Intellinet 561051 User Manual
Displayed below is the user manual for 561051 by Intellinet which is a product in the Network Switches category. This manual has pages.
Related Manuals

8‐PORTGIGABITETHERNETPOE+WEB‐
MANAGEDSWITCHWITH2SFPPORTS
USERMANUAL
MODEL561051
INT‐561051‐UM‐1015‐0

TableofContents
1ProductIntroduction................................................................................................................1
1.1ProductOverview.....................................................................................................1
1.1.1Features.............................................................................................................1
1.2ExternalComponentDescription.............................................................................2
1.2.1FrontPanel........................................................................................................2
1.2.2RearPanel.........................................................................................................4
1.3PackageContents......................................................................................................4
2InstallingandConnectingtheSwitch.......................................................................................5
2.1Installation................................................................................................................5
2.1.1DesktopInstallation..........................................................................................5
2.1.2Rack‐mountableInstallationin11‐inchCabinet...............................................5
2.1.3PowerontheSwitch.........................................................................................6
3HowtoLogintheSwitch..........................................................................................................7
3.1ConnectingComputer...............................................................................................7
3.2HowtoLogintotheSwitch.......................................................................................7
4SwitchConfiguration................................................................................................................9
4.1Toolbar....................................................................................................................10
4.1.1SAVE................................................................................................................10
4.1.2LOGOUT...........................................................................................................11
4.1.3REBOOT...........................................................................................................11
4.1.4REFRESH..........................................................................................................11
4.2System.....................................................................................................................12
4.2.1SystemInformation.........................................................................................12
4.2.2IPConfiguration..............................................................................................12
4.2.3UserConfiguration..........................................................................................13
4.2.4TimeSettings...................................................................................................14
4.2.5LogManagement............................................................................................15
4.2.6SNMPManagement........................................................................................18
4.3PortManagement...................................................................................................24
4.3.1PortConfiguration...........................................................................................24
4.3.2PortCounters..................................................................................................25
4.3.3BandwidthUtilization......................................................................................26
4.3.4PortMirroring.................................................................................................27
4.3.5JumboFrame...................................................................................................28
4.3.6PortErrorDisabledConfiguration...................................................................29
4.3.7ProtectedPorts...............................................................................................30
4.3.8EEE–EnergyEfficientEthernet.......................................................................32
4.4LinkAggregation.....................................................................................................33
4.4.1LAGSetting......................................................................................................34

4.4.2LAGManagement...........................................................................................35
4.4.3LAGPortSettings.............................................................................................36
4.4.4LACPSettings...................................................................................................37
4.4.5LACPPortSettings...........................................................................................37
4.4.6LAGStatus.......................................................................................................38
4.5VLAN.......................................................................................................................40
4.5.1WhatisVLAN?.................................................................................................40
4.5.2ManagementVLAN.........................................................................................44
4.5.3CreateVLAN....................................................................................................44
4.5.4InterfaceSettings............................................................................................45
4.5.5PorttoVLAN....................................................................................................49
4.5.6PortVLANMembership..................................................................................50
4.5.7ProtocolVLANGroupSettings........................................................................51
4.5.8ProtocolVLANPortSettings............................................................................52
4.5.9GVRPSetting...................................................................................................52
4.5.10GVRPPortSetting............................................................................................53
4.5.11GVRPVLAN......................................................................................................53
4.5.12GVRPStatistics................................................................................................54
4.6SpanningTreeProtocol(STP)..................................................................................55
4.6.1WhatisSTP?....................................................................................................55
4.6.2STPGlobalSettings..........................................................................................62
4.6.3STPPortSettings.............................................................................................63
4.6.4CISTInstanceSetting.......................................................................................65
4.6.5CISTPortSettings............................................................................................66
4.6.6MSTInstanceConfiguration............................................................................68
4.6.7MSTPortSettings............................................................................................70
4.6.8STPStatistics....................................................................................................71
4.7Multicast.................................................................................................................72
4.7.1Properties........................................................................................................72
4.7.2IGMPSnooping...............................................................................................72
4.7.3IGMPSnoopingStatics....................................................................................82
4.7.4MLDSnooping.................................................................................................83
4.7.5MLDSnoopingStatics......................................................................................87
4.7.6MulticastThrottlingSetting............................................................................88
4.7.7MulticastFilter................................................................................................88
4.8QoS‐QualityofService..........................................................................................91
4.8.1General/WhatisQoS?...................................................................................91
4.8.2QoSBasicMode..............................................................................................95
4.8.3QoSAdvancedMode.......................................................................................97
4.8.4RateLimit......................................................................................................101
4.8.5VoiceVLAN....................................................................................................104
4.9Security.................................................................................................................108

4.9.1StormControl................................................................................................108
4.9.2802.1x............................................................................................................109
4.9.3DHCPSnooping.............................................................................................116
4.9.4DynamicARPInspection...............................................................................122
4.9.5PortSettings..................................................................................................123
4.9.6DynamicARPInspectionStatistics................................................................123
4.9.7IPSourceGuard.............................................................................................124
4.9.8DOS................................................................................................................127
4.9.9Authentication,authorization,andaccounting(AAA)..................................129
4.9.10TACACS+server.............................................................................................132
4.9.11Radiusserver.................................................................................................133
4.9.12Access............................................................................................................135
4.10AccessControlList................................................................................................137
4.10.1WhatisACL?.................................................................................................137
4.10.2MAC‐BasedACL.............................................................................................137
4.10.3MAC‐BasedACE............................................................................................137
4.10.4IPv4‐BasedACL..............................................................................................139
4.10.5IPv4‐BasedACE.............................................................................................139
4.10.6IPv6‐BasedACL..............................................................................................143
4.10.7IPv6‐BasedACE.............................................................................................143
4.10.8ACLBinding...................................................................................................144
4.11MACAddressTable...............................................................................................144
4.11.1WhatisaMACAddressTable?......................................................................144
4.11.2StaticMACSettings.......................................................................................145
4.11.3MACFiltering.................................................................................................145
4.11.4DynamicAddressSetting..............................................................................145
4.11.5DynamicallyLearned.....................................................................................146
4.12LinkLayerDiscoveryProtocol(LLDP)....................................................................147
4.12.1WhatisLLDP.................................................................................................147
4.12.2LLDPGlobalSetting.......................................................................................147
4.12.3LLDPPortSettings.........................................................................................148
4.12.4LLDPLocalDevice..........................................................................................150
4.12.5LLDPRemoveDevice.....................................................................................151
4.12.6LLDPMEDNetworkPolicySettings...............................................................151
4.12.7MEDPortSettings.........................................................................................154
4.12.8LLDPOverloading..........................................................................................155
4.12.9LLDPStatistics...............................................................................................156
4.13Diagnostics............................................................................................................157
4.13.1CableDiagnostics..........................................................................................157
4.13.2SystemStatus................................................................................................158
4.13.3IPv4PingTest................................................................................................158
4.13.4IPv6PingTest................................................................................................158

4.13.5TraceRoute...................................................................................................159
4.14RMON...................................................................................................................160
4.14.1WhatisRMON?.............................................................................................160
4.14.2RMONStatistics.............................................................................................160
4.14.3RMONEventandEventLog..........................................................................160
4.14.4RMONAlarm.................................................................................................162
4.14.5RMONHistoryandHistoryLog.....................................................................165
4.15Maintenance.........................................................................................................166
4.15.1FactoryDefault..............................................................................................166
4.15.2RebootSwitch...............................................................................................167
4.15.3BackupManager...........................................................................................167
4.15.4UpgradeManager.........................................................................................168
4.15.5ConfigurationManager.................................................................................169
4.15.6EnablePassword...........................................................................................169
5Warranty..............................................................................................................................170
6Copyright..............................................................................................................................171
7FederalCommunicationCommissionInterferenceStatement............................................172

1
1 ProductIntroduction
ThankyouforpurchasingtheIntellinet8‐PortGigabitEthernetPoE+Web‐ManagedSwitch(561051).
Thisuserguidecoversallaspectsoftheinstallationofthisproduct.Notethatsomeofthe
configurationoptionsrequiretheusertohaveadvancedknowledgeofTCP/IPnetworks.
1.1 ProductOverview
TheIntellinet8‐PortGigabitEthernetPoE+Web‐ManagedSwitch(561051)isdesignedtopassboth
dataandelectricalpowertoanumberofPoE‐compatibledevicesviastandardCat5eorCat6network
cables.EquippedwitheightGigabitEthernetports(allofwhichsupport802.3at/afPoE/PoE+),this
switchcanpowerwirelessLANaccesspointsandbridges,VoIPphones,IPvideocamerasandmore
whiledeliveringnetworkspeedsofupto1000Mbps.
1.1.1 Features
ProvidespoweranddataconnectionforuptoeightPoEnetworkdevices
Foruseondesktopormountedinstandard19"rackSupportsAllpowerupto140W
IEEE802.3at/af‐compliantRJ45PoE/PoE+outputportsSupportsIEEE802.3xflowcontrolforFull‐
duplexModeandbackpressureforHalf‐duplexMode
PoEpowerbudgetof140wattsSupportsWEBmanagementinterface
SupportsIEEE802.3atandIEEE802.3af‐compliantPoEdevices(wirelessaccesspoints,VoIP
phones,IPcameras)Internalpoweradaptersupply
GreenEthernetpower‐savingtechnologydeactivatesunusedportsandadjustspowerlevels
basedonthecablelength

2
1.2 ExternalComponentDescription
1.2.1 FrontPanel
ThefrontpaneloftheSwitchconsistsof8x10/100/1000MbpsRJ‐45ports,1xConsoleport,2x
SFPports,1xResetbuttonandaseriesofLEDindicators.
10/100/1000MbpsRJ‐45ports(1~8):
Designedtoconnecttothedevicewithabandwidthof10Mbps,100Mbpsor1000Mbps.Eachhasa
corresponding10/100/1000MbpsLED.
Consoleport(Console):
ConnecttotheIntellinetswitchwithaserialportofacomputerorterminalformonitoringand
configurationpurposes.
SFPports(SFP1,SFP2):
DesignedtoinstalltheSFPmoduleandconnecttothedevicewithabandwidthof1000Mbps.Eachhasa
corresponding1000MbpsLED.
Resetbutton(Reset):
Whilethedeviceispoweredon,pressthebuttonfor2secondstoreboottheswitch,andpressthebutton
for5secondstorestoretheswitchtoitsoriginalfactorydefaultsettings.
LEDindicators:
TheLEDIndicatorswillallowyoutomonitor,diagnoseandtroubleshootanypotentialproblemwiththe
switch.
3
ThefollowingchartshowstheLEDindicatorsoftheSwitchalongwithexplanationofeachindicator.
LEDCOLORSTATUSSTATUSDESCRIPTION
PWRGreen
OnPowerOn
OffPowerOff
Link/Act
(1‐8)
10/100M:
Orange
OnAdeviceisconnectedtotheport.
OffNodeviceconnectedtotheport.
1000M:
GreenFlashingSendingorreceivingdata.
PoEGreen
On
APoweredDevice(PD)isconnectedtotheport,and
powerisbeingprovided.
Off
NoPDisconnectedtothecorrespondingport,orno
powerissuppliedtotheport.
Flashing
PoEoverloadorshortcircuit.DisconnectthePDright
away.
Max1
(1‐4Ports)
Green
On
WhenthepowerwhichoutputtoPDshasreached
themaximumpowerbudget(Thepowerofallthe
connectedPoEportsis≥55W).Nopowermaybe
suppliedifadditionalPDsareconnected.
Off
ThepowerofalltheconnectedPoEportsis<55W,or
NoPDconnectedtothecorrespondingport.
Flashing
WhenthepowerwhichoutputtoPDshasexceeded
themaximumpowerbudget(Thepowerofallthe
connectedPoEportis≥70W).
Max2
(5‐8Ports)
Green
On
WhenthepowerwhichoutputtoPDshasreached
themaximumpowerbudget(Thepowerofallthe
connectedPoEportsis≥55W).Nopowermaybe
suppliedifadditionalPDsareconnected.
Off
ThepowerofalltheconnectedPoEportsis<55W,or
NoPDconnectedtothecorrespondingport.
Flashing
WhenthepowerwhichoutputtoPDshasexceeded
themaximumpowerbudget(Thepowerofallthe
connectedPoEportis≥70W).
SFP1
SFP2
Green
OnAdeviceisconnectedtotheport
OffAdeviceisdisconnectedtotheport
FlashingSendingorreceivingdata

4
1.2.2 RearPanel
ACPowerConnector:
PowerissuppliedthroughanexternalACpoweradapter.Its
upportsAC100~240V,50/60Hz.
1.3 PackageContents
BeforeinstallingtheSwitch,makesurethatthefollowingthe"packinglist"listedOK.Ifanypartislost
anddamaged,pleasecontactyourlocalagentimmediately.Inaddition,makesurethatyouhavethe
toolsinstallswitchesandcablesbyyourhands.
8‐PortGigabitEthernetPoE+Web‐ManagedSwitchwith2SFPPorts
Fourrubberfeet,twomountingearsandeightsscrews
OneACpowercord
OneQuickInstallationGuide
InstallationCDwithUserManual
5
2 InstallingandConnectingtheSwitch
ThispartdescribeshowtoinstallyourPoEEthernetSwitchandmakeconnectionstoit.Pleaseread
thefollowingtopicsandperformtheproceduresintheorderbeingpresented.
2.1 Installation
Thefollowingstepswillhelppreventdamagetothedevicewhilealsohelpingtomaintainproper
security.
• Placetheswitchonastablesurfaceordesktoptominimizethechancesoffalling.
• MakesuretheswitchworksintheproperACinputrangeandmatchesthevoltagelabeledonthe
switch.
• Tokeeptheswitchfreefromlightningdamage,donotopentheswitch’schassisevenifitfailsto
receivepower.
• Makesurethatthereisproperheatdissipationfromandadequateventilationaroundtheswitch.
2.1.1 DesktopInstallation
Wheninstallingtheswitchonadesktop(ifnotinarack),attachtheenclosedrubberfeettothe
bottomcornersoftheswitchtominimizevibration.Allowadequatespaceforventilationbetweenthe
deviceandtheobjectsaroundit.
2.1.2 Rack‐mountableInstallationin11‐inchCabinet
TheSwitchcanbemountedinanEIAstandard‐sized,11‐inchrack,whichcanbeplacedinawiring
closetwithotherequipment.ToinstalltheSwitch,pleasefollowthesesteps:
a. AttachthemountingbracketsontheSwitch’ssidepanels(oneoneachside)andsecurethem
withthescrewsprovided.
b. Usethescrewsprovidedwiththe10”rackorcabinettomounttheswitchontherackandtighten
it.

6
2.1.3 PowerontheSwitch
TheswitchispoweredonbyconnectingittoanoutletusingtheAC100‐240V50/60Hzinternalhigh‐
performancepowersupply.
ACElectricalOutlet:
Itisrecommendedtouseasingle‐phase,three‐wirereceptaclewithaneutraloutletormultifunctional
computerprofessionalreceptacle.Besuretoconnectthemetalgroundconnectortothegrounding
sourceontheoutlet.
ACPowerCordConnection:
ConnecttheACpowerconnectoronthebackpaneloftheswitchtoanexternalreceptaclewiththe
includedpowercord,thencheckthatthepowerindicatorisON.WhenitisON,itindicatesthepower
connectionisokay.
PDportbynetworkcable.
7
3 HowtoLogintheSwitch
3.1 ConnectingComputer
UsestandardCat5/5eEthernetcable(UTP/STP)toconnecttheswitchtoendnodesasdescribedbelow.
Switchportswillautomaticallyadjusttothecharacteristics(MDI/MDI‐X,speed,duplex)ofthedeviceto
whichtheyareconnected.
Figure6‐PCConnect
TheLNK/ACT/SpeedLEDsforeachportlightwhenthelinkisavailable.
3.2 HowtoLogintotheSwitch
Connectionisdonebymeansofanystandardwebbrowser.ThedefaultsettingsoftheSwitchareshown
below.
ParameterDefaultValue
DefaultIPaddress 192.168.2.1
Defaultusername admin
Defaultpassword admin
YoucanlogontotheconfigurationwindowoftheSwitchthroughfollowingsteps:
1. ConnecttheSwitchwiththecomputerNICinterface.
2. CheckwhethertheIPaddressofthecomputeriswithinthisnetworksegment:192.168.2.xxx(“xxx”
ranges2~254),forexample,192.168.2.100.
3. PowerontheSwitchandverifythatyouhaveanactivelinkontheportyouareconnectedto.
4. Openthebrowser,andenterhttp://192.168.2.1andthenpress“Enter”.TheSwitchloginwindow
appears,asshownbelow.

8
5. EntertheUsernameandPassword(ThefactorydefaultUsernameisadminandPasswordisadmin),
andthenclick“LOGIN”tologintothewebconfiguration.

9
4 SwitchConfiguration
ThePoE+Web‐ManagedGigabitEthernetSwitchsoftwareprovidesrichLayer2functionalityfor
switchesinyournetworks.ThischapterdescribeshowtousetheWeb‐basedmanagementinterface
(WebUI)forthisswitch.
IntheWebUI,theleftcolumnshowstheconfigurationmenu.Thetoprowshowstheswitch’scurrent
linkstatus.Greensquaresindicatetheportlinkisup(port5intheexamplebelow),whileblack
squaresindicatetheportlinkisdown.Belowtheswitchpanel,youcanfindtoolbar(seesection4.1)
thatprovidesaccesstosomebasic,yetimportantfeatures.Therestofthescreenareadisplaysthe
configurationsettings.

10
4.1 Toolbar
4.1.1 SAVE
4.1.1.1 SaveConfigurationstoFLASH
Wheneveryoumakeanychangestotheconfigurationoftheswitch,andyouwantthosechangestobe
availableafterthenextrebootoftheswitch,youneedtosavetheconfiguration.Todothat,clickonSave
ConfigurationstoFlash,thenclickApply.
4.1.1.2 RestoretoDefaults
Inordertodeleteallcustomconfigurationdataandrestoretheswitchtoitsfactorydefaultstate,click
onRestoretoDefaults.
ClickonRestore,andconfirmthenextmessagebyclickingOK.
11
4.1.2 LOGOUT
Inordertologoutfromthewebadministratorinterface,clickonLOGOUTandthenconfirmthenext
messagebyclickingOK.
4.1.3 REBOOT
ClickRebootinordertorestarttheIntellinetswitch.Aftertherestarthasbeencompleted,youhavetore‐
authenticateattheloginpageinordertore‐gainaccess.
4.1.4 REFRESH
Reloadsthecontentsofthecurrentscreentoshowthemostcurrentinformation.

12
4.2 System
UsetheStatuspagestoviewsysteminformationandstatus.
4.2.1 SystemInformation
ThispageallowsyoutoconfigureSystem‐relatedinformationandbrowseinformationsuchasMAC
address,IPaddress,firmwareversion,loaderversion,amongothers.Inaddition,youcanmodifythe
valuesSystemName,SystemLocationandSystemContact:
4.2.2 IPConfiguration
OnthispageyousetupthemanagementIPaddressoftheIntellinetPoEswitch.Setthemodeto
eitherDHCPorStatic,andinthelattercaseprovidetheIPAddress,SubnetMaskandGateway.This
pageallowstodefinetheIPv4address.AlsorefertotheIPv6configuration.
13
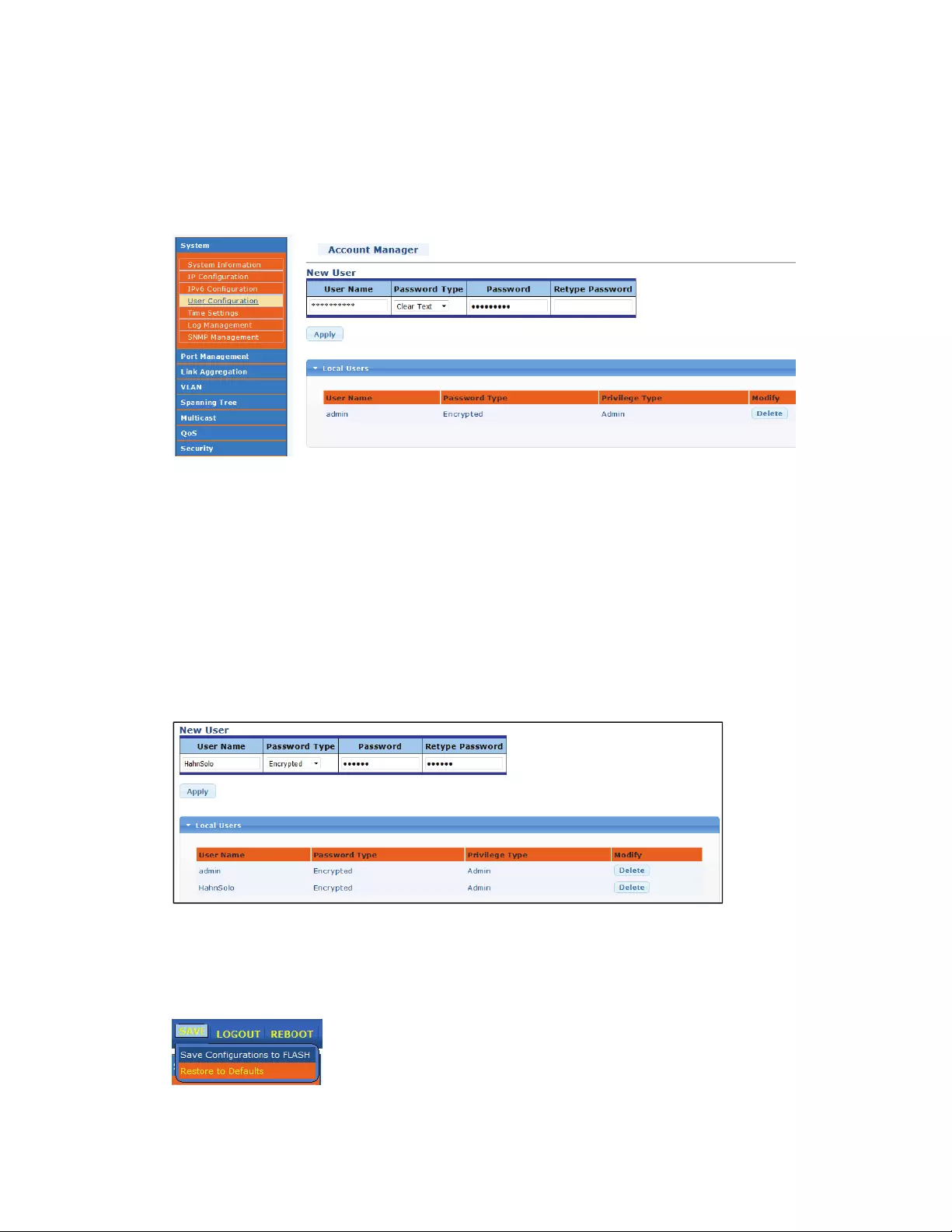
4.2.3 UserConfiguration
Onthisscreenyoucanchangethepasswordoftheadministratoraccount,andyoucanalsocreate
newuseraccounts.TheIntellinetPoEswitchonlyprovidesadministratorleveluseraccounts,which
simplifiesthesetup.
4.2.3.1 AddUserAccount
Typeinausername,apasswordandre‐typethepassword.Youalsocanselectthepassword
encryptiontype.Settoencryptedformaximumsecurity,orNoPasswordifyouwanttocreatean
administratoraccountthatrequiresnopasswordinordertologin.
4.2.3.2 EditPasswordforexistingUserAccount
Ifyouwanttochangeapasswordofanexistingaccount,youhavetoaddtheexistinguseraccountasa
newuseraccount.Byaddingauseraccountwithausernamethatalreadyexists,youcanoverwrite
thepasswordofthataccount.Theexamplebelowshowshowyouwouldchangethepasswordof
existinguser‘HahnSolo’.
4.2.3.3 DeleteUserAccount
ClickonDeleteoftheuseraccountwhichyouwanttodelete.Theaccountwillberemovedfromthe
configurationonceyouhavesavedtheconfigurationtotheflashmemoryoftheswitch.
14
4.2.4 TimeSettings
TheIntellinetPoEswitchisequippedwithaninternalclock,whichisusedtogivelogentriesaproper
timestamp.Therearetwowaystoconfiguretheclock.Youcaneitherconfiguretheswitchtoobtain
thetimeautomaticallyfromanSNTPserverontheInternetoronyourlocalnetworkbysettingthe
valueEnableSNTPtoEnable,oryoucanspecifythetimemanuallybysettingthevalueEnableSNTP
toDisable.
4.2.4.1 SettingupSystemTimeManually
WhenyoudisableSNTP,thescreenallowsyoutomanuallyenterthetime.
ManualTime:Specifythecorrectyear,month,day,hour,minuteandsecond
TimeZone:SelectthetimezonethatcorrespondstothelocationoftheIntellinetPoEswitch.
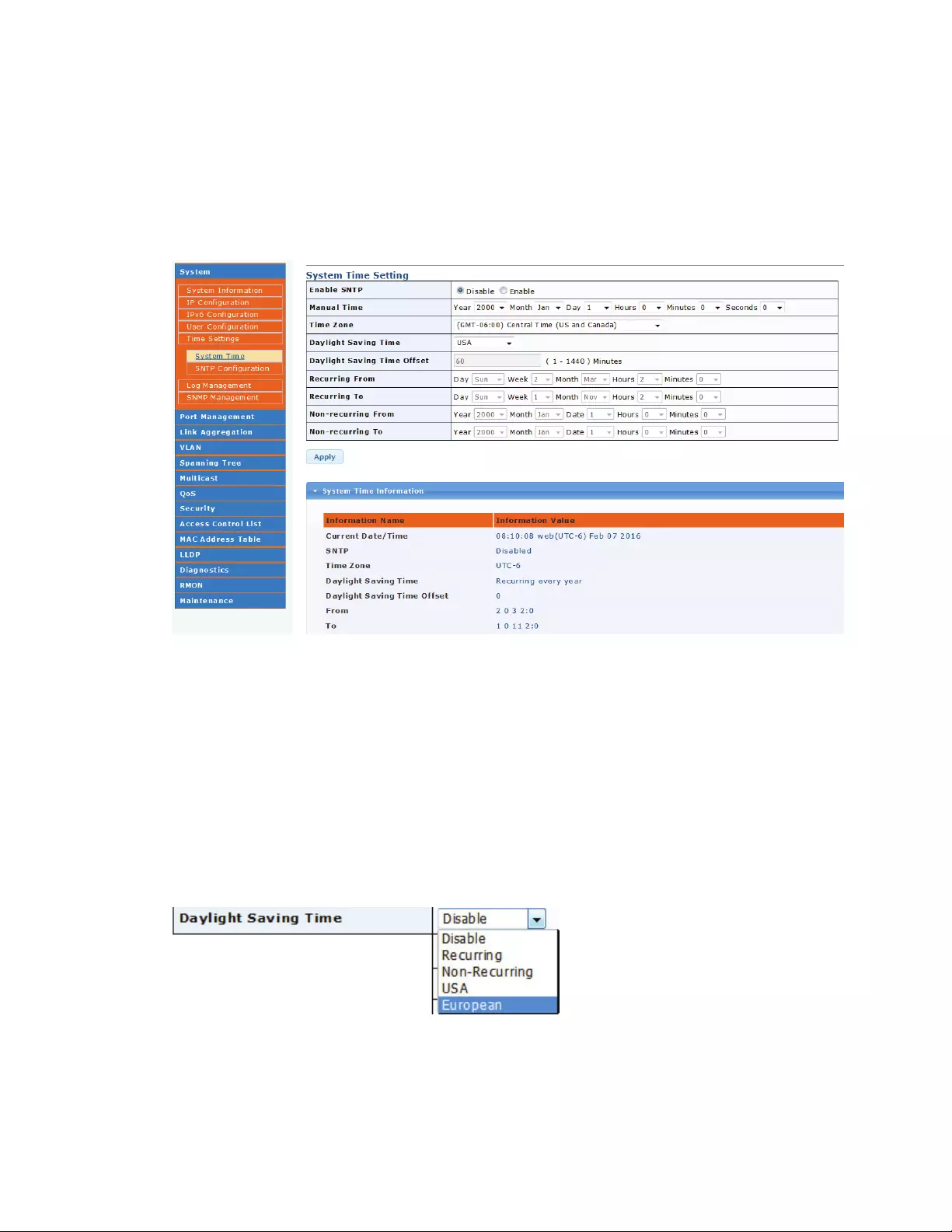
DaylightSavingTime:Iftheswitchislocatedinanareawithdaylightsavingtime,youcandefinethe
specificsofithere.Ifyoucan,ideallyyouwillwanttoselecteitherEuropeanorUSA,becauseinthat
casetheswitchwillautomaticallyadjustthetimeforyou.
SelectRecurringorNon‐Recurringinordertoenterthespecificdetailsaboutthedaylightsavingtime
manually.
15
4.2.4.2 SNTPSettings
IfyousettheIntellinetPoEtoobtainitstimefromanSNTPserver,thenyoumustspecificwhichSNTP
serveryouwanttouse.YoucanusebothinternalandexternalSNTPservers.Inbothcasesyouhaveto
ensurethattheIPconfigurationoftheswitchallowsittoaccesstheSNTPserver.Ifyouwishtousean
externalSNTPserversuchaspool.ntp.org,thenyoumustmakesurethattheswitchhasaccesstothe
InternetbyprovidingavalidGatewayIPaddress–seesection4.2.2IPConfiguration.
SNTPServerAddress:ThenetworkaddressoftheSNTP/NTPserver.
ServerPort:ThePortNumberofSNTP/NTPserver(default=123).
4.2.5 LogManagement
4.2.5.1 LoggingService
TheIntellinetPoEswitchhastheabilitytocreateahistorylogofimportantevents.Theselogscanbe
storedeitherintheswitchesownmemory,oronaremoteSyslogserver.Inordertoutilizethelogging
service,youmustfirstenableit.
16
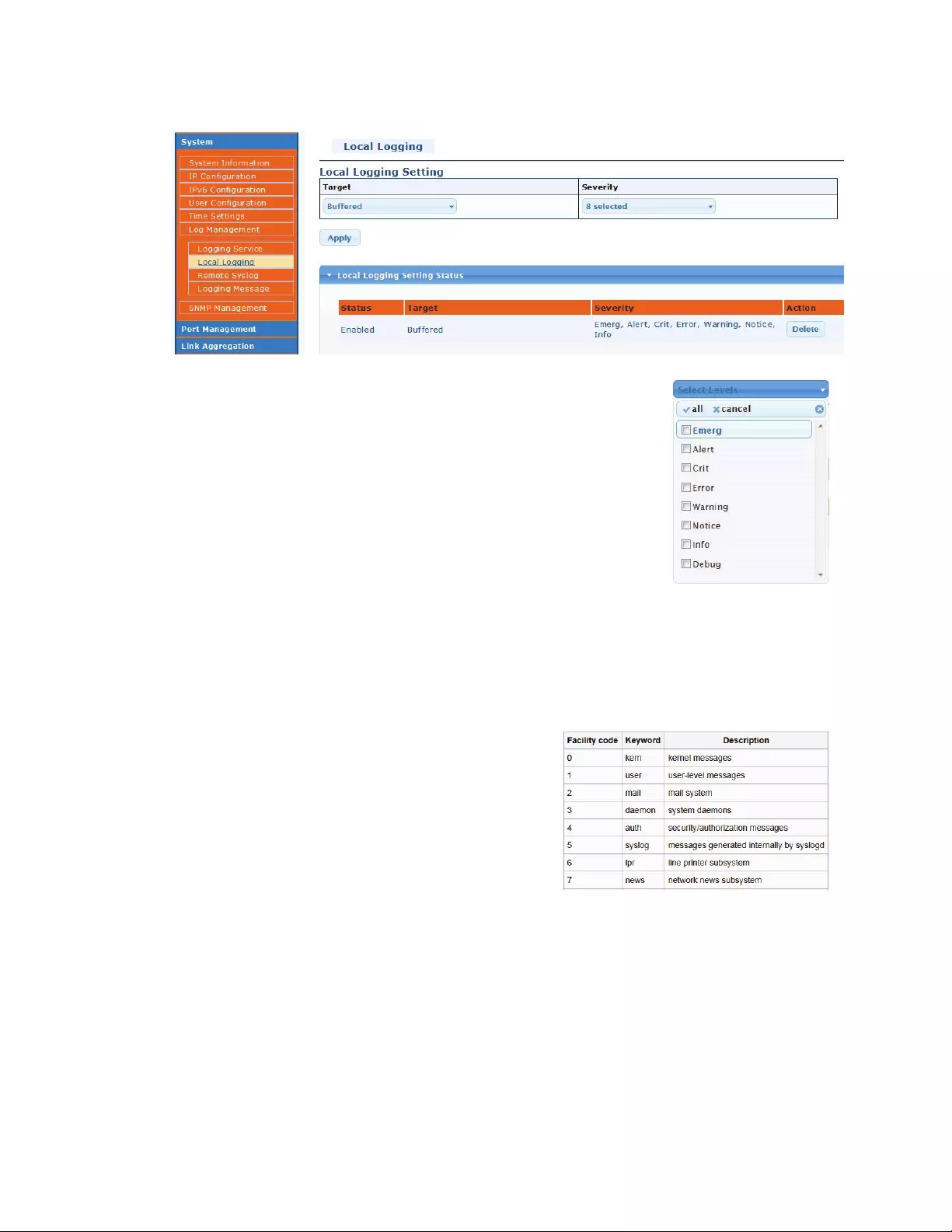
4.2.5.2 LocalLogging
Target:Selectthetargettostorelogmessage
Buffered:StorelogmessagesintheRAM.Alllogmessageswilldisappear
afterasystemreboot.
FLASH:StorelogmessagesintheFLASHmemory.Logmessageswillnot
disappearaftersystemreboot.
Severity:Definewhichlevelsofmessageswillbelogged.Debugwilllog
everysinglemessage,regardlesshowirrelevantitmaybe.Emergonthe
otherhandwillonlylogmissioncriticalinformation.
4.2.5.3 RemoteLogging
TodisplayRemoteLoggingwebpage,clickDiagnostics>LoggingSetting>RemoteLogging
ServerAddress:TheIPaddressofremotelogserver.
ServerPort:Theportnumberoftheremotelogserver
(default=514)..
Severity:Selecttheseverityoflogmessageswhichwill
berecorded.
Facility:Afacilitycodeisusedtospecifythetypeof
programthatisloggingthemessage.Messageswith
differentfacilitiesmaybehandleddifferently.Thelistof
facilitiesavailableisdefinedbyRFC3164,seechartontheright.
17
4.2.5.4 LoggingMessage
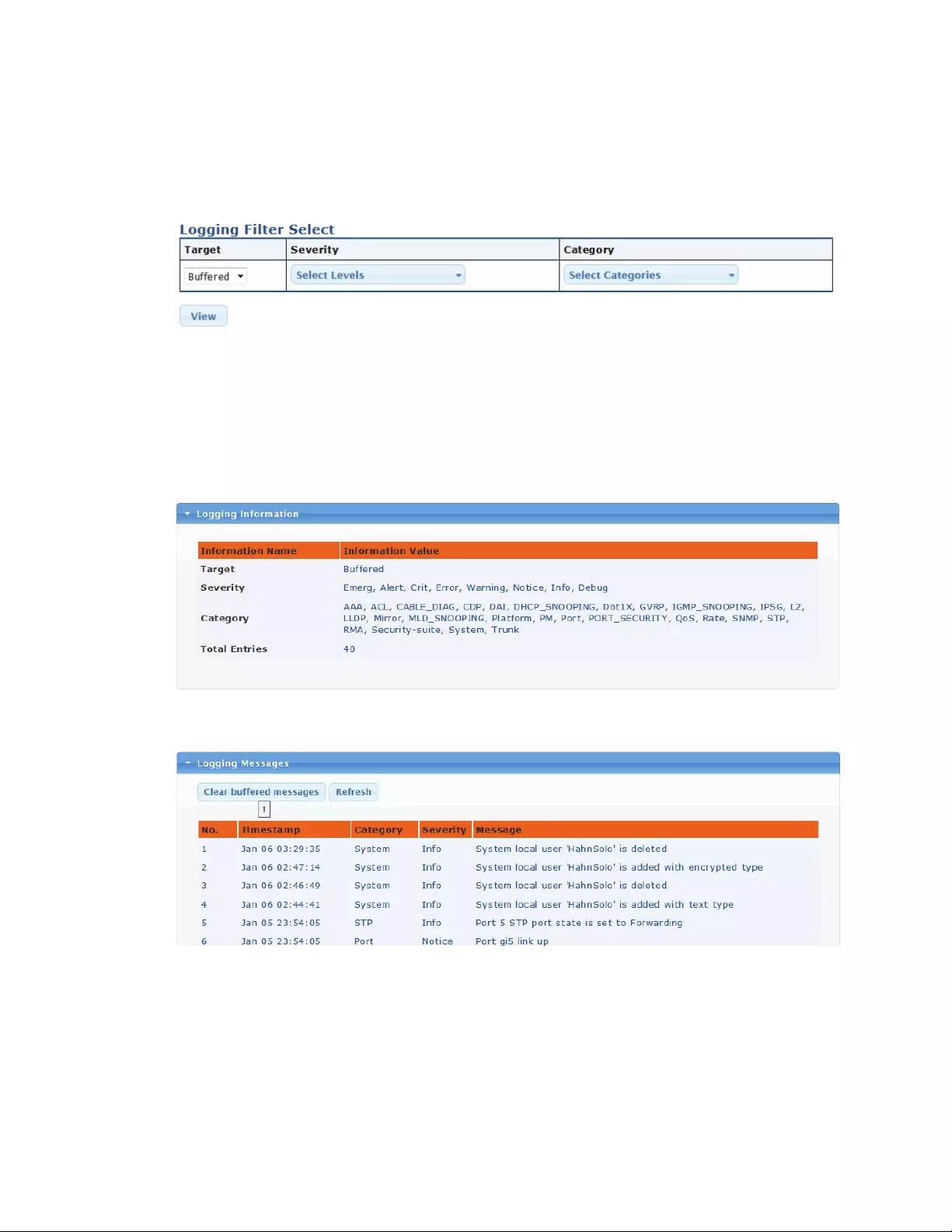
Thisinterfacescreenisdesignedtoletyouviewlogmessagesthathavebeenrecordedearlier.The
sectionLoggingFilterSelectallowsyoutodefineexactlywhattypeofloggingmessagesyouwishto
see.
Target:Thisdefinesthesourceofthelogmessages(eitherbufferedorFLASH).
Severity:Selecttheseverityoflogmessageswhichwillberecorded.
Category:Logmessagesarecategorized,andthecategoryfilterallowsyoutofilterout,which
messagesyouwishtosee.
Thesectionshownbelowdisplaysthecurrentfiltersettings.
Thesectionbelowshowsmessagesthathavebeenrecorded.

18
4.2.6 SNMPManagement
SimpleNetworkManagementProtocol(SNMP)isanOSILayer7(Application
Layer)designedspecificallyformanagingandmonitoringnetworkdevices.
SNMPenablesnetworkmanagementstationstoreadandmodifythesettings
ofgateways,routers,switches,andothernetworkdevices.UseSNMPto
configuresystemfeaturesforproperoperation,monitorperformanceand
detectpotentialproblemsintheSwitch,switchgroupornetwork.
4.2.6.1 SNMPSetting
State:SNMPdaemonstate
Enabled:EnableSNMPdaemon
Disabled:DisableSNMPdaemon

19
4.2.6.2 SNMPView
AnSNMPviewcanbeusedtolimitthetypeofinformationthatisaccessible,itisacombinationofa
setorafamilyofviewsubtreeswhereeachviewsubtreeisasubtreewithinthemanagedobject
namingtree.Aviewnamed“All”iscreatedautomaticallybytheswitch.Itcontainsallsupported
objects.
ItemDescription
ViewNameEnteranametoidentifytheSNMview.Thenamecancontainupto16
alphanumericcharacters.
SubtreeOIDAnobjectidentifiers(OID)identifiesavariablethatcanbereadorsetvia
SNMP.EnteranOIDstringforthesubtreeyouwishtoeitherincludeinor
excludefromtheSNMPview.
SubtreeOIDMaskThesubtreeOIDmaskcoupleswithasubtreeOIDtomakeMIBviewsubtrees.
ViewTypeSelectwhethertoincludeorexcludetheinformation.
20
4.2.6.3 SNMPAccessGroup
ThispageallowsconfiguringSNMPv3accessgroups.TheindexkeysareGroupName,SecurityModel
andSecurityLevel.
ItemDescription
GroupNameThisstringidentifiesthegroupname,lengthis1to16characters.
SecurityModelIndicatesthesecuritymodelforthisentry.
v1:SNMPv1.
v2c:SNMPv2c.
V3:SNMPv3orUser‐basedSecurityModel(USM)
SecurityLevelNotethatthesecuritylevelappliestoSNNPv3.Itindicatesthesecurity
modelthatthisentryshouldbelongto.
Possiblesecuritymodelsare:
Noauth:Noneauthenticationandnoneprivacysecuritylevelsare
assignedtothegroup.
auth:Authenticationandnoneprivacy.
priv:Authenticationandprivacy.
Note:
ReadViewNameReadviewnameisthenameoftheviewinwhichyoucanonlyviewthe
contentsoftheagent.Maximumlengthis16characters.
WriteViewNameWriteviewnameisthenameoftheviewinwhichyouenterdataand
configurethecontentsoftheagent.Maximumlengthis16characters.
NotifyViewNameNotifyviewnameisthenameoftheviewinwhichyouspecifyanotify,
inform,ortrap.
21
4.2.6.4 SNMPCommunity
ConfiguretheSNMPcommunityonthispage.
4.2.6.5 SNMPUser
ThispageisusedtocreateSNMPuserunderthegroup,Andthegroupwiththesamelevelofsecurity
andaccesscontrolpermissions.
22
4.2.6.6 SNMPv1,2NotificationRecipients
SNMPv1,2versionnotificationeventreceivinghostrelatedconfiguration,youcanconfiguretoinform
thehostintheformofthetrapmessageorloginformationaboutthecurrentequipment,canbeset
upgroupname,UDPportnumberandmessageofthetimeout.
4.2.6.7 SNMPv3NotificationRecipients
SNMPv3versionnotificationeventreceivinghostrelatedconfiguration,youcanconfiguretoinform
thehostintheformofthetrapmessageorloginformationaboutthecurrentequipment,canbeset
upgroupname,UDPportnumberandmessageofthetimeout.

23
4.2.6.8 SNMPEngineID
4.2.6.9 SNMPRemoteEngineID
ConfigureSNMPv3remoteEngineIDonthispage.
ItemDescription
RemoteIPAddressIndicatestheSNMPremoteengineIDaddress.ItallowsavalidIP
addressindotteddecimalnotation('x.y.z.w').
EngineIDAnoctetstringidentifyingtheengineIDthatthisentryshouldbelong
to.

24
4.3 PortManagement
TheIntellinet8‐PortGigabitPoE+SwitchisequippedwthbothRJ45portsandSFPmodules.Theport
managementfunctionallowstoconfiguretheseports.
4.3.1 PortConfiguration
Thispagedisplayscurrentportconfigurationsandstatus.Portscanalsobeconfiguredhere.
ItemDescription
PortSelectSelectportnumberforthisdropdownlist.
EnabledIndicatestheportstateoperation.
Enabled–Activatetheport.
Disabled–Shutdowntheport.
SpeedSetupthelinkspeedforthegivenswitchport.SelectAuto
(recommended)toalwaysconnectatthebestpossiblespeed,andselect
oneoftheindividualvaluesfrom10Mto1000Mtosettheportspeed
manually.
DuplexDefinetheduplexmodeoftheport.
‐Auto‐SetupAutonegotiation(recommended).
‐Full‐ForceFull‐Duplexmode.
‐Half‐ForceHalf‐Duplexmode.
FlowControlWhenAutoSpeedisselectedforaport,thissectionindicatestheflow
controlcapabilitythatisadvertisedtothelinkpartner.
Whenafixed‐speedsettingisselected,thatiswhatisused.
CurrentRxcolumnindicateswhetherpauseframesontheportare
obeyed.CurrentTxcolumnindicateswhetherpauseframesontheport
aretransmitted.TheRxandTxsettingsaredeterminedbytheresultof
thelastAuto‐Negotiation.Checktheconfiguredcolumntouseflow
control.ThissettingisrelatedtothesettingforConfiguredLinkSpeed.
25
4.3.2 PortCounters
Thispageprovidesanoverviewoftrafficandtrunkstatisticsforallswitchports.

26
4.3.3 BandwidthUtilization
TheBandwidthUtilizationpagedisplaysthepercentageofthetotalavailablebandwidthbeingusedonthe
ports.Bandwidthutilizationstatisticsisrepresentedbygraphs.
27
4.3.4 PortMirroring
Networkengineersoradministratorsuseportmirroringtoanalyzeanddebugdataordiagnoseerrors
onanetwork.Ithelpsadministratorskeepacloseeyeonnetworkperformanceandalertsthemwhen
problemsoccur.Itcanbeusedtomirroreitherinboundoroutboundtraffic(orboth)onsingleor
multipleinterfaces.Portmirroringisusedonanetworkswitchtosendacopyofnetworkpacketsseen
ononeswitchport(oranentireVLAN)toanetworkmonitoringconnectiononanotherswitchport.
Thetraffictobecopiedtothemirrorportisselectedasfollows:
‐Allframesreceivedonagivenport(alsoknownasingressorsourcemirroring).
‐Allframestransmittedonagivenport(alsoknownasegressordestinationmirroring).
28
4.3.5 JumboFrame
Incomputernetworking,jumboframesare
Ethernetframeswithmorethan1500bytes
ofpayload.Conventionally,jumboframes
cancarryupto9000bytesofpayload,but
variationsexist.Forinstance,theIntellinet8‐
PortGigabitPoE+switchsupportsJumbo
framesofupto9216bytes.
Setthejumboframesize(64–9216)andhitApplytosavethesettings.
Thetableaboveshowsthecurrentjumboframeconfiguration.
29
4.3.6 PortErrorDisabledConfiguration
TheIntellinet8‐PortGigabitPoE+Switchhastheabilitytodisableports,ifanerroroccurs.Bydoingso,it
canprotecttherestofthenetwork,ifanetworkclientononeportgeneratesalotofunwantedtraffic,i.e.
broadcastflooding.Belowyoucanactivate/deactivatetheeventsyouwishtomonitor,andyoucandefine
therecoveryinterval,whichisthetimeintervalinwhichtheportremainsdisabled(default=300seconds
(5minutes).

30
4.3.7 ProtectedPorts
Protectedportscanbeusedtopreventinterfaces(i.e.,networkclients)fromcommunicatingwitheach
other.Protectedportscanbeviewedas‘isolatedports.’
Forprotectedportgrouptobeapplied,thenetworkswitchmustfirstbeconfiguredforstandardVLAN
operation.Portsinaprotectedportgroupfallintooneofthesetwogroups:
1. Promiscuous(Unprotected)ports
a. PortsfromwhichtrafficcanbeforwardedtoallportsintheprivateVLAN
b. PortswhichcanreceivetrafficfromallportsintheprivateVLAN
2. Isolated(Protected)ports
a. Portsfromwhichtrafficcanonlybeforwardedtopromiscuousportsintheprivate
VLAN
b. PortswhichcanreceivetrafficfromonlypromiscuousportsintheprivateVLAN
TheconfigurationofpromiscuousandisolatedportsappliestoallprivateVLANs.Whentrafficcomes
inonapromiscuousportinaprivateVLAN,theVLANmaskfromtheVLANtableisapplied.When
trafficcomesinonanisolatedport,theprivateVLANmaskisappliedinadditiontotheVLANmask
fromtheVLANtable.Thisreducestheportstowhichforwardingcanbedonetojustthepromiscuous
portswithintheprivateVLAN.

31
Thescreenalsoshowsthecurrentstatusofprotectedv.unprotectedports.Intheexampleabove,ports1
and2areprotected(asinisolated),RJ45ports3–8aswellasSFPports91nd10areunprotected.
32
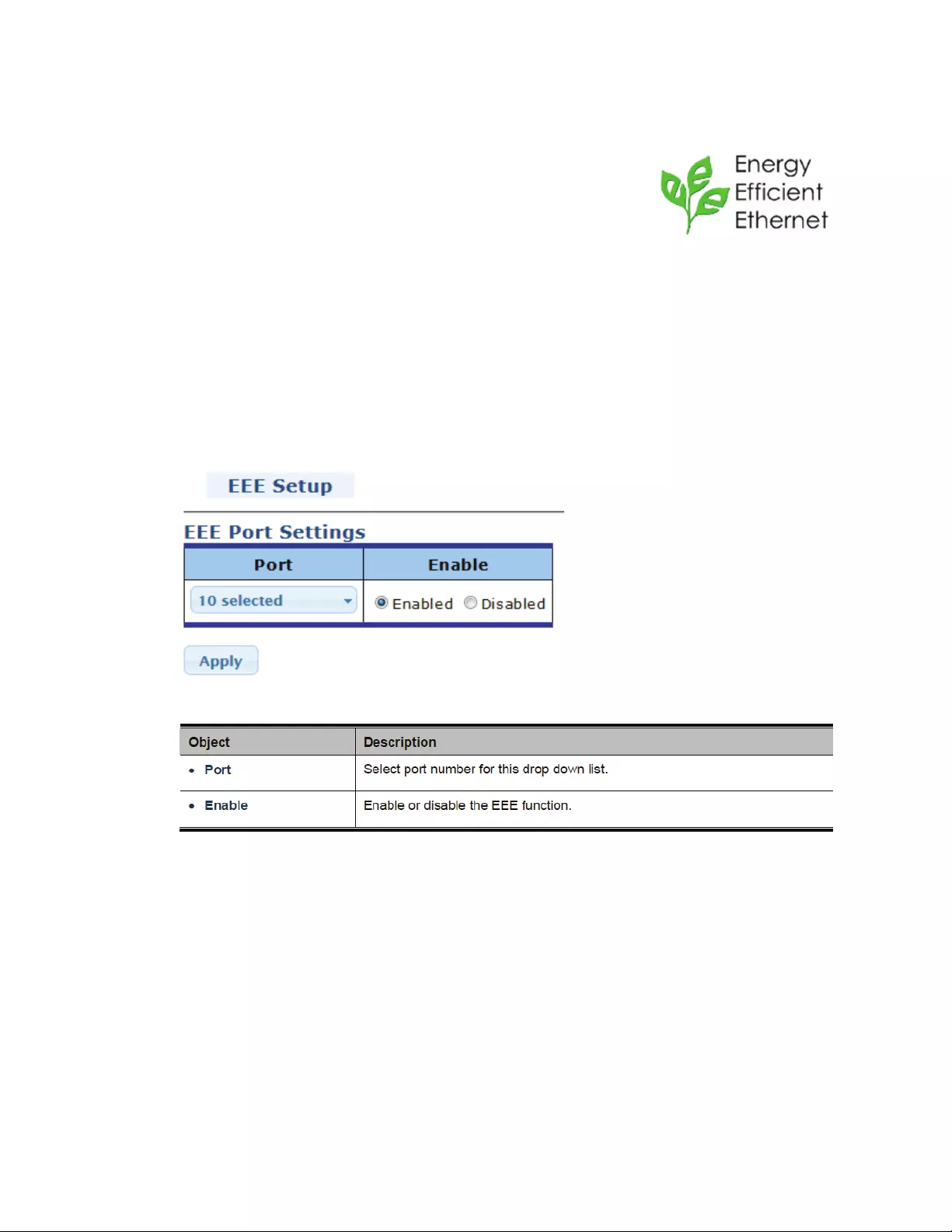
4.3.8 EEE–EnergyEfficientEthernet
Energy‐EfficientEthernet(EEE)isasetofenhancementstothetwisted‐pair
andbackplaneEthernetfamilyofcomputernetworkingstandardsthatallow
forlesspowerconsumptionduringperiodsoflowdataactivity.The
intentionwastoreducepowerconsumptionby50%ormore,while
retainingfullcompatibilitywithexistingequipment.TheInstituteof
ElectricalandElectronicsEngineers(IEEE),throughtheIEEE802.3aztaskforcedevelopedthestandard.EEE
isapowersavingoptionthatreducesthepowerusagewhenthereislowornotrafficutilization.EEE
worksbypoweringdowncircuitswhenthereisnotraffic.
Whenaportispowereddownforsavingpower,theoutgoingtrafficisstoredinabufferuntiltheport
ispoweredupagain.Usingthistechnique,morepowercanbesavedifthetrafficcanbebufferedup
untilalargeburstoftrafficcanbetransmitted.Keepinmind,thatbufferingtrafficwillgivesome
latencyinthetraffic.

33
4.4 LinkAggregation
Incomputernetworking,thetermlinkaggregationappliestovariousmethodsofcombining
(aggregating)multiplenetworkconnectionsinparallelinordertoincreasethroughputbeyondwhata
singleconnectioncouldsustain,andtoprovideredundancyincaseoneofthelinksshouldfail.
PortAggregationoptimizesportusagebylinkingagroupofportstogethertoformasingleLink
AggregatedGroup(LAG).PortAggregationmultipliesthebandwidthbetweenthetwoEthernet
switchesandprovideslinkredundancy.EachLAGiscomposedofportsofthesamespeed,settofull‐
duplexoperations.
AggregatedLinkscanbeassignedmanually(PortTrunk)orautomaticallybyenablingLinkAggregation
ControlProtocol(LACP)ontherelevantlinks.AggregatedLinksaretreatedbythesystemasasingle
logicalport.
TheIntellinet8‐PortGigabitPoE+switchsupportsthefollowingAggregationlinks:
1. StaticLAGs(PortTrunk)–Selectedportsareforcedtobeinatrunkgroup.
2. LinkAggregationControlProtocol(LACP)LAGs‐LACPLAGnegotiateaggregatedportlinkswith
otherLACPportslocatedonadifferentdevice.IftheotherdeviceportsarealsoLACPports,
thedevicesestablishaLAGbetweenthem.
Whenusingaportlinkaggregation,notethat:
Theportsusedinalinkaggregationmustallbeofthesamemediatype(RJ‐45,100Mbpsfiber).
Theportsthatcanbeassignedtothesamelinkaggregationhavecertainotherrestrictions(see
below).
Portscanonlybeassignedtoonelinkaggregation.
Theportsatbothendsofaconnectionmustbeconfiguredaslinkaggregationports.
Noneoftheportsinalinkaggregationcanbeconfiguredasamirrorsourceportoramirrortarget
port.
Alloftheportsinalinkaggregationhavetobetreatedasawholewhenmovedfrom/to,addedor
deletedfromaVLAN.
TheSpanningTreeProtocolwilltreatalltheportsinalinkaggregationasawhole.
Enablethelinkaggregationpriortoconnectinganycablebetweentheswitchestoavoidcreating
adataloop.
Disconnectalllinkaggregationportcablesordisablethelinkaggregationportsbeforeremovinga
portlinkaggregationtoavoidcreatingadataloop.
Itallowsamaximumof8portstobeaggregatedatthesametime.TheIntellintswitchsupportGigabit
Ethernetports(upto8groups).IfthegroupisdefinedasaLACPstaticlinkaggregationgroup,then
anyextraportselectedisplacedinastandbymodeforredundancyifoneoftheotherportsfails.Ifthe
groupisdefinedasalocalstaticlinkaggregationgroup,thenthenumberofportsmustbethesameas
thegroupmemberports.

34
4.4.1 LAGSetting
Thispageallowsconfiguringloadbalancealgorithmconfigurationsettings.
35
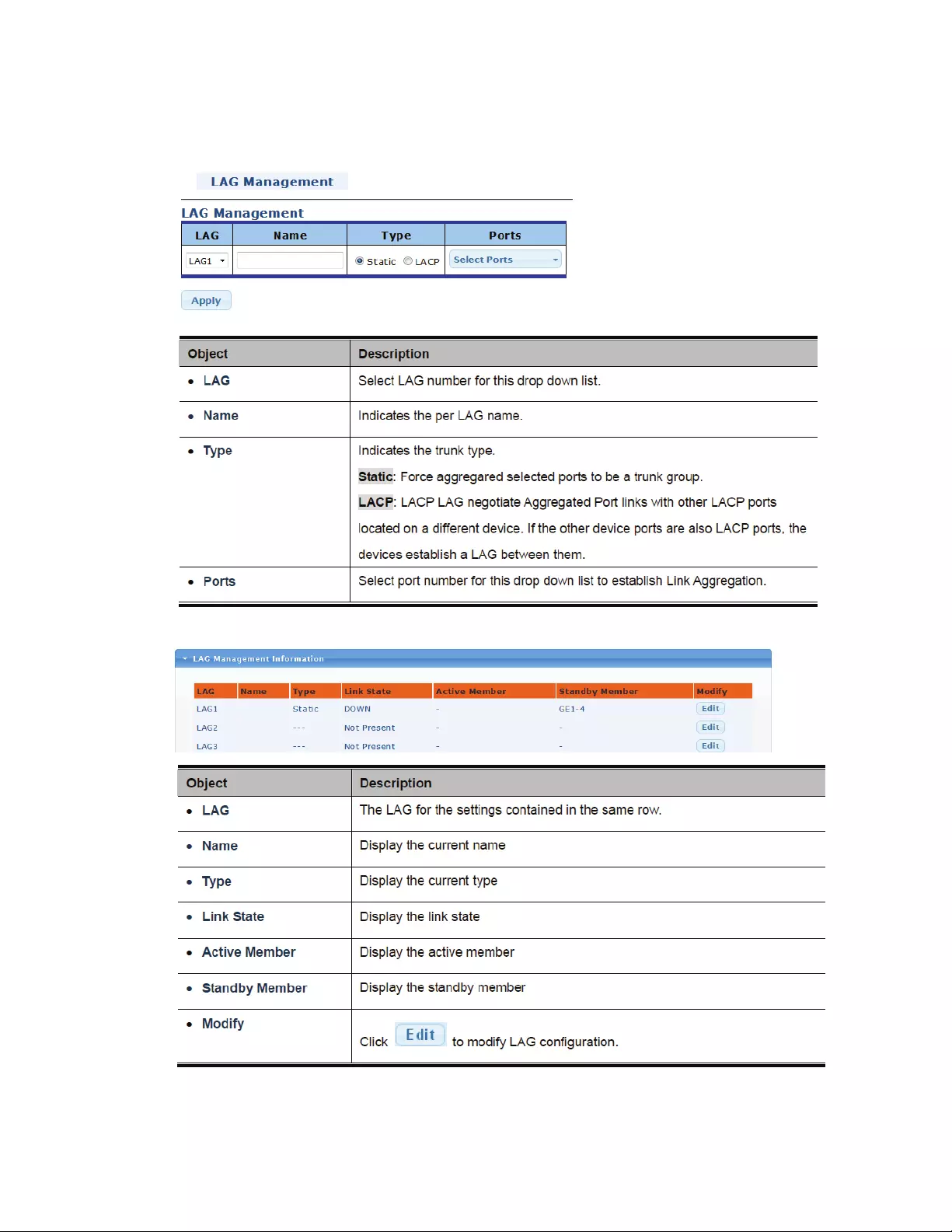
4.4.2 LAGManagement
ThispageisusedtoconfigurethebasicsettingsoftheLinkAggregationGroup.

36
4.4.3 LAGPortSettings
OnthisscreenyoudefinethepropertiesoftheportsbelongingtoaLinkAggregationGroup.

37
4.4.4 LACPSettings
Inatrunkgroup,eachswitchhastohaveapriority.Thatisthesystempriority.Thesmallerthe
number,thehigherthepriority.Theswitchwiththesmallestnumber(andthusthehighestpriority)is
theactiveLACPpeerofthetrunkgroup.
4.4.5 LACPPortSettings
ThispageisusedtoconfiguretheLACPportprioritysettings.
38
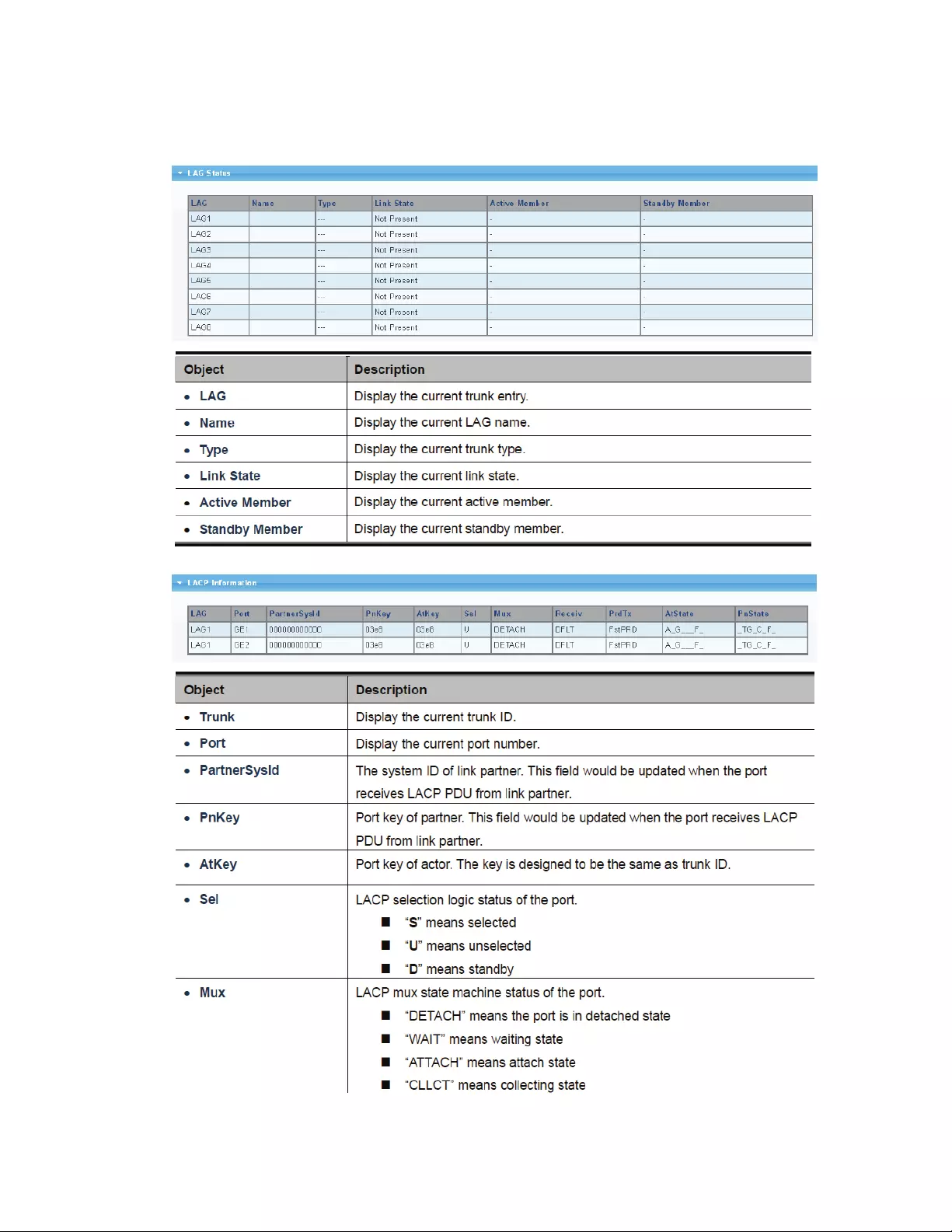
4.4.6 LAGStatus

39

40
4.5 VLAN
4.5.1 WhatisVLAN?
4.5.1.1 Overview
AVirtualLocalAreaNetwork(VLAN)isanetworktopologyconfiguredaccordingtoalogicalscheme
ratherthanthephysicallayout.VLANcanbeusedtocombineanycollectionofLANsegmentsintoan
autonomoususergroupthatappearsasasingleLAN.VLANalsologicallysegmentthenetworkinto
differentbroadcastdomainssothatpacketsareforwardedonlybetweenportswithintheVLAN.
Typically,aVLANcorrespondstoaparticularsubnet,althoughnotnecessarily.
VLANcanenhanceperformancebyconservingbandwidth,andimprovesecuritybylimitingtrafficto
specificdomains.AVLANisacollectionofendnodesgroupedbylogicinsteadofphysicallocation.End
nodesthatfrequentlycommunicatewitheachotherareassignedtothesameVLAN,regardlessof
wheretheyarephysicallyonthenetwork.Logically,aVLANcanbeequatedtoabroadcastdomain,
becausebroadcastpacketsareforwardedtoonlymembersoftheVLANonwhichthebroadcastwas
initiated.
Thingstonote:
• NomatterwhatbasisisusedtouniquelyidentifyendnodesandassignthesenodesVLAN
membership,packetscannotcrossVLANswithoutanetworkdeviceperformingaroutingfunction
betweentheVLANs.
• TheSwitchsupportsIEEE802.1QVLANs.Theportuntaggingfunctioncanbeusedtoremovethe
802.1Qtagfrompacketheaderstomaintaincompatibilitywithdevicesthataretag‐unaware.
• TheSwitch’sdefaultistoassignallportstoasingle802.1QVLANnamed“default.”
• The“default”VLANhasaVID=1.
• ThememberportsofPort‐basedVLANsmayoverlap,ifdesired.
4.5.1.2 Port‐basedVLANs
Port‐basedVLANlimittrafficthatflowsintoandoutofswitchports.Thus,alldevicesconnectedtoa
portaremembersoftheVLAN(s)theportbelongsto,whetherthereisasinglecomputerdirectly
connectedtoaswitch,oranentiredepartment.Onport‐basedVLAN.NICdonotneedtobeableto
identify802.1Qtagsinpacketheaders.NICsendandreceivenormalEthernetpackets.Ifthepacket's
destinationliesonthesamesegment,communicationstakeplaceusingnormalEthernetprotocols.
Eventhoughthisisalwaysthecase,whenthedestinationforapacketliesonanotherswitchport,
VLANconsiderationscomeintoplaytodecideifthepacketisdroppedbytheSwitchordelivered.
4.5.1.3 IEEE802.1QVLANs
IEEE802.1Q(tagged)VLANareimplementedontheSwitch.802.1QVLANrequiretagging,which
enablesthemtospantheentirenetwork(assumingallswitchesonthenetworkareIEEE802.1Q‐
compliant).VLANallowanetworktobesegmentedinordertoreducethesizeofbroadcastdomains.
AllpacketsenteringaVLANwillonlybeforwardedtothestations(overIEEE802.1Qenabledswitches)
thataremembersofthatVLAN,andthisincludesbroadcast,multicastandunicastpacketsfrom
unknownsources.VLANcanalsoprovidealevelofsecuritytoyournetwork.IEEE802.1QVLANwill
onlydeliverpacketsbetweenstationsthataremembersoftheVLAN.Anyportcanbeconfiguredas

41
eithertaggingoruntagging.TheuntaggingfeatureofIEEE802.1QVLANallowsVLANtoworkwith
legacyswitchesthatdon'trecognizeVLANtagsin30packetheaders.ThetaggingfeatureallowsVLAN
tospanmultiple802.1Q‐compliantswitchesthroughasinglephysicalconnectionandallowsSpanning
Treetobeenabledonallportsandworknormally.Anyportcanbeconfiguredaseithertaggingor
untagging.TheuntaggingfeatureofIEEE802.1QVLANallowVLANtoworkwithlegacyswitchesthat
don’trecognizeVLANtagsinpacketheaders.ThetaggingfeatureallowsVLANtospanmultiple
802.1Q‐compliantswitchesthroughasinglephysicalconnectionandallowsSpanningTreetobe
enabledonallportsandworknormally.
Somerelevantterms:
Tagging‐Theactofputting802.1QVLANinformationintotheheaderofapacket.
Untagging‐Theactofstripping802.1QVLANinformationoutofthepacketheader.
4.5.1.4 802.1QVLANTags
Thefiguretotheright
showsthe802.1Q
VLANtag.Thereare
fouradditionaloctets
insertedafterthe
sourceMACaddress.
Theirpresenceis
indicatedbyavalueof
0x8100intheEther
Typefield.Whena
packet'sEtherTypefieldisequalto1120x8100,thepacketcarriestheIEEE802.1Q/802.1ptag.The
tagiscontainedinthefollowingtwooctetsandconsistsof3bitsofuserpriority,1bitofCanonical
FormatIdentifier(CFI‐usedforencapsulatingTokenRingpacketssotheycanbecarriedacross
Ethernetbackbones),and12bitsofVLANID(VID).The3bitsofuserpriorityareusedby802.1p.The
VIDistheVLANidentifierandisusedbythe802.1Qstandard.BecausetheVIDis12bitslong,4094
uniqueVLANcanbeidentified.Thetagisinsertedintothepacketheadermakingtheentirepacket
longerby4octets.Alloftheinformationoriginallycontainedinthepacketisretained.
TheEtherTypeandVLANIDareinsertedaftertheMACsourceaddress,butbeforetheoriginalEther
Type/LengthorLogicalLinkControl.Becausethepacketisnowabitlongerthanitwasoriginally,the
CyclicRedundancyCheck(CRC)mustberecalculated.

42
4.5.1.5 PortVLANID
Packetsthataretagged(arecarryingthe802.1QVIDinformation)canbetransmittedfromone802.1Q
compliantnetworkdevicetoanotherwiththeVLANinformationintact.Thisallows802.1QVLANto
spannetworkdevices(andindeed,theentirenetwork–ifallnetworkdevicesare802.1Qcompliant).
OriginalEthernetNewTaggedPacketEveryphysicalportonaswitchhasaPVID.802.1Qportsarealso
assignedaPVID,forusewithintheswitch.IfnoVLANaredefinedontheswitch,allportsarethen
assignedtoadefaultVLANwithaPVIDequalto1.UntaggedpacketsareassignedthePVIDoftheport
onwhichtheywerereceived.ForwardingdecisionsarebaseduponthisPVID,insofarasVLANare
concerned.Tag gedpacketsareforwardedaccordingtotheVIDcontainedwithinthetag.Tag ged
packetsarealsoassignedaPVID,butthePVIDisnotusedtomakepacketforwardingdecisions,the
VIDis.
Tag‐awareswitchesmustkeepatabletorelatePVIDwithintheswitchtoVIDonthenetwork.The
switchwillcomparetheVIDofapackettobetransmittedtotheVIDoftheportthatistotransmitthe
packet.IfthetwoVIDaredifferenttheswitchwilldropthepacket.Becauseoftheexistenceofthe
PVIDforuntaggedpacketsandtheVIDfortaggedpackets,tag‐awareandtag‐unawarenetwork
devicescancoexistonthesamenetwork.AswitchportcanhaveonlyonePVID,butcanhaveasmany
VIDastheswitchhasmemoryinitsVLANtabletostorethem.Becausesomedevicesonanetwork
maybetag‐unaware,adecisionmustbemadeateachportonatag‐awaredevicebeforepacketsare
transmitted–shouldthepackettobetransmittedhaveatagornot?Ifthetransmittingportis
connectedtoatag‐unawaredevice,thepacketshouldbeuntagged.Ifthetransmittingportis
connectedtoatag‐awaredevice,thepacketshouldbetagged.
4.5.1.6 DefaultVLANs
TheSwitchinitiallyconfiguresoneVLAN,VID=1,called"default."Thefactorydefaultsettingassigns
allportsontheSwitchtothe"default".AsnewVLANareconfiguredinPort‐basedmode,their
respectivememberportsareremovedfromthe"default."
4.5.1.7 AssigningPortstoVLANs
BeforeenablingVLANsfortheswitch,youmustfirstassigneachporttotheVLANgroup(s)inwhichit
willparticipate.BydefaultallportsareassignedtoVLAN1asuntaggedports.Addaportasatagged
portifyouwantittocarrytrafficforoneormoreVLANs,andanyintermediatenetworkdevicesorthe
hostattheotherendoftheconnectionsupportsVLANs.ThenassignportsontheotherVLAN‐aware
networkdevicesalongthepaththatwillcarrythistraffictothesameVLAN(s),eithermanuallyor
dynamicallyusingGVRP.However,ifyouwantaportonthisswitchtoparticipateinoneormore
VLANs,butnoneoftheintermediatenetworkdevicesnorthehostattheotherendoftheconnection
supportsVLANs,thenyoushouldaddthisporttotheVLANasanuntaggedport.
Note:
VLAN‐taggedframescanpassthroughVLAN‐awareorVLAN‐unawarenetworkinterconnection
devices,buttheVLANtagsshouldbestrippedoffbeforepassingitontoanyend‐nodehostthatdoes
notsupportVLANtagging.

43
4.5.1.8 VLANClassification
Whentheswitchreceivesaframe,itclassifiestheframeinoneoftwoways.Iftheframeisuntagged,
theswitchassignstheframetoanassociatedVLAN(basedonthedefaultVLANIDofthereceiving
port).Butiftheframeistagged,theswitchusesthetaggedVLANIDtoidentifytheportbroadcast
domainoftheframe.
4.5.1.9 PortOverlapping
Portoverlappingcanbeusedtoallowaccesstocommonlysharednetworkresourcesamongdifferent
VLANgroups,suchasfileserversorprinters.NotethatifyouimplementVLANswhichdonotoverlap,
butstillneedtocommunicate,youcanconnectthembyenabledroutingonthisswitch.
4.5.1.10 UntaggedVLANs
Untagged(orstatic)VLANsaretypicallyusedtoreducebroadcasttrafficandtoincreasesecurity.A
groupofnetworkusersassignedtoaVLANformabroadcastdomainthatisseparatefromother
VLANsconfiguredontheswitch.Packetsareforwardedonlybetweenportsthataredesignatedforthe
sameVLAN.UntaggedVLANscanbeusedtomanuallyisolateusergroupsorsubnets.

44
4.5.2 ManagementVLAN
Whenitcomestoswitchmanagement,itscommontouseadedicatedVLANformanagement
purposes.ThatVLANyouwillhavecreatedalready(seesection4.5.3),andperhapsnamed
‘Management’.OnthisscreenyousimplyselecttheVLANasthemanagementVLAN.
4.5.3 CreateVLAN
Thispageallowsyoutosetup,editanddeleteVLANs.

45
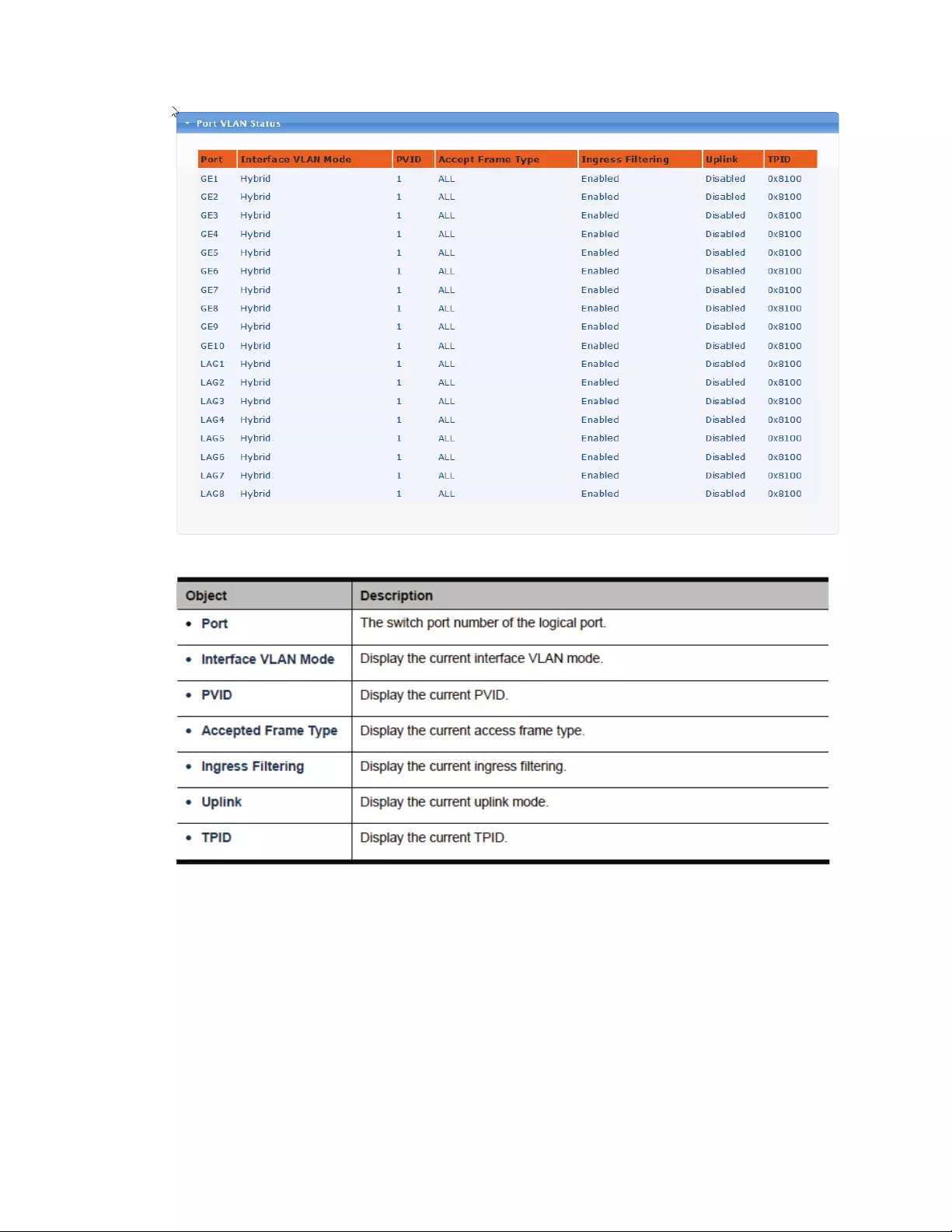
4.5.4 InterfaceSettings
ThisPageisusedforconfiguringtheManagedSwitchportVLAN.TheVLANperPortConfiguration
PagecontainsfieldsformanagingportsthatarepartofaVLAN.TheportdefaultVLANID(PVID)is
configuredontheVLANPortConfigurationPage.Alluntaggedpacketsarrivingtothedevicearetagged
bytheportsPVID.UnderstandnomenclatureoftheSwitch
IEEE802.1QTaggedandUntagged
Everyportonan802.1Qcompliantswitchcanbeconfiguredastaggedoruntagged.
Tagged:
PortswithtaggingenabledwillputtheVIDnumber,priorityandotherVLANinformationintothe
headerofallpacketsthatflowintothoseports.Ifapackethaspreviouslybeentagged,theportwill
notalterthepacket,thuskeepingtheVLANinformationintact.TheVLANinformationinthe
tagcanthenbeusedbyother802.1Qcompliantdevicesonthenetworktomakepacket‐forwarding
decisions.
Untagged:
Portswithuntaggingenabledwillstripthe802.1Qtagfromallpacketsthatflowintothoseports.Ifthe
packetdoesn'thavean802.1QVLANtag,theportwillnotalterthepacket.Thus,allpacketsreceived
byandforwardedbyanuntaggingportwillhaveno802.1QVLANinformation.(Rememberthatthe
PVIDisonlyusedinternallywithintheSwitch).Untaggingisusedtosendpacketsfroman802.1Q‐
compliantnetworkdevicetoanon‐compliantnetworkdevice.
IEEE802.1QTunneling(Q‐in‐Q)
IEEE802.1QTunneling(QinQ)isdesignedforserviceproviderscarryingtrafficformultiplecustomers
acrosstheirnetworks.QinQtunnelingisusedtomaintaincustomer‐specificVLANandLayer2protocol
configurationsevenwhendifferentcustomersusethesameinternalVLANIDs.Thisisaccomplishedby
insertingServiceProviderVLAN(SPVLAN)tagsintothecustomer’sframeswhentheyentertheservice
provider’snetwork,andthenstrippingthetagswhentheframesleavethenetwork.
Aserviceprovider’scustomersmayhavespecificrequirementsfortheirinternalVLANIDsandnumber
ofVLANssupported.VLANrangesrequiredbydifferentcustomersinthesameservice‐provider
networkmighteasilyoverlap,andtrafficpassingthroughtheinfrastructuremightbemixed.Assigning
auniquerangeofVLANIDstoeachcustomerwouldrestrictcustomerconfigurations,requireintensive
processingofVLANmappingtables,andcouldeasilyexceedthemaximumVLANlimitof4096.

46
TheManagedSwitchsupportsmultipleVLANtagsandcanthereforebeusedinMANapplicationsasa
providerbridge,aggregatingtrafficfromnumerousindependentcustomerLANsintotheMAN(Metro
AccessNetwork)space.OneofthepurposesoftheproviderbridgeistorecognizeanduseVLANtags
sothattheVLANsintheMANspacecanbeusedindependentofthecustomers’VLANs.Thisis
accomplishedbyaddingaVLANtagwithaMAN‐relatedVIDforframesenteringtheMAN.When
leavingtheMAN,thetagisstrippedandtheoriginalVLANtagwiththecustomer‐relatedVIDisagain
available.
ThisprovidesatunnelingmechanismtoconnectremotecostumerVLANsthroughacommonMAN
spacewithoutinterferingwiththeVLANtags.AlltagsuseEtherType0x8100or0x88A8,where0x8100
isusedforcustomertagsand0x88A8areusedforserviceprovidertags.Incaseswhereagivenservice
VLANonlyhastwomemberportsontheswitch,thelearningcanbedisabledfortheparticularVLAN
andcanthereforerelyonfloodingastheforwardingmechanismbetweenthetwoports.Thisway,the
MACtablerequirementsisreduced.

47
48
49
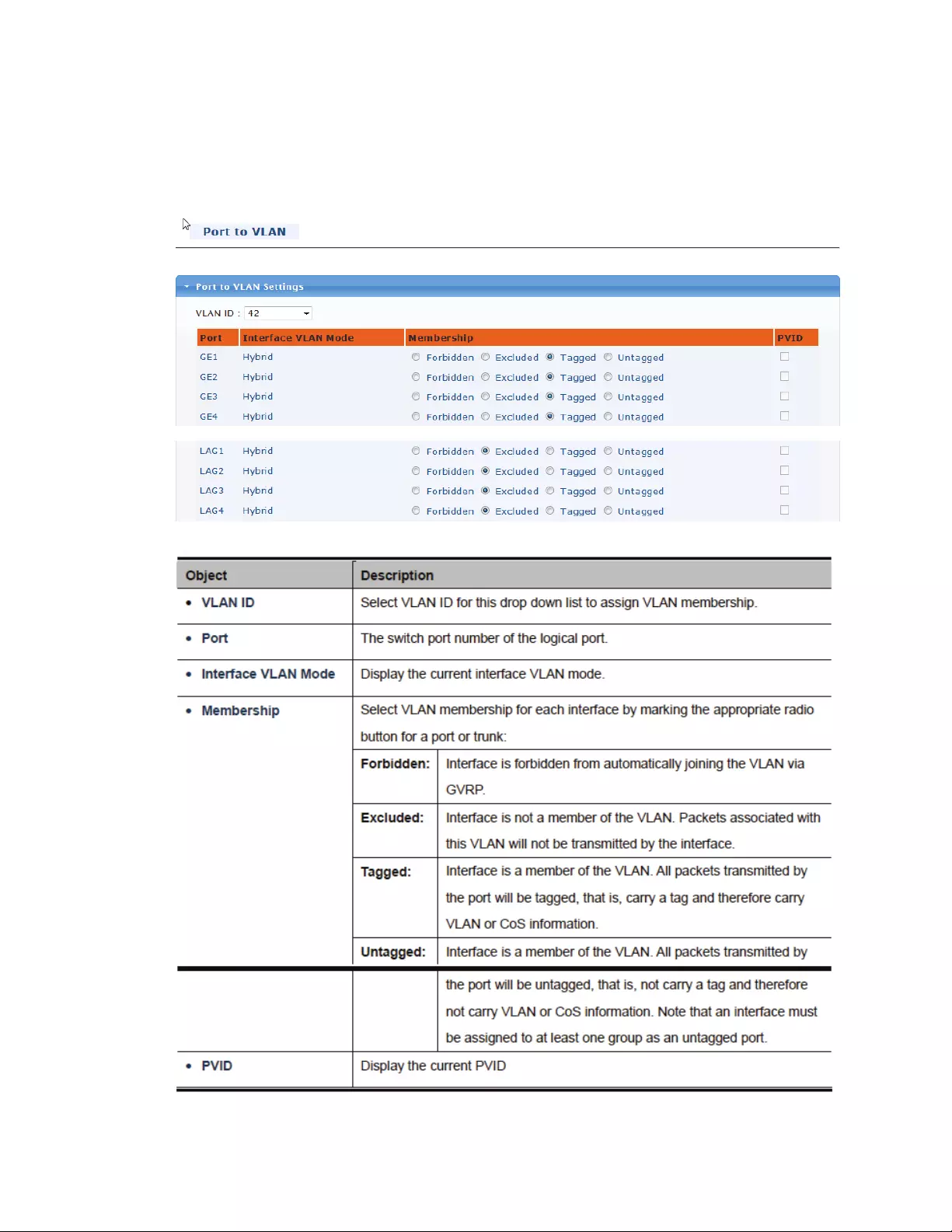
4.5.5 PorttoVLAN
WiththisfunctionyoucanassignportstoordeletethemfromexistingVLANs.GE1designatedGigabit
Ethernetport1,whileLAG1standsfirLinkAggregationGroup1.

50
4.5.6 PortVLANMembership
ThisscreenshowsanoverviewofallportsandLAGs,alongwiththeircorrespondingVLANstatus.
WhenyoueditaportorLAG,youcanremovetheportfrom
existingVLANsbyselectingtheVLANintherightboxandclicking
[Del].InordertoaddaporttoaVLAN,selecttheLANontheleft
side,andthenclick[Add].
Additionally,youcandefinethetaggingforthisport.Seethe
previoussectionfordetails.
51
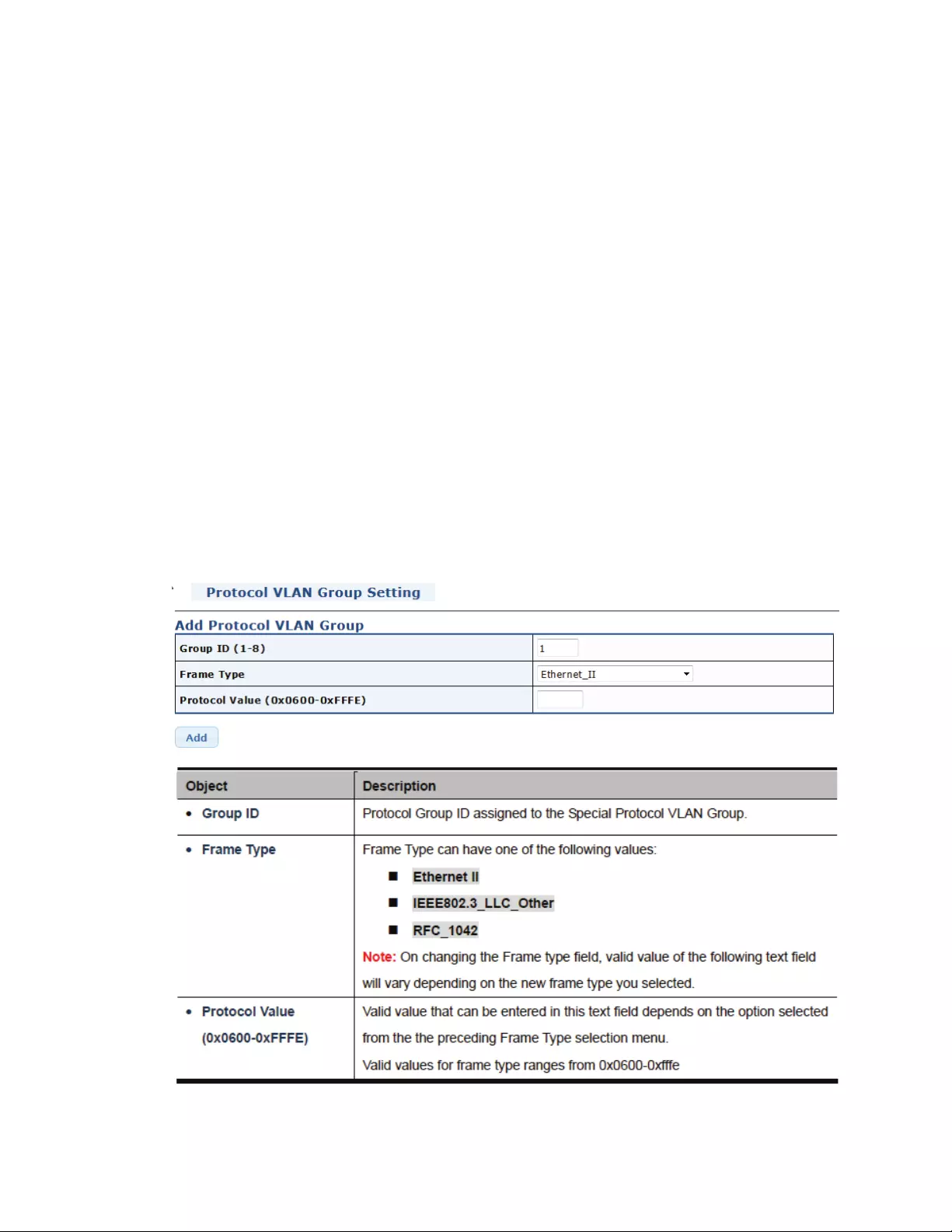
4.5.7 ProtocolVLANGroupSettings
Thenetworkdevicesrequiredtosupportmultipleprotocolscannotbeeasilygroupedintoacommon
VLAN.Thismayrequirenon‐standarddevicestopasstrafficbetweendifferentVLANsinorderto
encompassallthedevicesparticipatinginaspecificprotocol.Thiskindofconfigurationdeprivesusers
ofthebasicbenefitsofVLANs,includingsecurityandeasyaccessibility.Toavoidtheseproblems,you
canconfigurethisManagedSwitchwithprotocol‐basedVLANsthatdividethephysicalnetworkinto
logicalVLANgroupsforeachrequiredprotocol.Whenaframeisreceivedataport,itsVLAN
membershipcanthenbedeterminedbasedontheprotocoltypebeingusedbytheinboundpackets.
Toconfigureprotocol‐basedVLANs,followthesesteps:
1.FirstconfigureVLANgroupsfortheprotocolsyouwanttouse.Althoughnotmandatory,wesuggest
configuringaseparateVLANforeachmajorprotocolrunningonyournetwork.Donotaddport
membersatthistime.
2.CreateaprotocolgroupforeachoftheprotocolsyouwanttoassigntoaVLANusingtheProtocol
VLANConfigurationpage.
3.ThenmaptheprotocolforeachinterfacetotheappropriateVLANusingtheProtocolVLANPort
Configurationpage.
ThisPageallowsforconfiguresprotocol‐basedVLANGroupSetting

52
4.5.8 ProtocolVLANPortSettings
Oncethegrouphasbeenconfigured,youcanmapittoaVLAN/port.
4.5.9 GVRPSetting
GARPVLANRegistrationProtocol(GVRP)definesawayforswitchestoexchangeVLANinformationin
ordertoregisterVLANmembersonportsacrossthenetwork.VLANsaredynamicallyconfiguredbased
onjoinmessagesissuedbyhostdevicesandpropagatedthroughoutthenetwork.GVRPmustbe
enabledtopermitautomaticVLANregistration,andtosupportVLANswhichextendbeyondthelocal
switch.
Onthisconfigurationpageyoucanactivateordeactivatethisfeature.
53
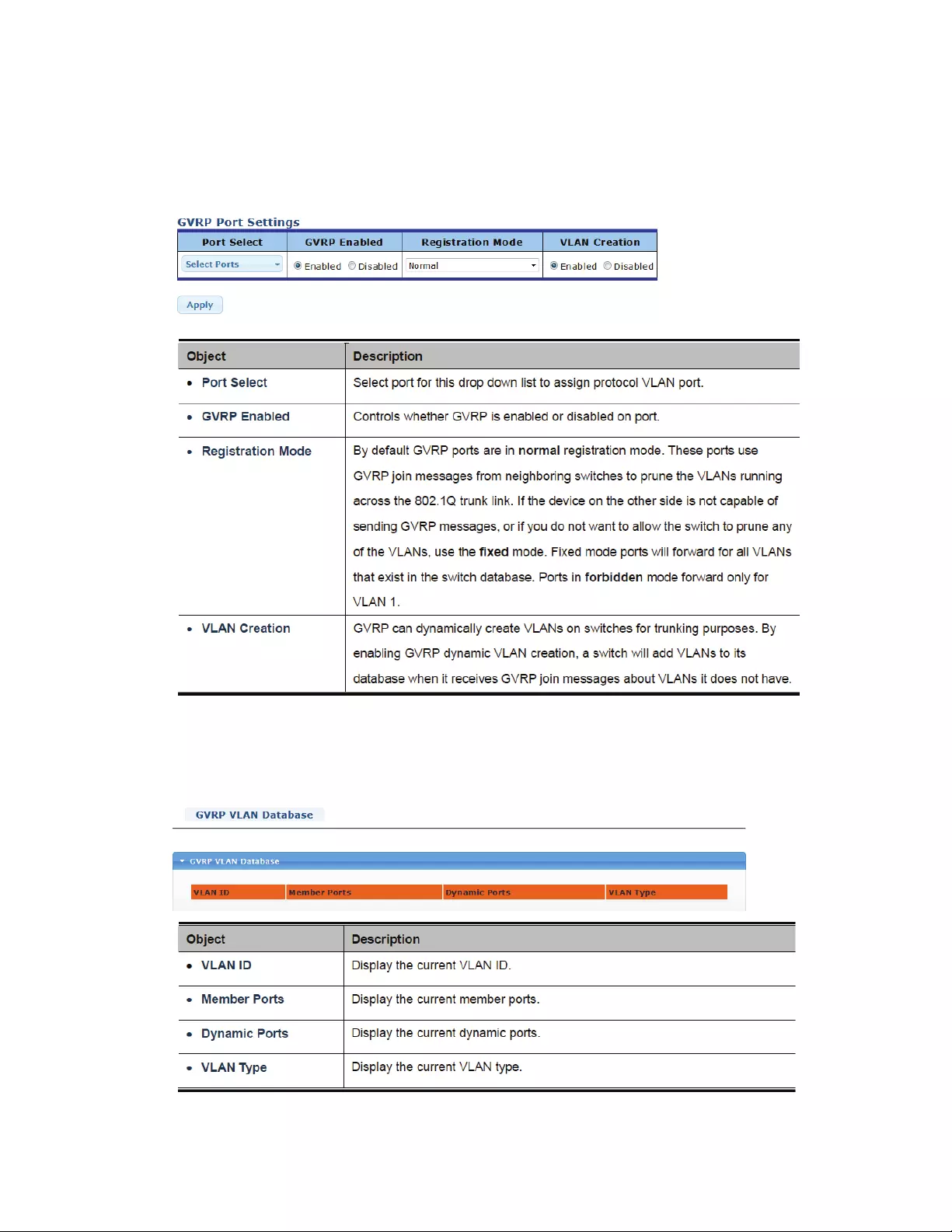
4.5.10 GVRPPortSetting
ThisconfigurationscreenallowsyoutoactivateordeactivateGVRPforeachport.Additionally,youcan
definetheregistrationmodeandallowordisallowthedynamiccreationofVLANs.
4.5.11 GVRPVLAN
ThisscreenprovidesanoverviewofthecurrentGVRPVLANsetup.
54
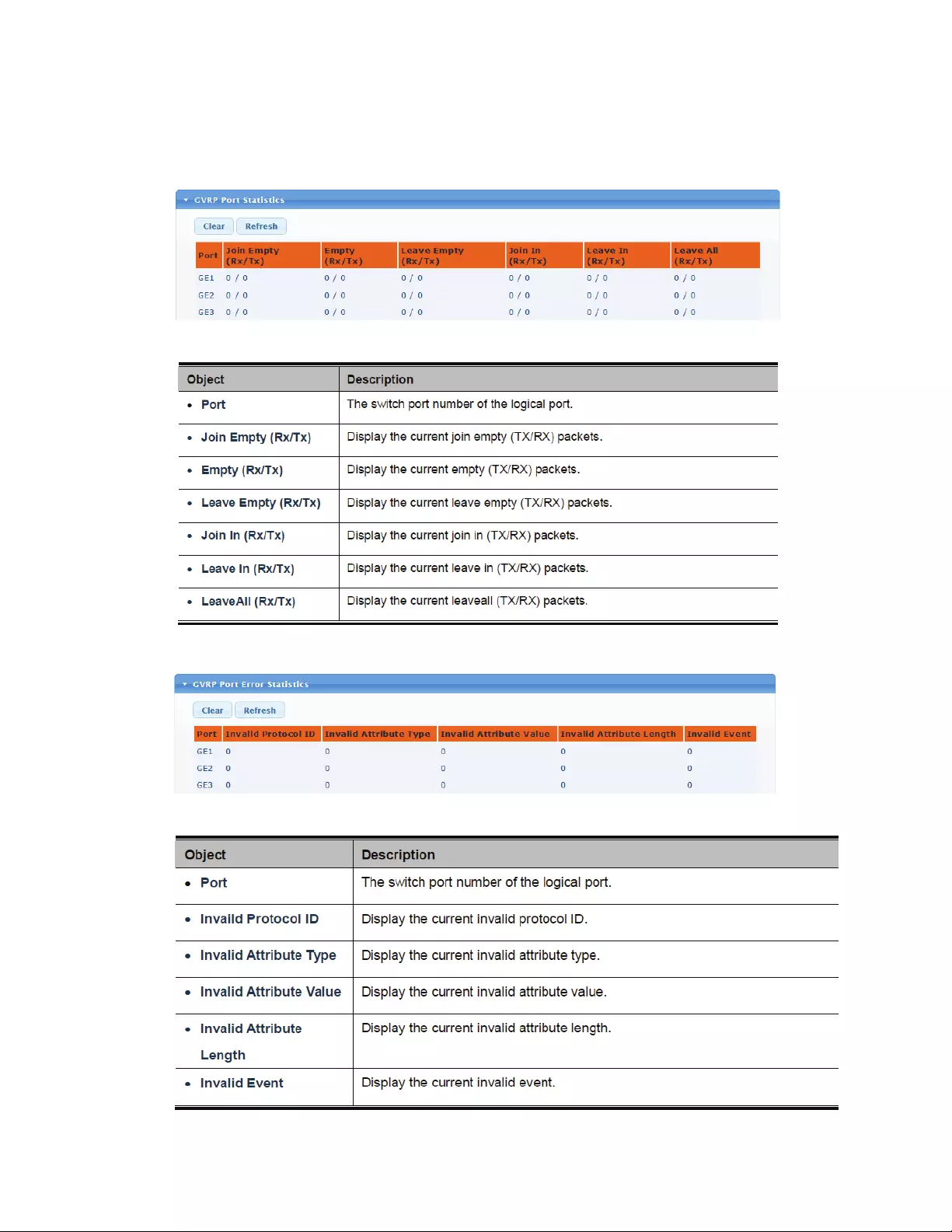
4.5.12 GVRPStatistics
GVRP Port and Error Statistics are shown on this page.

55
4.6 SpanningTreeProtocol(STP)
4.6.1 WhatisSTP?
TheSpanningTreeProtocolcanbeusedtodetectanddisablenetworkloops,andtoprovidebackup
linksbetweenswitches,bridgesorrouters.Thisallowstheswitchtointeractwithotherbridging
devicesinyournetworktoensurethatonlyonerouteexistsbetweenanytwostationsonthenetwork,
andprovidebackuplinkswhichautomaticallytakeoverwhenaprimarylinkgoesdown.Thespanning
treealgorithmssupportedbythisswitchincludetheseversions:
STP–SpanningTreeProtocol(IEEE802.1D)
RSTP–RapidSpanningTreeProtocol(IEEE802.1w)
MSTP–MultipleSpanningTreeProtocol(IEEE802.1s)
TheIEEE802.1DSpanningTreeProtocolandIEEE802.1wRapidSpanningTreeProtocolallowforthe
blockingoflinksbetweenswitchesthatformloopswithinthenetwork.Whenmultiplelinksbetween
switchesaredetected,aprimarylinkisestablished.Duplicatedlinksareblockedfromuseandbecome
standbylinks.Theprotocolallowsfortheduplicatelinkstobeusedintheeventofafailureofthe
primarylink.OncetheSpanningTreeProtocolisconfiguredandenabled,primarylinksareestablished
andduplicatedlinksareblockedautomatically.Thereactivationoftheblockedlinks(atthetimeofa
primarylinkfailure)isalsoaccomplishedautomaticallywithoutoperatorintervention.Thisautomatic
networkreconfigurationprovidesmaximumuptimetonetworkusers.However,theconceptsofthe
SpanningTreeAlgorithmandprotocolareacomplicatedandcomplexsubjectandmustbefully
researchedandunderstood.Itispossibletocauseseriousdegradationoftheperformanceofthe
networkiftheSpanningTreeisincorrectlyconfigured.Pleasereadthefollowingbeforemakingany
changesfromthedefaultvalues.
TheSwitchSTPperformsthefollowingfunctions:
Createsasinglespanningtreefromanycombinationofswitchingorbridgingelements.
Createsmultiplespanningtrees–fromanycombinationofportscontainedwithinasingle
switch,inuserspecifiedgroups.
Automaticallyreconfiguresthespanningtreetocompensateforthefailure,addition,or
removalofanyelementinthetree.
Reconfiguresthespanningtreewithoutoperatorintervention.
BridgeProtocolDataUnits
ForSTPtoarriveatastablenetworktopology,thefollowinginformationisused:
Theuniqueswitchidentifier
Thepathcosttotherootassociatedwitheachswitchport
Theportidentifier

56
STPcommunicatesbetweenswitchesonthenetworkusingBridgeProtocolDataUnits(BPDUs).Each
BPDUcontainsthefollowinginformation:
Theuniqueidentifieroftheswitchthatthetransmittingswitchcurrentlybelievesistheroot
switch
Thepathcosttotherootfromthetransmittingport
Theportidentifierofthetransmittingport
TheswitchsendsBPDUstocommunicateandconstructthespanning‐treetopology.Allswitches
connectedtotheLANonwhichthepacketistransmittedwillreceivetheBPDU.BPDUsarenotdirectly
forwardedbytheswitch,butthereceivingswitchusestheinformationintheframetocalculatea
BPDU,and,ifthetopologychanges,initiatesaBPDUtransmission.
ThecommunicationbetweenswitchesviaBPDUsresultsinthefollowing:
Oneswitchiselectedastherootswitch
Theshortestdistancetotherootswitchiscalculatedforeachswitch
Adesignatedswitchisselected.Thisistheswitchclosesttotherootswitchthroughwhich
packetswillbeforwardedtotheroot.
Aportforeachswitchisselected.Thisistheportprovidingthebestpathfromtheswitchto
therootswitch.
PortsincludedintheSTPareselected.
CreatingaStableSTPTopology
Itistomaketherootportafastestlink.IfallswitcheshaveSTPenabledwithdefaultsettings,the
switchwiththelowestMACaddressinthenetworkwillbecometherootswitch.Byincreasingthe
priority(loweringtheprioritynumber)ofthebestswitch,STPcanbeforcedtoselectthebestswitch
astherootswitch.WhenSTPisenabledusingthedefaultparameters,thepathbetweensourceand
destinationstationsinaswitchednetworkmightnotbeideal.Forinstance,connectinghigher‐speed
linkstoaportthathasahighernumberthanthecurrentrootportcancausearoot‐portchange.
STPPortStates
TheBPDUstakesometimetopassthroughanetwork.Thispropagationdelaycanresultintopology
changeswhereaportthattransitioneddirectlyfromaBlockingstatetoaForwardingstatecould
createtemporarydataloops.Portsmustwaitfornewnetworktopologyinformationtopropagate
throughoutthenetworkbeforestartingtoforwardpackets.Theymustalsowaitforthepacketlifetime
toexpireforBPDUpacketsthatwereforwardedbasedontheoldtopology.Theforwarddelaytimeris
usedtoallowthenetworktopologytostabilizeafteratopologychange.Inaddition,STPspecifiesa
seriesofstatesaportmusttransitionthroughtofurtherensurethatastablenetworktopologyis
createdafteratopologychange.
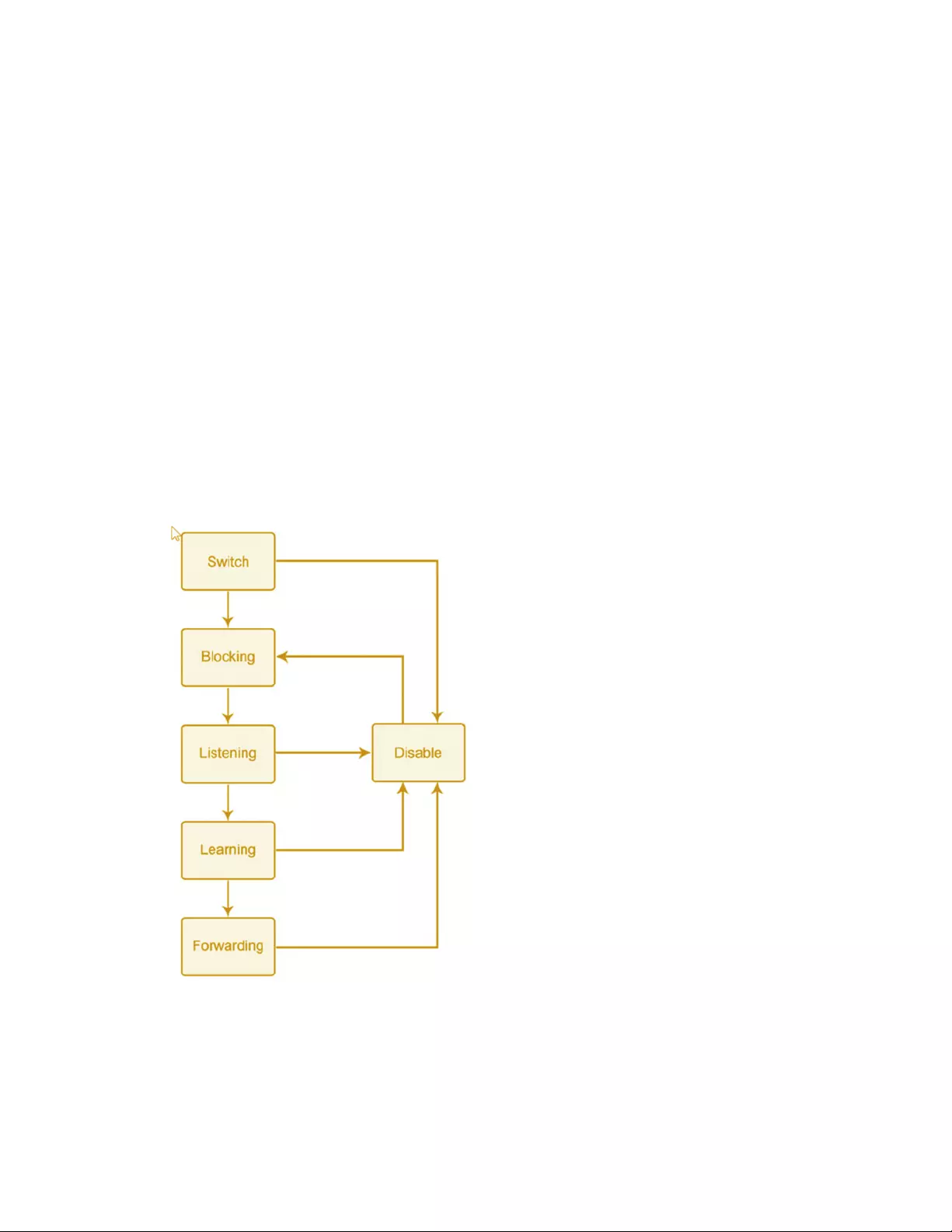
57
EachportonaswitchusingSTPexistsisinoneofthefollowingfivestates:
Blocking–theportisblockedfromforwardingorreceivingpackets
Listening–theportiswaitingtoreceiveBPDUpacketsthatmaytelltheporttogobacktothe
blockingstate
Learning–theportisaddingaddressestoitsforwardingdatabase,butnotyetforwarding
packets
Forwarding–theportisforwardingpackets
Disabled–theportonlyrespondstonetworkmanagementmessagesandmustreturntothe
blockingstatefirst
Aporttransitionsfromonestatetoanotherasfollows:
Frominitialization(switchboot)toblocking
Fromblockingtolisteningortodisabled
Fromlisteningtolearningortodisabled
Fromlearningtoforwardingortodisabled
Fromforwardingtodisabled
Fromdisabledtoblocking
Youcanmodifyeachportstatebyusingmanagementsoftware.WhenyouenableSTP,everyporton
everyswitchinthenetworkgoesthroughtheblockingstateandthentransitionsthroughthestatesof
listeningandlearningatpowerup.Ifproperlyconfigured,eachportstabilizestotheforwardingor
blockingstate.Nopackets(exceptBPDUs)areforwardedfrom,orreceivedby,STPenabledportsuntil
theforwardingstateisenabledforthatport.
58
TheSwitchallowsfortwolevelsofoperation:theswitchlevelandtheportlevel.Theswitchlevel
formsaspanningtreeconsistingoflinksbetweenoneormoreswitches.Theportlevelconstructsa
spanningtreeconsistingofgroupsofoneormoreports.TheSTPoperatesinmuchthesamewayfor
bothlevels.
Note:
Ontheswitchlevel,STPcalculatestheBridgeIdentifierforeachswitchandthensetstheRoot
BridgeandtheDesignatedBridges.Ontheportlevel,STPsetstheRootPortandtheDesignatedPorts.
Thefollowingaretheuser‐configurableSTPparametersfortheswitchlevel:
ParameterDescriptionDefaultValue
BridgeIdentifier AcombinationoftheUser‐set
priorityandtheswitch’sMAC
address.TheBridgeIdentifier
consistsoftwoparts:
a16‐bitpriorityanda48‐bit
EthernetMACaddress32768+
MAC.
32768+MAC
PriorityArelativepriorityforeach
switch.Lowernumbersgivea
higherpriorityandagreater
chanceofagivenswitchbeing
electedastherootbridge.
32768
HelloTimeThelengthoftimebetween
broadcastsofthehello
messagebytheswitch.
2seconds
MaximumAgeTimerMeasurestheageofareceived
BPDUforaportandensures
thattheBPDUisdiscarded
whenitsageexceedsthevalue
ofthemaximumagetimer.
20seconds
ForwardDelayTimerTheamounttimespentbya
portinthelearningand
listeningstateswaitingfora
BPDUthatmayreturntheport
totheblockingstate.
15seconds

59
Thefollowingaretheuser‐configurableSTPparametersfortheportorportgrouplevel:
DefaultSpanning‐TreeConfiguration
User‐ChangeableSTAParameters
TheSwitch’sfactorydefaultsettingshouldcoverthemajorityofinstallations.However,itisadvisable
tokeepthedefaultsettingsassetatthefactory;unless,itisabsolutelynecessary.Theuserchangeable
parametersintheSwitchareasfollows:
Priority–APriorityfortheswitchcanbesetfrom0to65535.0isequaltothehighestPriority.
HelloTime–TheHelloTimecanbefrom1to10seconds.Thisistheintervalbetweentwo
transmissionsofBPDUpacketssentbytheRootBridgetotellallotherSwitchesthatitisindeedthe
RootBridge.IfyousetaHelloTimeforyourSwitch,anditisnottheRootBridge,thesetHelloTime
willbeusedifandwhenyourSwitchbecomestheRootBridge.
Note:
TheHelloTimecannotbelongerthantheMax.Age.Otherwise,aconfigurationerrorwilloccur.

60
Max.Age–TheMaxAgecanbefrom6to40seconds.AttheendoftheMaxAge,ifaBPDUhasstill
notbeenreceivedfromtheRootBridge,yourSwitchwillstartsendingitsownBPDUtoallother
SwitchesforpermissiontobecometheRootBridge.IfitturnsoutthatyourSwitchhasthelowest
BridgeIdentifier,itwillbecometheRootBridge.
ForwardDelayTimer–TheForwardDelaycanbefrom4to30seconds.Thisisthetimeanyporton
theSwitchspendsinthelisteningstatewhilemovingfromtheblockingstatetotheforwardingstate.
Note:
Observethefollowingformulaswhensettingtheaboveparameters:
Max.Age_2x(ForwardDelay‐1second)
Max.Age_2x(HelloTime+1second)
PortPriority–APortPrioritycanbefrom0to240.Thelowerthenumber,thegreatertheprobability
theportwillbechosenastheRootPort.
PortCost–APortCostcanbesetfrom0to200000000.Thelowerthenumber,thegreaterthe
probabilitytheportwillbechosentoforwardpackets.
IllustrationofSTP
Asimpleillustrationofthreeswitchesconnectedinaloopisdepictedinthebelowdiagram.Inthis
example,youcananticipatesomemajornetworkproblemsiftheSTPassistanceisnotapplied.
IfswitchAbroadcastsapackettoswitchB,switchBwillbroadcastittoswitchC,andswitchCwill
broadcastittobacktoswitchAandsoon.Thebroadcastpacketwillbepassedindefinitelyinaloop,
potentiallycausinganetworkfailure.
Inthisexample,STPbreakstheloopbyblockingtheconnectionbetweenswitchBandC.Thedecision
toblockaparticularconnectionisbasedontheSTPcalculationofthemostcurrentBridgeandPort
settings.Now,ifswitchAbroadcastsapackettoswitchC,thenswitchCwilldropthepacketatport2
andthebroadcastwillendthere.Setting‐upSTPusingvaluesotherthanthedefaults,canbecomplex.
Therefore,youareadvisedtokeepthedefaultfactorysettingsandSTPwillautomaticallyassignroot
bridges/portsandblockloopconnections.InfluencingSTPtochooseaparticularswitchastheroot
bridgeusingthePrioritysetting,orinfluencingSTPtochooseaparticularporttoblockusingthePort
PriorityandPortCostsettingsis,however,relativelystraightforward.

61
BeforeApplyingtheSTARules
Inthisexample,onlythedefaultSTPvaluesareused.
AfterApplyingtheSTARules
TheswitchwiththelowestBridgeID(switchC)waselectedtherootbridge,andtheportswere
selectedtogiveahighportcostbetweenswitchesBandC.Thetwo(optional)Gigabitports(default
portcost=20,000)onswitchAareconnectedtoone(optional)GigabitportonbothswitchBandC.
TheredundantlinkbetweenswitchBandCisdeliberatelychosenasa100MbpsFastEthernetlink
(defaultportcost=200,000).Gigabitportscouldbeused,buttheportcostshouldbeincreasedfrom
thedefaulttoensurethatthelinkbetweenswitchBandswitchCistheblockedlink.

62
4.6.2 STPGlobalSettings
ThispageallowsyoutoconfiguretheSTPsystemsettings.ThesettingsareusedbyallSTPBridge
instancesintheIntellinet8‐PortGigabitPoE+switch.Themanagedswitchsupportsthefollowing
SpanningTreeprotocols:
Compatible‐‐SpanningTreeProtocol(STP):Providesasinglepathbetweenendstations,
avoidingandeliminatingloops.
Normal‐‐RapidSpanningTreeProtocol(RSTP):Detectsandusesofnetworktopologiesthat
providefasterspanningtreeconvergence,withoutcreatingforwardingloops.
Extension–MultipleSpanningTreeProtocol(MSTP):DefinesanextensiontoRSTPtofurther
developtheusefulnessofvirtualLANs(VLANs).This"Per‐VLAN"MultipleSpanningTree
ProtocolconfiguresaseparateSpanningTreeforeachVLANgroupandblocksallbutoneof
thepossiblealternatepathswithineachSpanningTree.
63
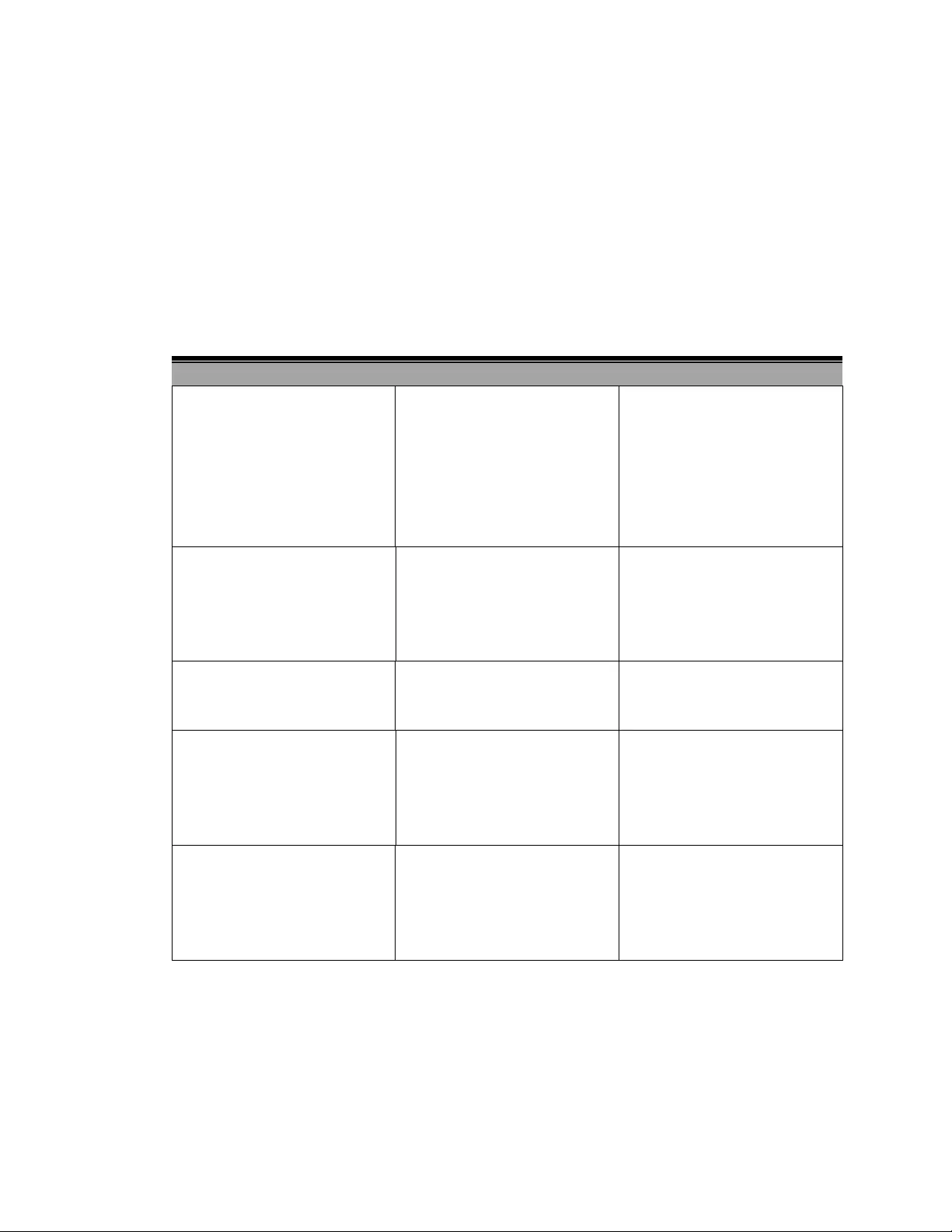
4.6.3 STPPortSettings
Allportrelatedsettingsareconfiguredonthisscreen.
64
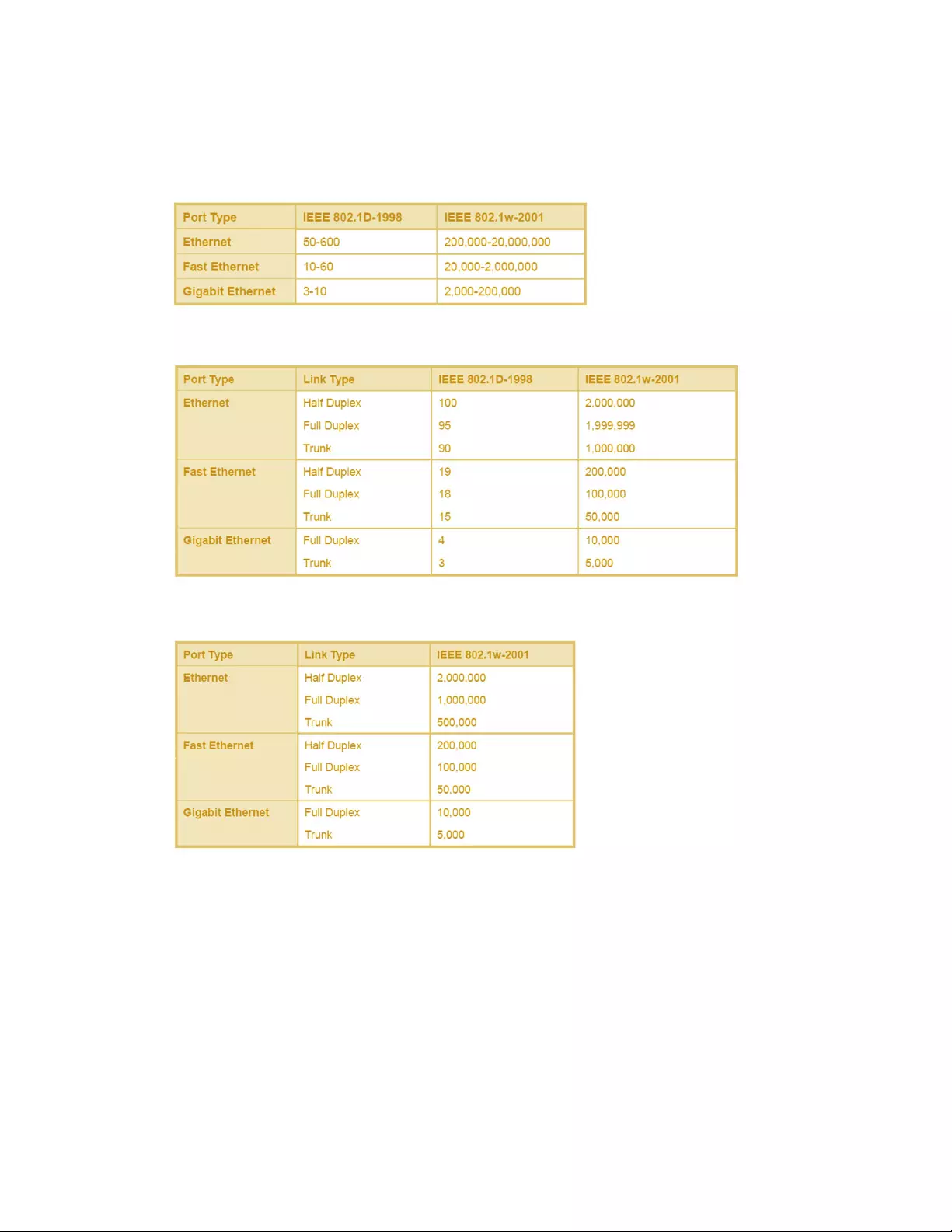
Bydefault,thesystemautomaticallydetectsthespeedandduplexmodeusedoneachport,and
configuresthepathcostaccordingtothevaluesshownbelow.Pathcost“0”isusedtoindicateauto‐
configurationmode.Whentheshortpathcostmethodisselectedandthedefaultpathcost
recommendedbytheIEEE8021wstandardexceeds65,535,thedefaultissetto65,535.
RecommendedSTPPathCostRange
Recommended STP Path Costs
DefaultSTPPathCosts
65
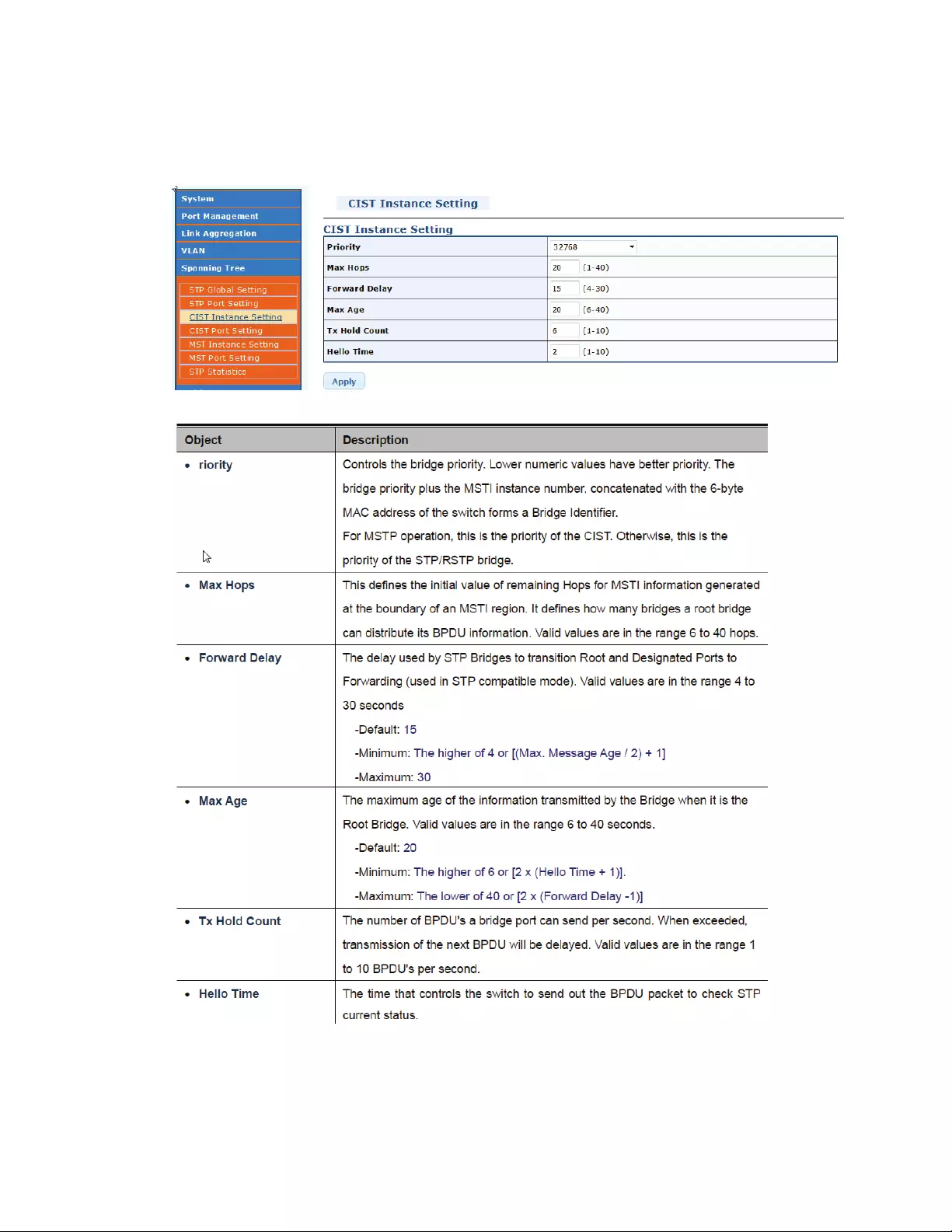
4.6.4 CISTInstanceSetting
ThisPageallowsyoutoconfigureCISTinstancesettings.
66
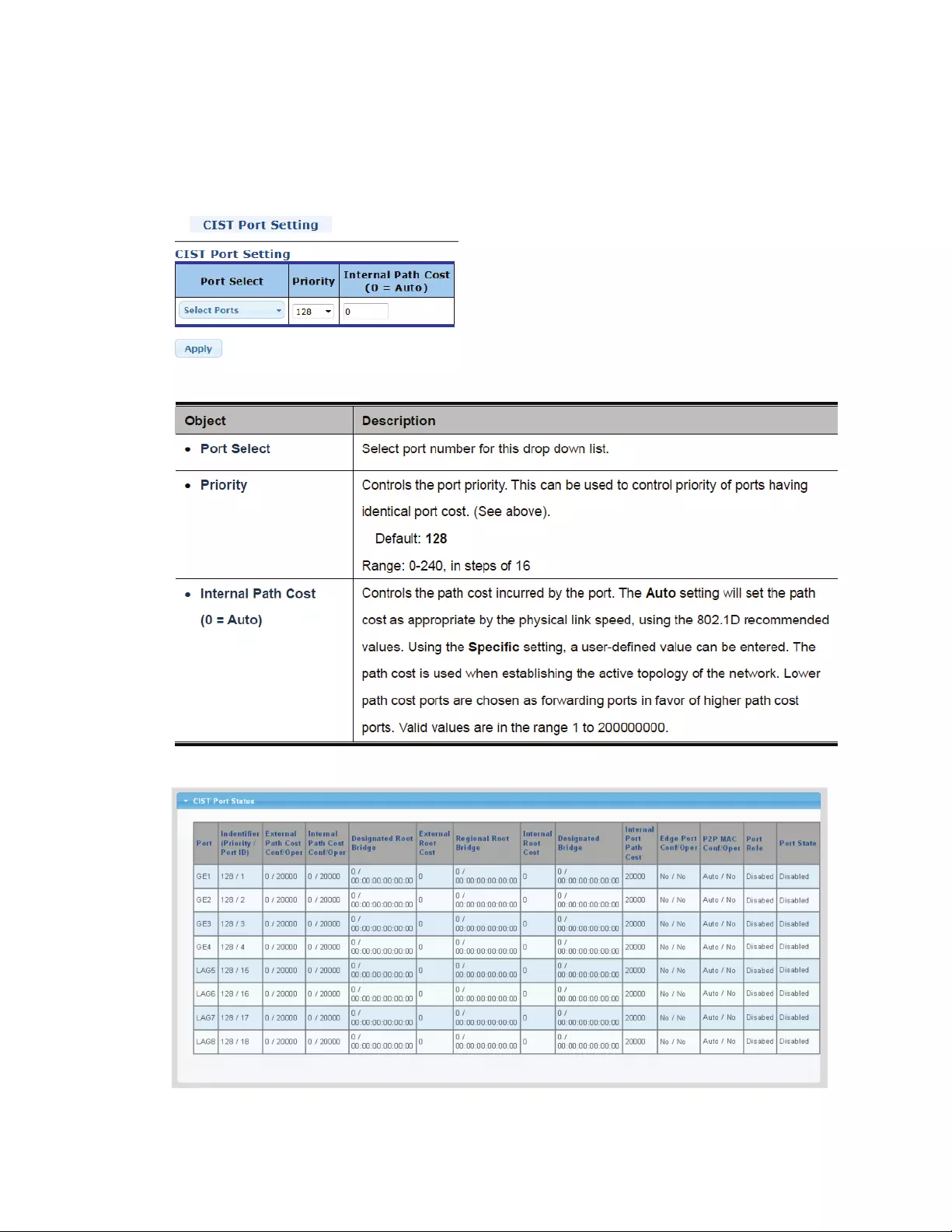
4.6.5 CISTPortSettings
ONthispageyoucanconfiguretheCISTpriorityandinternalpathcostoftheIntellinet8‐PortGigabit
PoESwitch.
CISTPortStatusPageScreenshot
67
68
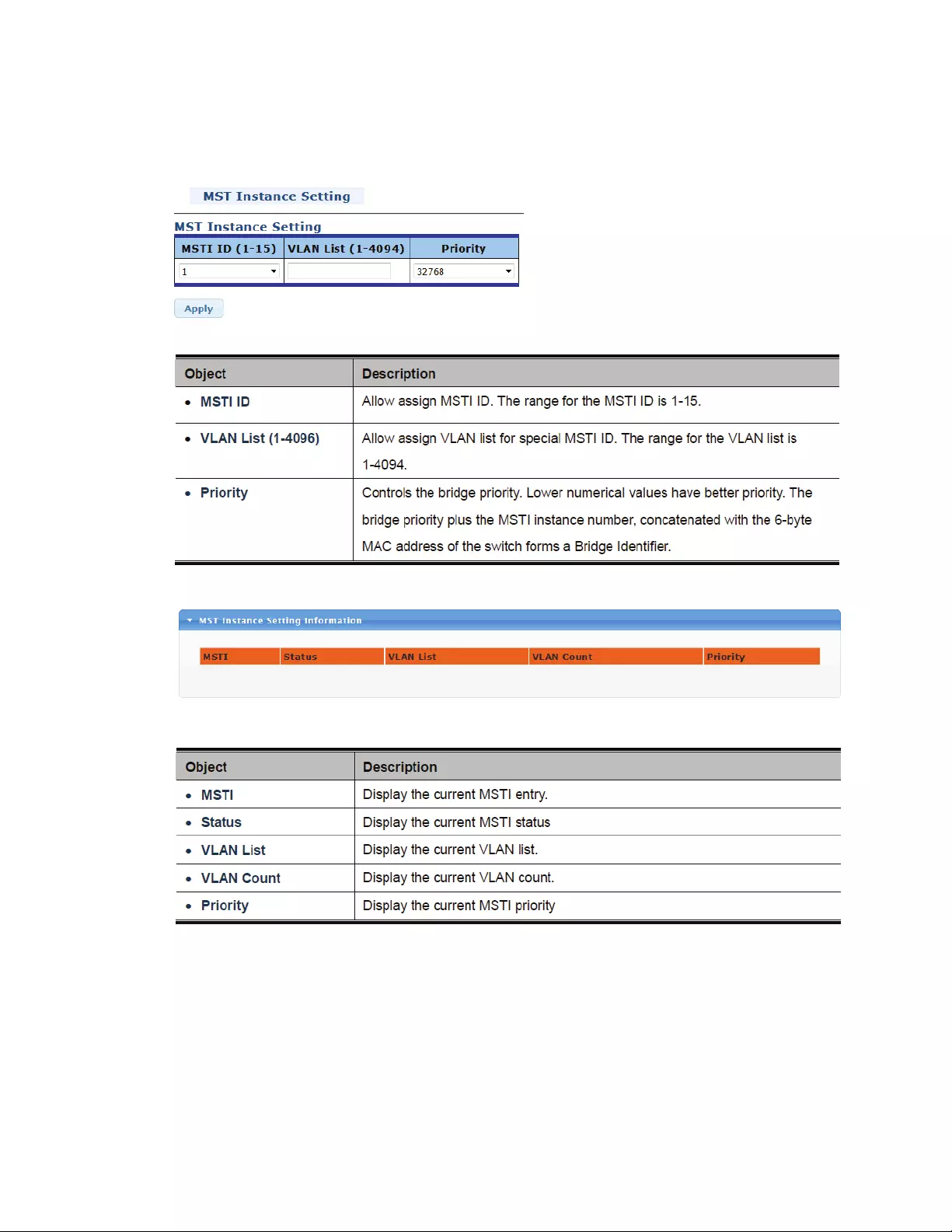
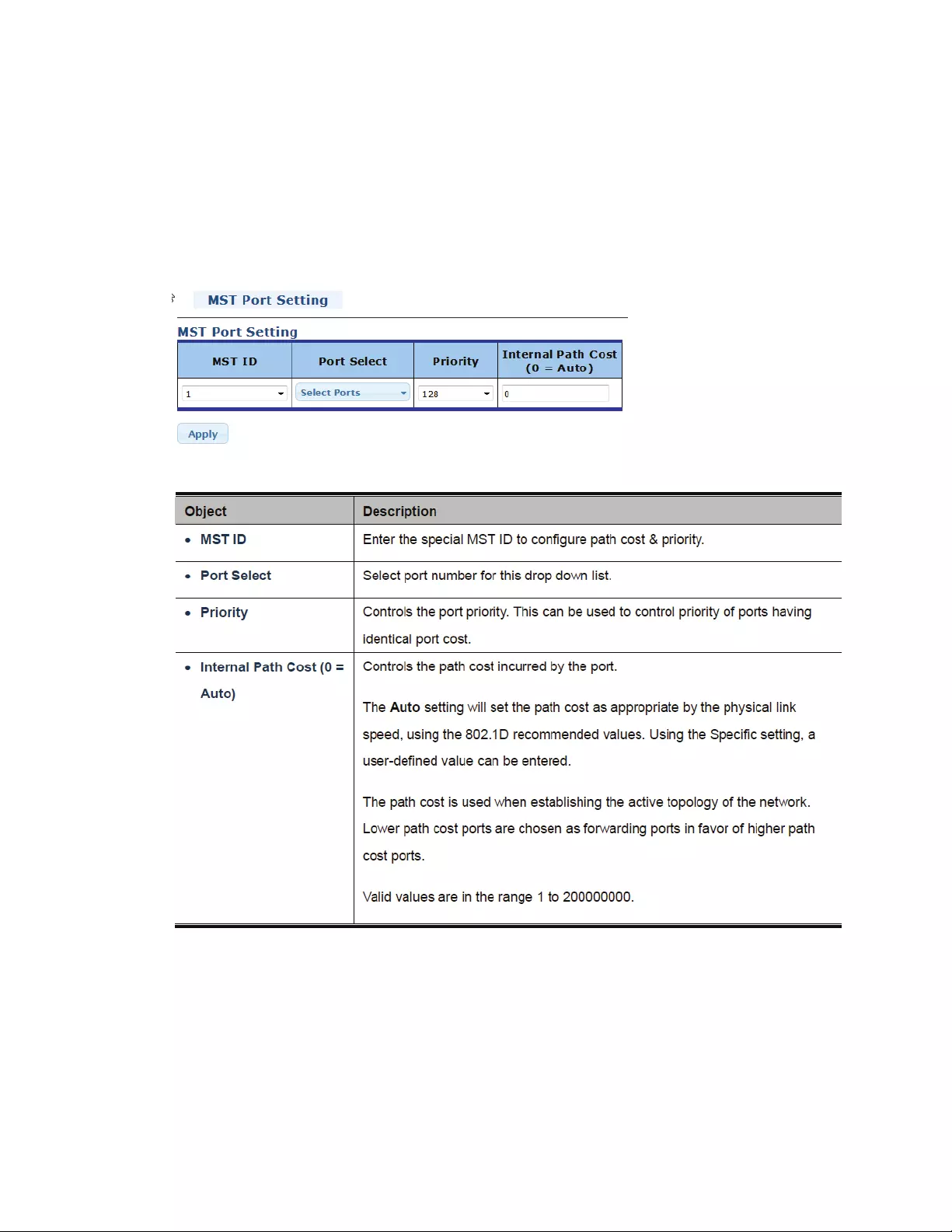
4.6.6 MSTInstanceConfiguration
ThispageallowstheusertoconfigureMSTInstanceConfiguration.

69
70
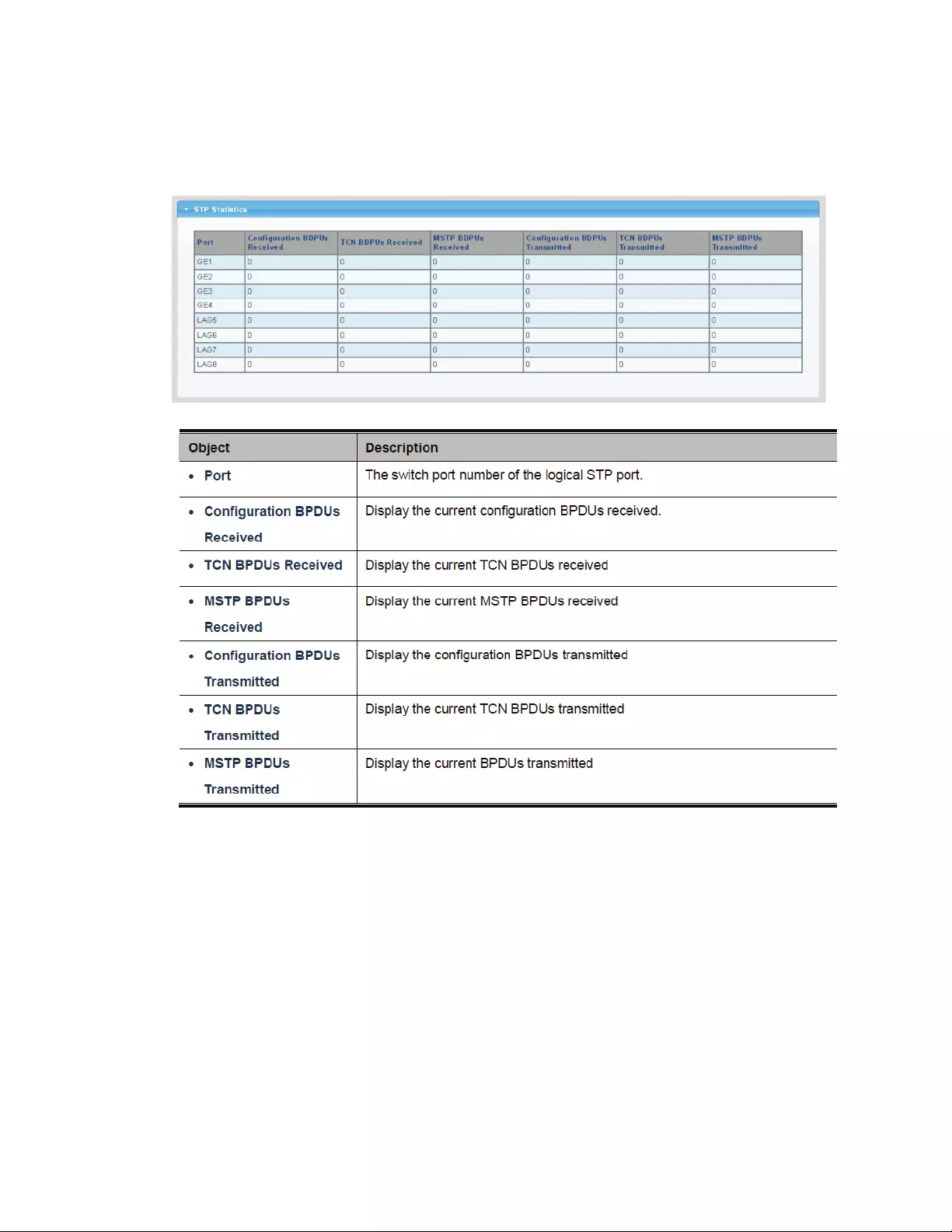
4.6.7 MSTPortSettings
ThispageallowstheusertoinspectthecurrentSTPMSTIportconfigurations,andpossiblychange
themaswell.AMSTIportisavirtualport,whichisinstantiatedseparatelyforeachactiveCIST
(physical)portforeachMSTIinstanceconfiguredandapplicablefortheport.TheMSTIinstancemust
beselectedbeforedisplayingactualMSTIportconfigurationoptions.ThispagecontainsMSTIport
settingsforphysicalandaggregatedports.Theaggregationsettingsareglobal.
71
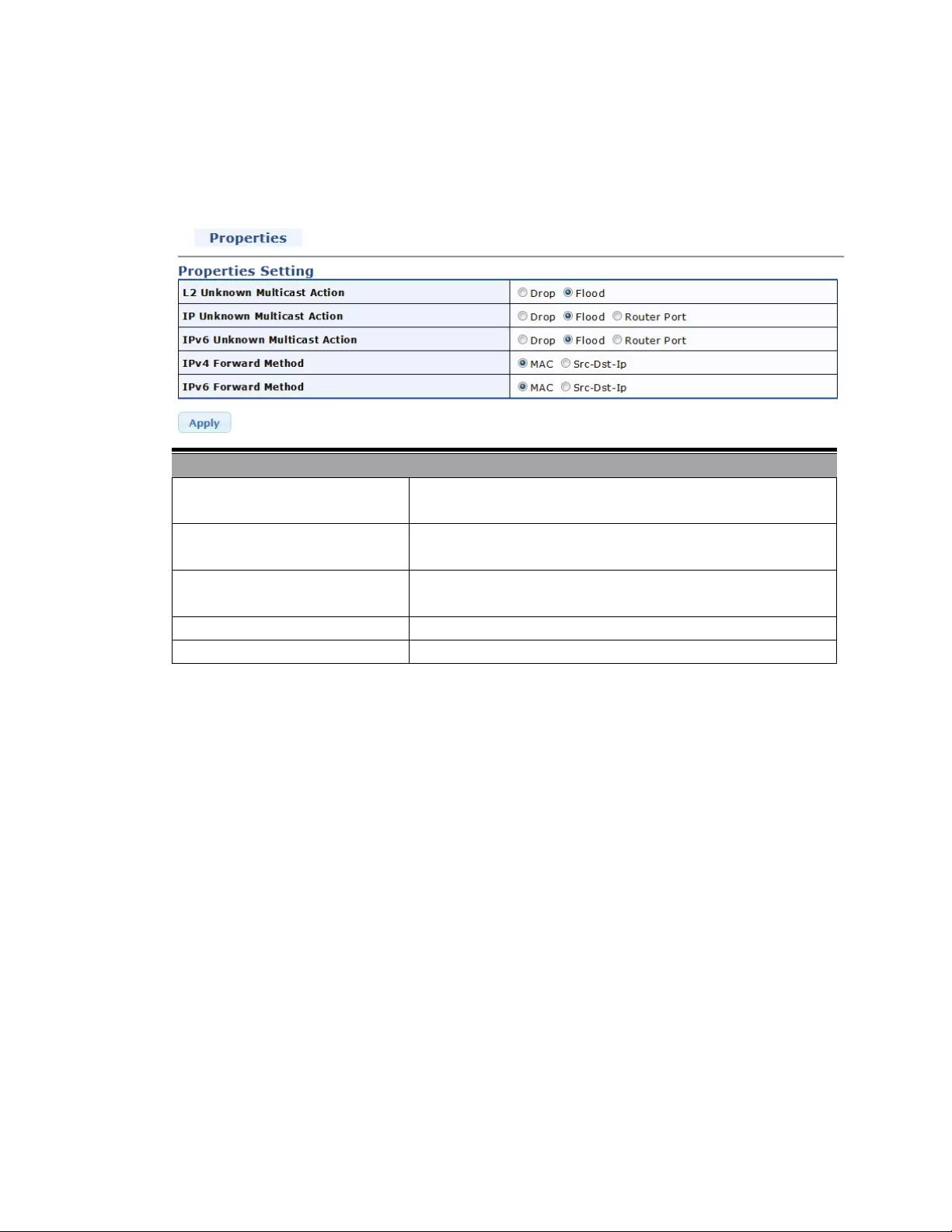
4.6.8 STPStatistics
72
4.7 Multicast
4.7.1 Properties
Thispageprovidesmulticastpropertiesrelatedconfiguration.
ParameterDescription
L2UnknownMulticastActionUnknownLayer2multicasttrafficcanbeeitherdropped,or
sendouttoallports(flood).
IPUnknownMulticastActionUnknownIPv4multicasttrafficmethod:
Drop,floodorsendtorouterport.
IPv6UnknownMulticastActionUnknownIPv6multicasttrafficmethod:
Drop,floodorsendtorouterport.
IPv4ForwardMethodForwardingbasedonMACorIPaddress.
IPv6ForwardMethodForwardingbasedonMACorIPaddress.
4.7.2 IGMPSnooping
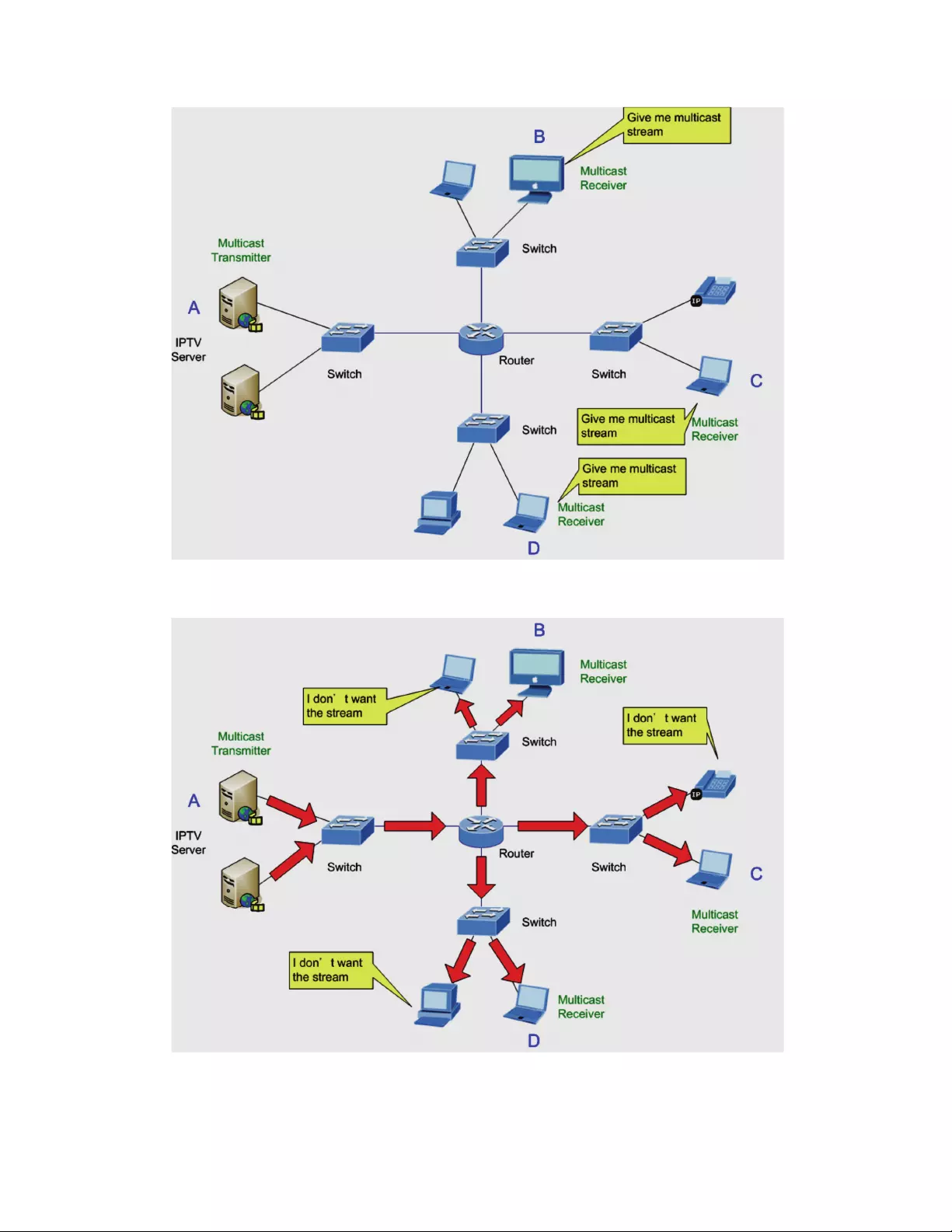
TheInternetGroupManagementProtocol(IGMP)letshostandroutersshareinformationabout
multicastgroupsmemberships.IGMPsnoopingisaswitchfeaturethatmonitorstheexchangeofIGMP
messagesandcopiesthemtotheCPUforfeatureprocessing.TheoverallpurposeofIGMPSnoopingis
tolimittheforwardingofmulticastframestoonlyportsthatareamemberofthemulticastgroup.
AbouttheInternetGroupManagementProtocol(IGMP)Snooping
Computersandnetworkdevicesthatwanttoreceivemulticasttransmissionsneedtoinformnearby
routersthattheywillbecomemembersofamulticastgroup.TheInternetGroupManagement
Protocol(IGMP)isusedtocommunicatethisinformation.IGMPisalsousedtoperiodicallycheckthe
multicastgroupformembersthatarenolongeractive.Inthecasewherethereismorethanone
multicastrouteronasubnetwork,onerouteriselectedasthe‘queried’.Thisrouterthenkeepstrack
ofthemembershipofthemulticastgroupsthathaveactivemembers.Theinformationreceivedfrom
IGMPisthenusedtodetermineifmulticastpacketsshouldbeforwardedtoagivensubnetworkor
not.Theroutercancheck,usingIGMP,toseeifthereisatleastonememberofamulticastgroupon
agivensubnetwork.Iftherearenomembersonasubnetwork,packetswillnotbeforwardedtothat
subnetwork.
73
MulticastService
MulticastFlooding
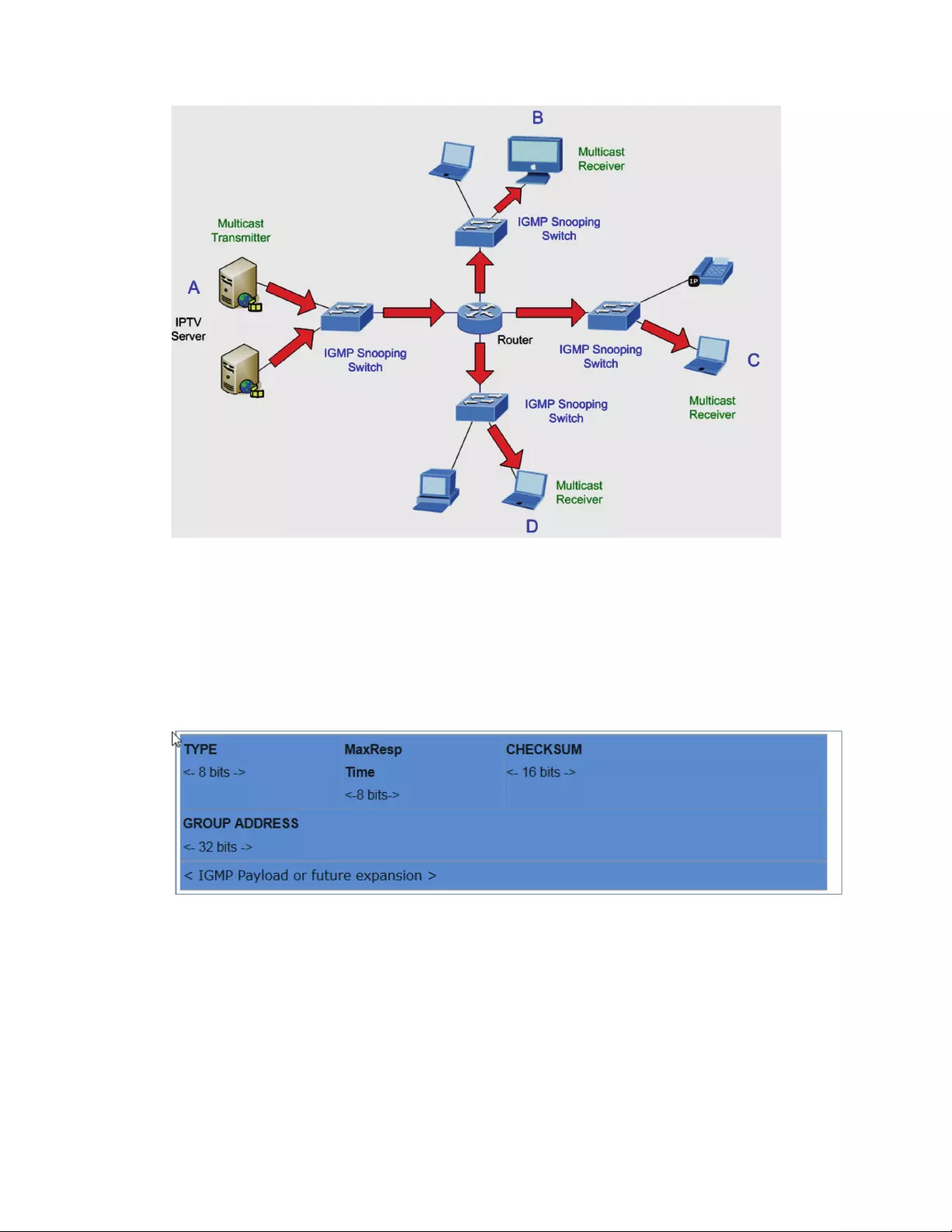
74
IGMPSnoopingMulticastStreamControl
IGMPVersions1and2
Multicastgroupsallowmemberstojoinorleaveatanytime.IGMPprovidesthemethodformembers
andmulticastrouterstocommunicatewhenjoiningorleavingamulticastgroup.IGMPversion1is
definedinRFC1112.Ithasafixedpacketsizeandnooptionaldata.
TheformatofanIGMPpacketisshownbelow:
Type
TypeofIGMPmessage.Therearethreetypes:MembershipQuery,MembershipReportand
LeaveGroup.
MaximumResponseTime
ThisfieldisusedonlyinMembershipQuerymessages.Thisfieldisthemaximumtimeahostis
allowedtoproduceandsendaMembershipReportmessageafterreceivingaMembership
Querymessage.
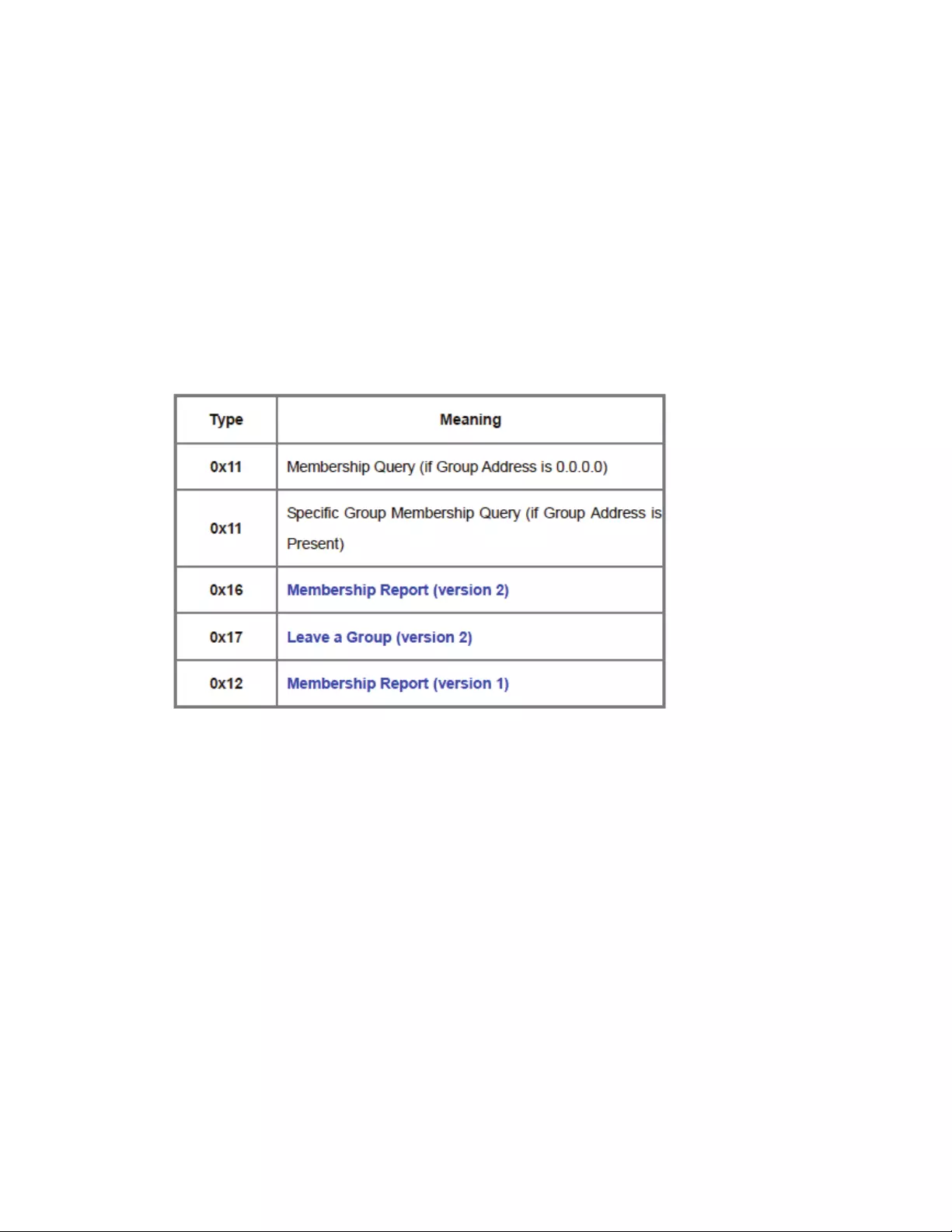
75
Checksum
Thisistheone'scomplimentoftheone'scomplementsumoftheentireIGMPmessage,which
basicallyworksouttobetheentirepayloadoftheIPdatagramtheIGMPdatagramis
encapsulatedwithin.
GroupAddress
Behaviorofthisfieldvariesbythetypeofmessagesent:
MembershipQuery:(setto)
GeneralQuery:Allzeroes
GroupSpecificQuery:multicastgroupaddress
MembershipReport:multicastgroupaddress
LeaveGroup:multicastgroupaddress
IGMPpacketsenablemulticastrouterstokeeptrackofthemembershipofmulticastgroups,ontheir
respectivesubnetworks.Thefollowingoutlineswhatiscommunicatedbetweenamulticastrouterand
amulticastgroupmemberusingIGMP.
AhostsendsanIGMP“report”tojoinagroup
Ahostwillneversendareportwhenitwantstoleaveagroup(forversion1).
Ahostwillsenda“leave”reportwhenitwantstoleaveagroup(forversion2).
MulticastrouterssendIGMPqueries(totheall‐hostsgroupaddress:224.0.0.1)periodicallytosee
whetheranygroupmembersexistontheirsubnetworks.Ifthereisnoresponsefromaparticular
group,therouterassumesthattherearenogroupmembersonthenetwork.
TheTime‐to‐Live(TTL)fieldofquerymessagesissetto1sothatthequerieswillnotbeforwardedto
othersubnetworks.
IGMPversion2introducessomeenhancementssuchasamethodtoelectamulticastqueriedforeach
LAN,anexplicitleavemessage,andquerymessagesthatarespecifictoagivengroup.Thestatesa
computerwillgothroughtojoinortoleaveamulticastgroupareshownbelow:

76
IGMPStateTransitions
IGMPQuerier–
Arouter,ormulticast‐enabledswitch,canperiodicallyasktheirhostsiftheywanttoreceivemulticast
traffic.Ifthereismorethanonerouter/switchontheLANperformingIPmulticasting,oneofthese
devicesiselected“querier”andassumestheroleofqueryingtheLANforgroupmembers.Itthen
propagatestheservicerequestsontoanyupstreammulticastswitch/routertoensurethatitwill
continuetoreceivethemulticastservice.
Note:
Multicastroutersusethisinformation,alongwithamulticastroutingprotocolsuchas
DVMRPorPIM,tosupportIPmulticastingacrosstheInternet.
4.7.2.1 IGMPSettings
ThispageprovidesIGMPSnoopingrelatedconfiguration.Mostofthesettingsareglobal,whereasthe
RouterPortconfigurationisrelatedtothecurrentunit,asreflectedbythepageheader.

77

78
4.7.2.2 IGMPSnoopingQuerierSettings
4.7.2.3 IGMPStaticGroup
MulticastfilteringcanbedynamicallyconfiguredusingIGMPSnoopingandIGMPQuerymessagesas
describedinabovesections.Forcertainapplicationsthatrequiretightercontrol,youmayneedto
staticallyconfigureamulticastserviceontheManagedSwitch.Firstaddalltheportsattachedto
participatinghoststoacommonVLAN,andthenassignthemulticastservicetothatVLANgroup.
‐Staticmulticastaddressesareneveragedout.‐Whenamulticastaddressisassignedtoaninterface
inaspecificVLAN,thecorrespondingtrafficcanonlybeforwardedtoportswithinthatVLAN.
79
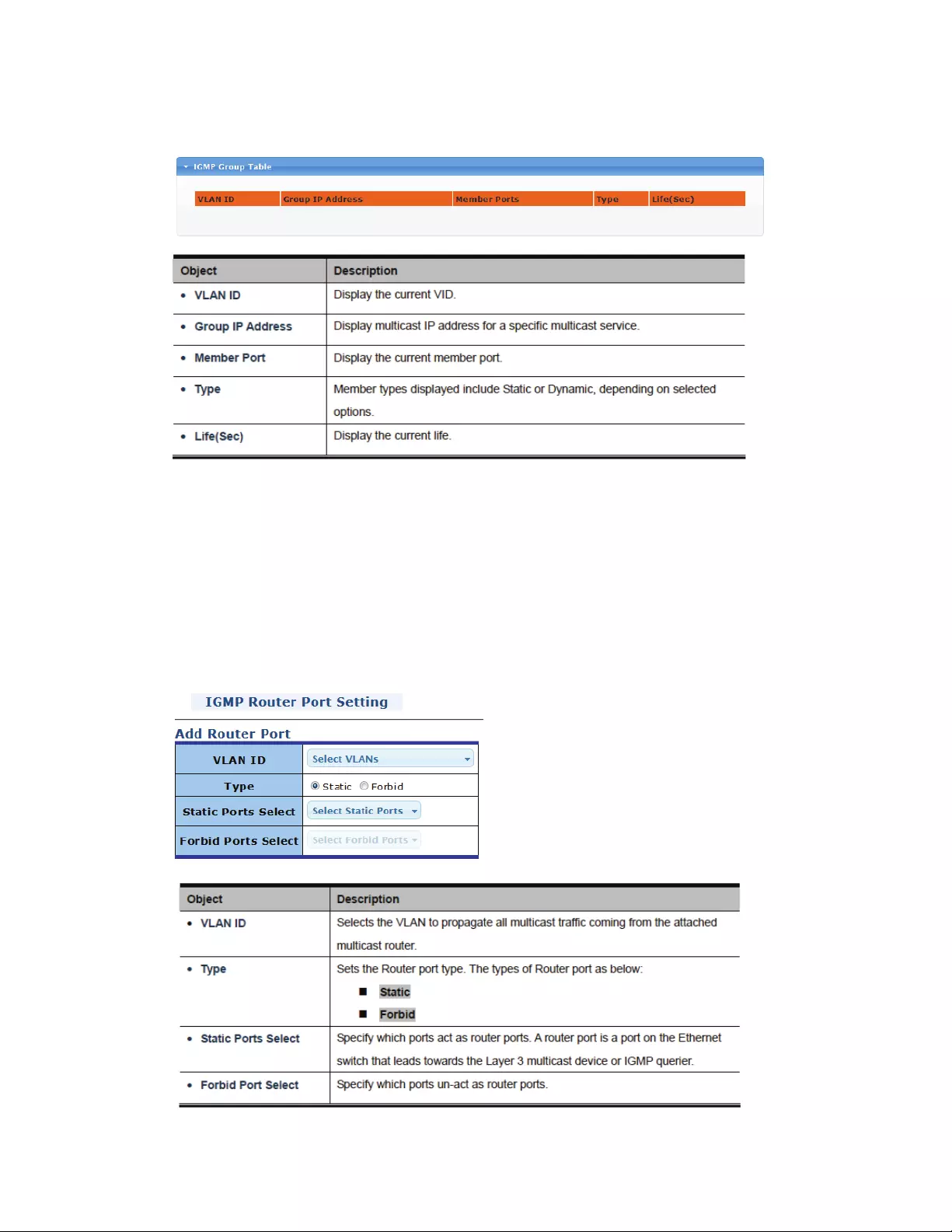
4.7.2.4 IGMPGroupTable
ThispageprovidesanoverviewoverthecurrentIGMPgrouptable(multicastdatabase).
4.7.2.5 IGMPRouterPortSettings
Dependingonyournetworkconnections,IGMPsnoopingmaynotalwaysbeabletolocatetheIGMP
querier.Therefore,iftheIGMPquerierisaknownmulticastrouter/switchconnectedoverthe
networktoaninterface(portortrunk)onyourManagedSwitch,youcanmanuallyconfigurethe
interface(andaspecifiedVLAN)tojoinallthecurrentmulticastgroupssupportedbytheattached
router.Thiscanensurethatmulticasttrafficispassedtoalltheappropriateinterfaceswithinthe
ManagedSwitch.

80
4.7.2.6 IGMPRouterTable
ThissectionprovidesstatisticalinformationaboutthecurrentIGMProutingtables.Thereareno
configurationoptionshere.
4.7.2.7 IGMPForwardAll
This page provides IGMP Forward All.

81
82
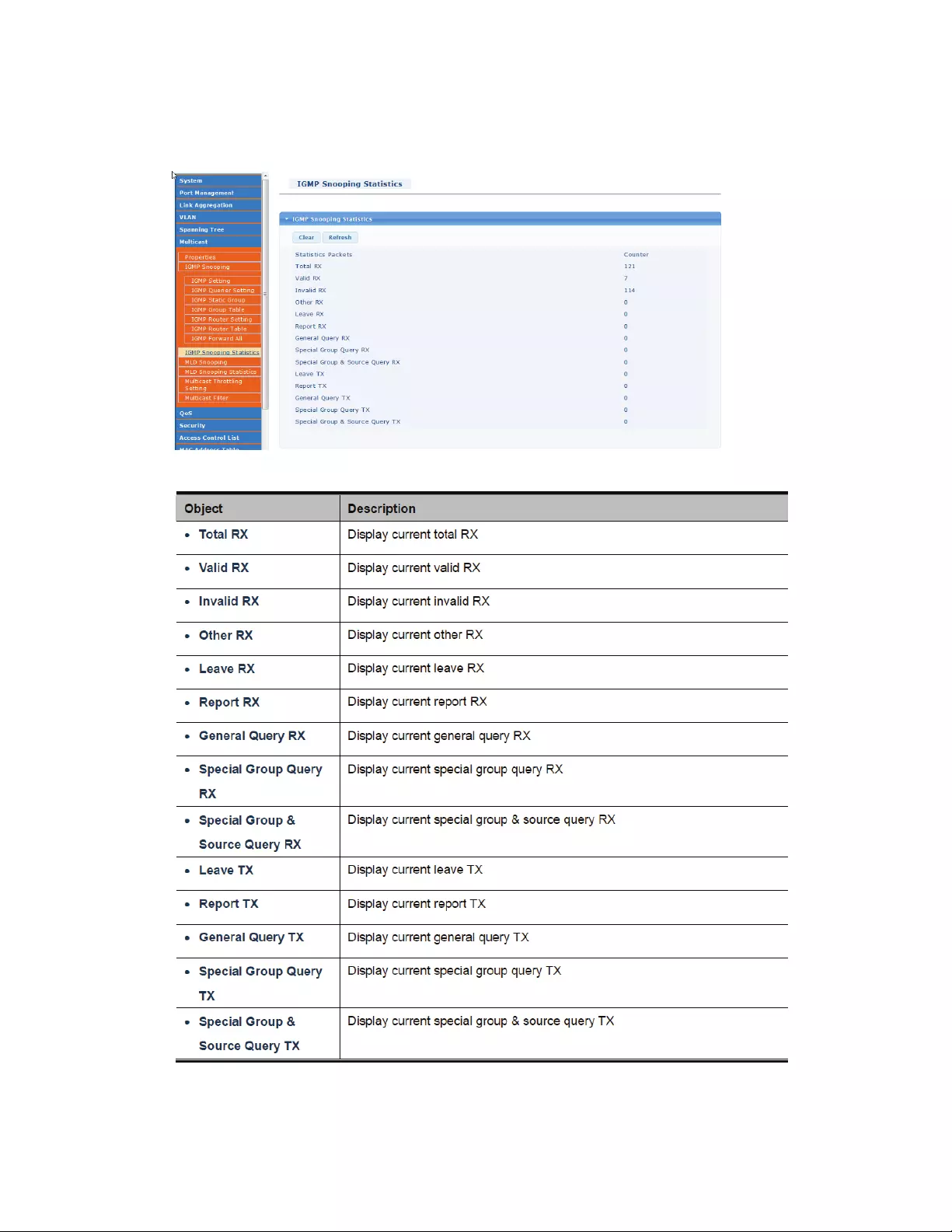
4.7.3 IGMPSnoopingStatics
ThispageprovidesIGMPSnoopingStatics.

83
4.7.4 MLDSnooping
4.7.4.1 MLDSetting
InIPv4,Layer2switchescanuseIGMPsnoopingtolimitthefloodingofmulticasttrafficbydynamically
configuringLayer2interfacessothatmulticasttrafficisforwardedtoonlythoseinterfacesassociated
withIPmulticastaddress.InIPv6,MLDsnoopingperformsasimilarfunction.WithMLDsnooping,IPv6
multicastdataisselectivelyforwardedtoalistofportsthatwanttoreceivethedata,insteadofbeing
floodedtoallportsinaVLAN.ThislistisconstructedbysnoopingIPv6multicastcontrolpackets.
MLDisaprotocolusedbyIPv6multicastrouterstodiscoverthepresenceofmulticastlisteners(nodes
configuredtoreceiveIPv6multicastpackets)onitsdirectlyattachedlinksandtodiscoverwhich
multicastpacketsareofinteresttoneighboringnodes.MLDisderivedfromIGMP;MLDversion1
(MLDv1)isequivalenttoIGMPv2,andMLDversion2(MLDv2)isequivalenttoIGMPv3.MLDisa
subprotocolofInternetControlMessageProtocolversion6(ICMPv6),andMLDmessagesareasubset
ofICMPv6messages,identifiedinIPv6packetsbyaprecedingNextHeadervalueof58.Thispage
providesMLD(MulticastListenerDiscovery)Snoopingrelatedconfiguration.Mostofthesettingsare
global,whereastheRouterPortconfigurationisrelatedtothecurrentunit,asreflectedbythepage
header.
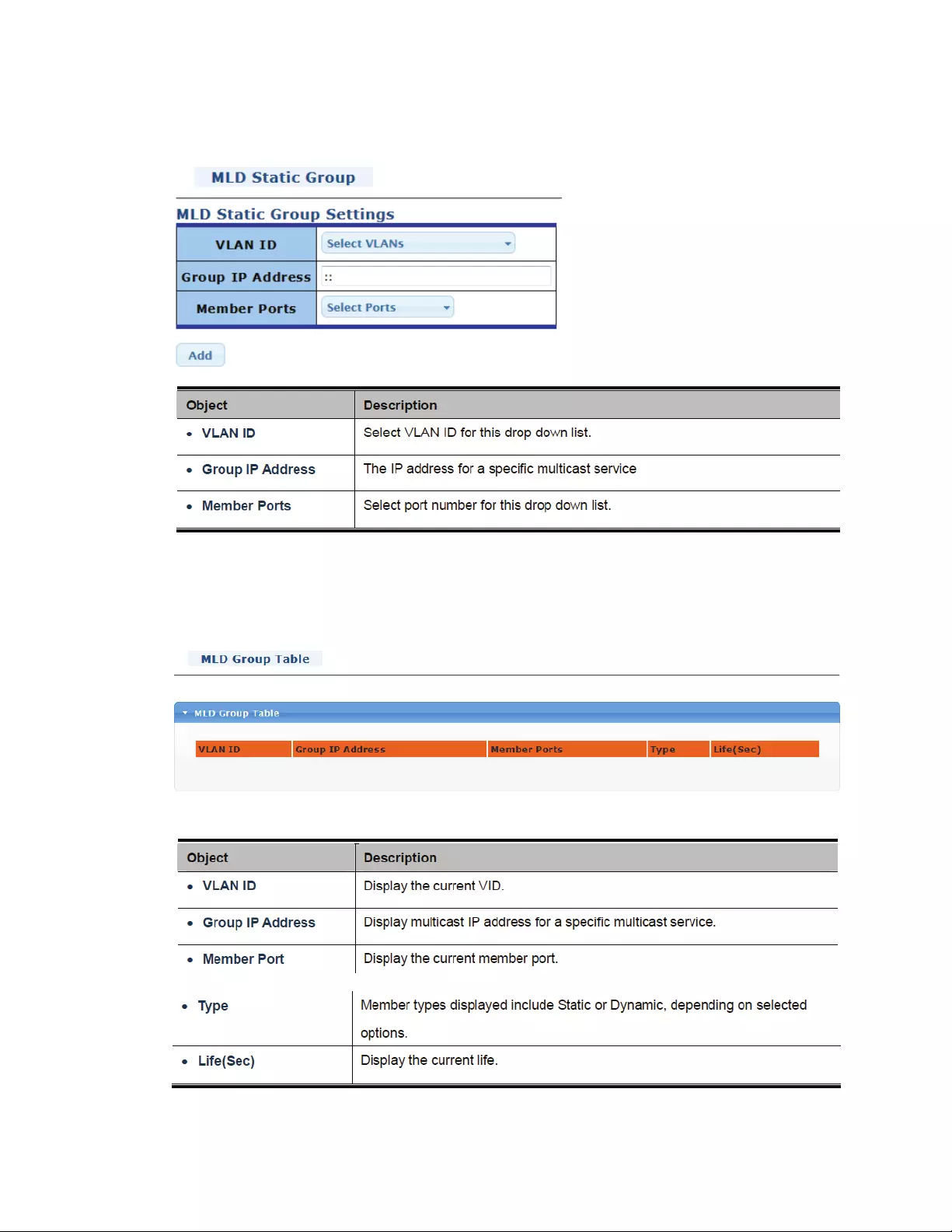
84
4.7.4.2 MLDStaticGroup
4.7.4.3 MLDGroupTable
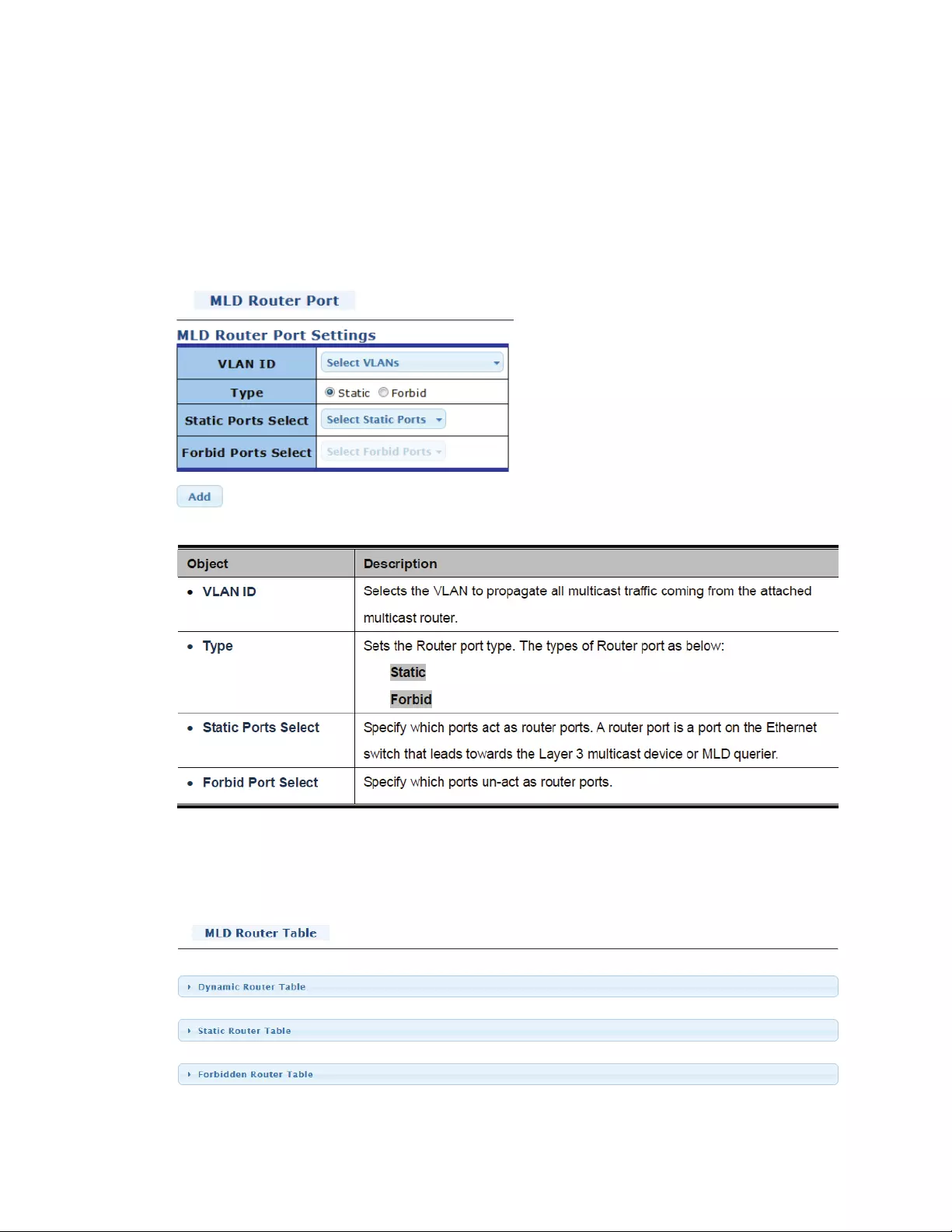
85
4.7.4.4 MLDRouterSettings
Dependingonyournetworkconnections,MLDsnoopingmaynotalwaysbeabletolocatetheMLD
querier.Therefore,iftheMLDquerierisaknownmulticastrouter/switchconnectedoverthenetwork
toaninterface(portortrunk)onyourManagedSwitch,youcanmanuallyconfiguretheinterface(and
aspecifiedVLAN)tojoinallthecurrentmulticastgroupssupportedbytheattachedrouter.Thiscan
ensurethatmulticasttrafficispassedtoalltheappropriateinterfaceswithintheManagedSwitch.
4.7.4.5 MLDRouterTable
ThispagecontainstheMLDroutertablesoftheIntellinet8‐PortGigabitPoE+Switch.
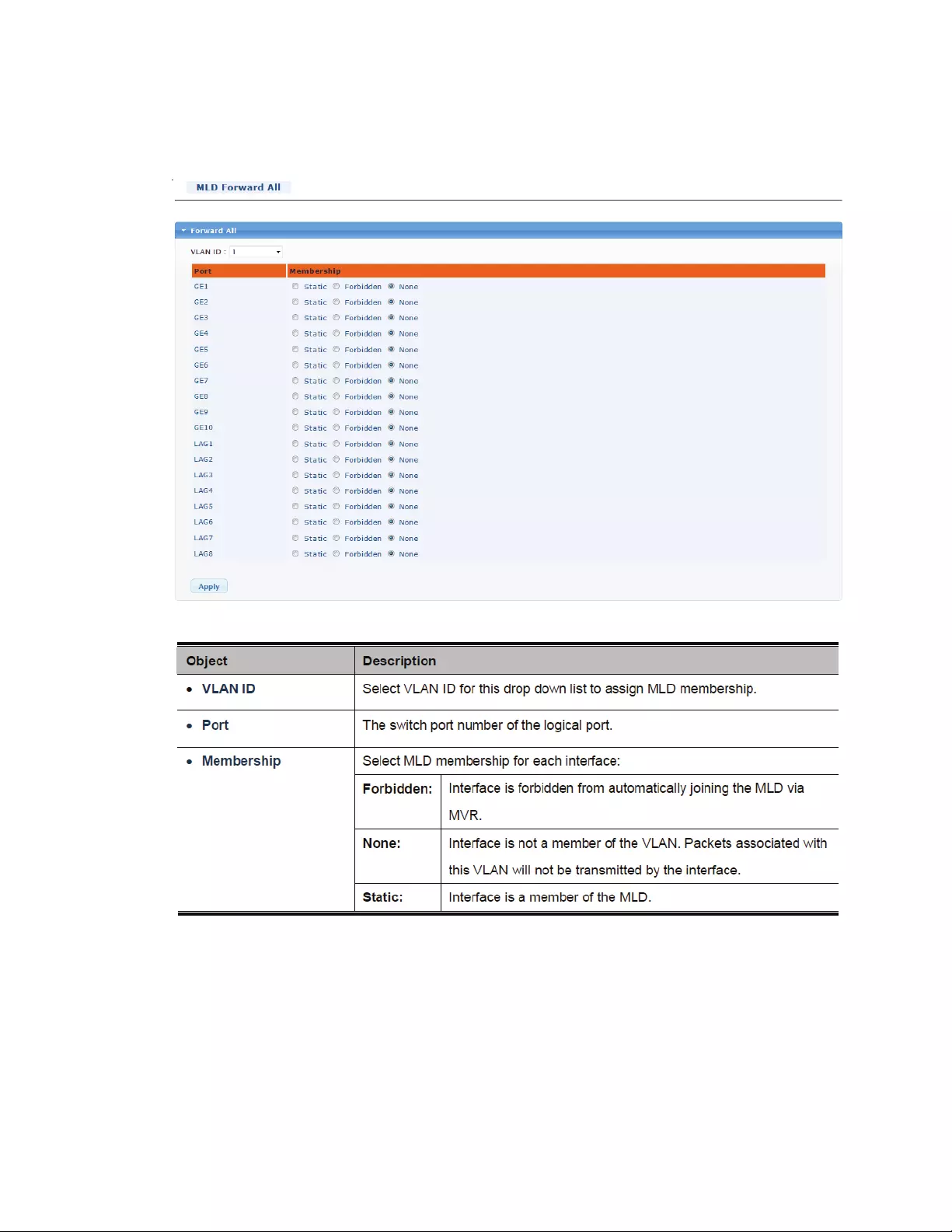
86
4.7.4.6 MLDForwardAll
DefinetheMLDForwardAllsettingsonthispage.

87
4.7.5 MLDSnoopingStatics
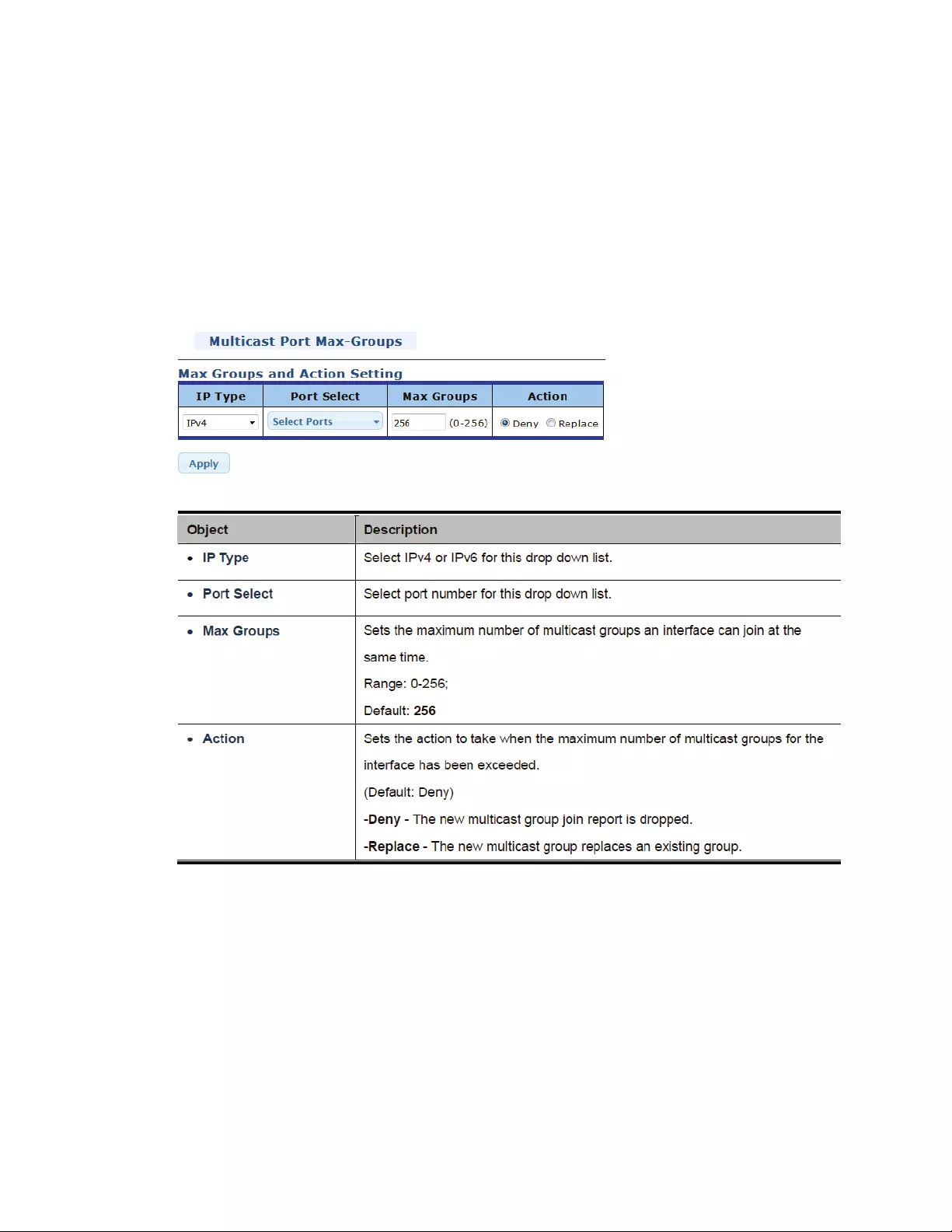
88
4.7.6 MulticastThrottlingSetting
Multicastthrottlingsetsamaximumnumberofmulticastgroupsthataportcanjoinatthesametime.
Whenthemaximumnumberofgroupsisreachedonaport,theswitchcantakeoneoftwoactions;
either“deny”or“replace”.Iftheactionissettodeny,anynewmulticastjoinreportswillbedropped.
Iftheactionissettoreplace,theswitchrandomlyremovesanexistinggroupandreplacesitwiththe
newmulticastgroup.Onceyouhaveconfiguredmulticastprofiles,youcanassignthemtointerfaces
ontheManagedSwitch.Alsoyoucansetthemulticastthrottlingnumbertolimitthenumberof
multicastgroupsaninterfacecanjoinatthesametime.
4.7.7 MulticastFilter
Incertainswitchapplications,theadministratormaywanttocontrolthemulticastservicesthatare
availabletoendusers.Forexample,anIP/TVserviceisbasedonaspecificsubscriptionplan.The
multicastfilteringfeaturefulfillsthisrequirementbyrestrictingaccesstospecifiedmulticastservices
onaswitchport.Multicastfilteringenablesyoutoassignaprofiletoaswitchportthatspecifies
multicastgroupsthatarepermittedordeniedontheport.Amulticastfilterprofilecancontainoneor
more,orarangeofmulticastaddresses;butonlyoneprofilecanbeassignedtoaport.
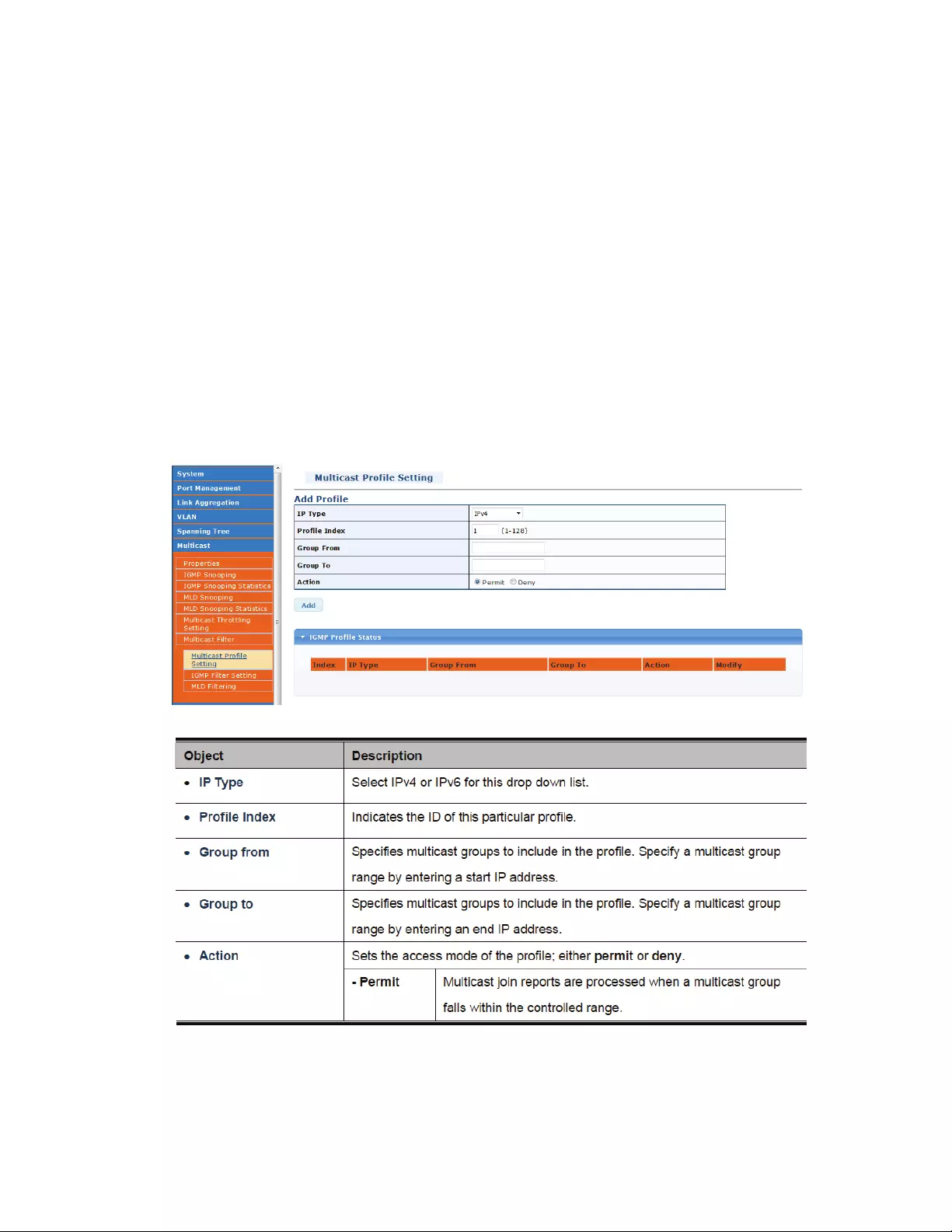
89
Whenenabled,multicastjoinreportsreceivedontheportarecheckedagainstthefilterprofile.Ifa
requestedmulticastgroupispermitted,themulticastjoinreportisforwardedasnormal.Ifa
requestedmulticastgroupisdenied,themulticastjoinreportisdropped.
WhenyouhavecreatedaMulticastprofilenumber,youcanthenconfigurethemulticastgroupsto
filterandsettheaccessmode.
CommandUsage
Eachprofilehasonlyoneaccessmode;eitherpermitordeny.
Whentheaccessmodeissettopermit,multicastjoinreportsareprocessedwhenamulticast
groupfallswithinthecontrolledrange.
Whentheaccessmodeissettodeny,multicastjoinreportsareonlyprocessedwhenthe
multicastgroupisnotinthecontrolledrange.
4.7.7.1 MulticastProfileSetting
90
4.7.7.2 IGMPFilterSetting
4.7.7.3 MLDFilterSetting

91
4.8 QoS‐QualityofService
4.8.1 General/WhatisQoS?
QualityofService(QoS)isanadvancedtrafficprioritizationfeaturethatallowsyoutoestablishcontrol
overnetworktraffic.QoSenablesyoutoassignvariousgradesofnetworkservicetodifferenttypesof
traffic,suchasmulti‐media,video,protocol‐specific,timecritical,andfile‐backuptraffic.
QoSreducesbandwidthlimitations,delay,loss,andjitter.Italsoprovidesincreasedreliabilityfor
deliveryofyourdataandallowsyoutoprioritizecertainapplicationsacrossyournetwork.Youcan
defineexactlyhowyouwanttheswitchtotreatselectedapplicationsandtypesoftraffic.
YoucanuseQoSonyoursystemtocontrolawidevarietyofnetworktrafficby:
Classifyingtrafficbasedonpacketattributes.
Assigningprioritiestotraffic(forexample,tosethigherprioritiestotime‐criticalorbusiness‐
criticalapplications).
Applyingsecuritypolicythroughtrafficfiltering.
Providepredictablethroughputformultimediaapplicationssuchasvideoconferencingorvoice
overIPbyminimizingdelayandjitter.Improveperformanceforspecifictypesoftrafficand
preserveperformanceastheamountoftrafficgrows.
Reducetheneedtoconstantlyaddbandwidthtothenetwork.
Managenetworkcongestion.
ToimplementQoSonyournetwork,youneedtocarryoutthefollowingactions:
1. Defineaserviceleveltodeterminetheprioritythatwillbeappliedtotraffic.
2. Applyaclassifiertodeterminehowtheincomingtrafficwillbeclassifiedandthustreatedbythe
Switch.
3. CreateaQoSprofilewhichassociatesaservicelevelandaclassifier.
4. ApplyaQoSprofiletoaport(s).
TheQoSpageoftheManagedSwitchcontainsthreetypesofQoSmode‐the802.1pmode,DSCP
modeorPort‐basemodecanbeselected.Boththethreemoderelyonpredefinedfieldswithinthe
packettodeterminetheoutputqueue.
802.1pTagPriorityMode–TheoutputqueueassignmentisdeterminedbytheIEEE802.1pVLAN
prioritytag.
IPDSCPMode‐TheoutputqueueassignmentisdeterminedbytheTOSorDSCPfieldintheIP
packets.
Port‐BasePriorityMode–Anypacketreceivedfromthespecifyhighpriorityportwilltreatedasa
highprioritypacket.
TheManagedSwitchsupportseightprioritylevelqueue,thequeueservicerateisbasedontheWRR
(WeightRoundRobin)andWFQ(WeightedFairQueuing)algorithm.TheWRRratioofhigh‐priorityand
low‐prioritycanbesetto“4:1and8:1.4.8.2General
92
4.8.1.1 QoSProperties
OnthisscreenyoucanactivateordeactivateQoS.
ParameterDescription
QoSModeDisable:QoSisdeactivated.
Basic:QoSisenabledinbasicmode.
Basic:QoSisenabledinadvancedmode.
Note:
InQoSadvancedmode,theIntellinet8‐PortGigabitPoE+switchusespoliciestosupportper‐flowQoS.
Thepolicyanditscomponentshavethefollowingcharacteristics:
• Apolicymaycontainsoneormoreclassmaps.
• Apolicycontainsoneormoreflows,eachwithauserdefinedQoS.
• AsinglepolicerappliestheQoStoasingleclassmap,andthustoasingleflow,basedonthe
policerQoSspecification.
• AnaggregatepolicerappliestheQoStooneormoreclassmaps,andthusoneormoreflows.
• PerflowQoSareappliedtoflowsbybindingthepoliciestothedesiredports.
4.8.1.2 QoSPortSettings
TheQoSPortSettingsandStatusscreen.
93
4.8.1.3 QueueSettings
Definetheschedulingmethodofthe8QoSqueuesonthisconfigurationscreen.
4.8.1.4 CoSMapping
ThisscreencontrolstomappingofClassofService(CoS)tothequeues.
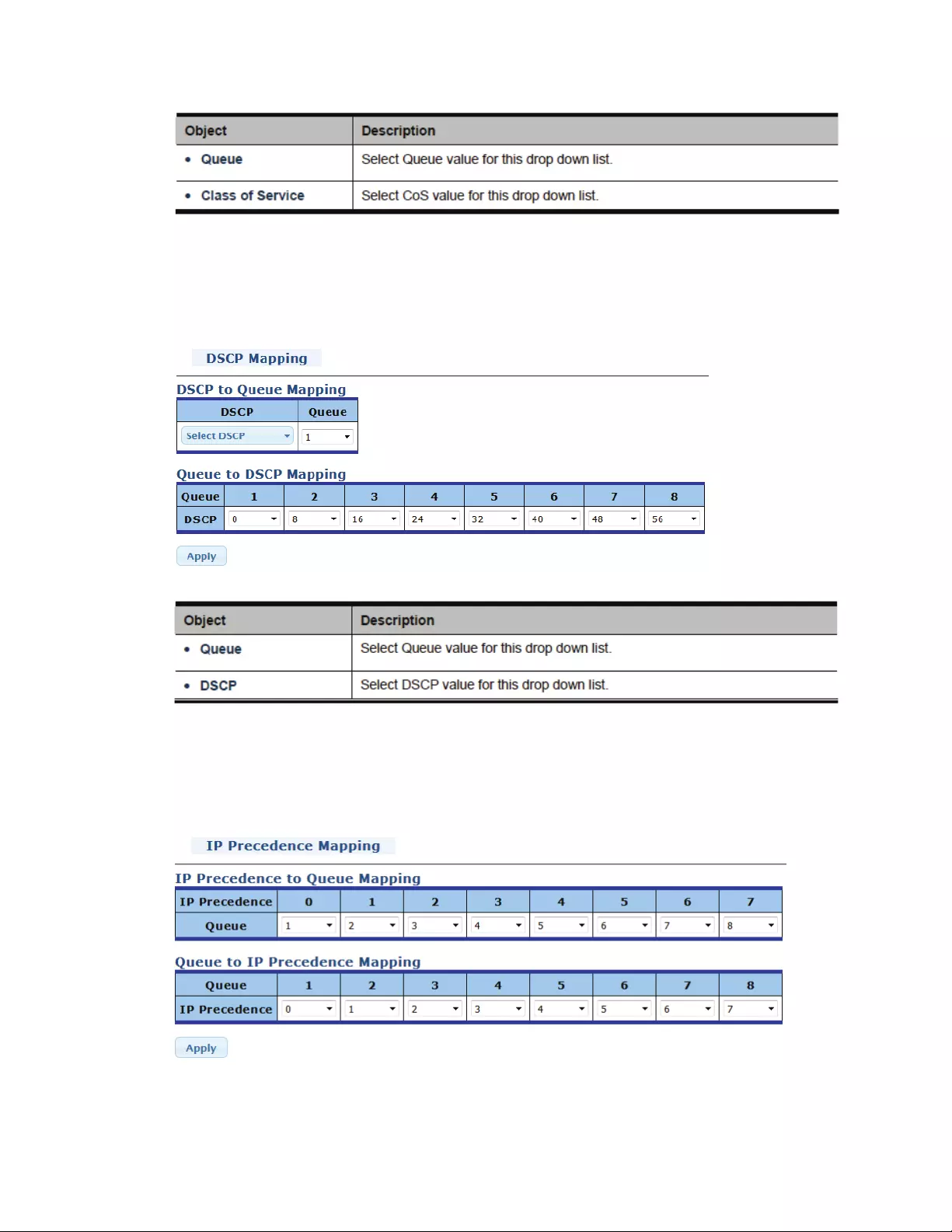
94
4.8.1.5 DSCPMapping
TheDSCPtoQueueandQueuetoDSCPMappingscreen
4.8.1.6 IPPrecedenceMapping
TheIPPrecedencetoQueueandQueuetoIPPrecedenceMappingscreen.
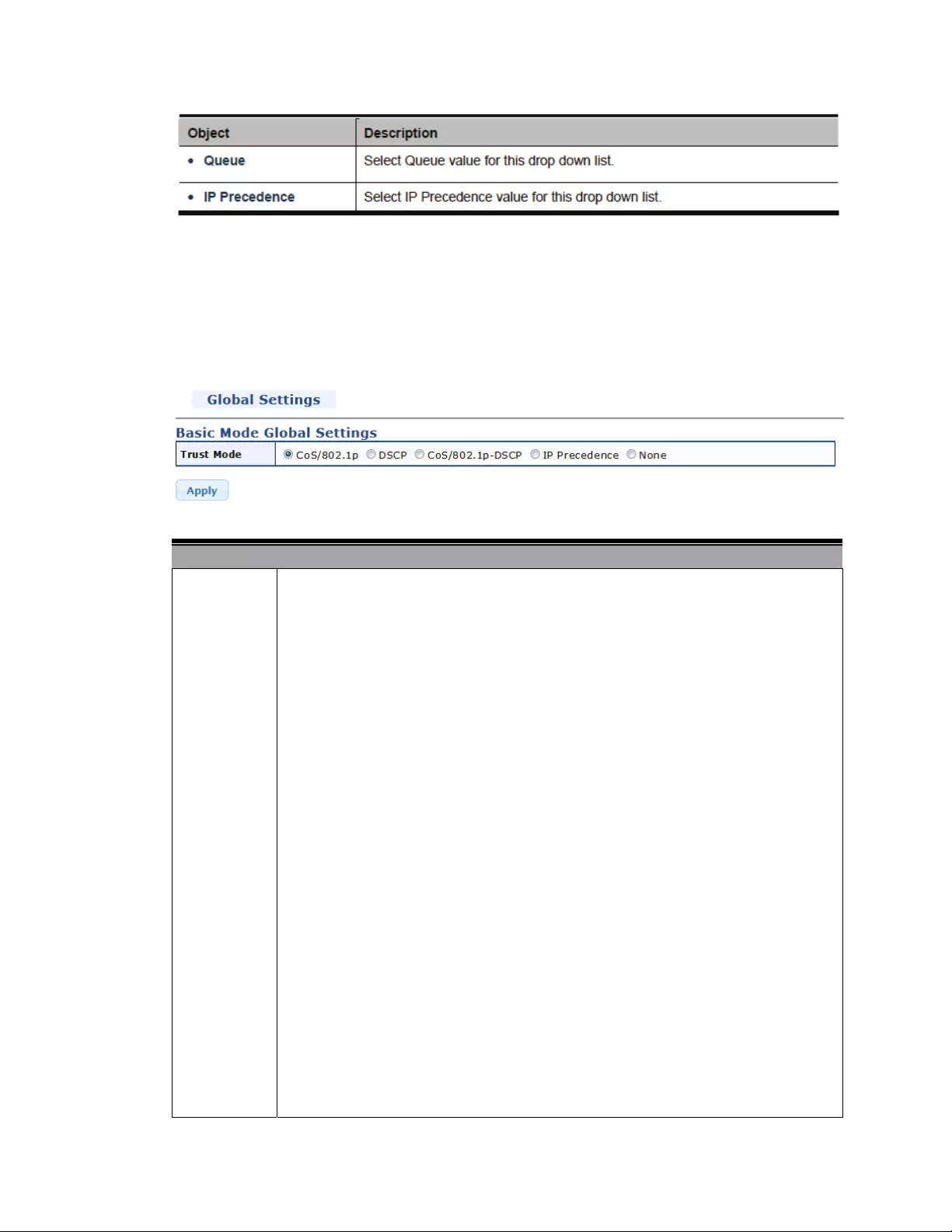
95
4.8.2 QoSBasicMode
4.8.2.1 GlobalSettings
OnthisinterfacescreenyoucandefinetheQoStrustmode.
ParameterDescription
TrustModeCoS/802.1p—ThisisaLayer2QoSwheretrafficismappedtoqueuesbasedonthe
VLANPriorityTag(VPT)fieldintheVLANtag.IfthereisnoVLANtagonthe
incomingpacket,thetrafficismappedtoqueuesbasedontheper‐portdefault
CoS/802.1pvalue.
DSCP—ThisisaLayer3QoS.WhereallIPtrafficismappedtoqueuesbasedonthe
DSCPfieldintheIPheader.IfthetrafficisnotIPtraffic,itismappedtothebest
effortqueue.
CoS/802.1p‐DSCP—Allnon‐IPtrafficismappedthroughtheuseofCoS/802.1p.All
IPtrafficismappedthroughDSCP.
IPPrecedence—TheIPheaderhasafieldcalledtheTypeofService(TOS)that
sitsbetweentheHeaderLengthfieldandtheTo talLengthfield.IPPrecedence
usesthefirstthreebitsoftheTOSfieldtogive8possibleprecedencevalues.
000(0)‐Routine
001(1)‐Priority
010(2)‐Immediate
011(3)‐Flash
100(4)‐FlashOverride
101(5)‐Critical
110(6)‐InternetworkControl
111(7)‐NetworkControl

96
4.8.2.2 QoSPortSetting
Oncethetrustmodehasbeenproperlyconfigured,thenextstepistochoosetheinterfaces(switch
port)towhichQoSisapplied.
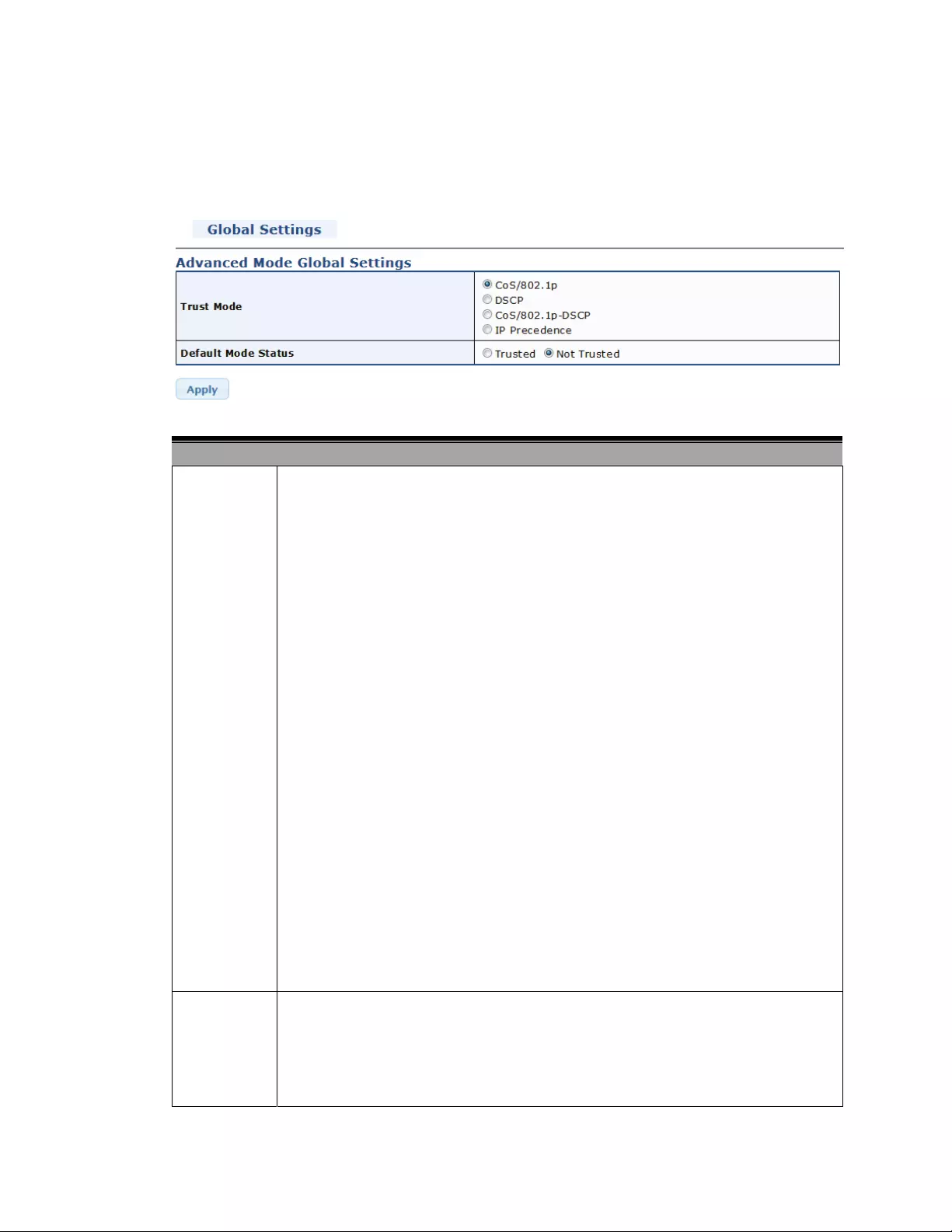
97
4.8.3 QoSAdvancedMode
4.8.3.1 GlobalSettings
OnthisinterfacescreenyoucandefinetheQoStrustmode.
ParameterDescription
TrustModeCoS/802.1p—ThisisaLayer2QoSwheretrafficismappedtoqueuesbasedonthe
VLANPriorityTag(VPT)fieldintheVLANtag.IfthereisnoVLANtagonthe
incomingpacket,thetrafficismappedtoqueuesbasedontheper‐portdefault
CoS/802.1pvalue.
DSCP—ThisisaLayer3QoS.WhereallIPtrafficismappedtoqueuesbasedonthe
DSCPfieldintheIPheader.IfthetrafficisnotIPtraffic,itismappedtothebest
effortqueue.
CoS/802.1p‐DSCP—Allnon‐IPtrafficismappedthroughtheuseofCoS/802.1p.All
IPtrafficismappedthroughDSCP.
IPPrecedence—TheIPheaderhasafieldcalledtheTypeofService(TOS)thatsits
betweentheHeaderLengthfieldandtheTotalLengthfield.IPPrecedenceuses
thefirstthreebitsoftheTOSfieldtogive8possibleprecedencevalues.
000(0)‐Routine
001(1)‐Priority
010(2)‐Immediate
011(3)‐Flash
100(4)‐FlashOverride
101(5)‐Critical
110(6)‐InternetworkControl
111(7)‐NetworkControl
Default
ModeStatus
Clicktheradiobuttonthatcorrespondstothedesiredmodestatus.Thisprovidesa
waytotrustCoS/DSCPwithouttheneedtocreateapolicy.
•Trusted—TrustCoS/DSCP.
•NotTrusted—DonottrustCoS/DSCP.ThedefaultCoSvaluesconfiguredonthe
interfaceareusedtoprioritizethetrafficthatarrivesontheinterface.
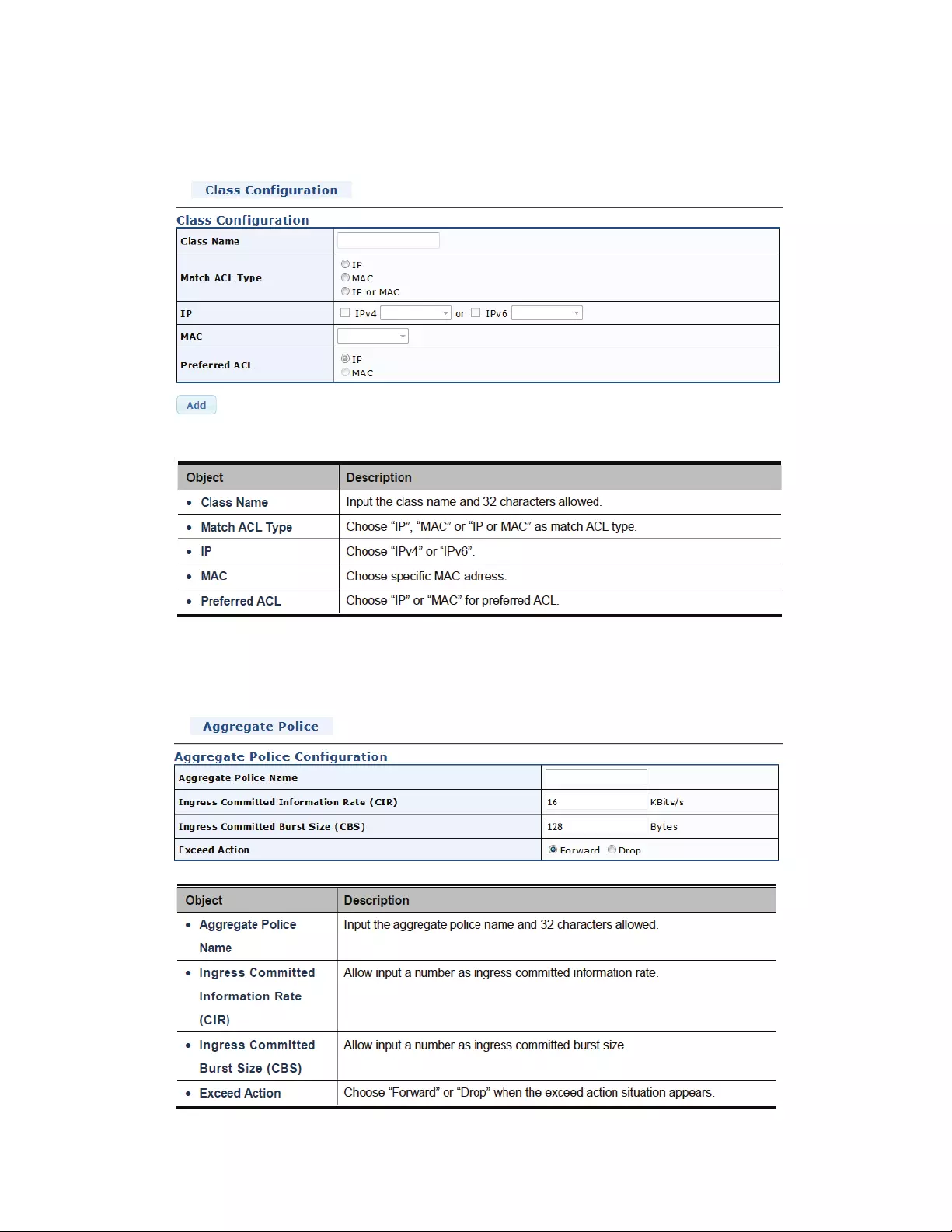
98
4.8.3.2 ClassConfiguration
QoSclassmappingisconfiguredonthispage.
4.8.3.3 AggregatePolice
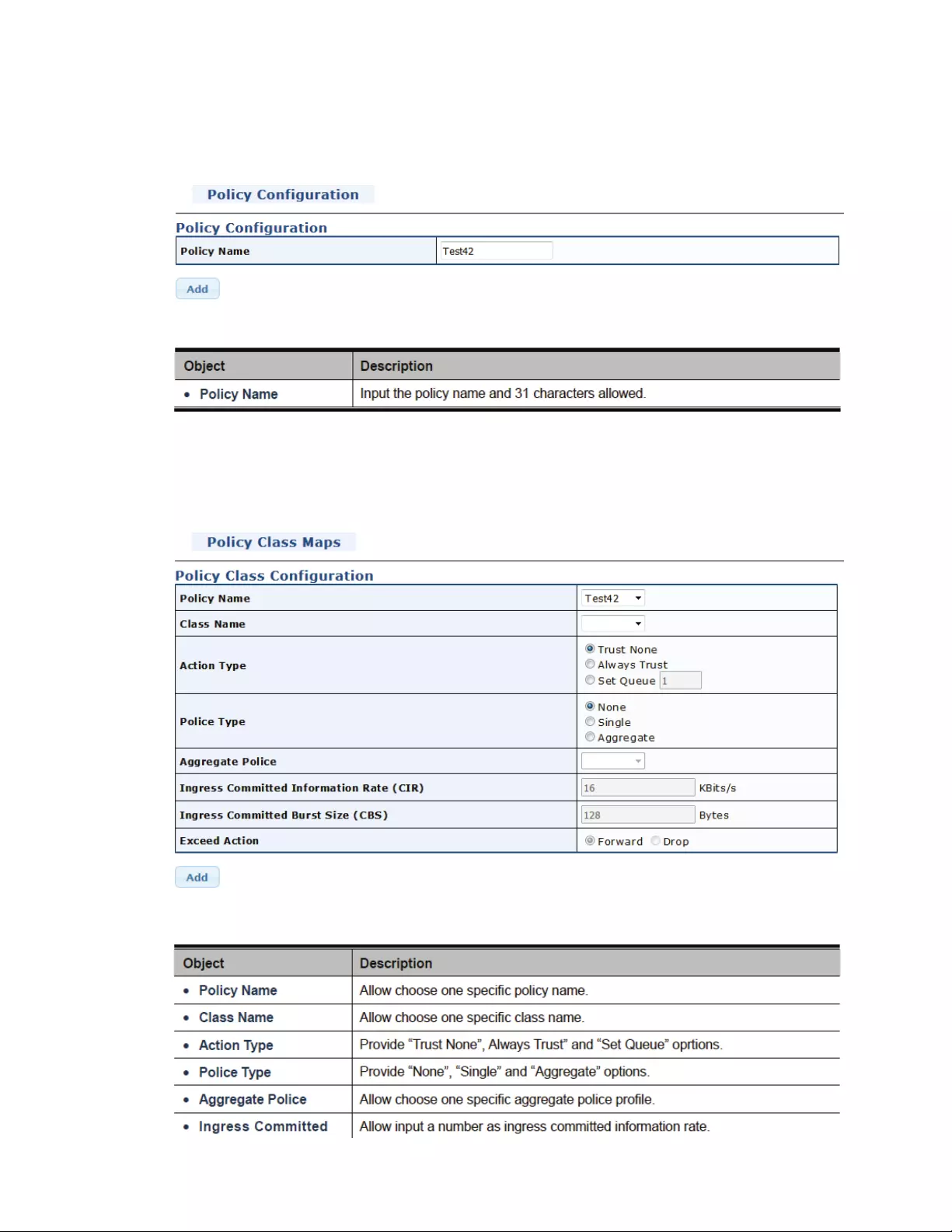
99
4.8.3.4 PolicyConfiguration
Provideanameforapolicyonthispage.
4.8.3.5 PolicyClassMaps
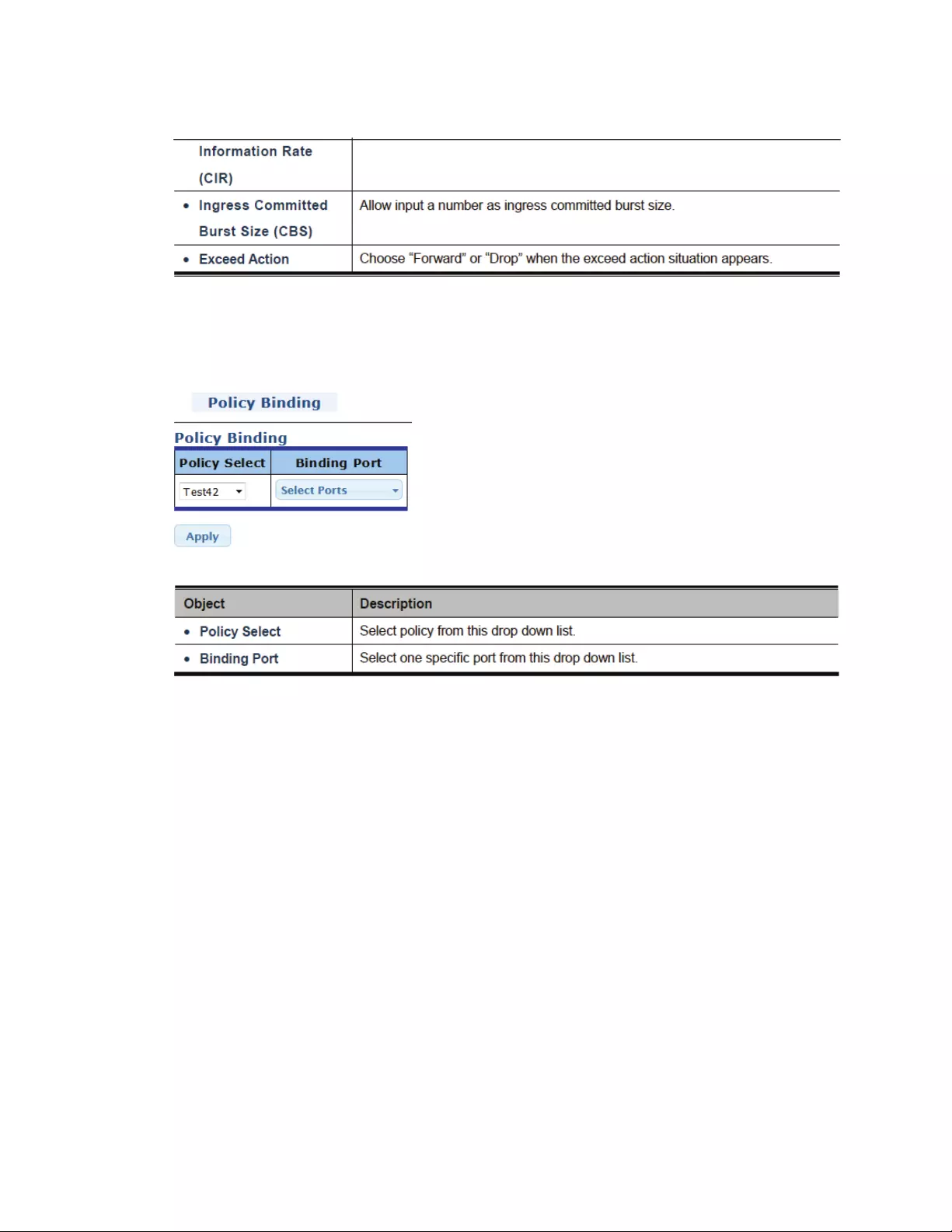
100
4.8.3.6 PolicyBinding
Onthispageyoucanlinkthepoliciestoaninterface(Networkport,orLAG).

101
4.8.4 RateLimit
Policing,orratelimiting,allowsyoutomonitorthedataratesforaparticularclassoftraffic.Whenthe
datarateexceedsuser‐configuredvalues,theIntellinetswitchdropspacketsimmediately.Because
policingdoesnotbufferthetraffic;transmissiondelaysarenotaffected.Whentrafficexceedsthedata
rateonaspecificclass,theswitchdropsthepackets.
Ratelimitingisconfiguredfortwotypesoftransmissions,whichareingressandegress.Ingresstraffic
isreceivedonanygivenport(incoming,orinbound),whereasegresstrafficistrafficsentout
(outgoing,outbound)toanothernetworkclient.
4.8.4.1 IngressBandwidthControl
Controlinboundbandwidthusagewiththisconfigurationscreen.
ParameterDescription
BurstSizeThemaximumsizepermittedforburstsofdata.Burstsizesaremeasuredin
bytes.Werecommendthisformulaforcalculatingthecorrectburstsize:
Burstsize=bandwidthxallowabletimeforbursttraffic/8.
PortPorts1to10.
StateDisableorenabletheingressbandwidthcontrol.
Rate(kbps)Theaveragenumberofkilobitspersecondpermittedforpacketsreceivedat
theinterface.Youcanspecifythebandwidthlimitasanabsolutenumberof
kilobitspersecond.
102
4.8.4.2 VLANIngressRateLimit
TrafficlimitingonVLANscanbeachievedbyratelimitingperVLAN.Ingresstrafficisthetrafficwhich
comesintotheportsoftheswitch.WhenVLANingressratelimitingisconfigured,itconstrainsthe
trafficfromalltheportsontheswitch.
ParameterDescription
VLANVLANID.
PortPorts1to10,LAG1toLAG8.
StateDisableorenabletheingressbandwidthcontrol.
Rate(kbps)Theaveragenumberofkilobitspersecondpermittedforpacketsreceivedat
theinterface.Youcanspecifythebandwidthlimitasanabsolutenumberof
kilobitspersecond.
4.8.4.3 EgressBandwidthControl
Theconfigurationoftheegressbandwidthisthesameastheingressbandwidth.SeesectionIngress
BandwidthControlabovefordetails.

103
4.8.4.4 EgressQueueBandwidthControl
Egressshapingperqueuelimitsthetransmissionrateofselectedoutgoingframesonaperqueue,per
portbasis.Todothis,theswitchshapes,orlimitstheoutputload.Thisdoesnotincludemanagement
frames,sotheydonotcounttowardstheratelimit.Egressqueuebandwidthcontrolisusedtohelp
preventcongestionforyourISP(InternetServiceProvider).
ParameterDescription
BurstSizeThemaximumsizepermittedforburstsofdata.Burstsizesaremeasuredin
bytes.Werecommendthisformulaforcalculatingthecorrectburstsize:
Burstsize=bandwidthxallowabletimeforbursttraffic/8.
PortPorts1to10.
QueueSelectthequeuefrom1to8.
StateDisableorenabletheingressbandwidthcontrol.
CIR(kbps)Thecommittedinformationrateinkilobitspersecond.
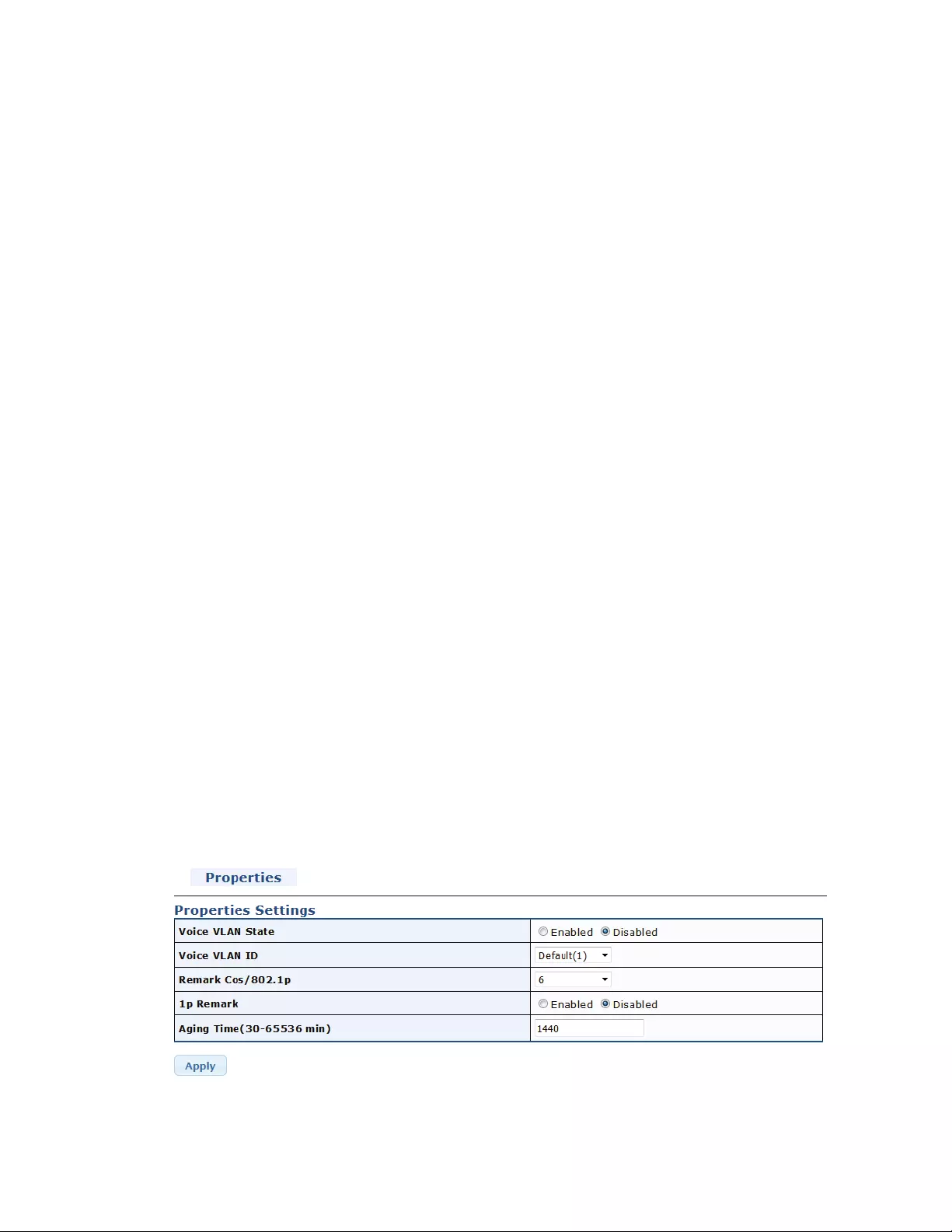
104
4.8.5 VoiceVLAN
4.8.5.1 WhatisVoiceVLAN?
VoiceVLANisspeciallyconfiguredforuservoicedatatraffic.BysettingaVoiceVLANandaddingthe
portsoftheconnectedvoicedevicetoVoiceVLAN,theuserwillbeabletoconfigureQoS(Qualityof
service)serviceforvoicedata,andimprovevoicedatatraffictransmissionprioritytoensurethecalling
quality.TheIntellinetswitchcanjudgeifthedatatrafficisthevoicedatatrafficfromspecified
equipmentaccordingtothesourceMACaddressfieldofthedatapacketenteringtheport.Thepacket
withthesourceMACaddresscomplyingwiththesystemdefinedvoiceequipmentOUI
(OrganizationallyUniqueIdentifier)willbeconsideredthevoicedatatrafficandtransmittedtothe
VoiceVLAN.
TheconfigurationisbasedonMACaddress,acquiringamechanisminwhicheveryvoiceequipment
transmittinginformationthroughthenetworkhasgotitsuniqueMACaddress.VLANwilltracethe
addressbelongstospecifiedMAC.ByThismeans,VLANallowsthevoiceequipmentalwaysbelongto
VoiceVLANwhenrelocatedphysically.ThegreatestadvantageoftheVLANistheequipmentcanbe
automaticallyplacedintoVoiceVLANaccordingtoitsvoicetrafficwhichwillbetransmittedat
specifiedpriority.Meanwhile,whenvoiceequipmentisphysicallyrelocated,itstillbelongstothe
VoiceVLANwithoutanyfurtherconfigurationmodification,whichisbecauseitisbasedonvoice
equipmentotherthanswitchport.
Note:
TheVoiceVLANfeatureenablesthevoicetraffictoforwardontheVoiceVLAN,andthentheswitchcan
beclassifiedandscheduledtonetworktraffic.ItisrecommendedtherearetwoVLANsonaport‐‐one
forvoice,onefordata.BeforeconnectingtheIPdevicetotheswitch,theIPphoneshouldconfigurethe
voiceVLANIDcorrectly.ItshouldbeconfiguredthroughitsownGUI.
4.8.5.2 Properties
TheVoiceVLANfeatureenablesvoicetraffictoforwardontheVoiceVLAN,andthentheIntellinet
switchcanbeclassifiedandscheduledtonetworktraffic.ItisrecommendedthattherearetwoVLANs
onaport‐‐oneforvoiceandonefordata.BeforeconnectingtheIPdevicetotheswitch,theIPphone
shouldconfigurethevoiceVLANIDcorrectlythroughitsownGUI.

105
4.8.5.3 Telephony OUI MAC
ConfigureVOICEVLANOUItableonthispage.
EachIPphonemanufacturercanbeidentifiedbyoneormoreOrganizationUniqueIdentifiers(OUIs).
AnOUIisthreebyteslongandisusuallyexpressedinhexadecimalformat.Itisimbeddedintothefirst
partofeachMACaddressofanEthernetnetworkdevice.YoucanfindtheOUIofanIPphoneinthe
firstthreecompletebytesofitsMACaddress.Typically,youwillfindthatalloftheIPphonesyouare
installinghavethesameOUIincommon.
The8‐PortIntellinetswitchidentifiesavoicedatapacketbycomparingtheOUIinformationinthe
packet’ssourceMACaddresswithanOUItablethatyouconfigurewhenyouinitiallysetupthevoice
VLAN.ThisisimportantwhentheAuto‐DetectionfeatureforaportandisadynamicvoiceVLANport.
WhenyouareconfiguringthevoiceVLANparameters,youmustenterthecompleteMACaddressofat
leastoneofyourIPphones.An“OUIMask”isautomaticallygeneratedandappliedbytheAT‐S107
managementsoftwaretoyieldthemanufacturer’sOUI.IftheOUIoftheremainingphonesfromthat
manufactureristhesame,thennootherIPphoneMACaddressesneedtobeenteredintothe
configuration.
However,itispossiblethatyoucanfindmorethanoneOUIfromthesamemanufactureramongtheIP
phonesyouareinstalling.ItisalsopossiblethatyourIPphonesarefromtwoormoredifferent
manufacturersinwhichcaseyouwillfinddifferentOUIsforeachmanufacturer.Ifyouidentifymore
thanoneOUIamongtheIPphonesbeinginstalled,thenoneMACaddressrepresentingeach
individualOUImustbeconfiguredinthevoiceVLAN.Youcanenteratotalof10OUIs.

106
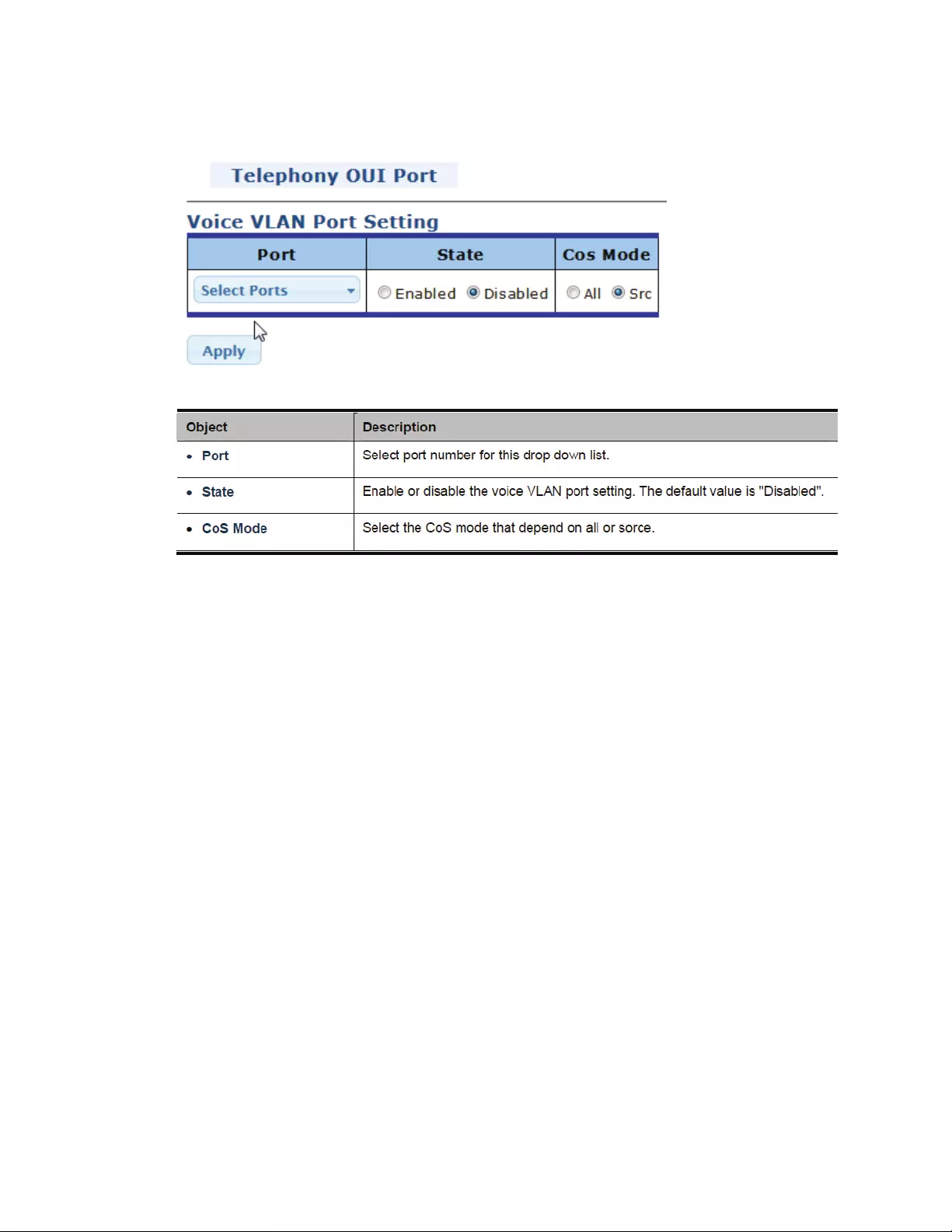
107
4.8.5.4 Telephony OUI Port

108
4.9 Security
4.9.1 StormControl
4.9.1.1 GlobalSettings
4.9.1.2 PortSettings

109
4.9.2 802.1x
Inthe802.1X‐world,theuseriscalledthesupplicant,theswitchistheauthenticator,andtheRADIUS
serveristheauthenticationserver.Theswitchactsastheman‐in‐the‐middle,forwardingrequestsand
responsesbetweenthesupplicantandtheauthenticationserver.Framessentbetweenthesupplicant
andtheswitcharespecial802.1Xframes,knownasEAPOL(EAPOverLANs)frames.EAPOLframes
encapsulateEAPPDUs(RFC3748).FramessentbetweentheswitchandtheRADIUSserverareRADIUS
packets.RADIUSpacketsalsoencapsulateEAPPDUstogetherwithotherattributesliketheswitch'sIP
address,name,andthesupplicant'sportnumberontheswitch.EAPisveryflexible,inthatitallows
fordifferentauthenticationmethods,likeMD5‐Challenge,PEAP,andTLS.Theimportantthingisthat
theauthenticator(theswitch)doesn'tneedtoknowwhichauthenticationmethodthesupplicantand
theauthenticationserverareusing,orhowmanyinformationexchangeframesareneededfora
particularmethod.TheswitchsimplyencapsulatestheEAPpartoftheframeintotherelevanttype
(EAPOLorRADIUS)andforwardsit.Whenauthenticationiscomplete,theRADIUSserversendsa
specialpacketcontainingasuccessorfailureindication.Besidesforwardingthisdecisiontothe
supplicant,theswitchusesittoopenuporblocktrafficontheswitchportconnectedtothe
supplicant.OverviewofUserAuthentication
ItisallowedtoconfiguretheManagedSwitchtoauthenticateusersloggingintothesystemfor
managementaccessusinglocalorremoteauthenticationmethods,suchastelnetandWebbrowser.
ThisManagedSwitchprovidessecurenetworkmanagementaccessusingthefollowingoptions:
RemoteAuthenticationDial‐inUserService(RADIUS)
Ter m inalAccessControllerAccessControlSystemPlus(TACACS+)
LocalusernameandPrivilegeLevelcontrol
TheIEEE802.1Xstandarddefinesaclient‐server‐basedaccesscontrolandauthenticationprotocolthat
restrictsunauthorizedclientsfromconnectingtoaLANthroughpubliclyaccessibleports.The
authenticationserverauthenticateseachclientconnectedtoaswitchportbeforemakingavailableany
servicesofferedbytheswitchortheLAN.
Untiltheclientisauthenticated,802.1XaccesscontrolallowsonlyExtensibleAuthenticationProtocol
overLAN(EAPOL)trafficthroughtheporttowhichtheclientisconnected.Afterauthenticationis
successful,normaltrafficcanpassthroughtheport.
Thissectionincludesthisconceptualinformation:
DeviceRoles
AuthenticationInitiationandMessageExchange
PortsinAuthorizedandUnauthorizedStates
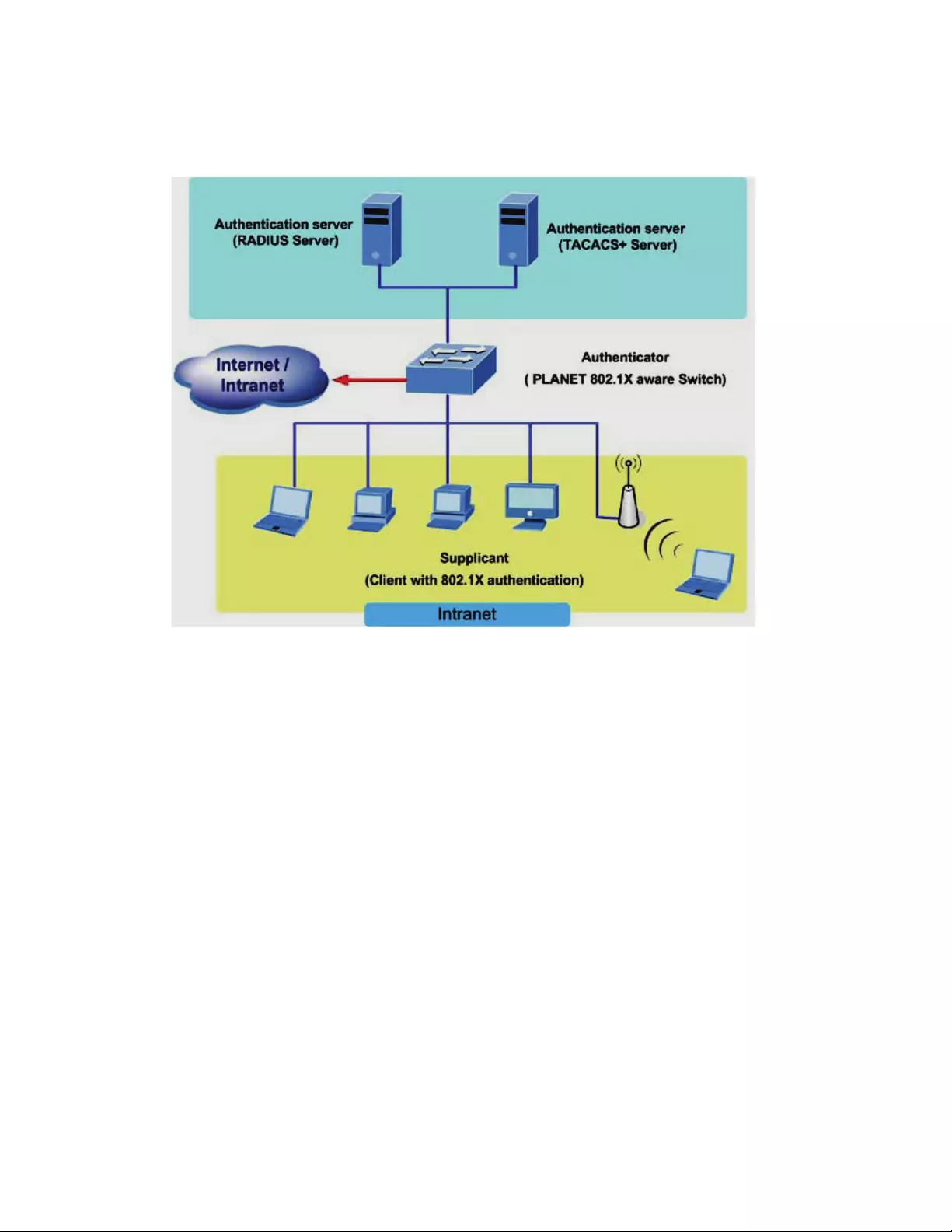
110
DeviceRoles:
With802.1Xport‐basedauthentication,thedevicesinthenetworkhavespecificrolesasshownbelow.
Client‐thedevice(workstation)thatrequestsaccesstotheLANandswitchservicesandrespondsto
requestsfromtheswitch.Theworkstationmustberunning802.1X‐compliantclientsoftwaresuchas
thatofferedintheMicrosoftWindowsXPoperatingsystem.(TheclientisthesupplicantintheIEEE
802.1Xspecification.)
Authenticationserver—performstheactualauthenticationoftheclient.Theauthenticationserver
validatestheidentityoftheclientandnotifiestheswitchwhetherornottheclientisauthorizedto
accesstheLANandswitchservices.Becausetheswitchactsastheproxy,theauthenticationserviceis
transparenttotheclient.Inthisrelease,theRemoteAuthenticationDial‐InUserService(RADIUS)
securitysystemwithExtensibleAuthenticationProtocol(EAP)extensionsistheonlysupported
authenticationserver;itisavailableinCiscoSecureAccessControlServerversion3.0.RADIUSoperates
inaclient/servermodelinwhichsecureauthenticationinformationisexchangedbetweentheRADIUS
serverandoneormoreRADIUSclients.
Switch(802.1Xdevice)—controlsthephysicalaccesstothenetworkbasedontheauthentication
statusoftheclient.Theswitchactsasanintermediary(proxy)betweentheclientandthe
authenticationserver,requestingidentityinformationfromtheclient,verifyingthatinformationwith
theauthenticationserver,andrelayingaresponsetotheclient.TheswitchincludestheRADIUSclient,
whichisresponsibleforencapsulatinganddecapsulatingtheExtensibleAuthenticationProtocol(EAP)
framesandinteractingwiththeauthenticationserver.WhentheswitchreceivesEAPOLframesand
relaysthemtotheauthenticationserver,theEthernetheaderisstrippedandtheremainingEAPframe
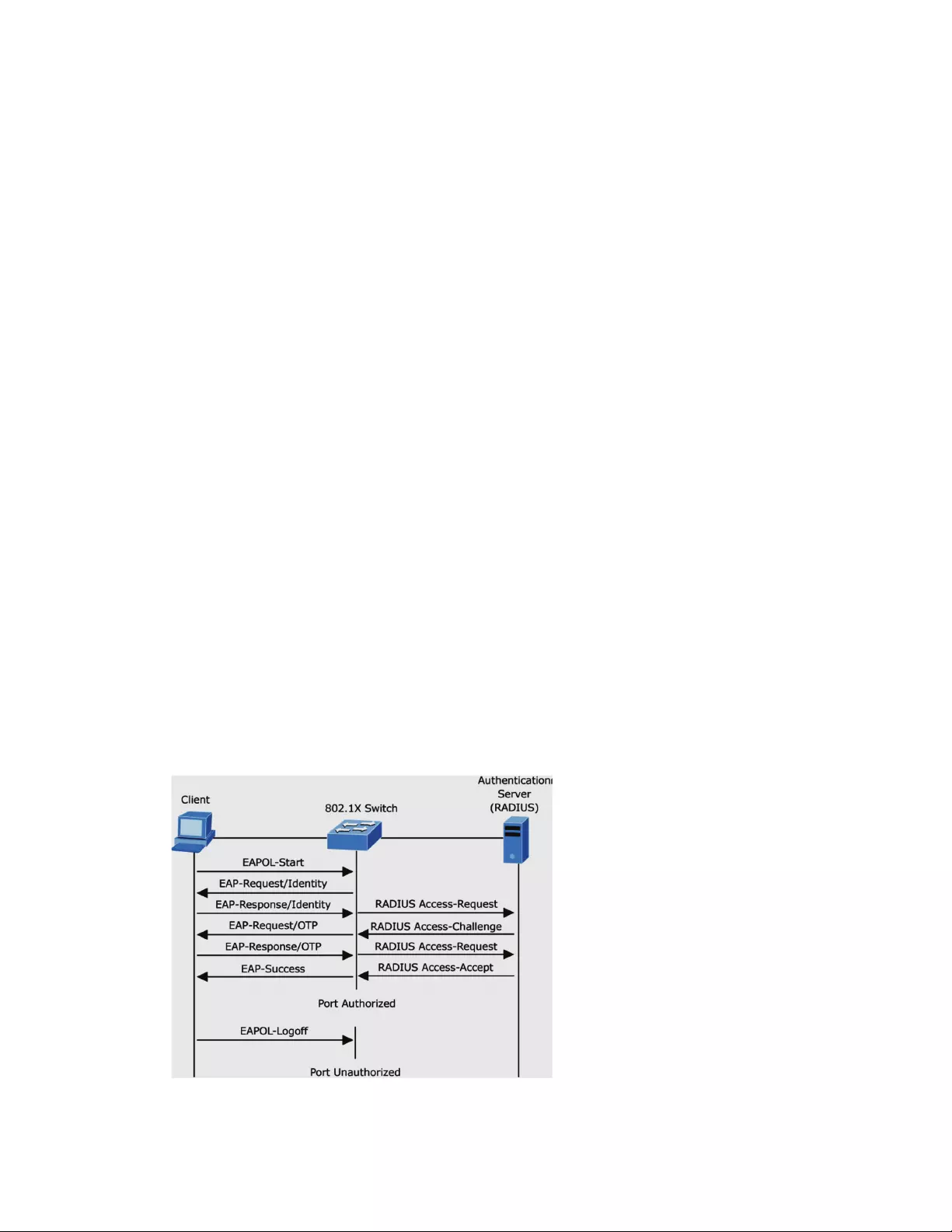
111
isre‐encapsulatedintheRADIUSformat.TheEAPframesarenotmodifiedorexaminedduring
encapsulation,andtheauthenticationservermustsupportEAPwithinthenativeframeformat.When
theswitchreceivesframesfromtheauthenticationserver,theserver'sframeheaderisremoved,
leavingtheEAPframe,whichisthenencapsulatedforEthernetandsenttotheclient.
AuthenticationInitiationandMessageExchange
Theswitchortheclientcaninitiateauthentication.Ifyouenableauthenticationonaportbyusingthe
dot1xport‐controlautointerfaceconfigurationcommand,theswitchmustinitiateauthentication
whenitdeterminesthattheportlinkstatetransitionsfromdowntoup.ItthensendsanEAP‐
request/identityframetotheclienttorequestitsidentity(typically,theswitchsendsaninitial
identity/requestframefollowedbyoneormorerequestsforauthenticationinformation).Upon
receiptoftheframe,theclientrespondswithanEAP‐response/identityframe.However,ifduring
boot‐up,theclientdoesnotreceiveanEAP‐request/identityframefromtheswitch,theclientcan
initiateauthenticationbysendinganEAPOL‐startframe,whichpromptstheswitchtorequestthe
client'sidentity.
Note:
If802.1Xisnotenabledorsupportedonthenetworkaccessdevice,anyEAPOLframesfromtheclient
aredropped.IftheclientdoesnotreceiveanEAP‐request/identityframeafterthreeattemptstostart
authentication,theclienttransmitsframesasiftheportisintheauthorizedstate.Aportinthe
authorizedstateeffectivelymeansthattheclienthasbeensuccessfullyauthenticated.
Whentheclientsuppliesitsidentity,theswitchbeginsitsroleastheintermediary,passingEAPframes
betweentheclientandtheauthenticationserveruntilauthenticationsucceedsorfails.Ifthe
authenticationsucceeds,theswitchportbecomesauthorized.ThespecificexchangeofEAPframes
dependsontheauthenticationmethodbeingused.Thepicturebelowshowsamessageexchange
initiatedbytheclientusingtheOne‐Time‐Password(OTP)authenticationmethodwithaRADIUS
server.
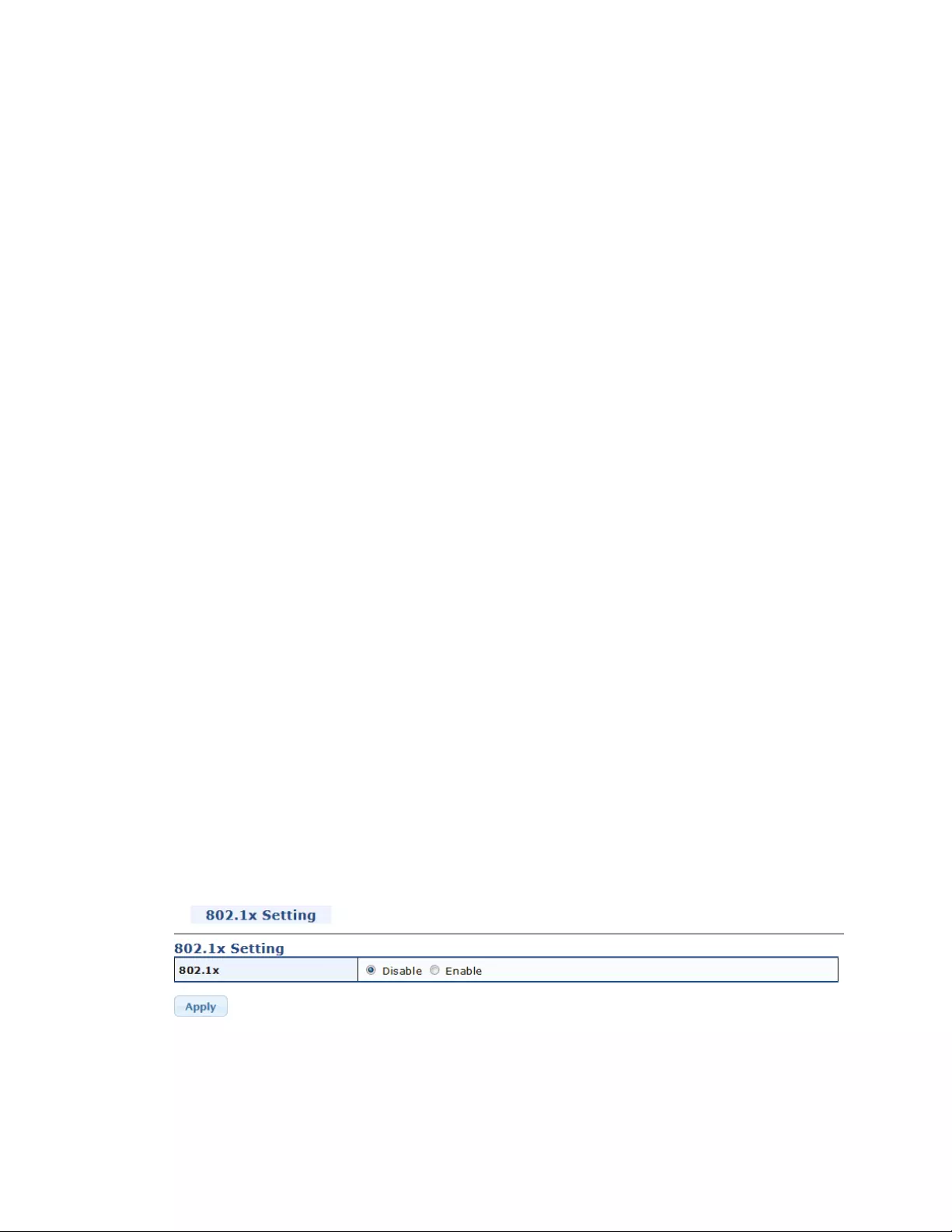
112
PortsinAuthorizedandUnauthorizedStates
Theswitchportstatedetermineswhetherornottheclientisgrantedaccesstothenetwork.Theport
startsintheunauthorizedstate.Whileinthisstate,theportdisallowsallingressandegresstraffic
exceptfor802.1Xprotocolpackets.Whenaclientissuccessfullyauthenticated,theporttransitionsto
theauthorizedstate,allowingalltrafficfortheclienttoflownormally.
Ifaclientthatdoesnotsupport802.1Xisconnectedtoanunauthorized802.1Xport,theswitch
requeststheclient'sidentity.Inthissituation,theclientdoesnotrespondtotherequest,theport
remainsintheunauthorizedstate,andtheclientisnotgrantedaccesstothenetwork.
Incontrast,whenan802.1X‐enabledclientconnectstoaportthatisnotrunningthe802.1Xprotocol,
theclientinitiatestheauthenticationprocessbysendingtheEAPOL‐startframe.Whennoresponseis
received,theclientsendstherequestforafixednumberoftimes.Becausenoresponseisreceived,
theclientbeginssendingframesasiftheportisintheauthorizedstate
Iftheclientissuccessfullyauthenticated(receivesanAcceptframefromtheauthenticationserver),
theportstatechangestoauthorized,andallframesfromtheauthenticatedclientareallowedthrough
theport.Iftheauthenticationfails,theportremainsintheunauthorizedstate,butauthenticationcan
beretried.Iftheauthenticationservercannotbereached,theswitchcanretransmittherequest.Ifno
responseisreceivedfromtheserverafterthespecifiednumberofattempts,authenticationfails,and
networkaccessisnotgranted.Whenaclientlogsoff,itsendsanEAPOL‐logoffmessage,causingthe
switchporttotransitiontotheunauthorizedstate.
Ifthelinkstateofaporttransitionsfromuptodown,orifanEAPOL‐logoffframeisreceived,theport
returnstotheunauthorizedstate.
4.9.2.1 802.1xSetting
ThispageallowsyoutoconfiguretheIEEE802.1Xauthenticationsystem.TheIEEE802.1Xstandard
definesaport‐basedaccesscontrolprocedurethatpreventsunauthorizedaccesstoanetworkby
requiringuserstofirstsubmitcredentialsforauthentication.Oneormorecentralservers,thebackend
servers,determinewhethertheuserisallowedaccesstothenetwork.Thesebackend(RADIUS)
serversareconfiguredonthe"Security→802.1XAccessControl→802.1XSetting"page.The
IEEE802.1Xstandarddefinesport‐basedoperation,butnon‐standardvariantsovercomesecurity
limitationsasshallbeexploredbelow.
Enableordisable802.1xontheIntellinetswitch.

113
4.9.2.2 802.1xPortSetting
OnthisinterfacescreenyoucandefinetheQoStrustmode.

114
4.9.2.3 GuestVLANSettings
WhenaGuestVLANenabledport'slinkcomesup,theswitchstartstransmittingEAPOLRequest
Identityframes.IfthenumberoftransmissionsofsuchframesexceedsMax.Reauth.Countandno
EAPOLframeshavebeenreceivedinthemeantime,theswitchconsidersenteringtheGuestVLAN.The
intervalbetweentransmissionofEAPOLRequestIdentityframesisconfiguredwithEAPOLTimeout.If
AllowGuestVLANifEAPOLSeenisenabled,theportwillnowbeplacedintheGuestVLAN.Ifdisabled,
theswitchwillfirstcheckitshistorytoseeifanEAPOLframehaspreviouslybeenreceivedontheport
(thishistoryisclearediftheportlinkgoesdownortheport'sAdminStateischanged),andifnot,the
portwillbeplacedintheGuestVLAN.OtherwiseitwillnotmovetotheGuestVLAN,butcontinue
transmittingEAPOLRequestIdentityframesattherategivenbyEAPOLTimeout.OnceintheGuest
VLAN,theportisconsideredauthenticated,andallattachedclientsontheportareallowedaccesson
thisVLAN.TheswitchwillnottransmitanEAPOLSuccessframewhenenteringtheGuestVLAN.While
intheGuestVLAN,theswitchmonitorsthelinkforEAPOLframes,andifonesuchframeisreceived,
theswitchimmediatelytakestheportoutoftheGuestVLANandstartsauthenticatingthesupplicant
accordingtotheportmode.IfanEAPOLframeisreceived,theportwillneverbeabletogobackinto
theGuestVLANifthe"AllowGuestVLANifEAPOLSeen"isdisabled.
115
4.9.2.4 AuthenticatedHosts
Seeallcurrentlyauthenticatedhostsonthisinformationscreen.
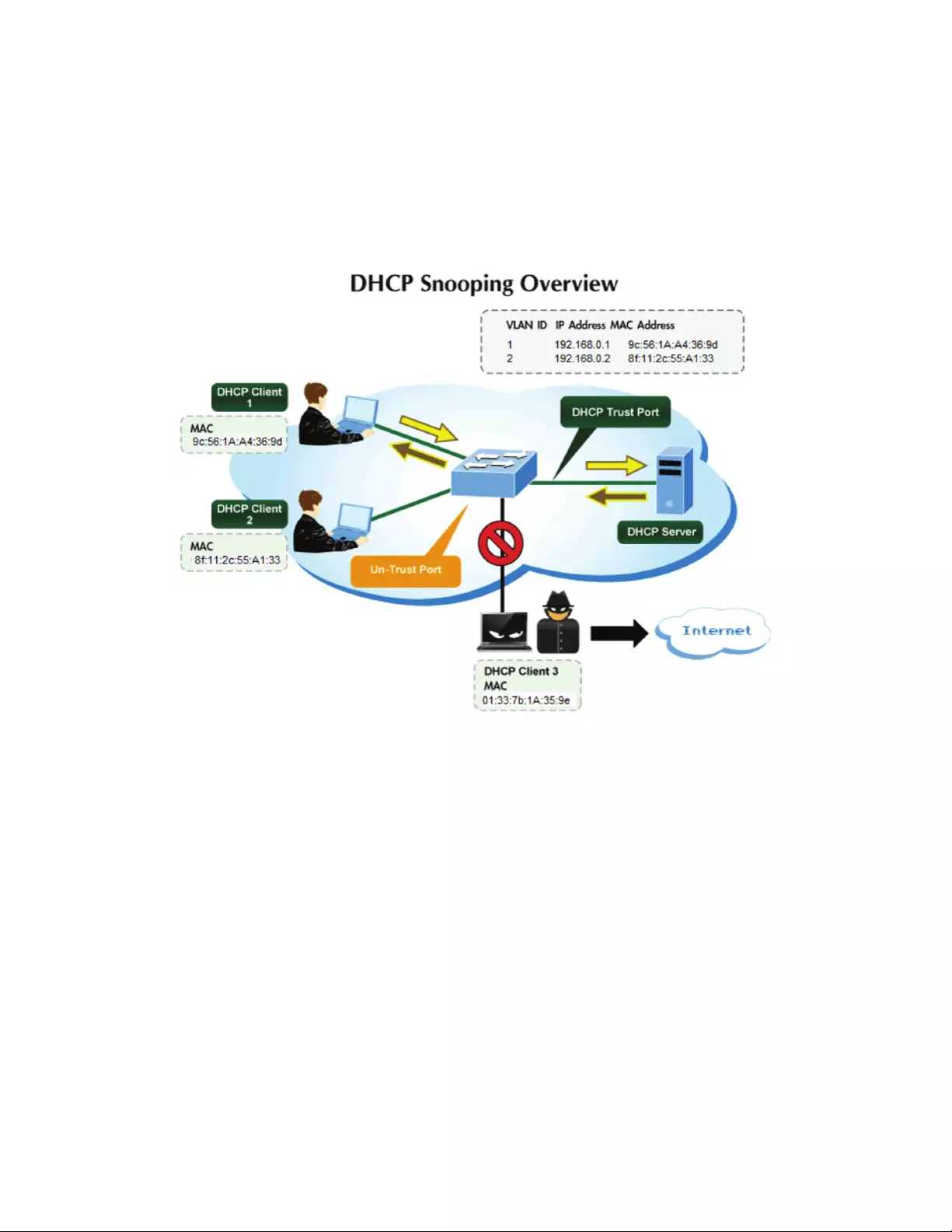
116
4.9.3 DHCPSnooping
TheaddressesassignedtoDHCPclientsonunsecureportscanbecarefullycontrolledusingthe
dynamicbindingsregisteredwithDHCPSnooping.DHCPsnoopingallowsaswitchtoprotectanetwork
fromrogueDHCPserversorotherdeviceswhichsendport‐relatedinformationtoaDHCPserver.This
informationcanbeusefulintrackinganIPaddressbacktoaphysicalport.
CommandUsage
NetworktrafficmaybedisruptedwhenmaliciousDHCPmessagesarereceivedfromanoutside
source.DHCPsnoopingisusedtofilterDHCPmessagesreceivedonanon‐secureinterfacefrom
outsidethenetworkorfirewall.WhenDHCPsnoopingisenabledgloballyandenabledonaVLAN
interface,DHCPmessagesreceivedonanuntrustedinterfacefromadevicenotlistedintheDHCP
snoopingtablewillbedropped.
Tableentriesareonlylearnedfortrustedinterfaces.Anentryisaddedorremoveddynamicallyto
theDHCPsnoopingtablewhenaclientreceivesorreleasesanIPaddressfromaDHCPserver.
EachentryincludesaMACaddress,IPaddress,leasetime,VLANidentifier,andportidentifier.
WhenDHCPsnoopingisenabled,DHCPmessagesenteringanuntrustedinterfacearefiltered
basedupondynamicentrieslearnedviaDHCPsnooping.

117
Filteringrulesareimplementedasfollows:
IftheglobalDHCPsnoopingisdisabled,allDHCPpacketsareforwarded.
IfDHCPsnoopingisenabledglobally,andalsoenabledontheVLANwheretheDHCPpacketis
received,allDHCPpacketsareforwardedforatrustedport.IfthereceivedpacketisaDHCP
ACKmessage,adynamicDHCPsnoopingentryisalsoaddedtothebindingtable.
IfDHCPsnoopingisenabledglobally,andalsoenabledontheVLANwheretheDHCPpacketis
received,buttheportisnottrusted,itisprocessedasfollows:
o IftheDHCPpacketisareplypacketfromaDHCPserver(includingOFFER,ACKorNAK
messages),thepacketisdropped.
o IftheDHCPpacketisfromaclient,suchasaDECLINEorRELEASEmessage,theswitch
forwardsthepacketonlyifthecorrespondingentryisfoundinthebindingtable.
o IftheDHCPpacketisfromaclient,suchasaDISCOVER,REQUEST,INFORM,DECLINE
orRELEASEmessage,thepacketisforwardedifMACaddressverificationisdisabled.
However,ifMACaddressverificationisenabled,thenthepacketwillonlybe
forwardediftheclient’shardwareaddressstoredintheDHCPpacketisthesameas
thesourceMACaddressintheEthernetheader.
o IftheDHCPpacketisnotarecognizabletype,itisdropped.
IfaDHCPpacketfromaclientpassesthefilteringcriteriaabove,itwillonlybeforwardedto
trustedportsinthesameVLAN.
IfaDHCPpacketisfromserverisreceivedonatrustedport,itwillbeforwardedtobothtrusted
anduntrustedportsinthesameVLAN.
IftheDHCPsnoopingisgloballydisabled,alldynamicbindingsareremovedfromthebinding
table.
AdditionalconsiderationswhentheswitchitselfisaDHCPclient–Theport(s)throughwhich
theswitchsubmitsaclientrequesttotheDHCPservermustbeconfiguredastrusted.Note
thattheswitchwillnotaddadynamicentryforitselftothebindingtablewhenitreceivesan
ACKmessagefromaDHCPserver.Also,whentheswitchsendsoutDHCPclientpacketsfor
itself,nofilteringtakesplace.However,whentheswitchreceives

118
4.9.3.1 DHCPSnoopingSettings
ActivateordeactivateDHCPsnoopingonthisconfigurationscreen.
4.9.3.2 LANSettings
CommandUsage
WhenDHCPsnoopingisenabledgloballyontheswitch,andenabledonthespecifiedVLAN,DHCP
packetfilteringwillbeperformedonanyuntrustedportswithintheVLAN.
WhentheDHCPsnoopingisgloballydisabled,DHCPsnoopingcanstillbeconfiguredforspecific
VLANs,butthechangeswillnottakeeffectuntilDHCPsnoopingisgloballyre‐enabled.
WhenDHCPsnoopingisgloballyenabled,andDHCPsnoopingisthendisabledonaVLAN,all
dynamicbindingslearnedforthisVLANareremovedfromthebindingtable.

119
4.9.3.3 DHCPSnoopingPortSettings
Configuresswitchportsastrustedoruntrusted.
CommandUsage
Atrustedinterfaceisaninterfacethatisconfiguredtoreceiveonlymessagesfromwithinthe
network.Anuntrustedinterfaceisaninterfacethatisconfiguredtoreceivemessagesfrom
outsidethenetworkorfirewall.
WhenDHCPsnoopingenabledbothgloballyandonaVLAN,DHCPpacketfilteringwillbe
performedonanyuntrustedportswithintheVLAN.
Whenanuntrustedportischangedtoatrustedport,allthedynamicDHCPsnoopingbindings
associatedwiththisportareremoved.
SetallportsconnectedtoDHCPserverswithinthelocalnetworkorfirewalltotrustedstate.Set
allotherportsoutsidethelocalnetworkorfirewalltountrustedstate.
4.9.3.4 DHCPSnoopingStatistics
120
4.9.3.5 RateLimit
AfterenablingDHCPsnooping,theswitchwillmonitoralltheDHCPmessagesandimplementsoftware
transmission.
4.9.3.6 Option82GlobalSettings
DHCPprovidesarelaymechanismforsendinginformationabouttheswitchanditsDHCPclientsto
DHCPservers.KnownasDHCPOption82,itallowscompatibleDHCPserverstousetheinformation
whenassigningIPaddresses,ortosetotherservicesorpoliciesforclients.Itisalsoaneffectivetoolin
preventingmaliciousnetworkattacksfromattachedclientsonDHCPservices,suchasIPSpoofing,
ClientIdentifierSpoofing,MACAddressSpoofing,andAddressExhaustion.
TheDHCPoption82enablesaDHCPrelayagenttoinsertspecificinformationintoaDHCPrequest
packetswhenforwardingclientDHCPpacketstoaDHCPserverandremovethespecificinformation
fromaDHCPreplypacketswhenforwardingserverDHCPpacketstoaDHCPclient.TheDHCPserver
canusethisinformationtoimplementIPaddressorotherassignmentpolicies.Specificallytheoption
worksbysettingtwosub‐options:
CircuitID(option1)
RemoteID(option2).
TheCircuitIDsub‐optionissupposedtoincludeinformationspecifictowhichcircuittherequestcame
inon.TheRemoteIDsub‐optionwasdesignedtocarryinformationrelatingtotheremotehostendof
thecircuit.ThedefinitionofCircuitIDintheswitchis4bytesinlengthandtheformatis"vlan_id"
"module_id""port_no".Theparameterof"vlan_id"isthefirsttwobytesrepresenttheVLANID.The
parameterof"module_id"isthethirdbyteforthemoduleID(instandaloneswitchitalwaysequal0,
inswitchitmeansswitchID).Theparameterof"port_no"isthefourthbyteanditmeanstheport
number.

121
4.9.3.7 Option82PortSettings
ThisfunctionisusedtosettheretransmittingpolicyofthesystemforthereceivedDHCPrequest
messagewhichcontainsoption82.Thedropmodemeansthatifthemessagehasoption82,thenthe
systemwilldropitwithoutprocessing;keepmodemeansthatthesystemwillkeeptheoriginal
option82segmentinthemessage,andforwardittotheservertoprocess;replacemodemeansthat
thesystemwillreplacetheoption82segmentintheexistingmessagewithitsownoption82,and
forwardthemessagetotheservertoprocess.
4.9.3.8 Option82Circuit‐IDSettings
Setcreationmethodforoption82,userscandefinetheparametersofcircute‐idsuboptionby
themselves.

122
4.9.4 DynamicARPInspection
4.9.4.1 DynamicARPInspectionSetting
DynamicARPInspection(DAI)isasecurefeature.Severaltypesofattackscanbelaunchedagainsta
hostordevicesconnectedtoLayer2networksby"poisoning"theARPcaches.Thisfeatureisusedto
blocksuchattacks.OnlyvalidARPrequestsandresponsescangothroughDUT.ThispageprovidesARP
Inspectionrelatedconfiguration.
OnthisconfigurationscreenyouactivateanddeactivateDAI.
4.9.4.2 VLANSettings
EnableordisableDAIfordifferentVLANIDs.

123
4.9.5 PortSettings
DAI-related port settings.
4.9.6 DynamicARPInspectionStatistics
ProvidesstatisticalinformationabouttheDAIfunction.
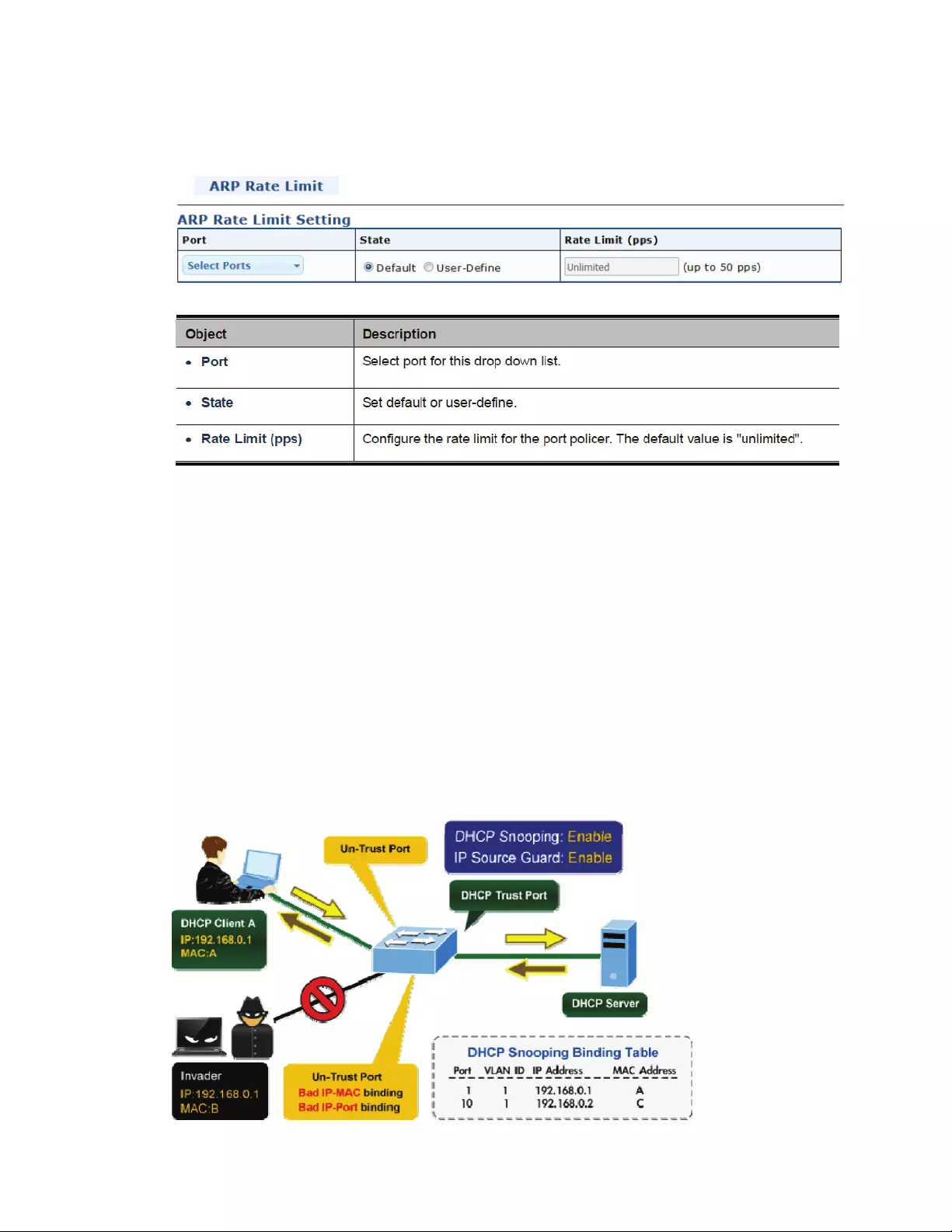
124
4.9.6.1 RateLimit
YoucanspecifyoptionalratelimitsforeachoftheportsandLAGshere.
4.9.7 IPSourceGuard
IPSourceGuardisasecurefeatureusedtorestrictIPtrafficonDHCPsnoopinguntrustedportsby
filteringtrafficbasedontheDHCPSnoopingTableormanuallyconfiguredIPSourceBindings.Ithelps
preventIPspoofingattackswhenahosttriestospoofandusetheIPaddressofanotherhost.After
receivingapacket,theportlooksupthekeyattributes(includingIPaddress,MACaddressandVLAN
tag)ofthepacketinthebindingentriesoftheIPsourceguard.Ifthereisamatchingentry,theport
willforwardthepacket.Otherwise,theportwillabandonthepacket.
IPsourceguardfilterspacketsbasedonthefollowingtypesofbindingentries:
IP‐portbindingentry
MAC‐portbindingentry
IP‐MAC‐portbindingentry
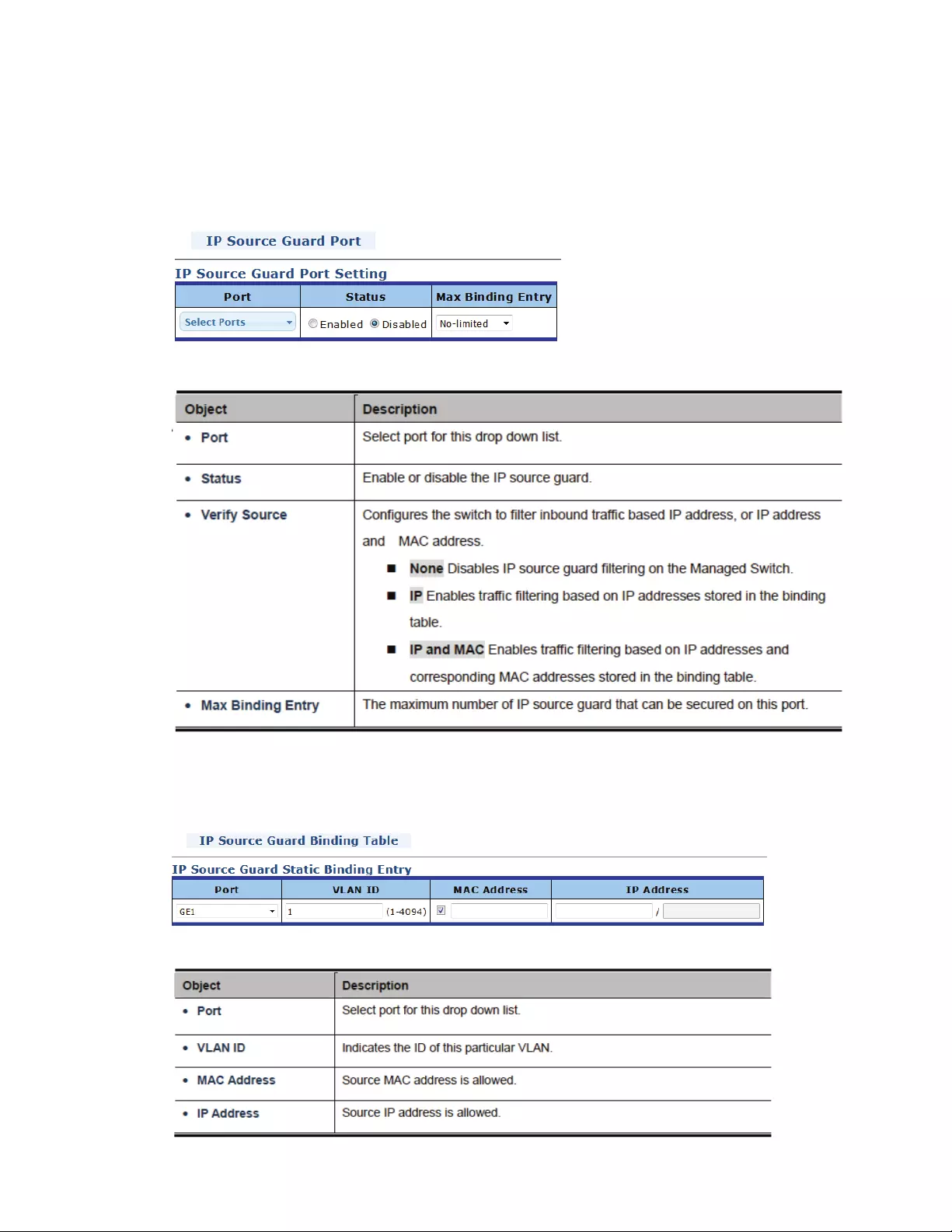
125
4.9.7.1 PortSettings
IPSourceGuardisasecurefeatureusedtorestrictIPtrafficonDHCPsnoopinguntrustedportsby
filteringtrafficbasedontheDHCPSnoopingTableormanuallyconfiguredIPSourceBindings.Ithelps
preventIPspoofingattackswhenahosttriestospoofandusetheIPaddressofanotherhost.
4.9.7.2 IPSourceGuardBindingTable

126
4.9.7.3 PortSecurity
ThispageallowsyoutoconfigurethePortSecurityLimitControlsystemandportsettings.Limit
Controlallowsforlimitingthenumberofusersonagivenport.AuserisidentifiedbyaMACaddress
andVLANID.IfLimitControlisenabledonaport,thelimitspecifiesthemaximumnumberofuserson
theport.Ifthisnumberisexceeded,anactionistaken.Theactioncanbeoneoffourdifferentas
describedbelow.
TheLimitControlmoduleisoneofarangeofmodulesthatutilizesalower‐layermodule,thePort
Securitymodule,whichmanagesMACaddresseslearnedontheport.TheLimitControlconfiguration
consistsoftwosections,asystem‐andaport‐wide.
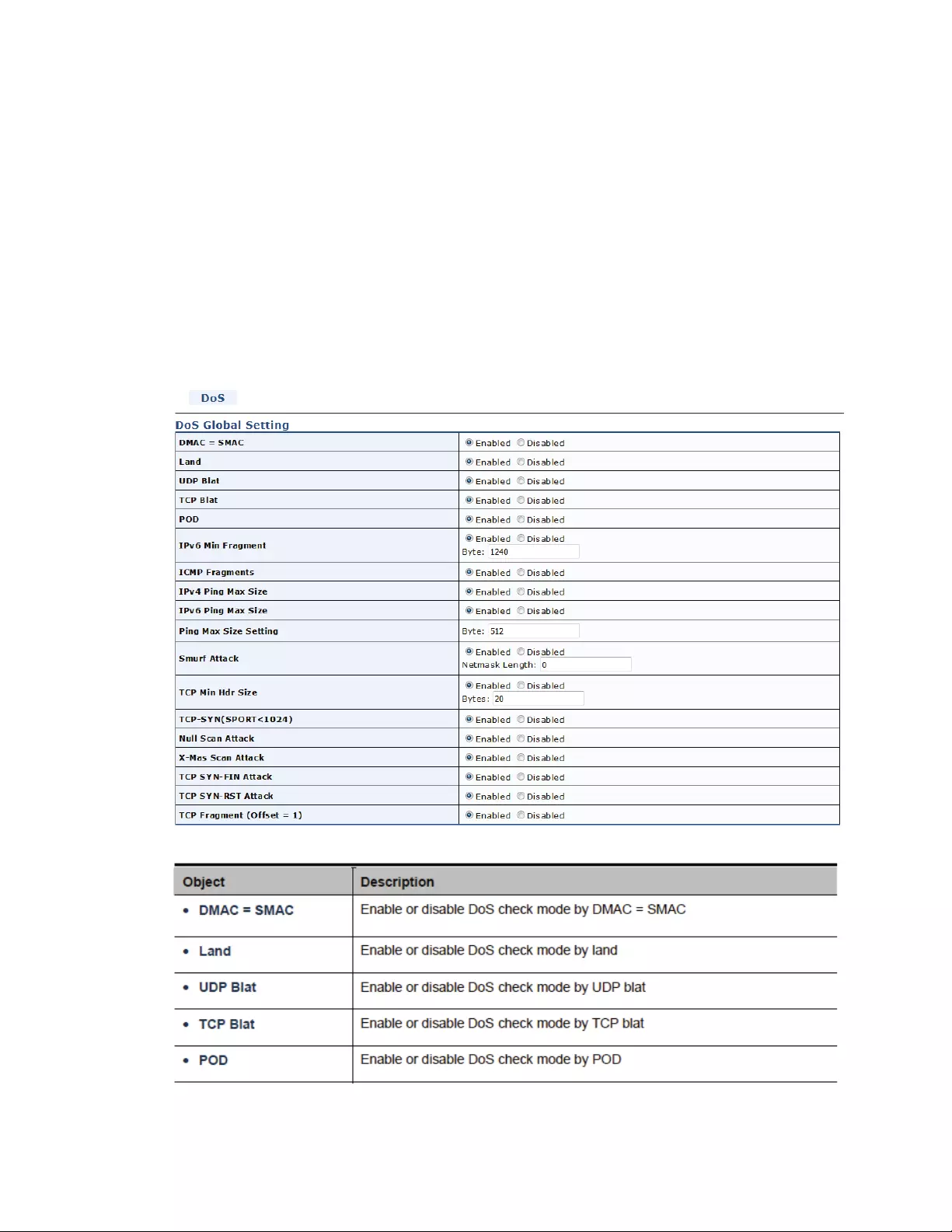
127
4.9.8 DOS
TheDoSisshortforDenialofService,whichisasimplebuteffectivedestructiveattackontheinternet.
TheserverunderDoSattackwilldropnormaluserdatapacketduetonon‐stopprocessingthe
attacker’sdatapacket,leadingtothedenialoftheserviceandworsecanleadtoleakofsensitivedata
oftheserver.Securityfeaturereferstoapplicationssuchasprotocolcheckwhichisforprotectingthe
serverfromattackssuchasDoS.Theprotocolcheckallowstheusertodropmatchedpacketsbasedon
specifiedconditions.ThesecurityfeaturesprovideseveralsimpleandeffectiveprotectionsagainstDos
attackswhileactingnoinfluenceonthelinearforwardingperformanceoftheswitch.
4.9.8.1 GlobalDoSSetting

128
4.9.8.2 DoSPortSetting
129
4.9.9 Authentication,authorization,andaccounting(AAA)
Authentication,authorization,andaccounting(AAA)providesaframeworkforconfiguringaccess
controlontheManagedSwitch.Thethreesecurityfunctionscanbesummarizedasfollows:
Authentication—Identifiesusersthatrequestaccesstothenetwork.
Authorization—Determinesifuserscanaccessspecificservices.
Accounting—Providesreports,auditing,andbillingforservicesthatusershaveaccessedon
thenetwork.
TheAAAfunctionsrequiretheuseofconfiguredRADIUSorTACACS+serversinthenetwork.The
securityserverscanbedefinedassequentialgroupsthatarethenappliedasamethodforcontrolling
useraccesstospecifiedservices.Forexample,whentheswitchattemptstoauthenticateauser,a
requestissenttothefirstserverinthedefinedgroup,ifthereisnoresponsethesecondserverwillbe
tried,andsoon.Ifatanypointapassorfailisreturned,theprocessstops.
TheManagedSwitchsupportsthefollowingAAAfeatures:
AccountingforIEEE802.1XauthenticatedusersthataccessthenetworkthroughtheManaged
Switch.
AccountingforusersthataccessmanagementinterfacesontheManagedSwitchthroughthe
consoleandTelnet.
AccountingforcommandsthatusersenteratspecificCLIprivilegelevels.Authorizationof
usersthataccessmanagementinterfacesontheManagedSwitchthroughtheconsoleand
Tel net.
ToconfigureAAAontheManagedSwitch,youneedtofollowthisgeneralprocess:
ConfigureRADIUSandTACACS+serveraccessparameters.See“ConfiguringLocal/Remote
LogonAuthentication”.
DefineRADIUSandTACACS+servergroupstosupporttheaccountingandauthorizationof
services.
Defineamethodnameforeachservicetowhichyouwanttoapplyaccountingor
authorizationandspecifytheRADIUSorTACACS+servergroupstouse.Applythemethod
namestoportorlineinterfaces.
Note:ThisguideassumesthatRADIUSandTACACS+servershavealreadybeenconfiguredtosupport
AAA.TheconfigurationofRADIUSandTACACS+serversoftwareisbeyondthescopeofthisguide,
refertothedocumentationprovidedwiththeRADIUSorTACACS+serversoftware.
4.9.9.1.1 LoginList

130
4.9.9.2 EnableList
4.9.9.3 AccountingList
Thispageallowstheusertoadd,editordeleteaccountinglistsettings.The“default”listcannotbe
deleted.
ParameterDescription
ListNameTheaccountlistnamemustbedifferentfromotherlistnames,i.e.,itmust
notbecalled“default”.
RecordType none:Noaccounting.
start‐stop:Recordstartandstopwithoutwaiting.
stop‐only:Recordstopwhenserviceterminates.
Method1Selectfirstpriority:
Tacacs+:UseremoteTACACS+servertoaccounting.

131
Radius:UseremoteRadiusservertoaccounting.
Method2Selectsecondpriority:
Tacacs+:UseremoteTACACS+servertoaccounting.
Radius:UseremoteRadiusservertoaccounting.
4.9.9.4 AccountingUpdate

132
4.9.10 TACACS+server
TACACS(TerminalAccessControllerAccessControlSystem)isanolderauthenticationprotocol
commontoUNIXnetworksthatallowsaremoteaccessservertoforwardauser'slogonpasswordto
anauthenticationservertodeterminewhetheraccesscanbeallowedtoagivensystem.
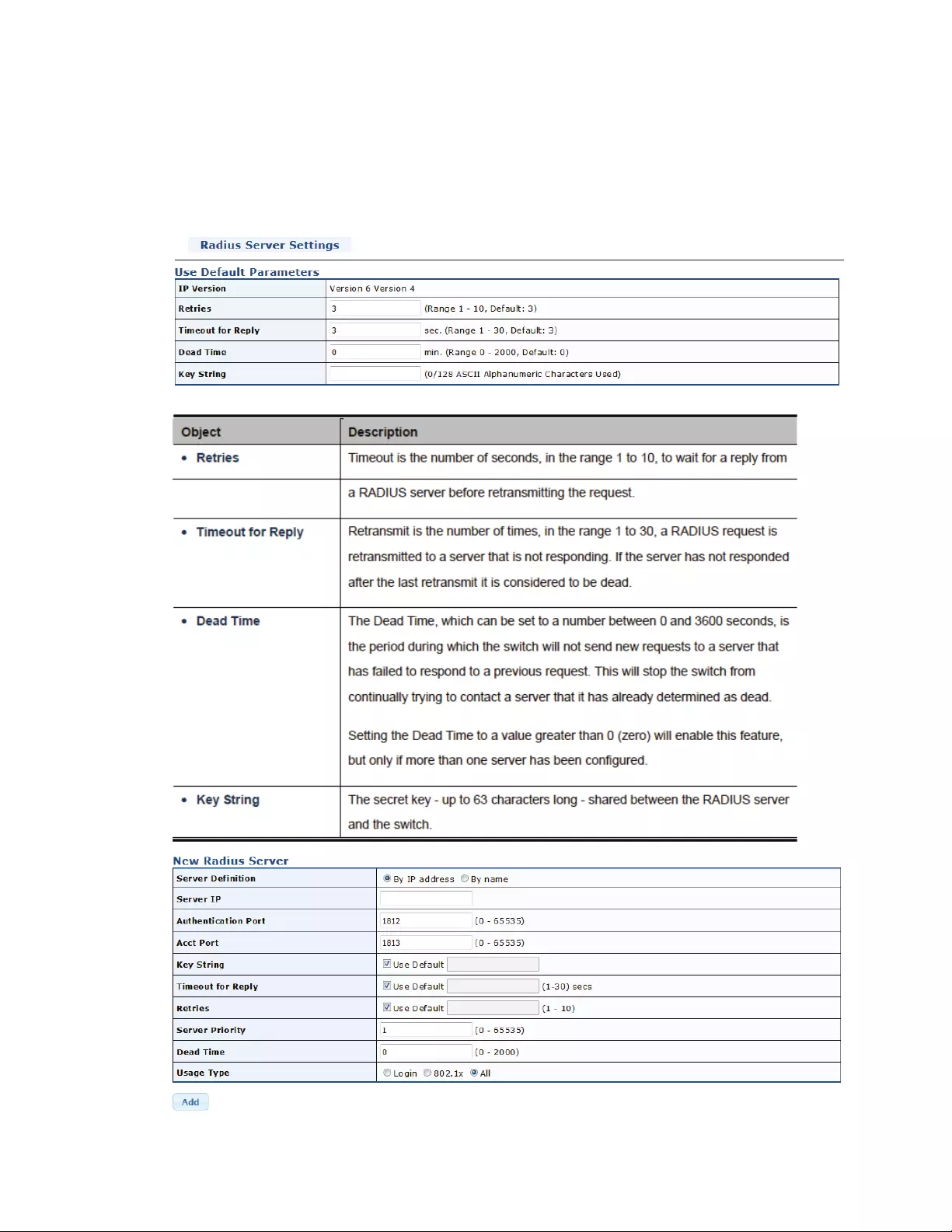
133
4.9.11 Radiusserver
RemoteAuthenticationDial‐InUserService(RADIUS)isanetworkingprotocolthatprovides
centralizedAuthentication,Authorization,andAccounting(AAA)managementforuserswhoconnect
anduseanetworkservice.
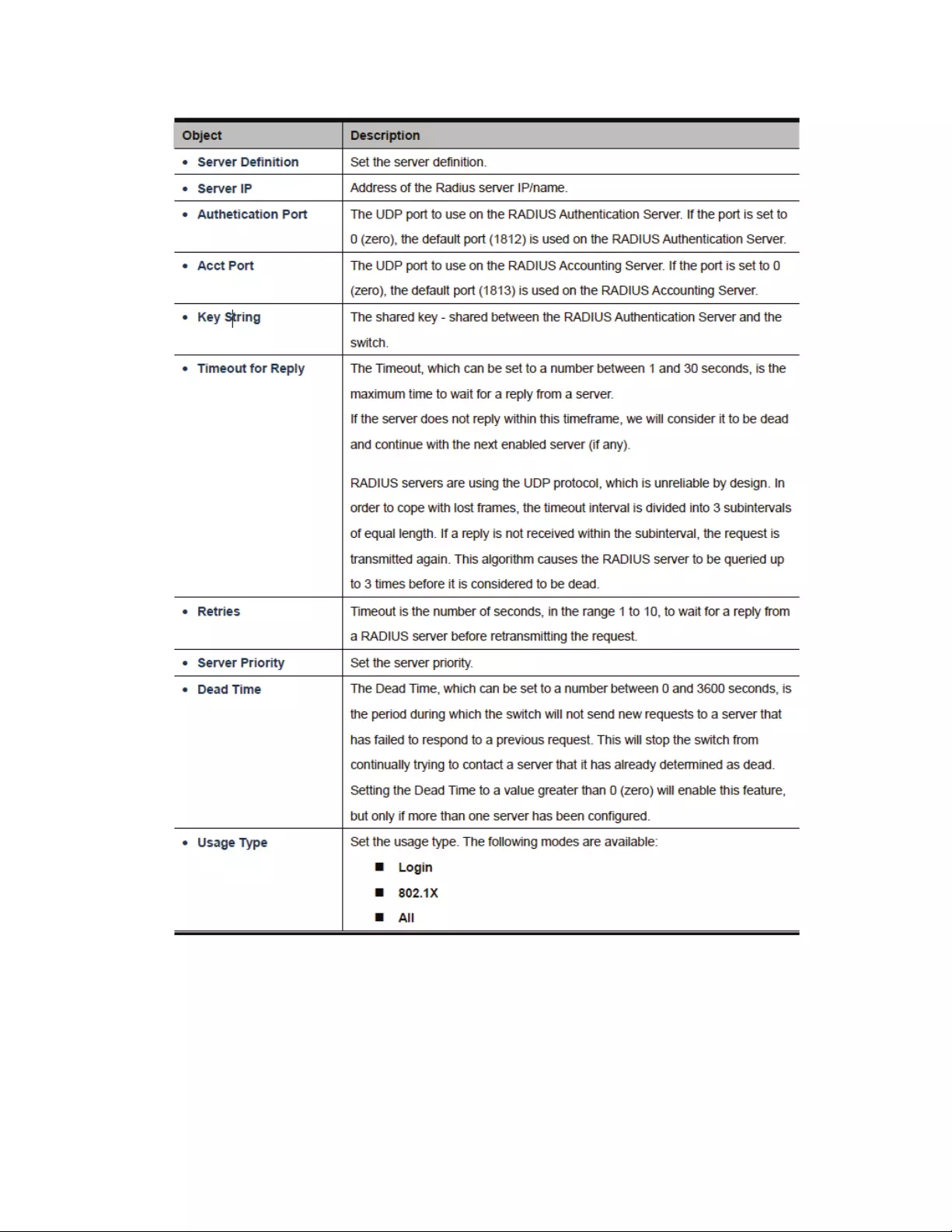
134
135
4.9.12 Access
TheIntellinetswitchallowsaccessviaHTTP(S),Telnetandconsoleport.Inthissectionyoudefinethe
authenticationandaccountingrelatedsettings.
4.9.12.1 ConsoleSettings
ParameterDescription
Login/Enable/ExecListSelecttheappropriatelistvalueforeachoftheseentries.
SessionTimeoutSpecifythelengthofinactivityinminutesafterwhichthesessionis
automaticallyterminated.
PasswordRetryCountEnterthenumberoffailedloginattemptsbeforethesilenttimeis
invoked.
SilentTimeUsethiscommandtosettheamountoftimethemanagementconsole
isinaccessibleafterthenumberofunsuccessfullogonattemptsexceeds
thethresholdsetbythepassword‐retrycount.
4.9.12.2 TelnetSettings
Verymuchthesameastheconsolesettings,howeveryoucandisableorenabletheservice.Allother
parametersareidentical.

136
4.9.12.3 HTTPSettings
InadditiontoTelnet andconsole‐basedaccess,themostcommonmethodofconnectingtothe
Intellinet8‐PortGigabitPoE+SwitchisviaHTTP(webbrowser).
ParameterDescription
HTTPServiceEnableordisableaccessviaHTTP..
LoginAuthenticationListSpecifytheappropriatevaluefromthedrop‐downlist.
SessionTimeoutSpecifythelengthofinactivityinminutesafterwhichthesessionis
automaticallyterminated.
4.9.12.4 HTTPSSettings
AsavariationofHTTP,thisaccessmethodismoresecurebyencryption.
TheparametersareidenticaltothoseofHTTP.

137
4.10 AccessControlList
4.10.1 WhatisACL?
ACLisanacronymforAccessControlList.ItisthelisttableofACEs,containingaccesscontrolentries
thatspecifyindividualusersorgroupspermittedordeniedtospecifictrafficobjects,suchasaprocess
oraprogram.EachaccessibletrafficobjectcontainsanidentifiertoitsACL.Theprivilegesdetermine
whethertherearespecifictrafficobjectaccessrights.
ACLimplementationscanbequitecomplex,forexample,whentheACEsareprioritizedforthevarious
situation.Innetworking,theACLreferstoalistofserviceportsornetworkservicesthatareavailable
onahostorserver,eachwithalistofhostsorserverspermittedordeniedtousetheservice.ACLcan
generallybeconfiguredtocontrolinboundtraffic,andinthiscontext,theyaresimilartofirewalls.
ACEisanacronymforAccessControlEntry.Itdescribesaccesspermissionassociatedwithaparticular
ACEID.TherearethreeACEframetypes(EthernetType,ARP,andIPv4)andtwoACEactions(permit
anddeny).TheACEalsocontainsmanydetailed,differentparameteroptionsthatareavailablefor
individualapplication.
4.10.2 MAC‐BasedACL
CreateaMACaddressbasedAccessControlListonthisscreen.TypeinthenamefortheACLandclick
“Add.”
4.10.3 MAC‐BasedACE
Onthispageyoucandefinetheaccesscontrolentries.
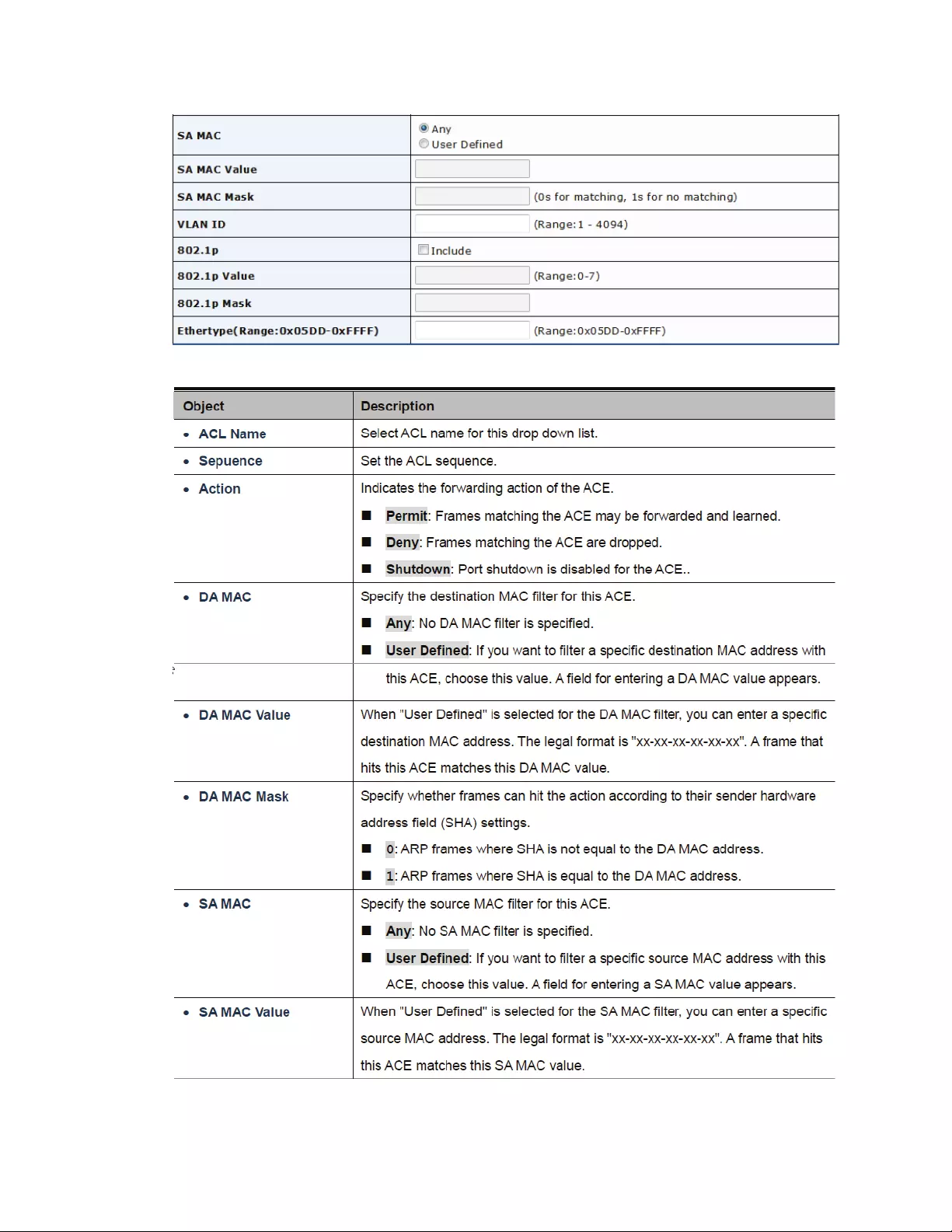
138
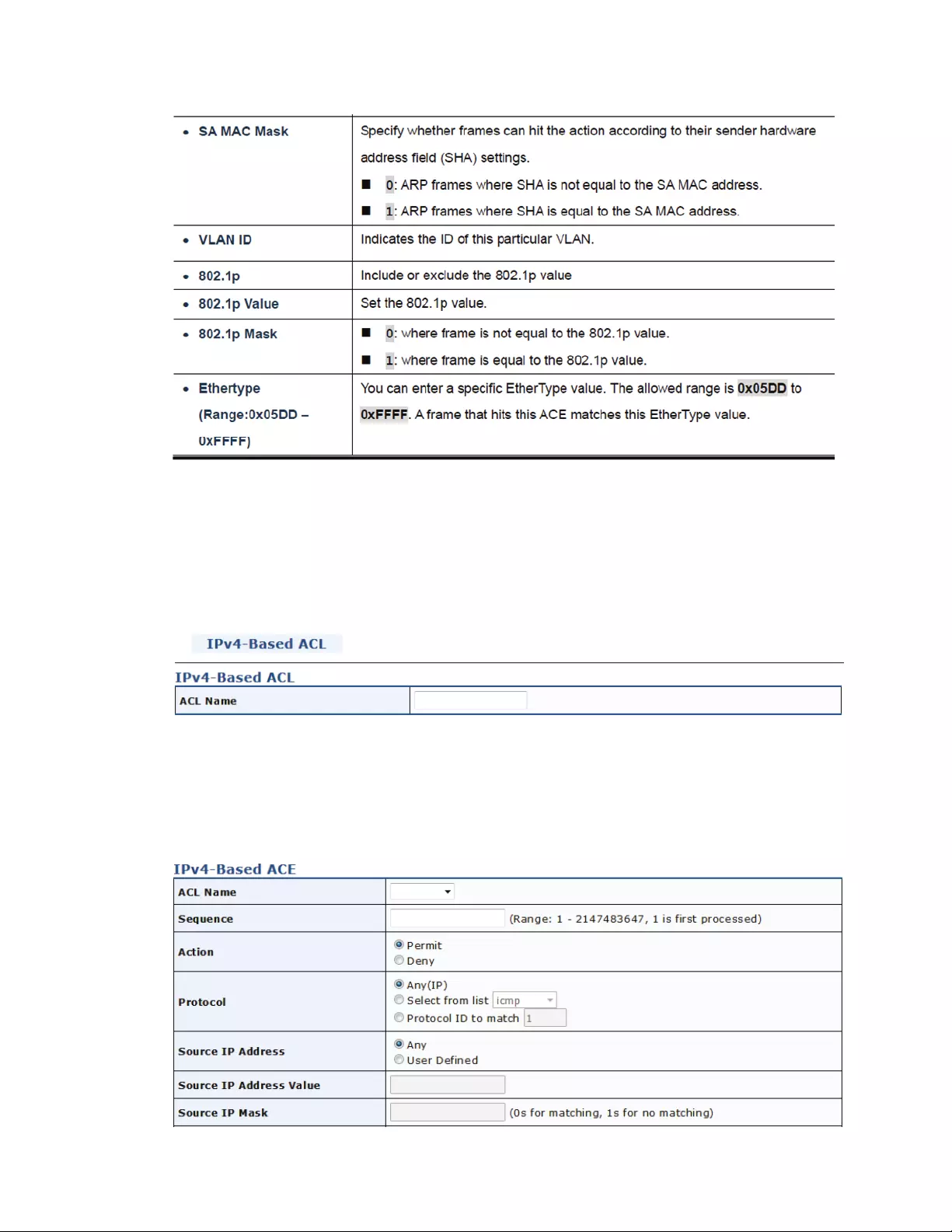
139
4.10.4 IPv4‐BasedACL
CreateaIPv4addressbasedAccessControlListonthisscreen.TypeinthenamefortheACLandclick
“Add.”
4.10.5 IPv4‐BasedACE
OnthispageyoucandefinetheaccesscontrolentriesforIPv4.
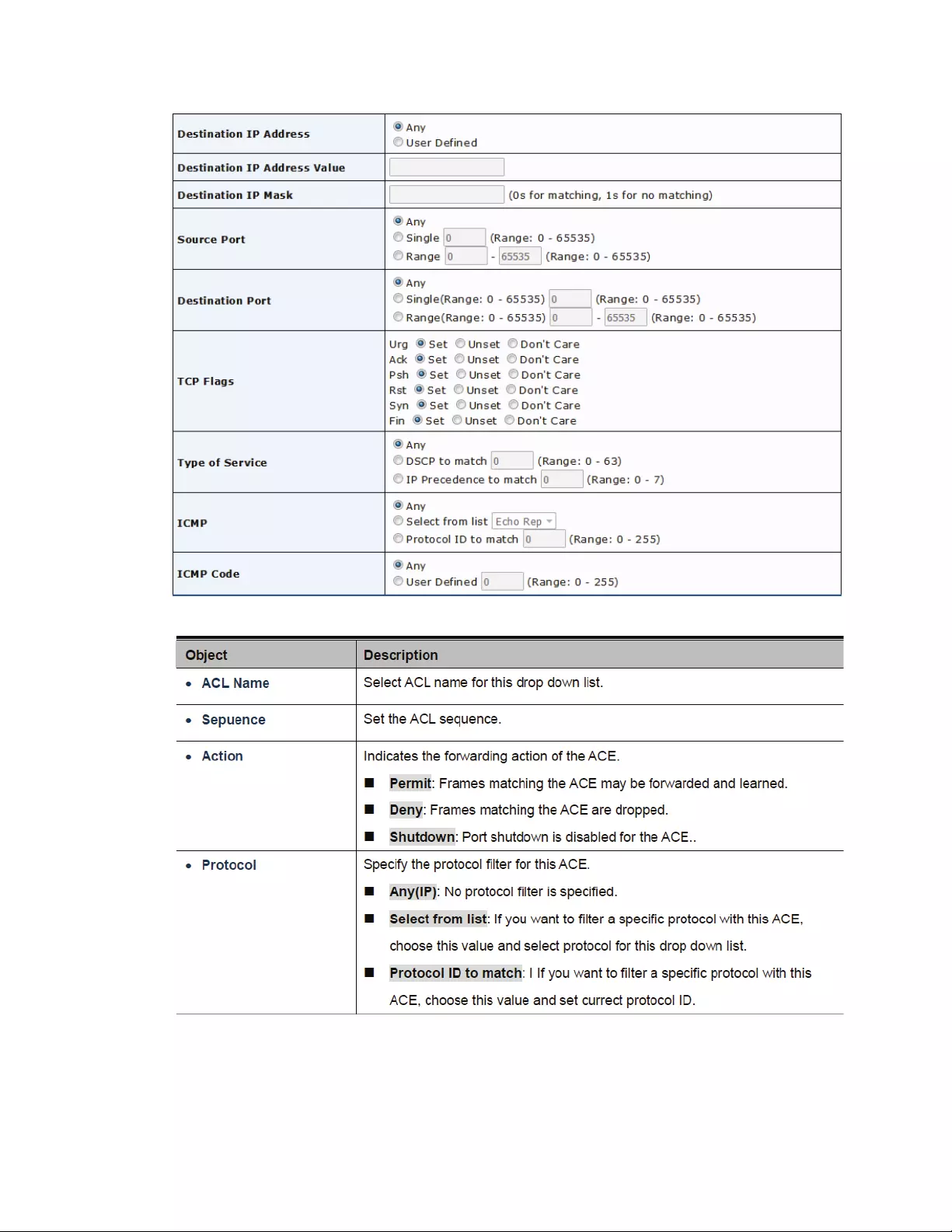
140
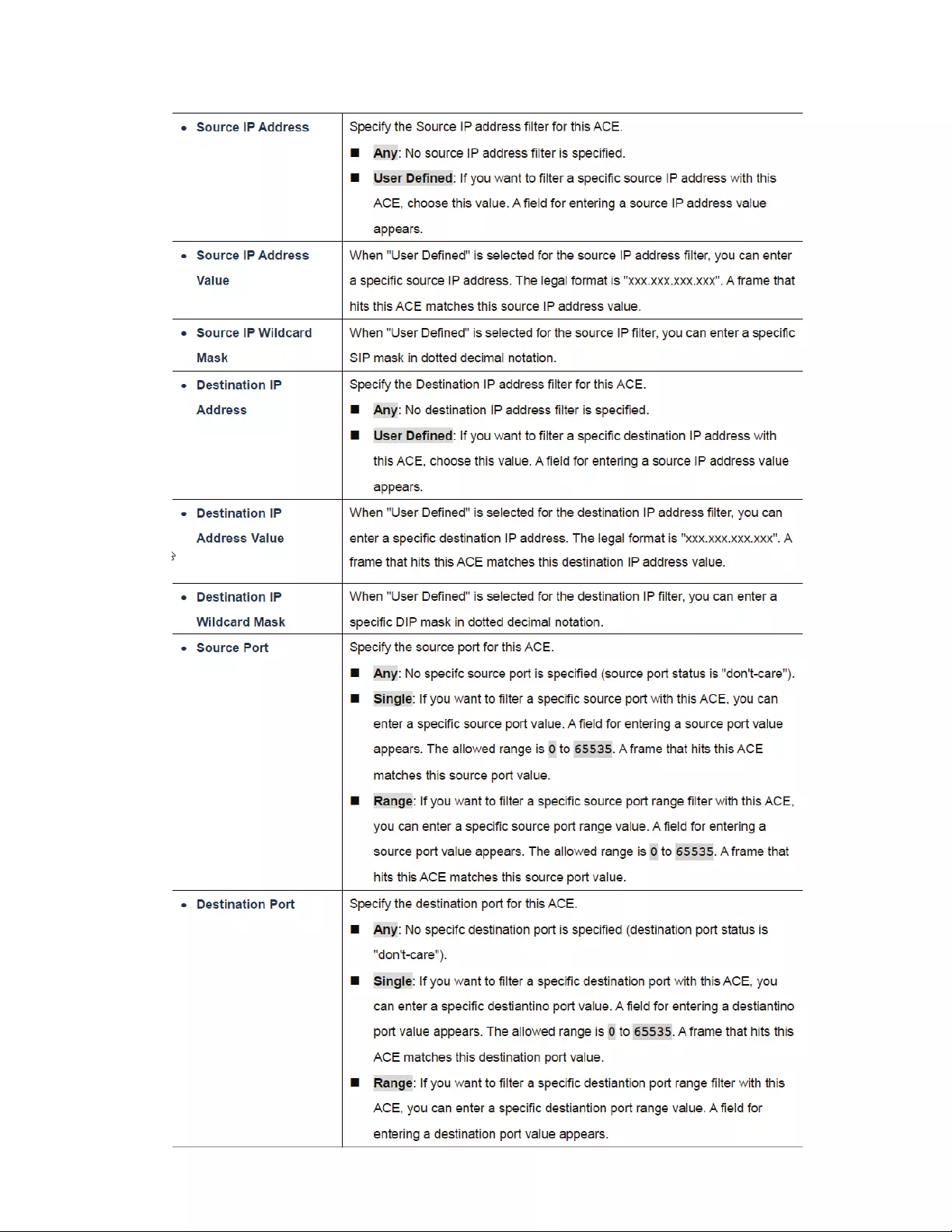
141
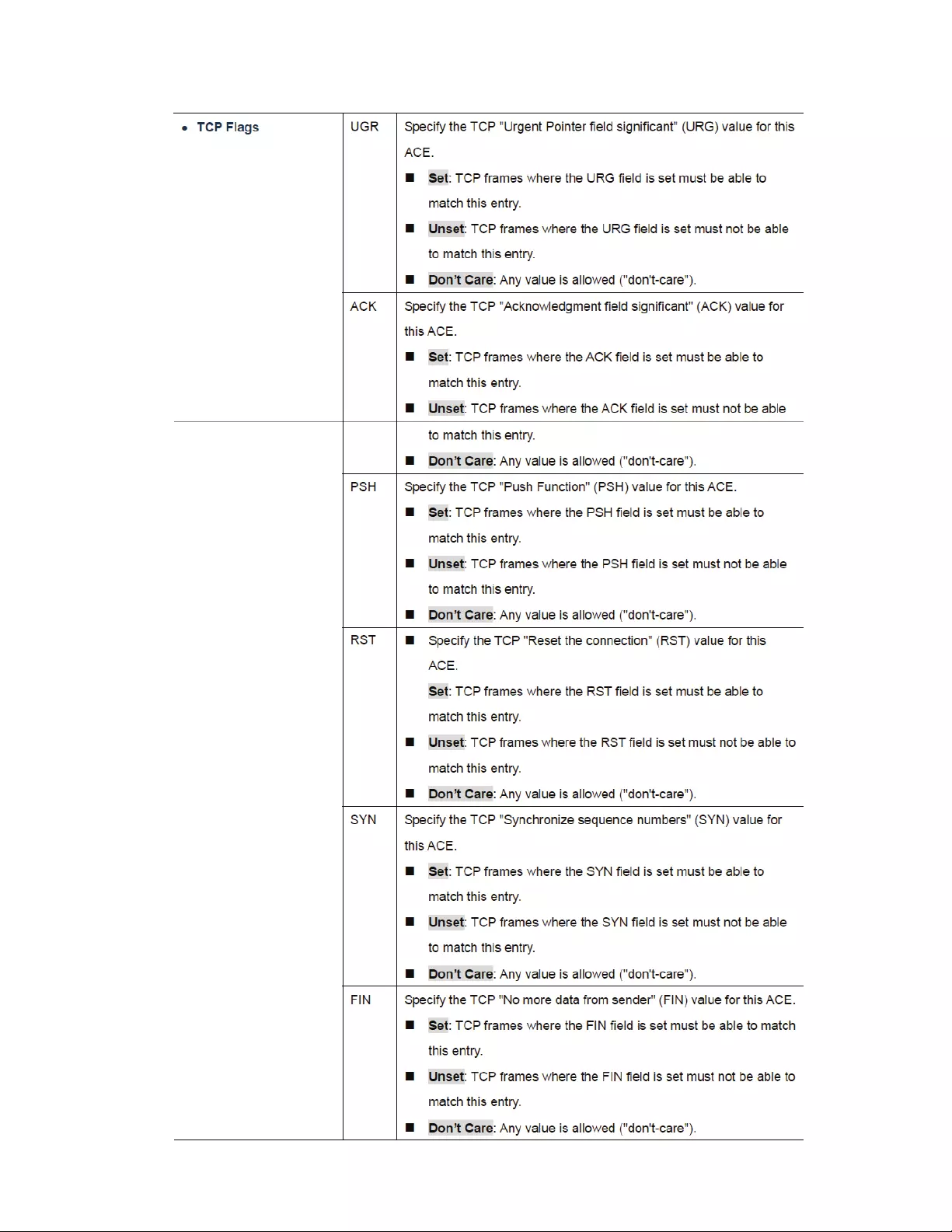
142

143
4.10.6 IPv6‐BasedACL
CreateanIPv6addressbasedACL.
4.10.7 IPv6‐BasedACE
VerysimilartoIPv4‐BasedACE(seeabove)withmuchofthesameparameters.
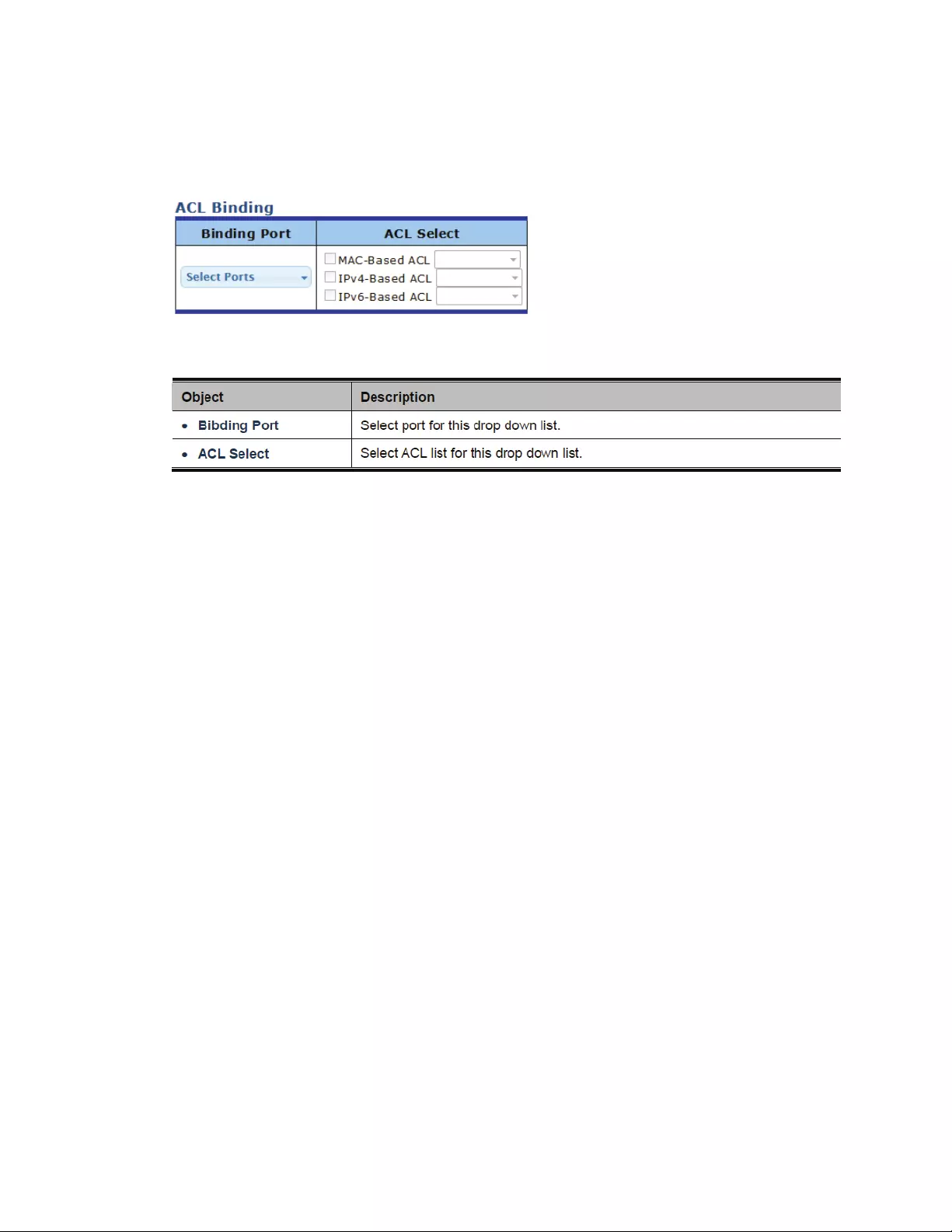
144
4.10.8 ACLBinding
Usethisconfigurationpageinordertolink(orbind)thephysicalportsorLAGstoanACL.
4.11 MACAddressTable
4.11.1 WhatisaMACAddressTable?
Amediaaccesscontroladdress(MACaddress)isauniqueidentifierassignedtonetworkinterfacesfor
communicationsonthephysicalnetworksegment.MACaddressesareusedasanetworkaddressfor
mostIEEE802networktechnologies,includingEthernetandWiFi.Layer2Ethernetswitches,suchas
theIntellinet8‐PortPoE+GigabitswitchusetheseMACaddressestoroutethepacketsfromsourceto
destination.Theswitchbuildsupatableovertime,inwhichitstorespairingsofMACaddressesand
physicalports.WheneverapackethastobedeliveredandthedestinationMACaddressisn’tinthe
MACaddresstable,theswitchisforcedtosendoutthedatapackettoallports,justlikeanold
Ethernethubwoulddo,andthatfloodsthenetworkwithunnecessarytraffic.However,oncethe
switchhaslearnttheportatwhichthedestinationclientisconnectedto,itwilladdthisinformationto
itsMACaddresstable,andfuturedeliveriesforthatMACaddresswillproceedmuchmoreefficiently.
MACaddressescanbestoredpermanently(static)ortemporarily(dynamic).

145
4.11.2 StaticMACSettings
YoucanaddastaticMACaddress;itremainsintheswitch'saddresstable,regardlessofwhetherthe
deviceisphysicallyconnectedtotheswitch.Thissavestheswitchfromhavingtore‐learnadevice's
MACaddresswhenthedisconnectedorpowered‐offdeviceisactiveonthenetworkagain.Youcan
add/modify/deleteastaticMACaddress.Additionally,bindingaMACaddresstoaspecificportcan
helpprotectagainstspoofingattacks.
ParameterDescription
MACAddressPhysical address of a network client.
PortSpecifytheportatwhichthenetworkclientisconnectedto.
VLANIftheclientispartofaVLAN,defineithereaccordingly.
4.11.3 MACFiltering
Theswitchcanfilterout(reject)trafficfrompre‐configuredMACaddresstoincreasesecurity.
4.11.4 DynamicAddressSetting
OnthisscreenyoudefinehowlongMACaddress–portpairingsarekeptintheMACaddresstable.
Thisiscalledagingtime.Thedefaultvalueis300seconds,butmayincreasethisvalueupto630
seconds.

146
4.11.5 DynamicallyLearned
ThisscreenshowsallMACaddressesthatarecurrentlystoredintheMACaddresstable.
Intheuppersectionoftheinterfaceyoucanfindtoolsthathelpyounarrowdownthetraffic.Youcan
filterbyport,VLANorpartofaMACaddress.
ThetablebelowshowsACaddressescurrentlyintheMACaddresstable.Bydefaultthescreenshows
allMACaddresses,butifyouhavespecifiedsomefiltersintheuppersection,theresultswillbe
narroweddownaccordingly.
ToaddaMACaddresstotheMACaddresstablepermanently,simplyclickthe“AddtoStaticMAC
Table”button.
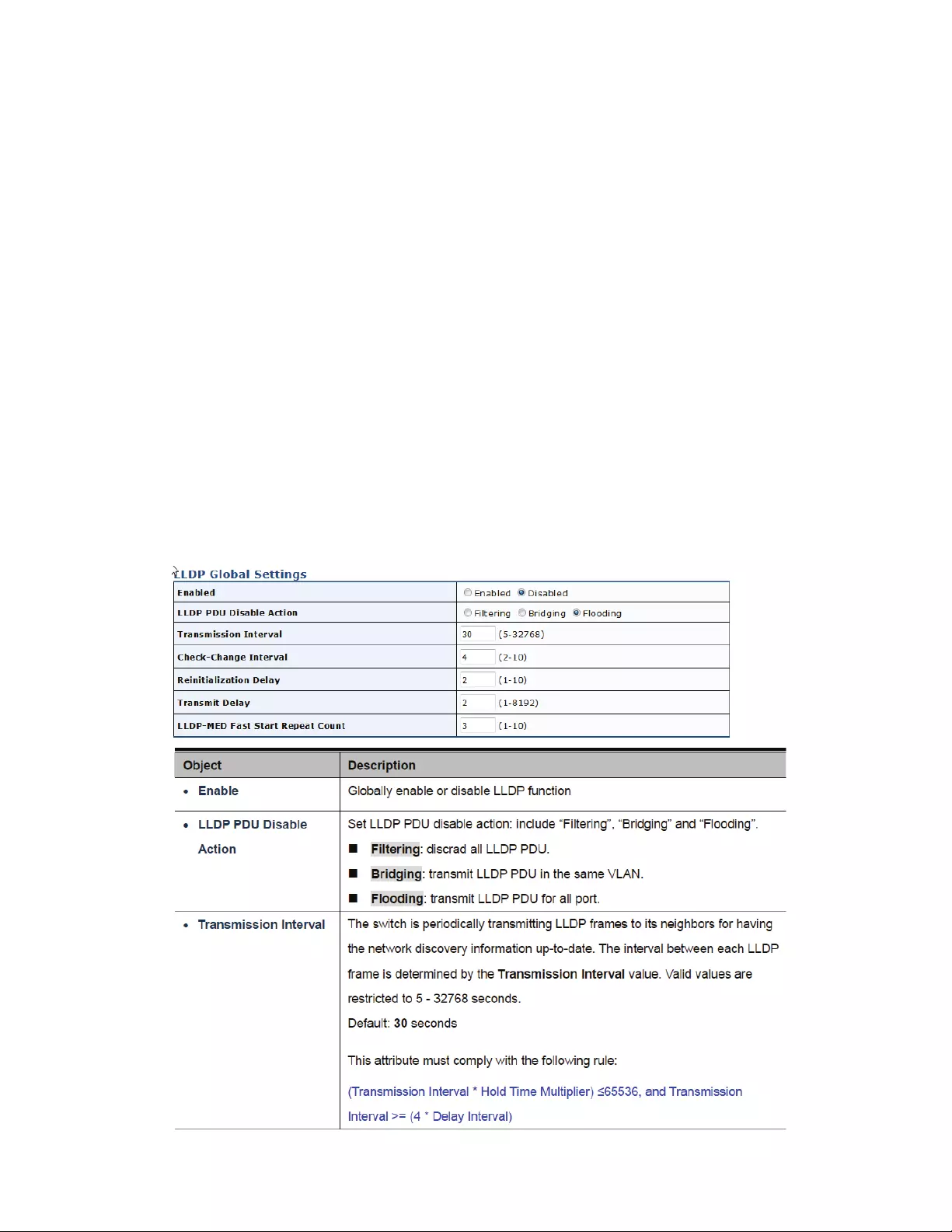
147
4.12 LinkLayerDiscoveryProtocol(LLDP)
4.12.1 WhatisLLDP
LinkLayerDiscoveryProtocol(LLDP)isusedtodiscoverbasicinformationaboutneighboringdevices
onthelocalbroadcastdomain.LLDPisaLayer2protocolthatusesperiodicbroadcaststoadvertise
informationaboutthesendingdevice.AdvertisedinformationisrepresentedinTypeLengthValue
(TLV)formataccordingtotheIEEE802.1abstandard,andcanincludedetailssuchasdevice
identification,capabilitiesandconfigurationsettings.LLDPalsodefineshowtostoreandmaintain
informationgatheredabouttheneighboringnetworknodesitdiscovers.
LinkLayerDiscoveryProtocol‐MediaEndpointDiscovery(LLDP‐MED)isanextensionofLLDPintended
formanagingendpointdevicessuchasVoiceoverIPphonesandnetworkswitches.TheLLDP‐MED
TLVsadvertiseinformationsuchasnetworkpolicy,power,inventory,anddevicelocationdetails.LLDP
andLLDP‐MEDinformationcanbeusedbySNMPapplicationstosimplifytroubleshooting,enhance
networkmanagement,andmaintainanaccuratenetworktopology.
4.12.2 LLDPGlobalSetting
This Page allows the user to inspect and configure the current LLDP port settings.
148
4.12.3 LLDPPortSettings
UsetheLLDPPortSettingtospecifythemessageattributesforindividualinterfaces,includingwhether
messagesaretransmitted,received,orbothtransmittedandreceived.

149

150
4.12.4 LLDPLocalDevice
UsetheLLDPLocalDeviceInformationscreentodisplayinformationabouttheswitch,suchasitsMAC
address,chassisID,managementIPaddress,andportinformation.
ThescreenalsodisplayLLDPstatusinformationofeachport.Clickingthe“Detail”buttonopensupa
pagethatpresentstheinformationinmuchgreaterdetail.

151
4.12.5 LLDPRemoveDevice
ThispageprovidesastatusoverviewforallLLDPremotedevices.Thedisplayedtablecontainsarow
foreachportonwhichanLLDPneighborisdetected.
4.12.6 LLDPMEDNetworkPolicySettings
NetworkPolicyDiscoveryenablestheefficientdiscoveryanddiagnosisofmismatchissueswiththe
VLANconfiguration,alongwiththeassociatedLayer2andLayer3attributes,whichapplyforasetof
specificprotocolapplicationsonthatport.Impropernetworkpolicyconfigurationsareavery
significantissueinVoIPenvironmentsthatfrequentlyresultinvoicequalitydegradationorlossof
service.Policiesareonlyintendedforusewithapplicationsthathavespecific'real‐time’network
policyrequirements,suchasinteractivevoiceand/orvideoservices.Thenetworkpolicyattributes
advertisedare:
1. Layer2VLANID(IEEE802.1Q‐2003)
2. Layer2priorityvalue(IEEE802.1D‐2004)
3. Layer3Diffservcodepoint(DSCP)value(IETFRFC2474)
Thisnetworkpolicyispotentiallyadvertisedandassociatedwithmultiplesetsofapplicationtypes
supportedonagivenport.
Theapplicationtypesspecificallyaddressedare:
1. Voice
2. GuestVoice
3. SoftphoneVoice
4. VideoConferencing
5. StreamingVideo
6. Control/Signaling(conditionallysupportaseparatenetworkpolicyforthemediatypesabove)
AlargenetworkmaysupportmultipleVoIPpoliciesacrosstheentireorganization,anddifferent
policiesperapplicationtype.LLDP‐MEDallowsmultiplepoliciestobeadvertisedperport,each
correspondingtoadifferentapplicationtype.DifferentportsonthesameNetworkConnectivity
Devicemayadvertisedifferentsetsofpolicies,basedontheauthenticateduseridentityorport
configuration.
ItshouldbenotedthatLLDP‐MEDisnotintendedtorunonlinksotherthanbetweenNetwork
ConnectivityDevicesandEndpoints,andthereforedoesnotneedtoadvertisethemultitudeof
networkpoliciesthatfrequentlyrunonanaggregatedlinkinteriortotheLAN.
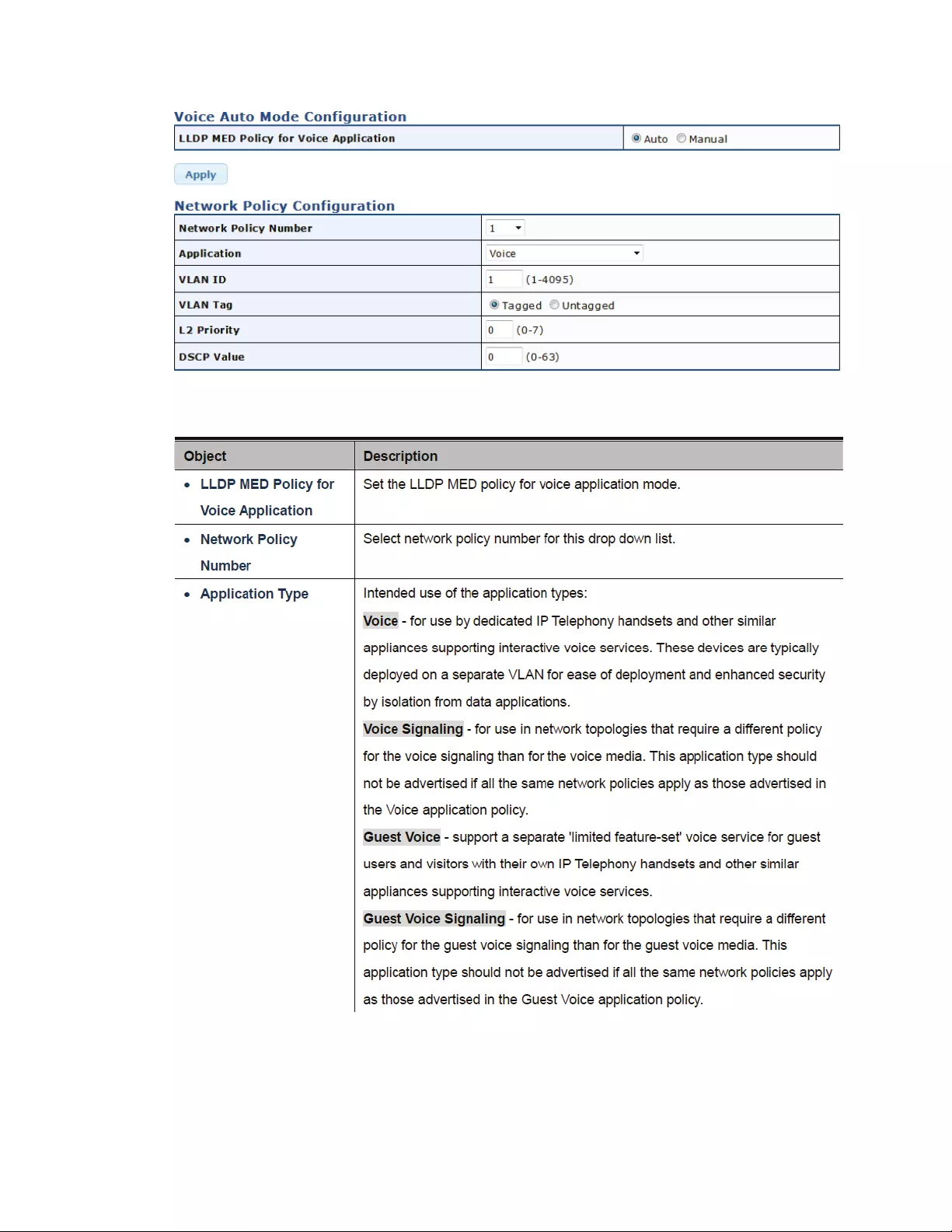
152

153
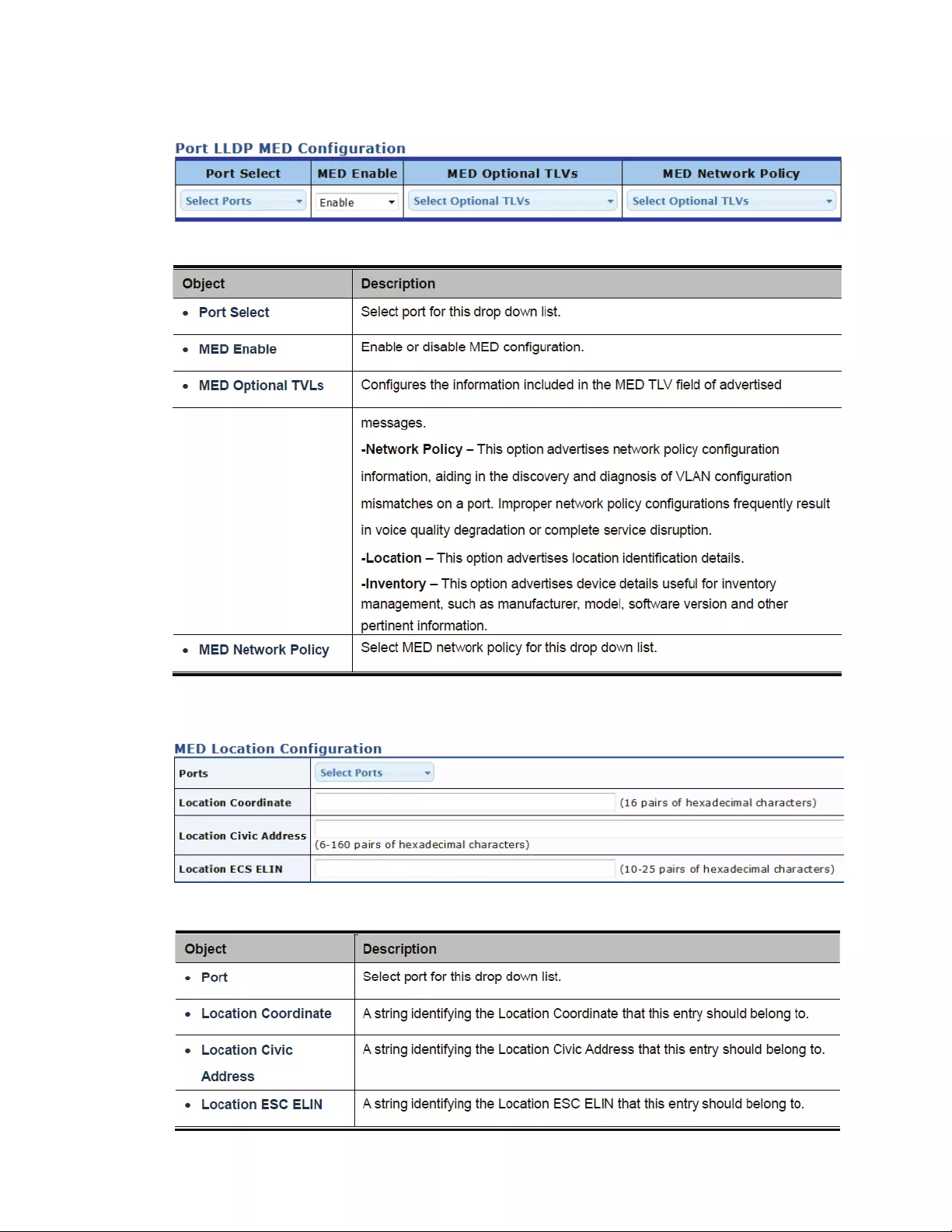
154
4.12.7 MEDPortSettings
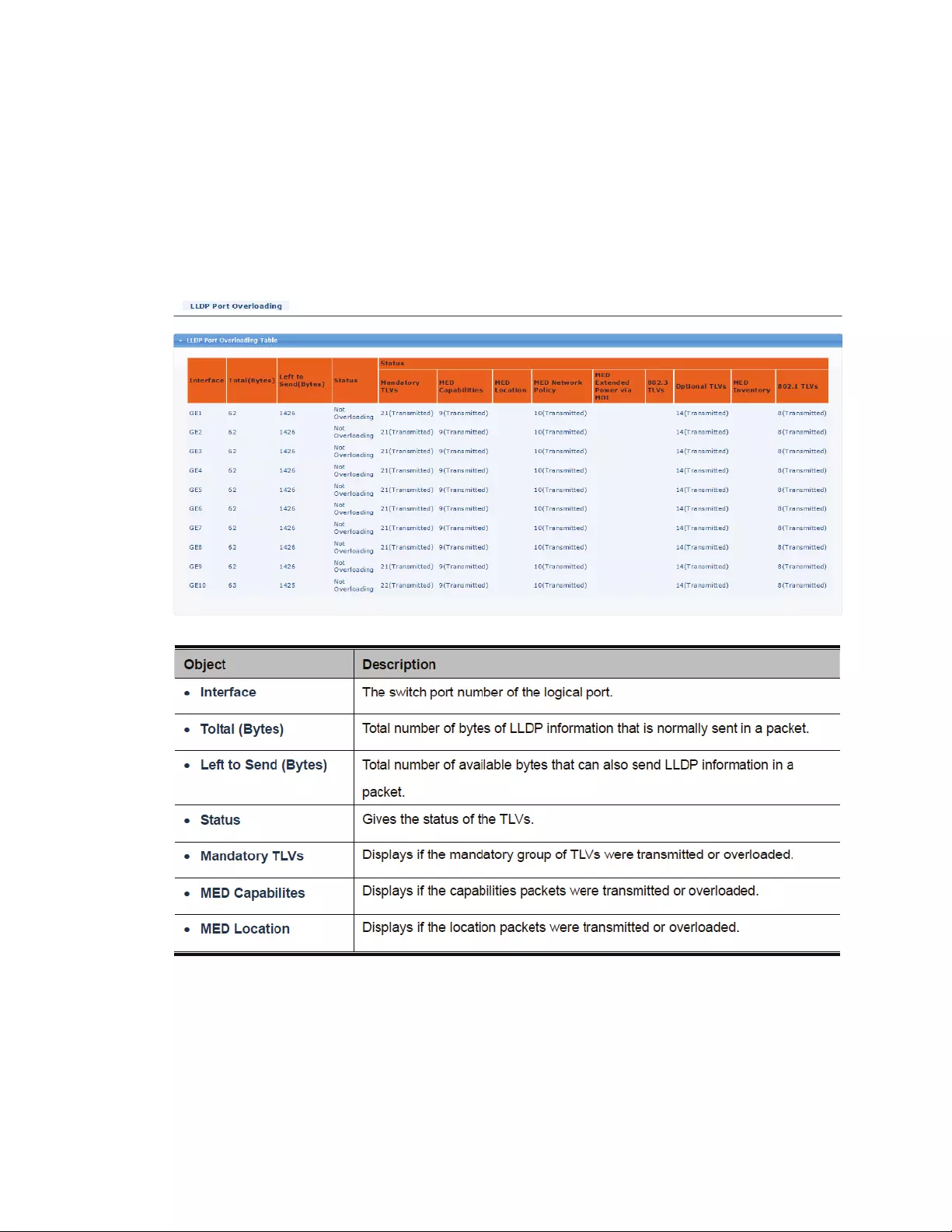
155
4.12.8 LLDPOverloading
LinkLayerDiscoveryProtocol(LLDP)isusedtoadvertiseinformationaboutadevicetoother
connecteddevices.OptionalinformationcanbesentthroughanLLDPpacketintheformofaType
LengthValue(TLV).Themoreinformationyouwanttoinclude,themoreTLVsyouadd.LLDP
informationissentinaprotocoldataunit(PDU).Eachinterfacethatinformationissentacrosshasa
maximumsizeofPDUthatitcanhandle.IftoomuchinformationisincludedinanLLDPpacket,itcan
exceedthemaximumPDUsize.ThisisknownasanLLDPoverload.
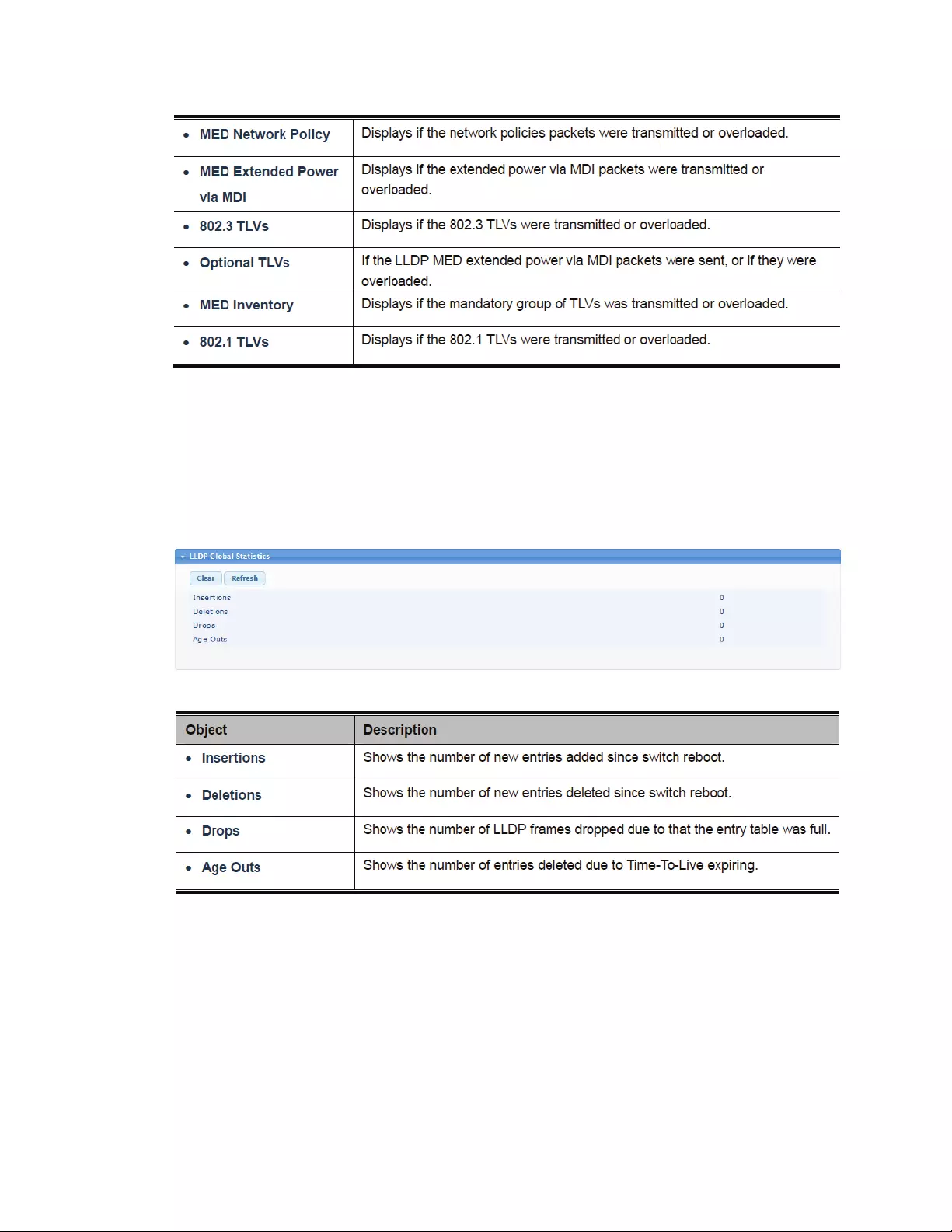
156
4.12.9 LLDPStatistics
UsetheLLDPDeviceStatisticsscreentogeneralstatisticsforLLDP‐capabledevicesattachedtothe
switch,andforLLDPprotocolmessagestransmittedorreceivedonalllocalinterfaces.

157
4.13 Diagnostics
This section provide the Physical layer and IP layer network diagnostics tools for
troubleshooting purposes. The diagnostic tools are designed for network
administrators to help them quickly diagnose problems.
4.13.1 CableDiagnostics
TheCableDiagnosticsperformstestsoncoppercables.Thesefunctionshavetheabilitytoidentifythe
cablelengthandoperatingconditions,andtoisolateavarietyofcommonfaultsthatcanoccuronthe
Cat5twisted‐paircabling.Theremightbetwostatusesasfollow:
Ifthelinkisestablishedonthetwisted‐pairinterfacein1000Base‐Tmode,theCable
Diagnosticscanrunwithoutdisruptionofthelinkorofanydatatransfer.
Ifthelinkisestablishedin100Base‐TXor10Base‐T,theCableDiagnosticscausethelinkto
dropwhilethediagnosticsarerunning.
Afterthediagnosticsarefinished,thelinkisreestablished.Andthefollowingfunctionsareavailable.
Couplingbetweencablepairs.
Cablepairtermination
CableLength
Note:
CableDiagnosticsisonlyaccurateforcablesoflengthfrom15to100meters.
Cablepairsarereferredtoaschannels,wherechannelArepresentspins3&4,channelBpins1&2,
channel7pins5&6andchannelDrepresentspins7&8.
Thepictureaboveshowsthetestresultsofport7,whichisconnectedtoaPCwitha3ftnetwork
cable.Duetotheshortcable,thelengthtestisn’tworking.
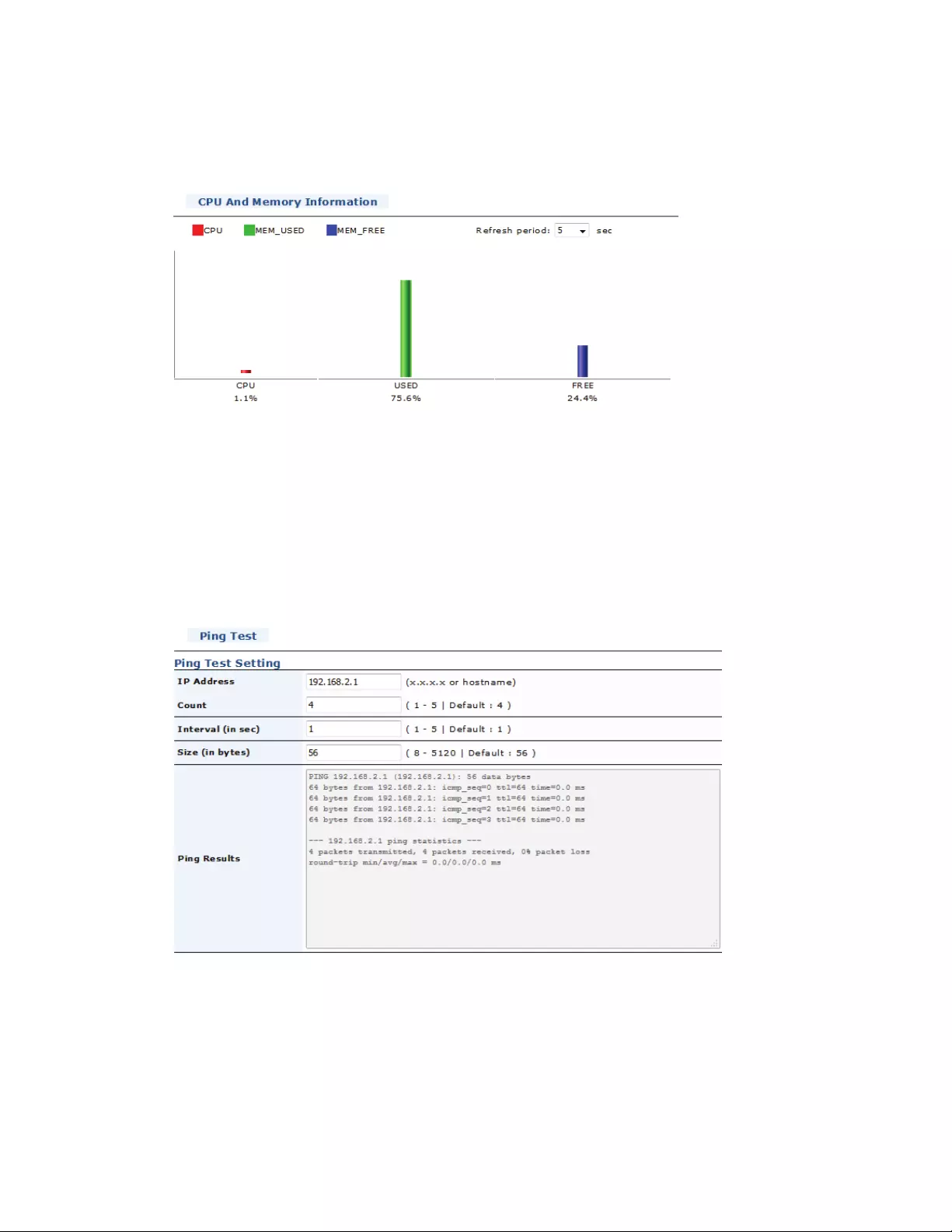
158
4.13.2 SystemStatus
Thispageprovidesinformationabouttheswitchitselfandsomeofitsvitalresources.
4.13.3 IPv4PingTest
Inordertotroubleshootconnectivityissues,theIntellinetswitchcanaideyouwithanintegratedping
tool.ThiscanbeveryusefulifyouareremotelyconnectingtotheIntellinetswitchandneedto
performaPINGinthelocalnetwork.
ProvidetheIPaddress,count(howmanypingstosend),thetimeintervalbetweeneachping,andthe
sizeofthepayload,clickApply(notshown)andwaitforthepingresultstobedisplayedonthescreen.
4.13.4 IPv6PingTest
VerymuchthesameastheIPv4test,exceptthisoneisdesignedfor,youguessedit,IPv6addresses.

159
4.13.5 TraceRoute
Tracerouteisacomputernetworkdiagnostictoolfordisplayingtheroute(path)andmeasuringtransit
delaysofpacketsacrossanInternetProtocol(IP)network.Thehistoryoftherouteisrecordedasthe
round‐triptimesofthepacketsreceivedfromeachsuccessivehost(remotenode)intheroute(path);
thesumofthemeantimesineachhopindicatesthetotaltimespenttoestablishtheconnection.
Tracerouteproceedsunlessall(three)sentpacketsarelostmorethantwice,thentheconnectionis
lostandtheroutecannotbeevaluated.Ping,ontheotherhand,onlycomputesthefinalround‐trip
timesfromthedestinationpoint.
Above:ExampleTrace
TypeintheIPaddressofthedestinationyouwithtotrace,andprovidethemaximumnumberofhops.
Note:YoucanonlytypeinanIPaddress.Hostnamesarenotallowed,despitetheinterfacescreen
claimingotherwise.

160
4.14 RMON
4.14.1 WhatisRMON?
RemoteMonitoring(RMON)isastandardmonitoringspecificationthatenablesvariousnetwork
monitorsandconsolesystemstoexchangenetwork‐monitoringdata.RMONisthemostimportant
expansionofthestandardSNMP.RMONisasetofMIBdefinitions,usedtodefinestandardnetwork
monitorfunctionsandinterfaces,enablingthecommunicationbetweenSNMPmanagementterminals
andremotemonitors.RMONprovidesahighlyefficientmethodtomonitoractionsinsidethesubnets.
MIDofRMONconsistsof10groups.Theswitchsupportsthemostfrequentlyusedgroup1,2,3and9:
Statistics:MaintainbasicusageanderrorstatisticsforeachsubnetmonitoredbytheAgent.
History:RecordperiodicalstatisticsamplesavailablefromStatistics.
Alarm:Allowmanagementconsoleuserstosetanycountorintegerforsampleintervalsand
alertthresholdsforRMONAgentrecords.
Event:AlistofalleventsgeneratedbyRMONAgent.
AlarmdependsontheimplementationofEvent.StatisticsandHistorydisplaysomecurrentorhistory
subnetstatistics.AlarmandEventprovideamethodtomonitoranyintegerdatachangeinthe
network,andprovidesomealertsuponabnormalevents(sendingTraporrecordinlogs).
4.14.2 RMONStatistics
ThispageprovidesRMONstatisticsfortheselectedport.Usethedrop‐downlisttoselecttheportyou
wishtoseethestatisticsfor,andafewsecondslatertheinformationwillappearonthescreen.Click
“Clear”inordertoresetthestatisticsfortheselectedport.
4.14.3 RMONEventandEventLog
YoucandefineaRMONeventonthispage.
161
TheRMONEventLogscreenallowsyoumonitorRMONevents.

162
4.14.4 RMONAlarm
AnRMONalarmmonitorsaspecificmanagementinformationbase(MIB)objectforaspecified
interval,triggersanalarmataspecifiedthresholdvalue(threshold),andresetsthealarmatanother
thresholdvalue.YoucanusealarmswithRMONeventstogeneratealogentryoranSNMPnotification
whentheRMONalarmtriggers.

163
164
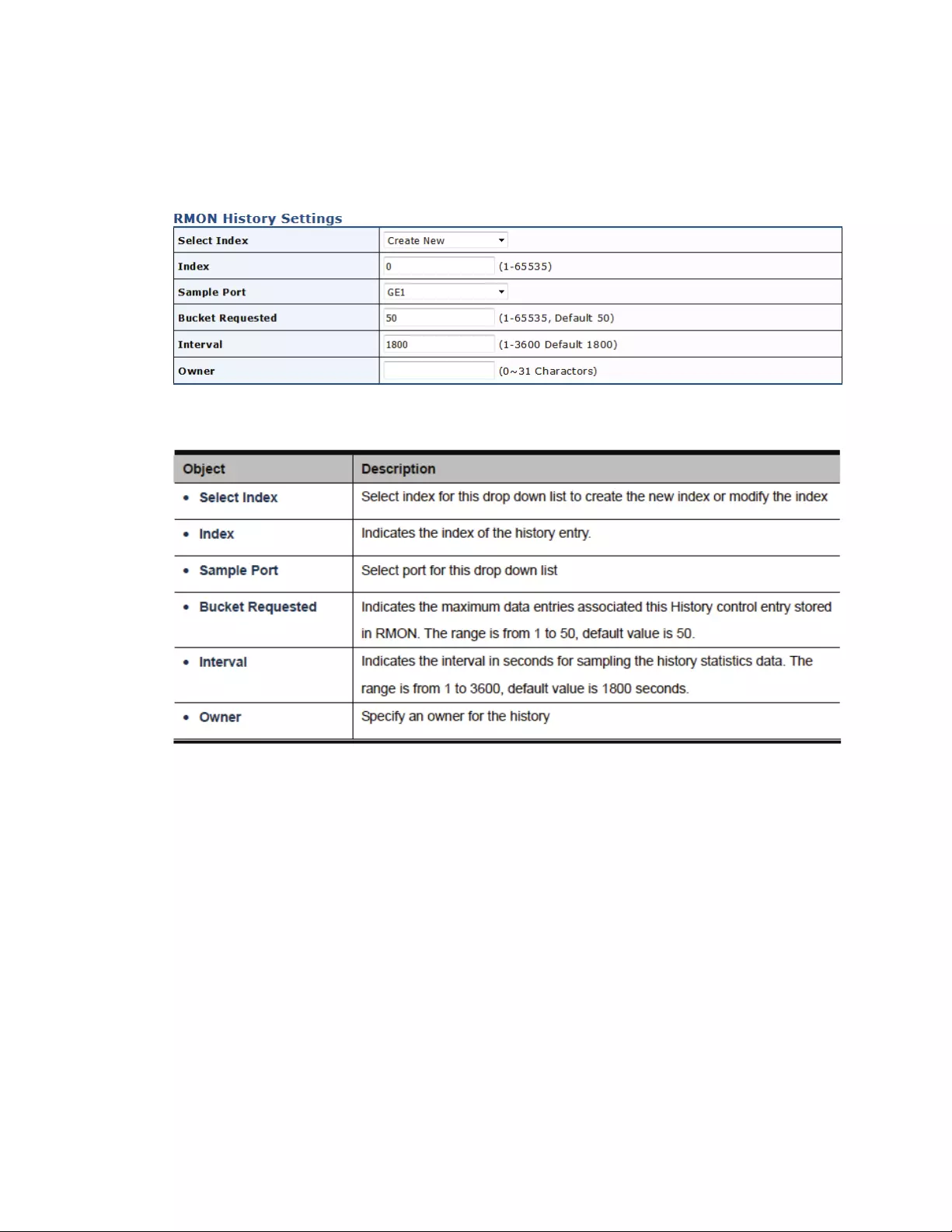
165
4.14.5 RMONHistoryandHistoryLog
RMONHistory(alsoknownasRMONgroup2)collectsahistorygroupofstatisticsonEthernet,Fast
Ethernet,andGigabitEthernetinterfacesforaspecifiedpollinginterval.

166
4.15 Maintenance
4.15.1 FactoryDefault
TherearetwowaystoresettheIntellinetswitchbacktoitsfactorydefaultsettings.
4.15.1.1 ViaResetButton
Presstheresetbuttonforatleast10secondswhiletheswitchisoperationinordertotriggerthe
factorydefaultreset.
4.15.1.2 ViaWebAdministratorMenu
ClickonRestoreandconfirmyourdecision.
167
4.15.2 RebootSwitch
IfyouneedtoreboottheIntellinetswitchfromaremotelocation,thisisthewaytodoit.Whenthe
rebootistriggered,theswitchwon’tbeaccessibleandoperationalforabout60seconds.
4.15.3 BackupManager
ThisfunctionallowsbackupofthecurrentimageorconfigurationoftheIntellinet8‐PortGigabitPoE+
switchtothelocalmanagementstation,i.e.,adesktopcomputer.
4.15.3.1 ViaTFTP
IsyouchooseTFTP,thenaTFTPserverhastobeavailablefortheswitchtoconnectto.Youneedto
providetheIPaddressofavalidTFTPserver,andyouwillhavetospecifywhattypeofbackupyou
wishtomake.
4.15.3.2 ViaHTTP
SelectHTTPforaneasierandquickerwaytostoretheconfigurationandlogdata.
ClickthebuttontosavethefileonyourlocalHDD.

168
4.15.4 UpgradeManager
Ifanewfirmwareneedstobeinstalled,youcanusethisscreentodoit.Youcaninstallanewfirmware
imageusingTFTP,orHTTP.Youcanalsousethisfeaturetoreloadapreviouslysavedconfiguration.
4.15.4.1 ViaTFTP
ToinstalltheupgradeviaTFTP,aTFTPservermustbeconfiguredtoacceptconnectionsfromthe
Intellinetswitch.ProvidetheIPaddressoftheTFTPserveralongwiththecorrectfilenamethatyou
wishtoinstall.
Presstobegin.
4.15.4.2 ViaHTTP
Inordertoinstalltheupgrade,selecttheappropriateupgradetype,thenclickon,selectthe
filefromyourlocalHDD.Thenpresstobegin.
169
4.15.5 ConfigurationManager
TheIntellinet8‐PortPoE+GigabitSwitchhastwoconfigurations.Thestartupandthebackup
configuration.WiththebackupmanageryoucansavetheseconfigurationstoaTFTPserver,ortothe
HDDofacomputer.
Withtheconfigurationmanageryoucancreatethestartupandbackupconfiguration,bycopyingthe
currentconfigurationoftheswitch(runningconfiguration)toeitherthestartuporbackup
configuration.
Oncethecurrentconfigurationhasbeensavedthisway,itcanbebackedupwiththebackupmanager.
4.15.6 EnablePassword
Thispageallowsyoutomodifytheenablepassword.Inthecommandlineinterface,youcanuse
“enable”tochangetheprivilegelevelto“Admin.”Afterthe“enable”commandisissued,youneedto
entertheenablepasswordtochangetheprivilegelevel.

170
5 Warranty
DeutschGarantieinformationenfindenSiehierunterintellinetnetwork.com/warranty.
EnglishForwarrantyinformation,gotointellinetnetwork.com/warranty.
EspañolSideseaobtenerinformaciónsobrelagarantía,visiteintellinetnetwork.com/warranty.
FrançaisPourconsulterlesinformationssurlagarantie,rendezvousàl’adresse
intellinetnetwork.com/warranty.
ItalianoPerinformazionisullagaranzia,accedereaintellinetnetwork.com/warranty.
PolskiInformacjedotyczącegwarancjiznajdująsięnastronieintellinetnetwork.com/warranty.
MéxicoPólizadeGarantíaIntellinet—DatosdelimportadoryresponsableanteelconsumidorIC
IntracomMéxico,S.A.P.I.deC.V.•Av.InterceptorPoniente#73,Col.ParqueIndustrialLaJoya,
CuautitlanIzcalli,EstadodeMéxico,C.P.54730,México.•Tel.(55)1500‐4500
Lapresentegarantíacubrelossiguientesproductoscontracualquierdefectodefabricaciónensus
materialesymanodeobra.
A.GarantizamoscámarasIPyproductosconpartesmóvilespor3años.
B.Garantizamoslosdemásproductospor5años(productossinpartesmóviles),bajolassiguientes
condiciones:
1.Todo s losproductosaqueserefiereestagarantía,amparasucambiofísico,sinningúncargoparael
consumidor.
2.Elcomercializadornotienetalleresdeservicio,debidoaquelosproductosquesegarantizanno
cuentanconreparaciones,nirefacciones,yaquesugarantíaesdecambiofísico.
3.Lagarantíacubreexclusivamenteaquellaspartes,equipososub‐ensamblesquehayansido
instaladasdefábricaynoincluyeenningúncasoelequipoadicionalocualesquieraquehayansido
adicionadosalmismoporelusuarioodistribuidor.
Parahacerefectivaestagarantíabastaráconpresentarelproductoaldistribuidoreneldomicilio
dondeueadquiridooeneldomiciliodeICIntracomMéxico,S.A.P.I.deC.V.,juntoconlosaccesorios
contenidosnsuempaque,acompañadodesupólizadebidamentellenadayselladaporlacasa
vendedoraindispensableelselloyfechadecompra)dondeloadquirió,obien,lafacturaoticketde
compraoriginaldondesemencioneclaramenteelmodelo,numerodeserie(cuandoaplique)yfecha
deadquisición.Estagarantíanoesválidaenlossiguientescasos:Sielproductosehubiesetilizadoen
condicionesdistintasalasnormales;sielproductonohasidooperadoconformealosinstructivosde
uso;osielproductohasidoalteradootratadodeserreparadoporelconsumidoroterceraspersonas.

171
6 Copyright
Copyright©2015ICIntracom.Allrightsreserved.Nopartofthispublicationmaybereproduced,
transmitted,transcribed,storedinaretrievalsystem,ortranslatedintoanylanguageorcomputer
language,inanyformorbyanymeans,electronic,mechanical,magnetic,optical,chemical,manualor
otherwise,withoutthepriorwrittenpermissionofthiscompany
Thiscompanymakesnorepresentationsorwarranties,eitherexpressedorimplied,withrespecttothe
contentshereofandspecificallydisclaimsanywarranties,merchantabilityorfitnessforanyparticular
purpose.Anysoftwaredescribedinthismanualissoldorlicensed"asis".Shouldtheprogramsprove
defectivefollowingtheirpurchase,thebuyer(andnotthiscompany,itsdistributor,oritsdealer)
assumestheentirecostofallnecessaryservicing,repair,andanyincidentalorconsequentialdamages
resultingfromanydefectinthesoftware.Further,thiscompanyreservestherighttorevisethis
publicationandtomakechangesfromtimetotimeinthecontentsthereofwithoutobligationtonotify
anypersonofsuchrevisionorchanges.

172
7 FederalCommunicationCommissionInterferenceStatement
ThisequipmenthasbeentestedandfoundtocomplywiththelimitsforaClassBdigitaldevice,
pursuanttoPart15ofFCCRules.Theselimitsaredesignedtoprovidereasonableprotectionagainst
harmfulinterferenceinaresidentialinstallation.Thisequipmentgenerates,uses,andcanradiateradio
frequencyenergyand,ifnotinstalledandusedinaccordancewiththeinstructions,maycauseharmful
interferencetoradiocommunications.However,thereisnoguaranteethatinterferencewillnotoccur
inaparticularinstallation.Ifthisequipmentdoescauseharmfulinterferencetoradioortelevision
reception,whichcanbedeterminedbyturningtheequipmentoffandon,theuserisencouragedto
trytocorrecttheinterferencebyoneormoreofthefollowingmeasures:
1.Reorientorrelocatethereceivingantenna.
2.Increasetheseparationbetweentheequipmentandreceiver.
3.Connecttheequipmentintoanoutletonacircuitdifferentfromthattowhichthereceiveris
connected.
4.Consultthedealeroranexperiencedradiotechnicianforhelp.
FCCCaution
Thisdeviceanditsantennamustnotbeco‐locatedoroperatinginconjunctionwithanyotherantenna
ortransmitter.ThisdevicecomplieswithPart15oftheFCCRules.Operationissubjecttothefollowing
twoconditions:(1)thisdevicemaynotcauseharmfulinterference,and(2)thisdevicemustacceptany
interferencereceived,includinginterferencethatmaycauseundesiredoperation.Anychangesor
modificationsnotexpresslyapprovedbythepartyresponsibleforcompliancecouldvoidtheauthority
tooperateequipment.
FCCRadiationExposureStatement:
ThisequipmentcomplieswithFCCradiationexposurelimitssetforthforanuncontrolledenvironment.
Thisequipmentshouldbeinstalledandoperatedwithminimumdistance20cmbetweentheradiator
&yourbody.
Safety
Thisequipmentisdesignedwiththeutmostcareforthesafetyofthosewhoinstallanduseit.
However,specialattentionmustbepaidtothedangersofelectricshockandstaticelectricitywhen
workingwithelectricalequipment.Allguidelinesofthisandofthecomputermanufacturemust
thereforebeallowedatalltimestoensurethesafeuseoftheequipment.
EUCountriesIntendedforUse
TheETSIversionofthisdeviceisintendedforhomeandofficeuseinAustria,Belgium,Bulgaria,
Cyprus,Czech,Denmark,Estonia,Finland,France,Germany,Greece,Hungary,Ireland,Italy,Latvia,
Lithuania,Luxembourg,Malta,Netherlands,Poland,Portugal,Romania,Slovakia,Slovenia,Spain,
Sweden,Turkey,andUnitedKingdom.TheETSIversionofthisdeviceisalsoauthorizedforuseinEFTA
memberstates:Iceland,Liechtenstein,Norway,andSwitzerland.
EUCountriesNotIntendedforUse
None

173
intellinetnetworkcom
©ICIntracom.Allrightsreserved.
IntellinetisatrademarkofICIntracom,registeredintheU.S.andothercountries.