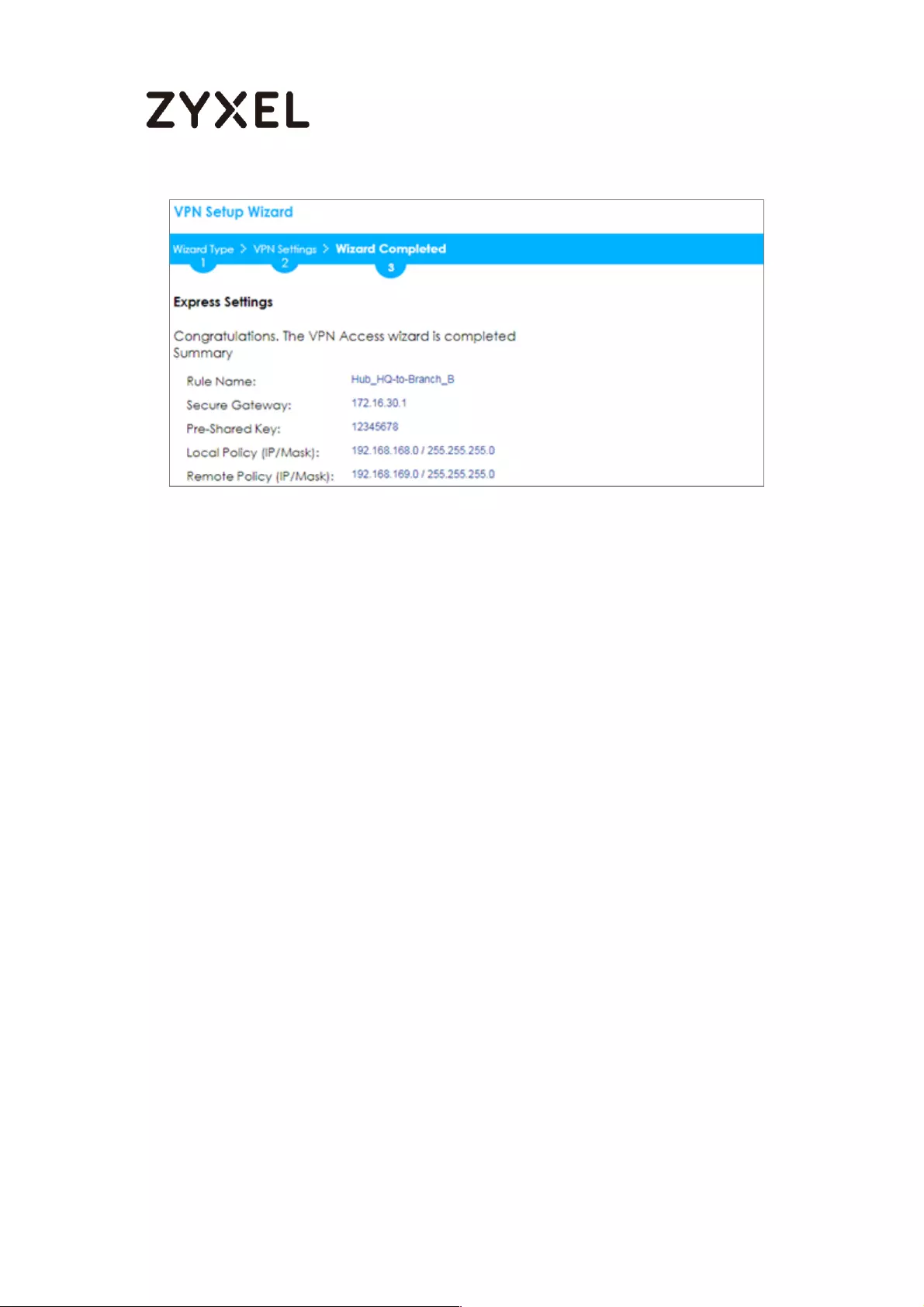
108/782
www.zyxel.com
Hub_HQ Concentrator
In the ZyWALL/USG, go to CONFIGURATION > VPN > IPSec VPN > Concentrator,
add a VPN Concentrator rule. Select VPN tunnels to be in the same member
group and click Save.
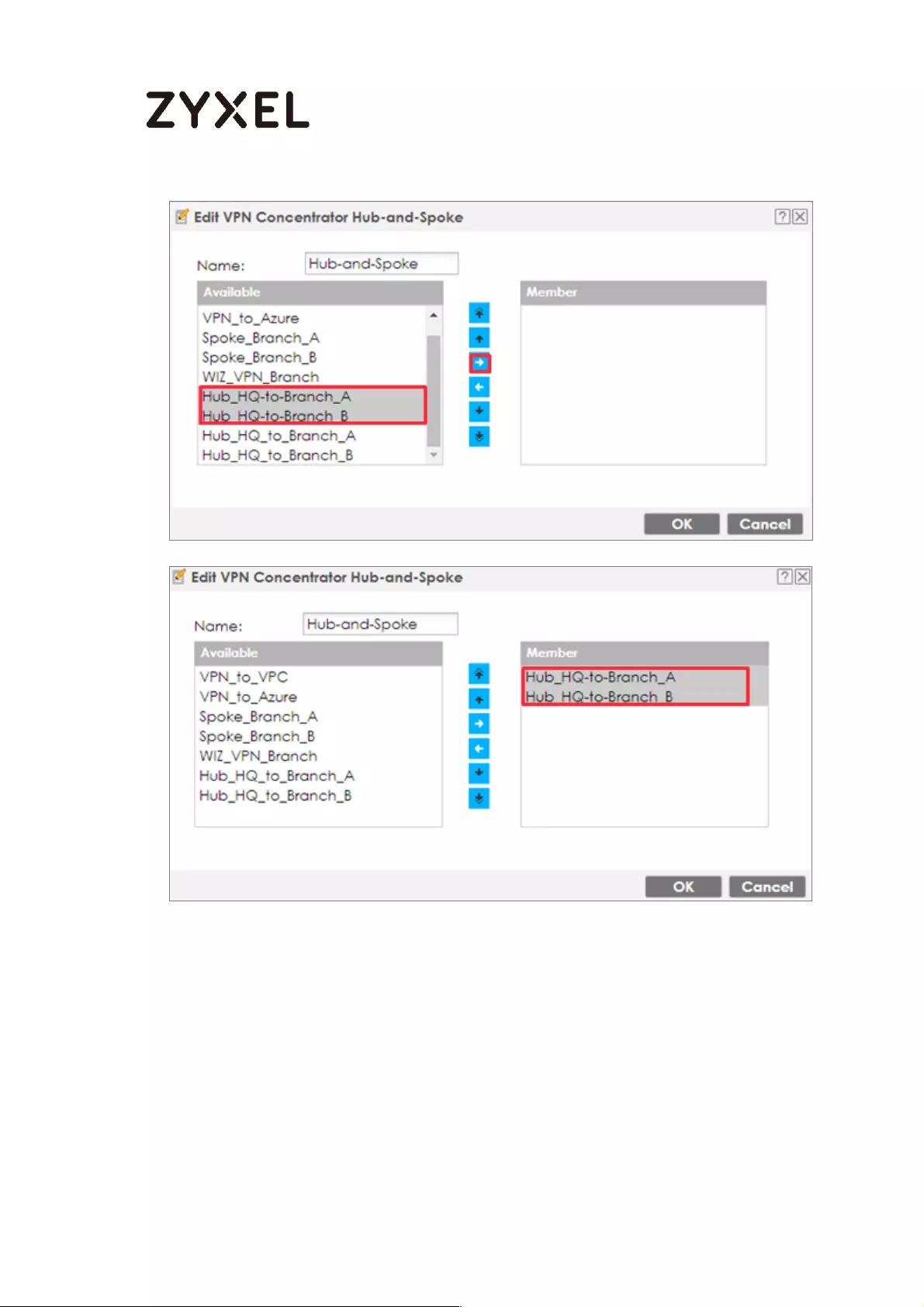
109/782
www.zyxel.com
Spoke_Branch_A
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
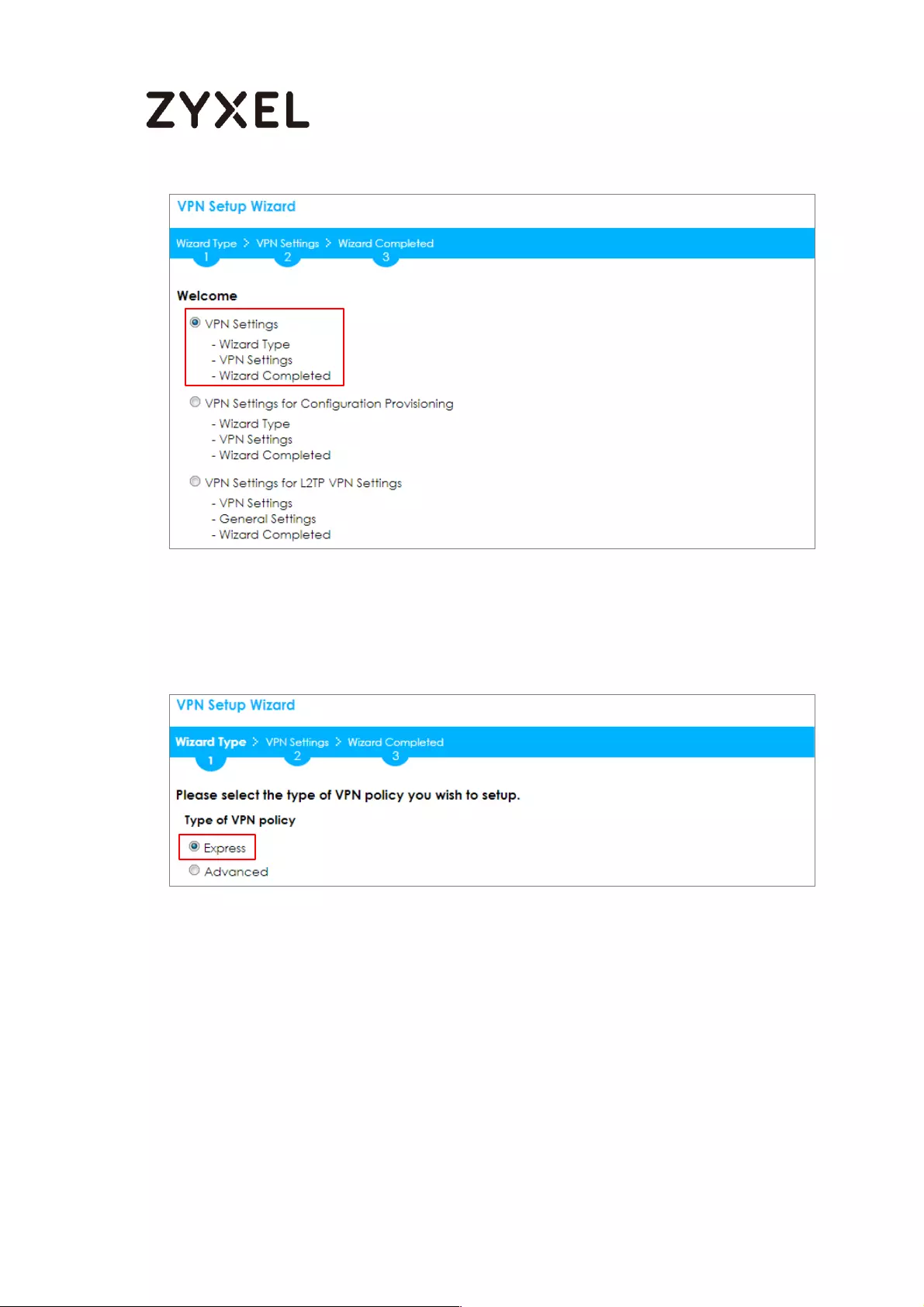
110/782
www.zyxel.com
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
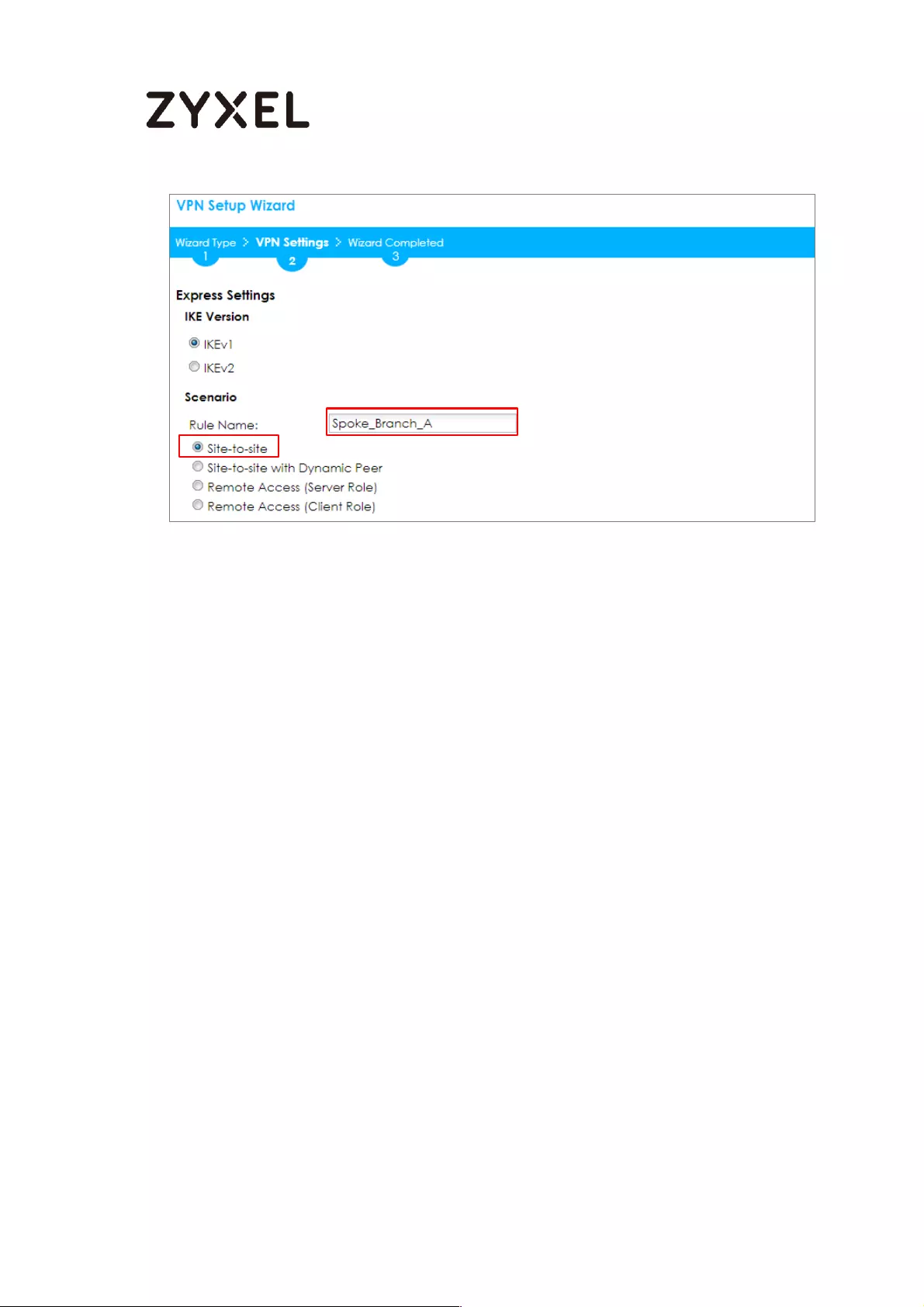
111/782
www.zyxel.com
Then, configure the Secure Gateway IP as the Hub_HQ’s Gateway IP address (in
the example, 172.16.10.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Hub_HQ’s Pre-Shared Key.
Set Local Policy to be the IP address range of the network connected to the
Spoke_Branch_A and Remote Policy to be the IP address range of the network
connected to the Hub_HQ. Click OK.
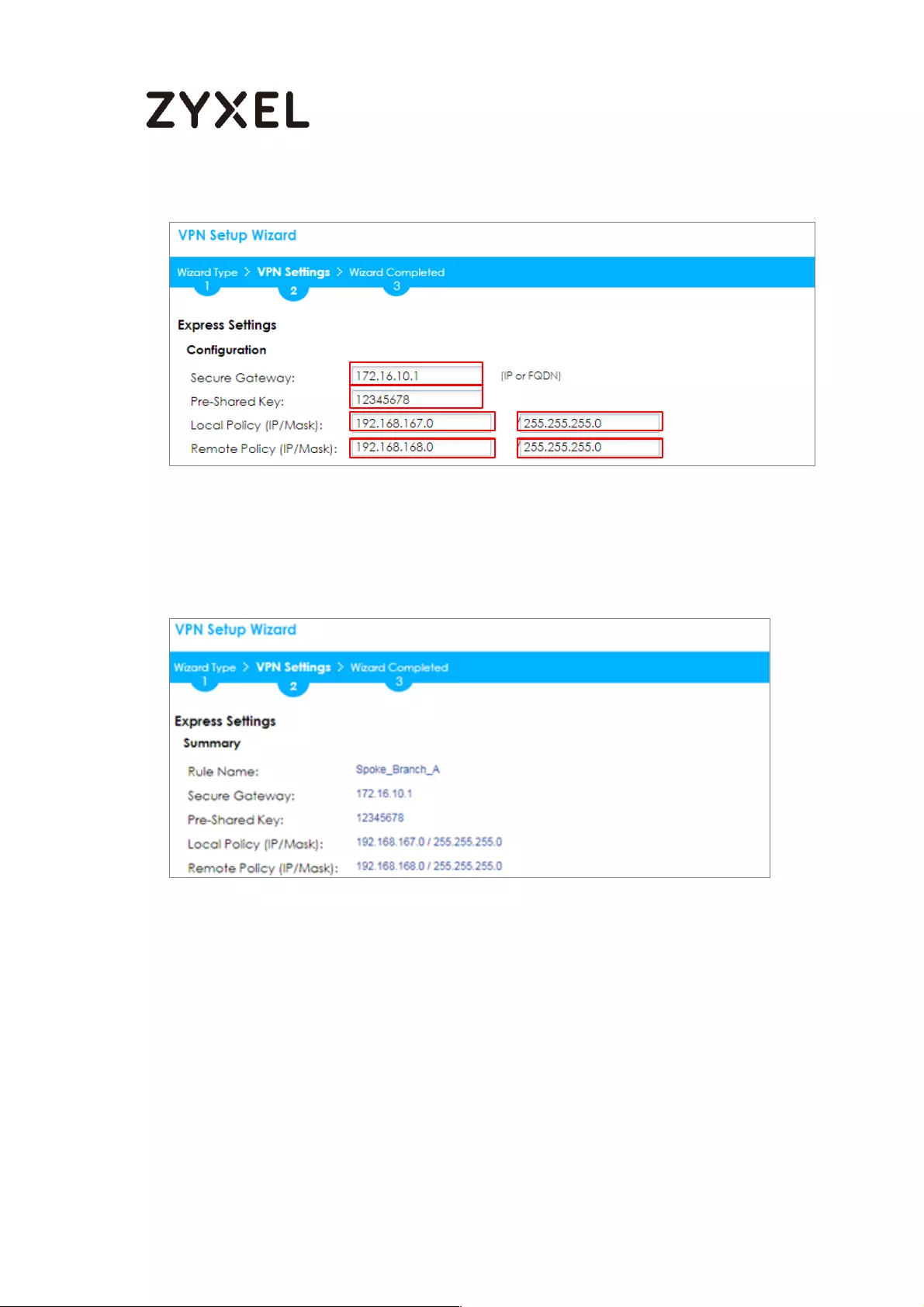
112/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings > Wizard
Completed
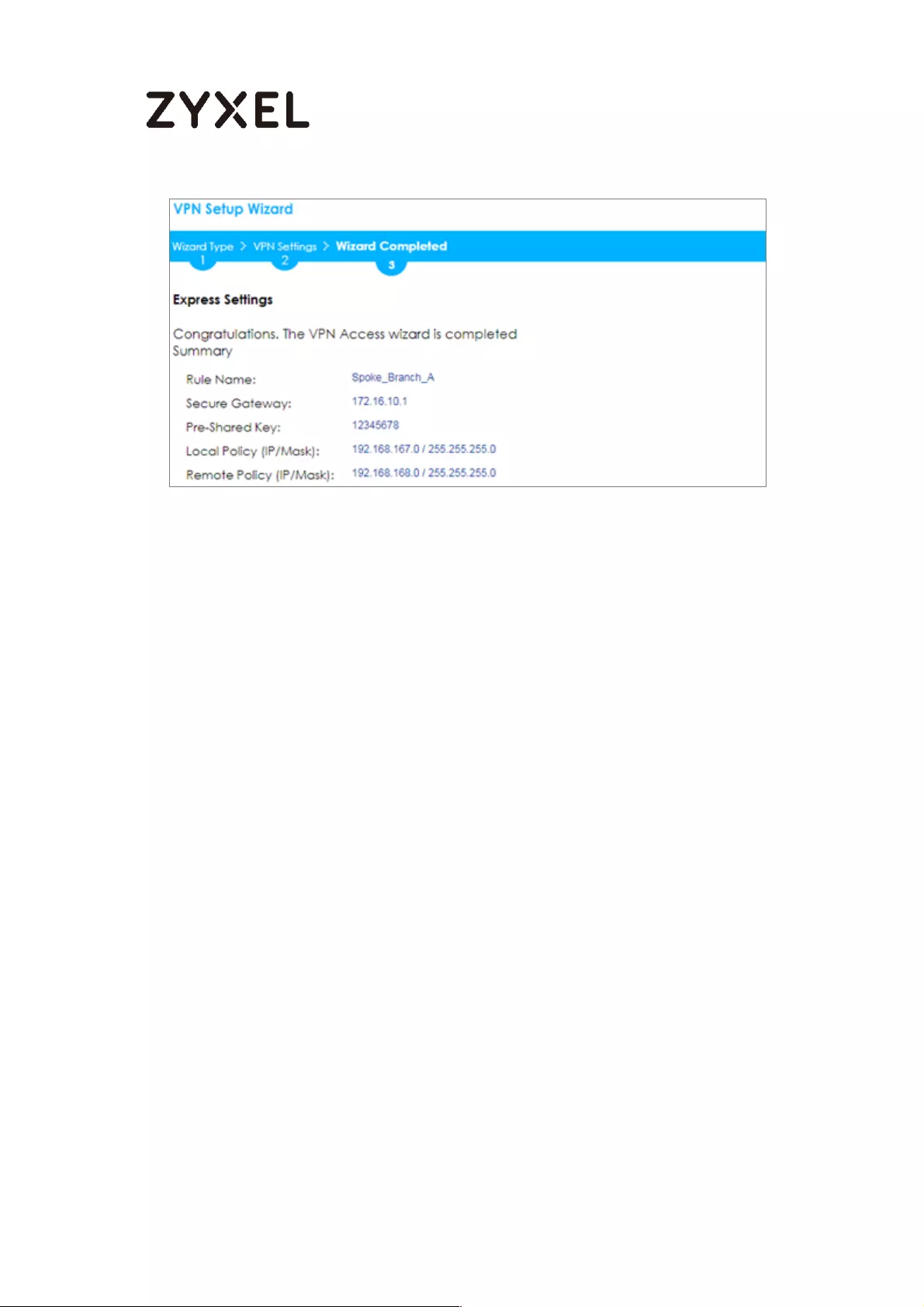
113/782
www.zyxel.com
Go to Network > Routing > Policy Route to add a Policy Route to allow traffic from
Spoke_Branch_A to Spoke_Branch_B.
Click Create new Object and set Address to be the local network behind the
Spoke_Branch_B. Select Source Address to be the local network behind the
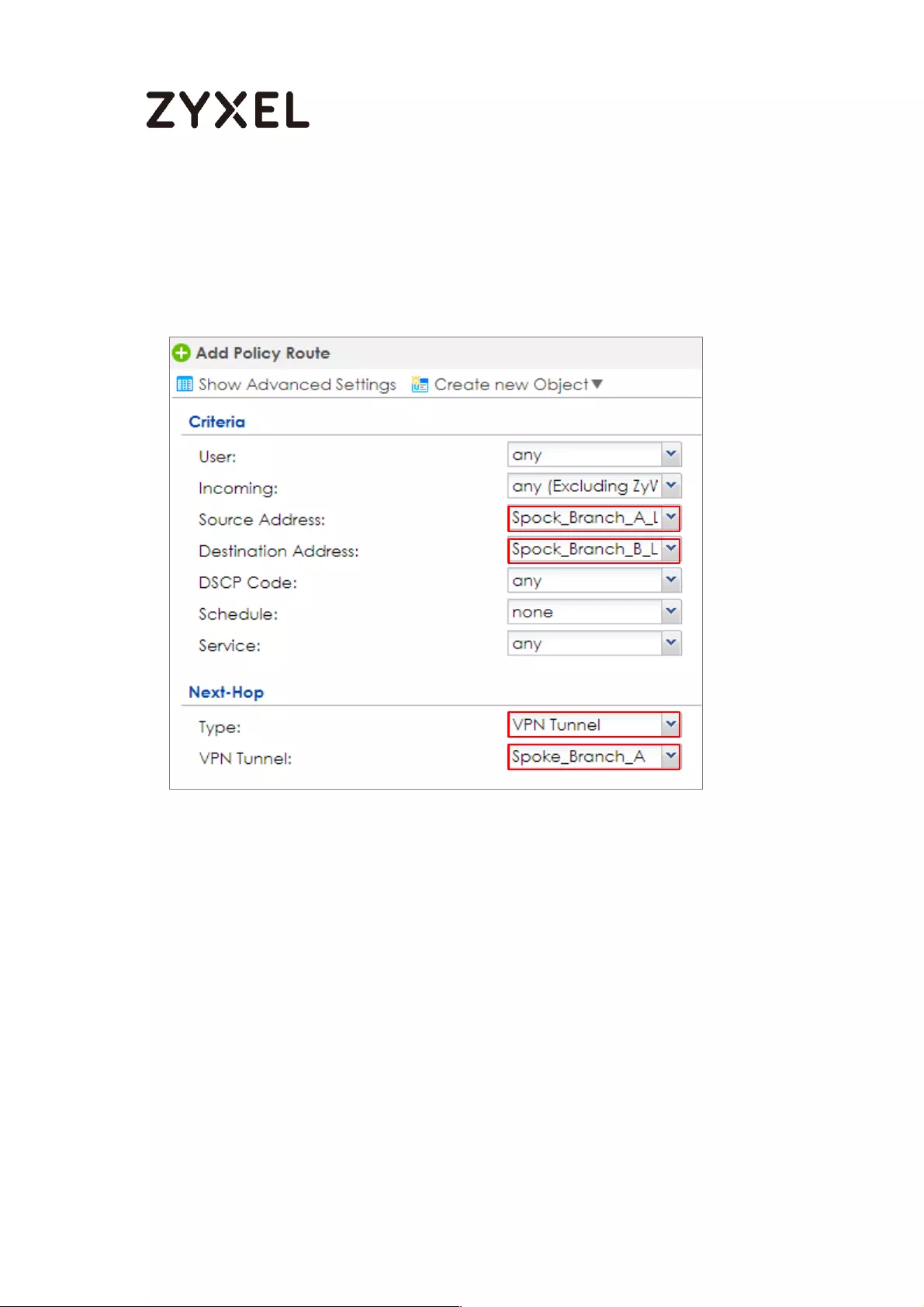
114/782
www.zyxel.com
Spoke_Branch_A. Then, scroll down the Destination Address list to choose the
newly created Spoke_Branch_B_LOCAL address. Click OK.
Network > Routing > Policy Route
Spoke_Branch_B
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
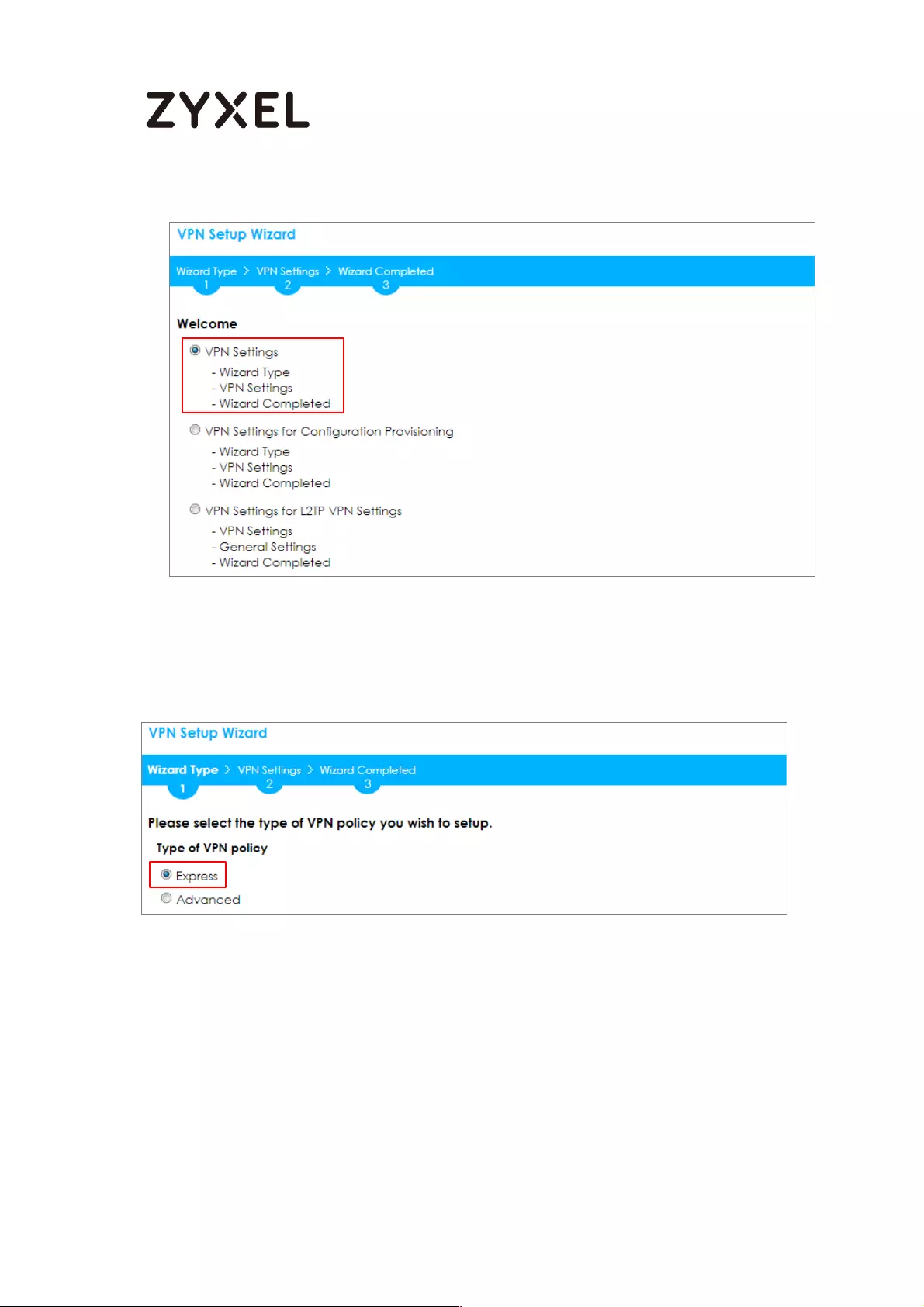
115/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
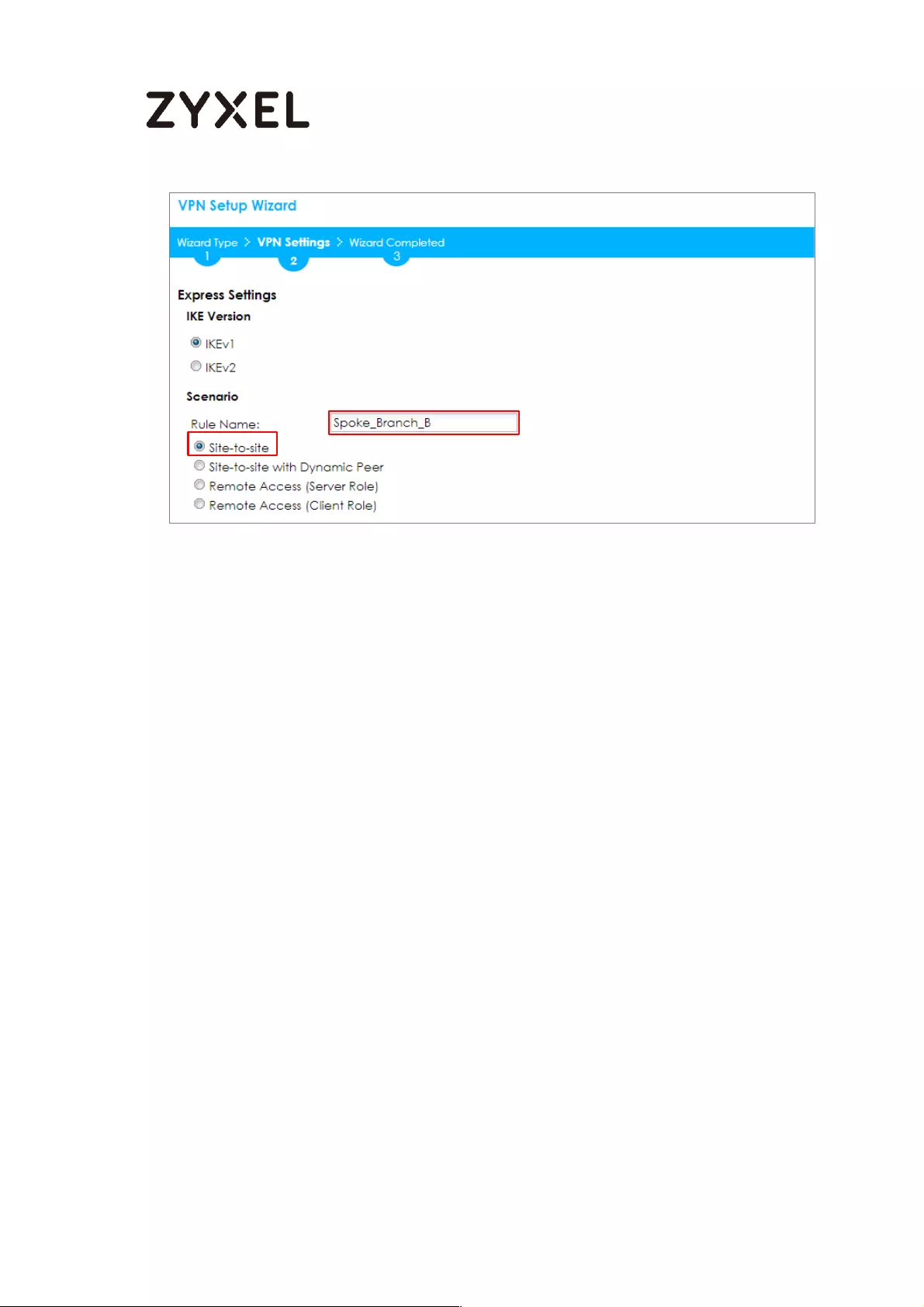
116/782
www.zyxel.com
Then, configure the Secure Gateway IP as the Hub_HQ’s Gateway IP address (in
the example, 172.16.10.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Hub_HQ’s Pre-Shared Key.
Set Local Policy to be the IP address range of the network connected to the
Spoke_Branch_B and Remote Policy to be the IP address range of the network
connected to the Hub_HQ. Click OK.
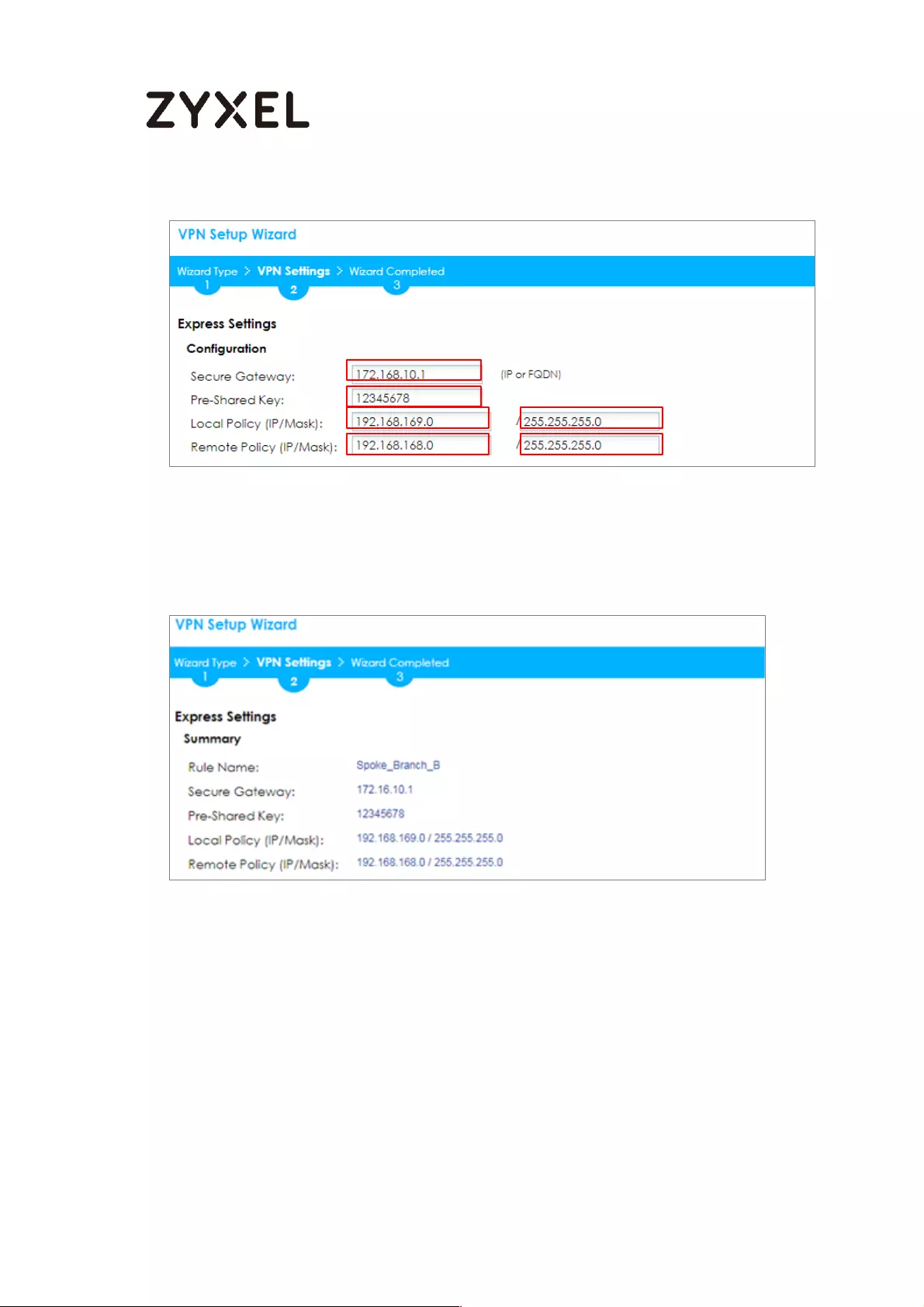
117/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings > Wizard
Completed
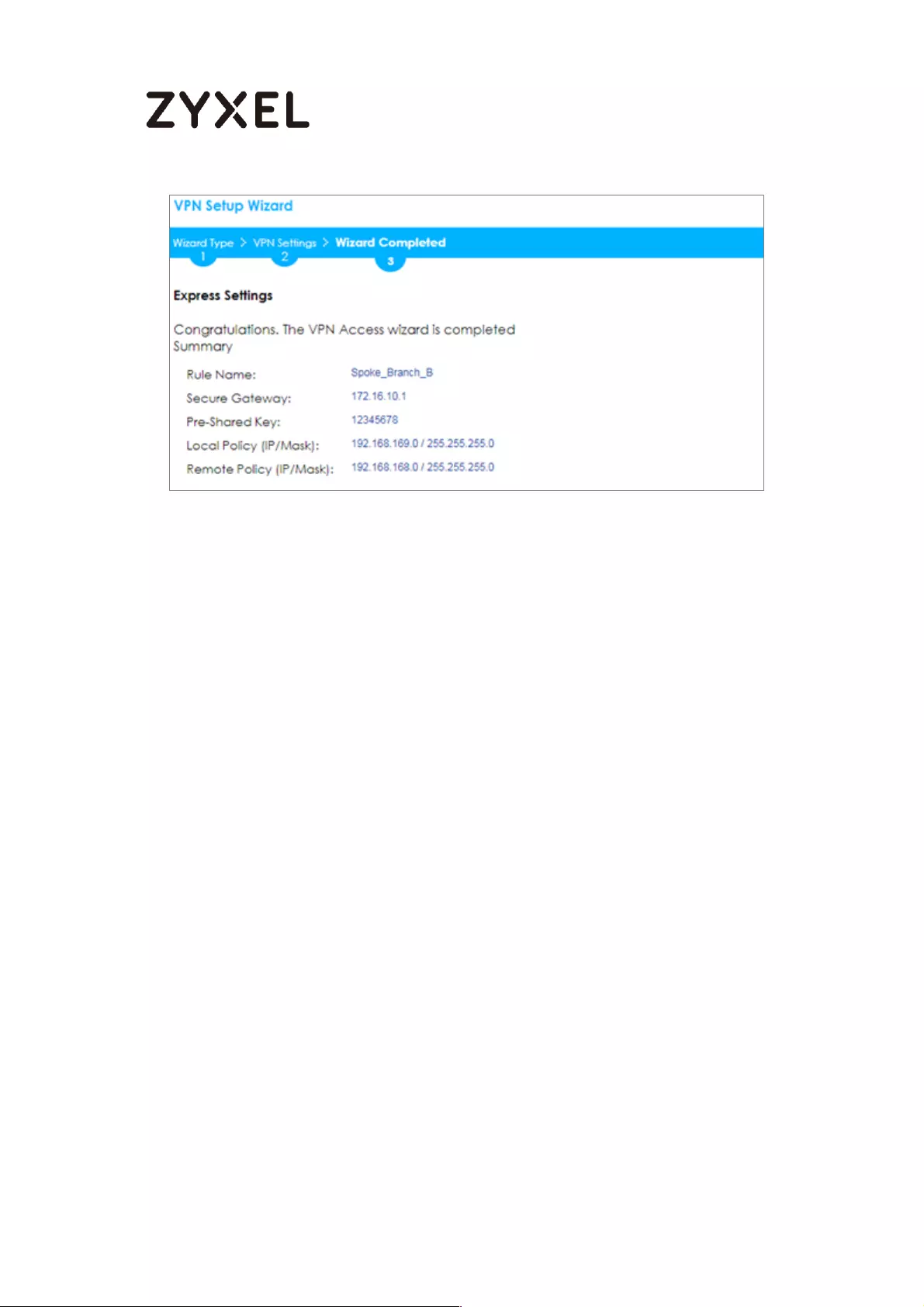
118/782
www.zyxel.com
Go to Network > Routing > Policy Route to add a Policy Route to allow traffic from
Spoke_Branch_B to Spoke_Branch_A.
Click Create new Object and set Address to be the local network behind the
Spoke_Branch_A. Select Source Address to be the local network behind the
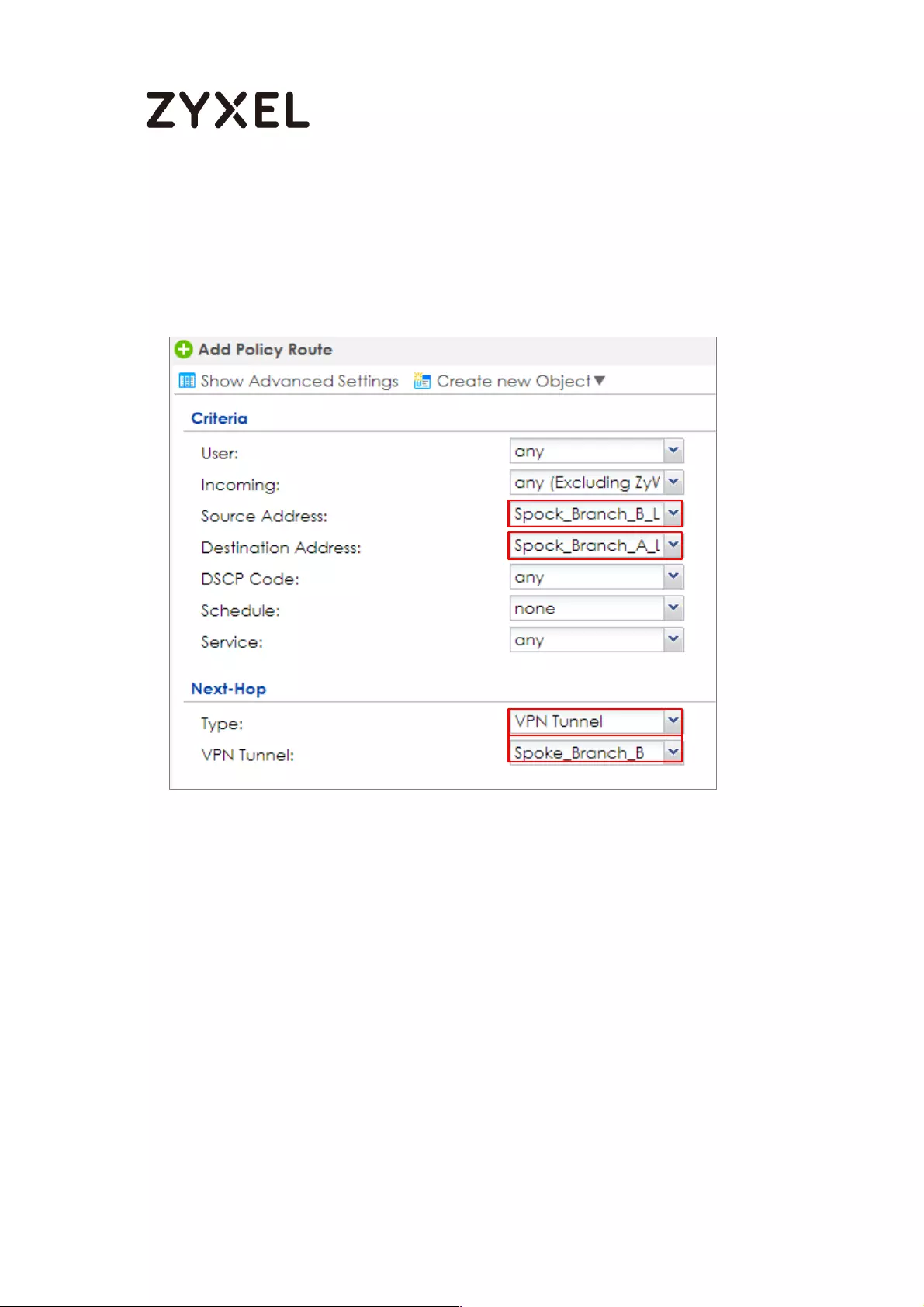
119/782
www.zyxel.com
Spoke_Branch_B. Then, scroll down the Destination Address list to choose the
newly created Spoke_Branch_A_LOCAL address. Click OK.
Network > Routing > Policy Route
Test the IPSec VPN Tunnel
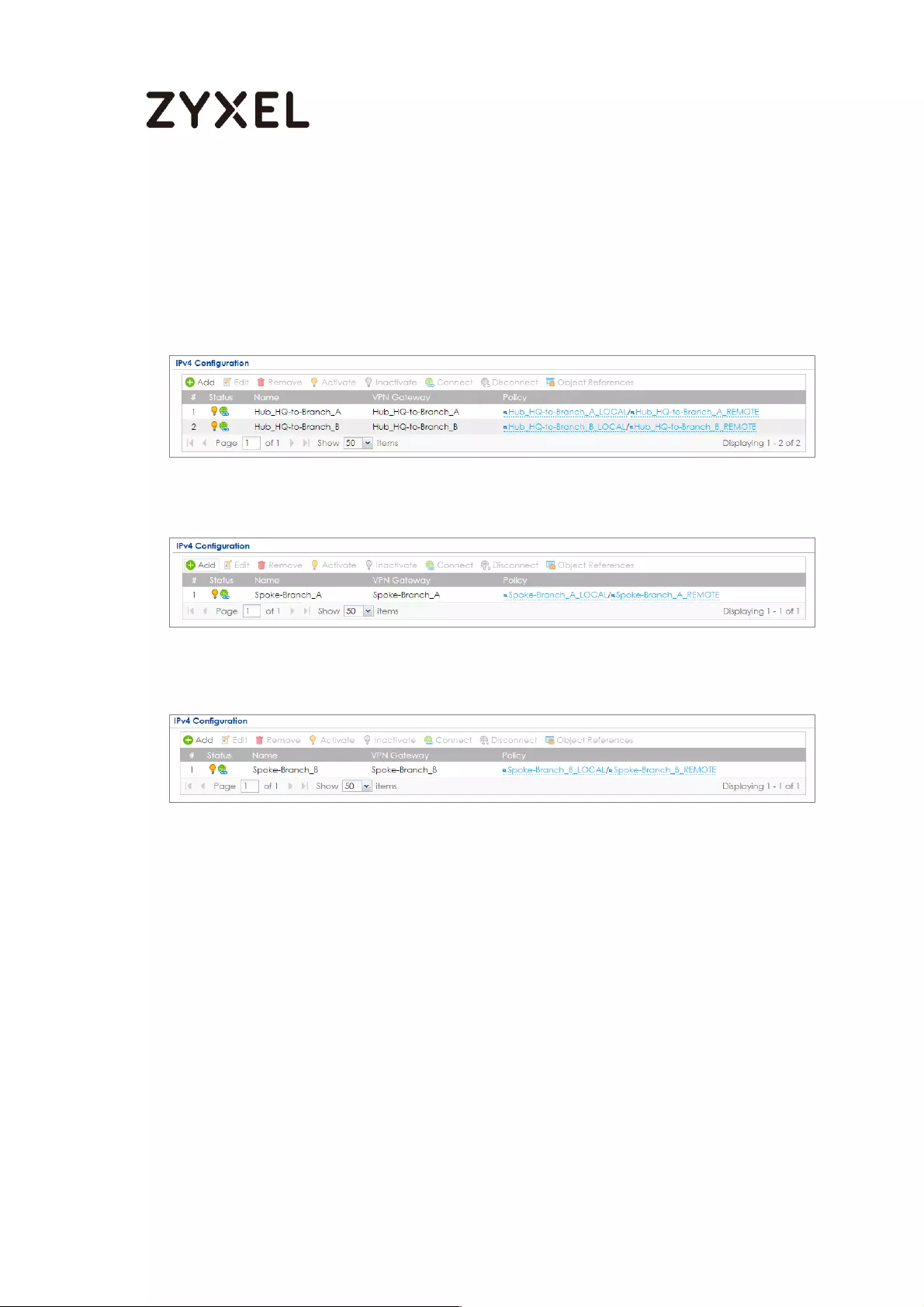
120/782
www.zyxel.com
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
Hub_HQ > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Spoke_Branch_A > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Spoke_Branch_B > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > IPSec > Hub_HQ-to-Branch_A
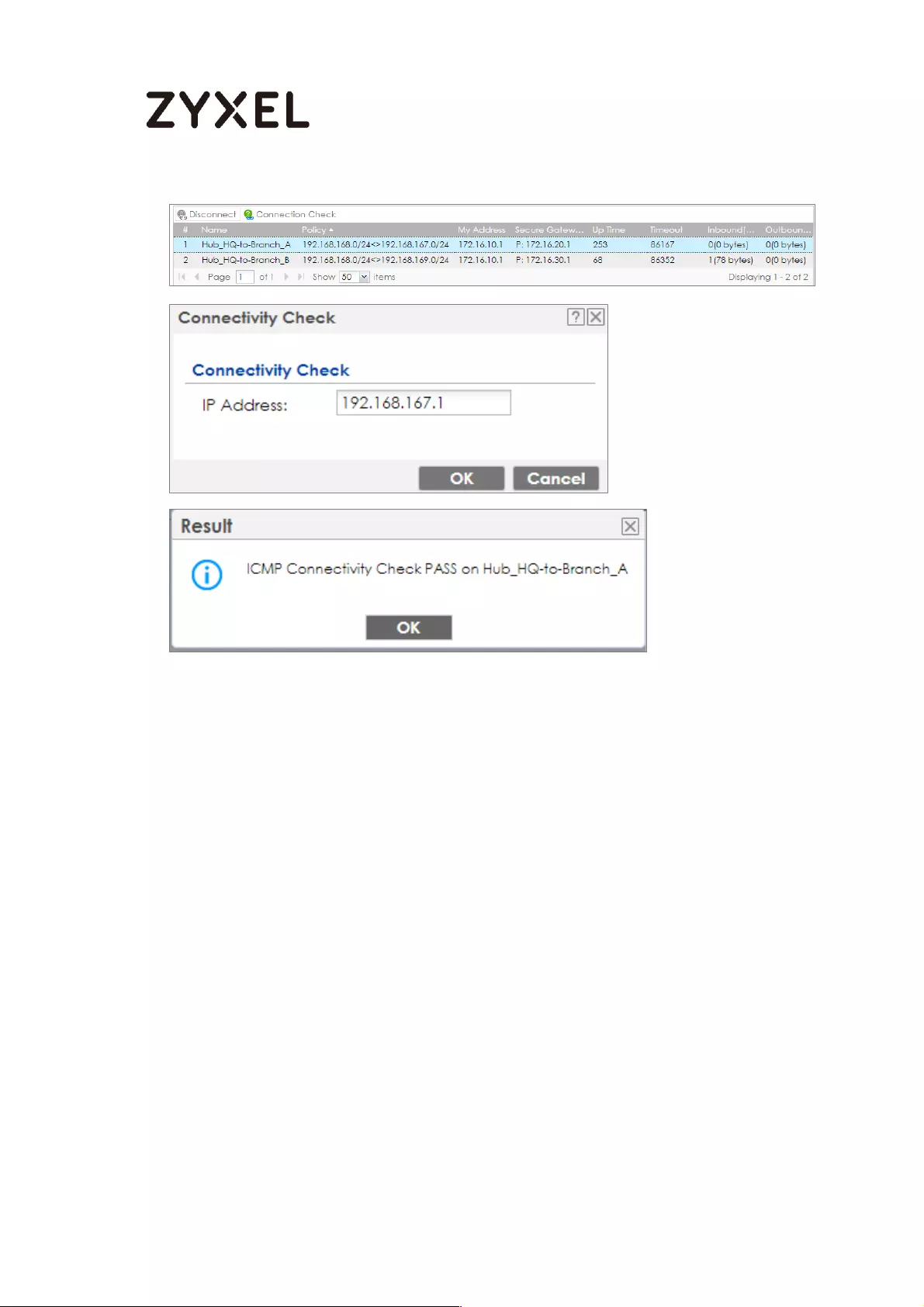
121/782
www.zyxel.com
Hub_HQ > MONITOR > VPN Monitor > IPSec > Hub_HQ-to-Branch_B
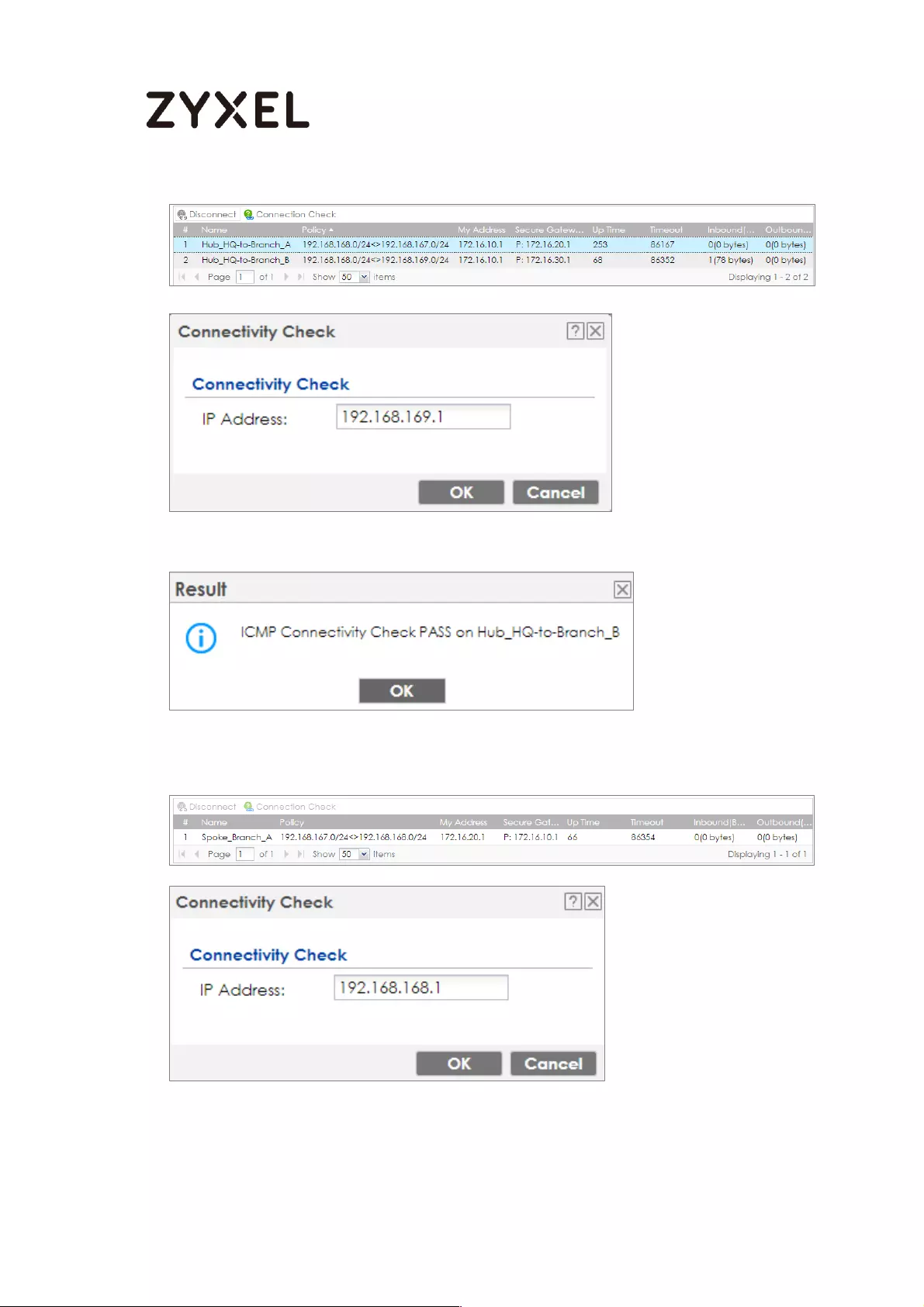
122/782
www.zyxel.com
Spoke_Branch_A > MONITOR > VPN Monitor > IPSec
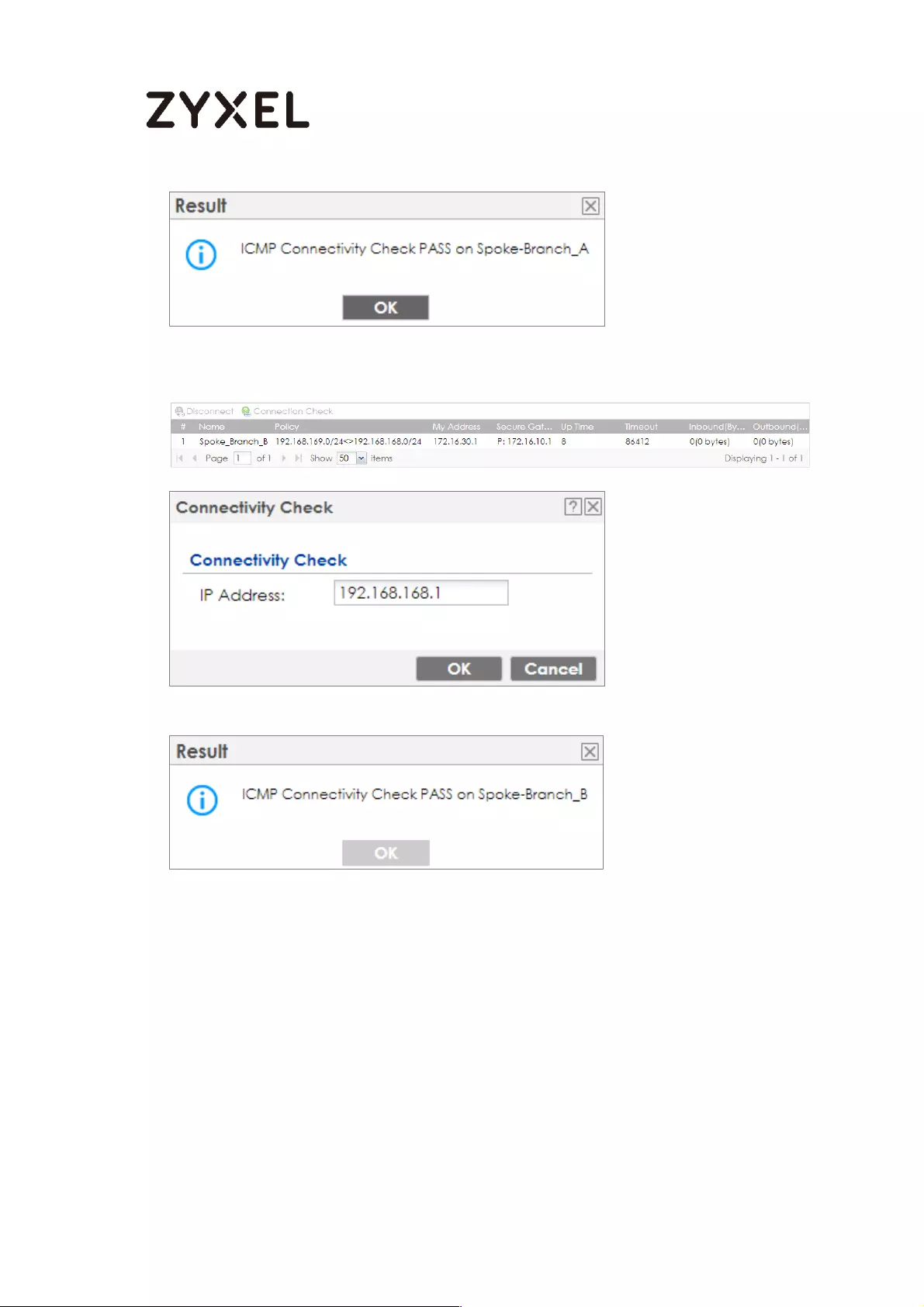
123/782
www.zyxel.com
Spoke_Branch_B > MONITOR > VPN Monitor > IPSec
What Could Go Wrong?
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. All ZyWALL/USG units must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.
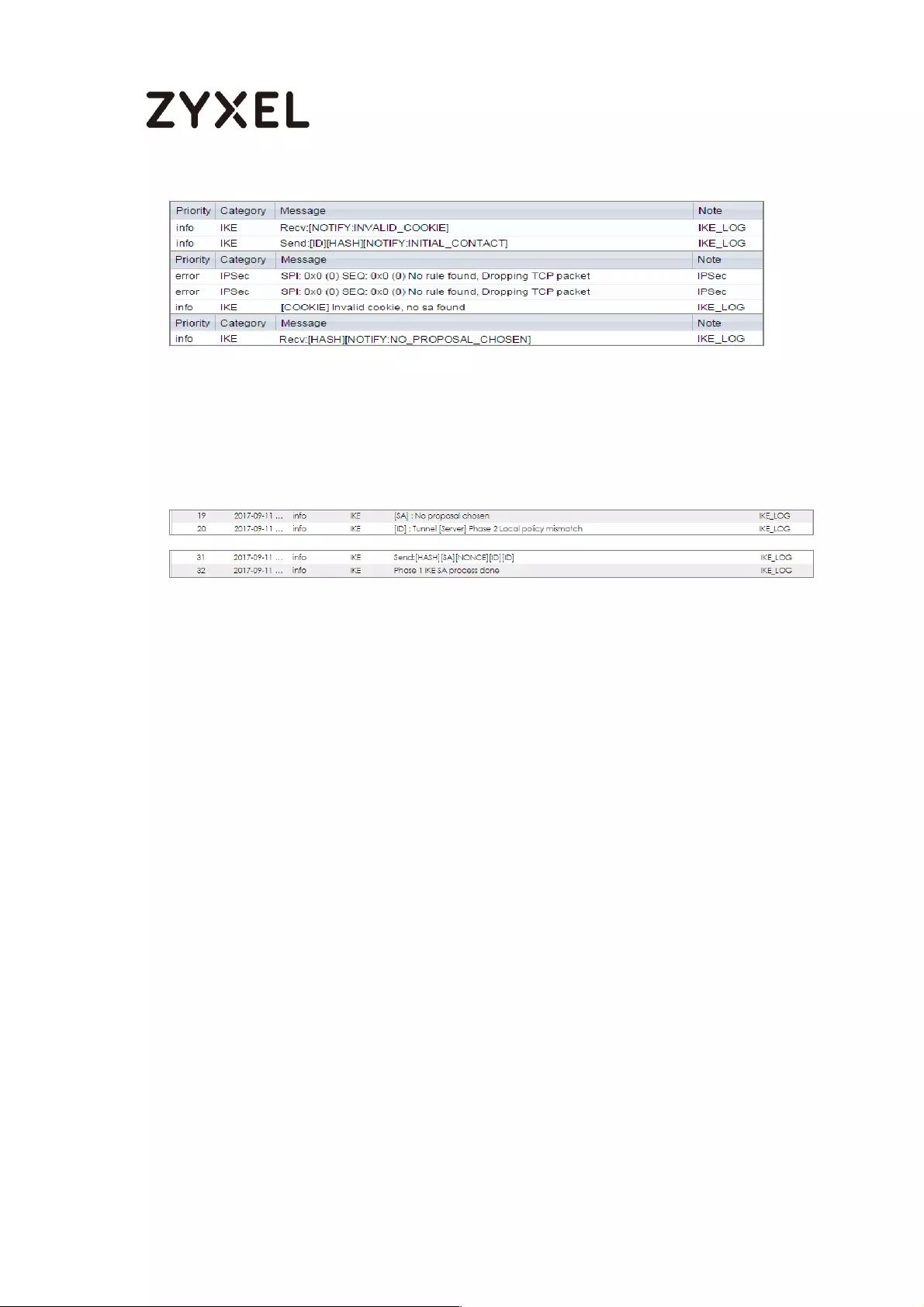
124/782
www.zyxel.com
If you see that Phase 1 IKE SA process done but still get [info] log message as
below, please check ZyWALL/USG and SonicWALL Phase 2 Settings. All
ZyWALL/USG units must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
Make sure the all ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE
uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
By default, NAT traversal is enabled on ZyWALL/USG, so please make sure the
remote IPSec device also has NAT traversal enabled.
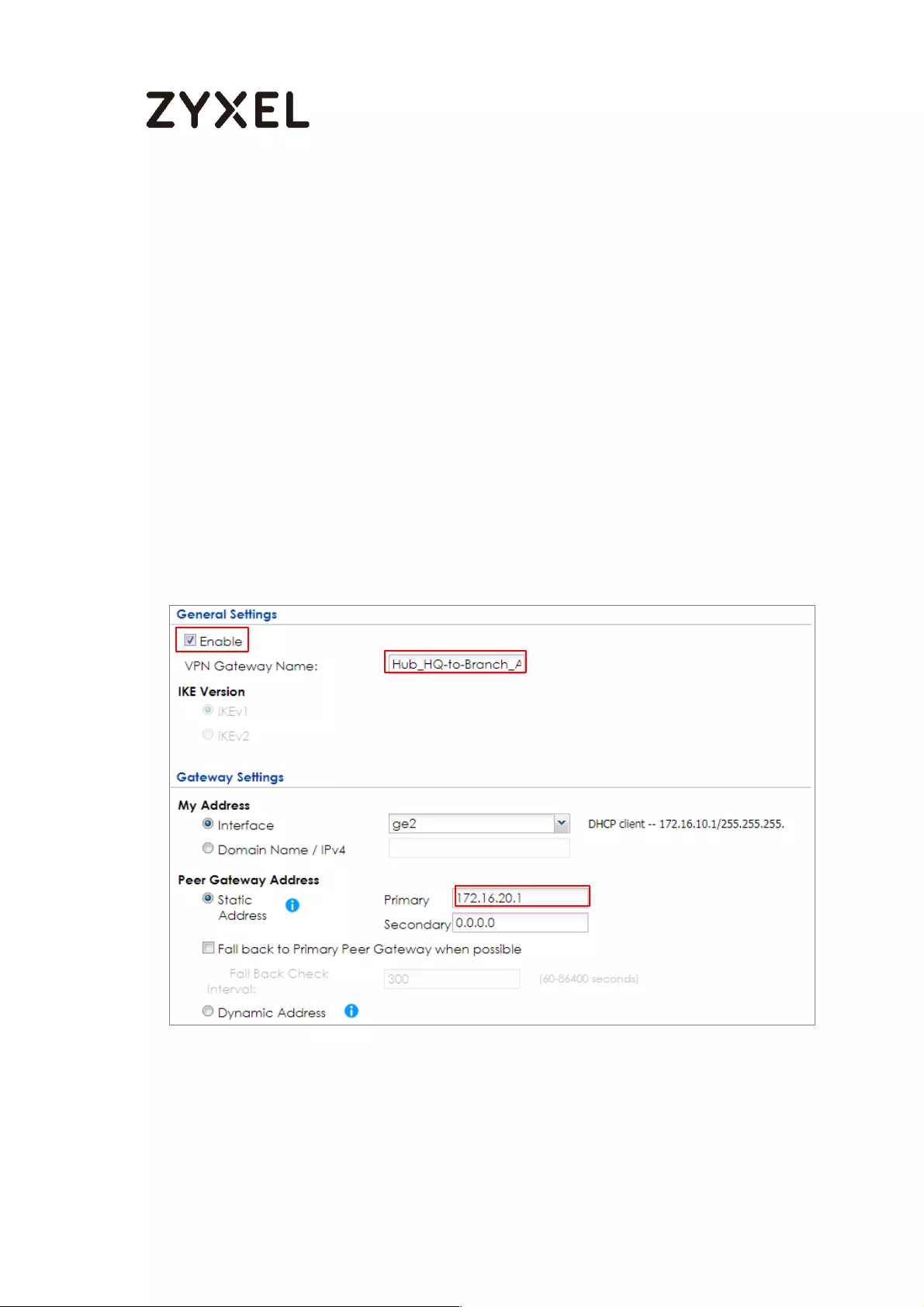
125/782
www.zyxel.com
Set Up the IPSec VPN Tunnel of ZyWALL/USG without Using VPN
Concentrator Hub_HQ-to-Branch_A
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Secure Gateway IP as the Branch A’s Gateway IP address (in the
example, 172.16.20.1). Type a secure Pre-Shared Key (8-32 characters) which must
match your Branch A’s Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway

126/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
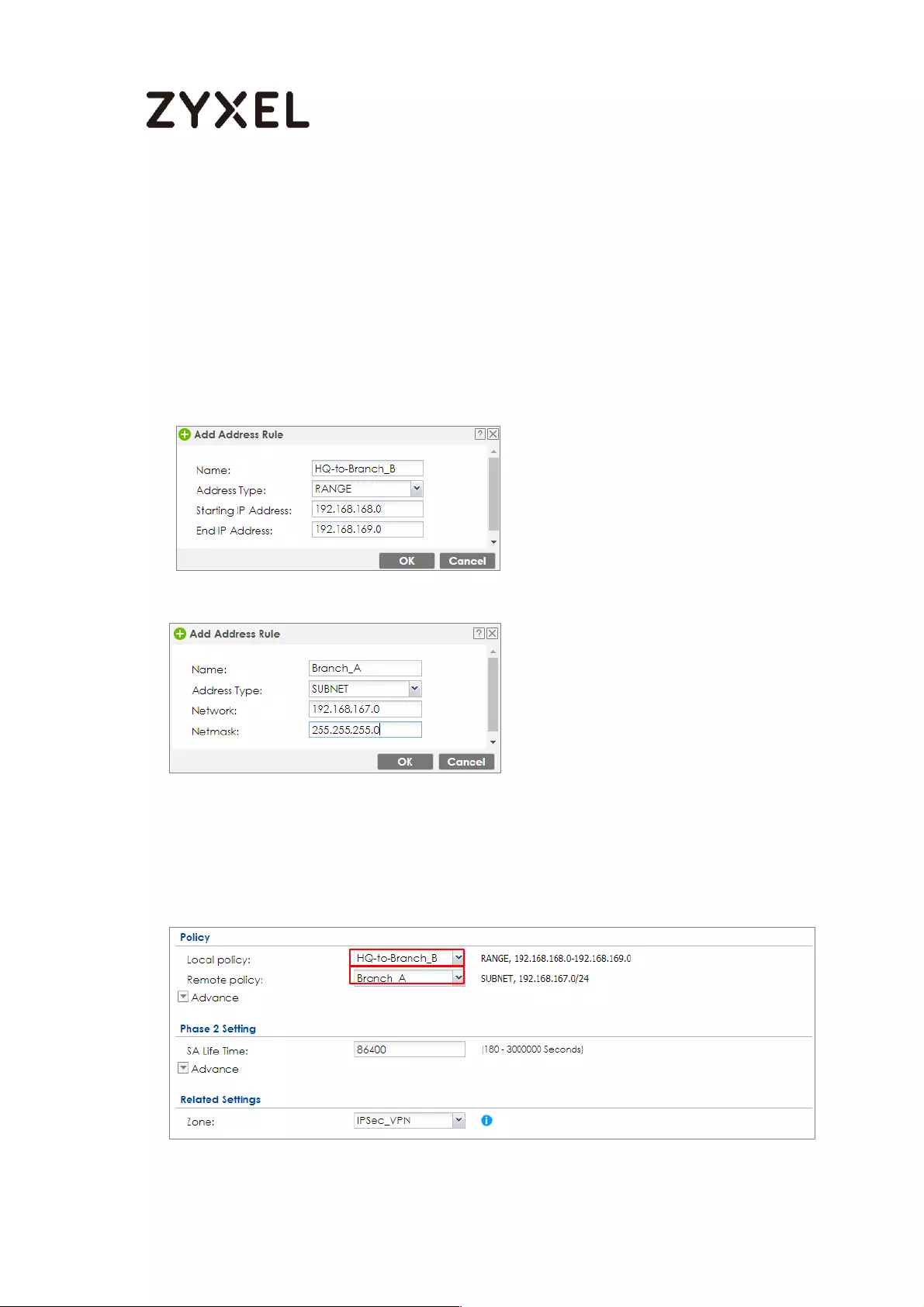
127/782
www.zyxel.com
Click Create new Object on the upper bar to add the address range of the local
network behind Hub_HQ to Branch_B and an address of local network behind
Branch A.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be HQ-to-Branch_B and Remote Policy to Branch_A which are
newly created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
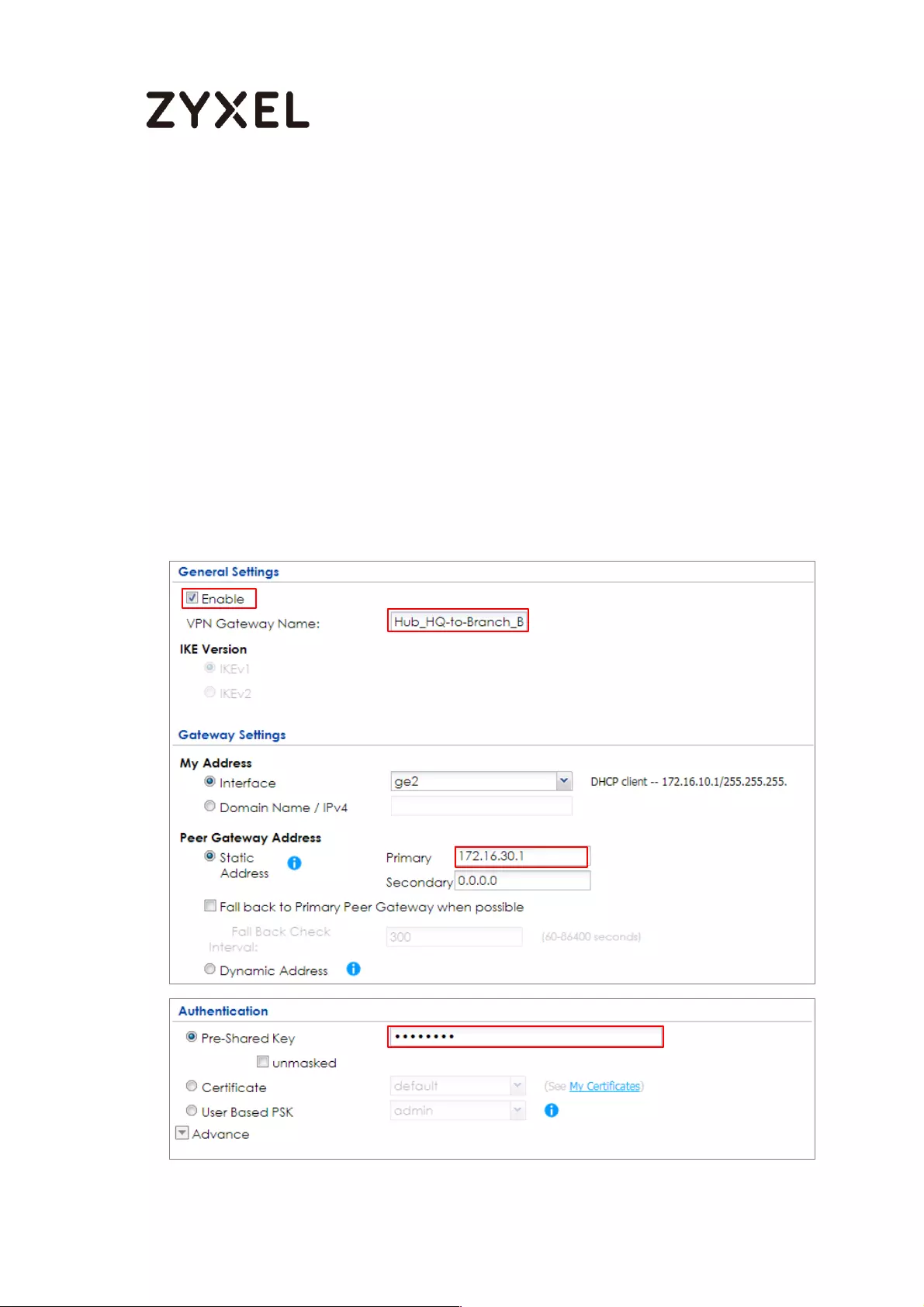
128/782
www.zyxel.com
Hub_HQ-to-Branch_B
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Secure Gateway IP as the Branch B’s Gateway IP address (in
the example, 172.16.30.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Branch B’s Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
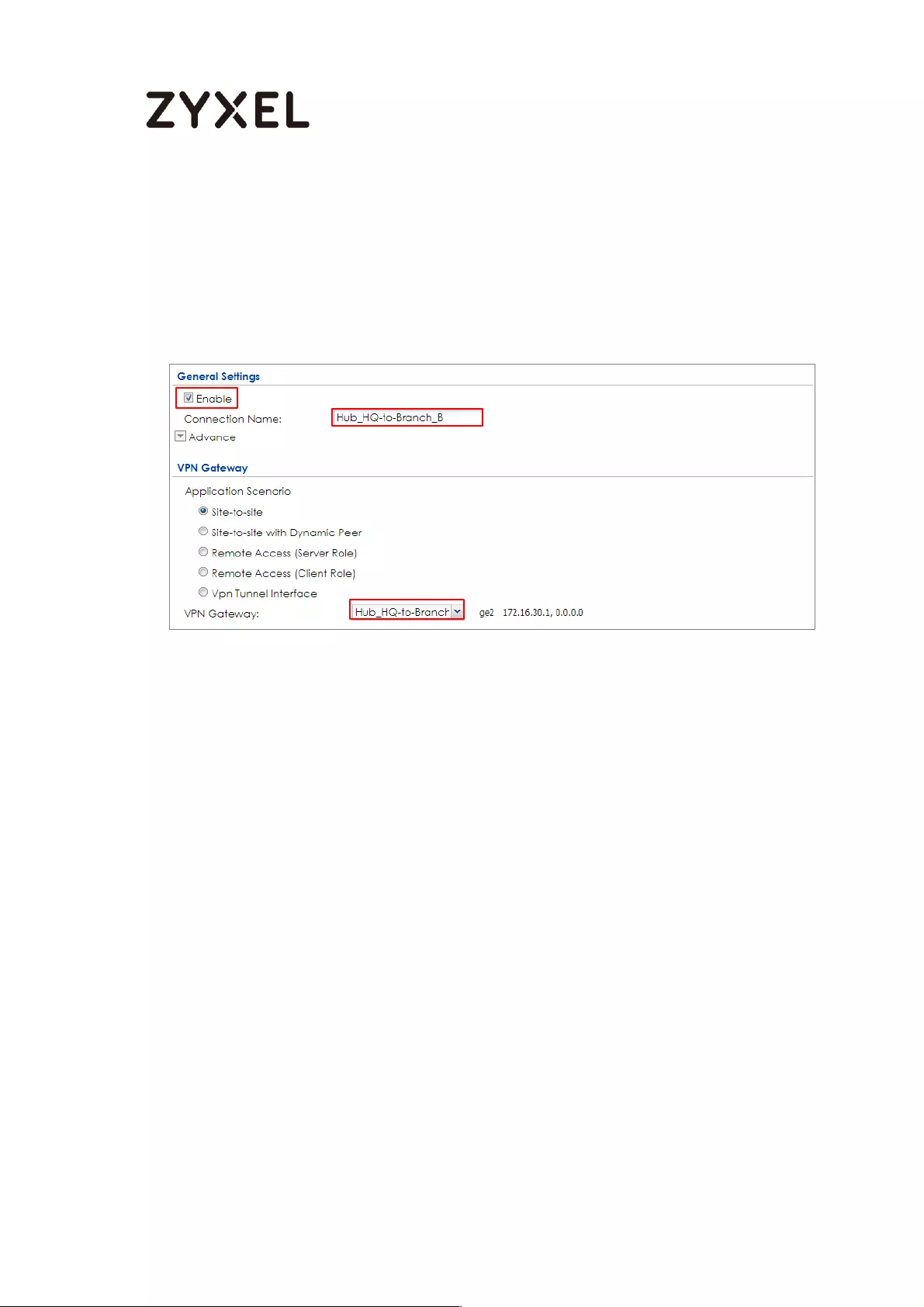
129/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
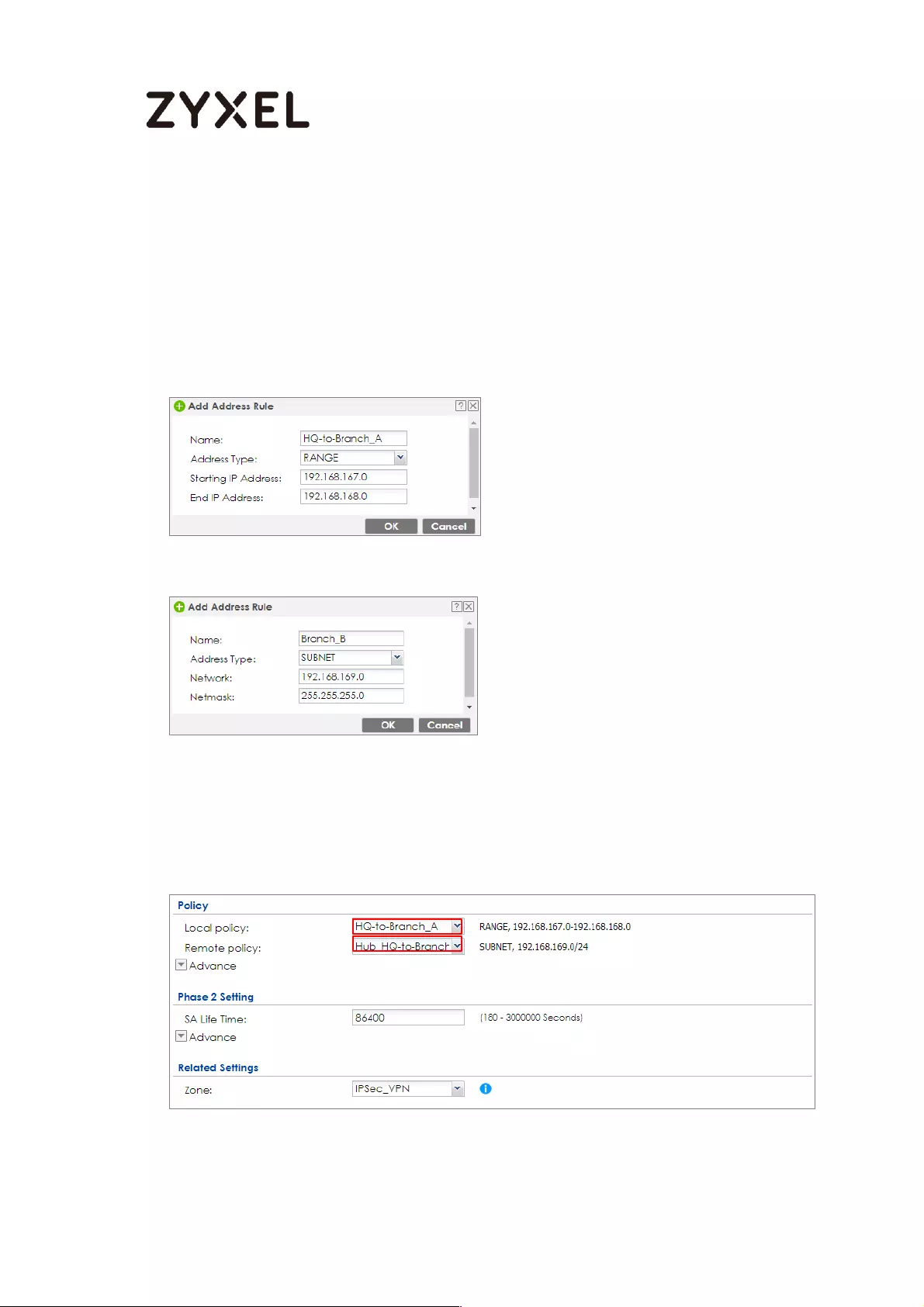
130/782
www.zyxel.com
Click Create new Object on the upper bar to add the address range of the local
network behind Hub_HQ to Branch_A and an address of local network behind
Branch B.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be HQ-to-Branch_B and Remote Policy to Branch_B which are
newly created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
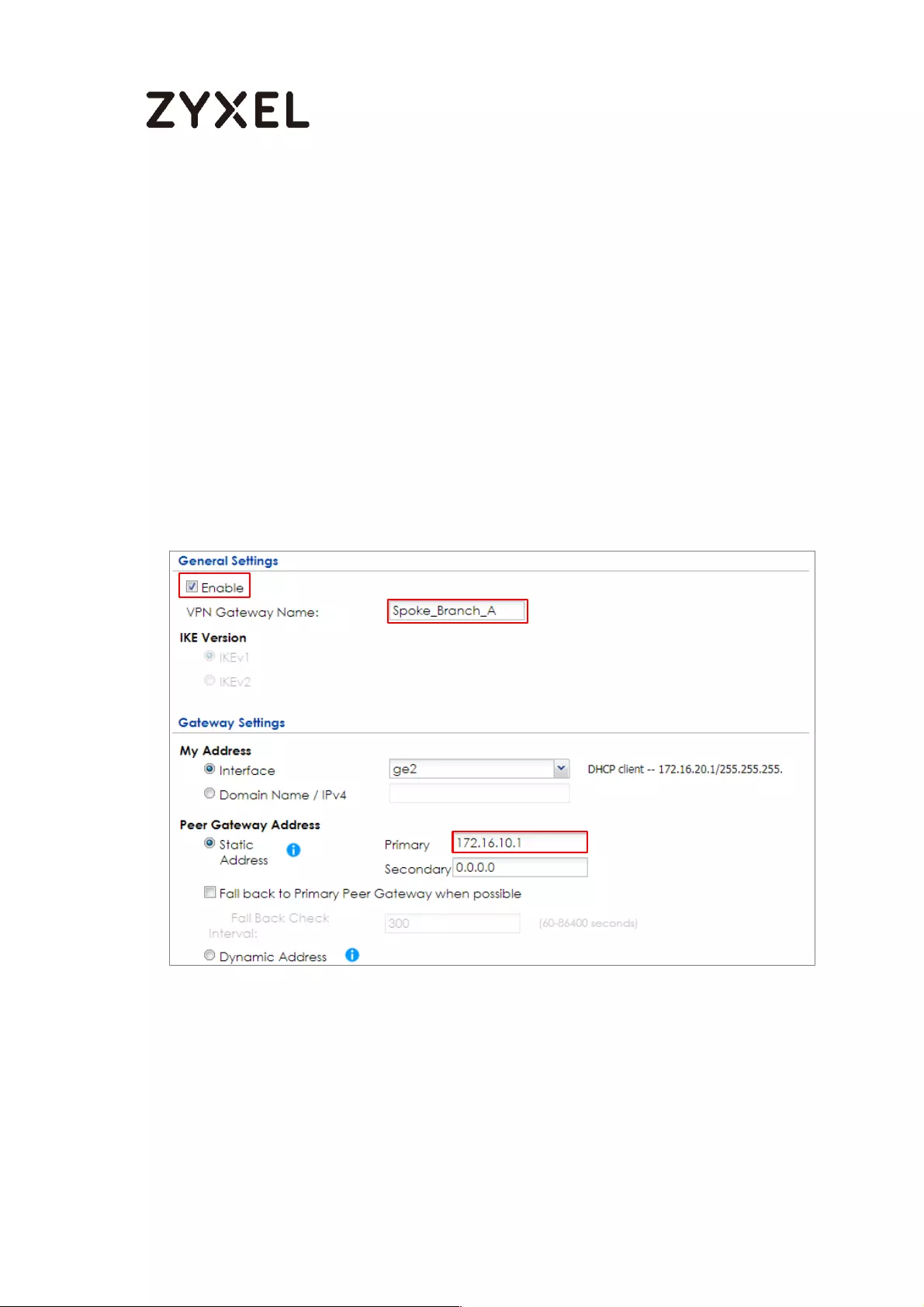
131/782
www.zyxel.com
Spoke_Branch_A
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Secure Gateway IP as the Hub_HQ’s Gateway IP address (in
the example, 172.16.10.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Hub_HQ’s Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
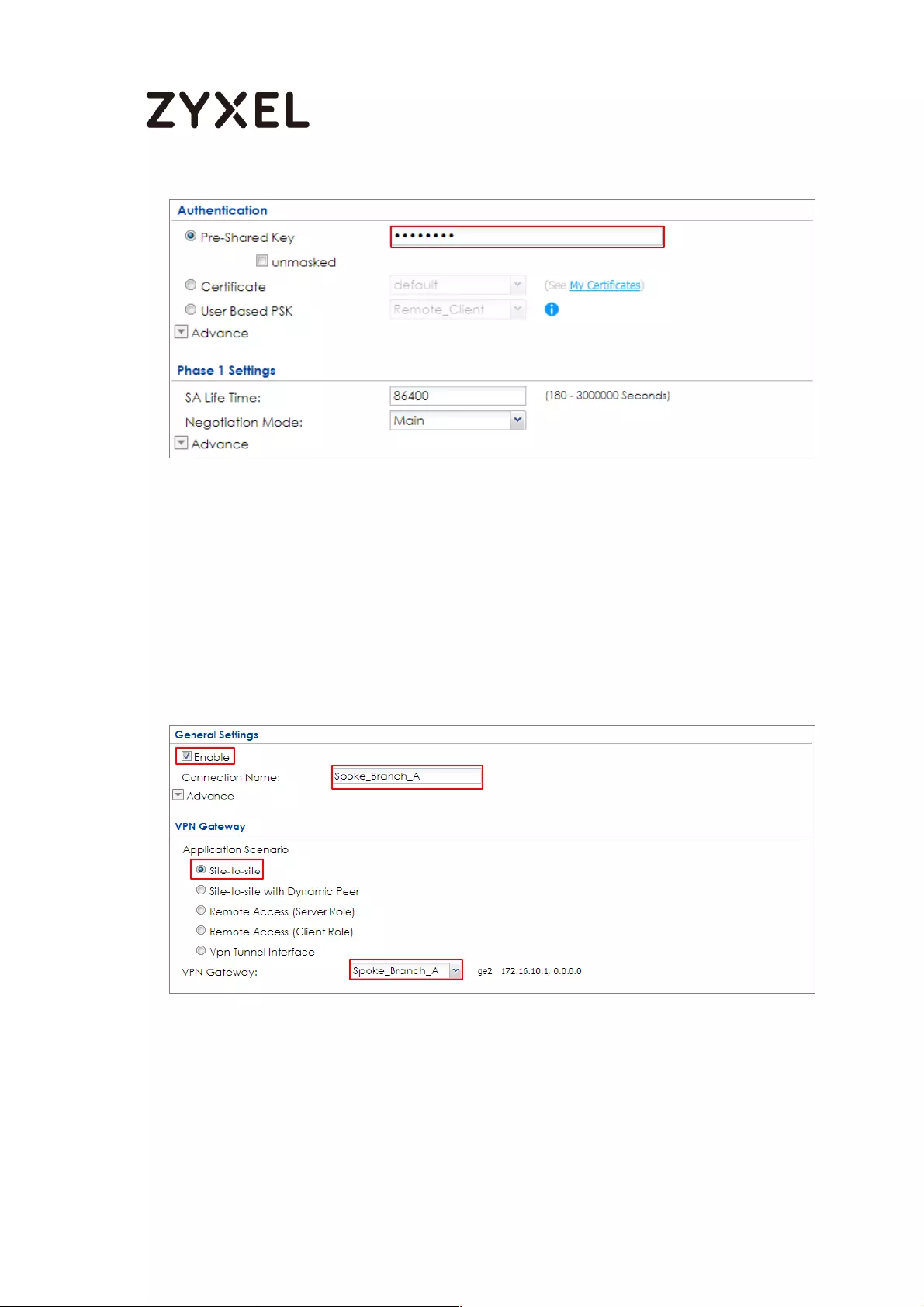
132/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
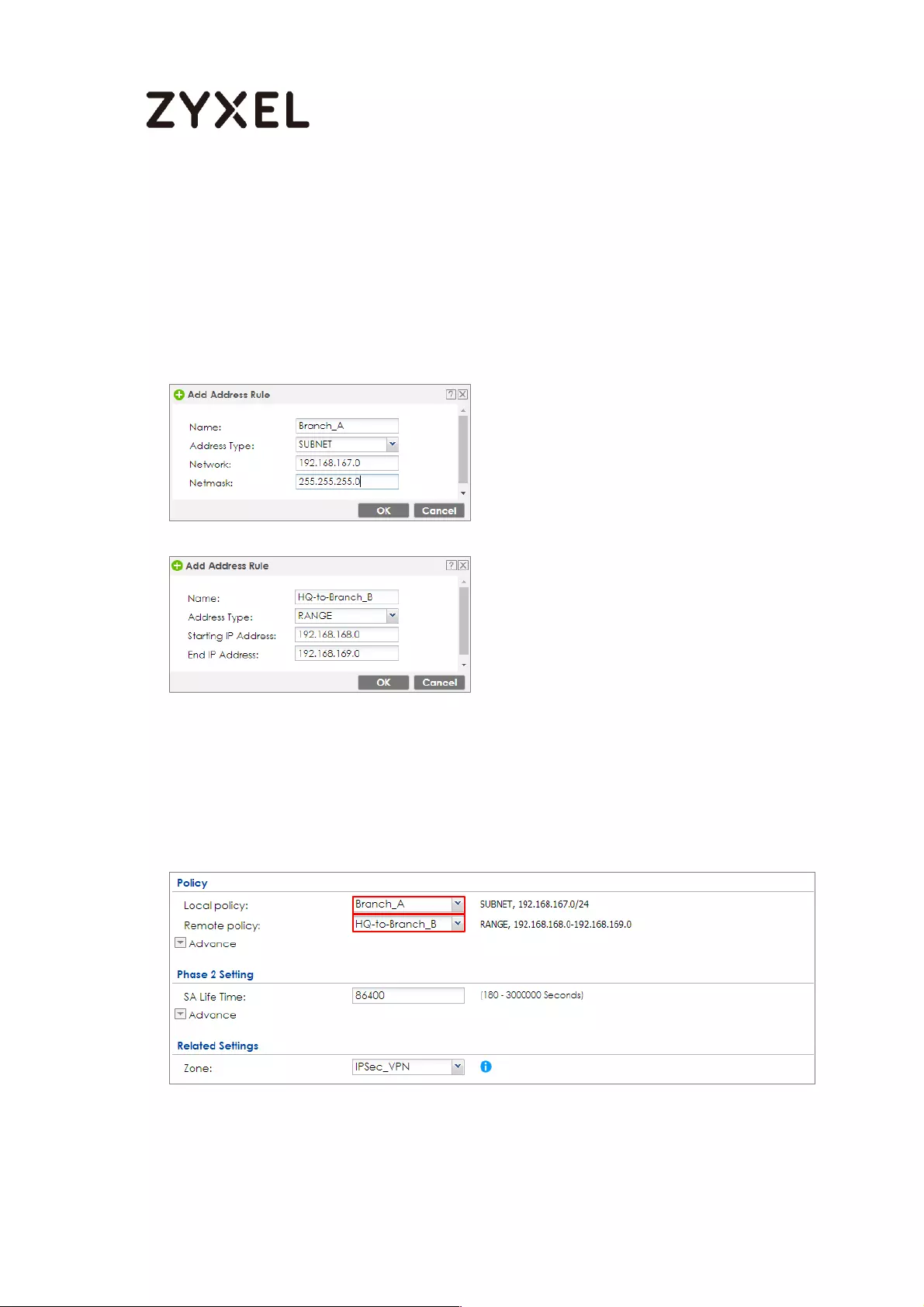
133/782
www.zyxel.com
Click Create new Object on the upper bar to add the address of the local
network behind Branch A and the address range of the local network behind
Hub_HQ to Branch_B.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be Branch_A and Remote Policy to HQ-to-Branch_B which are
newly created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
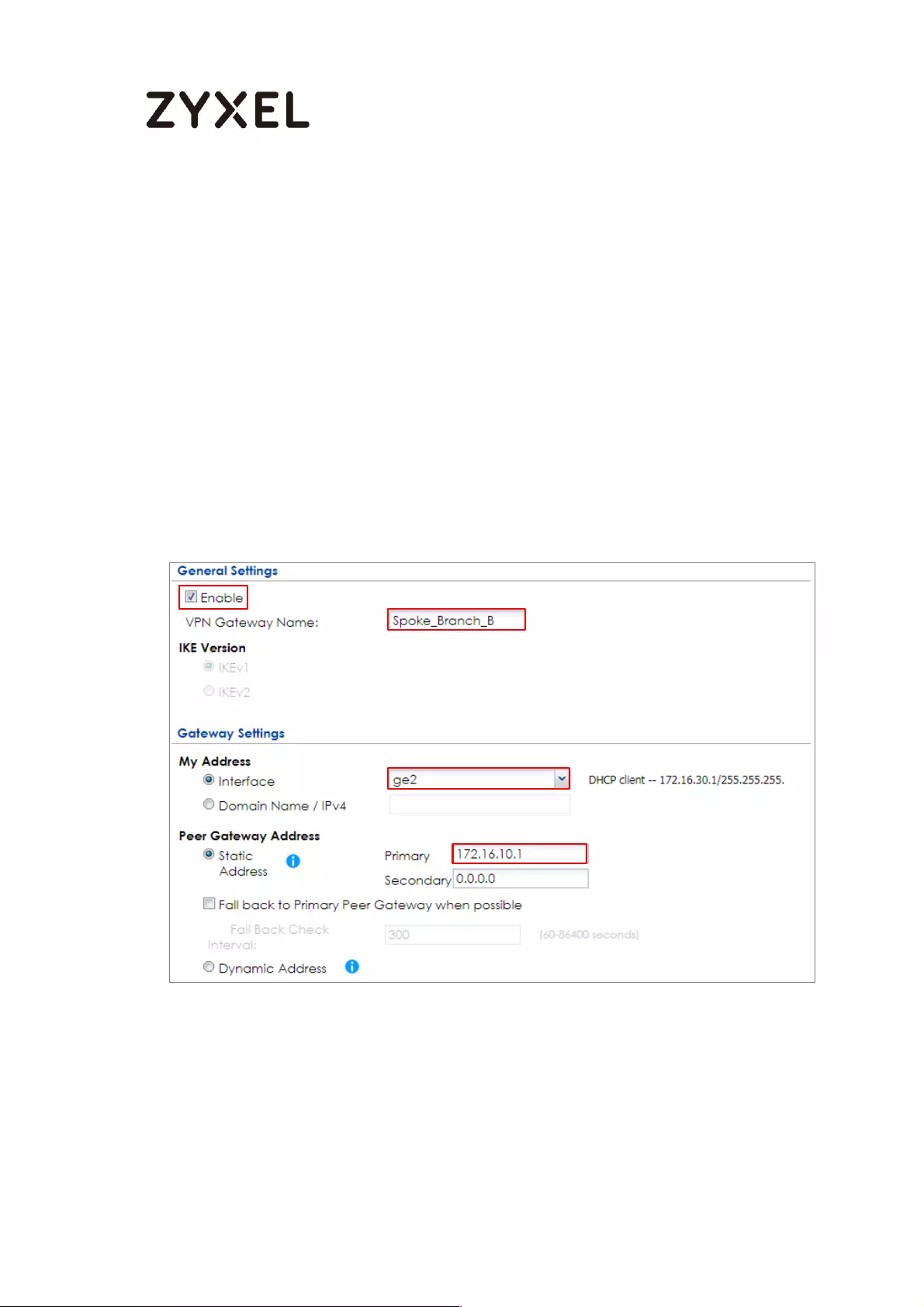
134/782
www.zyxel.com
Spoke_Branch_B
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Secure Gateway IP as the Hub_HQ’s Gateway IP address (in
the example, 172.16.10.1). Type a secure Pre-Shared Key (8-32 characters) which
must match your Hub_HQ’s Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
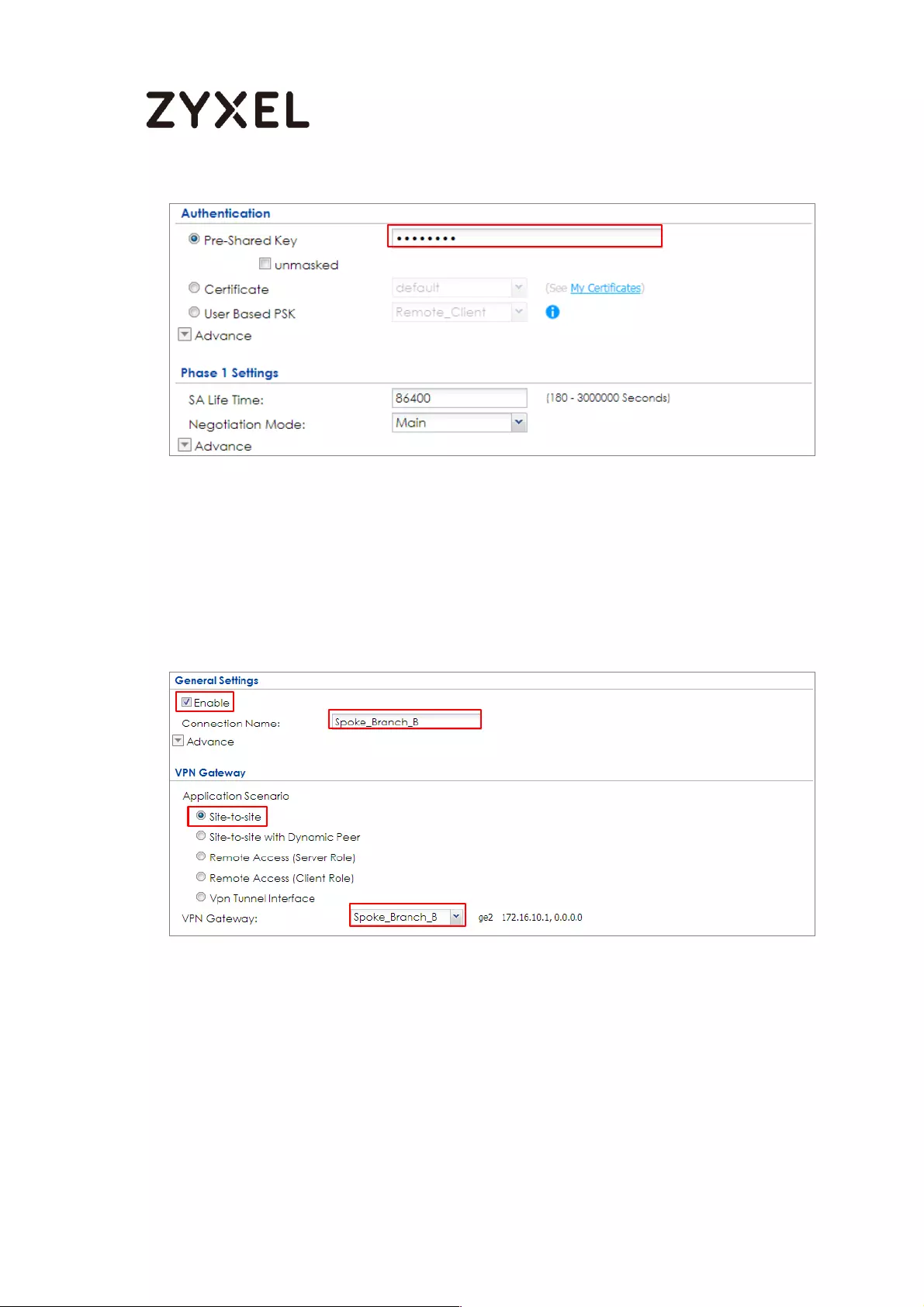
135/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
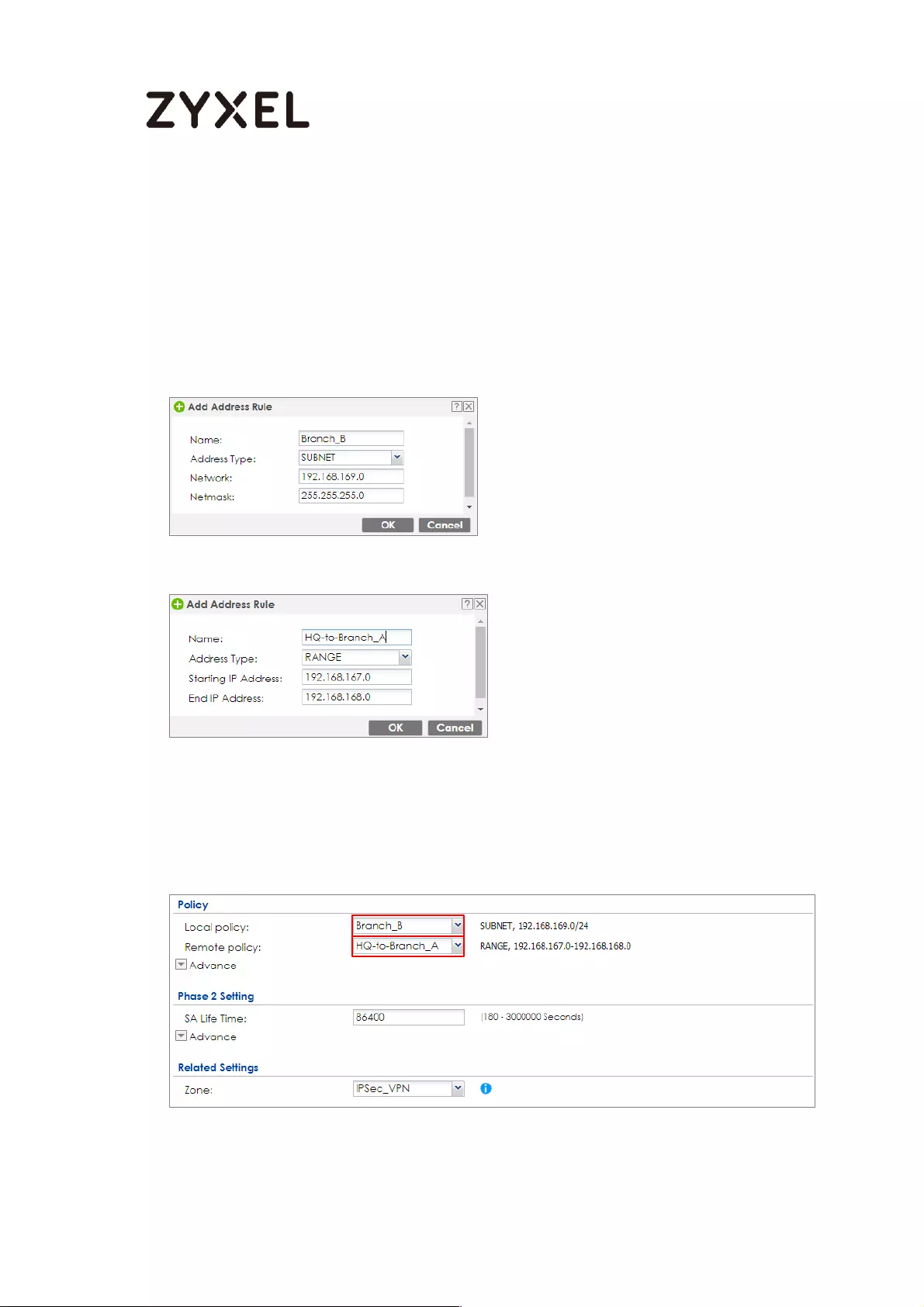
136/782
www.zyxel.com
Click Create new Object on the upper bar to add the address of local network
behind Branch B and address range of local network behind Hub_HQ to
Branch_A.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be Branch_B and Remote Policy to HQ-to-Branch_A which are
newly created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
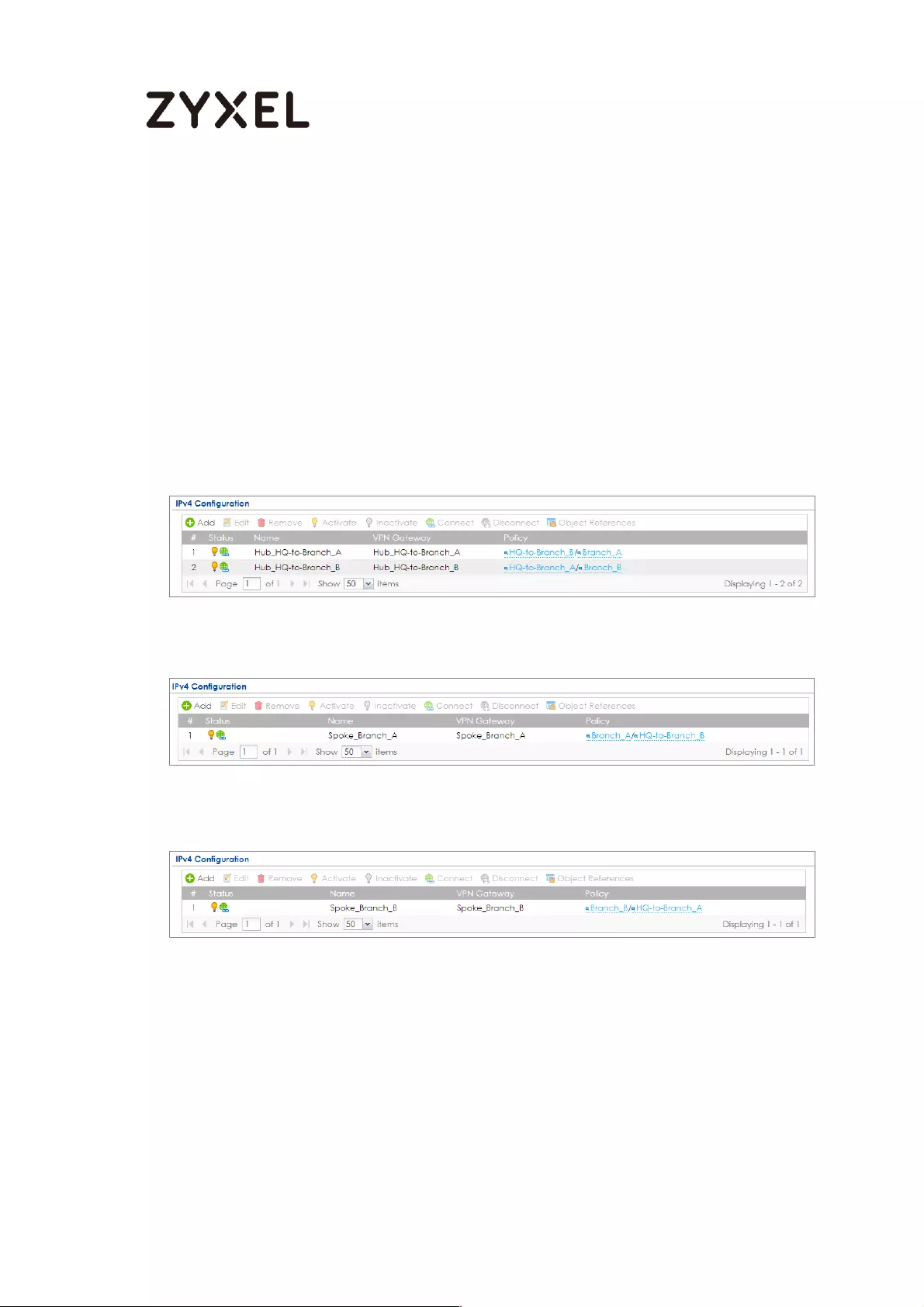
137/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
Hub_HQ > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Spoke_Branch_A > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Spoke_Branch_B > CONFIGURATION > VPN > IPSec VPN > VPN Connection

138/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > IPSec > Hub_HQ-to-Branch_A
Hub_HQ > MONITOR > VPN Monitor > IPSec > Hub_HQ-to-Branch_B

139/782
www.zyxel.com
Spoke_Branch_A > MONITOR > VPN Monitor > IPSec
Spoke_Branch_B > MONITOR > VPN Monitor > IPSec

140/782
www.zyxel.com
What Could Go Wrong?
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. All ZyWALL/USG units must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.

141/782
www.zyxel.com
If you see that Phase 1 IKE SA process done but still get [info] log message as
below, please check ZyWALL/USG and SonicWALL Phase 2 Settings. All
ZyWALL/USG units must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
Make sure the all ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE
uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
By default, NAT traversal is enabled on ZyWALL/USG, so please make sure the
remote IPSec device also has NAT traversal enabled.
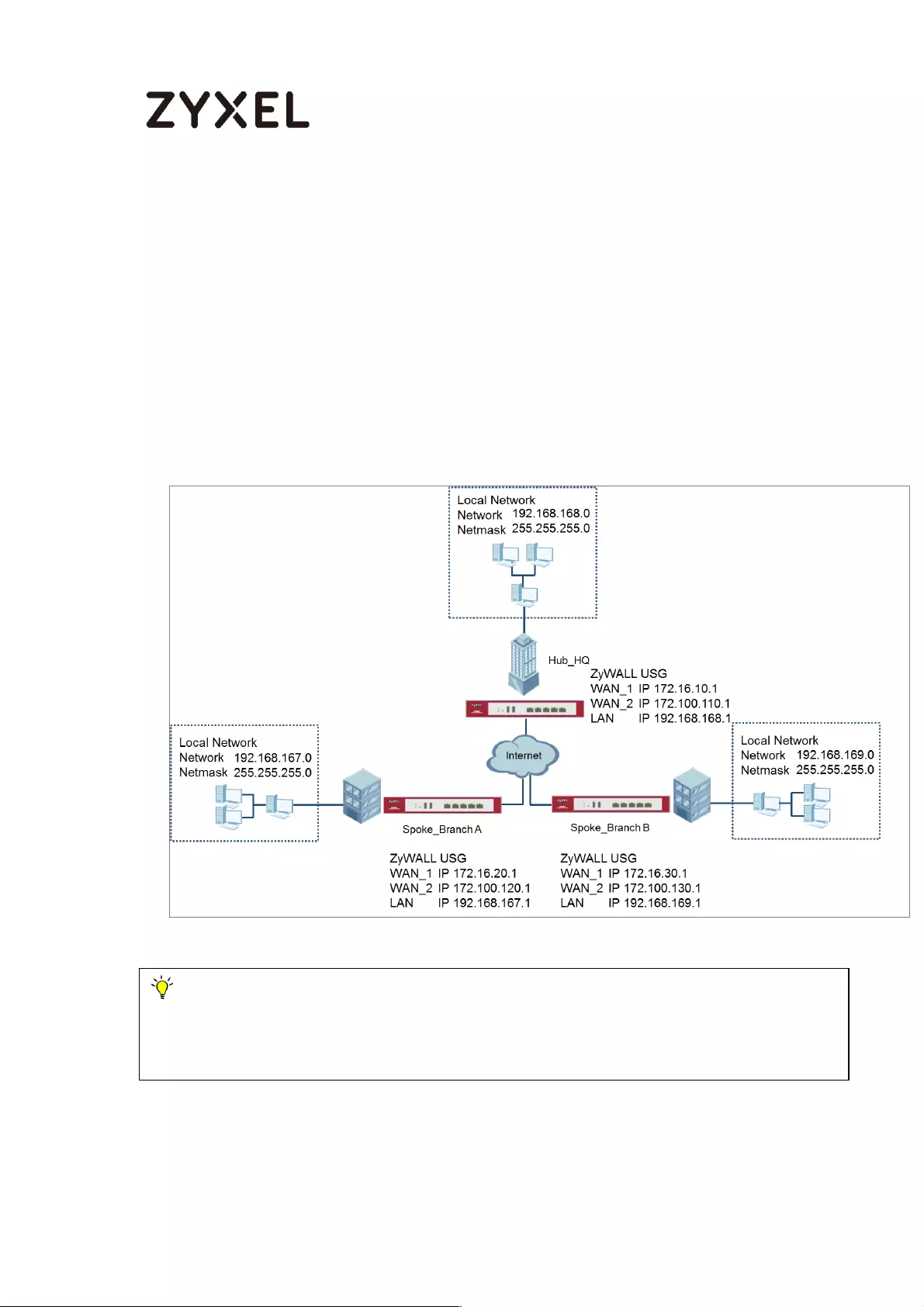
142/782
www.zyxel.com
How to Use Dual-WAN to Perform Fail-Over on VPN Using the
VPN Concentrator
This is an example of using Dual-WAN to perform fail-over on a hub-and-spoke
VPN with the HQ ZyWALL/USG as the hub and spoke VPNs to Branches A and B.
When the VPN tunnel is configured, traffic passes between branches via the hub
(HQ). Traffic can also pass between spoke-and-spoke through the hub. If the
primary WAN interface is unavailable, the backup WAN interface will be used.
When the primary WAN interface is available again, traffic will use that interface
again.
Hub & Spoken VPN Using the VPN Concentrator with Backup
WAN
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
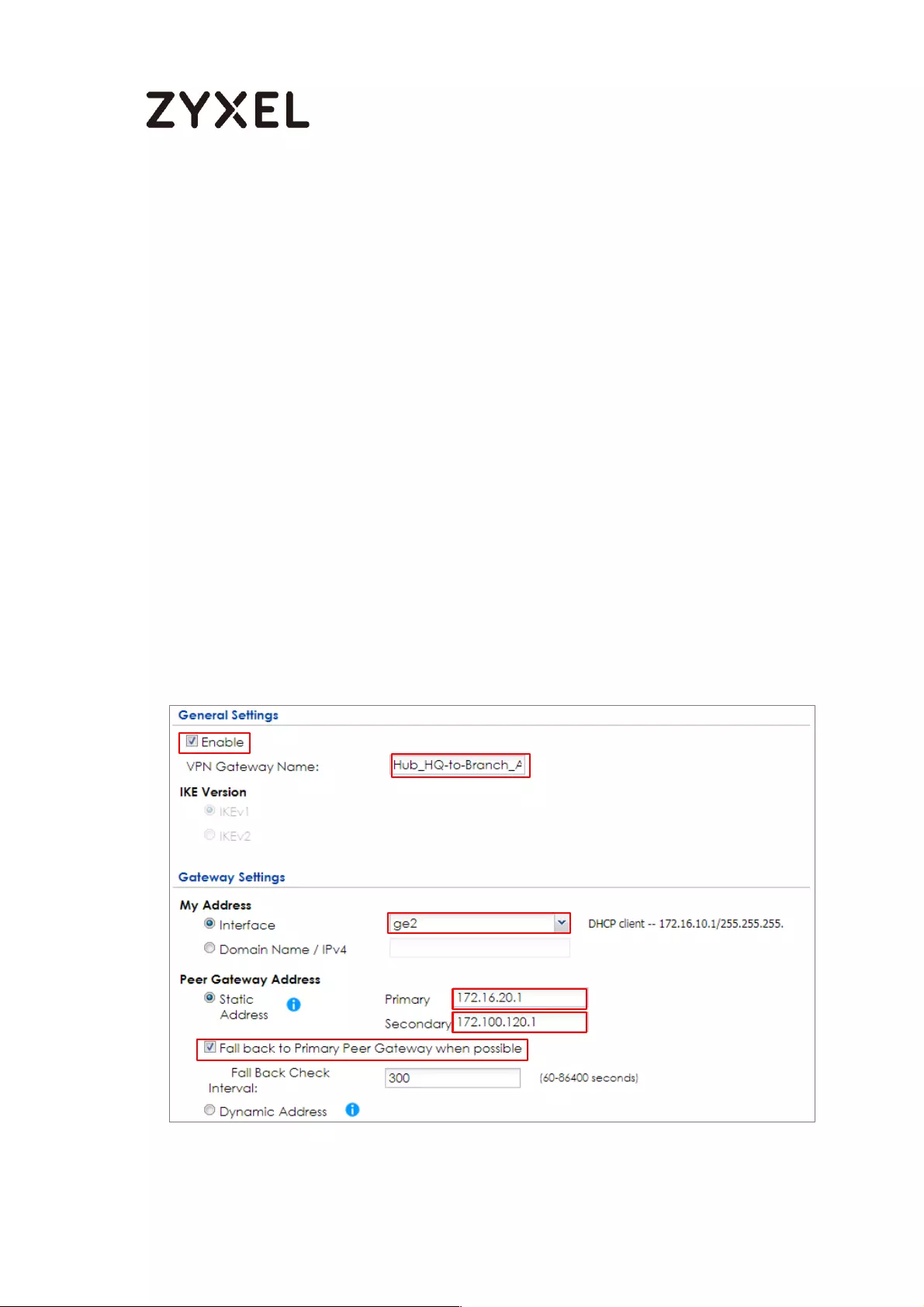
143/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG Hub_HQ-to-
Branch_A
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Primary Gateway IP as the Branch A’s wan1 IP address (in the
example, 172.16.20.1) and Secondary Gateway IP as the Branch A’s wan2 IP
address (in the example, 172.100.120.1). Select Fall back to Primary Peer Gateway
when possible and set desired Fall Back Check Interval time.
Type a secure Pre-Shared Key (8-32 characters) which must match your Branch
A’s Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
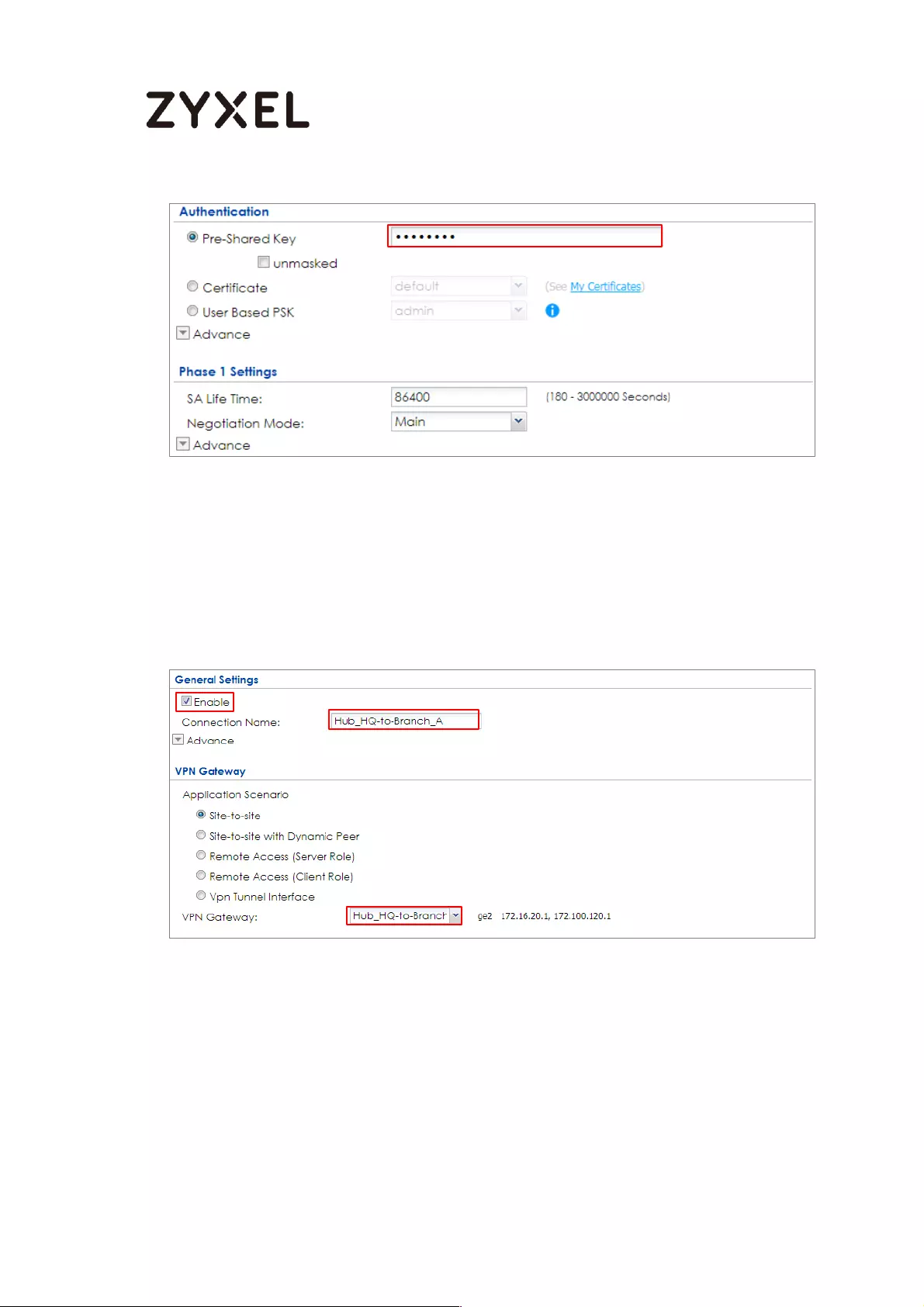
144/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
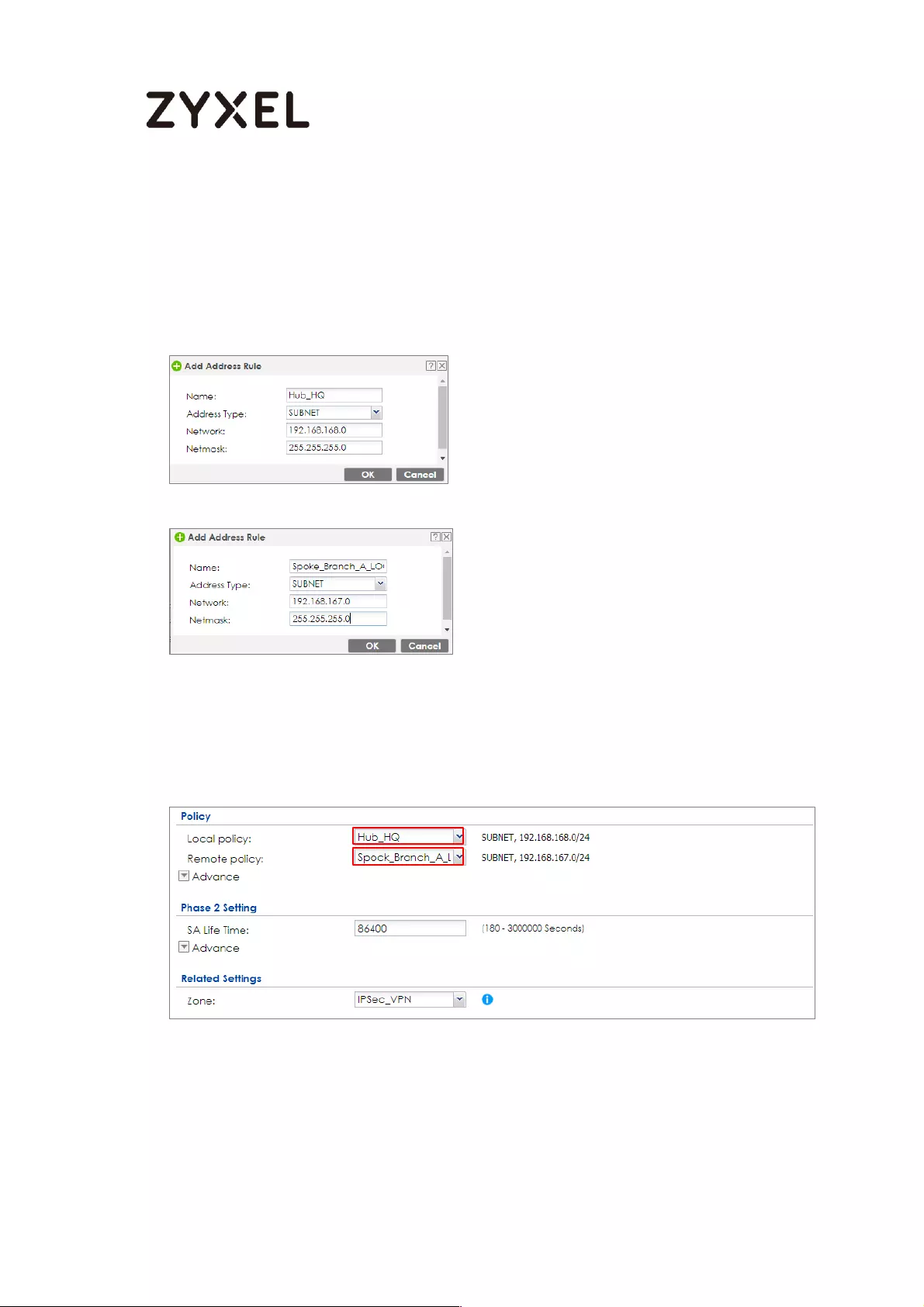
145/782
www.zyxel.com
Click Create new Object to add the address of local network behind Hub_HQ and
an address of local network behind Branch A.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be Hub_HQ and Remote Policy to Branch_A which are newly
created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
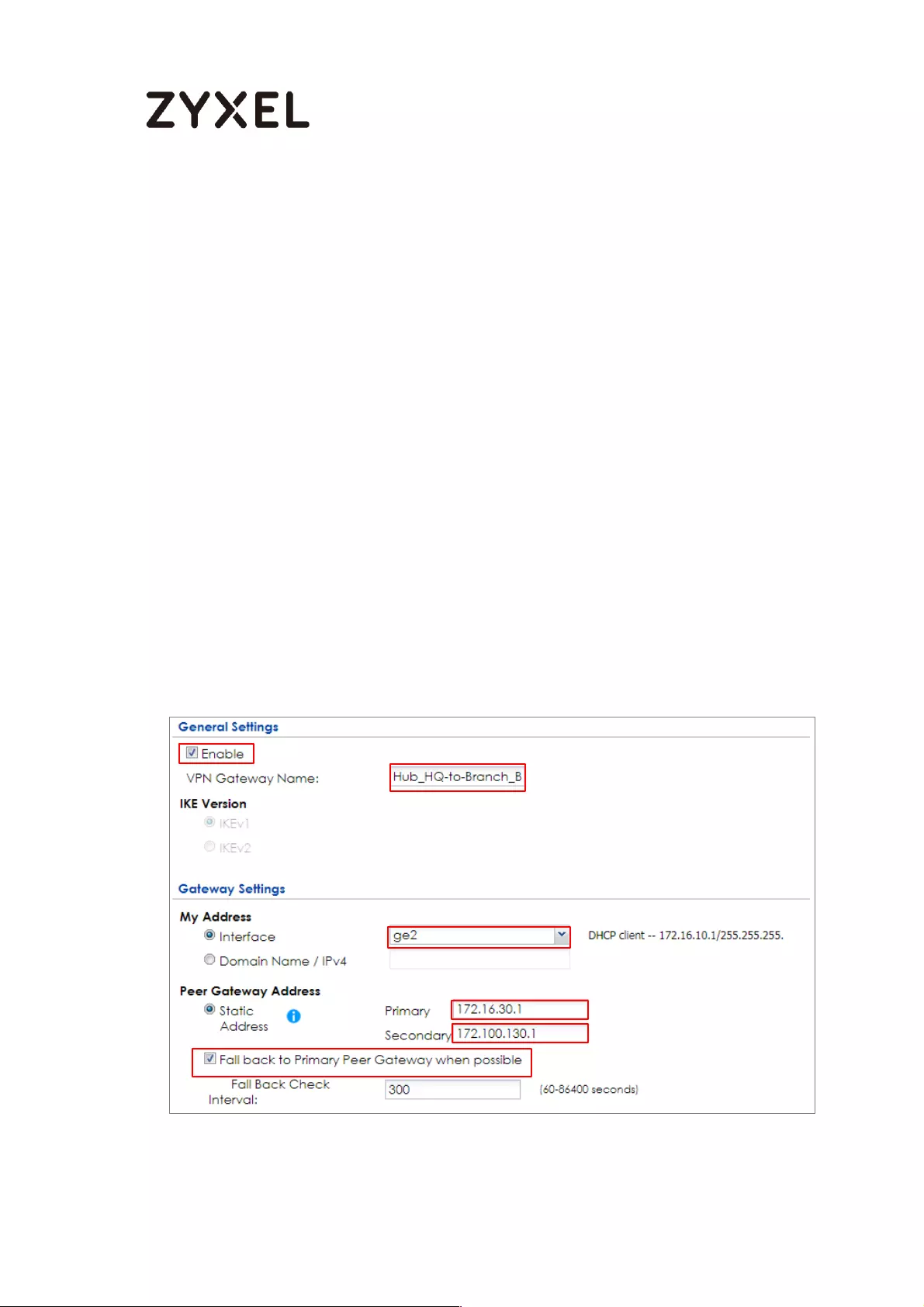
146/782
www.zyxel.com
Hub_HQ-to-Branch_B
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Primary Gateway IP as the Branch B’s wan1 IP address (in the
example, 172.16.30.1) and Secondary Gateway IP as the Branch B’s wan2 IP
address (in the example, 172.100.130.1). Select Fall back to Primary Peer Gateway
when possible and set desired Fall Back Check Interval time.
Type a secure Pre-Shared Key (8-32 characters) which must match your Branch
A’s Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
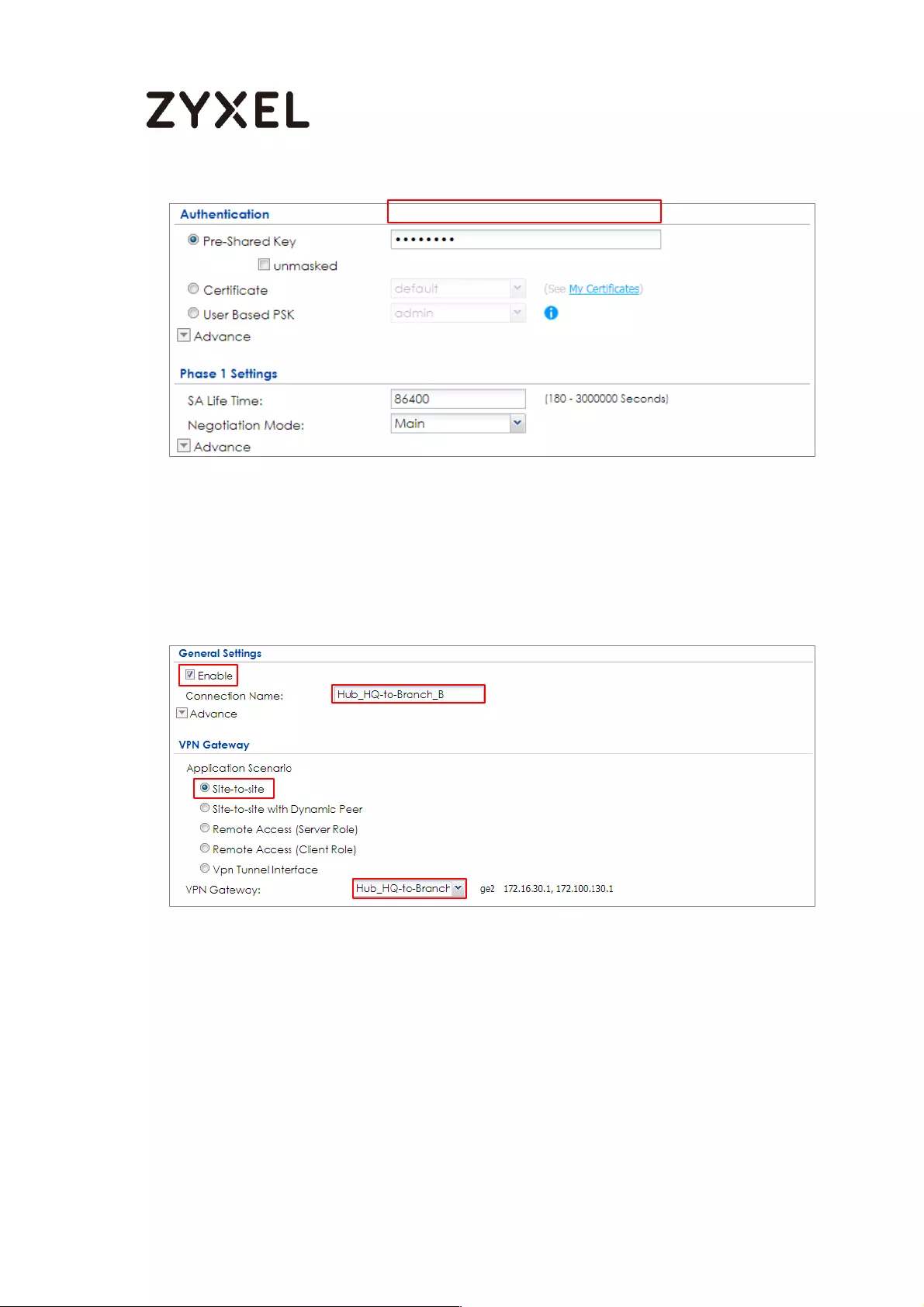
147/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection to enable VPN
Connection. Select scenario as Site-to-site and VPN Gateway which is configured
in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
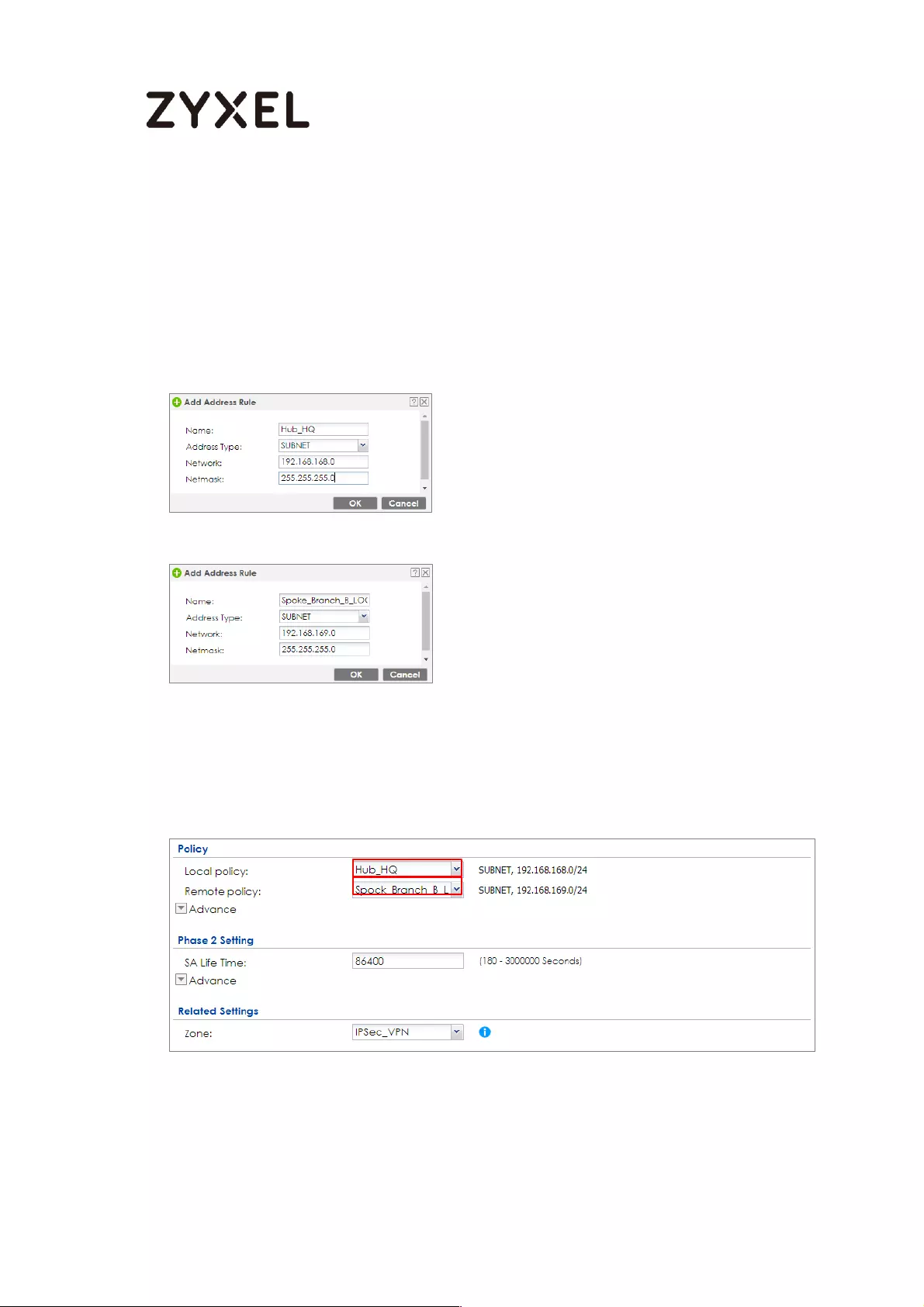
148/782
www.zyxel.com
Click Create new Object to add an address of local network behind Hub_HQ and
an address of local network behind Branch B.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be Hub_HQ and Remote Policy to Branch_B which are newly
created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
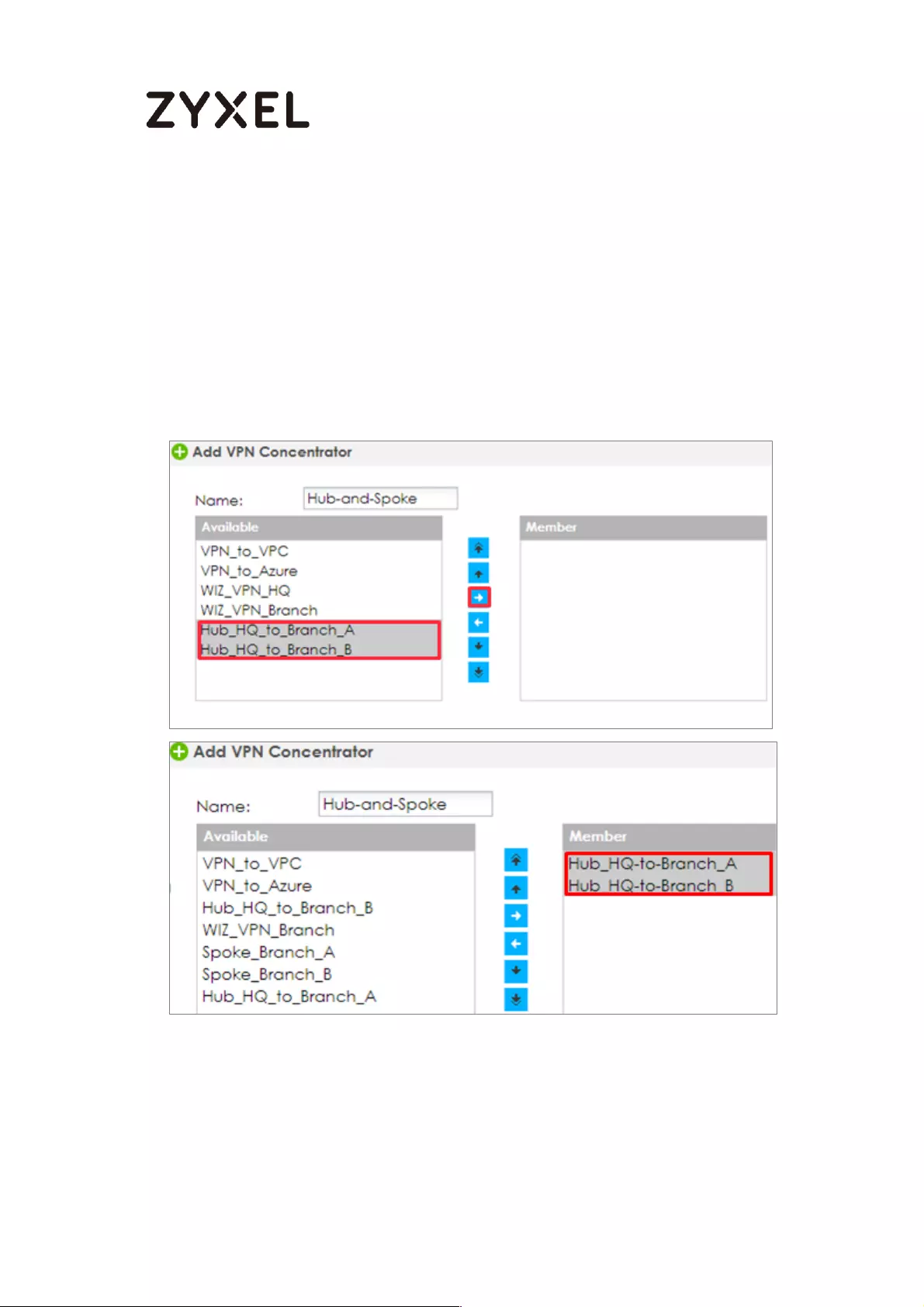
149/782
www.zyxel.com
Hub_HQ Concentrator
In the ZyWALL/USG, go to CONFIGURATION > VPN > IPSec VPN > Concentrator,
add a VPN Concentrator rule. Select VPN tunnels to the same member group and
click Save.
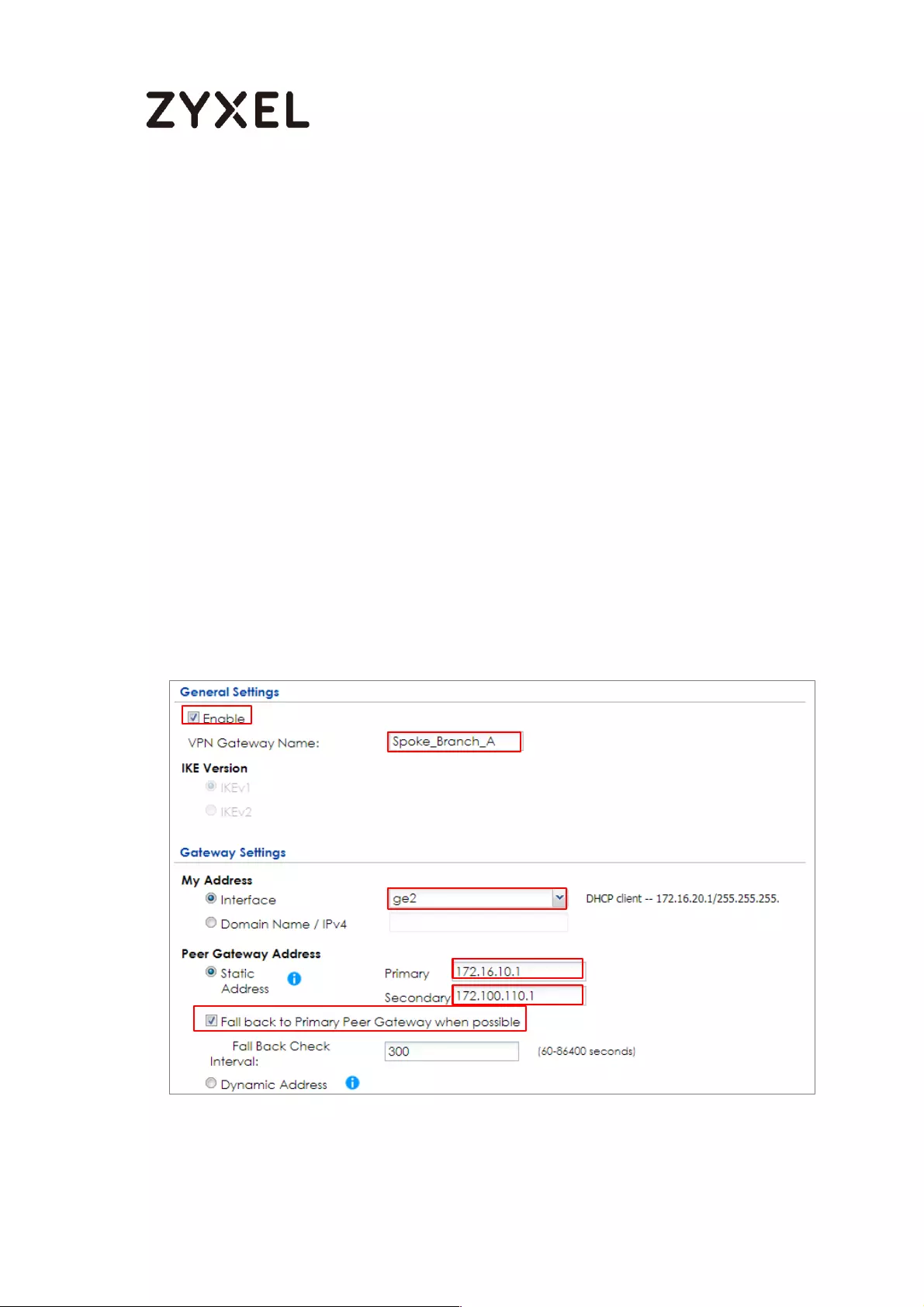
150/782
www.zyxel.com
Spoke_Branch_A
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Primary Gateway IP as the Hub_HQ’s wan1 IP address (in the
example, 172.16.10.1) and Secondary Gateway IP as the Hub_HQ’s wan2 IP
address (in the example, 172.100.110.1). Select Fall back to Primary Peer Gateway
when possible and set desired Fall Back Check Interval time.
Type a secure Pre-Shared Key (8-32 characters) which must match your Hub_HQ’s
Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
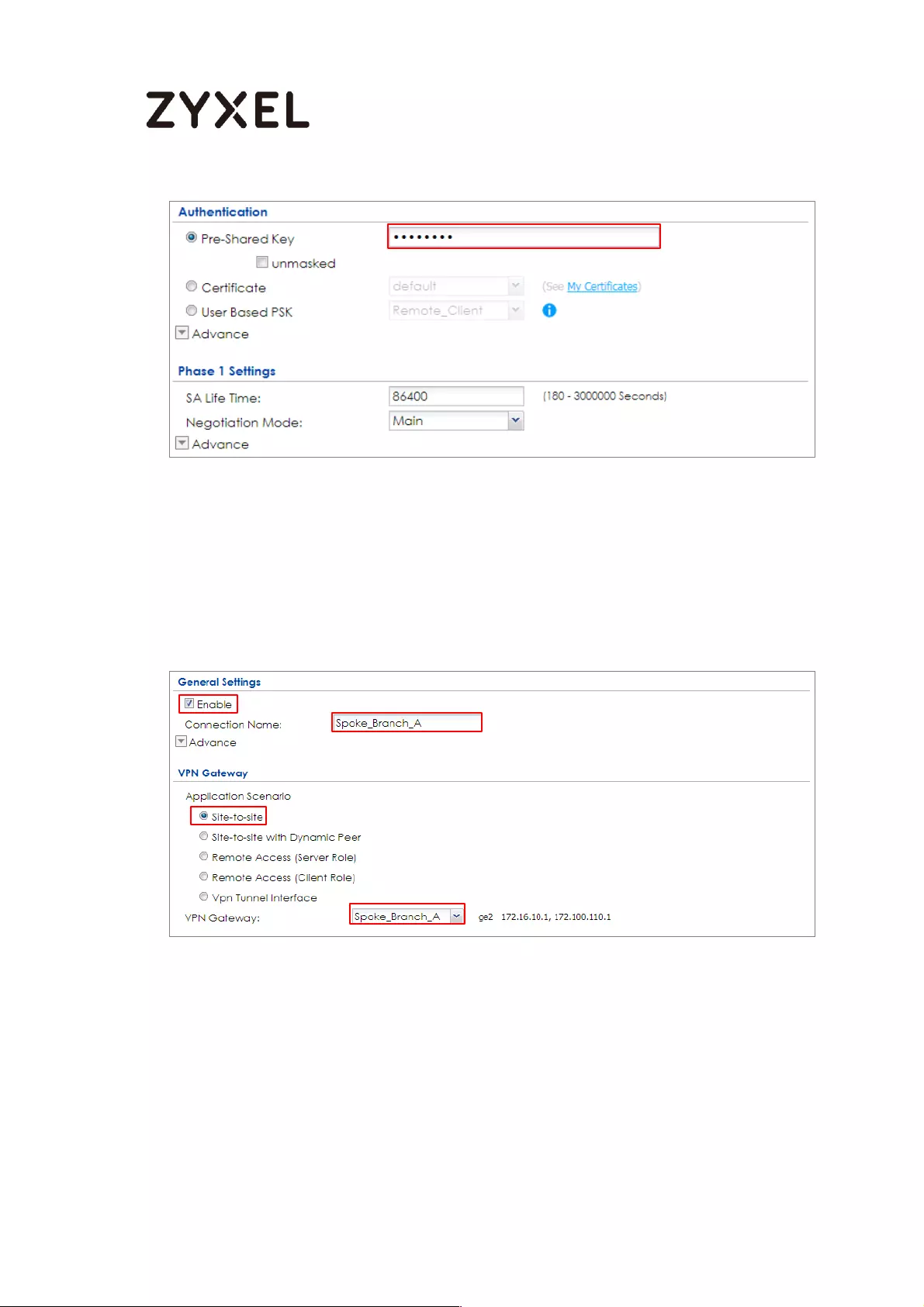
151/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway

152/782
www.zyxel.com
Click Create new Object to add the address of local network behind Branch A
and an address of local network behind Hub_HQ
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
Set Local Policy to be Spoke_Branch_A_LOCAL and Remote Policy to Hub_HQ
which are newly created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
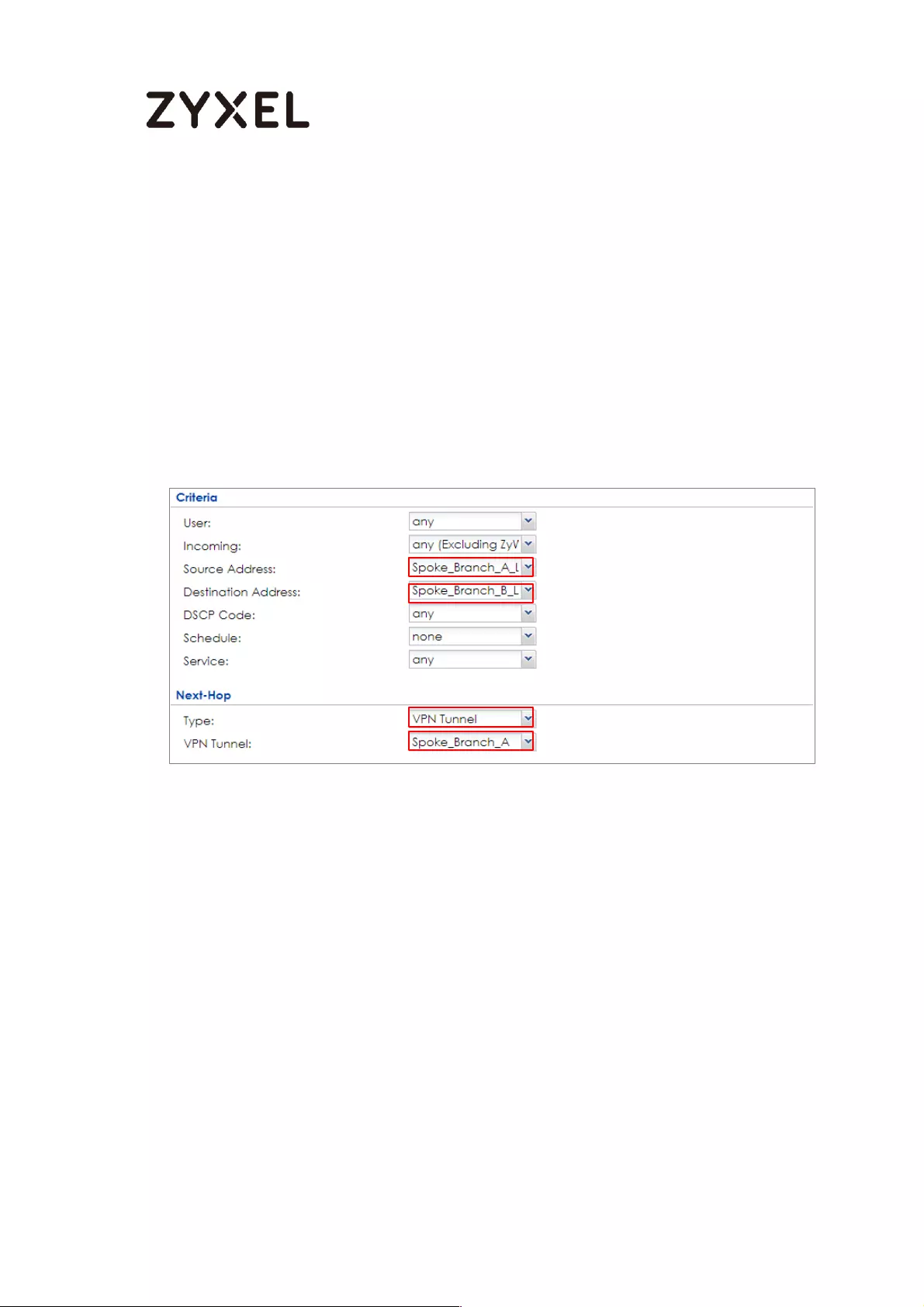
153/782
www.zyxel.com
Go to Network > Routing > Policy Route to add a Policy Route to allow traffic from
Spoke_Branch_A to Spoke_Branch_B.
Click Create new Object and set the address to be the local network behind the
Spoke_Branch_B. Select Source Address to be the local network behind the
Spoke_Branch_A. Then, scroll down the Destination Address list to choose the
newly created Spoke_Branch_B_LOCAL address. Click OK.
Network > Routing > Policy Route
Spoke_Branch_B
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, select Enable. Type
the VPN Gateway Name used to identify this VPN gateway.
Then, configure the Primary Gateway IP as the Hub_HQ’s wan1 IP address (in the
example, 172.16.10.1) and Secondary Gateway IP as the Hub_HQ’s wan2 IP
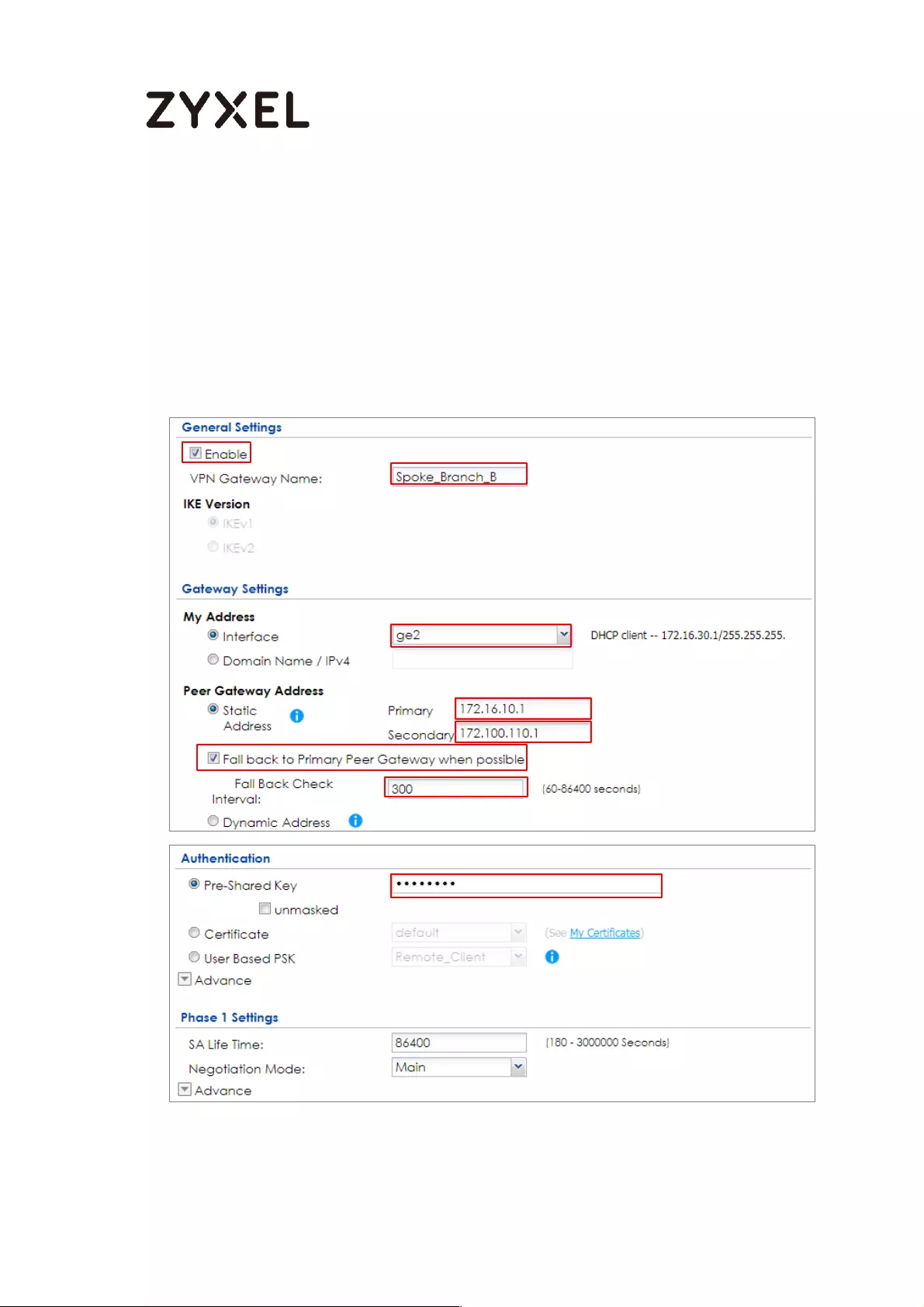
154/782
www.zyxel.com
address (in the example, 172.100.110.1). Select Fall back to Primary Peer Gateway
when possible and set desired Fall Back Check Interval time.
Type a secure Pre-Shared Key (8-32 characters) which must match your Hub_HQ’s
Pre-Shared Key and click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway
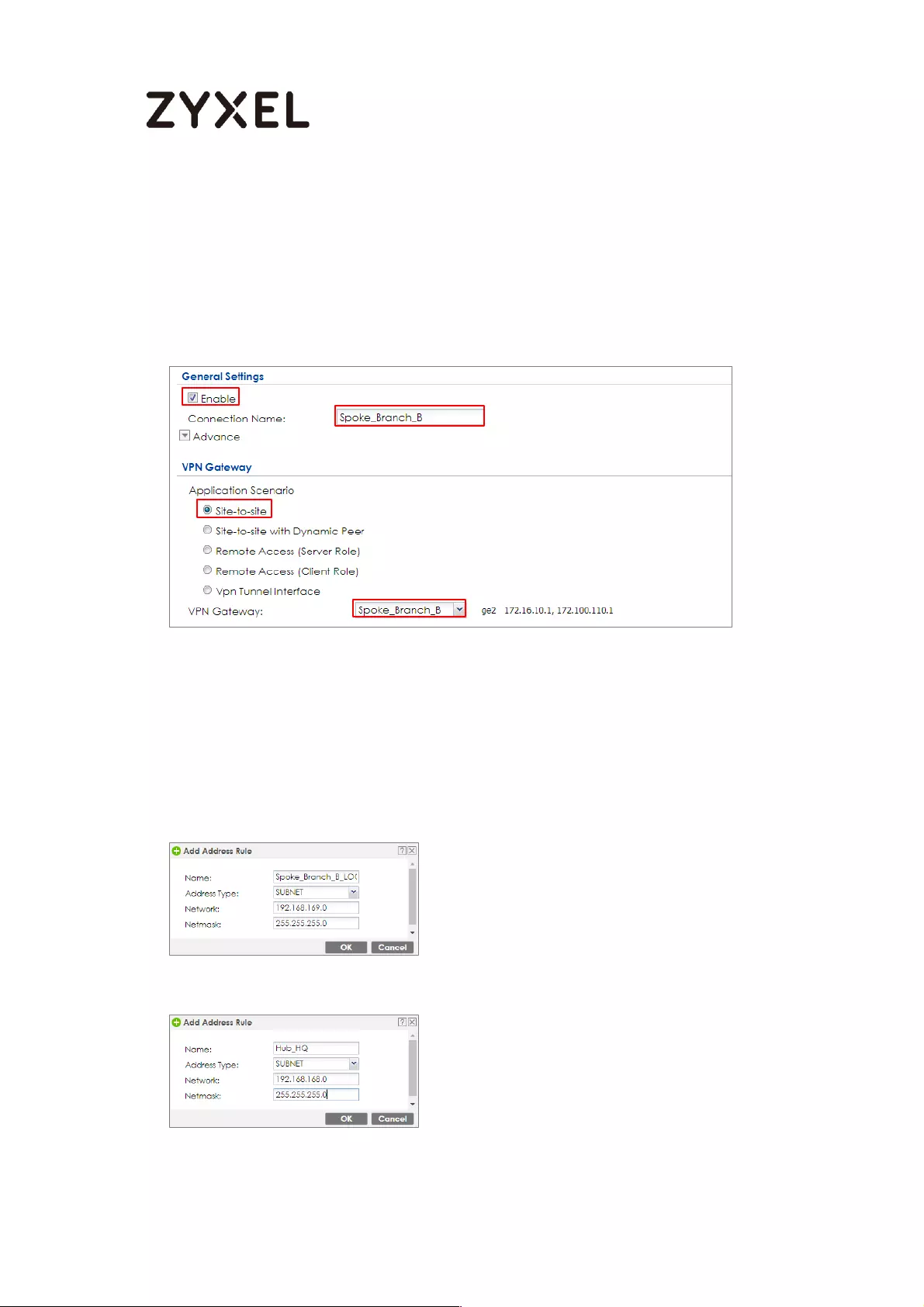
155/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection and select Enable.
Type the Connection Name used to identify this VPN connection. Select scenario
as Site-to-site and VPN Gateway which is configured in Step 1.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > General Settings and
VPN Gateway
Click Create new Object to add the address of local network behind Branch B
and an address of local network behind Hub_HQ.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Create new Object
Local Policy
Remote Policy
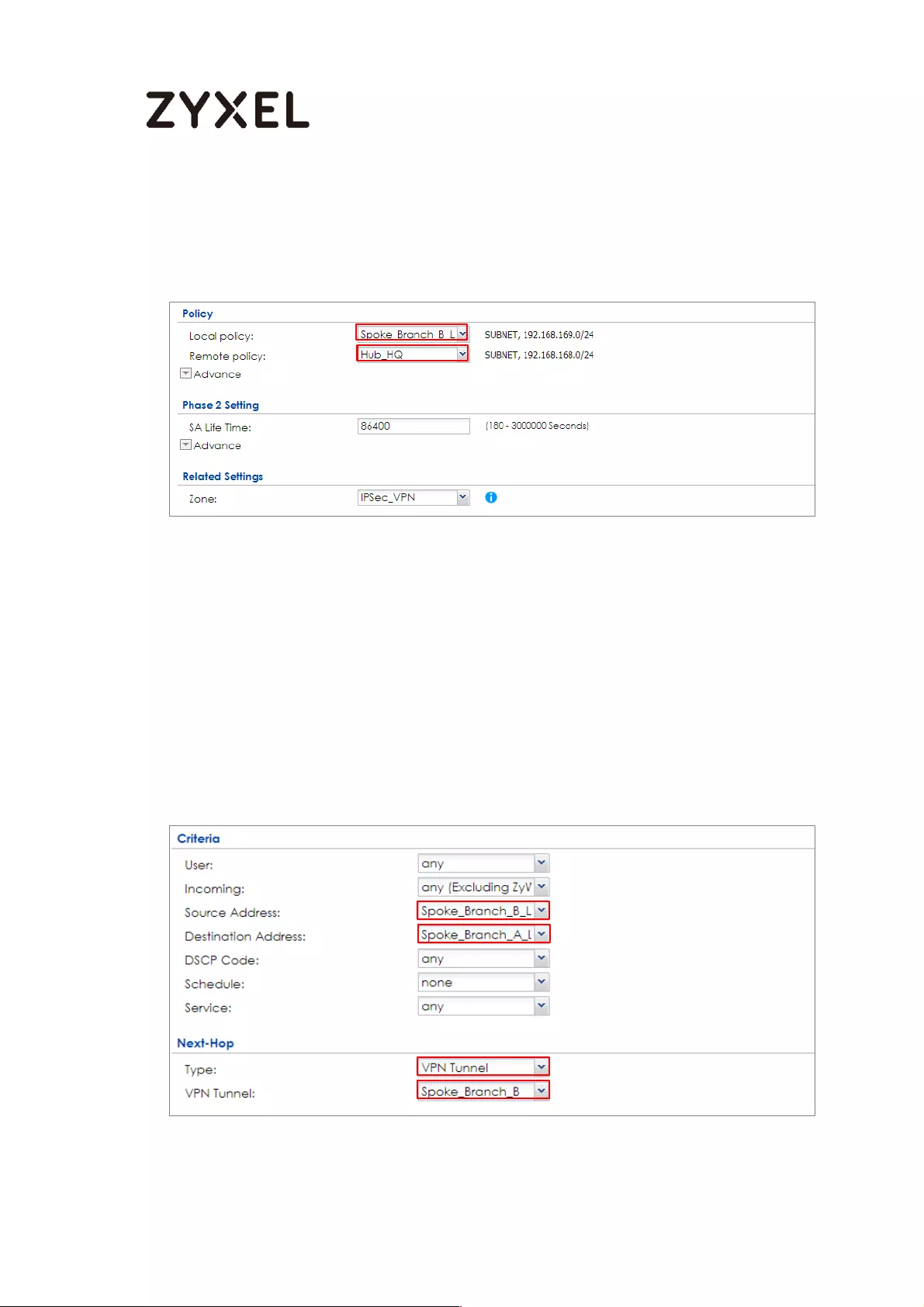
156/782
www.zyxel.com
Set Local Policy to be Spoke_Branch_B_LOCAL and Remote Policy to Hub_HQ
which are newly created. Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Policy
Go to Network > Routing > Policy Route to add a Policy Route to allow traffic from
Spoke_Branch_B to Spoke_Branch_A.
Click Create new Object and set the address to be the local network behind the
Spoke_Branch_A. Select Source Address to be the local network behind the
Spoke_Branch_B. Then, scroll down the Destination Address list to choose the
newly created Spoke_Branch_A_LOCAL address. Click OK.
Network > Routing > Policy Route
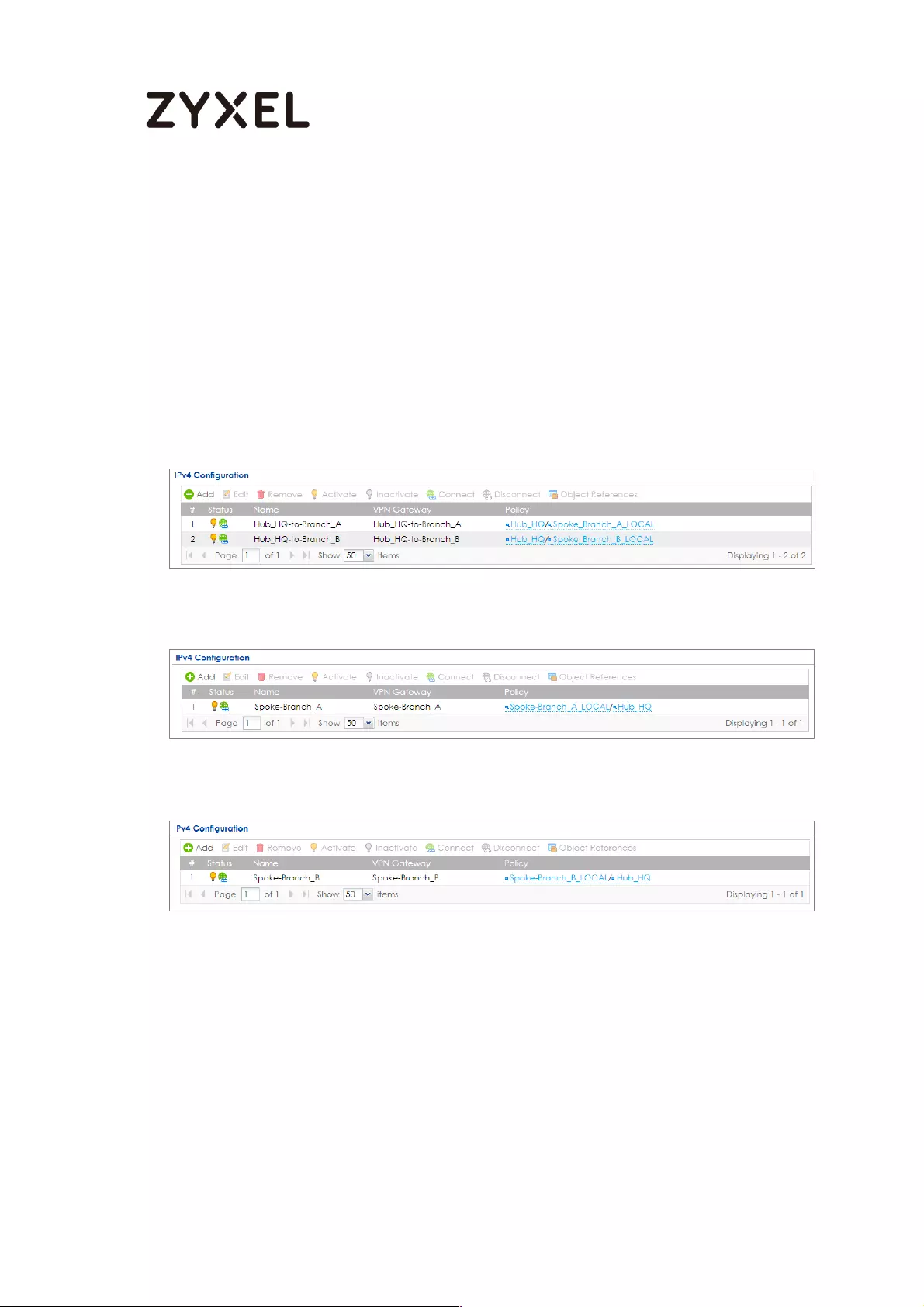
157/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
Hub_HQ > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Spoke_Branch_A > CONFIGURATION > VPN > IPSec VPN > VPN Connection
Spoke_Branch_B > CONFIGURATION > VPN > IPSec VPN > VPN Connection
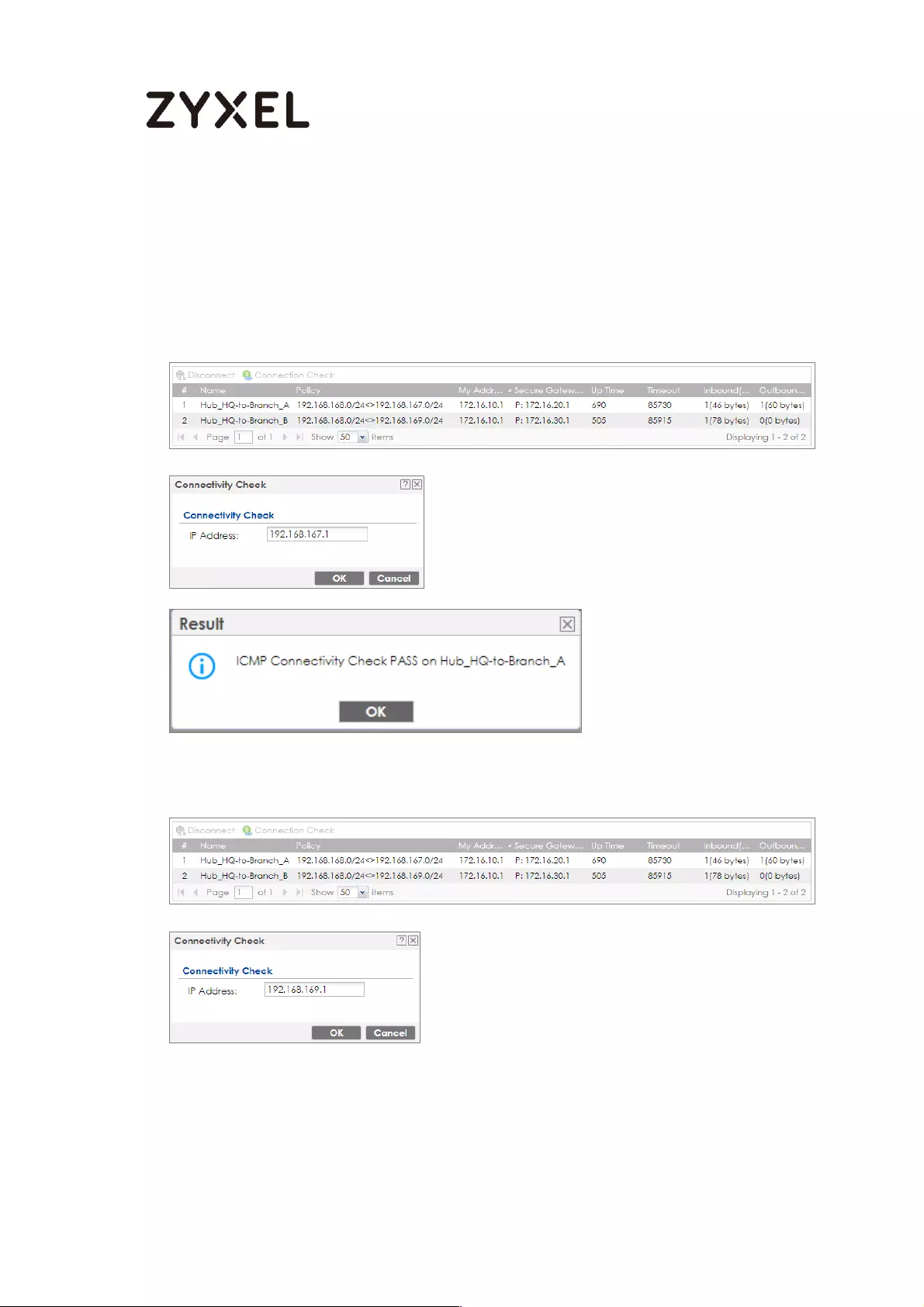
158/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > IPSec > Hub_HQ-to-Branch_A
Hub_HQ > MONITOR > VPN Monitor > IPSec > Hub_HQ-to-Branch_B
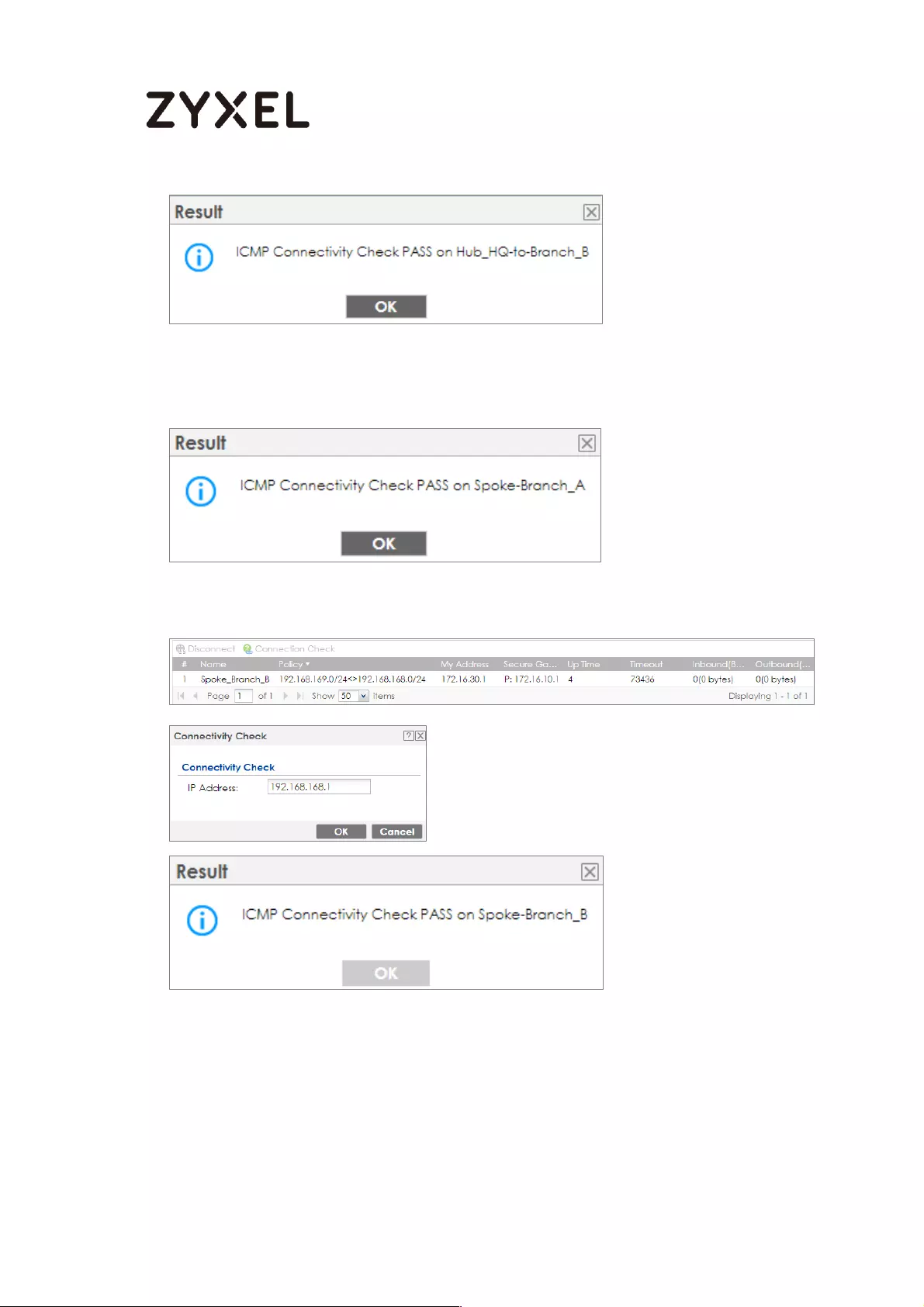
159/782
www.zyxel.com
Spoke_Branch_A > MONITOR > VPN Monitor > IPSec
Spoke_Branch_B > MONITOR > VPN Monitor > IPSec
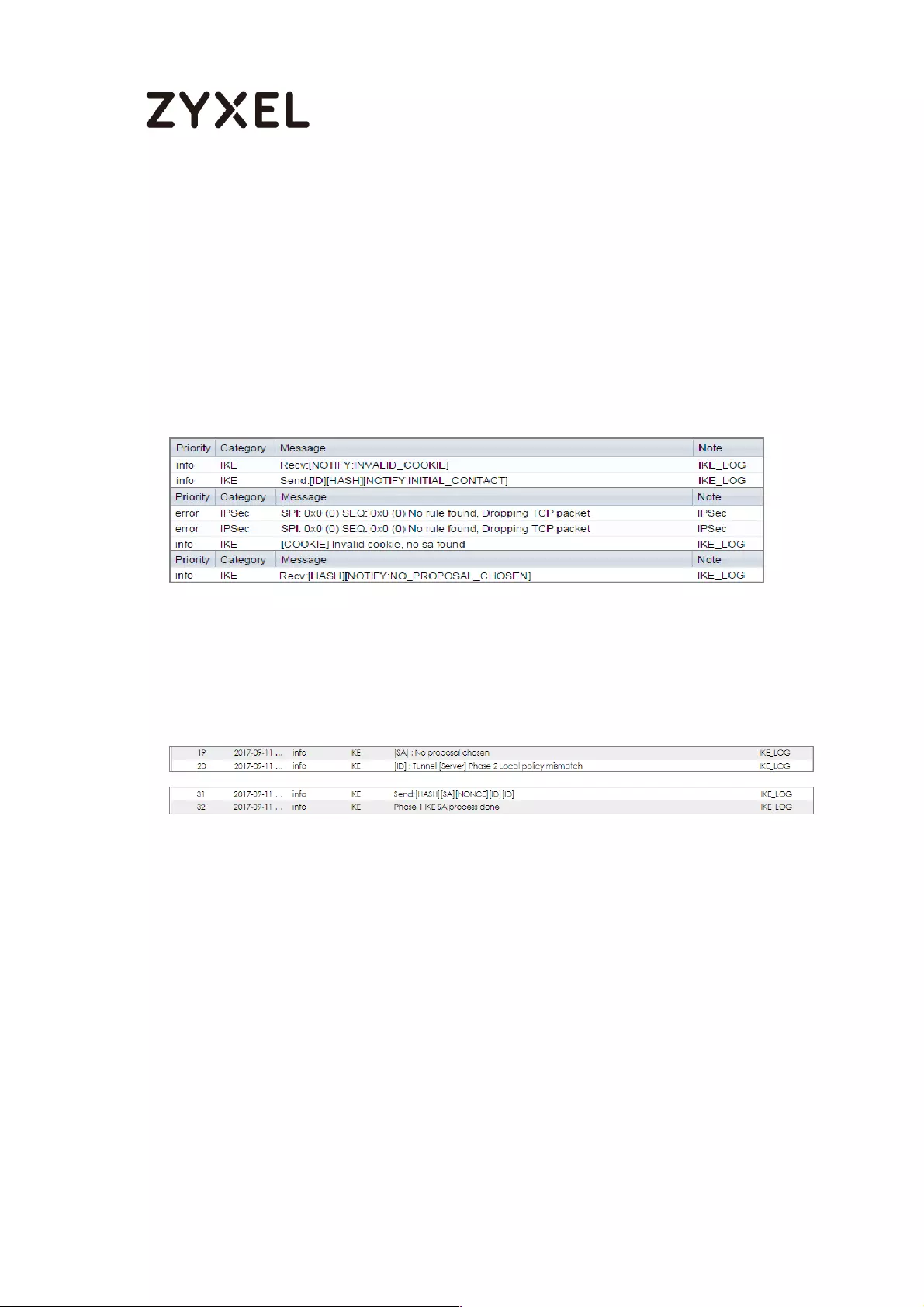
160/782
www.zyxel.com
What Could Go Wrong?
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. All ZyWALL/USG units must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.
If you see that Phase 1 IKE SA process done but still get [info] log message as
below, please check ZyWALL/USG Phase 2 Settings. All ZyWALL/USG units must
use the same Protocol, Encapsulation, Encryption, Authentication method and
PFS to establish the IKE SA.
Make sure the all ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE
uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
By default, NAT traversal is enabled on ZyWALL/USG, so please make sure the
remote IPSec device also has NAT traversal enabled.
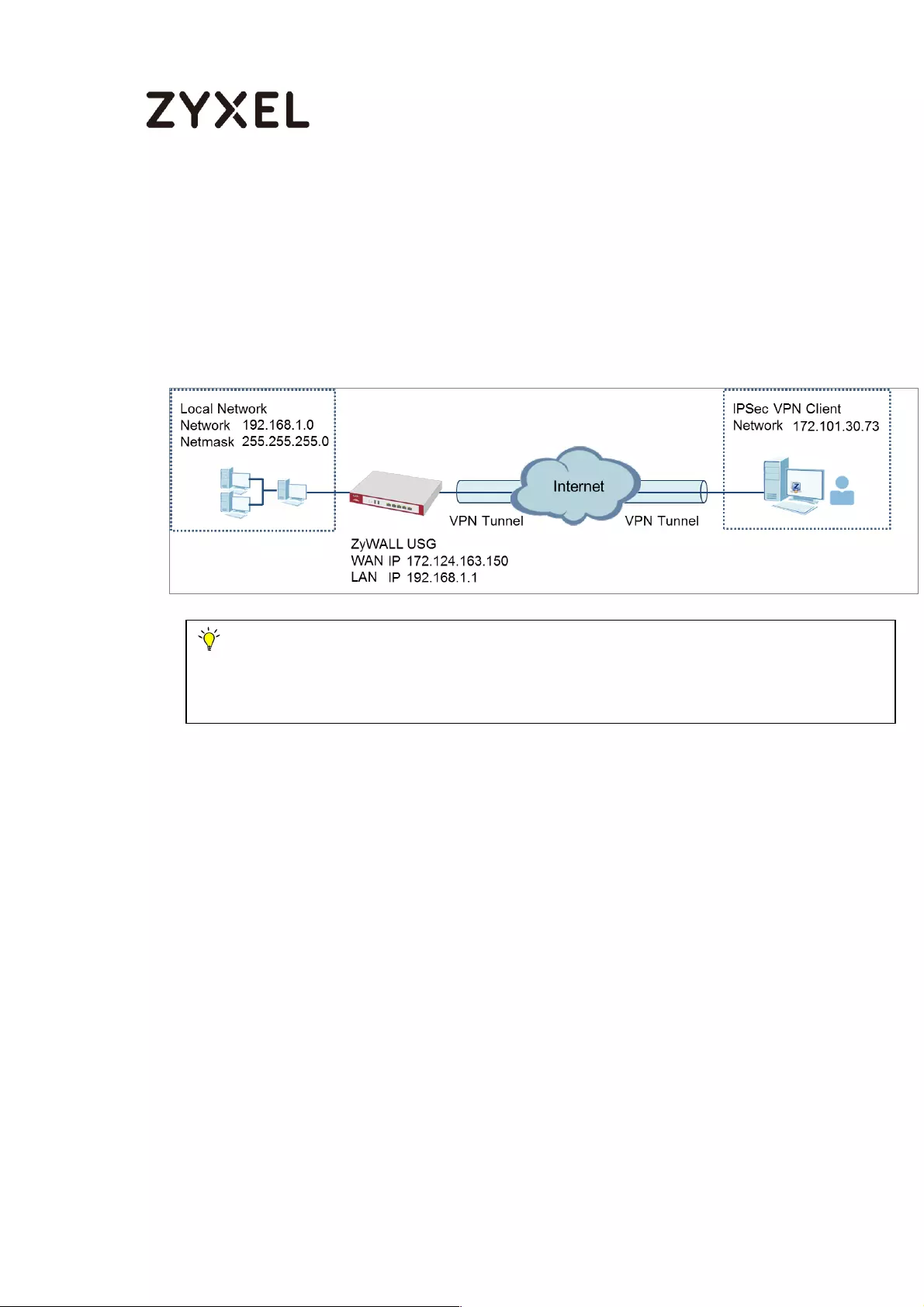
161/782
www.zyxel.com
How to Configure IPSec VPN with ZyWALL IPSec VPN Client
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
between a ZyWALL/USG and a ZyWALL IPSec VPN Client. The example instructs how
to configure the VPN tunnel between each site. When the VPN tunnel is configured,
each site can be accessed securely.
ZyWALL IPSec VPN Client with VPN Tunnel Connected
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This
example was tested using USG310 (Firmware Version: ZLD 4.25) and ZyWALL IPSec VPN
Client (Firmware Version: 3.6.204.61.4).
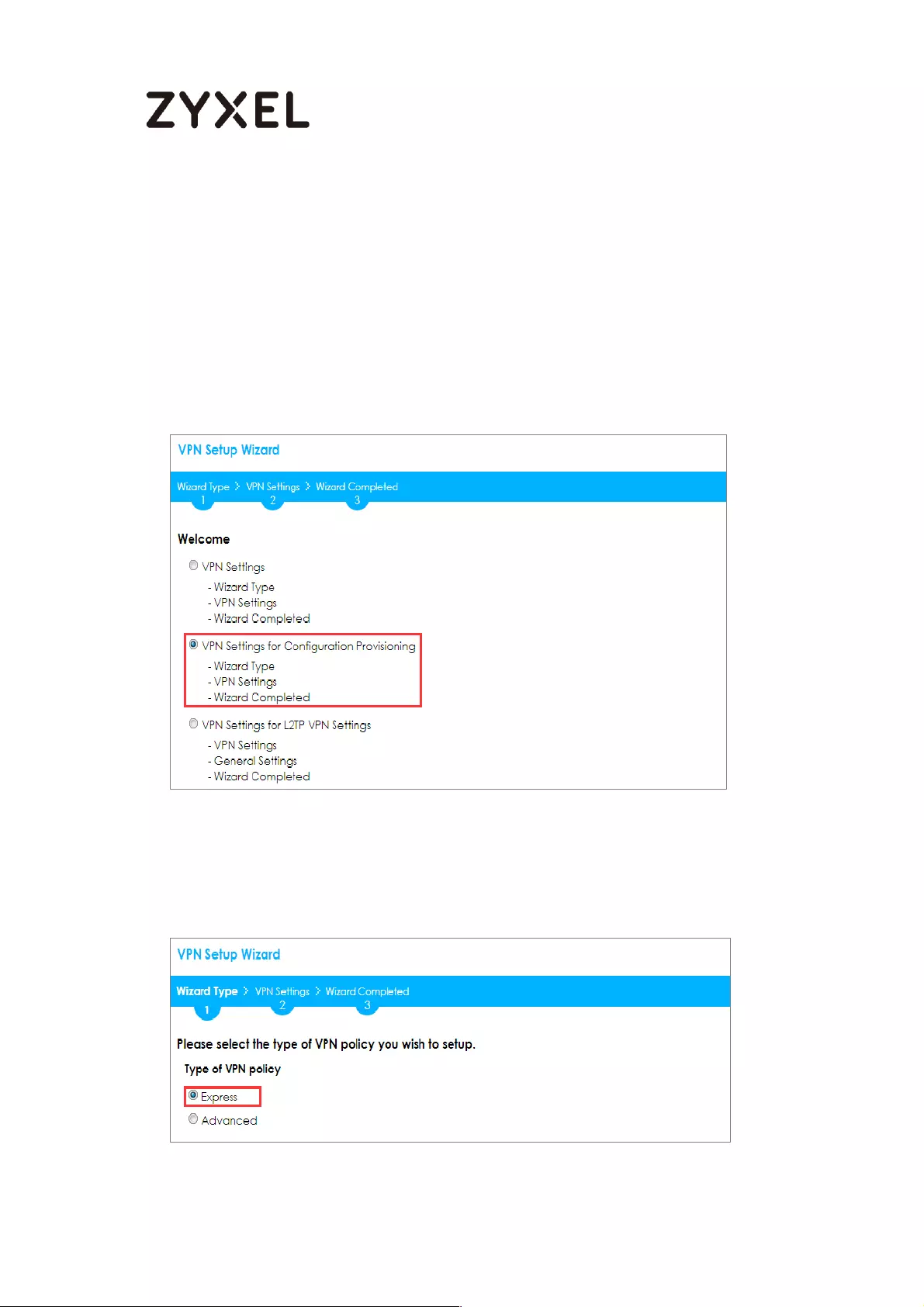
162/782
www.zyxel.com
Set Up the ZyWALL/USG IPSec VPN Tunnel
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
for Configuration Provisioning wizard to create a VPN rule that can be used with
the ZyWALL IPSec VPN Client. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
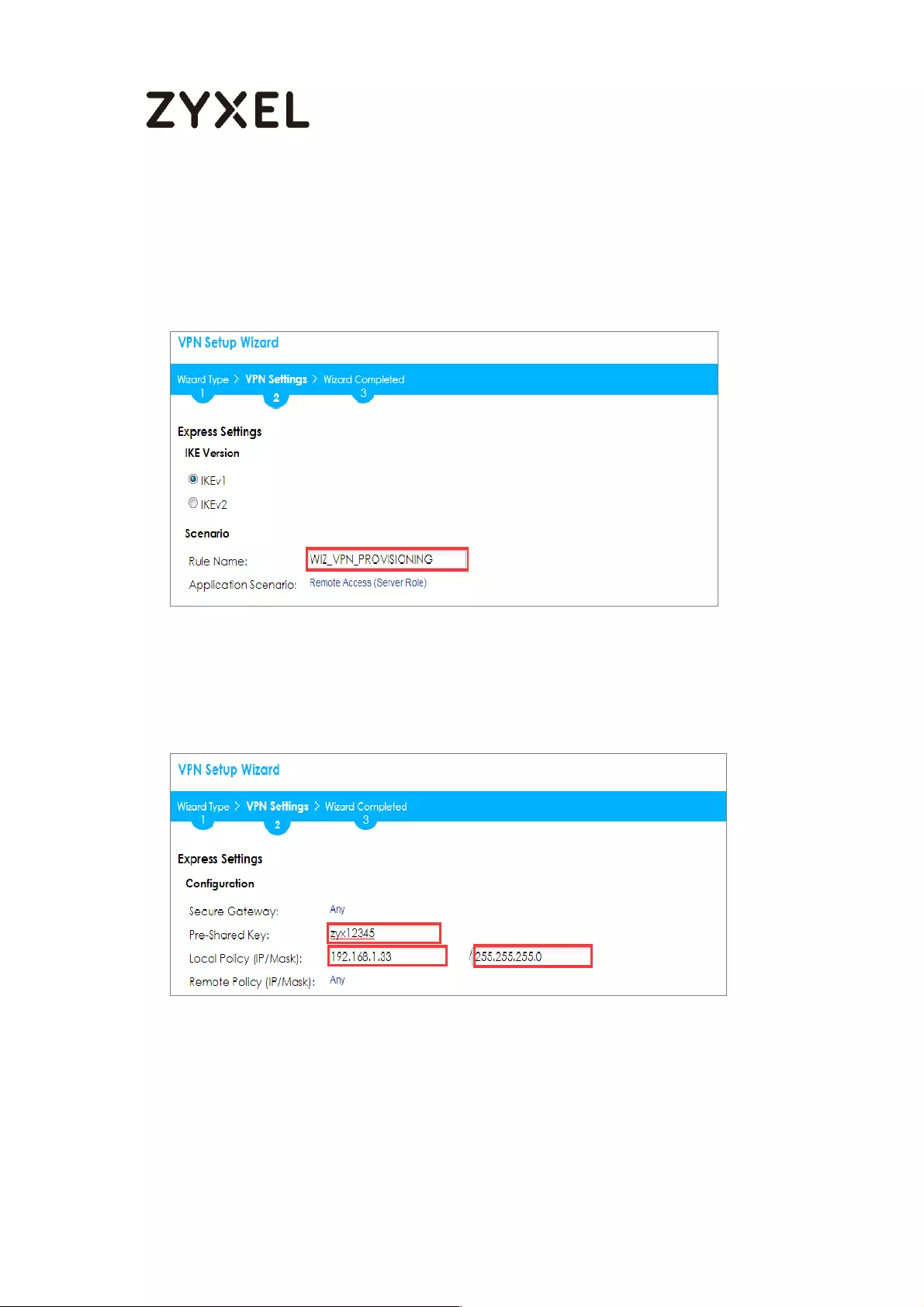
163/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings-1
Type a secure Pre-Shared Key (8-32 characters). Set Local Policy to be the IP
address range of the network connected to the ZyWALL/USG.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings-2
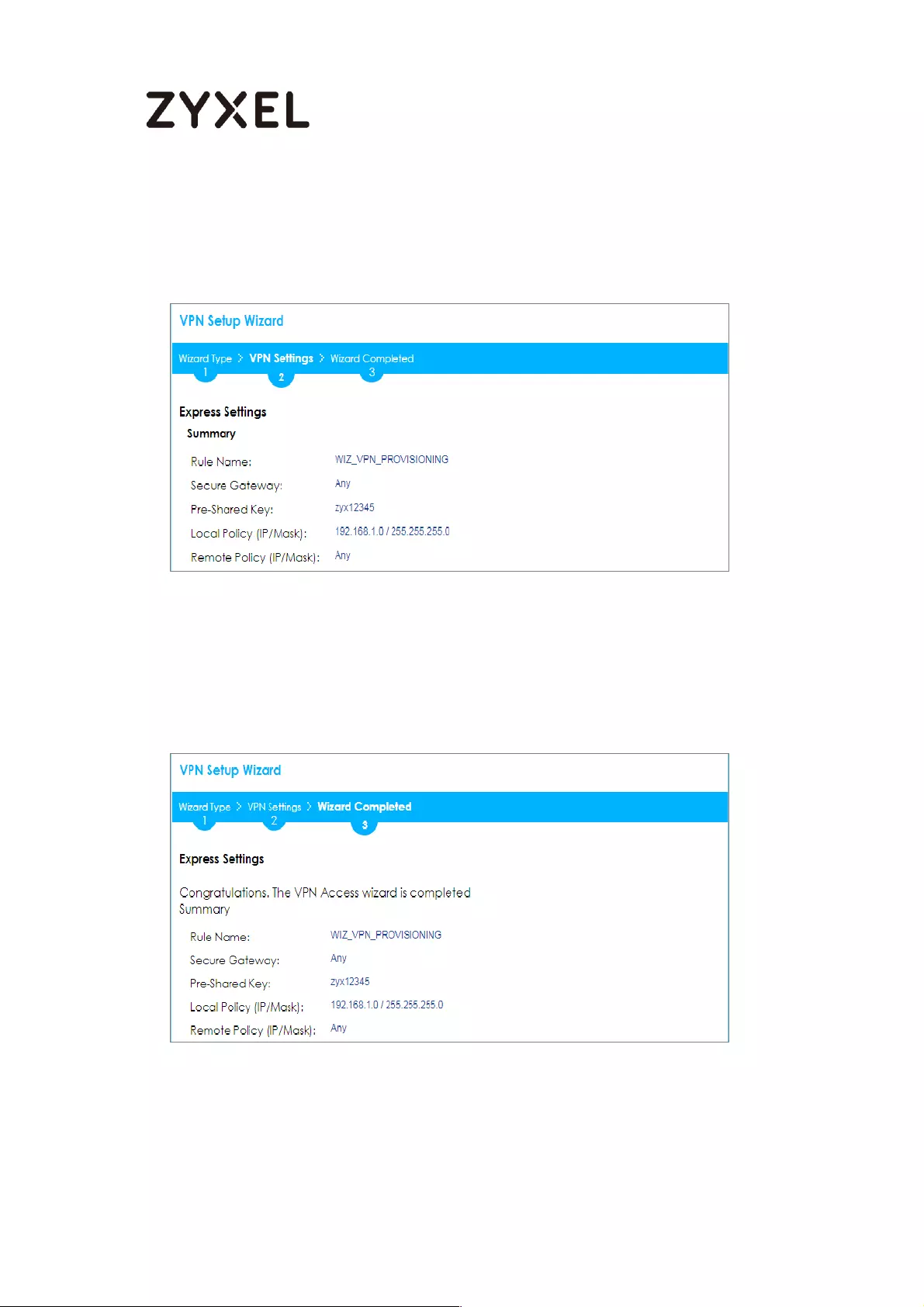
164/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings-3
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
Go to CONFIGURATION > Object > User/Group > Add A User and create a user
account for the ZyWALL IPSec VPN Client user.
CONFIGURATION > Object > User/Group > Add A User
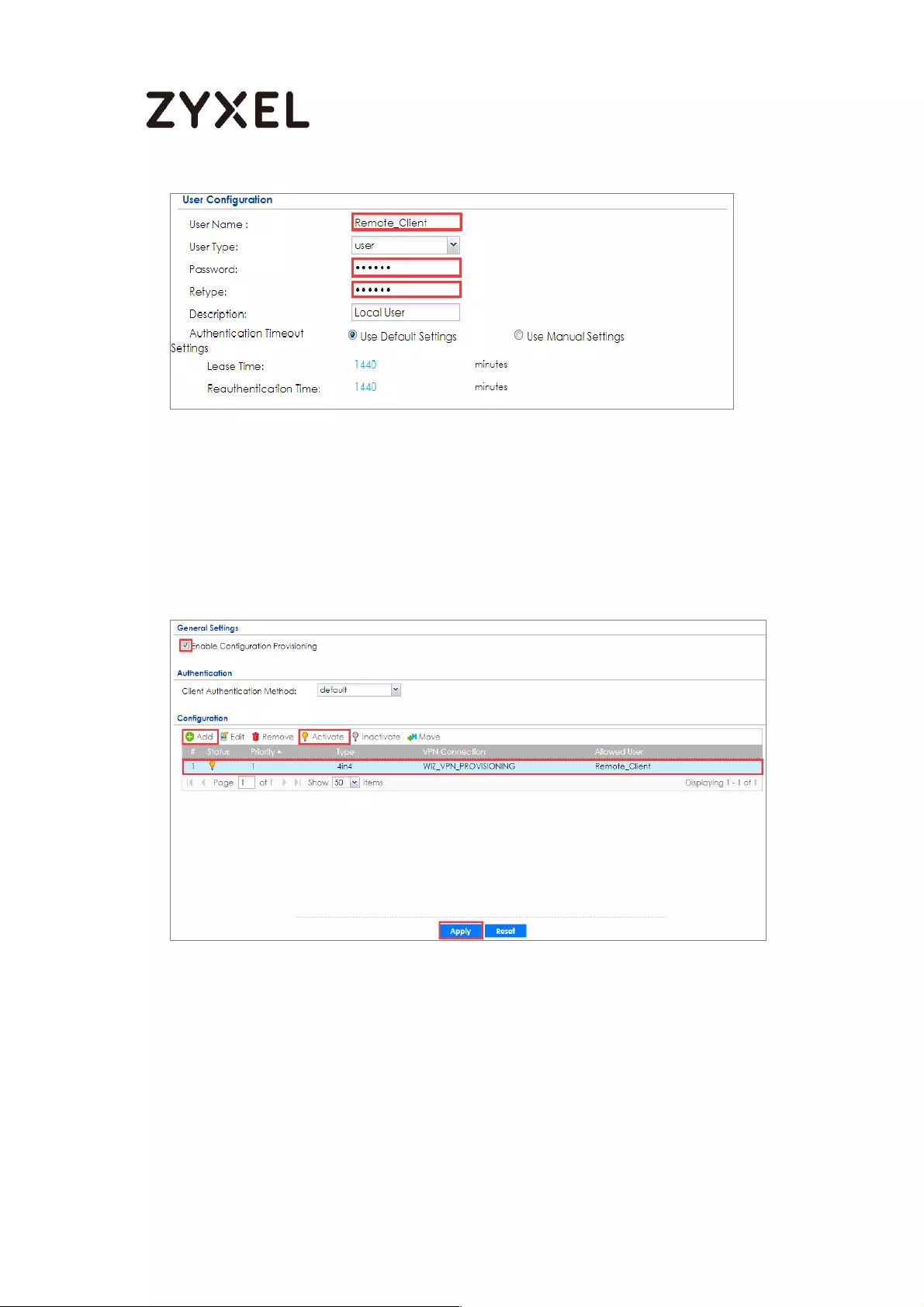
165/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > Configuration Provisioning. In the
General Settings section, select the Enable Configuration Provisioning. Then, go to
the Configuration section and click Add to bind a configured VPN Connection to
Allowed User. Click Activate and Apply to save the configuration.
CONFIGURATION > VPN > IPSec VPN > Configuration Provisioning

166/782
www.zyxel.com
Set Up the ZyWALL IPSec VPN Client
Download ZyWALL IPSec VPN Client software from ZyXEL Download Library:
http://www.zyxel.com/support/download_landing.shtml
Open ZyWALL IPSec VPN Client, select CONFIGURATION > Get from Server.
CONFIGURATION > Get from Server
Enter the WAN IP address or URL for the ZyWALL/USG in the Gateway Address. If
you changed the default HTTPS Port on the ZyWALL/USG, and then enter the new
one here. Enter the Login user name and Password exactly as configured on the
ZyWALL or external authentication server. Click Next, you will see it’s processing
VPN configuration from the server.
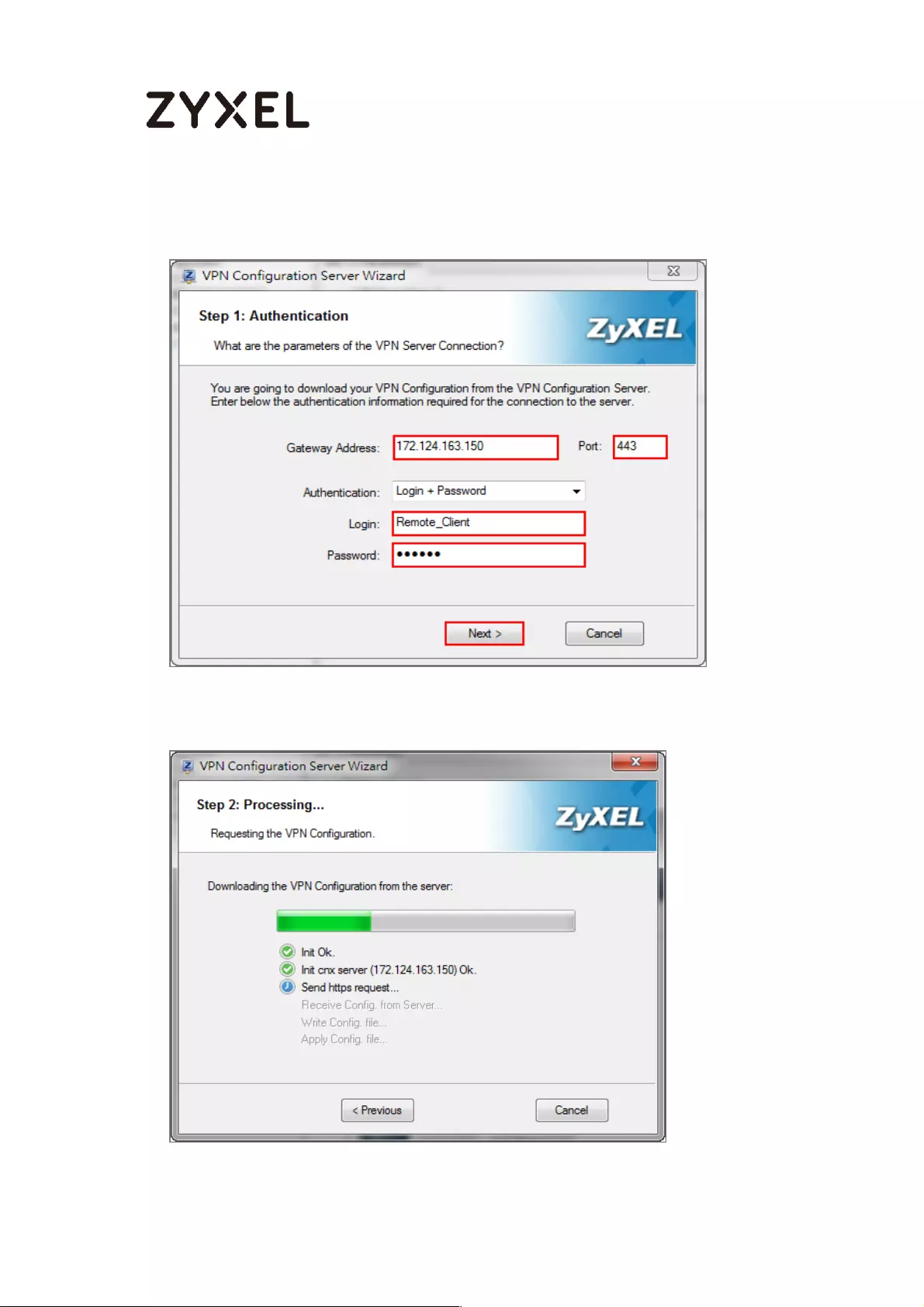
167/782
www.zyxel.com
CONFIGURATION > Get from Server > Step 1: Authentication
CONFIGURATION > Get from Server > Step 2: Processing
168/782
www.zyxel.com
Then, you will see the Configuration successful page, click OK to exit the wizard.
CONFIGURATION > Get from Server > Configuration successful
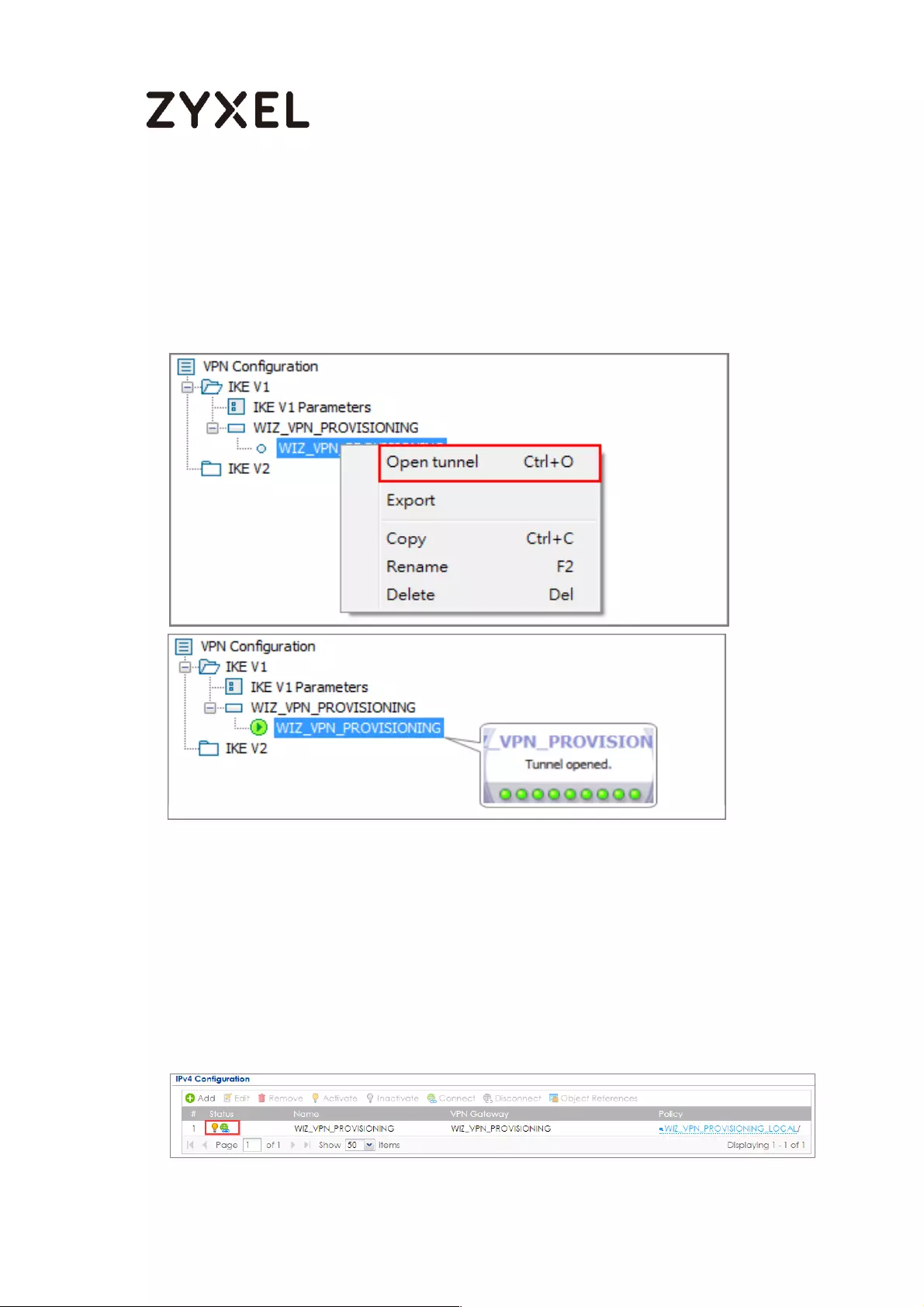
169/782
www.zyxel.com
Go to VPN Configuration > IKEv1, right click the WIZ_VPN_PROVISIONING and
select Open tunnel. You will see the Tunnel opened on the bottom right of the
screen.
VPN CONFIGURATION > IKE V1 > WIZ_VPN_PROVISIONING > Open tunnel
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the
Status connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
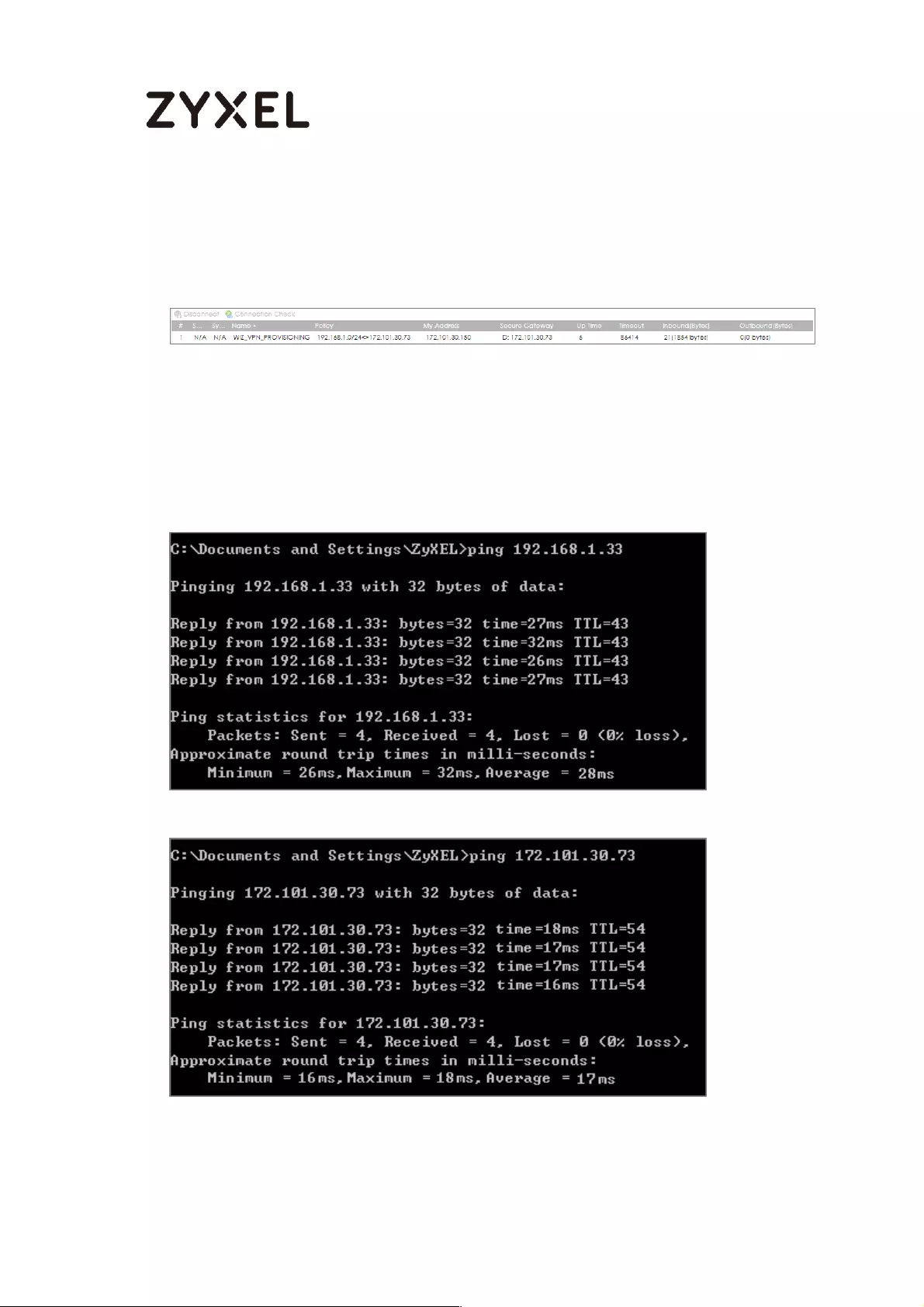
170/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC with ZyWALL IPSec VPN Client installed > Window 7 > cmd > ping 192.168.1.33
PC behind ZyWALL/USG > Window 7 > cmd > ping 172.101.30.73

171/782
www.zyxel.com
What Can Go Wrong?
If you see [info] log message such as below, please make sure both ZyWALL/USG
and ZyWALL IPSec VPN Client use the same Pre-Shared Key to establish the IKE
SA.
MONITOR > Log
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. ZyWALL/USG and ZyWALL IPSec VPN Client must use the same
Encryption, Authentication method, DH key group and ID Type/Content to
establish the IKE SA.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get [alert] or [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG
and ZyWALL IPSec VPN Client must use the same Active Protocol, Encapsulation,
Proposal, PFS and set correct Local Policy to establish the IKE SA.
MONITOR > Log
If you see [alert] log message as below, please make sure you create a user
account for the ZyWALL IPSec VPN Client user on ZyWALL/USG or the external
authentication server. Or please check your password matches the settings in
the user account.
MONITOR > Log
172/782
www.zyxel.com
Make sure the service HTTPS Port on IPSec VPN Client application is available.
Make sure the To-ZyWALL security policies allow IPSec VPN traffic to the
ZyWALL/USG. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses IP
protocol 50.
The ZyWALL/USG supports UDP port 500 and UDP port 4500 for NAT traversal. If
you enable this, make sure the To-ZyWALL security policies allow UDP port 4500
too.
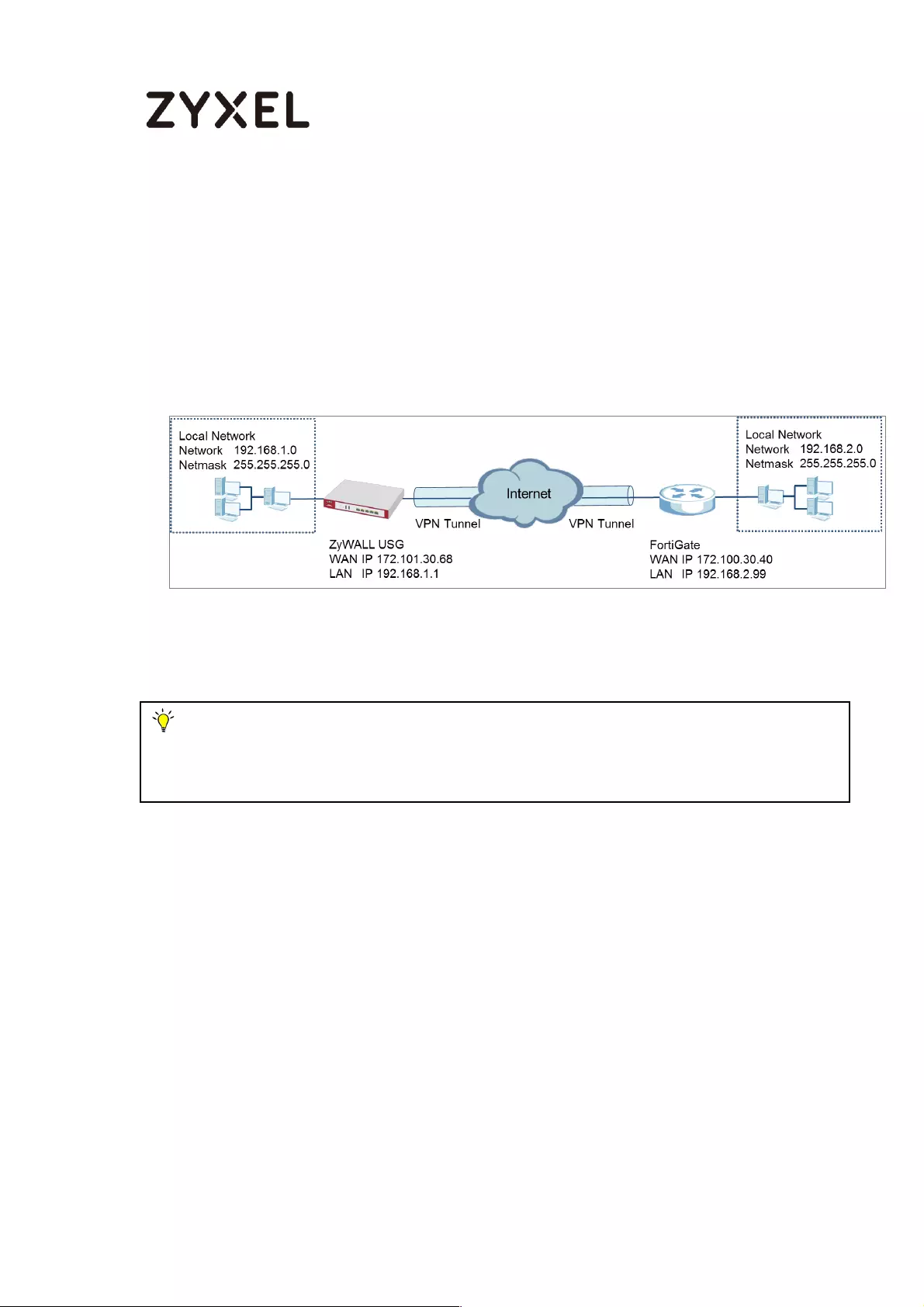
173/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN with FortiGate
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
between a ZYWALL/USG and a FortiGate router. The example instructs how to
configure the VPN tunnel between each site. The example instructs how to
configure the VPN tunnel between each site. When the VPN tunnel is configured,
each site can be accessed securely.
ZyWALL Site-to-site IPSec VPN with FortiGate Connected
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25) and FortiGate 100D (Firmware Version:
Forti OS 5.2.1).
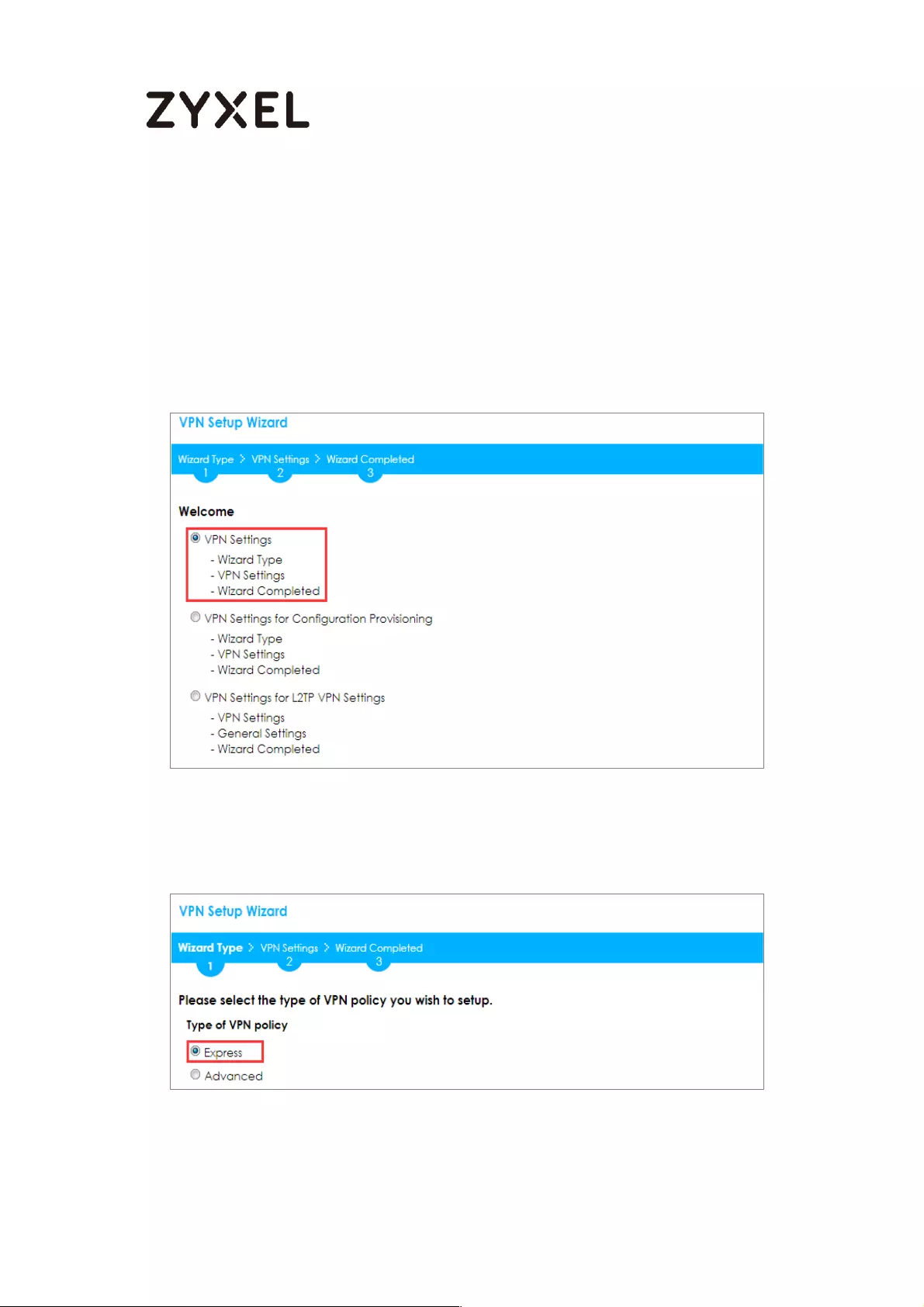
174/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the FortiGate. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
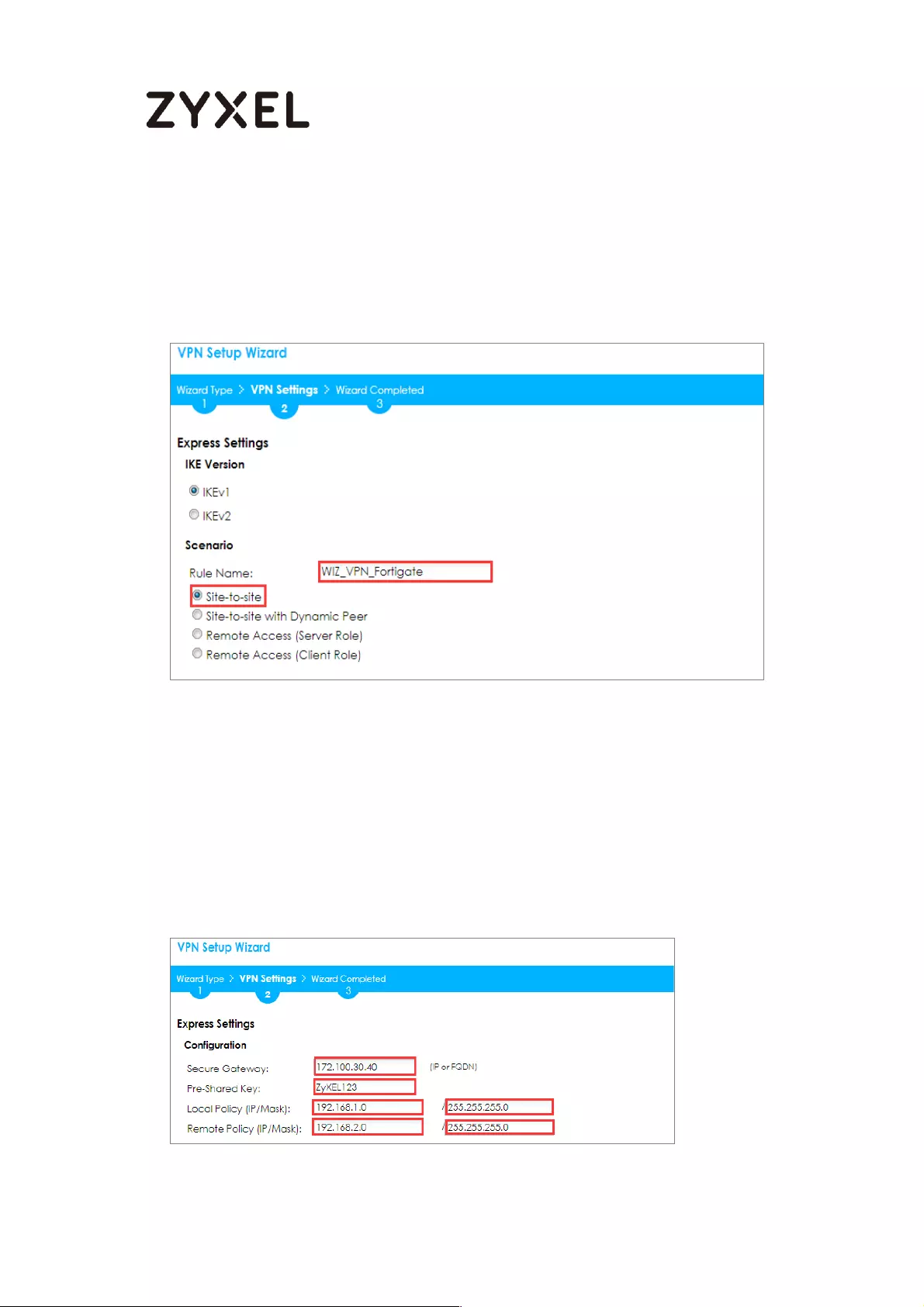
175/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the FortiGate’s WAN IP address (in the example,
172.100.30.40). Then, type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the FortiGate.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
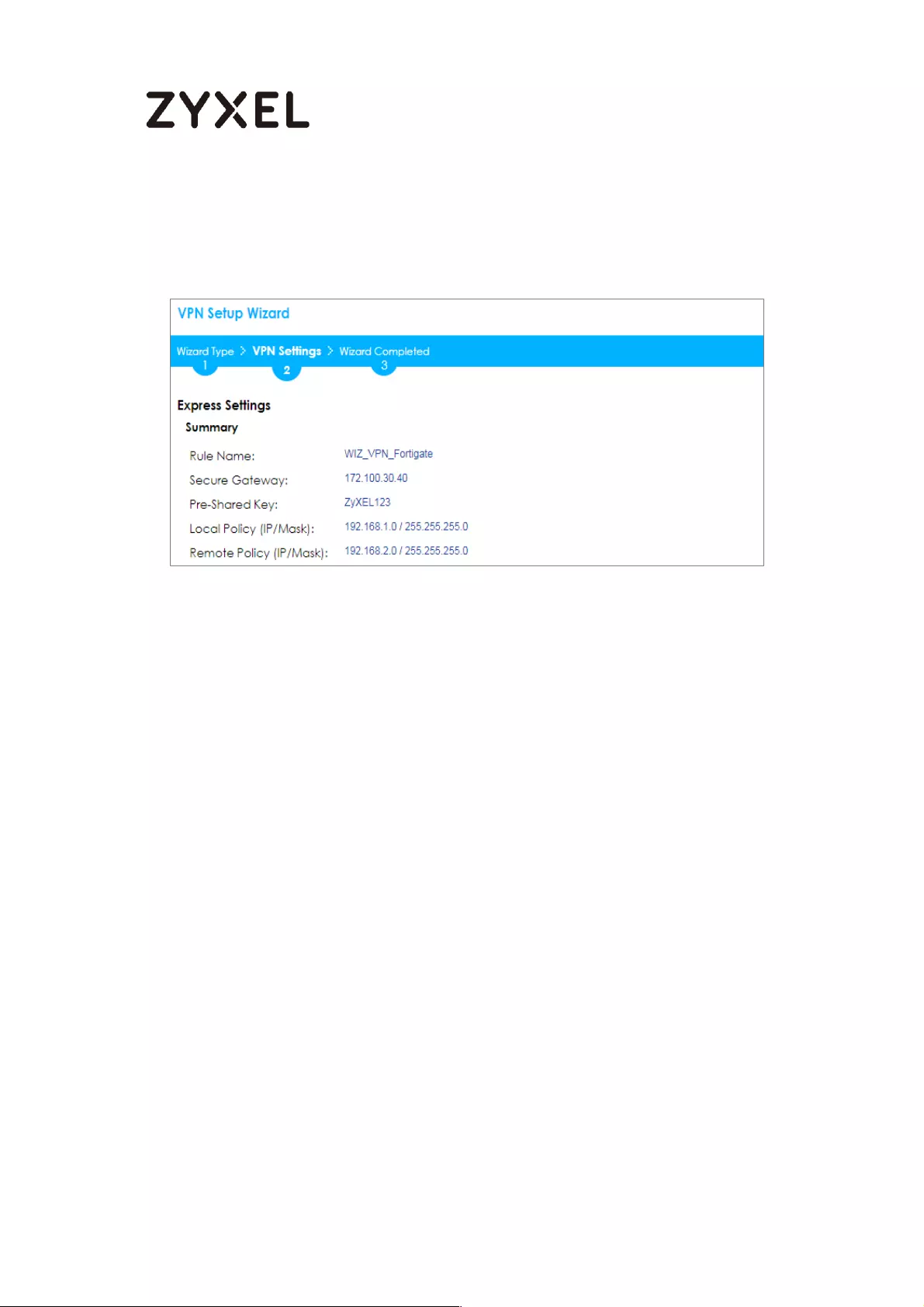
176/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
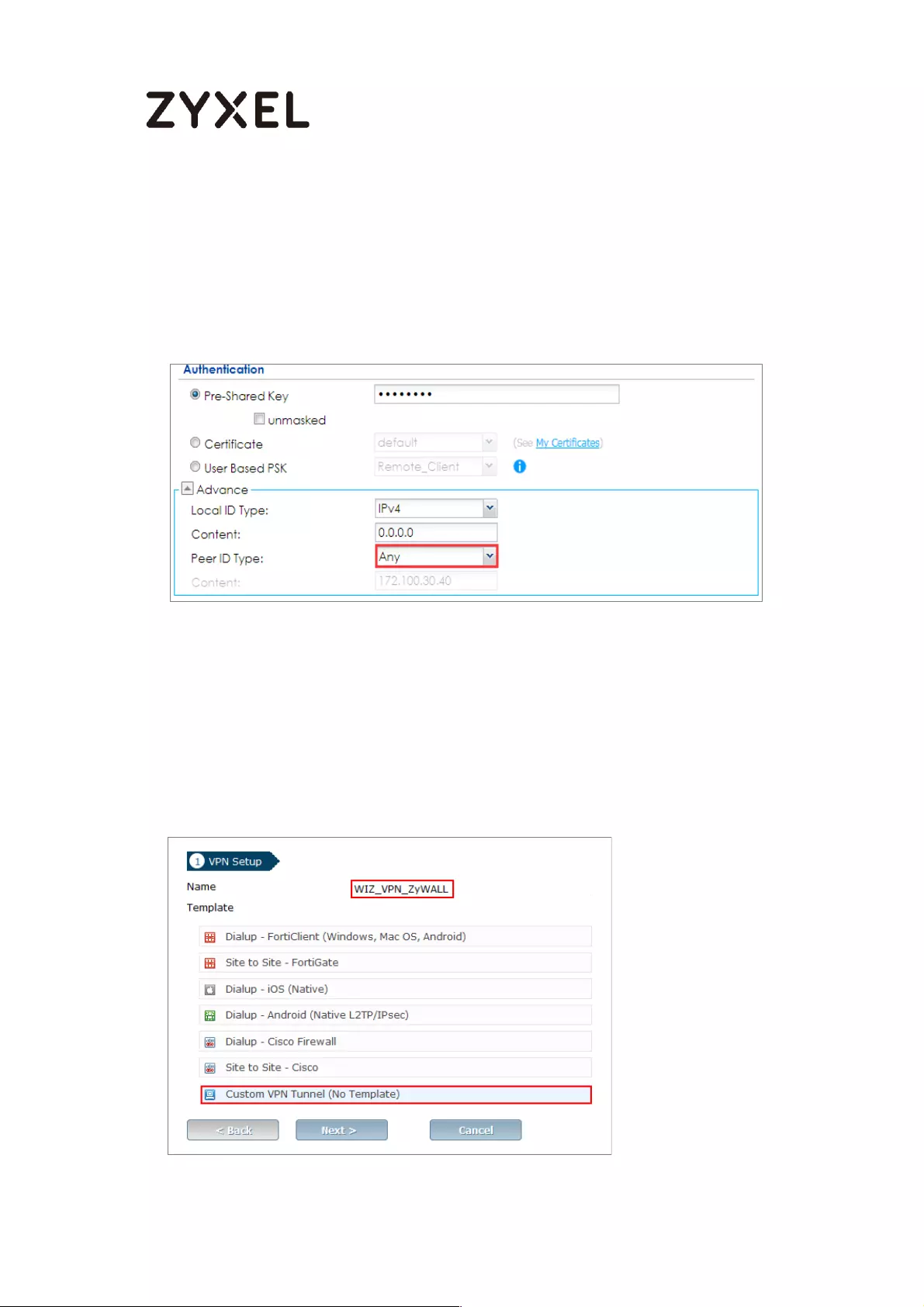
177/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
Set Up the IPSec VPN Tunnel on the FortiGate
In the FortiGate VPN > IPsec > Wizard > Custom VPN Tunnel (No Template), use the
VPN Setup to create a Site-to-site VPN rule Name.
VPN > IPsec > Wizard > Custom VPN Tunnel (No Template)
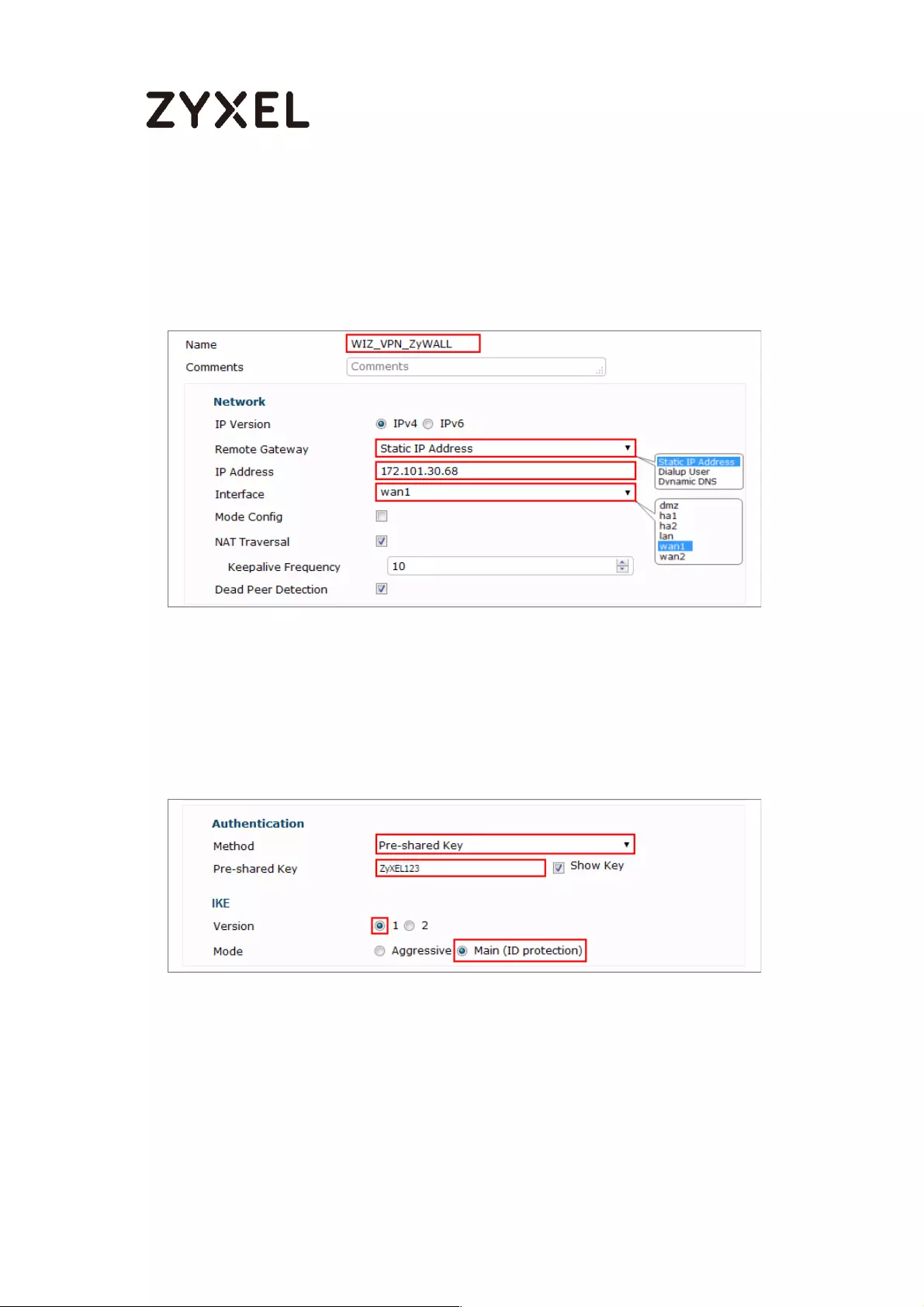
178/782
www.zyxel.com
Type the Name used to identify this VPN connection, configure Remote Gateway
IP as the peer ZyWALL/USG’s WAN IP address. Select the Interface which is
connected to the Internet.
VPN > IPsec > Wizard > Custom VPN Tunnel (No Template) > Network
Go to Authentication section, enter Pre-shared Key and choose negotiation
Mode the same as the peer ZyWALL/USG’s.
VPN > IPsec > Wizard > Custom VPN Tunnel (No Template) > Authentication

179/782
www.zyxel.com
Configure Phase 1 Proposal and Diffie-Hellman Group as the peer ZyWALL/USG
Advanced Settings’ Phase 1 Settings > Proposal and Key Group.
VPN > IPsec > Wizard > Custom VPN Tunnel (No Template) > Phase 1 Proposal
Go to Phase 2 Selectors > Advanced and configure Phase 2 Proposal as the peer
ZyWALL/USG Advanced Settings’ Phase 2 Settings > Proposal.
Set Local Address to be the IP address range of the network connected to the
FortiGate and Remote Address to be the IP address range of the network
connected to the ZyWALL/USG.
Make sure you uncheck Enable Perfect Forward Secrecy (PFS) if this function is
disabled in the peer ZyWALL/USG.
VPN > IPsec > Wizard > Custom VPN Tunnel (No Template) > Phase 2 Selectors
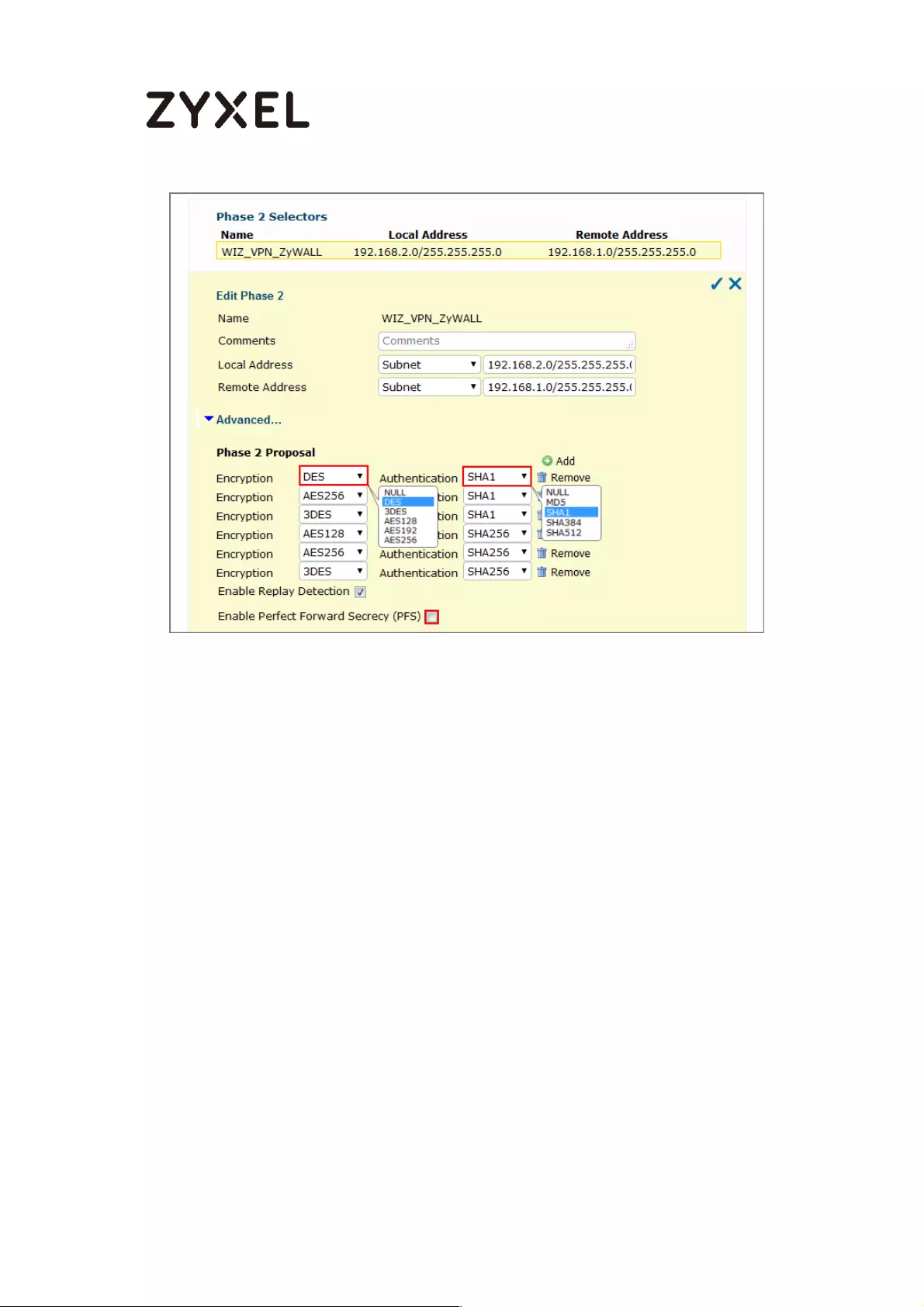
180/782
www.zyxel.com
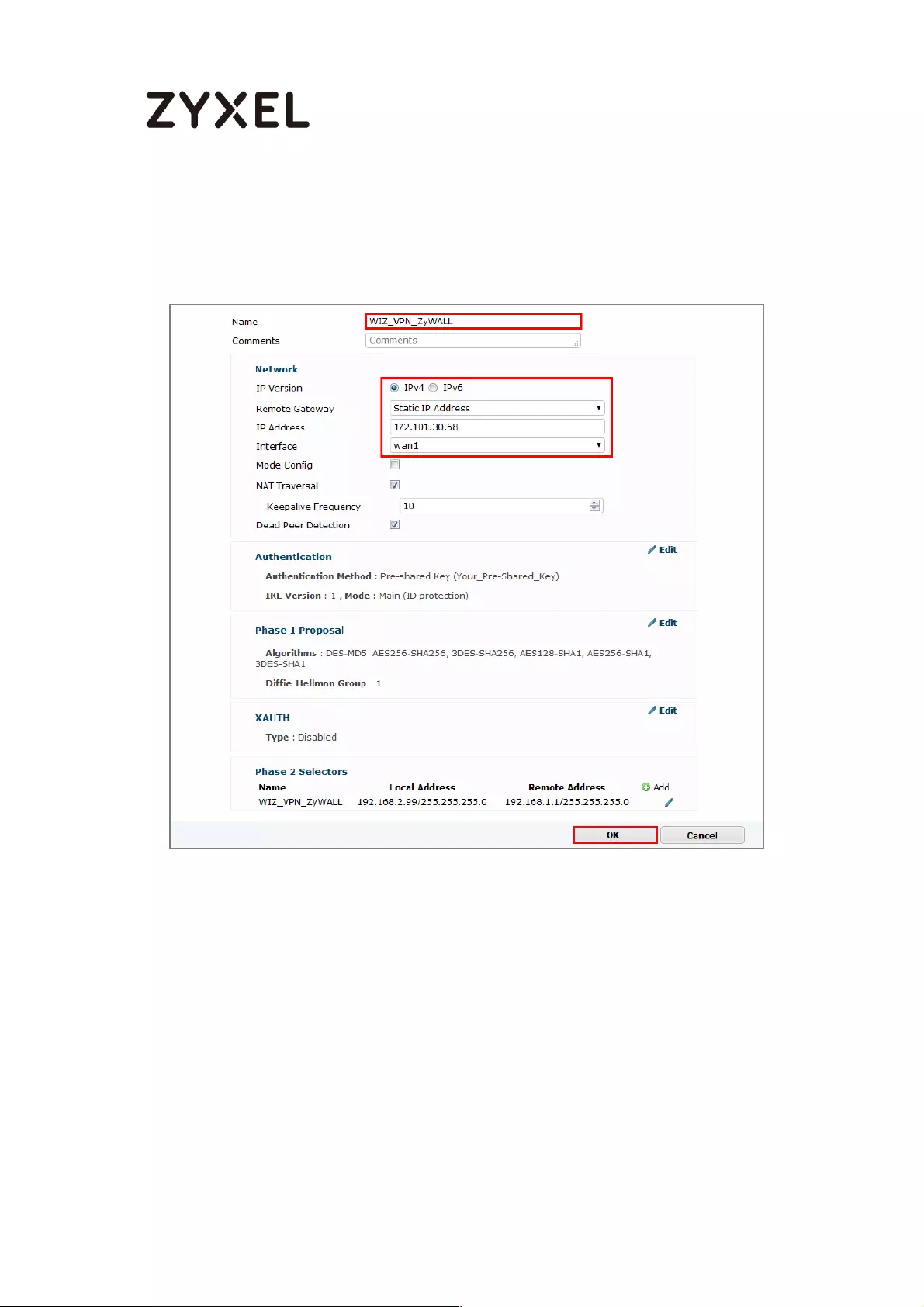
181/782
www.zyxel.com
This screen provides a summary of the VPN tunnel. Click OK to exit the
configuration page.
VPN > IPsec > Wizard > Custom VPN Tunnel (No Template)

182/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > IPSec
Go to FortiGate VPN > Monitor > IPsec Monitor and check the tunnel Status is up
and Incoming Data/Outgoing Data traffic.
VPN > Monitor > IPsec Monitor
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC behind ZyWALL/USG > Window 7 > cmd > ping 192.168.2.33
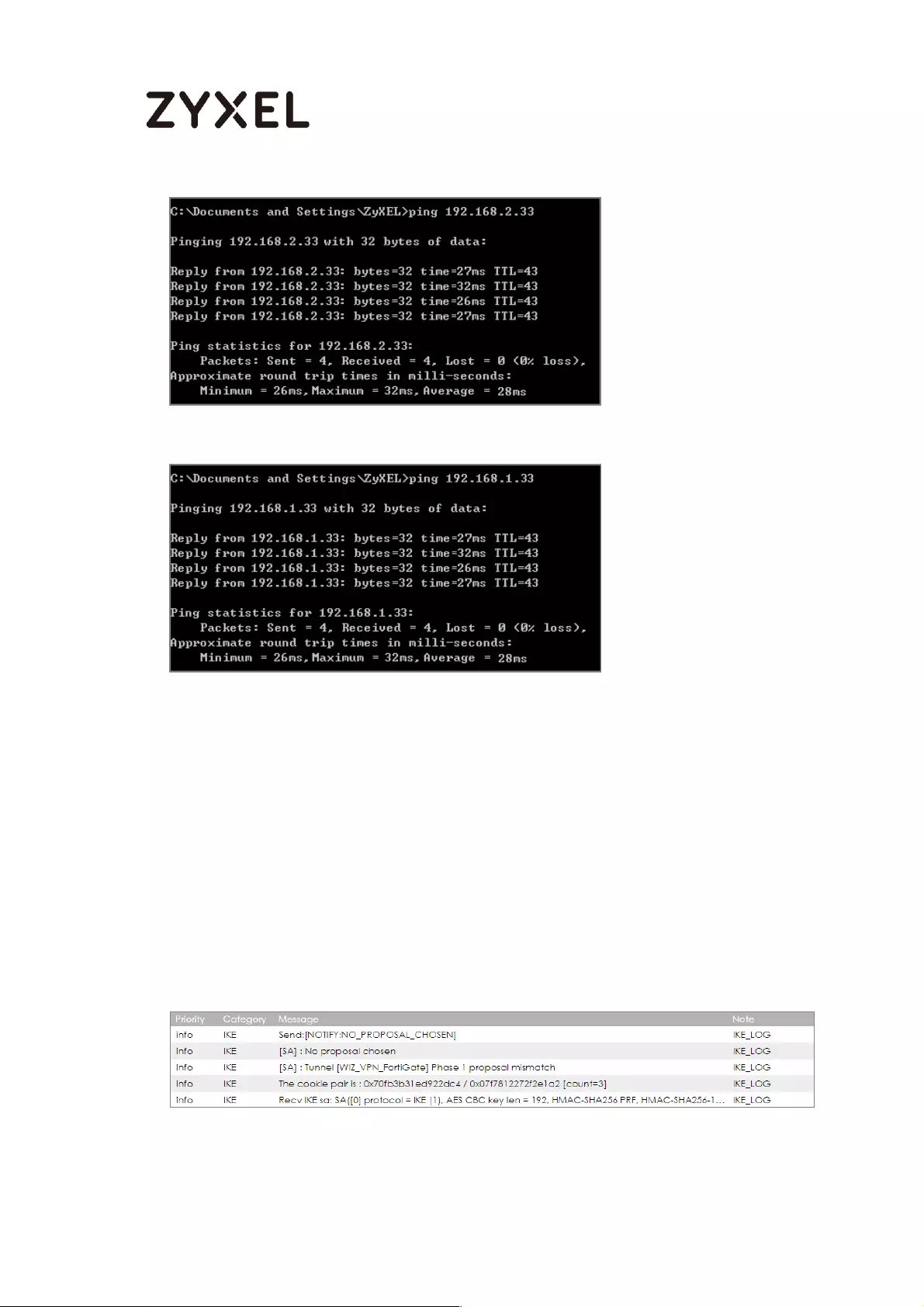
183/782
www.zyxel.com
PC behind FortiGate> Window 7 > cmd > ping 192.168.1.33
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG and FortiGate must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log message,
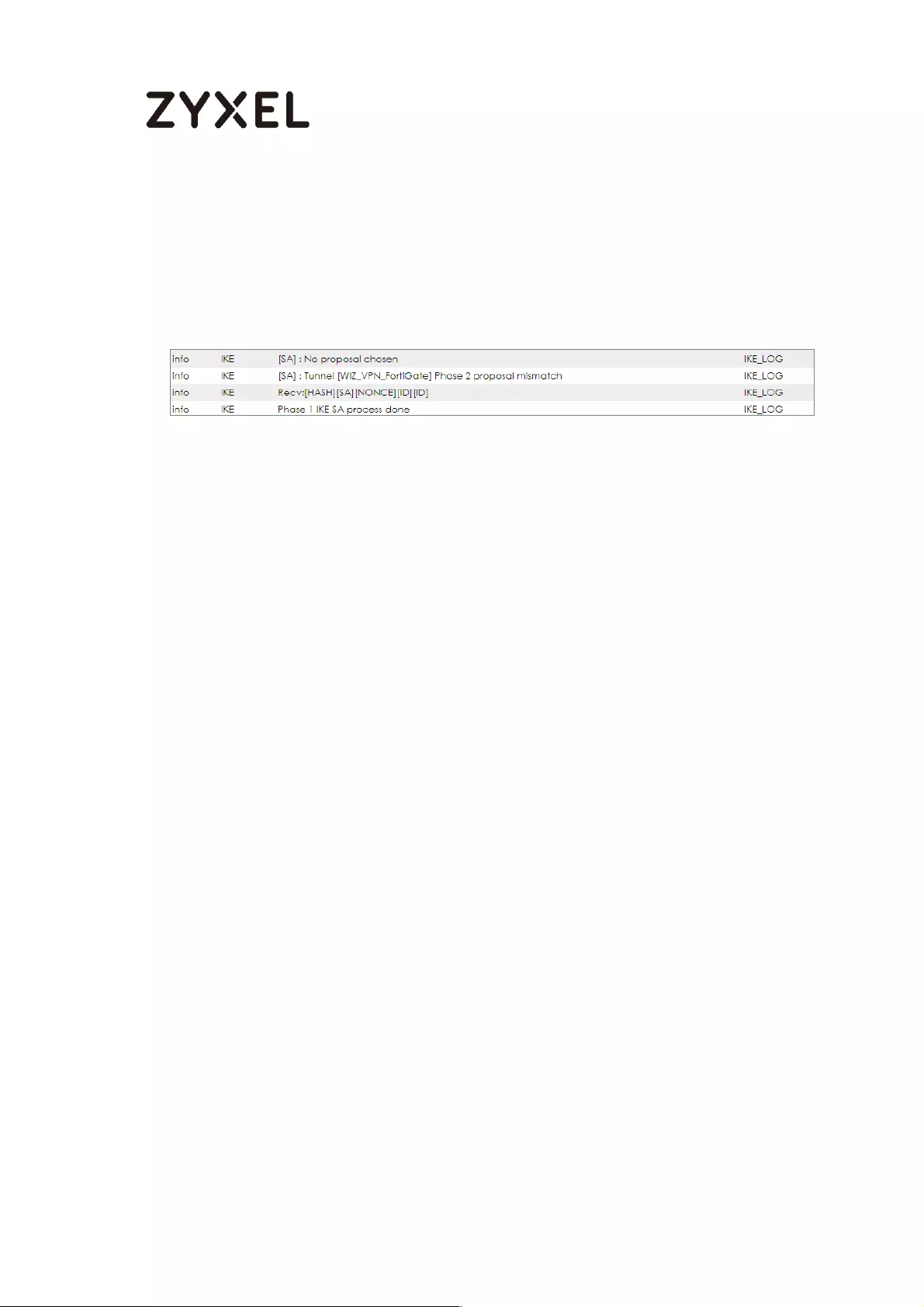
184/782
www.zyxel.com
please check ZyWALL/USG and FortiGate Phase 2 Settings. Both ZyWALL/USG
and FortiGate must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
MONITOR > Log
Make sure the both ZyWALL/USG and FortiGate security policies allow IPSec VPN
traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.
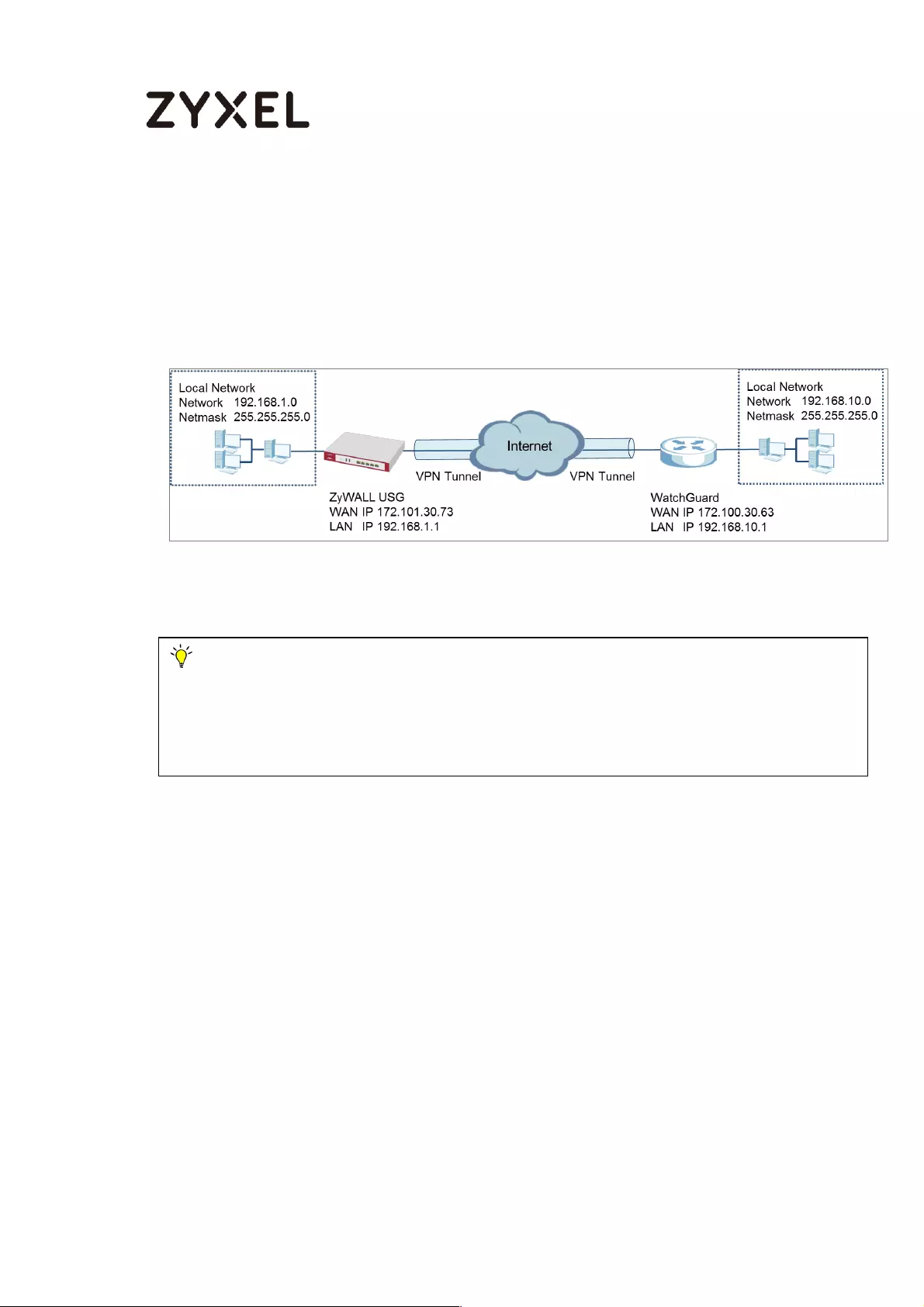
185/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN with WatchGuard
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
between a ZYWALL/USG and a WatchGuard router. The example instructs how to
configure the VPN tunnel between each site. When the VPN tunnel is configured,
each site can be accessed securely.
ZyWALL Site-to-site IPSec VPN with WatchGuard Connected
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25) and WatchGuard XTM 515 (Firmware
Version: 11.10.4).
186/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the WatchGuard. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2
settings and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
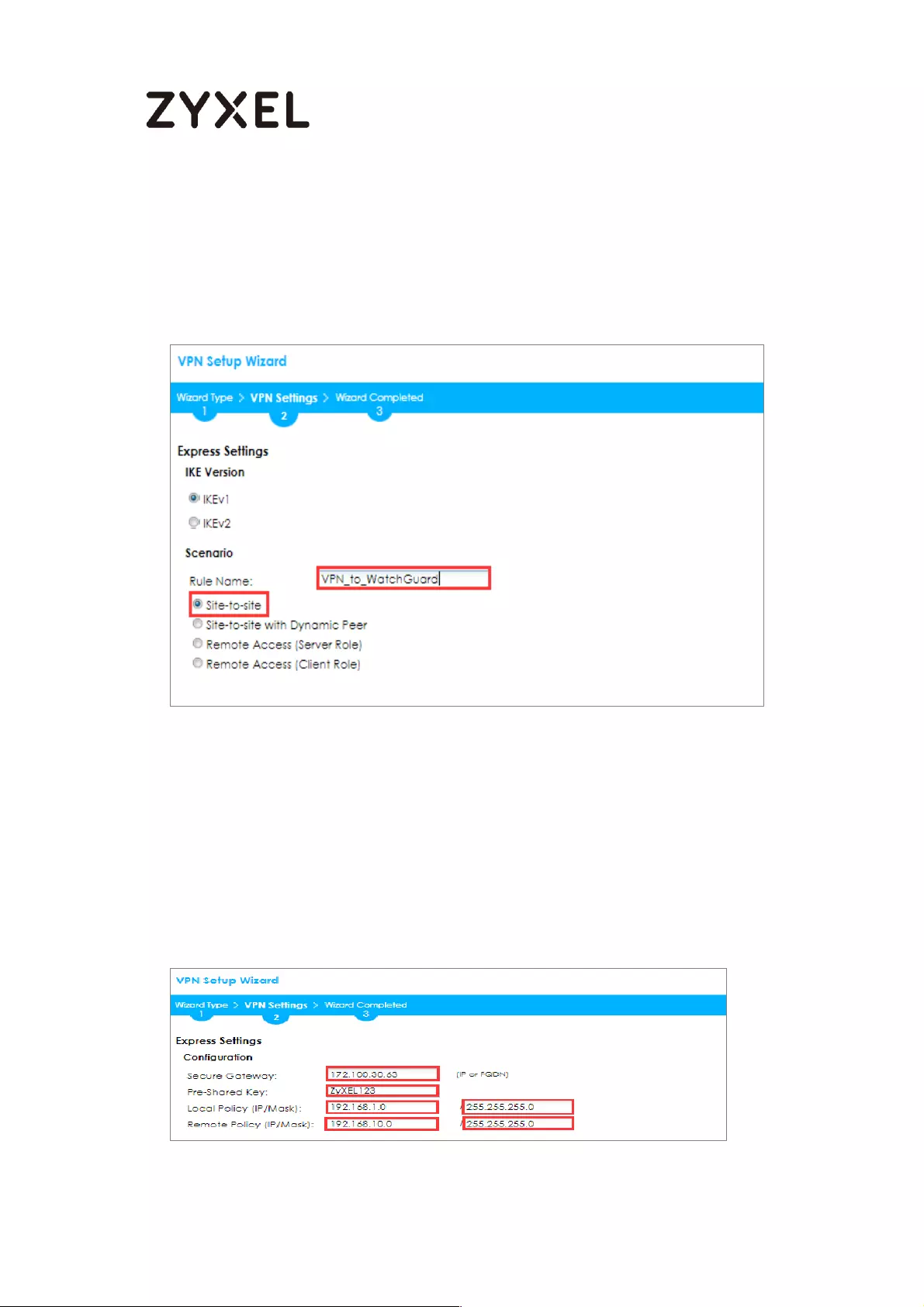
187/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the WatchGuard’s WAN IP address (in the
example, 172.100.30.63). Then, type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the WatchGuard. Click OK.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
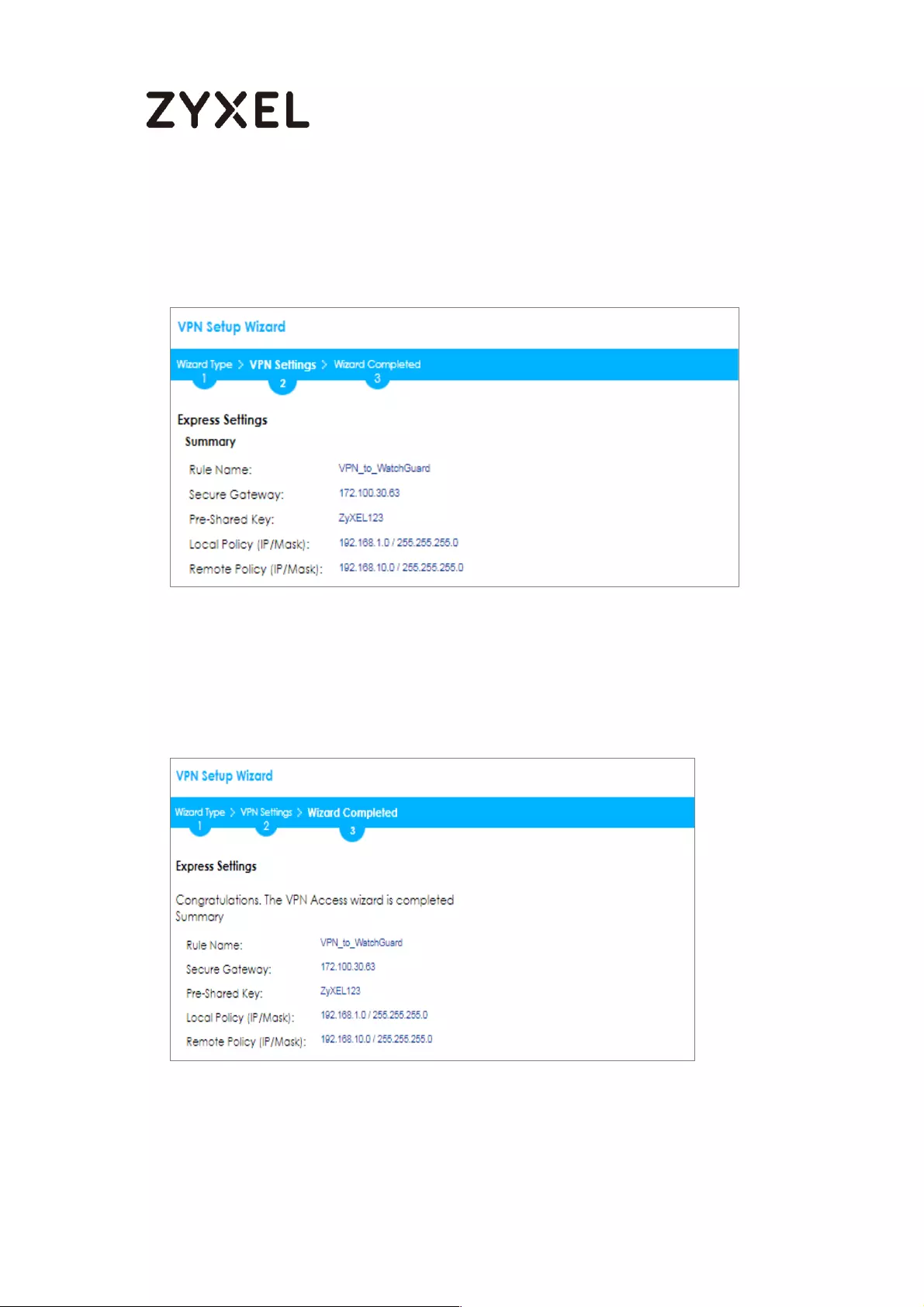
188/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings > Wizard completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, click Show Advanced
Settings. Configure Authentication > Local ID Type as IPv4 and set the Content as
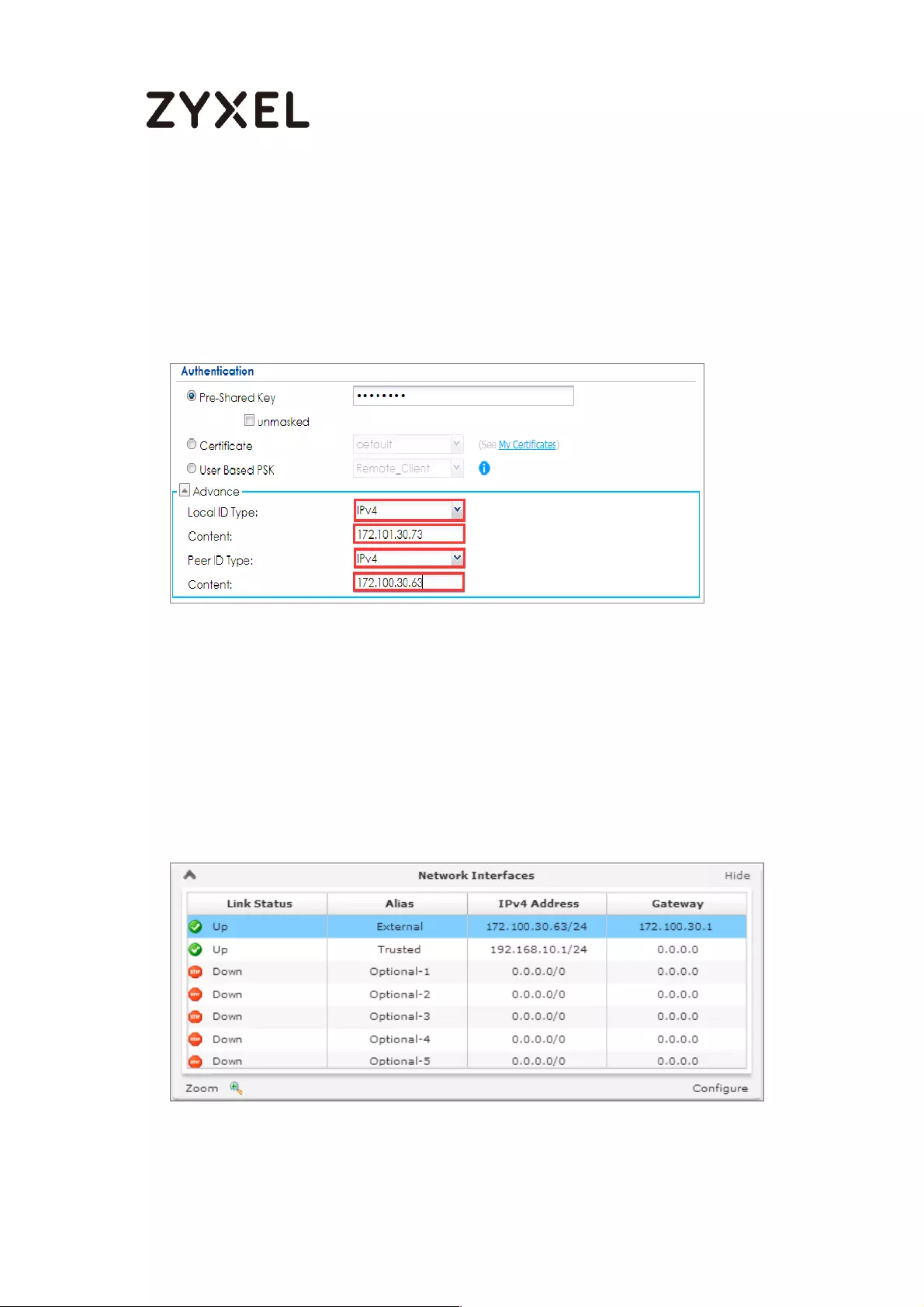
189/782
www.zyxel.com
your ZyWALL/USG’s WAN IP Address (in the example, 172.101.30.73). Then,
configure Authentication > Remote ID Type as IPv4 and set the Content as your
WatchGuard’s External IP Address (in the example, 172.100.30.63). Click OK.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
Set Up the IPSec VPN Tunnel on the WatchGuard
Go to Dashboard > Network Interfaces to check your External IP Address (the
Internet-facing interface) and Trusted IP Address (the Local IP address).
Dashboard > Network Interfaces

190/782
www.zyxel.com
In the WatchGuard VPN > Branch Office VPN > Gateway > General Settings
create a Site-to-site VPN Gateway Name and set a secure Pre-Shared Key.
VPN > Branch Office VPN > Gateway > General Settings > Credential Method
To add a Gateway Endpoint, click Add.
VPN > Branch Office VPN > Gateway > General Settings > Gateway Endpoints
The new Gateway Endpoint dialog box appears. Configure your Local Gateway
identity as WatchGuard’s External IP Address (in the example, 172.100.30.63) and
Remote Gateway identity as your ZyWALL/USG’s WAN IP Address (in the example,
172.101.30.73). Click OK.
VPN > Branch Office VPN > Gateway > General Settings > Gateway Endpoints
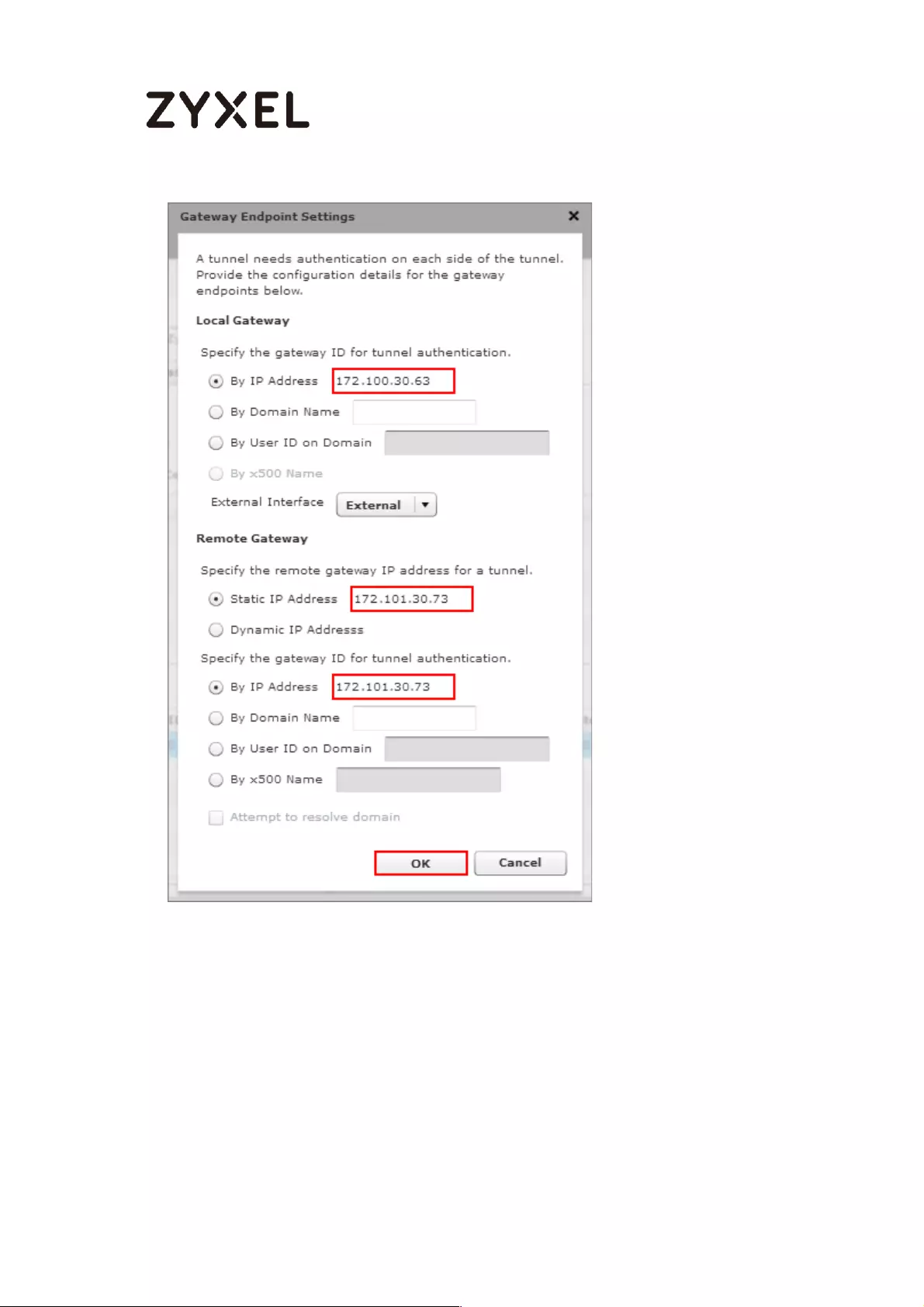
191/782
www.zyxel.com
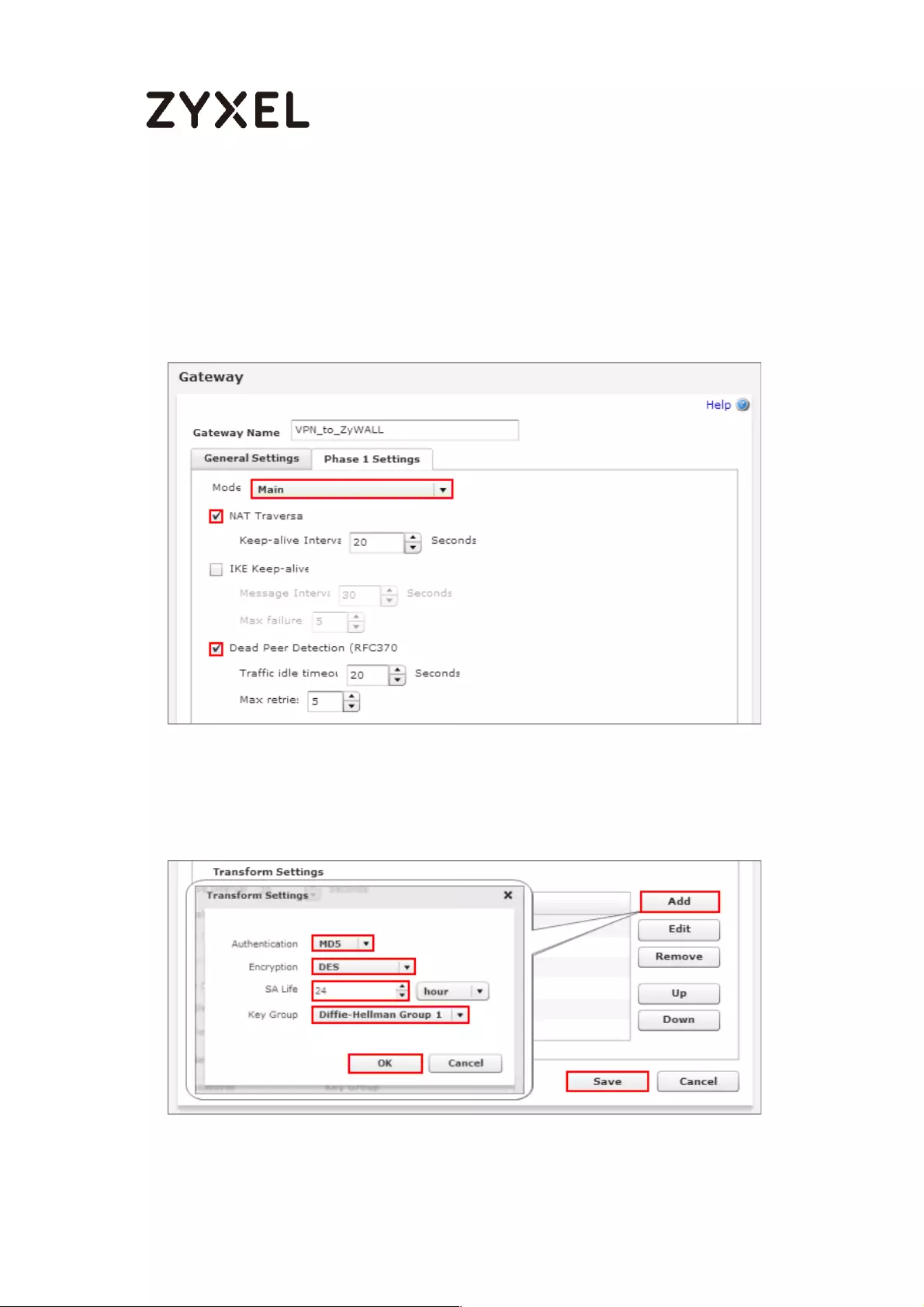
192/782
www.zyxel.com
Then, go to VPN > Branch Office VPN > Gateway > Phase 1 Settings to select
negotiation Mode the same as your ZyWALL/USG’s Phase 1 Settings. Make sure
you enable both NAT Traversa and Dead Peer Detection options if both options
are enabled in the ZyWALL/USG.
VPN > Branch Office VPN > Gateway > Phase 1 Settings
Use Transform Settings to create the same security settings as in the ZyWALL/USG
Phase 1 settings. Click OK and Save to exit the Transform Settings page.
VPN > Branch Office VPN > Gateway > Phase 1 Settings > Transform Settings
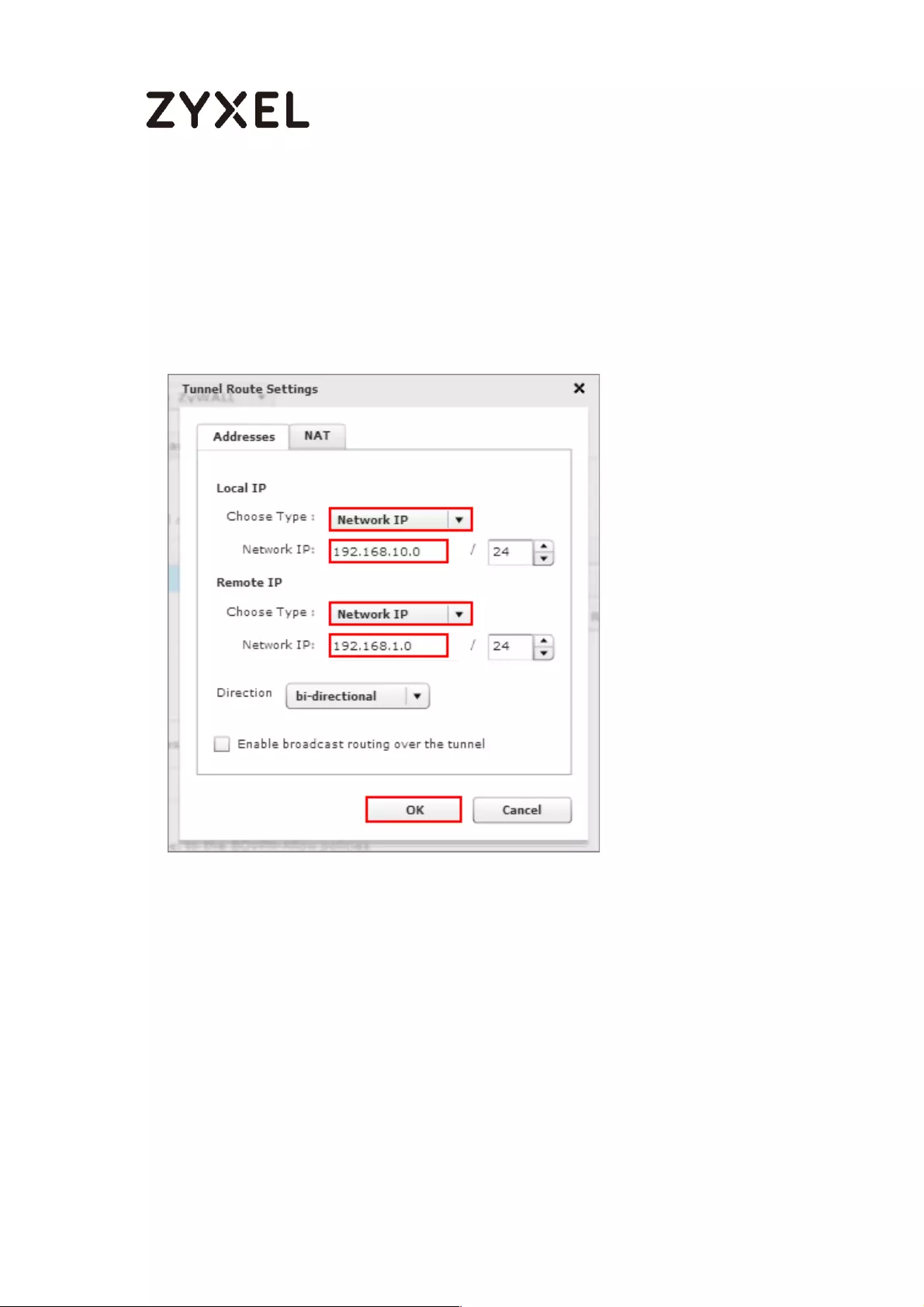
193/782
www.zyxel.com
Then, go to VPN > Branch Office VPN > Tunnel to add a Tunnel Route Settings. In
the Local IP section, set the Network IP to be the IP address range of the network
connected to the WatchGuard. In the Remote IP section, set the Network IP to be
the IP address range of the network connected to the ZyWALL/USG. Click OK.
VPN > Branch Office VPN > Tunnel > Address
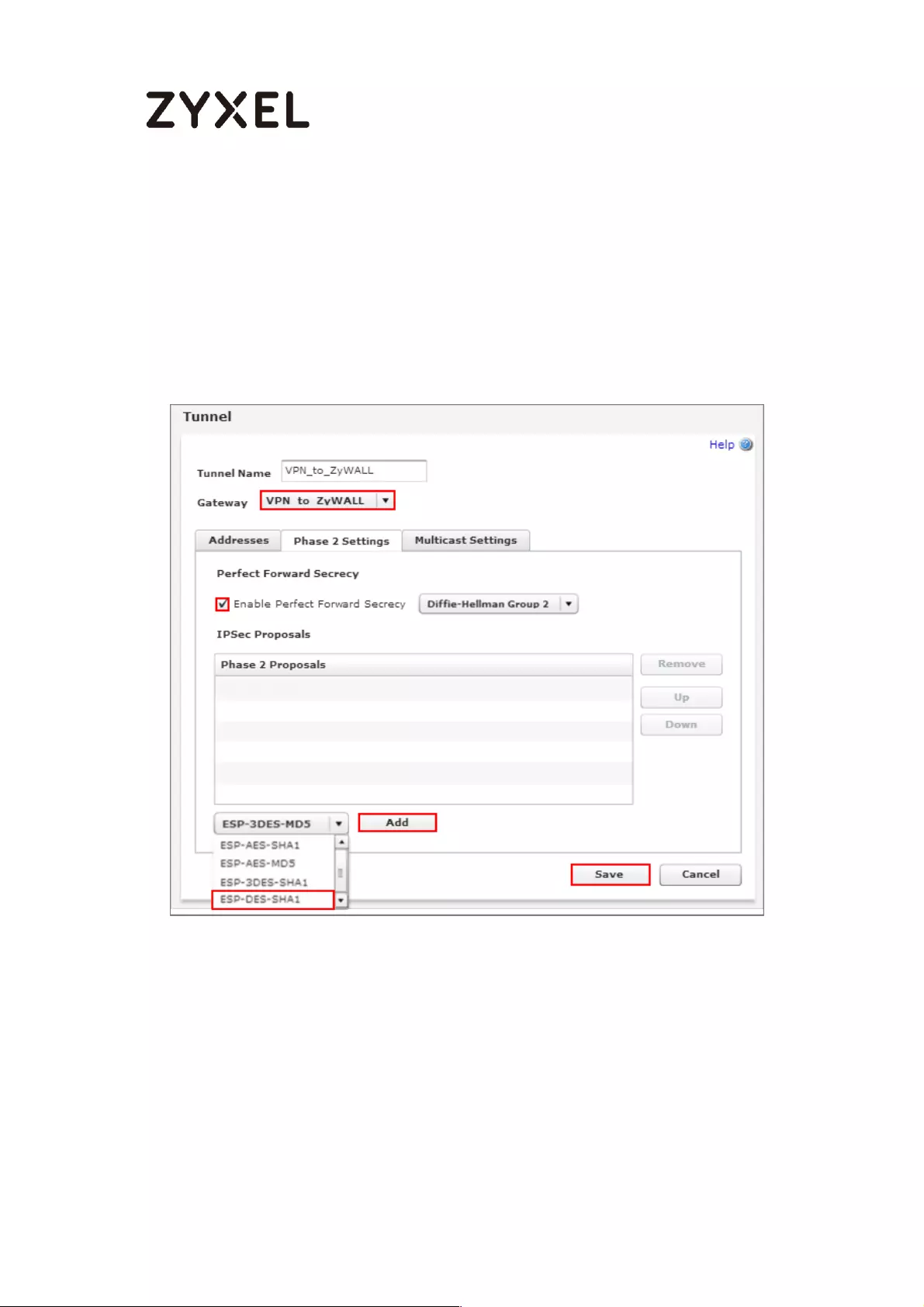
194/782
www.zyxel.com
Go to VPN > Branch Office VPN > Tunnel > Phase 2 Settings to create a Tunnel
Name. Then, select the Gateway. Make sure you enable Perfect Forward Secrecy
and select Diffie-Hellman Group 2. Then, scroll down Phase 2 Proposals and add
the encryption types to match your ZyWALL/USG’s VPN Connection > Phase 2
Settings. Click Save.
VPN > Branch Office VPN > Tunnel > Phase 2 Settings
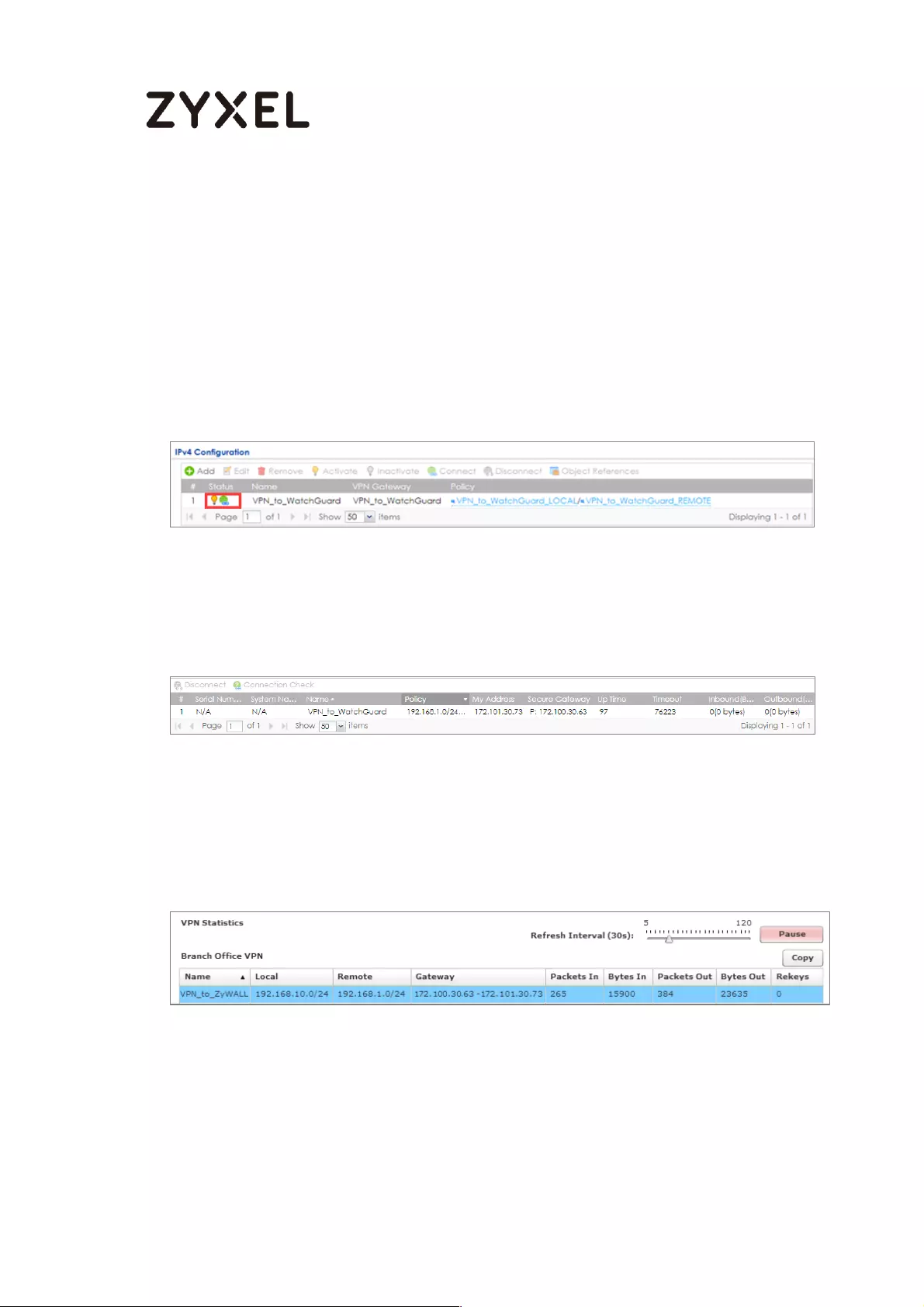
195/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > IPSec
Go to WatchGuard System Status > VPN Statistics > Branch Office VPN and check
the tunnel Status is up and Bytes In (Incoming Data) and Bytes Out (Outgoing
Data).
System Status > VPN Statistics > Branch Office
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
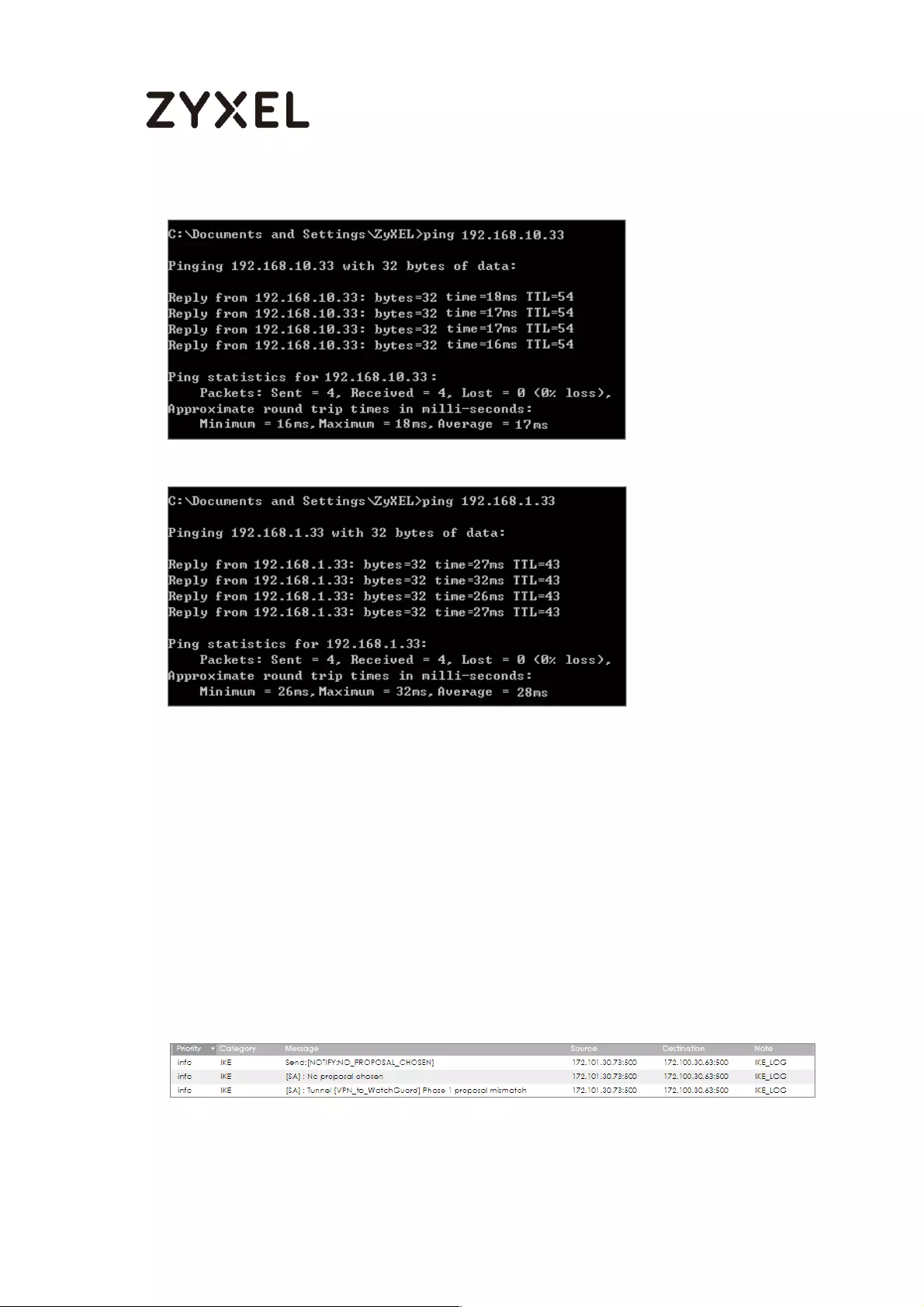
196/782
www.zyxel.com
PC behind ZyWALL/USG > Window 7 > cmd > ping 192.168.10.33
PC behind WatchGuard> Window 7 > cmd > ping 192.168.1.33
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG and WatchGuard must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log message,

197/782
www.zyxel.com
please check ZyWALL/USG and WatchGuard Phase 2 Settings. Both ZyWALL/USG
and WatchGuard must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
MONITOR > Log
Make sure the both ZyWALL/USG and WatchGuard security policies allow IPSec
VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol
50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.
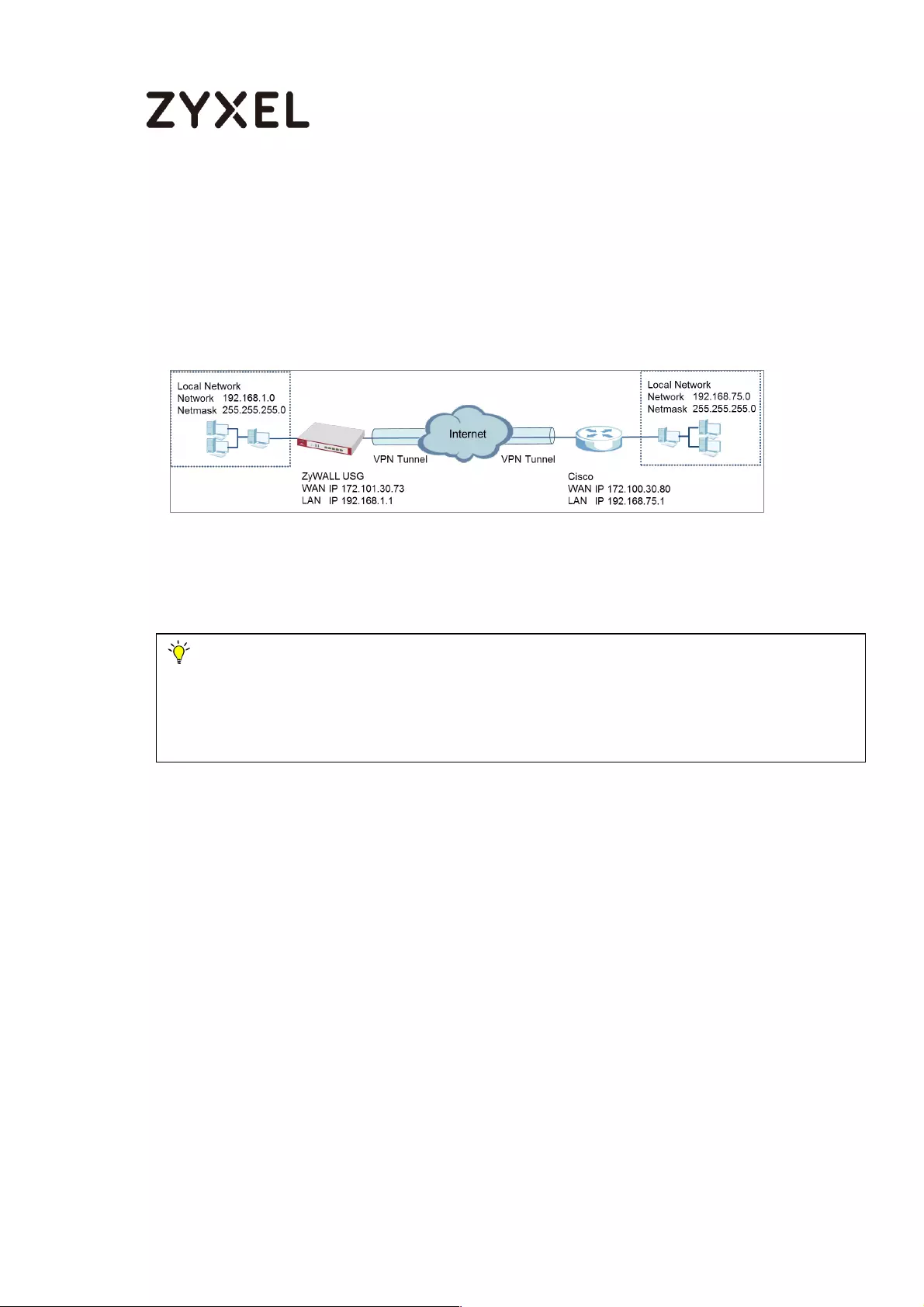
198/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN with Cisco
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
between a ZYWALL/USG and a Cisco router. The example instructs how to
configure the VPN tunnel between each site. When the VPN tunnel is configured,
each site can be accessed securely.
ZyWALL Site-to-site IPSec VPN with Cisco Connected
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25) and ISA500 (Firmware Version: 1.0.3).
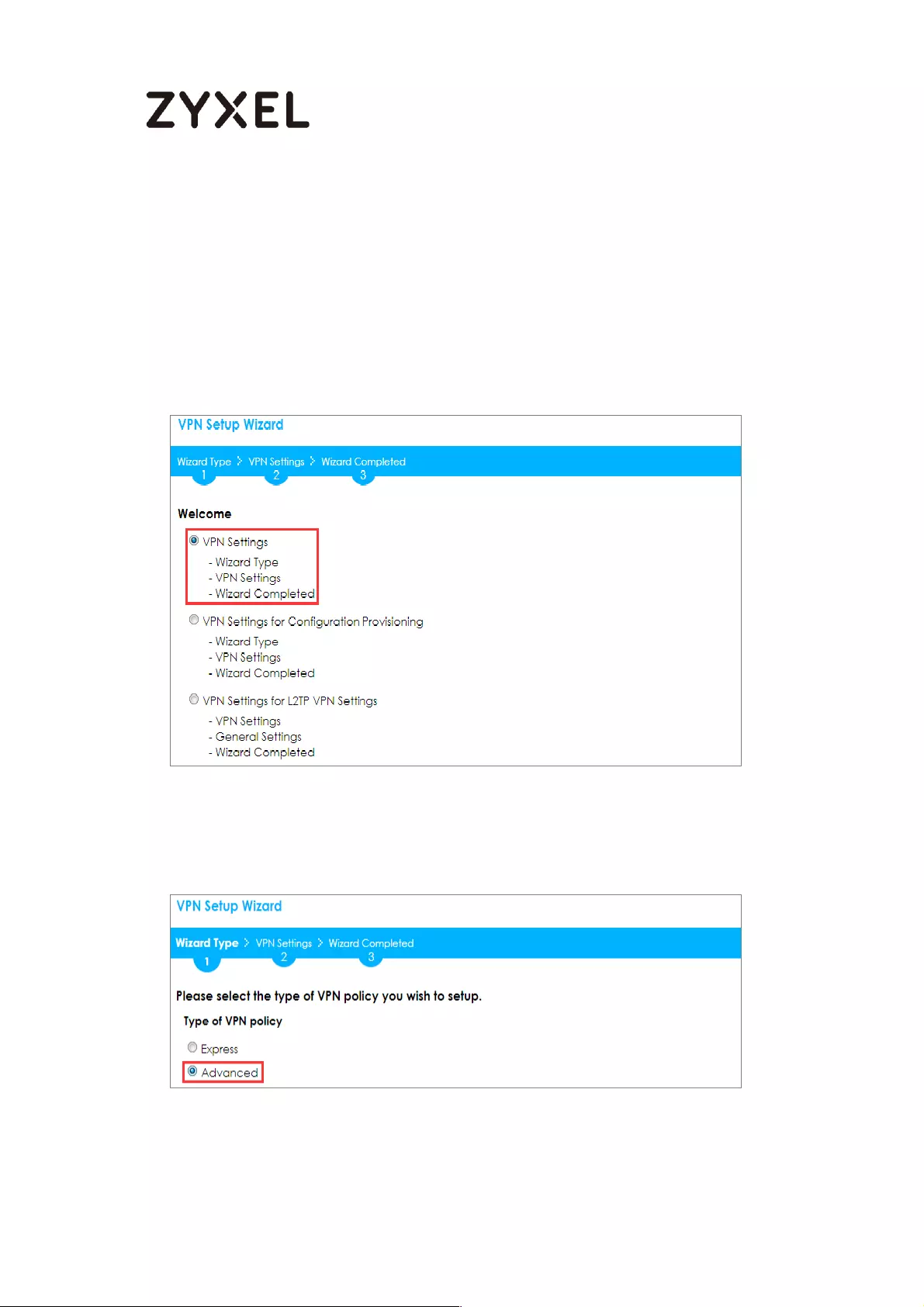
199/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the Cisco. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Advanced to create a VPN rule with the customize phase 1, phase 2
settings and authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
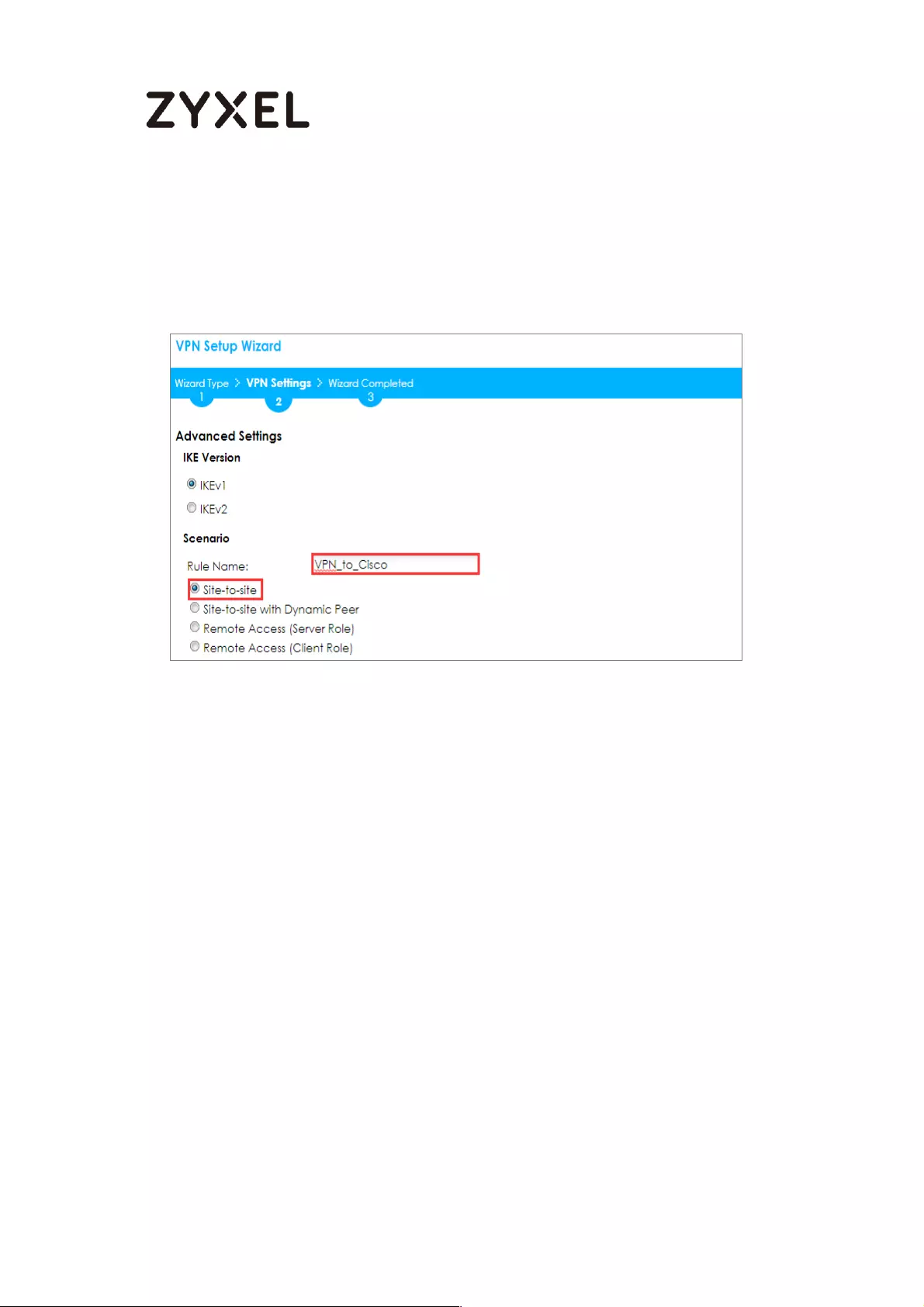
200/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Then, configure the Secure Gateway IP as the Cisco’s Gateway IP address (in the
example, 172.100.30.80); select My Address to be the interface connected to the
Internet.
Set the desired Negotiation, Encryption, Authentication, Key Group and SA Life
Time settings. Type a secure Pre-Shared Key (8-32 characters) which must match
your Cisco Pre-Shared Key. Click OK.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Phase 1 Setting)
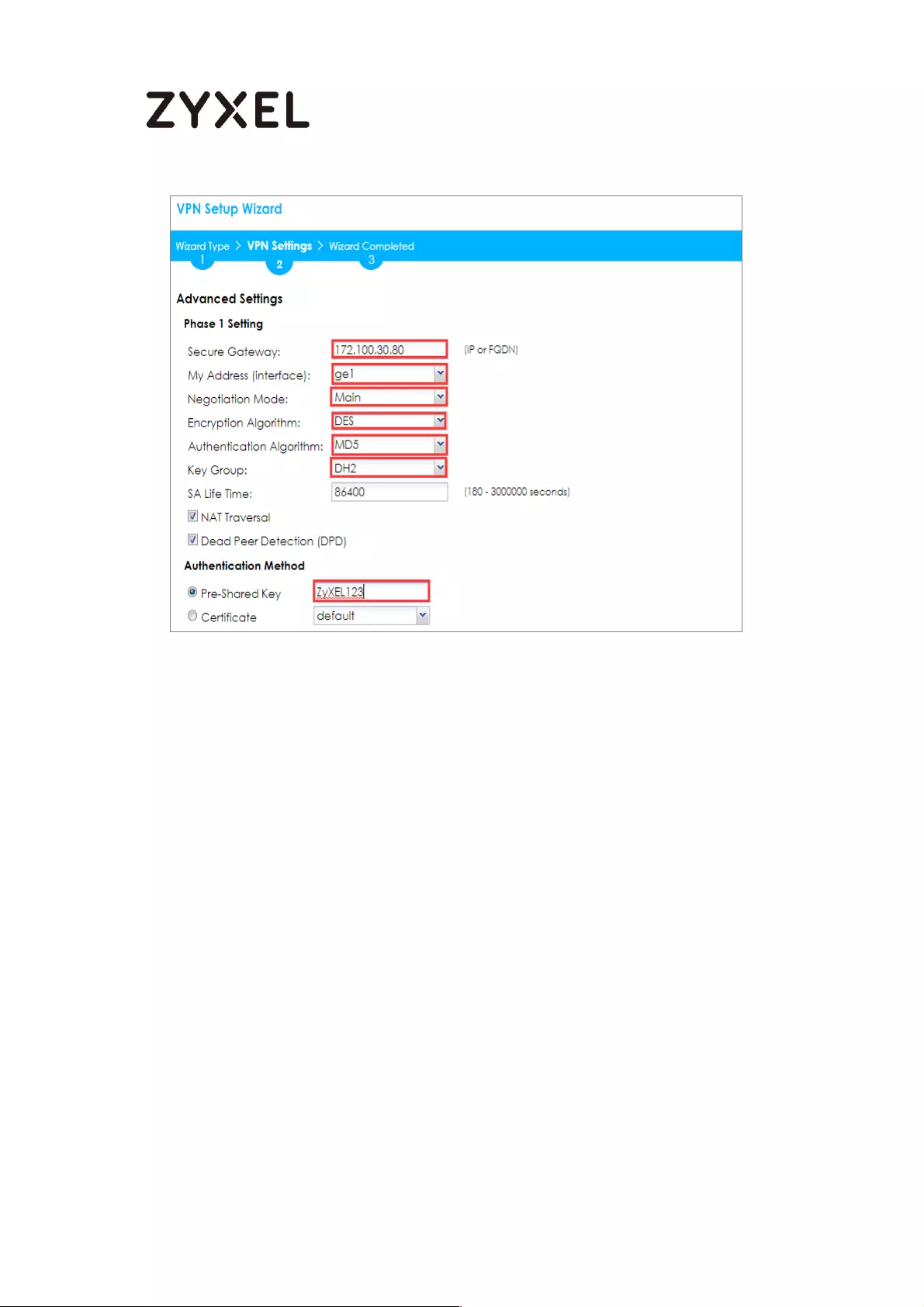
201/782
www.zyxel.com
Continue to Phase 2 Settings to select the desired Encapsulation, Encryption,
Authentication, and Perfect Forward Secrecy (PFS) settings.
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the Cisco. Click OK.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Phase 2 Setting)
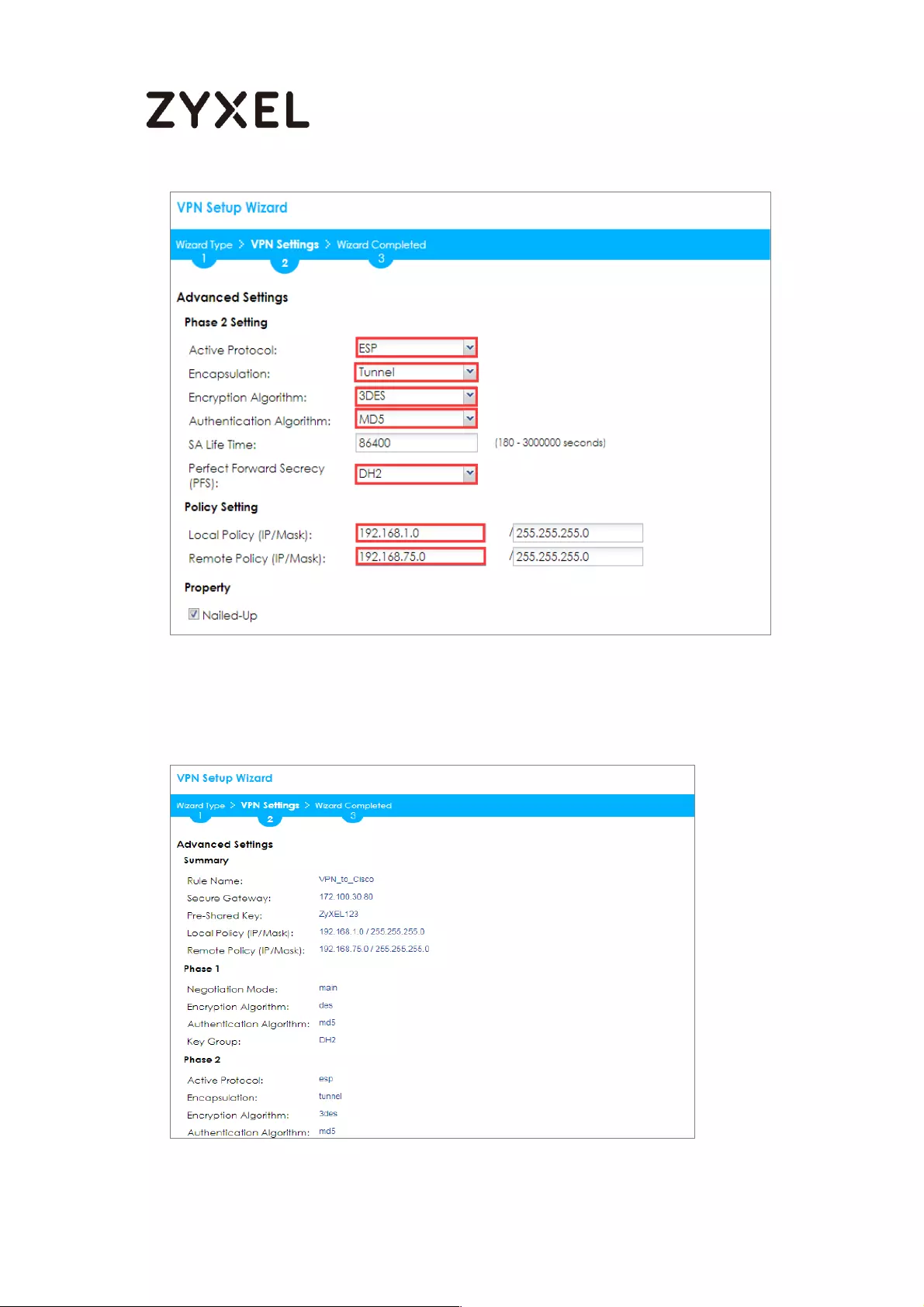
202/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
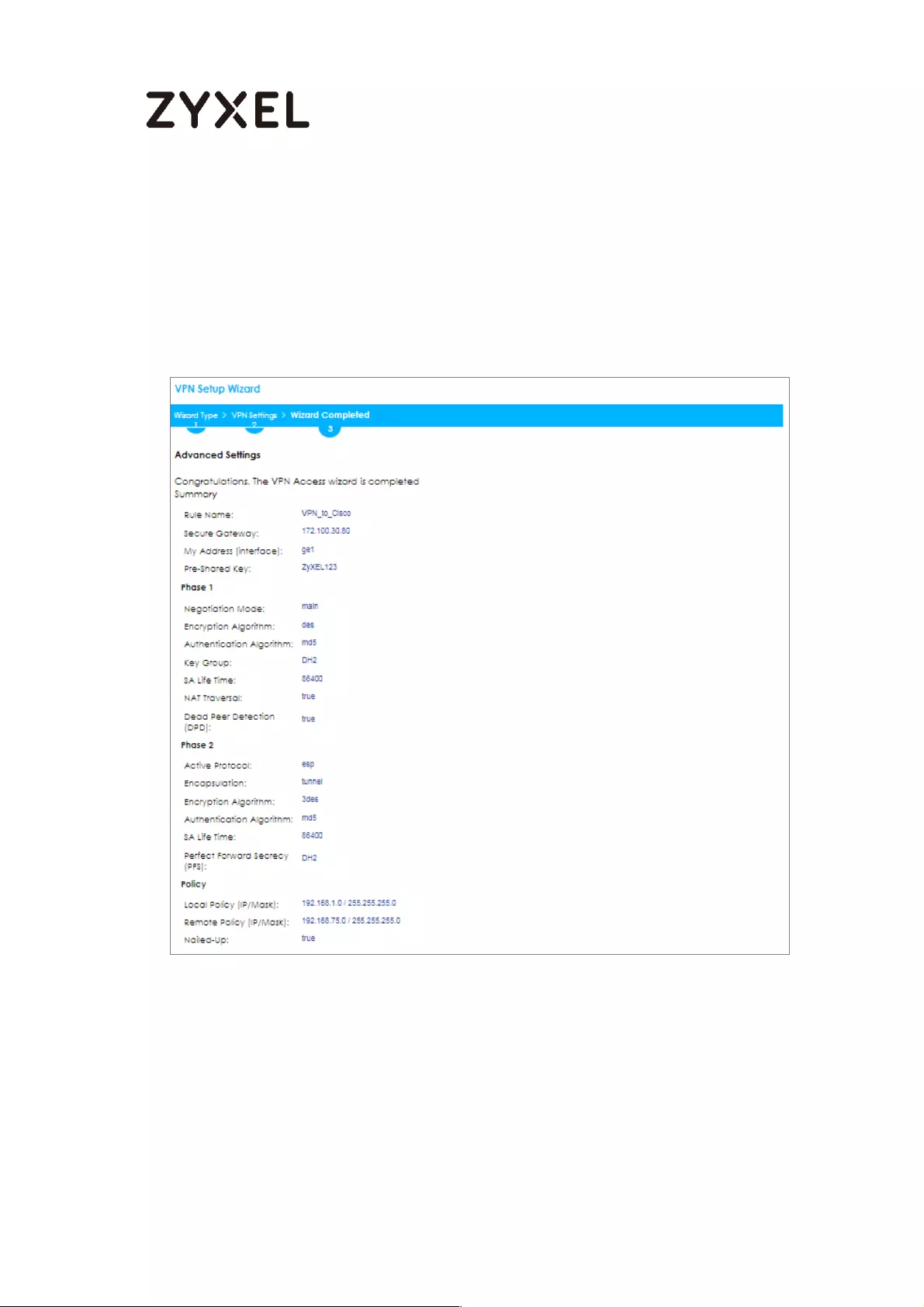
203/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
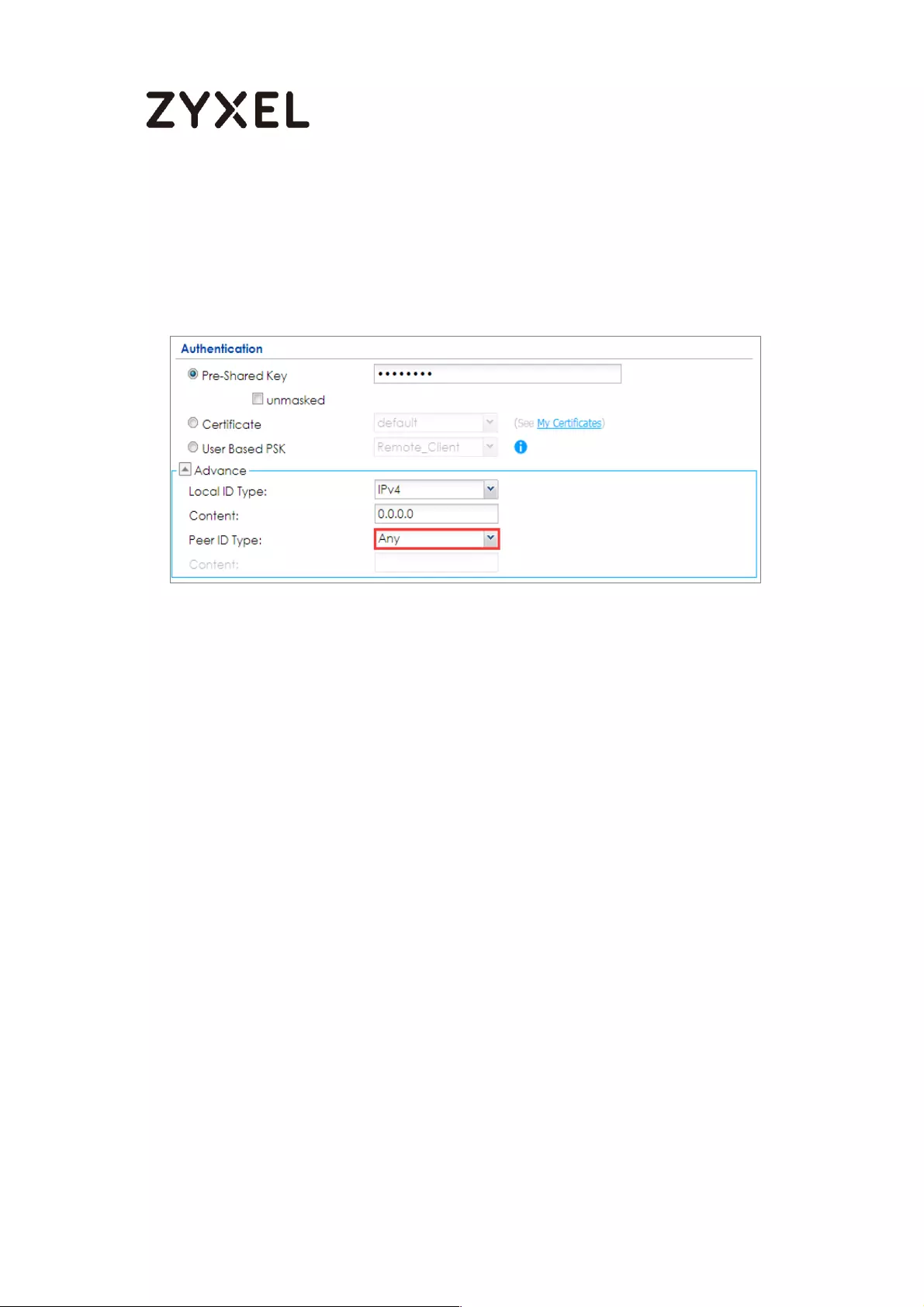
204/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced Settings >
Authentication > Peer ID Type
Set Up the IPSec VPN Tunnel on the Cisco
To create an Address Object Name of your peer ZyWALL/USG Local IP address,
go to Networking > Address Management > Address Objects and click Add
Address. Select Network as the Type. Configure IP Address and Netmask to be
the IP address range of the network connected to the ZyWALL/USG. Click OK.
Networking > Address Management > Address Objects
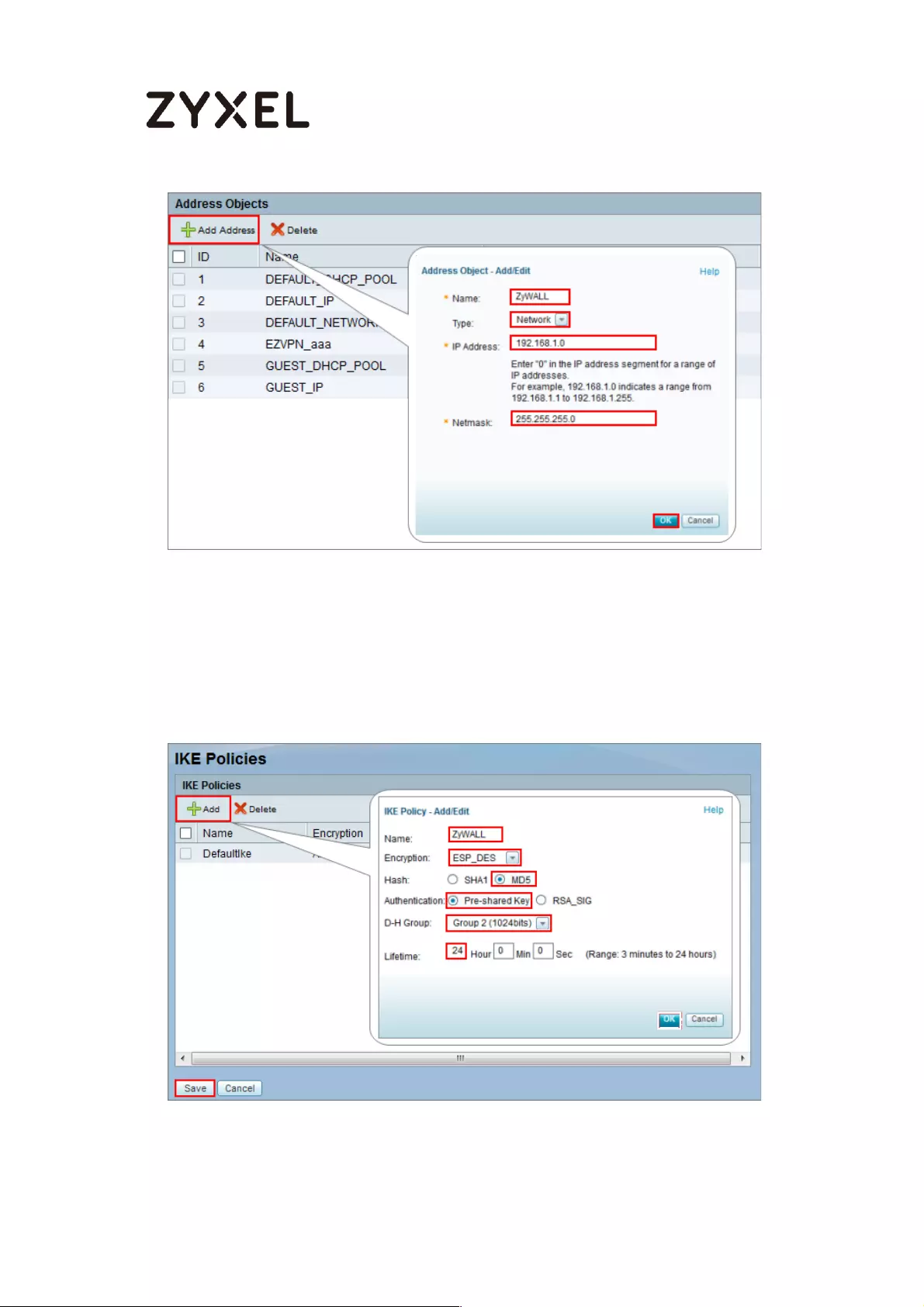
205/782
www.zyxel.com
Go to VPN > Site-to-site > IKE Policies, click Add to create a new IKE Policy Name.
Then, select Encryption, Hash, Pre-shared Key and D-H Group to match your
ZyWALL/USG’s VPN Gateway > Phase 1 Settings. Set Lifetime to 24 hours and click
OK then click Save to exit the IKE Policies page.
VPN > Site-to-site > IKE Policies
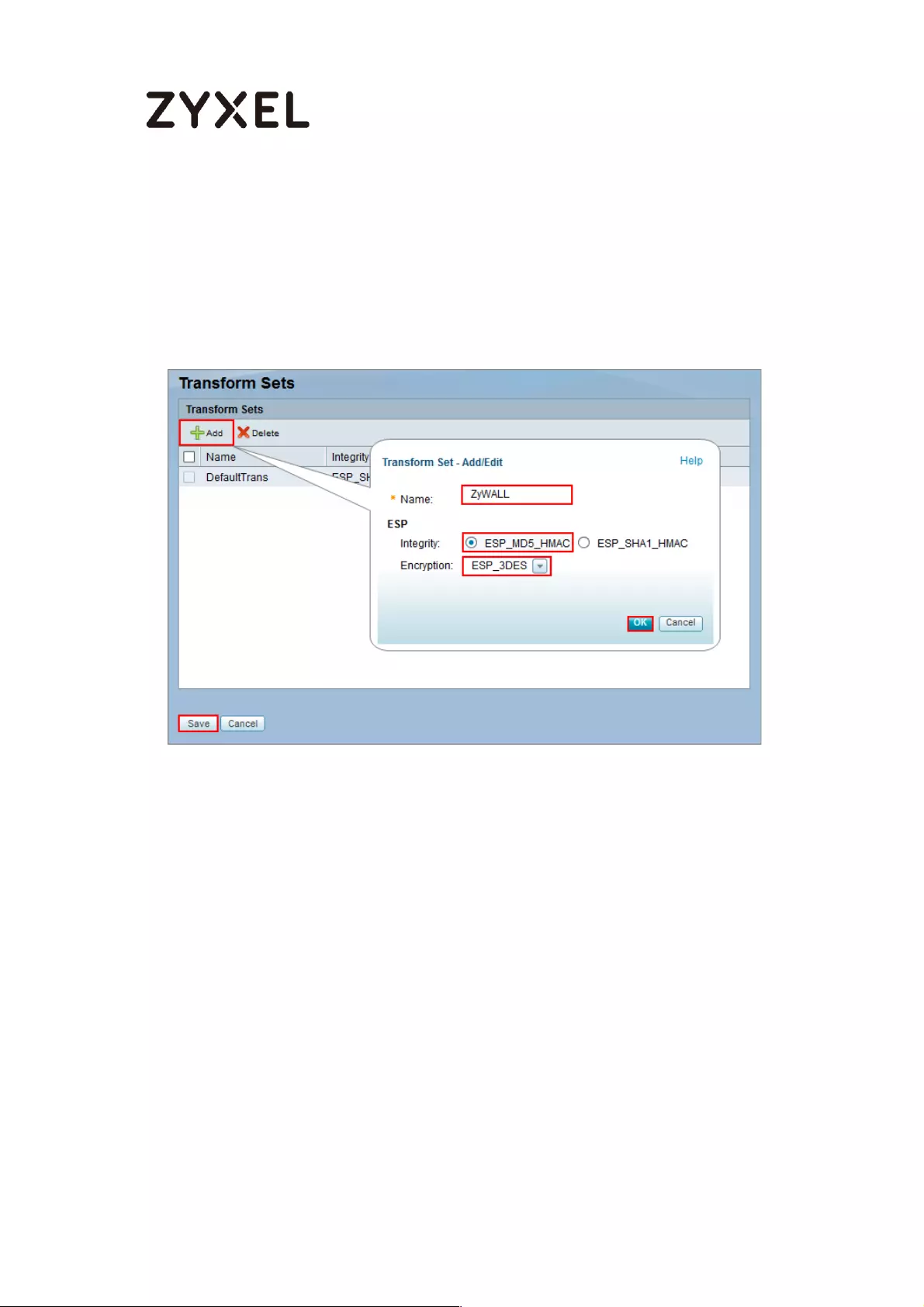
206/782
www.zyxel.com
Go to VPN > Site-to-site > Transform Sets, click Add to create a new Transform Set
name. Then, select Integrity and Encryption to match your ZyWALL/USG’s VPN
Connection > Phase 2 Settings. Click OK and click Save to exit the Transform Sets
page.
VPN > Site-to-site > Transform Sets
Go to VPN > Site-to-site > IPsec Policies and click Add. The new IPsec Policies
dialog box appears. Go to Basic Settings, create IPsec policy Description name
and click On the IPsec Policy Enable option.
Select Static IP as the Remote Type. Set Remote Address to be your ZyWALL/USG’s
WAN IP Address (in the example, 172.101.30.73). Enter the same Pre-Shared Key as
you created in ZyWALL/USG. Then, set WAN Interface to the Internet-facing
interface (found under Status > WAN Interface).
Select Local network to be the IP address range of the network connected to the
Cisco (found under Status > LAN Interface) and Remote network to be the IP
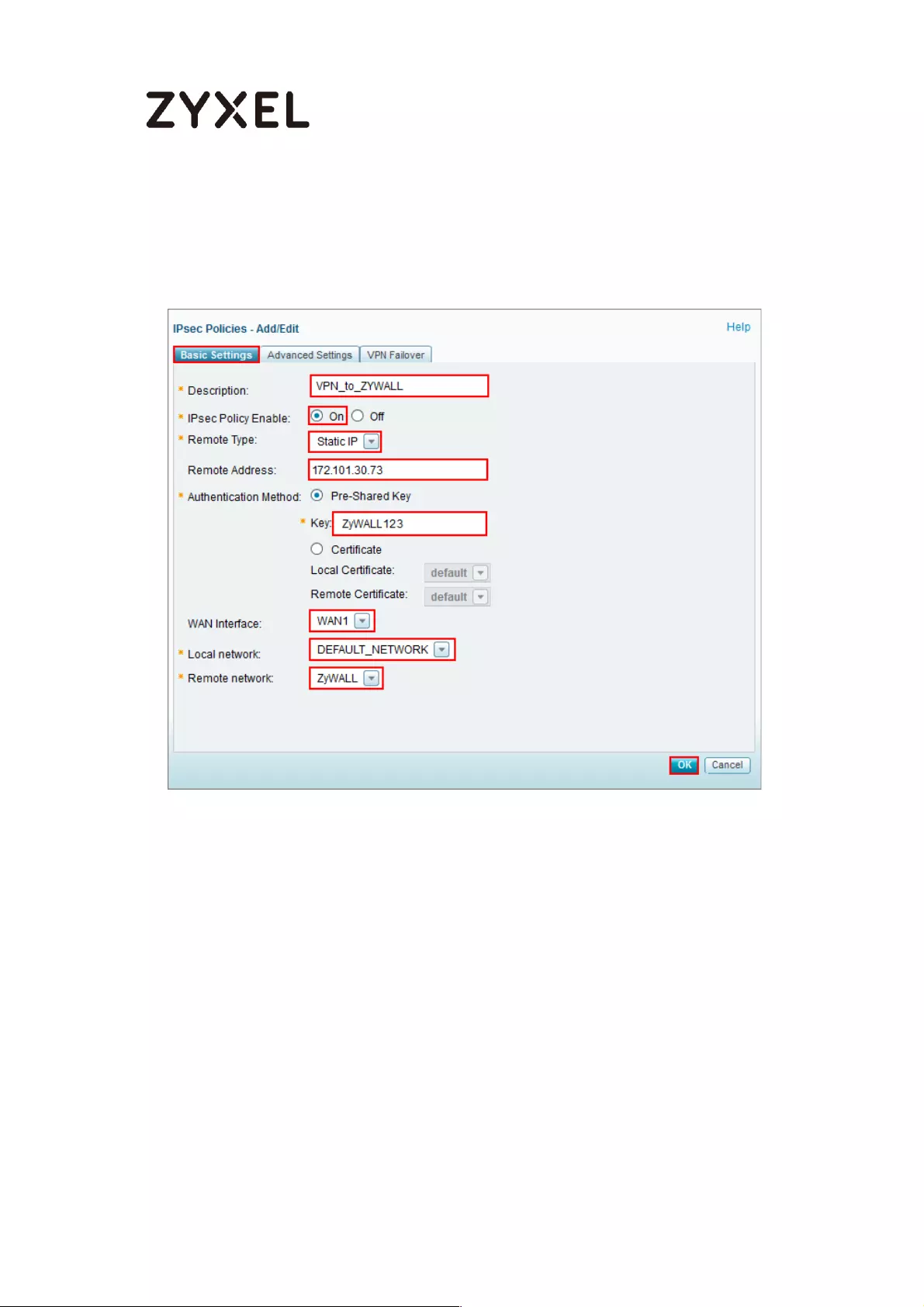
207/782
www.zyxel.com
address range of the network connected to the ZyWALL/USG (Address Object
created in Step 1)
VPN > Site-to-site > IPsec Policies > Basic Settings
Then, go to Advanced Settings enable PFS and DPD if you enable both options in
the ZyWALL/USG. Set IKE Policy to be the IKE Policy created in Step 2 (found
under IKE Policy Link); set Transform to be the Transform Set created in Step 3
(found under Transform Link) and SA-Lifetime to be 24 hours.
Click OK. The connection active dialog box appears. Click Activate Connection.
VPN > Site-to-site > IPsec Policies > Advanced Settings

208/782
www.zyxel.com
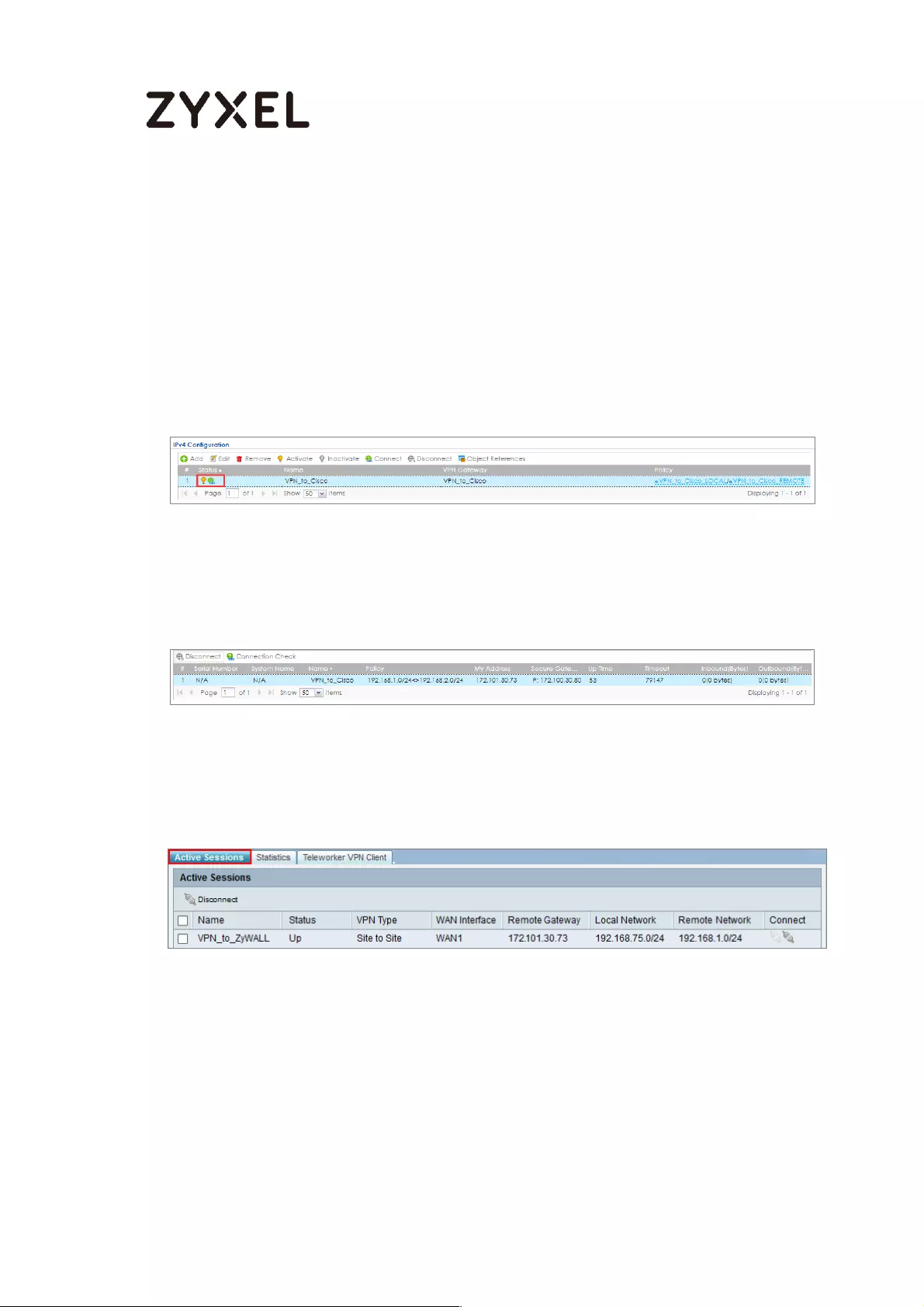
209/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > IPSec
Go to Cisco VPN > VPN Status > IPsec VPN Status > Active Sessions and check the
tunnel Status is up.
VPN > VPN Status > IPsec VPN Status > Active Sessions
Go to Cisco VPN > VPN Status > IPsec VPN Status > Statics and check the Tx
Packets (Transmit data) and Rx Packets (Receive data).
VPN > VPN Status > IPsec VPN Status > Statistics
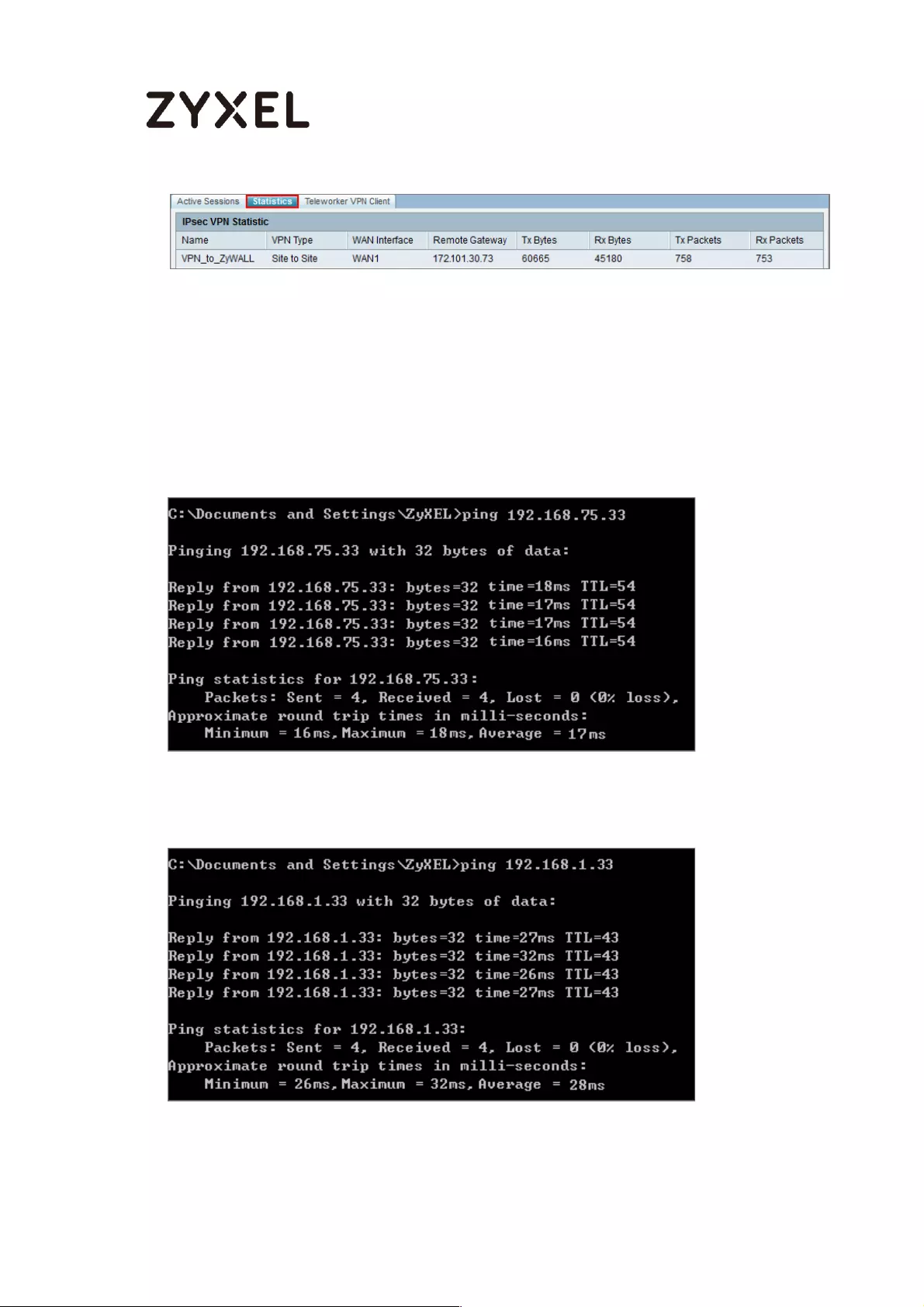
210/782
www.zyxel.com
To test whether a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC behind ZyWALL/USG > Window 7 > cmd > ping 192.168.75.33
PC behind Cisco> Window 7 > cmd > ping 192.168.1.33
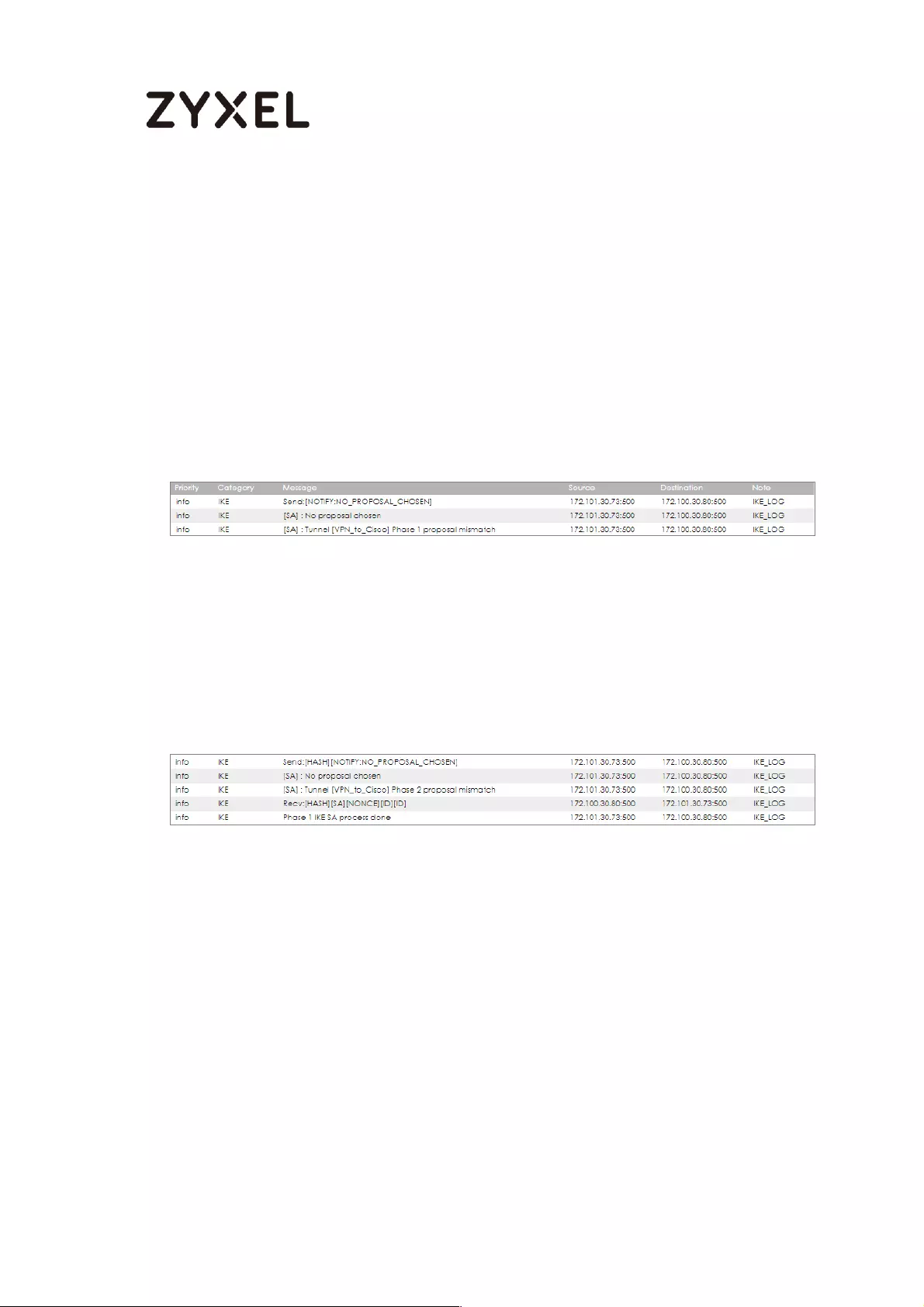
211/782
www.zyxel.com
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG and Cisco must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.
MONITOR > Log
If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG and Cisco Phase 2 Settings. Both ZyWALL/USG and
Cisco must use the same Protocol, Encapsulation, Encryption, Authentication
method and PFS to establish the IKE SA.
MONITOR > Log
Make sure the both ZyWALL/USG and Cisco security policies allow IPSec VPN
traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.
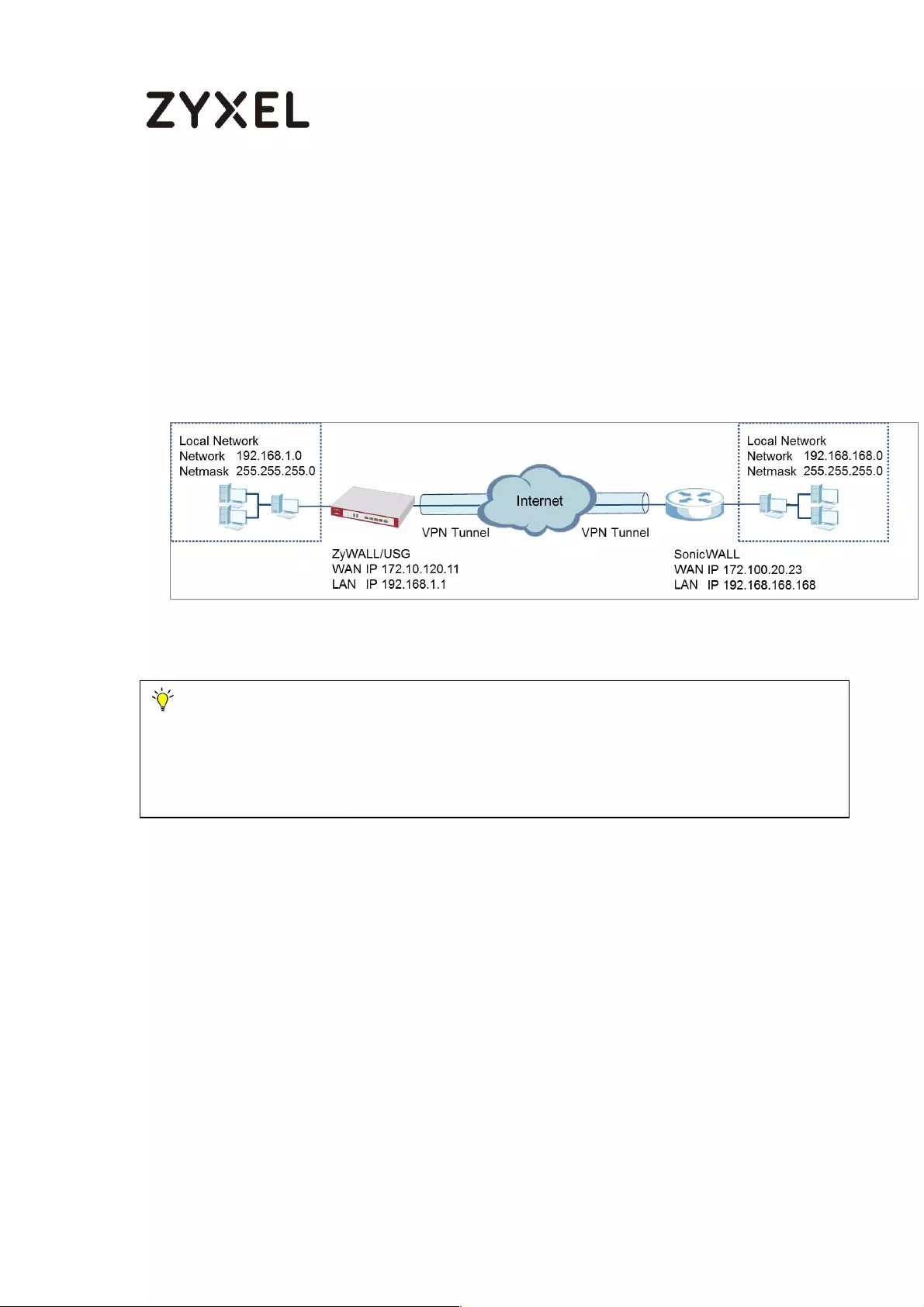
212/782
www.zyxel.com
How to Configure Site-to-site IPSec VPN with a SonicWALL
router
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
between a ZYWALL/USG and a SonicWALL router. The example instructs how to
configure the VPN tunnel between each site. When the VPN tunnel is configured,
each site can be accessed securely.
ZyWALL/USG Site-to-site IPSec VPN with SonicWALL
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25) and NSA240 (Firmware Version:
SonicOS Enhanced 5.8.0.1-31o)
213/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the SonicWALL. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Advanced to create a VPN rule with the customize phase 1, phase 2
settings and authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type

214/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway).
You may use 1-31 alphanumeric characters. This value is case-sensitive. Select the
rule to be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Then, configure the Secure Gateway IP as the SonicWALL’s Gateway IP address
(in the example, 172.100.20.23); select My Address to be the interface connected
to the Internet.
Set the desired Negotiation, Encryption, Authentication, Key Group and SA Life
Time settings. Type a secure Pre-Shared Key (8-32 characters) which must match
your SonicWALL Shared Secret.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Phase
1 Setting)
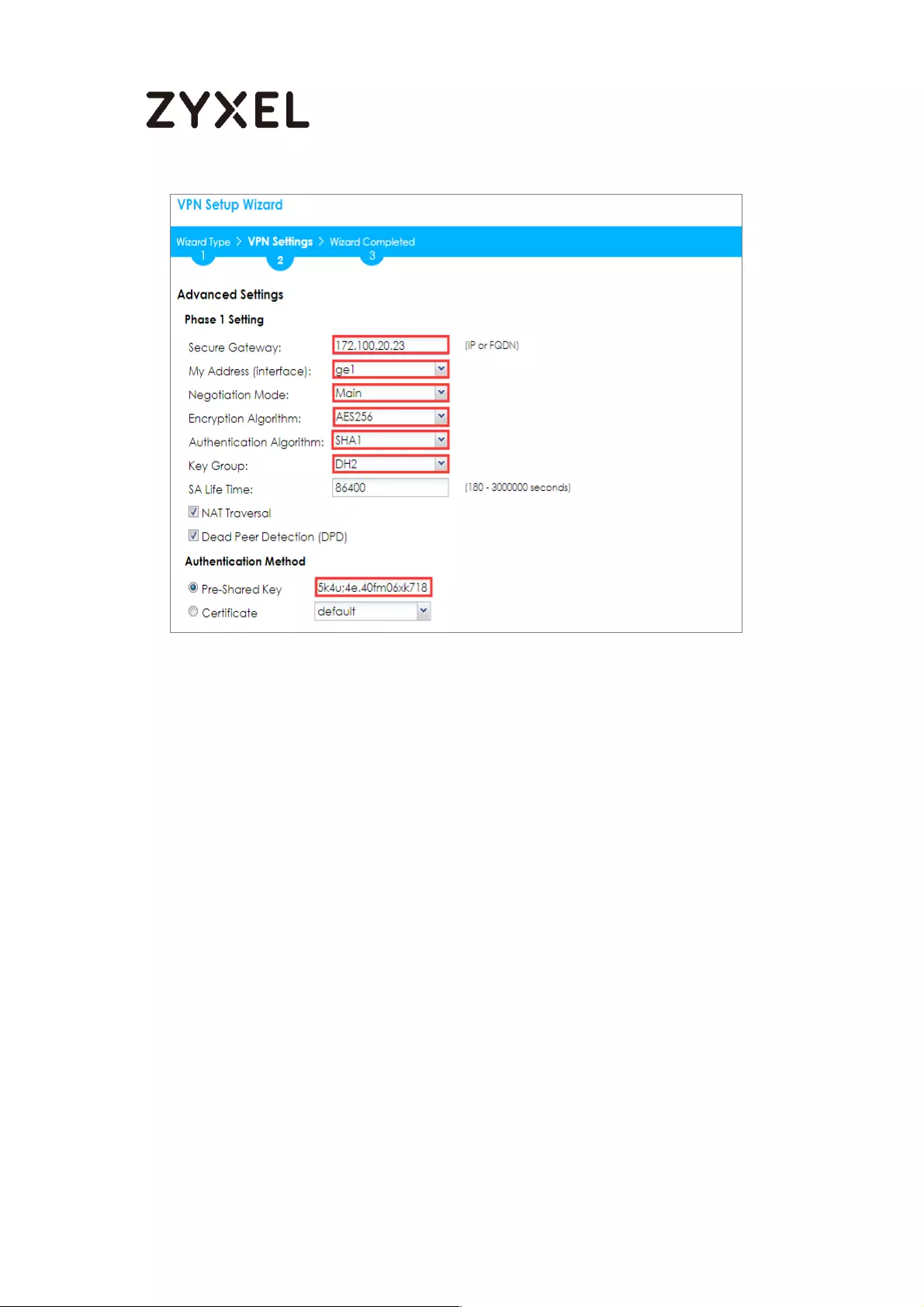
215/782
www.zyxel.com
Continue to Phase 2 Settings to select the desired Encapsulation, Encryption,
Authentication, and SA Life Time settings.
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the SonicWALL. Click OK.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Phase
2 Setting)
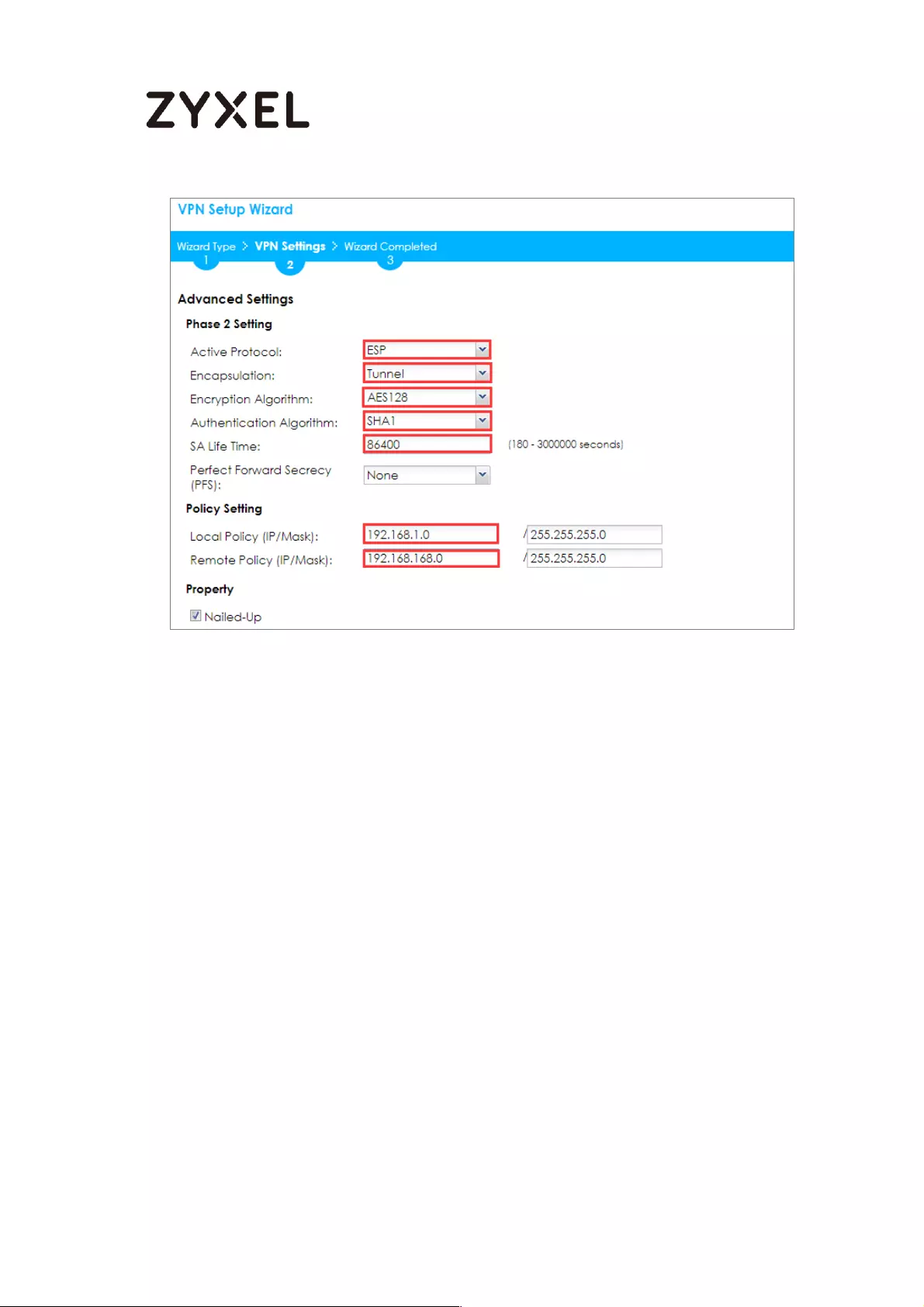
216/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings
(Summary)
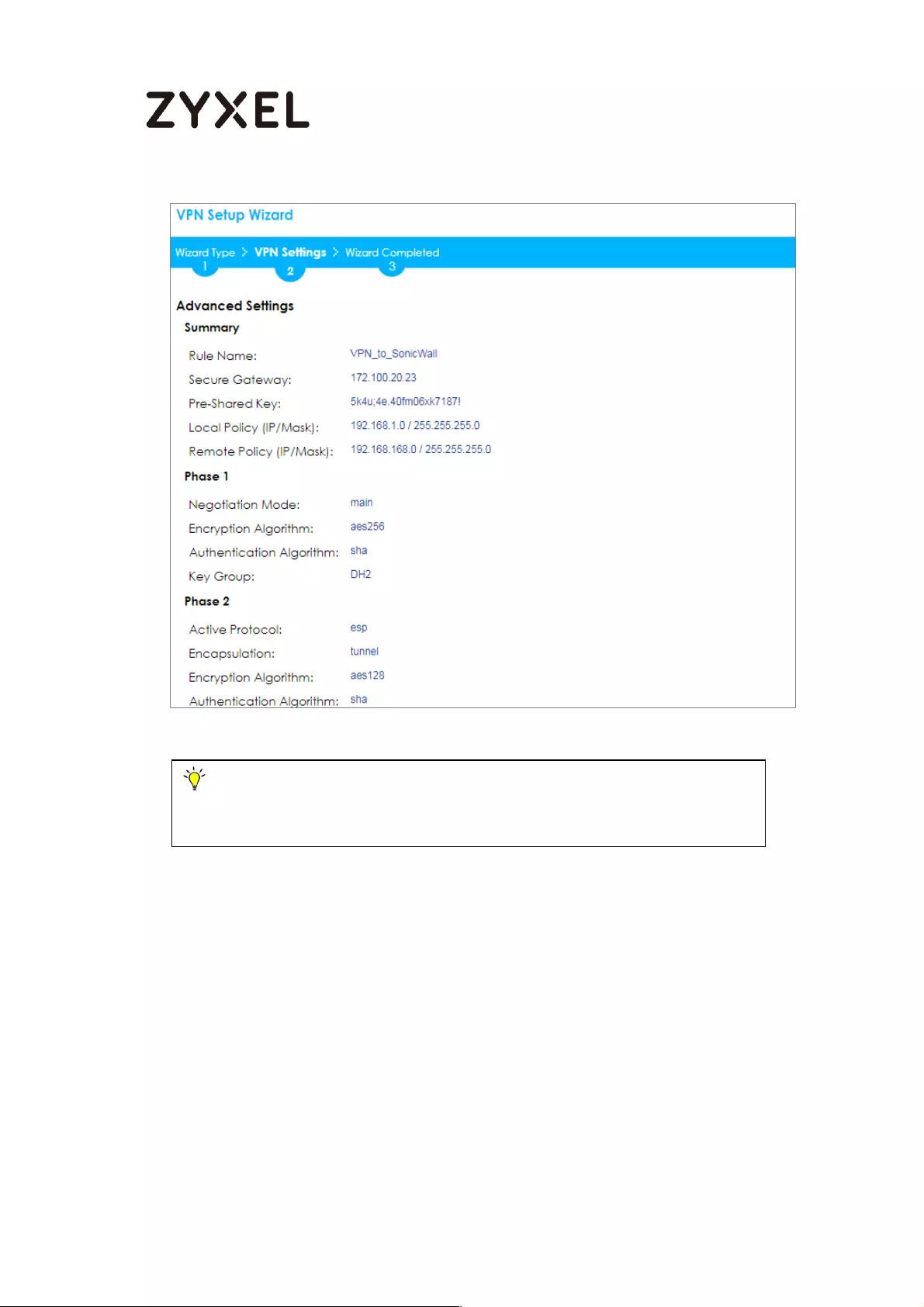
217/782
www.zyxel.com
Note: The Phase 1 and Phase 2 settings established here must match the
Phase 1 and Phase 2 settings configured later in the SonicWALL.

218/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in
the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear
in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings >
Wizard Completed
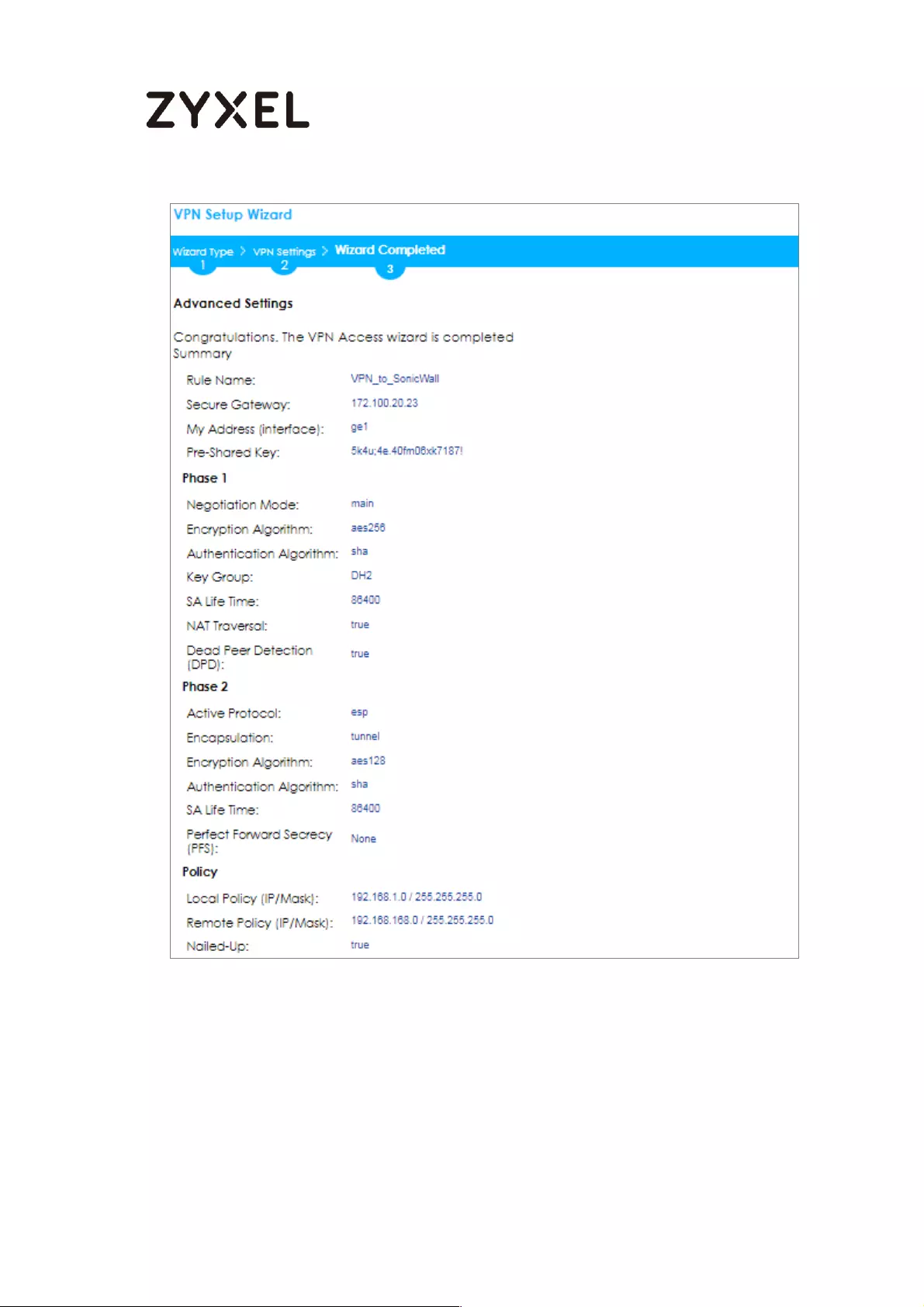
219/782
www.zyxel.com
Go to VPN Gateway > Show Advanced Settings > Authentication to configure
your Local ID Type and Peer ID Type to match your SonicWALL’s VPN > Settings >
VPN Policies > General > IKE Authentication > Local IKE ID and Peer IKE ID.
VPN Gateway > Show Advanced Settings > Authentication
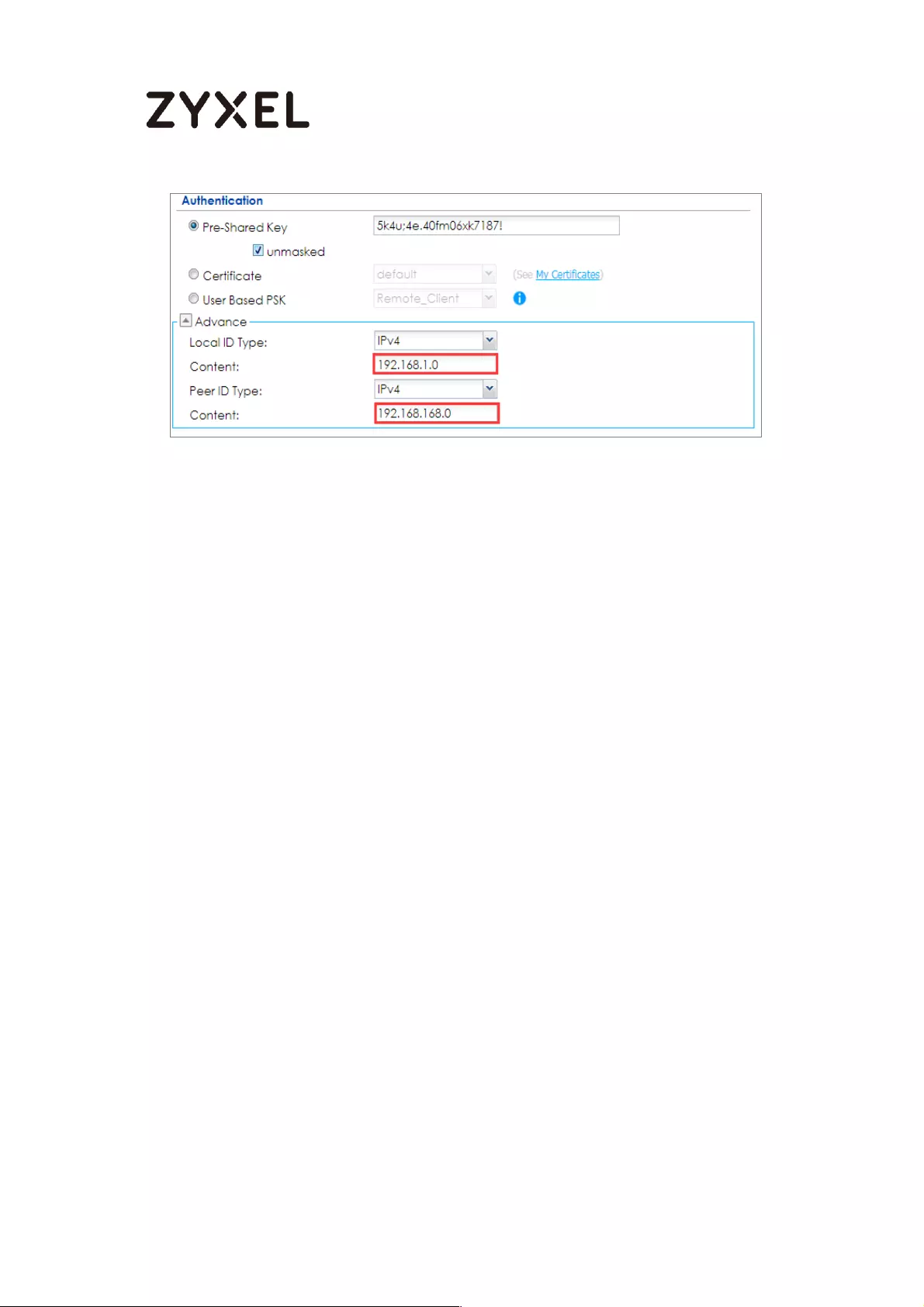
220/782
www.zyxel.com
Set Up the IPSec VPN Tunnel on the SonicWALL
In the SonicWALL VPN > Settings > VPN Policies, click Add to create a new VPN
policy. Select Policy Type to be the Site to Site, select Authentication Method to
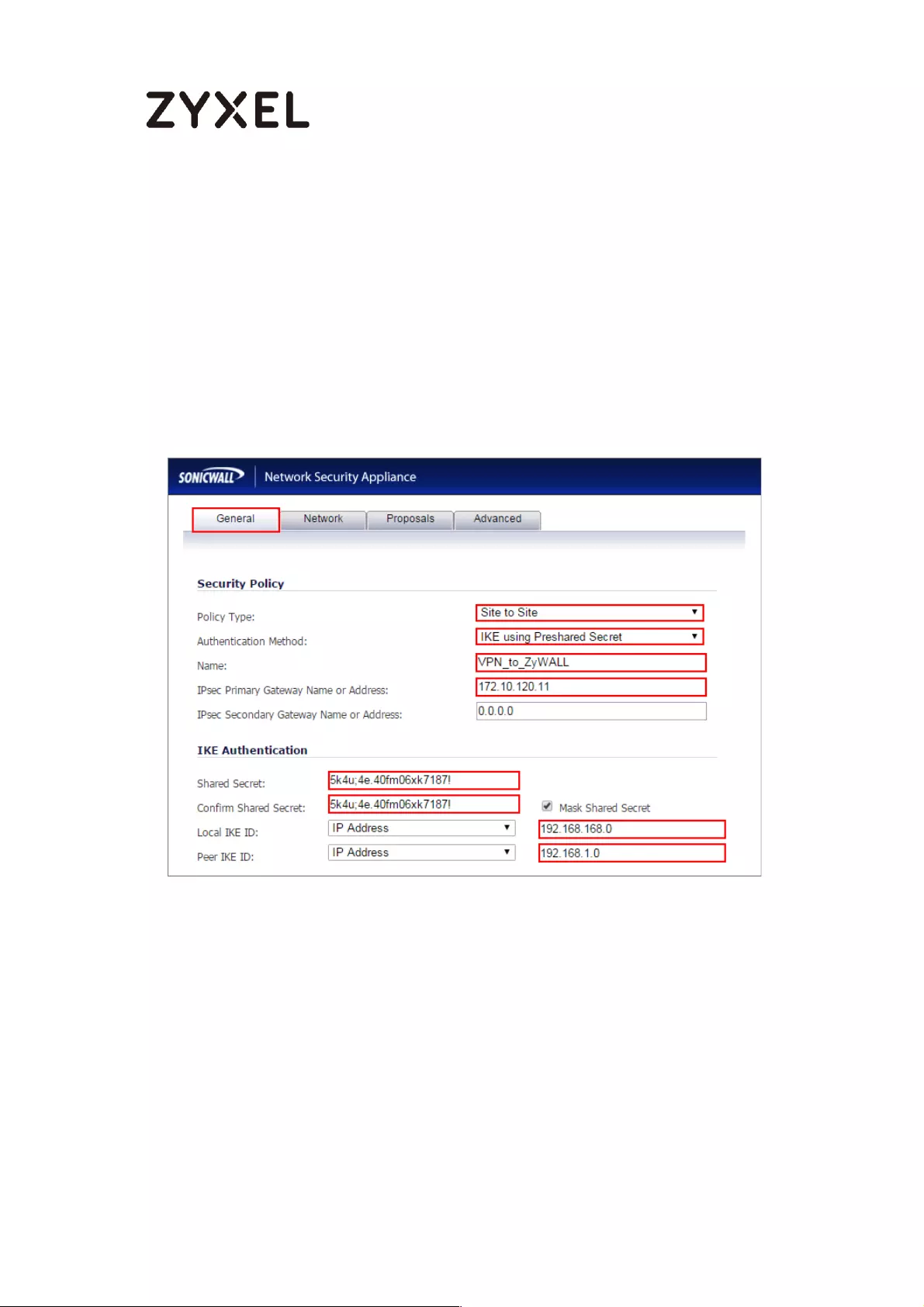
221/782
www.zyxel.com
be the IKE using Preshared Secret. Type the ZyWALL/USG's WAN IP Address to be
the IPsec Primary Gateway Name or Address (in the example, 172.10.120.11).
In the IKE Authentication section, set the Shared Secret to be the same as your
ZyWALL/USG’s Pre-Shared Key. Then, set the Local IKE ID and the Peer IKE ID to
match your ZyWALL/USG’s VPN Gateway > Show Advanced Settings >
Authentication > Local ID Type and Peer ID Type.
VPN > Settings > VPN Policies > General
In the SonicWALL VPN > Settings > VPN Policies > Network, choose Local Network
to be the IP address range of the network connected to the SonicWALL (found
under SonicWALL > Network > Interfaces > LAN).
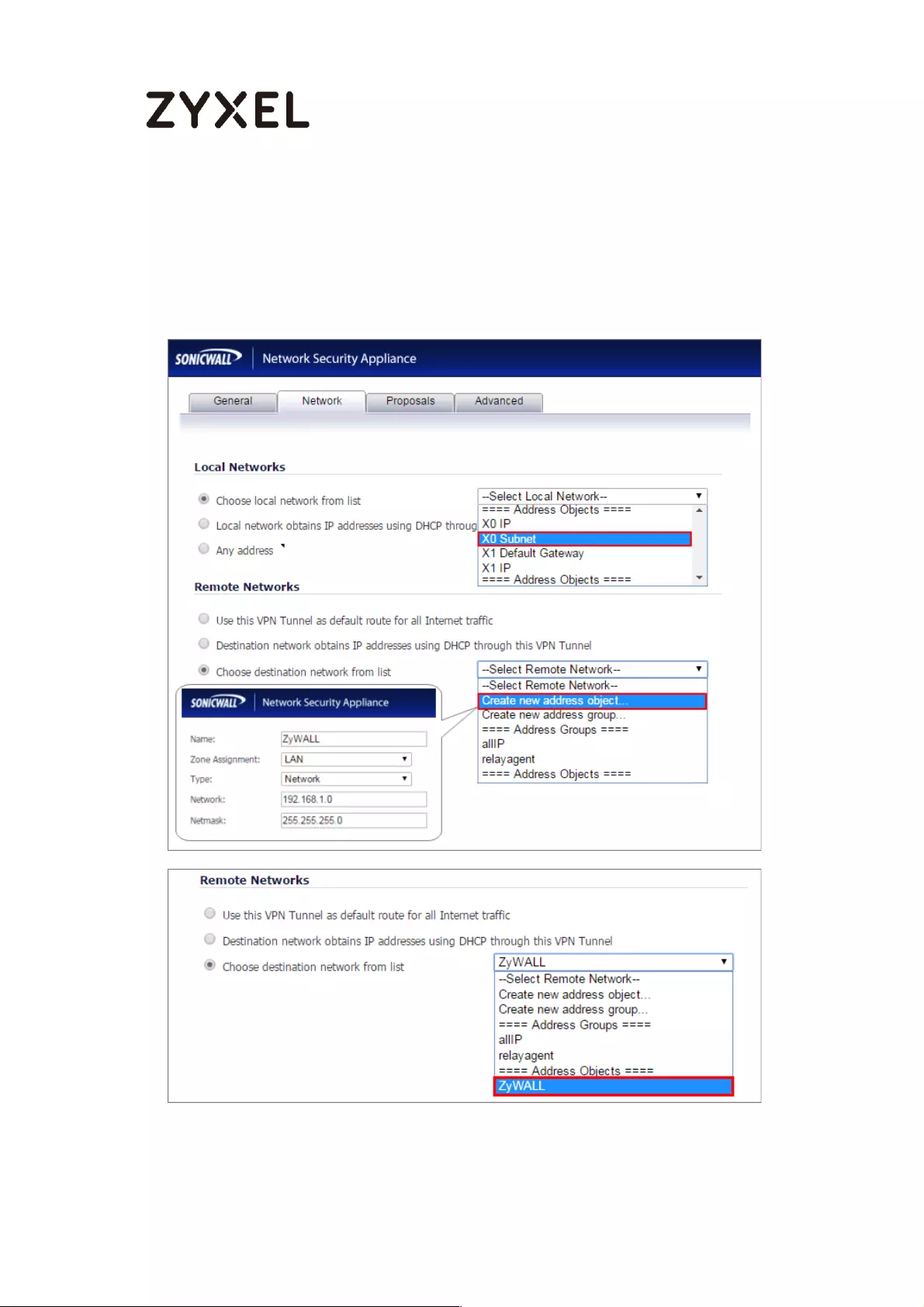
222/782
www.zyxel.com
Go to Remote Network and create a new address IP address range of the
network connected to the ZyWALL/USG. Then, scroll down the list to choose the
newly created Address Object to be the Remote Network.
VPN > Settings > VPN Policies > Network
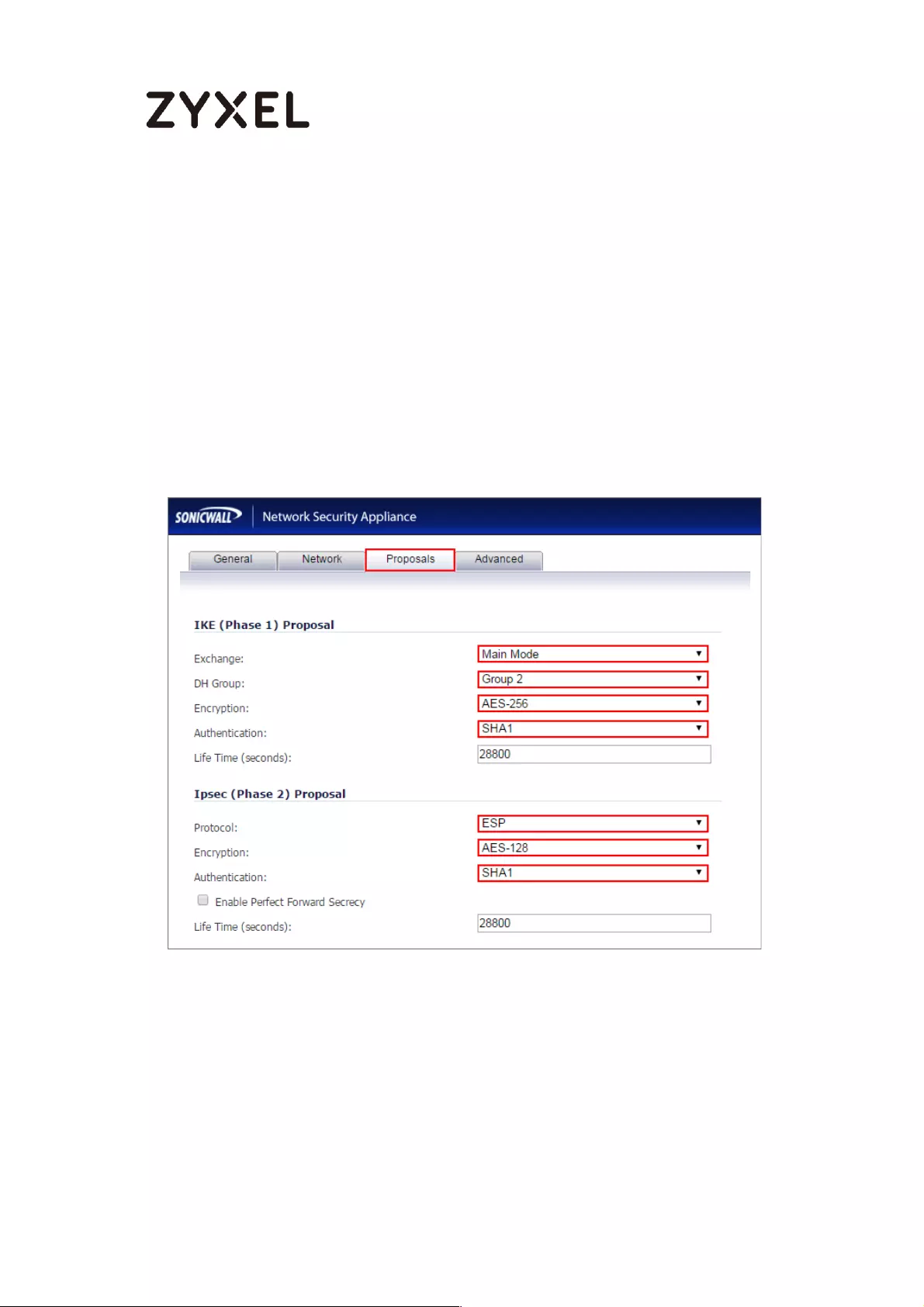
223/782
www.zyxel.com
In the SonicWALL VPN > Settings > VPN Policies > Proposals > IKE (Phase 1)
Proposal and set Exchange, DH Group, Encryption and Authentication to match
your ZyWALL/USG’s VPN Gateway > Show Advanced Settings > Phase 1 Settings.
Go to IKE (Phase 2) Proposal and set the Protocol, Encryption and Authentication
to match your ZyWALL/USG’s VPN Connection > Show Advanced Settings > Phase
2 Settings.
VPN > Settings > VPN Policies > Proposals
Select Enable VPN and click Refresh Active.
VPN > Settings > VPN Global Settings
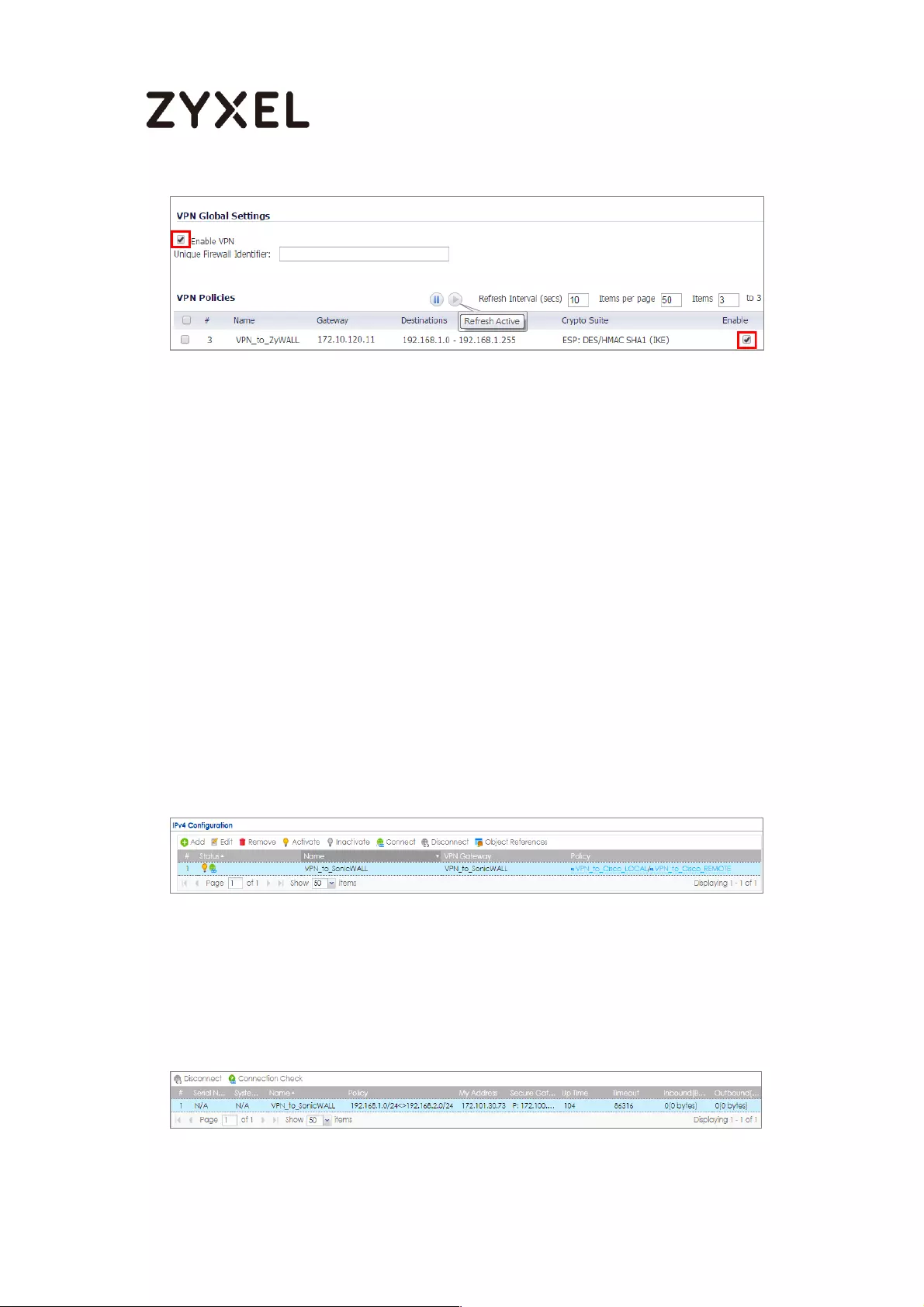
224/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > IPSec
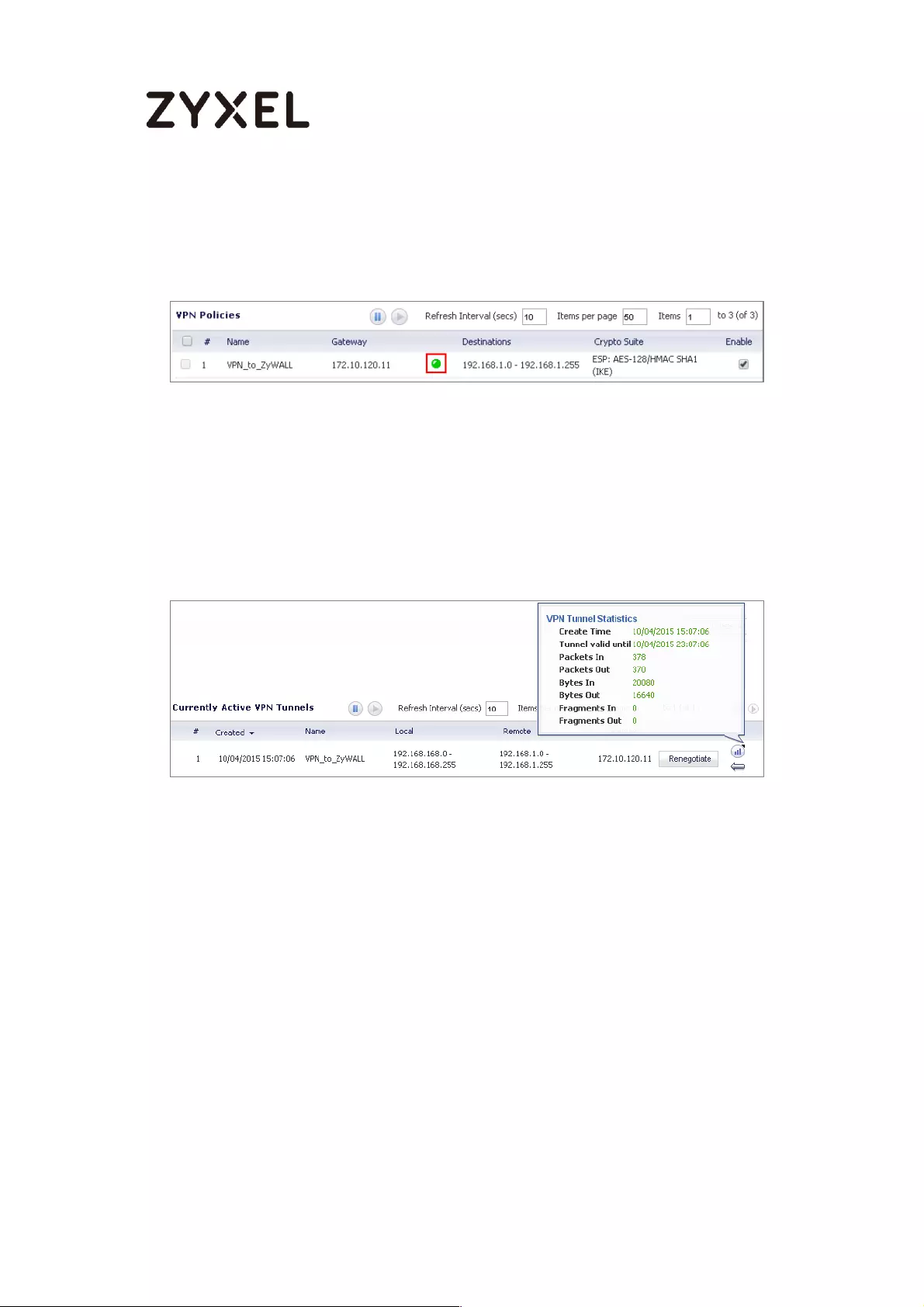
225/782
www.zyxel.com
Go to SonicWALL VPN > VPN Settings > VPN Policies, the status green light is on.
VPN > VPN Settings > VPN Policies
Go to SonicWALL VPN > VPN Settings > Currently Active VPN Tunnels > VPN Tunnel
Statics to check Tunnel valid time, Bytes In (Incoming Data) and Bytes Out
(Outgoing Data).
VPN > VPN Settings > Currently Active VPN Tunnels
To test whether a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC behind ZyWALL/USG > Window 7 > cmd > ping 192.168.168.33
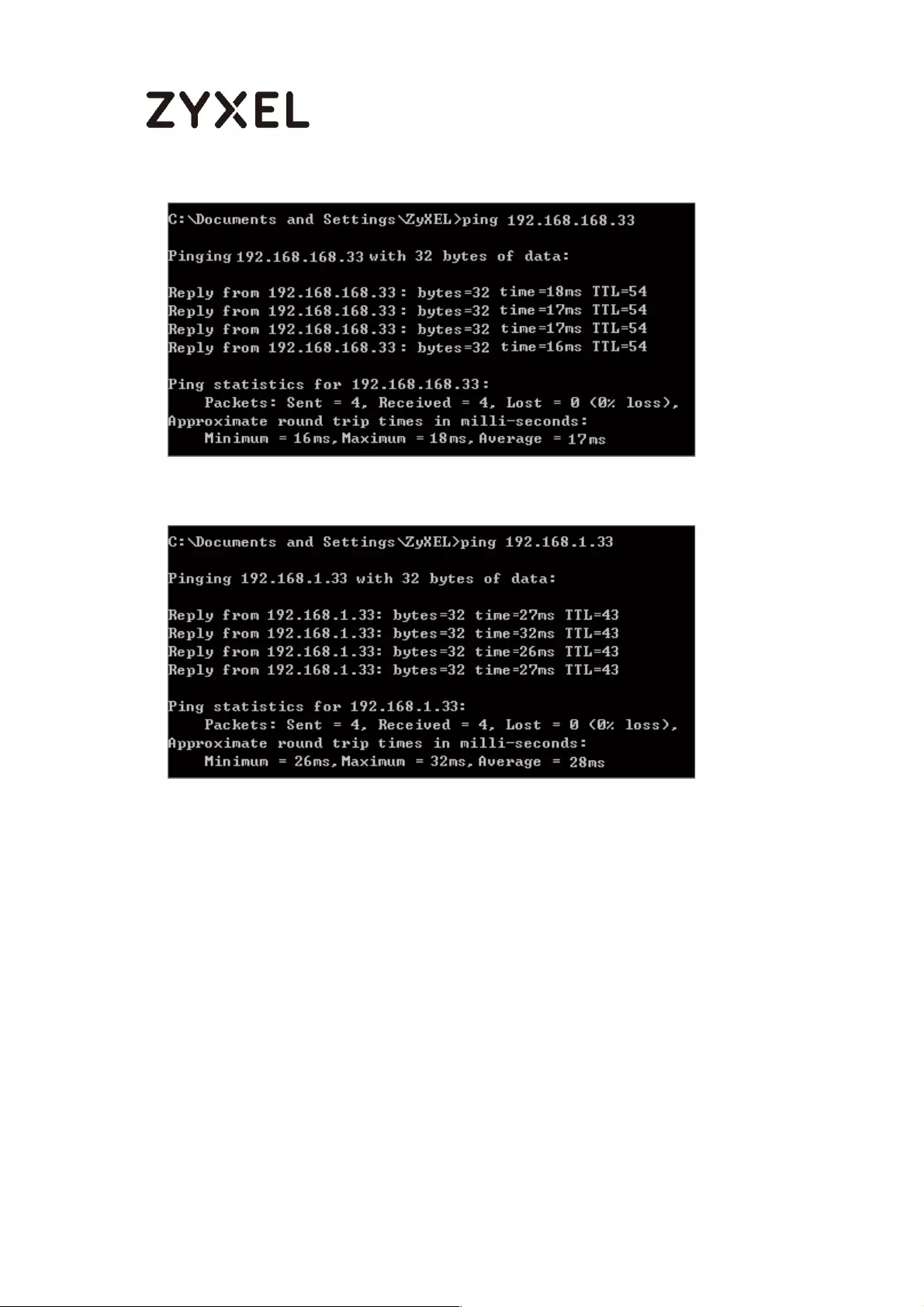
226/782
www.zyxel.com
PC behind SonicWALL> Window 7 > cmd > ping 192.168.1.33
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG and SonicWALL must use the same Pre-Shared Key,
Encryption, Authentication method, DH key group and ID Type to establish the
IKE SA.
MONITOR > Log
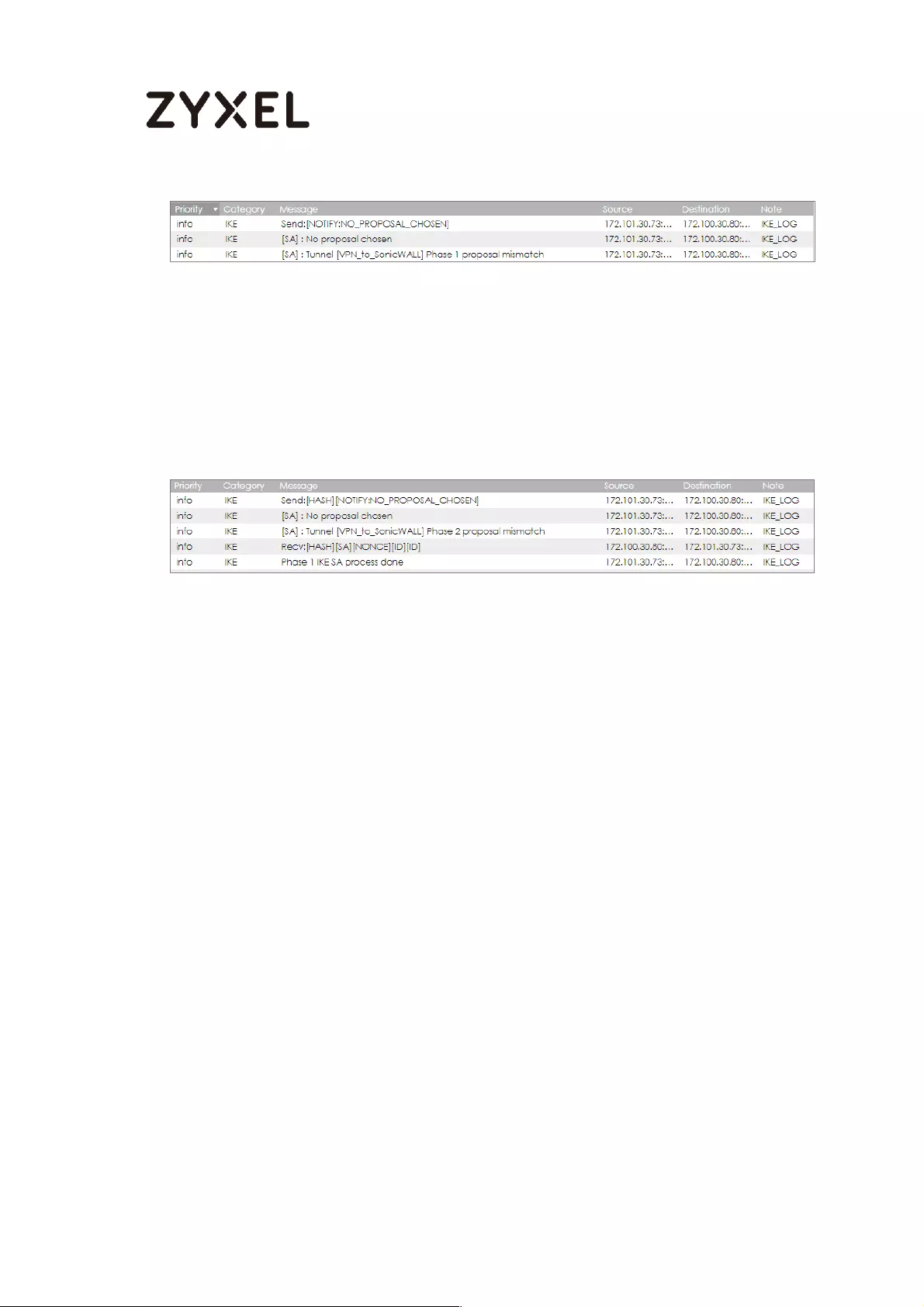
227/782
www.zyxel.com
If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG and SonicWALL Phase 2 Settings. Both ZyWALL/USG
and SonicWALL must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
MONITOR > Log
Make sure the both ZyWALL/USG and SonicWALL security policies allow IPSec
VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol
50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.

228/782
www.zyxel.com
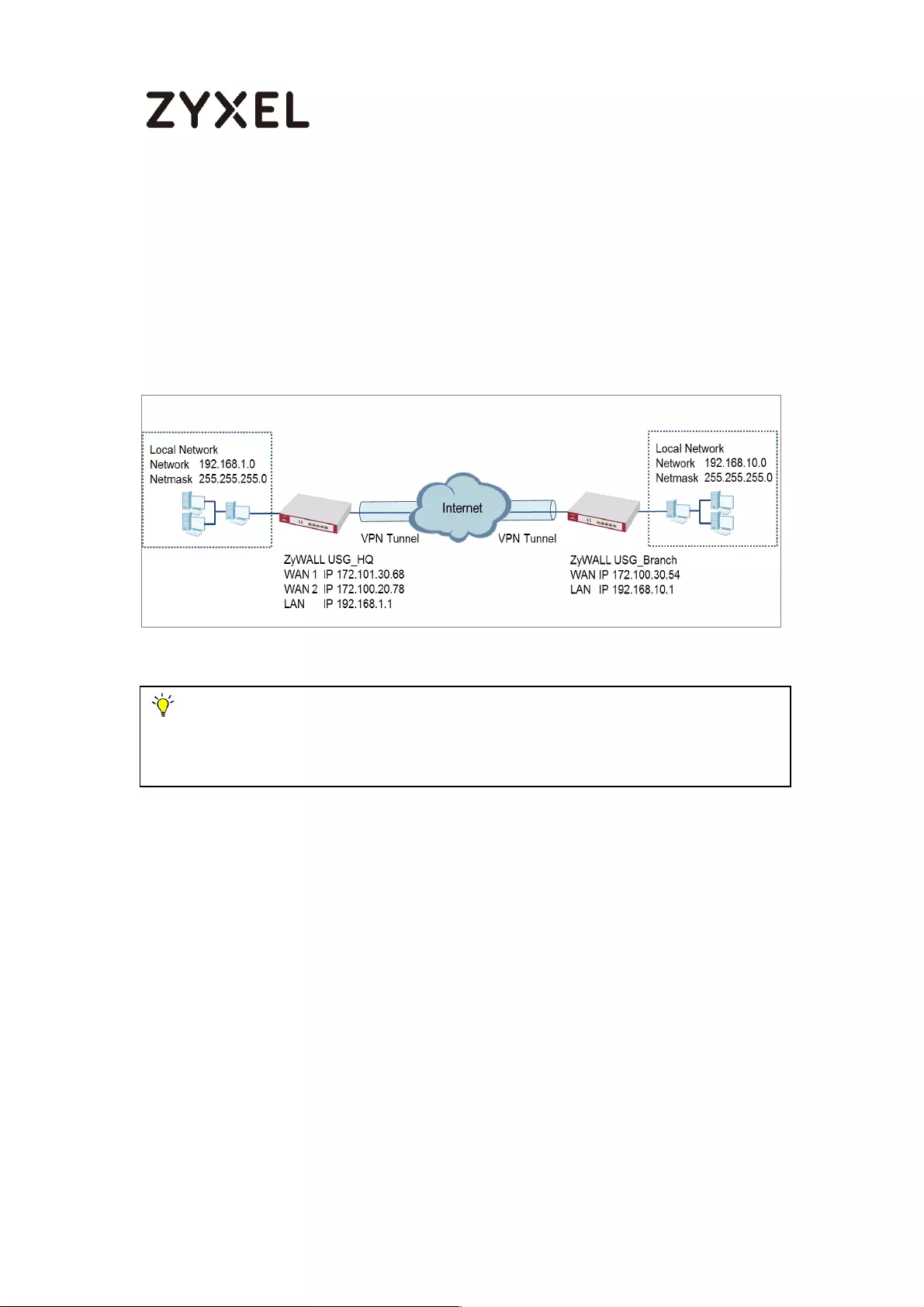
229/782
www.zyxel.com
How to Configure IPSec VPN Failover
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
with failover. The example instructs how to configure the VPN tunnel between
each site if one site has multi-WAN. When the multi-WAN VPN failover is
configured, IPSec VPN tunnels automatically fail over to a backup WAN
interface if the primary WAN interface becomes unavailable.
ZyWALL Site-to-site IPSec VPN with multiple WAN failover
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG110 (Firmware Version: ZLD 4.25).
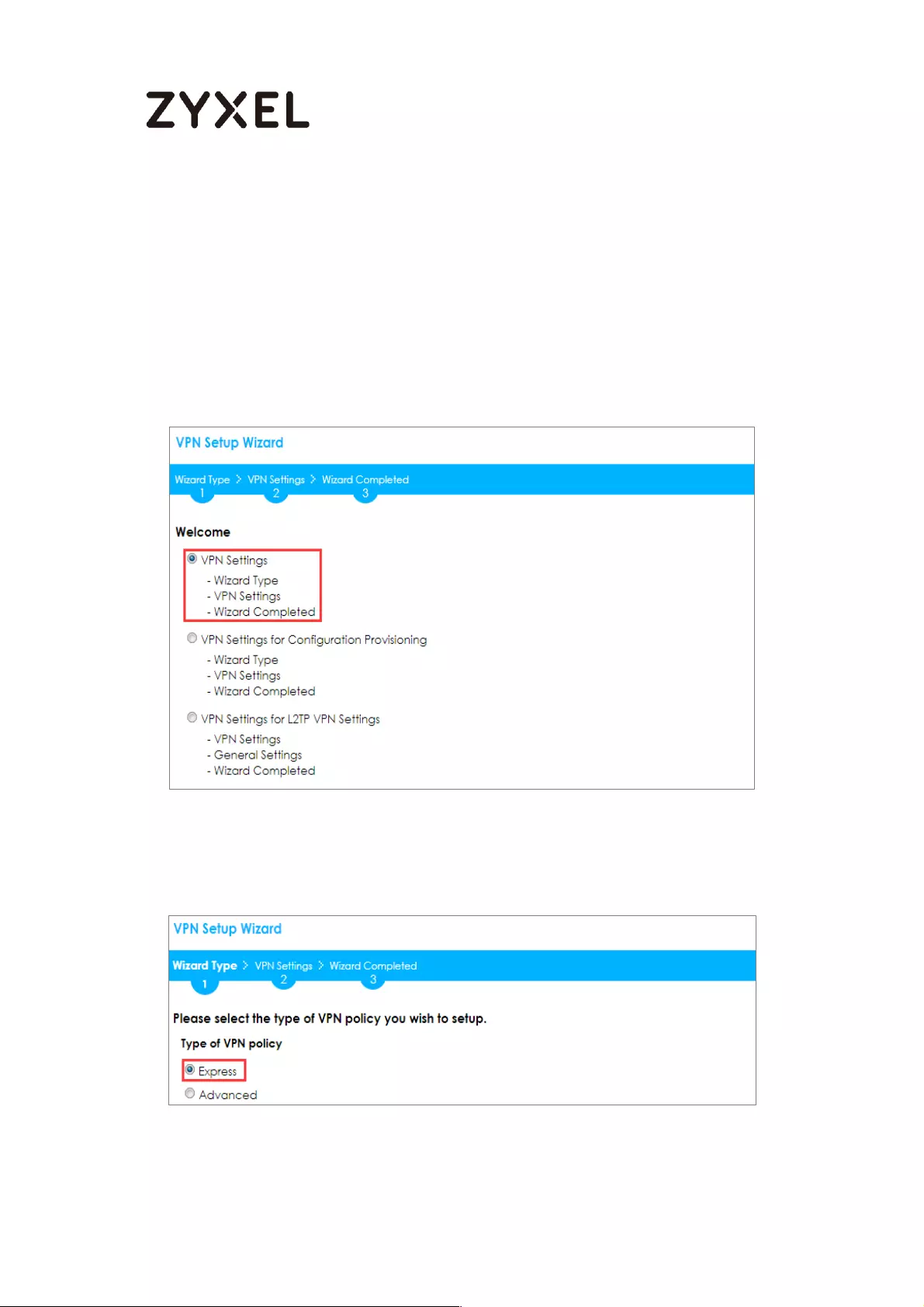
230/782
www.zyxel.com
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(HQ)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type

231/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Select the rule to
be Site-to-site. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.100.30.54). Type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the peer ZyWALL/USG.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)

232/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings > Wizard
Completed
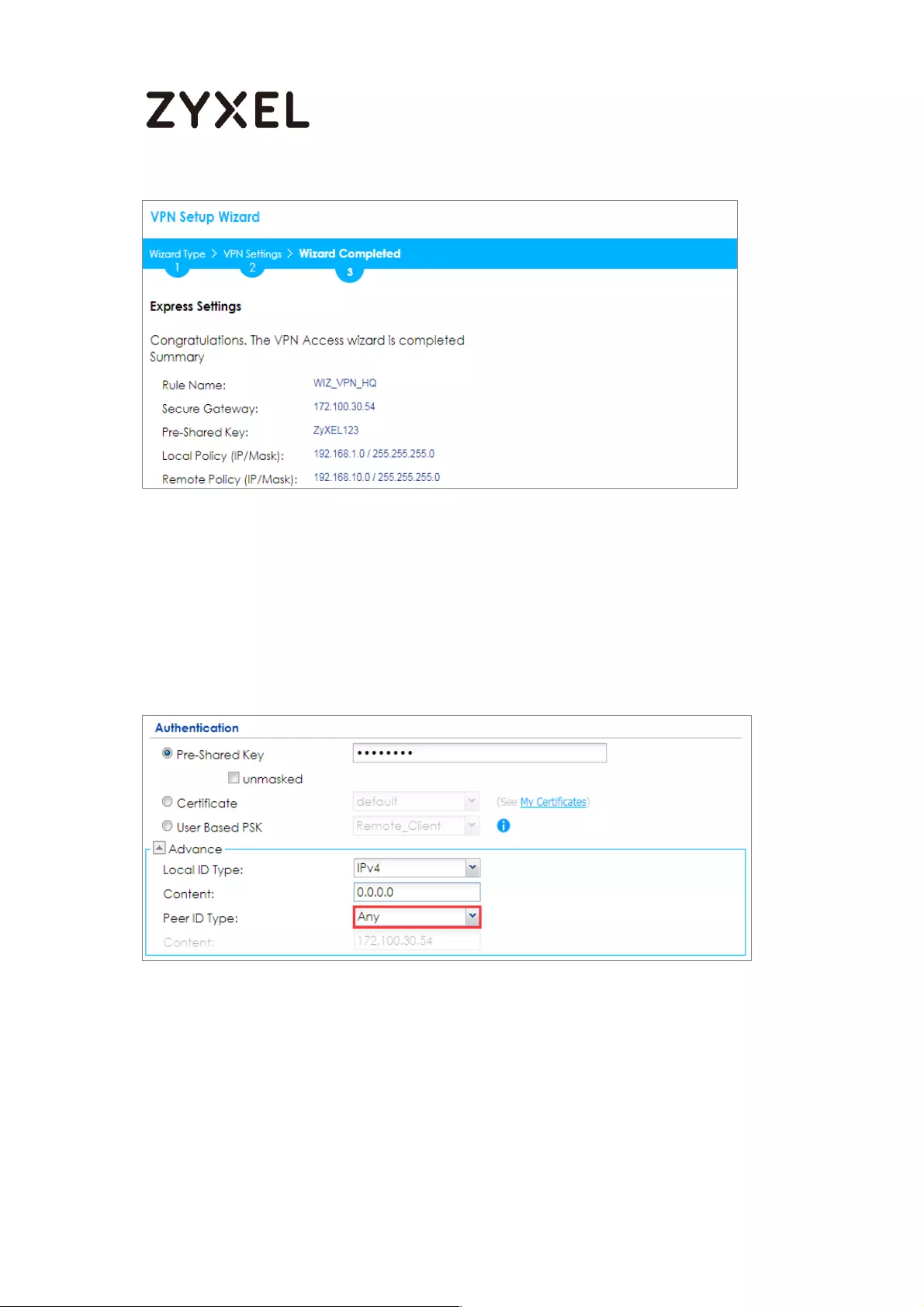
233/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec
router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate
Network (Branch)
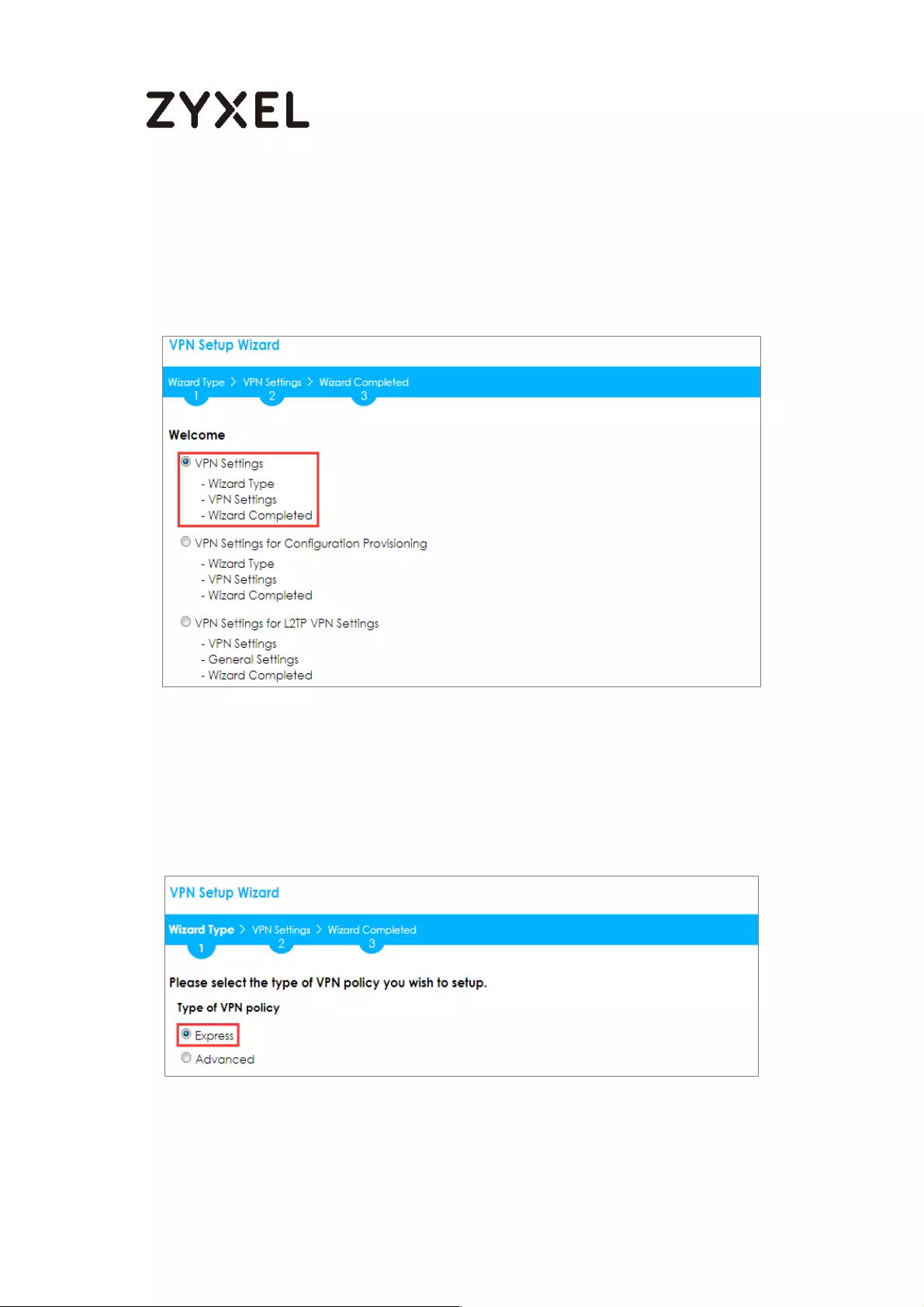
234/782
www.zyxel.com
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and to use a pre-shared key. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Click Next.

235/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.101.30.68). Type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the peer ZYWALL/USG.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
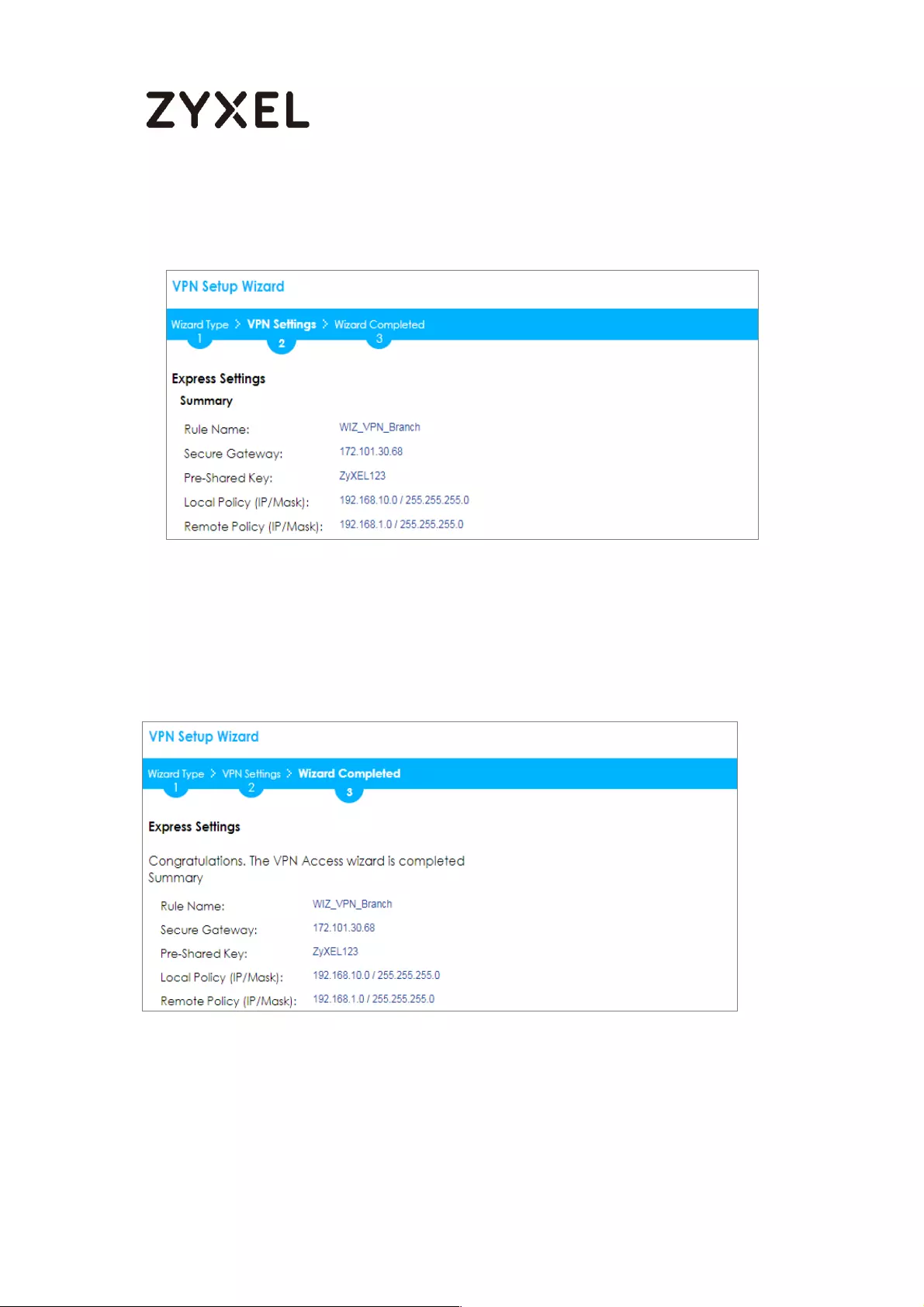
236/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear in the VPN
> IPSec VPN > VPN Gateway screen and the Phase 2 rule settings appear in the VPN >
IPSec VPN > VPN Connection screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings > Wizard
Completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec
router.
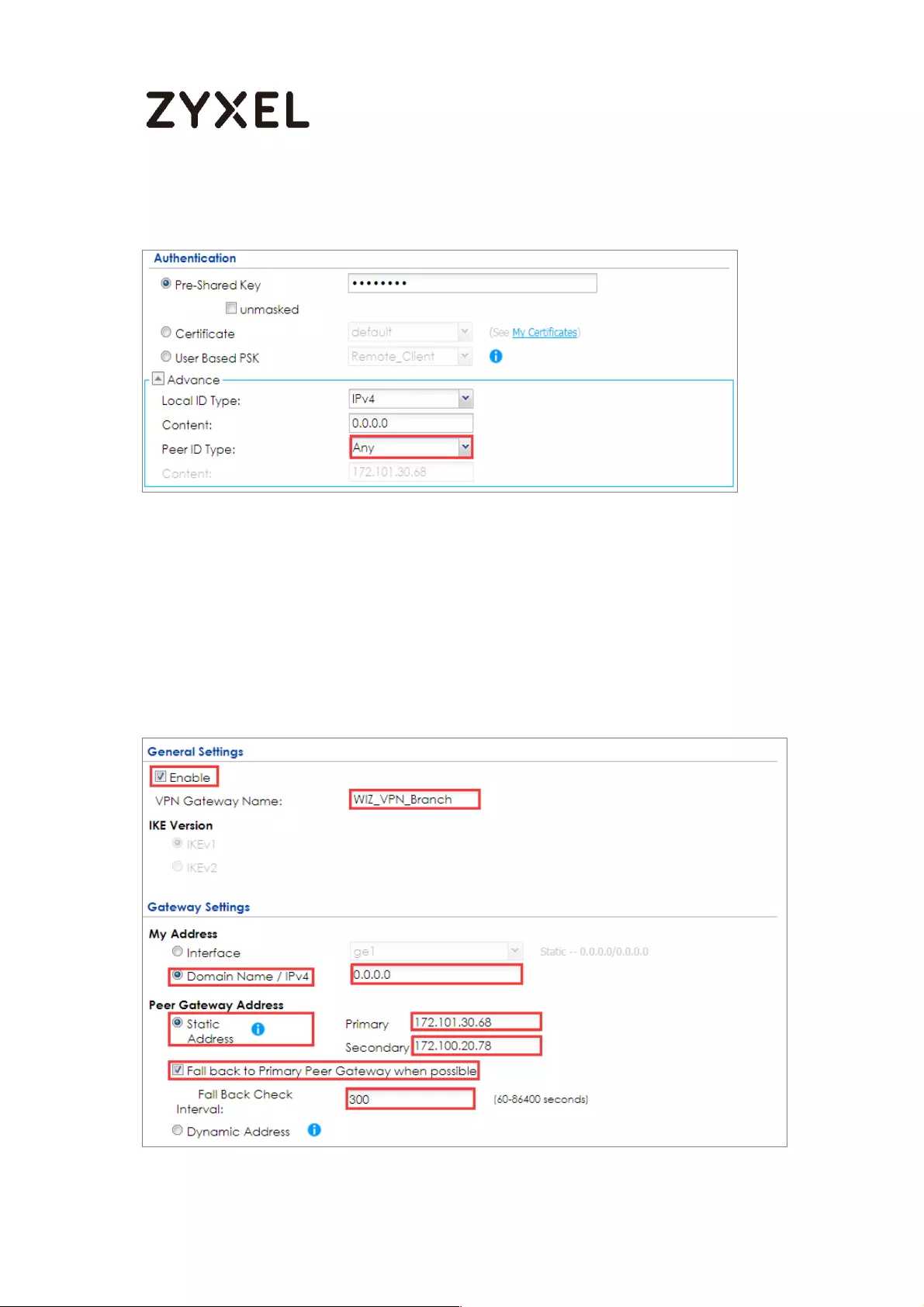
237/782
www.zyxel.com
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Go to Configuration > VPN > IPSec VPN > VPN Gateway > Gateway Settings. Set
My Address to be Domain Name/IP “0.0.0.0” (ZyWALL/USG will dial-up with the
active WAN interface first). Set Peer Gateway Address > Static Address > Primary
to be ZyWALL/USG_HQ WAN1 IP address and Secondary to be ZyWALL/USG_HQ
WAN2 IP address.
Configuration > VPN > IPSec VPN > VPN Gateway > Gateway Settings
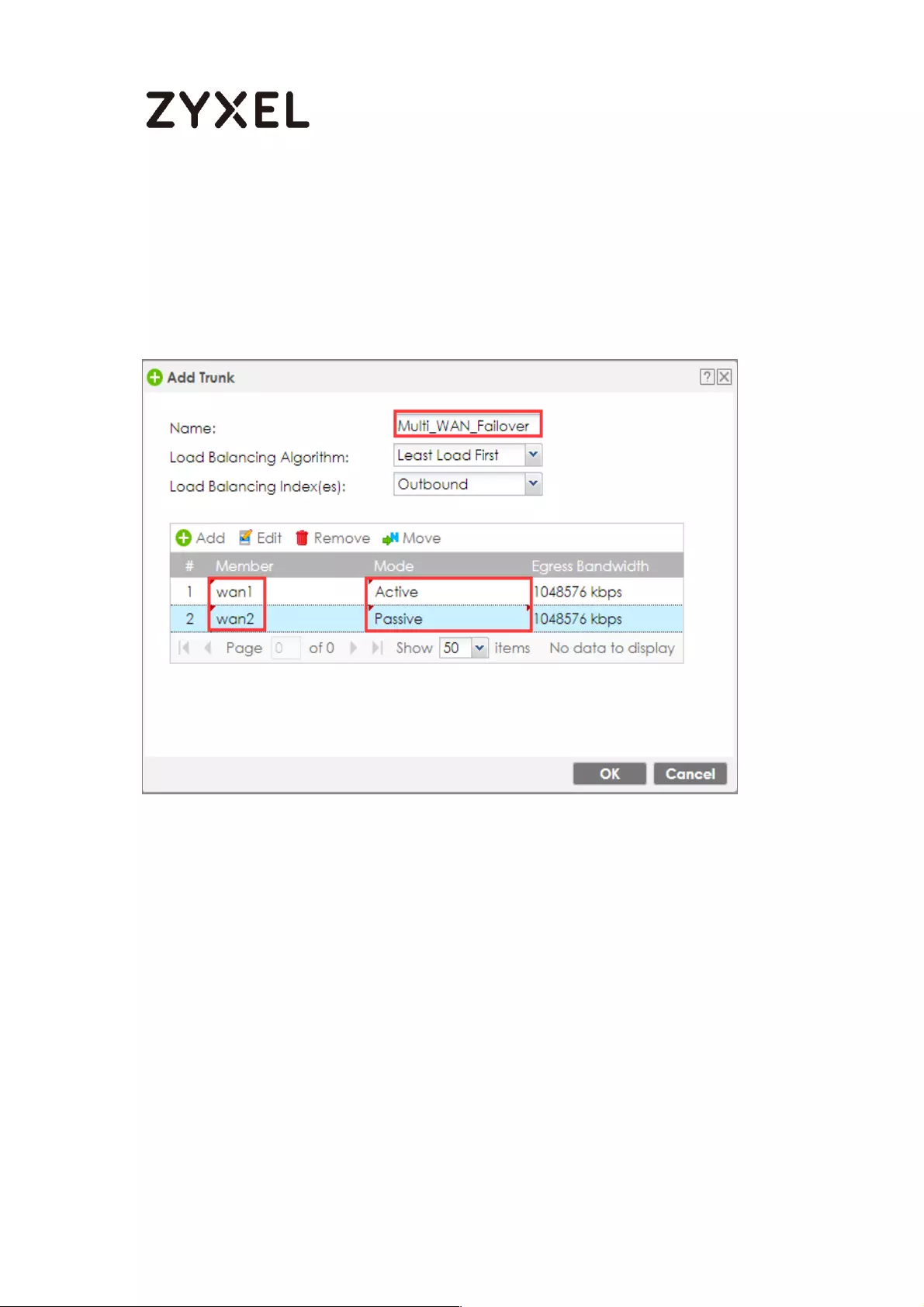
238/782
www.zyxel.com
Set up the WAN Trunk (ZyWALL/USG_HQ)
Go to CONFIGURATION > Interface > Trunk > User Configuration > Add. Select
wan1 and wan2 into the trunk Member and set wan2 Mode to be Passive.
CONFIGURATION > Interface > Trunk > User Configuration > Add
Go to CONFIGURATION > Interface > Trunk > Configuration. Select Disconnect
Connection before Falling Back. In the Default WAN Trunk, select User Configured
Trunk to be the customized WAN trunk added in the previous step
(Multi_WAN_Failover in this example).
CONFIGURATION > Interface > Trunk > User Configuration > Add
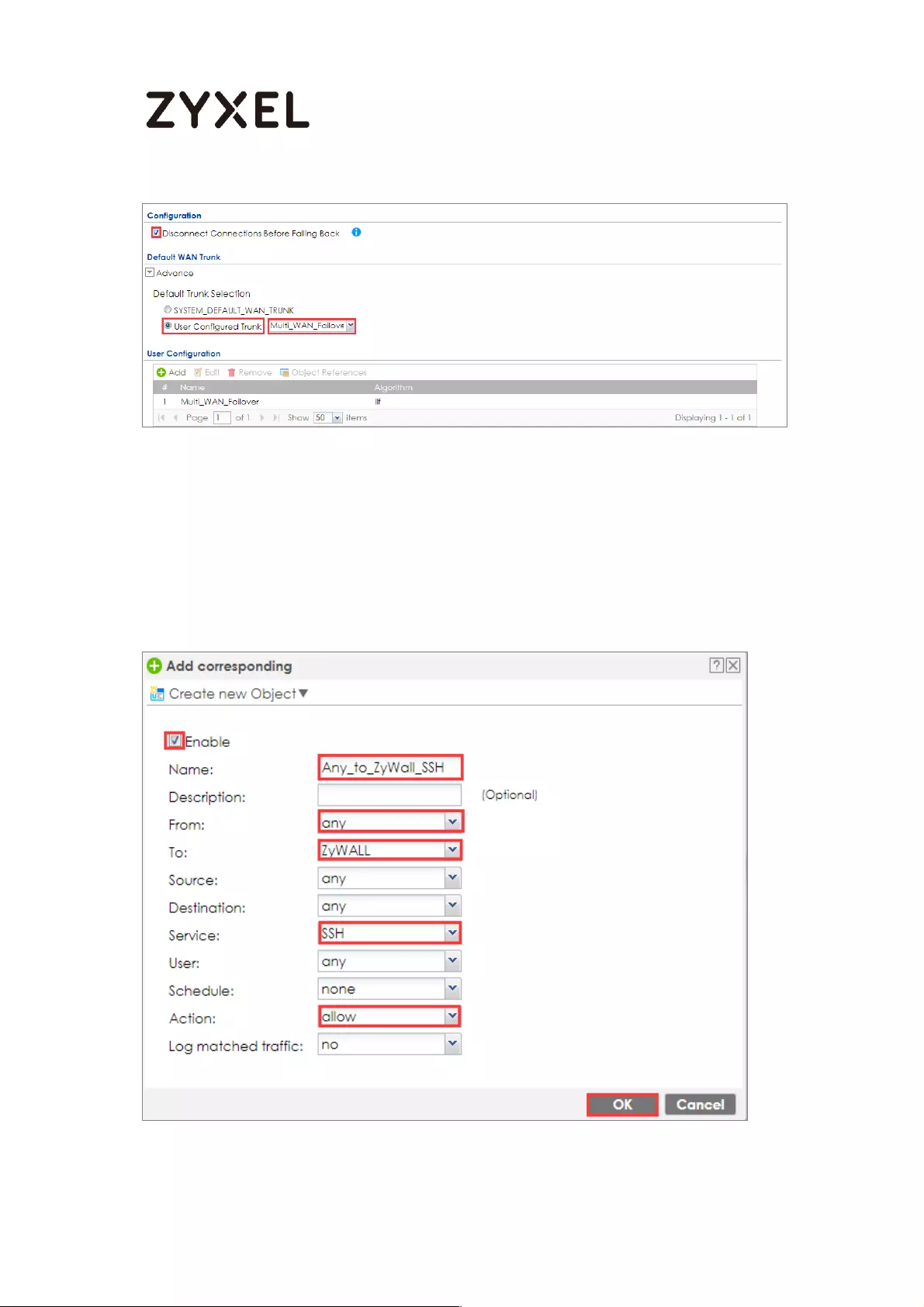
239/782
www.zyxel.com
Set up the Failover Command Line (ZyWALL/USG HQ)
Go to CONFIGURATION > Security Policy > Policy Control and add a To ZyWALL
rule to allow SSH service.
CONFIGURATION > Security Policy > Policy Control > Add corresponding

240/782
www.zyxel.com
If the Security Policy is created but still cannot access to ZyWALL, please go to
CONFIGURAITON > System > SSH to check do you Enable the General Settings
and make sure the Service Port is correct and the same in your terminal program.
Then, check the Service Control Action should be Accept.
CONFIGURAITON > System > SSH
Enter the command line in terminal mode (Using Tera Term in this example).
Tera Term command
Test the IPSec VPN Tunnel
8 Go to ZYWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
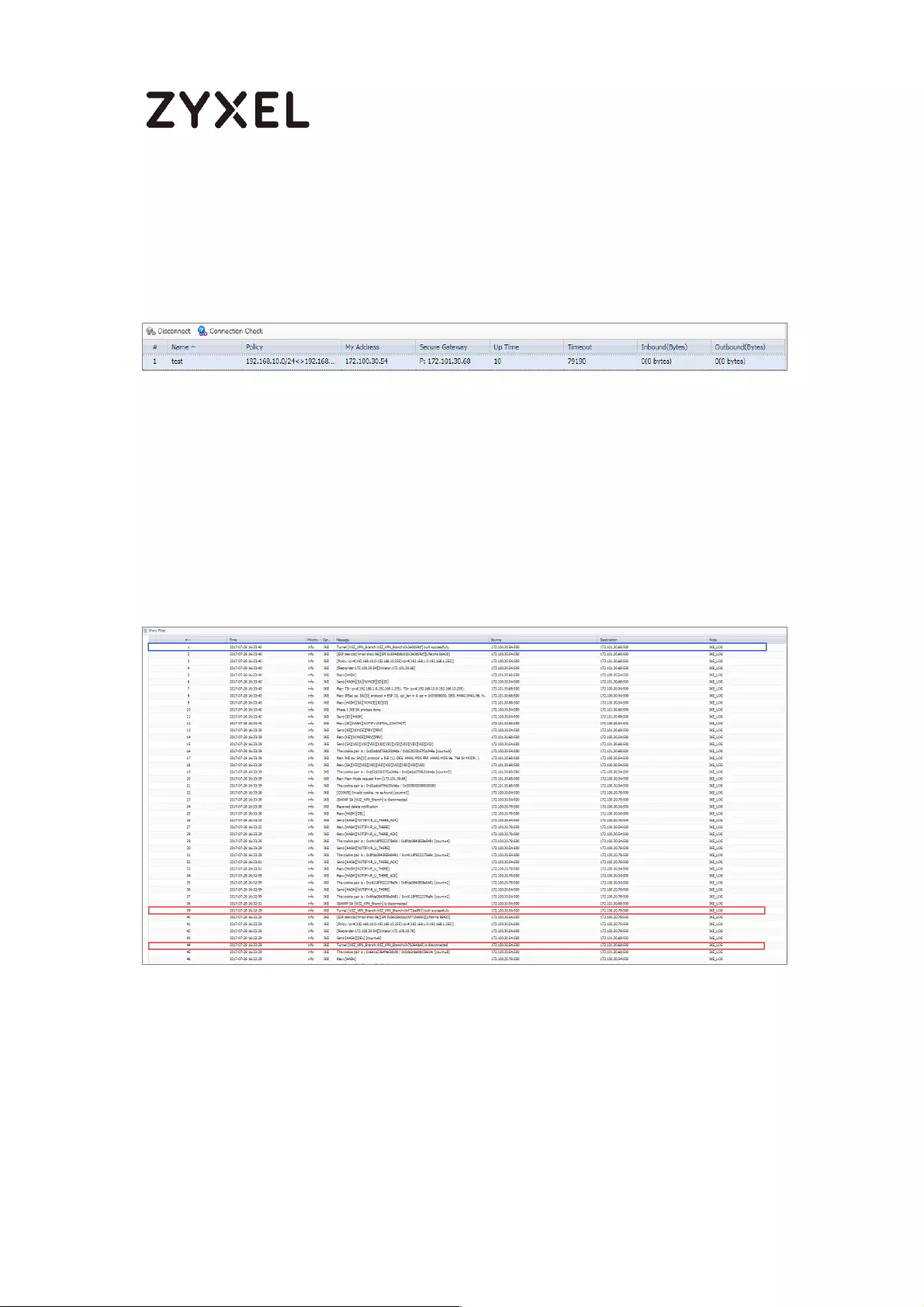
241/782
www.zyxel.com
9 Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
10 Go to ZyWALL/USG_Branch MONITOR > Log. Try to disconnect WAN1 interface
(172.1.1.30.68) and you will see the VPN tunnel failover to WAN2 interface
(172.100.20.78).
MONITOR > Log
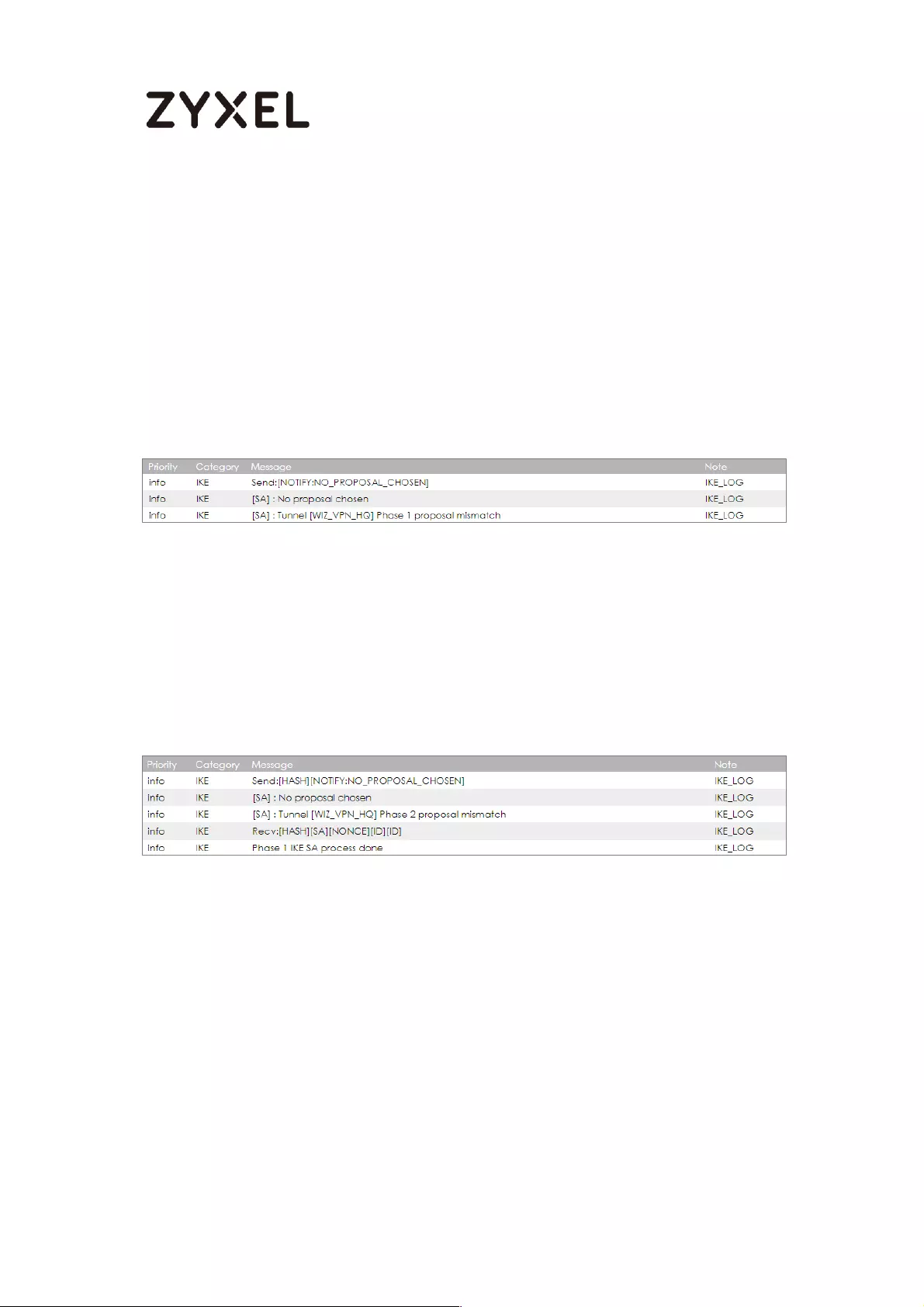
242/782
www.zyxel.com
What Could Go Wrong?
11 If you see below [info] or [error] log message, please check ZyWALL/USG Phase 1
Settings. Both ZyWALL/USG at the HQ and Branch sites must use the same Pre-
Shared Key, Encryption, Authentication method, DH key group and ID Type to
establish the IKE SA.
MONITOR > Log
12 If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG Phase 2 Settings. Both ZyWALL/USG at the HQ and
Branch sites must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
MONITOR > Log
13 Make sure the both ZyWALL/USG at the HQ and Branch sites security policies
allow IPSec VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses
IP protocol 50.
14 Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.

243/782
www.zyxel.com
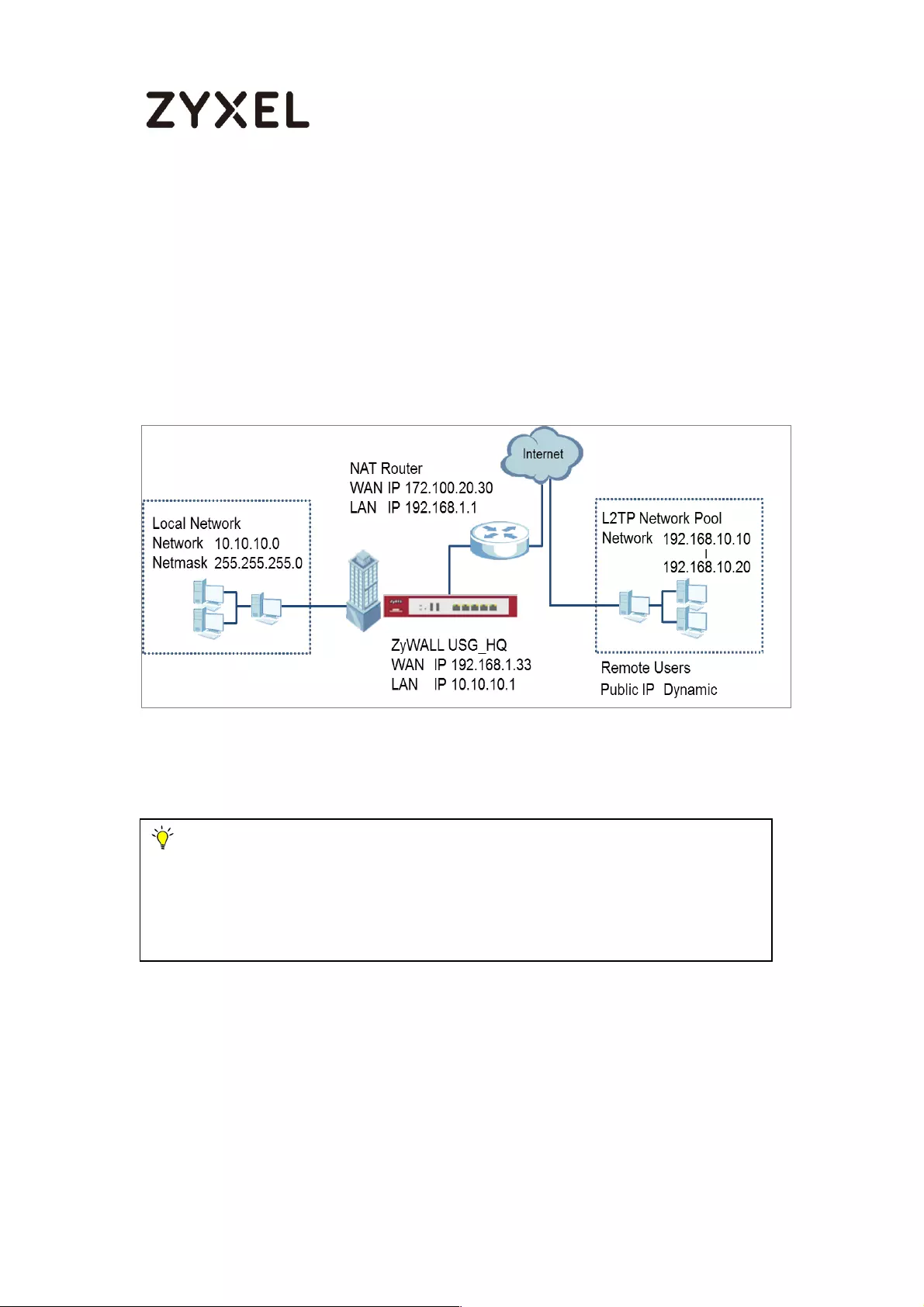
244/782
www.zyxel.com
How to Configure L2TP over IPSec VPN while the ZyWALL/USG
is behind a NAT router
This example shows how to use the VPN Setup Wizard to create a L2TP over
IPSec VPN tunnel between ZyWALL/USG devices. The example instructs how to
configure the VPN tunnel between each site while the ZyWALL/USG is behind a
NAT router. When the L2TP over IPSec VPN tunnel is configured, each site can
be accessed securely.
ZyWALL/USG L2TP over IPSec VPN while the ZyWALL/USG is behind a NAT router
Note:
All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks.
This example was tested using USG110 (Firmware Version: ZLD 4.25).
245/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the ZyWALL/USG_HQ
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
for L2TP VPN Settings wizard to create a L2TP VPN rule that can be used with the
remote Android Mobile Devices. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Then, configure the Rule Name and set My Address to be the wan1 interface
which is connected to the Internet. Type a secure Pre-Shared Key (8-32
characters).
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
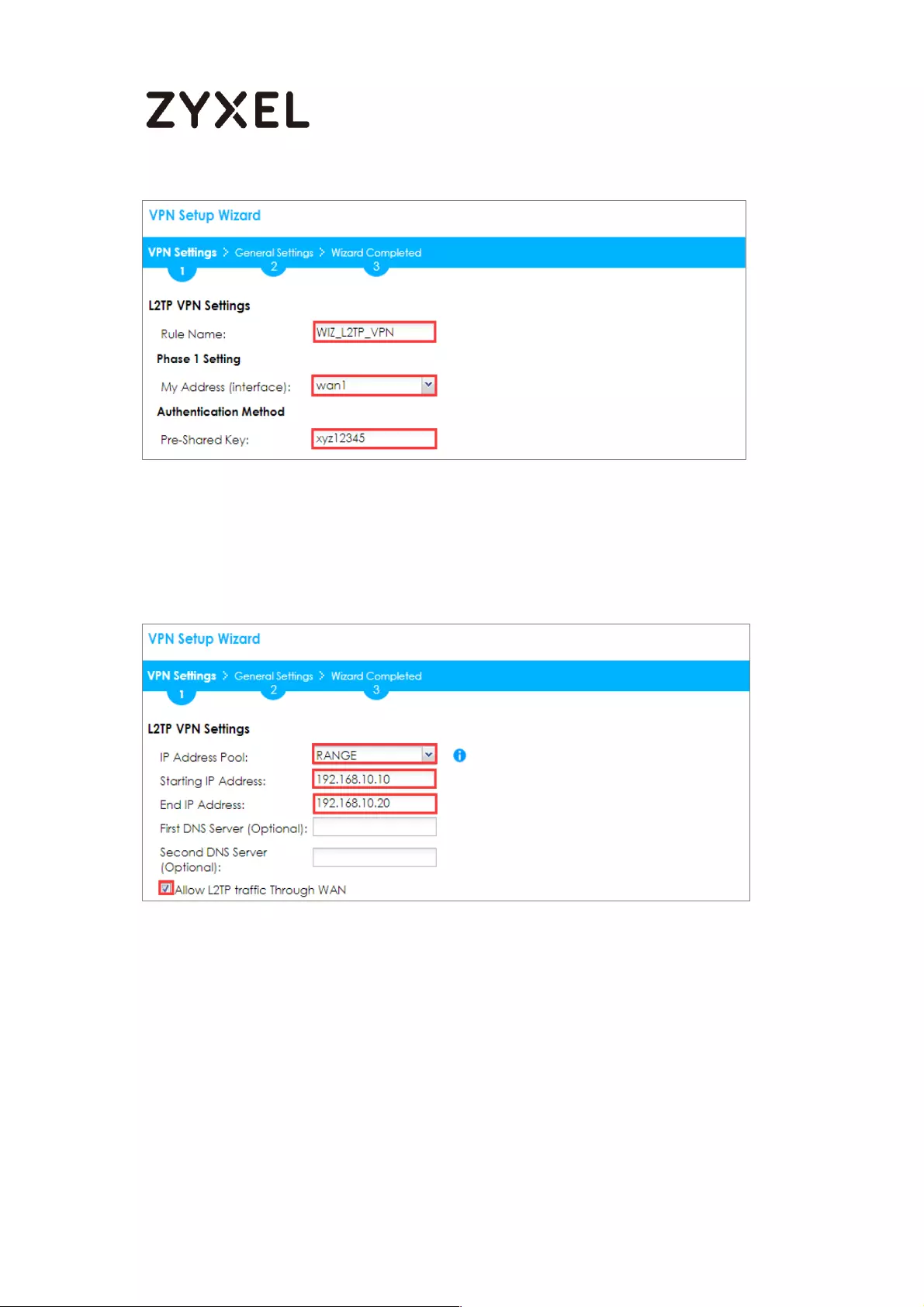
246/782
www.zyxel.com
Assign the remote users IP addresses range from 192.168.10.10 to 192.168.10.20 for use
in the L2TP VPN tunnel and check Allow L2TP traffic Through WAN to allow traffic from
L2TP clients to go to the Internet. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (L2TP VPN Settings)
15 This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (Summary)
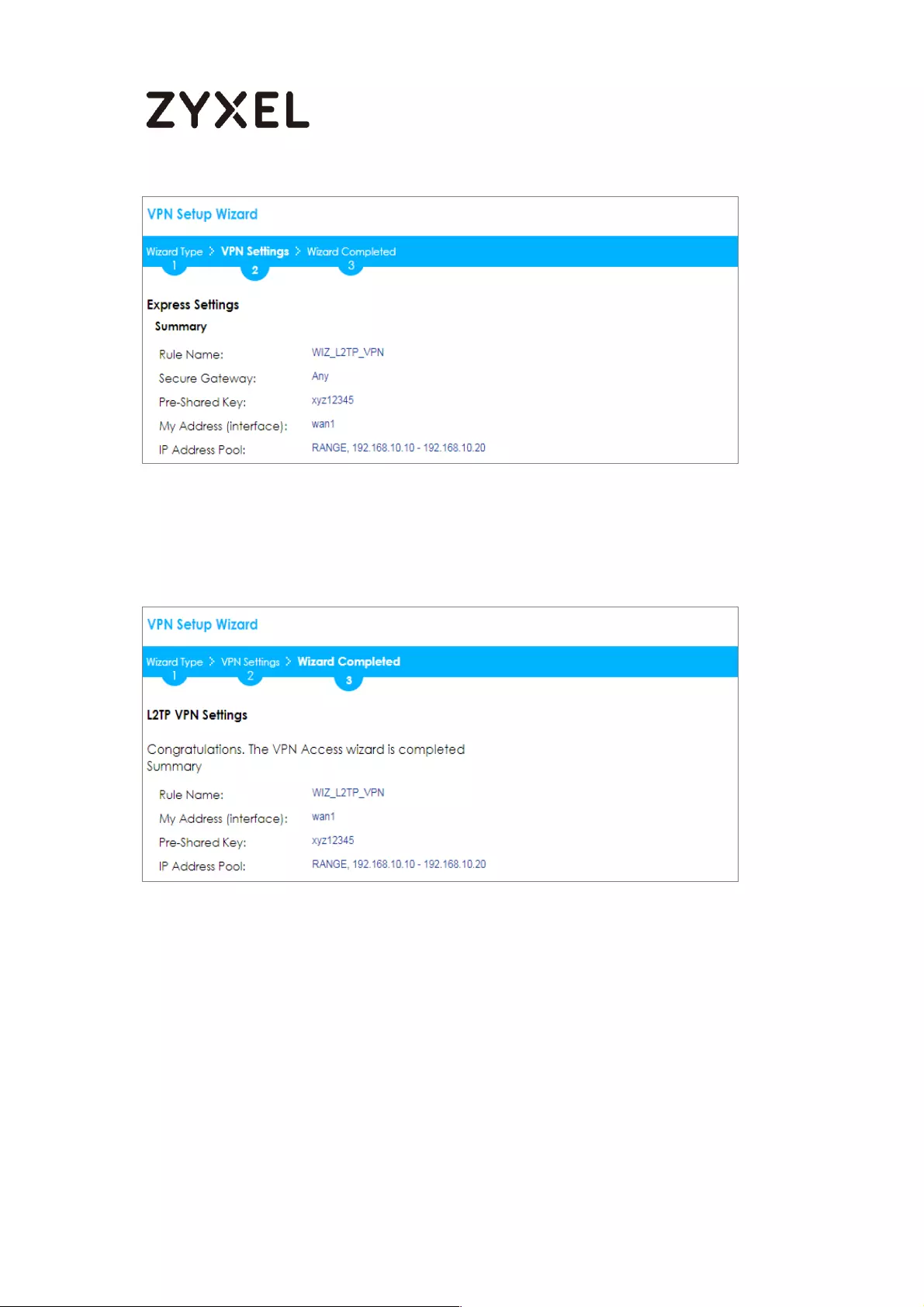
247/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The rule settings appear in the VPN >
L2TP VPN screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Wizard Completed
Go to CONFIGURATION > VPN Connection > Create new Object > Create Address,
create an address object as the NAT router’s WAN IP address (in the example,
172.100.20.30).
CONFIGURATION > VPN Connection > Create new Object > Create Address
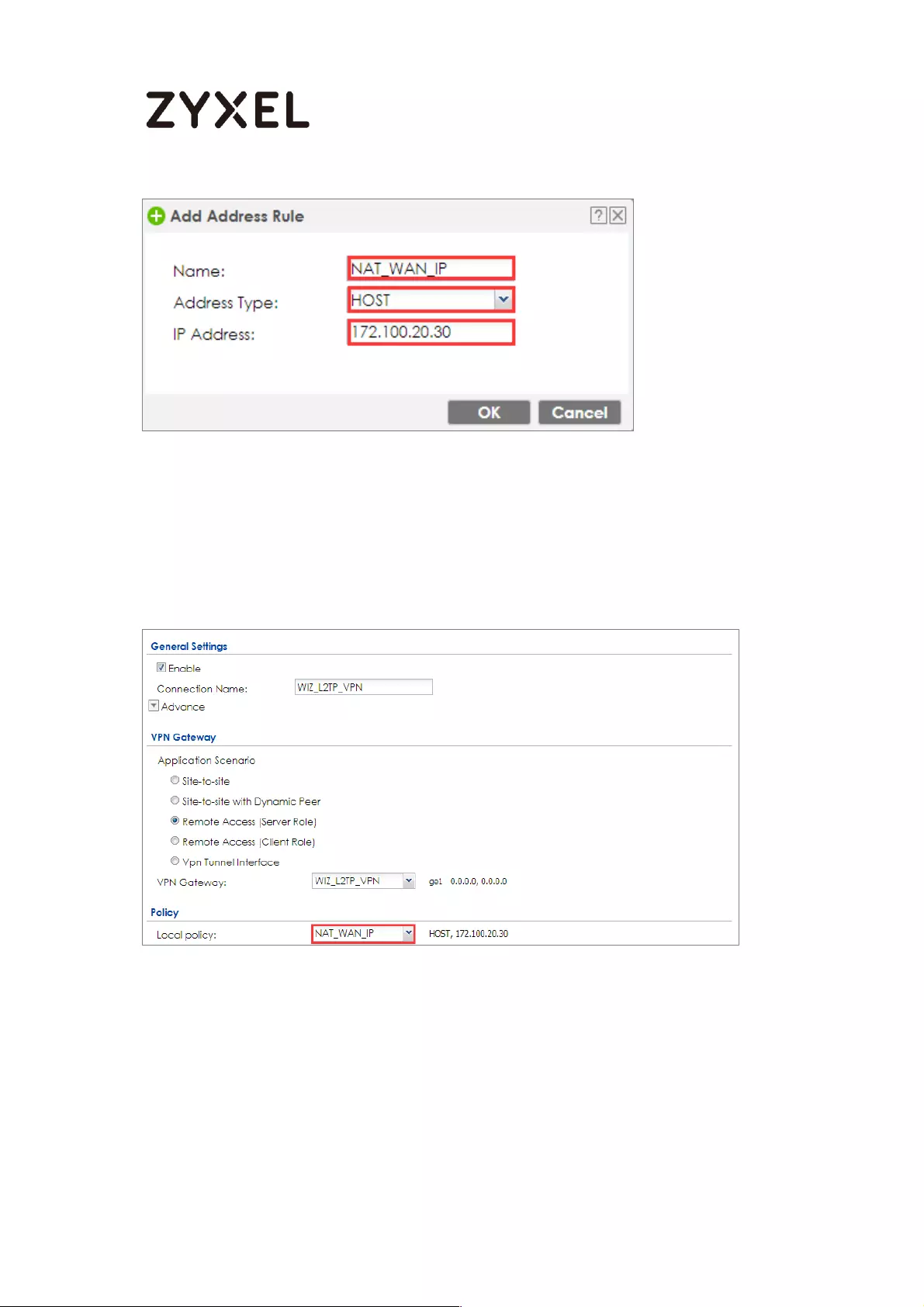
248/782
www.zyxel.com
Go to CONFIGURATION > VPN Connection > Policy > Local Policy, select it be to the
NAT router’s WAN IP address (in the example, 172.100.20.30).
CONFIGURATION > VPN Connection > Policy > Local Policy
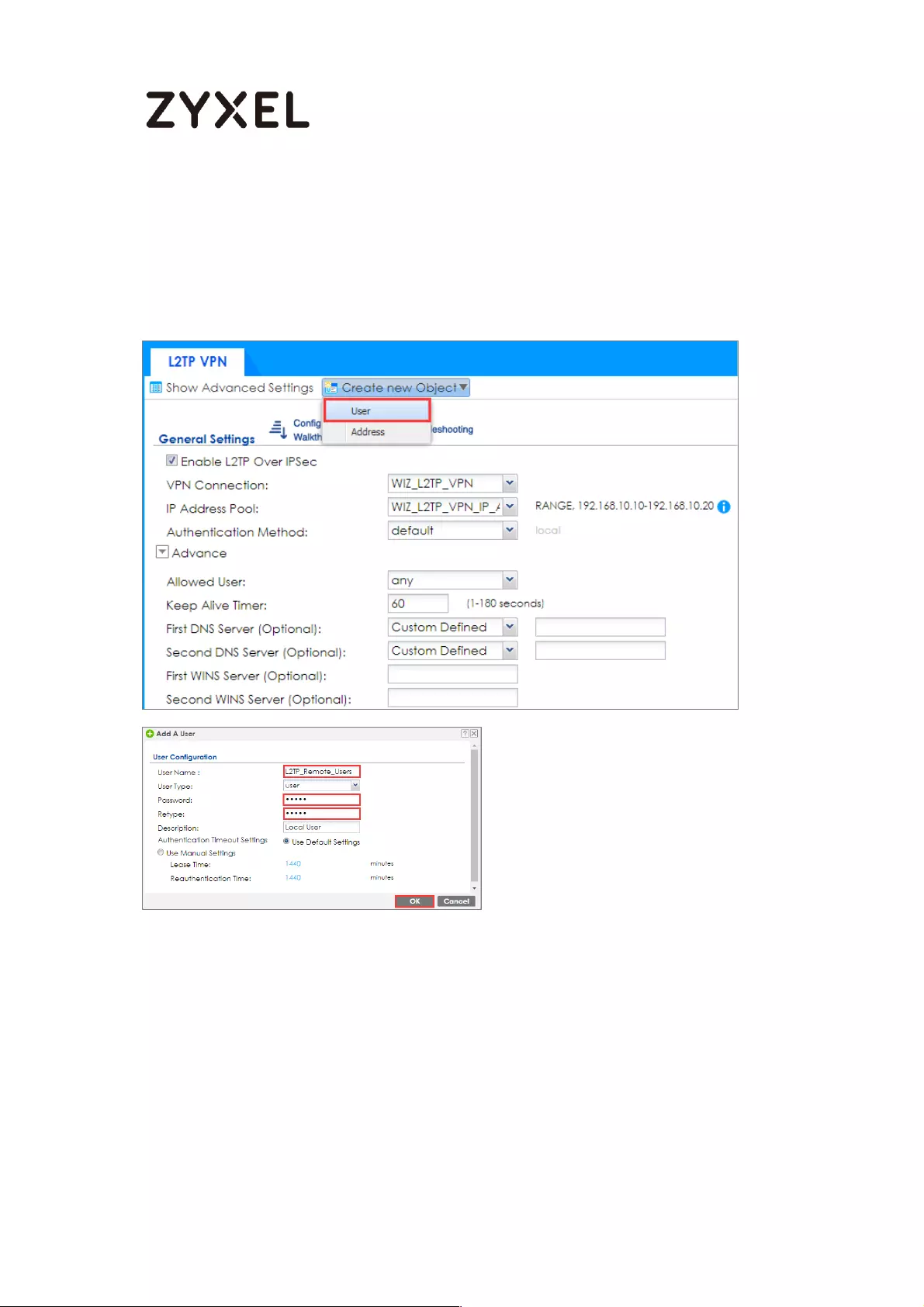
249/782
www.zyxel.com
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add
User Name and Password (4-24 characters). Then, set Allowed User to the newly
created object (L2TP_Remote_Users/zyx168 in this example).
CONFIGURATION > VPN > L2TP VPN > Create new Object > User
Set Up the NAT Router (Using ZyWALL USG device in this
example)
Go to CONFIGURATION > Network > NAT > Add. Select the Incoming Interface
on which packets for the NAT rule must be received. Specified the User-
Defined Original IP field and Type the translated destination IP address that this
NAT rule supports.

250/782
www.zyxel.com
CONFIGURATION > Network > NAT > Add
Go to CONFIGURATION > Object > Address > Add, create an address object as the
ZyWALL/USU_HQ’s WAN IP address (in the example, 192.168.1.33).
CONFIGURATION > Object > Address
Go to CONFIGURATION > Object > Service > Service Group, create a service
group for the following UDP ports:
UDP Port Number = 1701 → Used by L2TP
UDP Port Number = 500 → Used by IKE
UDP Port Number = 4500 → Used by NAT-T
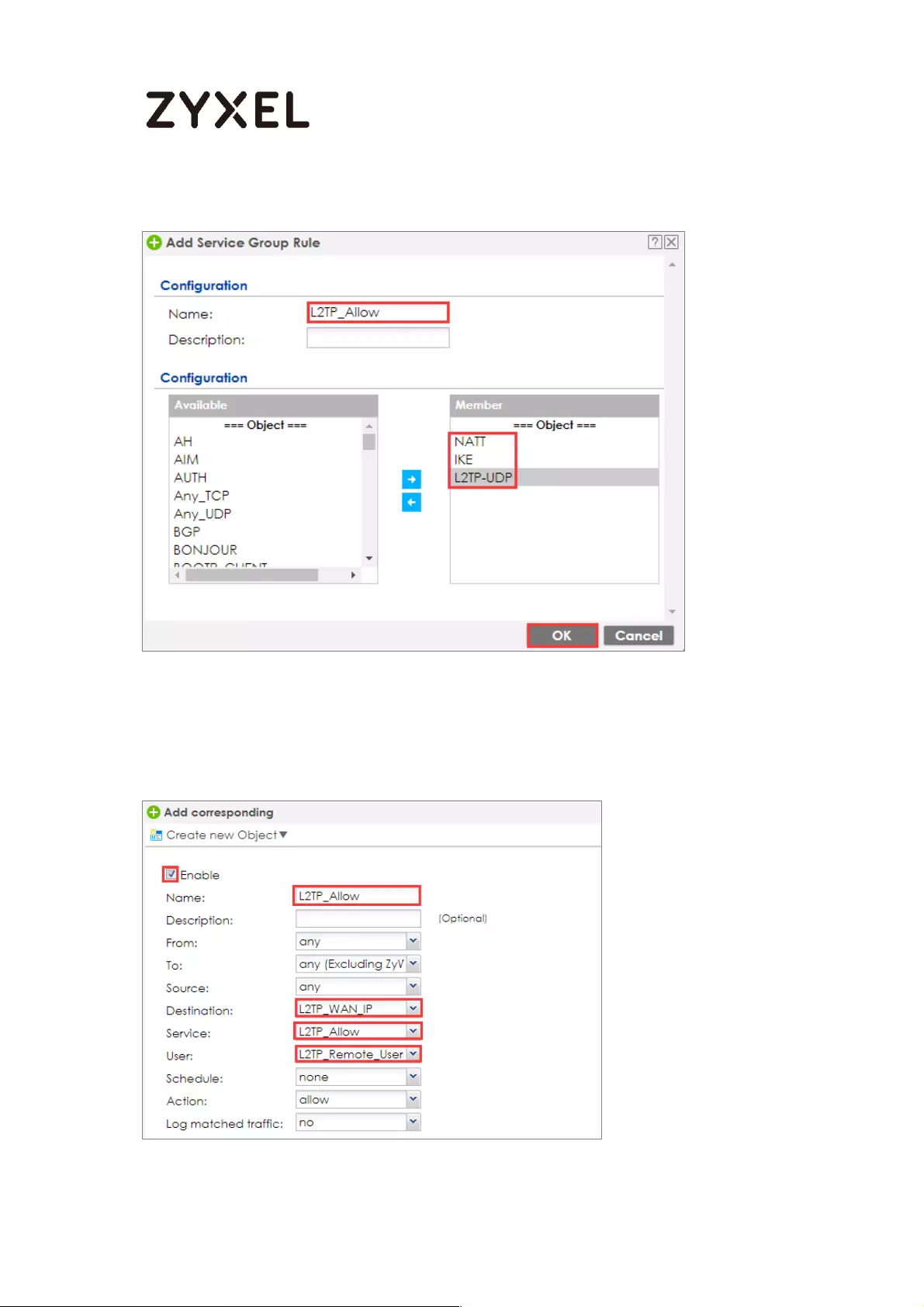
251/782
www.zyxel.com
CONFIGURATION > Service > Service Group
Go to CONFIGURATION > Security Policy > Policy Control, add corresponding
rule to allow L2TP services.
CONFIGURATION > Security Policy > Policy Control

252/782
www.zyxel.com
Test the L2TP over IPSec VPN Tunnel
Use a smartphone or a PC to establish a L2TP VPN connection to the
ZyWALL/USG. Configure the NAT's public IP address as the L2TP server address on
the client. In this example using iOS device to test the result:
To configure L2TP VPN in an iOS 8.4 device, go to Menu > Settings > VPN > Add VPN
Configuration and configure as follows.
Description is for you to identify the VPN configuration.
Set Server to the ZyWALL/USG’s WAN IP address (172.100.20.30 in this example).
Enter Account and Password which the same as Allowed User created in ZyWALL/USG
(L2TP_Remote_Users/zyx168 in this example).
Set Secret to the Pre-Shared Key of the IPSec VPN gateway the ZyWALL/USG uses
for L2TP VPN over IPSec (xyz12345 in this example).
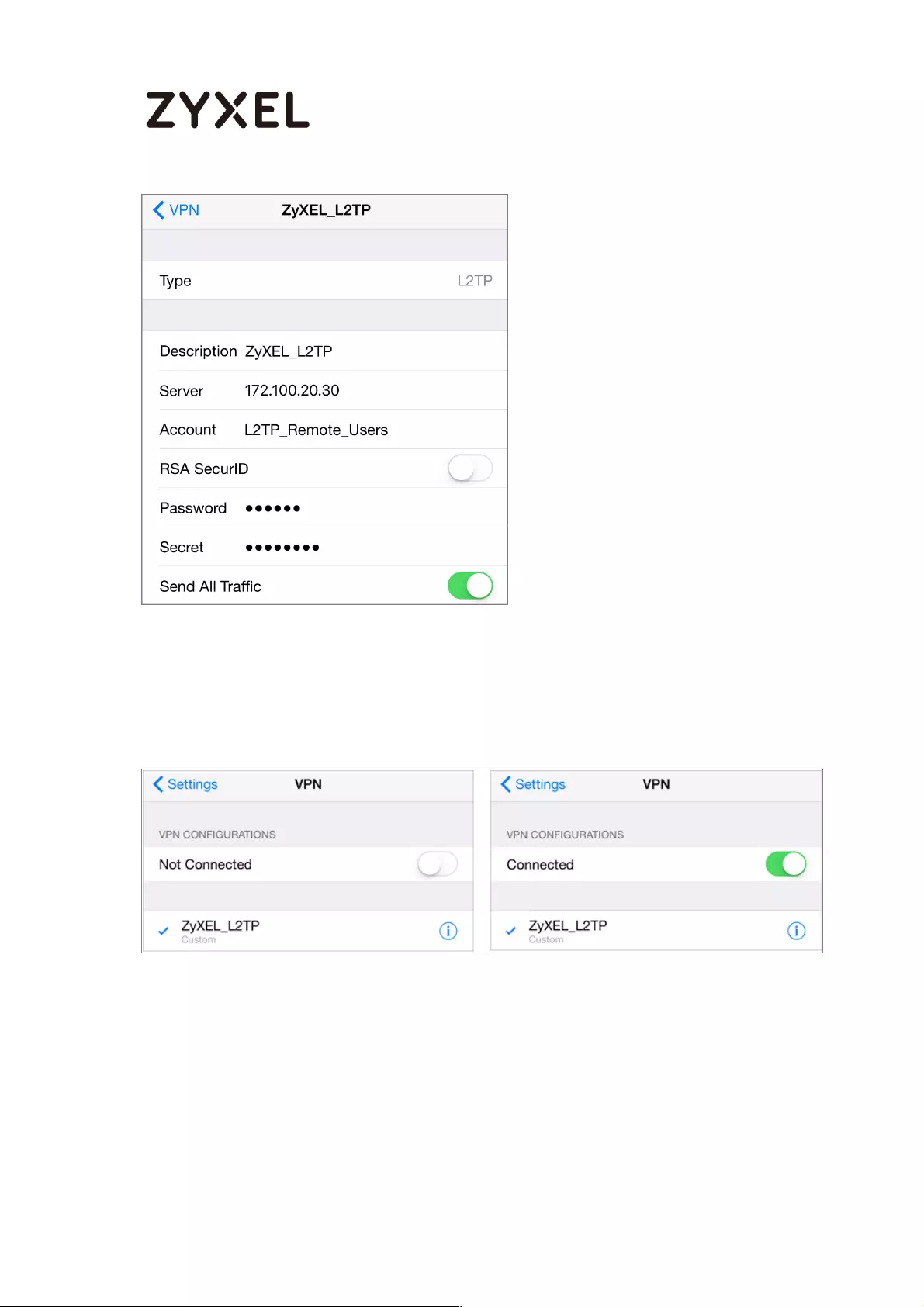
253/782
www.zyxel.com
After you create a VPN configuration, slide the button right to the on position to
initiate L2TP VPN session.
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection

254/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the Current
L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
Go to iOS mobile device Menu > Settings > VPN > ZyXEL_L2TP and verify the
Assigned IP Address and Connect Time.
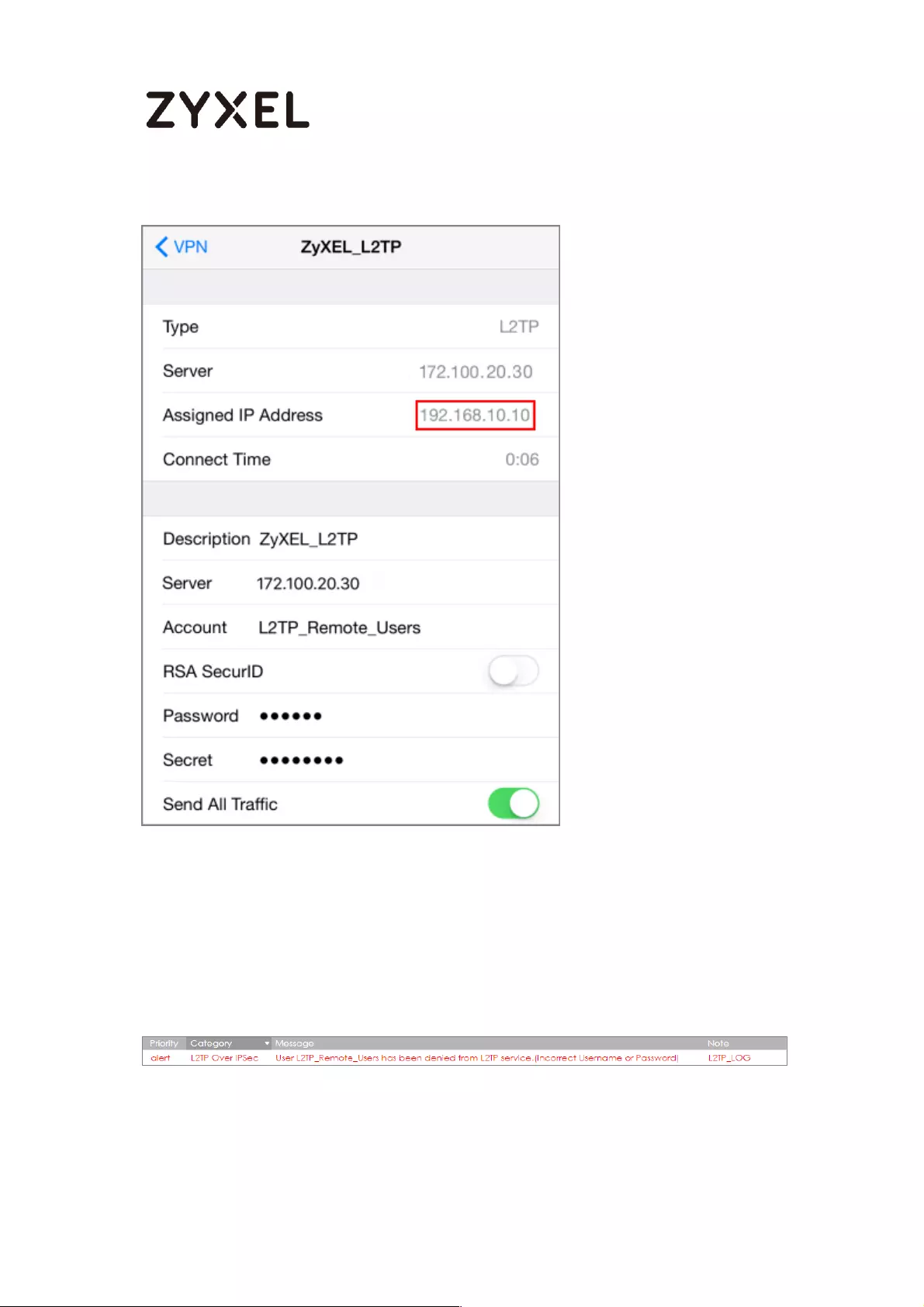
255/782
www.zyxel.com
Menu > Settings > VPN > ZyXEL_L2TP
What Could Go Wrong?
If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. iOS Mobile users must use the same
Username and Password as configured in ZyWALL/USG to establish the L2TP VPN.

256/782
www.zyxel.com
If you see [info] or [error] log message such as below, please check
ZyWALL/USG Phase 1 Settings. iOS Mobile users must use the same Secret as
configured in ZyWALL/USG to establish the IKE SA.
If you see that Phase 1 IKE SA process has completed but still get [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG
unit must set correct Local Policy to establish the IKE SA.
Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2, DMZ,
or WLAN zones, even if they are not in use.
If you cannot access devices in the local network, verify that the devices in the
local network set the USG’s IP as their default gateway to utilize the L2TP tunnel.
Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses UDP
port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
Verify that the Zone is set correctly in the Zone object. This should be set to IPSec_VPN
Zone so that security policies are applied properly.
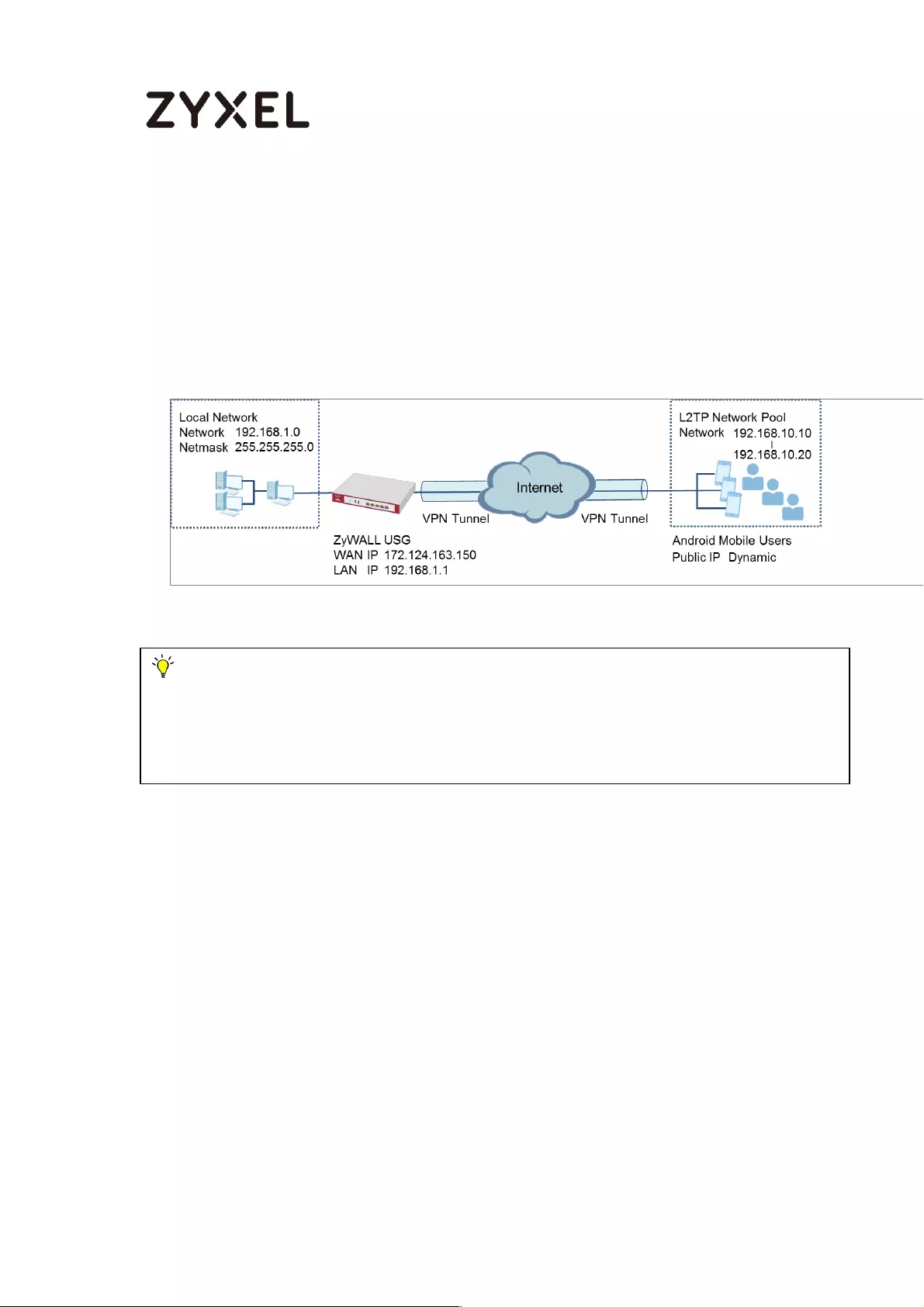
257/782
www.zyxel.com
How to Configure L2TP VPN with Android 5.0 Mobile Devices
This example shows how to use the VPN Setup Wizard to create a L2TP VPN
between a ZyWALL/USG and an Android 5.0 Mobile Device. The example instructs
how to configure the VPN tunnel between each site. When the VPN tunnel is
configured, each site can be accessed securely and allow traffic from L2TP
clients to go to the Internet.
ZyWALL/USG L2TP VPN with Android Mobile Devices Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: 4.25) and Android version (Firmware Version:
5.0)
258/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
for L2TP VPN Settings wizard to create a L2TP VPN rule that can be used with the
remote Android Mobile Devices. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Then, configure the Rule Name and set My Address to be the wan1 interface
which is connected to the Internet. Type a secure Pre-Shared Key (8-32
characters).
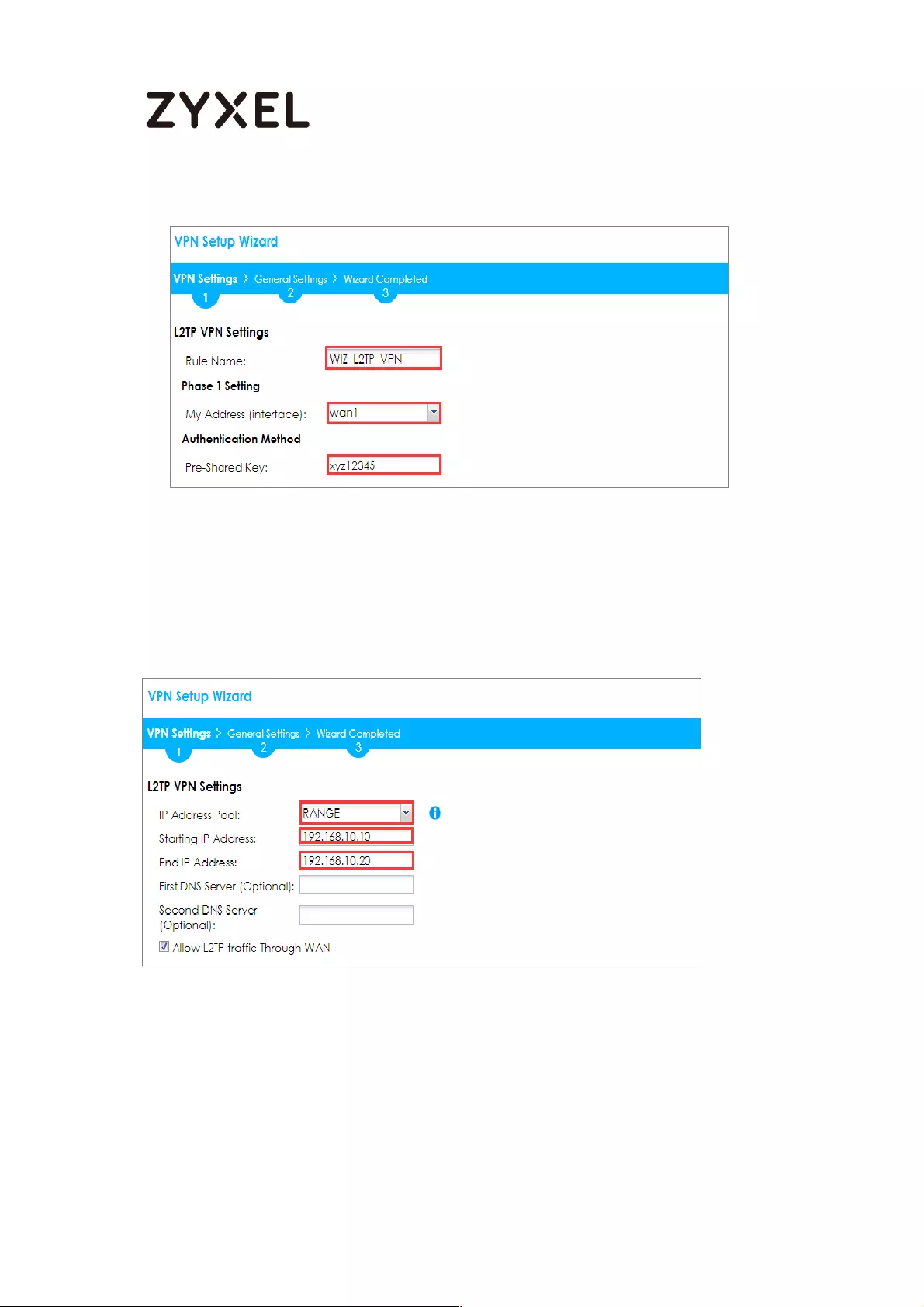
259/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
Assign the remote users IP addresses range from 192.168.10.10 to 192.168.10.20 for
use in the L2TP VPN tunnel and check Allow L2TP traffic Through WAN to allow
traffic from L2TP clients to go to the Internet. Click Next.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (L2TP VPN Settings)
This screen provides a read-only summary of the VPN tunnel. Click Save.
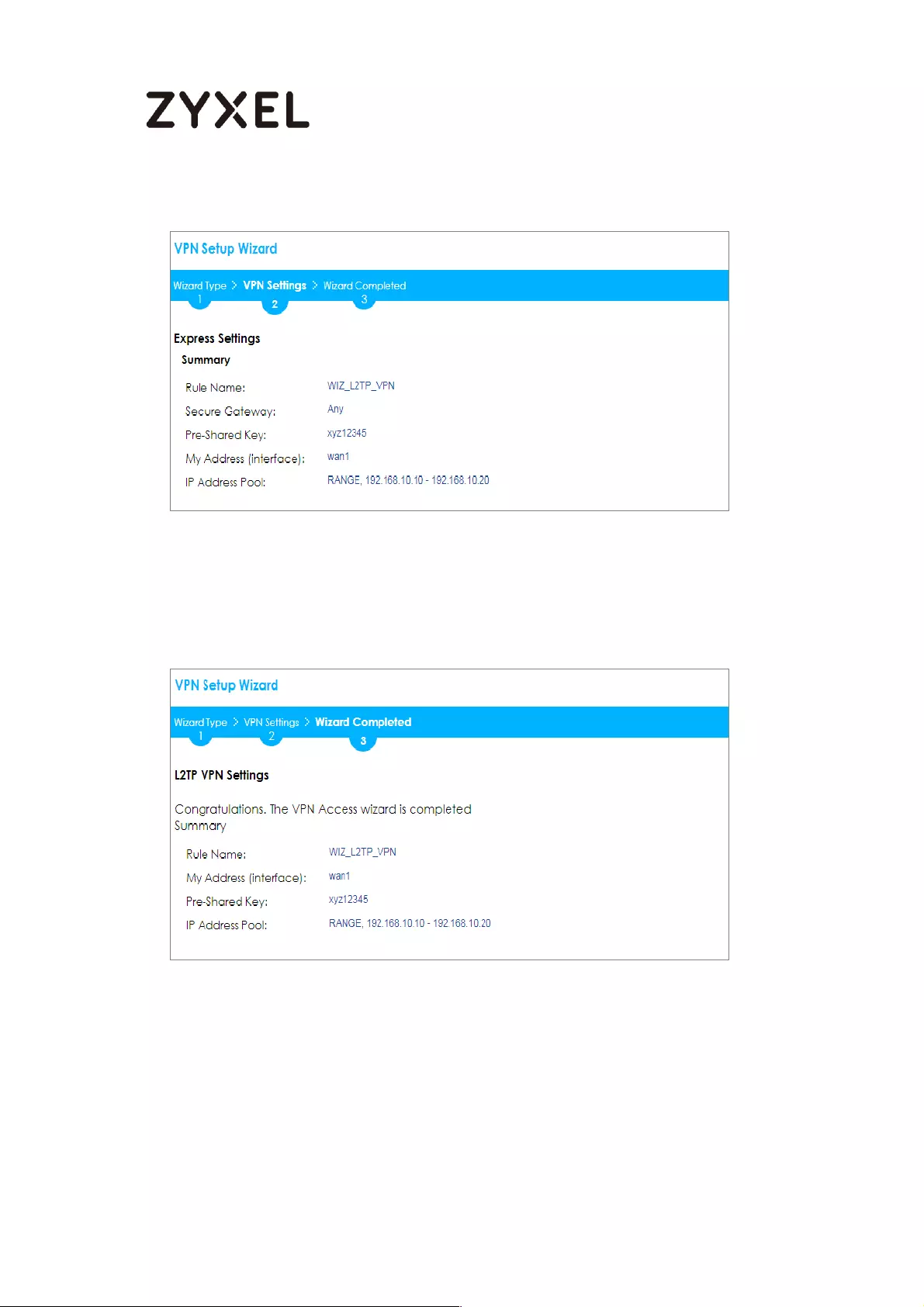
260/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The rule settings appear in the
VPN > L2TP VPN screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Wizard Completed
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add User
Name and Password (4-24 characters). Then, set Allowed User to the newly
created object (L2TP_Remote_Users/zyx168 in this example).
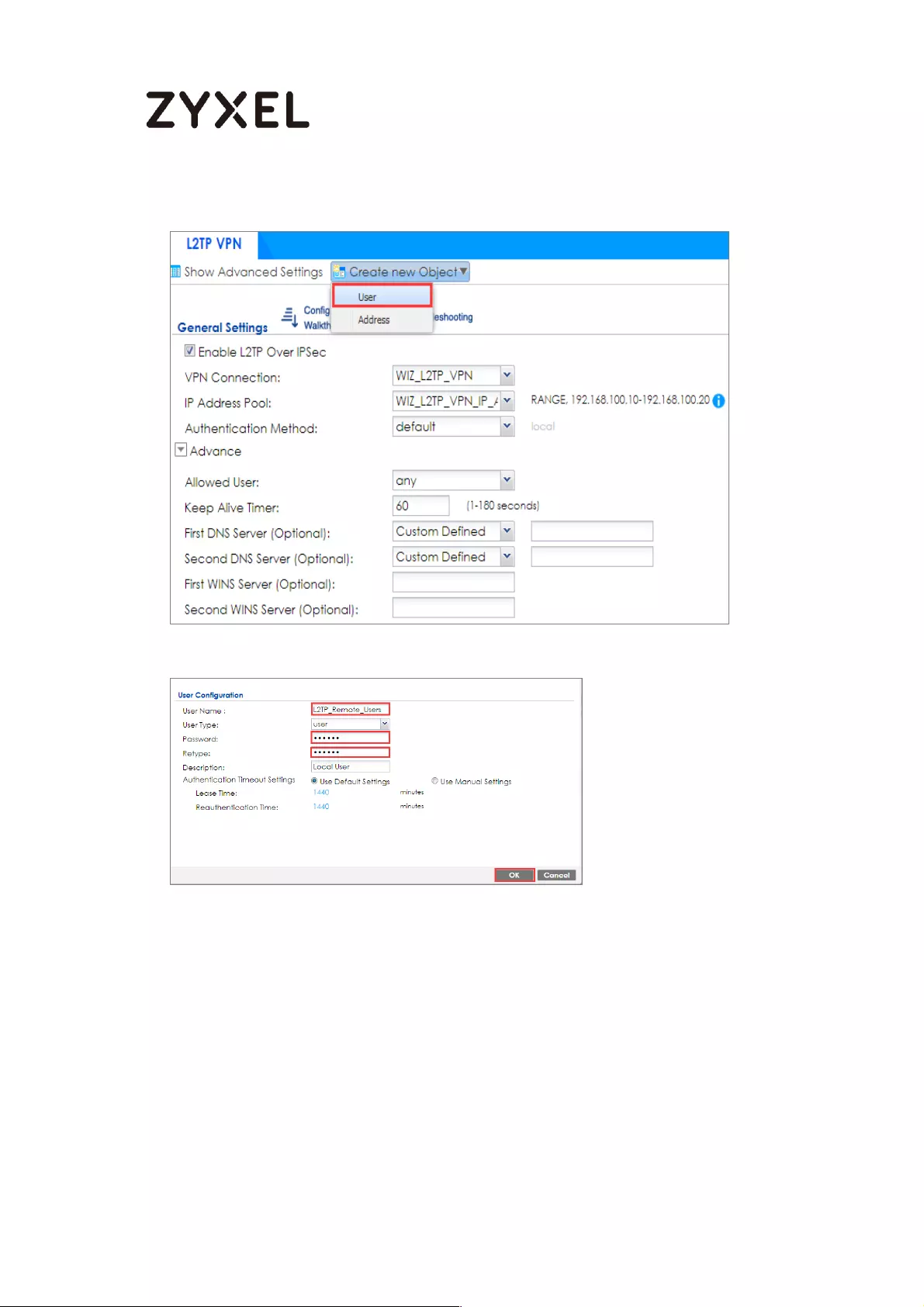
261/782
www.zyxel.com
CONFIGURATION > VPN > L2TP VPN > Create new Object > User
If some of the traffic from the L2TP clients need to go to the Internet, create a
policy route to send traffic from the L2TP tunnels out through a WAN trunk. Set
Incoming to Tunnel and select your L2TP VPN connection. Set the Source
Address to be the L2TP address pool. Set the Next-Hop Type to Trunk and select
the appropriate WAN trunk.
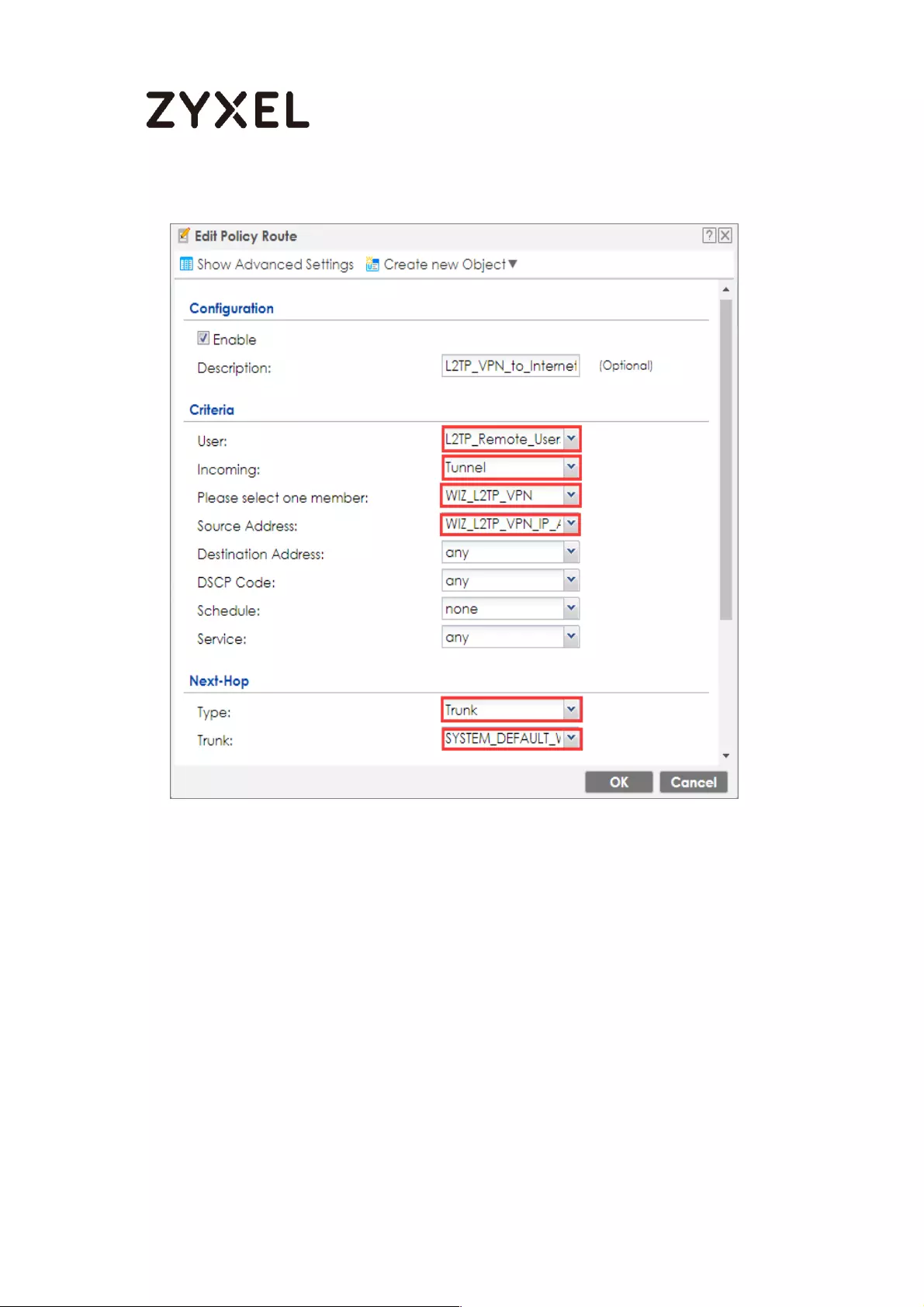
262/782
www.zyxel.com
CONFIGURATION > Network > Routing > Policy Route
Set Up the L2TP VPN Tunnel on the Android Device
To configure L2TP VPN on an Android device, go to Menu > Settings > Wireless &
Networks > VPN settings > Add VPN > Add L2TP/IPSec PSK VPN and configure as
follows.
VPN name is for the user to identify the VPN configuration.
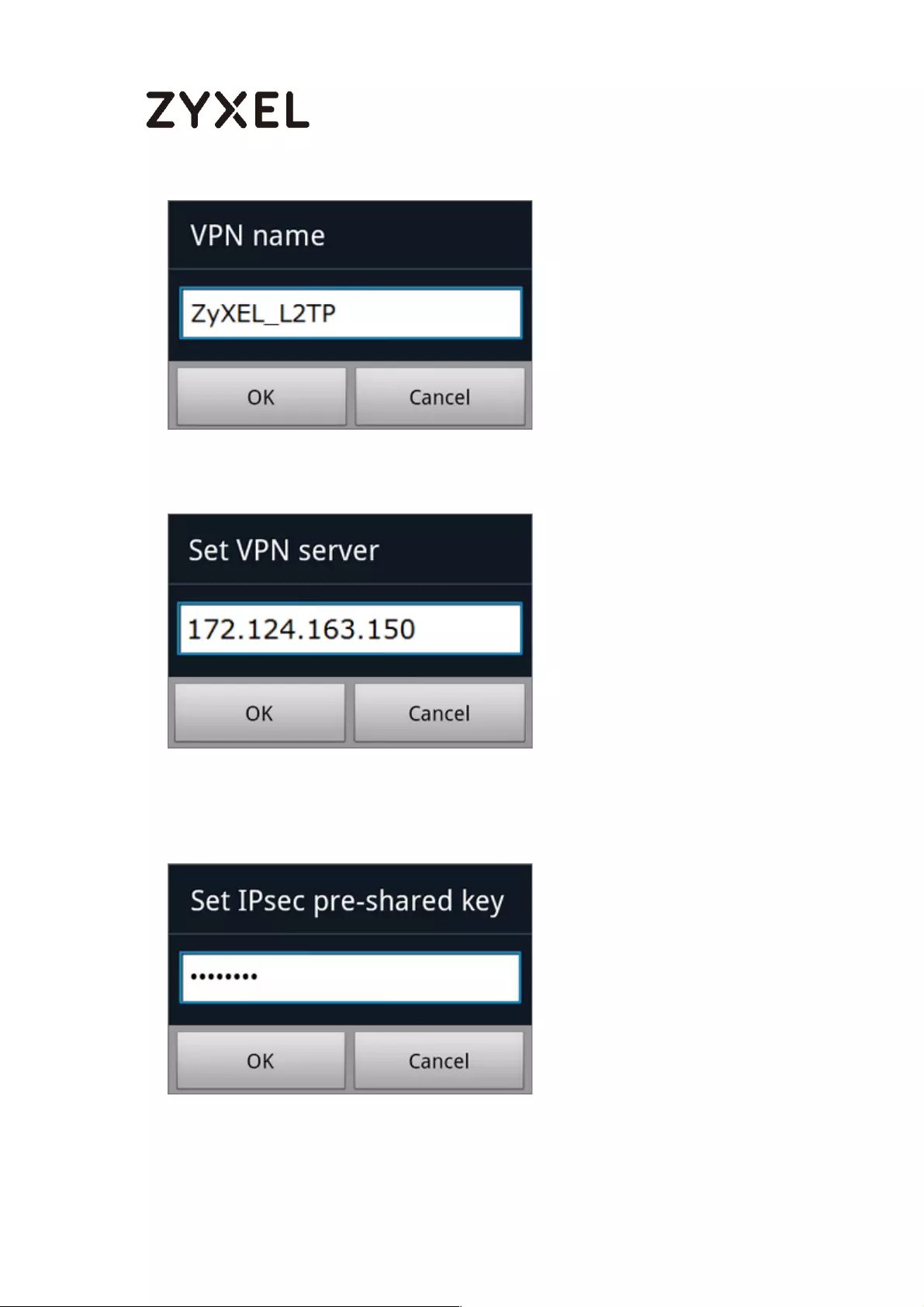
263/782
www.zyxel.com
Set VPN server to the ZyWALL/USG’s WAN IP address.
Set IPSec pre-shared key to the pre-shared key of the IPSec VPN gateway the
ZyWALL/USG uses for L2TP VPN over IPSec (zyx12345 in this example).
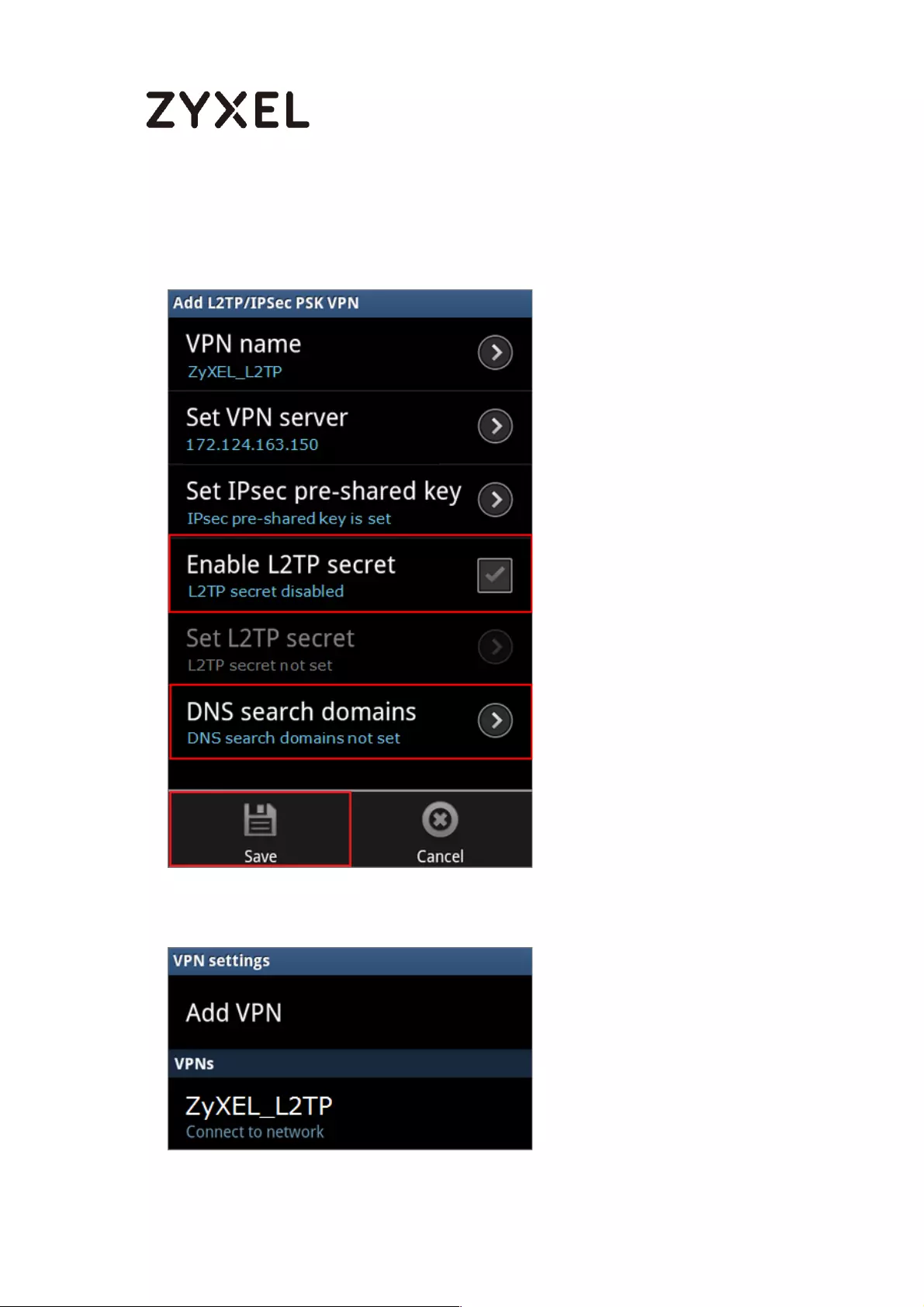
264/782
www.zyxel.com
Leave Enable L2TP secret disabled as default and turn on DNS search domains if
you need to use the internal DNS servers once your connection is made, enter the
DNS server address here. Click Save.
Click the VPN rule ZyXEL_L2TP to begin the VPN connection.
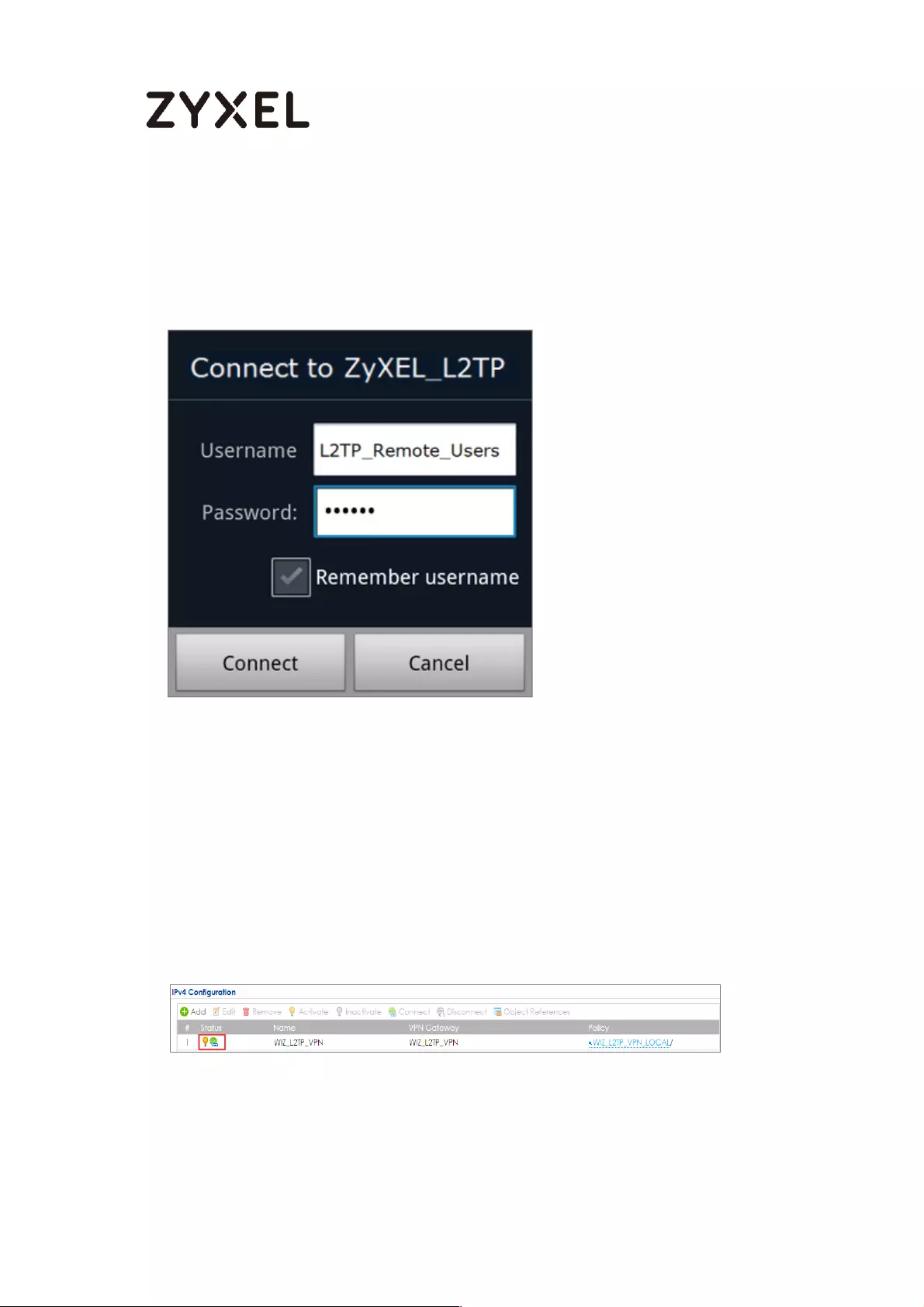
265/782
www.zyxel.com
When dialing the L2TP VPN, the user will have to enter Username/Password. They
are the same as Allowed User created in ZyWALL/USG (L2TP_Remote_Users/zyx168
in this example).
Test the L2TP over IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the
Status connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
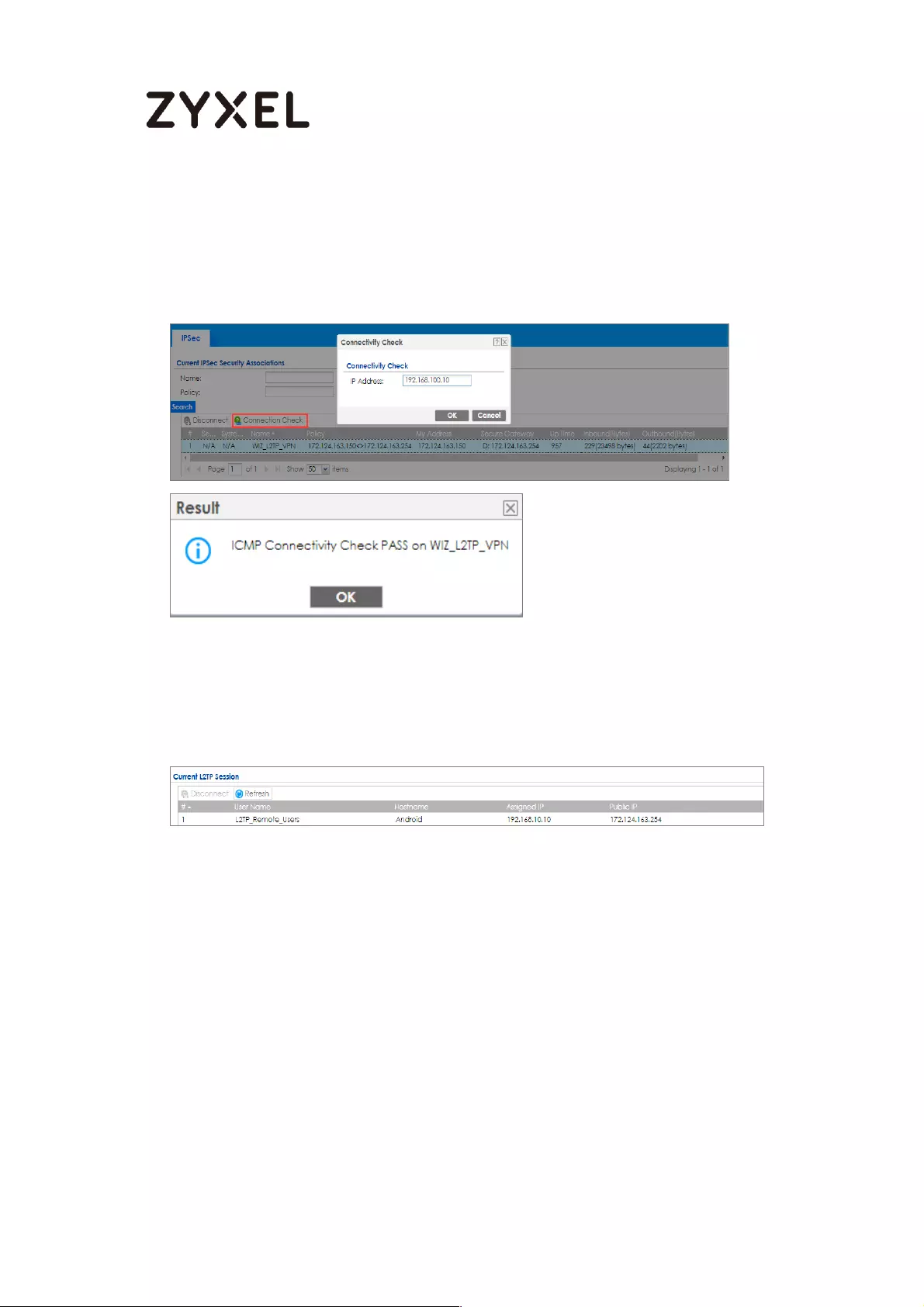
266/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > WIZ_L2TP_VPN
Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the
Current L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
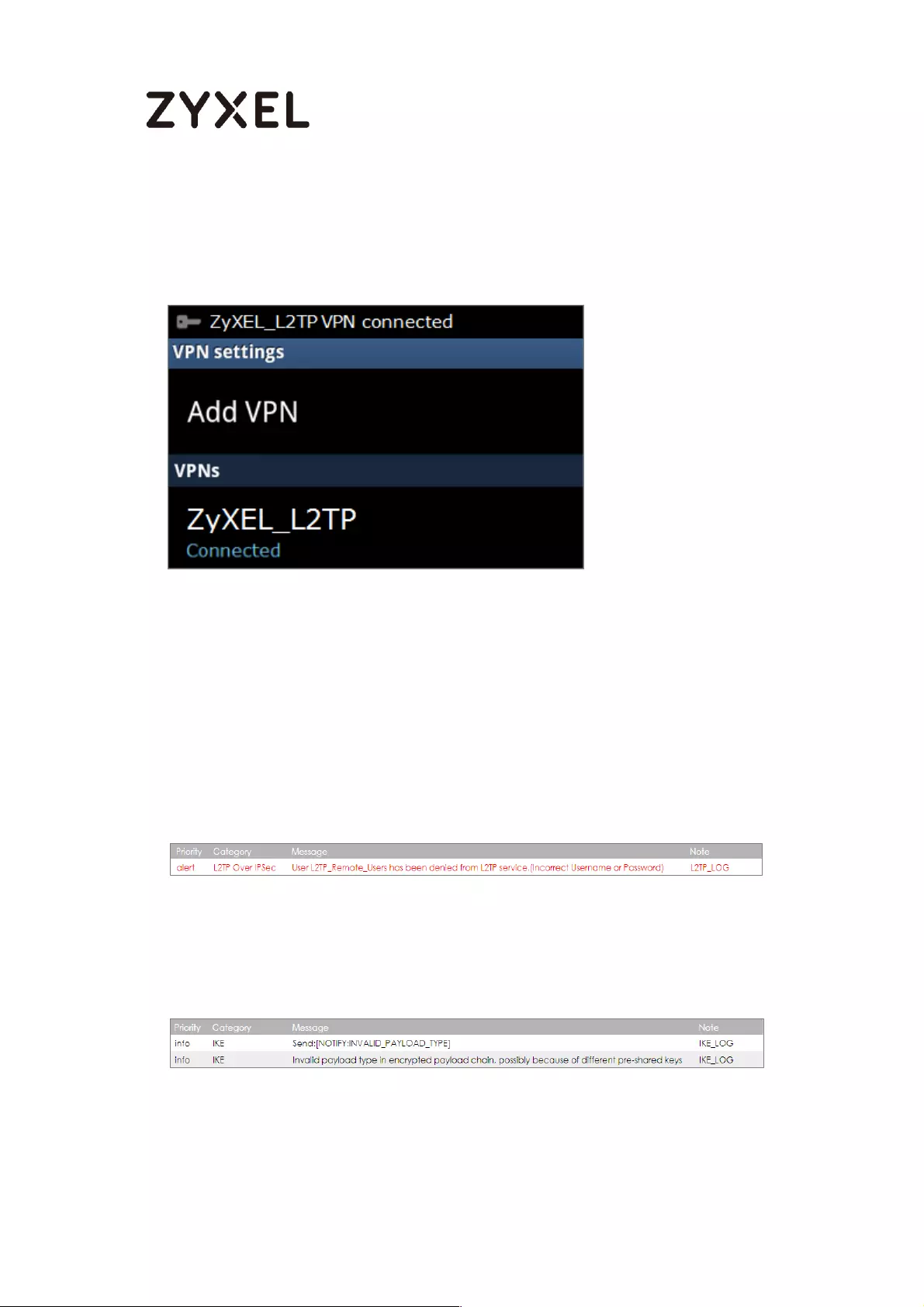
267/782
www.zyxel.com
Go to Android mobile device Menu > Settings > Wireless & Networks > VPN and
verify the connection status.
Menu > Settings > Wireless & Networks > VPN
What Could Go Wrong?
If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. Android Mobile users must use the same
Username and Password as configured in ZyWALL/USG to establish the L2TP VPN.
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. Android Mobile users must use the same Secret as configured in
ZyWALL/USG to establish the IKE SA.

268/782
www.zyxel.com
If you see that Phase 1 IKE SA process has completed but still get [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG unit
must set correct Local Policy to establish the IKE SA.
Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2,
DMZ, or WLAN zones, even if they are not in use.
If you cannot access devices in the local network, verify that the devices in the
local network set the USG’s IP as their default gateway to utilize the L2TP tunnel.
Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses
UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
Verify that the Zone is set correctly in the Zone object. This should be set to
IPSec_VPN Zone so that security policies are applied properly.
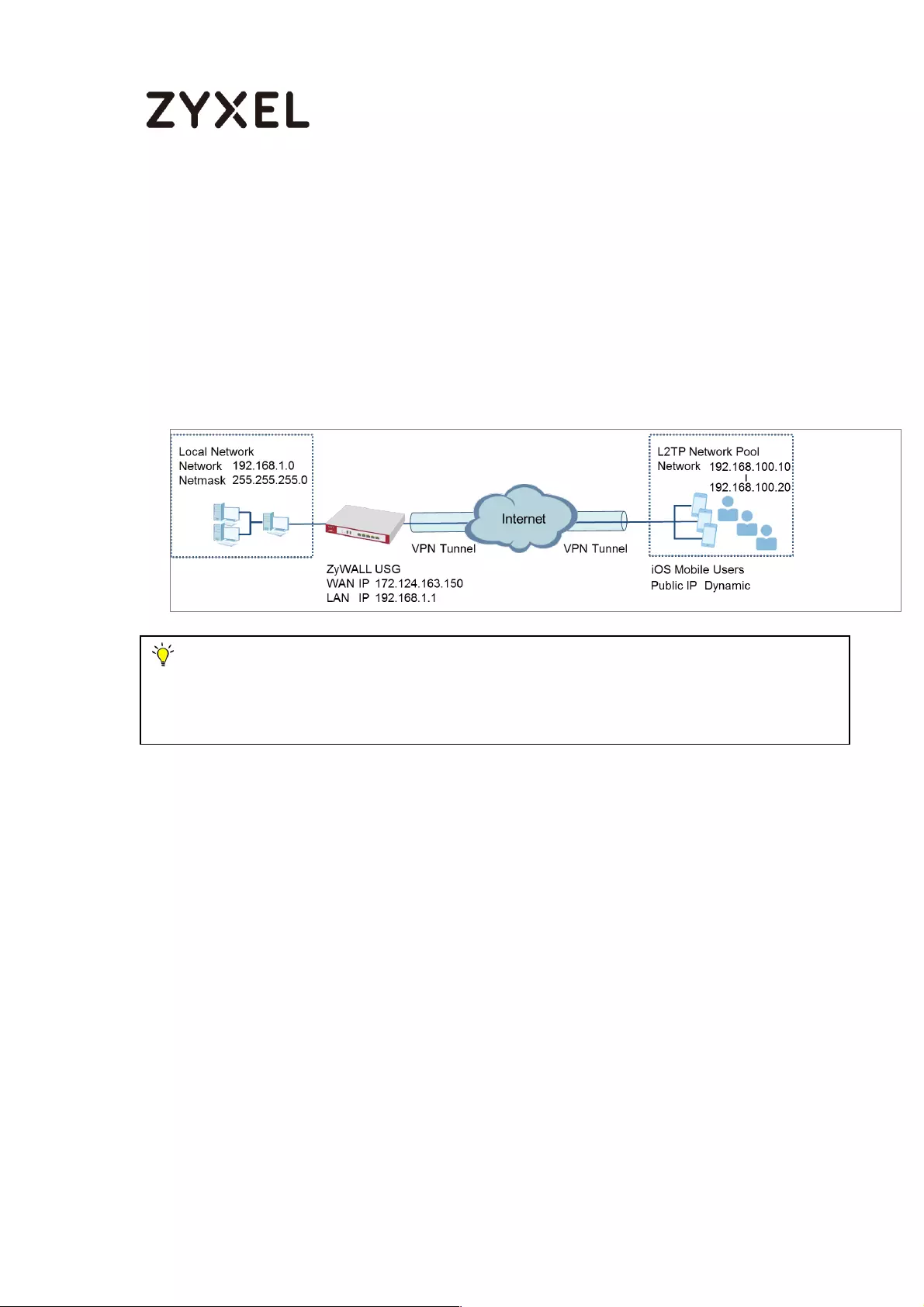
269/782
www.zyxel.com
How to Configure L2TP VPN with iOS 8.4 Mobile Devices
This example shows how to use the VPN Setup Wizard to create a L2TP VPN
between a ZyWALL/USG and an iOS 8.4 Mobile Device. The example instructs how
to configure the VPN tunnel between each site. When the VPN tunnel is
configured, each site can be accessed securely and allow traffic from L2TP
clients to go to the Internet.
ZyWALL/USG L2TP VPN with iOS Mobile Devices Example
Set Up the L2TP VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
for L2TP VPN Settings wizard to create a L2TP VPN rule that can be used with the
remote iOS Mobile Devices. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: 4.25) and iOS (Firmware Version: 8.4).
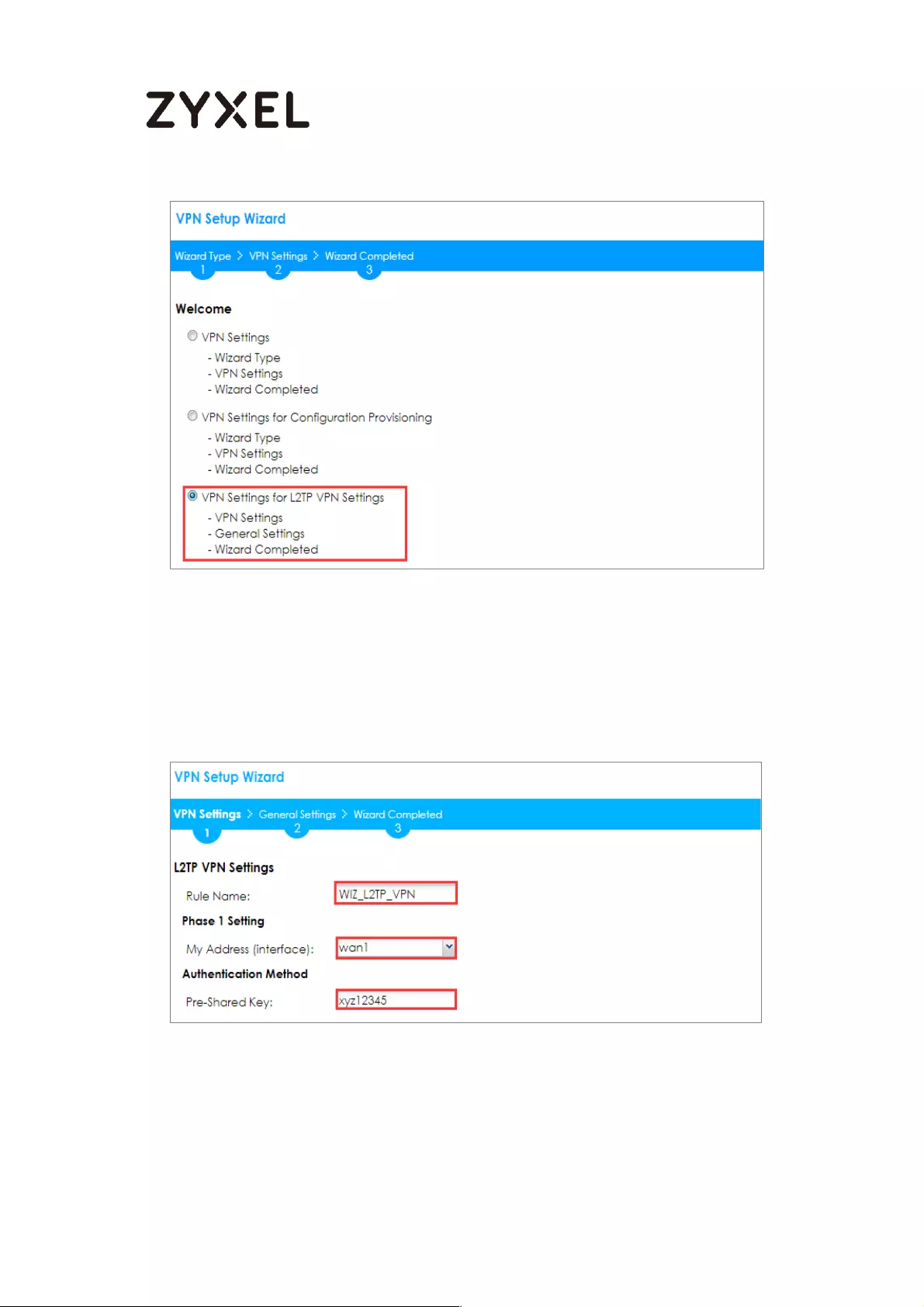
270/782
www.zyxel.com
Then, configure the Rule Name and set My Address to be the wan1 interface
which is connected to the Internet. Type a secure Pre-Shared Key (8-32
characters).
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
Assign the remote users IP addresses range from 192.168.100.10 to 192.168.100.20
for use in the L2TP VPN tunnel and check Allow L2TP traffic Through WAN to allow
traffic from L2TP clients to go to the Internet. Click Next.
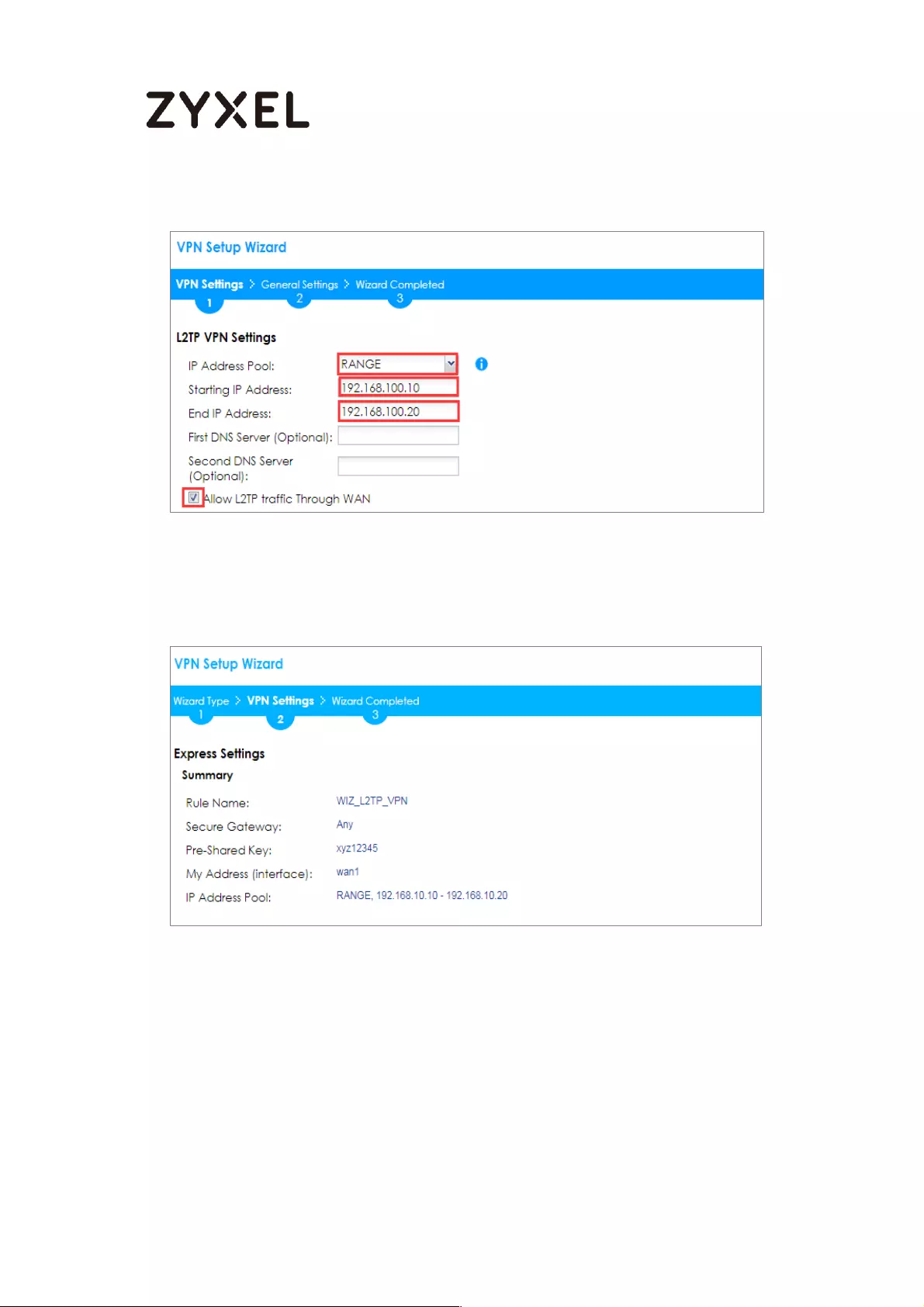
271/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (L2TP VPN Settings)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The rule settings appear in the
VPN > L2TP VPN screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Summary > Wizard
Completed
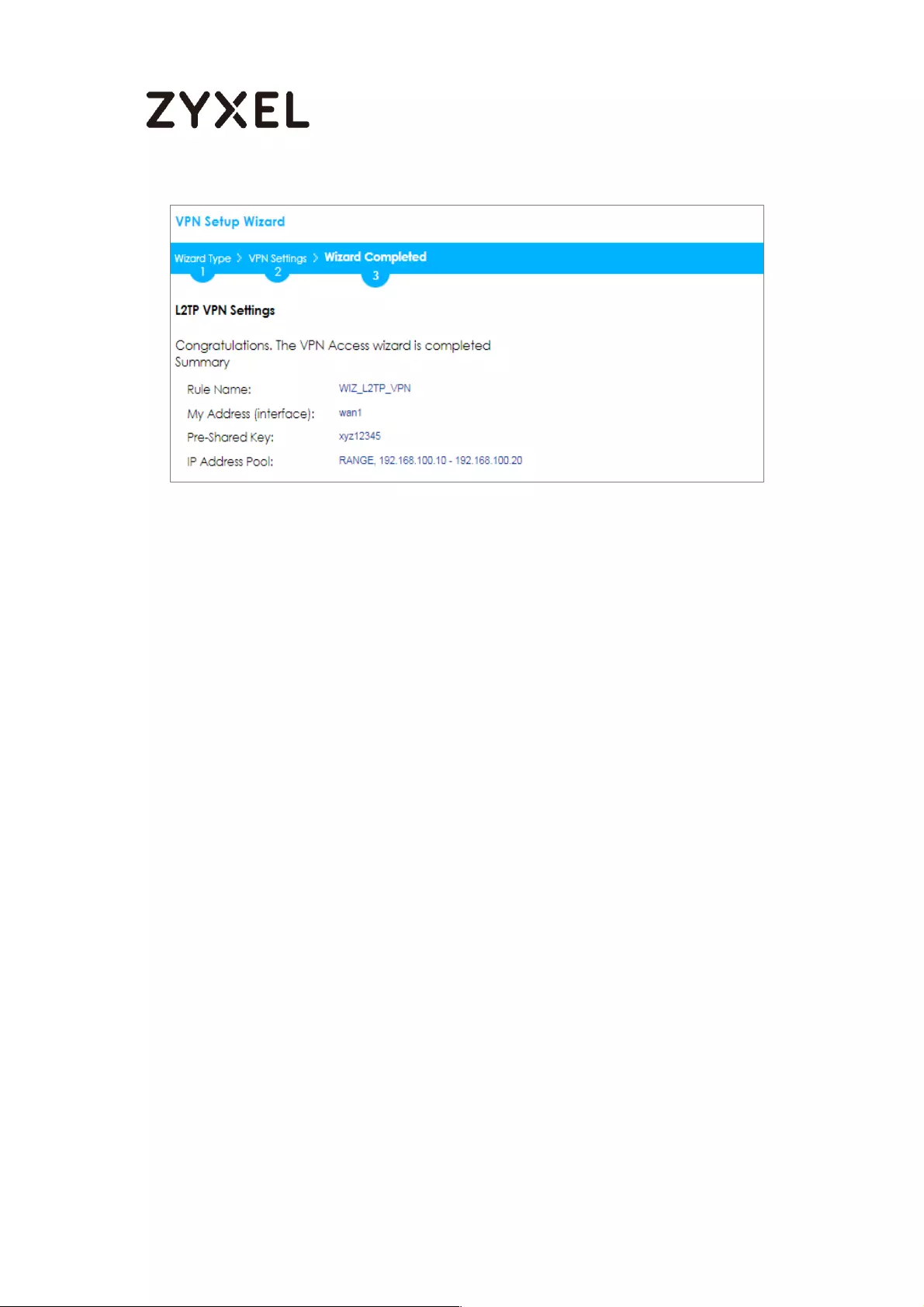
272/782
www.zyxel.com
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add User
Name and Password (4-24 characters). Then, set Allowed User to the newly
created object (L2TP_Remote_Users/zyx168 in this example).
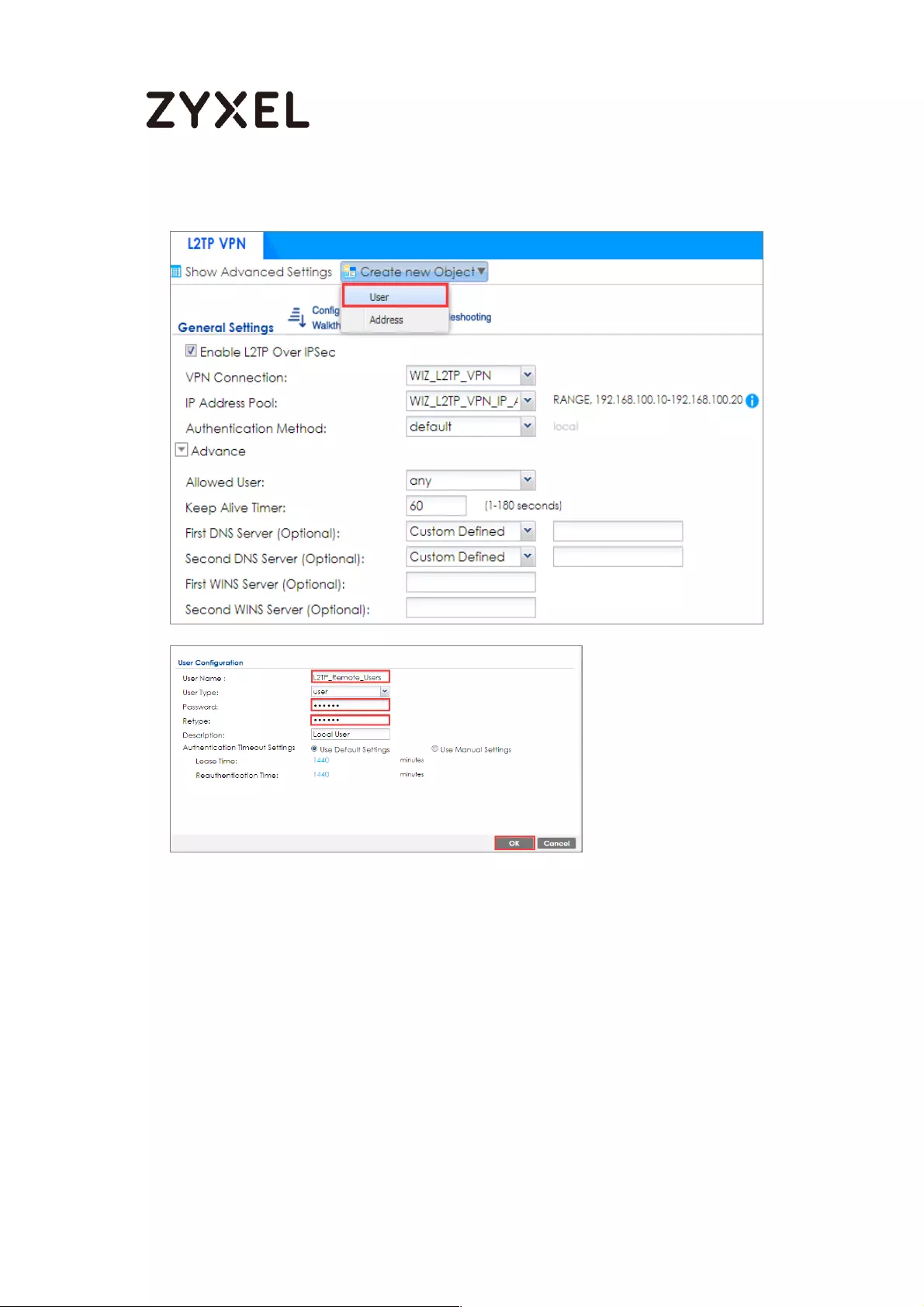
273/782
www.zyxel.com
CONFIGURATION > VPN > L2TP VPN > Create new Object > User
If some of the traffic from the L2TP clients need to go to the Internet, create a
policy route to send traffic from the L2TP tunnels out through a WAN trunk. Set
Incoming to Tunnel and select your L2TP VPN connection. Set the Source
Address to be the L2TP address pool. Set the Next-Hop Type to Trunk and select
the appropriate WAN trunk.
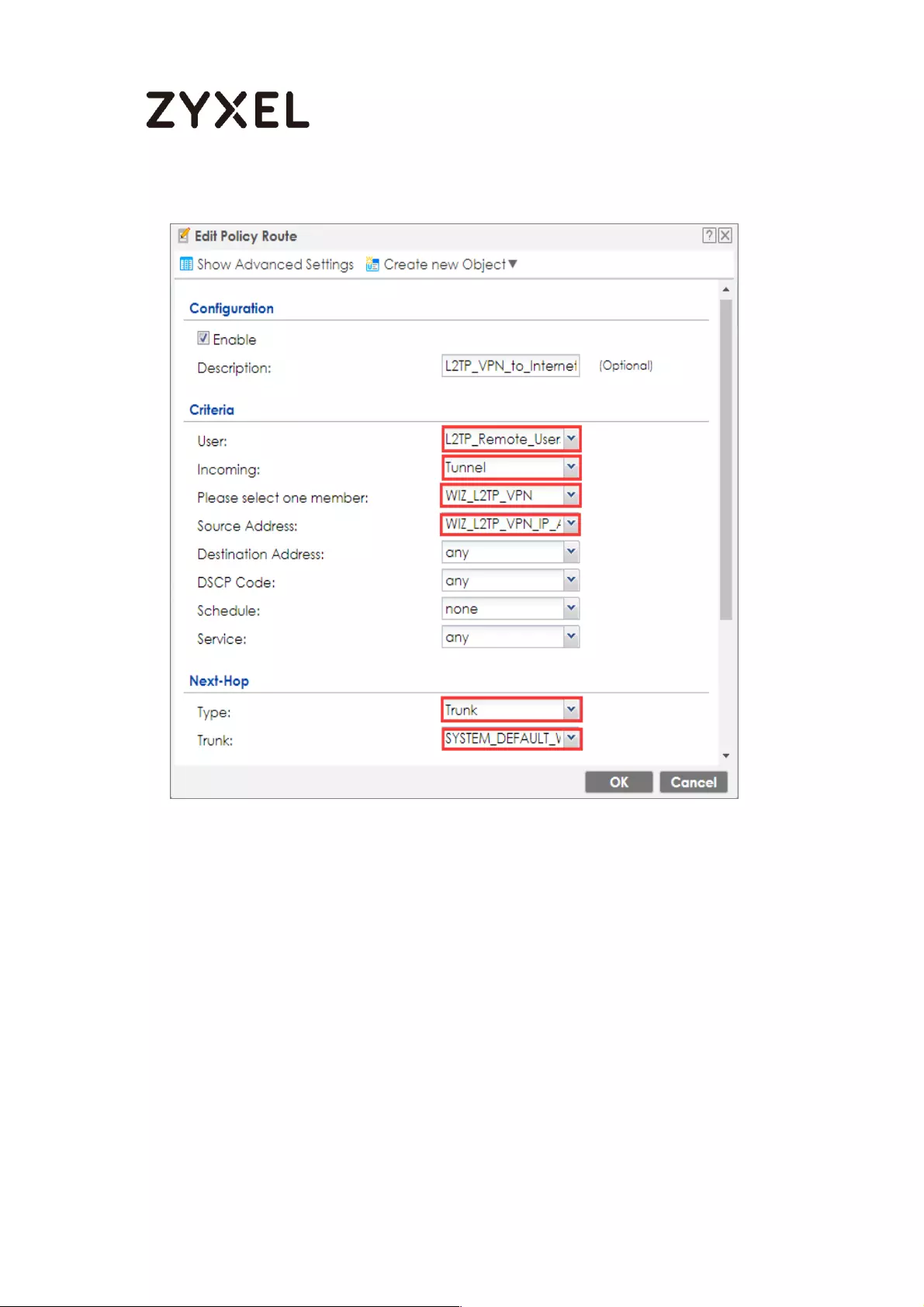
274/782
www.zyxel.com
CONFIGURATION > Network > Routing > Policy Route
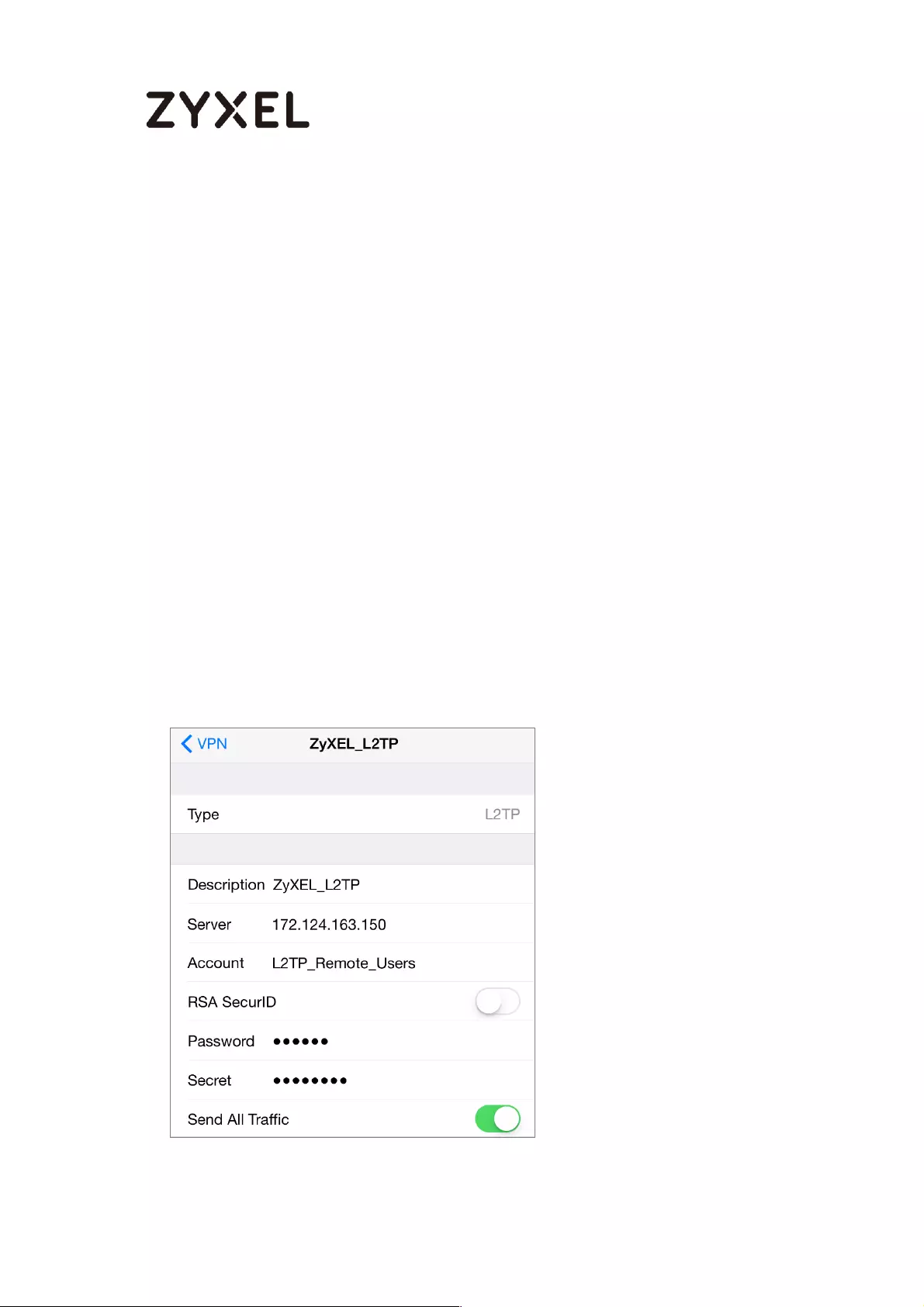
275/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the iOS Device
To configure L2TP VPN in an iOS 8.4 device, go to Menu > Settings > VPN > Add
VPN Configuration and configure as follows.
Description is for you to identify the VPN configuration.
Set Server to the ZyWALL/USG’s WAN IP address (172.124.163.150 in this example).
Enter Account and Password which the same as Allowed User created in
ZyWALL/USG (L2TP_Remote_Users/zyx168 in this example).
Set Secret to the Pre-Shared Key of the IPSec VPN gateway the ZyWALL/USG uses
for L2TP VPN over IPSec (zyx12345 in this example).
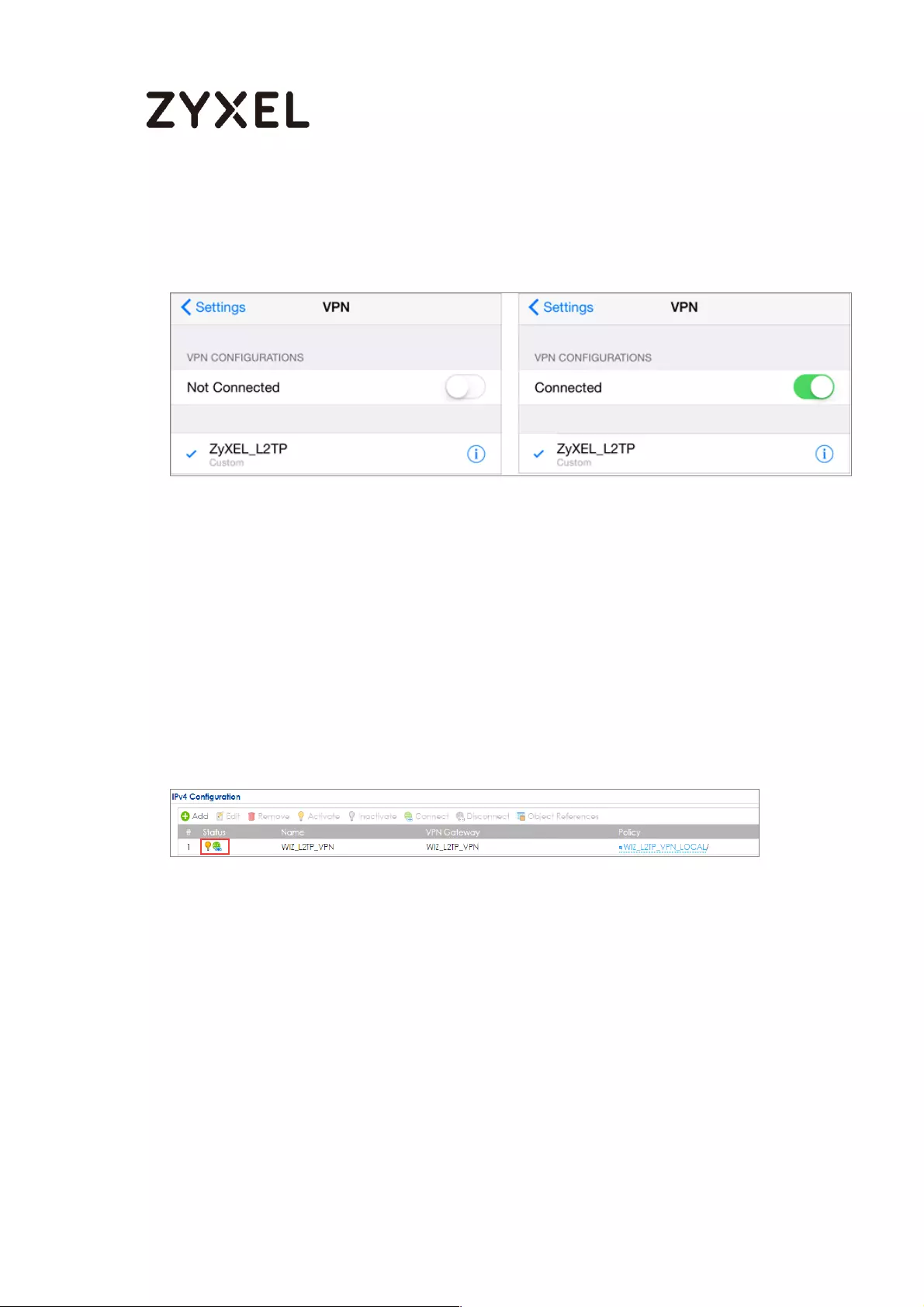
276/782
www.zyxel.com
After you create a VPN configuration, slide the button right to the on position to
initiate L2TP VPN session.
Test the L2TP over IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the
Status connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
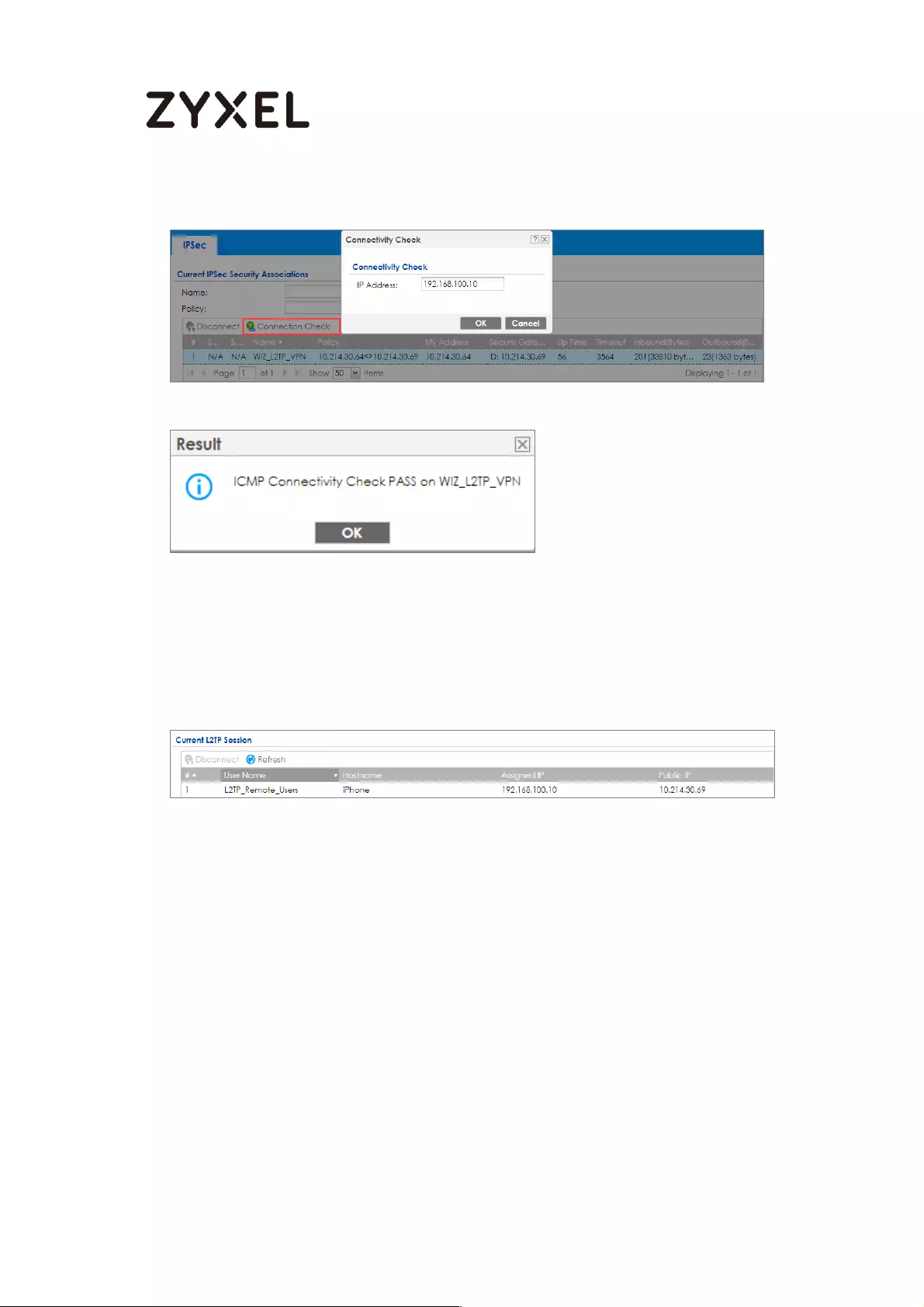
277/782
www.zyxel.com
Hub_HQ > MONITOR > VPN Monitor > IPSec > WIZ_L2TP_VPN
Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the
Current L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
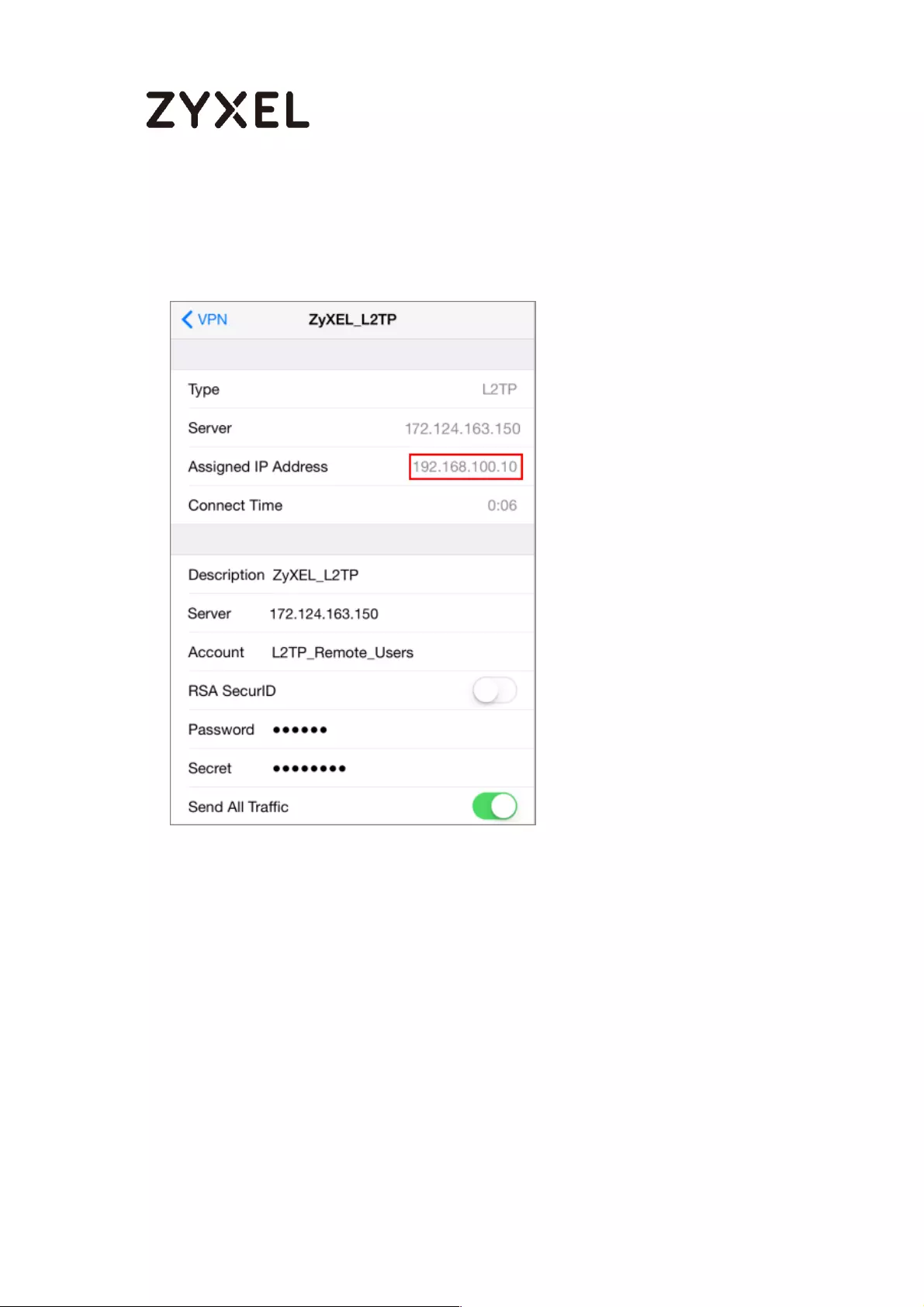
278/782
www.zyxel.com
Go to iOS mobile device Menu > Settings > VPN > ZyXEL_L2TP and verify the
Assigned IP Address and Connect Time.
Menu > Settings > VPN > ZyXEL_L2TP

279/782
www.zyxel.com
What Could Go Wrong?
If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. iOS Mobile users must use the same
Username and Password as configured in ZyWALL/USG to establish the L2TP VPN.
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. iOS Mobile users must use the same Secret as configured in
ZyWALL/USG to establish the IKE SA.
If you see that Phase 1 IKE SA process has completed but still get [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG unit
must set correct Local Policy to establish the IKE SA.
Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2,
DMZ, or WLAN zones, even if they are not in use.
If you cannot access devices in the local network, verify that the devices in the
local network set the USG’s IP as their default gateway to utilize the L2TP tunnel.

280/782
www.zyxel.com
Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses
UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
Verify that the Zone is set correctly in the Zone object. This should be set to
IPSec_VPN Zone so that security policies are applied properly.
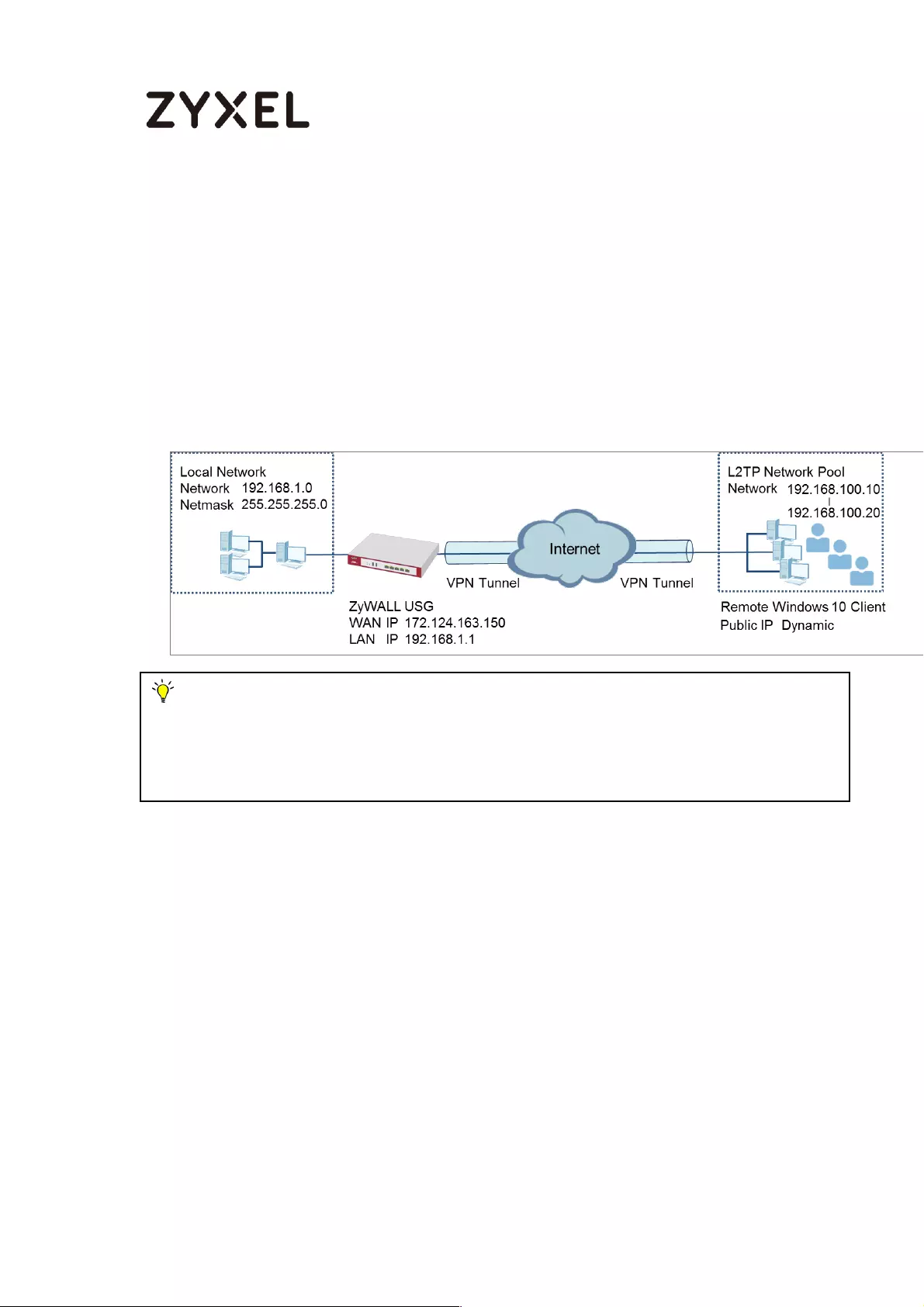
281/782
www.zyxel.com
How to Import ZyWALL/USG Certificate for L2TP over IPsec in
Windows 10
This is an example of using the L2TP VPN and VPN client software included in
Windows 10 operating systems. When the VPN tunnel is configured, users can
securely access the network behind the ZyWALL/USG and allow traffic from L2TP
clients to go to the Internet from a Windows 10 computer.
ZyWALL/USG L2TP VPN with Remote Windows 10 Client Example
Set Up the L2TP VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
for L2TP VPN Settings wizard to create a L2TP VPN rule that can be used with the
Window 10 clients. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: 4.25) and Windows 10 Pro (Version: 10.0.10240)
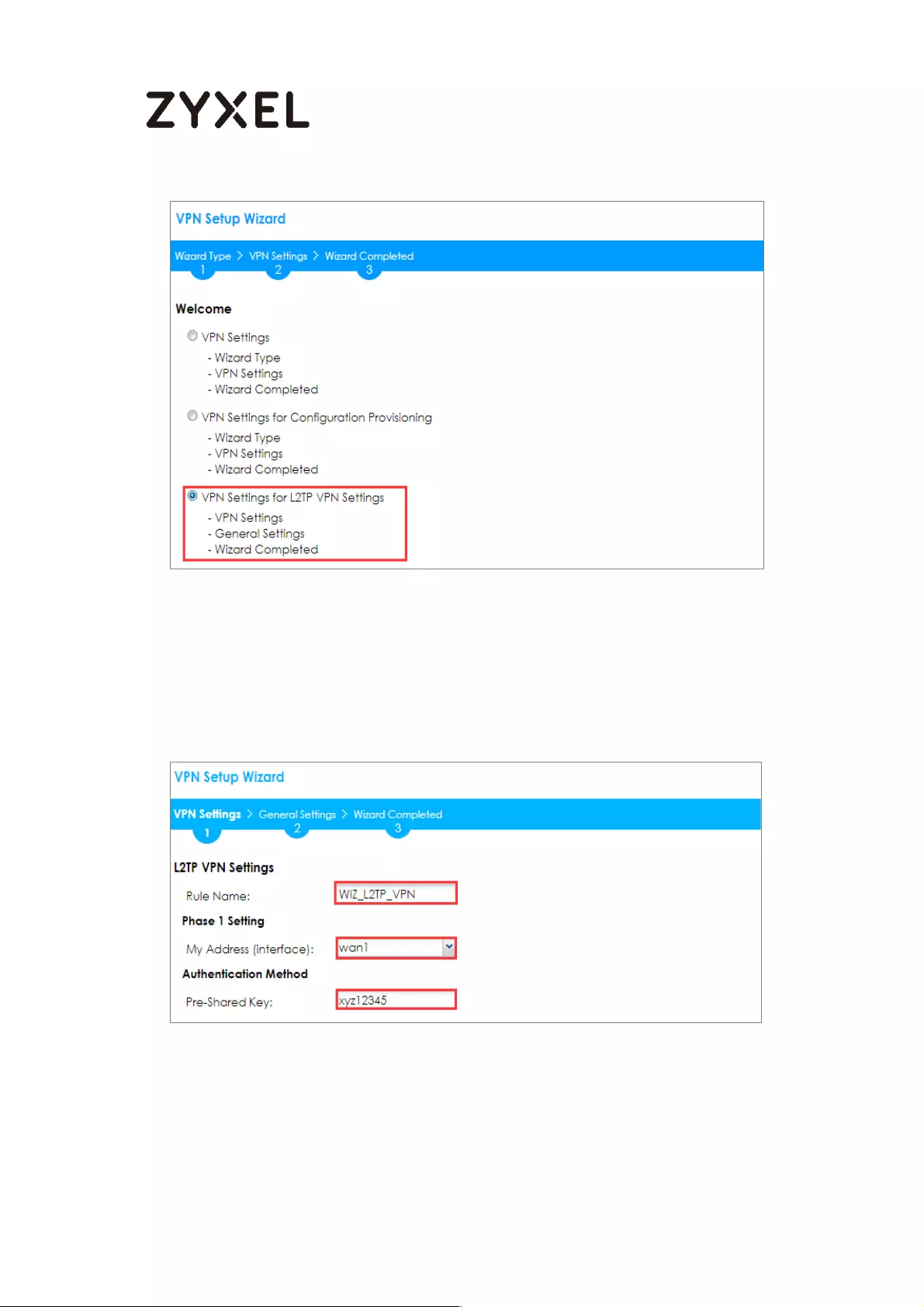
282/782
www.zyxel.com
Then, configure the Rule Name and set My Address to be the wan1 interface
which is connected to the Internet. Type a secure Pre-Shared Key (8-32
characters).
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
Assign the L2TP users’ IP address range from 192.168.100.10 to 192.168.100.20 for
use in the L2TP VPN tunnel and select Allow L2TP traffic Through WAN to allow
traffic from L2TP clients to go to the Internet. Click OK.
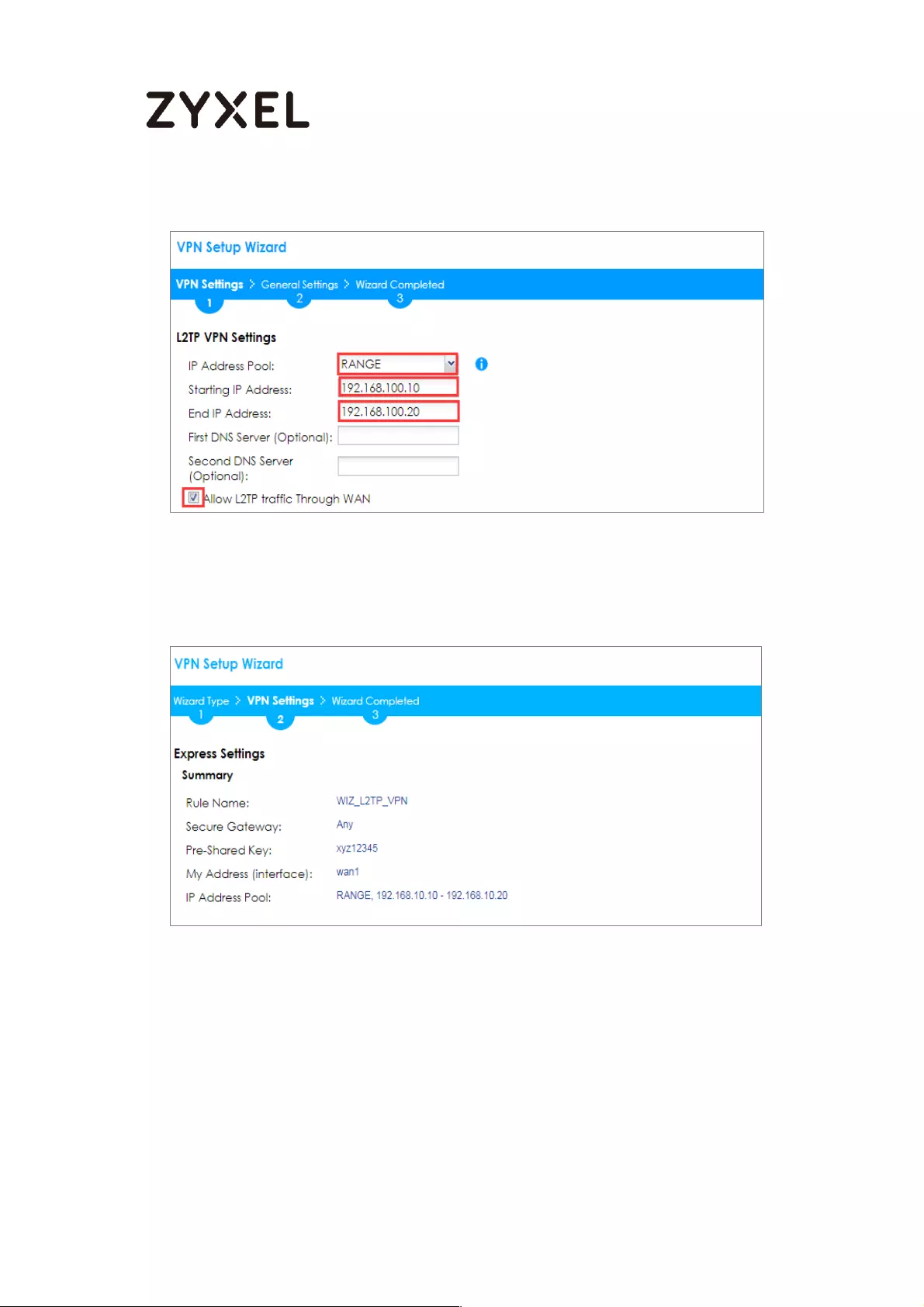
283/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (L2TP VPN Settings)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (Summary)
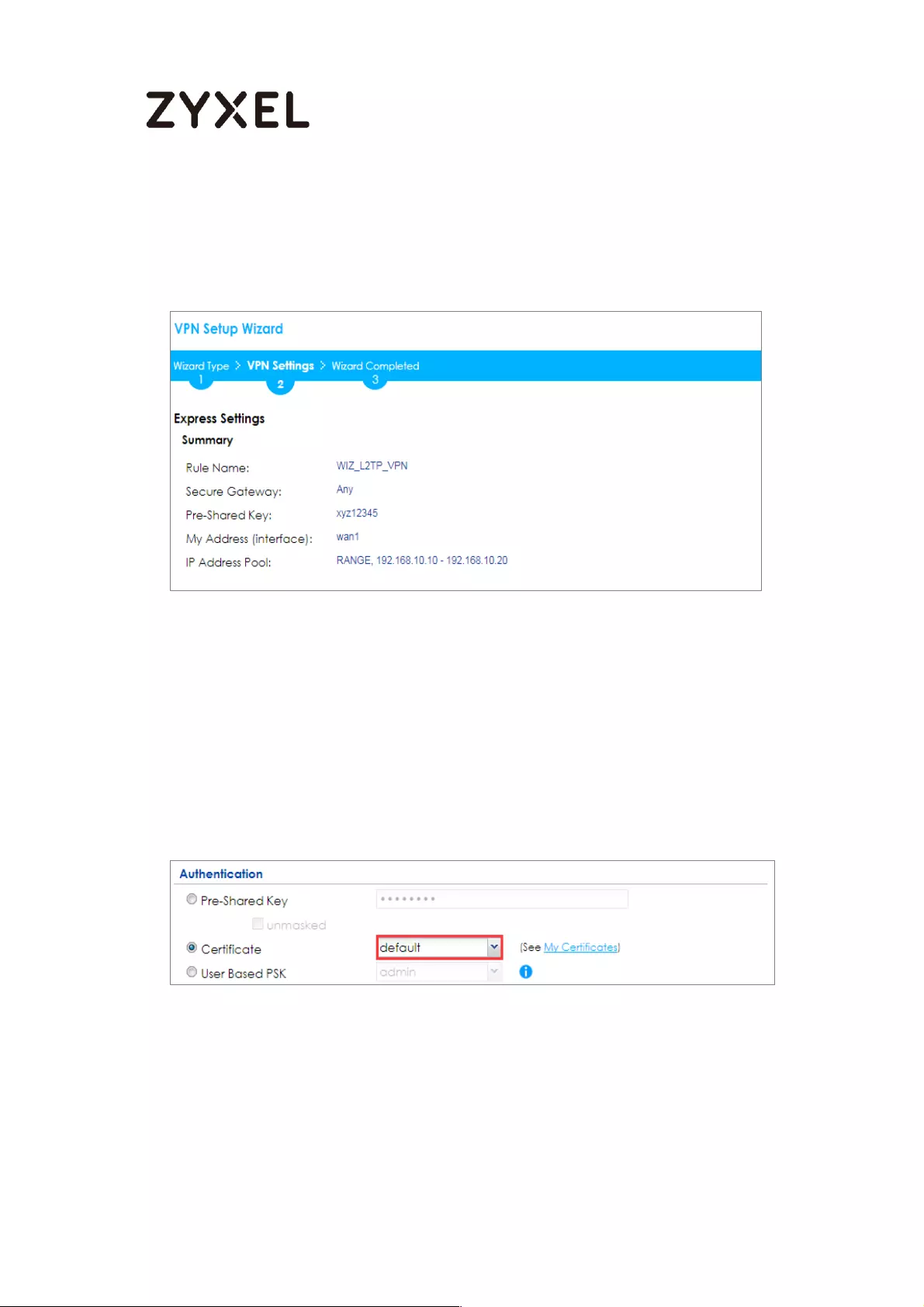
284/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The rule settings appear in the
VPN > L2TP VPN screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Wizard Completed
Go to CONFIGURATION > VPN > VPN Gateway > WIZ_L2TP_VPN, change
Authentication method to be Certificate and select the certificate which ZyWALL/USG
uses to identify itself to the Window 10 computer.
CONFIGURATION > VPN > VPN Gateway > WIZ_L2TP_VPN > Authentication >
Certificate
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add User
Name and Password (4-24 characters). Then, set Allowed User to the newly
created object (L2TP_Remote_Users/zyx168 in this example).
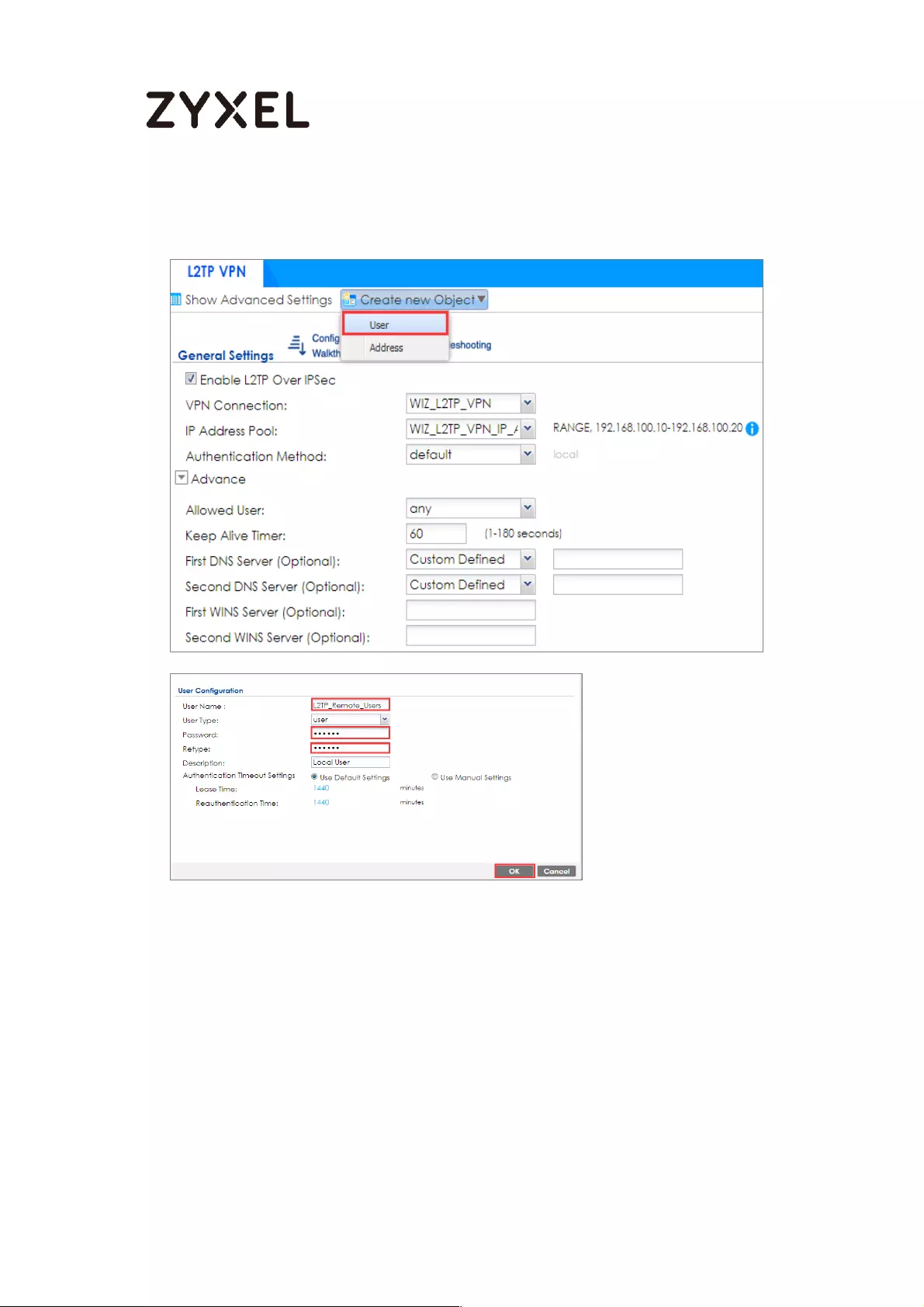
285/782
www.zyxel.com
CONFIGURATION > VPN > L2TP VPN > Create new Object > User
If some of the traffic from the L2TP clients need to go to the Internet, create a
policy route to send traffic from the L2TP tunnels out through a WAN trunk. Set
Incoming to Tunnel and select your L2TP VPN connection. Set the Source
Address to be the L2TP address pool. Set the Next-Hop Type to Trunk and select
the appropriate WAN trunk.
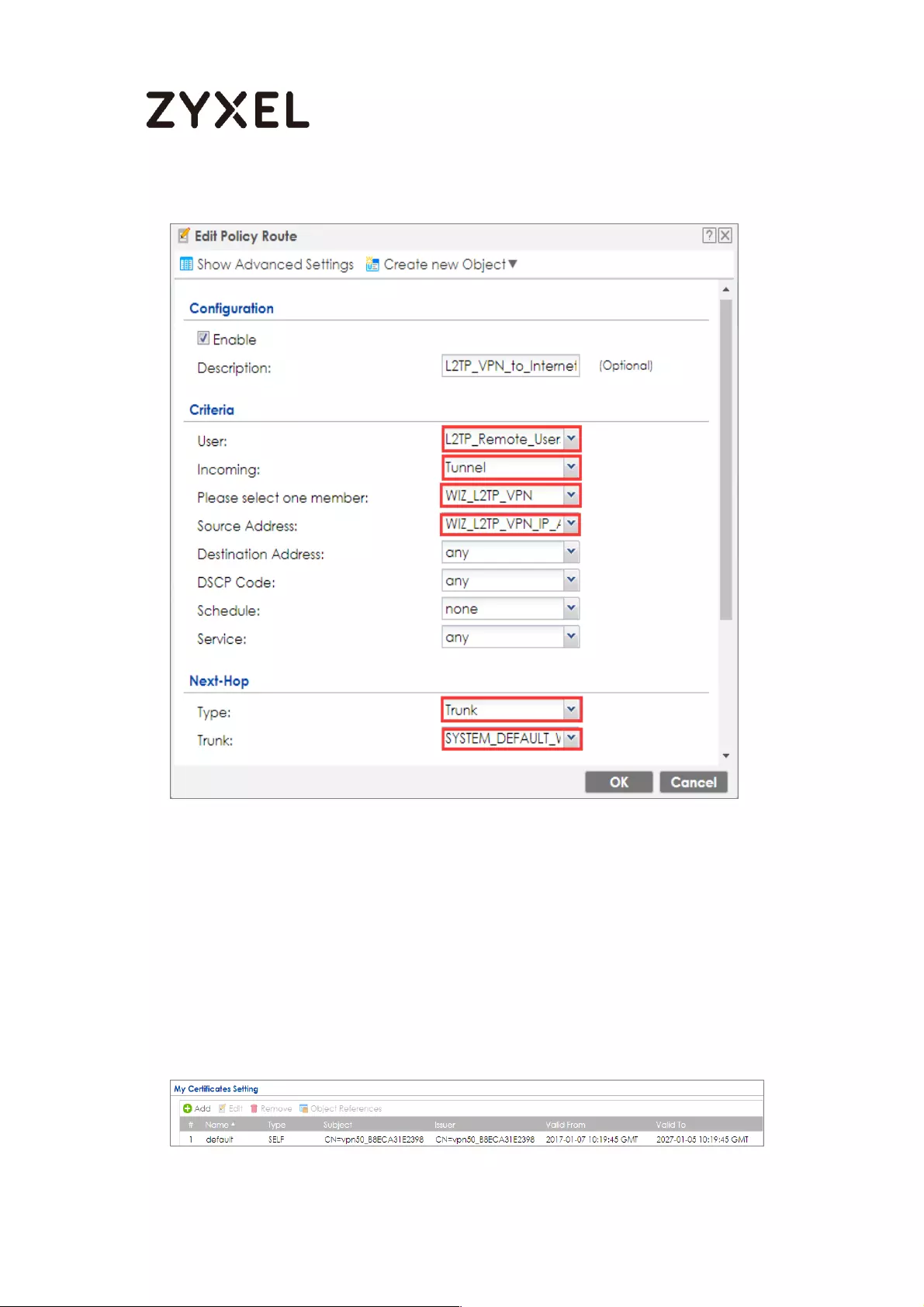
286/782
www.zyxel.com
CONFIGURATION > Network > Routing > Policy Route
Export a Certificate from ZyWALL/USG and Import it to Windows
10 Operating System
Go to ZyWALL/USG CONFIGURATION > Object > Certificate, select the certificate
(default in this example) and click Edit.
CONFIGURATION > Object > Certificate > default
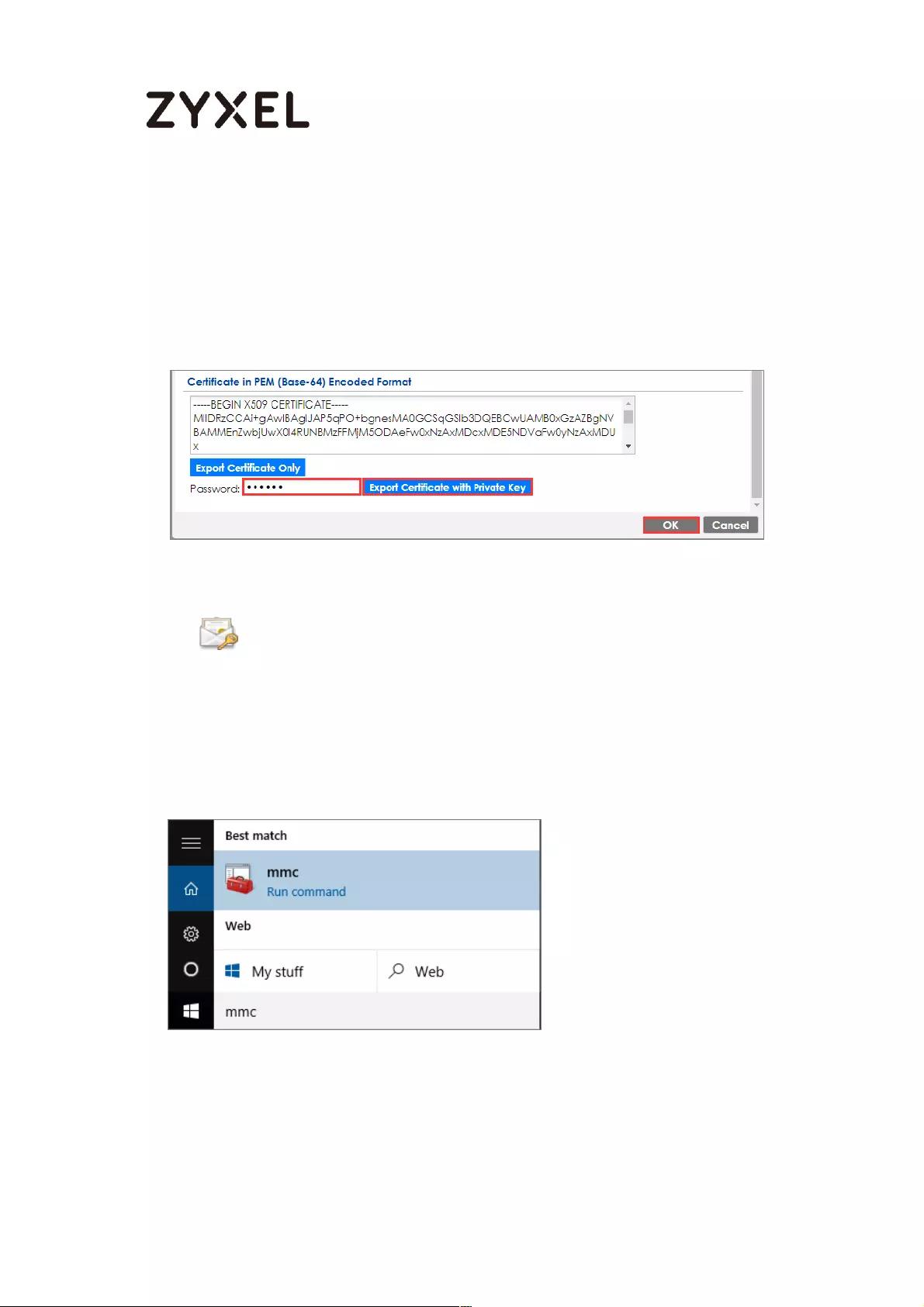
287/782
www.zyxel.com
Export default certificate from ZyWALL/USG with Private Key (zyx123 in this
example)
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with
Private Key
Save default certificate as *.p12 file to Windows 10 computer.
In Windows 10 Operating System, go to Start Menu > Search Box. Type mmc and
press Enter.
Start Menu > Search Box > mmc
In the mmc console window, click File > Add/Remove Snap-in...
File > Add/Remove Snap-in...
default.p12
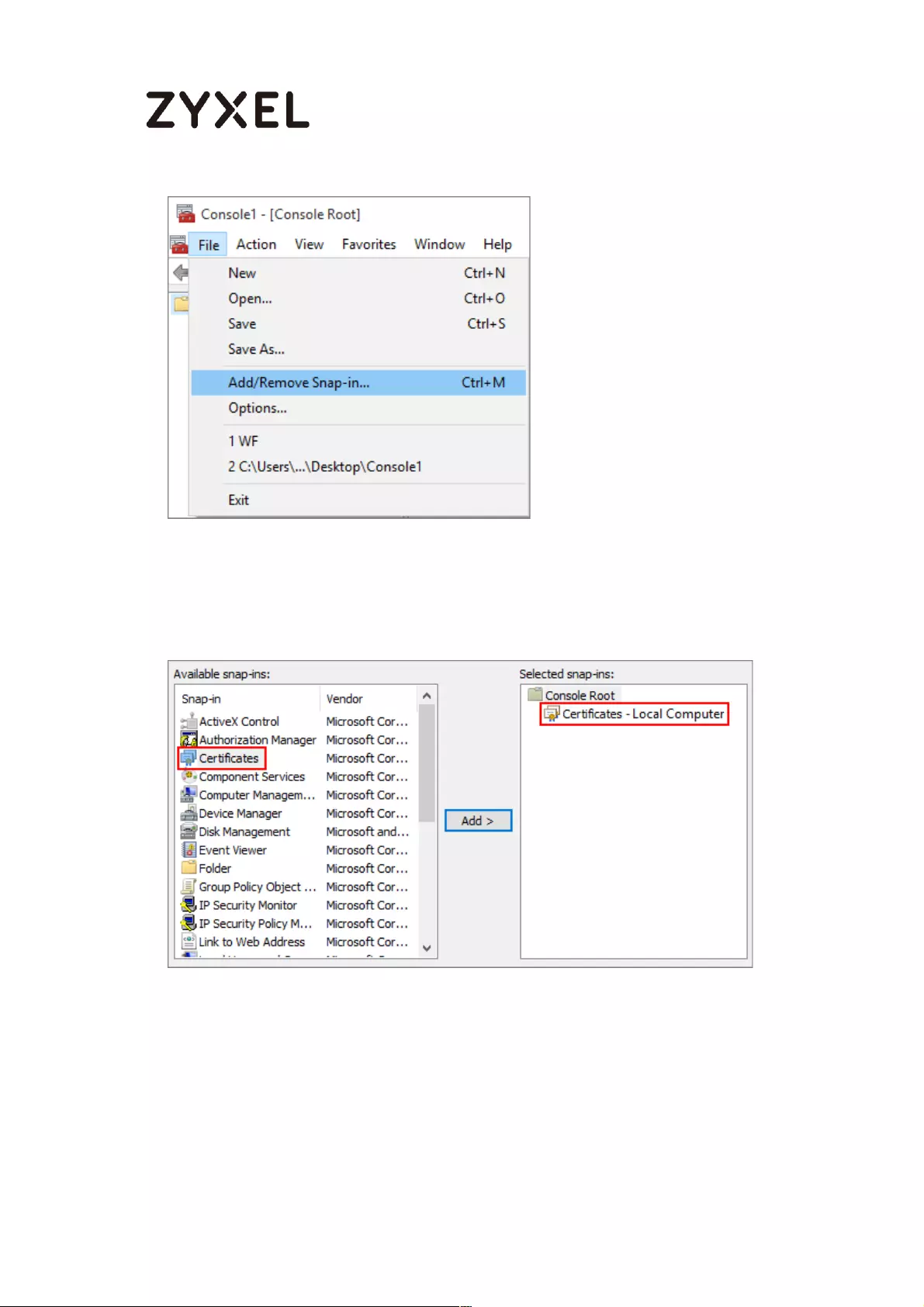
288/782
www.zyxel.com
In the Available snap-ins, select Certificates click Add. Then, click Finished.
Press OK to close the Snap-ins window.
Available snap-ins > Certificates > Add
In the mmc console window, go to Certificates (Local Computer) > Trusted Root
Certification Authorities, right click Certificate > All Tasks > Import…
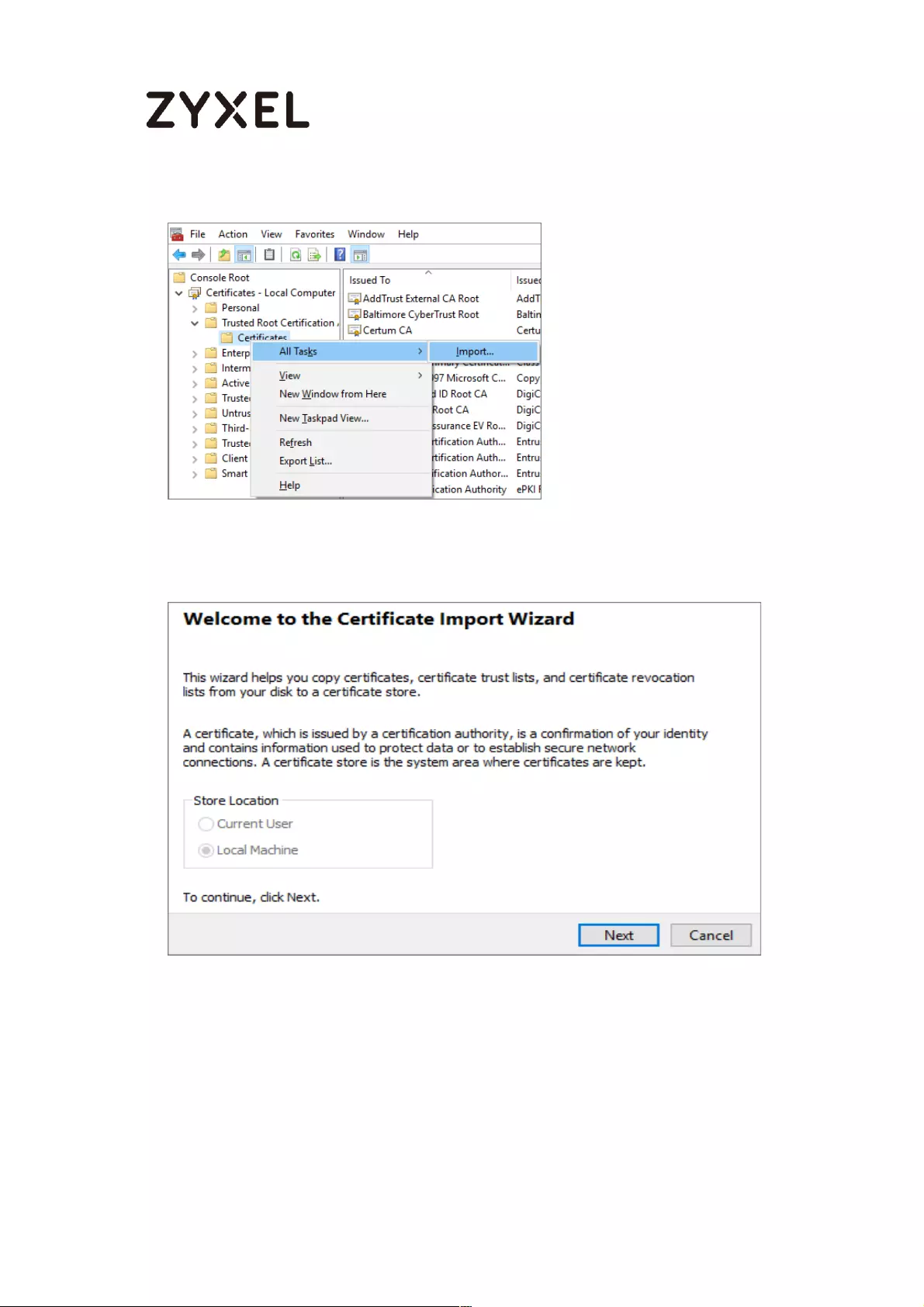
289/782
www.zyxel.com
Click Next.
Click Browse..., and locate the .p12 file you downloaded earlier. Then, click Next.
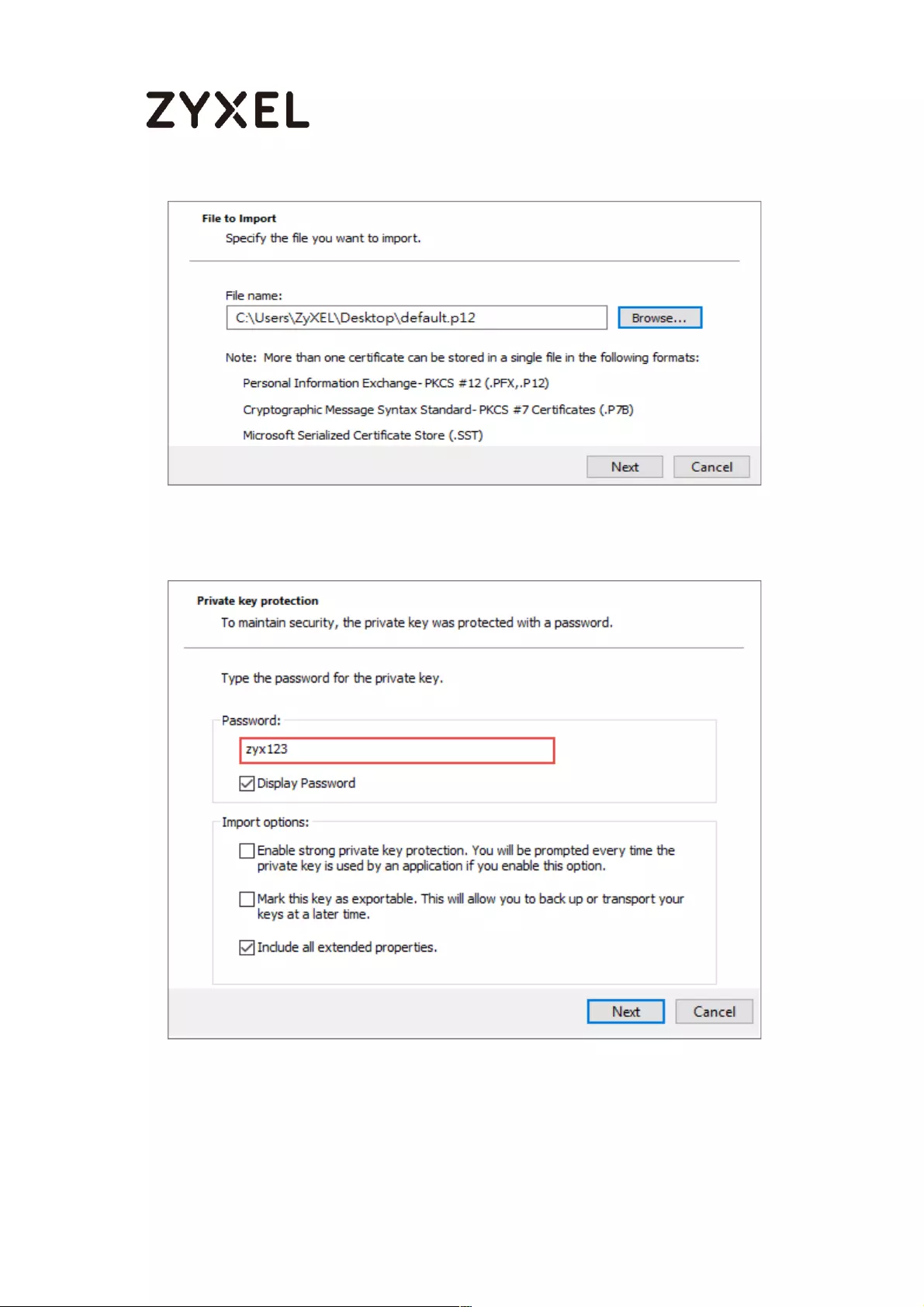
290/782
www.zyxel.com
Type zyx123 in the Password field and click Next.
Select Place all certificates in the following store and then click Browse and find
Trusted Root Certification Authorities. Click Next, then click Finish.
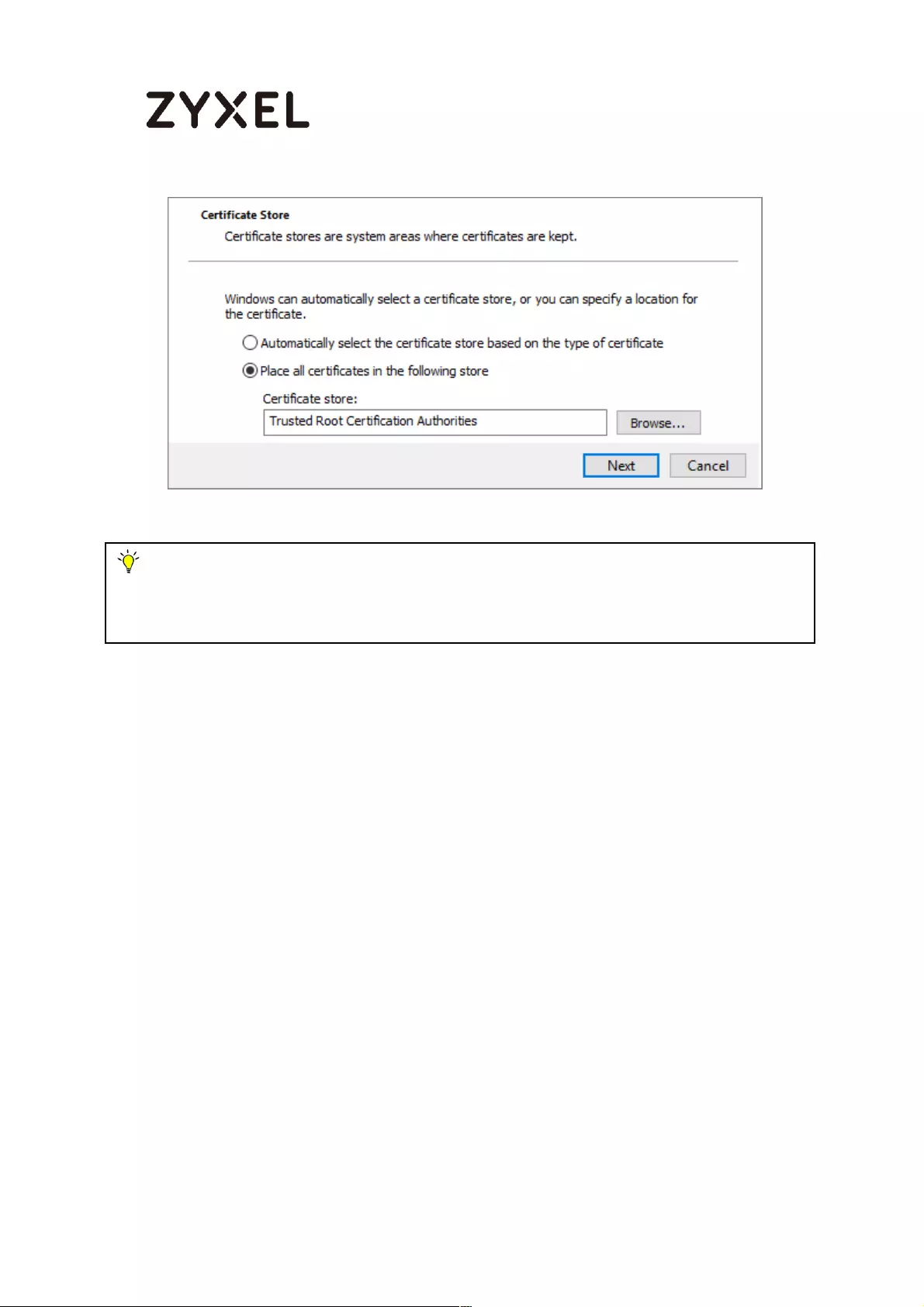
291/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the Windows 10
Note: Each ZyWALL/USG device has its own self-signed certificate by factory default.
When you reset to default configuration file, the original self-signed certificate is erased,
and a new self-signed certificate will be created when the ZyWALL/USG boots the next time.

292/782
www.zyxel.com
To configure L2TP VPN in Windows 10 operating system, go to Start > Settings >
Network & Internet > VPN > Add a VPN Connection and configure as follows.
VPN Provider set to Windows (built-in).
Configure Connection name for you to identify the VPN configuration.
Set Server name or address to be the ZyWALL/USG’s WAN IP address
(172.124.163.150 in this example).
Select VPN type to Layer 2 Tunneling Protocol with IPsec (L2TP/IPsec).
Enter User name and Password which the same as Allowed User created in
ZyWALL/USG (L2TP_Remote_Users/zyx168 in this example).
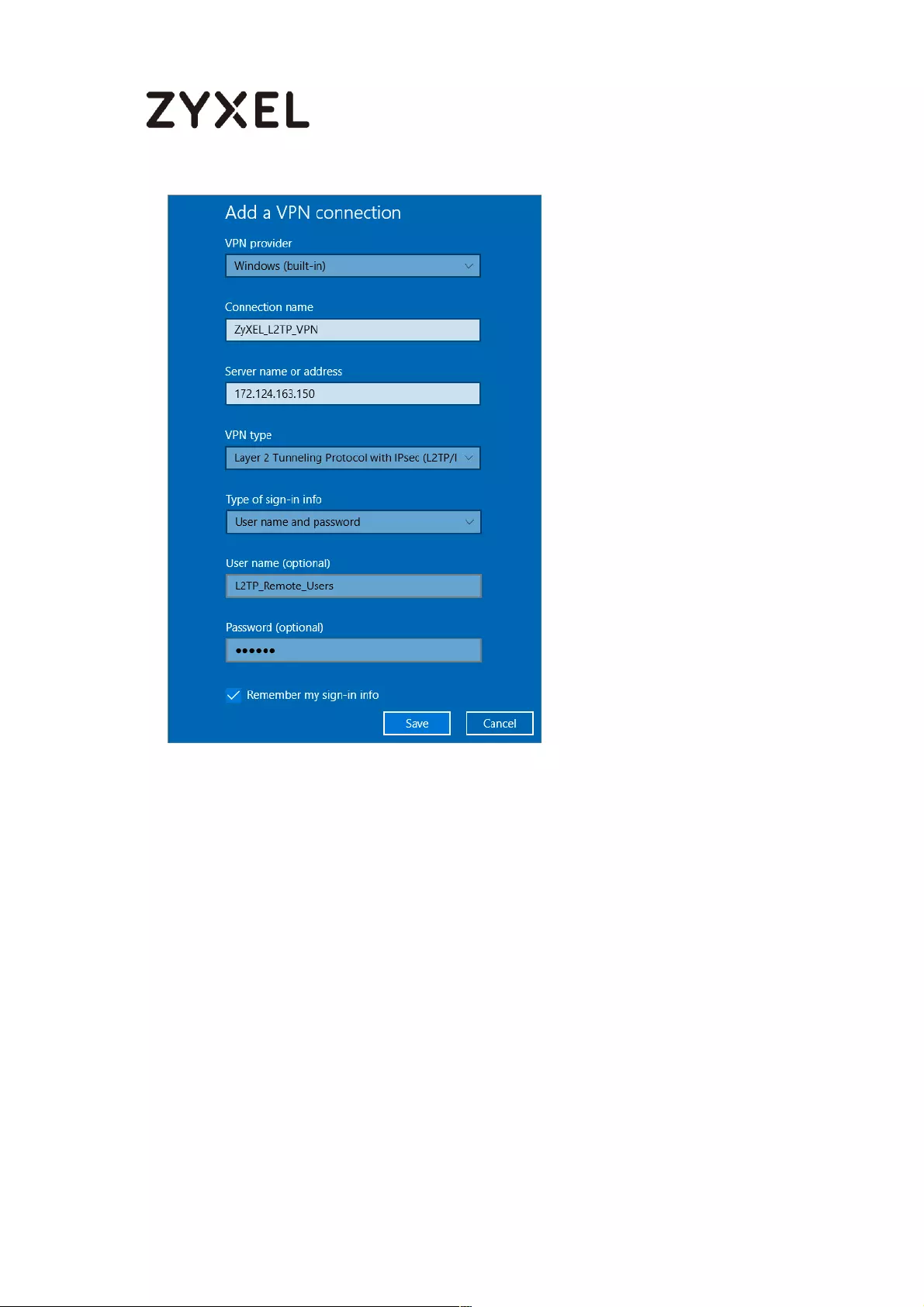
293/782
www.zyxel.com
Go to Control Panel > Network and Internet > Network Connections and right click
Properties. Continue to Security > Advanced settings and select Use Certificate for
authentication.
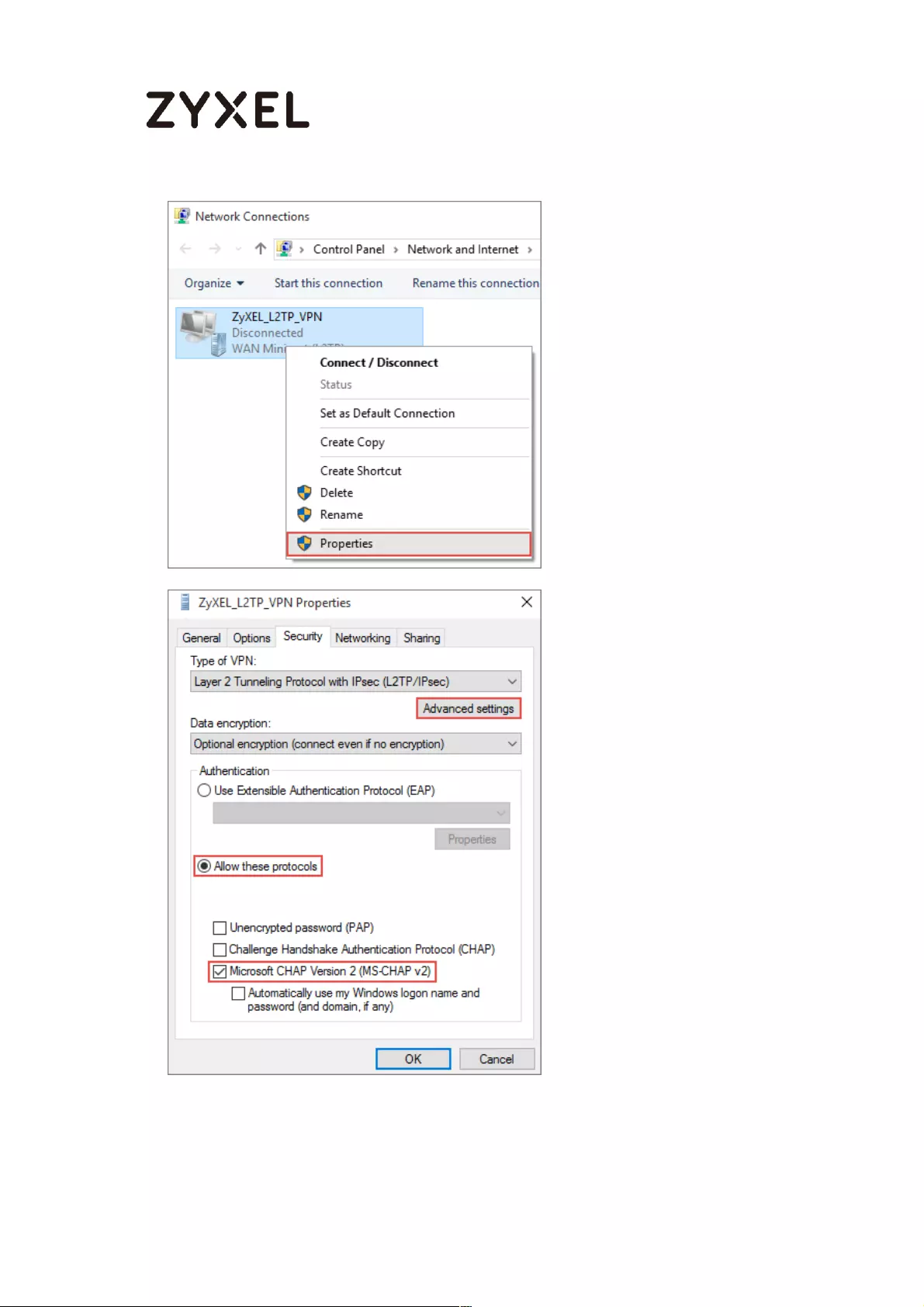
294/782
www.zyxel.com
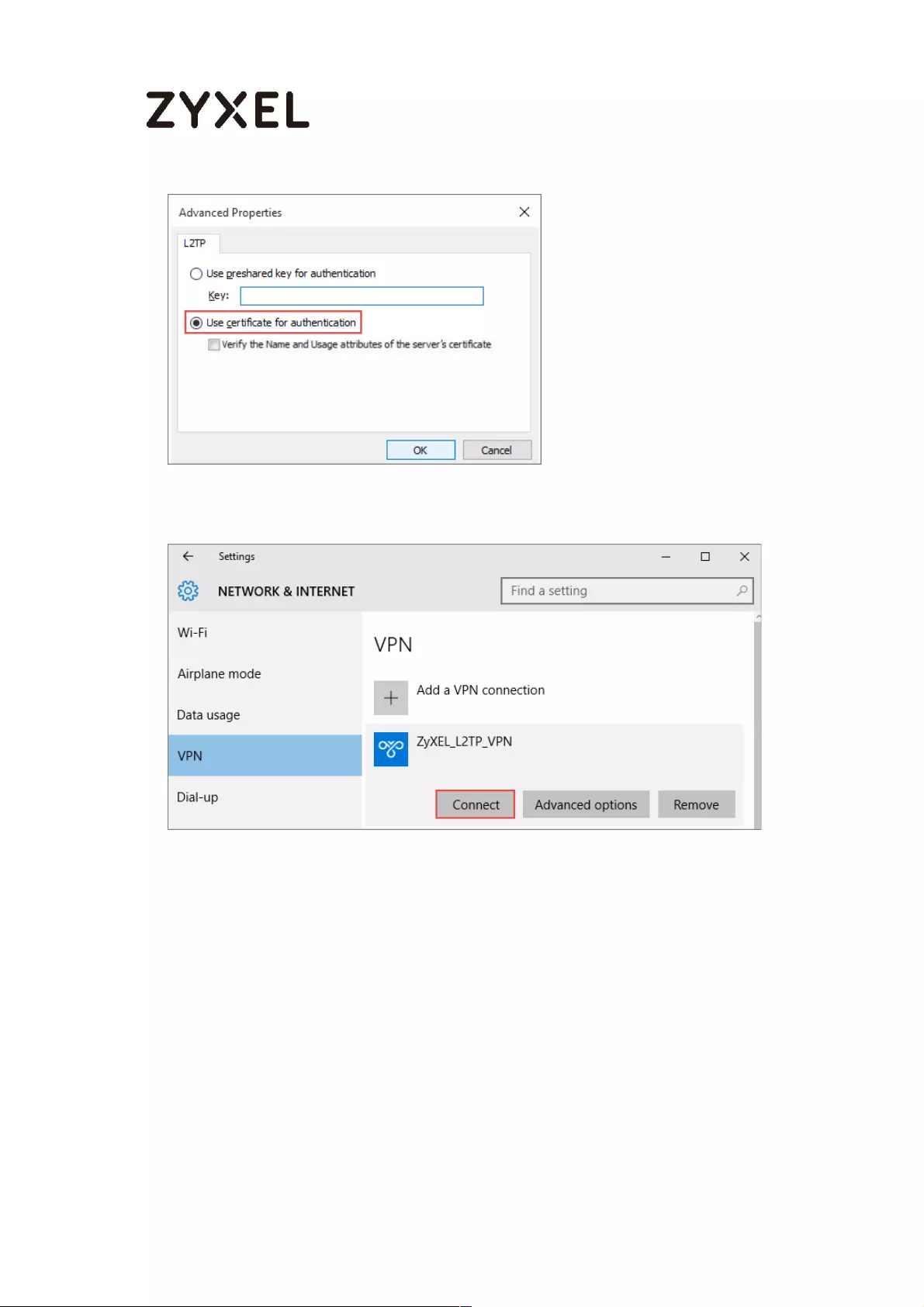
295/782
www.zyxel.com
Go to Network & Internet Settings window, click Connect.
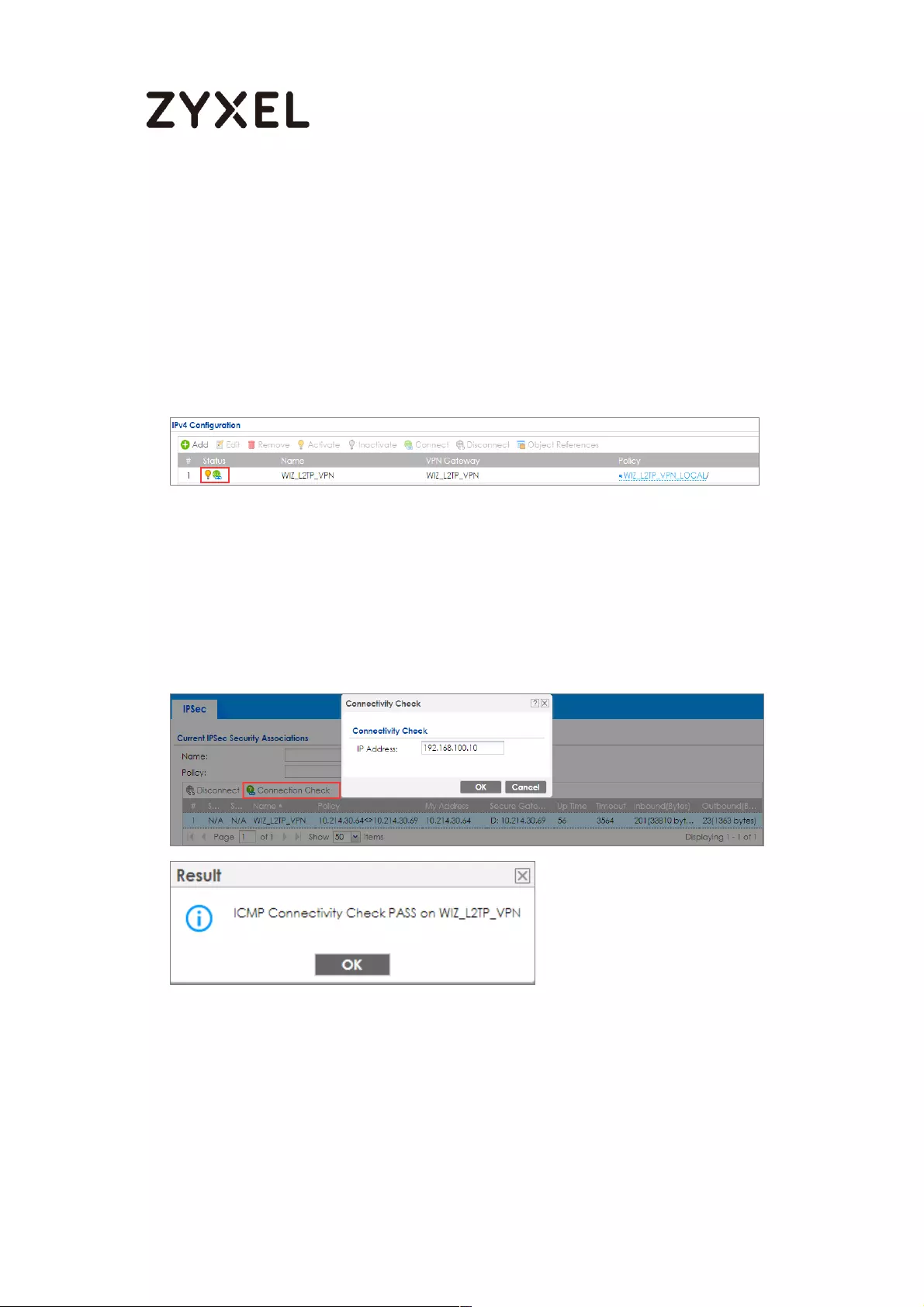
296/782
www.zyxel.com
Test the L2TP over IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the
Status connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > IPSec > WIZ_L2TP_VPN
Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the
Current L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
297/782
www.zyxel.com
Go to Window 10 operating system Start > Settings > Network & Internet > VPN and
show Connected status.
Menu > Settings > VPN > ZyXEL_L2TP
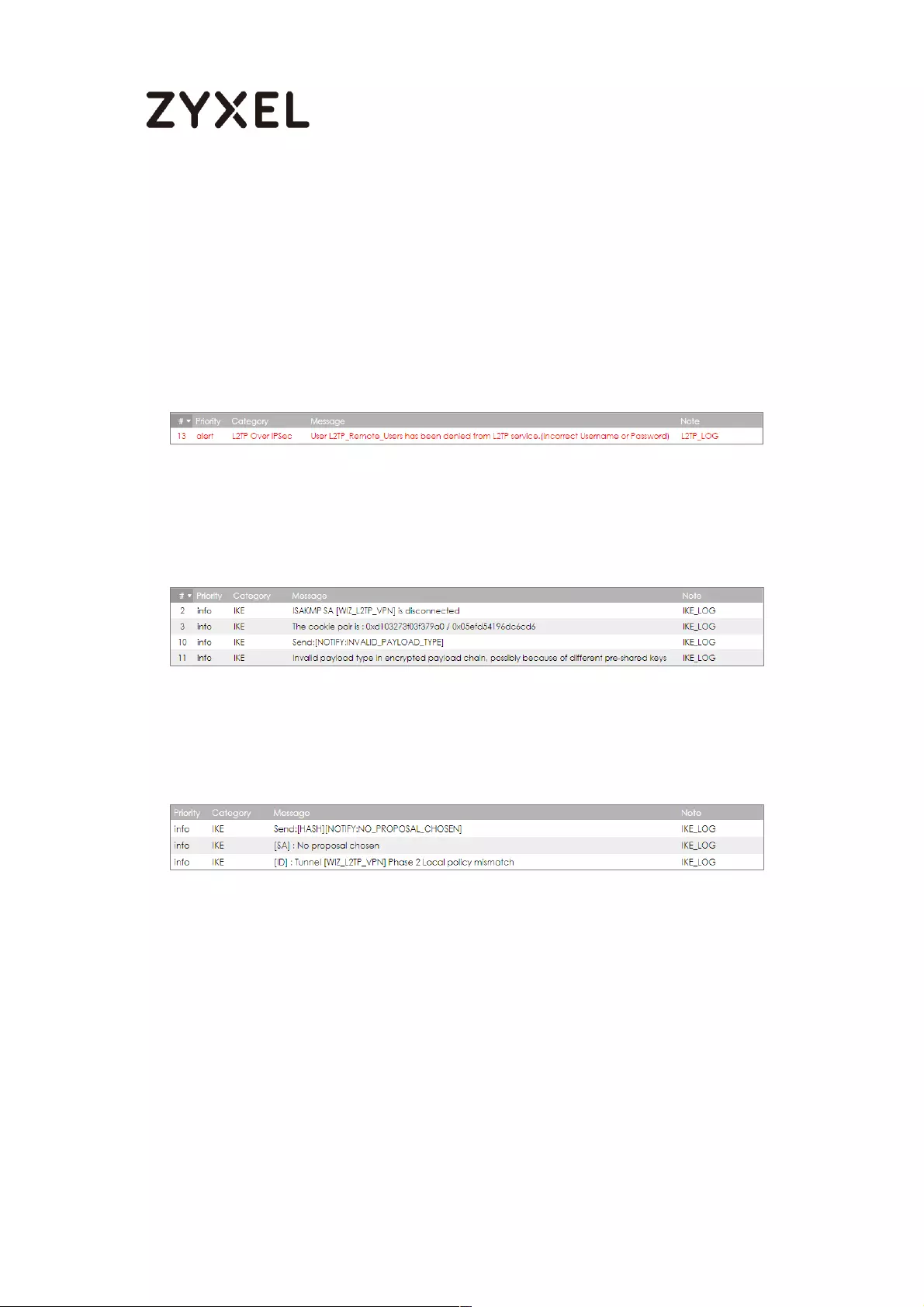
298/782
www.zyxel.com
What Could Go Wrong?
If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. Windows 10 users must use the same
Username and Password as configured in ZyWALL/USG to establish the L2TP VPN.
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. Windows 10 operating system users must use the same Pre-
Shared Key as configured in ZyWALL/USG to establish the IKE SA.
If you see that Phase 1 IKE SA process has completed but still get [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG unit
must set correct Local Policy to establish the IKE SA.
Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2,
DMZ, or WLAN zones, even if they are not in use.
If you cannot access devices in the local network, verify that the devices in the
local network set the USG’s IP as their default gateway to utilize the L2TP tunnel.
Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses
UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.

299/782
www.zyxel.com
Verify that the Zone is set correctly in the VPN Connection rule. This should be set
to IPSec_VPN Zone so that security policies are applied properly.
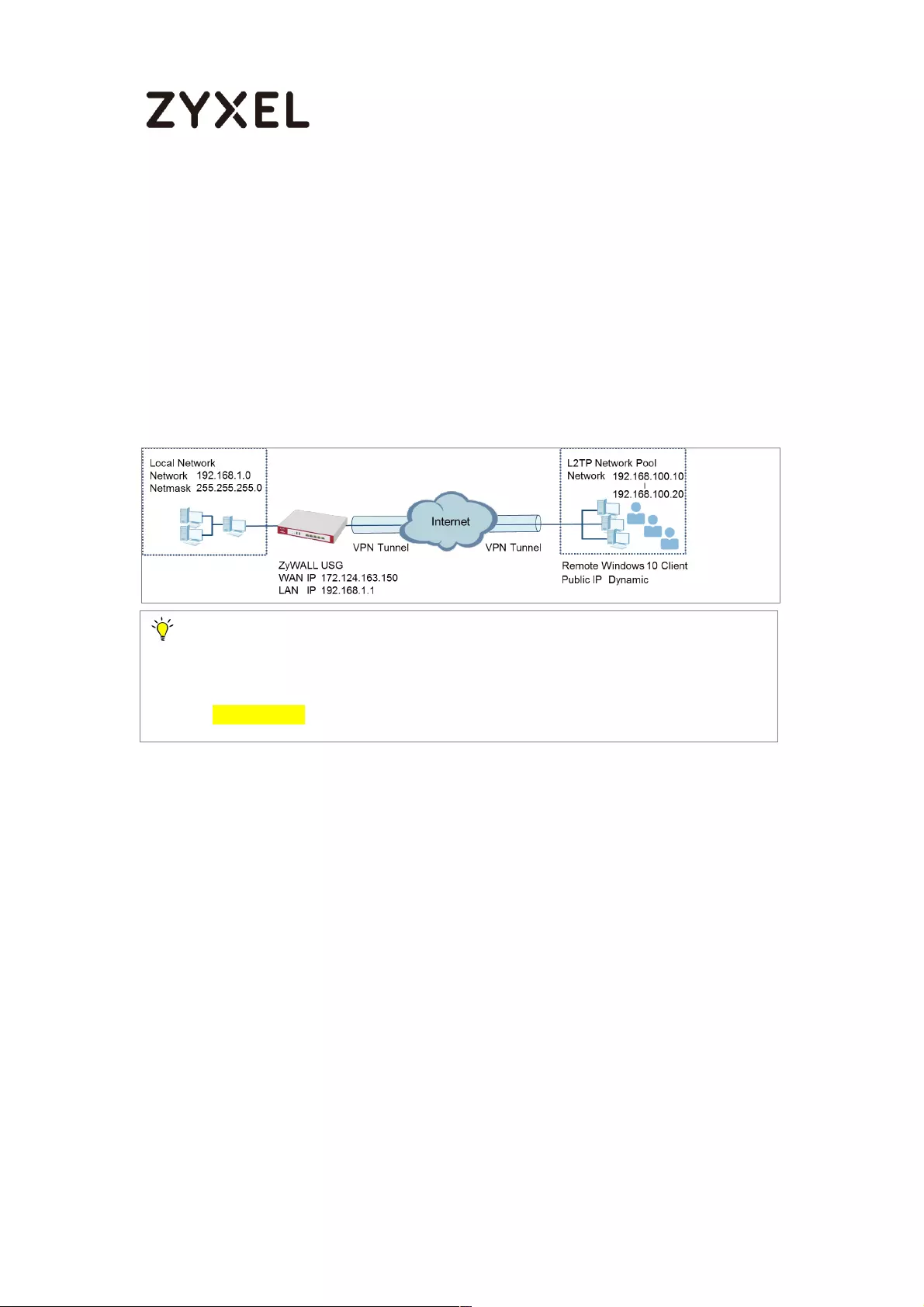
300/782
www.zyxel.com
How to Import ZyWALL/USG Certificate for L2TP over IPsec in
IOS mobile phone
This is an example of using the L2TP VPN and VPN client software included in Android
mobile phone operating systems. When the VPN tunnel is configured, users can
securely access the network behind the ZyWALL/USG and allow traffic from L2TP clients
to go to the Internet from an iOS mobile phone.
ZyWALL/USG L2TP VPN with Remote iOS Mobile Phone Client Example
Set Up the L2TP VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings for L2TP
VPN Settings wizard to create a L2TP VPN rule that can be used with the iOS mobile
phone clients. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG310 (Firmware Version: 4.25) and iOS
(Version: 10.0.10240)

301/782
www.zyxel.com
Then, configure the Rule Name and set My Address to be the wan1 interface which is
connected to the Internet. Type a secure Pre-Shared Key (8-32 characters).
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
Assign the L2TP users’ IP address range from 192.168.100.10 to 192.168.100.20 for use in
the L2TP VPN tunnel and select Allow L2TP traffic Through WAN to allow traffic from
L2TP clients to go to the Internet. Click OK.
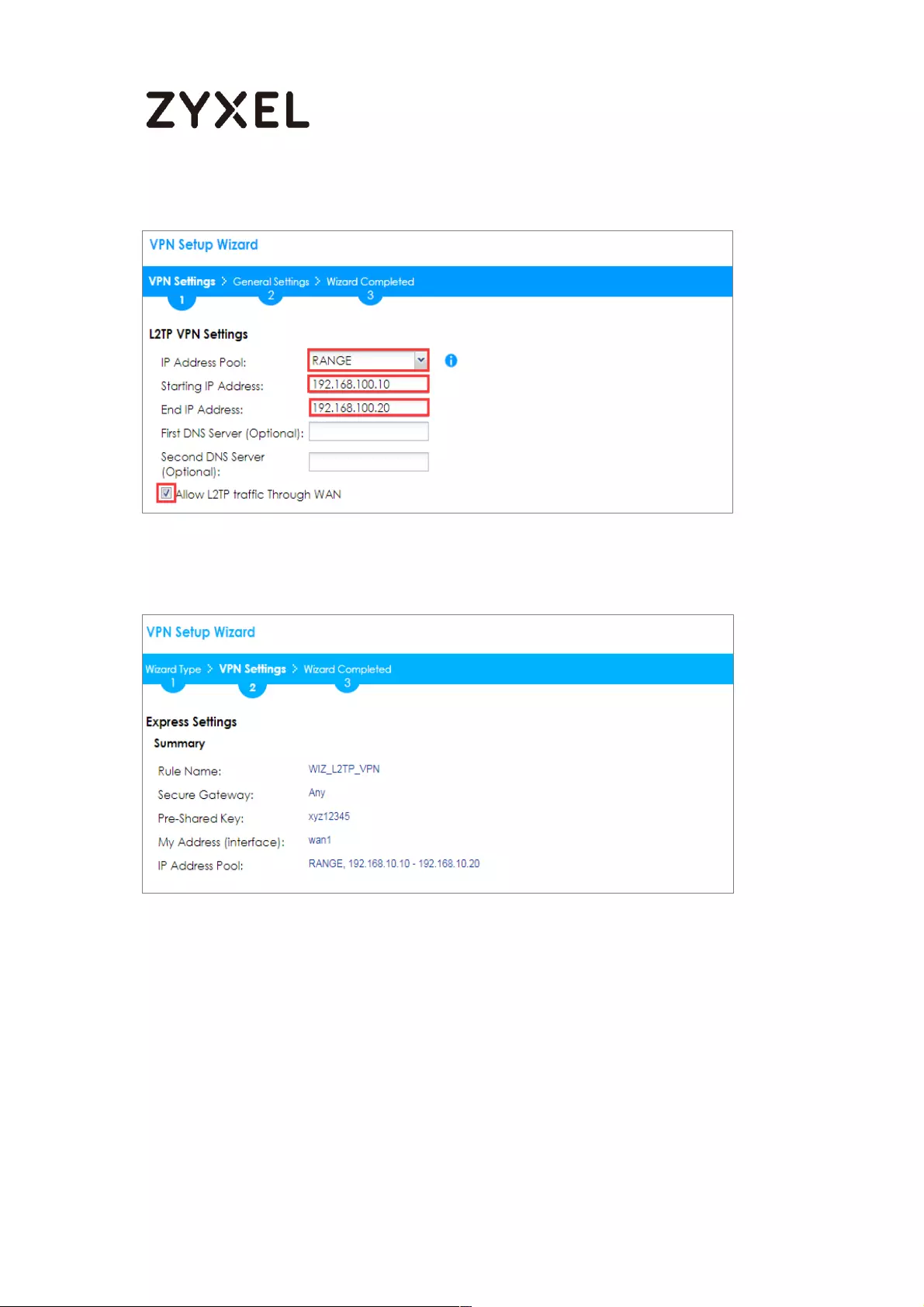
302/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (L2TP VPN Settings)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The rule settings appear in the VPN >
L2TP VPN screen. Click Close to exit the wizard.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Wizard Completed
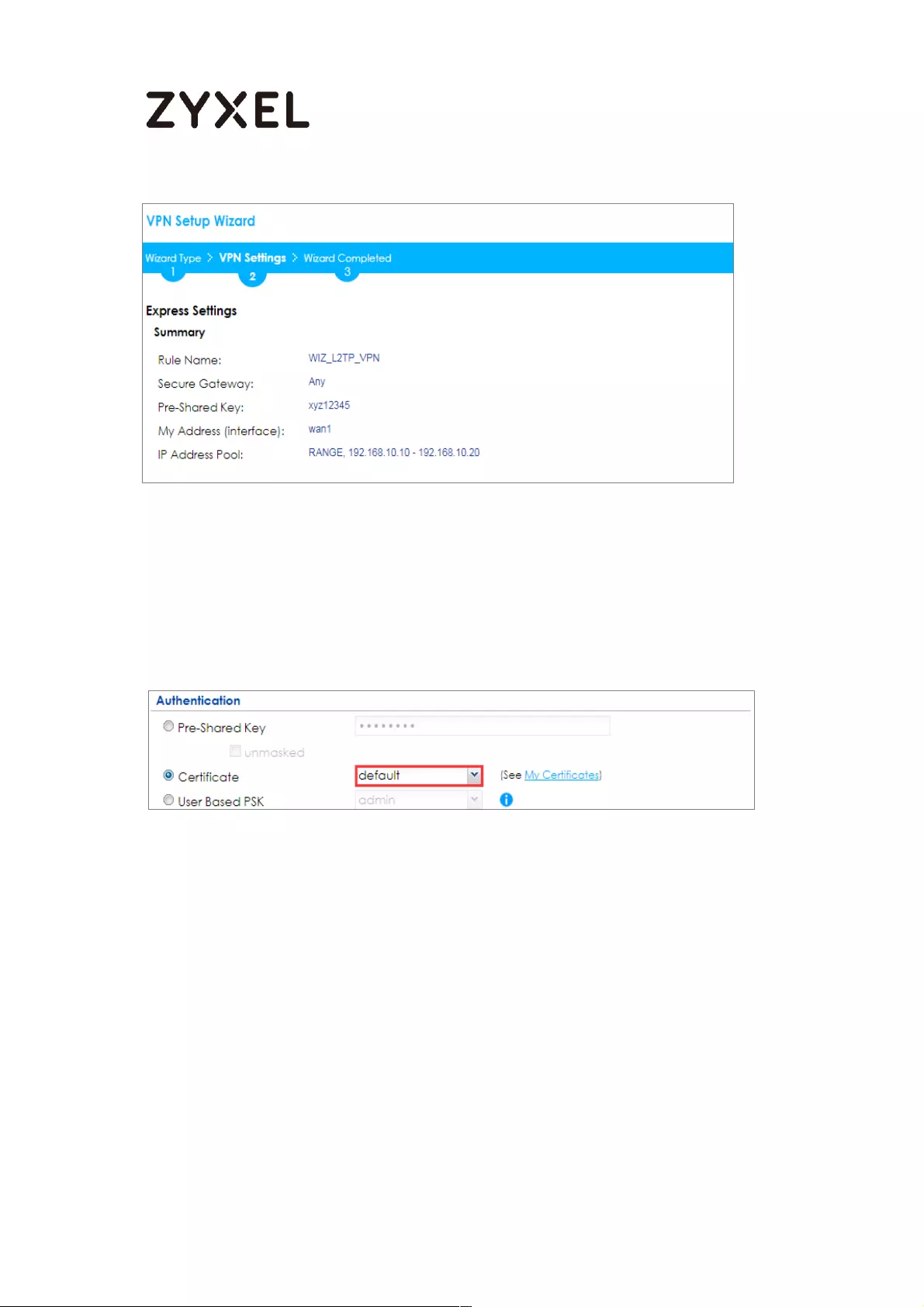
303/782
www.zyxel.com
Go to CONFIGURATION > VPN > VPN Gateway > WIZ_L2TP_VPN, change Authentication
method to be Certificate and select the certificate which ZyWALL/USG uses to identify
itself to the Android mobile phone.
CONFIGURATION > VPN > VPN Gateway > WIZ_L2TP_VPN > Authentication >
Certificate
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add User Name
and Password (4-24 characters). Then, set Allowed User to the newly created object
(L2TP_Remote_Users/zyx168 in this example).
CONFIGURATION > VPN > L2TP VPN > Create new Object > User

304/782
www.zyxel.com
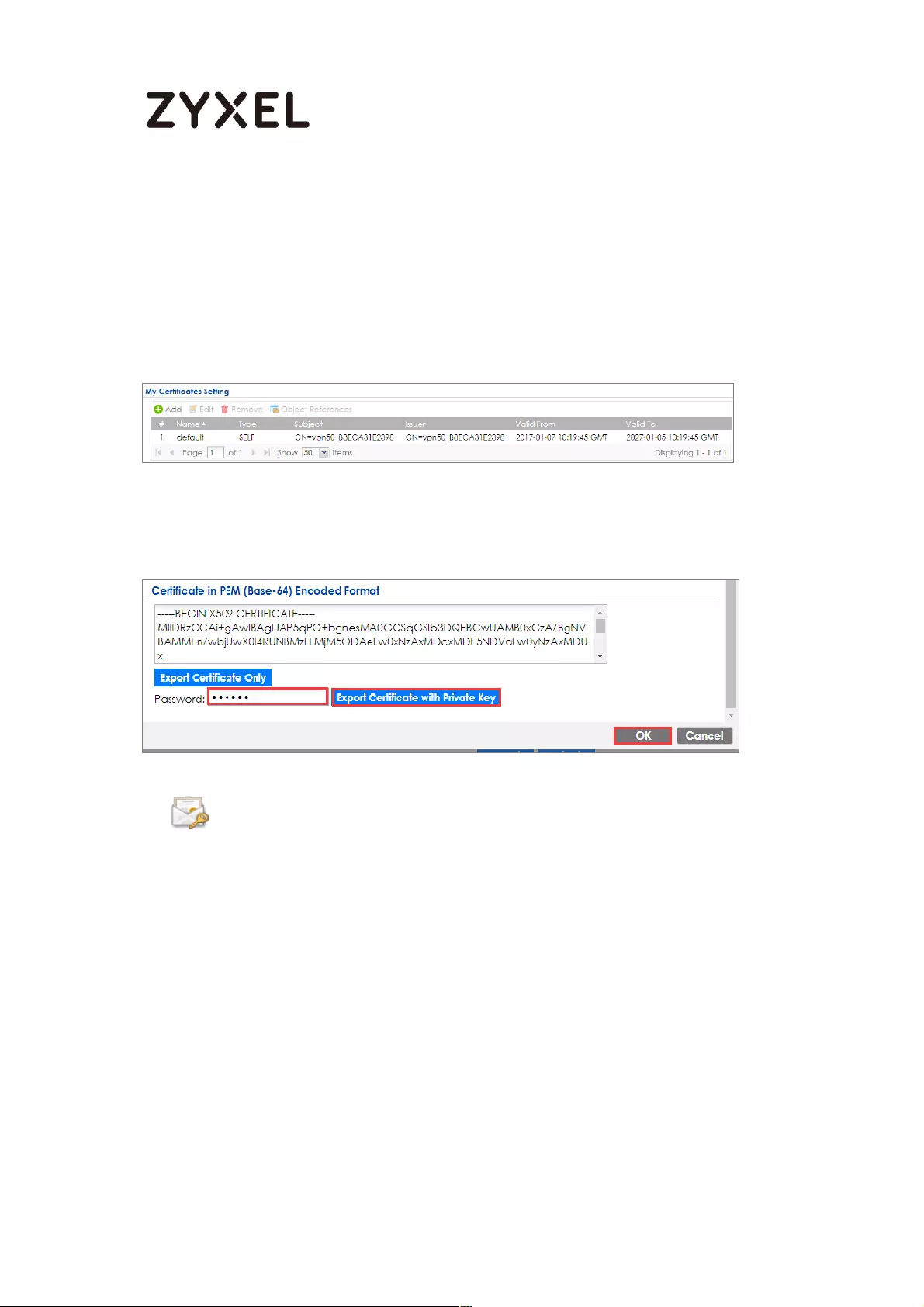
305/782
www.zyxel.com
Export a Certificate from ZyWALL/USG and Import it to iOS Mobile
Phone
Go to ZyWALL/USG CONFIGURATION > Object > Certificate, select the certificate
(default in this example) and click Edit.
CONFIGURATION > Object > Certificate > default
Export default certificate from ZyWALL/USG with Private Key (zyx123 in this example)
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with Private
Key
Save default certificate as *.p12 file to Android mobile phone computer.
Set Up the L2TP VPN Tunnel on the iOS Mobile Device
1 To configure L2TP VPN in iOS operating system, go to Start > Settings > Network &
Internet > VPN > Add a VPN Connection and configure as follows.
2 VPN Provider set to Windows (built-in).
3 Configure Connection name for you to identify the VPN configuration.
default.p12
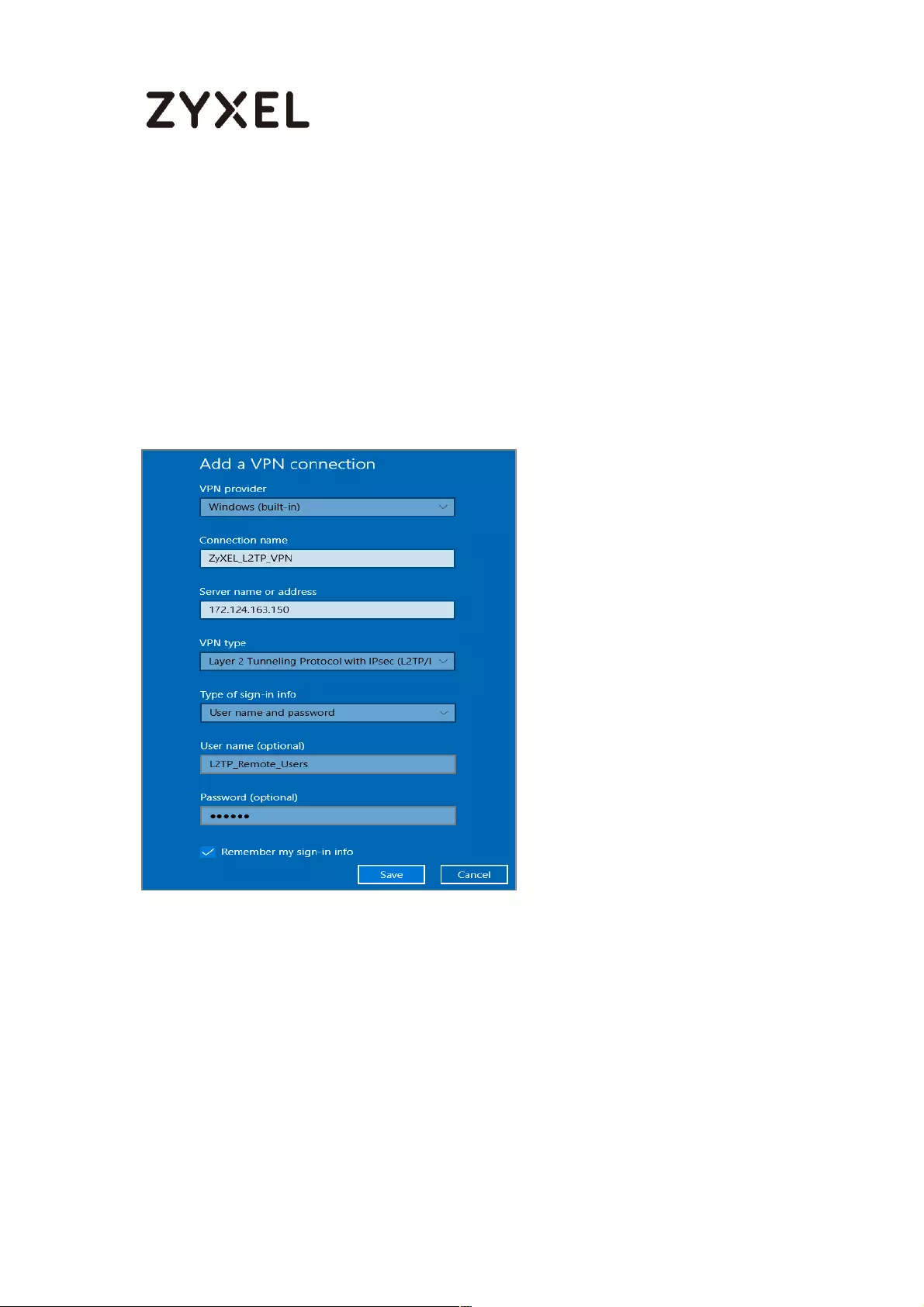
306/782
www.zyxel.com
4 Set Server name or address to be the ZyWALL/USG’s WAN IP address
(172.124.163.150 in this example).
5 Select VPN type to Layer 2 Tunneling Protocol with IPsec (L2TP/IPsec).
6 Enter User name and Password which the same as Allowed User created in
ZyWALL/USG (L2TP_Remote_Users/zyx168 in this example).
7 Go to Control Panel > Network and Internet > Network Connections and right
click Properties. Continue to Security > Advanced settings and select Use
Certificate for authentication.
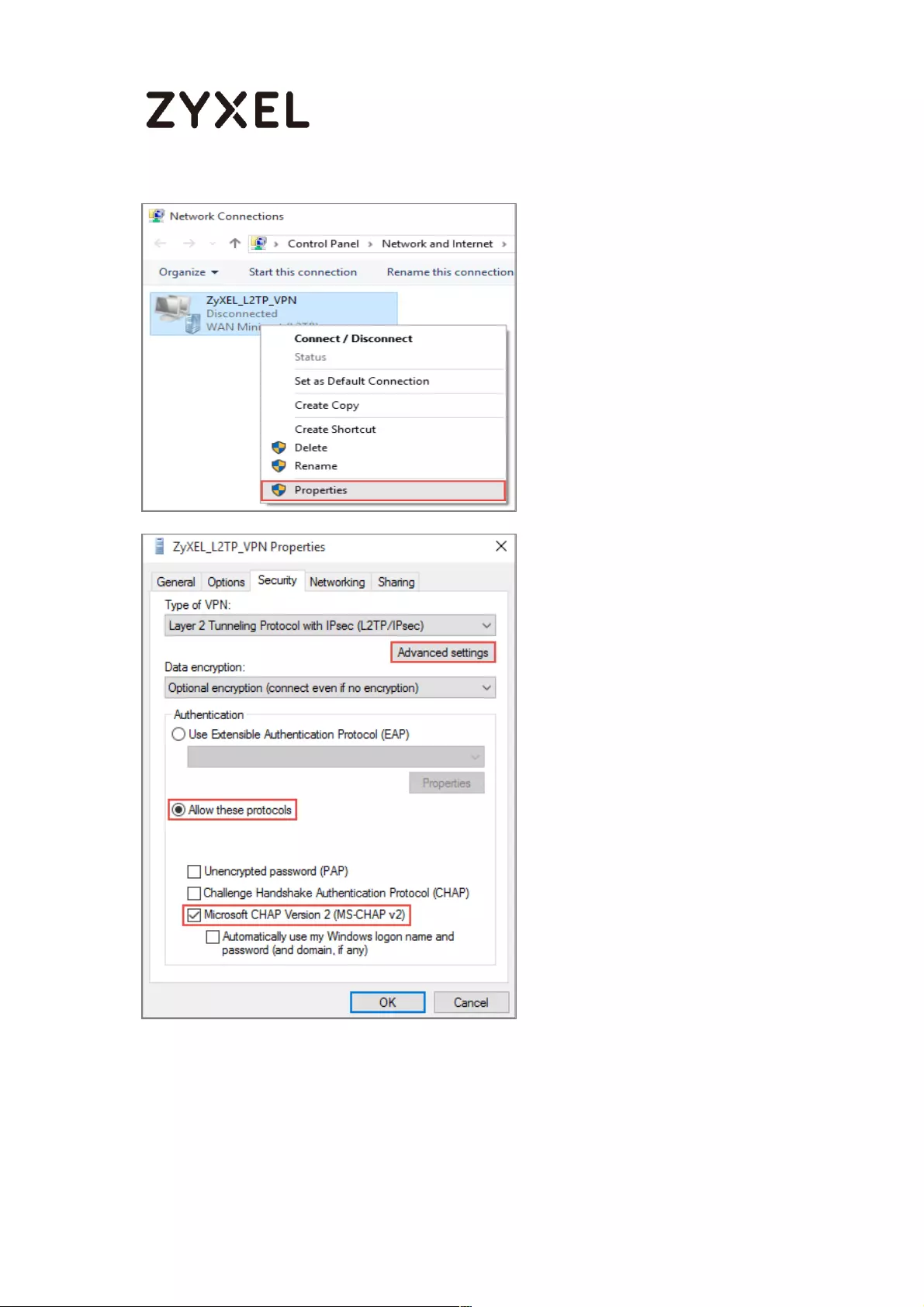
307/782
www.zyxel.com

308/782
www.zyxel.com
8 Go to Network & Internet Settings window, click Connect.
Test the L2TP over IPSec VPN Tunnel
1. Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the Status
connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
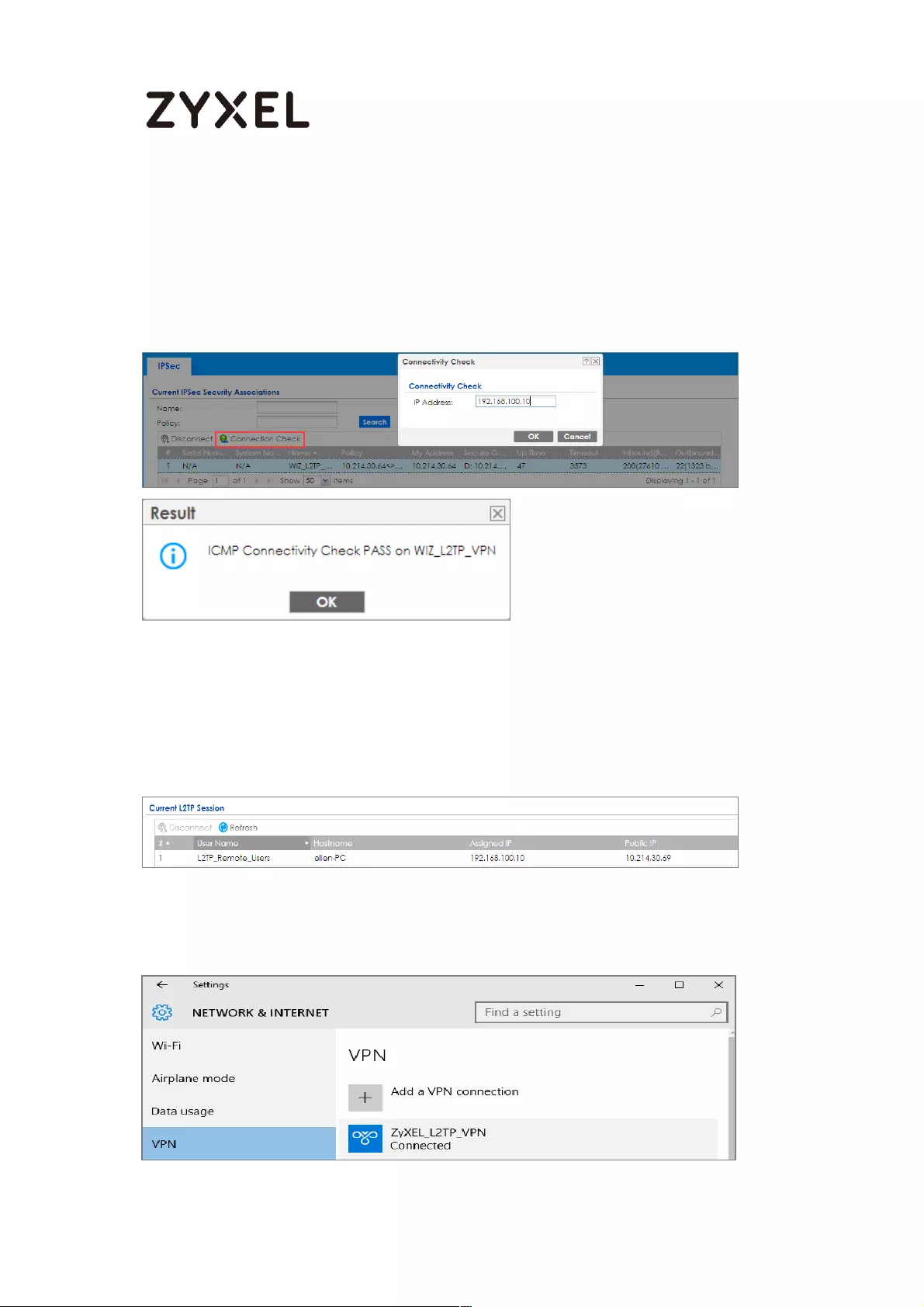
309/782
www.zyxel.com
2. Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > IPSec > WIZ_L2TP_VPN
3. Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the
Current L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
4. Go to iOS operating system Start > Settings > Network & Internet > VPN and show
Connected status.
Menu > Settings > VPN > ZyXEL_L2TP
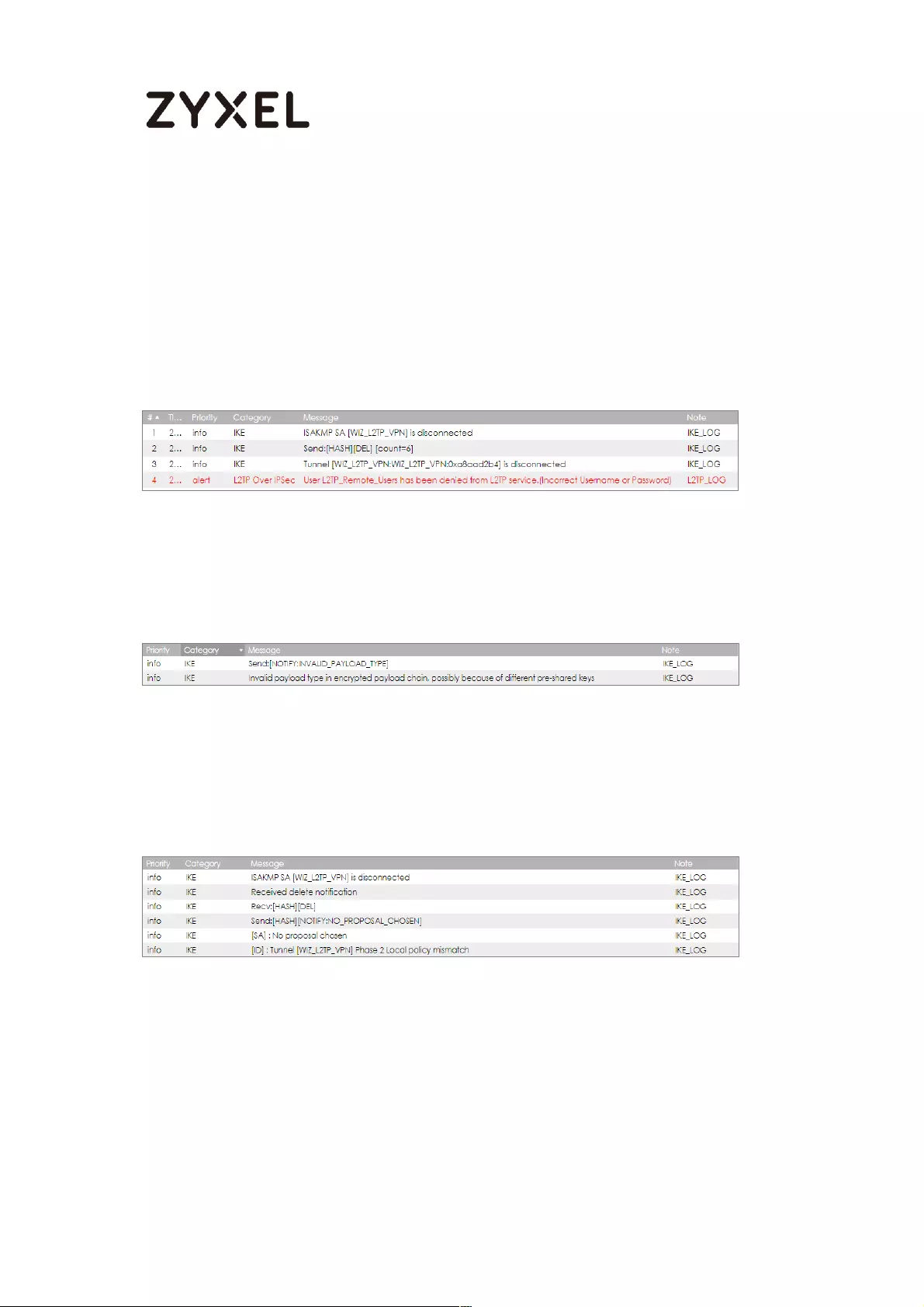
310/782
www.zyxel.com
What Could Go Wrong?
1. If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. iOS users must use the same Username and
Password as configured in ZyWALL/USG to establish the L2TP VPN.
2. If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. iOS users must use the same Pre-Shared Key as configured in
ZyWALL/USG to establish the IKE SA.
3. If you see that Phase 1 IKE SA process has completed but still get [info] log message
as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG unit must set
correct Local Policy to establish the IKE SA.
4. Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2,
DMZ, or WLAN zones, even if they are not in use.
5. If you cannot access devices in the local network, verify that the devices in the local
network set the USG’s IP as their default gateway to utilize the L2TP tunnel.
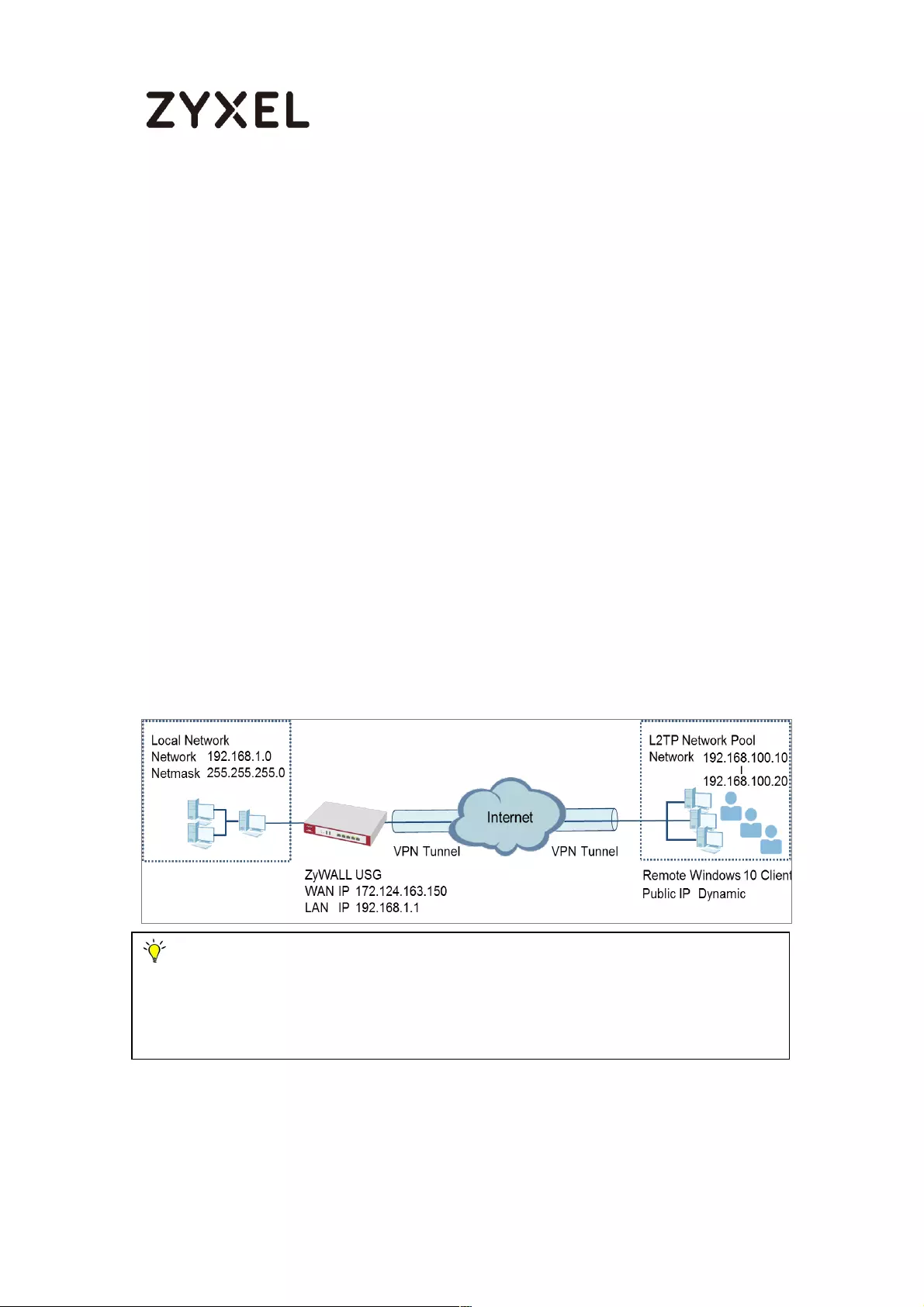
311/782
www.zyxel.com
6. Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses
UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
7. Verify that the Zone is set correctly in the VPN Connection rule. This should be set to
IPSec_VPN Zone so that security policies are applied properly.
How to Import ZyWALL/USG Certificate for L2TP over IPsec in
Android mobile phone
This is an example of using the L2TP VPN and VPN client software included in Android
mobile phone operating systems. When the VPN tunnel is configured, users can
securely access the network behind the ZyWALL/USG and allow traffic from L2TP
clients to go to the Internet from an Android mobile phone.
ZyWALL/USG L2TP VPN with Remote Android Mobile Phone Client Example
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG310 (Firmware Version: 4.25) and Android
(Version: 10.0.10240)
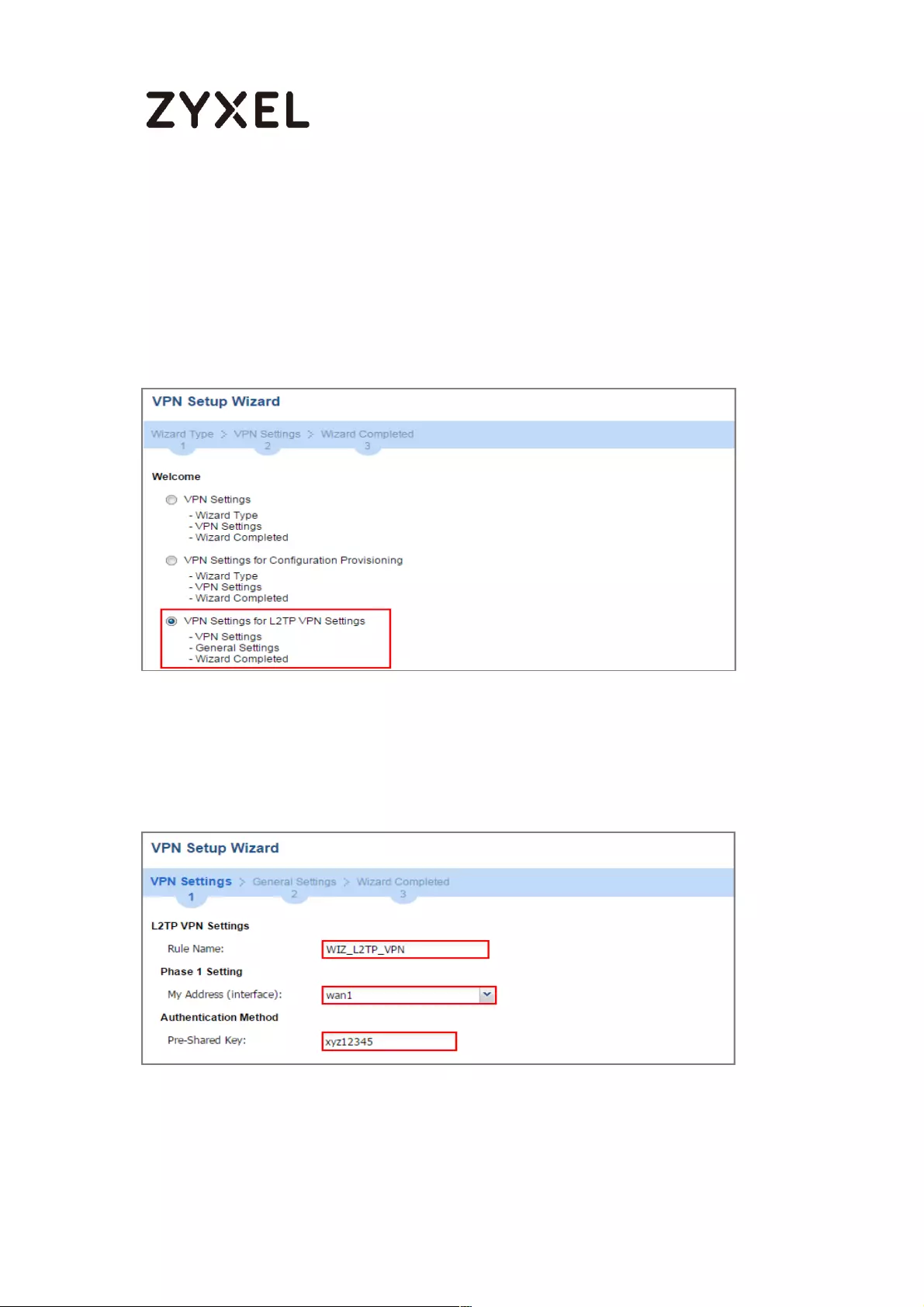
312/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings for
L2TP VPN Settings wizard to create a L2TP VPN rule that can be used with the Android
mobile phone clients. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Then, configure the Rule Name and set My Address to be the wan1 interface which is
connected to the Internet. Type a secure Pre-Shared Key (8-32 characters).
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings

313/782
www.zyxel.com
Assign the L2TP users’ IP address range from 192.168.100.10 to 192.168.100.20 for use in the L2TP
VPN tunnel and select Allow L2TP traffic Through WAN to allow traffic from L2TP clients to go to
the Internet. Click OK.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (L2TP VPN Settings)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The rule settings appear in the VPN >
L2TP VPN screen. Click Close to exit the wizard.
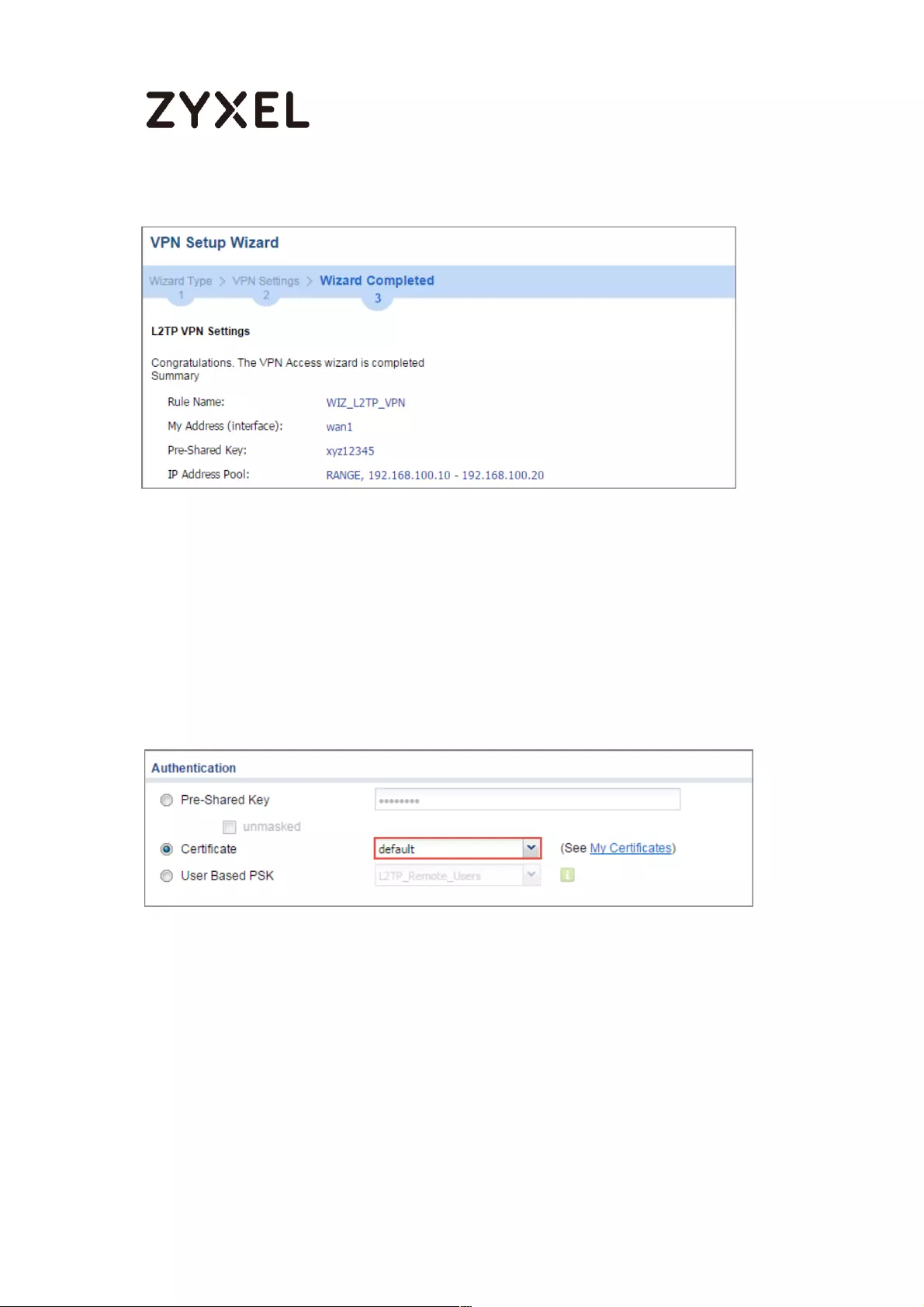
314/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Wizard Completed
Go to CONFIGURATION > VPN > VPN Gateway > WIZ_L2TP_VPN, change
Authentication method to be Certificate and select the certificate which ZyWALL/USG
uses to identify itself to the Android mobile phone.
CONFIGURATION > VPN > VPN Gateway > WIZ_L2TP_VPN > Authentication >
Certificate
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add User
Name and Password (4-24 characters). Then, set Allowed User to the newly created
object (L2TP_Remote_Users/zyx168 in this example).
CONFIGURATION > VPN > L2TP VPN > Create new Object > User
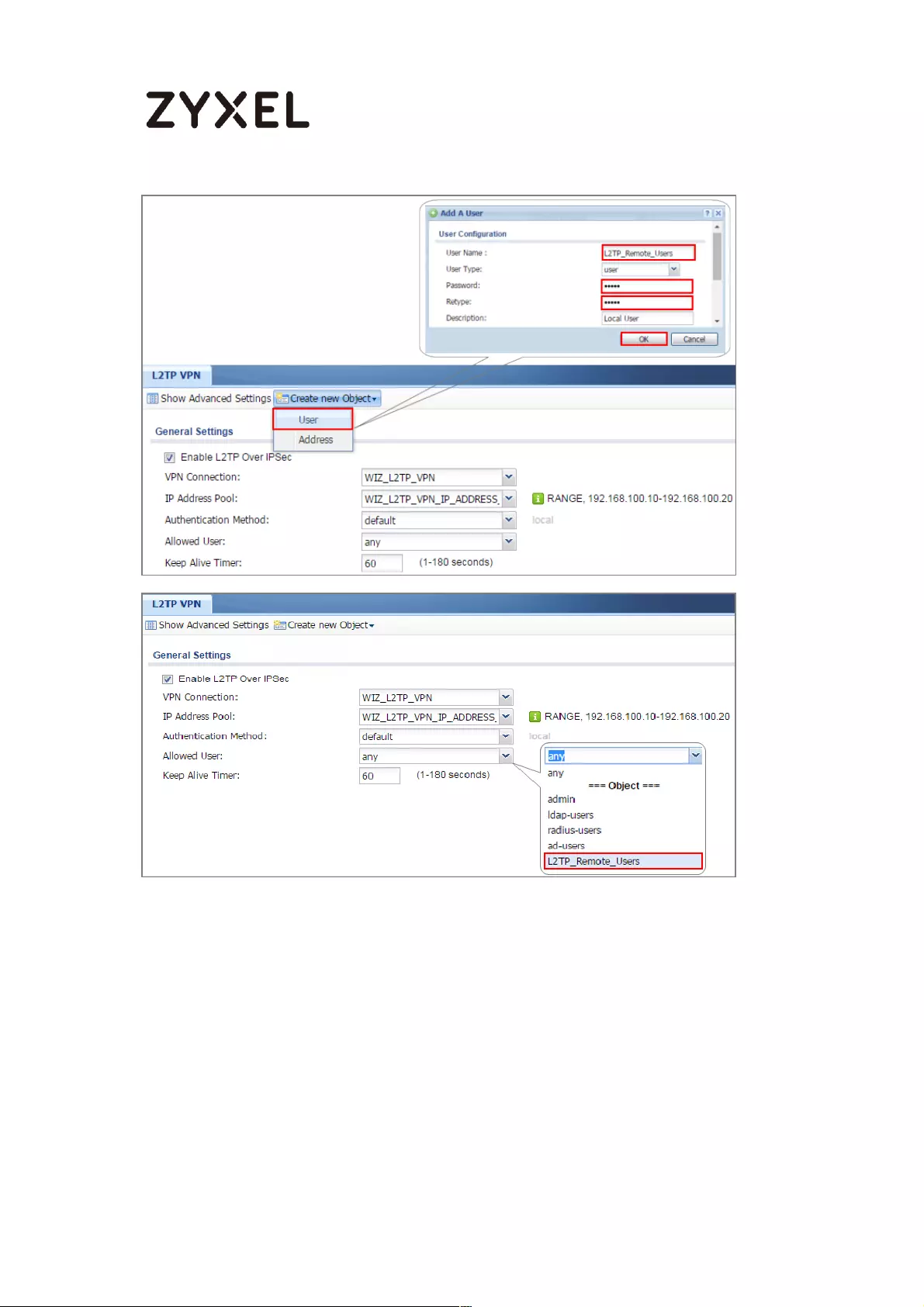
315/782
www.zyxel.com
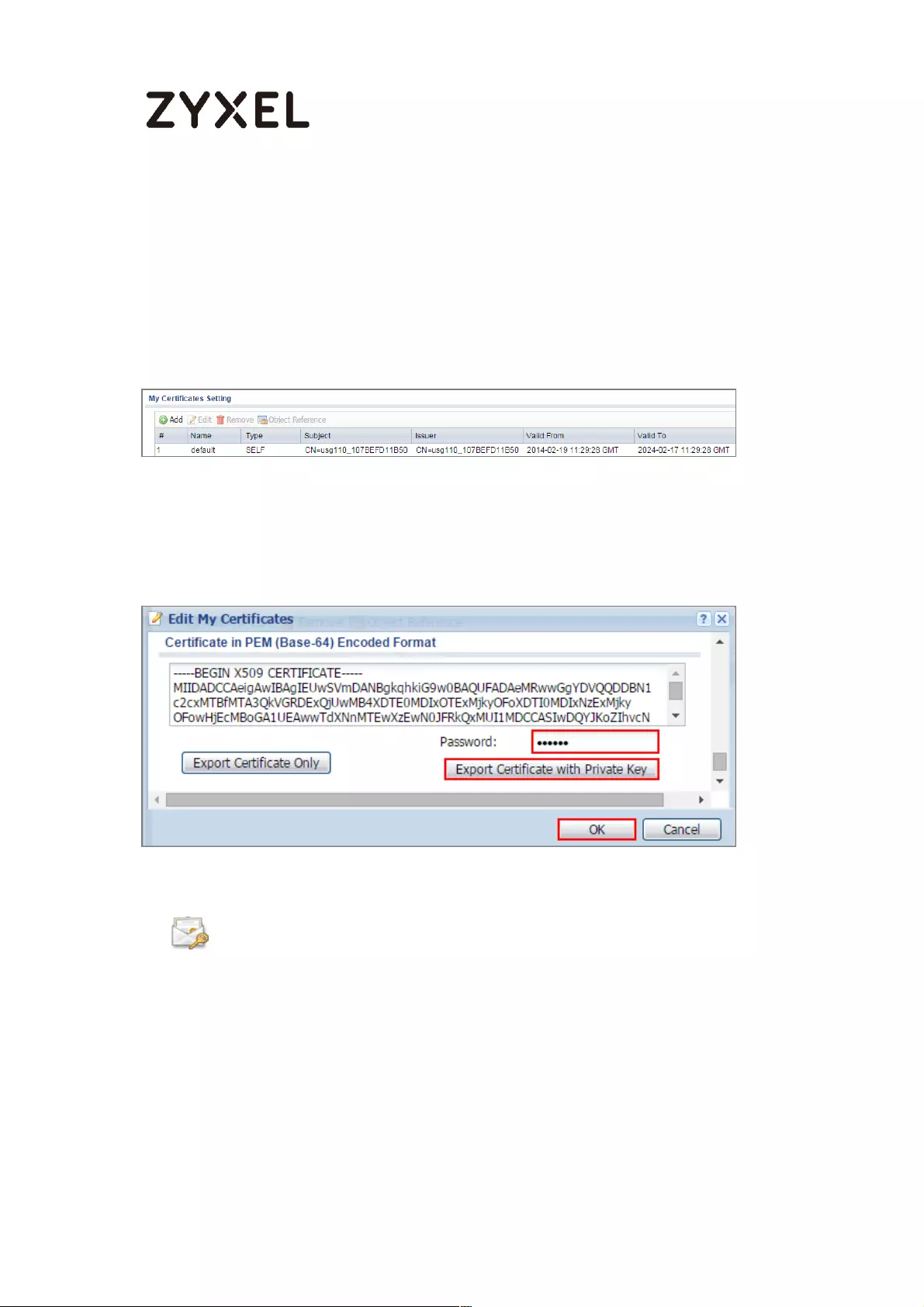
316/782
www.zyxel.com
Export a Certificate from ZyWALL/USG and Import it to Android
Mobile Phone
Go to ZyWALL/USG CONFIGURATION > Object > Certificate, select the certificate
(default in this example) and click Edit.
CONFIGURATION > Object > Certificate > default
Export default certificate from ZyWALL/USG with Private Key (zyx123 in this example)
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with
Private Key
Save default certificate as *.p12 file to Android mobile phone computer.
default.p12

317/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the Android Mobile Device
1 To configure L2TP VPN in Android, go to Start > Settings > Network & Internet >
VPN > Add a VPN Connection and configure as follows.
2 VPN Provider set to Windows (built-in).
3 Configure Connection name for you to identify the VPN configuration.
4 Set Server name or address to be the ZyWALL/USG’s WAN IP address
(172.124.163.150 in this example).
5 Select VPN type to Layer 2 Tunneling Protocol with IPsec (L2TP/IPsec).
6 Enter User name and Password which the same as Allowed User created in
ZyWALL/USG (L2TP_Remote_Users/zyx168 in this example).
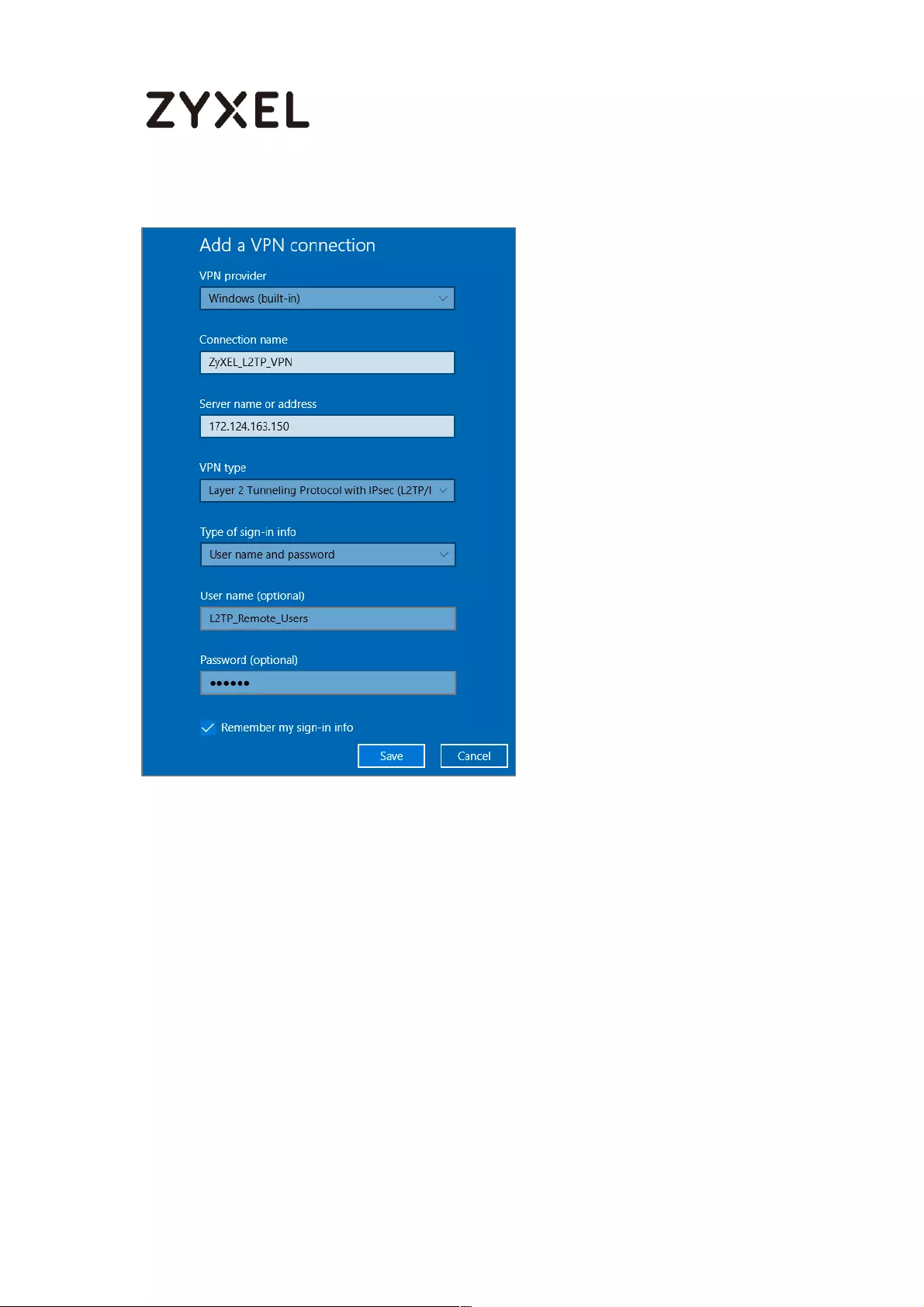
318/782
www.zyxel.com
Go to Control Panel > Network and Internet > Network Connections and right click
Properties. Continue to Security > Advanced settings and select Use Certificate for
authentication.
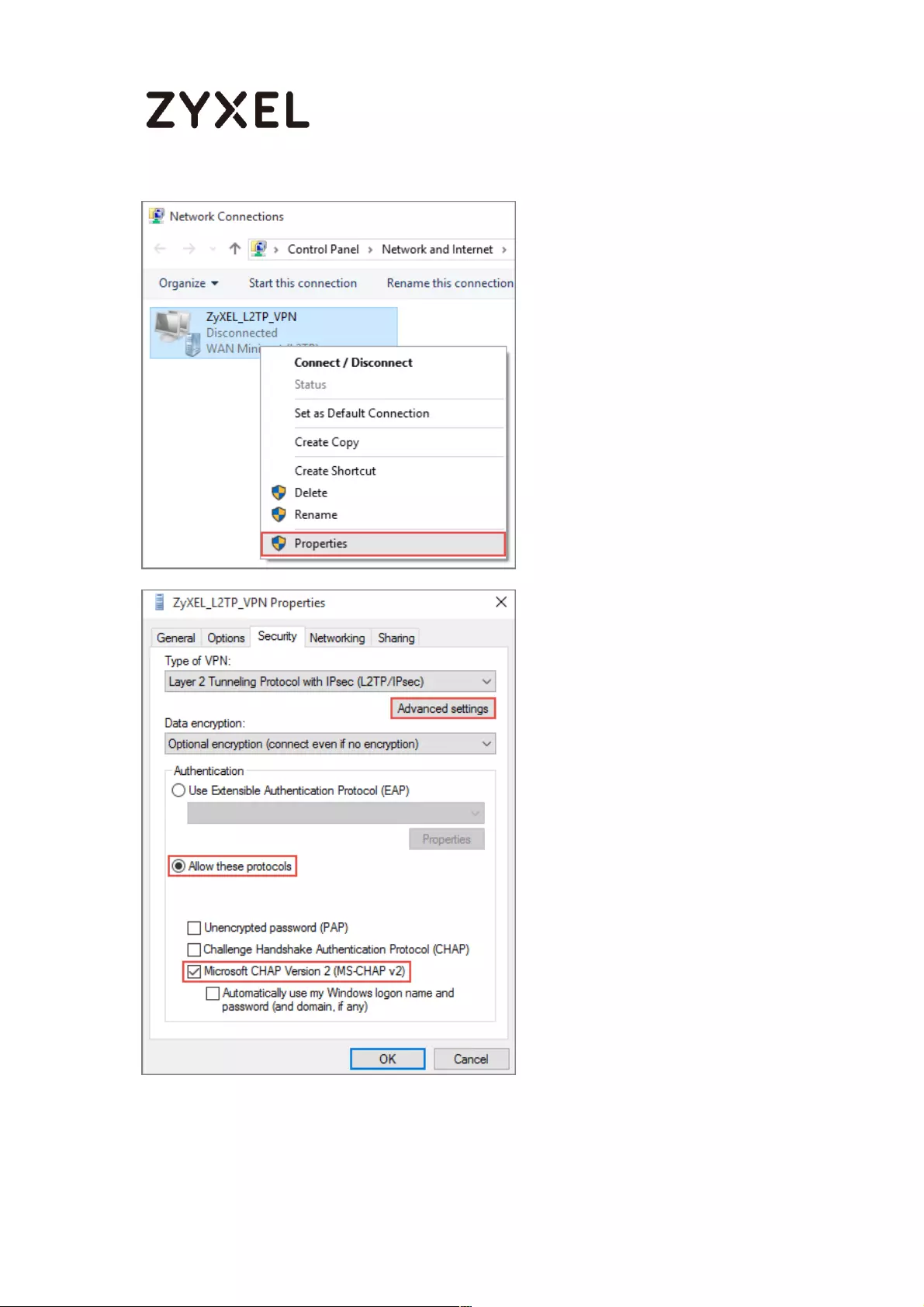
319/782
www.zyxel.com

320/782
www.zyxel.com
Go to Network & Internet Settings window, click Connect.
Test the L2TP over IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the Status
connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection

321/782
www.zyxel.com
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time and
the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to verify the
result of ICMP Connectivity.
Hub_HQ > MONITOR > VPN Monitor > IPSec > WIZ_L2TP_VPN
Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the Current
L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
Go to Android Start > Settings > Network & Internet > VPN and show Connected status.
Menu > Settings > VPN > ZyXEL_L2TP
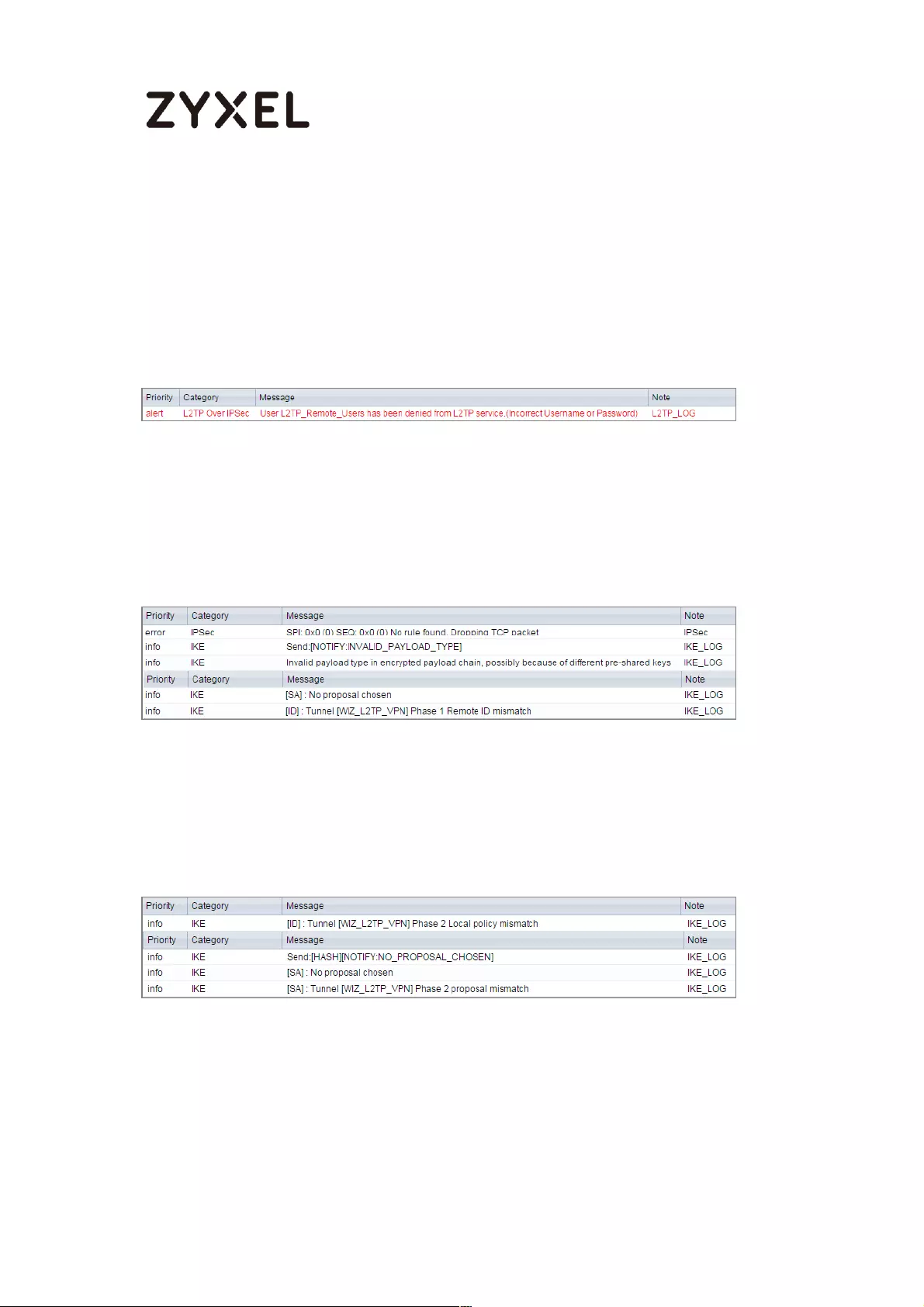
322/782
www.zyxel.com
What Could Go Wrong?
7 If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. Android users must use the same Username
and Password as configured in ZyWALL/USG to establish the L2TP VPN.
8 If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. Android users must use the same Pre-Shared Key as configured
in ZyWALL/USG to establish the IKE SA.
9 If you see that Phase 1 IKE SA process has completed but still get [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG unit
must set correct Local Policy to establish the IKE SA.
10 Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2,
DMZ, or WLAN zones, even if they are not in use.

323/782
www.zyxel.com
11 If you cannot access devices in the local network, verify that the devices in the
local network set the USG’s IP as their default gateway to utilize the L2TP tunnel.
12 Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses
UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
13 Verify that the Zone is set correctly in the VPN Connection rule. This should be set
to IPSec_VPN Zone so that security policies are applied properly.
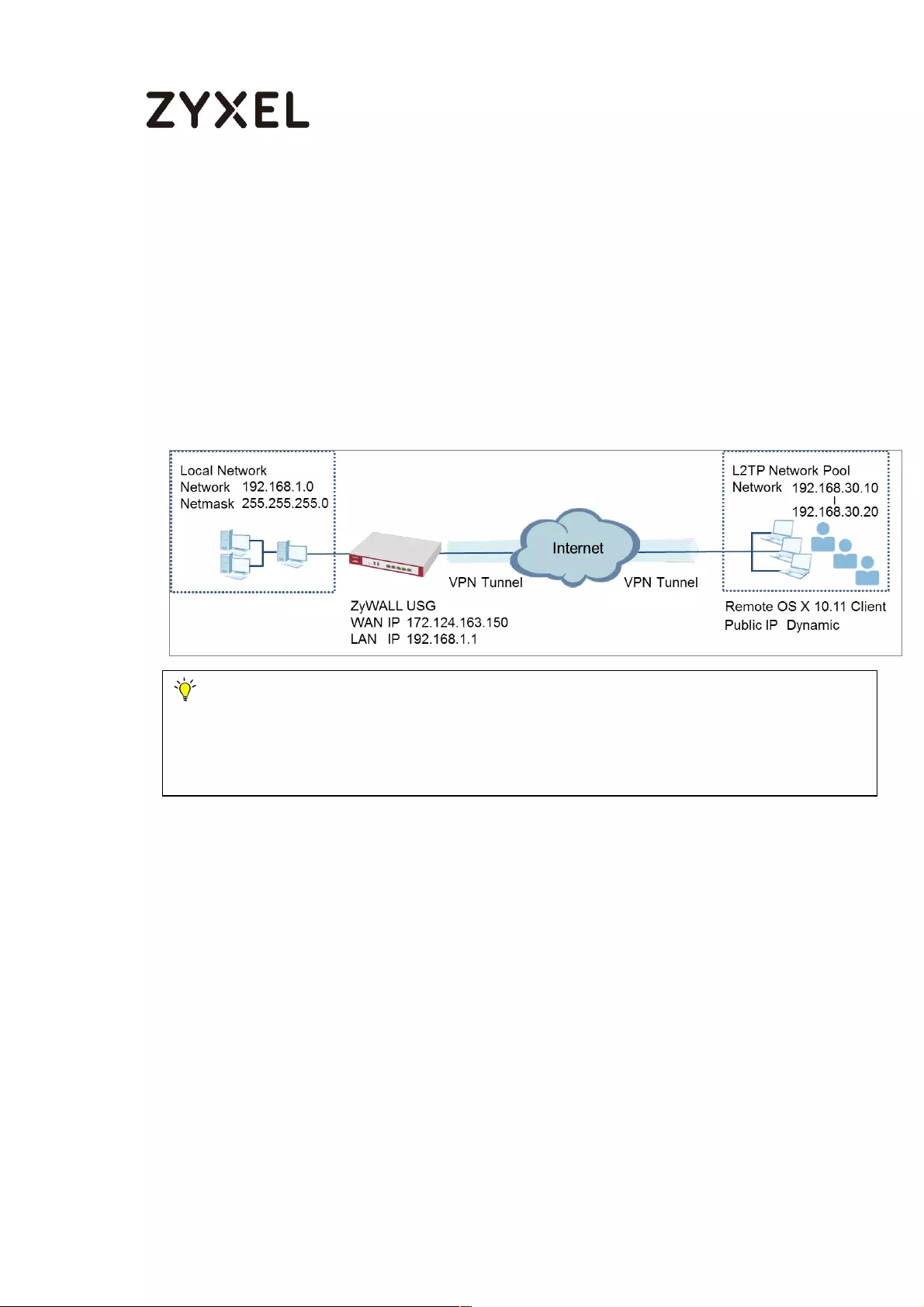
324/782
www.zyxel.com
How to Configure the L2TP VPN with Apple MAC OS X 10.11
Operating System
This is an example of using the L2TP VPN and VPN client software included in
Apple MAC OS X 10.11 El Capitan operating systems. When the VPN tunnel is
configured, users can securely access the network behind the ZyWALL/USG and
allow traffic from L2TP clients to go to the Internet from an Apple computer.
ZyWALL/USG L2TP VPN with Apple MAC OS X 10.11 El Capitan
Set Up the L2TP VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
for L2TP VPN Settings wizard to create a L2TP VPN rule that can be used with the
MAC OS X clients. Click Next.
Quick Setup > VPN Setup Wizard > Welcome
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25) and Apple MAC (Version: OS X10.11 El
Capitan).
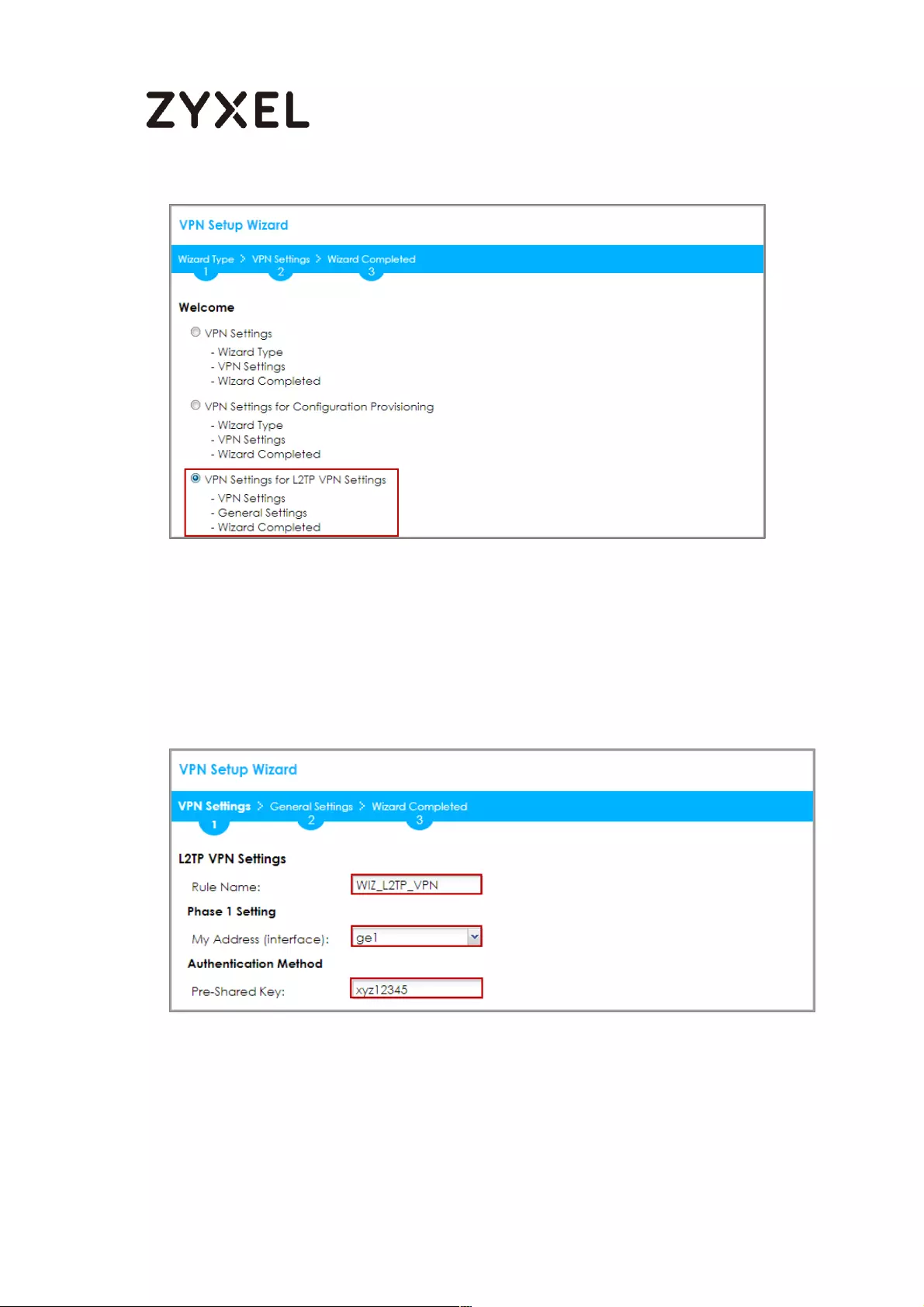
325/782
www.zyxel.com
Then, configure the Rule Name and set My Address to be the wan1 interface
which is connected to the Internet. Type a secure Pre-Shared Key (8-32
characters).
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
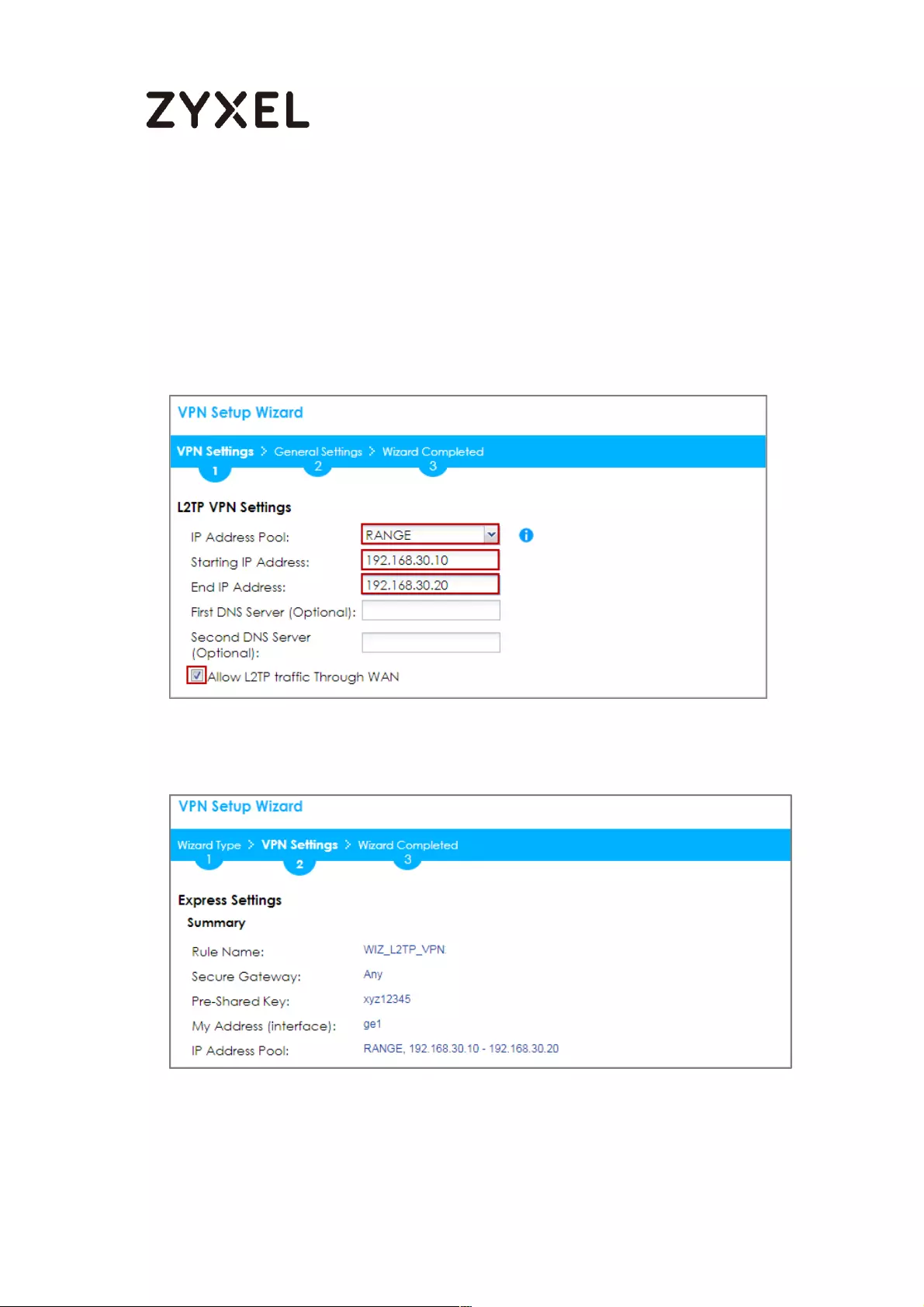
326/782
www.zyxel.com
Configure the L2TP users’ IP address range from 192.168.30.10 to 192.168.30.20 for
use in the L2TP VPN tunnel and check Allow L2TP traffic Through WAN. Click OK.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings
Continue to the next page to review your Summary and click Save.
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Summary
Quick Setup > VPN Setup Wizard > Welcome > VPN Settings > Summary > Wizard
Completed
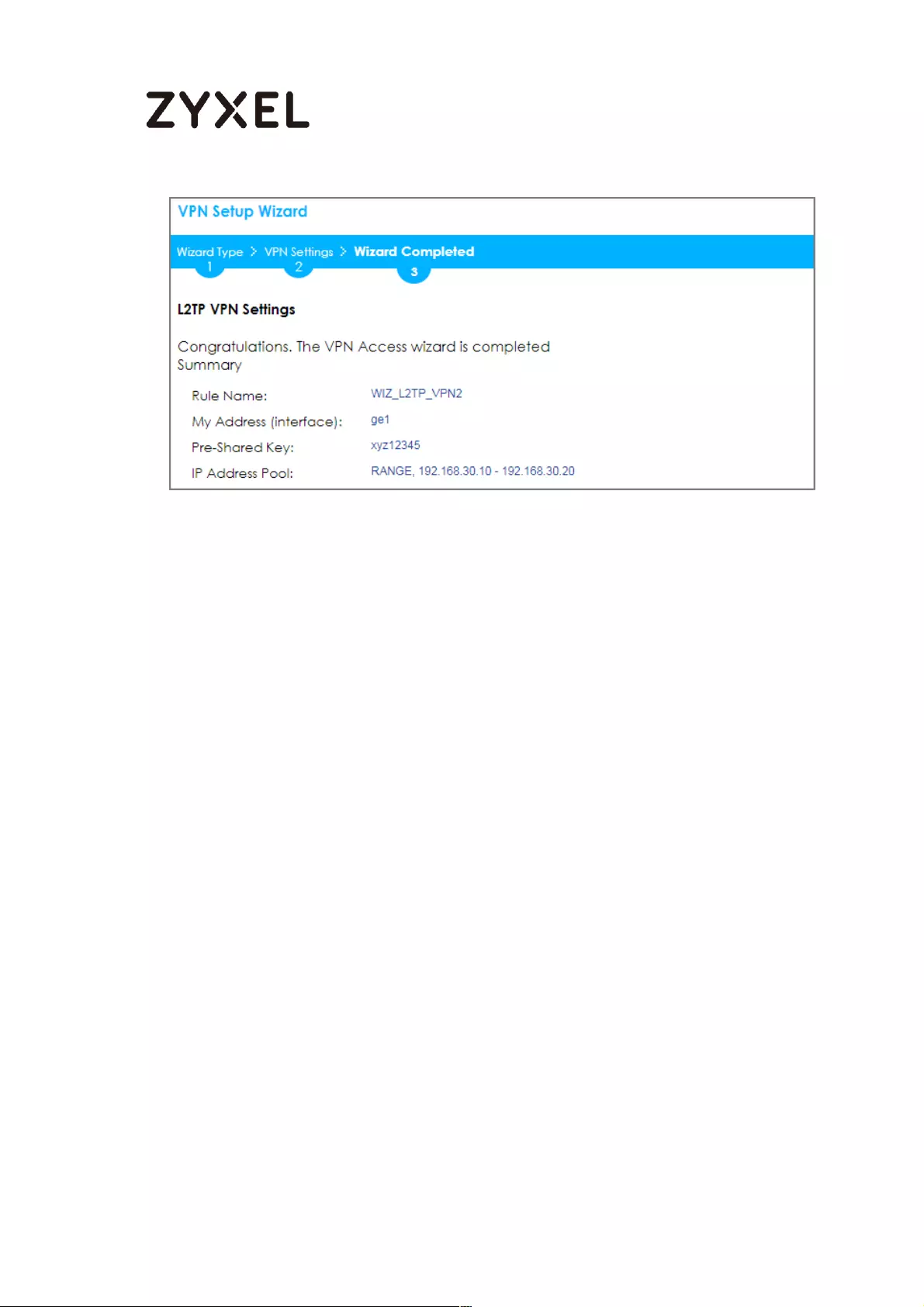
327/782
www.zyxel.com
Go to CONFIGURATION > VPN > L2TP VPN > Create new Object > User to add User
Name and Password (4-24 characters). Then, set Allowed User to the newly
created object (L2TP_Remote_Users/zyx168 in this example).
CONFIGURATION > VPN > L2TP VPN > Create new Object > User
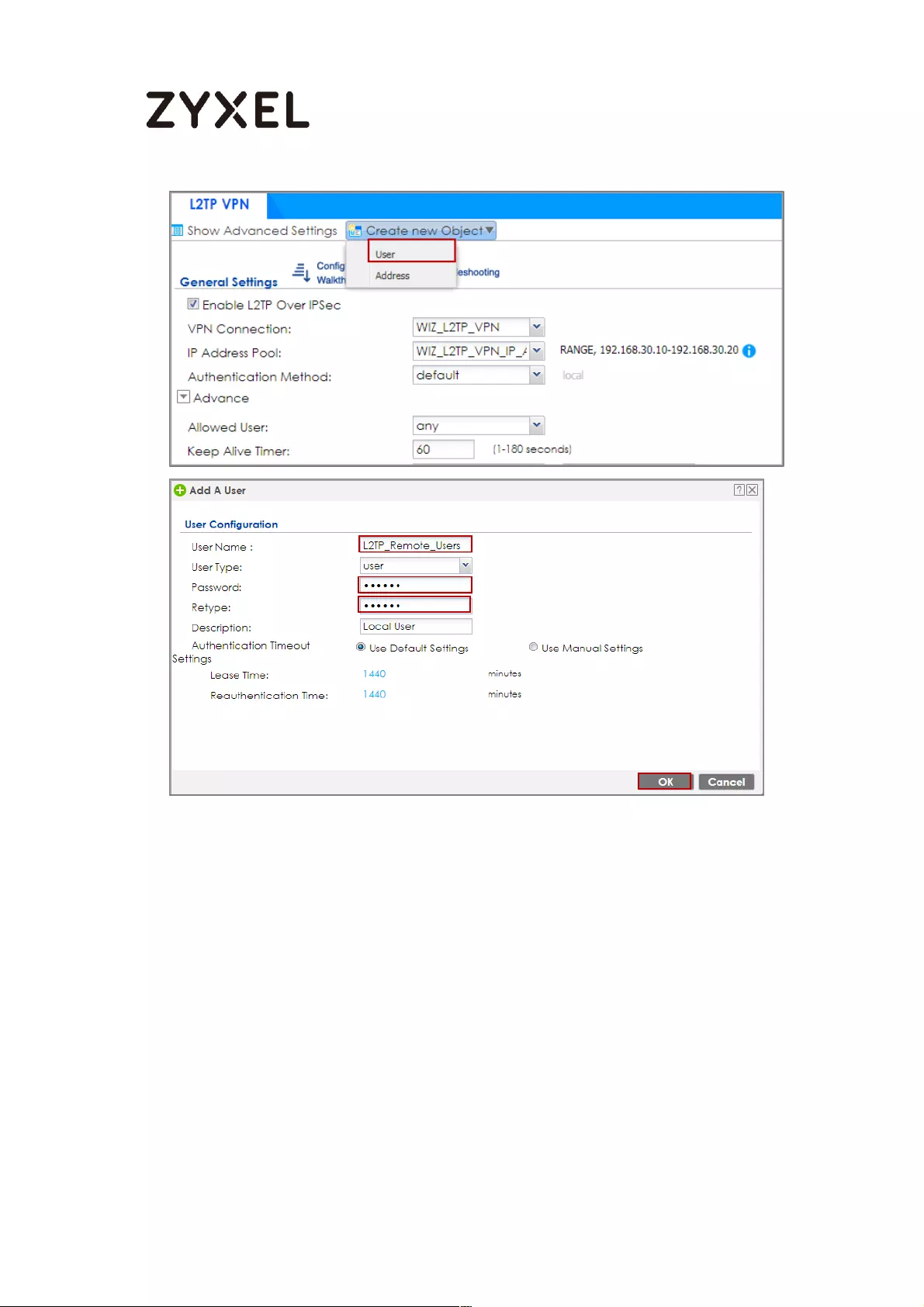
328/782
www.zyxel.com
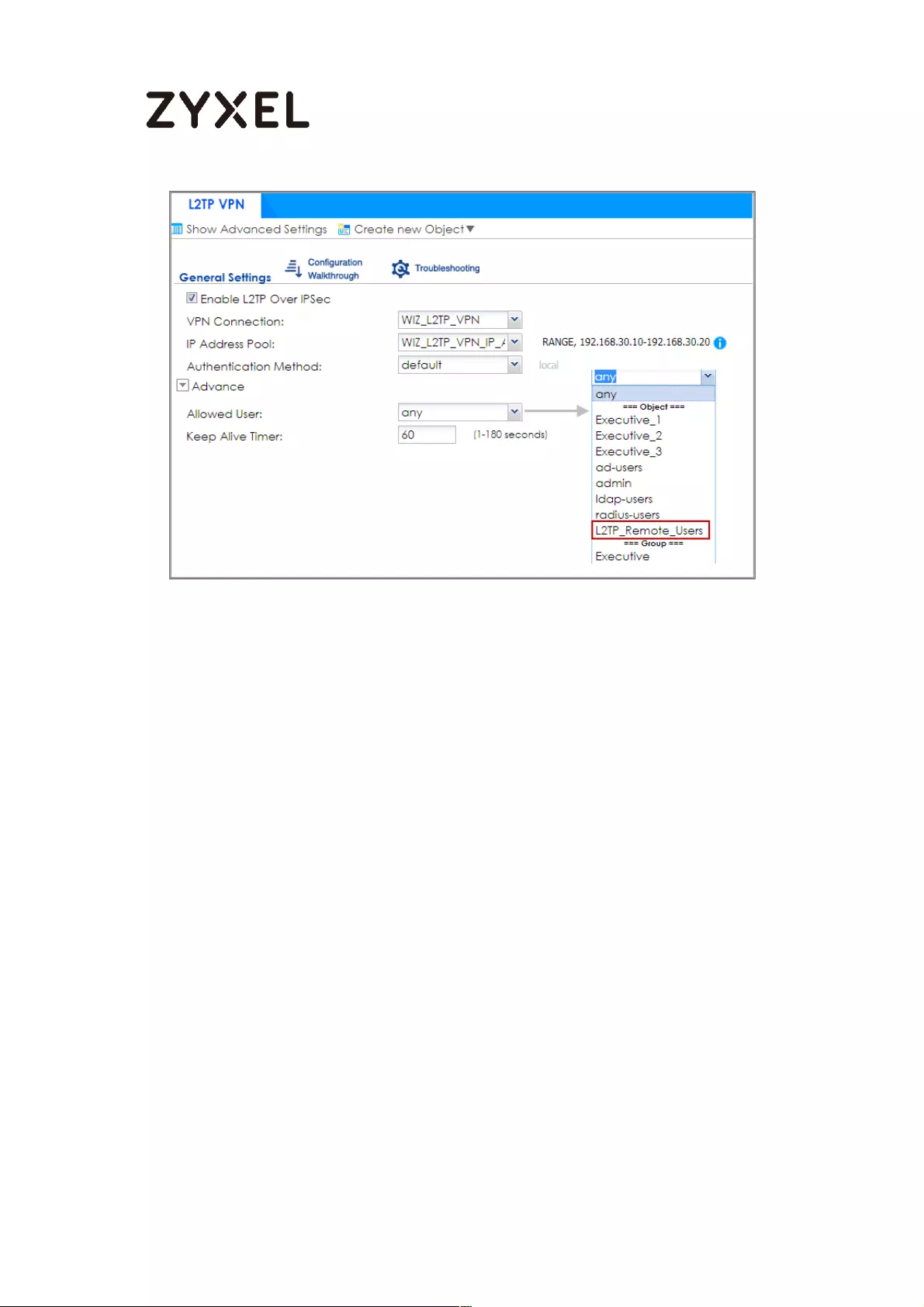
329/782
www.zyxel.com
Set Up the L2TP VPN Tunnel on the Apple MAC OS X 10.11 El
Capitan Operating System
To configure L2TP VPN in OS X 10.11 operation system, go to System Preferences…
> Network, click the "+" button at the bottom left of the connections to add a new
connection and configure as follows.
Set the Interface to be VPN, select VPN Type to be L2TP over IPSec.
Configure Service Name for you to identify the VPN configuration. Click Create.

330/782
www.zyxel.com
Configure Server Address to be the ZyWALL/USG’s WAN IP address
(172.124.163.150 in this example). Enter Account Name which should be the same
as Allowed User created in ZyWALL/USG (L2TP_Remote_Users in this example).
Then, click Authentication Settings....
In the User Authentication section, enter Password which should be the same as
Allowed User created in ZyWALL/USG (zyx123 in this example).
In the Machine Authentication section, enter Shared Secret to be the pre-shared
key of the IPSec VPN gateway the ZyWALL/USG uses for L2TP VPN over IPSec
(zyx12345 in this example). Click OK.
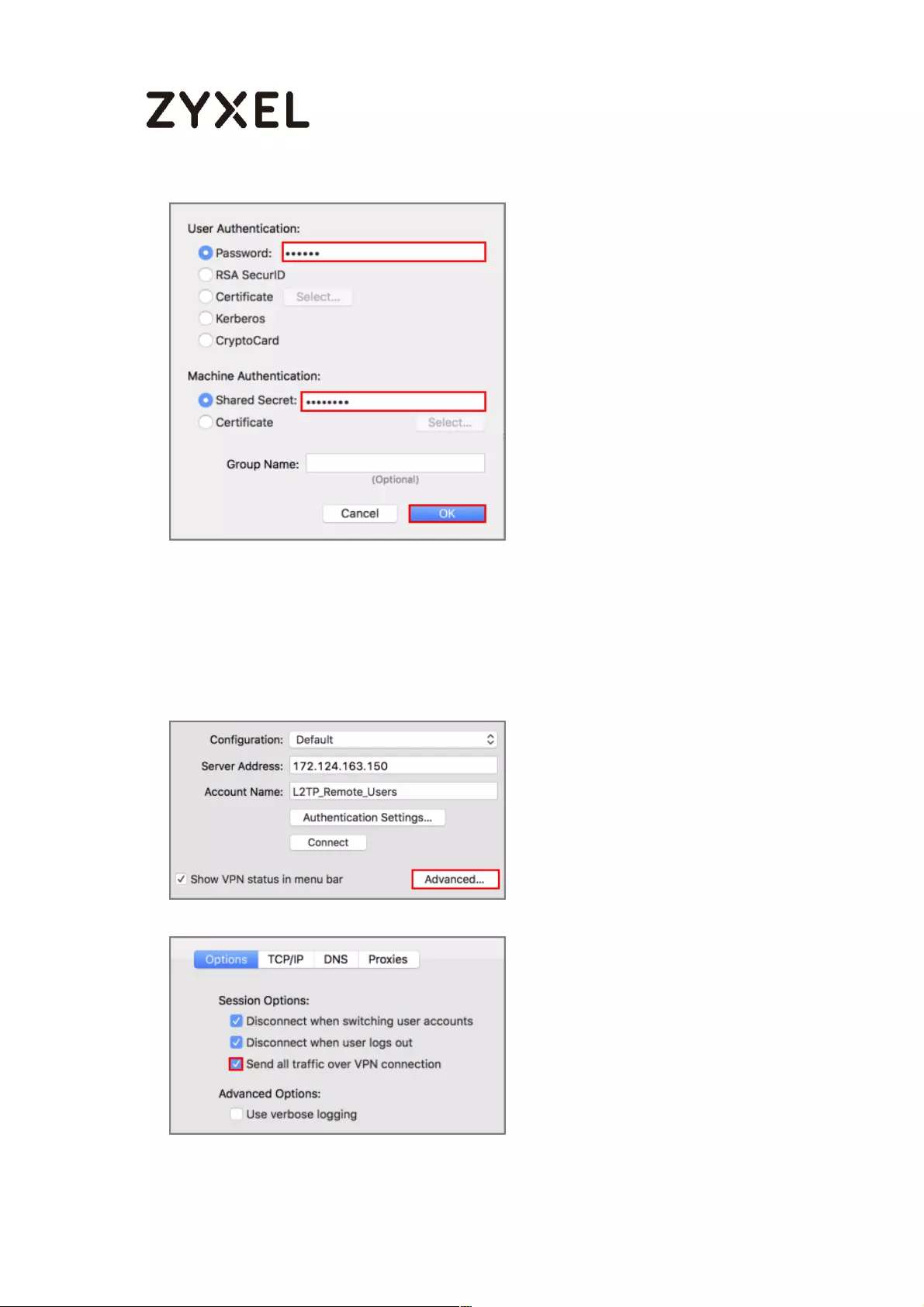
331/782
www.zyxel.com
Go back to Configuration and click Advanced…. Select Send all traffic over VPN
connection to allow the L2TP/IPSec VPN traffic between ZyWALL/USG and MAC
OS X system.
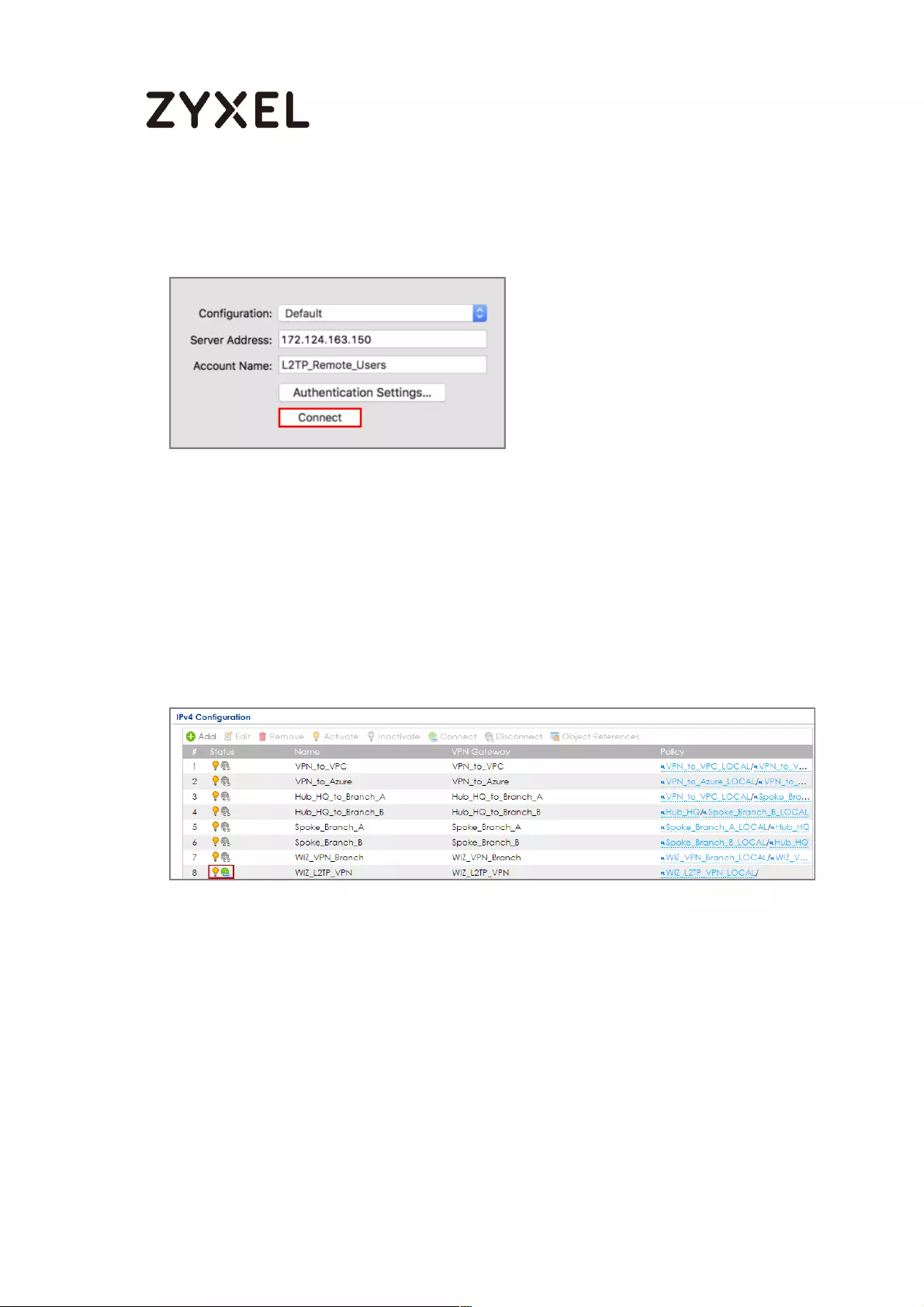
332/782
www.zyxel.com
Go back to Configuration and click Connect.
Test the L2TP over IPSec VPN Tunnel
Go to ZyWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, the
Status connect icon is lit when the interface is connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and the Inbound(Bytes)/Outbound(Bytes) traffic. Click Connectivity Check to
verify the result of ICMP Connectivity.
MONITOR > VPN Monitor > IPSec > WIZ_L2TP_VPN
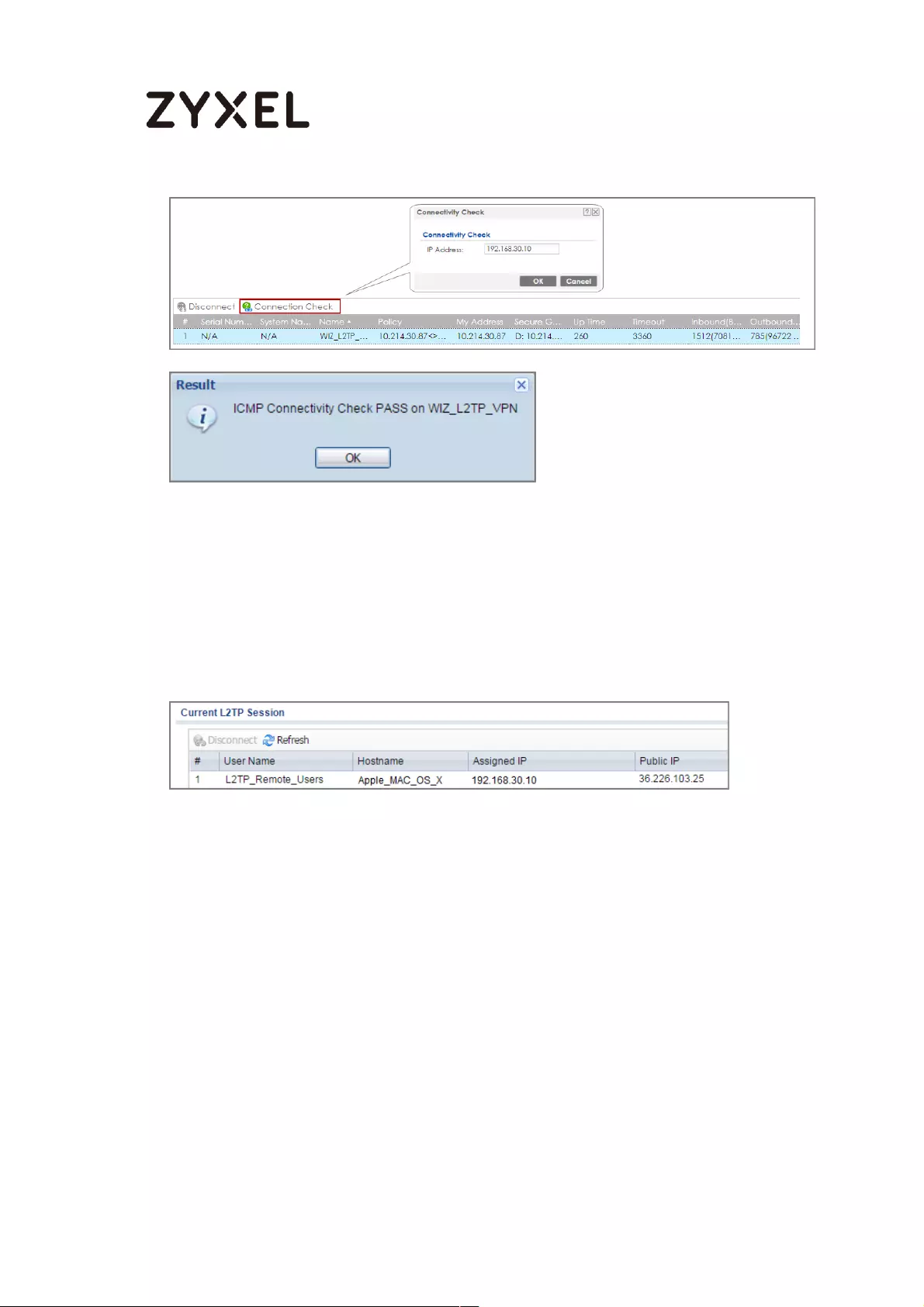
333/782
www.zyxel.com
功能有問題無法截圖
, connectivity check fail
Go to ZyWALL/USG MONITOR > VPN Monitor > L2TP over IPSec and verify the
Current L2TP Session.
MONITOR > VPN Monitor > L2TP over IPSec > L2TP_Remote_Users
Go to MAC OS X System Preferences… > Network and show Connected status,
Connect Time and assigned IP Address.
System Preferences… > Network
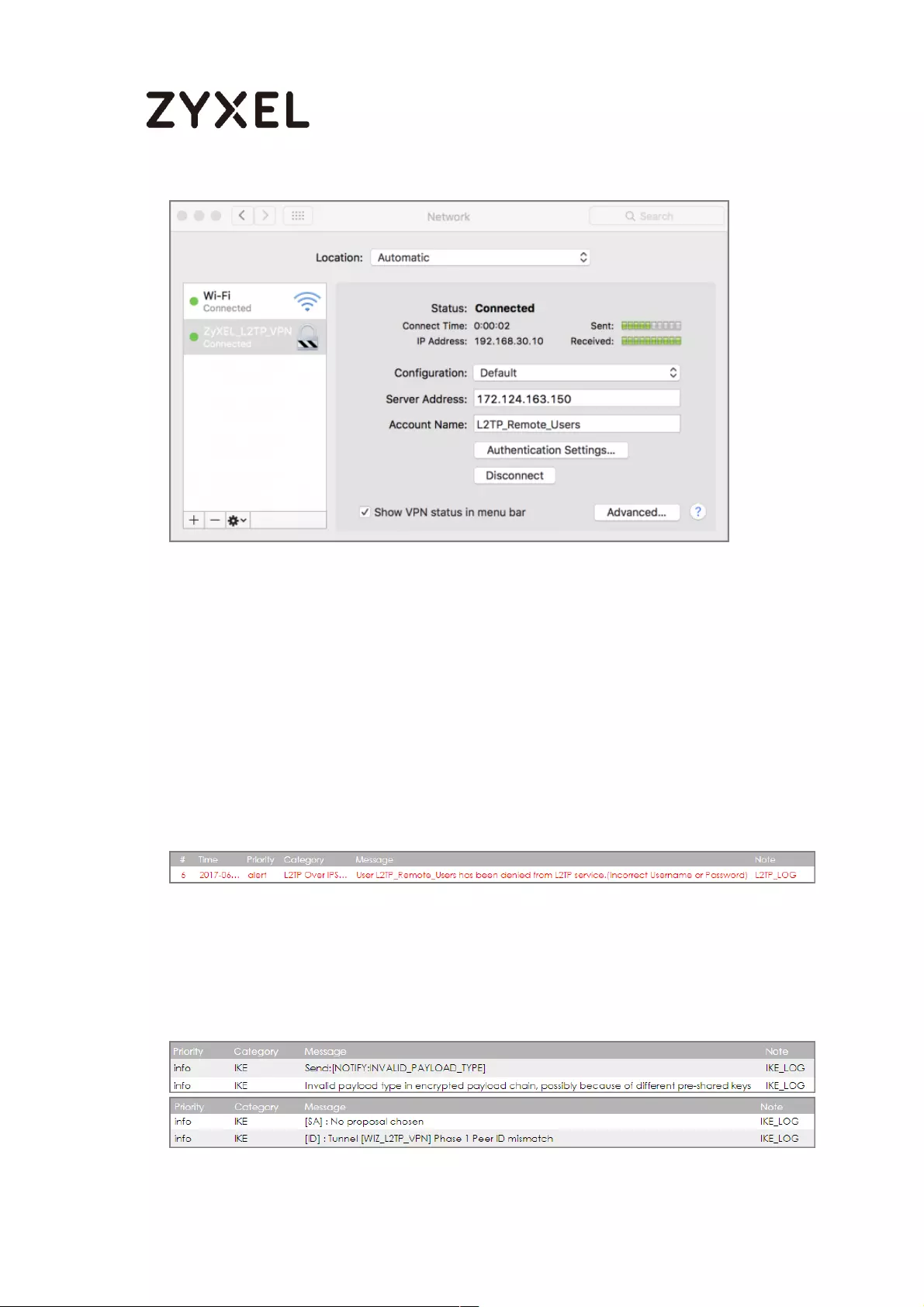
334/782
www.zyxel.com
What Could Go Wrong?
If you see [alert] log message such as below, please check ZyWALL/USG L2TP
Allowed User or User/Group Settings. Apple MAC OS X El Capitan operating
system users must use the same Username and Password as configured in
ZyWALL/USG to establish the L2TP VPN.
If you see [info] or [error] log message such as below, please check ZyWALL/USG
Phase 1 Settings. Apple MAC OS X El Capitan operating system users must use the
same Pre-Shared Key as configured in ZyWALL/USG to establish the IKE SA.
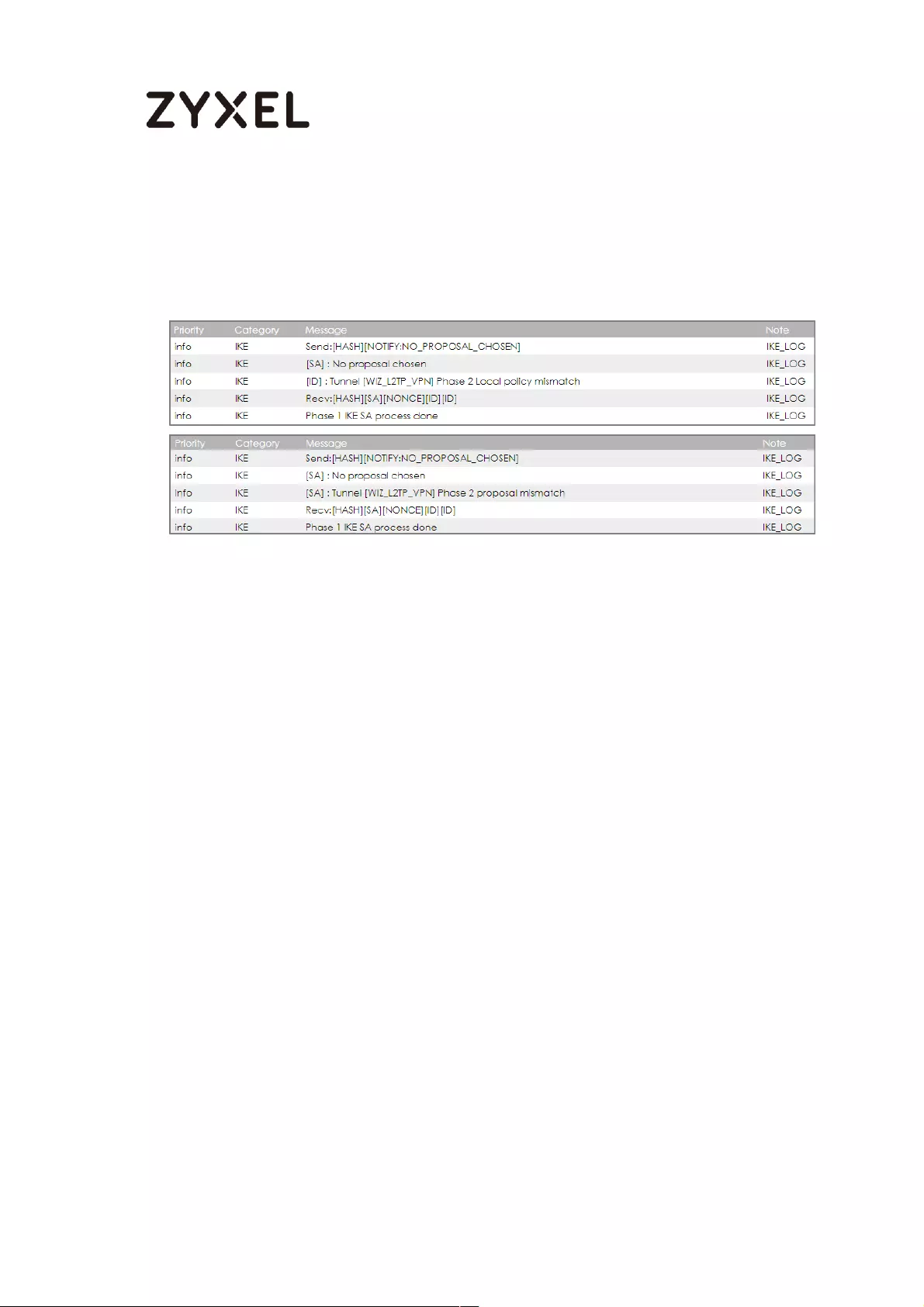
335/782
www.zyxel.com
If you see that Phase 1 IKE SA process has completed but still get [info] log
message as below, please check ZyWALL/USG Phase 2 Settings. ZyWALL/USG unit
must set correct Local Policy to establish the IKE SA.
Ensure that the L2TP Address Pool does not conflict with any existing LAN1, LAN2,
DMZ, or WLAN zones, even if they are not in use.
If you cannot access devices in the local network, verify that the devices in the
local network set the USG’s IP as their default gateway to utilize the L2TP tunnel.
Make sure the ZyWALL/USG units’ security policies allow IPSec VPN traffic. IKE uses
UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
Verify that the Zone is set correctly in the Zone object. This should be set to
IPSec_VPN Zone so that security policies are applied properly.
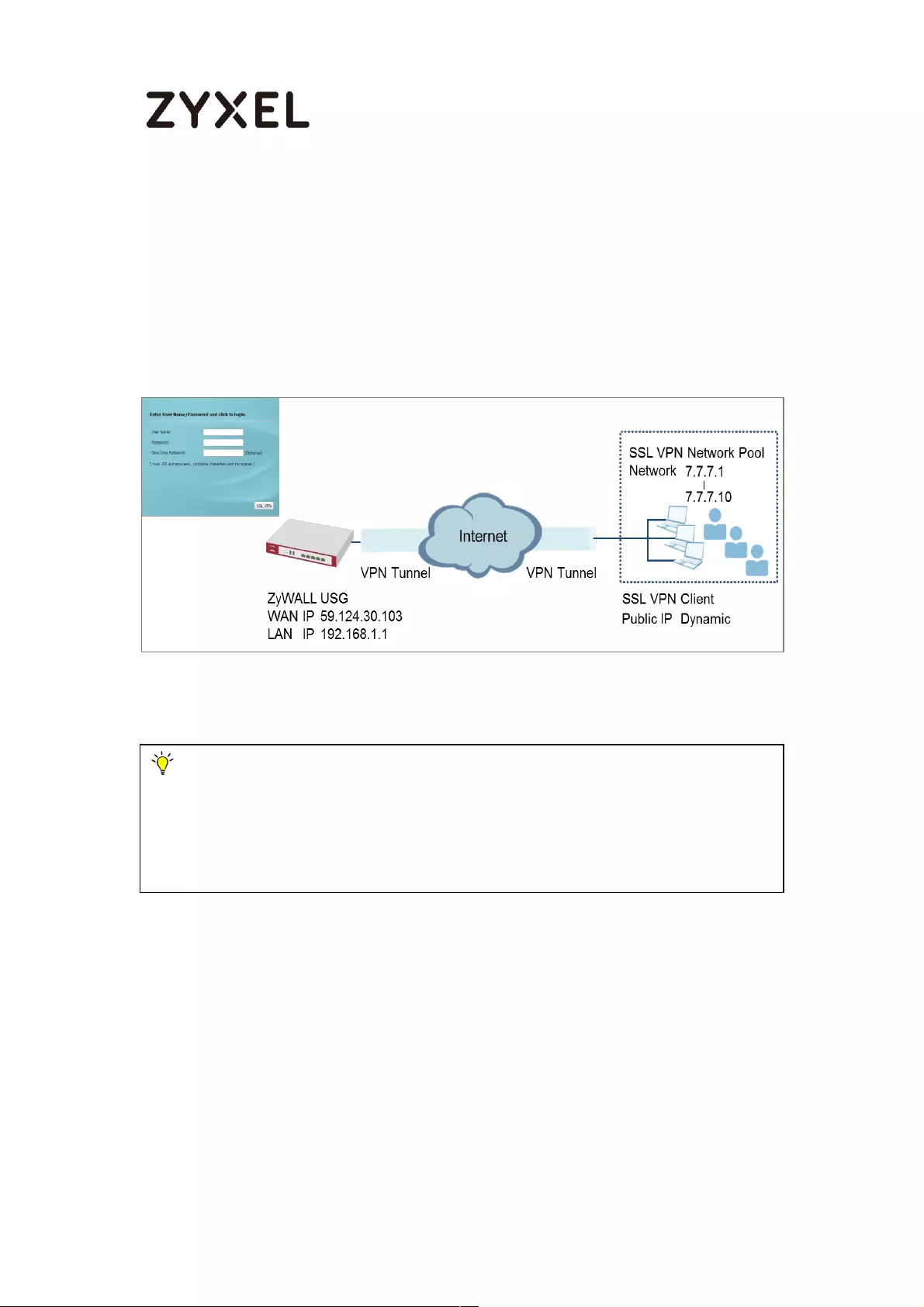
336/782
www.zyxel.com
How to configure if I want user can only see SSL VPN Login
button in web portal login page
This example shows how to strict portal access for SSL VPN clients. The example
instructs how to allow end users to only see the SSL VPN Login button in the web
portal login screen and the administrator can only manage the device from
LAN.
ZyWALL/USG only see SSL VPN Login button in web portal login page
Note:
All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This
example was tested using USG60 (Firmware Version: ZLD 4.25).
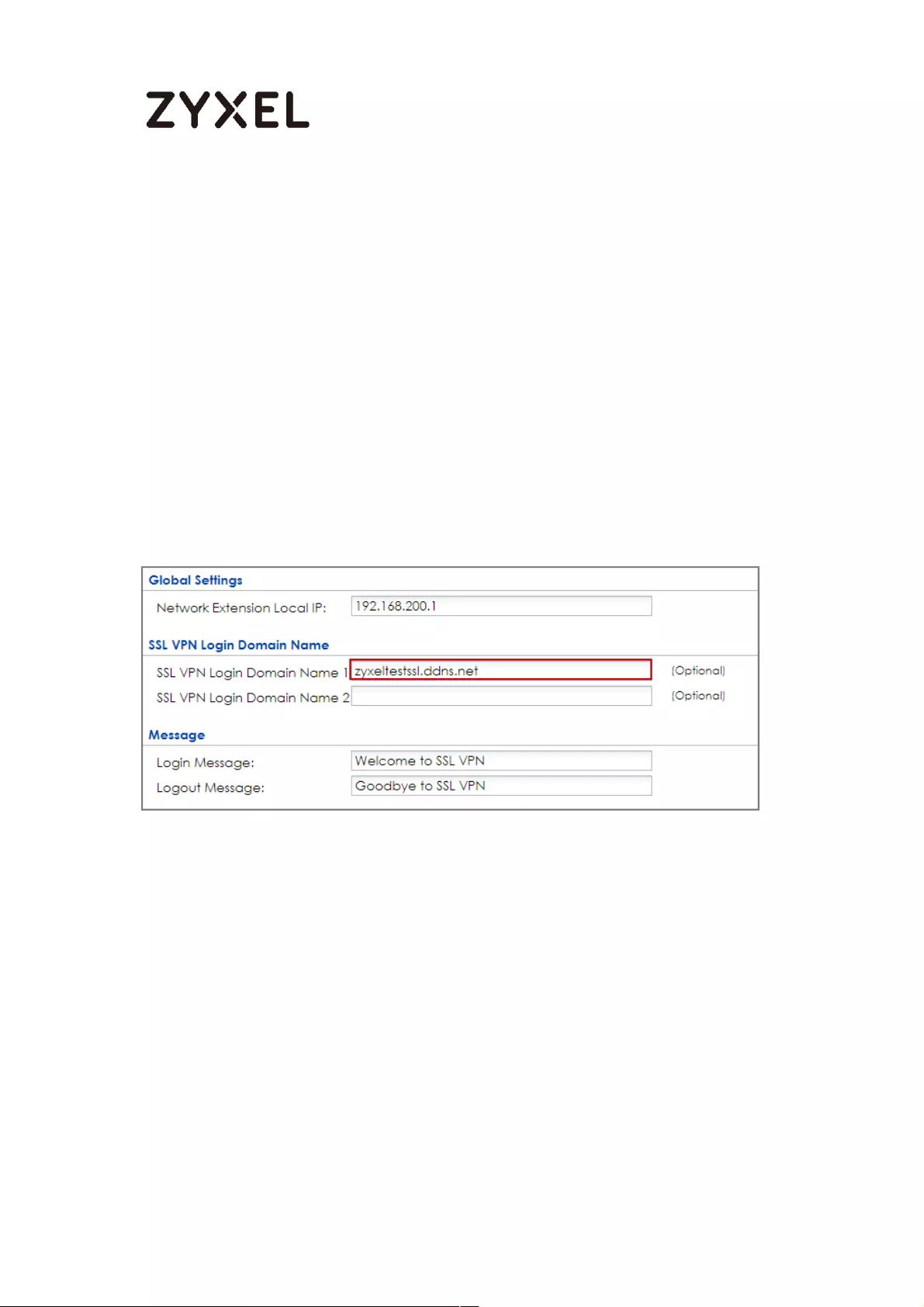
337/782
www.zyxel.com
Set Up the DNS Service
In this scenario, you need to have a DNS host to fulfill the requirement. In this
example, go to https://www.noip.com/ to register an account and create a
DNS host. The following mapping IP address is the public IP of the ZyWALL/USG's
WAN IP address.
Set Up the ZyWALL/USG SSL VPN Setting
In the ZyWALL/USG, go to CONFIGURATION > VPN > SSL VPN > Global Setting
> SSL VPN Login Domain Name and type in the DNS domain name.
CONFIGURATION > VPN > SSL VPN > Global Setting > SSL VPN Login Domain Name
Use SSL VPN, you need to allow users to access the HTTPS service. Go
to CONFIGURATION > Security Policy > Policy Control. Make sure the security
policy allows HTTPS traffic from the WAN interface to the ZyWALL (the example
shows the default settings).
CONFIGURATION > Security Policy > Policy Control
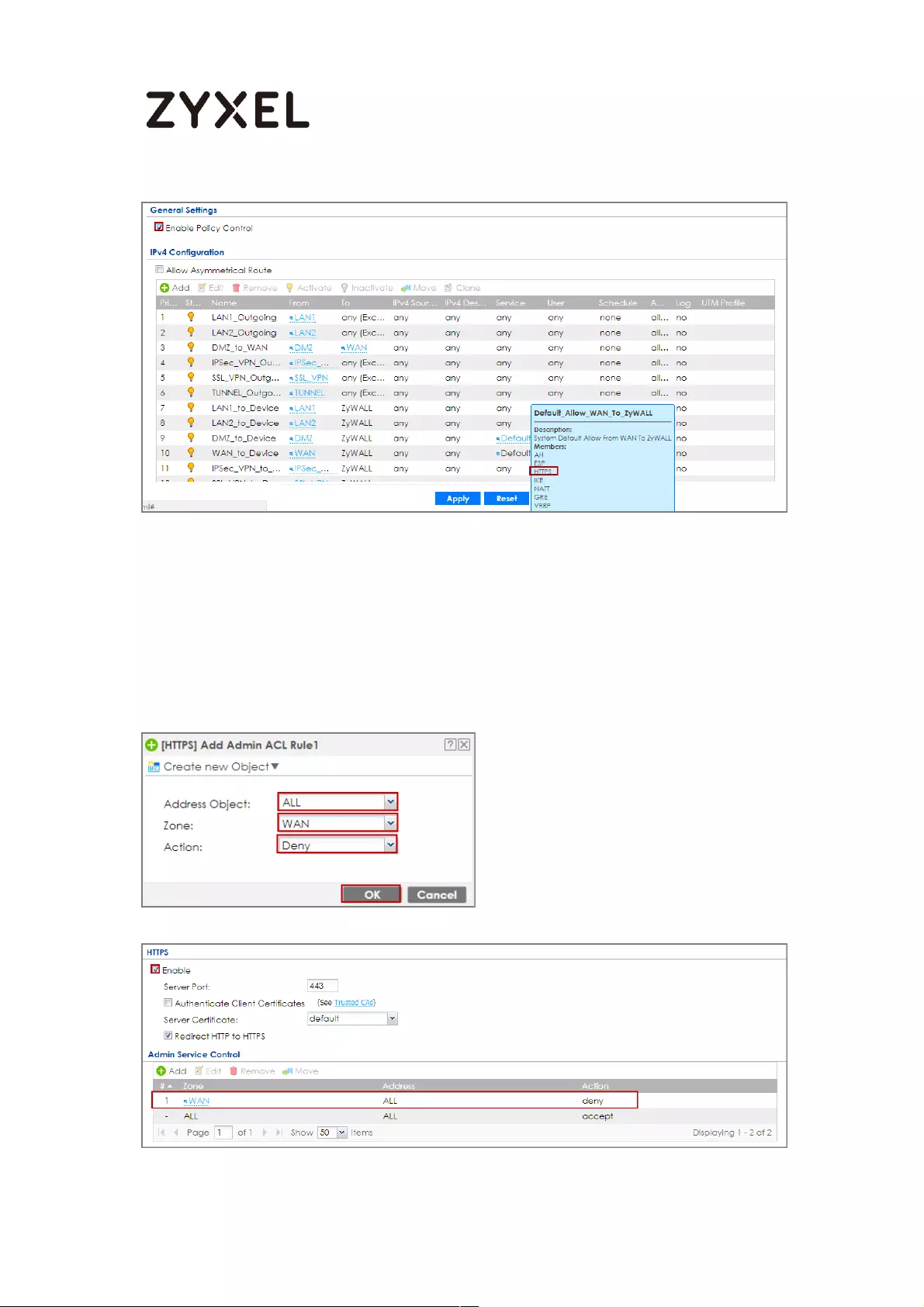
338/782
www.zyxel.com
Set Up the ZyWALL/USG System Setting
Go to CONFIGURATION > System > WWW > Admin Service Control > Add Admin
ACL Rule 1. Set the address access action as Deny for ALL address in WAN.
CONFIGURATION > System > WWW > Admin Service Control > Add Admin ACL Rule 1

339/782
www.zyxel.com
Test the SSL VPN
Type in the URL (https://sslvpnzyxeltest.ddns.net) and you will only see the SSL
VPN Login button in the web portal screen.
Type in the URL (https://sslvpnzyxeltest.ddns.net)
Login to the device via the WAN interface with the administrator's user name
and password. The screen will show Login denied.
340/782
www.zyxel.com
Login to the device via the WAN interface
Login to the device via the LAN interface with the administrator's user name and
password. The management portal will be displayed.

341/782
www.zyxel.com
Login to the device via the LAN interface

342/782
www.zyxel.com
Go to MONITOR > Log. You can see that the admin login has been denied
access from the WAN interface but it is allowed from the LAN interface.
MONITOR > Log

343/782
www.zyxel.com
How to Deploy SSL VPN with Apple Mac OS X 10.10
Operating System
This is an example of using the ZyWALL/USG SSL VPN client software in Apple MAC
OS X 10.10 Yosemite operating systems for secure connections to the network
behind the ZyWALL/USG. When the VPN tunnel is configured, users can securely
access the network from a Mac OS X 10.11 Yosemite computer.
ZyWALL/USG SSL VPN with Apple MAC OS X 10.10 Yosemite
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG110 (Firmware Version: ZLD 4.25) and Apple MAC (Version: OS X10.10
Yosemite).
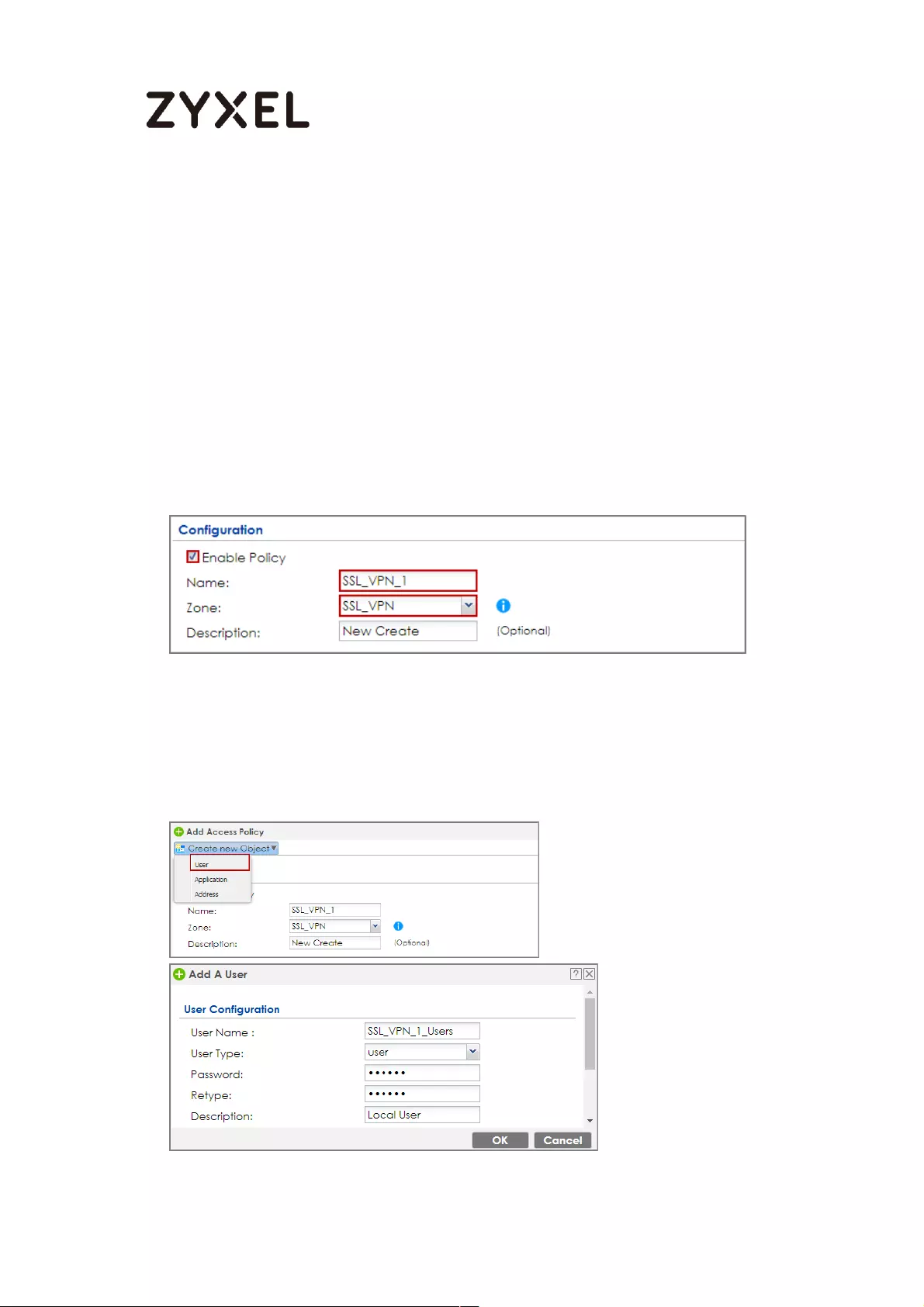
344/782
www.zyxel.com
Set Up the SSL VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > VPN > SSL VPN > Access Privilege to
add an Access Policy. Configure a Name for you to identify the SSL VPN
configuration.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy >
Configuration
Go to Create new Object > User to add User Name (SSL_VPN_1_Users in this
example) and Password (4-24 characters, zyx168 in this example), click OK.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy > Create
new Object > User
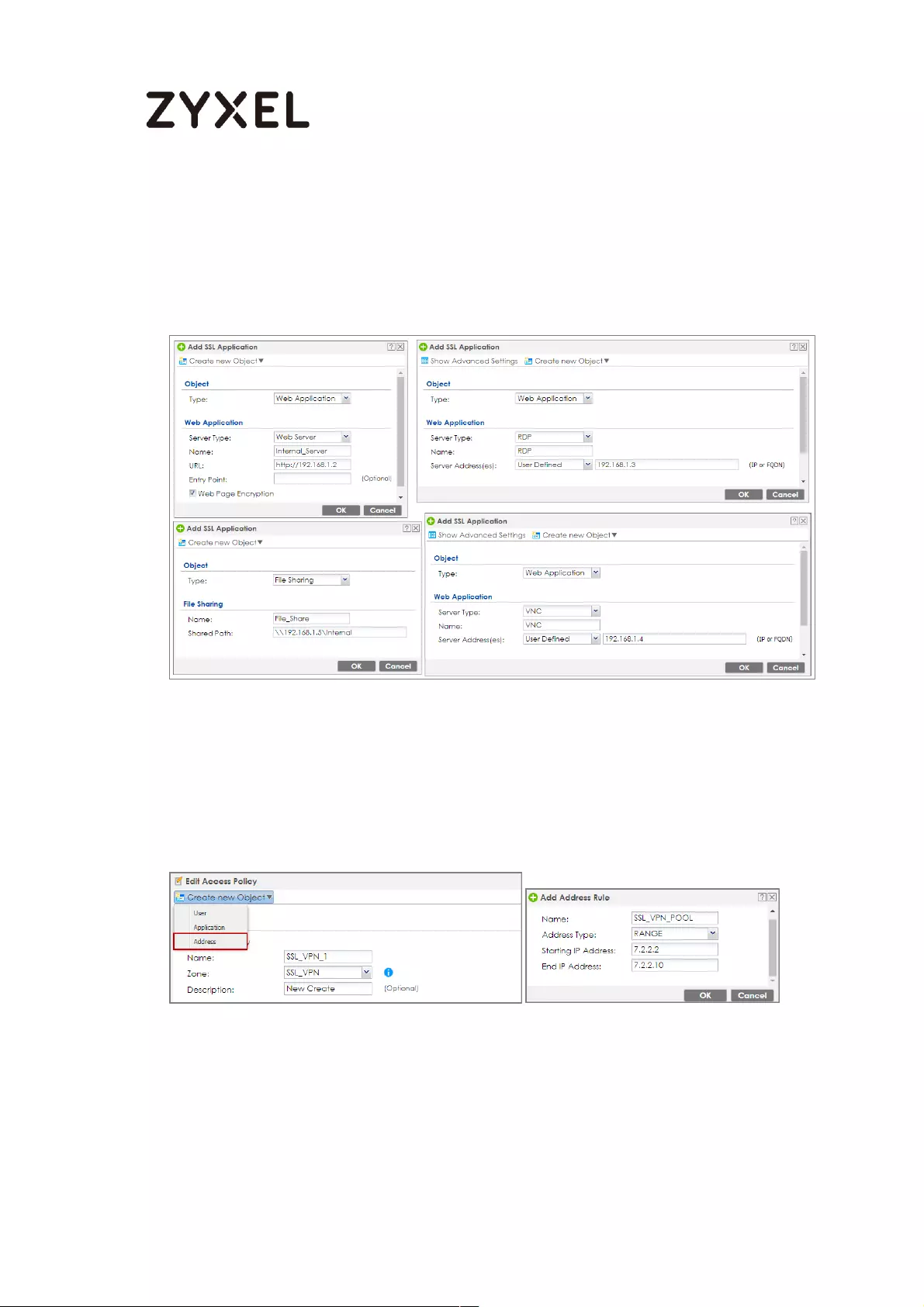
345/782
www.zyxel.com
Go to Create new Object > Application to add servers you allow SSL_VPN_1_Users
to access, click OK.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy > Create
new Object > Application
Go to Create new Object > Address to add the IP address pool for
SSL_VPN_1_Users.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy > Create
new Object > Address
Then, move the just created address object to Selected User/Group Objects.
Similarly, in SSL Application List (Optional) move the servers you want available to
SSL users to Selected Appellation Objects.
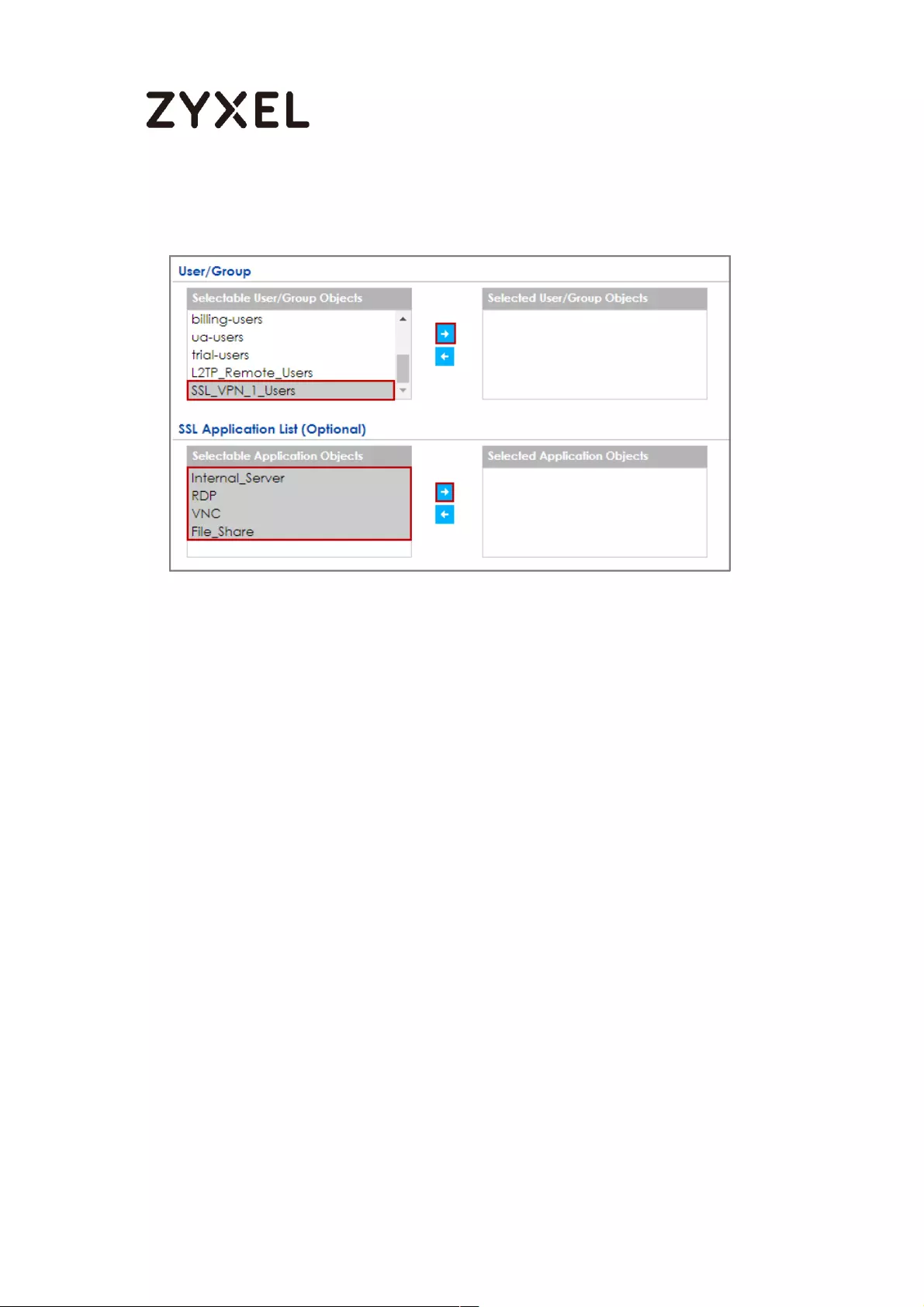
346/782
www.zyxel.com
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy >
User/Group & SSL Application
Scroll down to Network Extension (Optional) to select Enable Network Extension to
allow SSL VPN users to access the resources behind the ZyWALL/USG local
network.
Select network(s) name in the Selectable Address Objects list and click the right
arrow button to add to the Selected Address Objects list. You can select more
than one network.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy > Network
Extension (Optional)
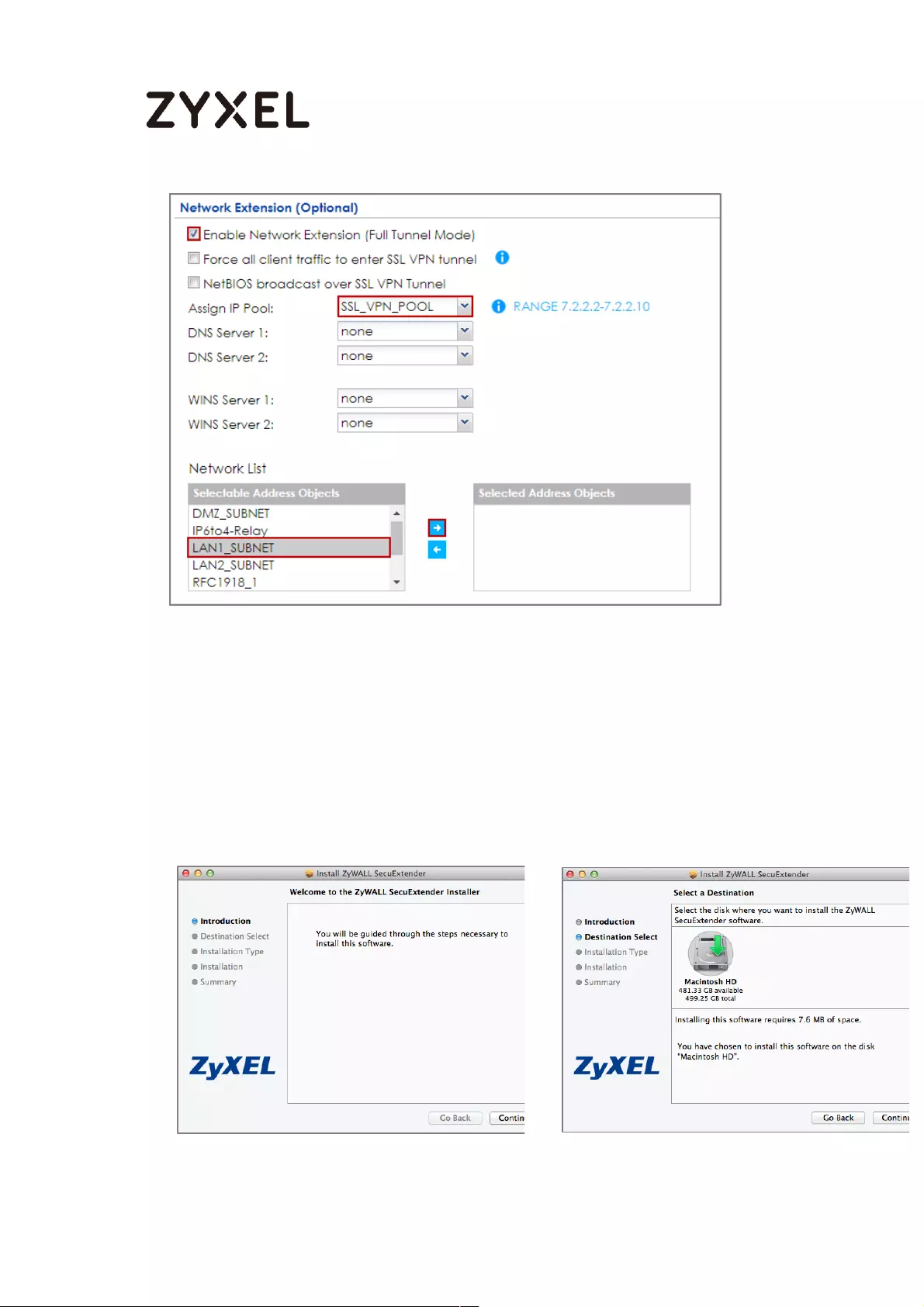
347/782
www.zyxel.com
Set Up the SSL VPN Tunnel on the Apple MAC OS X 10.10
Operating System
Download SSL VPN Client software: ZyWALL SecuExtender for MAC from the ZyXEL
Global Website and double-click on the downloaded file to install it.
348/782
www.zyxel.com
Go to ZyWALL SecuExtender > Preferences, click the "+" button at the bottom left
to add a new SSL VPN connection.

349/782
www.zyxel.com
Configure the Connection Name for you to identify the SSL VPN configuration.
Then, set the Remote Server Address to be the WAN IP of ZyWALL/USG (172.16.1.33
in this example). Click Save.
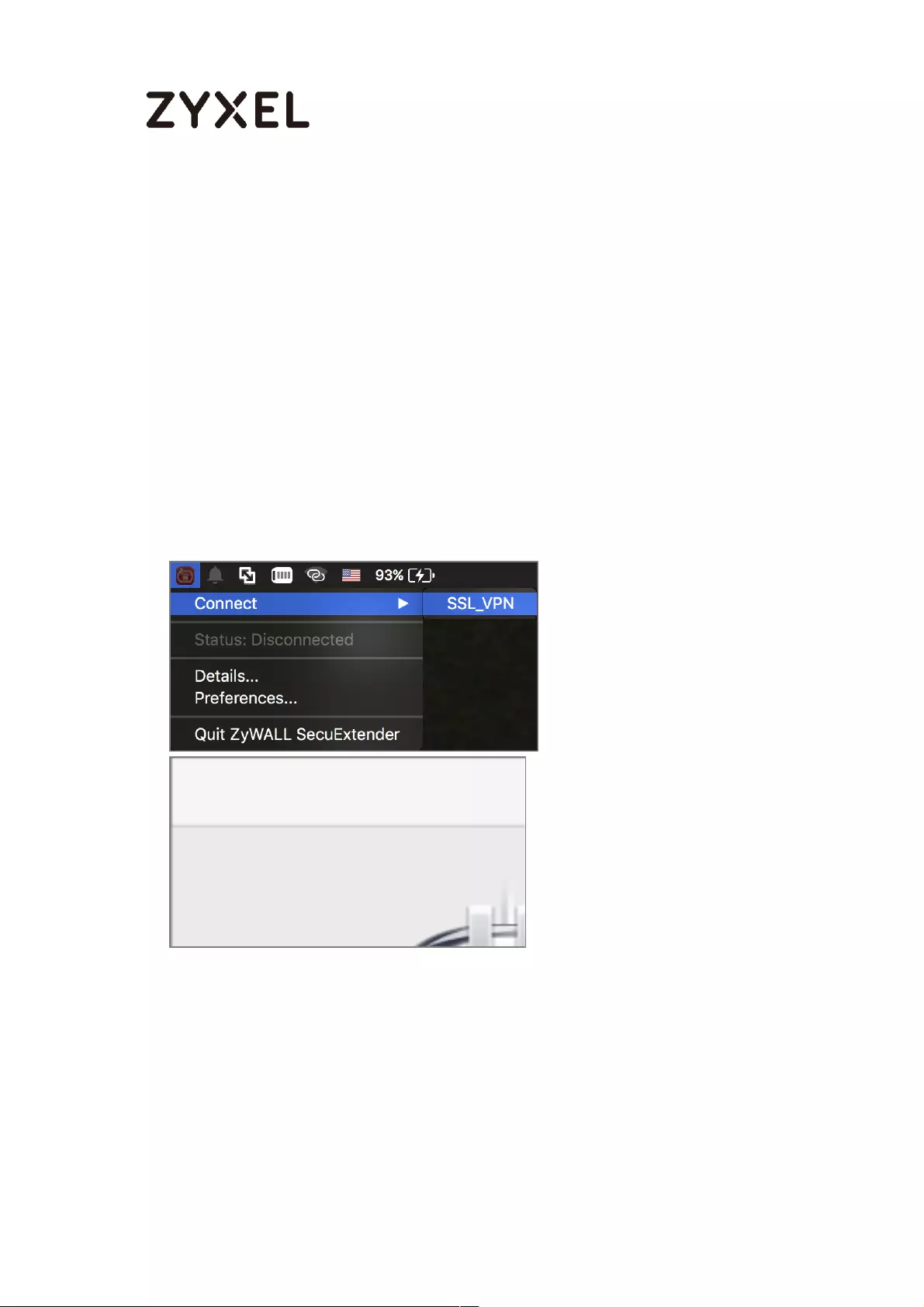
350/782
www.zyxel.com
Here are two methods to initiate SSL VPN connections:
From ZyWALL SecuExtender
From a Web Browser
From ZyWALL SecuExtender
Go to ZyWALL SecuExtender > Connect > SSL_VPN, to display the username and
password dialog box. Set Username and Password to be the same as your
ZyWALL/USG SSL VPN Selected User/Group name and password
(SSL_VPN_1_Users/zyx168 in this example).
From a Web Browser
Type ZyWALL/USG’s WAN IP into the browser, to display the login screen. Enter
User Name and Password to be the same as your ZyWALL/USG SSL VPN Selected
User/Group name and password (SSL_VPN_1_Users/zyx168 in this example). Click
SSL VPN.
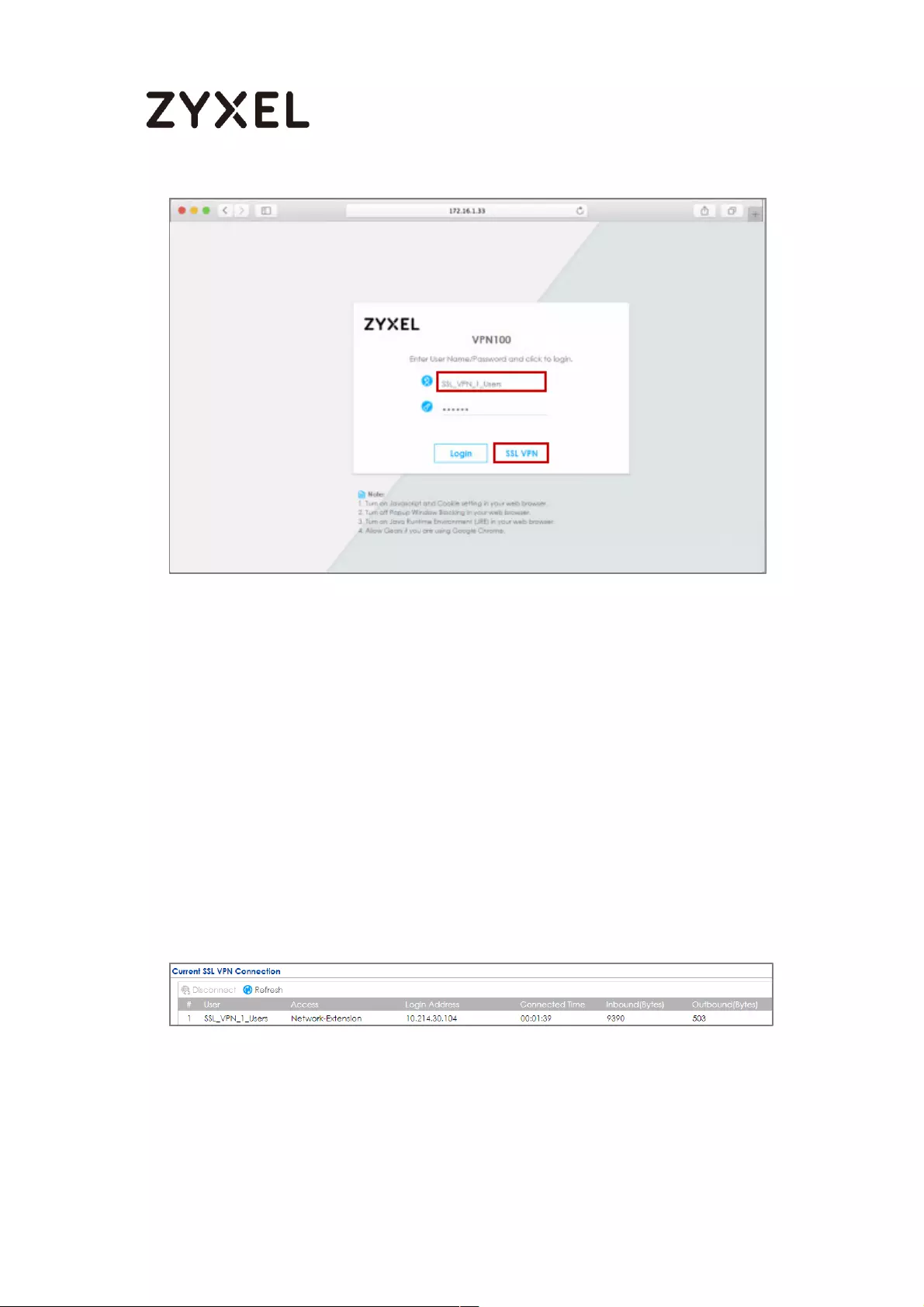
351/782
www.zyxel.com
Test the SSL VPN Tunnel
Go to ZyWALL/USG MONITOR > VPN Monitor > SSL and verify the tunnel Login
Address, Connected Time and the Inbound(Bytes)/Outbound(Bytes) traffic.
MONITOR > VPN Monitor > SSL > SSL_VPN_1_Users
Go to ZyWALL SecuExtender > Details and check Traffic Graph, Network Traffic
Statics and Log Details.
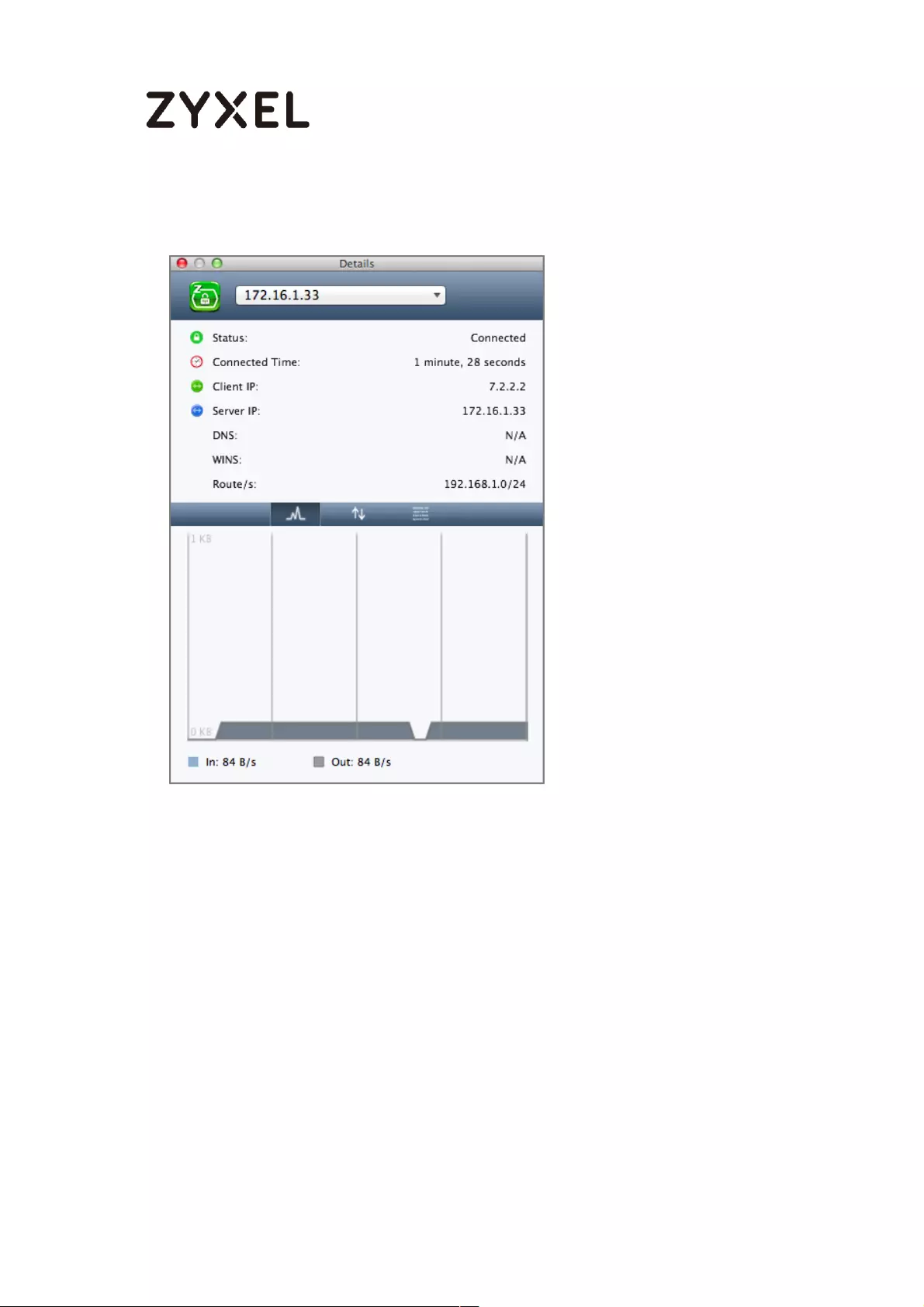
352/782
www.zyxel.com
ZyWALL SecuExtender > Details > Traffic Graph
ZyWALL SecuExtender > Details > Network Traffic Statics
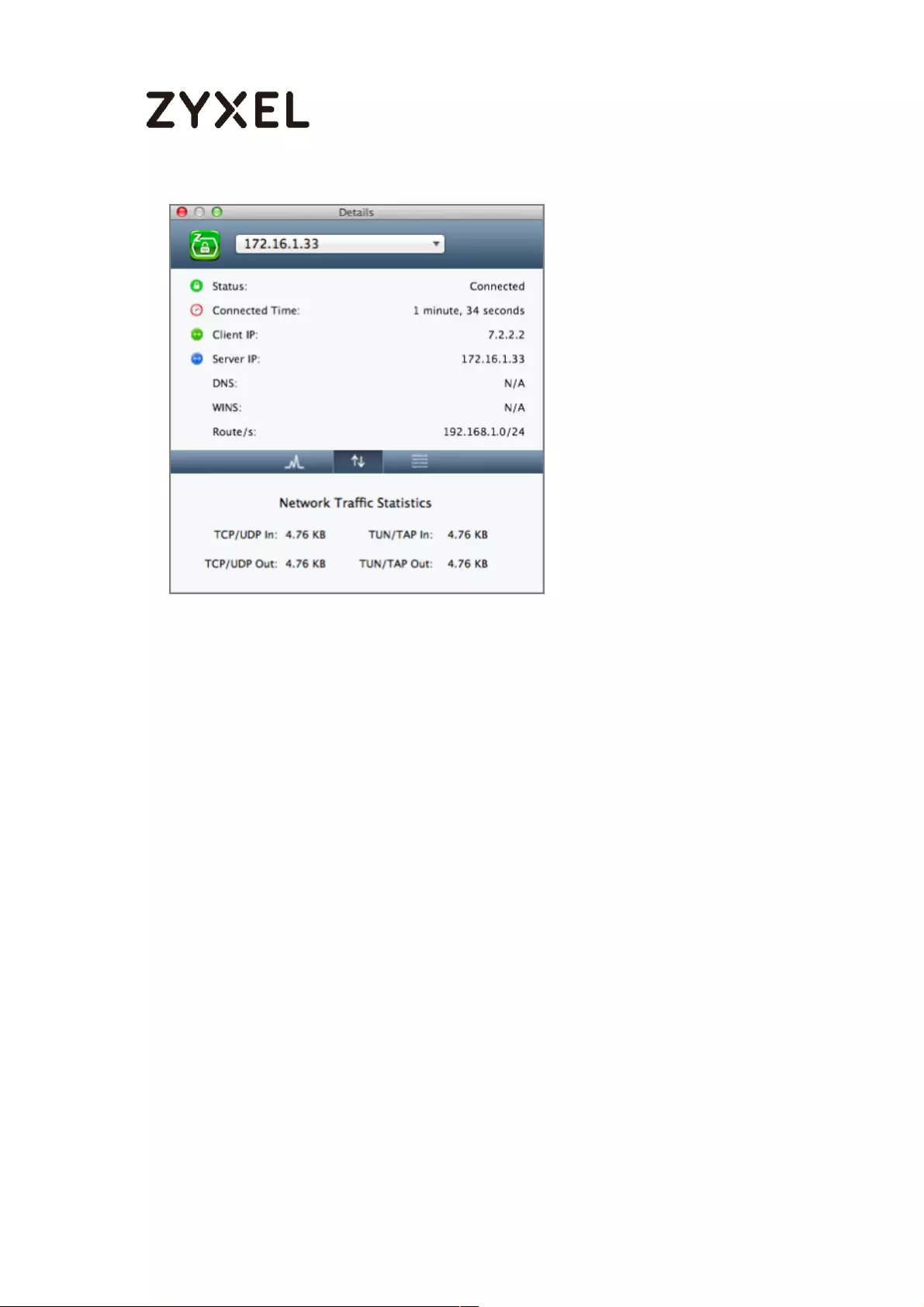
353/782
www.zyxel.com
ZyWALL SecuExtender > Details > Log Details
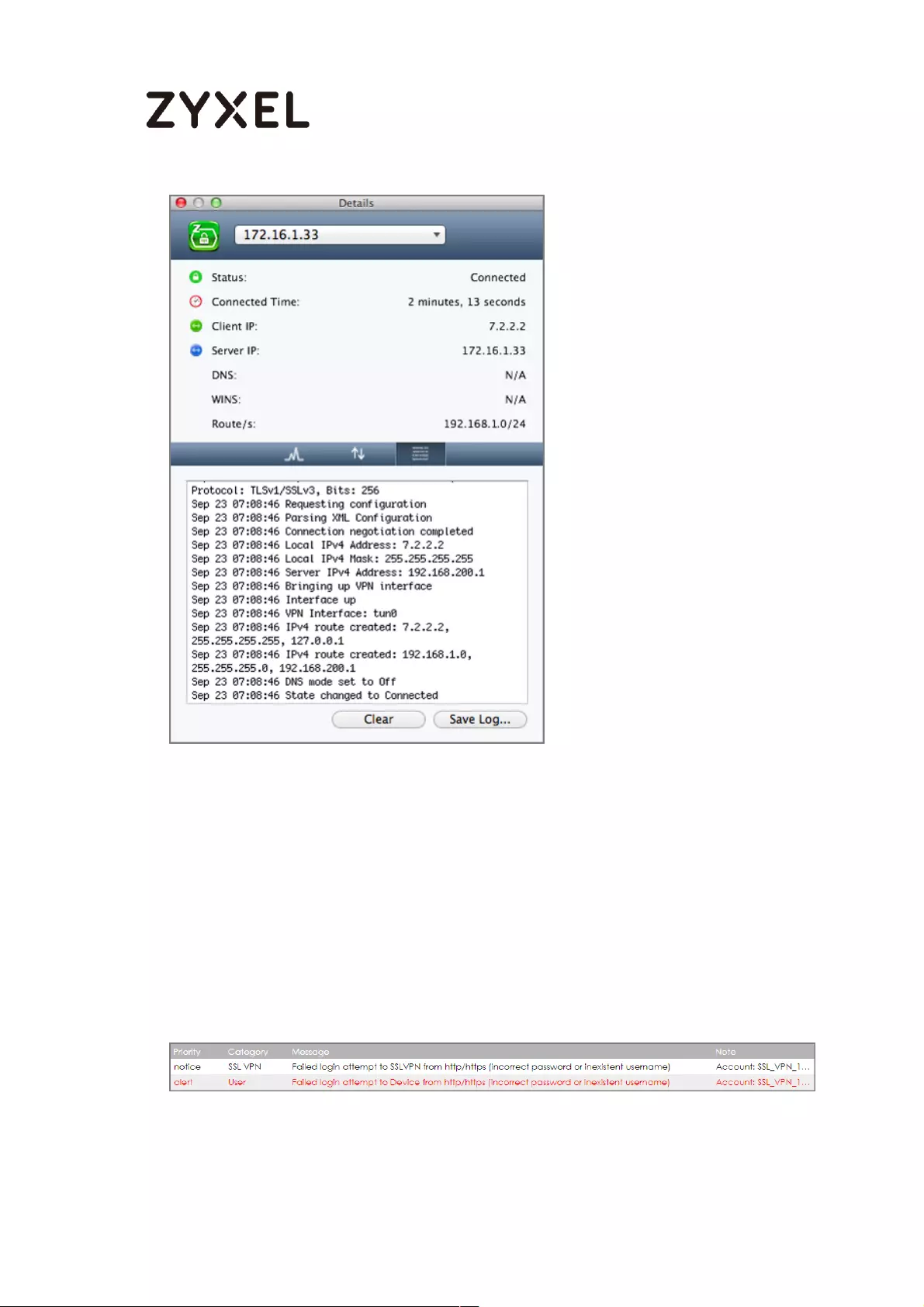
354/782
www.zyxel.com
What Could Go Wrong?
If you see [notice] or [alert] log message such as below, please check
ZyWALL/USG SSL Selected User/Group Objects settings. MAC OS X 10.10 Yosemite
users must use the same Username and Password as configured in ZyWALL/USG to
establish the SSL VPN tunnel.

355/782
www.zyxel.com
If you uploaded a logo to show in the SSL VPN user screens but it does not display
properly, check that the logo graphic is in GIF, JPG, or PNG format. The graphic
should use a resolution of 103 x 29 pixels to avoid distortion when displayed. The
ZyWALL/USG automatically resizes a graphic of a different resolution to 103 x 29
pixels. The file size must be 100 kilobytes or less. Transparent background is
recommended.
If users can log into the SSL VPN but cannot see some of the resource links check
the SSL application object’s configuration.
If the ZyWALL/USG redirects the user to the user aware screen, check whether the
user account is included in an SSL VPN access policy or not.
Changing the HTTP/HTTPS configuration disconnects SSL VPN network extension
sessions. Users need to re-connect if this happens.

356/782
www.zyxel.com
How To Configure SSL VPN for Remote Access Mobile
Devices
This is an example of using the ZyWALL/USG SSL VPN for remote access mobile
devices to securely connect to the File Sharing Server behind the ZyWALL/USG.
ZyWALL/USG SSL VPN for Secure External Access to Network Resources
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG1900 (Firmware Version: ZLD 4.25).
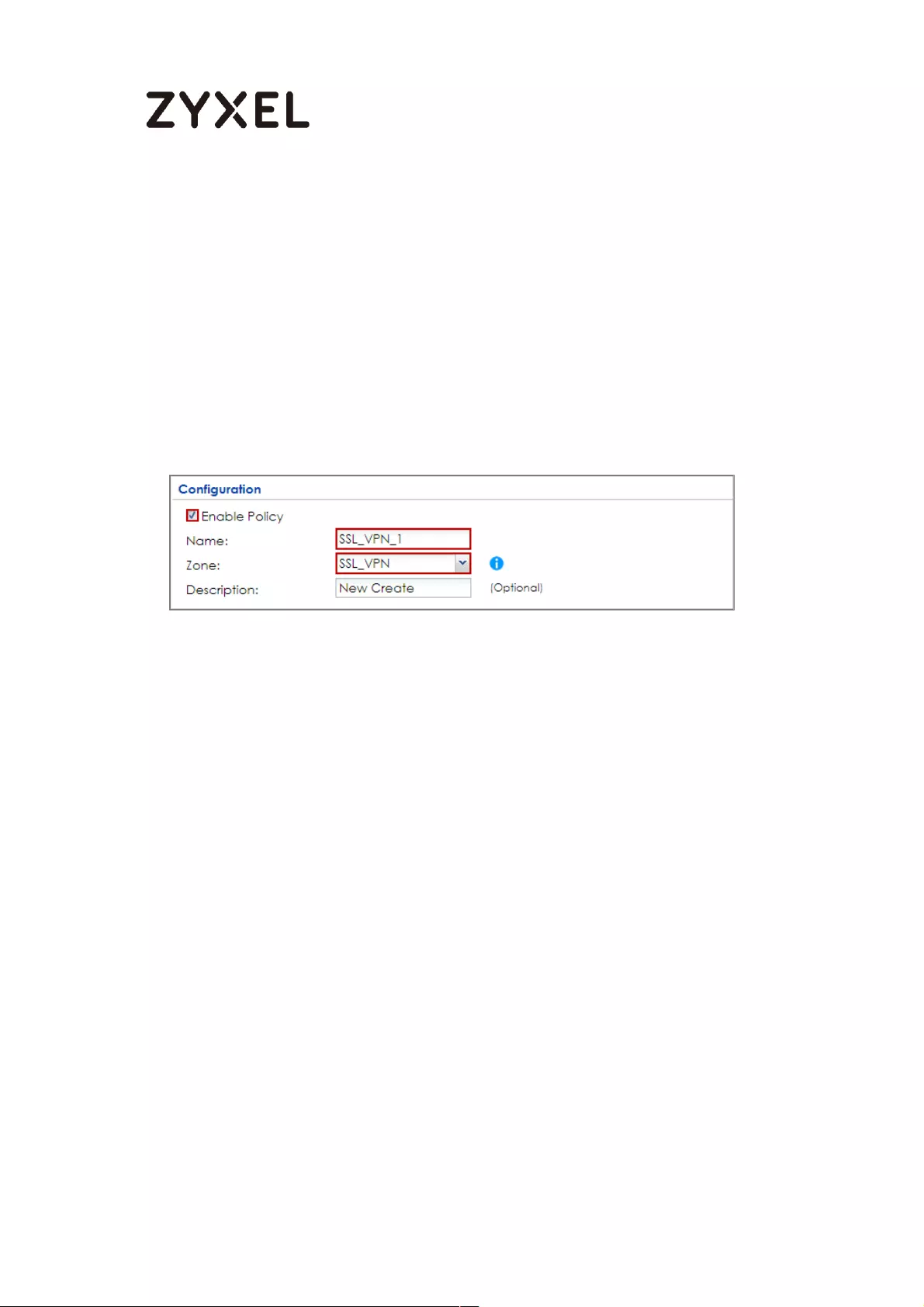
357/782
www.zyxel.com
Set Up the SSL VPN Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > VPN > SSL VPN > Access Privilege to
add an Access Policy. Configure a Name for you to identify the SSL VPN
configuration.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy >
Configuration
Go to Create new Object > User to add User Name (SSL_VPN_1_Users in this
example) and Password (4-24 characters, zyx168 in this example), click OK.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy > Create
new Object > User
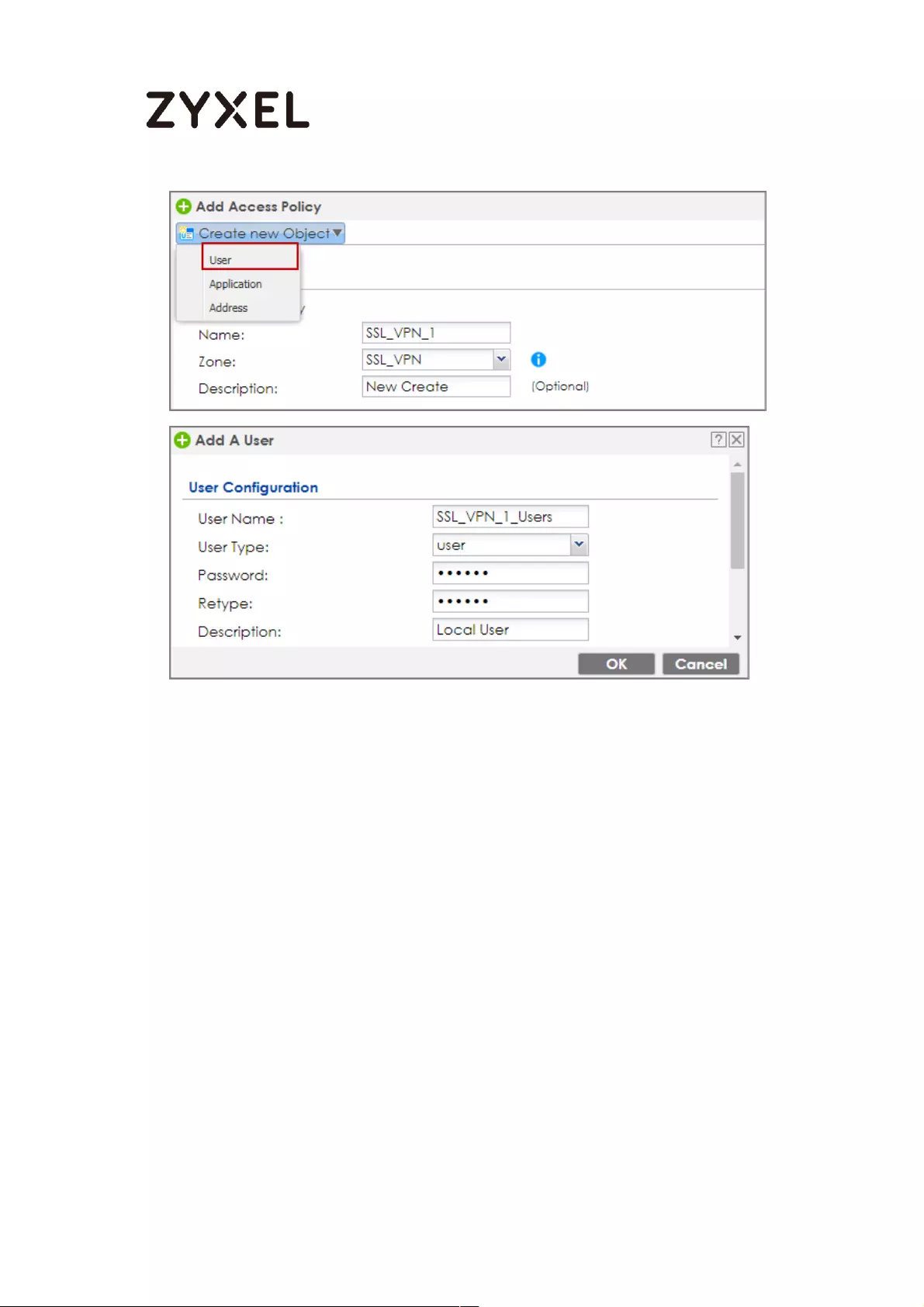
358/782
www.zyxel.com
Go to Create new Object > Application to add servers that you will allow
SSL_VPN_1_Users to access. Click OK.
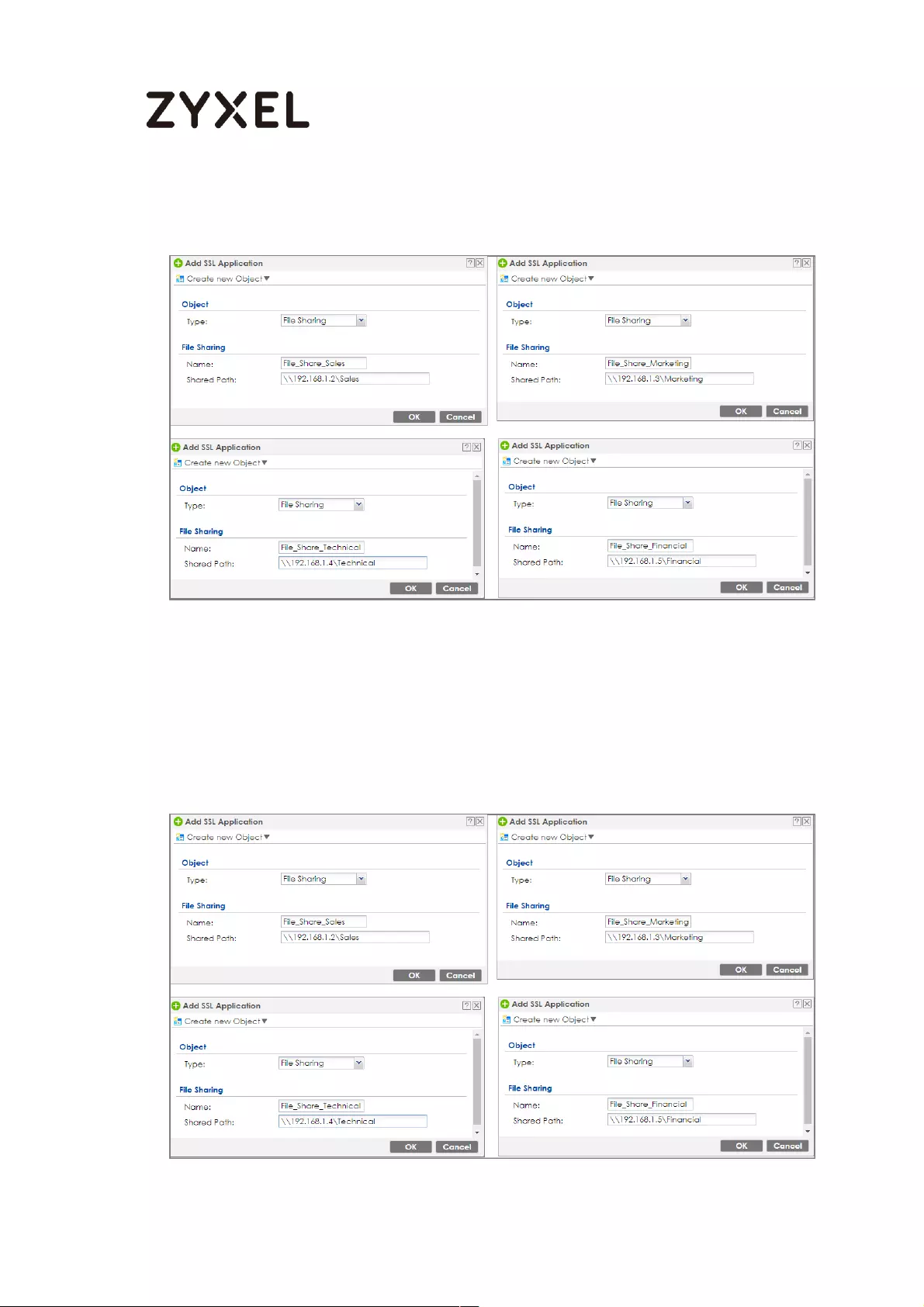
359/782
www.zyxel.com
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy > Create
new Object > Application
Then, move the just created address object to Selected User/Group Objects.
Similarly, in SSL Application List (Optional) move the servers you want available to
SSL users to Selected Application Objects.
CONFIGURATION > VPN > SSL VPN > Access Privilege > Access Policy >
User/Group & SSL Application
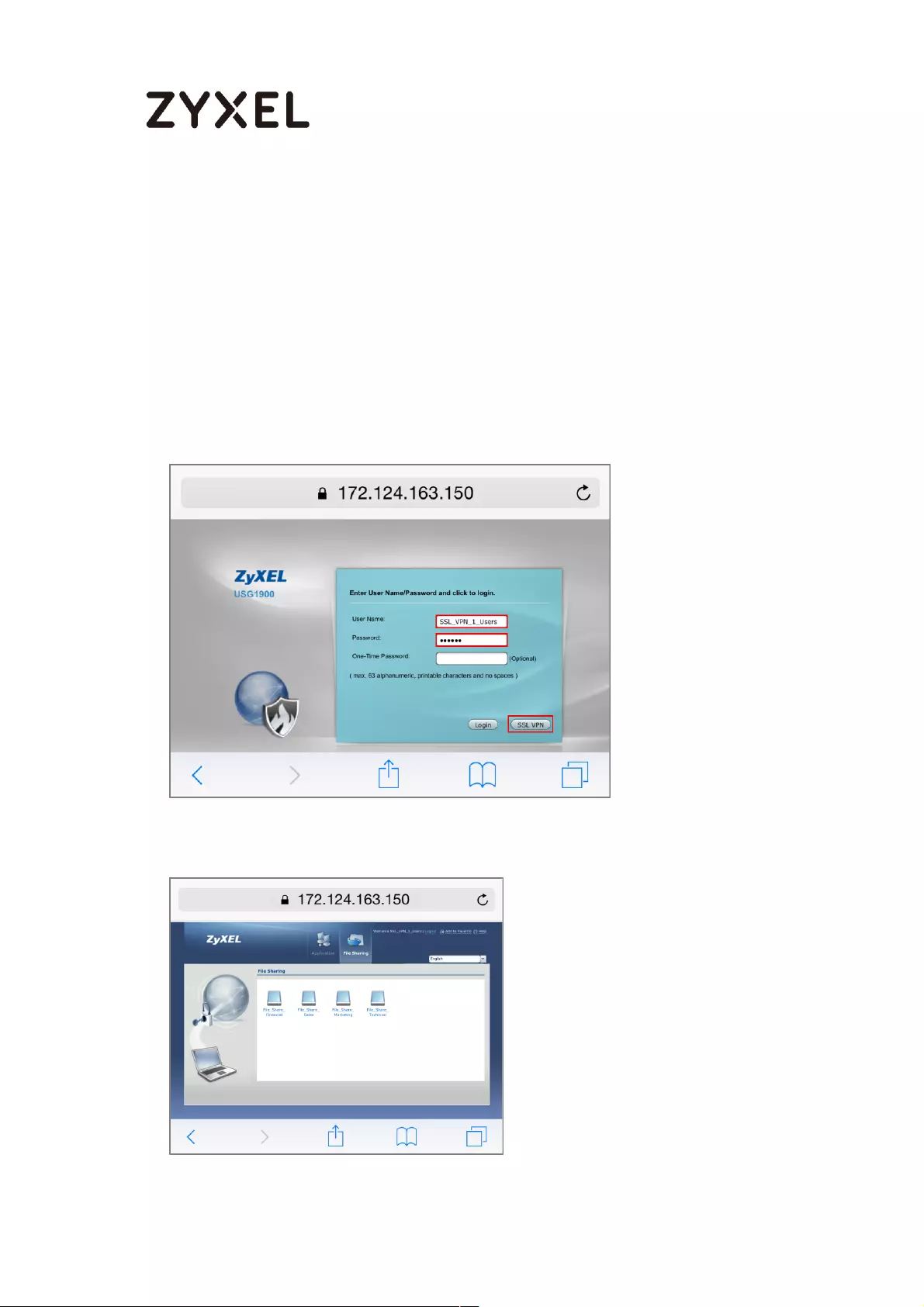
360/782
www.zyxel.com
Test the SSL VPN Tunnel
Type the ZyWALL/USG’s WAN IP into the browser, then the login screen appears.
Enter User Name and Password to be the same as your ZyWALL/USG SSL VPN
Selected User/Group name and password (SSL_VPN_1_Users/zyx168 in this
example). Click SSL VPN.
The File Sharing server appears.
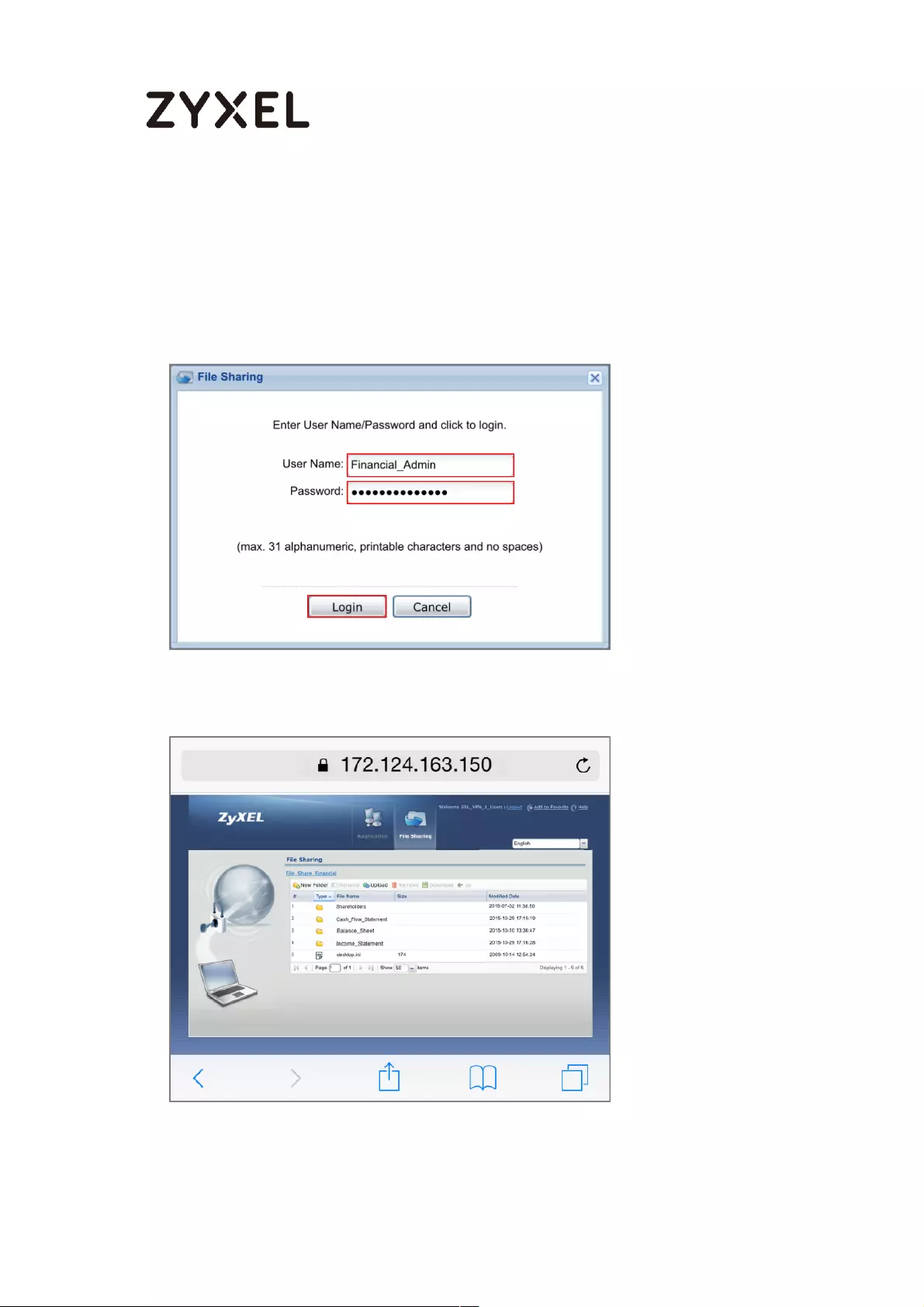
361/782
www.zyxel.com
Click the File Sharing folder you want to access, enter User Name/ Password of
your File Sharing server and click Login.
Now you can securely access the files.

362/782
www.zyxel.com
What Could Go Wrong?
If you see [notice] or [alert] log message such as below, please check
ZyWALL/USG SSL Selected User/Group Objects settings. Windows 10 users must use
the same Username and Password as configured in ZyWALL/USG to establish the
SSL VPN tunnel.
If you uploaded a logo to show in the SSL VPN user screens but it does not display
properly, check that the logo graphic is in GIF, JPG, or PNG format. The graphic
should use a resolution of 103 x 29 pixels to avoid distortion when displayed. The
ZyWALL/USG automatically resizes a graphic of a different resolution to 103 x 29
pixels. The file size must be 100 kilobytes or less. Transparent background is
recommended.
If users can log into the SSL VPN but cannot see some of the resource links check
the SSL application object’s configuration.
If the ZyWALL/USG redirects the user to the user aware screen, check whether the
user account is included in an SSL VPN access policy or not.
Changing the HTTP/HTTPS configuration disconnects SSL VPN network extension
sessions. Users need to re-connect if this happens.
363/782
www.zyxel.com
How to Configure an SSL VPN Tunnel (with SecuExtender
version 4.0.0.1) on the Windows 10 Operating System
Set up the SSL VPN Tunnel with Windows 10
Please download SecuExtender version 4.0.0.1 from the download library of
ZyXEL’s official website.
Before you start installing the SecuExtender, it is required to install the “Visual
C++ 2015 Redistributable” package first. Click Next, select I agree to the license
terms and conditions, and click Install to complete the Visual C++ 2015
Redistributable installation. After that, the setup wizard appears. Please note
that the users need to reboot their systems after the SecuExtender installation is
completed.
364/782
www.zyxel.com
365/782
www.zyxel.com

366/782
www.zyxel.com
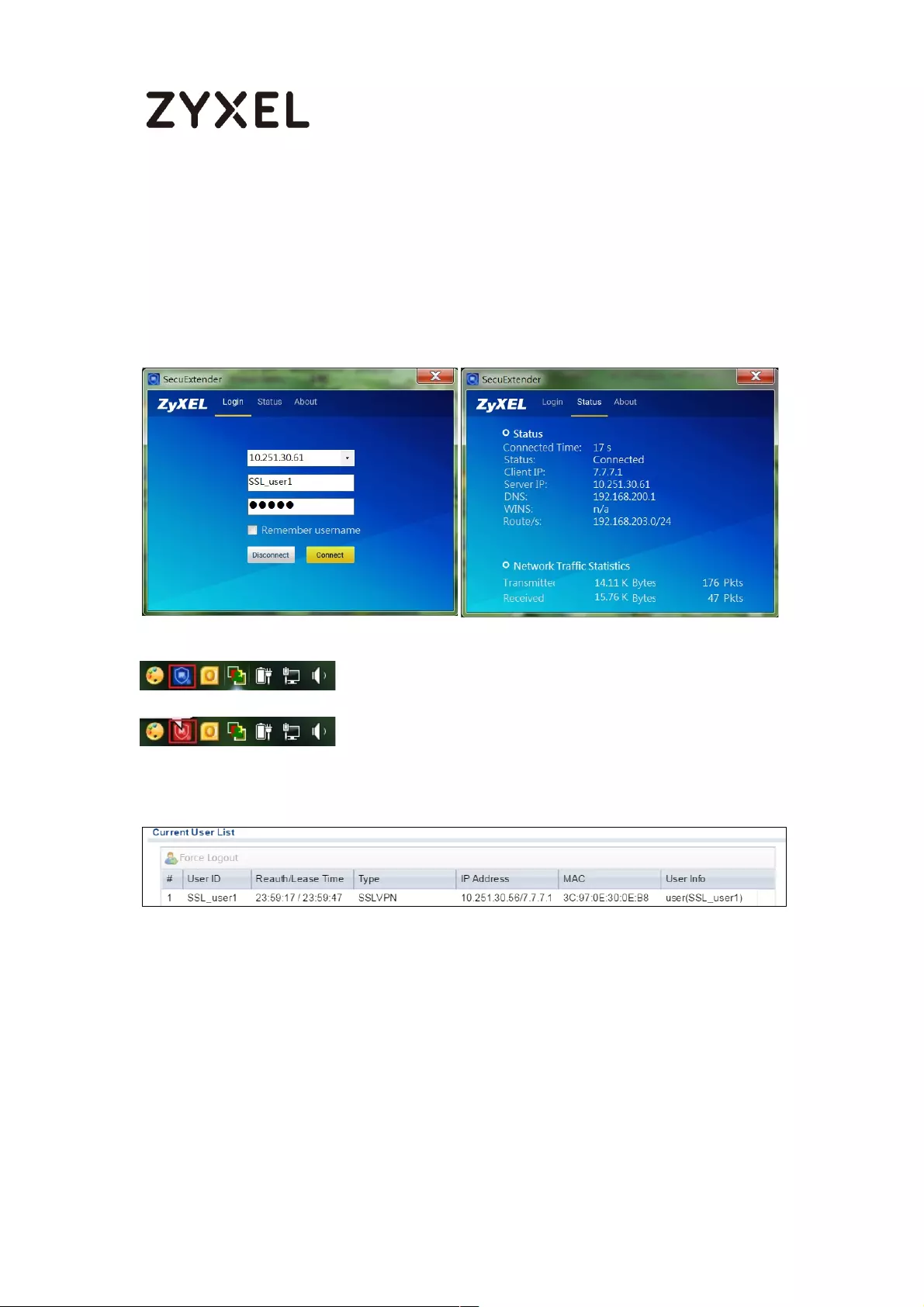
367/782
www.zyxel.com
Double-click the shortcut icon on your desktop. It is the same as the SSL VPN
standalone software on MAC OS X. Enter the server’s IP or domain name, user name,
and password to connect to the server. The example below shows that the client IP is
7.7.7.1 and you can also check the traffic statistic in the Status screen.
You can verify the connection status from the computer’s taskbar icon.
When connected, the icon is blue.
When disconnected, the icon is red.
You can also use the USG monitor screen to check the login list of the users.
What Can Go Wrong?
1 If you see a [notice] or [alert] log message such as shown below, please check
the ZyWALL/USG SSL’s Selected User/Group Objects settings. Windows 10 users
must use the same Username and Password as configured in the ZyWALL/USG to
establish the SSL VPN tunnel.
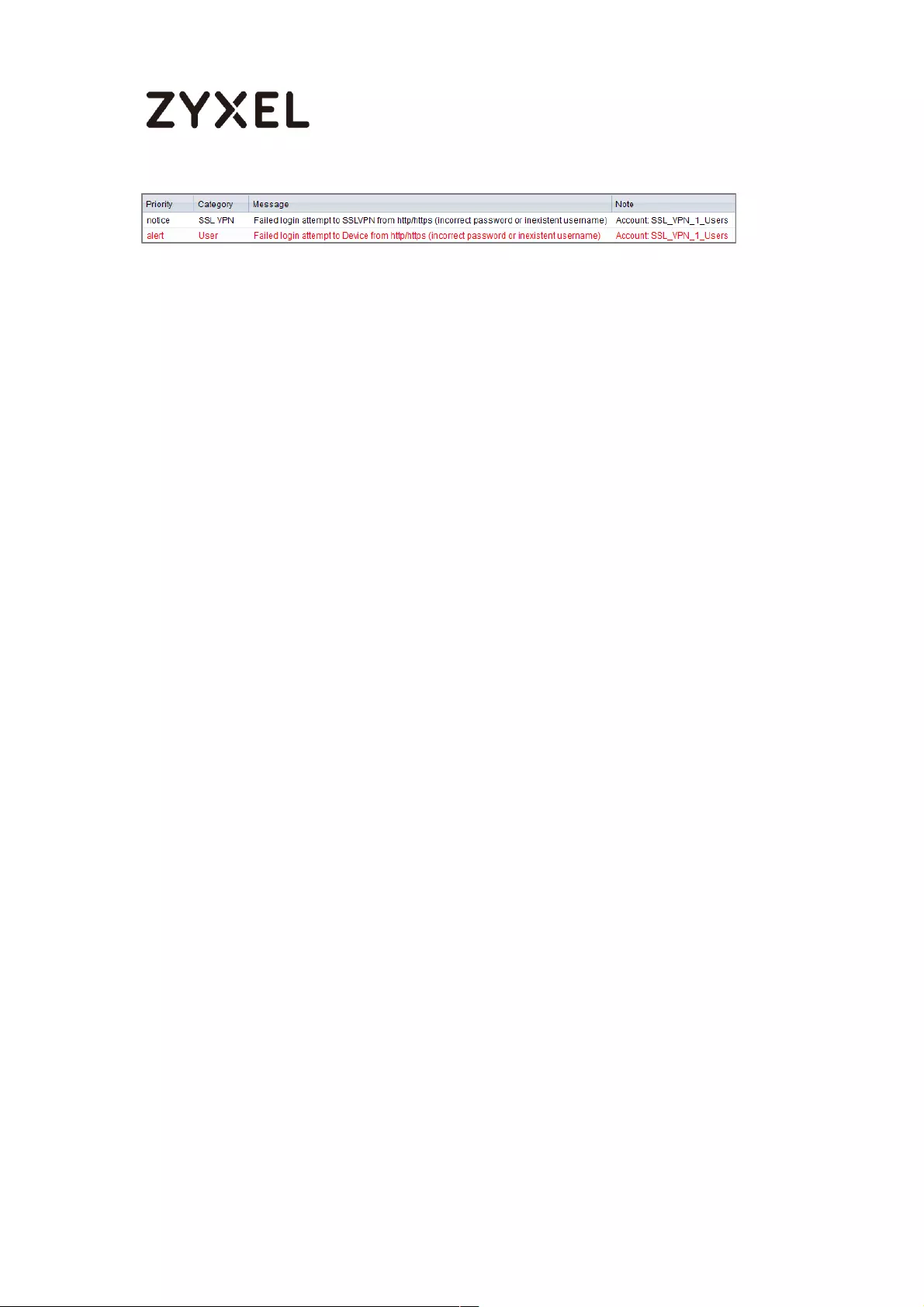
368/782
www.zyxel.com
2 If you have uploaded a logo to show on the SSL VPN user screens but it does not
display properly, check if the logo graphic is in GIF, JPG, or PNG format. The
graphic should use a resolution of 103 x 29 pixels to avoid distortion when
displayed. The ZyWALL/USG automatically resizes a graphic of a different
resolution to 103 x 29 pixels. The file size must be 100 kilobytes or less. Transparent
background is recommended.
3 If users can log into the SSL VPN but cannot see some of the resource links, check
the SSL application object’s configurations.
4 If the ZyWALL/USG redirects the user to the user aware screen, check whether the
user account is included in an SSL VPN access policy or not.
5 If you have changed the HTTP/HTTPS configuration, the SSL VPN network
extension sessions will be disconnected. The sessions need to be reconnected if
this happens.
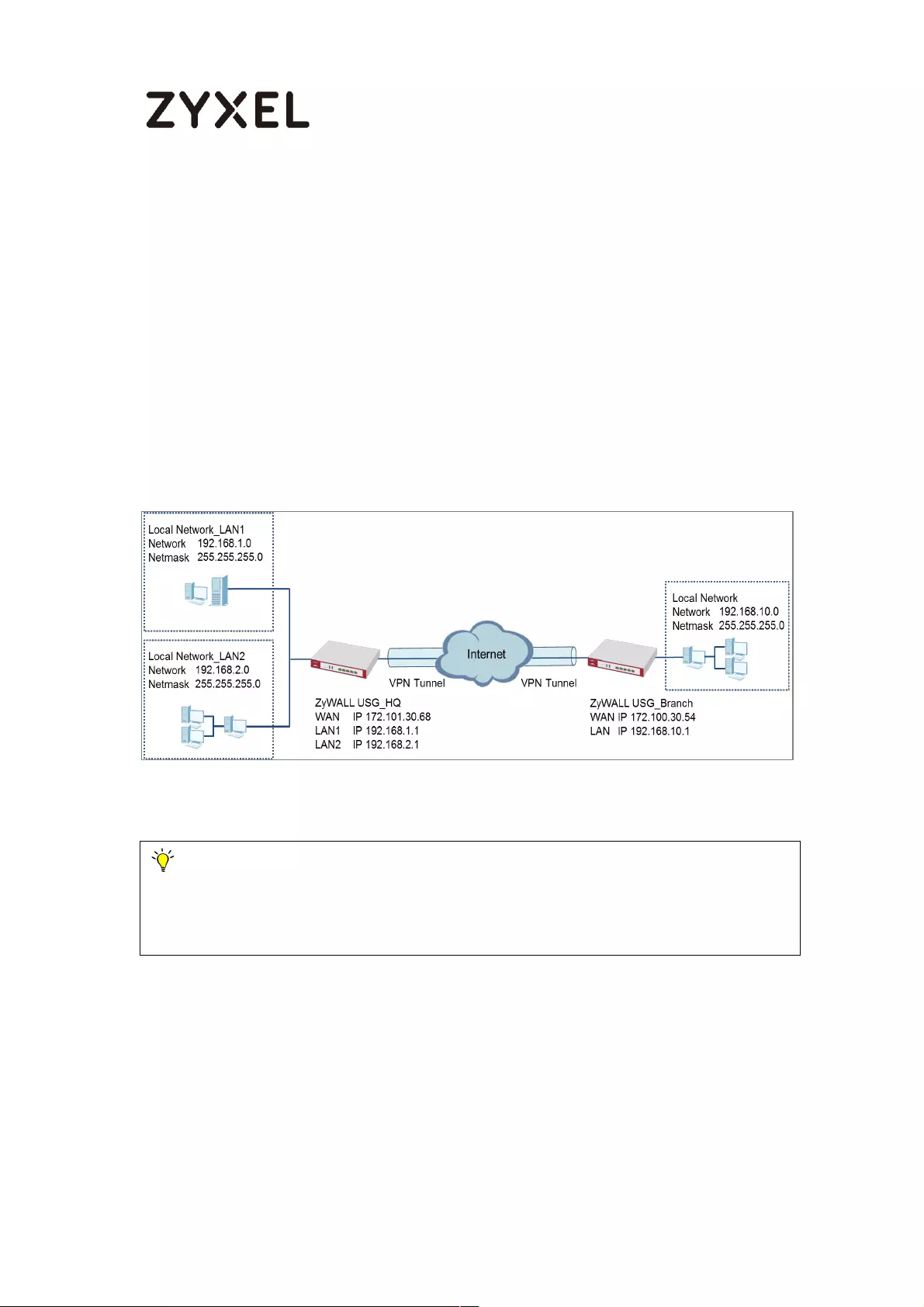
369/782
www.zyxel.com
How to redirect multiple LAN interface traffic to the VPN tunnel
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN
with multiple LAN access to the VPN tunnel. The example instructs how to
configure the VPN tunnel between each site and redirect multiple LAN interface
traffic to the VPN tunnel. When the VPN tunnel is configured, multiple LAN
subnets can be accessed securely.
ZyWALL Site-to-site IPSec VPN with multiple LAN access
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet masks.
This example was tested using USG310 (Firmware Version: ZLD 4.25).
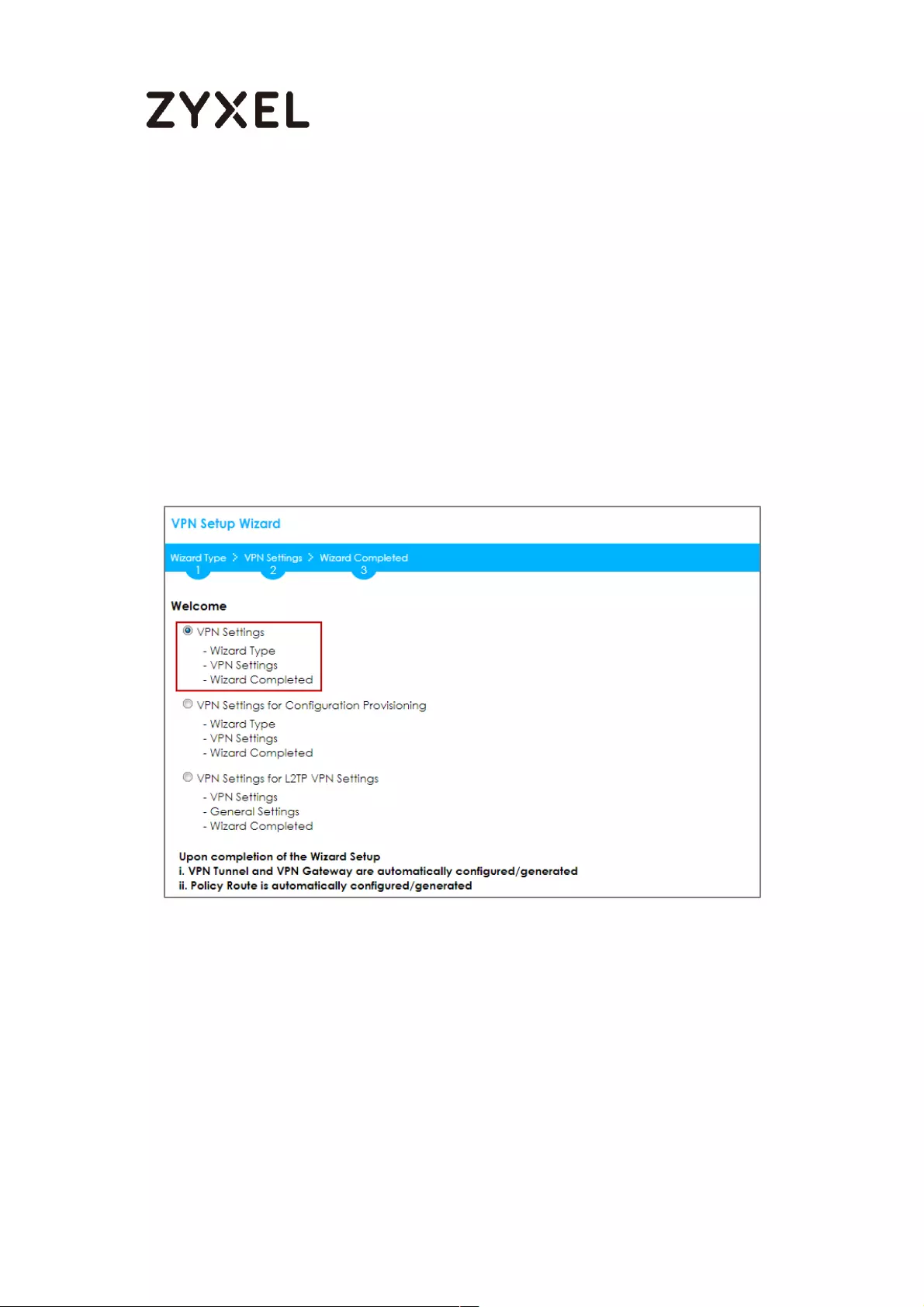
370/782
www.zyxel.com
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate Network
(HQ)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and use a pre-shared key to be the authentication method. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
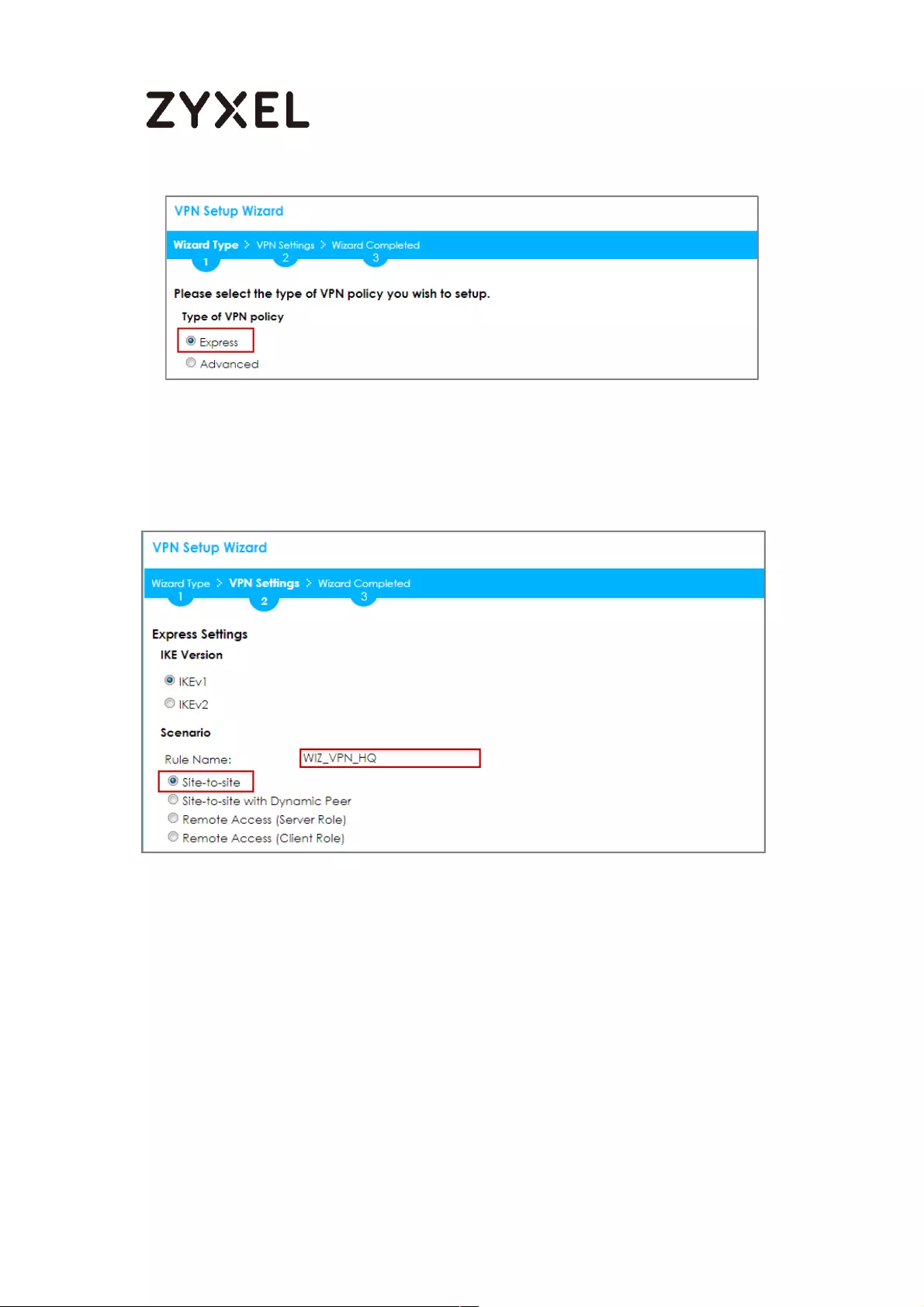
371/782
www.zyxel.com
Type the Rule Name used to identify this VPN connection (and VPN gateway). You may use 1-
31 alphanumeric characters. This value is case-sensitive. Select the rule to be Site-to-site. Click
Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.100.30.54). Type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the peer ZyWALL/USG.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
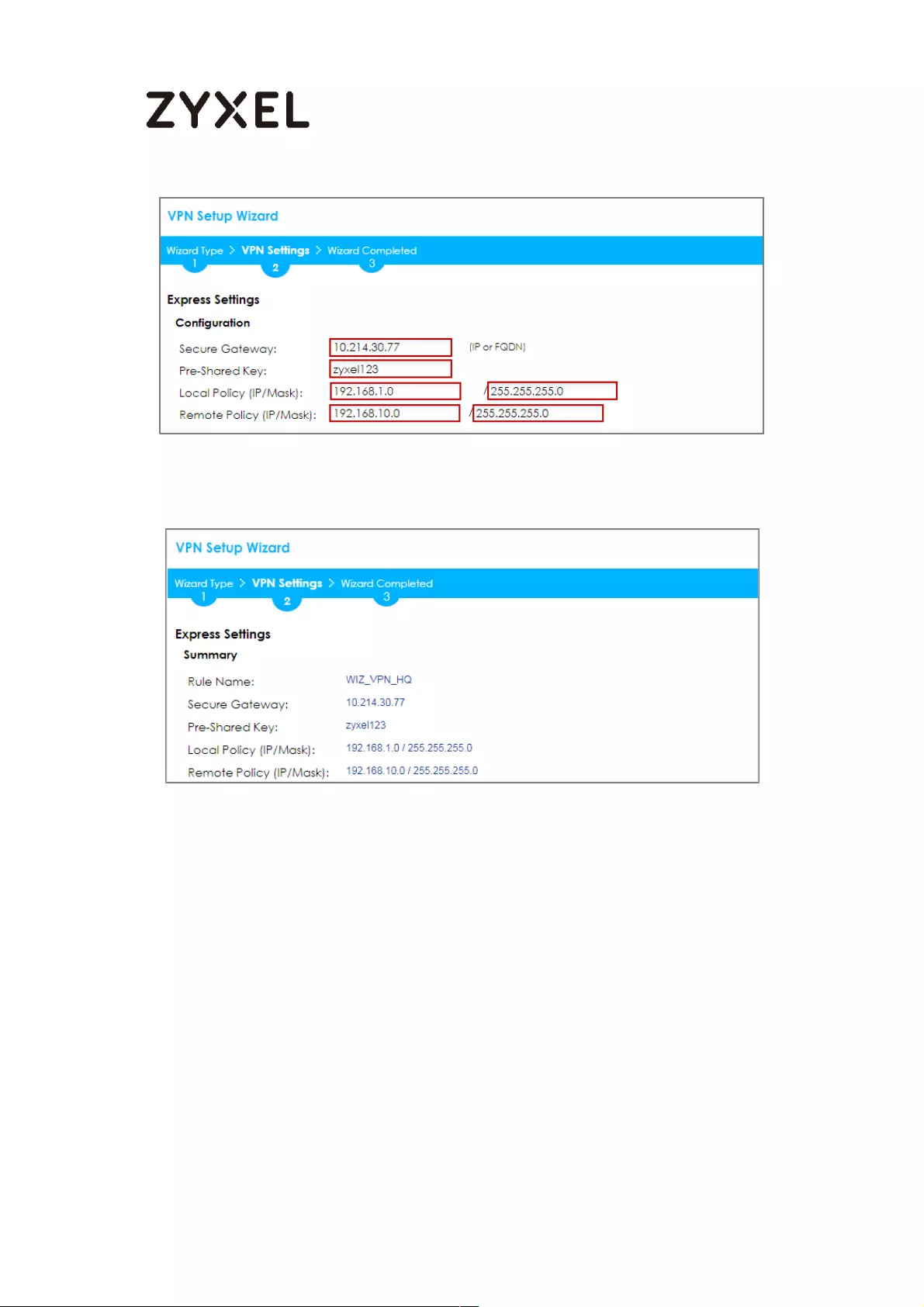
372/782
www.zyxel.com
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings > Wizard
Completed

373/782
www.zyxel.com
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec
router.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Set Up the ZyWALL/USG IPSec VPN Tunnel of Corporate
Network (Branch)
In the ZyWALL/USG, go to Quick Setup > VPN Setup Wizard, use the VPN Settings
wizard to create a VPN rule that can be used with the remote ZyWALL/USG. Click
Next.
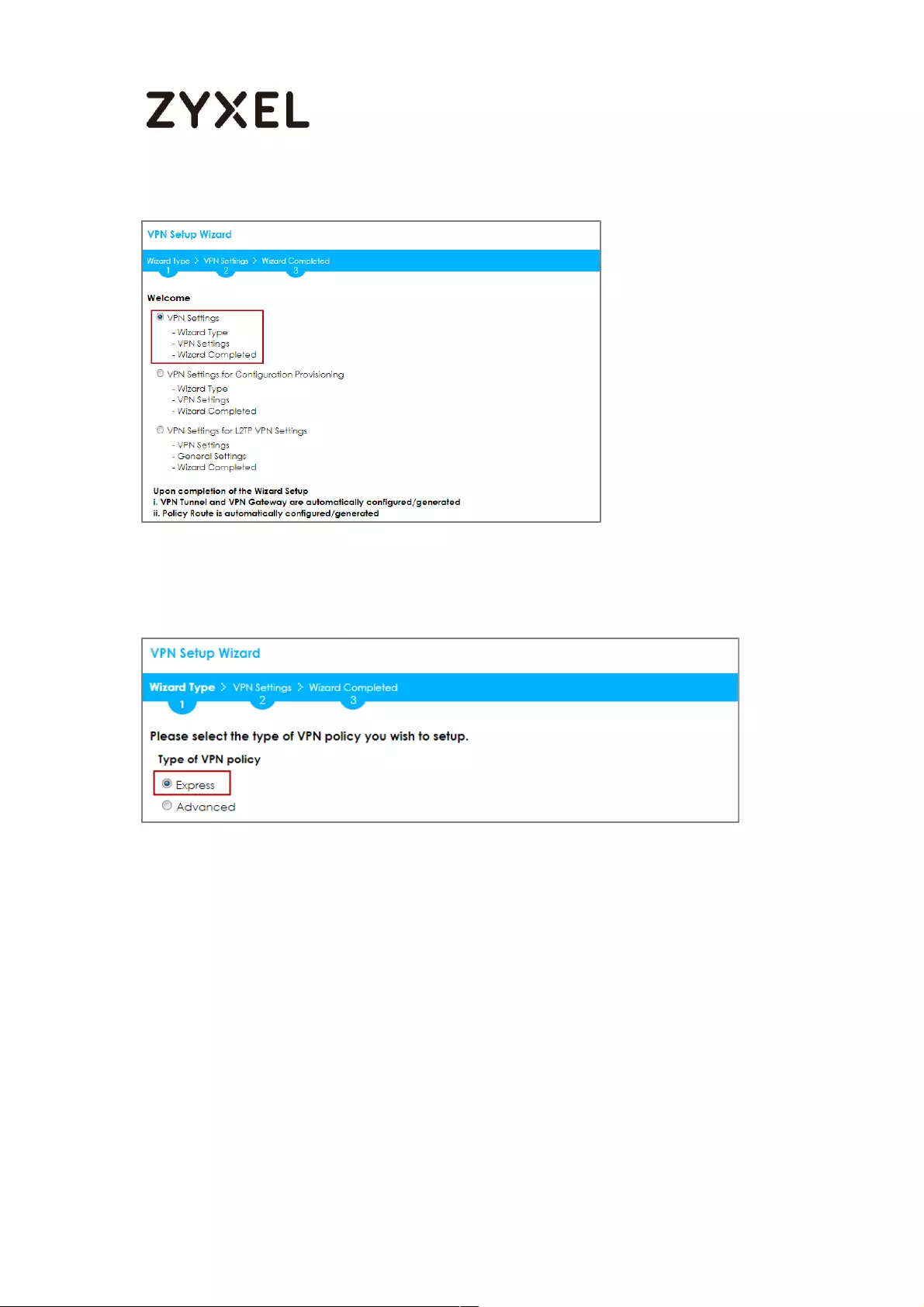
374/782
www.zyxel.com
Quick Setup > VPN Setup Wizard > Welcome
Choose Express to create a VPN rule with the default phase 1 and phase 2 settings
and to use a pre-shared key. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type
Type the Rule Name used to identify this VPN connection (and VPN gateway). You
may use 1-31 alphanumeric characters. This value is case-sensitive. Click Next.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Scenario)
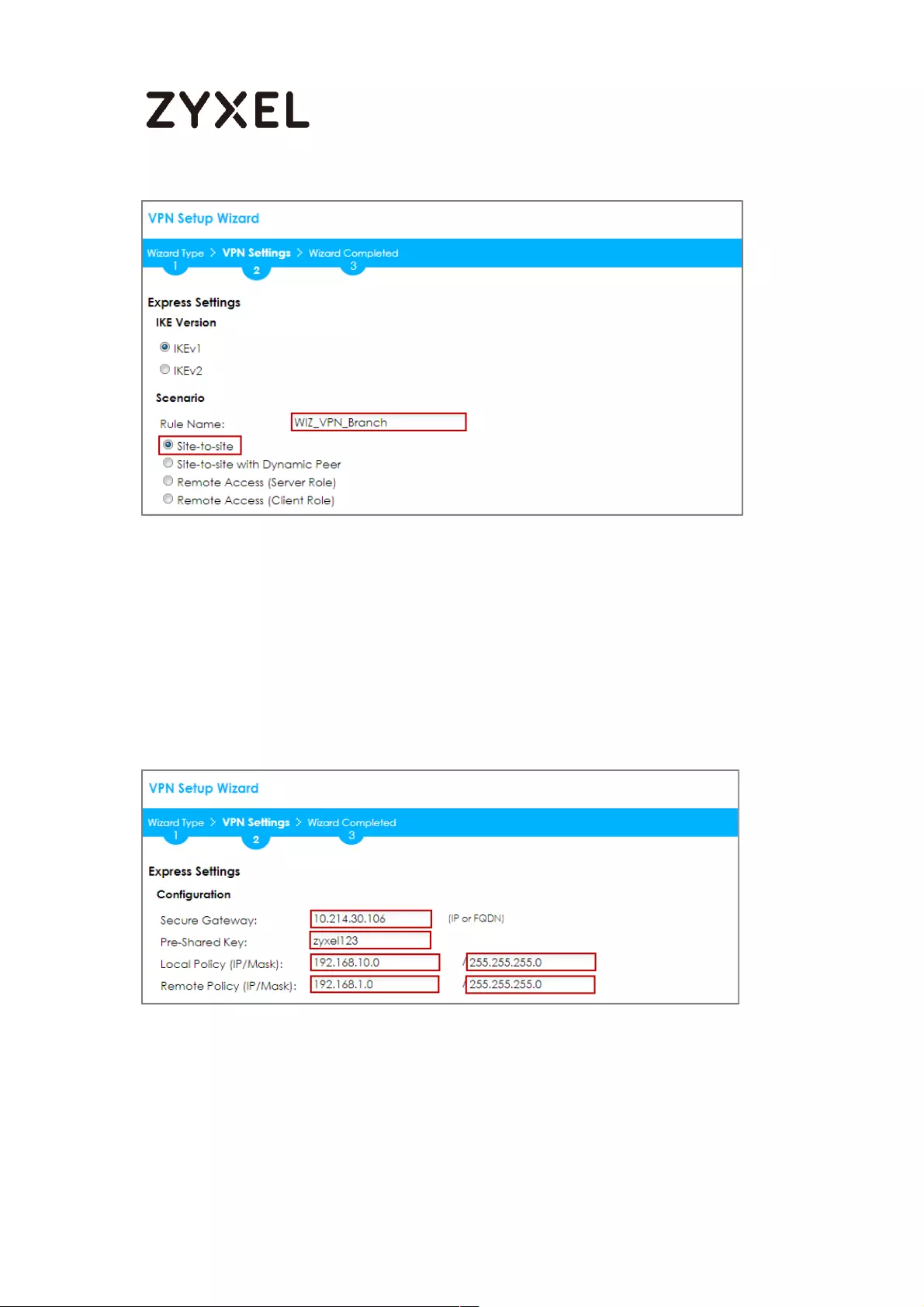
375/782
www.zyxel.com
Configure Secure Gateway IP as the peer ZyWALL/USG’s WAN IP address (in the
example, 172.101.30.68). Type a secure Pre-Shared Key (8-32 characters).
Set Local Policy to be the IP address range of the network connected to the
ZyWALL/USG and Remote Policy to be the IP address range of the network
connected to the peer ZYWALL/USG.
Quick Setup > VPN Setup Wizard > Wizard Type > VPN Settings (Configuration)
This screen provides a read-only summary of the VPN tunnel. Click Save.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings (Summary)
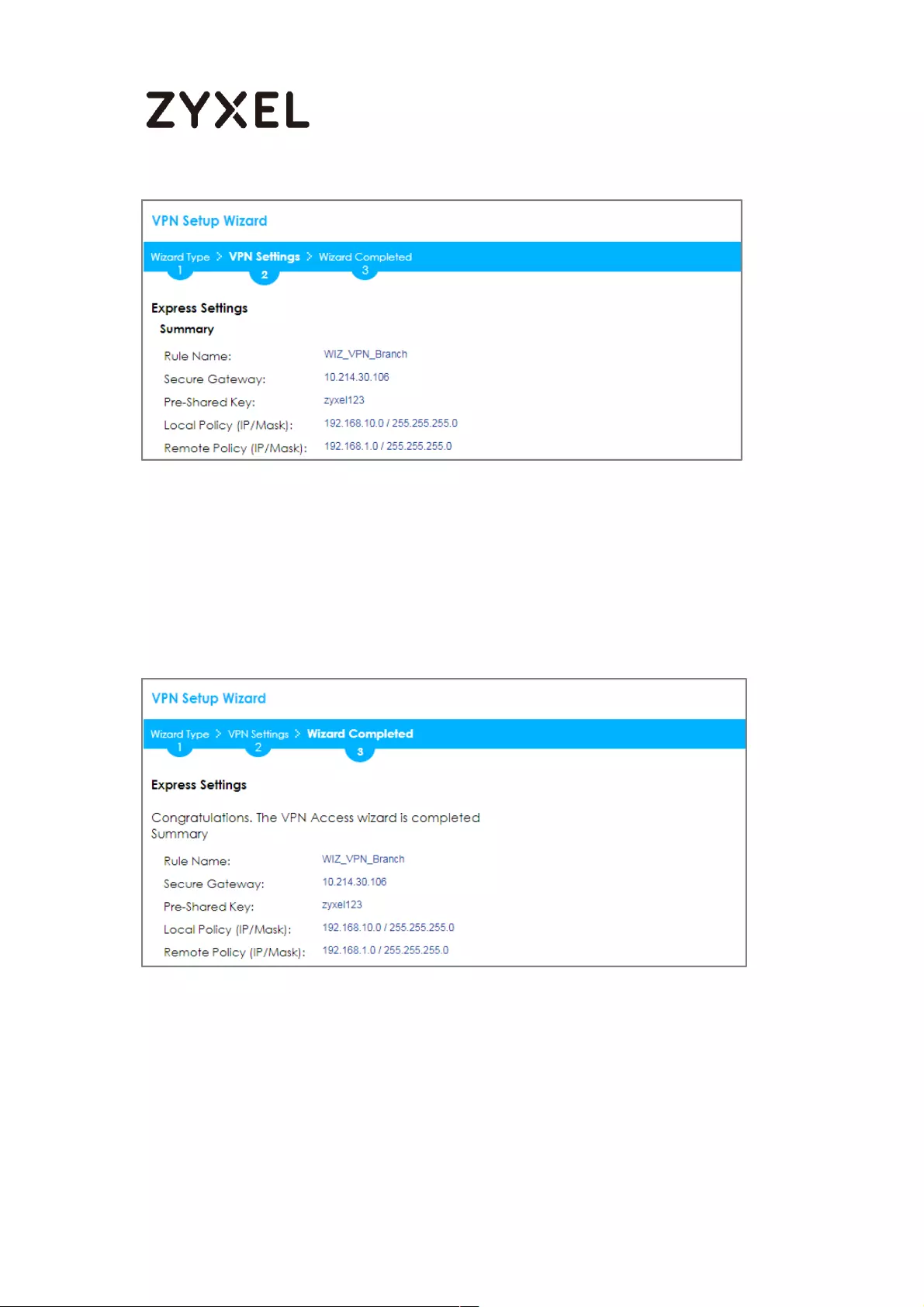
376/782
www.zyxel.com
Now the rule is configured on the ZyWALL/USG. The Phase 1 rule settings appear
in the VPN > IPSec VPN > VPN Gateway screen and the Phase 2 rule settings
appear in the VPN > IPSec VPN > VPN Connection screen. Click Close to exit the
wizard.
Quick Setup > VPN Setup Wizard > Welcome > Wizard Type > VPN Settings > Wizard
Completed
Go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway and click Show
Advanced Settings. Configure Authentication > Peer ID Type as Any to let the
ZyWALL/USG does not require to check the identity content of the remote IPSec
router.
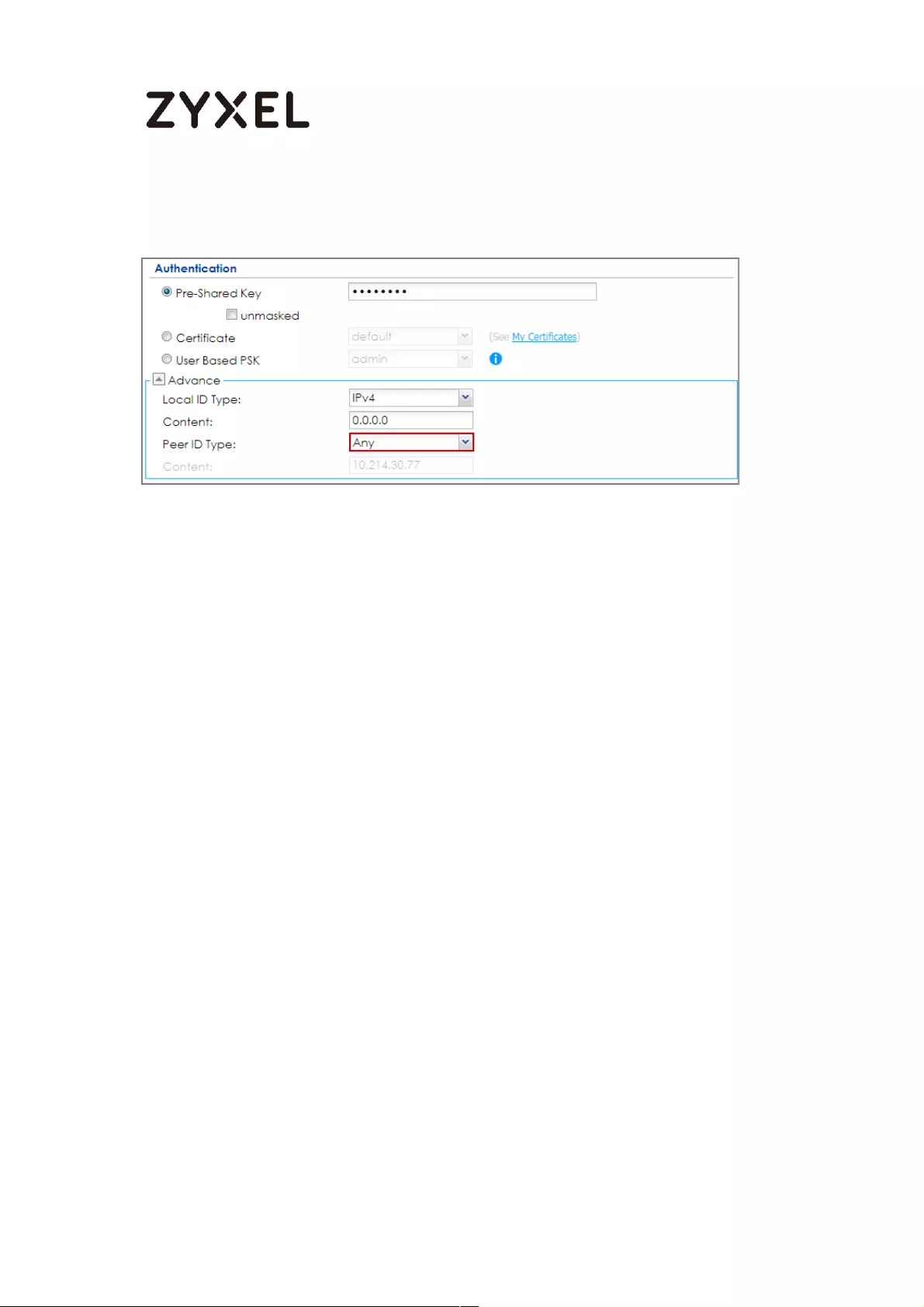
377/782
www.zyxel.com
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Show Advanced
Settings > Authentication > Peer ID Type
Set up the Policy Route (ZyWALL/USG_HQ)
Go to ZyWALL/USG_HQ CONFIGURATION > Network > Routing > Add. Set Source
Address to be the subnet (192.168.2.0/24 in this example) allows joining the VPN
tunnel. Set Destination Address to be the remote LAN subnet (192.168.10.0/24 in
this example).
378/782
www.zyxel.com
CONFIGURATION > Network > Routing > Add
Set up the Policy Route (ZyWALL/USG_Branch)
Go to ZyWALL/USG_Branch CONFIGURATION > Network > Routing > Add, create
Address to be the remote LAN subnet (192.168.2.0/24 in this example) allows
joining the VPN tunnel.
CONFIGURATION > Object > Address > Add
379/782
www.zyxel.com
Go to ZyWALL/USG_Branch CONFIGURATION > Network > Routing > Add. Set
Source Address to be the local subnet (192.168.10.0/24 in this example). Set
Destination Address to be the remote LAN subnet (192.168.2.0/24 in this example)
allows joining the VPN tunnel.
CONFIGURATION > Network > Routing > Add
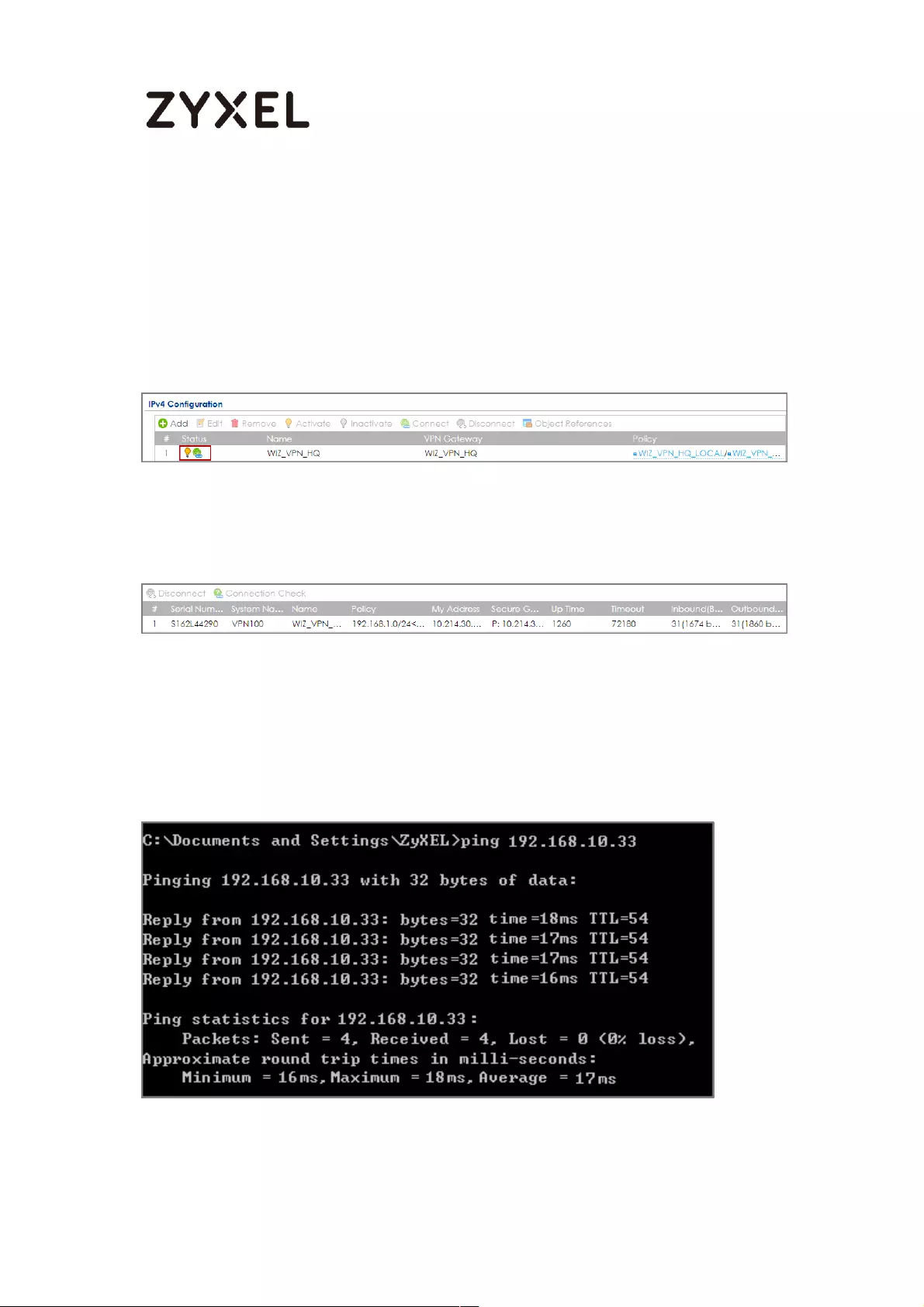
380/782
www.zyxel.com
Test the IPSec VPN Tunnel
Go to ZYWALL/USG CONFIGURATION > VPN > IPSec VPN > VPN Connection, click
Connect on the upper bar. The Status connect icon is lit when the interface is
connected.
CONFIGURATION > VPN > IPSec VPN > VPN Connection
Go to ZyWALL/USG MONITOR > VPN Monitor > IPSec and verify the tunnel Up Time
and Inbound(Bytes)/Outbound(Bytes) Traffic.
MONITOR > VPN Monitor > IPSec
To test whether or not a tunnel is working, ping from a computer at one site to a
computer at the other. Ensure that both computers have Internet access (via the
IPSec devices).
PC at HQ Office > Window 7 > cmd > ping 192.168.10.33
PC at Branch Office > Window 7 > cmd > ping 192.168.1.33
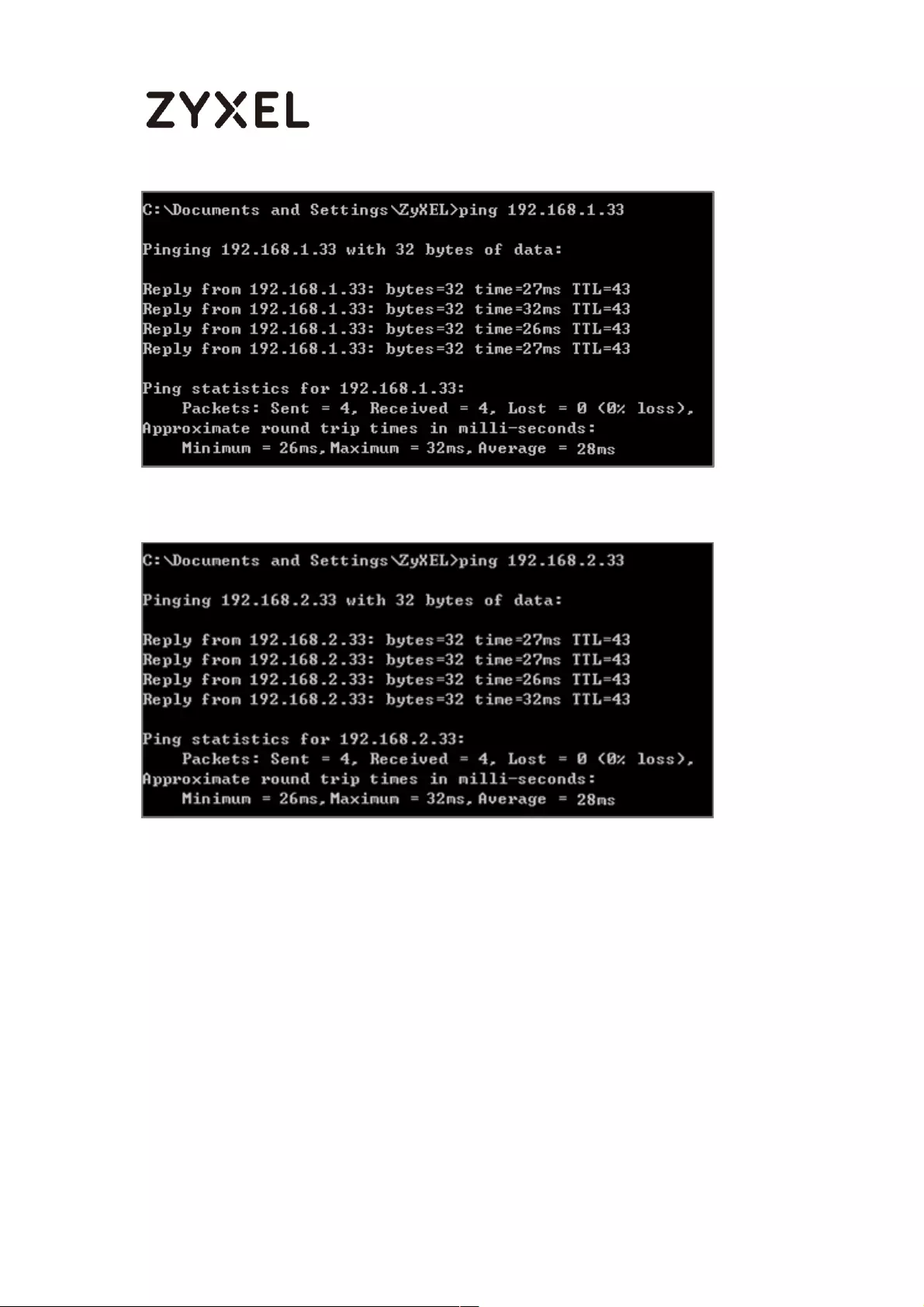
381/782
www.zyxel.com
PC at Branch Office > Window 7 > cmd > ping 192.168.2.33
What Could Go Wrong?
If you see below [info] or [error] log message, please check ZyWALL/USG Phase
1 Settings. Both ZyWALL/USG at the HQ and Branch sites must use the same Pre-
Shared Key, Encryption, Authentication method, DH key group and ID Type to
establish the IKE SA.
MONITOR > Log
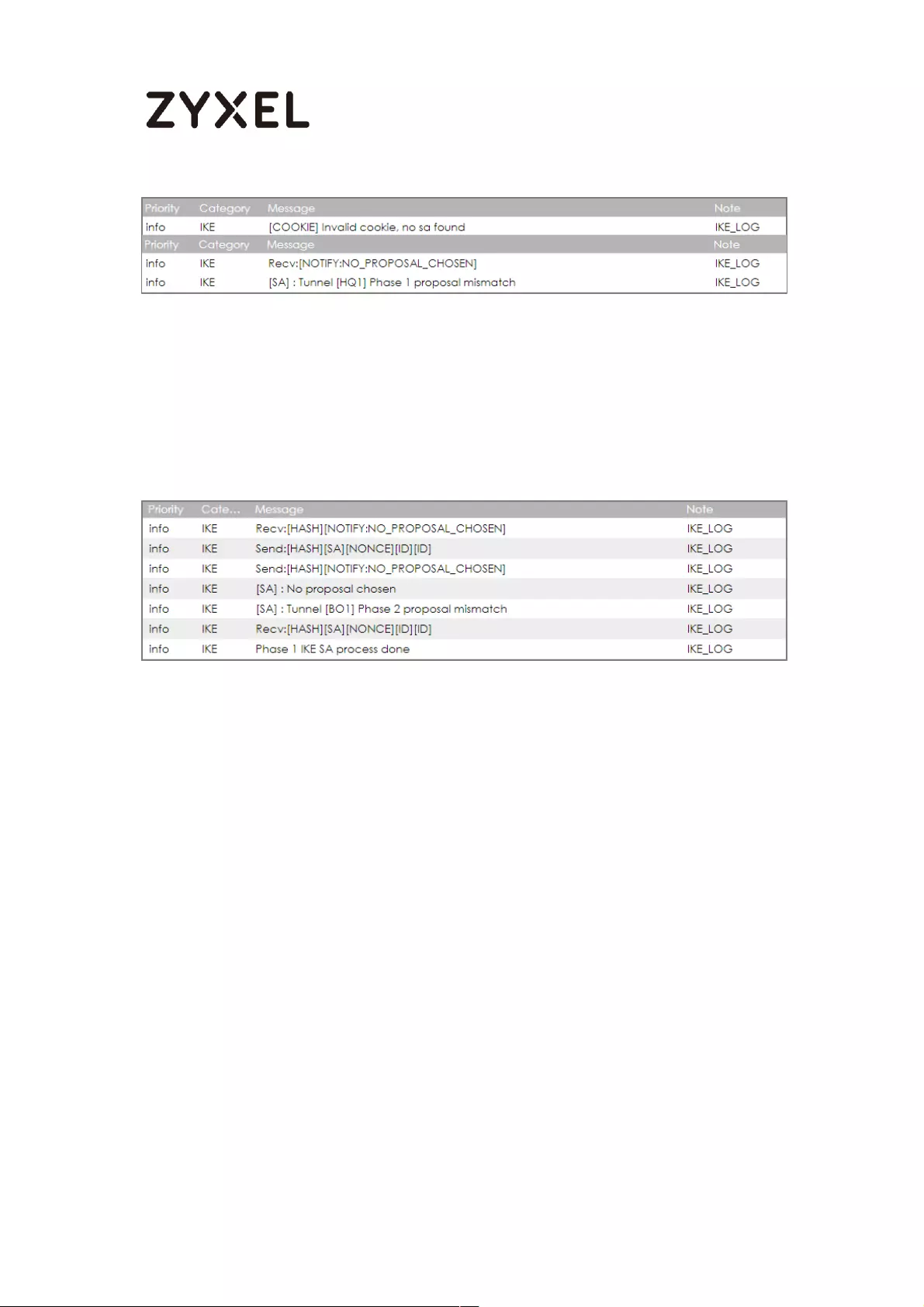
382/782
www.zyxel.com
If you see that Phase 1 IKE SA process done but still get below [info] log message,
please check ZyWALL/USG Phase 2 Settings. Both ZyWALL/USG at the HQ and
Branch sites must use the same Protocol, Encapsulation, Encryption,
Authentication method and PFS to establish the IKE SA.
MONITOR > Log
Make sure the both ZyWALL/USG at the HQ and Branch sites security policies
allow IPSec VPN traffic. IKE uses UDP port 500, AH uses IP protocol 51, and ESP
uses IP protocol 50.
Default NAT traversal is enable on ZyWALL/USG, please make sure the remote
IPSec device must also have NAT traversal enabled.

383/782
www.zyxel.com
How to Create VTI and Configure VPN Failover with VTI
This example illustrates how to create a VTI object and configure a policy route with
the VTI. Furthermore, it applies the VTI to the WAN trunk to achieve VPN load
balancing.
VPN Load Balance with VTI
VTI Deployment Flow
1 Configure the VPN gateways.
2 Configure a VPN tunnel for each VPN gateway with the application
scenario VPN Tunnel Interface.
3 Create a VTI for each VPN tunnel.
4 Create a trunk with the VTIs.
5 Configure a policy route.
6 Connect the VPN tunnels.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG110 (Firmware Version: ZLD 4.25).
384/782
www.zyxel.com
Set Up the ZyWALL/USG VTI of Corporate Network (HQ)
1 In the ZyWALL/USG, go to CONFIGURATION > VPN > IPSec VPN > VPN
Gateway > Add to create the VPN gateway HQ1 with wan1.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Add
2 In the same screen, create the VPN gateway HQ2 with wan2.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Add
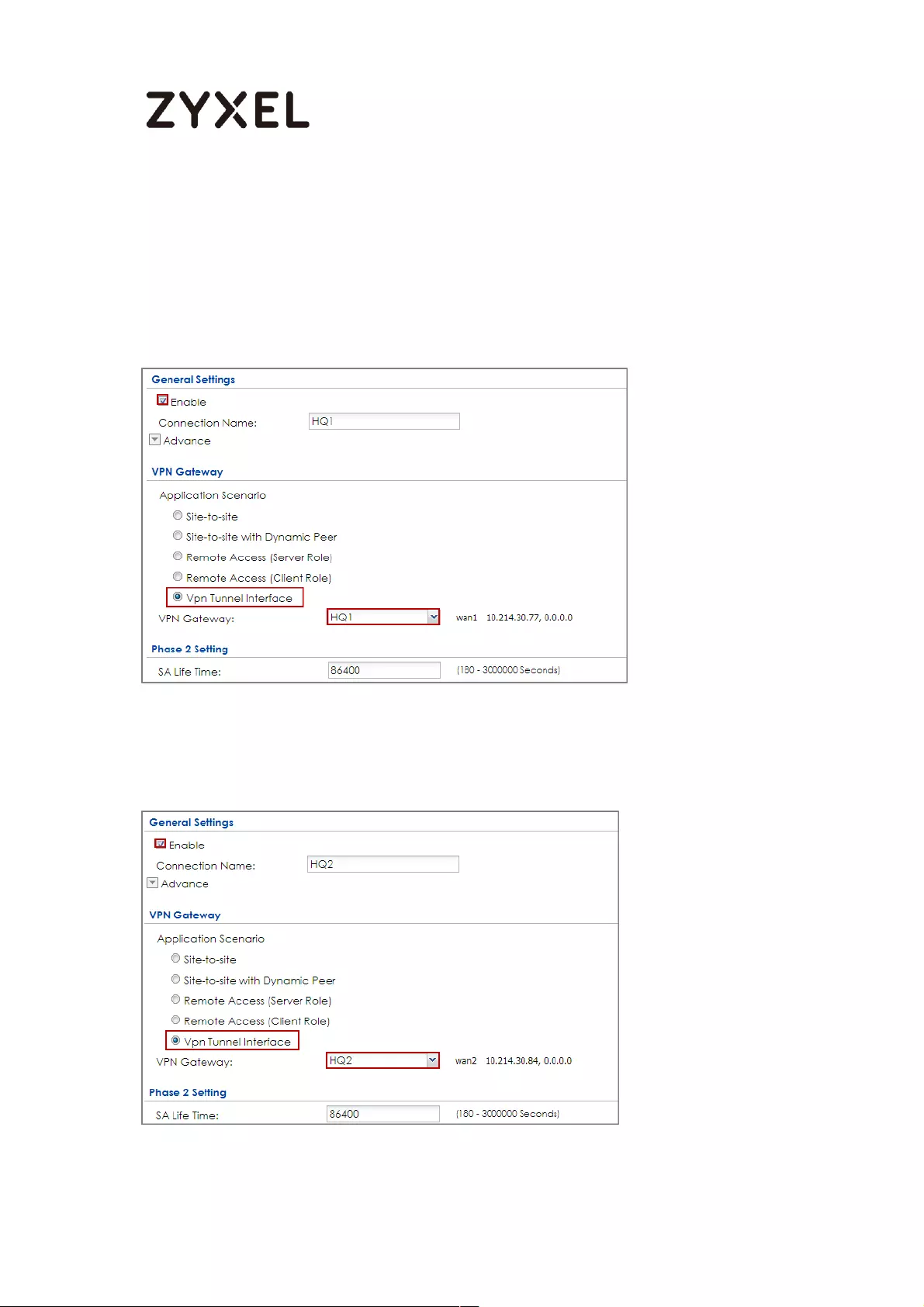
385/782
www.zyxel.com
3 Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection > Add and
configure a VPN tunnel for the VPN gateway HQ1. Select VPN Tunnel Interface as the
application scenario.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Add
4 In the same screen, create a VPN tunnel for the VPN gateway HQ2.
Select VPN tunnel Interface as the application scenario.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Add
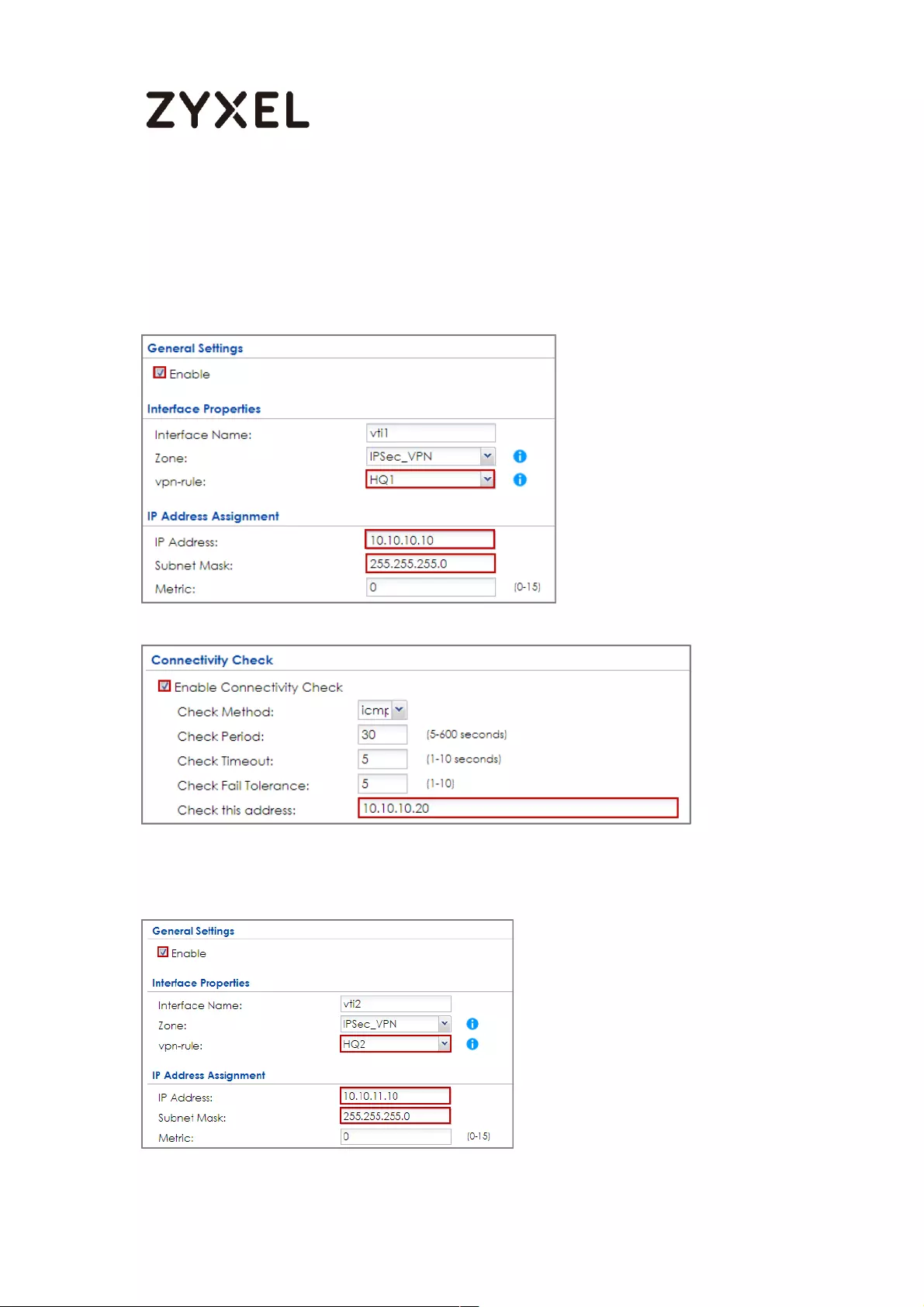
386/782
www.zyxel.com
5 Go to CONFIGURATION > Network > Interface > VTI > Add to create a VTI
for the VPN tunnel HQ1. Enable the connectivity check. Enter the IP address of vti1,
which is configured on USG2.
CONFIGURATION > Network > Interface > VTI > Add
CONFIGURATION > Network > Interface > VTI > vti1 > Connectivity Check
6 In the same screen, create a VTI for the VPN tunnel HQ2.
CONFIGURATION > Network > Interface > VTI > Add
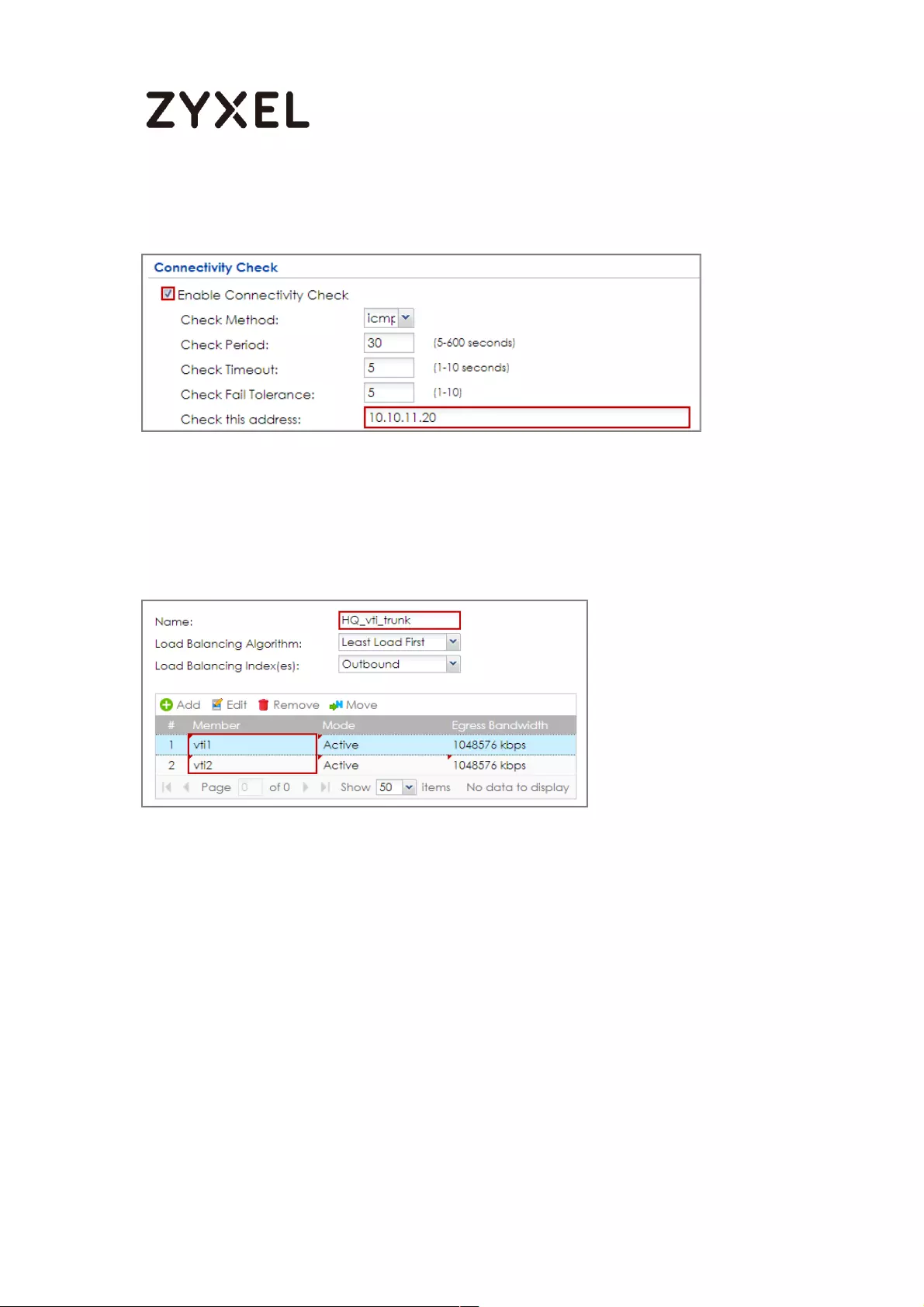
387/782
www.zyxel.com
CONFIGURATION > Network > Interface > VTI > vti2 > Connectivity Check
7 Go to CONFIGURATION > Network > Interface > Trunk > User
Configuration > Add to create a new trunk. Add vti1 and vti2 to the new trunk.
CONFIGURATION > Network > Interface > Trunk > User Configuration > Add
8 Go to CONFIGURATION > Network > Routing > Policy Route > Add to
configure a policy route.
Source Address: LAN1_SUBNET (192.168.1.0/24)
Destination Address: BO_subnet (192.168.11.0/24)
Next-Hop: HQ_vti_trunk
SNAT: none
CONFIGURATION > Network > Routing > Policy Route > Add
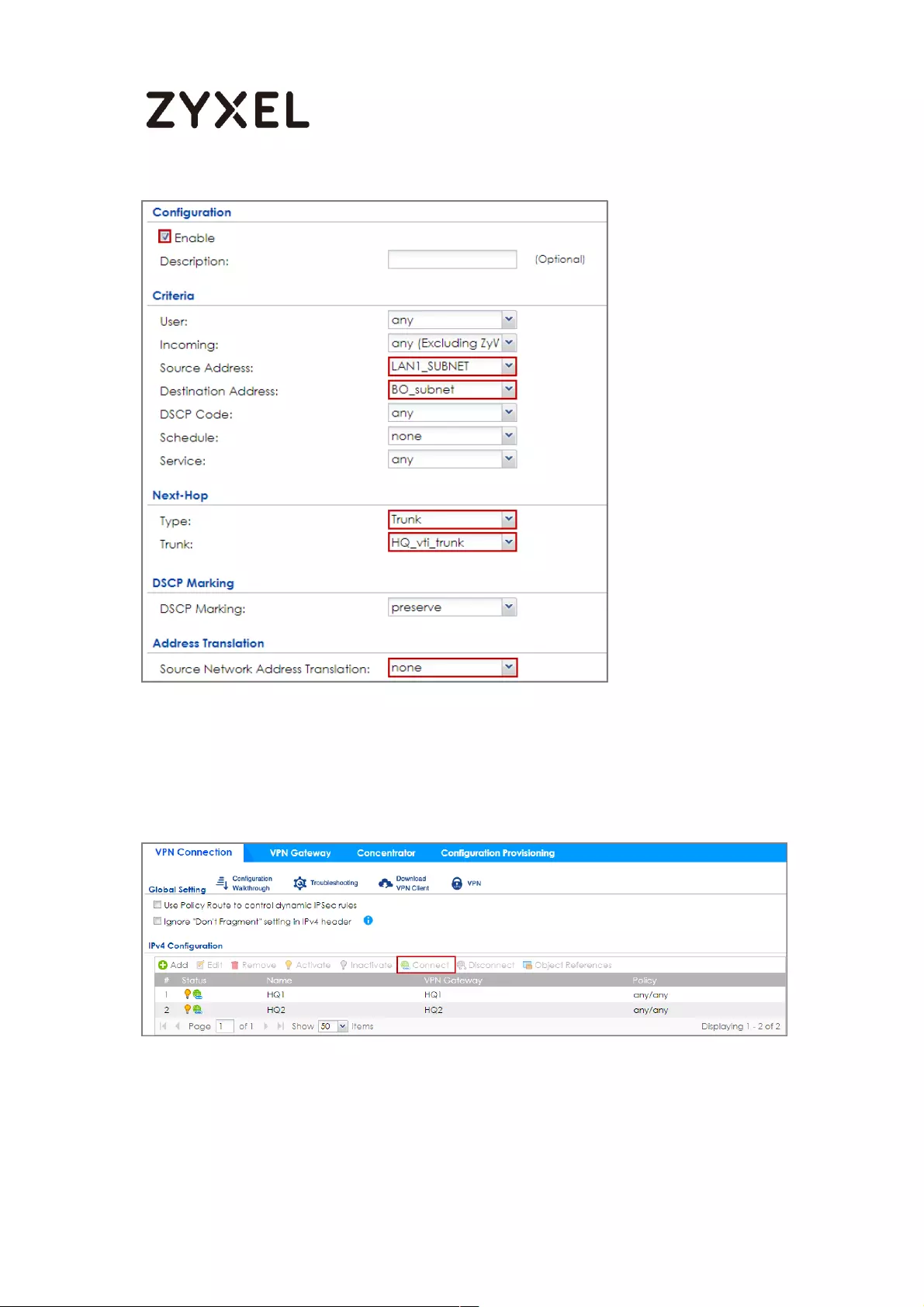
388/782
www.zyxel.com
9 Connect the VPN tunnels when the VTIs are ready. Go to
CONFIGURATION > VPN > IPSec VPN > VPN Connection to connect the VPN tunnels.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Connect
10 Go to CONFIGURATION > Network > Interface > VTI. You will see that the
status of the VTI is up when the corresponding VPN tunnel is established.
CONFIGURATION > Network > Interface > VTI
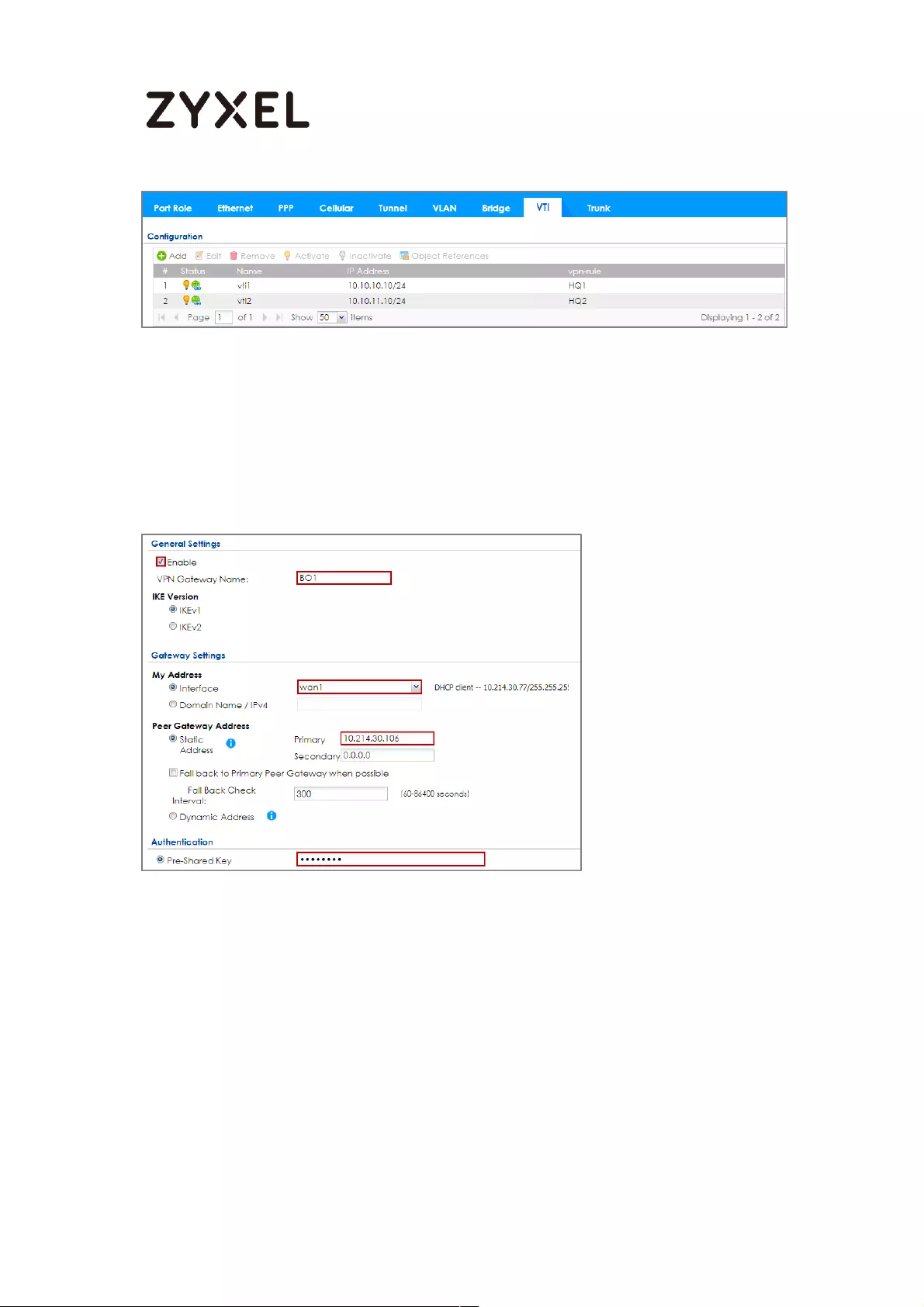
389/782
www.zyxel.com
Set Up the ZyWALL/USG VTI of Corporate Network (Branch)
1 In the ZyWALL/USG, go to CONFIGURATION > VPN > IPSec VPN > VPN
Gateway > Add to create the VPN gateway BO1 with wan1.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Add
2 In the same screen, create the VPN gateway BO2 with wan2.
CONFIGURATION > VPN > IPSec VPN > VPN Gateway > Add
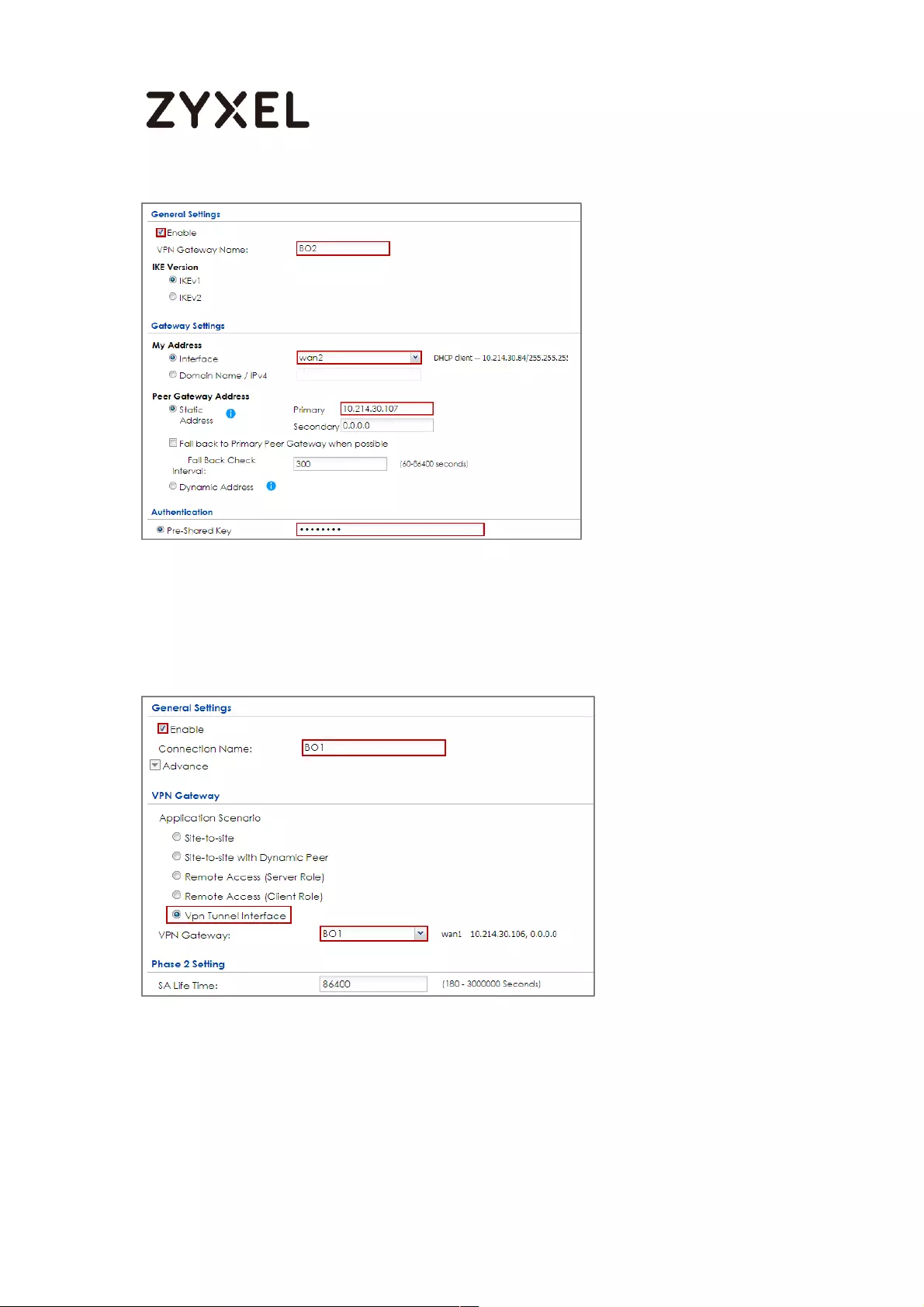
390/782
www.zyxel.com
3 Go to CONFIGURATION > VPN > IPSec VPN > VPN Connection > Add and
configure a VPN tunnel for the VPN gateway BO1. Select VPN Tunnel Interface as the
application scenario.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Add
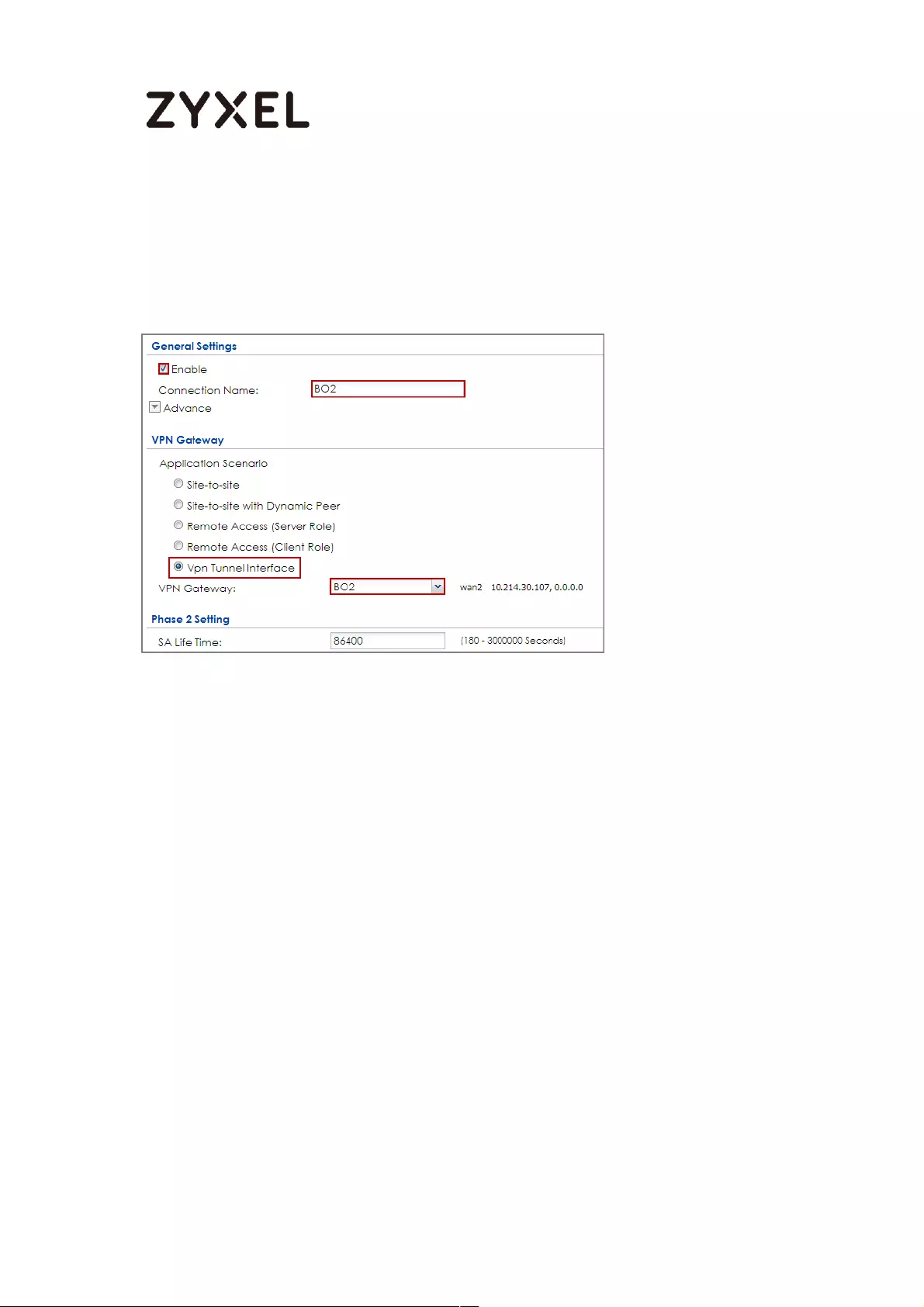
391/782
www.zyxel.com
4 In the same screen, create a VPN tunnel for the VPN gateway BO2.
Select VPN tunnel Interface as the application scenario.
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Add
5 Go to CONFIGURATION > Network > Interface > VTI > Add to create a VTI
for the VPN tunnel BO1. Be aware that the IP address of this VTI must be in the same
subnet as vti1 on USG1.
In this example, the IP address and subnet mask of vti1 on USG1 is 10.10.10.10 and
255.255.255.0 respectively. The IP address of vti1 on USG2 must be in the subnet of
10.10.10.0/24. Enable the connectivity check. Enter the IP address of vti1, which is
configured on USG1.
CONFIGURATION > Network > Interface > VTI > Add
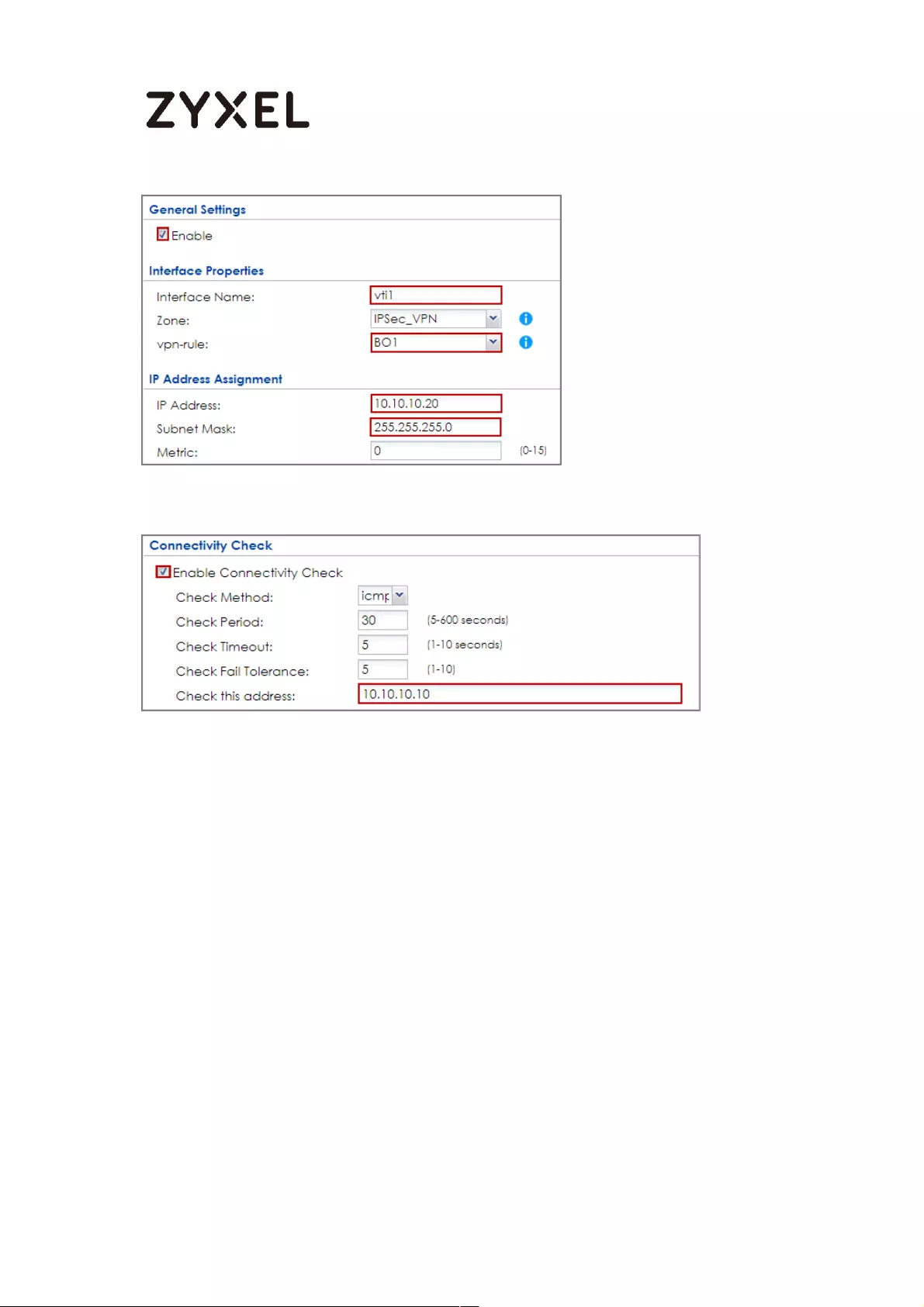
392/782
www.zyxel.com
CONFIGURATION > Network > Interface > VTI > vti1 > Connectivity Check
6 In the same screen, create a VTI for the VPN tunnel BO2. Be aware that
the IP address of this VTI must be in the same subnet as vti2 on USG1. In this example,
the IP address and subnet mask of vti2 on USG1 is 10.10.11.10 and 255.255.255.0
respectively. The IP address of vti2 on USG2 must be in the subnet of 10.10.11.0/24.
Enable the connectivity check. Enter the IP address of vti2, which is configured on
USG1.
CONFIGURATION > Network > Interface > VTI > Add
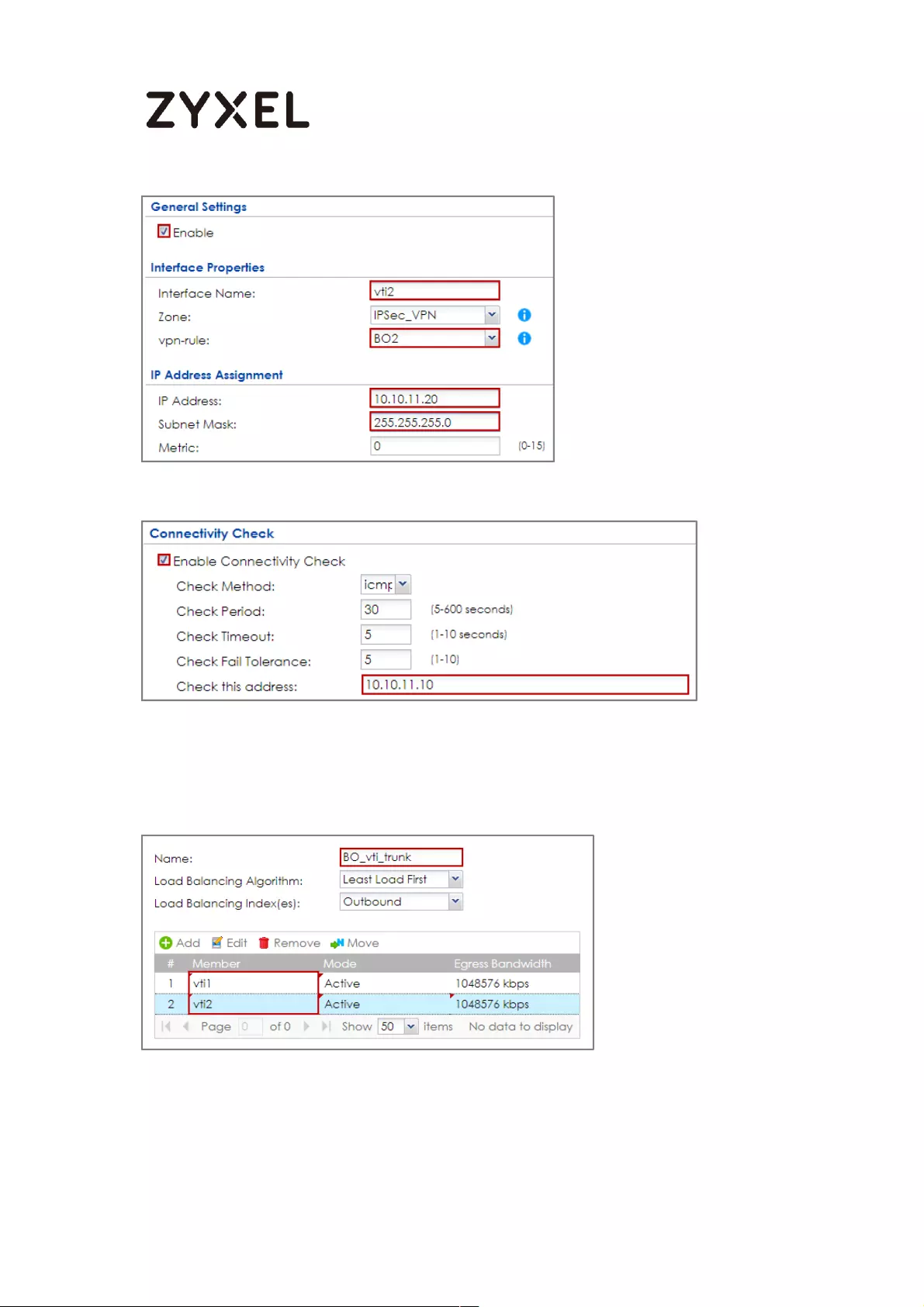
393/782
www.zyxel.com
CONFIGURATION > Network > Interface > VTI > vti1 > Connectivity Check
7 Go to CONFIGURATION > Network > Interface > Trunk > User
Configuration > Add to create a new trunk. Add vti1 and vti2 to the new trunk.
CONFIGURATION > Network > Interface > Trunk > User Configuration > Add
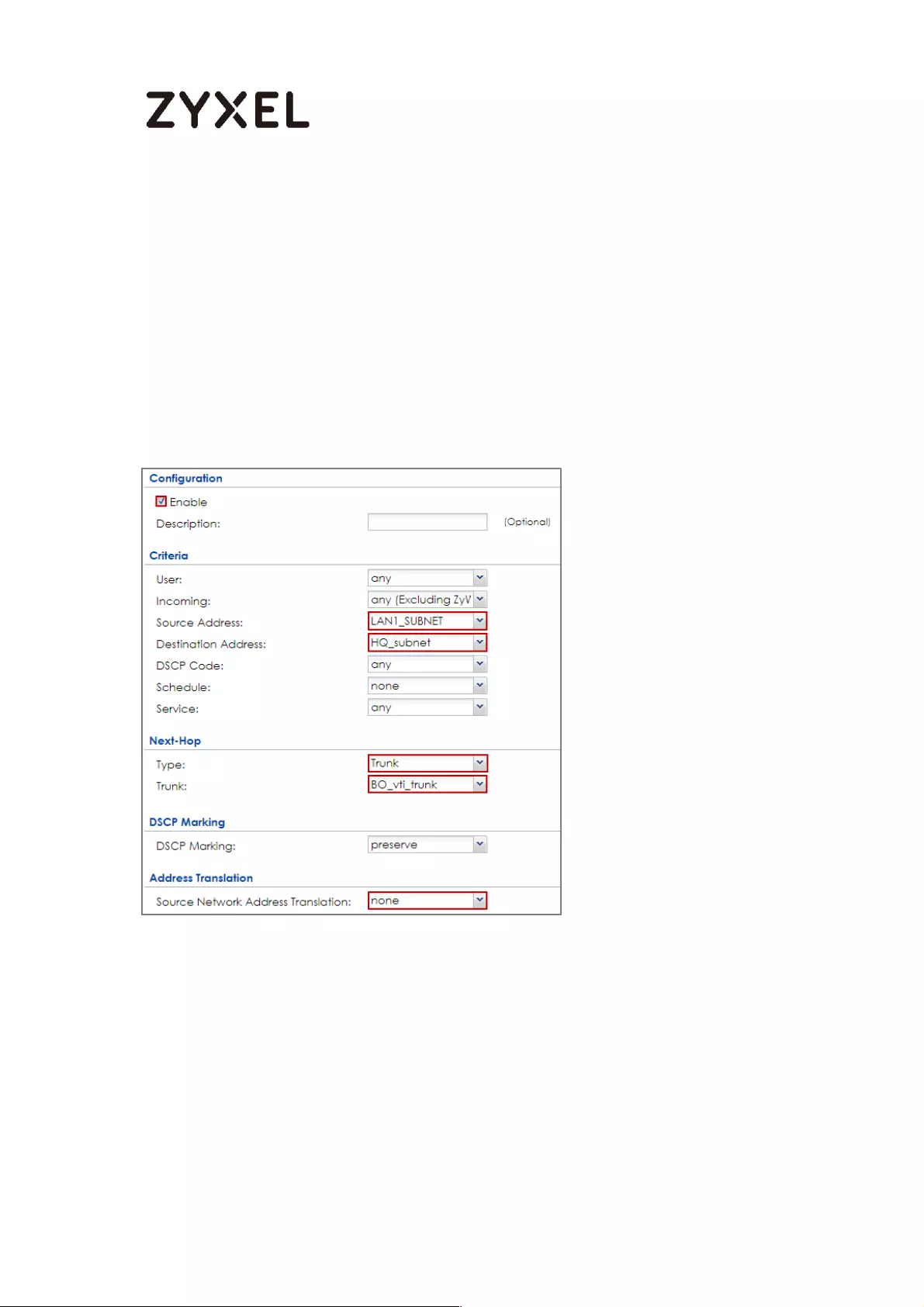
394/782
www.zyxel.com
8 Go to CONFIGURATION > Network > Routing > Policy Route > Add to
configure a policy route.
Source Address: LAN1_SUBNET (192.168.11.0/24)
Destination Address: HQ_subnet (192.168.1.0/24)
Next-Hop: BO_vti_trunk
SNAT: none
CONFIGURATION > Network > Routing > Policy Route > Add
9 Connect the VPN tunnels when the VTIs are ready. Go to
CONFIGURATION > VPN > IPSec VPN > VPN Connection to connect the VPN tunnels.
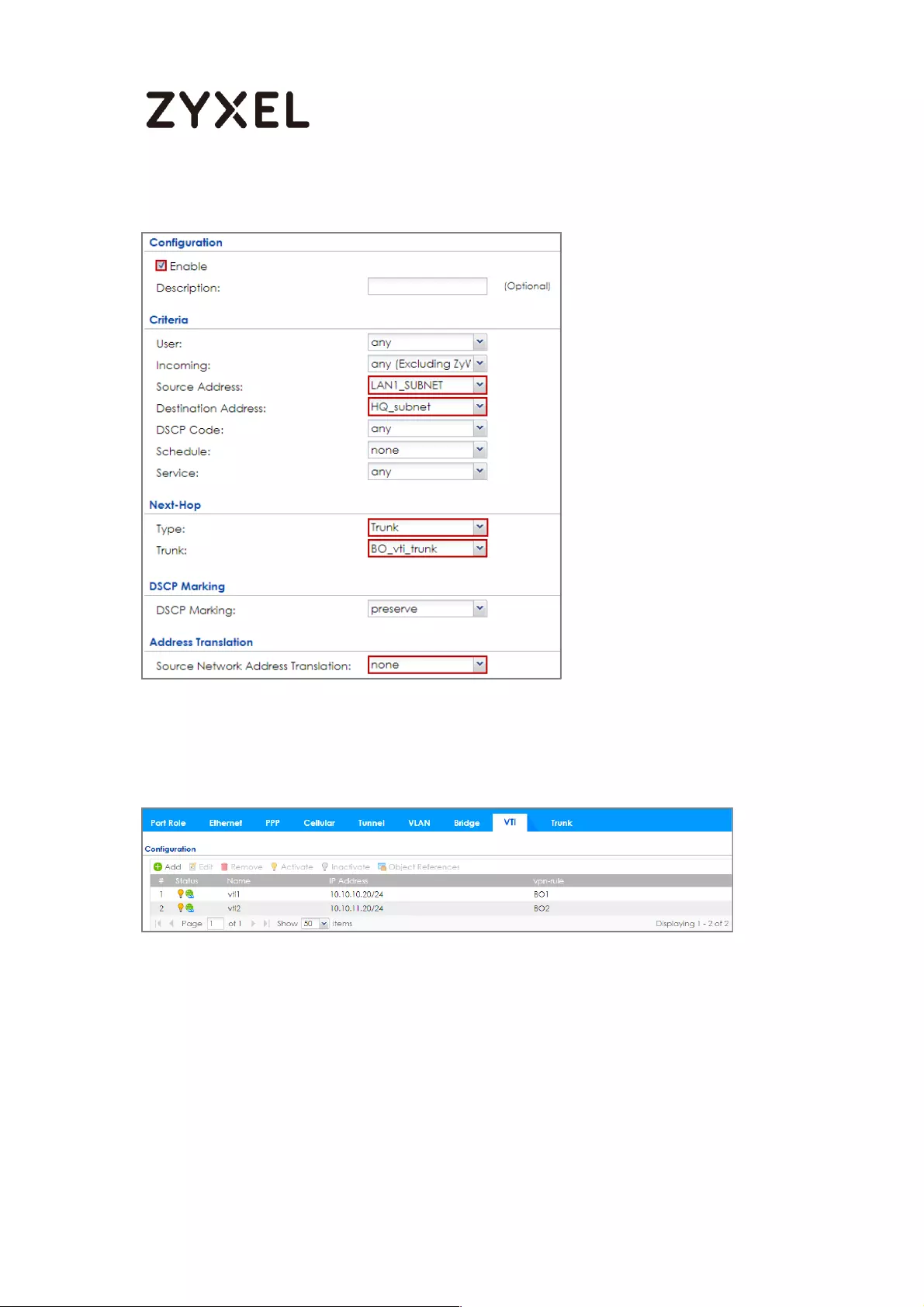
395/782
www.zyxel.com
CONFIGURATION > VPN > IPSec VPN > VPN Connection > Connect
10 Go to CONFIGURATION > Network > Interface > VTI. You will see that the
status of the VTI is up when the corresponding VPN tunnel is established.
CONFIGURATION > Network > Interface > VTI
Test the IPSec VPN Tunnel
1 To test whether or not a tunnel is working, ping from a PC in LAN1 of USG1
to a PC in LAN1 of USG2 and vice versa.
PC of USG1 (192.168.1.34) > Window 7 > cmd > ping 192.168.11.33
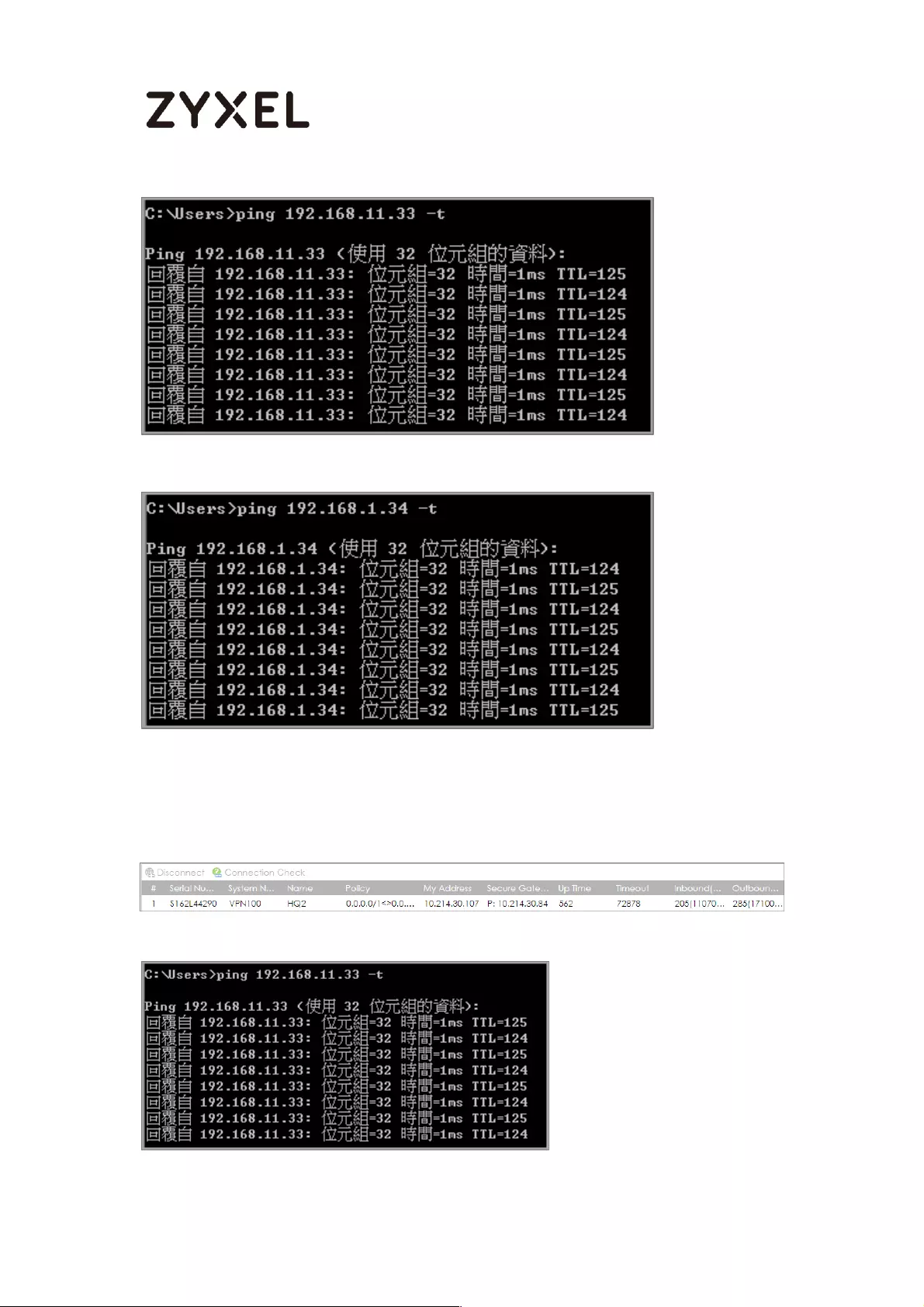
396/782
www.zyxel.com
PC of USG2 (192.168.11.33) > Window 7 > cmd > ping 192.168.1.34
2 To test whether or not VPN failover is working, unplug wan1 of USG1. Then
ping from a PC in LAN1 of USG1 to a PC in LAN1 of USG2 and vice versa.
Check the VPN status of the USG1 in the MONITOR > VPN Monitor > IPSec screen.
PC of USG1 (192.168.1.34) > Window 7 > cmd > ping 192.168.11.33
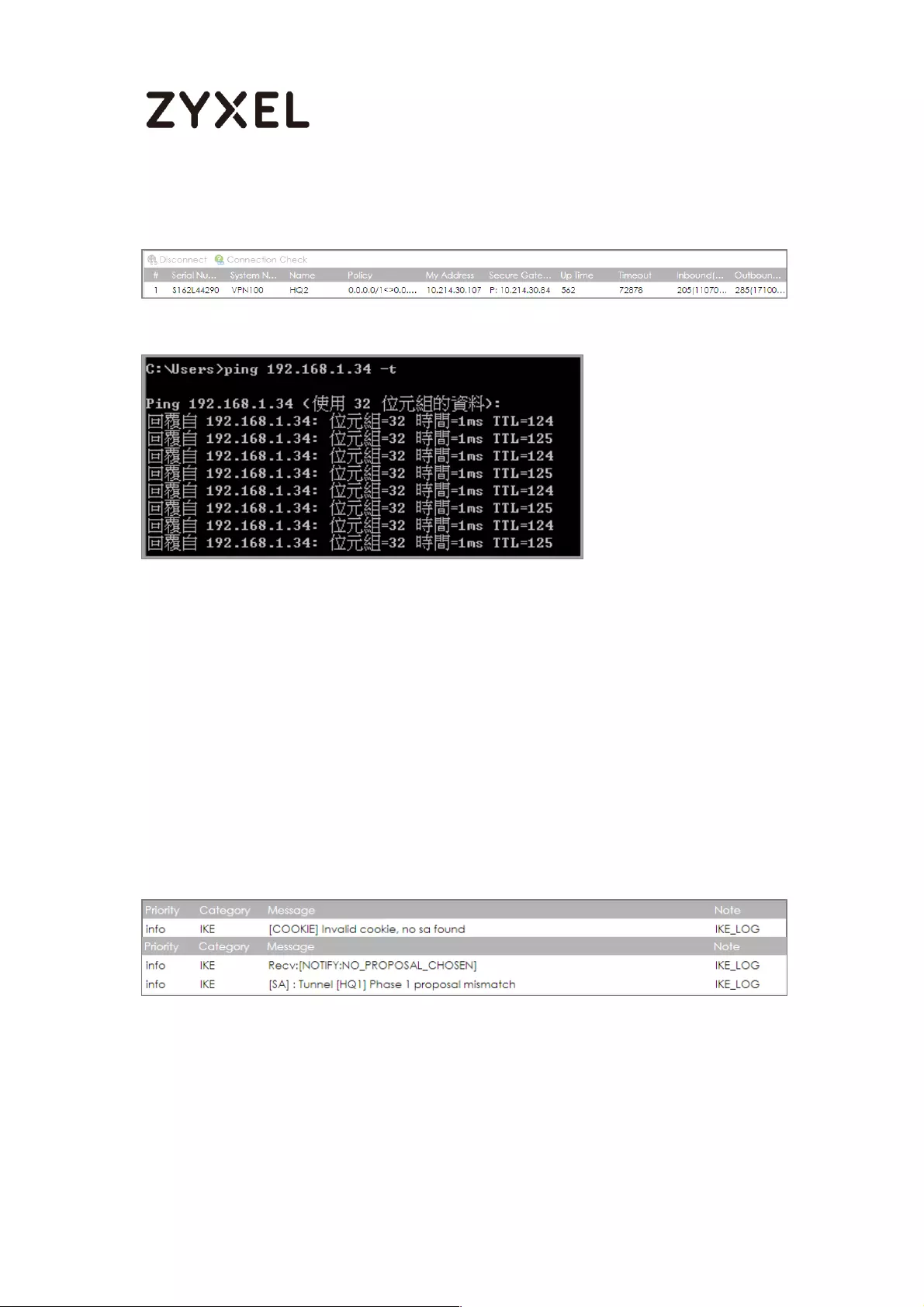
397/782
www.zyxel.com
Check the VPN status of the USG2 in the MONITOR > VPN Monitor > IPSec screen.
PC of USG2 (192.168.11.33) > Window 7 > cmd > ping 192.168.1.34
What Can Go Wrong?
1 If you see below [info] or [error] log message, please check ZyWALL/USG
Phase 1 Settings. Both ZyWALL/USG at the HQ and Branch sites must use
the same Pre-Shared Key, Encryption, Authentication method, DH key
group and ID Type to establish the IKE SA.
MONITOR > Log
2 If you see that Phase 1 IKE SA process done but still get below [info] log
message, please check ZyWALL/USG Phase 2 Settings. Both ZyWALL/USG
at the HQ and Branch sites must use the same Protocol, Encapsulation,
Encryption, Authentication method and PFS to establish the IKE SA.
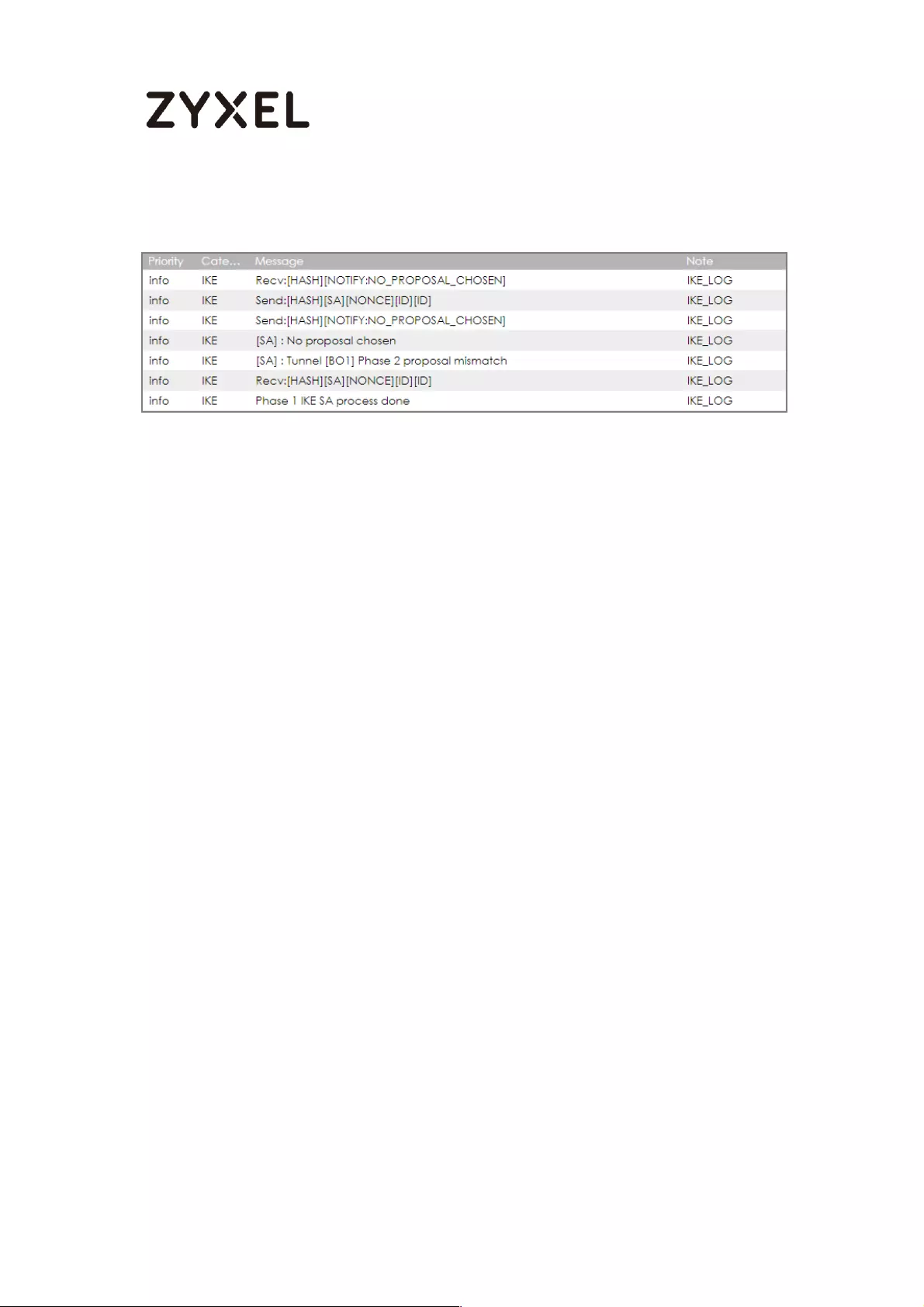
398/782
www.zyxel.com
MONITOR > Log
3 Make sure the both ZyWALL/USG at the HQ and Branch sites security
policies allow IPSec VPN traffic. IKE uses UDP port 500, AH uses IP
protocol 51, and ESP uses IP protocol 50.
4 Default NAT traversal is enable on ZyWALL/USG, please make sure the
remote IPSec device must also have NAT traversal enabled.
5 Make sure the both ZyWALL/USG at the HQ and Branch sites use static IP
address because VPN Tunnel Interface does not support dynamic peer.
6 Make sure policy routes are configured to control traffic between the
subnet of HQ and Branch through VTI.
7 Make sure that the IP address of VTI at the Branch must be in the same
subnet as vti1 on HQ. For example, the IP address and subnet mask of
vti1 on HQ is 10.10.10.10 and 255.255.255.0 respectively. The IP address of
vti1 on the Branch must be in the subnet of 10.10.10.0/24; the IP address
and subnet mask of vti2 on HQ is 10.10.11.10 and 255.255.255.0
respectively. The IP address of vti2 on the Branch must be in the subnet
of 10.10.10.0/24, and so on.
399/782
www.zyxel.com
How to configure the USG when using a Cloud Based SIP
system
This example shows how to configure USG when there is a Cloud Based SIP system. The
IP phones are more and more popular nowadays. USG supports the scenario as IP
phones located in LAN and connect to internet to register the SIP server.
SIP Phone connects to SIP server via USG.
int
USG
WAN IP
SIP
IP
IP
IP
Note: All network IP addresses and subnet masks are used as examples in this article. Please
replace them with your actual network IP addresses and subnet masks. This example was
tested using USG210 (Firmware Version: ZLD 4.25).
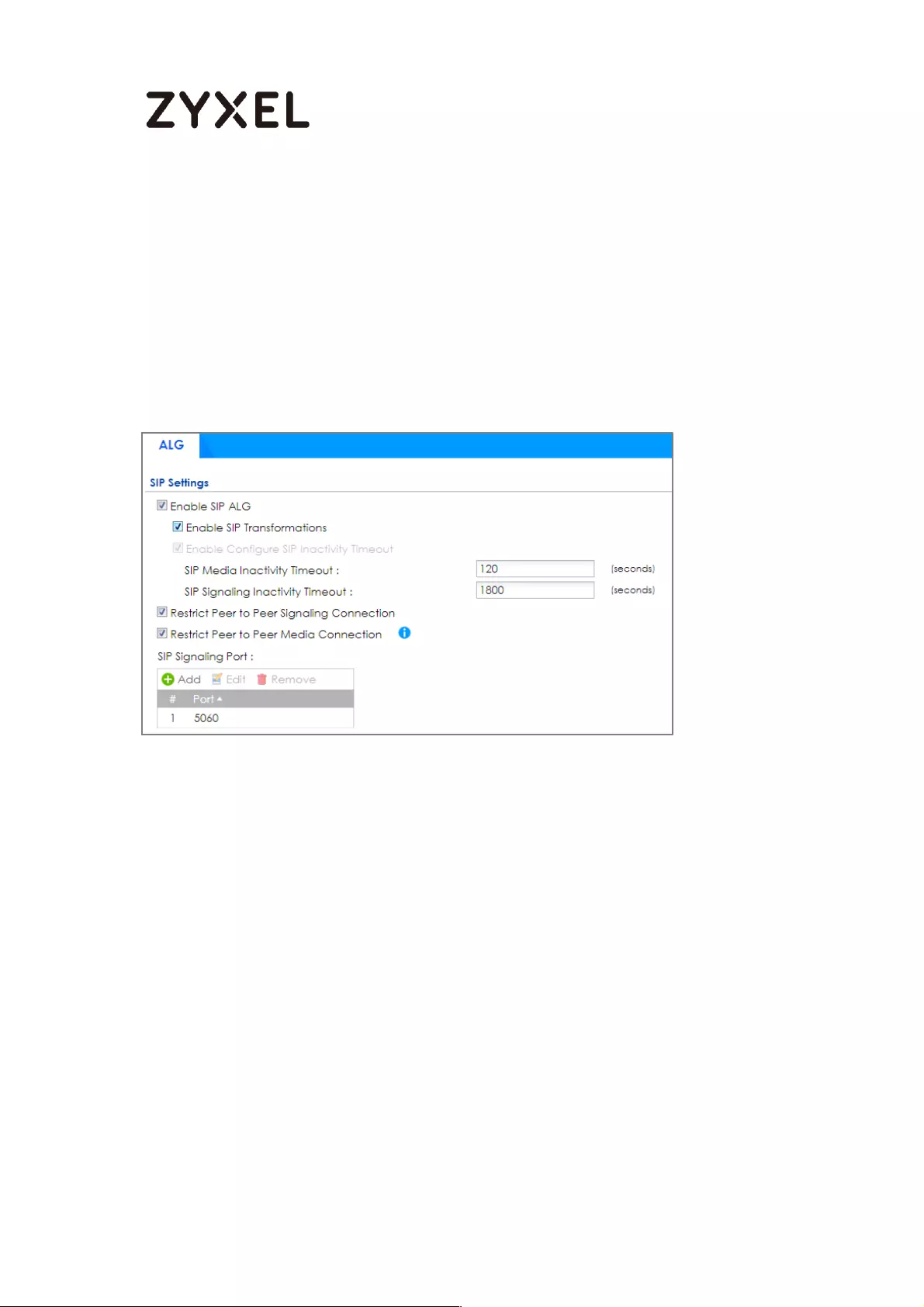
400/782
www.zyxel.com
Set Up the SIP ALG
Go to CONFIGURATION > Network > ALG, and check “Enable SIP ALG”. Also, check the
“Enable SIP Transformations” if the SIP content which is needed to be transform. Then
click “Apply”.
CONFIGURATION > Network > ALG
Direct-media and Direct-signalling are activated after ZLD 4.25. We can use the CLI to
show the status. When the two options are yes, it will change the original sip alg
behavior.
direct-siginalling will expect incoming calls from register only.
direct-media will expect media streams between signalling endpoints only.
Test result
Connect SIP phone to the USG, and check the register status. Register successfully.
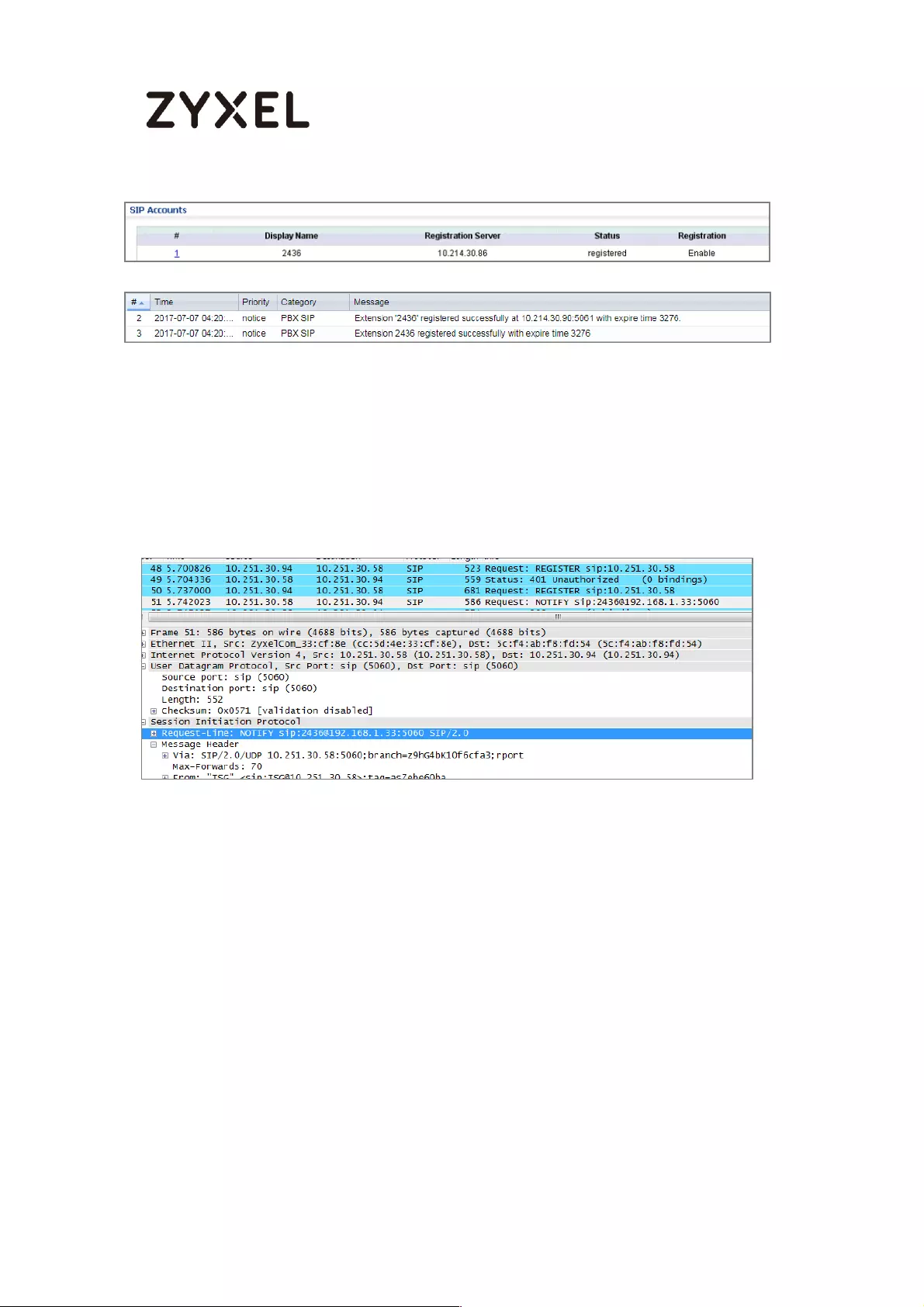
401/782
www.zyxel.com
Check the SIP register status on PBX.
What could go wrong?
SIP phone does not support transform itself, but the “SIP Transformations” does not be
checked.
SIP phone will contact with outside as not direct-signalling and direct media, but the
default setting on USG is on
How to block HTTPS websites by Domain Filter without
applying SSL Inspection
The Content Filter with HTTPs Domain Filter allows you to block HTTPs websites by
category service without SSL-Inspection. The filtering feature is based on more than 50
Managed Categories built in ZyWALL/USG such as pornography, gambling, hacking,
etc.
When user makes HTTPS request, the information contains a Server Name Indication
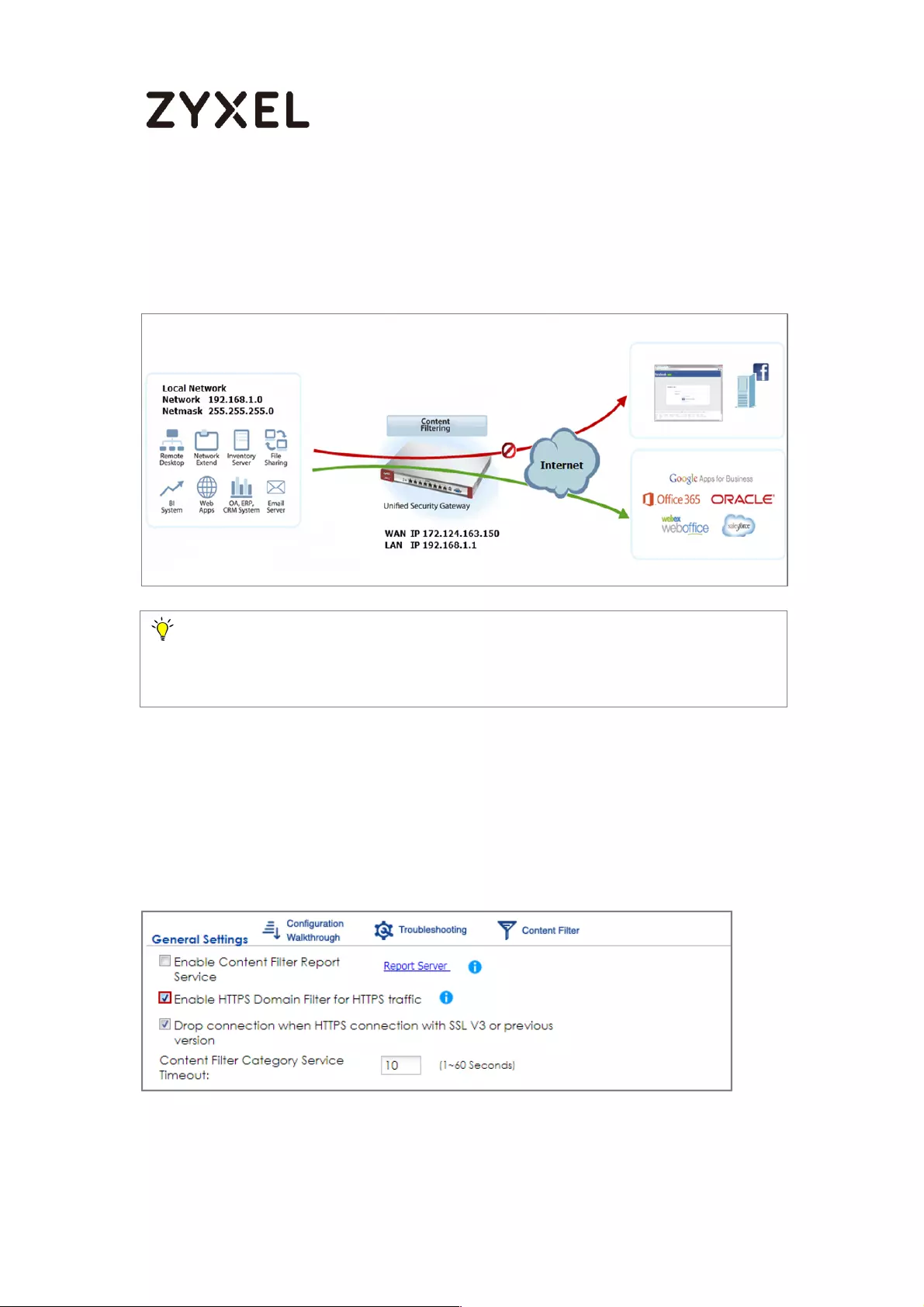
402/782
www.zyxel.com
(SNI) extension fields in server FQDN. Using the SNI to query category from Commtouch
engine, then take action when it matches the block category in Content Filter profile.
ZyWALL/USG Domain Filter Example
Set Up the Content Filter on the ZyWALL/USG
Go to CONFIGURATION > UTM Profile> Content Filter > Profile > General Settings. Select
Enable HTTPS Domain Filter for HTTPS traffic.
Go to CONFIGURATION > UTM Profile> Content Filter > Profile Management > Add Filter
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG310 (Firmware Version: 4.25)
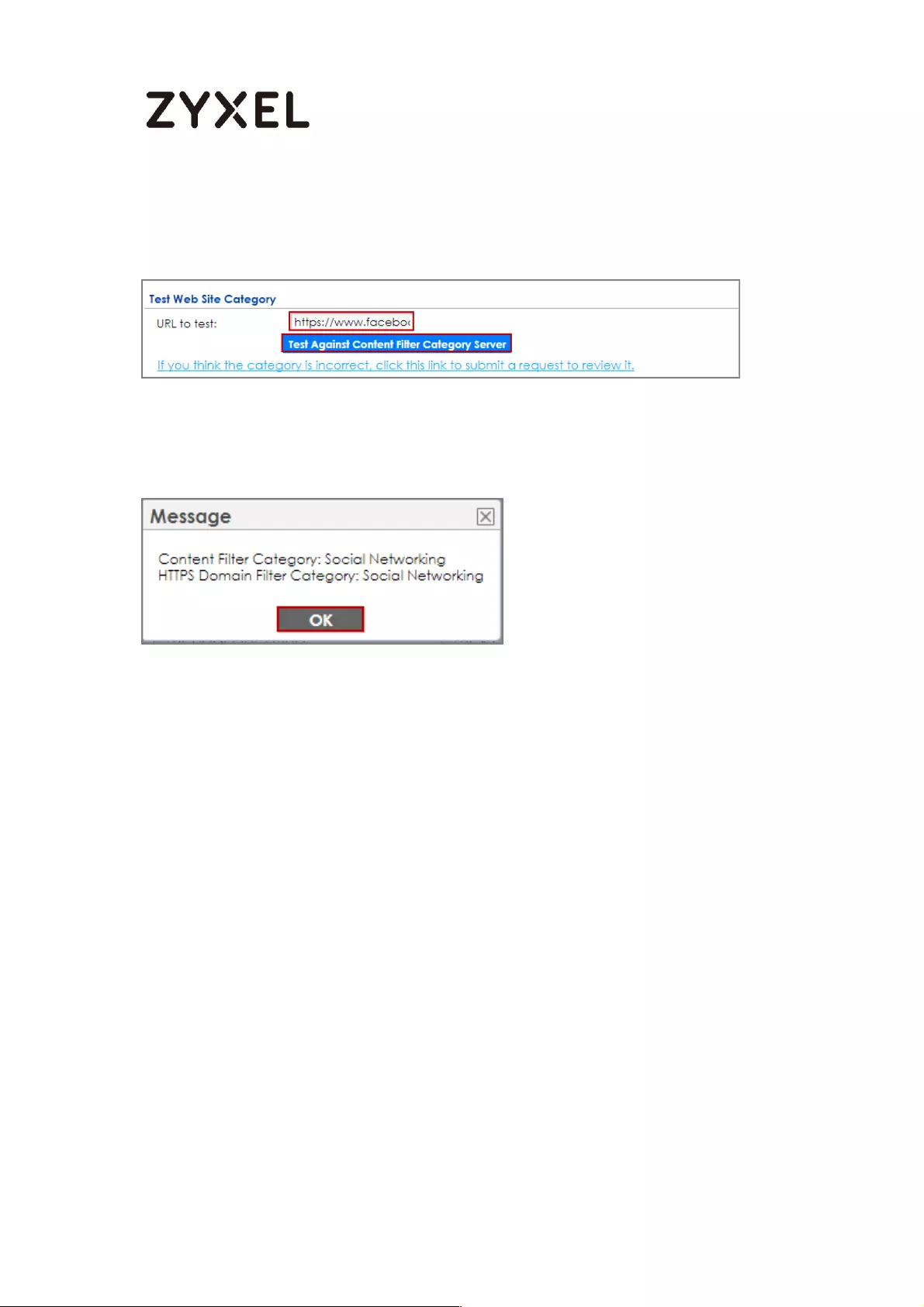
403/782
www.zyxel.com
Profile > Test Web Site Category. Type URL to test the category and click Test Against
Content Filter Category Server.
You will see the category recorded in the external content filter server’s database for
both HTTP and HTTPS Domain you specified.
Go to CONFIGURATION > UTM Profile> Content Filter > Profile Management > Add Filter
File > Custom Service. Configure a Name for you to identify the Content Filter Profile
and select Enable Content Filter Category Service. Select Block to prevent users from
accessing web pages that match the managed categories that you select below.
Select Log to record attempts to access web pages that match the unsafe categories
that you select below.
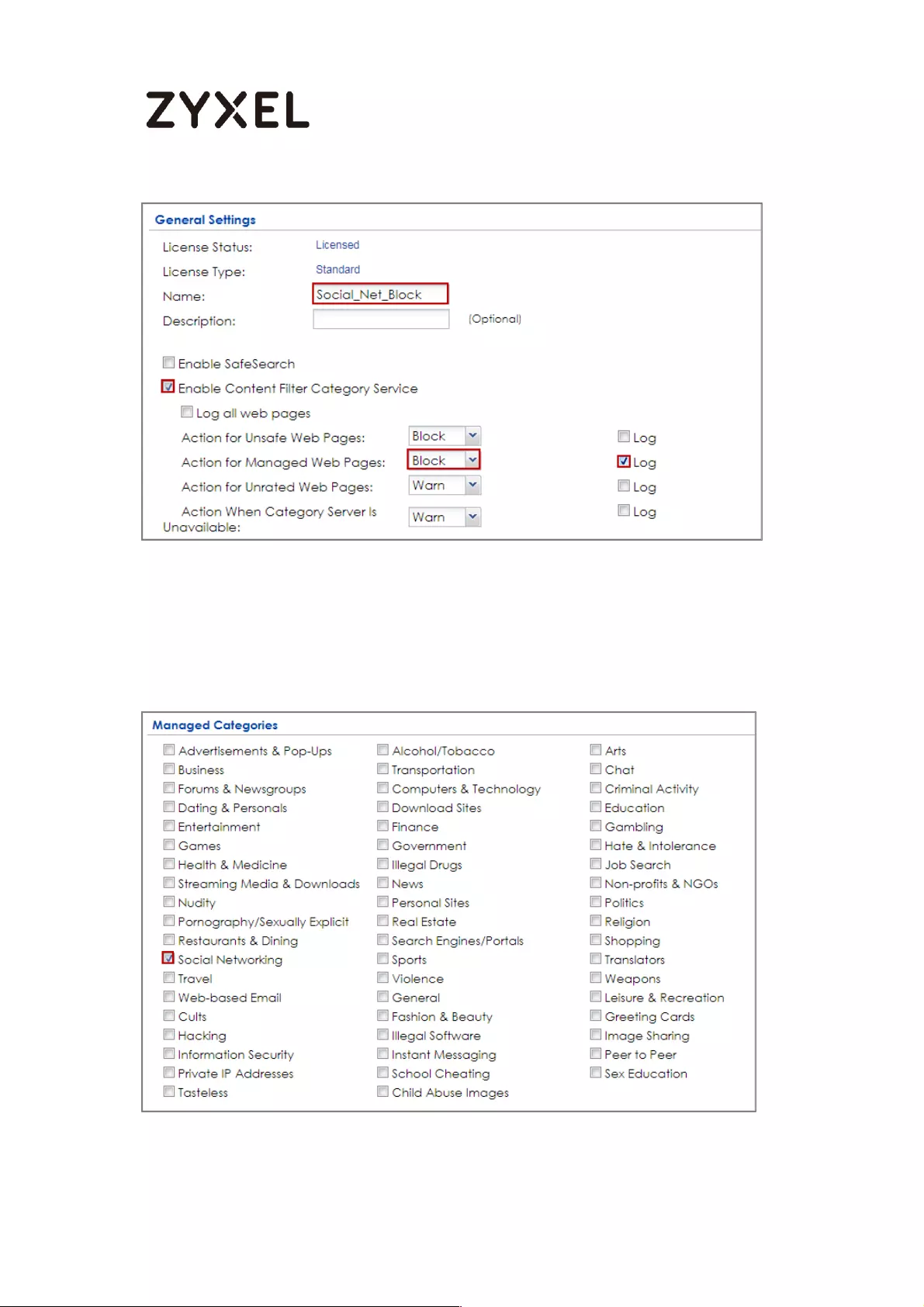
404/782
www.zyxel.com
Scroll down to the Managed Categories section, select categories in this section to
control access to specific types of Internet content. You must have the Content Filtering
license to filter these categories.
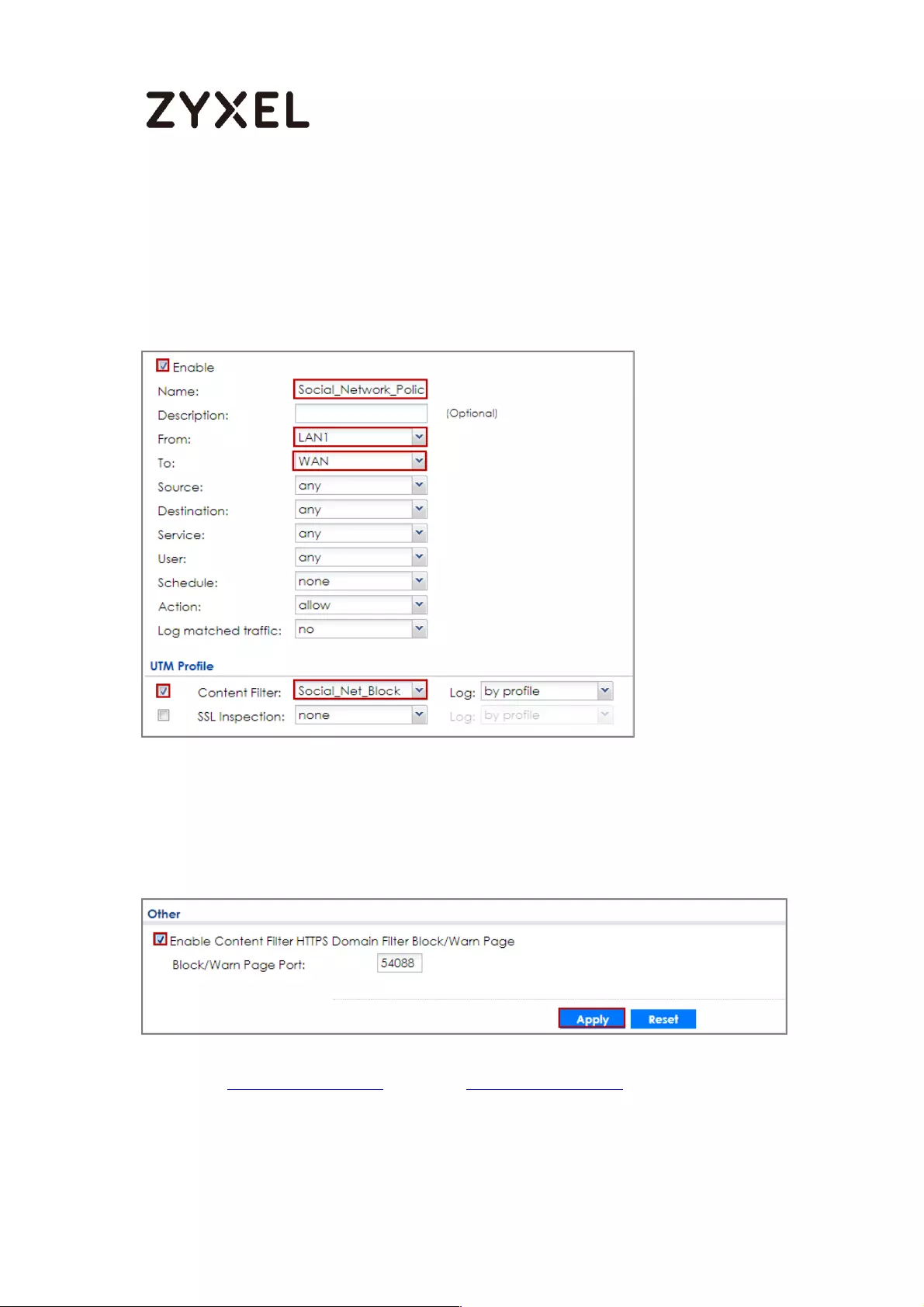
405/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
Go to CONFIGURATION > Security Policy > Policy Control, configure a Name for you to
identify the Security Policy profile. Scroll down to UTM Profile, select Content Filter and
select a profile from the list box (Social_Net_Block in this example).
Set Up the System Policy on the ZyWALL/USG
Go to CONFIGURATION > System > WWW > Show Advanced Settings > Other, click
Enable Content Filter HTTPS Domain Filter Block/Warn Page.
Test the Result
Type http://www.facebook.com/ or https://www.facebook.com/ into the browser, the
error message occurs.

406/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as below.
HTTP traffic log matches (Content Filter) and HTTPS traffic log matches (HTTPS Domain
Filter) in message field.
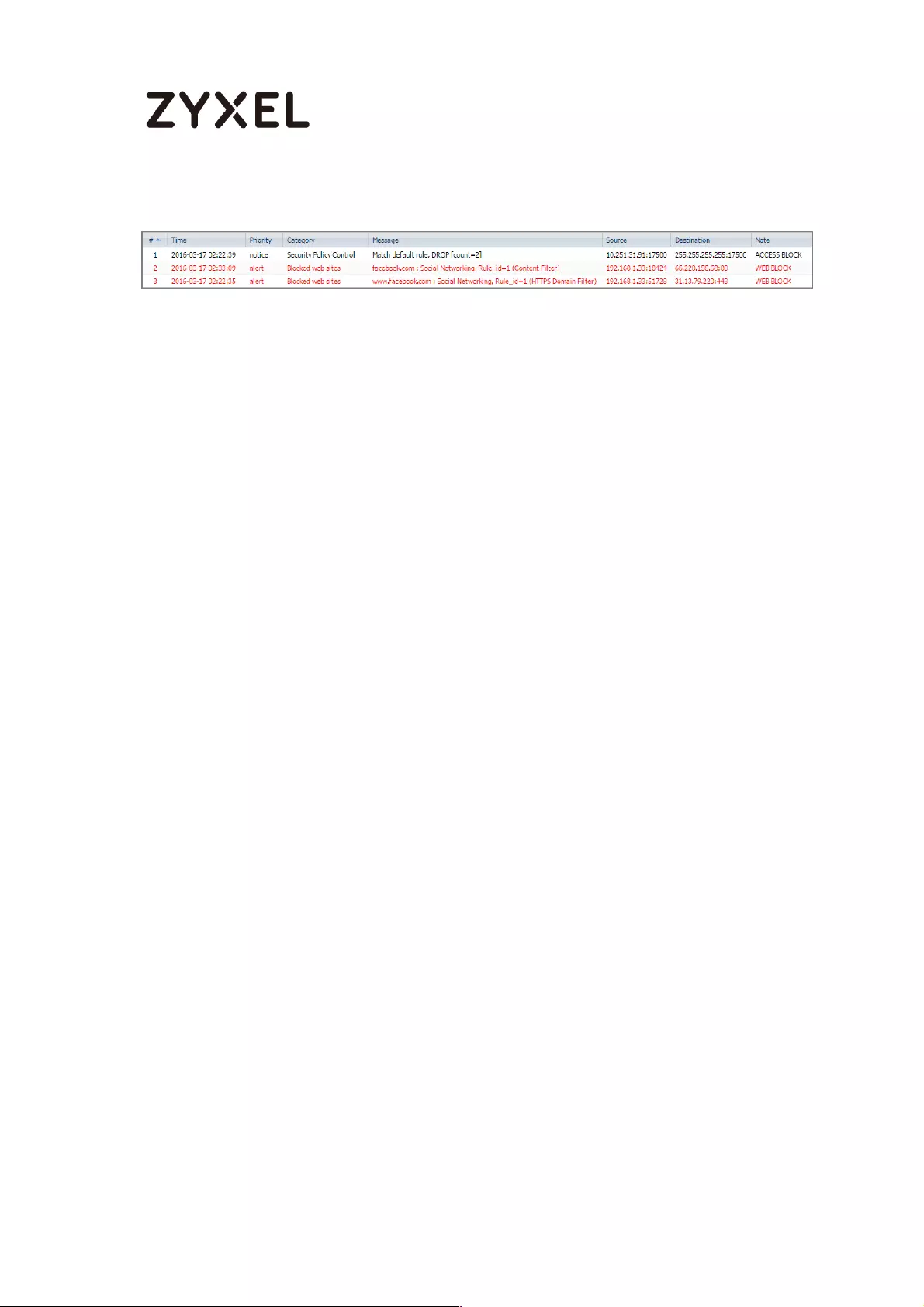
407/782
www.zyxel.com
Monitor > Log
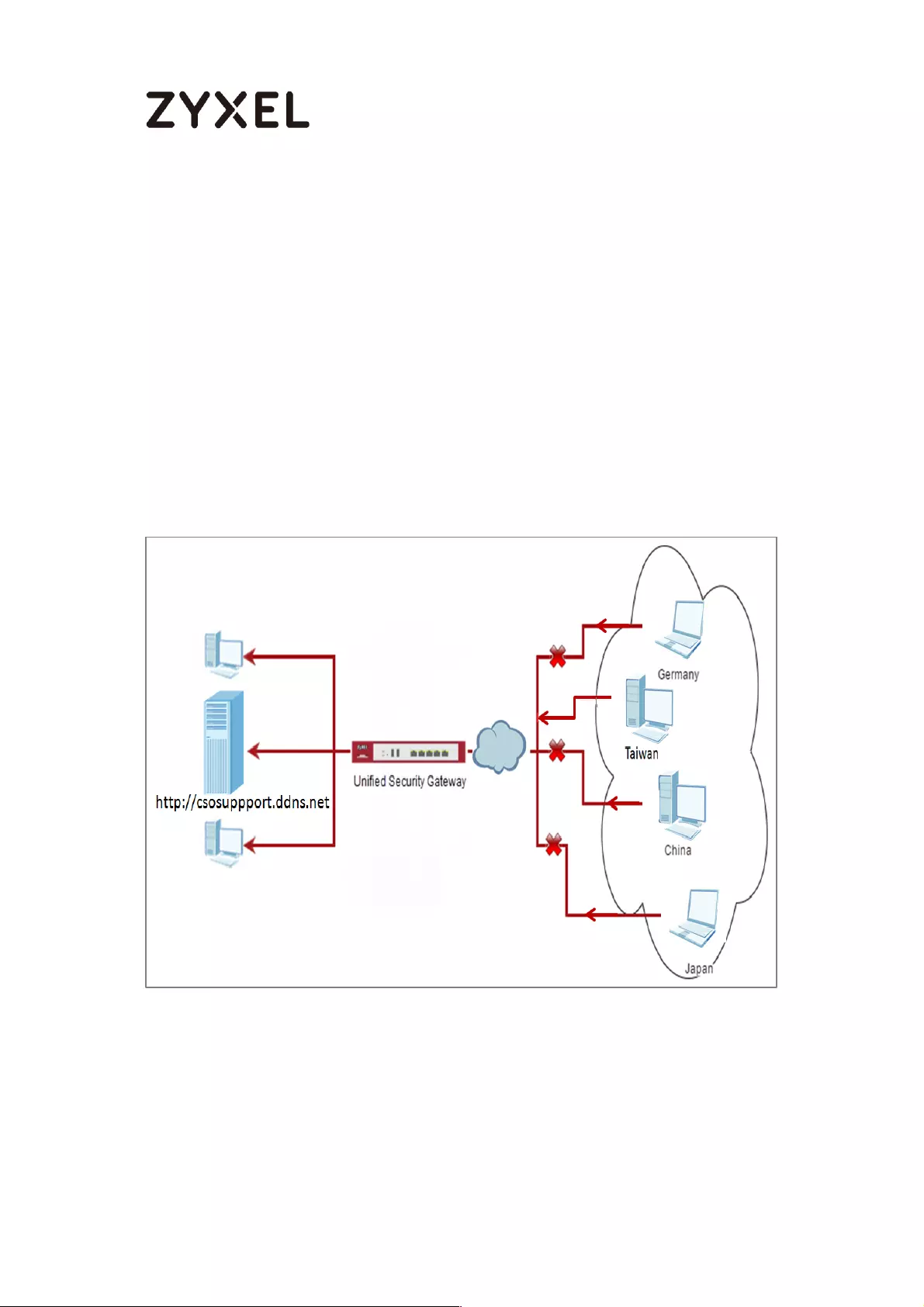
408/782
www.zyxel.com
How to Configure Content Filter 2.0 with Geo IP Blocking
The Content Filter 2.0 - Geo IP blocking offers identify the country based on IP address,
it allows you to block the client accessing to certain country based on organizational
policy.
When user makes HTTP or HTTPS request, ZyWALL/USG query IP address from MaxMind
database, then take action when it matches the block country in Content Filter profile.
If you have a local web site and your primary market is local people, then there is no
need to let any other countries index or waste bandwidth on your server.
Also this feature offer an easy and effective way to prevent bogus, bots, brute force
hacks, vulnerability scanners, and web crawlers from other countries.
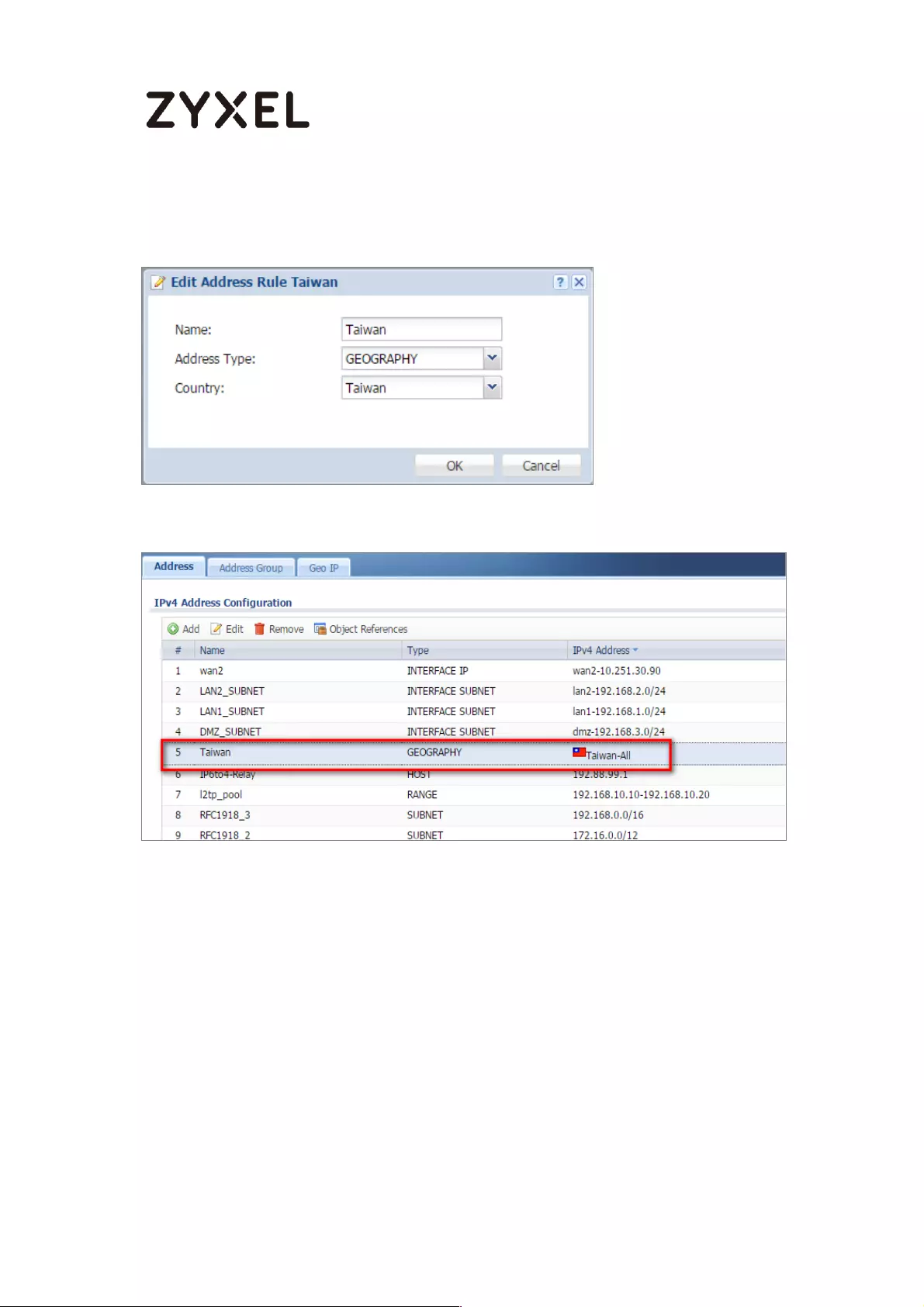
409/782
www.zyxel.com
Set Up the Address Objet with Geo IP on the ZyWALL/USG
Go to CONFIGURATION > Object > Address/Geo IP > Address > Add Address Rule.
Go to CONFIGURATION > Object > Address/Geo IP > Address, you can see the
customized GEOGRAPHY address.
Set Up the Security Policy on the ZyWALL/USG

410/782
www.zyxel.com
Go to CONFIGURATION > Security Policy > Policy Control, configure a Name for you
to identify the Security Policy profile. Set Geo IP traffic from WAN to LAN allow source
from local country (geo_allow_policy in this example).
Go to CONFIGURATION > Security Policy > Policy Control, configure a Name for you
to identify the Security Policy profile. Set traffic from WAN to LAN deny
(geo_block_policy in this example).
Test the Result
411/782
www.zyxel.com
Type http://csosuppport.ddns.net/ into the browser, and the http can be reached.
Go to the ZyWALL/USG Monitor > Log, you will see [notice] log message such as
below. Traffic matches Geo IP policy will be blocked and shows in message field.
What Could Go Wrong?
1. The Security Policy configured wrong. The traffic cannot access the LAN server.
2. The Content-Filter service ix expired. Since Geo-IP server is bind with Content-Filter
license, there must be available date for Content-Filter service.

412/782
www.zyxel.com
How to Configure Content Filter 2.0 with HTTPs Domain Filter
Application Scenario
The Content Filter with HTTPs Domain Filter allows you to block HTTPs websites by
category service without SSL-Inspection. The filtering feature is based on 64 categories
built in ZyWALL/USG such as pornography, gambling, hacking, etc.
When user makes HTTPS request, the information contains a Server Name Indication
(SNI) extension fields in server FQDN. Using the SNI to query category from local cache
then cloud database, then take action when it matches the block category in Content
Filter profile.
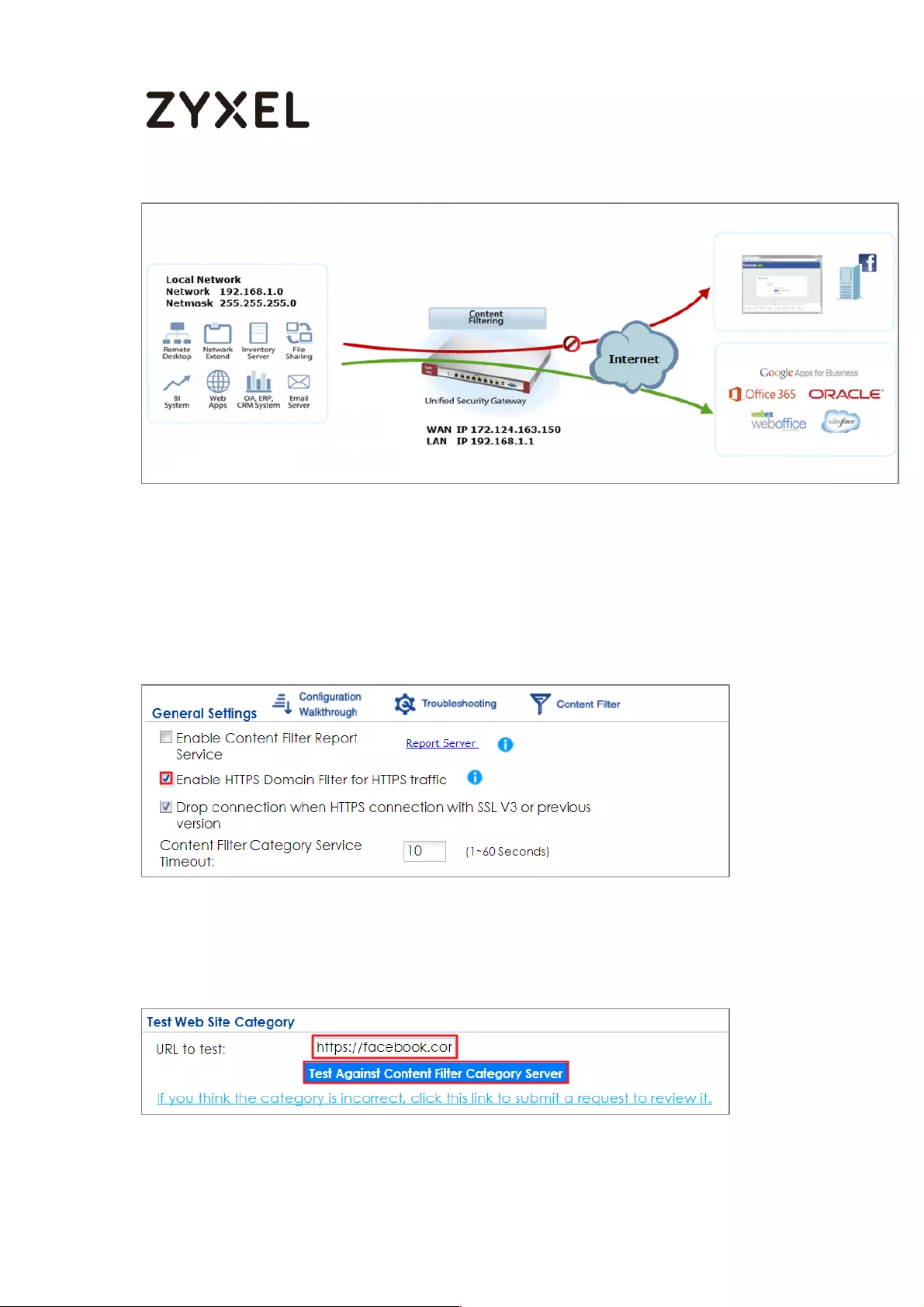
413/782
www.zyxel.com
Set Up the Content Filter on the ZyWALL/USG
Go to CONFIGURATION > UTM Profile> Content Filter > Profile > General Settings. Select
Enable HTTPS Domain Filter for HTTPS traffic.
Go to CONFIGURATION > UTM Profile> Content Filter > Profile Management > Add Filter
Profile > Test Web Site Category. Type URL to test the category and click Test Against
Content Filter Category Server.
414/782
www.zyxel.com
You will see the category recorded in the external content filter server’s database for
both HTTP and HTTPS Domain you specified.
Go to CONFIGURATION > UTM Profile> Content Filter > Profile Management > Add Filter
File > Custom Service. Configure a Name for you to identify the Content Filter Profile
and select Enable Content Filter Category Service. Select Block to prevent users from
accessing web pages that match the managed categories that you select below.
Select Log to record attempts to access web pages that match the unsafe categories
that you select below.
Scroll down to the Managed Categories section, select categories in this section to
control access to specific types of Internet content. You must have the Content Filtering
license to filter these categories.
415/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
Go to CONFIGURATION > Security Policy > Policy Control, configure a Name for you to
identify the Security Policy profile. Scroll down to UTM Profile, select Content Filter and
select a profile from the list box (Social_Net_Block in this example).
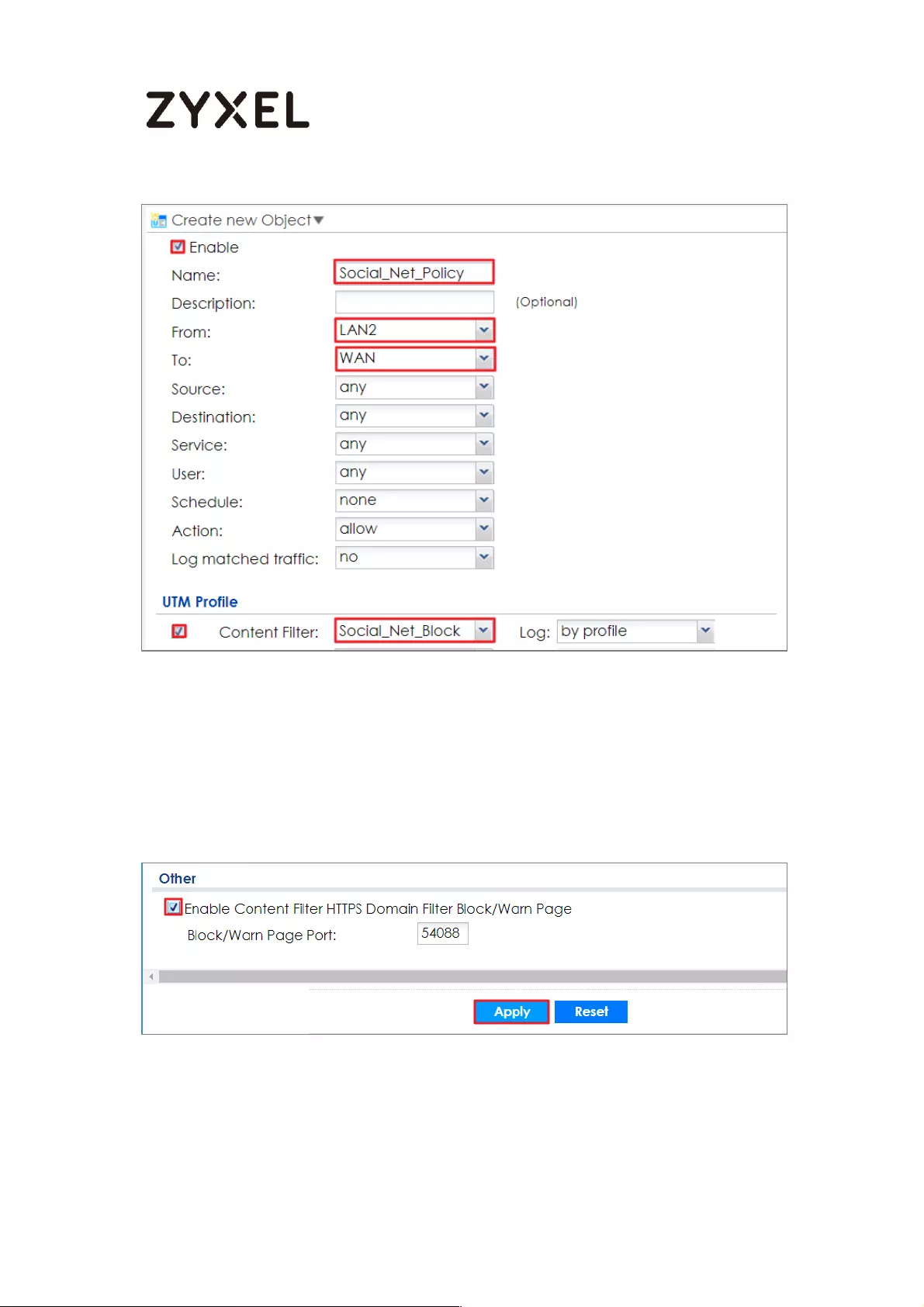
416/782
www.zyxel.com
Set Up the System Policy on the ZyWALL/USG
Go to CONFIGURATION > System > WWW > Show Advanced Settings > Other, click
Enable Content Filter HTTPS Domain Filter Block/Warn Page.
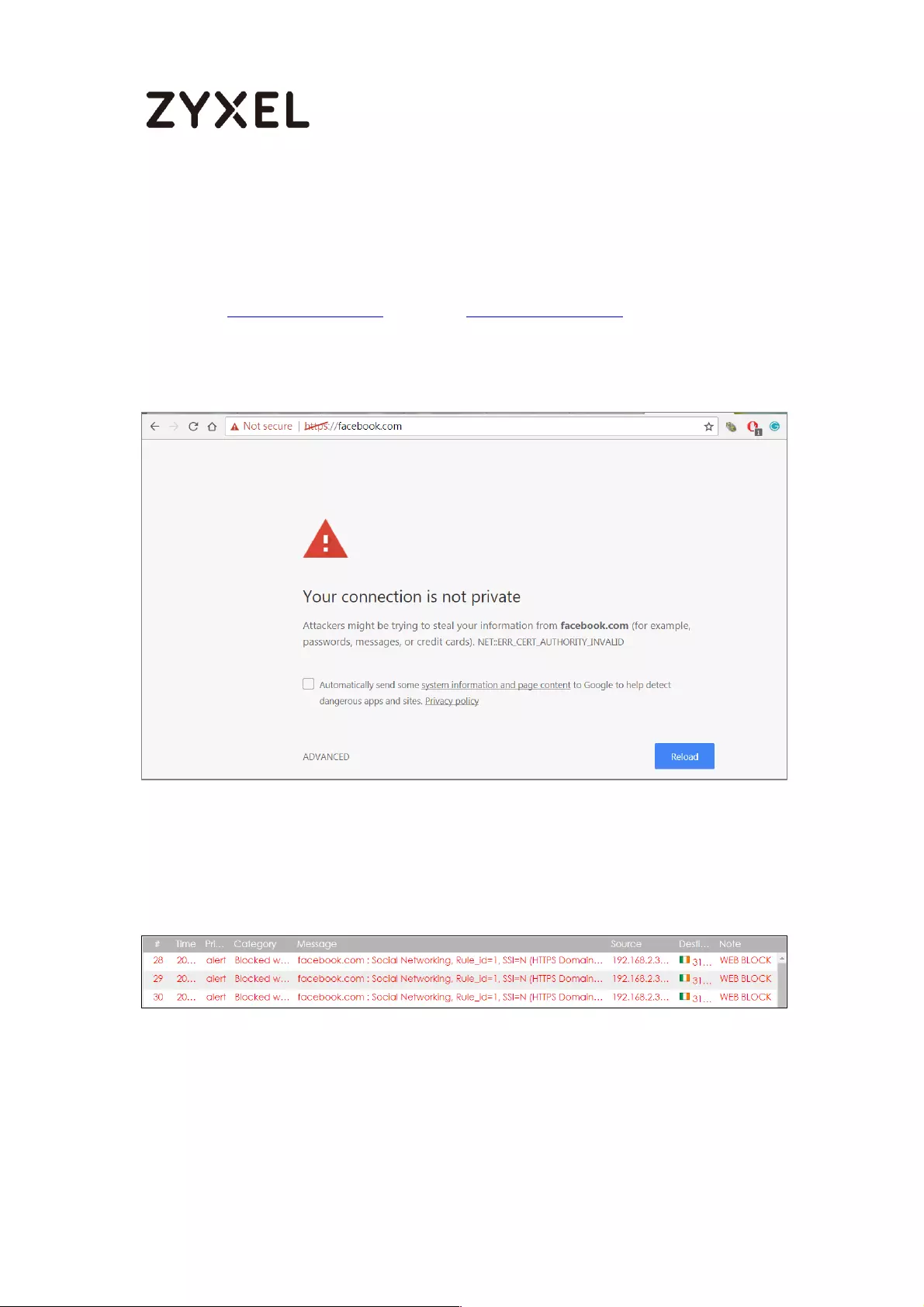
417/782
www.zyxel.com
Test the Result
Type http://www.facebook.com/ or https://www.facebook.com/ into the browser, the
error message occurs.
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as below.
HTTP traffic log matches (Content Filter) and HTTPS traffic log matches (HTTPS Domain
Filter) in message field.
Monitor > Log
What Could Wrong?
1. “Enable HTTPS Domain Filter for HTTPS traffic” is not checked.
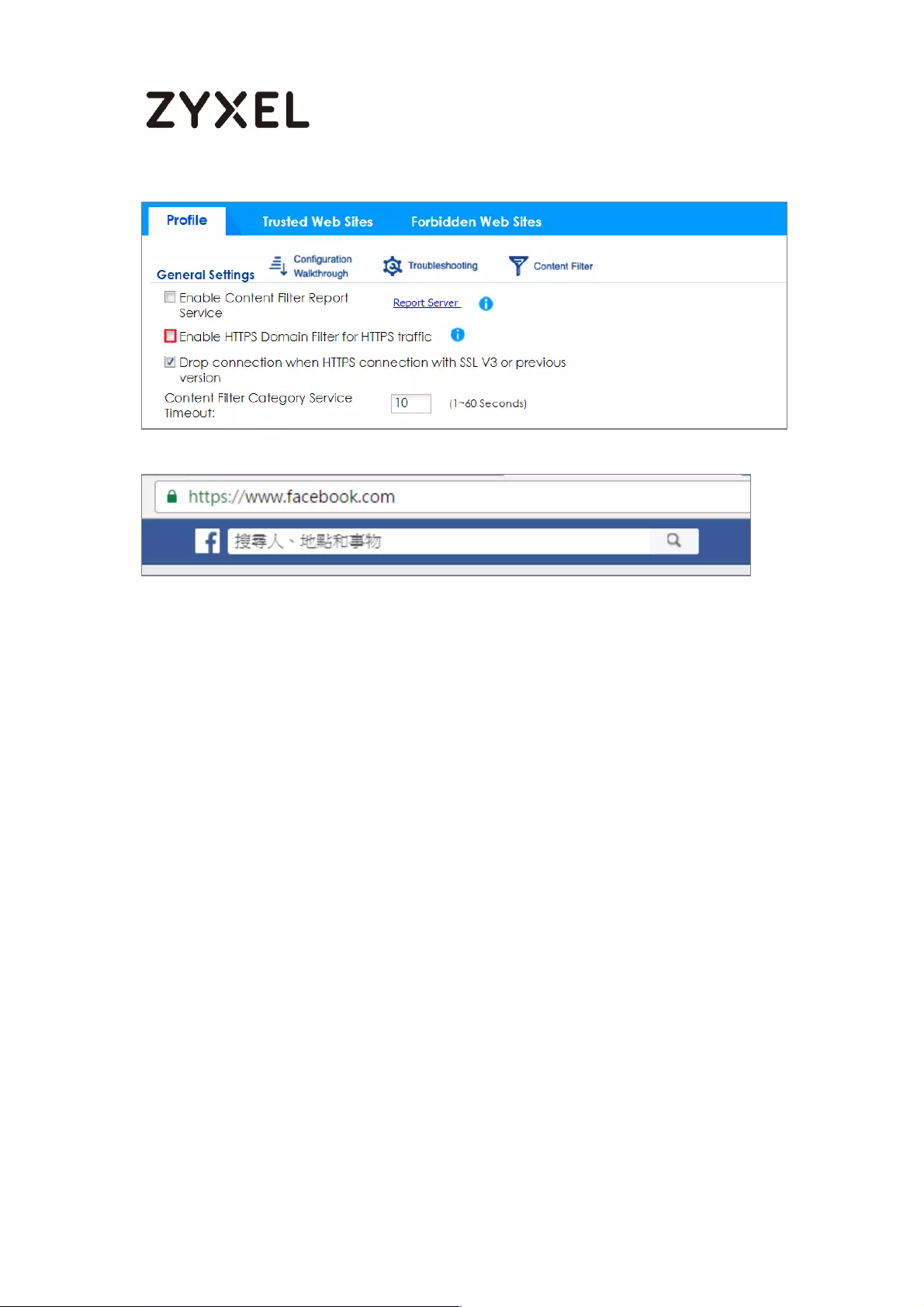
418/782
www.zyxel.com
HTTPs traffic will pass.
How to block the client accessing to certain country using
Geo IP and Content Filter
The Content Filter with Geo IP offers identify the country based on IP address, it allows
you to block the client accessing to certain country based on organizational policy.
When user makes HTTP or HTTPS request, ZyWALL/USG query IP address from MaxMind
database, then take action when it matches the block country in Content Filter profile.
ZyWALL/USG Geo IP Example

419/782
www.zyxel.com
Check Geo IP License Status on the ZyWALL/USG
Go to CONFIGURATION > Licensing > Registration > Service, the Geo IP Service should
be Licensed to configure this feature.
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG310 (Firmware Version: 4.25)
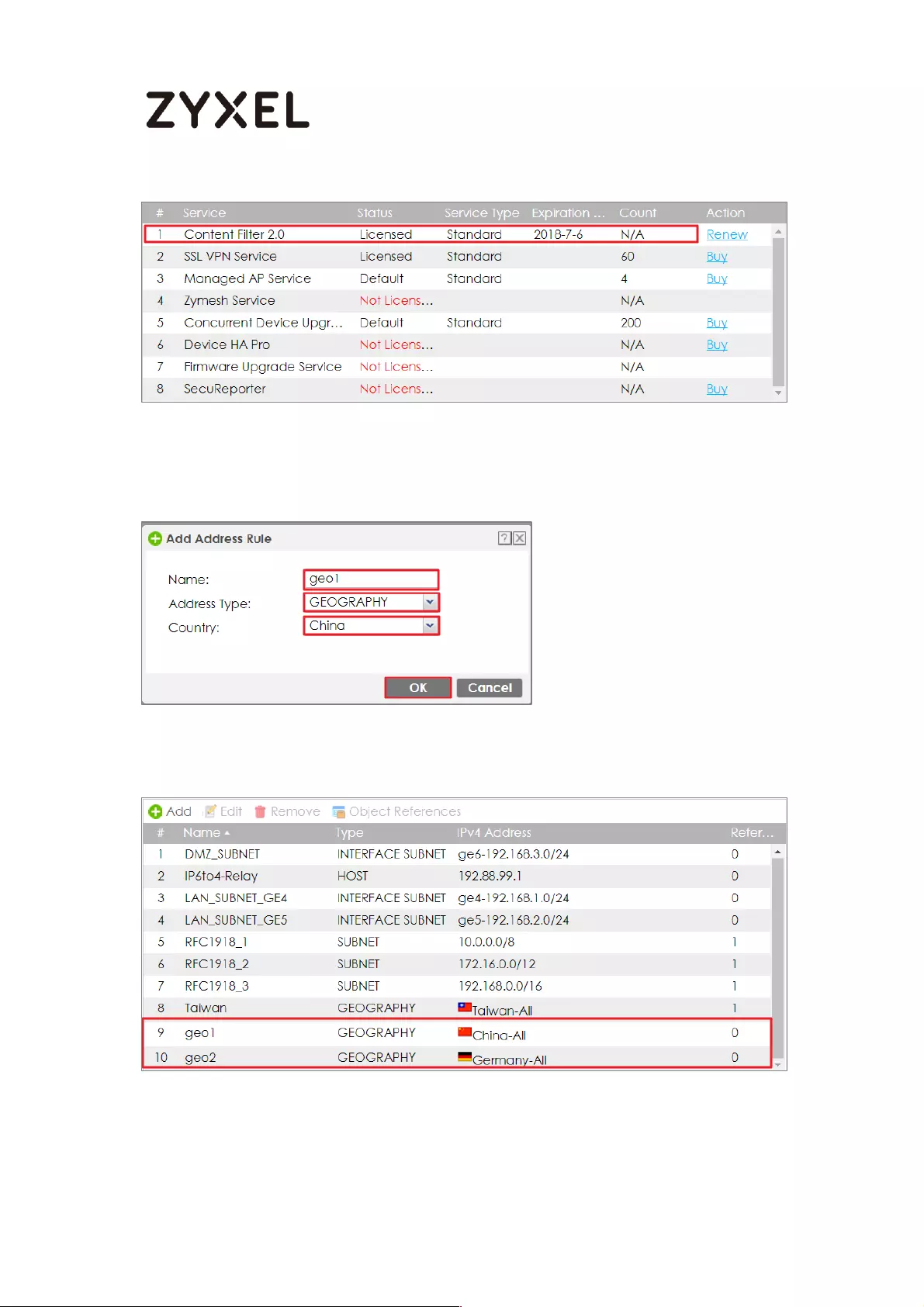
420/782
www.zyxel.com
Set Up the Address Objet with Geo IP on the ZyWALL/USG
Go to CONFIGURATION > Object > Address/Geo IP > Address > Add Address Rule.
Go to CONFIGURATION > Object > Address/Geo IP > Address, you can see the
customized GEOGRAPHY address.
Go to CONFIGURATION > Object > Address/Geo IP > Address Group> Add Address
Group Rule, add all customized GEOGRAPHY address into the same Member object.
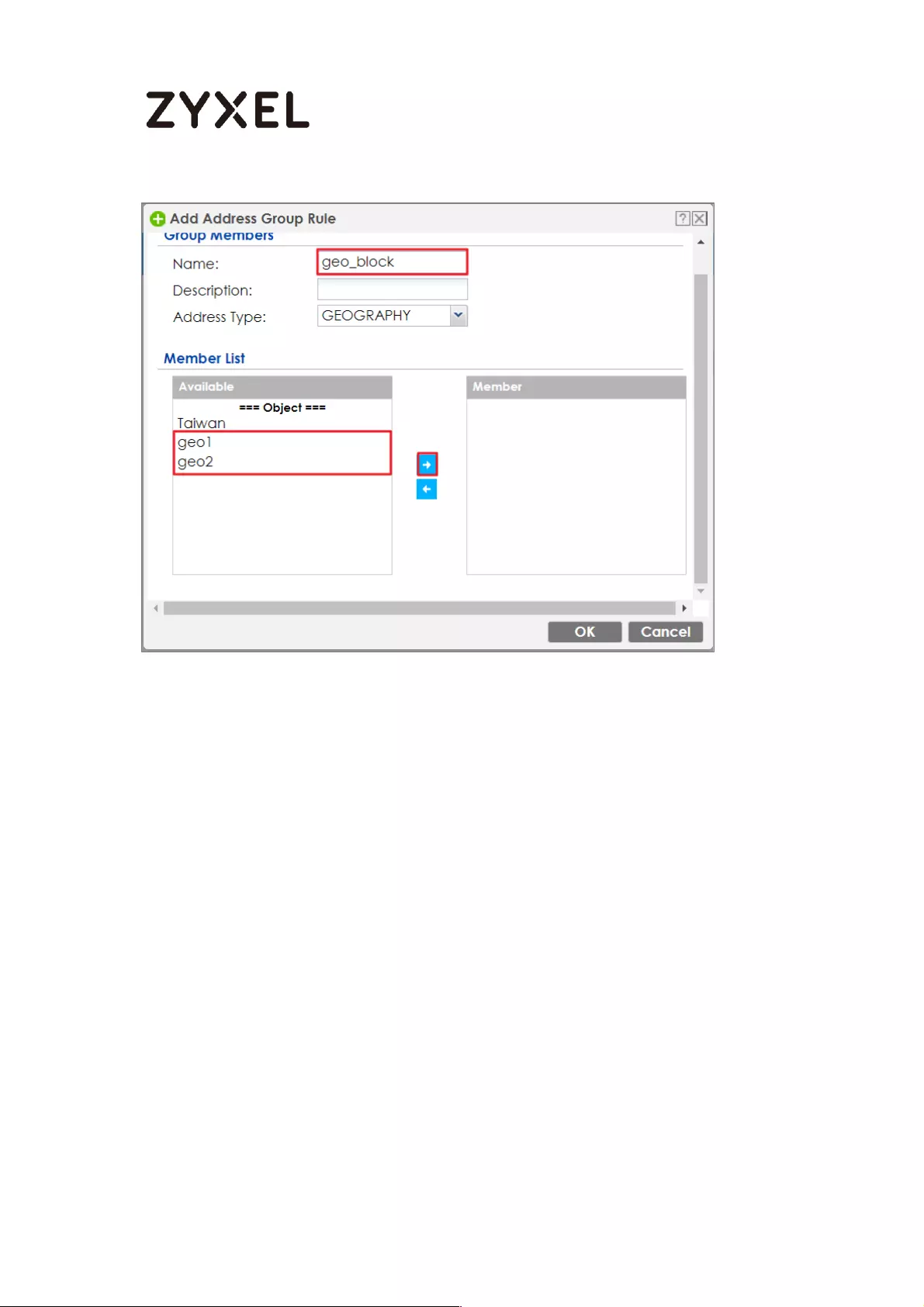
421/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
Go to CONFIGURATION > Security Policy > Policy Control, configure a Name for you to
identify the Security Policy profile. Set deny Geo IP traffic from LAN to WAN
(geo_block_policy in this example).

422/782
www.zyxel.com
Test the Result
Type http://www.pku.edu.cn/ or https://www.rwth-aachen.de/ into the browser, sites
can’t be reached.
423/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > Log, you will see [notice] log message such as
below. Traffic matches Geo IP policy will be blocked and shows in message field.
424/782
www.zyxel.com
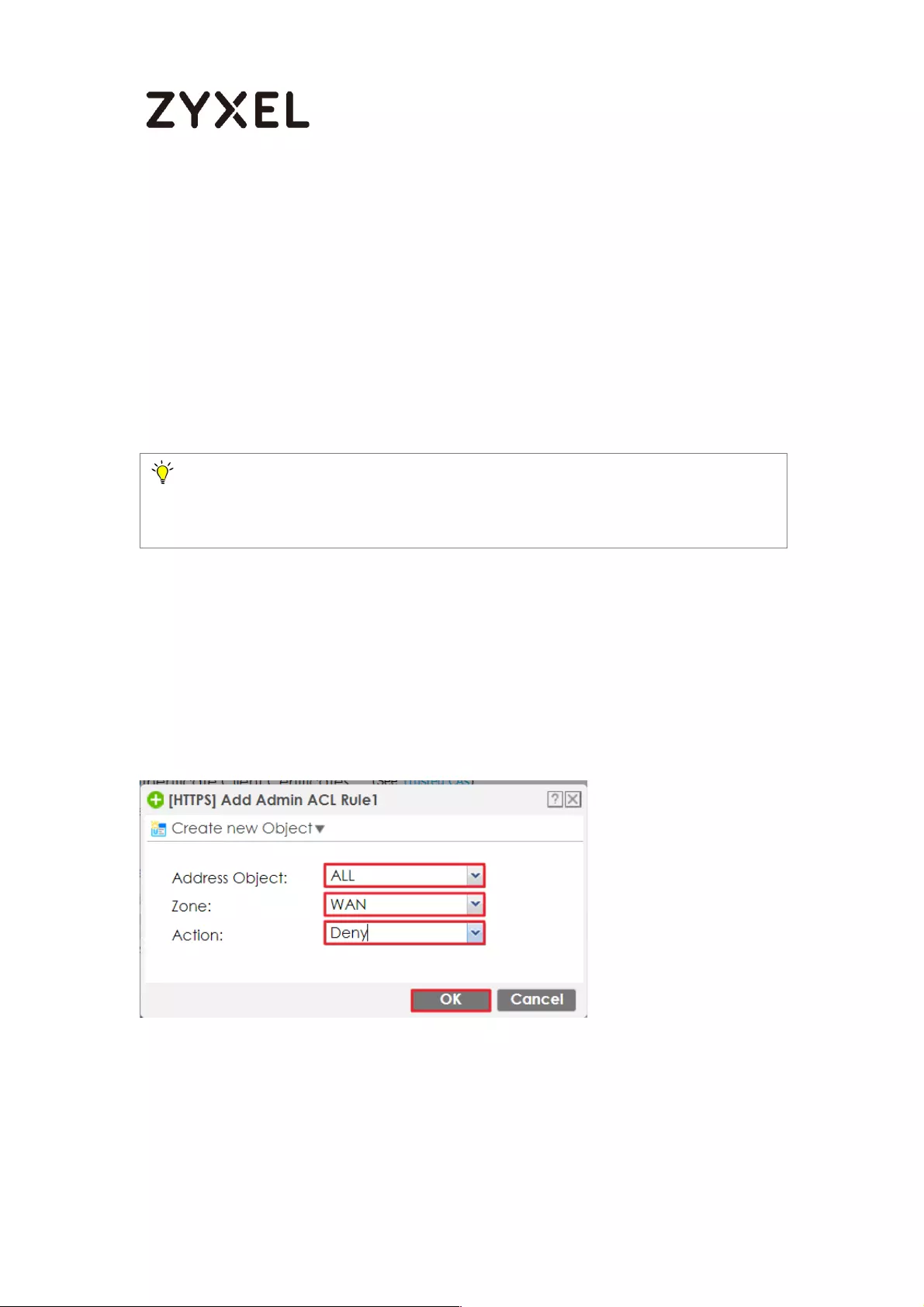
425/782
www.zyxel.com
How to Restrict Web Portal access from the Internet
This example shows how to use the VPN Setup Wizard to create a site-to-site VPN with
multiple LAN access to the VPN tunnel. The example instructs how to configure the VPN
tunnel between each site and redirect multiple LAN interface traffic to the VPN tunnel.
When the VPN tunnel is configured, multiple LAN subnets can be accessed securely.
ZyWALL/USG Restrict Web Portal Access from the Internet
Set Up the ZyWALL/USG System Setting
Go to CONFIGURATION > System > WWW > Admin Service Control > Add Admin ACL
Rule 1. Set the address access action as Deny for ALL address in WAN.
CONFIGURATION > System > WWW > Admin Service Control > Add Admin ACL Rule 1
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG60 (Firmware Version: ZLD 4.25).
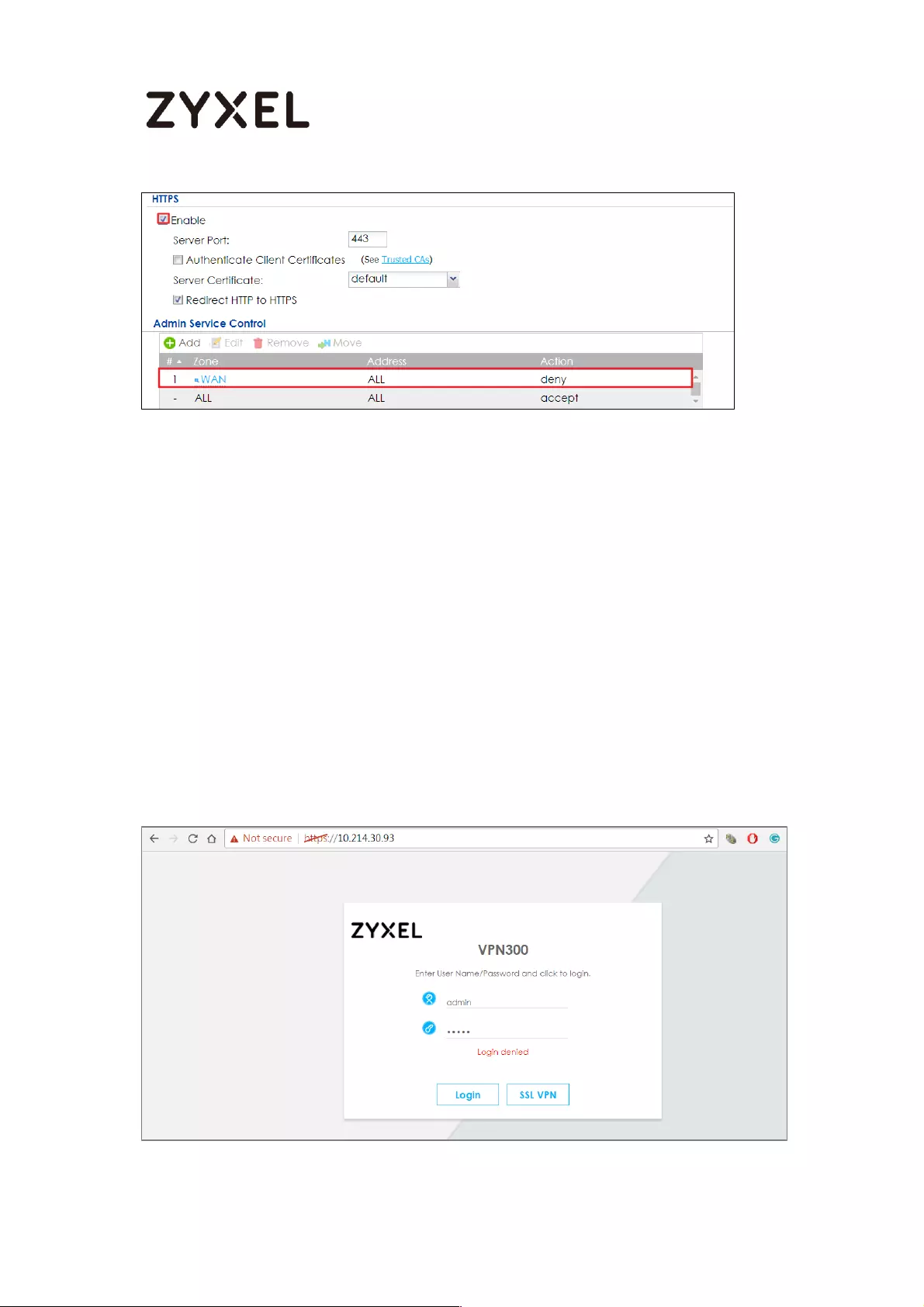
426/782
www.zyxel.com
Test the Web Access
Login to the device via the WAN interface with the administrator's user name and
password. The screen will show Login denied.
Login to the device via the WAN interface
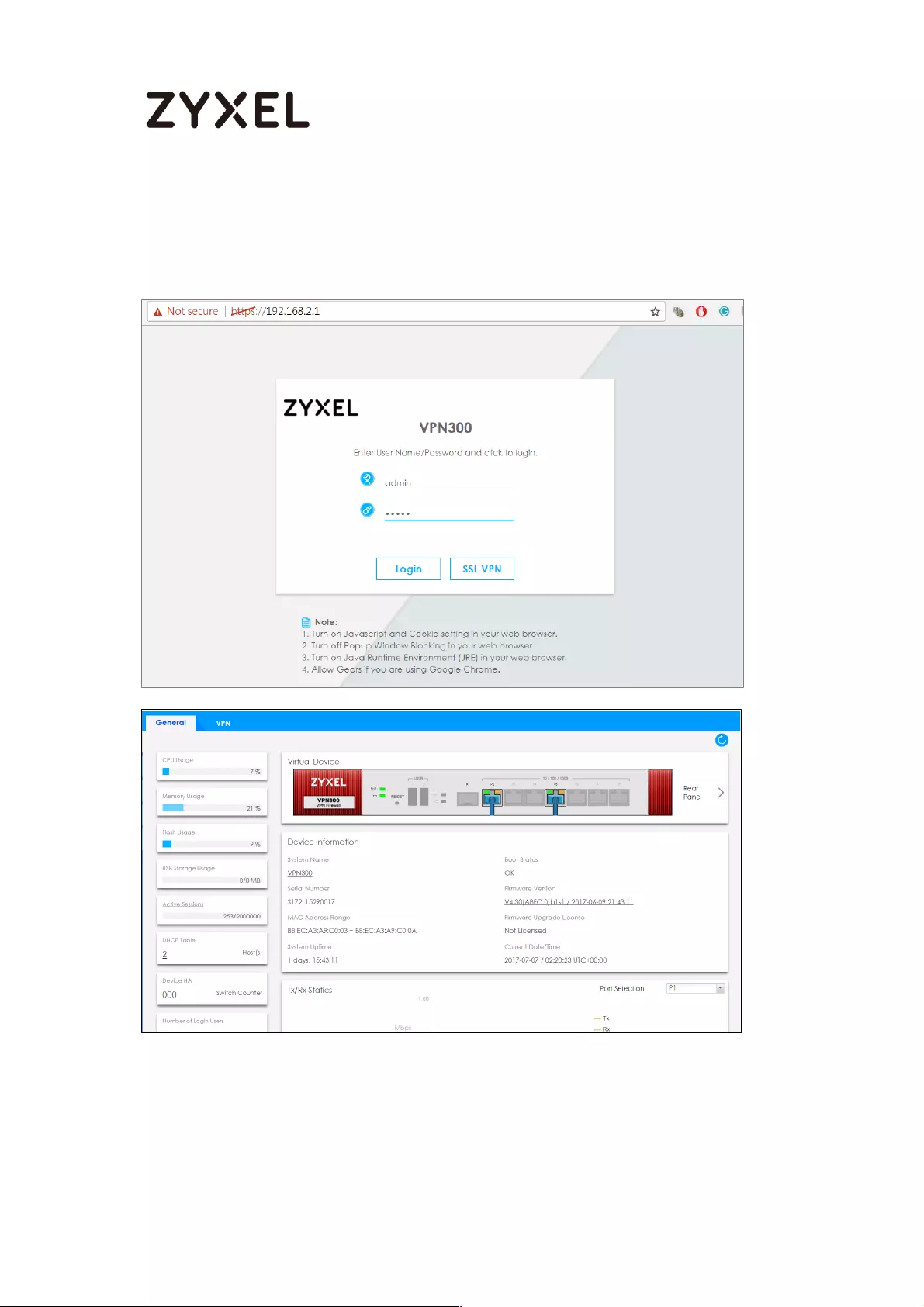
427/782
www.zyxel.com
Login to the device via the LAN interface with the administrator's user name and
password. The management portal will be displayed.
Login to the device via the LAN interface
Go to MONITOR > Log. You can see that the admin login has been denied access from
the WAN interface but it is allowed from the LAN interface.
MONITOR > Log
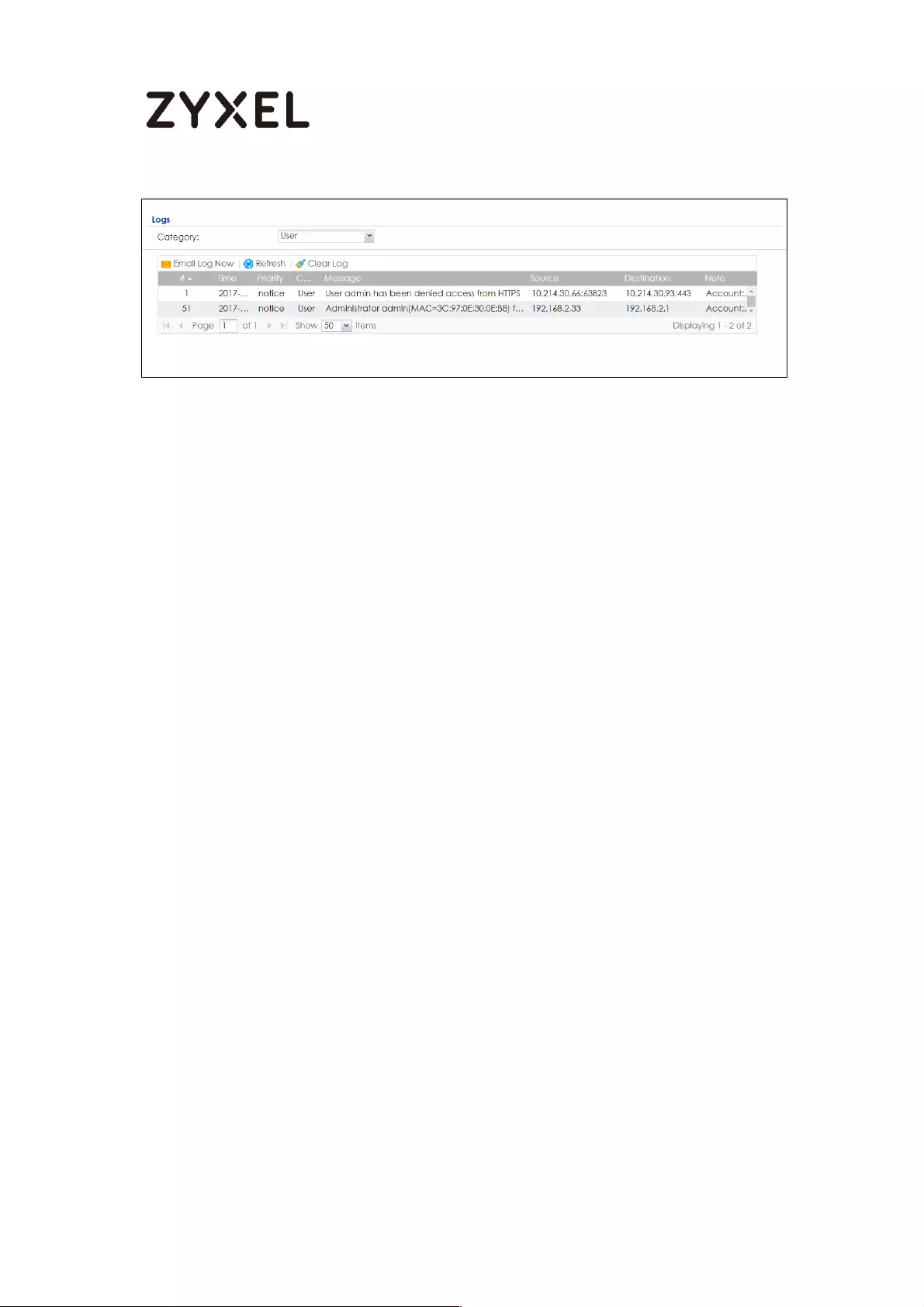
428/782
www.zyxel.com
429/782
www.zyxel.com
How to Setup and Configure Daily Report
This example shows how to set up the data collection and view various statistics about
traffic passing through your ZyWALL/USG. When the Daily Report is configured, you will
receive statistics report every day.
ZyWALL/USG Setup and Configure Daily Report
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG110 (Firmware Version: ZLD 4.25).
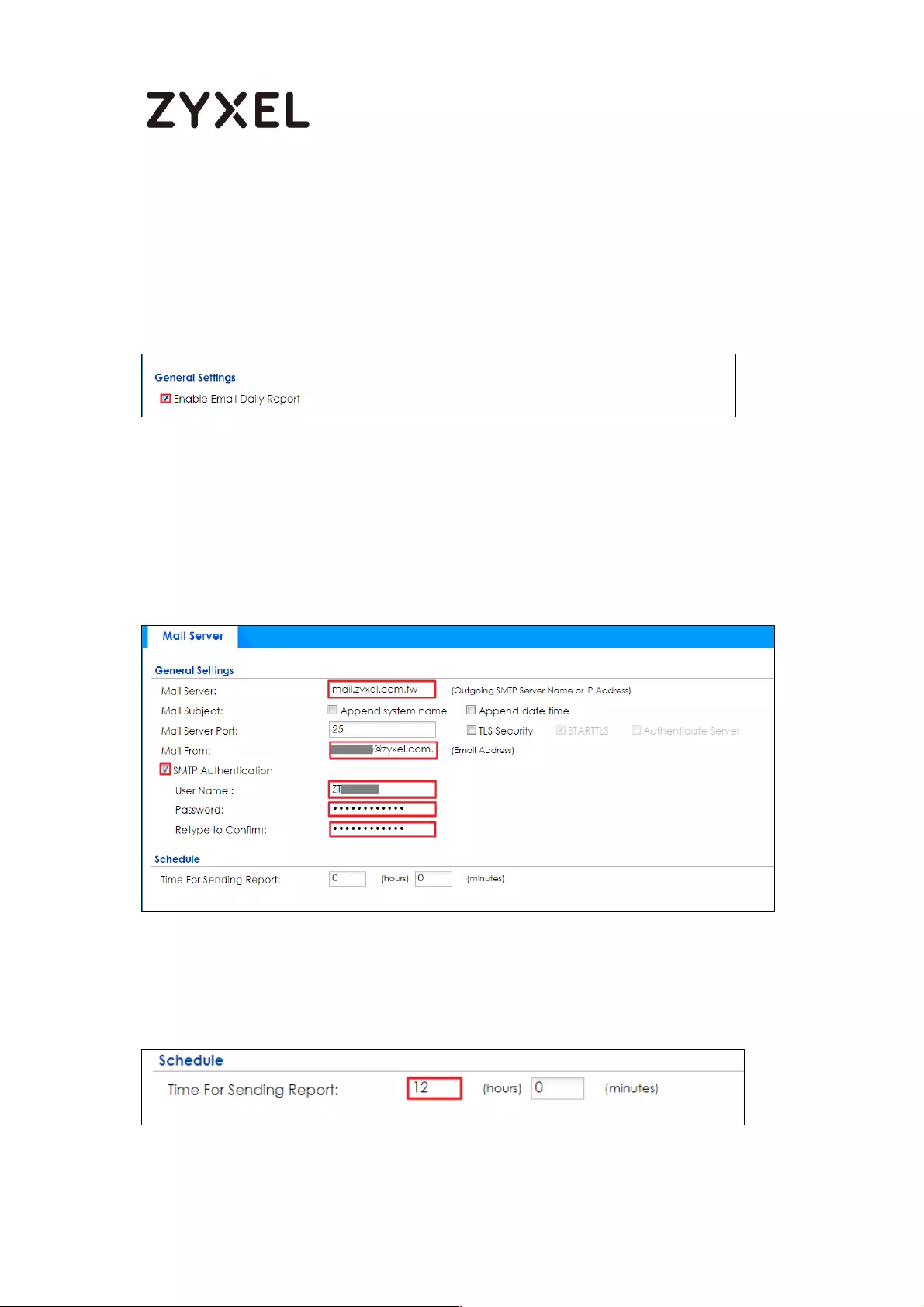
430/782
www.zyxel.com
Set Up the ZyWALL/USG Email Daily Report Setting
Go to CONFIGURATION > Log & Report > Email Daily Report > General Settings. Select
Enable Email Daily Report to send reports by e-mail every day.
CONFIGURATION > Log & Report > Email Daily Report > General Settings
Type the SMTP server name or IP address. In Mail From, type the e-mail address from
which the outgoing e-mail is delivered. In Mail To, type the e-mail address to which the
outgoing e-mail is delivered. Select SMTP Authentication if it is necessary to provide a
user name and password to the SMTP server.
CONFIGURATION > Log & Report > Email Daily Report > Email Settings
In the CONFIGURATION > Log & Report > Email Daily Report > Schedule. Select the time
of day (hours and minutes) when the log is e-mailed. Use 24-hour notation.
CONFIGURATION > Log & Report > Email Daily Report > Schedule
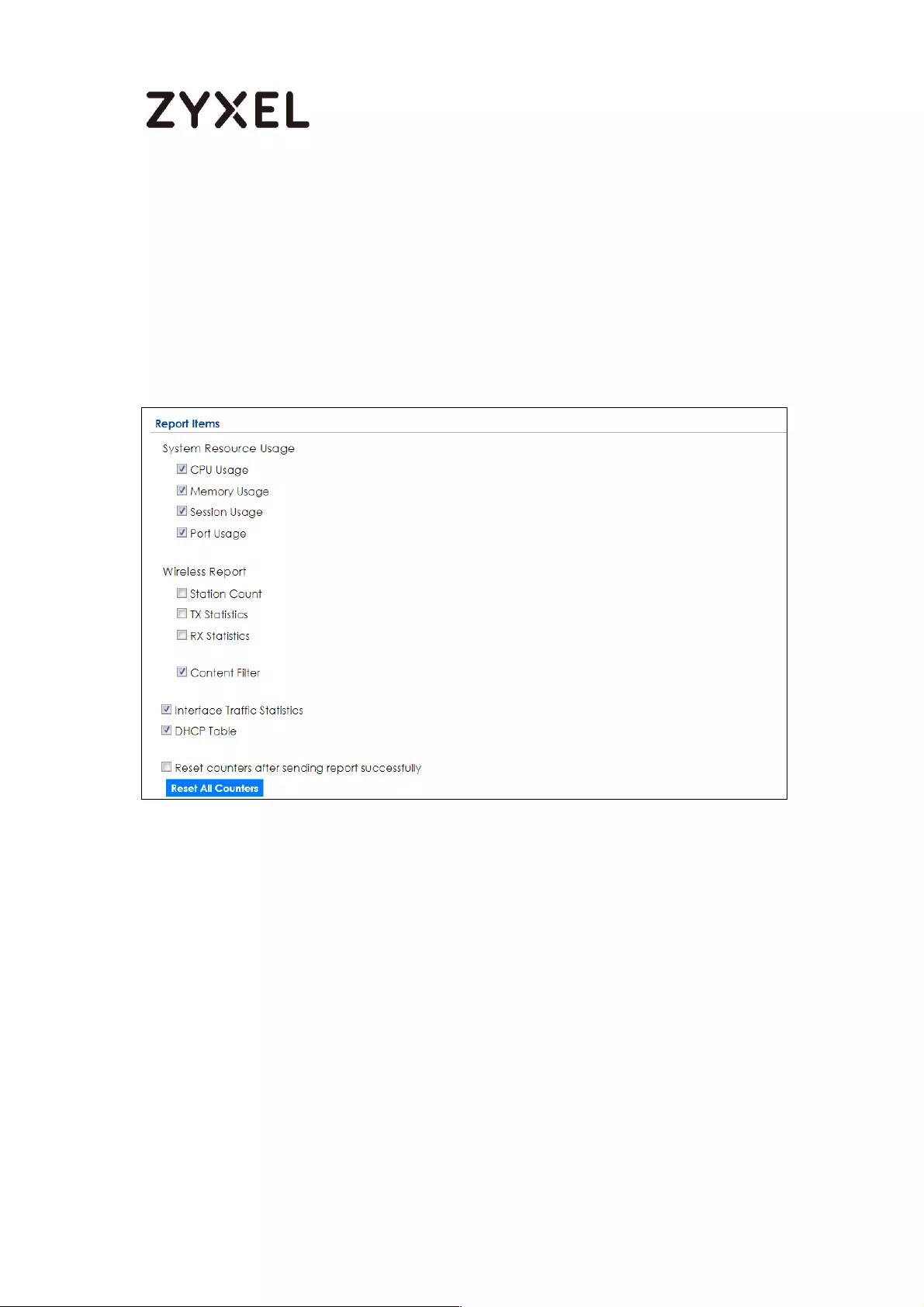
431/782
www.zyxel.com
Select the information to include in the report. Types of information include System
Resource Usage, Wireless Report, Threat Report, and Interface Traffic Statistics.
Select Reset counters after sending report successfully if you only want to see statistics
for a 24 hour period.
CONFIGURATION > Log & Report > Email Daily Report > Report Items
Test the Daily Log Report
Click Send Report Now to have the ZyWALL/USG send the daily e-mail report
immediately.
CONFIGURATION > Log & Report > Email Daily Report > Email Settings

432/782
www.zyxel.com
You will receive a daily report mail.
ZyXEL Daily Report Mail
433/782
www.zyxel.com
What Could Go Wrong?
Make sure your Email settings are all correct.
CONFIGURATION > Log & Report > Email Daily Report > Email Settings
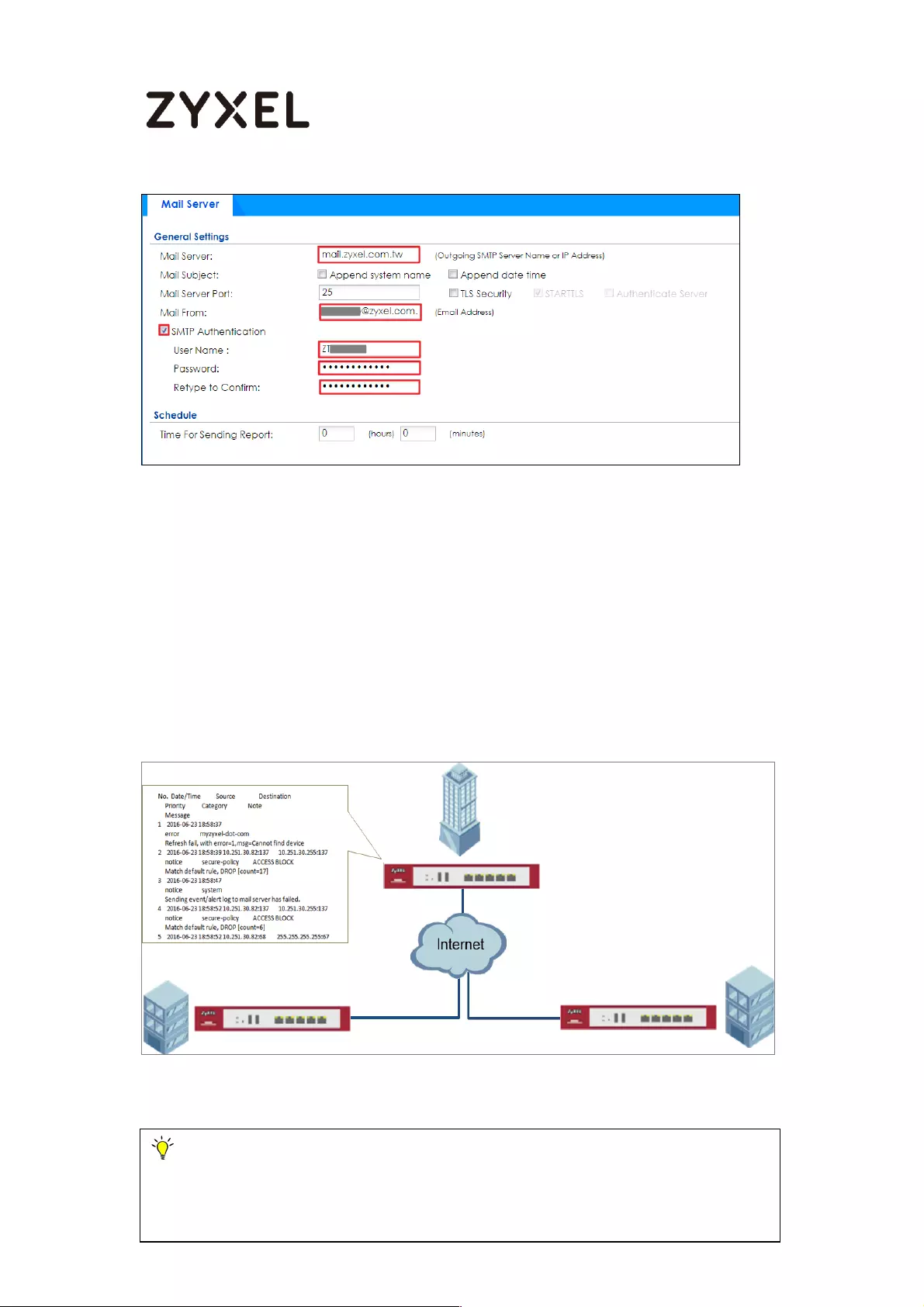
434/782
www.zyxel.com
Make sure your ZyWALL to WAN security policy allow.
How to Setup and Configure Email Logs
This example shows how to set up the e-mail profiles to mail ZyWALL/USG log messages
to the specific destinations. You can also specify which log messages to e-mail, and
where and how often to e-mail them. When the Email Logs is configured, you will
receive logs email report base on customized schedule.
ZyWALL/USG Setup and Configure E-mail Logs
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG110 (Firmware Version: ZLD 4.25).
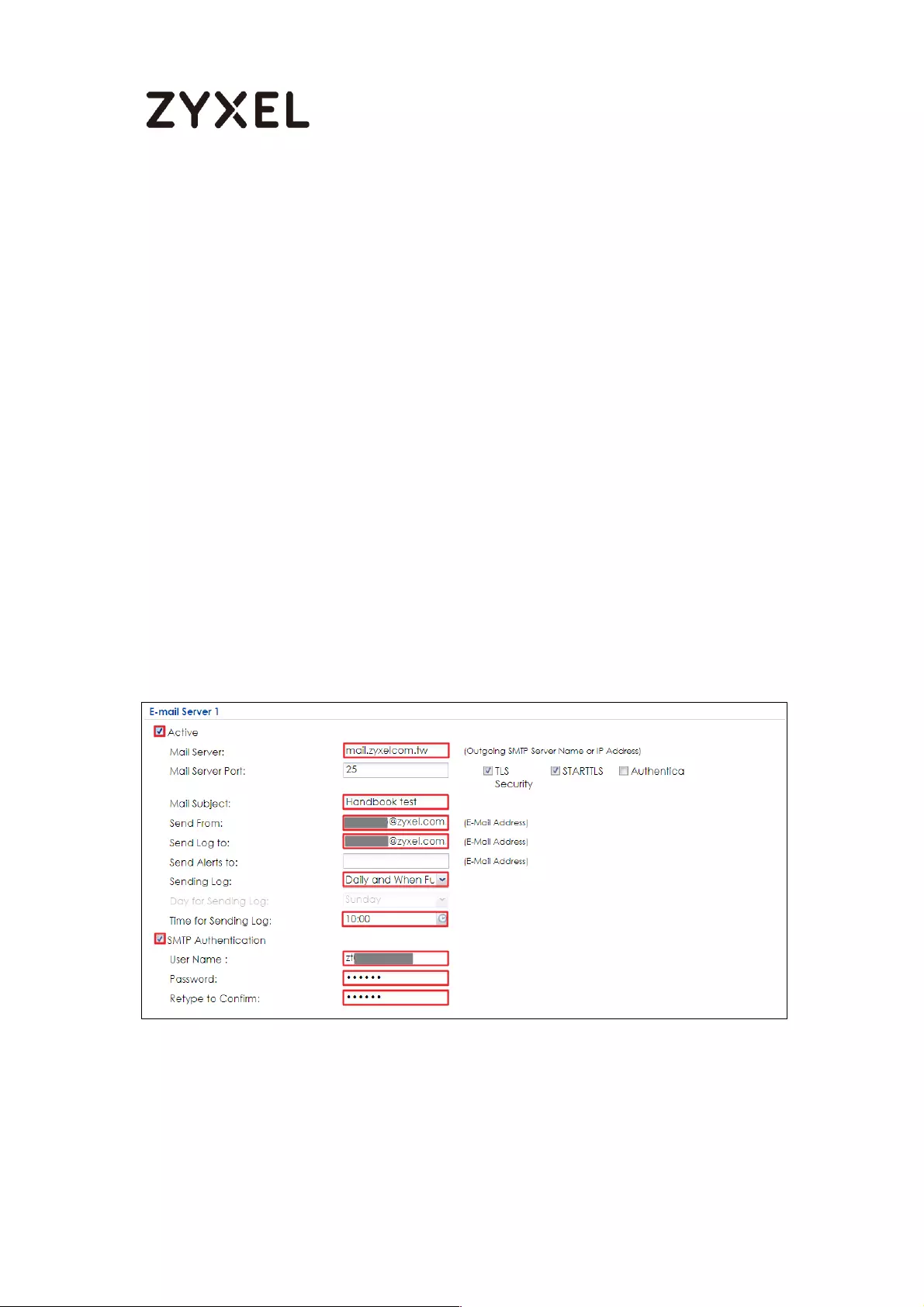
435/782
www.zyxel.com
Set Up the ZyWALL/USG Email Logs Setting
1. Go to CONFIGURATION > Log & Report > Log Settings > System Log > Edit > E-mail
Server 1. Select Active. Type the SMTP server name or IP address. In Mail From, type
the e-mail address from which the outgoing e-mail is delivered. In Mail To, type
the e-mail address to which the outgoing e-mail is delivered.
2. Day for Sending Log is available if the log is e-mailed weekly. Select the day of the
week the log is e-mailed.
3. Time for Sending Log is available if the log is e-mailed weekly or daily. Select the time
of day (hours and minutes) when the log is e-mailed. Use 24-hour notation.
4. Select SMTP Authentication if it is necessary to provide a user name and password
to the SMTP server.
CONFIGURATION > Log & Report > Log Settings > System Log > Edit > E-mail Server 1
5. Go to CONFIGURATION > Log & Report > Log Settings > System Log > Edit > Active
Log and Alert. Use the System Log drop-down list to change the log settings for all
of the log categories.
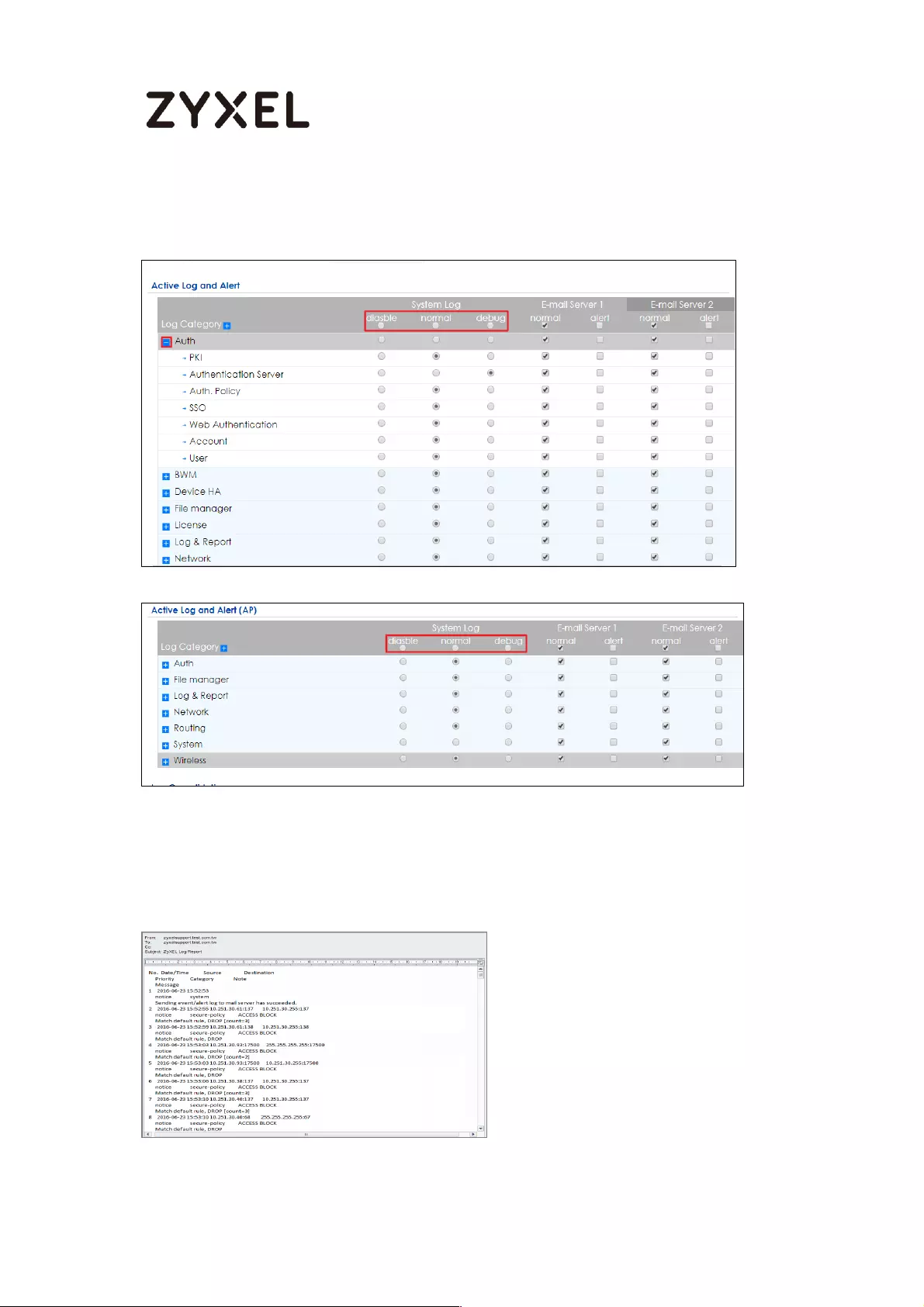
436/782
www.zyxel.com
CONFIGURATION > Log & Report > Log Settings > System Log > Edit > Active Log and
Alert.
Test the Email Log
You will receive a log mail depends on the time you set in the E-mail Server.
ZyXEL Log Mail
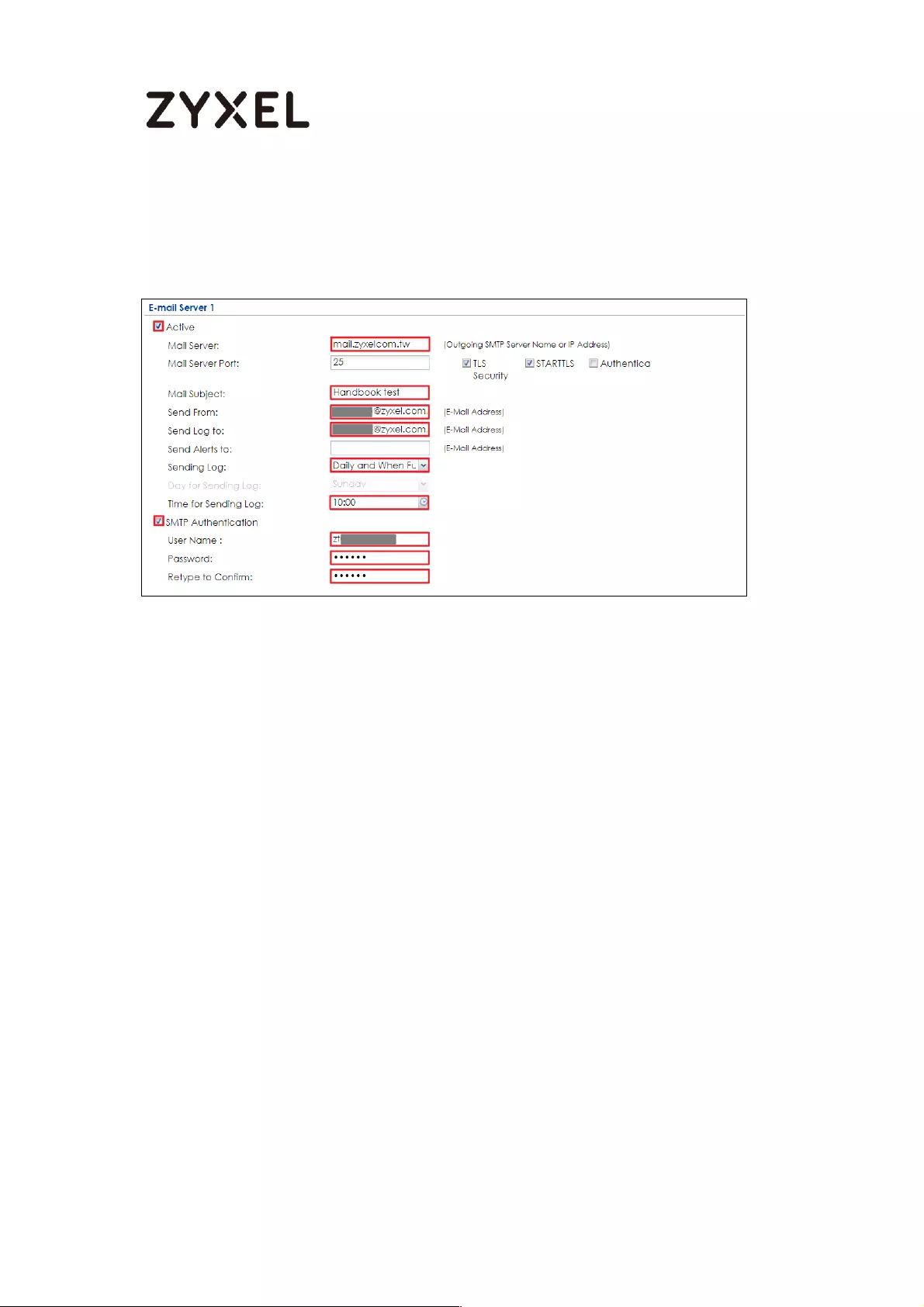
437/782
www.zyxel.com
What Could Go Wrong?
Make sure your Email settings are all correct.
CONFIGURATION > Log & Report > Email Daily Report > Email Settings
Make sure your ZyWALL to WAN security policy allow.

438/782
www.zyxel.com
How to Setup and send logs to a Syslog Server
This example shows how to set up the syslog server profiles to mail ZyWALL/USG log
messages to the specific destinations. You can also specify which log messages to
syslog server. When the syslog server is configured, you will receive the real time system
logs.
ZyWALL/USG Setup and Configure sending logs to a syslog and Vantage Reports
Server
Set Up the Syslog Server (Use Papertrail syslog in this example)
Register an account on Papertrail: https://papertrailapp.com
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG110 (Firmware Version: ZLD 4.25).
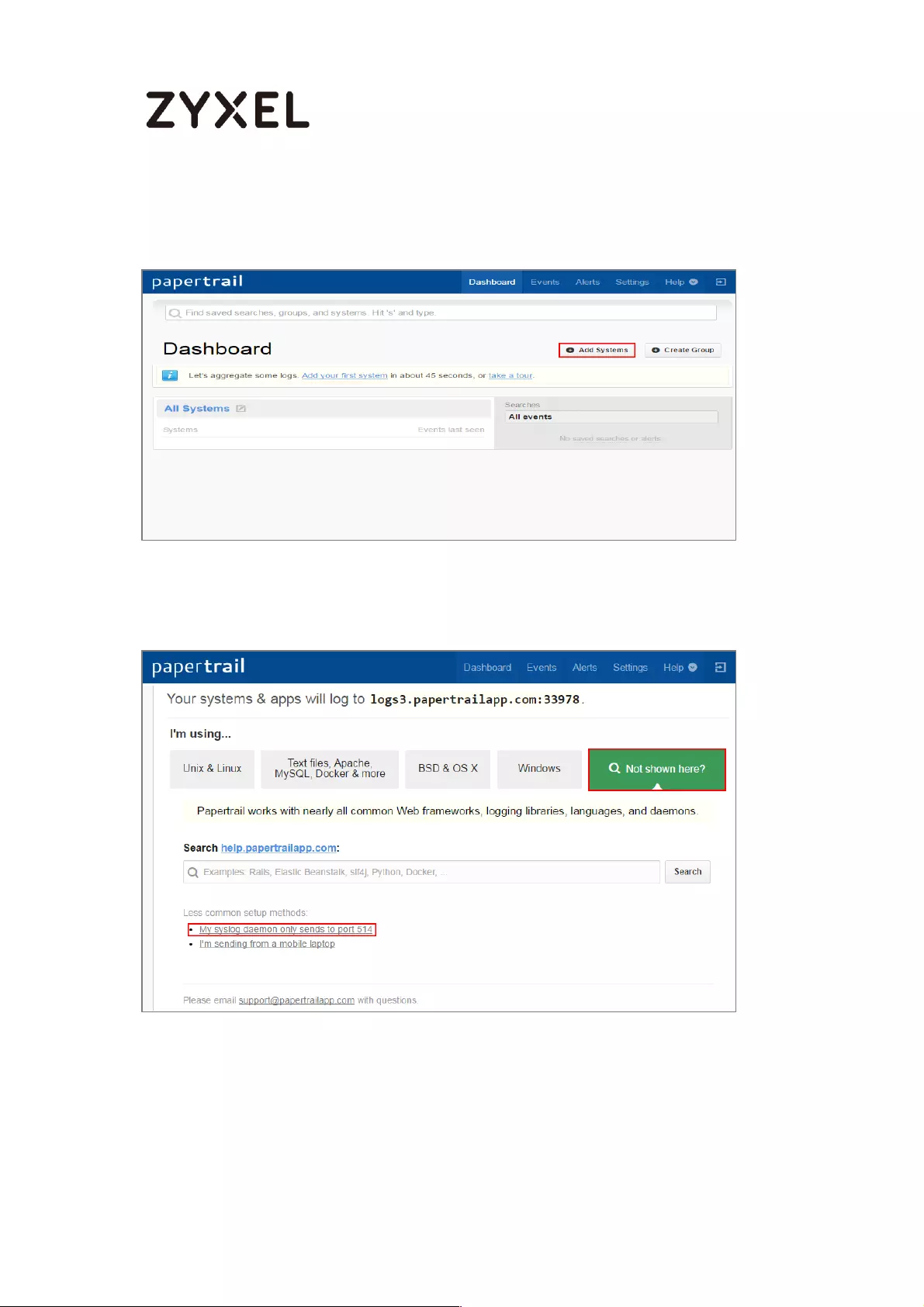
439/782
www.zyxel.com
Go to Dashboard > Add Systems.
Dashboard > Add Systems
Select Not shown here? and My syslog daemon only sends to port 514.
Dashboard > Add Systems > I’m using
Select My syslogd only uses the default port, set ZyWALL/USG public IP address
(111.250.188.9 in this example) and name the log system. Click Save.
Dashboard > Add Systems > > I’m using > Choose your situation
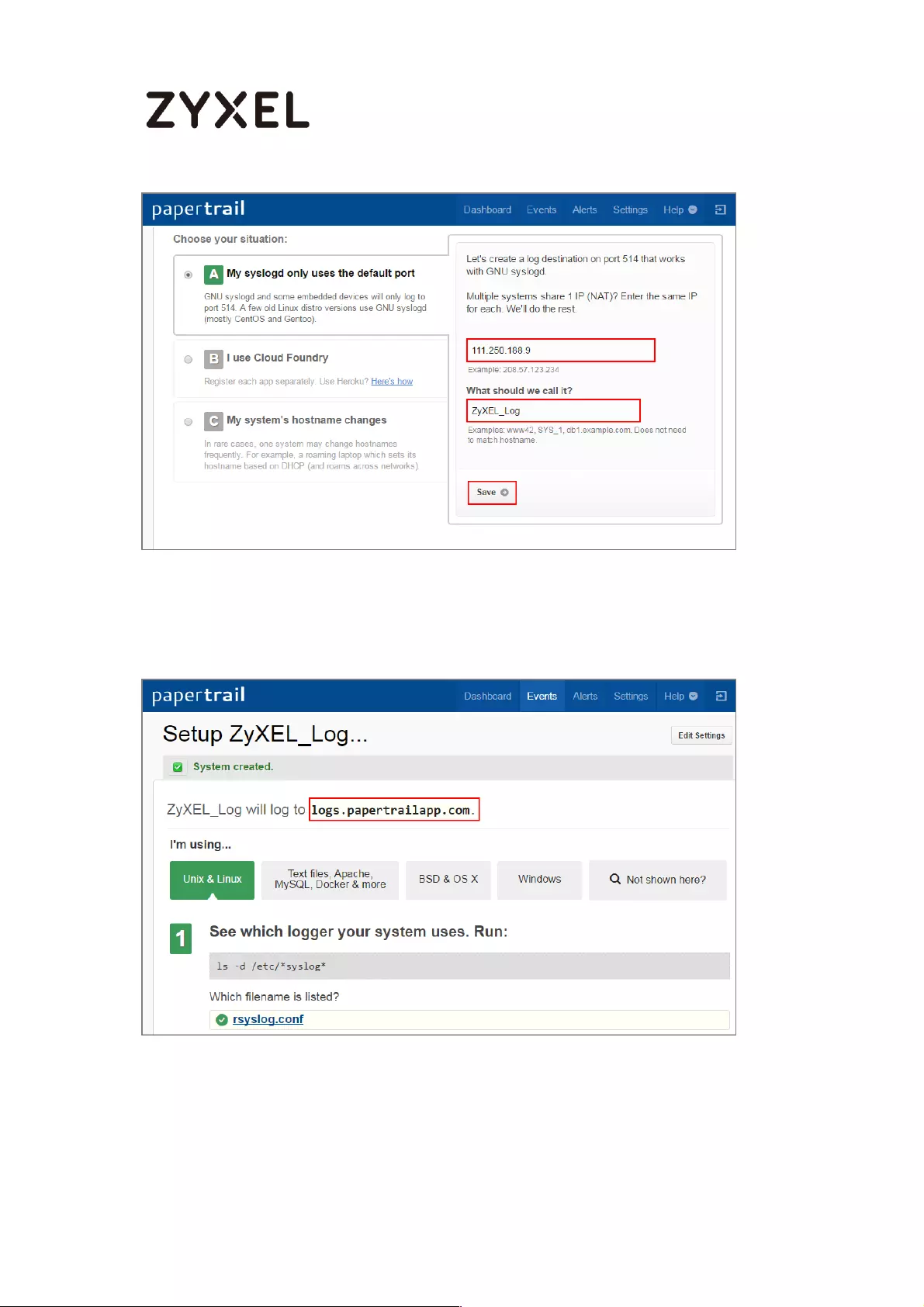
440/782
www.zyxel.com
Write down the Papertrail-provided domain name (logs.papertrialpp.com in this
example).
Dashboard > Add Systems > > I’m using > Choose your situation > System Created
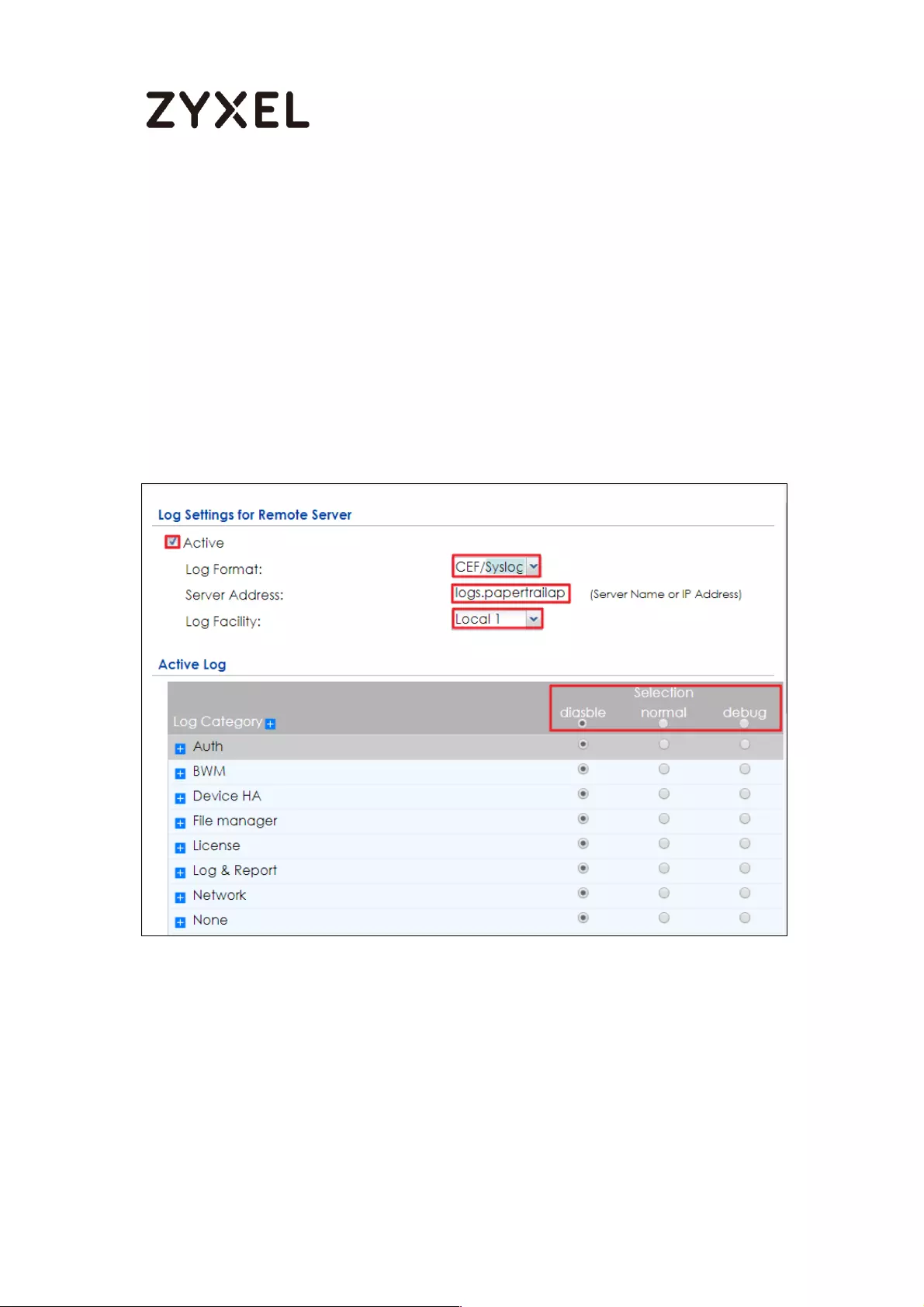
441/782
www.zyxel.com
Set Up the ZyWALL/USG Remote Server Setting
1. Go to CONFIGURATION > Log & Report > Log Settings > Remote Server > Edit. Set
Log Format to be CEF/Syslog. Type the Server Address to be the Papertrail-
provided domain name (logs.papertrialpp.com in this example).
2. Use the System Log drop-down list to change the log settings for all of the log
categories.
CONFIGURATION > Log & Report > Log Settings > Remote Server > Edit
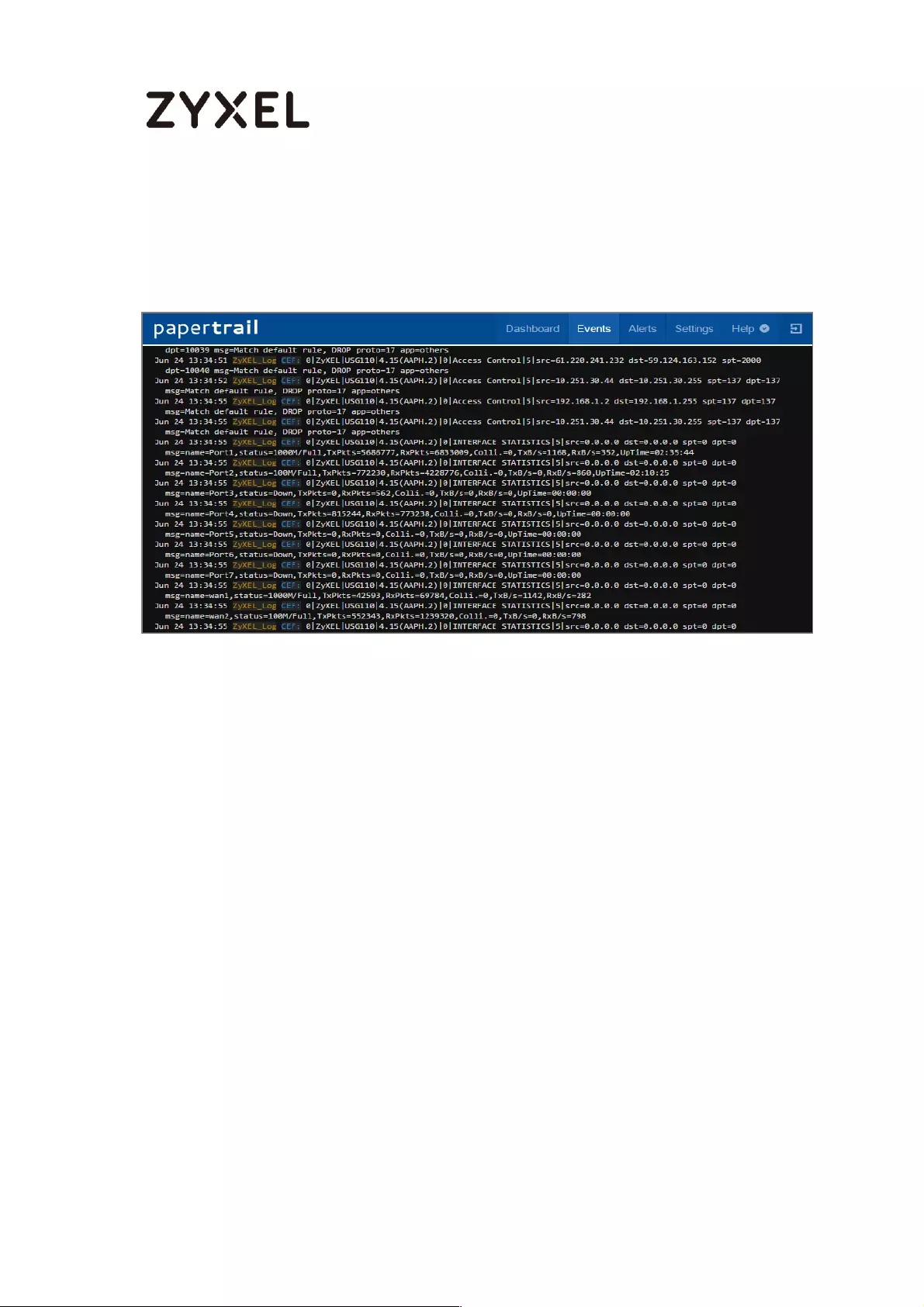
442/782
www.zyxel.com
Test the Remote Server
You will receive a log mail depends on the time you set in the E-mail Server.
ZyXEL Log Mail
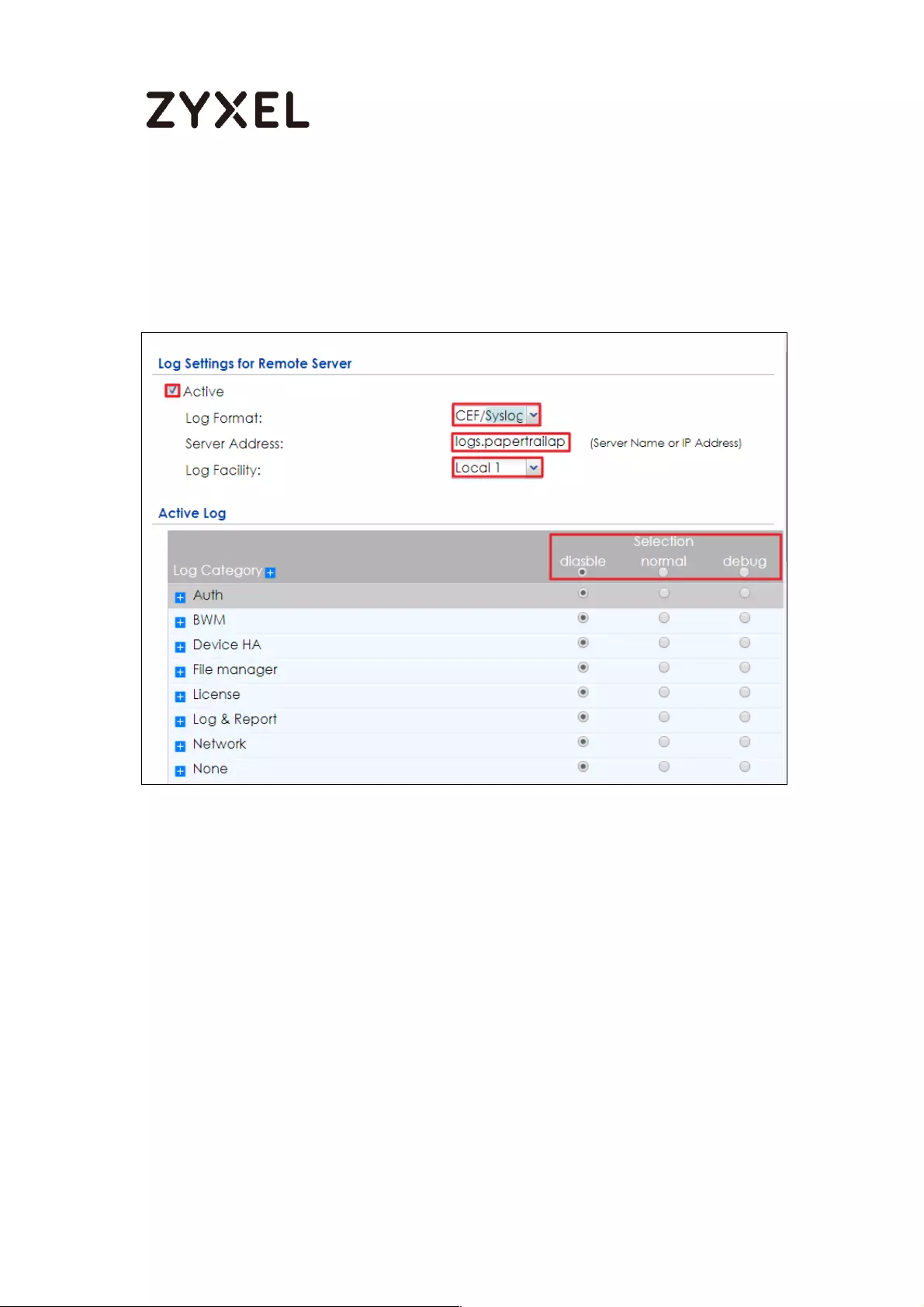
443/782
www.zyxel.com
What Could Go Wrong?
Make sure your Log settings for Remote Server are all correct.
CONFIGURATION > Log & Report > Log Settings > Remote Server
Make sure your ZyWALL to WAN security policy allow traffic to log server.
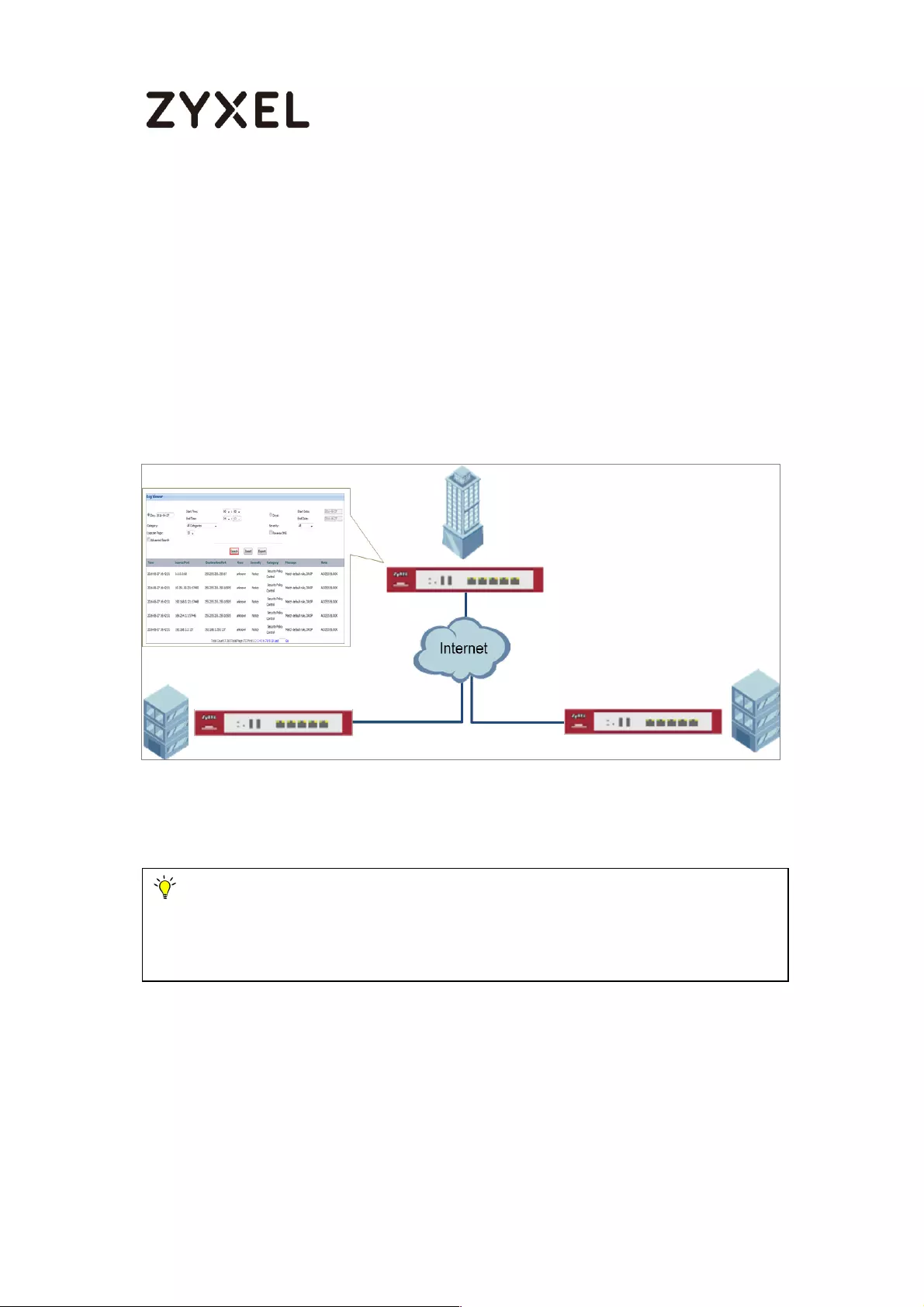
444/782
www.zyxel.com
How to Setup and send logs to a Vantage Reports Server
This example shows how to set up the Vantage Report Server profiles to mail
ZyWALL/USG log messages to the specific destinations. You can also specify which log
messages to Vantage Report Server. When the Vantage Report Server is configured,
you will receive the real time system logs.
ZyWALL/USG Setup and Configure sending logs to a syslog and Vantage Reports
Server
Note: All network IP addresses and subnet masks are used as examples in this
article. Please replace them with your actual network IP addresses and subnet
masks. This example was tested using USG110 (Firmware Version: ZLD 4.25).
445/782
www.zyxel.com
Set Up the VRPT Server
1. The Vantage Report server must have register an account in
http://www.myZyXEL.com.
2. Install VRPT software:
3. http://www.zyxel.com/support/DownloadLandingSR.shtml?c=gb&l=en&kbid=M-
01339&md=VRPT
4. Unzipped the file and click Vantage Reeport.exe to start installing Vantage Report.
Then, the Vantage Report installation wizard appears. Click Next.
446/782
www.zyxel.com
5. Enter the port number you want Vantage Report to use for web services. Make sure
this port number does not conflict with the other services in your network. Click
Next.
6. Check if any applications also use port 3316 (TCP), 514 (UDP) or 8080 (UDP) by
entering “netstat -a” into the command line. Uninstall them if any. Click OK.
When you finish installing Vantage Report, restart the Vantage Report server.
7. Open the browser window and go to http://a.b.c.d:xxxxxx/vrpt, where a.b.c.d is
the IP address of the Vantage Report server. If you open the configurator on the
same computer on which you installed Vantage Report server, enter localhost.
447/782
www.zyxel.com
Xxxx is the port number you entered during installation (10.251.30.61:8080/vrpt/ in
this example).
In the login screen, enter default login User Name and Password: root.
8. Go to Dashboard > License Information > Manage Device, click Add Device, the
Add Device screen appears on the left side. Enter the Name of the device you
want to add to Vantage Report. Enter the LAN MAC address of the device you
want to add. Select the model Type of the device you want to add. Click the
Add button.
Dashboard > License Information > Manage Device
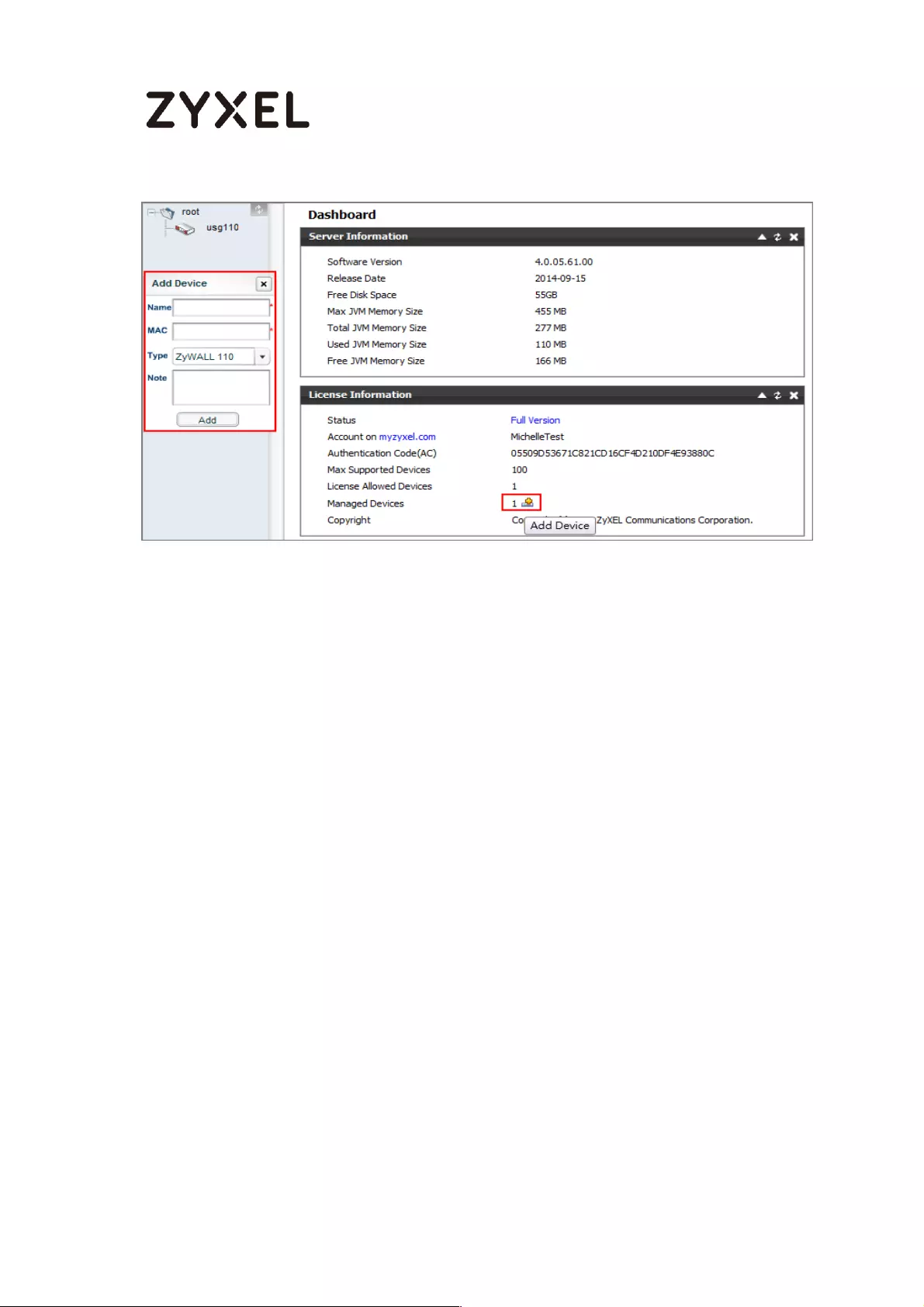
448/782
www.zyxel.com
Set Up the ZyWALL/USG Remote Server Setting
Go to CONFIGURATION > Log & Report > Log Settings > Remote Server > Edit. Set Log
Format to be VRPT/Syslog. Type the Server Address to be the Vantage Report server
IP address (10.251.30.61 in this example).
Use the System Log drop-down list to change the log settings for all of the log
categories.
CONFIGURATION > Log & Report > Log Settings > Remote Server > Edit
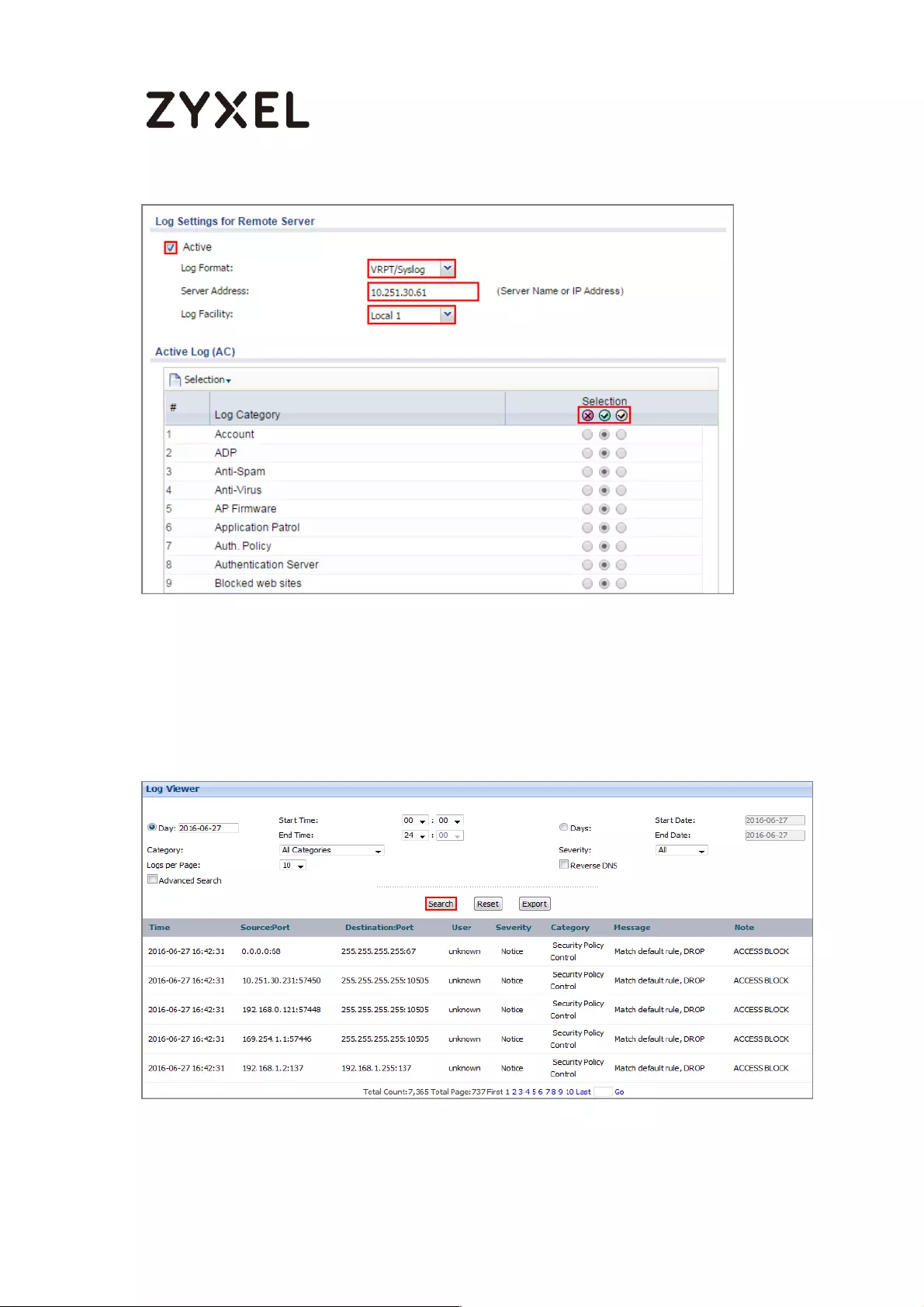
449/782
www.zyxel.com
Test the Remote Server
In the VRPT Sever, go to Logs > Log Viewer, click Search. The screen displays the device
log information. (It may take 5 - 10 minutes to display the log after just added the device)
VRPT Server > Logs > Log Viewer
What Could Go Wrong?
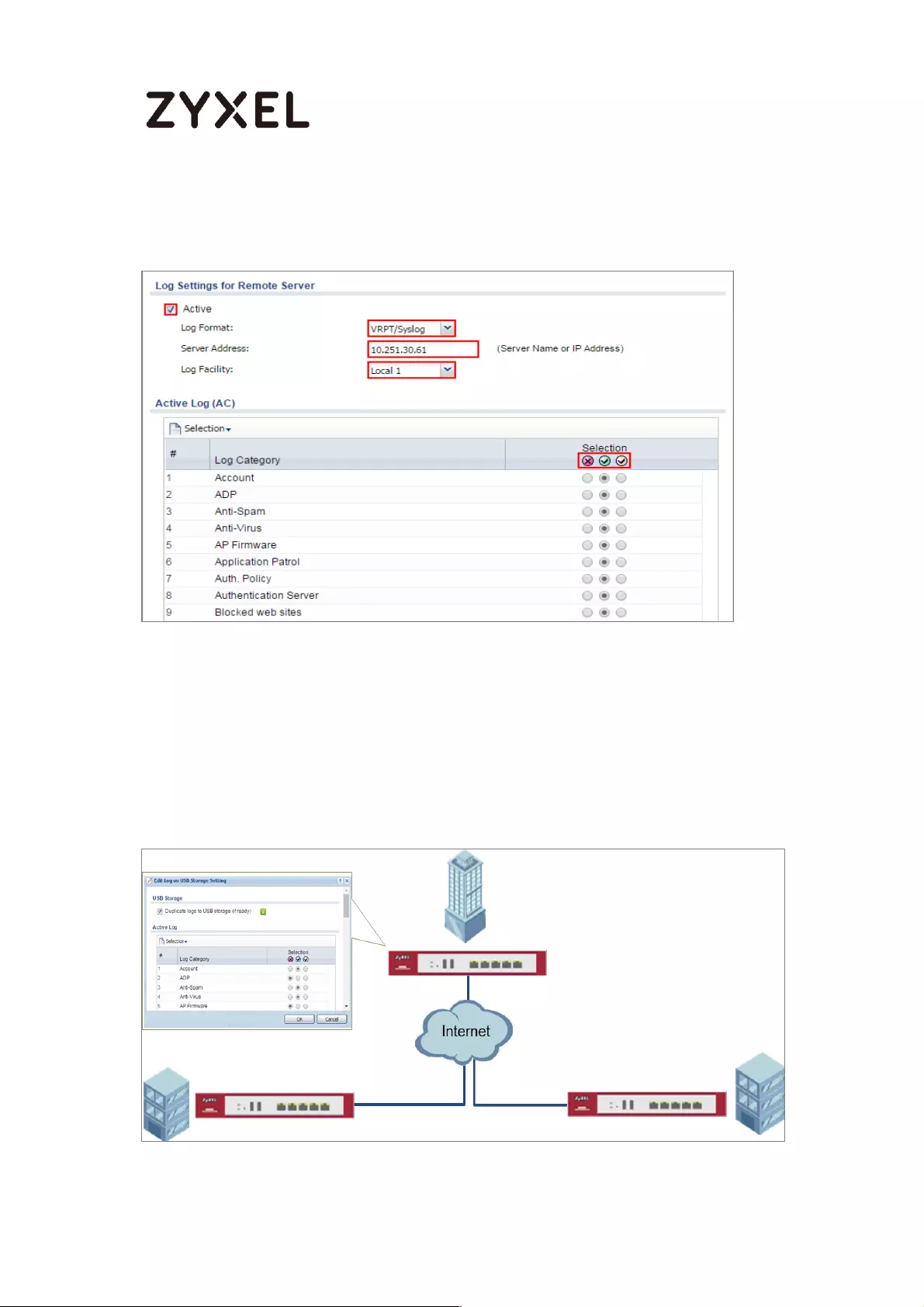
450/782
www.zyxel.com
Make sure your Log settings for Remote Server are all correct.
CONFIGURATION > Log & Report > Log Settings > Remote Server
Make sure your ZyWALL to WAN security policy allow traffic to log server.
How to Setup and send logs to the USB storage
This example shows how to use the USB device to store the system log information.
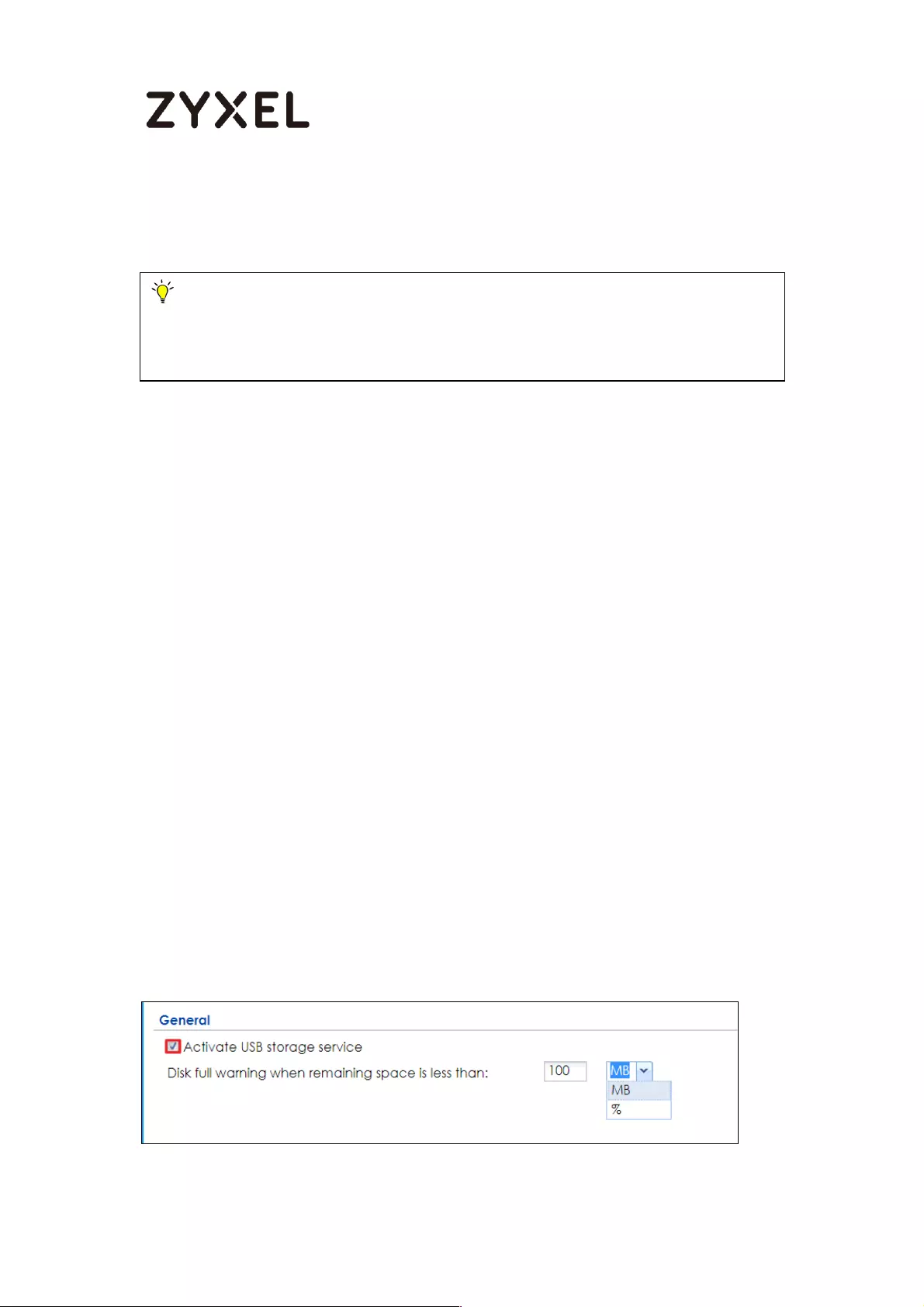
451/782
www.zyxel.com
ZyWALL/USG enable and send logs to the USB storage
Set Up the USB System Settings
Go to CONFIGURATION > System > USB Storage > Settings > General. Select Activate
USB storage service if you want to use the connected USB device(s).
Set a number and select a unit (MB or %) to have the ZyWALL/USG send a warning
message when the remaining USB storage space is less than the value you set here.
CONFIGURATION > System > USB Storage > Settings > General
Note: Only connect one USB device. It must allow writing (it cannot be read-
only) and use the FAT16, FAT32, EXT2, or EXT3 file system. This example was tested
using USG110 (Firmware Version: ZLD 4.25).
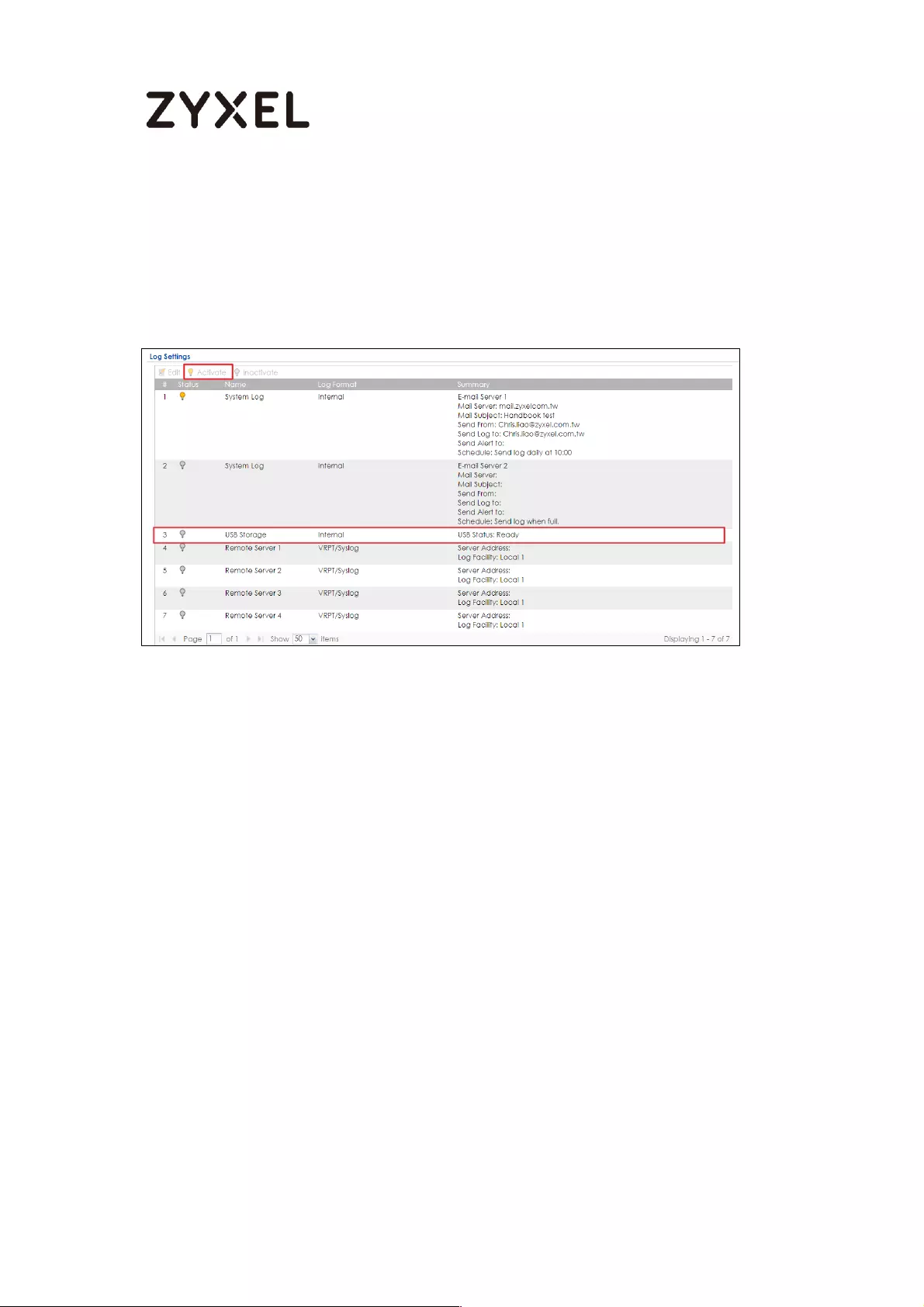
452/782
www.zyxel.com
Set Up the USB Log Storage
Go to CONFIGURATION > Log & Report > Log Settings, select USB Storage and click
Activate. Click Apply to save your changes.
CONFIGURATION > Log & Report > Log Settings
Go to CONFIGURATION > Log & Report > Log Settings > USB Storage > Edit. Select
Duplicate logs to USB storage (if ready) to have the ZyWALL/USG save a copy of its
system logs to a connected USB storage device. Use the Selection drop-down list to
change the log settings for all of the log categories.
CONFIGURATION > Log & Report > Log Settings
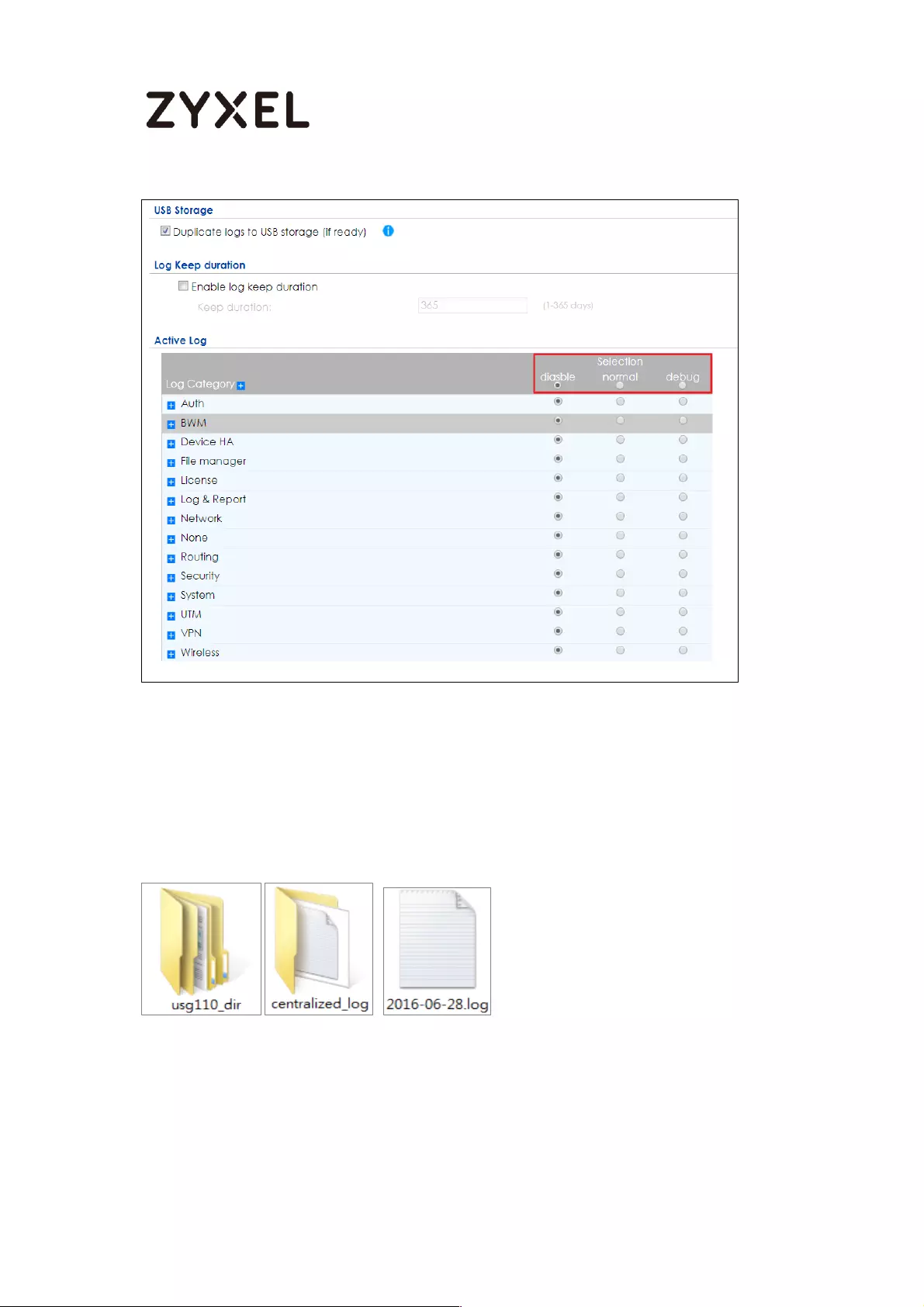
453/782
www.zyxel.com
Check the USG Log Files
Connect the USB to PC and you can find the files in the following path:\Model
Name_dir\centralized_log\YYYY-MM-DD.log
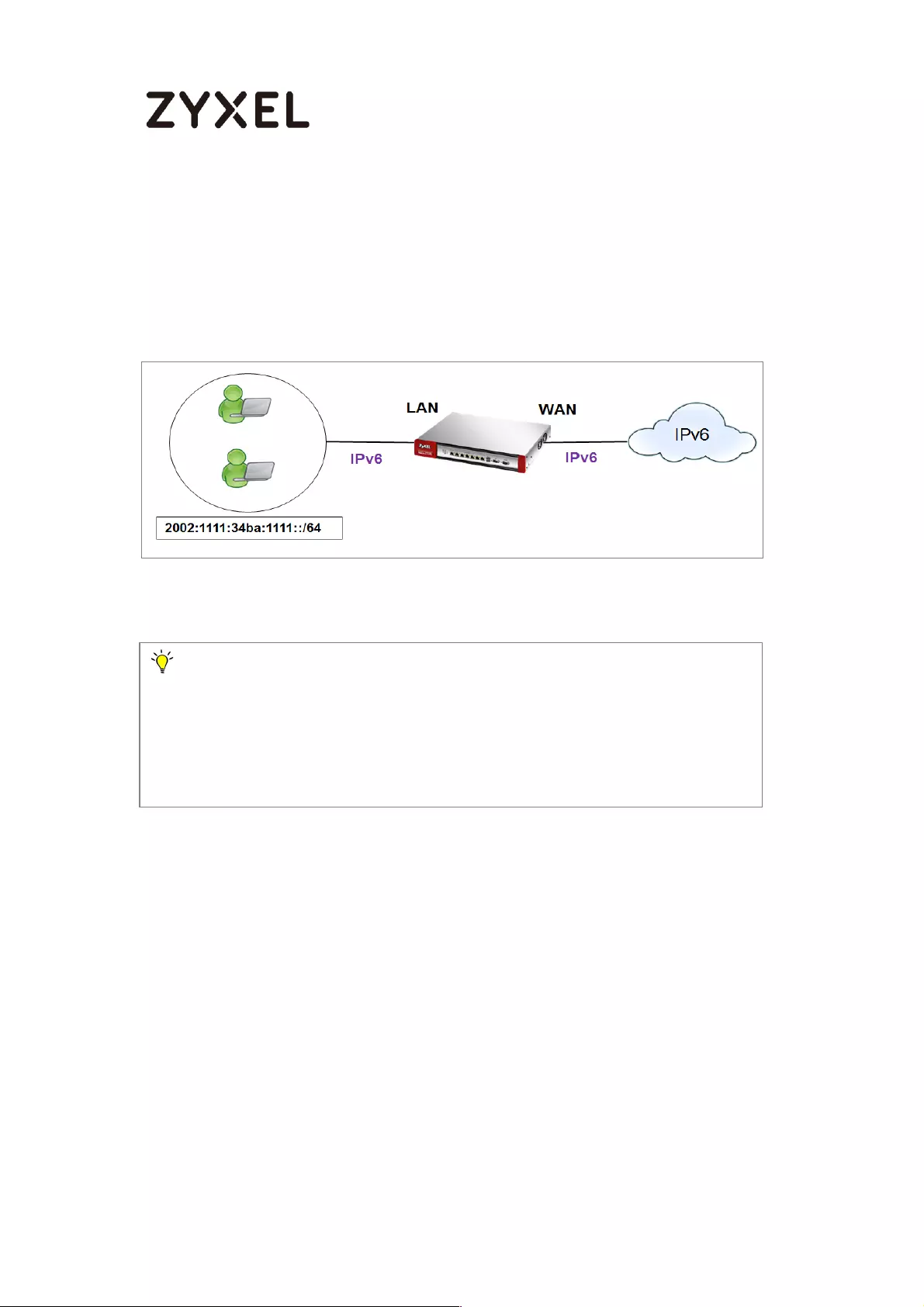
454/782
www.zyxel.com
How to Setup IPv6 Interfaces for Pure IPv6 Routing
This example shows how to configure your USG Z’s WAN and LAN interfaces which
connects two IPv6 networks. USG Z periodically advertises a network prefix of
2006:1111:1111:1111::/64 to the LAN through router advertisements.
ZyWALL/USG access the internet via IPv6
Note:
Instead of using router advertisement, you can use DHCPv6 to pass the
network settings to the computers on the LAN.
This example was tested using USG110 (Firmware Version: ZLD 4.25) and ZyWALL
310 (Firmware Version: ZLD 4.25).
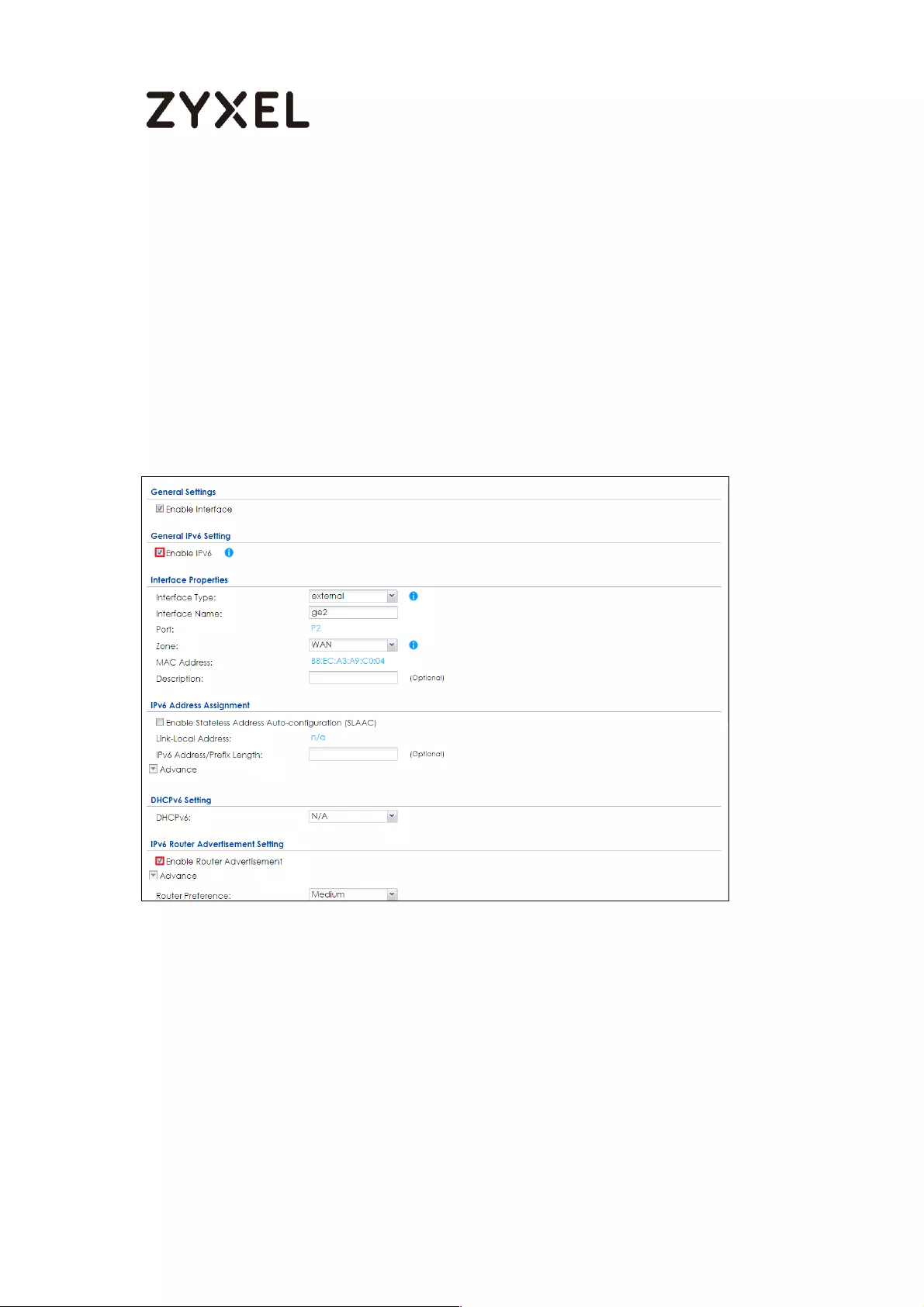
455/782
www.zyxel.com
Setting Up the IPv6 Interface
Wan
1. In the CONFIGURATION > Network > Interface > Ethernet screen’s IPv6
Configuration section, double-click the wan1.
2. The Edit Ethernet screen appears. Select Enable Interface and Enable IPv6. Select
Enable Auto-Configuration. Click OK.
Note: Your ISP or uplink router should enable router advertisement.
Lan
1. In the CONFIGURATION > Network > Interface > Ethernet screen, double-click the
lan1 in the IPv6 Configuration section.
2. The Edit Ethernet screen appears. Select Enable Interface and Enable IPv6. Select
Enable Router Advertisement and click Add and configure a network prefix for the
LAN1 (2006:1111:34ba:1111::/64 in this example). Click OK.
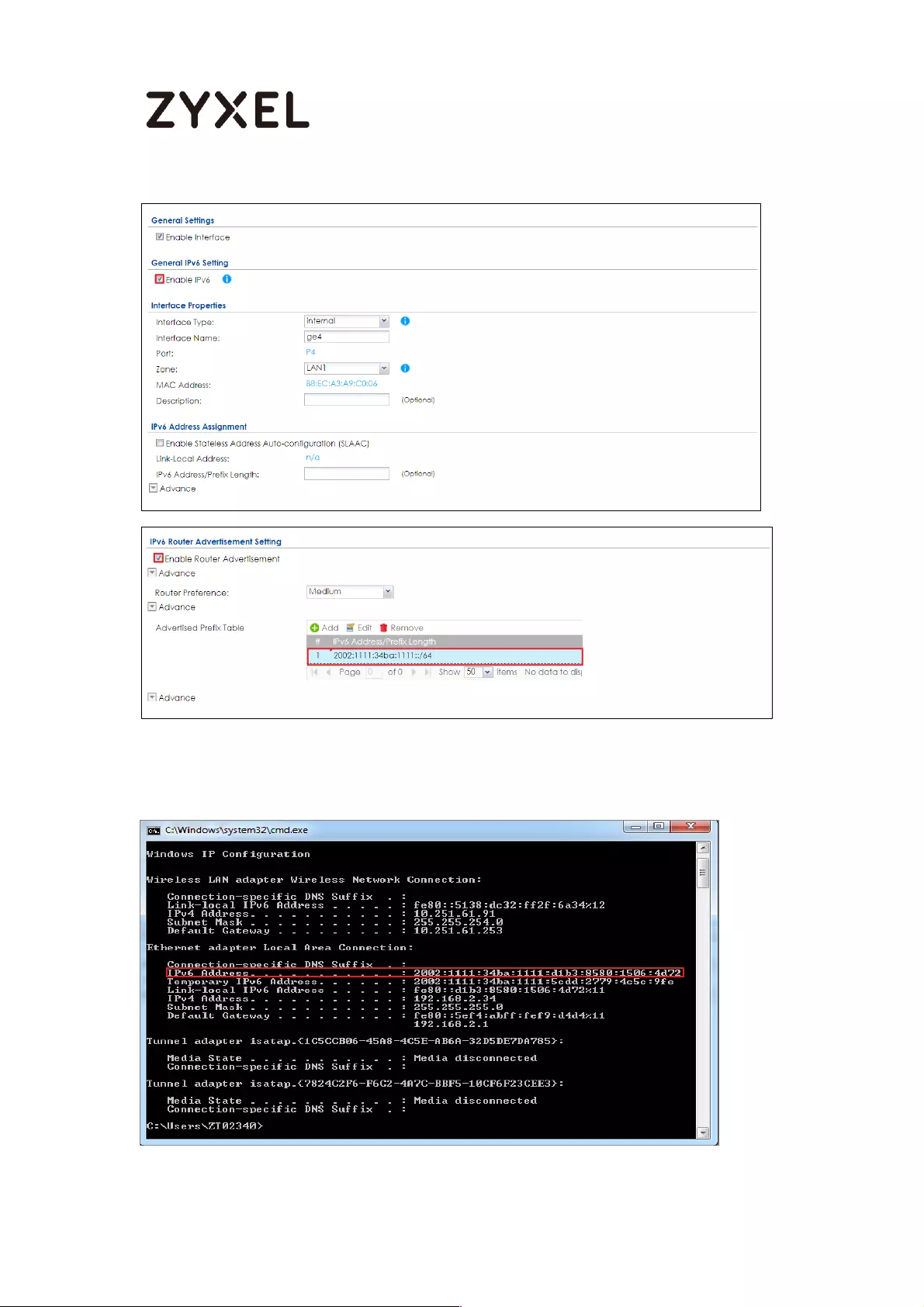
456/782
www.zyxel.com
3. Using command line ipconfig to check.
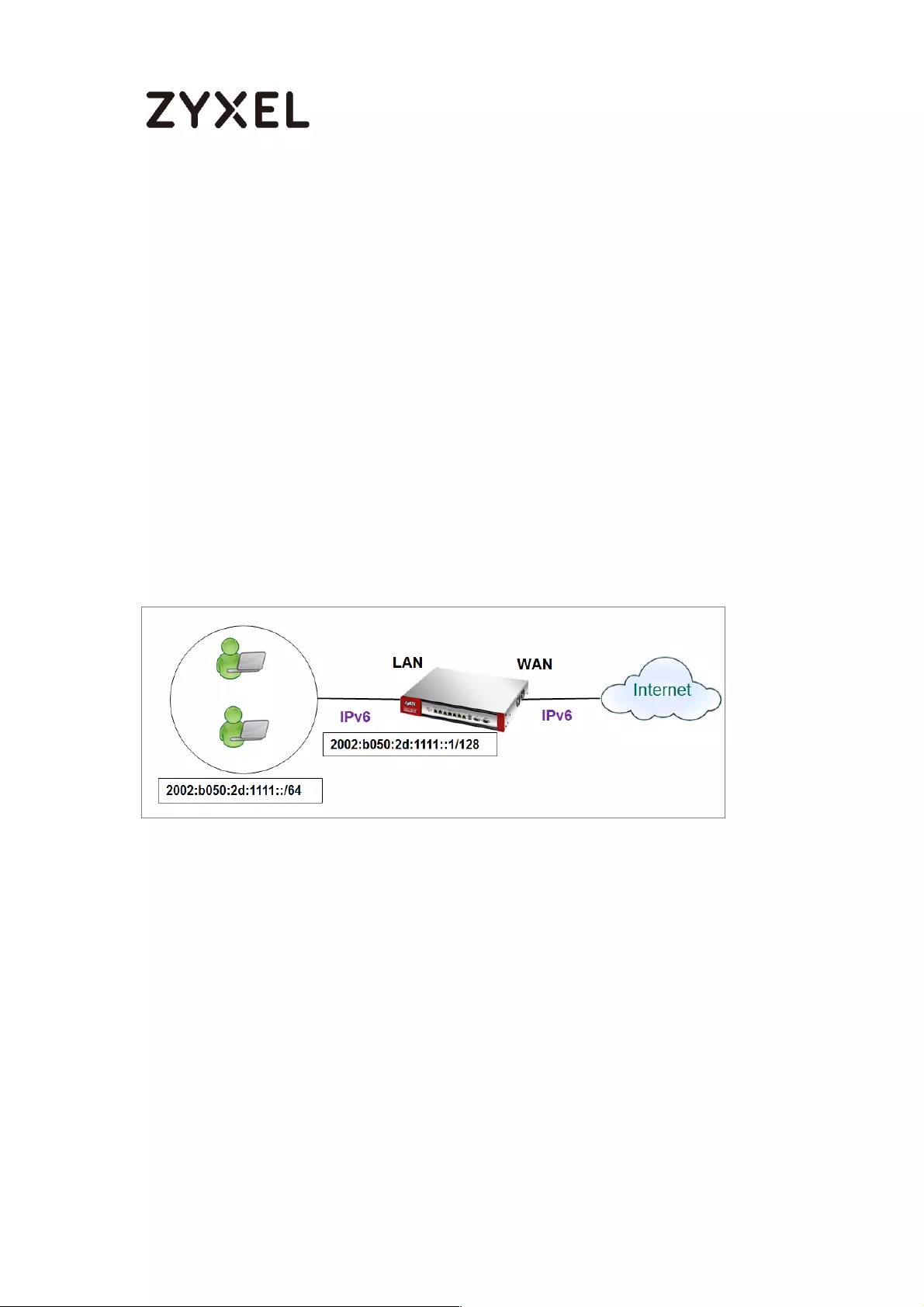
457/782
www.zyxel.com
Set up the Prefix Delegation and Router Advertisement
This example shows how to configure prefix delegation on the ZyWALL’s WAN and
router advertisement on the LAN.
Apply a network Prefix From Your ISP
First of all, you have to apply a network prefix from your ISP or the uplink router’s
administrator. The WAN port’s DUID is required when you apply the prefix. You can
check the DUID information in the WAN IPv6 Interface Edit screen.
This example assumes that you were given a network prefix of 2001:b050:2d::/48 and
you decide to
divide it and give 2001:b050:2d:1111::/64 to the LAN network. LAN1’s IP address is
2001:b050:2d:1111::1/128.
Setting Up the WAN IPv6 Interface
1. In the Configuration > Network > Interface > Ethernet screen’s IPv6 Configuration
section,
double-click the WAN interface.
2. The Edit Ethernet screen appears. Select Enable Interface and Enable IPv6.
Click Create new Object to add a DHCPv6 Request object with the Prefix Delegation
type.
Select Enable Auto-Configuration.
Select Client in the DHCPv6 field. (WAN1’s DUID appears.)
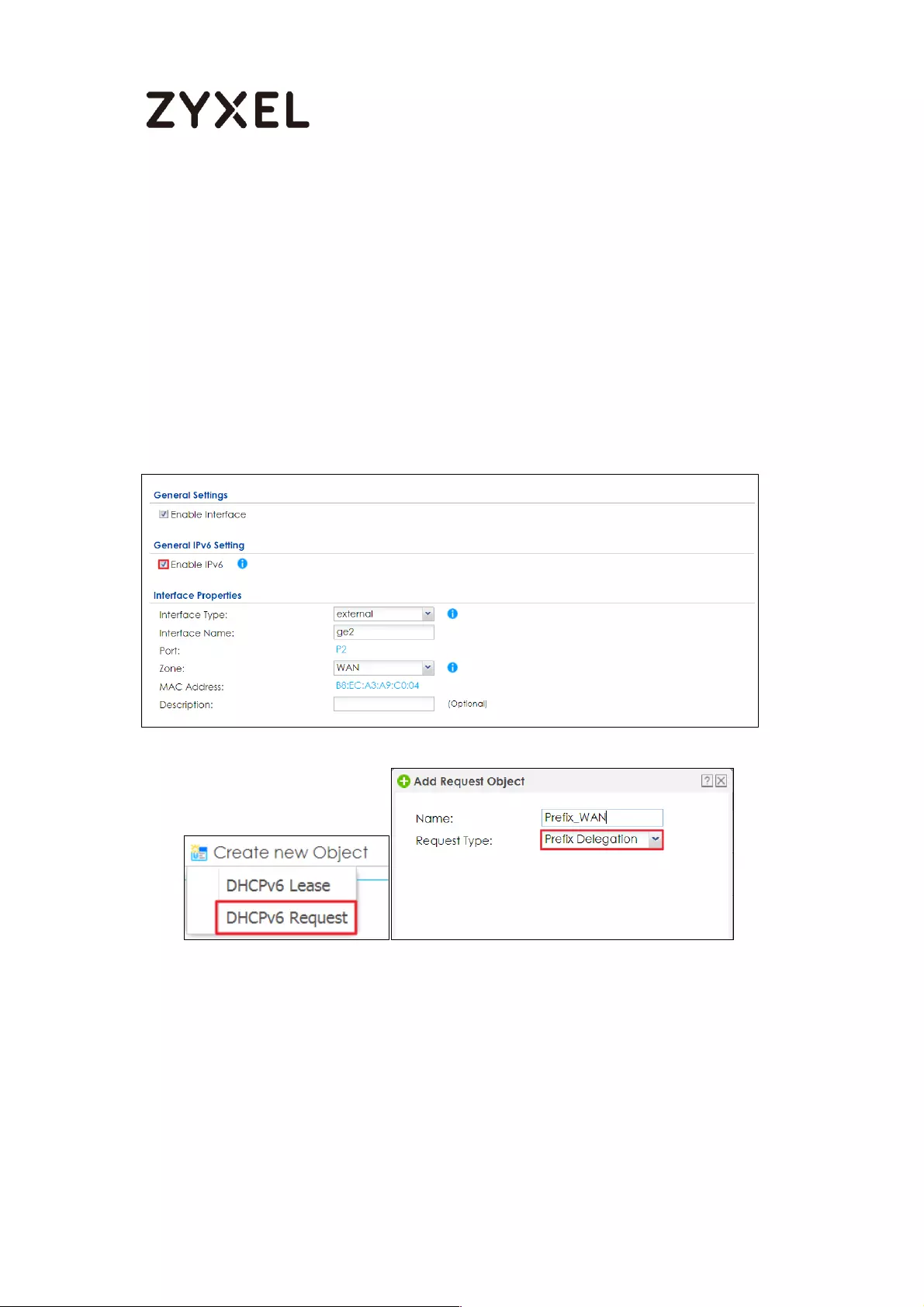
458/782
www.zyxel.com
Click Add in the DHCPv6 Request Options table and select the DHCPv6 request object
you just
created. You cannot see the prefix your ISP gave you in the Value field until you click
OK and then
come back to this screen again. It is 2001:b050:2d::/48 in this example.
Note: Your ISP or a DHCPv6 server in the same network as the WAN should assign an
IPv6 IP address for the WAN interface.
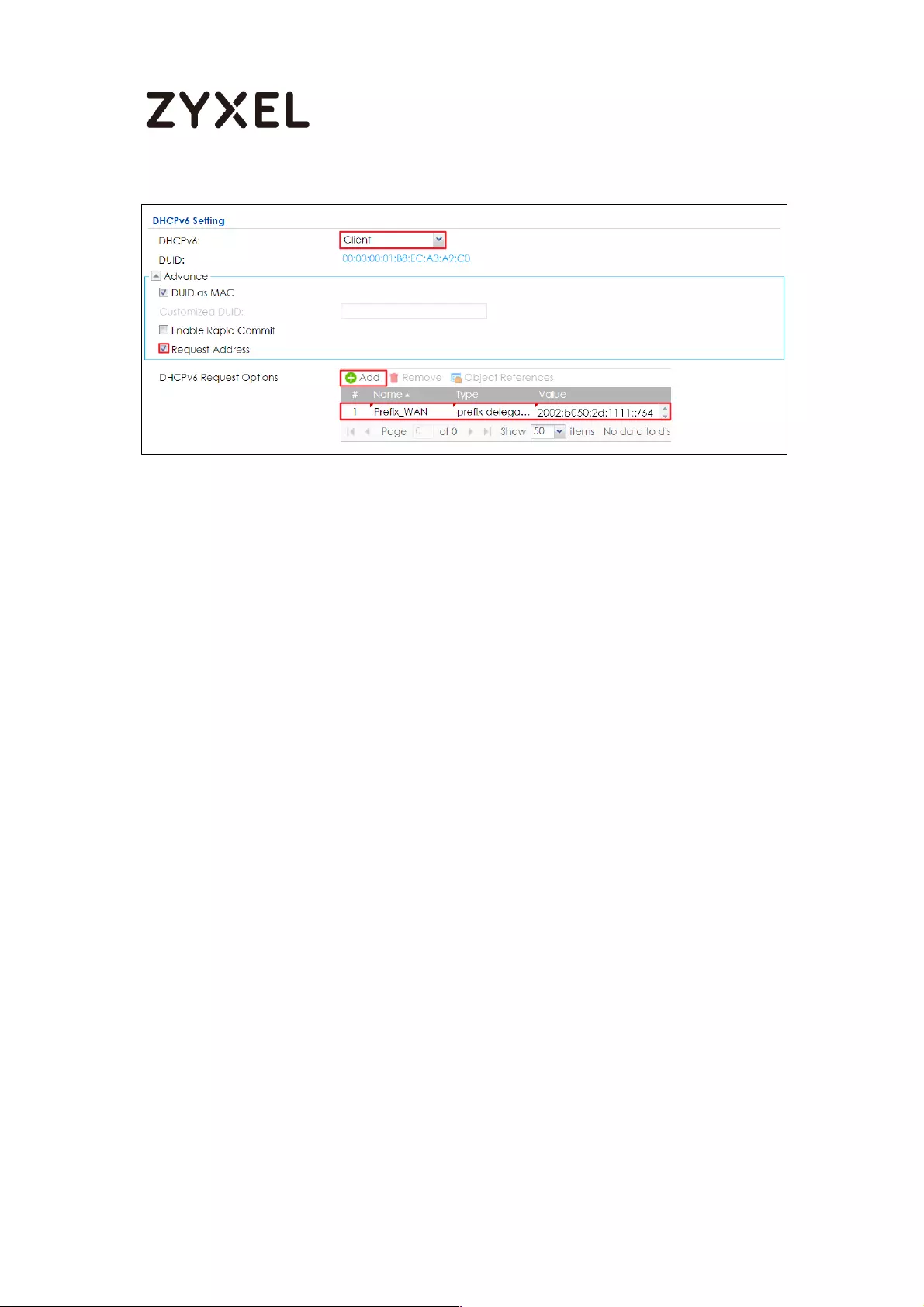
459/782
www.zyxel.com
Setting Up the WAN IPv6 Interface
1. In the Configuration > Network > Interface > Ethernet screen, double-click the lan
interface in the IPv6 Configuration section.
2. The Edit Ethernet screen appears. Click Show Advanced Settings to display more
settings on this screen.
Select Enable Interface and Enable IPv6.
In the Address from DHCPv6 Prefix Delegation table, click Add and select the DHCPv6
request object from the drop-down list, type ::1111:0:0:0:1/128 in the Suffix Address field.
(The combined address 2001:b050:2d:1111::1/128 will display as LAN1’s IPv6 address
after you click OK and come back to this screen again).
DHCPv6 Setting is N/A
Note: You can configure the IPv6 Address/Prefix Length field instead if the delegated
prefix is never changed.
3. In the Advertised Prefix from DHCPv6 Prefix Delegation table, click Add and select
the DHCPv6 request object from the drop-down list, type ::1111/64 in the Suffix Address
field. (The combined prefix 2001:b050:2d:1111::/64 will display for the LAN1’s network
prefix after you click OK and come back to this screen again)., pleae note that this is
the USG LAN interface IP.
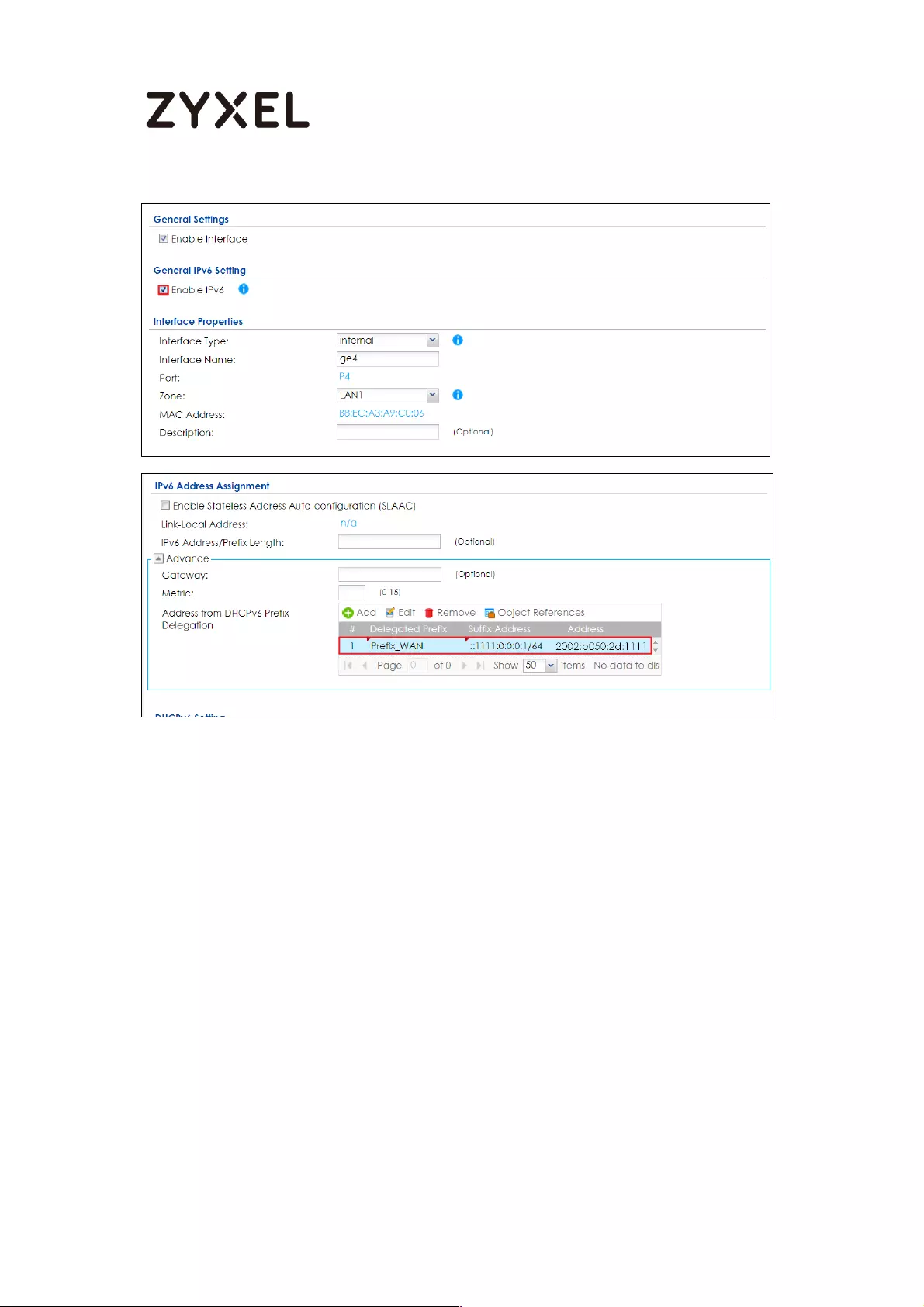
460/782
www.zyxel.com
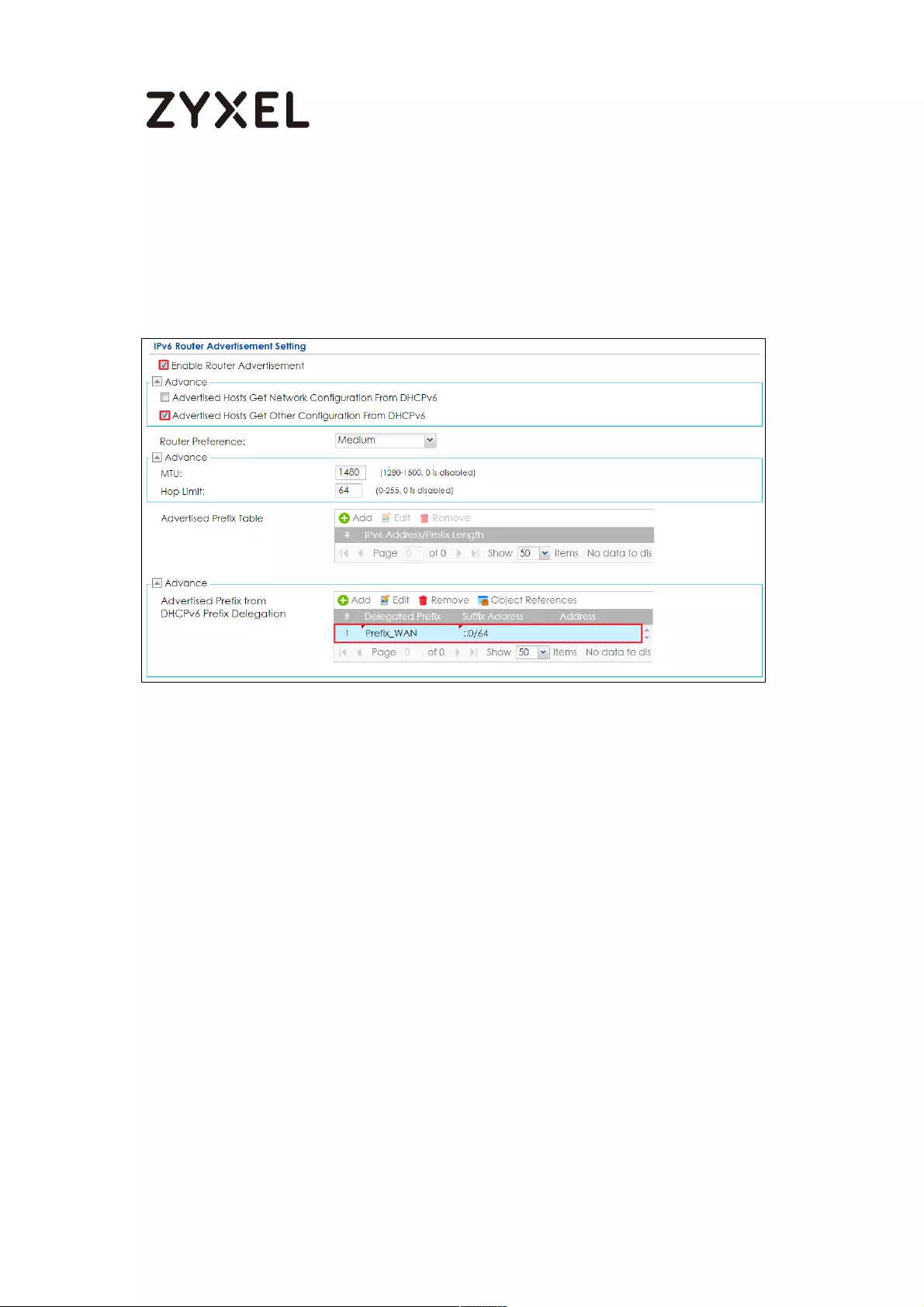
461/782
www.zyxel.com
1. Navigate to IPv6 Router Advertisement Setting, enable Router Advertisement, it would advertise
the prefix to the Lan host, also enable Adviertised Hosts Get Other Configuration From DHCPv6,
Lan hosts will get the DNS address from USG.
2. Configure Advertised Prefix from DHCPv6 Prefix Delegation, the Lan hosts will get the Prefix from
USG, Suffix address can set 0~F
Test
1. Connect a computer to the ZyWALL’s LAN interface.
2. Enable IPv6 support on you computer.
In Windows XP, you need to use the IPv6 install command in a Command
Prompt.
In Windows 7, IPv6 is supported by default. You can enable IPv6 in the Control
Panel > Network and Sharing Center > Local Area Connection screen.
3. Your computer should get an IPv6 IP address (starting with 2001:b050:2d:1111: for
this example) from the ZyWALL.
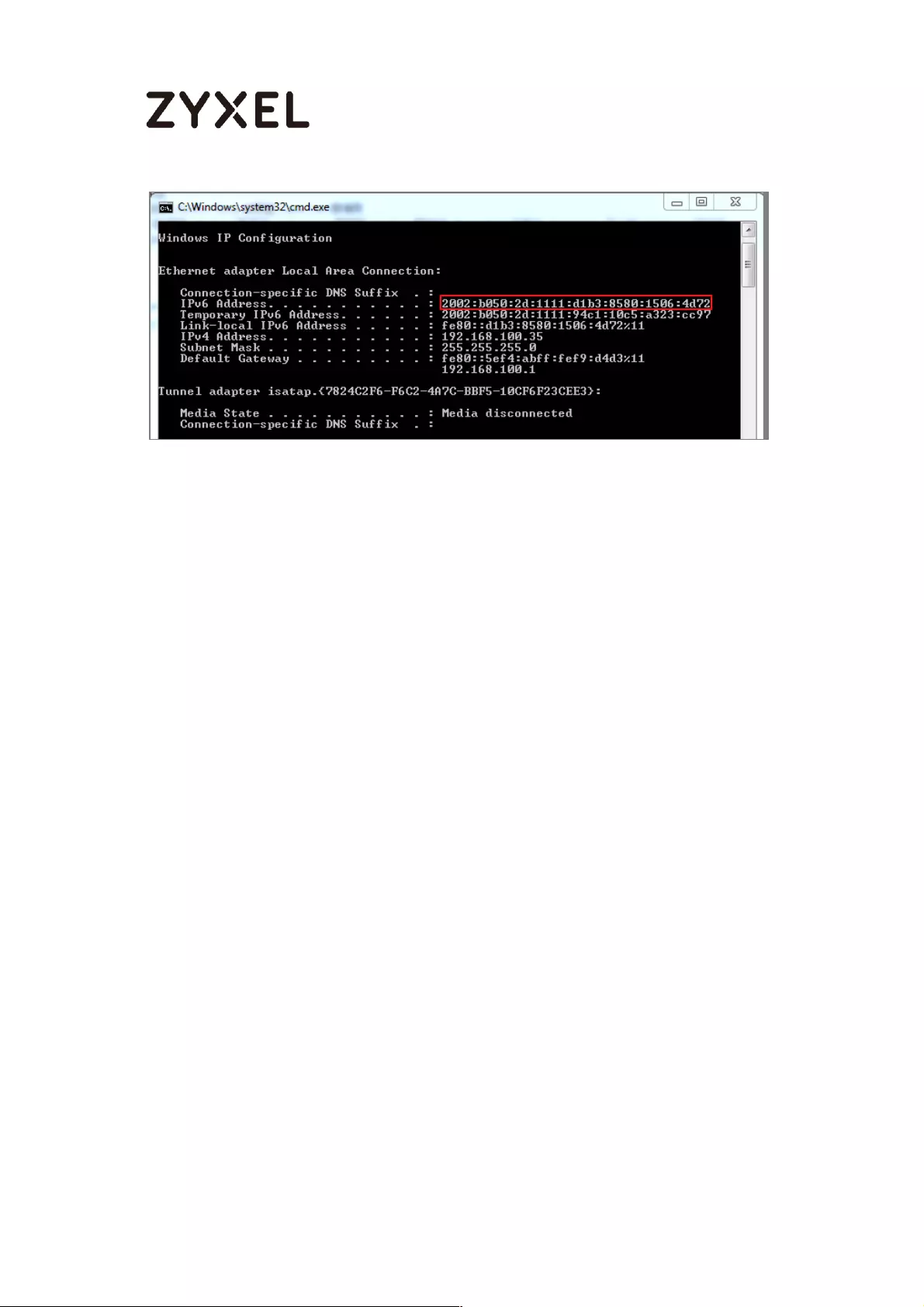
462/782
www.zyxel.com
4. Open a web browser and type http://www.kame.net. If your IPv6 settings are
correct, you can see a dancing turtle in the website.
What Can Go Wrong?
1. If you forgot to enable Auto-Configuration on the WAN1 IPv6 interface, you will
not have any default route to forward the LAN’s IPv6 packets.
2. To use prefix delegation, you must set the WAN interface to a DHCPv6 client,
enable router advertisements on the LAN interface as well as configure the
Advertised Prefix from DHCPv6 Prefix Delegation table.
3. If the Value field in the WAN1’s DHCPv6 Request Options table displays n/a,
contact your ISP for further support.
4. In Windows, some IPv6 related tunnels may be enabled by default such as Teredo
and 6to4 tunnels. It may cause your computer to handle IPv6 packets in an
unexpected way. It is recommended to disable those tunnels on your computer.
Assign the DNS address to the client
1. If you want to assign the DNS server address instead of ISP’s , then
please create the DNS server object.
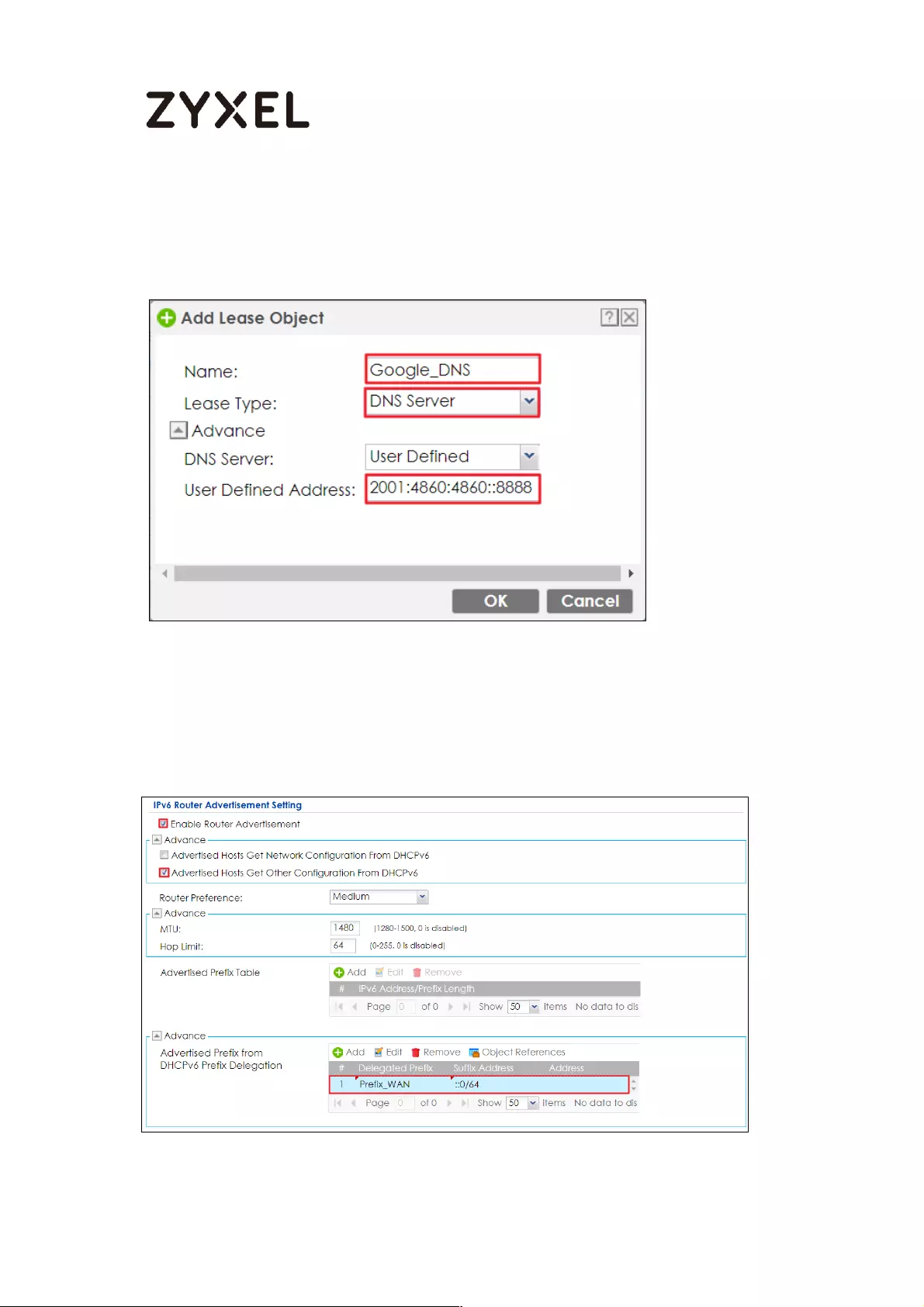
463/782
www.zyxel.com
Select DHCPv6 Lease and DNS server as lease type. For example set the
Google DNS IPv6 address 2001:4860:4860::8888
2. Select the drop-down list DHCPv6 as server type, add the DNS server object in
DHCPv6 lease options and enable Router Advertisement.
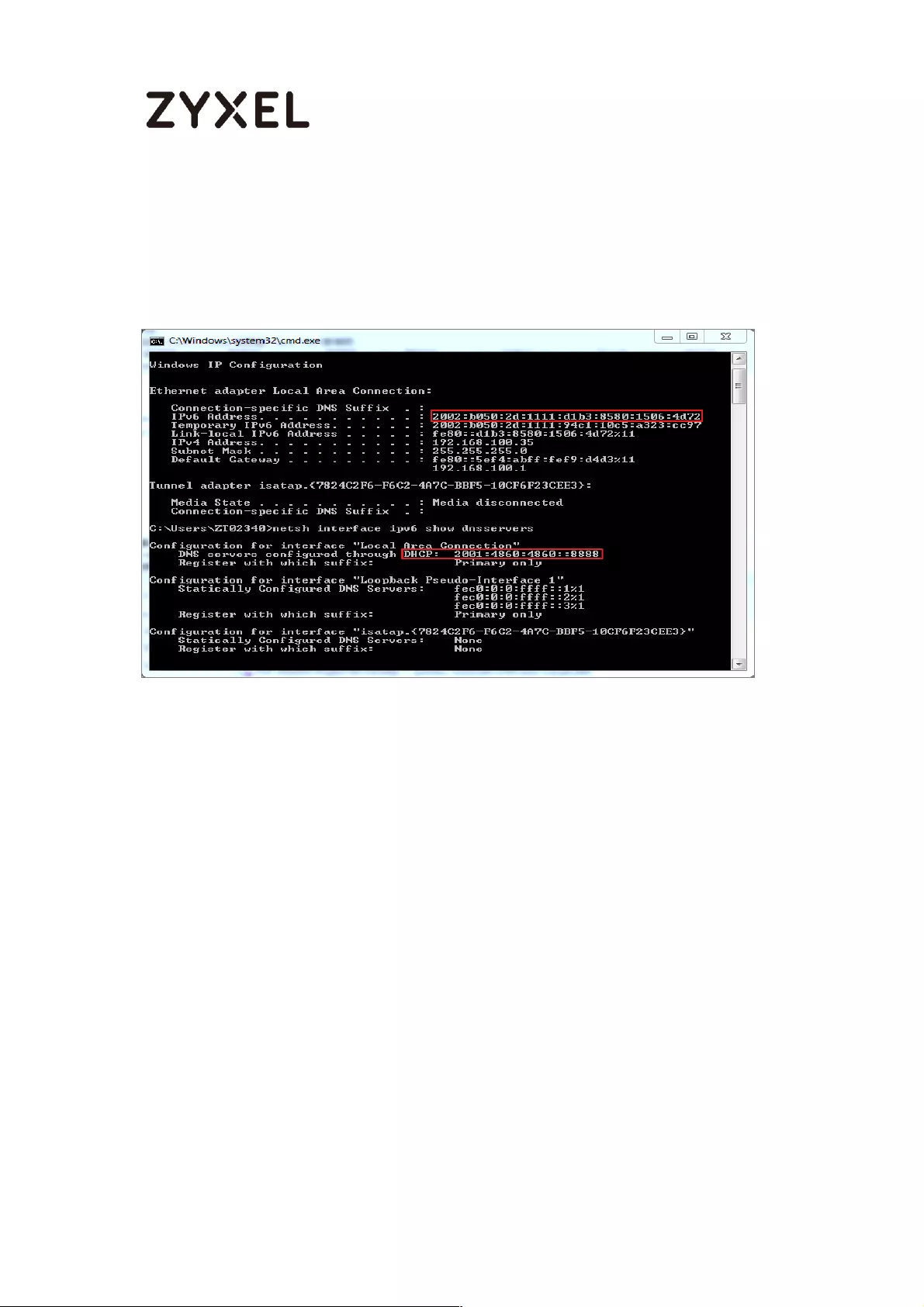
464/782
www.zyxel.com
Test
You can use command “netsh interface ipv6 show dnsservers” to check the DNS
server IP.
How to Perform and Use the Packet Capture Feature on the
ZyWALL/USG
This example shows how to use the Packet Capture feature to capture network traffic
going through the ZyWALL/USG’s interfaces. Studying these packet captures may help
you identify network problems.
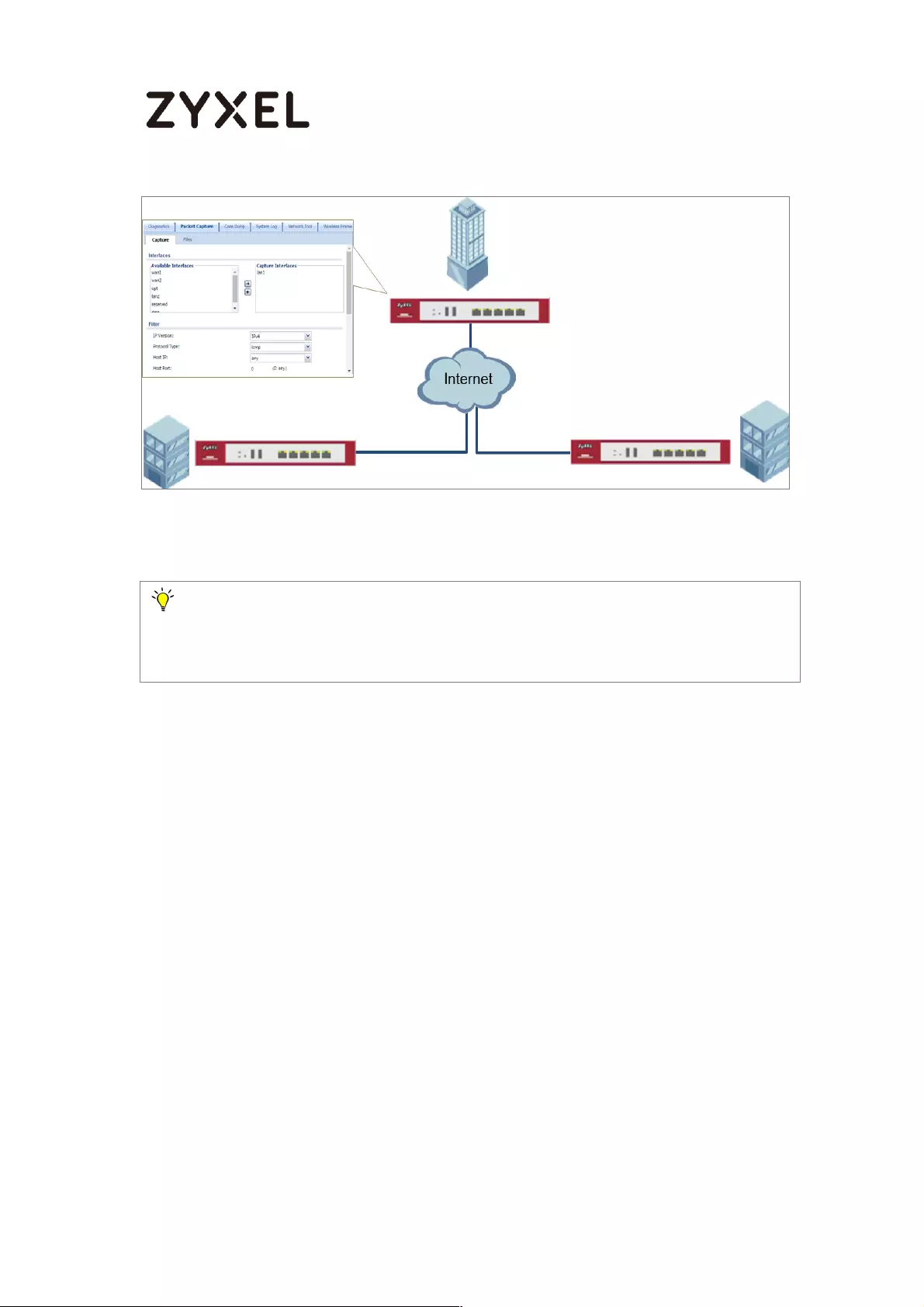
465/782
www.zyxel.com
ZyWALL/USG Packet Capture Feature Settings
Set Up the Packet Capture Feature
8 Go to MAINTENANCE > Diagnostics > Packet Capture > Capture > Interfaces.
Select interfaces for which to capture packets and click the right arrow button to
move them to the Capture Interfaces list.
Note: New capture files overwrite existing files of the same name. Change the File
Suffix field’s setting to avoid this. This example was tested using USG110 (Firmware
Version: ZLD 4.25).
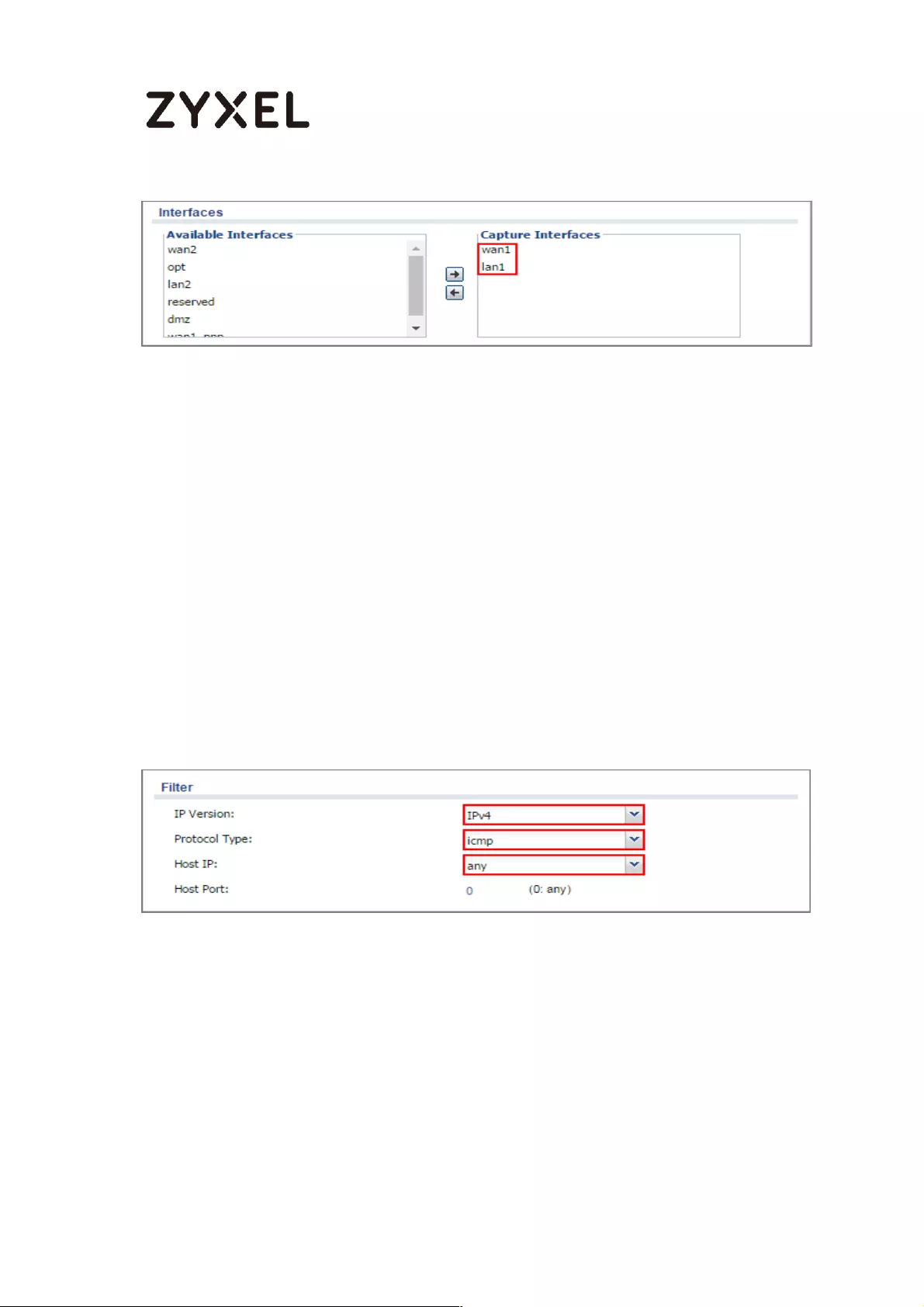
466/782
www.zyxel.com
9 Go to MAINTENANCE > Diagnostics > Packet Capture > Capture > Filter.
Select IP Version (IPv4 or IPv6) for which to capture packets or select any to capture
packets for all IP versions.
Select the Protocol Type of traffic for which to capture packets. Select any to capture
packets for all types of traffic.
Select a Host IP address object for which to capture packets. Select any to capture
packets for all hosts. Select User Defined to be able to enter an IP address.
10 Go to MAINTENANCE > Diagnostics > Packet Capture > Capture > Misc setitng.
Select Continuously capture and overwrite old ones to have the ZyWALL/USG keep
capturing traffic and overwriting old packet capture entries when the available
storage space runs out. Select Save data to onboard storage only or Save data to USB
storage (If status shows service deactivated, go to CONFIGURATION > Object > USB
Storage, select Activate USB storage service)
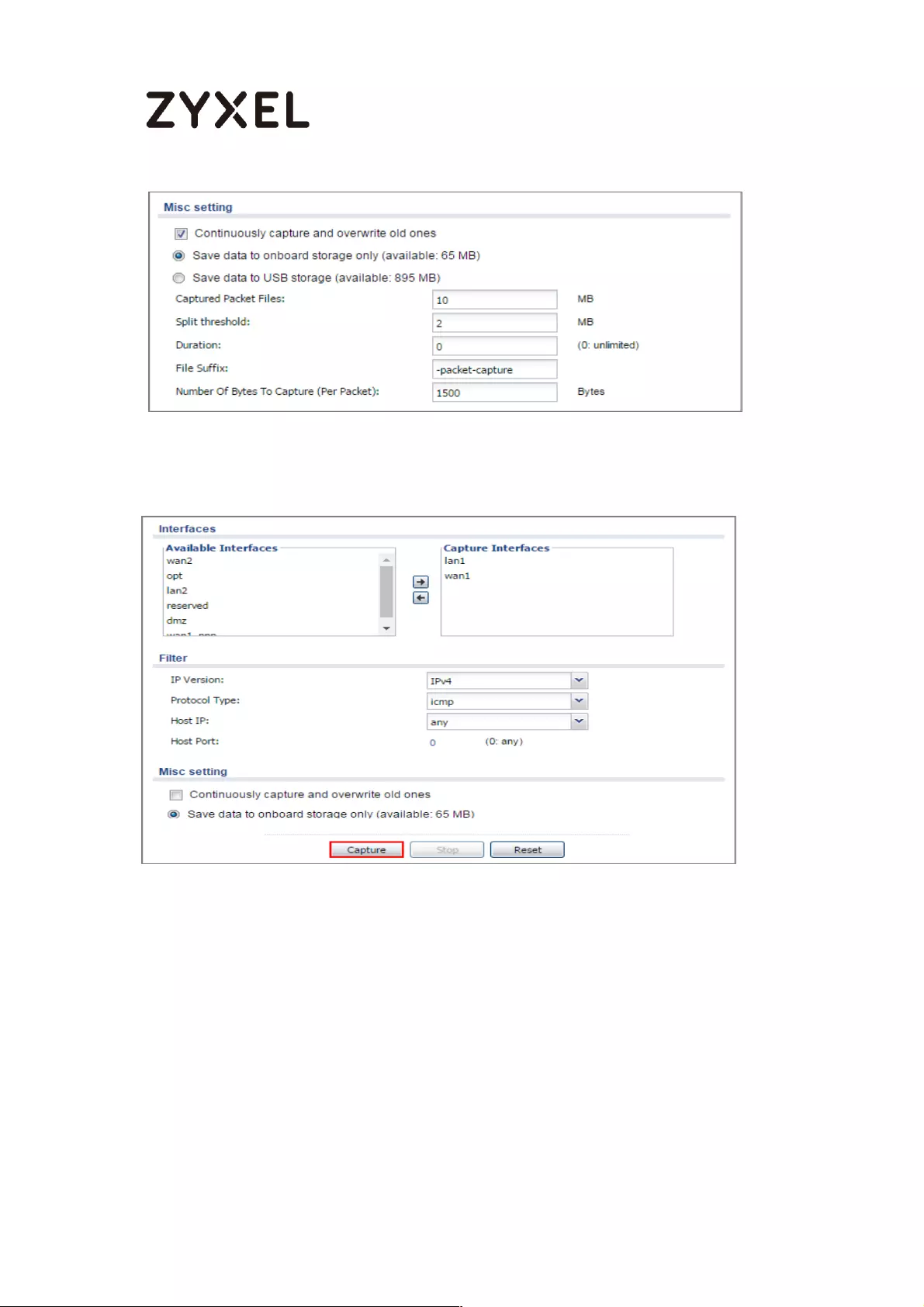
467/782
www.zyxel.com
11 Click Capture.
12 Click Stop when collection is done.
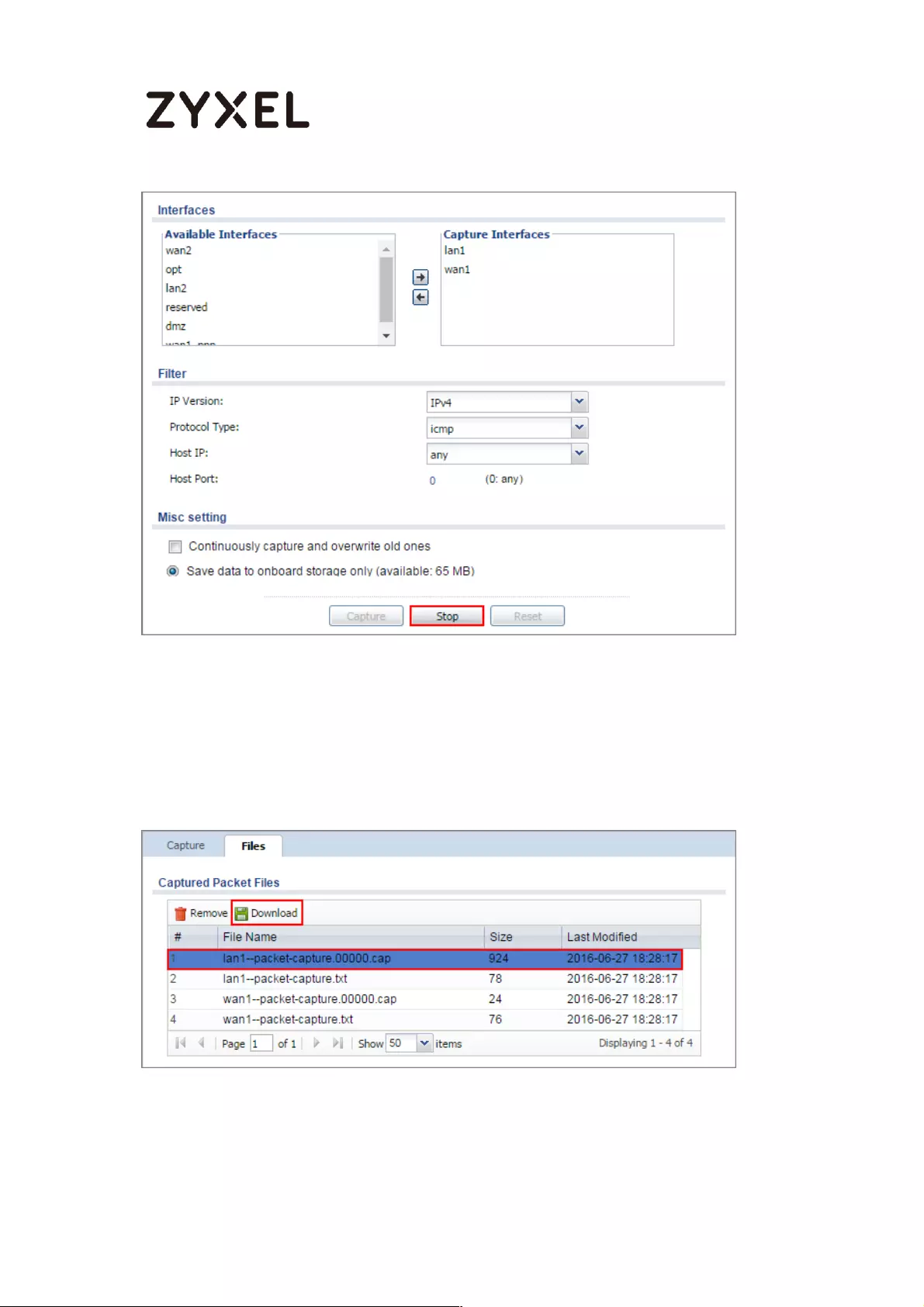
468/782
www.zyxel.com
Check the Capture Files
1 Go to MAINTENANCE > Diagnostics > Packet Capture > Files, select
the .cap file and click Download.
2 Open .cap files with Wireshark
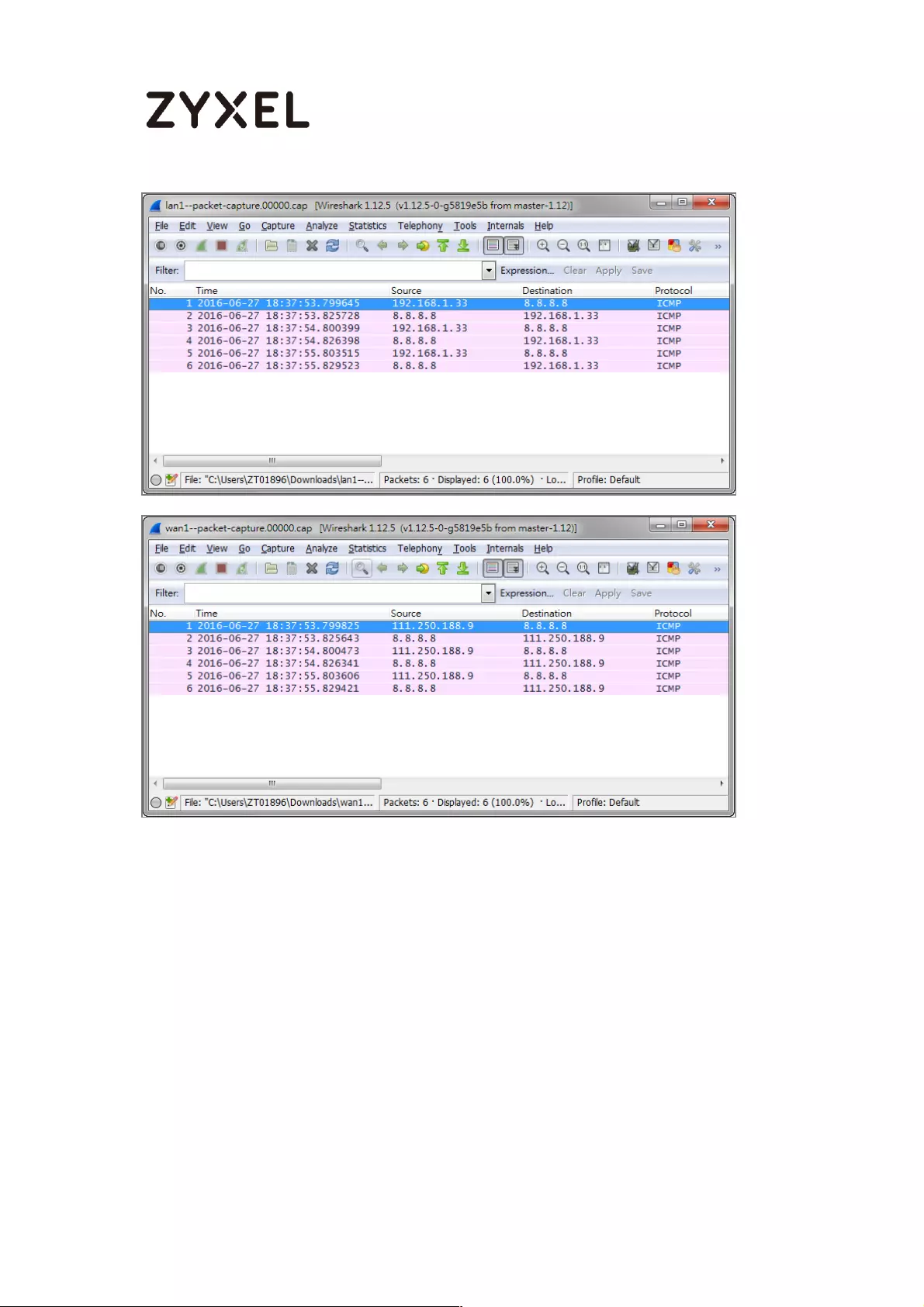
469/782
www.zyxel.com
How to Automatically Reboot the ZyWALL/USG by Schedule
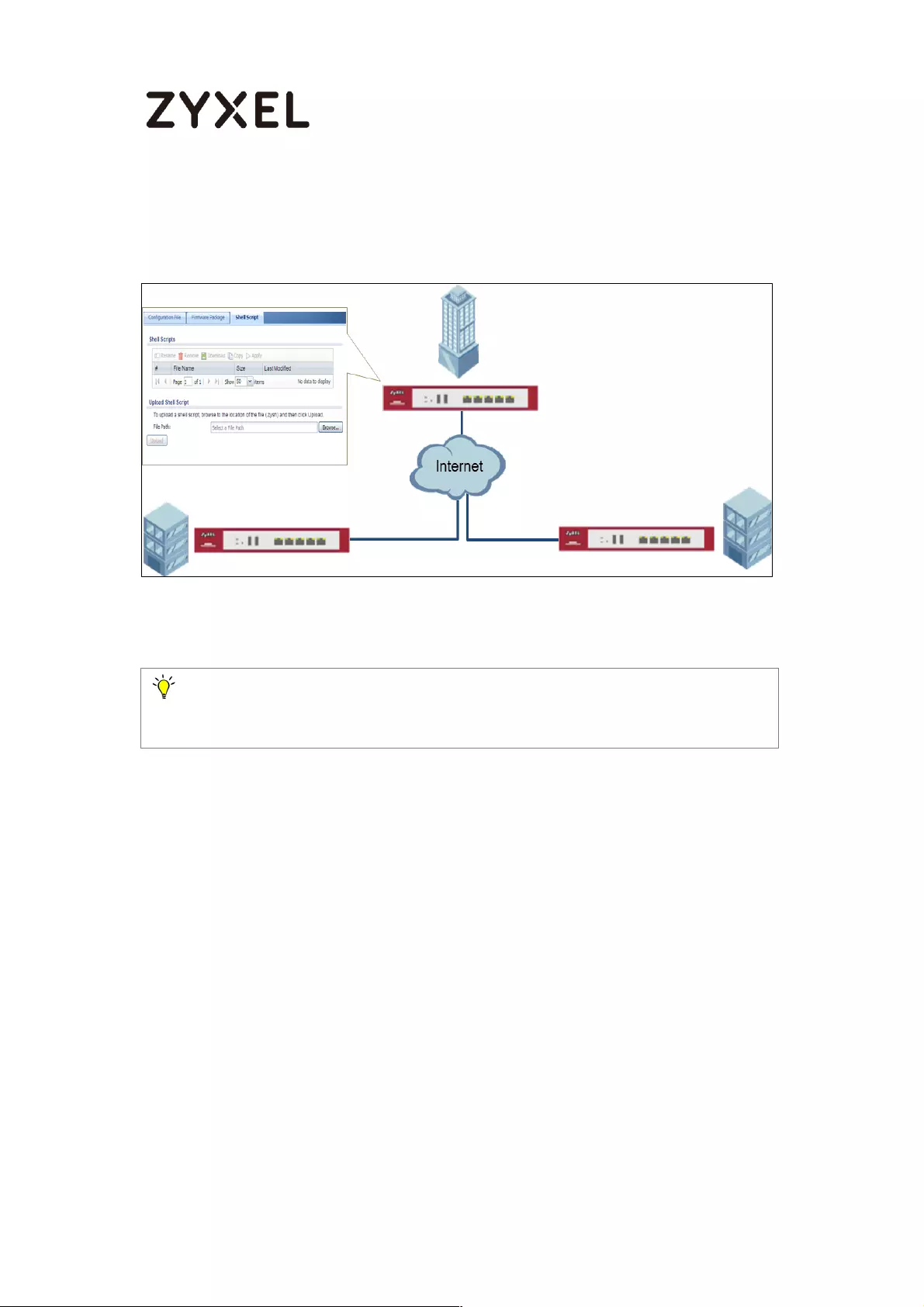
470/782
www.zyxel.com
This example shows how to use shell script and schedule run to reboot device
automatically for maintenance purpose.
ZyWALL/USG Auto Schedule Reboot Settings
Set Up the Shell Script
1 Run Windows Notepad application and input below command:
Note: This example was tested using USG110 (Firmware Version: ZLD 4.25).
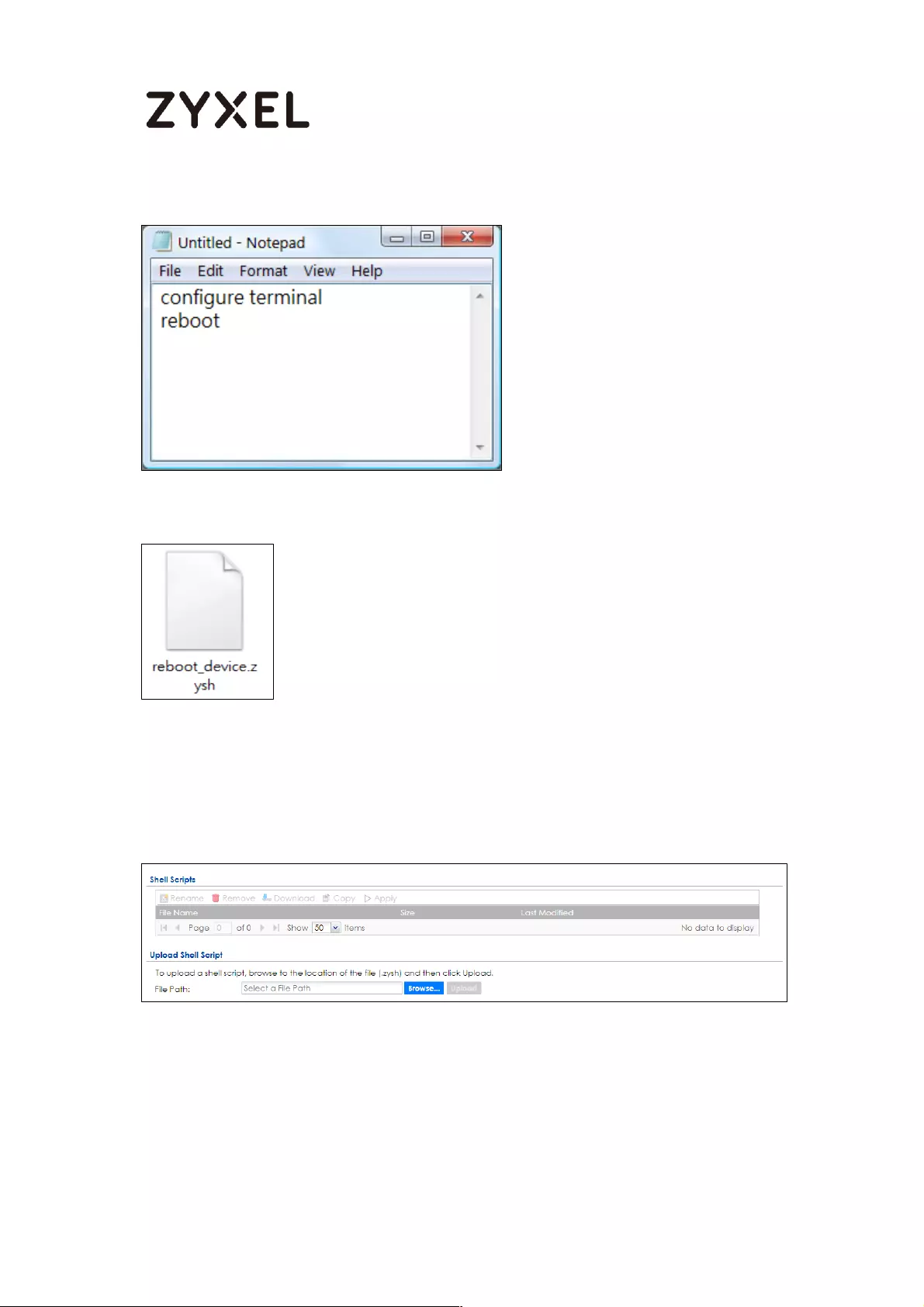
471/782
www.zyxel.com
2 Save this file as "reboot_device.zysh"
3 In the ZyWALL/USG, go to MAINTENANCE > File Manager > Shell Script. Click
Browse... to find the reboot_device.zysh file. Click Upload to begin the upload
process.
Set Up the Schedule Run
1 Login the device via console/telnet/SSH (using PuTTY in this example)

472/782
www.zyxel.com
2 Issuing below commands based on three different (daily, weekly and monthly)
user scenarios:
a. Router(config)# schedule-run 1 reboot_device.zysh daily 10:00
(The device will reboot at 10:00 everyday)
b. Router(config)# schedule-run 1 reboot_device.zysh weekly 10:00 sun
(The device will reboot at 10:00 every Sunday)

473/782
www.zyxel.com
c. Router(config)# schedule-run 1 reboot_device.zysh monthly 10:00 23
(The device will reboot at 10:00 every month on 23th)
Check the Reboot Status
3 Login the device via console/telnet/SSH, the reboot runs as scheduled
4 Go to Configuration > System> Date/Time, check Current Date/Time.
Figure Configuration > System >Date/Time
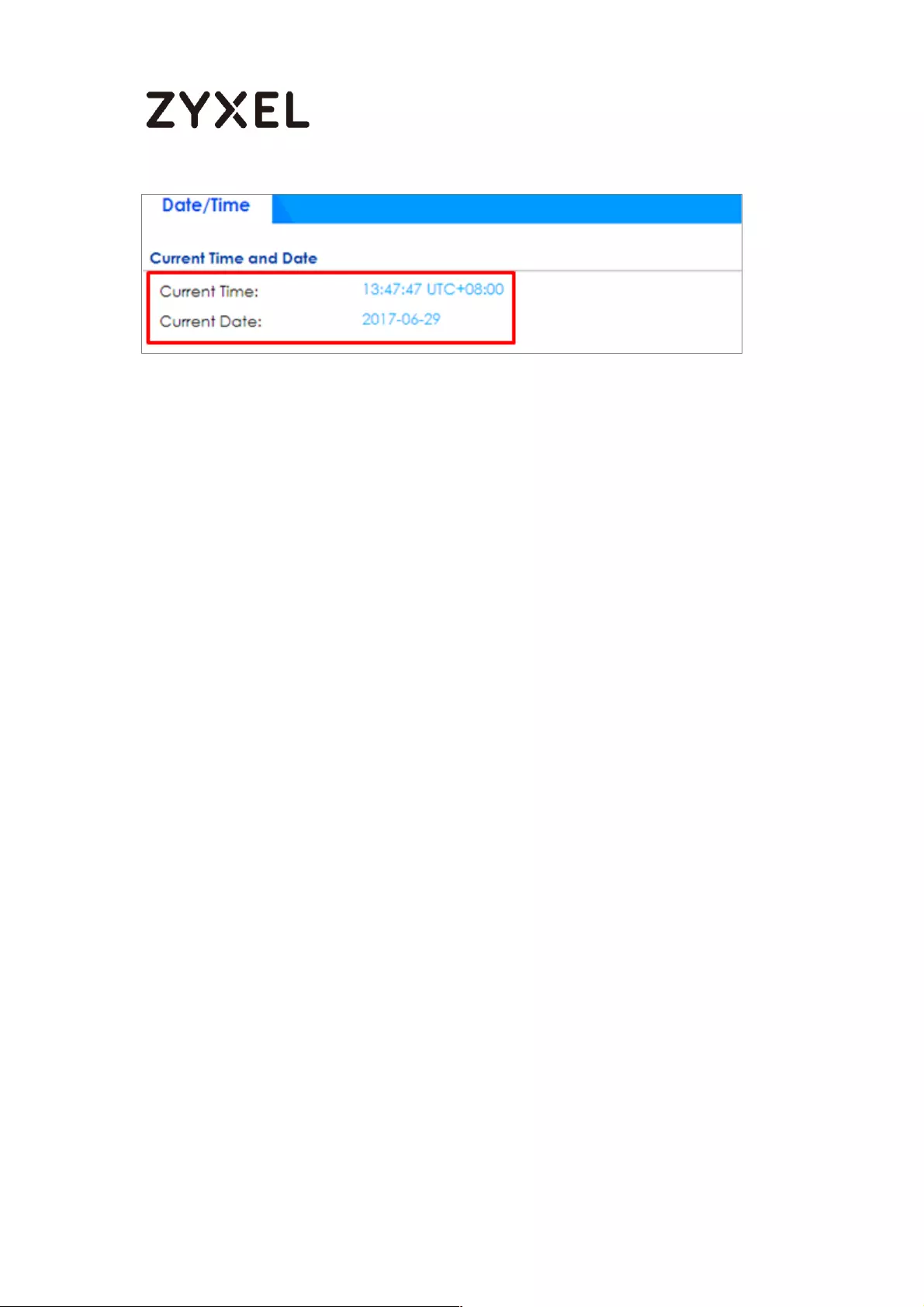
474/782
www.zyxel.com
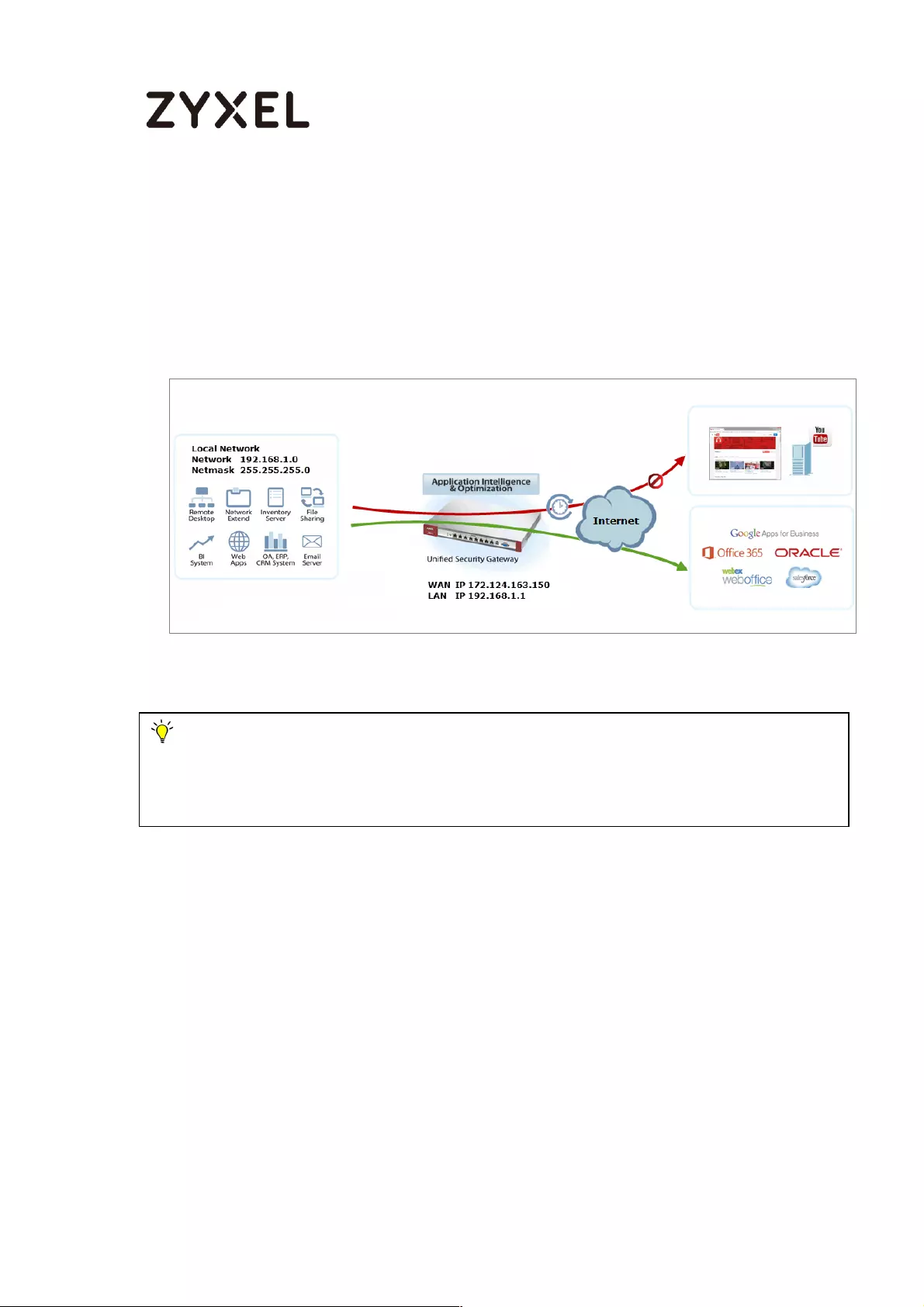
475/782
www.zyxel.com
How To Schedule YouTube Access
This is an example of using the ZyWALL/USG UTM Profile and Security Policy to control
access to the network. If an application should not have network access during
certain hours, you can use Application Patrol, SSL Inspection and Schedule settings to
make sure that these applications cannot access the Internet.
ZyWALL/USG with Scheduled YouTube Access Settings Example
Set Up the Schedule on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Object > Schedule > Recurring > Add
Schedule Recurring Rule. Configure a Name for you to identify the Schedule
Recurring Rule. Specify the Day Time hour and minute when the schedule begins
and ends each day. In the Weekly schedule, select each day of the week that the
recurring schedule is effective.
CONFIGURATION > Object > Schedule > Recurring
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
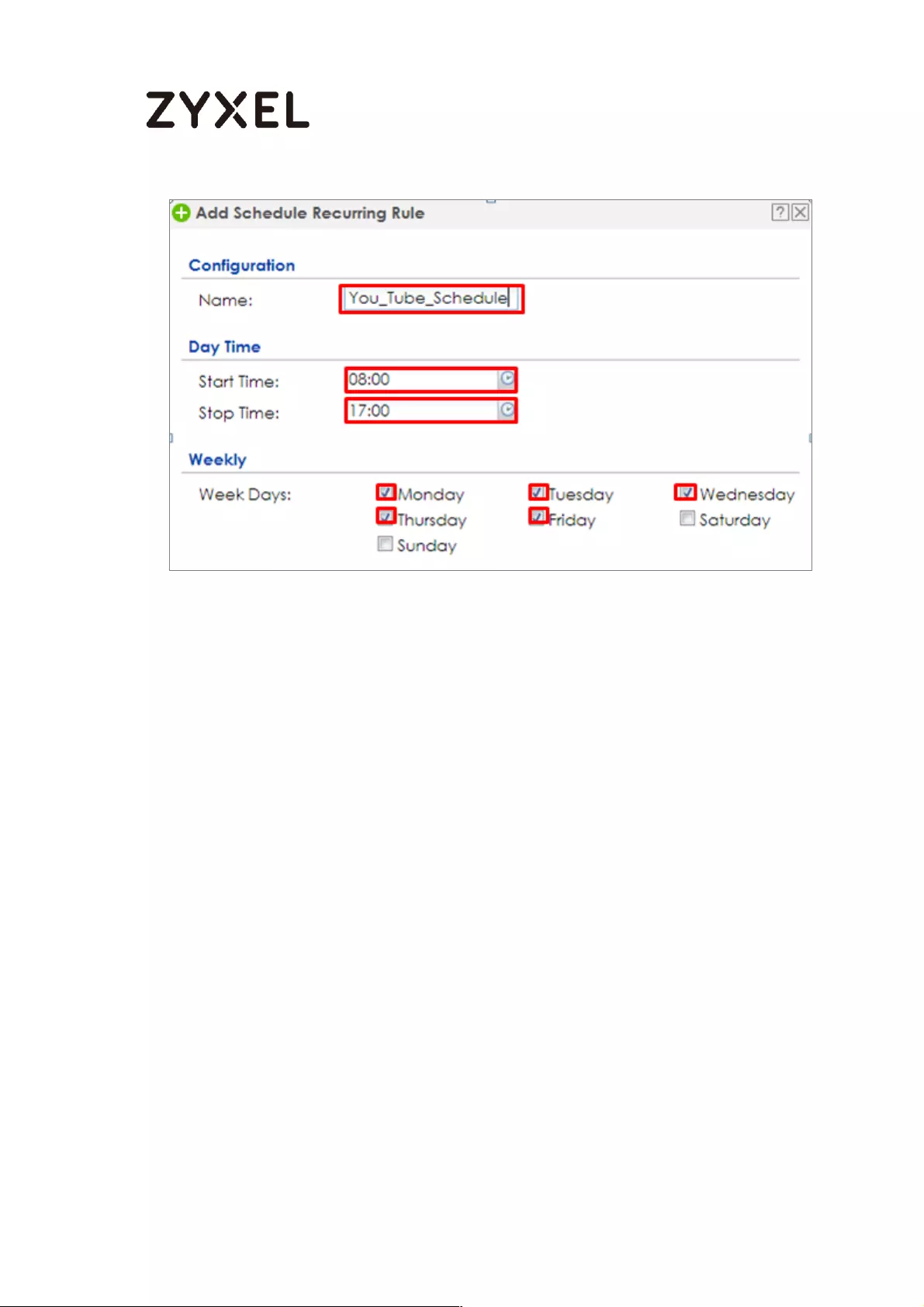
476/782
www.zyxel.com
Create the Application Objects on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Object > Application > Add
Application Rule. Configure a Name for you to identify the Application Profile. Then,
click Add to create an Application Object.
CONFIGURATION > Object > Application > Add Application Rule
In the Application Object, select By Service, type a keyword and click Search to
display all signatures containing that keyword. Check all Query Result and Click OK.
CONFIGURATION > Object > Application > Add Application Rule > Add Application
Object
Set Up SSL Inspection on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile > SSL Inspection > Add
rule, configure a Name for you to identify the SSL Inspection profile.

477/782
www.zyxel.com
Then, select the CA Certificate to be the certificate used in this profile. Select
Block to Action for Connection with SSL v3 and select Log type to be log alert. Leave
other actions as default settings.
CONFIGURATION > UTM Profile > SSL Inspection > Add rule
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy Control,
configure a Name for you to identify the Security Policy profile. For From and To
policies, select the direction of travel of packets to which the policy applies.
Select the Schedule that defines when the policy applies (Youtube_Schedule in
this example).
Scroll down to UTM Profile, check Application Patrol and select a profile from the
list box (Youtube_profile in this example). Then, check SSL Inspection and select a
profile from the list box (Youtube in this example).
CONFIGURATION > Security Policy > Policy Control
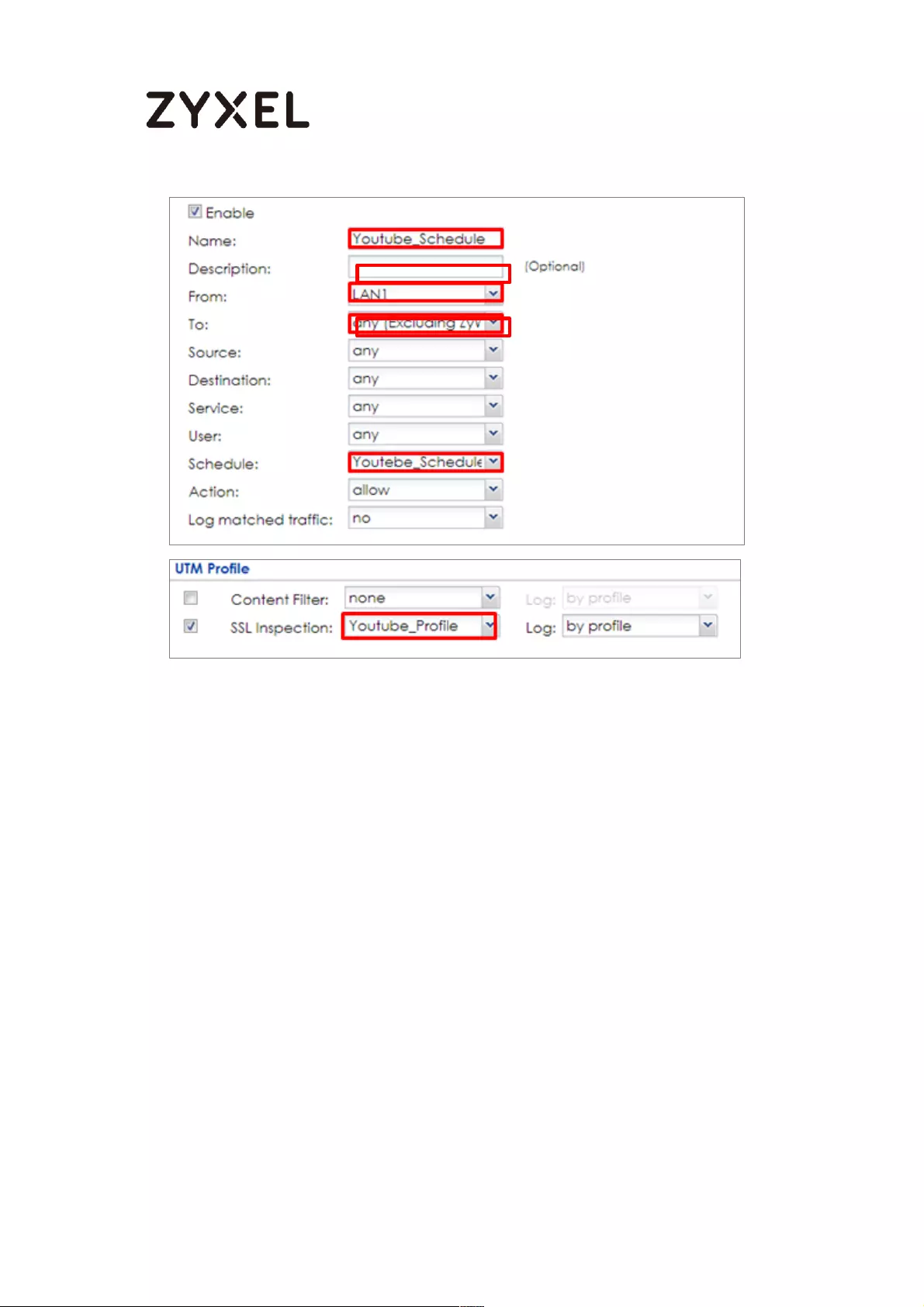
478/782
www.zyxel.com
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System
When SSL inspection is enabled and an access website does not trust the
ZyWALL/USG certificate, the browser will display a warning page of security
certificate problems.
Go to ZyWALL/USG CONFIGURATION > Object > Certificate > default > Edit to
export default certificate from ZyWALL/USG with Private Key (zyx123 in this
example).
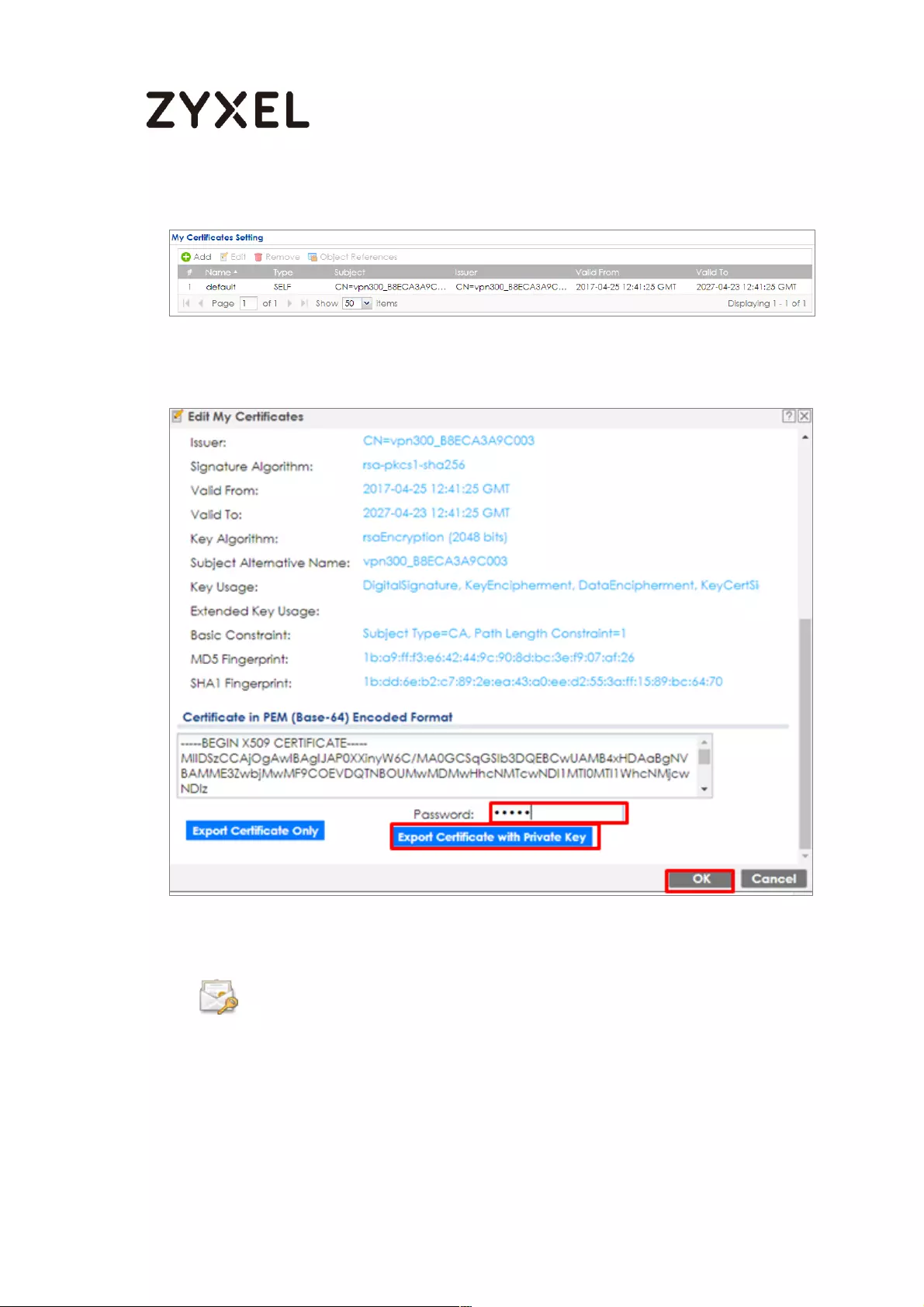
479/782
www.zyxel.com
CONFIGURATION > Object > Certificate > default
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with
Private Key
Save default certificate as *.p12 file to Windows 7 Operation System.
In Windows 7 Operating System Start Menu > Search Box, type mmc and press
Enter.
Start Menu > Search Box > mmc
default.p12
480/782
www.zyxel.com
In the mmc console window, click File > Add/Remove Snap-in...
File > Add/Remove Snap-in...
In the Available snap-ins, select the Certificates and click Add button. Select
Computer account > Local Computer. Then, click Finished and OK to close the
Snap-ins window.
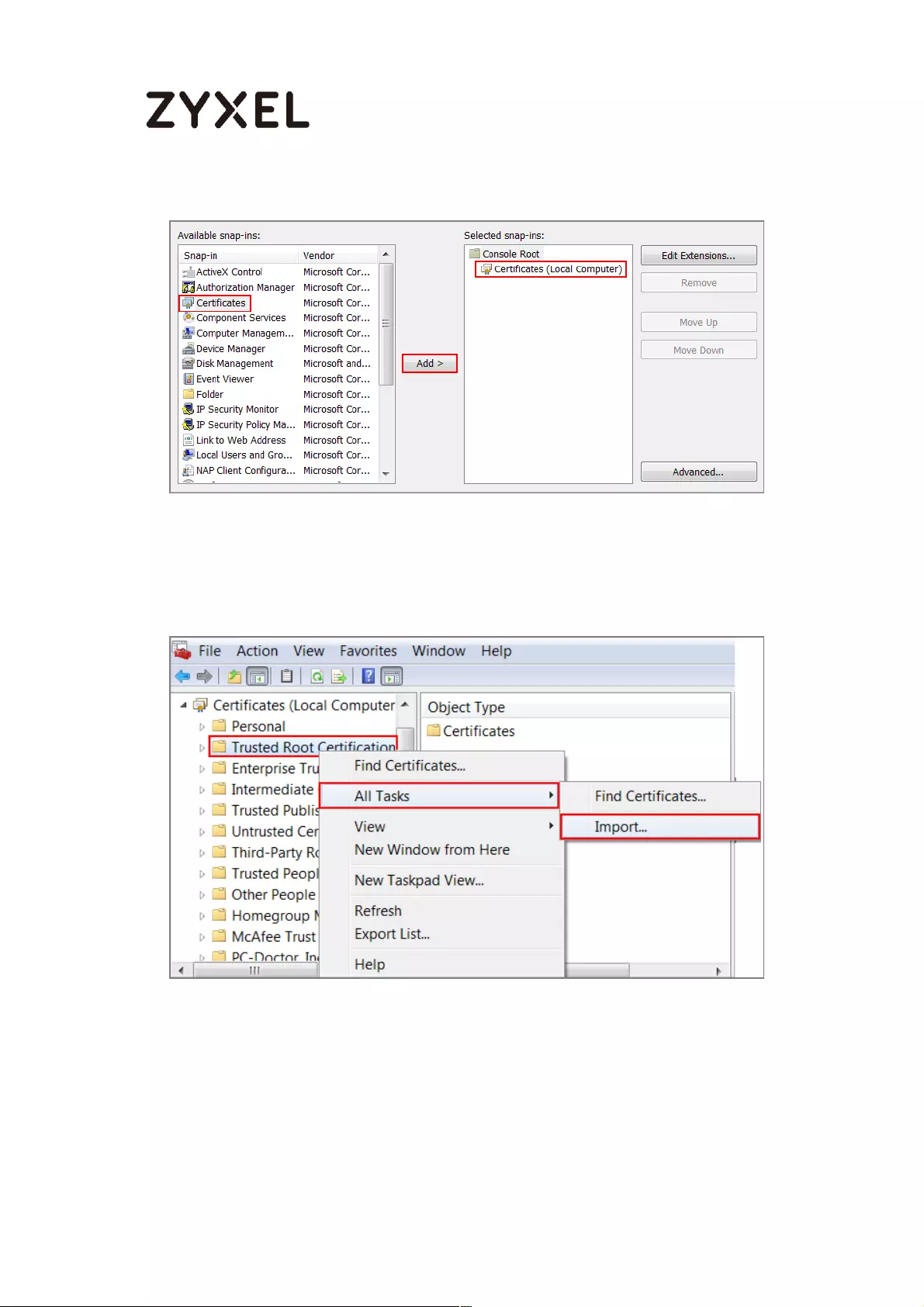
481/782
www.zyxel.com
Available snap-ins > Certificates > Add
In the mmc console window, open the Certificates (Local Computer) > Trusted
Root Certification Authorities, right click Certificate > All Tasks > Import…
Click Next, Then, Browse..., and locate the .p12 file you downloaded earlier. Then,
click Next.
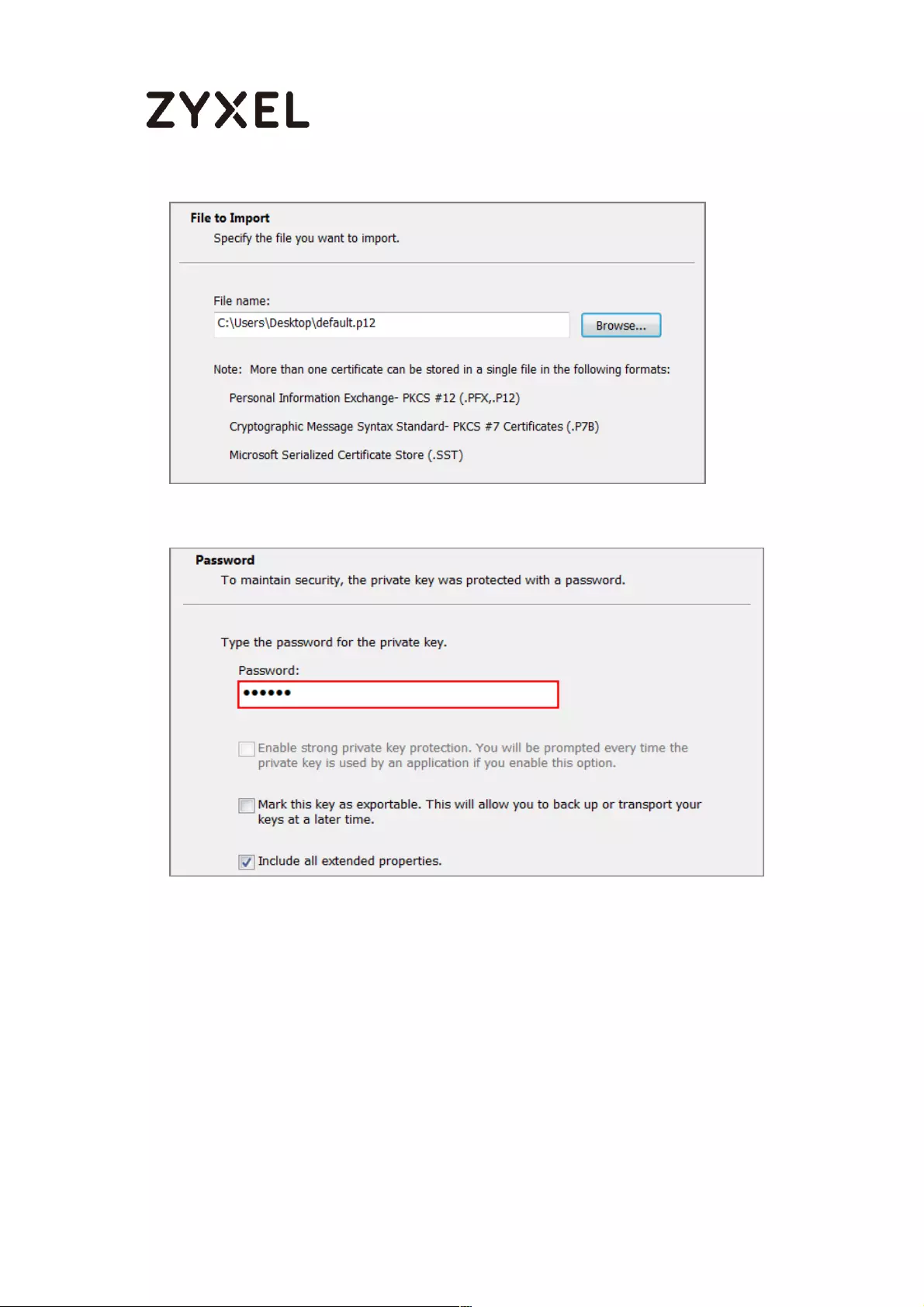
482/782
www.zyxel.com
Click Next, type zyx123 in the Password field and click Next again
Select Place all certificates in the following store and then click Browse and find
Trusted Root Certification Authorities. Click Next, then click Finish.
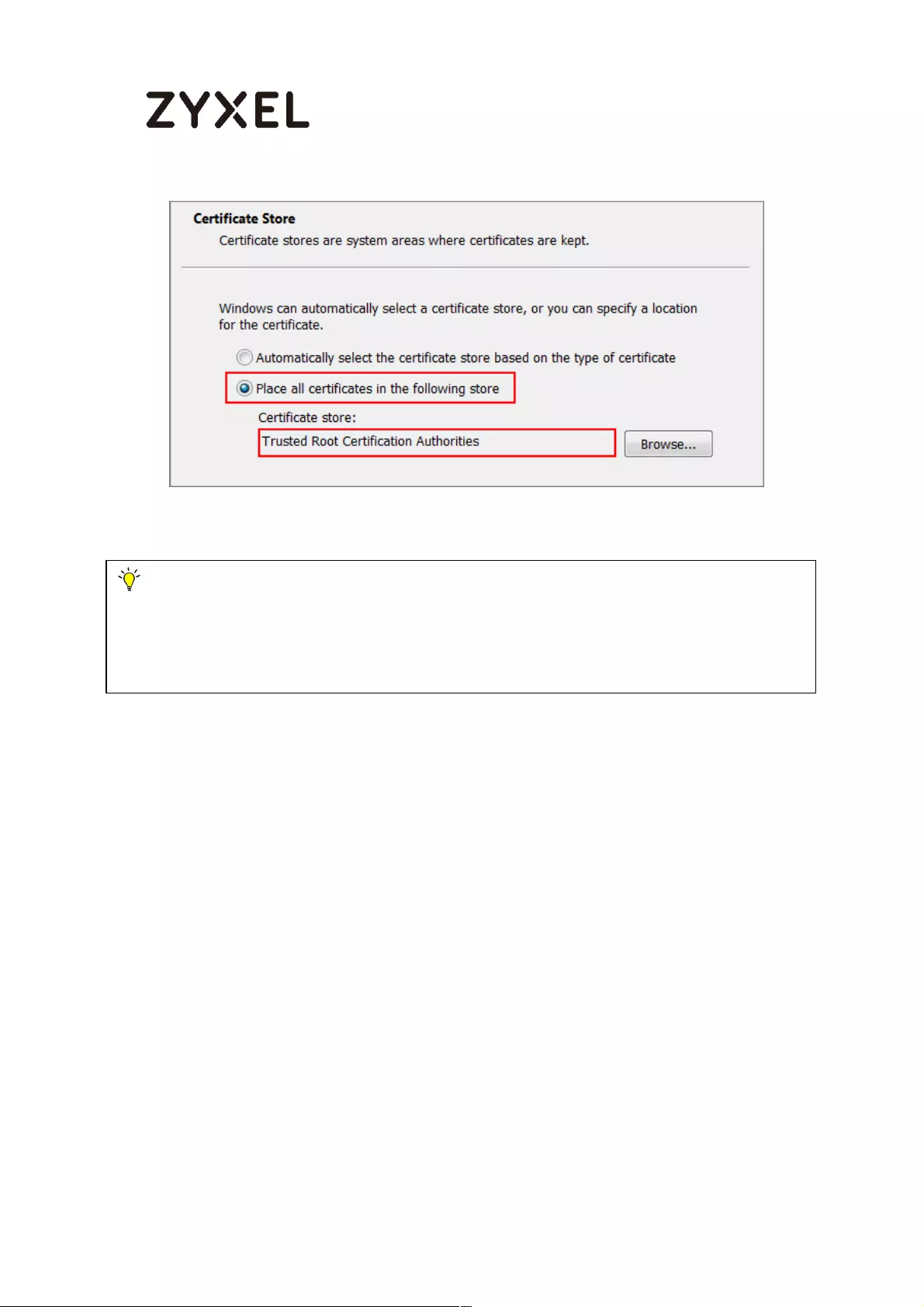
483/782
www.zyxel.com
Note: Each ZyWALL/USG device has its own self-signed certificate by factory default.
When you reset to the default configuration file, the original self-signed certificate is erased,
and a new self-signed certificate will be created when the ZyWALL/USG boots the next time.
484/782
www.zyxel.com
Test the Result
Type http://www.youtube.com/ or https://www.youtube.com/ into the browser.
An error message occurs.
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as
below.
What Could Go Wrong?
If you are not be able to configure any Application Patrol policies or it’s not
working, there are two possible reasons:
You have not subscribed for the Application Patrol service.
You have subscribed for the Application Patrol service but the license is
expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from

485/782
www.zyxel.com
the portal page (https://portal.myzyxel.com/) to register or extend your
Application Patrol license.
After you apply the Application Patrol service, the running session will continue till
it’s finished.
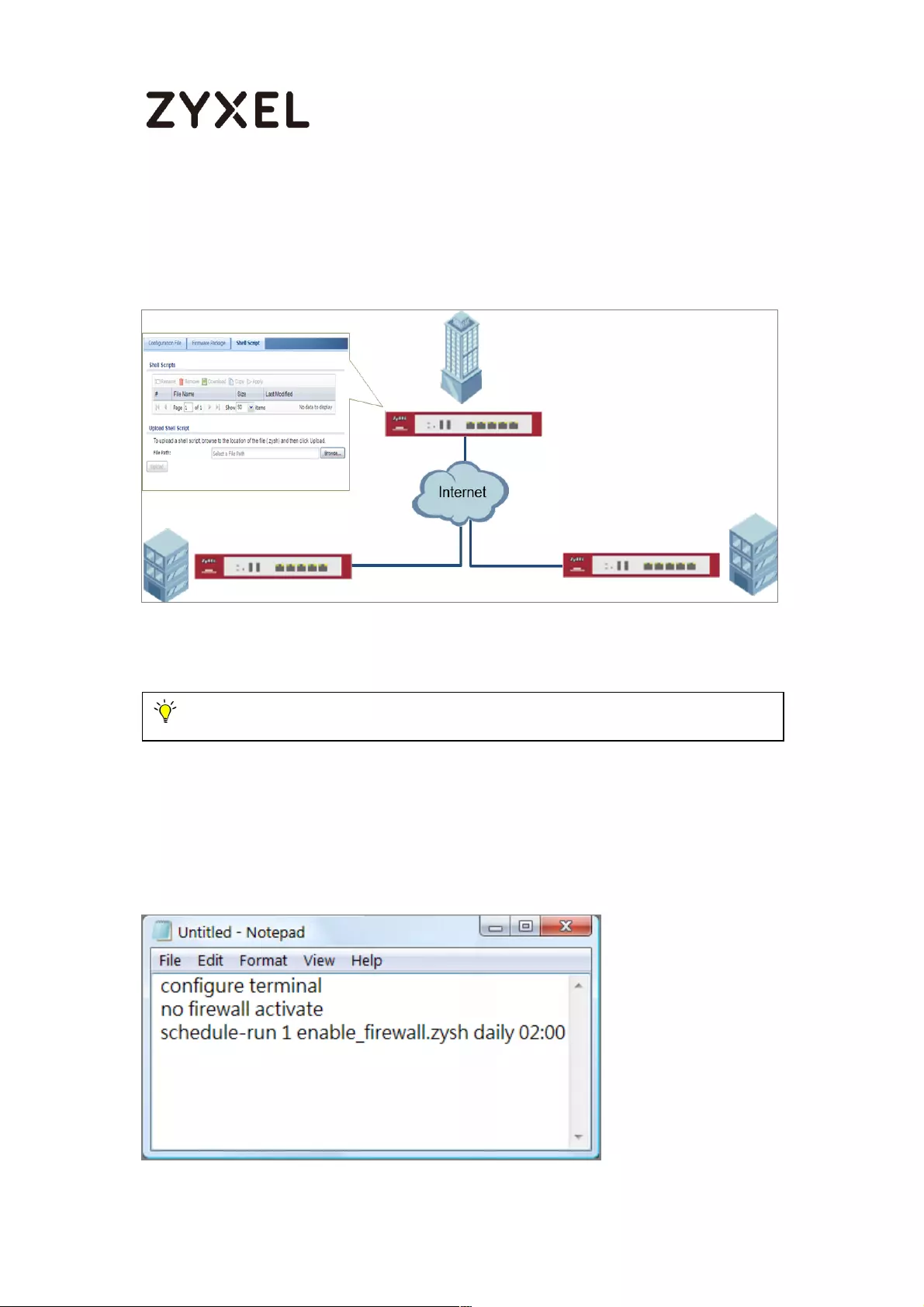
486/782
www.zyxel.com
How to continuously run a ZySH script
This example shows how to use shell script and continuously run a ZySH script
automatically for maintenance purpose.
ZyWALL/USG continuously run a ZySH script Settings
Set Up the Shell Script
1 Run Windows Notepad application and input below command:
Note: This example was tested using USG110 (Firmware Version: ZLD 4.25).

487/782
www.zyxel.com
2 Save this file as "disable_firewall.zysh"
3 Run Windows Notepad application and input below command:
4 Save this file as "enable_firewall.zysh"
5 In the ZyWALL/USG, go to MAINTENANCE > File Manager > Shell Script. Click
Browse... to find the disable_firewall.zysh and enable_firewall.zysh file. Click Upload to
begin the upload process.
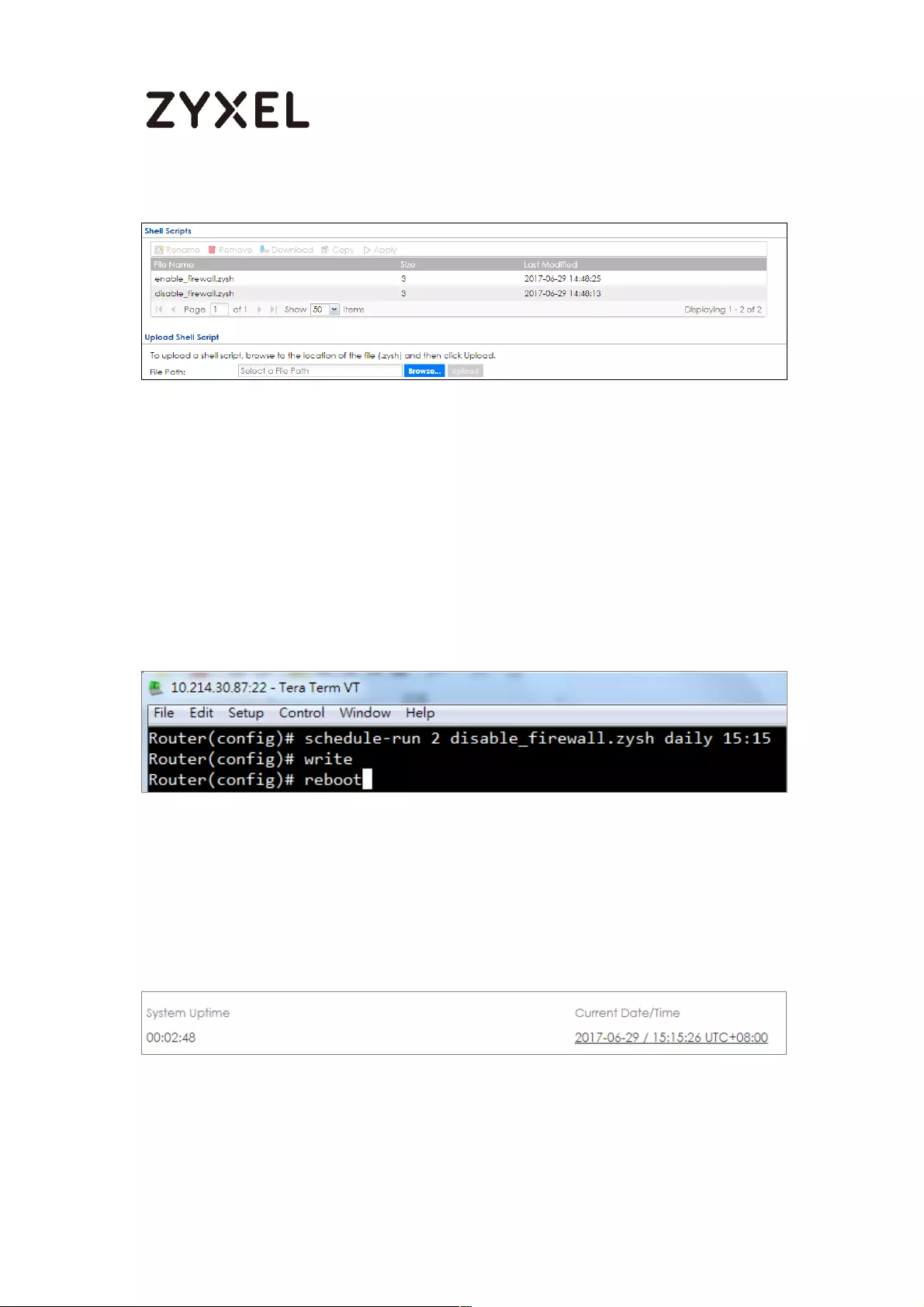
488/782
www.zyxel.com
Set Up the Schedule Run
6 Issuing below commands:
Router> configure terminal
Router(config)# schedule-run 1 disable_firewall.zysh daily 15:15
Check the Result
1 In the ZyWALL/USG, go to DASHBOARD.
DASHBOARD
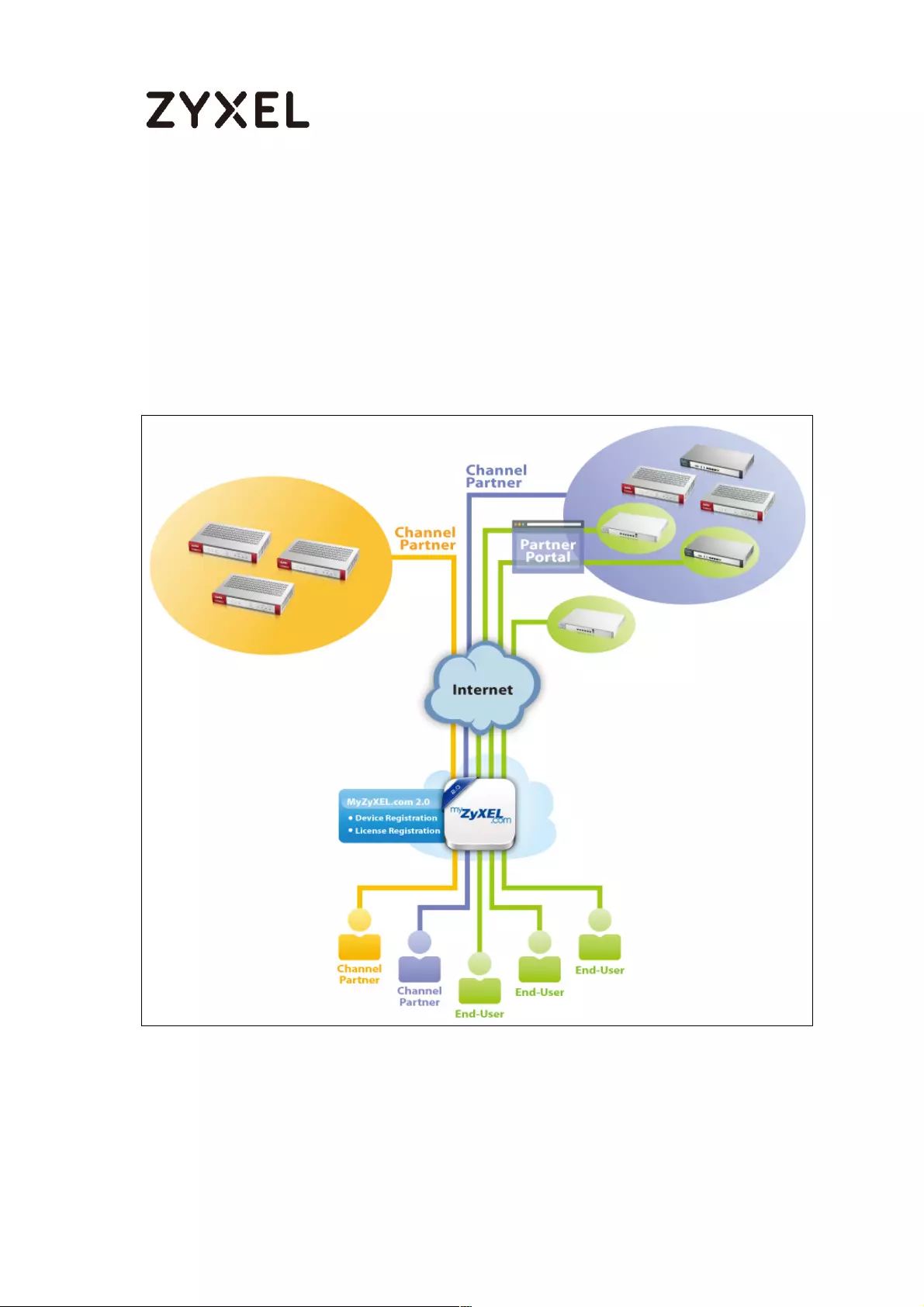
489/782
www.zyxel.com
How To Register Your Device and Services at myZyXEL.com
myZyXEL.com is ZyXEL’s online services center where you can register your ZyXEL
device and manage subscription services available for the device. To update
signature files or use a subscription service, you have to register the device and
activate the corresponding service at myZyXEL.com.
MyZyXEL.com 2.0 Management Architecture
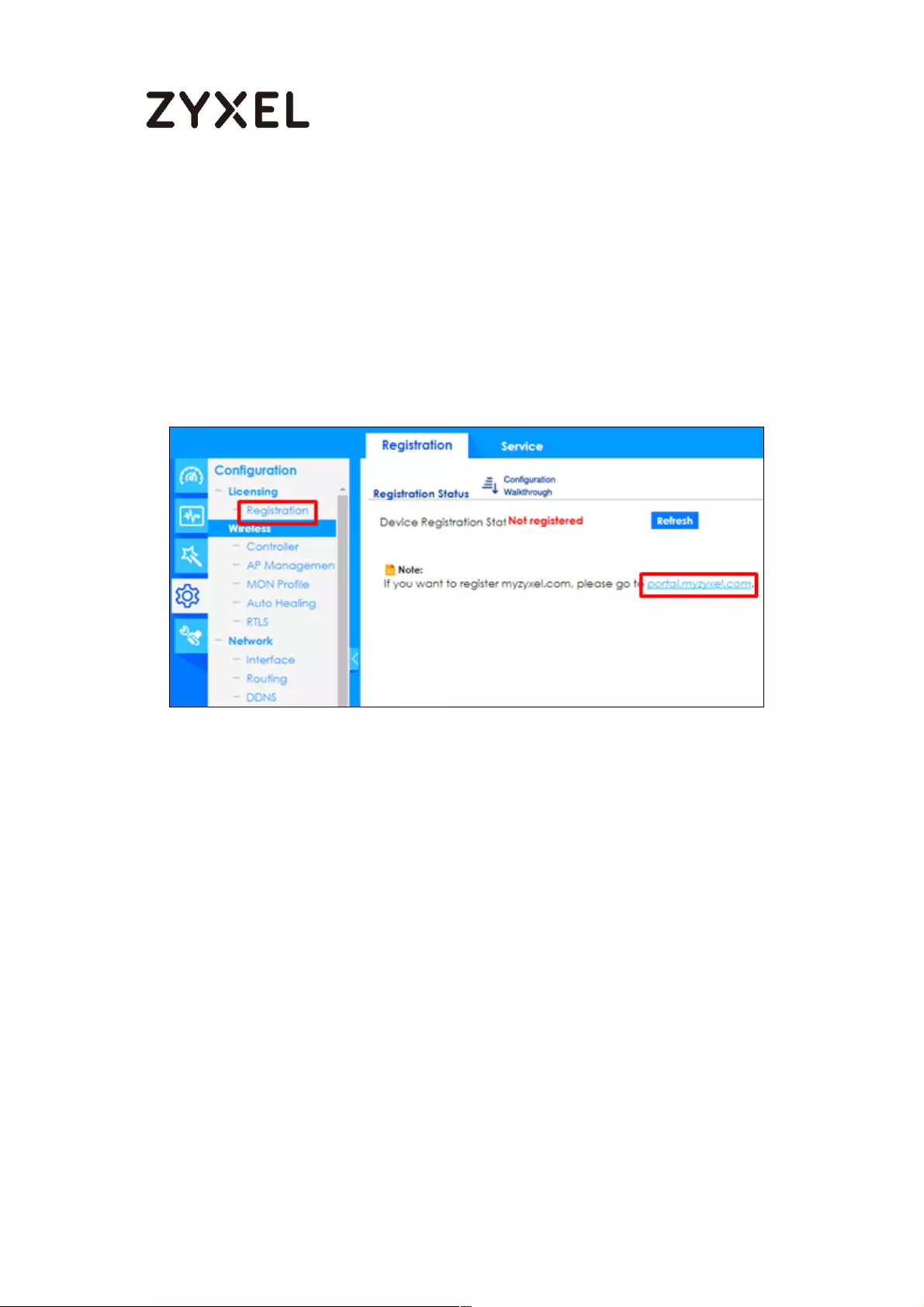
490/782
www.zyxel.com
Account Creation
After you click the link from the Registration screen of your ZyXEL device’s Web
Configurator or click the myZyXEL.com 2.0 icon from the portal page
(https://portal.myzyxel.com/), the Sign In screen displays.
CONFIGURATION > Licensing > Registration
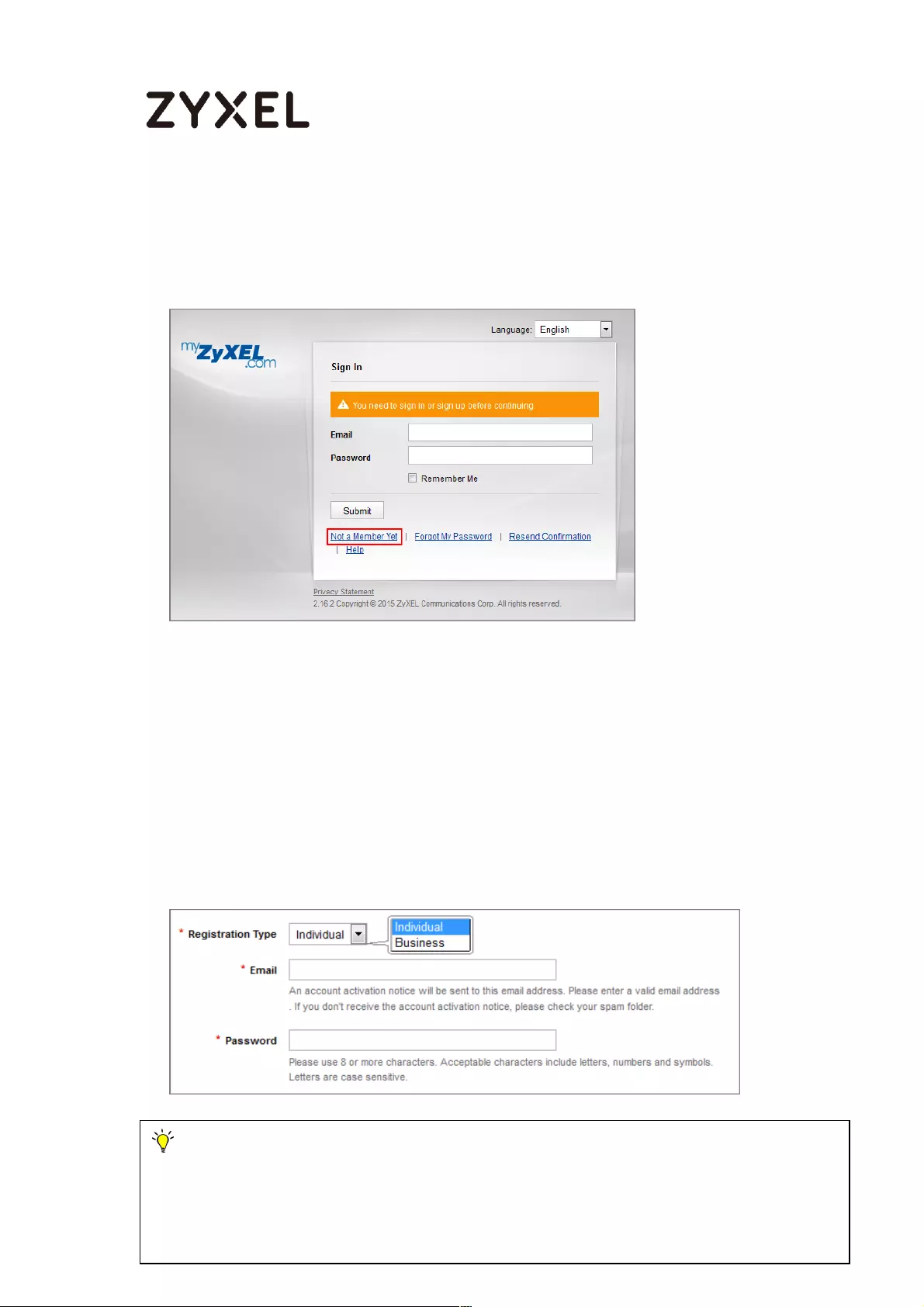
491/782
www.zyxel.com
Click Not a Member Yet to open the Sign Up screen where you can create an
account.
myZyXEL.com > Not a Member Yet
Select Registration Type to create an Individual account or a Business account.
Individual account is for non-commercial, end user of ZyXEL products. Business
account is for commercial users; VAT # is required (the requirement varies in
selection of different countries)
myZyXEL.com > Not a Member Yet > Sign-up
Note: The business account can be changed into a channel partner account by an
administrator. With a channel partner account, you can register multiple devices and/or
services at a time and check service status reports. Contact your sales representative to
have a channel partner account.
492/782
www.zyxel.com
After you click Submit, myZyXEL.com 2.0 will send you an account activation
notification e-mail. Click the URL link from the e-mail to activate your account and
log into myZyXEL.com 2.0.
After E-mail activate, sign in myZyXEL.com 2.0 to register or mange your devices
and services. If you are a business account, please go to account page and
press the Reseller Request button.
Device Registration
Click Device Registration in the navigation panel to open the screen. Use this
screen to register your device with myZyXEL.com.
Enter the device’s (first) MAC Address and Serial Number, which can be found on
the sticker on the back of the device. Click Submit.
If you access myZyXEL.com from the Registration screen of your ZyXEL device’s
Web Configurator, the device MAC Address and Serial Number displays
automatically.
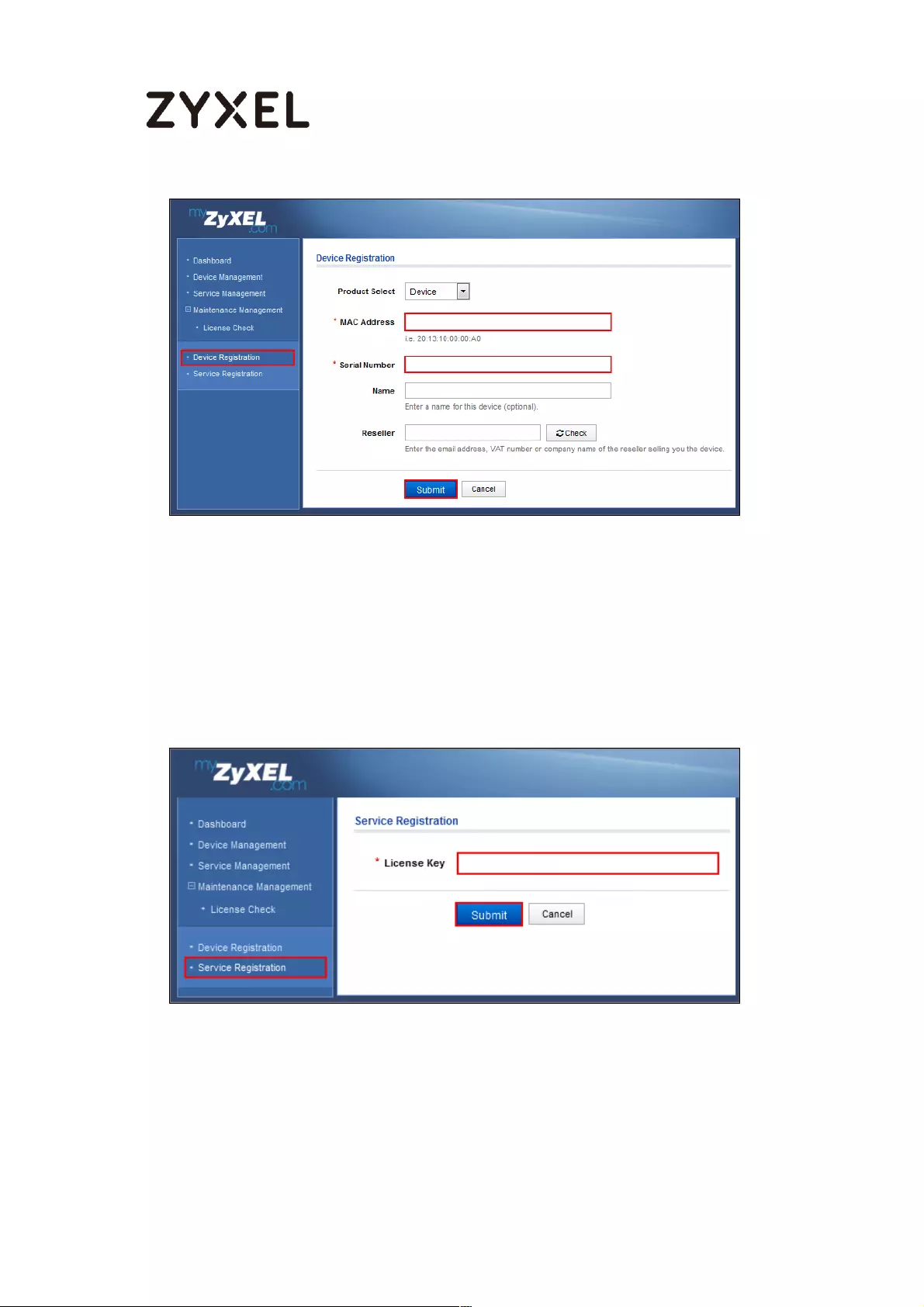
493/782
www.zyxel.com
Service Registration (In the Case of Standard License)
Click Service Registration in the navigation panel to open the screen. Fill in the
License Key as shown on E-iCard License.
Go to the Service Management page and click the Link button. Select the device
then click the Activate button to initiate the services license. You will get a Service
Activation Notice Email when you activate a new service.
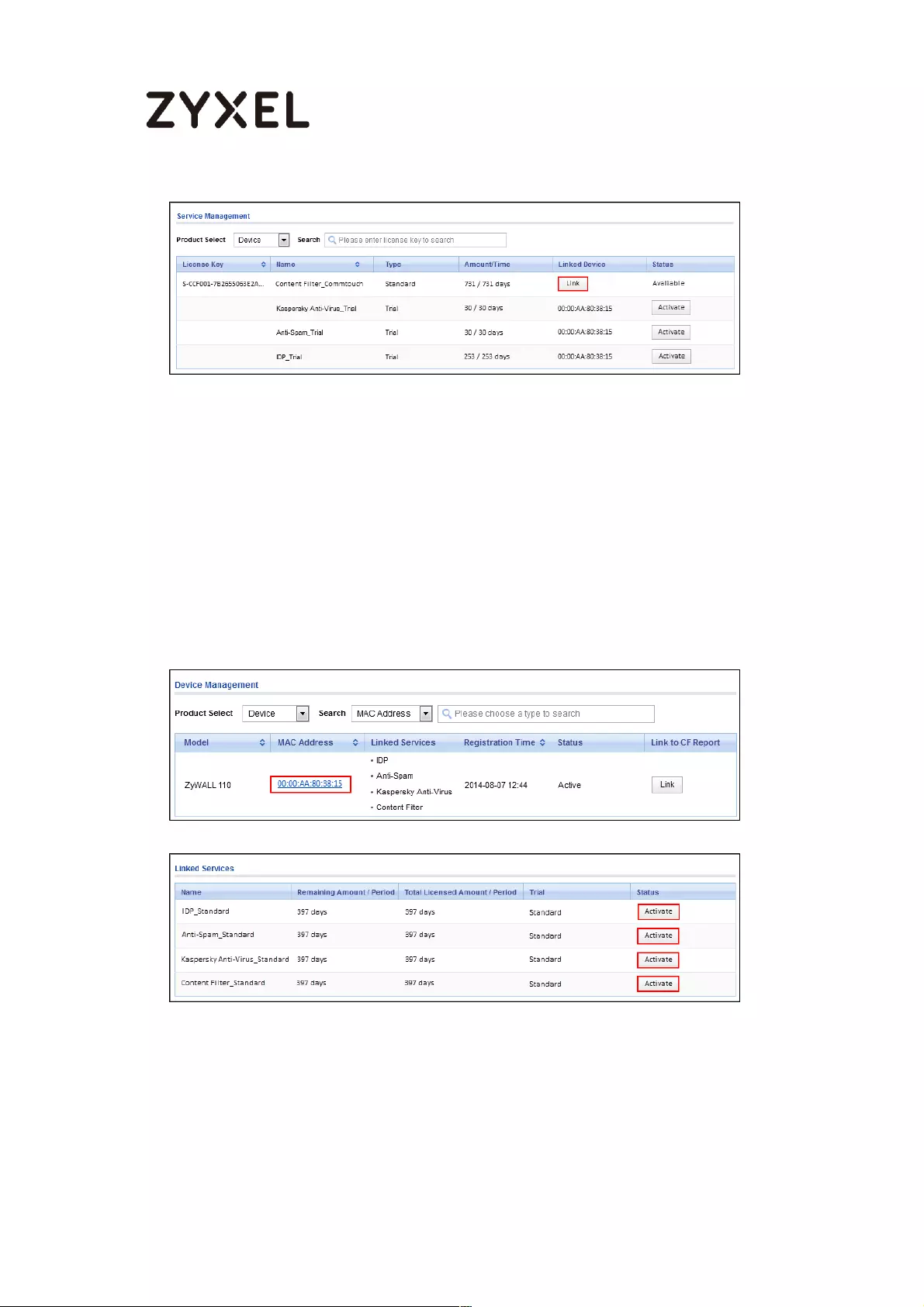
494/782
www.zyxel.com
Device Management (In the Case of Registering Bundled
Licenses)
Go to Device Management and click on the MAC Address hyper link of your
device. In the Linked Services page, click the Activate button to initiate the
services license. You will get a Service Activation Notice Email when you activate
a new service.
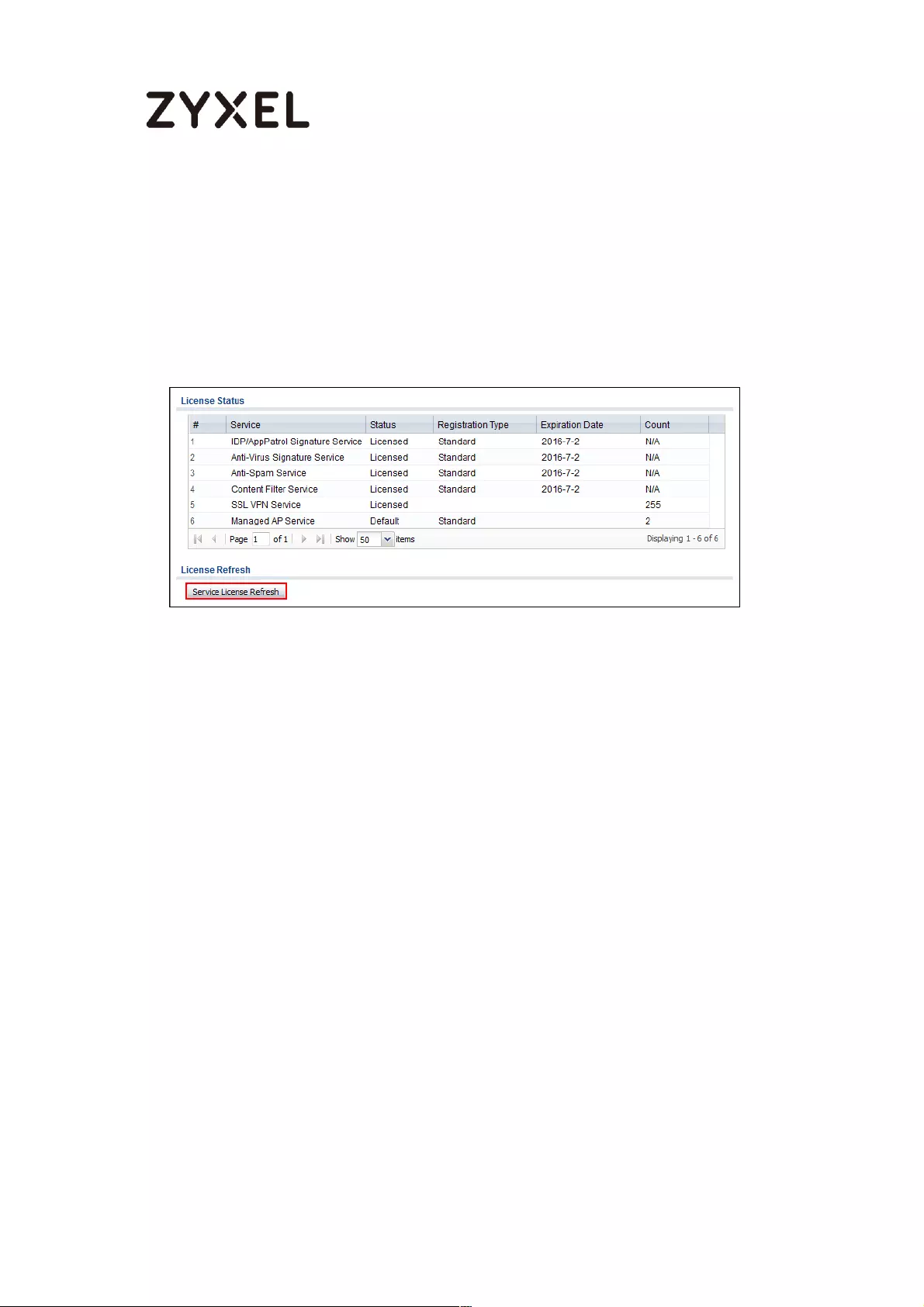
495/782
www.zyxel.com
Refresh Service
After service activated, please go to the ZyWALL/USG CONFIGURATION >
Licensing > Registration > Service and click the Service License Refresh button to
update the Status.
What Could Go Wrong?
If you can’t activate your device’s service license, please check if you entered a
correct license key. Or your login session connecting to the device’s Web GUI or
to myZyXEL.com might have been timed out. Please try to login again.
If the device fails to register and connect to myzyxel.com, please ensure that the
WAN interface IP address can public access to Internet is working properly.
If you forget your password of myzyxel.com account, please click the “Forgot My
Password” link on the login screen and enter your email address. MyZyXEL.com 2.0
will send an email to you with a link to change your password.
496/782
www.zyxel.com
If you forget your registered email address on myZyXEL.com, please go to the link
below and submit a request to ZyXEL support team for further support:
http://www.zyxel.com/form/Support_Feedback.shtml
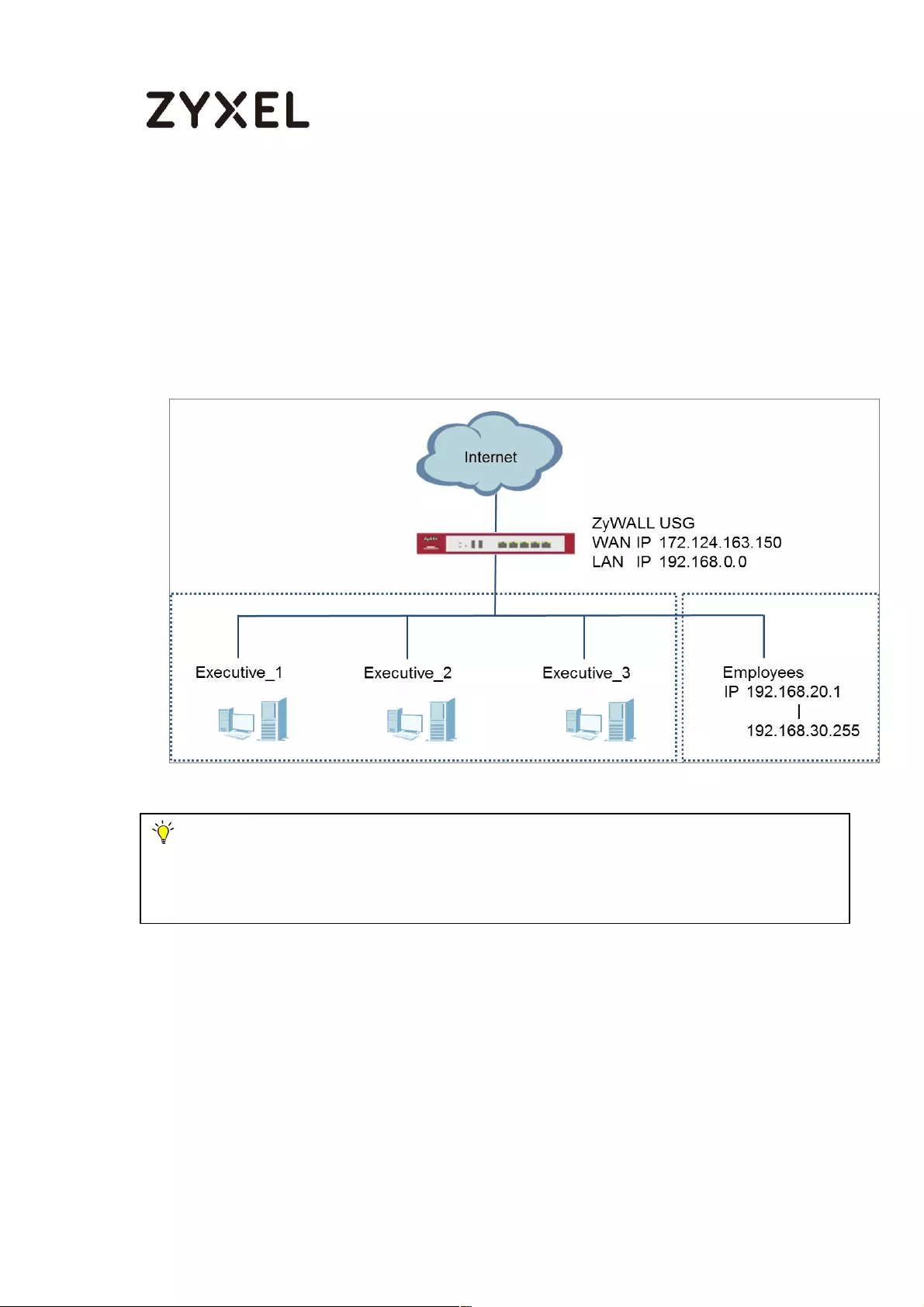
497/782
www.zyxel.com
How To Exempt Specific Users From Security Control
This is an example of using a ZyWALL/USG Security Policy to exempt three
corporate executives from security control, while controlling Internet access for
other employees’ accounts.
Exempt Specific Users from Security Control Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
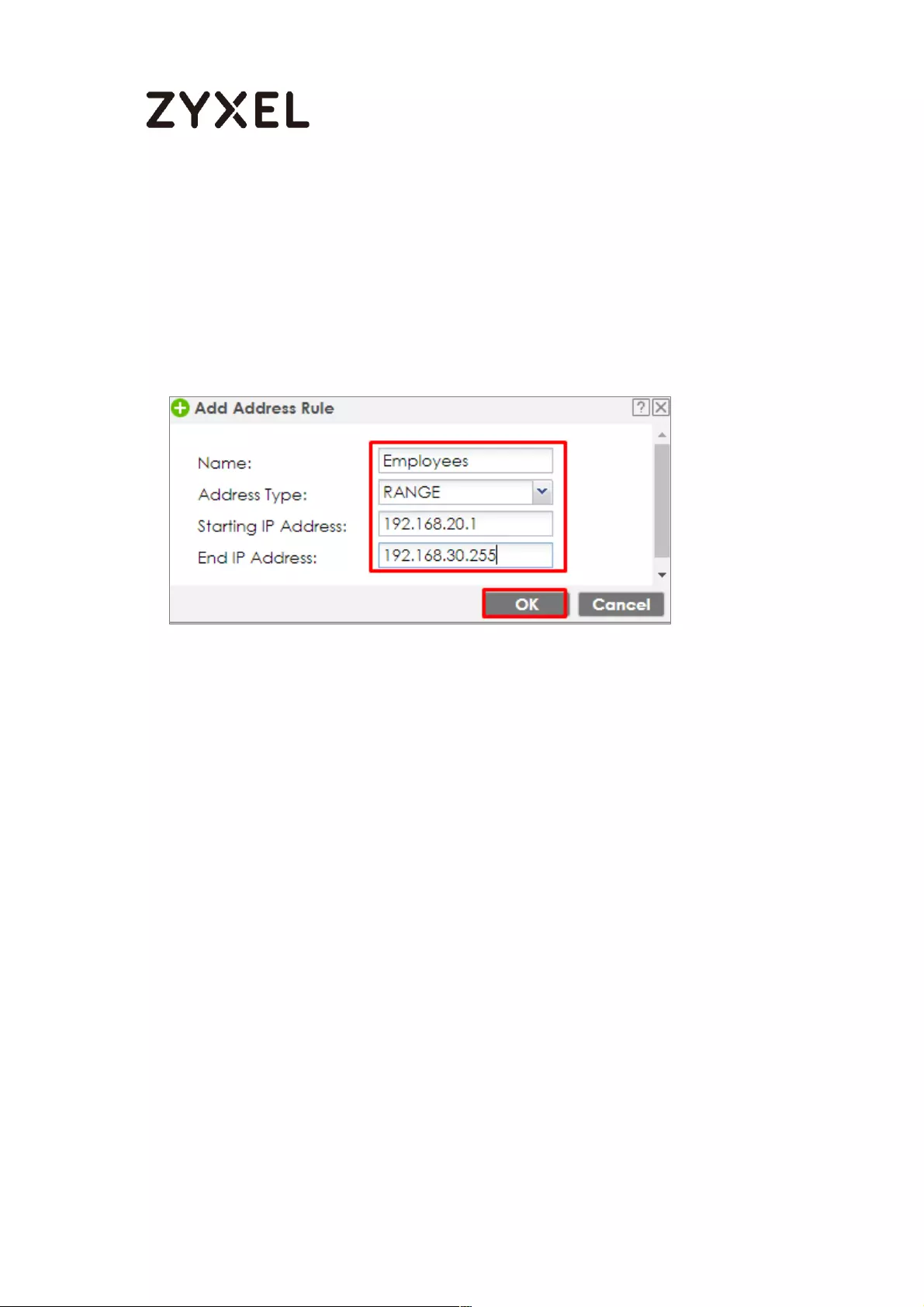
498/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG for Employees
In the ZyWALL/USG, go to CONFIGURATION > Object > Address > Add Address
Rule to create address range for employees.
CONFIGURATION > Object > Address > Add Address Rule
Set up Security Policy for employees, go to CONFIGURATION > Security Policy >
Policy Control > Add corresponding, configure a Name for you to identify the
employees’ Security Policy profile.
For From and To policies, select the direction of travel of packets to which the
policy applies. Select Source to be the Employees to apply the policy to all traffic
coming from them. In order to view the test result later on, set Log matched traffic
to be log.
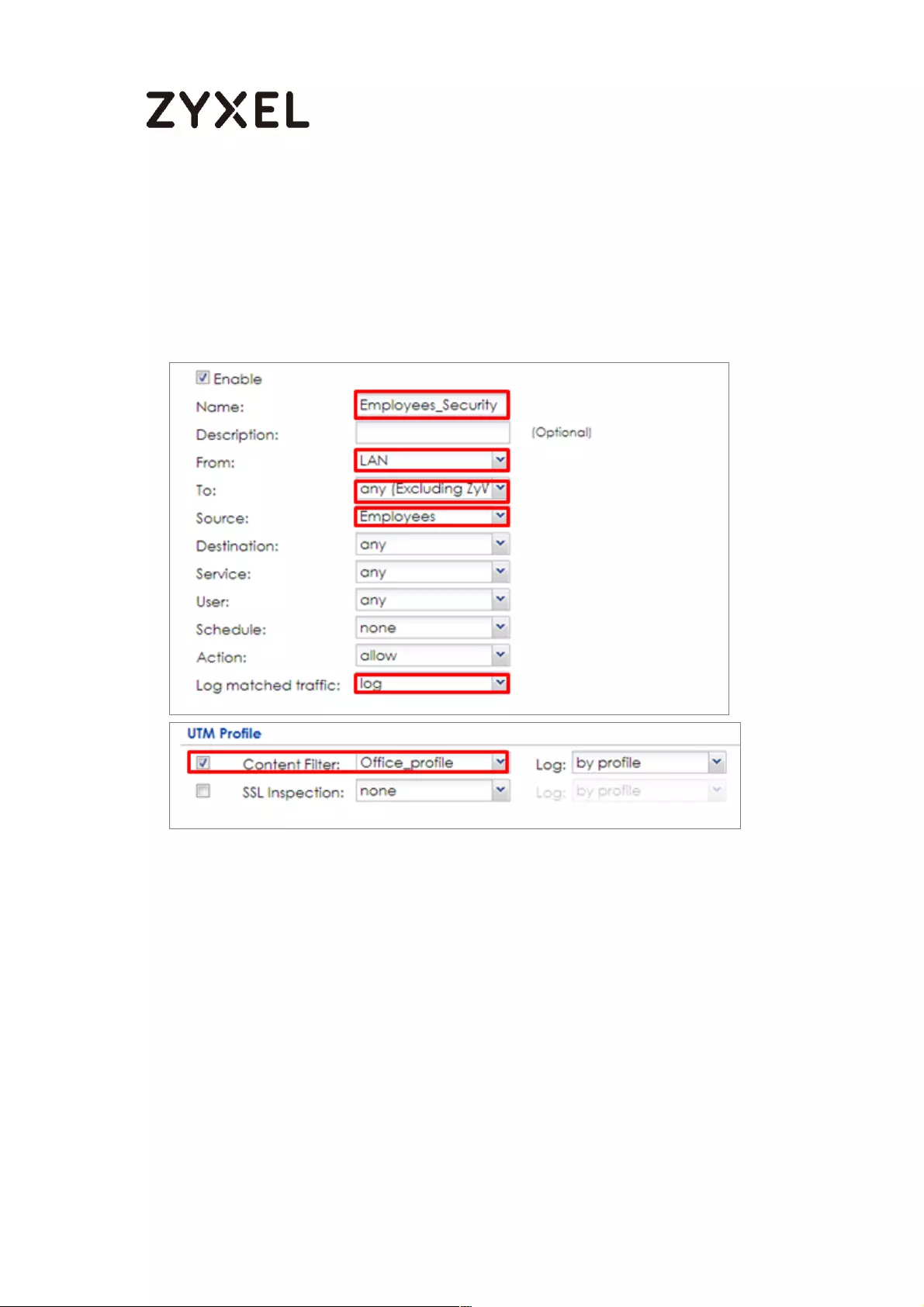
499/782
www.zyxel.com
Scroll down to UTM Profile, select the general policy that allows employees to
access the Internet. (Using built-in Office profile in this example blocks the non-
productive services, such as Advertisement & Pop-Ups, Gambling and Peer to
Peer services…etc.).
CONFIGURATION > Security Policy > Policy Control > Add corresponding >
Employees_Security
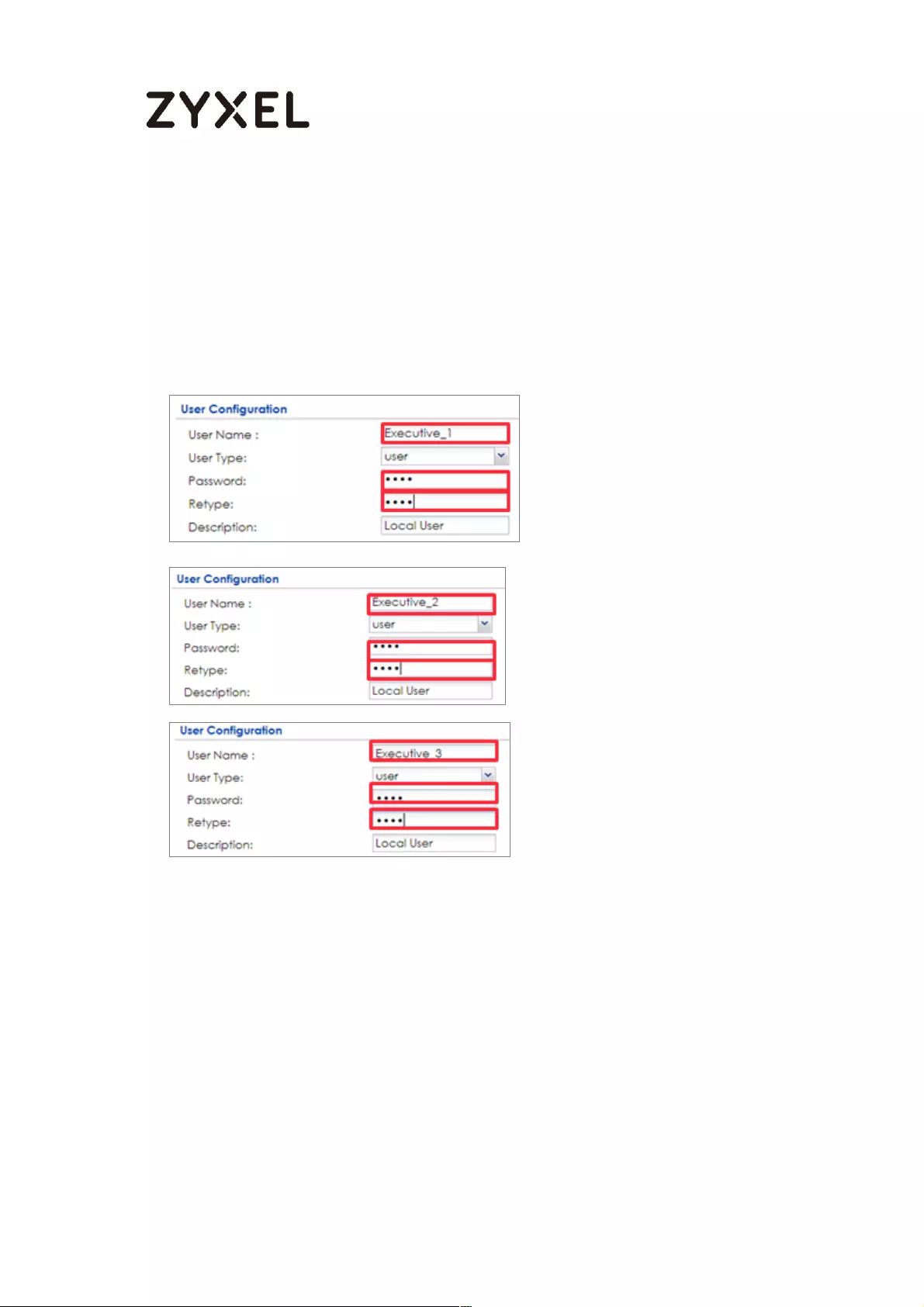
500/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG for Executives
In the ZyWALL/USG, go to CONFIGURATION > Object > User/Group > Add A User
to create User Name/Password for each executive.
CONFIGURATION > Object > User/Group > Add A User
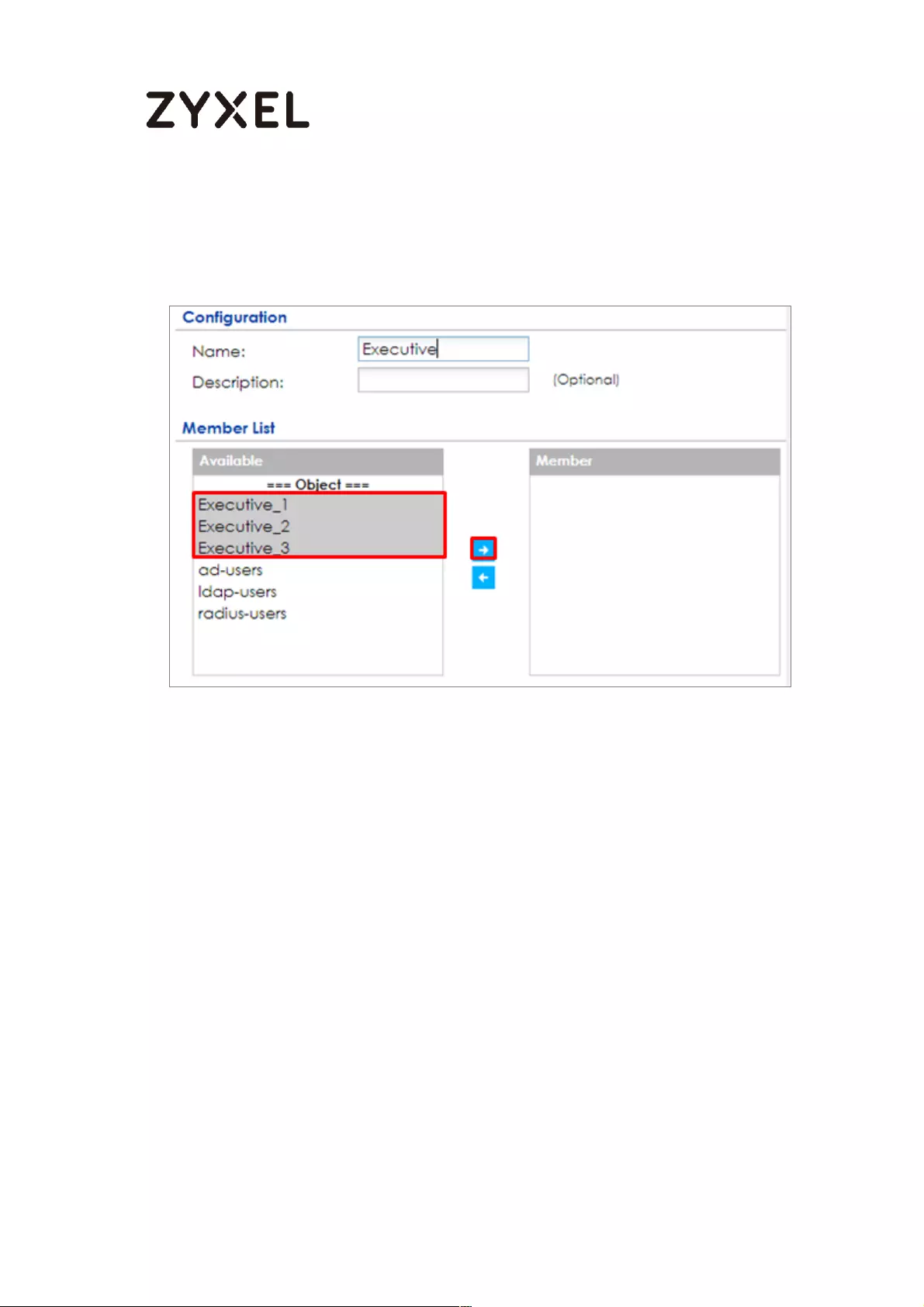
501/782
www.zyxel.com
Then, go to CONFIGURATION > Object > User/Group > Group > Add Group to
create a Group Members’ Name and move the just created executives user
object to Member.
CONFIGURATION > Object > Address Group > Add Address Group Rule
Set up Security Policy for executives, go to CONFIGURATION > Security Policy >
Policy Control > Add corresponding, configure a Name for you to identify the
executives’ Security Policy profile.
For From and To policies, select the direction of travel of packets to which the
policy applies. Select User to be the Executives to apply the policy to all traffic
coming from them.
In order to view the test result later on, set Log matched traffic to be log.
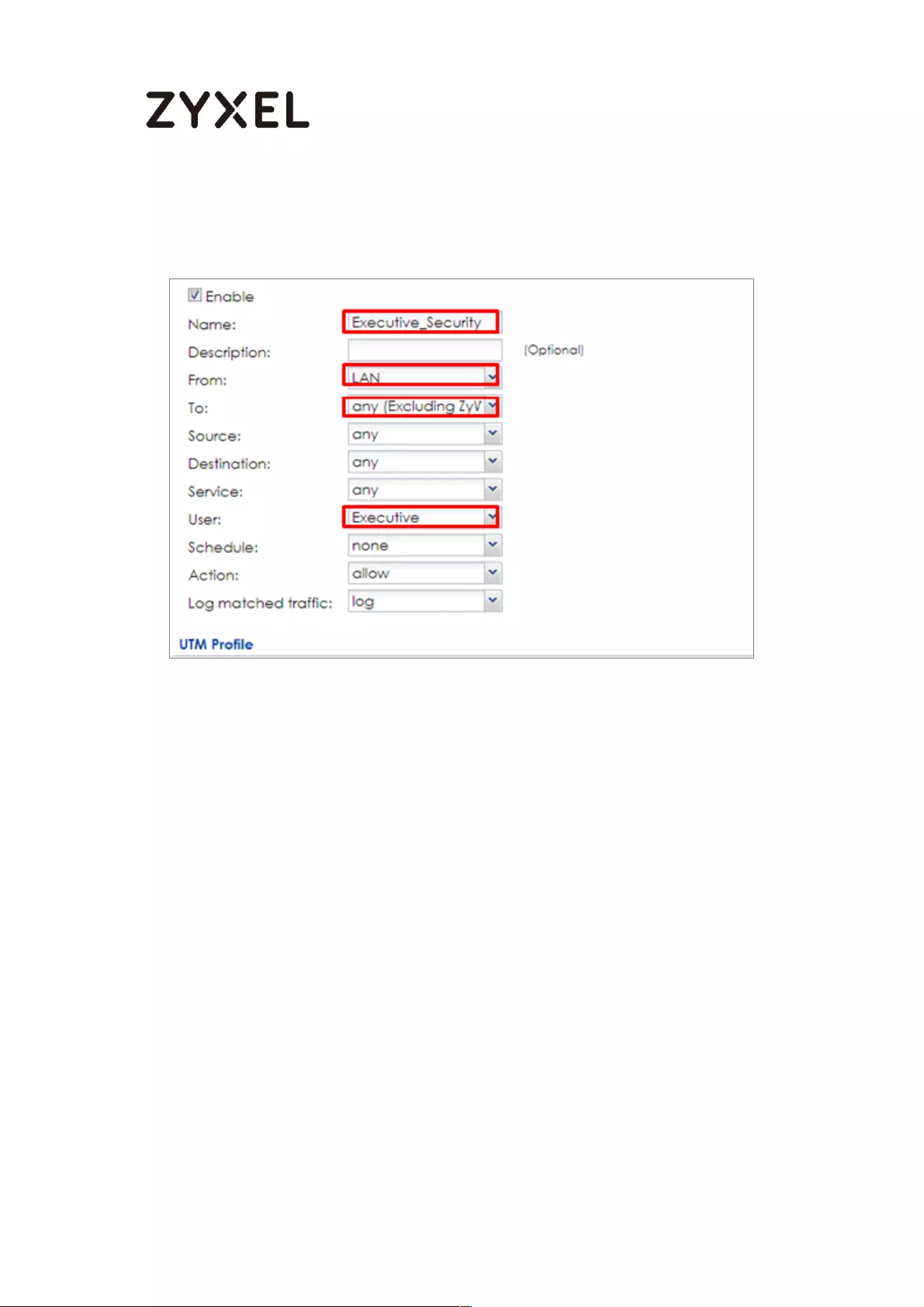
502/782
www.zyxel.com
Leave all UTM Profiles disabled.
CONFIGURATION > Security Policy > Policy Control > Add corresponding >
Employees_Security
Test the Result
Connect to the Internet from two computers: one from executive_1 and one from
an employee address (192.168.30.9).
Go to the ZyWALL/USG Monitor > Log, you will see [notice] log message such as
below. In this example result, a connection from executive_1 has user login
message and always with ACCESS FORWARD information. A connection from
employee address (192.168.30.9) and some of the services are with ACCESS
BLOCK information
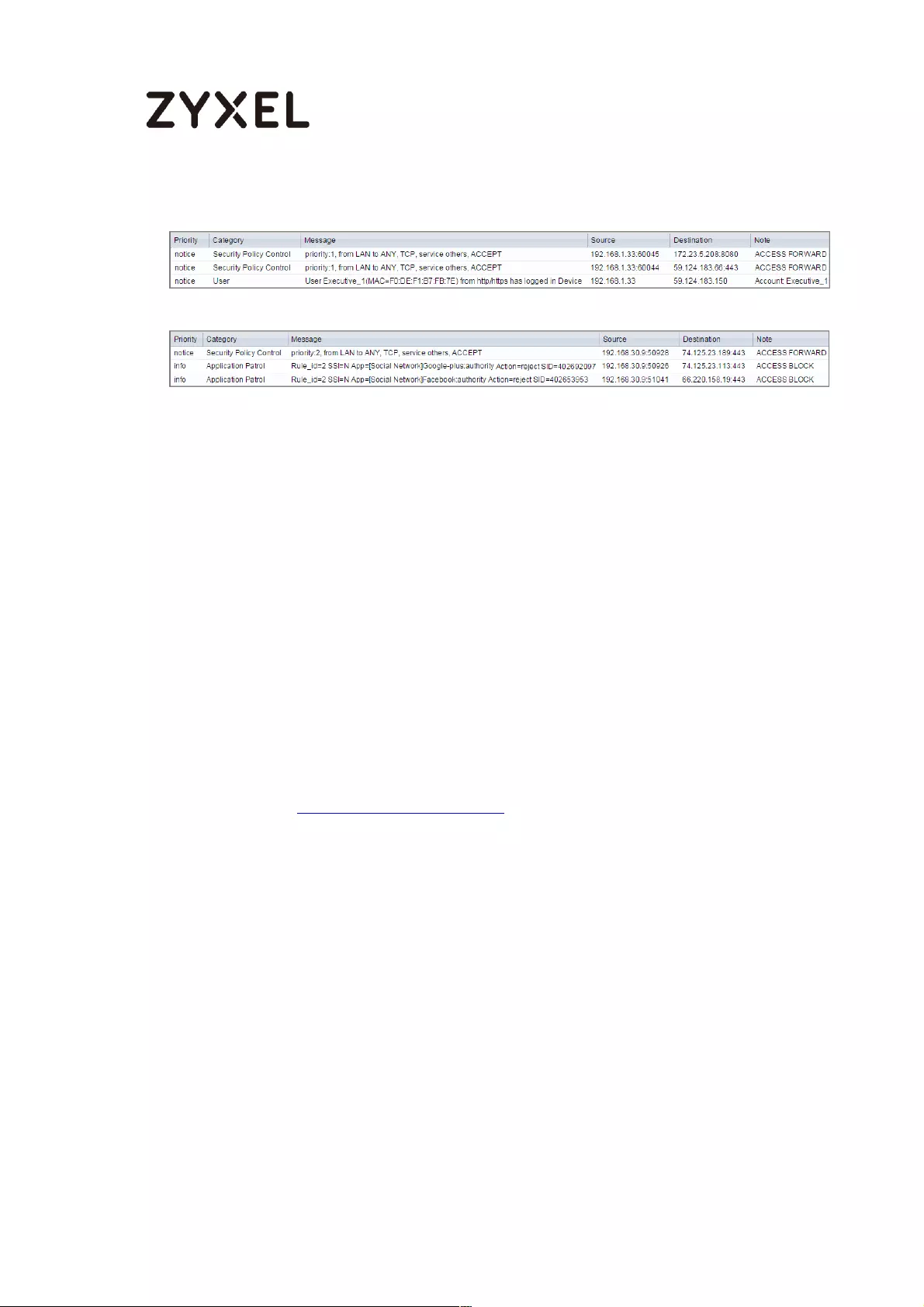
503/782
www.zyxel.com
Monitor > Log
What Could Go Wrong?
If you are not be able to configure any UTM policies or it’s not working, there are
two possible reasons:
You have not subscribed for the UTM service.
You have subscribed for the UTM service but the license is expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your UTM
license.
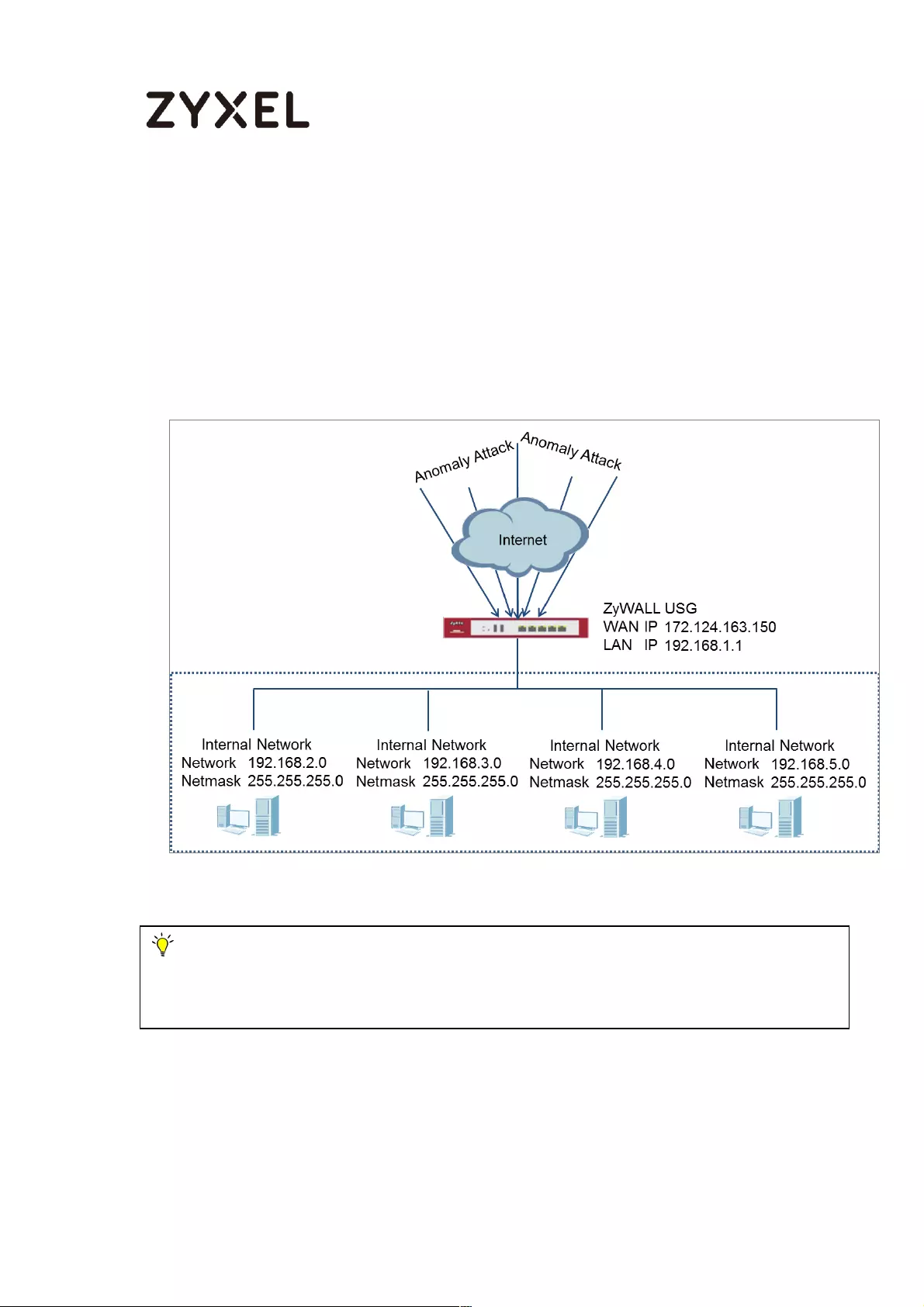
504/782
www.zyxel.com
How To Detect and Prevent TCP Port Scanning with ADP
This is an example of using a ZyWALL/USG ADP (Anomaly Detection and
Prevention) Profile to protect against anomalies based on violations of protocol
standards (RFCs – Requests for Comments) and abnormal traffic flows such as
port scans.
ZyWALL/USG with ADP Profile Setting Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
505/782
www.zyxel.com
Set Up the ADP Profile on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > ADP > Profile, click
the Add icon. A pop-up screen will appear allowing you to choose a base profile.
Select a base profile to go to the profile details screen.
CONFIGURATION > Security Policy > ADP > Profile > Base Profile
The Traffic Anomaly screen will display. A Name is automatically generated that you can
edit. Enable or disable individual scan or flood types by selecting a row and
clicking Activate or Inactivate.
In the Scan Detection section, selecting levels in the Sensitivity drop-down menu
and set Block Period for the duration applies blocking to the source IP address.

506/782
www.zyxel.com
In the Flood Detection section, set Block Period for the duration applies blocking
to the destination IP address. Set a Threshold number (the number of packets per
second that match the flood detection criteria) for your network. Click OK.
CONFIGURATION > Security Policy > ADP > Profile > Base Profile > Traffic Anomaly
Click the Protocol Anomaly tab. A Name is automatically generated that you can
edit. Enable or disable individual rules by selecting a row and clicking Activate or
Inactivate. Edit the default log options and actions by selecting a row and
making a selection in the Log or Action drop-down menus. Click OK.
CONFIGURATION > Security Policy > ADP > Profile > Base Profile > Protocol
Anomaly
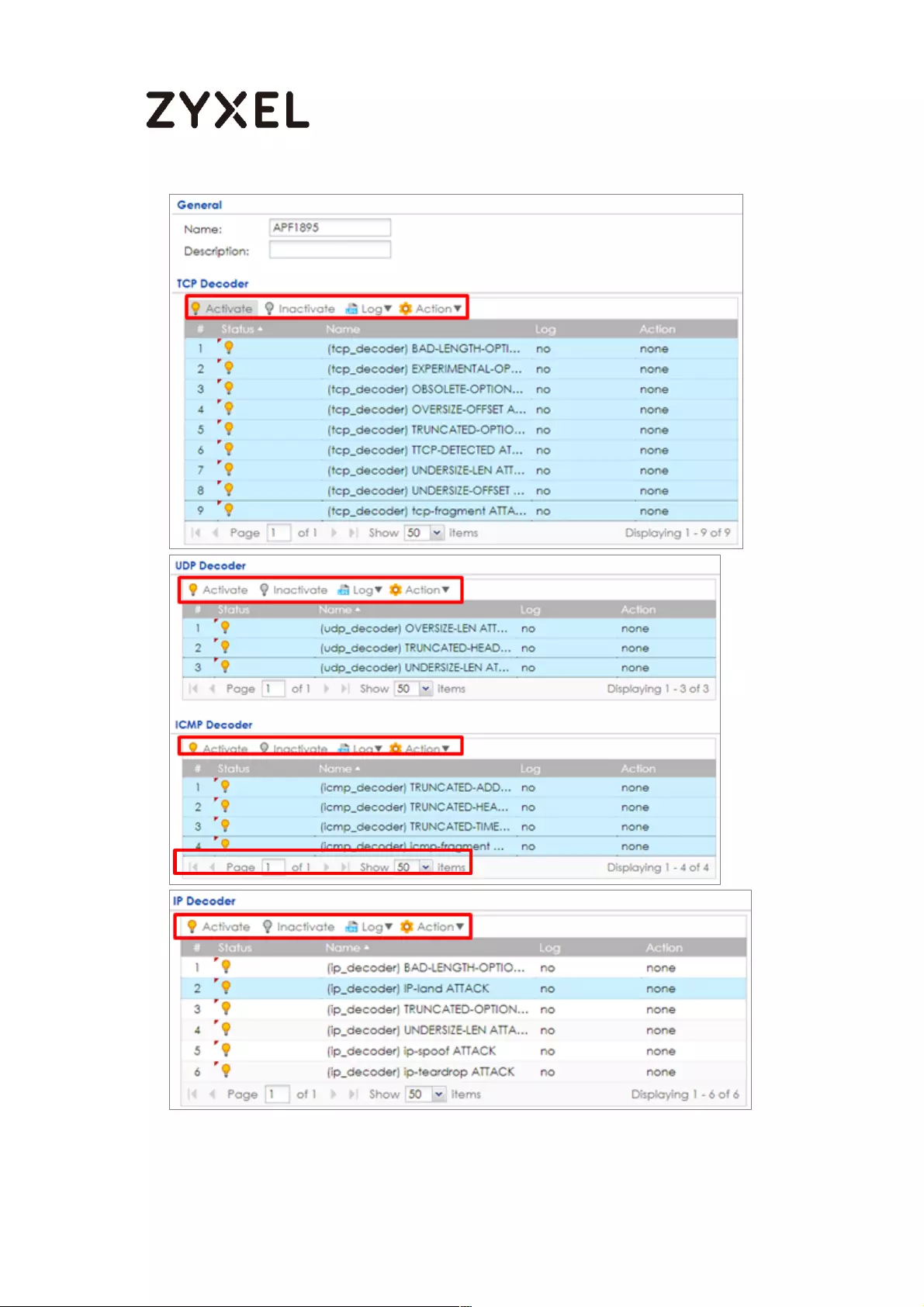
507/782
www.zyxel.com
Go to CONFIGURATION > Security Policy > ADP > General, select Enable Anomaly

508/782
www.zyxel.com
Detection and Prevention. Then, select the just created Anomaly Profile and click
Apply.
CONFIGURATION > Security Policy > ADP > General
Test the Result
Download Nmap free security scanner for testing the result:
https://nmap.org/download.html
Open the Nmap GUI, set the Target to be the WAN IP of ZyWALL/USG
(172.124.163.150 in this example) and set Profile to be Intense Scan. Click Scan.

509/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > Log, you will see [warn] log message such as
below.
Monitor > Log
What Could Go Wrong?
You may find that certain rules are triggering too many false positives or false
negatives. A false positive is when valid traffic is flagged as an attack. A false
negative is when invalid traffic is wrongly allowed to pass through the
ZyWALL/USG. As each network is different, false positives and false negatives are
common on initial ADP deployment. You could create a new ‘monitor profile’
that creates logs but all actions are disabled. Observe the logs over time and try
to eliminate the causes of the false alarms. When you’re satisfied that they have
been reduced to an acceptable level, you could then create an ‘inline profile’
whereby you configure appropriate actions to be taken when a packet matches
a detection.
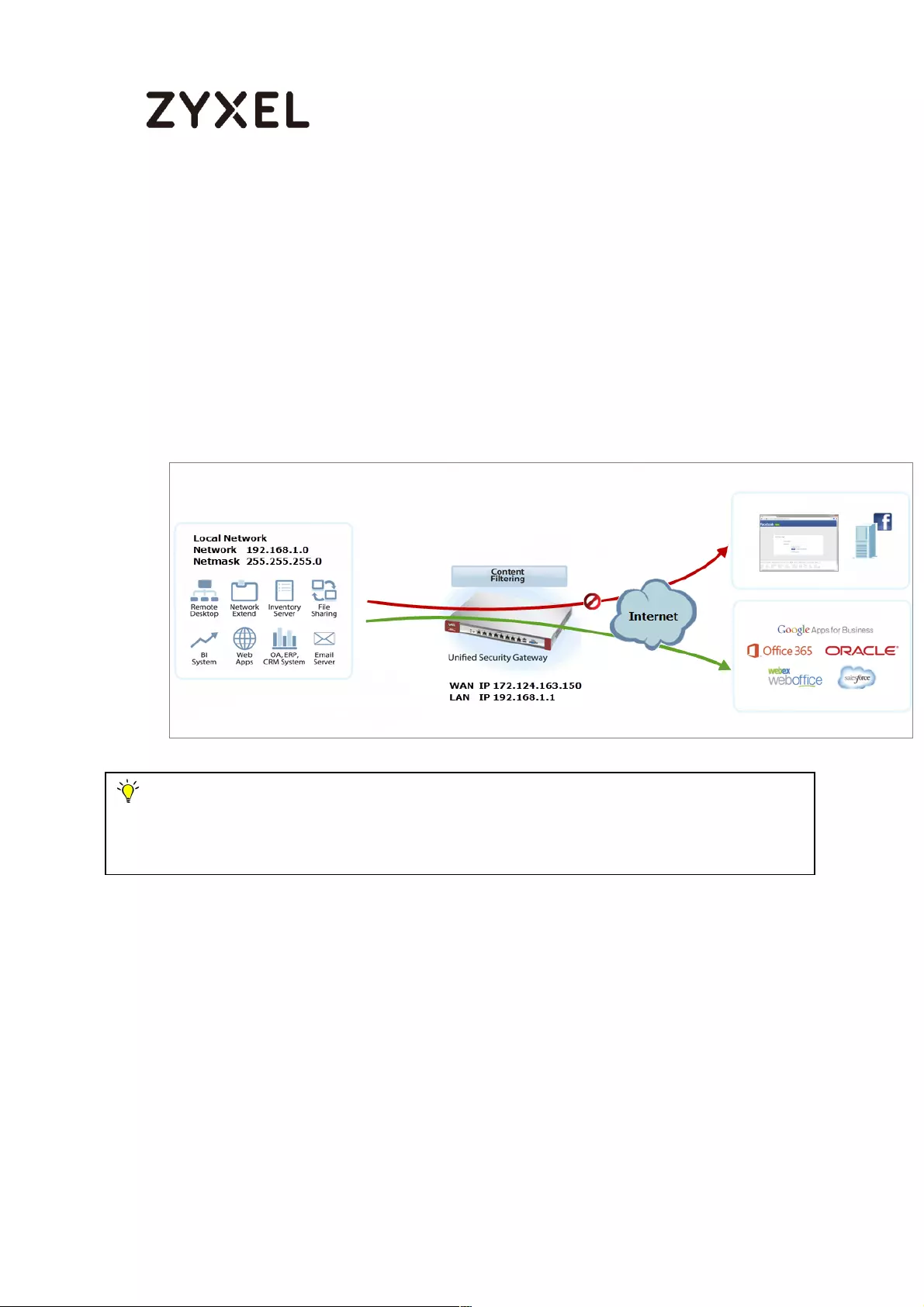
510/782
www.zyxel.com
How To Block Facebook
This is an example of using a ZyWALL/USG UTM Profile in a Security Policy to block
access to a specific social network service. You can use Content Filter, SSL
Inspection and Policy Control to make sure that a certain web page cannot be
accessed through both HTTP and HTTPS protocols.
ZyWALL/USG with Block Facebook Settings Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
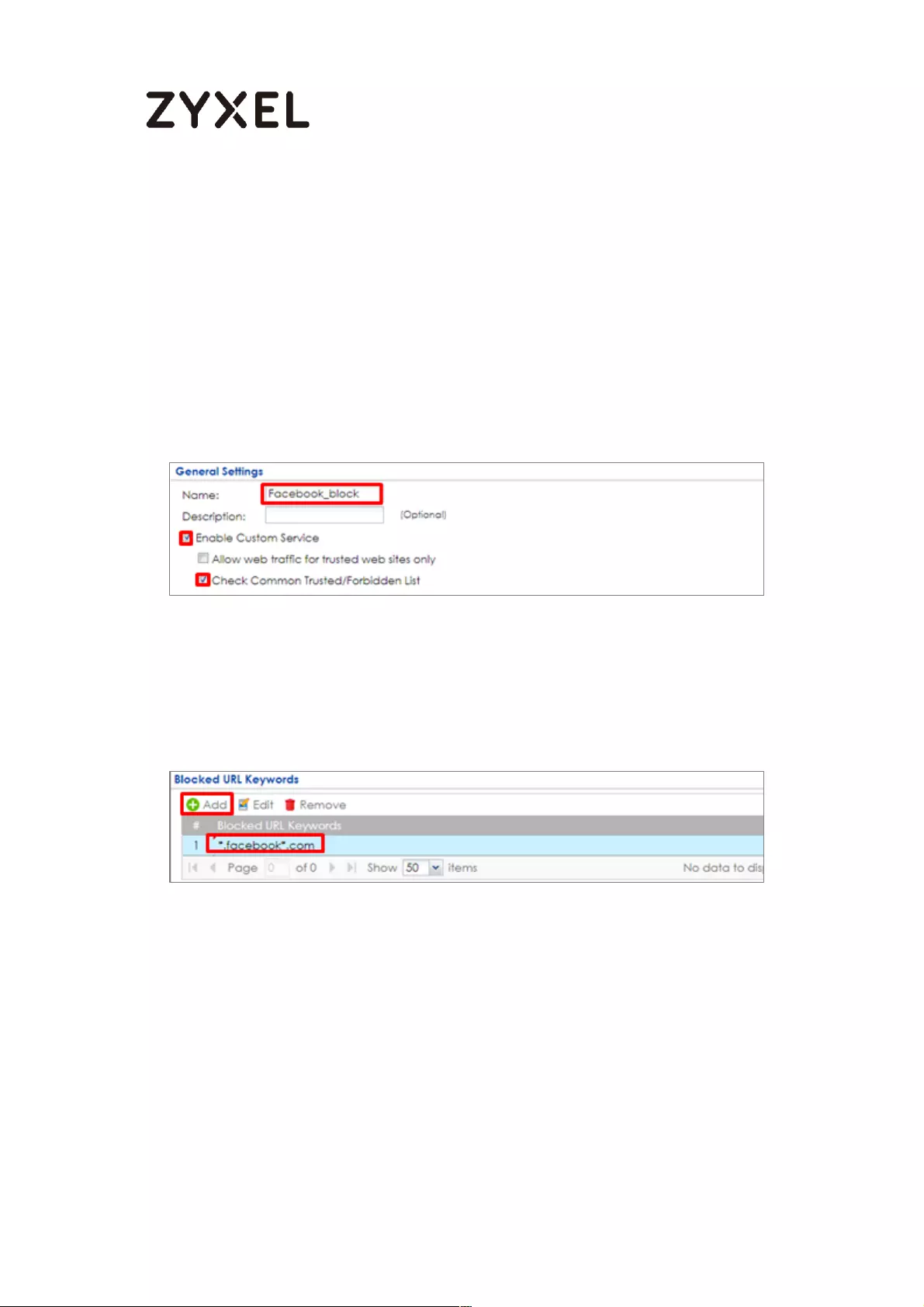
511/782
www.zyxel.com
Set Up the Content Filter on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile> Content Filter > Profile
Management > Add Filter File > Custom Service. Configure a Name for you to
identify the Content Filter Profile and select Enable Custom Service.
CONFIGURATION > UTM Profile> Content Filter > Profile > Profile Management >
Add Filter File > Custom Service > General Settings
Scroll down to the Blocked URL Keywords section, click Add and use "*" as a
wildcard to match any string in trusted/forbidden web sites and blocked URL
keywords (*.facebook*.com in this example). Click OK.
CONFIGURATION > UTM Profile> Content Filter > Profile > Profile Management >
Add Filter File > Custom Service > Blocked URL Keywords
Set Up the SSL Inspection on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile > SSL Inspection > Add
rule, configure a Name for you to identify the SSL Inspection profile.
Then, select the CA Certificate to be the certificate used in this profile. Select
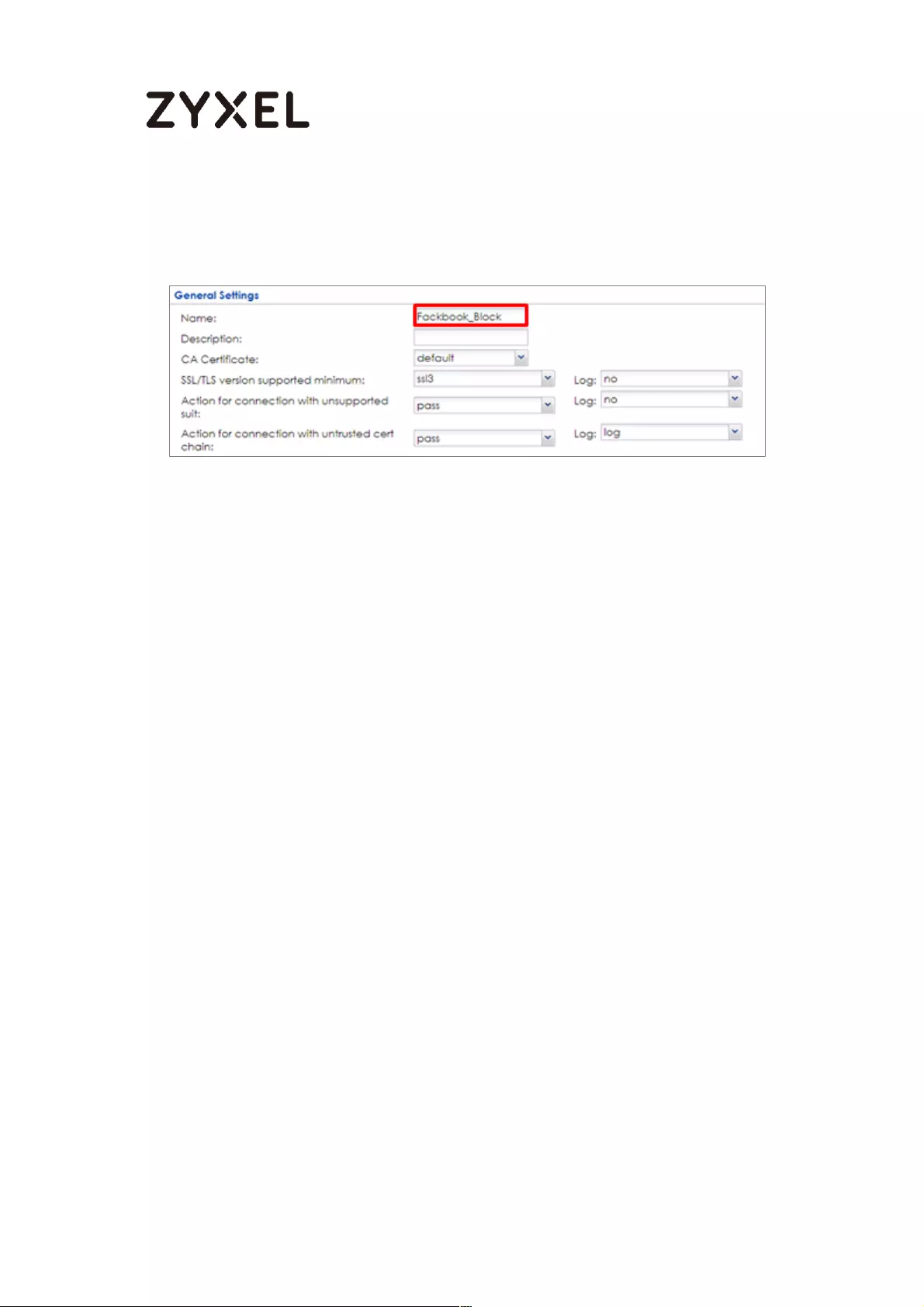
512/782
www.zyxel.com
Block to Action for Connection with SSL v3 and select Log type to be log alert.
Leave other actions as default settings.
CONFIGURATION > UTM Profile > SSL Inspection > Add rule

513/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy Control,
configure a Name for you to identify the Security Policy profile. For From and To
policies, select the direction of travel of packets to which the policy applies.
Select the Schedule that defines when the policy applies (Facebook_Block in this
example).
Scroll down to UTM Profile, select Content Filter and select a profile from the list
box (Facebook_Block in this example). Then, select SSL Inspection and select a
profile from the list box (Facebook_Block in this example).
CONFIGURATION > Security Policy > Policy Control
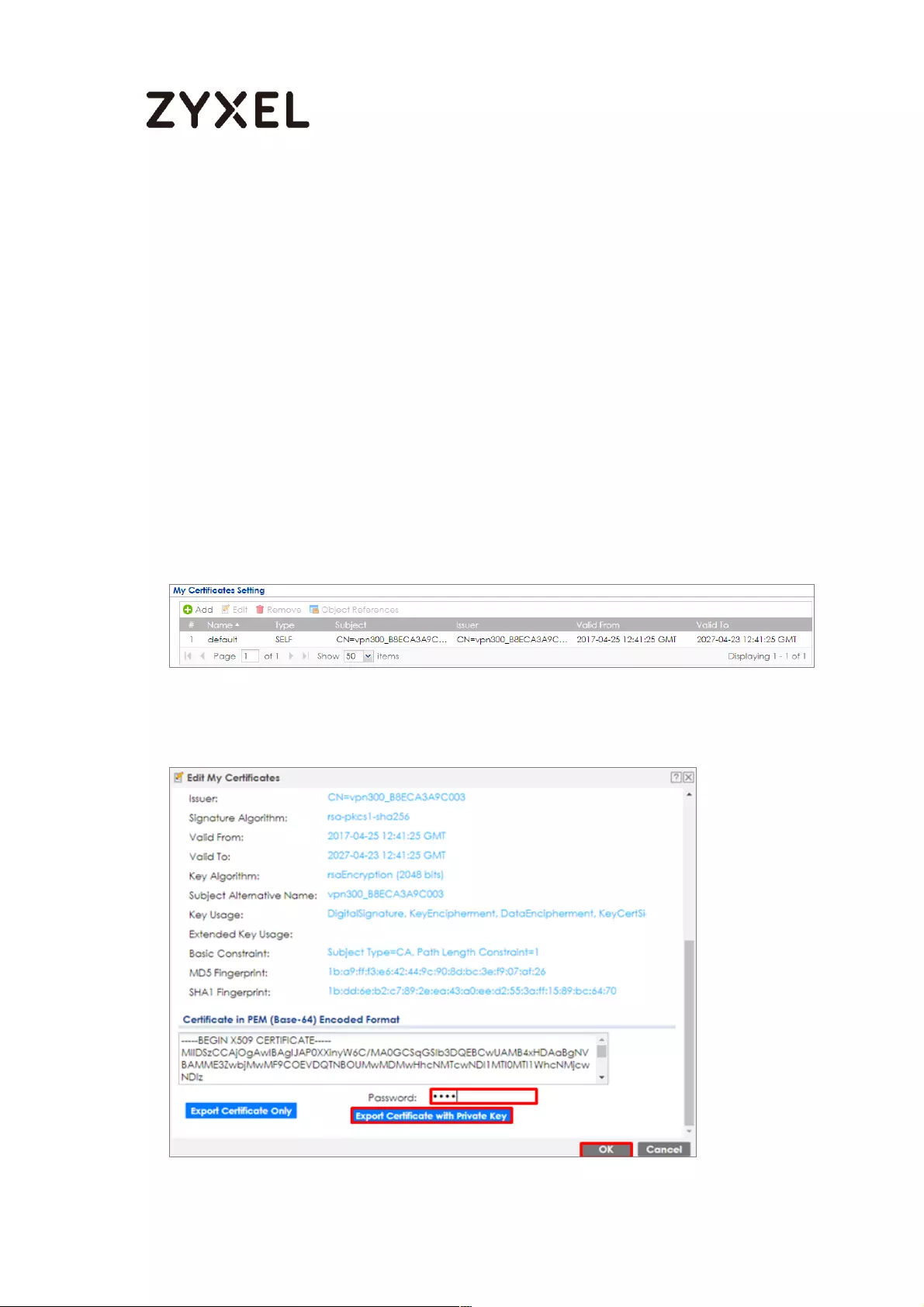
514/782
www.zyxel.com
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System
When SSL inspection is enabled and an access website does not trust the
ZyWALL/USG certificate, the browser will display a warning page of security
certificate problems.
Go to ZyWALL/USG CONFIGURATION > Object > Certificate > default > Edit to
export default certificate from ZyWALL/USG with Private Key (zyx123 in this
example).
CONFIGURATION > Object > Certificate > default
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with
Private Key
515/782
www.zyxel.com
Save default certificate as *.p12 file to Windows 7 Operation System.
In Windows 7 Operating System Start Menu > Search Box, type mmc and press
Enter.
Start Menu > Search Box > mmc
default.p12

516/782
www.zyxel.com
In the mmc console window, click File > Add/Remove Snap-in...
File > Add/Remove Snap-in...
In the Available snap-ins, select the Certificates and click Add button. Select
Computer account > Local Computer. Then, click Finished and OK to close the
Snap-ins window.
Available snap-ins > Certificates > Add

517/782
www.zyxel.com
In the mmc console window, open the Certificates (Local Computer) > Trusted
Root Certification Authorities, right click Certificate > All Tasks > Import…
Click Next. Then, Browse..., and locate the .p12 file you downloaded earlier. Then,
click Next.
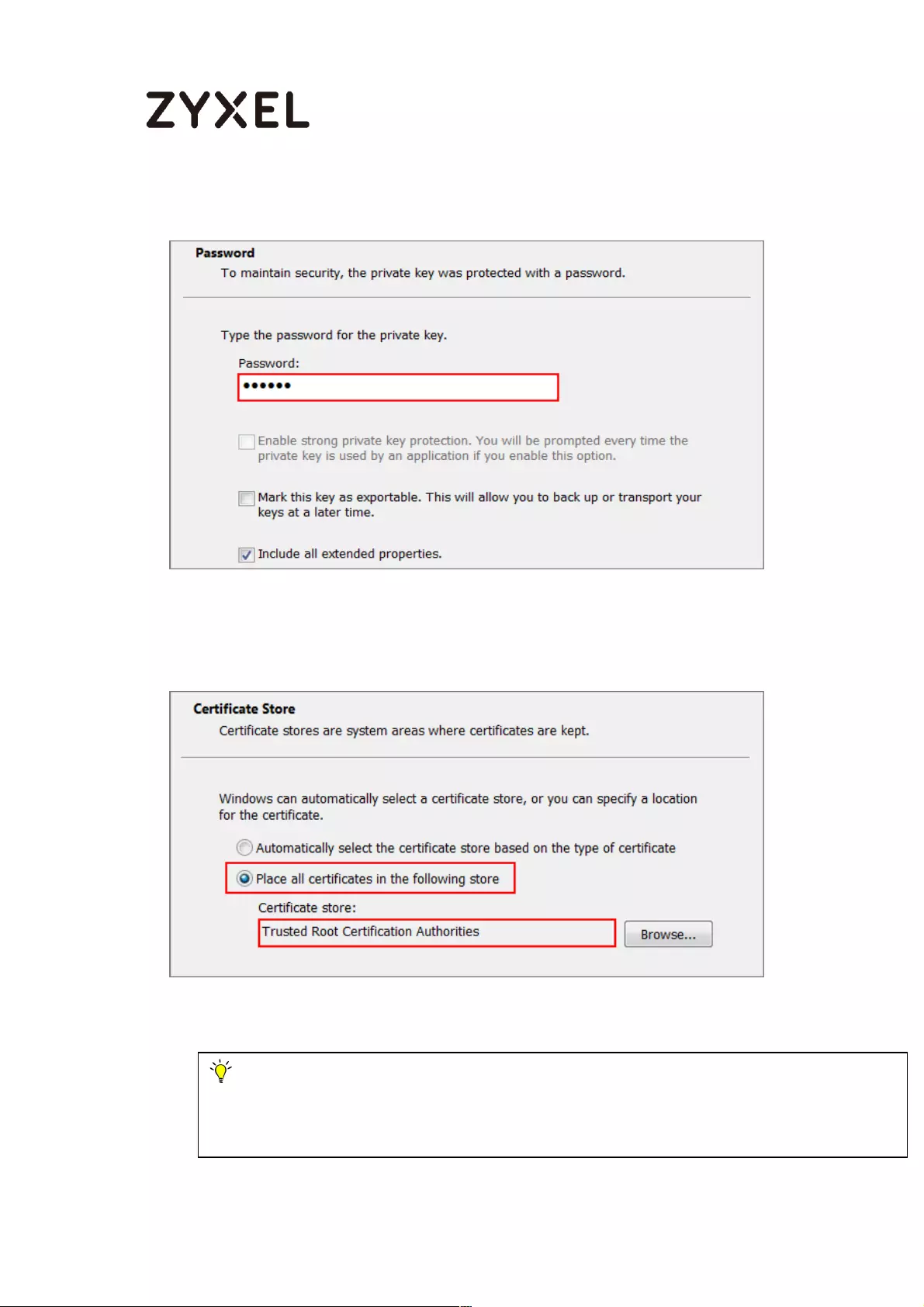
518/782
www.zyxel.com
Click Next, type zyx123 in the Password field and click Next again
Select Place all certificates in the following store and then click Browse and find
Trusted Root Certification Authorities. Click Next, then click Finish.
Note: Each ZyWALL/USG device has its own self-signed certificate by factory default.
When you reset to default configuration file, the original self-signed certificate is erased,
and a new self-signed certificate will be created when the ZyWALL/USG boots the next time.
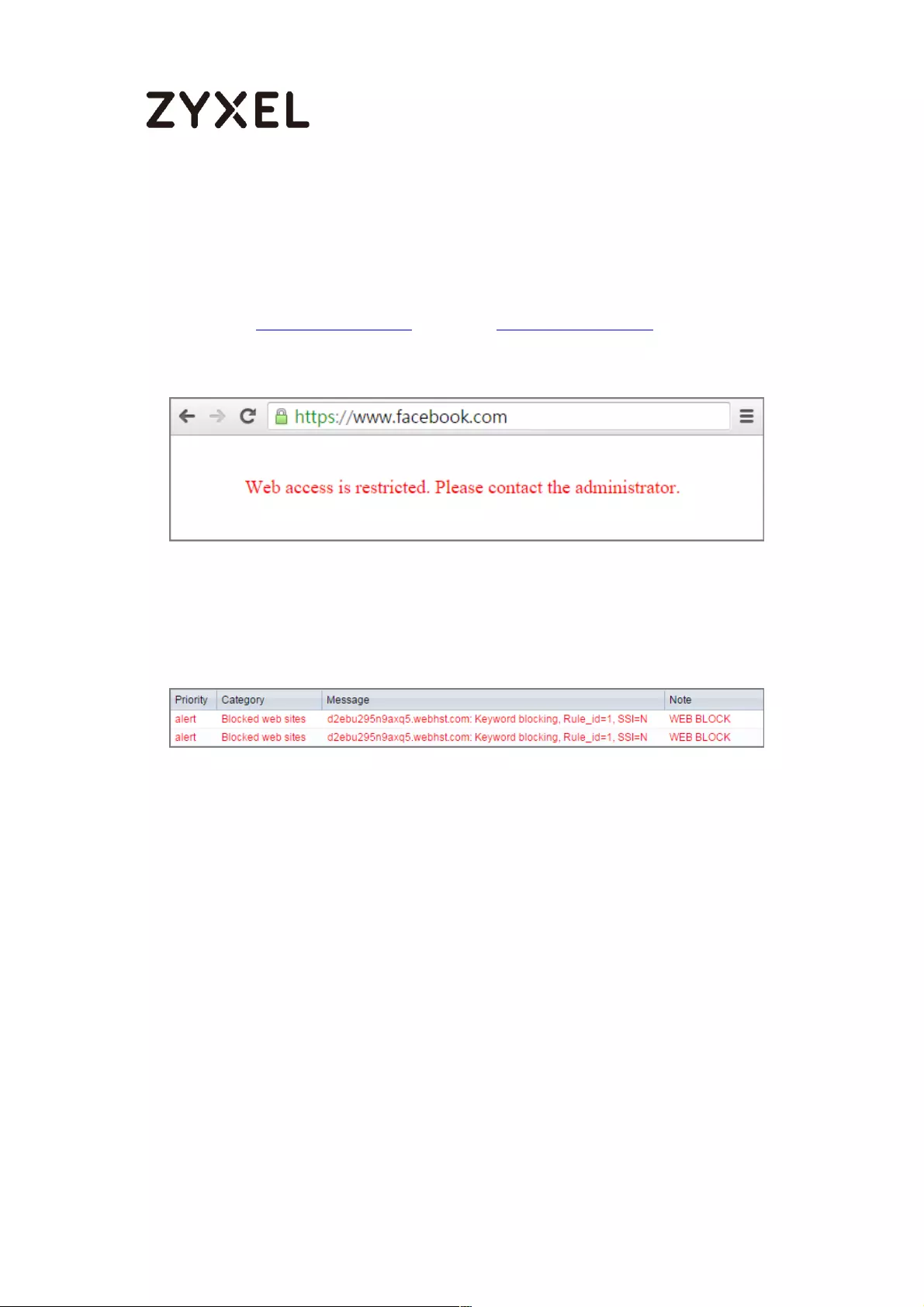
519/782
www.zyxel.com
Test the Result
Type http://www.facebook.com/ or https://www.facebook.com/ into the
browser, the error message occurs.
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as
below.
Monitor > Log
520/782
www.zyxel.com
What Could Go Wrong?
If you are not be able to configure any Content Filter policies or it’s not working,
there are two possible reasons:
You have not subscribed for the Content Filter service.
You have subscribed for the Content Filter service but the license is
expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your Content
Filter license.
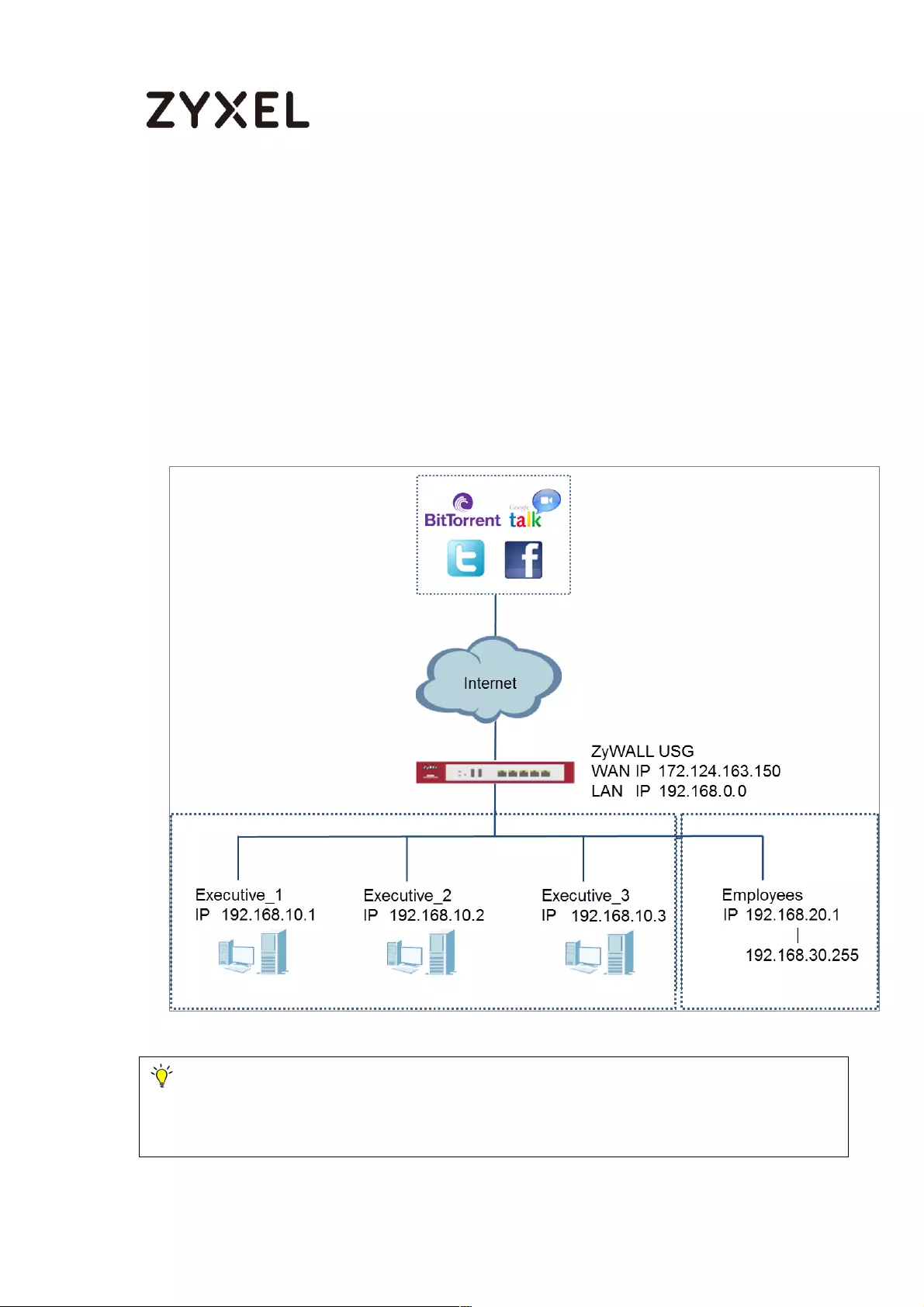
521/782
www.zyxel.com
How To Exempt Specific Users From a Blocked Website
This is an example of using a ZyWALL/USG Security Policy to exempt three
corporate executives from a blocked Website, while controlling Internet access
for other employees’ accounts.
With executives connect to a blocked Website using PCs with static IP addresses,
you could set up address group to allow their traffic.
ZyWALL/USG with Exempt Specific Users From a Blocked Website Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
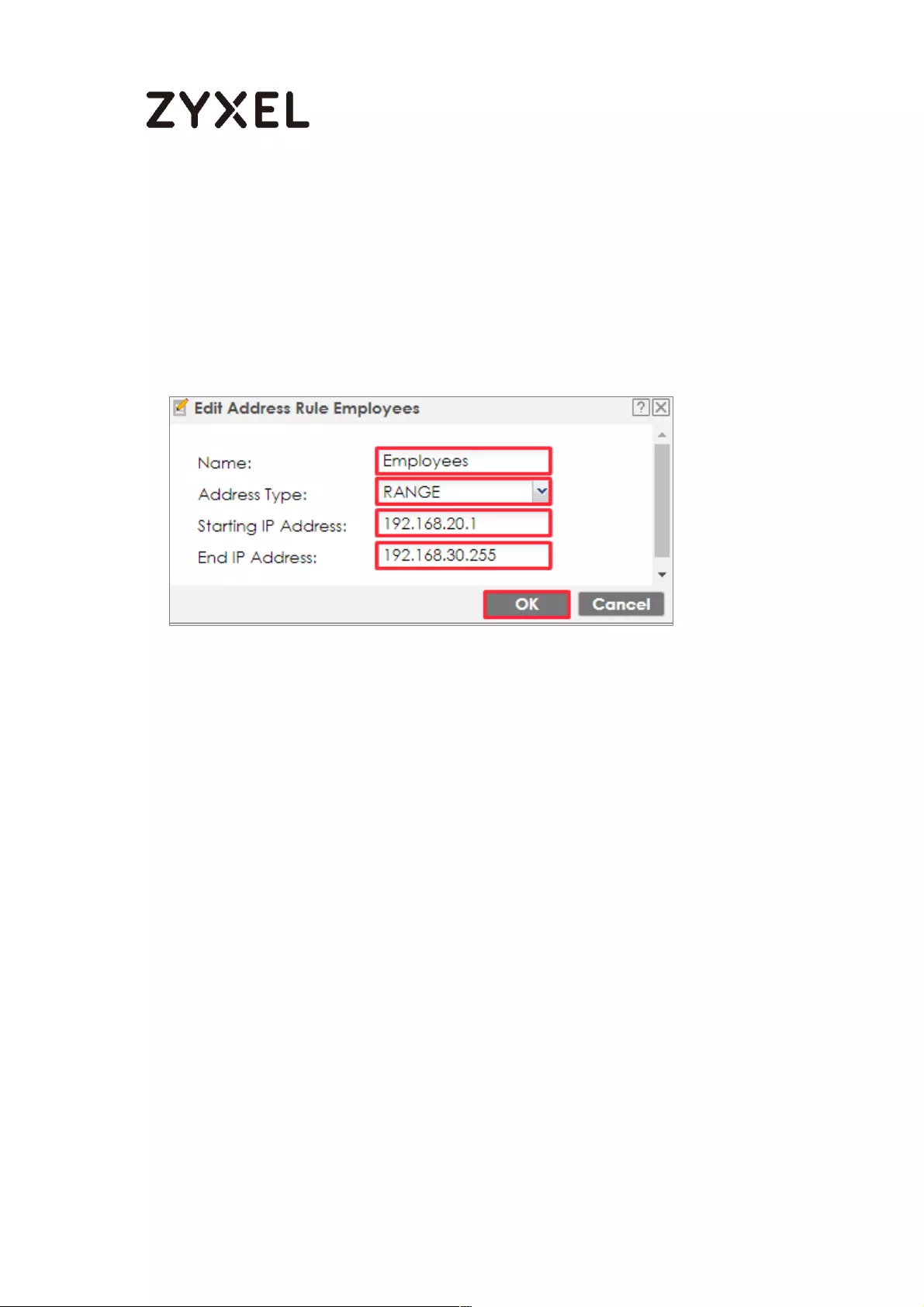
522/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG for Employees
In the ZyWALL/USG, go to CONFIGURATION > Object > Address > Add Address
Rule to create address range for employees.
CONFIGURATION > Object > Address > Add Address Rule
Set up Security Policy for employees, go to CONFIGURATION > Security Policy >
Policy Control > Add corresponding, configure a Name for you to identify the
employees’ Security Policy profile.
For From and To policies, select the direction of travel of packets to which the
policy applies. Select Source to be the Employees to apply the policy to all traffic
coming from them.

523/782
www.zyxel.com
Scroll down to UTM Profile, select the general policy that allows employees to
access the Internet. (Using built-in Office profile in this example blocks the non-
productive services, such as Advertisement & Pop-Ups, Gambling and Peer to
Peer services…etc.).
CONFIGURATION > Security Policy > Policy Control > Add corresponding >
Employees_Security
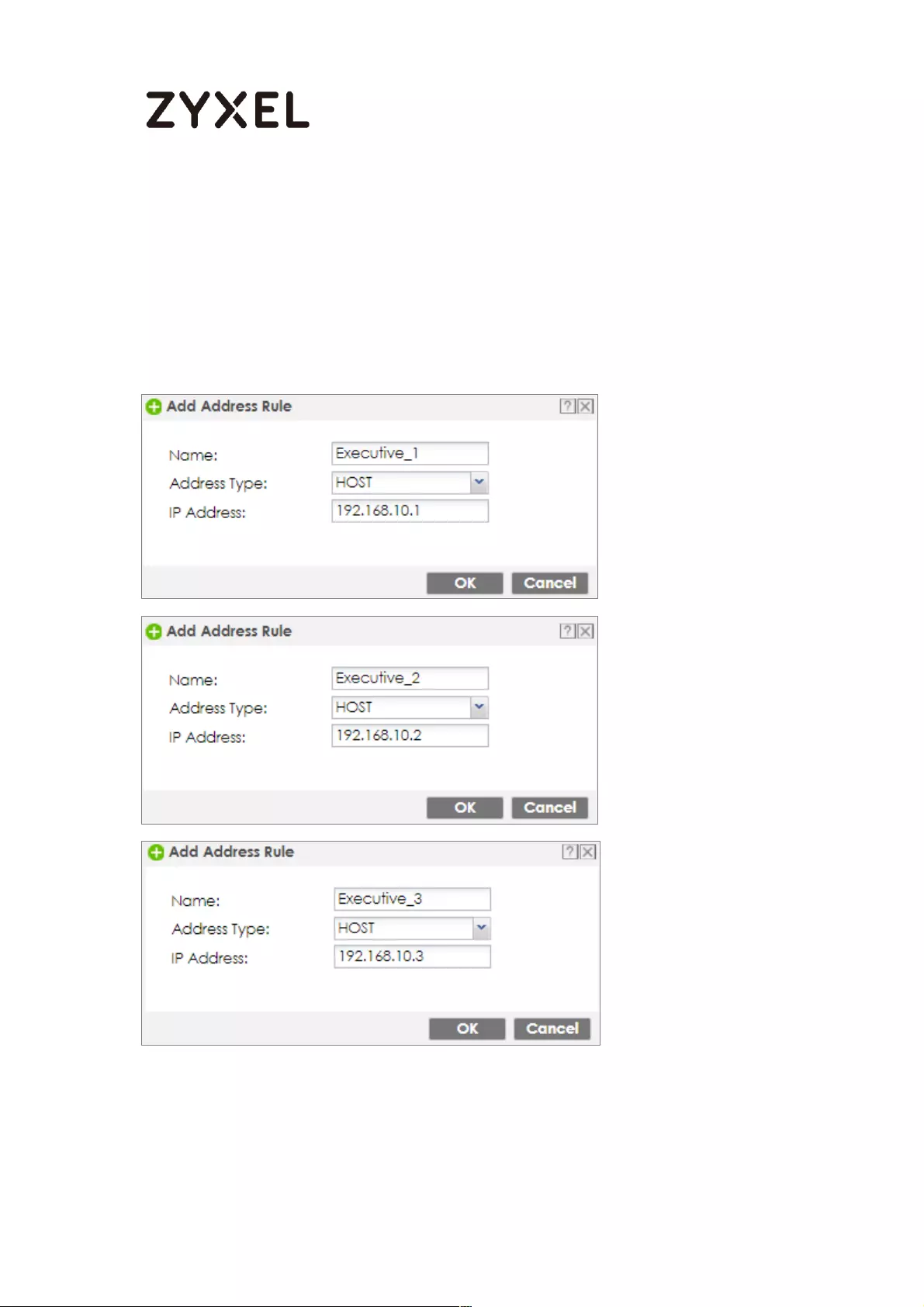
524/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG for Executives
In the ZyWALL/USG, go to CONFIGURATION > Object > Address > Add Address
Rule to create address for each executives.
CONFIGURATION > Object > Address > Add Address Rule
Then, go to CONFIGURATION > Object > Address Group > Add Address Group
Rule to create a Group Members’ Name and move the just created executives
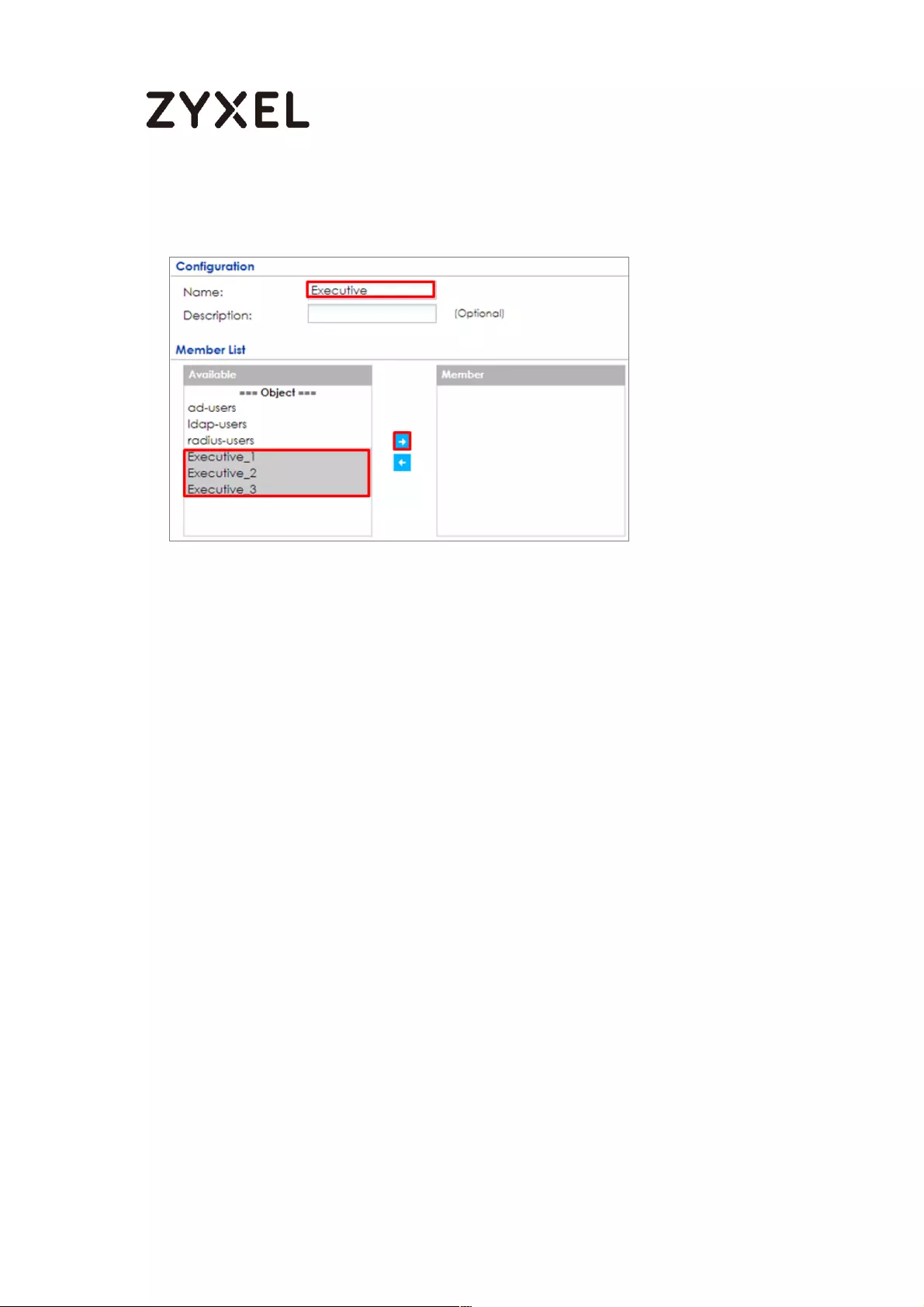
525/782
www.zyxel.com
address object to Member.
CONFIGURATION > Object > Address Group > Add Address Group Rule
Set up Security Policy for executives, go to CONFIGURATION > Security Policy >
Policy Control > Add corresponding, configure a Name for you to identify the
executives’ Security Policy profile.
For From and To policies, select the direction of travel of packets to which the
policy applies. Select Source to be the Executives to apply the policy to all traffic
coming from them. In order to view the results later, to have the ZyWALL/USG
generate Log matched traffic (log).
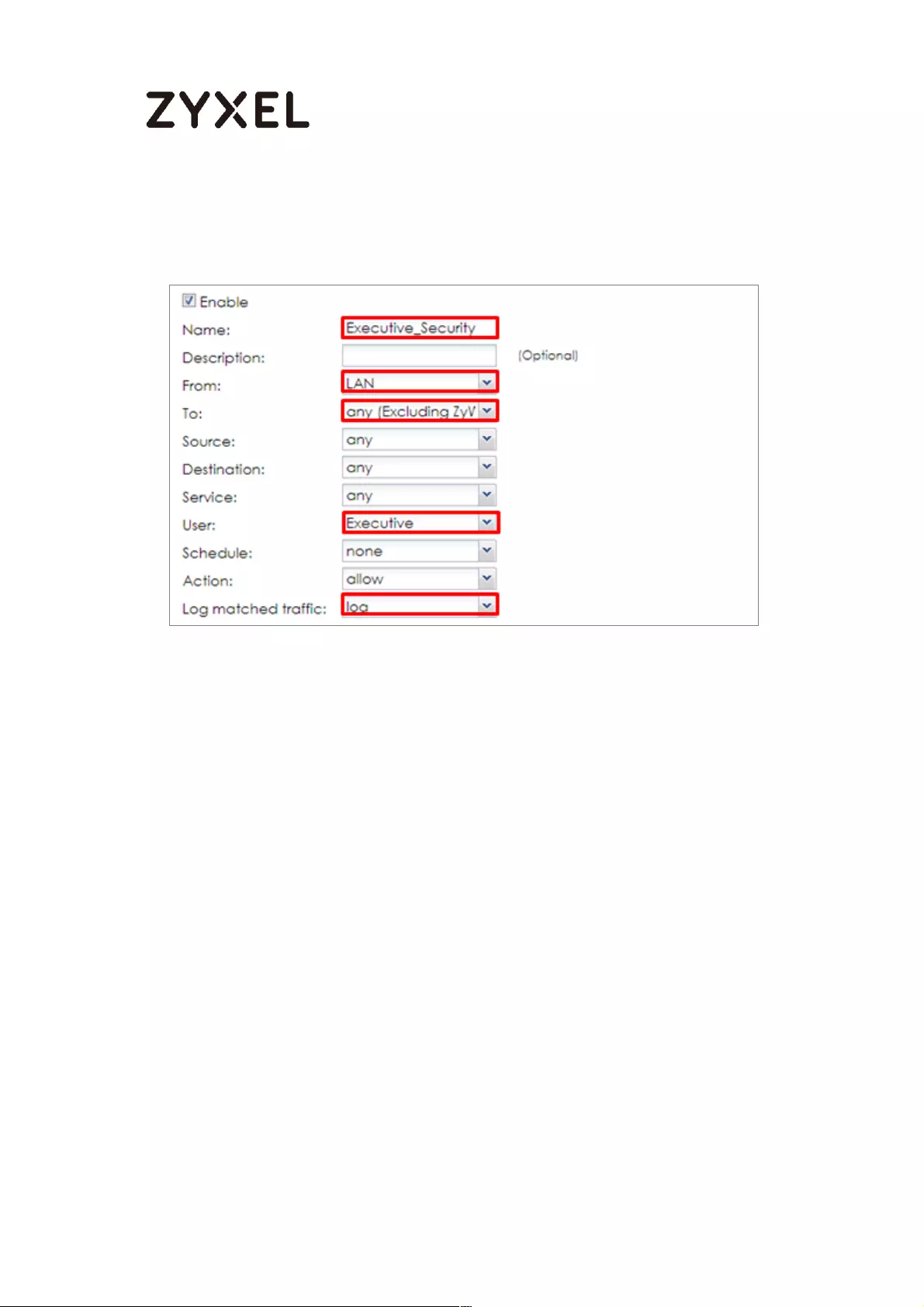
526/782
www.zyxel.com
Leave all UTM Profiles disabled.
CONFIGURATION > Security Policy > Policy Control > Add corresponding >
Executives_Security
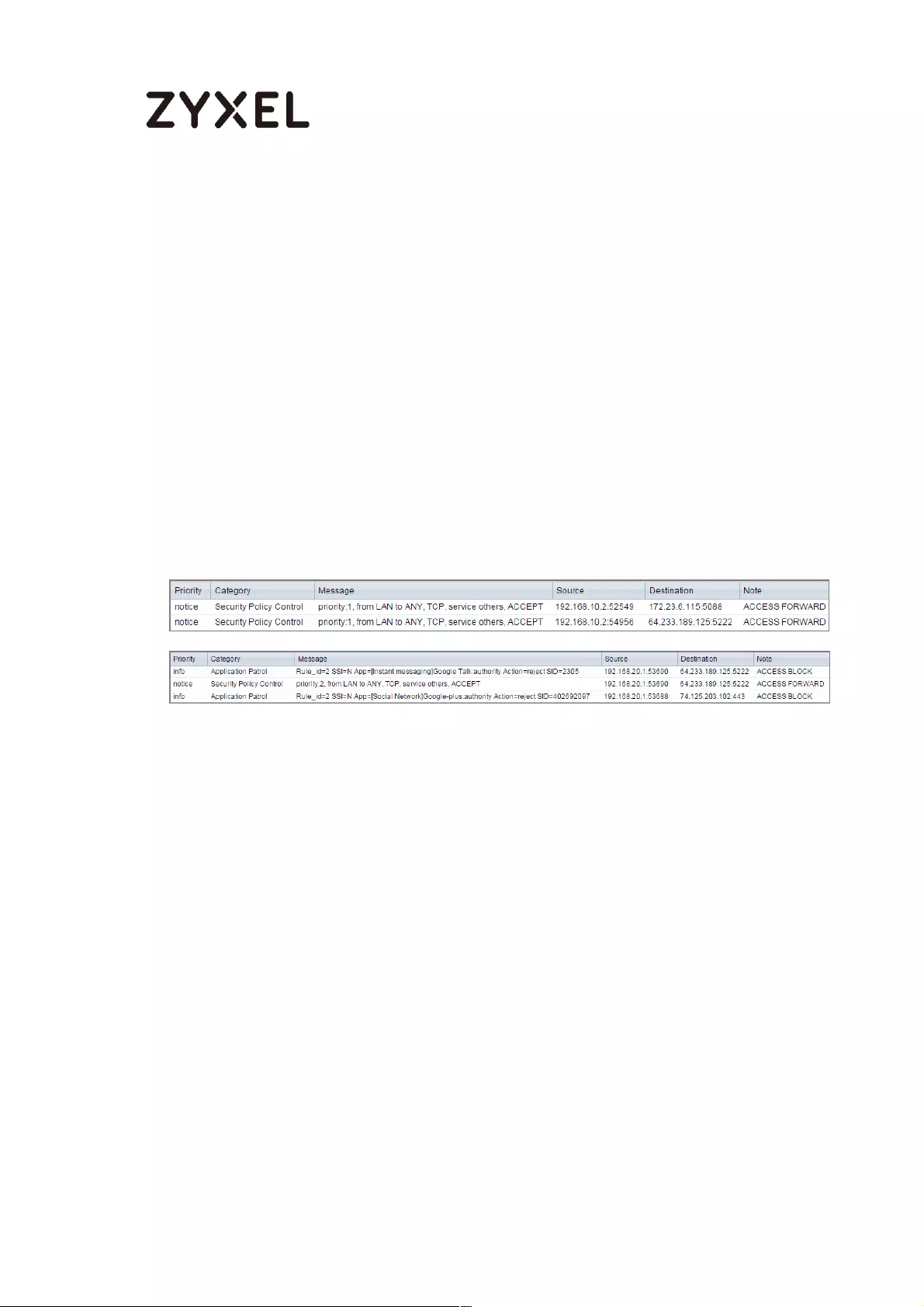
527/782
www.zyxel.com
Test the Result
Connect to the Internet from two computers: one from executive_2 address
(192.168.10.2) and one from an employee address (192.168.20.1) and both access
to https://hangouts.google.com/.
Go to the ZyWALL/USG Monitor > Log, you will see [notice] and [info] log message
such as below. In this example result, connections from executive_2 address
(192.168.10.2) use Security Policy priority: 1. Connections from employee address
(192.168.20.1) use Security Policy priority: 2 and UTM Profile Rule_id=2.

528/782
www.zyxel.com
What Could Go Wrong?
If you are not be able to configure any UTM policies or it’s not working, there are
two possible reasons:
You have not subscribed for the UTM service.
You have subscribed for the UTM service but the license is expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your UTM
license.

529/782
www.zyxel.com
How To Control Access To Google Drive
This is an example of using a ZyWALL/USG UTM Profile in a Security Policy to block
access to a specific file transfer service. You can use Application Patrol and
Policy Control to make sure that a certain file transfer service cannot be
accessed through both HTTP and HTTPS protocols.
ZyWALL/USG with Control Access To Google Drive Settings Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
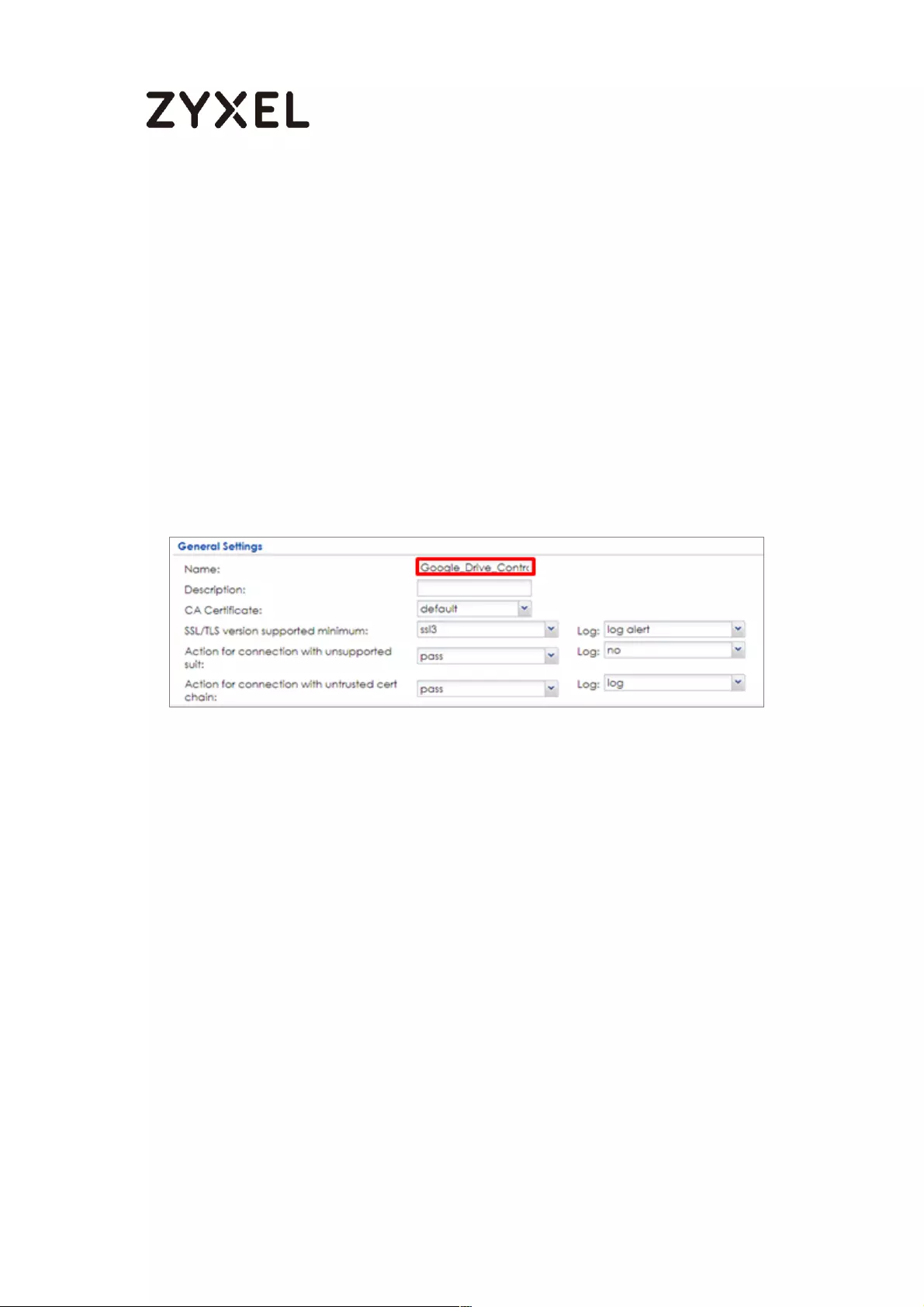
530/782
www.zyxel.com
Set Up the SSL Inspection on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile > SSL Inspection > Add
rule, configure a Name for you to identify the SSL Inspection profile.
Then, select the CA Certificate to be the certificate used in this profile. Select
Block to Action for Connection with SSL v3 and select Log type to be log alert. Leave
other actions as default settings.
CONFIGURATION > UTM Profile > SSL Inspection > Add rule
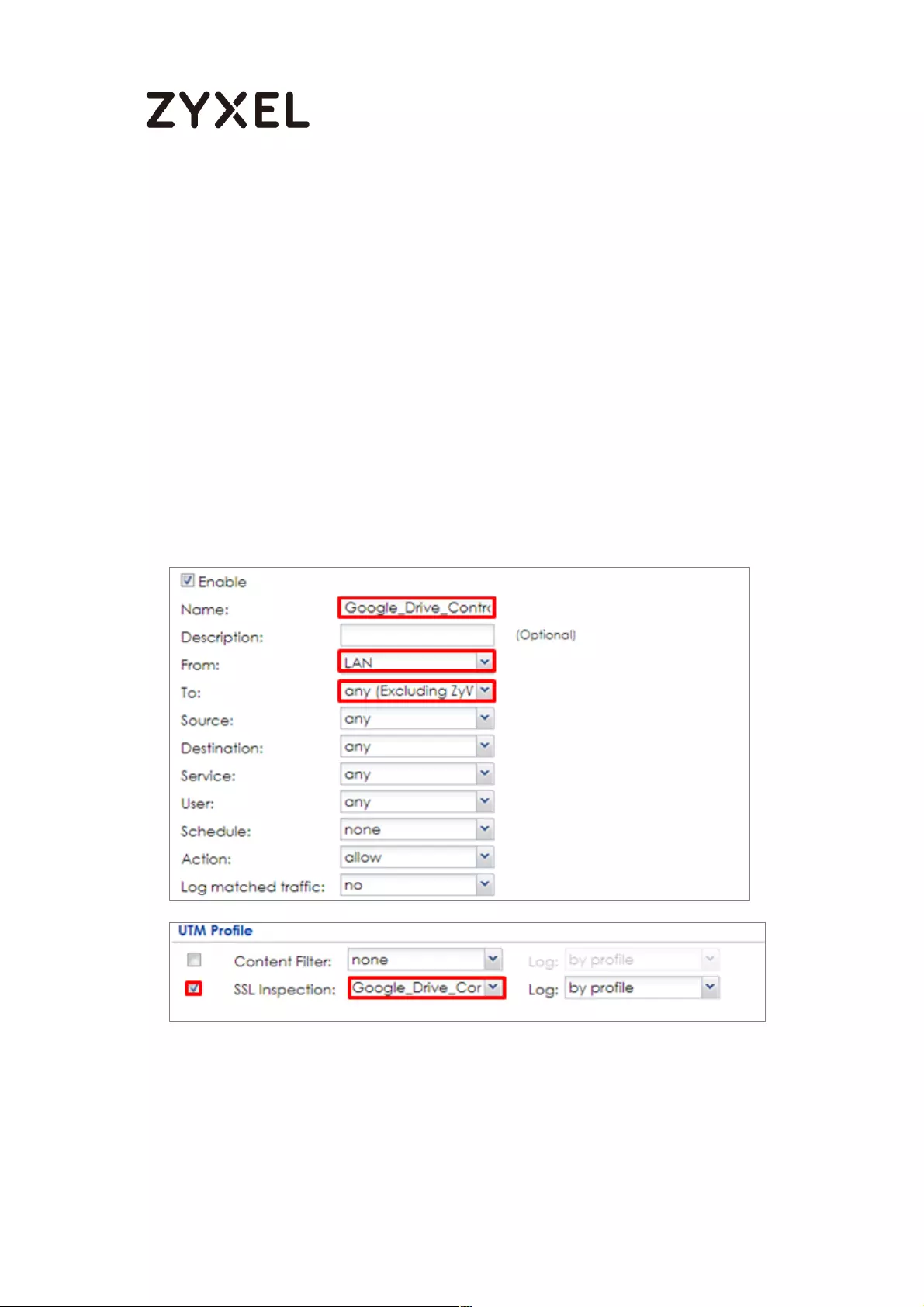
531/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy Control,
configure a Name for you to identify the Security Policy profile. For From and To
policies, select the direction of travel of packets to which the policy applies.
Scroll down to UTM Profile, select Content Filter and select a profile from the list
box (Facebook_Block in this example). Then, select SSL Inspection and select a
profile from the list box (Facebook_Block in this example).
CONFIGURATION > Security Policy > Policy Control
Export Certificate from ZyWALL/USG and Import it to Windows 7

532/782
www.zyxel.com
Operation System
When SSL inspection is enabled and an access website does not trust the
ZyWALL/USG certificate, the browser will display a warning page of security
certificate problems.
Go to ZyWALL/USG CONFIGURATION > Object > Certificate > default > Edit to
export default certificate from ZyWALL/USG with Private Key (zyx123 in this
example).
CONFIGURATION > Object > Certificate > default
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with
Private Key
Save default certificate as *.p12 file to Windows 7 Operation System.
533/782
www.zyxel.com
In Windows 7 Operating System Start Menu > Search Box, type mmc and press
Enter.
Start Menu > Search Box > mmc
In the mmc console window, click File > Add/Remove Snap-in...
File > Add/Remove Snap-in...
default.p12

534/782
www.zyxel.com
In the Available snap-ins, select the Certificates and click Add button. Select
Computer account > Local Computer. Then, click Finished and OK to close the
Snap-ins window.
Available snap-ins > Certificates > Add
In the mmc console window, open the Certificates (Local Computer) > Trusted
Root Certification Authorities, right click Certificate > All Tasks > Import…

535/782
www.zyxel.com
Click Next. Then, Browse..., and locate the .p12 file you downloaded earlier. Then,
click Next.
Click Next, type zyx123 in the Password field and click Next again
536/782
www.zyxel.com
Select Place all certificates in the following store and then click Browse and find
Trusted Root Certification Authorities. Click Next, then click Finish.
Note: Each ZyWALL/USG device has its own self-signed certificate by factory default.
When you reset to default configuration file, the original self-signed certificate is erased,
and a new self-signed certificate will be created when the ZyWALL/USG boots the next time.
537/782
www.zyxel.com
Test the Result
Type http://drive.google.com/ or https://drive.google.com/ into the browser, the
error message occurs.
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as
below.
Monitor > Log
538/782
www.zyxel.com
What Could Go Wrong?
If you are not be able to configure any Application Patrol policies or it’s not
working, there are two possible reasons:
You have not subscribed for the Application Patrol service.
You have subscribed for the Application Patrol service but the license is
expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your
Application Patrol license.
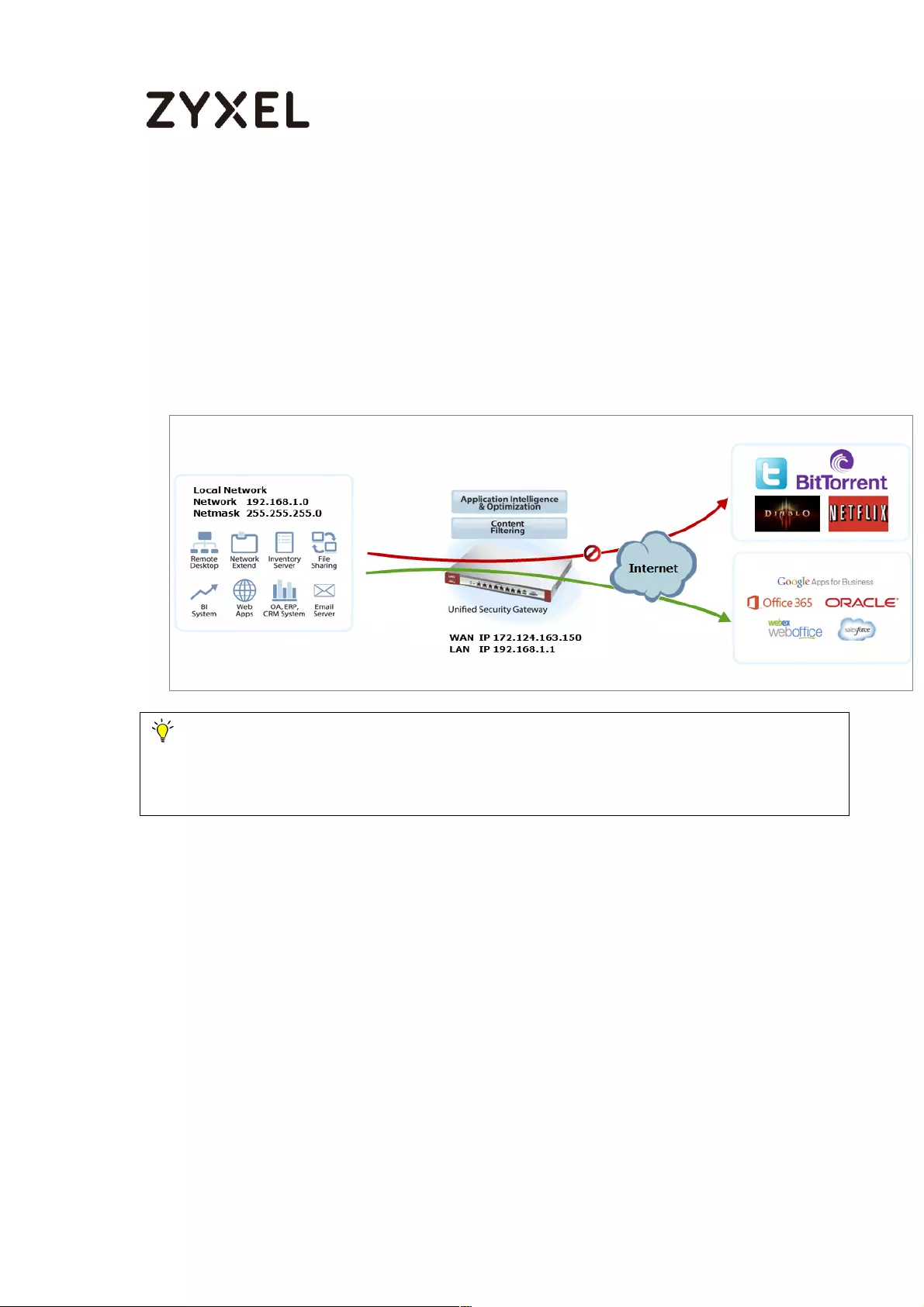
539/782
www.zyxel.com
How To Block HTTPS Websites Using Content Filtering and SSL
Inspection
This is an example of using a ZyWALL/USG Content Filtering, SSL Inspection and
Security Policy to block access to malicious or not business-related websites.
ZyWALL/USG with Block HTTPS Websites Using Content Filtering and SSL Inspection
Settings Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
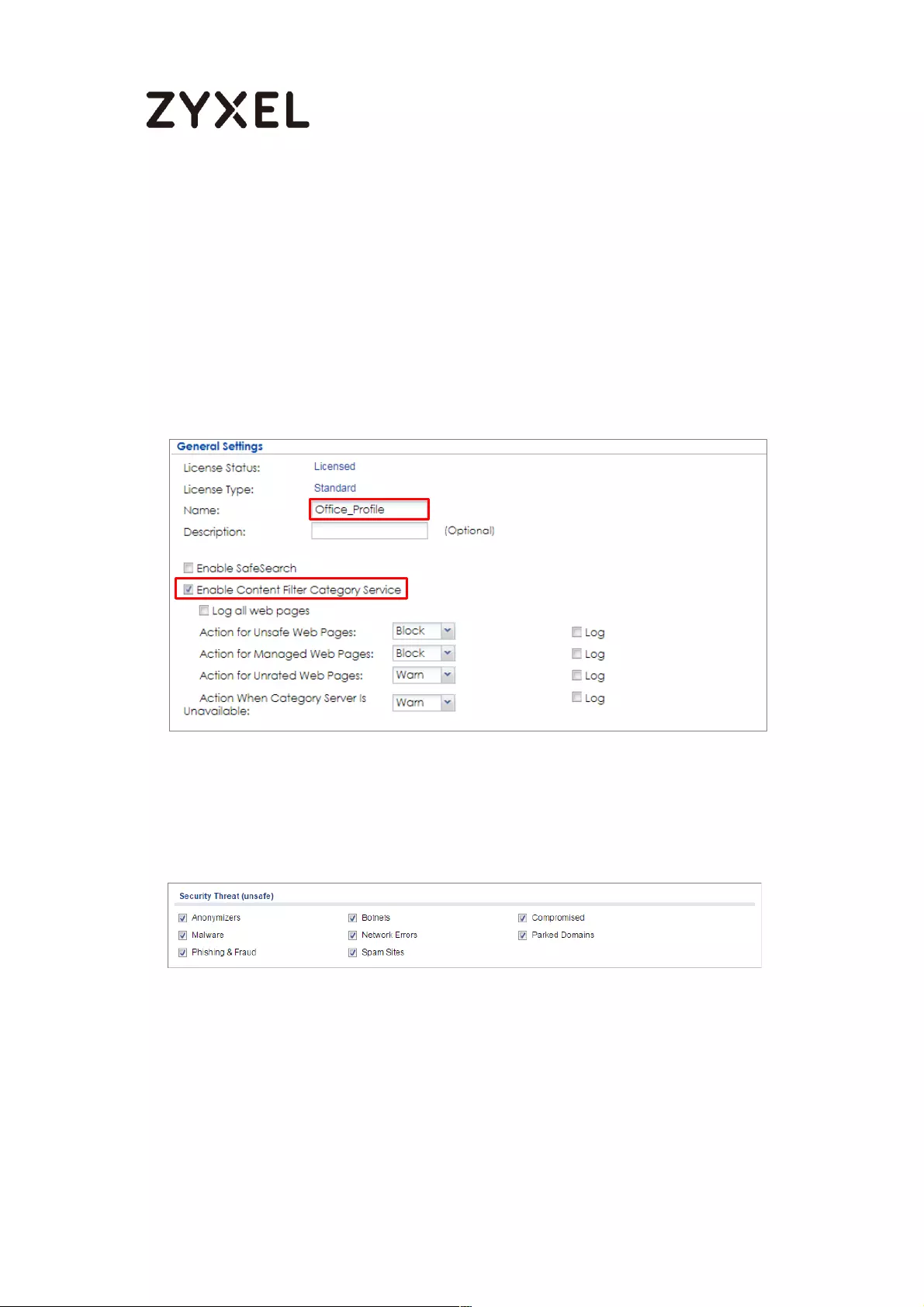
540/782
www.zyxel.com
Set Up the Content Filter on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile> Content Filter > Profile
Management > Add Filter File > Category Service. Configure a Name for you to
identify the Content Filter Profile and select Enable Custom Service.
CONFIGURATION > UTM Profile> Content Filter > Profile > Profile Management >
Add > Category Service > General Settings
Scroll down to the Security Threat (unsafe) section and select all categories of
web pages that are known to pose a threat to your computers.
CONFIGURATION > UTM Profile> Content Filter > Profile > Profile Management >
Add Filter File > Category Service > Security Threat (unsafe)
Scroll down to the Managed Categories section and select the categories that
are not business-related. Click OK.
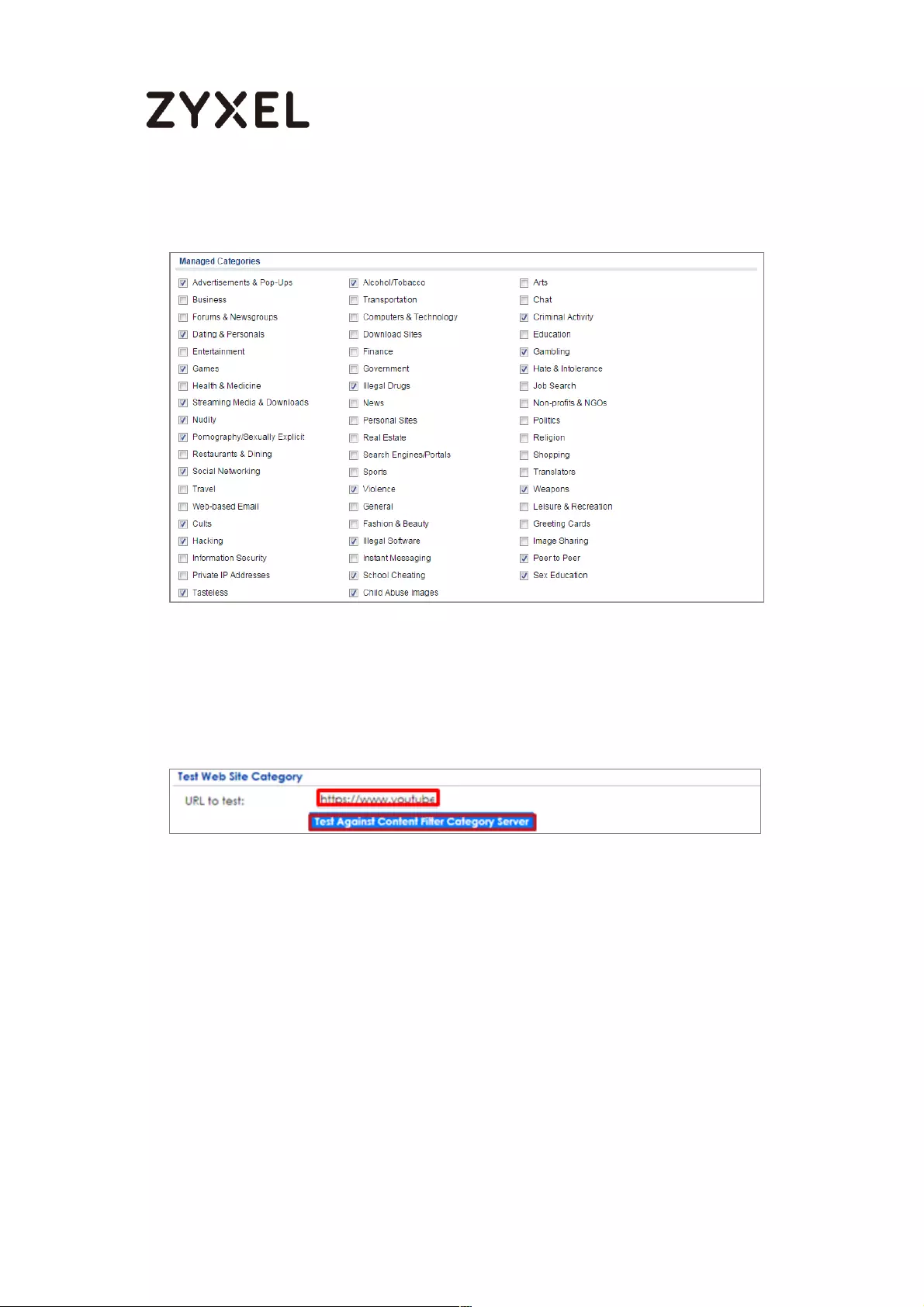
541/782
www.zyxel.com
CONFIGURATION > UTM Profile> Content Filter > Profile > Profile Management >
Add Filter File > Category Service > Managed Categories
If you are not sure which category a web page belongs to, you can enter a web
site URL in the text box of Test Web Site Category.
CONFIGURATION > UTM Profile> Content Filter > Profile > Profile Management >
Add Filter File > Category Service > Test Web Site Category
Set Up SSL Inspection on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile > SSL Inspection > Add
rule, and configure a Name for you to identify the SSL Inspection profile.
Then, select the CA Certificate to be the certificate used in this profile. Select to
pass or block SSLv2/unsupported suit/untrusted cert chain traffic that matches
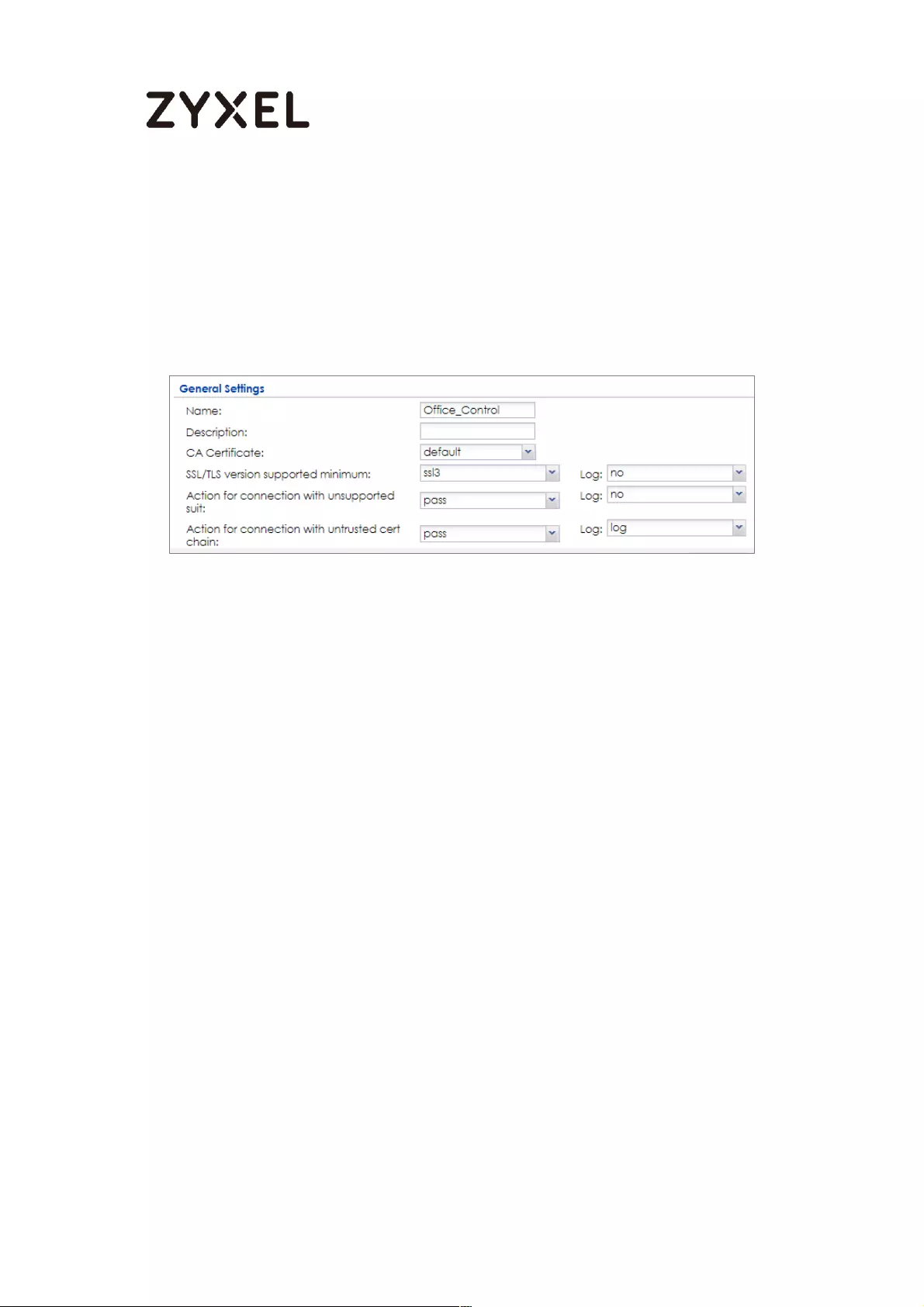
542/782
www.zyxel.com
traffic bound to this policy here.
Select desired Log type whether to have the ZyWALL/USG generate a log (log),
log and alert (log alert) or neither (no) by default when traffic matches this policy.
CONFIGURATION > UTM Profile > SSL Inspection > Add rule
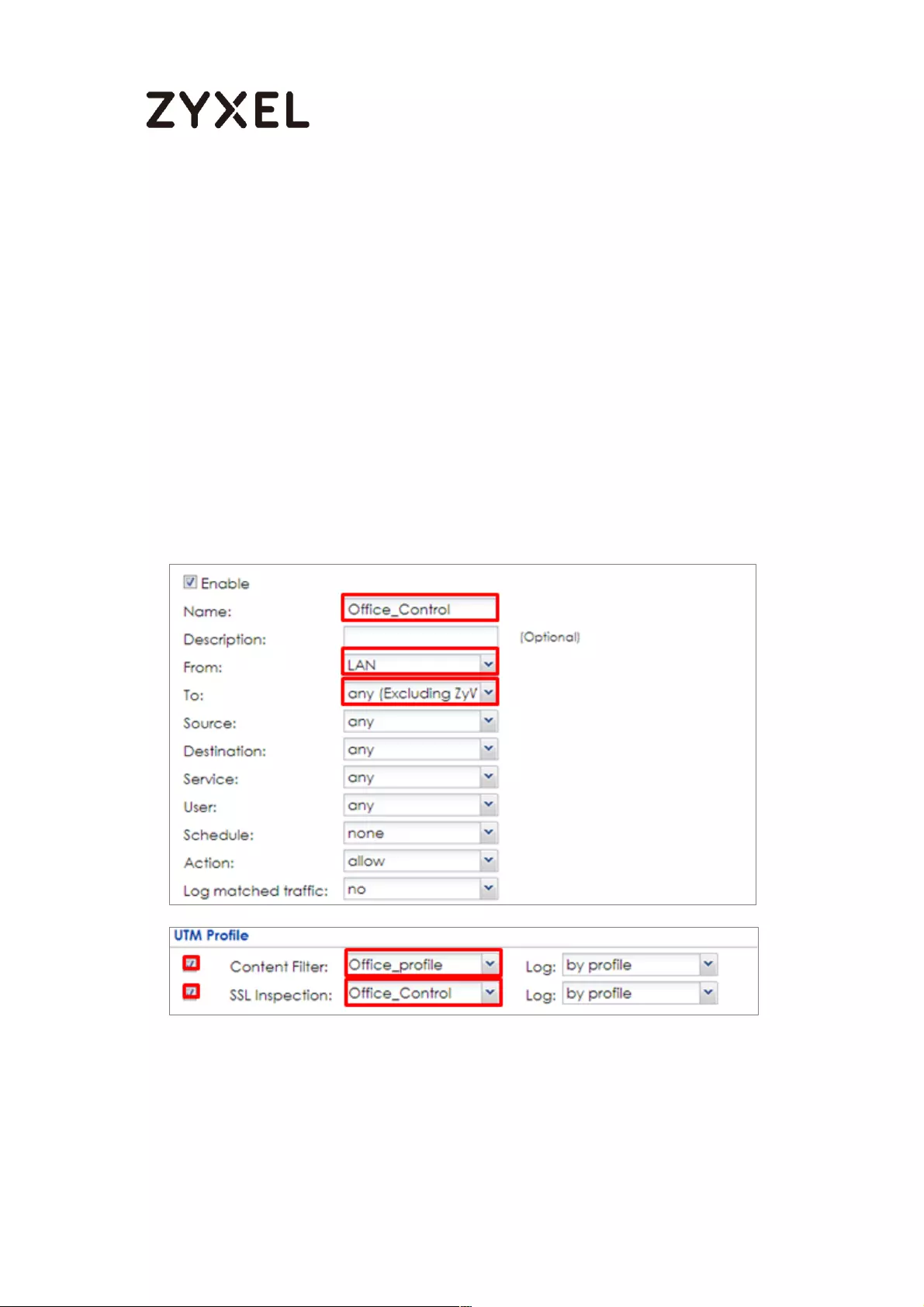
543/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy Control,
configure a Name for you to identify the Security Policy profile. For From and To
policies, select the direction of travel of packets to which the policy applies.
Scroll down to UTM Profile, select Content Filter and select a profile from the list
box (Office_profile in this example). Then, select SSL Inspection and select a
profile from the list box (Office_Control in this example).
CONFIGURATION > Security Policy > Policy Control

544/782
www.zyxel.com
Export Certificate from ZyWALL/USG and Import it to Windows 7
Operation System
When SSL inspection is enabled and an access website does not trust the
ZyWALL/USG certificate, the browser will display a warning page of security
certificate problems.
Go to ZyWALL/USG CONFIGURATION > Object > Certificate > default > Edit to
export default certificate from ZyWALL/USG with Private Key (zyx123 in this
example).
CONFIGURATION > Object > Certificate > default
CONFIGURATION > Object > Certificate > default > Edit > Export Certificate with
Private Key
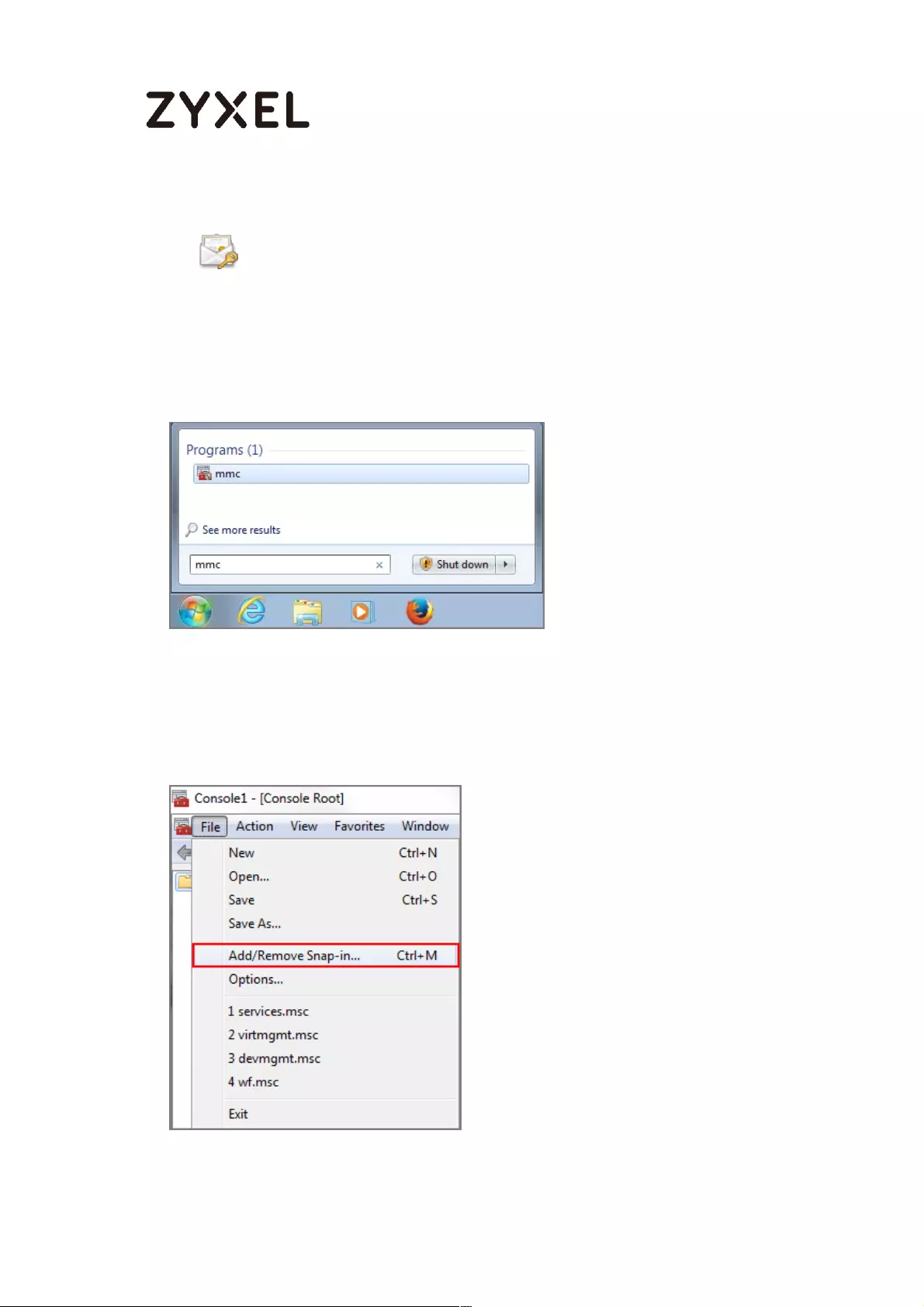
545/782
www.zyxel.com
Save default certificate as *.p12 file to Windows 7 Operation System.
In Windows 7 Operating System Start Menu > Search Box, type mmc and press
Enter.
Start Menu > Search Box > mmc
In the mmc console window, click File > Add/Remove Snap-in...
File > Add/Remove Snap-in...
default.p12
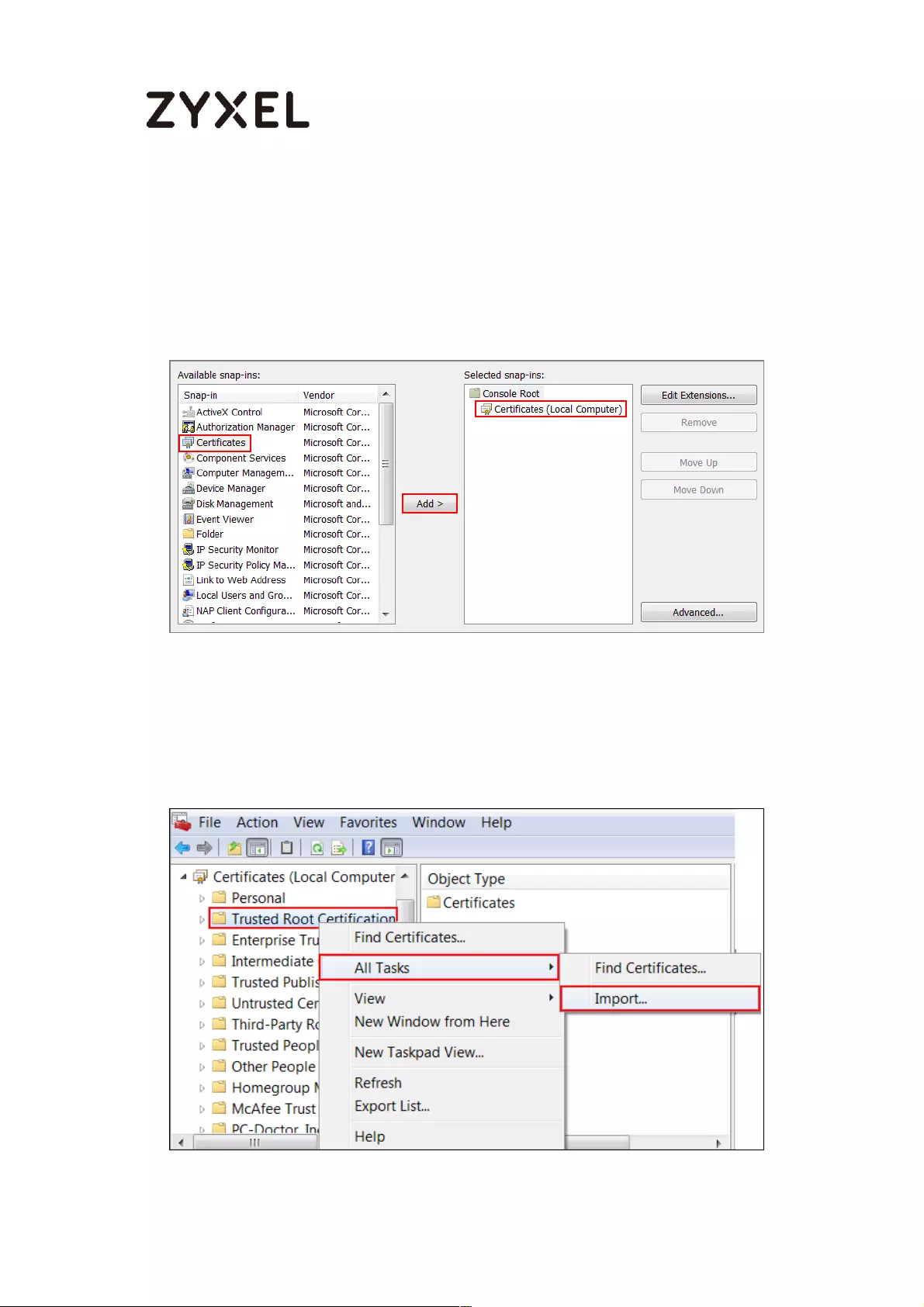
546/782
www.zyxel.com
In the Available snap-ins, select the Certificates and click Add button. Select
Computer account > Local Computer. Then, click Finished and OK to close the
Snap-ins window.
Available snap-ins > Certificates > Add
In the mmc console window, open the Certificates (Local Computer) > Trusted
Root Certification Authorities, right click Certificate > All Tasks > Import…
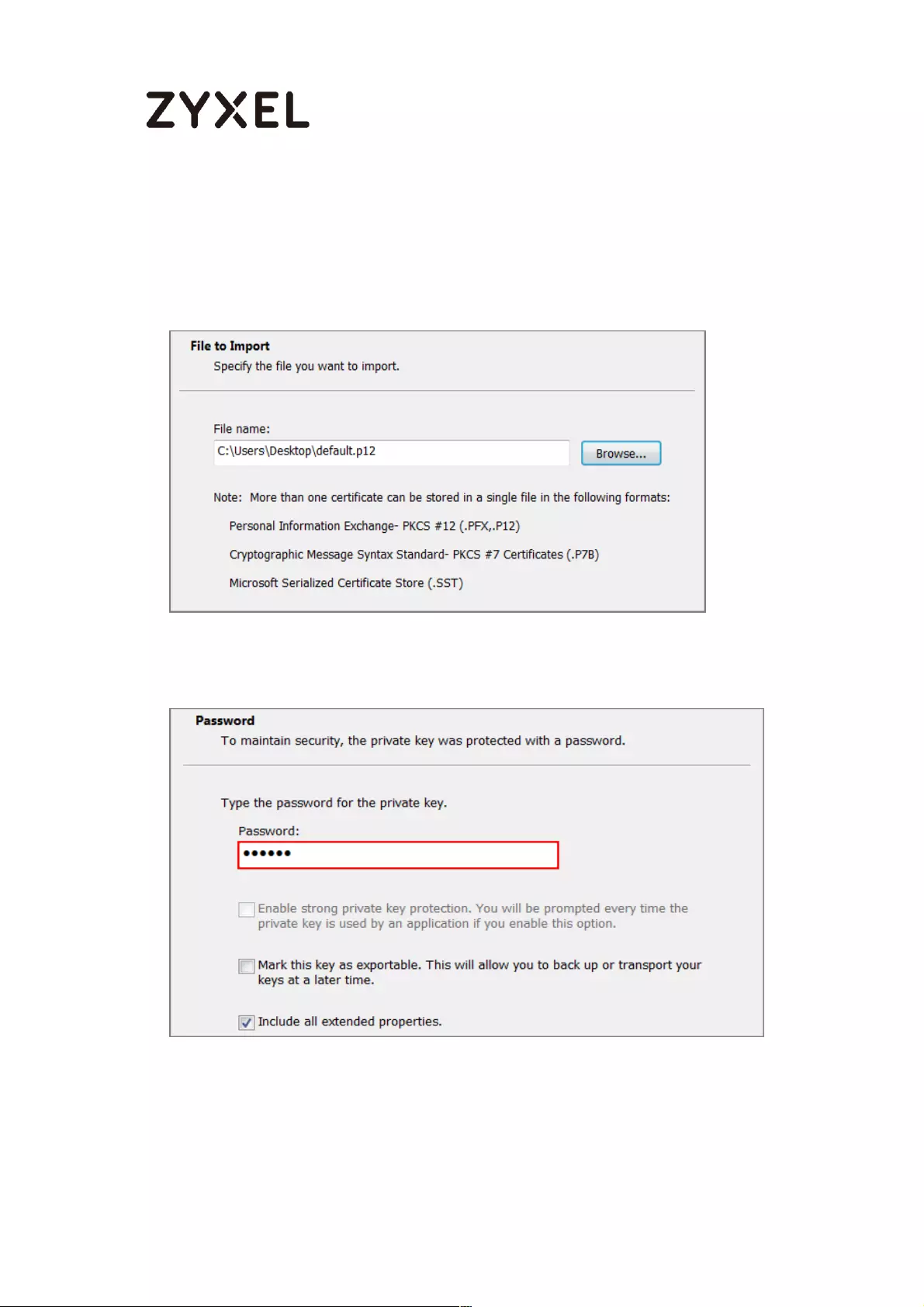
547/782
www.zyxel.com
Click Next. Then, Browse..., and locate the .p12 file you downloaded earlier. Then,
click Next.
Click Next, type zyx123 in the Password field and click Next again
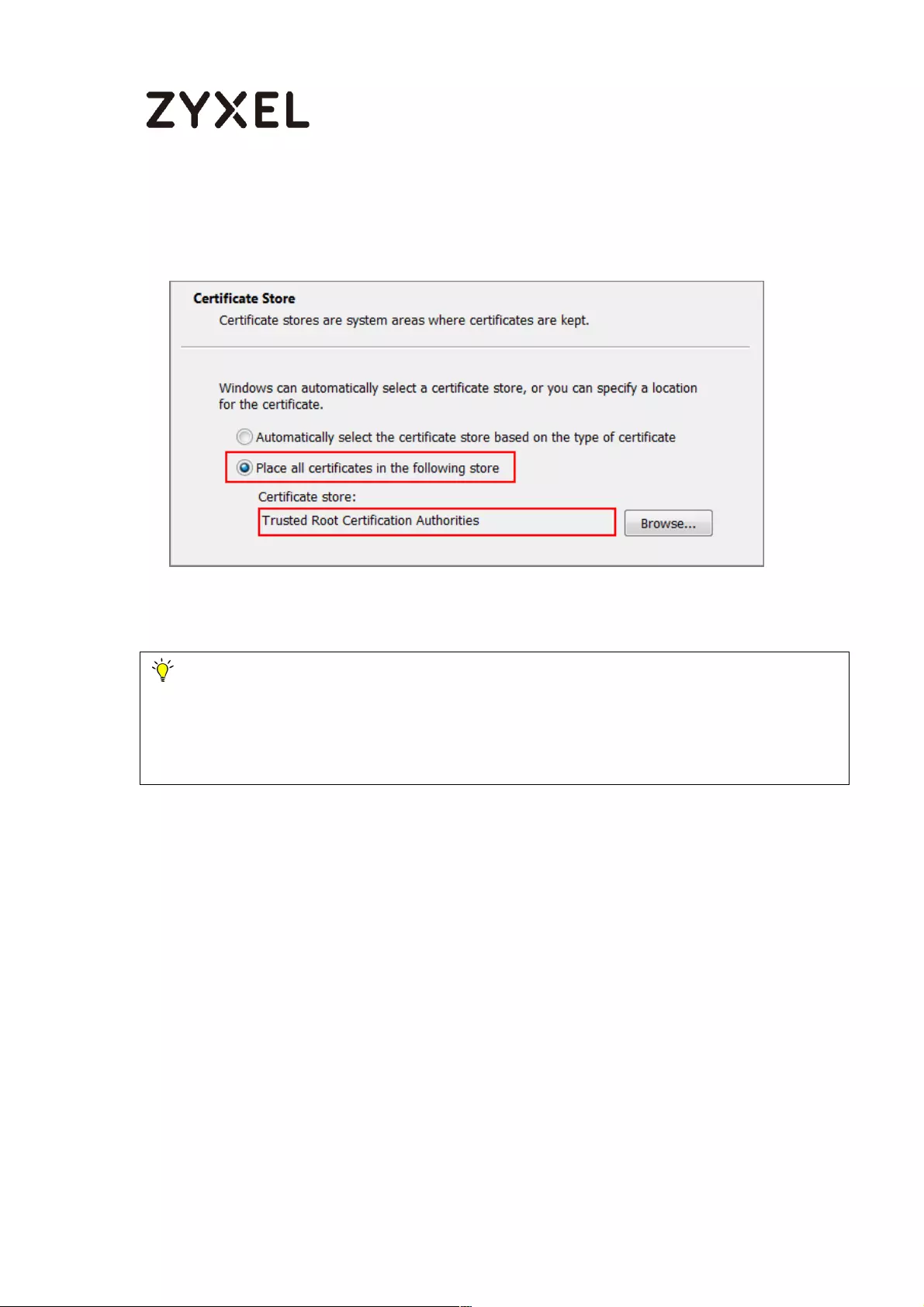
548/782
www.zyxel.com
Select Place all certificates in the following store and then click Browse and find
Trusted Root Certification Authorities. Click Next, then click Finish.
Note: Each ZyWALL/USG device has its own self-signed certificate by factory default.
When you reset to default configuration file, the original self-signed certificate is erased,
and a new self-signed certificate will be created when the ZyWALL/USG boots the next time.
549/782
www.zyxel.com
Test the Result
Type http://www.bittorrent.com/ or http://us.battle.net/d3/en/ into the browser.
The error message occurs.
Go to the ZyWALL/USG Monitor > Log to see [alert] log message such as below.
Monitor > Log
550/782
www.zyxel.com
What Could Go Wrong?
If you are not be able to configure any Content Filter policies or it’s not working,
there are two possible reasons:
You have not subscribed for the Content Filter service.
You have subscribed for the Content Filter service but the license is
expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your Content
Filter license.
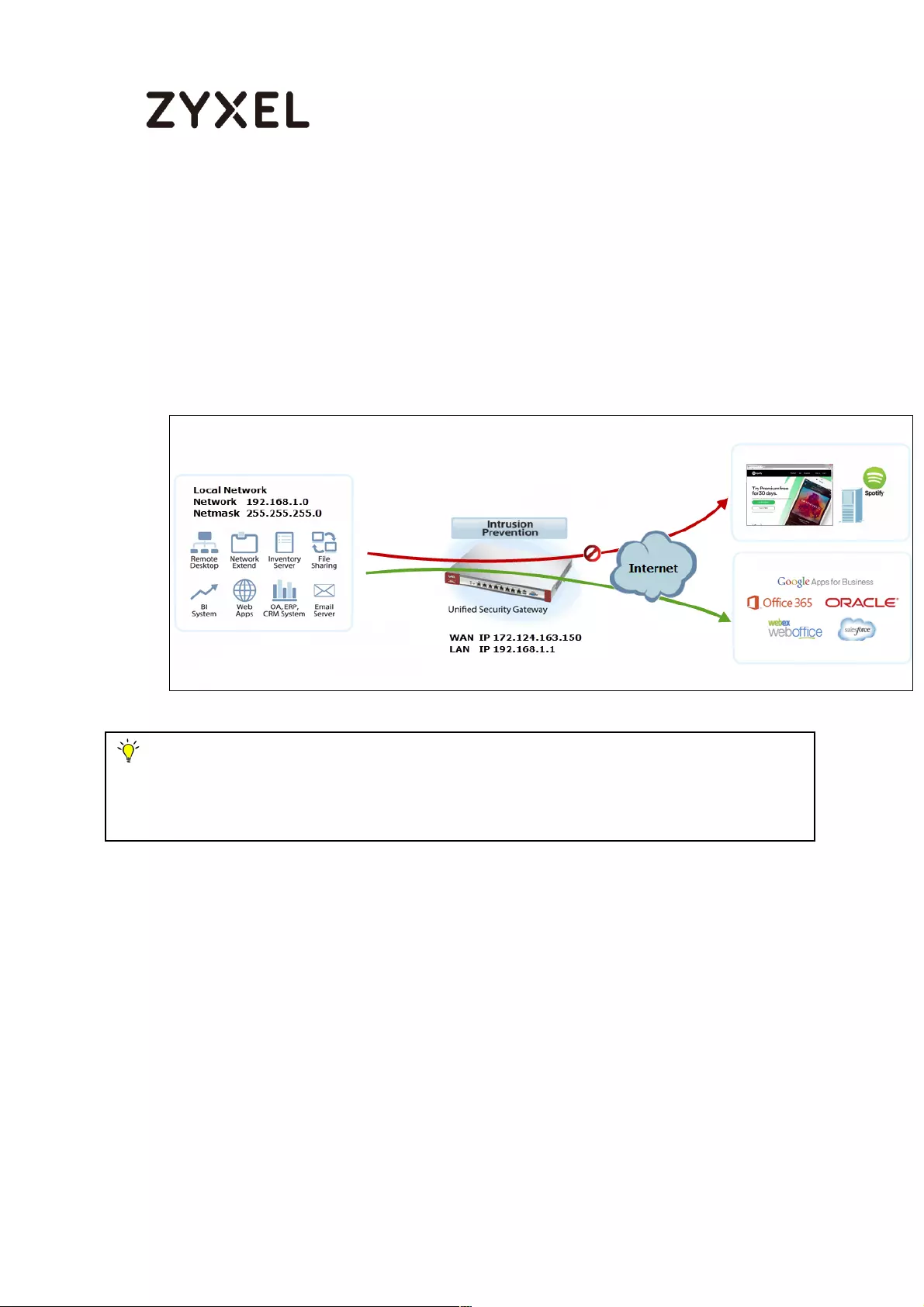
551/782
www.zyxel.com
How To Block the Spotify Music Streaming Service
This is an example of using a ZyWALL/USG IDP Profile to block DNS query packet.
When the Spotify software launches, it will send a DNS query for Spofity's public
server. In this example, you can create a custom IDP to block DNS query packet
if this packet includes the Spotify signature.
ZyWALL/USG with Block the Spotify Service Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
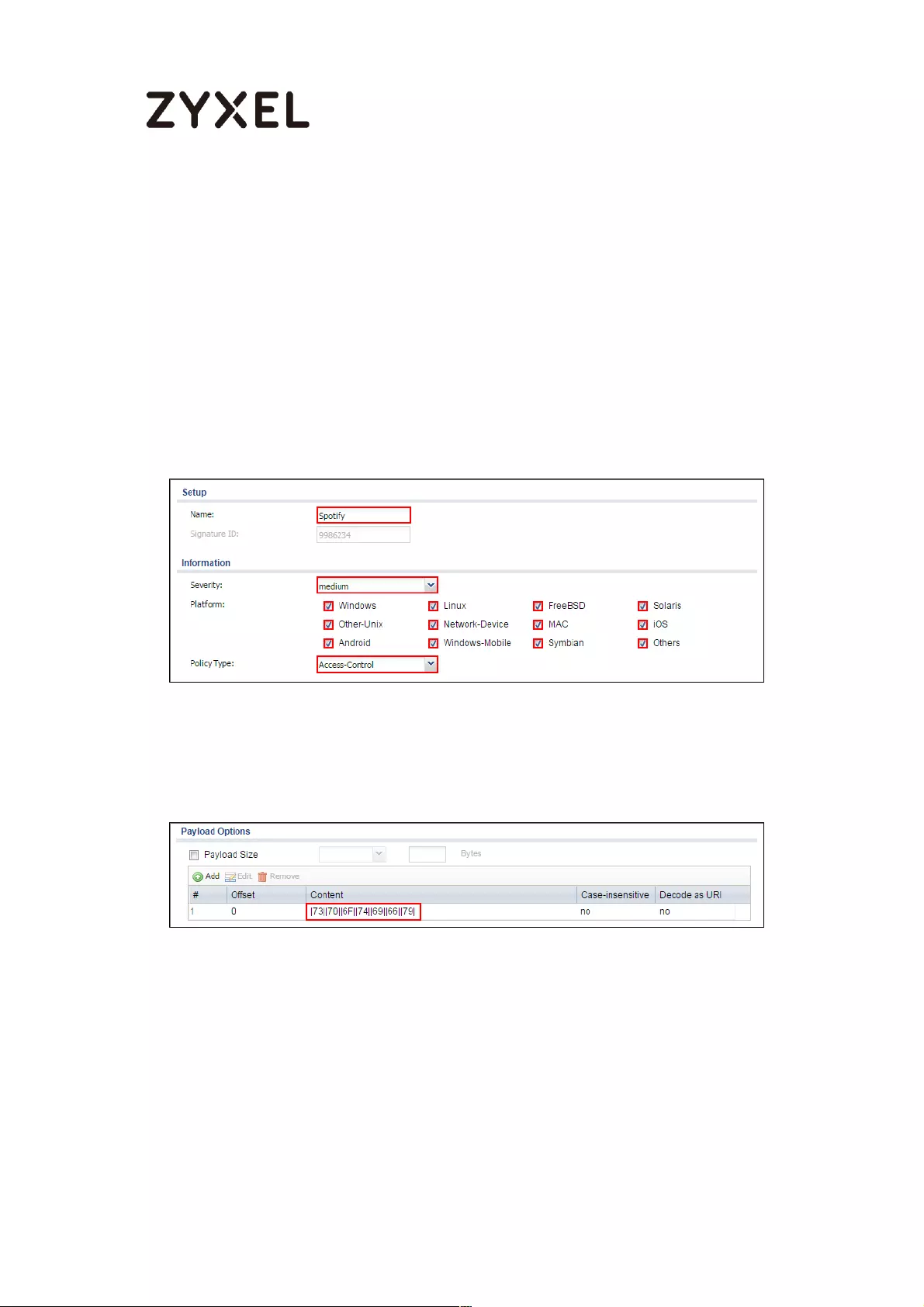
552/782
www.zyxel.com
Set Up IDP Profile on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile > IDP > Custom
Signatures > Add Custom Signatures, configure a Name for you to identify the IDP
Profile. Select medium as the Severity level. Select all Platform. Select Policy Type
to be Access-Control here to limit access network resources such as servers.
CONFIGURATION > Security Policy > IDP > Custom Signatures > Add Custom
Signatures > Setup & Information
Scroll down to the Payload Options section, the type Spotify's software signature:
|73||70||6F||74||69||66||79|into the Content field. Click OK.
CONFIGURATION > Security Policy > IDP > Custom Signatures > Add Custom
Signatures > Payload Options
In the ZyWALL/USG, go to CONFIGURATION > UTM Profile > IDP > Profile > Base
Profile. A pop-up screen will appear and select a Base Profile to go to the profile
details screen.
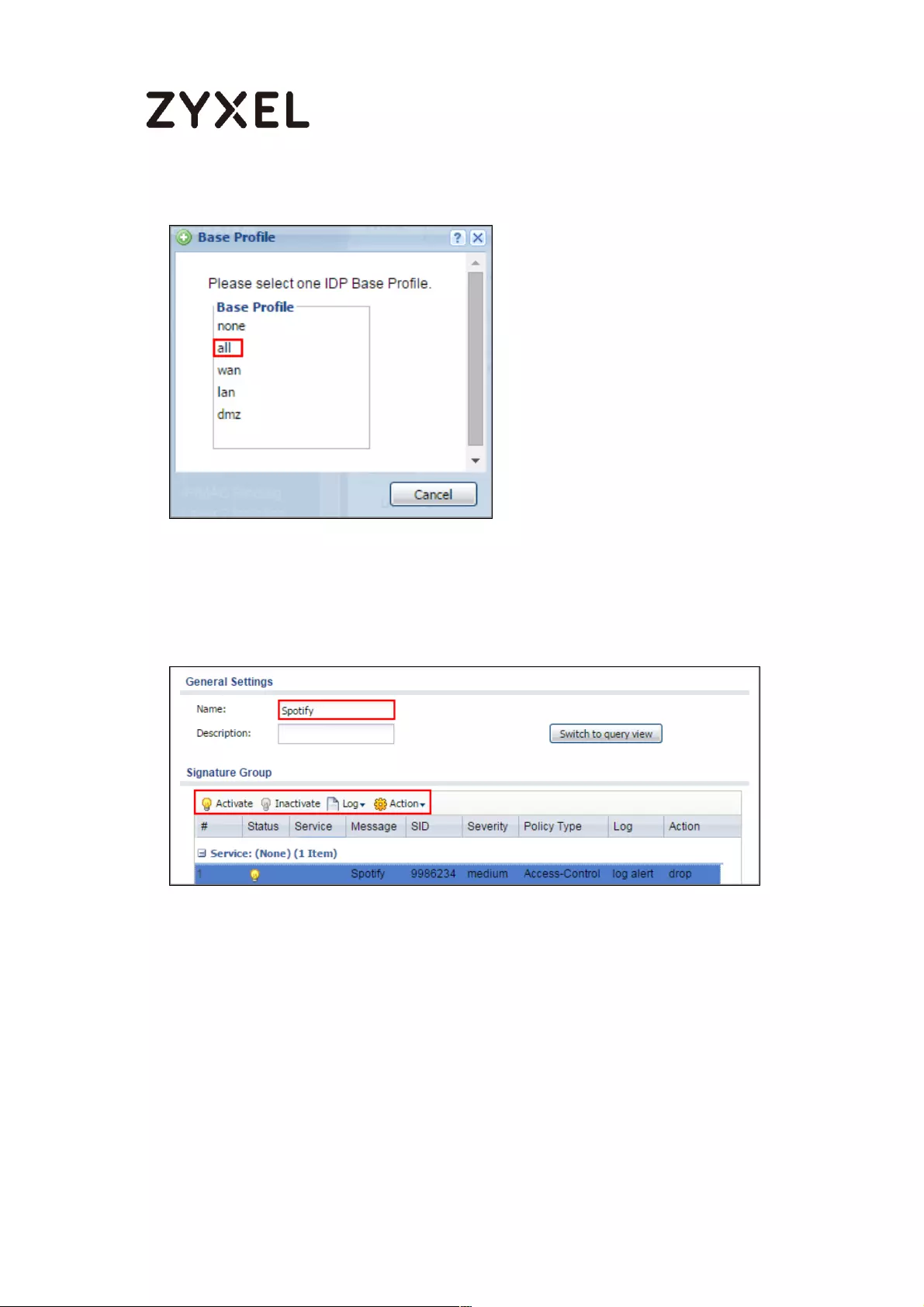
553/782
www.zyxel.com
CONFIGURATION > UTM Profile > IDP > Profile > Base Profile
Configure a Name for you to identify the IDP Profile. Activate the newly created
IDP Profile and select Action to be drop. Select Log type to be log alert in order to
view the result later.
CONFIGURATION > UTM Profile > IDP > Profile > Base Profile > Add Profile
Test the Result
Type http://www.spotify.com/ or https://www.spotify.com / into the browser, the
error message occurs.

554/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > Log, you will see [crit] log message such as
below.
Monitor > Log
What Could Go Wrong?
If you are not be able to configure any IDP policies or it’s not working, there are
two possible reasons:
You have not subscribed for the IDP service.
You have subscribed for the IDP service but the license is expired.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your
Application Patrol license.
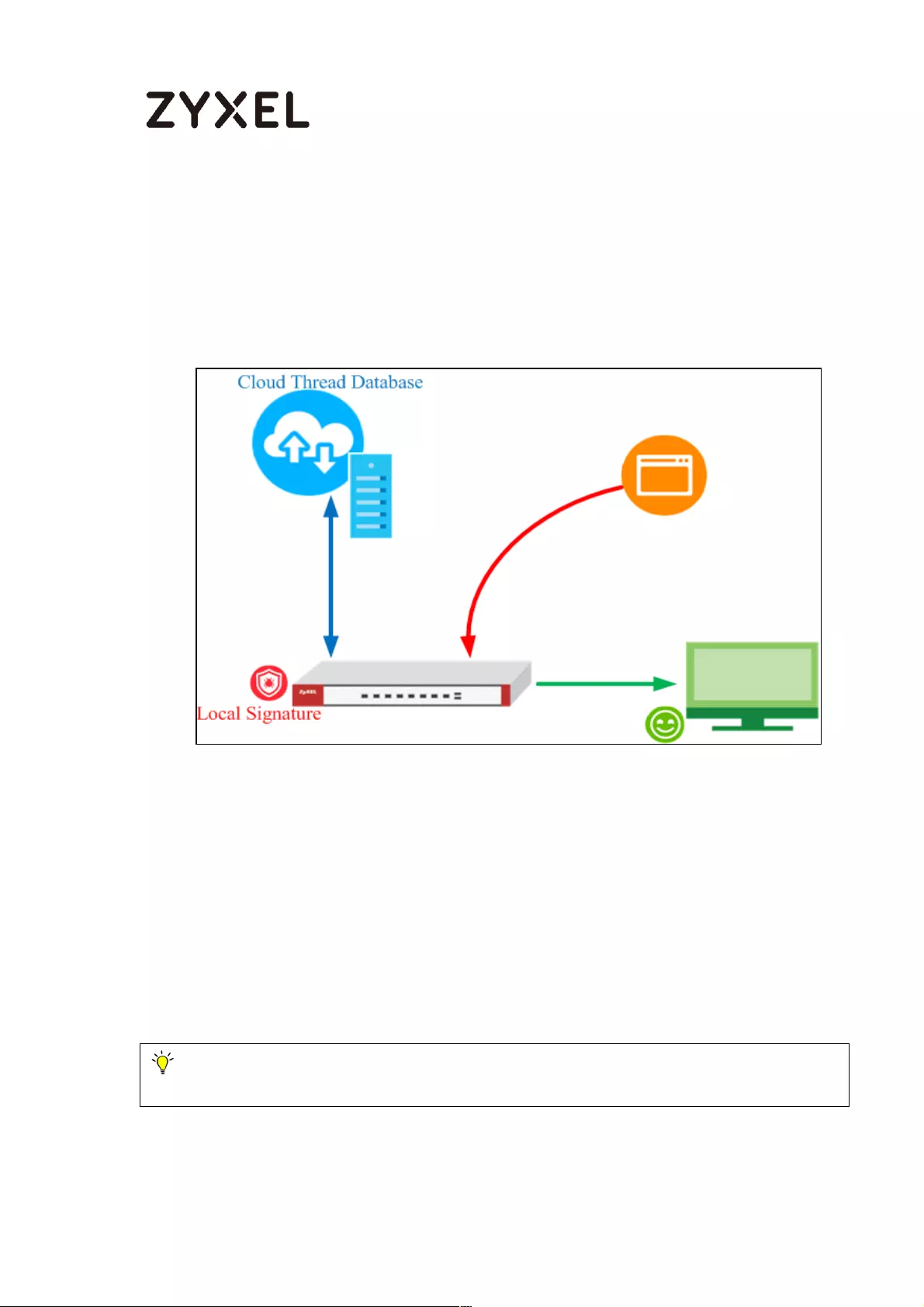
555/782
www.zyxel.com
How does Anti-Malware work
There are many virus exist on the internet. And it may auto-downloaded
on unexpected situation when you surfing between websites. The Anti-
Malware is a good choose to protecting your computer to downloads
unsafe application or files.
After you enabled Anti-Malware function, it will enabled “Cloud Threat
Database” and “Anti-Malware Signature” in the same time.
The Cloud Threat Database is means your downloaded files will
decompressed by device first, and then check files with cloud data base
server if it exist unsafe file or not.
The Anti-Malware Signature is means your downloaded files will checked
by local signatures that exist on device itself. It is helpful when your device
unable access to internet at that moment.
Note: In the default setting, the Cloud Threat Database is enabled and with higher priority
when scanning the files.
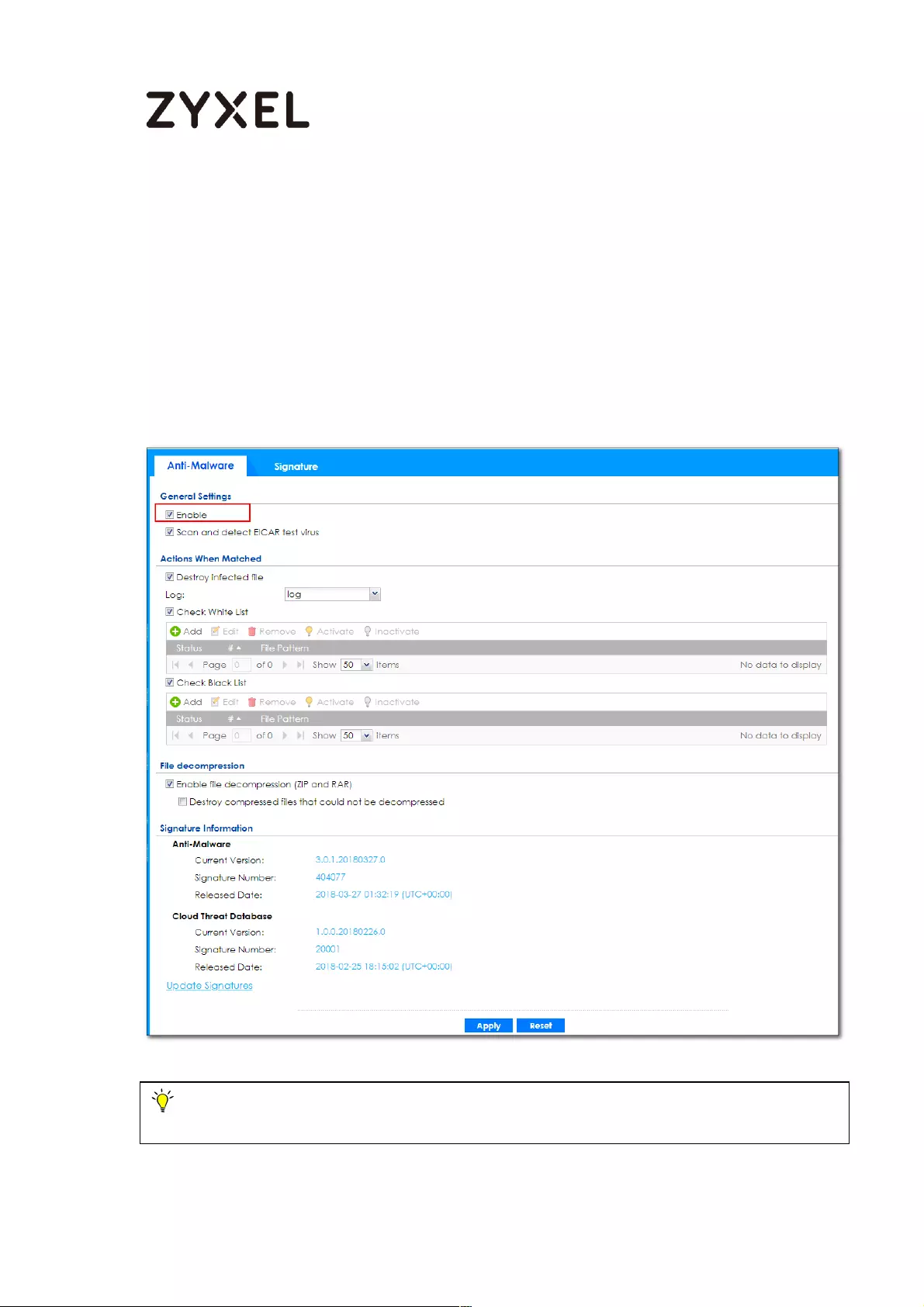
556/782
www.zyxel.com
Enable Anti-Malware function to protecting your traffic
Go to CONFIGURATION > Security Service > Anti-Malware > Tick in
enable checkbox to enable Anti-Malware function.
Configuration > Security Service > Anti-Malware > Tick in enable
checkbox
Note: The Anti-Malware license is required. So you must enabled Anti-Malware function
on your myzyxel.com account.

557/782
www.zyxel.com
Test the result
After you enabled Anti-Malware function and your PC downloaded
the virus file from internet. You device will detected it and drop the
file directly.
Then your file is unable opened or replaced by “0”.
Additional configuration
White List: You can use wildcard to allowing specific type files.
Black List: You can use wildcard to drop specific type files.
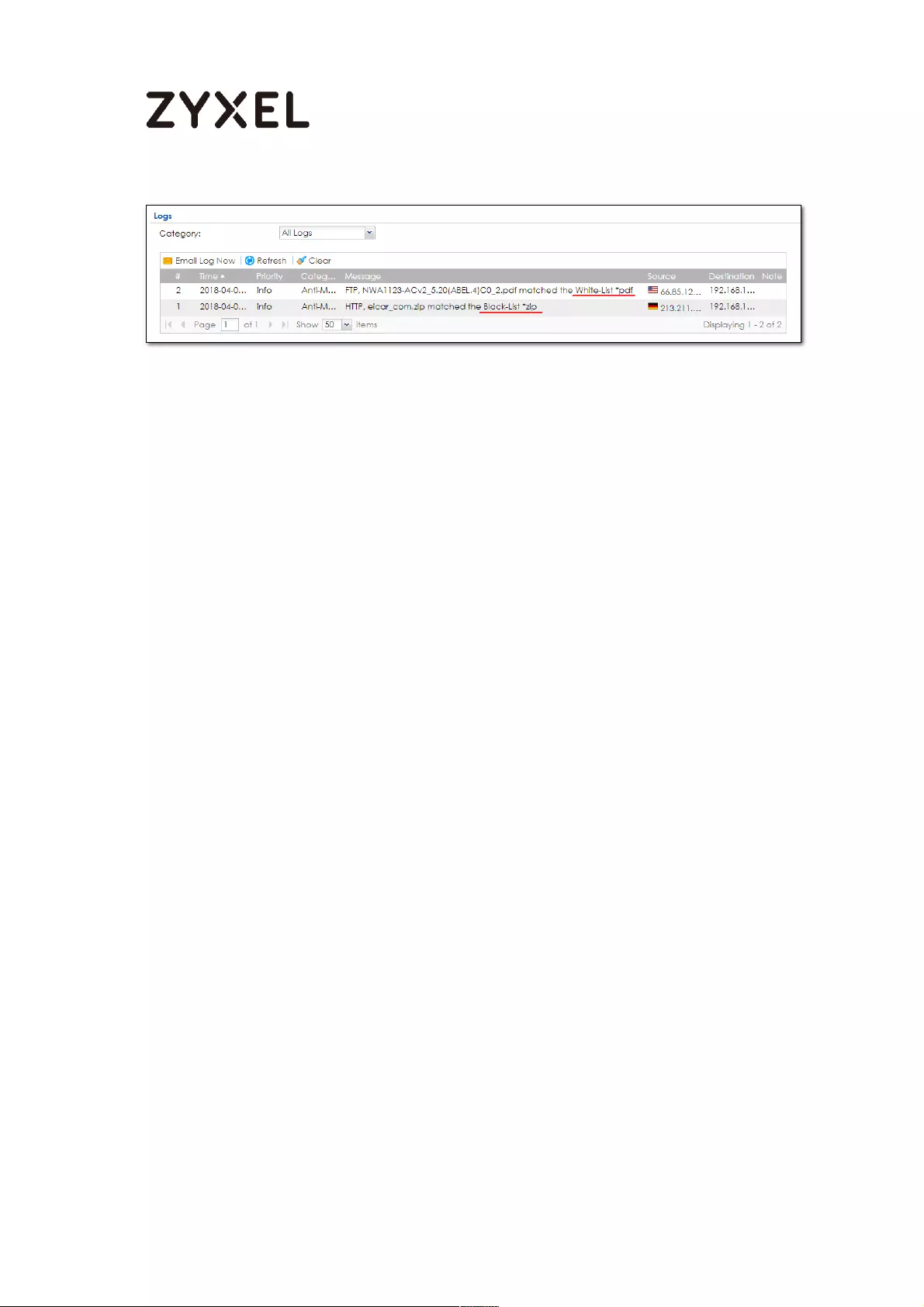
558/782
www.zyxel.com
What can go wrong
1 The Anti-Malware service license is required
2 The Anti-Malware is able decompress the file. But it is not support multi-
layer zip files.
3 In the default setting, could thread batabase is enabled. You can use
the CLI command to activate/deactivate cloud base service. It means
the scanning priority will been changed.
a. Router(config)# debug anti-virus ctdb activate
b. Router(config)# debug anti-virus ctdb deactivate
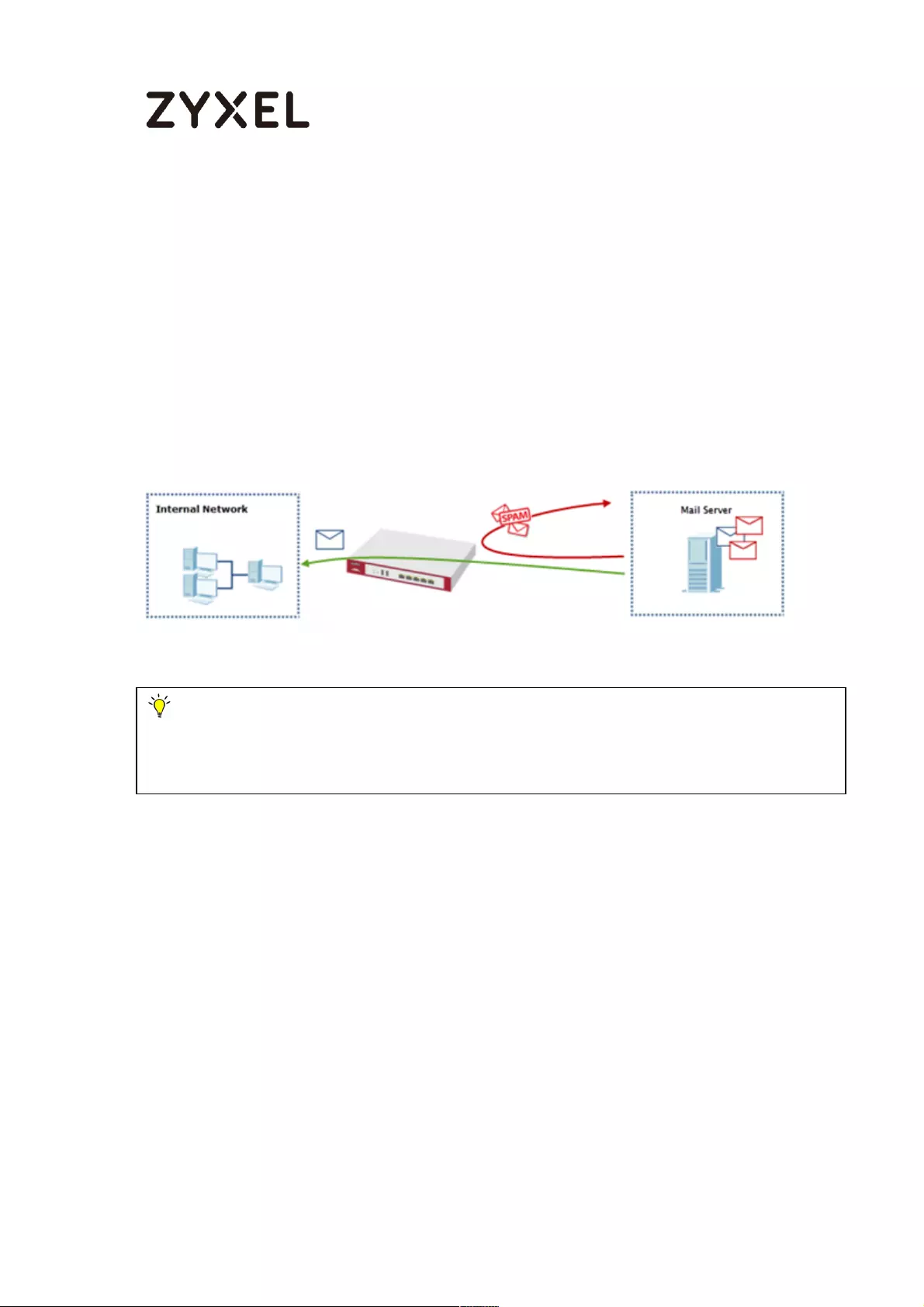
559/782
www.zyxel.com
How to Configure an Email Security Policy with Mail Scan
and DNSBL
This is an example of using ATP Series’ UTM Profile to mark or discard
spam (unsolicited commercial or junk e-mail). Use the Email Security
white list to identify legitimate e-mail. Use the Email Security black list
to identify spam e-mail. The ATP Series can also check e-mail against
a DNS Black List (DNSBL) of IP addresses of servers that are suspected
of being used by spammers.
ATP Series with Email Security Profile to mark or discard spam e-mail
Example
Figure 1 Using Email Security to Detect Spam
Set Up the Email Security on ATP Series
In the ATP Series, go to CONFIGURATION > Security Service> Email Security; Enable
this feature on General Settings page. Select Check IP Reputation (SMTP only) to
have the ATP Series scan for spam e-mail by IP Reputation. Select Check Mail
Content to identify Spam Email by content, such as malicious content. Select
Check Virus Outbreak to scan viruses attached in emails. On advance section,
leave Query Timeout Settings to be the default settings.
Select from the list of available Scan Options and desired Log type whether to have
the ATP Series generate a log (log), log and alert (log alert) or neither (no) by
default when traffic matches this policy. Click Apply to save the configuration
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using ATP200 (Firmware Version: ZLD 4.32).
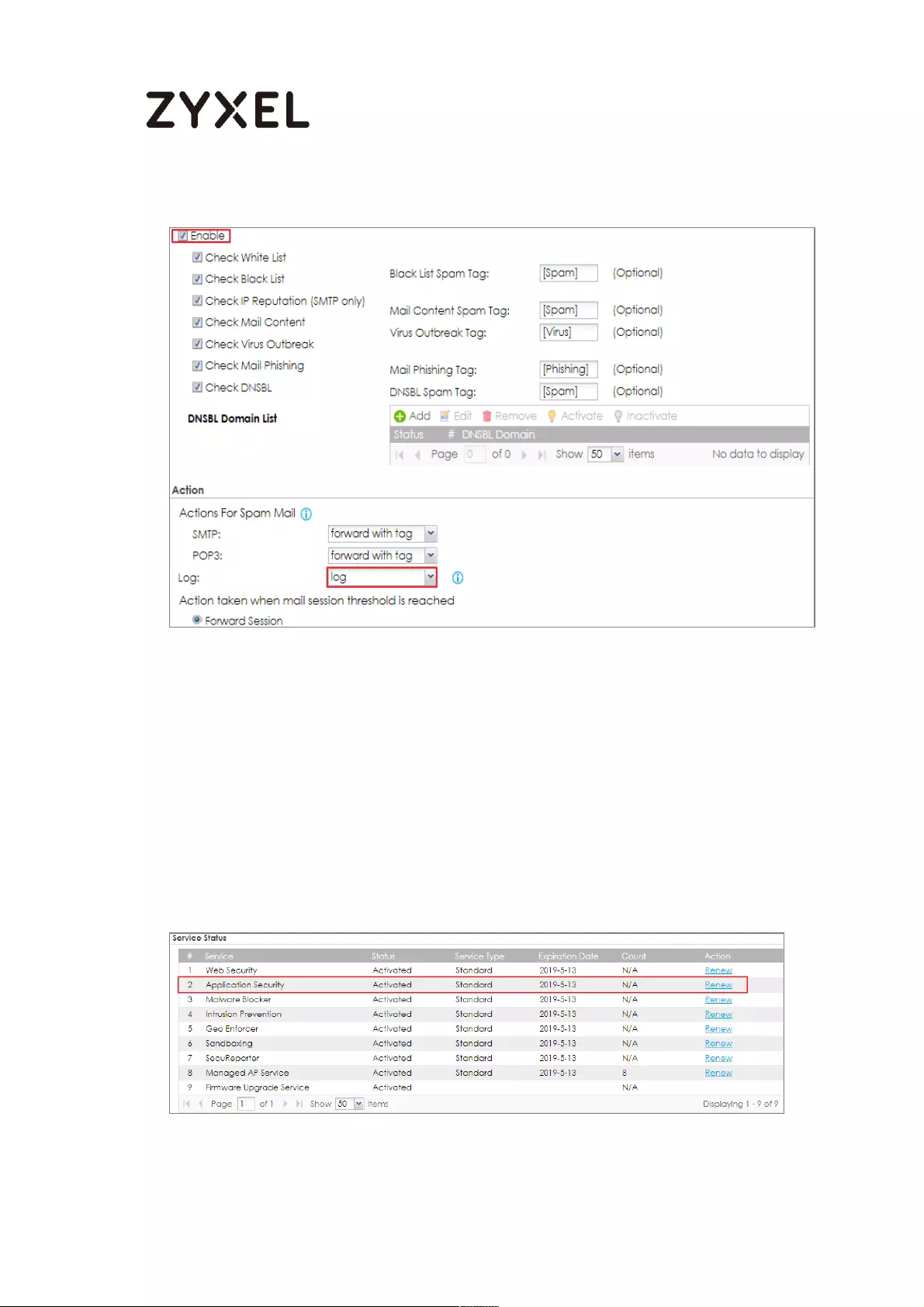
560/782
www.zyxel.com
CONFIGURATION > Security Service > Email Security
1. Register the device to myZyxel.com.
2. Activate Application Security.
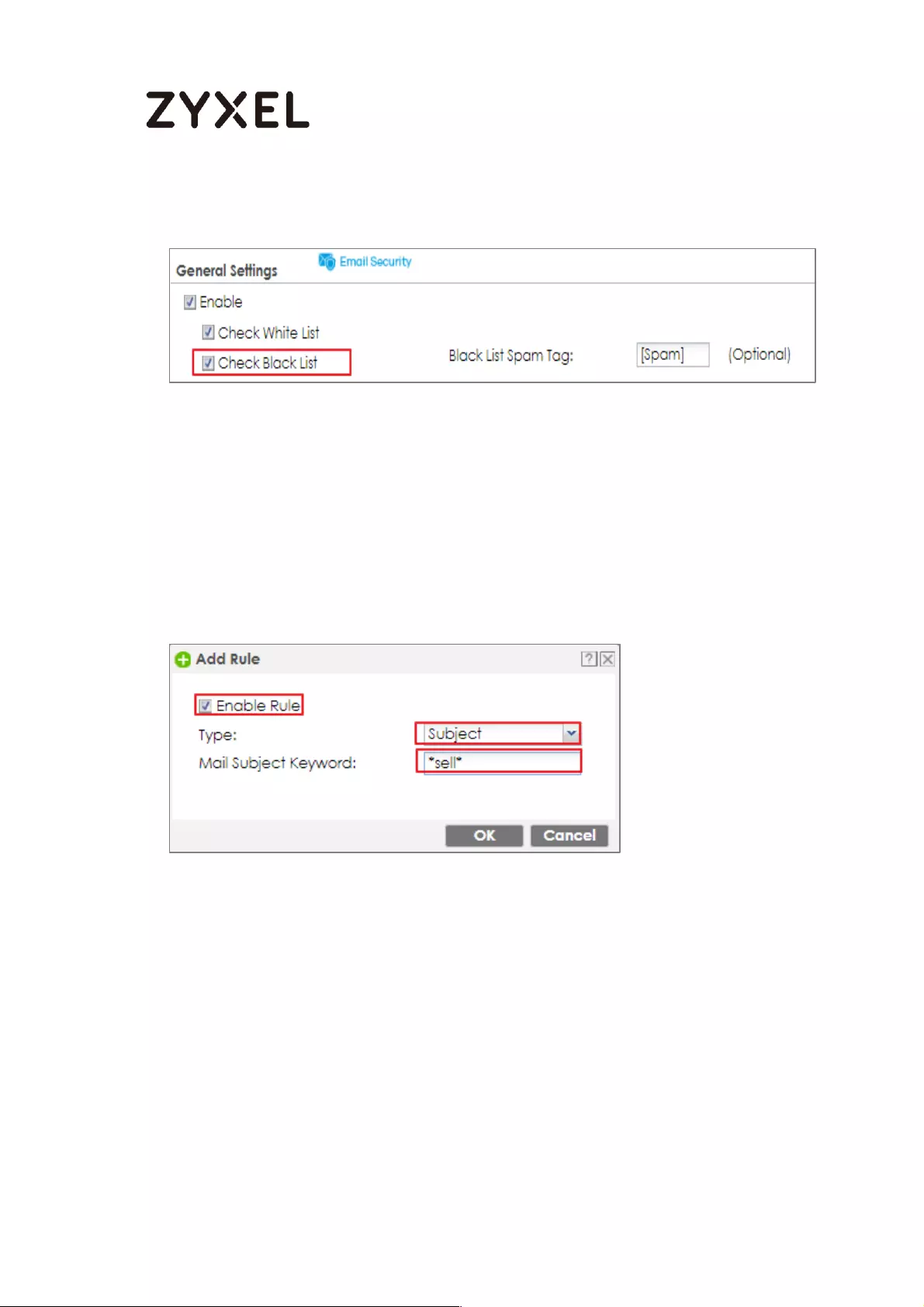
561/782
www.zyxel.com
3. Go to CONFIGURATION > Security Service> Email Security>Enable Check Black List
to have the ATP Series treat e-mail that matches (an active) black list entry as spam.
4. Continue to Rule Summary on Black/White List, click the Add icon. A
pop-up screen will appear allowing you to configure Content
(Subject, IP/IPv6 Address, E-Mail Address and Mail Header), Use
wildcards (*) to configure Mail Subject Keyword. (*sell* in this
example). Click OK to return to the General screen.
CONFIGURATION > Security Service> Black/White List
5. In the ATP Series, go to CONFIGURATION > Security Service> Email Security>Enable
Check DNSBL
Press Add and enter the DNSBL Domain for a DNSBL service (zen.spamhaus.org in
this example). Click Apply.
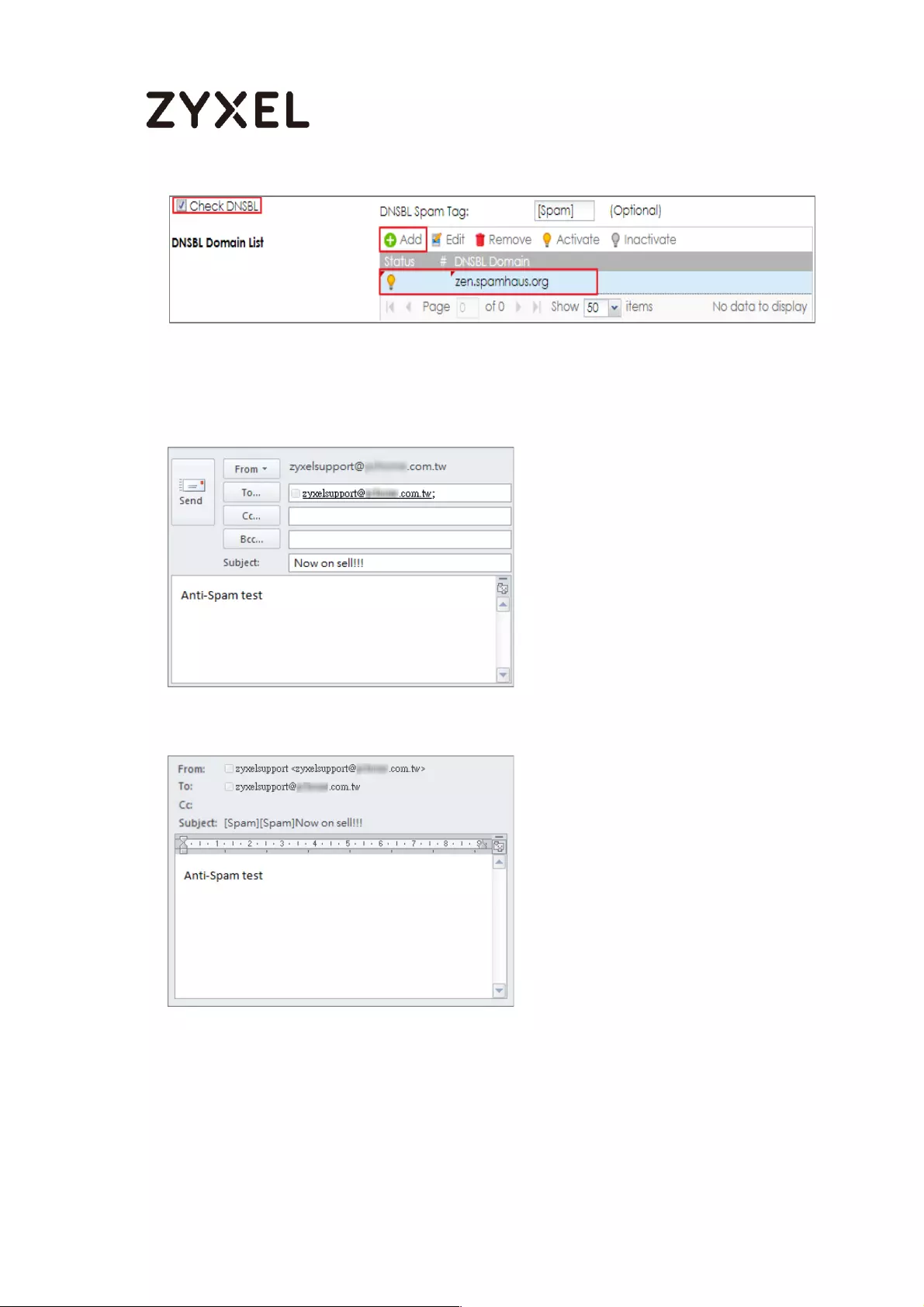
562/782
www.zyxel.com
Test the result
1. Send the mail subject with “sell”.
2. You will receive the mail subject with [Spam] tag.

563/782
www.zyxel.com
What can go wrong
1. If Email Security is not working, there are two possible reasons:
You have not subscribed for the Email Security service.
You have subscribed for the Email Security service but the license
(Application Security) is expired.
2. You can click the link from the CONFIGURATION > Licensing > Registration
screen of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0
icon from the portal page (https://portal.myzyxel.com/) to register or extend
your Application Security license.

564/782
www.zyxel.com
How to Configure Botnet!Filter on ATP series?
Botnets are organized groups of infected computers. Those infected PCs will try
to connect to the command-and-control server and ask for commands.
When the attacker sends command to the command-and-control server, it will
relay those commands to the clients (infected computers) and perform attacks
on particular targets.
The following steps will walk you through an example of how to configure
Botnet Filter (IP blocking and URL blocking) on the ATP.
565/782
www.zyxel.com
Prerequisites before setting up Botnet Filter function
1. License status check
2. Update the Botnet Filter signature
License activation
Before setting up the Botnet Filter function, users need to make sure their licenses are
purchased and activated.
To check the license activation status:
Go to configuration > Licensing > Registration > Service and check on the
“Application Security” service which includes the Botnet Filtering function.
Update Botnet Filter Signatures
To make sure the device has the most updated signature, we suggest users to update
their Botnet Filter signature before using this function.
To update the Botnet Filter signature:
Go to Configuration > Security Service > Botnet Filter. Then click “Update Signatures”
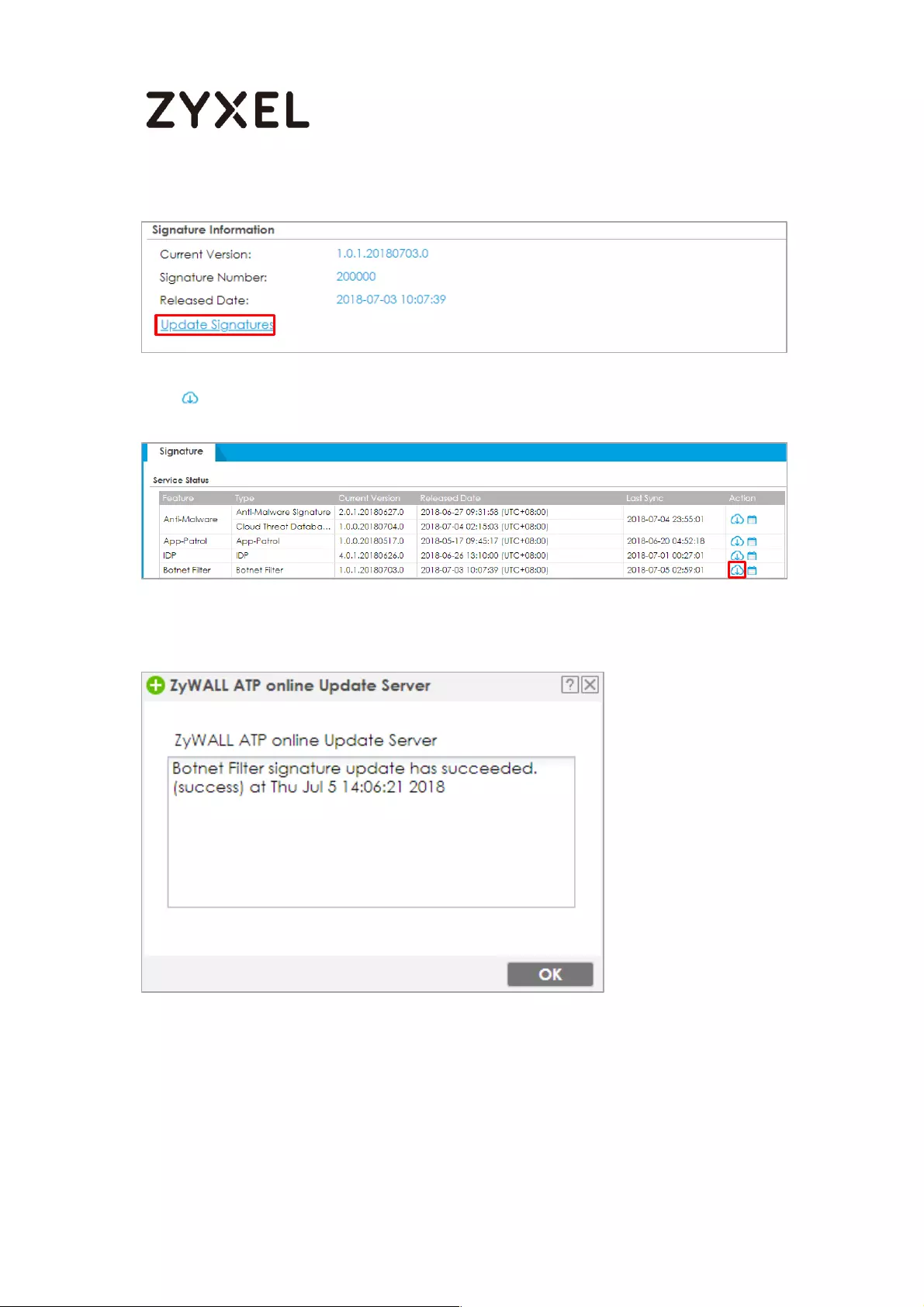
566/782
www.zyxel.com
Then the device will redirect users to the “Service Status” page. Click on the cloud
icon and the device will start signature downloading process
Once the signature updating process was done. The GUI will pop up the following
message to notify users.
Now the Botnet Filtering function is ready to go.
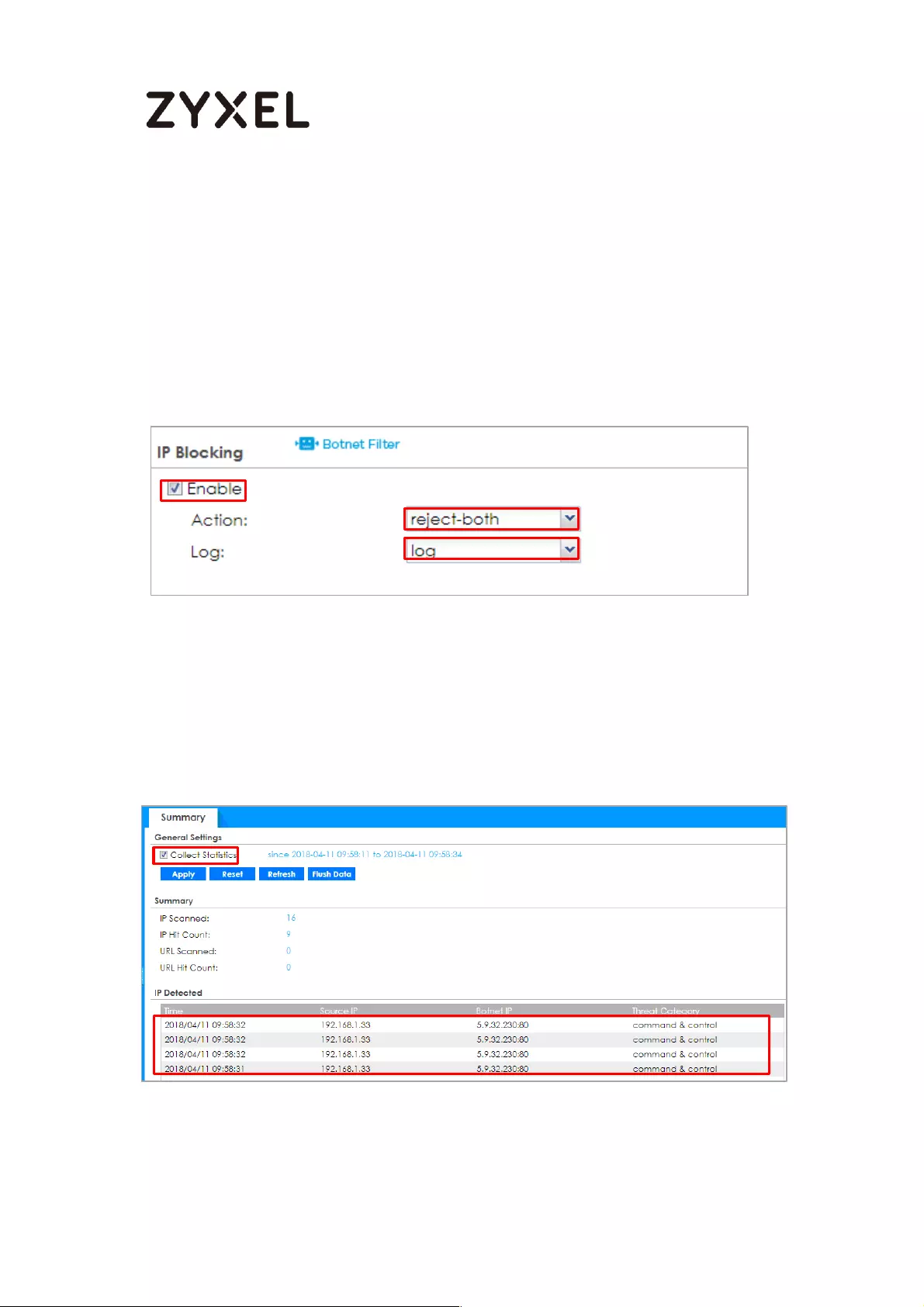
567/782
www.zyxel.com
Set Up the IP Blocking on the ATP series
Go to Configuration > Security Service > Botnet Filter.
Select the Enable IP Blocking check box. There’re some actions can be selected
“reject-both”, user can decide if they’d like to “forward”, “reject-sender” or “reject-
receiver” the blocked IP . In addition, users can select if they want to log the related
events or not.
Test the Result
User access IP: 5.9.32.230
Go to Monitor > Security Statistics > Botnet Filter to check summary.
IP: 5.9.32.230 is blocked due to command & control.
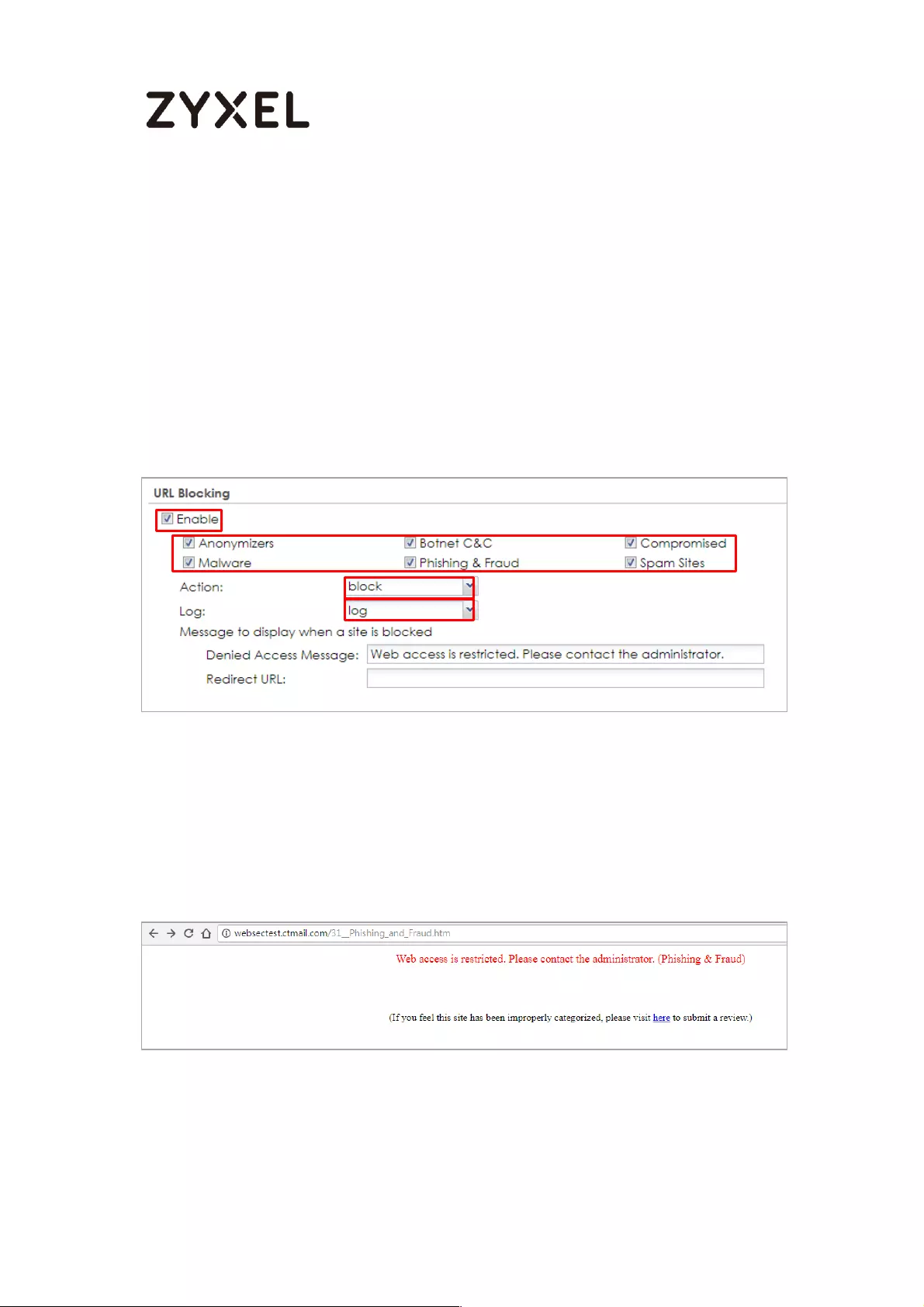
568/782
www.zyxel.com
Set up the URL Blocking on the ATP series
Go to Configuration > Security Service > Botnet Filter.
Select the Enable URL Blocking check box, check the categories that need to be
blocked. Users can only check those categories as their requirement. Choose the
Action the device will take (In this example we select “block” to block certain URLs)
and if they want to Log those events on the device.
Test the Result
Browse the Phishing website URL from the host browser. Users will be redirected to an
error page in the browser that nofifies users they are visiting to the “Phishing & Fraud”
categorized URL
Go to Monitor > Security Statistics > Botnet Filter to check summary where users will
see the related threat log was recorded
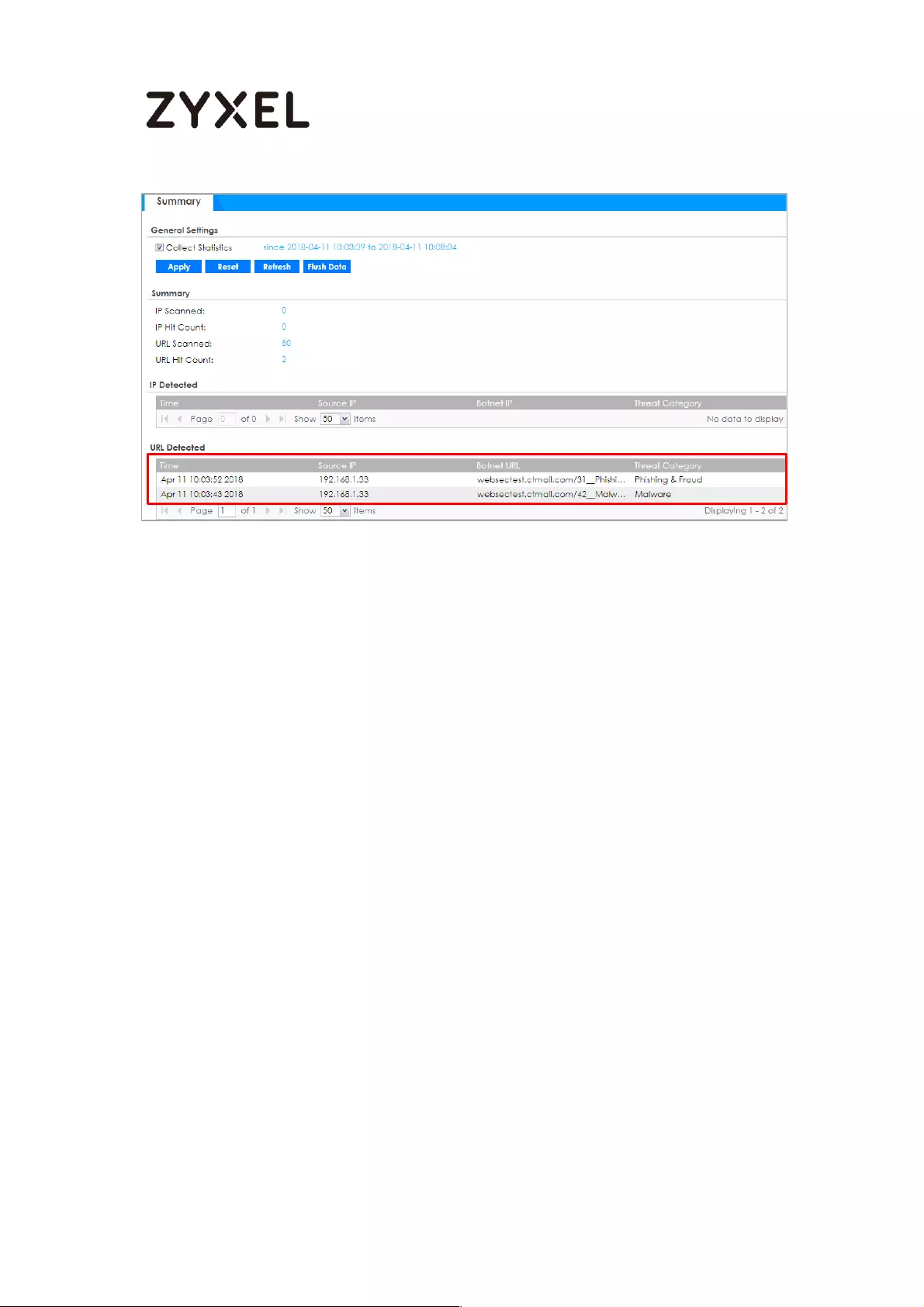
569/782
www.zyxel.com
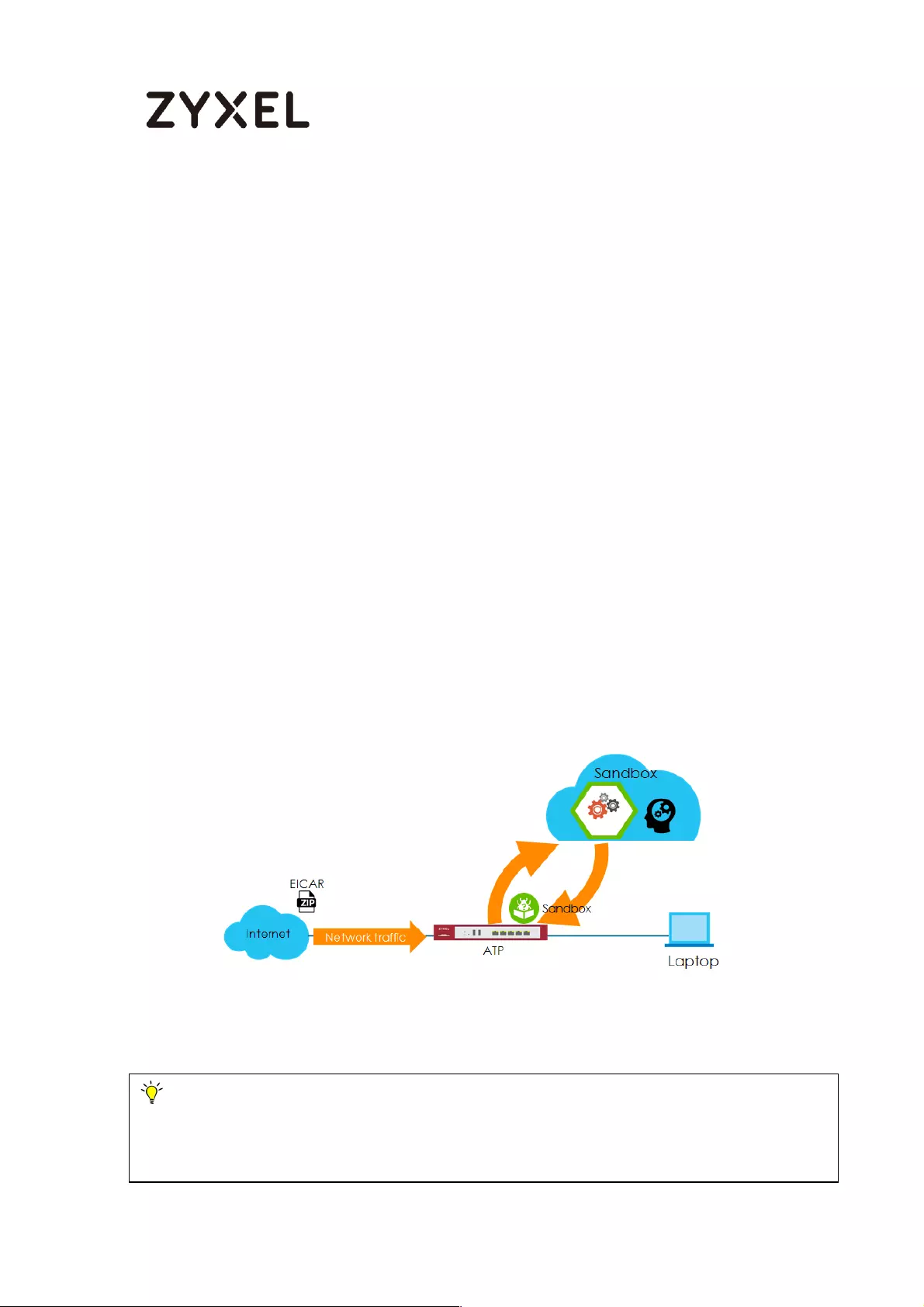
570/782
www.zyxel.com
How to Use Sandboxing to Detect Unknown Malware
The traditional security service such as Anti-Virus and IDP are signature-
based solution, so they have no chance to detect unknown threats.
ZyWALL ATP enhances UTM service and integrates Sandbox solution as a
second layer of defense to detect and mitigate advanced threats. Zyxel
Sandbox is a cloud-based service that can identify previously unknown
malware. Each new threat discovered by Sandbox will be converted to
known signatures in the cloud threat database of Anti-Malware. The Anti-
Malware examines file for threats before deciding to block or pass to
Sandbox. If the file has never been inspected by Sandbox, ZyWALL ATP
copies this file to the caches and then forwards the file. A copy of the file
is sent to Sandbox for analysis and the analysis result is recorded on
device’s local cache. Once ZyWALL ATP detects the file again, it can
identify the file and take the action based on the previous analysis result
on local cache. With the cooperation of Anti-Malware, ATP can
immediately block threat which previous detected by Sandbox. This
example illustrates how to configure Sandboxing on ATP gateway to
detect unknown malware.
Figure 1 Using Sandboxing to Detect Unknown Malware
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses. This example was tested using
the ATP200 (Firmware Version: ZLD 4.32).
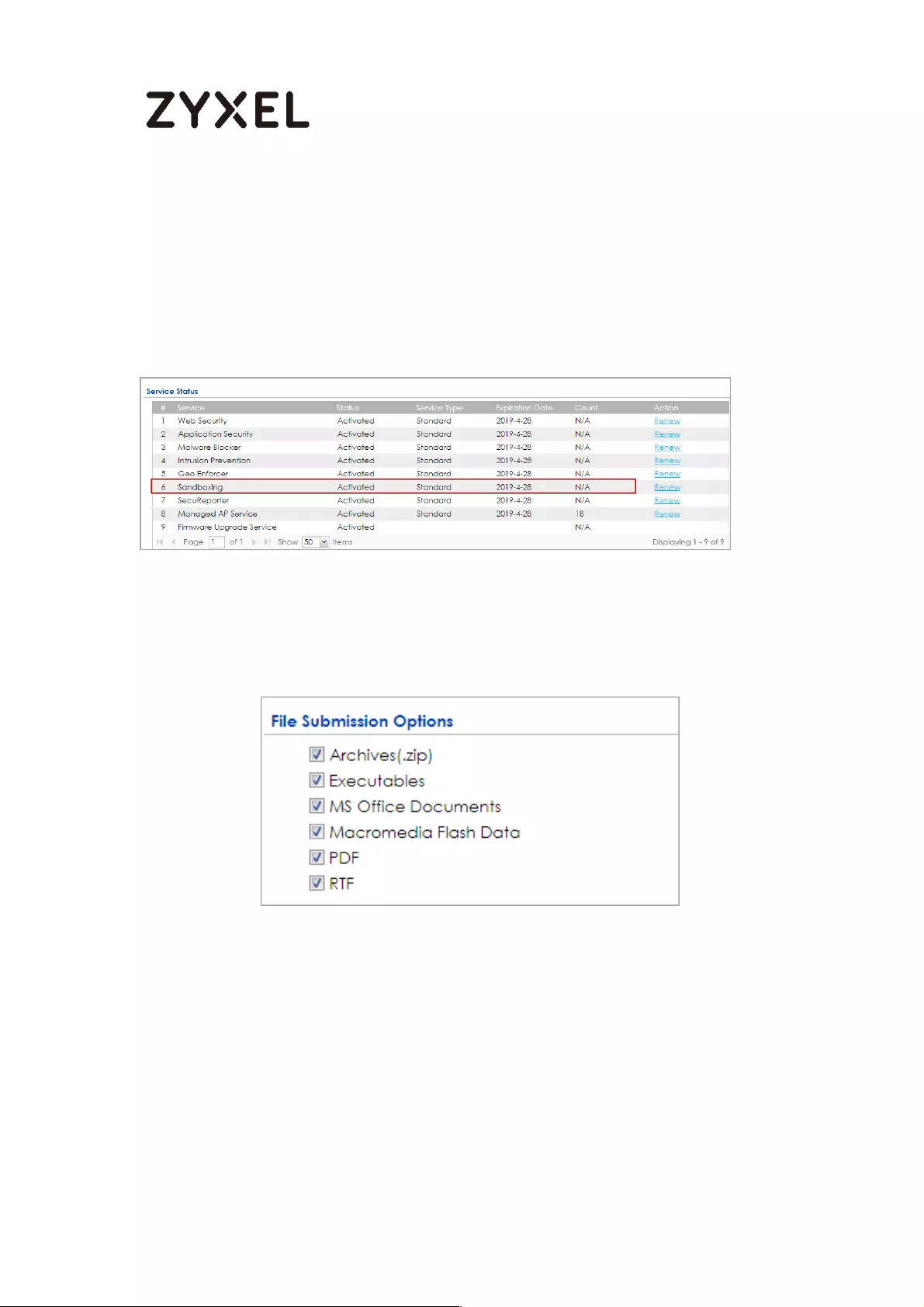
571/782
www.zyxel.com
Set Up Sandboxing on ATP
1. Register the device to myZyxel.com.
2. Activate Sandboxing license.
3. In the ATP, go to CONFIGURATION > Security Service > Sandboxing >
File Submission Options, the default supported file types are listed.
Use the command to check the status of each file type. If the
status is “no”, the file type is not scanned by Sandboxing.
Router> show sandbox file-type all
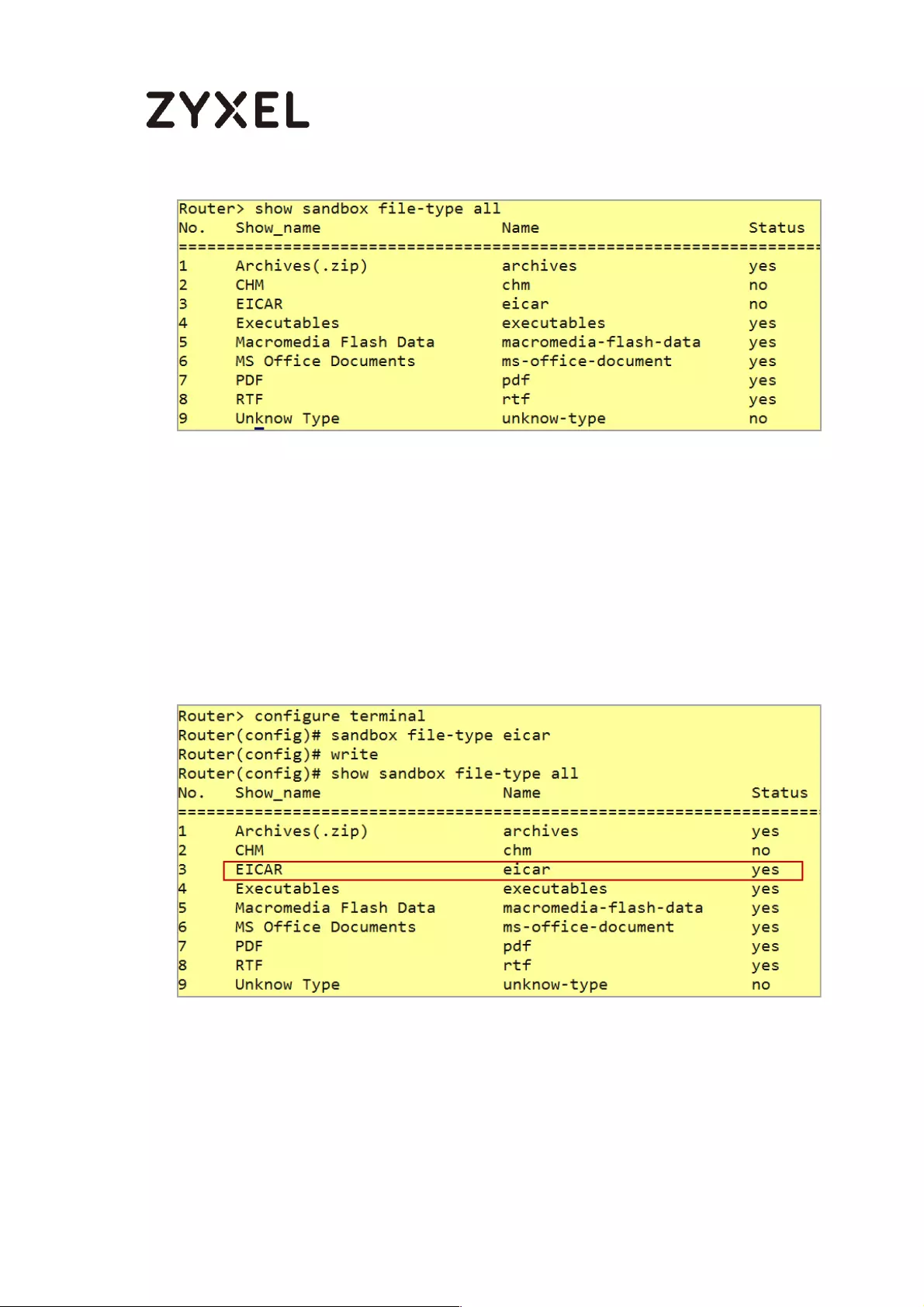
572/782
www.zyxel.com
Use the following commands to make Sandboxing access and
check a certain file type.
Router> configure terminal
Router(config)# sandbox file-type eicar
Router(config)# write
4. Go to CONFIGURATION > Security Service > Sandboxing > General,
enable Sandboxing and select action and log for malicious and
suspicious files to monitor the result.
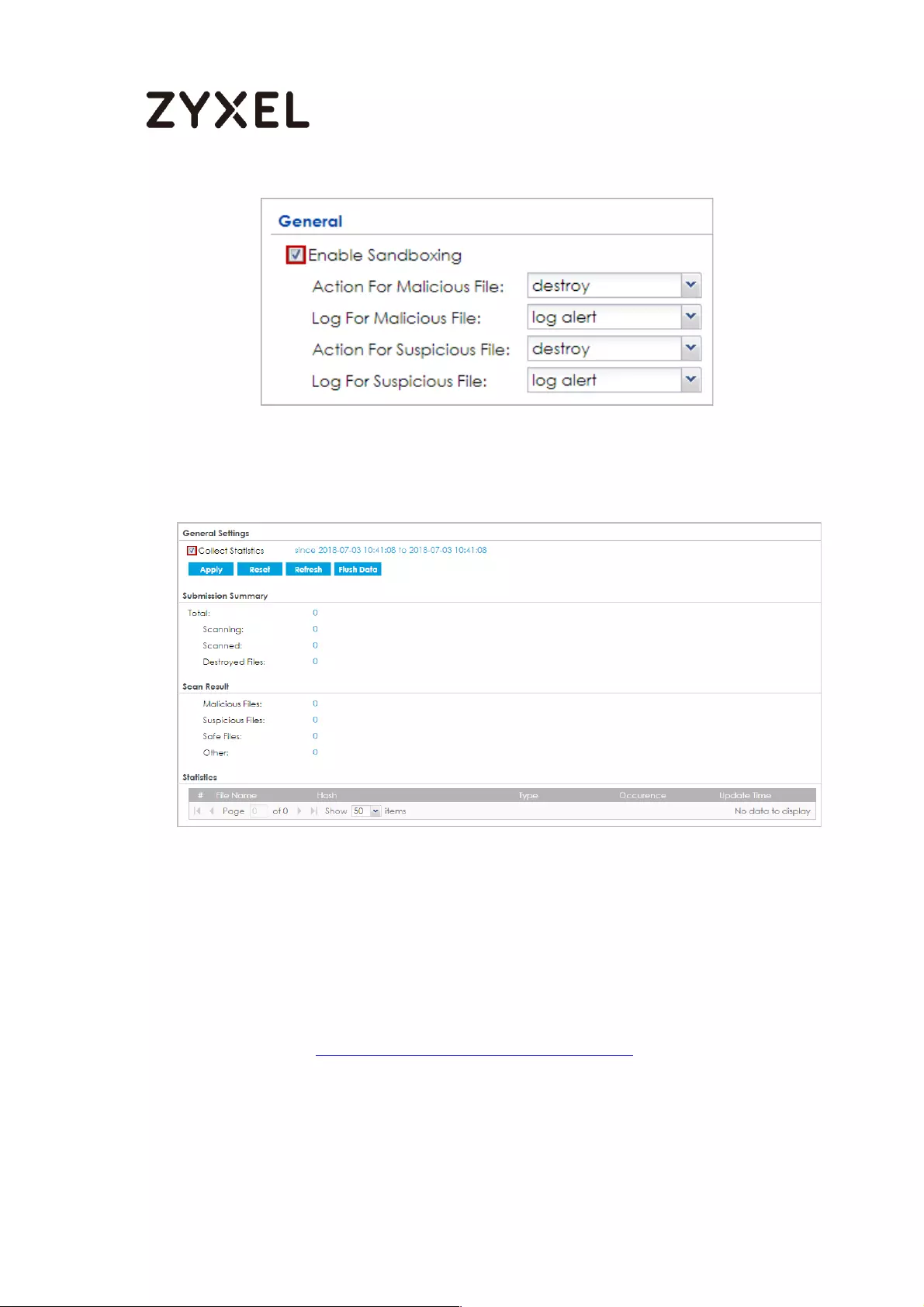
573/782
www.zyxel.com
5. Enable Collect Statistics to monitor the scan results and statistics.
MONITOR > Security Statistics > Sandboxing
Test the Result
4 Go to http://www.eicar.org/85-0-Download.html to download
eicar_com.zip file.
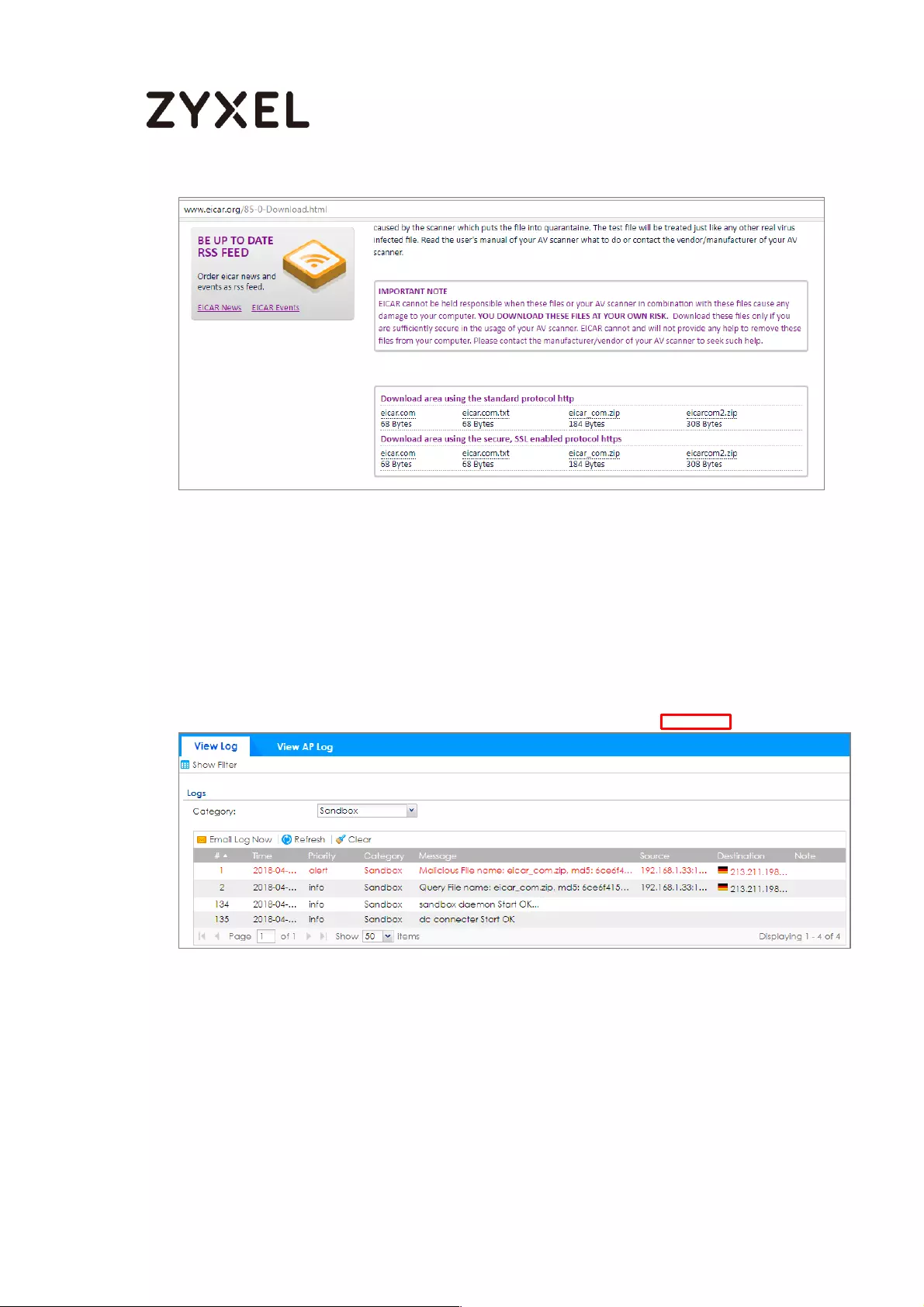
574/782
www.zyxel.com
5 When you download eicar_com.zip for the first time, it is
considered to be an unknown malware. The file is allowed to pass
and a copy of eicar_com.zip will be sent to Sandbox for further
scan.
MONITOR > Log > View Log > Sandboxing
The eicar_com.zip file is detected by Sandbox as a malicious file.
MONITOR > Security Statistics > Sandboxing
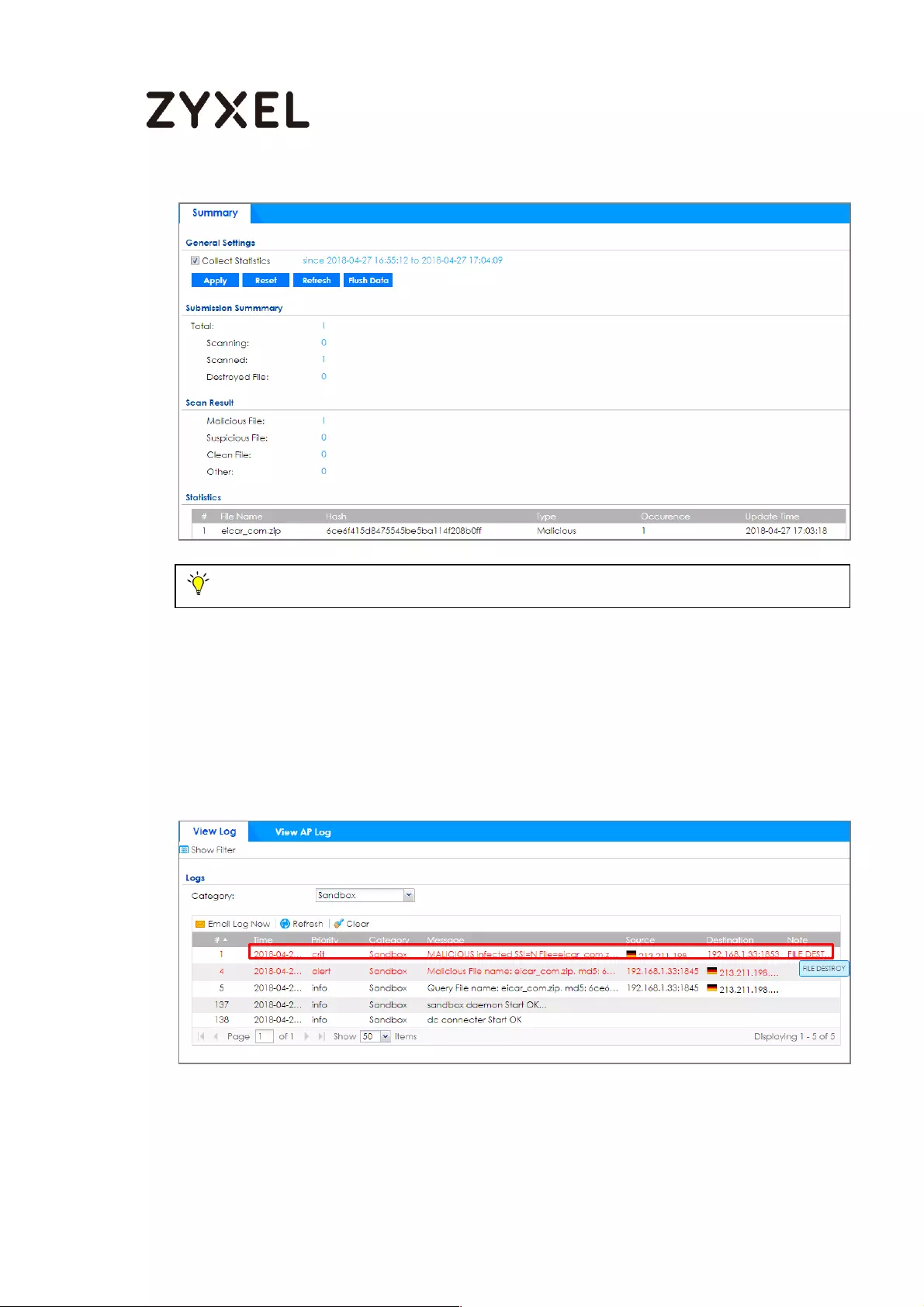
575/782
www.zyxel.com
6 Download eicar_com.zip file again. ZyWALL ATP destroyed the
eicar_com.zip file at the second time when you download the
file and generate the log.
MONITOR > Log > View Log > Sandboxing
MONITOR > Security Statistics > Sandboxing
Note: Disable anti-virus software on your laptop in order to test Sandbox.

576/782
www.zyxel.com
What Can Go Wrong?
7 SSL inspection needs to be enabled and applied to the
corresponding security policy rule for HTTPS traffic.
8 Only Windows (Win XP, Win 7, Win 10) and Mac OSX operating
system are supported.
9 The local cache of the analysis result will be deleted when the
device reboots.
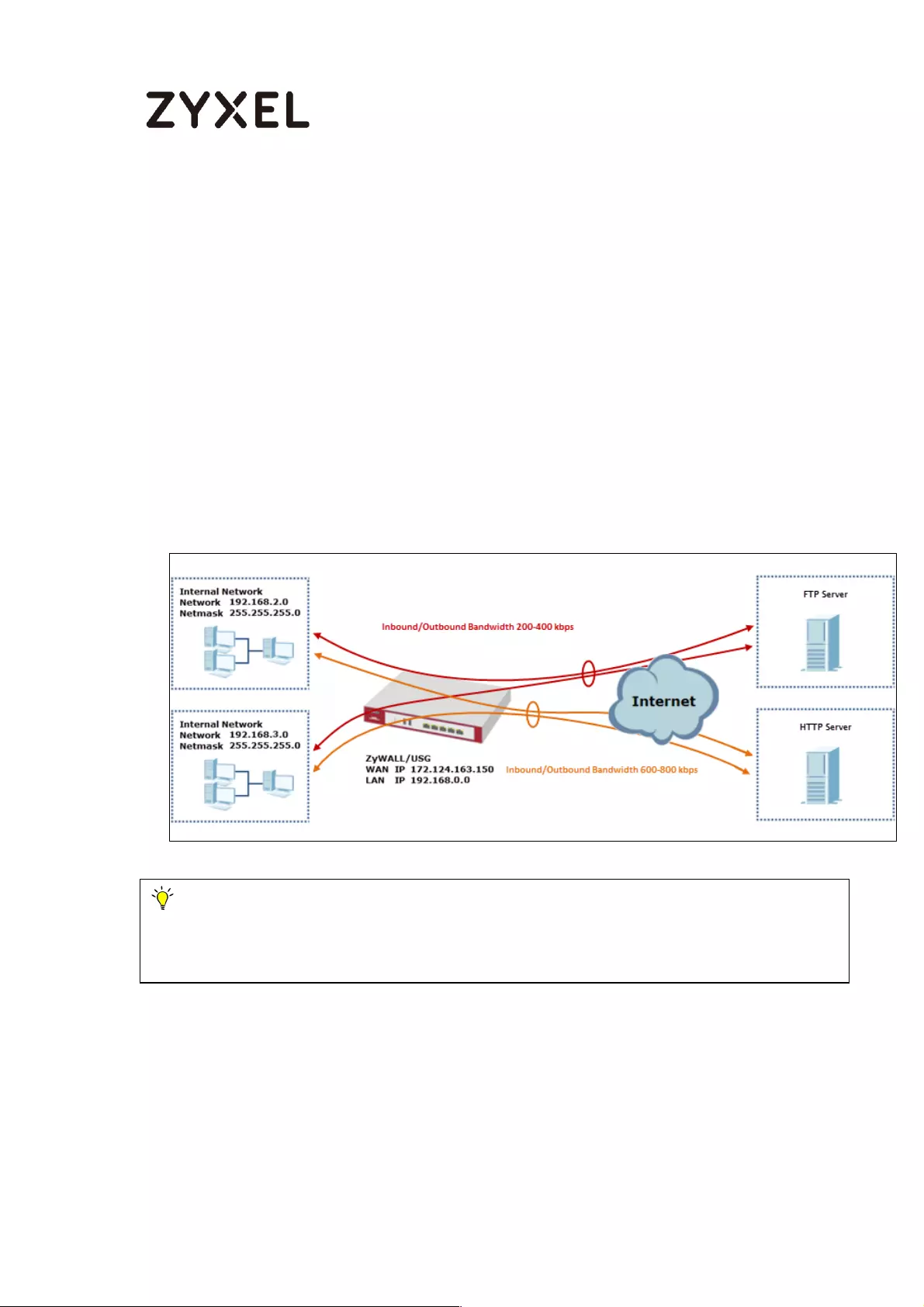
577/782
www.zyxel.com
How to Configure Bandwidth Management for FTP and HTTP
Traffic
This is an example of using ZyWALL/USG Bandwidth Management (BWM) to
control the bandwidth allocation for FTP and HTTP traffic. You can use source
interface, destination interface, destination port, schedule, user, source,
destination information, DSCP code and service type as criteria to create a
sequence of specific conditions to allocate bandwidth for the matching
packets. When the BWM is configured, you can limit bandwidth consuming
services, such as FTP, while providing consistent HTTP service with bandwidth
guarantees.
ZyWALL/USG with Bandwidth Management for HTTP and FTP Traffic Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. The total
available bandwidth assumption is 1,600 kbps. This example was tested using USG310
(Firmware Version: ZLD 4.25).

578/782
www.zyxel.com
Set Up the Bandwidth Management for FTP on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > Configuration > Add Policy,
select Enable and type FTP Any-to-WAN as the policy’s Description.
Leave the Incoming Interface to any and select the Outgoing Interface to be
wan1. Select Service Type to be the Service Object and select FTP from the list
box.
Set the Guaranteed Bandwidth Inbound to 200 (kbps) and set Priority 5 (low-to-
medium). Set the Maximum to 400 (kbps). Set the Guaranteed Bandwidth
Outbound to 200 (kbps) and set Priority 5. Set the Maximum to 400 (kbps).
In order to view the result later, set the Log setting to be log alert. Click OK to
return to the General screen.
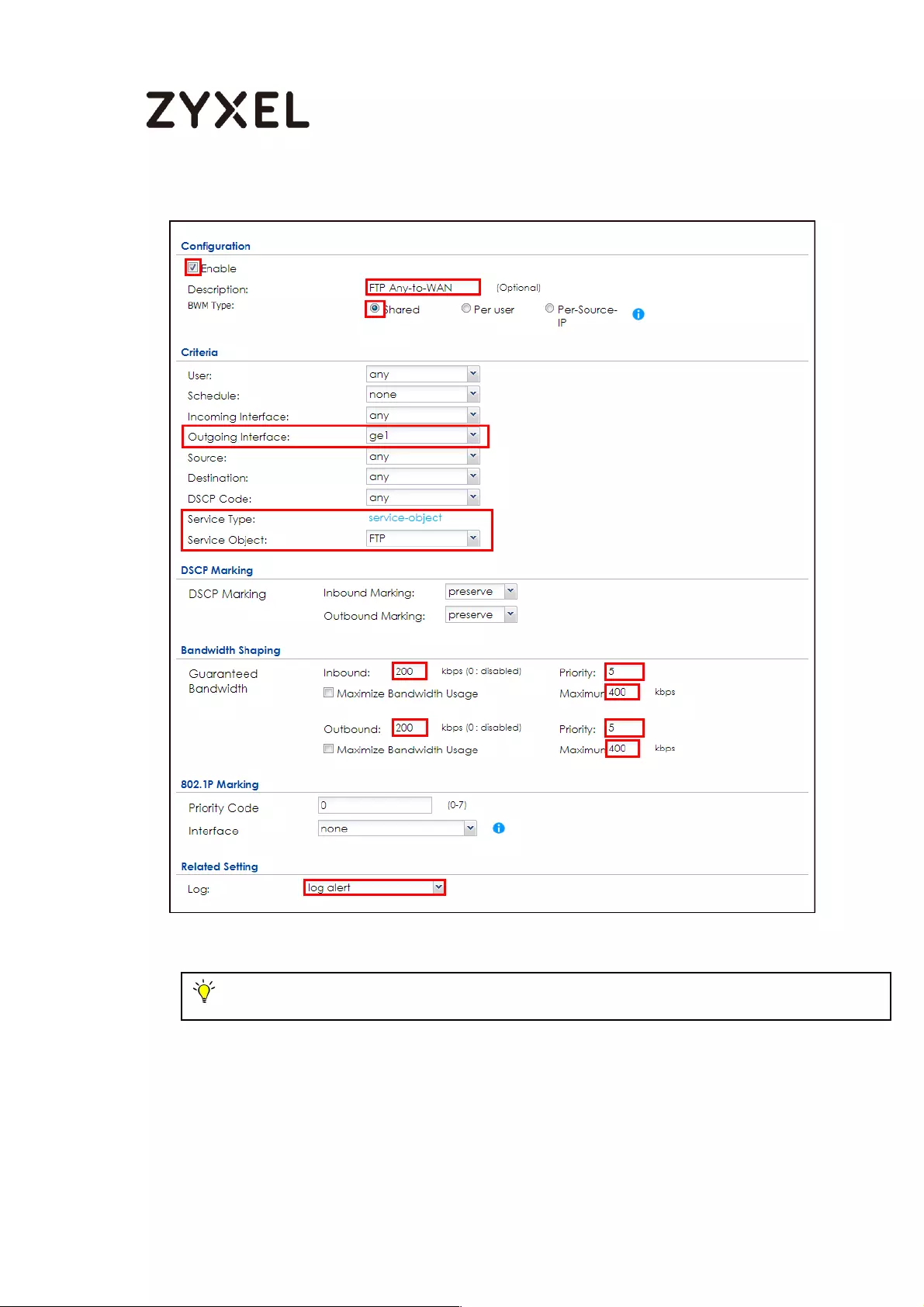
579/782
www.zyxel.com
CONFIGURATION > BWM > Configuration > Add Policy
Set Up the Bandwidth Management for HTTP on the
Note: In Bandwidth Management, the highest priority is (1) the lowest priority is (7).

580/782
www.zyxel.com
ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > Configuration > Add Policy,
select Enable and type HTTP Any-to-WAN as the policy’s Description (Optional).
Leave the Incoming Interface to any and select the Outgoing Interface to be
wan1. Select Service Type to be the Service Object and select HTTP from the list
box.
Set the Guaranteed Bandwidth Inbound to 600 (kbps) and set higher Priority 3. Set
the Maximum to 800 (kbps). Set the Guaranteed Bandwidth Outbound Priority 3.
In order to view the result later, set the Log setting to be log alert. Click OK to
return to the General screen.
CONFIGURATION > BWM > Configuration > Add Policy
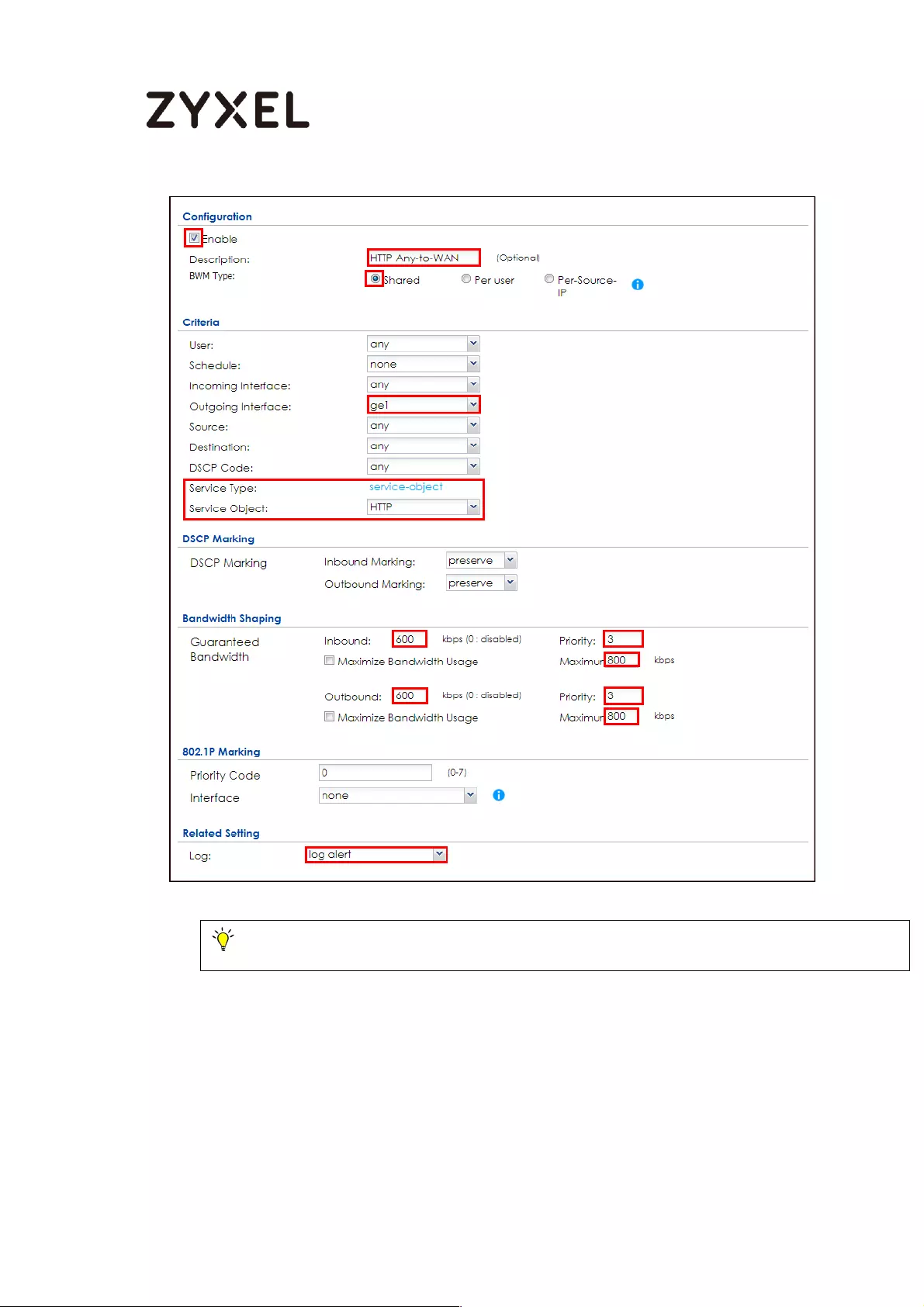
581/782
www.zyxel.com
Set Up the Bandwidth Management Global Setting on the
Note: In Bandwidth Management, the highest priority is (1) the lowest priority is (7).
582/782
www.zyxel.com
ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > BWM Global Setting, select
Enable.
CONFIGURATION > BWM > BWM Global Setting
Test the Result
Access the Internet to generate FTP traffic and HTTP traffic. In this example, a 123
MB file is downloading from an FTP server. The FTP file should download slowly.

583/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as
below.
Monitor > Log
What Could Go Wrong?
If the “outbound” in the guaranteed bandwidth settings apply to traffic going
from the connection initiator to the outgoing interface. “Inbound” refers to the
reverse direction.
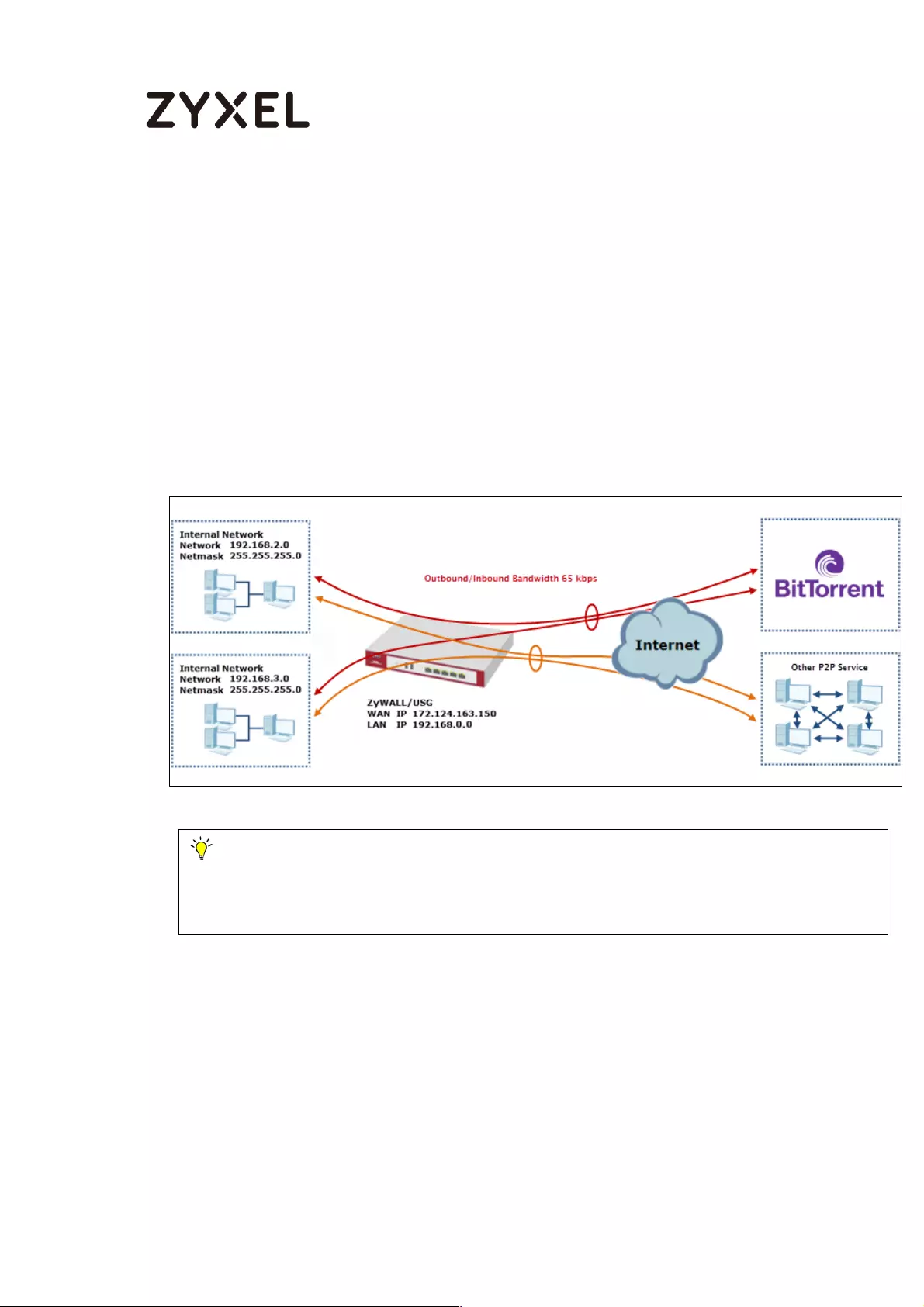
584/782
www.zyxel.com
How to Limit BitTorrent or Other Peer-to-Peer Traffic
This is an example of using ZyWALL/USG Bandwidth Management (BWM) to
control the bandwidth allocation for peer-to-peer traffic. You can use source
interface, destination interface, destination port, schedule, user, source,
destination information, DSCP code and service type as criteria to create a
sequence of specific conditions to allocate bandwidth for the matching
packets. When the BWM is configured, you can limit bandwidth consuming
Application traffic, such as Peer-to-Peer (P2P) service.
ZyWALL/USG with Bandwidth Management for Peer-to-Peer Traffic Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. The total
available bandwidth assumption is 1,600 kbps. This example was tested using USG310
(Firmware Version: ZLD 4.25).
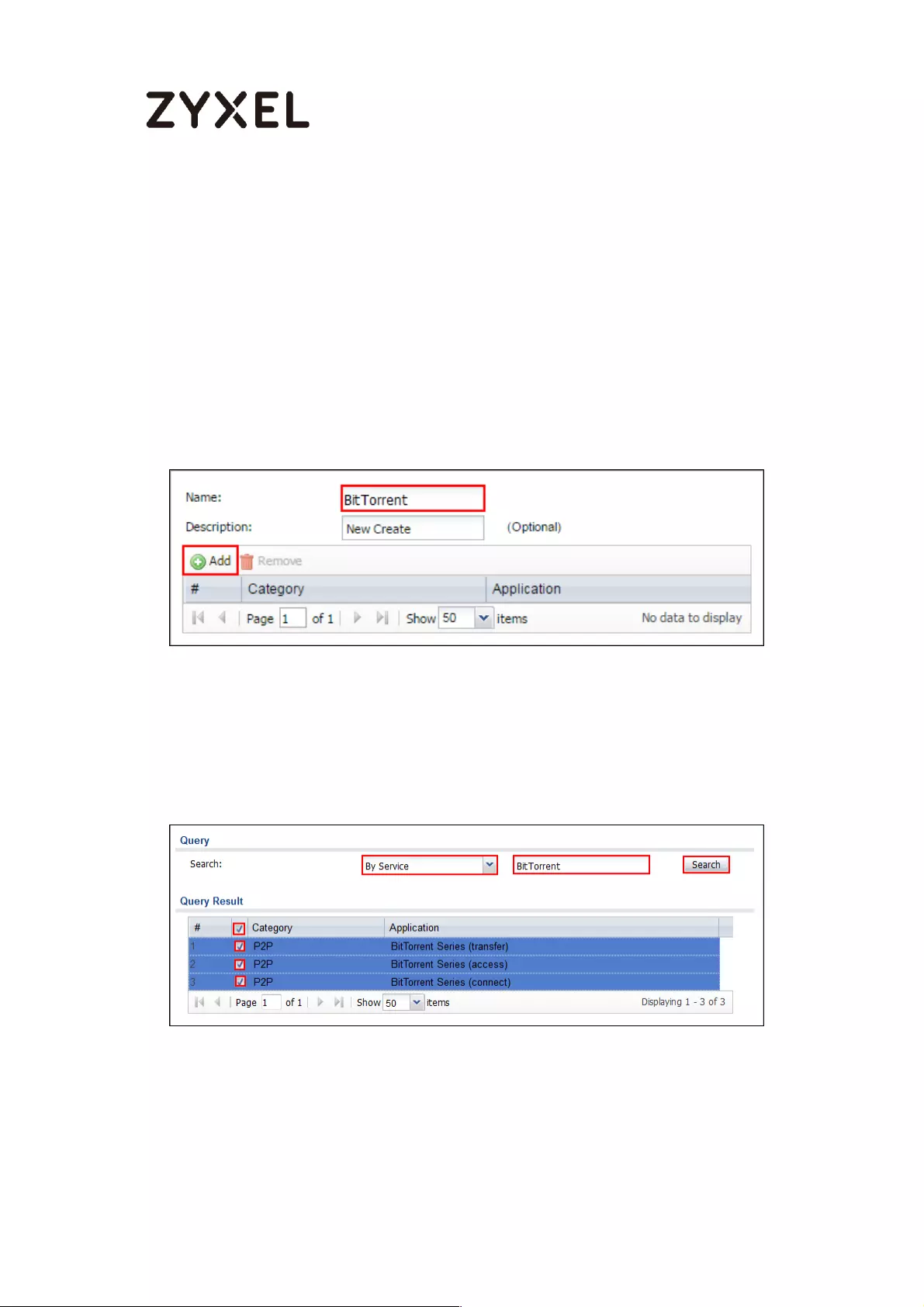
585/782
www.zyxel.com
Set Up the Application Patrol Profile on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Object > Application > Add
Application Rule. Configure a Name for you to identify the Application Profile.
Then, click Add to create an Application Object.
CONFIGURATION > Object > Application > Add Application Rule
In the Application Object, select By Service, type a keyword and click Search to
display all signatures containing that keyword. Select all Query Result and Click
OK.
CONFIGURATION > Object > Application > Add Application Rule > Add
Application Object

586/782
www.zyxel.com
Set Up the Bandwidth Management for BitTorrent on the
ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > Configuration > Add Policy,
select Enable and type BitTorrent Any-to-Any as the policy’s Description.
Leave the Incoming Interface to any and select the Outgoing Interface to be
wan1. Select Service Type to be the Service Object and select BitTorrent from the
list box.
Set the Guaranteed Bandwidth Inbound to 65 (kbps) and set Priority 5 (low-to-
medium). Set the Maximum to 512(kbps). Set the Guaranteed Bandwidth
Outbound to 65 (kbps) and set Priority 5. Set the Maximum to 512 (kbps). Click OK
to return to the General screen.
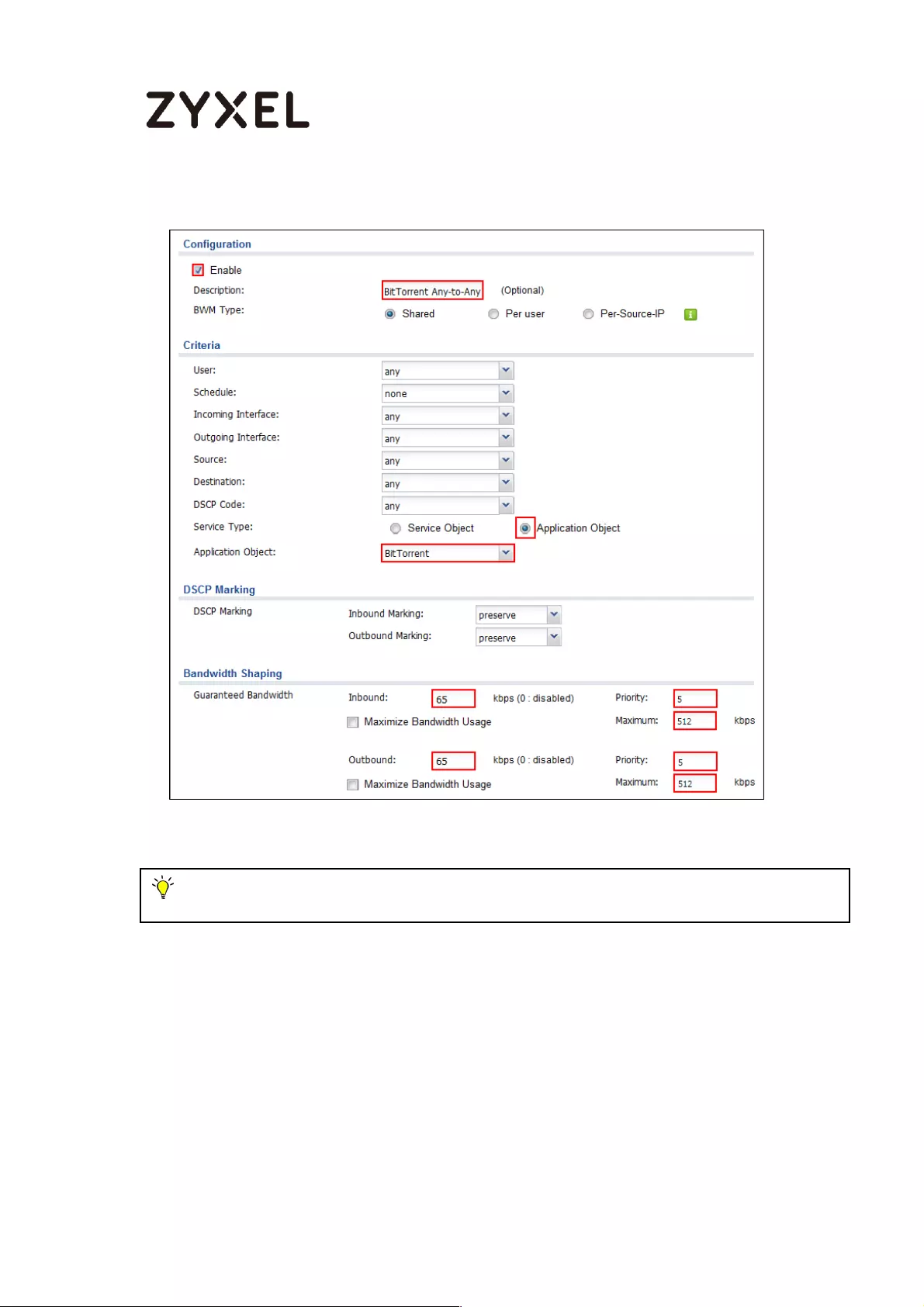
587/782
www.zyxel.com
CONFIGURATION > BWM > Configuration > Add Policy
Note: In Bandwidth Management, the highest priority is (1) the lowest priority is (7).
588/782
www.zyxel.com
Set Up the Bandwidth Management Global Setting on the
ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > BWM Global Setting, select
Enable.
CONFIGURATION > BWM > BWM Global Setting
Test the Result
Download BitTorrent application for testing the result:
http://www.bittorrent.com/downloads
In this example, an 826 MB file is downloading, the Down Speed limited to
maximum 65 kB/s.
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as
below.
Monitor > Log
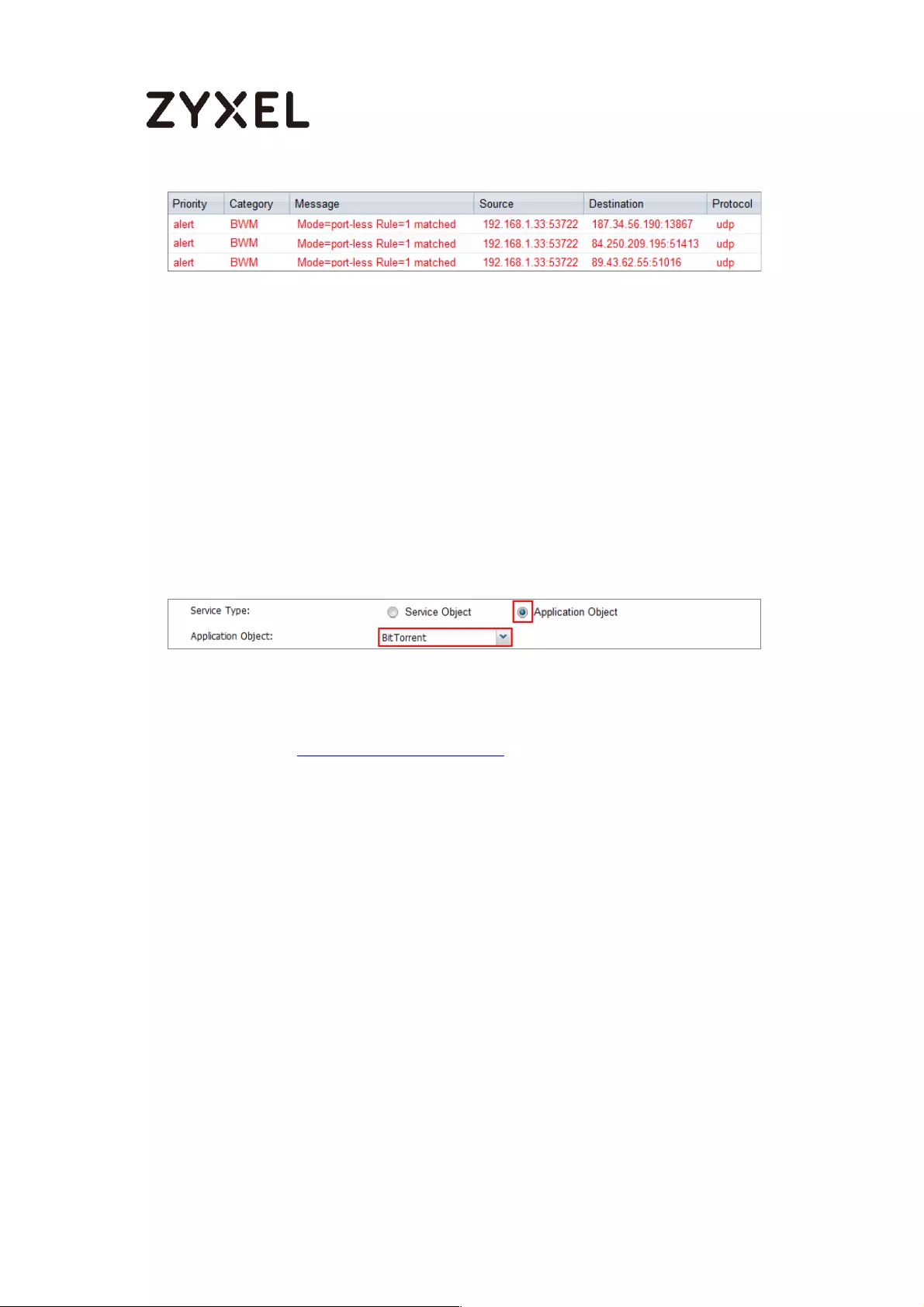
589/782
www.zyxel.com
What Could Go Wrong?
If the “outbound” in the guaranteed bandwidth settings apply to traffic going
from the connection initiator to the outgoing interface. “Inbound” refers to the
reverse direction.
Make sure you have registered the Application Patrol service on the ZyWALL/USG
to use Application Object as the Service Type in the bandwidth management
rules.
You can click the link from the CONFIGURATION > Licensing > Registration screen
of your ZyXEL device’s Web Configurator or click the myZyXEL.com 2.0 icon from
the portal page (https://portal.myzyxel.com/) to register or extend your
Application Patrol license.
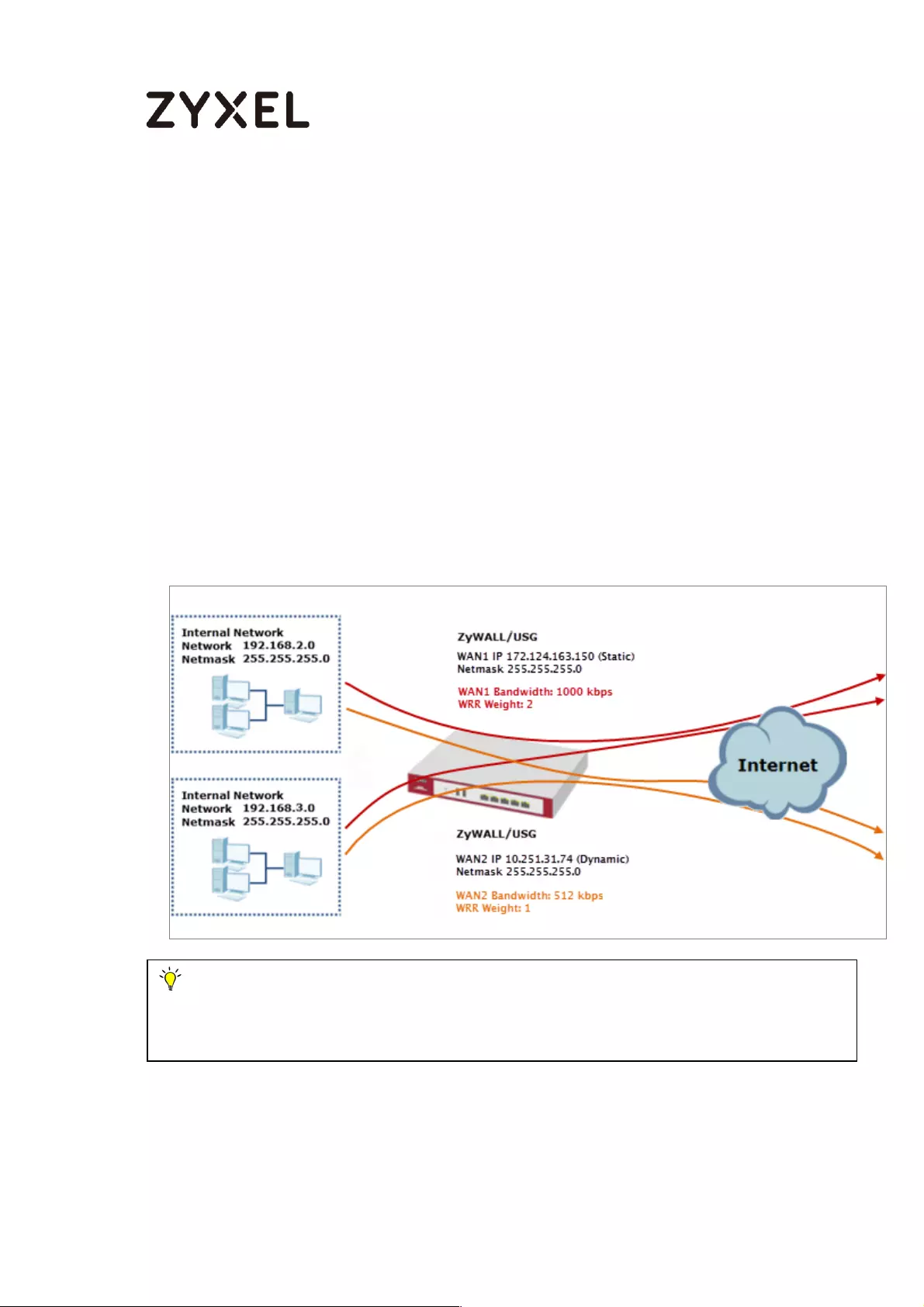
590/782
www.zyxel.com
How to Configure a Trunk for WAN Load Balancing with a
Static or Dynamic IP Address
This is an example of using ZyWALL/USG Trunk for two WAN connections to the
Internet. The available bandwidth for the connections is 1000 kbps (wan1 with
static IP address) and 512 Kbps (wan2 with dynamic IP address) respectively. As
these connections have different bandwidths, we will use the Weighted Round
Robin (WRR) algorithm to send traffic to wan1 and wan2 in a 2:1 ratio.
ZyWALL/USG with WAN Load Balancing Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
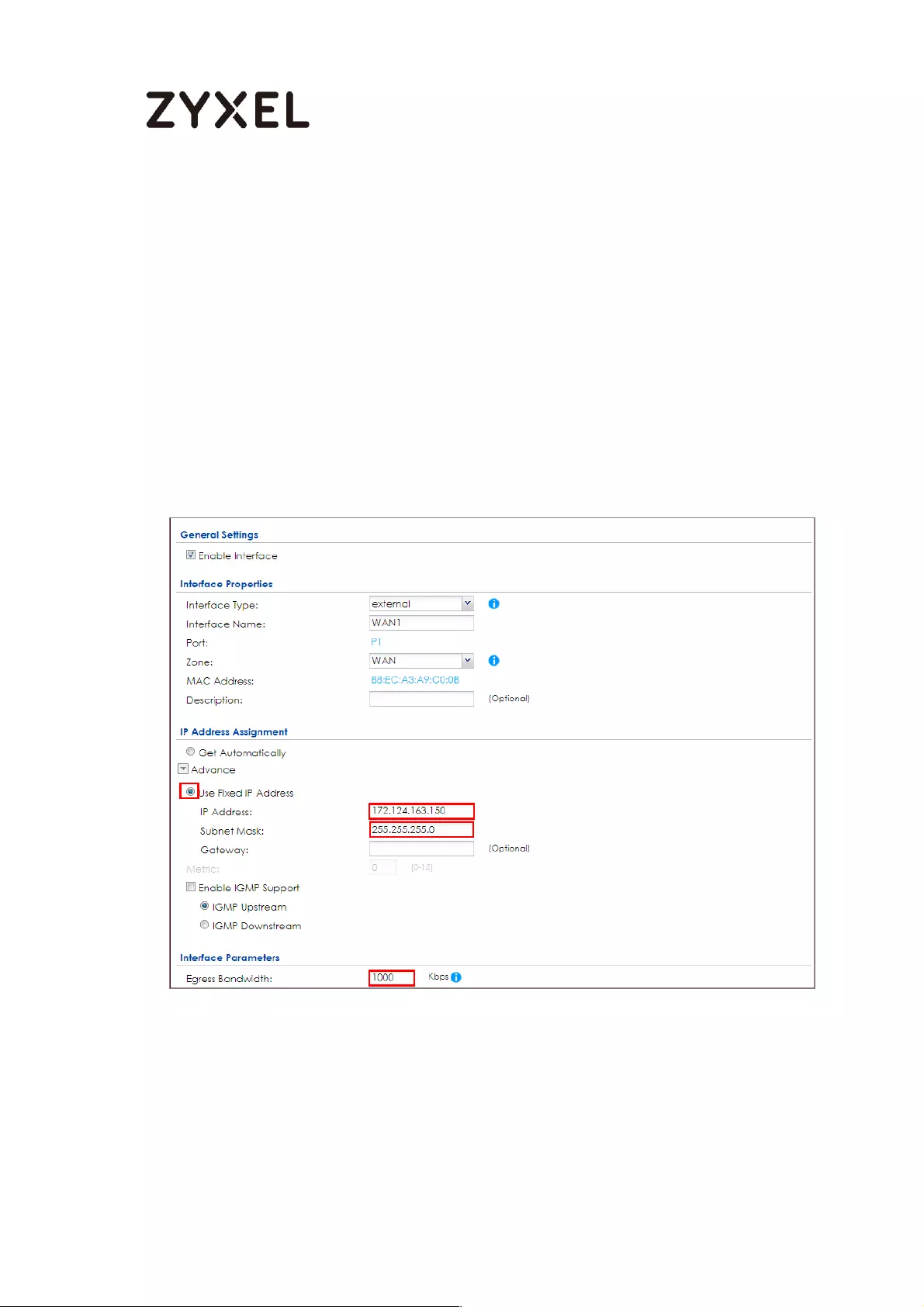
591/782
www.zyxel.com
Set Up the Available Bandwidth on WAN1 Interfaces on the
ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Interface > Ethernet > WAN1 > Egress
Bandwidth and enter the available bandwidth (1000 kbps) in the Egress
Bandwidth field. Click OK.
CONFIGURATION > Interface > Ethernet > WAN1
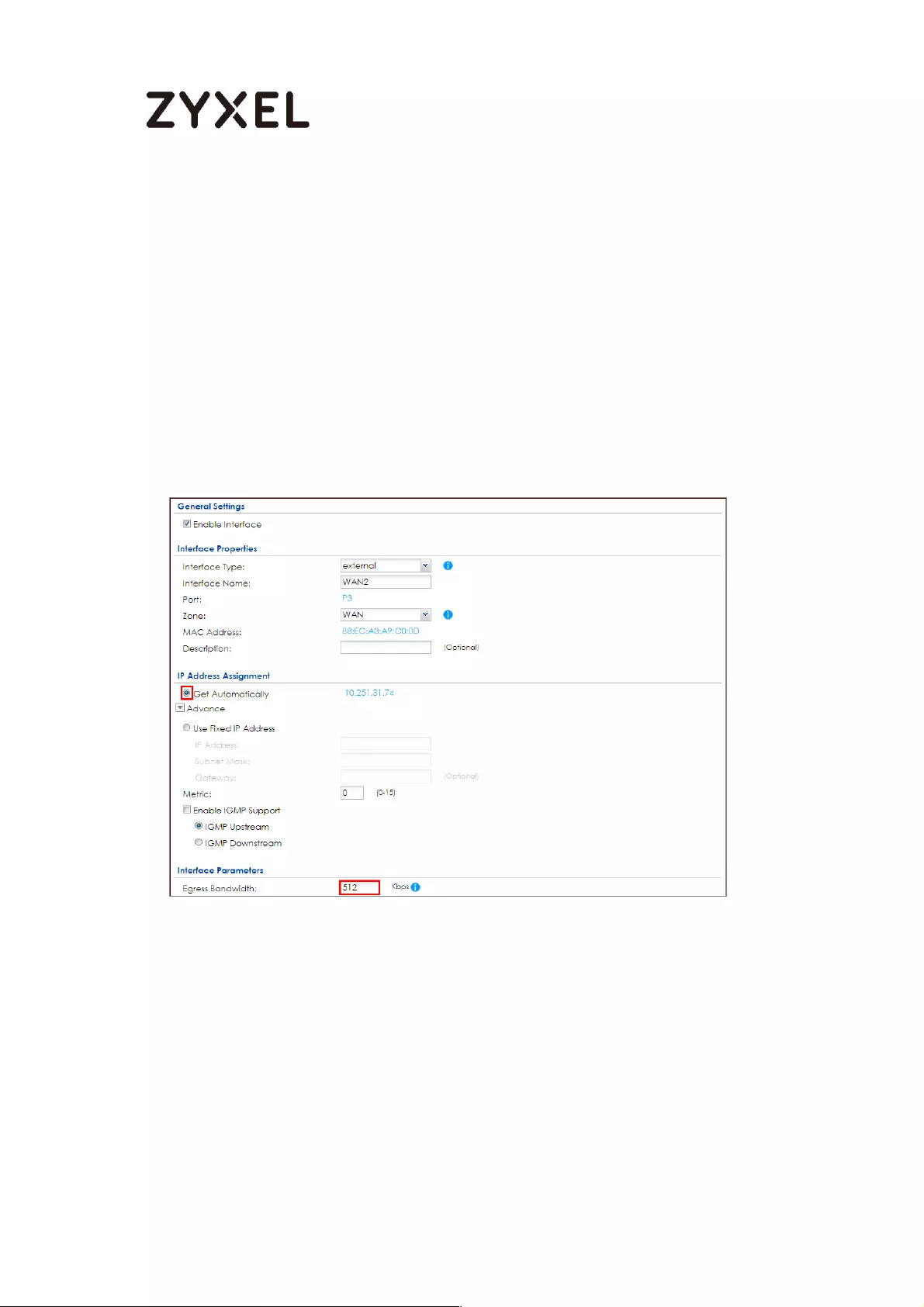
592/782
www.zyxel.com
Set Up the Available Bandwidth on WAN2 Interfaces on the
ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Interface > Ethernet > WAN2 > Egress
Bandwidth and enter the available bandwidth (512 kbps) in the Egress Bandwidth
field. Click OK.
CONFIGURATION > Interface > Ethernet > WAN2
Set Up the WAN Trunk on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Interface > Trunk > User
Configuration > Add Trunk. Configure a Name for you to identify the Trunk profile
and set the Load Balancing Algorithm field to be the Weighted Round Robin.
Add WAN1 and enter 2 in the Weight column. Add WAN2 and enter 1 in the
Weight column. Click OK to return to the Configuration screen.

593/782
www.zyxel.com
CONFIGURATION > Interface > Trunk > User Configuration > Add Trunk
In the Configuration screen, go to Default WAN Trunk section, select User
Configured Trunk and select the newly created Trunk from the list box. Click
Apply.
CONFIGURATION > Interface > Trunk > Default WAN Trunk
Test the Result
Browse any website to test the result.
The Weighted Round Robin (WRR) algorithm is best suited for situations where the
bandwidths set for the two WAN interfaces are different. An interface with a
larger weight (WAN1) gets more chances to transmit traffic than an interface with
a smaller weight (WAN2).
MONITOR > Interface Summary > Interface Statistics
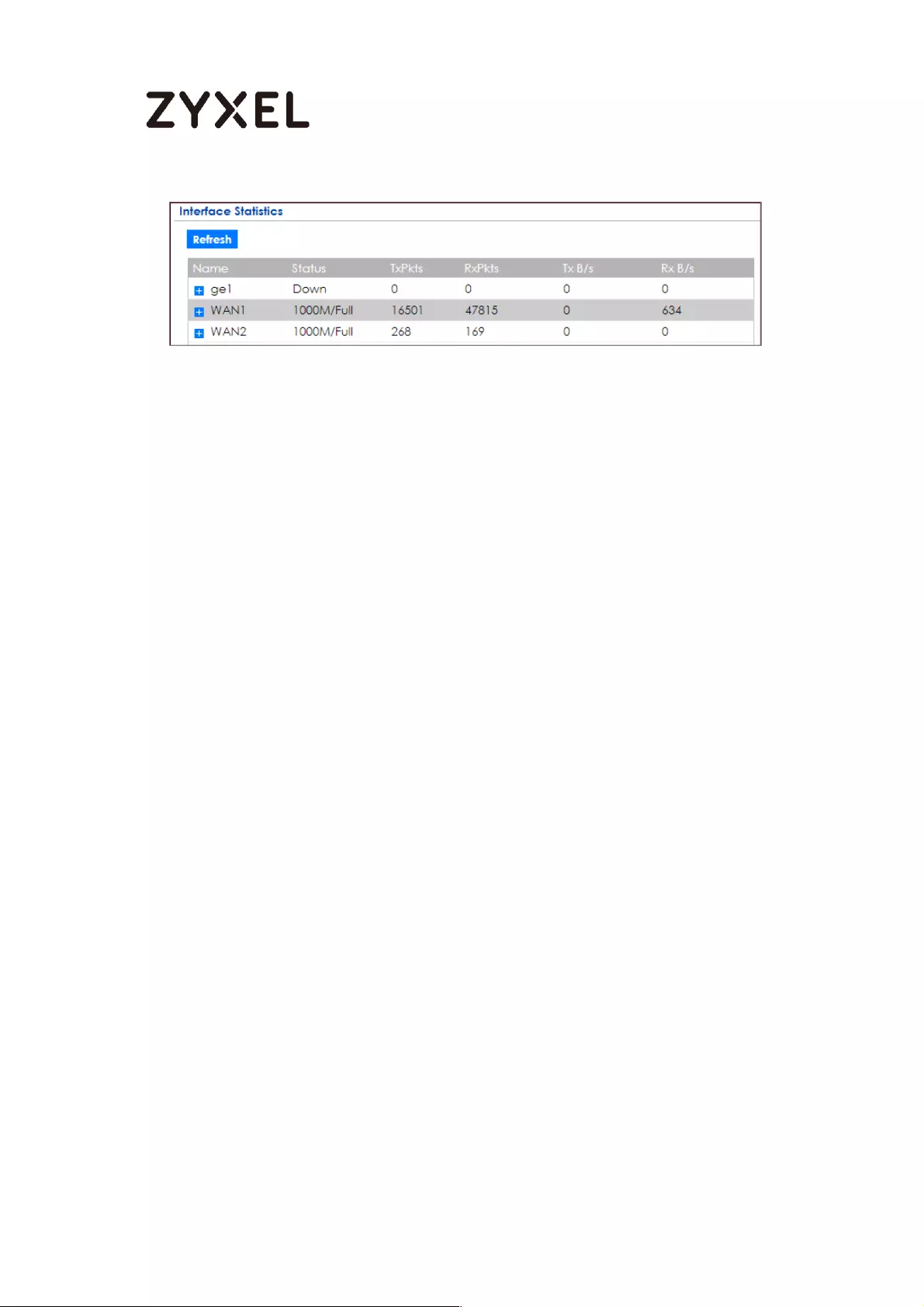
594/782
www.zyxel.com
What Could Go Wrong?
If there is no traffic passing through either WAN1 or WAN2 interfaces, check that
the Mode of both WAN1 & WAN2 should be Active. If a trunk is in Passive mode,
the ZyWALL/USG will use this connection only when all of the connections set to
Active mode are down.
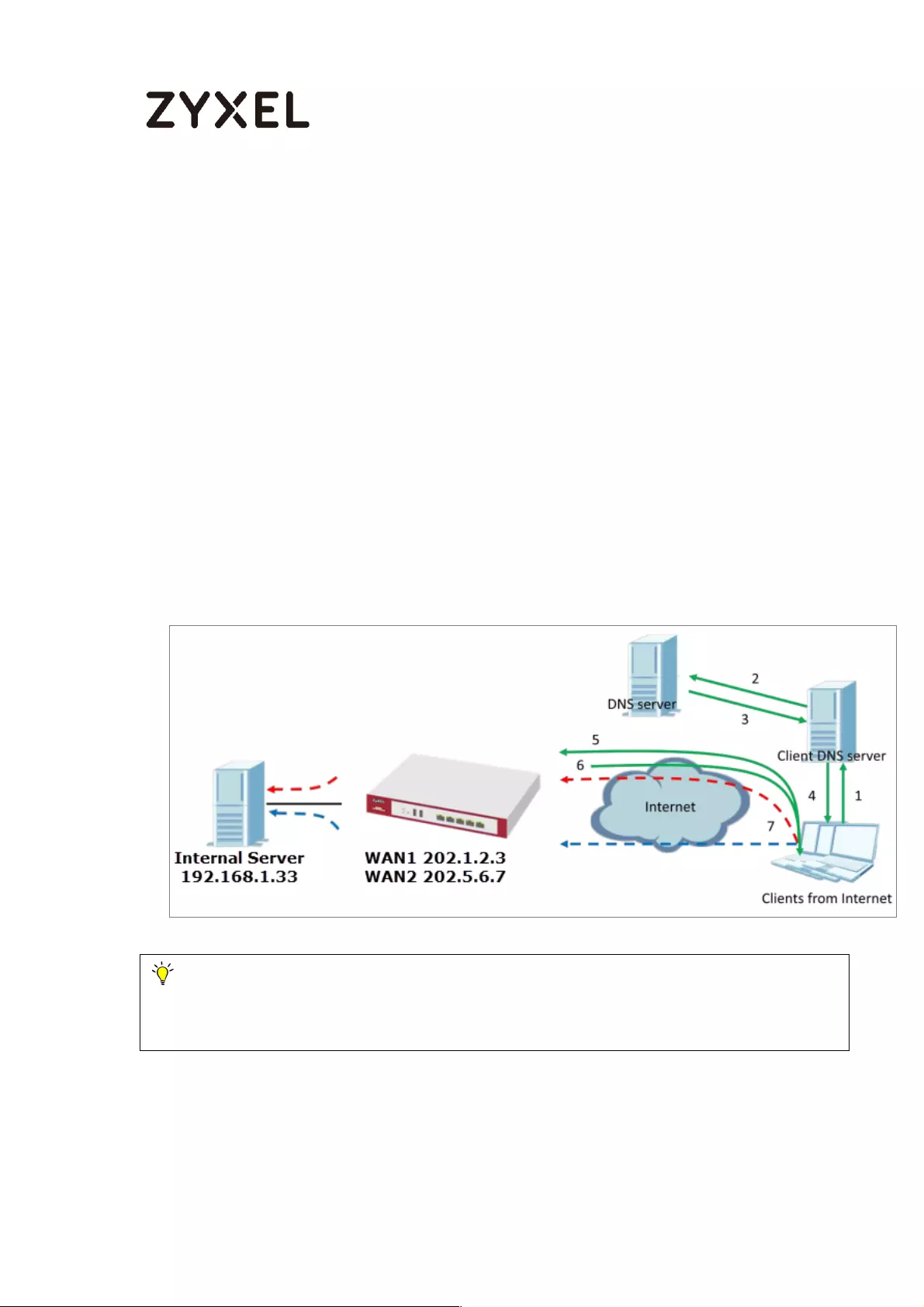
595/782
www.zyxel.com
How to Configure DNS Inbound Load Balancing to balance
DNS Queries Among Interfaces
This is an example of using the ZyWALL/USG dynamically responding to DNS
query messages with its least loaded interface’s IP address. The DNS query
senders will then transmit packets to that interface instead of an interface that
has a heavy load. This example assumes that your company’s domain name is
www.example.com. You want your ZyWALL/USG’s WAN1 (202.1.2.3) and WAN2
(202.5.6.7) to use DNS inbound load balancing to balance traffic loading coming
from the Internet.
ZyWALL/USG with DNS Inbound Load Balancing Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
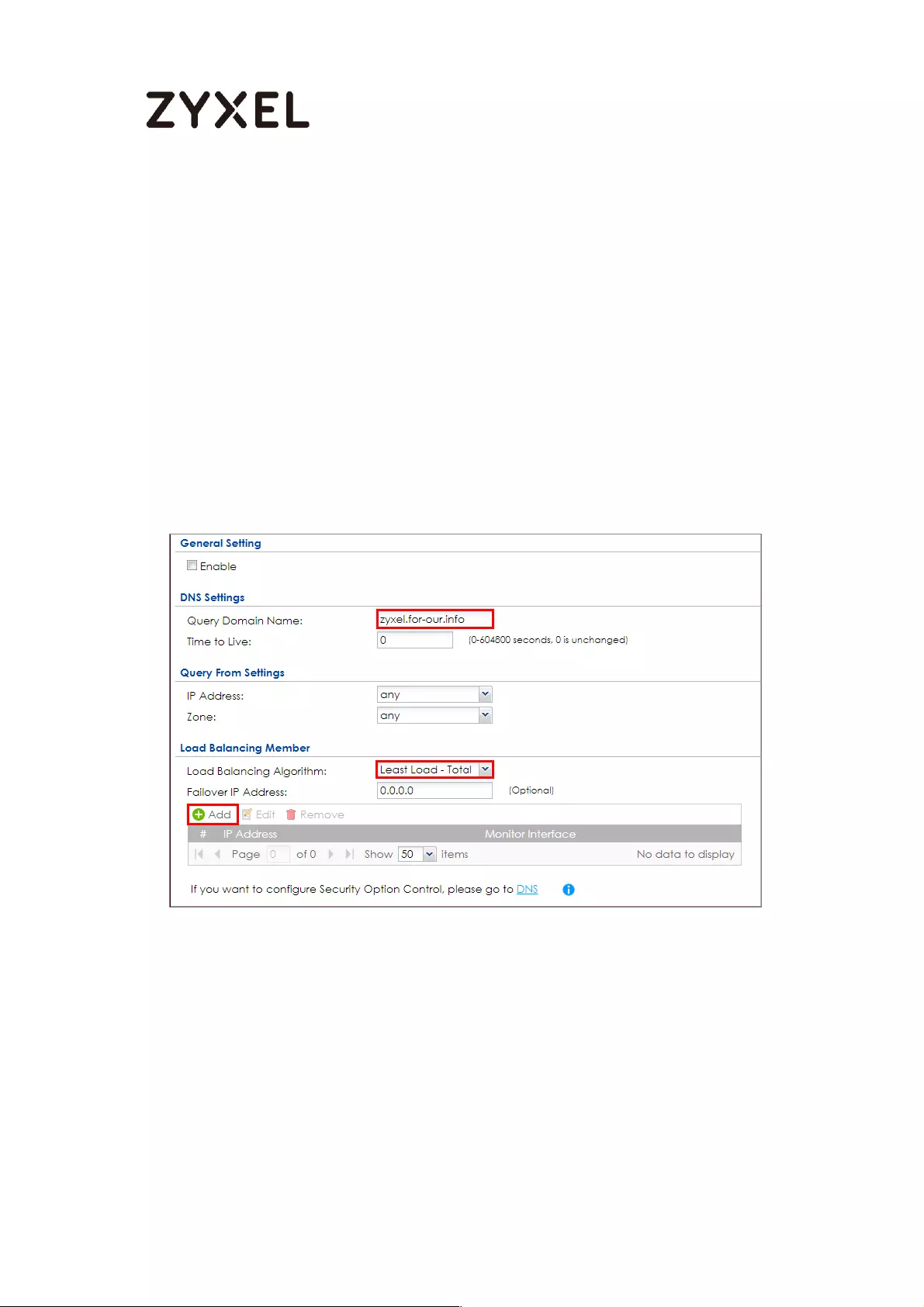
596/782
www.zyxel.com
Set Up the DNS Inbound Load Balancing on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > DNS Inbound LB. Edit the
Query Domain Name, set the Load Balancing Algorithm field to be the Least Load
- Total. Click Add to create a new Load Balancing Member.
CONFIGURATION > Network > DNS Inbound LB
CONFIGURATION > Network > DNS Inbound LB
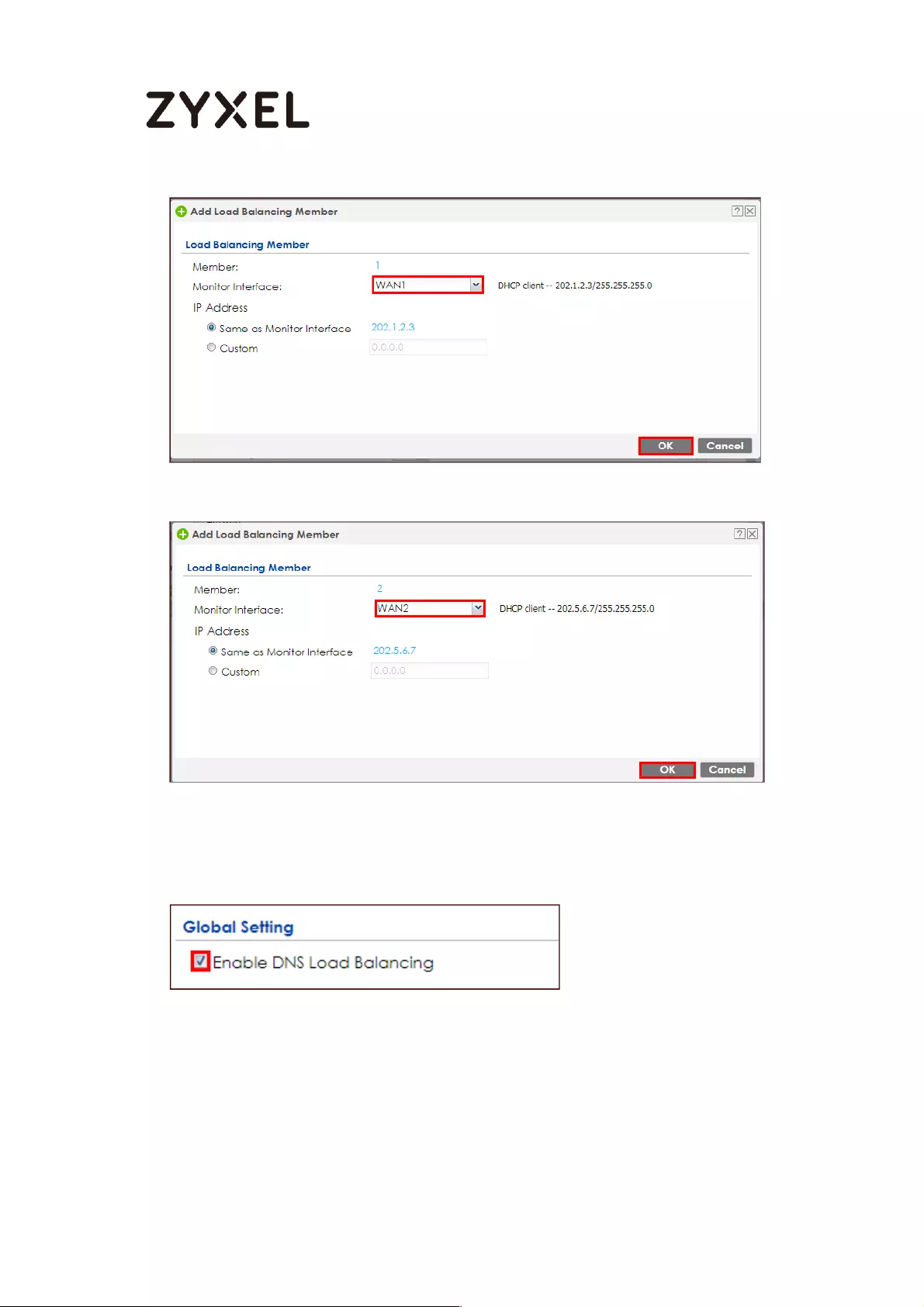
597/782
www.zyxel.com
CONFIGURATION > Network > DNS Inbound LB
Go to the Global Setting page to select Enable DNS Load Balancing.
CONFIGURATION > Network > DNS Inbound LB
Set Up the NAT Rule on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > NAT. Configure the Virtual

598/782
www.zyxel.com
Server to forward the traffic from WAN to Internal Server (192.168.1.33). Click OK.
CONFIGURATION > Network > NAT
Test the Result
Open the browser and query http://zyxel.for-our.info/.
599/782
www.zyxel.com
Create a Security Policy in order to view the testing result. Set Destination to be
the Internal Server IP address (192.168.1.33 in this example) and set Log type to be
the Log Alert.
Go to the ZyWALL/USG Monitor > Log, you will see [alert] log message such as
below. The Source Interface is the WAN1 or WAN2 interface which is handling the
least amount of outgoing and incoming traffic.
What Could Go Wrong?
If you cannot access the Internal Server, please check that the NAT configuration
matches the Internal Server IP address and Port number. If the NAT configuration is
correct, please check the system status of your Internal Server is up.
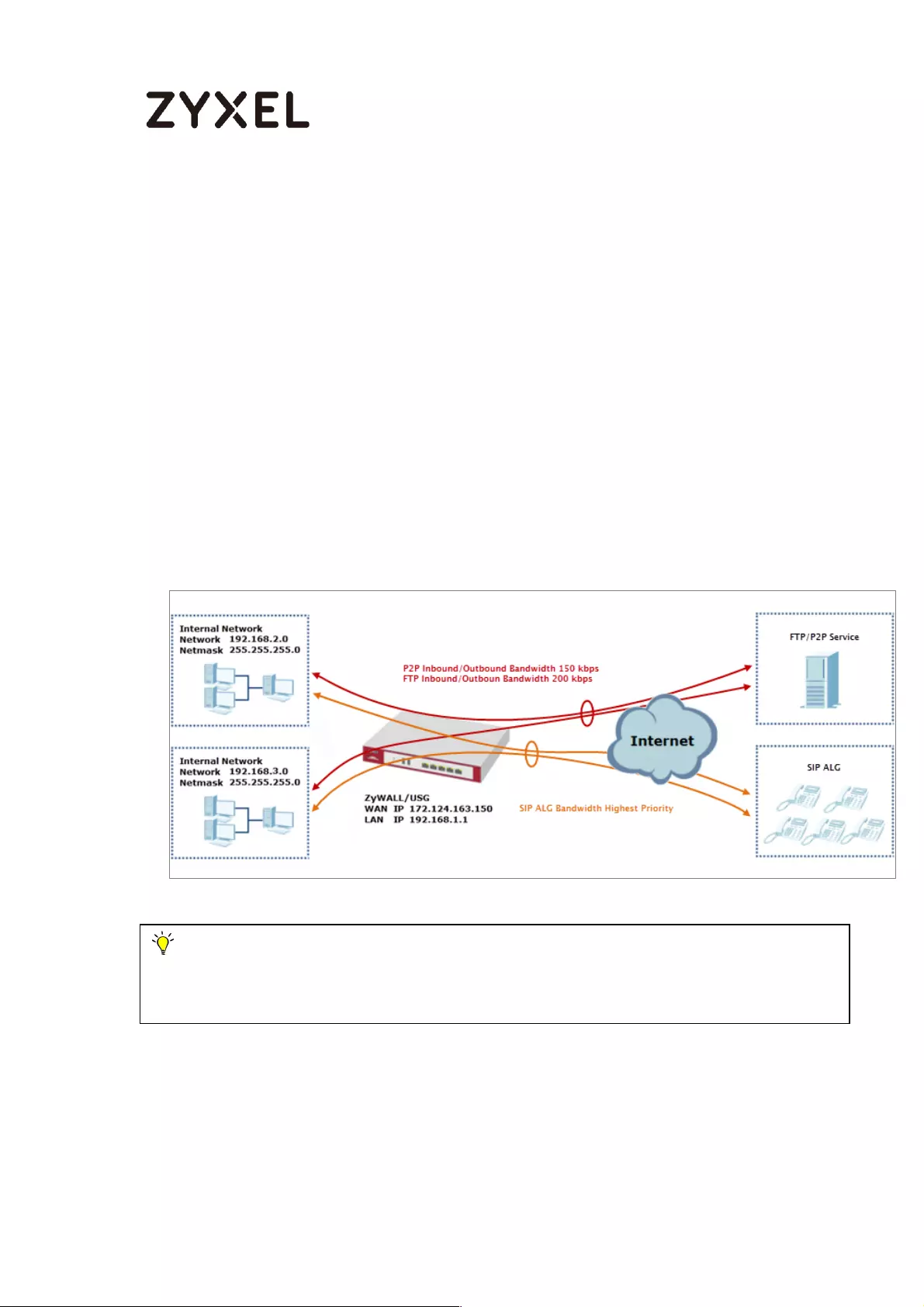
600/782
www.zyxel.com
How to Manage Voice Traffic
This is an example of using Application Layer Gateway (ALG) to allow the SIP
(Session Initiation Protocol) voice traffic through the ZyWALL/USG. To achieve
high-quality voice transmissions, use ZyWALL/USG provides Bandwidth
Management (BWM) function to effectively manage bandwidth according to
flexible criteria. You can limit bandwidth consuming services, such as Peer-to-
Peer (P2P) and FTP service while providing a higher priority and consistent
bandwidth for voice traffic.
ZyWALL/USG with Voice Traffic Management Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
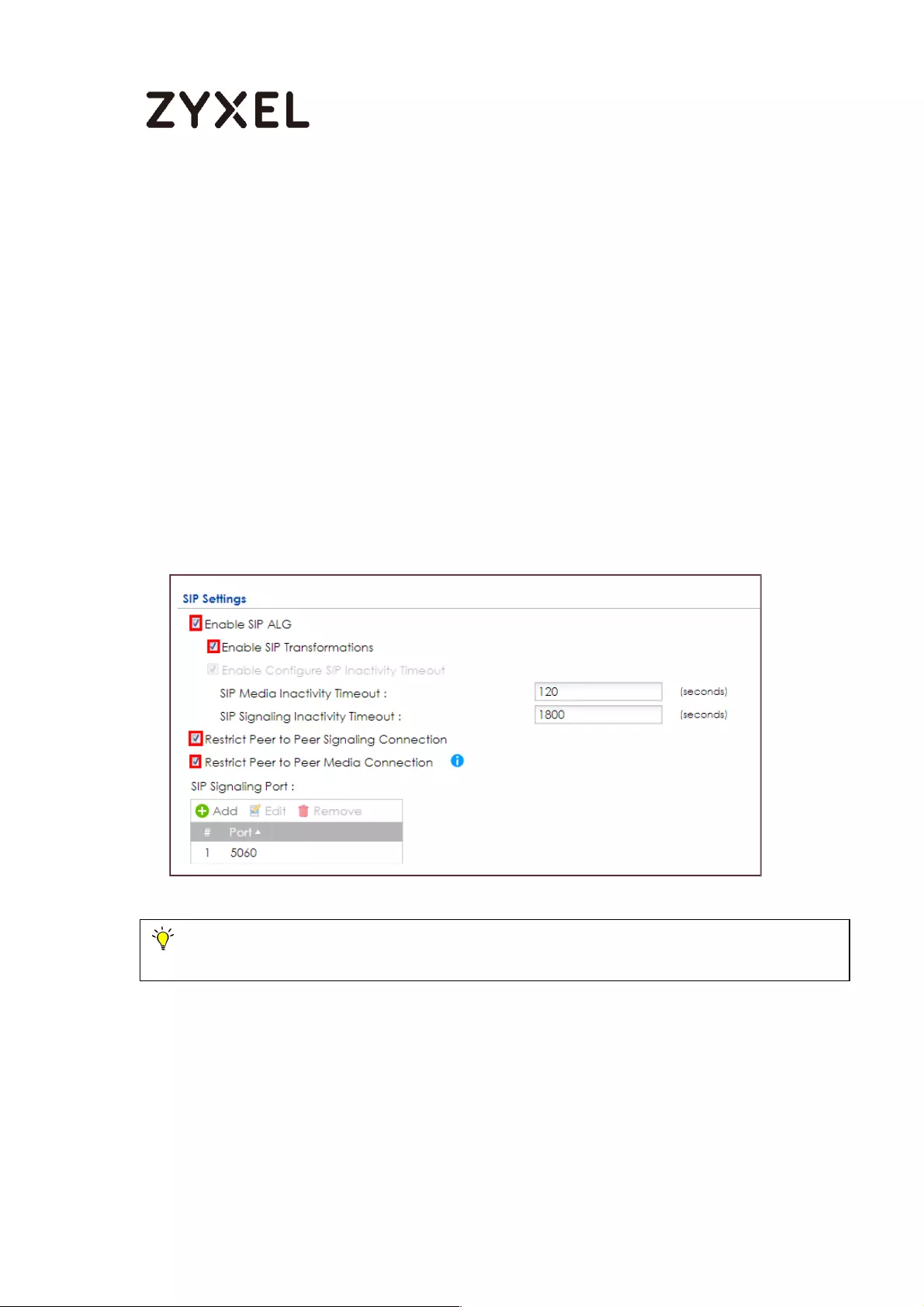
601/782
www.zyxel.com
Set Up the SIP ALG on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > SIP > SIP Settings, select
Enable SIP ALG, Enable SIP Transformations (optional), Restrict Peer to Peer
Signaling Connection and Restrict Peer to Peer Media Connection. Make sure the
SIP Signaling Port is configured the same as your VoIP phone SIP signaling port.
Click Apply.
CONFIGURATION > BWM > Configuration > Add Policy
Set Up the Bandwidth Management for SIP on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > BWM Global Settings, select
Note: If you are using a custom or additional UDP port number (not 5060) for SIP traffic,
use the Add icon to add SIP Signaling Port numbers.
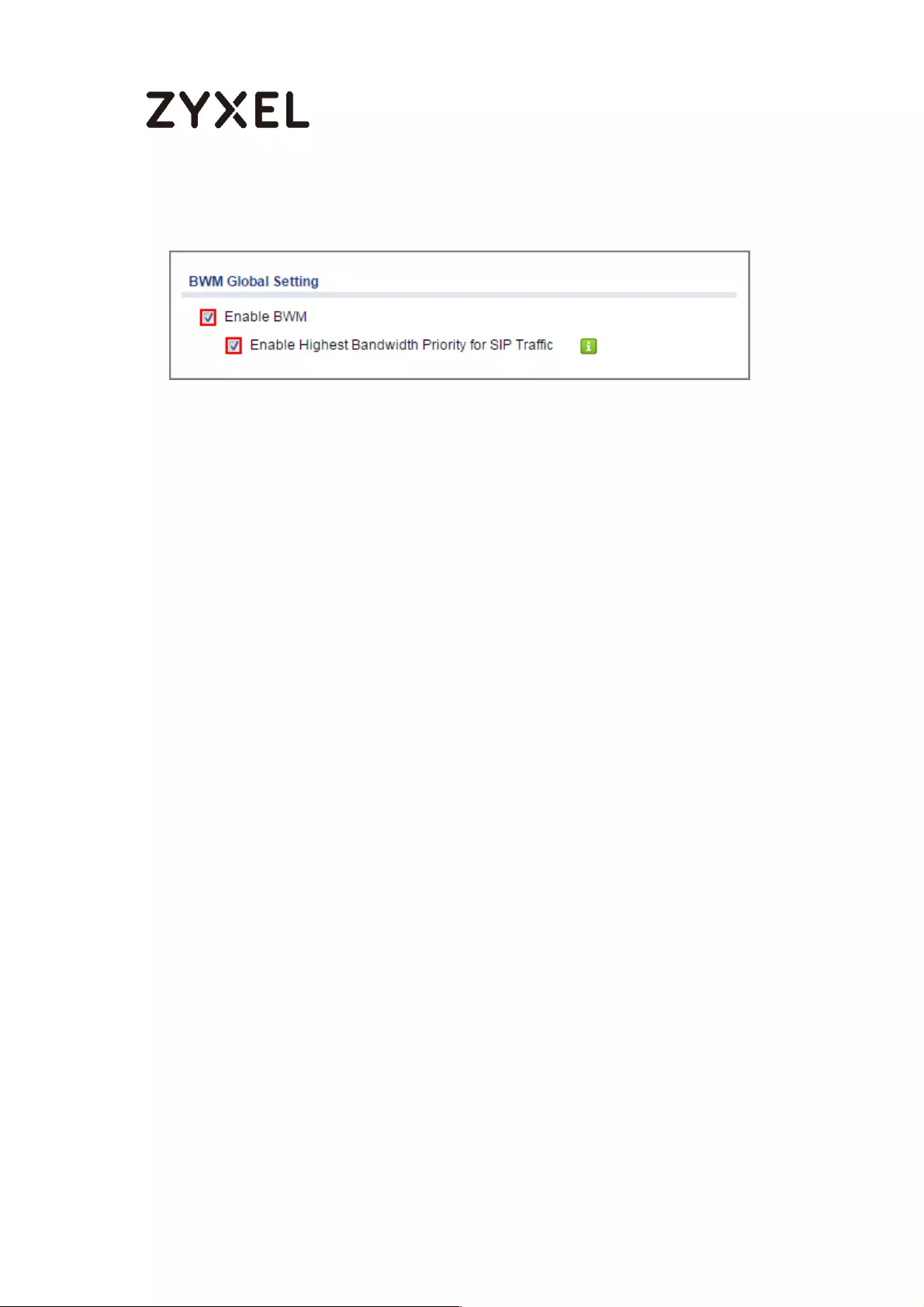
602/782
www.zyxel.com
Enable BWM and Enable Highest Bandwidth Priority for SIP Traffic.
CONFIGURATION > BWM > BWM Global Settings > Enable BWM
Set Up the Bandwidth Management for P2P on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > Configuration > Add Policy,
select Enable and type P2P Any-to-WAN as the policy’s Description.
Leave the Incoming Interface to any and select the Outgoing Interface to be
WAN1. Select Service Type to be the Application Object and select P2P from the
list box.
Set the Guaranteed Bandwidth Inbound to 100 (kbps) and set Priority 5. Set the
Maximum to 150 (kbps). Set the Guaranteed Bandwidth Outbound to 100 (kbps)
and set Priority 5. Set the Maximum to 150 (kbps). Click OK to return to the
General screen.
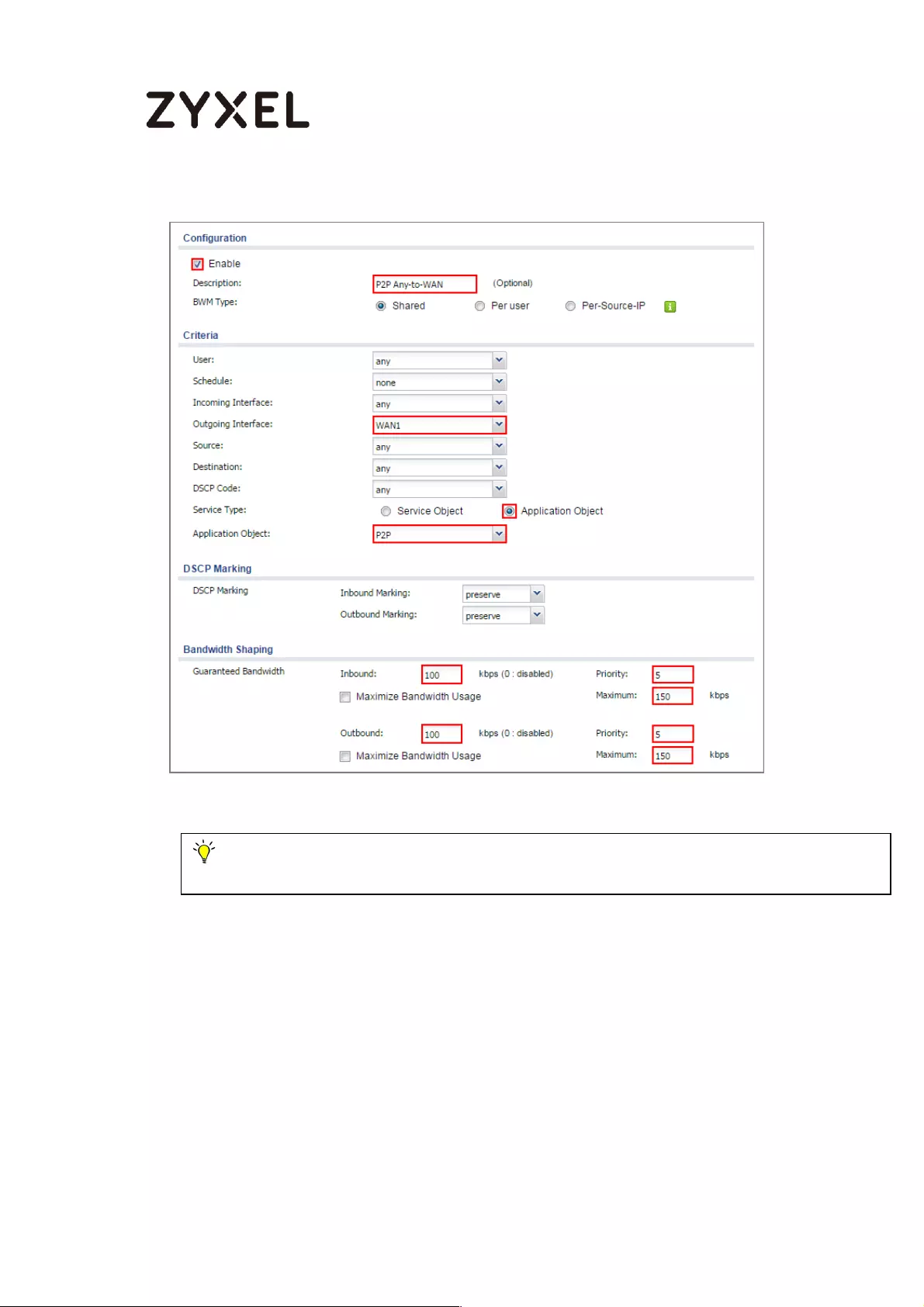
603/782
www.zyxel.com
CONFIGURATION > BWM > Configuration > Add Policy
Set Up the Bandwidth Management for FTP on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > BWM > Configuration > Add Policy,
select Enable and type FTP Any-to-Any as the policy’s Description.
Note: In Bandwidth Shaping, the highest priority is (1) the lowest priority is (7).
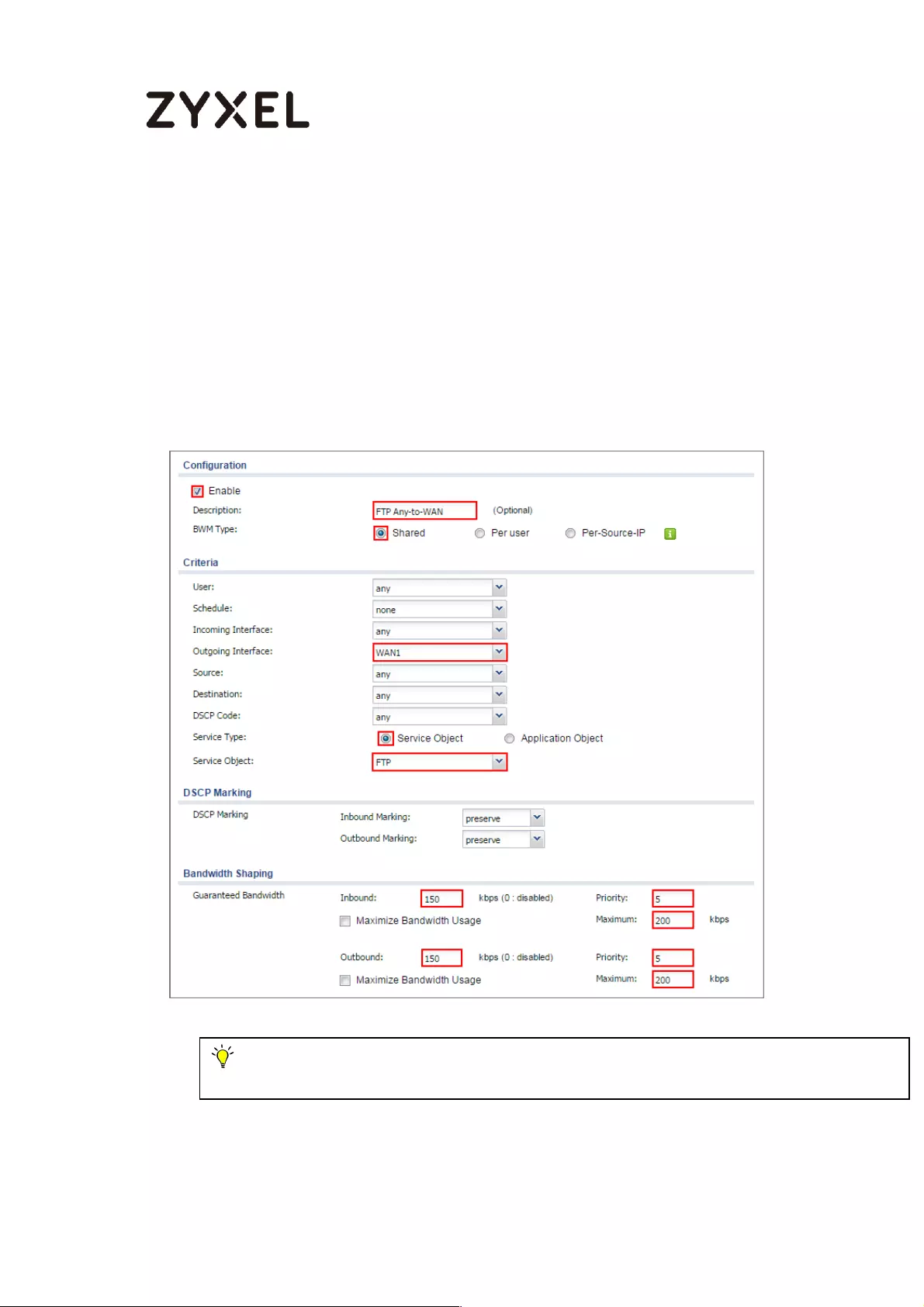
604/782
www.zyxel.com
Leave the Incoming Interface to any and select the Outgoing Interface to be
WAN1. Select Service Type to be the Service Object and select FTP from the list
box.
Set the Guaranteed Bandwidth Inbound to 150 (kbps) and set Priority 5. Set the
Maximum to 200 (kbps). Set the Guaranteed Bandwidth Outbound to 150 (kbps)
and set Priority 5. Set the Maximum to 200 (kbps). Click OK to return to the
General screen.
CONFIGURATION > BWM > Configuration > Add Policy
Note: In Bandwidth Shaping, the highest priority is (1) the lowest priority is (7).

605/782
www.zyxel.com
Test the Result
Add a Security Policy rule to view the SIP log:
CONFIGURATION > BWM > Configuration > Add Policy
Dial Phone Number 1001 (192.168.10.2 in this example) from Phone Number 1002
(192.168.100.2 in this example), go to the ZyWALL/USG Monitor > Log, you will see
[alert] log message such as below. The Destination IP address is the SIP Server IP
address.
Monitor > Log
Go to the ZyWALL/USG Monitor > Traffic Statics and review the SIP traffic and other
services to optimize the Guaranteed and Maximum BMW of bandwidth
consuming services.
Monitor > Traffic Statics
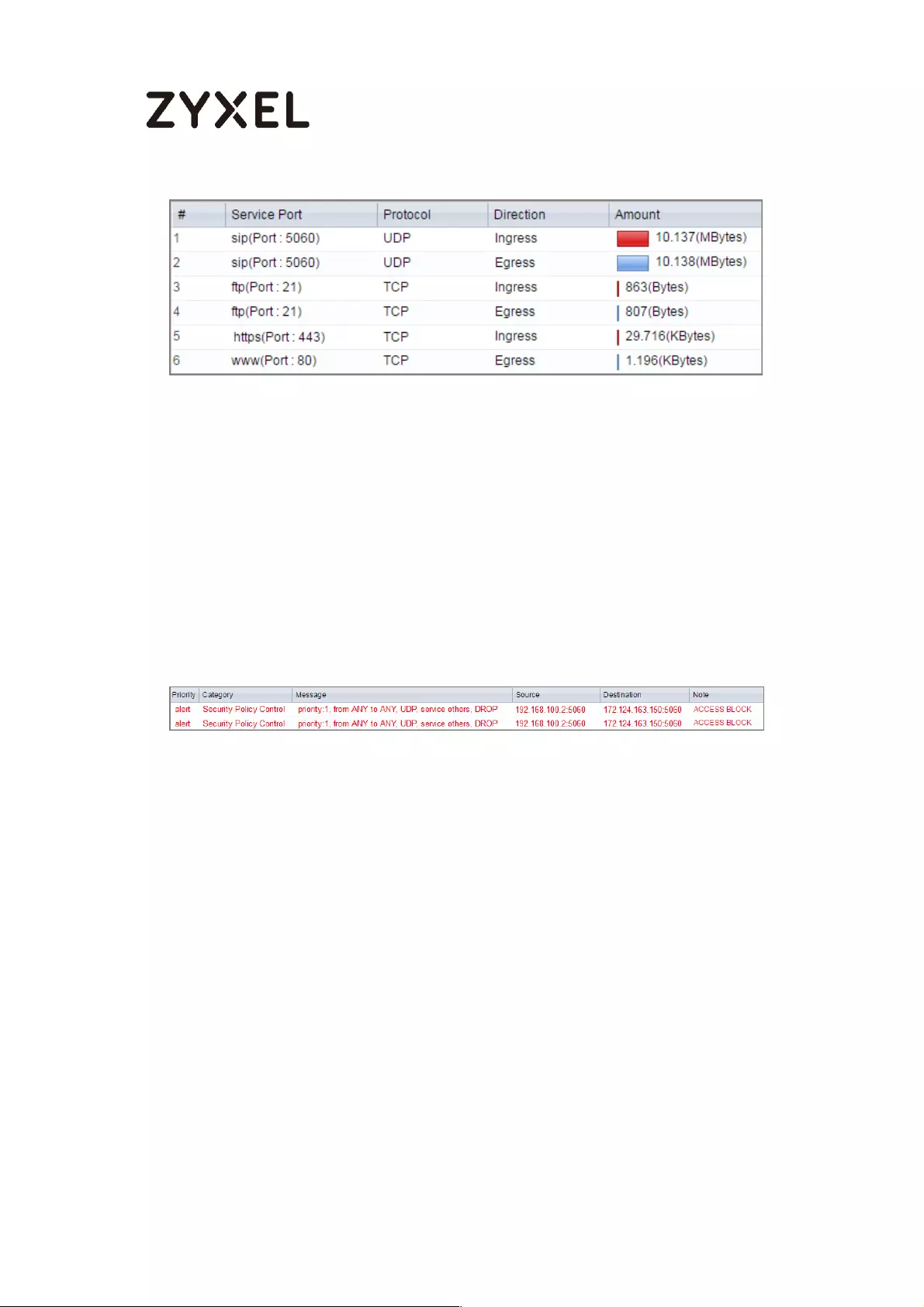
606/782
www.zyxel.com
What Could Go Wrong?
If you see [alert] log message such as below, the voice traffic is blocked by the
priority 1 Security Policy. The ZyWALL/USG checks the security policy in order and
applies the first security policy the traffic matches. If the voice traffic matches a
policy that comes earlier in the list, it may be unexpectedly blocked. Please
change your policy setting or move the voice traffic policy to the higher priority.
Monitor > Log
607/782
www.zyxel.com
How to Manage ZyWALL/USG Configuration Files
This is an example of how to rename, download, copy, apply and upload
configuration files. Once your ZyWALL/USG is configured and functioning
properly, it is highly recommended that you back up your configuration file
before making further configuration changes. The backup configuration file will
be useful in case you need to return to your previous settings.
The system-default.conf file contains the ZyWALL/USG’s default settings. This
configuration file is included when you upload a firmware package.
The startup-config.conf file is the configuration file that the ZyWALL/USG is
currently using. If you make and save changes during your management session,
the changes are applied to this configuration file.
The lastgood.conf is the most recently used (valid) configuration file that was
saved when the device last restarted.
ZyWALL/USG with Configuration Files Example
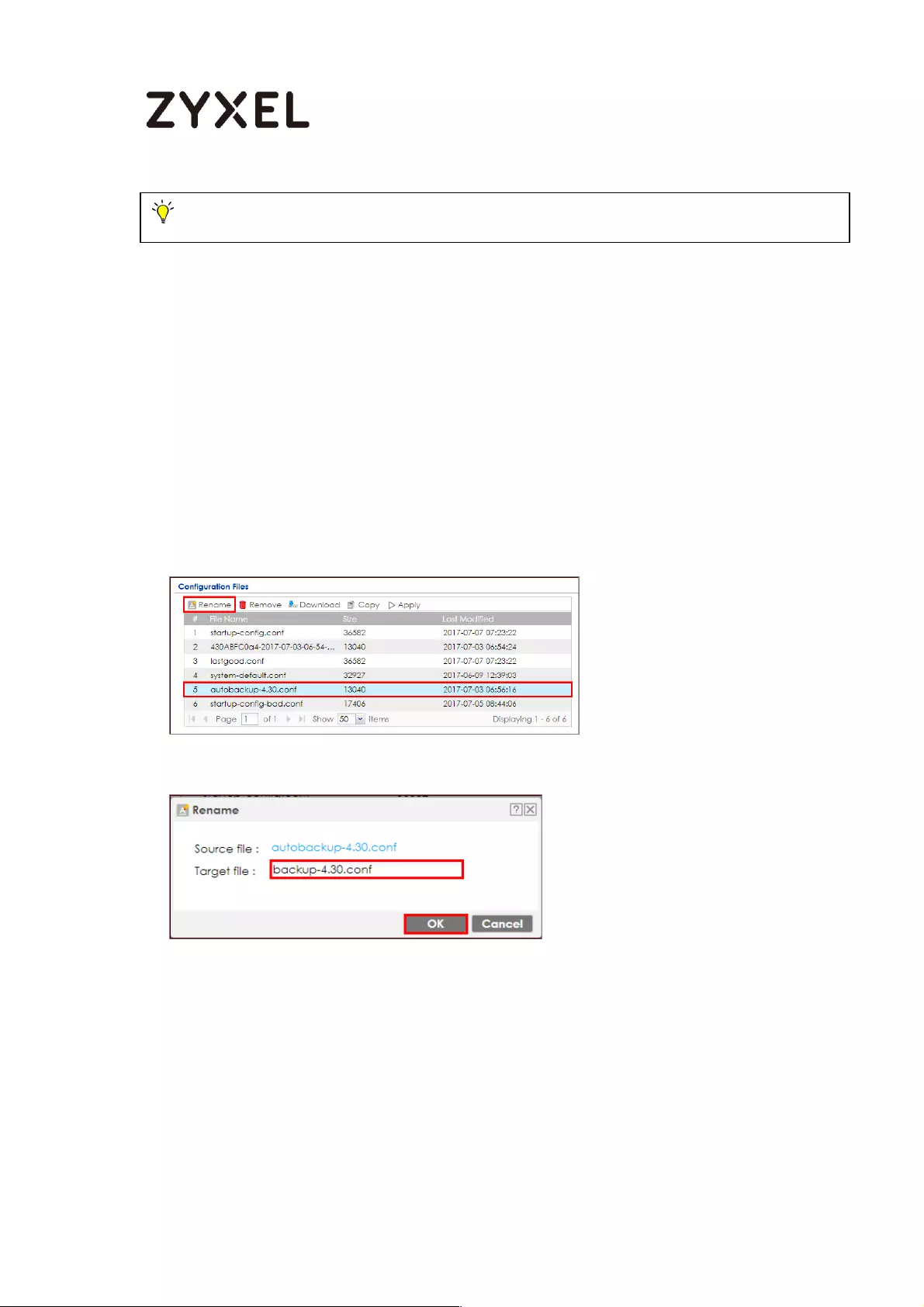
608/782
www.zyxel.com
Rename the Configuration Files from the ZyWALL/USG
In the ZyWALL/USG, go to MAINTENANCE > File Manager > Configuration File,
select the configuration file and click Rename. A pop-up screen will appear
allowing you to edit the Target file name. Click OK to save the Rename
configuration.
MAINTENANCE > File Manager > Configuration File
MAINTENANCE > File Manager > Configuration File > Rename
Download the Configuration Files on the ZyWALL/USG
In the ZyWALL/USG, go to MAINTENANCE > File Manager > Configuration File,
select the configuration file and click Download to back up your configuration file
from ZyWALL/USG to your computer.
Note: This example was using USG310 (Firmware Version: ZLD 4.25).
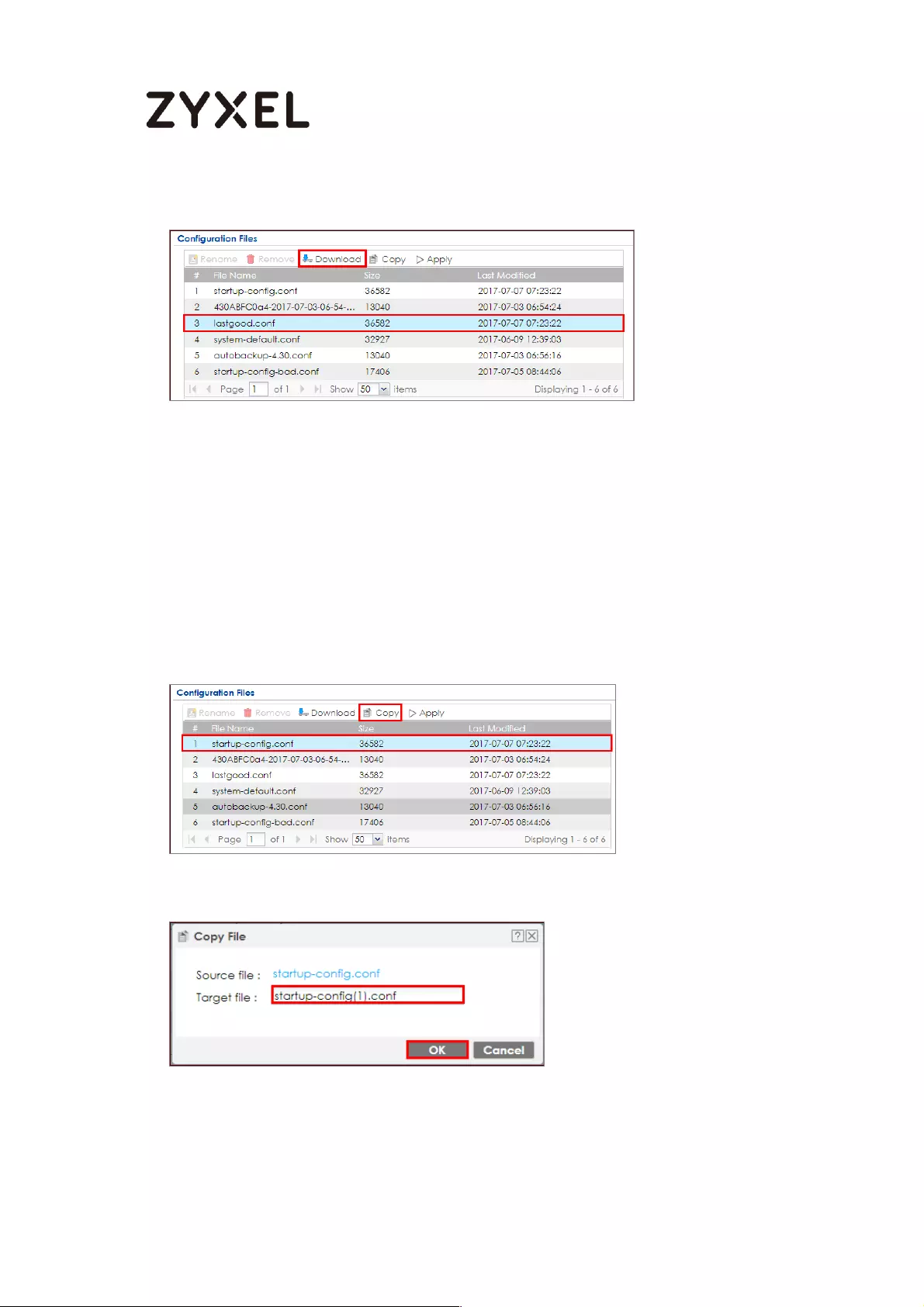
609/782
www.zyxel.com
MAINTENANCE > File Manager > Configuration File
Copy the Configuration Files on the ZyWALL/USG
In the ZyWALL/USG, go to MAINTENANCE > File Manager > Configuration File,
select the configuration file and click Copy. A pop-up screen will appear allowing
you to edit the Target file name. Click OK to save the Copy configuration.
MAINTENANCE > File Manager > Configuration File
MAINTENANCE > File Manager > Configuration File > Copy

610/782
www.zyxel.com
Apply the Configuration Files on the ZyWALL/USG
In the ZyWALL/USG, go to MAINTENANCE > File Manager > Configuration File,
select a specific configuration file to have ZyWALL/USG use it. For example, select
the system-default.conf file and click Apply to reset all of the ZyWALL/USG settings
to the factory defaults. Or select the lastgood.conf which is the most recently
used (valid) configuration file that was saved when the device last restarted. If
you uploaded and applied a configuration file with an error, select this file then
click Apply to return to a valid configuration.
MAINTENANCE > File Manager > Configuration File
A pop-up screen will appear allowing you to edit the Target file name. Select
Immediately stop applying the configuration file and roll back to the previous
configuration to get the ZyWALL/USG started with a fully valid configuration file as
quickly as possible. Click OK to have the ZyWALL/USG start applying the
configuration file.
MAINTENANCE > File Manager > Configuration File > Apply Configuration File
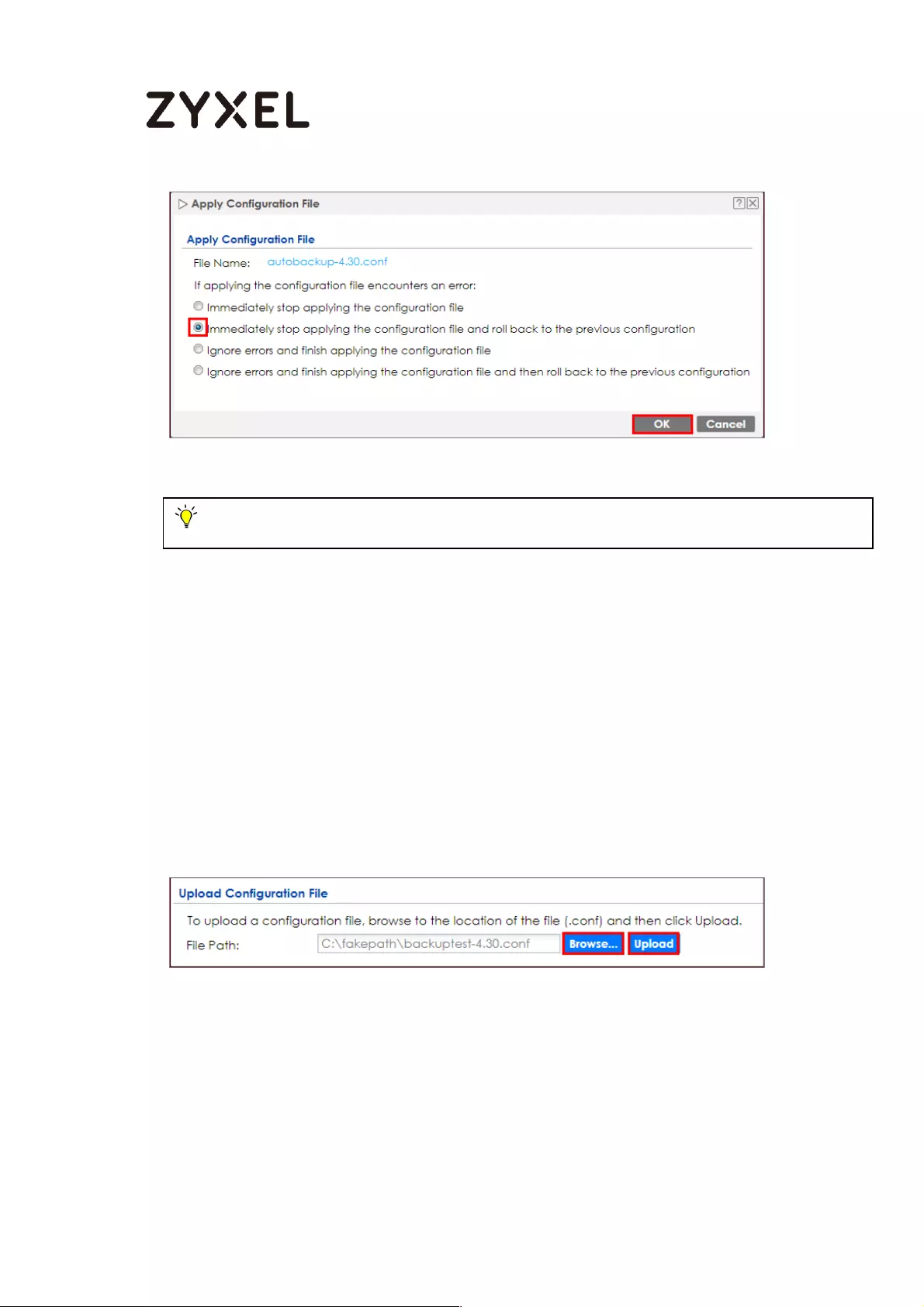
611/782
www.zyxel.com
Upload the Configuration Files from the ZyWALL/USG
In the ZyWALL/USG, go to MAINTENANCE > File Manager > Configuration File >
Upload Configuration File, select Browse to upload a new or previously saved
configuration file from your computer to your ZyWALL/USG. You cannot upload a
configuration file named system-default.conf or lastgood.conf. If you upload
startup-config.conf, it will replace the current configuration and immediately
apply the new settings.
MAINTENANCE > File Manager > Configuration File
What Could Go Wrong?
If you cannot apply a configuration file and the device shows error message, go
to Monitor > Log to check the [alert] log message and make the correction of the
Note: Do not shut down the ZyWALL/USG while the configuration file is being applied.
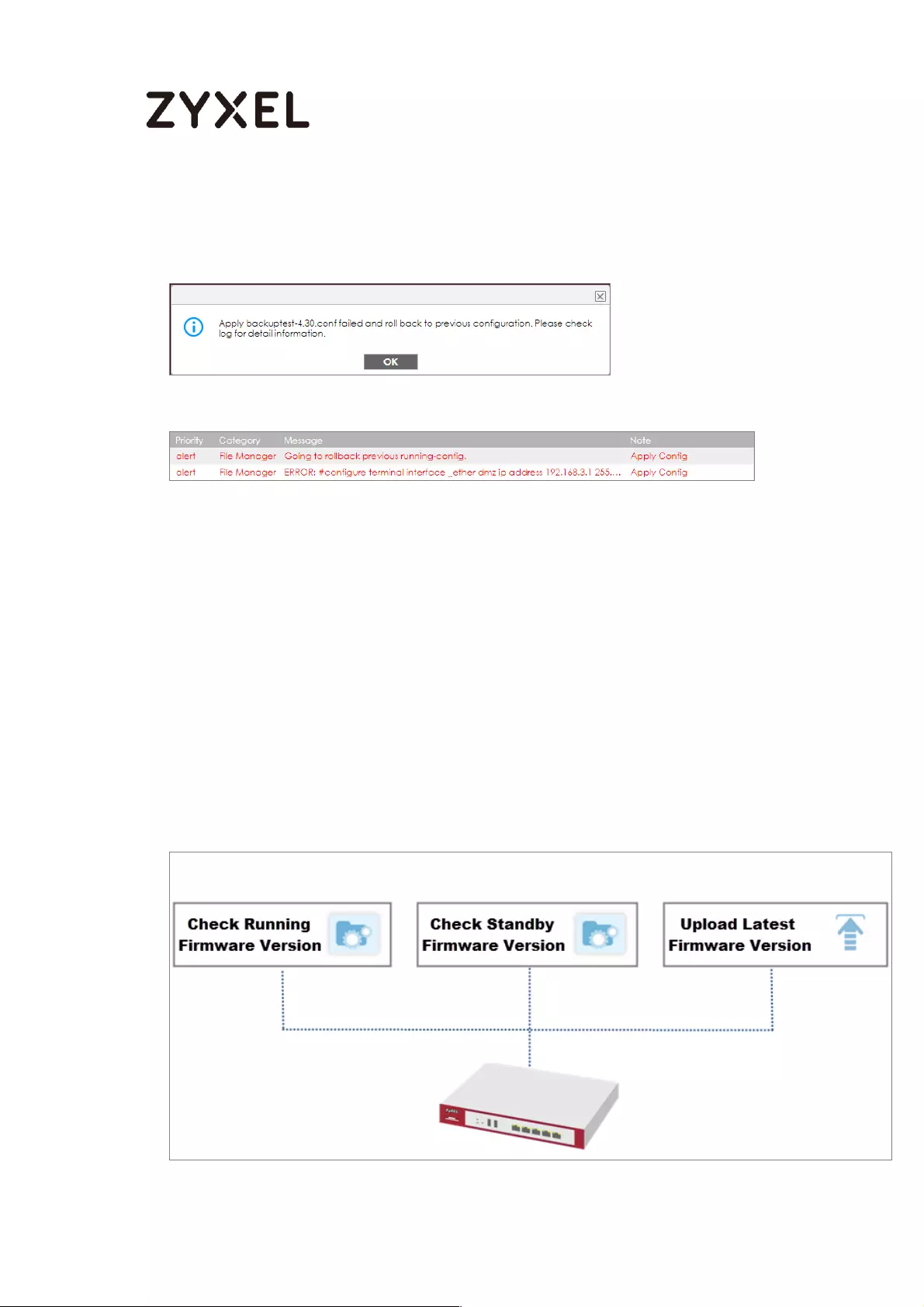
612/782
www.zyxel.com
configuration file. In this example, the [alert] log message shows the configuration
file has an incomplete static DHCP address so that the device can't apply it.
MAINTENANCE > File Manager > Configuration File > Apply Configuration File
Monitor > Log
How to Manage ZyWALL/USG Firmware
This is an example of using ZyWALL/USG to check your current firmware version
and upload firmware to the ZyWALL/USG. You can upload firmware to be the
Running firmware or Standby firmware.
ZyWALL/USG with Firmware Management Example
613/782
www.zyxel.com
Download the Current Firmware Version from ZyXEL.com
Go to www.zyxel.com/support/download_landing.shtml and download the
current firmware package.
Note: The firmware update can take up to five minutes. Do not turn off or reset the
ZyWALL/USG while the firmware update is in progress. This example was using USG110
(Firmware Version: ZLD 4.25).
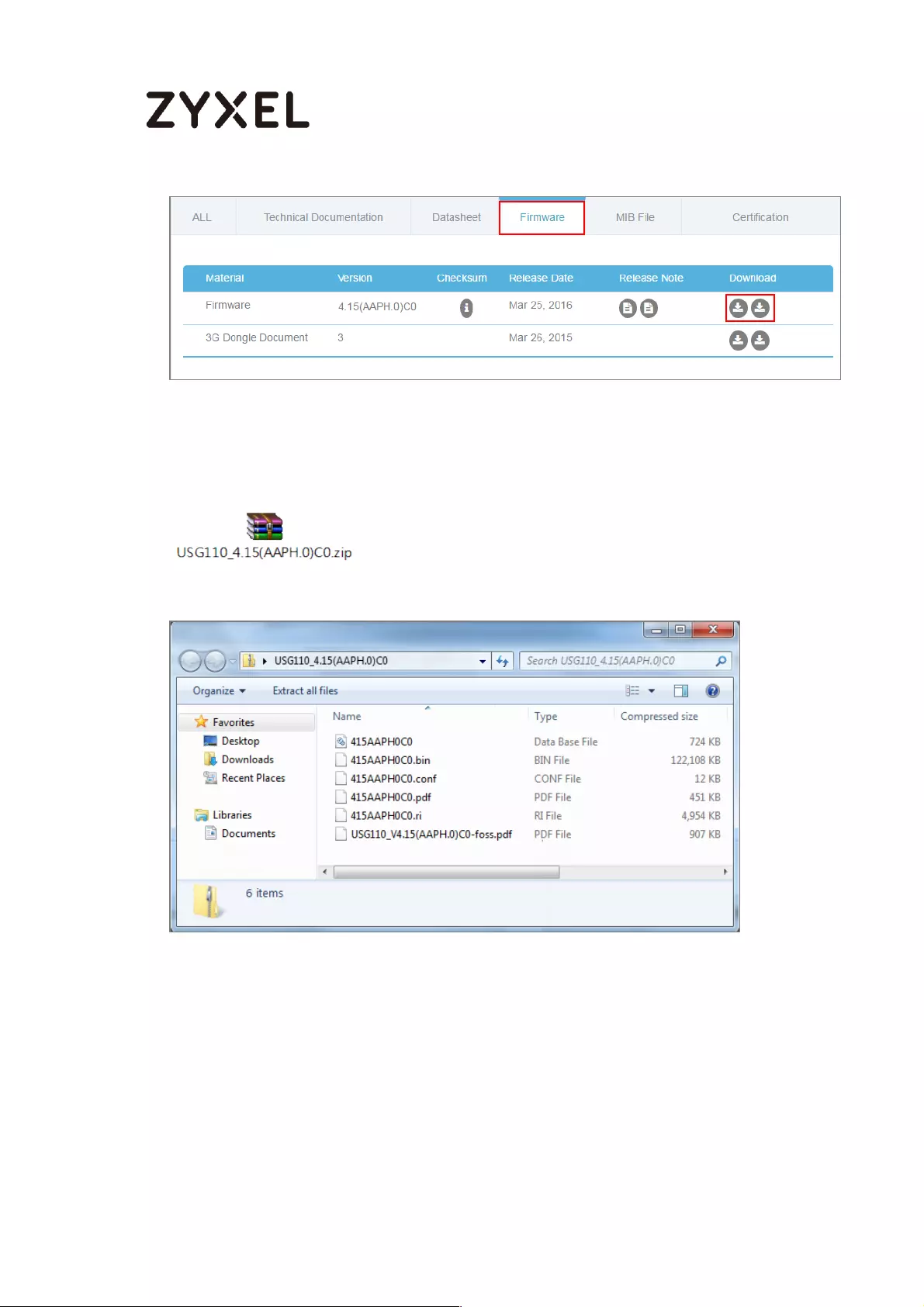
614/782
www.zyxel.com
Extract firmware zip file.
Upload the Firmware on the ZyWALL/USG
In the ZyWALL/USG, go to MAINTENANCE > File Manager > Firmware Package >
Upload File. Click the To upload image file in system space pull-down menu and
select (1) or (2). The default Standby system space is (2), so if you want to upload
new firmware to be the Running firmware, then select the Running system space
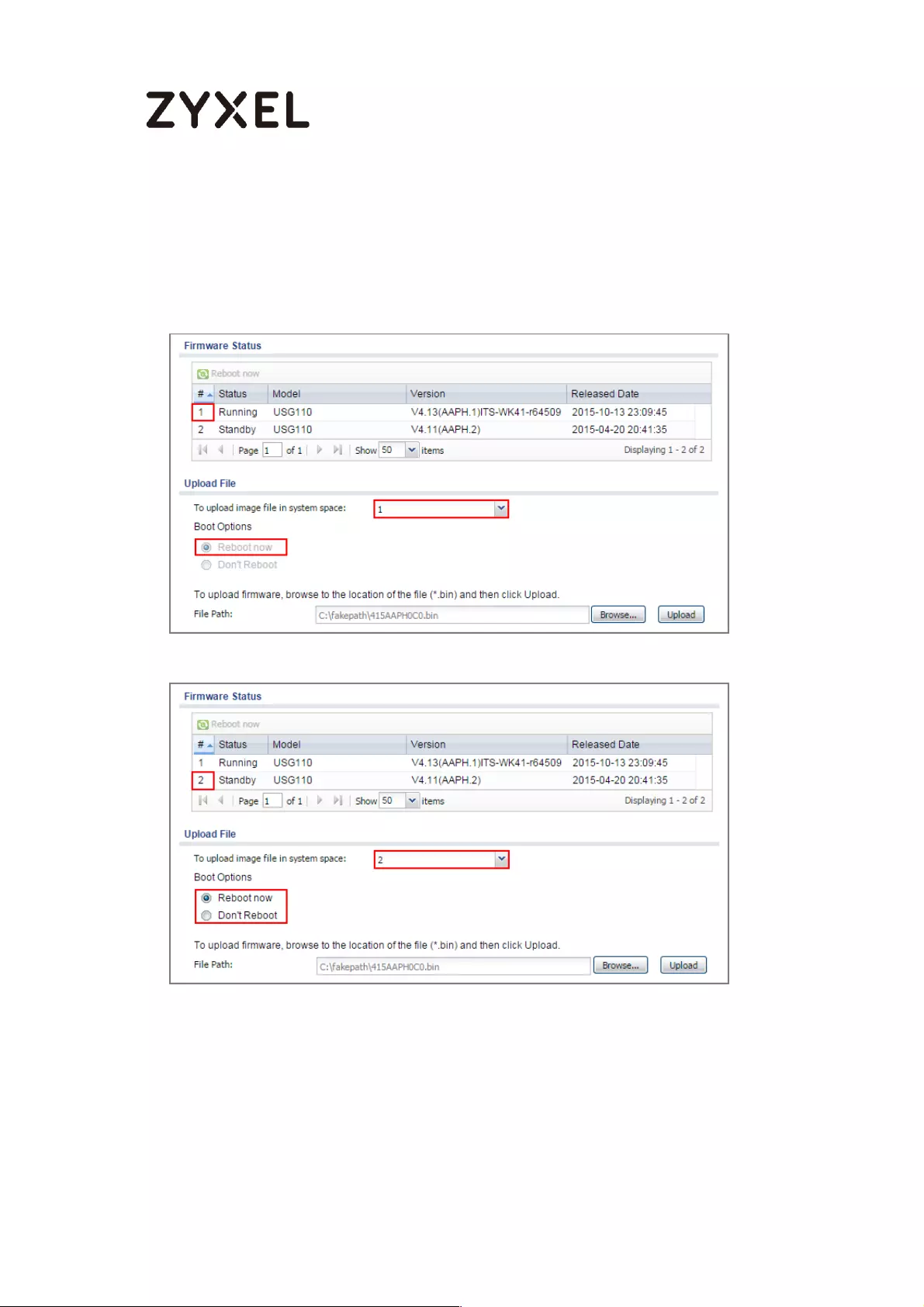
615/782
www.zyxel.com
(1). The ZyWALL/USG will reboot automatically.
If you upload firmware to the Standby system space (2), you have the option to
select Reboot now or Don’t Reboot.
MAINTENANCE > File Manager > Firmware Package > Upload File > (1)
MAINTENANCE > File Manager > Firmware Package > Upload File > (2)
To upload firmware, click Browse to the location of the file (*.bin) and then click
Upload.
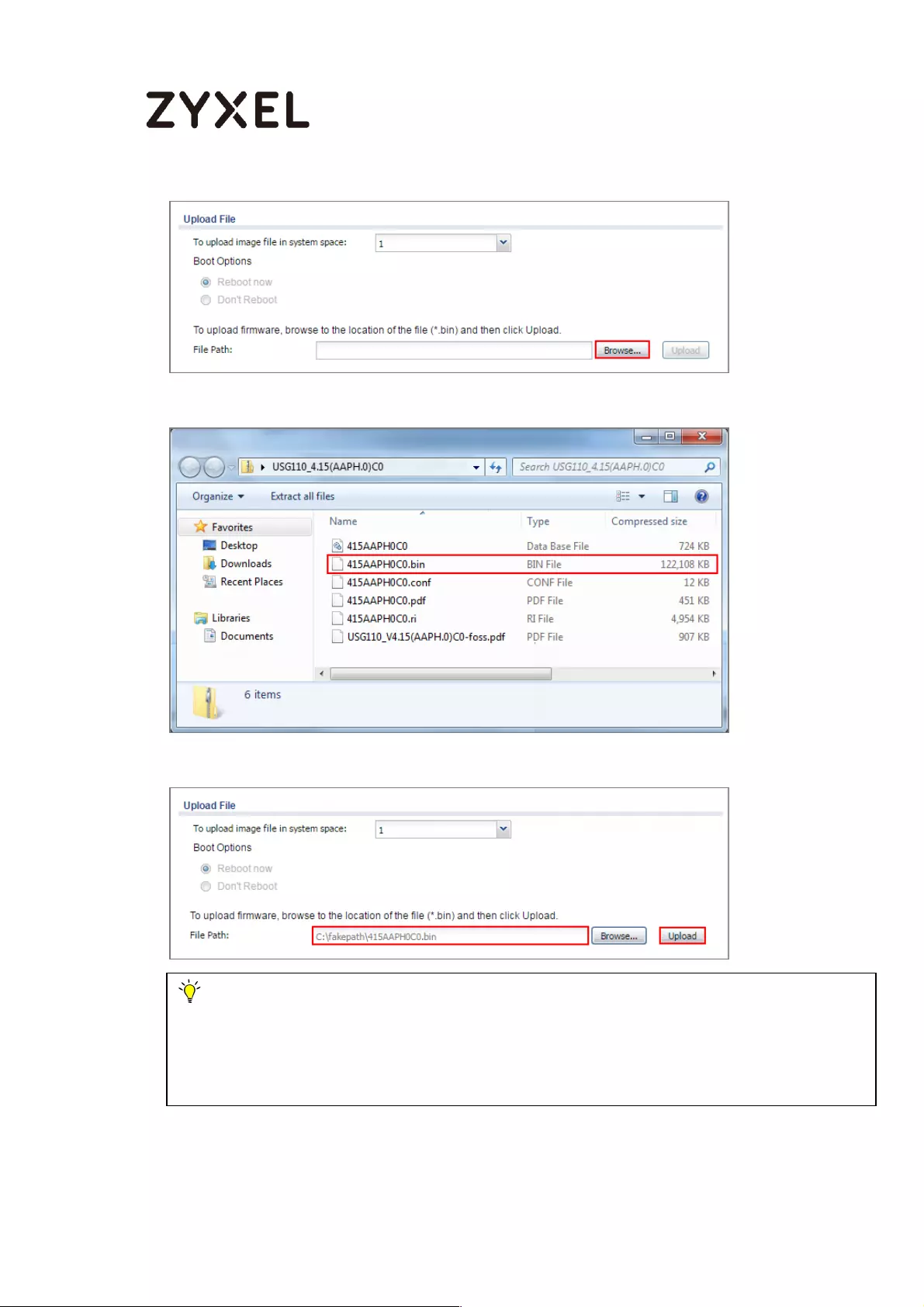
616/782
www.zyxel.com
Note: The default Running system space is (1), the Standby system space is (2). If you
select the Standby firmware and click Reboot now or you upload file to Standby system
space (2) and select Boot Options to be Reboot now. After reboot process complete, the
Running system space will be (2). Standby system space will be (1).

617/782
www.zyxel.com
What Could Go Wrong?
If you cannot download the firmware, please check if you enable the Destroy
compressed files that could not be decompressed function in Anti-Virus.
ZyWALL/USG firmware package is ZIP file, the ZyWALL/USG classifies the firmware
package as not being able to decompress will delete it. Please disable this option
while downloading the firmware package.
618/782
www.zyxel.com
How to Get Started Using the Wizards
When you log into the Web Configurator for the first time or when you reset the
ZyWALL/USG to its default configuration, the Installation Setup Wizard screen
displays. This is an example of using ZyWALL/USG Wizards to configure Internet
connection settings, wireless settings and device registration services.
ZyWALL/USG with Installation Setup Wizard Example
Set Up the Internet Access (Ethernet) Wizard on the
ZyWALL/USG
In the ZyWALL/USG Installation Setup Wizard Welcome page, click Next to start
configuring. Click the double arrow in the upper right corner to display (
≪
Note: You need internet access to activate your ZyWALL/USG subscription services. This
example was tested using USG310 (Firmware Version: ZLD 4.25).
619/782
www.zyxel.com
)#or#hide#(≫
) the help.
Installation Setup Wizard > Welcome
In the Internet Access page, you can configure Internet connections from two

620/782
www.zyxel.com
Internet service providers (ISPs). Connect your ISP devices to your ZyWALL/USG
WAN port, select I have two ISPs if you want to configure two Internet connections
or leave it cleared to configure just one.
Choose the Encapsulation option to be Ethernet, leave Zone as default setting
Internet connection belongs to the WAN zone.
In the IP Address Assignment section, select Auto if your ISP did not assign you a
fixed IP address or select Static if your ISP did assign you a fixed IP address. Click
Next.
Installation Setup Wizard > Welcome > Internet Access
Enter the IP Address, IP Subnet Mask and Gateway IP Address exactly as given by
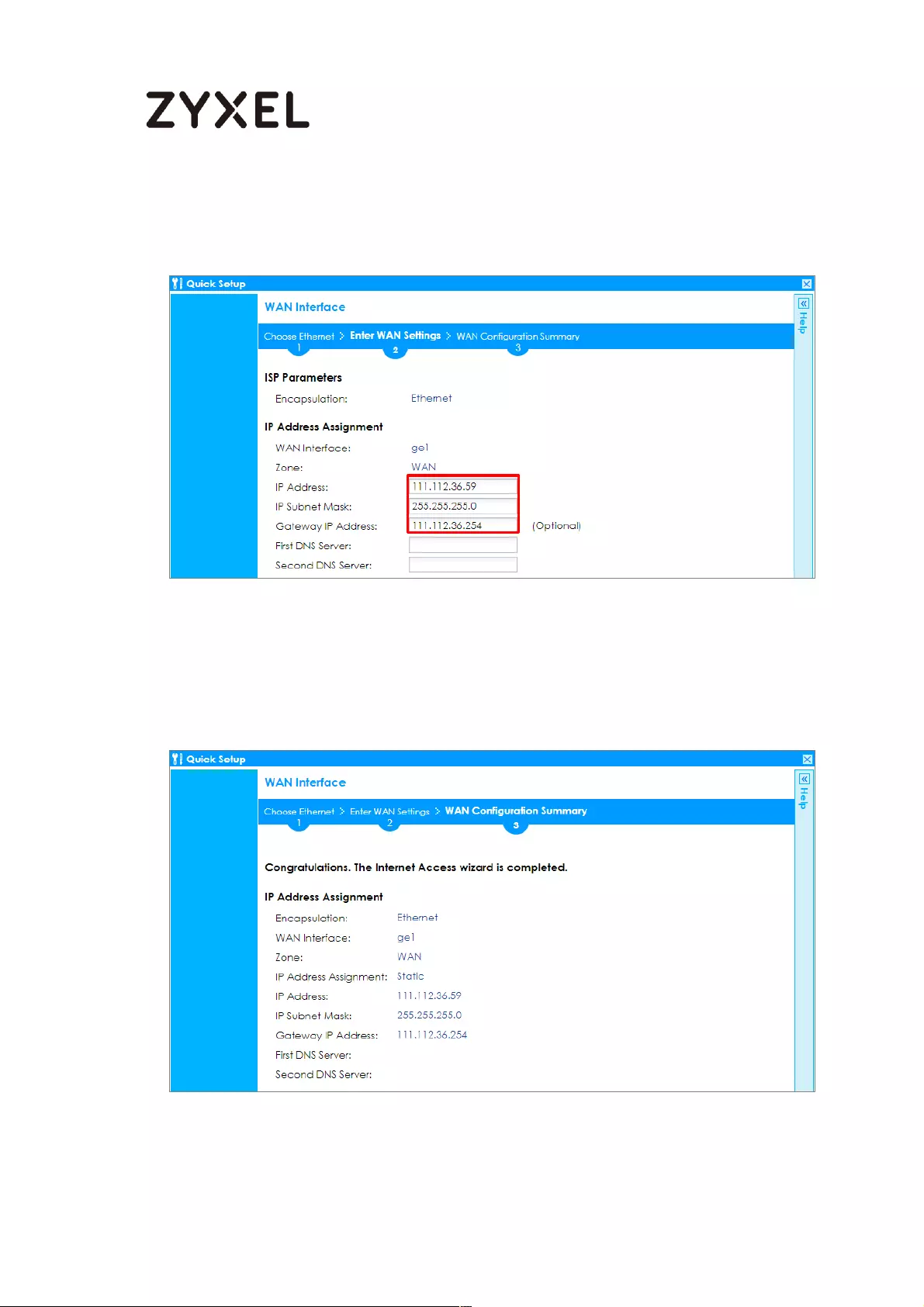
621/782
www.zyxel.com
your ISP or network administrator. First/Second DNS Servers are optional. Click
Next.
Installation Setup Wizard > Welcome > Internet Access
The Internet Access Succeed page will display the summary of Internet access of
the First Setting. If you select I have two ISPs in Internet Access > ISP Setting, click
Next to configure the second WAN interface or continue to the Wireless Settings
page.
Installation Setup Wizard > Welcome > Internet Access > Internet Access Succeed
622/782
www.zyxel.com
Set Up the Internet Access (PPPoE) Wizard on the ZyWALL/USG
In the ZyWALL/USG Installation Setup Wizard Welcome page, click Next to start
configuring for Internet. Click the double arrow in the upper right corner to display
(
≪)#or#hide#(≫
) the help.
Installation Setup Wizard > Welcome
In the Internet Access page, you can configure Internet connections from two
Internet service providers (ISPs). Connect your ISP devices to your ZyWALL/USG
WAN port, select I have two ISPs if you want to configure two Internet connections
or leave it cleared to configure just one.
Choose the Encapsulation option to be PPP over Ethernet, leave Zone as default
setting Internet connection belongs to the WAN zone. Leave the IP Address

623/782
www.zyxel.com
Assignment section to be the Auto and click Next.
Installation Setup Wizard > Welcome > Internet Access
Select the Authentication Type to be the authentication method by the remote
node. Enter the User Name and Password exactly as given by your ISP or
network administrator. Select Nailed-UP if you want to keep the connection
always up or type the desired Idle Timeout value in seconds. Click Next.
Installation Setup Wizard > Welcome > Internet Access
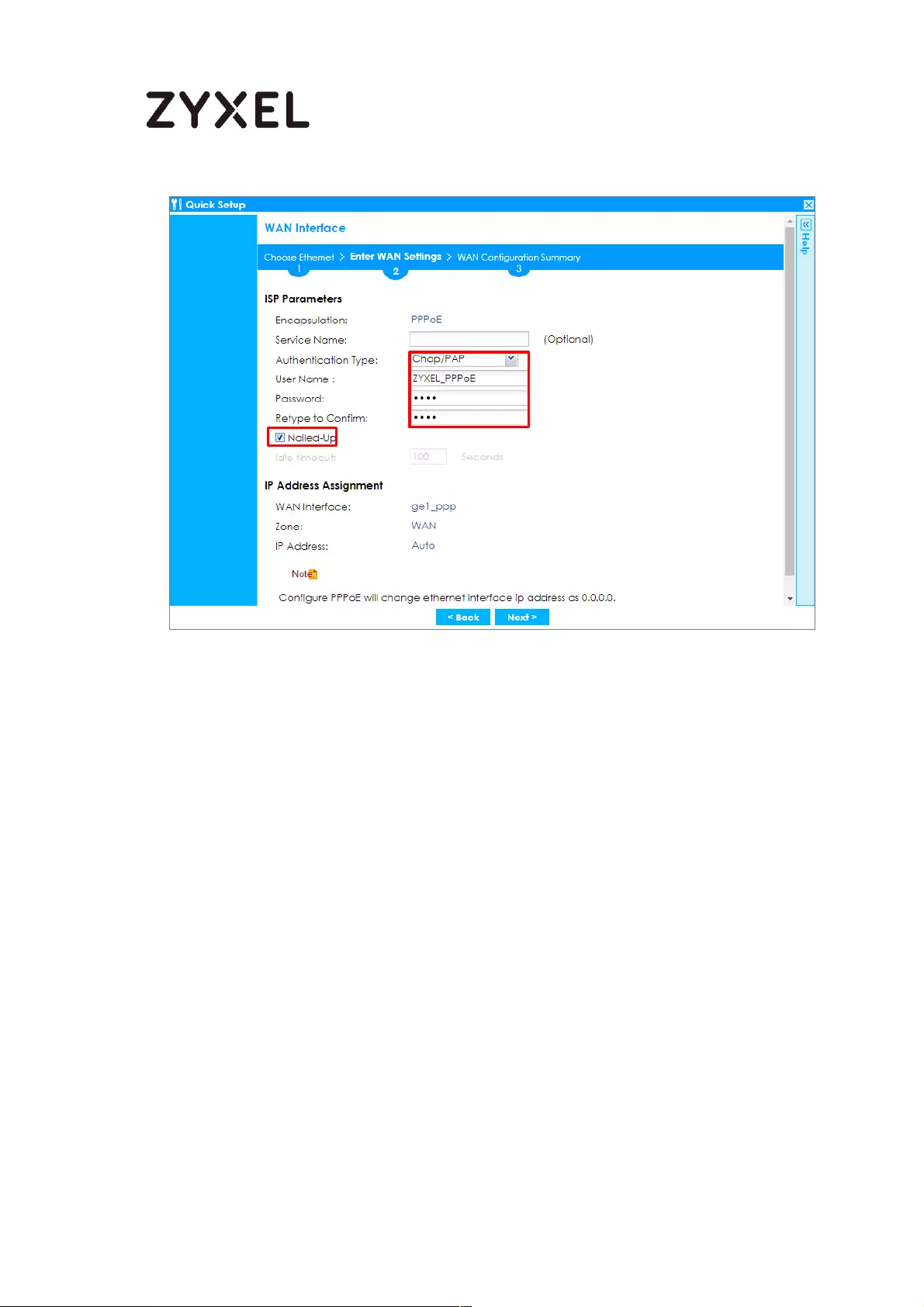
624/782
www.zyxel.com
The Internet Access Succeed page will display the summary of Internet access of
the First Setting. If you select I have two ISPs in Internet Access > ISP Setting, click
Next to configure the second WAN interface.
Installation Setup Wizard > Welcome > Internet Access > Internet Access Succeed
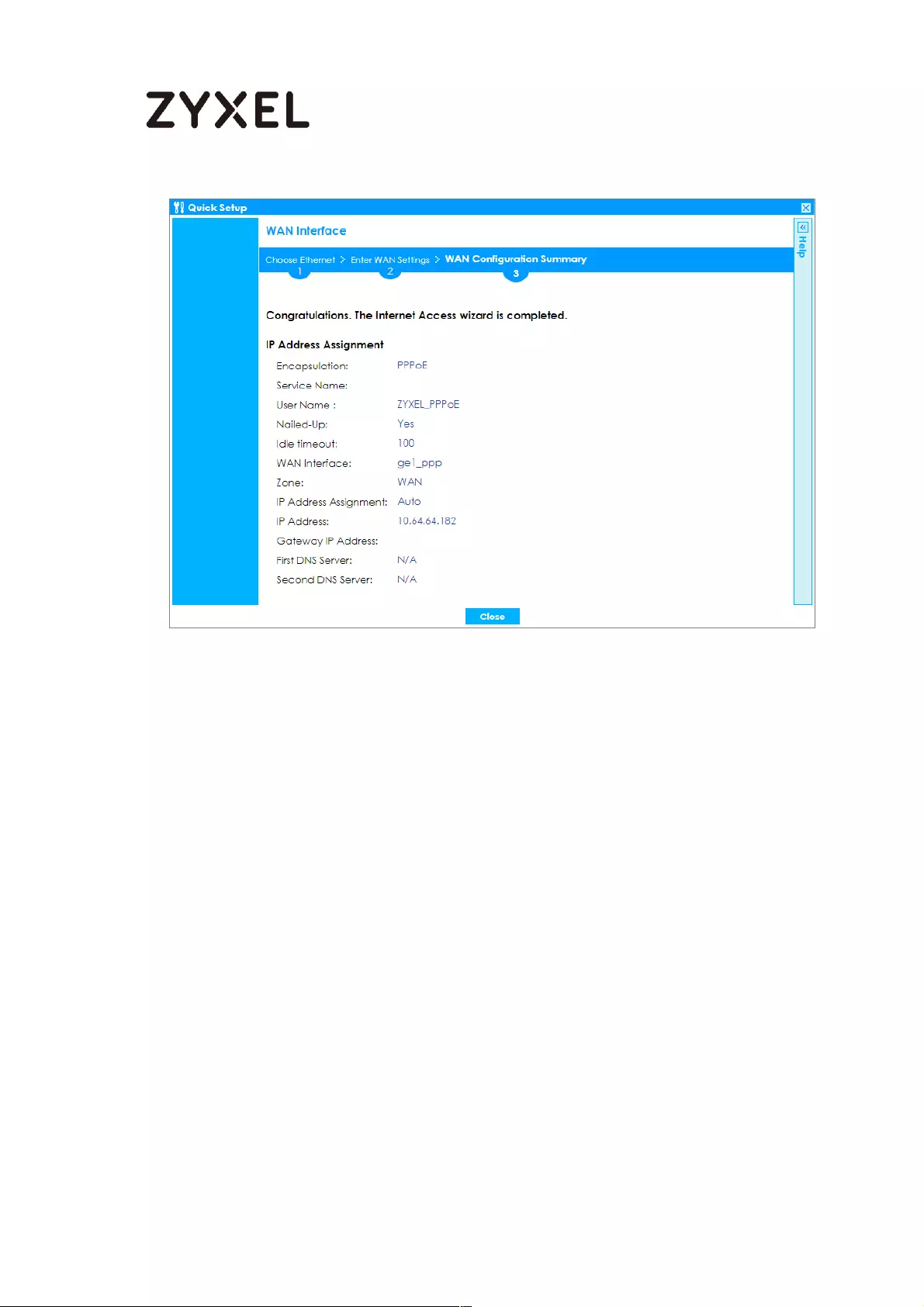
625/782
www.zyxel.com
Set Up the Internet Access (PPTP) Wizard on the ZyWALL/USG
In the ZyWALL/USG Installation Setup Wizard Welcome page, click Next to start
configuring for Internet. Click the double arrow in the upper right corner to display
(
≪)#or#hide#(≫
) the help.
Installation Setup Wizard > Welcome
626/782
www.zyxel.com
In the Internet Access page, you can configure Internet connections from two
Internet service providers (ISPs). Connect your ISP devices to your ZyWALL/USG
WAN port, select I have two ISPs if you want to configure two Internet connections
or leave it cleared to configure just one.
Choose the Encapsulation option to be the PPTP, leave Zone as default setting
Internet connection belongs to the WAN zone. Leave the IP Address Assignment
section to be the Auto and click Next.
Installation Setup Wizard > Welcome > Internet Access

627/782
www.zyxel.com
Select the Authentication Type to be the authentication method by the remote
node. Enter the User Name and Password exactly as given by your ISP or
network administrator. Select Nailed-UP if you want to keep the connection
always up or type the desired Idle Timeout value in seconds. Click Next.
Enter the Base IP Address, IP Subnet Mask, Gateway IP Address assigned to you
by your ISP. Type the Server IP address of the PPTP Server. Click Next.
Installation Setup Wizard > Welcome > Internet Access

628/782
www.zyxel.com
The Internet Access Succeed page will display the summary of Internet access of
the First Setting. If you select I have two ISPs in Internet Access > ISP Setting, click
Next to configure the second WAN interface.
Installation Setup Wizard > Welcome > Internet Access > Internet Access Succeed

629/782
www.zyxel.com
Set Up the Wireless Settings Wizard on the ZyWALL/USG
In the Wireless Settings page, select Yes if you want the ZyWALL/USG to enable AP
Controller feature in your network; select No if you want to skip this setting. Click
Next.
Installation Setup Wizard > Welcome > Internet Access > Internet Access Succeed
> Wireless Settings
630/782
www.zyxel.com
Configure descriptive SSID name (1-32 characters) for the wireless LAN. Select Pre-
Shared Key (8-63 characters) to add security on this wireless network. Otherwise,
select None to allow any wireless client to associate this network without
authentication.
Select Hidden SSID to hide the SSID from site tool scanning.
Select Enable Intra-BSS Traffic blocking if you want to prevent crossover traffic
from within the same wireless network. Wireless clients in that network can still
access the wired network but cannot communicate with each other.
For Built-in Wireless AP only, ZyWALL/USGs with W in the model name have a built-
in AP. Select an interface to bridge with the built-in AP wireless network. Devices
connected to this interface will then be in the same broadcast domain as devices
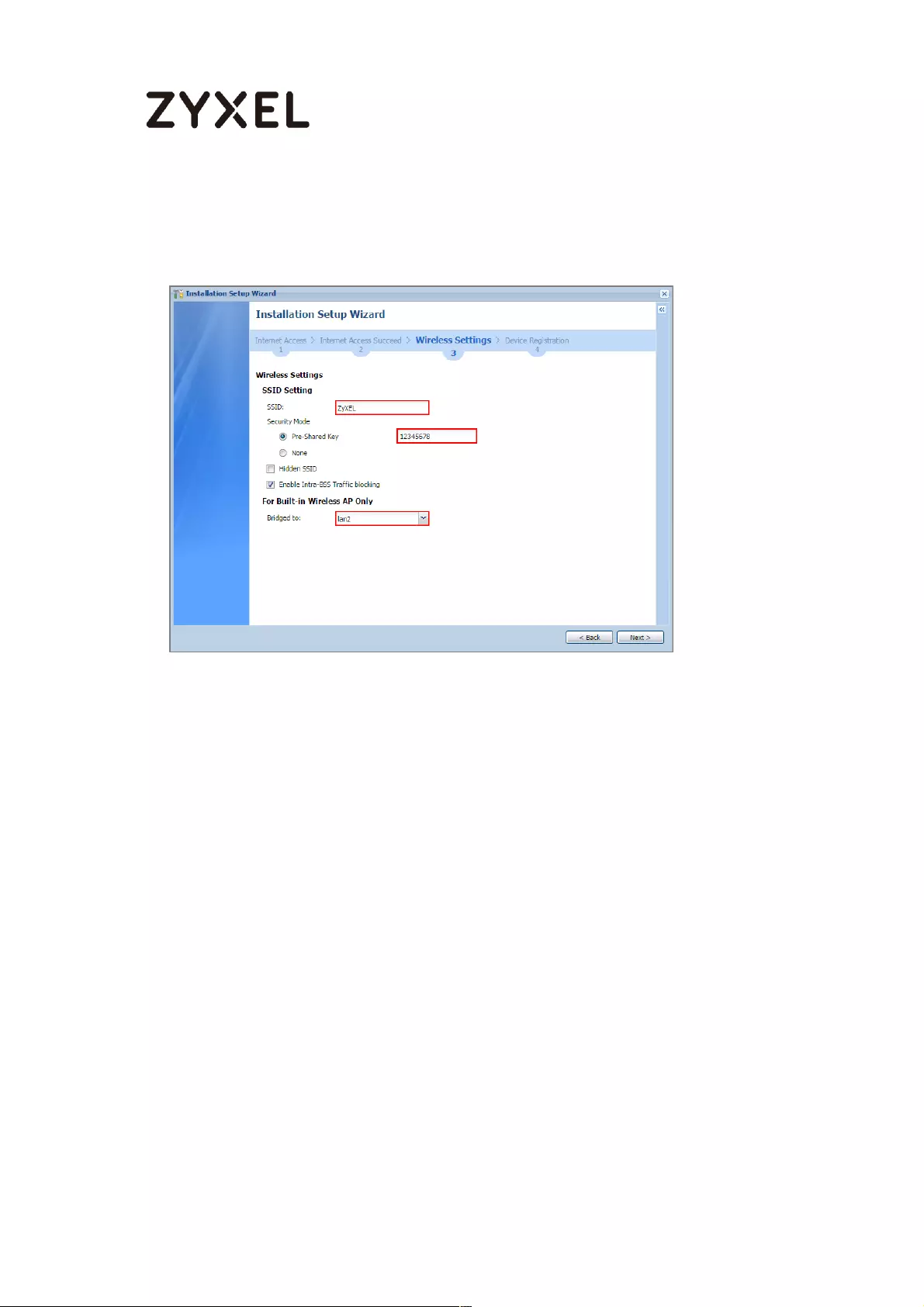
631/782
www.zyxel.com
in the AP wireless network.
Installation Setup Wizard > Welcome > Internet Access > Internet Access Succeed
> Wireless Settings
Set Up the Device Registration on the ZyWALL/USG
The ZyWALL/USG must be connected to the Internet in order to register.
Click portal.myzyxel.com to register the device, you need the ZyWALL/USG’s serial
number and LAN MAC address to register it. See How To Register Your Device and
632/782
www.zyxel.com
Services at myZyXEL.com for more details. Use the Configuration > Licensing >
Registration > Service screen to update your service subscription status. Click
Finish.
Installation Setup Wizard > Welcome > Internet Access > Internet Access Succeed
> Wireless Settings > Device Registration
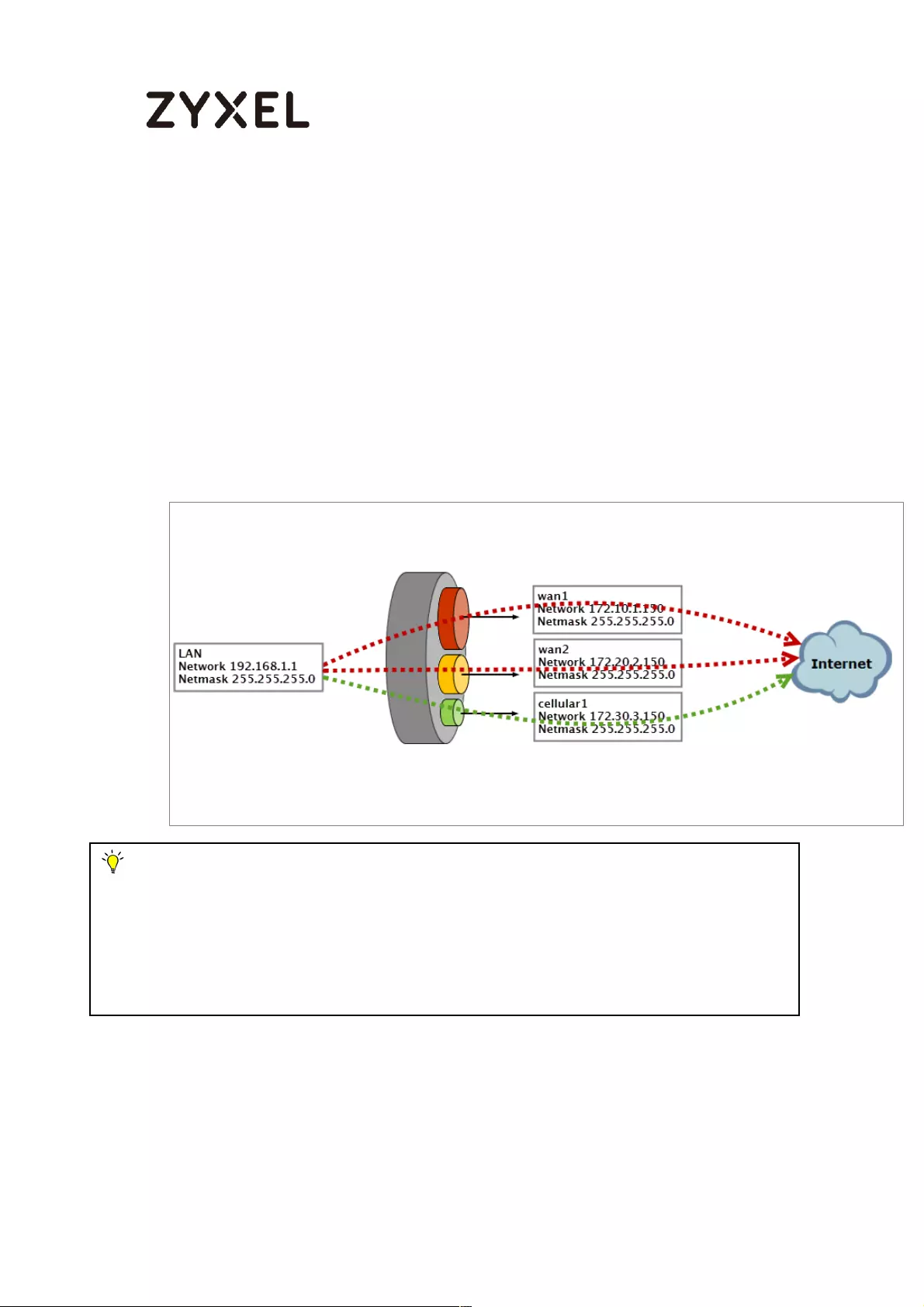
633/782
www.zyxel.com
How to Configure the 3G/LTE Interface on the ZyWALL/USG
as a WAN Backup
This is an example of using ZyWALL/USG to configure 3G/LTE interface as a WAN
backup that ensures the ZyWALL/USG provides the continuously Internet
connections when the primary WAN interface is down. After configuration, it can
provide additional mobile broadband WAN connectivity or a redundant link for
maximum reliability.
ZyWALL/USG with 3G/LTE Interface as a WAN Backup Example
Note: This example includes weighted load balancing (Weighted Round Robin) so that
most of your Internet traffic is handled by ISP connected to wan1 before it fails over to
3G/LTE.
All network IP addresses and subnet masks are used as examples in this article. Please
replace them with your actual network IP addresses and subnet masks. This example was
tested using USG310 (Firmware Version: ZLD 4.25).
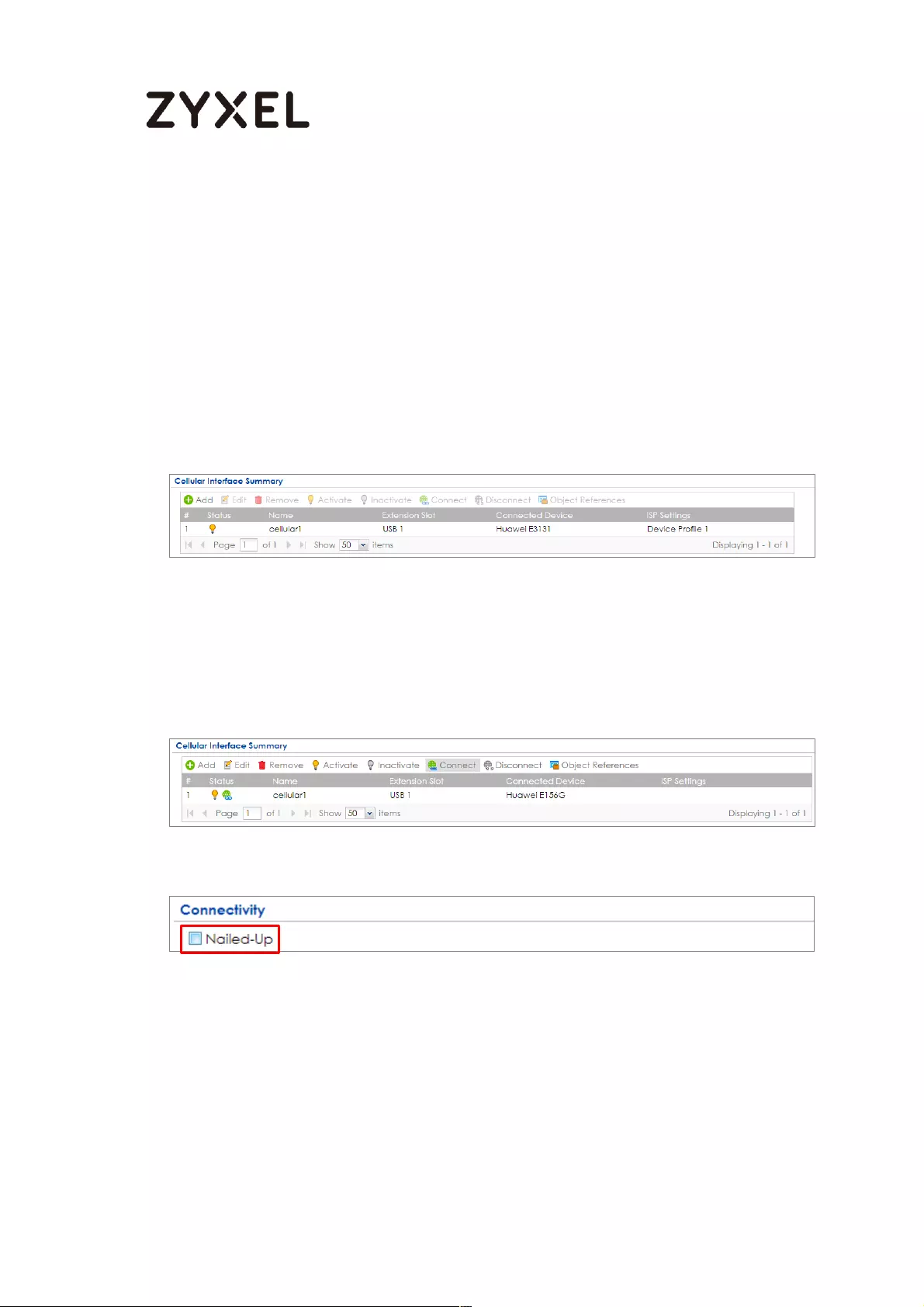
634/782
www.zyxel.com
Set Up the 3G/LTE Interface on the ZyWALL/USG
Connect a compatible mobile broadband USB device to use a cellular
connection.
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Cellular, the
connected device will automatically display in the Cellular Interface Summary.
Click Activate and then the Apply button at the bottom of this page.
CONFIGURATION > Network > Interface > Cellular > Activate
The default Connectivity method is Nailed-Up. The connection should always be
up after you activate the cellular interface. You can click Edit and go to the
Connectivity section to clear the Nailed-Up check box to have the ZyWALL/USG
to establish the connection only when there is traffic.
CONFIGURATION > Network > Interface > Cellular > Connect
CONFIGURATION > Network > Interface > Cellular > Edit
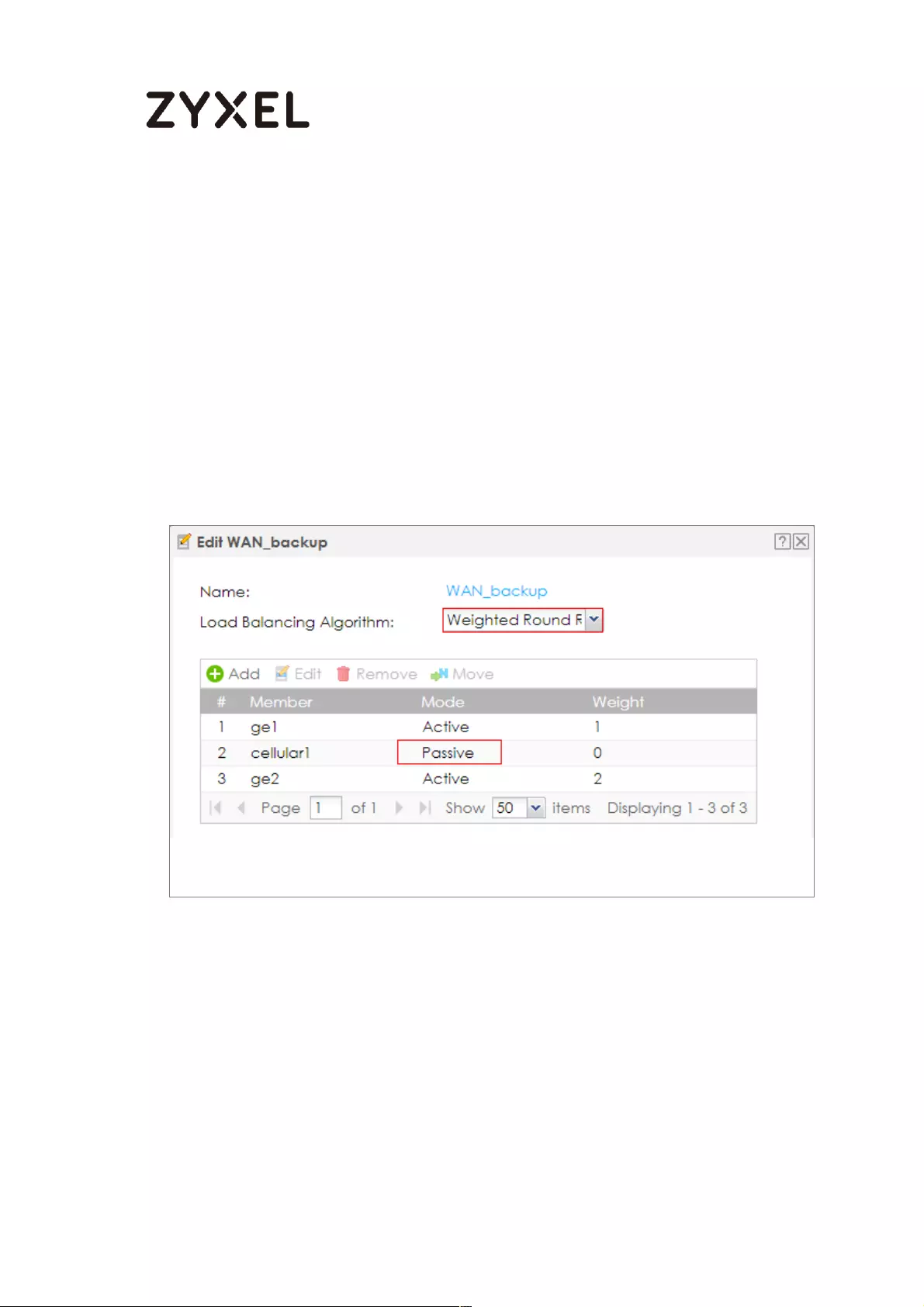
635/782
www.zyxel.com
Set Up the Trunk on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Trunk > User
Configuration > Add Trunk, configure a Name for you to identify the Trunk profile
and set the Load Balancing Algorithm field to be the Weighted Round Robin.
Add wan1 and enter 3 in the Weight column. Add wan2 and enter 2 in the Weight
column. Add cellular1, change Mode to be the Passive mode, enter 1 in the
Weight column. Click OK to return to the Configuration screen.
CONFIGURATION > Network > Interface > Trunk > User Configuration > Add Trunk
In the Configuration screen, go to Default WAN Trunk section, select User
Configured Trunk and select the newly created Trunk from the list box. Click
Apply.
CONFIGURATION > Network > Interface > Trunk > Default WAN Trunk > User
Configured Trunk
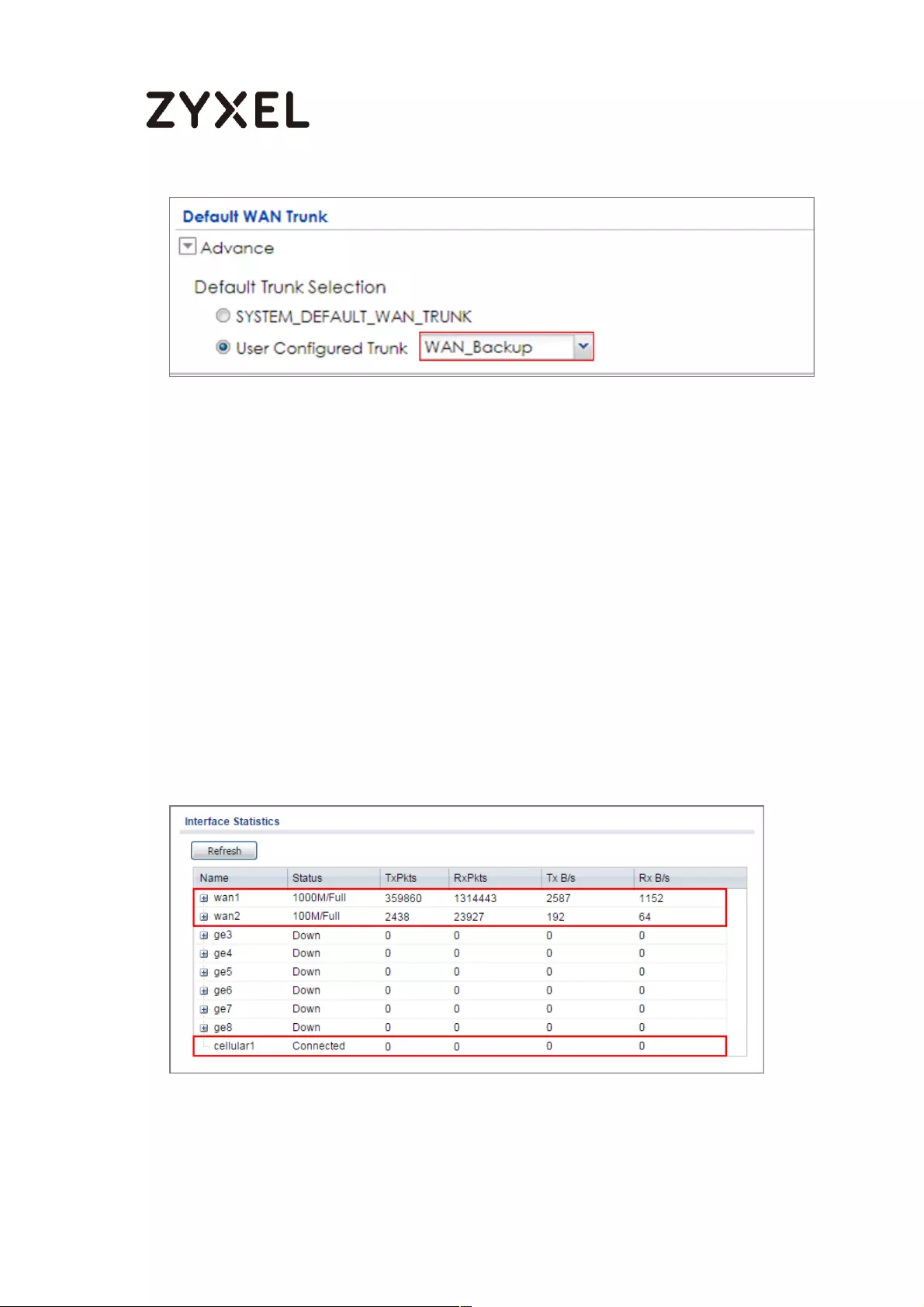
636/782
www.zyxel.com
Test the Result
Check the Interface Statistics when wan1 and wan2 connections are up. You can
see both wan1 and wan2 Status are up, Tx B/s displays the transmission speed
and Rx B/s displays the reception speed; cellular1 Status is connected but there is
no traffic going through this interface.
MONITOR > Interface Status > Interface Statistics
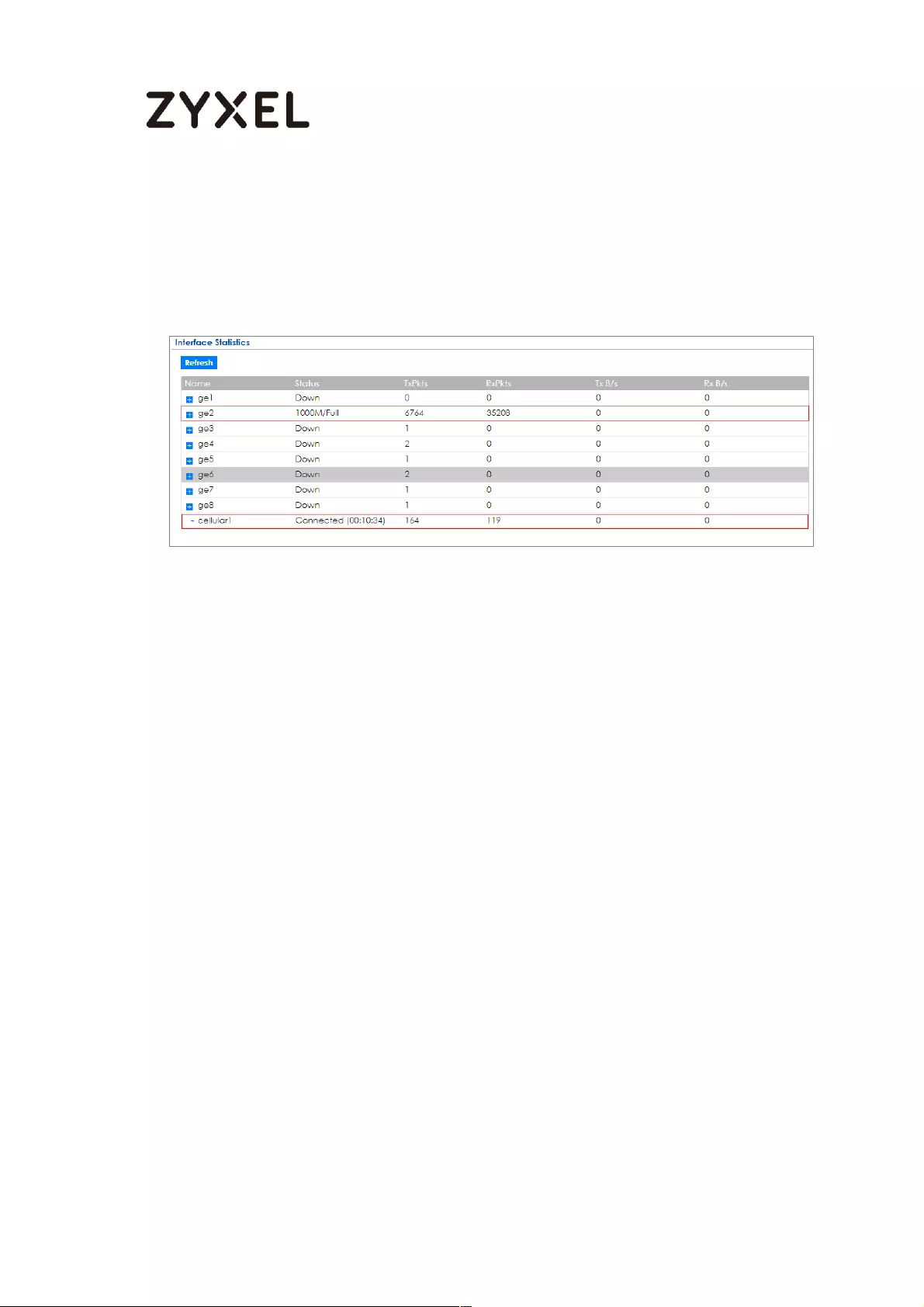
637/782
www.zyxel.com
After disconnecting both wan1 and wan2, you can see both wan1 and wan2
Status are Down and no traffic goes through these two interfaces. The backup
cellular1 Status is connected and all the traffic is going through this interface.
MONITOR > Interface Status > Interface Statistics
What Could Go Wrong?
If there is no traffic going through cellular interface when other interfaces are
down, please make sure you have a compatible mobile broadband device
installed or connected. Go to
http://www.zyxel.com/support/download_landing.shtml and see the 3G Dongle
Document to check the compatible mobile broadband devices. Also, make sure
the cellular interface is enabled and the cellular interface has the correct user
name, password, and PIN code configured with the correct casing.
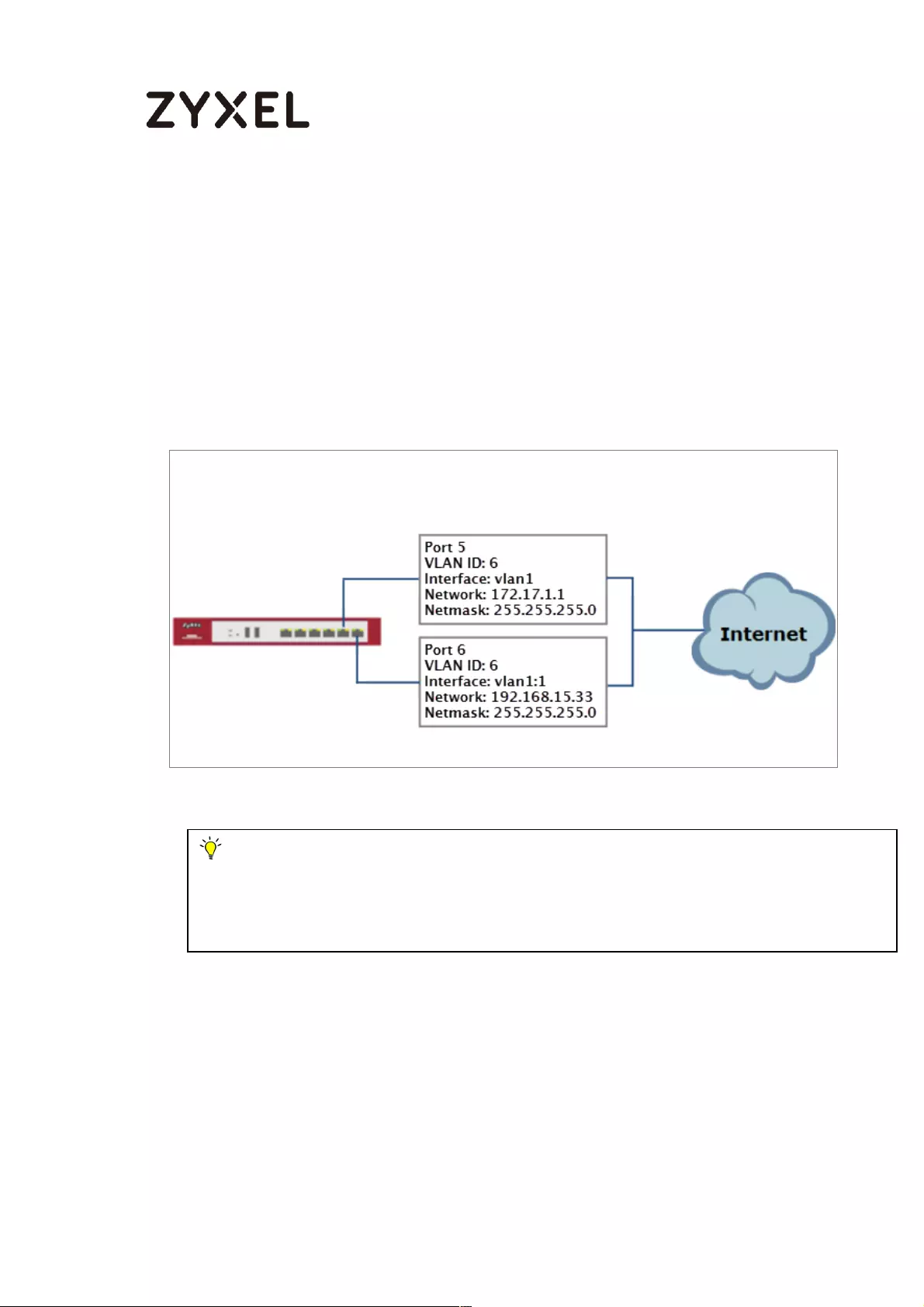
638/782
www.zyxel.com
How to Configure Two Different WAN Interfaces with
Different IP Addresses in the Same VLAN
This is an example of using ZyWALL/USG to configure two different WAN
interfaces with different IP addresses in the same VLAN. After configuration, you
can have the same VLAN ID for two different WAN interfaces.
ZyWALL/USG with Two Different WAN Interfaces with Different IP Addresses in the
Same VLAN Example
Note: This example requires the ZyWALL/USG models which can apply port grouping.
All network IP addresses and subnet masks are used as examples in this article. Please
replace them with your actual network IP addresses and subnet masks. This example was
tested using ZyWALL USG300 (Firmware Version: ZLD 4.25).
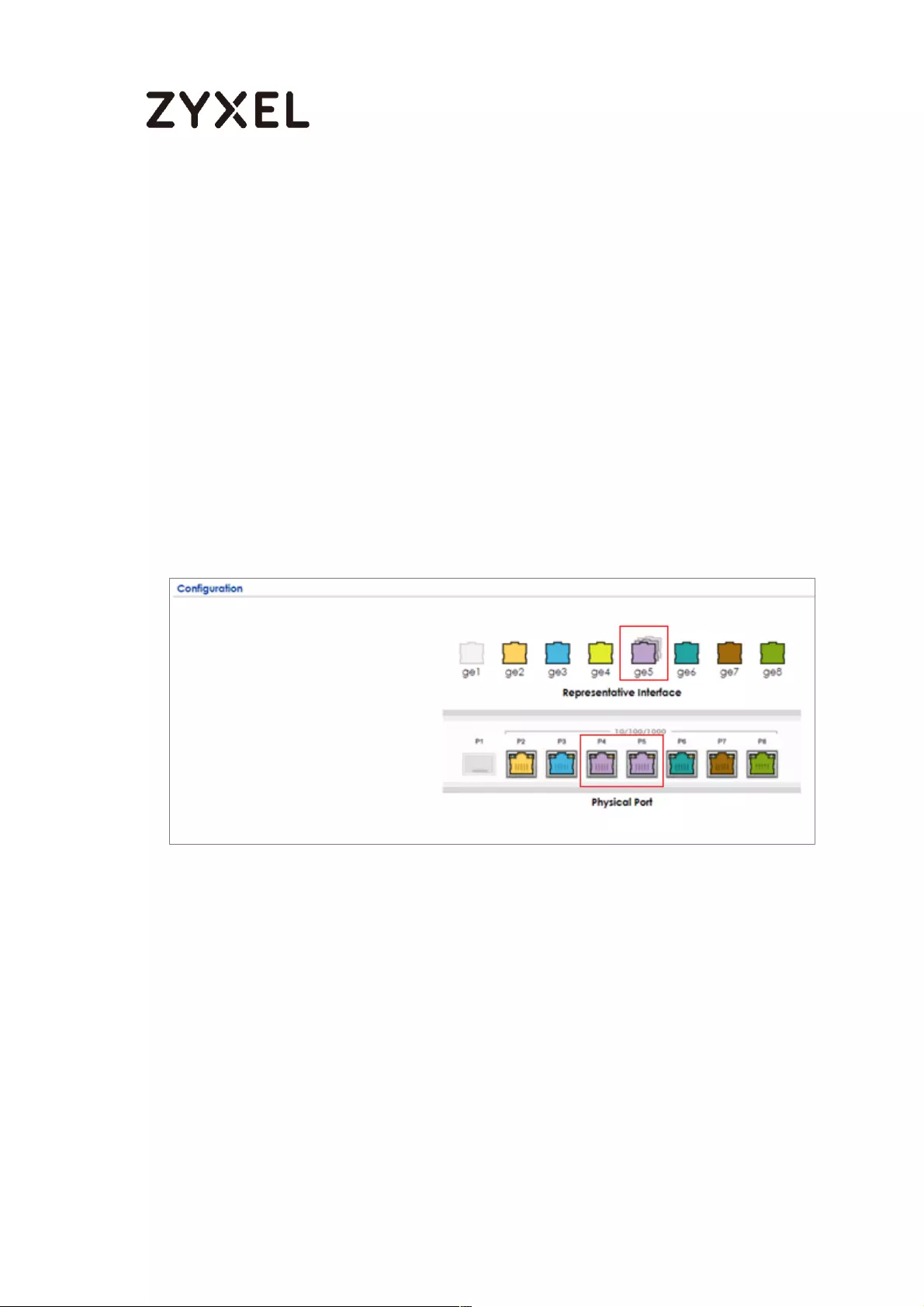
639/782
www.zyxel.com
Set Up the Port Grouping on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Port Grouping,
select the ports that you want to assign to a representative Interface (in this
example, Port 4 and Port 5 are configured as ge5).
CONFIGURATION > Network > Interface > Port Grouping
Set Up the VLAN on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > VLAN. Set
Interface Type to be External. Set Zone to be WAN, configure Base Port to be ge5.
Enter the VLAN ID and configure the fixed IP address (172.17.1.1/24 in this
example). Click OK to go back to the Configuration page.
CONFIGURATION > Network > Interface > VLAN
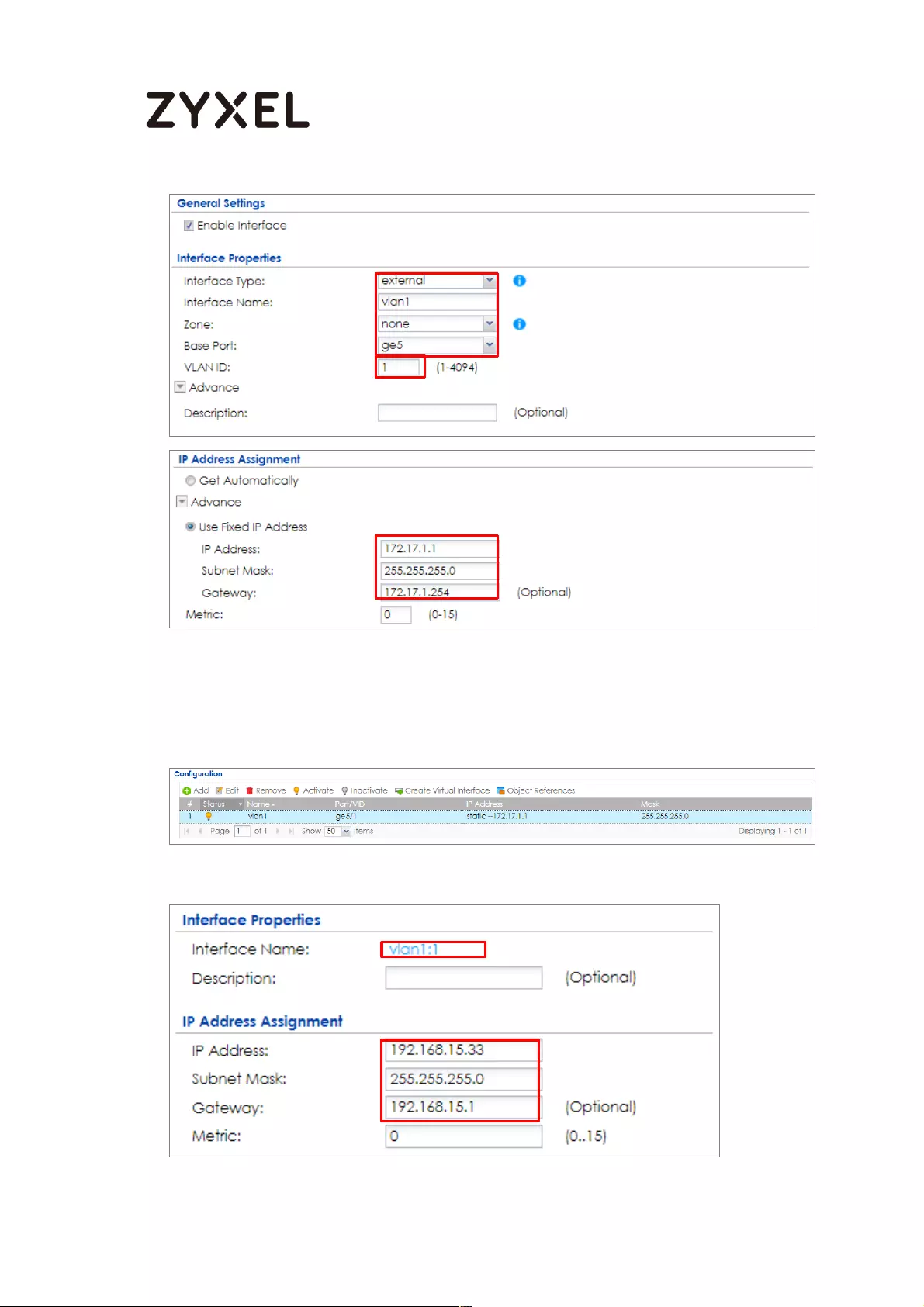
640/782
www.zyxel.com
In the Configuration page, select the vlan1 entry and click Create Virtual
Interface on the upper bar. Configure the Fixed IP address (192.168.15.33/24 in this
example). Click OK.
CONFIGURATION > Network > Interface > VLAN > vlan1
CONFIGURATION > Network > Interface > VLAN > vlan1:1
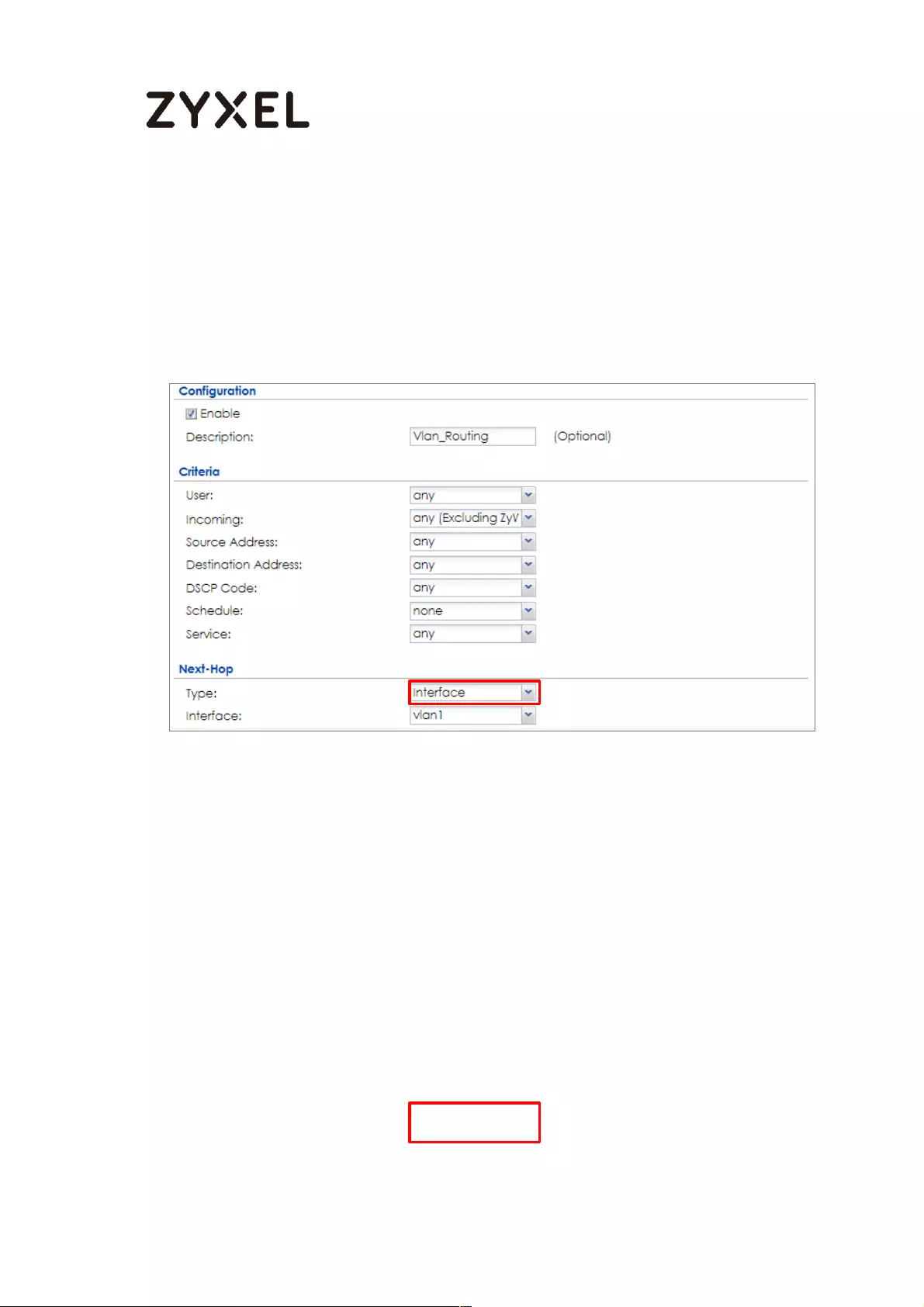
641/782
www.zyxel.com
Set Up the Routing on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Routing, set Next-Hop
Type to be Interface and set Interface to be the vlan1.
CONFIGURATION > Network > Routing
Test the Result
Check the Interface Statistics, you can see vlan1 Status is up, Tx B/s displays the
transmission speed and Rx B/s displays the reception speed. Port 5 and Port 6 are
configured in the same vlan1 but use different IP addresses.
MONITOR > Interface Status > Interface Statistics
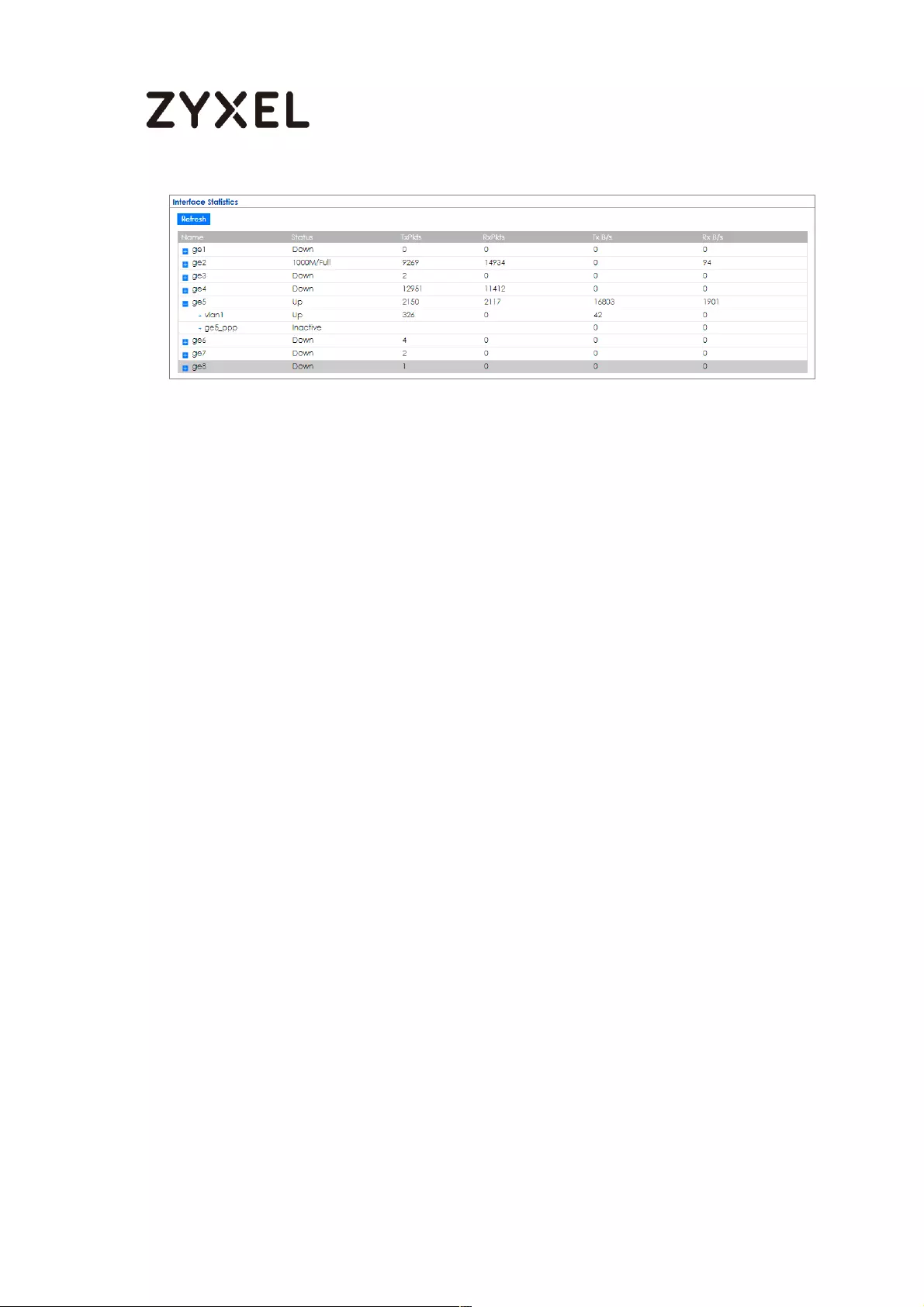
642/782
www.zyxel.com
What Could Go Wrong?
If you cannot configure a particular VLAN interface on top of an Ethernet
interface, please whether this VLAN has just been created on top of other
Ethernet interface.
How to Let a Server Use the Same Public IP Address as the
WAN Interface Using the Bridge Interface
This is an example of using ZyWALL/USG to configure an internal server in bridge
mode without applying network address translation (NAT). The Internet users can
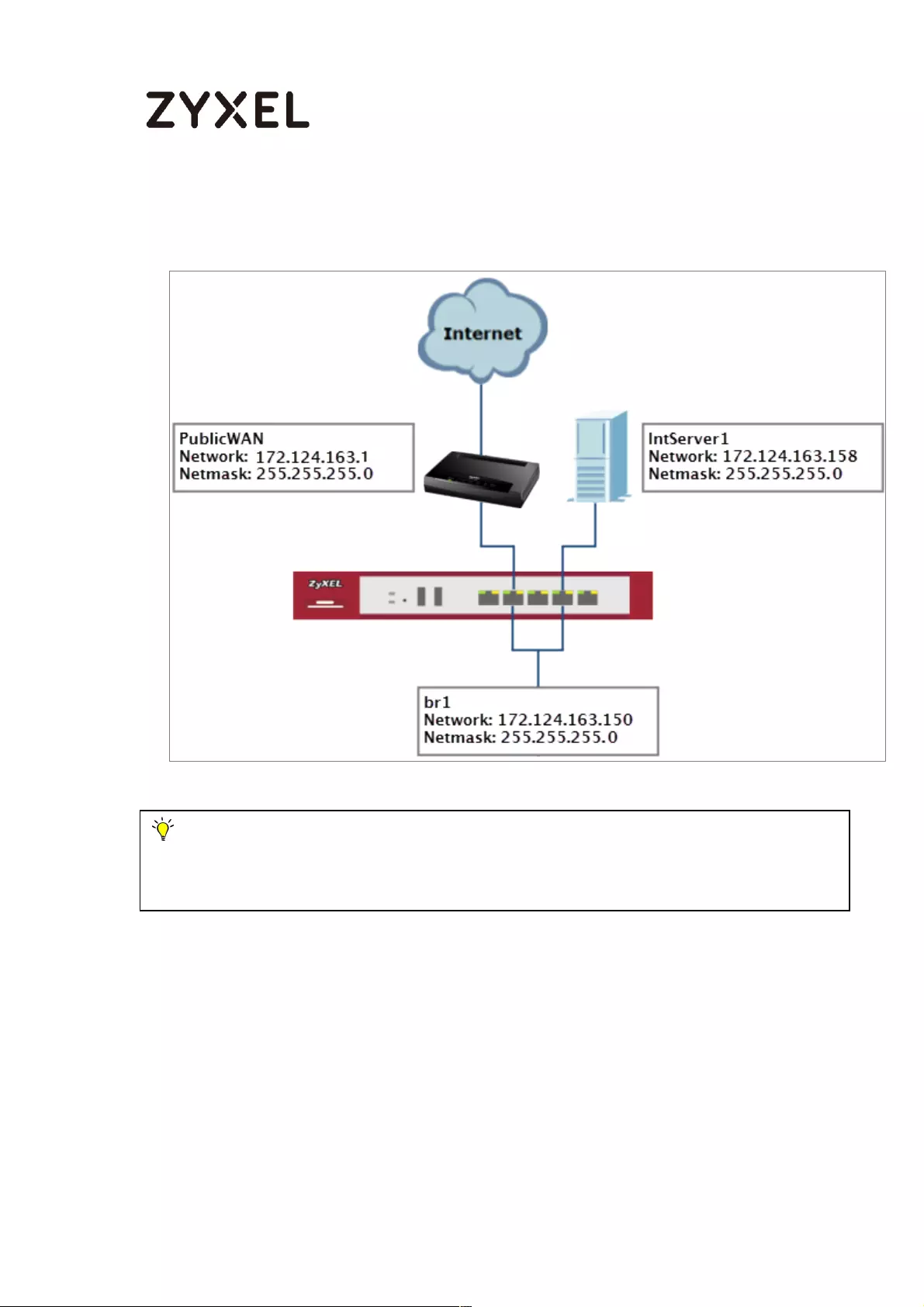
643/782
www.zyxel.com
reach this server directly by its public IP address.
ZyWALL/USG with Bridge Interface Example
Set Up the Bridge Interface on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Bridge > add
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
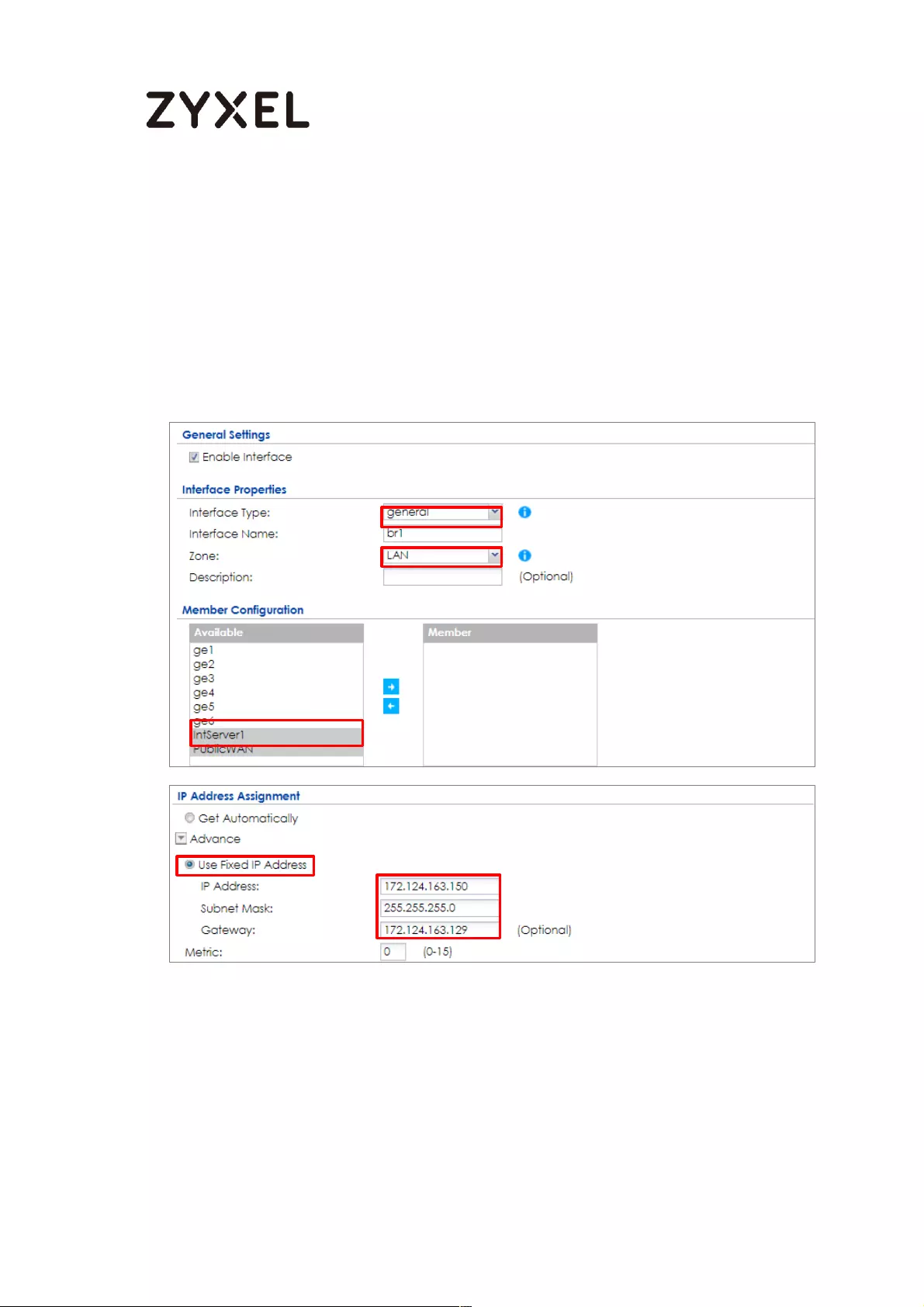
644/782
www.zyxel.com
Bridge, select Interface Type to be the general type, select Zone to be the LAN
zone. In the Member Configuration, select internal server (IntServer1 interface in
this example) and public IP address (Public WAN interface in this example) to be
in the same member group.
In the IP Address Assignment section, select Used Fixed IP Address and configure
br1 IP address (172.124.163.150/24 in this example).
CONFIGURATION > Network > Interface > Bridge > add Bridge
After creating the bridge interface, connect the server's network cable to
IntServer1 port and set the server's IP to be in the same subnet (172.124.163.158 in
this example).
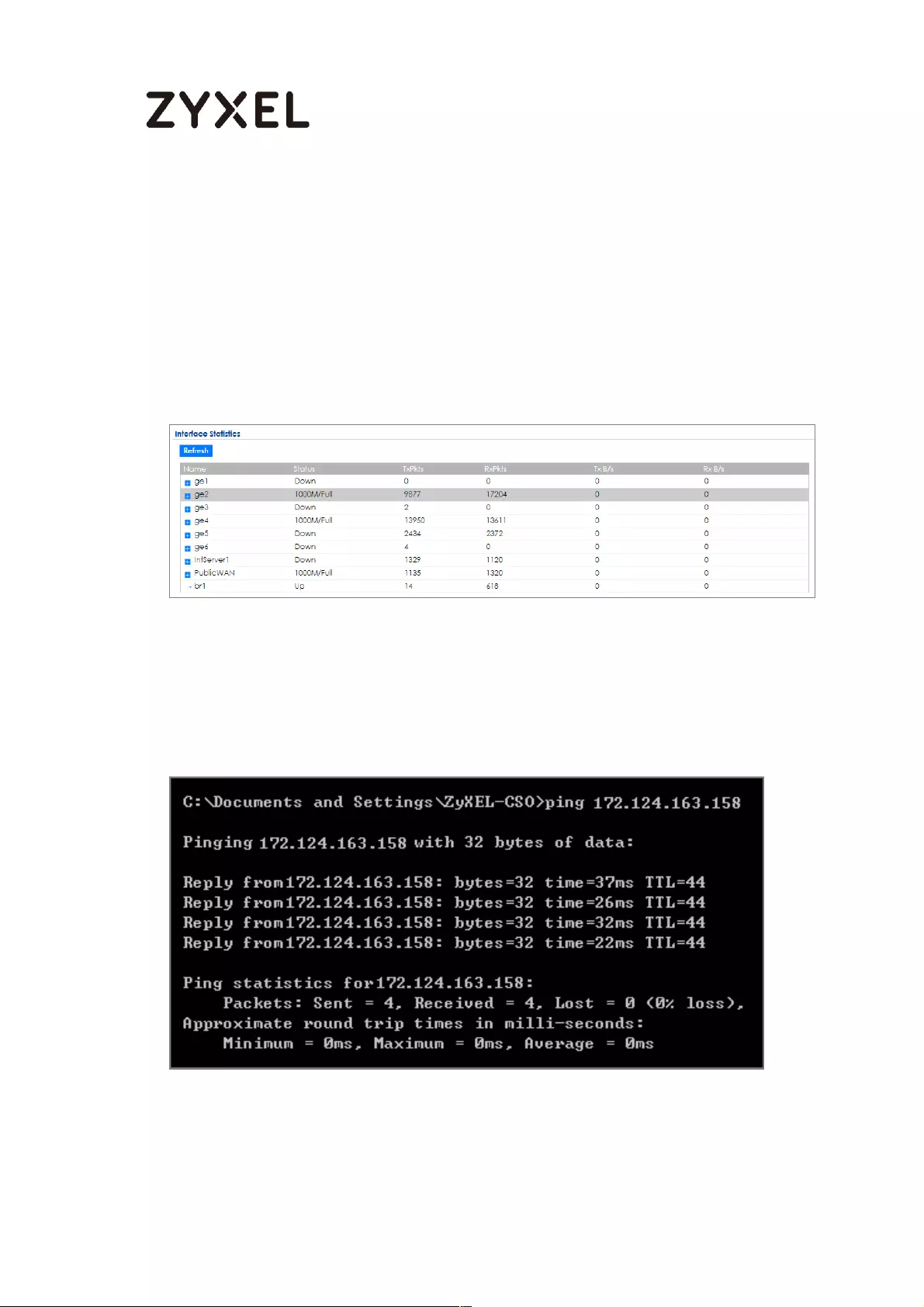
645/782
www.zyxel.com
Test the Result
Check the Interface Statistics, you can see br1 Status is up, Tx B/s displays the
transmission speed and Rx B/s displays the reception speed. IntServer1 and
PublicWAN are configured in the same vlan1 but using different IP address.
MONITOR > Interface Status > Interface Statistics
Server can access Internet successfully by using its IP address (172.124.163.158 in
this example) and Internet users can also reach this server by this public address
as well.
Windows 7 > cmd > ping 172.124.163.158

646/782
www.zyxel.com
What Could Go Wrong?
If you cannot configure a particular bridge IP address, please check is this IP
address already created on other Ethernet interface.
How to Allow Public Access to a Server Behind
ZyWALL/USG
This is an example of using ZyWALL/USG to configure a securely access to internal
server behind ZyWALL/USG with network address translation (NAT). The Internet
users can reach this server directly by its public IP address and a NAT mapping
rule will forward the traffic from the Internet to the Intranet. It provides security and
decrease the number of IP addresses an organization needs.
ZyWALL/USG enables Public Access to a Server with NAT
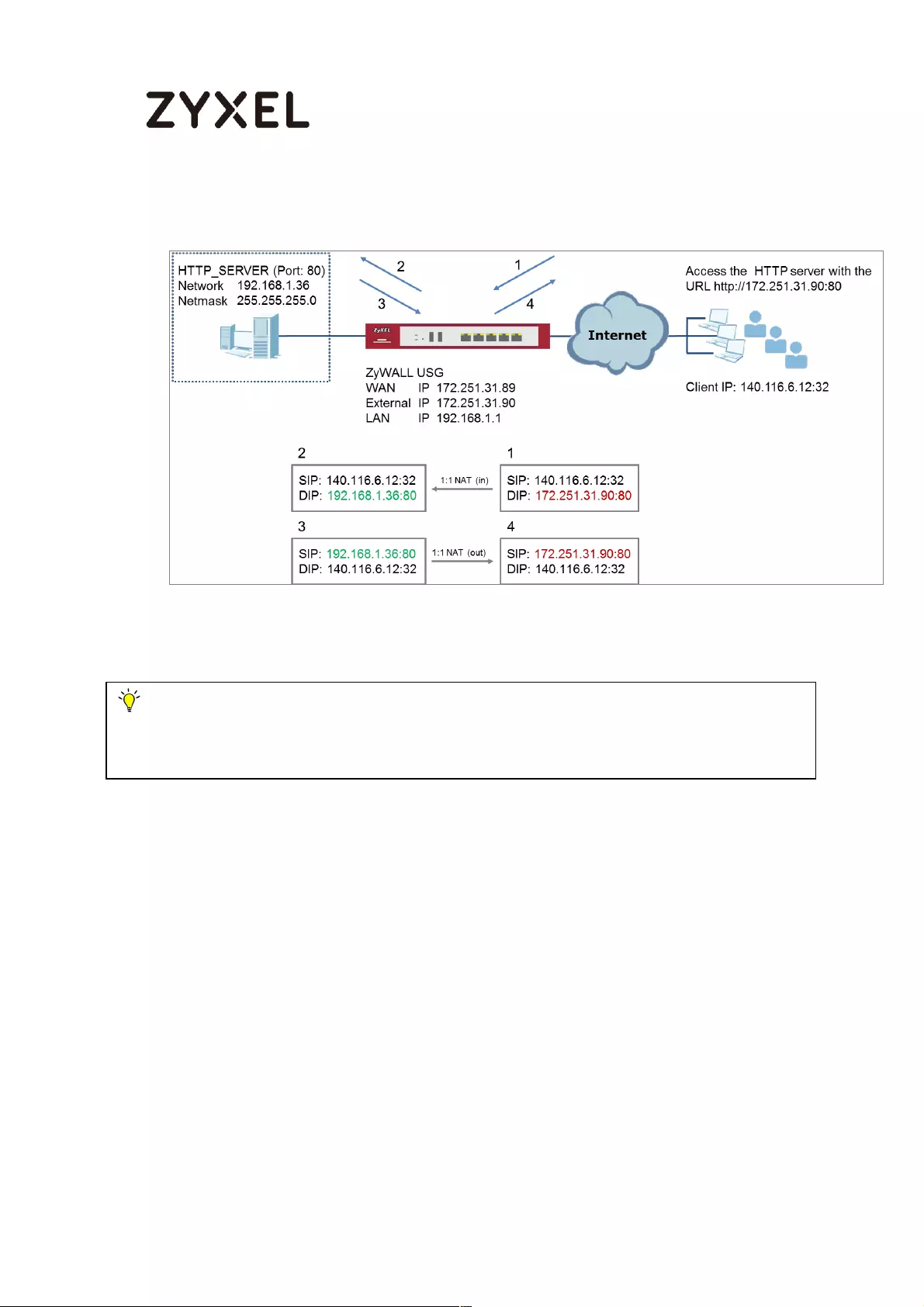
647/782
www.zyxel.com
Set Up the NAT on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > NAT > add NAT, select
Enable Rule. Select 1:1 NAT. Set Incoming Interface to be the wan1 interface.
Type User-Defined Original IP (172.251.31.90 in this example) and type User-
Defined Mapped IP (192.168.1.34 in this example). Set Port Mapping Type to
Service, set Original Service and Mapped Service to HTTP in this example. Click
OK.
CONFIGURATION > Network > NAT > add NAT
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).

648/782
www.zyxel.com
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy Control >
add corresponding, select Enable. Configure a Name for your to identify the
security policy (http_server_access in this example). Set From: WAN and To: LAN1.
Set Destination to the lan subnet where your server is (LAN_SUBNET_GE3 in this
example). Set Service to HTTP, set Action to allow. Click OK.
CONFIGURATION > Security Policy > Policy Control > add corresponding
649/782
www.zyxel.com
Test the Result
Type http://172.251.31.90/ into the browser, it displays the HTTP service page.
What Could Go Wrong?
If you cannot access your server via public IP address, please make sure all your
public IP addresses are routing properly. To do one by one assign them to the
ZyWALL’s WAN port. Test to make sure you have internet access with the public IP
address.
If you cannot access the ZyWALL from the internet with any IP address on your
public IP, this is a routing issue on the service end. Please contact the ISP to fix the
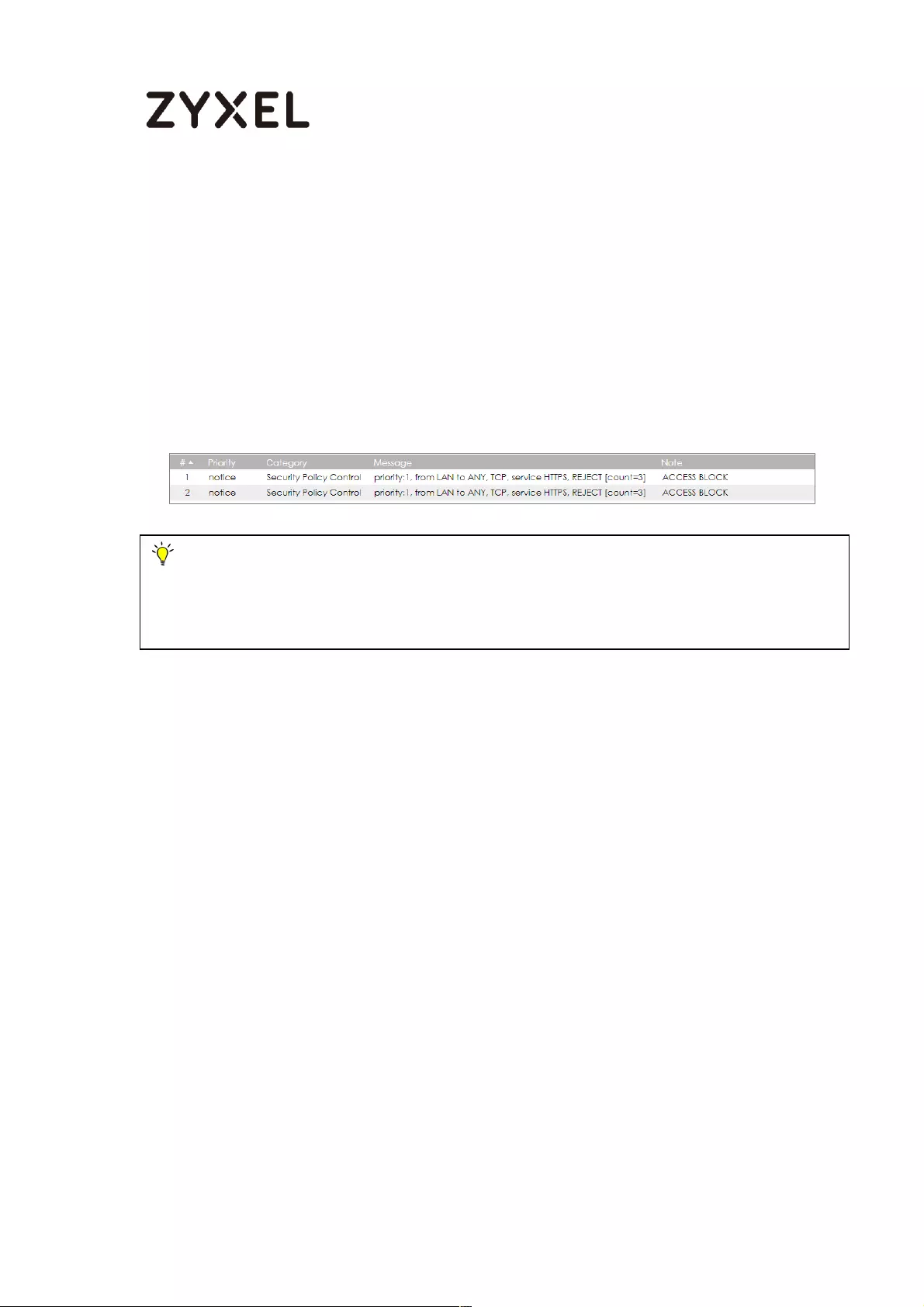
650/782
www.zyxel.com
routing for the public IPs.
If you see [notice] log message as below, the HTTPS traffic is blocked by the
priority 1 Security Policy. The ZyWALL/USG checks the security policy in order and
applies the first security policy the traffic matches. If the HTTPS traffic matches a
policy that comes earlier in the list, it may be unexpectedly blocked. Please
change your policy setting or move the policy to the higher priority.
Monitor > Log
Note: The default setting of Security Policy is without log notification (except
PolicyDefault), if you want to check which policy may potentially block the traffic, please
select this policy and set the Log matched traffic to be log or log alert.
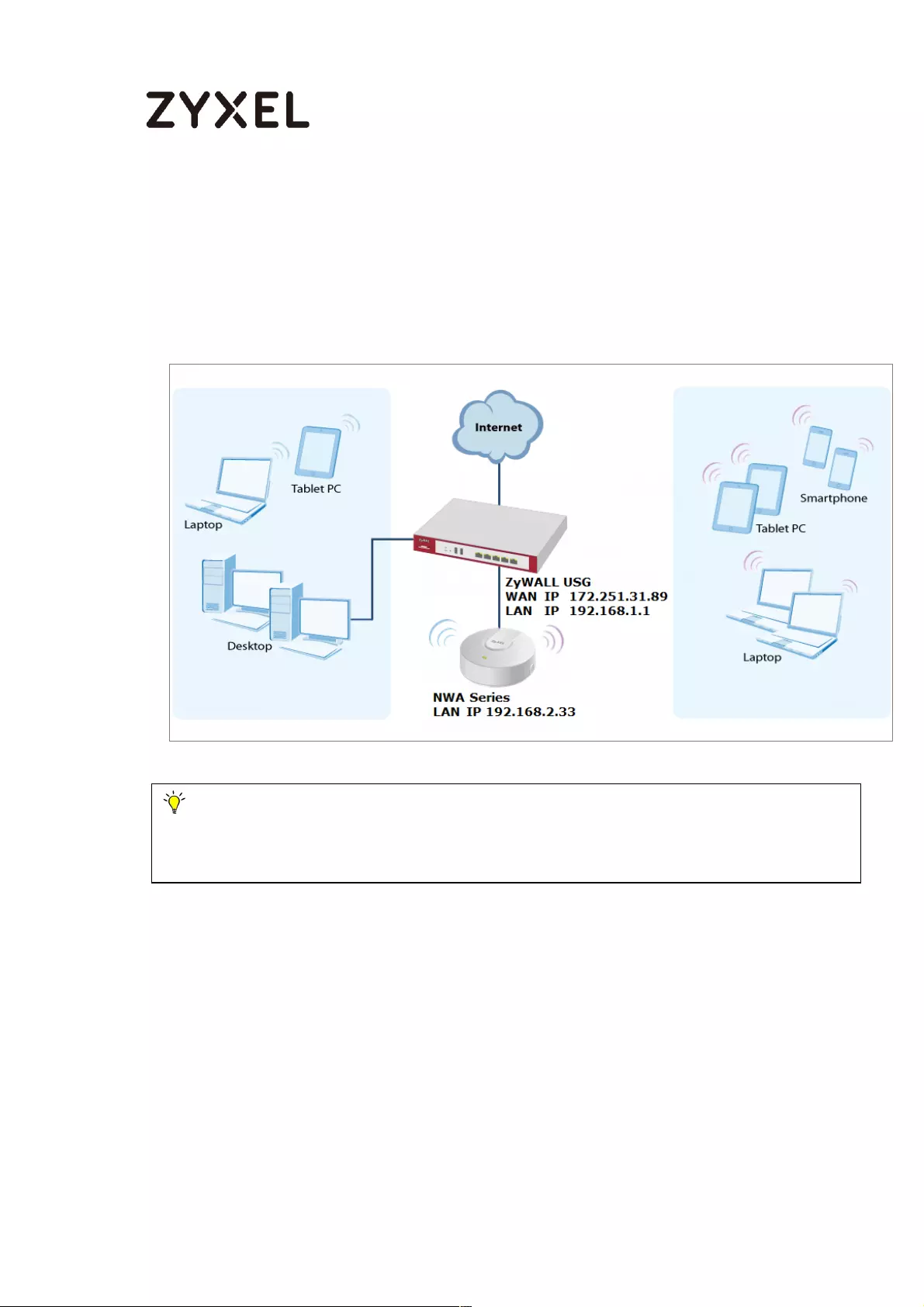
651/782
www.zyxel.com
How to Set Up a WiFi Network with ZyXEL APs
This is an example of using ZyWALL/USG to manage the Access Points (APs) and
allow wireless access to the network.
ZyWALL/USG as AP Controller Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
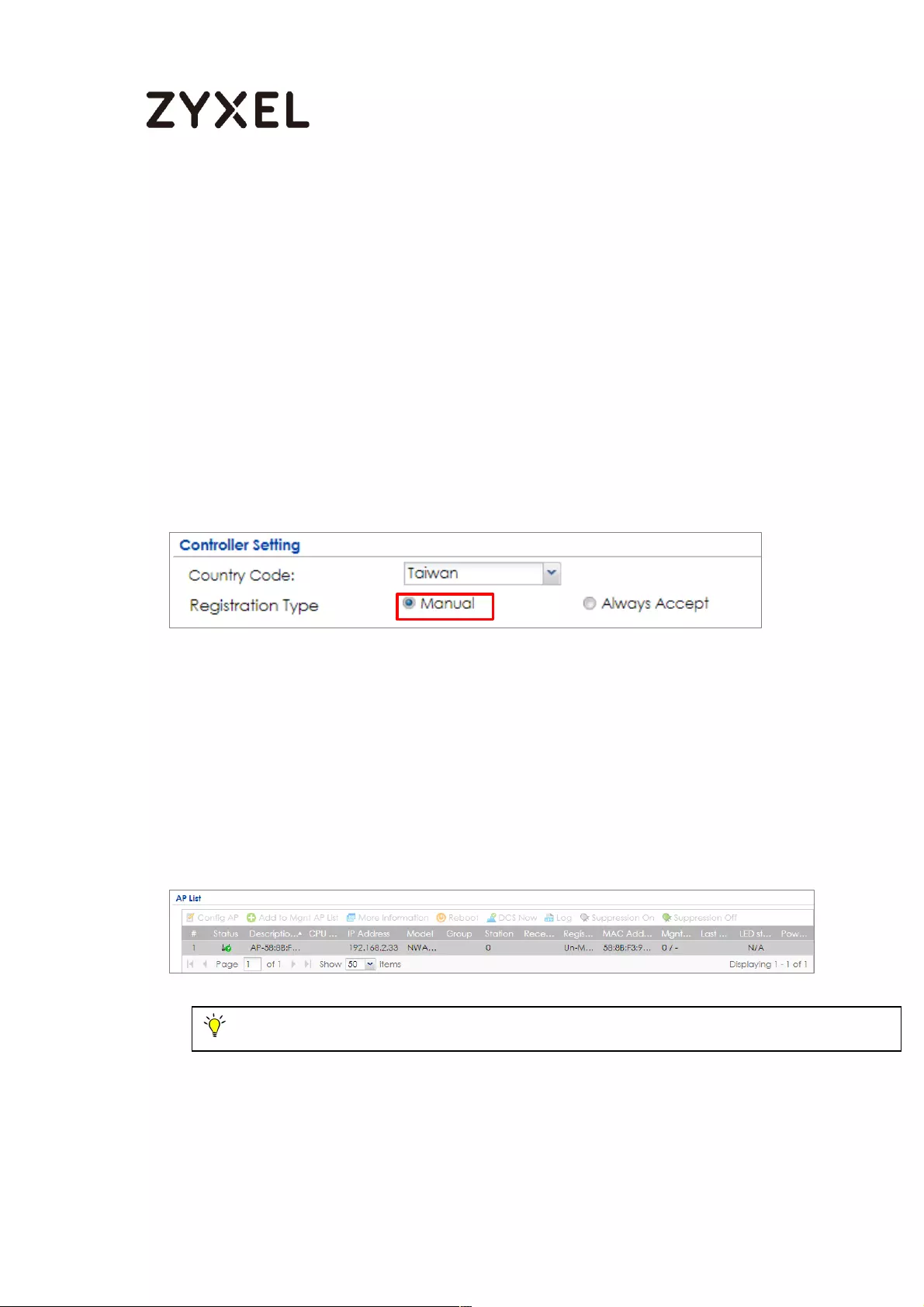
652/782
www.zyxel.com
Set Up the AP Management on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Wireless > Controller > Configuration,
set Registration Type to Manual. This is recommended as the registration
mechanism cannot automatically differentiate between friendly and rogue APs.
CONFIGURATION > Wireless > Controller > Configuration
Connect the ZyXEL AP unit to the lan interface.
Go to MONITOR > Wireless > AP Information > AP List and the ZyXEL AP is listed. A
green question mark displays in the Status column since the AP is not yet
managed by the ZyWALL/USG. Select the listed AP and click Add to Mgnt AP List
on the upper bar.
Monitor > Wireless > AP Information > AP List
Go to CONFIGURATION > Object > AP Profile > SSID > SSID List to configure a
name to identify the SSID.
CONFIGURATION > Object > AP Profile > SSID > SSID List
Note: The APs may take few minutes to appear in the AP List.
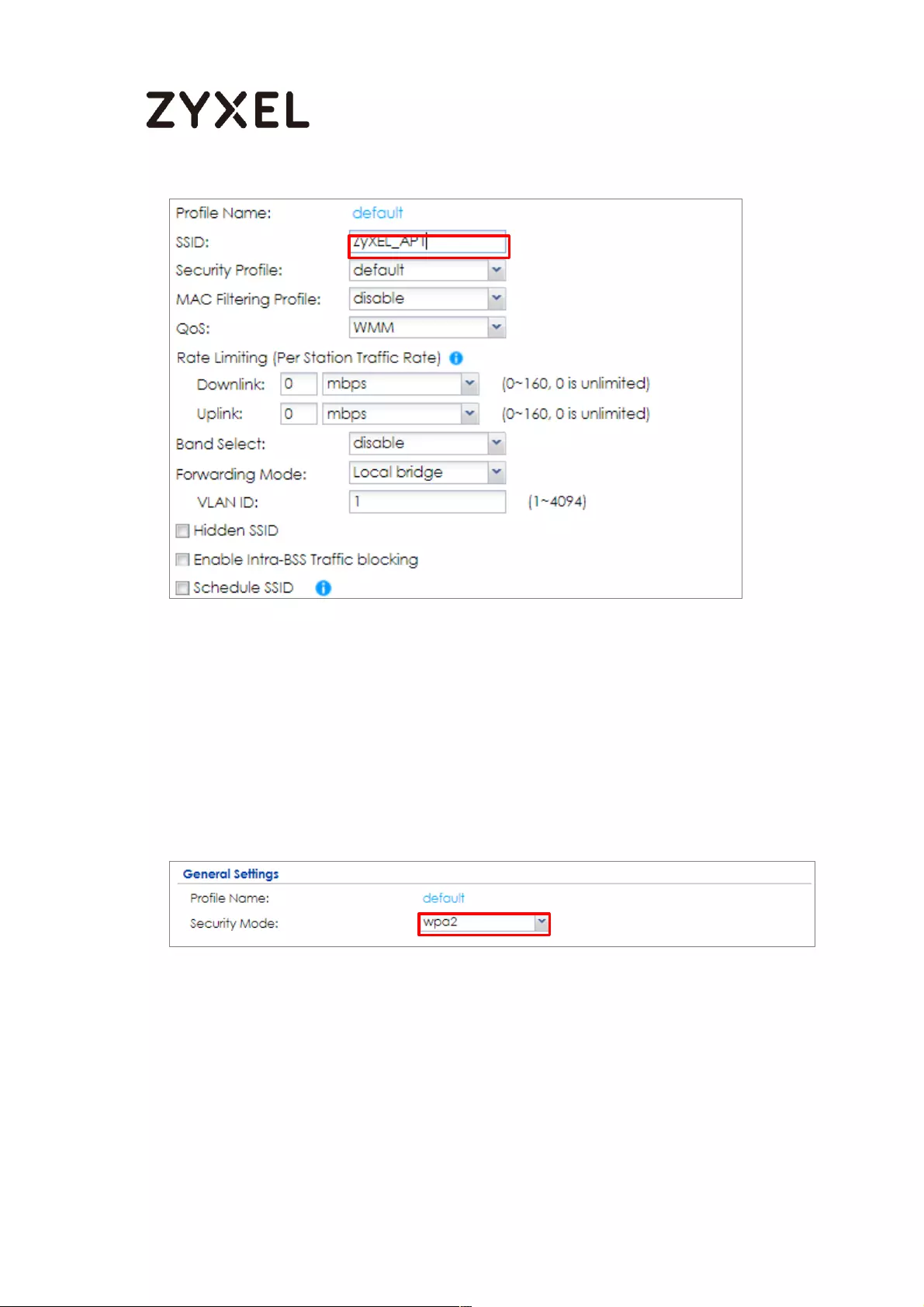
653/782
www.zyxel.com
Go to CONFIGURATION > Object > AP Profile > SSID > Security List to select the
Security Mode to be the wpa2. Then, set a Pre-Shared Key (8-63 characters) and
select the Cipher Type to be the auto to have ZyWALL/USG automatically
chooses the best available cipher based on the cipher currently in use by the
wireless network. Click OK.
CONFIGURATION > Object > AP Profile > SSID > Security List
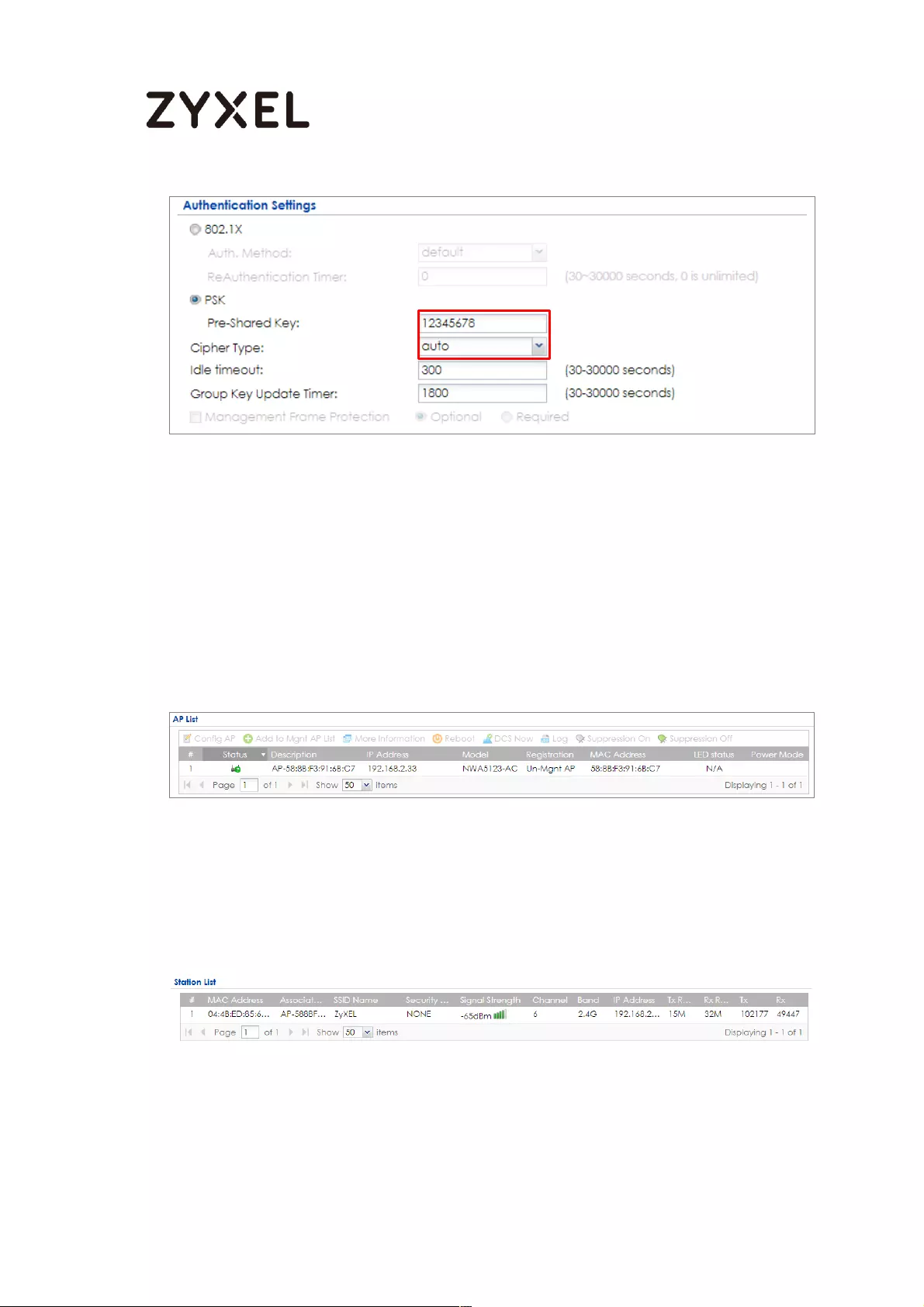
654/782
www.zyxel.com
Test the Result
Go to the ZyWALL/USG Monitor > Wireless > AP Information > AP List, you can
check the list of APs which are currently connected to it and the details
information such as Registration type, Model and Recent On-line Time /Last Off-
line Time.
MONITOR > Wireless > AP Information > AP List
Go to the ZyWALL/USG Monitor > Wireless > Station Info > Station List, you can
check the list of wireless stations associated with a managed AP and the details
information such as SSID Name, Signal Strength and the transmit (Tx)/receive (Rx) data
rate.
MONITOR > Wireless > Station Info > Station List
Using a mobile device to connect to SSID: ZyXEL_AP1 and type the password
(zyxel123) for authentication. Go to the ZyWALL/USG Monitor > Log, you will see
[info] log message as shown below. The ZyWALL/USG will assign an IP address to
655/782
www.zyxel.com
the mobile device and the mobile device can access the Internet.
MONITOR > Log
What Could Go Wrong?
If you can’t see AP information in the AP List, please check the number of APs
connected to the ZyWALL/USG has exceeded the maximum Managed AP
number it can support. You can check the maximum support number of each
ZyWALL/USG in the Datasheet from ZyXEL Download Library -
http://www.zyxel.com/support/download_landing.shtml
If your mobile device can’t find the AP SSID you configured, please go to
CONFIGURATION > Object > AP Profile > SSID > SSID List and check if the Hidden
SSID option is enabled.
If your mobile device can’t access to the Internet via AP connects to the
ZyWALL/USG, please check if the LAN outgoing security policy allow access to the
Internet.
If your mobile device is not connected to the AP automatically even you’ve
joined the Wifi network before and you see [Wlan Station Info] log message as
shown below, please check if this AP is removed from your mobile device’s saved
Wifi network list.
MONITOR > Log

656/782
www.zyxel.com
How to Set Up Guest WiFi Network Accounts
This is an example of using ZyWALL/USG to configure guest WiFi accounts to allow
limited wireless access to the Internet using only HTTP, HTTPS, and DNS protocols.
For the wireless network setup, please see the tutorial about How to Set Up WiFi
with ZyXEL AP.
ZyWALL/USG with Guest WiFi Accounts Example

657/782
www.zyxel.com
Set Up the WiFi Guest Account, Address Range and Service
Rule on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Object > User/Group > User > Add A
User to configure the User Name the guest Wi-Fi user and set User Type to guest.
Set a secured Password (4-31 characters) and enter it again for confirmation.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
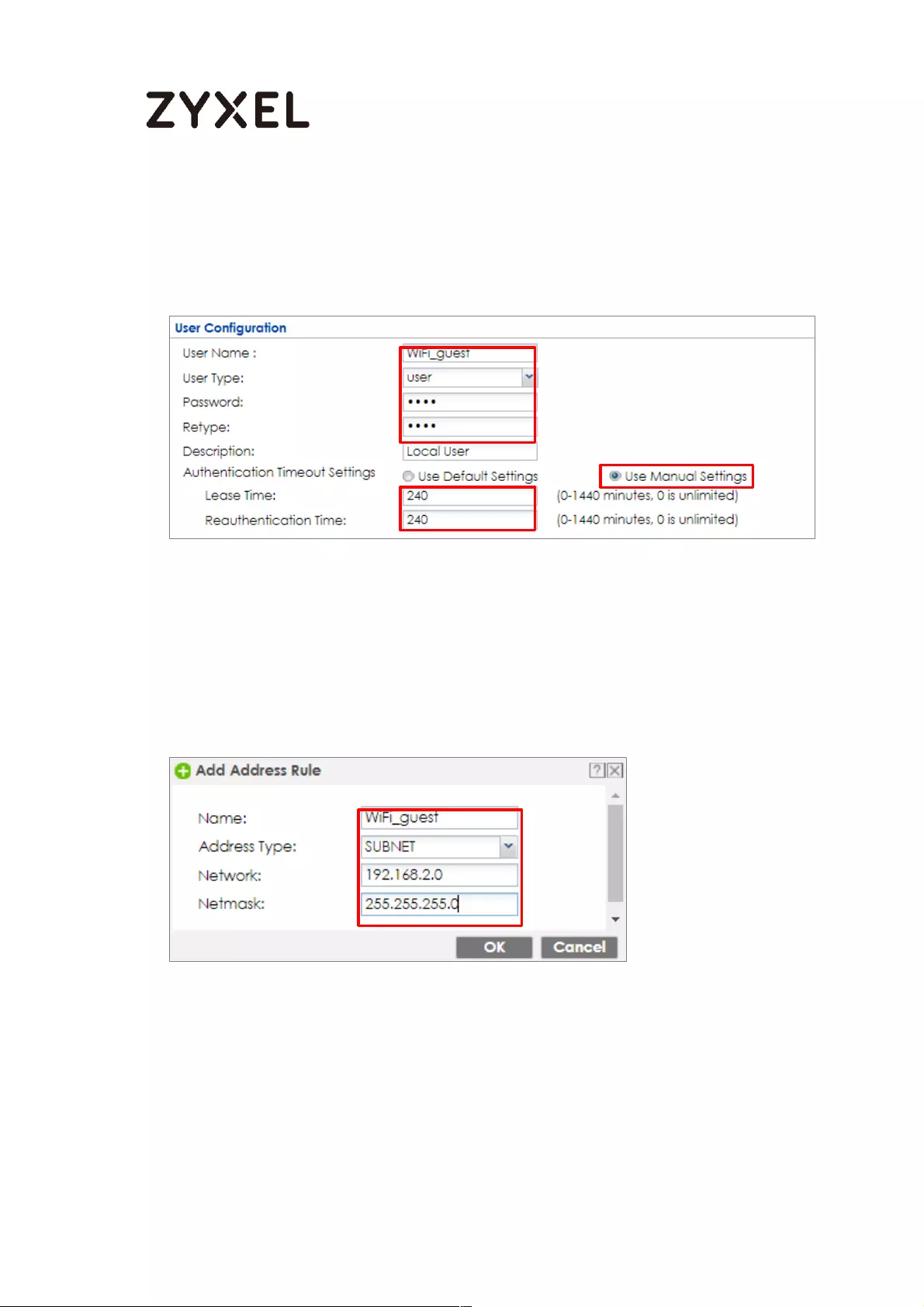
658/782
www.zyxel.com
Set the Authentication Timeout Settings to be Use Manual Settings to enter the
number of minutes this user has to renew the current session before the user is
logged out.
CONFIGURATION > Object > User/Group > User > Add A User
In the ZyWALL/USG, go to CONFIGURATION > Object > Address > Add Address
Rule to create the guest Wi-Fi user access subnet. In this example, AP is
connected to ZyWALL/USG LAN interface 192.168.2.0/24. Configure the Name for
you to identify the Wi-Fi guest subnet. Set the Network to be 192.168.2.0 and set
the Netmask to be 255.255.255.0. Click OK.
CONFIGURATION > Object > Address > Add Address Rule
In the ZyWALL/USG, go to CONFIGURATION > Object > Service > Service Group >
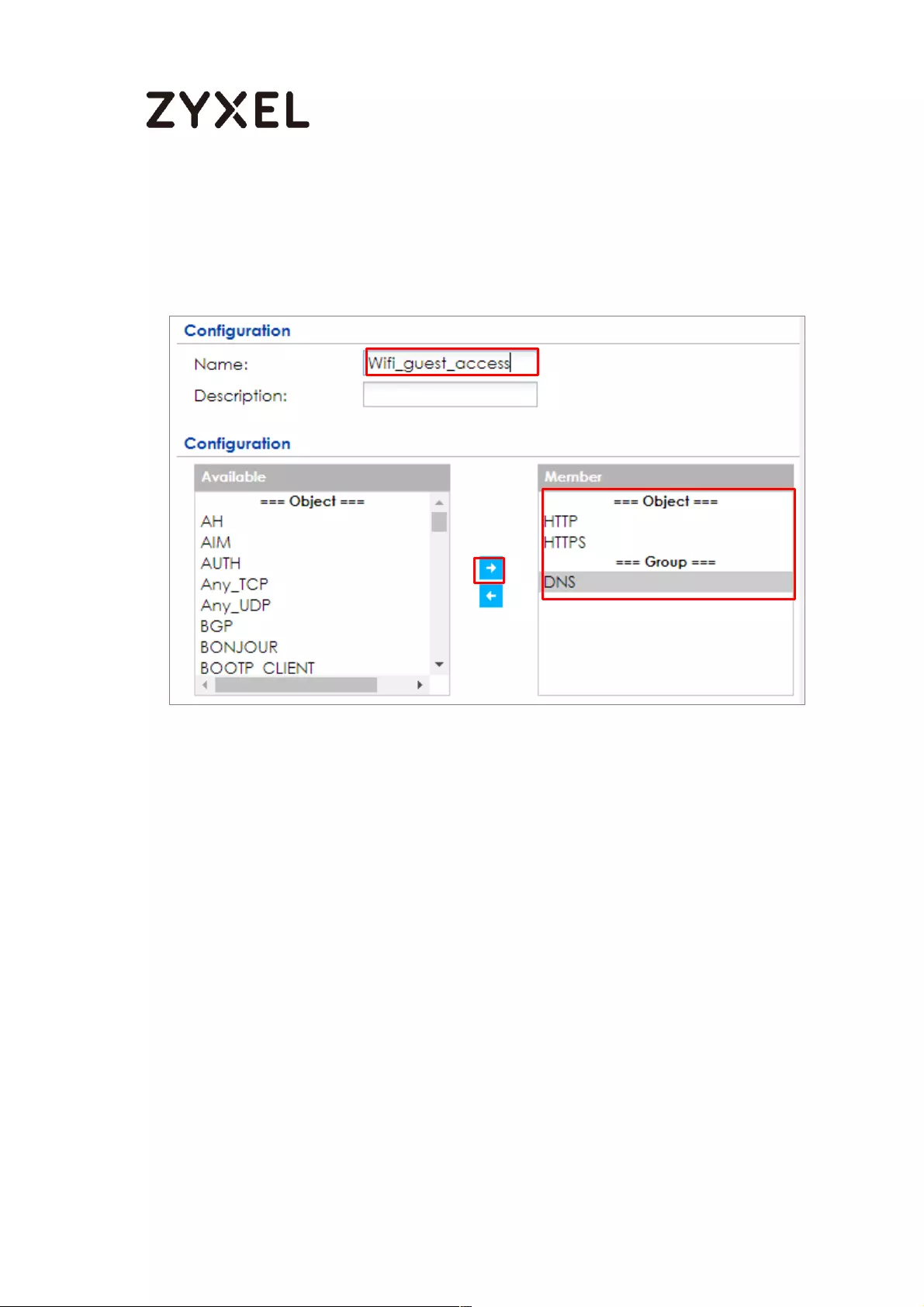
659/782
www.zyxel.com
Add Service Group Rule to create the allowed protocols for guest Wi-Fi user.
Configure the Name for you to identify the Service Group. Set HTTP, HTTPS and
DNS to be in the same member group and click OK.
CONFIGURATION > Object > Service > Service Group > Add Service Group Rule
Set Up the Web Authentication on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Web Authentication > Web
Authentication Policy Summary > Auth. Policy Add to configure policy to redirect
HTTP traffic to the user login screen. Configure the Description (Optional) for you to
identify the auth. Policy. Then, scroll down the Source Address list to choose the
newly created wifi-guest. Set the Authentication to be required. Select Force User
Authentication.
CONFIGURATION > Web Authentication > Web Authentication Policy Summary >
Auth. Policy Add
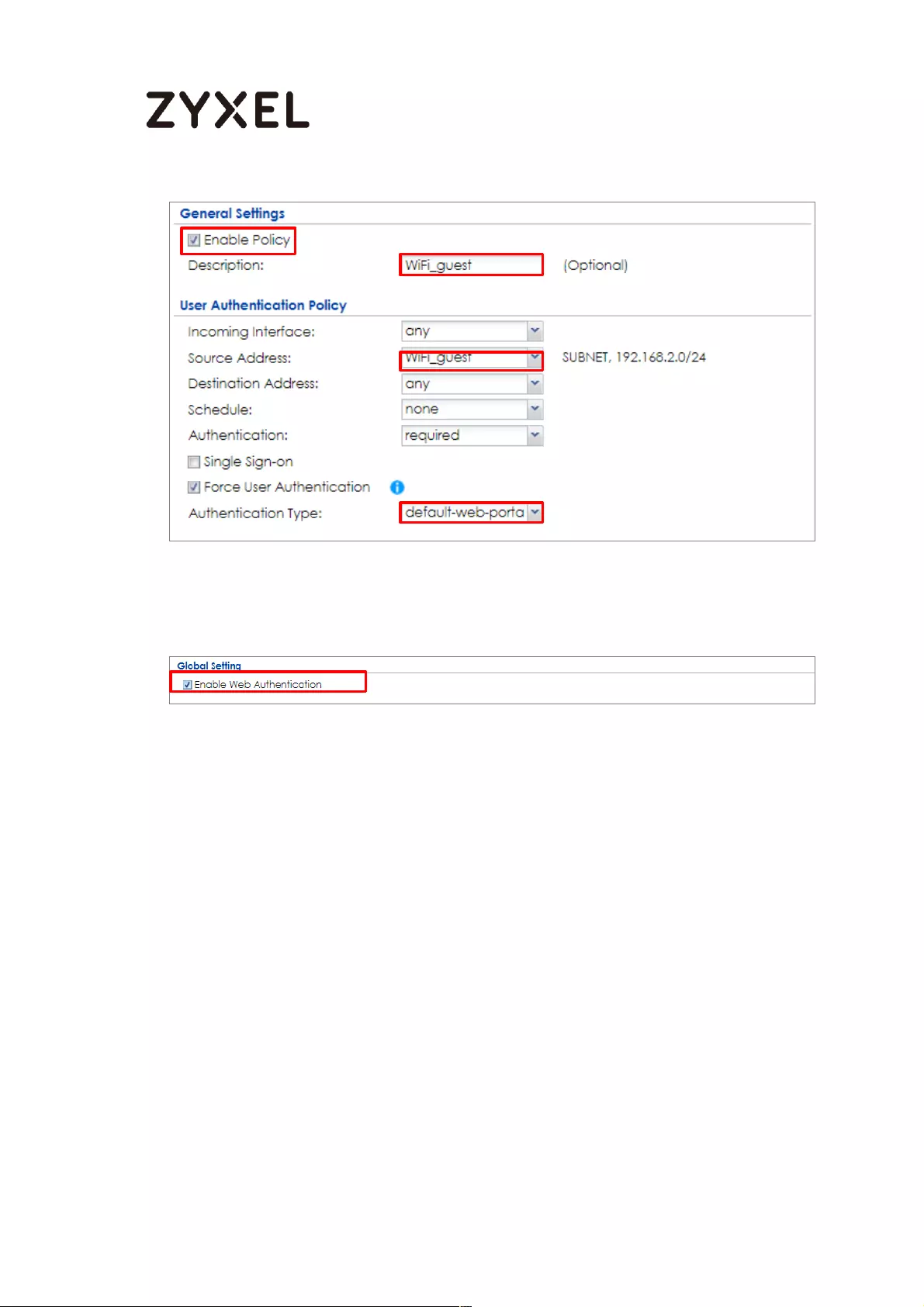
660/782
www.zyxel.com
In the ZyWALL/USG, go to CONFIGURATION > Web Authentication > General
Settings and select Enable Web Authentication.
CONFIGURATION > Web Authentication > General Settings
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy > Add
corresponding. Configure a Name for you to identify the Security Policy profile.
Set From: LAN and To: any (Excluding ZyWALL). Set Service to be the Service
Group Rule (wifi_guest_access in this example). Set User to be the Wi-Fi guest user
(wifi_guest_access in this example). Select Log type to log alert in order to view
the result later.
CONFIGURATION > Security Policy > Policy > Add corresponding
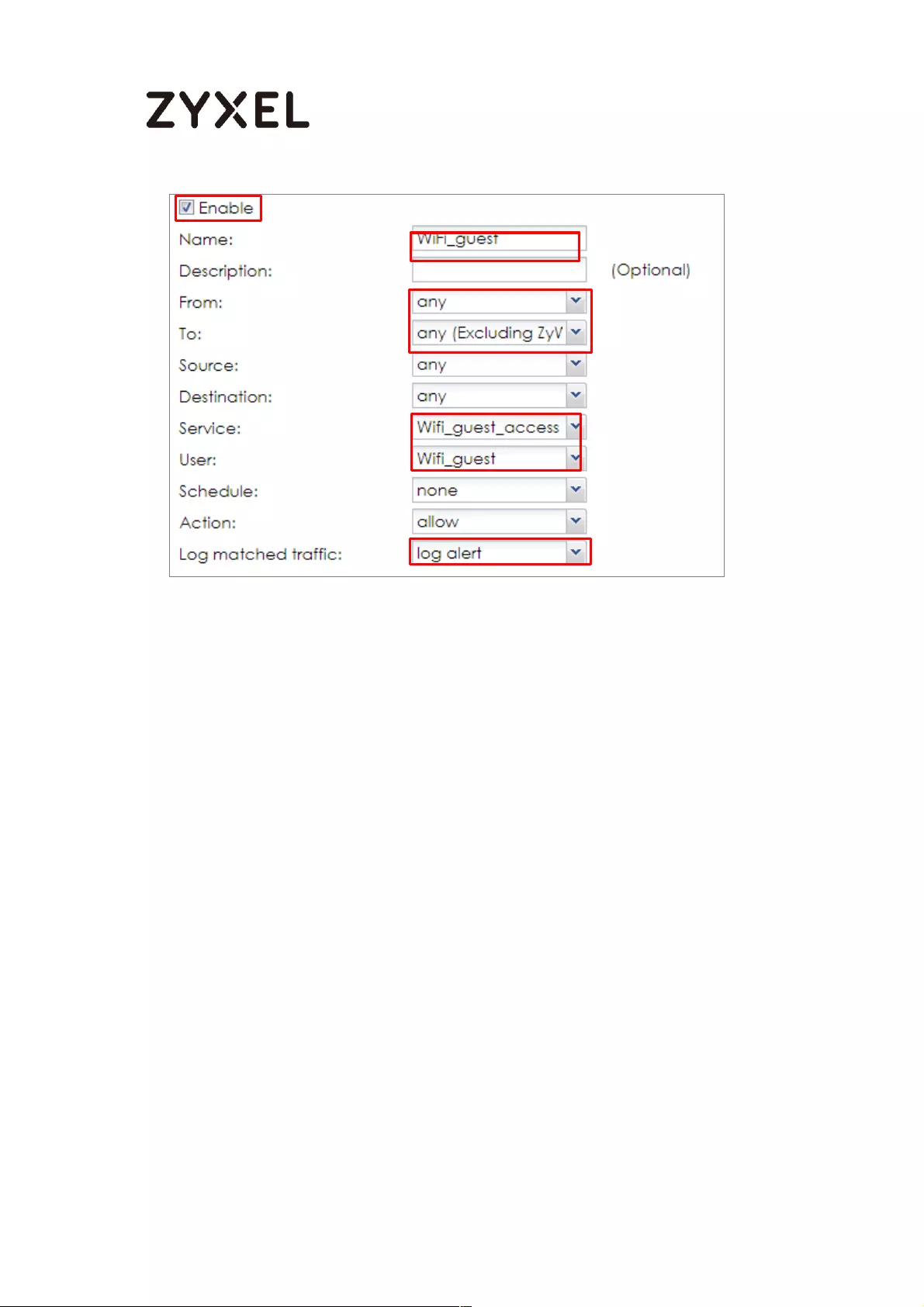
661/782
www.zyxel.com
Test the Result
Using a mobile device to connect to the AP which is connected to the
ZyWALL/USG. When you try to access the Internet, it will redirect to the user login
screen.

662/782
www.zyxel.com
Type the Wi-Fi guest User Name and Password, click Login.
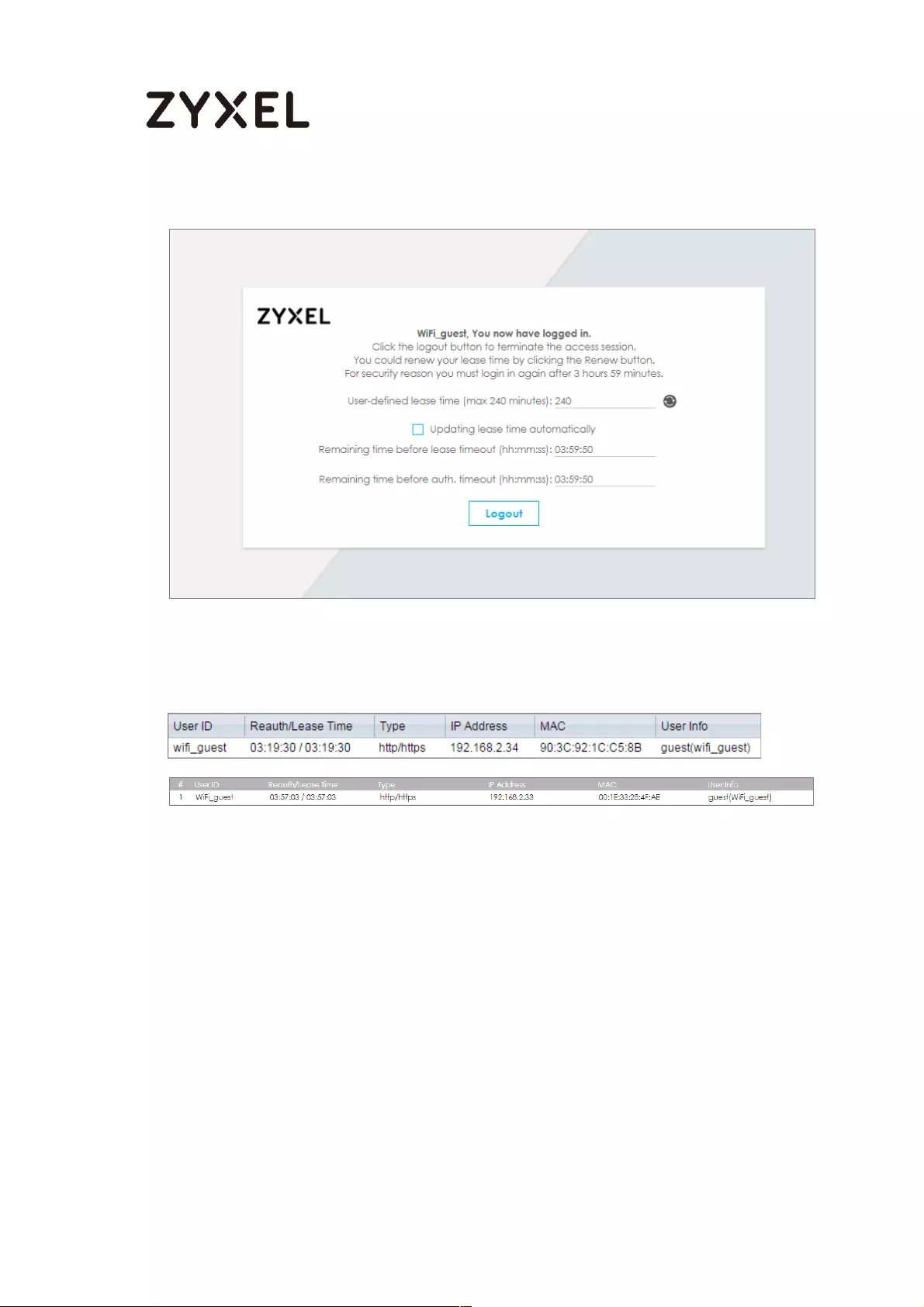
663/782
www.zyxel.com
The access session page will appear.
Go to the ZyWALL/USG Monitor > System Status > Login Users, you will see current
login user list shown as below.
Monitor > System Status > Login Users
Attempt to access FTP server (prohibited service in this example) and it gets an
error message.
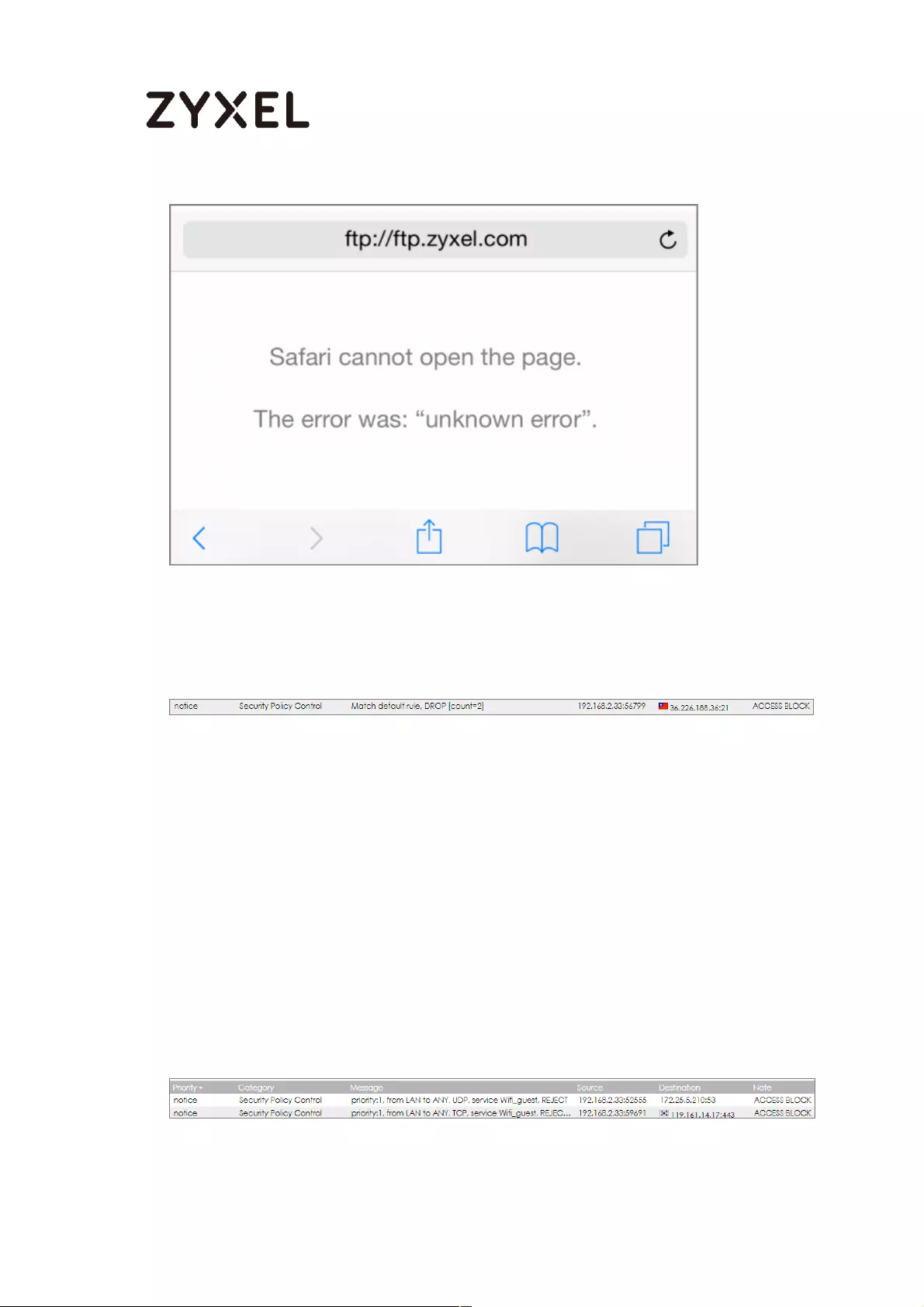
664/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > Log, you will see [notice] log message shown as
below. The access to FTP service port 21 is blocked in this example.
Monitor > Log
What Could Go Wrong?
If you see [notice] log shown as below, the Wi-Fi guest traffic is blocked by the
priority 1 Security Policy. The ZyWALL/USG checks the security policy in order and
applies the first security policy to the matched traffic. If the Wi-Fi guest traffic
matches a policy that comes earlier in the list, it may be unexpectedly blocked.
Please change your policy setting or move the Wi-Fi guest policy to the higher
priority.
Monitor > Log
665/782
www.zyxel.com
Note: The default setting of Security Policy is without log notification (except
PolicyDefault), if you want to check which policy may potentially block the traffic, please
select this policy and set the Log matched traffic to be log or log alert.

666/782
www.zyxel.com
How to create a Wi-Fi VLAN interfaces to separate staff
network and Guest network
This example shows how to create Wi-Fi VLAN interfaces to separate staff network and
Guest network. Suppose there should be no limitation for the staff network, but restrict
the guests not access the USG.
Separate the Staff and Guest network
Iini
Staff
Network
Guest
Network
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG210 (Firmware Version: ZLD 4.25)
667/782
www.zyxel.com
Set up Wi-Fi VLAN interfaces
Create VLAN interfaces
Go to CONFIGURATION > Object > Zone. Create a zone for the guest.
CONFIGURATION > Object > Zone
Go to CONFIGURATION > Network > Interface > VLAN. Create VLAN16 for Staff_WiFi
and VLAN17 for Guest_WiF
CONFIGURATION > Network > Interface > VLAN > VLAN16
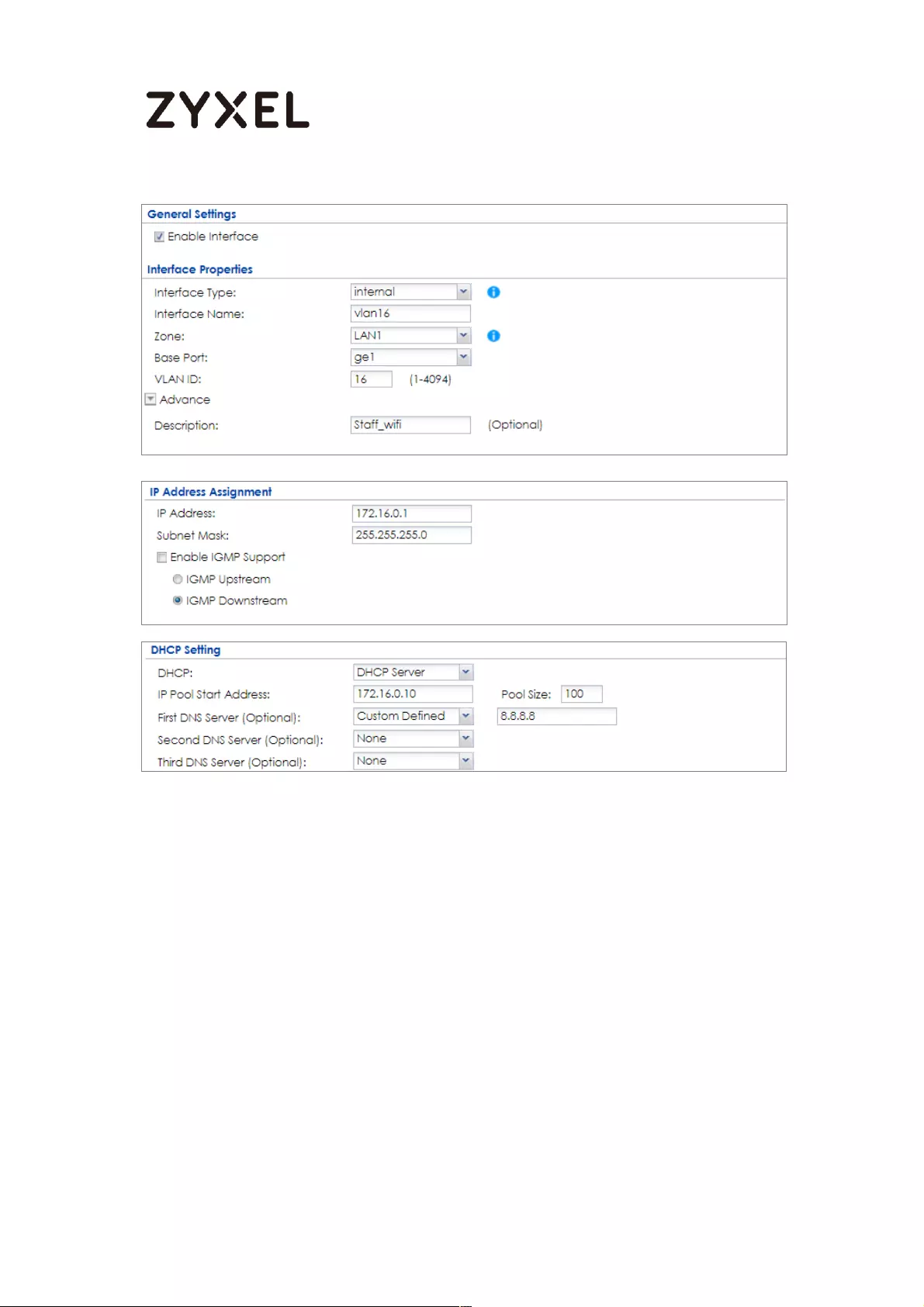
668/782
www.zyxel.com
CONFIGURATION > Network > Interface > VLAN > VLAN17

669/782
www.zyxel.com
There will be two VLAN interfaces.
CONFIGURATION > Network > Interface > VLAN
Set Up the User
Go to Configuration > Object > User/Group > User, and create users for the staff and
the guest
Configuration > Object > User/Group > User > staff

670/782
www.zyxel.com
Configuration > Object > User/Group > User > guest
There will be two users.
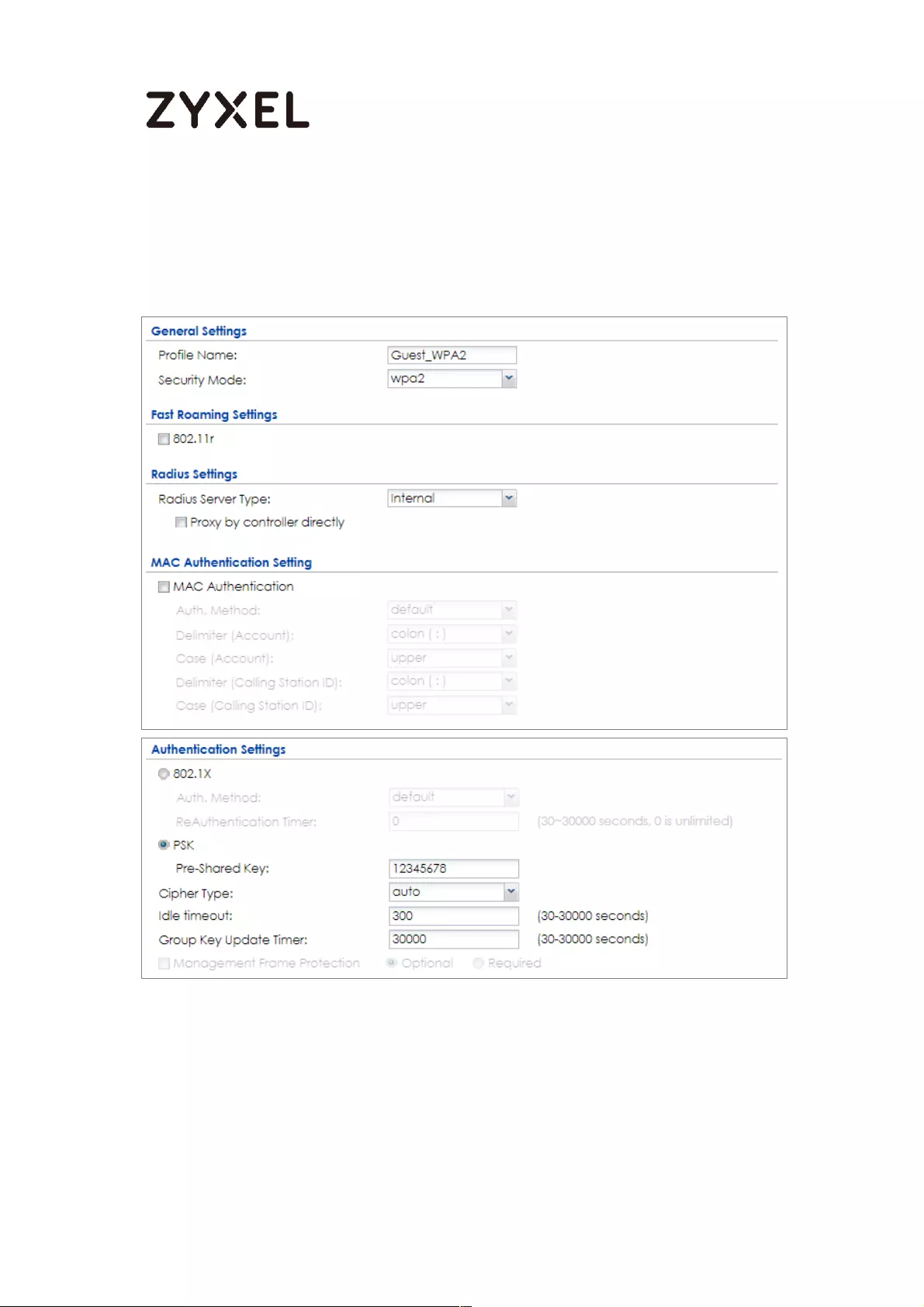
671/782
www.zyxel.com
Set Up the AP Profile
Go to CONFIGURATION > Object > AP Profile > SSID > Security List, and create two
security profiles.
CONFIGURATION > Object > AP Profile > SSID > Security List > Guest_WPA2
CONFIGURATION > Object > AP Profile > SSID > Security List > Staff_WPA2
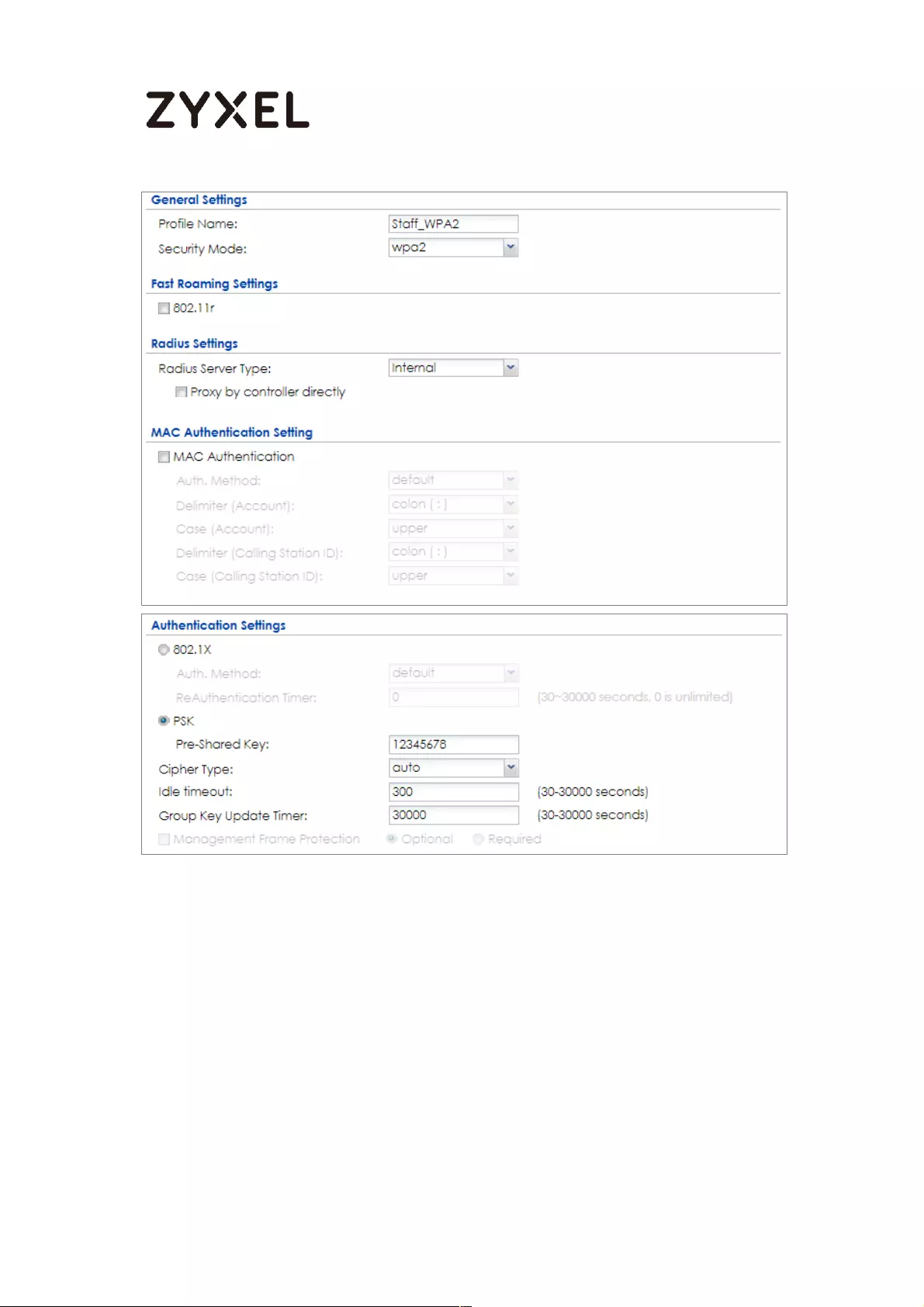
672/782
www.zyxel.com
Go to CONFIGURATION > Object > AP Profile > SSID > SSID List, and create two SSID
profiles.
CONFIGURATION > Object > AP Profile > SSID > SSID List > Staff_Wifi
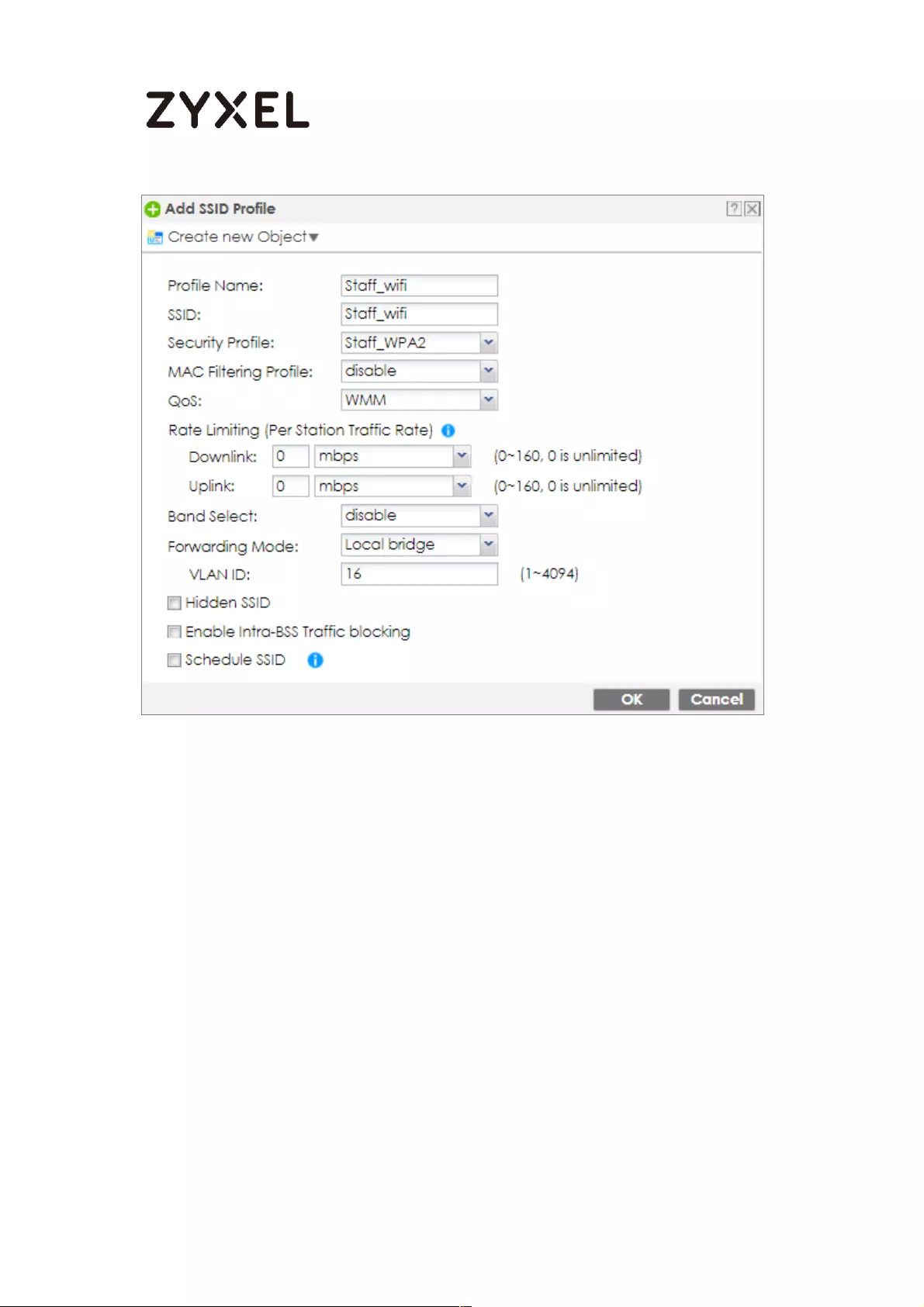
673/782
www.zyxel.com
CONFIGURATION > Object > AP Profile > SSID > SSID List > Guest_Wifi
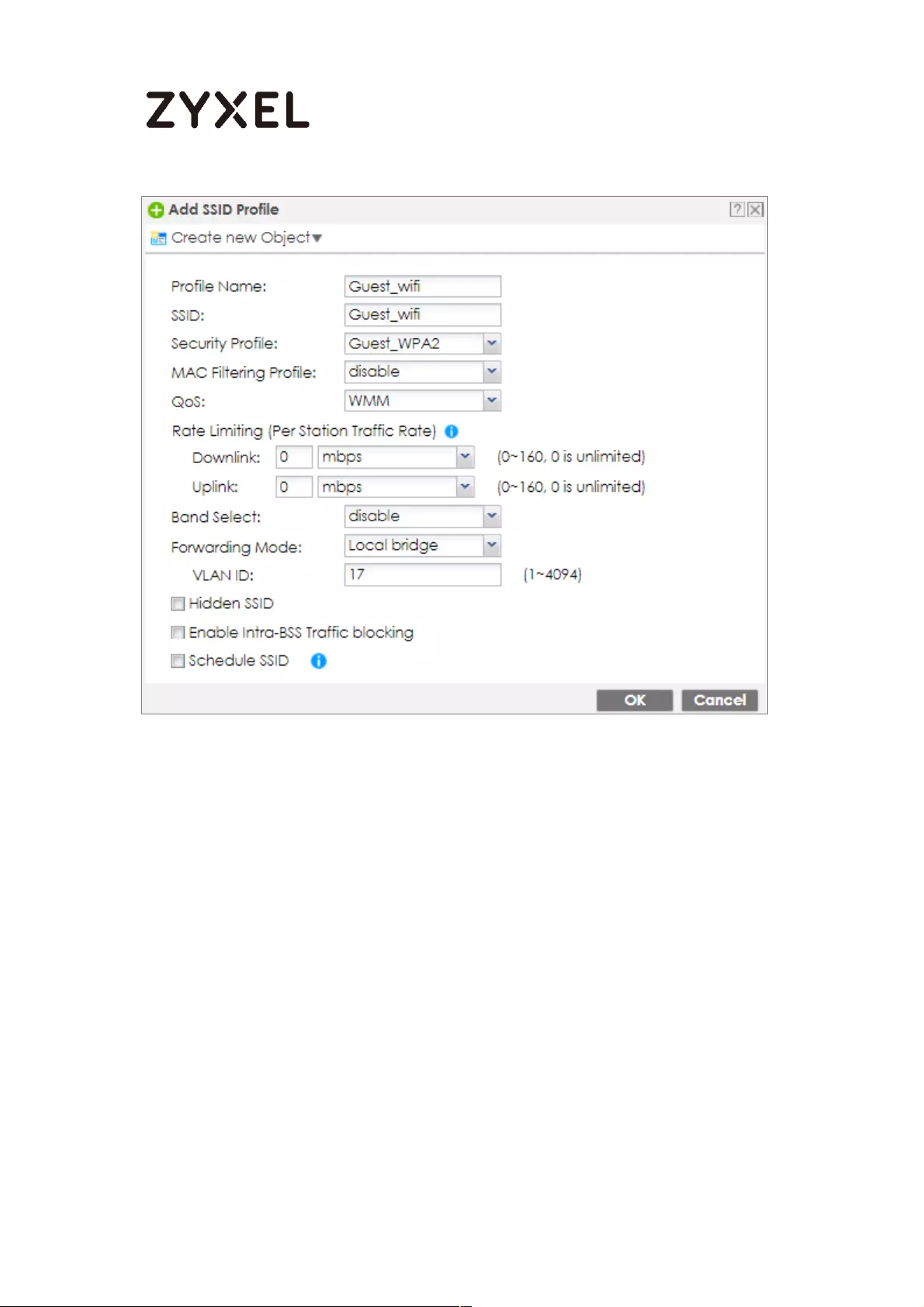
674/782
www.zyxel.com
Go to CONFIGURATION > Wireless > AP Management > AP Group, and add an AP
Group as WiFi.
CONFIGURATION > Wireless > AP Management > AP Group
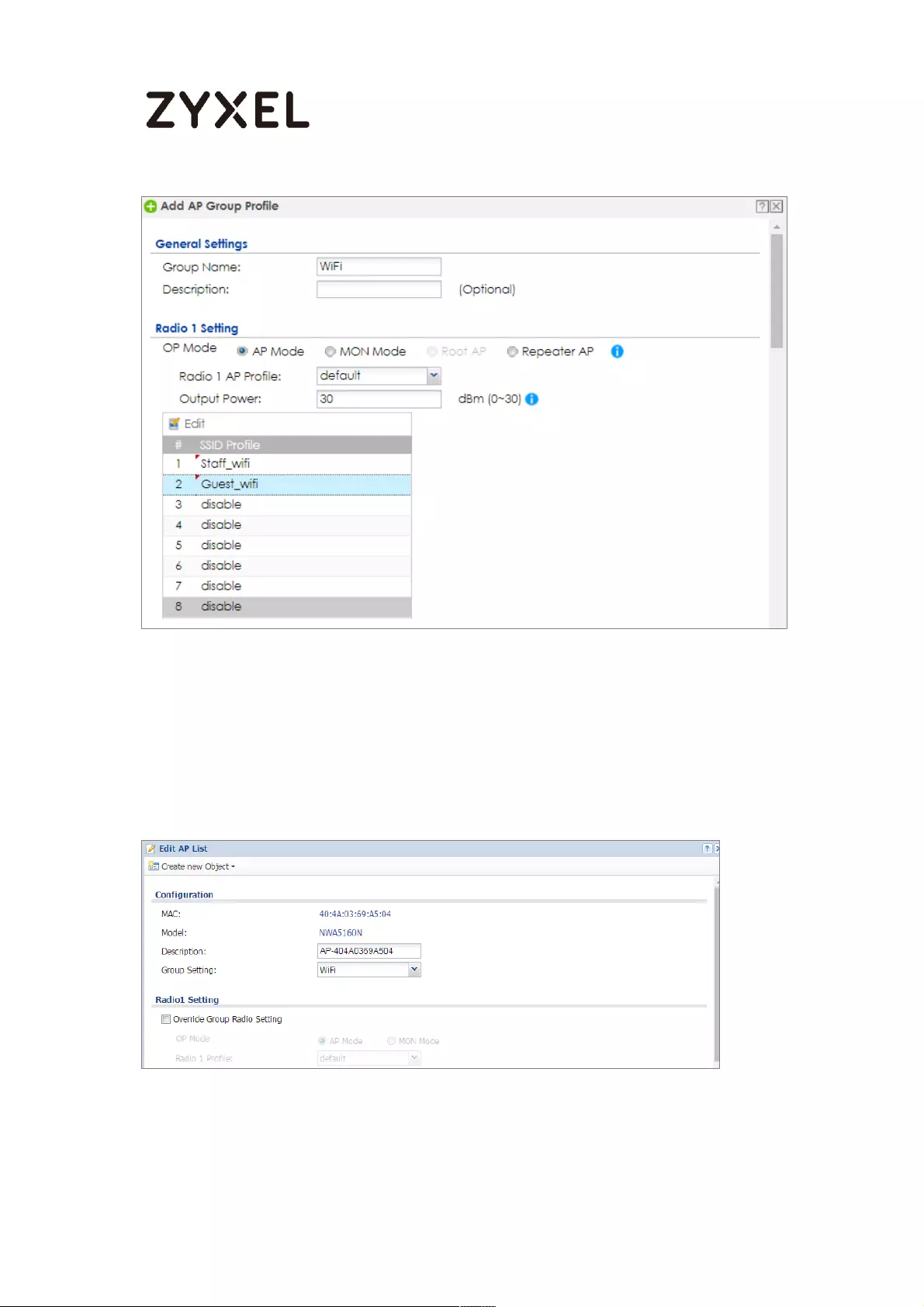
675/782
www.zyxel.com
Go to CONFIGURATION > Wireless > AP Management > Mgnt. AP List, and Edit the AP
List. Change the Group setting as WiFi
CONFIGURATION > Wireless > AP Management > Mgnt. AP List,
Set Up the Security policy rule
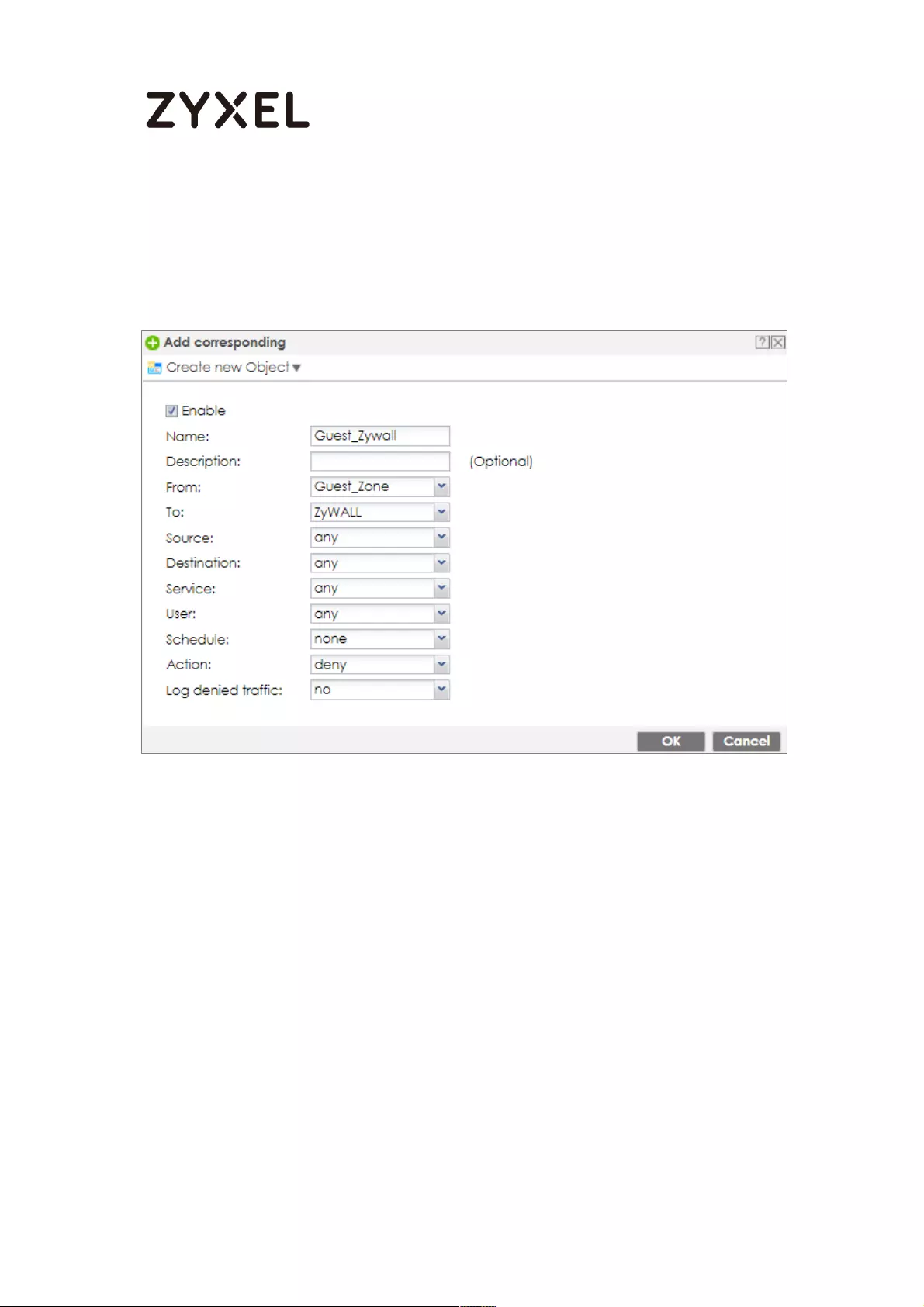
676/782
www.zyxel.com
Go to CONFIGURATION > Security Policy > Policy Control > Policy. Add one rule to
restrict Guest access USG, and another one to allow to access internet.
CONFIGURATION > Security Policy > Policy Control > Policy > Guest_ZyWALL
CONFIGURATION > Security Policy > Policy Control > Policy > Guest_Internet
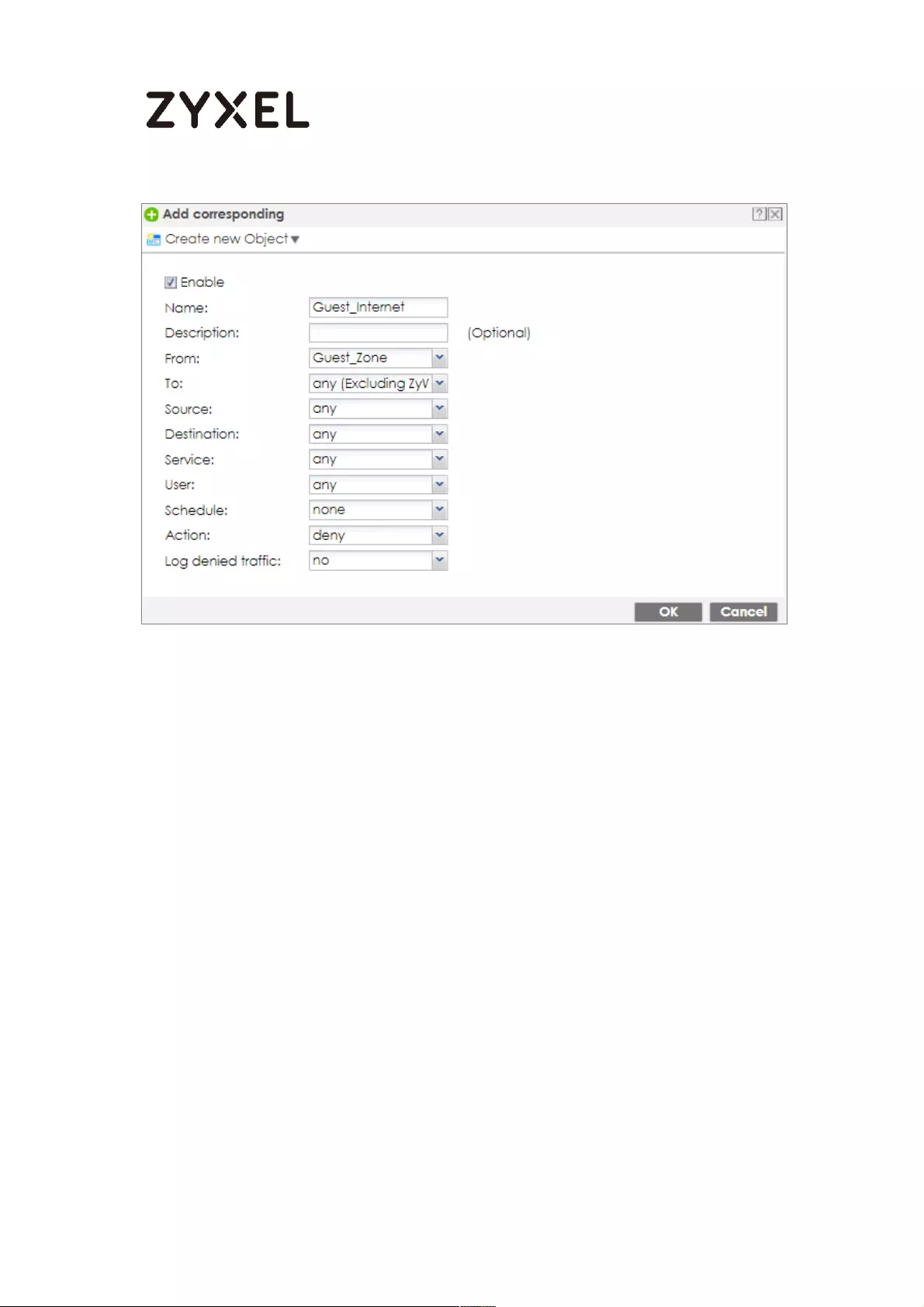
677/782
www.zyxel.com
Test result
Connect to the SSID Staff_WiFi, and ping the USG interface.
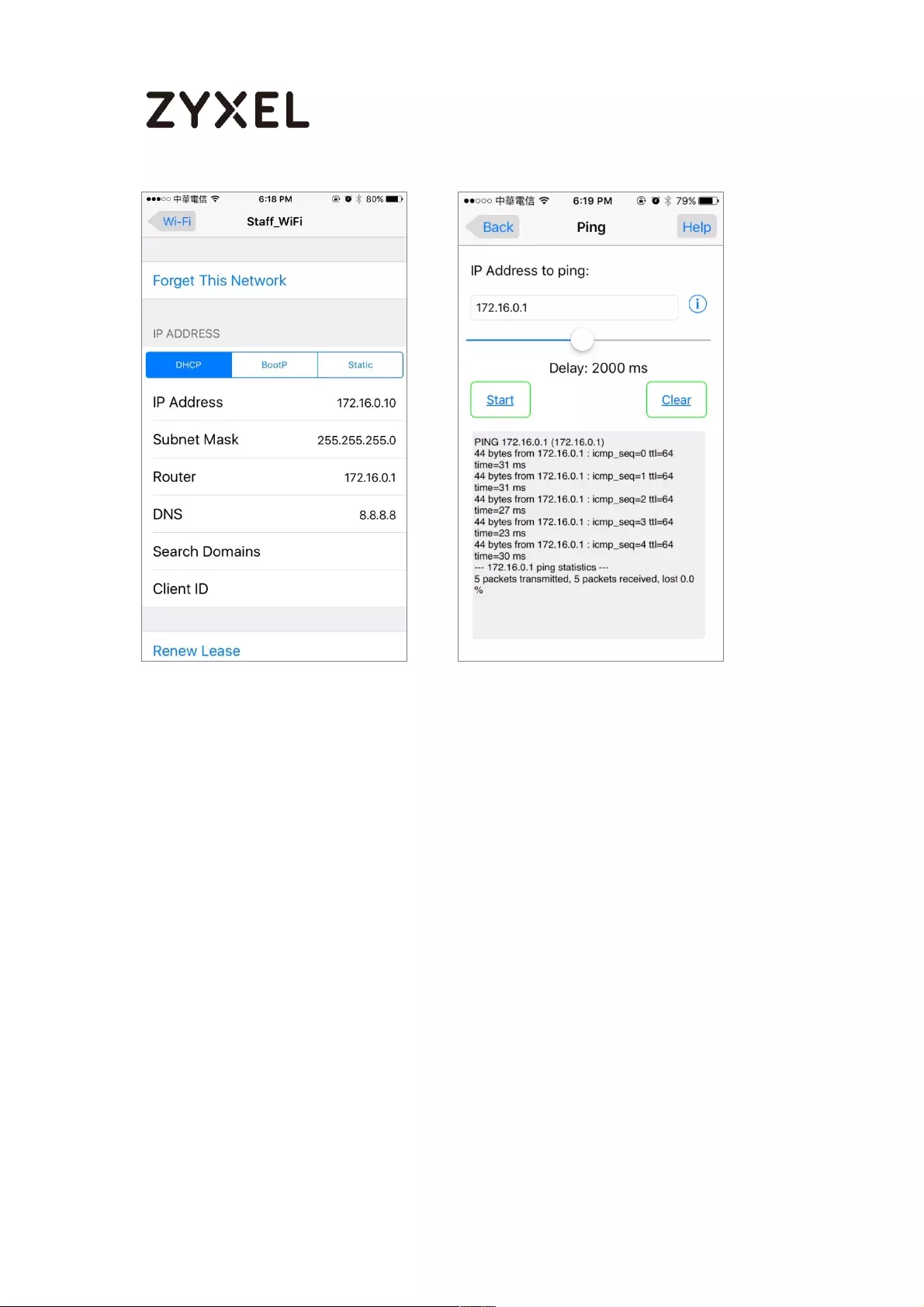
678/782
www.zyxel.com
Connect to the SSID Guest_WiFi, and ping the USG interface
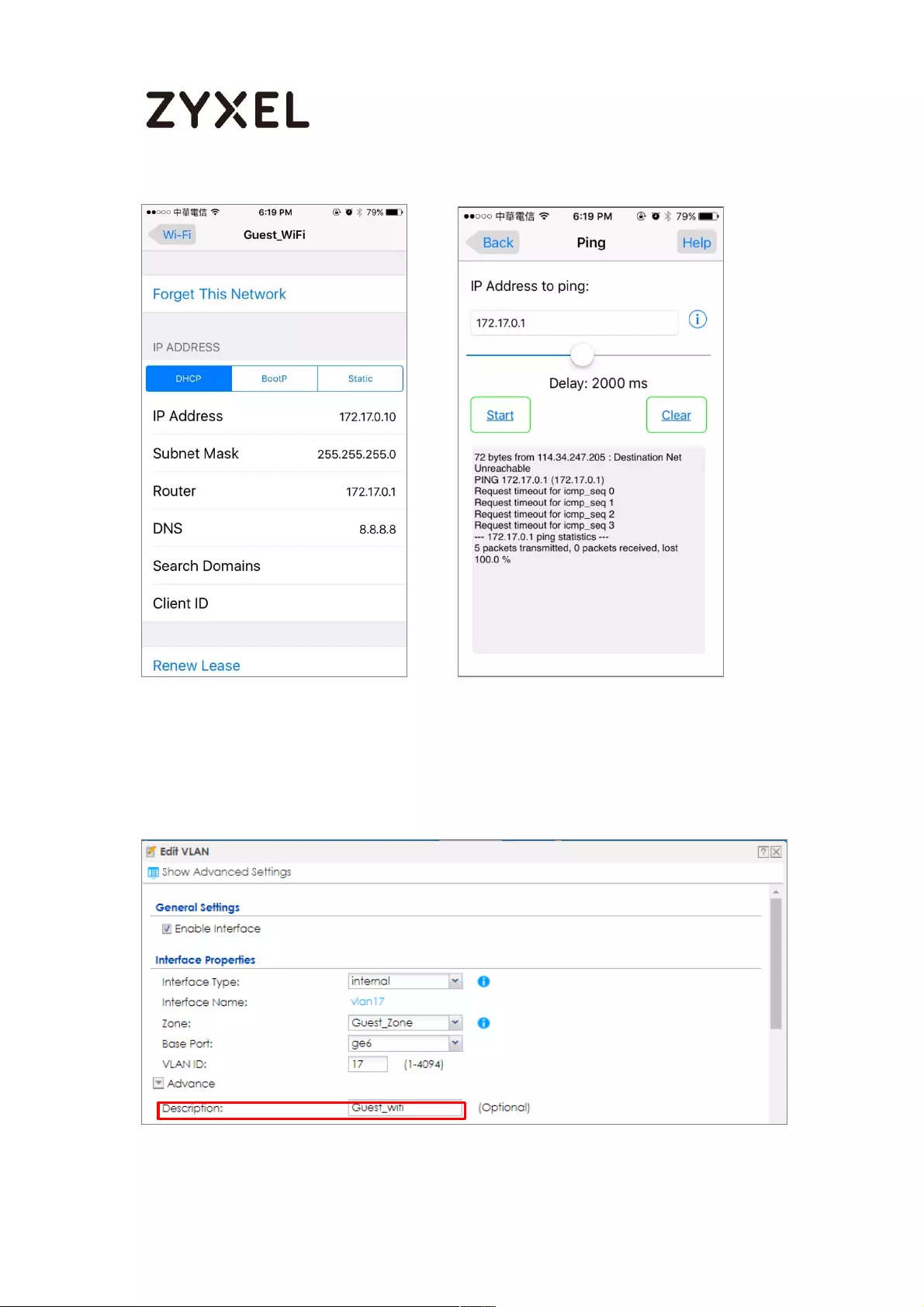
679/782
www.zyxel.com
What could go wrong
Choose the wrong zone for the Guest VLAN interface.
Not change the AP to the correct group
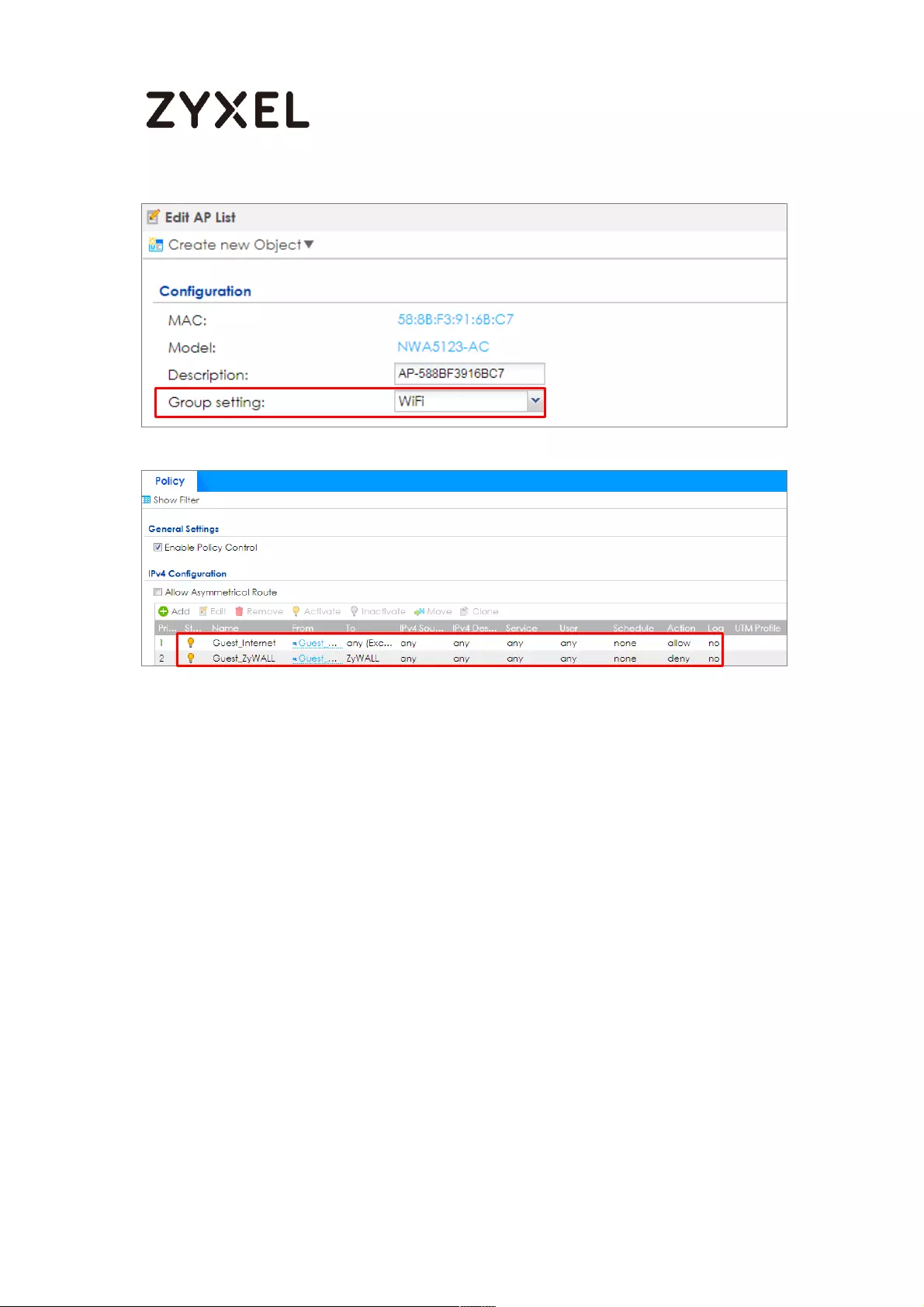
680/782
www.zyxel.com
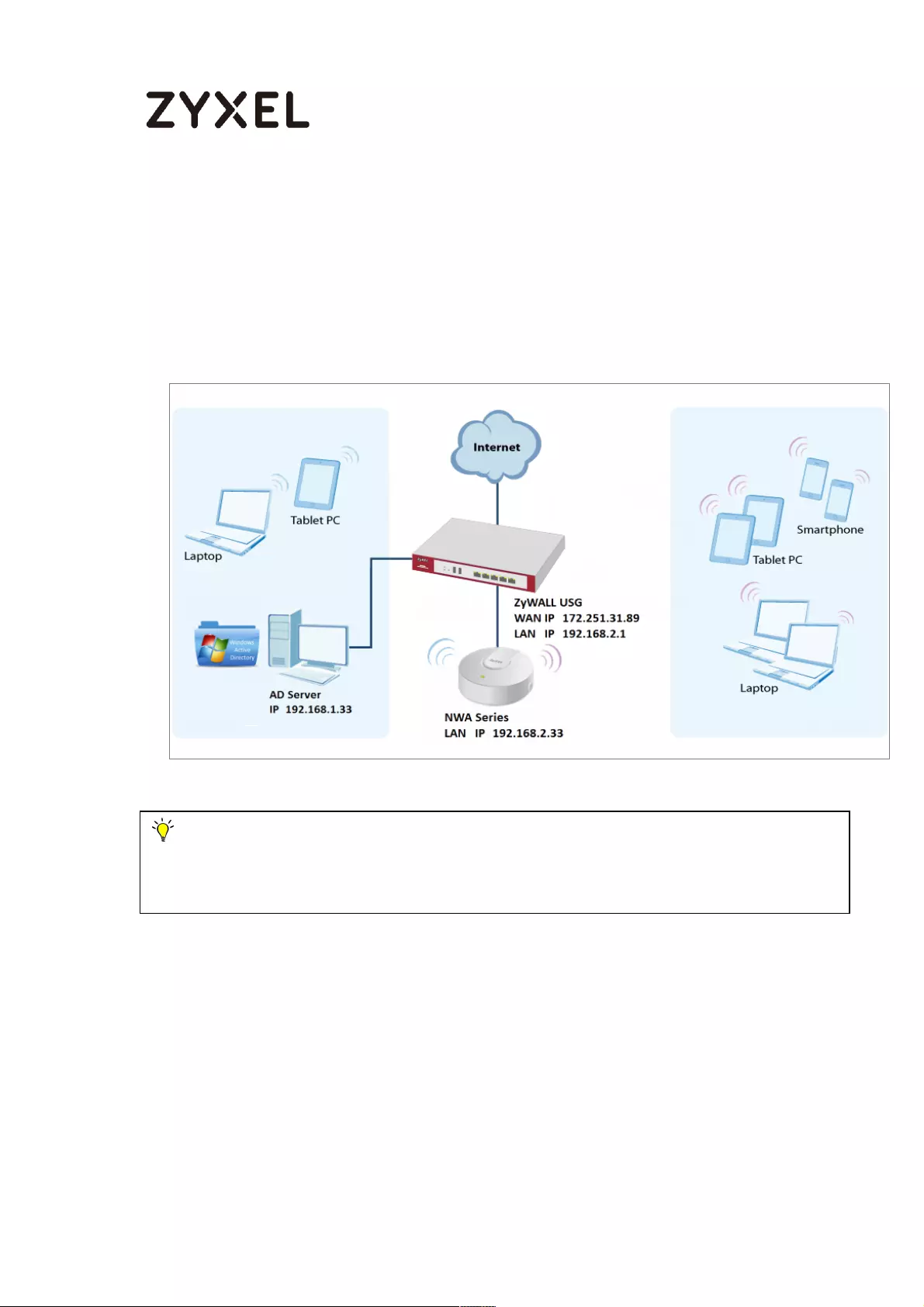
681/782
www.zyxel.com
How to Set Up WiFi Networks with Microsoft Active Directory
Authentication
This is an example of using ZyWALL/USG to configure guest WiFi accounts with
Microsoft Active Directory (AD) to authenticate your WiFi guests. For the wireless
network setup, please go to How to Set Up WiFi with ZyXEL AP.
ZyWALL/USG with AD Guest WiFi Accounts Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
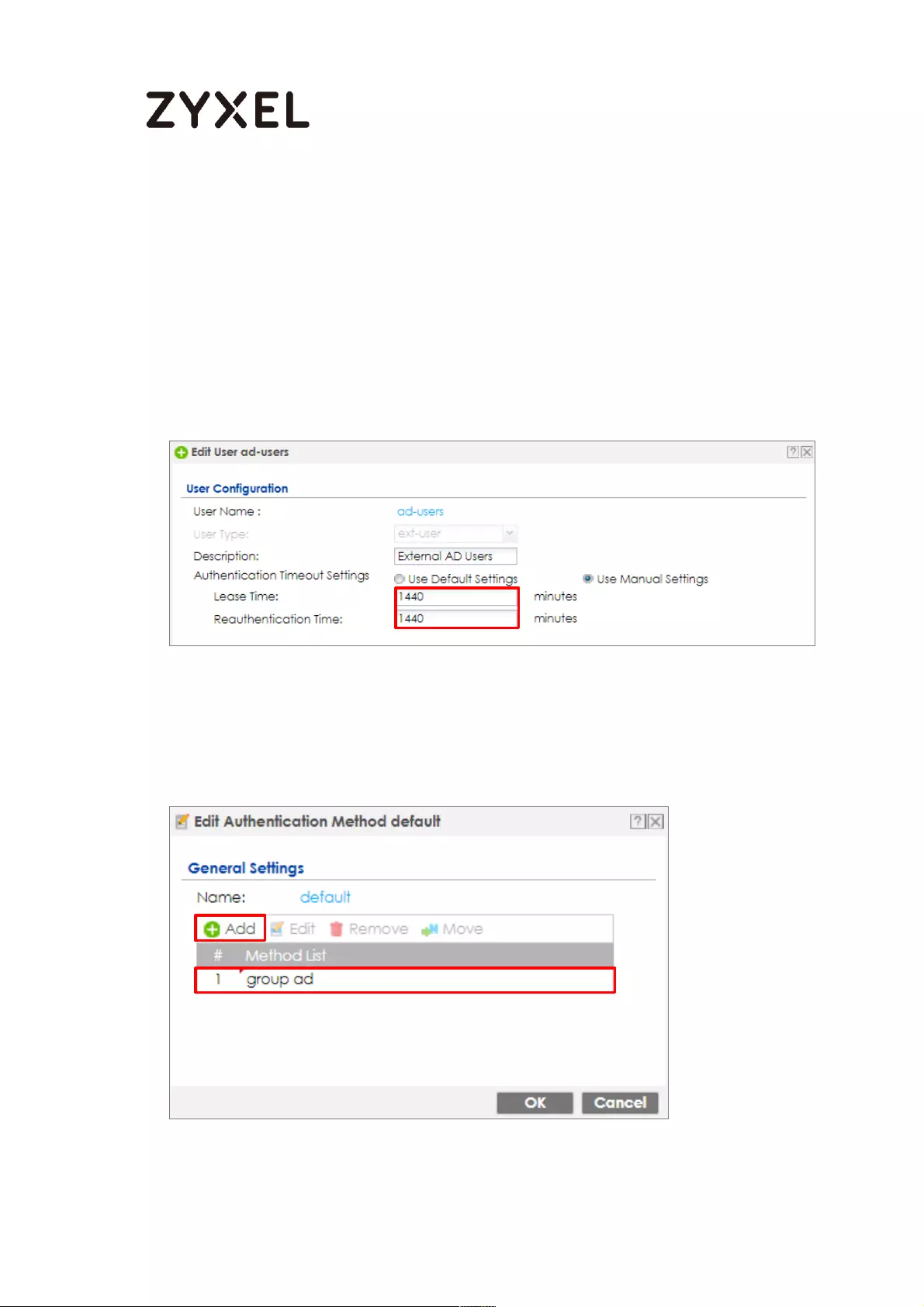
682/782
www.zyxel.com
Set Up the Wi-Fi Guest Account and Authentication Method on
the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Object > User/Group > User > ad-
users, set the Authentication Timeout Settings to Use Manual Settings and enter
the number of minutes this user has to renew the current session before the user is
logged out.
CONFIGURATION > Object > User/Group > User > ad-users
In the ZyWALL/USG, go to CONFIGURATION > Object > Authentication Method >
default > Edit Authentication Method default, click Add to insert group ad in the
table. Click OK.
CONFIGURATION > Object > User/Group > User > ad-users
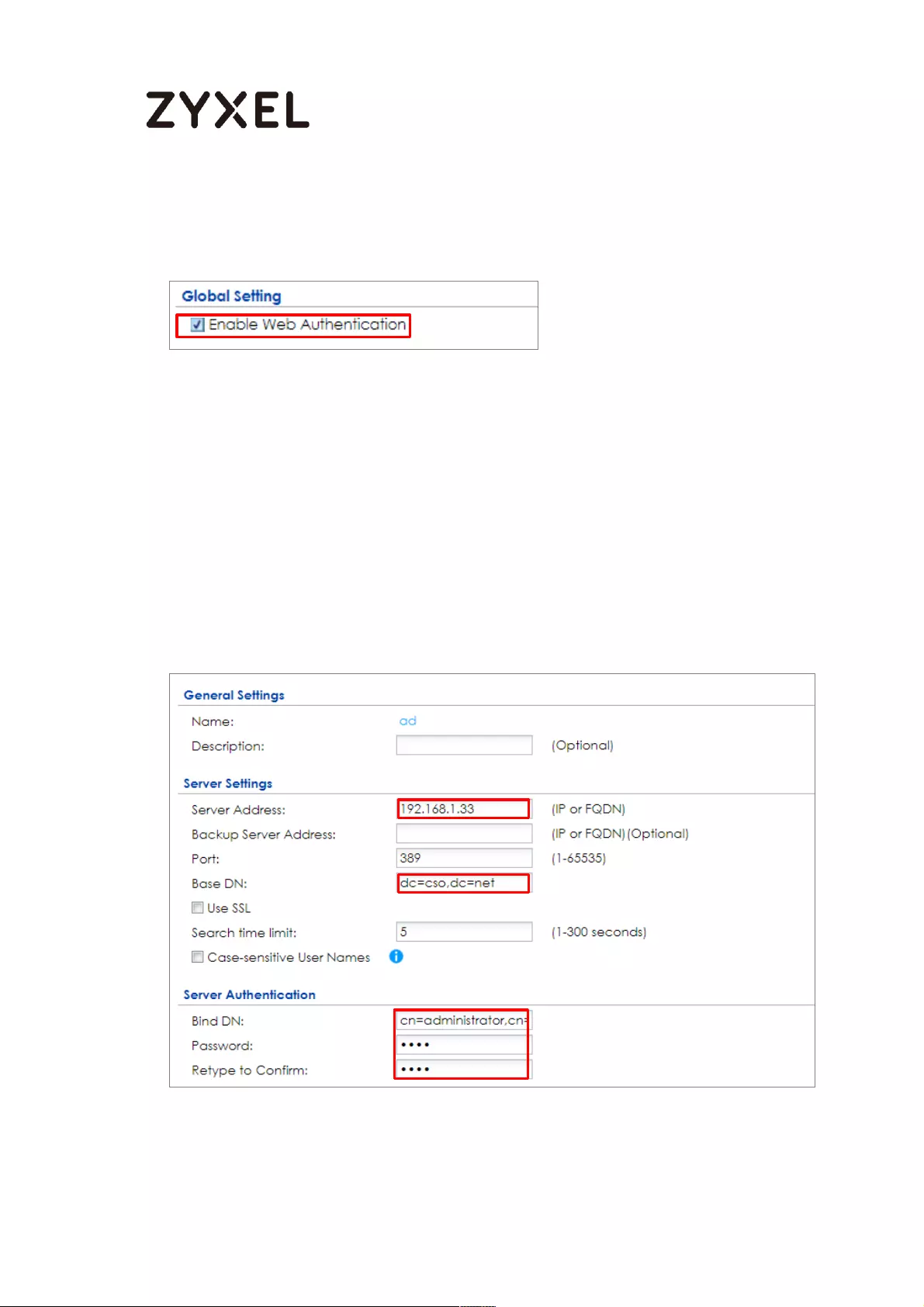
683/782
www.zyxel.com
In the ZyWALL/USG, go to CONFIGURATION > Web Authentication > General
Settings and select Enable Web Authentication.
CONFIGURATION > Web Authentication > General Settings
Set Up the Active Directory Server Account on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Object > AAA Server > Active
Directory > Add Active Directory to configure the AD sever. Enter the Server
Address (192.168.1.33 in this example) and Based DN (dc=cso,dc=net in this
example). Specify the Bind DN for logging into the AD server
(cn=Administrator,cn=users,dc=cso,dc=net in this example). If required, enter the
Password for the ZyWALL/USG to bind (or log in) to the AD server.
CONFIGURATION > Object > AAA Server > Active Directory > Add Active Directory
Scroll down to the Configuration Validation section, use a user account from the
server specified above to test if the configuration is correct. Enter the account’s
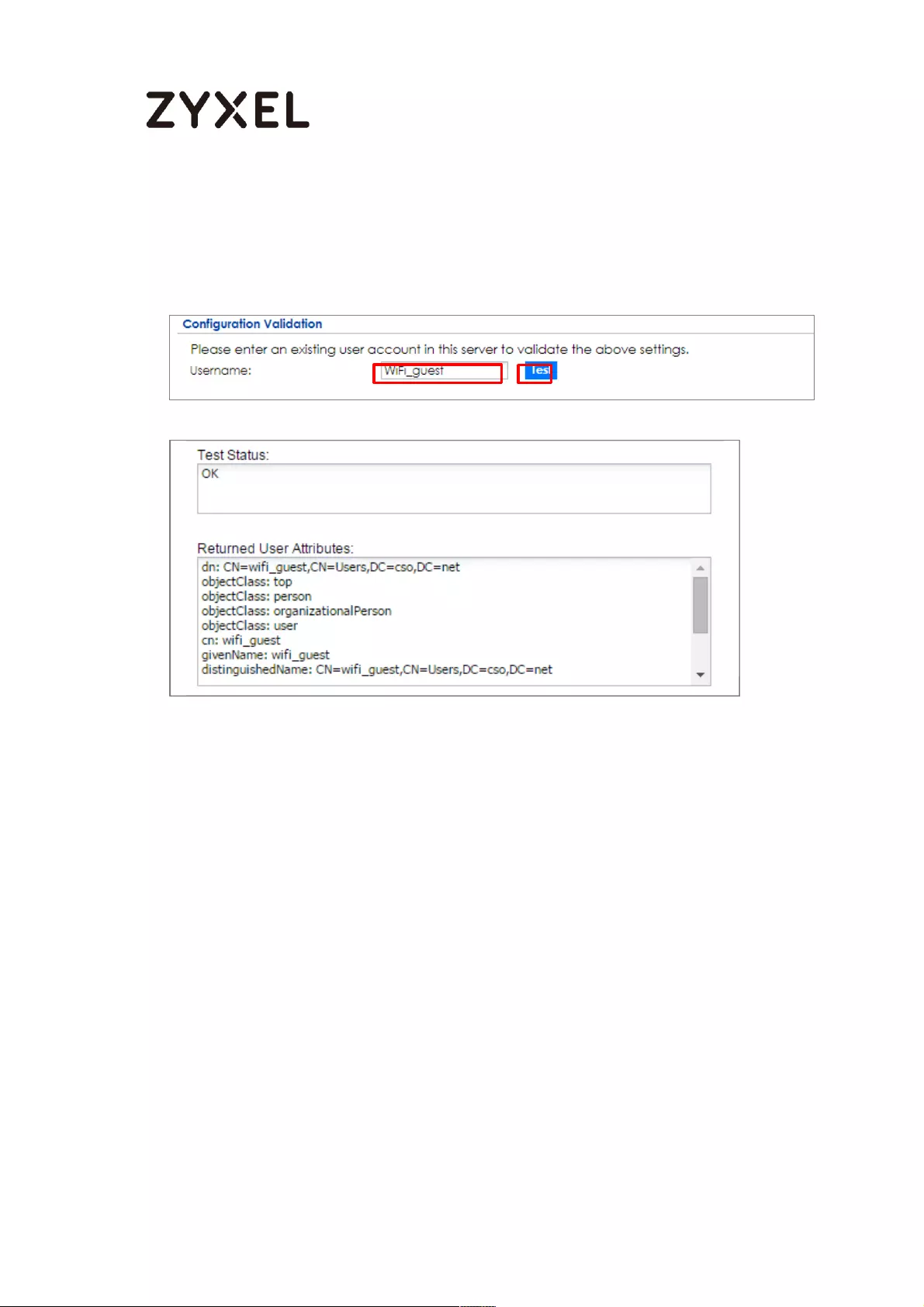
684/782
www.zyxel.com
user name (wifi_guest in this example) in the Username field and click Test. A pop-
up screen will appear allowing you to view the test result. Click OK to save the
configuration.
CONFIGURATION > Object > AAA Server > Active Directory > Add Active Directory
Set Up the Security Policy on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Security Policy > Policy > Add
corresponding. Configure a Name for you to identify the Security Policy profile.
Set From: LAN and To: any (Excluding ZyWALL). Set Service to be the service rule
for Wi-Fi guest (wifi_guest_access in this example). Set User to be the Wi-Fi guest
user (ad-users in this example). Select Log type to be log alert in order to view
the result later.
CONFIGURATION > Security Policy > Policy > Add corresponding
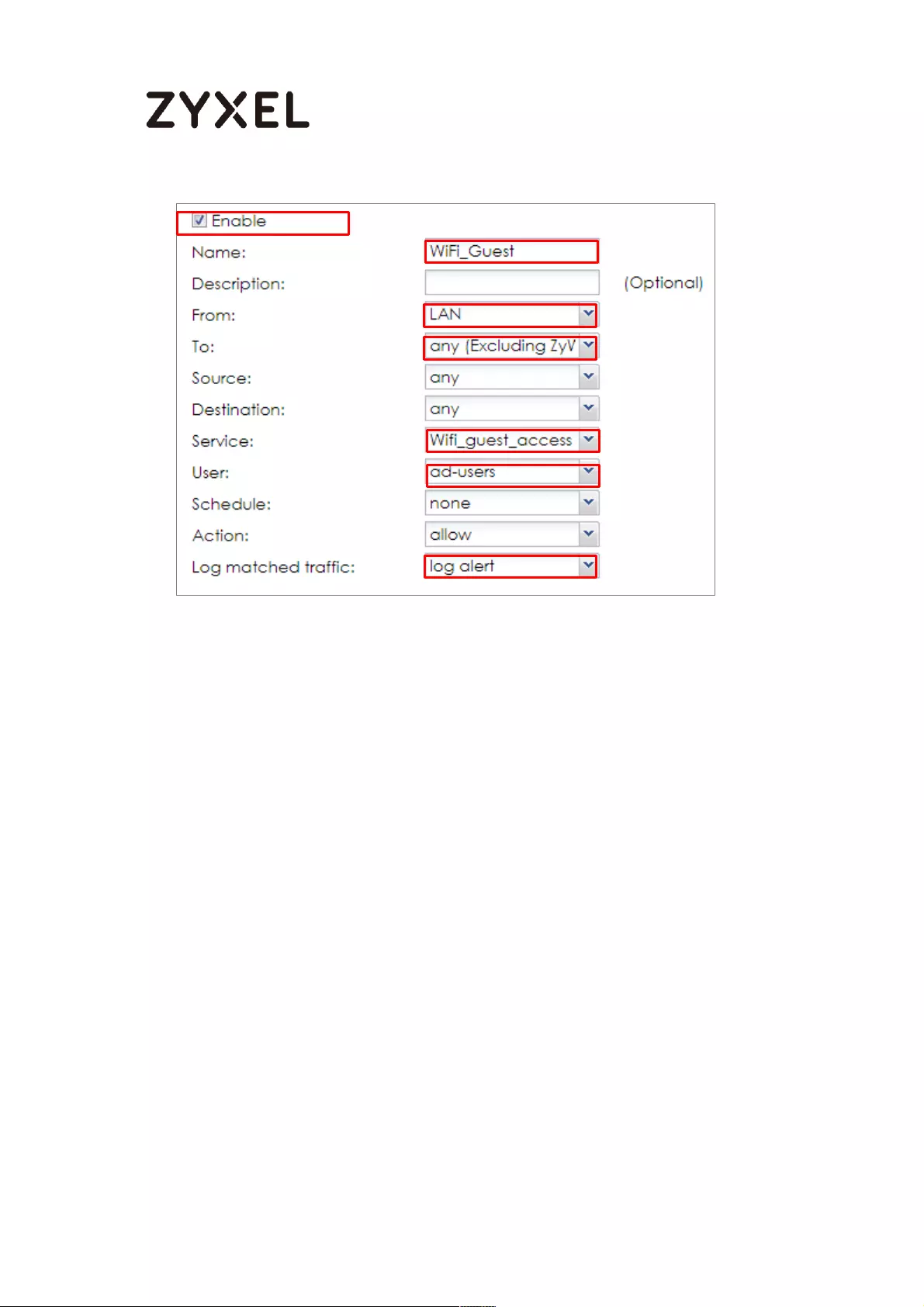
685/782
www.zyxel.com
Test the Result
Using a mobile device to connect to the AP which is connected to the
ZyWALL/USG. When you try to access the Internet, it will redirect to the user login
screen.
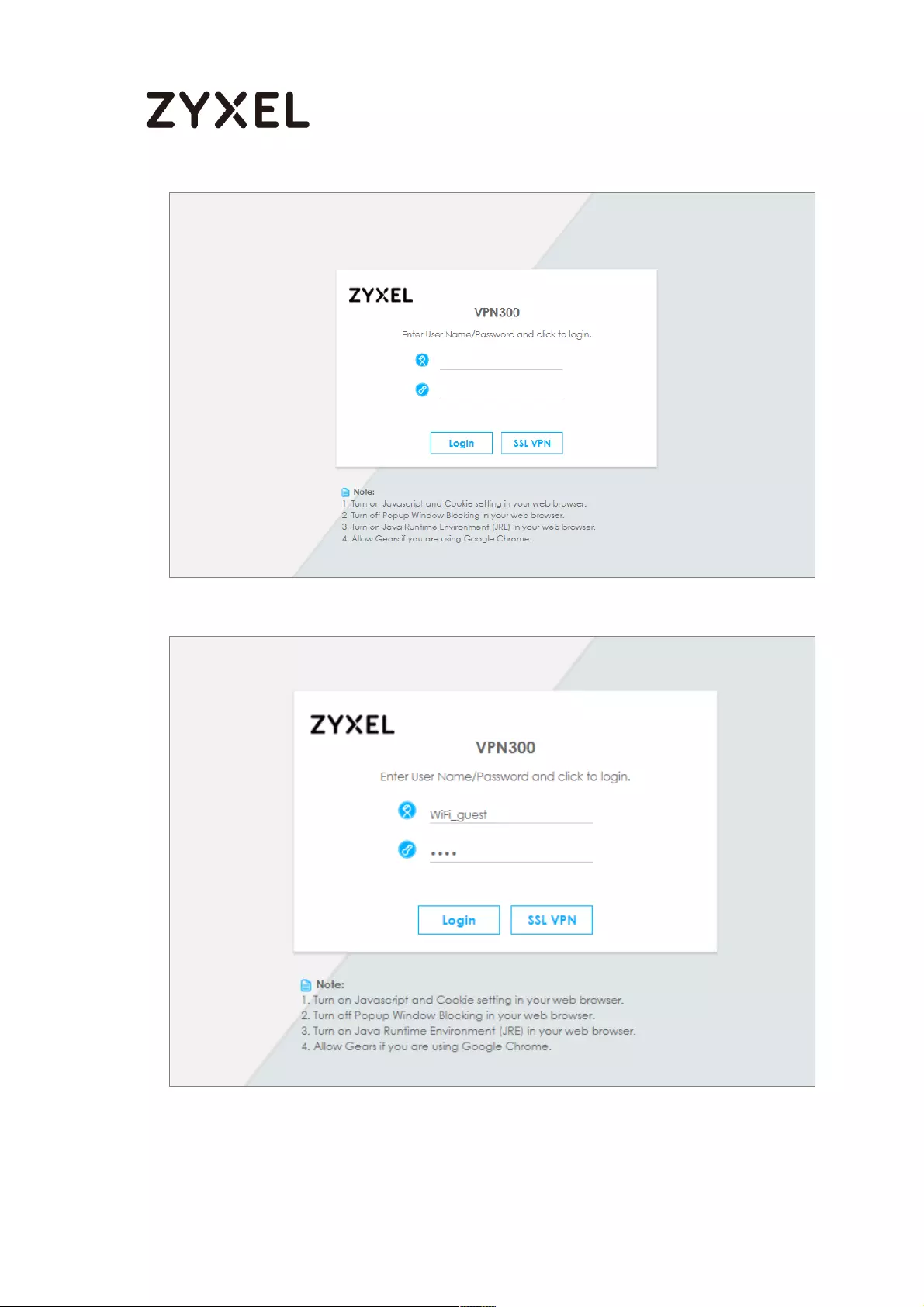
686/782
www.zyxel.com
Type the Wi-Fi guest User Name and Password, click Login.
The access session page will appear.
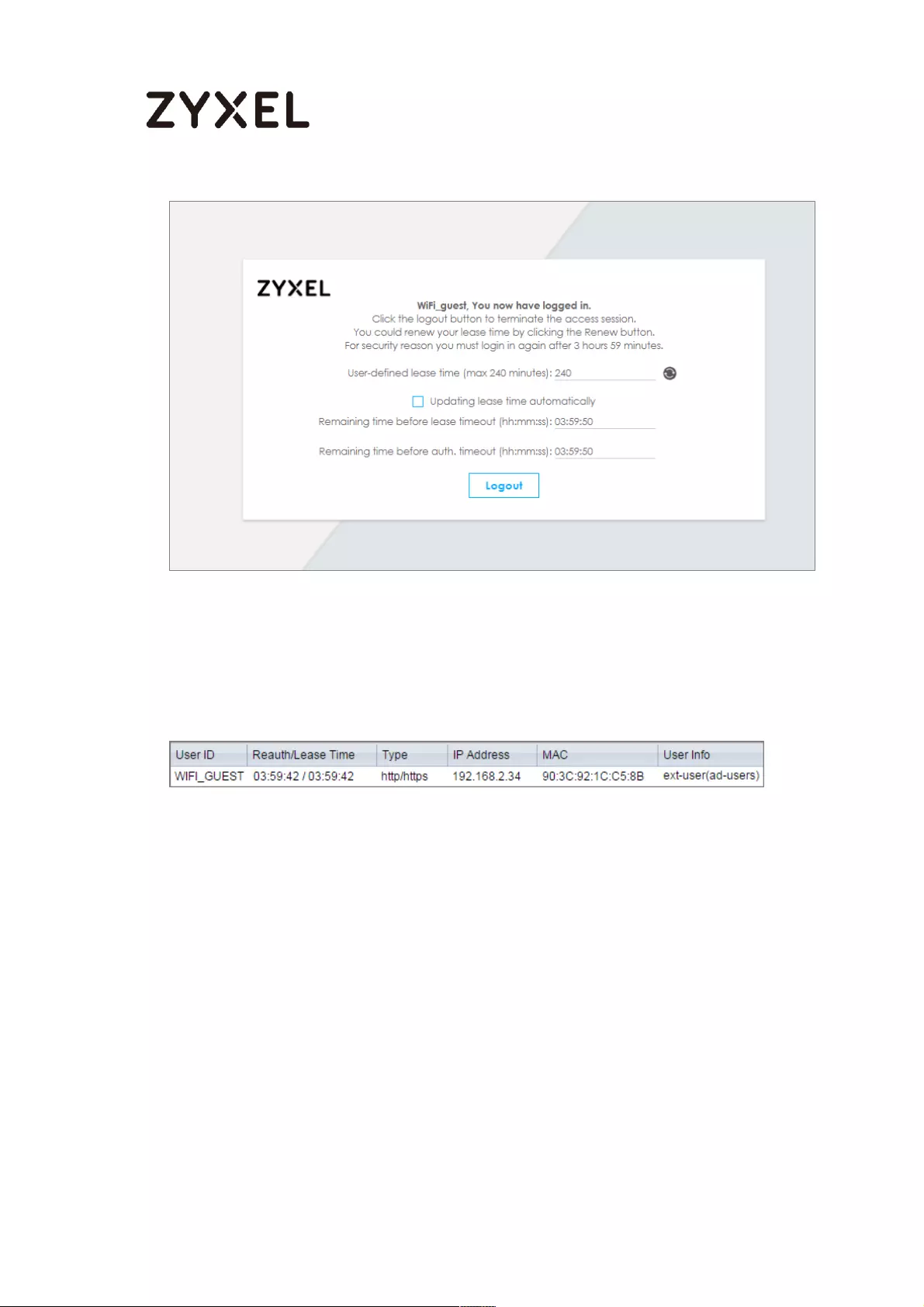
687/782
www.zyxel.com
Go to the ZyWALL/USG Monitor > System Status > Login Users, you will see current
login user list as below.
Monitor > System Status > Login Users
What Could Go Wrong?
If you see [notice] log shown as below, the Wi-Fi guest traffic is blocked by the
priority 1 Security Policy. The ZyWALL/USG checks the security policy in order and
applies the first security policy the traffic matches. If the Wi-Fi guest traffic
matches a policy that comes earlier in the list, it may be unexpectedly blocked.
Please change your policy setting or move the Wi-Fi guest policy to the higher
priority.
Monitor > Log
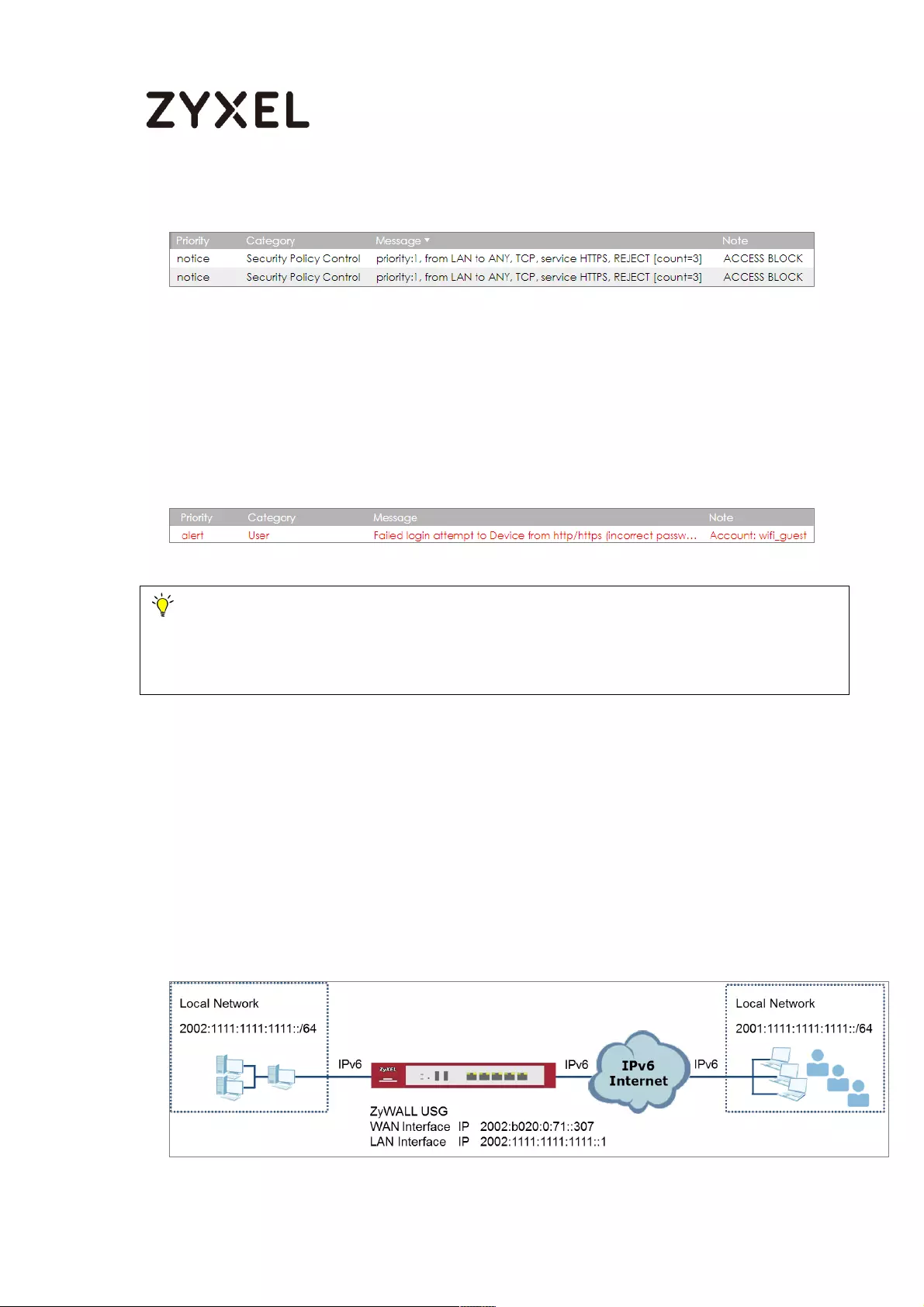
688/782
www.zyxel.com
If you see [alert] log message shown as below, the Wi-Fi guest traffic failed. Please
make sure you enable Web Authentication and check your AD server is working
properly.
Monitor > Log
How to Set Up IPv6 Interfaces for Pure IPv6 Routing
This example shows how to configure your ZyWALL/USG WAN and LAN interfaces
which connects two IPv6 networks. ZyWALL/USG periodically advertises a network
prefix of 2002:1111:1111:1111::/64 to the LAN through router advertisements.
ZyWALL/USG with Pure IPv6 Network Example
Note: The default setting of Security Policy is without log notification (except
PolicyDefault), if you want to check which policy may potentially block the traffic, please
select this policy and set the Log matched traffic to be log or log alert.

689/782
www.zyxel.com
Enable the IPv6 on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > System > IPv6 > Global Setting,
select the Enable IPv6 and click Apply at the bottom of the screen.
CONFIGURATION > System > IPv6 > Global Setting
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).
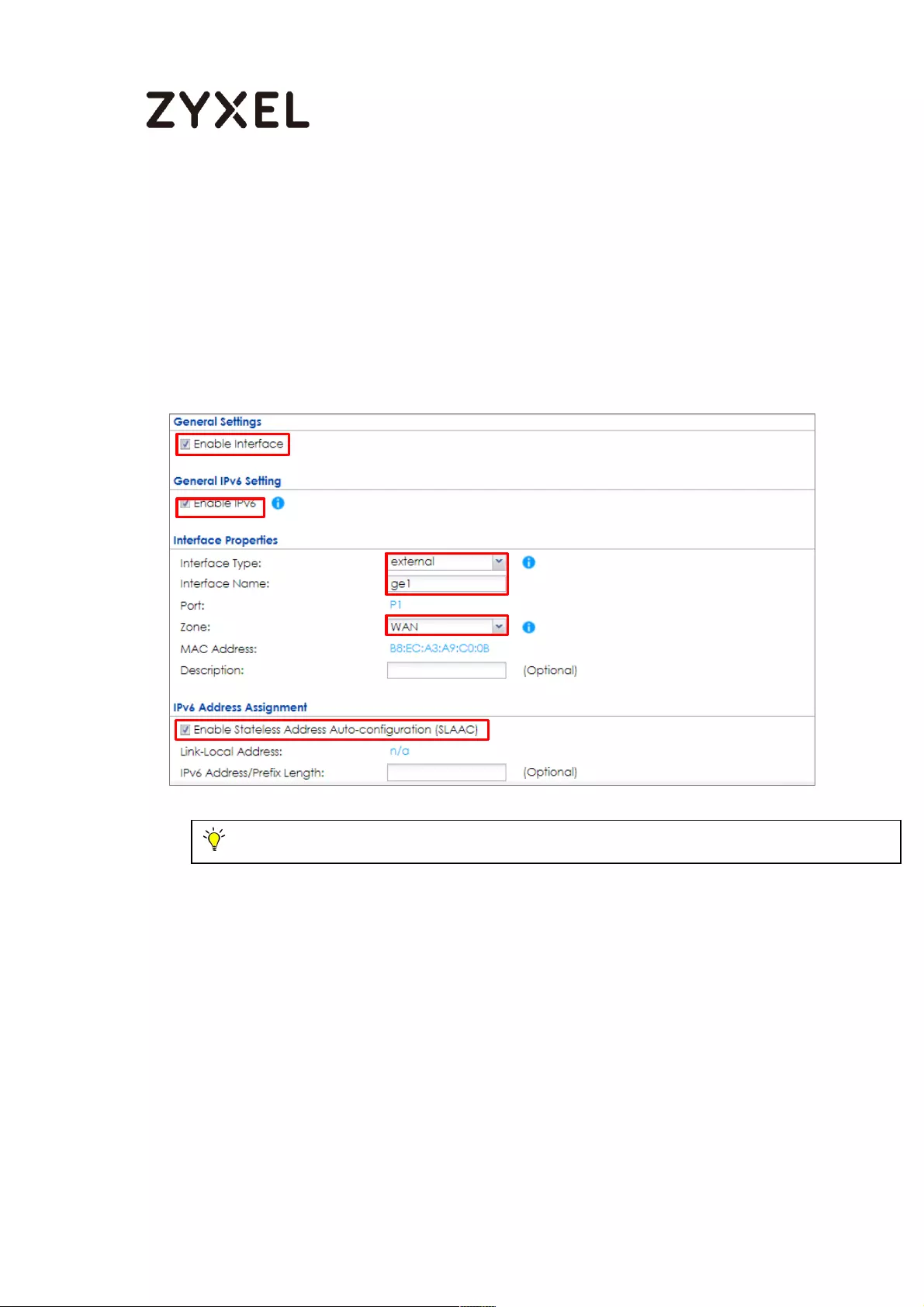
690/782
www.zyxel.com
Set Up the WAN IPv6 Interface on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Ethernet >
wan1. Select Enable Interface and Enable IPv6. Select Enable Stateless Address
Auto-configuration (SLAAC). Click OK.
CONFIGURATION > Network > Interface > Ethernet > wan1
Set Up the LAN IPv6 Interface on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Ethernet >
lan1. Select Enable Interface and Enable IPv6. Select Enable Stateless Address
Auto-configuration (SLAAC). Select Enable Router Advertisement and click Add to
configure a network prefix for the LAN1 (2002:1111:1111:1111::/64 in this example).
Note: Your ISP or uplink router should enable router advertisement.
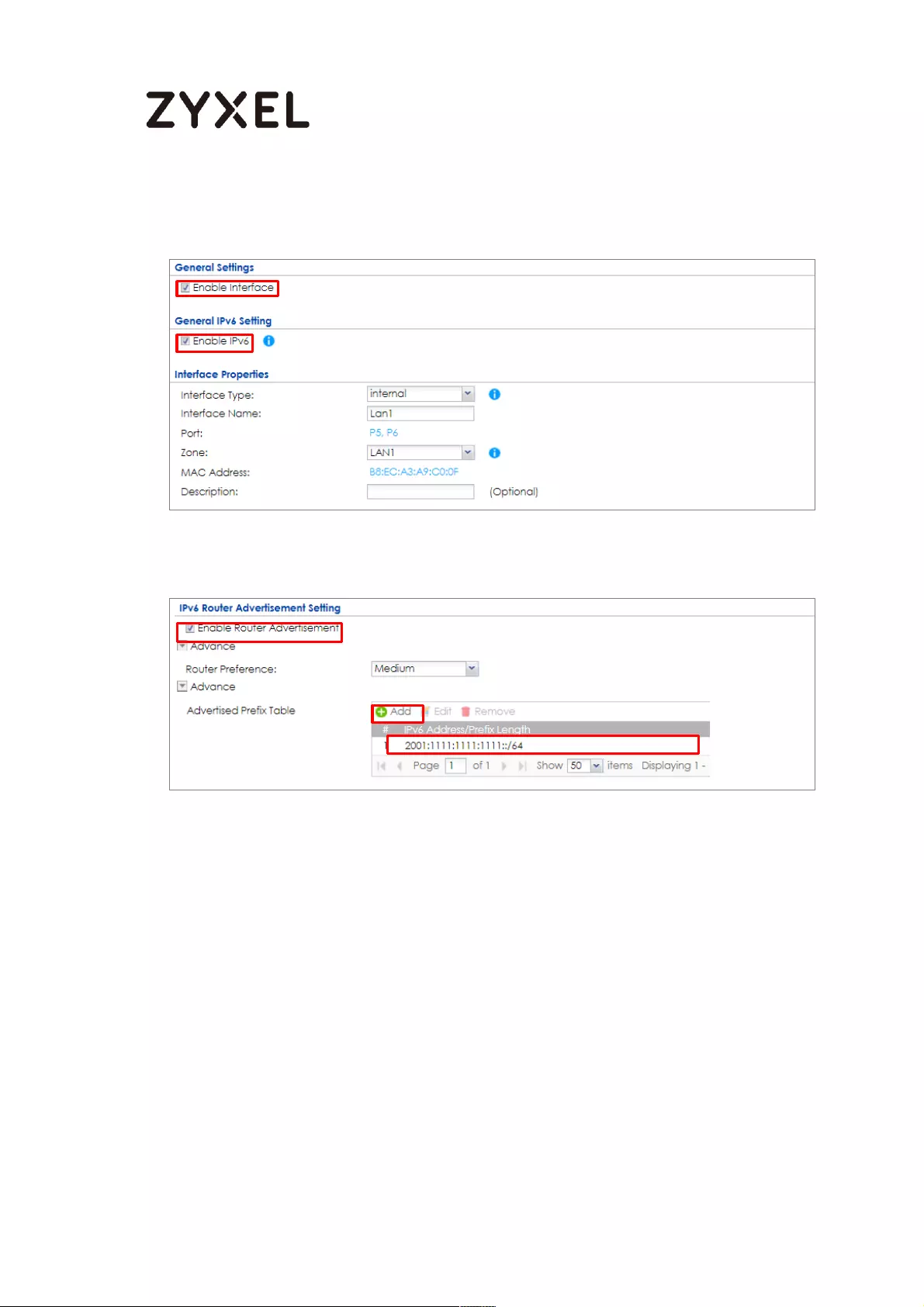
691/782
www.zyxel.com
Click OK.
CONFIGURATION > Network > Interface > Ethernet > lan1 > General Settings
CONFIGURATION > Network > Interface > Ethernet > lan1 > IPv6 Router
Advertisement Setting
Test the Result
Connect a computer to the ZyWALL/USG’s LAN1.
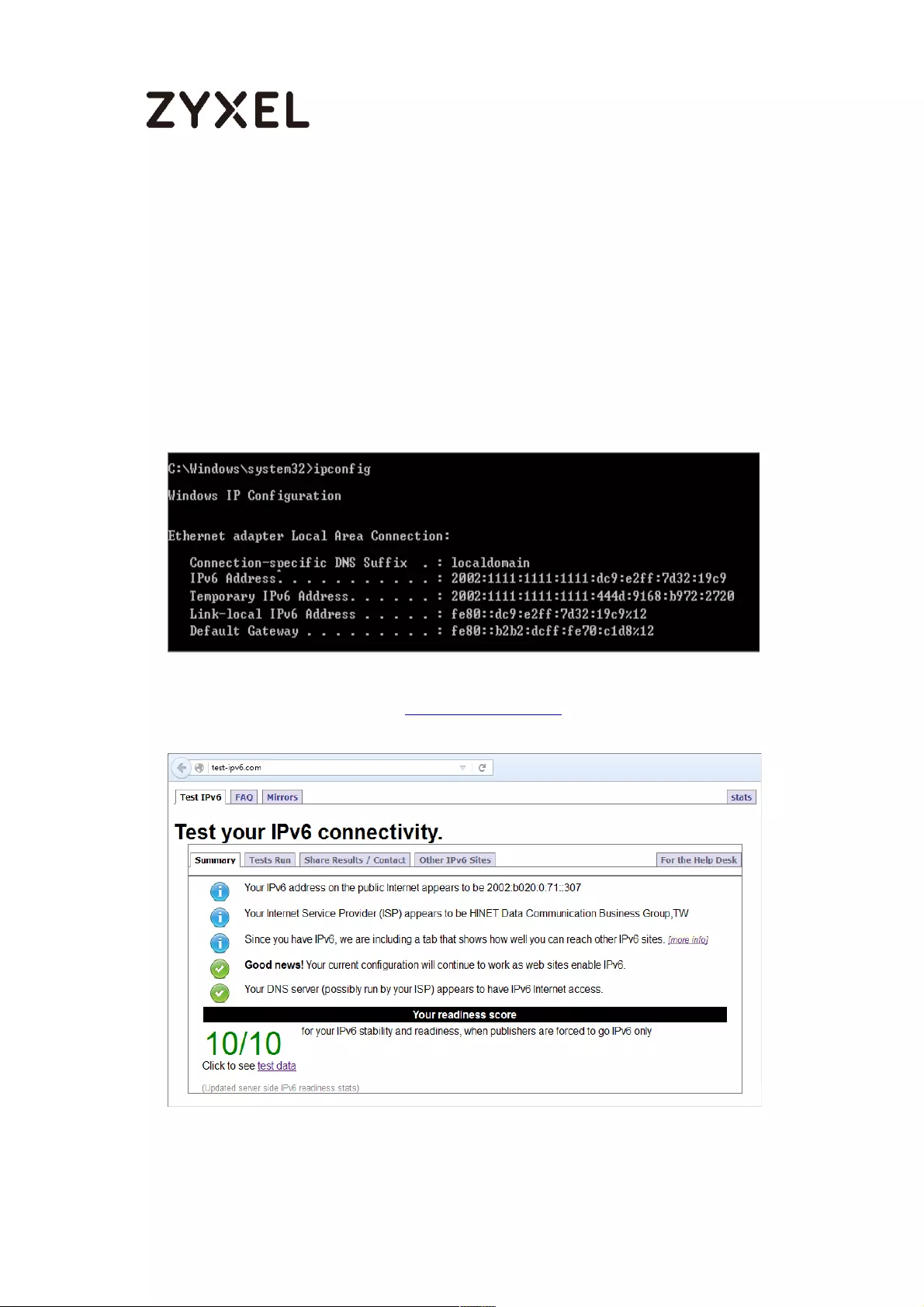
692/782
www.zyxel.com
Enable IPv6 support on your computer. In Windows XP, you need to use the IPv6
install command in a Command Prompt. In Windows 7, IPv6 is supported by
default. You can enable IPv6 in the Control Panel > Network and Sharing Center >
Local Area Connection screen
Your computer should get an IPv6 IP address (starting with 2002:1111:1111:1111:
for this example) from the ZyWALL/USG.
Window 7 > cmd > ipconfig
Open a web browser and type http://test-ipv6.com/. You can see the IPv6
connectivity result shown as below:

693/782
www.zyxel.com
What Could Go Wrong?
If your IPv6 connection is not working, please make sure you enable Auto-
Configuration on the WAN1 IPv6 interface. If not, you will not have any default
route to forward the LAN’s IPv6 packets.
In Windows, some IPv6 related tunnels may be enabled by default such as Teredo
and 6to4 tunnels. It may cause your computer to handle IPv6 packets in an
unexpected way. It is recommended to disable those tunnels on your computer.
How to Set Up an IPv6 6to4 Tunnel
This example shows how to configure your ZyWALL/USG to create IPv6 6to4 Tunnel.
In this example, the ZyWALL/USG acts as a 6to4 router which connects the IPv4.
After configuration, the ZyWALL/USG can assign an IPv6 to clients behind it and
pass IPv6 traffic through IPv4 environment to access remote IPv6 network.
ZyWALL/USG with IPv6 6to4 Tunnel Example

694/782
www.zyxel.com
Set Up the LAN IPv6 Interface on the ZyWALL/USG
The second and third sets of 16-bit IP address from the left must be converted
from wan1 IP (122.100.220.238 in this example). It becomes 7a64:dcee in
hexadecimal. (You can go to https://isc.sans.edu/tools/ipv6.html#form to convert
an IPv4 address into it's default 6-to-4 equivalent). You are free to use the fourth
set of 16-bit IP address from the left in order to allocate different network
addresses (prefixes) to IPv6 interfaces. In this example, the LAN1 network address
is assigned to use 2002:7a64:dcee:1::/64 and the LAN1 IP address is set to
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).

695/782
www.zyxel.com
2002:7a64:dcee:1::111/128.
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Ethernet >
lan1, Select Enable Interface and Enable IPv6. Type 2002:7a64:dcee:1::111/128 in
the IPv6 Address/Prefix Length field for the LAN1’s IP address.
Enable Router Advertisement. Then click Add in the Advertised Prefix Table to add
2002:7a64:dcee:1::/64. The LAN1 hosts will get the network prefix through the
router advertisement messages sent by the LAN1 IPv6 interface periodically. Click
OK.
CONFIGURATION > Network > Interface > Ethernet > lan1 > General Settings
CONFIGURATION > Network > Interface > Ethernet > lan1 > IPv6 Router
Advertisement Setting

696/782
www.zyxel.com
Set Up the 6to4 Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Tunnel > Add,
Select Enable. Enter tunnel0 as the Interface Name and select 6to4 as the Tunnel
Mode. In the 6to4 Tunnel Parameter section, this example just simply uses the
default 6to4 Prefix, 2002:://16. Enter your Relay Router’s IP address (192.88.99.1 in
this example). Select wan1 as the Gateway. Click OK.
CONFIGURATION > Network > Interface > Tunnel
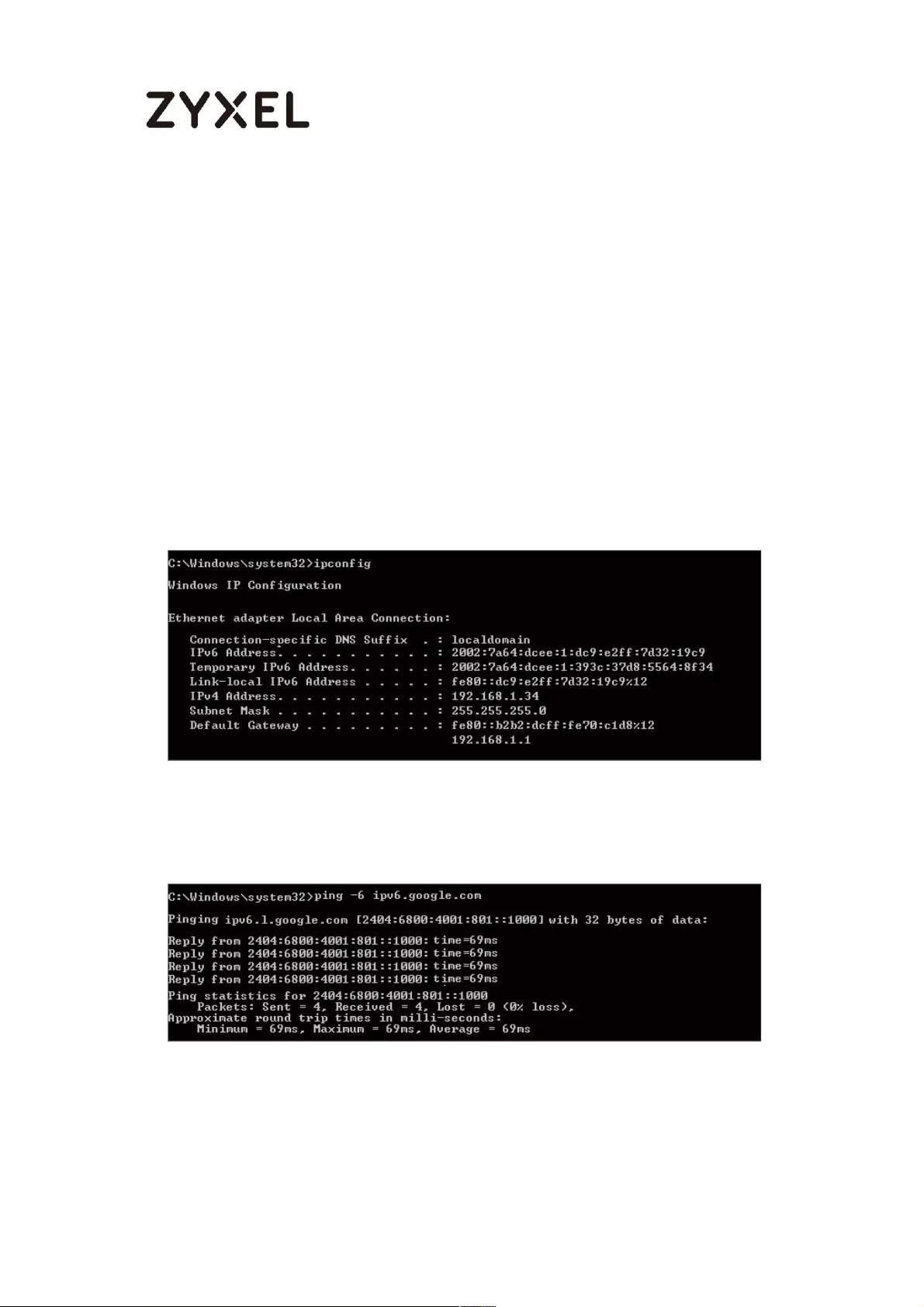
697/782
www.zyxel.com
Test the Result
Connect a computer to the ZyWALL/USG’s LAN1.
Enable IPv6 support on your computer. In Windows XP, you need to use the IPv6
install command in a Command Prompt. In Windows 7, IPv6 is supported by
default. You can enable IPv6 in the Control Panel > Network and Sharing Center >
Local Area Connection screen.
Your computer should get an IPv6 IP address (starting with 2002:7a64:dcee:1: in
this example) from the ZyWALL/USG.
Window 7 > cmd > ipconfig
Type ping -6 ipv6.google.com in a Command Prompt to test. You should get a
response.
Window 7 > cmd > ping -6 ipv6.google.com

698/782
www.zyxel.com
What Could Go Wrong?
If your IPv6 connection is not working, please make sure you disable Auto-
Configuration on the LAN1 IPv6 interface. Enabling it will cause two default routes,
however, the ZyWALL/USG only needs a default route generated by your relay
router setting. Also, make sure you enable the WAN1 IPv4 interface. In 6to4, the
ZyWALL/USG uses the WAN1 IPv4 interface to forward your 6to4 packets over the
IPv4 network.
In Windows, some IPv6 related tunnels may be enabled by default such as Teredo
and 6to4 tunnels. It may cause your computer to handle IPv6 packets in an
unexpected way. It is recommended to disable those tunnels on your computer.
How to Set Up an IPv6-in-IPv4 Tunnel
This example shows how to configure your ZyWALL/USG to create IPv6-in-IPv4
Tunnel. In this example, the ZyWALL/USG acts as IPv6-in-IPv4 routers which
connect the IPv4 Internet and an individual IPv6 network. This configuration
example only shows the settings on ZyWALL/USG_Z. You can use similar settings to
configure ZyWALL/USG_Y.
ZyWALL/USG with IPv6-in-IPv4 Tunnel Example
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses and subnet masks. This example
was tested using USG310 (Firmware Version: ZLD 4.25).

699/782
www.zyxel.com
Set Up the LAN IPv6 Interface on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Ethernet >
lan1. Select Enable Interface and Enable IPv6. Type 2002:7a64:dcee:1::111/128 in
the IPv6 Address/Prefix Length field for the LAN1’s IP address.
Enable Router Advertisement. Then click Add in the Advertised Prefix Table to add
2002:7a64:dcee:1::/64. The LAN1 hosts will get the network prefix through the
router advertisement messages sent by the LAN1 IPv6 interface periodically. Click
OK.
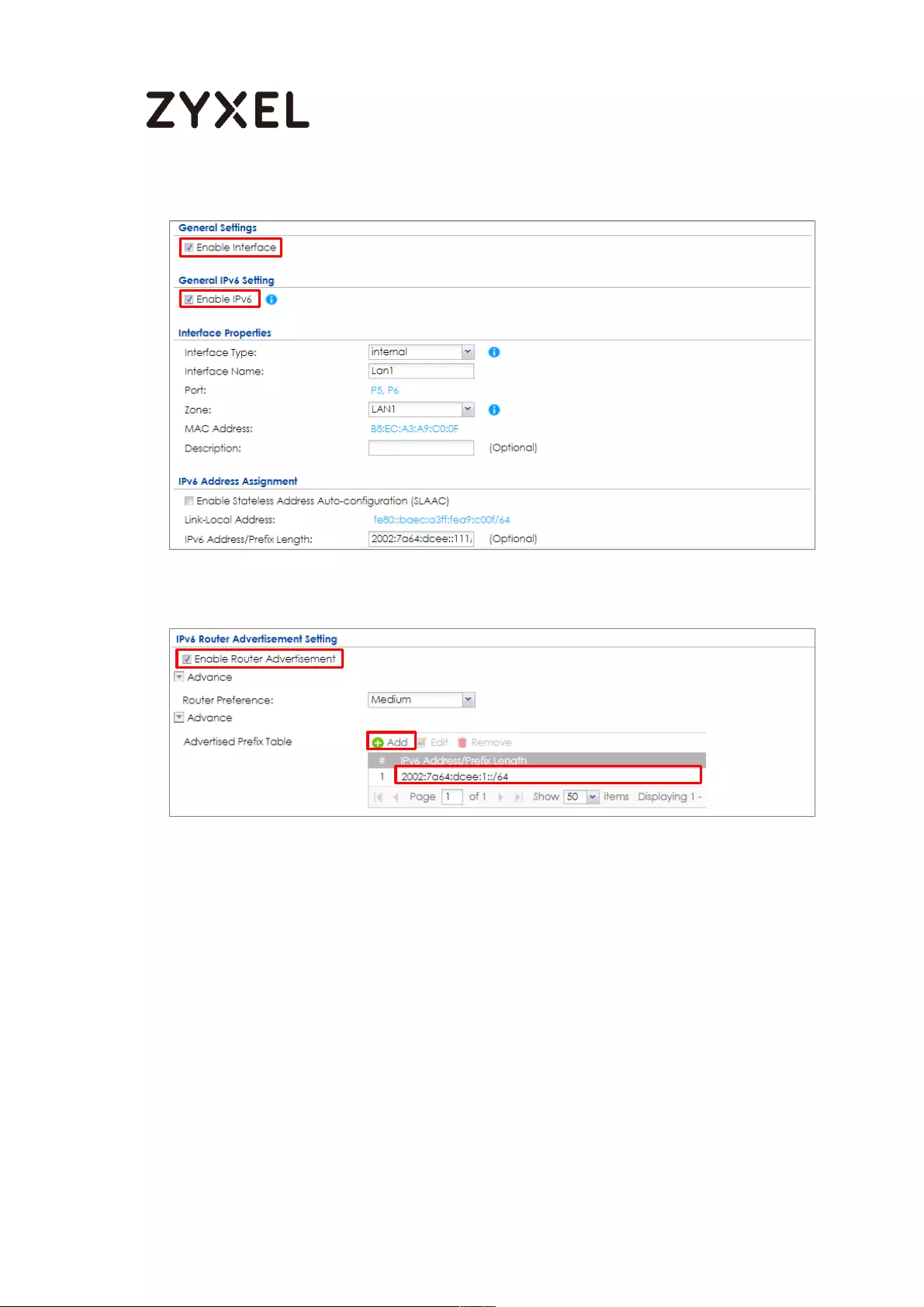
700/782
www.zyxel.com
CONFIGURATION > Network > Interface > Ethernet > lan1 > General Settings
CONFIGURATION > Network > Interface > Ethernet > lan1 > IPv6 Router
Advertisement Setting
Set Up the 6to4 Tunnel on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Interface > Tunnel > Add
and select Enable. Enter tunnel0 as the Interface Name and select IPv6-in-IPv4 as
the Tunnel Mode. Select wan1 as the gateway interface. Enter your Remote
Gateway Address (172.121.123.150 in this example). Click OK.

701/782
www.zyxel.com
CONFIGURATION > Network > Interface > Tunnel
Set Up the Policy Route on the ZyWALL/USG
In the ZyWALL/USG, go to CONFIGURATION > Network > Routing > IPv6
Configuration > Add, click Create New Object to create an IPv6 address object
with the address prefix of 2002:7a64:dcee:1::/64. Select Enable. Select the address
object you just created in the Source Address field. Select any in the Destination
Address field. Select Interface as the next-hop type and then tunnel0 as the
interface. Click OK.
CONFIGURATION > Network > Routing > Policy Route > IPv6 Configuration
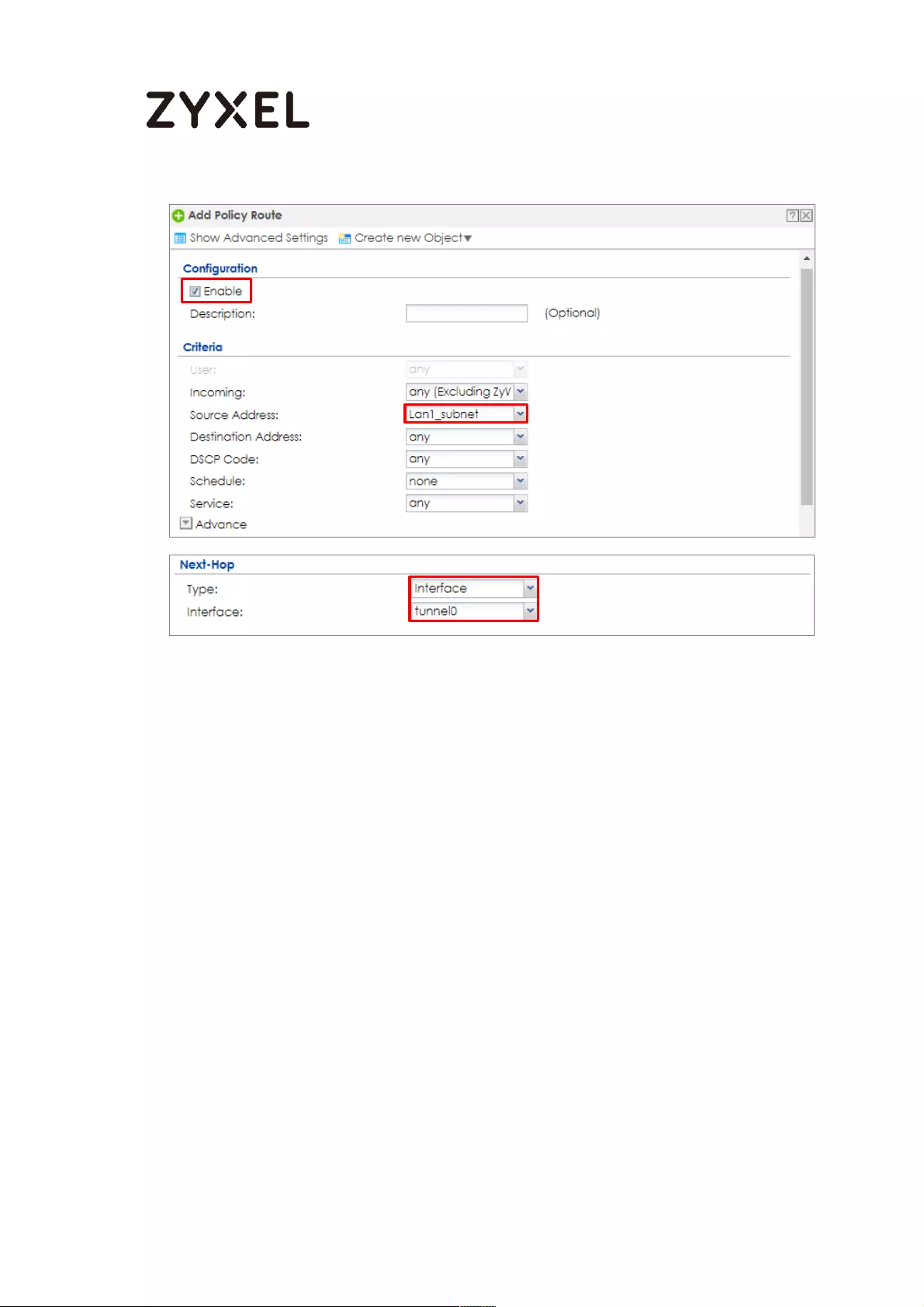
702/782
www.zyxel.com
Test the Result
Connect a computer to the ZyWALL/USG’s LAN1.
Enable IPv6 support on your computer. In Windows XP, you need to use the IPv6
install command in a Command Prompt. In Windows 7, IPv6 is supported by
default. You can enable IPv6 in the Control Panel > Network and Sharing Center >
Local Area Connection screen.
Your computer should get an IPv6 IP address (starting with 2002:7a64:dcee:1: for
this example) from the ZyWALL/USG.
Window 7 > cmd > ipconfig

703/782
www.zyxel.com
Use the ping -6 [IPv6 IP address] command in a Command Prompt to test whether
you can ping a computer behind ZyWALL/USG_Y. You should get a response.
Window 7 > cmd > ping -6 2001:b020:0:71::46
What Could Go Wrong?
If your IPv6 connection is not working, please make sure you enable the WAN1
IPv4 interface. In IPv6-in-IPv4, the ZyWALL/USG uses the WAN1 IPv4 interface to
forward your 6to4 packets to the IPv4 network.
In Windows, some IPv6 related tunnels may be enabled by default such as Teredo
and 6to4 tunnels. It may cause your computer to handle IPv6 packets in an
unexpected way. It is recommended to disable those tunnels on your computer.
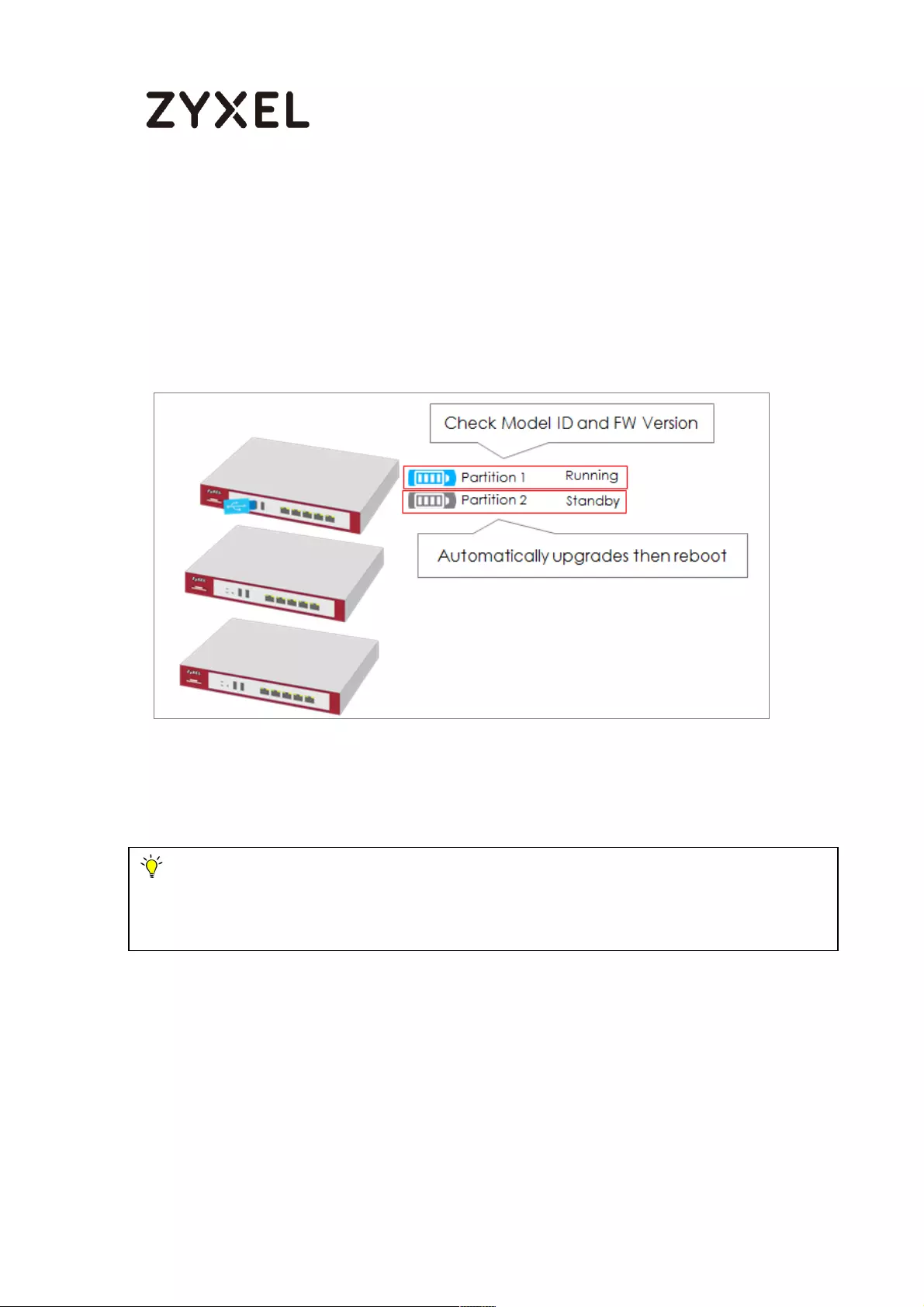
704/782
www.zyxel.com
How to Update Firmware Automatically from a USB Storage
This example illustrates how to update the ZyWALL/USG’s firmware automatically from
a USB storage. With this feature, it is more efficient for users to upgrade the firmware
for numerous devices without Internet or GUI access. The user can also downgrade
the firmware by using this feature.
Figure 1 Automatic USB Firmware Upgrade
Automatic USB Firmware Upgrade Flow
1 Enable the USB firmware upgrade function by CLI command.
2 Save the firmware on the USB.
3 Plug the USB into the device.
4 The device checks running partition for the model ID and the firmware version.
5 Upgrade the firmware to the standby partition and then the device reboots.
Note: This feature does not support Device HA Pro firmware auto upgrade to passive
devices. Do not use USB firmware upgrade on the devices with Device HA Pro function
activated. This example was tested using the USG210 (Firmware Version: ZLD 4.25).
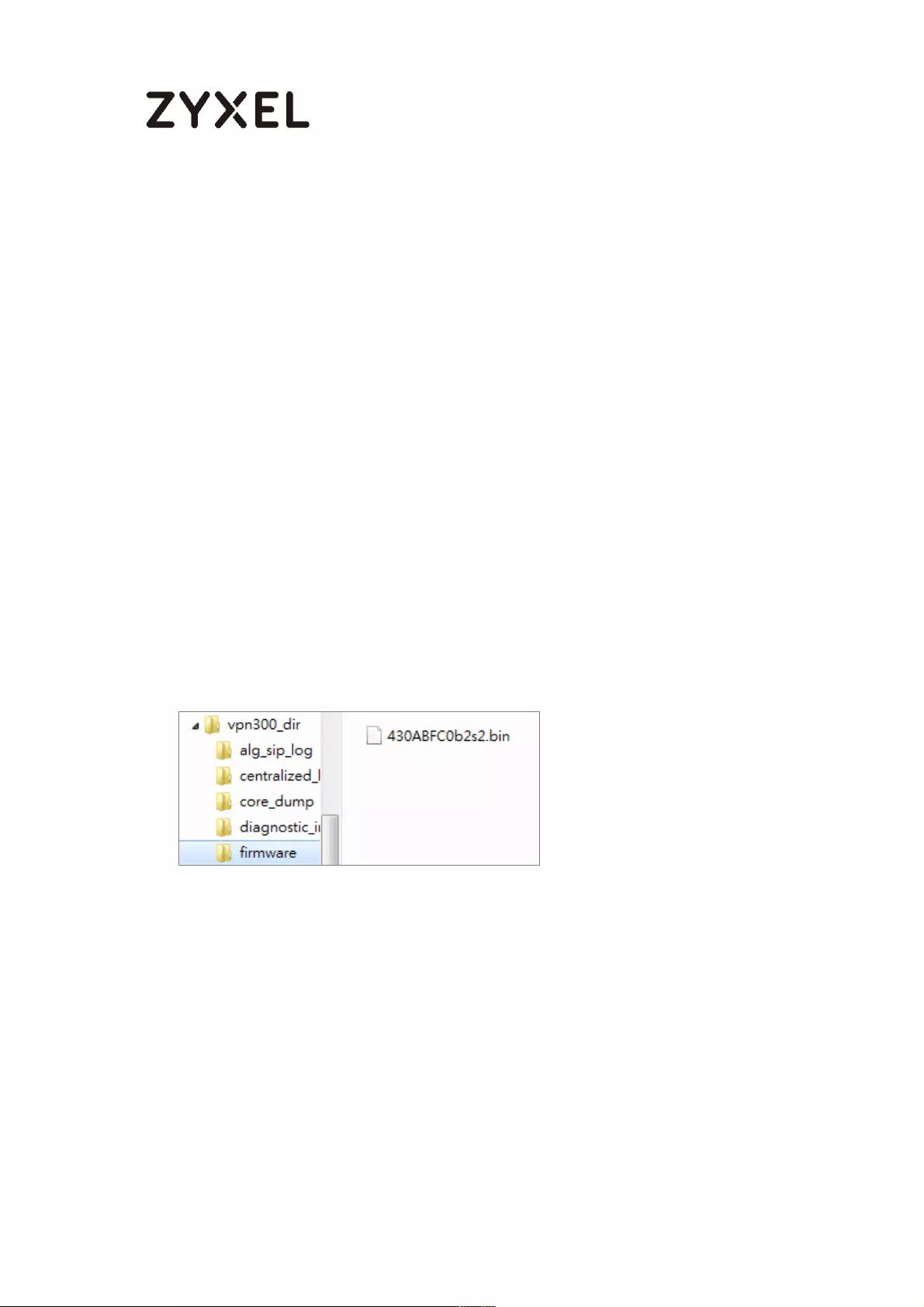
705/782
www.zyxel.com
Enable the USB Firmware Upgrade Function by CLI Command
For security concerns, the function is disabled by default. The administrator needs
to enable the function by the following CLI command:
Router(config)# usb-storage update-firmware enable
Save the Firmware on the USB
There are two ways to create the firmware folder on the USB storage.
1 Follow the folder structure to create the firmware folder manually. It does
not matter if the letters of the folder name are capitalized or not. For
example: D:\vpn300_dir\firmware
Create the Firmware Folder Manually: Root Directory\vpn300_dir\firmware
2 Plug the USB storage to the device and the device will automatically
create the folder Vpn300_dir, which includes the following sub-folders.
Save the .bin file to the firmware folder.
centralized_log
core_dump
diagnostic_info
firmware
packet_trace
706/782
www.zyxel.com
Firmware Folder is Created Automatically
Plug the USB into the Device
Once the .bin file in the firmware folder is detected, the device will copy it to the RAM.
Plug the USB storage into the USB port
The following message shows on the console if the device fails to copy the .bin file.
Router> USB update-firmware failed: firmware copy fail
The Device Checks Running Partition for the Model ID and the
Firmware Version
The device checks the USB firmware with the running partition only. It does not check
the standby partition.
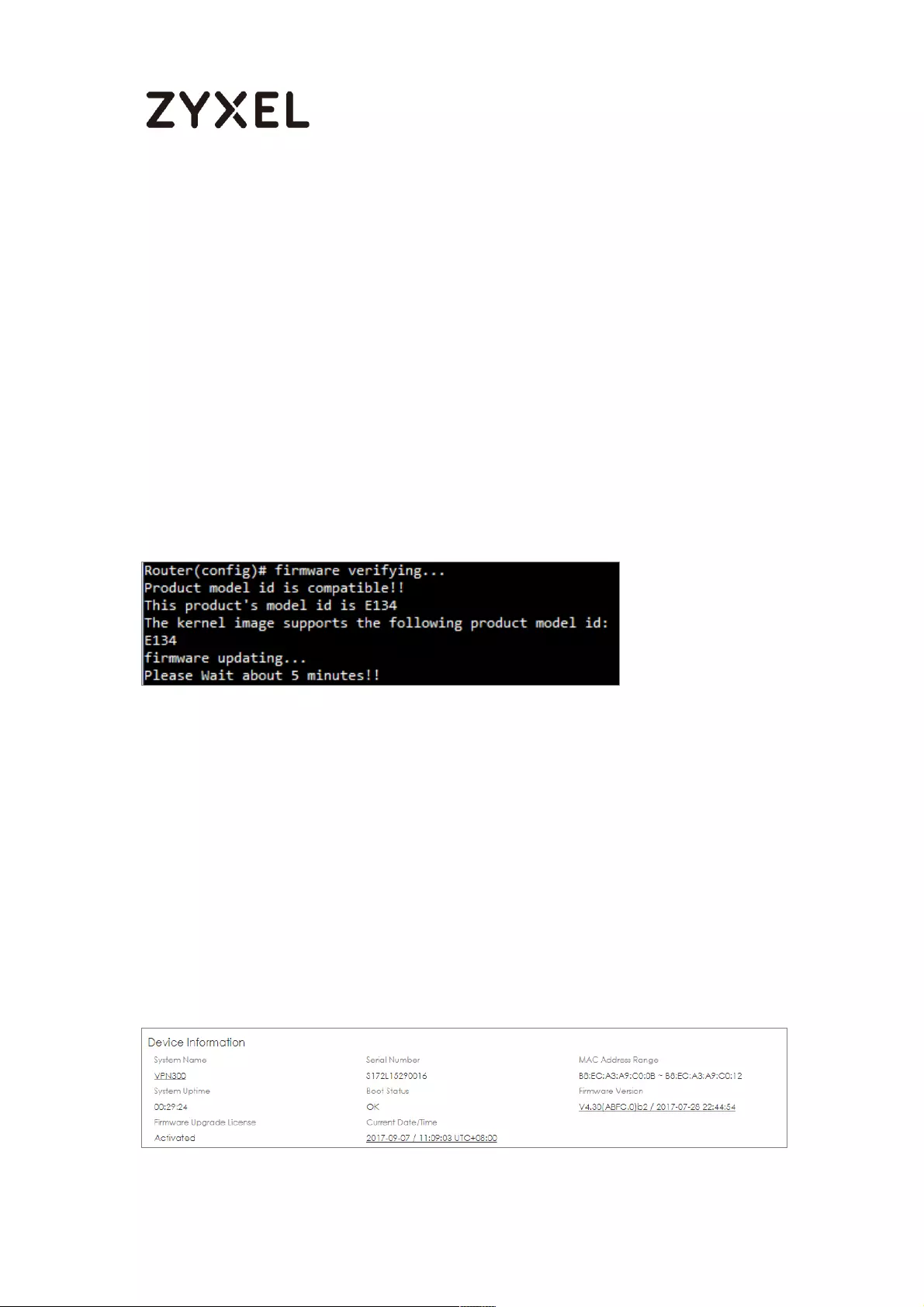
707/782
www.zyxel.com
1 Check model ID:
If incompatible, the device deletes the firmware in the RAM.
If compatible, the device checks the firmware version.
2 Check firmware version:
If it is the same as the running firmware, the device deletes the firmware in the
RAM.
If it is not the same as the running version, the device starts to upgrade to the
standby partition.
Check Model ID and Firmware Version
Check Firmware Status
The device upgrades the standby partition and then reboots. After been upgraded to
the standby partition, the device automatically reboots to switch from running to
standby partition. The SYS LED starts to blink when the device begins to upgrade its
firmware until the rebooting process is completed.
Check the Firmware Version on the Dashboard
708/782
www.zyxel.com
MONITOR > Log > View log
What Can Go Wrong?
1 The USB storage must use the FAT16, FAT32, EXT2, or EXT3 file system.
Otherwise, it may not be detected by the ZyWALL/USG.
2 The device only checks the firmware under the specific folder.
Therefore, make sure the firmware is saved in the correct folder under
the root directory: \ProductName_dir\firmware. For example:
\vpn300_dir\firmware
3 If there are multiple firmware files in the firmware folder of one model,
the device only checks the first one in order.
Multiple firmware files of one model in the same folder is not supported.
4 Make sure the product model ID of the USB firmware is compatible with
the device. The device writes logs on the console and device log if the
firmware model ID is incompatible.

709/782
www.zyxel.com
Console Message
MONITOR > Log > View log
5 Make sure the version of the USB firmware is different from that of the
running partition. The device writes logs on the console and device log if
the firmware version is the same as the running firmware.
Console Message
MONITOR > Log > View log
6 This feature does not support the Device HA Pro firmware auto upgrade
to passive devices. Do not use USB firmware upgrade on devices with

710/782
www.zyxel.com
Device HA Pro function activated. When using USB firmware upgrade on
a device HA or in a device HA Pro scenario, make sure you plug the USB
storage to the passive device for firmware upgrade first. After the
passive device has finished firmware upgrading through the USB, plug
the USB storage to the active device for firmware upgrade.
How to Configure DHCP Option 60 – Vendor Class Identifier
The following figure depicts how the ZyWALL/USG uses DHCP option 60. By matching
the VCI strings, a DHCP client can choose one specific DHCP server on the WAN
network. This function is useful when there are several DHCP servers providing different
services in an environment. Clients that need Internet service can be directed to the
DHCP server which provides Internet connection information with the same option 60
string. IPTV clients may relay to another DHCP server which obtains IPTV service
information.
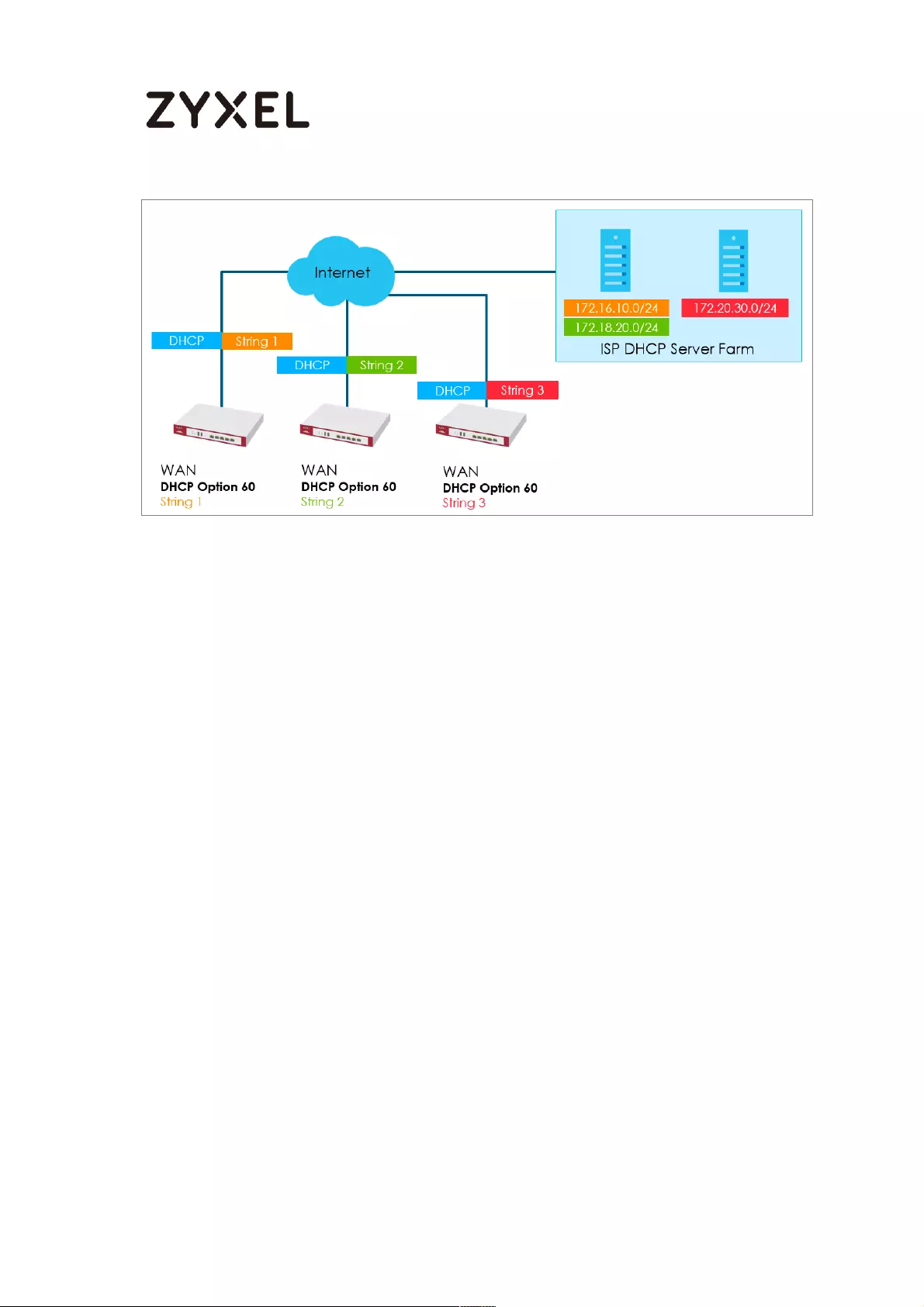
711/782
www.zyxel.com
Figure 1 DHCP Option 60 Vendor Class Identifier
DHCP Option 60 Deployment Flow
1 Enable the WAN ports as DHCP clients (enabled by default).
2 Navigate to the WAN interface configuration screen.
3 Type in user defined option 60 string in the Advance setting section.
Setting Up DHCP Option 60 on the Web GUI
1 In the ZyWALL/USG’s navigation panel, go to Configuration > Network >
Interface.
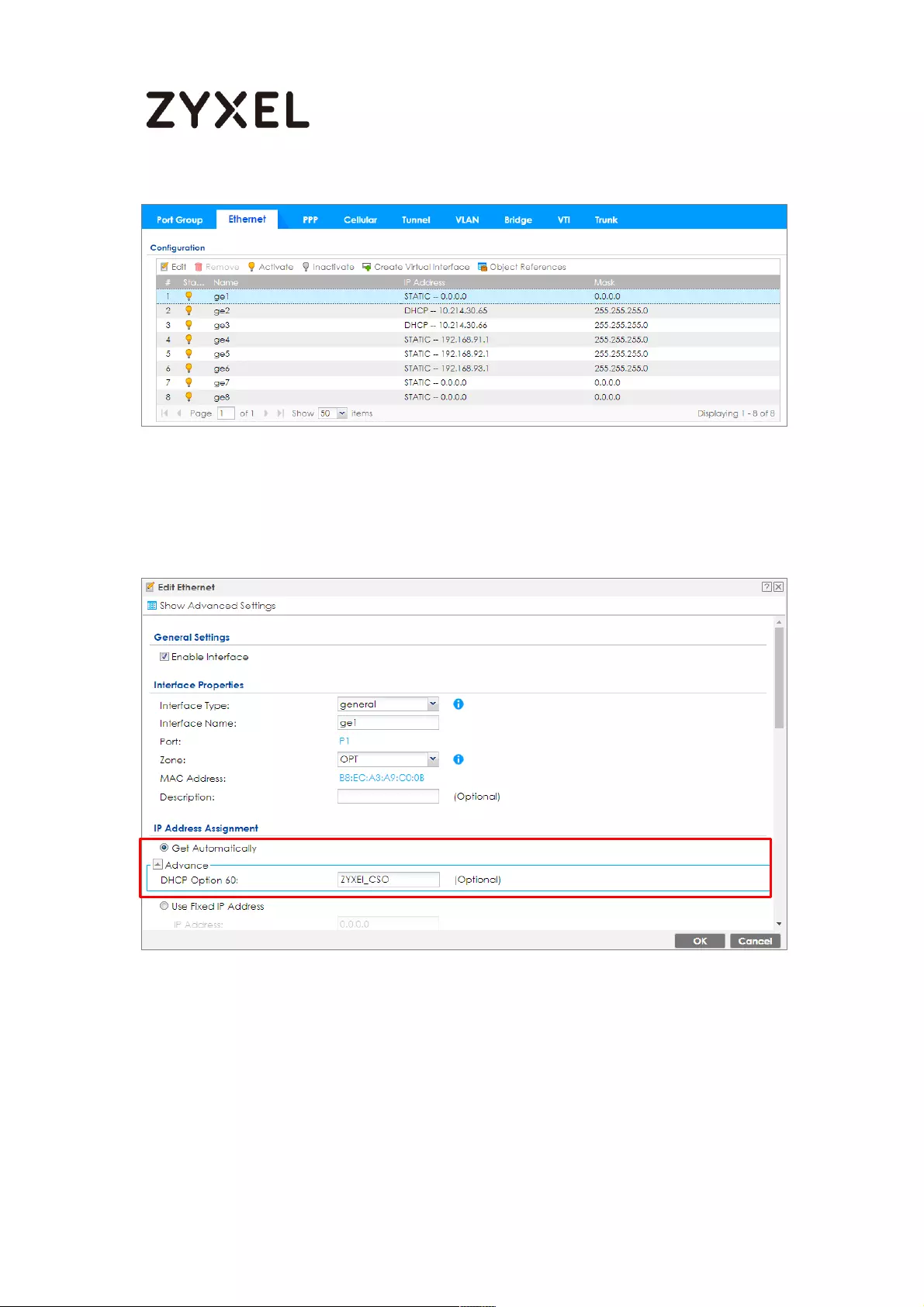
712/782
www.zyxel.com
2 Click the Ethernet tab, go to WAN > Edit. Enter the VCI string in the Advance
section of DHCP Option 60.
Setting Up DHCP Option 60 on the CLI
Under the specific interface path, use these commands to:
Enable option 60
Router(config-if-wan1)# ip address dhcp option-60 {VCI_STRING}
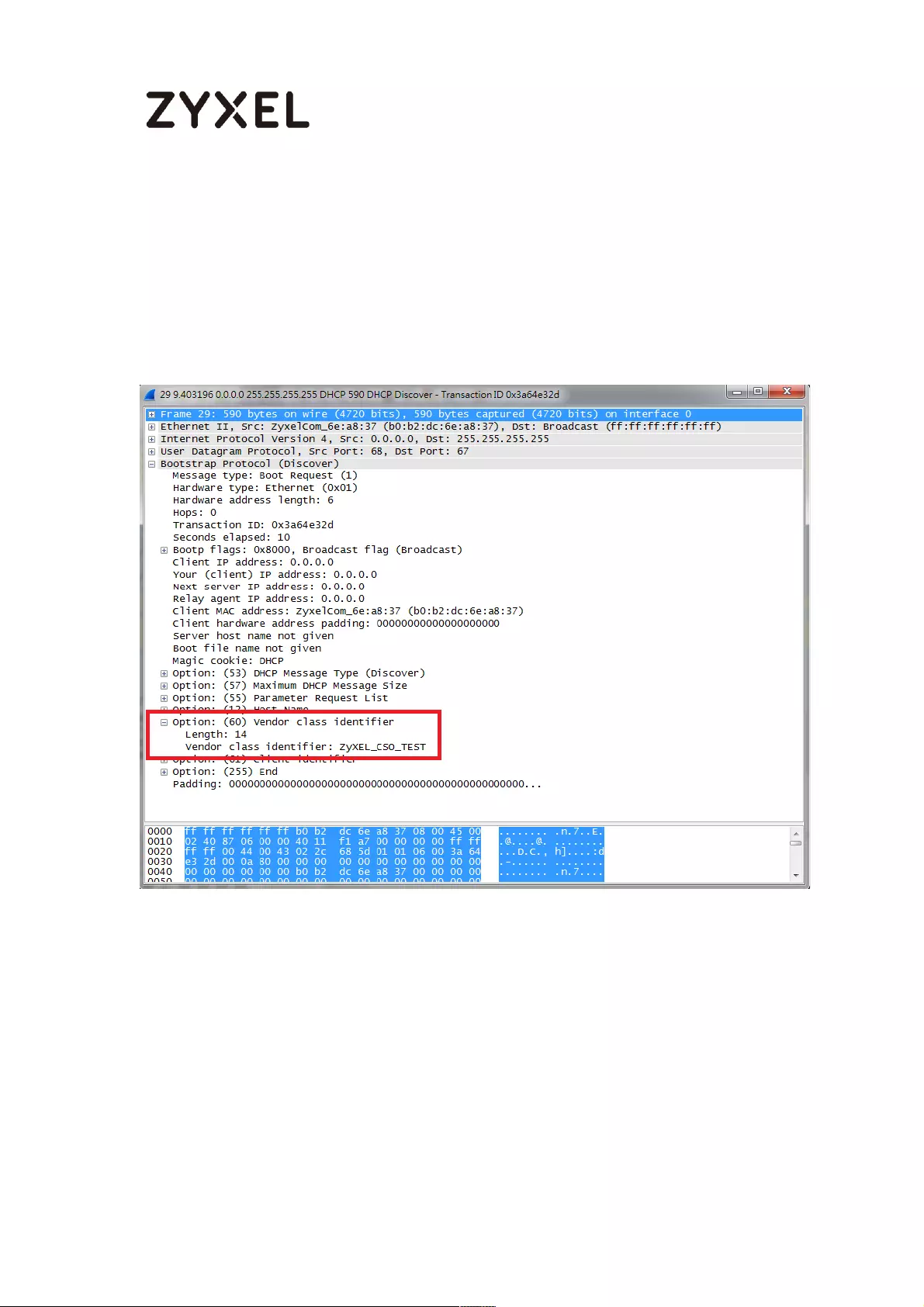
713/782
www.zyxel.com
Disable option 60
Router(config-if-wan1)# no ip address dhcp option-60
Test DHCP Option 60
To test the DHCP option 60 function, use a packet capture software to check if option
60 string exists in the DHCP discover message sent from the ZyWALL/USG WAN port.
What Can Go Wrong?
1 Avoid using the same option 60 string on two or more DHCP servers. It
may cause duplicate DHCP serving confliction.
2 Since packets with option 60 are clear, do not consider it as a secure
way for DHCP server authentication.
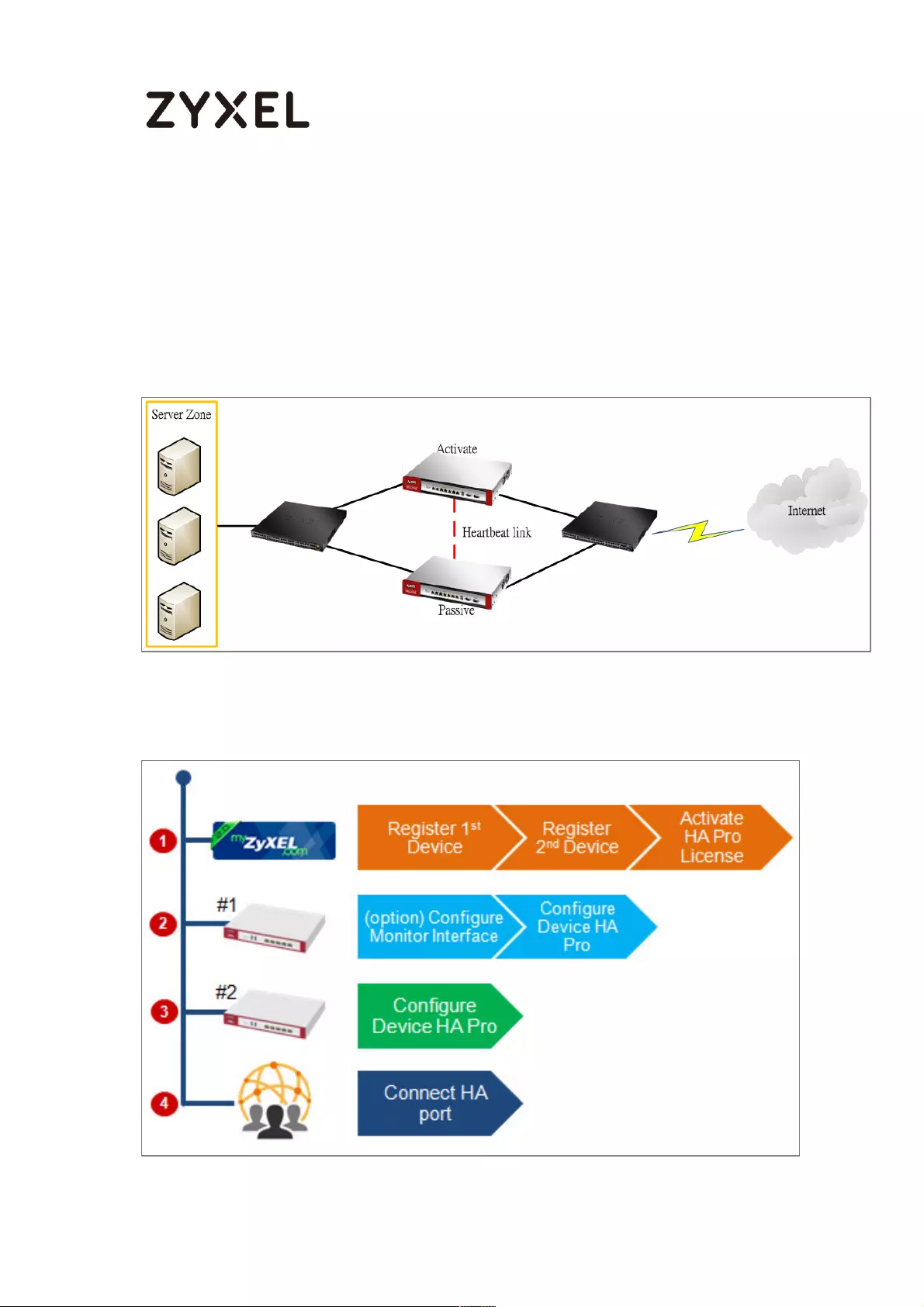
714/782
www.zyxel.com
How to Configure Device HA Pro
The Device HA feature acts as a failover when one of the devices in the network is
dead or can’t access the Internet. Therefore, this is a popular feature for network
environments. In the previous firmware version, the USG supports AP (Activate-
Passive/Master-Backup) mode. In V4.25, the Device HA feature is enhanced and
named Device HA Pro.
In Device HA Pro, a “heartbeat link” is added for monitoring the interface status and
synchronizing settings. Follow the steps below to deploy the Device HA Pro feature in
your network environment.
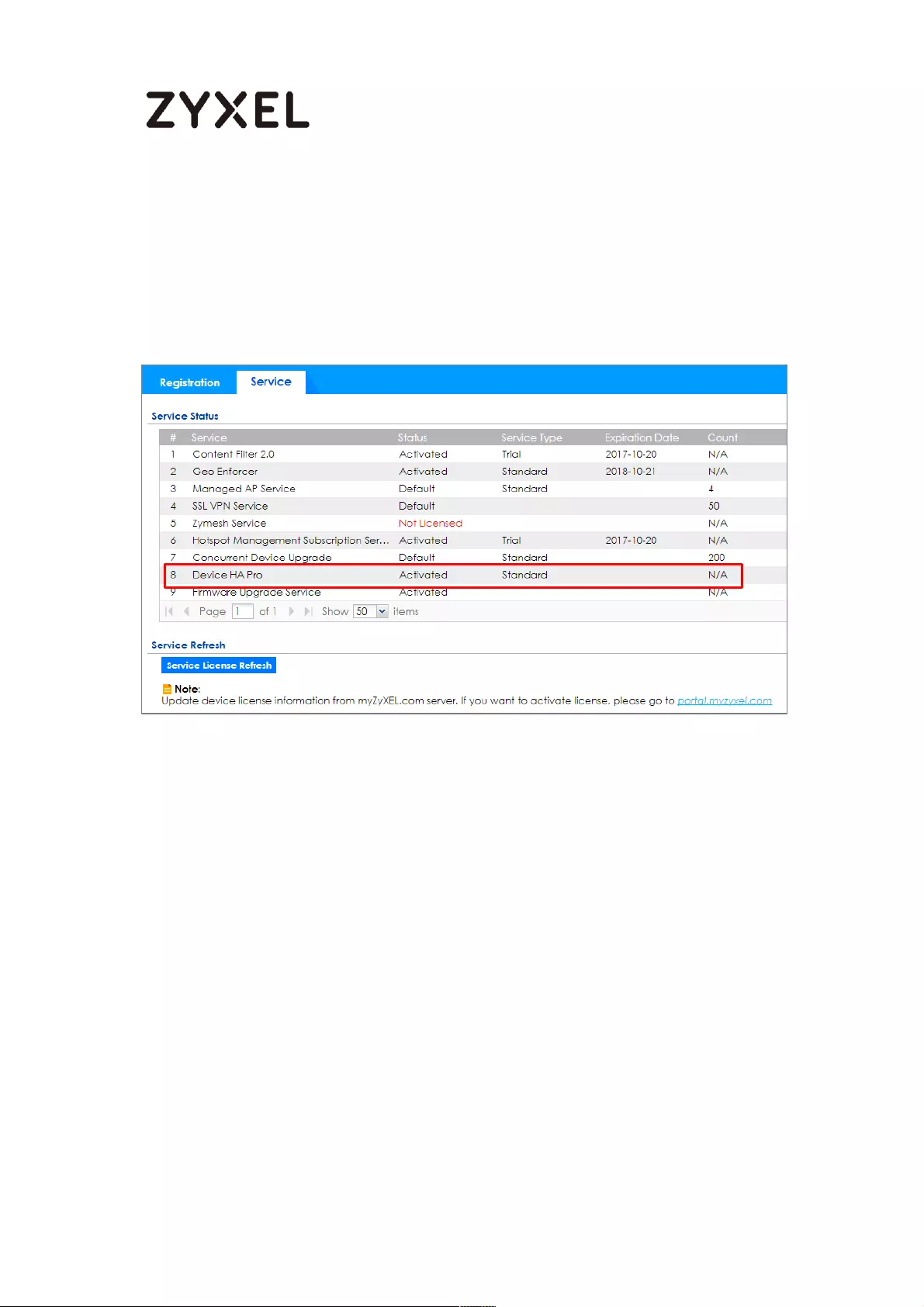
715/782
www.zyxel.com
Device HA Pro License
The Device HA Pro feature is license required. You must register both of your devices
on the myZyXEL.com server first. Then make sure the Device HA Pro license is available
on both of your devices.
Behavior of the Device HA Pro
The behavior of the Device HA Pro includes a heartbeat link to monitor the
“activate” device’s interface status. If one of the monitored interfaces is dead or
fails, the “passive” device’s status will become “activate”. (This means only 1
device’s status can be “activate” at a time.)
Be aware that the Device HA status of the devices might constantly change due
to the network environment situation. In the current firmware design, Device HA
Pro will not fallback when the primary device interface is working normally again.
Device-HA Pro Setting Screen
A. Enable configuration provisioning on the activated device
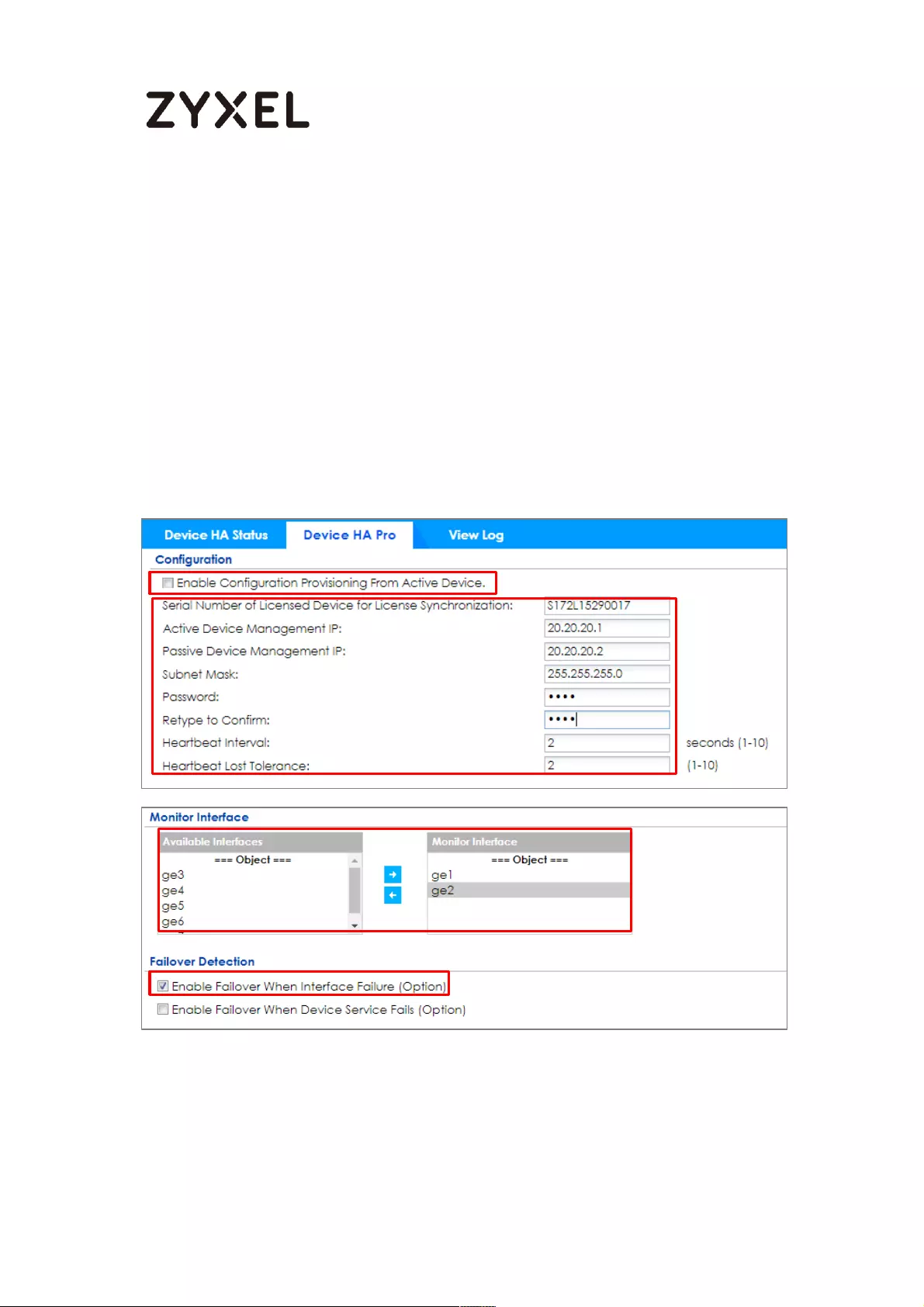
716/782
www.zyxel.com
This function is for the secondary device. If you are configuring the primary
device, this function is unnecessary.
B. Serial number of the licensed device for license synchronization
Entering the serial number of license from the myZyXEL.com server.
C. Configure the Device HA Pro interface
Enter the management IP address of the active and passive devices. Also, enter
the password for synchronizing configuration with each other.
D. Monitoring Interfaces
Select the interfaces which you would like to monitor.
E. Synchronization
Enable failover when one of the interfaces fails.
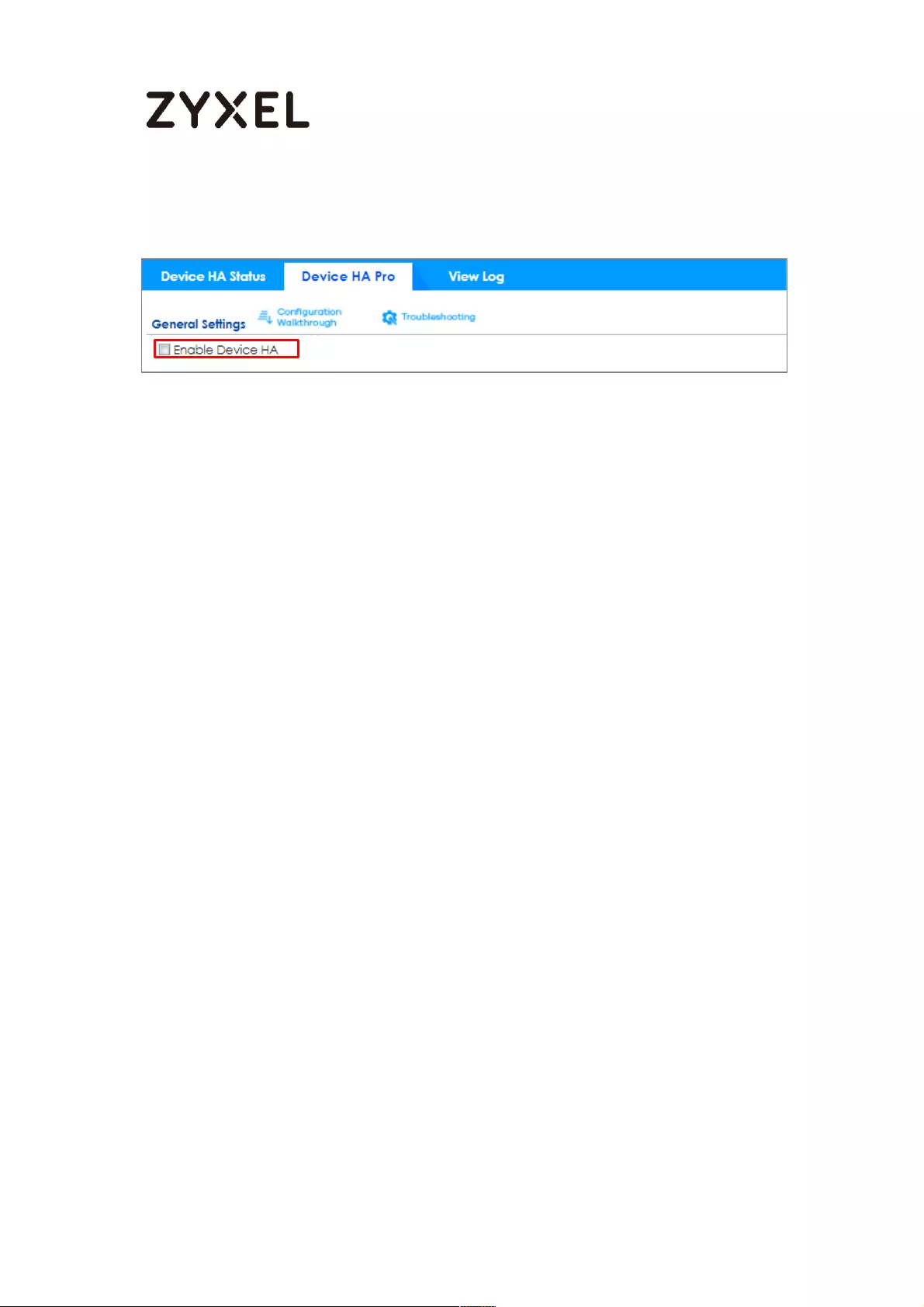
717/782
www.zyxel.com
The Main Function of the Device HA Pro
Heartbeat Link
The heartbeat port is a new physical port on the device.
After you have enabled Device HA Pro, the devices will transmit multicast packets
(UDP 694) to check each device’s status.
When the passive device is working properly, the system LED light will be on. Only
the heartbeat port’s LED light can be on.
Suggestions
1. Transfer all the licenses to the primary device. This helps to avoid the system
from recounting licenses every time.
2. Enable the connectivity check function on the monitored interfaces. When
an interface doesn’t receive any response from the remote server for a
certain period of time, the device will consider the interface status as fail.
Then the Device HA Pro feature will change the status of the interface.
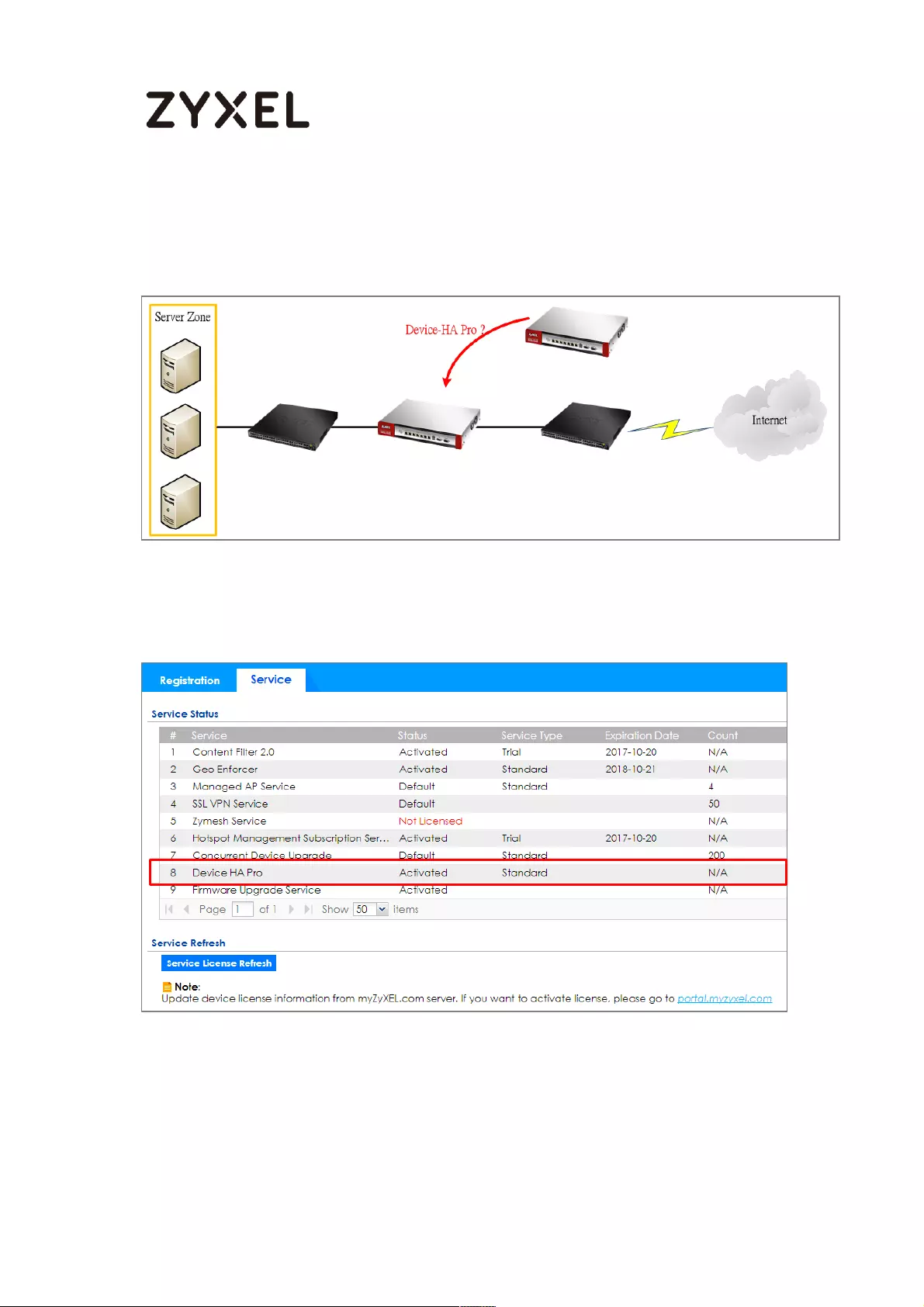
718/782
www.zyxel.com
How do I Configure Device HA Pro in My Current Environment?
License
The Device HA Pro feature is license required. Please go to register both of your devices
on myZyXEL.com and make sure the devices have the license after syncing with the
myZyXEL.com server.
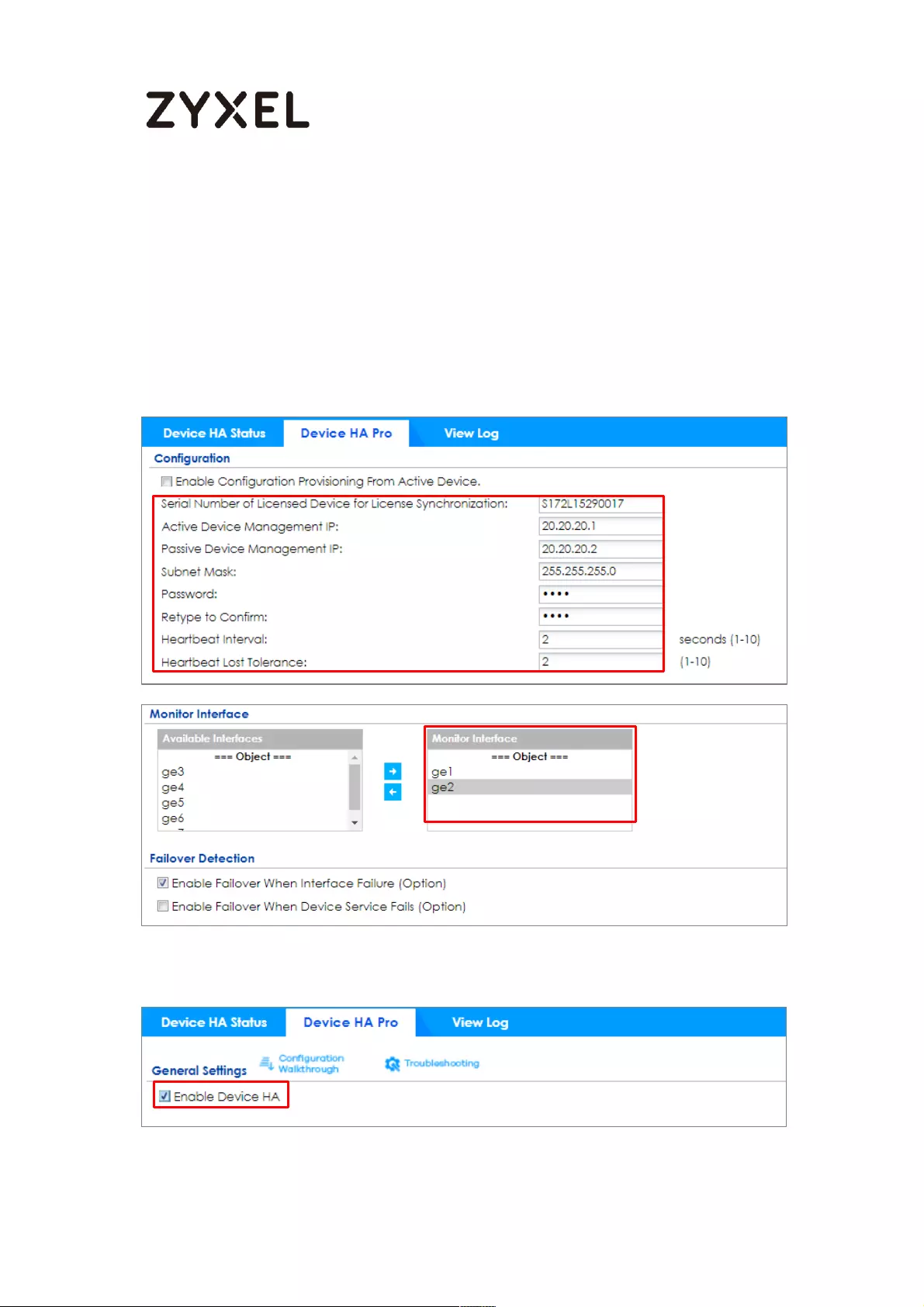
719/782
www.zyxel.com
Configurations on the Primary Device
1. Go to the Configuration > Device HA > Device HA Pro screen.
2. Enter the device’s license serial number from the myZyXEL.com server.
3. Enter the management IP address after enabling the Device HA Pro feature.
4. Select the interfaces which you would like to monitor.
5. Enable failover when an interface fails.
6. Click Apply.
Go to the Configuration > Device HA > General screen.
Select Enable Device HA and click Apply to enable Device HA Pro.
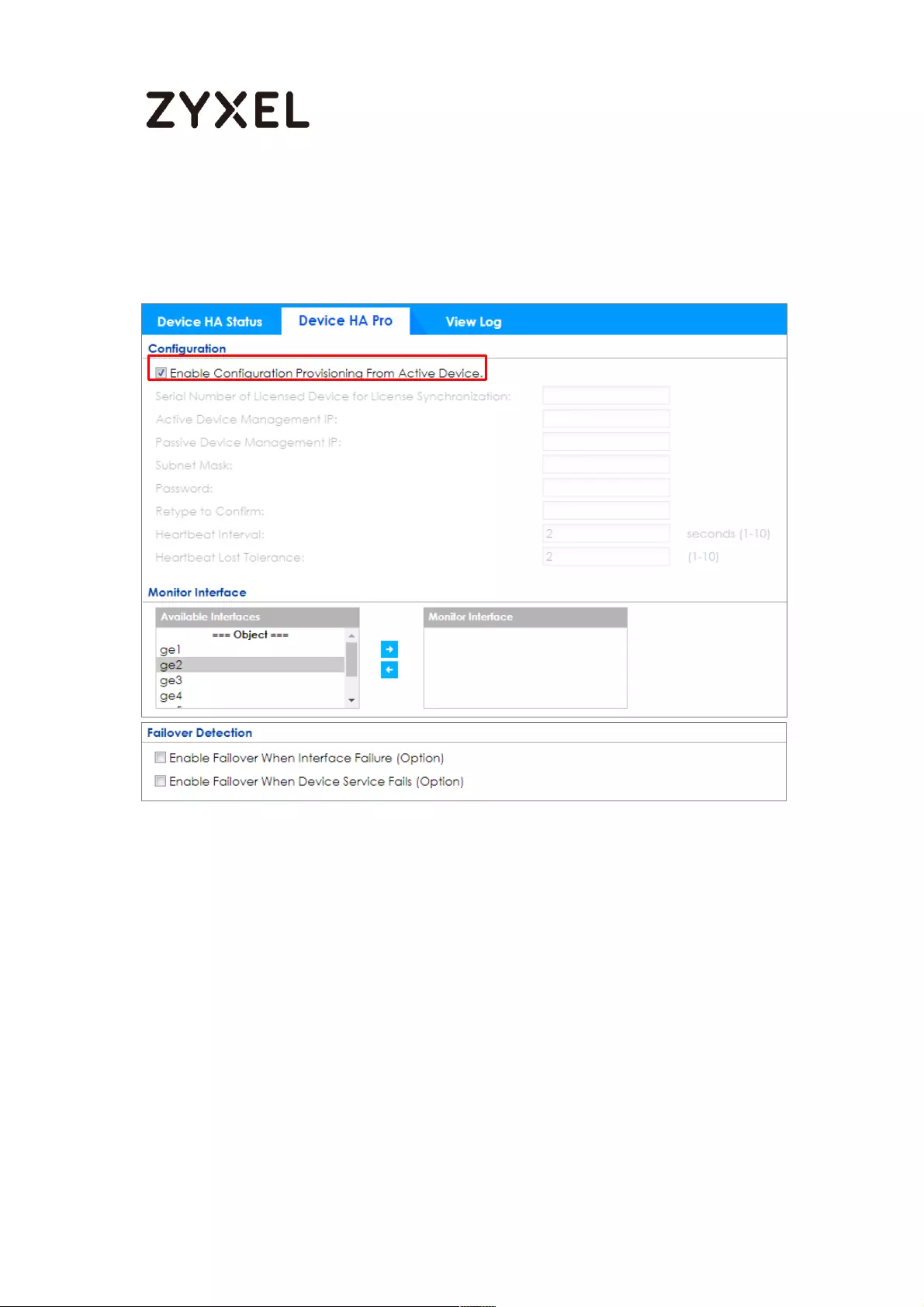
720/782
www.zyxel.com
Configurations on the Secondary Device
Go to the Configuration > Device HA > Device-HA Pro screen.
Select Enable Configuration Provisioning from Active Device.
Click Apply.

721/782
www.zyxel.com
Go to the Configuration > Device HA > General screen.
Select Enable Device HA and click Apply.
Before the Device HA Pro feature is enabled on the secondary device, a warning
message will pop-up for you to confirm. Click OK to enable it.
不會顯示這個訊息
1. Connecting the Device HA Pro Port
The Device HA Pro port is a new physical port on the DUT. You can use a cable to
connect the devices with each other.

722/782
www.zyxel.com
What can go wrong?
1. Why I can’t see correct license status from myzyxel.com server?
On the Device-HA Pro setting, there is a function “Serial number of the licensed
device for license synchronization”. You should entering device’s S/N which with
licenses. So you can transfer all of the licenses to “Activate” device, and entering
this device’s S/N in frame.
2. Why nothing happened after enabled Device-HA Pro?
After you enabled Device-HA Pro, the secondary device will not forward any
traffic any more except the latest physical port. So you must confirm the physical
port already connected with each other.
3. Why after Device-HA failover to secondary device, it will not fallback to primary
device?
Because Device-HA Pro purpose is for networking environment stability, so after
mechanism failover to secondary device it will keeping the latest status even
primary device is back. It can avoid the network service unstable.
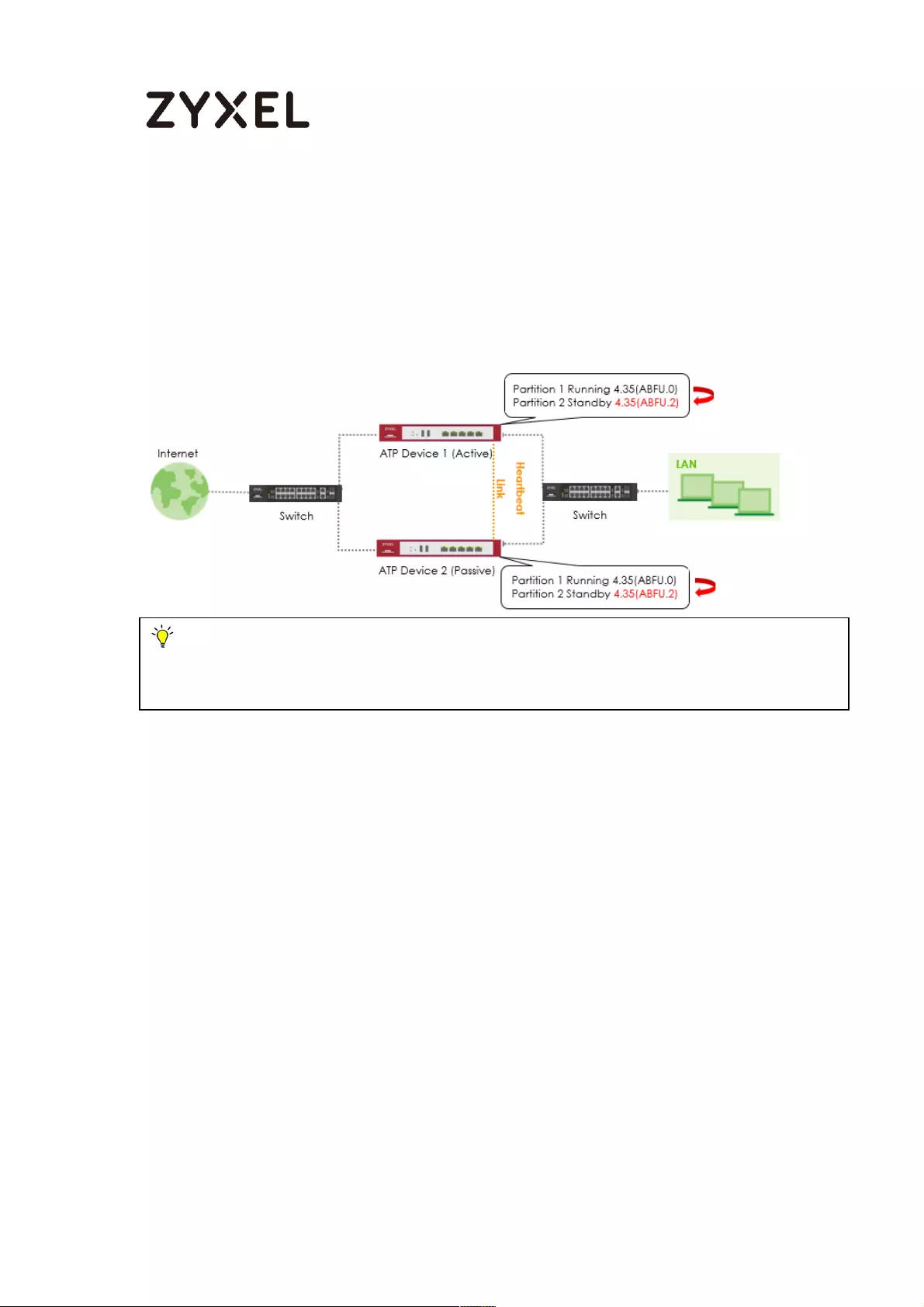
723/782
www.zyxel.com
How to Upgrade Firmware on HA Pro Synchronized Devices?
This example illustrates how to upgrade firmware from 4.35(ABFU.0) to
4.35(ABFU.2) on device HA Pro.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses. This example was tested using
the ATP500 (Firmware Version: ZLD 4.35).
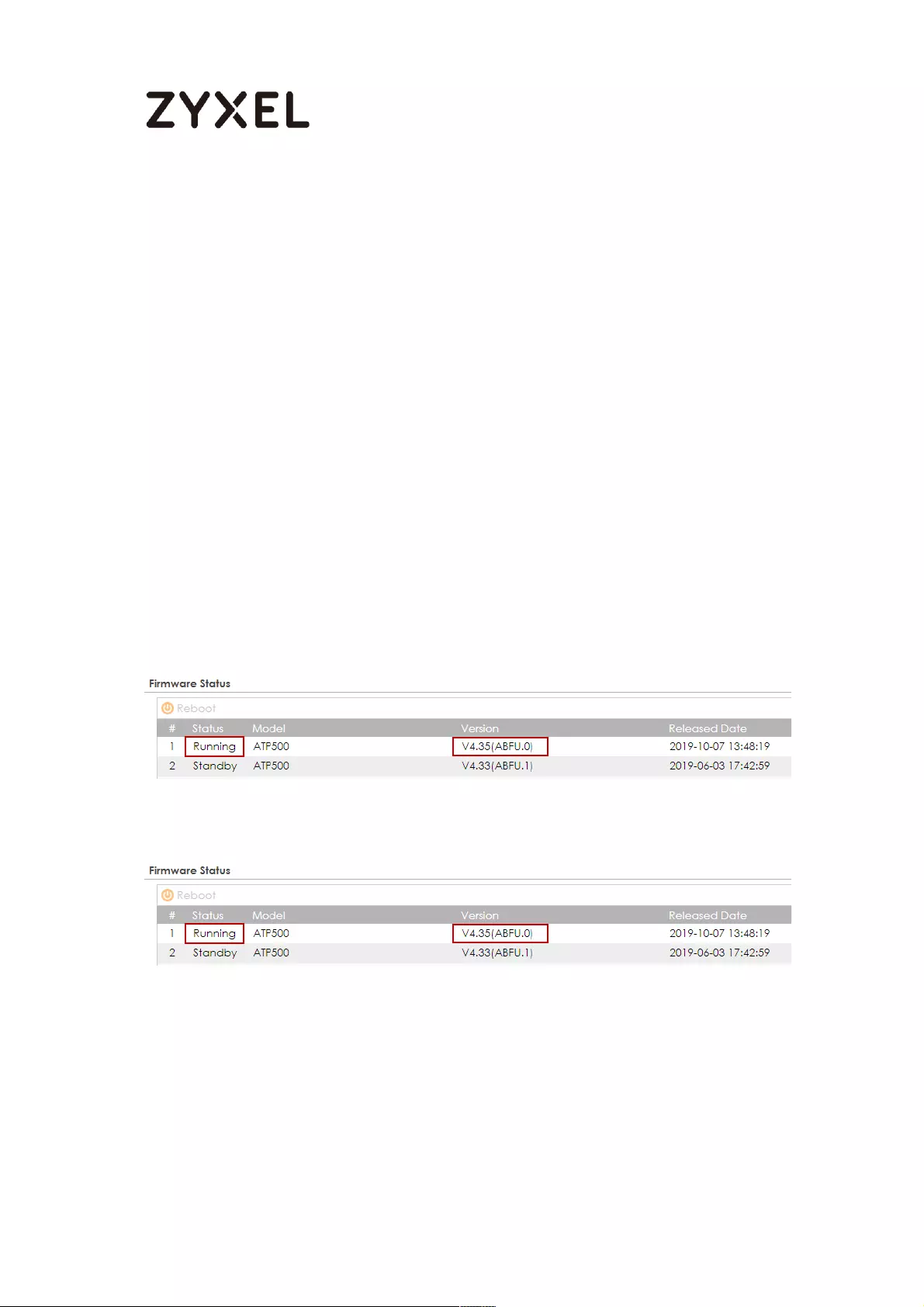
724/782
www.zyxel.com
Firmware Upgrade Flow
1. Make sure the running firmware version of active and passive are the same.
2. Make sure the running firmware of active and passive are in the same
partition.
3. Make sure the heartbeat port link is well connected and passive device is
fully synchronized with the active device.
4. Upload the firmware to the active device in standby partition.
Running Firmware Version
The running firmware on both active and passive devices must be the same.
Active (Device 1)- Running Firmware 4.35(ABFU.0)
Passive (Device 2)- Running Firmware 4.35(ABFU.0)
Running Firmware Partition
The running firmware partition of active and passive must be in the same position.
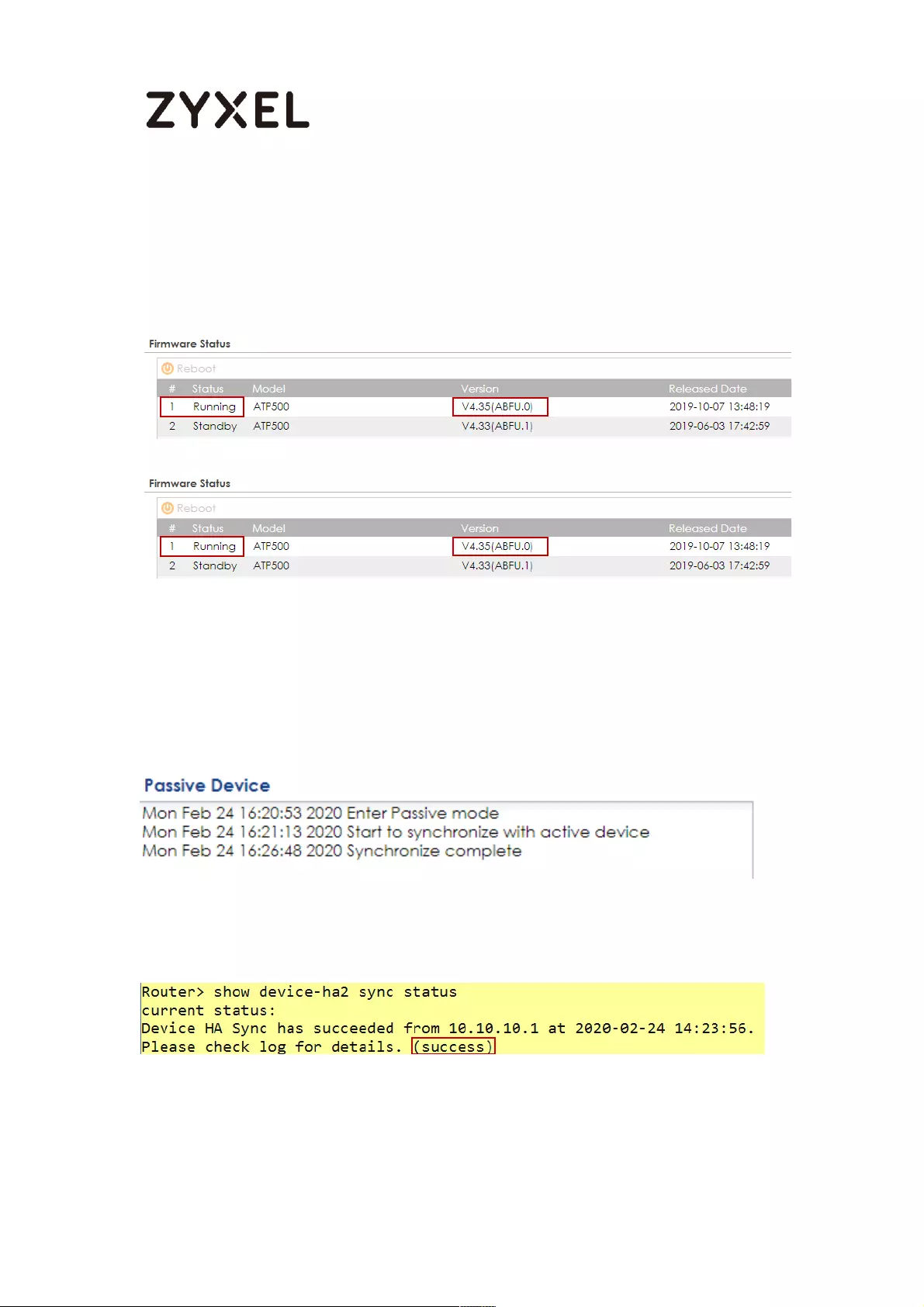
725/782
www.zyxel.com
For example,
The running firmware of the active device is in partition 1.
Then the running firmware of the passive device must also be in partition 1.
Active (Device 1)- Running Firmware in partition 1
Passive (Device 2)- Running Firmware in partition 1
Synchronization Status
Go to CONFIGURATION > Device HA > View Log > Passive Device and check if the
synchronization is complete.
You can also check the status on the console of the passive device.
Router> show device-ha2 sync status

726/782
www.zyxel.com
Upload the Firmware to the Active Device
On the Active (Device 1) device, go to MAINTENANCE > File Manager > Firmware
Management and upload the firmware to the Standby partition.
Click Yes to reboot device immediately after the firmware if uploaded
successfully.
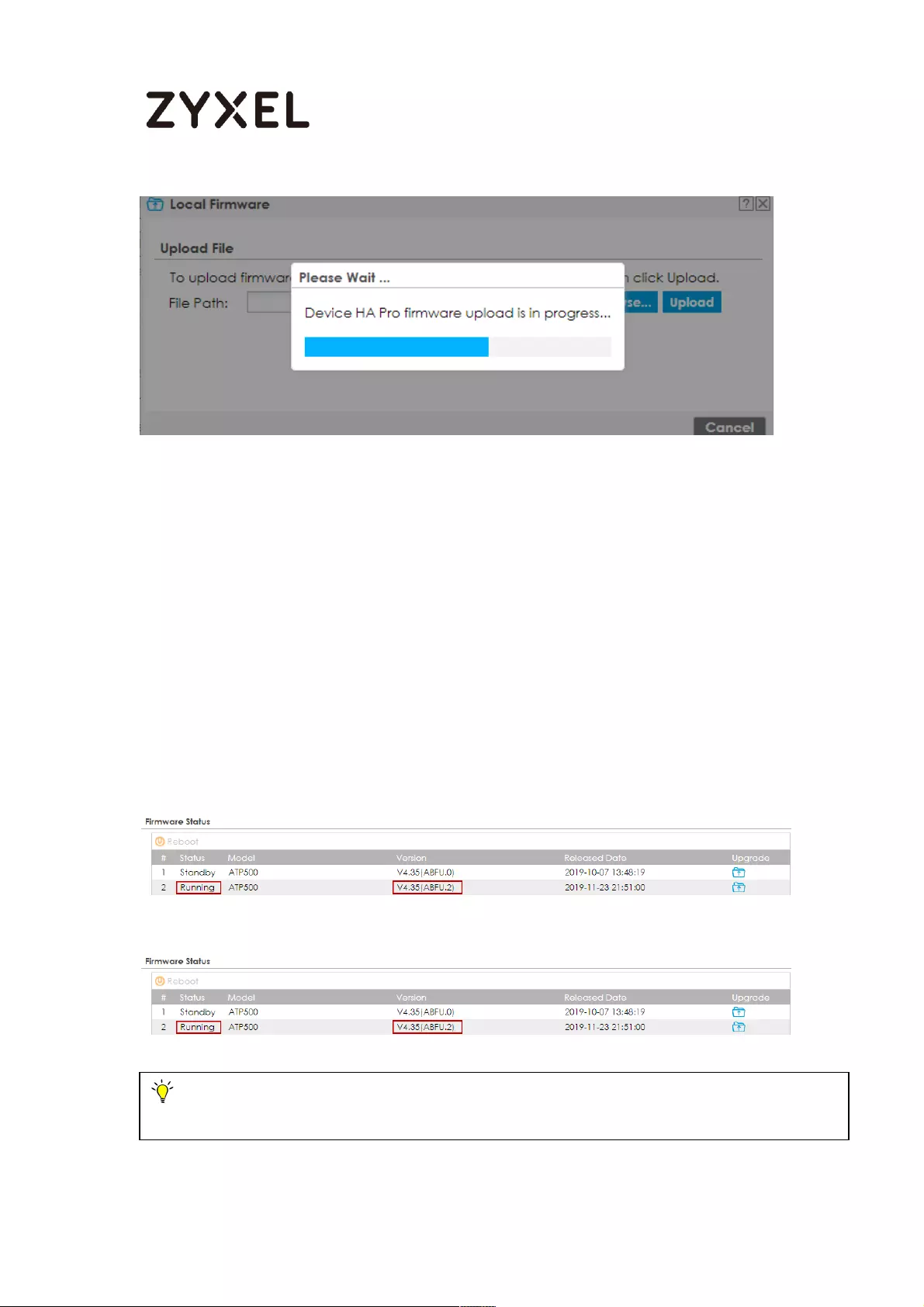
727/782
www.zyxel.com
Test the Result
The firmware will be uploaded in the Passive device (Device 2) first. After the firmware
is successfully uploaded to the Passive device (Device 2), the Passive device (Device
2) becomes active mode. Then the original Active device (Device 1) starts firmware
upgrading.
After firmware upgrading is finished on two devices, Device 2 becomes active mode
of HA Pro. Device 1 becomes passive mode.
Active (Device 2)- Running Firmware 4.35(ABFU.2)
Passive (Device 1)- Running Firmware 4.35(ABFU.2)
Note: Do not modify any settings before the Device 1 finished firmware upgrading and
configuration synchronization.

728/782
www.zyxel.com
How to Downgrade Firmware on HA Pro Synchronized Devices?
This example illustrates how to downgrade firmware from 4.35(ABFU.2) to
4.33(ABFU.1) on device HA Pro.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses. This example was tested using
the ATP500 (Firmware Version: ZLD 4.35).
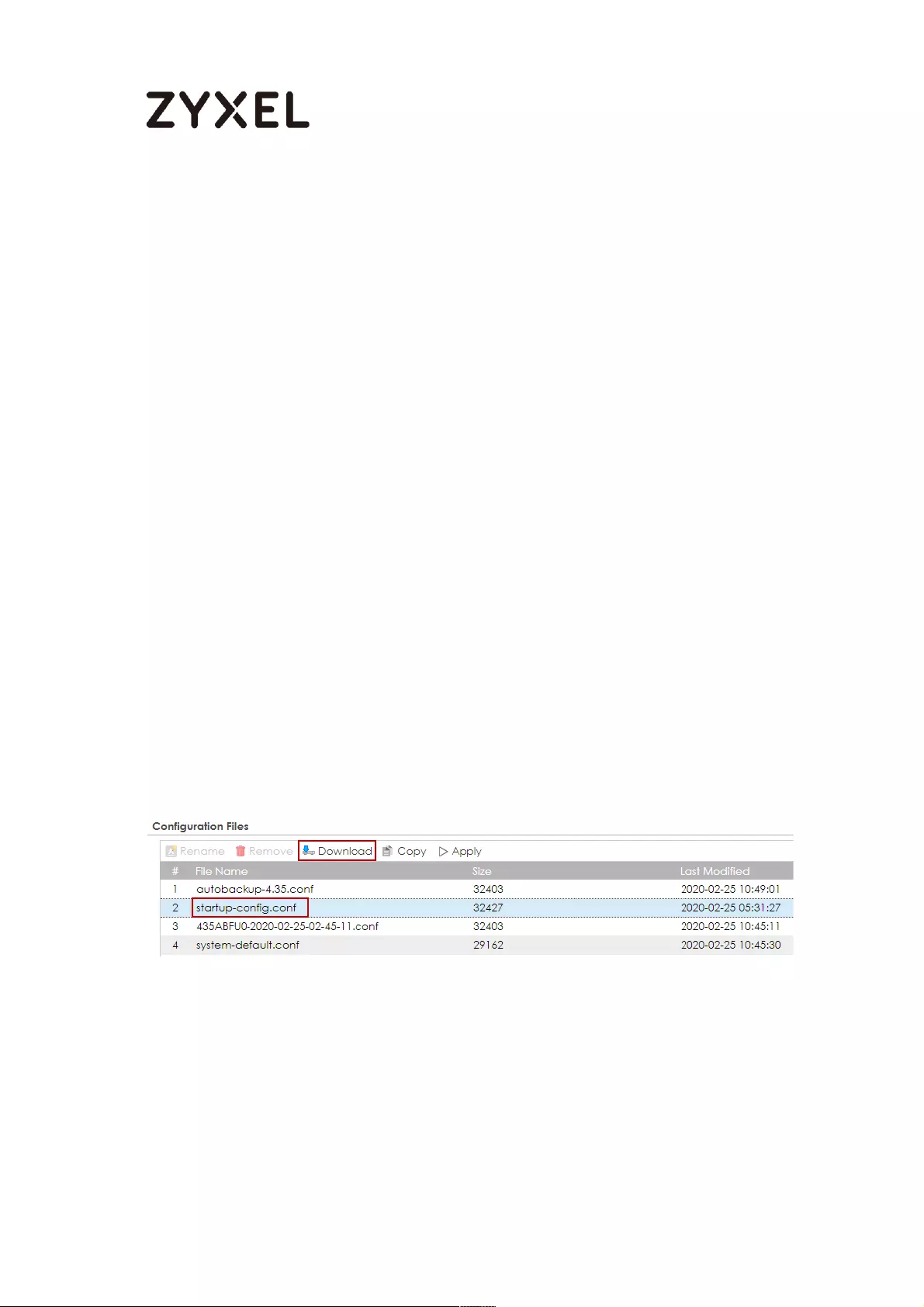
729/782
www.zyxel.com
Firmware Downgrade Flow
1. Back up the latest startup-config.conf of the Active device (Device 1).
2. Switch the passive device (Device 2) to active mode.
3. Disconnect all Ethernet cables and heartbeat port link on Device 1.
4. Downgrade the firmware to Device 1 and apply the backup configuration
file startup-config.conf to Device 1.
5. Disconnect all Ethernet cables on Device 2.
6. Connect all Ethernet cables on Device 1.
7. Downgrade the firmware to Device 2 and reset it to factory default settings.
8. Deploy HA Pro on Device 2 from the beginning and connect the heartbeat
port link to perform full synchronization.
Configuration File Backup
On Active device (Device 1), download the configuration file startup-config.conf.
MAINTENANCE > File Manager > Configuration File
Switch Passive Device to Active Mode
Disconnect any of monitored interfaces of Active device (Device 1) to have the
Passive device (Device 2) take over the active role. In this example, ge2 and ge4
730/782
www.zyxel.com
are selected as monitor interface. Disconnect one of monitor interfaces to make
Device 2 switch to active role.
CONFIGURATION > Device HA > Device HA Pro > Monitor Interface
Ethernet Cable and Heartbeat Port Disconnection
After Device 2 enters active mode, disconnect all Ethernet cables and the
heartbeat port link on Device 1.
Firmware Downgrade on Device 1
On Device 1, enter the command to disable HA Pro.
Router> configure terminal
Router(config)# no device-ha2 activate
Router(config)# write
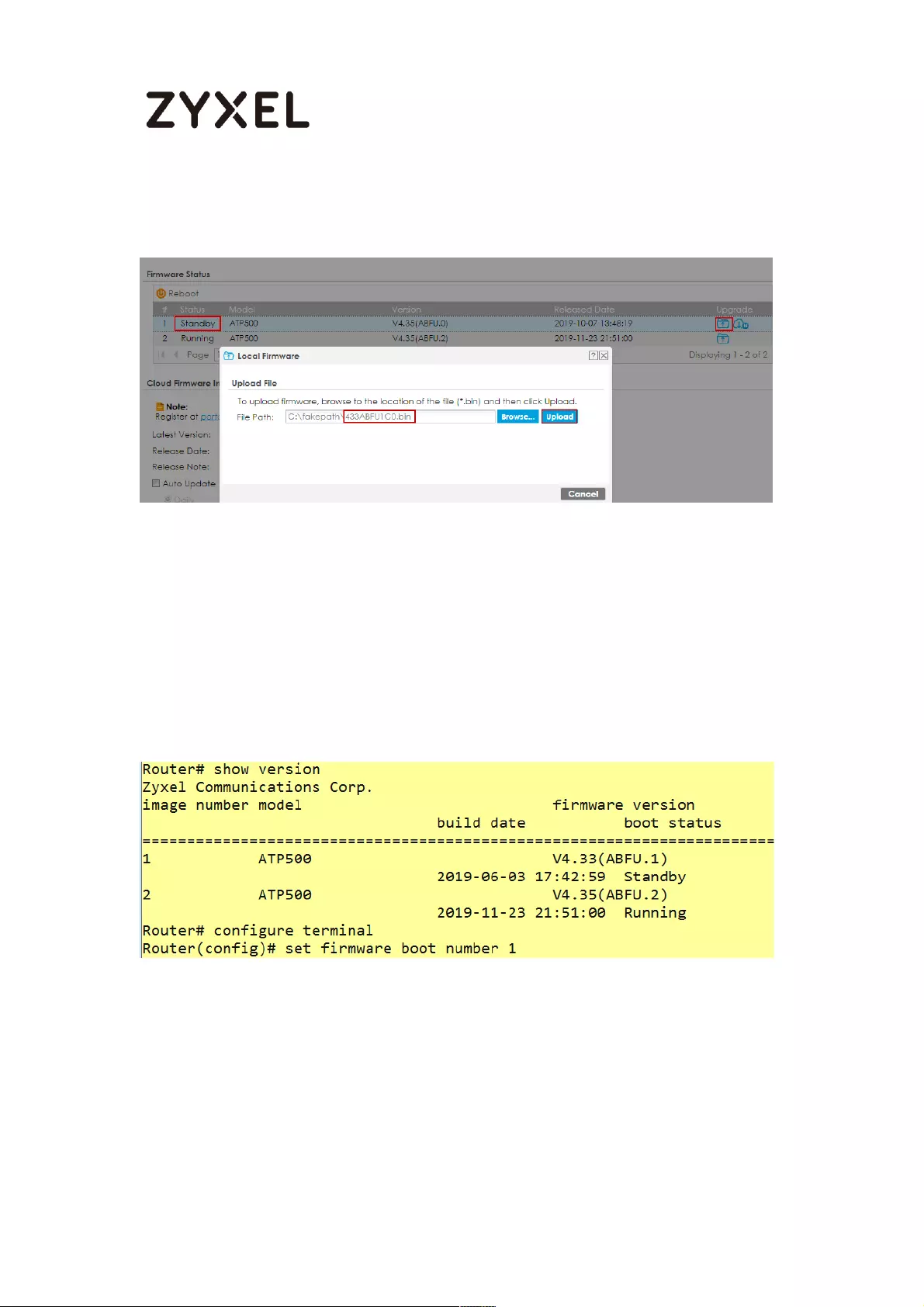
731/782
www.zyxel.com
Go to MAINTENANCE > File Manager > Firmware Management and upload the
old firmware to the standby partition.
After the old firmware 4.33(ABFU.1) is uploaded and device reboots, you may get
the error message “Failed to apply startup configuration file and failover to
previous firmware ...” because the configurations between two ZLD versions are
different. The device boots up with previous firmware 4.35(ABFU.2).
Use the commands to manually switch to the firmware partition 4.33(ABFU.1).
Router> configure terminal
Router(config)# set firmware boot number 1
Backup Configuration Apply
1. If the device is downgraded to an older ZLD version, for example, from ZLD
4.35 to 4.33, the hash method for local users on different ZLD versions are
732/782
www.zyxel.com
different. Hence, you need to edit the password manually before applying
the configuration file to Device 1 with firmware 4.33(ABFU.1). You might need
to refer to Appendix of this document to edit the configuration file.
2. Upload the edited configuration file to Device 1 and apply the configuration
on console by entering the command.
Router(config)# apply /conf/HA_config.conf ignore-error
Connect All Ethernet Cables Back on Device 1
After firmware downgrade and configuration apply are finished on Device 1,
disconnect all Ethernet cables on Device 2. Connect all Ethernet cables back on
Device 1. Now only Device 1 is online and acts as Active role.
Firmware Downgrade on Device 2
On Device 2, follow the same steps in Firmware Downgrade on Device 1 for
firmware downgrade. Go to MAINTENANCE > File Manager > Firmware
Management and upload the old firmware to the standby partition.
Note: Some features in ZLD 4.35 were not implemented in ZLD 4.33, so some
configurations in 4.35 cannot be applied to device with firmware 4.33. Hence, we suggest
you apply the configuration file with ignore error.
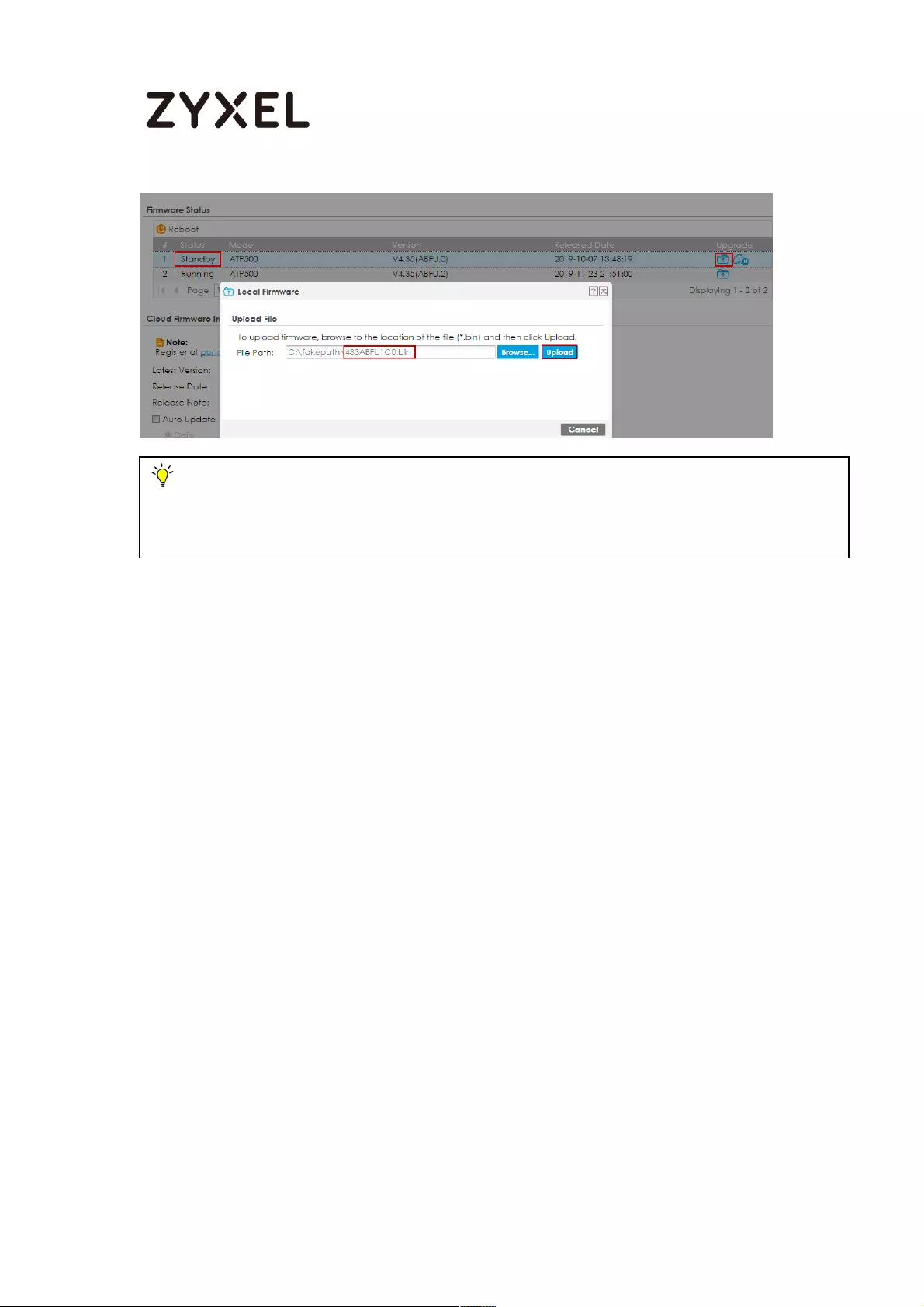
733/782
www.zyxel.com
Enable Device HA Pro on Device 2
After firmware downgrade is finished on Device 2, reset Device 2 to factory
default settings. Enable Device HA Pro on Device 2. Connect heartbeat port
between Device 1 and Device 2 to have Device 2 perform full synchronization.
Test the Result
After firmware upgrading is finished on two devices, Device 1 is active mode of HA Pro.
Device 2 becomes passive mode after it is fully synchronized with Device 1 while
heartbeat port is connected.
Active (Device 1)- Running Firmware 4.33(ABFU.1)
Note: On Device 2, upload the old firmware to the same firmware partition as Device 1.
For example, the old firmware is uploaded to partition 1 on Device 1. Then the old firmware
must also be uploaded to partition 1 on Device 2.
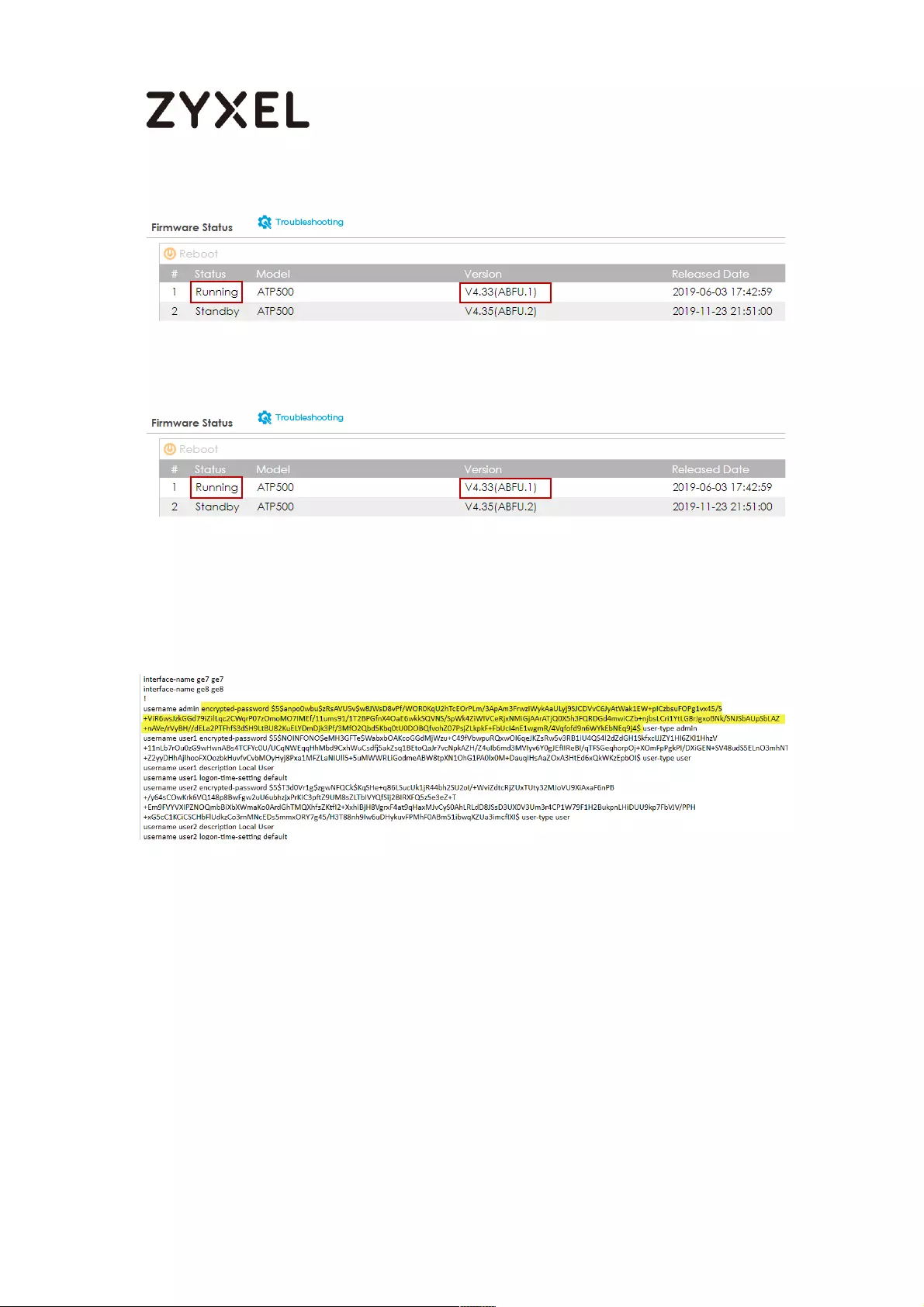
734/782
www.zyxel.com
Passive (Device 2)- Running Firmware 4.33(ABFU.1)
Appendix. Edit the Configuration File
Open the backup configuration file and search for the following CLI.
username admin encrypted password xxxxxx user type admin
Set a new password and replace the following CLI with the original one. In this
example, 12345 is the password for admin. Then save the settings after the
configuration file is edited.
username admin password yournewpassword user type admin
username user1 password yournewpassword user type admin
username user2 password yournewpassword user type admin
735/782
www.zyxel.com
Note: Remember to set password for every user because the hash method for all local
users are different between two different ZLD version.
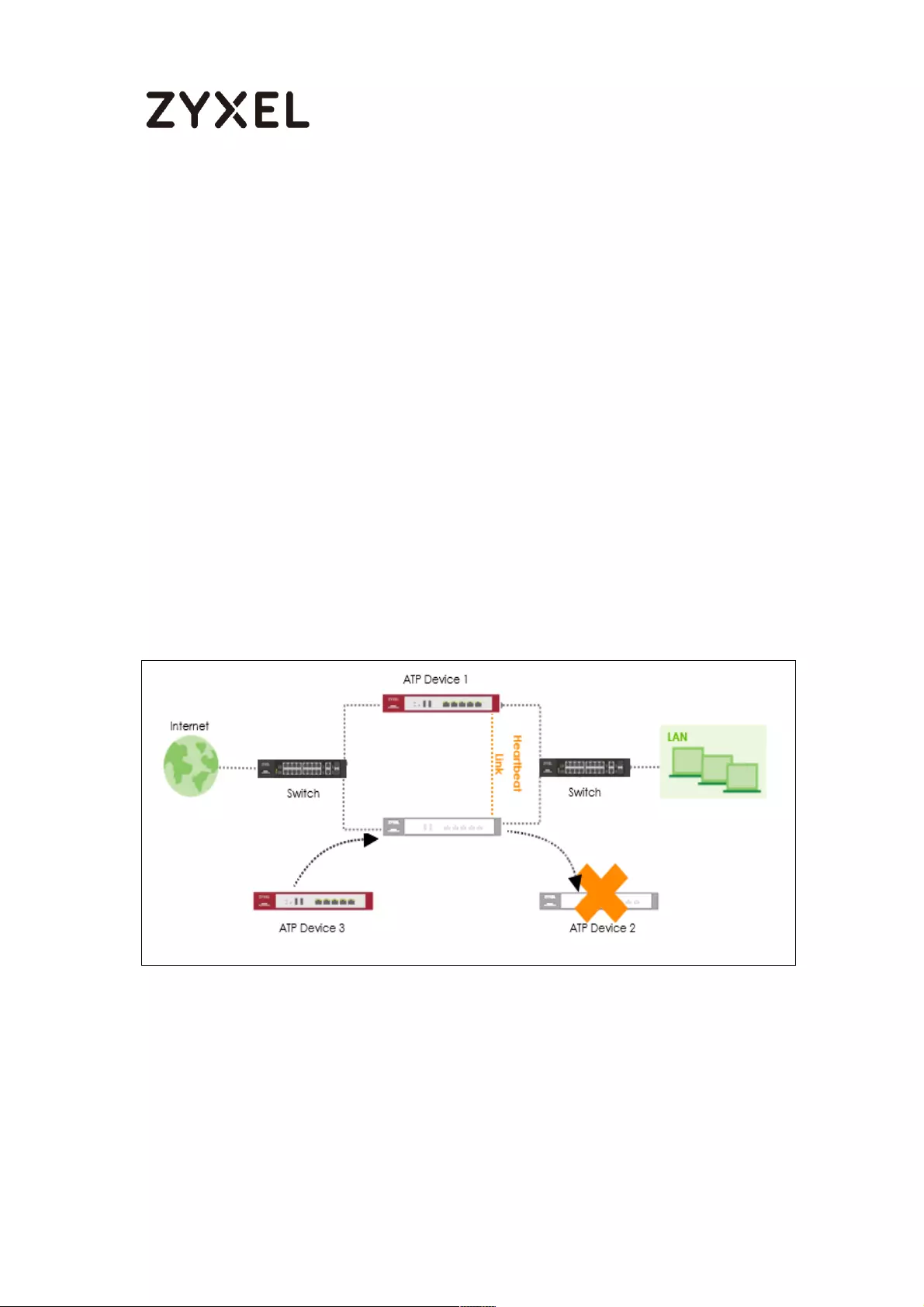
736/782
www.zyxel.com
How to replace one defect device of HA Pro
In case, one of HA Device is broke down or out of service; client needs to
purchase the new one and deploy back on the live Device HA-Pro
environment. This guide will lead user on how to swap one of the HA Pro
synchronized devices when the device was RMAed.
Scenario and Topology
For example, if Device 2 is out of service, and client needs to swap it to the
new Device.
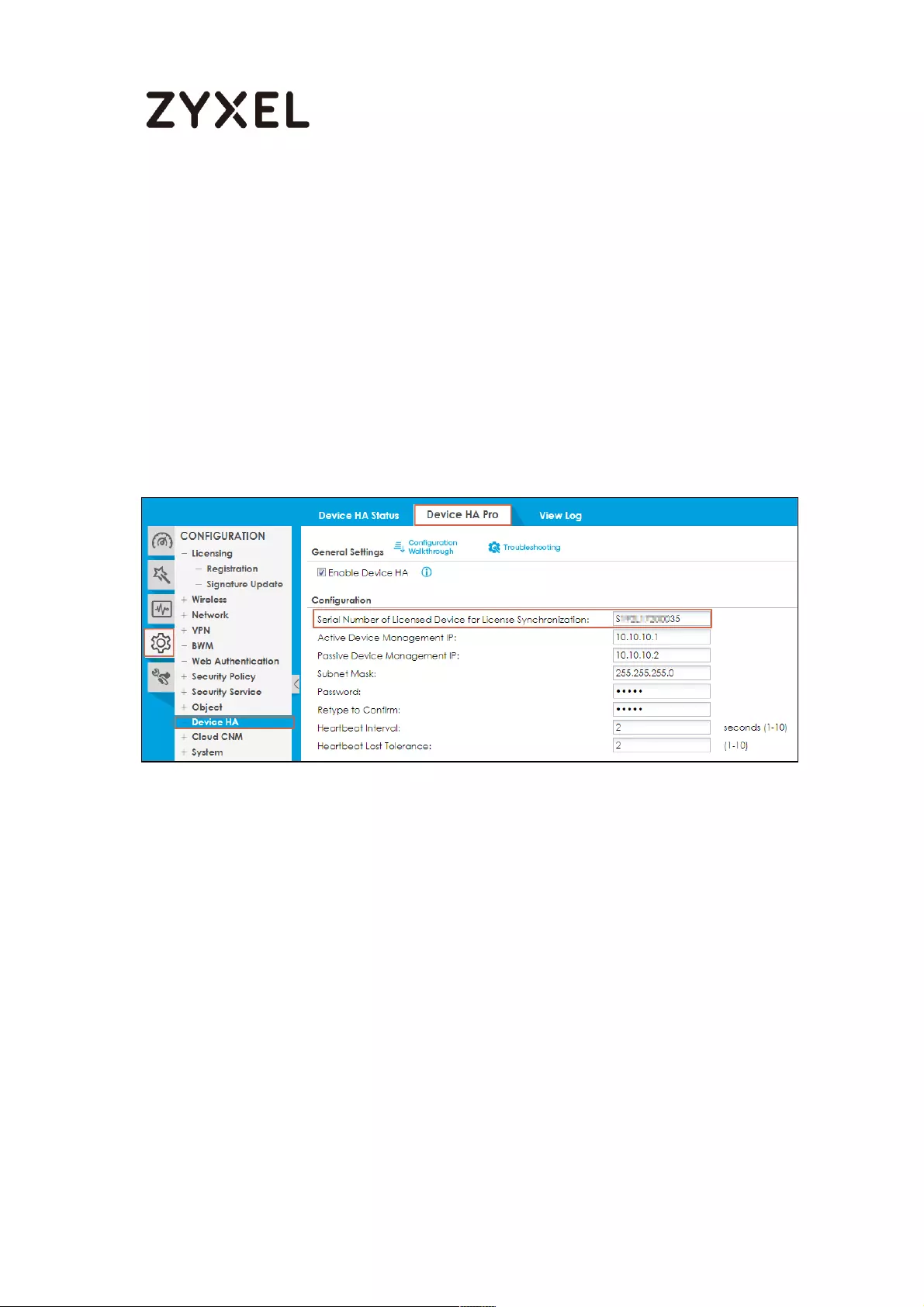
737/782
www.zyxel.com
Before redeploy the HA-Pro environment
1. Make sure all licenses of Device 2 are transferred to Device 1 from
myzyxel.com before Device 2 deliver to RMA
2. Confirm the Serial Number of Device 1 is entered on HA-Pro page.
Go to Configuration> Device HA>Device HA-Pro
3. Click the Service License on Device 1 Refresh button to check license
update correctly from myzyxel.com
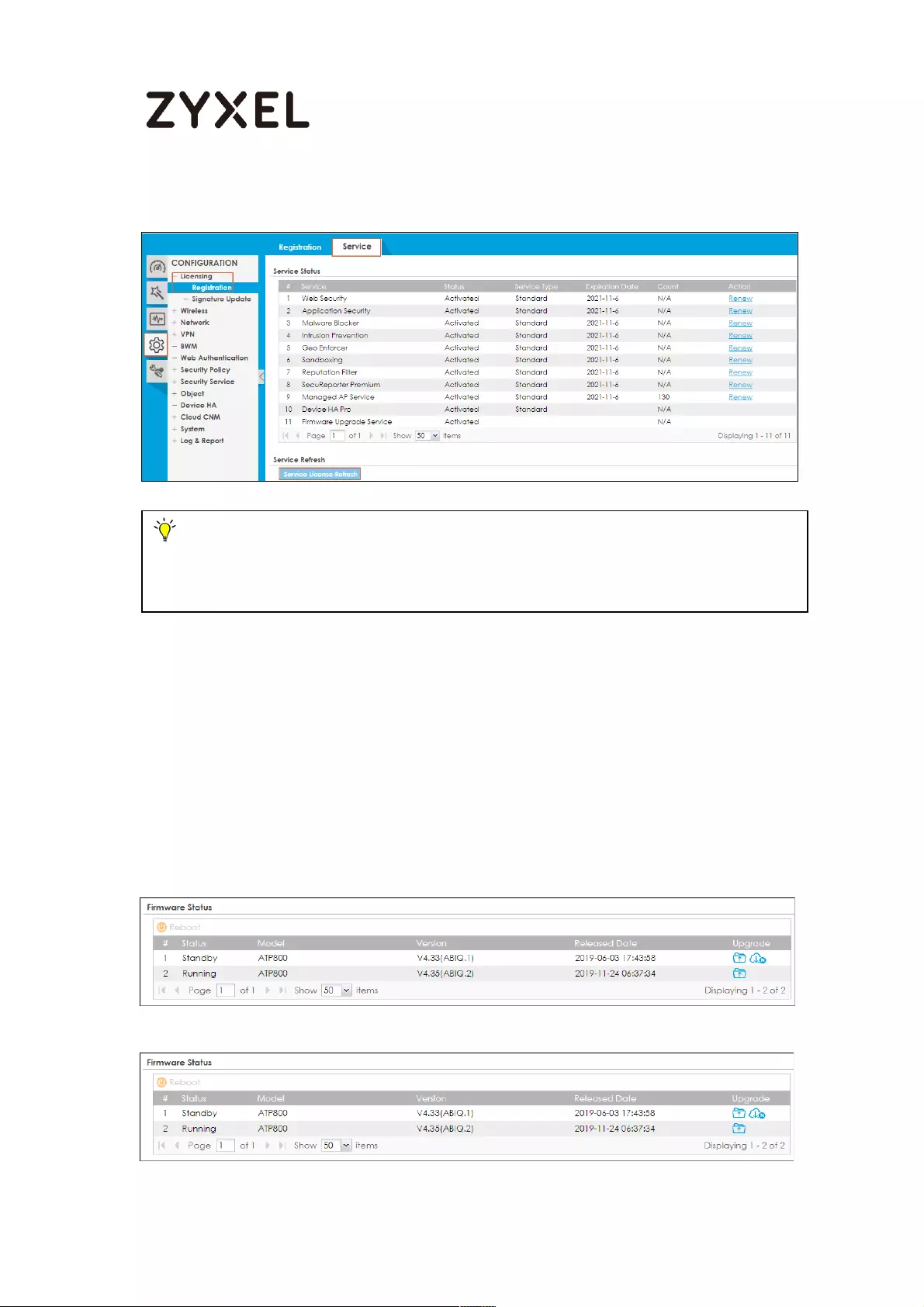
738/782
www.zyxel.com
Go to Configuration>Licensing>Registration>Service>Press Service License Refresh
After received the New device (Device 3)
1. Backup the Device 1 current configuration.
2. Make sure the Device 3 is reset to default setting
3. On Device 3, the running firmware version must the same as the Device 1.
4.
On Device 3, the partition of running firmware must be the same position as the Device 1.
Active (Device 1)- Running Firmware 4.35(ABIQ.2)
Passive (Device 3)- Running Firmware 4.35(ABIQ.2)
Note: If RMA device which was initial active role (S/N was filled on HA-PRO page),
user needs to modify the S/N to another Device (On Serial Number of Licensed Device
for License Synchronization)
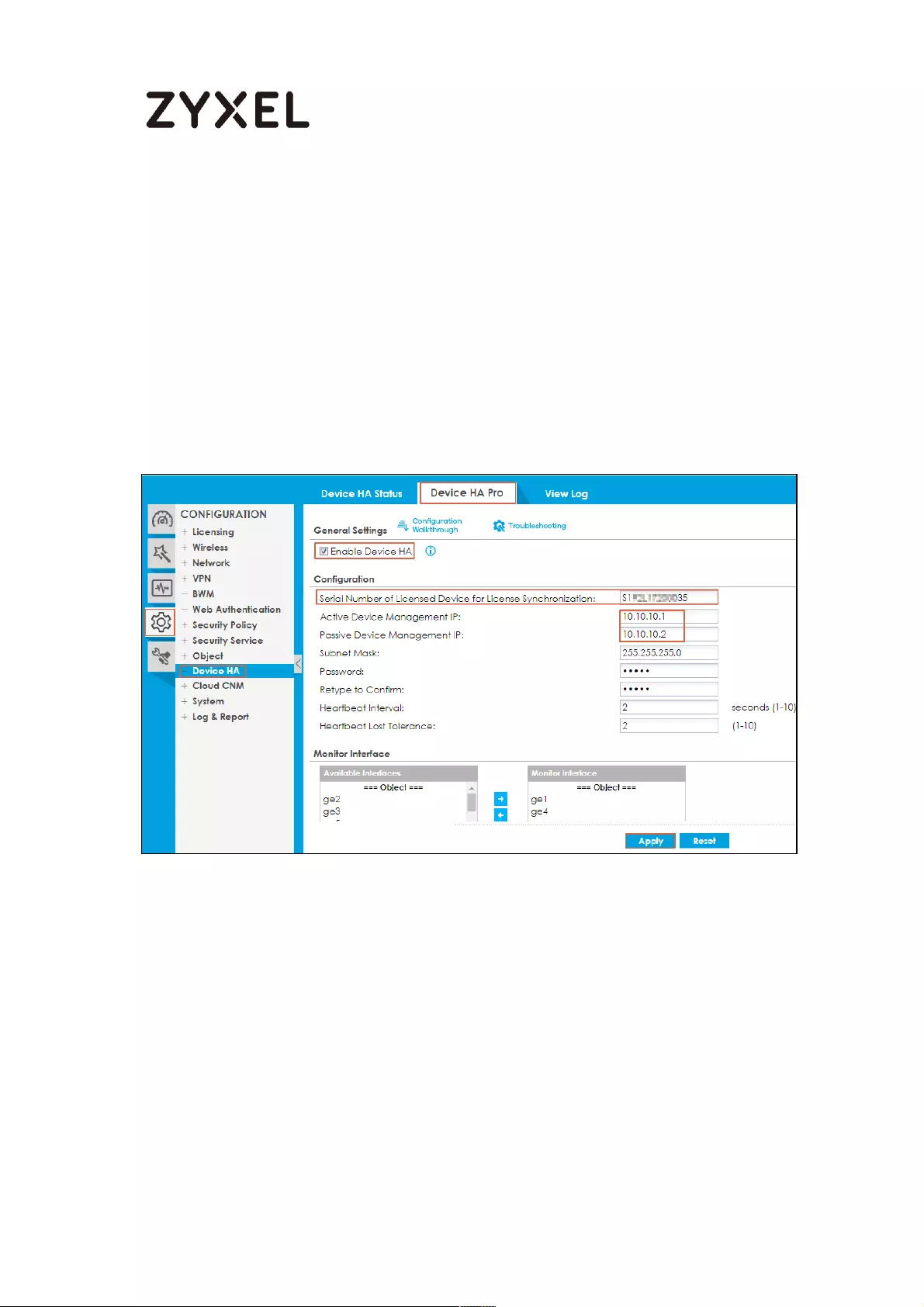
739/782
www.zyxel.com
Configuration on Device 1
Go to Configuration >Device HA>Device HA Pro, Enable Device HA
Make sure the configuration on each field are correct.
(Management IP of active, and passive device, password…)
Next, Press Apply button.
Configuration on Device 3
Go to Configuration >Device HA>Device HA Pro> Tick Enable Configuration
Provisioning From Active Device 1nd Enable Device HA then press Apply
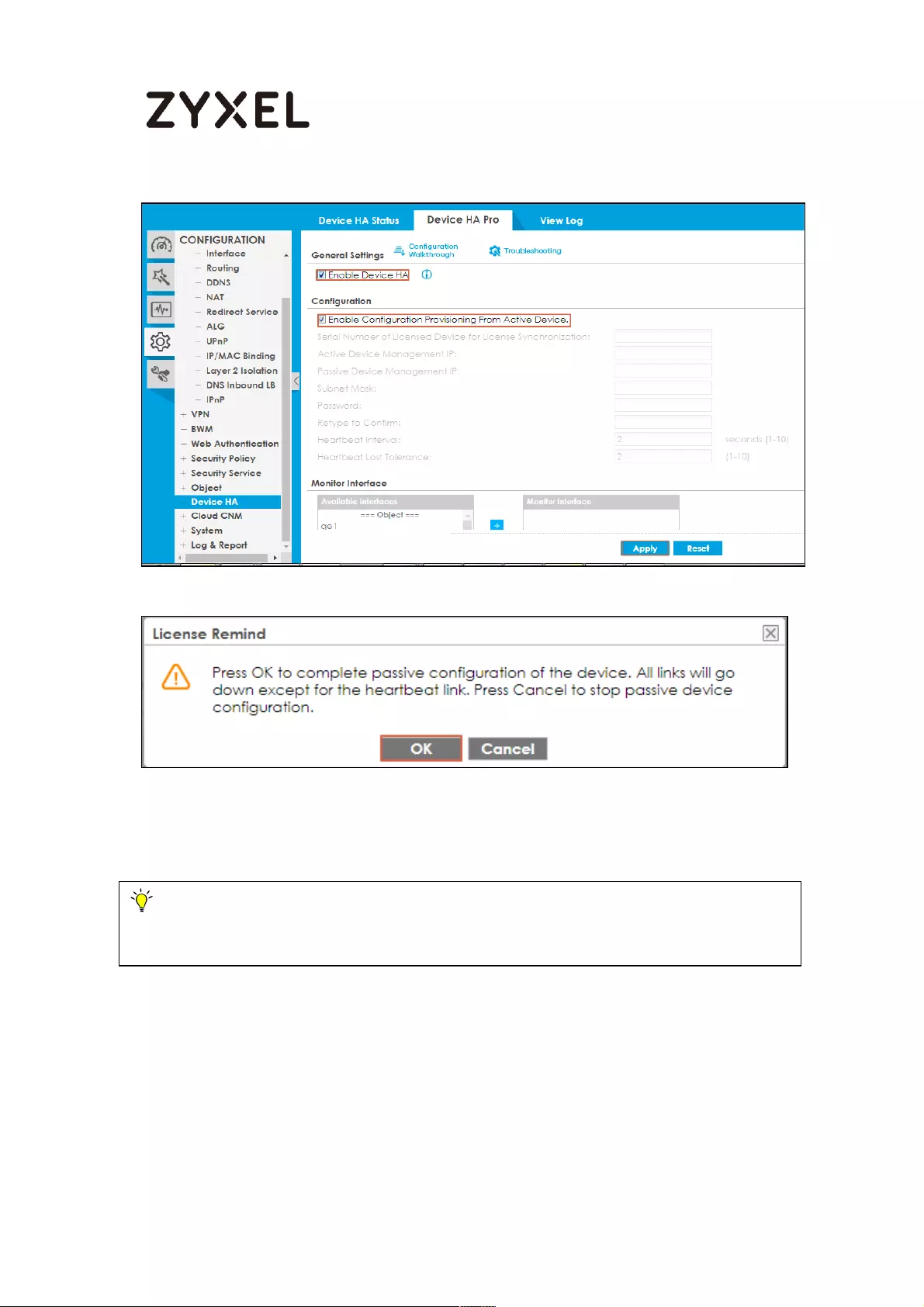
740/782
www.zyxel.com
Press OK to complete passive configuration
Next, connect the heartbeat port (the last Copper Ethernet port) link and
waiting for the full sync.
In this example, ATP800 heartbeat port is Port 12.
The sync status also can be check from Console
To type CLI:
# show device-ha2 device-status
# show device-ha2 passive device-status
Until you get the information of active and passive device.
Note: Before sync completely, do not change any configuration
It takes time (around 10 minutes) for the first time full configuration synchronizes
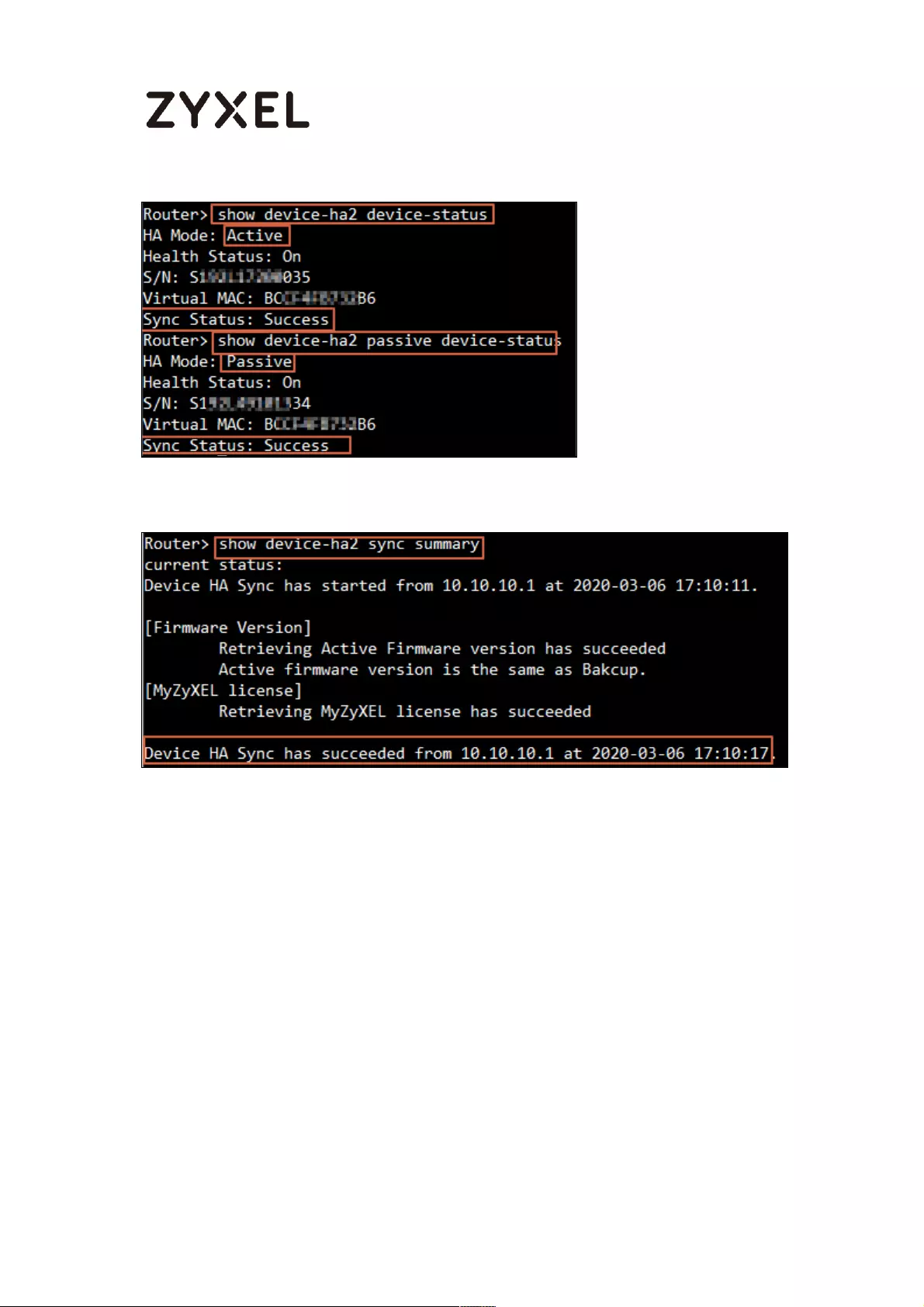
741/782
www.zyxel.com
Then go back to console of the passive device to type CLI
# show device-ha2 sync summary
Verification
After the above configuration complete, Go to Configuration>Device HA>
check Device HA status and View Log
Device 1 (Active Role)

742/782
www.zyxel.com
Device 3 (Passive Role)
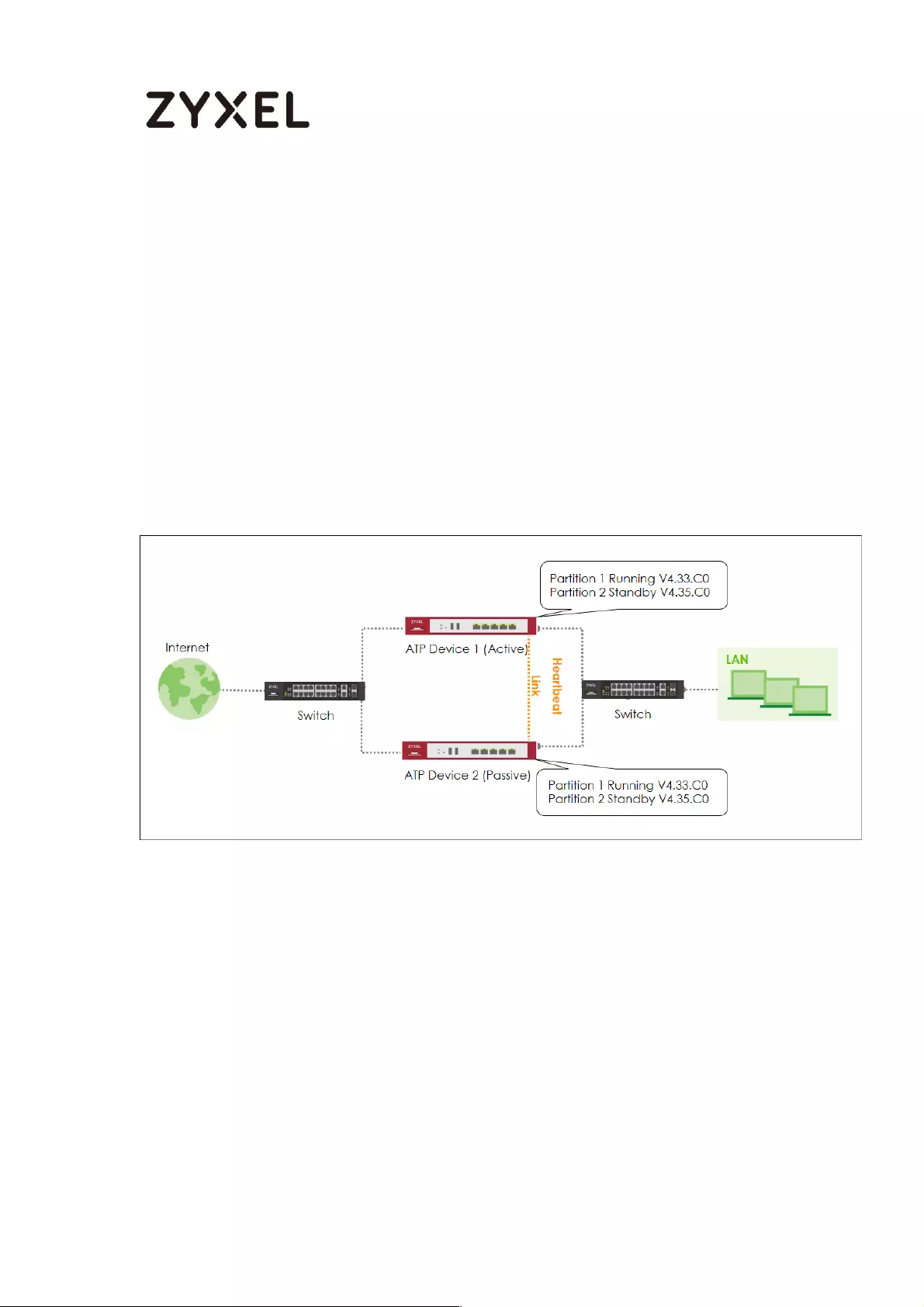
743/782
www.zyxel.com
How to reboot the Active device to the standby partition when
two partitions has different firmware version
In some of situation the new firmware with stability issue after upgraded, and user
must to rollback to stable version.
In this scenario user has running Device-HA on partion#1 with 4.33 firmware for a few
months, and upgraded 4.35 firmware to partion#2. But after 1~2 days 4.35 has some
of stability issue even user did not change any configuration. So user would like to
rollback partuion#1. Then user can follow these steps to rollback to standby partition.
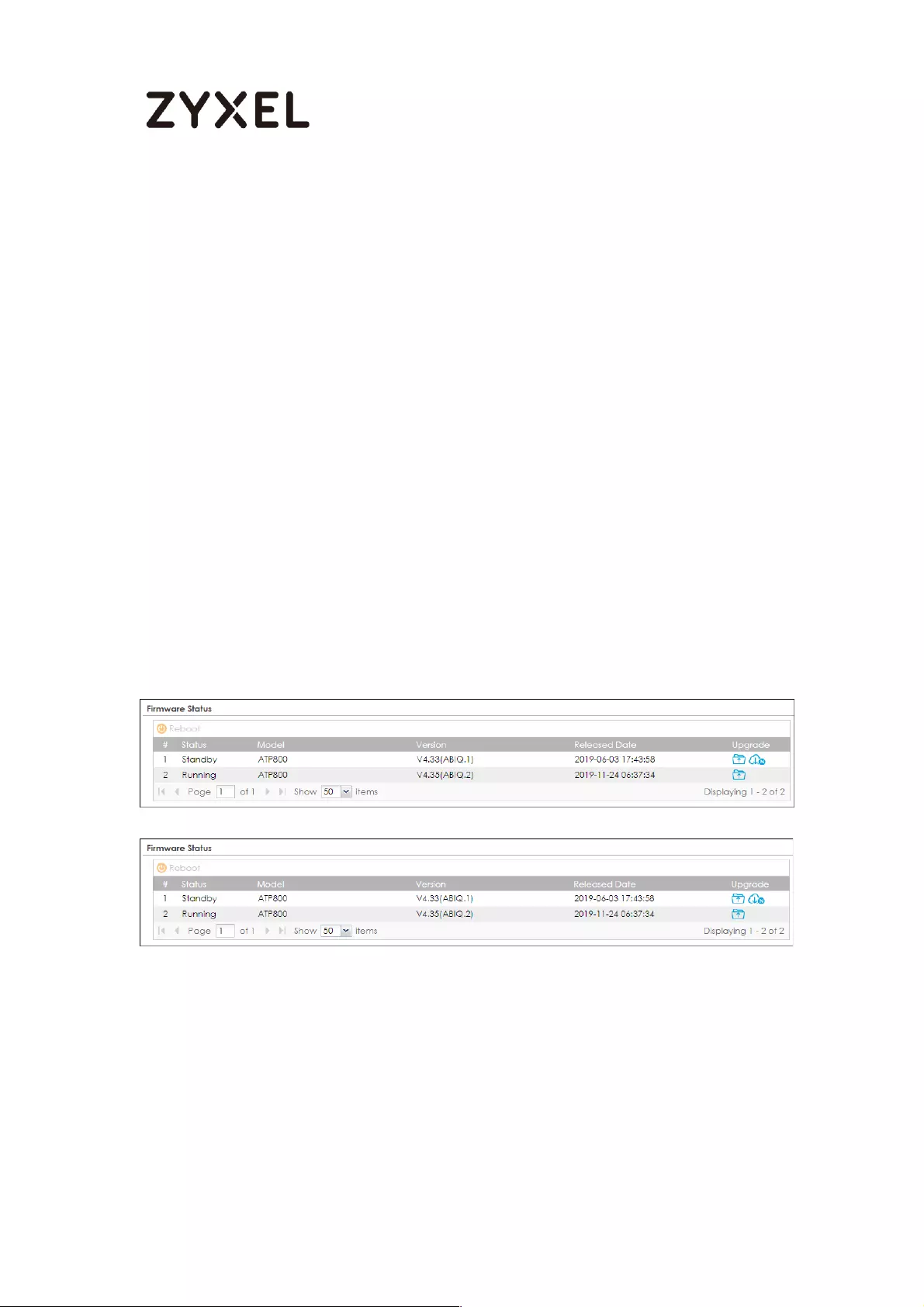
744/782
www.zyxel.com
Change Partition Flow
1. Make sure the running and standby firmware version of active and passive
devices are the same.
2. Reboot passive device(Device 2) by standby partition
3. Reboot active device(Device 1) by standby partition
4. Make sure passive device(Device 1) sync process completed successfully.
5. Configuration changed scenario.
Check Firmware Version on Active and Passive devices
Go to Maintenance > File Manager > Firmware Management.
The running and standby firmware on both of devices must be the same
Active(Device 1)- Running Firmware 4.35(ABIQ.2), Standby Firmware 4.33(ABIQ.1)
Passive(Device 2)- Running Firmware 4.35(ABIQ.2), Standby Firmware 4.33(ABIQ.1)

745/782
www.zyxel.com
Reboot passive device(Device 1) by standby partition
Device 2- Reboot device by standby partition
Access device by Device-HA management IP address.
Go to Maintenance > File Manager > Firmware Management.
Select standby partition, and click Reboot button.
After device boots up successfully, the device 2 role will stay as Passive.
All of traffic will pass by Active device continually.
Reboot active device(Device 1) by standby partition
Device 1- Reboot device by standby partition
Go to Maintenance > File Manager > Firmware Management.
Select standby partition, and click Reboot button.
After device boots up successfully, device 2 role will become to “Active”.
All traffic will handle by Active device (device 2).
Note: Since partitions have their own startup-config.conf. So reboot device by different
partitions will not overwrite configuration again. In this example, partition#1 already exist
4.33 configuration. So there is no configuration need to changed.
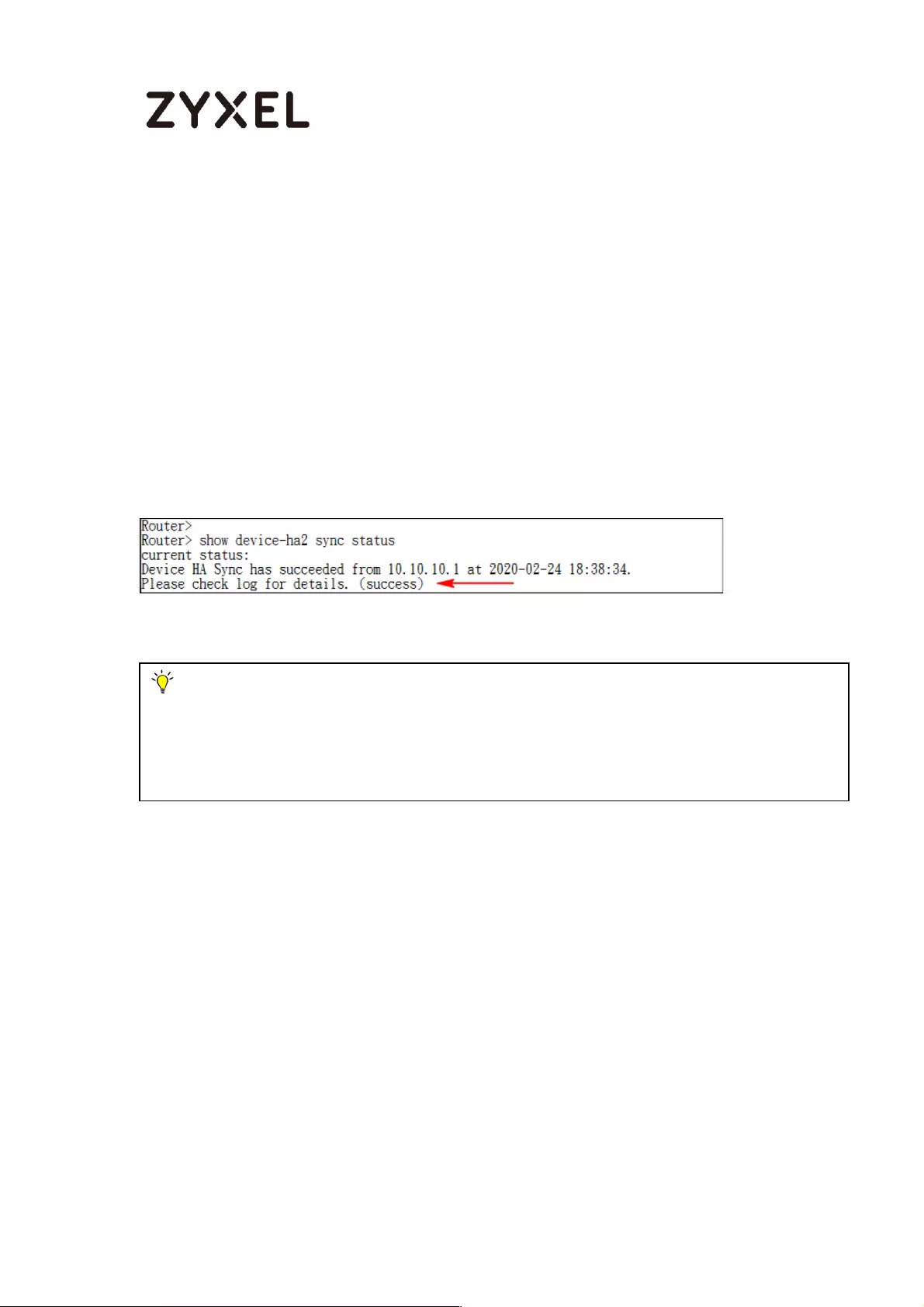
746/782
www.zyxel.com
After device 1 boot up, device 1 role will become to “Passive”.
Make sure passive device(Device 1) sync process successfully
After passive device boots up successfully, it will start to Device-HA Sync process.
You can use CLI command on passive device to make sure sync status.
Router> show device-ha2 sync status
Configuration changed scenario
In almost downgrading scenario, the configuration already been changed in
4.35 firmware. But old firmware may unable apply configuration successfully. So
we must compare 4.33 and 4.35 configuration together, and add the rules
manually after switched to 4.33 partition.
Note: There are 2 ways to force device sync configurations itself. It can start process but
just initial by different role.
On Active device: Router(config)# _device-ha2 send-sync all
On Passive device: Router> debug device-ha2 passive sync now

747/782
www.zyxel.com
(1) Access to device FTP server by admin & password to download
configurations.
A. Download running(4.33) partition configuration.
Go to “/conf” folder and download startup-config.conf
B. Download standby(4.35) partition configuration.
Go to “/standby_conf” folder and download startup-config.conf
(2) Open both of configuration by text and use any compare tool to
check what difference between your configurations. And then try to add
configuration by CLI command. (e.g. https://text-compare.com/)
(3) In some of scenario device will reply “% Command not found” to you
since system doesn’t support such command. You can ignore following
items:
a. Local Users
User password uses different hashing algorithms, so password will be
different.
b. New Feature Enhancement
New feature only works in new firmware. So use CLI command to enter
them will be fail. (e.g. IP reputation)
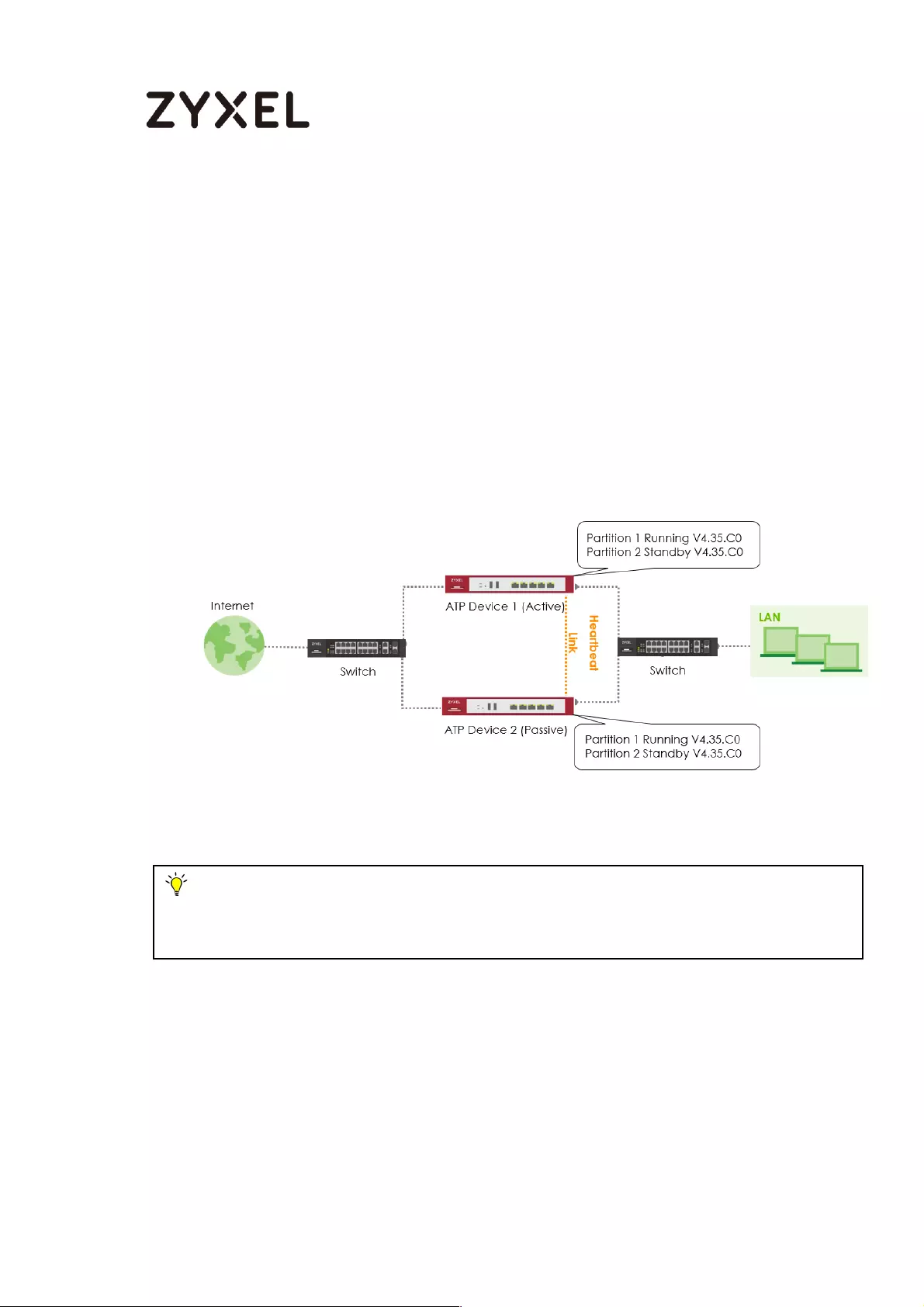
748/782
www.zyxel.com
How to restore configuration file in Device HA mode?
For some maintenance and troubleshooting purpose, user may need to restore
configuration file in device HA mode. Assuming HA had been setting ready and works
perfect for a while, below steps are to guide the user on how to restore configuration
file in device HA mode.
Figure
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses. This example was tested using
the ATP500 (Firmware Version: ZLD 4.35.P2).

749/782
www.zyxel.com
Configuration file restore flow
1. Unplug all active device network link (Device 1). Let network service runs on
passive device.
2. Upload configuration file to active device (Device 1).
3. Apply configuration file on active device (Device 1).
4. Connect all network cables on Device 1. Network service is running on Device
1 from now on.
5. Reset passive device to system default.
6. Deploy Device HA.
7. Make sure that passive device sync process successfully.
Unplug all active device network link (Device 1), let network
service runs on passive device.
Disconnect all Ethernet cables and heartbeat link on active device. As now,
network service is running on passive device (Device 2).
-Active device offline to restore configuration file.
-Passive device provide network service.
Upload configuration file to active device (Device 1).
Before you upload the configuration file on active device (Device 1), verify if the
virtual-mac and license-sync serial number is correct.
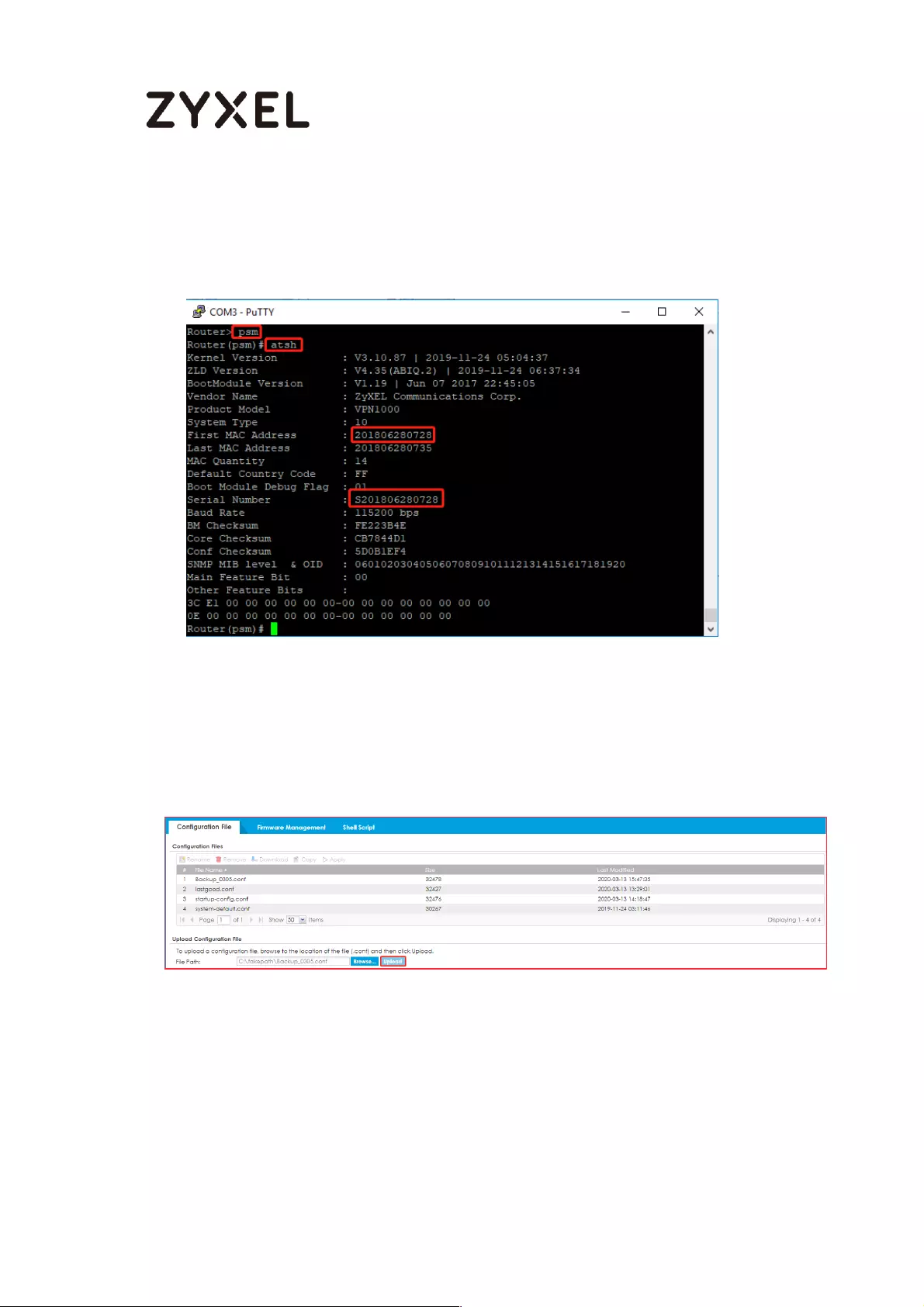
750/782
www.zyxel.com
It supposed to be same as original active device (Device 1). We can check by CLI
Router > psm
Router(psm)# atsh
If virtual mac and serial are correct, then proceed to upload configuration file
on active device (Device 1).
On device 1, go to MAINTENANCE > File Manager > Configuration File and
upload configuration file.
Apply configuration file on active device (Device 1)
Connected serial cable to active device (Device 1) and apply configuration file
via CLI

751/782
www.zyxel.com
Router# apply /conf/Backup_0305.conf
After completed configuration restore, we need to save the running
configuration to startup configuration file.
Router(config)# write
Connect all network cables on Device 1.
Disconnect all network cables on Device 2, and then connect all network
cables on Device 1(Excluding heartbeat link). Network service is running on
Device 1 from now on.
Reset passive device to system default.
Connected serial cable to passive device (Device 2), and reset to factory
default.
Router# apply /conf/system-default.conf
Deploy Device HA
Activate device HA on passive device and connect heartbeat port.
Connect serial cable to original passive device (Device 2) and active device via
CLI
Router(config)# device-ha2 activate
Note: Assume this scenario is USG series. You should set the Device HA mode
before your activeate Device HA.
Router(config)# device-ha mode device-ha-2
Router(config)# device-ha2 activate
On Passive device: Router> debug device-ha2 passive sync now
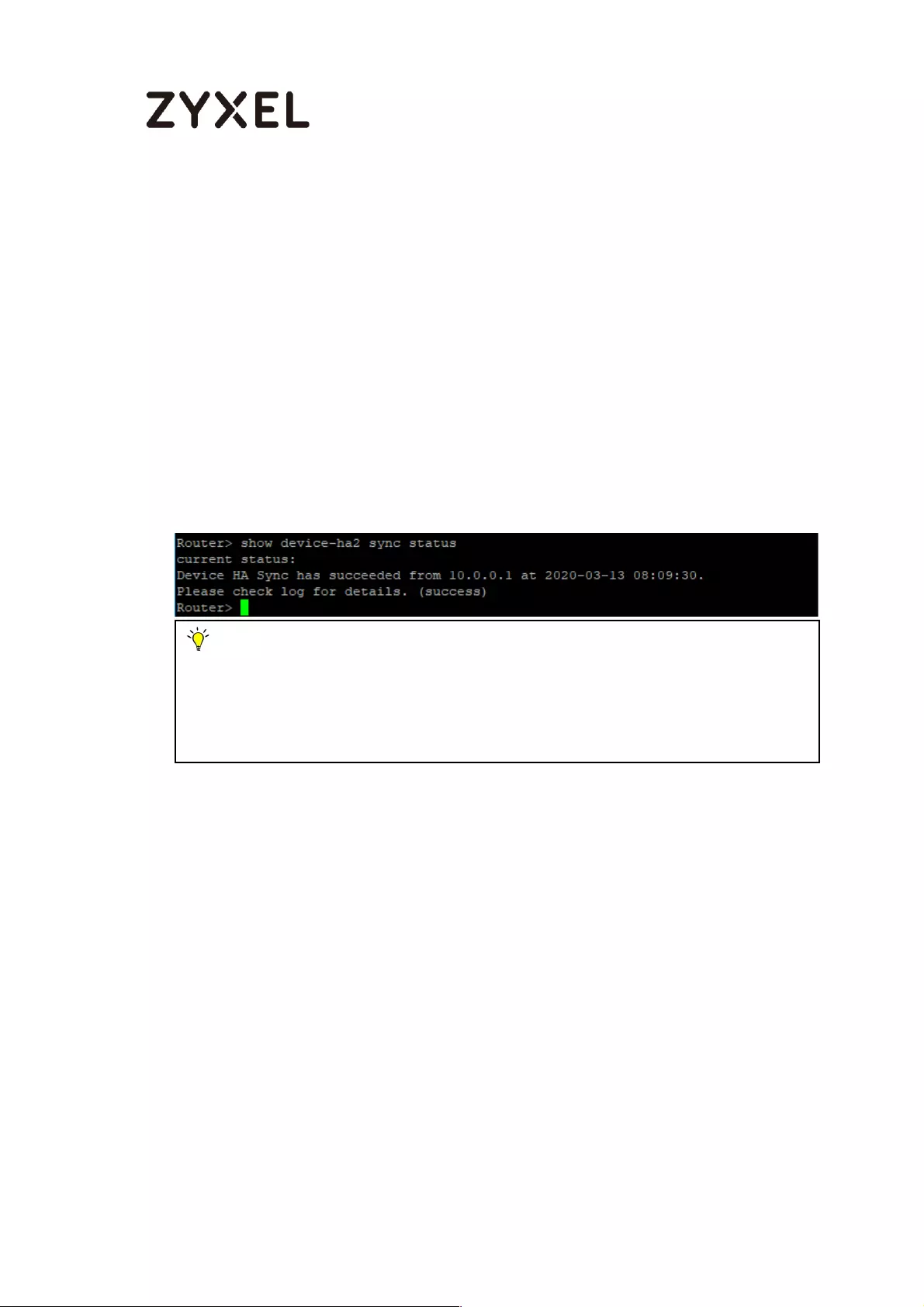
752/782
www.zyxel.com
Make sure that passive device (Device 2) sync process
successfully
it starts to Device-HA Sync process. You can use CLI on passive device to
check sync status. When it has done, you can see status indicated that
"Device HA Sync has succeeded from X.X.X.X at YYYY-MM-DD HH:MM:SS"
Router> show device-ha2 sync status
Note: There are 2 ways to force device sync configurations itself. It can start
process from different role.
On Passive device: Router# device-ha2 sync_from_active
On Active device: Router# device-ha2 sync_to_passive
On Passive device: Router> debug device-ha2 passive sync now
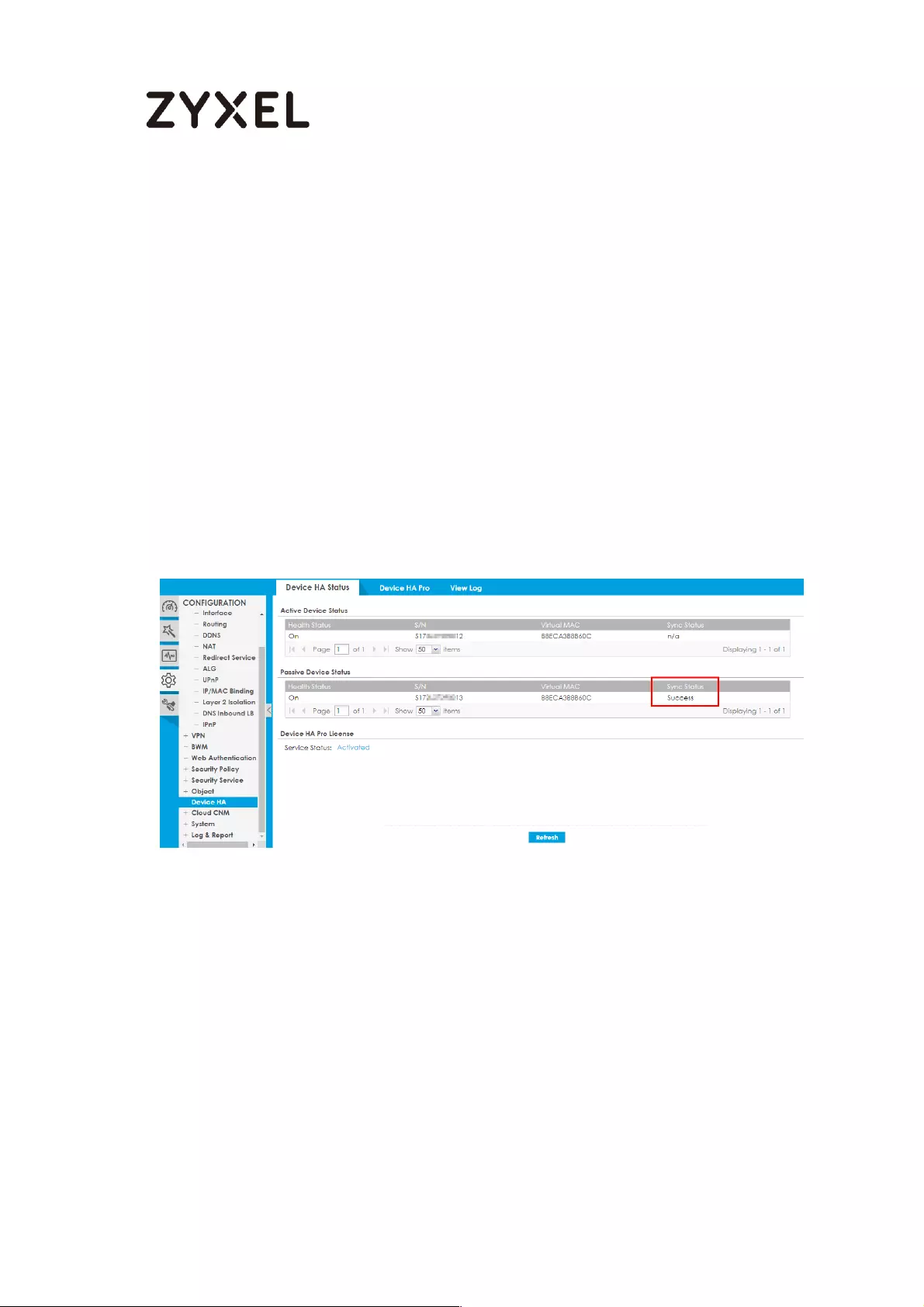
753/782
www.zyxel.com
How to Check HA Pro Synchronization Status
There are two types to check HA Pro synchronization, one is using web gui to
check, the other one is using console or Secure Shell (SSH), below is the step to
check the HA Pro synchronization status.
Check the sync status on web GUI
To check status with GUI, go to Configuration > Device HA > Device HA Status,
if device HA Pro setup successfully the sync status will display success
Go to Configuration > Device HA > View log, the log here will display related
HA log on passive device. The synchronization on passive device must show
Synchronized complete.
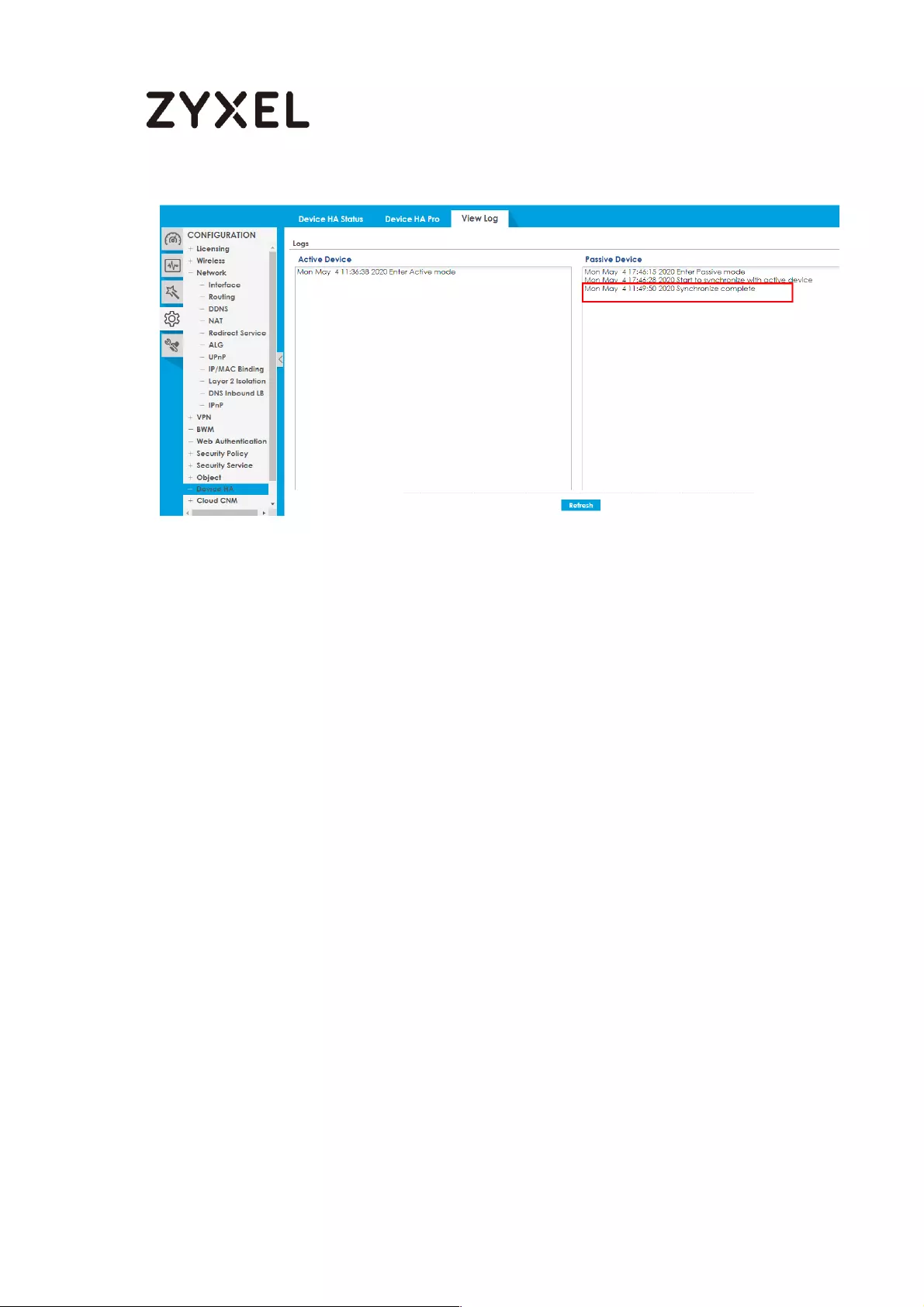
754/782
www.zyxel.com
Check the sync status on console
Using CLI may help you do a quick check, and can get more information
A. Check the synchronization status on Active device
4. Type command: show device-ha2 status
To check the basic information on active device
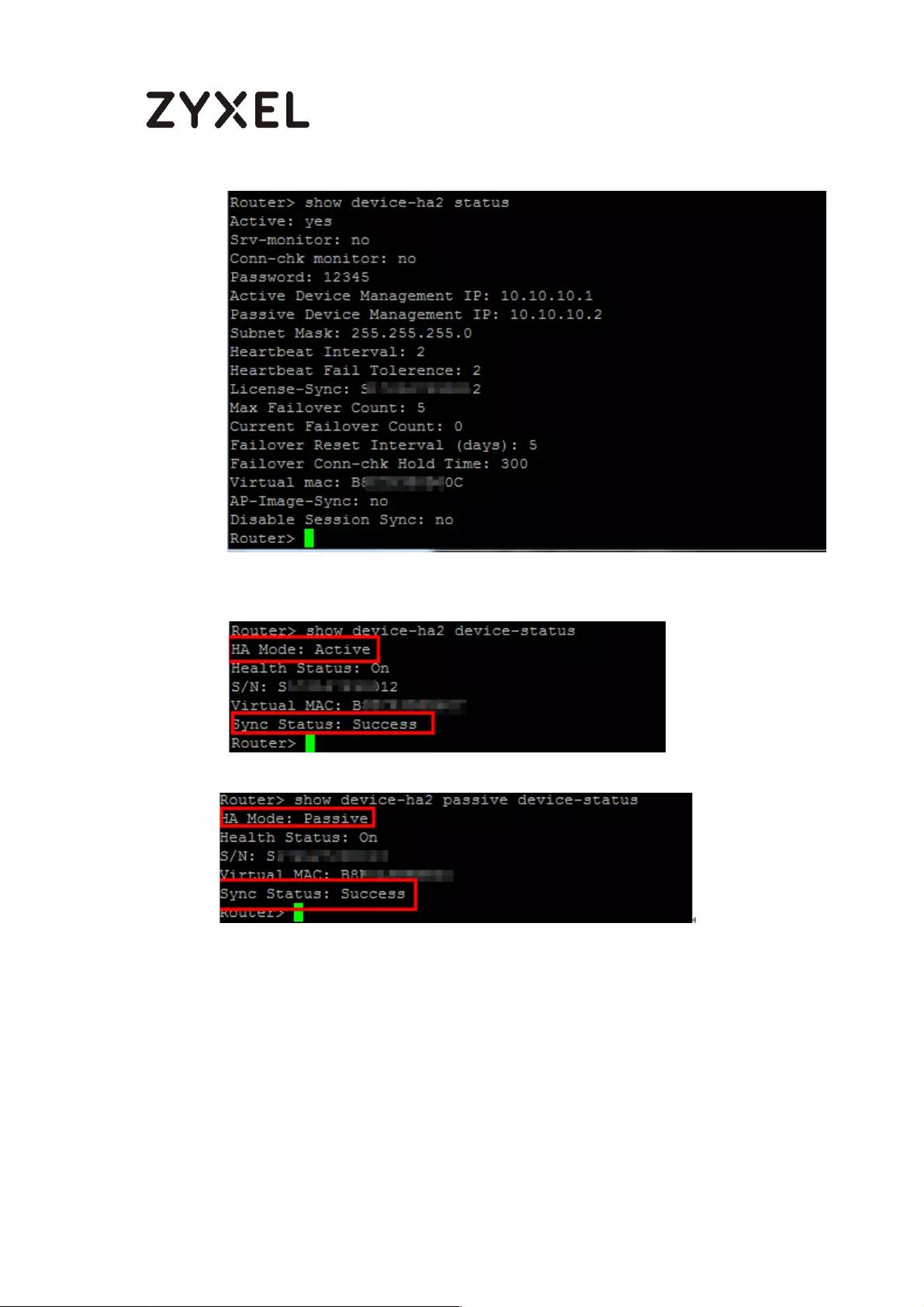
755/782
www.zyxel.com
5. Type the command below to check the status.
Router> show device-ha2 device-status
Type command: show device-ha2 passive device-status
B. Check the synchronization status on Passive device
1. Check the sync status of the device
Type command: show device-ha2 sync summary
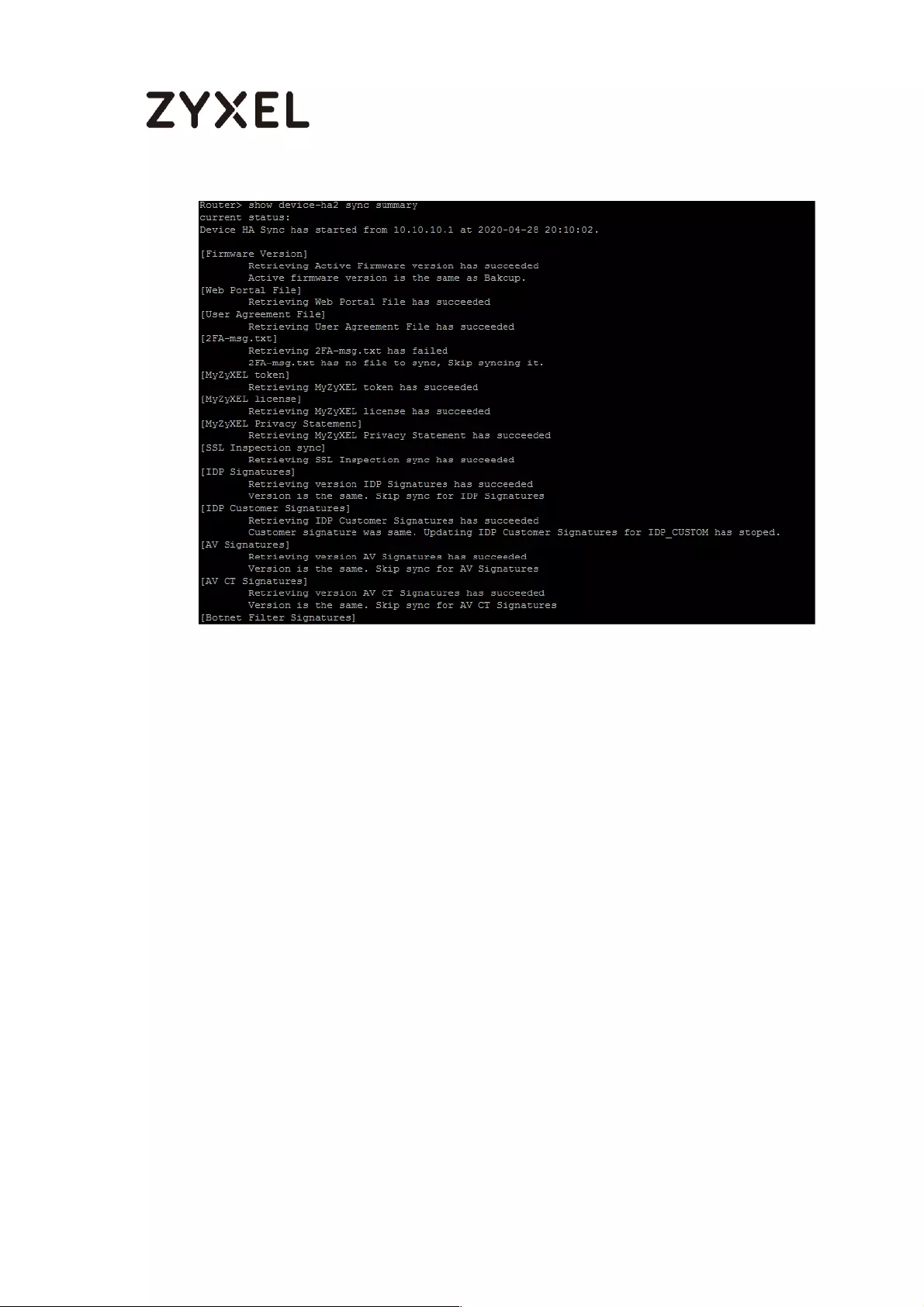
756/782
www.zyxel.com
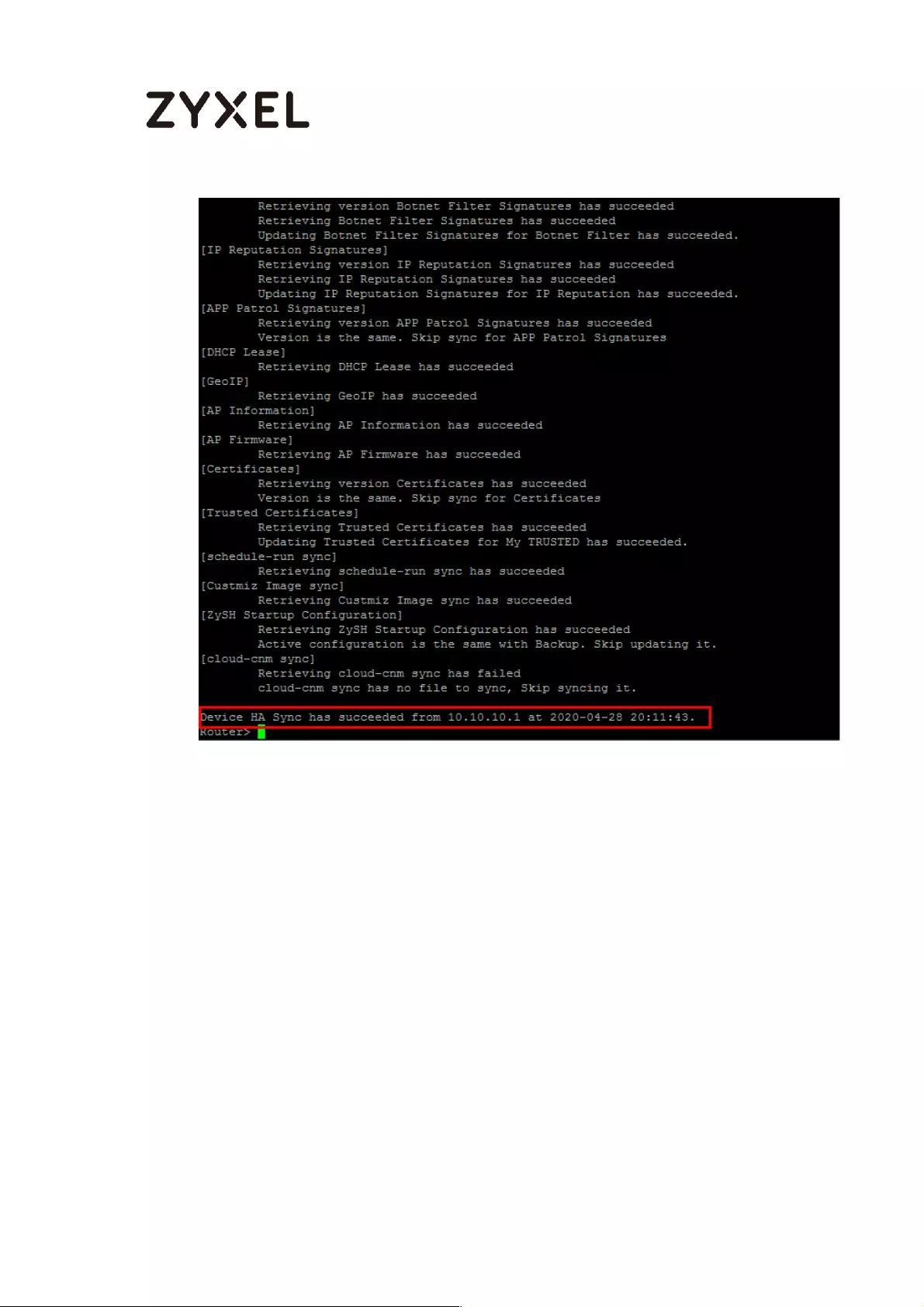
757/782
www.zyxel.com
It’s very important that the last line the status of the Device HA Sync need
to be success.
C. Fail cases
1. If Device HA sync failed, please disconnect all the links. Then reset device
to factory default and try again.
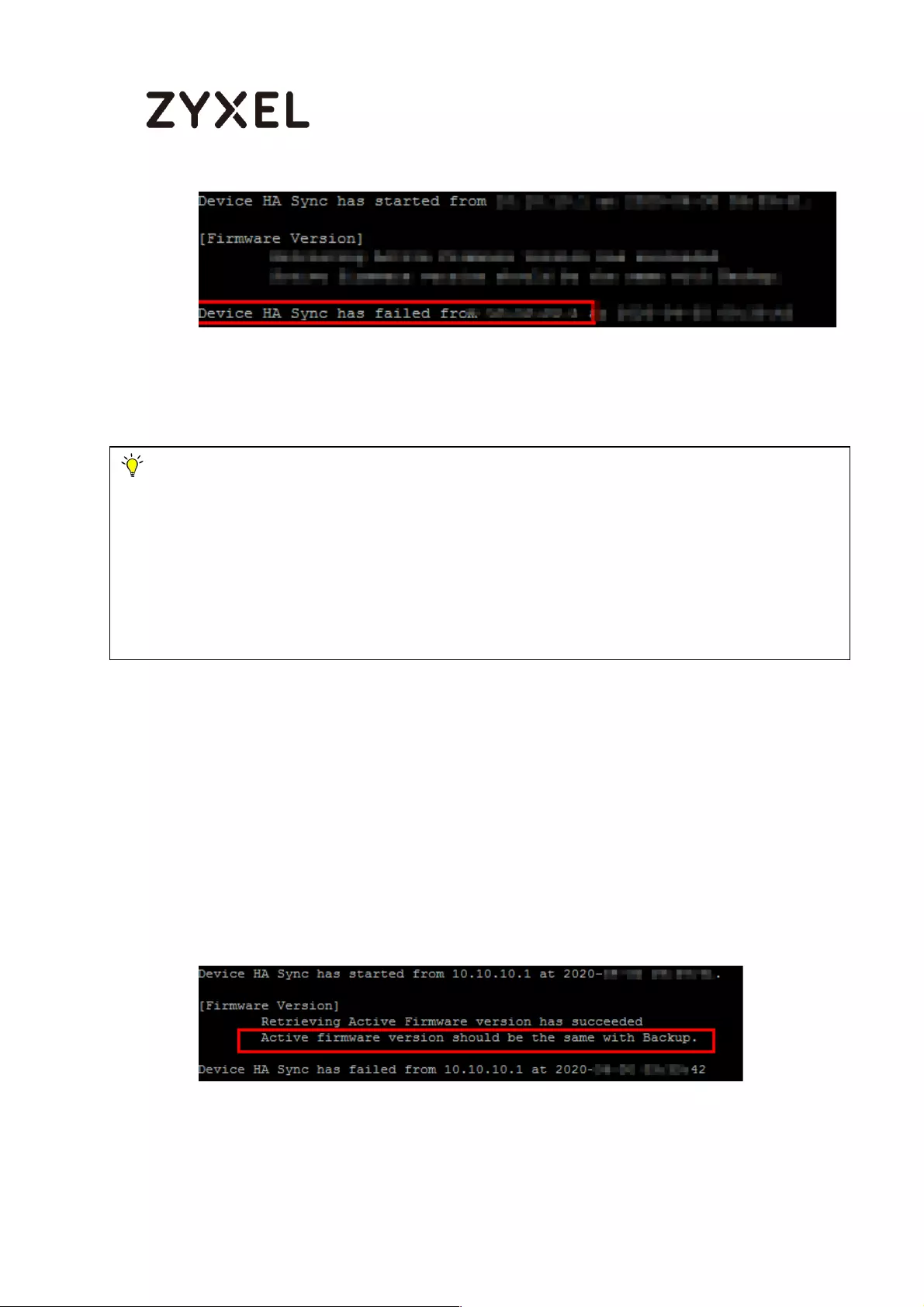
758/782
www.zyxel.com
D. Exception case
1. After upgrade firmware, if check the log immediately, the log will
display fail, no need to worry when the log displayed fail when
upgrade the firmware.
It is normal behavior, since the other device has not upgrade the
firmware yet.
So the log will display fail.
Note: After device upgrade the firmware, on active device type command “Router>show
device-ha2 sync summary” will display fail. It need to type below command on active
device to sync again.
Router> debug device-ha2 passive sync now, after Device HA sync from passive,
the status of the Device HA Sync will display success.
Here is the step below
759/782
www.zyxel.com
What Can Go Wrong?
1. For device HA or HA Pro, signature synchronization is required.
2. Cloud query is not supported.
3. It doesn't support for IPv6.
Caution:
Any Fail, please disconnect all the links. Then reset device to factory
default and try again.
Don’t copy configuration file from first device and upload to second
device to deploy.
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses. This example was tested using
the ATP500 (Firmware Version: ZLD 4.35).
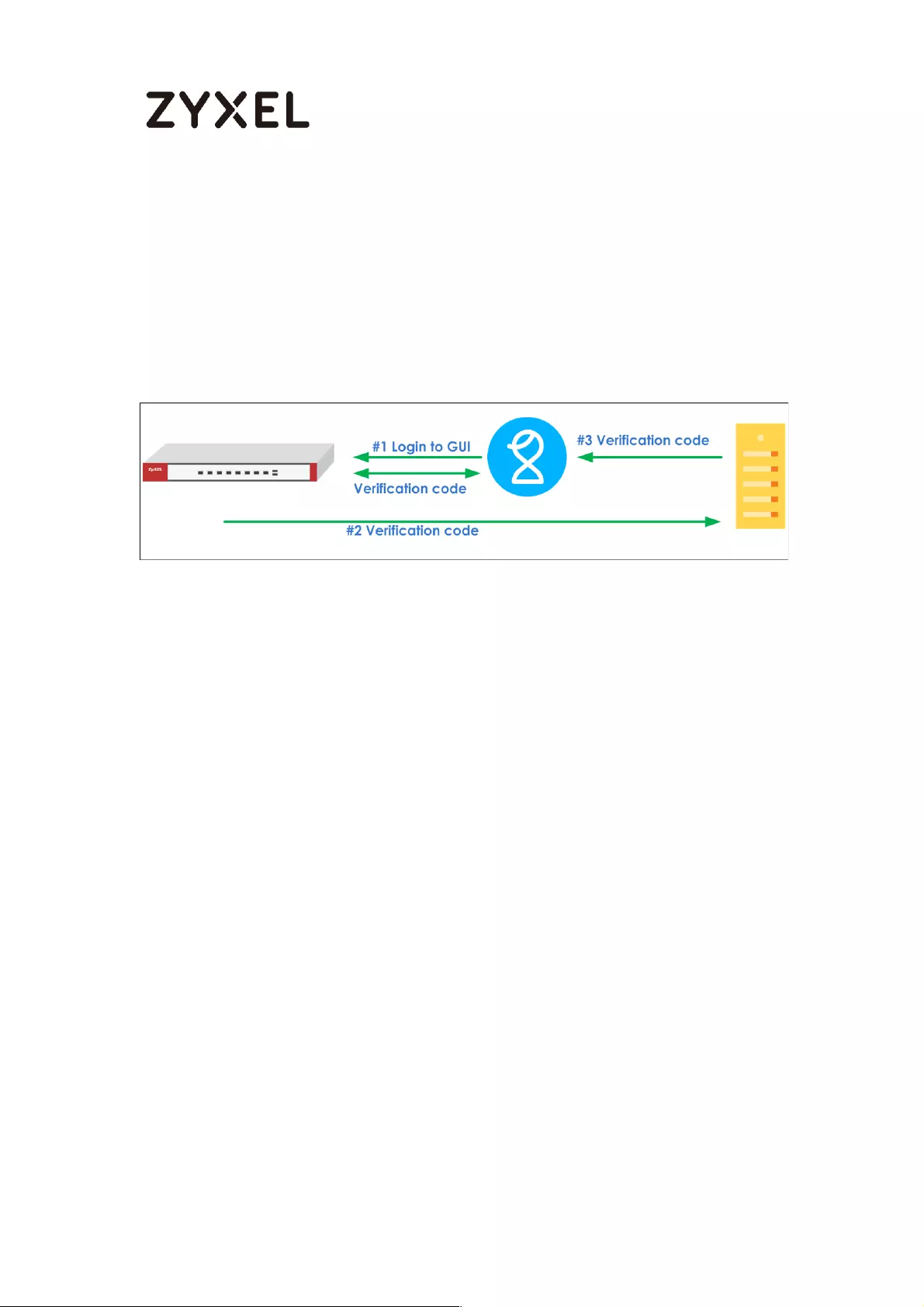
760/782
www.zyxel.com
How to setup Two-Factor Authentication for admin login
2 Factor Authentication is a function can prevent your device login by hacker.
It needs additional verification code after logged into WebGUI/SSH/Telnet
You can follow these steps to setup 2 factor authentication when logging to
system.
Setup SMTP function on your device
Go to CONFIGURATION > System > Notification > Mail Server Field your SMTP serve
configuration.
a. Mail server
b. Mail server ports
c. Mail From
d. SMTP Authentication
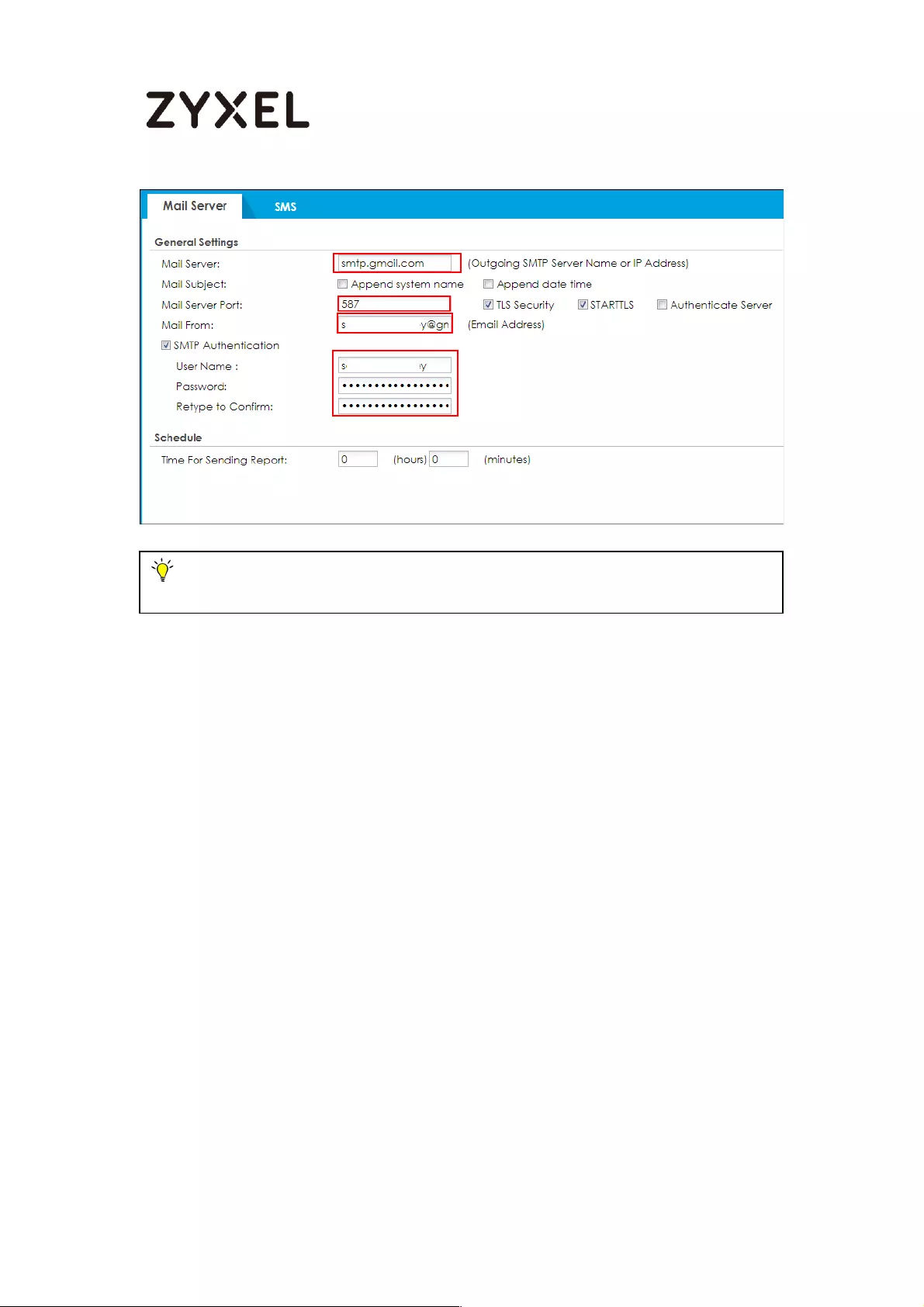
761/782
www.zyxel.com
Create admin type user on device
Go to Configuration > Object > User/Group > User Click Add button to create an
user and user type is admin.
And also entered email address of this user.
Note: Must make sure SMTP Server configuration is correct otherwise user will
unable receive mail successfully.
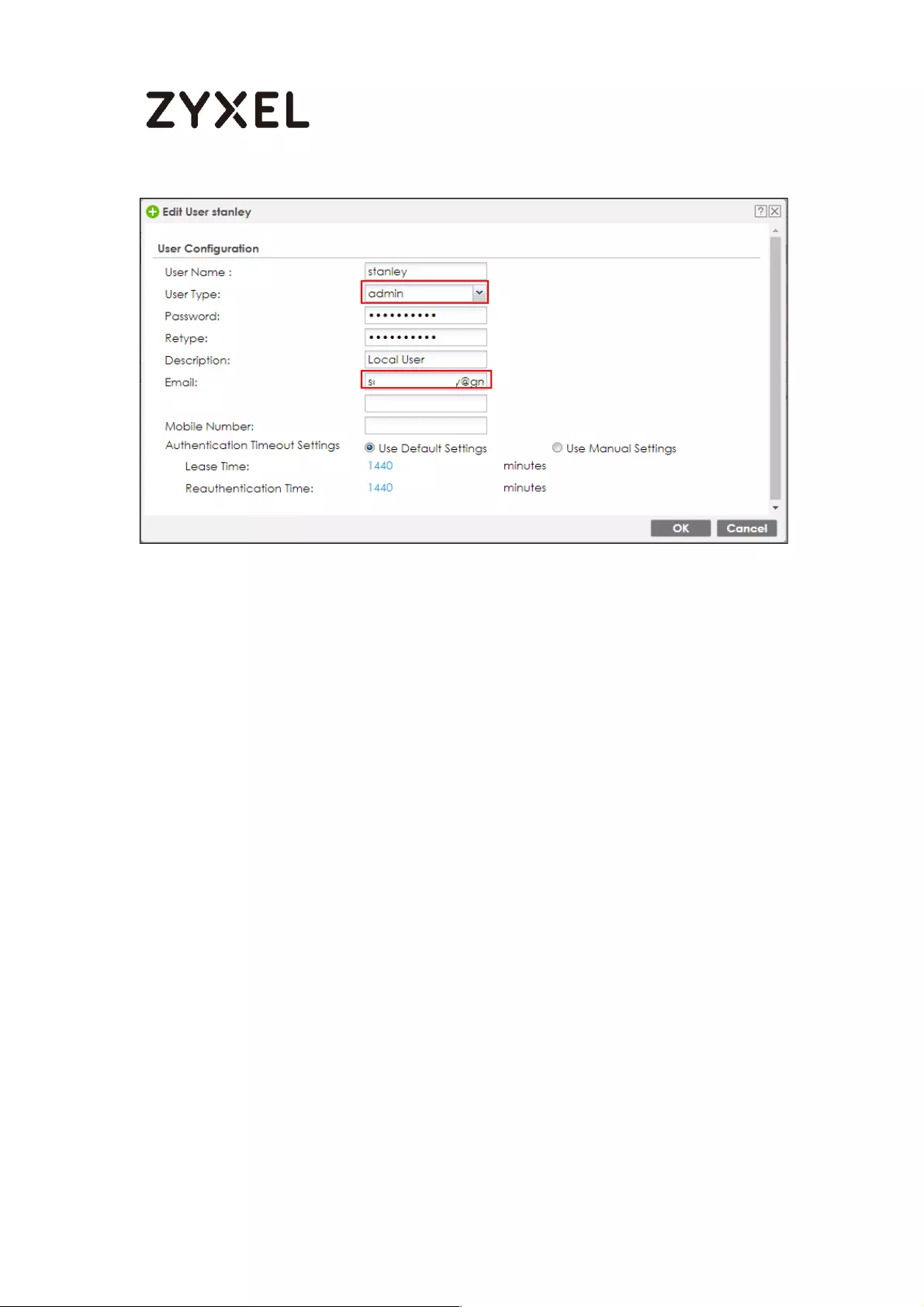
762/782
www.zyxel.com
Setup Two-Factor Authentication for admin on your device
Go to Configuration > Object > Auth Method > Two-Factor Authentication >
Admin Access
Enable the function and add admin user which you added in step2 in the rule,
and you can select what services are 2 Factor authentication needed.

763/782
www.zyxel.com
Test the Result
After setup these steps and login to device by admin user, the verification code
is required.
Web Service:
SSH Service:
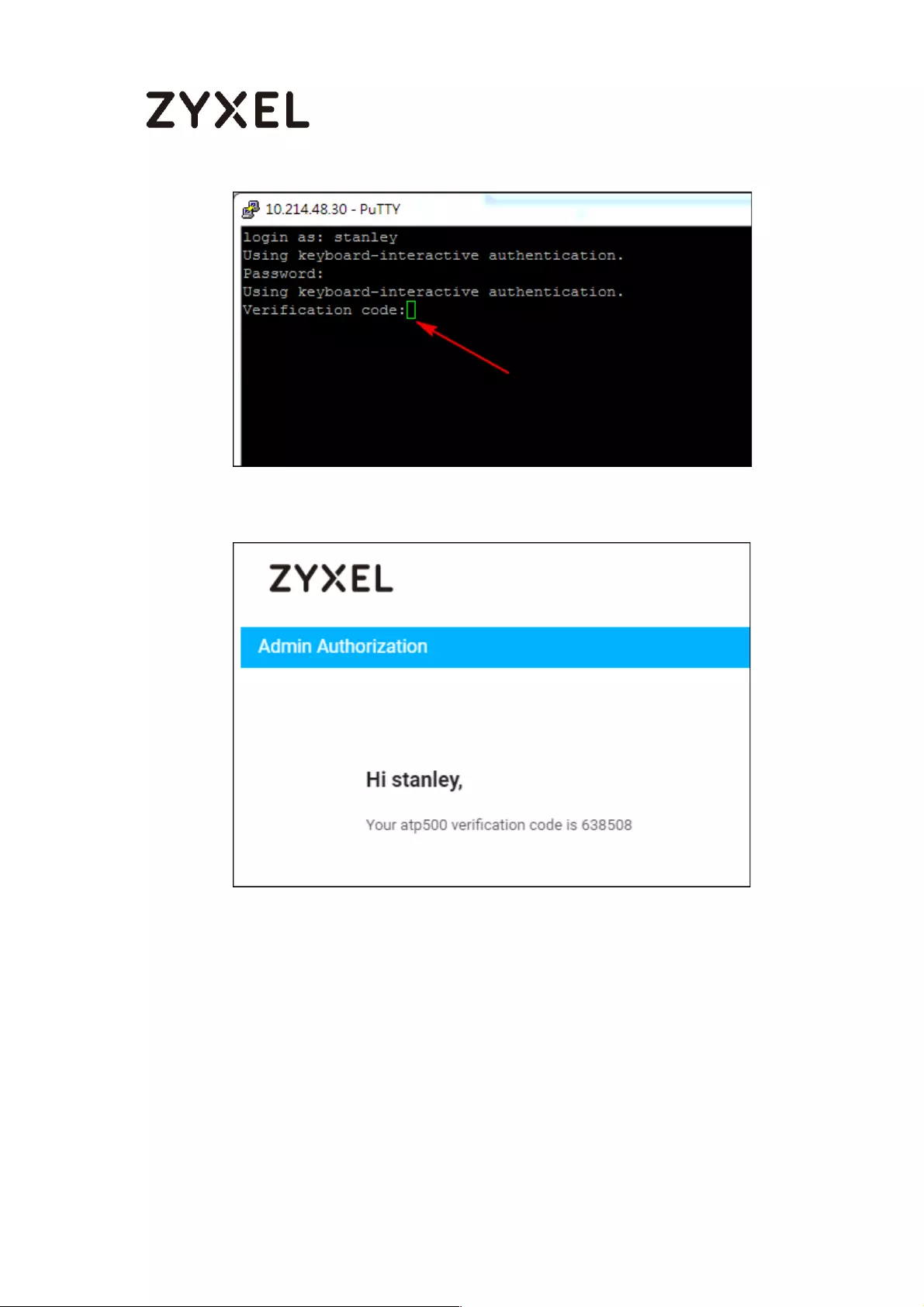
764/782
www.zyxel.com
You will receive verification code by Email.
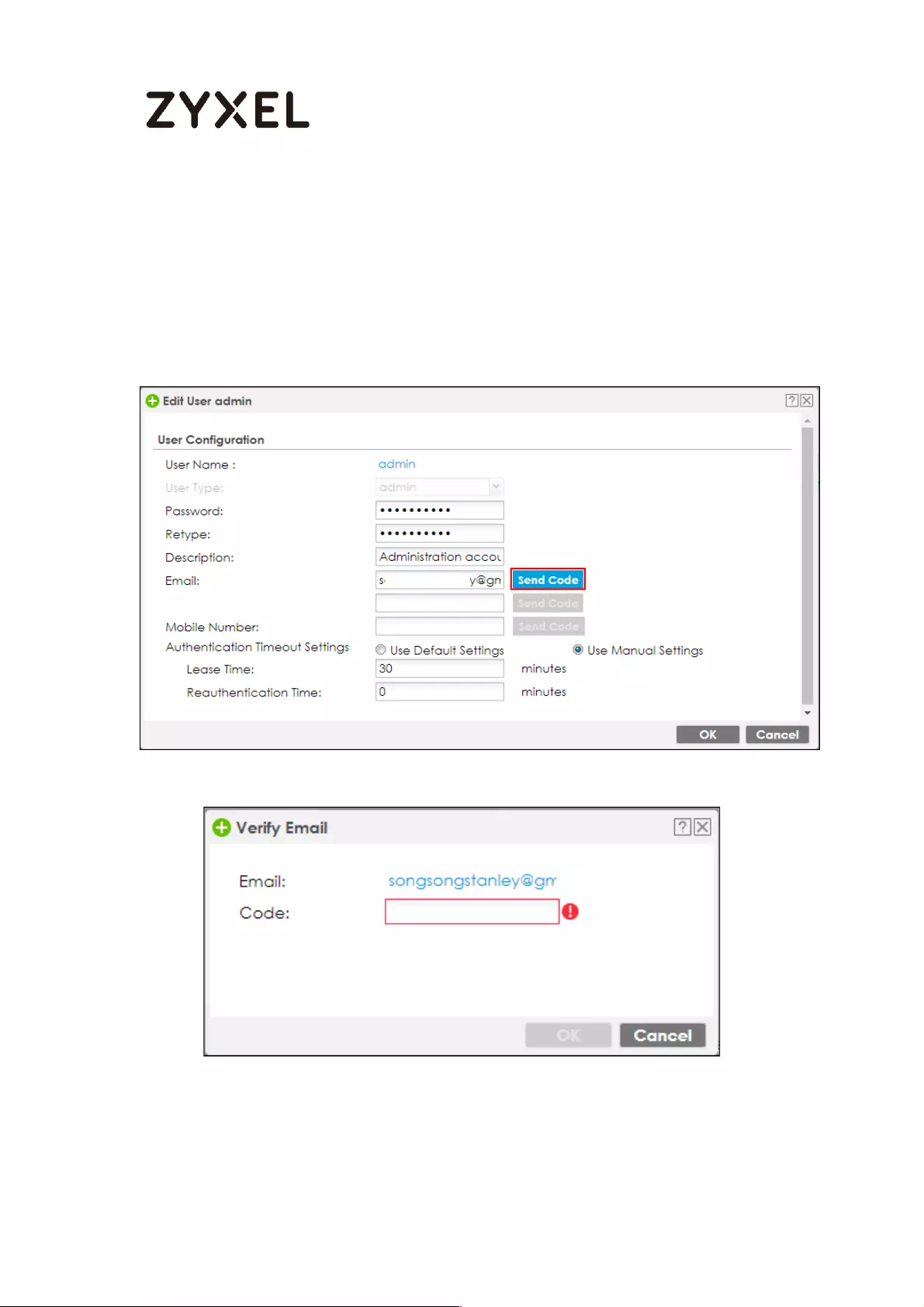
765/782
www.zyxel.com
What Can Go Wrong?
1. Must make sure SMTP server configuration is correct.
2. If you would like to add “admin” into the 2FA rule, you must do verify admin
email first
2-1 Enter Email address and click “send code” button
2.2 After clicked “Send Code”, you will receive code by Email.
2.3 Enter code that you received.
2.4 After admin Email is verified, it will display success.
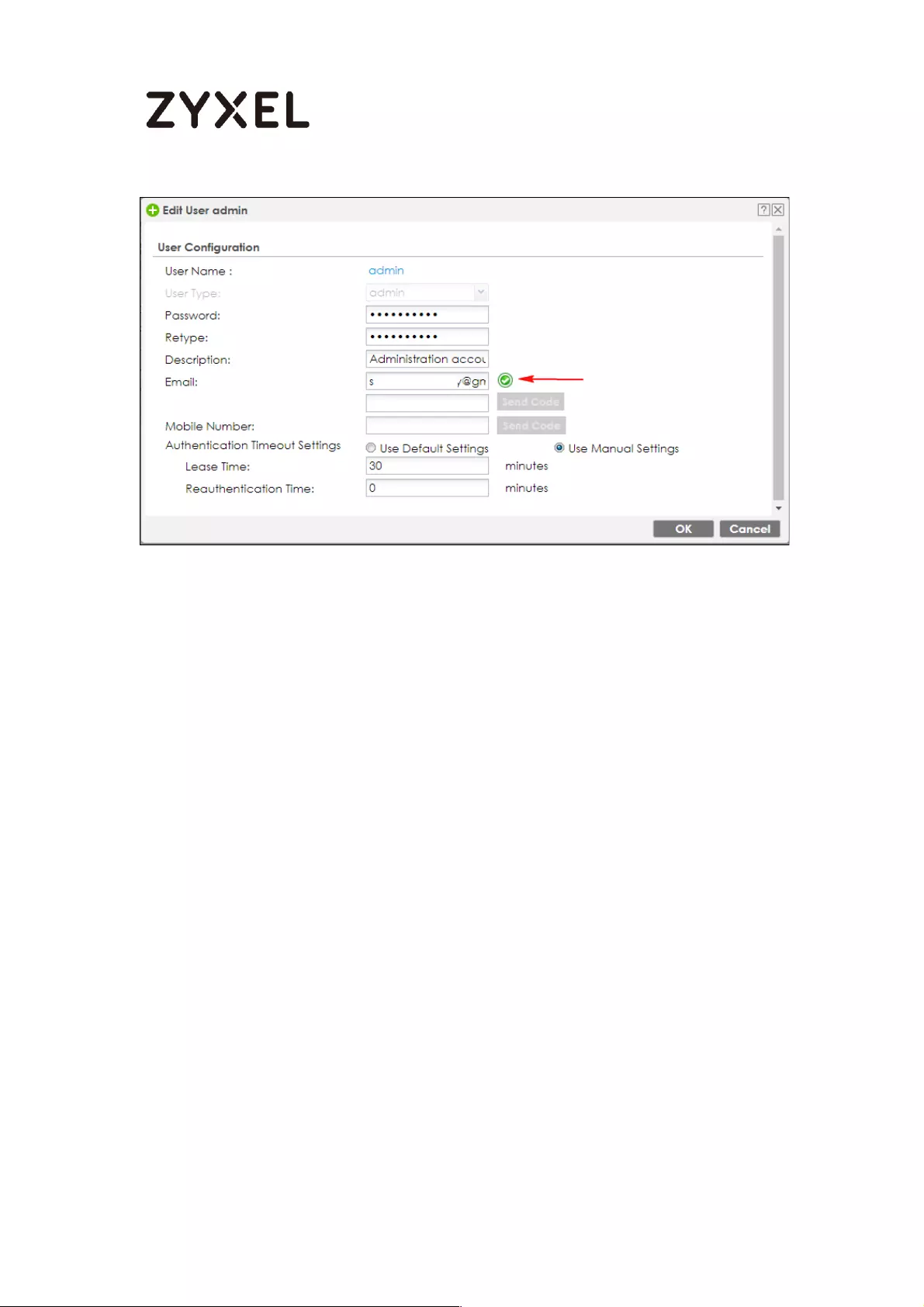
766/782
www.zyxel.com
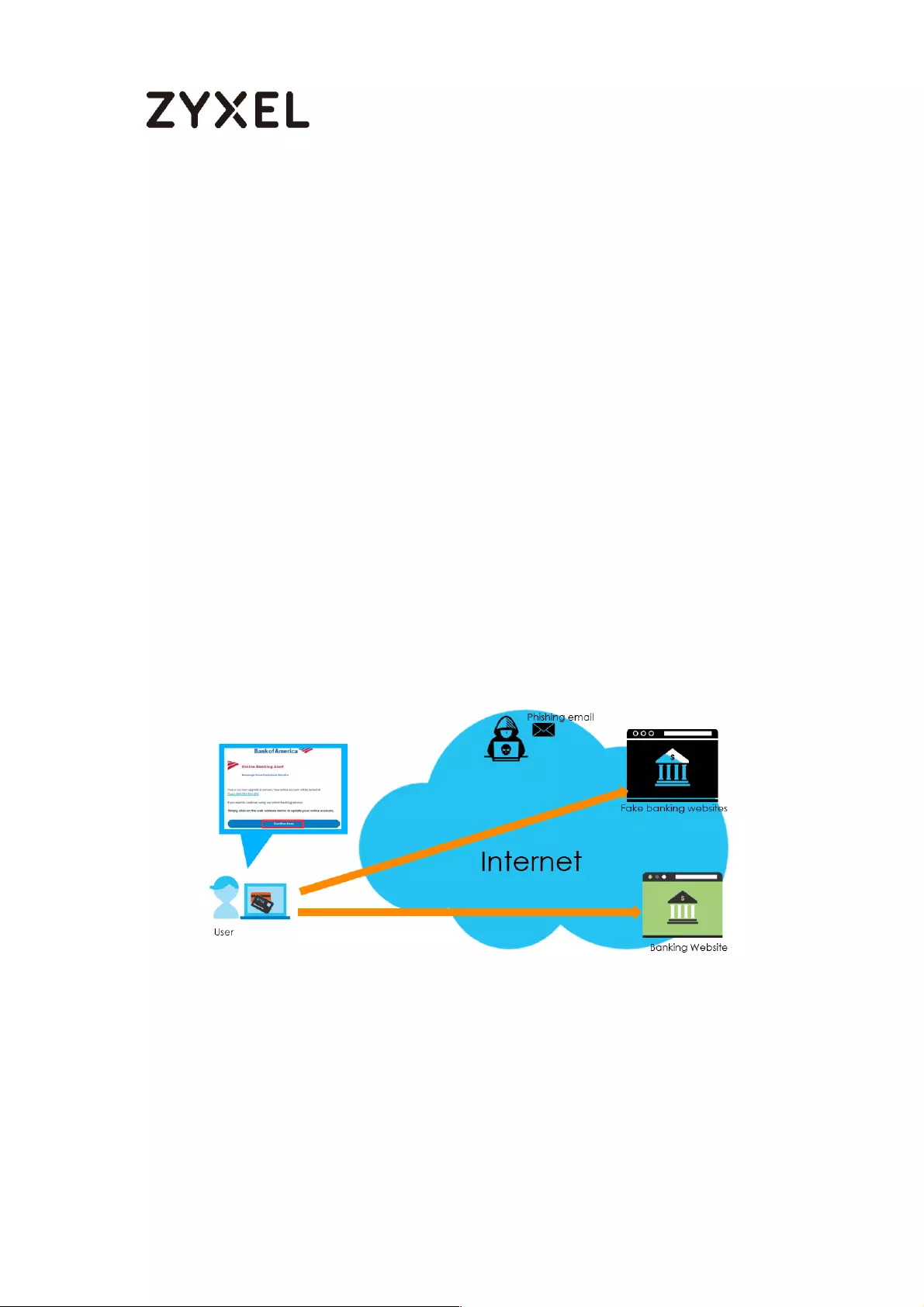
767/782
www.zyxel.com
How to configure Email Security for Phishing mail?
(This feature is only supported on ATP series)
The following depicts a sample configuration of Email security for Phishing
mail.
Phishing is a type of online scam where criminals send an email with a
fake website and asking you to provide sensitive information.
An example of phishing attack:
1. Attacker creates an fake banking websites which copy the content
from real banking website
2. Attacker sends user an phishing emails with an embed URLs to ask
change the new banking password
3. User opens the mail then click to the embed URLs, it redirects user
access to fake banking websites.
4. User enters the current banking account when they attempt
change the password
5. Attacker gets the user’s banking account and can steal user’s
money
Figure 1 Using Sandboxing to Detect Unknown Malware
How it works
Gateway inspects the email content to detect the embedded URLs. With Anti-
phishing enhancement, ATP gateway inspects the mail content to detect the
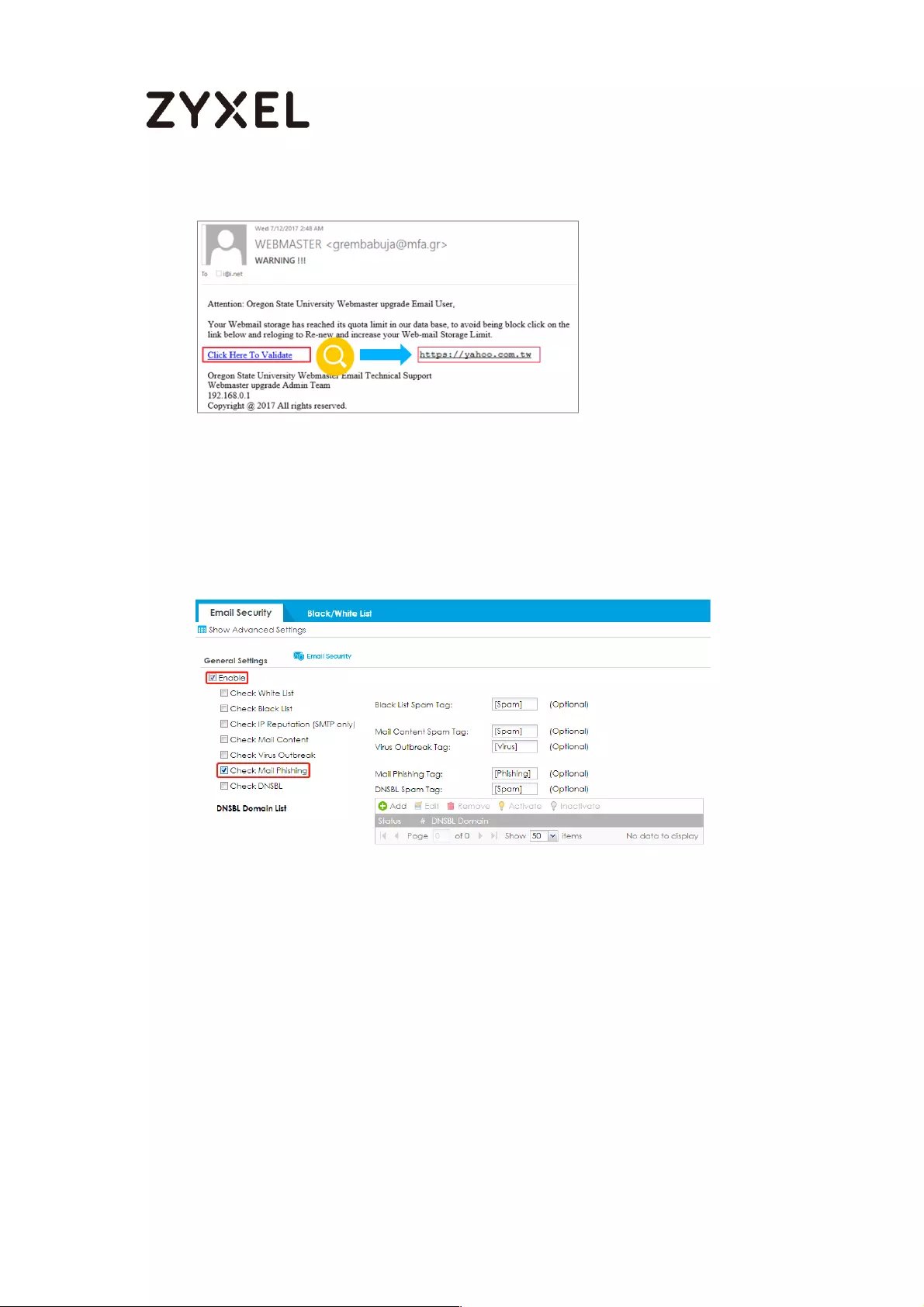
768/782
www.zyxel.com
embedded URLs.
Figure 2 Phishing mail example
Set up Phishing on ATP
In the ATP, Go to Configuration > Security Service > Email Security to enable
Check Mail Phishing that allows gateway inspects the embed URLs in the email

769/782
www.zyxel.com
Test the Result
1 Go to Monitor > Security Statistics > Email Security to observe mail
phishing logs
Monitor > Security Statistics > Email Security
2 Go to Monitor > Security Statistics > Email Security to collect Email
security statistics
What Can Go Wrong?
1 Make sure the Anti-Spam default service port is SMTP or POP3 by CLI
Router# show utm-manager anti-spam defaultport

770/782
www.zyxel.com
2 It does not support SSL inspection.
3 The ATP can inspect email up to 50KB. If the mail size greater than 50KB, gateway
will inspect the first 50KB from the header
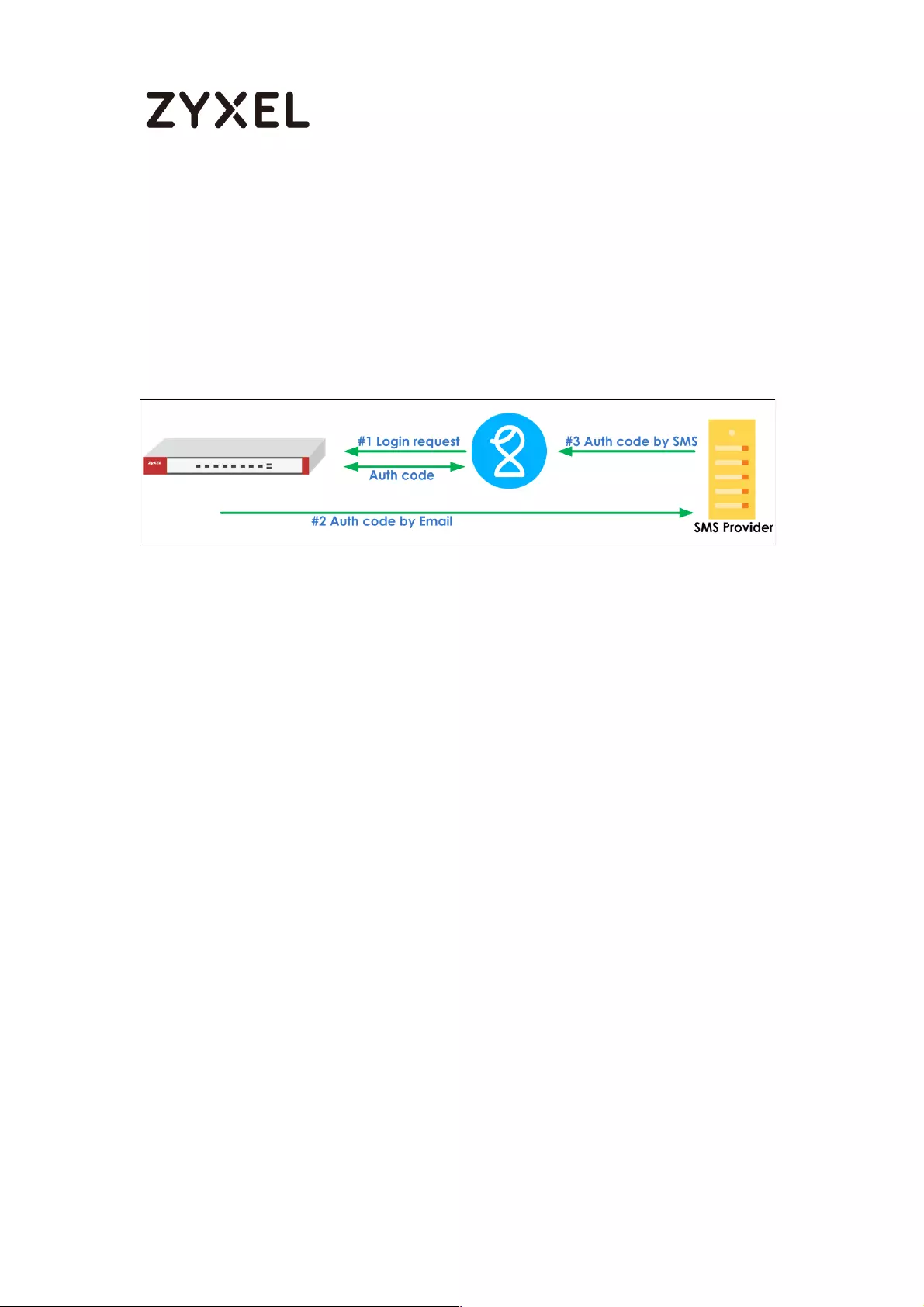
771/782
www.zyxel.com
How to setup Email to SMS
The Email to SMS function can help to send the SMS to client. The SMS
message is initialed from device to SMS provider, and then SMS provider
send the SMS to client. This function can help to make sure user receives
SMS if client without Internet connection.
You can follow these steps to Email to SMS.
Setup SMTP function on your device
Go to CONFIGURATION > System > Notification > Mail Server Field your SMTP serve
configuration.
A. Mail server
B. Mail server ports
C. Mail From
D. SMTP Authentication
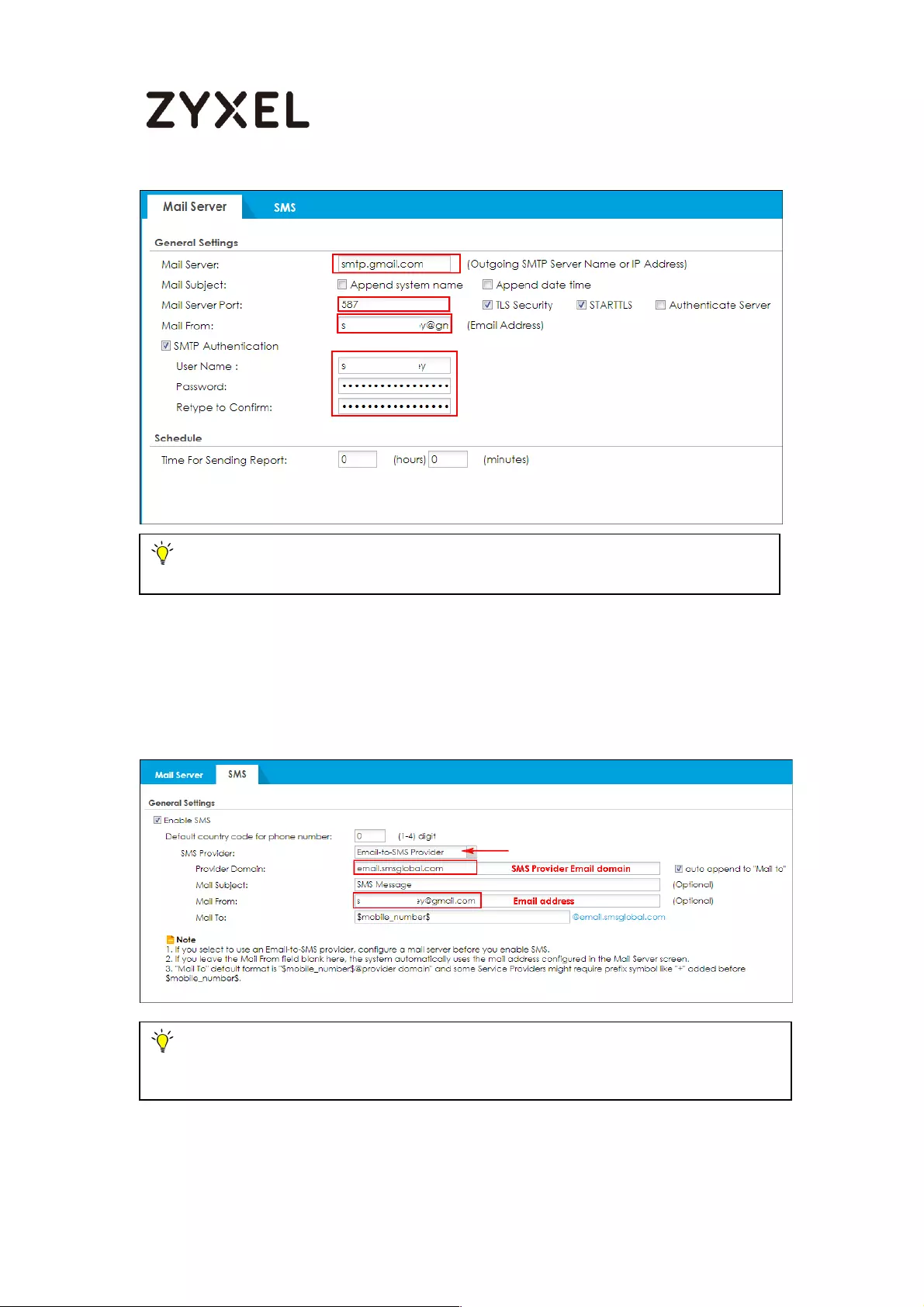
772/782
www.zyxel.com
Setup Email to SMS Provider configuration
Go to “Configuration > system > Notification > SMS Select “SMS Provider” as Email
to SMS Provider. Enter SMS Provider Email server domain name.
And configuring sender mail address in “Mail From”
Note: Must make sure SMTP Server configuration is correct otherwise message
will unable send to SMS provider successfully.
Note: Your SMS provider has to allow the email address which configured in “Mail
From” to prevent the email is denied by SMS provider’s mailbox.
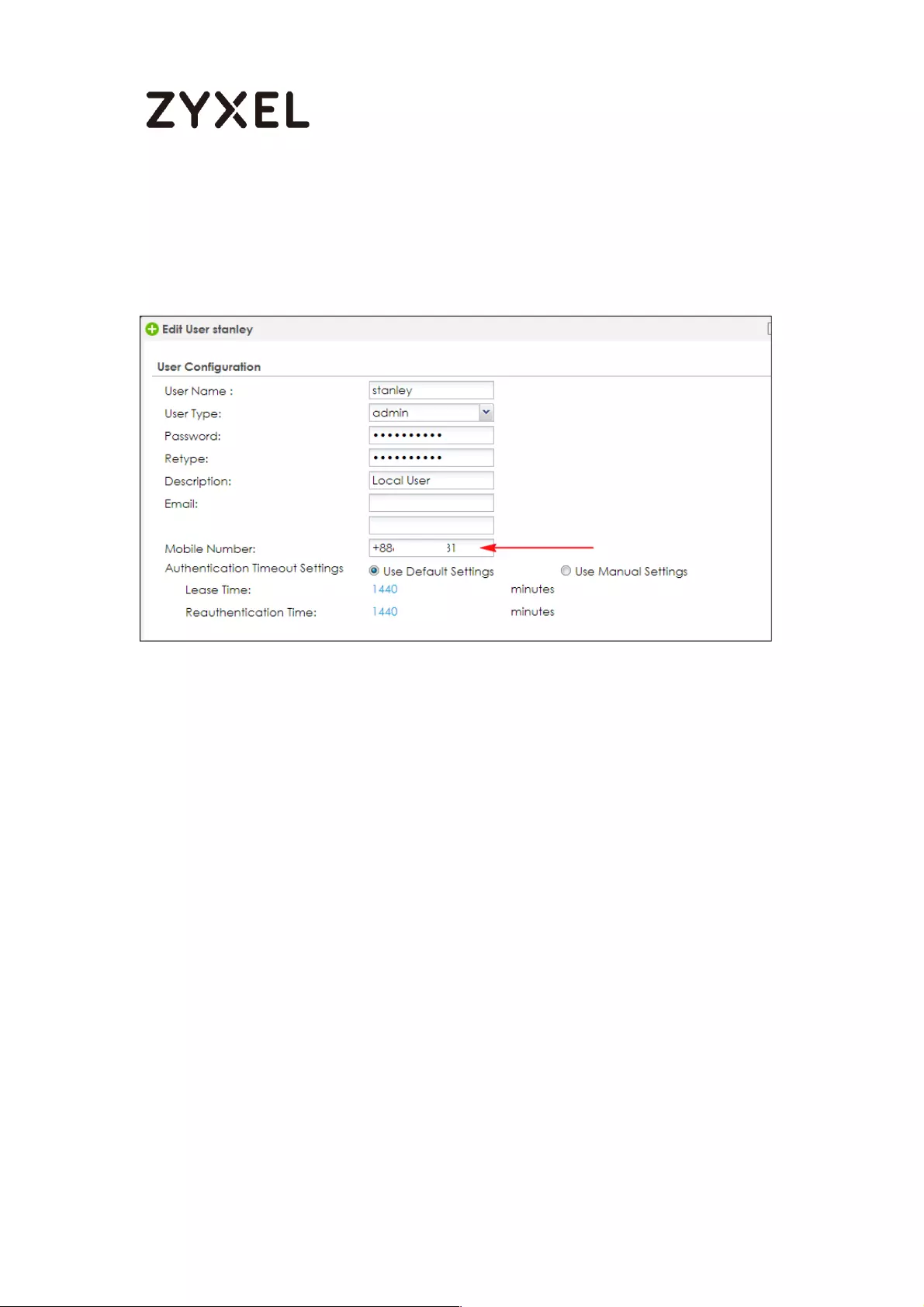
773/782
www.zyxel.com
Create admin type user on device
Go to Configuration > Object > User/Group > User Click Add button to create an
user and user type is admin. And also entered phone number of this user.
Setup Two-Factor Authentication for admin on your device
Go to Configuration > Object > Auth Method > Two-Factor Authentication >
Admin Access
Enable the function and add admin user which you added in step3 in the rule,
and you can select what services are 2 Factor authentication needed. Enable
SMS function to send verification code by SMS.
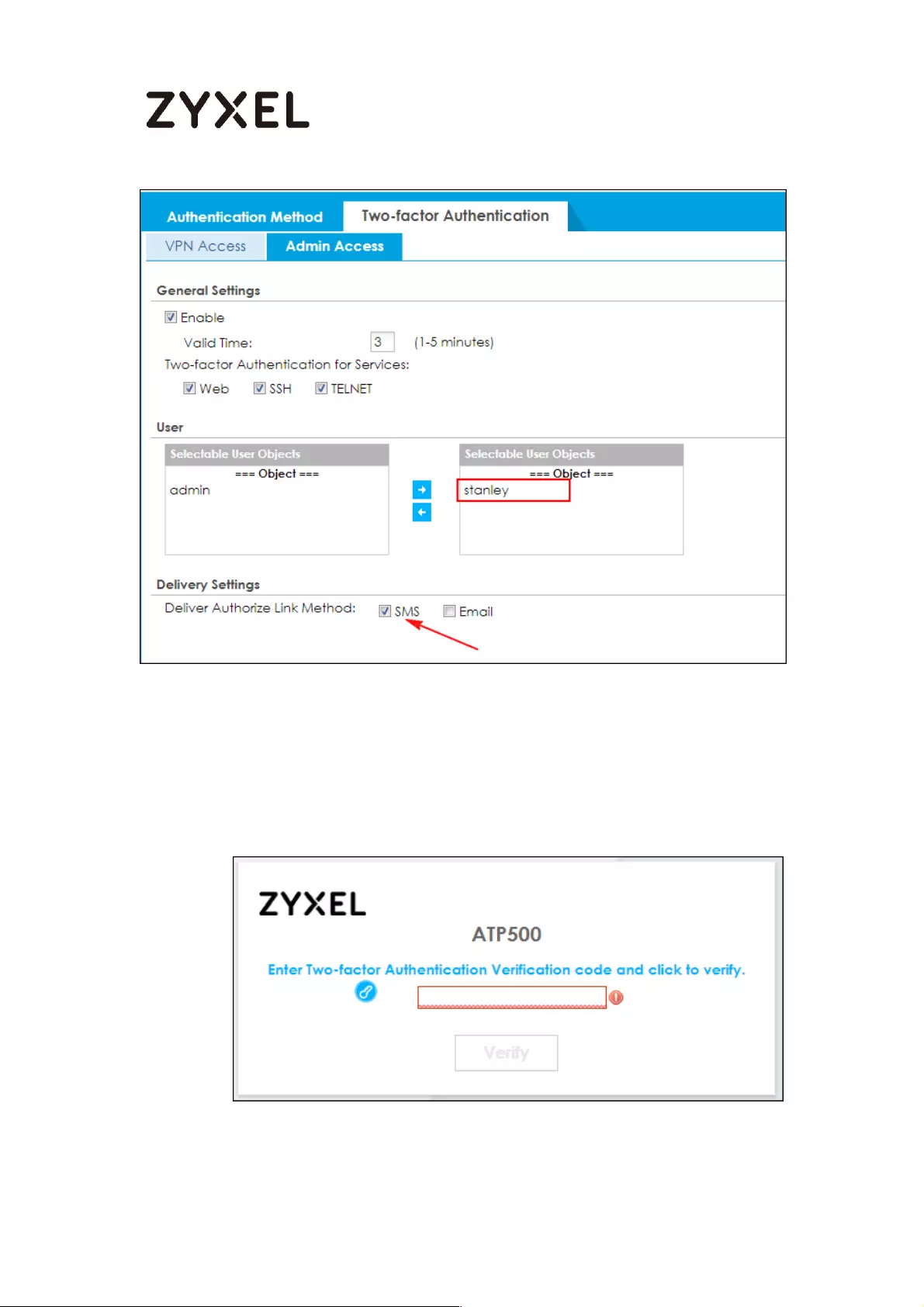
774/782
www.zyxel.com
Test the Result
After setup these steps and login to device by admin user, the verification code
is required.
Web Service:
SSH Service:
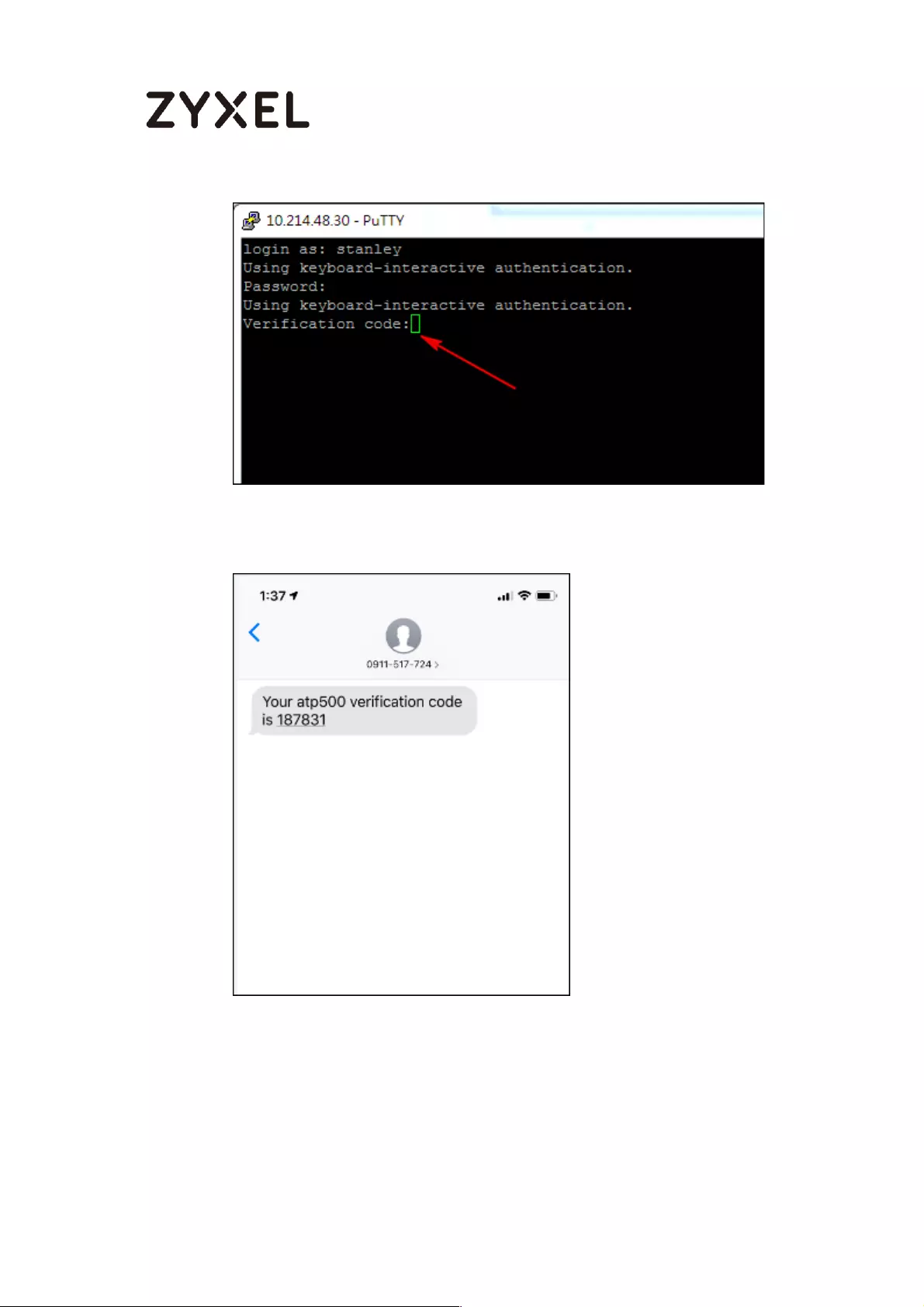
775/782
www.zyxel.com
You will receive verification code by SMS.

776/782
www.zyxel.com
What Can Go Wrong?
1 Must make sure SMTP server configuration is correct.
2 Must make sure your SMS provider is supported Mail to SMS function.
3 Make sure your email address is allowed by your SMS provider.
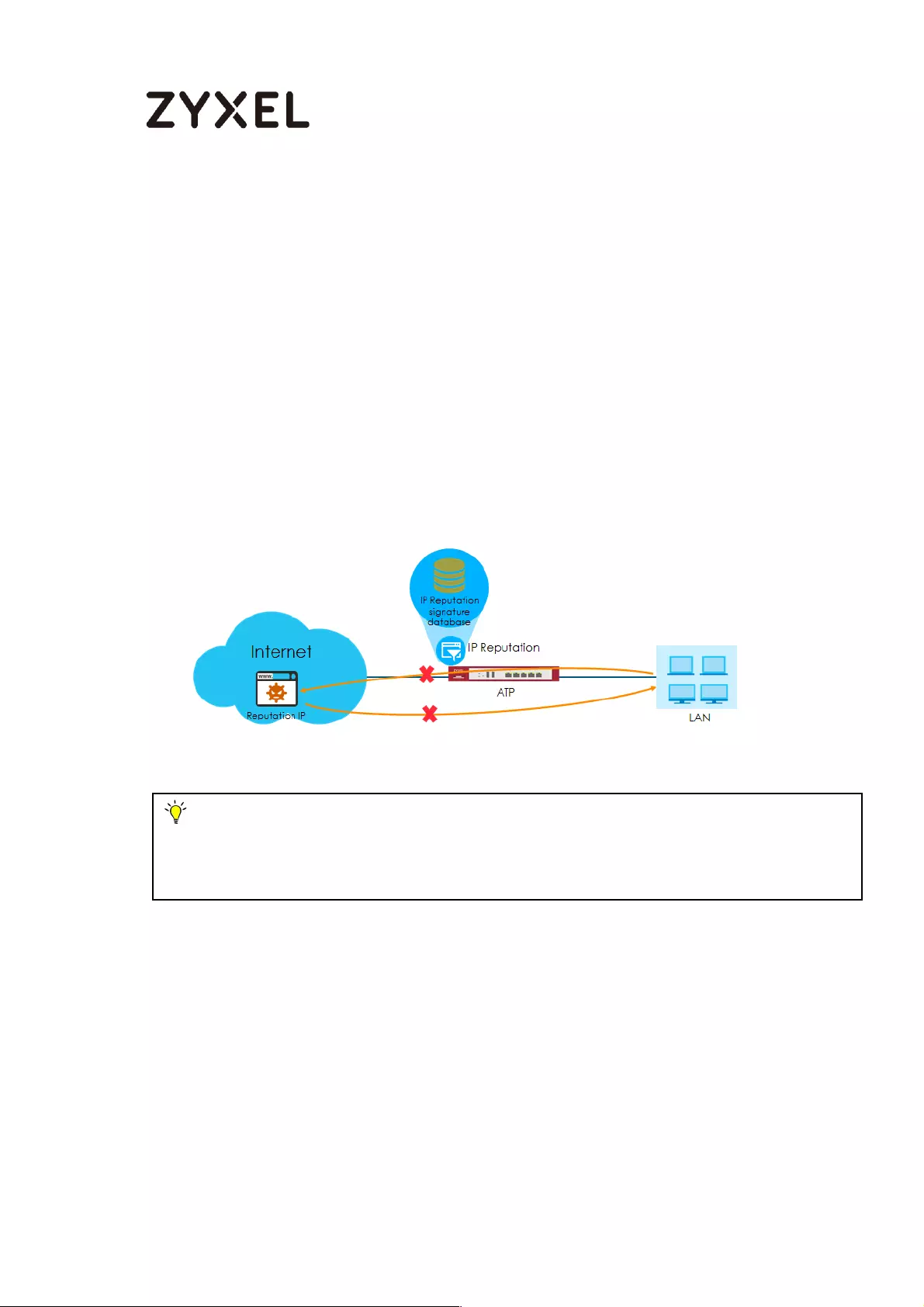
777/782
www.zyxel.com
How to Use IP Reputation to Detect Threats
(This feature is only supported on ATP series)
As cyber threats such as scanners, botnets, phishing, etc. grow
increasingly, how to identify suspect IP addresses of threats efficiently
becomes a crucial task.
With regularly updated IP database, ATP prevents threats by blocking
connection to/from known IP addresses based on signature database. It
filters source and destination addresses in your network traffic to take the
proper risk prevention actions.
This example illustrates how to configure IP Reputation on ATP gateway
to detect cyber threats for both incoming and outgoing traffic.
Figure
Note: All network IP addresses and subnet masks are used as examples in this article.
Please replace them with your actual network IP addresses. This example was tested using
the ATP500 (Firmware Version: ZLD 4.35).
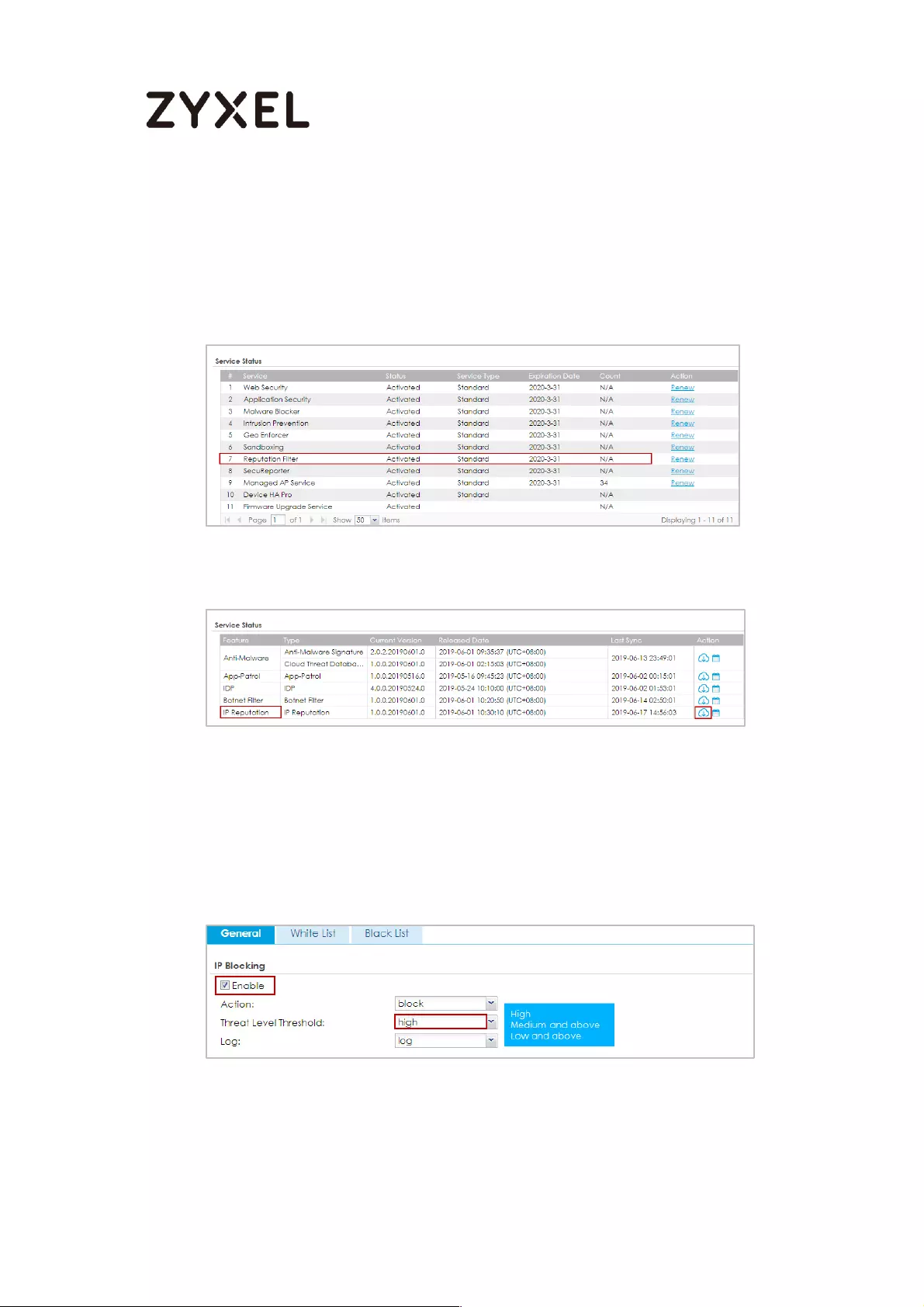
778/782
www.zyxel.com
Activating Reputation Filter Service
1 Register ATP gateway to myZyxel.com.
2 Activate Reputation Filter license.
3 On ATP, go to CONFIGURATION > Licensing > Signature Update. Click
the Update icon to check for new signatures.
Enabling IP Blocking on ATP
Go to CONFIGURATION > Security Service > Reputation Filter > IP Reputation >
General. Click Enable to detect reputation IPs. The threat level threshold is
measured by the query score of IP signature database.
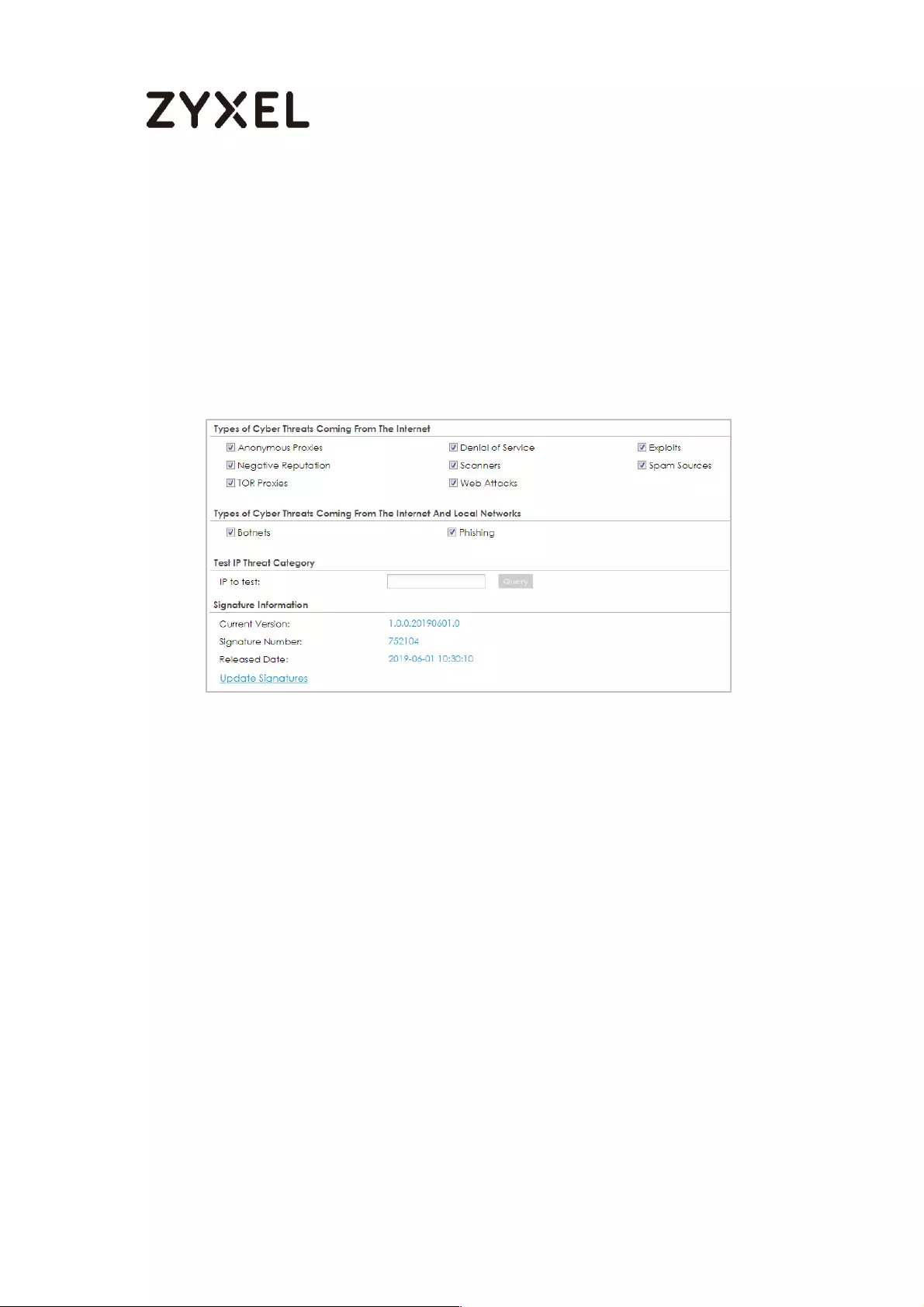
779/782
www.zyxel.com
Selecting specific type of IP addresses to block
In Types of Cyber Threats Coming From The Internet, select the type of threats that
are known to pose a security threat for incoming traffic.
In Types of Cyber Threats Coming From The Internet And Local Networks, select
the type of threats that are known to pose a security threat for both incoming
and outgoing traffic.
Adding IP addresses to white list and black list
Go to CONFIGURATION > Security Service > Reputation Filter > IP Reputation >
White List and Black List to manually adding IP addresses to the White List and
Black List.
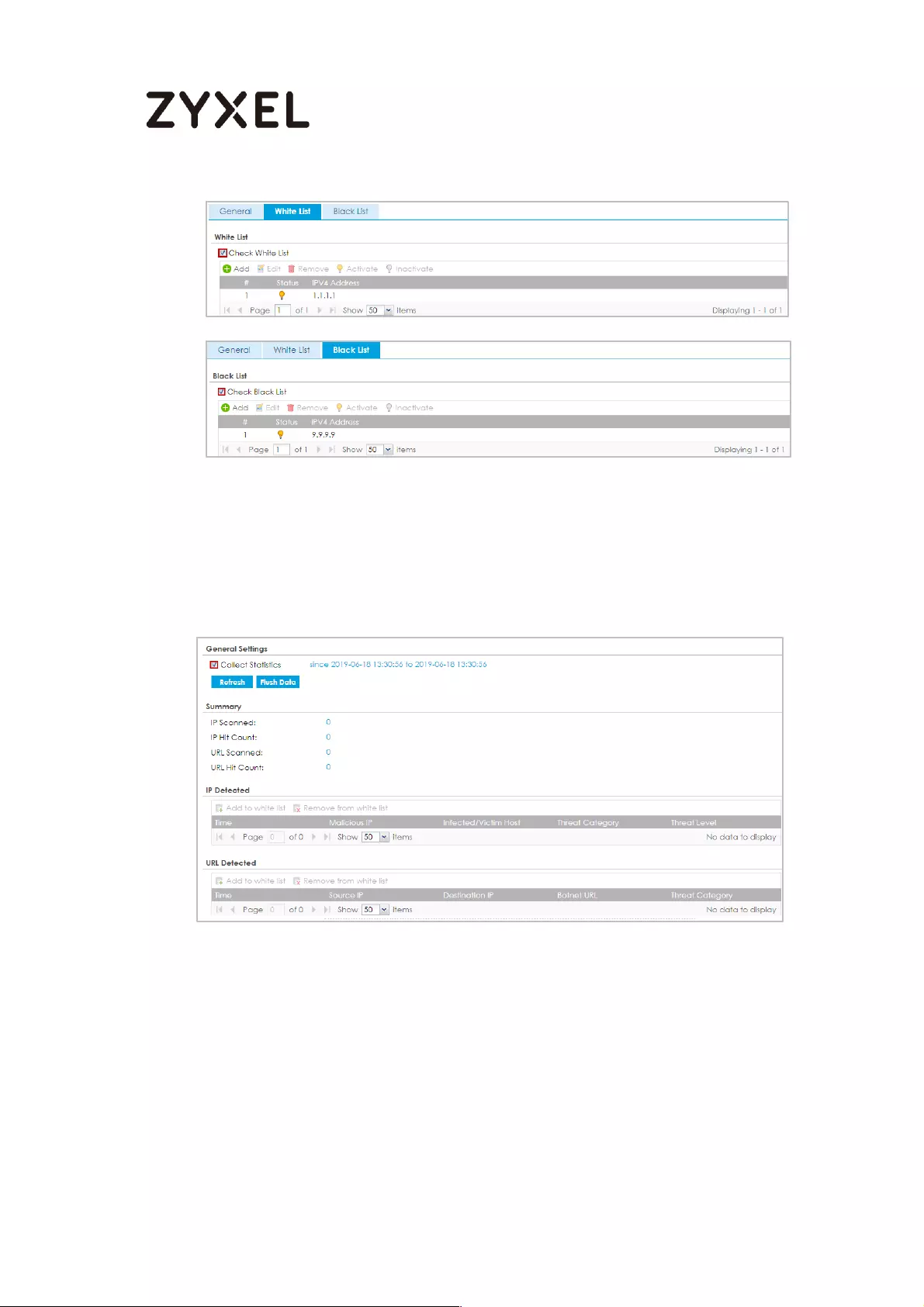
780/782
www.zyxel.com
Monitoring statistics for IP detection
Enable Collect Statistics to monitor the scanned result and detected IP.
MONITOR > Security Statistics > Reputation Filter
Test the Result
1 Select Anonymous Proxies for detecting incoming traffic and Botnet
for outgoing traffic.
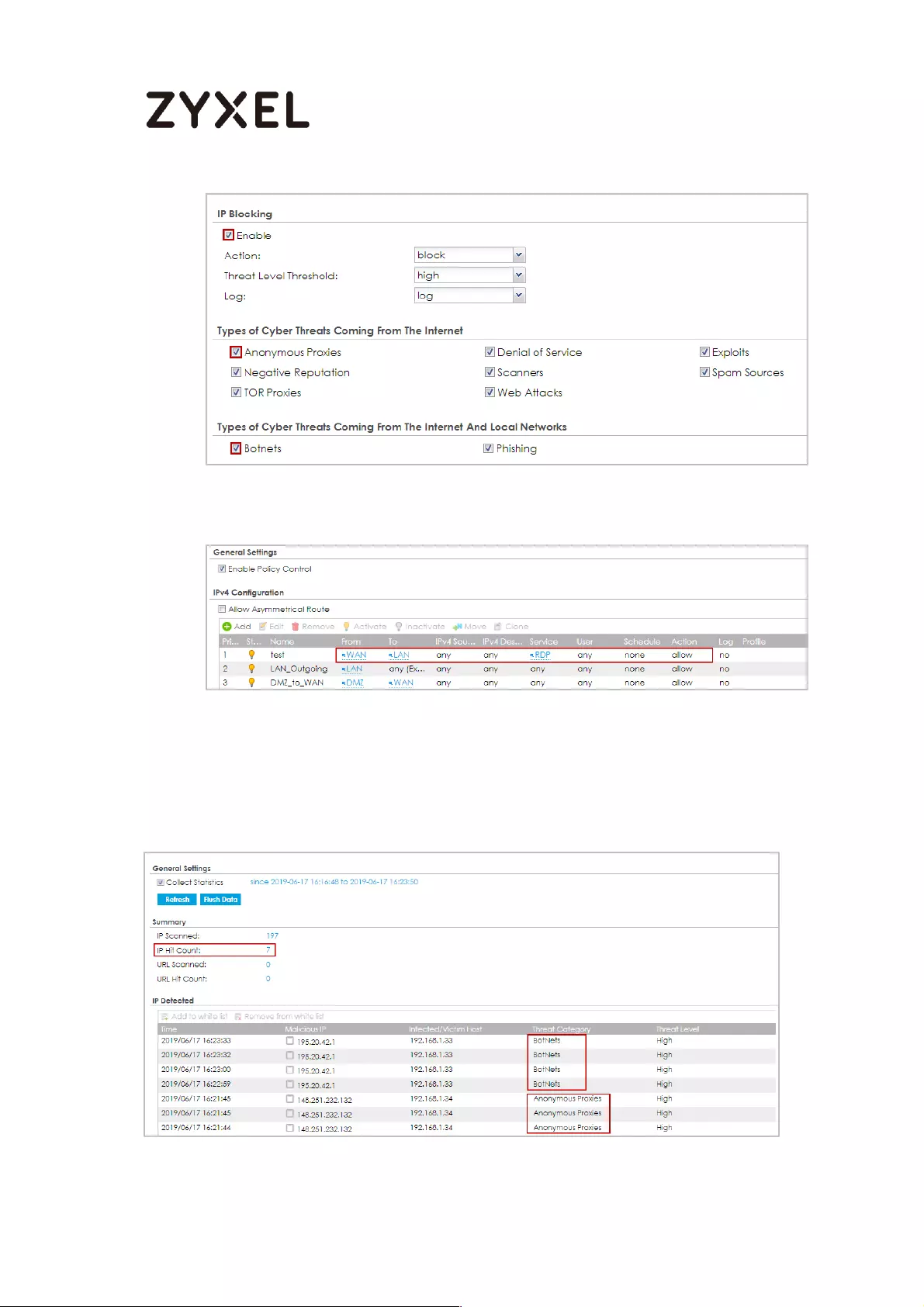
781/782
www.zyxel.com
2 For incoming traffic, set a NAT rule and add a security policy rule for
allowing traffic from WAN to LAN.
For outgoing traffic, ping an IP address in the threat category
"Botnets" from LAN.
3 Check statistics for detected IPs.
MONITOR > Security Statistics > Reputation Filter

782/782
www.zyxel.com
On dashboard, you can find top 5 countries that are detected the most by IP
Reputation.
Dashboard > Advanced Threat Protection
What Can Go Wrong?
4. For device HA or HA Pro, signature synchronization is required.
5. Cloud query is not supported.
6. It doesn't support for IPv6.