Table of Contents
- Table of Contents
- Safety Warnings
- Chapter 1. Product Overview
- Chapter 2. Basic Operations
- Chapter 3. Upgrade Memory on QNAP Turbo NAS (RAM Module Installation)
- Chapter 4. Expansion Card Installation
- Chapter 5. Install M.2 SSDs
- Chapter 6. Install and Hot-swap Drives
- Chapter 7. Using the LCD Panel
- Technical Support
- GNU GENERAL PUBLIC LICENSE
QNAP TS-1685 User Manual
Displayed below is the user manual for TS-1685 by QNAP which is a product in the NAS & Storage Servers category. This manual has pages.
Related Manuals

2018-03-28
QNAP Turbo NAS
TS-1685 Hardware User Manual
© 2018. QNAP Systems, Inc. All Rights Reserved.

2
Thank you for choosing QNAP products! This user manual provides description of the
hardware of the T urbo NAS and relevant guideline of certain functions. Please read carefully
and strictly adhere to the instructions of the manual.
Th is user manual is applicable to the following Turbo NAS models:
TS-1685
NOTE
• The “Turbo NAS” is hereaft er referred to as “NAS”.
• The prod uct you purchased may not support cer tain functions de d icated to specific
models.
• All fea t ures, functionality, and other product specifications are subject to change
without prior notice or obligation.
• Information presented is subject to change w ithout notice.
• No part of this publication may be reproduced, stored in a retrieval system, or
transmitted, in any f orm or by any means, mechanica l, electronic, photoco p ying,
recording, or otherwise, without prior written permission of QNAP Systems, Inc.
• QNAP and the QNAP logo are registered trademarks of QNAP Systems, Inc. Other
products and company names mentioned herein may be the trademarks of their
respective companies.

3
DISCLAIMER
In no eve nt shall QNAP Sy stems, Inc . (QNAP) liability e xceed the price paid for the p roduct
from direct, indirect, special, incidental, or consequential damages resulting from the use
of the product, its accompanying software, or its documentation. QNAP makes no warranty
or representation, expressed, implied, or statutory, with respect to its products or the
contents or use of this documentation and all accompanying software, and specifically
disclaims its quality, performance, merchanta bi li ty, or fitness for any particular purpose.
QNAP r es er ves the right to revise or update its products, software, or documentation
without obligation to notify any individual or entity.
Note:
Back up your system periodically to avoid any potential data loss. QNAP disclaims any
responsibility of all sor ts of data loss or recovery.
Should you return any components of th e NAS package for refund or mainte nance,
make sure they ar e carefully pac ked for shipping. Any form of damages due to
improper packaging will not be compensated.

4
Regulatory Notice
FCC Class B Notice
The TS-1685 complies with Part 15 of the FCC Rules. Operation is subject to the following
two conditions:
1. This device may not cause harmful interference.
2. This device must accept any interference received, including interference that may
cause u n d esired operation .
Note: This equipment ha s been tested and found to comply with the limits for a Class B
digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference in a resid entia l in s talla tion. T h is
equipment generates, uses, and can radiate radio frequency energy and, if not insta lled
and used in accordance with the instr uctions, may cause harmful interference to radio
comm unications. However, there is n o guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference to radio or
television receptio n, which can be dete rm ined by turning the e quipment off and on, the
user is encouraged to try to correct the interferen ce by on e o r mo r e of t h e fol lowing
measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circ uit d iff erent from that to which the
receiver is connected.
• Consult the dealer or an experienced radio/television technician for help.
Modifications: Any modifications made to this device that are not a p proved by QNAP
Sys tems, Inc. may void the authority gra nted to the user by the FCC to operate this
equipment.
5
CE NOTICE
The TS-1685 series complies with CE compliance clas ses B.
RESTRICTED ACCESS LOCATION
This equipment must be only located where both of the following apply:
Only authorized and knowledgeable personnel can access the equipment
Access to the equipment is restricted through the use of lock and key or other means of
security and this access is controlled by those in charge of the location.
6
Symbols in this document
Warning
This icon indicates the instructions must be strictly followed. Failure
to do so could result in injury to human body or death.
Caution
This icon indicates the action may lead to disk clearance or loss OR
failure to f ollow the instru ctions could result in data damage, disk
damage, or pro d uct damage.

7
Table of Contents
Table of Contents ............................................................................................... 7
Safety Warnings ................................................................................................. 8
Chapter 1. Product Overview ........................................................................... 9
1.1 HARDWARE SPECIFICATION ............................................................................. 9
1.2 ORDERING INFORMATION ............................................................................. 10
1.3 COMPONENTS ........................................................................................... 12
Chapter 2. Basic Operations .......................................................................... 15
2.1 POWER BUTTON ......................................................................................... 15
2.2 RESET BU TTON .......................................................................................... 15
2.3 USB ONE TOUCH COPY ............................................................................... 16
2.4 LED ...................................................................................................... 17
2.5 BEEP ALARM ............................................................................................ 19
Chapter 3. Upgrade Memory on QNAP Turbo NAS (RAM Module Installation) 20
Chapter 4. Expansion Card Installation ......................................................... 25
Chapter 5. Install and Hot-swap Drives ......................................................... 29
5.1 DRIVE BAY NUMBERING .................................................................................... 29
5.2 INSTALLING DRIVES ........................................................................................ 29
5.3 RAID RECOVERY - HOT-SWAPPING DRIVES ............................................................ 34
5.4 RAID RECOVERY - ACCIDENTAL REMOVAL OF A HEALTHY DRIVE .................................... 35
Chapter 6. Using the LCD Panel ..................................................................... 37
Technical Support ............................................................................................ 42
GNU GENERAL PUBLIC LICENSE ....................................................................... 43

8
Safety Warnings
1. The NAS can operate normally in temperatures of 0ºC - 40ºC (32ºF - 104ºF) and
relative humidity of 5% - 95%. Please make sure the environment is well-ventilated.
2. The power cord and devices connected to the NAS must provide correct supply voltage
(100W, 90–264V).
3. Do no t place the NAS in direct s unlight or ne ar chemicals. Make sure the temperature
and humidity of t he environment are in optimized level.
4. Unplug the po wer cord and all connecte d cables before cleaning. Wipe the NAS with a
dry towel. Do not use chemical or aerosol to clean the NAS.
5. Do not place any objects on the NAS for the server’ s normal operation and to avoid
overheat.
6. Use the flat head screws in the product package to lock the hard disks in the NAS when
installing hard disk s for proper oper ation.
7. Do no t place the NAS near an y liquid.
8. Do not place the NAS on any uneven surface to avoid falling off and da mage.
9. Make sure the voltage is correct in the location where the NAS is installed. Contact the
distributor or the local power supply company for the information.
10. Do not place any object on the power cord.
11. Do no t atte m pt to repair the NAS in any occasions. Improper disassembly of the
product may expose the users to electric shock or other risks. For any enquiries,
please conta ct the distributor.
12. The NAS should only be installed in the server room and maintained by the authorized
server manager or IT administrator. The server room is locked by key or keycard
access and only certified staff is allowed to enter the server room.
Warning:
Danger of explosion if battery is incorrectly replaced. Replace only with the same or
equivalent type recommended by the manufacturer. Dispose of used batteries
according to the manufacturer’s instruc t io ns.
Do NOT touch the fan inside the system to avoid serio us injurie s.
9
Chapter 1. Product Overview
Caution: Any unauthorized modif ications pe rformed on QNAP products will result in
the warranty being voided. QNAP is not responsible for any form of damage or loss of data
cause d by such modifications. U na uthorized modifications inc l ude, but are not limited to,
changes made to the default system firmware, installation of unofficial third party
applications, and changes to the hardware performed by unauthorized technicians.
1.1 Hardware Specification
TS-1685
CPU Intel® Xeon® Processor D-1521 quad-core 2.4 GHz
Intel® Xeon® Processor D-1531 6-core 2.2 GHz
System memory
16GB non-ECC RAM (8GB UDIMM*2)
32GB non-ECC RAM (16GB UDIMM*2)
64GB non-ECC RAM (16GB UDIMM*4)
64GB ECC RAM (16GB RDIMM*4)
128GB ECC RAM (32GB RDIMM*4)
Flash memory 512 MB (USB DOM)
CPU replaceable No
Memory replaceable Yes
Memory slots 4 x Long-DIMM slots
3.5" drive slots 12 x SATA 6 Gb/s (3.5-inch HDD, 2.5-inch HDD& SSD)
2.5" drive slots 4 x SATA 6 Gb/s (2.5-inch SSD)
M.2 SSD slots 6 x M.2 2242/2260/2280/22110 SATA 6 Gb/s
PCIe slots
3:
Slot 1: PCIe Gen.3 x8
Slot 2: PCIe Gen.2 x4
Slot 3: PCIe Gen.3 x8
10 GbE LAN ports 2 x 10GBASE-T
GbE LAN ports 4
LED panel Mono-LCD display with backlight
Enter and Select buttons for configuration
USB ports Front: 1 x USB 3.0 port
Rear: 2 x USB 3.0 port
Audio outputs 1 x built-in speaker
10
1 x 3.5mm Line-out jack
Note: Only one of the
above audio output por ts can work at a time.
If a speaker is connected, the sound will output through the
speaker.
LED indicators Status, USB One Touch Copy, HDD 1-12, SSD 1-4, M.2 SSD 1-6
Buttons Power, USB One Touch Copy, Reset
IR sensor QNAP RM-IR0 04 remote control (MCE compatible)
Security Kensingto n security slo t
Form factor Tower
Power Supply 100-240V~, 3-1.5A, 60-50Hz, 25 0W PSU
100-240V~, 3-1.5A, 60-50Hz, 550W PSU
System fans 3 x 9.2cm system fan (12V DC)
CPU fans 2 x 9cm fan
1.2 Ordering Information
NAS SKUs
TS-1685-D1521-8G Intel® Xeon® Processor D-1521, 8GB non-ECC RAM
(4GB UDIMM*2), 250W PSU
TS-1685-D1521-16G Intel® Xeon® Processor D-1521, 16GB non-ECC RAM
(8GB UDIMM*2), 250W PSU
TS-1685-D1521-16G-550W Intel® Xeon® Processor D-1521, 16GB non-ECC RAM
(8GB UDIMM*2), 550W PSU
TS-1685-D1521-32G Intel® Xeon® Processor D-1521, 32GB non-ECC RAM
(16GB UDIMM*2), 250W PSU
TS-1685-D1521-32G-550W Intel® Xeon® Processor D-1521, 32GB non-ECC RAM
(16GB UDIMM*2), 550W PSU
TS-1685-D1531-16G Intel® Xeon® Processor D-1531, 16GB non-ECC RAM
(8GB UDIMM*2), 250W PSU
TS-1685-D1531-32G Intel® Xeon® Processor D-1531, 32GB non-ECC RAM
(16GB UDIMM*2), 250W PSU
TS-1685-D1531-32G-550W Intel® Xeon® Processor D-1531, 32GB non-ECC RAM
(16GB UDIMM*2), 550W PSU
TS-1685-D1531-64G Intel® Xeon® Processor D-1531, 64GB non-ECC RAM
(16GB UDIMM*4), 250W PSU
TS-1685-D1531-64GR Intel® Xeon® Processor D-1531, 64GB ECC RAM (16GB
RDIMM*4), 250W PSU
TS-1685-D1531-128GR Intel® Xeon® Processor D-
1531, 128GB ECC RAM (32GB

11
RDIMM*4), 250W PSU
TS-1685-D1531-64GR-550W Intel® Xeon® Processor D-1531, 64GB ECC RAM (16GB
RDIMM*4), 550W PSU
TS-1685-D1531-128GR-550W Intel® Xeon® Processor D-
1531, 128GB ECC RAM (32GB
RDIMM*4), 550W PSU
12
1.3 Components
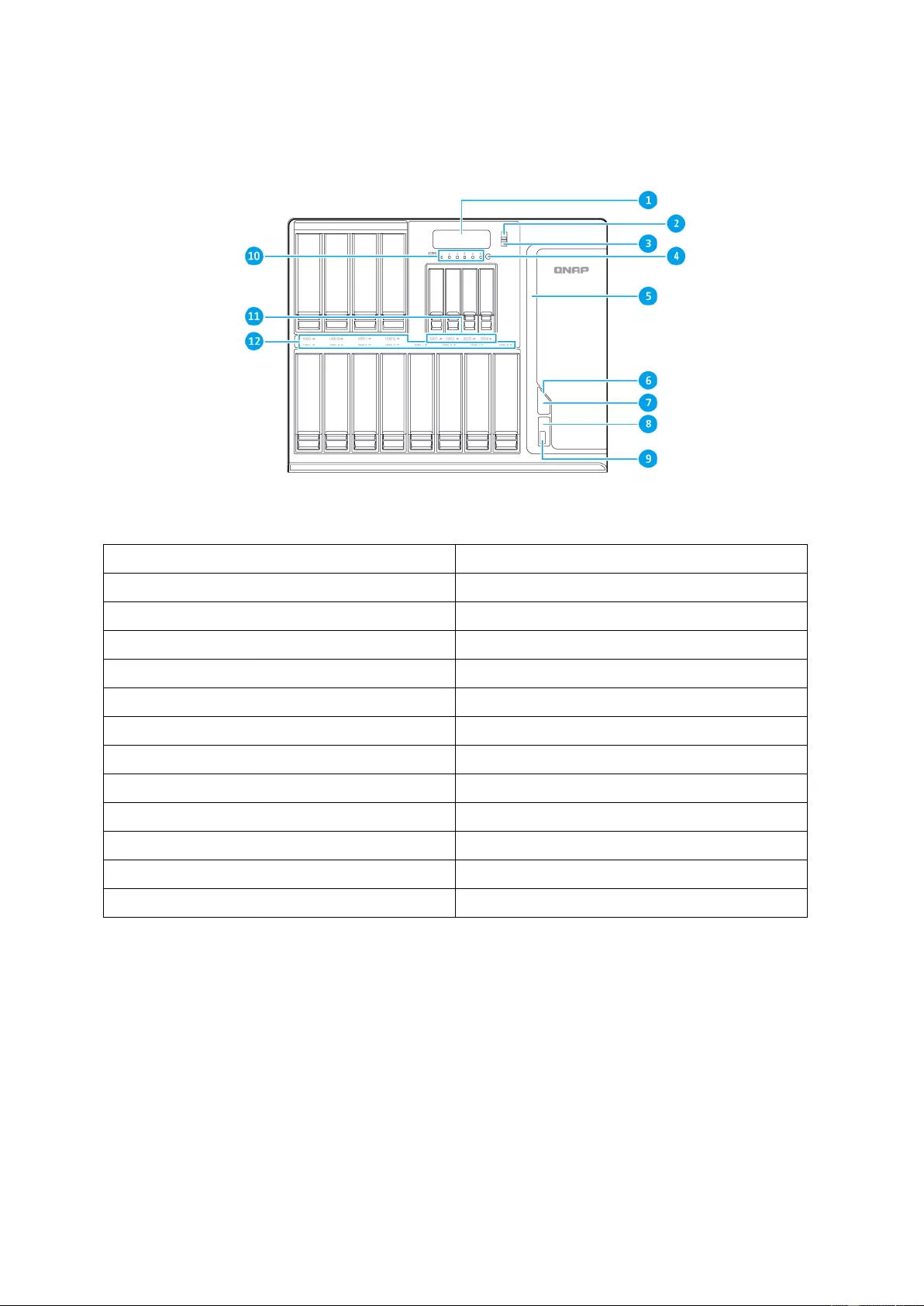
Front View
No. Component
1 LCD panel
2 Enter button
3 Select butto n
4 IR senso r
5 Power LED (adjustable brightness)
6 Power button
7 Status LED
8 USB One-touch Copy button
9 USB 3.0 One-touch C opy port
10 M.2 SSD LEDs
11 SSD LEDs
12 HDD LEDs
13
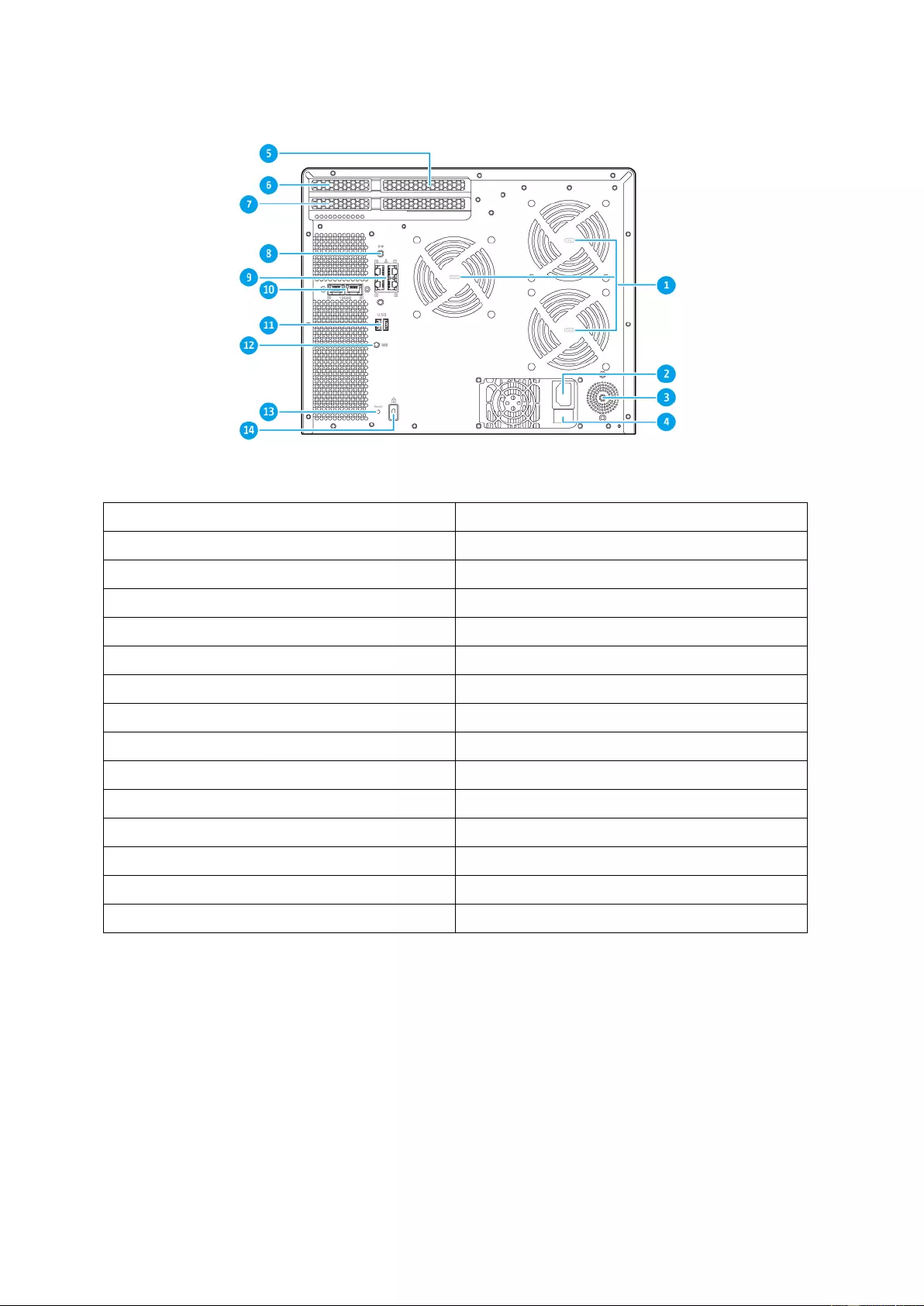
Back View
No. Component
1 Syst em f a n s 1 -3
2 Power input
3 Speaker
4 Power switch
5 PCIe slot 1 (f ull height)
6 PCIe slot 2 (low profile)
7 PCIe slot 3 (low profile)
8 3.5 mm speaker jack
9 Gigabit ports
10 10 GbE 10GBASE-T port
11 USB 3.0 ports
12 Console port
13 Reset button
14 Kensington security slot
14
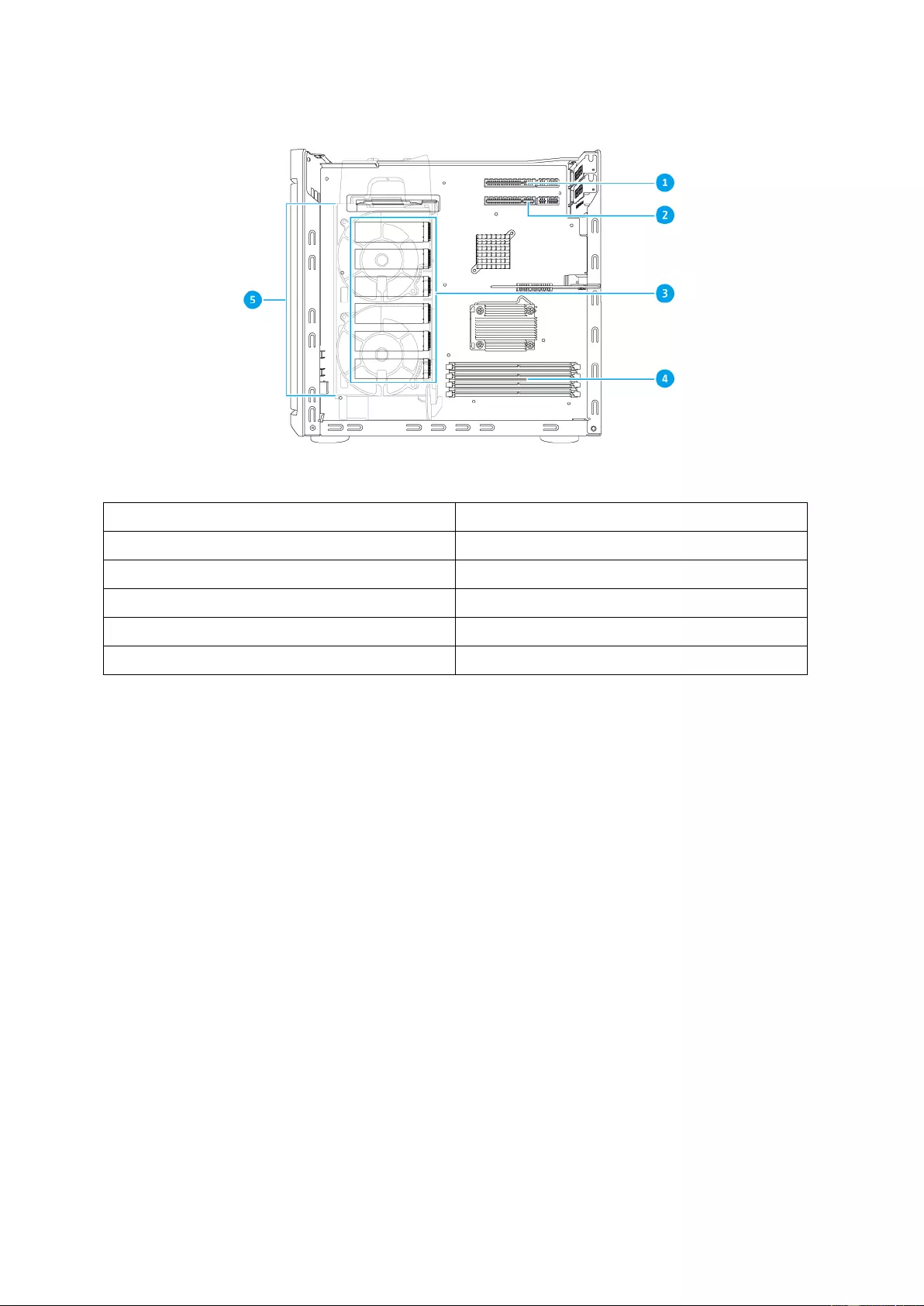
Side View
No. Component
1 PCIe slot 2 socket (low profile)
2 PCIe slot 3 socket (low profile)
3 M.2 SSD slots
4 Memory slots
5 CPU fans
15
Chapter 2. Basic Operations
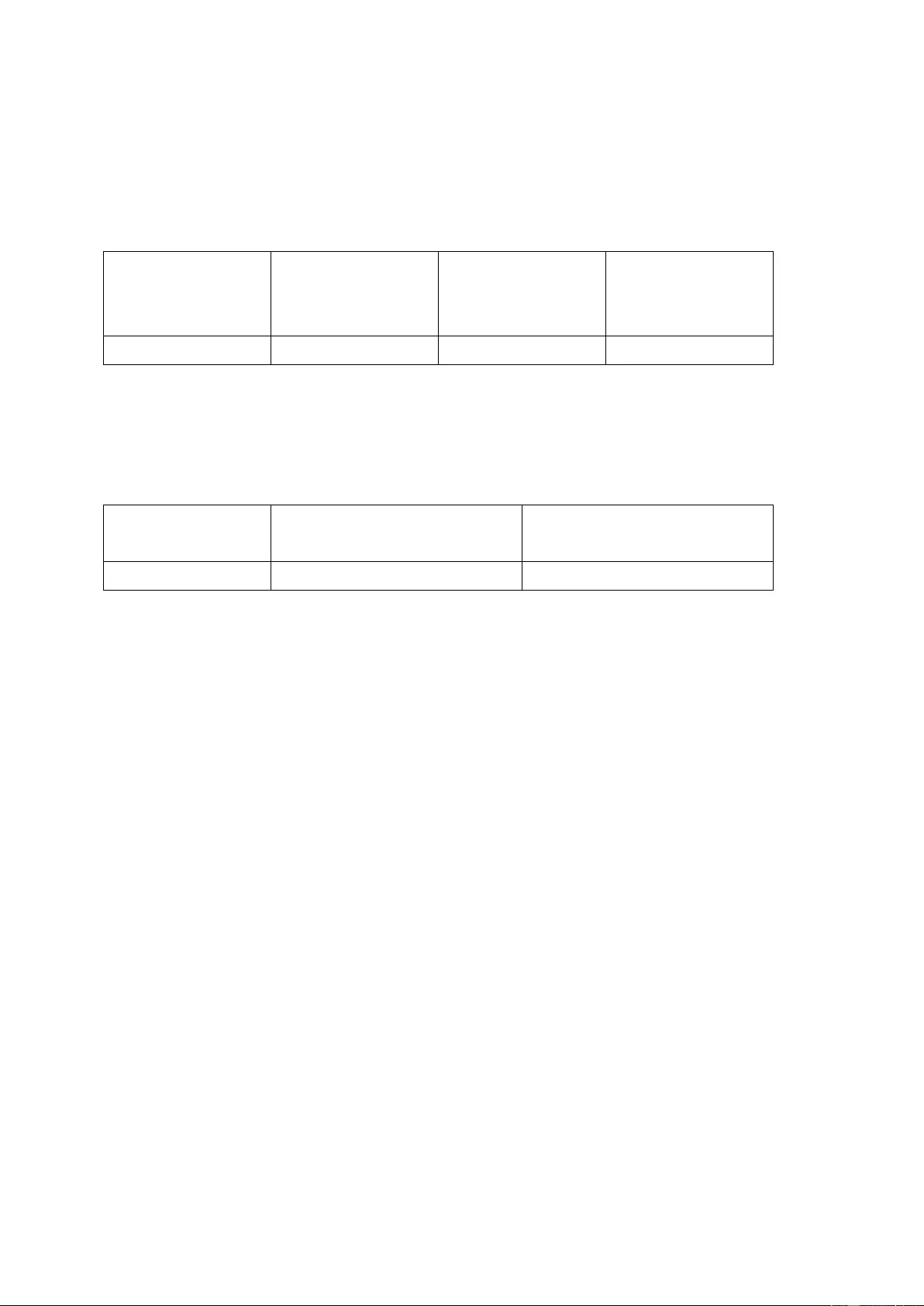
2.1 Power button
Power button: Press to turn on or turn off.
System Power button
(Turn on)
Power button
(Hardware turn
off)
Power button
(Force turn off)
All models Press once 1.5 sec 5 sec
2.2 Reset button
Reset button: Press to reset the system settings.
System Basic system reset
(1 beep)
Advanced syst e m reset
(2 beeps)
All models 3 sec 10 sec
Basic system reset (3 sec)
Press the reset button for 3 seconds, a beep sound will be heard. The following settings are
reset to default:
Sys tem administration password: admin
TCP/IP configuration: Obtain the IP address settings automatically via DHC P
TCP/IP configuration: Disable Jumbo Frame
TCP/IP configuration: If port trunking is ena bled (dua l LAN models only), the port
trunking mode will be reset to “Active Backup (F ailover)”.
System Port: 8080 (system service port)
Security Level: Low (Allow all con nections )
LCD panel password: (blank)
VLAN will be d isabled.
Service binding: All t he NAS services run on all ava ilable network interfaces.
Advanced system res et (10 sec)
Press the res et button for 10 seconds; you will hear two beeps at the third and the tenth
seconds. The NAS will reset all the system settings to def ault as it does by we b-based
system reset in “Control Panel” > “System Settings” > “Backup / Restore” > “Restore to
Factory Default” except all the data are reserved. The settings such as the users, user
groups, and the network share folders previously created will be cleared. T o retrieve the old
16
data after the adv anced system reset, create the same network sha r e f olders on th e NA S
and the data will be ac cessible again.
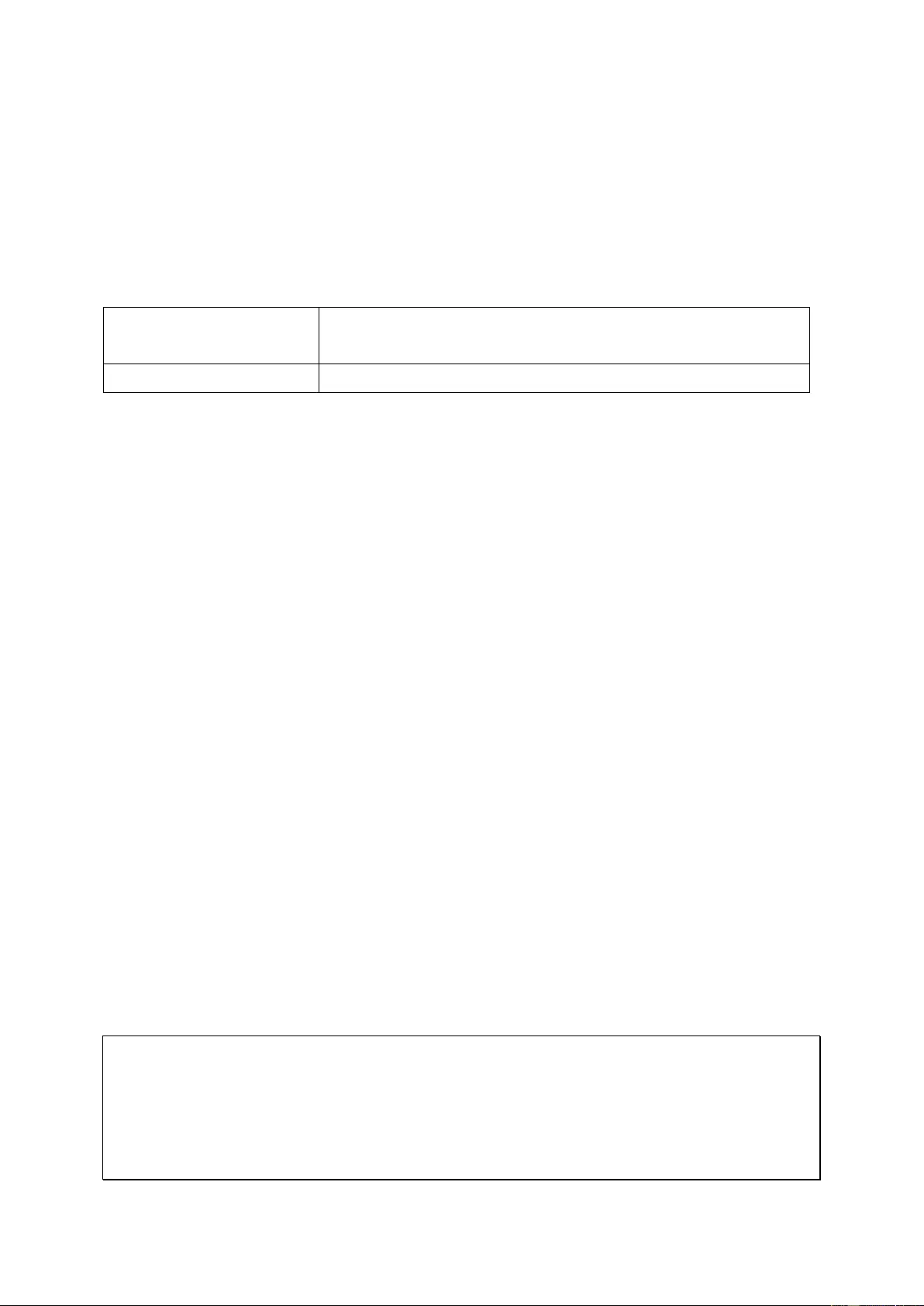
2.3 USB One Touch Copy
System Number of seconds (press the one touch copy button
to trigger data copy)
All NAS models 0.5 sec
Data Copy by the Front USB Port
The NAS supports instant data copy backup from the external USB device to the NAS or the
other w ay round by the fro nt one touc h co py butto n. To use this funct ion, f o llow the s te ps
below:
1. Make sure a drive is installed and formatted on the NAS. The default network share
Qusb or Usb is created.
2. Turn on the N AS.
3. Log into QTS as an administra tor.
4. Go to “Main Menu” > “Backup Station” > ”USB One Touch Co p y”.
5. Under One touch backup for external device, select USB One Touch Copy.
6. Configure the behavior of USB One Touch Copy.
7. Connect the USB storage device to the front USB port of the NAS.
8. Press the Copy button. The USB LED will flash. The data will be copied to or f rom the
USB device according to the NAS sett ings.
Note:
This feature adopts incremental backup. After the first time data backup, the NAS only
copies the changed files since the last backup.
This feature is only available on certain NAS models. Please refer to the product
specification table for details at w ww.qnap.com.
17
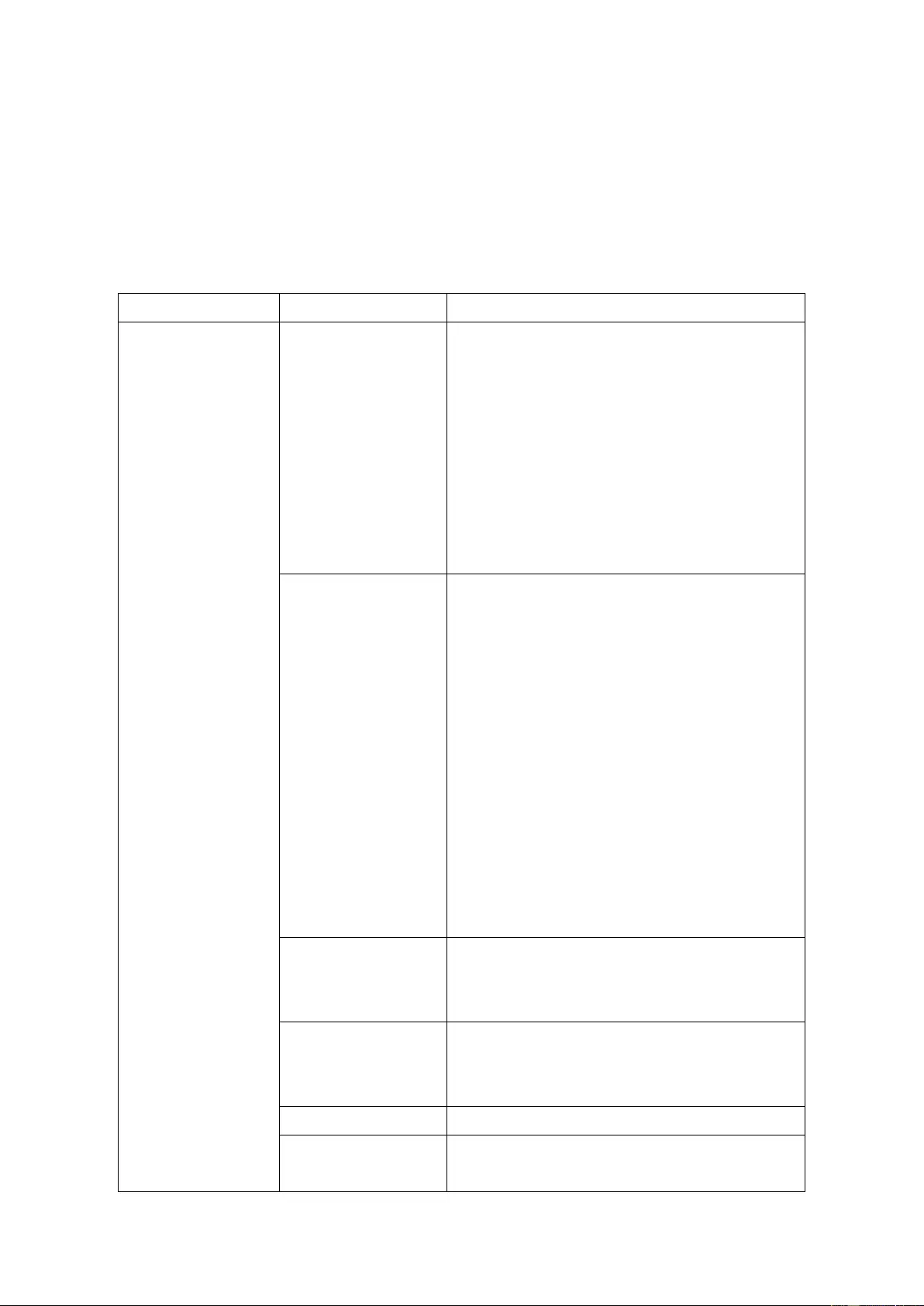
2.4 LED
The LED indicators of the NAS indicate the system status and information. When the NAS is
turned o n, c heck the following items to make sure t he system status is normal. Note that
the following LED information is applicable o nly when users have properly installed the
drive, and connected the N AS to the network and the power supply.
LED LED Status Description
Sys tem Status
Flashes green and
red alternately
every 0.5 sec
1. The hard drive on the NAS is being
formatted.
2. The NAS is being initialized.
3. The system firmware is being
updated.
4. RAID rebuild ing is in process.
5. Online RAID capacity expansion is in
process.
6. Online RAID le vel migration is in pro cess.
Red
1. The drive is invalid.
2. The disk volume has reached its full
capacity.
3. T he disk volume is going to be full.
4. The sys t em fan is out of functio n.
5. An error occurs when accessing
(read/write) the disk data.
6. A bad sector is detected on the drive.
7. The NAS is in degraded read-only mode
(2 member drives fail in a RAID 5 or RAID
6 configuration, the disk data can still be
read).
8. Hardware self-test error.
Flashes red every
0.5 sec
The NAS is in degraded mode (one member
drive fails in RAID 1, RAID 5 or RAID 6
configuration).
Flashes green
every 0.5 sec
1. The NAS is starting up.
2. The NAS is not conf igured.
3. A hard disk drive is not formatted.
Green The NAS is ready.
Deep flashes of
orange The NAS is in sleep mode.
18
Off All the drives on the NAS are in standby
mode.
LAN Orange
The disk data is being accessed from t he
network and a read / writ e er ro r oc cu rs
during the process.
Flashes orange The NAS is connected to the network.
HDD/SSD/M.2
SSD
Flashes red The NAS is being accessed from the
network.
Red A drive read/write error occurs.
Flashes green The disk data is being accessed.
Green The drive can be accessed.
USB
Flashes blue every
0.5 sec
1. A USB device (connected to the front USB
port) is being detected.
2. A USB device (connected to the front USB
port) is being removed from the NAS.
3. The USB device (connected to the front
USB port of the NAS) is being accessed.
The data is being copied to or from the
external USB device.
Blue A front USB dev ice is detecte d (after the
device is mounted).
Off
No USB device detected.
The NAS has finished copying the data to or
from the USB device connected to the front
USB port.
19
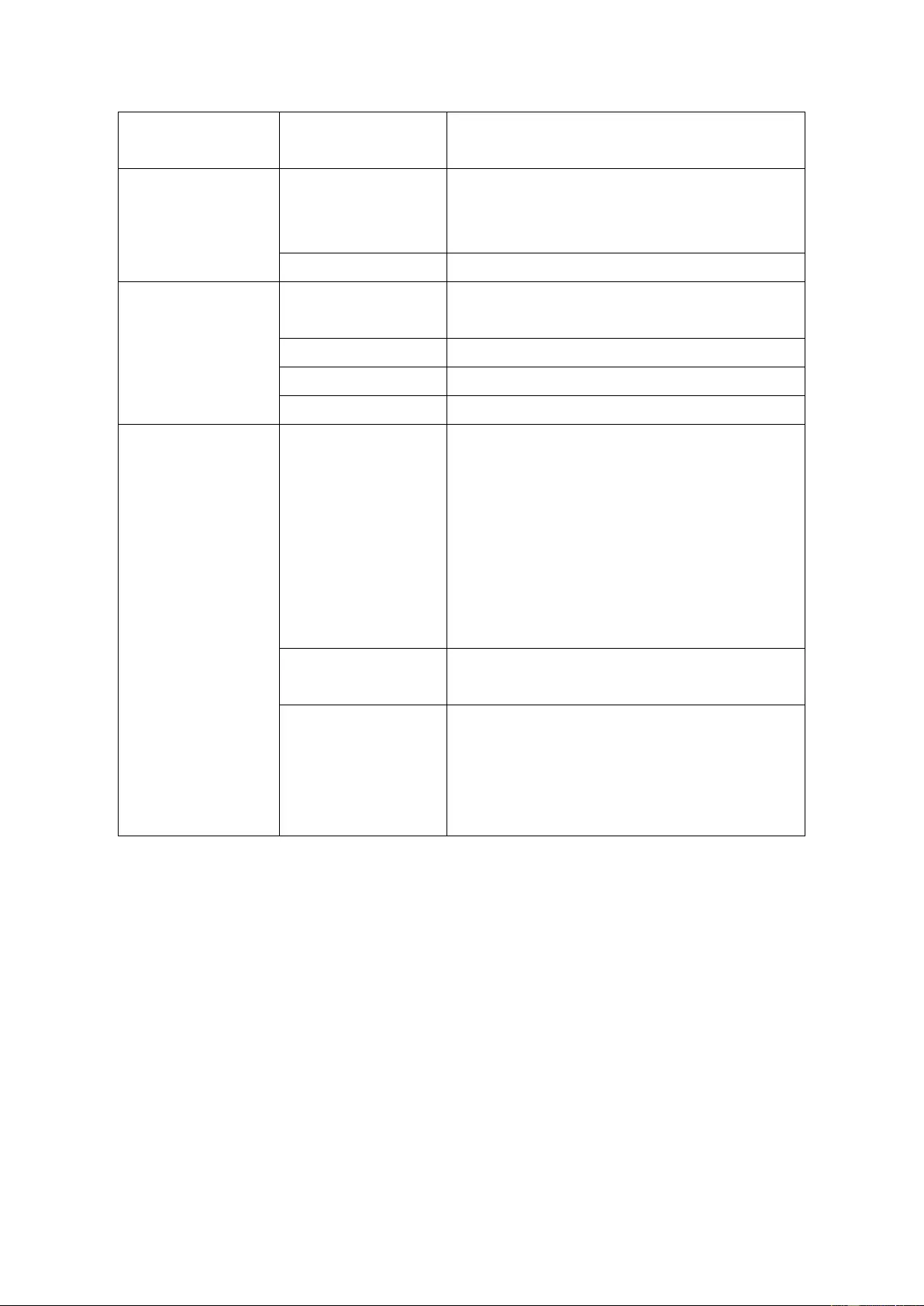
2.5 Beep Al ar m
The beep alarm can be disabled in “Control Panel” > “System Settings” > “Hardware”.
Beep sound Number of Times Description
Short beep (0.5 sec) 1
1. The N A S is starting up.
2. The NAS is being shut down
(software shutdow n).
3. The user presses the reset button to
reset the NAS.
4. The system firmware has been
updated.
Short beep (0.5 sec) 3 The NAS data cannot be copied to the
external storage device from the front
USB port.
Long beep (1.5 sec) 3, every 5 min The system fan is out of function.
Long beep (1.5 sec)
2
1. The disk volume is going to be full.
2. The d isk volume has rea ched its full
capacity.
3. The drives on the NAS are in
degraded mode.
4. The user starts the drive rebuilding
process.
5. A drive is plugged in or out.
1
1. The NAS is turned off by force
shutdown (hardware shutdown).
2. The NAS has been turned on and is
ready.

20
Chapter 3. Upgrade Memory on QNAP Turbo NAS (RAM Module
Installation)
Warning:
The following instructions s hould only be performed by an authorized or trained
technician.
Strictly adhere to the instructions in this section to install RAM modules in NAS. Failure
to do so could result in property damage, bodily harm or even death.
Before starting, please ensure that you turn off the NAS, disconne ct the power
adaptor, network cable(s), and also remove any other device/cable that is attached to
the NAS.
Please ensure that you wear an antistatic wrist strap during the entire process to
prev ent electrostatic disc harge. The crocod ile clip should be conne cted to the ground.
When installing more than one memory module, it is recommended t o u se the same
size and ideally the same type/model in every slot.
QNAP provid es RAM modules (optional purchase) for users to upgrade the NAS memory.
Follow the below steps to install an extra memory module on the NAS to upgrade the
memory.
The TS-1685 allows users to upgrade the memory in their QNAP NAS devices. Ensure that
the type of RAM is compatible with the NAS before installing.
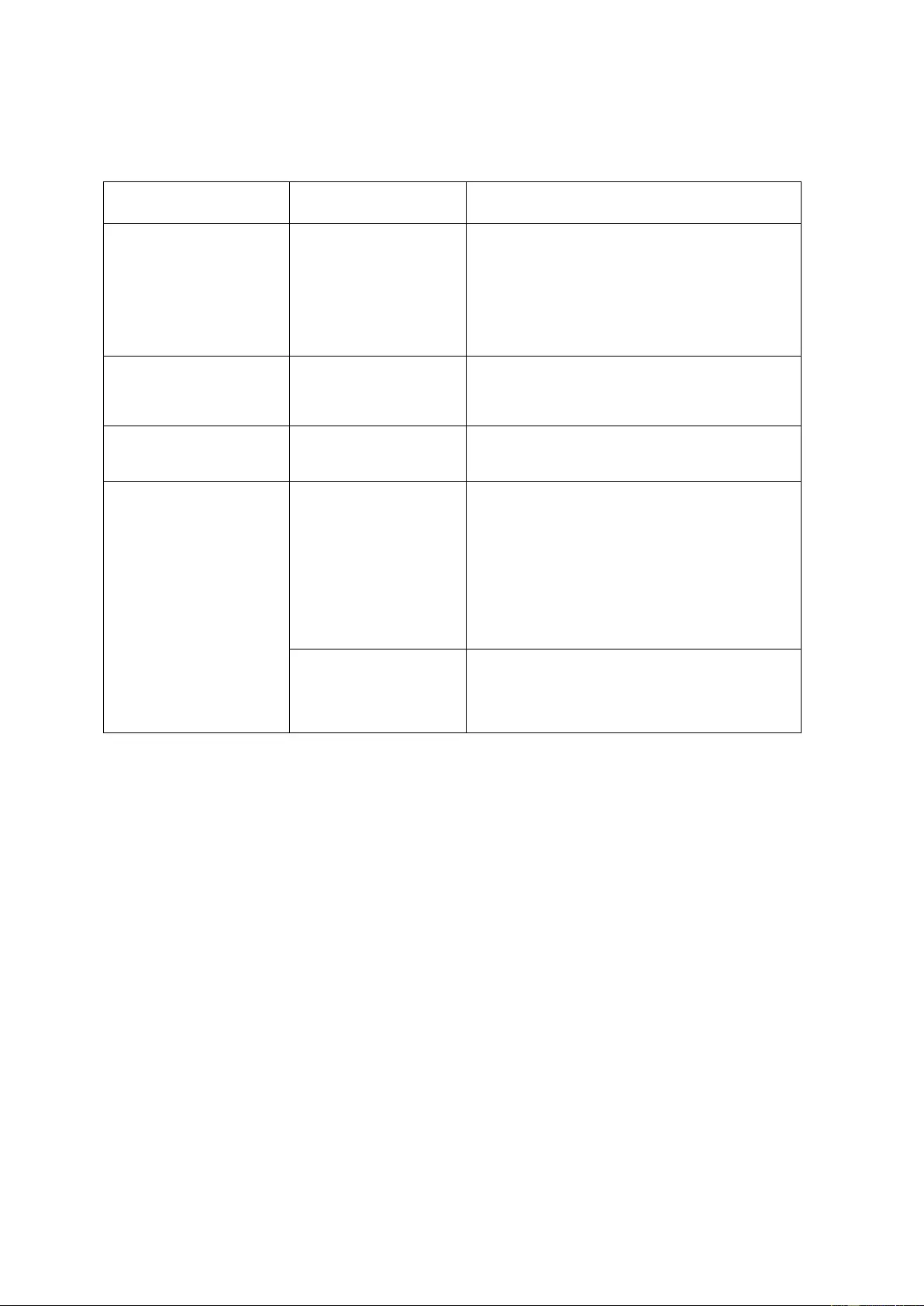
To determine how much memory is currently in the system:
1. Log into QTS as administrator.
2. Go to “Control Panel” > “System Settings” > “System Status” to open the System
Status window.
3. To go Sy s t em Info rma t ion and check for System memory or Total memory.
21
To install or replace RAM modules:
1. Power off the system by pressing the power button for 1.5 seconds or until the system
beeps once. Wait for all the LEDs on the front of the system to turn off.
2. Disconnect the power cord, network cables, and any other cables a ttached to the
device.
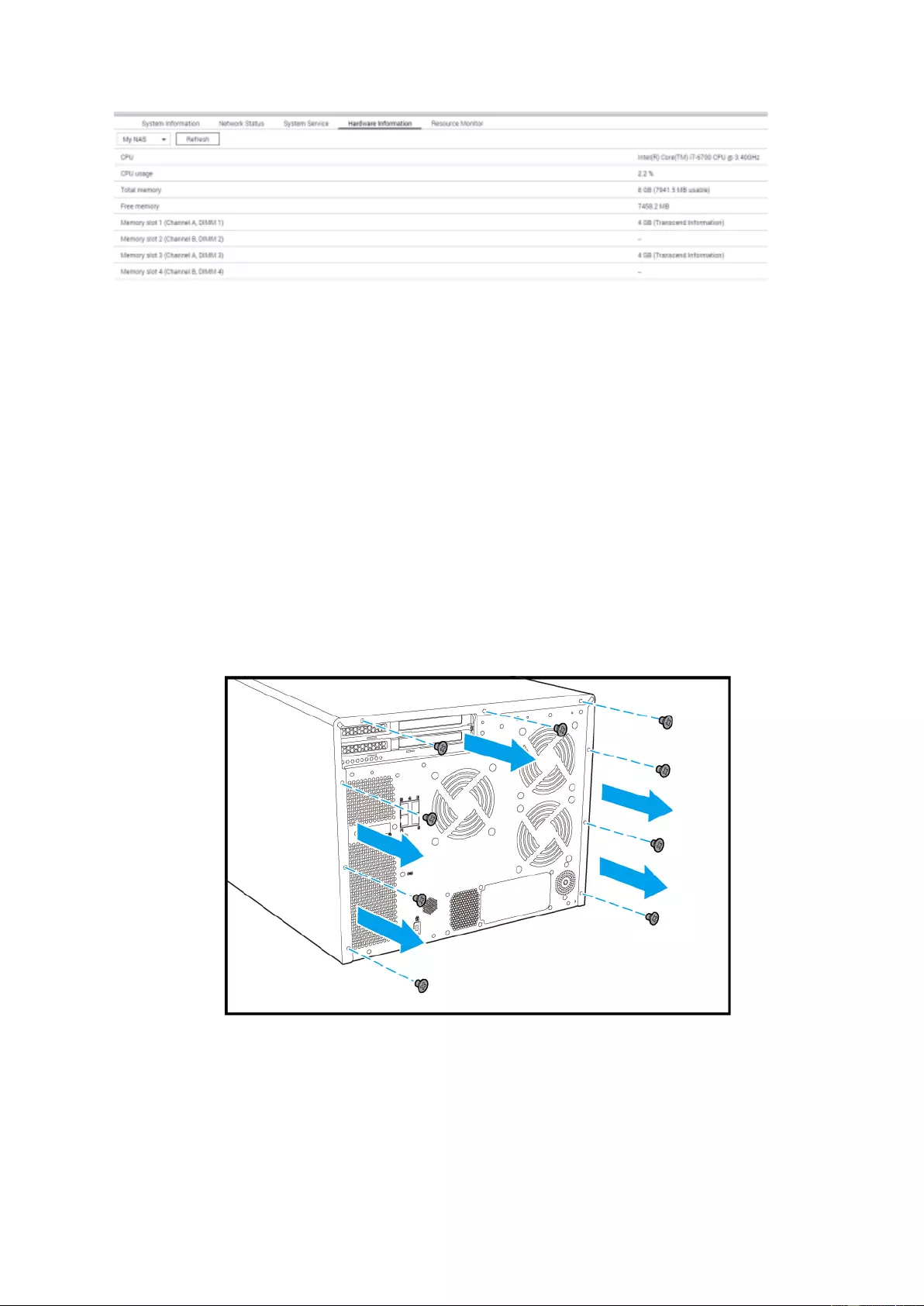
3. Before opening the NAS, wear an antistatic wrist strap and connect the crocodile clamp
to ground to prev ent electrostatic discharge from damaging equipment.
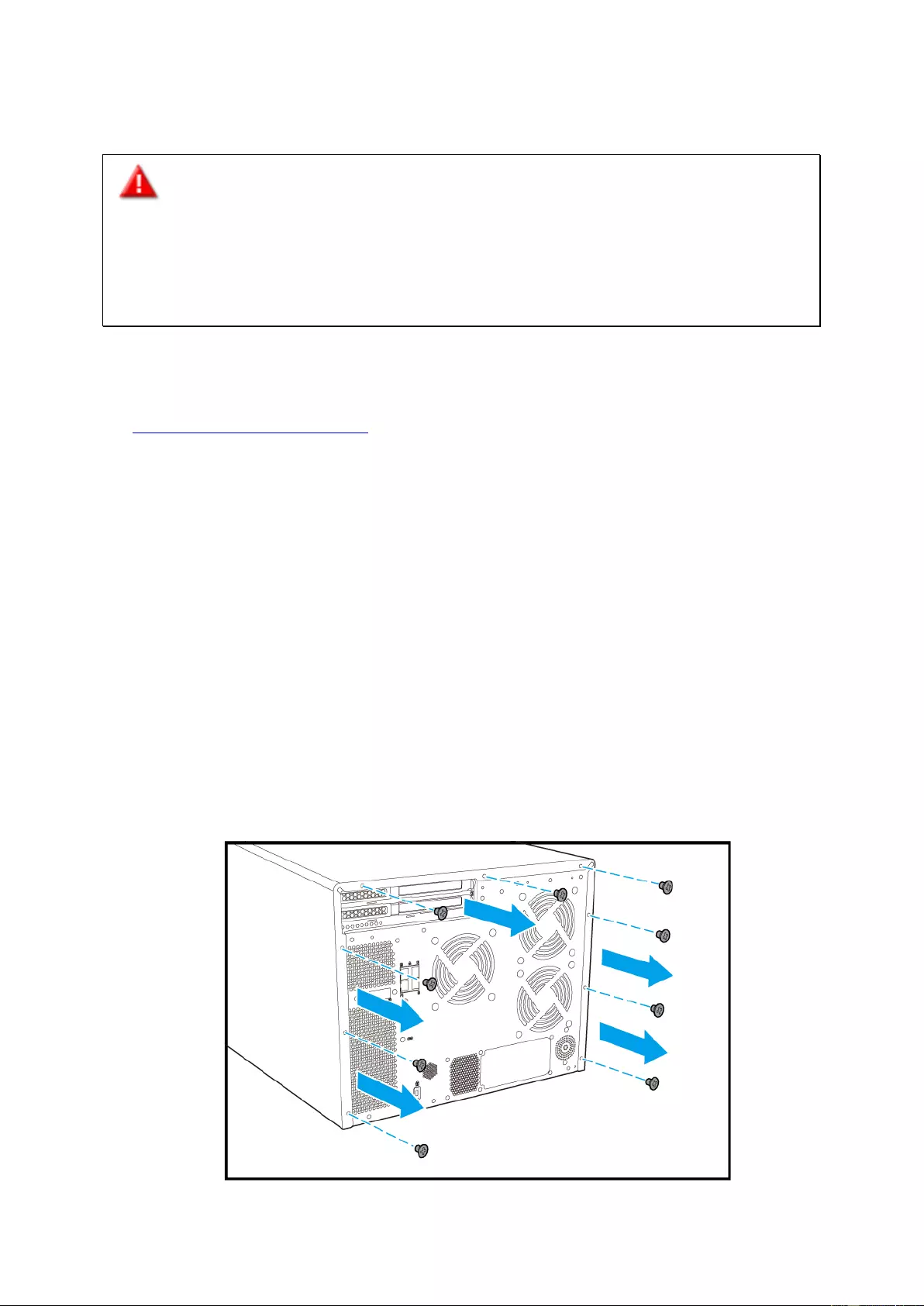
4. Remove the screws on the bac k of the NAS that are connecting the ca se cover to t he
chassis.
5. Gently remove case cover from case.
22
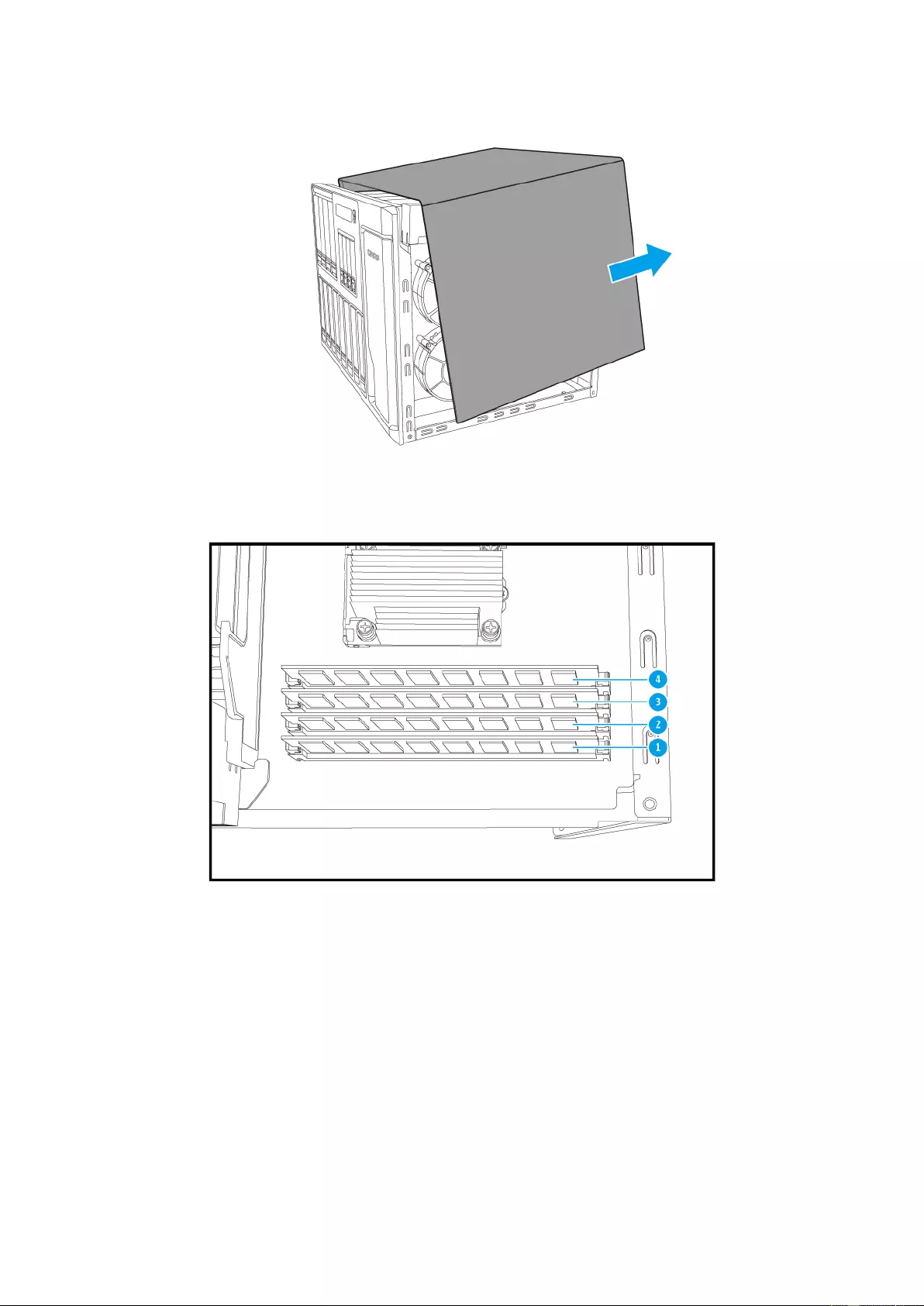
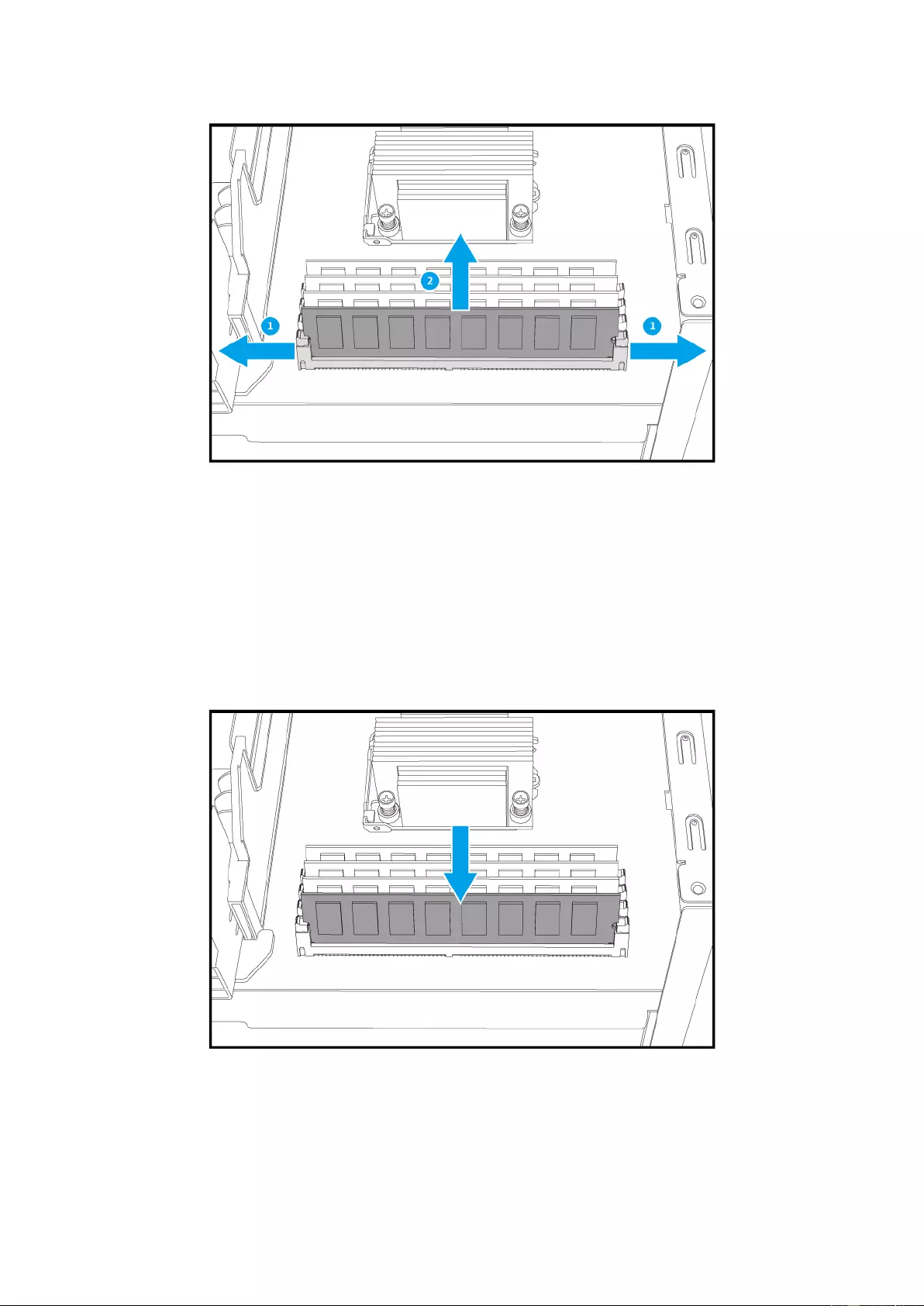
6. Unlock the RAM slot by pressing down on the retention clamps on the sides of the RAM
slot. If replacing RAM, remove existing module from socket.
23
7. Install new RAM:
i. Grip the ne w RAM on the edg es to avoid touching conta cts or circuitry on the
module.
ii. Line up the notch on the RAM to the break in the slot. Ensure that first RAM
module is inserted into slot 1 (see below for slot positioning).
iii. Set the stick into the slot and apply equal pressure onto both ends of the stick
until the clamps on the side click and fully lock the RAM in.
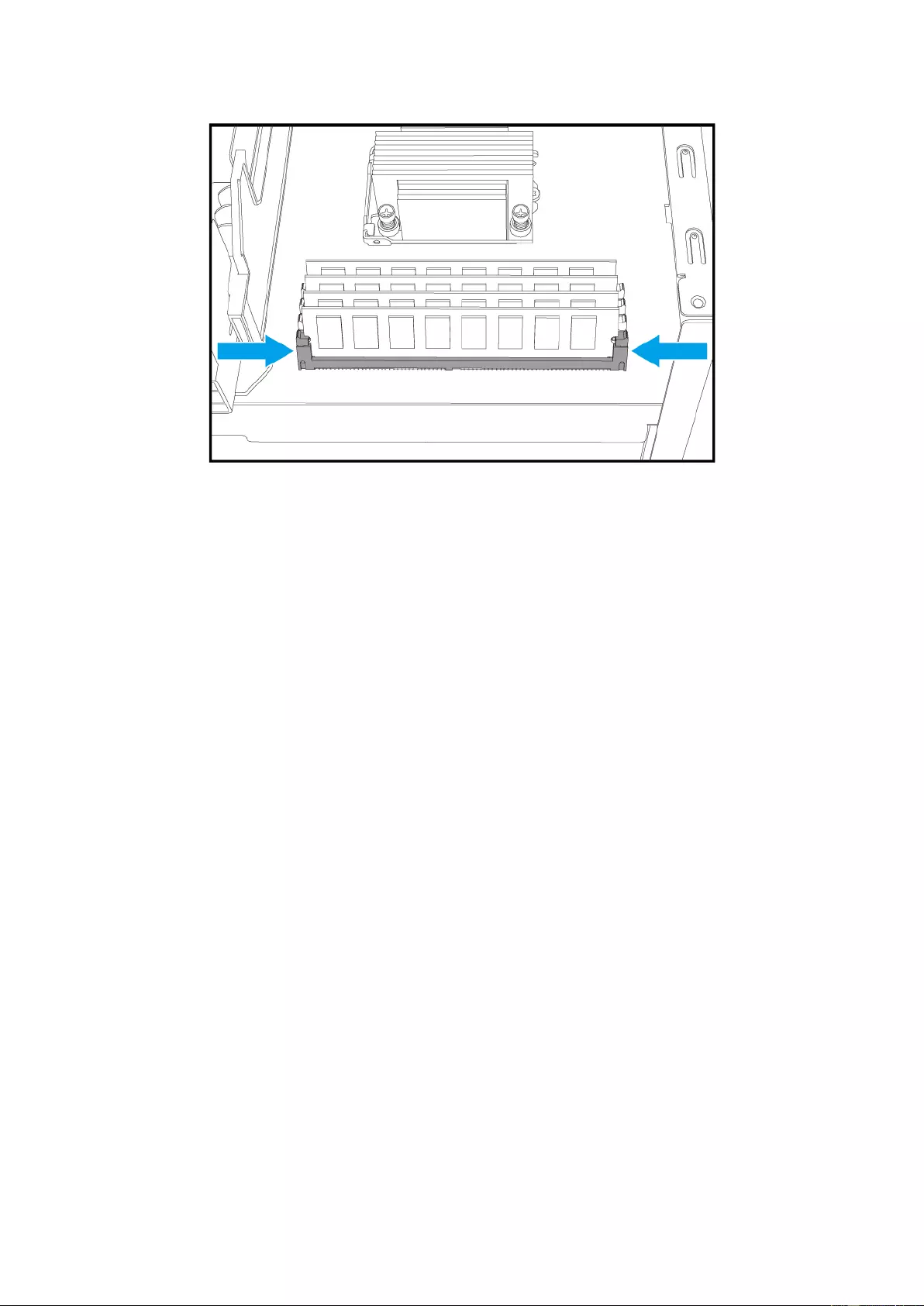
24
8. Close the case cover and fasten the screws.
9. Connect the power adaptor and cables to the NAS. Power on NAS.
10. Optional: Check tha t the memory has been correctly installed.
25
Chapter 4. Expansion Card Installation
Warning:
The following instructions s hould only be performed by an authorized or trained
technician.
Strictly adhe re to the instructions in this section to install PCIe a dd-in card(s) in NAS.
Failure to do so could result in property damage, bodily harm or even death.
The TS-1685 provides 2 low-profile & one full height PCIe expansion slots so that users can
add functionality to their NAS. Re fer to the compatibility list
at http://qnap.com/compatibility.
Follow the steps below to install a PCIe card:
1. P ower off the syste m by pressing the po wer butto n for 1.5 sec onds or until the s ystem
beeps once. Wait for all the LEDs on the front to turn off.
2. Disconnect the power cord, network cables, and any other cables a ttached to the
device.
3. Before opening the NAS , wear an antistatic wr ist str ap and connect the crocodile clamp
to ground to prev ent electrostatic discha rge from damaging equipment.
4. Remove the screws on the bac k of the NAS that are connecting the case cov er to the
chassis.
26
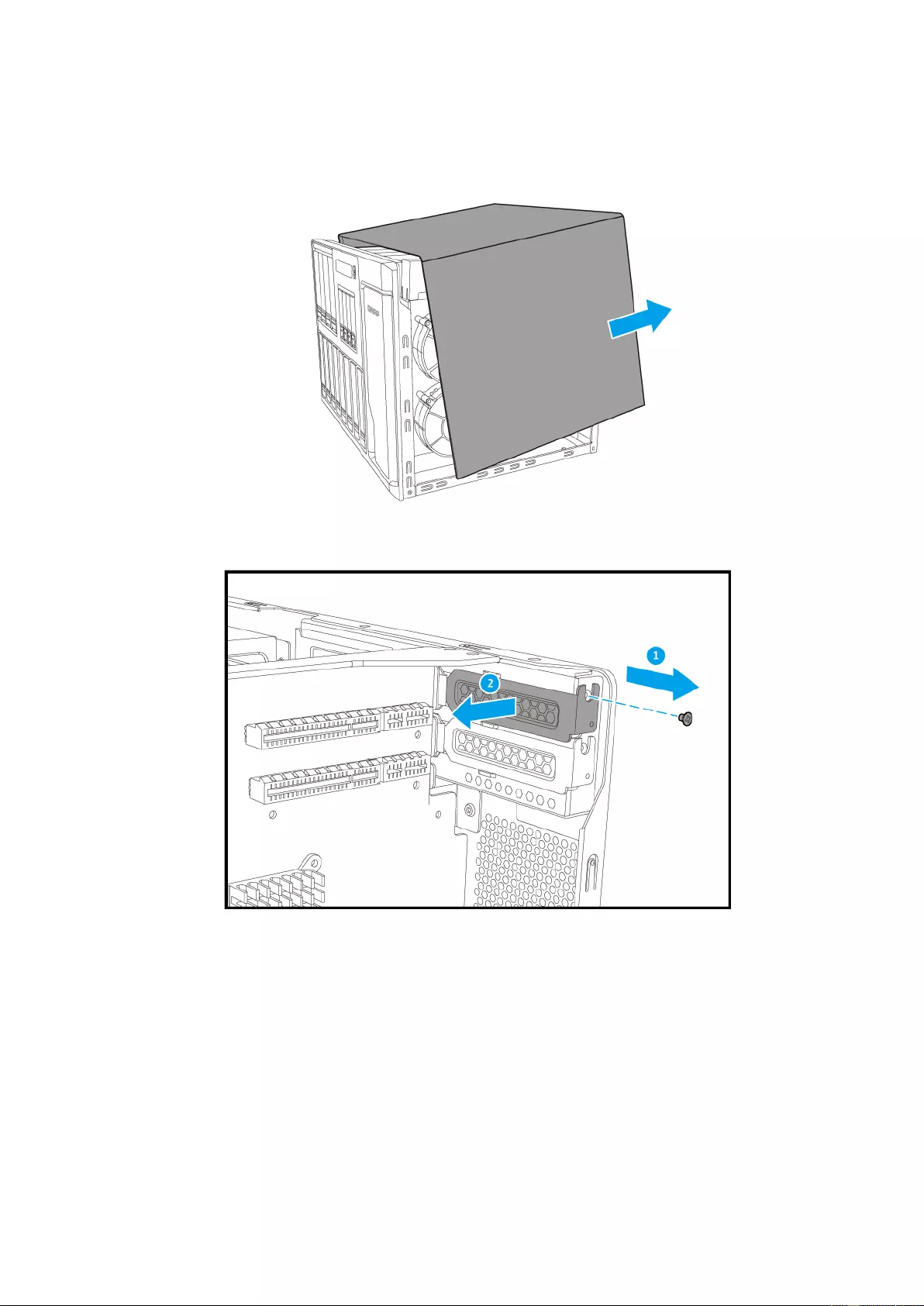
5. Gently remove case cover from case.
6. Remove the screw of the PCIe cover. Remove the cover.
27
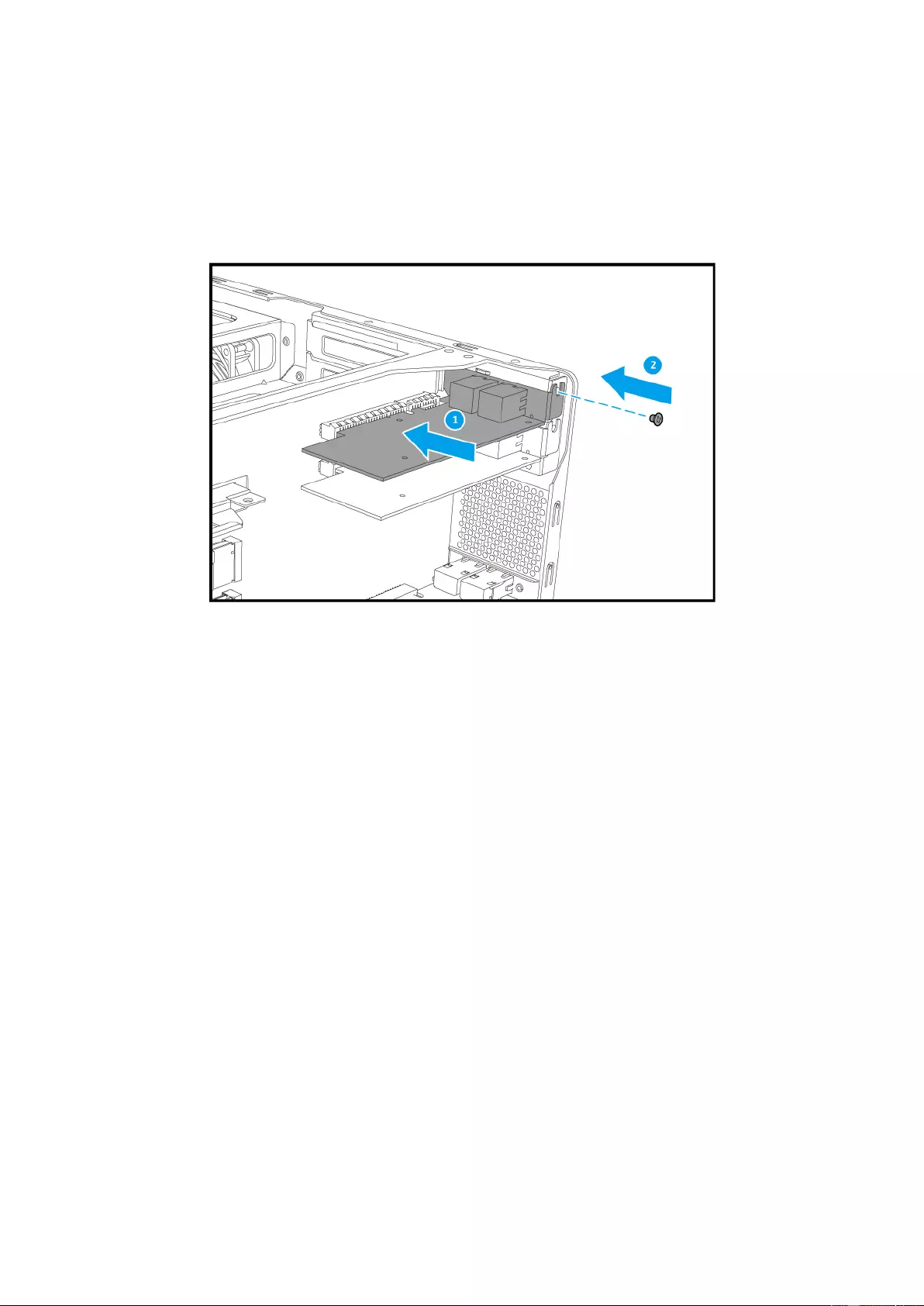
7. Hold the network expansion card by grasping the edges. Align the notch on the network
expansion card to the break in the PCIe slot. Fully insert the network expansion card to
the ex pansion slot.
8. Fasten screw to lock the card in.
9. Close the case cover and fasten the screws.
10. Connect the power adaptor and cables to the NAS.
Chapter 5. Install M.2 SSDs
5.1 M.2 SSD Heat Sink Installation
M.2 cooling modules are package d with the TS-1685. For reliable operation, it is
recommended that you install the M.2 cooling module on your M.2 SSD. You may also
install third party heatsinks on the SSD controller directly.
To install M.2 cooling module:
1. Disassemble the M.2 cooling module.
i. Slide the clip away from the tray.
ii. Separate the heatsink from the tray.
2. Peel off the blue protective film from the heatsink.
3. Ins ta ll the hea tsink onto the t op of the M.2 S SD.

28
i. Determine the top side of the M. 2 S S D by inserting it in the M.2 socket of your
NAS.
ii. Mount t he heatsink onto the top of the M.2 SSD.
Note: the figures below display the mounted heatsink locations for different sized M.2
SSDs.
4. Place the M.2 SSD/heatsink module onto the tray.
5. Optiona l: Install spacer in between the M.2 SSD and the tra y if the clip is too loose.
6. Insert the clip.
i. Gently squeeze the heatsink and the tray together, and inser t the clip at a
35-egree angle.
ii. Slide the clip in .
5.2 M.2 SSD Installation
Note: Do not attempt to bend or remove the orange temperature sensor near the M.2 SSD
socket.
To install M.2 SSD:
1. Power off the system by pressing the power button for 1.5 seconds or until the system
beeps o nce. Wait for all the LEDs on the front to turn off.
2. Disconnect the power cord, network cables, a nd an y other cables attached to the
device.
3. Before opening the NAS, wear an antistatic wrist strap and connect the crocodile clamp
to ground to prev ent electrostatic discha rge from damaging equipment.
4. Remove the screws on the back of the NAS that are connecting the case cover to the
chassis.
5. Gently remove case cover from case.
6. Remove the fan module.
i. Disconnect the fan cable from the system board.
29
ii. Remove t he screw connecting the fan module to the cha ssis.
iii. Press down the clip and remove fan module.
7. Install M.2 SSD.
i. Attach riser screw based on the M.2 SSD size
ii. Insert M.2 SSD into M.2 socket.
iii. Attach screw to riser to hold M.2 SSD in place.
8. Attach the fan module.
i. Insert fan module into chassis.
ii. Attach screw to fan module.
iii. Connect fan cable.
9. Close the case cover and fasten the screws.
10. Connect the power adaptor and cables to the NAS.
Chapter 6. Install and Hot-swap Drives
The TS-1685 is co mpatible with 2.5-inch/3.5-inch SATA drives. For drive compatibility list,
go to http://www.qnap.com/compatibility.
Caution:
QNAP is not responsible f or produc t damage/malfunction o r data los s due to misuse or
improper installation of hard disks.
Note when a drive is installed in a QNAP NAS for the first time, the drive will be
automatically formatted and all the data on disk will be cleared.
For information on QTS NAS migration, go to docs.qnap.com and check “Migr ating from
Old NAS” section.
5.1 Drive Bay Numbering
Identify the drive position in the diagram below.
5.2 Installing Drives
To install drives, follow the steps below:
30
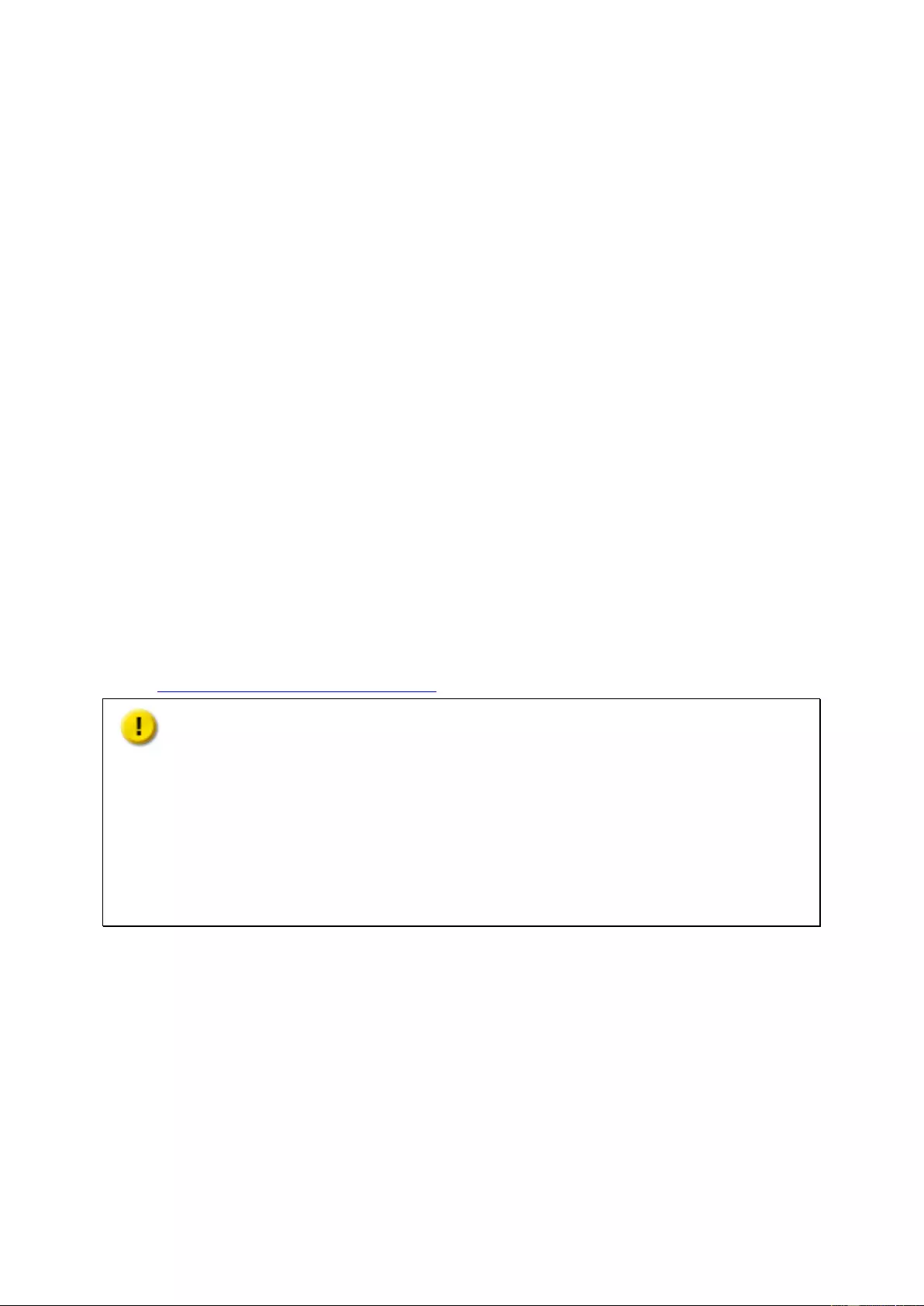
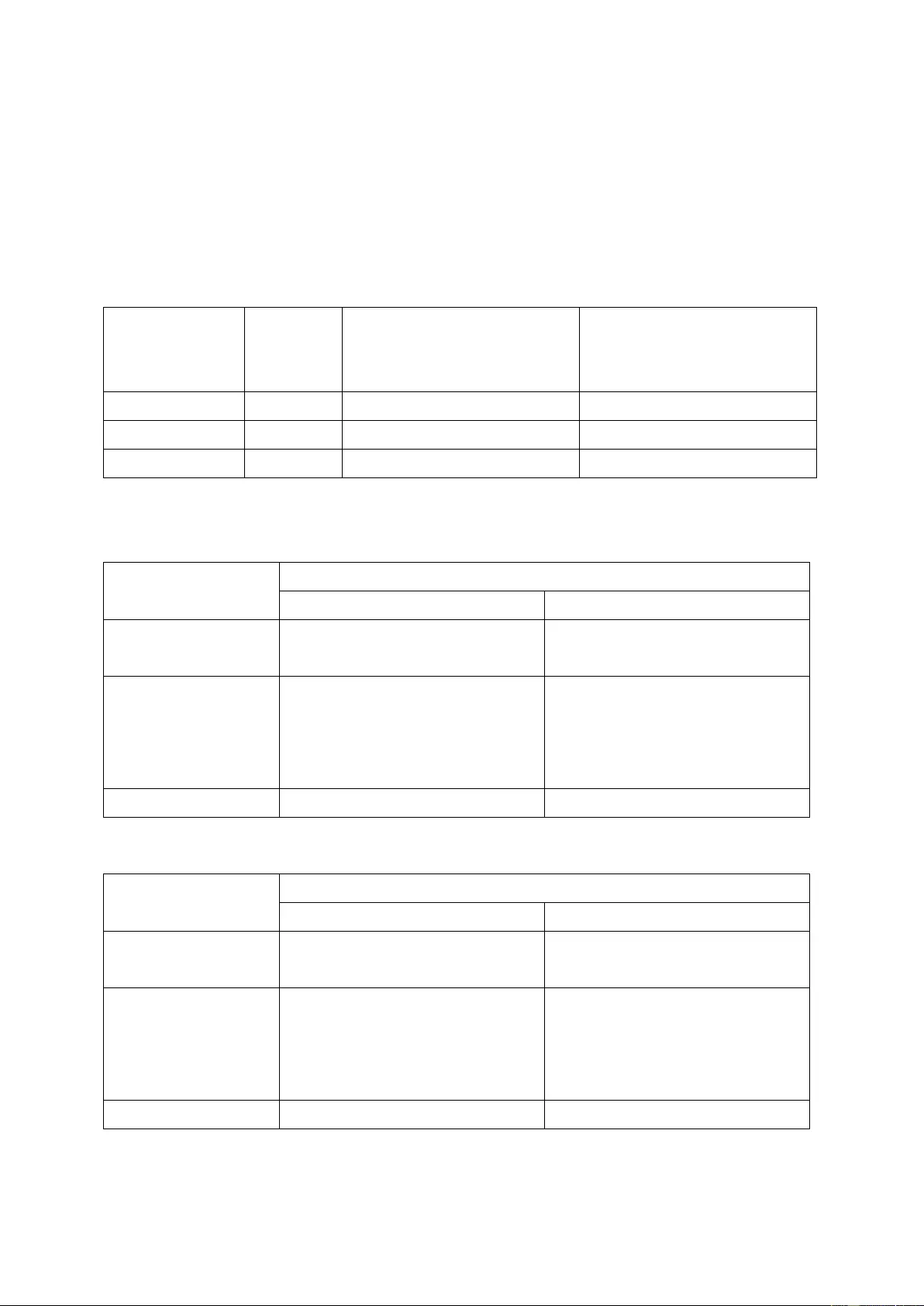
1. Remove drive tray from NAS:
a. Push the blue lock switch on the tray down to the unlock p osition.
b. Push t he button below the blue switch to release the lever.
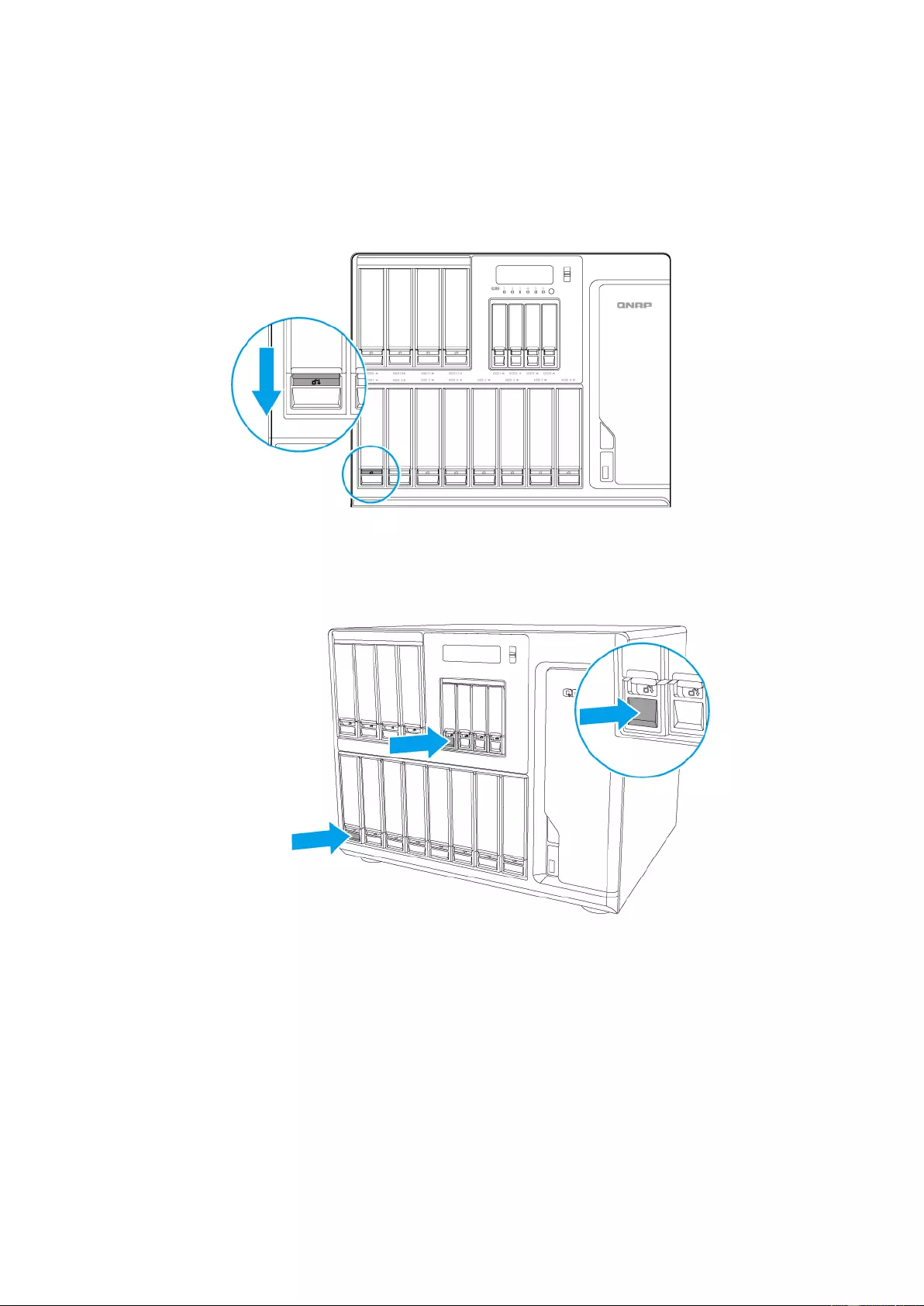
31
c. Pull out tray using lever.
2. Ins ta lling a drive on the tray.
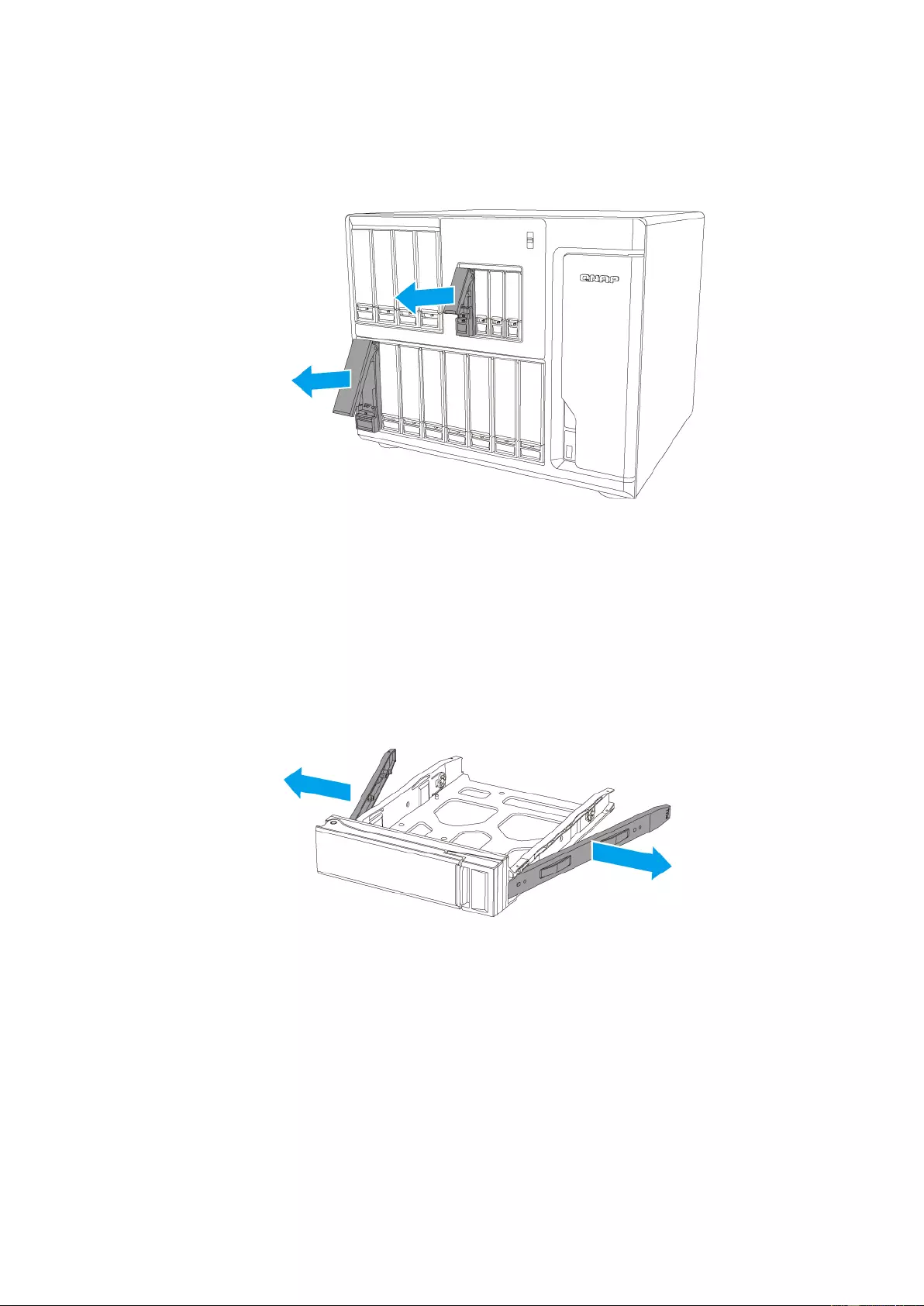
a. 3.5” HDD:
i. Remove the fastening panels from the sides of a 3.5” drive tray.
ii. Place the drive on the tray so that the holes on the sides of the drive are
aligned with the ho les on the sides of the tray.
iii. Attach the fastening panels to lock the drive to the tray.
Note: Screws may be inserted for increased stability.
32
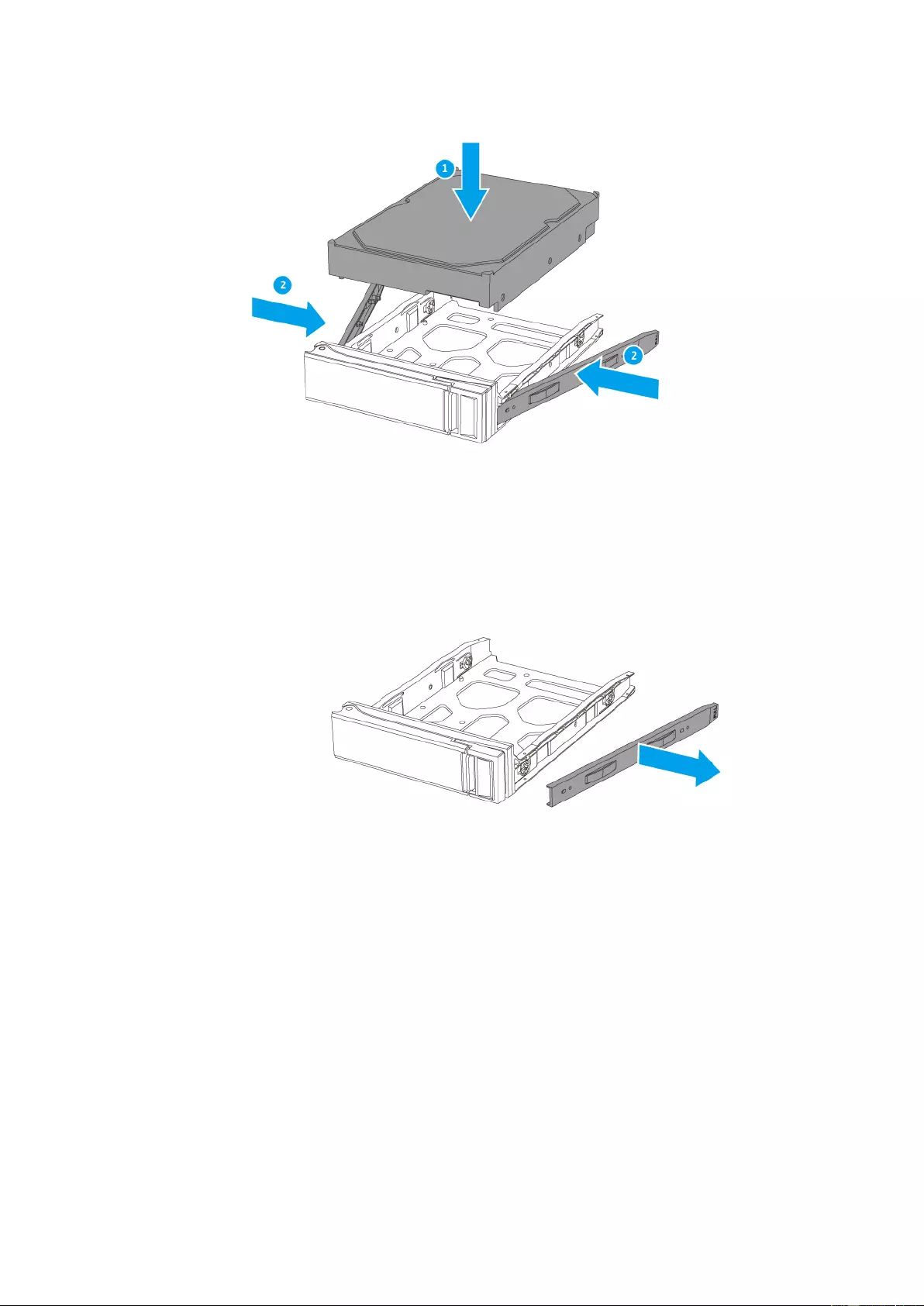
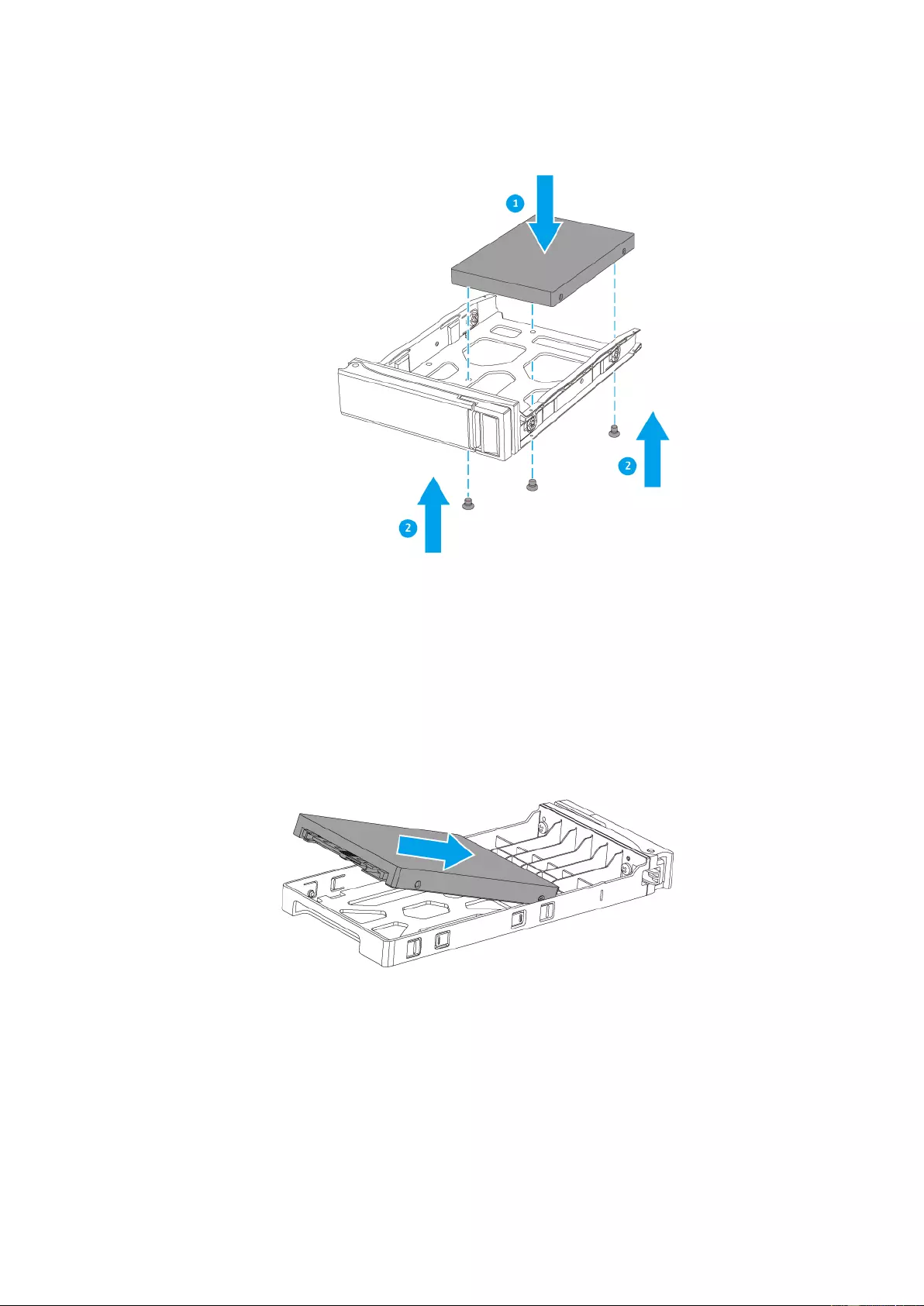
b. 2.5” HDD:
i. Remov e the right fastening panel from the 3.5” drive tray.
ii. Place the 2.5” drive on the tr ay so that the SA TA connector is f acing out and
that three holes on the bottom of the drive are aligned with three holes on
the bottom of the tray.
iii. Attach the screws to lock the drive to the tray.
33
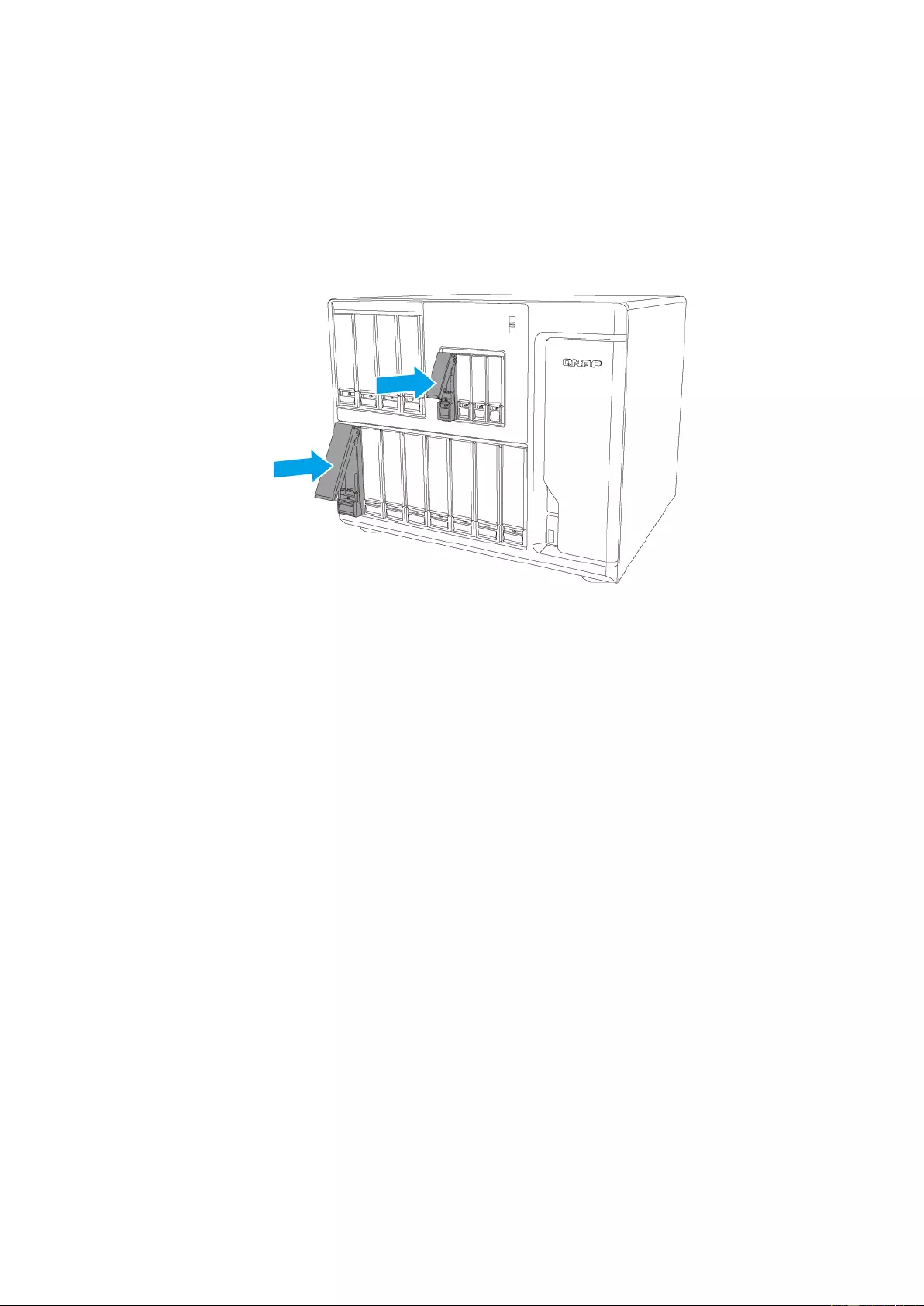
c. SSD:
i. Insert an SSD into an SSD tray so that SATA connector is perfectly aligned
with the opening at end of the tray.
OR
Insert an SSD into a 3.5” drive tray using the same method as in 2b.
34
3. Load tray back into drive bay.
i. Insert the drive tray into the NAS. Verify that the tray is correctly oriented (top of
HDD facing right) and fully pushed in.
ii. Close the latch, and lock the switch.
4. To verify that the drive has been correctly installed and recognized by the operating
system, log into QTS as administrato r and go to “Storage Manager” > “Storage ” >
“Disks/VJOB” and confirm the disk is in the System Component or NAS Host section.
5.3 RAID Recovery - Hot-Swapping Drives
The QNAP NAS supports hot-swapp ing drives. When one drive fails in RAID 1/5, up to two
drives fail in RAID 6/RAID 10*, replacing failed drives with a healthy ones will automatically
trigger QTS to rebuild the RAID. Follow the steps below to hot-swap drives when drive
failures occur in a RAID configuration. See section 6.2 for detailed instr uctions on how to
install a new drive.
* One drive each in the RAID 1 pair
Follow instructions below for hot-swapping:
1. Log into QTS as administrator and check the stora ge p ool status i n “Sto r age Ma nager”
> “Storage” > “Storage Space”. There will be a list of all available storage pools.

35
2. If one drive fails in RAID 1/5, up to two drives fail in RAID 6/RAID 10*, the storage pool
status will be labeled as “Degraded” and the Volume/RAID group status should be
labeled as “Warning”.
3. Go to “Storage Manager” > “Storage” > “Disks/VJBOD” to determine which disk needs
to be replace d .
4. Take out bad drive from NAS enclosure and remove the drive from the tray.
5. Install replacement drive onto tray.
Note: the capacity of the new drive must be equal to or greater than the capacity of the
old drive.
7. Insert tray with drive instal led into NAS.
Important: Wait for two beeps after removing the faulty drive before inserting
replacement drive into NAS. The NAS should also beep twice after replacement drive is
installed.
8. The volume should automat ically rebuild. Go to “Storage Manager” > “Storage ” >
“Storage Space” to confirm.
5.4 RAID Recovery - Accidental Removal of a Healthy Drive
The QNAP NAS supports RAID recovery when a healthy drive is unexpectedly removed from
a RAID 1/5/6 during hot-swapping or RAID 0/JBOD configuration in QTS. Note that RAID 10
does not support this feature.
When a healthy drive is unexpectedly removed from a RAID group, the status o f the RAID
will change to “Not ac tive”. To recover from an “Not active” status:
1. Re-insert all drives back into the NAS in its original order. This includes any bad drive(s)
that will need to be replaced after recovery.
2. Log into QTS as administrator and go to “Storage Manager” > “ St o rage ” > “Storage
Space”.
3. Double click on the affected Storage Pool to open the Storage Pool Management
window.
36
4. In the “St orag e Pool Management” window, click on the “Manage” button and select
“Recover”.
The process will take about 60 seconds for QTS to complete. When recovery is completed,
the RAID gro up should be restored to its initial status.
See char t below for RAID status during this process.
Initial
Status
Status After Healthy
Drive is Removed
Statu s After Driv e is
Re-Inserted and Storage
Pool is Recovered
RAID 0/JBOD Ready Not active Ready
RAID 1/5/6 Ready Degraded Rebuilding
RAID 1/5/6 Degraded Not active Degraded
The chart below describes the events of an error when using RAID 5.
RAID 5 (Minimum 3 Disks)
QTS Standard
One drive fails Degraded mode (may still read
and write).
Degraded mode (may still read
and write).
One drive fails
an d there are bad
sectors found in
the other drive(s)
Read only protect mode (for
immediate data b a ckup & drive
replacement).
RAID crash.
2 drives fail RAID crash. RAID crash.
The chart below describes the events of an error when using RAID 6.
RAID 6 (Minimum 4 Disks)
QTS Standard
One or two drives
drive fail
Degraded mode. (may still read
and write).
Degraded mode. (may still read
and write).
Two drives fail
an d there are bad
sectors found in
the other drive(s)
Read only protect mode (for
immediate data b a ckup & drive
replacement).
RAID crash.
3 drives fail RAID crash. RAID crash.
37
Chapter 7. Using the LCD Panel
The NAS provides a handy LCD panel for users to perform disk configuration and view the
system information.
When the NAS has started up, the server name and IP address w ill be shown.
N A S 5 F 4 D E 3
4 . 3 . 0 ( 2 0 1 7 0 2 1 4 )
After a few seconds, the panel will be automatically turned off. Then you can begin to
configure settings or view system information.
N A S 5 F 4 D E 3
1 6 9 . 2 5 4 . 1 0 0 . 1 0 0
Viewing and configuring system settings
When the name and firmware version of the NAS appear on the panel, press “ENTER” for
two seconds to view the Main Menu, which will automatically disappear if no further actions
are performed in ten seconds.
There are eight options on the Main Menu:
1. TCP/IP
2. Physical disk
3. Volume
4. System
5. Shut down
6. Reboot
7. Password
8. Back
1. TCP/IP
In TCP /IP, you can see the following information:
LAN1 IP Address
LAN1 Subnet Mask
LAN1 Gatewa y

38
LAN 1 PRI. DNS
LAN 1 SEC. DNS
(You can configure the above settings for every interface.)
Enter Network Settings
Network Settings – DHCP
Network Settings – Static IP*
Network Settings – BACK
Back to Main Menu
* In Network Settings – Static IP, users can configure the IP address, subnet mask,
gateway, and DNS of LAN 1 and LAN 2.
2. Phys ical disk
In Physical disk, you can see the f ollowing options:
Disk Info
Back to Main Menu
Disk info shows the temperature and the capacity of the drive.
D
i
s
k
:
1
T
e
m
p
:
5
0
°
C
S
i
z
e
:
2
3
2
G
B
3. Volume
This section shows the capacities of volumes and L UNs. You can view the name and
capacity of a volume/LUN. If there are multiple volumes/LUNs, press "Select" to view
the information of a s pecific volume/LUN .
D
a
t
a
V
o
l
1
7
5
0
G
B
L
U
N
_
0
7
5
0
G
B
4. System
This sec tion shows the syste m temperature and the ro tation speed of the syste m fan.
C
P
U
T
e
m
p
:
5
0
°
C
S
y
s
T
e
m
p
:
5
5
°
C
S
y
s
F
a
n
:
8
6
5
R
P
M
39
5. Shut down
You can use this option to turn off the NAS. Press "SELECT", select "Yes", and then
press "ENTER" to confirm.
6. Reboot
You can use this option to restart the NAS. Press "SELECT", select "Yes", and pre ss
"ENTER" to confirm.
7. Password
The default password for the LCD panel is empty. If you want to change the password,
select "Yes" to continue..
C
h
a
n
g
e
P
a
s
s
w
o
r
d
Y
e
s
→
N
o
You can enter up to 8 digits for your password.
Press “SELEC T” to increment the digit and press “ENTER” to add a new digit.
After inputting your desired password, press “ENTER”.
When the cursor moves next to "OK", press “ENTER” to confirm the password.
N
e
w
P
a
s
s
w
o
r
d
:
2
3
4
→
O
K
V
e
r
i
f
Y
P
a
s
s
w
o
r
d
:
2
3
4
→
O
K
8. Back
Select this option to return to the main menu.
40
System Messages
When an error occurs, a message will appear on the LCD panel. Press “ENTER” to view the
message and press “ENTER” again to go to the next message.
S
y
s
t
e
m
E
r
r
o
r
!
P
l
s
.
C
h
e
c
k
L
o
g
s
System Message Description
Sys. Fan Failed The system fan fails
Sys. Ov erheat The system is overheating
HDD Ov erheat The drive is overheating
CPU Overheat The CPU is overheating
Network Lost Both LAN 1 and LAN 2 are disconnected in failover or
load-balancing mode
LAN1 Lost LAN 1 is disconnected
LAN2 Lost LAN 2 is disconnected
HDD Failure The drive failed
Vol1 Full The volume is f ull
HDD Ejected The drive is ejected
RX#3 HDD Ejected A drive has been ejected from th e expansion unit 3.
M.2 SSD Ejected A M.2 SSD has been ejected a nd may be defectiv e as
hot-plugging is not supported for M.2 drives.
PCIe SSD Ejected A PCIe SSD has been ejected and may be defective as
hot-plugging is not supported for PCIe devices/
Vol1 Degraded The volume is in degraded mode
Vol1 Unmounted The volume is unmounted
Vol1 Nonactivate The volume is not activated
System Startup
S
Y
S
T
E
M
B
O
O
T
I
N
G
>
>
>
There are several phases in the system startup process:
• System Booting: BIOS and hardware initialization, and system booting (no
actions need to be performed)
• Loading Driver: Loading QTS and its drivers (no actions need to be performed)
• Mount Volume: Pr ep a r e volumes (n o a c tions need to be performed)
• Starting Service: Starting NAS system services (no actions need to be

41
performed). Note that applications start only after the system finishes booting
For TS-1685, the LCD panel displays additional booting information after you power on the
NAS:
B
I
O
S
X
X
X
X
X
X
X
C
h
e
c
k
i
n
g
M
e
m
o
r
y
• BIOS XXXXXX – XXXXXX is the BIOS version, which can be used for technical
support to help identify and resolve issues.
• Startup phases:
o Checking Memory – The system checks t h e installed mem ory.
o P owering up all disks – Power up all disks sequentially.
o Hardware initialization – Initialize additional hardware components, such as
PCIe SSD, Graphic card, Thunderbolt adapter, etc.
o Booting - Boot from the DOM. If the startup stops at this step, the DOM may
be defective. Please seek technical support.
o Starting System – Starting QTS. If the startup stops at this step, the QTS
installation may have encountered problems. Please seek technical support.
• The remaining startup phases are the same as those of other NAS models

43
GNU GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright © 2007 Free Software Foundation, Inc. <http://fsf.org/>
Eve ryone is permitted to copy and distr ibute verbatim co pies of this license docume nt, but
changing it is not allowed.
Preamble
The GNU General Public License is a free, copyleft license for software and other kinds of
works.
The licenses for most software and other practical works are designed to take away your
freedom to share and change the works. By contrast, the GNU General Public License is
intended to guarantee your freedom to s hare and change all versions of a program--to
make sure it remains free software for all its users. W e, the Free Software Foundation, use
the GNU General Public License for most of our software; it applies also to any other work
released this way by its authors. You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public
Licenses are designed to make sure that you have the freedom to distribute copies of free
software (and charge for them if you wish), that you receive source code or can get it if you
want it, that you can change the software or use pieces of it in new free programs, and that
you know you can do these things.
To protect your rights, we need to prevent others from denying you these rights or asking
you to surrender the rights. Therefore, you have certain responsibilities if you distribute
copies of the software, or if you modify it: responsibilities to respect the freedom of others.
For example, if you distribute copies of such a program, whether gratis or for a fee, you
must pass on to the recipients the s ame freedoms that yo u received. You must make sure
that they, too, receive or can get the source code. And you must show them these terms so
they know their rights.
Developers that use the GNU GPL protect your rights with two steps: (1) assert cop yr ight
on the software, and (2) o ffer you this License giving you legal permission to copy,
distribute and/or modify it.

44
For the developers' and authors' protection, the GPL clear ly explains that there is no
war ranty for this free software. Fo r both users' and authors' sake, the GP L requires that
modified v ersions be marked as changed, so that their problems will not be a t tributed
erroneously to authors of previous versions.
Some devices are designed to deny users access to install or run modified versions of the
software inside them, although the manufacturer can do so. This is f undamentally
incompatible w ith the aim of protecting users ' freedom to change the software. The
systematic pattern of such abuse occurs in the area of products for individuals to use, which
is precisely where it is most unacceptable. Therefore, we have designed this version of the
GPL to prohibit the practice for those products. If such problems arise substantially in other
domains, we stand ready to extend this provision to those domains in future versions of the
GPL, as needed to protect the freedom of users.
Finally, every program is threatened constantly by software patents. State s should not
allow patents to restrict development and use of software on general-purpose compute rs,
but in those that do, we wish to avoid the special danger that patents applied to a free
program could make it effectively proprietary . To prevent this, the GPL assures that patents
cannot be used to render the program non-free.
The precise terms and conditions for copying, distr ibut ion and modificat i on follow.
TERMS AND CONDITIONS
0. Definitions.
“This License” refers to version 3 of the GNU General Public License.
“Copyright” also m eans cop yri g h t-like laws tha t a p ply to other kinds of works, such as
semiconductor masks.
“The Program” refers to any copyrightable work licensed under this License. Each licensee
is addressed as “you”. “Licensees” and “recipients” may be individuals or organizations.
T o “modify” a work means to copy from or adapt all or part of the work in a fashion requiring
copyright per mission, othe r than the m aking of an e xact copy. The resulting wor k is called
a “modified version” of the earlier work or a work “based on” the earlier work.
A “covered work” means either the unmodified Program or a work based on the Program.

45
To “propagate” a work mea ns to do anything with it that, without per mission, would mak e
you directly or secondarily liable for infringement under applicable copyright law, e xcept
exe cuting it on a computer or modifying a private copy. Propagation includes copying,
distribution (with or without modification), making available to the p ublic, and in some
countries other activities as well.
To “c onvey” a work means any kind of propagation that enables other parties to make or
receive copies. Mere interaction with a user through a computer network, with no transfer
of a copy, is not conveying.
An interactive user interface displays “Appropriate Legal Notices” to the extent that it
includes a convenient and prominently visible feature that (1) displays an appropriate
copyright notice, and (2) tells the user that there is no warranty for the work (except to the
exte nt that w arranties are provided), that licensees may convey the work under this
License, and how to view a copy of this License. If the interface presents a list of user
comm ands or options, such a s a menu, a prominent item in the list meets t his criterion.
1. Source Code.
The “source code” for a work means the preferred form of the work for making
modifications to it. “Object code” means any non-source form of a work.
A “Standard I nterface” means an interface that either is an official standard defined by a
recognized standards body, or, in the case of interfaces specified for a particular
programming language, one that is widely used among developers working in that
language.
The “System Libraries” of an executable work include anything, other than the work as a
whole, that (a) is include d in the nor mal form of packa ging a Major Compone nt, but which
is not part of that Major Component, and (b) serves only to enable use of the work with that
Major Com ponent, or to implement a Standard Interf ace for which an implementation is
a v ailab le to t he p ublic in source code form. A “Major Component”, in this context, means a
major essential component (kernel, window system, and so on) of the specific operating
system (if any) on which the executable work runs, or a compiler used to produce the work,
or an object code interpreter used to run it.
The “Corresponding Source” for a work in object code form means all the source code
needed to generate, install, and (for an executable work) run the object code and to modify

46
the work, including scripts to control those ac tivities . However, it does not include the
work's System Libraries, or general-purpose tools or generally available free programs
which are used unmodified in performing those activities but which are not part of the work.
For exampl e, Co rresp ond ing Source includes interf ace definition files associated with
source files for the work, and the source code for shared libraries and dynamically linked
subprograms that the work is specifically designed to require , such as by intimate data
comm unication or control flow between those subprograms and other parts of the work.
The Corresponding Source need not include anything that users can regenerate
automatical ly f rom other parts of the Corresponding Source.
The Corresponding Source for a work in source code form is that same work.
2. Basic Permissions.
All rights gr anted under th is License are gr anted for the term of copyright o n the Progr am,
and are irrevocable provided the stated conditions are met. This License explicitly affirms
your unlimited permission t o run the un m odified Program. The output fr om running a
cove red work is cover e d by this License only if the output, giv e n its content, constitutes a
covered work. This License acknowledges your rights of fair use or other equivalent, as
provided b y copyright law.
You m ay make, run and propa gate covered works that y ou do not convey, without
conditions so long as your lice nse otherwise remains in force. You may convey cove red
works to others for the sole purpose of having them make modifications exclusively for you,
or pro vide you with fac ilities for running those works, provided that you comply with the
terms of this License in conveying all material for which you do not control copyright. Those
thus making or running the covered works for you must do so exclusively on your behalf,
under your direction and c ontrol, on terms that prohibit them f rom making any copies of
yo ur copyrighted material outside their relationship with you.
Conveying under any other circumstances is permitted solely under the conditions stated
below. Sublicensing is not allowed; section 10 makes it unnecessary.
3. Protec ting Users' Legal Rights From Anti-Circumvention Law.
No covered work shall be deemed part of an effective technological measure under any
applicable law fulfilling obligations under article 11 of the WIPO copyright treaty adopted on
20 December 1996, or simila r laws prohibiting or restricting circumven tion of such
measures.

47
When you convey a covered work, you waive any legal power to forbid circumvention of
technological measures to the extent such circumvention is effected by exercising rights
under this License with respect to the covered work, and you disclaim any intention to limit
operation or modification of the work as a means of enforcing, against the work's users,
your or third parties' legal rights to forbid circumvention of technological measures.
4. Conveying Ve rbatim Copies.
You may convey verbatim copies of the Program's source code as you receive it, in any
medium, pro vided that you conspicuously and appropriately publish on each copy an
appropriate copyright notice; keep intact all notices stating that this License and any
non-permissive terms added in accord with section 7 apply to the code; keep intact all
notices of the absence of any warranty; and give a ll recipients a copy of this Licens e along
with the Program.
You may charge any price or no price for each copy that you convey, and you may offer
support or warranty protection for a fee.
5. Conveying Modified Source Versions.
You may convey a work based on the Pro gr am, or the modifications to pro duce it fro m the
Program, in the form of source code under the terms of section 4, provided that you also
meet all of these conditions:
a) The work must carry prominent notices stating that you modified it, and giving a
relevant date.
b) The wor k must carry prominent no tices s tating that it is re leased under this License and
any conditions added under section 7. This requirement modifies the requirement in
section 4 to “keep intact all notices”.
c) You must license the entire work, as a whole, under this License to anyone who comes
into posses sion of a copy. This License will therefore apply, along with any ap pl icable
section 7 a d ditional terms, to the whole of the work, and all its parts, regardless of how
they are packaged . This Lice nse give s no permiss ion to licens e the work in any other w ay,
but it does no t invalidate such permission if you have separately received it.
d) If the work has inter active user interfaces, each must display Appropriate Legal Notices;
howev er, if the Program has interactiv e interfaces that do not display Appropriate Legal
Notices, your work need not make them do so.
A compilation of a covered work with other separate and independent works, which are not
by their nature extensions of the covered work, and which are not combined with it such as

48
to form a larger program, in or on a volume of a storage or distribution medium, is called an
“aggregate” if the compilation and its resulting copyright are not used to limit the access or
legal rights of the compilation's users beyond what the individual works permit. Inclusion of
a cov ered work in an aggregate does not cause this License to apply to the other parts of
the aggregate.
6. Conveying Non-Source Forms.
You may convey a covered work in object code form under the terms of sections 4 and 5,
provided tha t you also conve y the machine-readable Corresponding Source under the
terms of this License, in one of these ways:
a) Con vey the object code in, or embodied in, a physical product (including a physical
distribution me d ium), accompanied by the Corresponding Source fixed on a durable
physical medium customarily used for software interchange.
b) Convey the object code in, or embodied in, a physical product (including a phy sical
distribution me d ium), accompanied by a written offer, valid for at least three years and
valid for as long as you offer spare parts or customer support for that product model, to
give an yo ne who posse sses the o bject code eithe r (1) a co py of the Corre sponding Source
for all the software in the product that is covered by this License, on a durable physical
medium customarily used for software interchange, for a price no more than your
reasonable cost of physically performing this conveying of source, or (2) access to copy the
Corresponding Source from a network server at no charge.
c) Convey individual copies of the object code with a copy of the written offer to provide the
Corre sponding Source . This alter native is allowed only occasionally and noncommercially,
and only if you received the object code with suc h an offer, in accord with subsection 6b.
d) Convey the object code by offering access from a designated place (gratis or for a
charge), and offer equivalent access to the Corresponding Source in the same way through
the same place at no further charge. You need not require recipients to copy the
Correspo nding Source along with the object co de. If the place to copy the objec t code is a
network server, the Corresponding Source may be on a different server (operated by you or
a third party) that supports equivalent copying facilities, pro vided you maintain clear
directions next to the object code saying where to find the Corresponding Source.
Regardless of what server hosts the Corresponding Source, you remain obligated to ensure
that it is available for as long as needed to satisfy these requirements.
e) Conv ey the object code using peer-to-peer transmission, provided you inform other
peers where the object code and Corresponding Source of the work are being offered to the
general public at no cha rge under subsection 6d.
A separable portion of the object code, whose source code is excluded from the

49
Corresponding Source as a System Library, need not be included in conveying the object
code work.
A “User Product” is either (1) a “consumer product”, which means any tangible personal
property which is normally used for personal, family, or household purposes, or (2)
anything designed or sold for incorporation into a dwelling. In determining whether a
product is a consumer product, doubtful cases shall be resolved in favor of coverage. For a
particular product received by a particular user, “normally used” refers to a typical or
common use of that class of product, regardless of the status of the particular user or of the
way in which the particular user actually uses, or expects or is expected to use, the product.
A product is a consumer product regardless of whether the product has substantial
commer cial, industrial or non-consumer uses, unless such uses represent the only
significant mode of use of the product.
“Ins ta llation Information” for a User Product mea ns any methods, procedures,
authorization keys, or other information required to install and execute modified versions
of a covered work in that User Product from a modified version of its Corresponding Source.
The information must suffice to ensure that the continued functioning of th e modified
object code is in no case prevented or interfered with solely because modification has been
made.
If you convey an object code work under this section in, or with, or specifically for use in,
a User Product, and the conveying occurs as part of a transaction in which the right of
possession and us e of the User Produc t is transferred to the recipient in perpetuity or for a
fixed ter m (regar dless of ho w the tr ans ac tion is char a cter ized), the Corre sponding Sour ce
conveyed under this section must be accompanied by the Installation Information. But this
requirement does not apply if neither you nor any third party retains the a b ility to install
modified obje ct code on the User Product (for example, the work ha s been installed in
ROM).
The requirement to provide Installation Information does not include a requirement to
continue to provide support service, warranty , or updates for a work that has been modified
or installed by the recipient, or for the User Product in which it has been modified o r
installed. Ac cess to a network may be denied when the modification itself materially and
adversely affects the operation of the network or violates the rules and protocols for
comm unication across the network .
Correspo nding Source co nveyed, and Installation I nformation provided, in accord with this

50
section must be in a format that is publicly documented (and with an implementation
available to t he public in source code form), and must re q uire no special password or key
for unpack ing, reading or copying.
7. Additional Terms.
“Additional per missions” are terms that supplement the terms of this License by m aking
exceptions from one or more of its conditions. Additio nal per miss ions that are applica ble to
the entire Program shall be treated as though they were included in this License, to the
exte nt that they are va lid under applicable law . If addit ional perm issions apply only to part
of the Progr am, that pa rt ma y be used se parately under those permiss ions, b ut the e ntire
Program remains governed by this License without regard to the additi onal permissions.
When you convey a copy of a covered work, you may at your option remove any additional
permissions from that copy, or from any part of it. (Additiona l permissions ma y be written
to require their own removal in certain cases when you modify the work.) You may place
additional per missions on ma terial, added by y ou to a cov ered work, fo r which yo u have or
can give appropriate copyright permission.
Notwithstanding any other provision of this License, for material you add to a covered work,
yo u may (if authorized by the copyright holders of that ma terial) supplement the terms of
this License with terms:
a) Disclaim ing warr anty or limit ing liability diffe rently fr om the ter ms of sections 15 and 16
of this License; or
b) Requiring preservation of specified reasonable legal notices or author attributions in that
material or in the Appropriate Legal Notices displayed by works containing it; or
c) Prohibiting misrepresentation of the origin of that material, or requiring that modified
versions of such material be marked in reasonable ways as different from the original
version; or
d) Limiting the use for publicity purposes of names of licensors or authors of the material;
or
e) Declining to grant rights under trademark law for use of some trade names, trademarks,
or servi c e mar ks ; or
f) Requiring indemnification of lice nsors and authors of that material by anyone who
conveys the material (or modified v ersions of it) with contr actual assumptions of liability to
the recipient, f or an y liability that the se contractual assumptions direc tly impose o n those
licensors and authors.
All other non-permissive additional terms are considered “further restrictions” within the

51
meaning of section 10. If the Program as you received it, or any part of it, contains a notice
stating that it is governed by this License along with a term that is a further restriction, you
may remove that term. If a license document contains a further restriction but permits
relicensing or conveying under this License, you may add to a covered work material
gov erned by the terms of that licens e document, pro vided that the further restriction does
not survive such relicensing or convey ing.
If yo u a d d terms to a cov ered work in accord with this section, you must place, in the
relevant source files, a statement of the additional terms that apply to those files, or a
notice indicating where to f ind the a pp licable terms.
Additional terms, permissive or non-permissive, may be stated in the form of a separately
written license, or stated as exceptions; the above requirements apply either way.
8. Termination.
You may not propagate or modify a covered work except a s expressly pro v ided under this
License. Any attempt otherwise to propa g a te or modify it is void, and will automatica l ly
terminate y our rights under this L icense (including any p a t ent licenses granted under the
third paragraph of section 11 ).
Howev er, if you cease all violat ion of this License, then your license from a part icular
copyright holder is reinstated (a ) provisionally, unless and until the copyright holder
explic itly a nd finally terminates your license , and ( b) permanently, if the copyright holder
fails to notify you of the violation by some reasonable means prior to 60 days after the
cessation.
Moreover, your license from a particular copyright holder is reinstated permanently if the
copyright holder notifies you of the violation by some reasonable means, this is the first
time you have received notice of violation of this License (for any work) from that copyright
holder, and you cure the violation prior to 30 days after your receipt of the notice.
Termination of your rights under this section does not terminate the licenses of parties who
have received copies or rights from you under this License. If your rights have been
terminated and not permanently reinstated, you do not qualify to receive new licenses for
the same material under section 10.
9. Acceptance Not Required for Having Copies.
Y ou are not required to accept this License in order to receive or run a copy of the Program.

52
Ancillary propagation of a covered work occurring solely as a consequence of using
peer-to-peer transmission to receive a copy likewise does not require acceptance. However,
nothing othe r than this License grants you permission to propa gate or modify any cove red
work. These actions infringe copyright if yo u do not accept this License. Therefore, by
modifying or propagating a covered work, you indicate your acceptance of this License to
do so.
10. Automatic Licensing of Downstream Recipients.
Each time you convey a covered work, the recipient automatically receives a license from
the origina l licenso rs, to run, modify a nd propagate t hat work, subjec t to this Lice nse. Y o u
are not responsible for enforcing compliance by third parties with this License.
An “ent ity t ransactio n” is a transaction transferring cont rol of an org anization, or
substantially a ll assets of one, or subdividing an organizat ion, or merging or ganizations. If
propaga tion of a covered work results from an entity transaction, each party to that
transaction who receives a copy of the work also receives whatever licenses to the work the
party's predecessor in interest had or could give under the previous paragraph, plus a right
to possession of the Corresponding Source of the work from the predecessor in interest, if
the predecessor has it or can get it with reasonable efforts.
You may not impose any further restrictions on the exercise of the rights granted or
affirmed under this License. For example, you may not impose a license fee, royalty, or
other charge for exercise of rights granted under this License, and you may n ot initiate
litigation (including a cross-claim or counterclaim in a lawsu it) alleging that any pa tent
claim is infringe d by making, using, selling, offering for sale, or importing the Prog ram or
any portion of it.
11. Patents.
A “contributor” is a copyright holder who authorizes use under this L icense of the Pro gram
or a work on which the Program is based. The work thus licensed is called the contributor's
“cont ribu t or version ”.
A contributor's “essential patent claims” are a ll patent claims owned or controlled by the
contributor, whether already acquired or hereafter acquired, that would be infringed by
some manner, permitted by this License, of making, using, or selling its contributor version,
but do not include cla im s that would be infringed only as a consequence of further
modification of the contributor version. For purposes of this definition, “control” includes
the right to grant patent sublicenses in a manner consistent with the requirements of this

53
License.
Each contributor grants you a non-exclusive, worldwide , royalty-free patent license under
the contributor's essential patent claims, to make, use, sell, offer for sale, import and
otherwise run, modify and propagate the contents of its contributor version.
In the following three paragraphs, a “patent license” is any express agreement or
commitment, however denom inate d, not to enforce a patent (such as an expres s
permission to prac tice a patent or cov enant not to s ue for patent infringement). To “grant”
such a patent license to a party means to make such an agreement or commitment not to
enforce a patent against the party.
If you convey a covered work, knowingly relying on a patent license, and the Corresponding
Source of the work is not available for anyone to copy, free of charge and under the terms
of this License, through a publicly available network server or other readily accessible
means, then you must either (1) cause the Corresponding Source to be so available, or (2)
arrange to deprive yourself of the benefit of the patent license for this particular work, or (3)
arrange, in a manner consistent with the requirements of this License, to extend the patent
license to downstream recipients. “Knowingly relying” m eans you have actual knowledge
that, but fo r the patent license, yo ur conveying the covered work in a country, or your
recipient's use of the covered work in a country, would infringe one or more identifiable
patents in that country that you have reason to believe are valid.
If, pursuant to or in connection with a sin gle transaction or arrangement, you convey, or
propagate by procuring conveyance of , a covered work, and grant a patent license to some
of the par ties receiving the covered work authorizing them to use, propagate, modify or
convey a specific copy of the covered work, then the patent license y ou grant is
automatically extended to all recipients of the covered work and works based on it.
A paten t license is “discriminatory” if it does not include within the scope of its coverage,
prohibits the exercise of , or is conditioned on the non-exercise of one or more of the rights
that are specifically granted under this License. Y ou may not convey a covered work if you
are a party to an arrangement with a third party tha t is in the business of distributing
software, under which you make payment to the third party based on the extent of your
activity of conveying the work, and under which the third party grants, to any of the parties
who would receive the covered work from you, a discriminatory patent license (a) in
connection with copies of the covered work conveyed by you (or copies made from those
copies), or (b) primarily for a nd in connection with specific products or compilations that

54
contain the co vered work, unless you entered into that arr angement, or that patent license
was granted, prior to 28 March 2007.
Nothing in this Licens e shall be construe d as excluding or limiting any implied license or
other defenses to infringement that may otherwise be available to you under applicable
patent law.
12. No Surrender of Others' Freedom.
If conditions are imposed on you (whether by court order, agreement or otherwise) that
contr adict the conditions of this License, they do not excuse you from the conditions of this
License. If you cannot convey a covered work so as to satisfy simultaneously your
obligat ions unde r this L icense and an y o ther pertine nt ob ligat ions , the n as a conseq ue nce
yo u may not conve y it at all. F or example, if yo u agree to terms that obligate you to collect
a royalty for further conveying from those to whom you conv ey the Progr am, the only way
yo u could satisfy both tho se terms and this License would be to re frain entirely from
conveying the Program.
13. Use with the GNU Affero General Public License.
Notwithstanding any other provision of this License, you have permission to link or combine
any covered work with a work licensed under version 3 of the GNU Affero General Public
License into a single combined work, and to convey the resulting work. The terms of this
License will continue to apply to the part which is the covered work, but the special
requirements of the GNU Affero General Public License, section 13, concerning interaction
through a network will apply to the com bination as such.
14. Revised Versions of this License.
The Free Software Foundation may publish revised and/or new versions of the GNU General
Public License from time to time. Such new versions will be similar in spirit to the present
version, but may differ in detail to address new problems or concerns.
Each version is given a d istinguishing version number. If the Program specifies that a
certain numbered version of the GNU General Public License “or any later version” applies
to it, you have the option of follow ing the terms and conditions either of that numbered
version or of any later version published by the Free Software Foundation. If the Program
does not specify a version number of the GNU General Public License, you may choose any
version ever p ublished by the Free Software Foundation.
If the Progr am specifies that a pro xy can decide which future versions of the GNU General

55
Public License can be used, that proxy's public statement of acceptance of a version
permanently authorizes you to choose that version for the Program.
Later license versions may give you additional or different permissions. However, no
additional obligations are imposed on any author or copyright holder a s a result of your
choosing to follow a later version.
15. Disclaimer of Warranty.
THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE
LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR
OTHER PARTIES PROVIDE THE PROGRAM “AS IS” WITHOUT WARRANTY OF ANY KIND,
EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE
ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU.
SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY
SERVICING, REPAIR OR CORRECTION.
16. Limitation of Liability.
IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL
ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MODIFIES AND/OR CONVEYS THE
PROGRAM AS PERMITTED ABOVE, BE LIABLE TO Y OU FOR DAMAGES, INCLUDING ANY
GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE
USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF
DA T A OR DA T A BEING RENDERED INACCURA TE OR LOSSES SUST AINED BY YOU OR THIRD
PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS),
EVEN IF SUCH H OLD ER OR OTHER PARTY HAS BEEN ADVIS ED OF TH E POSSIBI L ITY OF
SUCH DAMAGES.
17. Interpretation of Sections 15 and 16.
If the discla imer of warranty and limitation of liability pro vided above c annot be giv en local
legal effect according to their terms, reviewing courts shall apply local law that most closely
ap pro xim ate s a n ab so lute wa iv er o f al l civ il liab il it y in co nne ctio n w ith t he Pr ogr a m, un les s
a warranty or assumption of liability accompanies a copy of the Program in return for a fee.
END OF TERMS AND CONDITIONS