Table of Contents
- SBG5500 Series
- User’s Guide
- Technical Reference
- Dashboard
- WAN/Internet
- LAN
- Routing
- Network Address Translation (NAT)
- Firewall
- VPN
- Bandwidth Management
- Network Management
- Log / Report
- Service / License
- Device Name
- Host Name List
- Date / Time
- User Account
- USB Storage
- Diagnostic
- Firmware Upgrade
- Backup / Restore
- Language
- Restart / Shutdown
- Troubleshooting
- Customer Support
- Legal Information
- Index
Zyxel SBG5500-A User Manual
Displayed below is the user manual for SBG5500-A by Zyxel which is a product in the Wired Routers category. This manual has pages.
Related Manuals

Default Login Details
User’s Guide
SBG5500 Series
SBG5500-A / SBG5500-B
Small Business Gateway
Copyright © 2017 Zyxel Communications Corporation
LAN IP Address http://192.168.1.1
User Name admin
Password 1234
Version 1.10 Edition 1, 12/2017

SBG5500 Series User’s Guide
2
IMPORTANT!
READ CAREFULLY BEFORE USE.
KEEP THIS GUIDE FOR FUTURE REFERENCE.
This is a User’s Guide for a series of products. Not all products support all firmware features. Screenshots
and graphics in this book may differ slightly from your product due to differences in your product
firmware or your computer operating system. Every effort has been made to ensure that the information
in this manual is accurate.
Related Documentation
•Quick Start Guide
The Quick Start Guide shows how to connect the SBG and access the Web Configurator wizards. It
contains information on setting up your network and configuring for Internet access.
•More Information
Go to support.zyxel.com to find other information on the SBG.
SBG5500 Series User’s Guide
3
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this guide.
Warnings tell you about things that could harm you or your device.
Note: Notes tell you other important information (for example, other things you may need to
configure or helpful tips) or recommendations.
Syntax Conventions
• All models in this series may be referred to as the “SBG” in this guide.
• Product labels, screen names, field labels and field choices are all in bold font.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For example, Configuration >
Log / Report > Log Settings means you first click Configuration in the navigation panel, then the Log
sub menu and finally the Log Settings tab to get to that screen.
Icons Used in Figures
Figures in this user guide may use the following generic icons. The SBG icon is not an exact
representation of your device.
SBG Generic Router Wireless Router / Access Point
Switch Firewall USB Storage Device
USB Dongle Cell Tower Printer
Server
SBG

Contents Overview
SBG5500 Series User’s Guide
4
Contents Overview
User’s Guide ......................................................................................................................................12
Introducing the SBG ............................................................................................................................. 13
The Web Configurator ......................................................................................................................... 20
Wizard .................................................................................................................................................... 26
Technical Reference ........................................................................................................................44
Dashboard ............................................................................................................................................ 45
WAN/Internet ........................................................................................................................................ 48
LAN ......................................................................................................................................................... 85
Routing ................................................................................................................................................. 108
Network Address Translation (NAT) ................................................................................................... 122
Firewall ................................................................................................................................................. 138
VPN ....................................................................................................................................................... 159
Bandwidth Management .................................................................................................................. 194
Network Management ...................................................................................................................... 212
Log / Report ....................................................................................................................................... 215
Service / License ................................................................................................................................. 225
Device Name ...................................................................................................................................... 227
Host Name List ..................................................................................................................................... 228
Date / Time .......................................................................................................................................... 230
User Account ...................................................................................................................................... 233
USB Storage ......................................................................................................................................... 236
Diagnostic ........................................................................................................................................... 240
Firmware Upgrade .............................................................................................................................. 247
Backup / Restore ................................................................................................................................ 250
Language ............................................................................................................................................ 252
Restart / Shutdown ............................................................................................................................. 253
Troubleshooting .................................................................................................................................. 254

Table of Contents
SBG5500 Series User’s Guide
5
Table of Contents
Document Conventions ......................................................................................................................3
Contents Overview .............................................................................................................................4
Table of Contents .................................................................................................................................5
Part I: User’s Guide.......................................................................................... 12
Chapter 1
Introducing the SBG...........................................................................................................................13
1.1 Overview ......................................................................................................................................... 13
1.2 Ways to Manage the SBG ............................................................................................................. 13
1.3 Good Habits for Managing the SBG ............................................................................................ 14
1.4 Applications for the SBG ............................................................................................................... 14
1.4.1 Internet Access ...................................................................................................................... 14
1.4.2 SBG’s USB Support ................................................................................................................. 16
1.5 LEDs (Lights) ..................................................................................................................................... 17
1.6 The RESET Button ............................................................................................................................. 18
Chapter 2
The Web Configurator........................................................................................................................20
2.1 Overview ......................................................................................................................................... 20
2.1.1 Accessing the Web Configurator ....................................................................................... 20
2.2 Web Configurator Layout .............................................................................................................. 21
2.2.1 Title Bar ................................................................................................................................... 22
2.2.2 Navigation Panel .................................................................................................................. 22
2.2.3 Main Window ......................................................................................................................... 25
Chapter 3
Wizard .................................................................................................................................................26
3.1 Overview ......................................................................................................................................... 26
3.2 Wizard Basic Setup ......................................................................................................................... 27
3.3 Wizard IPsec VPN Setup ................................................................................................................. 32
3.3.1 VPN Express Settings ............................................................................................................. 33
3.3.2 VPN Advanced Settings ....................................................................................................... 35
3.4 Wizard IPv6 Setup ........................................................................................................................... 40

Table of Contents
SBG5500 Series User’s Guide
6
Part II: Technical Reference........................................................................... 44
Chapter 4
Dashboard..........................................................................................................................................45
4.1 Overview ......................................................................................................................................... 45
4.2 The Dashboard Screen .................................................................................................................. 45
Chapter 5
WAN/Internet......................................................................................................................................48
5.1 Overview ......................................................................................................................................... 48
5.1.1 What You Can Do in this Chapter ....................................................................................... 49
5.1.2 What You Need to Know ..................................................................................................... 49
5.1.3 Before You Begin ................................................................................................................... 52
5.2 The WAN Status Screen .................................................................................................................. 52
5.2.1 The xDSL Statistics Screen ..................................................................................................... 53
5.2.2 The SFP Status Screen ........................................................................................................... 55
5.3 The WAN Setup Screen .................................................................................................................. 56
5.3.1 Add/Edit Internet Connection .............................................................................................57
5.4 The Mobile Screen .......................................................................................................................... 68
5.5 The Port Setting Screen .................................................................................................................. 72
5.6 The Multi-WAN Screen .................................................................................................................... 73
5.6.1 Edit Multi-WAN ....................................................................................................................... 74
5.6.2 How to Configure Multi-WAN for Load Balancing and Failover ...................................... 75
5.7 The Dynamic DNS screen .............................................................................................................. 76
5.7.1 Edit Dynamic DNS ................................................................................................................. 77
5.8 The xDSL Advanced screen .......................................................................................................... 79
5.9 Technical Reference ...................................................................................................................... 81
Chapter 6
LAN ......................................................................................................................................................85
6.1 Overview ......................................................................................................................................... 85
6.1.1 What You Can Do in this Chapter ....................................................................................... 85
6.1.2 What You Need To Know ..................................................................................................... 86
6.1.3 Before You Begin ................................................................................................................... 87
6.2 The LAN Status Screen ................................................................................................................... 87
6.3 The LAN Setup Screen .................................................................................................................... 88
6.3.1 Edit LAN Setup ....................................................................................................................... 89
6.3.2 Edit LAN Setup IPv6 ............................................................................................................... 91
6.4 The Static DHCP Screen ................................................................................................................. 94
6.4.1 Edit Static DHCP .................................................................................................................... 94
6.5 The Additional Subnet Screen ....................................................................................................... 96
6.6 The Wake on LAN Screen .............................................................................................................. 96
6.6.1 Wake On LAN: Add/Edit ....................................................................................................... 97

Table of Contents
SBG5500 Series User’s Guide
7
6.7 The VLAN / Interface Group Screen ............................................................................................ 98
6.7.1 VLAN / Interface Group: Add/Edit ...................................................................................... 99
6.8 The DNS Entry Screen ................................................................................................................... 103
6.9 The DNS Forwarder Screen .......................................................................................................... 103
6.9.1 DNS Forwarder: Add/Edit ................................................................................................... 104
6.10 Technical Reference .................................................................................................................. 105
6.10.1 LANs, WANs and the SBG ................................................................................................. 105
6.10.2 DHCP Setup ....................................................................................................................... 105
6.10.3 DNS Server Addresses ....................................................................................................... 106
6.10.4 LAN TCP/IP ......................................................................................................................... 106
Chapter 7
Routing ..............................................................................................................................................108
7.1 Overview ...................................................................................................................................... 108
7.1.1 What You Can Do in this Chapter ..................................................................................... 108
7.2 The Routing Status Screen ........................................................................................................... 109
7.3 The Policy Route Screen .............................................................................................................. 115
7.3.1 Add/Edit Policy Route ........................................................................................................ 116
7.4 The Static Route Screen ............................................................................................................... 118
7.4.1 Add/Edit Static Route ......................................................................................................... 119
7.5 The RIP Screen ............................................................................................................................... 120
Chapter 8
Network Address Translation (NAT)................................................................................................122
8.1 Overview ....................................................................................................................................... 122
8.1.1 What You Can Do in this Chapter ..................................................................................... 122
8.1.2 What You Need To Know ................................................................................................... 122
8.2 The Port Forwarding Screen ....................................................................................................... 123
8.2.1 Add/Edit Port Forwarding .................................................................................................. 125
8.3 The Port Triggering Screen ........................................................................................................... 126
8.3.1 Add/Edit Port Triggering Rule ............................................................................................ 128
8.4 The Address Mapping Screen ..................................................................................................... 129
8.4.1 Add/Edit Address Mapping Rule ....................................................................................... 130
8.5 The Default Server Screen ........................................................................................................... 131
8.5.1 Edit Default Server ............................................................................................................... 132
8.6 The ALG Screen ............................................................................................................................ 133
8.7 Technical Reference .................................................................................................................... 134
8.7.1 NAT Definitions ..................................................................................................................... 134
8.7.2 What NAT Does ................................................................................................................... 134
8.7.3 How NAT Works .................................................................................................................... 135
8.7.4 NAT Application .................................................................................................................. 135
Chapter 9
Firewall ..............................................................................................................................................138

Table of Contents
SBG5500 Series User’s Guide
8
9.1 Overview ....................................................................................................................................... 138
9.1.1 What You Can Do in this Chapter ..................................................................................... 138
9.1.2 What You Need to Know ................................................................................................... 139
9.2 The Firewall Overview Screen ..................................................................................................... 140
9.3 The DoS Screen ............................................................................................................................. 141
9.4 The Firewall Rules Screen ............................................................................................................. 141
9.4.1 Add/Edit a Firewall Rule ..................................................................................................... 143
9.5 The Device Service Screen .......................................................................................................... 144
9.5.1 Edit a Device Service .......................................................................................................... 146
9.5.2 Add/Edit a Trust Domain .................................................................................................... 146
9.6 The Zone Control Screen ............................................................................................................. 147
9.7 The Scheduler Rule Screen .......................................................................................................... 148
9.7.1 Add/Edit a Scheduler Rule ................................................................................................. 149
9.8 The Service Screen ...................................................................................................................... 149
9.8.1 Add/Edit a Service ............................................................................................................. 150
9.9 The MAC Filter Screen .................................................................................................................. 151
9.9.1 MAC Filter: Add/Edit ........................................................................................................... 152
9.10 The Certificate Screen ............................................................................................................... 153
9.11 The AAA Server ........................................................................................................................... 154
9.11.1 Add/Edit an LDAP Server .................................................................................................155
9.11.2 Add/Edit an RADIUS Server .............................................................................................. 157
Chapter 10
VPN....................................................................................................................................................159
10.1 Overview ..................................................................................................................................... 159
10.2 What You Can Do in this Chapter ............................................................................................ 159
10.3 What You Need to Know ........................................................................................................... 159
10.4 The VPN Status Screen ............................................................................................................... 162
10.5 The IPsec VPN Screen ................................................................................................................ 163
10.5.1 Add/Edit a VPN Gateway ................................................................................................ 165
10.5.2 Add/Edit a VPN Connection ........................................................................................... 171
10.5.3 The Default_L2TP_VPN_GW IPsec VPN Rule ................................................................... 174
10.5.4 PPTP VPN Troubleshooting Tips ........................................................................................ 175
10.6 The PPTP VPN Screen ................................................................................................................. 176
10.6.1 PPTP VPN Troubleshooting Tips ........................................................................................ 178
10.7 The L2TP VPN Screen .................................................................................................................. 179
10.7.1 L2TP Setup - Server ............................................................................................................ 179
10.7.2 L2TP Setup - Client ............................................................................................................. 181
10.7.3 L2TP VPN Troubleshooting Tips ......................................................................................... 182
10.8 The L2TP Client Status Screen .................................................................................................... 185
10.9 Technical Reference .................................................................................................................. 186
10.9.1 IPsec Architecture ............................................................................................................. 186
10.9.2 Encapsulation .................................................................................................................... 187

Table of Contents
SBG5500 Series User’s Guide
9
10.9.3 IKE Phases .......................................................................................................................... 188
10.9.4 Negotiation Mode ............................................................................................................ 189
10.9.5 IPsec and NAT ................................................................................................................... 190
10.9.6 VPN, NAT, and NAT Traversal ........................................................................................... 190
10.9.7 ID Type and Content ........................................................................................................ 191
10.9.8 Pre-Shared Key .................................................................................................................. 192
10.9.9 Diffie-Hellman (DH) Key Groups ...................................................................................... 192
Chapter 11
Bandwidth Management ................................................................................................................194
11.1 Overview .................................................................................................................................... 194
11.1.1 What You Can Do in this Chapter ................................................................................... 194
11.1.2 What You Need to Know ................................................................................................. 194
11.2 The General Screen .................................................................................................................. 196
11.3 The Queue Setup Screen ........................................................................................................... 197
11.3.1 Adding a QoS Queue ...................................................................................................... 198
11.4 The Classification Setup Screen ................................................................................................ 199
11.4.1 Add/Edit a QoS Class ....................................................................................................... 200
11.5 The Policer Setup Screen ........................................................................................................... 204
11.5.1 Add/Edit a QoS Policer ................................................................................................... 205
11.6 The Shaper Setup Screen .......................................................................................................... 206
11.6.1 Add/Edit a QoS Shaper .................................................................................................... 207
11.7 Technical Reference .................................................................................................................. 207
Chapter 12
Network Management ....................................................................................................................212
12.1 Overview ..................................................................................................................................... 212
12.1.1 What You Can Do in This Chapter .................................................................................. 212
12.2 The SNMP Screen ........................................................................................................................ 212
Chapter 13
Log / Report .....................................................................................................................................215
13.1 Overview ..................................................................................................................................... 215
13.1.1 What You Can Do in this Chapter ................................................................................... 215
13.1.2 What You Need To Know ................................................................................................. 215
13.2 The Log Viewer Screen .............................................................................................................. 216
13.3 Log Settings ................................................................................................................................. 217
13.3.1 Edit Log on USB Settings .................................................................................................... 218
13.3.2 Edit System and Email ....................................................................................................... 220
13.3.3 Edit Remote Server Log Settings ...................................................................................... 222
Chapter 14
Service / License..............................................................................................................................225

Table of Contents
SBG5500 Series User’s Guide
10
14.1 Overview ..................................................................................................................................... 225
14.2 The License Screen ..................................................................................................................... 225
Chapter 15
Device Name ...................................................................................................................................227
15.1 Overview ..................................................................................................................................... 227
15.2 The Device Name Screen ......................................................................................................... 227
Chapter 16
Host Name List..................................................................................................................................228
16.1 Overview ..................................................................................................................................... 228
16.2 The Host Name Screen .............................................................................................................. 228
16.2.1 Add Host Name ................................................................................................................. 228
Chapter 17
Date / Time .......................................................................................................................................230
17.1 Overview ..................................................................................................................................... 230
17.2 The Date / Time Screen ............................................................................................................. 230
Chapter 18
User Account....................................................................................................................................233
18.1 Overview .................................................................................................................................... 233
18.2 What You Can Do in this Chapter ............................................................................................ 233
18.3 The User Account Screen .......................................................................................................... 233
18.3.1 Add/Edit a Users Account ...............................................................................................234
Chapter 19
USB Storage ......................................................................................................................................236
19.1 Overview ..................................................................................................................................... 236
19.1.1 What You Need To Know ................................................................................................. 236
19.1.2 Before You Begin ............................................................................................................... 237
19.2 The USB Storage Screen ............................................................................................................. 237
19.2.1 Add a USB Share ............................................................................................................... 239
Chapter 20
Diagnostic.........................................................................................................................................240
20.1 Overview ..................................................................................................................................... 240
20.1.1 What You Can Do in this Chapter ................................................................................... 240
20.1.2 What You Need to Know ................................................................................................. 240
20.2 The Network Tools Screen .......................................................................................................... 241
20.3 The 802.1ag Screen .................................................................................................................... 241
20.4 The OAM Ping Screen ................................................................................................................ 242
20.5 The Packet Capture Screen ...................................................................................................... 244

Table of Contents
SBG5500 Series User’s Guide
11
Chapter 21
Firmware Upgrade ...........................................................................................................................247
21.1 Overview ..................................................................................................................................... 247
21.2 The Firmware Screen .................................................................................................................. 247
21.3 The Mobile Profile Screen .......................................................................................................... 249
Chapter 22
Backup / Restore .............................................................................................................................250
22.1 Overview ..................................................................................................................................... 250
22.2 The Backup / Restore Screen .................................................................................................... 250
Chapter 23
Language .........................................................................................................................................252
23.1 Overview ..................................................................................................................................... 252
23.2 The Language Screen ................................................................................................................ 252
Chapter 24
Restart / Shutdown...........................................................................................................................253
24.1 Overview ..................................................................................................................................... 253
24.2 The Restart / Shutdown Screen ................................................................................................. 253
Chapter 25
Troubleshooting................................................................................................................................254
25.1 Power, Hardware Connections, and LEDs ............................................................................... 254
25.2 SBG Access and Login ............................................................................................................... 255
25.3 Internet Access ........................................................................................................................... 256
25.4 USB Device Connection ............................................................................................................ 257
Appendix A Customer Support ..................................................................................................... 259
Appendix B Legal Information....................................................................................................... 265
Index .................................................................................................................................................270

12
PART I
User’s Guide

SBG5500 Series User’s Guide
13
CHAPTER 1
Introducing the SBG
1.1 Overview
The SBG is a VDSL router and Gigabit Ethernet (GbE) gateway. It has one DSL port and Gigabit Ethernet
for super-fast Internet access over telephone lines. The SBG5500-A can use the DSL port over POTS (Plain
Old Telephone Service) with an R-J11 connection, while the SBG5500-B uses DSL port over ISDN (Internet
Service Digital Network) with an RJ45 connection.
The SBG features a Gigabit Ethernet (GbE) WAN with Small Form Factor Pluggable (SFP) interface. SFP is
also known as Fiber Optics interface. The GbE WAN with SFP has a dual-personality combo design (GbE
+ Fiber) which enables increased bandwidth and extended coverage.
Features
• One DSL Port for Internet Connection
• Combo GbE and SFP Port for Internet Connection
• One USB Port for 3G/4G Connection and File Sharing
• Five GbE Ports for LAN Connection
• Firewall with Secure Network Management
• Secure Access via VPN (IPsec, PPTP, L2TP)
• Backward compatible with ADSL, ADSL2 and ADSL2+ in case VDSL is not available.
• Supports both Packet Transfer Mode (PTM) and Asynchronous Transfer Mode (ATM).
Only use firmware for your SBG’s specific model. Refer to the label on
the bottom of your SBG.
Use the USB port for file sharing or using a 3G/4G dongle for cellular WAN (Internet) backup connections.
1.2 Ways to Manage the SBG
Use any of the following methods to manage the SBG.
• Web Configurator. This is recommended for everyday management of the SBG using a (supported)
web browser.
• TR-069. SBG uses an auto-configuration server used to remotely configure your device via TR-069.

Chapter 1 Introducing the SBG
SBG5500 Series User’s Guide
14
1.3 Good Habits for Managing the SBG
Do the following things regularly to make the SBG more secure and to manage the SBG more
effectively.
• Change the password. Use a password that’s not easy to guess and that consists of different types of
characters, such as numbers and letters. The password must have 6-64 printable characters [0-9][a-z]
[A-Z][!@#$%*].
• Write down the password and put it in a safe place.
• Back up the configuration (and make sure you know how to restore it). Restoring an earlier working
configuration may be useful if the device becomes unstable or even crashes. If you forget your
password, you will have to reset the SBG to its factory default settings. If you backed up an earlier
configuration file, you would not have to totally re-configure the SBG. You could simply restore your
last configuration.
1.4 Applications for the SBG
Here are some example uses for which the SBG is well suited.
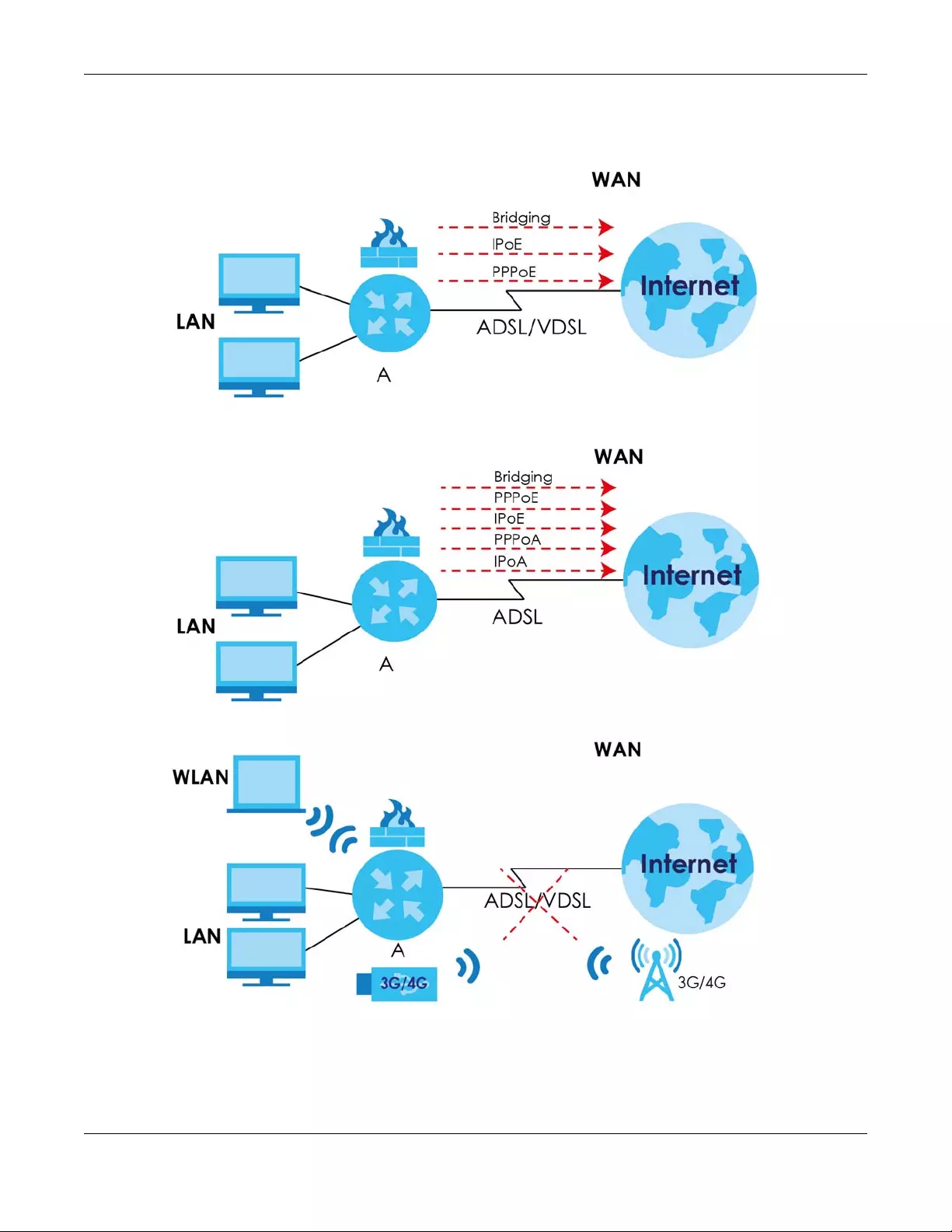
1.4.1 Internet Access
As a small business gateway your SBG has multiple WAN interfaces, including, 3G/4G, DSL, fiber and
Gigabit Ethernet to share the network traffic load. You can configure multiple WAN load balance and
failover rules to distribute traffic amongst the different interfaces.
If you have DSL Internet service, connect the DSL port to the DSL or modem jack on a splitter or your
telephone jack. You can also have multiple WAN services over one ADSL or VDSL. The SBG cannot work
in ADSL and VDSL mode at the same time.
If you prefer not to use a DSL line or you already have a broadband modem/router in your network, use
the Ethernet WAN or SFP port. The SFP and GbE ports work as a Combo port, which means there are two
physical ports in the SBG, but they share a same port number and GbE works as a backup for the SFP
port if both are connected. You can also use a 3G/4G dongle for cellular backup WAN (Internet)
connections.
Note: If you connect all WAN ports the priority order will be DSL, Combo, and USB port.
Note: The ADSL and VDSL lines share the same WAN (layer-2) interfaces that you configure in
the SBG. Refer to Section 5.3 on page 56 for the Configuration > WAN / Internet > WAN
Setup screen.
Chapter 1 Introducing the SBG
SBG5500 Series User’s Guide
15
Computers can connect to the SBG’s LAN ports.
Figure 1 SBG’s Internet Access Application: ADSL/VDSL
Figure 2 SBG’s Internet Access Application: ADSL
Figure 3 SBG’s Internet Access Application: 3G/4G WAN Backup
SBG
SBG
SBG
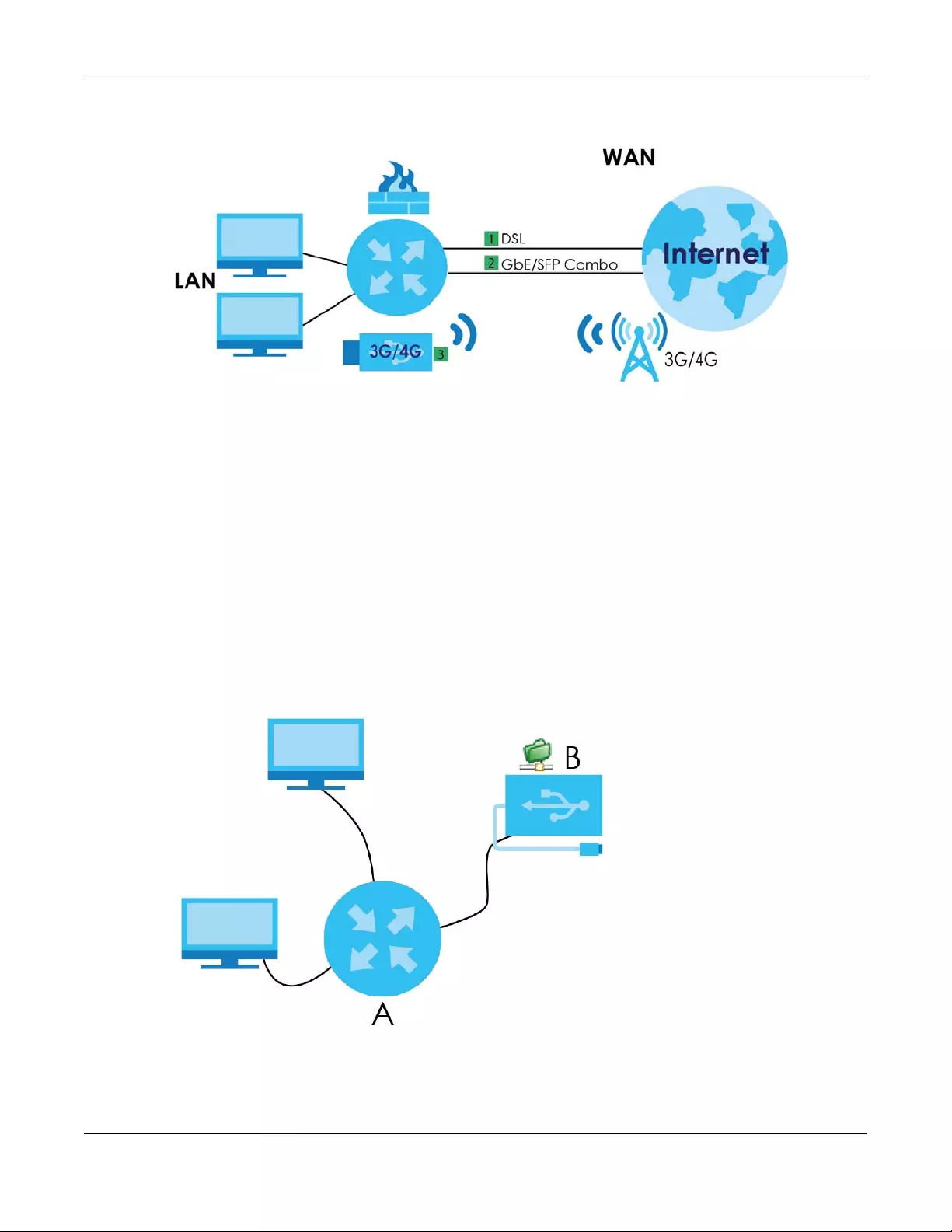
Chapter 1 Introducing the SBG
SBG5500 Series User’s Guide
16
Figure 4 SBG’s Internet Access Application: DSL + SFP/GbE Combo + 3G/4G WAN Priority
You can also configure IP filtering on the SBG for secure Internet access. When the IP filter is on, all
incoming traffic from the Internet to your network is blocked by default unless it is initiated from your
network. This means that probes from the outside to your network are not allowed, but you can safely
browse the Internet and download files.
1.4.2 SBG’s USB Support
Use the USB port for file sharing or insert a 3G/4G dongle for cellular backup WAN (Internet) connections.
File Sharing
Use the USB port (built-in USB 2.0) to share files on USB memory sticks or USB hard drives (B). Use FTP to
access the files on the USB device.
Figure 5 USB File Sharing Application
SBG
SBG
Chapter 1 Introducing the SBG
SBG5500 Series User’s Guide
17
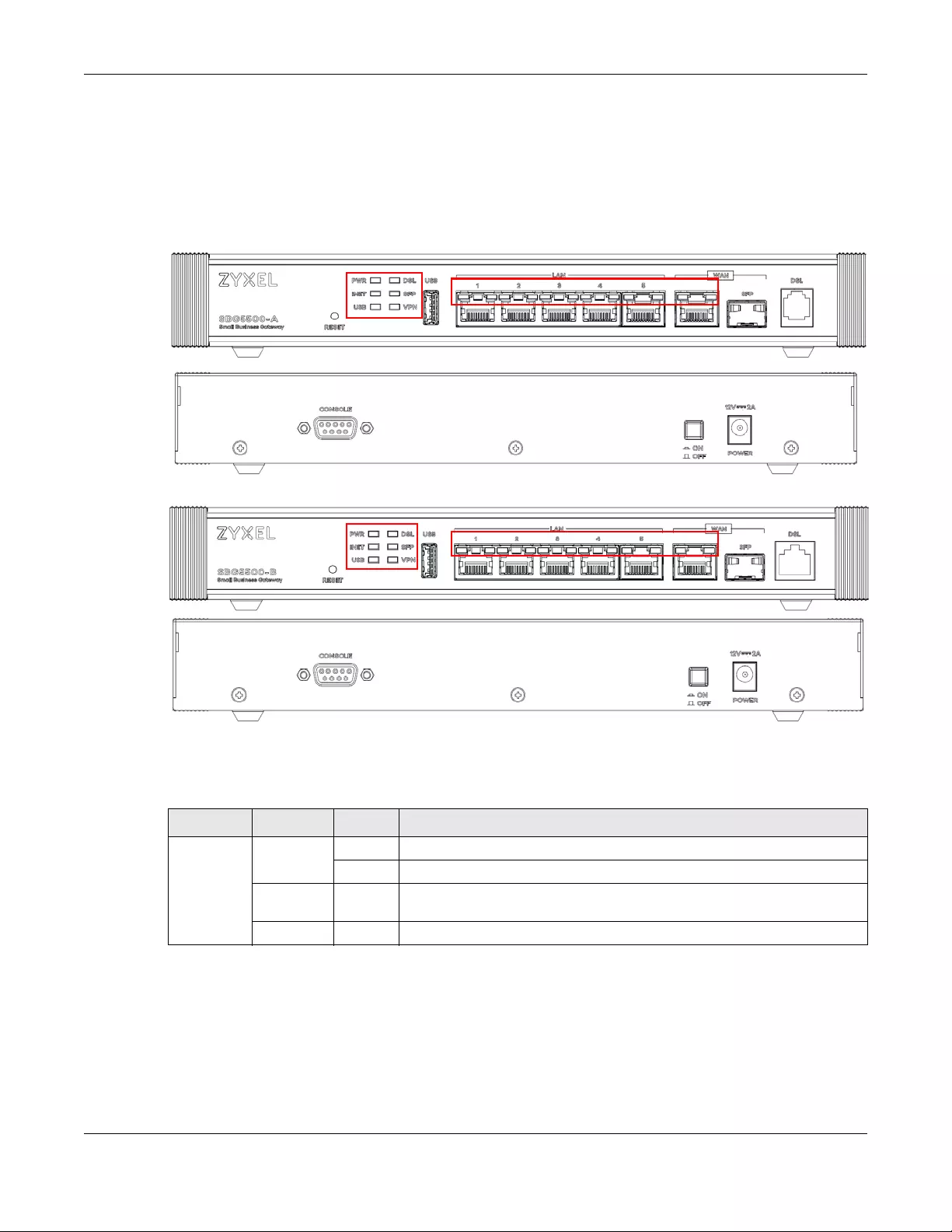
1.5 LEDs (Lights)
This section describes the LEDs on the SBG.
The following figure shows the front and rear panels of the SBG.
Figure 6 SBG5500-A Front and Rear Panels
Figure 7 SBG5500-B Front and Rear Panels
None of the LEDs are on if the SBG is not receiving power. The location of the LEDs are highlighted in the
figures above,
Table 1 LED Descriptions
LED COLOR STATUS DESCRIPTION
POWER Green On The SBG is receiving power and ready for use.
Blinking The SBG is self-testing.
Red On The SBG detected an error while self-testing, or there is a device
malfunction.
Off The SBG is not receiving power.
Chapter 1 Introducing the SBG
SBG5500 Series User’s Guide
18
1.6 The RESET Button
If you forget your password or cannot access the web configurator, you will need to use the RESET
button at the back of the device to reload the factory-default configuration file. This means that you will
lose all configurations that you had previously and the password will be reset to “1234”.
1Make sure the POWER LED is on (not blinking).
INTERNET Green On The SBG has an IP connection but no traffic.
Your device has a WAN IP address (either static or assigned by a DHCP
server), PPP negotiation was successfully completed (if used) and the DSL
connection is up.
Blinking The SBG is sending or receiving IP traffic.
Red On The DSL port is connected to a DSL jack or the Ethernet WAN port is
connected to an Ethernet port but the SBG cannot access the Internet.
There is an Internet connection problem.
Off There is no Internet connection or the gateway is in bridged mode.
USB Green On The SBG recognizes a USB connection.
Off The SBG does not detect a USB connection.
DSL Green/
Amber
On The ADSL/VDSL line is up.
Blinking The SBG is initializing the ADSL/VDSL line.
Off The ADSL/VDSL line is down.
SFP Green On The SBG has established an SFP connection.
Blinking The SBG is sending or receiving data to/from the SFP connection.
Off The SBG has not established an SFP connection.
VPN Green On The SBG VPN tunnel is up.
Off The SBG VPN tunnel is down.
ETHERNET
LAN 1-4 (On
Connector)
Green
(Left LED)
1GM
On The SBG has a successful Ethernet connection with a device on the Local
Area Network (LAN).
Blinking The SBG is sending or receiving data to/from the LAN.
Off The SBG does not have an Ethernet connection with the LAN.
Amber
(Right LED)
10-100M
On The SBG has a successful Ethernet connection with a device on the Local
Area Network (LAN).
Blinking The SBG is sending or receiving data to/from the LAN.
Off The SBG does not have an Ethernet connection with the LAN.
ETHERNET
WAN (On
Connector)
Green
(Left LED)
1GM
On The Gigabit Ethernet connection is working.
Blinking The SBG is sending or receiving data to/from the Gigabit Ethernet link.
Off There is no Gigabit Ethernet link.
Amber
(Right LED)
10-100M
On The Gigabit Ethernet connection is working.
Blinking The SBG is sending or receiving data to/from the Gigabit Ethernet link.
Off There is no Gigabit Ethernet link.
Table 1 LED Descriptions (continued)
LED COLOR STATUS DESCRIPTION

Chapter 1 Introducing the SBG
SBG5500 Series User’s Guide
19
2To set the device back to the factory default settings, press the RESET button for five seconds or until the
POWER LED begins to blink and then release it. When the POWER LED begins to blink, the defaults have
been restored and the device restarts.
SBG5500 Series User’s Guide
20
CHAPTER 2
The Web Configurator
2.1 Overview
The web configurator is an HTML-based management interface that allows easy device setup and
management via Internet browser. Use Internet Explorer 8.0 and later versions, Mozilla Firefox 3 and later
versions, Chrome, or Safari 2.0 and later versions. The recommended screen resolution is 1024 by 768
pixels.
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by default in
Windows XP SP (Service Pack) 2.
• JavaScript (enabled by default).
• Java permissions (enabled by default).
2.1.1 Accessing the Web Configurator
1Make sure your SBG hardware is properly connected (refer to the Quick Start Guide).
2Launch your web browser. If the SBG does not automatically re-direct you to the login screen, go to
http://192.168.1.1.
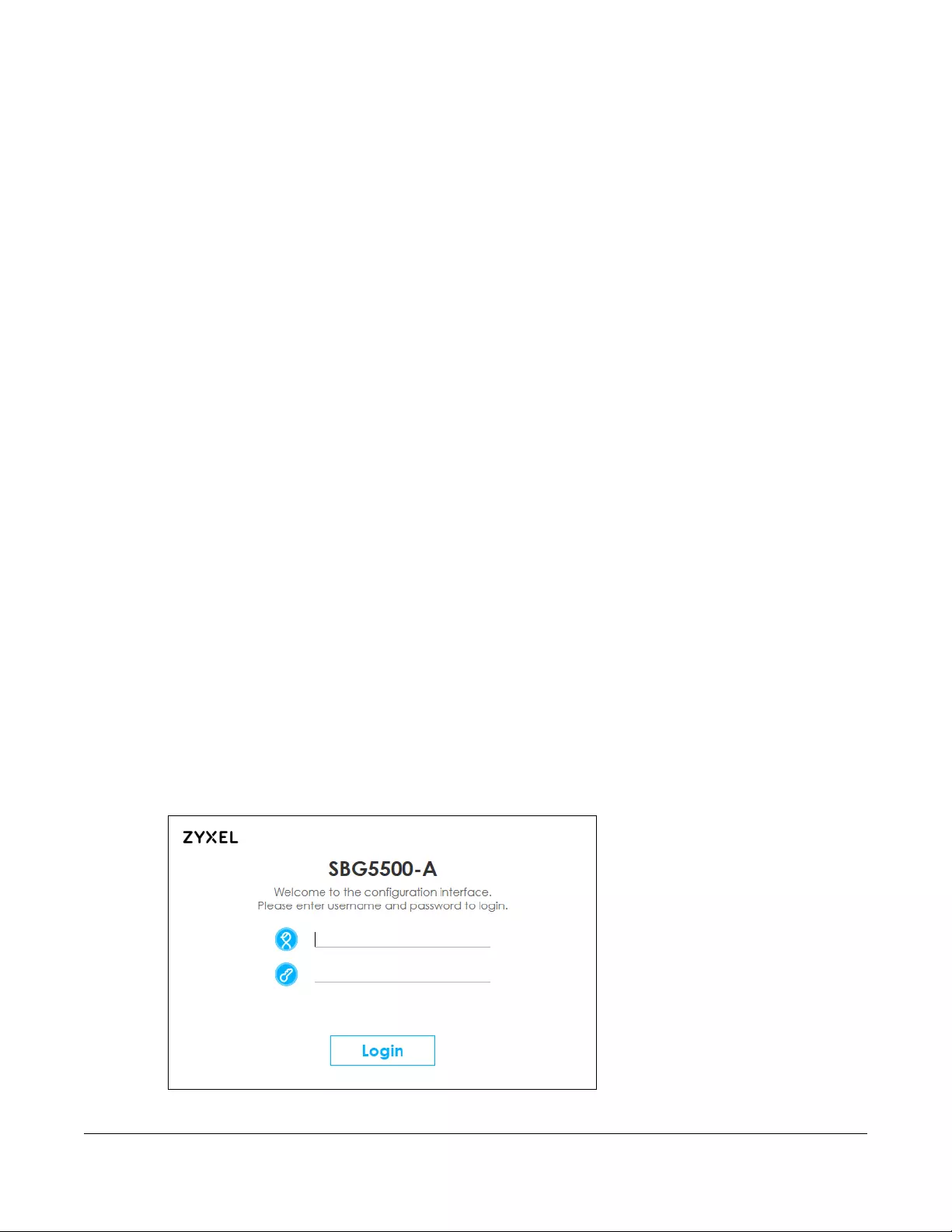
3A password screen displays. To access the administrative web configurator and manage the SBG, type
the default username admin and password 1234 in the password screen and click Login. If advanced
account security is enabled (see Section 18.3 on page 233) the number of dots that appears when you
type the password changes randomly to prevent anyone watching the password field from knowing the
length of your password. If you have changed the password, enter your password and click Login.
Figure 8 Password Screen
Chapter 2 The Web Configurator
SBG5500 Series User’s Guide
21
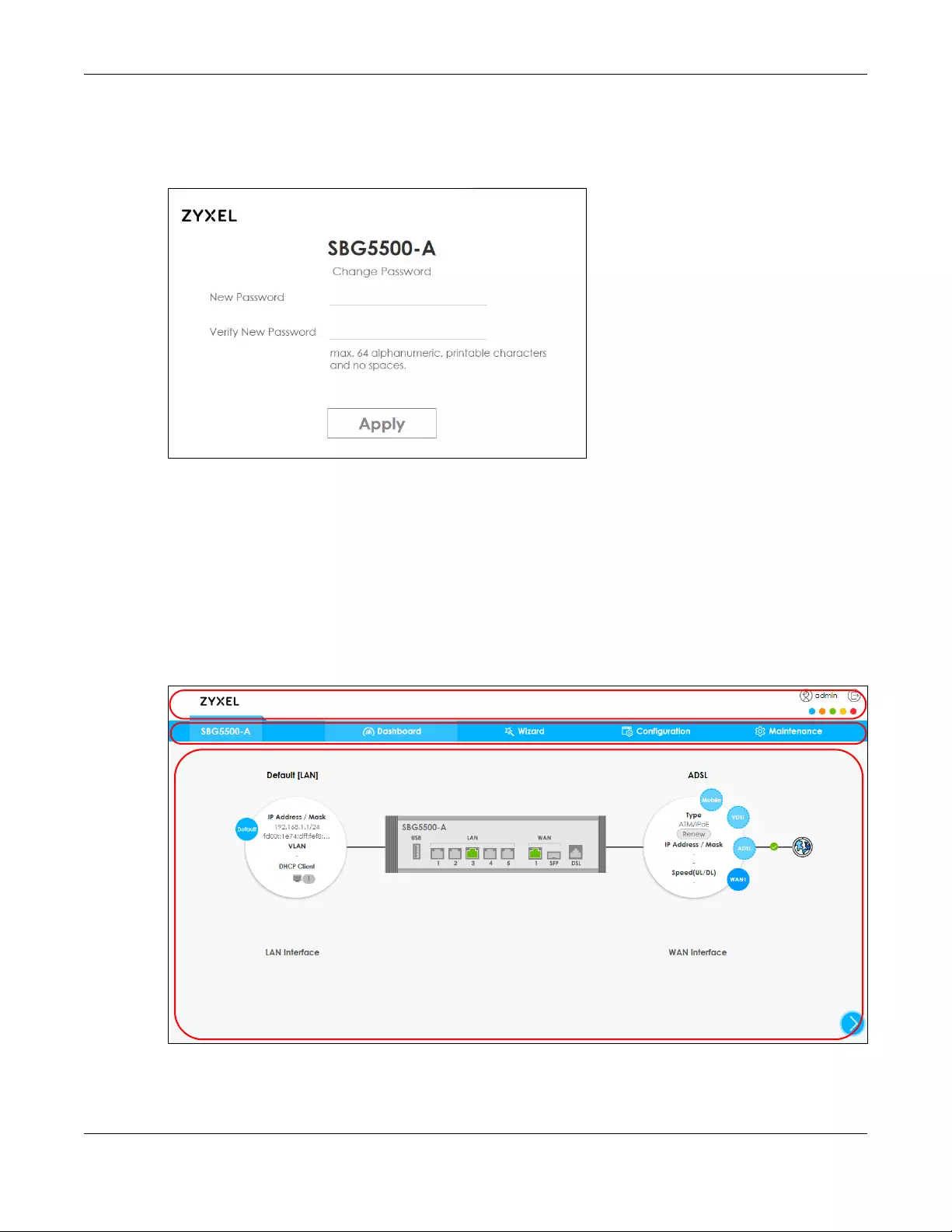
4The following screen displays if you have not yet changed your password from the default. Enter a new
password, retype it to confirm and click Apply. After changing the password your SBG will log out
automatically. so you can log in with your new password.
Figure 9 Change Password Screen
5The Wizard appears automatically after login. Use the Wizard to configure SBG’s basic settings. See
Chapter 3 on page 26 for more information.
6The Dashboard page appears after the Wizard set up, here you can view the SBG’s interface and
system information.
2.2 Web Configurator Layout
Figure 10 Screen Layout
As illustrated above, the main screen is divided into these parts:
•A - title bar
A
B
C

Chapter 2 The Web Configurator
SBG5500 Series User’s Guide
22
•B - navigation panel
•C - main window
2.2.1 Title Bar
The title bar provides some icons in the upper right corner.
The icons provide the following functions.
2.2.2 Navigation Panel
Use the menu items on the navigation panel to open screens to configure SBG features. The following
tables describe each menu item.
Table 2 Web Configurator Icons in the Title Bar
ICON DESCRIPTION
Logout: Click this icon to log out of the web configurator.
Click a color from the palette to change the color of your web configurator.
Table 3 Navigation Panel Summary
LINK TAB FUNCTION
Dashboard Click this to go to the main Web Configurator screen.
Wizard Use this screen to configure the SBG’s basic settings. For more information
see Chapter 3 on page 26.
Configuration
Configuration
Site Map
Click this to view a summary of all the available screens in the
Configuration menu.
WAN / Internet
WAN Status WAN Status Use this screen to view the WAN ports’ status.
xDSL Statistics Use this screen to view detailed DSL traffic statistics.
SFP Status Use this screen to view details about the SFP connection.
WAN Setup Use this screen to view and configure ISP parameters, WAN IP address
assignment, and other advanced properties. You can also add new WAN
connections.
Mobile Use this screen to configure the mobile 3G/4G connection.
Port Setting Use this screen to set flexible ports as part of LAN or WAN interfaces.
Multi-WAN Use this screen to configure the multiple WAN load balance and failover
rules to distribute traffic among different interfaces.
Dynamic
DNS Use this screen to allow a static hostname alias for a dynamic IP address.
xDSL
Advanced Use this screen to enable or disable DSL PHyR, ADSL, and VDSL functions.
LAN / Home Network
Chapter 2 The Web Configurator
SBG5500 Series User’s Guide
23
LAN Status LAN Status Use this screen to view the status of all network traffic going through the
LAN ports of the SBG.
DHCP Client Use this screen to view the status of all devices connected to the SBG. You
can also set screen refresh time to see updates on new devices.
ARP Table Use this screen to view the ARP table. It displays the IP and MAC address
of each DHCP connection.
Multicast Status Use this screen to look at IGMP/MLD group status and traffic statistics.
LAN Setup Use this screen to configure LAN TCP/IP settings, and other advanced
properties.
Static DHCP Use this screen to assign specific IP addresses to individual MAC
addresses.
Additional
Subnet Use this screen to configure IP alias and public static IP.
Wake on LAN Use this screen to remotely wake up a hibernating device on the local
network.
VLAN /
Interface
Group
Use this screen to create a new interface group, which is a new LAN
bridge interface (subnet).
DNS Entry Use this screen to view and configure a domain name and DNS routes on
the SBG.
DNS
Forwarder Use this screen to view and configure domain zone forwarder on the SBG.
Routing
Routing
Status Use this screen to view the IPv4 and IPv6 routing flow.
Policy Route Use this screen to view and set up policy routes on the SBG.
Static Route Use this screen to view and set up static routes on the SBG.
RIP Use this screen to set up RIP (Routing Information Protocol) settings on the
SBG.
NAT
Port
Forwarding Use this screen to make your local servers visible to the outside world.
Port
Triggering Use this screen to change your SBG’s port triggering settings.
Address
Mapping Use this screen to change your SBG’s address mapping settings.
Default
Server Use this screen to configure a default server which receives packets from
ports that are not specified in the Port Forwarding screen.
ALG Use this screen to enable or disable NAT ALG and SIP ALG.
Firewall / Security
Firewall
Overview Use this screen to enable the firewall.
DoS Use this screen to activate protection against Denial of Service (DoS)
attacks.
Firewall Rules Use this screen to add and view existing firewall rules to the SBG.
Device
Service Use this screen to manage the services (such as HTTP and SSH) in the SBG.
Zone Control Use this screen to set the firewall’s default actions based on the direction
of travel of packets.
Table 3 Navigation Panel Summary (continued)
LINK TAB FUNCTION
Chapter 2 The Web Configurator
SBG5500 Series User’s Guide
24
Scheduler
Rule Use this screen to configure the days and times when a configured
restriction (such as User Access control) is enforced.
Service Use this screen to add Internet services.
MAC Filter Use this screen to block or allow traffic from devices of certain MAC
addresses to the SBG.
Certificate Use this screen to view a summary list of certificates and manage
certificates and certification requests.
AAA Server Use this screen to manage the list of LDAP and RADIUS servers the SBG
can use in authenticating users.
VPN
VPN Status Use this screen to look at the status of VPN tunnels that are currently
established.
IPsec VPN Use this screen to display and manage IPsec VPN gateways and
connections.
PPTP VPN Use this screen to configure the PPTP VPN settings in the SBG.
L2TP VPN Use this screen to configure L2TP over IPsec tunnels.
L2TP Client
Status Use this screen to view details about the L2TP clients.
Bandwidth Management
General Use this screen to enable QoS and traffic prioritizing. You can also
configure the QoS rules and actions.
Queue Setup Use this screen to configure QoS queues.
Classification
Setup Use this screen to define a classifier.
Policer Setup Use these screens to configure QoS policers.
Shaper Setup Use this screen to limit outgoing traffic transmission rate on the selected
interface.
Network Management
SNMP Use this screen to configure SNMP communities and services.
Log/Report
Log Viewer Use this screen to view the system logs on the SBG.
Log Settings Use this screen to change specify settings to recording your logs on the
SBG.
Maintenance
Maintenance
Site Map
Click this to view a summary of all the available screens in the
Maintenance menu.
Service / License Use this screen to view the status of your licenses and update any license
information.
Device Name Use this screen to give your SBG a name.
LAN Site Host
Name
Use this screen to add connected devices to the SBG.
Date / Time Use this screen to change your SBG5500-N’s time and date.
User Account Use this screen to manage user accounts, which includes configuring the
username, password, retry times, file sharing, captive portal, and
customizing the login message.
USB Storage Use this screen to enable USB storage sharing.
Table 3 Navigation Panel Summary (continued)
LINK TAB FUNCTION
Chapter 2 The Web Configurator
SBG5500 Series User’s Guide
25
2.2.3 Main Window
The main window displays information and configuration fields. It is discussed in the rest of this
document.
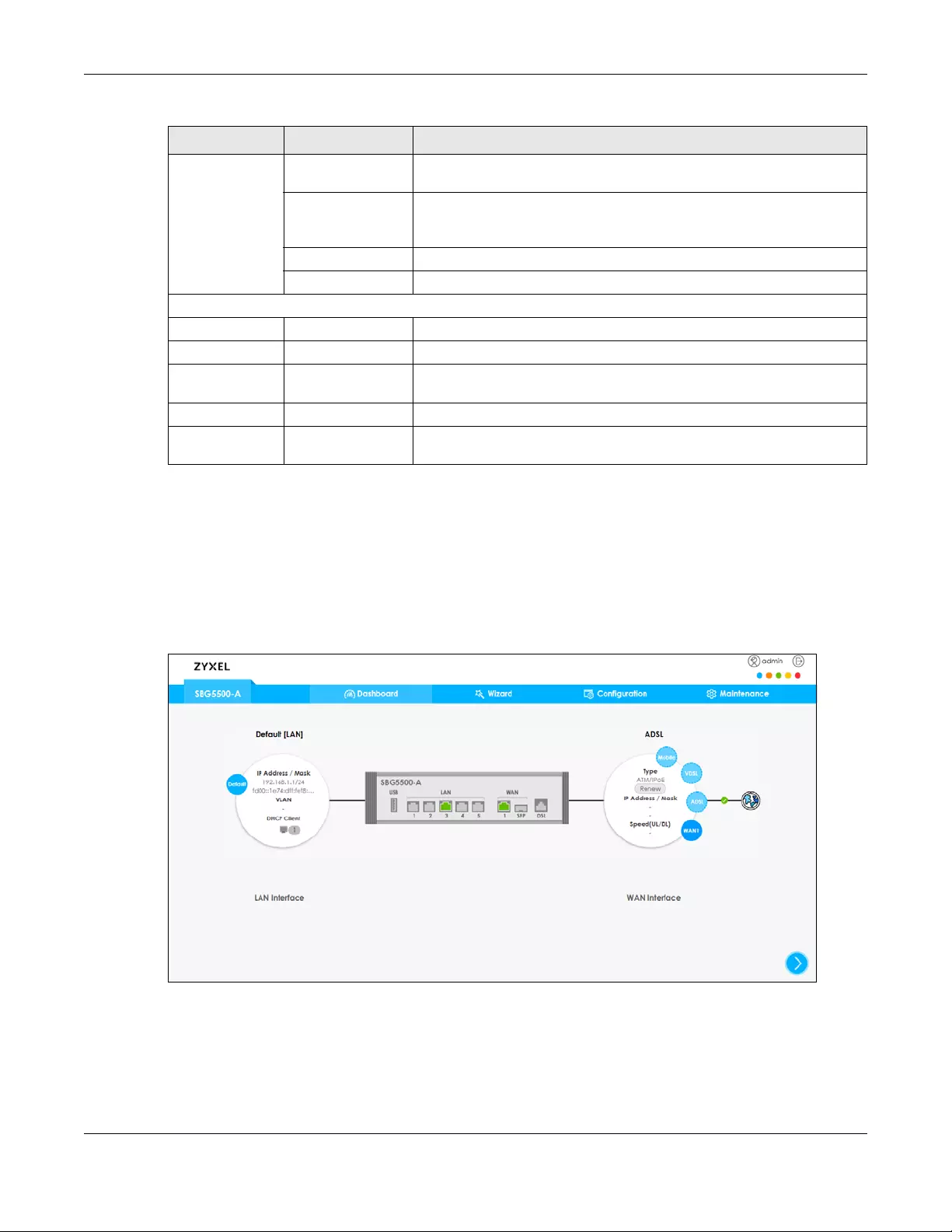
If you click Dashboard a graphic shows the connection status of the SBG’s ports. The connected
interfaces are in color and disconnected interfaces are gray.
Figure 11 Dashboard Screen
Diagnostic Network Tools Use this screen to ping an IP address or trace the route packets take to a
host
802.1ag Use this screen to configure CFM (Connectivity Fault Management) MD
(maintenance domain) to perform connectivity tests and view test
reports.
OAM Ping Use this screen to verify the connectivity of a specific PVC.
Packet Capture Use this screen to capture packets going through the SBG.
Firmware Upgrade
Firmware Use this screen to upload firmware to your device.
Mobile Profile Use this screen to update the mobile profile on the SBG.
Backup / Restore Use this screen to backup and restore your device’s configuration
(settings) or reset the factory default settings.
Language Use this screen to change the SBG web configurator’s language,
Restart /
Shutdown
Use this screen to reboot the SBG without turning the power off.
Table 3 Navigation Panel Summary (continued)
LINK TAB FUNCTION
SBG5500 Series User’s Guide
26
CHAPTER 3
Wizard
3.1 Overview
The Web Configurator's quick setup Wizard helps you configure Internet and VPN connection settings.
This chapter provides information on configuring the Wizard screens in the Web Configurator. See the
feature-specific chapters in this User’s Guide for background information.
Before you begin configuring your SBG register your device at myZyxel portal and check your current
license status.
The Wizard consists of the following setups:
• Wizard Basic Setup - Use Basic Setup to set up a WAN (Internet) connection. This Wizard creates
matching ISP account settings in the SBG if you use PPPoE. See Section 3.2 on page 27.
•Wizard IPsec VPN Setup - Use IPsec VPN Setup to configure an IPsec VPN (Virtual Private Network) rule
for a secure connection to another computer or network. See Section 3.3 on page 32.
•Wizard IPv6 Setup - Use IPv6 Setup to configure the IPv6 settings on your SBG. See Section 3.4 on page
40.
Figure 12 Wizard Setup
Note: See the technical reference chapters (starting on page 44) for background information
on the features in this chapter.
Chapter 3 Wizard
SBG5500 Series User’s Guide
27
3.2 Wizard Basic Setup
The Wizard appears automatically after you log in the first time. Or you can go to the Wizard tab in the
navigation panel. Click the Welcome to Basic Setup down arrow to configure an interface to connect
to the Internet. Click Next to continue the Wizard, Back to return to the previous screen.
Figure 13 Wizard Basic Setup
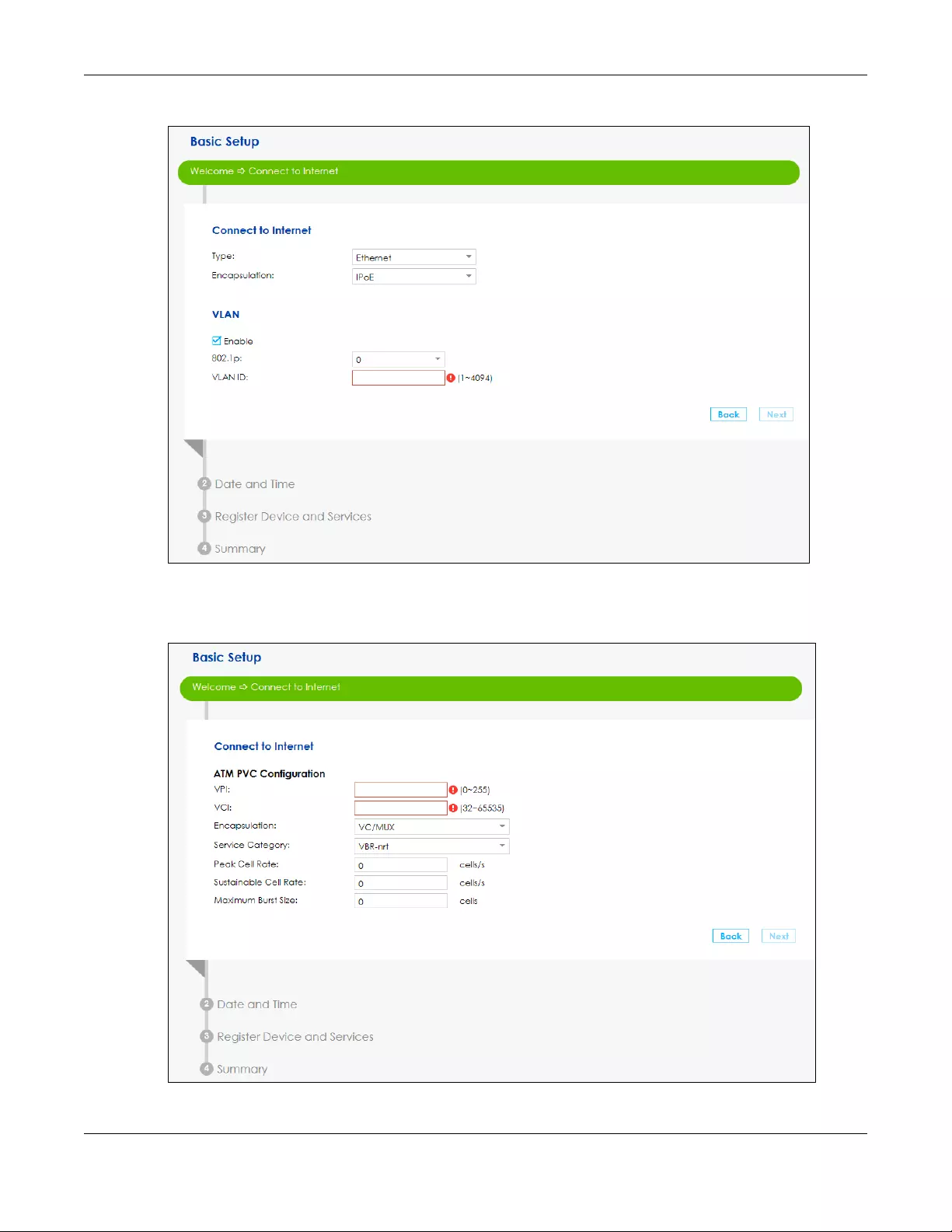
1Enter your Internet connection information in this screen. The screen and fields to enter may vary
depending on your current connection type and the Encapsulation you choose. You can also use this
screen to enable the VLAN tag in the SBG. Assign it a priority level (802.1p) and a VLAN ID for traffic
through this connection. Click Next.
Chapter 3 Wizard
SBG5500 Series User’s Guide
28
Figure 14 Connect to the Internet
2If you select the ADSL over ATM connection type, enter the VPI and VCI assigned to you and the
method of multiplexing used by your ISP.
Figure 15 ATM PVC Configuration
Chapter 3 Wizard
SBG5500 Series User’s Guide
29
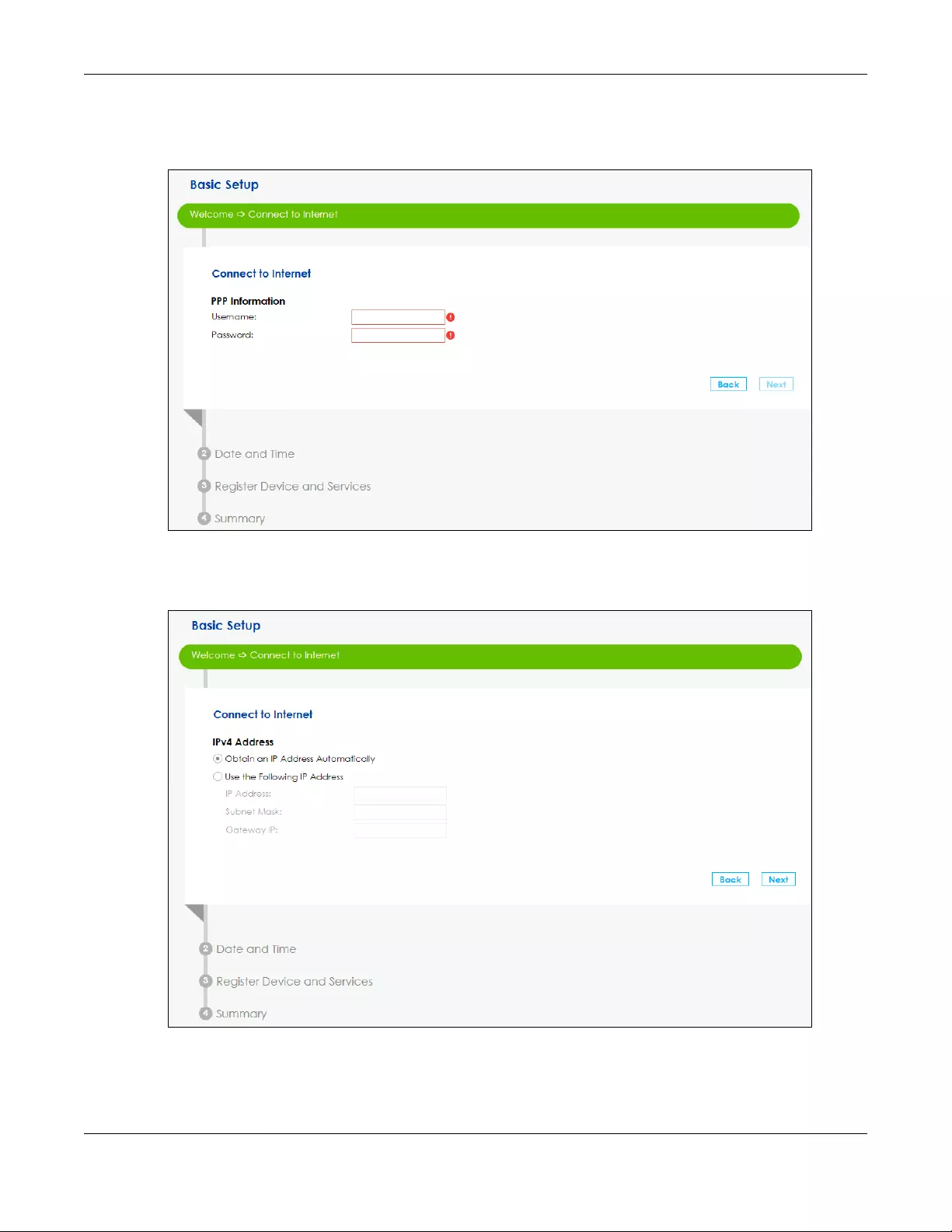
3If you select PPPoE or PPPoA as your encapsulation, type the Username given to you by your ISP and
type the Password associated with the user name.
Figure 16 PPP information
4Use this screen to specify which IPv4 address the SBG uses to connect to the Internet. If your ISP gave
you this information, enter it here. Otherwise select Obtain an IP Address Automatically.
Figure 17 IPv4 Address
5Choose whether SBG gets DNS server addresses from the ISP automatically or uses the DNS server
addresses you got from the ISP. A DNS server is used for mapping a domain name to its corresponding IP
address and vice versa.
Chapter 3 Wizard
SBG5500 Series User’s Guide
30
Figure 18 DNS Server
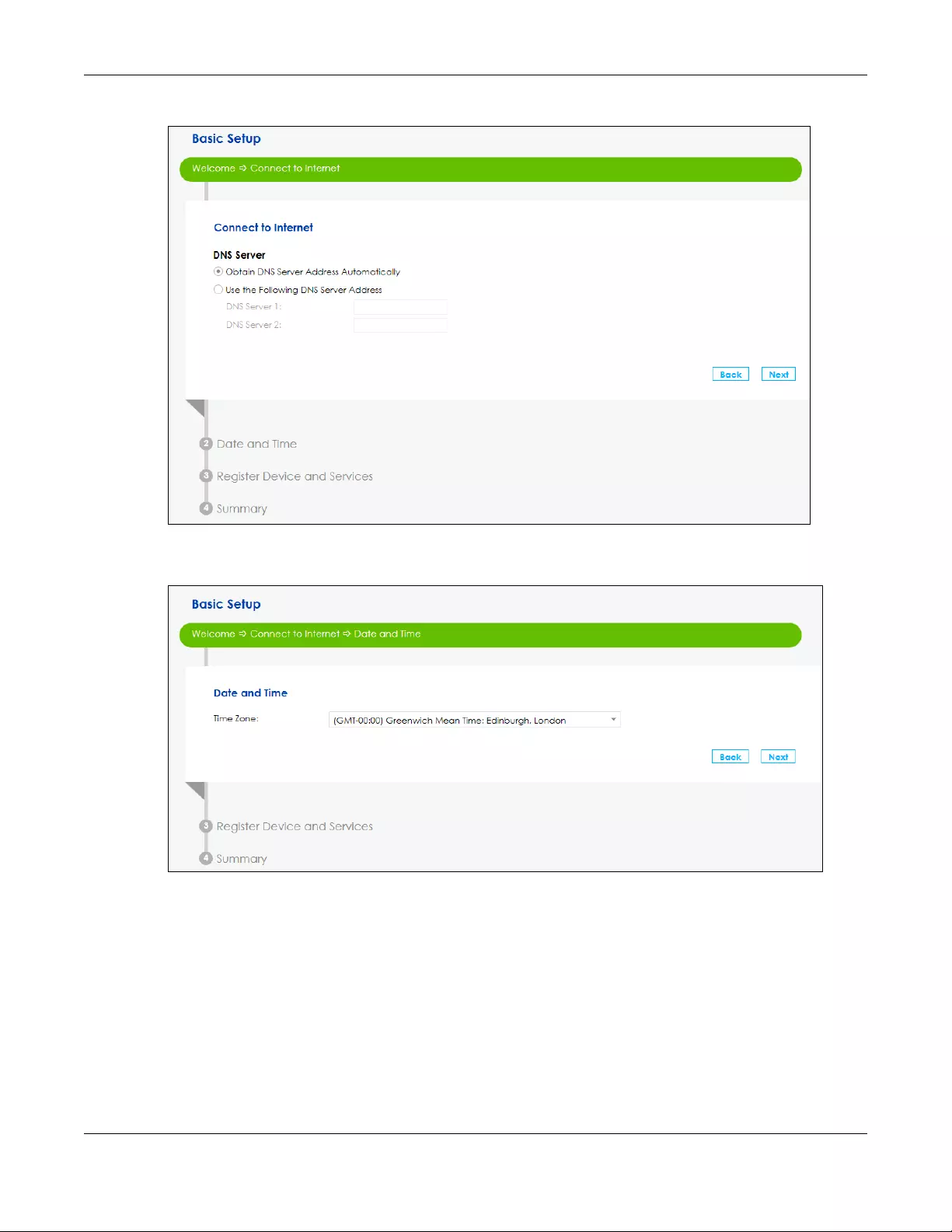
6Choose the time zone for your device’s location. Click Save.
Figure 19 Date and Time
7The SBG saves your settings and attempts to connect to the Internet. If the SBG failed to connect to the
Internet or if you want to modify any of the settings you previously configured you can click Back or go
to the Configuration > WAN/Internet > WAN Setup screen. Click Connection Test for the SBG to try
reconnecting with the same settings.
Chapter 3 Wizard
SBG5500 Series User’s Guide
31
Figure 20 Basic Setup Completed
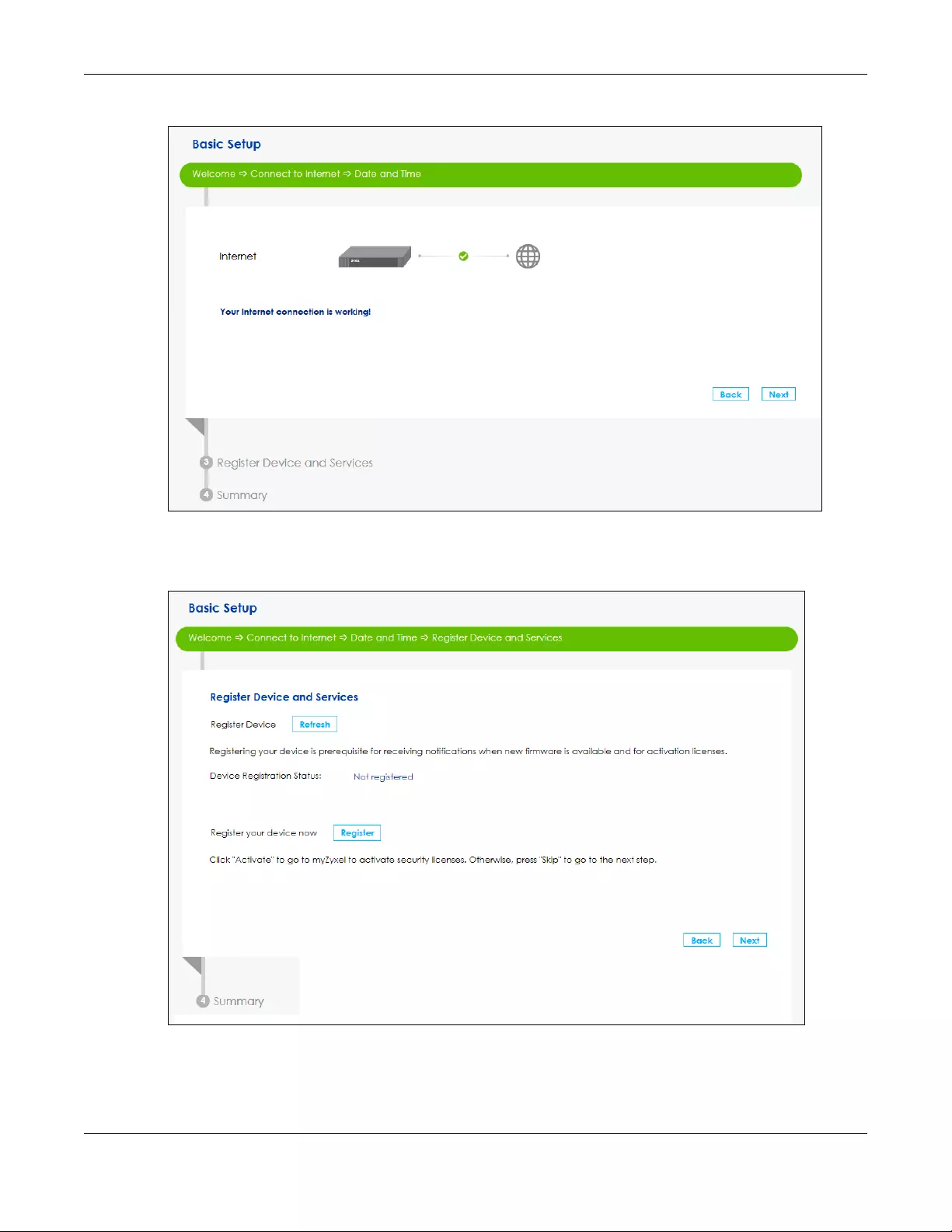
8You can register your device and manage subscription services available for your SBG at myZyxel portal
for online services.
Figure 21 Register Device and Services
9Once you completed the basic setup a summary of your settings displays. Click Finish to continue with
the Wizard setup.
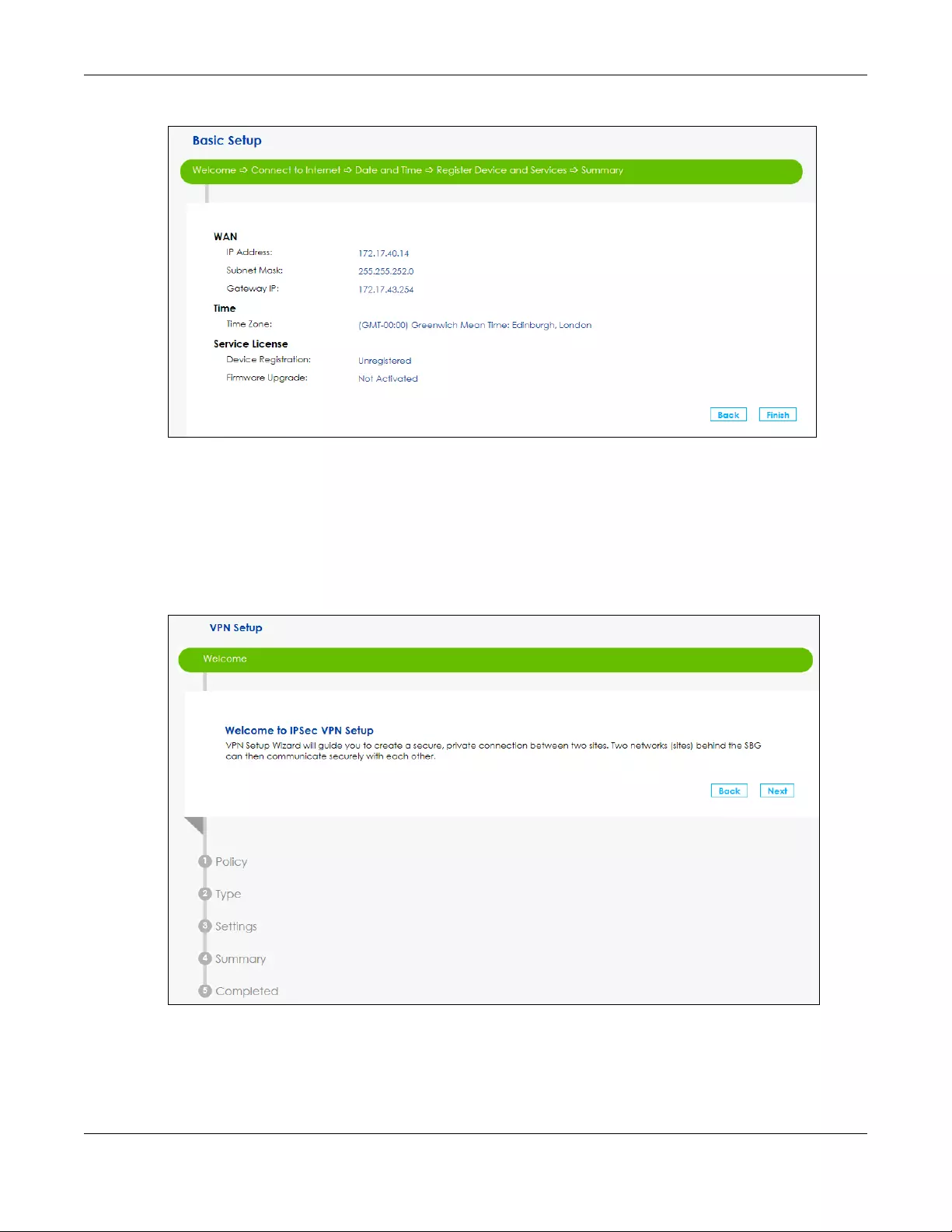
Chapter 3 Wizard
SBG5500 Series User’s Guide
32
Figure 22 Summary
3.3 Wizard IPsec VPN Setup
Click the IPsec VPN Setup down arrow to configure a VPN (Virtual Private Network) rule for a secure
connection to another computer or network.
Figure 23 Wizard IPsec VPN Setup
There are two types of VPN policies you can configure in the SBG. Select one and click Next.
•Express - Select Express to create a VPN rule with the default phase 1 and phase 2 settings and use a
pre-shared key as the authentication method. See Section 3.3.1 on page 33.
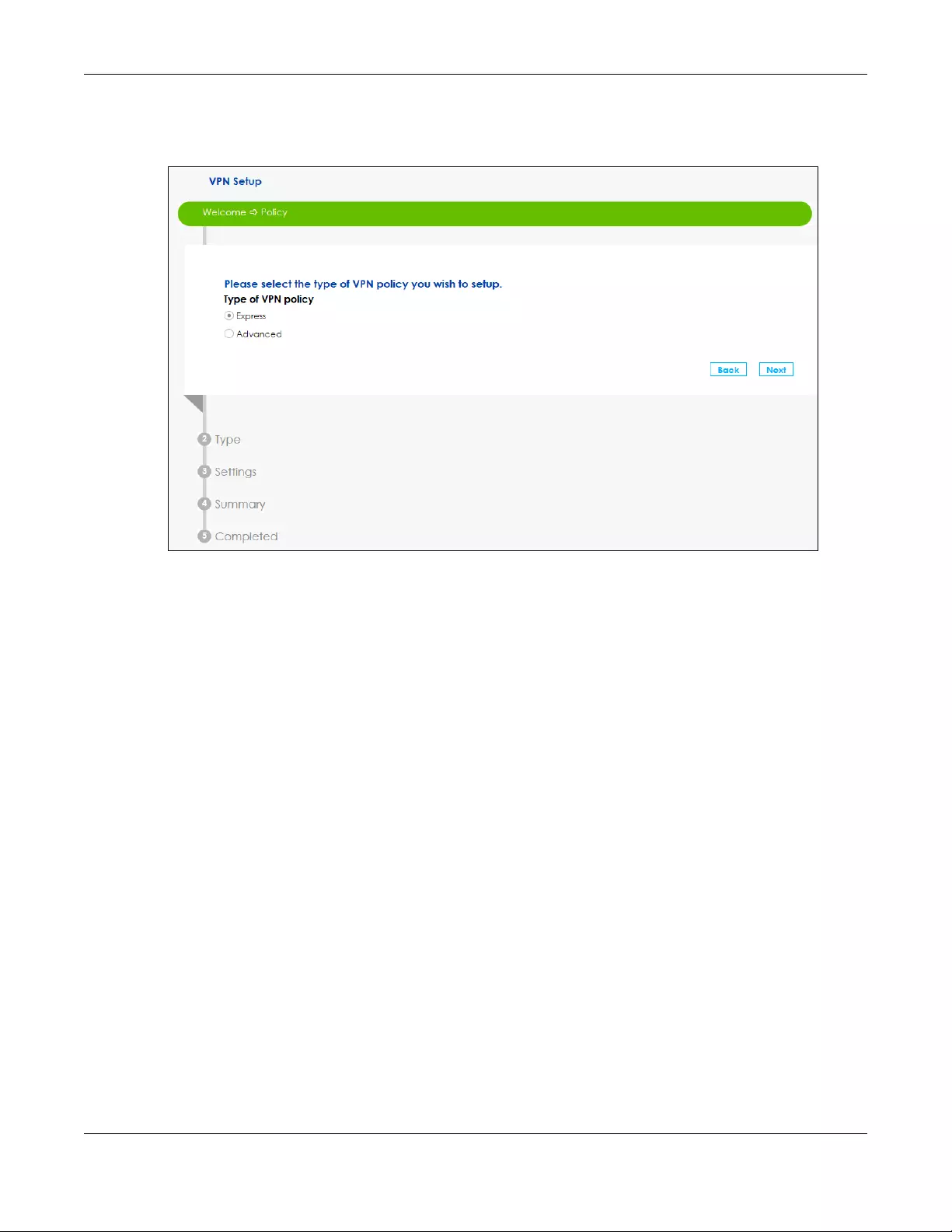
Chapter 3 Wizard
SBG5500 Series User’s Guide
33
• Advanced - Select Advanced to change default settings an/or use certificates instead of a pre-
shared key in the VPN rule. See Section 3.3.2 on page 35.
Figure 24 VPN Policy Type
3.3.1 VPN Express Settings
The following screens will display if you select Express in the previous screen.
1Type the Rule Name used to identify this VPN connection (and VPN gateway). Then select the IKE
Version and Scenario that best describes your intended VPN connection. For more information on each
label see Section 10.5 on page 163.
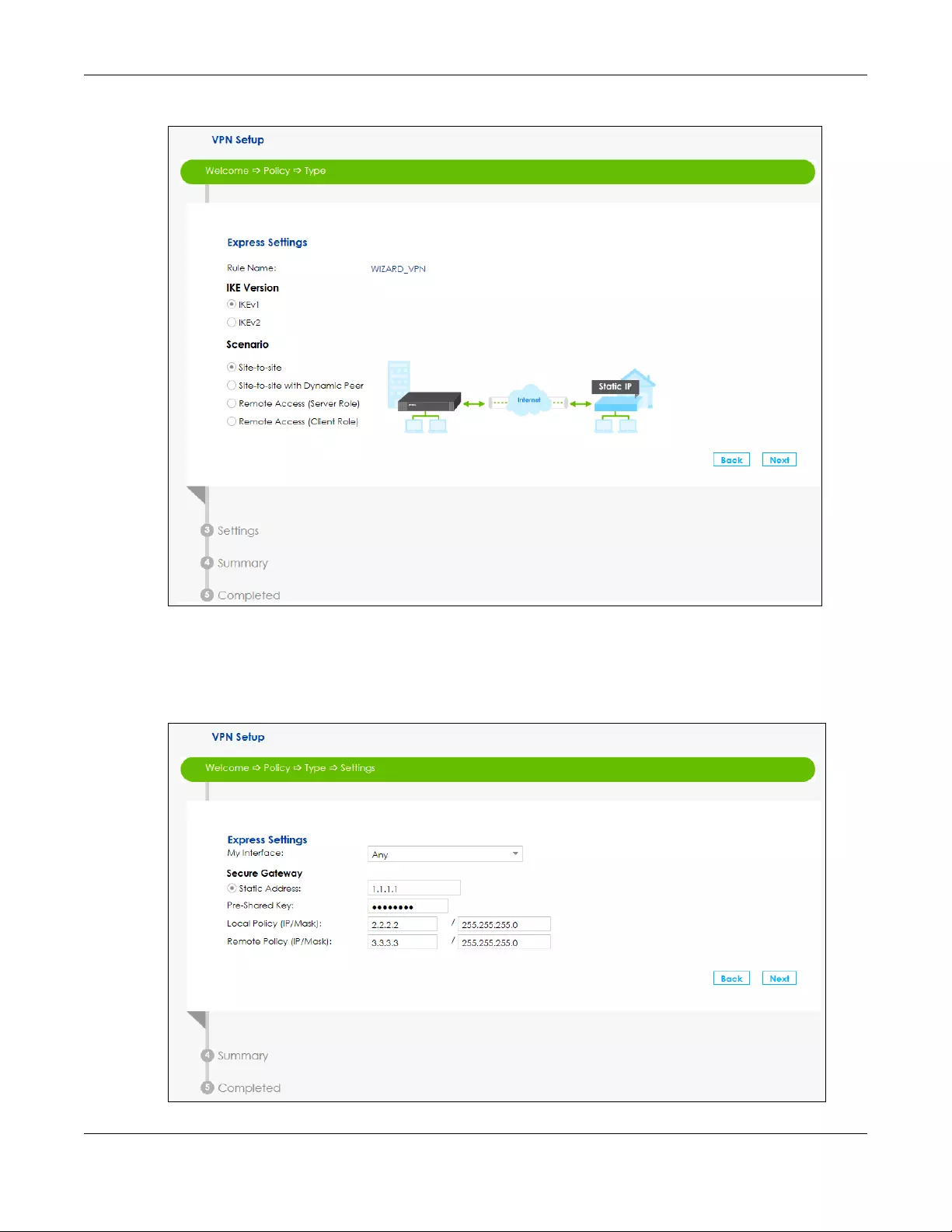
Chapter 3 Wizard
SBG5500 Series User’s Guide
34
Figure 25 VPN Express Settings
2In My Interface select the type of encapsulation this connection is to use. Configure a Secure Gateway
IP as the peer SBG’s WAN IP address. Type a secure Pre-Shared Key. Set Local Policy to be the IP address
range of the network connected to the SBG and Remote Policy to be the IP address range of the
network connected to the peer SBG.
Figure 26 Secure Gateway
Chapter 3 Wizard
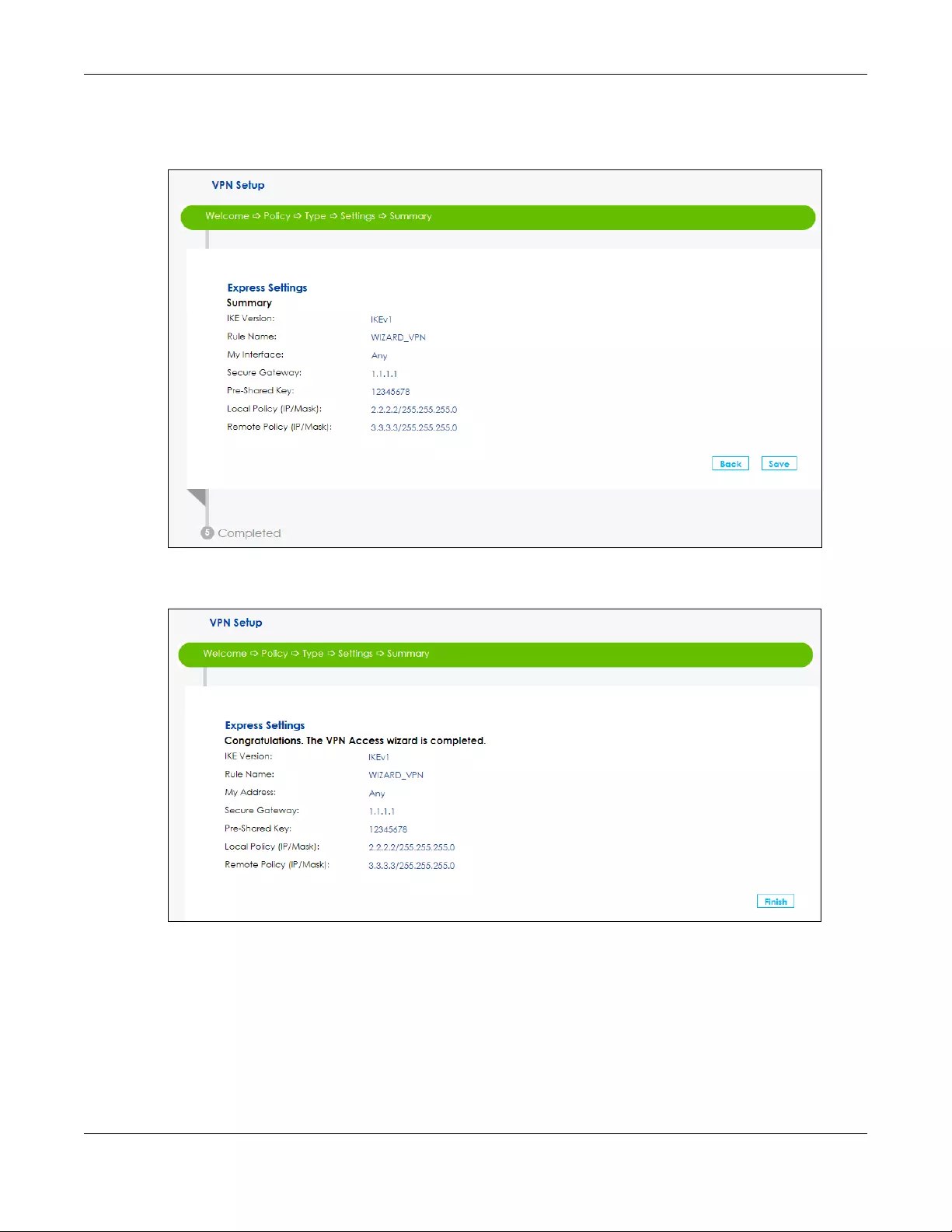
SBG5500 Series User’s Guide
35
3This screen shows a read-only summary of the VPN tunnel’s configuration. Click Save to apply your
changes.
Figure 27 Summary
4Your SBG saves your settings. Now the VPN rule is configured on the SBG.
Figure 28 VPN Express Settings Completed
3.3.2 VPN Advanced Settings
The following screens will display if you select Advanced in the VPN Policy screen.
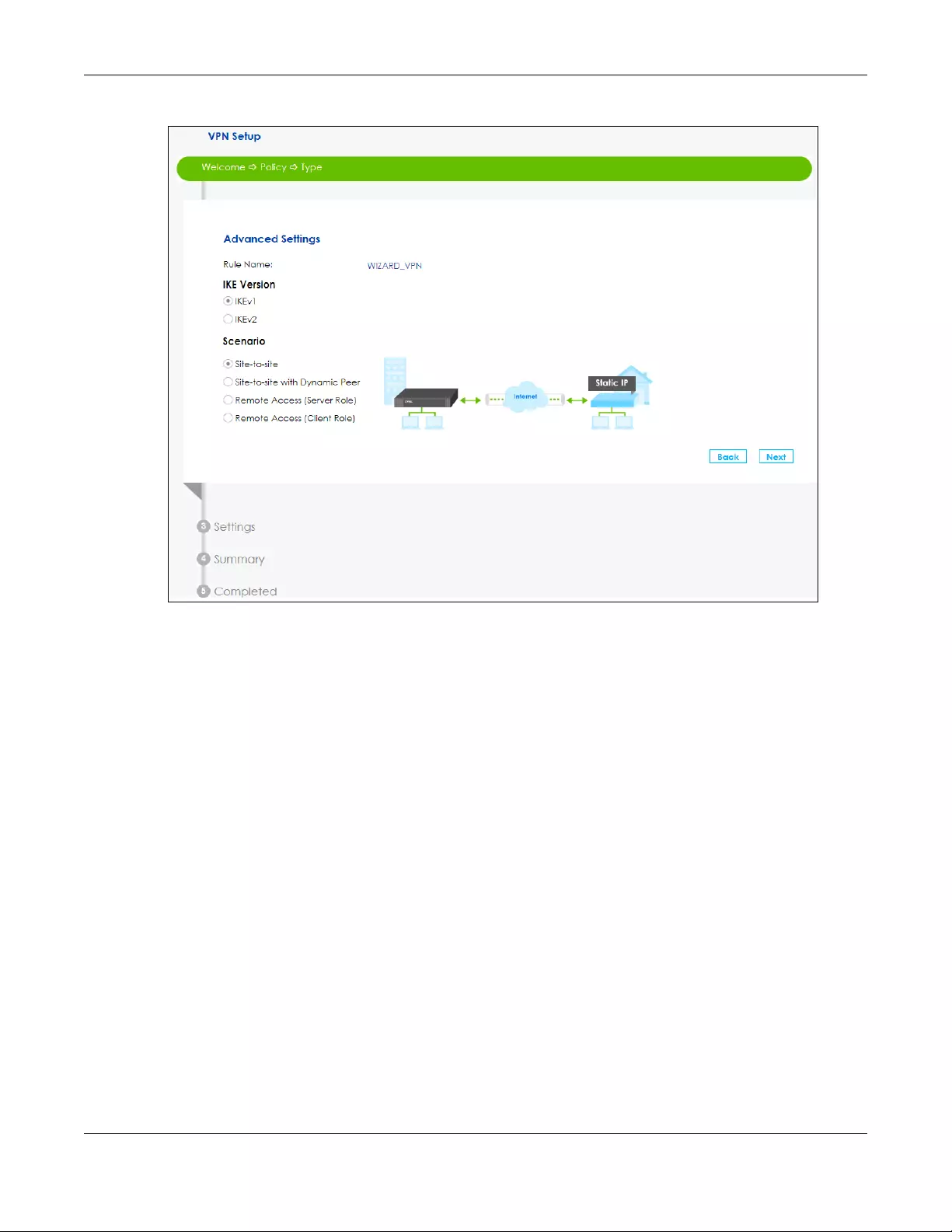
1Type the Rule Name used to identify this VPN connection (and VPN gateway). Then select the IKE
Version and the Scenario that best describes your intended VPN connection. Then click Next. For more
information on each label see Section 10.5 on page 163.
Chapter 3 Wizard
SBG5500 Series User’s Guide
36
Figure 29 VPN Advanced Settings
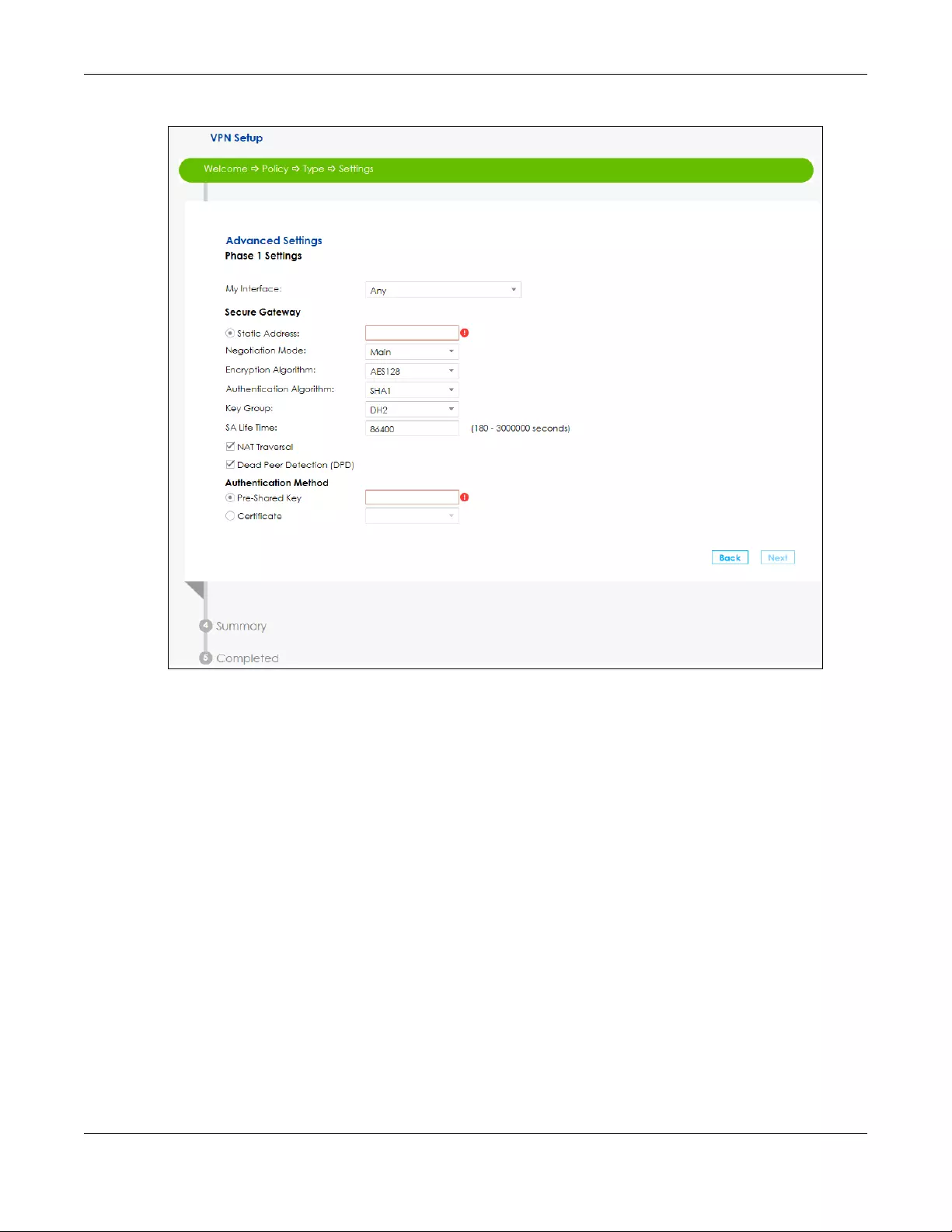
2Use the following screen to setup Phase 1 Settings. Select an Encryption, Authentication Algorithm, and
Key Group, and define how often the SBG renegotiates the IKE SA in the Life Time field. For more
information on each label see Section 10.5 on page 163.
Chapter 3 Wizard
SBG5500 Series User’s Guide
37
Figure 30 Phase 1 Settings
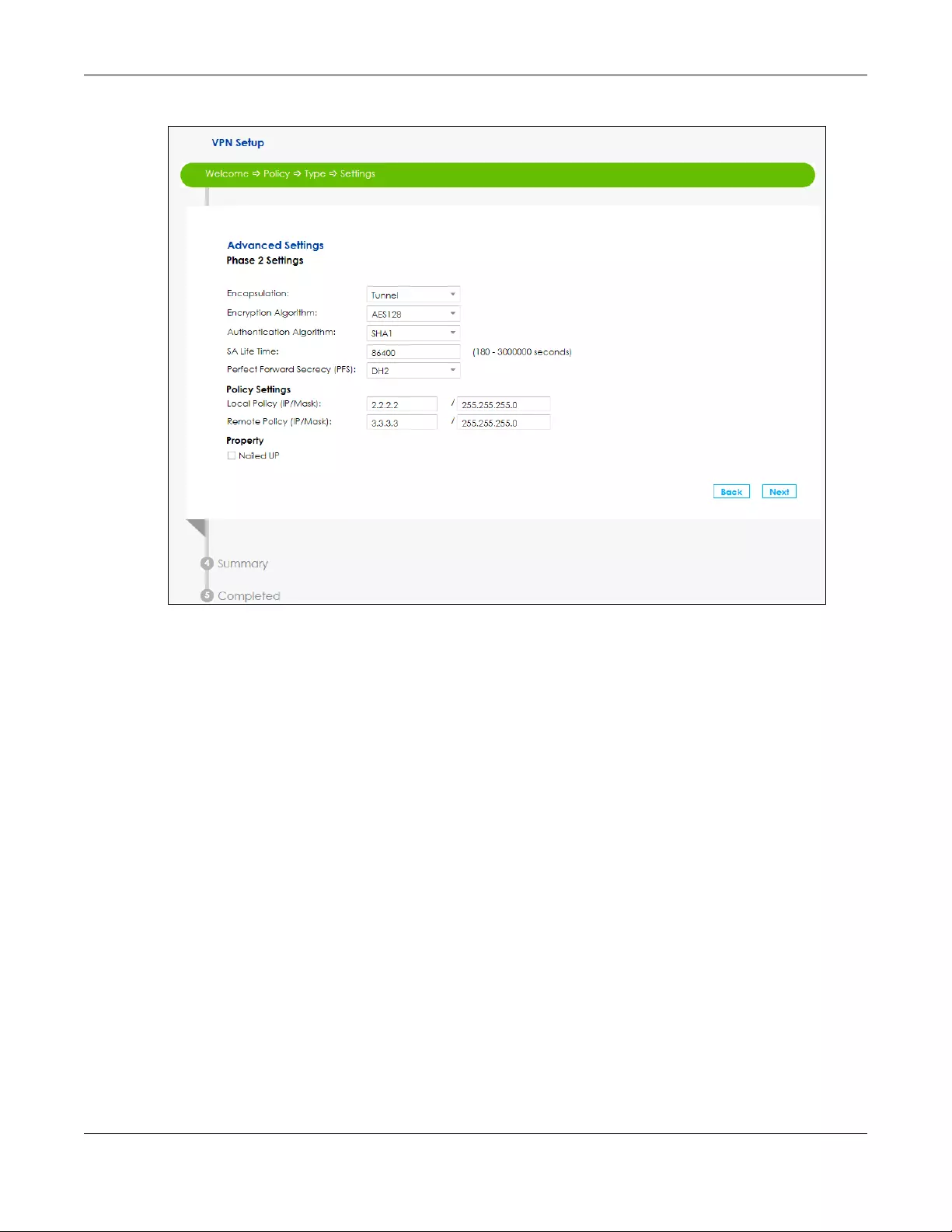
3Use the following screen to setup Phase 2 Settings. Phase 2 in an IKE uses the SA that was established in
phase1 to negotiate Security Associations (SAs) for IPsec. For more information on each label on this
screen see Section 10.5 on page 163. Click Next.
Chapter 3 Wizard
SBG5500 Series User’s Guide
38
Figure 31 Phase 2 Settings
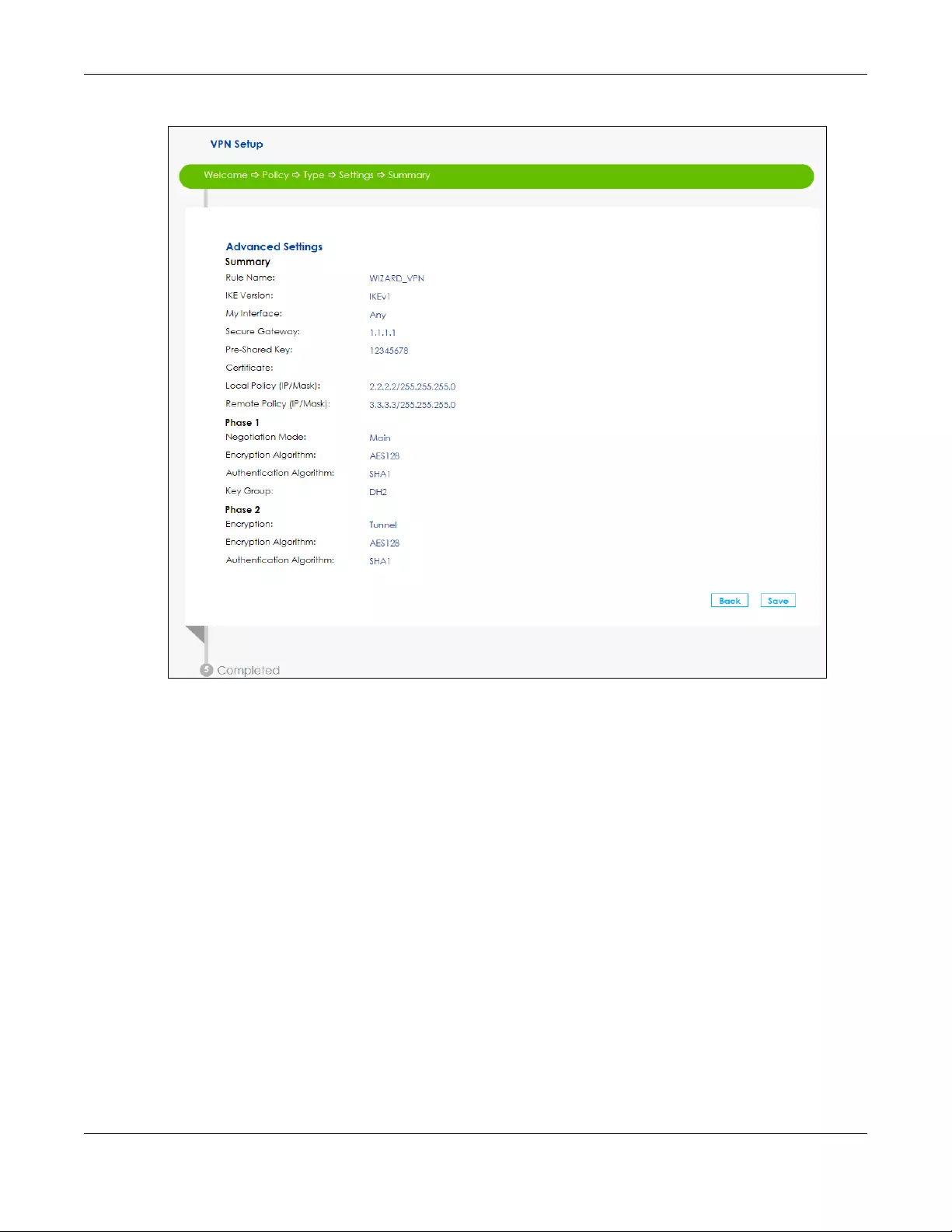
4A read-only summary of the VPN tunnel’s configuration will display. If you want to save your changes
click Save; otherwise go Back to modify any previous configurations.
Chapter 3 Wizard
SBG5500 Series User’s Guide
39
Figure 32 Summary
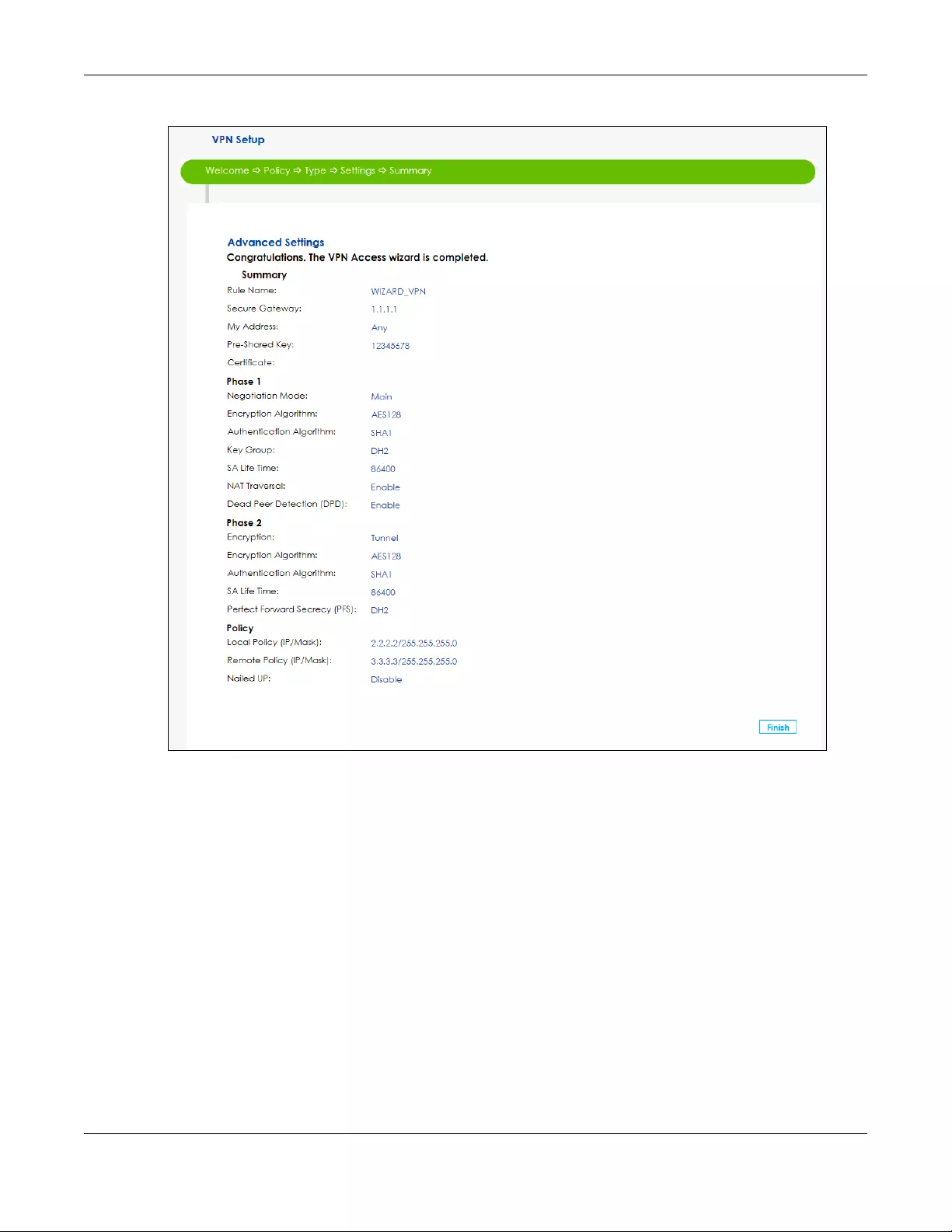
5Your SBG saves your settings. Now the rule is configured on the SBG. Click Finish to exit the VPN Setup
Wizard.
Chapter 3 Wizard
SBG5500 Series User’s Guide
40
Figure 33 VPN Advanced Settings Completed
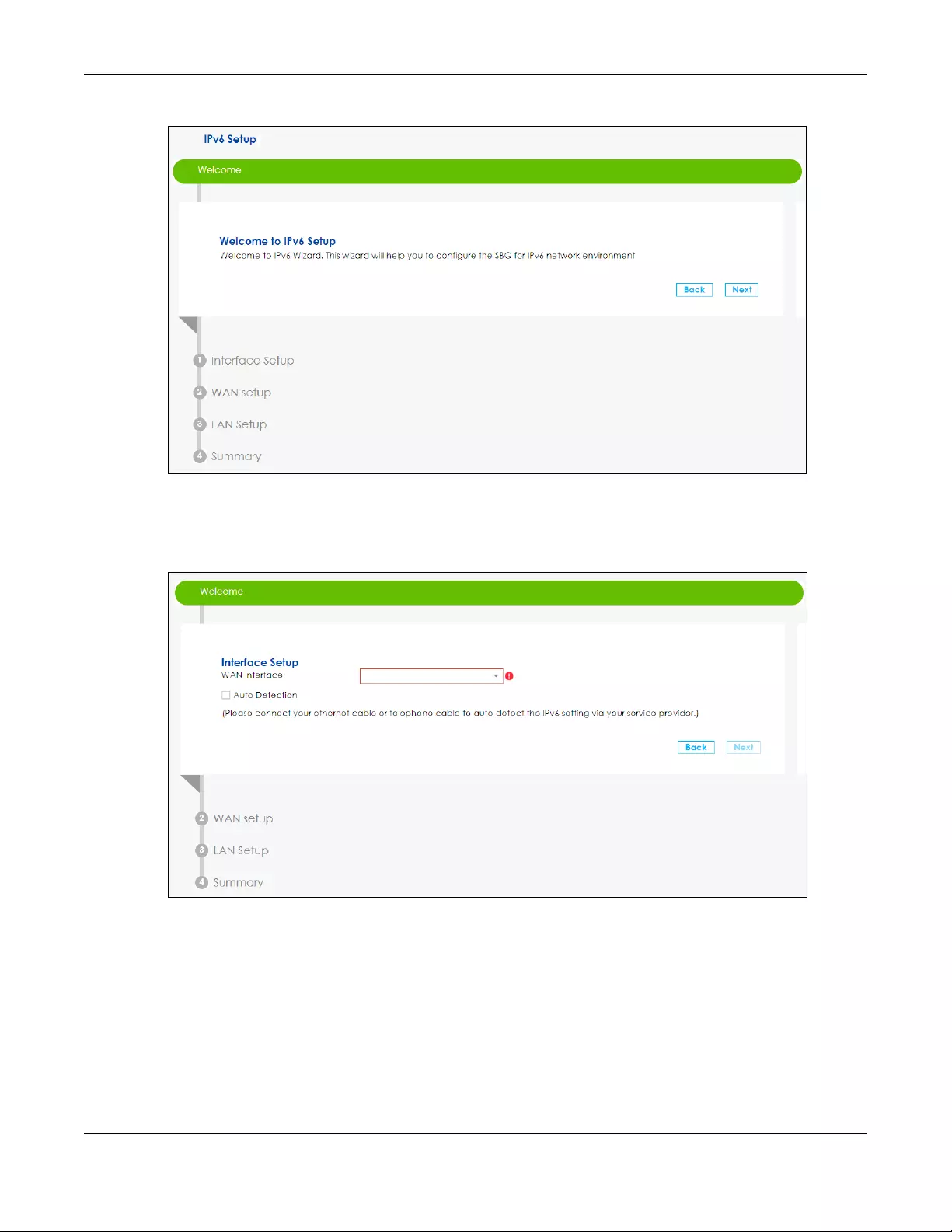
3.4 Wizard IPv6 Setup
Click the IPv6 Setup down arrow to configure the IPv6 settings on the SBG. Click Next to continue the
Wizard, Back to return to the previous screen.
Chapter 3 Wizard
SBG5500 Series User’s Guide
41
Figure 34 Wizard IPv6 Setup
6Select the WAN interface on which you want to have an IPv6 connection. Select Auto Detection for the
SBG to automatically detect the IPv6 Internet connection type, and the Wizard IPv6 setup is completed.
If you want to enter a static IPv6 address or obtain it from a DHCP server click Next.
Figure 35 Interface Setup
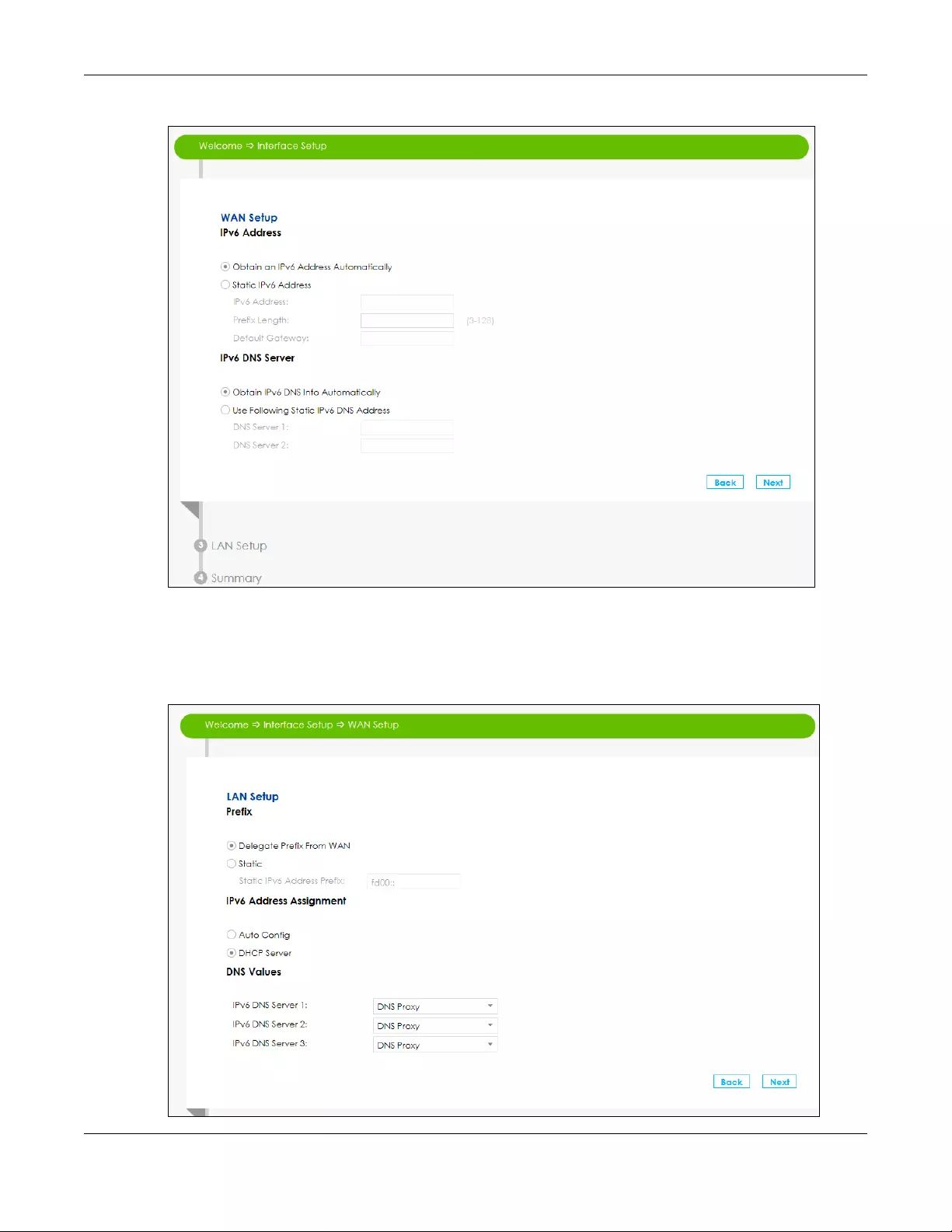
7If you did not select Auto Detection the following screen displays. Use this screen to enter a static IPv6
address assigned by your ISP, and/or obtain an IPv6 address from a DHCPv6 server. The IP address
assigned by a DHCP server has priority over the IP address automatically generated by the SBG.
Chapter 3 Wizard
SBG5500 Series User’s Guide
42
Figure 36 WAN Setup
8Use this screen to configure the LAN IPv6 settings of the SBG. Select Delegate Prefix From WAN to
automatically obtain an IPv6 network prefix from the previously selected interface. Or select Static to
configure a static IPv6 address for the SBG’s LAN IPv6 address. Select the type of service that you are
registered from your DNS service provider. Click Next to save your settings.
Figure 37 LAN Setup
Chapter 3 Wizard
SBG5500 Series User’s Guide
43
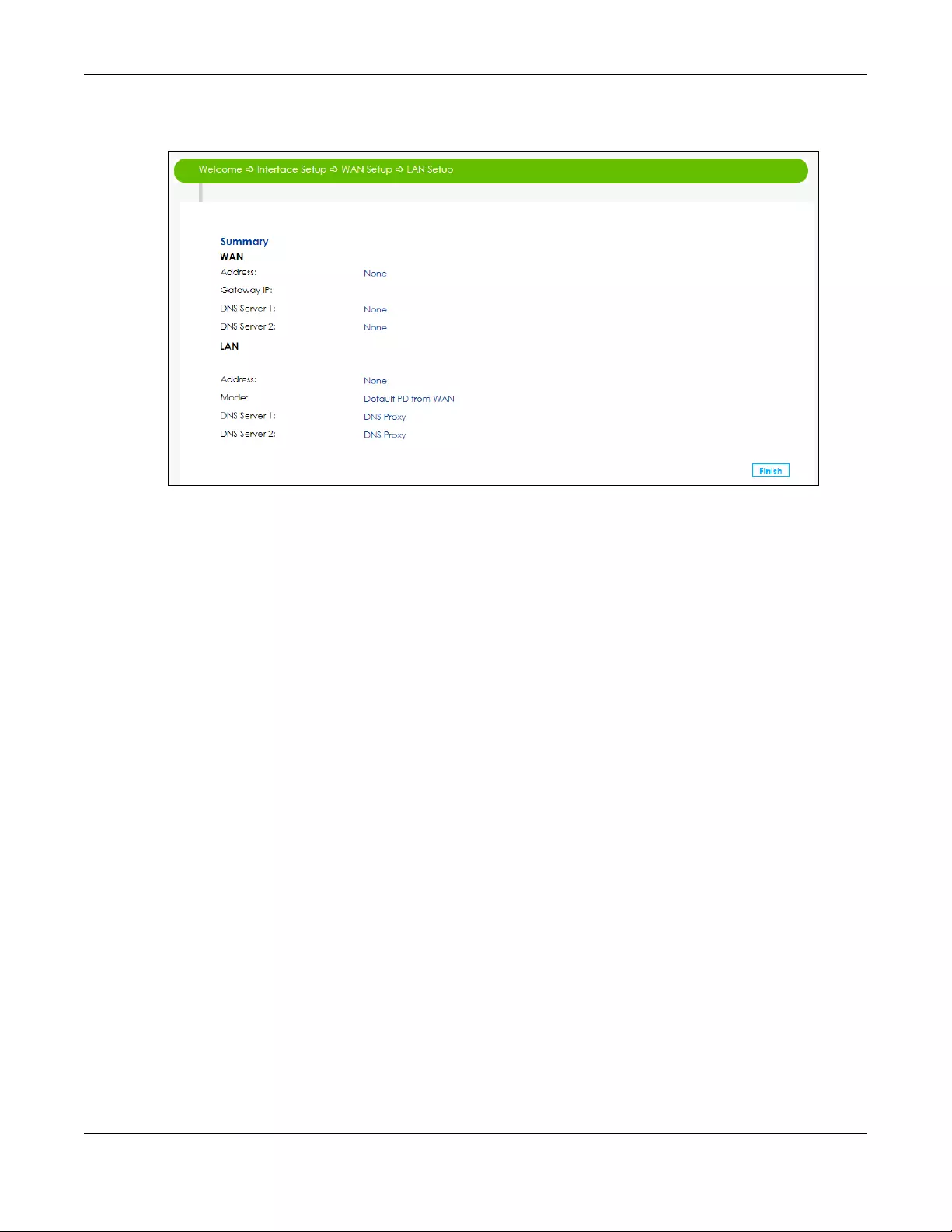
9A read-only summary of the IPv6 settings will display. Click Finish to exit the Wizard IPv6 Setup.
Figure 38 Summary

44
PART II
Technical Reference
SBG5500 Series User’s Guide
45
CHAPTER 4
Dashboard
4.1 Overview
After you log into the Web Configurator, the Dashboard screen appears. This shows the network
connection status of the SBG and clients connected to it.
You can use the Dashboard screen to look at the current status of the SBG, system resources, and
interfaces (LAN and WAN).
4.2 The Dashboard Screen
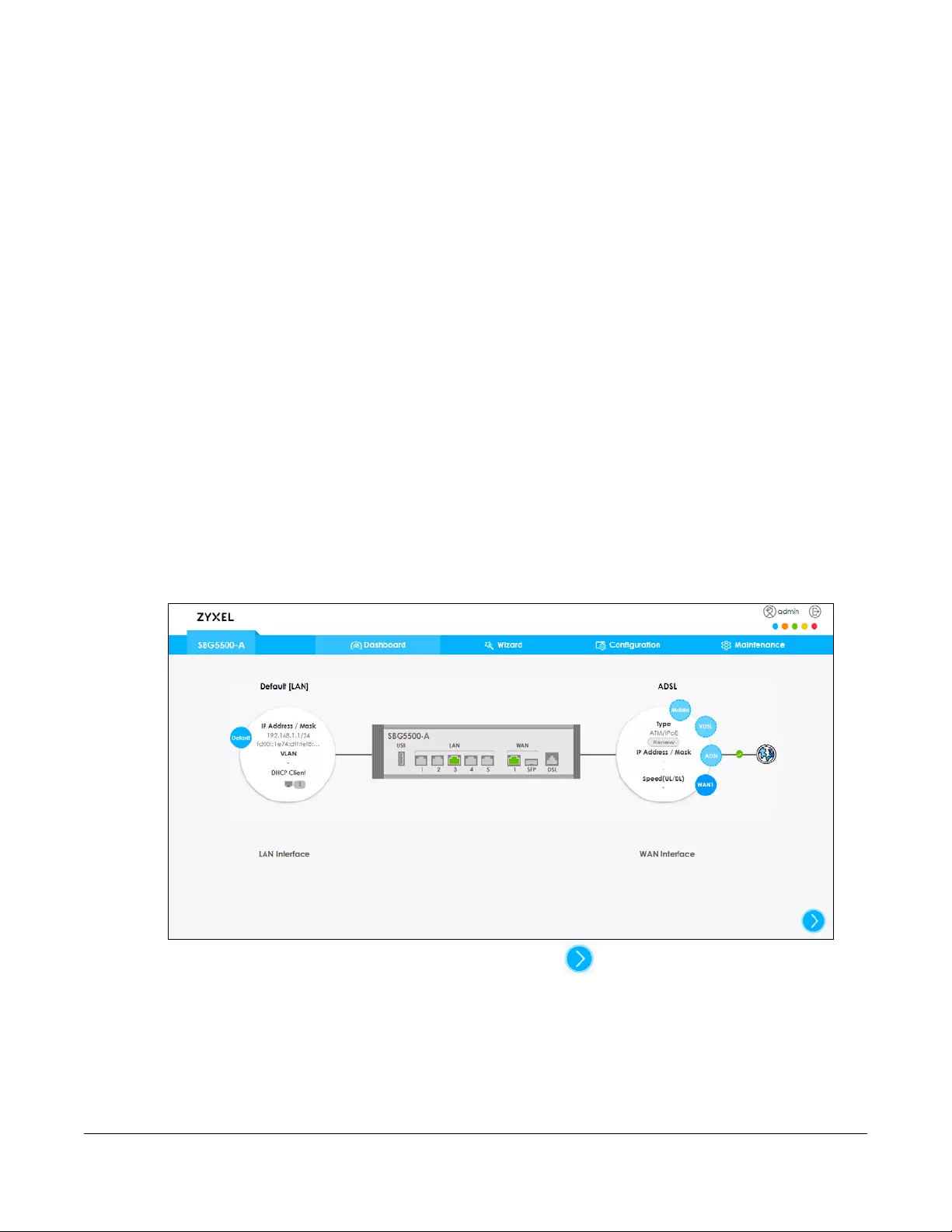
Use this screen to view the connections status of the SBG. When you click the Dashboard tab a network
map opens. You can view the number of devices connected to the SBG. Click on each interface icon
to view details about the SBG interfaces.
Figure 39 Dashboard Screen
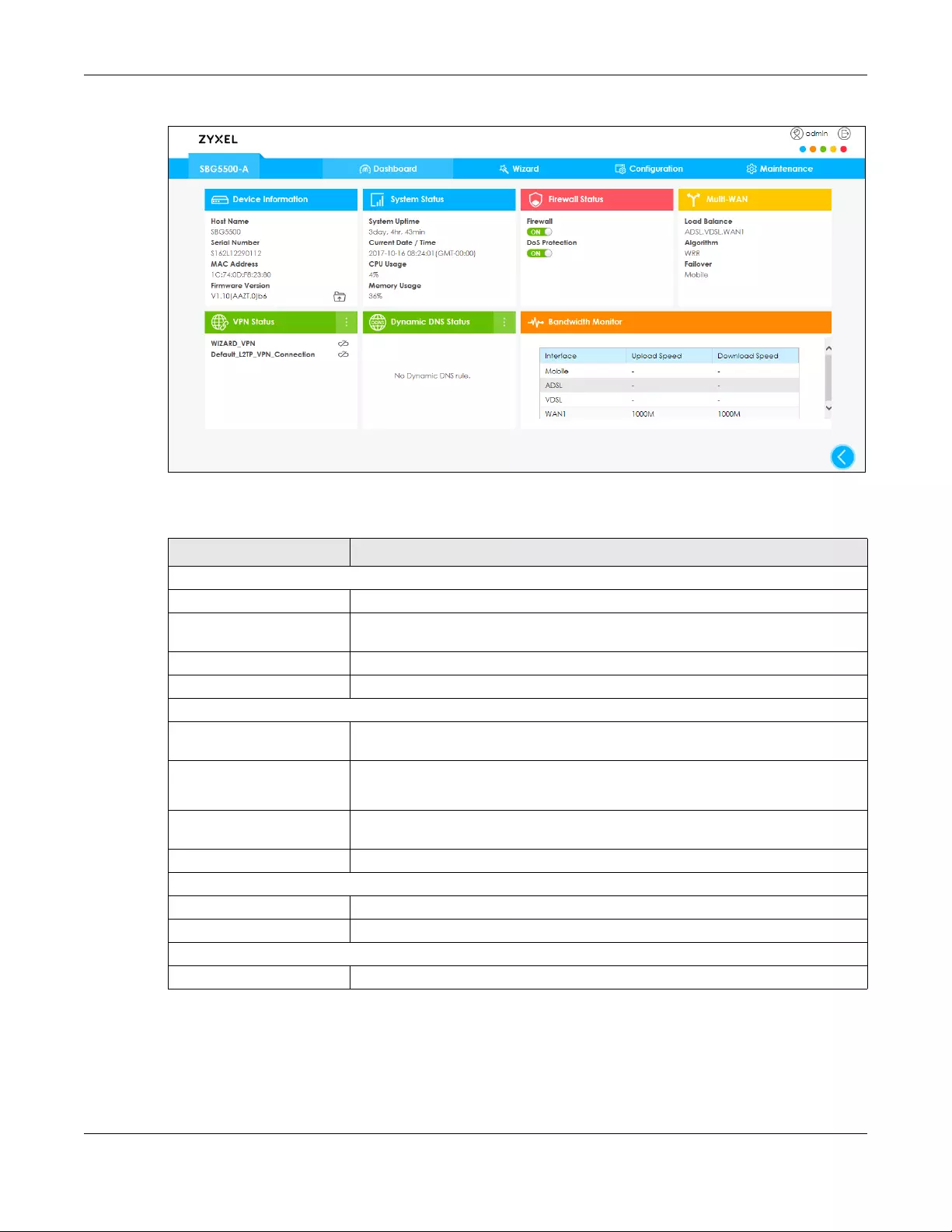
If you prefer to view the status in a list, click the arrow icon to show the Dashboard’s list view.
Chapter 4 Dashboard
SBG5500 Series User’s Guide
46
Figure 40 Dashboard List View Screen
Each field is described in the following table.
Table 4 Dashboard List View Screen
LABEL DESCRIPTION
Device Information
Host Name This field displays the name used to identify the SBG on any network.
Serial Number This field displays the serial number of this SBG. The serial number is used for device
tracking and control.
MAC Address This field displays the MAC address used by the SBG.
Firmware Version This field displays the present firmware version.
System Status
System Uptime This field displays how long the SBG has been running since it last restarted or was
turned on.
Current Date/Time This field displays the time in the SBG.
Each time you reload this page, the SBG synchronizes the date with the time server.
CPU Usage This field displays what percentage of the SBG’s processing capability is currently
being used.
Memory Usage This field displays what percentage of the SBG’s RAM is currently being used.
Firewall Status
Firewall Click the slide button to enable and disable the firewall on the SBG.
DoS Protection Click the slide button to activate protection against DoS attacks.
Multi-WAN
Load Balance This shows the active WAN interfaces in the SBG.

Chapter 4 Dashboard
SBG5500 Series User’s Guide
47
Algorithm This field displays the type of load balancing algorithm currently used by the SBG.
WRR (Weighted Round Robin) to balance the traffic load between interfaces based
on their respective weights.
LLF (Least Load First) to send new session traffic through the least utilized trunk
member.
SPILLOVER to send network traffic through the first interface in the group member list
until there is enough traffic that the second interface needs to be used (and so on).
Failover This field displays the passive interfaces used for failover in the SBG.
VPN Status This field displays the SBG’s VPN connections and if the IP Sec SA is connected or
disconnected.
Dynamic DNS Status This field display the SBG’s dynamic DNS and the interface each DDNS uses.
Bandwidth Monitor
Interface This field displays the name of each interface in the SBG.
Upload Speed This displays interface’s current upload link speed.
Download Speed This displays interface’s current download link speed.
Table 4 Dashboard List View Screen
LABEL DESCRIPTION
SBG5500 Series User’s Guide
48
CHAPTER 5
WAN/Internet
5.1 Overview
This chapter discusses the SBG’s WAN/Internet screens. Use these screens to configure your SBG for
Internet access.
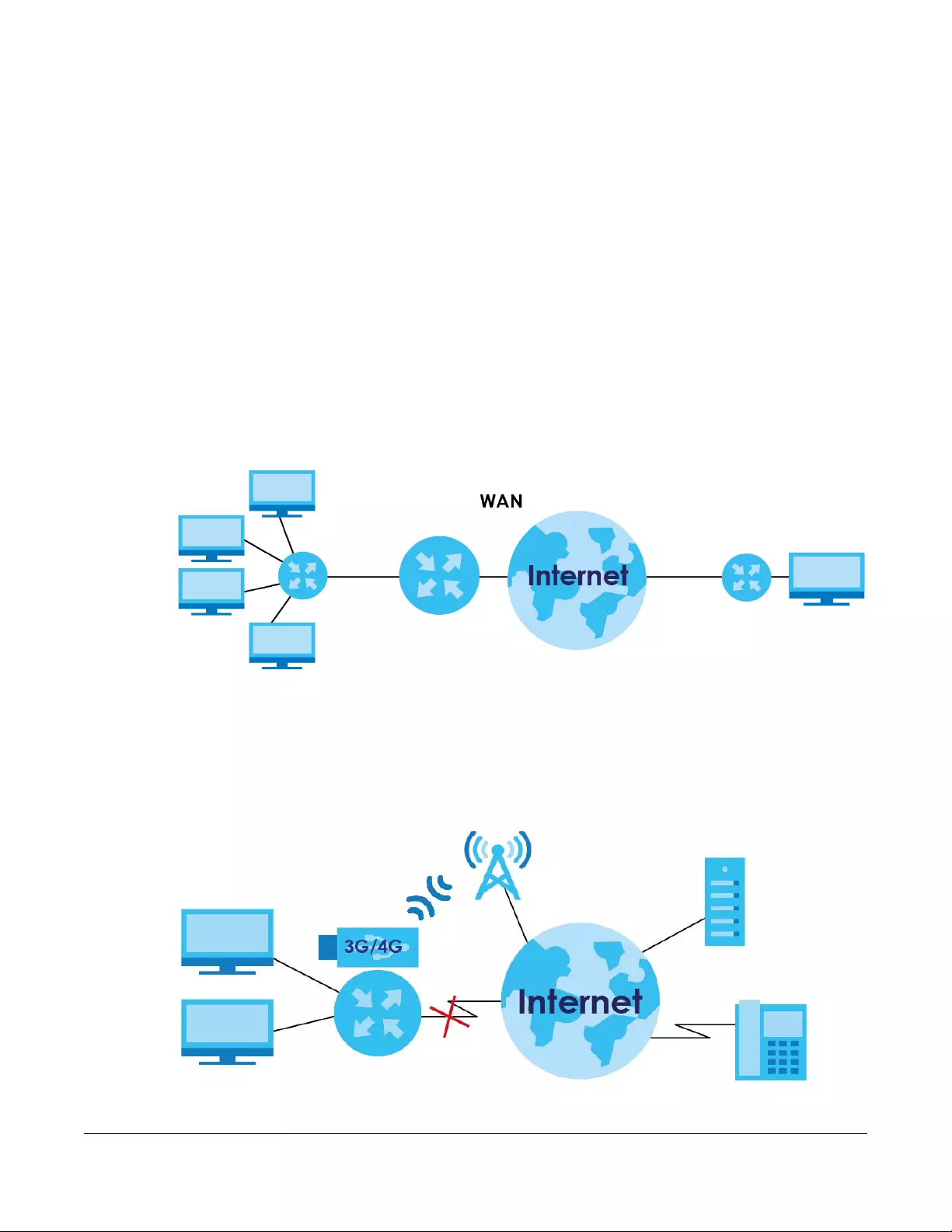
A WAN (Wide Area Network) connection is an outside connection to another network or the Internet. It
connects your private networks, such as a LAN (Local Area Network) and other networks, so that a
computer in one location can communicate with computers in other locations.
Figure 41 LAN and WAN
3G (third generation) standards for the sending and receiving of voice, video, and data in a mobile
environment.
You can attach a 3G/4G wireless adapter to the USB port and set the SBG to use this 3G connection as
your WAN or a backup when the wired WAN connection fails.
Figure 42 3G/4G WAN Connection
SBG
SBG
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
49
5.1.1 What You Can Do in this Chapter
• Use the WAN Status screen to view the WAN traffic statistics (Section 5.3 on page 56).
• Use the WAN Setup screen to view, remove or add a WAN interface. You can also configure the WAN
settings on the SBG for Internet access (Section 5.3 on page 56).
• Use the Mobile screen to configure a 3G/4G WAN connection (Section 5.4 on page 68).
• Use the Port Setting screen to set flexible ports as part of LAN or WAN interfaces. (Section 5.5 on page
72).
• Use the Multi-WAN screen to configure the multiple WAN load balancing and failover rules to
distribute traffic among different interfaces (Section 5.6 on page 73).
• Use the Dynamic DNS screen to enable DDNS and configure the DDNS settings on the SBG (Section
5.7 on page 76).
• Use the xDSL Advanced screen to enable Annex M, DSL PhyR and other functions (Section 5.8 on
page 79).
5.1.2 What You Need to Know
The following terms and concepts may help as you read this chapter.
Encapsulation Method
Encapsulation is used to include data from an upper layer protocol into a lower layer protocol. To set up
a WAN connection to the Internet, you need to use the same encapsulation method used by your ISP
Table 5 WAN Setup Overview
LAYER-2 INTERFACE INTERNET CONNECTION
CONNECTION DSL LINK TYPE MODE ENCAPSULATION CONNECTION SETTINGS
ADSL/VDSL over
PTM
N/A Routing PPPoE PPP information, IPv4/IPv6 IP address,
routing feature, DNS server, VLAN,
QoS, and MTU
IPoE IPv4/IPv6 IP address, routing feature,
DNS server, VLAN, QoS, and MTU
Bridge N/A VLAN and QoS
ADSL over ATM EoA Routing PPPoE/PPP0A ATM PCV configuration, PPP
information, IPv4/IPv6 IP address,
routing feature, DNS server, VLAN,
QoS, and MTU
IPoE/IPoA ATM PCV configuration, IPv4/IPv6 IP
address, routing feature, DNS server,
VLAN, QoS, and MTU
Bridge N/A ATM PCV configuration, and QoS
Ethernet N/A Routing IPoE/PPPoE PPP information, IPv4/IPv6 IP address,
routing feature, DNS server, VLAN,
QoS, and MTU
Bridge N/A VLAN and QoS
3G N/A Nailed Up PPP/IPoE Dial string, APN (Access Point Name),
IP address, DNS server
On Demand PPP/IPoE Dial string, APN, Maximum idle time
out, IP address, DNS server

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
50
(Internet Service Provider). If your ISP offers a dial-up Internet connection using PPPoE (PPP over
Ethernet), they should also provide a username and password (and service name) for user
authentication.
WAN IP Address
The WAN IP address is an IP address for the SBG, which makes it accessible from an outside network. It is
used by the SBG to communicate with other devices in other networks. It can be static (fixed) or
dynamically assigned by the ISP each time the SBG tries to access the Internet.
If your ISP assigns you a static WAN IP address, they should also assign you the subnet mask and DNS
server IP address(es).
ATM
Asynchronous Transfer Mode (ATM) is a WAN networking technology that provides high-speed data
transfer. ATM uses fixed-size packets of information called cells. With ATM, a high QoS (Quality of Service)
can be guaranteed. ATM uses a connection-oriented model and establishes a virtual circuit (VC)
between Finding Out More
PTM
Packet Transfer Mode (PTM) is packet-oriented and supported by the VDSL2 standard. In PTM, packets
are encapsulated directly in the High-level Data Link Control (HDLC) frames. It is designed to provide a
low-overhead, transparent way of transporting packets over DSL links, as an alternative to ATM.
3G
3G (Third Generation) is a digital, packet-switched wireless technology. Bandwidth usage is optimized as
multiple users share the same channel and bandwidth is only allocated to users when they send data. It
allows fast transfer of voice and non-voice data and provides broadband Internet access to mobile
devices.
IPv6 Introduction
IPv6 (Internet Protocol version 6), is designed to enhance IP address size and features. The increase in
IPv6 address size to 128 bits (from the 32-bit IPv4 address) allows up to 3.4 x 1038 IP addresses. The SBG
can use IPv4/IPv6 dual stack to connect to IPv4 and IPv6 networks, and supports IPv6 rapid deployment
(6RD).
IPv6 Addressing
The 128-bit IPv6 address is written as eight 16-bit hexadecimal blocks separated by colons (:). This is an
example IPv6 address 2001:0db8:1a2b:0015:0000:0000:1a2f:0000.
IPv6 addresses can be abbreviated in two ways:
• Leading zeros in a block can be omitted. So 2001:0db8:1a2b:0015:0000:0000:1a2f:0000 can be
written as 2001:db8:1a2b:15:0:0:1a2f:0.
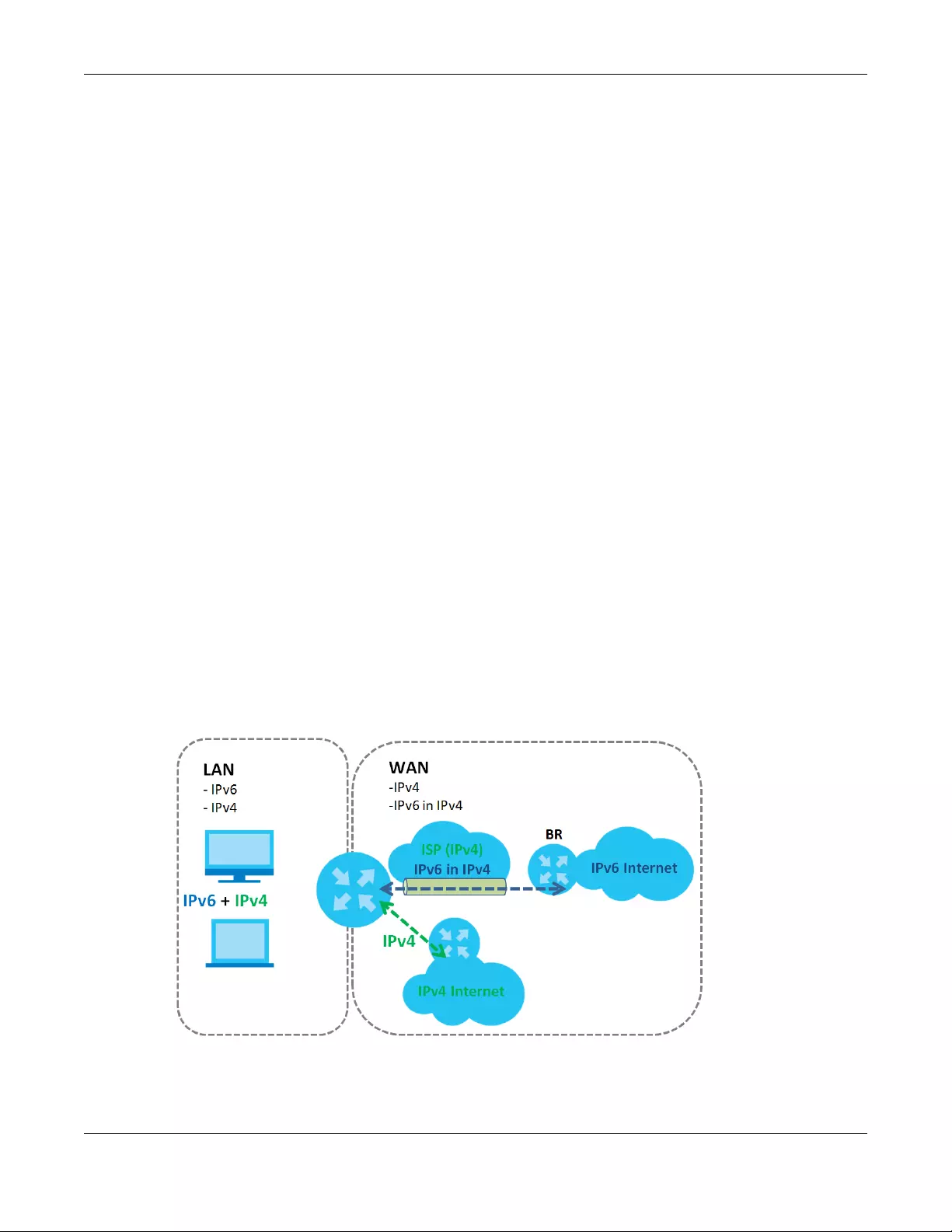
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
51
• Any number of consecutive blocks of zeros can be replaced by a double colon. A double colon can
only appear once in an IPv6 address. So 2001:0db8:0000:0000:1a2f:0000:0000:0015 can be
written as 2001:0db8::1a2f:0000:0000:0015, 2001:0db8:0000:0000:1a2f::0015,
2001:db8::1a2f:0:0:15 or 2001:db8:0:0:1a2f::15.
IPv6 Prefix and Prefix Length
Similar to an IPv4 subnet mask, IPv6 uses an address prefix to represent the network address. An IPv6
prefix length specifies how many most significant bits (start from the left) in the address compose the
network address. The prefix length is written as “/x” where x is a number. For example,
2001:db8:1a2b:15::1a2f:0/32
means that the first 32 bits (2001:db8) is the subnet prefix.
IPv6 Subnet Masking
Both an IPv6 address and IPv6 subnet mask compose of 128-bit binary digits, which are divided into
eight 16-bit blocks and written in hexadecimal notation. Hexadecimal uses four bits for each character
(1 ~ 10, A ~ F). Each block’s 16 bits are then represented by four hexadecimal characters. For example,
FFFF:FFFF:FFFF:FFFF:FC00:0000:0000:0000.
IPv6 Rapid Deployment
Use IPv6 Rapid Deployment (6rd) when the local network uses IPv6 and the ISP has an IPv4 network.
When the SBG has an IPv4 WAN address and you set IPv4/IPv6 Mode to IPv4 Only, you can enable 6rd
to encapsulate IPv6 packets in IPv4 packets to cross the ISP’s IPv4 network.
The SBG generates a global IPv6 prefix from its IPv4 WAN address and tunnels IPv6 traffic to the ISP’s
Border Relay router (BR in the figure) to connect to the native IPv6 Internet. The local network can also
use IPv4 services. The SBG uses it’s configured IPv4 WAN IP to route IPv4 traffic to the IPv4 Internet.
Figure 43 IPv6 Rapid Deployment
SBG
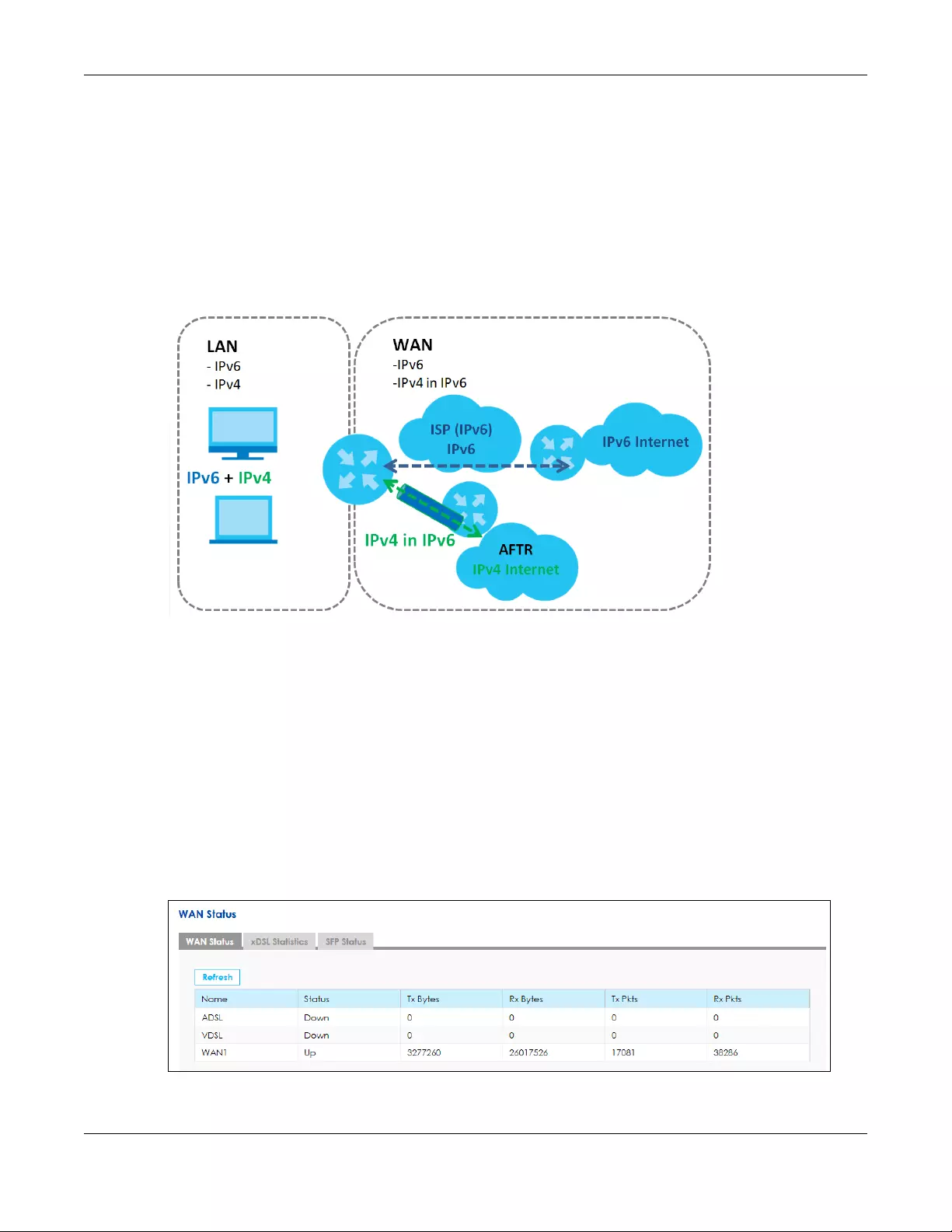
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
52
Dual Stack Lite
Use Dual Stack Lite when local network computers use IPv4 and the ISP has an IPv6 network. When the
SBG has an IPv6 WAN address and you set IPv4/IPv6 Mode to IPv6 Only, you can enable Dual Stack Lite
to use IPv4 computers and services.
The SBG tunnels IPv4 packets inside IPv6 encapsulation packets to the ISP’s Address Family Transition
Router (AFTR in the graphic) to connect to the IPv4 Internet. The local network can also use IPv6 services.
The VDSL Router uses it’s configured IPv6 WAN IP to route IPv6 traffic to the IPv6 Internet.
Figure 44 Dual Stack Lite
5.1.3 Before You Begin
You need to know your Internet access settings such as encapsulation and WAN IP address. Get this
information from your ISP.
5.2 The WAN Status Screen
Use this screen to show the number of bytes received and sent on the SBG. Click Configuration > WAN /
Internet to open the WAN Status screen.
Figure 45 Configuration > WAN / Internet > WAN Status
SBG
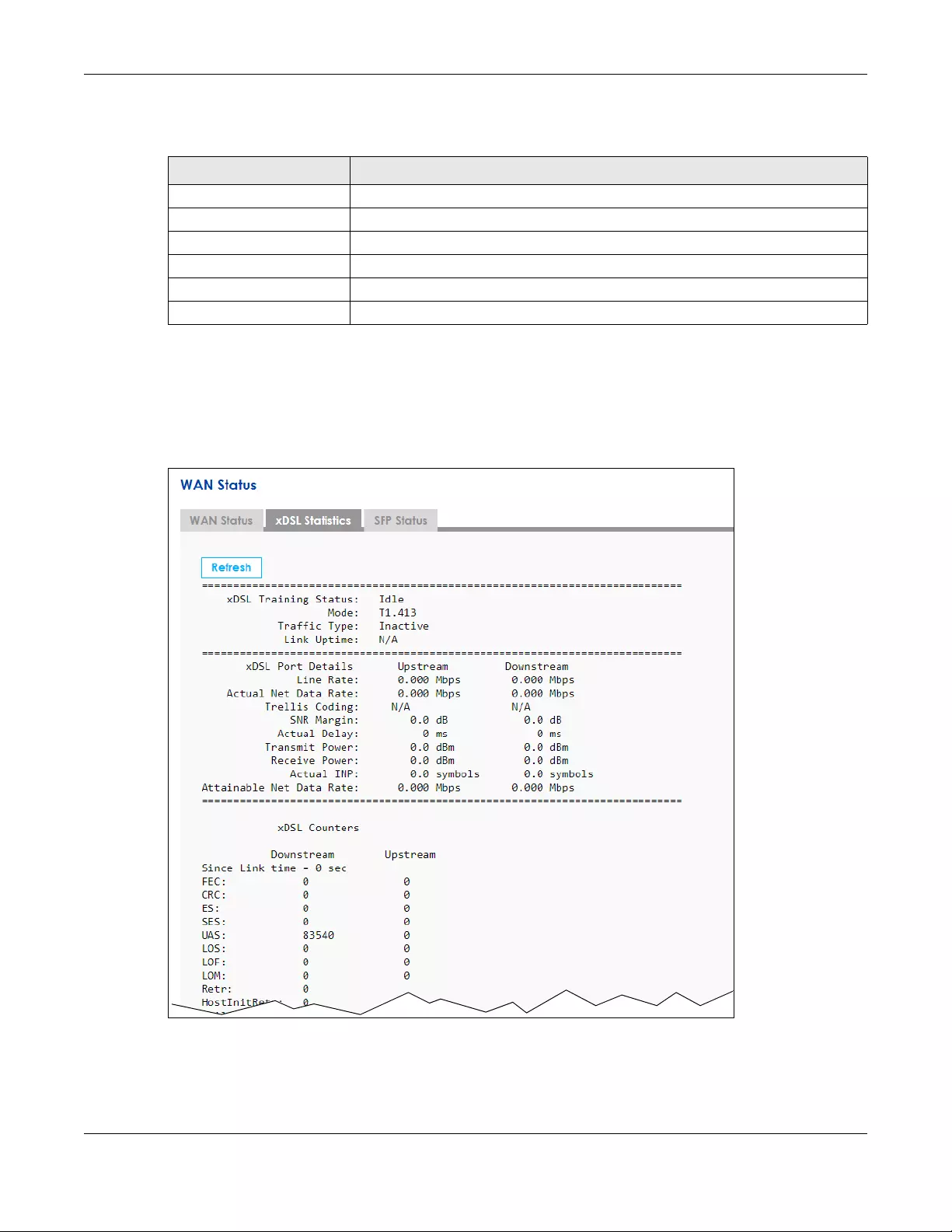
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
53
The following table describes the labels in this screen.
5.2.1 The xDSL Statistics Screen
Use this screen to view detailed DSL statistics. Click Configuration > WAN / Internet > WAN Status and
click on the xDSL Statistics tab.
Figure 46 Configuration > WAN / Internet > WAN Status > xDSL Statistics
Table 6 Configuration > WAN / Internet > WAN Status
LABEL DESCRIPTION
Name This displays the name of the WAN interface.
Status This shows Up if the connection to this interface is up, otherwise it will display Down.
Tx Bytes This indicates the number of bytes transmitted on this interface.
Rx Bytes This indicates the number of bytes received on this interface.
Tx Pkts This indicates the number of transmitted packets on this interface.
Rx Pkts This indicates the number of received packets on this interface.
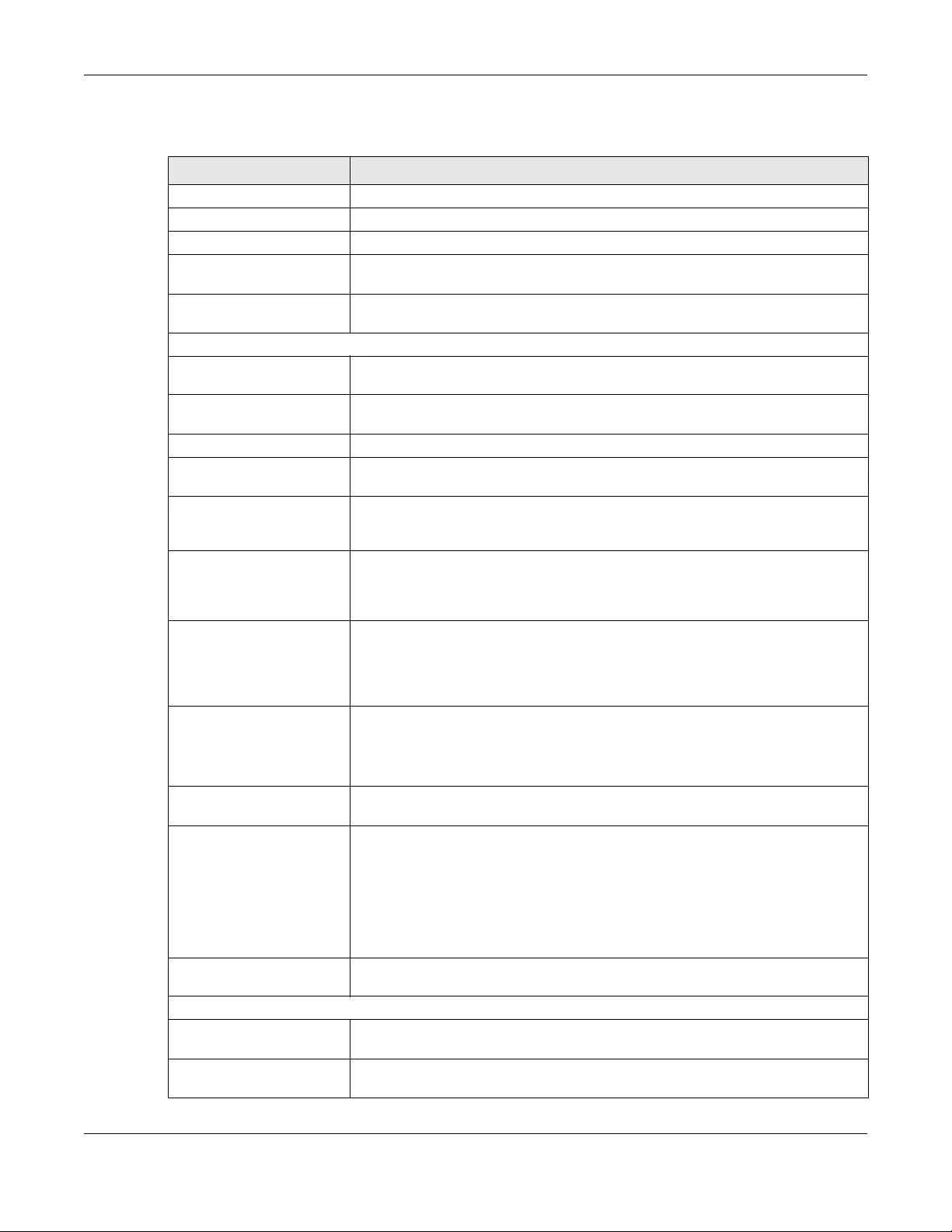
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
54
The following table describes the labels in this screen.
Table 7 Configuration > WAN / Internet > WAN Status > xDSL Statistics
LABEL DESCRIPTION
Refresh Click this to refresh the statistics.
xDSL Training Status This displays the current state of setting up the DSL connection.
Mode This displays the ITU standard used for this connection.
Traffic Type This displays the type of traffic the DSL port is sending and receiving. Inactive displays
if the DSL port is not currently sending or receiving traffic.
Link Uptime This displays how long the port has been running (or connected) since the last time it
was started.
xDSL Port Details
Upstream These are the statistics for the traffic direction going out from the port to the service
provider.
Downstream These are the statistics for the traffic direction coming into the port from the service
provider.
Line Rate These are the data transfer rates at which the port is sending and receiving data.
Actual Net Data Rate These are the rates at which the port is sending and receiving the payload data
without transport layer protocol headers and traffic.
Trellis Coding This displays whether or not the port is using Trellis coding for traffic it is sending and
receiving. Trellis coding helps to reduce the noise in ADSL transmissions. Trellis may
reduce throughput but it makes the connection more stable.
SNR Margin This is the upstream and downstream Signal-to-Noise Ratio margin (in dB). A DMT sub-
carrier’s SNR is the ratio between the received signal power and the received noise
power. The signal-to-noise ratio margin is the maximum that the received noise
power could increase with the system still being able to meet its transmission targets.
Actual Delay This is the upstream and downstream interleave delay. It is the wait (in milliseconds)
that determines the size of a single block of data to be interleaved (assembled) and
then transmitted. Interleave delay is used when transmission error correction (Reed-
Solomon) is necessary due to a less than ideal telephone line. The bigger the delay,
the bigger the data block size, allowing better error correction to be performed.
Transmit Power This is the upstream and downstream far end actual aggregate transmit power (in
dBm).
Upstream is how much power the port is using to transmit to the service provider.
Downstream is how much port the service provider is using to transmit to the port.
Receive Power Upstream is how much power the service provider is receiving from the port.
Downstream is how much power the port is receiving from the service provider.
Actual INP Sudden spikes in the line’s level of external noise (impulse noise) can cause errors
and result in lost packets. This could especially impact the quality of multimedia
traffic such as voice or video. Impulse noise protection (INP) provides a buffer to
allow for correction of errors caused by error correction to deal with this. The number
of DMT (Discrete Multi-Tone) symbols shows the level of impulse noise protection for
the upstream and downstream traffic. A higher symbol value provides higher error
correction capability, but it causes overhead and higher delay which may increase
error rates in received multimedia data.
Attainable Net Data Rate These are the highest theoretically possible transfer rates at which the port could
send and receive payload data without transport layer protocol headers and traffic.
xDSL Counters
Downstream These are the statistics for the traffic direction coming into the port from the service
provider.
Upstream These are the statistics for the traffic direction going out from the port to the service
provider.
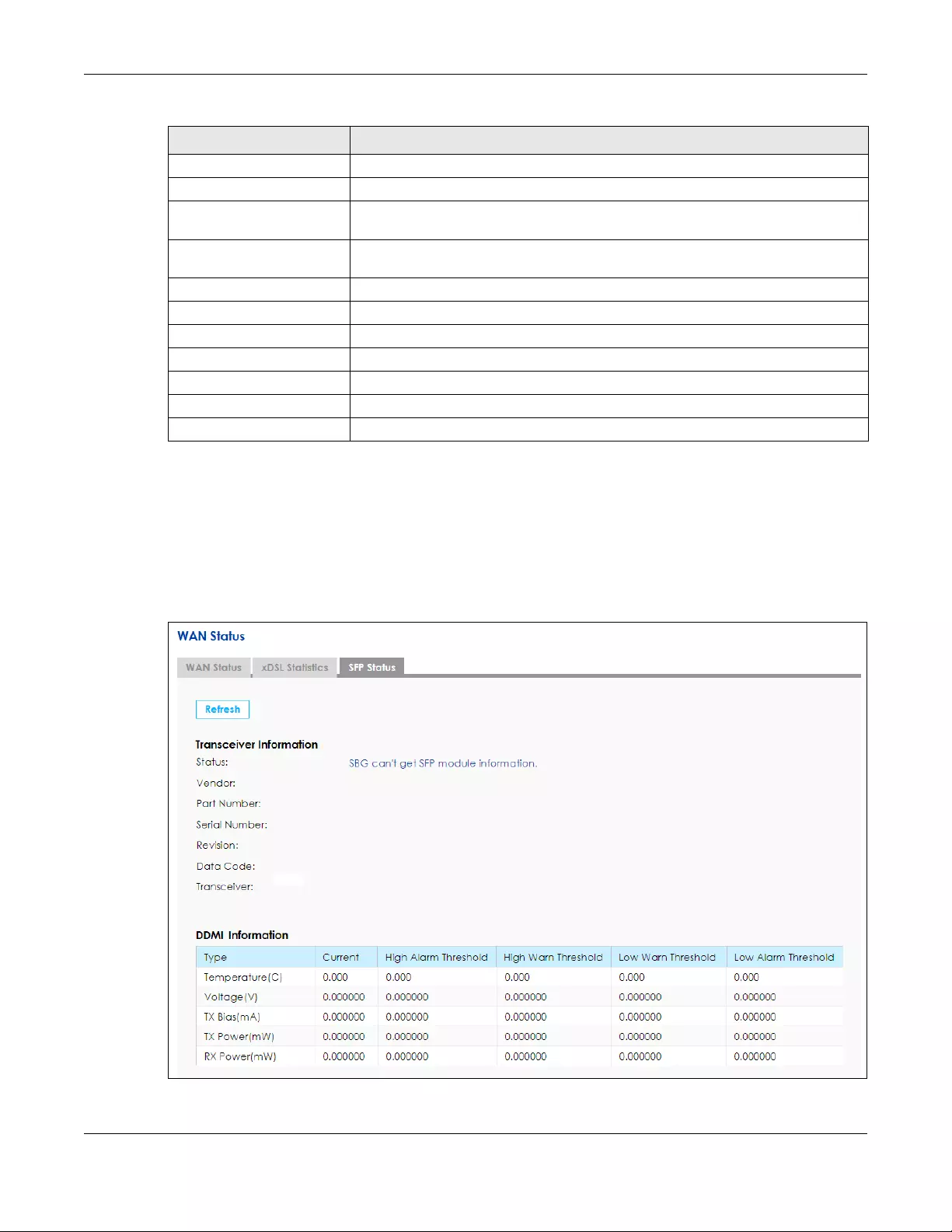
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
55
5.2.2 The SFP Status Screen
Use this screen to view details about the SBG’s SFP connection and DDMI. Digital Diagnostics Monitoring
Interface (DDMI) SFP enables a real time link to be established between the SBG and the SFP
transceiver. View operating parameters within the fiber link. Click Configuration > WAN / Internet > WAN
Status and click on the SFP Status tab.
Figure 47 Configuration > WAN / Internet > WAN Status > SFP Status
FEC This is the number of Far End Corrected blocks.
CRC This is the number of Cyclic Redundancy Checks.
ES This is the number of Errored Seconds meaning the number of seconds containing at
least one errored block or at least one defect.
SES This is the number of Severely Errored Seconds meaning the number of seconds
containing 30% or more errored blocks or at least one defect. This is a subset of ES.
UAS This is the number of UnAvailable Seconds.
LOS This is the number of Loss Of Signal seconds.
LOF This is the number of Loss Of Frame seconds.
LOM This is the number of Loss of Margin seconds.
Retr This is the number of DSL retraining count in BRCM DSL driver.
HostInitRetr This is the number of the retraining counts the host initiated.
FailedRetr This is the number of failed retraining counts
Table 7 Configuration > WAN / Internet > WAN Status > xDSL Statistics
LABEL DESCRIPTION
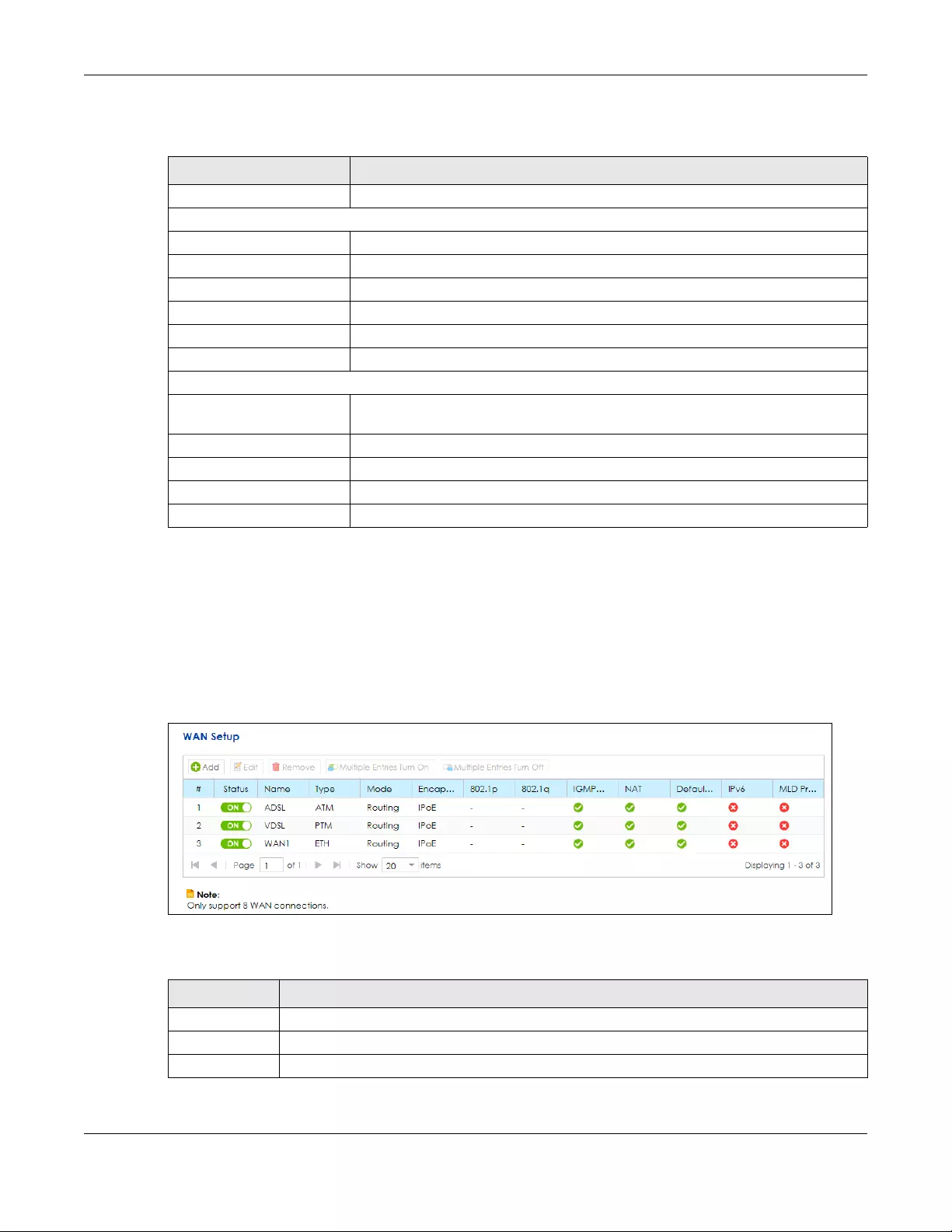
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
56
The following table describes the labels in this screen.
5.3 The WAN Setup Screen
Use this screen to change your SBG’s Internet access settings. Click Configuration > WAN / Internet >
WAN Setup from the menu. The summary table shows you the configured WAN services (connections)
on the SBG.
Figure 48 Configuration > WAN / Internet > WAN Setup
The following table describes the labels in this screen.
Table 8 Configuration > WAN / Internet > WAN Status > SFP Status
LABEL DESCRIPTION
Refresh Click Refresh to update this screen.
Transceiver Information
Status This field displays the status of the SFP transceiver.
Vendor This field displays the SFP transceiver’s vendor name.
Serial Number This field displays the SFP transceiver’s serial number provided by the vendor.
Revision This field displays the SFP transceiver’s serial number revision level for part number.
Data Code This field displays the SFP transceiver’s manufacturing data code.
Transceiver This field displays the SFP transceiver’s compatibility.
DDMI Information
Current This field displays the current value for the temperature, voltage, TX Bias, TX Power,
RX power.
High Alarm Threshold This field displays the threshold value for a high alarm.
High Warn Threshold This field displays the threshold value for a high warning.
Low Warn Threshold This field displays the threshold value for a low warning.
Low Alarm Threshold This field displays the threshold value for a low warning.
Table 9 Configuration > WAN / Internet > WAN Setup
LABEL DESCRIPTION
Add Click this button to create a new WAN connection.
Edit Click Edit to modify the WAN connection.
Remove Click Remove to delete a WAN connection.
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
57
5.3.1 Add/Edit Internet Connection
Click Add or Edit in the Configuration > WAN / Internet > WAN Setup screen to configure a WAN
connection. The screen varies depending on the interface type, mode, encapsulation, and IPv4/IPv6
mode you select.
5.3.1.1 Routing Mode
Use Routing mode if your ISP give you one IP address only and you want multiple computers to share an
Internet account.
The screen varies when you select other interface type, encapsulation, and IPv6/IPv4 mode.
Multiple Entries
Turn On
Select one or more WAN connections and click this to enable them.
Use the [Shift] or [Ctrl] key to select multiple entries.
Multiple Entries
Turn Off
Select one or more WAN connections and click this to disable them.
Use the [Shift] or [Ctrl] key to select multiple entries.
# This is the index number of the WAN connection.
Status This field displays whether the connection is active or not. A green ON button signifies that this
connection is active. A gray OFF button signifies that this connection is not active.
Click the slide button to enable and disable the connection.
Name This is the service name of the connection.
Type This shows whether it is an ATM, PTM, or Ethernet connection.
Mode This shows whether the connection is in routing or bridge mode.
Encapsulation This is the method of encapsulation used by this connection.
802.1p This indicates the IEEE 802.1p priority level assigned to traffic sent through this connection. This
displays N/A when there is no priority level assigned.
802.1q This indicates the VLAN ID number assigned to traffic sent through this connection. This displays
N/A when there is no VLAN ID number assigned.
IGMP Proxy This shows whether the SBG act as an IGMP proxy (green check mark) or not (red X) on this
connection.
NAT This shows whether NAT is activated (green check mark) or not (red X) for this connection.
Default
Gateway
This shows whether the SBG use the WAN interface of this connection as the system default
gateway (green check mark) or not (red X).
IPv6 This shows whether IPv6 is activated (green check mark) or not (red X) for this connection. IPv6 is
not available when the connection uses the bridging service.
MLD Proxy This shows whether Multicast Listener Discovery (MLD) is activated (green check mark) or not
(red X) for this connection. MLD is not available when the connection uses the bridging service.
Table 9 Configuration > WAN / Internet > WAN Setup (continued)
LABEL DESCRIPTION
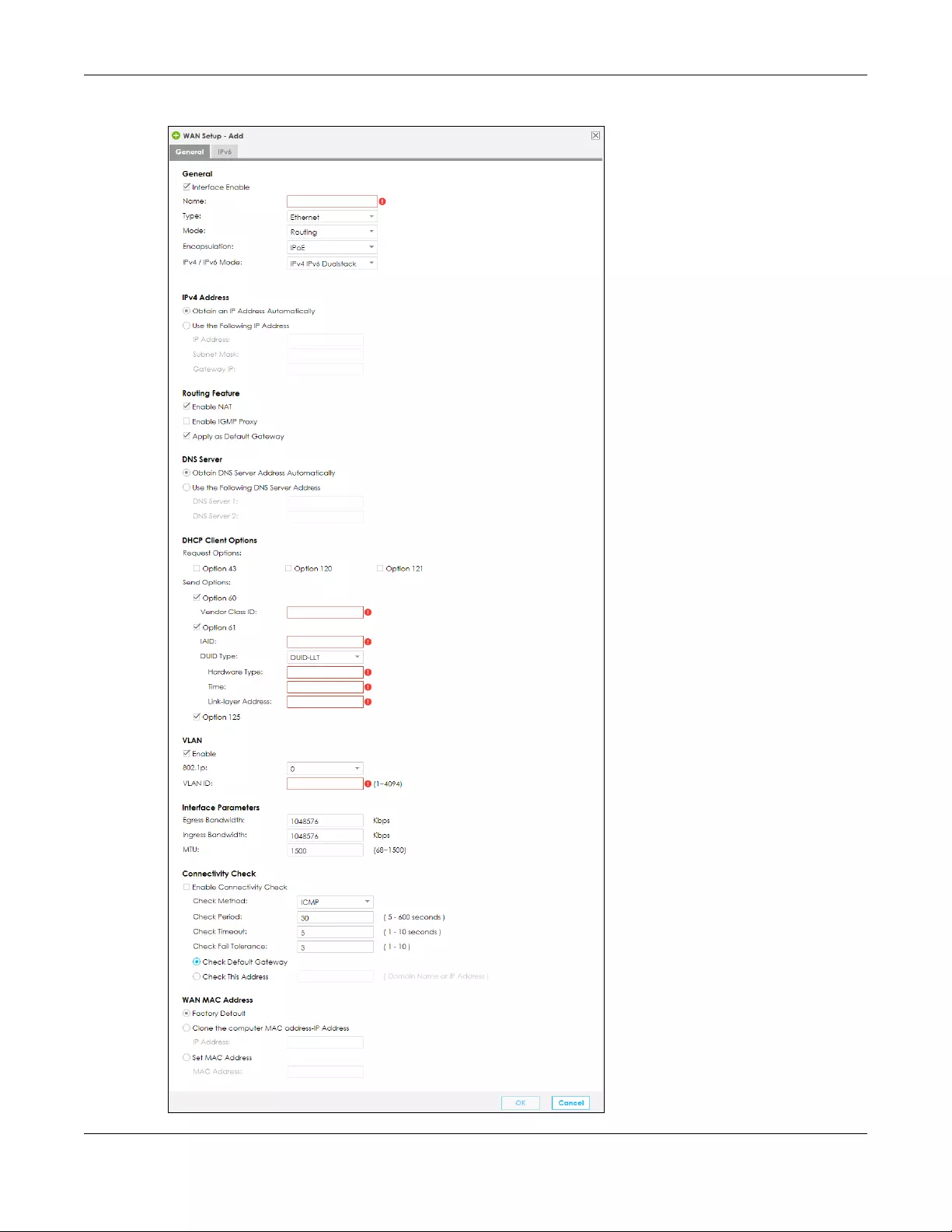
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
58
Figure 49 WAN / Internet > WAN Setup > Add/Edit: Routing Mode

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
59
The following table describes the labels in this screen.
Table 10 WAN Internet > WAN Setup > Add/Edit: Routing Mode
LABEL DESCRIPTION
General
Interface
Enable
Select this to activate the WAN configuration settings.
Name Specify a descriptive name for this connection.
Type Select whether it is ADSL/VDSL over PTM, ADSL over ATM, or Ethernet connection.
•ADSL/VDSL over PTM: The SBG uses the VDSL technology for data transmission over the DSL
port.
•ADSL over ATM: The SBG uses the ADSL technology for data transmission over the DSL port.
•Ethernet: The SBG transmits data over the Ethernet WAN port. Select this if you have a DSL
router or modem in your network already.
Mode Select Routing if your ISP give you one IP address only and you want multiple computers to share
an Internet account.
Encapsulation Select the method of encapsulation used by your ISP from the drop-down list box. This option is
available only when you select Routing in the Mode field.
•PPP over Ethernet (PPPoE): PPPoE (Point to Point Protocol over Ethernet) provides access
control and billing functionality in a manner similar to dial-up services using PPP. Select this if
you have a username and password for Internet access.
•IP over Ethernet (IPoE): In this type of Internet connection, IP packets are routed between the
Ethernet interface and the WAN interface and then formatted so that they can be
understood in a bridged environment.
•PPP over ATM (PPPoA): PPPoA allows just one PPPoA connection over a PVC.
•IP over ATM (IPoA): IPoA allows just one RFC 1483 routing connection over a PVC.
If your connection type is ADSL/VDSL over PTM or Ethernet, the choices are PPPoE and IPoE.
If your connection type is ADSL over ATM, the choices are PPPoE, PPPoA, IPoE and IPoA.
IPv4/IPv6 Mode Select IPv4 Only if you want the SBG to run IPv4 only.
Select IPv4 IPv6 Dualstack to allow the SBG to run IPv4 and IPv6 at the same time.
Select IPv6 Only if you want the SBG to run IPv6 only.
PPP Information This is available only when you select PPPoE or PPPoA in the Encapsulation field.
User Name Enter the user name exactly as your ISP assigned. If assigned a name in the form user@domain
where domain identifies a service name, then enter both components exactly as given.
Password Enter the password associated with the user name above. Click Password Unmask to view the
password you entered.
Connection
Trigger
Select Auto Connect if you do not want the connection to time out. Select On Demand to
specify the time of idle before the connection times out.
Idle Timeout This value specifies the time in minutes that elapses before the router automatically disconnects
from the PPPoE server.
This field is not configurable if you select Auto Connect.
PPPoE
Passthrough
This field is available when you select PPPoE encapsulation.
In addition to the SBG’s built-in PPPoE client, you can enable PPPoE pass through to allow up to
ten hosts on the LAN to use PPPoE client software on their computers to connect to the ISP via
the SBG. Each host can have a separate account and a public WAN IP address.
PPPoE pass through is an alternative to NAT for application where NAT is not appropriate.
Disable PPPoE pass through if you do not need to allow hosts on the LAN to use PPPoE client
software on their computers to connect to the ISP.
ATM PVC Configuration (These fields appear when the Type is set to ADSL over ATM.)
VPI The valid range for the VPI is 0 to 255. Enter the VPI assigned to you.

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
60
VCI The valid range for the VCI is 32 to 65535 (0 to 31 is reserved for local management of ATM
traffic). Enter the VCI assigned to you.
Encapsulation Select the method of multiplexing used by your ISP from the drop-down list box. Choices are:
•LLC/SNAP-BRIDGING: In LCC encapsulation, bridged PDUs are encapsulated by identifying
the type of the bridged media in the SNAP header. This is available only when you select IPoE
or PPPoE in the Select DSL Link Type field.
•VC/MUX: In VC multiplexing, each protocol is carried on a single ATM virtual circuit (VC). To
transport multiple protocols, the SBG needs separate VCs. There is a binding between a VC
and the type of the network protocol carried on the VC. This reduces payload overhead
since there is no need to carry protocol information in each Protocol Data Unit (PDU)
payload.
Service
Category
Select UBR Without PCR for applications that are non-time sensitive, such as e-mail.
Select CBR (Continuous Bit Rate) to specify fixed (always-on) bandwidth for voice or data traffic.
Select VBR-nrt (non real-time Variable Bit Rate) for connections that do not require closely
controlled delay and delay variation.
Select Realtime VBR (real-time Variable Bit Rate) for applications with bursty connections that
require closely controlled delay and delay variation.
Peak Cell Rate Divide the DSL line rate (bps) by 424 (the size of an ATM cell) to find the Peak Cell Rate (PCR). This
is the maximum rate at which the sender can send cells. Type the PCR here.This field is not
available when you select UBR Without PCR.
Sustainable Cell
Rate
The Sustainable Cell Rate (SCR) sets the average cell rate (long-term) that can be transmitted.
Type the SCR, which must be less than the PCR. Note that system default is 0 cells/sec.
This field is available only when you select VBR-nrt or Realtime VBR.
Maximum Burst
Size
Maximum Burst Size (MBS) refers to the maximum number of cells that can be sent at the peak
rate. Type the MBS, which is less than 65535.
This field is available only when you select VBR-nrt or Realtime VBR.
IPv4 Address This is available only when you select IPv4 Only or IPv4 IPv6 Dualstack in the IPv4 / IPv6 Mode
field.
Obtain an IP
Address
Automatically
A static IP address is a fixed IP that your ISP gives you. A dynamic IP address is not fixed; the ISP
assigns you a different one each time you connect to the Internet. Select this if you have a
dynamic IP address.
Use the
Following IP
Address
Select this option if the ISP assigned a fixed IP address.
IP Address Enter the static IP address provided by your ISP.
Subnet Mask Enter the subnet mask provided by your ISP.
Gateway IP
Address Enter the gateway IP address provided by your ISP.
Routing Feature This is available only when you select IPv4 Only or IPv4 IPv6 DualStack in the IPv4 / IPv6 Mode
field.
Enable NAT Select this option to activate NAT on this connection.
Enable
IGMP Proxy Internet Group Multicast Protocol (IGMP) is a network-layer protocol used to establish
membership in a Multicast group - it is not used to carry user data.
Select this option to have the SBG act as an IGMP proxy on this connection. This allows the SBG
to get subscribing information and maintain a joined member list for each multicast group. It can
reduce multicast traffic significantly.
Apply as
Default
Gateway
Select this option to have the SBG use the WAN interface of this connection as the system
default gateway.
Table 10 WAN Internet > WAN Setup > Add/Edit: Routing Mode (continued)
LABEL DESCRIPTION
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
61
DNS Server This is available only when you select IPv4 Only or IPv4 IPv6 Dualstack in the IPv4 / IPv6 Mode
field.
Obtain DNS
Server Address
Automatically
Select this if you want the SBG to use the DNS server addresses assigned by your ISP.
Use the
Following DNS
Server Address
Select this if you want the SBG to use the DNS server addresses you configure manually.
DNS Server 1 Enter the first DNS server address.
DNS Server 2 Enter the second DNS server address.
DHCP Client
Options
This is available only when you select IPv4 Only or IPv4 IPv6 Dualstack in the IPv4 / IPv6 Mode
field.
Request Options Select Option 43 to have the SBG automatically add vendor specific information in the DHCP
packets to request the vendor specific options from the DHCP server.
Select Option 120 to have the SBG get the IP address or a fully-qualified domain name of SIP
server from the DHCP server.
Select Option 121 to have the SBG get static route rules from the DHCP server.
Send Options
Option 60 Select this and enter the device identity you want the SBG to add in the DHCP discovery packets
that go to the DHCP server.
Vendor
Class ID Enter the Vendor Class Identifier, such as the type of the hardware or firmware.
Option 61 Select this and enter any string that identifies the device.
IAID Enter the Identity Association Identifier (IAID) of the device, for example, the WAN connection
index number.
DUID Type Select DUID-LLT to have the SBG use DUID-LLT (DUID Based on Link-layer Address Plus Time) for
identification when exchanging DHCPv6 messages. You need to enter the hardware type, a
time value and the MAC address of the device.
Select DUID-EN to have the SBG use DUID-EN (DUID Assigned by Vendor Based upon Enterprise
Number) for identification when exchanging DHCPv6 messages. You need to enter the vendor’s
registered enterprise number.
Select DUID-LL to have the SBG use DUID-LL (DUID Based on Link-layer Address) for identification
when exchanging DHCPv6 messages. You need to enter the device’s hardware type and
hardware address (MAC address).
Hardware
Type Enter the device’s hardware type, assigned by the IANA.
Time Enter the time that the DUID is generated.
Link-layer
Address Enter the SBG’s hardware address, that is the MAC address.
Enterprise
Number Enter the vendor’s registered private enterprise number. An enterprise number is a unique
number that identifies a company.
Identifier Enter a unique identifier assigned by the vendor.
Option 125 Select this to have the SBG automatically generate and add vendor specific parameters in the
DHCP discovery packets that go to the DHCP server.
6RD Enable IPv6 rapid deployment to tunnel IPv6 traffic from the local network through the ISP’s IPv4
network.
The 6RD (IPv6 rapid deployment) fields display when you set the IPv4 / IPv6 Mode field to IPv4
Only.
Table 10 WAN Internet > WAN Setup > Add/Edit: Routing Mode (continued)
LABEL DESCRIPTION
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
62
Automatically
configured by
DHCPC
Select this to have the SBG detect IPv4 address automatically through DHCP.
This option is configurable only when you set the method of encapsulation to IPoE.
Manual
Configuration
Select this to manually configure an IPv4 address of the relay server.
Service Provider
IPv6 Prefix
Enter an IPv6 prefix for tunneling IPv6 traffic to the ISP’s Border Relay router and connecting to
the native IPv6 Internet.
IPv4 Mask
Length
Enter the subnet mask number (1~32) for the IPv4 network.
Border Relay
IPv4 Address
When you select Manual Configuration, specify the relay server IPv4 address.
VLAN These fields disappear when the Type is set to ADSL/VDSL over PTM and the method of
encapsulation is PPPoA or IPoA.
Enable Select this option to add the VLAN tag (specified below) to the outgoing traffic through this
connection.
802.1p IEEE 802.1p defines up to 8 separate traffic types by inserting a tag into a MAC-layer frame that
contains bits to define class of service.
Select the IEEE 802.1p priority level (from 0 to 7) to add to traffic through this connection. The
greater the number, the higher the priority level.
VLAN ID Type the VLAN ID number (from 1 to 4094) for traffic through this connection.
Interface Parameters
Egress
Bandwidth
Enter the maximum amount of traffic, in kilobits per second, the SBG can send through the
interface to the network. Allowed values are 0 - 1048576.
Ingress
Bandwidth
This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the SBG can receive from the
network through the interface. Allowed values are 0 - 1048576.
MTU Enter the MTU (Maximum Transfer Unit) size for this traffic.
Type the maximum size of each data packet, in bytes, that can move through this interface. If a
larger packet arrives, the SBG divides it into smaller fragments. Allowed values are 68 -1492.
Usually, this value is 1500.
Connectivity
Check
The interface can regularly check the connection to the gateway you specified to make sure it
is still available. You specify how often the interface checks the connection, how long to wait for
a response before the attempt is a failure, and how many consecutive failures are required
before the SBG stops routing to the gateway. The SBG resumes routing to the gateway the first
time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select ICMP to have the SBG regularly ping the gateway you specify to make sure it is still
available.
Select TCP to have the SBG regularly perform a TCP handshake with the gateway you specify to
make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance
Enter the number of consecutive failures before the SBG stops routing through the gateway.
Table 10 WAN Internet > WAN Setup > Add/Edit: Routing Mode (continued)
LABEL DESCRIPTION
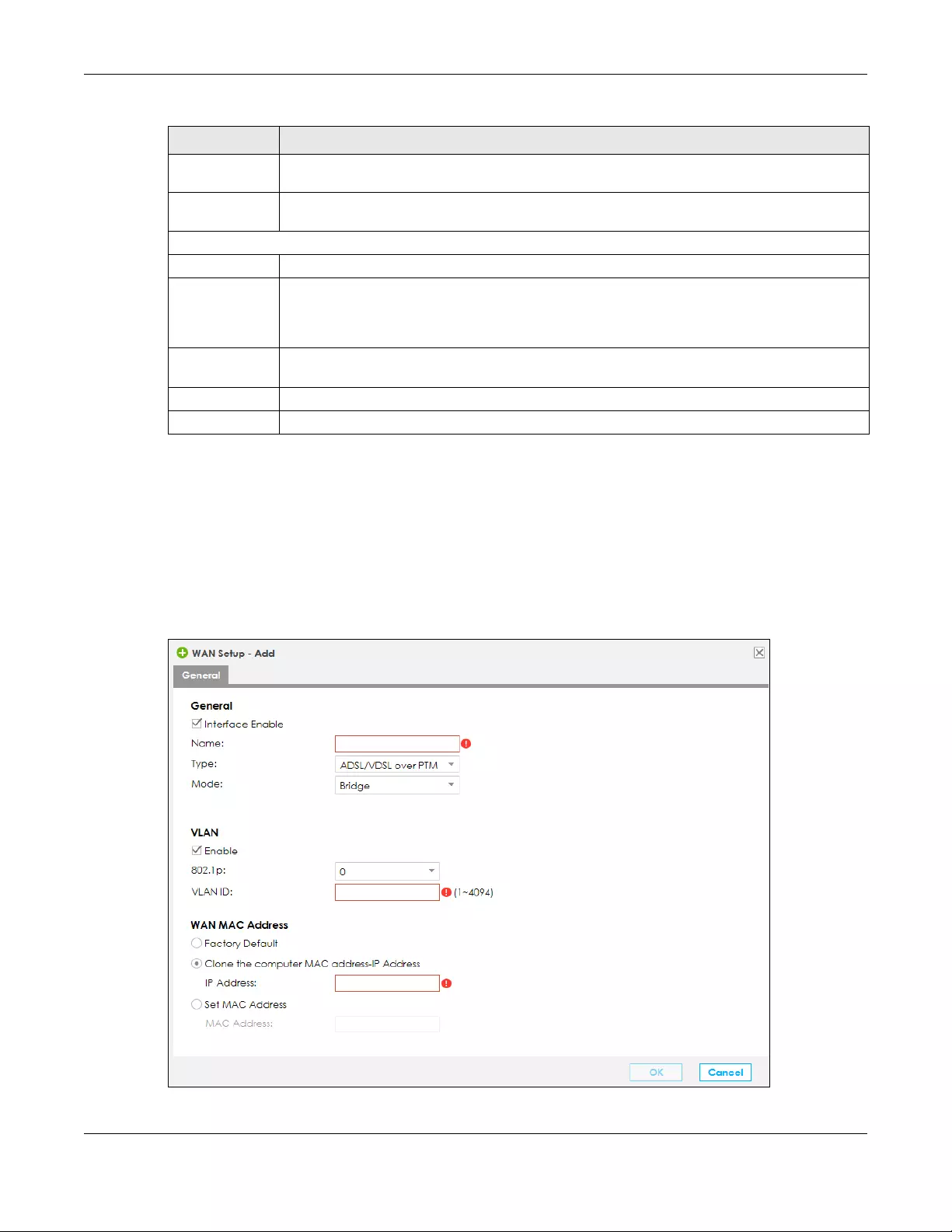
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
63
5.3.1.2 Bridge Mode
Click the Add or Edit in the Configuration > WAN / Internet > WAN Setup screen. Select Bridge as the
device mode. The screen varies depending on the interface type you select.
ADSL/VDSL over PTM or Ethernet
If you select ADSL/VDSL over PTM or Ethernet as the interface type, the following screen appears.
Figure 50 WAN / Internet > WAN Setup > Add/Edit: Bridge Mode (ADSL/VDSL over PTM or Ethernet)
Check Default
Gateway
Select this to use the default gateway for the connectivity check.
Check This
Address
Select this to specify a domain name or IP address for the connectivity check. Enter that domain
name or IP address in the field next to it.
WAN MAC Address
Factory Default Select this to use the factory default MAC address,
Clone the
Computer MAC
address-IP
Address
Select this to clone the MAC address from a computer on your LAN. Type the IP address of the
computer with the MAC address you are cloning.
Set MAC
Address
Select this if you know the MAC address you want to use.
OK Click OK to save your changes back to the SBG.
Cancel Click Cancel to exit this screen without saving.
Table 10 WAN Internet > WAN Setup > Add/Edit: Routing Mode (continued)
LABEL DESCRIPTION

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
64
The following table describes the fields in this screen.
ADSL over ATM
If you select ADSL over ATM as the interface type, the following screen appears.
Table 11 WAN / Internet > WAN Setup > Add/Edit: Bridge Mode (ADSL/VDSL over PTM or Ethernet)
LABEL DESCRIPTION
General
Interface Enable Select this to activate the WAN configuration settings.
Name Enter a service name of the connection.
Type Select ADSL/VDSL over PTM as the interface that you want to configure. The SBG uses the VDSL
technology for data transmission over the DSL port. Otherwise, select Ethernet to have the SBG
transmits data over the Ethernet WAN port.
Mode Select Bridge when your ISP provides you more than one IP address and you want the
connected computers to get individual IP address from ISP’s DHCP server directly. If you select
Bridge, you cannot use routing functions, such as QoS, Firewall, DHCP server and NAT on traffic
from the selected LAN port(s).
VLAN
Enable Select this to add the VLAN Tag (specified below) to the outgoing traffic through this
connection.
802.1p IEEE 802.1p defines up to 8 separate traffic types by inserting a tag into a MAC-layer frame that
contains bits to define class of service.
Select the IEEE 802.1p priority level (from 0 to 7) to add to traffic through this connection. The
greater the number, the higher the priority level.
VLAN ID Type the VLAN ID number (from 0 to 4094) for traffic through this connection.
WAN MAC Address
Factory Default Select this to use the factory default MAC address,
Clone the
Computer MAC
address-IP
Address
Select this to clone the MAC address from a computer on your LAN. Type the IP address of the
computer with the MAC address you are cloning.
Set MAC
address
Select this if you know the MAC address you want to use.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
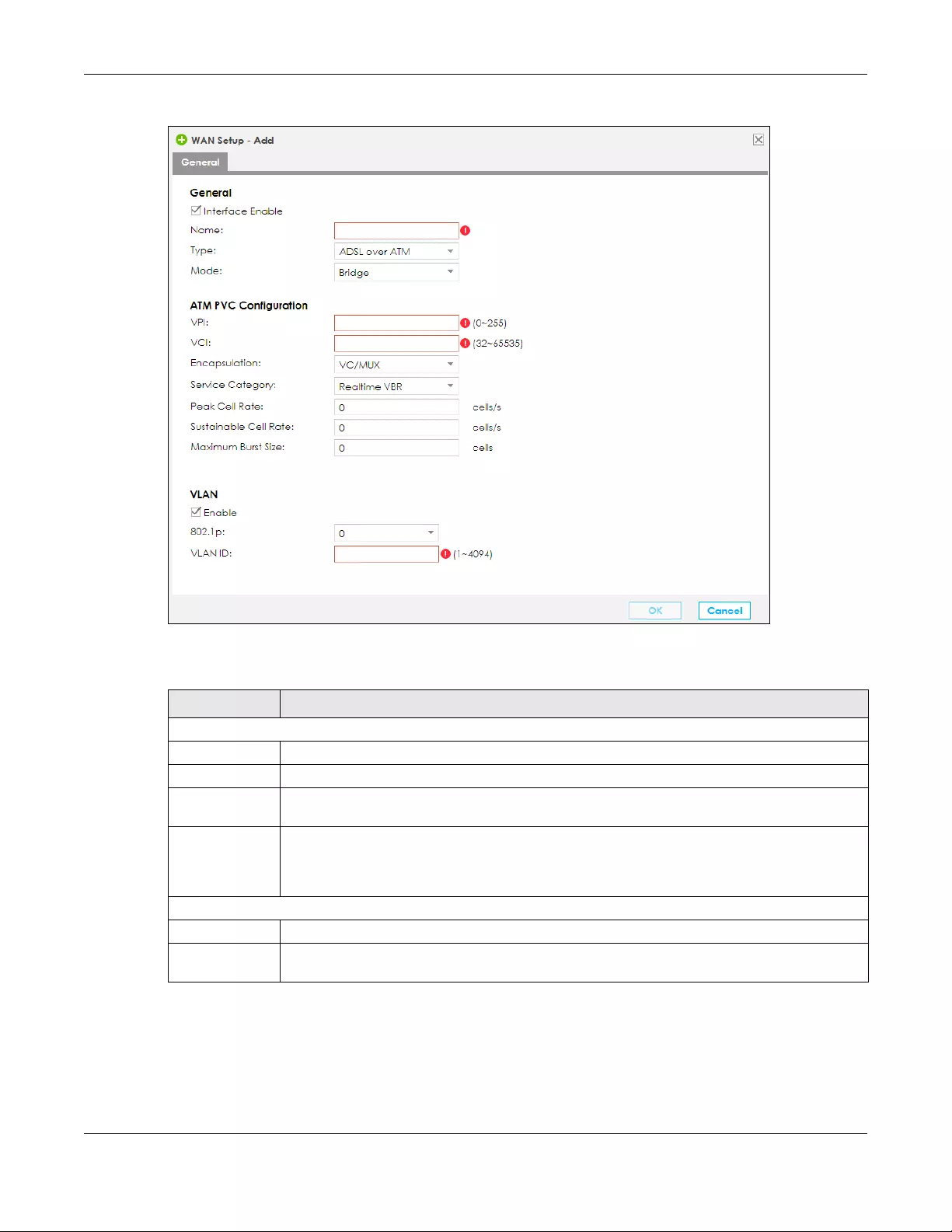
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
65
Figure 51 WAN / Internet > WAN Setup > Add/Edit: Bridge Mode (ADSL over ATM)
The following table describes the fields in this screen.
Table 12 WAN / Internet > WAN Setup > Add/Edit: Bridge Mode (ADSL over ATM)
LABEL DESCRIPTION
General
Interface Enable Select this to activate the WAN configuration settings.
Name Enter a service name of the connection.
Type Select ADSL over ATM as the interface for which you want to configure here. The SBG uses the
ADSL technology for data transmission over the DSL port.
Mode Select Bridge when your ISP provides you more than one IP address and you want the
connected computers to get individual IP address from ISP’s DHCP server directly. If you select
Bridge, you cannot use routing functions, such as QoS, Firewall, DHCP server and NAT on traffic
from the selected LAN port(s).
ATM PVC Configuration (These fields appear when the Type is set to ADSL over ATM.)
VPI The valid range for the VPI is 0 to 255. Enter the VPI assigned to you.
VCI The valid range for the VCI is 32 to 65535 (0 to 31 is reserved for local management of ATM
traffic). Enter the VCI assigned to you.
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
66
5.3.1.3 IPv6
Click the Add or Edit in the Configuration > WAN / Internet > WAN Setup screen. Click the IPv6 tab to
configure an IPv6 WAN interface connection. This screen is available only when you select IPv6 Only or
IPv4 IPv6 Dualstack in the IPv4 / IPv6 Mode field of the WAN Setup > Add/Edit screen.
Encapsulation Select the method of multiplexing used by your ISP from the drop-down list box. Choices are:
•LLC/SNAP-BRIDGING: In LCC encapsulation, bridged PDUs are encapsulated by identifying
the type of the bridged media in the SNAP header. This is available only when you select
IPoE or PPPoE in the Select DSL Link Type field.
•VC/MUX: In VC multiplexing, each protocol is carried on a single ATM virtual circuit (VC). To
transport multiple protocols, the SBG needs separate VCs. There is a binding between a VC
and the type of the network protocol carried on the VC. This reduces payload overhead
since there is no need to carry protocol information in each Protocol Data Unit (PDU)
payload.
Service
Category
Select UBR Without PCR for applications that are non-time sensitive, such as e-mail.
Select CBR (Continuous Bit Rate) to specify fixed (always-on) bandwidth for voice or data traffic.
Select VBR-nrt (non real-time Variable Bit Rate) for connections that do not require closely
controlled delay and delay variation.
Select Realtime VBR (real-time Variable Bit Rate) for applications with bursty connections that
require closely controlled delay and delay variation.
Peak Cell Rate Divide the DSL line rate (bps) by 424 (the size of an ATM cell) to find the Peak Cell Rate (PCR). This
is the maximum rate at which the sender can send cells. Type the PCR here.This field is not
available when you select UBR Without PCR.
Sustainable Cell
Rate
The Sustainable Cell Rate (SCR) sets the average cell rate (long-term) that can be transmitted.
Type the SCR, which must be less than the PCR. Note that system default is 0 cells/sec.
This field is available only when you select VBR-nrt or Realtime VBR.
Maximum Burst
Size
Maximum Burst Size (MBS) refers to the maximum number of cells that can be sent at the peak
rate. Type the MBS, which is less than 65535.
This field is available only when you select Non Realtime VBR or Realtime VBR.
VLAN This section is available only when you select ADSL/VDSL over PTM in the Type field.
Enable Select this to add the VLAN Tag (specified below) to the outgoing traffic through this
connection.
802.1p IEEE 802.1p defines up to 8 separate traffic types by inserting a tag into a MAC-layer frame that
contains bits to define class of service.
Select the IEEE 802.1p priority level (from 0 to 7) to add to traffic through this connection. The
greater the number, the higher the priority level.
VLAN ID Type the VLAN ID number (from 0 to 4094) for traffic through this connection.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 12 WAN / Internet > WAN Setup > Add/Edit: Bridge Mode (ADSL over ATM) (continued)
LABEL DESCRIPTION
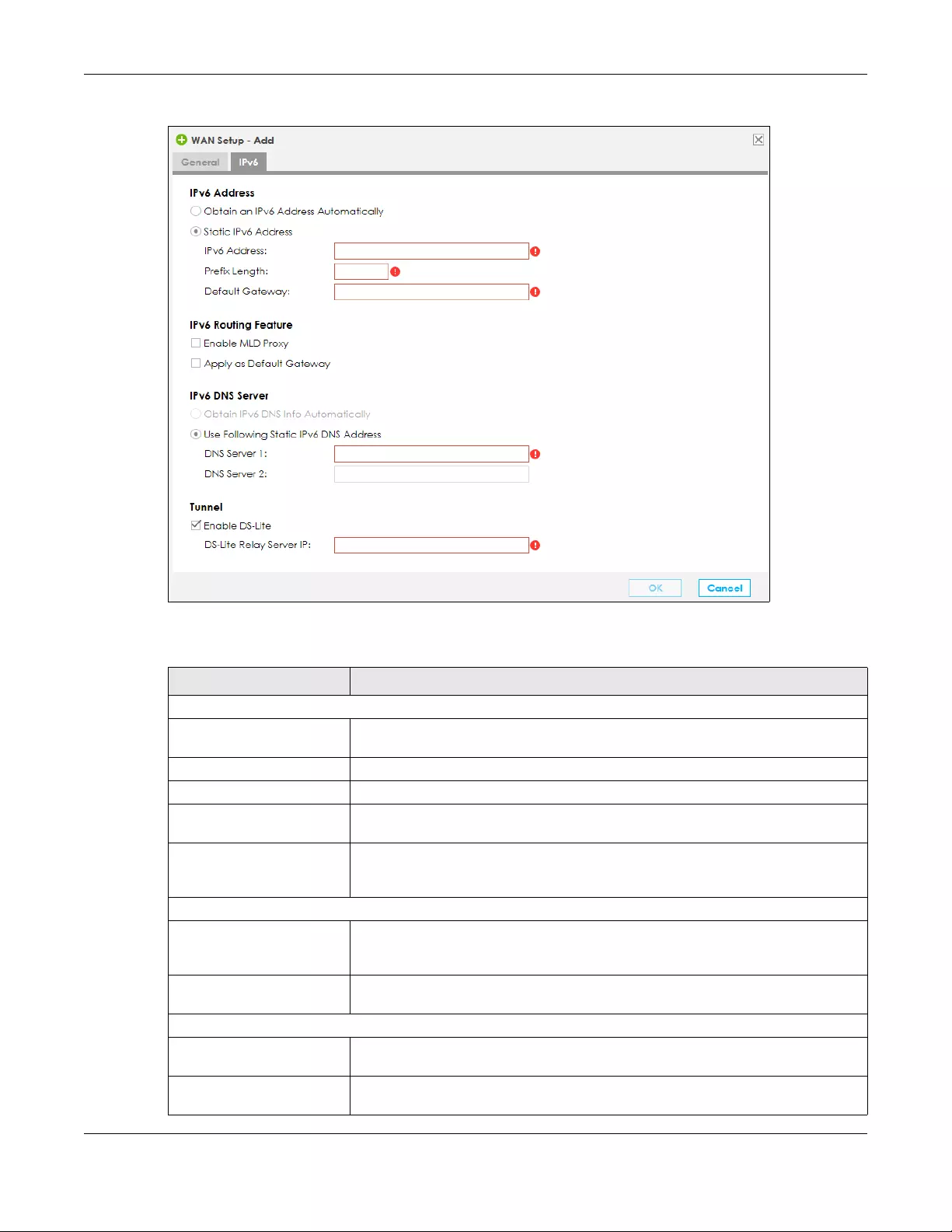
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
67
Figure 52 WAN / Internet > WAN Setup > IPv6
The following table describes the labels in this screen.
Table 13 WAN / Internet > WAN Setup > IPv6
LABEL DESCRIPTION
IPv6 Address
Obtain an IPv6 Address
Automatically
Select this if you want to have the SBG use the IPv6 prefix from the connected
router’s Router Advertisement (RA) to generate an IPv6 address.
Static IPv6 Address Select this if you have a fixed IPv6 address assigned by your ISP.
IPv6 Address Enter the IPv6 address assigned by your ISP.
Prefix Length Enter the address prefix length to specify how many most significant bits in an IPv6
address compose the network address.
Default Gateway Enter the IP address of the next-hop gateway. The gateway is a router or switch on
the same segment as your SBG's interface(s). The gateway helps forward packets to
their destinations.
IPv6 Routing Feature
Enable MLD Proxy Select this check box to have the SBG act as an MLD proxy on this connection. This
allows the SBG to get subscription information and maintain a joined member list for
each multicast group. It can reduce multicast traffic significantly.
Apply as Default Gateway Select this option to have the SBG use the WAN interface of this connection as the
system default gateway.
IPv6 DNS Server
Obtain IPv6 DNS Info
Automatically
Select this to have the SBG get the IPv6 DNS server addresses from the ISP
automatically.
Use Following Static IPv6
DNS Address
Select Static to have the SBG use the IPv6 DNS server addresses you configure
manually.
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
68
5.4 The Mobile Screen
Use this screen to configure your 3G/4G settings. Click Configuration > WAN / Internet > Mobile.
Note: The actual data rate you obtain varies depending on the 3G/4G USB dongle you use,
the signal strength to the service provider’s base station, and so on.
DNS Server 1 Enter the first IPv6 DNS server address assigned by the ISP.
DNS Server 2 Enter the second IPv6 DNS server address assigned by the ISP.
Tunnel
(This is available only when you select IPv6 Only in the IPv4 / IPv6 Mode field.)
Enable DS-Lite Enable Dual Stack Lite to let local computers use IPv4 through an ISP’s IPv6 network.
DS-Lite Relay Server IP Specify the transition router’s IPv6 address.
OK Click OK to save your changes back to the SBG.
Cancel Click Cancel to exit this screen without saving.
Table 13 WAN / Internet > WAN Setup > IPv6
LABEL DESCRIPTION
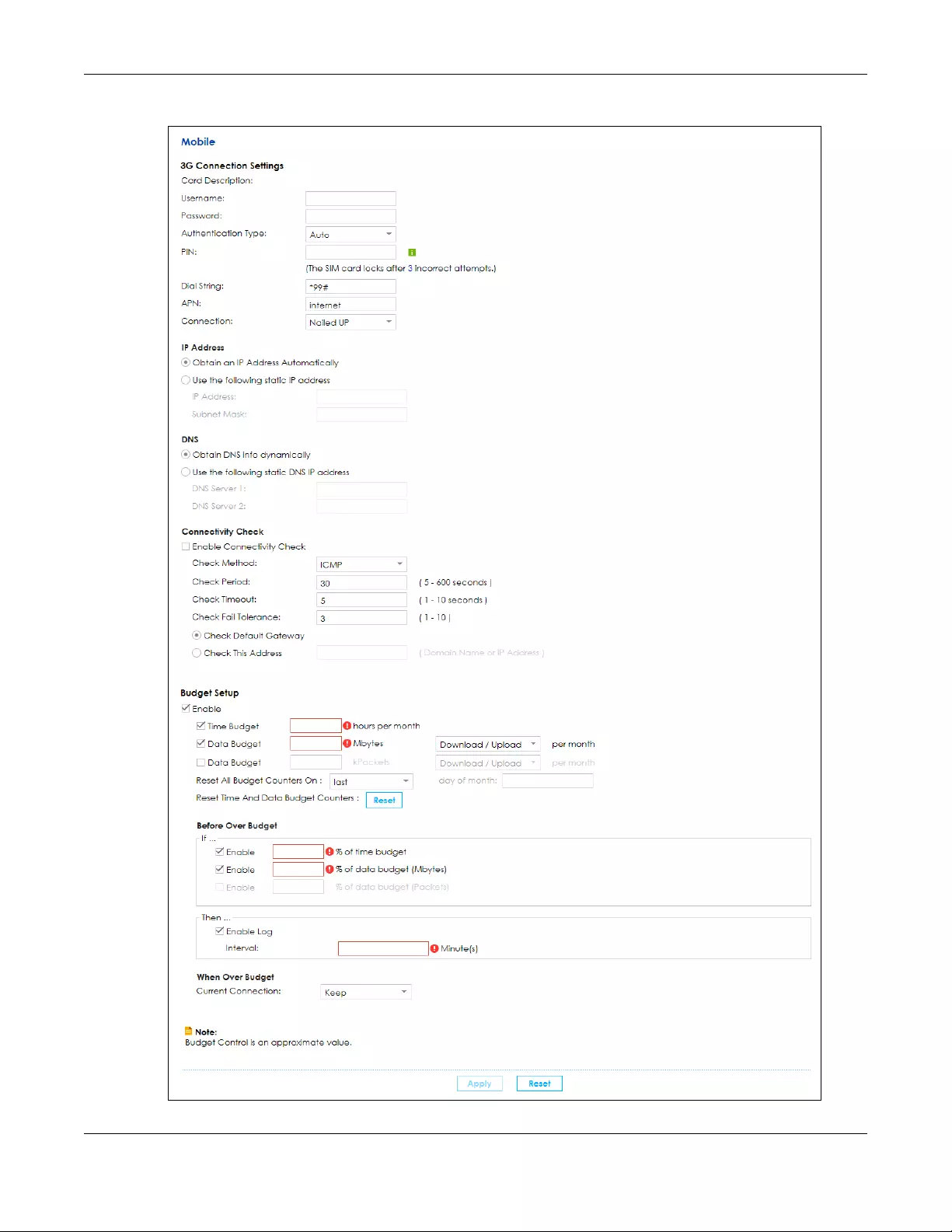
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
69
Figure 53 Configuration > WAN / Internet > Mobile
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
70
The following table describes the labels in this screen.
Table 14 Configuration > WAN / Internet > Mobile
LABEL DESCRIPTION
3G Connection Settings
Card
Description
This field displays the manufacturer and model name of your 3G/4G card if you inserted one in
the SBG. Otherwise, it displays N/A.
Username Type the user name (of up to 64 ASCII printable characters) given to you by your service
provider.
Password Type the password (of up to 64 ASCII printable characters) associated with the user name
above.
Authentication
Type
Select an authentication type protocol for outgoing connection requests. Select Auto for the
SBG to accept any protocol when requested by the remote node. Select CHAP to accept only
CHAP and PAP for the SBG to accept only PAP.
PIN A PIN (Personal Identification Number) code is a key to a 3G/4G card. Without the PIN code, you
cannot use the 3G card.
If your ISP enabled PIN code authentication, enter the 4-digit PIN code (0000 for example)
provided by your ISP. If you enter the PIN code incorrectly, the 3G/4G card may be blocked by
your ISP and you cannot use the account to access the Internet.
If your ISP disabled PIN code authentication, leave this field blank.
Dial string Enter the phone number (dial string) used to dial up a connection to your service provider’s base
station. Your ISP should provide the phone number.
For example, *99# is the dial string to establish a GPRS or 3G or 4G connection in Taiwan.
APN Enter the APN (Access Point Name) provided by your service provider. Connections with
different APNs may provide different services (such as Internet access or MMS (Multi-Media
Messaging Service)) and charge method.
You can enter up to 32 ASCII printable characters. Spaces are allowed.
Connection Select Nailed UP if you do not want the connection to time out.
Select on Demand if you do not want the connection up all the time and specify an idle time-
out in the Max Idle Timeout field.
Max Idle
Timeout
This value specifies the time in minutes that elapses before the SBG automatically disconnects
from the ISP.
IP Address
Obtain an IP
Address
Automatically
Select this option If your ISP did not assign you a fixed IP address.
Use the
following static
IP address
Select this option If the ISP assigned a fixed IP address.
IP Address Enter your WAN IP address in this field if you selected Use the following static IP address.
Subnet Mask Enter the Subnet Mask provided by your ISP.
DNS
Obtain DNS info
dynamically
Select this to have the SBG get the DNS server addresses from the ISP automatically.
Use the
following static
DNS IP address
Select this to have the SBG use the DNS server addresses you configure manually.
DNS server 1 Enter the first DNS server address assigned by the ISP.
DNS server 2 Enter the second DNS server address assigned by the ISP.
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
71
Connectivity
Check
The interface can regularly check the connection to the gateway you specified to make sure it
is still available. You specify how often the interface checks the connection, how long to wait for
a response before the attempt is a failure, and how many consecutive failures are required
before the SBG stops routing to the gateway. The SBG resumes routing to the gateway the first
time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select ICMP to have the SBG regularly ping the gateway you specify to make sure it is still
available.
Select TCP to have the SBG regularly perform a TCP handshake with the gateway you specify to
make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance
Enter the number of consecutive failures before the SBG stops routing through the gateway.
Check Default
Gateway
Select this to use the default gateway for the connectivity check.
Check This
Address
Select this to specify a domain name or IP address for the connectivity check. Enter that domain
name or IP address in the field next to it.
Budget Setup
Enable Select this option to set a monthly limit for the user account of the installed 3G card. You must
insert a 3G card before you enable budget control on the SBG.
You can set a limit on the total traffic and/or call time. The SBG takes the actions you specified
when a limit is exceeded during the month.
Time Budget Select this option and specify the amount of time (in hours) that the 3G connection can be used
within one month.
If you change the value after you configure and enable budget control, the SBG resets the
statistics.
Data Budget Select this option and specify the amount of data in Mega bytes or the number of packets that
can be transmitted via the 3G connection within one month.
Select Download to set a limit on the downstream traffic (from the ISP to the SBG).
Select Upload to set a limit on the upstream traffic (from the SBG to the ISP).
Select Download/Upload to set a limit on the total traffic in both directions.
If you change the value after you configure and enable budget control, the SBG resets the
statistics.
Reset All Budget
Counters On
Select the last or a specific day of the month to reset all budget counters. If the date you
specified is not available in a month, such as 30th or 31th of February, the SBG resets the budget
on the last day of the month.
Reset Time And
Data Budget
Counters
Click this button to reset the time and data budgets immediately. The count starts over with the
3G connection’s full configured monthly time and data budgets. This does not affect the normal
monthly budget restart.
Before Over
Budget
Enter a number from 1 to 99 in the percentage fields. The SBG takes actions when the specified
percentage of time budget or data limit is exceeded. If you change the value after you
configure and enable budget control, the SBG resets the statistics.
Enable Log Select this to activate the logging function at the interval you set in the Interval field.
Interval Enter the time interval (in minutes) at which the SBG creates log messages.
Table 14 Configuration > WAN / Internet > Mobile (continued)
LABEL DESCRIPTION
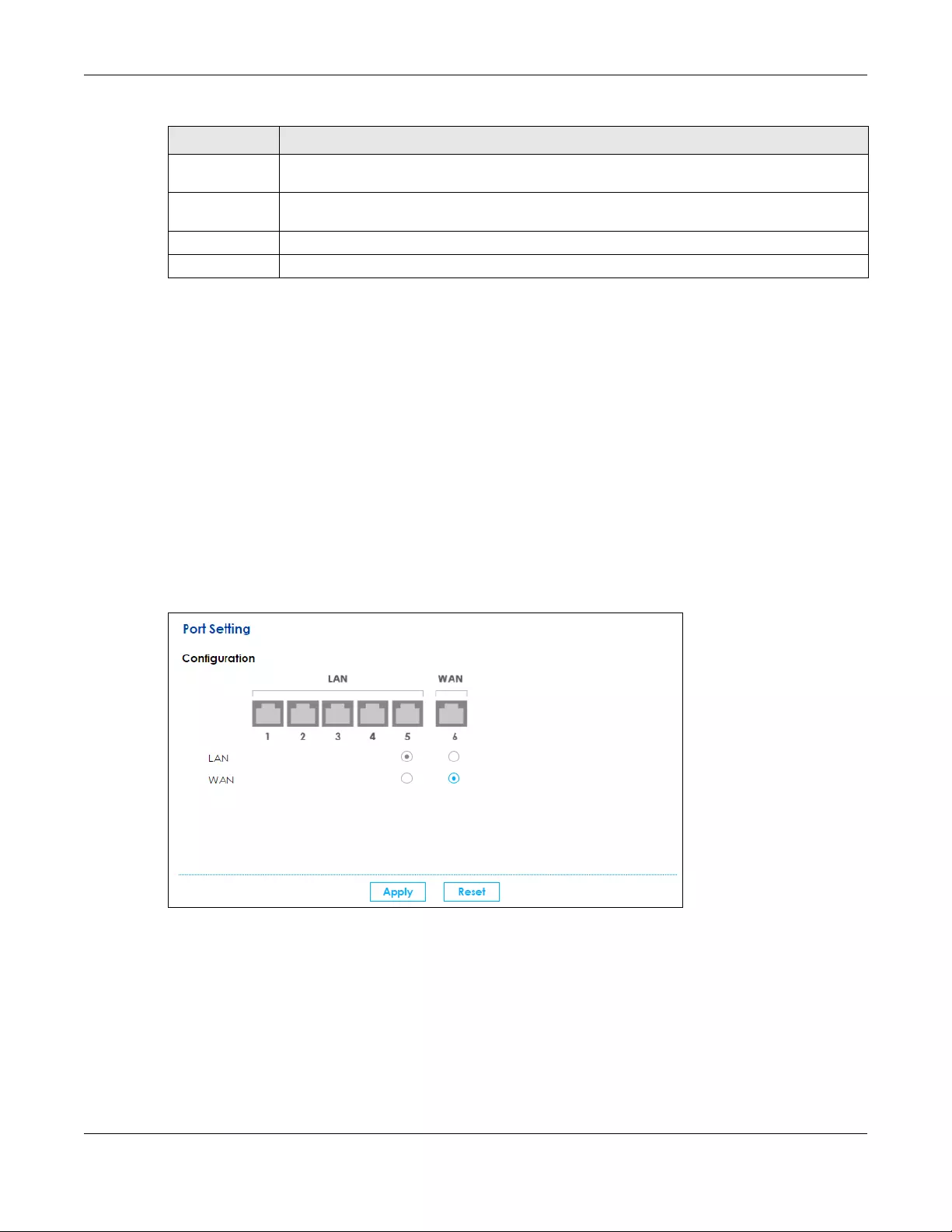
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
72
5.5 The Port Setting Screen
Click Configuration > WAN / Internet > Port Setting to display the following screen. Use the Port Setting
screen to set the SBG flexible ports as part of the LAN or WAN interfaces. This creates a hardware
connection between physical ports at the layer 2 (data link, MAC address level). This provides wire-
speed throughput but no security.
Note the following if you are configuring from a computer connected to a LAN or WAN port and
change the port's role:
• A port's IP address varies as its role changes. Make sure your computer's IP address is in the same
subnet as the SBG's LAN or WAN IP address.
• Use the appropriate LAN or WAN IP address to access the SBG.
Figure 54 Configuration > WAN / Internet > Port Setting
The physical Ethernet ports are shown at the bottom and the Ethernet interfaces are shown at the
bottom of the screen. Use the radio buttons to select for which interface (network) you want to use
each physical port. For example, select a port’s LAN radio button to use the port as part of the LAN
interface. The port will use the SBG’s LAN IP address and MAC address.
Note: You will notice when Port 5 is WAN, Port 6 can only be WAN, this is because Port 6 has a
better performance as WAN and Port 5 works as failover.
Click Apply to save your changes and apply them to the SBG.
When Over
Budget
Specify the actions the SBG takes when the time or data limit is exceeded.
Current
connection
Select Keep to maintain the existing 3G connection or Drop to disconnect it when the data
transmission is over the set budget.
Apply Click Apply to save your changes back to the SBG.
Reset Click Cancel to return to the previous configuration.
Table 14 Configuration > WAN / Internet > Mobile (continued)
LABEL DESCRIPTION
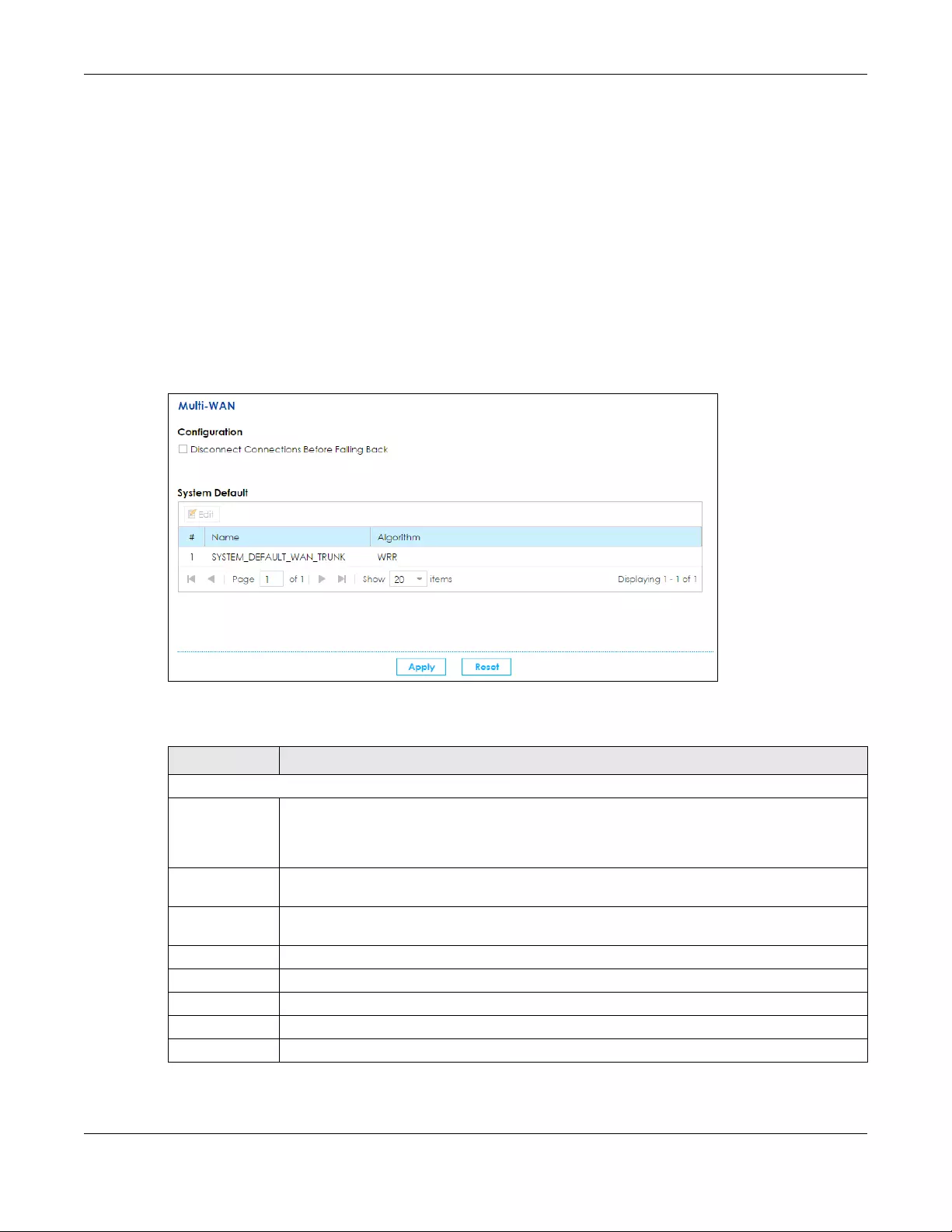
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
73
Click Reset to change the port groups to their current configuration (last-saved values).
5.6 The Multi-WAN Screen
Use the Multi-WAN screen to configure the multiple WAN load balance and failover rules to distribute
traffic among different interfaces. This helps to increase overall network throughput and reliability. Load
balancing divides traffic loads between multiple interfaces. This allows you to improve quality of service
and maximize bandwidth utilization for multiple ISP links.
You can only configure one rule for each interface. Click Configuration > WAN / Internet > Multi-WAN to
display the following screen.
Figure 55 Configuration > WAN / Internet > Multi-WAN
The following table describes the labels in this screen.
Table 15 Configuration > WAN / Internet > Multi-WAN
LABEL DESCRIPTION
Configuration
Disconnect
Connections
Before Falling
Back
Select this to terminate existing connections on an interface which is set to passive mode when
any interface set to active mode in the same trunk comes back up.
System Default The SBG automatically adds all external interfaces into the pre-configured system default
SYSTEM_DEFAULT_WAN_TRUNK. You cannot delete it.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify the
entry’s settings.
# This field is a sequential value, and it is not associated with any interface.
Name This field displays the label to identify the trunk.
Algorithm This field displays the load balancing method the trunk is set to use.
Apply Click Apply to save your changes to the SBG.
Reset Click Reset to return the screen to its last-saved settings.
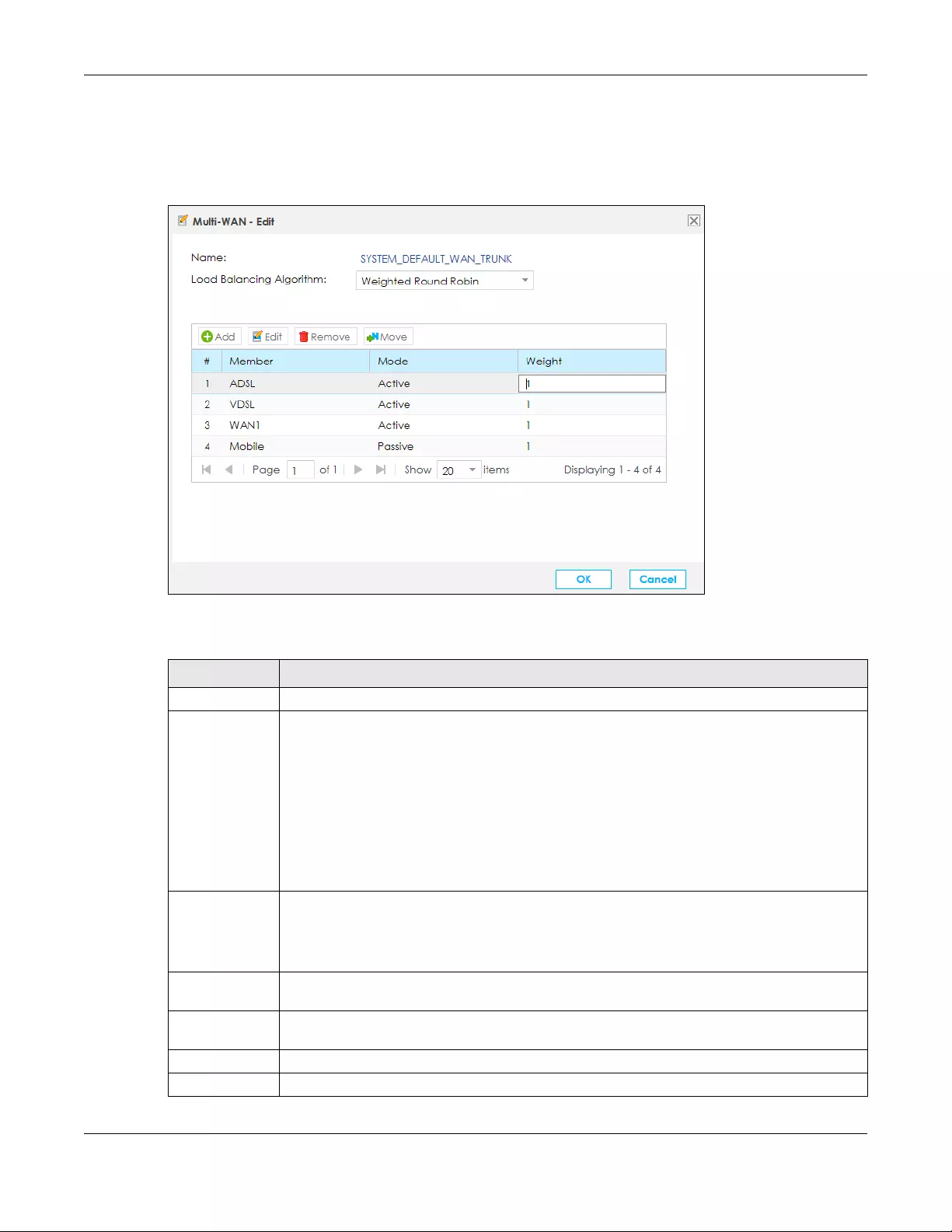
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
74
5.6.1 Edit Multi-WAN
Select an existing multi-WAN and click Edit in the Multi-WAN screen to configure it.
Figure 56 Multi-WAN: Edit
The following table describes the labels in this screen.
Table 16 Multi-WAN: Edit
LABEL DESCRIPTION
Name This field displays the label to identify the trunk.
Load Balancing
Algorithm
Select a load balancing method to use from the drop-down list box.
Select Weighted Round Robin to balance the traffic load between interfaces based on their
respective weights. An interface with a larger weight gets more chances to transmit traffic than
an interface with a smaller weight. For example, if the weight ratio of wan1 and wan2 interfaces
is 2:1, the SBG chooses wan1 for 2 sessions’ traffic and wan2 for 1 session’s traffic in each round
of 3 new sessions.
Select Least Load First to send new session traffic through the least utilized trunk member.
Select Spillover to send network traffic through the first interface in the group member list until
there is enough traffic that the second interface needs to be used (and so on).
Load Balancing
Index(es)
This field is available if you selected to use the Least Load First or Spillover method.
Select Outbound, Inbound, or Outbound + Inbound to set the traffic to which the SBG applies the
load balancing method. Outbound means the traffic traveling from an internal interface (ex.
LAN) to an external interface (ex. WAN). Inbound means the opposite.
The table lists the trunk’s member interfaces. You can add, edit, remove, or move entries for user
configured trunks.
Add Click this to add a member interface to the trunk. Select an interface and click Add to add a
new member interface after the selected member interface.
Edit Select an entry and click Edit to modify the entry’s settings.
Remove To remove a member interface, select it and click Remove.
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
75
5.6.2 How to Configure Multi-WAN for Load Balancing and Failover
This example shows you how to configure multi-WAN for three WAN connections: an Ethernet WAN
connection, an ADSL WAN connection, and a 3G/4G (mobile) WAN connection. The available
bandwidth for the Ethernet WAN connection is 3 Mbps, and the available bandwidth for the ADSL WAN
connection is 1 Mbps.
As these two wired WAN connections have different bandwidths, you can set multi-WAN to send traffic
over these WAN connections in a 3:2 ratio. Most 3G/4G WAN connections charge the user for the
amount of data sent, so you can set multi-WAN to send traffic over the 3G/4G WAN connection only if
all other WAN connections are unavailable.
Move To move an interface to a different number in the list, click the Move icon. In the field that
appears, specify the number to which you want to move the interface.
#This column displays the priorities of the group’s interfaces. The order of the interfaces in the list is
important since they are used in the order they are listed.
Member Click this table cell and select an interface to be a group member.
Mode Click this table cell and select Active to have the SBG always attempt to use this connection.
Select Passive to have the SBG only use this connection when all of the connections set to
active are down. You can only set one of a group’s interfaces to passive mode.
Weight This field displays with the weighted round robin load balancing algorithm. Specify the weight
(1~10) for the interface. The weights of the different member interfaces form a ratio.This ratio
determines how much traffic the SBG assigns to each member interface.The higher an
interface’s weight is (relative to the weights of the interfaces), the more sessions that interface
should handle.
Ingress
Bandwidth
This field displays with the least load first load balancing algorithm. It displays the maximum
number of kilobits of data the SBG is to allow to come in through the interface per second.
Note: You can configure the bandwidth of an interface in the corresponding
interface edit screen.
Egress
Bandwidth
This field displays with the least load first or spillover load balancing algorithm. It displays the
maximum number of kilobits of data the SBG is to send out through the interface per second.
Note: You can configure the bandwidth of an interface in the corresponding
interface edit screen.
Total Bandwidth This field displays with the spillover load balancing algorithm. It displays the maximum number of
kilobits of data the SBG is to send out and allow to come in through the interface per second.
Note: You can configure the bandwidth of an interface in the corresponding
interface edit screen.
Spillover This field displays with the spillover load balancing algorithm. Specify the maximum bandwidth
of traffic in kilobits per second (1~1048576) to send out through the interface before using
another interface. When this spillover bandwidth limit is exceeded, the SBG sends new session
traffic through the next interface. The traffic of existing sessions still goes through the interface on
which they started.
The SBG uses the group member interfaces in the order that they are listed.
OK Click OK to save your changes back to the SBG.
Cancel Click Cancel to exit this screen without saving.
Table 16 Multi-WAN: Edit (continued)
LABEL DESCRIPTION
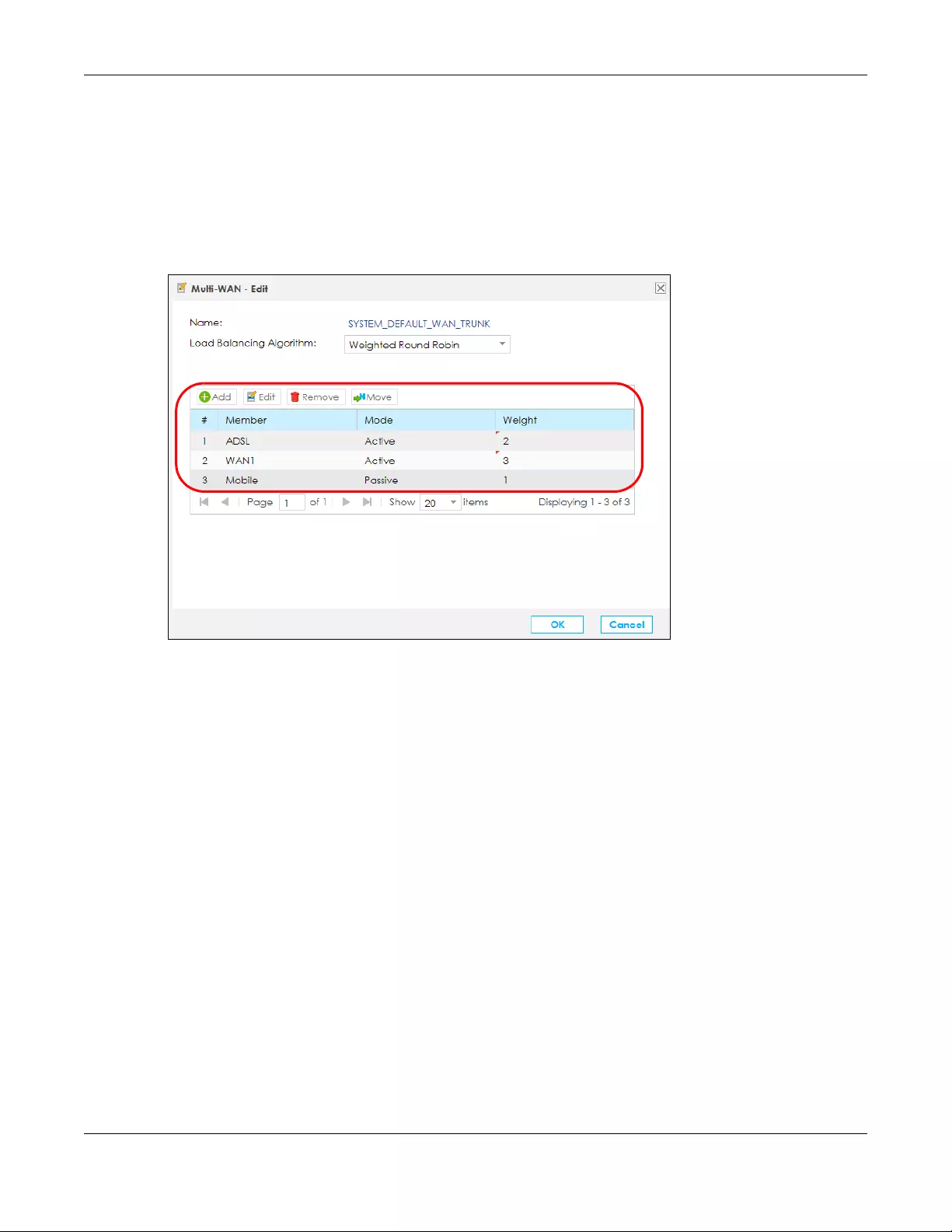
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
76
5.6.2.1 Configuring Multi-WAN
1Click Configuration > WAN / Internet > Multi-WAN > Edit. By default, all available WAN connections on
the SBG are in active mode with a weight of 1, except for the mobile WAN connection which is set to
passive mode.
2Select the Ethernet WAN (WAN1) connection and click Edit. Change the weight field to 3 and change
ADSL’s weight to 2. Click the OK button.
3You have finished the configuration. When both the Ethernet WAN and ADSL connections are up, the
SBG will send traffic over these two connections in a 3:2 ratio. When only one of these two connections
are up, the SBG will use that connection exclusively. Only when both of these two connections are
down will the SBG use the mobile WAN connection.
5.6.2.2 What Can Go Wrong?
• There can only be one WAN connection configured as passive mode at a time. If there is already a
WAN connection configured as passive mode, you will not be able to add or edit another WAN
connection in passive mode until the first WAN connection is changed to active mode or deleted.
• The SBG will automatically add newly created WAN connections (from the WAN / Internet > WAN
Setup screen) to the multi-WAN configuration as active mode with a weight of 1. If you are creating a
new WAN connection for other purposes (such as exclusive VPN use), you will need to delete that
WAN connection from the multi-WAN configuration. Deleting a WAN connection from the multi-WAN
screen does not delete the WAN connection from the WAN Setup page.
• A WAN connection can only be listed once in the multi-WAN configuration table.
5.7 The Dynamic DNS screen
Use this screen to change your SBG’s DDNS. Click Configuration > WAN / Internet > Dynamic DNS. The
screen appears as shown.
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
77
Figure 57 Configuration > WAN / Internet > Dynamic DNS
The following table describes the labels in this screen.
5.7.1 Edit Dynamic DNS
Click Add or select an existing dynamic DNS and click Edit in the Dynamic DNS screen to configure it.
Table 17 Configuration > WAN / Internet > Dynamic DNS
LABEL DESCRIPTION
Dynamic DNS
Add Click this to add a dynamic DNS.
Edit Select an entry and click Edit to modify the dynamic DNS’s settings.
Remove To remove an Dynamic DNS, select it and click Remove.
Multiple Entries Turn On Select one or more dynamic DNS entries and click this to enable them.
Multiple Entries Turn Off Select one or more dynamic DNS entries and click this to disable them.
# This is the number of an individual dynamic DNS.
Status This field displays whether the dynamic DNS is active or not. A green ON button
signifies that this dynamic DNS is active. A gray OFF button signifies that this dynamic
DNS is not active.
Profile Name This field displays the descriptive profile name for this entry.
DDNS Server This shows your Dynamic DNS service provider.
Domain Name This shows the domain name assigned to your SBG by your Dynamic DNS provider.
Interface This field displays the interface to use for updating the IP address mapped to the
domain name.
Current IP This shows the IP address your Dynamic DNS provider has currently associated with
the Profile Name.
Result Accept - displays when DDNS profile was updated to server successfully.
Not Accept - displays when DDNS profile is there was a problem during sync process.
Login Fail - displays when a DDNS profile is incorrect and it failed
Time This shows the last time the IP address the Dynamic DNS provider has associated with
the profile name was updated.
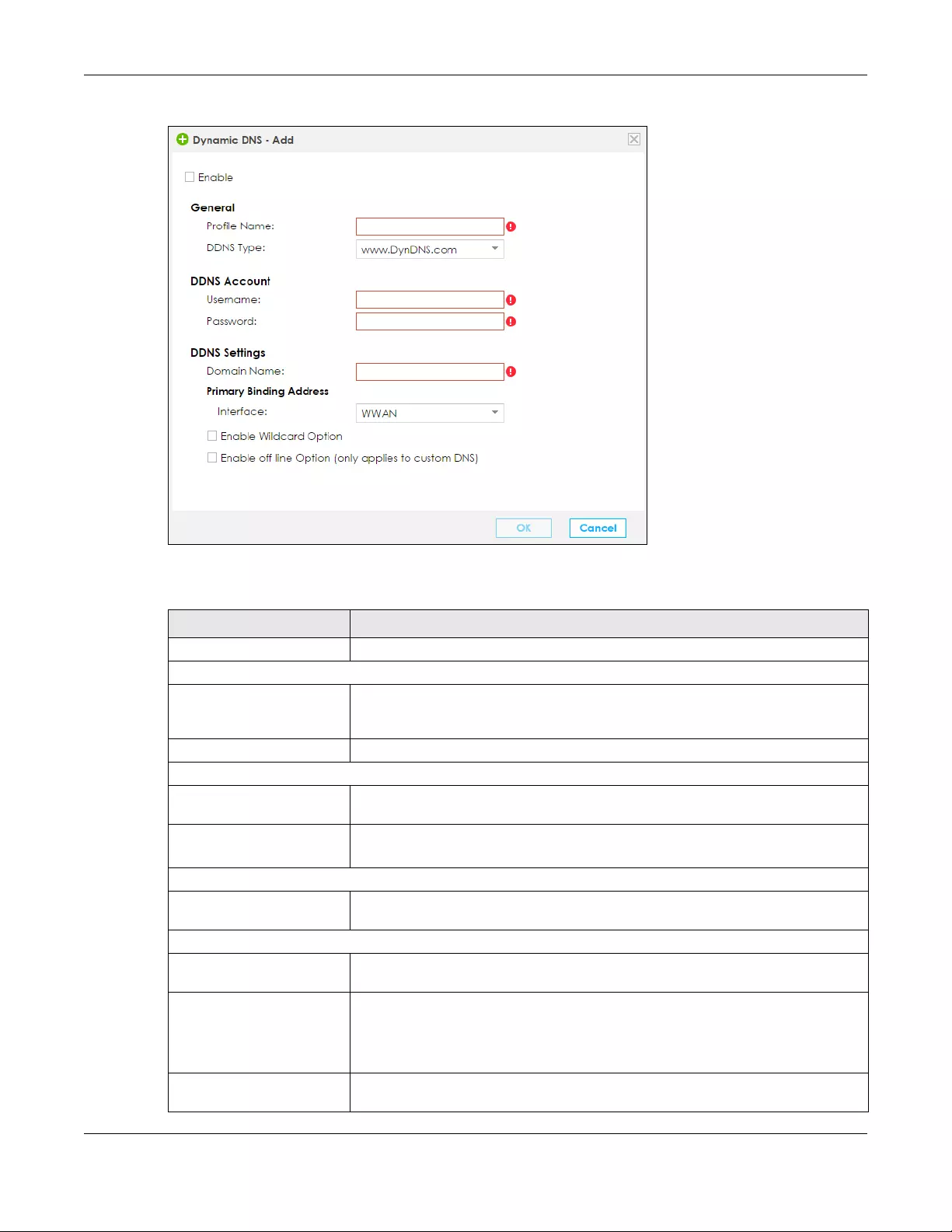
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
78
Figure 58 Dynamic DNS: Add/Edit
The following table describes the labels on this screen.
Table 18 Dynamic DNS: Add/Edit
LABEL DESCRIPTION
Enable Select Enable to use this dynamic DNS.
General
Profile Name When you are adding a dynamic DNS entry, type a descriptive name for this DDNS
entry in the SBG. You may use 1-32 alphanumeric characters, underscores(_), or
dashes (-), but the first character cannot be a number. This value is case-sensitive.
DDNS Type Select your Dynamic DNS service provider from the drop-down list box.
DDNS Account
Username Type the user name used when you registered your domain name. You can use up
to 32 alphanumeric characters and the underscore. Spaces are not allowed.
Password Type the password provided by the DDNS provider. You can use up to 32
alphanumeric characters and the underscore. Spaces are not allowed.
DDNS Settings
Domain Name Type the domain name you registered. You can use up to 256 alphanumeric
characters.
Primary Binding Address
Interface Select the interface to use for updating the IP address mapped to the domain
name.
Enable Wildcard Option Select the check box to enable DynDNS Wildcard.
Enable the wildcard feature to alias subdomains to be aliased to the same IP
address as your (dynamic) domain name. This feature is useful if you want to be able
to use, for example, www.yourhost.dyndns.org and still reach your hostname.
Enable off line Option (only
applies to custom DNS)
This option applies for custom DNS. Check with your Dynamic DNS service provider to
have traffic redirected to a URL (that you can specify) while you are off line.
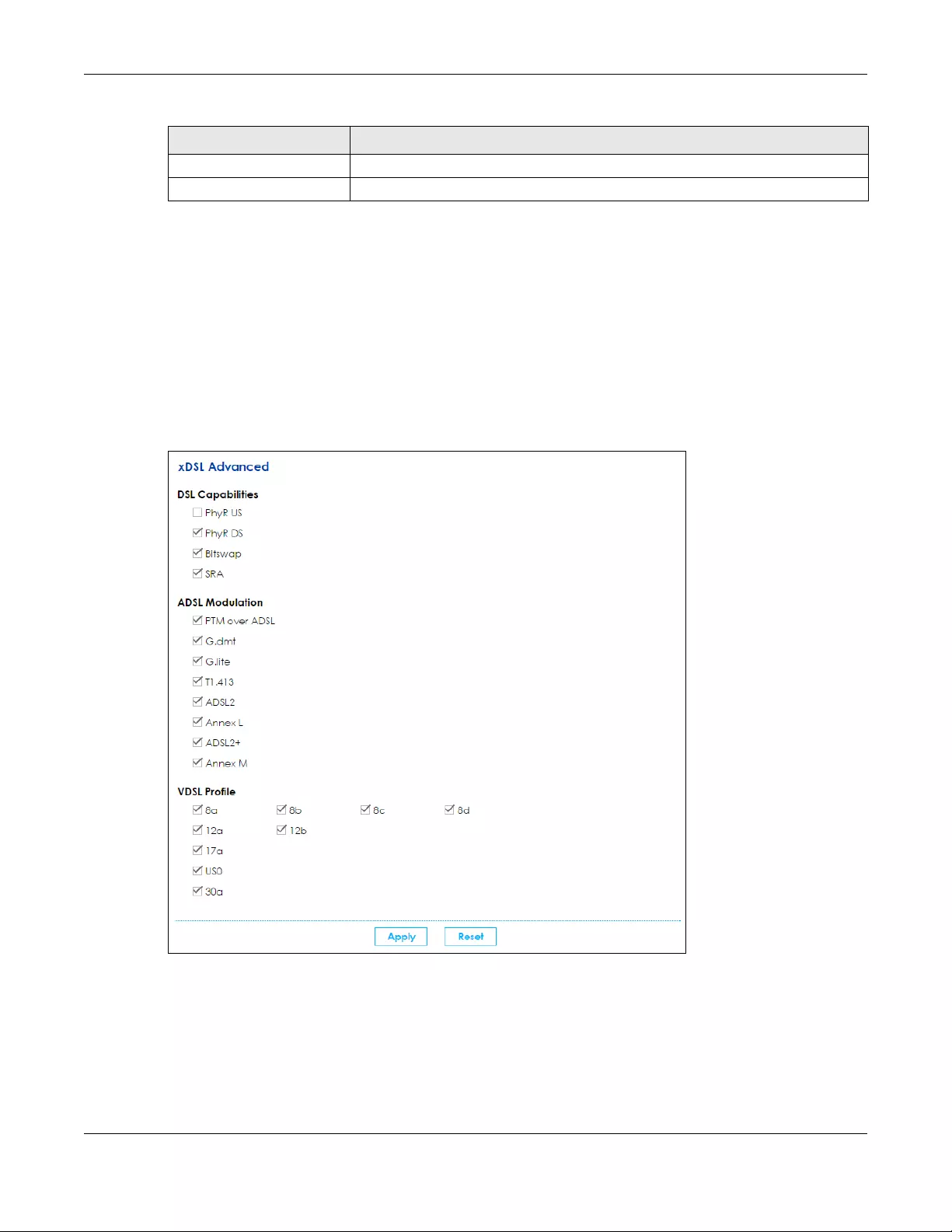
Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
79
5.8 The xDSL Advanced screen
Use the xDSL Advanced screen to enable or disable PTM over ADSL, Annex M, and DSL PhyR functions.
The SBG supports the PhyR retransmission scheme. PhyR is a retransmission scheme designed to provide
protection against noise on the DSL line. It improves voice, video and data transmission resilience by
utilizing a retransmission buffer.
Click Configuration > WAN / Internet > xDSL Advanced to display the following screen.
Figure 59 Configuration > WAN / Internet > xDSL Advanced
OK Click OK to save your changes back to the SBG and exit this screen.
Cancel Click Cancel to exit this screen without saving.
Table 18 Dynamic DNS: Add/Edit
LABEL DESCRIPTION

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
80
The following table describes the labels in this screen.
Table 19 Configuration > WAN / Internet > xDSL Advanced
LABEL DESCRIPTION
DSL Capabilities
PhyR US Enable or disable PhyR US (upstream) for upstream transmission to the WAN. PhyR US should be
enabled if data being transmitted upstream is sensitive to noise. However, enabling PhyR US can
decrease the US line rate. Enabling or disabling PhyR will require the CPE to retrain. For PhyR to
function, the DSLAM must also support PhyR and have it enabled.
PhyR DS Enable or disable PhyR DS (downstream) for downstream transmission from the WAN. PhyR DS
should be enabled if data being transmitted downstream is sensitive to noise. However,
enabling PhyR DS can decrease the DS line rate. Enabling or disabling PhyR will require the CPE
to retrain. For PhyR to function, the DSLAM must also support PhyR and have it enabled.
Bitswap Enable to allow the SBG to adapt to line changes when you are using G.dmt.
Bit-swapping is a way of keeping the line more stable by constantly monitoring and redistributing
bits between channels.
SRA Enable or disable Seamless Rate Adaption (SRA). Enable to have the SBG automatically adjust
the connection’s data rate according to line conditions without interrupting service.
ADSL Modulation
PTM over ADSL Enable to use PTM over ADSL. Since PTM has less overhead than ATM, some ISPs use PTM over
ADSL for better performance.
G.dmt ITU G.992.1 (better known as G.dmt) is an ITU standard for ADSL using discrete multitone
modulation. G.dmt full-rate ADSL expands the usable bandwidth of existing copper telephone
lines, delivering high-speed data communications at rates up to 8 Mbit/s downstream and 1.3
Mbit/s upstream.
G.lite ITU G.992.2 (better known as G.lite) is an ITU standard for ADSL using discrete multitone
modulation. G.lite does not strictly require the use of DSL filters, but like all variants of ADSL
generally functions better with splitters.
T1.413 ANSI T1.413 is a technical standard that defines the requirements for the single asymmetric
digital subscriber line (ADSL) for the interface between the telecommunications network and
the customer installation in terms of their interaction and electrical characteristics.
ADSL2 It optionally extends the capability of basic ADSL in data rates to 12 Mbit/s downstream and,
depending on Annex version, up to 3.5 Mbit/s upstream (with a mandatory capability of ADSL2
transceivers of 8 Mbit/s downstream and 800 kbit/s upstream).
Annex L Annex L is an optional specification in the ITU-T ADSL2 recommendation G.992.3 titled Specific
requirements for a Reach Extended ADSL2 (READSL2) system operating in the frequency band
above POTS, therefore it is often referred to as Reach Extended ADSL2 or READSL2.The main
difference between this specification and commonly deployed Annex A is the maximum
distance that can be used. The power of the lower frequencies used for transmitting data is
boosted up to increase the reach of this signal up to 7 kilometers (23,000 ft).
ADSL2+ ADSL2+ extends the capability of basic ADSL by doubling the number of downstream channels.
The data rates can be as high as 24 Mbit/s downstream and up to 1.4 Mbit/s upstream
depending on the distance from the DSLAM to the customer's premises.
Annex M You can enable Annex M for the SBG to use double upstream mode to increase the maximum
upstream transfer rate.
VDSL Profile VDSL2 profiles differ in the width of the frequency band used to transmit the broadband
signal.Profiles that use a wider frequency band can deliver higher maximum speeds.
8a, 8b, 8c, 8d,
12a, 12b, 17a,
US0, 30a
The G.993.2 VDSL standard defines a wide range of profiles that can be used in different VDSL
deployment settings, such as in a central office, a street cabinet or a building.
The SBG must comply with at least one profile specified in G.993.2. but compliance with more
than one profile is allowed.
Apply Click Apply to save your changes back to the SBG.
Reset Click this button to return the screen to its last-saved settings.

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
81
5.9 Technical Reference
The following section contains additional technical information about the SBG features described in this
chapter.
Encapsulation
Be sure to use the encapsulation method required by your ISP. The SBG can work in bridge mode or
routing mode. When the SBG is in routing mode, it supports the following methods.
IP over Ethernet
IP over Ethernet (IPoE) is an alternative to PPPoE. IP packets are being delivered across an Ethernet
network, without using PPP encapsulation. They are routed between the Ethernet interface and the
WAN interface and then formatted so that they can be understood in a bridged environment. For
instance, it encapsulates routed Ethernet frames into bridged Ethernet cells.
PPP over ATM (PPPoA)
PPPoA stands for Point to Point Protocol over ATM Adaptation Layer 5 (AAL5). A PPPoA connection
functions like a dial-up Internet connection. The SBG encapsulates the PPP session based on RFC 1483
and sends it through an ATM PVC (Permanent Virtual Circuit) to the Internet Service Provider’s (ISP)
DSLAM (digital access multiplexer). Please refer to RFC 2364 for more information on PPPoA. Refer to RFC
1661 for more information on PPP.
PPP over Ethernet (PPPoE)
Point-to-Point Protocol over Ethernet (PPPoE) provides access control and billing functionality in a
manner similar to dial-up services using PPP. PPPoE is an IETF standard (RFC 2516) specifying how a
personal computer (PC) interacts with a broadband modem (DSL, cable, wireless, etc.) connection.
For the service provider, PPPoE offers an access and authentication method that works with existing
access control systems (for example RADIUS).
One of the benefits of PPPoE is the ability to let you access one of multiple network services, a function
known as dynamic service selection. This enables the service provider to easily create and offer new IP
services for individuals.
Operationally, PPPoE saves significant effort for both you and the ISP or carrier, as it requires no specific
configuration of the broadband modem at the customer site.
By implementing PPPoE directly on the SBG (rather than individual computers), the computers on the
LAN do not need PPPoE software installed, since the SBG does that part of the task. Furthermore, with
NAT, all of the LANs’ computers will have access.
ATM Traffic Classes
These are the basic ATM traffic classes defined by the ATM Forum Traffic Management 4.0 Specification.
Constant Bit Rate (CBR)

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
82
Constant Bit Rate (CBR) provides fixed bandwidth that is always available even if no data is being sent.
CBR traffic is generally time-sensitive (doesn't tolerate delay). CBR is used for connections that
continuously require a specific amount of bandwidth. A PCR is specified and if traffic exceeds this rate,
cells may be dropped. Examples of connections that need CBR would be high-resolution video and
voice.
Variable Bit Rate (VBR)
The Variable Bit Rate (VBR) ATM traffic class is used with bursty connections. Connections that use the
Variable Bit Rate (VBR) traffic class can be grouped into real time (VBR-RT) or non-real time (VBR-nRT)
connections.
The VBR-RT (real-time Variable Bit Rate) type is used with bursty connections that require closely
controlled delay and delay variation. It also provides a fixed amount of bandwidth (a PCR is specified)
but is only available when data is being sent. An example of an VBR-RT connection would be video
conferencing. Video conferencing requires real-time data transfers and the bandwidth requirement
varies in proportion to the video image's changing dynamics.
The VBR-nRT (non real-time Variable Bit Rate) type is used with bursty connections that do not require
closely controlled delay and delay variation. It is commonly used for "bursty" traffic typical on LANs. PCR
and MBS define the burst levels, SCR defines the minimum level. An example of an VBR-nRT connection
would be non-time sensitive data file transfers.
Unspecified Bit Rate (UBR)
The Unspecified Bit Rate (UBR) ATM traffic class is for bursty data transfers. However, UBR doesn't
guarantee any bandwidth and only delivers traffic when the network has spare bandwidth. An example
application is background file transfer.
IP Address Assignment
A static IP is a fixed IP that your ISP gives you. A dynamic IP is not fixed; the ISP assigns you a different one
each time. The Single User Account feature can be enabled or disabled if you have either a dynamic or
static IP. However the encapsulation method assigned influences your choices for IP address and
default gateway.
Introduction to VLANs
A Virtual Local Area Network (VLAN) allows a physical network to be partitioned into multiple logical
networks. Devices on a logical network belong to one group. A device can belong to more than one
group. With VLAN, a device cannot directly talk to or hear from devices that are not in the same
group(s); the traffic must first go through a router.
In Multi-Tenant Unit (MTU) applications, VLAN is vital in providing isolation and security among the
subscribers. When properly configured, VLAN prevents one subscriber from accessing the network
resources of another on the same LAN, thus a user will not see the printers and hard disks of another user
in the same building.
VLAN also increases network performance by limiting broadcasts to a smaller and more manageable
logical broadcast domain. In traditional switched environments, all broadcast packets go to each and
every individual port. With VLAN, all broadcasts are confined to a specific broadcast domain.

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
83
Introduction to IEEE 802.1Q Tagged VLAN
A tagged VLAN uses an explicit tag (VLAN ID) in the MAC header to identify the VLAN membership of a
frame across bridges - they are not confined to the switch on which they were created. The VLANs can
be created statically by hand or dynamically through GVRP. The VLAN ID associates a frame with a
specific VLAN and provides the information that switches need to process the frame across the network.
A tagged frame is four bytes longer than an untagged frame and contains two bytes of TPID (Tag
Protocol Identifier), residing within the type/length field of the Ethernet frame) and two bytes of TCI (Tag
Control Information), starts after the source address field of the Ethernet frame).
The CFI (Canonical Format Indicator) is a single-bit flag, always set to zero for Ethernet switches. If a
frame received at an Ethernet port has a CFI set to 1, then that frame should not be forwarded as it is to
an untagged port. The remaining twelve bits define the VLAN ID, giving a possible maximum number of
4,096 VLANs. Note that user priority and VLAN ID are independent of each other. A frame with VID
(VLAN Identifier) of null (0) is called a priority frame, meaning that only the priority level is significant and
the default VID of the ingress port is given as the VID of the frame. Of the 4096 possible VIDs, a VID of 0 is
used to identify priority frames and value 4095 (FFF) is reserved, so the maximum possible VLAN
configurations are 4,094.
Multicast
IP packets are transmitted in either one of two ways - Unicast (1 sender - 1 recipient) or Broadcast (1
sender - everybody on the network). Multicast delivers IP packets to a group of hosts on the network -
not everybody and not just 1.
Internet Group Multicast Protocol (IGMP) is a network-layer protocol used to establish membership in a
Multicast group - it is not used to carry user data. IGMP version 2 (RFC 2236) is an improvement over
version 1 (RFC 1112) but IGMP version 1 is still in wide use. If you would like to read more detailed
information about interoperability between IGMP version 2 and version 1, please see sections 4 and 5 of
RFC 2236. The class D IP address is used to identify host groups and can be in the range 224.0.0.0 to
239.255.255.255. The address 224.0.0.0 is not assigned to any group and is used by IP multicast
computers. The address 224.0.0.1 is used for query messages and is assigned to the permanent group of
all IP hosts (including gateways). All hosts must join the 224.0.0.1 group in order to participate in IGMP.
The address 224.0.0.2 is assigned to the multicast routers group.
At start up, the SBG queries all directly connected networks to gather group membership. After that, the
SBG periodically updates this information.
DNS Server Address Assignment
Use Domain Name System (DNS) to map a domain name to its corresponding IP address and vice versa,
for instance, the IP address of www.zyxel.com is 204.217.0.2. The DNS server is extremely important
because without it, you must know the IP address of a computer before you can access it.
The SBG can get the DNS server addresses in the following ways.
1The ISP tells you the DNS server addresses, usually in the form of an information sheet, when you sign up.
If your ISP gives you DNS server addresses, manually enter them in the DNS server fields.
TPID
2 Bytes
User Priority
3 Bits
CFI
1 Bit
VLAN ID
12 Bits

Chapter 5 WAN/Internet
SBG5500 Series User’s Guide
84
2If your ISP dynamically assigns the DNS server IP addresses (along with the SBG’s WAN IP address), set the
DNS server fields to get the DNS server address from the ISP.
IPv6 Addressing
The 128-bit IPv6 address is written as eight 16-bit hexadecimal blocks separated by colons (:). This is an
example IPv6 address 2001:0db8:1a2b:0015:0000:0000:1a2f:0000.
IPv6 addresses can be abbreviated in two ways:
• Leading zeros in a block can be omitted. So 2001:0db8:1a2b:0015:0000:0000:1a2f:0000 can be
written as 2001:db8:1a2b:15:0:0:1a2f:0.
• Any number of consecutive blocks of zeros can be replaced by a double colon. A double colon can
only appear once in an IPv6 address. So 2001:0db8:0000:0000:1a2f:0000:0000:0015 can be
written as 2001:0db8::1a2f:0000:0000:0015, 2001:0db8:0000:0000:1a2f::0015,
2001:db8::1a2f:0:0:15 or 2001:db8:0:0:1a2f::15.
IPv6 Prefix and Prefix Length
Similar to an IPv4 subnet mask, IPv6 uses an address prefix to represent the network address. An IPv6
prefix length specifies how many most significant bits (start from the left) in the address compose the
network address. The prefix length is written as “/x” where x is a number. For example,
2001:db8:1a2b:15::1a2f:0/32
means that the first 32 bits (2001:db8) is the subnet prefix.
SBG5500 Series User’s Guide
85
CHAPTER 6
LAN
6.1 Overview
A Local Area Network (LAN) is a shared communication system to which many networking devices are
connected. It is usually located in one immediate area such as a building or floor of a building.
Use the LAN screens to help you configure a LAN DHCP server and manage IP addresses.
6.1.1 What You Can Do in this Chapter
• Use the LAN Status screen to show the status of interfaces currently connected to the SBG (Section 6.2
on page 87).
• Use the LAN Setup screen to set the LAN IP address, subnet mask, and DHCP settings of your SBG
(Section 6.2 on page 87).
• Use the Static DHCP screen to assign IP addresses on the LAN to specific individual computers based
on their MAC Addresses (Section 6.4 on page 94).
• Use the Additional Subnet screen to configure IP alias and public static IP (Section 6.5 on page 96).
• Use the Wake on LAN screen to remotely turn on a device on the network (Section 6.6 on page 96).
• Use the VLAN / Interface Group screen to create multiple networks on the SBG (Section 6.7 on page
98).
• Use the DNS Entry screen to view, configure or remove DNS routes (Section 6.8 on page 103).
• Use the DNS Forwarder screen to view and configure domain zone forwarder on the SBG (Section 6.9
on page 103).
SBG

Chapter 6 LAN
SBG5500 Series User’s Guide
86
6.1.2 What You Need To Know
6.1.2.1 About LAN
IP Address
IP addresses identify individual devices on a network. Every networking device (including computers,
servers, routers, printers, etc.) needs an IP address to communicate across the network. These
networking devices are also known as hosts.
Subnet Mask
Subnet masks determine the maximum number of possible hosts on a network. You can also use subnet
masks to divide one network into multiple sub-networks.
DHCP
A DHCP (Dynamic Host Configuration Protocol) server can assign your SBG an IP address, subnet mask,
DNS and other routing information when it's turned on.
DNS
DNS (Domain Name System) is for mapping a domain name to its corresponding IP address and vice
versa. The DNS server is extremely important because without it, you must know the IP address of a
networking device before you can access it. The DNS server addresses you enter when you set up DHCP
are passed to the client machines along with the assigned IP address and subnet mask.
There are two ways that an ISP disseminates the DNS server addresses.
• The ISP tells you the DNS server addresses, usually in the form of an information sheet, when you sign
up. If your ISP gives you DNS server addresses, enter them in the DNS Server fields in the LAN Setup
screen.
• Some ISPs choose to disseminate the DNS server addresses using the DNS server extensions of IPCP (IP
Control Protocol) after the connection is up. If your ISP did not give you explicit DNS servers, chances
are the DNS servers are conveyed through IPCP negotiation. The SBG supports the IPCP DNS server
extensions through the DNS proxy feature.
Please note that DNS proxy works only when the ISP uses the IPCP DNS server extensions. It does not
mean you can leave the DNS servers out of the DHCP setup under all circumstances. If your ISP gives you
explicit DNS servers, make sure that you enter their IP addresses in the LAN Setup screen.
RADVD (Router Advertisement Daemon)
When an IPv6 host sends a Router Solicitation (RS) request to discover the available routers, RADVD with
Router Advertisement (RA) messages in response to the request. It specifies the minimum and maximum
intervals of RA broadcasts. RA messages containing the address prefix. IPv6 hosts can be generated
with the IPv6 prefix an IPv6 address.
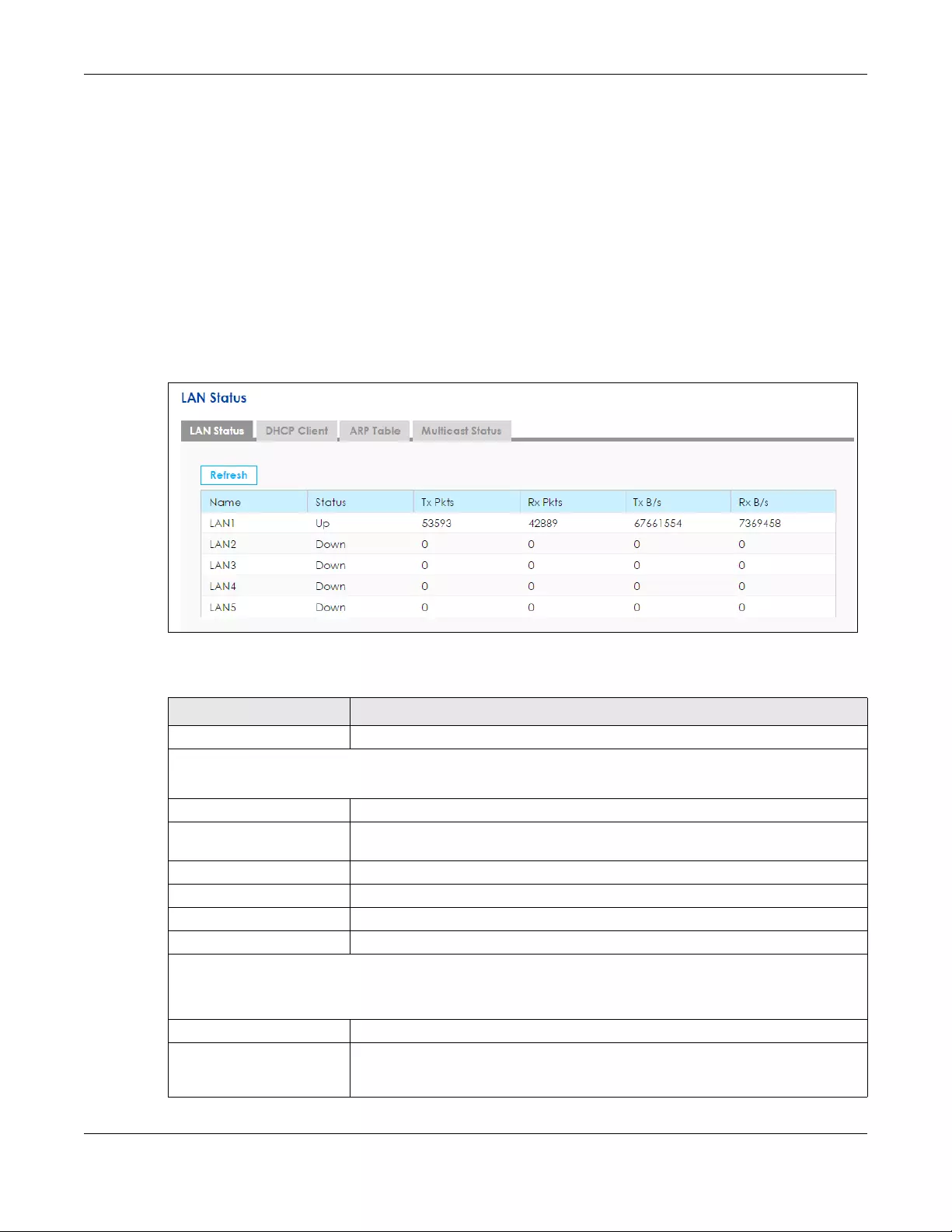
Chapter 6 LAN
SBG5500 Series User’s Guide
87
6.1.3 Before You Begin
Find out the MAC addresses of your network devices if you intend to add them to the DHCP Client List
screen.
6.2 The LAN Status Screen
Use the LAN Status Screen to view the status of all interfaces connected to the SBG, details about DHCP
clients. Click on Configuration > LAN / Home Network > LAN Status to open the following screen. The
tables change depending on the table you click on.
Figure 60 Configuration > LAN / Home Network > LAN Status
The following table describes the labels in the screen.
Table 20 Configuration > LAN / Home Network > LAN Status
LABEL DESCRIPTION
Refresh Click this to update the table.
LAN Status
Click this to show the interfaces currently connected to the SBG.
Name This shows the name of the LAN interface.
Status This shows Up if the SBG detect a connection through this port. Otherwise it shows
Down.
Tx Pkts This is the number of transmitted packets on this port.
Rx Pkts This is the number of received packets on this port.
Tx B/s This displays the transmission speed in bytes per second on this port.
Rx B/s This displays the reception speed in bytes per second on this port.
DHCP Client
Click this to look at the IP addresses currently assigned to DHCP clients and the IP addresses reserved for specific
MAC addresses.
# This field is a sequential value, and it is not associated with a specific entry.
Device Name This field displays the name used to identify this device on the network (the
computer name). The SBG learns these from the DHCP client requests.“None” shows
here for a static DHCP entry.
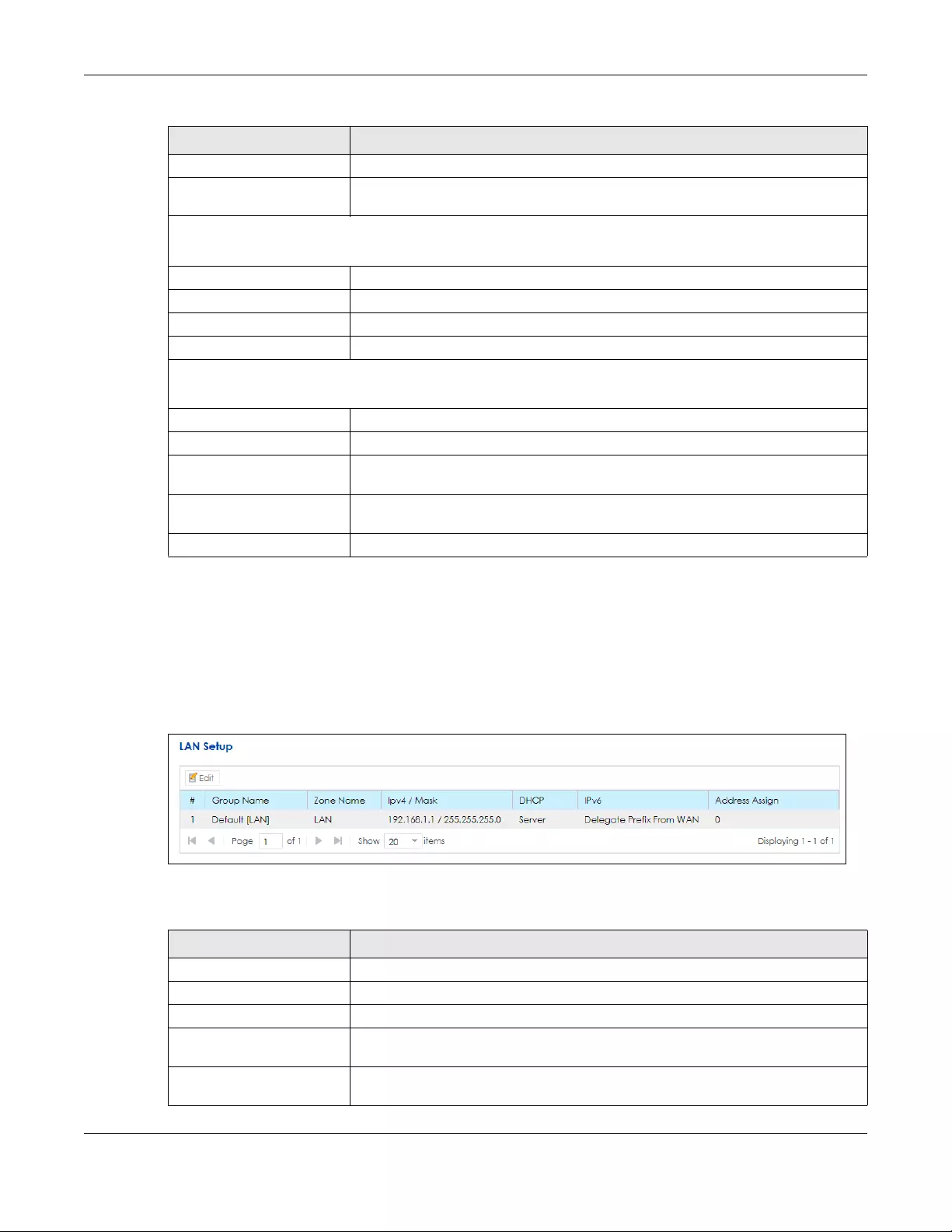
Chapter 6 LAN
SBG5500 Series User’s Guide
88
6.3 The LAN Setup Screen
Use this screen to set the Local Area Network IP address and subnet mask of your SBG. Click
Configuration > LAN / Home Network to open the LAN Setup screen.
Figure 61 Configuration > LAN / Home Network > LAN Setup
The following table describes the labels in this screen.
IP Address This field displays the DHCP client’s IP address.
MAC Address This field displays the MAC address to which the IP address is currently assigned or for
which the IP address is reserved.
ARP Table
Click this to view IP-to-MAC address mapping(s).
# This is the ARP table entry number.
IP Address This is the learned IPv4 or IPv6 IP address of a device connected to a port.
MAC Address This is the MAC address of the device with the listed IP address.
Interface This is the interface used by the ARP entry.
Multicast Status
Click this to look at the current list of multicast groups the SBG has joined and which ports have joined it.
# This is the multicast status table entry number.
Type This is the protocol used by the interface.
Interface This field displays the name of an interface on the SBG that belongs to an IGMP
multicast group.
Multicast Group This field displays the name of the IGMP multicast group to which the interface
belongs.
Host This shows the clients that are part of this multicast group.
Table 20 Configuration > LAN / Home Network > LAN Status
LABEL DESCRIPTION
Table 21 Configuration > LAN / Home Network > LAN Setup
LABEL DESCRIPTION
Edit Select an entry and click Edit to modify it.
# This field is a sequential value, and it is not associated with a specific entry.
Group Name This field shows the interface group name.
Zone Name This field shows the security zone (LAN, WLAN, DMZ, or EXTRA) in which the LAN
interface is included.
IPv4 / Mask This field displays the LAN IPv4 address assigned to your SBG and the subnet mask of
your network in dotted decimal notation.
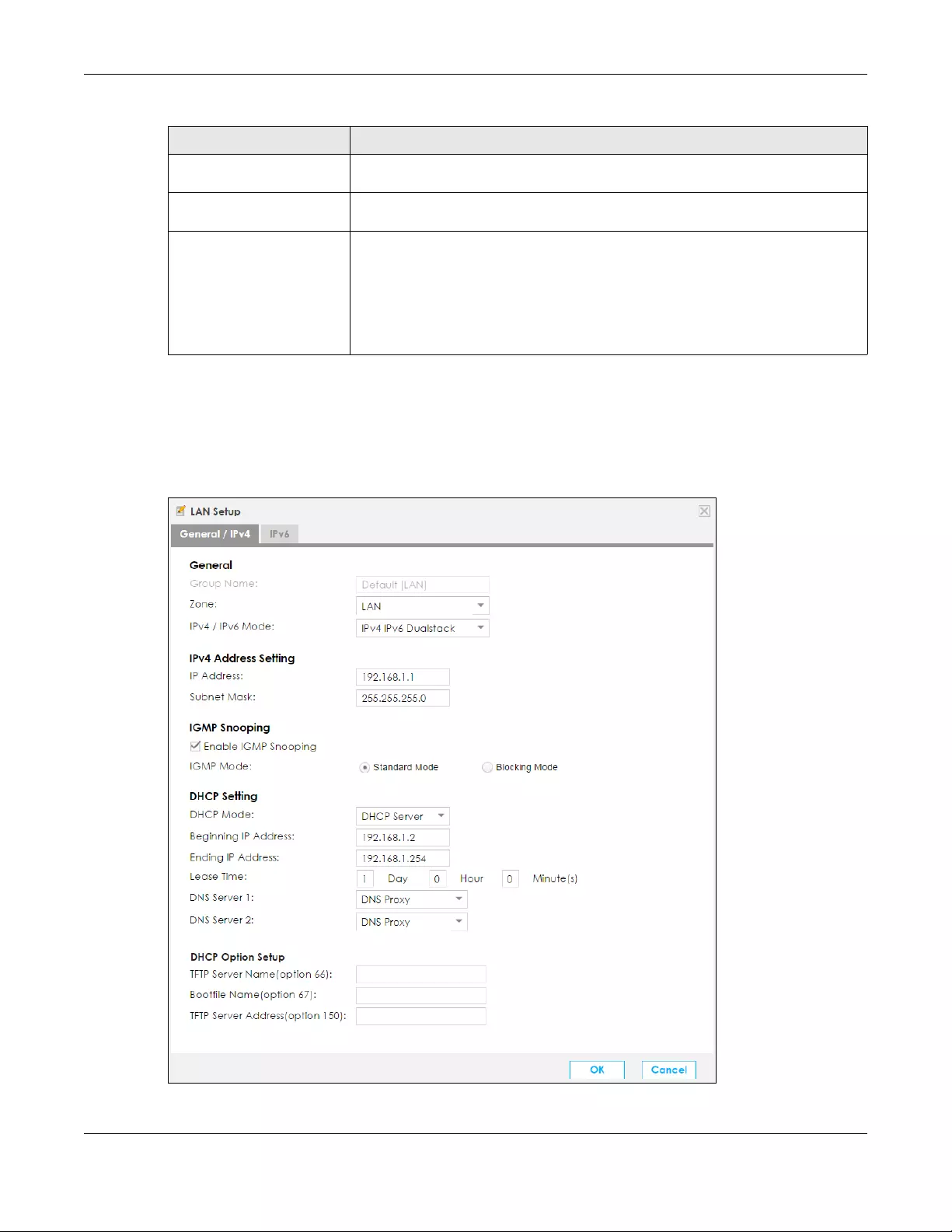
Chapter 6 LAN
SBG5500 Series User’s Guide
89
6.3.1 Edit LAN Setup
In Configuration > LAN / Home Network screen select an entry and click Edit to open the following
screen.
Figure 62 LAN Setup: Edit > General / IPv4
DHCP This shows whether the SBG acts as DHCP Server or DHCP Relay agent. It shows
Disable if the DHCP server has been stopped in the SBG.
IPv6 This shows the IPv6 prefix and prefix length you configured when you enable IPv6 on
the LAN interface and set
Address Assign This field displays 1 when the IPv6 address is assigned using IPv6 stateful
autoconfiguration (DHCPv6) or 0 when the SBG uses IPv6 stateless
autoconfiguration.
• Stateless: The SBG send IPv6 prefix information in router advertisements
periodically and in response to router solicitations.
• Stateful: The DHCPv6 server is enabled to have the SBG act as a DHCPv6 server
and pass IPv6 addresses to DHCPv6 clients.
Table 21 Configuration > LAN / Home Network > LAN Setup
LABEL DESCRIPTION

Chapter 6 LAN
SBG5500 Series User’s Guide
90
The following table describes the fields in this screen.
Table 22 LAN Setup: Edit > General / IPv4
LABEL DESCRIPTION
General
Group Name Select the interface group name for which you want to configure LAN settings. See Section 6.7
on page 98 for how to create a new interface group/VLAN.
Zone Select the security zone (LAN, WLAN, DMZ, or EXTRA) in which to include the LAN interface. A
newly created local network (interface group) belongs to the LAN zone by default.
IPv4 / IPv6 Mode Select IPv4 only if you want the SBG to run IPv4 only.
Select IPv4 IPv6 Dualstack to allow the SBG to run IPv4 and IPv6 at the same time.
IPv4 Address Setting
IP Address Enter the LAN IP address you want to assign to your SBG in dotted decimal notation, for
example, 192.168.1.1 (factory default).
Subnet Mask Type the subnet mask of your network in dotted decimal notation, for example 255.255.255.0
(factory default). Your SBG automatically computes the subnet mask based on the IP Address
you enter, so do not change this field unless you are instructed to do so.
IGMP Snooping
Enable IGMP
Snooping
Select the check box to allow the SBG to passively learn multicast group.
IGMP Mode Select Standard Mode to have the SBG forward multicast packets to a port that joins the
multicast group and broadcast unknown multicast packets from the WAN to all LAN ports.
Select Blocking Mode to have the SBG block all unknown multicast packets from the WAN.
DHCP Setting
DHCP Mode Select DHCP Server to have the SBG act as a DHCP server.
Select DHCP Relay to have the SBG act as a DHCP relay agent and forward DHCP request to the
DHCP server you specify.
Select DHCP Disable to stop the DHCP server on the SBG.
Beginning IP
Address
This field specifies the first of the contiguous addresses in the IP address pool.
Ending IP
Address
This field specifies the last of the contiguous addresses in the IP address pool.
Lease Time This is the period of time DHCP-assigned addresses use. DHCP automatically assigns IP addresses
to clients when they log in. DHCP centralizes IP address management on central computers that
run the DHCP server program. DHCP leases addresses, for a period of time, which means that
past addresses are “recycled” and made available for future reassignment to other systems.
This field is only available when you select DHCP Server in the DHCP Mode field.
DNS Server 1 Specify the IP address of the first DNS server for the DHCP clients to use. Use one of the following
ways to specify the IP address.
DNS Proxy - the clients use the IP address of the SBG LAN interface. The SBG redirects clients’ DNS
queries to a DNS server for resolving domain names.
Static - enter a static IP address.
From Wan Interface - select the WAN interface that receives the DNS server address from its
DHCP server.

Chapter 6 LAN
SBG5500 Series User’s Guide
91
6.3.2 Edit LAN Setup IPv6
Click the IPv6 tab in Configuration > LAN / Home Network > LAN Setup > Edit to configure IPv6 LAN
settings on the SBG. This screen is available only when you select IPv4 IPv6 Dualstack in the IPv4 / IPv6
Mode field of the LAN Setup > Edit > General / IPv4 screen.
DNS Server 2 Specify the IP address of the secondary DNS server for the DHCP clients to use. Use one of the
following ways to specify the IP address.
DNS Proxy - the clients use the IP address of the SBG LAN interface. The SBG redirects clients’ DNS
queries to a DNS server for resolving domain names.
Static - enter a static IP address.
From Wan Interface - select the WAN interface that receives the DNS server address from its
DHCP server.
Remote DHCP
Server
Enter the DHCP server’s address so the SBG forwards DHCP requests to this address.
This field is only available when you select DHCP Relay.
DHCP Option
Setup
These fields display when you select DHCP Server in the DHCP Mode field. You may need to
configure them when you have VoIP phones on your LAN.
TFTP Server
Name (option
66)
Enter the name of a TFTP server to assign it to the DHCP clients.
Bootfile Name
(option 67)
Enter the name of a bootfile to assign it to the DHCP clients.
TFTP Server
Address (option
150)
Enter the IP address of a TFTP server to assign it to the DHCP clients.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 22 LAN Setup: Edit > General / IPv4 (continued)
LABEL DESCRIPTION
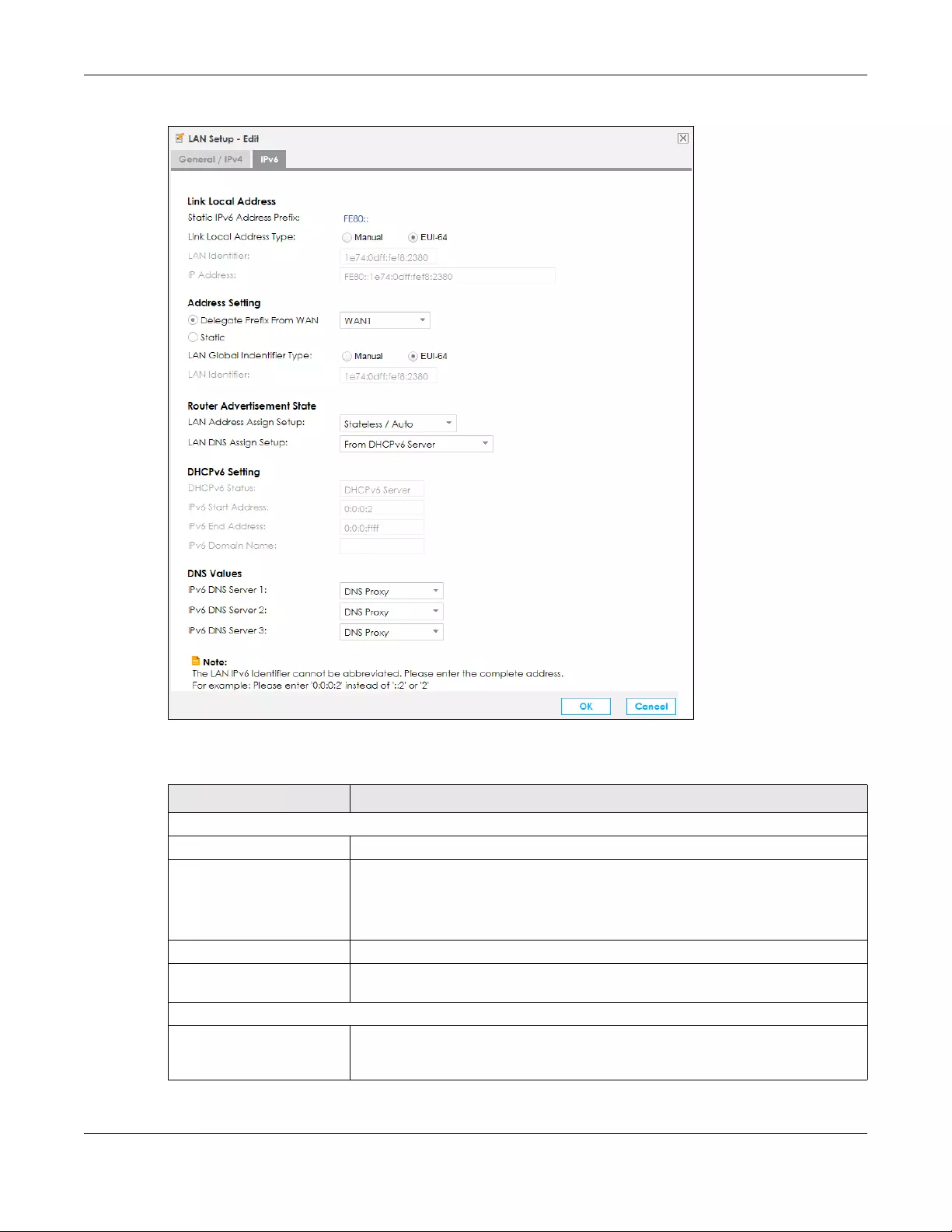
Chapter 6 LAN
SBG5500 Series User’s Guide
92
Figure 63 LAN Setup: Edit > IPv6
The following table describes the labels in this screen.
Table 23 Configuration > LAN / Home Network > LAN Setup: Edit > IPv6
LABEL DESCRIPTION
Link Local Address
Static IPv6 Address Prefix This shows the static IPv6 address prefix used to represent the SBG network address.
Link Local Address Type Select EUI-64 to give clients a 64-bit Extended Unique Identifier (EUI) to link locally
without DHCP.
Select Manual to manually enter an interface ID for the LAN interface’s global IPv6
address.
LAN Identifier Enter an interface ID for the LAN interface’s global IPv6 address.
IP address This field shows an IPv6 address created using the Static IPv6 Address Prefix and the
LAN Identifier you input.
Address Setting
Delegate Prefix From WAN Select this option and a WAN interface with IPv6 enabled to automatically obtain
an IPv6 network prefix from the service provider or an uplink router through the
specified WAN interface.
Chapter 6 LAN
SBG5500 Series User’s Guide
93
Static Select this option to configure a fixed IPv6 address for the SBG’s LAN interface.
Note: This fixed address is for local hosts to access the Web Configurator
only as the global LAN IPv6 address might be changed by your ISP
any time. This address is not the routing gateway’s address for LAN
IPv6 hosts.
Static IPv6 Address Prefix Enter the address prefix to represent the SBG’s static LAN IPv6 address.
Prefix Length If you select Static, enter the IPv6 prefix length that the SBG uses to generate the LAN
IPv6 address.
An IPv6 prefix length specifies how many most significant bits (starting from the left)
in the address compose the network address. This field displays the bit number of the
IPv6 subnet mask.
LAN Global Identifier Type Select EUI-64 to allow clients to assign themselves a 64-bit Extended Unique Identifier
(EUI) without DHCP.
Select Manual if you want to enter the LAN identifier the clients use.
LAN Identifier Enter the LAN identifier clients use without DHCP.
IP Address This field shows an IPv6 address created using the Static IPv6 Address Prefix and the
LAN Identifier you input.
Route Advertisement State
LAN Address Assign Setup Select how you want to obtain an IPv6 address:
•Stateless / Auto: The SBG uses IPv6 stateless autoconfiguration. RADVD (Router
Advertisement Daemon) is enabled to have the SBG send IPv6 prefix information
in router advertisements periodically and in response to router solicitations.
DHCPv6 server is disabled.
•Stateful / DHCP: The SBG uses IPv6 stateful autoconfiguration. The DHCPv6 server
is enabled to have the SBG act as a DHCPv6 server and pass IPv6 addresses to
DHCPv6 clients.
LAN DNS Assign Setup Select how the SBG provide DNS server and domain name information to the clients:
•From Router Advertisement: The SBG provides DNS information through router
advertisements.
•From DHCPv6 Server: The SBG provides DNS information through DHCPv6.
DHCPv6 Setting
DHCPv6 Status This shows the status of the DHCPv6. DHCPv6 Server displays if you configured the
SBG to act as a DHCPv6 server which assigns IPv6 addresses and/or DNS information
to clients.
IPv6 Start Address If DHCPv6 is enabled, specify the first IPv6 address in the pool of addresses that can
be assigned to DHCPv6 clients.
IPv6 End Address If DHCPv6 is enabled, specify the last IPv6 address in the pool of addresses that can
be assigned to DHCPv6 clients.
IPv6 Domain Name If DHCPv6 is enabled, specify the domain name to be assigned to DHCPv6 clients.
IPv6 DNS Values
IPv6 DNS Server 1-3 Select From WAN Interface if your ISP dynamically assigns IPv6 DNS server
information.
Select Static if you have the IPv6 address of a DNS server. Enter the DNS server IPv6
addresses the SBG passes to the DHCP clients.
Select DNS Proxy if you have the DNS proxy service. The SBG redirects clients’ DNS
queries to a DNS server for resolving domain names.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 23 Configuration > LAN / Home Network > LAN Setup: Edit > IPv6
LABEL DESCRIPTION
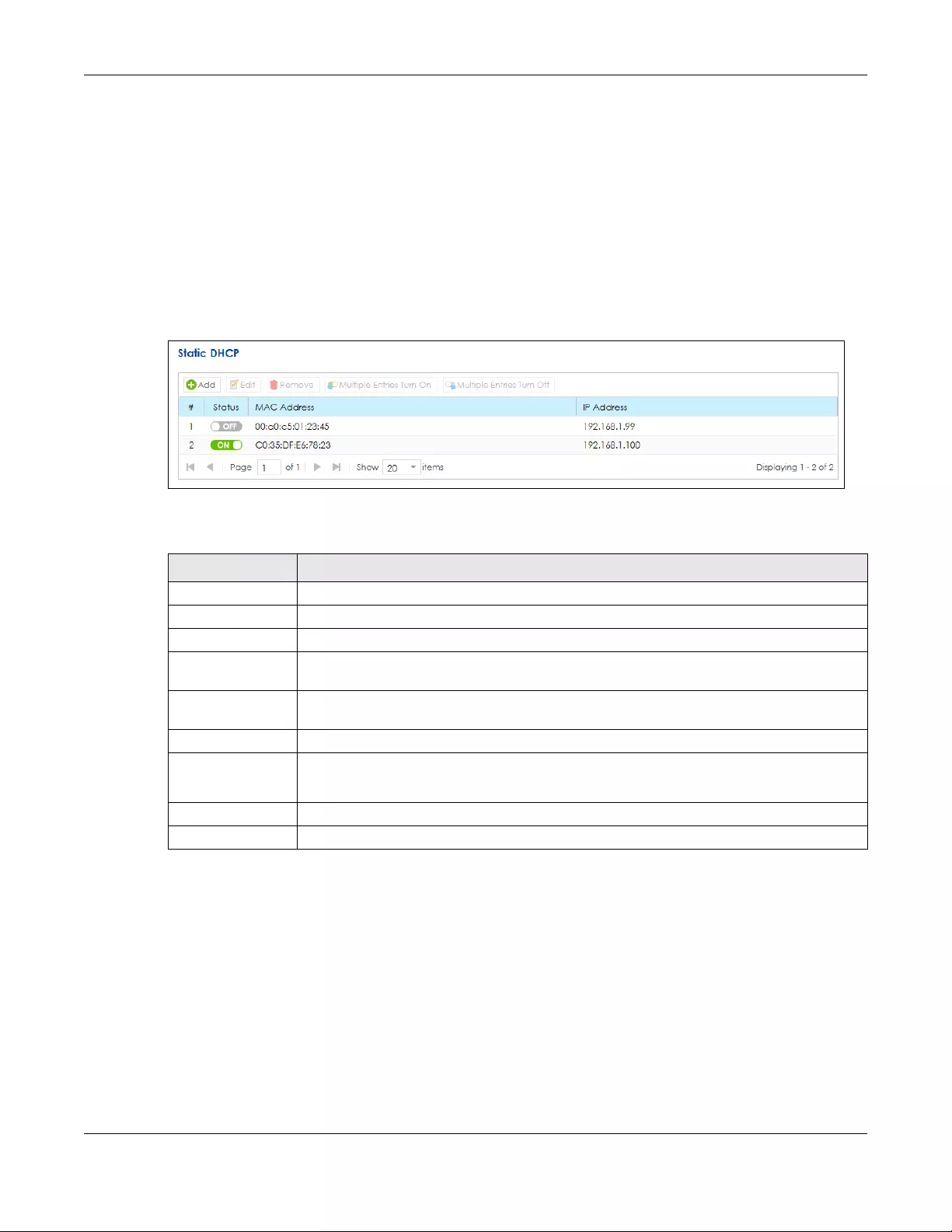
Chapter 6 LAN
SBG5500 Series User’s Guide
94
6.4 The Static DHCP Screen
This table allows you to assign IP addresses on the LAN to specific individual computers based on their
MAC Addresses.
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC address is assigned
at the factory and consists of six pairs of hexadecimal characters, for example, 00:A0:C5:00:00:02.
Use this screen to change your SBG’s static DHCP settings. Click Configuration > LAN / Home Network >
Static DHCP to open the following screen.
Figure 64 Configuration > LAN / Home Network > Static DHCP
The following table describes the labels in this screen.
6.4.1 Edit Static DHCP
If you click Add in the Static DHCP screen or Edit next to a static DHCP entry, the following screen
displays.
Table 24 Network Setting > LAN > Static DHCP
LABEL DESCRIPTION
Add Click this to add a new static DHCP entry.
Edit Click Edit to configure a static DHCP entry.
Remove Click Remove to delete a static DHCP entry.
Multiple Entries Turn
On
Select one or more static DHCP entry and click this to enable them.
Multiple Entries Turn
Off
Select one or more static DHCP entry and click this to disable them.
# This is the index number of the DHCP entry.
Status This field displays whether the entry is active.
Click the slide button to turn on or turn off the entry.
MAC Address This field displays the MAC address of a computer on the LAN.
IP Address This field displays the IP address relative to the MAC address field listed above.
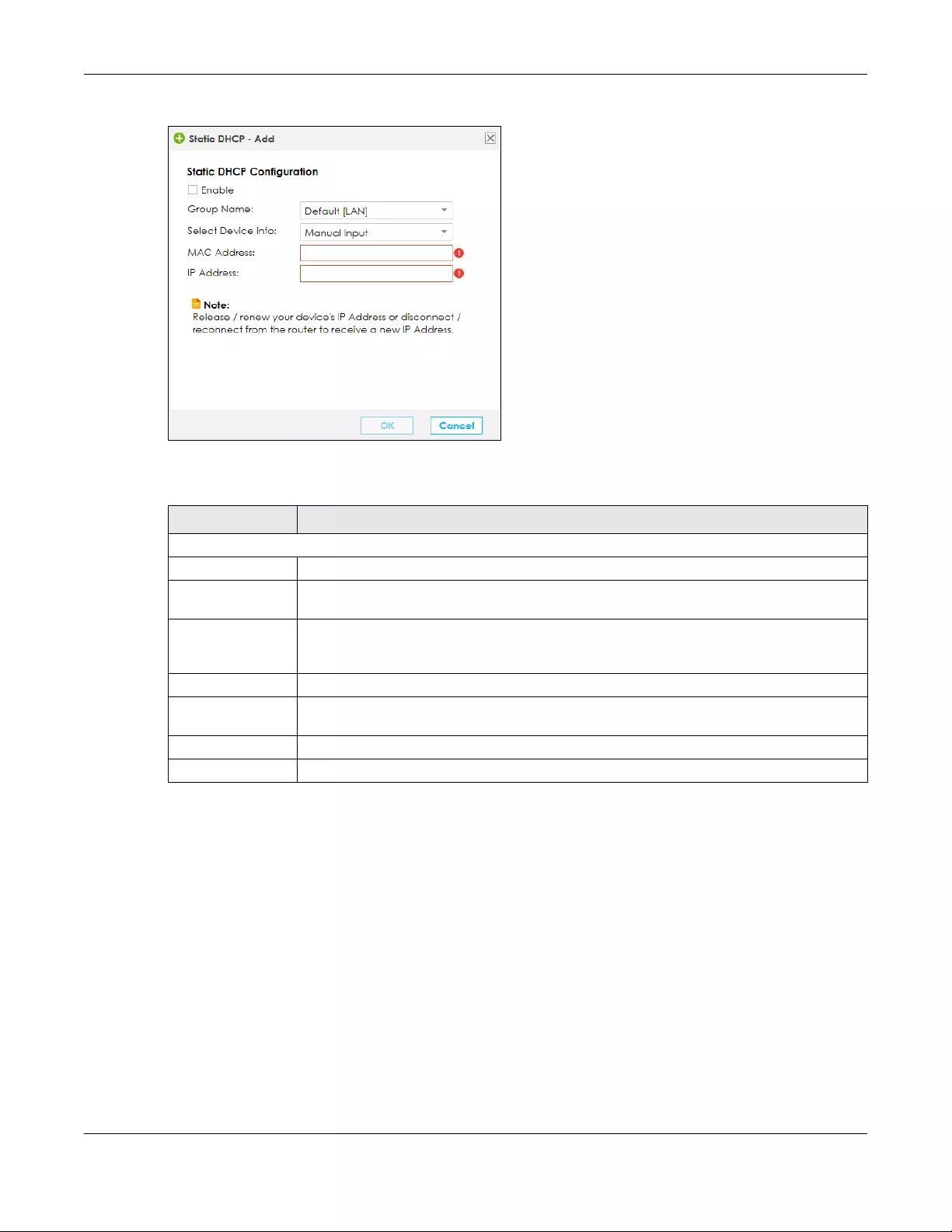
Chapter 6 LAN
SBG5500 Series User’s Guide
95
Figure 65 Static DHCP: Add/Edit
The following table describes the labels in this screen.
Table 25 Static DHCP: Add/Edit
LABEL DESCRIPTION
Static DHCP Configuration
Enable Select this to activate the rule.
Group Name Select the interface group name for which you want to configure static DHCP settings. See
Section 6.7 on page 98 for how to create a new interface group.
Select Device Info If you select Manual Input, you can manually type in the MAC address and IP address of a
computer on your LAN. You can also choose the name of a computer from the drop list and
have the MAC Address and IP Address auto-detected.
MAC Address If you select Manual Input, enter the MAC address of a computer on your LAN.
IP Address If you select Manual Input, enter the IP address that you want to assign to the computer on
your LAN with the MAC address that you will also specify.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
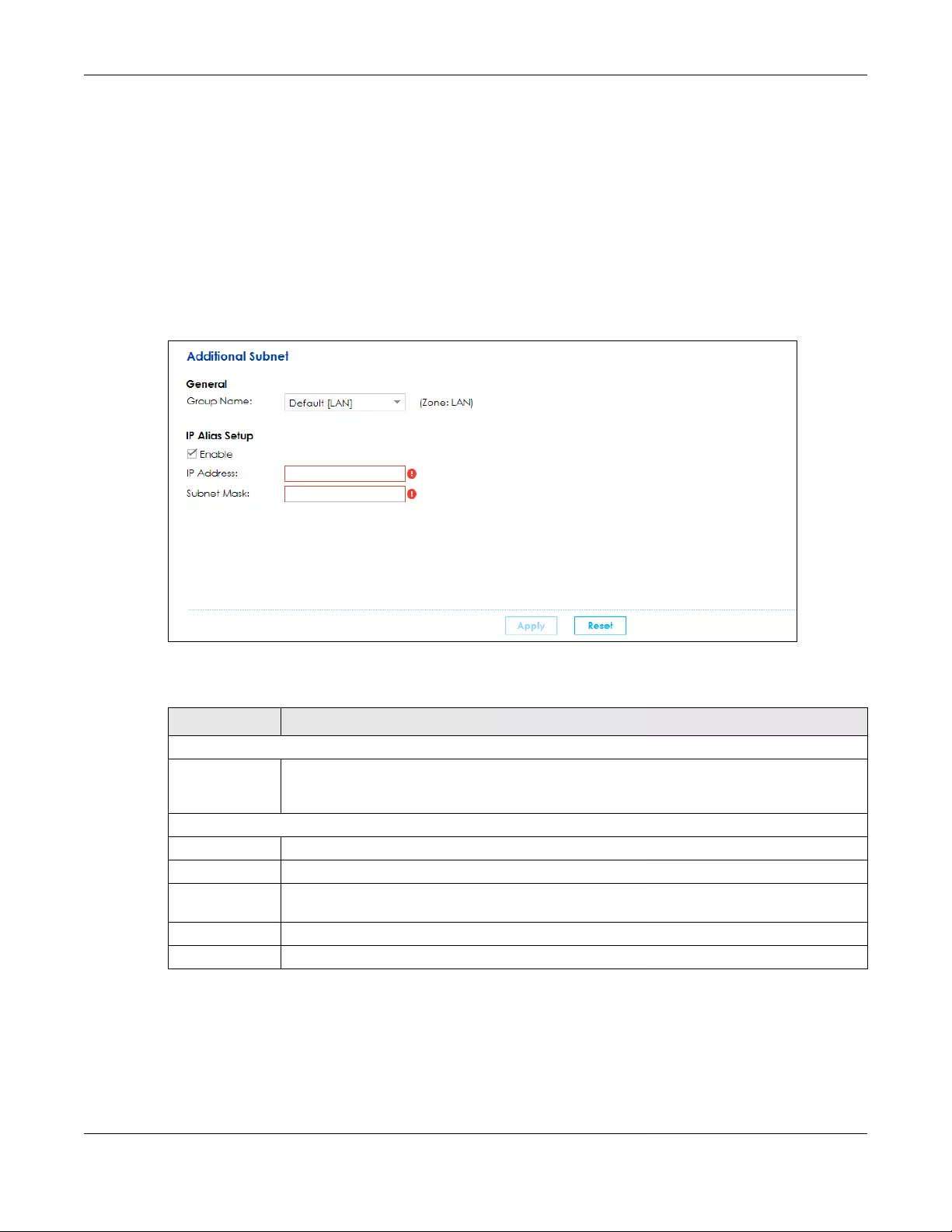
Chapter 6 LAN
SBG5500 Series User’s Guide
96
6.5 The Additional Subnet Screen
Use the Additional Subnet screen to configure IP alias.
IP alias allows you to partition a physical network into different logical networks over the same Ethernet
interface. The SBG supports multiple logical LAN interfaces via its physical Ethernet interface with the
SBG itself as the gateway for the LAN network. When you use IP alias, you can also configure firewall
rules to control access to the LAN's logical network (subnet).
Click Configuration > LAN / Home Network > Additional Subnet to display the screen shown next.
Figure 66 Configuration > LAN / Home Network > Additional Subnet
The following table describes the labels in this screen.
6.6 The Wake on LAN Screen
Use this screen to turn on a device on the LAN network. To use this feature, the remote device must also
support Wake On LAN.
Table 26 Configuration > LAN / Home Network > Additional Subnet
LABEL DESCRIPTION
General
Group Name Select the interface group name for which you want to configure the IP alias settings. See
Section 6.7 on page 98 for how to create a new interface group. A newly created local network
(interface group) belongs to the LAN zone by default.
IP Alias Setup
Enable Select the check box to configure a LAN network for the SBG.
IP Address Enter the IP address of your SBG in dotted decimal notation.
Subnet Mask Your SBG will automatically calculate the subnet mask based on the IP address that you assign.
Unless you are implementing subnetting, use the subnet mask computed by the SBG.
Apply Click Apply to save your changes.
Reset Click Reset to return the screen to its last-saved settings.
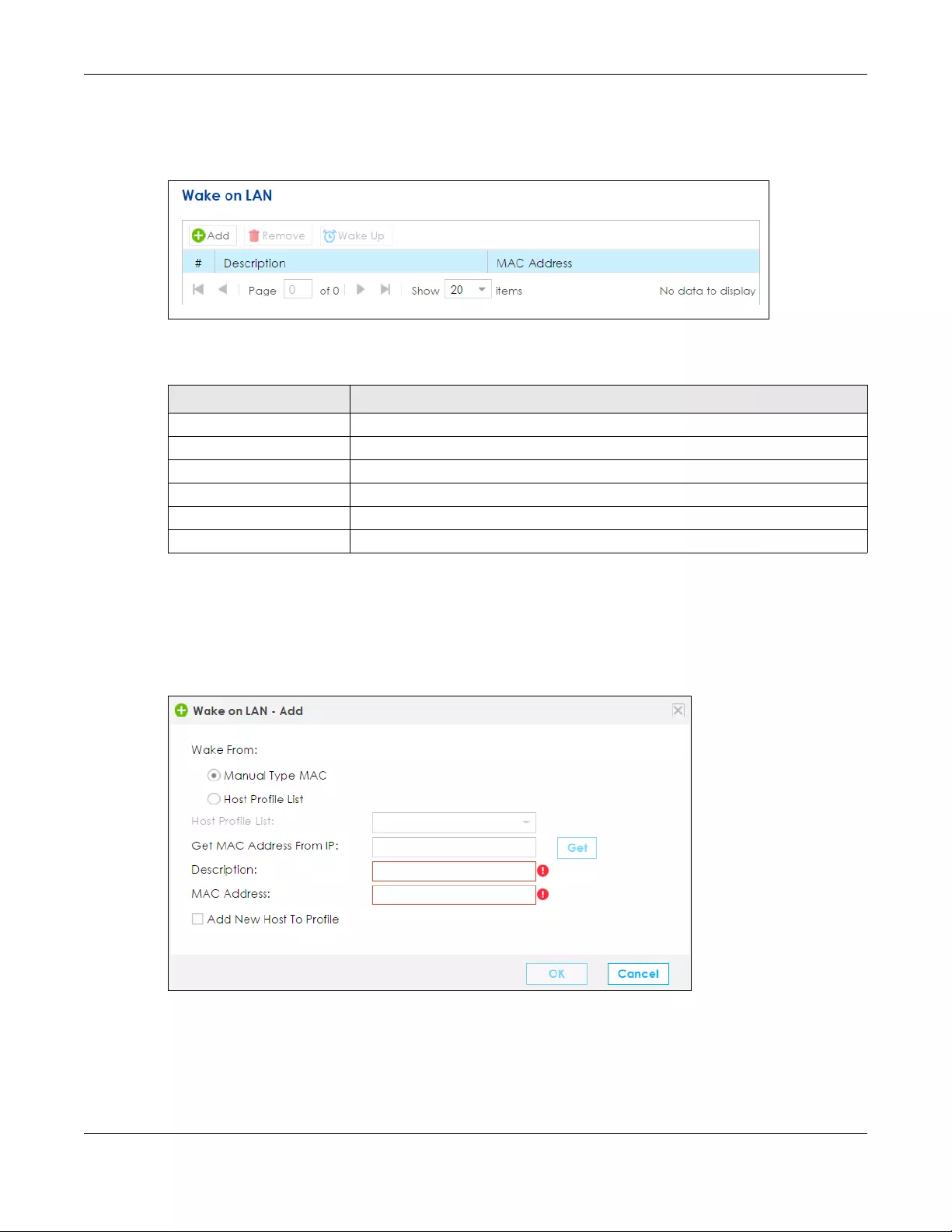
Chapter 6 LAN
SBG5500 Series User’s Guide
97
You need to know the MAC address of the LAN device. It may be on a label on the device or in its
documentation.
Figure 67 Configuration > LAN / Home Network > Wake on LAN
The following table describes the labels in this screen.
6.6.1 Wake On LAN: Add/Edit
Use this screen to add a device and turn it on using Wake on LAN. Click Edit to open the following
screen.
Figure 68 Wake On LAN: Edit
Table 27 Configuration > LAN / Home Network > Wake on LAN
LABEL DESCRIPTION
Add Click this to add a new device to Wake on LAN.
Remove Select a static DHCP entry and click Remove to delete it.
Wake Up Select a device and click this to enable the Wake on LAN feature.
# This field is a sequential value, and it is not associated with any entry.
Description This field shows a descriptive name for a device on the LAN network.
MAC Address This field shows the MAC address for a device on the LAN network.
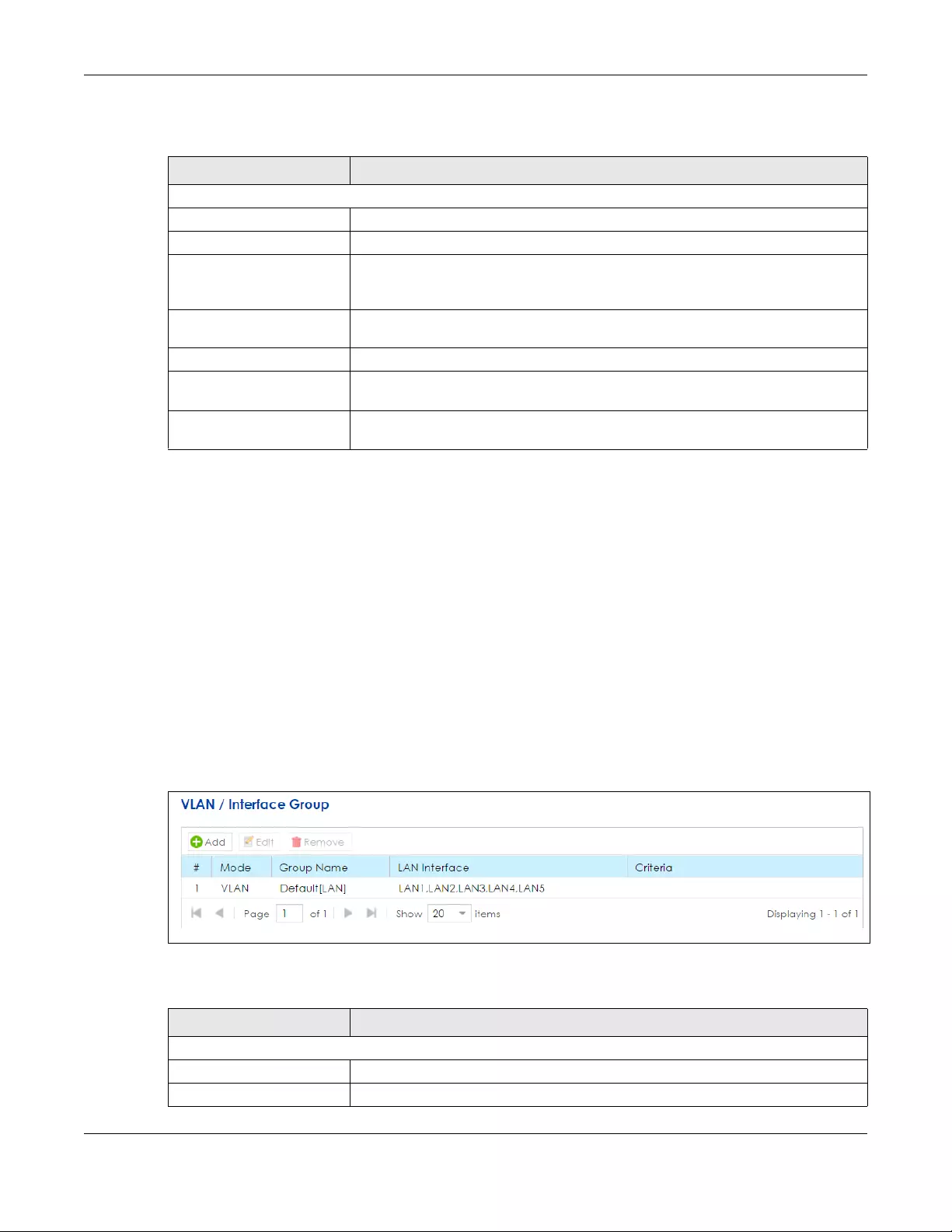
Chapter 6 LAN
SBG5500 Series User’s Guide
98
The following table describes the labels in this screen.
6.7 The VLAN / Interface Group Screen
Use Interface Group to create multiple networks on the SBG. You can manually add a LAN interface to
a new group. Alternatively, you can have the SBG automatically add the incoming traffic and the LAN
interface on which traffic is received to an interface group when its DHCP Vendor ID option information
matches one listed for the interface group.
Use the LAN screen to configure the private IP addresses the DHCP server on the SBG assigns to the
clients in the default and/or user-defined groups. If you set the SBG to assign IP addresses based on the
client’s DHCP Vendor ID option information, you must enable DHCP server and configure LAN TCP/IP
settings for both the default and user-defined groups.
Click Configuration > LAN / Home Network > VLAN / Interface Group to open the following screen.
Figure 69 Configuration > LAN / Home Network > VLAN / Interface Group
The following table describes the labels on this screen.
Table 28 Configuration > LAN / Home Network > Wake on LAN
LABEL DESCRIPTION
Wake From
Manual Type MAC Select this to enter the MAC address of the device to turn it on remotely.
Host Profile List Select this to look at the list of hosts connected to the SBG.
Host Profile List This is drop-down list that shows the IP addresses that can be found in the SBG’s LAN
Site Host list, see Section 16.2 on page 228. Select a host and it will then
automatically update the Description and MAC address fields.
Get MAC Address From IP If you selected Manual Type MAC you can enter a device’s IP address and click Get
to obtain its MAC address.
Description Enter a descriptive name for the device you want to turn on.
MAC Address Enter the MAC address of the device to turn it on. A MAC address consists of six
hexadecimal character pairs.
Add New Host to Profile Select this check box to add this Host to the LAN Site Host list in the Maintenance >
LAN Site Host Name screen, see Section 16.2 on page 228.
Table 29 Configuration > LAN / Home Network > VLAN / Interface Group
LABEL DESCRIPTION
VLAN/ Interface Group
Add Click Add to create a new interface group.
Edit Click Edit to configure an interface group.
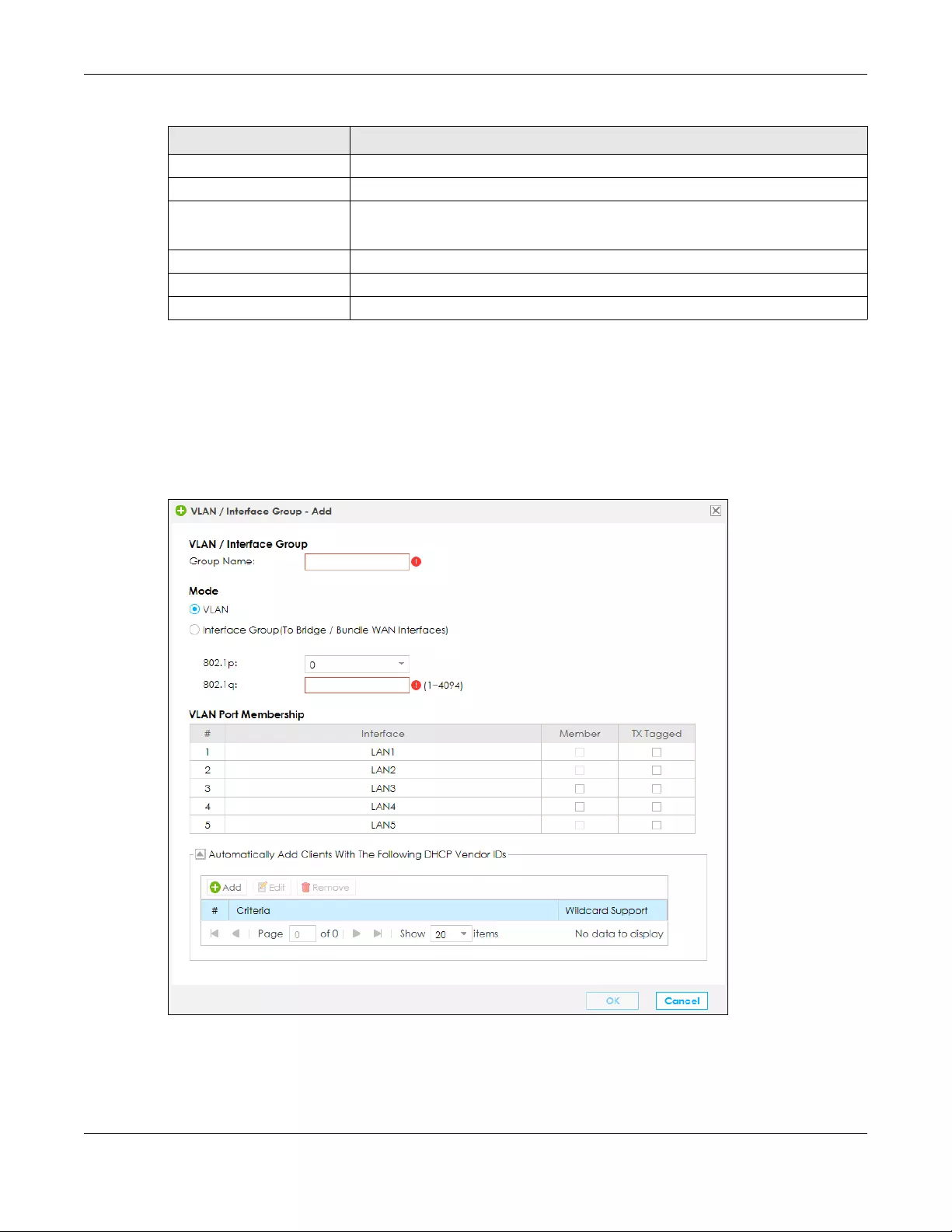
Chapter 6 LAN
SBG5500 Series User’s Guide
99
6.7.1 VLAN / Interface Group: Add/Edit
If you click Add in the VLAN / Interface Group screen or select an existing group and click Edit the screen
displays as shown below.
The screen varies depending on whether you create a VLAN Group or an Interface Group.
Figure 70 VLAN / Interface Group: Add/Edit (VLAN Group)
Remove Click Remove to delete an interface group.
# This shows the index number of the interface group.
Mode This shows VLAN when this is a VLAN group.
This shows Interface Group when this is an interface group.
Group Name This shows the descriptive name of the group.
LAN Interface This shows the LAN interfaces in the group.
Criteria This shows the filtering criteria for the group.
Table 29 Configuration > LAN / Home Network > VLAN / Interface Group
LABEL DESCRIPTION
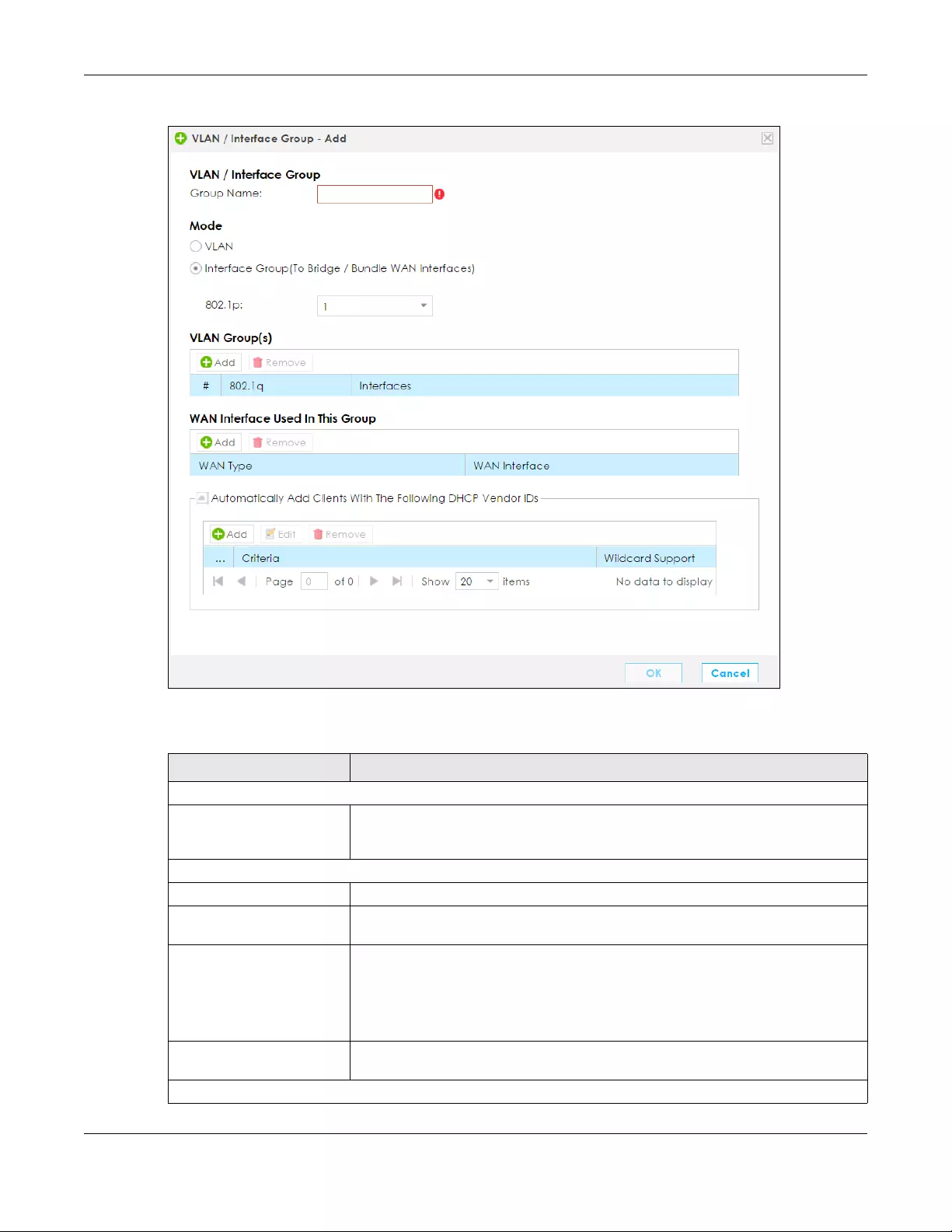
Chapter 6 LAN
SBG5500 Series User’s Guide
100
Figure 71 VLAN / Interface Group: Add/Edit (Interface Group)
The following table describes the labels in this screen.
Table 30 VLAN / Interface Group > Add/Edit
LABEL DESCRIPTION
VLAN / Interface Group
Group Name Enter the descriptive name of the VLAN or Interface Group. You can enter up to 65
characters. You can use numbers, letters, hyphens (-) and underscores(_). Spaces
are not allowed.
Mode
VLAN Click this check box to create a VLAN group.
Interface Group (To Bridge /
Bundle WAN Interfaces)
Click this check box to create an interface group,
802.1p IEEE 802.1p defines up to 8 separate traffic types by inserting a tag into a MAC layer
frame that contains bits to define class of service.
Select the IEEE 802.1p priority (from 0 to 7) to add to traffic the SBG sends through
tagged member ports of this group. The greater the number, the higher the priority
level.
802.1q Type the VLAN ID number (from 1 to 4094) for traffic through tagged member ports
of this group. A VLAN ID cannot be assigned to more than one group.
VLAN Port Membership
Chapter 6 LAN
SBG5500 Series User’s Guide
101
6.7.1.1 Add WAN Interface Used In This Group
Click Add in the WAN Interface Used In This Group table to display the following screen.
# This shows the index number of the interface.
Interface This shows the SBG LAN interfaces.
Member Select this check box to add the LAN interface to the group. Clear the Tagged
check box to add the LAN interface as an untagged member port.
A LAN interface can be added as an untagged member port of at most one group.
Ethernet LAN interfaces that have already been added as an untagged member
port of another group will have this check box disabled. It is still possible to add these
LAN interfaces to the group as tagged member ports.
TX Tagged Select this check box to add the LAN interface to the group as a tagged member
port.
VLAN Group(s)
Add Click this to add a new VLAN group.
Remove Select a VLAN group and click this to delete it.
# This shows the index number of the VLAN group.
802.1q This shows the VLAN ID number (from 1 to 4094) for traffic through tagged member
ports of this group. A VLAN ID cannot be assigned to more than one group.
Interfaces This shows the LAN ports included in the VLAN group and if traffic leaving the port will
be tagged with the VLAN ID.
WAN Interface Used In This Group
Add Click this to add a new WAN interface for an interface group.
Remove Select a WAN interface and click this to delete it.
WAN Type This field displays the current WAN connection type.
WAN Interface This field displays the current WAN interface.
Automatically Add Clients
With The Following DHCP
Vendor IDs
Click Add to identify LAN hosts to add to the interface group by criteria such as the
type of the hardware or firmware.
Add Click this to add a new rule.
Edit Select a rule and click this to modify it.
Remove Select a rule and click this to delete it.
# This shows the index number of the rule.
Criteria This shows the filtering criteria. The LAN interface on which the matched traffic is
received will belong to this group automatically.
Wildcard Support This shows if wildcard on DHCP option 60 is enabled.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 30 VLAN / Interface Group > Add/Edit
LABEL DESCRIPTION
Chapter 6 LAN
SBG5500 Series User’s Guide
102
Figure 72 WAN Interface Use In This Group: Add
The following table describes the labels in this screen.
6.7.1.2 Add Clients With The Following DHCP Vendor IDs
Click Add in the Clients With The Following DHCP Vendor IDs table to display the following screen.
Figure 73 Clients With The Following DHCP Vendor IDs: Add
The following table describes the labels in this screen.
Table 31
LABEL DESCRIPTION
WAN Type Select the current WAN connection type.
WAN Interface Select the current WAN interface.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 32 Clients With The Following DHCP Vendor IDs: Add
LABEL DESCRIPTION
Criteria
DHCP Option 60 Select this to enter STB’s Vendor Class IDentifiers (DHCP Option 60).
Type the class vendor ID you want the SBG to add in the DHCP Discovery packets that go
to the DHCP server in the Vendor Class ID field.
Enable Wildcard Select this option to be able to use wildcards in the Vendor Class Identifier configured for
DHCP option 60.
Chapter 6 LAN
SBG5500 Series User’s Guide
103
6.8 The DNS Entry Screen
Use this screen to view and configure DNS routes on the SBG. Click Configuration > LAN / Home Network
> DNS Entry screen.
Figure 74 Configuration > LAN / Home Network > DNS Entry
The following table describes the labels in this screen.
6.9 The DNS Forwarder Screen
A domain zone forwarder contains a DNS server’s IP address. The SBG can query the DNS server to
resolve domain zones for features like VPN, DDNS and the time server. A domain zone is a fully qualified
domain name without the host. For example, zyxel.com.tw is the domain zone for the www.zyxel.com.tw
fully qualified domain name. Use this screen to create domain zone forwarder records. Click
Configuration > LAN / Home Network > DNS Forwarder to open the following screen.
DHCP Option 61 Click this to enter the Identity Association IDentifier (IAD Option 61) of the matched traffic
such as the MAC address of the device.
Type the DHCP Unique Identifier (DUID) you want the SBG to add in the DHCP Discovery
packets that go to the DHCP server.
DHCP Option 125 Click this to enter the vendor specific information of the matched traffic, such as the
Enterprise Number, Manufacture OUI, Serial Number and Product Class of the device.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 32 Clients With The Following DHCP Vendor IDs: Add
LABEL DESCRIPTION
Table 33 Configuration > LAN / Home Network > DNS Entry
LABEL DESCRIPTION
Add Click this to create a new DNS rule.
Edit Click Edit to modify a DNS rule.
Remove Click Remove to delete an existing DNS rule.
# This is the index number of the rule.
Host Name This indicates the host or domain name.
IP Address This indicates the IP address assigned to this computer.
Chapter 6 LAN
SBG5500 Series User’s Guide
104
Figure 75 Configuration > LAN / Home Network > DNS Forwarder
The following table describes the labels in this screen.
6.9.1 DNS Forwarder: Add/Edit
If you click Add in the DNS Forwarder screen or select an domain zone forwarder record and click Edit,
the following screen displays.
Figure 76 DNS Forwarder: Add/Edit
Table 34 Configuration > LAN / Home Network > DNS Forwarder
LABEL DESCRIPTION
Add Click this to add a domain zone forwarder record.
Edit Select an existing domain zone forwarder record and click Edit to modify it.
Remove Click this to delete a domain zone forwarder record.
# This is the index number of the domain zone entry.
Domain Name This shows the domain zone.
Mode This shows whether the DNS server is user-designed or from the ISP.
DNS Server If the Mode is User Defined Address, this field displays the IP address of the DNS server
Interface This shows the interface through which the SBG sends DNS queries to a DNS server.
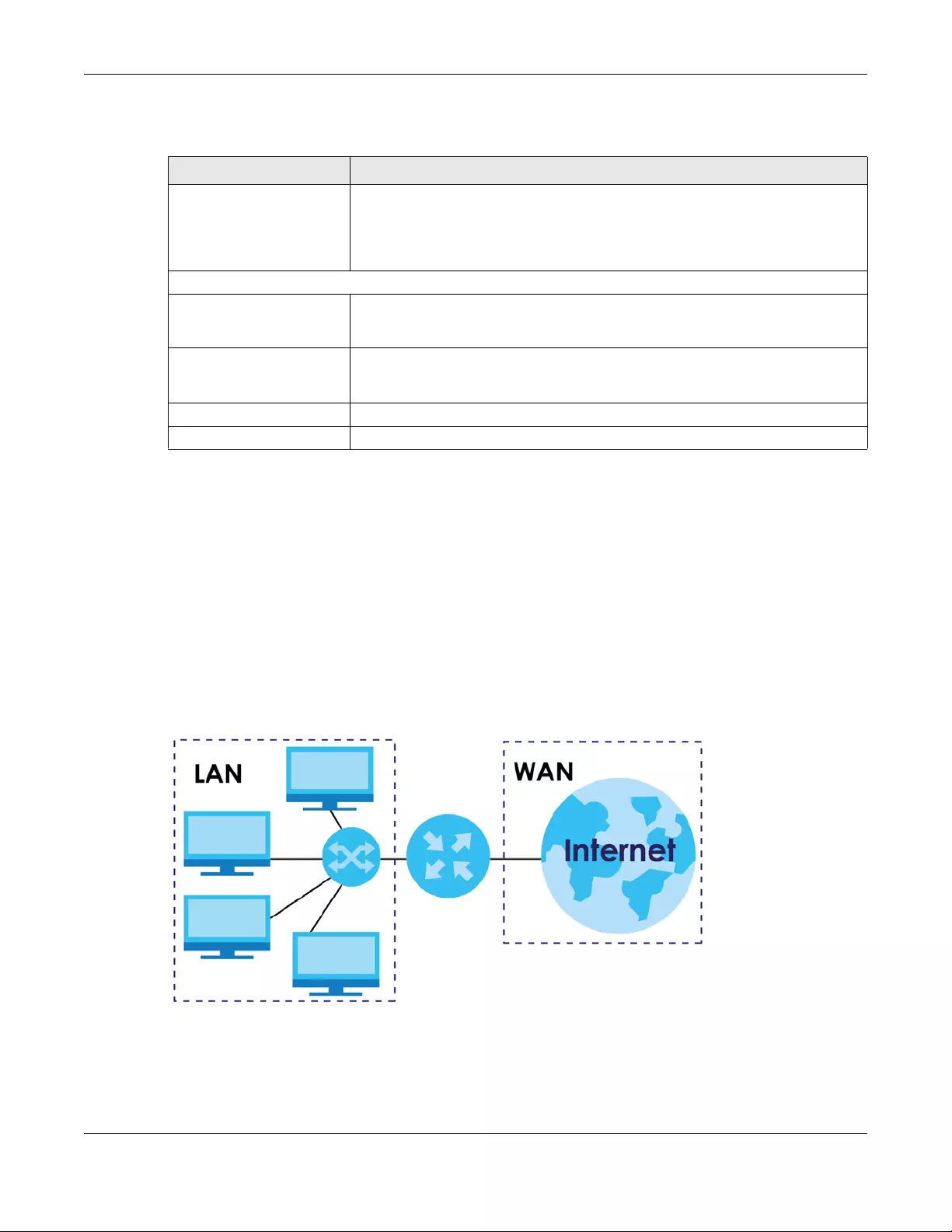
Chapter 6 LAN
SBG5500 Series User’s Guide
105
The following table describes the labels in this screen.
6.10 Technical Reference
This section provides some technical background information about the topics covered in this chapter.
6.10.1 LANs, WANs and the SBG
The actual physical connection determines whether the SBG ports are LAN or WAN ports. There are two
separate IP networks, one inside the LAN network and the other outside the WAN network as shown
next.
Figure 77 LAN and WAN IP Addresses
6.10.2 DHCP Setup
DHCP (Dynamic Host Configuration Protocol, RFC 2131 and RFC 2132) allows individual clients to obtain
TCP/IP configuration at start-up from a server. You can configure the SBG as a DHCP server or disable it.
Table 35 Configuration > LAN / Home Network > DNS Forwarder
LABEL DESCRIPTION
Domain Name Enter the domain zone in this field. A domain zone is a fully qualified domain name
without the host. For example, *.zyxel.com.tw is a wildcard domain zone for the
www.zyxel.com.tw fully qualified domain name. For example, whenever the SBG
looks up a domain name that ends in zyxel.com.tw domain name, it can send a
query to the recorded name server IP address.
DNS Server
DNS Server From ISP Select DNS Server(s) from ISP if your ISP dynamically assigns DNS server information.
You also need to select an interface through which the ISP provides the DNS server
IP address(es). The interface should be activated and set to be a DHCP client.
DNS Server Select DNS Server if you have the IP address of a DNS server. Enter the DNS server's IP
address in the field to the right. Use the Interface field to select the interface through
which the SBG sends DNS queries to a DNS server.
OK Click OK to save your customized settings and exit this screen.
Cancel Click Cancel to exit this screen without saving.
SBG

Chapter 6 LAN
SBG5500 Series User’s Guide
106
When configured as a server, the SBG provides the TCP/IP configuration for the clients. If you turn DHCP
service off, you must have another DHCP server on your LAN, or else the computer must be manually
configured.
IP Pool Setup
The SBG is pre-configured with a pool of IP addresses for the DHCP clients (DHCP Pool). See the product
specifications in the appendices. Do not assign static IP addresses from the DHCP pool to your LAN
computers.
6.10.3 DNS Server Addresses
DNS (Domain Name System) maps a domain name to its corresponding IP address and vice versa. The
DNS server is extremely important because without it, you must know the IP address of a computer
before you can access it. The DNS server addresses you enter when you set up DHCP are passed to the
client machines along with the assigned IP address and subnet mask.
There are two ways that an ISP disseminates the DNS server addresses.
• The ISP tells you the DNS server addresses, usually in the form of an information sheet, when you sign
up. If your ISP gives you DNS server addresses, enter them in the DNS Server fields in the DHCP Setup
screen.
• Some ISPs choose to disseminate the DNS server addresses using the DNS server extensions of IPCP (IP
Control Protocol) after the connection is up. If your ISP did not give you explicit DNS servers, chances
are the DNS servers are conveyed through IPCP negotiation. The SBG supports the IPCP DNS server
extensions through the DNS proxy feature.
Please note that DNS proxy works only when the ISP uses the IPCP DNS server extensions. It does not
mean you can leave the DNS servers out of the DHCP setup under all circumstances. If your ISP gives
you explicit DNS servers, make sure that you enter their IP addresses in the DHCP Setup screen.
6.10.4 LAN TCP/IP
The SBG has built-in DHCP server capability that assigns IP addresses and DNS servers to systems that
support DHCP client capability.
IP Address and Subnet Mask
Similar to the way houses on a street share a common street name, so too do computers on a LAN share
one common network number.
Where you obtain your network number depends on your particular situation. If the ISP or your network
administrator assigns you a block of registered IP addresses, follow their instructions in selecting the IP
addresses and the subnet mask.
If the ISP did not explicitly give you an IP network number, then most likely you have a single user
account and the ISP will assign you a dynamic IP address when the connection is established. If this is
the case, it is recommended that you select a network number from 192.168.0.0 to 192.168.255.0 and
you must enable the Network Address Translation (NAT) feature of the SBG. The Internet Assigned
Number Authority (IANA) reserved this block of addresses specifically for private use; please do not use
any other number unless you are told otherwise. Let's say you select 192.168.1.0 as the network number;
which covers 254 individual addresses, from 192.168.1.1 to 192.168.1.254 (zero and 255 are reserved). In

Chapter 6 LAN
SBG5500 Series User’s Guide
107
other words, the first three numbers specify the network number while the last number identifies an
individual computer on that network.
Once you have decided on the network number, pick an IP address that is easy to remember, for
instance, 192.168.1.1, for your SBG, but make sure that no other device on your network is using that IP
address.
The subnet mask specifies the network number portion of an IP address. Your SBG will compute the
subnet mask automatically based on the IP address that you entered. You don't need to change the
subnet mask computed by the SBG unless you are instructed to do otherwise.
Private IP Addresses
Every machine on the Internet must have a unique address. If your networks are isolated from the
Internet, for example, only between your two branch offices, you can assign any IP addresses to the
hosts without problems. However, the Internet Assigned Numbers Authority (IANA) has reserved the
following three blocks of IP addresses specifically for private networks:
• 10.0.0.0 — 10.255.255.255
• 172.16.0.0 — 172.31.255.255
• 192.168.0.0 — 192.168.255.255
You can obtain your IP address from the IANA, from an ISP or it can be assigned from a private network.
If you belong to a small organization and your Internet access is through an ISP, the ISP can provide you
with the Internet addresses for your local networks. On the other hand, if you are part of a much larger
organization, you should consult your network administrator for the appropriate IP addresses.
Note: Regardless of your particular situation, do not create an arbitrary IP address; always
follow the guidelines above. For more information on address assignment, please refer
to RFC 1597, “Address Allocation for Private Internets” and RFC 1466, “Guidelines for
Management of IP Address Space”.
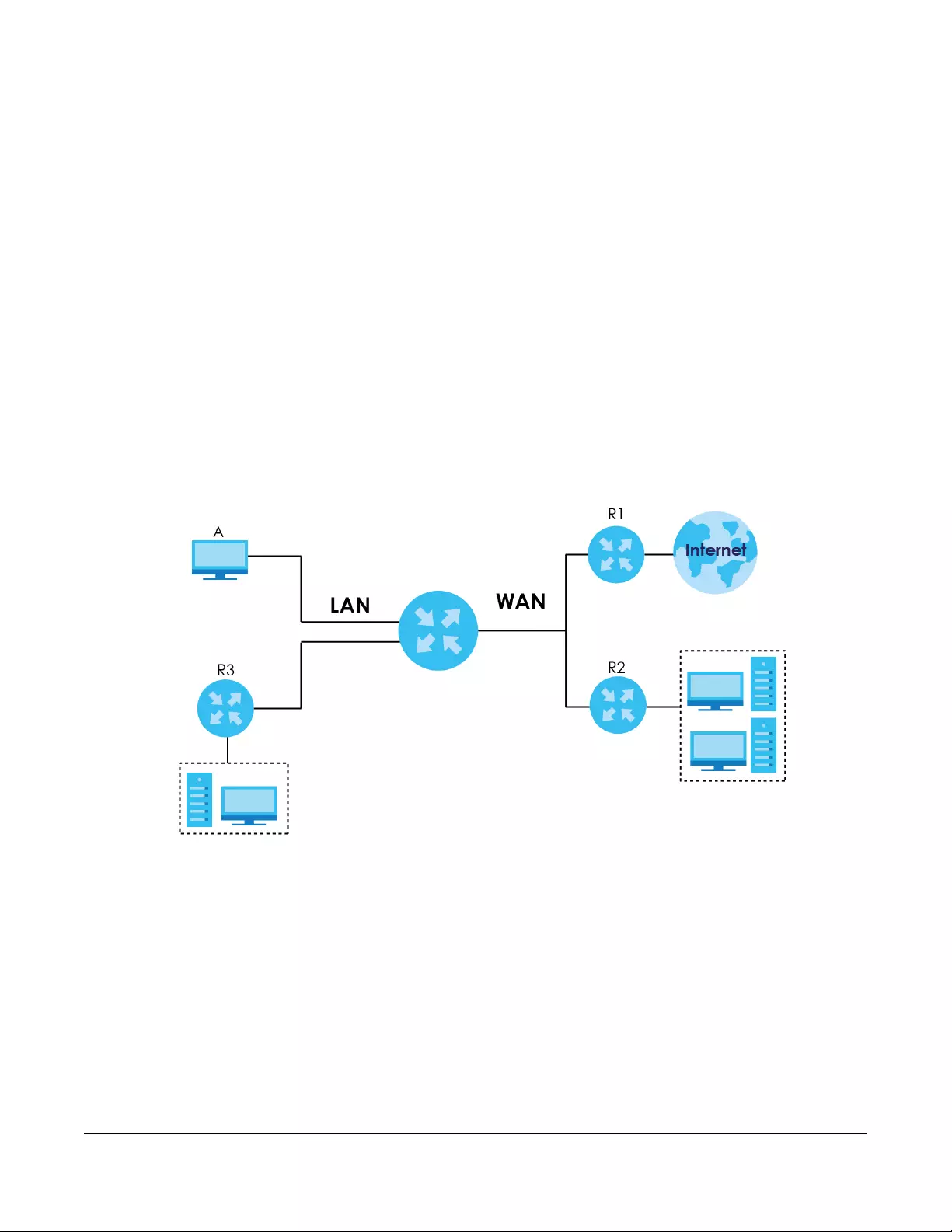
SBG5500 Series User’s Guide
108
CHAPTER 7
Routing
7.1 Overview
The SBG usually uses the default gateway to route outbound traffic from computers on the LAN to the
Internet. To have the SBG send data to devices not reachable through the default gateway, use static
routes.
For example, the next figure shows a computer (A) connected to the SBG’s LAN interface. The SBG
routes most traffic from A to the Internet through the SBG’s default gateway (R1). You create one static
route to connect to services offered by your ISP behind router R2. You create another static route to
communicate with a separate network behind a router R3 connected to the LAN.
Figure 78 Example of Routing Topology
7.1.1 What You Can Do in this Chapter
• Use the Routing Status screen to view the IPv4 and IPv6 routing flow(Section 7.2 on page 109).
• Use the Policy Route screen to configure policy routing on the SBG (Section 7.3 on page 115).
• Use the Static Route screen to view and set up static routes on the SBG (Section 7.4 on page 118).
• Use the RIP screen to set up RIP settings on the SBG (Section 7.5 on page 120).
SBG
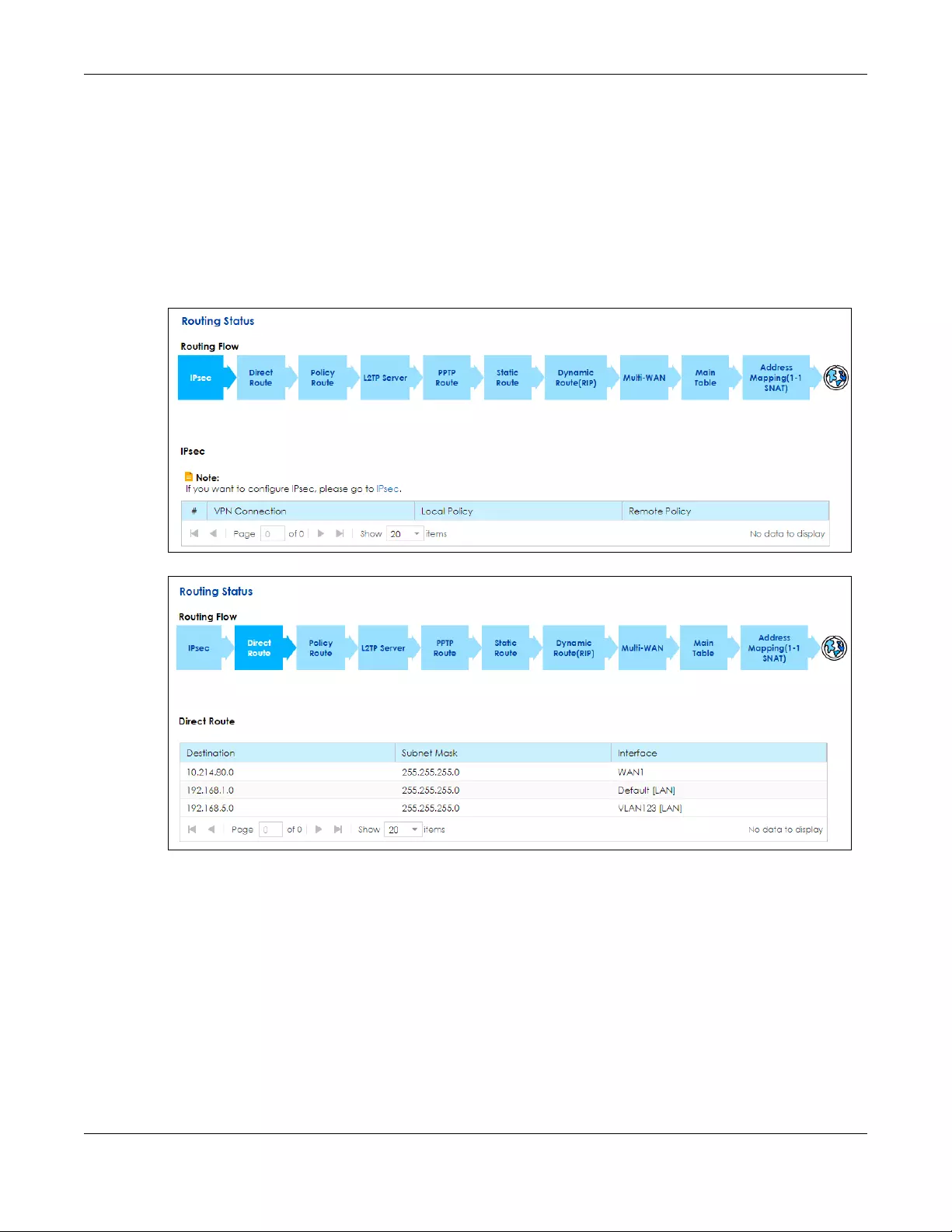
Chapter 7 Routing
SBG5500 Series User’s Guide
109
7.2 The Routing Status Screen
The Routing Status screen allows you to view the current routing flow and quickly link to specific routing
settings. Click a function box in the Routing Flow section, the related routes (activated) will display in the
Routing Table section. To access this screen, click Configuration > Routing > Routing Status.
Note: Once a packet matches the criteria of a routing rule, the SBG takes the corresponding
action and does not perform any further flow checking.
Figure 79 Configuration > Routing > Routing Status (IPsec)
Figure 80 Configuration > Routing > Routing Status (Direct Route)
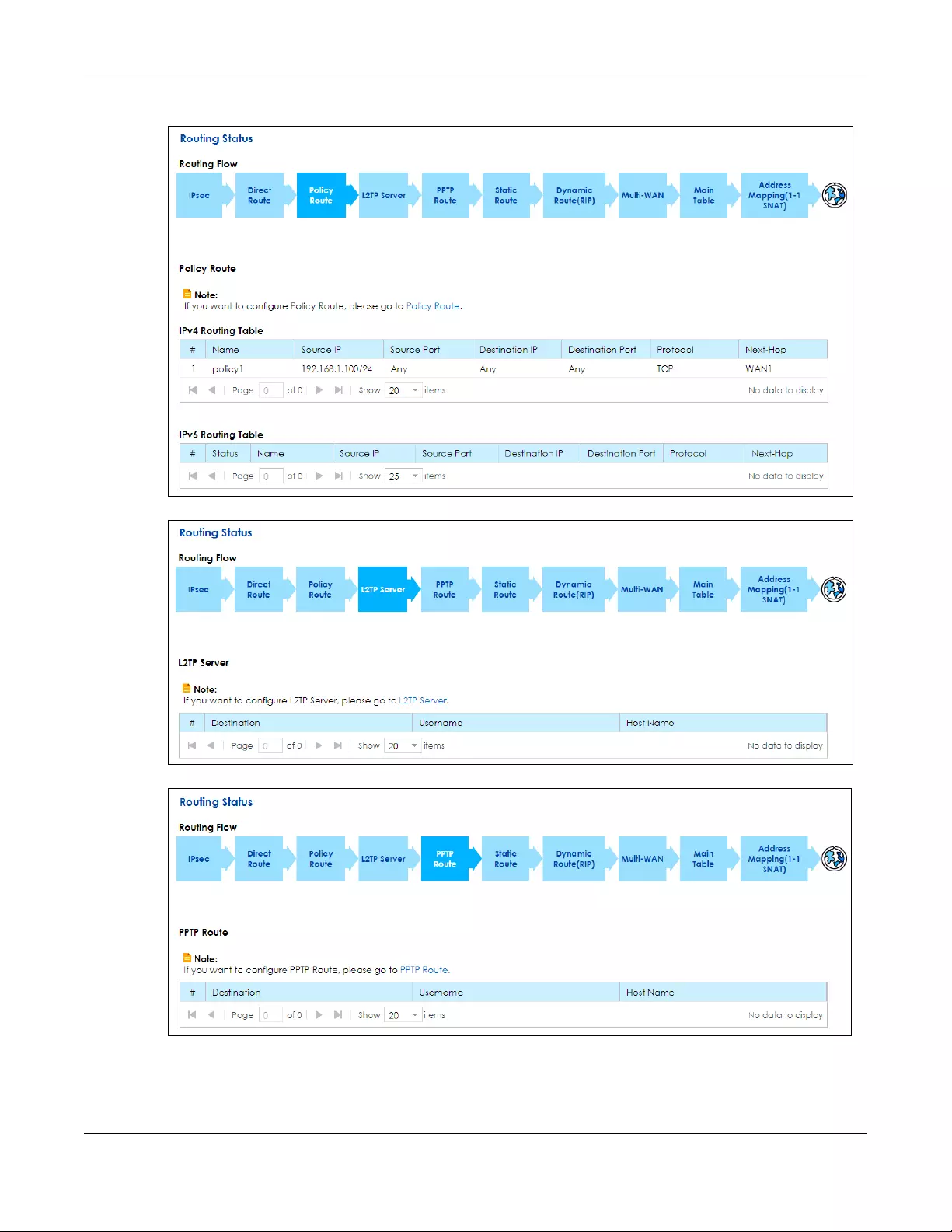
Chapter 7 Routing
SBG5500 Series User’s Guide
110
Figure 81 Configuration > Routing > Routing Status (Policy Route)
Figure 82 Configuration > Routing > Routing Status (L2TP Server)
Figure 83 Configuration > Routing > Routing Status (PPTP Route)
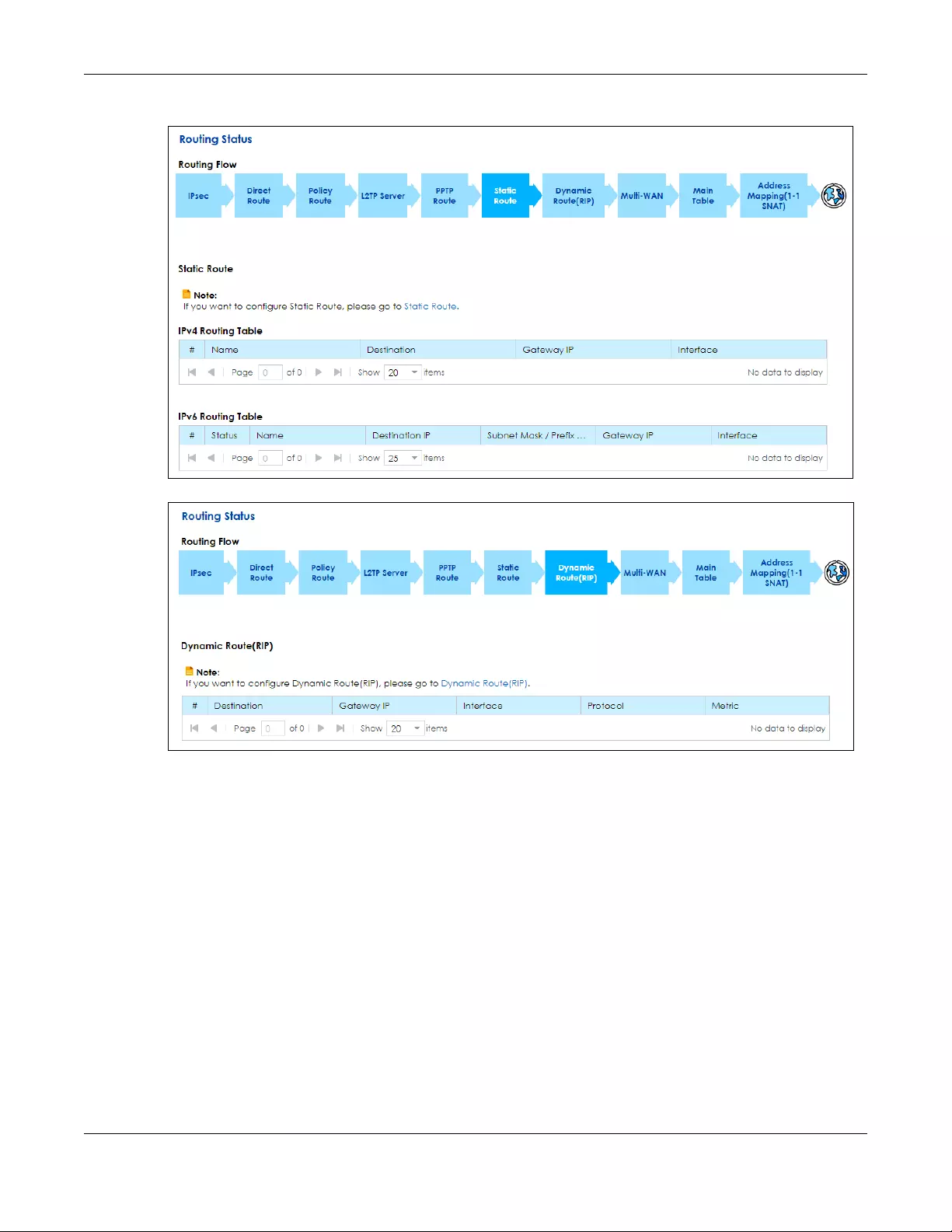
Chapter 7 Routing
SBG5500 Series User’s Guide
111
Figure 84 Configuration > Routing > Routing Status (Static Route)
Figure 85 Configuration > Routing > Routing Status (Dynamic Route (RIP))
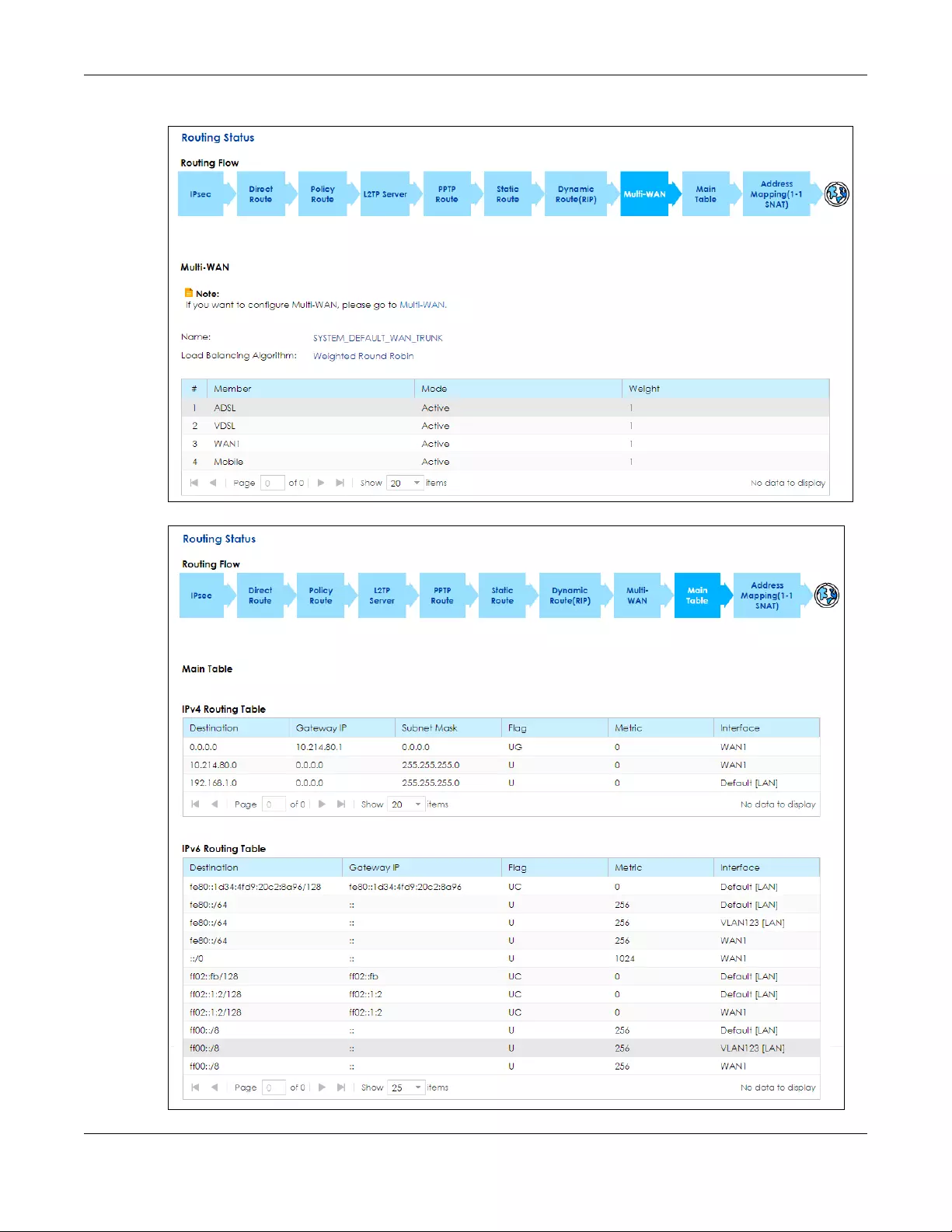
Chapter 7 Routing
SBG5500 Series User’s Guide
112
Figure 86 Configuration > Routing > Routing Status (Multi-WAN)
Figure 87 Configuration > Routing > Routing Status (Main Table)
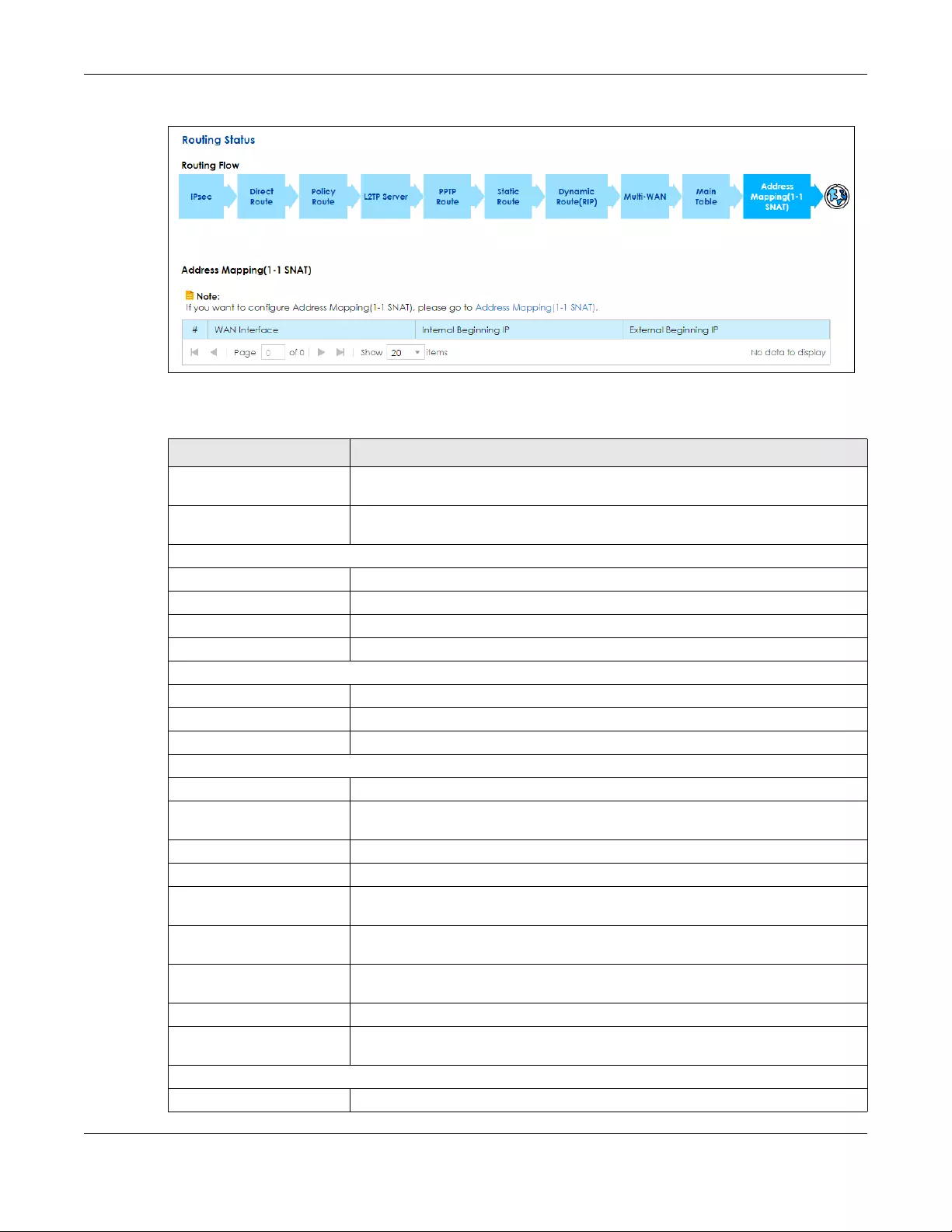
Chapter 7 Routing
SBG5500 Series User’s Guide
113
Figure 88 Configuration > Routing > Routing Status (Address Mapping (1-1 SNAT))
The following table describes the labels in this screen.
Table 36 Configuration > Routing > Routing Status
LABEL DESCRIPTION
Routing Flow This section shows you the flow of how the SBG determines where to route a packet.
Click a function box to display the related settings in the next section.
This section shows the corresponding settings according to the function box you
click in the Routing Flow section.
The following fields are available if you click IPsec in the Routing Flow section.
# This is the IPsec VPN policy index number.
VPN Connection This field displays the identification name for this VPN policy.
Local Policy This field displays the local policy.
Remote Policy This field displays the remote policy.
The following fields are available if you click Direct Route in the Routing Flow section.
Destination This is the destination IP address of a route.
Subnet Mask This is the subnet mask of a route.
Interface This is the name of an interface associated with the route.
The following fields are available if you click Policy Route in the Routing Flow section.
# This is the number of an individual policy route.
Status This field displays whether the policy route is active or not. A lit light bulb signifies that
this route is active. A gray light bulb signifies that this route is not active.
Name This field displays the descriptive name of the policy route.
Source IP This is the name of the source IP address (group) object. Any means all IP addresses.
Destination IP This is the name of the destination IP address (group) object. Any means all IP
addresses.
Source Port This displays the port (0-65535) the source IP address(es) are using in this policy route
rule.
Destination Port This displays the port (0-65535) the destination IP address(es) are using in this policy
route rule.
Protocol This shows the kind of protocol used by this policy route rule (TCP, UDP or None).
Next-Hop This is the next hop to which packets are directed. It helps forward packets to their
destinations and can be a router, VPN tunnel, outgoing interface or trunk.
The following fields are available if you click L2TP Server and PPTP Route in the Routing Flow section.
# This is the PPTP/L2TP VPN policy index number.
Chapter 7 Routing
SBG5500 Series User’s Guide
114
Destination This is the original destination IP address(es) to which the packets are transmitted.
Username This field displays the client’s login name for this connection.
Host Name This is the client's host name of this connection.
The following fields are available if you click Static Route in the Routing Flow section.
# This is the number of an individual static route.
Status This field displays whether the static route is active or not. A lit light bulb signifies that
this route is active. A gray light bulb signifies that this route is not active.
Name This field displays the descriptive name of the static route.
Destination IP This is the destination IP address. Any means all IP addresses.
Subnet Mask / Prefix Length This parameter specifies the IP network subnet mask and prefix length of the final
destination.
Gateway IP This is the IP address of the gateway. The gateway is a router or switch on the same
network segment as the device's LAN or WAN port. The gateway helps forward
packets to their destinations.
Interface This is the WAN interface used for this static route.
The following fields are available if you click Dynamic Route (RIP) in the Routing Flow section.
# This is the number of an individual dynamic route.
Destination This indicates the destination IP address of this route.
Gateway IP This indicates the IP address of the gateway that helps forward this route’s traffic.
Interface This indicates the name of the interface through which the route is forwarded.
Protocol This shows the kind of protocol used by this route rule (TCP, UDP or None).
Metric This is the route’s priority among the displayed routes.
The following fields are available if you click Multi-WAN in the Routing Flow section.
Name This is the name to identify the trunk.
Load Balancing Algorithm This shows the load balancing method used by the trunk.
# This field is a sequential value, and it is not associated with any interface.
Member This field displays the member interface of the trunk.
Mode This field displays Active when the SBG always attempt to use this connection.
Displays Passive to have the SBG only use this connection when all of the
connections set to active are down.
Weight This field displays with the weighted round robin load balancing algorithm.
The following fields are available if you click Main Table in the Routing Flow section
Destination This indicates the destination IPv4 address or IPv6 address and prefix of this route.
Gateway IP This indicates the IPv4 or IPv6 address of the gateway that helps forward this route’s
traffic.
Subnet Mask This indicates the destination subnet mask of the IPv4 route.
Table 36 Configuration > Routing > Routing Status
LABEL DESCRIPTION

Chapter 7 Routing
SBG5500 Series User’s Guide
115
7.3 The Policy Route Screen
Click Configuration > Routing to open the Policy Route screen. Use this screen to see the configured
policy routes and turn policy routing based bandwidth management on or off.
A policy route defines the matching criteria and the action to take when a packet meets the criteria.
The action is taken only when all the criteria are met. The criteria can include the user name, source
address and incoming interface, destination address, schedule, IP protocol (ICMP, UDP, TCP, etc.) and
port.
The actions that can be taken include:
• Routing the packet to a different gateway, outgoing interface, VPN tunnel, or trunk.
• Limiting the amount of bandwidth available and setting a priority for traffic.
IPPR follows the existing packet filtering facility of RAS in style and in implementation. If you enabled IPv6
you can also configure policy routes used for your IPv6 networks on this screen.
Flag This indicates the route status.
U-Up: The route is up.
UC-Up Cache: The route is up and it is a cache entry.
!-Reject: The route is blocked and will force a route lookup to fail.
G-Gateway: The route uses a gateway to forward traffic.
H-Host: The target of the route is a host.
R-Reinstate: The route is reinstated for dynamic routing.
D-Dynamic (redirect): The route is dynamically installed by a routing daemon or
redirect.
M-Modified (redirect): The route is modified from a routing daemon or redirect.
Metric The metric represents the “cost of transmission”. A router determines the best route
for transmission by choosing a path with the lowest “cost”. The smaller the number,
the lower the “cost”. This is the route’s priority among the displayed routes.
Interface This indicates the name of the interface through which the route is forwarded.
The following fields are available if you click Address Mapping (1-1 SNAT) in the Routing Flow section
# This is the index number of the rule.
WAN Interface This shows the WAN interface through which the address mapping is forwarded.
Internal beginning IP This is the starting Inside Local IP Address (ILA).
External Beginning IP This is the starting Inside Global IP Address (IGA).
Table 36 Configuration > Routing > Routing Status
LABEL DESCRIPTION
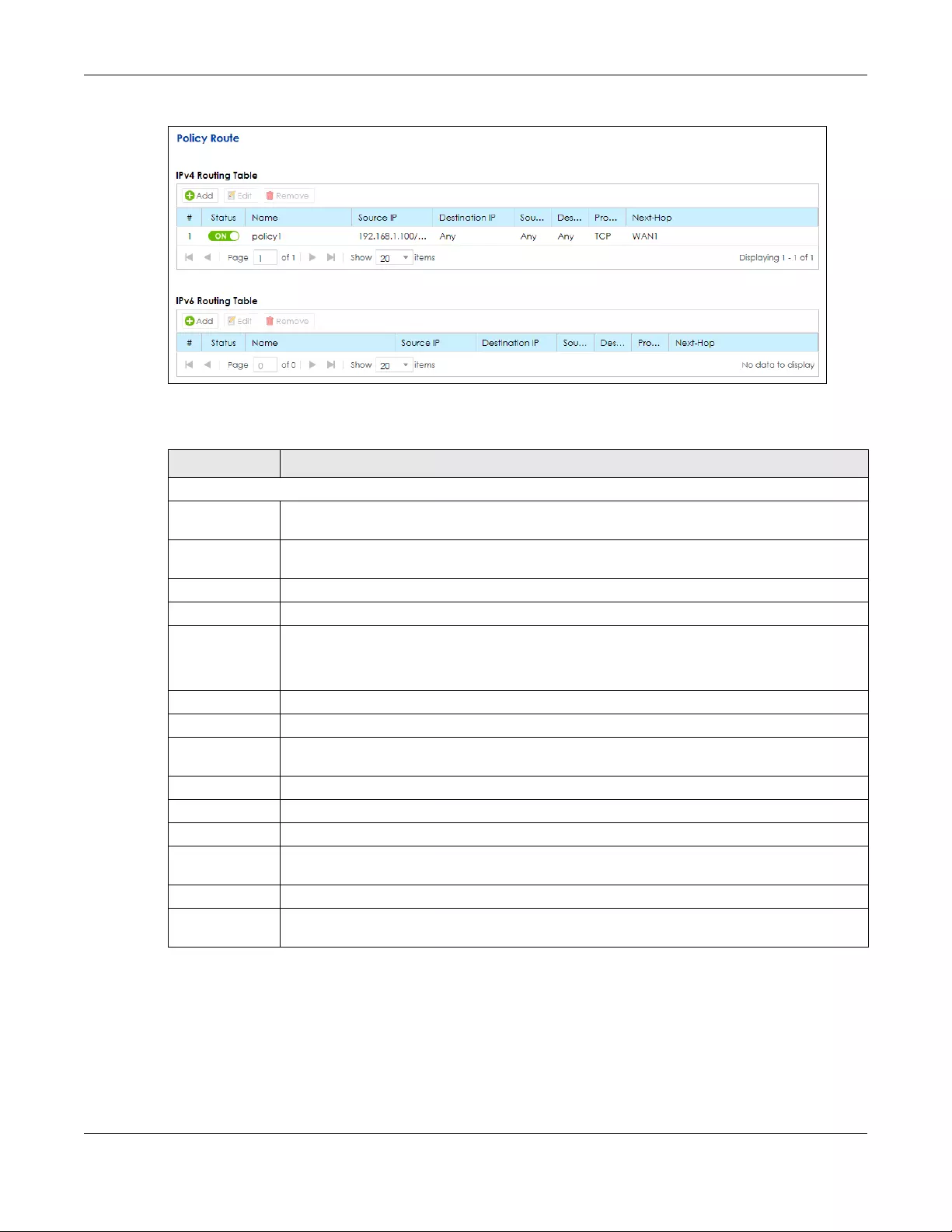
Chapter 7 Routing
SBG5500 Series User’s Guide
116
Figure 89 Configuration > Routing > Policy Route
The following table describes the labels in this screen.
7.3.1 Add/Edit Policy Route
Click Add in the Policy Route screen or click the Edit. Use this screen to configure the required
information for a policy route.
Table 37 Configuration > Routing > Policy Route
LABEL DESCRIPTION
IPv4 / IPv6 Routing Table
Add Click this to create a new entry. Select an entry and click Add to create a new entry after the
selected entry.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify the
entry’s settings.
Remove To remove an existing entry, select it and click Remove.
#This is the number of an individual policy route.
Status This field displays whether the policy route is active or not. A green ON button signifies that this
route is active. A gray OFF button signifies that this route is not active.
Click the slide button to enable and disable the policy router.
Name This field displays the descriptive name of the policy route.
Source IP This is the source IP address(es) from which the packets are sent. Any means all IP addresses.
Destination IP This is the destination IP address(es) to which the packets are transmitted. Any means all IP
addresses.
Source Port This displays the port(0-65535) the source IP address(es) are using in this policy route rule.
Destination Port This displays the port(0-65535) the destination IP address(es) are using in this policy route rule.
Source MAC This displays the source MAC address. Blank space means all MAC addresses.
Destination
MAC
This displays the destination MAC address. Blank space means all MAC addresses.
Protocol This shows the kind of protocol used by this policy route rule (TCP, UDP or None).
Next Hop This is the next hop to which packets are directed. It helps forward packets to their destinations
and can be a router, VPN tunnel, outgoing interface or trunk.
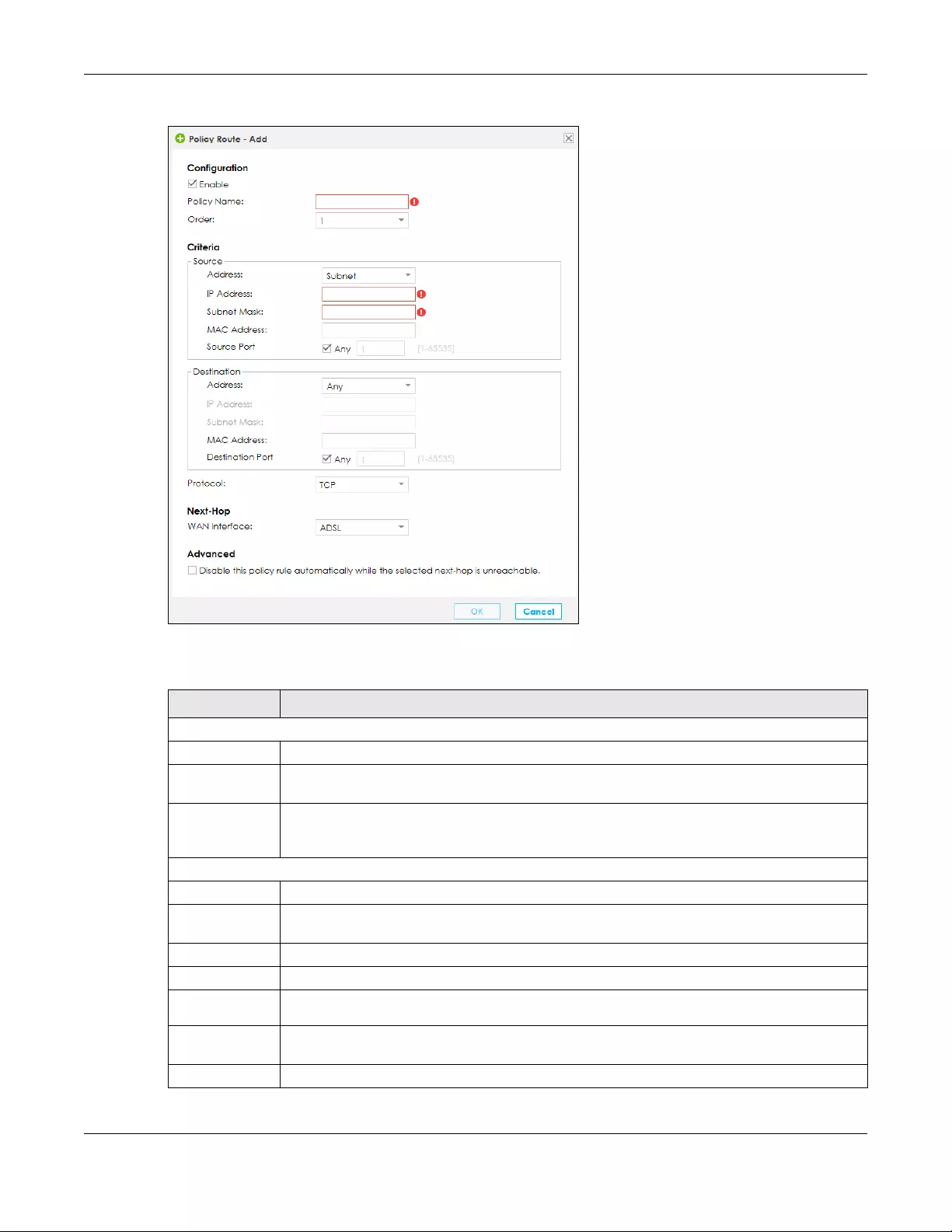
Chapter 7 Routing
SBG5500 Series User’s Guide
117
Figure 90 Policy Route: Add/Edit
The following table describes the labels in this screen.
Table 38 Policy Route: Add/Edit (Sheet 1 of 2)
LABEL DESCRIPTION
Configuration
Enable Select this to activate the policy route.
Policy Name Enter a descriptive name for the policy. It should begin with a letter and cannot exceed 31
characters [0-9][A-Z] [a-z][_-].
Order Select an existing number for where you want to put this policy route to move the policy route to
the number you selected after clicking OK. Ordering your rules is important because the SBG
applies the rules in the order that you specify.
Criteria
Source Use this section to configure where the packets are coming from in this policy route.
Address Select Any if the policy route will receive packets from all IP addresses. Select IP Address to
specify the source IP address. Otherwise, select Subnet to specify the source subnet mask.
IP Address Enter a source IP address object from which the packets are sent.
Subnet Mask Enter a subnet mask address object from which the packets are sent.
MAC
Address Enter a MAC address object from which the packets are sent.
Source Port Enter the port number (1-65535) from which the packets are sent. The SBG applies the policy
route to the packets sent from the corresponding service port. Any means all service ports.
Destination Use this section to configure where the packets are going from in this policy route.
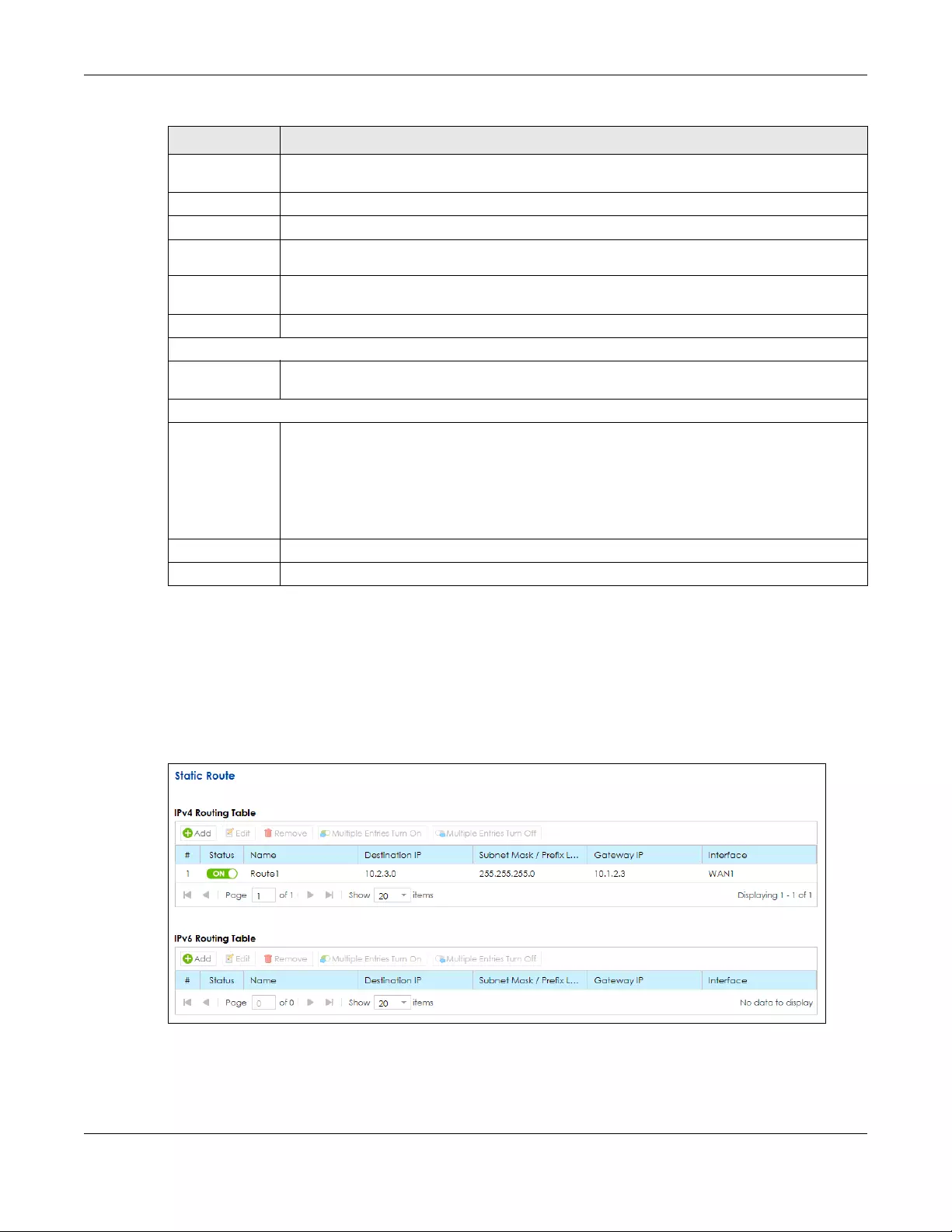
Chapter 7 Routing
SBG5500 Series User’s Guide
118
7.4 The Static Route Screen
Use this screen to view and configure the static route rules on the SBG. Click Configuration > Routing >
Static Route to open the following screen.
Figure 91 Configuration > Routing > Static Route
Address Select Any if the policy route packets will go to all IP addresses. Otherwise select IP Address to
specify the destination IP address, or select Subnet to specify the destination subnet mask.
IP Address Enter a source IP address object to which the packets go.
Subnet Mask Enter a subnet mask address object to which the packets go.
MAC
Address Enter a MAC address object to which the packets go.
Destination
Port Enter the port number (1-65535) to which the packets go. The SBG applies the policy route to the
packets that go to the corresponding service port. Any means all service ports.
Protocol Select TCP or UDP if you want to specify a protocol for the policy route. Otherwise select None.
Next-Hop
WAN Interface Select the WAN interface to route the matched packets through the specified outgoing
interface to a gateway (which is connected to the interface).
Advanced
Disable this
policy rule
automatically
while the
selected next-
hop is
unreachable
Select this if you want the SBG to disable a policy rule if next-hop is unreachable.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 38 Policy Route: Add/Edit (Sheet 2 of 2)
LABEL DESCRIPTION
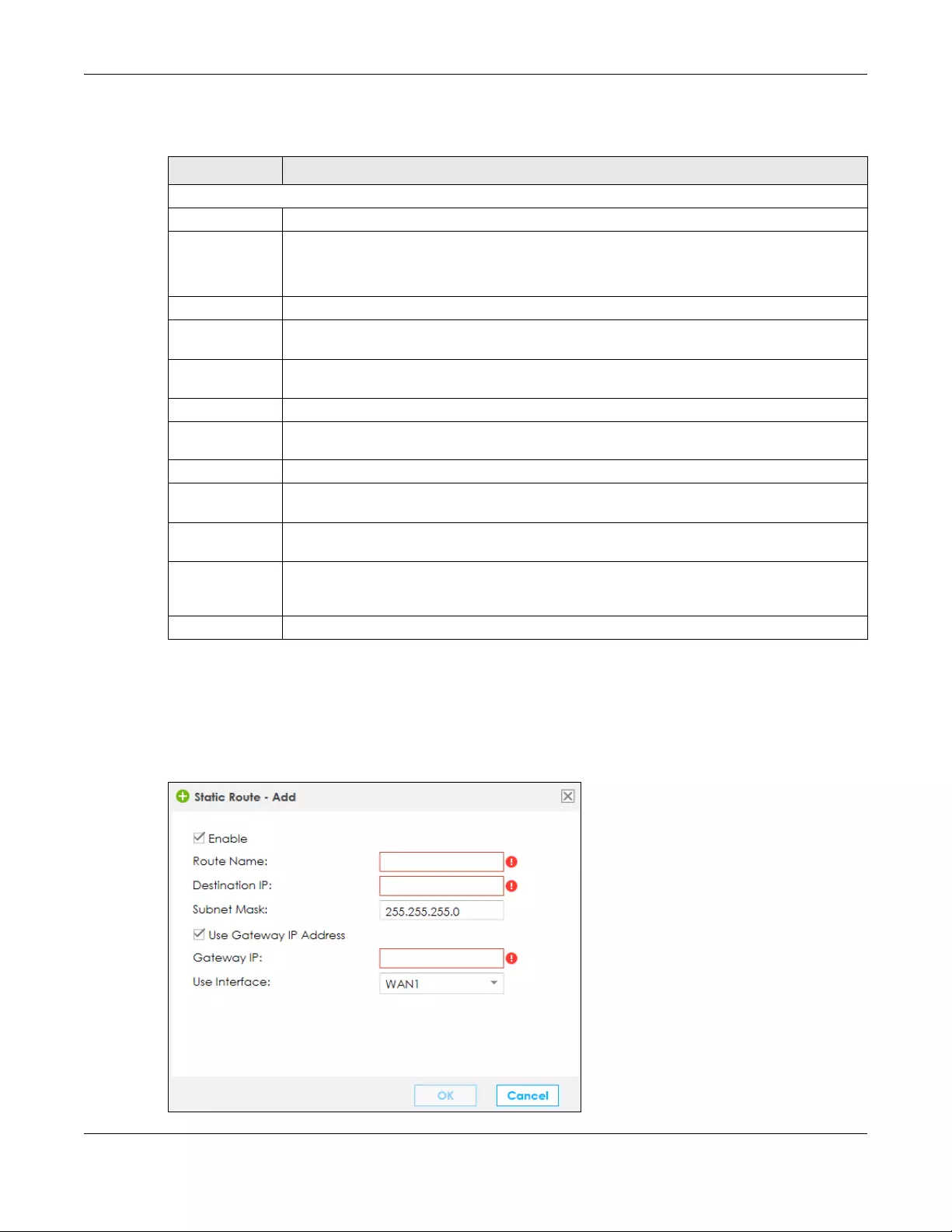
Chapter 7 Routing
SBG5500 Series User’s Guide
119
The following table describes the labels in this screen.
7.4.1 Add/Edit Static Route
Use this screen to add or edit a static route. Click Add new static route in the Routing screen or the Edit
icon next to the static route you want to edit. The screen shown next appears.
Figure 92 Static Route: Add/Edit
Table 39 Configuration > Routing > Static Route
LABEL DESCRIPTION
IPv4 / IPv6 Routing Table
Add Click this to configure a new static route.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify the
static route’s settings.
Click the slide button to enable and disable the static router.
Remove To remove an existing static route, select it and click Remove.
Multiple Entries
Turn On
Select one or more static routes and click this to enable them.
Multiple Entries
Turn Off
Select one or more static route and click this to disable them.
#This is the index number of the static route.
Status This field displays whether the static route is active or not. A green ON button signifies that this
static route is active. A gray OFF button signifies that this static route is not active.
Name This is the name that describes or identifies this route.
Destination IP This parameter specifies the IP network address of the final destination. Routing is always based
on network number.
Subnet Mask /
Prefix Length
This parameter specifies the IP network subnet mask and prefix length of the final destination.
Gateway IP This is the IP address of the gateway. The gateway is a router or switch on the same network
segment as the device's LAN or WAN port. The gateway helps forward packets to their
destinations.
Interface This is the WAN interface used for this static route.

Chapter 7 Routing
SBG5500 Series User’s Guide
120
The following table describes the labels in this screen.
7.5 The RIP Screen
Routing Information Protocol (RIP, RFC 1058 and RFC 1389) allows a device to exchange routing
information with other routers.
Click Configuration > Routing > RIP to open the RIP screen.
Table 40 Routing: Add/Edit
LABEL DESCRIPTION
Enable This field allows you to activate/deactivate this static route.
Select this to enable the static route. Clear this to disable this static route without having to
delete the entry.
Route Name Enter a descriptive name for the static route.
Destination IP
Address
Enter the IPv4 or IPv6 network address of the final destination.
Subnet Mask Enter the IP subnet mask here.
If you are using IPv4 and need to specify a route to a single host, use a subnet mask of
255.255.255.255 in the subnet mask field to force the network number to be identical to the host
ID.
Prefix Length Enter the IPv6 prefix length that specifies how many most significant bits (starting from the left) in
the address compose the network address.
Use Gateway IP
Address
The gateway is a router or switch on the same network segment as the device's LAN or WAN
port. The gateway helps forward packets to their destinations.
Select this if you want to use the gateway IP address.
Gateway IP Enter the IP address of the gateway.
Use Interface Select the WAN interface you want to use for this static route.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
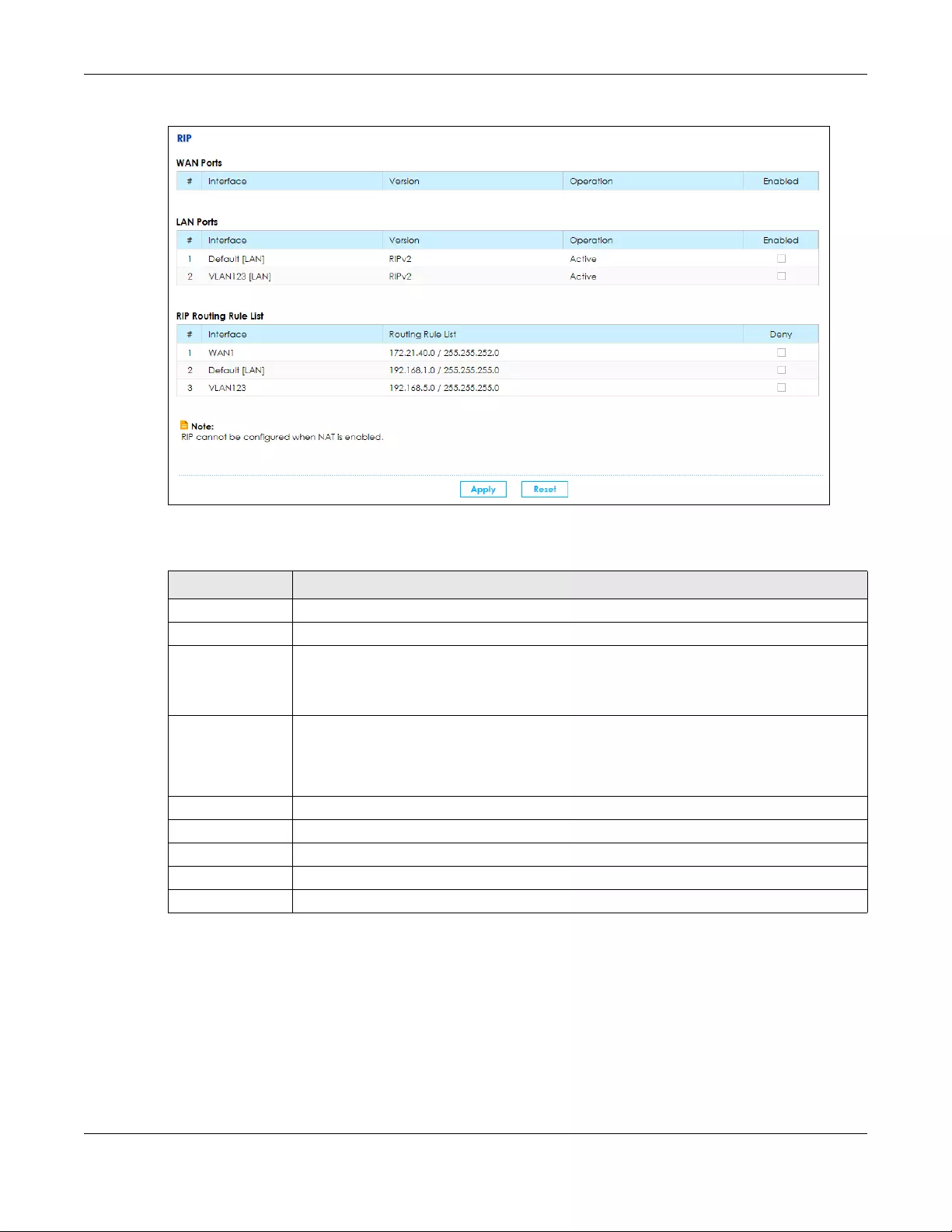
Chapter 7 Routing
SBG5500 Series User’s Guide
121
Figure 93 Configuration > Routing > RIP
The following table describes the labels in this screen.
Table 41 Configuration > Routing > RIP
LABEL DESCRIPTION
#This is the index number of the entry.
Interface This is the name of the interface in which the RIP setting is used.
Version The RIP version controls the format and the broadcasting method of the RIP packets that the
SBG sends (it recognizes both formats when receiving). RIP version RIPv1 is universally
supported but RIP version RIPv2 carries more information. RIP version RIPv1 is probably
adequate for most networks, unless you have an unusual network topology.
Operation Select Passive to have the SBG update the routing table based on the RIP packets received
from neighbors but not advertise its route information to other routers in this interface.
Select Active to have the SBG advertise its route information and also listen for routing
updates from neighboring routers.
Enabled Select the check box to activate the settings.
Routing Rule List This shows the destination IP address and subnet mask of the routing entries.
Deny Select the check box to deny routing entries to report (send out) through the interfaces.
Apply Click Apply to save your changes.
Cancel Click Cancel to exit this screen without saving.

SBG5500 Series User’s Guide
122
CHAPTER 8
Network Address Translation
(NAT)
8.1 Overview
This chapter discusses how to configure NAT on the SBG. NAT (Network Address Translation - NAT, RFC
1631) is the translation of the IP address of a host in a packet, for example, the source address of an
outgoing packet, used within one network to a different IP address known within another network.
8.1.1 What You Can Do in this Chapter
• Use the Port Forwarding screen to configure forward incoming service requests to the server(s) on your
local network (Section 8.2 on page 123).
• Use the Port Triggering screen to add and configure the SBG’s trigger port settings (Section 8.3 on
page 126).
• Use the Address Mapping screen to configure the SBG's address mapping settings (Section 8.4 on
page 129).
• Use the Default Server screen to configure a default server (Section 8.5 on page 131).
• Use the ALG screen to enable and disable the NAT and SIP (VoIP) ALG in the SBG (Section 8.6 on
page 133).
8.1.2 What You Need To Know
Inside/Outside
Inside/outside denotes where a host is located relative to the SBG, for example, the computers of your
subscribers are the inside hosts, while the web servers on the Internet are the outside hosts.
Global/Local
Global/local denotes the IP address of a host in a packet as the packet traverses a router, for example,
the local address refers to the IP address of a host when the packet is in the local network, while the
global address refers to the IP address of the host when the same packet is traveling in the WAN side.
NAT
In the simplest form, NAT changes the source IP address in a packet received from a subscriber (the
inside local address) to another (the inside global address) before forwarding the packet to the WAN
side. When the response comes back, NAT translates the destination address (the inside global address)
back to the inside local address before forwarding it to the original inside host.

Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
123
Port Forwarding
A port forwarding set is a list of inside (behind NAT on the LAN) servers, for example, web or FTP, that you
can make visible to the outside world even though NAT makes your whole inside network appear as a
single computer to the outside world.
Finding Out More
See Section 8.7 on page 134 for advanced technical information on NAT.
8.2 The Port Forwarding Screen
Use the Port Forwarding screen to forward incoming service requests to the server(s) on your local
network.
You may enter a single port number or a range of port numbers to be forwarded, and the local IP
address of the desired server. The port number identifies a service; for example, web service is on port 80
and FTP on port 21. In some cases, such as for unknown services or where one server can support more
than one service (for example both FTP and web service), it might be better to specify a range of port
numbers. You can allocate a server IP address that corresponds to a port or a range of ports.
Please refer to RFC 1700 for further information about port numbers.
Note: Many residential broadband ISP accounts do not allow you to run any server processes
(such as a Web or FTP server) from your location. Your ISP may periodically check for
servers and may suspend your account if it discovers any active services at your
location. If you are unsure, refer to your ISP.
Configuring Servers Behind Port Forwarding (Example)
Let's say you want to assign ports 21-25 to one FTP, Telnet and SMTP server (A in the example), port 80 to
another (B in the example) and assign a default server IP address of 192.168.1.35 to a third (C in the
example). You assign the LAN IP addresses and the ISP assigns the WAN IP address. The NAT network
appears as a single host on the Internet.
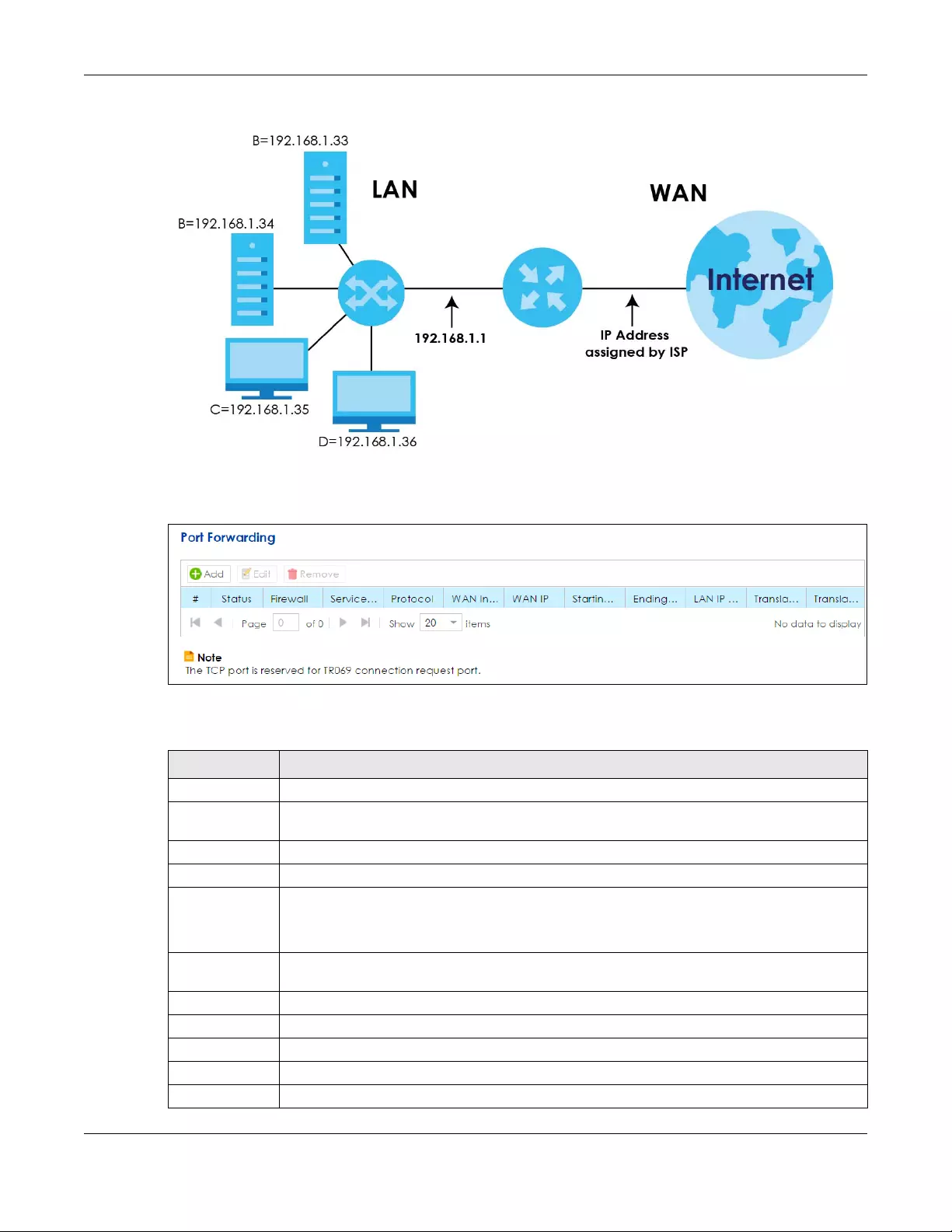
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
124
Figure 94 Multiple Servers Behind NAT Example
Click Configuration > NAT > Port Forwarding to open the following screen.
Figure 95 Configuration > NAT > Port Forwarding
The following table describes the fields in this screen.
Table 42 Configuration > NAT > Port Forwarding
LABEL DESCRIPTION
Add Click this to add a new rule.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify the rule’s
settings.
Remove To remove an existing rule, select it and click Remove.
#This is the index number of the rule.
Status This field displays whether the rule is active or not. A green ON button signifies that this rule is
active. A gray OFF button signifies that this rule is not active.
Click the slide button to turn on or turn off the rule.
Firewall This shows a firewall exception icon if there is an exception filter rule on the SBG firewall for this
port forwarding rule, otherwise this field is empty.
Service Name This shows the service’s name.
Protocol This shows the IP protocol supported by this virtual server, whether it is TCP, UDP, or TCP/UDP.
WAN Interface This shows the WAN interface through which the service is forwarded.
WAN IP This field displays the incoming packet’s destination IP address.
Starting Port This is the first external port number that identifies a service.
SBG
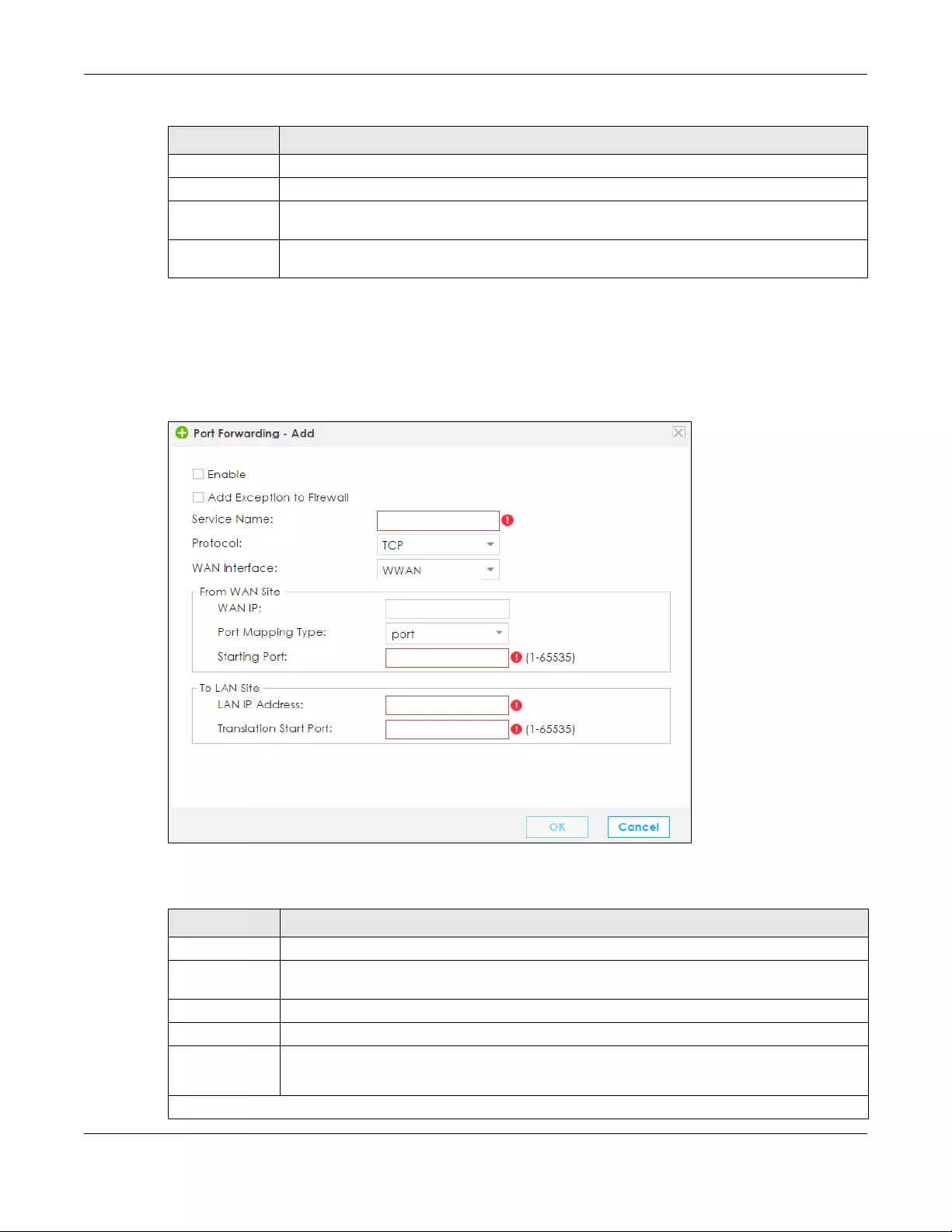
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
125
8.2.1 Add/Edit Port Forwarding
Click Add in the Port Forwarding screen or select an existing rule and click Edit to open the following
screen.
Figure 96 Port Forwarding: Add/Edit
The following table describes the labels in this screen.
Ending Port This is the last external port number that identifies a service.
LAN IP Address This is the service’s internal IP address.
Translation Start
Port
This is the first internal port number that identifies a service.
Translation End
Port
This is the last internal port number that identifies a service.
Table 42 Configuration > NAT > Port Forwarding (continued)
LABEL DESCRIPTION
Table 43 Port Forwarding: Add/Edit
LABEL DESCRIPTION
Enable Clear the check box to inactivate the rule. Select the check box to activate it.
Add Exception
to Firewall
Select this option to create an incoming filter rule in the Firewall to allow the packets.
Service Name Enter a name to identify this rule using keyboard characters (A-Z, a-z, 1-2 and so on).
Protocol Select the protocol supported by this virtual server. Choices are TCP, UDP, or TCP/UDP.
WAN Interface Select the WAN interface through which the service is forwarded.
You must have already configured a WAN connection with NAT enabled.
From WAN Site

Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
126
8.3 The Port Triggering Screen
Some services use a dedicated range of ports on the client side and a dedicated range of ports on the
server side. With regular port forwarding you set a forwarding port in NAT to forward a service (coming in
from the server on the WAN) to the IP address of a computer on the client side (LAN). The problem is that
port forwarding only forwards a service to a single LAN IP address. In order to use the same service on a
different LAN computer, you have to manually replace the LAN computer's IP address in the forwarding
port with another LAN computer's IP address.
Trigger port forwarding solves this problem by allowing computers on the LAN to dynamically take turns
using the service. The SBG records the IP address of a LAN computer that sends traffic to the WAN to
request a service with a specific port number and protocol (a “trigger” port). When the SBG's WAN port
receives a response with a specific port number and protocol (“open” port), the SBG forwards the traffic
to the LAN IP address of the computer that sent the request. After that computer’s connection for that
service closes, another computer on the LAN can use the service in the same manner. This way you do
not need to configure a new IP address each time you want a different LAN computer to use the
application.
For example:
WAN IP Enter the WAN IP address for which the incoming service is destined. If the packet’s destination
IP address doesn’t match the one specified here, the port forwarding rule will not be applied.
Port Mapping
Type
Select Port if you only want to enter the starting port. Select Ports if you want to enter both
starting and ending ports (1-65535).
Starting Port Enter the original destination port for the packets.
To forward only one port, enter the port number again in the End Port field.
To forward a series of ports, enter the start port number here and the end port number in the End
Port field.
Ending Port Enter the last port of the original destination port range.
To forward only one port, enter the port number in the Start Port field above and then enter it
again in this field.
To forward a series of ports, enter the last port number in a series that begins with the port
number in the Start Port field above.
To LAN Site
LAN IP Address Enter the inside IP address of the virtual server here.
Translation Start
Port
This shows the port number to which you want the SBG to translate the incoming port. For a
range of ports, enter the first number of the range to which you want the incoming ports
translated.
Translation End
Port
This shows the last port of the translated port range.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 43 Port Forwarding: Add/Edit (continued)
LABEL DESCRIPTION
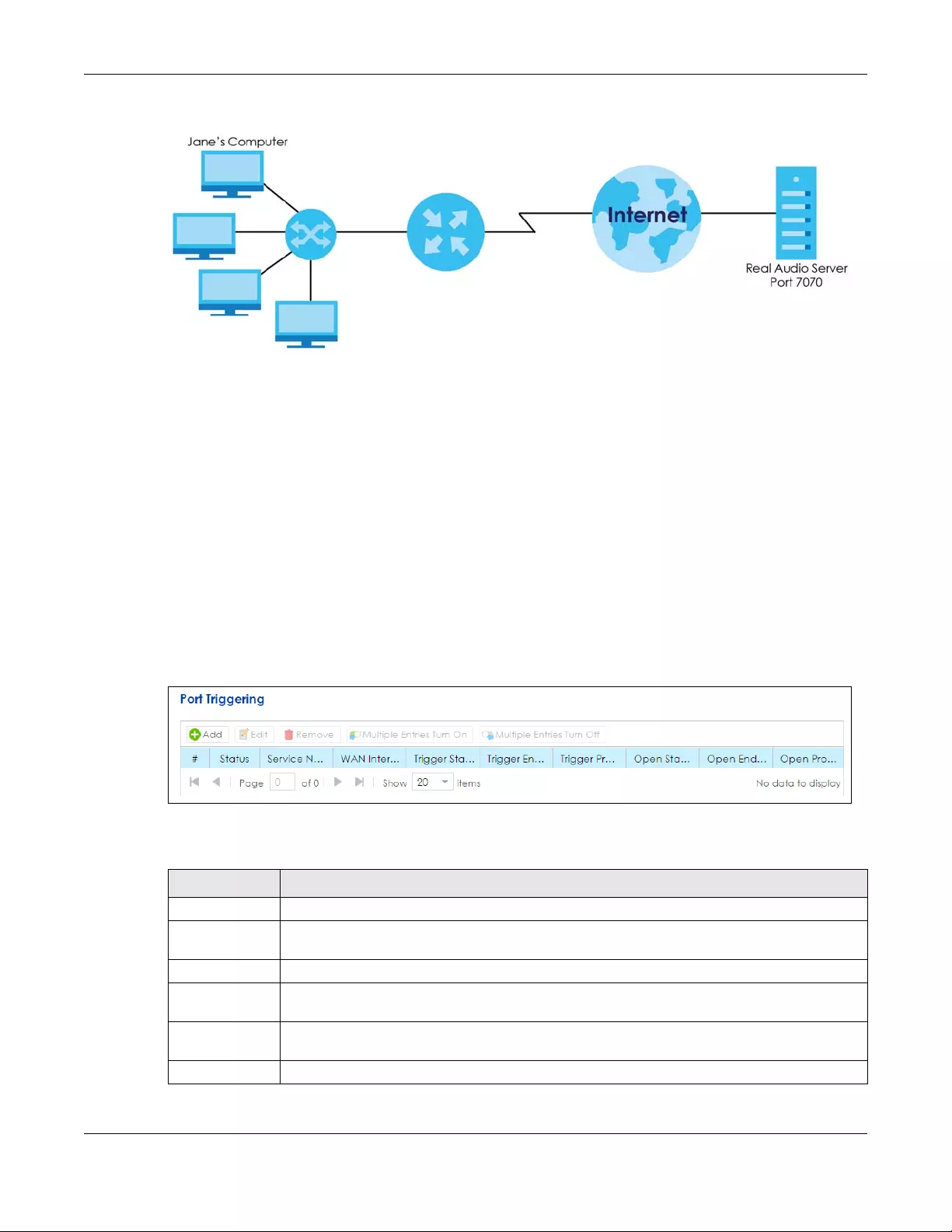
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
127
Figure 97 Trigger Port Forwarding Process: Example
1Jane requests a file from the Real Audio server (port 7070).
2Port 7070 is a “trigger” port and causes the SBG to record Jane’s computer IP address. The SBG
associates Jane's computer IP address with the “open” port range of 6970-7170.
3The Real Audio server responds using a port number ranging between 6970-7170.
4The SBG forwards the traffic to Jane’s computer IP address.
5Only Jane can connect to the Real Audio server until the connection is closed or times out. The SBG
times out in three minutes with UDP (User Datagram Protocol) or two hours with TCP/IP (Transfer Control
Protocol/Internet Protocol).
Click Configuration > NAT > Port Triggering to open the following screen. Use this screen to view your
SBG’s trigger port settings.
Figure 98 Configuration > NAT > Port Triggering
The following table describes the labels in this screen.
SBG
Table 44 Network Setting > NAT > Port Triggering
LABEL DESCRIPTION
Add Click this to create a new rule.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify the rule’s
settings.
Remove To remove an existing rule, select it and click Remove.
Multiple Entries
Turn On
Select one or more rules and click this to enable them.
Multiple Entries
Turn Off
Select one or more rules and click this to disable them.
#This is the index number of the rule.
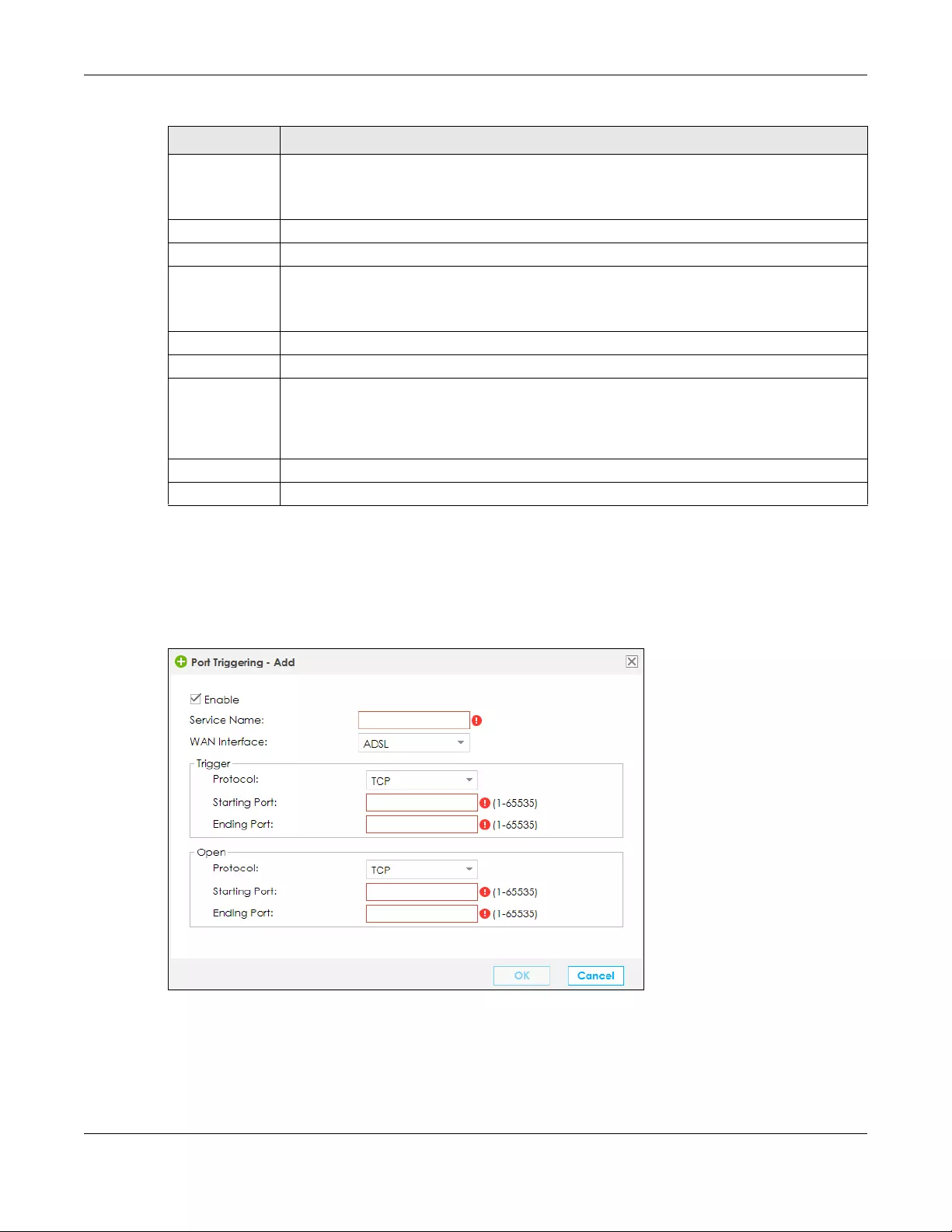
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
128
8.3.1 Add/Edit Port Triggering Rule
This screen lets you create new port triggering rules. Click Add in the Port Triggering screen or select a
rule and click Edit to open the following screen.
Figure 99 Port Triggering: Add/Edit
Status This field displays whether the rule is active or not. A green ON button signifies that this rule is
active. A gray OFF button signifies that this rule is not active.
Click the slide button to turn on or turn off the rule.
Service Name This field displays the name of the service used by this rule.
WAN Interface This field shows the WAN interface through which the service is forwarded.
Trigger Start Port The trigger port is a port (or a range of ports) that causes (or triggers) the SBG to record the IP
address of the LAN computer that sent the traffic to a server on the WAN.
This is the first port number that identifies a service.
Trigger End Port This is the last port number that identifies a service.
Trigger Protocol This is the trigger transport layer protocol.
Open Start Port The open port is a port (or a range of ports) that a server on the WAN uses when it sends out a
particular service. The SBG forwards the traffic with this port (or range of ports) to the client
computer on the LAN that requested the service.
This is the first port number that identifies a service.
Open End Port This is the last port number that identifies a service.
Open Protocol This is the open transport layer protocol.
Table 44 Network Setting > NAT > Port Triggering (continued)
LABEL DESCRIPTION
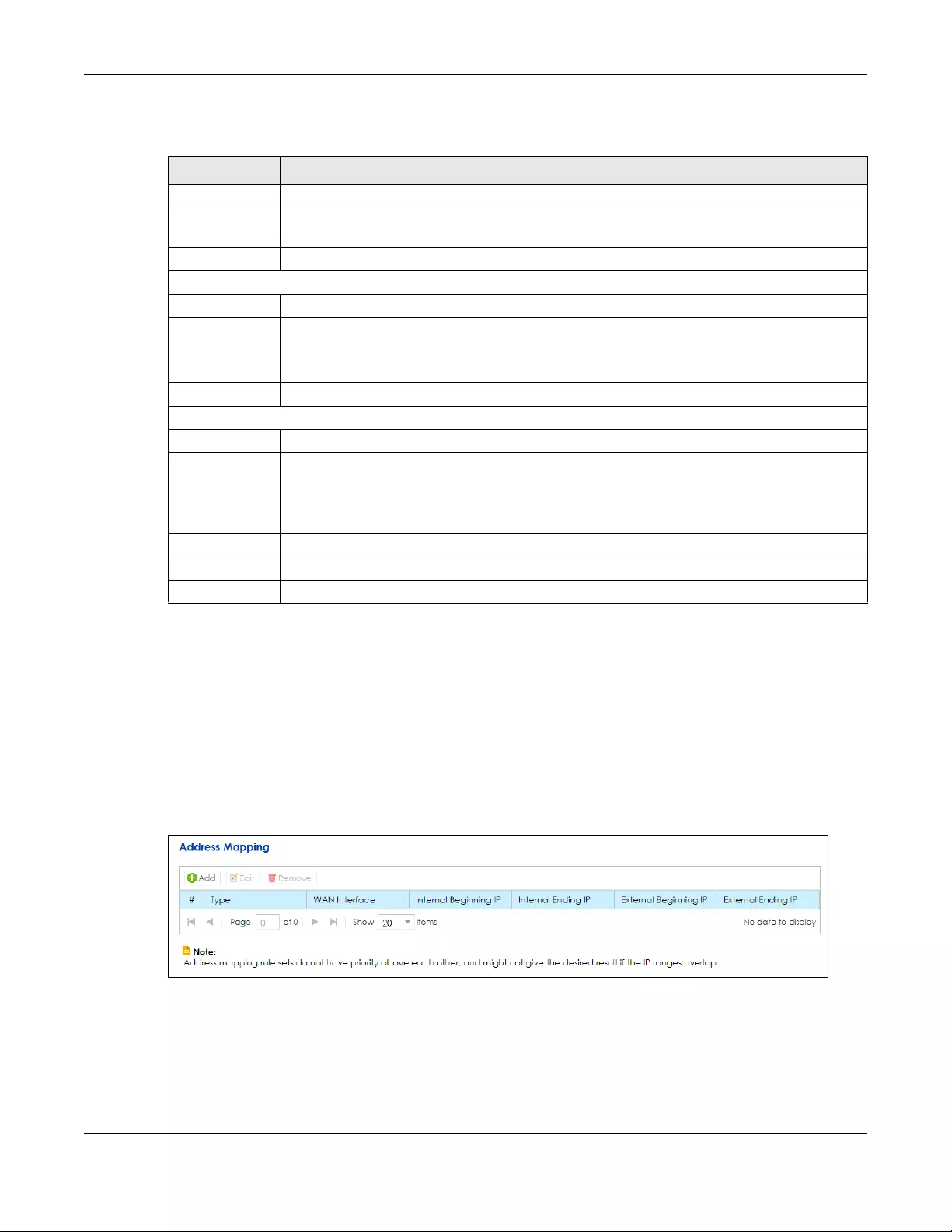
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
129
The following table describes the labels in this screen.
8.4 The Address Mapping Screen
Use this screen to change your SBG’s address mapping settings. Ordering your rules is important,
because the SBG applies the rules in the order that you specify. When a rule matches the current
packet, the SBG takes the corresponding action and the remaining rules are ignored.
Click Configuration > NAT > Address Mapping to display the following screen.
Figure 100 Configuration > NAT > Address Mapping
Table 45 Port Triggering: Configuration Add/Edit
LABEL DESCRIPTION
Enable Select the check box to activate this rule.
Service Name Enter a name to identify this rule. It should begin with a letter and cannot exceed 20 characters
[0-9][A-Z] [a-z][_-].
WAN Interface Select a WAN interface for which you want to configure port triggering rules.
Trigger
Protocol Select the transport layer protocol from TCP, UDP, or TCP/UDP.
Starting Port The trigger port is a port (or a range of ports) that causes (or triggers) the SBG to record the IP
address of the LAN computer that sent the traffic to a server on the WAN.
Type a port number or the starting port number in a range of port numbers (1-65535).
Ending Port Type a port number or the ending port number in a range of port numbers (1-65535).
Open
Protocol Select the transport layer protocol from TCP, UDP, or TCP/UDP.
Starting Port The open port is a port (or a range of ports) that a server on the WAN uses when it sends out a
particular service. The SBG forwards the traffic with this port (or range of ports) to the client
computer on the LAN that requested the service.
Type a port number or the starting port number in a range of port numbers (1-65535).
Ending Port Type a port number or the ending port number in a range of port numbers (1-65535).
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
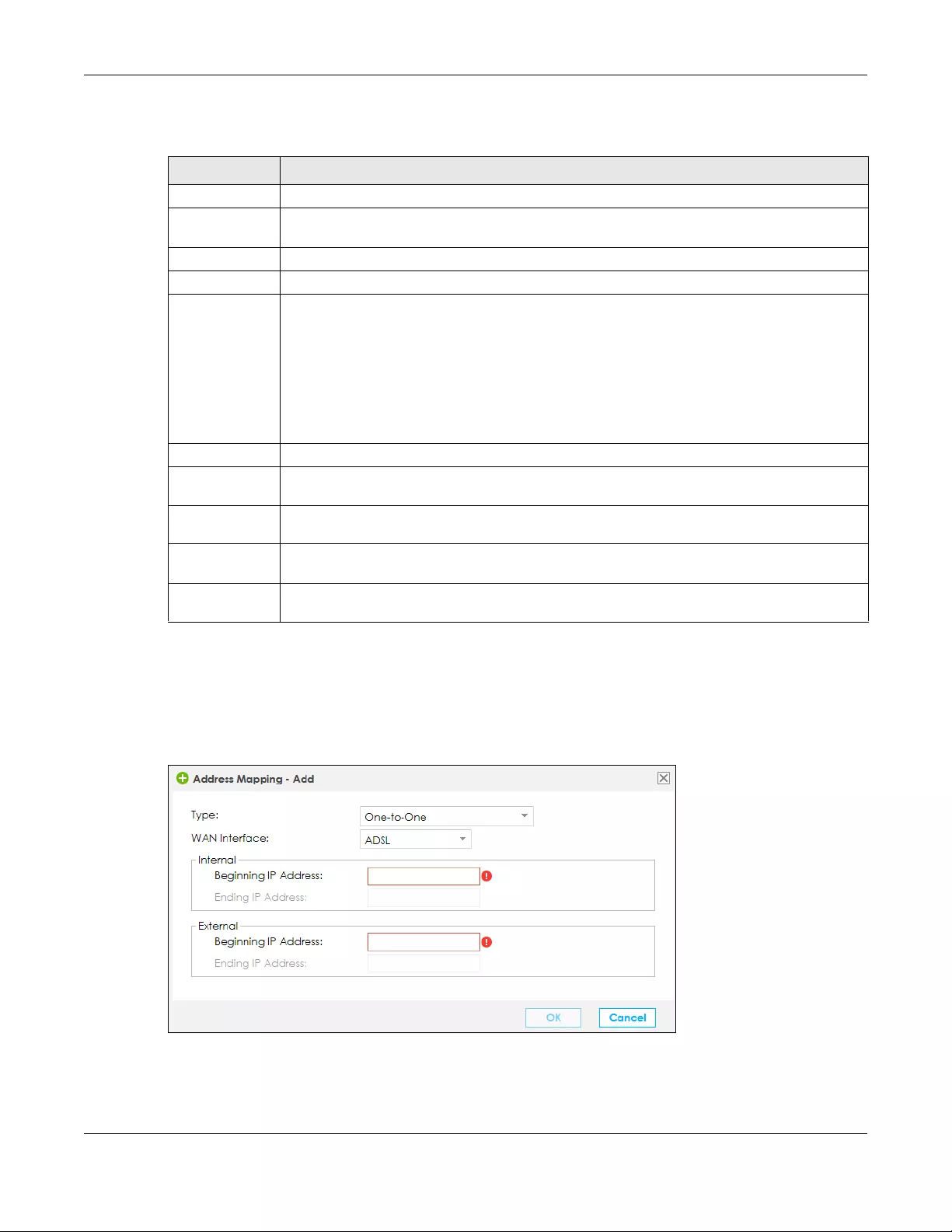
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
130
The following table describes the fields in this screen.
8.4.1 Add/Edit Address Mapping Rule
To add or edit an address mapping rule, click Add or select a rule and click Edit icon in the Address
Mapping screen to display the screen shown next.
Figure 101 Address Mapping: Add/Edit
Table 46 Configuration > NAT > Address Mapping
LABEL DESCRIPTION
Add Click this to create a new address mapping rule.
Edit Double-click an address mapping rule or select it and click Edit to open a screen where you can
modify the rule’s settings.
Remove To remove an existing address mapping rule, select it and click Remove.
# This is the index number of the rule.
Type This is the address mapping type.
One-to-One: This mode maps one local IP address to one global IP address. Note that port
numbers do not change for the One-to-one NAT mapping type.
Many-to-One / Source NAT: This mode maps multiple local IP addresses to one global IP address.
This is equivalent to SUA (that is, PAT, port address translation), the SBG's Single User Account
feature that previous routers supported only.
Many-to-Many: This mode maps multiple local IP addresses to shared global IP addresses.
WAN Interface This shows the WAN interface through which the address mapping is forwarded.
Internal
Beginning IP
This is the starting Inside Local IP Address (ILA).
Internal Ending
IP
This is the ending Inside Local IP Address (ILA). This field is blank for One-to-One mapping types.
External
Beginning IP
This is the starting Inside Global IP Address (IGA). Enter 0.0.0.0 here if you have a dynamic IP
address from your ISP. You can only do this for the Many-to-One mapping type.
External Ending
IP
This is the ending Inside Global IP Address (IGA). This field is blank for One-to-One and Many-to-
One mapping types.

Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
131
The following table describes the fields in this screen.
8.5 The Default Server Screen
In addition to the servers for specified services, NAT supports a default server IP address. A default server
receives packets from ports that are not specified in the NAT Port Forwarding Setup screen. Click
Configuration > NAT > Default Server to open the following screen.
Figure 102 Configuration > NAT > Default Server
Table 47 Address Mapping: Add/Edit
LABEL DESCRIPTION
Type Choose the IP/port mapping type from one of the following.
One-to-One: This mode maps one local IP address to one global IP address. Note that port
numbers do not change for the One-to-one NAT mapping type.
Many-to-One / Source NAT: This mode maps multiple local IP addresses to one global IP address.
This is equivalent to SUA (that is, PAT, port address translation), the SBG's Single User Account
feature that previous routers supported only.
Many-to-Many: This mode maps multiple local IP addresses to shared global IP addresses.
WAN Interface Select the WAN interface through which the service is forwarded.
Internal
Beginning IP
Address
Enter the starting Inside Local IP Address (ILA).
Ending IP
Address
Enter the ending Inside Local IP Address (ILA). This field is blank for One-to-One mapping types.
External
Beginning IP
Address
Enter the starting Inside Global IP Address (IGA). Enter 0.0.0.0 here if you have a dynamic IP
address from your ISP. You can only do this for the Many-to-One / Source NAT mapping type.
Ending IP
Address
Enter the ending Inside Global IP Address (IGA). This field is blank for One-to-One and Many-to-
One mapping types.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
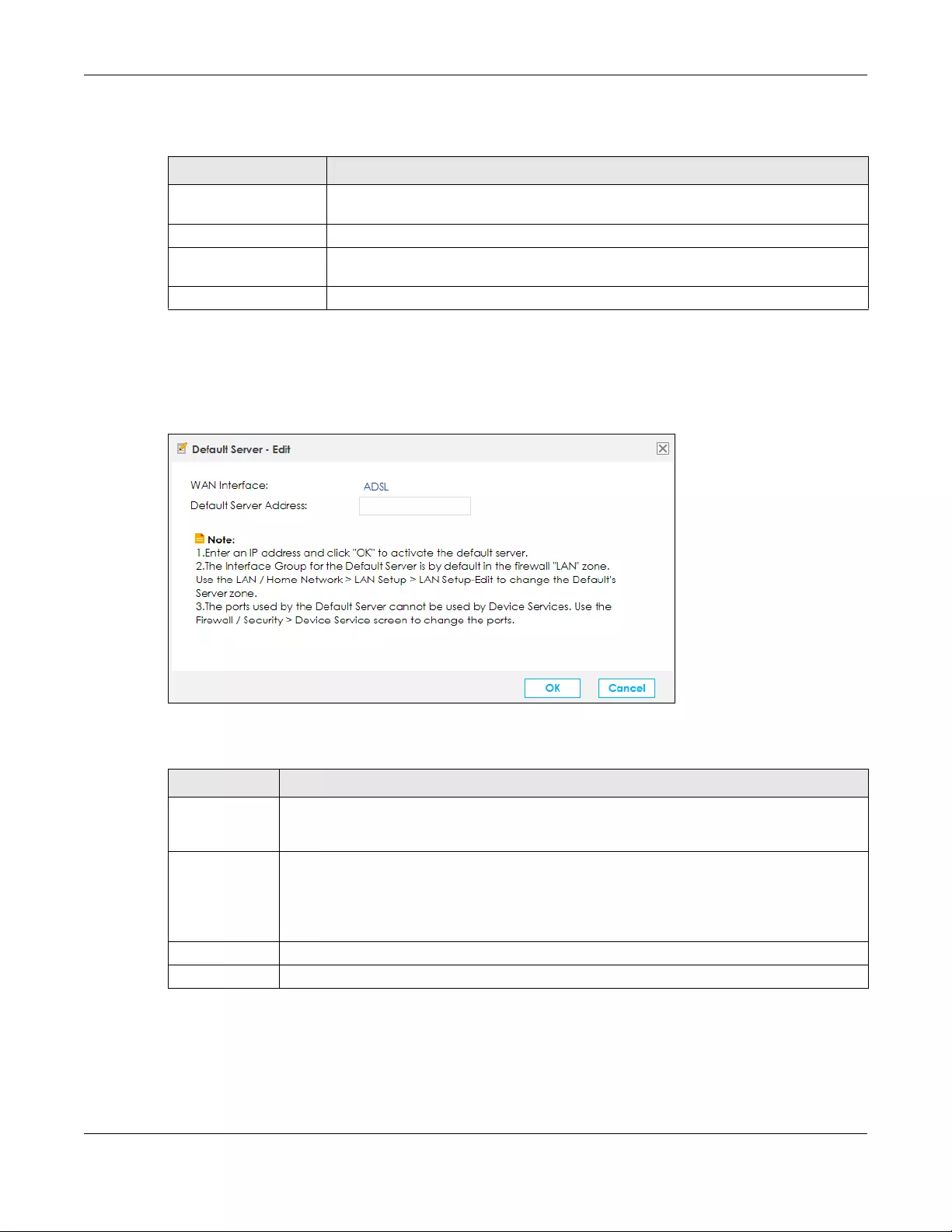
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
132
The following table describes the labels in this screen.
8.5.1 Edit Default Server
This screen lets you edit interface groups. Select an interface and click Edit to open the following screen.
Figure 103 Default Server: Edit
The following table describes the fields in this screen.
Table 48 Configuration > NAT > Default Server
LABEL DESCRIPTION
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the default server’s IP address.
# This is the index number of the WAN interface.
WAN Interface This shows the name of the interface group that was created in the Configuration > LAN
/ Home Network > VLAN / Interface Group screen.
Default Server Address This shows the IP address of the default server.
Table 49 Default Server: Edit
LABEL DESCRIPTION
WAN Interface This shows the name of the interface group that was created in the Configuration > LAN / Home
Network > VLAN / Interface Group screen. The host must be in the same VLAN as the selected
VLAN / Interface Group.
Default Server
Address
Enter the IP address of the default server which receives packets from ports that are not
specified in the NAT Port Forwarding screen.
Note: If you do not assign a Default Server Address, the SBG discards all packets
received for ports that are not specified in the NAT Port Forwarding screen.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
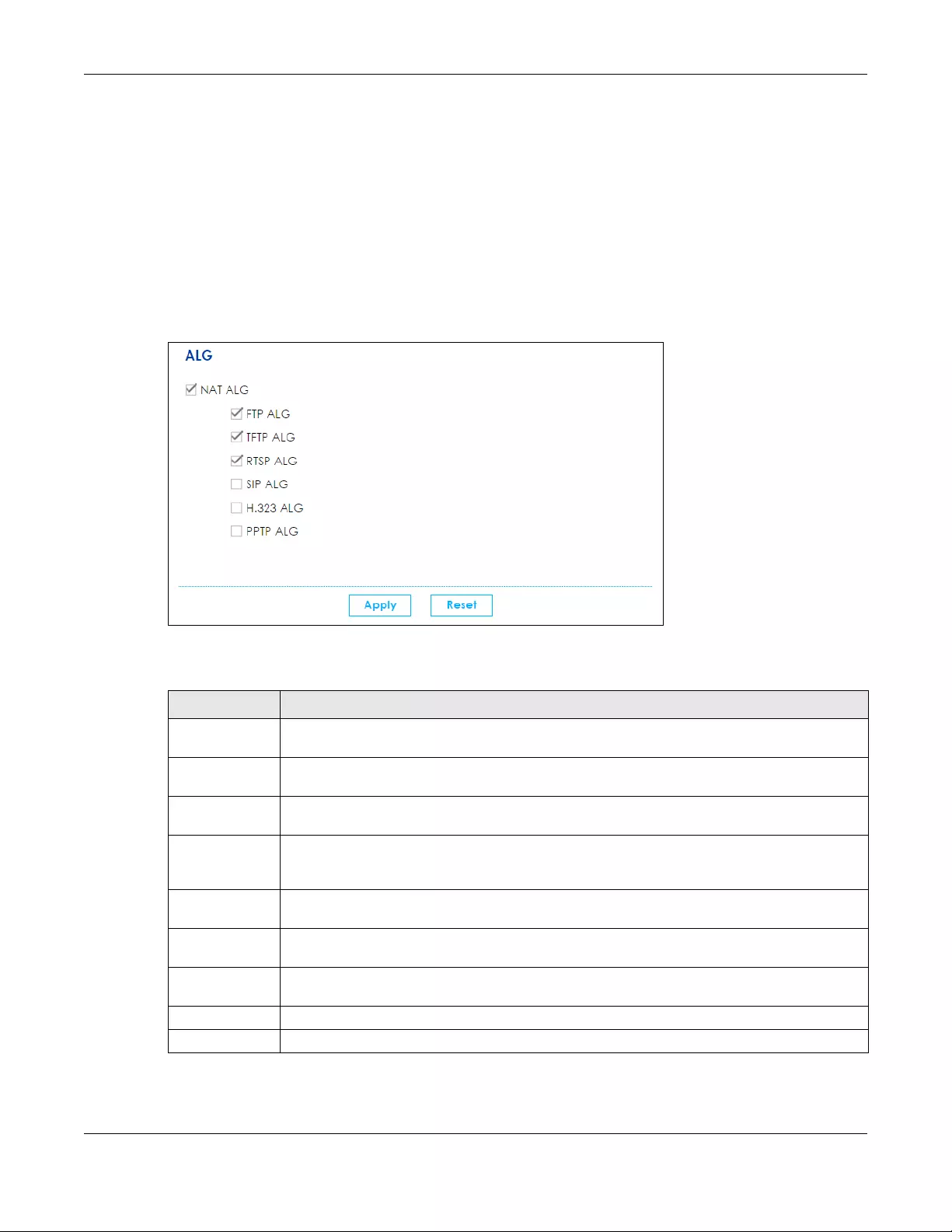
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
133
8.6 The ALG Screen
Some NAT routers may include a SIP Application Layer Gateway (ALG). A SIP ALG allows SIP calls to pass
through NAT by examining and translating IP addresses embedded in the data stream. When the SBG
registers with the SIP register server, the SIP ALG translates the SBG’s private IP address inside the SIP data
stream to a public IP address. You do not need to use STUN or an outbound proxy if your SBG is behind a
SIP ALG.
Use this screen to enable and disable the NAT, SIP (VoIP) and/or RTSP ALG in the SBG. To access this
screen, click Configuration > NAT > ALG.
Figure 104 Configuration > NAT > ALG
The following table describes the fields in this screen.
Table 50 Configuration > NAT > ALG
LABEL DESCRIPTION
NAT ALG Enable this to make sure applications such as FTP and file transfer in IM applications work
correctly with port-forwarding and address-mapping rules.
FTP ALG Turn on the FTP ALG to detect FTP (File Transfer Program) traffic and help build FTP sessions
through the SBG’s NAT.
TFTP ALG Turn on the TFTP ALG to detect TFTP (Trivial File Transfer Protocol) traffic and help build TFTP
sessions through the SBG’s NAT.
RTSP ALG Enable this to have the SBG detect RTSP traffic and help build RTSP sessions through its NAT. The
Real Time Streaming (media control) Protocol (RTSP) is a remote control for multimedia on the
Internet.
SIP ALG Enable this to make sure SIP (VoIP) works correctly with port-forwarding and address-mapping
rules.
H.323 ALG Turn on the H.323 ALG to detect H.323 traffic (used for audio communications) and help build
H.323 sessions through the SBG’s NAT.
PPTP ALG Turn on the PPTP ALG to detect PPTP (Point-to-point Tunneling Protocol) traffic and help build
PPTP sessions through the SBG’s NAT.
Apply Click Apply to save your changes.
Reset Click Reset to return the screen to its last-saved settings.

Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
134
8.7 Technical Reference
This part contains more information regarding NAT.
8.7.1 NAT Definitions
Inside/outside denotes where a host is located relative to the SBG, for example, the computers of your
subscribers are the inside hosts, while the web servers on the Internet are the outside hosts.
Global/local denotes the IP address of a host in a packet as the packet traverses a router, for example,
the local address refers to the IP address of a host when the packet is in the local network, while the
global address refers to the IP address of the host when the same packet is traveling in the WAN side.
Note that inside/outside refers to the location of a host, while global/local refers to the IP address of a
host used in a packet. Thus, an inside local address (ILA) is the IP address of an inside host in a packet
when the packet is still in the local network, while an inside global address (IGA) is the IP address of the
same inside host when the packet is on the WAN side. The following table summarizes this information.
NAT never changes the IP address (either local or global) of an outside host.
8.7.2 What NAT Does
In the simplest form, NAT changes the source IP address in a packet received from a subscriber (the
inside local address) to another (the inside global address) before forwarding the packet to the WAN
side. When the response comes back, NAT translates the destination address (the inside global address)
back to the inside local address before forwarding it to the original inside host. Note that the IP address
(either local or global) of an outside host is never changed.
The global IP addresses for the inside hosts can be either static or dynamically assigned by the ISP. In
addition, you can designate servers, for example, a web server and a telnet server, on your local
network and make them accessible to the outside world. If you do not define any servers (for Many-to-
One and Many-to-Many Overload mapping), NAT offers the additional benefit of firewall protection.
With no servers defined, your SBG filters out all incoming inquiries, thus preventing intruders from probing
your network. For more information on IP address translation, refer to RFC 1631, The IP Network Address
Translator (NAT).
Table 51 NAT Definitions
ITEM DESCRIPTION
Inside This refers to the host on the LAN.
Outside This refers to the host on the WAN.
Local This refers to the packet address (source or destination) as the packet travels on the LAN.
Global This refers to the packet address (source or destination) as the packet travels on the WAN.
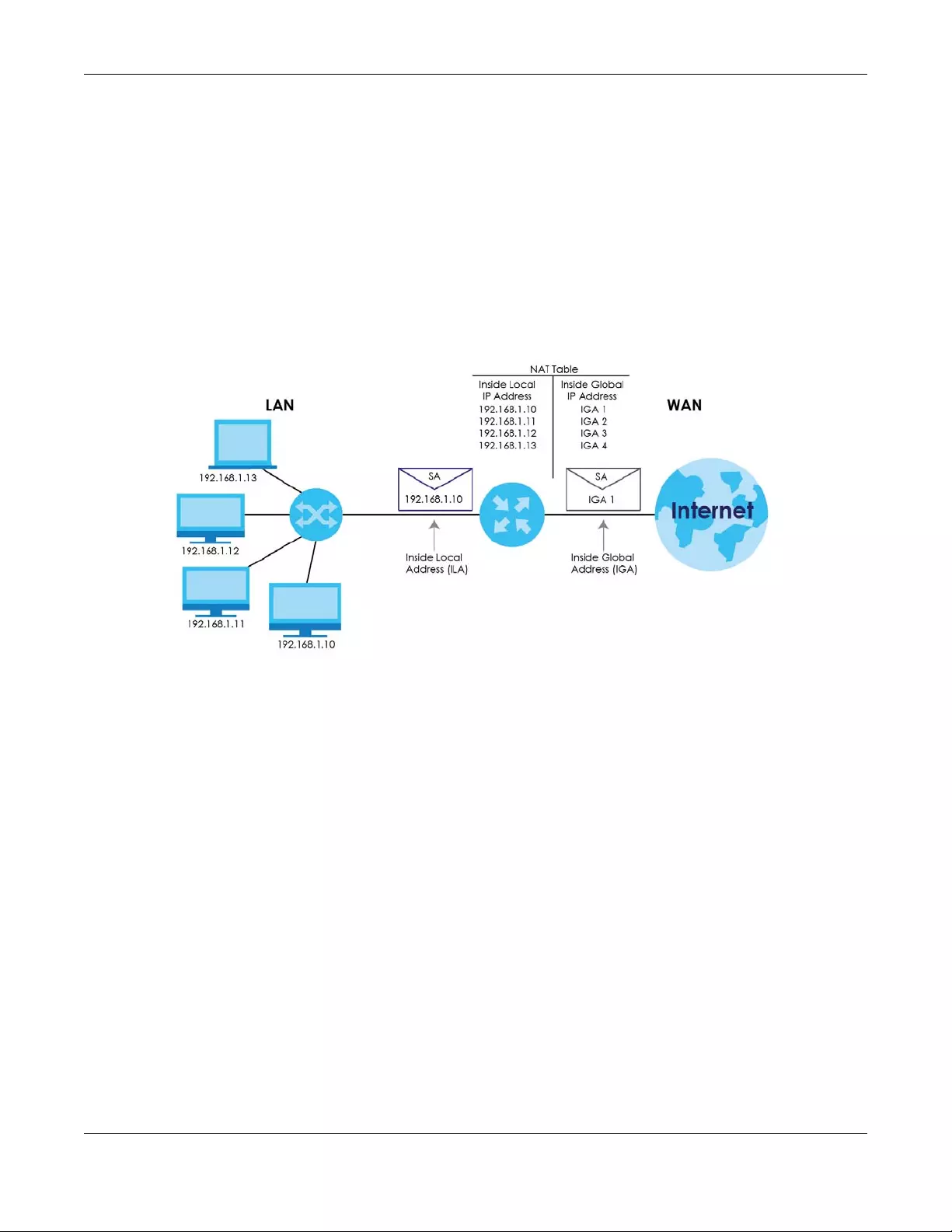
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
135
8.7.3 How NAT Works
Each packet has two addresses – a source address and a destination address. For outgoing packets,
the ILA (Inside Local Address) is the source address on the LAN, and the IGA (Inside Global Address) is
the source address on the WAN. For incoming packets, the ILA is the destination address on the LAN,
and the IGA is the destination address on the WAN. NAT maps private (local) IP addresses to globally
unique ones required for communication with hosts on other networks. It replaces the original IP source
address (and TCP or UDP source port numbers for Many-to-One and Many-to-Many Overload NAT
mapping) in each packet and then forwards it to the Internet. The SBG keeps track of the original
addresses and port numbers so incoming reply packets can have their original values restored. The
following figure illustrates this.
Figure 105 How NAT Works
8.7.4 NAT Application
The following figure illustrates a possible NAT application, where three inside LANs (logical LANs using IP
alias) behind the SBG can communicate with three distinct WAN networks.
SBG
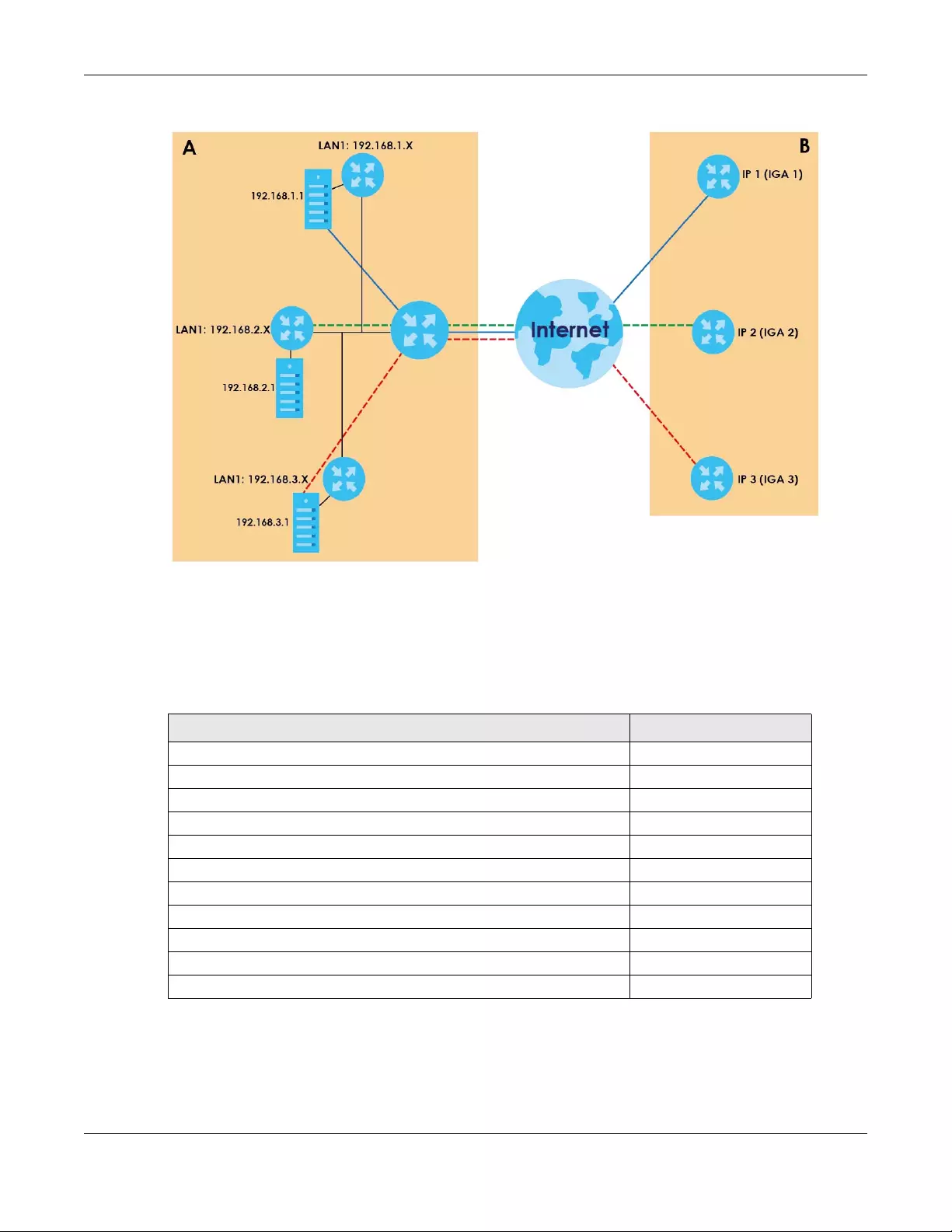
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
136
Figure 106 NAT Application With IP Alias
Port Forwarding: Services and Port Numbers
The most often used port numbers are shown in the following table. Please refer to RFC 1700 for further
information about port numbers. Please also refer to the Supporting CD for more examples and details
on port forwarding and NAT.
Port Forwarding Example
Let's say you want to assign ports 21-25 to one FTP, Telnet and SMTP server (A in the example), port 80 to
another (B in the example) and assign a default server IP address of 192.168.1.35 to a third (C in the
Table 52 Services and Port Numbers
SERVICES PORT NUMBER
ECHO 7
FTP (File Transfer Protocol) 21
SMTP (Simple Mail Transfer Protocol) 25
DNS (Domain Name System) 53
Finger 79
HTTP (Hyper Text Transfer protocol or WWW, Web) 80
POP3 (Post Office Protocol) 110
NNTP (Network News Transport Protocol) 119
SNMP (Simple Network Management Protocol) 161
SNMP trap 162
PPTP (Point-to-Point Tunneling Protocol) 1723
SBG
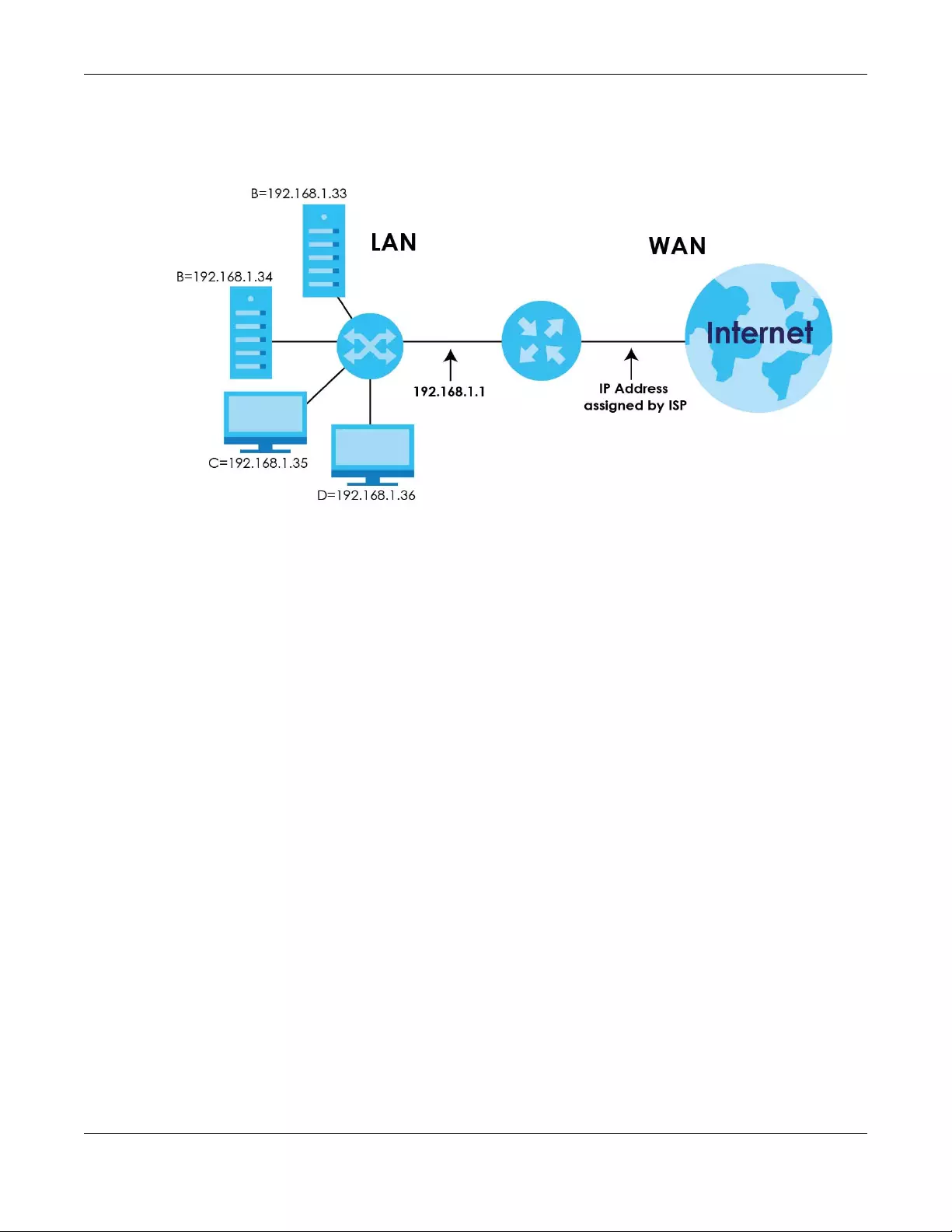
Chapter 8 Network Address Translation (NAT)
SBG5500 Series User’s Guide
137
example). You assign the LAN IP addresses and the ISP assigns the WAN IP address. The NAT network
appears as a single host on the Internet.
Figure 107 Multiple Servers Behind NAT Example
SBG
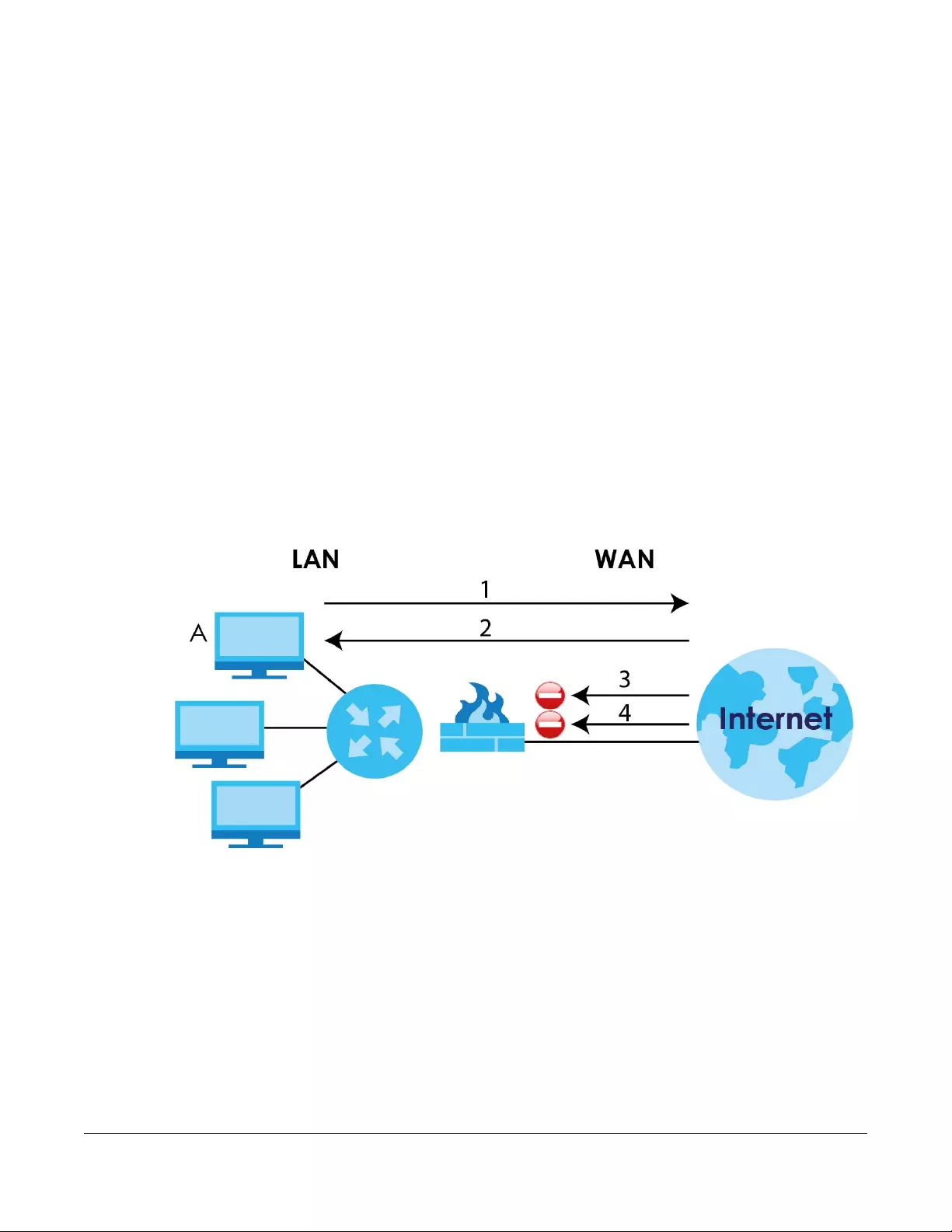
SBG5500 Series User’s Guide
138
CHAPTER 9
Firewall
9.1 Overview
This chapter shows you how to enable and configure the SBG’s security settings. Use the firewall to
protect your SBG and network from attacks by hackers on the Internet and control access to it. By
default the firewall:
• allows traffic that originates from your LAN computers to go to all other networks.
• blocks traffic that originates on other networks from going to the LAN.
The following figure illustrates the default firewall action. User A can initiate an IM (Instant Messaging)
session from the LAN to the WAN (1). Return traffic for this session is also allowed (2). However other traffic
initiated from the WAN is blocked (3 and 4).
Figure 108 Default Firewall Action
9.1.1 What You Can Do in this Chapter
• Use the Firewall Overview screen to activate the firewall feature on the SBG (Section 9.2 on page
140).
• Use the DoS screen to activate protection against Denial of Service (DoS) attacks (Section 9.3 on
page 141).
• Use the Firewall Rules screen to view the configured firewall rules and add, edit or remove incoming/
outgoing filtering rules (Section 9.4 on page 141).
• Use the Device Service screen to configure through which interfaces, which services can access the
SBG (Section 9.5 on page 144).
SBG

Chapter 9 Firewall
SBG5500 Series User’s Guide
139
• Use the Zone Control screen to set the firewall’s default actions based on the direction of travel of
packets (Section 9.6 on page 147).
• Use the Scheduler Rule screen to view, add or edit time schedule rules (Section 9.7 on page 148).
• Use the Service screen to add or remove predefined Internet services and configure firewall rules
(Section 9.8 on page 149).
• Use the MAC Filter screen to allow LAN clients access to the SBG (Section 9.9 on page 151).
• Use the Certificate screen to generate certification requests and import the SBG signed certificates
(Section 9.10 on page 153).
• Use the AAA Server screen to provide access control to your network (Section 9.11 on page 154).
9.1.2 What You Need to Know
SYN Attack
A SYN attack floods a targeted system with a series of SYN packets. Each packet causes the targeted
system to issue a SYN-ACK response. While the targeted system waits for the ACK that follows the SYN-
ACK, it queues up all outstanding SYN-ACK responses on a backlog queue. SYN-ACKs are moved off the
queue only when an ACK comes back or when an internal timer terminates the three-way handshake.
Once the queue is full, the system will ignore all incoming SYN requests, making the system unavailable
for legitimate users.
DoS
Denials of Service (DoS) attacks are aimed at devices and networks with a connection to the Internet.
Their goal is not to steal information, but to disable a device or network so users no longer have access
to network resources. The SBG is pre-configured to automatically detect and thwart all known DoS
attacks.
DDoS
A DDoS attack is one in which multiple compromised systems attack a single target, thereby causing
denial of service for users of the targeted system.
LAND Attack
In a LAND attack, hackers flood SYN packets into the network with a spoofed source IP address of the
target system. This makes it appear as if the host computer sent the packets to itself, making the system
unavailable while the target system tries to respond to itself.
Ping of Death
Ping of Death uses a "ping" utility to create and send an IP packet that exceeds the maximum 65,536
bytes of data allowed by the IP specification. This may cause systems to crash, hang or reboot.
SPI
Stateful Packet Inspection (SPI) tracks each connection crossing the firewall and makes sure it is valid.
Filtering decisions are based not only on rules but also context. For example, traffic from the WAN may
only be allowed to cross the firewall in response to a request from the LAN.
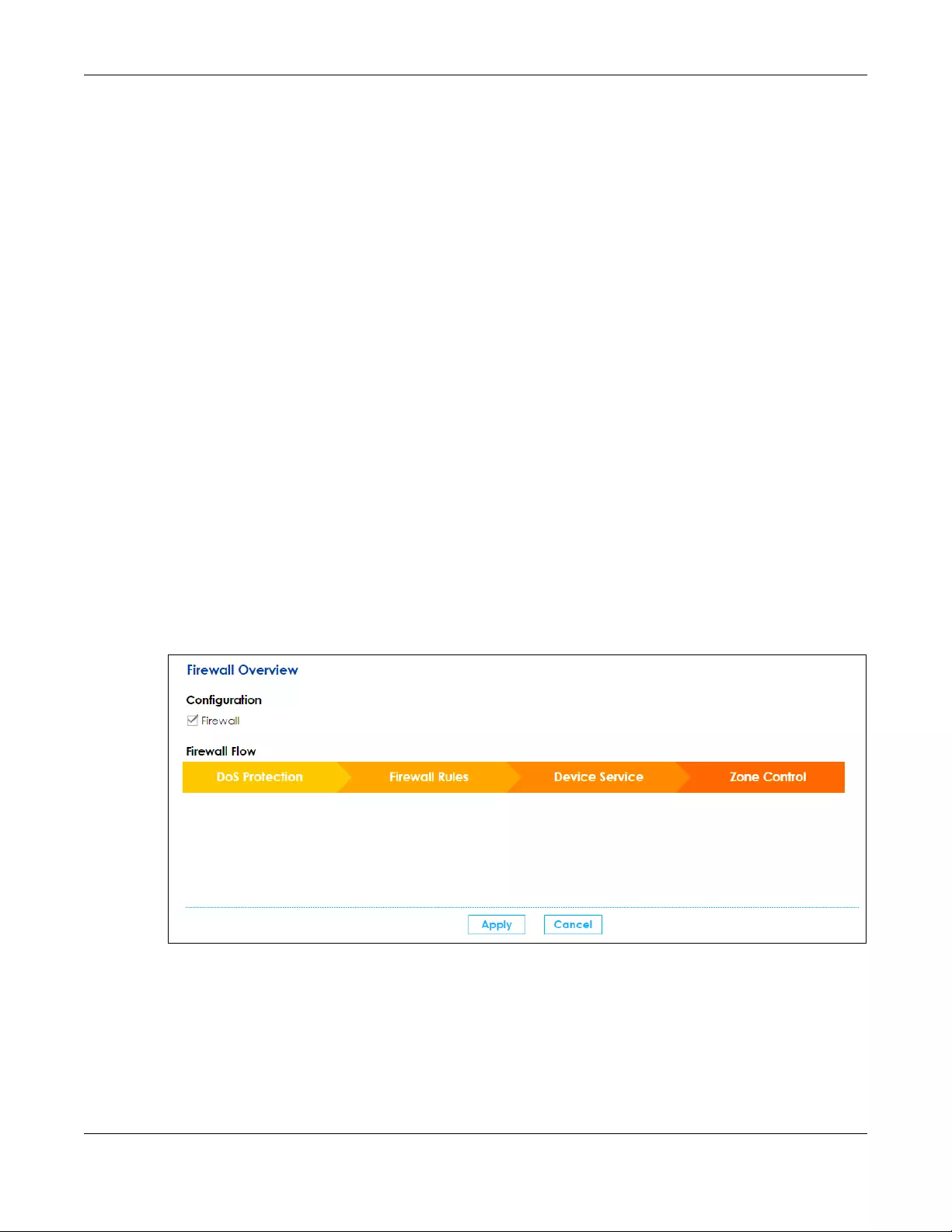
Chapter 9 Firewall
SBG5500 Series User’s Guide
140
Certification Authority
A Certification Authority (CA) issues certificates and guarantees the identity of each certificate owner.
There are commercial certification authorities like CyberTrust or VeriSign and government certification
authorities. The certification authority uses its private key to sign certificates. Anyone can then use the
certification authority's public key to verify the certificates. You can use the SBG to generate
certification requests that contain identifying information and public keys and then send the
certification requests to a certification authority.
AAA Servers Supported by the SBG
The following lists the types of authentication server the SBG supports.
•Local user database
The SBG uses the built-in local user database to authenticate administrative users logging into the SBG’s
Web Configurator or network access users logging into the network through the SBG.
•RADIUS
RADIUS (Remote Authentication Dial-In User Service) authentication is a popular protocol used to
authenticate users by means of an external or built-in RADIUS server. RADIUS authentication allows you
to validate a large number of users from a central location.
9.2 The Firewall Overview Screen
Use this screen to enable the firewall on the SBG. Click Configuration > Firewall / Security > Firewall
Overview to display the General screen.
Figure 109 Configuration > Firewall / Security > Firewall Overview
Click the check box to activate the firewall feature on the SBG, then click Apply to save your changes.
You can also use the Firewall Flow to go through the SBG’s firewall features.
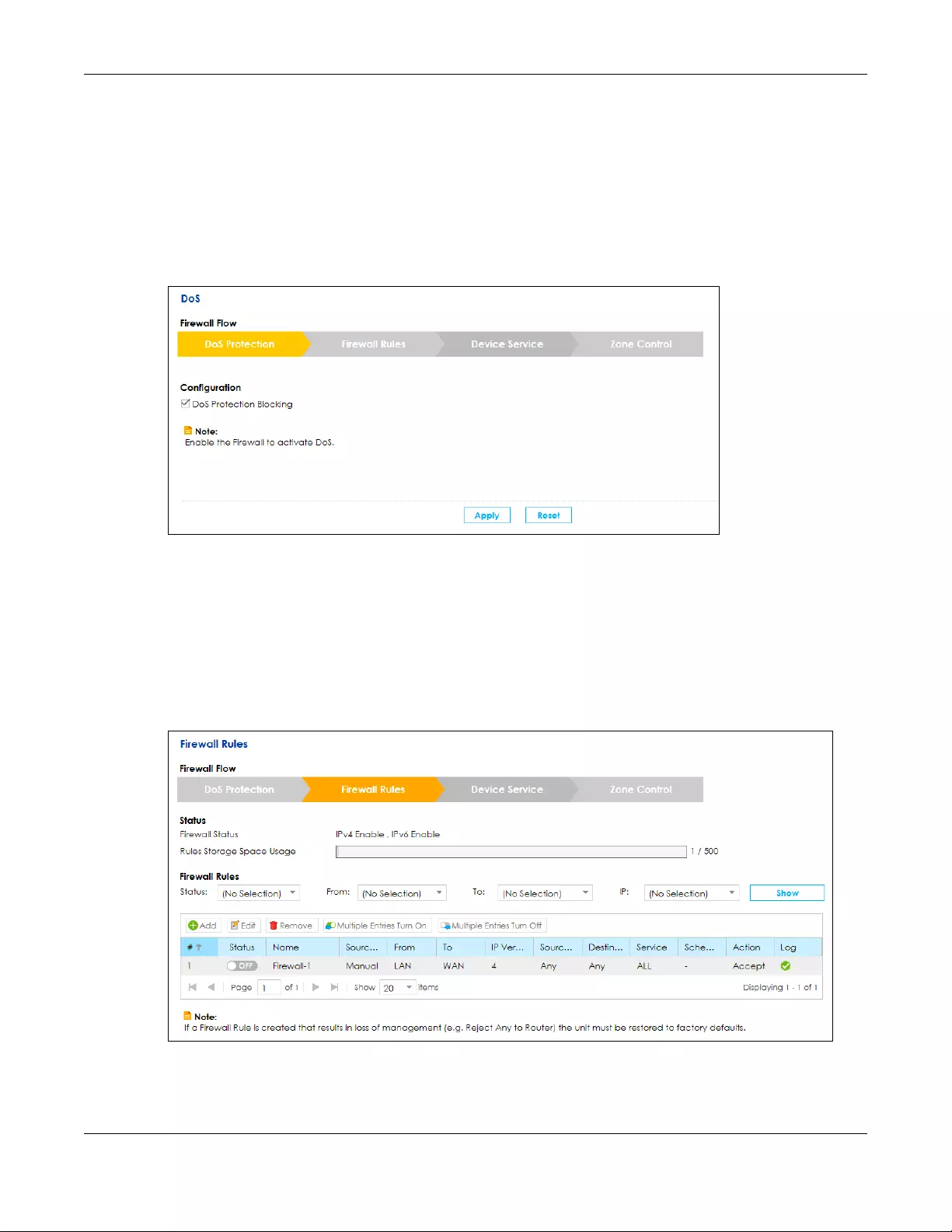
Chapter 9 Firewall
SBG5500 Series User’s Guide
141
9.3 The DoS Screen
DoS (Denial of Service) attacks can flood your Internet connection with invalid packets and connection
requests, using so much bandwidth and so many resources that Internet access becomes unavailable.
Click Configuration > Firewall / Security > DoS to display the following screen. Click the DoS Protection
Blocking check box to activate protection against DoS attacks. Then click Apply to save your settings.
Figure 110 Configuration > Firewall / Security > DoS
9.4 The Firewall Rules Screen
This screen displays a list of the configured firewall rules. Note the order in which the rules are listed,
ordering your rules is important because the SBG applies the rules in the order that you specify. Click
Configuration > Firewall / Security > Firewall Rules to display in the following screen.
Figure 111 Configuration > Firewall / Security > Firewall Rules
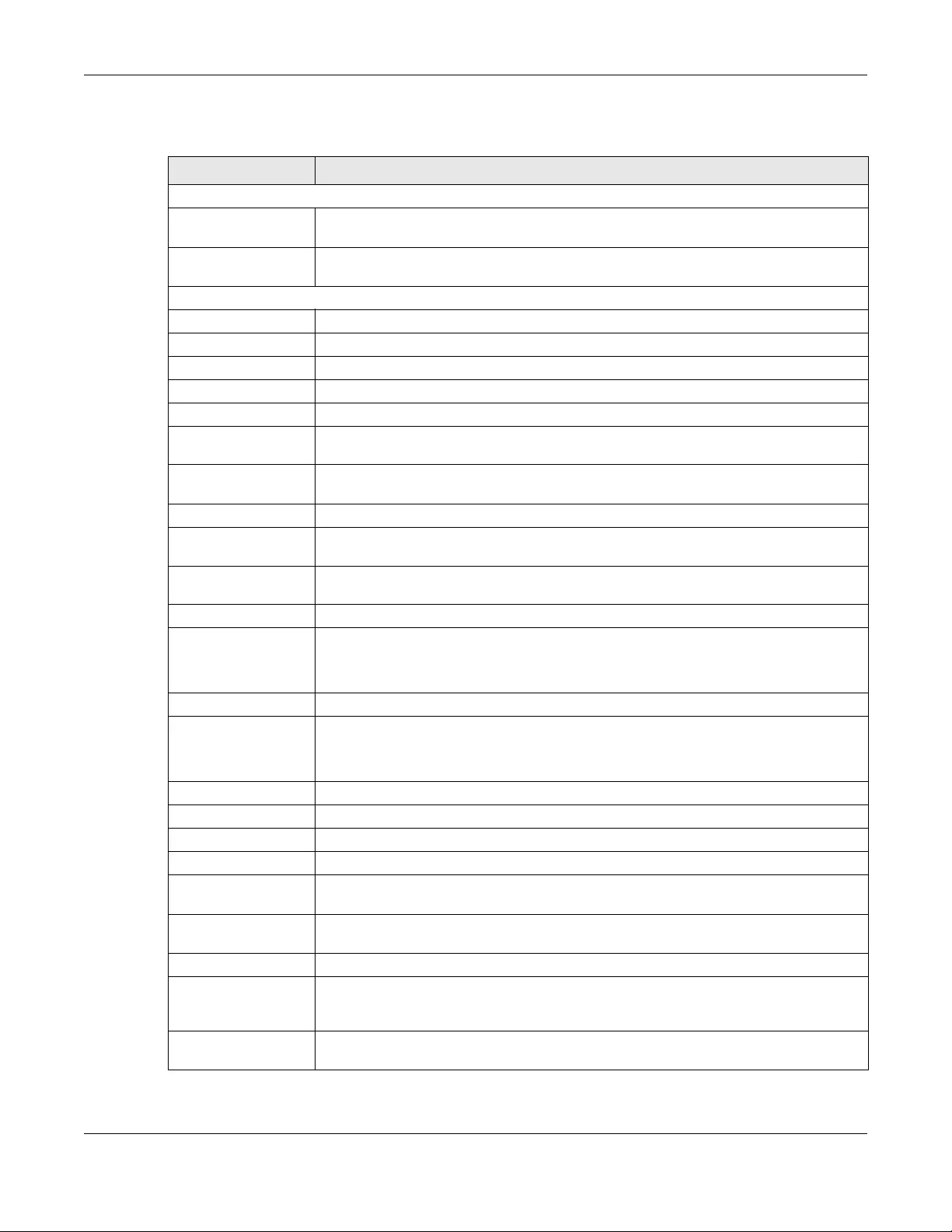
Chapter 9 Firewall
SBG5500 Series User’s Guide
142
The following table describes the labels in this screen.
Table 53 Configuration > Firewall / Security > Firewall Rules
LABEL DESCRIPTION
Status
Firewall Status This shows IPv4 Enable, IPv6 Enable when the firewall is enabled, otherwise it shows Disable.
You can change this in the Firewall Overview screen (Section 9.2 on page 140).
Rules Storage Space
Usage
This bar shows the percentage of the SBG’s space that has been used. If the usage is
almost full, you may need to remove an existing filter rule before you create a new one.
Firewall Rules
Status Select Enable to view all active firewall rules, or Disable to view all inactivate firewall rules.
From Select the source security zone of traffic to which the rule applies.
To Select the destination security zone of traffic to which the rule applies.
IP Select v4 to filter IPv4 address firewall rules or v6 for IPv6 addresses firewall rules.
Show Click this button to search the firewall rules with the filters you used.
Add Click this to create a new rule. Select a rule and click Add to create a new rule after the
selected entry.
Edit Double-click a rule or select it and click Edit to open a screen where you can modify the
rule’s settings.
Remove To remove an existing rule, select it and click Remove.
Multiple Entries Turn
On
Select one or more rules and click this to enable them.
Multiple Entries Turn
Off
Select one or more rules and click this to disable them.
# This is the index number of the rule.
Status This field displays whether the firewall rule is active or not. A green ON button signifies that
this firewall rule is active. A gray OFF button signifies that this firewall rule is not active.
Click the slide button to turn on or turn off the rule.
Name This displays the descriptive name of the rule.
Source Type This displays Manual when you create firewall rules on this screen.
This displays Auto when you have added an exception to the Firewall in the NAT > Port
Forwarding screen, see Section 8.2.1 on page 125.
From This displays the source security zone of traffic to which the rule applies.
To This displays the destination security zone of traffic to which the rule applies.
IP version This displays 4 if the rule applies to IPv4 addresses or 6 if it applies to IPv6 addresses.
Source IP This displays the source IP addresses to which this rule applies. Any means all IP addresses.
Destination IP This displays the destination IP addresses to which this rule applies. Any means all IP
addresses.
Service This displays the transport layer protocol that defines the service and the direction of traffic
to which this rule applies.
Schedule This field displays the scheduler rule used for this firewall rule.
Action This displays whether the rule allows packets (Accept), silently discards packets (Drop), or
discards packets and sends an ICMP destination-unreachable packet to the sender
(Reject).
Log This displays whether the SBG logs when it performs the ACL rule’s selected action on the
traffic traveling between the two zones.
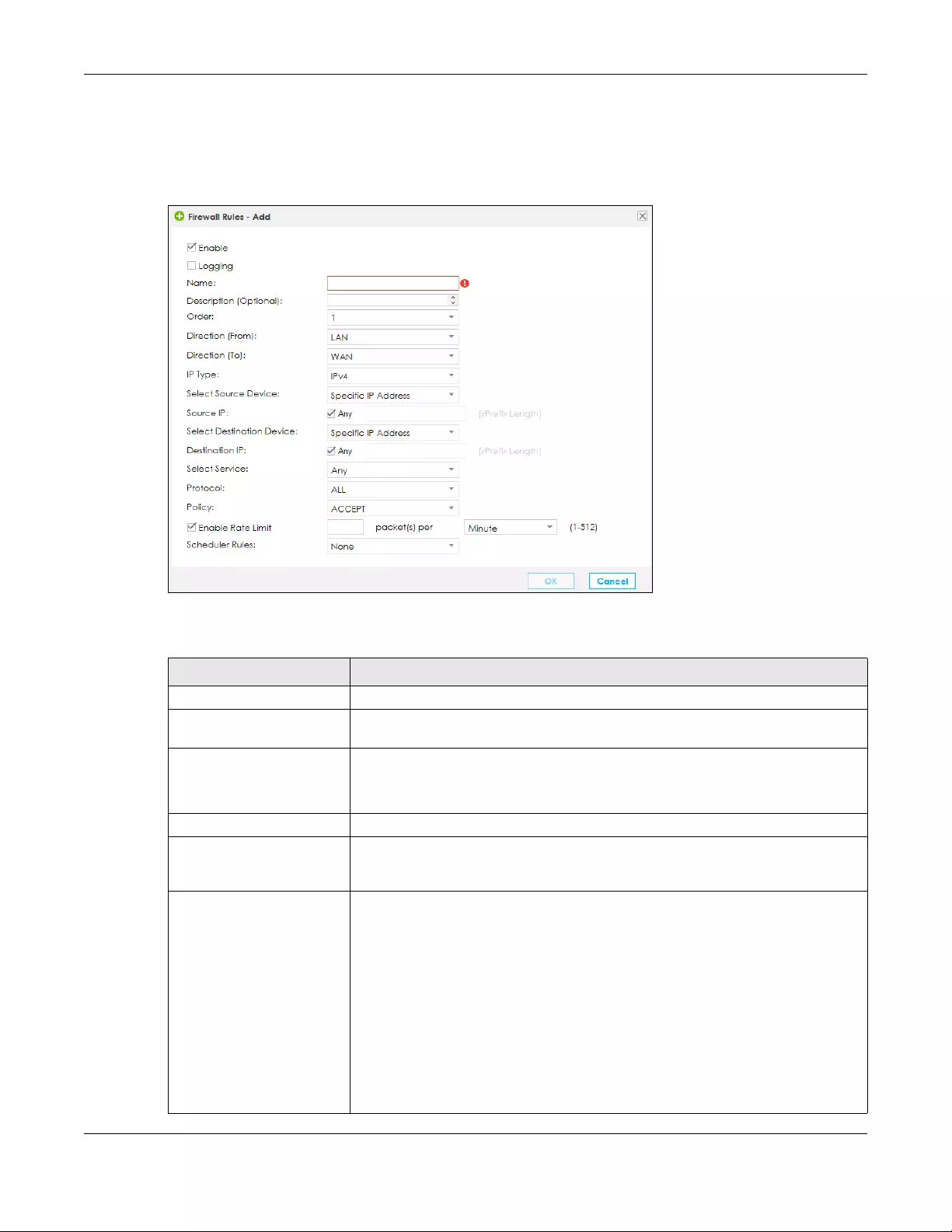
Chapter 9 Firewall
SBG5500 Series User’s Guide
143
9.4.1 Add/Edit a Firewall Rule
Click Add or select a firewall rule and click Edit to open the following screen.
Figure 112 Firewall Rules: Add/Edit
The following table describes the labels in this screen.
Table 54 Firewall Rules: Add/Edit
LABEL DESCRIPTION
Enable Select this to turn on the firewall rule.
Logging Select this to have the SBG log when it performs the firewall rule’s selected action on
the traffic traveling between the two zones.
Name Enter a descriptive name of up to 16 alphanumeric characters, not including
spaces.
You must enter the filter name to add a firewall rule.
Description (Optional) Enter a description to help you identify the purpose of the firewall rule.
Order Select an existing number for where you want to put this firewall rule to move the
firewall rule to the number you selected after clicking OK. Ordering your rules is
important because the SBG applies the rules in the order that you specify.
Direction Use the From and To define the direction of travel of packets to which to apply this
firewall rule. Select from which zone the packets come in and to which zone they
are destined. For example, From LAN To WAN means packets traveling from a
computer or subnet on the LAN zone to the WAN zone.
From Any means traffic coming from the WAN, LAN, WLAN, DMZ, and EXTRA zones
(but not the ROUTER zone).
To Any (excl. Router) means traffic going to the WAN, LAN, WLAN, DMZ, and EXTRA
zones (but not the ROUTER zone).
EXTRA is a local zone to use as needed depending on your network topology.
To ROUTER applies to traffic that destined for the SBG. Use this to control which
computers can manage the SBG.
Chapter 9 Firewall
SBG5500 Series User’s Guide
144
9.5 The Device Service Screen
Use this screen to configure through which interfaces, which services can access the SBG. You can also
specify the port numbers the services must use to connect to the SBG.
Use the Trust Domain section in this screen to view a list of public IP addresses which are allowed to
access the SBG through the services configured above.
Click Configuration > Firewall / Security > Device Service to open the following screen.
IP Type Select the type of IP you want to apply this firewall rule (IPv4 or IPv6).
Select Source Device Select the source device to which the firewall rule applies. If you select Specific
Address IP, enter the source IP address in the field below.
Source IP Enter the source IP address, or select Any to apply firewall rule to any source IP
addresses.
Select Destination Device Select the destination device to which the firewall rule applies. If you select Specific
Address IP, enter the source IP address in the field below.
Destination IP If you do not select Any, enter the destiniation IP address in this field.
Select Service Select the transport layer protocol that defines your customized port from the drop-
down list box. The specific protocol rule sets you add in the Configuration > Firewall /
Security > Service > Add screen display in this list.
Protocol This field is displayed only when you select Any in Select Service.
Choose the IP port (ALL, TCP, UDP, ICMP, or ICMP6) that defines your customized port
from the drop-down list box.
Policy Use the drop-down list box to select whether to discard (DROP), deny and send an
ICMP destination-unreachable message to the sender of (REJECT) or allow the
passage of (ACCEPT) packets that match this rule.
Enable Rate Limit Select this check box to set a limit on the upstream/downstream transmission rate for
the specified protocol.
Specify how many packet(s) per Minute or Second the transmission rate is.
Scheduler Rules Select a scheduler rule for this firewall rule form the drop-down list box. The scheduler
rules available are the ones you create in the Configuration > Firewall / Security >
Scheduler Rule screen.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 54 Firewall Rules: Add/Edit
LABEL DESCRIPTION
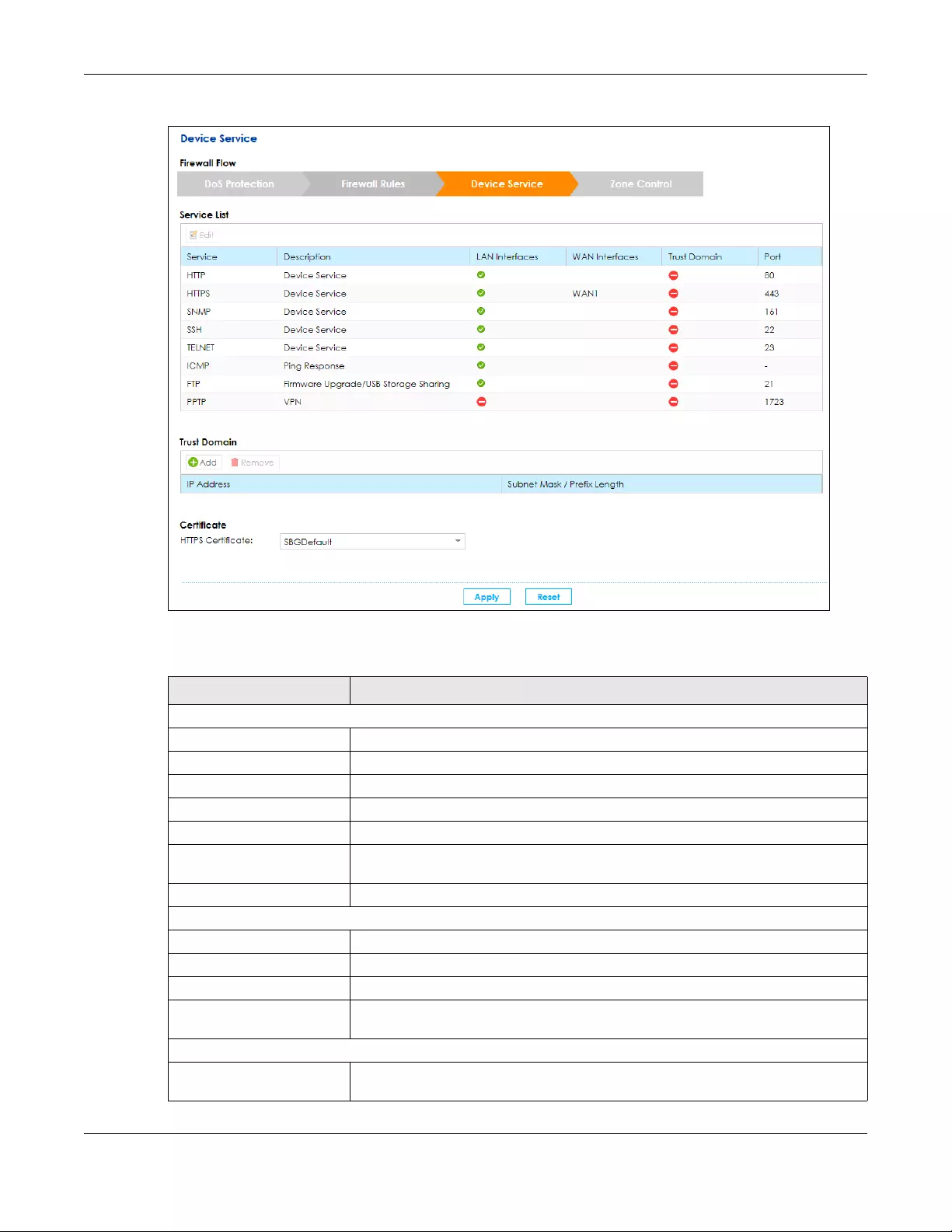
Chapter 9 Firewall
SBG5500 Series User’s Guide
145
Figure 113 Configuration > Firewall / Security > Device Service
The following table describes the labels in this screen.
Table 55 Configuration > Firewall / Security > Device Service
LABEL DESCRIPTION
Service List
Edit Select a service control and click Edit to modify it.
Service This is the service you may use to access the SBG.
Description This shows a description of the service.
LAN Interfaces This shows a check icon if the service is allowed access to the SBG from the LAN.
WAN Interfaces This shows the interfaces this service is allowed access to the SBG from the WAN.
Trust Domain This shows a check icon if the service is allowed access to the SBG from the Trust
Domain.
Port This field displays the server port number for the service.
Trust Domain
Add Click this to add a trusted host IP address,
Remove Click this to remove the trusted IP address.
IP Address This field shows a trusted host IP address.
Subnet Mask / Prefix Length This shows the prefix length that specifies how many most significant bits are in the
trusted host IP address,
Certificate
HTTPS Certificate Select a certificate the HTTPS server (the SBG) uses to authenticate itself to the HTTPS
client. You must have certificates already configured in the Certificates screen.
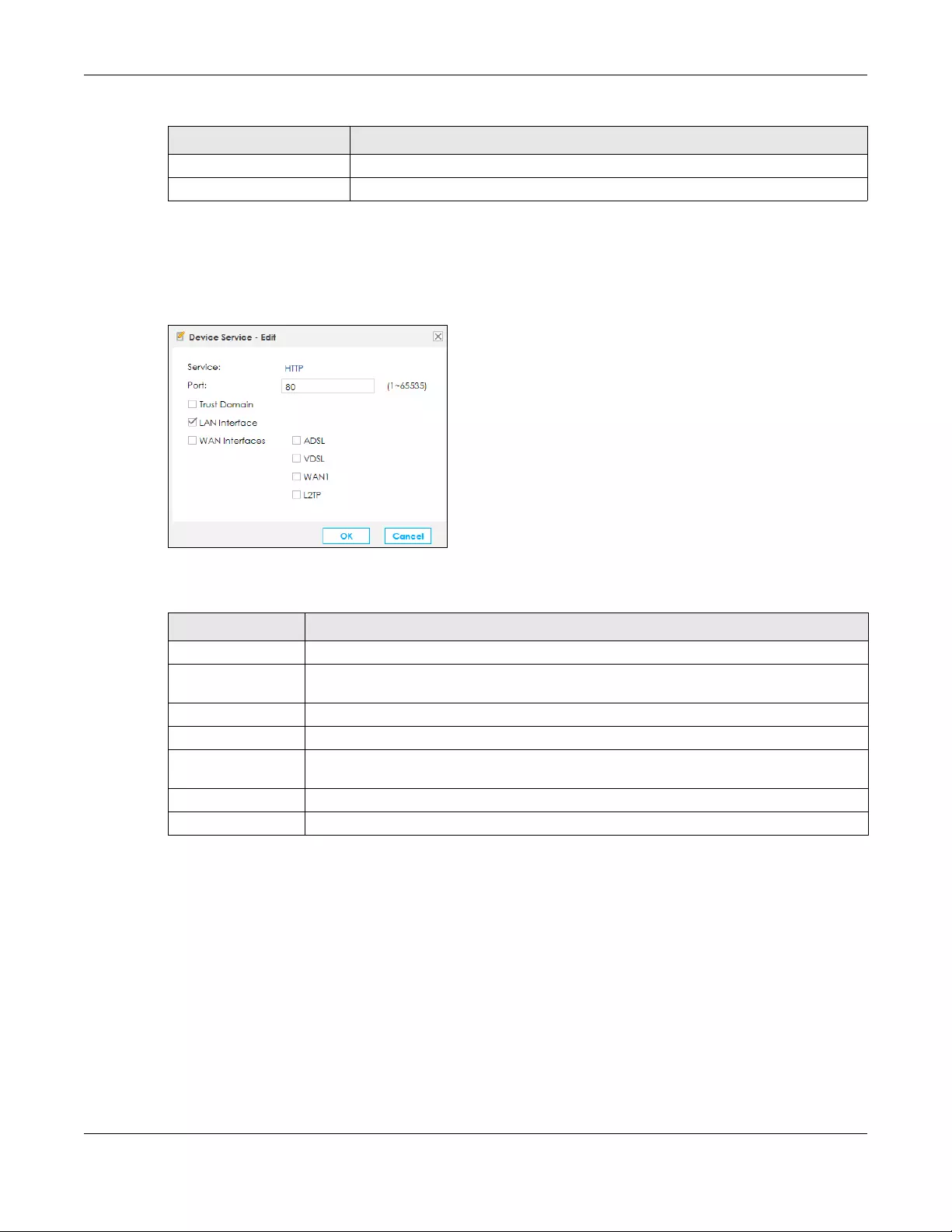
Chapter 9 Firewall
SBG5500 Series User’s Guide
146
9.5.1 Edit a Device Service
Double click a Service or select one and click Edit to open the following screen.
Figure 114 Device Service: Edit
The following table describes the labels in this screen.
9.5.2 Add/Edit a Trust Domain
Use this screen to configure a public IP address which is allowed to access the SBG. Double click an IP
Address or select one and click Edit to open the following screen.
Apply Click Apply to save your changes.
Reset Click Reset to restore your previously saved settings.
Table 55 Configuration > Firewall / Security > Device Service
LABEL DESCRIPTION
Table 56 Device Service: Edit
LABEL DESCRIPTION
Service This is the service you may use to access the SBG.
Port You may change the server port number for a service if needed, however you must use the
same port number in order to use that service for remote management.
Trust Domain Click the check box if the services is allowed access to the SBG from the trust domain.
LAN Interface Click the check box if the services are allowed access to the SBG from the LAN.
WAN Interface Click the check box if the services are allowed access to the SBG from all WAN connections,
or specify the interfaces individually.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
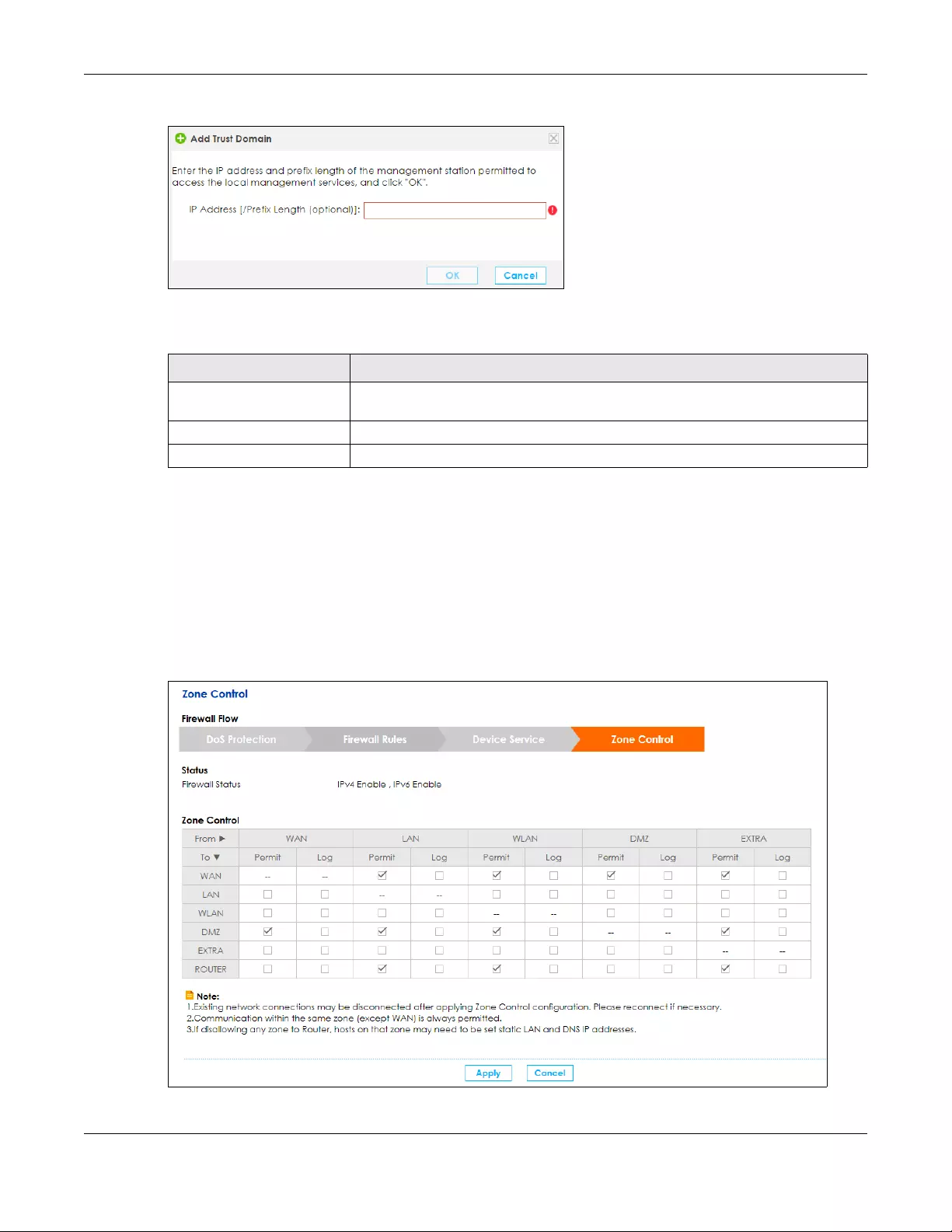
Chapter 9 Firewall
SBG5500 Series User’s Guide
147
Figure 115 Trust Domain: Add/Edit
The following table describes the labels in this screen.
9.6 The Zone Control Screen
Use this screen to set the firewall’s default actions. Firewall rules are grouped based on the direction of
travel of packets to which they apply.
Click Configuration > Firewall / Security > Zone Control to display the following screen.
Figure 116 Configuration > Firewall > Security > Zone Control
Table 57 Trust Domain: Add/Edit
LABEL DESCRIPTION
IP Address [/Prefix Length
(optional)]
Enter a public IPv4 IP address which is allowed to access the service on the SBG from
the WAN. You can also enter the prefix length of the IP address.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Chapter 9 Firewall
SBG5500 Series User’s Guide
148
The following table describes the labels in this screen.
9.7 The Scheduler Rule Screen
Use the Scheduler Rule screen to define time periods and days during which the SBG performs
scheduled rules of certain features (such as a Firewall). Click Configuration > Firewall / Security >
Scheduler Rule to open the following screen.
Figure 117 Configuration > Firewall / Security > Scheduler Rule
The following table describes the labels in this screen.
Table 58 Configuration > Firewall / Security > Zone Control
LABEL DESCRIPTION
Status
Firewall Status This shows IPv4 Enable, IPv6 Enable when the firewall is enabled, otherwise it shows Disable. You
can change this in the Firewall Overview screen (Section 9.2 on page 140).
Zone Control
From/To The firewall rules are grouped by the direction of packet travel and their zones (WAN, LAN,
WLAN, DMZ, EXTRA and ROUTER). By default, the firewall allows passage of packets traveling in
the same zone (a LAN to a LAN, a WAN to a WAN). Here are some example descriptions of the
directions of travel.
From LAN To LAN means packets traveling from a computer on one LAN subnet to a computer
on another LAN subnet on the LAN interface of the device.
You can define the EXTRA zone to include the VPN connection. The Router zone can only be
controlled in ingress direction “to” because it is reserved for the router’s CPU. However, packets
sent from the router zone are always permitted. For example, if your packet come from a LAN
zone and is going to the Router zone. The SBG will apply the firewall rules to the LAN packets if
you did not click the Permit check box.
When Permit box is unchecked and Log box is checked, it means the “dropped” packets will be
logged. When both Permit and Log boxes are checked, it means the “permitted” packets will
be logged.
Permit Click the check box Permit to allow the passage of the packets.
Log Click the check box Log to create a log when an action from Firewall rule is taken.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 59 Configuration > Firewall / Security > Scheduler Rule
LABEL DESCRIPTION
Add Click this to create a new scheduler rule. Select a rule and click Add to create a new rule after
the selected entry.
Edit Double-click a scheduler rule or select it and click Edit to open a screen where you can modify
the rule’s settings.
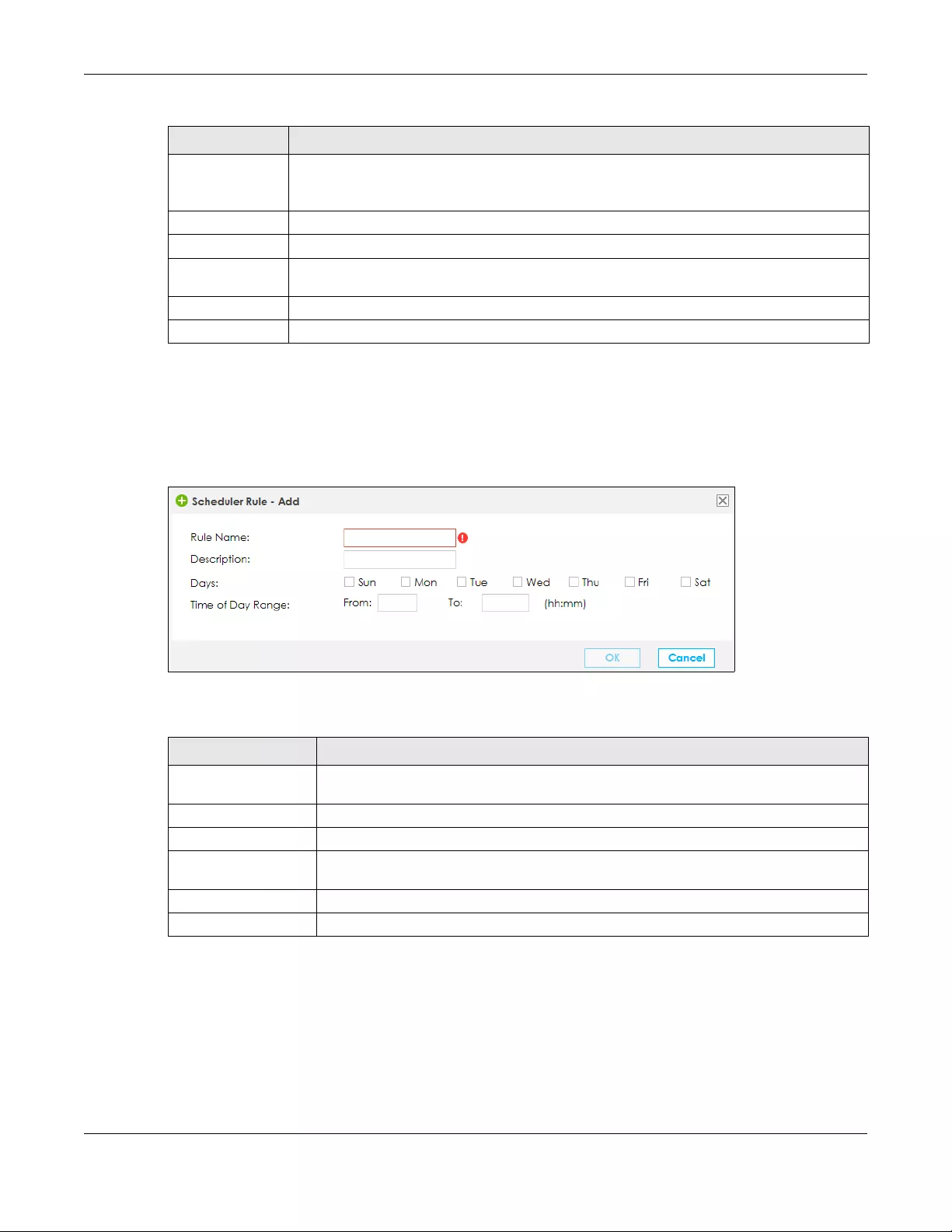
Chapter 9 Firewall
SBG5500 Series User’s Guide
149
9.7.1 Add/Edit a Scheduler Rule
Click Add in the Scheduler Rule screen, or select a rule and click Edit to open the following screen. Use
this screen to configure a restricted access schedule.
Figure 118 Scheduler Rule: Add/Edit
The following table describes the labels in this screen.
9.8 The Service Screen
You can configure customized services and port numbers in the Service screen. For a comprehensive list
of port numbers and services, visit the IANA (Internet Assigned Number Authority) website.
Click Configuration > Firewall / Security > Service to display the following screen.
Remove To remove an existing scheduler rule, select it and click Remove.
Note: You cannot delete a scheduler rule once it is applied to a certain feature.
# This is the index number of the rule.
Rule Name This is the name of the rule.
Days This shows the day(s) on which this rule is enabled. Green days show when the rule is enabled,
Gray days show when the rule is disabled.
Time This shows the period of time on which this rule is enabled.
Description This shows the description of this rule.
Table 59 Configuration > Firewall / Security > Scheduler Rule
LABEL DESCRIPTION
Table 60 Scheduler Rule: Add/Edit
LABEL DESCRIPTION
Rule Name Enter a name (up to 31 printable characters English keyboard characters, not including
spaces) for this schedule.
Description Enter a description for this scheduler rule.
Days Select the check boxes for the days that you want the SBG to perform this scheduler rule.
Time of Day Range Enter the time period of each day, in 24-hour format, during which the rule will be
enforced.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
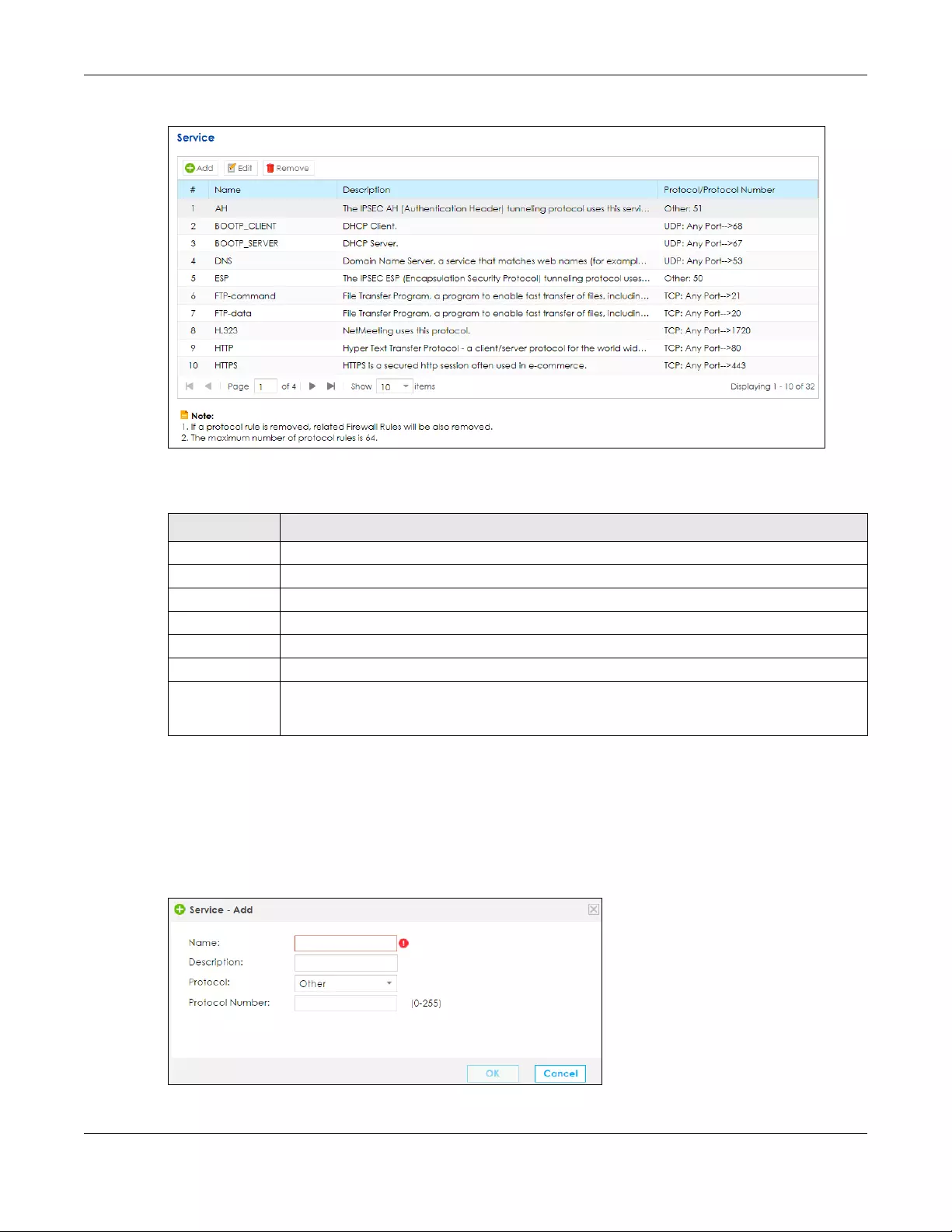
Chapter 9 Firewall
SBG5500 Series User’s Guide
150
Figure 119 Configuration > Firewall / Security > Service
The following table describes the labels in this screen.
9.8.1 Add/Edit a Service
Use this screen to add a customized service rule that you can use in the firewall’s ACL rule configuration.
Click Add or select an existing service rule and click Edit in the Service screen to display the following
screen.
Figure 120 Service: Add/Edit
Table 61 Configuration > Firewall / Security > Service
LABEL DESCRIPTION
Add Click this to add a new service.
Edit Click this to modify an existing service,
Remove Click this to remove a service,
#This is the index number of the service.
Name This is the name of your customized service.
Description This is the description of your customized service.
Protocol/
Protocol
Number
This shows the IP protocol (TCP, UDP, ICMP, or TCP/UDP) and the port number or range of ports
that defines your customized service. Other and the protocol number displays if the service uses
another IP protocol.
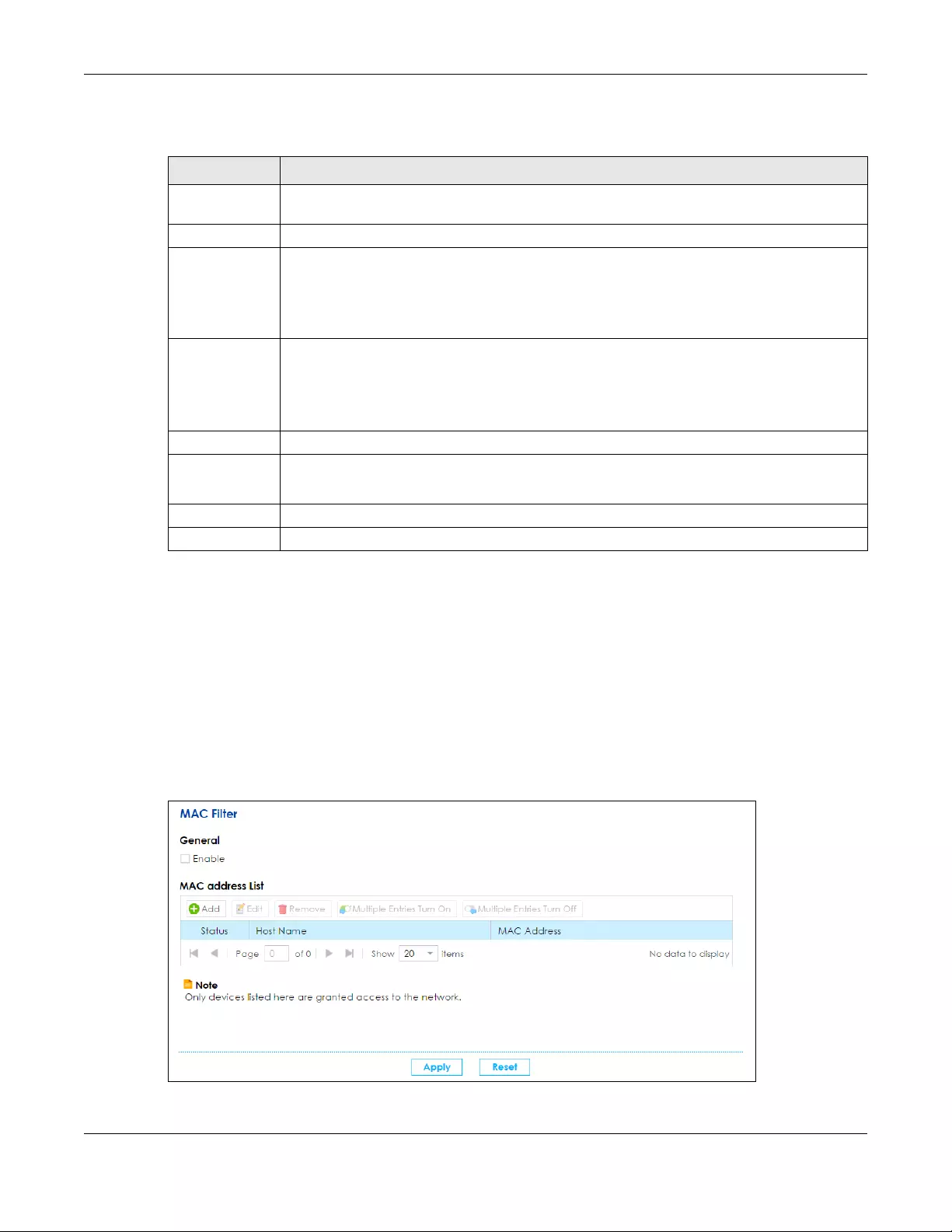
Chapter 9 Firewall
SBG5500 Series User’s Guide
151
The following table describes the labels in this screen.
9.9 The MAC Filter Screen
You can configure the SBG to permit access to clients based on their MAC addresses in the MAC Filter
screen. Every Ethernet device has a unique MAC (Media Access Control) address. The MAC address is
assigned at the factory and consists of six pairs of hexadecimal characters, for example,
00:A0:C5:00:00:02. You need to know the MAC addresses of the devices to configure this screen.
Click Configuration > Firewall / Security > MAC Filter to open the following screen.
Figure 121 Configuration > Firewall / Security > MAC Filter
Table 62 Service: Add/Edit
LABEL DESCRIPTION
Name Enter a unique name (up to 32 printable English keyboard characters, including spaces) for your
customized port.
Description Enter a description for your customized port.
Protocol Choose the IP protocol (TCP, UDP, ICMP, Other, or ICMPv6) that defines your customized port
from the drop-down list box.
Select Other to be able to enter a protocol number.
Select ICMPv6 to be able to select a packet type.
Source/
Destination Port
These fields are displayed if you select TCP or UDP as the IP port.
Select Single to specify one port only or Range to specify a span of ports that define your
customized service. If you select Any, the service is applied to all ports.
Type a single port number or the range of port numbers that define your customized service.
ICMPv6 Type Select an ICMPv6 packet type.
Protocol
Number
This field is displayed if you select Other as the protocol.
Enter the protocol number of your customized port.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Chapter 9 Firewall
SBG5500 Series User’s Guide
152
The following table describes the labels in this screen.
9.9.1 MAC Filter: Add/Edit
Click Add or select an existing MAC filter rule and click Edit to display the following screen.
Figure 122 MAC Filter: Add/Edit
The following table describes the labels in this screen.
Table 63 Configuration > Firewall / Security > MAC Filter
LABEL DESCRIPTION
General
Enable Select Enable to activate the MAC filter function.
MAC Address List
Add Click this to create a new MAC filter rule. Select a rule and click Add to create a new rule
after the selected entry.
Edit Double-click a MAC filter rule or select it and click Edit to open a screen where you can
modify the rule’s settings.
Remove To remove an existing MAC filter rule, select it and click Remove.
Multiple Entries Turn On Select one or more MAC filter rules and click this to enable them.
Multiple Entries Turn Off Select one or more MAC filter rules and click this to disable them.
Status This field displays whether the MAC filter rule is active or not. A green ON button signifies
that this MAC filter rule is active. A gray OFF button signifies that this MAC filter rule is not
active.
Click the slide button to turn on or turn off the rule.
Host Name This field displays host name of the LAN clients that are allowed access to the SBG.
MAC Address This field displays the MAC addresses of the LAN clients that are allowed access to the
SBG in these address fields.
Apply Click Apply to save your changes.
Reset Click Reset to restore your previously saved settings.
Table 64 MAC Filter: Add/Edit
LABEL DESCRIPTION
Enable Select this to enable the MAC filter rule. The rule will not be applied if Enable is not
selected.
Host Name Enter the host name of the LAN clients that are allowed access to the SBG.
MAC Address Enter the MAC addresses of the LAN clients that are allowed access to the SBG in these
address fields. Enter the MAC addresses in a valid MAC address format, that is, six
hexadecimal character pairs, for example, 12:34:56:78:9a:bc.
Chapter 9 Firewall
SBG5500 Series User’s Guide
153
9.10 The Certificate Screen
The SBG can use certificates (also called digital IDs) to authenticate users. Certificates are based on
public-private key pairs. A certificate contains the certificate owner’s identity and public key.
Certificates provide a way to exchange public keys for use in authentication. Click Configuration >
Firewall /Security > Certificate to open the following screen.
Figure 123 Configuration > Firewall / Security > Certificate
The following table describes the labels in this screen.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 64 MAC Filter: Add/Edit
LABEL DESCRIPTION
Table 65 Configuration > Firewall / Security > Certificate
LABEL DESCRIPTION
My Certificate Settings / Trusted CA Settings
Add Click this to create a new certificate. Select a rule and click Add to create a new certificate
after the selected entry.
Remove To remove an existing certificate, select it and click Remove.
More Information Select a certificate and click More Information to view all details about the certificate.
Import Click this button to save the certificate that you have enrolled from a certification authority
from your computer to the SBG.
# This is the index number of the rule.
Name This field displays the descriptive name used to identify this certificate. It is recommended
that you give each certificate a unique name.
Subject This field displays identifying information about the certificate’s owner, such as CN
(Common Name), OU (Organizational Unit or department), O (Organization or company)
and C (Country). It is recommended that each certificate have unique subject information.
Chapter 9 Firewall
SBG5500 Series User’s Guide
154
9.11 The AAA Server
You can use a AAA (Authentication, Authorization, Accounting) server to provide access control to your
network. The AAA server can be a RADIUS server. Use the AAA Server screens to create and manage
objects that contain settings for using AAA servers. Click Configuration > Firewall / Security > AAA Server
to open the following screen.
Figure 124 Configuration > Firewall / Security > AAA Server
The following table describes the labels in this screen.
Type This field displays general information about the certificate.
It displays Self when the certificate is self-signed.
It displays Import when the certificate used is imported.
Issuer This field displays identifying information about the certificate’s issuing certification authority,
such as a common name, organizational unit or department, organization or company and
country.
Valid From This field displays the date that the certificate becomes applicable. The text displays in red
and includes a Not Yet Valid! message if the certificate has not yet become applicable.
Valid To This field displays the date that the certificate expires. The text displays in red and includes
an Expiring! or Expired! message if the certificate is about to expire or has already expired.
Table 65 Configuration > Firewall / Security > Certificate
LABEL DESCRIPTION
Configuration > Firewall / Security > AAA Server
LABEL DESCRIPTION
LDAP Server Summary
Add Click this to create a new server. Select a rule and click Add to create a new server
after the selected entry.
Edit Double-click a server or select it and click Edit to open a screen where you can
modify the server’s settings.
Remove To remove an existing server, select it and click Remove.
# This field displays the index number.
Name This field displays the name of the LDAP server entry.
Server Address This field displays the address of the LDAP server.
Base DN This field displays the domain name of the LDAP server.
Chapter 9 Firewall
SBG5500 Series User’s Guide
155
9.11.1 Add/Edit an LDAP Server
Click Add icon or select a server and click Edit to display the following screen. Use this screen to create
a new LDAP entry or edit an existing one.
Figure 125 LDAP Server: Add/Edit
RADIUS Server Summary
Add Click this to create a new server. Select a rule and click Add to create a new server
after the selected entry.
Edit Double-click a server or select it and click Edit to open a screen where you can
modify the server’s settings.
Remove To remove an existing server, select it and click Remove.
# This field displays the index number.
Name This field displays the name of the RADIUS server entry.
Server Address This field displays the address of the RADIUS server.
Configuration > Firewall / Security > AAA Server
LABEL DESCRIPTION

Chapter 9 Firewall
SBG5500 Series User’s Guide
156
The following table describes the labels in this screen.
Table 66 LDAP Server: Add/Edit
LABEL DESCRIPTION
General Settings
Name Enter a descriptive name for identification purposes. It cannot exceed 64 characters
[0-9][A-Z] [a-z][_-].
Description Enter the description of each server, if any. You can use up to 128 printable ASCII
characters.
Server Settings
Server Address Enter an IP address or Fully-Qualified Domain Name (FQDN) of the LDAP
authentication server.
Backup Server Address If the LDAP server has a backup authentication server, enter its IP address or FQDN
here.
Port Specify the port number on the LDAP server to which the SBG sends authentication
requests. Enter a number between 1 and 65535.
Base DN Specify the directory (up to 127 alphanumerical characters). For example, o=Zyxel,
c=US.
This is only for LDAP.
Use SSL Select Use SSL to establish a secure connection to the LDAP server(s).
Search time limit Specify the timeout period (between 1 and 300 seconds) before the SBG
disconnects from the LDAP server. In this case, user authentication fails.
Search timeout occurs when either the user information is not in the LDAP server(s) or
the LDAP server(s) is down.
Case-sensitive User Names Select this if the server checks the case of the user names.
Server Authentication
Bind DN Specify the bind DN for logging into the LDAP server. Enter up to 127 alphanumerical
characters.
For example, cn=zyxelAdmin specifies zyxelAdmin as the user name.
Password If required, enter the password (up to 15 alphanumerical characters) for the SBG to
bind (or log in) to the AD or LDAP server.
Retype to Confirm Retype your new password for confirmation.
User Login Settings
Login Name Attribute Enter the type of identifier the users are to use to log in. For example “name” or “e-
mail address”.
Alternative Login Name
Attribute
If there is a second type of identifier that the users can use to log in, enter it here. For
example “name” or “e-mail address”.
Group Membership
Attribute
An LDAP server defines attributes for its accounts. Enter the name of the attribute
that the SBG is to check to determine to which group a user belongs. The value for
this attribute is called a group identifier; it determines to which group a user belongs.
You can add ext-group-user objects to identify groups based on these group
identifier values.
For example you could have an attribute named “memberOf” with values like
“sales”, “RD”, and “management”. Then you could also create a ext-group-user
object for each group. One with “sales” as the group identifier, another for “RD” and
a third for “management”.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
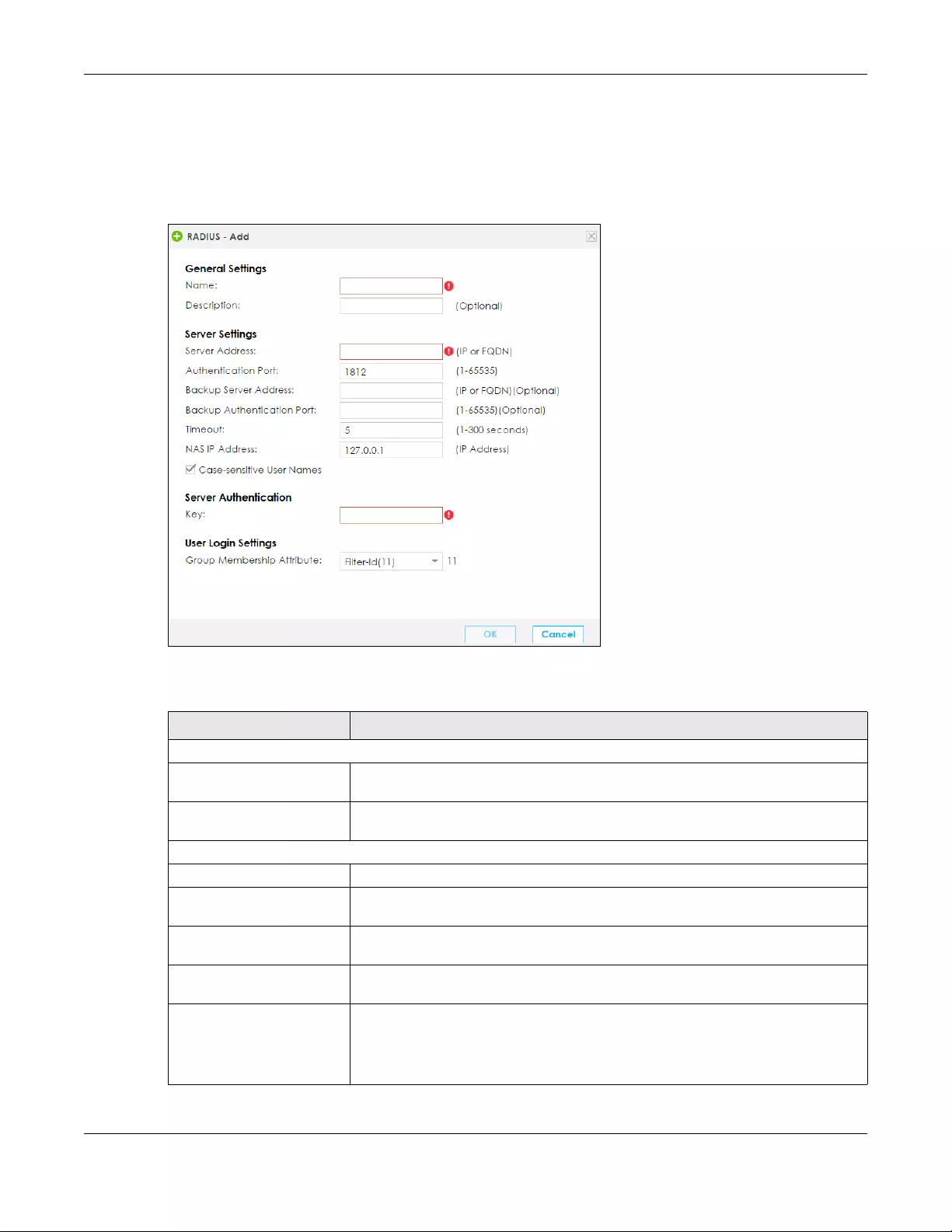
Chapter 9 Firewall
SBG5500 Series User’s Guide
157
9.11.2 Add/Edit an RADIUS Server
Click Add icon or select a server and click Edit to display the following screen. Use this screen to create
a new RADIUS entry or edit an existing one.
Figure 126 RADIUS Server: Add/Edit
The following table describes the labels in this screen.
Table 67 RADIUS Server: Add/Edit
LABEL DESCRIPTION
General Settings
Name Enter a descriptive name (up to 64 alphanumerical characters) for identification
purposes.
Description Enter the description of each server, if any. You can use up to 128 printable ASCII
characters.
Server Settings
Server Address Enter the IP address or FQDN of the RADIUS authentication server.
Authentication Port Specify the port number on the RADIUS server to which the SBG sends
authentication requests. Enter a number between 1 and 65535.
Backup Server Address If the RADIUS server has a backup authentication server, enter its IP address or FQDN
here.
Backup Authentication Port Specify the port number on the RADIUS server to which the SBG sends
authentication requests. Enter a number between 1 and 65535.
Timeout Specify the timeout period (between 1 and 300 seconds) before the SBG
disconnects from the RADIUS server. In this case, user authentication fails.
Search timeout occurs when either the user information is not in the RADIUS server or
the RADIUS server is down.
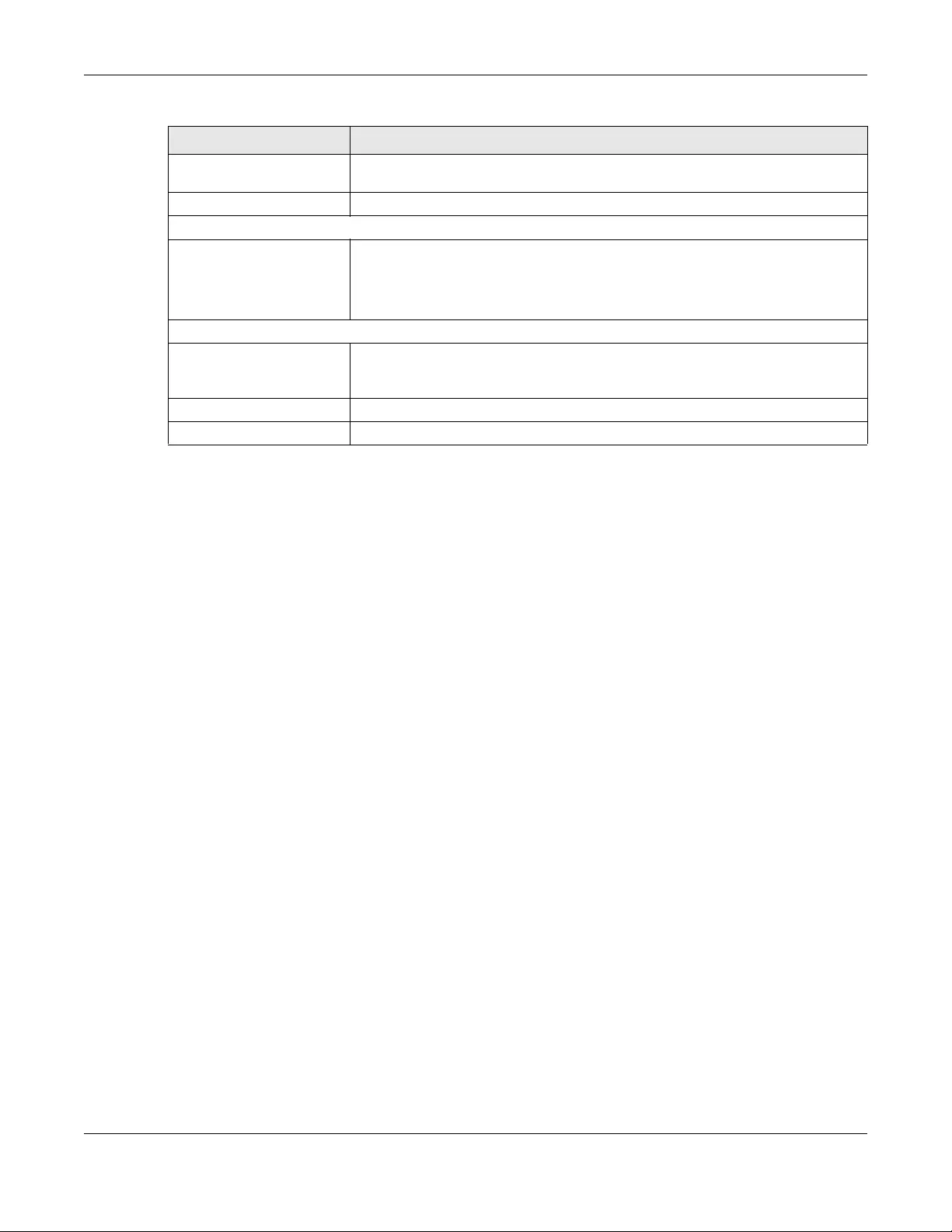
Chapter 9 Firewall
SBG5500 Series User’s Guide
158
NAS IP Address If the RADIUS server requires the SBG to provide the Network Access Server IP
address attribute with a specific value, enter it here.
Case-sensitive User Names Select this if the server checks the case of the user names.
Server Authentication
Key Enter a password (up to 32 characters) as the key to be shared between the
external authentication server and the SBG.
The key is not sent over the network. This key must be the same on the external
authentication server and the SBG.
User Login Settings
Group Membership
Attribute
A RADIUS server defines attributes for its accounts. Select the name and number of
the attribute that the SBG is to check to determine to which group a user belongs. If
it does not display, select User Defined and specify the attribute’s number.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 67 RADIUS Server: Add/Edit
LABEL DESCRIPTION

SBG5500 Series User’s Guide
159
CHAPTER 10
VPN
10.1 Overview
A virtual private network (VPN) provides secure communications between sites without the expense of
leased site-to-site lines. A secure VPN is a combination of tunneling, encryption, authentication, access
control and auditing. It is used to transport traffic over the Internet or any insecure network that uses
TCP/IP for communication.
10.2 What You Can Do in this Chapter
• Use the VPN Status screen to look at the VPN tunnels currently established in the SBG (Section 10.4 on
page 162).
• Use the IPsec VPN screen to display and manage active IPsec VPN connections (Section 10.5 on
page 163).
• Use the PPTP VPN screen to configure the PPTP VPN settings in the SBG(Section 10.6 on page 176).
• Use the L2TP VPN screen to configure the SBG’s L2TP VPN settings(Section 10.7 on page 179).
• Use the L2TP Client Status screen to view connection details for L2TP clients (Section 10.8 on page
185).
10.3 What You Need to Know
IPsec VPN
Internet Protocol Security (IPsec) is a standards-based VPN that offers flexible solutions for secure data
communications across a public network like the Internet. IPsec is built around a number of
standardized cryptographic techniques to provide confidentiality, data integrity and authentication at
the IP layer.
The following figure provides one perspective of a VPN tunnel.
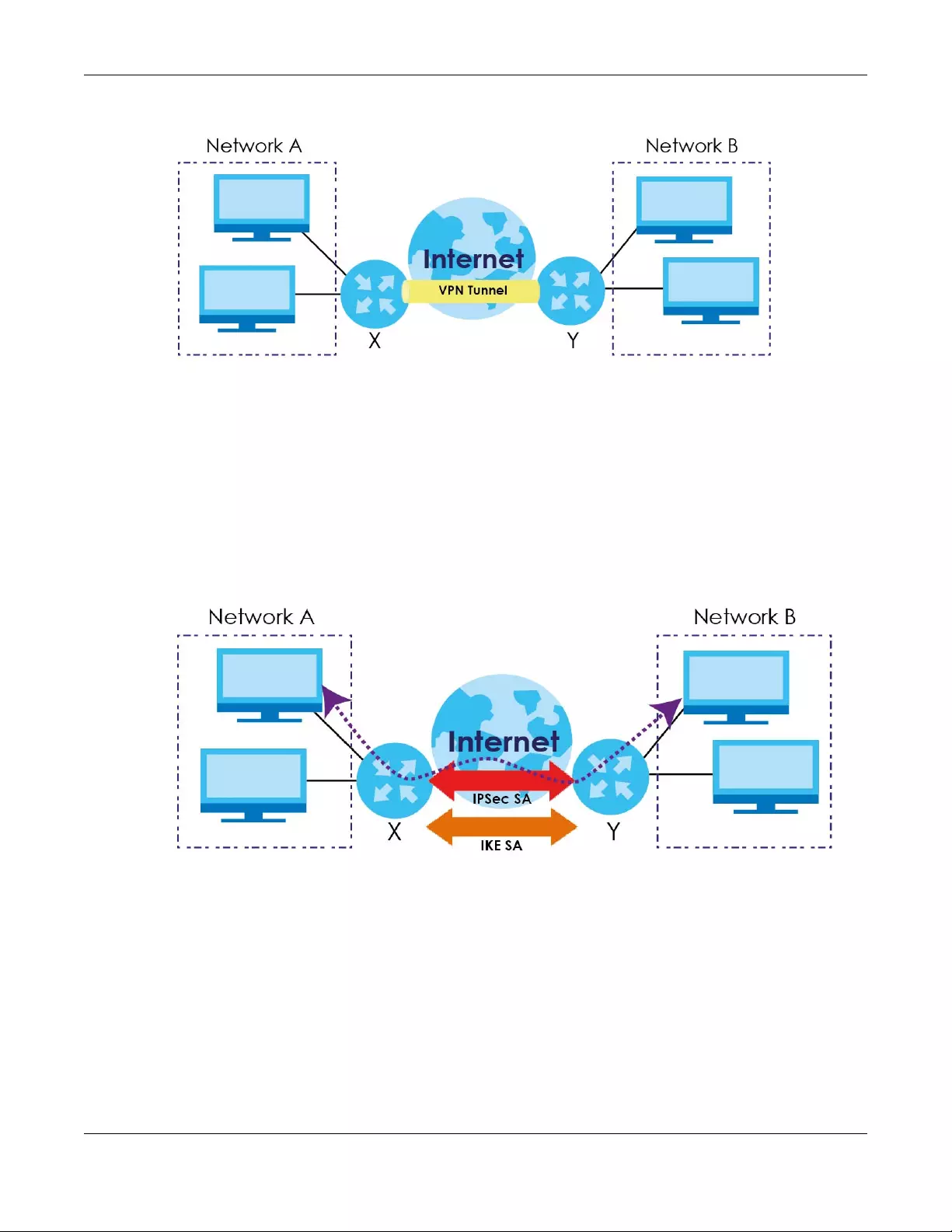
Chapter 10 VPN
SBG5500 Series User’s Guide
160
Figure 127 IPsec VPN: Overview
The VPN tunnel connects the SBG (X) and the remote IPsec router (Y). These routers then connect the
local network (A) and remote network (B).
A VPN tunnel is usually established in two phases. Each phase establishes a security association (SA), a
contract indicating what security parameters the SBG and the remote IPsec router will use.
The first phase establishes an Internet Key Exchange (IKE) SA between the SBG and remote IPsec router.
The second phase uses the IKE SA to securely establish an IPsec SA through which the SBG and remote
IPsec router can send data between computers on the local network and remote network. The
following figure illustrates this.
Figure 128 VPN: IKE SA and IPsec SA
In this example, a computer in network A is exchanging data with a computer in network B. Inside
networks A and B, the data is transmitted the same way data is normally transmitted in the networks.
Between routers X and Y, the data is protected by tunneling, encryption, authentication, and other
security features of the IPsec SA. The IPsec SA is established securely using the IKE SA that routers X and Y
established first.
PPTP VPN
Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables secure transfer of data from a
remote client to a private server, creating a VPN using TCP/IP-based networks. PPTP supports on-
demand, multi-protocol and virtual private networking over public networks, such as the Internet.
SBG
SBG
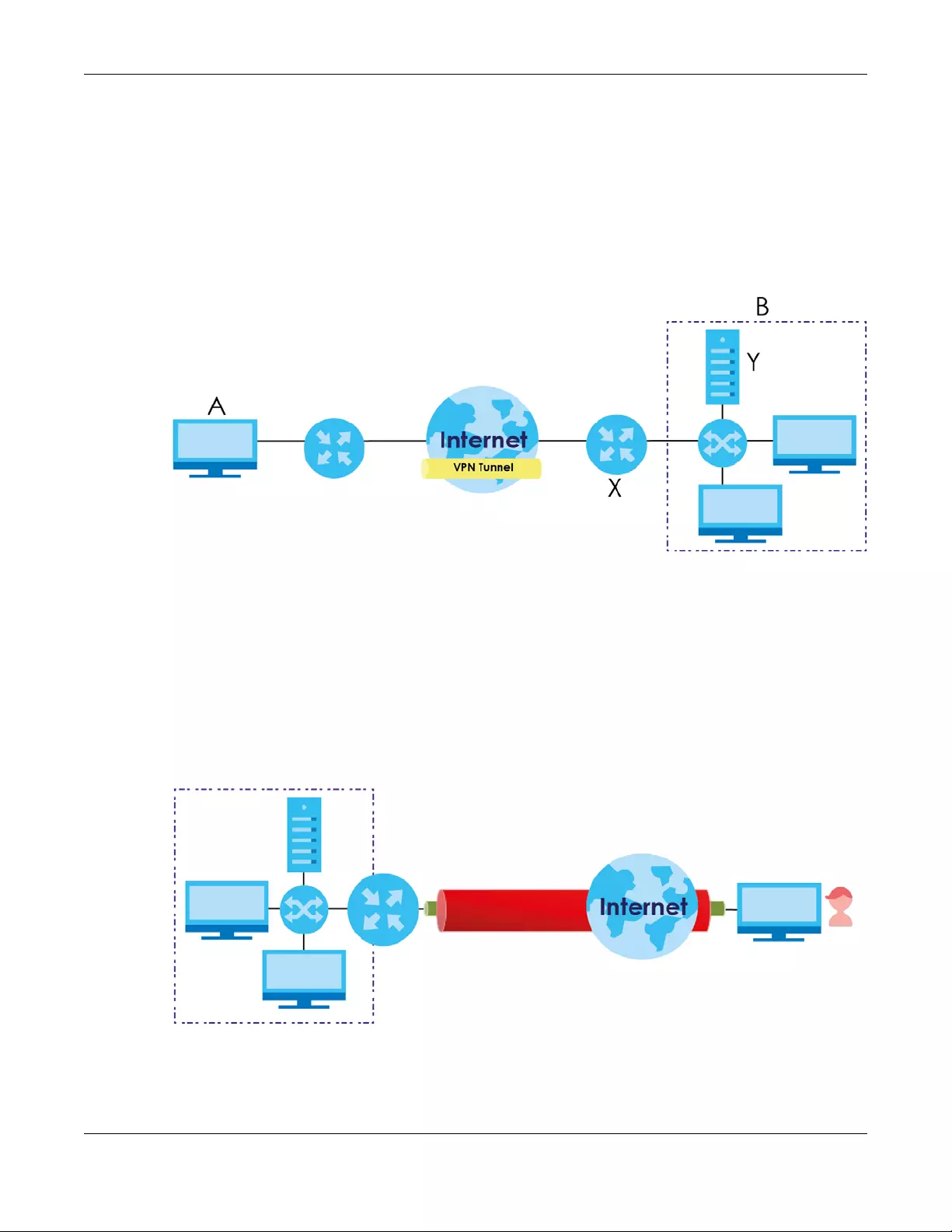
Chapter 10 VPN
SBG5500 Series User’s Guide
161
PPTP sets up two sessions and uses Generic Routing Encapsulation (GRE, RFC 2890) to transfer
information between the computers. It is convenient and easy-to-use, but you have to make sure that
firewalls support both PPTP sessions.
PPTP works on a client-server model and is suitable for remote access applications. For example, an
employee (A) can connect to the PPTP VPN gateway (X) as a PPTP client to gain access to the
company network resources from outside the office. When you connect to a remote network (B)
through a PPTP VPN, all of your traffic goes through the PPTP VPN gateway (X).
Figure 129 PPTP VPN Example
L2TP VPN
The Layer 2 Tunneling Protocol (L2TP) works at layer 2 (the data link layer) to tunnel network traffic
between two peers over another network (like the Internet). In L2TP VPN, an IPsec VPN tunnel is
established first and then an L2TP tunnel is built inside it.
L2TP VPN lets remote users use the L2TP and IPsec client software included with their computers’
operating systems to securely connect to the network behind the SBG. The remote users do not need
their own IPsec gateways or VPN client software.
Figure 130 L2TP VPN Overview
SBG
SBG
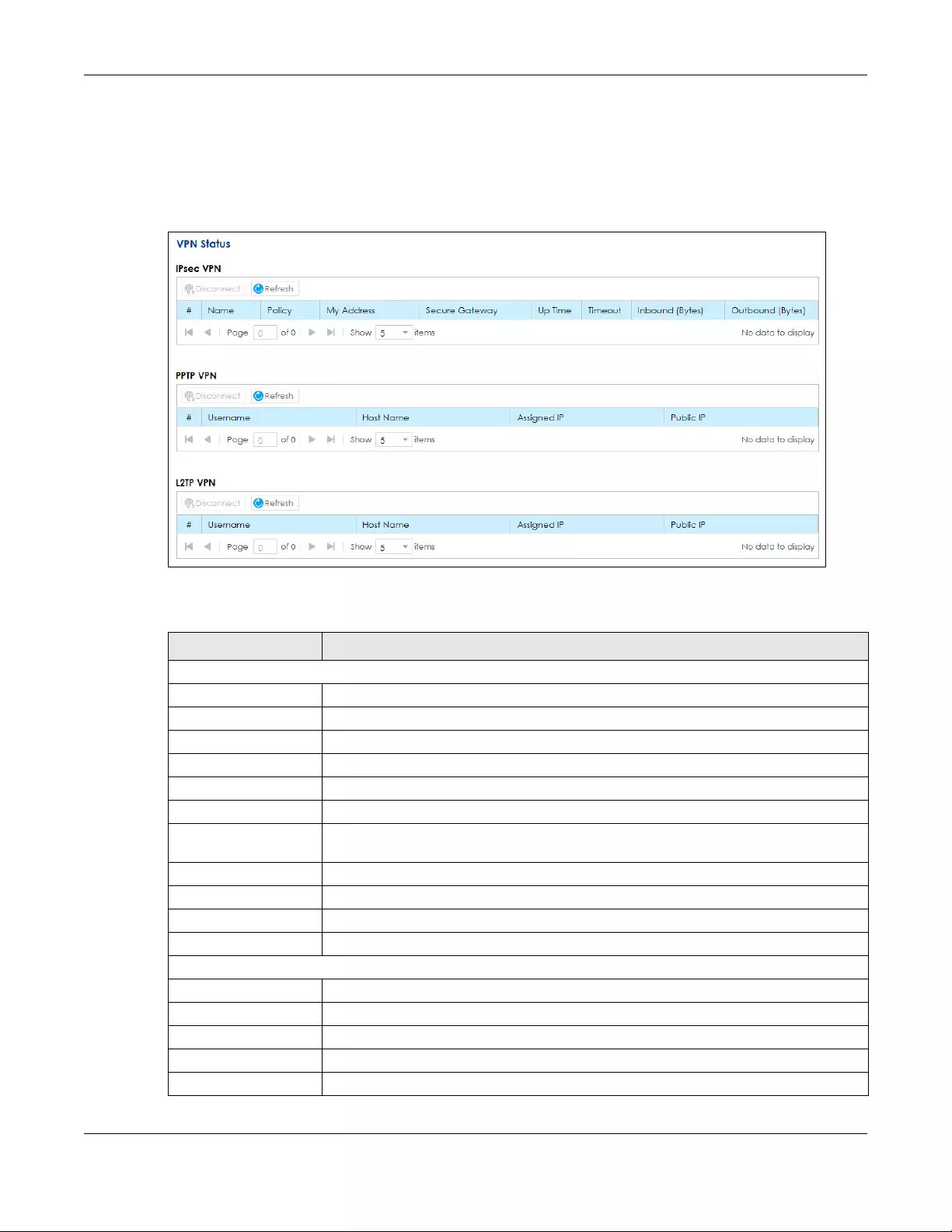
Chapter 10 VPN
SBG5500 Series User’s Guide
162
10.4 The VPN Status Screen
Use this screen to look at the VPN tunnels that are currently established. To access this screen, click
Configuration > VPN > VPN Status.
Figure 131 Configuration > VPN > VPN Status
The following table describes the labels in this screen.
Table 68 Configuration > VPN > VPN Status
LABEL DESCRIPTION
IPsec VPN
Disconnect Select a VPN policy and click Disconnect to disable it.
Refresh Click this to renew the table.
# This is the IPsec VPN policy index number.
Name This field displays the identification name for this VPN policy.
Policy This field displays the local policy and the remote policy, respectively.
My Address This field displays the interface the VPN gateway uses.
Secure Gateway This field displays the peer gateway address of the IPsec router with which you are
making the VPN connection.
Up Time This field displays the period of time the VPN tunnel has been up.
Timeout This field displays the timeout period before the SBG disconnects from this VPN tunnel.
Inbound (Bytes) This field displays the number of bytes received by the SBG on this VPN tunnel.
Outbound (Bytes) This field displays the number of bytes transmitted by the SBG on this VPN tunnel.
PPTP VPN / L2TP VPN
Disconnect Select a VPN client connection and click this to disable it.
Refresh Click this to renew the table.
# This is the PPTP/L2TP VPN policy index number.
Username This field displays the client’s login name for this connection.
Host Name This is the client's host name of this connection.
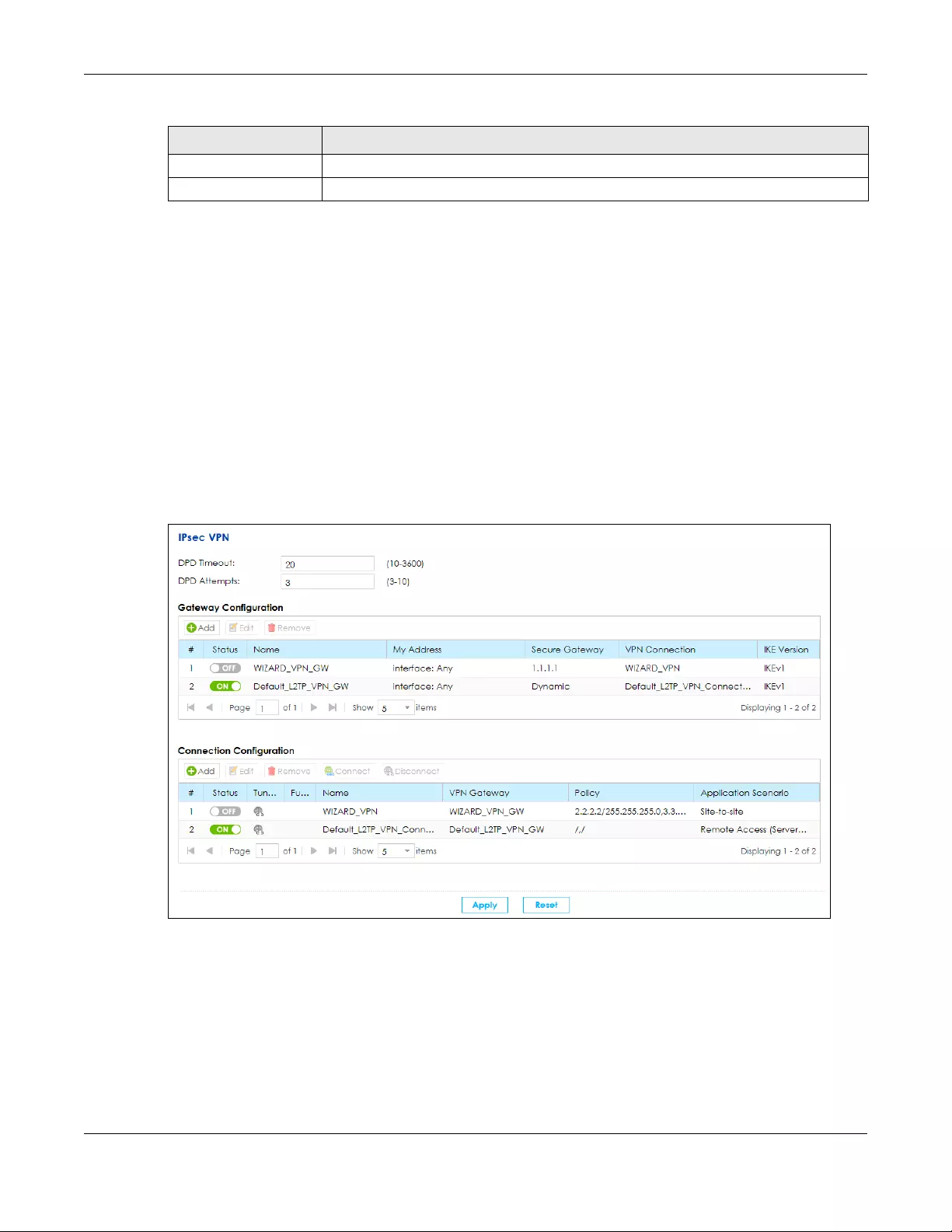
Chapter 10 VPN
SBG5500 Series User’s Guide
163
10.5 The IPsec VPN Screen
Click Configuration > VPN > IPsec VPN to open the following screen.
Use Gateway Configuration to manage the SBG’s VPN gateway policies. A VPN gateway specifies the
IPsec routers at either end of a VPN tunnel and the IKE SA settings (phase 1 settings). You can also
activate and deactivate each VPN gateway.
Use Connection Configuration to specify which IPsec VPN gateway an IPsec VPN connection policy
uses, which devices behind the IPsec routers can use the VPN tunnel, and the IPsec SA settings (phase 2
settings). You can also activate or deactivate and connect or disconnect each VPN connection (each
IPsec SA).
Figure 132 Configuration > VPN > IPsec VPN
Assigned IP This is the local point-to-point IP address assigned to the client.
Public IP This is the client’s public IP address for this connection.
Table 68 Configuration > VPN > VPN Status
LABEL DESCRIPTION
Chapter 10 VPN
SBG5500 Series User’s Guide
164
The following table describes the labels in this screen.
Table 69 Configuration > VPN > IPsec VPN
LABEL DESCRIPTION
DPD Timeout Use Dead Peer Detection (DPD) so the SBG makes sure the remote IPsec router is there
before it transmits data through the IKE SA. The remote IPsec router must support DPD.
Enter the number of seconds for DPD Timeout. The SBG sends a message to the remote
IPsec router. If the remote IPsec router responds, the SBG keeps the tunnel up.
DPD Attempts If the remote IPsec router does not respond, enter how many attempts the SBG should
make before it shuts down the tunnel.
Note: If you enabled Nailed Up in the VPN > IPsec VPN > VPN Connection
screen, the SBG shuts down the tunnel and will automatically establish a
new tunnel.
Gateway Configuration
Add Click this to configure a new entry.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an existing entry, select it and click Remove.
# This field displays the VPN gateway index number.
Status This field displays whether the IPsec VPN gateway is active or not. A green ON button
signifies that this IPsec VPN gateway is active. A gray OFF button signifies that this IPsec
VPN gateway is not active.
Name This field displays the identification name for this VPN gateway.
My Address This field displays the interface the VPN gateway uses.
Secure Gateway This field displays the peer gateway address of the IPsec router with which you are
making the VPN connection.
IP Version This field displays whether the VPN gateway uses IPv4 or IPv6 addresses.
VPN Connection This field displays which VPN connection use this gateway.
IKE Version This field displays the IKE Version the VPN gateway uses.
Connection Configuration
Add Click this to configure a new entry.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an existing entry, select it and click Remove.
Connect To connect an IPsec SA, select it and click Connect.
Disconnect To disconnect an IPsec SA, select it and click Disconnect.
# This field displays the VPN connection index number.
Status This field displays whether the IPsec VPN connection is active or not. A green ON button
signifies that this IPsec VPN connection is active. A gray OFF button signifies that this IPsec
VPN connection is not active.
Tunnel This shows a lit up globe if the VPN tunnel is connected or and a gray globe when it is
disconnected.
Name This field displays the identification name for this VPN policy.
VPN Gateway This field displays the VPN gateway the VPN connection uses.
Encapsulation This field displays the type of encapsulation the IPsec SA uses,
Algorithm This field displays the encryption algorithm used in the IKE SA.
Policy This field displays the remote and local policy.

Chapter 10 VPN
SBG5500 Series User’s Guide
165
10.5.1 Add/Edit a VPN Gateway
Click Add to create a new VPN gateway policy. You can also double click a VPN gateway policy or
select one and click Edit to go to the following screen.
Application Scenario This field is read-only and shows the scenario that the SBG supports.
Site-to-site - The remote IPsec router needs to have a static IP address or a domain name.
This SBG can initiate the VPN tunnel.
Site-to-site with Dynamic Peer - Choose this if the remote IPsec router has a dynamic IP
address. Only the remote IPsec router can initiate the VPN tunnel.
Remote Access (Server Role) - Choose this to allow incoming connections from IPsec VPN
clients. The clients have dynamic IP addresses and are also known as dial-in users. Only
the clients can initiate the VPN tunnel.
Remote Access (Client Role) - Choose this to connect to an IPsec server. This SBG is the
client (dial-in user) and can initiate the VPN tunnel.
Apply Click Apply to save your changes.
Reset Click Reset to restore your previously saved settings.
Table 69 Configuration > VPN > IPsec VPN
LABEL DESCRIPTION
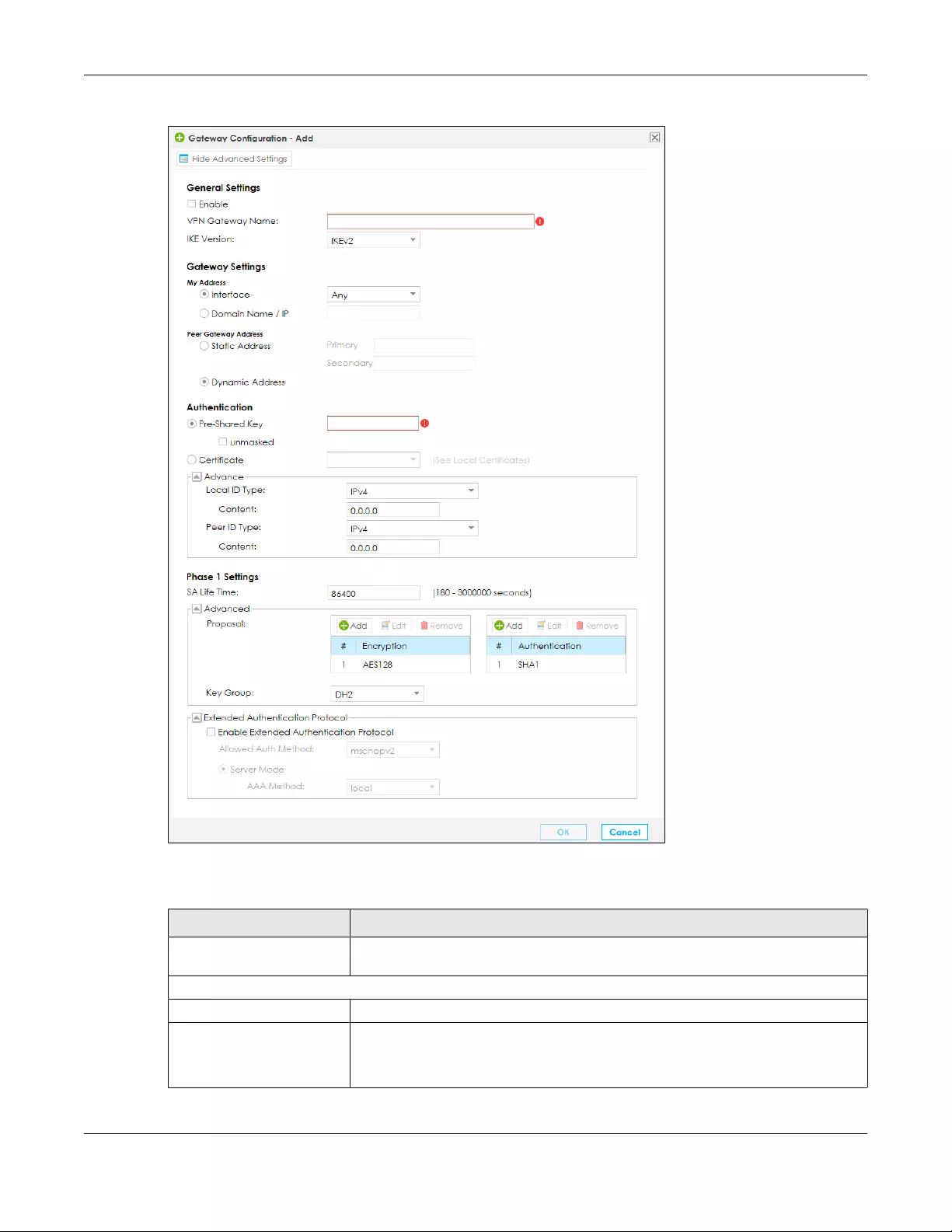
Chapter 10 VPN
SBG5500 Series User’s Guide
166
Figure 133 VPN Gateway: Add/Edit
The following table describes the labels in this screen.
Table 70 VPN Gateway: Add/Edit
LABEL DESCRIPTION
Show Advanced Settings /
Hide Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
General Settings
Enable Select the check box to activate this VPN gateway policy.
VPN Gateway Name Enter a name used to identify this VPN gateway.
The VPN Gateway Name of an IPsec rule must be unique and cannot be changed
once it has been created.
Chapter 10 VPN
SBG5500 Series User’s Guide
167
IKE Version Select IKEv1 or IKEv2. IKEv1 applies to IPv4 traffic only. IKEv2 applies to both IPv4 and
IPv6 traffic. IKE (Internet Key Exchange) is a protocol used in setting up security
associations that allows two parties to send data securely. See Section 10.3 on page
159 for more information on IKEv1 and IKEv2.
Gateway Settings
My address Select how the IP address of the SBG in the IKE SA is defined.
If you select Interface, select the Ethernet interface, WWAN interface, virtual
Ethernet interface, ADSL/VDSL interface. The IP address of the SBG in the IKE SA is the
IP address of the interface.
If you select Domain Name / IP, enter the domain name or the IP address of the SBG.
The IP address of the SBG in the IKE SA is the specified IP address or the IP address
corresponding to the domain name. 0.0.0.0 is not generally recommended as it has
the SBG accept IPsec requests destined for any interface address on the SBG.
Peer Gateway Address Select how the IP address of the remote IPsec router in the IKE SA is defined.
Select Static Address to enter the domain name or the IP address of the remote
IPsec router. You can provide a Secondary IP address or domain name for the SBG
to try if it cannot establish an IKE SA with the first one.
Enter a Secondary IP address, if the connection to the Primary address goes down
and the SBG changes to using the secondary connection, the SBG will reconnect to
the primary address when it becomes available again and stop using the secondary
connection. Users will lose their VPN connection briefly while the SBG changes back
to the primary connection. To use this, the peer device at the secondary address
cannot be set to use a nailed-up VPN connection. In the Fallback Check Interval
field, set how often to check if the primary address is available.
Select Dynamic Address if the remote IPsec router has a dynamic IP address (and
does not use DDNS).
Authentication Note: The SBG and remote IPsec router must use the same
authentication method to establish the IKE SA.
Pre-Shared Key Select this to have the SBG and remote IPsec router use a pre-shared key (password)
to identify each other when they negotiate the IKE SA. Type the pre-shared key in
the field to the right. The pre-shared key can be
• 8 - 32 keyboard characters except (=) equals sign, (-) dash, (/) slash, (\) backslash,
or (",') quotation marks.
• 8 - 32 pairs of hexadecimal (0-9, A-F) characters, preceded by “0x”.
If you want to enter the key in hexadecimal, type “0x” at the beginning of the key.
For example, "0x0123456789ABCDEF" is in hexadecimal format; in
“0123456789ABCDEF” is in ASCII format. If you use hexadecimal, you must enter
twice as many characters since you need to enter pairs.
The SBG and remote IPsec router must use the same pre-shared key.
Select unmasked to see the pre-shared key in readable plain text.
Note: All remote access application scenario of IPsec rules must use the
same pre-shared key.
Table 70 VPN Gateway: Add/Edit
LABEL DESCRIPTION
Chapter 10 VPN
SBG5500 Series User’s Guide
168
Certificate In order to use Certificate for IPsec authentication, you need to add new host
certificates in the Firewall / Security > Certificate screen.
Select this to have the SBG and remote IPsec router use certificates to authenticate
each other when they negotiate the IKE SA. Then select the certificate the SBG uses
to identify itself to the remote IPsec router.
This certificate is one of the certificates in Certificate. If this certificate is self-signed,
import it into the remote IPsec router. If this certificate is signed by a CA, the remote
IPsec router must trust that CA.
Note: The IPsec routers must trust each other’s certificates.
The SBG uses one of its Trusted CA to authenticate the remote IPsec router’s
certificate. The trusted certificate can be a self-signed certificate or that of a trusted
CA that signed the remote IPsec router’s certificate.
Advance
Local ID Type This field is read-only if the SBG and remote IPsec router use certificates to identify
each other. Select which type of identification is used to identify the SBG during
authentication. Choices are:
IPv4 - the SBG is identified by an IP address.
DNS - the SBG is identified by a domain name.
Email Address - the SBG is identified by the string specified in the Content field.
My Address - the SBG is identified by he IP address specified in the My Address field.
Content This field is read-only if the SBG and remote IPsec router use certificates to identify
each other. Type the identity of the SBG during authentication. The identity depends
on the Local ID Type.
IPv4 - type an IP address. This is not recommended in the following situations:
• There is a NAT router between the SBG and remote IPsec router.
• You want the remote IPsec router to be able to distinguish between IPsec SA
requests that come from IPsec routers with dynamic WAN IP addresses.
In these situations, use a different IP address, or use a different Local ID Type.
DNS - type the fully qualified domain name (FQDN). This value is only used for
identification and can be any string that matches the peer ID string.
Email Address - the SBG is identified by the string you specify here; you can use up to
63 ASCII characters including spaces, although trailing spaces are truncated. This
value is only used for identification and can be any string.
Peer ID Type Select which type of identification is used to identify the remote IPsec router during
authentication. Choices are:
IPv4 - the remote IPsec router is identified by an IP address.
DNS - the remote IPsec router is identified by a domain name.
Email Address - the remote IPsec router is identified by the string specified in this field.
Any - the SBG does not check the identity of the remote IPsec router If the SBG and
remote IPsec router use certificates, there is one more choice.
Table 70 VPN Gateway: Add/Edit
LABEL DESCRIPTION
Chapter 10 VPN
SBG5500 Series User’s Guide
169
Content This field is disabled if the Peer ID Type is Any. Type the identity of the remote IPsec
router during authentication. The identity depends on the Peer ID Type.
If the SBG and remote IPsec router do not use certificates,
IPv4 - type an IP address; see the note at the end of this description.
DNS - type the fully qualified domain name (FQDN). This value is only used for
identification and can be any string that matches the peer ID string.
Email Address - the remote IPsec router is identified by the string you specify here;
you can use up to 31 ASCII characters including spaces, although trailing spaces are
truncated. This value is only used for identification and can be any string.
Note: If Peer ID Type is IPv4, please read the rest of this section.
If you type 0.0.0.0, the SBG uses the IP address specified in the Secure Gateway
Address field. This is not recommended in the following situations:
• There is a NAT router between the SBG and remote IPsec router.
• You want the remote IPsec router to be able to distinguish between IPsec SA
requests that come from IPsec routers with dynamic WAN IP addresses.
In these situations, use a different IP address, or use a different Peer ID Type.
Phase 1 Settings Phase 1 Encryption and Authentication can have up to 3 algorithm pairs. You
cannot use phase 1 Encryption, Authentication, and Key Group pairs that already
exist in other enabled IPsec rules.
When the default IPsec rule Default_L2TP_VPN_GW is enabled, if you want to add a
new Remote Access IPsec rule, you can use phase 1 Encryption, Authentication, and
Key Group pair DES, MD5, and DH2 or DES, SHA1, and DH2, or any algorithm
combination with DH1 or DH5.
SA Life Time Define the length of time before an IKE or IPsec SA automatically renegotiates in this
field. It may range from 1 to 99,999 seconds.
A short SA Life Time increases security by forcing the two VPN gateways to update
the encryption and authentication keys. However, every time the VPN tunnel
renegotiates, all users accessing remote resources are temporarily disconnected.
Negotiation Mode Select the negotiation mode to use to negotiate the IKE SA. Choices are:
Main - this encrypts the SBG’s and remote IPsec router’s identities but takes more
time to establish the IKE SA.
Aggressive - this is faster but does not encrypt the identities The SBG and the remote
IPsec router must use the same negotiation mode.
Note: This field is only available when you select IKEv1 in the IKE Version
field.
Advanced
Proposal Use this section to manage the encryption algorithm and authentication algorithm
pairs the SBG accepts from the remote IPsec router for negotiating the IKE SA.
Add Click this to add phase 1 Encryption and Authentication.
Edit Select an entry and click the Edit to modify it.
Remove Select an entry and click Remove to delete it.
# This field is a sequential value, and it is not associated with a specific proposal. The
sequence of proposals should not affect performance significantly.
Table 70 VPN Gateway: Add/Edit
LABEL DESCRIPTION
Chapter 10 VPN
SBG5500 Series User’s Guide
170
Encryption Select which key size and encryption algorithm to use in the IKE SA. Choices are:
3DES - a 168-bit key with the DES encryption algorithm
AES128 - a 128-bit key with the AES encryption algorithm
AES192 - a 192-bit key with the AES encryption algorithm
AES256 - a 256-bit key with the AES encryption algorithm
The SBG and the remote IPsec router must use the same algorithms and keys. Longer
keys require more processing power, resulting in increased latency and decreased
throughput.
# This is the Authentication index number.
Authentication Select which hash algorithm to use to authenticate packet data in the IPsec SA.
Choices are SHA1, SHA256, and SHA512 is generally considered stronger than MD5,
but it is also slower.
The remote IPsec router must use the same authentication algorithm.
Key Group Select which Diffie-Hellman key group (DHx) you want to use for encryption keys.
Choices are:
None - disable DHx.
DH2 - use a 1024-bit random number.
DH5 - use a 1536-bit random number.
DH14 - use a 2048-bit random number.
The longer the key, the more secure the encryption, but also the longer it takes to
encrypt and decrypt information. Both routers must use the same DH key group.
NAT Traversal Select this if any of these conditions are satisfied.
• This IKE SA might be used to negotiate IPsec SAs that use ESP as the active
protocol.
• There are one or more NAT routers between the SBG and remote IPsec router,
and these routers do not support IPsec pass-thru or a similar feature.
The remote IPsec router must also enable NAT traversal, and the NAT routers have to
forward packets with UDP port 500 and UDP 4500 headers unchanged.
This field applies for IKEv1 only. NAT Traversal is always performed when you use
IKEv2.
Dead Peer Detection
(DPD) Select this check box if you want the SBG to make sure the remote IPsec router is
there before it transmits data through the IKE SA. The remote IPsec router must
support DPD. If there has been no traffic for at least 15 seconds, the SBG sends a
message to the remote IPsec router. If the remote IPsec router responds, the SBG
transmits the data. If the remote IPsec router does not respond, the SBG shuts down
the IKE SA.
If the remote IPsec router does not support DPD, see if you can use the VPN
connection connectivity check.
This field applies for IKEv1 only. Dead Peer Detection (DPD) is always performed
when you use IKEv2.
X Auth / Extended
Authentication Protocol
This part of the screen displays X-Auth when using IKEv1 and Extended
Authentication Protocol when using IKEv2.
X-Auth This displays when using IKEv1. When different users use the same VPN tunnel to
connect to the SBG (telecommuters sharing a tunnel for example), use X-auth to
enforce a user name and password check. This way even though telecommuters all
know the VPN tunnel’s security settings, each still has to provide a unique user name
and password.
Table 70 VPN Gateway: Add/Edit
LABEL DESCRIPTION
Chapter 10 VPN
SBG5500 Series User’s Guide
171
10.5.2 Add/Edit a VPN Connection
Click Add to create a new VPN Connection. You can also double click a VPN Connection or select one
and click Edit to go to the following screen.
Enable Extended
Authentication When multiple IPsec routers use the same VPN tunnel to connect to a single VPN
tunnel (telecommuters sharing a tunnel for example), use extended authentication
to enforce a user name and password check. This way even though they all know
the VPN tunnel’s security settings, each still has to provide a unique user name and
password.
Select the check box if one of the routers (the SBG or the remote IPsec router)
verifies a user name and password from the other router using the local user
database and/or an external server.
Allowed Auth Method This displays when using IKEv2. Select the authentication method, which specifies
how the SBG authenticates this information.
Server Mode Select this if the SBG authenticates the user name and password from the remote
IPsec router. You also have to select the AAA server to use for authentication if you
use IKEv1.
AAA Method This displays when using IKEv2. Select the AAA server to use to authenticate the user
name and password from the remote IPsec router.
OK Click OK to save your settings and exit this screen.
Cancel Click Cancel to exit this screen without saving.
Table 70 VPN Gateway: Add/Edit
LABEL DESCRIPTION
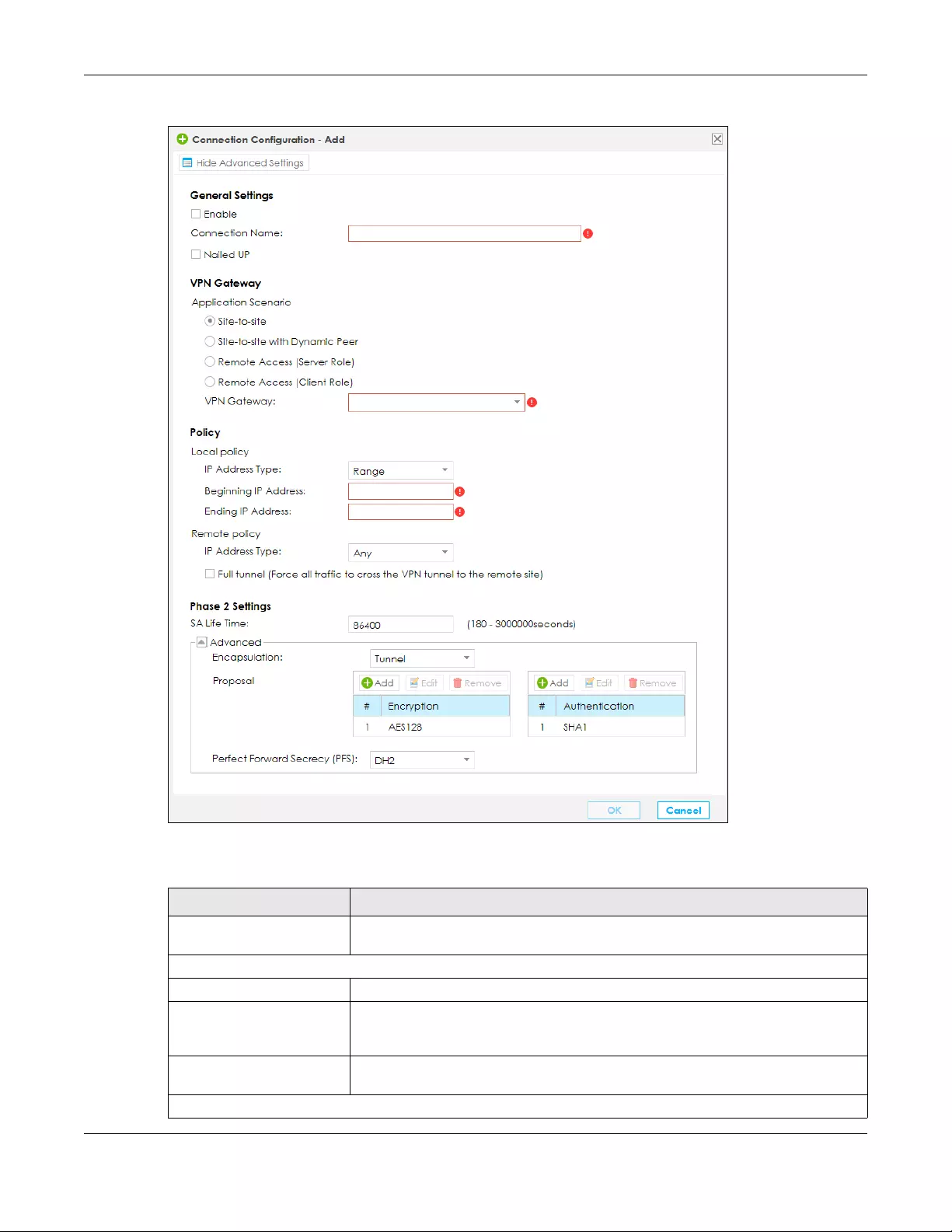
Chapter 10 VPN
SBG5500 Series User’s Guide
172
Figure 134 VPN Connection: Add/Edit
The following table describes the labels in this screen.
Table 71 VPN Connection: Add/Edit
LABEL DESCRIPTION
Show Advanced Settings /
Hide Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
General Settings
Enable Select the check box to activate this VPN connection.
Connection Name Type the name used to identify this IPsec SA. You may use 1-48 alphanumeric
characters, underscores (_), or dashes (-), but the first character cannot be a
number. This value is case-sensitive.
Nailed Up Select this if you want the SBG to automatically renegotiate the IPsec SA when the
SA life time expires.
VPN Gateway
Chapter 10 VPN
SBG5500 Series User’s Guide
173
Application Scenario Select the scenario that best describes your intended VPN connection.
Site-to-site - Choose this if the remote IPsec router has a static IP address or a
domain name. This SBG can initiate the VPN tunnel.
Site-to-site with Dynamic Peer - Choose this if the remote IPsec router has a dynamic
IP address. Only the remote IPsec router can initiate the VPN tunnel.
Remote Access (Server Role) - Choose this to allow incoming connections from IPsec
VPN clients. The clients have dynamic IP addresses and are also known as dial-in
users. Only the clients can initiate the VPN tunnel.
Remote Access (Client Role) - Choose this to connect to an IPsec server. This SBG is
the client (dial-in user) and can initiate the VPN tunnel.
VPN Gateway Select the VPN gateway this VPN connection is to use.
Policy
Local policy Type the IP address of a computer on your network. You can also specify a subnet.
This must match the remote IP address configured on the remote IPsec device.
Remote Policy Type the IP address of a computer behind the remote IPsec device. You can also
specify a subnet. This must match the local IP address configured on the remote
IPsec device.
Full Tunnel Select this check box if you need the SBG to send packets through the VPN Tunnel.
Phase 2 Settings
SA Life Time Type the maximum number of seconds the IPsec SA can last. Shorter life times
provide better security. The SBG automatically negotiates a new IPsec SA before the
current one expires, if there are users who are accessing remote resources.
Advanced
Encapsulation Select which type of encapsulation the IPsec SA uses. Choices are:
Tunnel - this mode encrypts the IP header information and the data.
Transport - this mode only encrypts the data.
The SBG and remote IPsec router must use the same encapsulation.
Proposal Use this section to manage the encryption algorithm and authentication algorithm
pairs the SBG accepts from the remote IPsec router for negotiating the IPsec SA.
Add Click this to create a new entry.
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
# This field is a sequential value, and it is not associated with a specific proposal. The
sequence of proposals should not affect performance significantly.
Table 71 VPN Connection: Add/Edit
LABEL DESCRIPTION
Chapter 10 VPN
SBG5500 Series User’s Guide
174
10.5.3 The Default_L2TP_VPN_GW IPsec VPN Rule
A default IPsec VPN rule (Default_L2TP_VPN_GW) is predefined. It can be edited but cannot be
removed. This rule is used for L2TP VPN exclusively and is disabled by default.
The following table lists the default settings for the Default_L2TP_VPN_GW IPsec VPN.
Encryption This field is applicable when the Active Protocol is ESP. Select which key size and
encryption algorithm to use in the IPsec SA. Choices are:
None - no encryption key or algorithm
3DES - a 168-bit key with the DES encryption algorithm
AES128 - a 128-bit key with the AES encryption algorithm
AES192 - a 192-bit key with the AES encryption algorithm
AES256 - a 256-bit key with the AES encryption algorithm
The SBG and the remote IPsec router must both have at least one proposal that uses
use the same encryption and the same key.
Longer keys are more secure, but require more processing power, resulting in
increased latency and decreased throughput.
Authentication Select which hash algorithm to use to authenticate packet data in the IPsec SA.
Choices are SHA1, SHA256, and SHA512. SHA is generally considered stronger than
MD5, but it is also slower.
The SBG and the remote IPsec router must both have a proposal that uses the same
authentication algorithm.
Perfect Forward Secrecy
(PFS)
Select whether or not you want to enable Perfect Forward Secrecy (PFS) and, if you
do, which Diffie-Hellman key group to use for encryption. Choices are:
DH2 - enable PFS and use a 1024-bit random number
DH5 - enable PFS and use a 1536-bit random number
DH14 - enable PFS and use a 2048-bit random number
PFS changes the root key that is used to generate encryption keys for each IPsec SA.
The longer the key, the more secure the encryption, but also the longer it takes to
encrypt and decrypt information. Both routers must use the same DH key group.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 71 VPN Connection: Add/Edit
LABEL DESCRIPTION
Table 72 Default settings for Default_L2TP_VPN_GW
GENERAL AUTHENTICATION
Enabled No Pre-Shared Key none
Nailed-up No Certificate none
NAT Traversal Yes Local ID Type IP
Application Scenario Remote Access Content 0.0.0.0
My Address Any Remote ID Type Any
PHASE 1 PHASE 2
Life time 86400 Life time 3600
Chapter 10 VPN
SBG5500 Series User’s Guide
175
10.5.4 PPTP VPN Troubleshooting Tips
This section lists the common troubleshooting tips for PPTP VPN.
1A PPTP client device (such as a PC, smart phone, tablet) cannot connect to the SBG.
TIP: This could be due to one of the following reasons:
a. The client device is not connected to the Internet successfully.
Action: Check the client device’s Internet connection.
b. Incorrect server address configured on the client device.
(1) If the Local WAN Interface is “Any”:
From the SBG’s GUI, click Status. The client device should be configured with one of the WAN
interface IP addresses.
(2) If the Local WAN Interface is an interface (IP address shown to the right):
Use that IP address for the client device to connect.
c. The WAN interface which the SBG’s PPTP VPN is using is not connected.
Action: From the SBG’s GUI, click Status. Check if the WAN interface the client device is connected has
an IP address present.
d. The PPTP VPN is not enabled.
Action: From the SBG’s GUI, click VPN > PPTP VPN. Check Enable check box and click Apply.
e. PPTP is not configured correctly on the client device.
Action: Check the PPTP VPN configuration on the client device.
f. The client entered an incorrect username or password.
Negotiation Mode Main Tunnel Mode ESP
Encryption /
Authentication
3DES / SHA1
3DES / MD5
AES256 / SHA1
Encryption DES
3DES
AES256
Authentication MD5
SHA1
Key Group DH2 Perfect Forward Secrecy
(PFS)
No
Dead Peer Detection
(DPD)
Yes Encapsulation Transport
XAUTH No
Table 72 Default settings for Default_L2TP_VPN_GW (continued)
GENERAL AUTHENTICATION

Chapter 10 VPN
SBG5500 Series User’s Guide
176
Action: From the SBG’s GUI, click Maintenance > User Account. The client should use one of the
accounts to make the connection.
g. The SBG has already reached the maximum number of concurrent PPTP VPN connections.
Action: There are too many clients connected. Wait a while and then retry.
2A PPTP client is disconnected unexpectedly.
Tip: A PPTP connection will be dropped when one of the followings occurs on the SBG:
a. The client has no activity for a period of time.
b. The client loses connectivity to the SBG for a period of time.
c. PPTP VPN is disabled on the SBG.
d. When any one of these configuration changes is applied on the SBG: WAN interface used for PPTP
VPN, IP address pool, access group.
e. The SBG’s WAN interface on which the PPTP connection is established is disconnected.
3A PPTP client is connected successfully but cannot access the local host or server behind the SBG.
Tip: This may be caused by one of the followings:
a. The local host or server is disconnected.
b. The access group is not configured correctly. From the SBG’s GUI, go to VPN > PPTP VPN to check.
Note that all local hosts are by default accessible unless access group is configured.
c. IP Address Pool for PPTP VPN conflicts with any WAN, LAN, DMZ, WLAN, or L2TP VPN subnet configured
on the SBG. Note that the IP Address Pool for PPTP VPN has a 24-bit netmask and should not conflict with
any others listed above even if they are not in use.
4A PPTP client is connected successfully but cannot browse the Internet.
Tip: From the SBG’s GUI, click VPN > PPTP VPN. Check if DNS Server is configured. A client cannot browse
the Internet without DNS resolved. Note that when a new DNS server is configured, the client must
disconnect then reconnect in order for the new DNS Server to take effect.
5An Android device cannot connect to the SBG’s PPTP VPN.
Tip: Devices running an Android OS older than version 4.1 have issues with PPTP/MPPE encryption. Avoid
using devices that run an Android OS older than version 4.1 for PPTP VPN connection.
10.6 The PPTP VPN Screen
Use this screen to configure settings for a Point to Point Tunneling Protocol (PPTP) server.
Click Configuration > VPN > PPTP VPN to open the following screen.
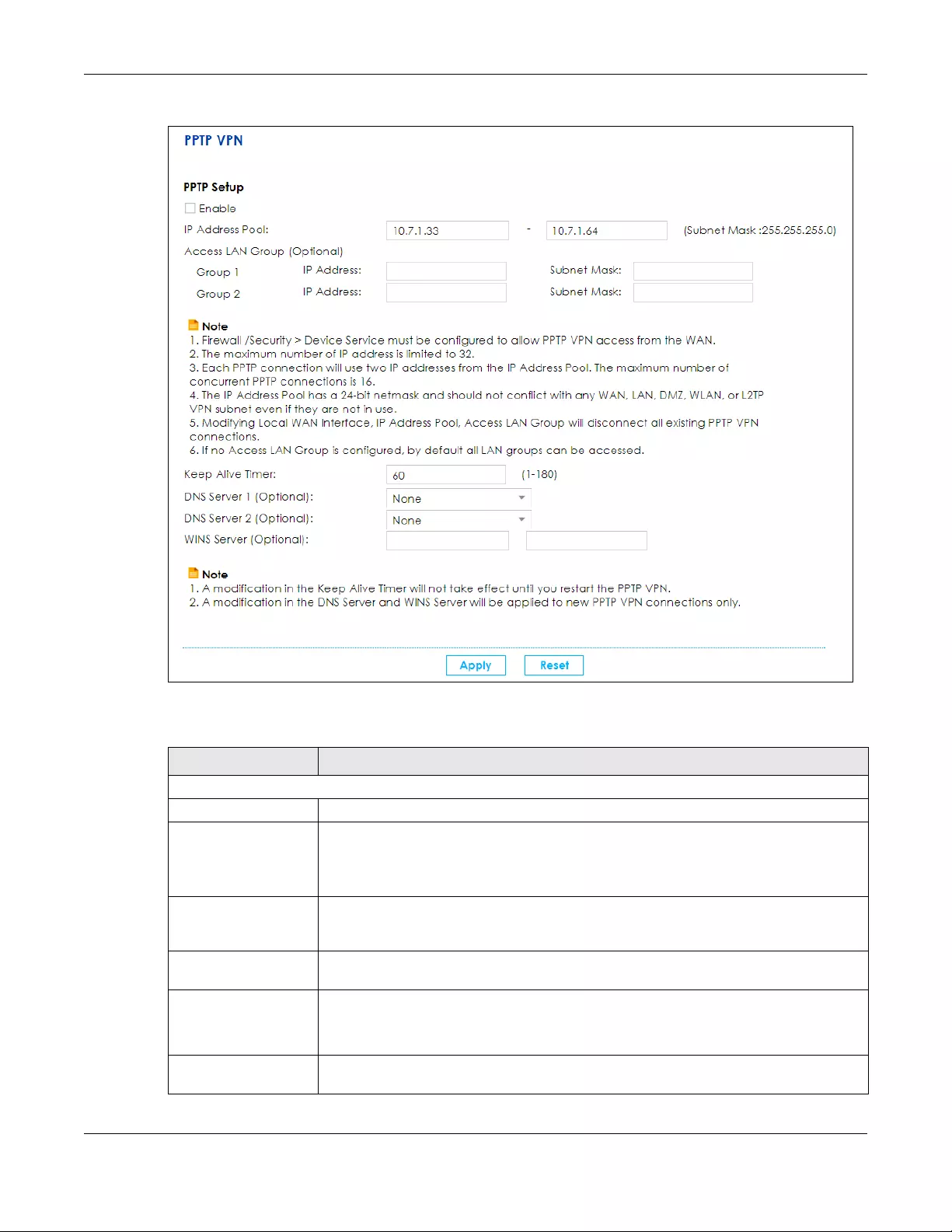
Chapter 10 VPN
SBG5500 Series User’s Guide
177
Figure 135 Configuration > VPN > PPTP VPN
The following table describes the labels in this screen.
Table 73 Configuration > VPN > PPTP VPN
LABEL DESCRIPTION
PPTP Setup
Enable Use this field to turn the SBG’s PPTP VPN function on or off.
IP Address Pool Enter the pool of IP addresses that the SBG uses to assign to the PPTP VPN clients.
Note: This is with a 24-bit netmask and should not conflict with any configured
WAN, LAN, DMZ, WLAN, or L2TP VPN subnet even if they are not in use.
Access LAN Group
(optional)
Specify up to 2 LAN groups (subnets) which a PPTP VPN client is allowed to access. If none
is specified, all LAN groups can be accessed. Enter the IP address and Subnet Mask for
the LAN group(s).
Keep Alive Timer The SBG sends a Hello message after waiting this long without receiving any traffic from
the remote user. The SBG disconnects the VPN tunnel if the remote user does not respond.
Preferred DNS Server
(Optional)
Specify the IP addresses of DNS servers to assign to the remote users.
You can choose from one of the DNS servers from the list, or choose User Defined to enter
the static IP addresses for the first and second DNS servers manually.
Alternative DNS Server
(Optional)
Specify the second DNS server address.

Chapter 10 VPN
SBG5500 Series User’s Guide
178
10.6.1 PPTP VPN Troubleshooting Tips
This section lists the common troubleshooting tips for PPTP VPN.
1A PPTP client device (such as a PC, smart phone, tablet) cannot connect to the SBG.
TIP: This could be due to one of the following reasons:
a. The client device is not connected to the Internet successfully.
Action: Check the client device’s Internet connection.
b. Incorrect server address configured on the client device.
(1) If the Local WAN Interface is “Any”:
(2) If the Local WAN Interface is an interface (IP address shown to the right):
Use that IP address for the client device to connect.
c. The WAN interface which the SBG’s PPTP VPN is using is not connected.
Action: From the SBG’s GUI, click Status. Check if the WAN interface the client device is connected has
an IP address present.
d. The PPTP VPN is not enabled.
Action: From the SBG’s GUI, click VPN > PPTP VPN. Check Enable check box and click Apply.
e. PPTP is not configured correctly on the client device.
Action: Check the PPTP VPN configuration on the client device.
f. The client entered an incorrect username or password.
Action: From the SBG’s GUI, click Maintenance > User Account. The client should use one of the
accounts to make the connection.
g. The SBG has already reached the maximum number of concurrent PPTP VPN connections.
Action: There are too many clients connected. Wait a while and then retry.
2A PPTP client is disconnected unexpectedly.
Tip: A PPTP connection will be dropped when one of the followings occurs on the SBG:
WINS Server (Optional) The WINS (Windows Internet Naming Service) server keeps a mapping table of the
computer names on your network and the IP addresses that they are currently using.
Type the IP addresses of up to two WINS servers to assign to the remote users.
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to restore your previous settings.
Table 73 Configuration > VPN > PPTP VPN
LABEL DESCRIPTION

Chapter 10 VPN
SBG5500 Series User’s Guide
179
a. The client has no activity for a period of time.
b. The client loses connectivity to the SBG for a period of time.
c. PPTP VPN is disabled on the SBG.
d. When any one of these configuration changes is applied on the SBG: WAN interface used for PPTP
VPN, IP address pool, access group.
e. The SBG’s WAN interface on which the PPTP connection is established is disconnected.
3A PPTP client is connected successfully but cannot access the local host or server behind the SBG.
Tip: This may be caused by one of the followings:
a. The local host or server is disconnected.
b. The access group is not configured correctly. From the SBG’s GUI, go to VPN > PPTP VPN to check.
Note that all local hosts are by default accessible unless access group is configured.
c. IP Address Pool for PPTP VPN conflicts with any WAN, LAN, DMZ, WLAN, or L2TP VPN subnet configured
on the SBG. Note that the IP Address Pool for PPTP VPN has a 24-bit netmask and should not conflict with
any others listed above even if they are not in use.
4A PPTP client is connected successfully but cannot browse the Internet.
Tip: From the SBG’s GUI, click VPN > PPTP VPN. Check if DNS Server is configured. A client cannot browse
the Internet without DNS resolved. Note that when a new DNS server is configured, the client must
disconnect then reconnect in order for the new DNS Server to take effect.
5An Android device cannot connect to the SBG’s PPTP VPN.
Tip: Devices running an Android OS older than version 4.1 have issues with PPTP/MPPE encryption. Avoid
using devices that run an Android OS older than version 4.1 for PPTP VPN connection.
10.7 The L2TP VPN Screen
Click Configuration > VPN > L2TP VPN to open the following screen. Use this screen to configure the SBG
L2TP VPN settings.
10.7.1 L2TP Setup - Server
The following screen displays when you select Server in the Type field.
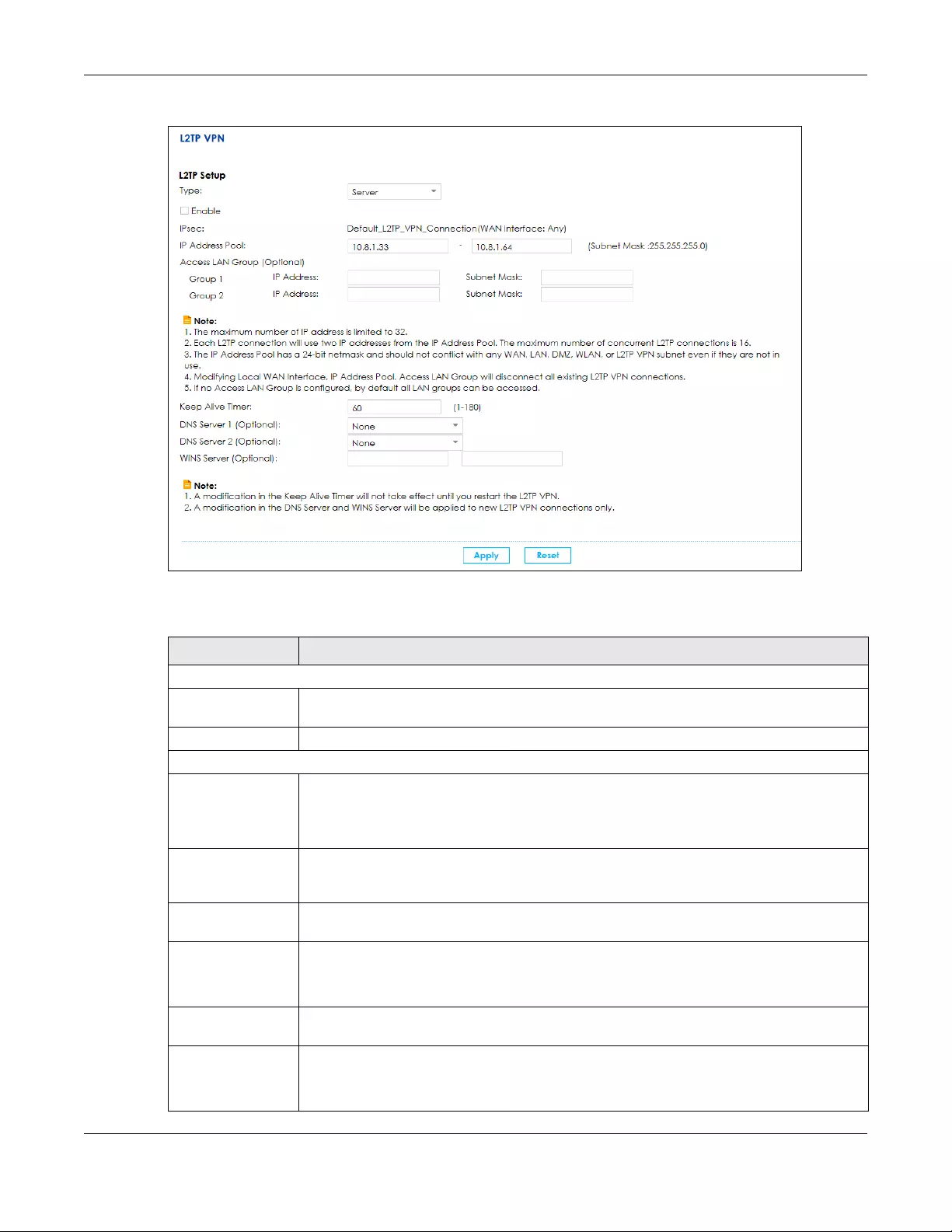
Chapter 10 VPN
SBG5500 Series User’s Guide
180
Figure 136 Configuration > VPN > L2TP VPN > Server
The following table describes the fields in this screen.
Table 74 Configuration > VPN > L2TP VPN > Server
LABEL DESCRIPTION
L2TP Setup
Type Select Server to have the SBG Series act as a L2TP VPN server . Also, the screen varies
depending on which option you select here.
Enable Select the check box to enable the SBG’s L2TP VPN function as a server.
IPsec
IP Address Pool Enter the pool of IP addresses that the SBG uses to assign to the L2TP VPN clients.
Note: These addresses use a 24-bit netmask and should not conflict with any WAN,
LAN, DMZ, WLAN, or PPTP VPN subnet even if they are not in use.
Access LAN Group
(optional)
Specify up to 2 LAN groups (subnets) which a L2TP VPN client is allowed to access. If none is
specified, all LAN groups can be accessed. Enter the IP address and Subnet Mask for the LAN
group(s).
Keep Alive Timer The SBG sends a Hello message after waiting this long without receiving any traffic from the
remote user. The SBG disconnects the VPN tunnel if the remote user does not respond.
DNS Server 1
(Optional)
Specify the IP addresses of DNS servers to assign to the remote users.
You can choose from one of the DNS servers from the list, or choose User Defined to enter the
static IP addresses for the first and second DNS servers manually.
DNS Server 2
(Optional)
Specify the second DNS server address.
WINS Server
(Optional)
The WINS (Windows Internet Naming Service) server keeps a mapping table of the computer
names on your network and the IP addresses that they are currently using.
Type the IP addresses of up to two WINS servers to assign to the remote users.
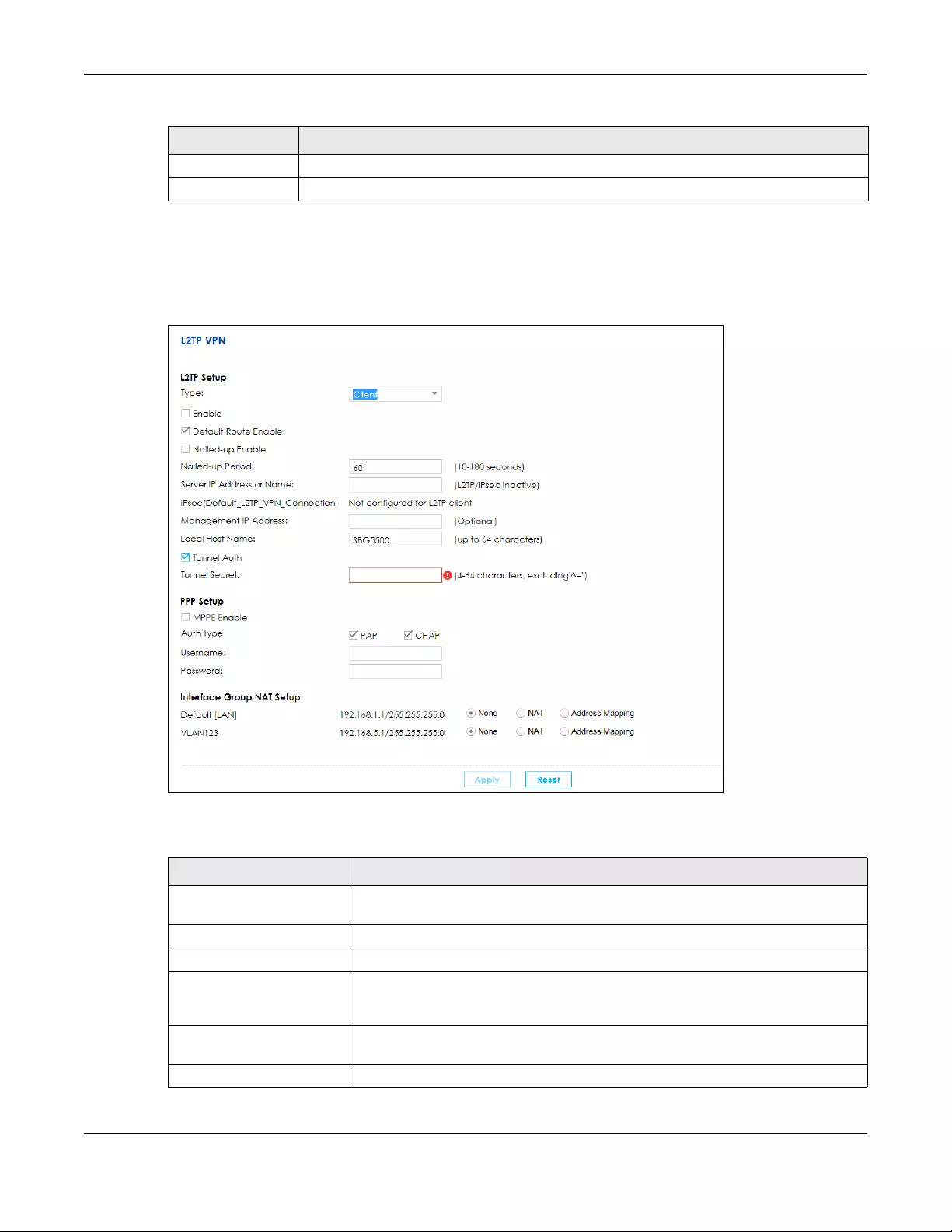
Chapter 10 VPN
SBG5500 Series User’s Guide
181
10.7.2 L2TP Setup - Client
The following screen displays when you select Client in the Type field.
Figure 137 Configuration > VPN > L2TP VPN > Client
The following table describes the labels in this screen.
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to restore your previous settings.
Table 74 Configuration > VPN > L2TP VPN > Server
LABEL DESCRIPTION
Table 75 Configuration > VPN > L2TP VPN > Client
LABEL DESCRIPTION
Type Select Client to have the SBG act as a L2TP VPN client. Also, the screen varies
depending on which option you select here.
Enable Select the check box to enable the SBG’s L2TP VPN function as a client.
Default Route Enable Select the check box to use the L2TP VPN connection as the system default route.
Nailed-up Enable Select this if you want the SBG to automatically reconnect when the L2TP VPN
connection is down. The attempt to reconnect will continue until the L2TP VPN
connection is up again.
Nailed-up Period Enter a value in seconds for the SBG to wait before re-initiating L2TP VPN
connections. The valid range for the period is 10-180 seconds.
Server IP Address or Name Enter the IP address or domain name of the LNS (L2TP Network Server).
Chapter 10 VPN
SBG5500 Series User’s Guide
182
10.7.3 L2TP VPN Troubleshooting Tips
This section lists the common troubleshooting tips for L2TP VPN.
1A L2TP client device (such as a PC, smart phone, tablet) cannot connect to the SBG.
TIP: This could be due to one of the following reasons:
a. The client device is not connected to the Internet successfully.
Action: Check the client device’s Internet connection.
Management IP Address Enter the SBG's public routable IP address for management purposes, and an
administrator will be able to reach the SBG via L2TP VPN connection and the
address input here.
Local Host Name Enter the L2TP local host name.
Tunnel Auth When performing tunnel authentication on the LNS (L2TP Network Server), please
select the check box to enable tunnel authentication, and enter a valid Tunnel
Secret in the next column.
Tunnel Secret Enter a valid Tunnel Secret consisting of 4-64 characters, and the following special
characters are not allowed: '/\=".
PPP Setup
MPPE Enable Click the check box to use MPPE, Microsoft Point to Point Encryption. It enables 40-bit
encryption as well as 128-bit encryption.
Note: PPP CHAP must be enabled as well.
Auth Type Select PAP or/and CHAP as your authentication method(s).
PAP (Password Authentication Protocol ) - The L2TP server will crosscheck the
username and password sent by the client with the database for authentication
purposes.
CHAP (Challenge Handshake Authentication Protocol) - When it’s enabled, MS-
CHAP and MS-CHAP-v2 are both supported. Also, CHAP needs to be enabled if you
wish to activate MPPE.
Username Enter the username for PPP authentication. It must be consistent with the
configuration made on LNS (L2TP Network Server). Otherwise the L2TP VPN
connection will not be established.
Password Enter the password for PPP authentication. It must be consistent with the
configuration made on LNS (L2TP Network Server). Otherwise the L2TP VPN
connection will not be established.
Interface Group NAT Setup
Default Select None, NAT, or Address Mapping to apply to the L2TP VPN connection.
None - NAT is not applied to the L2TP VPN connection.
NAT - Select this option to turn on the NAT function on the VPN connection.
Address Mapping - Select this option to apply the specified address mapping rule(s)
to the VPN connection. The address mapping rules are configured using the
Configuration > NAT > Address Mapping screen.
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to restore your previous settings.
Table 75 Configuration > VPN > L2TP VPN > Client
LABEL DESCRIPTION

Chapter 10 VPN
SBG5500 Series User’s Guide
183
b. Incorrect server address configured on the client device.
Action: From the SBG’s GUI, click VPN > IPsec VPN.
(1) If the Local Gateway Address for Default_L2TP_VPN_GW is set to “Any”:
(2) If the Local Gateway Address for Default_L2TP_VPN_GW is an IP address:
Use that IP address for the client device to connect.
c. The WAN interface which the SBG’s L2TP VPN is using is not connected.
Action: From the SBG’s GUI, click Status. Check if the WAN interface used by L2TP VPN is connected.
d. The client device has an incorrect IPsec pre-shared key configured.
Action: From the SBG’s GUI, click VPN > L2TP VPN. The client device should use the same pre-shared key.
e. The L2TP VPN is not fully enabled.
Action: From the SBG’s GUI,
(1) Click VPN > L2TP VPN. Select the Enable check box and click Apply.
(2) Click VPN > L2TP VPN. Select the Enable check box and click Apply.
f. L2TP or IPsec is not configured correctly on the client device.
Action: Check the L2TP VPN configuration on the client device.
g. The client entered an incorrect user name or password.
Action: From the SBG’s GUI, click Maintenance > User Account. The client should use one of the
accounts to make the connection.
h. The SBG exceeds the maximum number of concurrent L2TP VPN connections.
Action: There are too many clients connected. Wait a while and then retry.
2A windows L2TP client fails to connect to the SBG with an "invalid certificate" message.
Tip: Windows sometimes may show this error even if the client device has been configured with a
correct pre-shared key for authentication. This usually happens at the first connection attempt after a
new connection profile is created. Reconfigure the pre-shared key on the client Windows device and
retry the connection.
3An L2TP client device cannot reconnect after it is disconnected.
Tip: If a client reconnects right after it is disconnected, the reconnection may fail. Wait 60 seconds
before reconnecting.
4An L2TP client is disconnected unexpectedly.
Tip: An L2TP connection will be dropped when one of the followings occurs on the SBG:
(1) Client has no activity for a period of time.
Chapter 10 VPN
SBG5500 Series User’s Guide
184
(2) Client loses connectivity to the SBG for a period of time.
(3) Any IPsec VPN configuration change is applied on the SBG.
(4) Either Default_L2TP_VPN_GW IPsec configuration or L2TP VPN is disabled on the SBG.
(5) When any one of these configuration changes is applied on the SBG: WAN Interface used for L2TP
VPN, IP Address Pool, Access Group.
(6) The SBG WAN interface on which the L2TP connection established is disconnected.
5An L2TP client is connected successfully but cannot access the local host or server behind the SBG.
Tip: This may be caused by one of the followings:
(1) The local host or server is disconnected.
(2) The Access Group is not configured correctly. From the SBG’s GUI, go to the VPN > L2TP VPN screen
to check. Note that all local hosts are by default accessible unless Access Group is configured.
(3) IP Address Pool for L2TP VPN is conflicting with any WAN, LAN, DMZ, WLAN, or PPTP VPN subnet
configured on the SBG. Note that IP Address Pool for L2TP VPN has 24-bit netmask and should not
conflict with any others listed above even if they are not in use.
6An L2TP client is connected successfully but cannot browse Internet.
Tip: From the SBG’s GUI, click VPN > L2TP VPN. Check if DNS Server is configured. A client cannot browse
Internet without DNS resolved. Note that when a new DNS Server is configured, the client must
disconnect then reconnect in order for the new DNS Server to take effect.
7The L2TP client can no longer connect to SBG after the Encryption or Authentication for the
Default_L2TP_VPN_GW IPsec VPN rule is changed.
Tip: A user usually do not need change the default Encryption or Authentication algorithms in the
Default_L2TP_VPN IPsec VPN rule. The default Encryption and Authentication algorithms should support
the built-in L2TP/IPsec client software in the popular operating systems (Windows (XP, Vista, 7), Android,
and iOS).
Refer to Table 71 on page 172 for the default setting of the Default_L2TP_VPN_GW IPsec VPN rule.
As a reference, Table 76 on page 184 lists the IPsec proposals provided by a built-in L2TP client in the
popular operating systems during IPsec phase 1 negotiation. The first proposal that can be supported by
the phase 1 setting in the Default_L2TP_VPN_GW IPsec VPN rule will be accepted by the SBG. The
algorithms in red in Table 76 on page 184 indicate the ones that will be accepted based on Table 72 on
page 174.
Table 76 Phase 1 IPsec proposals provided by the built-in L2TP client in popular operating systems
(Encryption/Authentication/Key Group)
WINDOWS XP WINDOWS VISTA WINDOWS 7 IOS 5.1 ANDROID 4.1
1 3DES/SHA1/DH15 3DES/SHA1/DH15 AES/SHA1/DH15 AES/SHA1/DH2 AES/SHA1/DH2
23DES/SHA1/DH2 3DES/SHA1/DH2 3DES/SHA1/DH15 AES/MD5/DH2 AES/MD5/DH2
3 3DES/MD5/DH2 3DES/SHA1/DH2 3DES/SHA1/DH2 3DES/SHA1/DH2
4 DES/SHA1/DH1 3DES/MD5/DH2 3DES/MD5/DH2
Chapter 10 VPN
SBG5500 Series User’s Guide
185
After phase 1 tunnel is established, IPsec phase 2 negotiations begin. Table 77 on page 185 lists the IPsec
phase 2 proposals provided by a built-in L2TP client in the popular operating systems. The first proposal
that can be supported by the phase 2 setting in the Default_L2TP_VPN_GW IPsec VPN rule will be
accepted by the SBG. The algorithms in red in Table 77 on page 185 indicate the ones that will be
accepted based on Table 72 on page 174.
10.8 The L2TP Client Status Screen
Use the L2TP Client Status screen to view details about the L2TP clients. Click Configuration > VPN > L2TP
Client Status to open the following screen.
5DES/MD5/DH1 DES/SHA1/DH2
6DES/MD5/DH2
Table 77 Phase 2 IPsec proposals provided by the built-in L2TP client in popular operating systems
(Tunnel Mode/Encryption/Authentication) [Encapsulation = Transport]
WINDOWS XP WINDOWS VISTA WINDOWS 7 IOS 5.1 ANDROID 4.1
1ESP/3DES/MD5
ESP/3DES/SHA1
ESP/AES/SHA1 ESP/AES/SHA1 ESP/AES/SHA1
ESP/AES/MD5
ESP/3DES/SHA1
ESP/3DES/MD5
ESP/AES/SHA1
ESP/AES/MD5
ESP/3DES/SHA1
ESP/3DES/MD5
ESP/DES/SHA1
ESP/DES/MD5
2 AH/-/SHA1 and
ESP/3DES/-
ESP/3DES/SHA1 ESP/3DES/SHA1
3 AH/-/MD5 and
ESP/3DES/-
AH/-/SHA1 and
ESP/AES/-
ESP/DES/SHA1
4 AH/-/SHA1 and
ESP/3DES/SHA1
AH/-/SHA1 and
ESP/3DES/-
ESP/-/SHA1
5 AH/-/MD5 and
ESP/3DES/MD5
AH/-/SHA1 and
ESP/3DES/SHA1
AH/-/SHA1
6 ESP/DES/MD5 ESP/
DES/SHA1
ESP/-/SHA1
AH/-/SHA1
Table 76 Phase 1 IPsec proposals provided by the built-in L2TP client in popular operating systems
(Encryption/Authentication/Key Group)
WINDOWS XP WINDOWS VISTA WINDOWS 7 IOS 5.1 ANDROID 4.1
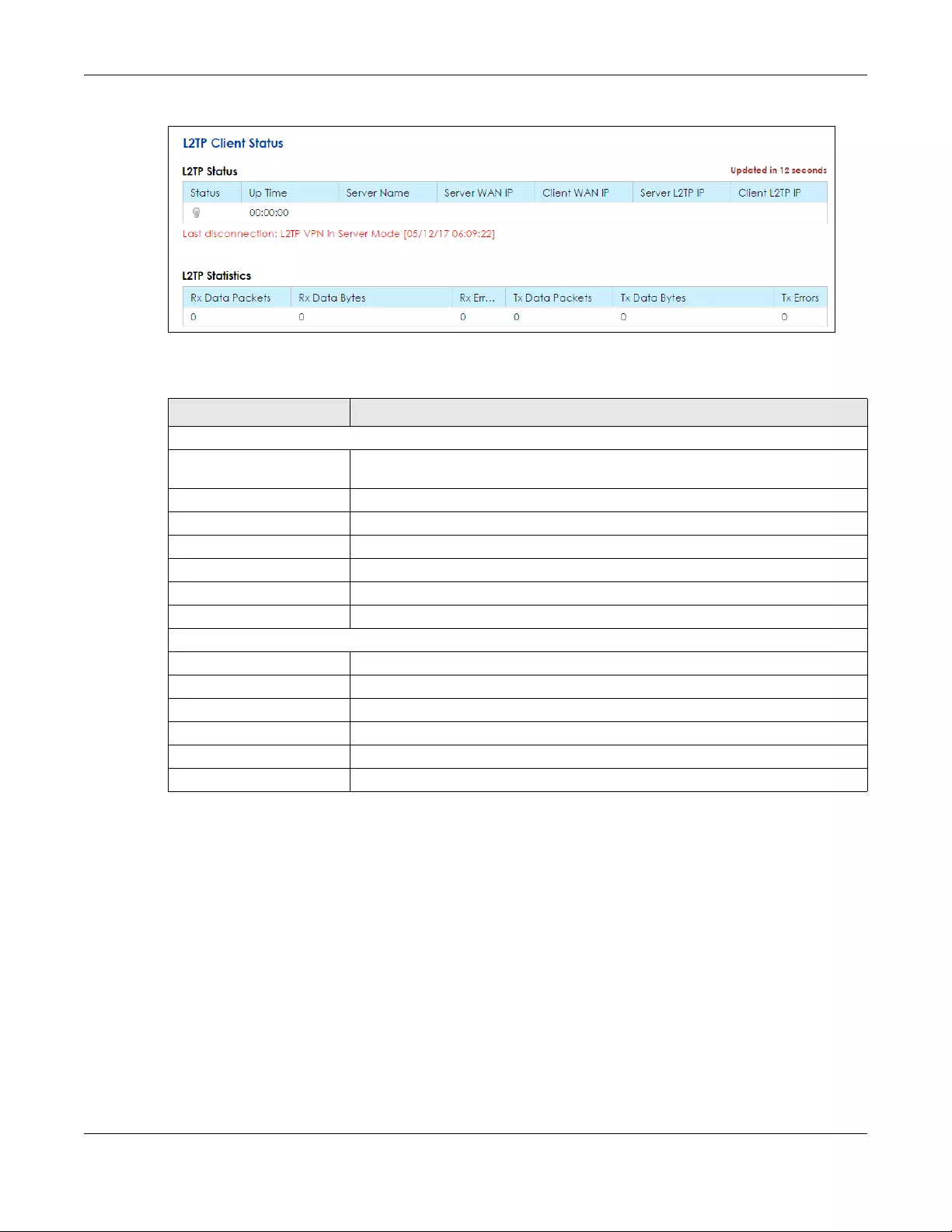
Chapter 10 VPN
SBG5500 Series User’s Guide
186
Figure 138 Configuration > VPN > L2TP Client Status
The following table describes the labels in this screen.
10.9 Technical Reference
This section provides some technical background information about the topics covered in this chapter.
10.9.1 IPsec Architecture
The overall IPsec architecture is shown as follows.
Table 78 Configuration > VPN > L2TP Client Status
LABEL DESCRIPTION
L2TP Status
Status This field displays whether the L2TP VPN is active or not. A yellow bulb signifies that
this VPN is active. A gray bulb signifies that this VPN is not active.
Up Time This field displays the period of time this connection has been up.
Server Name This field displays the name of the L2TP Network Server.
Server WAN IP This field displays the WAN IP address of the L2TP Network Server.
Client WAN IP This field displays the WAN IP address of the L2TP client.
Server L2TP IP This field displays the assigned L2TP IP address of the L2TP network server.
Client L2TP IP This field displays the assigned L2TP IP address of the L2TP client.
L2TP Statistics
Rx Data Packets This indicates the number of packets received in this L2TP connection.
Rx Data Bytes This indicates the number of bytes received in this L2TP connection.
Rx Errors This indicates the number of received packet errors in this L2TP connection.
Tx Data Packets This indicates the number of packets transmitted in this L2TP connection.
Tx Data Bytes This indicates the number of bytes transmitted in this L2TP connection.
Tx Errors This indicates the number of transmitted packet errors in this L2TP connection.
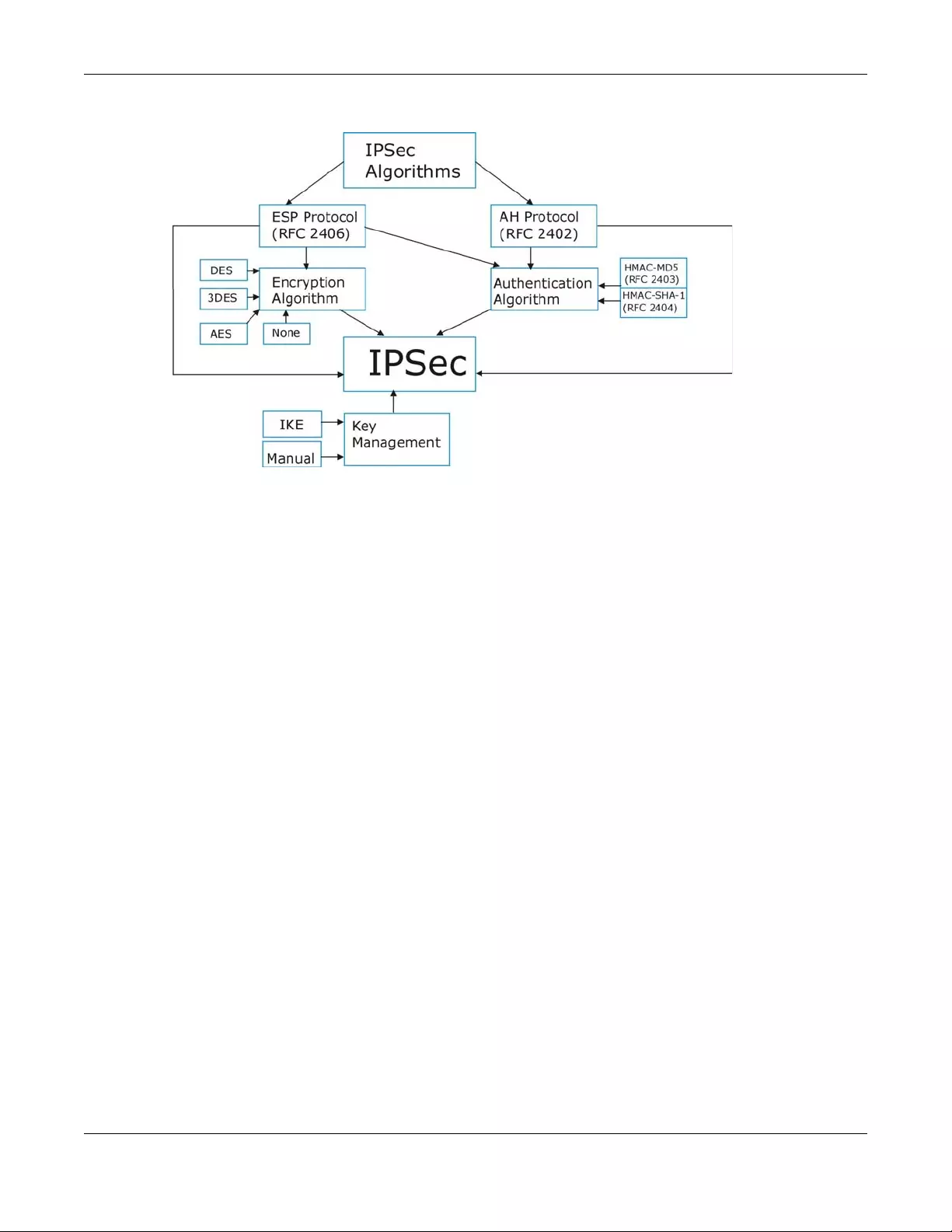
Chapter 10 VPN
SBG5500 Series User’s Guide
187
Figure 139 IPsec Architecture
IPsec Algorithms
The ESP (Encapsulating Security Payload) Protocol (RFC 2406) and AH (Authentication Header) protocol
(RFC 2402) describe the packet formats and the default standards for packet structure (including
implementation algorithms).
The Encryption Algorithm describes the use of encryption techniques such as DES (Data Encryption
Standard) and Triple DES algorithms.
The Authentication Algorithms, HMAC-MD5 (RFC 2403) and HMAC-SHA-1 (RFC 2404, provide an
authentication mechanism for the AH and ESP protocols.
Key Management
Key management allows you to determine whether to use IKE (ISAKMP) or manual key configuration in
order to set up a VPN.
10.9.2 Encapsulation
The two modes of operation for IPsec VPNs are Transport mode and Tunnel mode. At the time of writing,
the SBG supports Tunnel mode only.
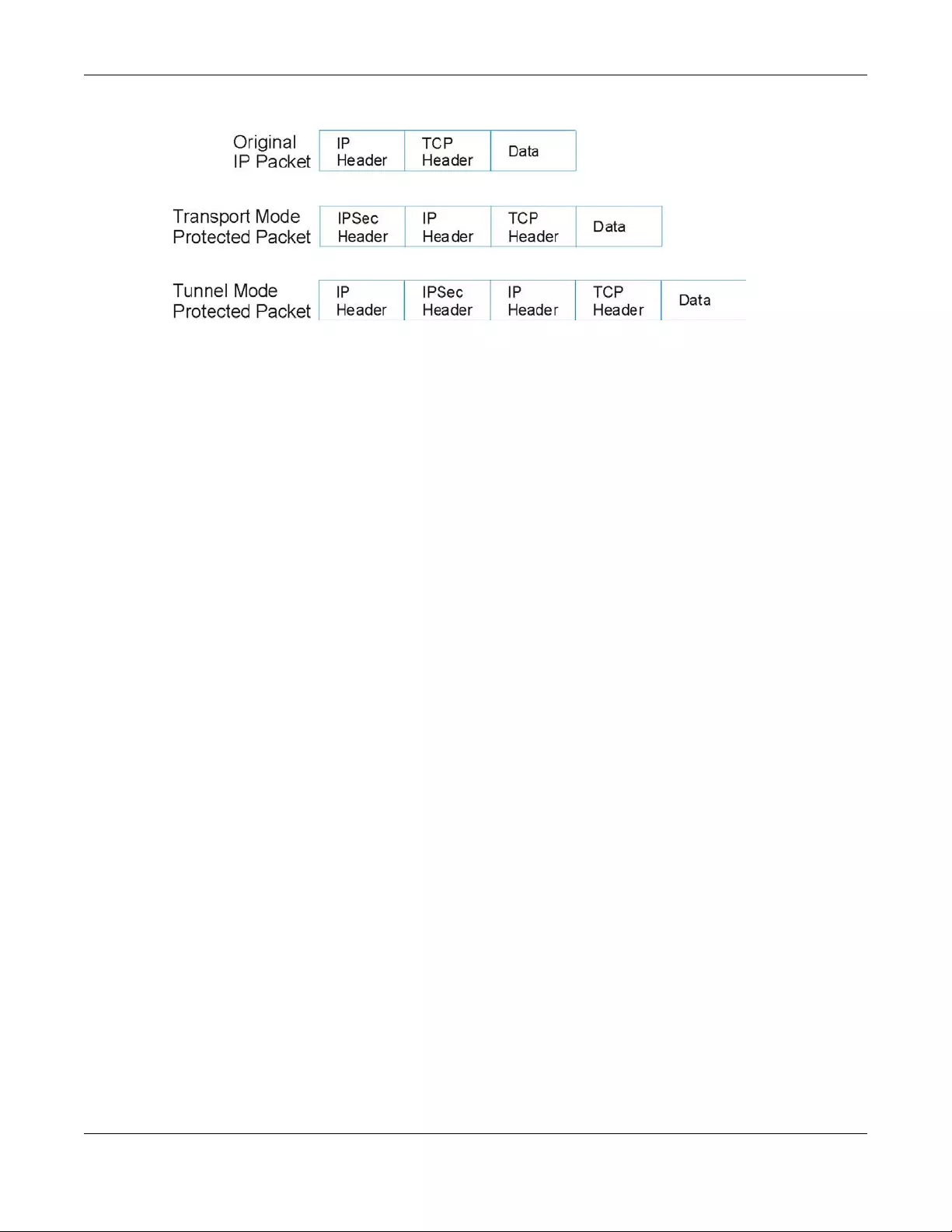
Chapter 10 VPN
SBG5500 Series User’s Guide
188
Figure 140 Transport and Tunnel Mode IPsec Encapsulation
Transport Mode
Transport mode is used to protect upper layer protocols and only affects the data in the IP packet. In
Transport mode, the IP packet contains the security protocol (AH or ESP) located after the original IP
header and options, but before any upper layer protocols contained in the packet (such as TCP and
UDP).
With ESP, protection is applied only to the upper layer protocols contained in the packet. The IP header
information and options are not used in the authentication process. Therefore, the originating IP address
cannot be verified for integrity against the data.
With the use of AH as the security protocol, protection is extended forward into the IP header to verify
the integrity of the entire packet by use of portions of the original IP header in the hashing process.
Tunnel Mode
Tunnel mode encapsulates the entire IP packet to transmit it securely. A Tunnel mode is required for
gateway services to provide access to internal systems. Tunnel mode is fundamentally an IP tunnel with
authentication and encryption. This is the most common mode of operation. Tunnel mode is required for
gateway to gateway and host to gateway communications. Tunnel mode communications have two
sets of IP headers:
•Outside header: The outside IP header contains the destination IP address of the VPN gateway.
•Inside header: The inside IP header contains the destination IP address of the final system behind the
VPN gateway. The security protocol appears after the outer IP header and before the inside IP
header.
10.9.3 IKE Phases
There are two phases to every IKE (Internet Key Exchange) negotiation – phase 1 (Authentication) and
phase 2 (Key Exchange). A phase 1 exchange establishes an IKE SA and the second one uses that SA to
negotiate SAs for IPsec.
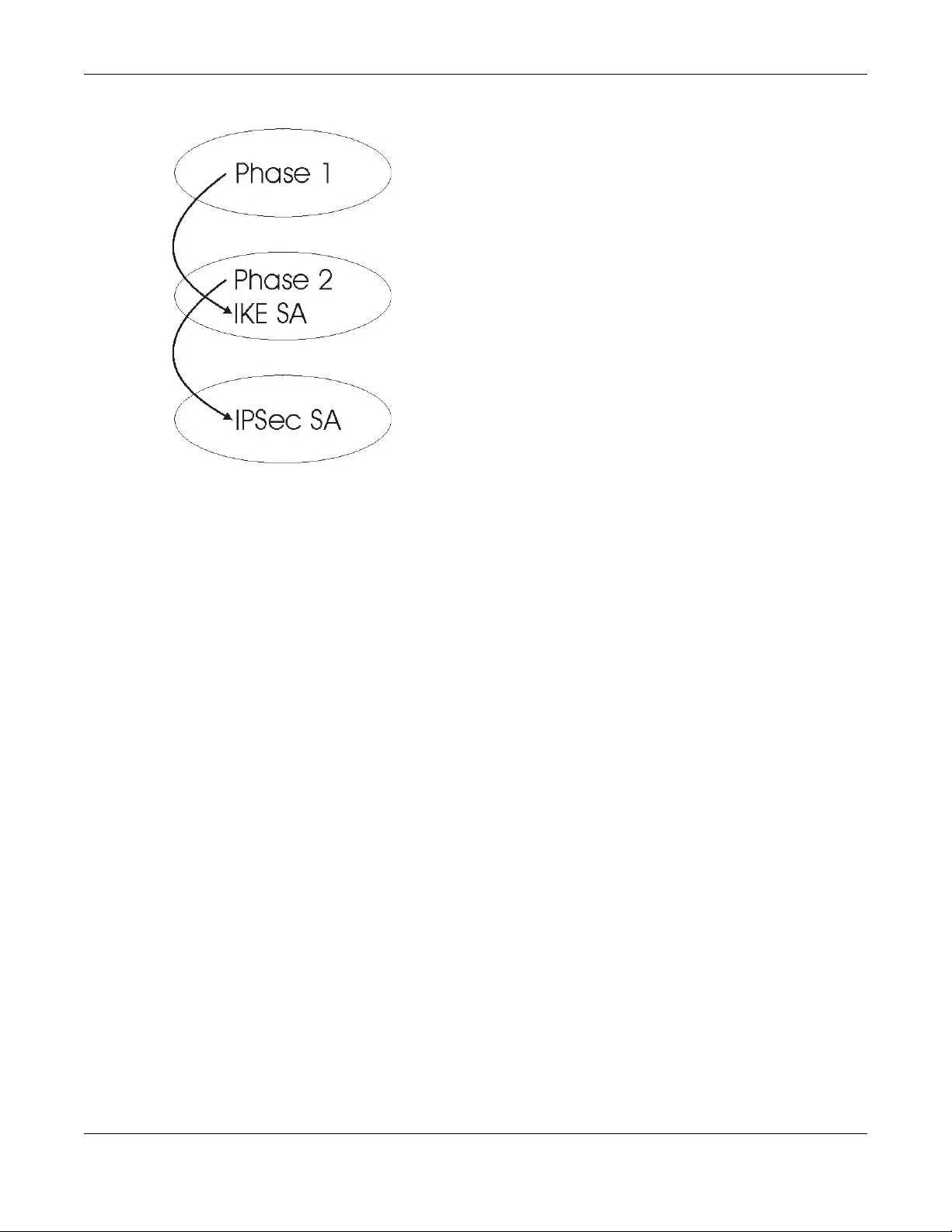
Chapter 10 VPN
SBG5500 Series User’s Guide
189
Figure 141 Two Phases to Set Up the IPsec SA
In phase 1 you must:
• Choose a negotiation mode.
• Authenticate the connection by entering a pre-shared key.
• Choose an encryption algorithm.
• Choose an authentication algorithm.
• Choose a Diffie-Hellman public-key cryptography key group (DH1 or DH2).
• Set the IKE SA lifetime. This field allows you to determine how long an IKE SA should stay up before it
times out. An IKE SA times out when the IKE SA lifetime period expires. If an IKE SA times out when an
IPsec SA is already established, the IPsec SA stays connected.
In phase 2 you must:
• Choose an encryption algorithm.
• Choose an authentication algorithm
• Choose a Diffie-Hellman public-key cryptography key group.
• Set the IPsec SA lifetime. This field allows you to determine how long the IPsec SA should stay up
before it times out. The SBG automatically renegotiates the IPsec SA if there is traffic when the IPsec
SA lifetime period expires. If an IPsec SA times out, then the IPsec router must renegotiate the SA the
next time someone attempts to send traffic.
10.9.4 Negotiation Mode
The phase 1 Negotiation Mode you select determines how the Security Association (SA) will be
established for each connection through IKE negotiations.
•Main Mode ensures the highest level of security when the communicating parties are negotiating
authentication (phase 1). It uses 6 messages in three round trips: SA negotiation, Diffie-Hellman
exchange and an exchange of nonces (a nonce is a random number). This mode features identity
protection (your identity is not revealed in the negotiation).

Chapter 10 VPN
SBG5500 Series User’s Guide
190
•Aggressive Mode is quicker than Main Mode because it eliminates several steps when the
communicating parties are negotiating authentication (phase 1). However the trade-off is that faster
speed limits its negotiating power and it also does not provide identity protection. It is useful in remote
access situations where the address of the initiator is not know by the responder and both parties
want to use pre-shared key authentication.
10.9.5 IPsec and NAT
Read this section if you are running IPsec on a host computer behind the SBG.
NAT is incompatible with the AH protocol in both Transport and Tunnel mode. An IPsec VPN using the AH
protocol digitally signs the outbound packet, both data payload and headers, with a hash value
appended to the packet. When using AH protocol, packet contents (the data payload) are not
encrypted.
A NAT device in between the IPsec endpoints will rewrite either the source or destination address with
one of its own choosing. The VPN device at the receiving end will verify the integrity of the incoming
packet by computing its own hash value, and complain that the hash value appended to the received
packet doesn't match. The VPN device at the receiving end doesn't know about the NAT in the middle,
so it assumes that the data has been maliciously altered.
IPsec using ESP in Tunnel mode encapsulates the entire original packet (including headers) in a new IP
packet. The new IP packet's source address is the outbound address of the sending VPN gateway, and
its destination address is the inbound address of the VPN device at the receiving end. When using ESP
protocol with authentication, the packet contents (in this case, the entire original packet) are
encrypted. The encrypted contents, but not the new headers, are signed with a hash value appended
to the packet.
Tunnel mode ESP with authentication is compatible with NAT because integrity checks are performed
over the combination of the "original header plus original payload," which is unchanged by a NAT
device.
Transport mode ESP with authentication is not compatible with NAT.
10.9.6 VPN, NAT, and NAT Traversal
NAT is incompatible with the AH protocol in both transport and tunnel mode. An IPsec VPN using the AH
protocol digitally signs the outbound packet, both data payload and headers, with a hash value
appended to the packet, but a NAT device between the IPsec endpoints rewrites the source or
destination address. As a result, the VPN device at the receiving end finds a mismatch between the
hash value and the data and assumes that the data has been maliciously altered.
NAT is not normally compatible with ESP in transport mode either, but the SBG’s NAT Traversal feature
provides a way to handle this. NAT traversal allows you to set up an IKE SA when there are NAT routers
between the two IPsec routers.
Table 79 VPN and NAT
SECURITY PROTOCOL MODE NAT
AH Transport N
AH Tunnel N
ESP Transport N
ESP Tunnel Y
Chapter 10 VPN
SBG5500 Series User’s Guide
191
Figure 142 NAT Router Between IPsec Routers
Normally you cannot set up an IKE SA with a NAT router between the two IPsec routers because the NAT
router changes the header of the IPsec packet. NAT traversal solves the problem by adding a UDP port
500 header to the IPsec packet. The NAT router forwards the IPsec packet with the UDP port 500 header
unchanged. In the above figure, when IPsec router A tries to establish an IKE SA, IPsec router B checks
the UDP port 500 header, and IPsec routers A and B build the IKE SA.
For NAT traversal to work, you must:
• Use ESP security protocol (in either transport or tunnel mode).
• Use IKE keying mode.
• Enable NAT traversal on both IPsec endpoints.
• Set the NAT router to forward UDP port 500 to IPsec router A.
Finally, NAT is compatible with ESP in tunnel mode because integrity checks are performed over the
combination of the "original header plus original payload," which is unchanged by a NAT device. The
compatibility of AH and ESP with NAT in tunnel and transport modes is summarized in the following table.
Y* - This is supported in the SBG if you enable NAT traversal.
10.9.7 ID Type and Content
With aggressive negotiation mode (see Section 10.9.4 on page 189), the SBG identifies incoming SAs by
ID type and content since this identifying information is not encrypted. This enables the SBG to distinguish
between multiple rules for SAs that connect from remote IPsec routers that have dynamic WAN IP
addresses.
Regardless of the ID type and content configuration, the SBG does not allow you to save multiple active
rules with overlapping local and remote IP addresses.
With main mode (see Section 10.9.4 on page 189), the ID type and content are encrypted to provide
identity protection. In this case the SBG can only distinguish between different incoming SAs that
connect from remote IPsec routers that have dynamic WAN IP addresses. The SBG can distinguish
incoming SAs because you can select between three encryption algorithms (DES, 3DES and AES), two
authentication algorithms (MD5 and SHA1) and eight key groups when you configure a VPN rule (see
Table 80 VPN and NAT
SECURITY PROTOCOL MODE NAT
AH Transport N
AH Tunnel N
ESP Transport Y*
ESP Tunnel Y
Chapter 10 VPN
SBG5500 Series User’s Guide
192
Section 10.6 on page 176). The ID type and content act as an extra level of identification for incoming
SAs.
The type of ID can be a domain name, an IP address or an e-mail address. The content is the IP address,
domain name, or e-mail address.
10.9.7.1 ID Type and Content Examples
Two IPsec routers must have matching ID type and content configuration in order to set up a VPN
tunnel.
The two SBGs in this example can complete negotiation and establish a VPN tunnel.
The two SBGs in this example cannot complete their negotiation because SBG B’s Local ID type is IP, but
SBG A’s Remote ID type is set to E-mail. An “ID mismatched” message displays in the IPSEC LOG.
10.9.8 Pre-Shared Key
A pre-shared key identifies a communicating party during a phase 1 IKE negotiation (see Section 10.9.3
on page 188 for more on IKE phases). It is called “pre-shared” because you have to share it with another
party before you can communicate with them over a secure connection.
10.9.9 Diffie-Hellman (DH) Key Groups
Diffie-Hellman (DH) is a public-key cryptography protocol that allows two parties to establish a shared
secret over an unsecured communications channel. Diffie-Hellman is used within IKE SA setup to
establish session keys. 768-bit, 1024-bit 1536-bit, 2048-bit, and 3072-bit Diffie-Hellman groups are
Table 81 Local ID Type and Content Fields
LOCAL ID TYPE= CONTENT=
IP Type the IP address of your computer.
FQDN Type a domain name (up to 31 characters) by which to identify this SBG.
User-FQDN Type an e-mail address (up to 31 characters) by which to identify this SBG.
The domain name or e-mail address that you use in the Local ID Content field is used
for identification purposes only and does not need to be a real domain name or e-
mail address.
Table 82 Matching ID Type and Content Configuration Example
SBG A SBG B
Local ID type: User-FQDN Local ID type: IP
Local ID content: tom@yourcompany.com Local ID content: 1.1.1.2
Remote ID type: IP Remote ID type: E-mail
Remote ID content: 1.1.1.2 Remote ID content: tom@yourcompany.com
Table 83 Mismatching ID Type and Content Configuration Example
SBG A SBG B
Local ID type: IP Local ID type: IP
Local ID content: 1.1.1.10 Local ID content: 1.1.1.2
Remote ID type: User-FQDN Remote ID type: IP
Remote ID content: aa@yahoo.com Remote ID content: 1.1.1.0

Chapter 10 VPN
SBG5500 Series User’s Guide
193
supported. Upon completion of the Diffie-Hellman exchange, the two peers have a shared secret, but
the IKE SA is not authenticated. For authentication, use pre-shared keys.

SBG5500 Series User’s Guide
194
CHAPTER 11
Bandwidth Management
11.1 Overview
Quality of Service (QoS) refers to both a network’s ability to deliver data with minimum delay, and the
networking methods used to control the use of bandwidth. Without QoS, all traffic data is equally likely
to be dropped when the network is congested. This can cause a reduction in network performance and
make the network inadequate for time-critical application such as video-on-demand.
Configure QoS on the SBG to group and prioritize application traffic and fine-tune network
performance. Setting up QoS involves these steps:
1Configure classifiers to sort traffic into different flows.
2Assign priority and define actions to be performed for a classified traffic flow.
The SBG assigns each packet a priority and then queues the packet accordingly. Packets assigned a
high priority are processed more quickly than those with low priority if there is congestion, allowing time-
sensitive applications to flow more smoothly. Time-sensitive applications include both those that require
a low level of latency (delay) and a low level of jitter (variations in delay) such as Voice over IP (VoIP) or
Internet gaming, and those for which jitter alone is a problem such as Internet radio or streaming video.
This chapter contains information about configuring QoS and editing classifiers.
11.1.1 What You Can Do in this Chapter
• The General screen lets you enable or disable QoS and set the upstream bandwidth (Section 11.2 on
page 196).
• The Queue Setup screen lets you configure QoS queue assignment (Section 11.3 on page 197).
• The Classification Setup screen lets you add, edit or delete QoS classifiers (Section 11.4 on page 199).
• The Policer Setup screen lets you add, edit or delete QoS policers (Section 11.5 on page 204).
• The Shaper Setup screen lets you limit outgoing traffic transmission rate on the selected interface
(Section 11.6 on page 206)
11.1.2 What You Need to Know
The following terms and concepts may help as you read through this chapter.
QoS versus Cos
QoS is used to prioritize source-to-destination traffic flows. All packets in the same flow are given the
same priority. CoS (class of service) is a way of managing traffic in a network by grouping similar types of
traffic together and treating each type as a class. You can use CoS to give different priorities to different
packet types.
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
195
CoS technologies include IEEE 802.1p layer 2 tagging and DiffServ (Differentiated Services or DS). IEEE
802.1p tagging makes use of three bits in the packet header, while DiffServ is a new protocol and
defines a new DS field, which replaces the eight-bit ToS (Type of Service) field in the IP header.
Tagging and Marking
In a QoS class, you can configure whether to add or change the DSCP (DiffServ Code Point) value, IEEE
802.1p priority level and VLAN ID number in a matched packet. When the packet passes through a
compatible network, the networking device, such as a backbone switch, can provide specific
treatment or service based on the tag or marker.
Traffic Shaping
Bursty traffic may cause network congestion. Traffic shaping regulates packets to be transmitted with a
pre-configured data transmission rate using buffers (or queues). Your SBG uses the Token Bucket
algorithm to allow a certain amount of large bursts while keeping a limit at the average rate.
Traffic Policing
Traffic policing is the limiting of the input or output transmission rate of a class of traffic on the basis of
user-defined criteria. Traffic policing methods measure traffic flows against user-defined criteria and
identify it as either conforming, exceeding or violating the criteria.
The SBG supports three incoming traffic metering algorithms: Token Bucket Filter (TBF), Single Rate Two
Color Maker (srTCM), and Two Rate Two Color Marker (trTCM). You can specify actions which are
performed on the colored packets. See Section 11.7 on page 207 for more information on each
metering algorithm.
Traffic
Time
Traffic Rate
Traffic
Time
Traffic Rate
(Before Traffic Shaping) (After Traffic Shaping)
Traffic
Time
Traffic Rate
Traffic
Time
Traffic Rate
(Before Traffic Policing) (After Traffic Policing)
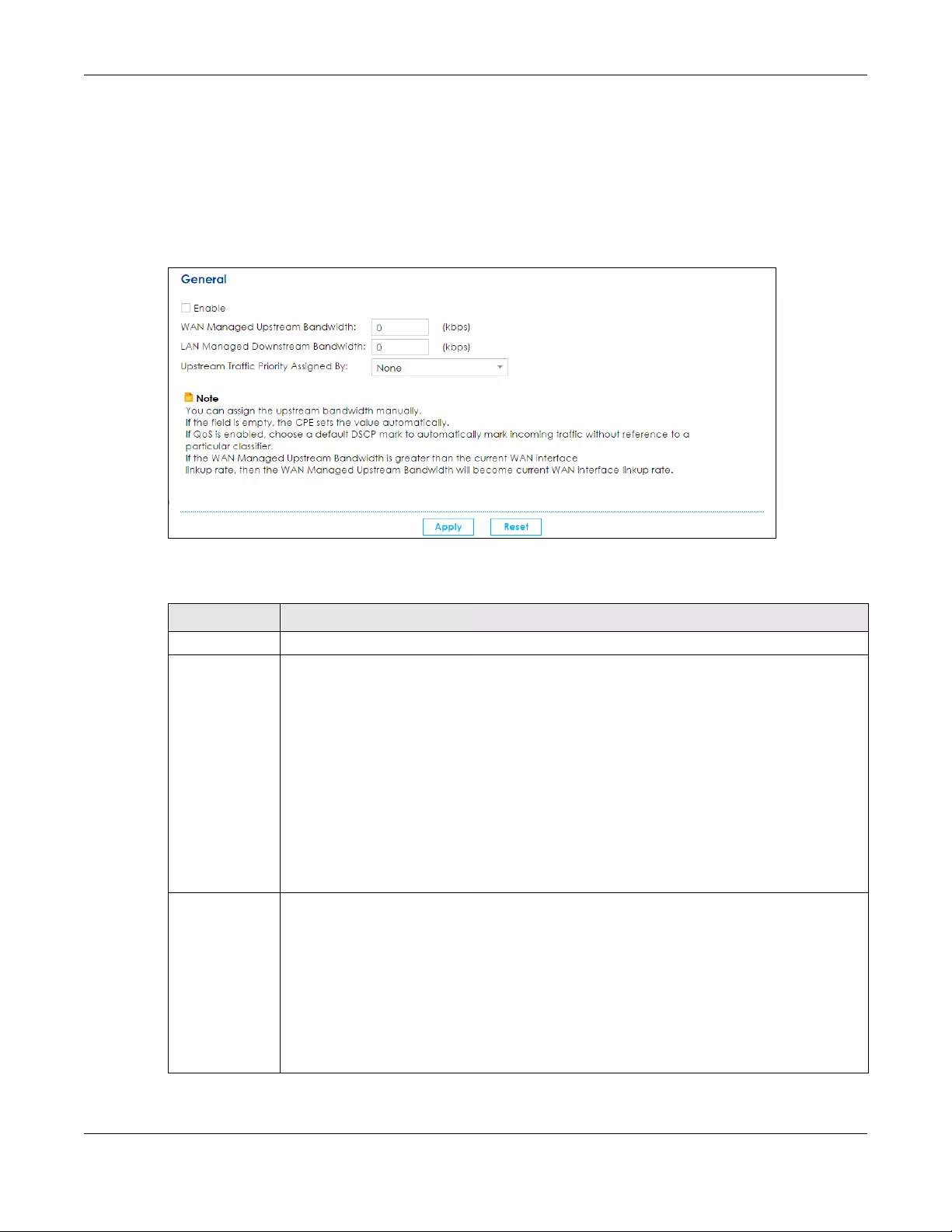
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
196
11.2 The General Screen
Click Configuration > Bandwidth Management > General to open the screen as shown next.
Use this screen to enable or disable QoS and set the upstream bandwidth. See Section 11.1 on page 194
for more information.
Figure 143 Configuration > Bandwidth Management > General
The following table describes the labels in this screen.
Table 84 Configuration > Bandwidth Management > General
LABEL DESCRIPTION
Enable Select the Enable check box to turn on QoS to improve your network performance.
WAN Managed
Upstream
Bandwidth
Enter the amount of upstream bandwidth for the WAN interfaces that you want to allocate using
QoS.
The recommendation is to set this speed to match the interfaces’ actual transmission speed. For
example, set the WAN interfaces’ speed to 100000 kbps if your Internet connection has an
upstream transmission speed of 100 Mbps.
You can set this number higher than the interfaces’ actual transmission speed. The SBG uses up
to 95% of the DSL port’s actual upstream transmission speed even if you set this number higher
than the DSL port’s actual transmission speed.
You can also set this number lower than the interfaces’ actual transmission speed. This will cause
the SBG to not use some of the interfaces’ available bandwidth.
If you leave this field blank, the SBG automatically sets this number to be 95% of the WAN
interfaces’ actual upstream transmission speed.
LAN Managed
Downstream
Bandwidth
Enter the amount of downstream bandwidth for the LAN interfaces (including WLAN) that you
want to allocate using QoS.
The recommendation is to set this speed to match the WAN interfaces’ actual transmission
speed. For example, set the LAN managed downstream bandwidth to 100000 kbps if you use a
100 Mbps wired Ethernet WAN connection.
You can also set this number lower than the WAN interfaces’ actual transmission speed. This will
cause the SBG to not use some of the interfaces’ available bandwidth.
If you leave this field blank, the SBG automatically sets this to the LAN interfaces’ maximum
supported connection speed.
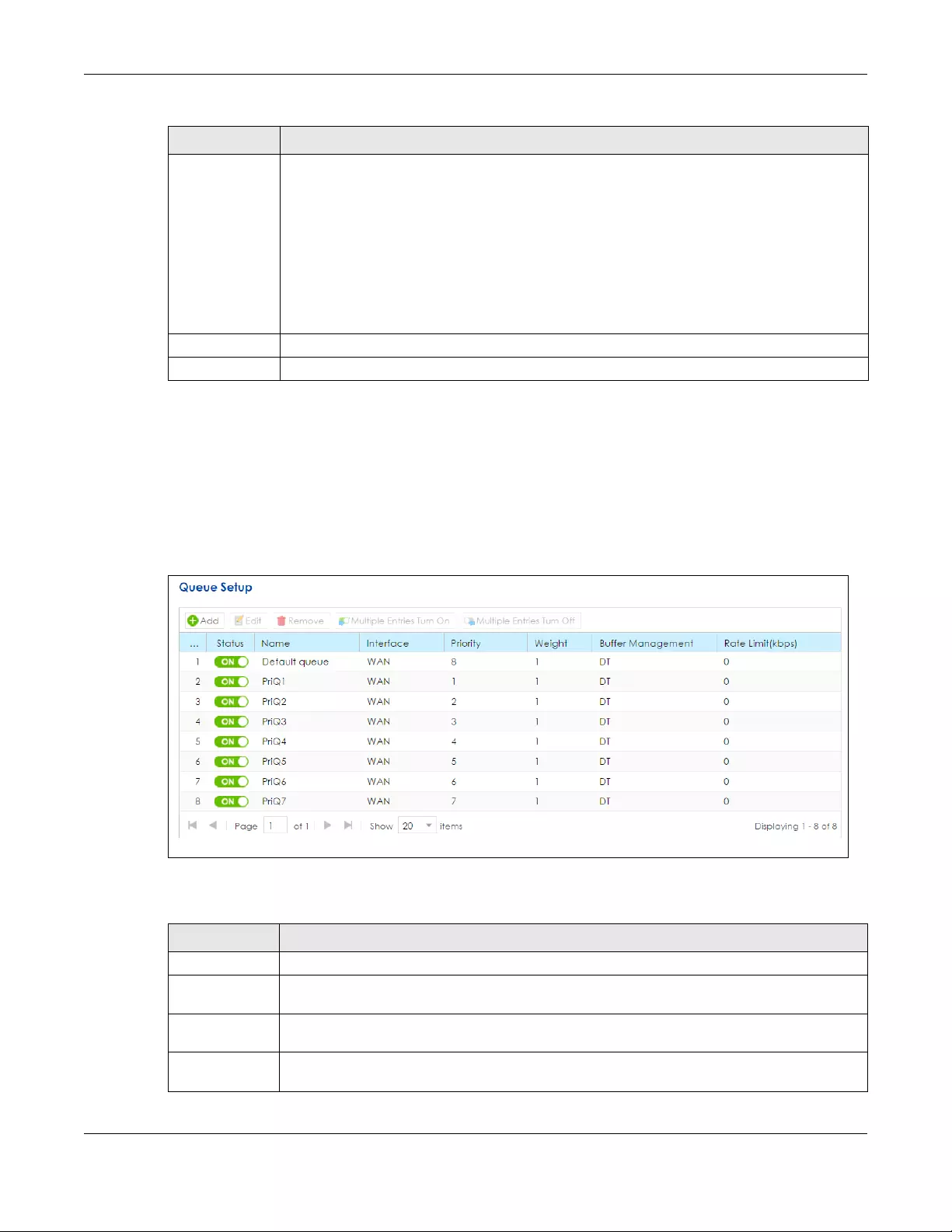
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
197
11.3 The Queue Setup Screen
Click Configuration > Bandwidth Management > Queue Setup to open the screen as shown next.
Use this screen to configure QoS queue assignment.
Figure 144 Configuration > Bandwidth Management > Queue Setup
The following table describes the labels in this screen.
Upstream traffic
priority Assigned
by
Select how the SBG assigns priorities to various upstream traffic flows.
•None: Disables auto priority mapping and has the SBG put packets into the queues
according to your classification rules. Traffic which does not match any of the classification
rules is mapped into the default queue with the lowest priority.
•Ethernet Priority: Automatically assign priority based on the IEEE 802.1p priority level.
•IP Precedence: Automatically assign priority based on the first three bits of the TOS field in the
IP header.
•Packet Length: Automatically assign priority based on the packet size. Smaller packets get
higher priority since control, signaling, VoIP, internet gaming, or other real-time packets are
usually small while larger packets are usually best effort
• data packets like file transfers.
Apply Click Apply to save your changes.
Reset Click Reset to restore your previously saved settings.
Table 84 Configuration > Bandwidth Management > General (continued) (continued)
LABEL DESCRIPTION
Table 85 Network Setting > QoS > Queue Setup
LABEL DESCRIPTION
Add Click this button to create a new queue entry.
Edit Double-click a queue entry or select it and click Edit to open a screen where you can modify
the queue’s settings.
Remove To remove an existing queue entry, select it and click Remove. Note that subsequent rules move
up by one when you take this action.
Multiple Entries
Turn On
Select a queue and click this to enable it.
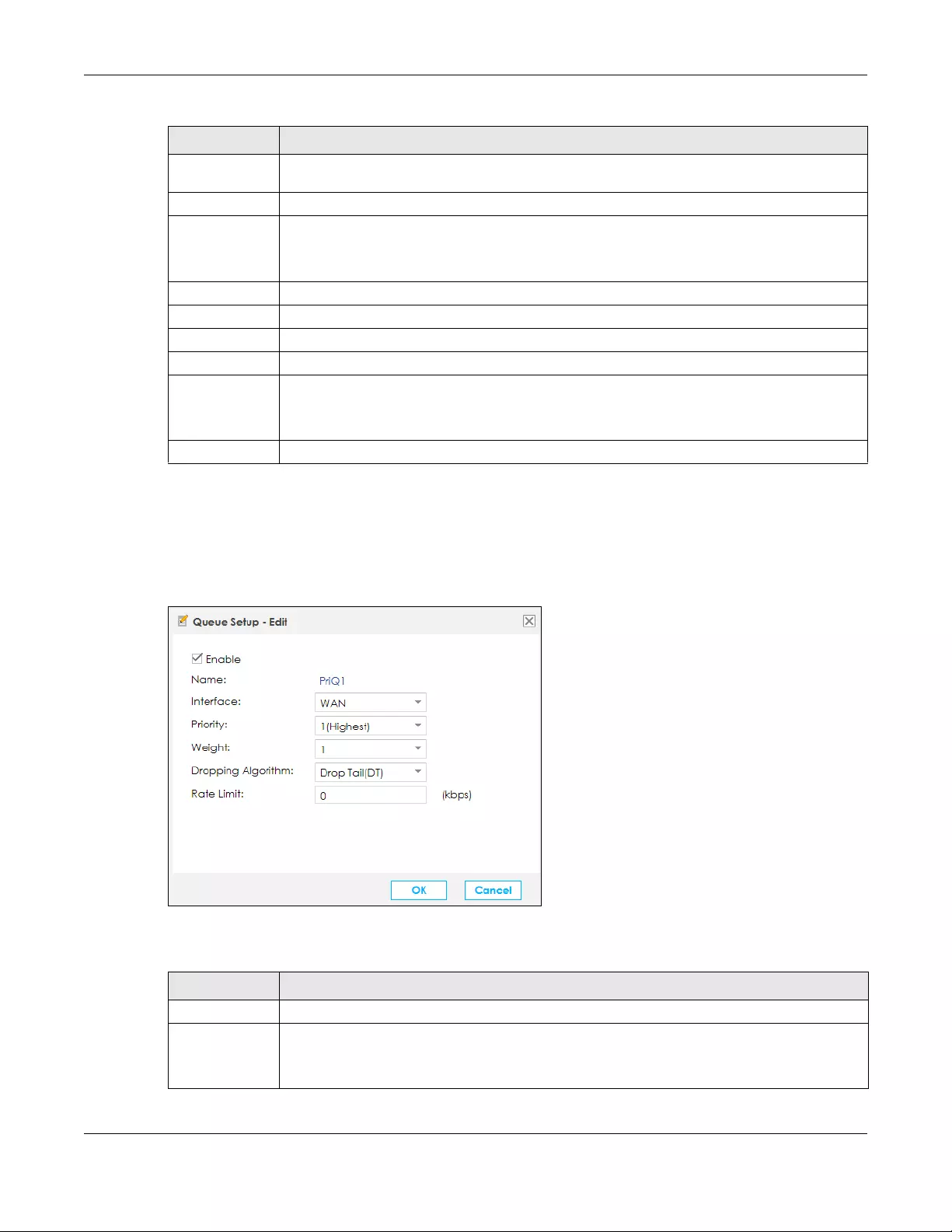
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
198
11.3.1 Adding a QoS Queue
Click Add or the select an existing queue and click Edit icon in the Queue Setup screen to configure a
queue.
Figure 145 Queue Setup: Add/Edit
The following table describes the labels in this screen.
Multiple Entries
Turn Off
Select a queue and click this to disable it.
#This is the index number of the queue entry.
Status This field displays whether the queue is active or not. A green ON button signifies that this queue
is active. A gray OFF button signifies that this queue is not active.
Click the slide button to turn on or turn off the queue.
Name This shows the descriptive name of this queue.
Interface This shows the name of the SBG’s interface through which traffic in this queue passes.
Priority This shows the priority of this queue.
Weight This shows the weight of this queue.
Buffer
Management
This shows the queue management algorithm used for this queue.
Queue management algorithms determine how the SBG should handle packets when it
receives too many (network congestion).
Rate Limit This shows the maximum transmission rate allowed for traffic on this queue.
Table 85 Network Setting > QoS > Queue Setup (continued)
LABEL DESCRIPTION
Table 86 Queue Setup: Add/Edit
LABEL DESCRIPTION
Enable Select to enable or disable this queue.
Name Enter the descriptive name of this queue. You can use up to 31 alphanumeric characters, it must
begin with a letter. The valid characters are [0-9][a-z] [A-Z][_-].
This field is not configurable if you are editing an existing queue.
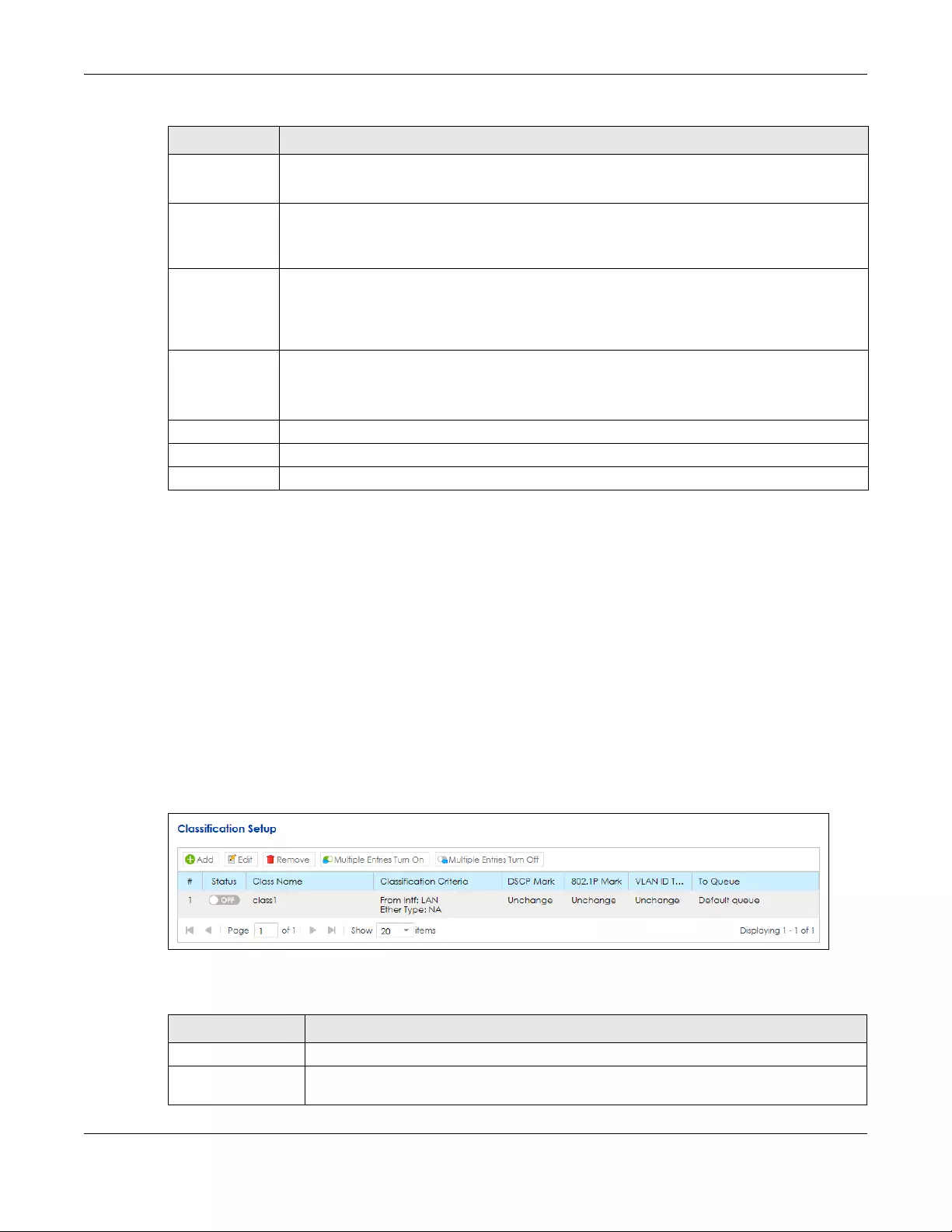
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
199
11.4 The Classification Setup Screen
Use this screen to add, edit or delete QoS classifiers. A classifier groups traffic into data flows according
to specific criteria such as the source address, destination address, source port number, destination port
number or incoming interface. For example, you can configure a classifier to select traffic from the
same protocol port (such as Telnet) to form a flow.
You can give different priorities to traffic that the SBG forwards out through the WAN interface. Give high
priority to voice and video to make them run more smoothly. Similarly, give low priority to many large file
downloads so that they do not reduce the quality of other applications.
Click Configuration > Bandwidth Management > Classification Setup to open the following screen.
Figure 146 Configuration > Bandwidth Management > Classification Setup
The following table describes the labels in this screen.
Interface Select the interface to which this queue is applied.
This field is read-only if you are editing the queue.
Priority Select the priority level (from 1 to 8) of this queue.
The smaller the number, the higher the priority level. Traffic assigned to higher priority queues
gets through faster while traffic in lower priority queues is dropped if the network is congested.
Weight Select the weight (from 1 to 8) of this queue.
If two queues have the same priority level, the SBG divides the bandwidth across the queues
according to their weights. Queues with larger weights get more bandwidth than queues with
smaller weights.
Dropping
Algorithm
This field displays Drop Tail (DT). Drop Tail (DT) is a simple queue management algorithm that
allows the SBG buffer to accept as many packets as it can until it is full. Once the buffer is full,
new packets that arrive are dropped until there is space in the buffer again (packets are
transmitted out of it).
Rate Limit Specify the maximum transmission rate (in Kbps) allowed for traffic on this queue.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 86 Queue Setup: Add/Edit (continued)
LABEL DESCRIPTION
Table 87 Configuration > Bandwidth Management > Classification Setup
LABEL DESCRIPTION
Add Click this to create a new classifier.
Edit Double-click a classifier or select it and click Edit to open a screen where you can modify
the classifier’s settings.
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
200
11.4.1 Add/Edit a QoS Class
Click Add in the Classification Setup screen or the Edit icon next to a classifier to open the following
screen.
Remove To remove an existing classifier, select it and click Remove. Note that subsequent rules move
up by one when you take this action.
Multiple Entries Turn
On
Select one or more classifier and click this to enable them.
Multiple Entries Turn
Off
Select one or more classifier and click this to disable them.
#This field displays the order in which this classifier is applied.
Status This field displays whether the classifier is active or not. A green ON button signifies that this
classifier is active. A gray OFF button signifies that this classifier is not active.
Click the slide button to turn on or turn off the classifier.
Class Name This is the name of the classifier.
Classification
Criteria
This shows criteria specified in this classifier, for example the interface from which traffic of
this class should come and the source MAC address of traffic that matches this classifier.
DSCP Mark This is the DSCP number added to traffic of this classifier.
802.1P Mark This is the IEEE 802.1p priority level assigned to traffic of this classifier.
VLAN ID Tag This is the VLAN ID number assigned to traffic of this classifier.
To Queue This is the name of the queue in which traffic of this classifier is put.
Table 87 Configuration > Bandwidth Management > Classification Setup (continued)
LABEL DESCRIPTION
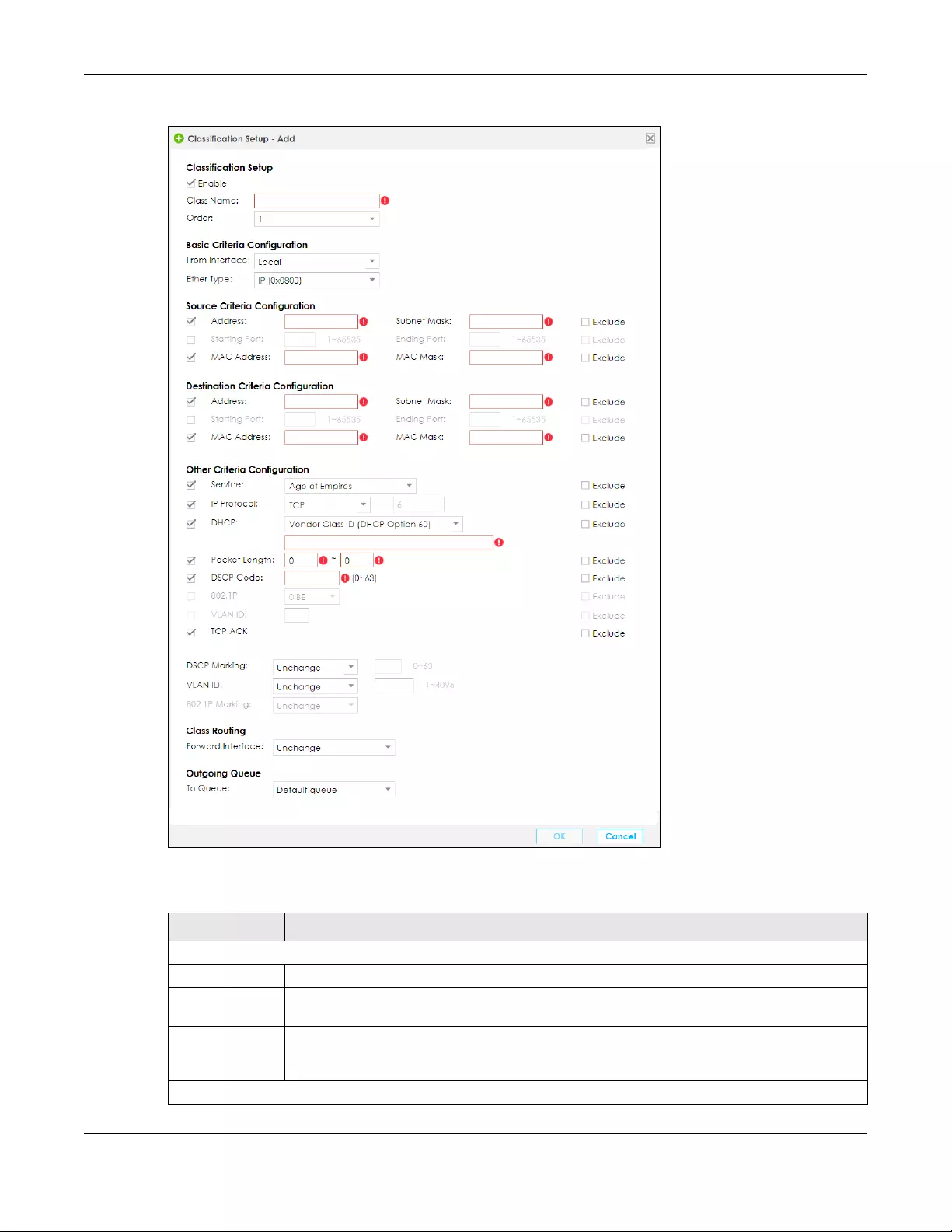
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
201
Figure 147 Classification Setup: Add/Edit
The following table describes the labels in this screen.
Table 88 Classification Setup: Add/Edit
LABEL DESCRIPTION
Classification Setup
Enable Select this to enable this classifier.
Class Name Enter a descriptive name for the classifier. You can use up to 31 alphanumeric characters, it
must begin with a letter. The valid characters are [0-9][a-z] [A-Z][_-].
Order Select an existing number for where you want to put this classifier to move the classifier to the
number you selected after clicking OK. Ordering your classifiers is important because the SBG
applies the classifiers in the order that you specify.
Basic Criteria Configuration
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
202
From Interface If you want to classify the traffic by an ingress interface, select an interface from the From
Interface drop-down list box.
Ether Type Select a predefined application to configure a class for the matched traffic.
If you select IP, you also need to configure source or destination MAC address, IP address,
DHCP options, DSCP value or the protocol type.
If you select 802.1Q, you can configure an 802.1p priority level.
Source Criteria Configuration
Address Select the check box and enter the source IP address in dotted decimal notation. A blank
source IP address means any source IP address.
Subnet
Netmask Enter the source subnet mask.
Starting Port Enter the starting port of the source.
Ending Port Enter the ending port of the source,
MAC Address Select the check box and enter the source MAC address of the packet.
MAC Mask Type the mask for the specified MAC address to determine which bits a packet’s MAC address
should match.
Enter “f” for each bit of the specified source MAC address that the traffic’s MAC address should
match. Enter “0” for the bit(s) of the matched traffic’s MAC address, which can be of any
hexadecimal character(s). For example, if you set the MAC address to 00:13:49:00:00:00 and
the mask to ff:ff:ff:00:00:00, a packet with a MAC address of 00:13:49:12:34:56 matches this
criteria.
Exclude Select this option to exclude the packets that match the specified criteria from this classifier.
Destination Criteria Configuration
Address Select the check box and enter the source IP address in dotted decimal notation. A blank
source IP address means any source IP address.
Subnet
Netmask Enter the source subnet mask.
Starting Port Enter the starting port of the source.
Ending Port Enter the ending port of the source,
MAC Address Select the check box and enter the source MAC address of the packet.
MAC Mask Type the mask for the specified MAC address to determine which bits a packet’s MAC address
should match.
Enter “f” for each bit of the specified source MAC address that the traffic’s MAC address should
match. Enter “0” for the bit(s) of the matched traffic’s MAC address, which can be of any
hexadecimal character(s). For example, if you set the MAC address to 00:13:49:00:00:00 and
the mask to ff:ff:ff:00:00:00, a packet with a MAC address of 00:13:49:12:34:56 matches this
criteria.
Exclude Select this option to exclude the packets that match the specified criteria from this classifier.
Other Criteria Configuration
Service This field is available only when you select IP in the Ether Type field.
This field simplifies classifier configuration by allowing you to select a predefined application.
When you select a predefined application, you do not configure the rest of the filter fields.
IP Protocol This field is available only when you select IP in the Ether Type field.
Select this option and select the protocol (service type) from TCP, UDP, ICMP or IGMP. If you
select User defined, enter the protocol (service type) number.
Table 88 Classification Setup: Add/Edit (continued)
LABEL DESCRIPTION

Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
203
DHCP This field is available only when you select IP in the Ether Type field.
Select this option and select a DHCP option.
If you select Vendor Class ID (DHCP Option 60), enter the Vendor Class Identifier (Option 60) of
the matched traffic, such as the type of the hardware or firmware.
If you select User Class ID (DHCP Option 77), enter a string that identifies the user’s category or
application type in the matched DHCP packets.
Packet
Length This field is available only when you select IP in the Ether Type field.
Select this option and enter the minimum and maximum packet length (from 46 to 1500) in the
fields provided.
DSCP Code This field is available only when you select IP in the Ether Type field.
Select this option and specify a DSCP (DiffServ Code Point) number between 0 and 63 in the
field provided.
802.1P This field is available only when you select 802.1Q in the Ether Type field.
Select this option and select a priority level (between 0 and 7) from the drop-down list box.
"0" is the lowest priority level and "7" is the highest.
VLAN ID This field is available only when you select 802.1Q in the Ether Type field.
Select this option and specify a VLAN ID number.
TCP ACK This field is available only when you select IP in the Ether Type field.
If you select this option, the matched TCP packets must contain the ACK (Acknowledge) flag.
Exclude Select this option to exclude the packets that match the specified criteria from this classifier.
DSCP Marking This field is available only when you select IP in the Ether Type field.
If you select Mark, enter a DSCP value with which the SBG replaces the DSCP field in the
packets.
If you select Unchange, the SBG keep the DSCP field in the packets.
VLAN ID If you select Remark, enter a VLAN ID number with which the SBG replaces the VLAN ID of the
frames.
If you select Remove, the SBG deletes the VLAN ID of the frames before forwarding them out.
If you select Add, the SBG treat all matched traffic untagged and add a second VLAN ID.
If you select Unchange, the SBG keep the VLAN ID in the packets.
802.1P Marking Select a priority level with which the SBG replaces the IEEE 802.1p priority field in the packets.
If you select Unchange, the SBG keep the 802.1p priority field in the packets.
Class Routing
Forward
Interface
Select a WAN interface through which traffic of this class will be forwarded out. If you select
Unchange, the SBG forward traffic of this class according to the default routing table.
Outgoing Queue
To Queue Select a queue that applies to this class.
You should have configured a queue in the Queue Setup screen already.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 88 Classification Setup: Add/Edit (continued)
LABEL DESCRIPTION
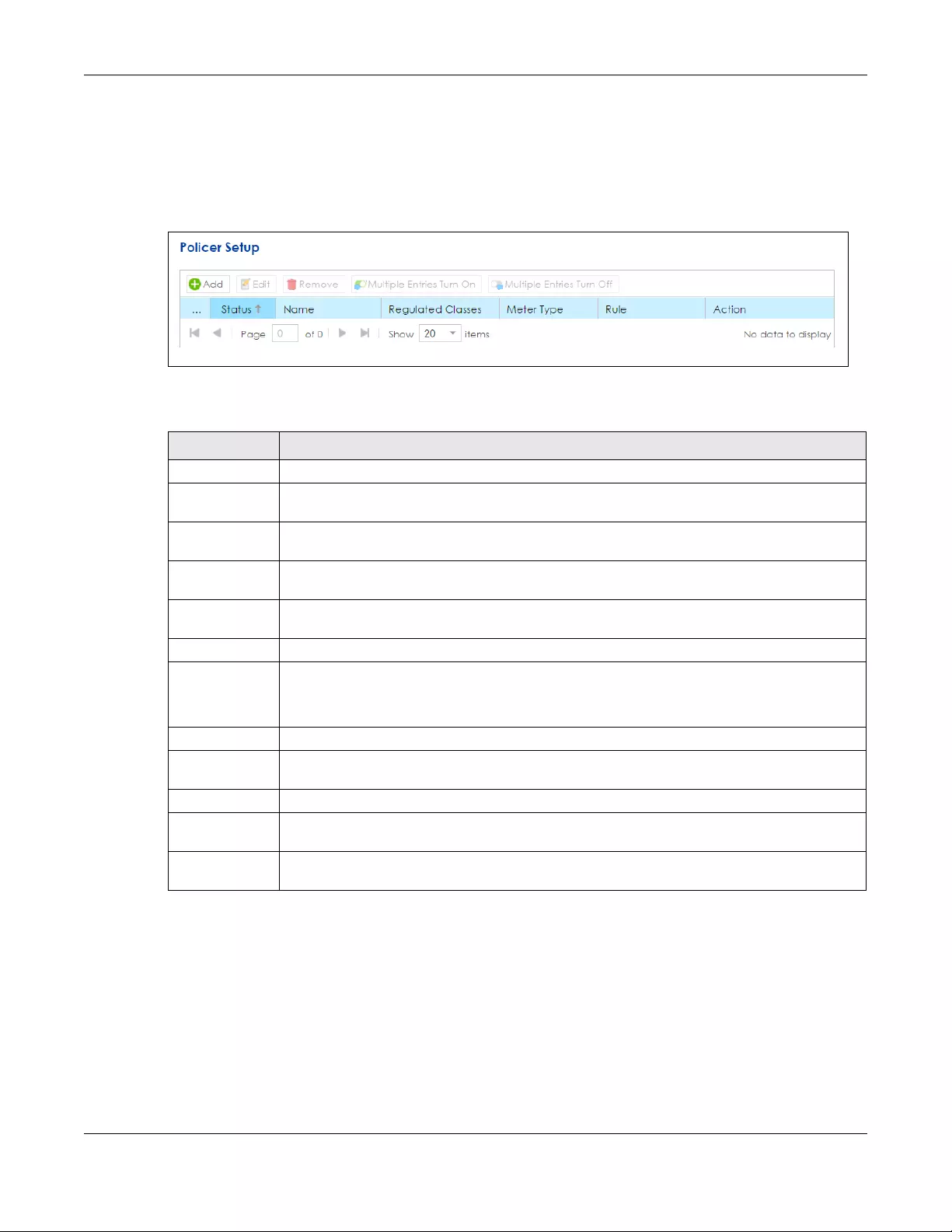
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
204
11.5 The Policer Setup Screen
Use this screen to configure QoS policers that allow you to limit the transmission rate of incoming traffic.
Click Configuration > Bandwidth Management > Policer Setup. The screen appears as shown.
Figure 148 Configuration > Bandwidth Management > Policer Setup
The following table describes the labels in this screen.
Table 89 Network Setting > QoS > Policer Setup
LABEL DESCRIPTION
Add Click this to create a new policer.
Edit Double-click a policer or select it and click Edit to open a screen where you can modify the
policer’s settings.
Remove To delete an existing policer, select it and click Remove. Note that subsequent rules move up by
one when you take this action.
Multiple Entries
Turn On
Select one or more policers and click this to enable them.
Multiple Entries
Turn Off
Select one ore more policers and click this to disable them.
#This is the index number of the policer.
Status This field displays whether the policer is active or not. A green ON button signifies that this policer
is active. A gray OFF button signifies that this policer is not active.
Click the slide button to turn on or turn off the policer.
Name This field displays the descriptive name of this policer.
Regulated
Classes
This field displays the name of a QoS classifier.
Meter Type This field displays the type of QoS metering algorithm used in this policer.
Rule These are the rates and burst sizes against which the policer checks the traffic of the member
QoS classes.
Action This shows the how the policer has the SBG treat different types of traffic belonging to the
policer’s member QoS classes.
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
205
11.5.1 Add/Edit a QoS Policer
Click Add in the Policer Setup screen or select a policer and click Edit next to a policer to show the
following screen.
Figure 149 Policer Setup: Add/Edit
The following table describes the labels in this screen.
Table 90 Policer Setup: Add/Edit
LABEL DESCRIPTION
Policer Setting
Enable Select the check box to activate this policer.
Name Enter the descriptive name of this policer. You can use up to 31 alphanumeric characters, it must
begin with a letter. The valid characters are [0-9][a-z] [A-Z][_-].
Meter Type This shows the traffic metering algorithm used in this policer.
The Simple Token Bucket algorithm uses tokens in a bucket to control when traffic can be
transmitted. Each token represents one byte. The algorithm allows bursts of up to b bytes which is
also the bucket size.
The Single Rate Three Color Marker (srTCM) is based on the token bucket filter and identifies
packets by comparing them to the Committed Information Rate (CIR), the Committed Burst Size
(CBS) and the Excess Burst Size (EBS).
Committed
Rate
Specify the committed rate. When the incoming traffic rate of the member QoS classes is less
than the committed rate, the device applies the conforming action to the traffic.
Committed
Burst Size
Specify the committed burst size for packet bursts. This must be equal to or less than the peak
burst size (two rate three color) or excess burst size (single rate three color) if it is also configured.
This is the maximum size of the (first) token bucket in a traffic metering algorithm.
Excess Burst Size Specify the burst size of packet bursts above which the SBG will perform the non-conforming
action.
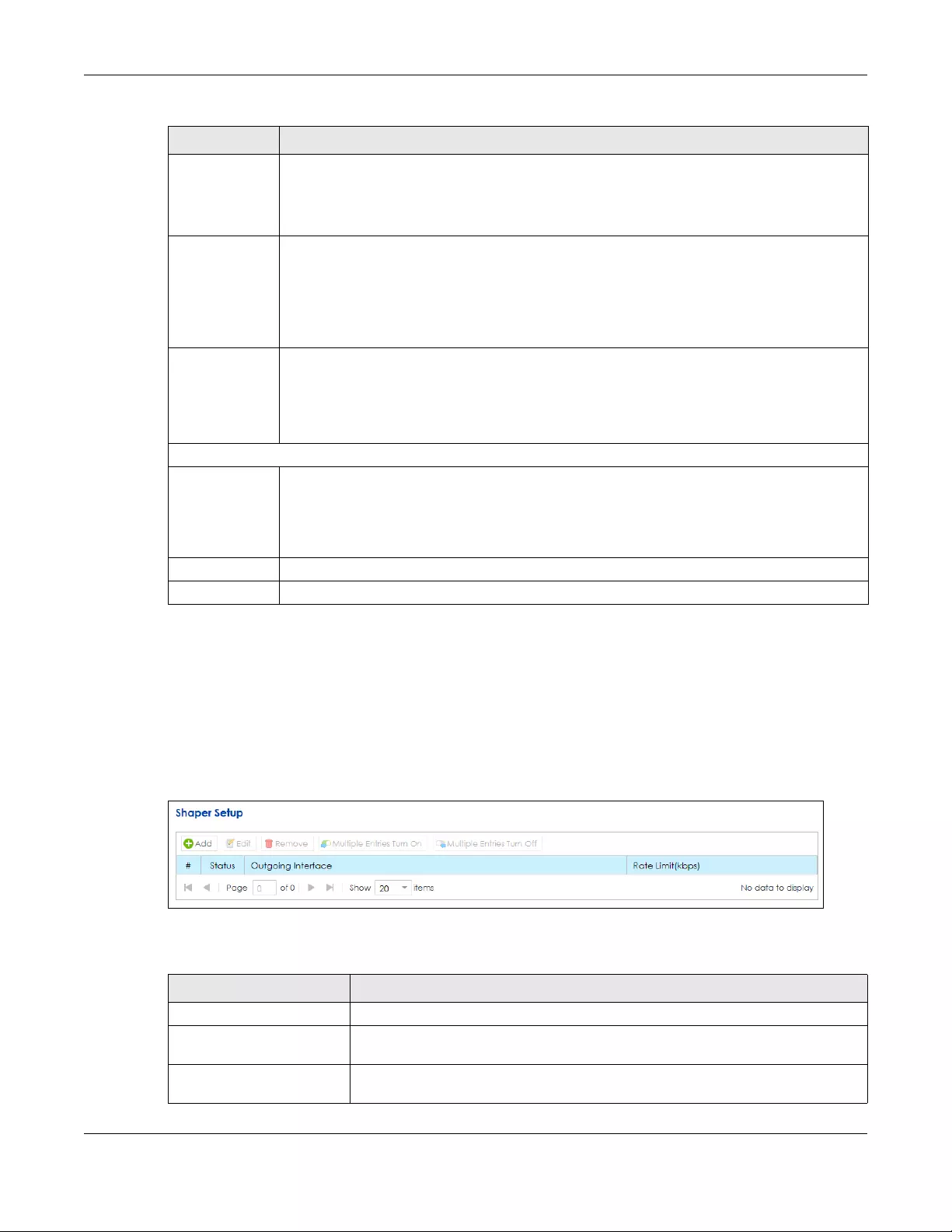
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
206
11.6 The Shaper Setup Screen
This screen shows that you can use the token bucket algorithm to allow a certain amount of large bursts
while keeping a limit for processing outgoing traffic at the average rate. Click Configuration >
Bandwidth Management > Shaper Setup. The screen appears as shown:
Figure 150 Configuration > Bandwidth Management > Shaper Setup
The following table describes the labels in this screen.
Conforming
Action
Specify what the SBG does for packets within the committed rate and burst size (green-marked
packets).
•Pass: Send the packets without modification.
•DSCP Mark: Change the DSCP mark value of the packets. Enter the DSCP mark value to use.
Partial
Conforming
Action
Specify what the SBG does for packets that exceed the committed rate and burst size but are
within the excess burst size or peak rate and burst size (yellow-marked packets).
•Drop: Discard the packets.
•Pass: Send the packets without modification.
•DSCP Mark: Change the DSCP mark value of the packets. Enter the DSCP mark value to use.
The packets may be dropped if there is congestion on the network.
Non-
Conforming
Action
Specify what the SBG does for packets that exceed the excess burst size or peak rate and burst
size (red-marked packets).
•Drop: Discard the packets.
•DSCP Mark: Change the DSCP mark value of the packets. Enter the DSCP mark value to use.
The packets may be dropped if there is congestion on the network.
Regulated Classes Member Setting
Available
Member
Select a QoS classifier to apply this QoS policer to traffic that matches the QoS classifier.
Highlight a QoS classifier in the Available box and use the → button to move it to the Member
box.
To remove a QoS classifier from the Member box, select it and use the ← button.
OK Click OK to save your changes.
Cancel Click Cancel to exit this screen without saving.
Table 90 Policer Setup: Add/Edit (continued)
LABEL DESCRIPTION
Table 91 Configuration > Bandwidth Management > Shaper Setup
LABEL DESCRIPTION
Add Click this to create a new shaper.
Edit Double-click a shaper or select it and click Edit to open a screen where you can
modify the shaper’s settings.
Remove To remove an existing shaper, select it and click Remove. Note that subsequent rules
move up by one when you take this action.

Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
207
11.6.1 Add/Edit a QoS Shaper
Click Add in the Shaper Setup screen or select a shaper and click Edit to show the following screen.
Figure 151 Shaper Setup: Add/Edit
The following table describes the labels in this screen.
11.7 Technical Reference
The following section contains additional technical information about the SBG features described in this
chapter.
IEEE 802.1Q Tag
The IEEE 802.1Q standard defines an explicit VLAN tag in the MAC header to identify the VLAN
membership of a frame across bridges. A VLAN tag includes the 12-bit VLAN ID and 3-bit user priority.
Multiple Entries Turn On Select one or more shapers and click this to enable them.
Multiple Entries Turn Off Select one or more shapers and click this to disable them.
# This is the index number of the entry.
Status This field displays whether the shaper is active or not. A green ON button signifies that
this shaper is active. A gray OFF button signifies that this shaper is not active.
Click the slide button to turn on or turn off the shaper.
Outgoing Interface This shows the name of the SBG’s interface through which traffic in this shaper
applies.
Rate Limit (kbps) This shows the average rate limit of traffic bursts for this shaper.
Table 91 Configuration > Bandwidth Management > Shaper Setup
LABEL DESCRIPTION
Table 92 Shaper Setup: Add/Edit
LABEL DESCRIPTION
Enable Select the check box to activate this shaper.
Outgoing Interface Select the SBG’s interface through which traffic in this shaper applies.
Rate Limit Enter the average rate limit of traffic bursts for this shaper.
OK Click this button to save your changes to the SBG.
Cancel Click this button to exit this screen without saving.
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
208
The VLAN ID associates a frame with a specific VLAN and provides the information that devices need to
process the frame across the network.
IEEE 802.1p specifies the user priority field and defines up to eight separate traffic types. The following
table describes the traffic types defined in the IEEE 802.1d standard (which incorporates the 802.1p).
DiffServ
QoS is used to prioritize source-to-destination traffic flows. All packets in the flow are given the same
priority. You can use CoS (class of service) to give different priorities to different packet types.
DiffServ (Differentiated Services) is a class of service (CoS) model that marks packets so that they
receive specific per-hop treatment at DiffServ-compliant network devices along the route based on the
application types and traffic flow. Packets are marked with DiffServ Code Points (DSCPs) indicating the
level of service desired. This allows the intermediary DiffServ-compliant network devices to handle the
packets differently depending on the code points without the need to negotiate paths or remember
state information for every flow. In addition, applications do not have to request a particular service or
give advanced notice of where the traffic is going.
DSCP and Per-Hop Behavior
DiffServ defines a new Differentiated Services (DS) field to replace the Type of Service (TOS) field in the IP
header. The DS field contains a 2-bit unused field and a 6-bit DSCP field which can define up to 64
service levels. The following figure illustrates the DS field.
DSCP is backward compatible with the three precedence bits in the ToS octet so that non-DiffServ
compliant, ToS-enabled network device will not conflict with the DSCP mapping.
The DSCP value determines the forwarding behavior, the PHB (Per-Hop Behavior), that each packet
gets across the DiffServ network. Based on the marking rule, different kinds of traffic can be marked for
different kinds of forwarding. Resources can then be allocated according to the DSCP values and the
configured policies.
Table 93 IEEE 802.1p Priority Level and Traffic Type
PRIORITY
LEVEL TRAFFIC TYPE
Level 7 Typically used for network control traffic such as router configuration messages.
Level 6 Typically used for voice traffic that is especially sensitive to jitter (jitter is the variations in delay).
Level 5 Typically used for video that consumes high bandwidth and is sensitive to jitter.
Level 4 Typically used for controlled load, latency-sensitive traffic such as SNA (Systems Network
Architecture) transactions.
Level 3 Typically used for “excellent effort” or better than best effort and would include important business
traffic that can tolerate some delay.
Level 2 This is for “spare bandwidth”.
Level 1 This is typically used for non-critical “background” traffic such as bulk transfers that are allowed but
that should not affect other applications and users.
Level 0 Typically used for best-effort traffic.
DSCP (6 bits) Unused (2 bits)
Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
209
IP Precedence
Similar to IEEE 802.1p prioritization at layer-2, you can use IP precedence to prioritize packets in a layer-3
network. IP precedence uses three bits of the eight-bit ToS (Type of Service) field in the IP header. There
are eight classes of services (ranging from zero to seven) in IP precedence. Zero is the lowest priority
level and seven is the highest.
Automatic Priority Queue Assignment
If you enable QoS on the SBG, the SBG can automatically base on the IEEE 802.1p priority level, IP
precedence and/or packet length to assign priority to traffic which does not match a class.
The following table shows you the internal layer-2 and layer-3 QoS mapping on the SBG. On the SBG,
traffic assigned to higher priority queues gets through faster while traffic in lower index queues is
dropped if the network is congested.
Table 94 Internal Layer2 and Layer3 QoS Mapping
PRIORITY
QUEUE
LAYER 2 LAYER 3
IEEE 802.1P USER
PRIORITY
(ETHERNET
PRIORITY)
TOS (IP
PRECEDENCE) DSCP IP PACKET LENGTH
(BYTE)
0 1 0 000000
12
2 0 0 000000 >1100
3 3 1 001110
001100
001010
001000
250~1100
4 4 2 010110
010100
010010
010000
5 5 3 011110
011100
011010
011000
<250
6 6 4 100110
100100
100010
100000
5 101110
101000
7 7 6 110000
111000
7

Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
210
Token Bucket
The token bucket algorithm uses tokens in a bucket to control when traffic can be transmitted. The
bucket stores tokens, each of which represents one byte. The algorithm allows bursts of up to b bytes
which is also the bucket size, so the bucket can hold up to b tokens. Tokens are generated and added
into the bucket at a constant rate. The following shows how tokens work with packets:
• A packet can be transmitted if the number of tokens in the bucket is equal to or greater than the size
of the packet (in bytes).
• After a packet is transmitted, a number of tokens corresponding to the packet size is removed from
the bucket.
• If there are no tokens in the bucket, the SBG stops transmitting until enough tokens are generated.
• If not enough tokens are available, the SBG treats the packet in either one of the following ways:
In traffic shaping:
• Holds it in the queue until enough tokens are available in the bucket.
In traffic policing:
•Drops it.
• Transmits it but adds a DSCP mark. The SBG may drop these marked packets if the network is
overloaded.
Configure the bucket size to be equal to or less than the amount of the bandwidth that the interface
can support. It does not help if you set it to a bucket size over the interface’s capability. The smaller the
bucket size, the lower the data transmission rate and that may cause outgoing packets to be dropped.
A larger transmission rate requires a big bucket size. For example, use a bucket size of 10 kbytes to get
the transmission rate up to 10 Mbps.
Single Rate Three Color Marker
The Single Rate Three Color Marker (srTCM, defined in RFC 2697) is a type of traffic policing that identifies
packets by comparing them to one user-defined rate, the Committed Information Rate (CIR), and two
burst sizes: the Committed Burst Size (CBS) and Excess Burst Size (EBS).
The srTCM evaluates incoming packets and marks them with one of three colors which refer to packet
loss priority levels. High packet loss priority level is referred to as red, medium is referred to as yellow and
low is referred to as green.
The srTCM is based on the token bucket filter and has two token buckets (CBS and EBS). Tokens are
generated and added into the bucket at a constant rate, called Committed Information Rate (CIR).
When the first bucket (CBS) is full, new tokens overflow into the second bucket (EBS).
All packets are evaluated against the CBS. If a packet does not exceed the CBS it is marked green.
Otherwise it is evaluated against the EBS. If it is below the EBS then it is marked yellow. If it exceeds the
EBS then it is marked red.
The following shows how tokens work with incoming packets in srTCM:
• A packet arrives. The packet is marked green and can be transmitted if the number of tokens in the
CBS bucket is equal to or greater than the size of the packet (in bytes).
• After a packet is transmitted, a number of tokens corresponding to the packet size is removed from
the CBS bucket.

Chapter 11 Bandwidth Management
SBG5500 Series User’s Guide
211
• If there are not enough tokens in the CBS bucket, the SBG checks the EBS bucket. The packet is
marked yellow if there are sufficient tokens in the EBS bucket. Otherwise, the packet is marked red. No
tokens are removed if the packet is dropped.
Two Rate Three Color Marker
The Two Rate Three Color Marker (trTCM, defined in RFC 2698) is a type of traffic policing that identifies
packets by comparing them to two user-defined rates: the Committed Information Rate (CIR) and the
Peak Information Rate (PIR). The CIR specifies the average rate at which packets are admitted to the
network. The PIR is greater than or equal to the CIR. CIR and PIR values are based on the guaranteed
and maximum bandwidth respectively as negotiated between a service provider and client.
The trTCM evaluates incoming packets and marks them with one of three colors which refer to packet
loss priority levels. High packet loss priority level is referred to as red, medium is referred to as yellow and
low is referred to as green.
The trTCM is based on the token bucket filter and has two token buckets (Committed Burst Size (CBS)
and Peak Burst Size (PBS)). Tokens are generated and added into the two buckets at the CIR and PIR
respectively.
All packets are evaluated against the PIR. If a packet exceeds the PIR it is marked red. Otherwise it is
evaluated against the CIR. If it exceeds the CIR then it is marked yellow. Finally, if it is below the CIR then
it is marked green.
The following shows how tokens work with incoming packets in trTCM:
• A packet arrives. If the number of tokens in the PBS bucket is less than the size of the packet (in bytes),
the packet is marked red and may be dropped regardless of the CBS bucket. No tokens are removed
if the packet is dropped.
• If the PBS bucket has enough tokens, the SBG checks the CBS bucket. The packet is marked green
and can be transmitted if the number of tokens in the CBS bucket is equal to or greater than the size
of the packet (in bytes). Otherwise, the packet is marked yellow.
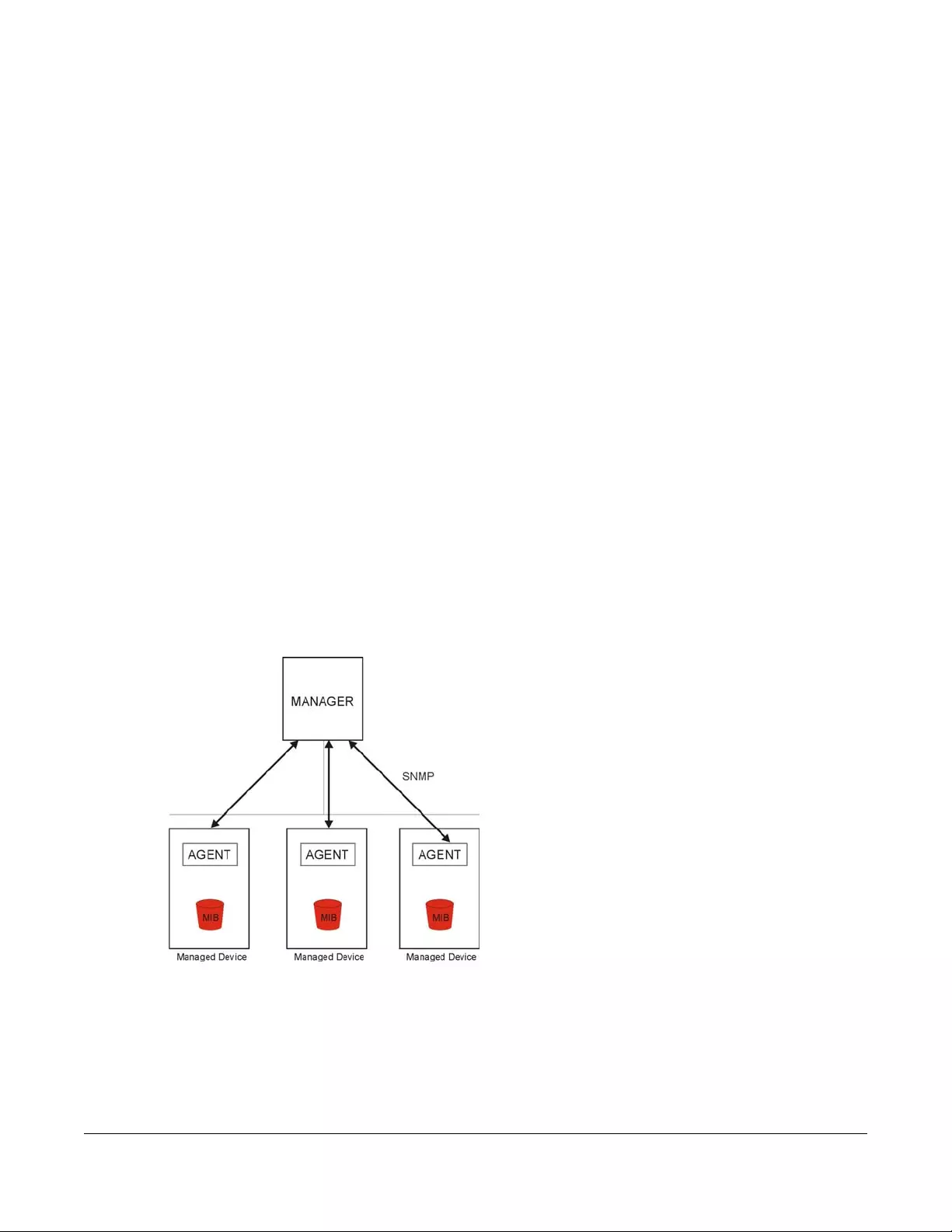
SBG5500 Series User’s Guide
212
CHAPTER 12
Network Management
12.1 Overview
This chapter describes the SBG’s Configuration > Network Management screens. Use this screens to
configure your SBG’s SNMP.
12.1.1 What You Can Do in This Chapter
Use the SNMP screen to configure the SBG’s SNMP settings (Section 12.2 on page 212)
12.2 The SNMP Screen
Simple Network Management Protocol is a protocol used for exchanging management information
between network devices. Your SBG supports SNMP agent functionality, which allows a manager station
to manage and monitor the SBG through the network. The SBG supports SNMP version one (SNMPv1)
and version two (SNMPv2c). The next figure illustrates an SNMP management operation.
Figure 152 SNMP Management Model
An SNMP managed network consists of two main types of component: agents and a manager.
An agent is a management software module that resides in a managed device (the SBG). An agent
translates the local management information from the managed device into a form compatible with
SNMP. The manager is the console through which network administrators perform network management
functions. It executes applications that control and monitor managed devices.
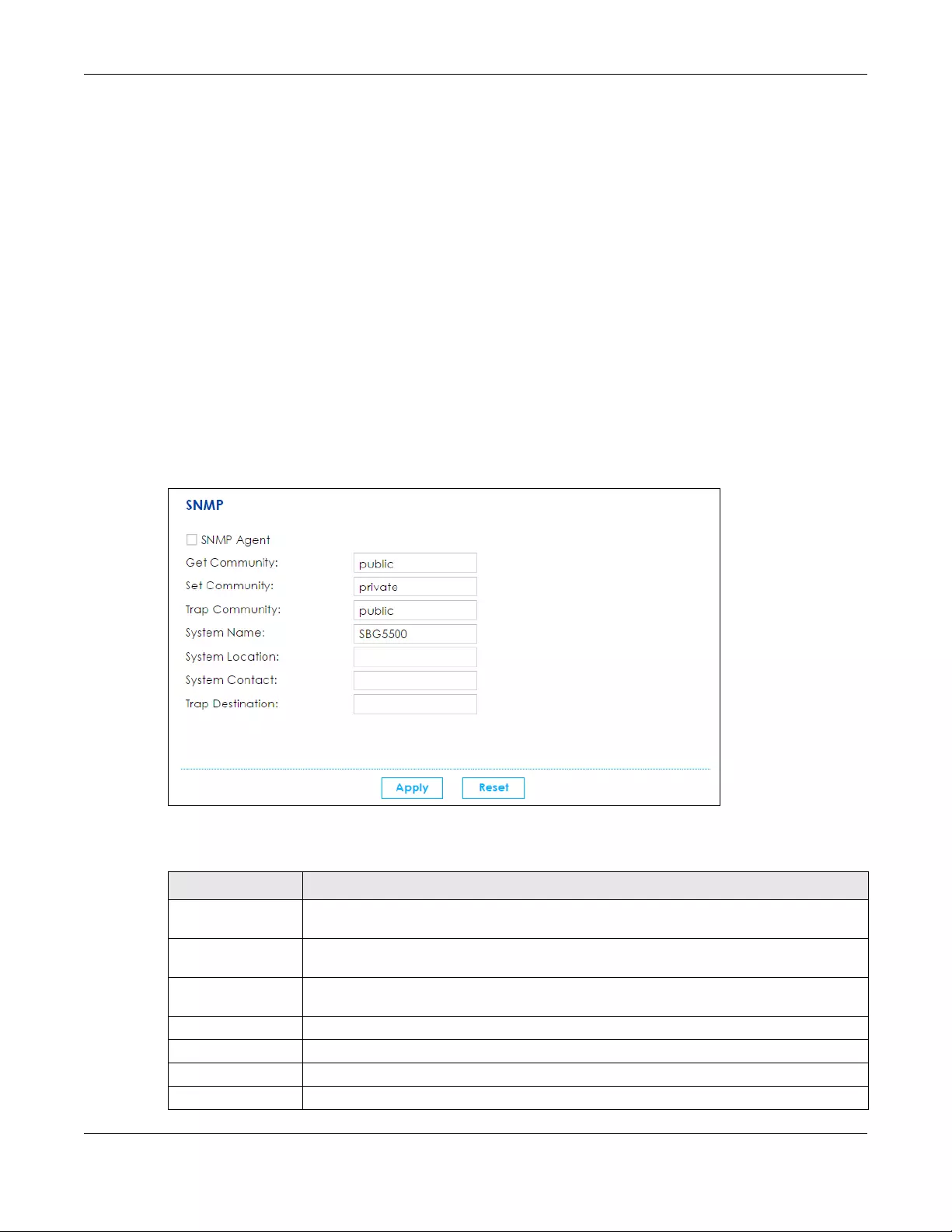
Chapter 12 Network Management
SBG5500 Series User’s Guide
213
The managed devices contain object variables/managed objects that define each piece of
information to be collected about a device. Examples of variables include such as number of packets
received, node port status etc. A Management Information Base (MIB) is a collection of managed
objects. SNMP allows a manager and agents to communicate for the purpose of accessing these
objects.
SNMP itself is a simple request/response protocol based on the manager/agent model. The manager
issues a request and the agent returns responses using the following protocol operations:
• Get - Allows the manager to retrieve an object variable from the agent.
• GetNext - Allows the manager to retrieve the next object variable from a table or list within an agent.
In SNMPv1, when a manager wants to retrieve all elements of a table from an agent, it initiates a Get
operation, followed by a series of GetNext operations.
• Set - Allows the manager to set values for object variables within an agent.
• Trap - Used by the agent to inform the manager of some events.
Click Configuration > Network Management > SNMP to open the following screen. Use this screen to
configure the SBG SNMP settings.
Figure 153 Configuration > Network Management > SNMP
The following table describes the fields in this screen.
Table 95 Configuration > Network Management > SNMP
LABEL DESCRIPTION
SNMP Agent Select the check box to allow a manager station to manage and monitor the SBG through
the network via SNMP.
Get Community Enter the password for the incoming Get and GetNext requests from the management
station. The default is public and allows all requests.
Set Community Enter the Set community, which is the password for incoming Set requests from the
management station. The default is public and allows all requests.
Trap Community Enter the Trap Community, which is the password sent with each trap to the SNMP manager.
System Name Enter the system name of the SBG.
System Location Specify the geographic location of the SBG.
System Contact Enter the name of the person in charge of the SBG.

Chapter 12 Network Management
SBG5500 Series User’s Guide
214
Trap Destination Type the IP address of the station to send your SNMP traps to.
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to restore your previously saved settings.
Table 95 Configuration > Network Management > SNMP (continued)
LABEL DESCRIPTION

SBG5500 Series User’s Guide
215
CHAPTER 13
Log / Report
13.1 Overview
The web configurator allows you to choose which categories of events and/or alerts to have the SBG
log and then display the logs or have the SBG send them to an administrator (as e-mail) or to a syslog
server.
13.1.1 What You Can Do in this Chapter
• Use the Log Viewer screen to see the system logs (Section 13.2 on page 216).
• Use the Log Settings screen to specify settings for recording log messages and alerts, e-mailing them,
storing them on a connected USB storage device, and sending them to remote syslog servers(Section
13.3 on page 217).
13.1.2 What You Need To Know
The following terms and concepts may help as you read this chapter.
Alerts and Logs
An alert is a type of log that warrants more serious attention. They include system errors, attacks (access
control) and attempted access to blocked web sites. Some categories such as System Errors consist of
both logs and alerts. You may differentiate them by their color in the View Log screen. Alerts display in
red and logs display in black.
Syslog Overview
The syslog protocol allows devices to send event notification messages across an IP network to syslog
servers that collect the event messages. A syslog-enabled device can generate a syslog message and
send it to a syslog server.
Syslog is defined in RFC 3164. The RFC defines the packet format, content and system log related
information of syslog messages. Each syslog message has a facility and severity level. The syslog facility
identifies a file in the syslog server. Refer to the documentation of your syslog program for details. The
following table describes the syslog severity levels.
Table 96 Syslog Severity Levels
CODE SEVERITY
0 Emergency: The system is unusable.
1 Alert: Action must be taken immediately.
2 Critical: The system condition is critical.
3 Error: There is an error condition on the system.
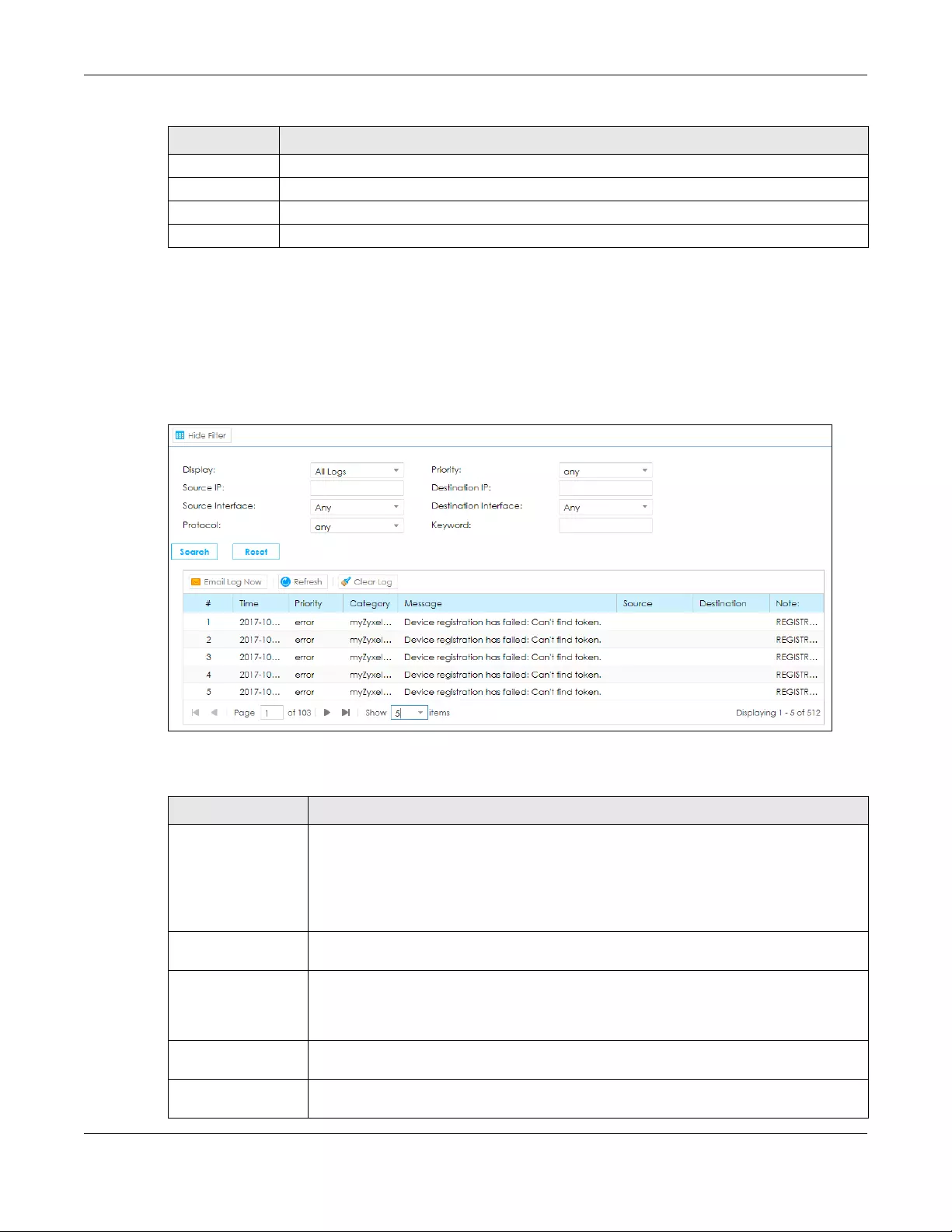
Chapter 13 Log / Report
SBG5500 Series User’s Guide
216
13.2 The Log Viewer Screen
Use the Log viewer screen to see the system logs. Click Configuration > Log / Report > Log Viewer to
open the following screen.
Figure 154 Configuration > Log / Report > Log Viewer
The following table describes the fields in this screen.
4 Warning: There is a warning condition on the system.
5 Notice: There is a normal but significant condition on the system.
6 Informational: The syslog contains an informational message.
7 Debug: The message is intended for debug-level purposes.
Table 96 Syslog Severity Levels
CODE SEVERITY
Table 97 Configuration > Log / Report > Log Viewer
LABEL DESCRIPTION
Show (Hide) Filter Click this button to show or hide the filter settings.
If the filter settings are hidden only Display filter is available.
If the filter settings are shown, the Display, Priority, Source Address, Destination IP Address,
Source Interface, Destination Interface, Protocol, Keyword, Search and Reset fields are
available.
Display Select the type of log message(s) you want to view. You can also view All Logs at one time,
or you can view the Debug Log.
Priority This displays when you show the filter. Select the priority of log messages to display. The log
displays the log messages with this priority or higher. Choices are: any, emerg, alert, crit,
error, warn, notice, and info, from highest priority to lowest priority. This field is read-only if the
Display field is set to Debug Log.
Source IP This displays when you show the filter. Type the source IP address of the incoming packet
that generated the log message. Do not include the port in this filter.
Source Interface This displays when you show the filter. Type the source interface of the incoming packet that
generated the log message.

Chapter 13 Log / Report
SBG5500 Series User’s Guide
217
13.3 Log Settings
The Log Settings screen controls log messages and alerts. A log message stores the information for
viewing or regular e-mailing later, and an alert is e-mailed immediately. Usually, alerts are used for
events that require more serious attention, such as system errors and attacks.
The Log Settings Edit screens control what information the SBG saves in each log. You can also specify
which log messages to e-mail for the system log, and where and how often to e-mail them. These
screens also set for which events to generate alerts and where to email the alerts.
To access this screen click Configuration > Log / Report > Log Settings.
Protocol This displays when you show the filter. Select a service protocol whose log messages you
would like to see.
Destination IP This displays when you show the filter. Type the IP address of the destination of the incoming
packet when the log message was generated. Do not include the port in this filter.
Destination Interface This displays when you show the filter. Type the interface of the destination of the incoming
packet when the log message was generated.
Keyword Type a keyword of the policy service available from SBG to search for a log.
Search This displays when you show the filter. Click this button to update the log using the current
filter settings.
Reset Click this to return the filters to its original settings.
Email Log Now Click this to send the log file(s) to the E-mail address you specify in the Log Settings screen.
Refresh Click this to renew the log screen.
Clear Log Click this to delete all the logs.
#This field is a sequential value and is not associated with a specific entry.
Time This field displays the time the log was recorded.
Priority This field displays the priority of the log message. It has the same range of values as the
Priority field above.
Category This field displays type of logs to display.
Messages This field states the reason for the log.
Source This field displays the source IP address and the port number in the event that generated
the log message.
Destination This field displays the destination IP address and the port number of the event that
generated the log message.
Note This field displays any additional information about the log message.
Table 97 Configuration > Log / Report > Log Viewer
LABEL DESCRIPTION
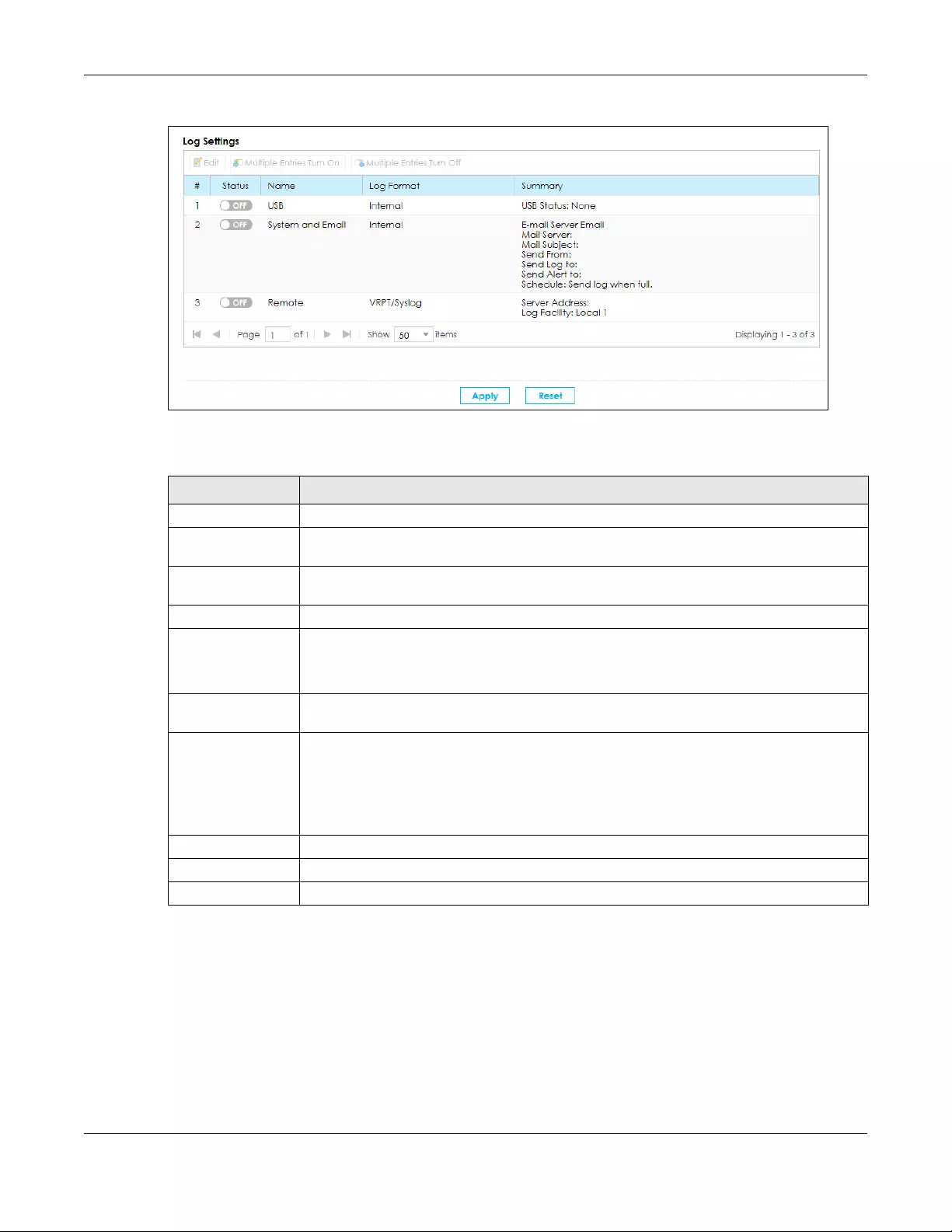
Chapter 13 Log / Report
SBG5500 Series User’s Guide
218
Figure 155 Configuration > Log / Report > Log Settings
The following table describes the labels in this screen.
13.3.1 Edit Log on USB Settings
The Edit Log on USB Settings screen controls the detailed settings for saving logs to a connected USB
storage device. Go to the Log Settings screen (see Section 13.3 on page 217), and double-click the USB
setting or select it and click Edit to open the following screen.
Table 98 Configuration > Log / Report > Log Settings
LABEL DESCRIPTION
Edit Double-click an entry or select it and click Edit to open a screen where you can modify it.
Multiple Entries Turn
On
Select one or more entries and click this to enable them.
Multiple Entries Turn
Off
Select one or more entries and click this to disable them.
# This field is a sequential value, and it is not associated with a specific log.
Status This field displays whether the log setting is active or not. A green ON signifies that this log
setting is active. A gray OFF signifies that this log setting is not active.
Click the slide button to turn on or turn off the entry.
Name This field displays the type of log setting entry (system log, logs stored on a USB storage device
connected to the SBG, or one of the remote servers).
Log Format This field displays the format of the log.
Internal - system log; you can view the log on the View Log tab.
VRPT/Syslog - Zyxel’s Vantage Report, syslog-compatible format.
CEF/Syslog - Common Event Format, syslog-compatible format.
Summary This field is a summary of the settings for each log.
Apply Click Apply to save your changes.
Reset Click Reset to restore your previously saved settings.
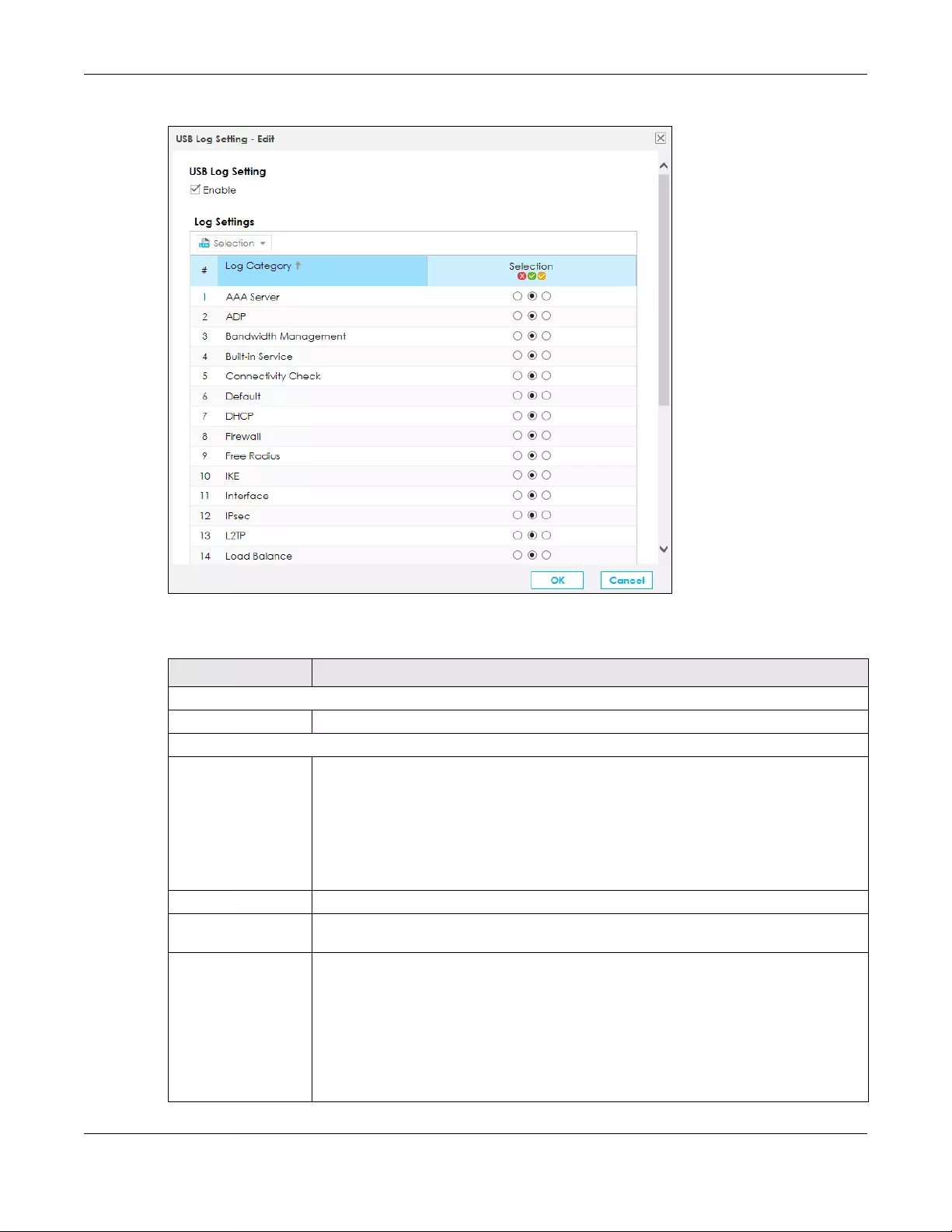
Chapter 13 Log / Report
SBG5500 Series User’s Guide
219
Figure 156 Configuration > Log / Report > Log Settings > Edit (USB)
The following table describes the labels in this screen.
Table 99 Configuration > Log / Report > Log Settings > Edit (USB)
LABEL DESCRIPTION
USB Log Setting
Enable Select the check box to turn on the USB Log Setting.
Log Settings
Selection Use the Selection drop-down list to change the log settings for all of the log categories.
disable all logs (red X) - do not send the remote server logs for any log category.
enable normal logs (green check mark) - send the remote server log messages and alerts
for all log categories.
enable normal logs and debug logs (yellow check mark) - send the remote server log
messages, alerts, and debugging information for all log categories.
# This field is a sequential value, and it is not associated with a specific entry.
Log Category This field displays each category of messages. The Default category includes debugging
messages generated by open source software.
Selection Select what information you want to log from each Log Category (except All Logs; see
below). Choices are:
disable all logs (red X) - do not log any information from this category
enable normal logs (green check mark) - log regular information and alerts from this
category
enable normal logs and debug logs (yellow check mark) - log regular information, alerts,
and debugging information from this category
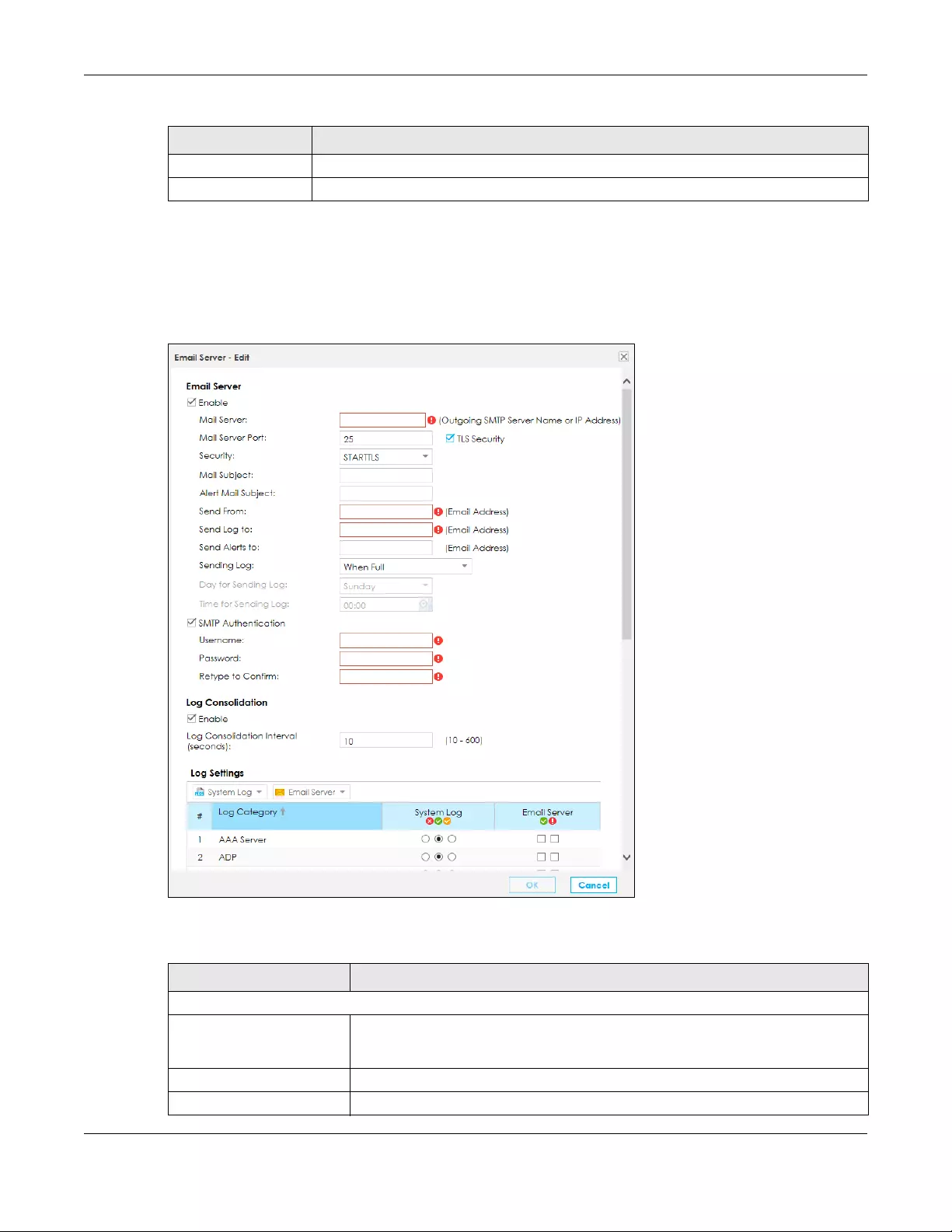
Chapter 13 Log / Report
SBG5500 Series User’s Guide
220
13.3.2 Edit System and Email
The Log Settings Edit screen controls the detailed settings for each log in the system log (which includes
the e-mail profiles). Double-click a log setting or select it and click Edit to open the following screen.
Figure 157 Configuration > Log / Report > Log Settings > Edit (System and Email)
The following table describes the labels in this screen.
OK Click this to save your changes and return to the previous screen.
Cancel Click this to return to the previous screen without saving your changes.
Table 99 Configuration > Log / Report > Log Settings > Edit (USB)
LABEL DESCRIPTION
Table 100 Configuration > Log / Report > Log Settings > Edit (System and Email)
LABEL DESCRIPTION
E-mail Server
Enable Select this to send log messages and alerts according to the information in this
section. You specify what kinds of log messages are included in log information and
what kinds of log messages are included in alerts in the Log Settings section.
Mail Server Type the name or IP address of the outgoing SMTP server.
Mail Server Port Enter the same port number here as is on the mail server for mail traffic.
Chapter 13 Log / Report
SBG5500 Series User’s Guide
221
TLS Security Select the check box if you want encrypted communications between the mail
server and the SBG.
Security Select SSL/TLS to use Secure Sockets Layer (SSL) or Transport Layer Security (TLS).
Select STARTTLS to upgrade a plain text connection to a secure connection using
SSL/TLS.
Mail Subject Type the subject line for the outgoing e-mail.
Alert Mail Subject Type the subject line for the outgoing alert e-mail.
Send From Type the e-mail address from which the outgoing e-mail is delivered. This address is
used in replies.
Send Log to Type the e-mail address to which the outgoing e-mail is delivered.
Send Alerts to Type the e-mail address to which alerts are delivered.
Sending Log Select how often log information is e-mailed. Choices are: When Full, Hourly and
When Full, Hourly and When Full, Daily and When Full, and Weekly and When Full.
Day for Sending Log This field is available if the log is e-mailed weekly. Select the day of the week the log
is emailed.
Time for Sending Log This field is available if the log is e-mailed weekly, daily or hourly. Select the time of
day (hours and minutes) when the log is e-mailed. Use 24-hour notation.
SMTP Authentication Select this check box if it is necessary to provide a user name and password to the
SMTP server.
Username This box is effective when you select the SMTP Authentication check box. Type the
user name to provide to the SMTP server when the log is e-mailed.
Password This box is effective when you select the SMTP Authentication check box. Type the
password to provide to the SMTP server when the log is e-mailed.
Retype to Confirm Type the password again to make sure that you have entered is correctly.
Log Consolidation
Enable Select this to activate log consolidation. Log consolidation aggregates multiple log
messages that arrive within the specified Log Consolidation Interval. In the Log
Viewer tab, the text “[count=x]”, where x is the number of original log messages, is
appended at the end of the Message field, when multiple log messages were
aggregated.
Log Consolidation Interval
(seconds)
Type how often, in seconds, to consolidate log information. If the same log message
appears multiple times, it is aggregated into one log message with the text
“[count=x]”, where x is the number of original log messages, appended at the end
of the Message field.
Log Settings
System Log Use the System Log drop-down list to change the log settings for all of the log
categories.
disable all logs (red X) - do not log any information for any category for the system
log or e-mail any logs to e-mail server 1 or 2.
enable normal logs (green check mark) - create log messages and alerts for all
categories for the system log. If e-mail server 1 or 2 also has normal logs enabled, the
SBG will e-mail logs to them.
enable normal logs and debug logs (yellow check mark) - create log messages,
alerts, and debugging information for all categories. The SBG does not e-mail
debugging information, even if this setting is selected.
Table 100 Configuration > Log / Report > Log Settings > Edit (System and Email)
LABEL DESCRIPTION

Chapter 13 Log / Report
SBG5500 Series User’s Guide
222
13.3.3 Edit Remote Server Log Settings
The Log Settings Edit screen controls the detailed settings for each log in the remote server (syslog). Go
to the Log Settings screen (Section 13.3 on page 217), select a remote server and click Edit.
E-mail Server Use the E-Mail Server drop-down list to change the settings for e-mailing logs to e-
mail server for all log categories.
Using the System Log drop-down list to disable all logs overrides your e-mail server
settings.
enable normal logs (green check mark) - e-mail log messages for all categories to e-
mail server.
enable alert logs (red exclamation point) - e-mail alerts for all categories to e-mail
server.
# This field is a sequential value, and it is not associated with a specific address.
Log Category This field displays each category of messages. It is the same value used in the Display
and Category fields in the Log Viewer tab. The Default category includes debugging
messages generated by open source software.
System Log Select which events you want to log by Log Category. There are three choices:
disable all logs (red X) - do not log any information from this category
enable normal logs (green check mark) - create log messages and alerts from this
category
enable normal logs and debug logs (yellow check mark) - create log messages,
alerts, and debugging information from this category; the SBG does not e-mail
debugging information, however, even if this setting is selected.
E-mail Server Select whether each category of events should be included in the log messages
when it is e-mailed (green check mark) and/or in alerts (red exclamation point) for
the e-mail settings specified in E-Mail Server. The SBG does not e-mail debugging
information, even if it is recorded in the System log.
OK Click this to save your changes and return to the previous screen.
Cancel Click this to return to the previous screen without saving your changes.
Table 100 Configuration > Log / Report > Log Settings > Edit (System and Email)
LABEL DESCRIPTION
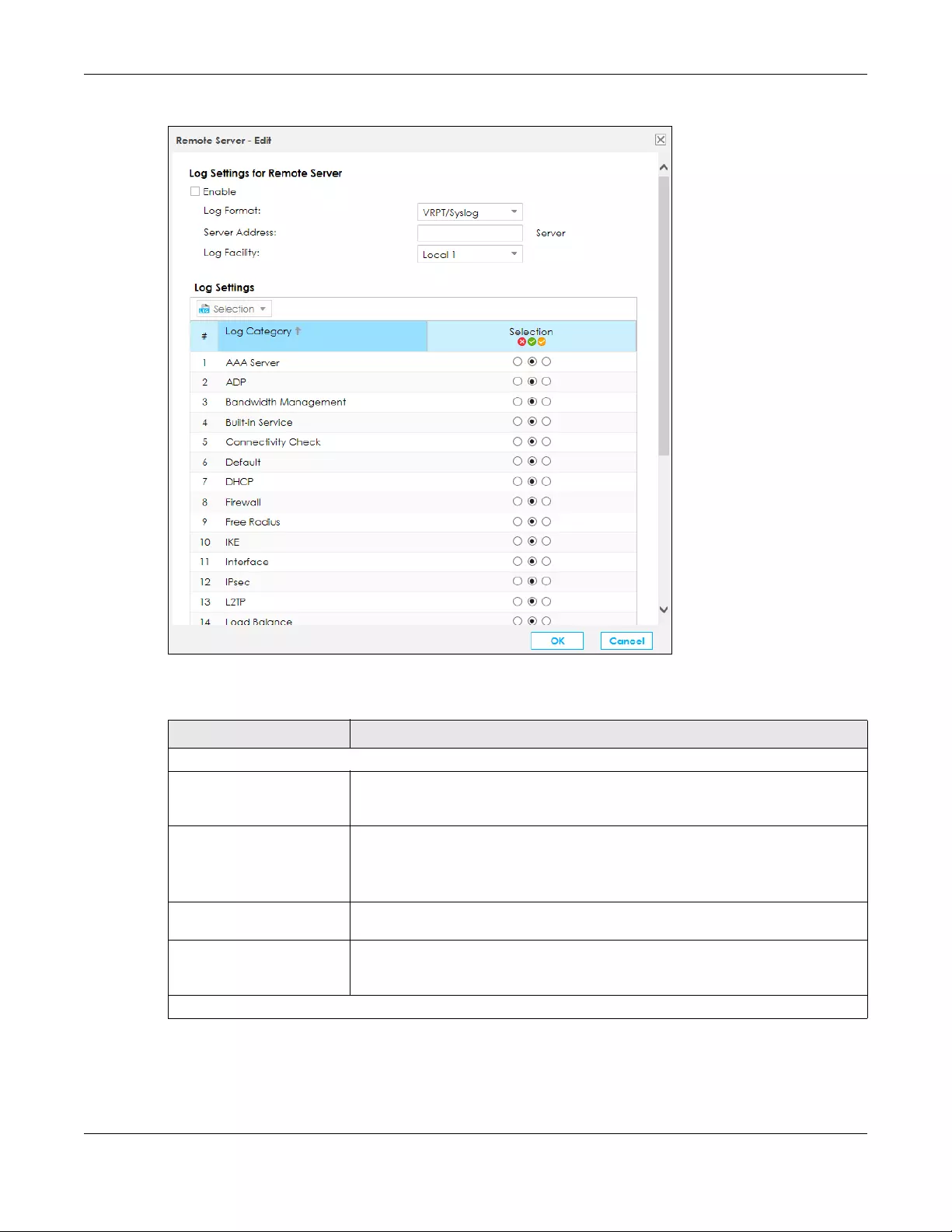
Chapter 13 Log / Report
SBG5500 Series User’s Guide
223
Figure 158 Configuration > Log / Report > Log Settings > Edit (Remote)
The following table describes the labels in this screen.
Table 101 Configuration > Log / Report > Log Settings > Edit (Remote)
LABEL DESCRIPTION
Log Settings for Remote Server
Enable Select this check box to send log information according to the information in this
section. You specify what kinds of messages are included in log information in the
Log Settings section.
Log Format This field displays the format of the log information. It is read-only.
VRPT/Syslog - Zyxel’s Vantage Report, syslog-compatible format.
CEF/Syslog - Common Event Format, syslog-compatible format.
Server Address Type the server name or the IP address of the syslog server to which to send log
information.
Log Facility Select a log facility. The log facility allows you to log the messages to different files in
the syslog server. Please see the documentation for your syslog program for more
information.
Log Settings
Chapter 13 Log / Report
SBG5500 Series User’s Guide
224
Selection Use the Selection drop-down list to change the log settings for all of the log
categories.
disable all logs (red X) - do not send the remote server logs for any log category.
enable normal logs (green check mark) - send the remote server log messages and
alerts for all log categories.
enable normal logs and debug logs (yellow check mark) - send the remote server
log messages, alerts, and debugging information for all log categories.
# This field is a sequential value, and it is not associated with a specific address.
Log Category This field displays each category of messages. It is the same value used in the
Display and Category fields in the Log Viewer tab. The Default category includes
debugging messages generated by open source software.
Selection Select what information you want to log from each Log Category (except All Logs;
see below). Choices are:
disable all logs (red X) - do not log any information from this category
enable normal logs (green check mark) - log regular information and alerts from this
category
enable normal logs and debug logs (yellow check mark) - log regular information,
alerts, and debugging information from this category
OK Click this to save your changes and return to the previous screen.
Cancel Click this to return to the previous screen without saving your changes.
Table 101 Configuration > Log / Report > Log Settings > Edit (Remote)
LABEL DESCRIPTION
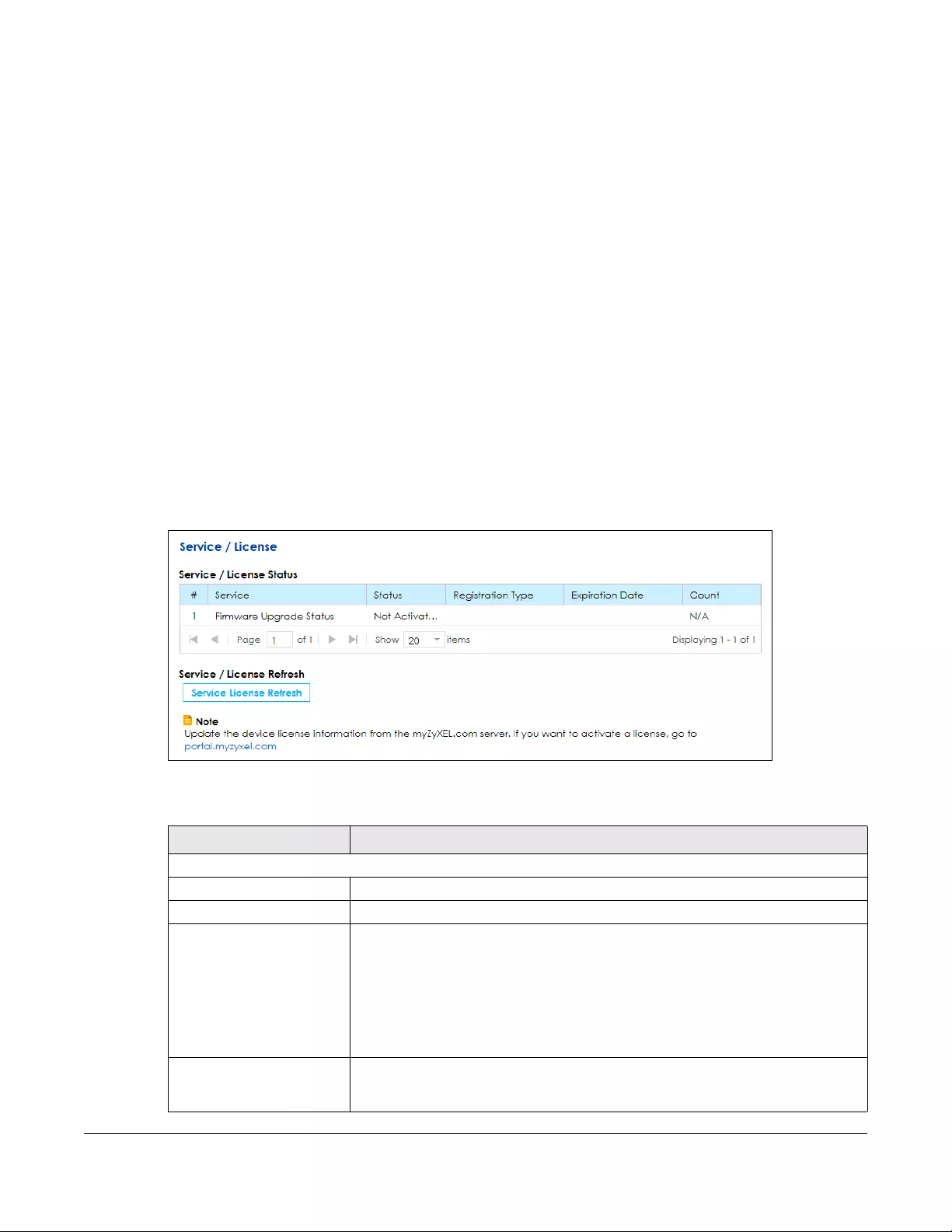
SBG5500 Series User’s Guide
225
CHAPTER 14
Service / License
14.1 Overview
Use the Service / License screen to display the status of your service registrations. To activate or extend
a standard service subscription, purchase an iCard and enter the iCard’s PIN number (license key) at
myZyxel.com.
14.2 The License Screen
Click Maintenance > Service / License to open the following screen.
Figure 159 Maintenance > Service / License
The following table describes the labels on this screen.
Table 102 Maintenance > Service / License
LABEL DESCRIPTION
Service / License Status
# This is the entry’s position in the list.
Service This lists the services that are available on the SBG.
Status This field displays the status of your service registration.
Not Activated displays if you have not successfully registered and activated the
service.
Expired displays if your subscription to the service has expired.
Licensed displays if you have successfully registered the SBG and activated the
service.
Registration Type This field displays whether you applied for a trial application (Trial) or registered a
service with your iCard’s PIN number (Standard). This field is blank when a service is
not activated. It always displays Standard for a default service.

Chapter 14 Service / License
SBG5500 Series User’s Guide
226
Expiration Date This field displays the date your service expires. This field is blank when a service does
not expire.
Count This field displays the maximum number of users that may connect to the SBG at the
same time or how many managed APs the SBG can support with your current
license.
It displays 0 if this field does not apply to a service.
Service / License Refresh
Service License Refresh Click this button to renew service license information (such as the registration status
and expiration day).
Table 102 Maintenance > Service / License
LABEL DESCRIPTION
SBG5500 Series User’s Guide
227
CHAPTER 15
Device Name
15.1 Overview
Use the Device Name screen to change the SBG’s name in the network.
15.2 The Device Name Screen
Click Maintenance > Device Name to view the following screen.
Figure 160 Maintenance > Device Name
The following table describes the labels in this screen.
Table 103 Maintenance > Device Name
LABEL DESCRIPTION
General Settings
Host Name Enter a descriptive name to identify your SBG. This name can be up to 64
alphanumeric characters long. Spaces are not allowed, but dashes (-) underscores
(_) and periods (.) are accepted.
Domain Name Enter the domain name (if you know it) here. This name is propagated to DHCP
clients connected to interfaces with the DHCP server enabled. This name can be up
to 254 alphanumeric characters long.
Device Information
Serial Number This displays the serial number of the SBG.
MAC Address This displays the MAC address of the SBG.
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to renew this screen.
SBG5500 Series User’s Guide
228
CHAPTER 16
Host Name List
16.1 Overview
Use the Host Name List screen to add connected devices to the SBG’s host list. Configure these devices
to turn on with the Wake on LAN screen, see Section 6.6 on page 96.
16.2 The Host Name Screen
Click Maintenance > Host Name List to view the following screen. Use this screen to view and manage
the clients that you added to the host list.
Figure 161 Maintenance > Host Name List
The following table describes the labels in this screen.
16.2.1 Add Host Name
Click Add to create a new host. The screen appears as shown.
Table 104 Maintenance > Host Name List
LABEL DESCRIPTION
Add Click Add to create a new host.
Remove Select a host and click Remove to delete it.
# This is the index number of the host.
Description This field displays a descriptive name for the host.
MAC Address This field displays the host’s MAC Address.
Chapter 16 Host Name List
SBG5500 Series User’s Guide
229
Figure 162 Maintenance > Host Name List: Add
The following table describes the labels in this screen.
Table 105 Maintenance > Host Name List: Add
LABEL DESCRIPTION
Refer To Select MAC Filter List if you want to select the devices that you added in the MAC
Filter List.
Select ARP Table to view the IPv4 or IPv6 devices that are connected to an SBG’s
port,
Select Manual Type MAC to enter the MAC address of the host device manually.
You can also enter a device’s IP address and click Get to obtain its MAC address.
Member List Select a member device from the drop-down list.
Get MAC Address From IP Enter the IP address of a device connected to the SBG, click Get and the SBG will
automatically obtain the MAC address of the device with this IP address.
Description Enter a description for this host.
MAC Address Enter the host’s MAC address, This field is configured automatically if you enter the
device’s IP address in the Get MAC Address From IP field and click Get.
OK Click OK to save your changes back to the SBG.
Cancel Click Cancel to exit this screen without saving.
SBG5500 Series User’s Guide
230
CHAPTER 17
Date / Time
17.1 Overview
This chapter shows you how to configure system related settings, such as system time and the daylight
saving setup.
17.2 The Date / Time Screen
To change your SBG’s time and date, click Maintenance > Date / Time. The screen appears as shown.
Use this screen to configure the SBG’s time based on your local time zone.
Figure 163 Maintenance > Date / Time
Chapter 17 Date / Time
SBG5500 Series User’s Guide
231
The following table describes the labels in this screen.
Table 106 Maintenance > Date / Time
LABEL DESCRIPTION
Current Date / Time
Current Time This field displays the time of your SBG.
Each time you reload this page, the SBG synchronizes the time with the time server.
Current Date This field displays the date of your SBG.
Each time you reload this page, the SBG synchronizes the date with the time server.
Time and Date Setup
Time Protocol This displays the protocol currently used by your SBG to obtain date and time.
Time Server (1-5) Select an NTP time server from the drop-down list box.
Otherwise, select Other and enter the IP address or URL (up to 29 extended ASCII
characters in length) of your time server.
Select None if you don’t want to configure the time server.
Check with your ISP/network administrator if you are unsure of this information.
Time Zone Setup
Time Zone Choose the time zone of your location. This will set the time difference between your
time zone and Greenwich Mean Time (GMT).
Daylight Saving Setup Daylight Saving time is a period from late spring to early fall when many countries set
their clocks ahead of normal local time by one hour to give more daytime light in
the evening.
Enable Select Enable if you use Daylight Saving time.
Start Configure the day and time when Daylight Saving time starts if you enabled Daylight
Saving. You can select a specific date in a particular month or a specific day of a
specific week in a particular month. The Time field uses the 24 hour format. Here are
a couple of examples:
Daylight Saving time starts in most parts of the United States on the second Sunday
of March. Each time zone in the United States starts using Daylight Saving Time at 2
A.M. local time. So in the United States, set the day to Second, Sunday, the month to
March and the time to 02:00 in the Time field.
Daylight Saving Time starts in the European Union on the last Sunday of March. All of
the time zones in the European Union start using Daylight Saving time at the same
moment (1 A.M. GMT or UTC). So in the European Union you would set the day to
Last, Sunday and the month to March. The time you select in the Time field depends
on your time zone. In Germany for instance, you would select 02:00 in the Time field
because Germany's time zone is one hour ahead of GMT or UTC (GMT+1).
End Configure the day and time when Daylight Saving time ends if you enabled Daylight
Saving. You can select a specific date in a particular month or a specific day of a
specific week in a particular month. The Time field uses the 24 hour format. Here are
a couple of examples:
Daylight Saving Time ends in the United States on the first Sunday of November. Each
time zone in the United States stops using Daylight Saving Time at 2 A.M. local time.
So in the United States you would set the day to First, Sunday, the month to
November and the time to 02:00 in the Time field.
Daylight Saving Time ends in the European Union on the last Sunday of October. All
of the time zones in the European Union stop using Daylight Saving Time at the same
moment (1 A.M. GMT or UTC). So in the European Union you would set the day to
Last, Sunday, and the month to October. The time you select in the Time field
depends on your time zone. In Germany for instance, you would select 02:00 in the
Time field because Germany's time zone is one hour ahead of GMT or UTC (GMT+1).

Chapter 17 Date / Time
SBG5500 Series User’s Guide
232
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to restore your previously saved settings.
Table 106 Maintenance > Date / Time
LABEL DESCRIPTION
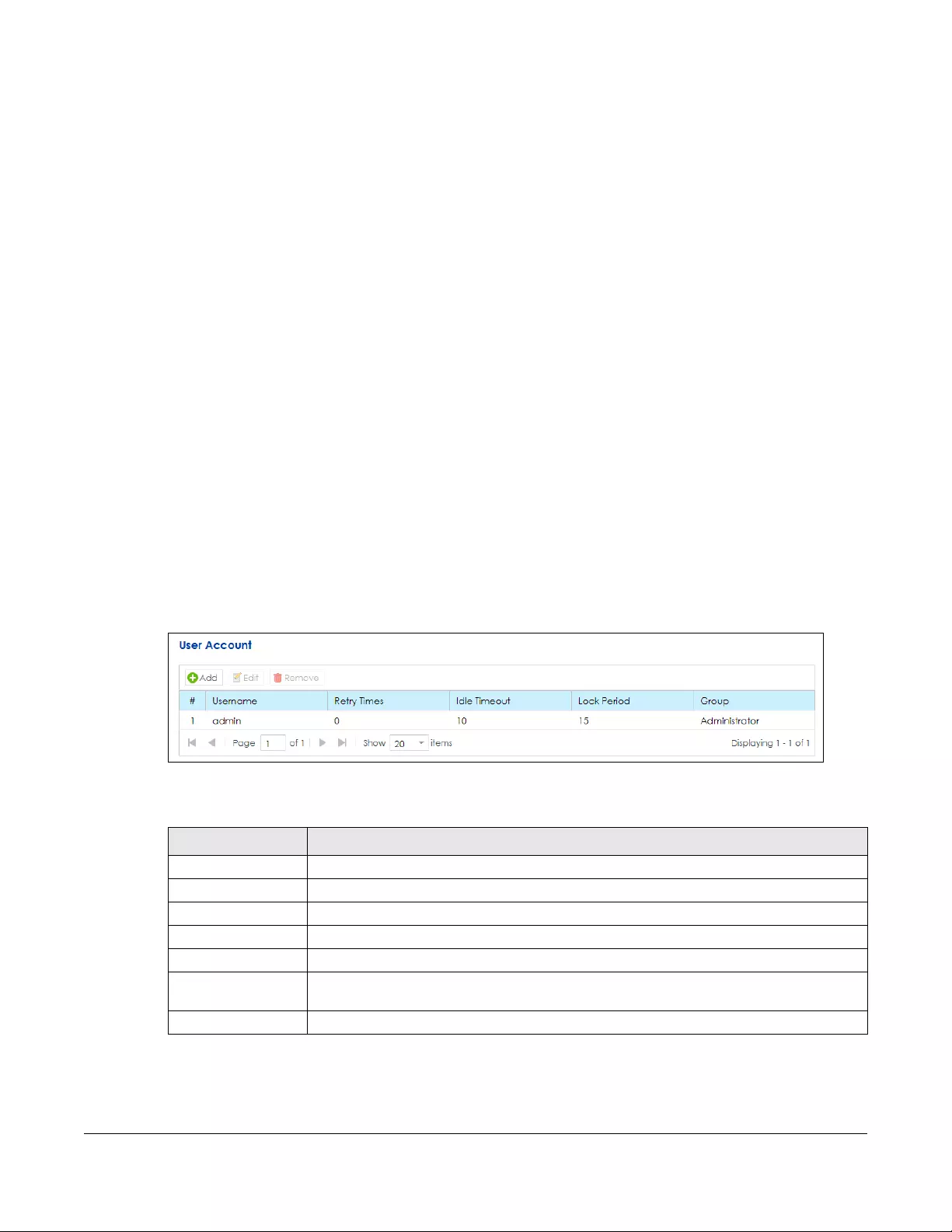
SBG5500 Series User’s Guide
233
CHAPTER 18
User Account
18.1 Overview
Use the User Account screen to manage user accounts, which includes configuring the username,
password, retry times, and users timeout period.
18.2 What You Can Do in this Chapter
Use the User Account screen to view and manage all user accounts (Section 18.3 on page 233).
18.3 The User Account Screen
Click Maintenance > User Account to open the following screen.
Figure 164 Maintenance > User Account
The following table describes the labels in this screen.
Table 107 Maintenance > User Account
LABEL DESCRIPTION
Add Click this to configure a new user account.
Edit Select an existing user account and click this to modify its settings.
Remove Click this to delete a user account.
#This is the index number of the user.
Username This field displays the name of the user.
Retry Times This field indicates how many times a user can re-enter his/her account information before
the SBG locks the user out.
Idle Timeout This field indicates the number of minutes that the system can idle before being logged out.
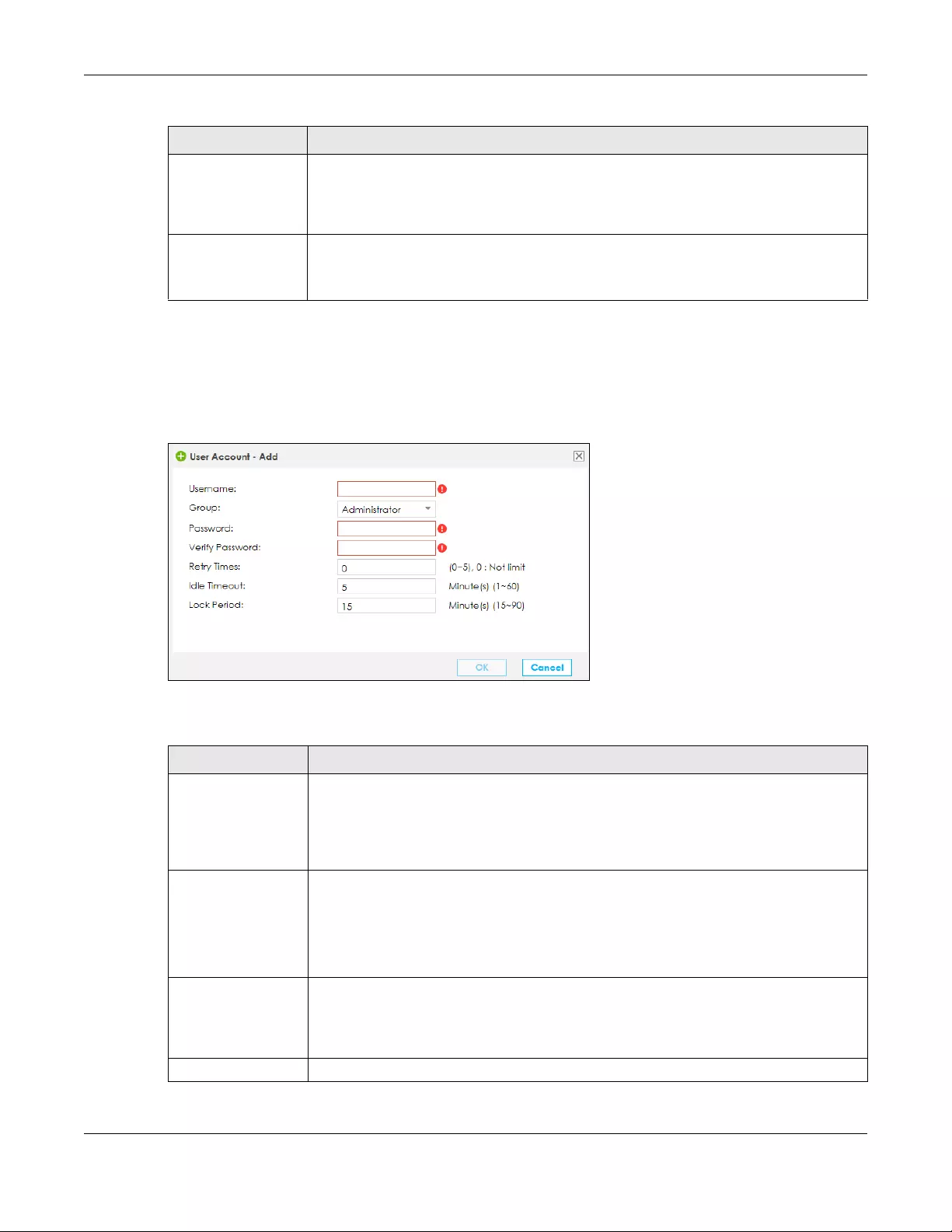
Chapter 18 User Account
SBG5500 Series User’s Guide
234
18.3.1 Add/Edit a Users Account
Use this screen to add or edit a users account. Click Add in the User Account screen or the select an
existing user account and click Edit. The screen shown next appears.
Figure 165 Users Configuration: Add/Edit
The following table describes the labels in this screen.
Lock Period This field indicates the number of minutes for the lockout period. A user cannot log into the
SBG during the lockout period, even if he/she enters correct account information.
An account will be locked if the account password is entered incorrectly too many times.
You can specify how many times a password can be re-entered in the Retry Times field.
Group This field displays the login account type of the user.
Different login account types have different privilege levels. The web configurator screens
and privileges vary depending on which account type you use to log in.
Table 107 Maintenance > User Account (continued)
LABEL DESCRIPTION
Table 108 Users Configuration: Add/Edit
LABEL DESCRIPTION
User Name This field is read-only if you are editing the user account.
Enter a descriptive name for the user account. The user name can be up to 15
alphanumeric characters (0-9, A-Z, a-z, -, _ with no spaces). With advanced account
security enabled, the user names must be a minimum length of six characters and include
both letters and numbers.
Group This field is read-only if you are editing the user account.
Select a type of login account. The web configurator screens and privileges vary
depending on which account type you use to log in. Administrator accounts can configure
the SBG while User accounts can only view some status information.
Users logged in with either type of account can access the Internet.
Password Specify the password associated to this account. The password can be 6 to 15
alphanumeric characters (0-9, A-Z, a-z, -, _ with no spaces), not containing the user name. It
must contain both letters and numbers.
The characters are displayed as asterisks (*) in this field.
Verify Password Enter the exact same password that you just entered in the above field.

Chapter 18 User Account
SBG5500 Series User’s Guide
235
Retry Times The SBG can lock a user out if you use a wrong user name or password to log in the SBG.
Enter up to how many times a user can re-enter his/her account information before the SBG
locks the user out.
Idle Timeout Enter the number of minutes that the system can idle before being logged out.
Lock Period Enter the number of minutes for the lockout period. A user cannot log into the SBG during
the lockout period, even if he/she enters correct account information.
OK Click OK to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 108 Users Configuration: Add/Edit (continued)
LABEL DESCRIPTION
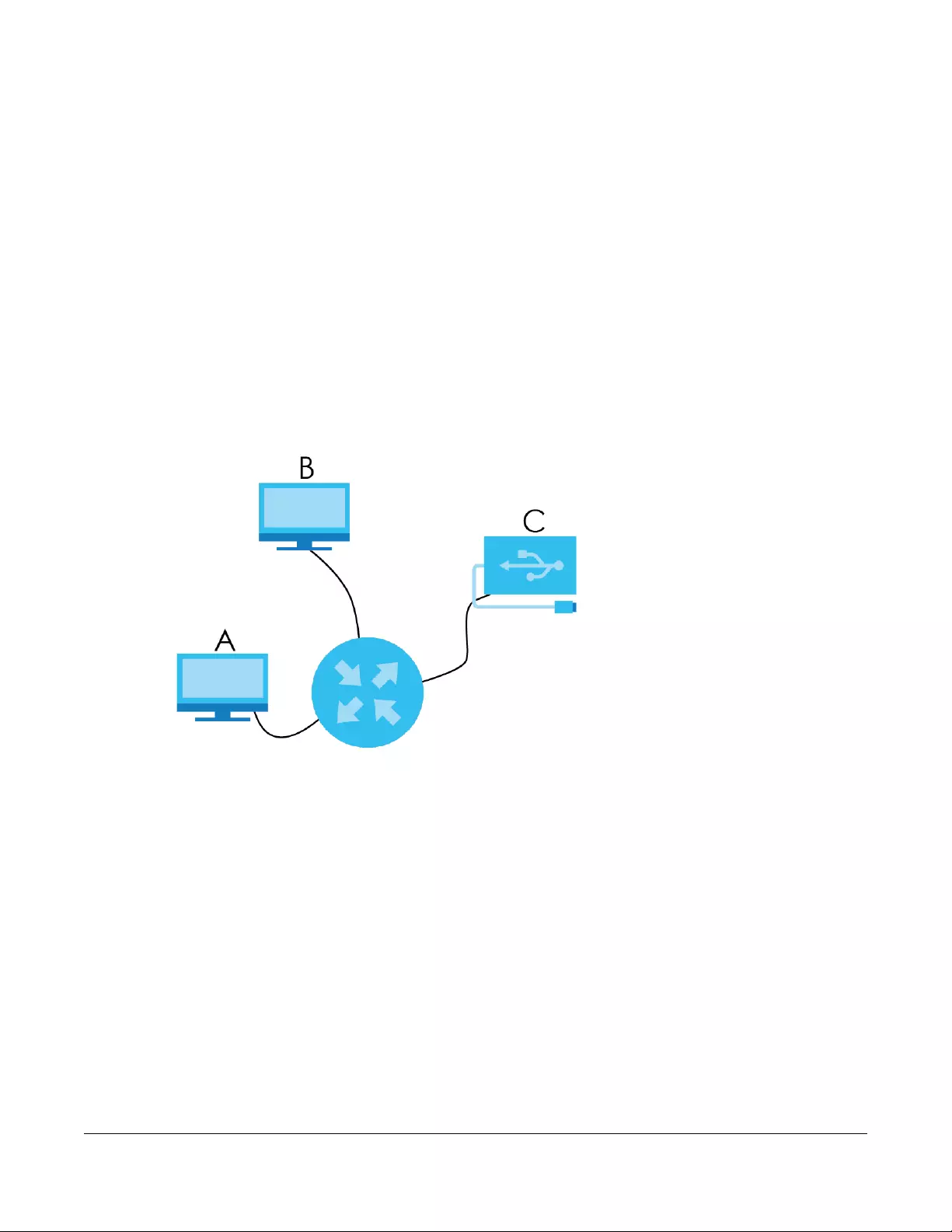
SBG5500 Series User’s Guide
236
CHAPTER 19
USB Storage
19.1 Overview
Use the USB Storage screen to share files on a USB memory stick or hard drive connected to your SBG
with users on your network.
The following figure is an overview of the SBG’s file server feature. Computers A and B can access files
on a USB device (C) which is connected to the SBG.
Figure 166 File Sharing Overview
19.1.1 What You Need To Know
The following terms and concepts may help as you read this chapter.
Workgroup name
This is the name given to a set of computers that are connected on a network and share resources such
as a printer or files. Windows automatically assigns the workgroup name when you set up a network.
Shares
When settings are set to default, each USB device connected to the SBG is given a folder, called a
“share”. If a USB hard drive connected to the SBG has more than one partition, then each partition will
be allocated a share. You can also configure a “share” to be a sub-folder or file on the USB device.
SBG

Chapter 19 USB Storage
SBG5500 Series User’s Guide
237
File Systems
A file system is a way of storing and organizing files on your hard drive and storage device. Often
different operating systems such as Windows or Linux have different file systems. The file sharing feature
on your SBG supports File Allocation Table (FAT) and FAT32.
Common Internet File System
The SBG uses Common Internet File System (CIFS) protocol for its file sharing functions. CIFS compatible
computers can access the USB file storage devices connected to the SBG. CIFS protocol is supported on
Microsoft Windows, Linux Samba and other operating systems (refer to your systems specifications for
CIFS compatibility).
19.1.2 Before You Begin
Make sure the SBG is connected to your network and turned on.
1Connect the USB device to one of the SBG’s USB port. Make sure the SBG is connected to your network.
2The SBG detects the USB device and makes its contents available for browsing. If you are connecting a
USB hard drive that comes with an external power supply, make sure it is connected to an appropriate
power source that is on.
Note: If your USB device cannot be detected by the SBG, see the troubleshooting for
suggestions.
19.2 The USB Storage Screen
Use this screen to set up file sharing through the SBG. The SBG’s LAN users can access the shared folder
(or share) from the USB device inserted in the SBG. To access this screen click Maintenance > USB
Storage.
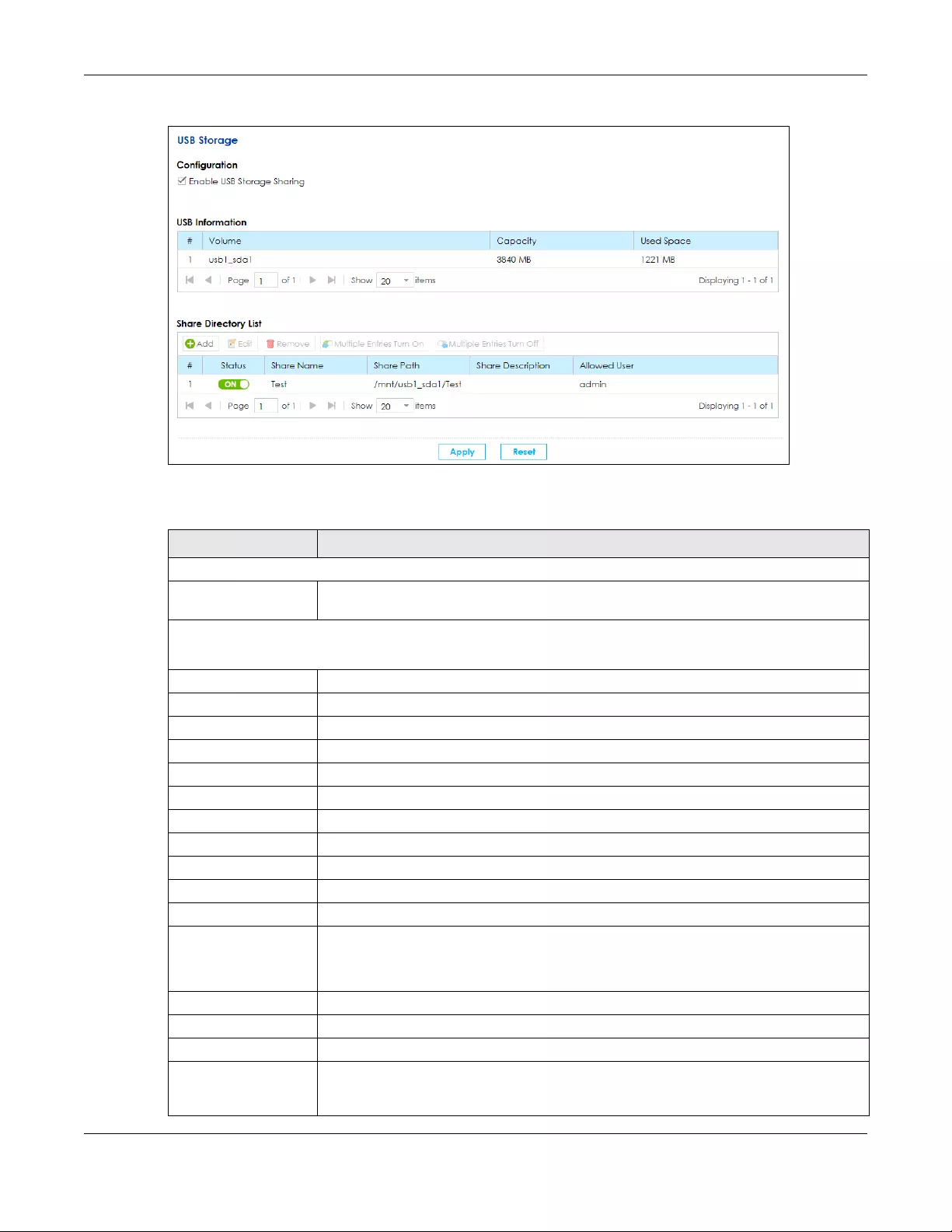
Chapter 19 USB Storage
SBG5500 Series User’s Guide
238
Figure 167 Maintenance > USB Storage
The following table describes the labels in this screen.
Table 109 Maintenance > USB Storage
LABEL DESCRIPTION
Configuration
Enable USB Storage
Sharing
Click the check box to activate file sharing through the SBG.
USB Information
This section is available only when a USB device is connected and detected by the SBG.
# This is the index number of the USB.
Volume This is the volume name the SBG gives to an inserted USB device.
Capacity This is the total available memory size (in megabytes) on the USB device.
Used Space This is the memory size (in megabytes) already used on the USB device.
Share Directory List This table is available when you connect a USB to the SBG.
Add Click Add to create a new share.
Edit Select a share and click Edit to modify it.
Remove Select a share and click Remove to delete it.
Multiple Entries Turn On Select one or more shares and click this to enable them.
Multiple Entries Turn Off Select one or more shares and click this to disable them.
# This is the index number of the share.
Status This field displays whether the share is active or not. A green ON button signifies that this
share is active. A gray OFF button signifies that this share is not active.
Click the slide button to turn on or turn off the share.
Share Name This field displays the name of the file you shared.
Share Path This field displays the location in the USB of the file you shared.
Share Description This field displays a description of the file you shared.
Allowed User This field displays which username(s) can access this share (Admin or any username
added in the Maintenance > User Account screen). This field will be empty if the file is
Public and anybody connected to the SBG can access it.
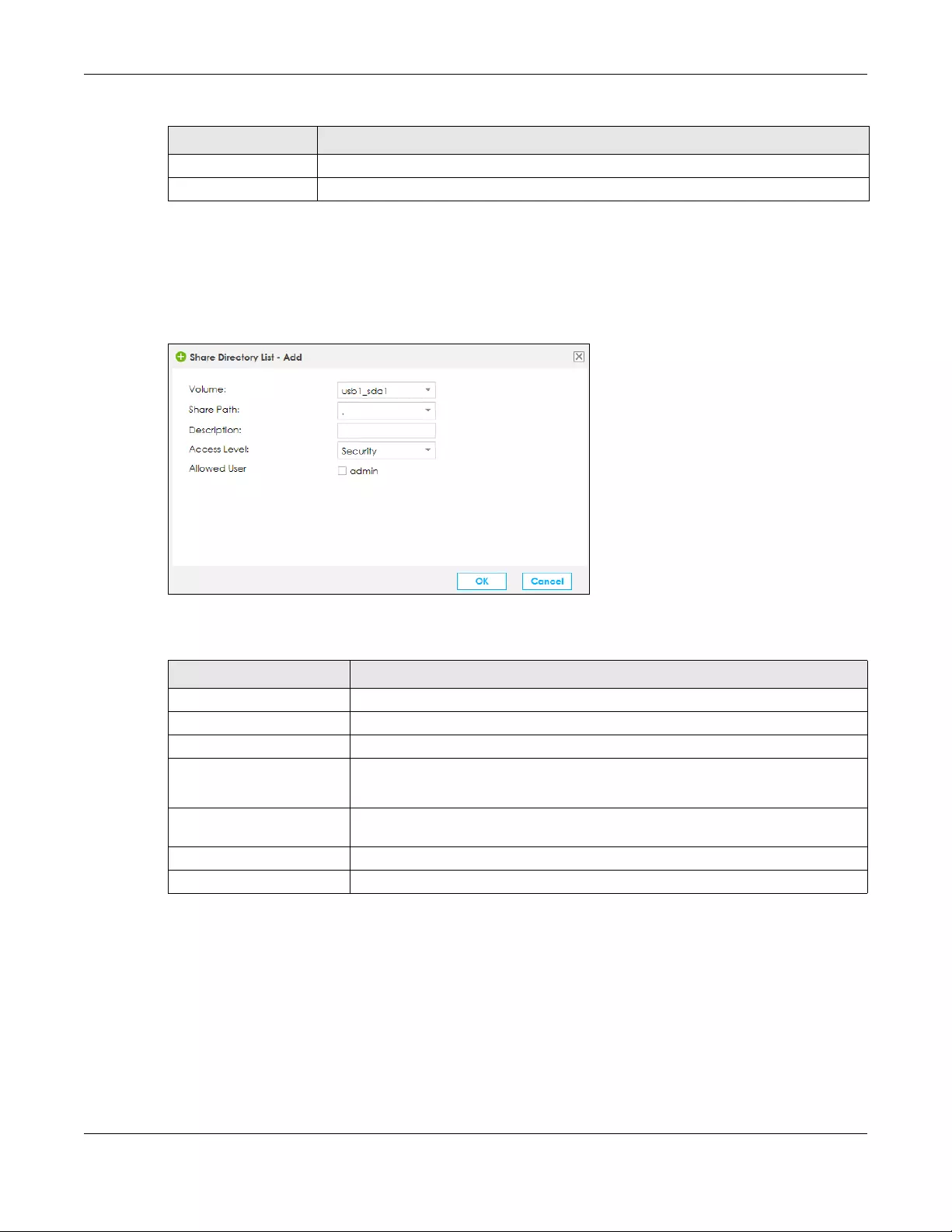
Chapter 19 USB Storage
SBG5500 Series User’s Guide
239
19.2.1 Add a USB Share
If a USB is connected to the USB port in the SBG you can view the Share Directory List table. Click Add to
add a shared file to the SBG’s network. The following screen will display.
Figure 168 USB Storage: Add
The following table describes the labels in this screen.
Apply Click Apply to save your changes back to the SBG.
Reset Click Reset to restore your previously saved settings.
Table 109 Maintenance > USB Storage
LABEL DESCRIPTION
Table 110 USB Storage: Add
LABEL DESCRIPTION
Volume Select the name of the USB where the file you want to share is located.
Share Path Select a file drop-down list to share.
Description Enter a descriptive name for this file.
Access Level Select Security if you want to specify the user names that can access this file.
Select Public so anyone connected to the SBG can access this file.
Allowed User This option displays when you select Security in Access Level. Select the check box
of the user names you want to grant access to this file.
OK Click OK to save your changes back to the SBG.
Cancel Click Cancel to exit this screen without saving.

SBG5500 Series User’s Guide
240
CHAPTER 20
Diagnostic
20.1 Overview
The Diagnostic screens display information to help you identify problems with the SBG.
The route between a CO VDSL switch and one of its CPE may go through switches owned by
independent organizations. A connectivity fault point generally takes time to discover and impacts
subscriber’s network access. In order to eliminate the management and maintenance efforts, IEEE
802.1ag is a Connectivity Fault Management (CFM) specification which allows network administrators to
identify and manage connection faults. Through discovery and verification of the path, CFM can
detect, analyze and isolate connectivity faults in bridged LANs.
20.1.1 What You Can Do in this Chapter
• The Network Tools screen lets you ping an IP address or trace the route packets take to a host
(Section 20.2 on page 241).
• The 802.1ag screen lets you perform CFM actions (Section 20.3 on page 241).
• The OAM Ping screen lets you send an ATM OAM (Operation, Administration, and Maintenance)
packet to verify the connectivity of a specific PVC (Section 20.4 on page 242).
• The Packet Capture screen to capture packets going through the SBG (Section 20.5 on page 244).
20.1.2 What You Need to Know
The following terms and concepts may help as you read through this chapter.
How CFM Works
A Maintenance Association (MA) defines a VLAN and associated Maintenance End Point (MEP) ports
on the device under a Maintenance Domain (MD) level. An MEP port has the ability to send
Connectivity Check Messages (CCMs) and get other MEP ports information from neighbor devices’
CCMs within an MA.
CFM provides two tests to discover connectivity faults.
• Loopback test - checks if the MEP port receives its Loop Back Response (LBR) from its target after it
sends the Loop Back Message (LBM). If no response is received, there might be a connectivity fault
between them.
• Link trace test - provides additional connectivity fault analysis to get more information on where the
fault is. If an MEP port does not respond to the source MEP, this may indicate a fault. Administrators
can take further action to check and resume services from the fault according to the line
connectivity status report.
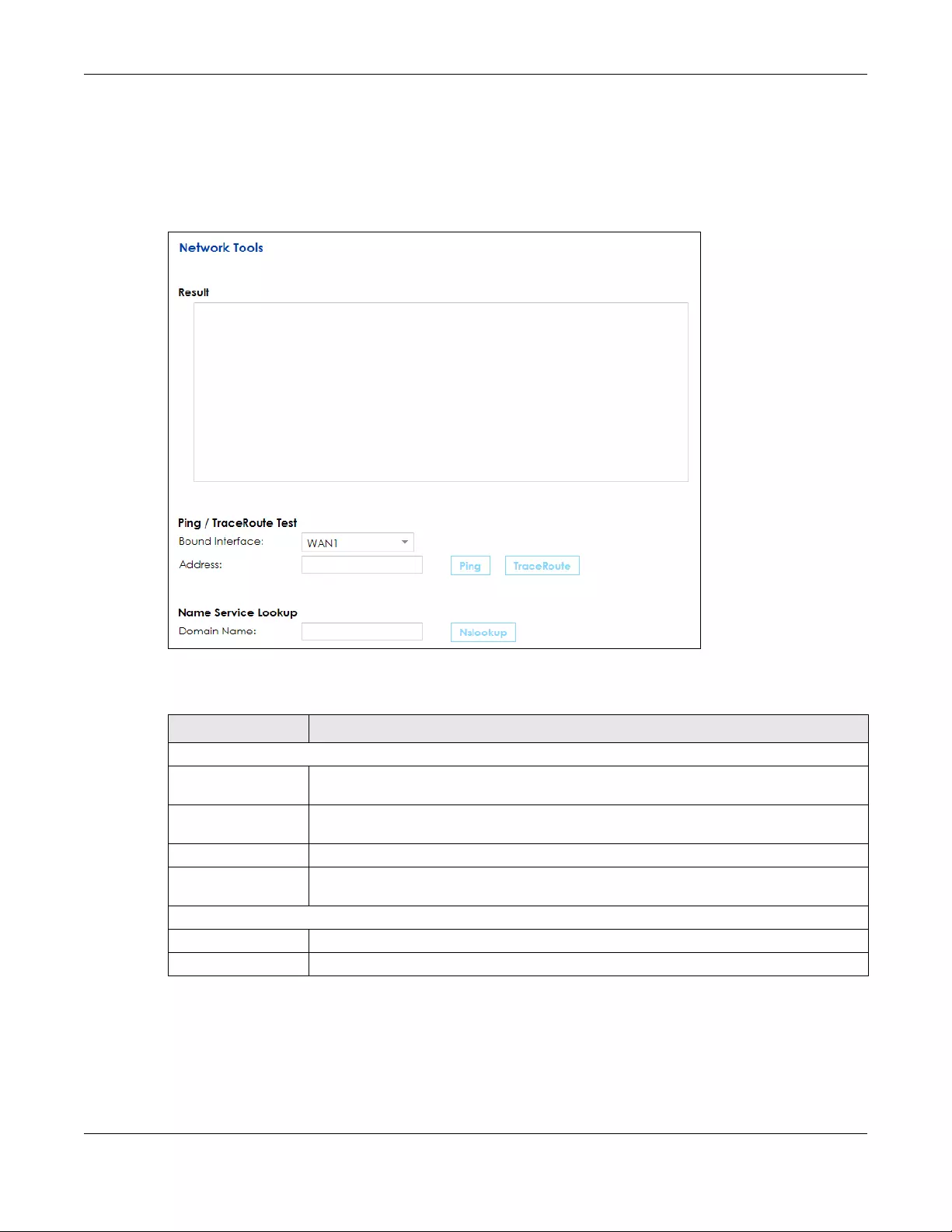
Chapter 20 Diagnostic
SBG5500 Series User’s Guide
241
20.2 The Network Tools Screen
Use this screen to ping, traceroute, or nslookup an IP address. Click Maintenance > Diagnostic > Network
Tools to open the screen shown next.
Figure 169 Maintenance > Diagnostic > Network Tools
The following table describes the fields in this screen.
20.3 The 802.1ag Screen
Click Maintenance > Diagnostic > 802.1ag to open the following screen. Use this screen to perform CFM
actions.
Table 111 Maintenance > Diagnostic > Network Tools
LABEL DESCRIPTION
Ping / TraceRoute Test
Bound Interface Choose a connected interface from the drop-down list (LAN, WAN) to perform the ping/
tracer route test.
Address Type the URL or IP address of a computer that you want to perform ping, traceroute, or
nslookup in order to test a connection.
Ping Click this to ping the IP address that you entered.
TraceRoute Click this button to perform the traceroute function. This determines the path a packet
takes to the specified computer.
Name Service lookup
Domain name Type a domain name in this field for the name service lookup.
Nslookup Click this button to perform a DNS lookup on the IP address of a computer you enter.
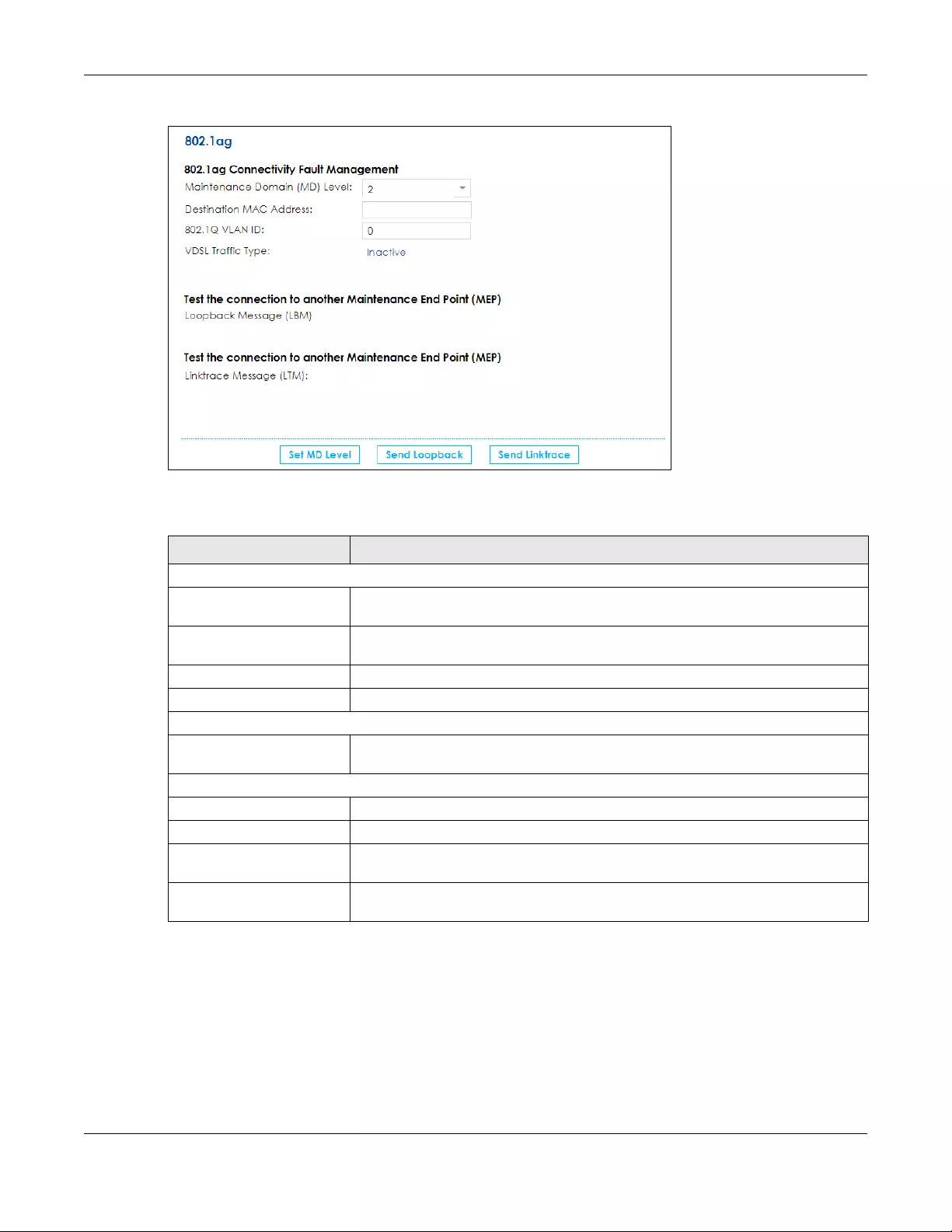
Chapter 20 Diagnostic
SBG5500 Series User’s Guide
242
Figure 170 Maintenance > Diagnostic > 802.1ag
The following table describes the labels in this screen.
20.4 The OAM Ping Screen
Click Maintenance > Diagnostic > OAM Ping to open the screen shown next. Use this screen to perform
an OAM (Operation, Administration and Maintenance) F4 or F5 loopback test on a PVC. The SBG sends
an OAM F4 or F5 packet to the DSLAM or ATM switch and then returns it to the SBG. The test result then
displays in the text box.
Table 112 Maintenance > Diagnostic > 802.1 ag
LABEL DESCRIPTION
802.1ag Connectivity Fault Management
Maintenance Domain (MD)
Level
Select a level (0-7) under which you want to create an MA.
Destination MAC Address Enter the target device’s MAC address to which the SBG performs a CFM loopback
test.
802.1Q VLAN ID Type a VLAN ID (0-4095) for this MA.
VDSL Traffic Type This shows whether the VDSL traffic is activated.
Test the connection to another Maintenance End Point (MEP)
Loopback Message (LBM) This shows how many Loop Back Messages (LBMs) are sent and if there is any inorder
or outorder Loop Back Response (LBR) received from a remote MEP.
Test the connection to another Maintenance End Point (MEP)
Linktrace Message (LTM) This shows the destination MAC address in the Link Trace Response (LTR).
Set MD level Click this button to configure the MD (Maintenance Domain) level.
Send Loopback Click this button to have the selected MEP send the LBM (Loop Back Message) to a
specified remote end point.
Send Linktrace Click this button to have the selected MEP send the LTMs (Link Trace Messages) to a
specified remote end point.
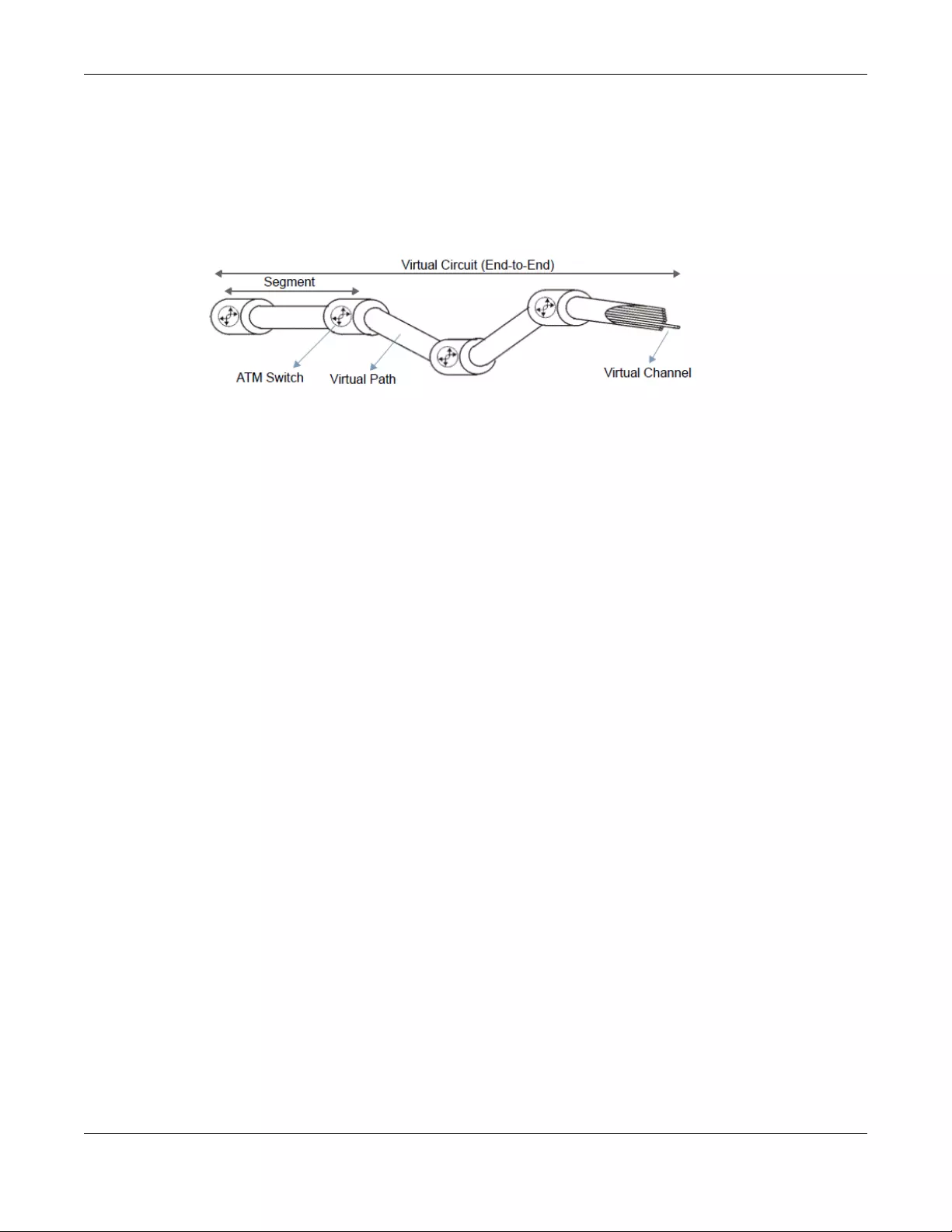
Chapter 20 Diagnostic
SBG5500 Series User’s Guide
243
ATM sets up virtual circuits over which end systems communicate. The terminology for virtual circuits is as
follows:
• Virtual Channel (VC) Logical connections between ATM devices
• Virtual Path (VP) A bundle of virtual channels
• Virtual Circuits A series of virtual paths between circuit end points
Figure 171 Virtual Circuit Topology
Think of a virtual path as a cable that contains a bundle of wires. The cable connects two points and
wires within the cable provide individual circuits between the two points. In an ATM cell header, a VPI
(Virtual Path Identifier) identifies a link formed by a virtual path; a VCI (Virtual Channel Identifier)
identifies a channel within a virtual path. A series of virtual paths make up a virtual circuit.
F4 cells operate at the virtual path (VP) level, while F5 cells operate at the virtual channel (VC) level. F4
cells use the same VPI as the user data cells on VP connections, but use different predefined VCI values.
F5 cells use the same VPI and VCI as the user data cells on the VC connections, and are distinguished
from data cells by a predefined Payload Type Identifier (PTI) in the cell header. Both F4 flows and F5
flows are bidirectional and have two types.
• segment F4 flows (VCI=3)
• end-to-end F4 flows (VCI=4)
• segment F5 flows (PTI=100)
• end-to-end F5 flows (PTI=101)
OAM F4 or F5 tests are used to check virtual path or virtual channel availability between two DSL
devices. Segment flows are terminated at the connecting point which terminates a VP or VC segment.
End-to-end flows are terminated at the end point of a VP or VC connection, where an ATM link is
terminated. Segment loopback tests allow you to verify integrity of a PVC to the nearest neighboring
ATM device. End-to-end loopback tests allow you to verify integrity of an end-to-end PVC.
Note: The DSLAM to which the SBG is connected must also support ATM F4 and/or F5 to use
this test.
Note: This screen is available only when you configure an ATM layer-2 interface.
Chapter 20 Diagnostic
SBG5500 Series User’s Guide
244
Figure 172 Maintenance > Diagnostic > OAM Ping
The following table describes the labels in this screen.
20.5 The Packet Capture Screen
Use this screen to capture network traffic going through the SBG’s interfaces. Studying these packet
captures may help you identify network problems. Click Maintenance > Diagnostic > Packet Capture to
open the packet capture screen.
Note: New capture files overwrite existing files of the same name. Change the File Suffix field’s
setting to avoid this.
Table 113 Maintenance > Diagnostic > OAM Ping
LABEL DESCRIPTION
Result
Select a PVC on which you want to perform the loopback test.
F4 Segment Press this to perform an OAM F4 segment loopback test.
F4 End-End Press this to perform an OAM F4 end-to-end loopback test.
F5 Segment Press this to perform an OAM F5 segment loopback test.
F5 End-End Press this to perform an OAM F5 end-to-end loopback test.
Chapter 20 Diagnostic
SBG5500 Series User’s Guide
245
Figure 173 Maintenance > Diagnostic > Packet Capture
The following table describes the labels in this screen.
Table 114 Maintenance > Diagnostic > Packet Capture
LABEL DESCRIPTION
Status This displays USB not found if there is no USB detected in the port.
This displays Ready when the USB is ready for capture.
This displays Unmount USB to confirm you can remove your USB drive safely.
This displays Capturing when the packet is in process of being captured.
This displays Completed when the packet capture process is finished.
Interface Enabled interfaces appear under Interface. Select interfaces for which to capture
packets.
File Name Enter the label that identifies the file. The file name format is interface name-file
suffix.pcap.
Setting

Chapter 20 Diagnostic
SBG5500 Series User’s Guide
246
Capture Until Stop Click this check box to have the SBG capture packets according to the settings
configured here.
You can configure the SBG while a packet capture is in progress although you
cannot modify the packet capture settings.
The SBG’s throughput or performance may be affected while a packet capture is in
progress.
After the SBG finishes the capture it saves a separate capture file for each selected
interface. The total number of packet capture files that you can save depends on
the file sizes and the available flash storage space. Once the flash storage space is
full, adding more packet captures will fail.
Count Packet Specify a maximum number of individual packet for each capture files. After a
packet capture file reaches this number, the SBG won’t start another capture.
Capture Duration Set a time limit in seconds for the capture. The SBG stops the capture and generates
the capture file when either this period of time has passed.
Capture File Size Specify a maximum size limit in megabytes for individual packet capture files. After a
packet capture file reaches this size, the SBG won’t start another capture, but
replaces the existing packet capture file.
Filter
Host IP Select a host IP address object for which to capture packets.
Host Port Specify the port number or port range of traffic to capture.
Protocol Type Select the protocol of traffic for which to capture packets.
Start Capture After applying the desired filters click Start Capture for the SBG to capture network
traffic on the interfaces.
Stop Capture Click Stop Capture so the SBG ends the capture process.
Check Status Click Check Status to refresh the USB status in Status.
Unmount USB Click Unmount USB to remove your USB drive safely.
Table 114 Maintenance > Diagnostic > Packet Capture
LABEL DESCRIPTION
SBG5500 Series User’s Guide
247
CHAPTER 21
Firmware Upgrade
21.1 Overview
This chapter explains how to upload new firmware package, to update USB 3G dongle support, to your
SBG. You can download new firmware releases and USB 3G dongle support packages from your
nearest Zyxel FTP site (or www.zyxel.com) to use to upgrade your device’s performance.
Only use firmware for your device’s specific model. Refer to the label on
the bottom of your SBG.
21.2 The Firmware Screen
Click Maintenance > Firmware Upgrade to open the following screen. The upload process uses HTTP
(Hypertext Transfer Protocol) and may take up to two minutes. After a successful upload, the system will
reboot.
Do NOT turn off the SBG while firmware upload is in progress!
Figure 174 Maintenance > Firmware Upgrade
The following table describes the labels in this screen.
Table 115 Maintenance > Firmware Upgrade
LABEL DESCRIPTION
Firmware Status
#This is a sequential value, and it is not associated with the entry.

Chapter 21 Firmware Upgrade
SBG5500 Series User’s Guide
248
After you see the firmware updating screen, wait two minutes before logging into the SBG again.
Figure 175 Firmware Uploading
The SBG automatically restarts in this time causing a temporary network disconnect. In some operating
systems, you may see the following icon on your desktop.
Figure 176 Network Temporarily Disconnected
Status This indicates whether the firmware is Running, or not running but already uploaded to the
SBG and is on Standby. It displays N/A if there is no firmware uploaded to that system space.
Model This shows the model name of this Zyxel device.
Version This is the SBG’s present firmware version.
Released Date This shows the date the present firmware was released.
Upgrade Click the Upgrade icon to open a new screen, where you Browse the location of the .bin file
you want to Upload to the SBG. Remember that you must decompress compressed (.zip)
files before you can upload them. The upgrade process may take up to two minutes.
Note: Do not turn off the SBG while firmware upgrade is in progress.
Cloud Firmware Information
Latest Version This is the firmware’s latest version. Click Check Now for the SBG to check for new firmware
releases.
Released Date This is the date that the latest version of the firmware was created.
Release Note This is a comment associated with the latest firmware.
Firmware Upgrade License Status
Service / License
Status
This is the current status of the license.
Table 115 Maintenance > Firmware Upgrade
LABEL DESCRIPTION
Chapter 21 Firmware Upgrade
SBG5500 Series User’s Guide
249
After two minutes, log in again and check your new firmware version in the Status screen.
If the upload was not successful, the following screen will appear. Click OK to go back to the Firmware
Upgrade screen.
Figure 177 Error Message
21.3 The Mobile Profile Screen
Use this screen to update the mobile profile on the SBG. The mobile profile is a WWAN package that
contains configuration to identify and activate the supported 3G USB dongles.
Note: To update the supported 3G USB dongle list, download the latest mobile profile from
the ZyXEL website and upload it to the SBG.
Click Maintenance > Firmware Upgrade > Mobile Profile to open the following screen. The upload
process uses HTTP (Hypertext Transfer Protocol) and may take up to two minutes.
Do NOT turn off the SBG while profile upload is in progress!
Figure 178 Maintenance > Firmware Upgrade > Mobile Profile
The following table describes the labels in this screen.
Table 116 Maintenance > Firmware Upgrade > Mobile Profile
LABEL DESCRIPTION
Mobile Profile Status
#This is a sequential value, and it is not associated with the entry.
Version This is the version of the SBG’s present mobile profile.
Upgrade Click the Upgrade icon to open a new screen, where you Browse the location of the file you
want to Upload to the SBG.
Note: Do not turn off the SBG while profile upgrade is in progress.
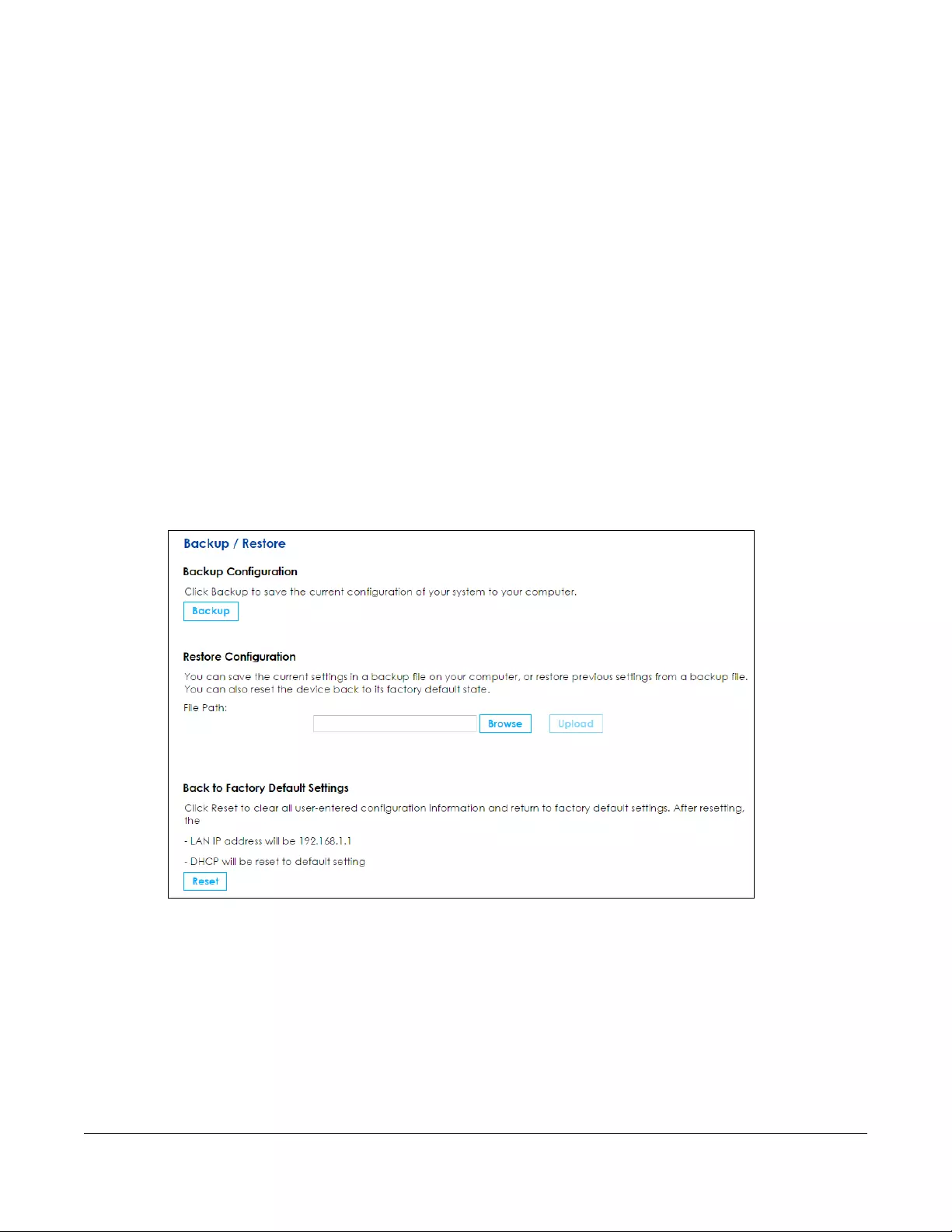
SBG5500 Series User’s Guide
250
CHAPTER 22
Backup / Restore
22.1 Overview
The Backup / Restore screen allows you to backup and restore device configurations. You can also
reset your device settings back to the factory default.
22.2 The Backup / Restore Screen
Click Maintenance > Backup / Restore. Information related to factory defaults, backup configuration,
and restoring configuration appears in this screen, as shown next.
Figure 179 Maintenance > Backup / Restore
Backup Configuration
Backup Configuration allows you to back up (save) the SBG’s current configuration to a file on your
computer. Once your SBG is configured and functioning properly, it is highly recommended that you
back up your configuration file before making configuration changes. The backup configuration file will
be useful in case you need to return to your previous settings.
Click Backup to save the SBG’s current configuration to your computer.
Chapter 22 Backup / Restore
SBG5500 Series User’s Guide
251
Restore Configuration
Restore Configuration allows you to upload a new or previously saved configuration file from your
computer to your SBG.
Do not turn off the SBG while configuration file upload is in progress.
After the SBG configuration has been restored successfully, the login screen appears. Login again to
restart the SBG.
The SBG automatically restarts in this time causing a temporary network disconnect. In some operating
systems, you may see the following icon on your desktop.
Figure 180 Network Temporarily Disconnected
If you uploaded the default configuration file you may need to change the IP address of your computer
to be in the same subnet as that of the default device IP address (192.168.1.1).
If the upload was not successful, the following screen will appear. Click OK to go back to the Backup /
Restore screen.
Figure 181 Configuration Upload Error
Reset to Factory Defaults
Click the Reset button to clear all user-entered configuration information and return the SBG to its
factory defaults. The following warning screen appears.
Table 117 Restore Configuration
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Choose File to find it.
Browse Click this to find the file you want to upload. Remember that you must decompress compressed
(.ZIP) files before you can upload them.
Upload Click this to begin the upload process.
SBG5500 Series User’s Guide
252
CHAPTER 23
Language
23.1 Overview
Use the Language screen to change the language in which the screen are displayed in the web
configurator.
23.2 The Language Screen
Click Maintenance > Language to open the following screen.
Figure 182 Maintenance > Language
Select the language of your preference and click Apply to save your changes to the SBG. The following
screen will display. After clicking Yes the SBG will automatically change all the screens to the selected
language.
Figure 183 Maintenance > Language > Apply
SBG5500 Series User’s Guide
253
CHAPTER 24
Restart / Shutdown
24.1 Overview
Use this screen to restart the device. Restart is different to reset; restart returns the device to its default
configuration.
24.2 The Restart / Shutdown Screen
System restart allows you to reboot the SBG remotely without turning the power off. You may need to do
this if the SBG hangs, for example.
Click Maintenance > Restart / Shutdown. Click Restart to have the SBG reboot. This does not affect the
SBG's configuration. If you applied changes in the Web configurator, these were saved automatically
and do not change when you reboot.
Figure 184 Maintenance > Restart / Shutdown
SBG5500 Series User’s Guide
254
CHAPTER 25
Troubleshooting
This chapter offers some suggestions to solve problems you might encounter. The potential problems are
divided into the following categories.
•Power, Hardware Connections, and LEDs
•SBG Access and Login
•Internet Access
•USB Device Connection
25.1 Power, Hardware Connections, and LEDs
The SBG does not turn on. None of the LEDs turn on.
1Make sure the SBG is turned on.
2Make sure you are using the power adaptor or cord included with the SBG.
3Make sure the power adaptor or cord is connected to the SBG and plugged in to an appropriate power
source. Make sure the power source is turned on.
4Turn the SBG off and on.
5If the problem continues, contact the vendor.
One of the LEDs does not behave as expected.
1Make sure you understand the normal behavior of the LED. See Section 1.5 on page 17.
2Check the hardware connections.
3Inspect your cables for damage. Contact the vendor to replace any damaged cables.
4Turn the SBG off and on.
5If the problem continues, contact the vendor.
Chapter 25 Troubleshooting
SBG5500 Series User’s Guide
255
25.2 SBG Access and Login
I forgot the IP address for the SBG.
1The default LAN IP address is 192.168.1.1.
2If you changed the IP address and have forgotten it, you might get the IP address of the SBG by looking
up the IP address of the default gateway for your computer. To do this in most Windows computers, click
Start > Run, enter cmd, and then enter ipconfig. The IP address of the Default Gateway might be the IP
address of the SBG (it depends on the network), so enter this IP address in your Internet browser.
3If this does not work, you have to reset the device to its factory defaults. See Section 1.6 on page 18.
I forgot the password.
1The default admin password is 1234.
2If this does not work, you have to reset the device to its factory defaults. See Section 1.6 on page 18.
I cannot see or access the Login screen in the web configurator.
1Make sure you are using the correct IP address.
• The default IP address is 192.168.1.1.
• If you changed the IP address (Section 6.2 on page 87), use the new IP address.
• If you changed the IP address and have forgotten it, see the troubleshooting suggestions for I
forgot the IP address for the SBG.
2Check the hardware connections, and make sure the LEDs are behaving as expected. See Section 1.5
on page 17.
3Make sure your Internet browser does not block pop-up windows and has JavaScripts and Java
enabled.
4If it is possible to log in from another interface, check the service control settings for HTTP and HTTPS
(Configuration > Firewall / Security > Device Service).
5Reset the device to its factory defaults, and try to access the SBG with the default IP address. See
Section 1.6 on page 18.
6If the problem continues, contact the network administrator or vendor, or try one of the advanced
suggestions.
Advanced Suggestions
Chapter 25 Troubleshooting
SBG5500 Series User’s Guide
256
• Make sure you have logged out of any earlier management sessions using the same user account
even if they were through a different interface or using a different browser.
• Try to access the SBG using another service, such as Telnet. If you can access the SBG, check the
remote management settings and firewall rules to find out why the SBG does not respond to HTTP.
I can see the Login screen, but I cannot log in to the SBG.
1Make sure you have entered the password correctly. The default admin password is 1234. The field is
case-sensitive, so make sure [Caps Lock] is not on.
2You cannot log in to the web configurator while someone is using Telnet to access the SBG. Log out of
the SBG in the other session, or ask the person who is logged in to log out.
3Turn the SBG off and on.
4If this does not work, you have to reset the device to its factory defaults. See Section 25.1 on page 254.
I cannot Telnet to the SBG.
See the troubleshooting suggestions for I cannot see or access the Login screen in the web configurator.
Ignore the suggestions about your browser.
I cannot use FTP to upload / download the configuration file. / I cannot use FTP to upload new
firmware.
See the troubleshooting suggestions for I cannot see or access the Login screen in the web configurator.
Ignore the suggestions about your browser.
25.3 Internet Access
I cannot access the Internet.
1Check the hardware connections, and make sure the LEDs are behaving as expected. See the Quick
Start Guide and Section 1.5 on page 17.
2Make sure you entered your ISP account information correctly in the Configuration > WAN / Internet >
WAN Setup or Mobile screen. These fields are case-sensitive, so make sure [Caps Lock] is not on.
3Disconnect all the cables from your device and reconnect them.
Chapter 25 Troubleshooting
SBG5500 Series User’s Guide
257
4If the problem continues, contact your ISP.
I cannot access the Internet through a DSL connection.
1Make sure you have the DSL WAN port connected to a telephone jack (or the DSL or modem jack on a
splitter if you have one).
2Make sure you configured a proper DSL WAN interface (Configuration > WAN / Internet > WAN Setup
screen) with the Internet account information provided by your ISP and that it is enabled.
3Check that the LAN interface you are connected to is in the same interface group as the DSL
connection (Configuration > LAN / Home Network > VLAN / Interface Group).
4If you set up a WAN connection using bridging service, make sure you turn off the DHCP feature in the
Configuration > LAN / Home Network > LAN Setup screen to have the clients get WAN IP addresses
directly from your ISP’s DHCP server.
I cannot connect to the Internet using a second DSL connection.
ADSL and VDSL connections cannot work at the same time. You can only use one type of DSL
connection, either ADSL or VDSL connection at one time.
I cannot access the Internet anymore. I had access to the Internet (with the SBG), but my Internet
connection is not available anymore.
1Your session with the SBG may have expired. Try logging into the SBG again.
2Check the hardware connections, and make sure the LEDs are behaving as expected. See the Quick
Start Guide and Section 1.5 on page 17.
3Turn the SBG off and on.
4If the problem continues, contact your ISP.
25.4 USB Device Connection
The SBG fails to detect my USB device.
1Disconnect the USB device.

Chapter 25 Troubleshooting
SBG5500 Series User’s Guide
258
2Reboot the SBG.
3If you are connecting a USB hard drive that comes with an external power supply, make sure it is
connected to an appropriate power source that is on.
4Re-connect your USB device to the SBG.

SBG5500 Series User’s Guide
259
APPENDIX A
Customer Support
In the event of problems that cannot be solved by using this manual, you should contact your vendor. If
you cannot contact your vendor, then contact a Zyxel office for the region in which you bought the
device.
See http://www.zyxel.com/homepage.shtml and also
http://www.zyxel.com/about_zyxel/zyxel_worldwide.shtml for the latest information.
Please have the following information ready when you contact an office.
Required Information
• Product model and serial number.
• Warranty Information.
• Date that you received your device.
• Brief description of the problem and the steps you took to solve it.
Corporate Headquarters (Worldwide)
Taiwan
• Zyxel Communications Corporation
• http://www.zyxel.com
Asia
China
• Zyxel Communications (Shanghai) Corp.
Zyxel Communications (Beijing) Corp.
Zyxel Communications (Tianjin) Corp.
• http://www.zyxel.cn
India
•Zyxel Technology India Pvt Ltd
• http://www.zyxel.in
Kazakhstan
•Zyxel Kazakhstan
• http://www.zyxel.kz

Appendix A Customer Support
SBG5500 Series User’s Guide
260
Korea
• Zyxel Korea Corp.
• http://www.zyxel.kr
Malaysia
• Zyxel Malaysia Sdn Bhd.
• http://www.zyxel.com.my
Pakistan
• Zyxel Pakistan (Pvt.) Ltd.
• http://www.zyxel.com.pk
Philippines
• Zyxel Philippines
• http://www.zyxel.com.ph
Singapore
• Zyxel Singapore Pte Ltd.
• http://www.zyxel.com.sg
Taiwan
• Zyxel Communications Corporation
• http://www.zyxel.com/tw/zh/
Thailand
• Zyxel Thailand Co., Ltd
• http://www.zyxel.co.th
Vietnam
• Zyxel Communications Corporation-Vietnam Office
• http://www.zyxel.com/vn/vi
Europe
Austria
•Zyxel Deutschland GmbH
• http://www.zyxel.de
Belarus
•Zyxel BY
• http://www.zyxel.by

Appendix A Customer Support
SBG5500 Series User’s Guide
261
Belgium
• Zyxel Communications B.V.
• http://www.zyxel.com/be/nl/
• http://www.zyxel.com/be/fr/
Bulgaria
•Zyxel България
• http://www.zyxel.com/bg/bg/
Czech Republic
• Zyxel Communications Czech s.r.o
• http://www.zyxel.cz
Denmark
• Zyxel Communications A/S
• http://www.zyxel.dk
Estonia
• Zyxel Estonia
• http://www.zyxel.com/ee/et/
Finland
• Zyxel Communications
• http://www.zyxel.fi
France
•Zyxel France
• http://www.zyxel.fr
Germany
•Zyxel Deutschland GmbH
• http://www.zyxel.de
Hungary
• Zyxel Hungary & SEE
• http://www.zyxel.hu
Italy
• Zyxel Communications Italy
• http://www.zyxel.it/

Appendix A Customer Support
SBG5500 Series User’s Guide
262
Latvia
•Zyxel Latvia
• http://www.zyxel.com/lv/lv/homepage.shtml
Lithuania
•Zyxel Lithuania
• http://www.zyxel.com/lt/lt/homepage.shtml
Netherlands
• Zyxel Benelux
• http://www.zyxel.nl
Norway
• Zyxel Communications
• http://www.zyxel.no
Poland
• Zyxel Communications Poland
• http://www.zyxel.pl
Romania
• Zyxel Romania
• http://www.zyxel.com/ro/ro
Russia
• Zyxel Russia
• http://www.zyxel.ru
Slovakia
• Zyxel Communications Czech s.r.o. organizacna zlozka
• http://www.zyxel.sk
Spain
• Zyxel Communications ES Ltd
• http://www.zyxel.es
Sweden
• Zyxel Communications
• http://www.zyxel.se
Switzerland
•Studerus AG

Appendix A Customer Support
SBG5500 Series User’s Guide
263
• http://www.zyxel.ch/
Turkey
• Zyxel Turkey A.S.
• http://www.zyxel.com.tr
UK
• Zyxel Communications UK Ltd.
• http://www.zyxel.co.uk
Ukraine
•Zyxel Ukraine
• http://www.ua.zyxel.com
Latin America
Argentina
• Zyxel Communication Corporation
• http://www.zyxel.com/ec/es/
Brazil
• Zyxel Communications Brasil Ltda.
• https://www.zyxel.com/br/pt/
Ecuador
• Zyxel Communication Corporation
• http://www.zyxel.com/ec/es/
Middle East
Israel
• Zyxel Communication Corporation
• http://il.zyxel.com/homepage.shtml
Middle East
• Zyxel Communication Corporation
• http://www.zyxel.com/me/en/

Appendix A Customer Support
SBG5500 Series User’s Guide
264
North America
USA
• Zyxel Communications, Inc. - North America Headquarters
• http://www.zyxel.com/us/en/
Oceania
Australia
• Zyxel Communications Corporation
• http://www.zyxel.com/au/en/
Africa
South Africa
• Nology (Pty) Ltd.
• http://www.zyxel.co.za
SBG5500 Series User’s Guide
265
APPENDIX B
Legal Information
Copyright
Copyright © 2017 by Zyxel Communications Corporation.
The contents of this publication may not be reproduced in any part or as a whole, transcribed, stored in a retrieval system, translated into any
language, or transmitted in any form or by any means, electronic, mechanical, magnetic, optical, chemical, photocopying, manual, or
otherwise, without the prior written permission of Zyxel Communications Corporation.
Published by Zyxel Communications Corporation. All rights reserved.
Disclaimer
Zyxel does not assume any liability arising out of the application or use of any products, or software described herein. Neither does it convey any
license under its patent rights nor the patent rights of others. Zyxel further reserves the right to make changes in any products described herein
without notice. This publication is subject to change without notice.
Regulatory Notice and Statement
UNITED STATES of AMERICA
The following information applies if you use the product within USA area.
FCC EMC Statement
• The device complies with Part 15 of FCC rules. Operation is subject to the following two conditions:
(1) This device may not cause harmful interference, and
(2) This device must accept any interference received, including interference that may cause undesired operation.
• Changes or modifications not expressly approved by the party responsible for compliance could void the user’s authority to operate the
device.
• This product has been tested and complies with the specifications for a Class B digital device, pursuant to Part 15 of the FCC Rules. These
limits are designed to provide reasonable protection against harmful interference in a residential installation. This device generates, uses, and
can radiate radio frequency energy and, if not installed and used according to the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a particular installation.
• If this device does cause harmful interference to radio or television reception, which is found by turning the device off and on, the user is
encouraged to try to correct the interference by one or more of the following measures:
• Reorient or relocate the receiving antenna
• Increase the separation between the devices
• Connect the equipment to an outlet other than the receiver’s
• Consult a dealer or an experienced radio/TV technician for assistance
FCC Part 68 Statement (for SBG5500-A only)
• This equipment complies with Part 68 of the FCC rules and the requirements adopted by the ACTA. On the back of this equipment is a label
that contains, among other information, a product identifier in the format US:1RODL01ASBG5500-A. If requested, this number must be
provided to the telephone company.
• List all applicable certification jack Universal Service Order Codes (“USOC”) for the equipment. USOC JACK: RJ11C
• A plug and jack used to connect this equipment to the premises wiring and telephone network must comply with the applicable FCC Part 68
rules and requirements adopted by the ACTA. A compliant telephone cord and modular plug is provided with this product. It is designed to
be connected to a compatible modular jack that is also compliant. See installation instructions for details.
• The REN is used to determine the number of devices that may be connected to a telephone line. Excessive RENs on a telephone line may
result in the devices not ringing in response to an incoming call. In most but not all areas, the sum of RENs should not exceed five (5.0). To be
certain of the number of devices that may be connected to a line, as determined by the total RENs, contact the local telephone company.
For products approved after July 23, 2001, the REN for this product is part of the product identifier that has the format US:AAAEQ##TXXXX. The
digits represented by ## are the REN without a decimal point (e.g., 03 is a REN of 0.3). For earlier products, the REN is separately shown on the
label.
• If this equipment US: 1RODL01ASBG5500-A causes harm to the telephone network, the telephone company will notify you in advance that
temporary discontinuance of service may be required. But if advance notice isn't practical, the telephone company will notify the customer
as soon as possible. Also, you will be advised of your right to file a complaint with the FCC if you believe it is necessary.
• The telephone company may make changes in its facilities, equipment, operations or procedures that could affect the operation of the
equipment. If this happens the telephone company will provide advance notice in order for you to make necessary modifications to
maintain uninterrupted service.
Appendix B Legal Information
SBG5500 Series User’s Guide
266
• If trouble is experienced with this equipment US: 1RODL01ASBG5500-A, for repair or warranty information, please contact Zyxel
Communication Inc.; 1130 N Miller street Anaheim, CA 92806-2001, USA; TEL: 002 +1 714-6320882. If the equipment is causing harm to the
telephone network, the telephone company may request that you disconnect the equipment until the problem is resolved.
• Connection to party line service is subject to state tariffs. Contact the state public utility commission, public service commission or
corporation commission for information.
• If your home has specially wired alarm equipment connected to the telephone line, ensure the installation of this US: 1RODL01ASBG5500-A
does not disable your alarm equipment. If you have questions about what will disable alarm equipment, consult your telephone company or
a qualified installer.
CANADA
The following information applies if you use the product within Canada area
Industry Canada ICES statement
CAN ICES-3 (B)/NMB-3(B)
Industry Canada CS-03 Statement
• This product meets the applicable Innovation, Science and Economic Development Canada technical specifications.
• The Ringer Equivalence Number (REN) indicates the maximum number of devices allowed to be connected to a telephone interface. The
termination of an interface may consist of any combination of devices subject only to the requirement that the sum of the RENs of all the
devices not exceed five.
Déclaration de conformité
• Le présent produit est conforme aux spécifications techniques applicables d'Innovation, Sciences et Développement économique Canada.
• L'indice d'équivalence de la sonnerie (IES) sert à indiquer le nombre maximal de dispositifs qui peuvent être raccordés à une interface
téléphonique. La terminaison d'une interface peut consister en une combinaison quelconque de dispositifs, à la seule condition que la
somme des IES de tous les dispositifs n'excède pas cinq.
EUROPEAN UNION
The following information applies if you use the product within the European Union.
List of national codes
Safety Warnings
• Do not use this product near water, for example, in a wet basement or near a swimming pool.
• Do not expose your device to dampness, dust or corrosive liquids.
COUNTRY ISO 3166 2 LETTER CODE COUNTRY ISO 3166 2 LETTER CODE
Austria AT Liechtenstein LI
Belgium BE Lithuania LT
Bulgaria BG Luxembourg LU
Croatia HR Malta MT
Cyprus CY Netherlands NL
Czech Republic CZ Norway NO
Denmark DK Poland PL
Estonia EE Portugal PT
Finland FI Romania RO
France FR Serbia RS
Germany DE Slovakia SK
Greece GR Slovenia SI
Hungary HU Spain ES
Iceland IS Switzerland CH
Ireland IE Sweden SE
Italy IT Turkey TR
Latvia LV United Kingdom GB

Appendix B Legal Information
SBG5500 Series User’s Guide
267
• Do not store things on the device.
• Do not obstruct the device ventilation slots as insufficient airflow may harm your device. For example, do not place the device in an
enclosed space such as a box or on a very soft surface such as a bed or sofa.
• Do not install, use, or service this device during a thunderstorm. There is a remote risk of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• Do not open the device or unit. Opening or removing covers can expose you to dangerous high voltage points or other risks.
• Only qualified service personnel should service or disassemble this device. Please contact your vendor for further information.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Do not remove the plug and connect it to a power outlet by itself; always attach the plug to the power adaptor first before connecting it to
a power outlet.
• Do not allow anything to rest on the power adaptor or cord and do NOT place the product where anyone can walk on the power adaptor
or cord.
• Please use the provided or designated connection cables/power cables/ adaptors. Connect it to the right supply voltage (for example,
110V AC in North America or 230V AC in Europe). If the power adaptor or cord is damaged, it might cause electrocution. Remove it from the
device and the power source, repairing the power adapter or cord is prohibited. Contact your local vendor to order a new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a remote risk of electric shock from lightning.
• CAUTION: Risk of explosion if battery is replaced by an incorrect type, dispose of used batteries according to the instruction. Dispose them at
the applicable collection point for the recycling of electrical and electronic devices. For detailed information about recycling of this
product, please contact your local city office, your household waste disposal service or the store where you purchased the product.
• The following warning statements apply, where the disconnect device is not incorporated in the device or where the plug on the power
supply cord is intended to serve as the disconnect device,
- For permanently connected devices, a readily accessible disconnect device shall be incorporated external to the device;
- For pluggable devices, the socket-outlet shall be installed near the device and shall be easily accessible.
• CLASS 1 LASER PRODUCT
APPAREIL À LASER DE CLASS 1
PRODUCT COMPLIES WITH 21 CFR 1040.10 AND 1040.11.
PRODUIT CONFORME SELON 21 CFR 1040.10 ET 1040.11.
Environment Statement
ErP (Energy-related Products)
Zyxel products put on the EU market in compliance with the requirement of the European Parliament and the Council published Directive 2009/
125/EC establishing a framework for the setting of ecodesign requirements for energy-related products (recast), so called as "ErP Directive
(Energy-related Products directive) as well as ecodesign requirement laid down in applicable implementing measures, power consumption has
satisfied regulation requirements which are:
• Network standby power consumption < 8W, and/or
• Off mode power consumption < 0.5W, and/or
• Standby mode power consumption < 0.5W.
(Wireless setting, please refer to "Wireless" chapter for more detail.)
European Union - Disposal and Recycling Information
The symbol below means that according to local regulations your product and/or its battery shall be disposed of separately from domestic
waste. If this product is end of life, take it to a recycling station designated by local authorities. At the time of disposal, the separate collection of
your product and/or its battery will help save natural resources and ensure that the environment is sustainable development.
Die folgende Symbol bedeutet, dass Ihr Produkt und/oder seine Batterie gemäß den örtlichen Bestimmungen getrennt vom Hausmüll entsorgt
werden muss. Wenden Sie sich an eine Recyclingstation, wenn dieses Produkt das Ende seiner Lebensdauer erreicht hat. Zum Zeitpunkt der
Entsorgung wird die getrennte Sammlung von Produkt und/oder seiner Batterie dazu beitragen, natürliche Ressourcen zu sparen und die Umwelt
und die menschliche Gesundheit zu schützen.
El símbolo de abajo indica que según las regulaciones locales, su producto y/o su batería deberán depositarse como basura separada de la
doméstica. Cuando este producto alcance el final de su vida útil, llévelo a un punto limpio. Cuando llegue el momento de desechar el
producto, la recogida por separado éste y/o su batería ayudará a salvar los recursos naturales y a proteger la salud humana y
medioambiental.
Le symbole ci-dessous signifie que selon les réglementations locales votre produit et/ou sa batterie doivent être éliminés séparément des ordures
ménagères. Lorsque ce produit atteint sa fin de vie, amenez-le à un centre de recyclage. Au moment de la mise au rebut, la collecte séparée
de votre produit et/ou de sa batterie aidera à économiser les ressources naturelles et protéger l'environnement et la santé humaine.
Il simbolo sotto significa che secondo i regolamenti locali il vostro prodotto e/o batteria deve essere smaltito separatamente dai rifiuti domestici.
Quando questo prodotto raggiunge la fine della vita di servizio portarlo a una stazione di riciclaggio. Al momento dello smaltimento, la raccolta
separata del vostro prodotto e/o della sua batteria aiuta a risparmiare risorse naturali e a proteggere l'ambiente e la salute umana.
Appendix B Legal Information
SBG5500 Series User’s Guide
268
Symbolen innebär att enligt lokal lagstiftning ska produkten och/eller dess batteri kastas separat från hushållsavfallet. När den här produkten når
slutet av sin livslängd ska du ta den till en återvinningsstation. Vid tiden för kasseringen bidrar du till en bättre miljö och mänsklig hälsa genom att
göra dig av med den på ett återvinningsställe.
台灣
安全警告 - 為了您的安全,請先閱讀以下警告及指示 :
• 請勿將此產品接近水、火焰或放置在高溫的環境。
• 避免設備接觸
- 任何液體 - 切勿讓設備接觸水、雨水、高濕度、污水腐蝕性的液體或其他水份。
- 灰塵及污物 - 切勿接觸灰塵、污物、沙土、食物或其他不合適的材料。
• 雷雨天氣時,不要安裝,使用或維修此設備。有遭受電擊的風險。
• 切勿重摔或撞擊設備,並勿使用不正確的電源變壓器。
• 若接上不正確的電源變壓器會有爆炸的風險。
• 請勿隨意更換產品內的電池。
• 如果更換不正確之電池型式,會有爆炸的風險,請依製造商說明書處理使用過之電池。
• 請將廢電池丟棄在適當的電器或電子設備回收處。
• 請勿將設備解體。
• 請勿阻礙設備的散熱孔,空氣對流不足將會造成設備損害。
• 請插在正確的電壓供給插座 ( 如 : 北美 / 台灣電壓 110V AC,歐洲是 230V AC)。
• 假若電源變壓器或電源變壓器的纜線損壞,請從插座拔除,若您還繼續插電使用,會有觸電死亡的風險。
• 請勿試圖修理電源變壓器或電源變壓器的纜線,若有毀損,請直接聯絡您購買的店家,購買一個新的電源變壓器。
• 請勿將此設備安裝於室外,此設備僅適合放置於室內。
• 請勿隨一般垃圾丟棄。
• 請參閱產品背貼上的設備額定功率。
• 請參考產品型錄或是彩盒上的作業溫度。
• 產品沒有斷電裝置或者採用電源線的插頭視為斷電裝置的一部分,以下警語將適用 :
- 對永久連接之設備, 在設備外部須安裝可觸及之斷電裝置;
- 對插接式之設備, 插座必須接近安裝之地點而且是易於觸及的。
About the Symbols
Various symbols are used in this product to ensure correct usage, to prevent danger to the user and others, and to prevent property damage.
The meaning of these symbols are described below. It is important that you read these descriptions thoroughly and fully understand the
contents.
Explanation of the Symbols
Viewing Certifications
Go to http://www.zyxel.com to view this product’s documentation and certifications.
SYMBOL EXPLANATION
Alternating current (AC):
AC is an electric current in which the flow of electric charge periodically reverses direction.
Direct current (DC):
DC if the unidirectional flow or movement of electric charge carriers.
Earth; ground:
A wiring terminal intended for connection of a Protective Earthing Conductor.
Class II equipment:
The method of protection against electric shock in the case of class II equipment is either double insulation or
reinforced insulation.

Appendix B Legal Information
SBG5500 Series User’s Guide
269
Zyxel Limited Warranty
Zyxel warrants to the original end user (purchaser) that this product is free from any defects in material or workmanship for a specific period (the
Warranty Period) from the date of purchase. The Warranty Period varies by region. Check with your vendor and/or the authorized Zyxel local
distributor for details about the Warranty Period of this product. During the warranty period, and upon proof of purchase, should the product
have indications of failure due to faulty workmanship and/or materials, Zyxel will, at its discretion, repair or replace the defective products or
components without charge for either parts or labor, and to whatever extent it shall deem necessary to restore the product or components to
proper operating condition. Any replacement will consist of a new or re-manufactured functionally equivalent product of equal or higher value,
and will be solely at the discretion of Zyxel. This warranty shall not apply if the product has been modified, misused, tampered with, damaged by
an act of God, or subjected to abnormal working conditions.
Note
Repair or replacement, as provided under this warranty, is the exclusive remedy of the purchaser. This warranty is in lieu of all other warranties,
express or implied, including any implied warranty of merchantability or fitness for a particular use or purpose. Zyxel shall in no event be held
liable for indirect or consequential damages of any kind to the purchaser.
To obtain the services of this warranty, contact your vendor. You may also refer to the warranty policy for the region in which you bought the
device at http://www.zyxel.com/web/support_warranty_info.php.
Registration
Register your product online to receive e-mail notices of firmware upgrades and information at www.zyxel.com for global products, or at
www.us.zyxel.com for North American products.
Trademarks
ZyNOS (Zyxel Network Operating System) and ZON (Zyxel One Network) are registered trademarks of Zyxel Communications, Inc. Other
trademarks mentioned in this publication are used for identification purposes only and may be properties of their respective owners.
Open Source Licenses
This product contains in part some free software distributed under GPL license terms and/or GPL like licenses. Open source licenses are provided
with the firmware package. You can download the latest firmware at www.zyxel.com. To obtain the source code covered under those Licenses,
please contact support@zyxel.com.tw to get it.

Index
SBG5500 Series User’s Guide
270
Index
A
activation
SIP ALG 133
administrator password 21
AH 187
algorithms 187
applications
Internet access 14
applications, NAT 135
B
backup
configuration 250
blinking LEDs 17
broadcast 83
C
Canonical Format Indicator See CFI
CCMs 240
certifications 266
viewing 268
CFI 83
CFM 240
CCMs 240
link trace test 240
loopback test 240
MA 240
MD 240
MEP 240
MIP 240
client list 94
configuration
backup 250
reset 251
restoring 251
static route 119, 234
Connectivity Check Messages, see CCMs
contact information 259
copyright 265
CoS 208
CoS technologies 195
customer support 259
D
DDoS 139
default server address 132
Denials of Service, see DoS
DH 192
DHCP 86, 105
Differentiated Services, see DiffServ 208
Diffie-Hellman key groups 192
DiffServ 208
marking rule 208
disclaimer 265
DMZ 131
DNS 86, 106
DNS server address assignment 83
Domain Name 136
Domain Name System, see DNS
Domain Name System. See DNS.
DoS 139
DS field 208
DS, dee differentiated services
DSCP 208
Dynamic Host Configuration Protocol, see DHCP
E
ECHO 136
Encapsulation 81

Index
SBG5500 Series User’s Guide
271
MER 81
PPP over Ethernet 81
encapsulation 49, 187
ESP 187
F
file sharing 16
Finger 136
firewalls 138
add protocols 149
DDoS 139
DoS 139
LAND attack 139
Ping of Death 139
SYN attack 139
firmware 247
forwarding ports 123
FTP 136
H
HTTP 136
I
ID type and content 191
IEEE 802.1Q 83
IGA 134
IGMP 83
version 83
IKE phases 188
ILA 134
Inside Global Address, see IGA
inside header 188
Inside Local Address, see ILA
Internet
wizard setup 27
Internet access 14
wizard setup 27
Internet Key Exchange 188
Internet Protocol Security. See IPsec.
Internet Protocol version 6 50
Internet Service Provider, see ISP
IP address 86, 106
ping 241
private 107
WAN 50
IP Address Assignment 82
IP alias
NAT applications 136
IPsec 159
algorithms 187
architecture 186
NAT 190
IPsec. See also VPN.
IPv6 50
addressing 50, 84
prefix 51, 84
prefix delegation 52
prefix length 51, 84
ISP 49
L
L2TP VPN 161
LAN 85
client list 94
DHCP 86, 105
DNS 86, 106
IP address 86, 88, 106
subnet mask 86, 106
LAND attack 139
Layer 2 Tunneling Protocol Virtual Private Network, see
L2TP VPN 161
LBR 240
link trace 240
Link Trace Message, see LTM
Link Trace Response, see LTR
login 20
passwords 20, 21
logs 215
Loop Back Response, see LBR
loopback 240
LTM 240
LTR 240

Index
SBG5500 Series User’s Guide
272
M
MA 240
Maintenance Association, see MA
Maintenance Domain, see MD
Maintenance End Point, see MEP
Management Information Base (MIB) 213
managing the device
good habits 14
MD 240
MEP 240
MTU (Multi-Tenant Unit) 82
multicast 83
N
NAT 122, 124, 134
applications 135
IP alias 136
example 135
global 134
IGA 134
ILA 134
inside 134
IPsec 190
local 134
outside 134
port forwarding 123
port number 136
services 136
SIP ALG 133
activation 133
traversal 190
NAT example 137
negotiation mode 189
Network Address Translation, see NAT
Network Map 45
NNTP 136
O
outside header 188
P
passwords 20, 21
Per-Hop Behavior, see PHB 208
PHB 208
Ping of Death 139
Point-to-Point Tunneling Protocol 136
POP3 136
port forwarding 123
ports 17
PPP over Ethernet, see PPPoE
PPPoE 49, 81
Benefits 81
PPTP 136
prefix delegation 52
pre-shared key 192
private IP address 107
product registration 269
protocol 49
Q
QoS 194, 208
marking 195
setup 194
tagging 195
versus CoS 194
Quality of Service, see QoS
R
registration
product 269
reset 18, 251
restart 253
restoring configuration 251
RFC 1058. See RIP.
RFC 1389. See RIP.
RFC 3164 215
RIP 120
router features 14
Routing Information Protocol. See RIP

Index
SBG5500 Series User’s Guide
273
S
security associations. See VPN.
Security Parameter Index, see SPI
Services 136
setup
static route 119, 234
Simple Network Management Protocol, see SNMP
Single Rate Three Color Marker, see srTCM
SIP ALG 133
activation 133
SMTP 136
SNMP 136, 212, 213
agents 212
Get 213
GetNext 213
Manager 212
managers 212
MIB 213
Set 213
Trap 213
versions 212
SNMP trap 136
SPI 139
srTCM 210
static route 108
configuration 119, 234
example 108
static VLAN
status 45
status indicators 17
subnet mask 86, 106
SYN attack 139
syslog
protocol 215
severity levels 215
system
firmware 247
passwords 20, 21
reset 18
status 45
T
Tag Control Information See TCI
Tag Protocol Identifier See TPID
TCI
The 50
TPID 83
trademarks 269
transport mode 188
trTCM 211
tunnel mode 188
Two Rate Three Color Marker, see trTCM
U
unicast 83
upgrading firmware 247
USB features 16
V
VID
Virtual Local Area Network See VLAN
Virtual Private Network. See VPN.
VLAN 82
Introduction 82
number of possible VIDs
priority frame
static
VLAN ID 83
VLAN Identifier See VID
VLAN tag 83
VPN 159
established in two phases 160
IPsec 159
local network 160
remote IPsec router 160
remote network 160
security associations (SA) 160
VPN. See also IKE SA, IPsec SA.
W
WAN
